29.3.23 Virus The Hacker News
Trojanized installers for the TOR anonymity browser are being used to target users in Russia and Eastern Europe with clipper malware designed to siphon cryptocurrencies since September 2022.
ARTICLES MARCH H MARCH(103) APRIL(113) MAY(110) JUNE(93) July(113) November(58) December(100)
Spyware Vendors Caught Exploiting Zero-Day Vulnerabilities on Android and iOS Devices
29.3.23 OS The Hacker News
A number of zero-day vulnerabilities that were addressed last year were exploited by commercial spyware vendors to target Android and iOS devices, Google's Threat Analysis Group (TAG) has revealed.
The two distinct campaigns were both limited and highly targeted, taking advantage of the patch gap between the release of a fix and when it was actually deployed on the targeted devices.
"These vendors are enabling the proliferation of dangerous hacking tools, arming governments that would not be able to develop these capabilities in-house," TAG's Clement Lecigne said in a new report.
"While use of surveillance technologies may be legal under national or international laws, they are often found to be used by governments to target dissidents, journalists, human rights workers, and opposition party politicians."
The first of the two operations took place in November 2022 and involved sending shortened links over SMS messages to users located in Italy, Malaysia, and Kazakhstan.
Upon clicking, the URLs redirected the recipients to web pages hosting exploits for Android or iOS, before they were redirected again to legitimate news or shipment-tracking websites.
The iOS exploit chain leveraged multiple bugs, including CVE-2022-42856 (a then zero-day), CVE-2021-30900, and a pointer authentication code (PAC) bypass, to install an .IPA file onto the susceptible device.
The Android exploit chain comprised three exploits – CVE-2022-3723, CVE-2022-4135 (a zero-day at the time of abuse), and CVE-2022-38181 – to deliver an unspecified payload.
While CVE-2022-38181, a privilege escalation bug affecting Mali GPU Kernel Driver, was patched by Arm in August 2022, it's not known if the adversary was already in possession of an exploit for the flaw prior to the release of the patch.
Another point of note is that Android users who clicked on the link and opened it in Samsung Internet Browser were redirected to Chrome using a method called intent redirection.
The second campaign, observed in December 2022, consisted of several zero-days and n-days targeting the latest version of Samsung Internet Browser, with the exploits delivered as one-time links via SMS to devices located in the U.A.E.
The web page, similar to those that were used by Spanish spyware company Variston IT, ultimately implanted a C++-based malicious toolkit capable of harvesting data from chat and browser applications.
The flaws exploited constitute CVE-2022-4262, CVE-2022-3038, CVE-2022-22706, CVE-2023-0266, and CVE-2023-26083. The exploit chain is believed to have been used by a customer or partner of Variston IT.
That said, the scale of the two campaigns and the nature of the targets are currently unknown.
The revelations come just days after the U.S. government announced an executive order restricting federal agencies from using commercial spyware that presents a national security risk.
"These campaigns are a reminder that the commercial spyware industry continues to thrive," Lecigne said. "Even smaller surveillance vendors have access to zero-days, and vendors stockpiling and using zero-day vulnerabilities in secret pose a severe risk to the Internet."
"These campaigns may also indicate that exploits and techniques are being shared between surveillance vendors, enabling the proliferation of dangerous hacking tools."
Mélofée: Researchers Uncover New Linux Malware Linked to Chinese APT Groups
29.3.23 APT The Hacker News
An unknown Chinese state-sponsored hacking group has been linked to a novel piece of malware aimed at Linux servers.
French cybersecurity firm ExaTrack, which found three samples of the previously documented malicious software that date back to early 2022, dubbed it Mélofée.
One of the artifacts is designed to drop a kernel-mode rootkit that's based on an open source project referred to as Reptile.
"According to the vermagic metadata, it is compiled for a kernel version 5.10.112-108.499.amzn2.x86_64," the company said in a report. "The rootkit has a limited set of features, mainly installing a hook designed for hiding itself."
Both the implant and the rootkit are said to be deployed using shell commands that download an installer and a custom binary package from a remote server.
The installer takes the binary package as an argument and then extracts the rootkit as well as a server implant module that's currently under active development.
Mélofée's features are no different from other backdoors of its kind, enabling it to contact a remote server and receive instructions that allow it to carry out file operations, create sockets, launch a shell, and execute arbitrary commands.
The malware's ties to China come from infrastructure overlaps with groups such as APT41 (aka Winnti) and Earth Berberoka (aka GamblingPuppet).
Earth Berberoka is the name given to a state-sponsored actor chiefly targeting gambling websites in China since at least 2020 using multi-platform malware like HelloBot and Pupy RAT.
According to Trend Micro, some samples of the Python-based Pupy RAT have been concealed using the Reptile rootkit.
Also discovered by ExaTrack is another implant codenamed AlienReverse, which shares code similarities with Mélofée and makes use of publicly-available tools like EarthWorm and socks_proxy.
"The Mélofée implant family is another tool in the arsenal of Chinese state sponsored attackers, which show constant innovation and development," the company said.
"The capabilities offered by Mélofée are relatively simple, but may enable adversaries to conduct their attacks under the radar. These implants were not widely seen, showing that the attackers are likely limiting its usage to high value targets."
Trojanized TOR Browser Installers Spreading Crypto-Stealing Clipper Malware
29.3.23 Virus The Hacker News
Trojanized installers for the TOR anonymity browser are being used to target users in Russia and Eastern Europe with clipper malware designed to siphon cryptocurrencies since September 2022.
"Clipboard injectors [...] can be silent for years, show no network activity or any other signs of presence until the disastrous day when they replace a crypto wallet address," Vitaly Kamluk, director of global research and analysis team (GReAT) for APAC at Kaspersky, said.
Another notable aspect of clipper malware is that its nefarious functions are not triggered unless the clipboard data meet specific criteria, making it more evasive.
It's not immediately clear how the installers are distributed, but evidence points to the use of torrent downloads or some unknown third-party source since the Tor Project's website has been subjected to blockades in Russia in recent years.
Regardless of the method used, the installer launches the legitimate executable, while also simultaneously launching the clipper payload that's designed to monitor the clipboard content.
"If the clipboard contains text, it scans the contents with a set of embedded regular expressions," Kamluk noted. "Should it find a match, it is replaced with one randomly chosen address from a hardcoded list."
Each sample is packed with thousands of possible replacement addresses that's selected at random. It also comes with the ability to disable the malware by means of a special hotkey combination (Ctrl+Alt+F10), an option likely added during the testing phase.
The Russian cybersecurity firm said it recorded roughly 16,000 detections, of which a majority are registered in Russia and Ukraine, followed by the U.S., Germany, Uzbekistan, Belarus, China, the Netherlands, the U.K., and France. In all, the threat has been spotted in 52 countries worldwide.
The scheme is estimated to have netted the operators almost $400,00 in illicit profits through the theft of Bitcoin, Litecoin, Ether, and Dogecoin. The amount of Monero assets plundered is not known owing to the privacy features built into the service.
It's suspected that the campaign could be larger in scope due to the possibility that the threat actors could be leveraging other software installers and hitherto unseen delivery methods to target unwary users.
To secure against such threats, it's always recommended to download software only from reliable and trusted sources.
North Korean APT43 Group Uses Cybercrime to Fund Espionage Operations
29.3.23 APT The Hacker News
A new North Korean nation-state cyber operator has been attributed to a series of campaigns orchestrated to gather strategic intelligence that aligns with Pyongyang's geopolitical interests since 2018.
Google-owned Mandiant, which is tracking the activity cluster under the moniker APT43, said the group's motives are both espionage- and financially-motivated, leveraging techniques like credential harvesting and social engineering to further its objectives.
The monetary angle to its attack campaigns is an attempt on the part of the threat actor to generate funds to meet its "primary mission of collecting strategic intelligence."
Victimology patterns suggest that targeting is focused on South Korea, the U.S., Japan, and Europe, spanning government, education, research, policy institutes, business services, and manufacturing sectors.
The threat actor was also observed straying off course by striking health-related verticals and pharma companies from October 2020 through October 2021, underscoring its ability to swiftly change priorities.
"APT43 is a prolific cyber operator that supports the interests of the North Korean regime," Mandiant researchers said in a detailed technical report published Tuesday.
"The group combines moderately-sophisticated technical capabilities with aggressive social engineering tactics, especially against South Korean and U.S.-based government organizations, academics, and think tanks focused on Korean peninsula geopolitical issues."
APT43's activities are said to align with the Reconnaissance General Bureau (RGB), North Korea's foreign intelligence agency, indicating tactical overlaps with another hacking group dubbed Kimsuky (aka Black Banshee, Thallium, or Velvet Chollima).
What's more, it has been observed using tools previously associated with other subordinate adversarial syndicates within RGB, such as the Lazarus Group (aka TEMP.Hermit).
Attack chains mounted by APT43 involve spear-phishing emails containing tailored lures to entice victims. These messages are sent using spoofed and fraudulent personas that masquerade as key individuals within the target's area of expertise to gain their trust.
It's also known to take advantage of contact lists stolen from compromised individuals to identify more targets and steal cryptocurrency to fund its attack infrastructure. The stolen digital assets are then laundered using hash rental and cloud mining services to obscure the forensic trail and convert them into clean cryptocurrency.
The ultimate goal of the attacks is to facilitate credential collection campaigns through domains that mimic a wide range of legitimate services and use the gathered data to create online personas.
"The prevalence of financially-motivated activity among North Korean groups, even among those which have historically focused on cyber espionage, suggests a widespread mandate to self-fund and an expectation to sustain themselves without additional resourcing," Mandiant said.
APT43's operations are actualized through a large arsenal of custom and publicly available malware such as LATEOP (aka BabyShark), FastFire, gh0st RAT, Quasar RAT, Amadey, and an Android version of a Windows-based downloader called PENCILDOWN.
The findings come less than a week after German and South Korean government agencies warned about cyber attacks mounted by Kimsuky using rogue browser extensions to steal users' Gmail inboxes.
"APT43 is highly responsive to the demands of Pyongyang's leadership," the threat intelligence firm said, noting the group "maintains a high tempo of activity."
"Although spear-phishing and credential collection against government, military, and diplomatic organizations have been core taskings for the group, APT43 ultimately modifies its targeting and tactics, techniques and procedures to suit its sponsors, including carrying out financially-motivated cybercrime as needed to support the regime."
Microsoft Introduces GPT-4 AI-Powered Security Copilot Tool to Empower Defenders
29.3.23 Security The Hacker News
Microsoft on Tuesday unveiled Security Copilot in limited preview, marking its continued quest to embed AI-oriented features in an attempt to offer "end-to-end defense at machine speed and scale."
Powered by OpenAI's GPT-4 generative AI and its own security-specific model, it's billed as a security analysis tool that enables cybersecurity analysts to quickly respond to threats, process signals, and assess risk exposure.
To that end, it collates insights and data from various products like Microsoft Sentinel, Defender, and Intune to help security teams better understand their environment; determine if they are susceptible to known vulnerabilities and exploits; identify ongoing attacks, their scale, and receive remediation instructions; and summarize incidents.
Users, for instance, can ask Security Copilot about suspicious user logins over a specific time period, or even employ it to create a PowerPoint presentation outlining an incident and its attack chain. It can also accept files, URLs, and code snippets for analysis.
Redmond said its proprietary security-specific model is informed by more than 65 trillion daily signals, emphasizing that the tool is privacy-compliant and customer data "is not used to train the foundation AI models."
"Today the odds remain stacked against cybersecurity professionals," Vasu Jakkal, Microsoft's corporate vice president of Security, Compliance, Identity, and Management, pointed out.
"Too often, they fight an asymmetric battle against prolific, relentless and sophisticated attackers. To protect their organizations, defenders must respond to threats that are often hidden among noise."
Security Copilot is the latest AI push from Microsoft, which has been steadily integrating generative AI features into its software offerings over the past two months, including Bing, Edge browser, GitHub, LinkedIn, and Skype.
The development also comes weeks after the tech giant launched Microsoft 365 Copilot, integrating AI capabilities within its suite of productivity and enterprise apps such as Office, Outlook, and Teams.
Pakistan-Origin SideCopy Linked to New Cyberattack on India's Ministry of Defence
28.3.23 BigBrothers The Hacker News
An advanced persistent threat (APT) group that has a track record of targeting India and Afghanistan has been linked to a new phishing campaign that delivers Action RAT.
According to Cyble, which attributed the operation to SideCopy, the activity cluster is designed to target the Defence Research and Development Organization (DRDO), the research and development wing of India's Ministry of Defence.
Known for emulating the infection chains associated with SideWinder to deliver its own malware, SideCopy is a threat group of Pakistani origin that shares overlaps with Transparent Tribe. It has been active since at least 2019.
Attack chains mounted by the group involve using spear-phishing emails to gain initial access. These messages come bearing a ZIP archive file that contains a Windows shortcut file (.LNK) masquerading as information about the K-4 ballistic missile developed by DRDO.
Executing the .LNK file leads to the retrieval of an HTML application from a remote server, which, in turn, displays a decoy presentation, while also stealthily deploying the Action RAT backdoor.
The malware, in addition to gathering information about the victim machine, is capable of running commands sent from a command-and-control (C2) server, including harvesting files and dropping follow-on malware.
Also deployed is a new information-stealing malware referred to as AuTo Stealer that's equipped to gather and exfiltrate Microsoft Office files, PDF documents, database and text files, and images over HTTP or TCP.
"The APT group continuously evolves its techniques while incorporating new tools into its arsenal," Cyble noted.
This is not the first time SideCopy has employed Action RAT in its attacks directed against India. In December 2021, Malwarebytes disclosed a set of intrusions that breached a number of ministries in Afghanistan and a shared government computer in India to steal sensitive credentials.
The latest findings arrive a month after the adversarial crew was spotted targeting Indian government agencies with a remote access trojan dubbed ReverseRAT.
IcedID Malware Shifts Focus from Banking Fraud to Ransomware Delivery
28.3.23 Virus The Hacker News
Multiple threat actors have been observed using two new variants of the IcedID malware in the wild with more limited functionality that removes functionality related to online banking fraud.
IcedID, also known as BokBot, started off as a banking trojan in 2017. It's also capable of delivering additional malware, including ransomware.
"The well-known IcedID version consists of an initial loader which contacts a Loader [command-and-control] server, downloads the standard DLL Loader, which then delivers the standard IcedID Bot," Proofpoint said in a new report published Monday.
One of the new versions is a Lite variant that was previously highlighted as being dropped as a follow-on payload by the Emotet malware in November 2022. Also newly observed in February 2023 is a Forked variant of IcedID.
Both these variants are designed to drop what's called a Forked version of IcedID Bot that leaves out the web injects and backconnect functionality that would typically be used for banking fraud, the enterprise security firm noted.
"It is likely a cluster of threat actors is using modified variants to pivot the malware away from typical banking trojan and banking fraud activity to focus on payload delivery, which likely includes prioritizing ransomware delivery," Proofpoint noted.
The February campaign has been tied to a new group christened TA581, with the threat actor distributing the Forked variant using weaponized Microsoft OneNote attachments. Another malware used by TA581 is the Bumblebee loader.
In all, the Forked IcedID variant has been employed in seven different campaigns to date, some of which have been undertaken by initial access brokers (IABs).
The use of existing Emotet infections to deliver the Lite variant has raised the possibility of a potential partnership between Emotet developers and IcedID operators.
"While historically IcedID's main function was a banking trojan, the removal of banking functionality aligns with the overall landscape shift away from banking malware and an increasing focus on being a loader for follow-on infections, including ransomware," the researchers said.
Stealthy DBatLoader Malware Loader Spreading Remcos RAT and Formbook in Europe
28.3.23 Virus The Hacker News
A new phishing campaign has set its sights on European entities to distribute Remcos RAT and Formbook via a malware loader dubbed DBatLoader.
"The malware payload is distributed through WordPress websites that have authorized SSL certificates, which is a common tactic used by threat actors to evade detection engines," Zscaler researchers Meghraj Nandanwar and Satyam Singh said in a report published Monday.
The findings build upon a previous report from SentinelOne last month that detailed phishing emails containing malicious attachments that masquerade as financial documents to activate the infection chain.
Some of the file formats used to distribute the DBatLoader payload concern the use of a multi-layered obfuscated HTML file and OneNote attachments.
The development adds to growing abuse of OneNote files as an initial vector for malware distribution since late last year in response to Microsoft's decision to block macros by default in files downloaded from the internet.
DBatLoader, also called ModiLoader and NatsoLoader, is a Delphi-based malware that's capable of delivering follow-on payloads from cloud services like Google Drive and Microsoft OneDrive, while also adopting image steganography techniques to evade detection engines.

One notable aspect of the attack is the use of mock trusted directories such as "C:\Windows \System32" (note the trailing space after Windows) to bypass User Account Control (UAC) and escalate privileges.
A caveat here is that the directories cannot be directly created from within the Windows Explorer user interface, instead requiring the attacker to rely on a script to accomplish the task and copy to the folder a rogue DLL and a legitimate executable (easinvoker.exe) that's vulnerable to DLL hijacking in order to load the DLL payload.
This enables the attackers to conduct elevated activities without alerting users, including establishing persistence and adding the "C:\Users" directory to the Microsoft Defender exclusion list to avoid getting scanned.
To mitigate risks posed by DBatLoader, it's advised to monitor process executions that involve filesystem paths with trailing spaces and consider configuring Windows UAC to Always notify.
President Biden Signs Executive Order Restricting Use of Commercial Spyware
28.3.23 BigBrothers The Hacker News
U.S. President Joe Biden on Monday signed an executive order that restricts the use of commercial spyware by federal government agencies.
The order said the spyware ecosystem "poses significant counterintelligence or security risks to the United States Government or significant risks of improper use by a foreign government or foreign person."
It also seeks to ensure that the government's use of such tools is done in a manner that's "consistent with respect for the rule of law, human rights, and democratic norms and values."
To that end, the order lays out the various criteria under which commercial spyware could be disqualified for use by U.S. government agencies. They include -
The purchase of commercial spyware by a foreign government or person to target the U.S. government,
A commercial spyware vendor that uses or discloses sensitive data obtained from the cyber surveillance tool without authorization and operates under the control of a foreign government that's engaged in espionage activities aimed at the U.S.,
A foreign threat actor that uses commercial spyware against activists and dissidents with the goal of limiting freedom of expression or perpetrating human rights abuses,
A foreign threat actor that uses commercial spyware to keep tabs on a U.S. citizen without legal authorization, safeguards, and oversight, and
The sales of commercial spyware to governments that have a record of engaging in systematic acts of political repression and other human rights violations.
"This Executive Order will also serve as a foundation to deepen international cooperation to promote responsible use of surveillance technology, counter the proliferation and misuse of such technology, and spur industry reform," the White House said in a statement.
About 50 U.S. government officials in senior positions located in at least 10 countries are estimated to have been infected or targeted by such spyware to date, the Wall Street Journal reported, a number larger than previously known.
While the order stops short of an outright ban, the development comes as sophisticated and invasive surveillance tools are being increasingly deployed to access electronic devices remotely using zero-click exploits and extract valuable information about targets without their knowledge or consent.
Last week, the New York Times reported that Artemis Seaford, a former security policy manager at Meta, had her phone wiretapped and hacked by Greece's national intelligence agency using Predator, a spyware developed by Cytrox.
That said, the order also leaves open the possibility of other kinds of spyware devices, including IMSI catchers, being used by government agencies to glean valuable intelligence.
Viewed in that light, it's also an acknowledgment that the spyware-for-sale industry plays an important role in intelligence-gathering operations even as the technology constitutes a growing counterintelligence and national security risk to government personnel.
Earlier this month, the Federal Bureau of Investigation (FBI) confirmed that the agency has in the past purchased the location data of U.S. citizens from data brokers as a means to sidestep the traditional warrant process.
The FBI is also alleged to have bought a license for Israeli company NSO Group's Pegasus during 2020 and 2021, acknowledging that it was used for research and development purposes.
The Drug Enforcement Administration (DEA), in a similar fashion, uses Graphite, a spyware tool produced by another Israeli company named Paragon, for counternarcotics operations. It's not immediately not clear if other U.S. federal agencies currently use any commercial spyware.
Apple Issues Urgent Security Update for Older iOS and iPadOS Models
28.3.23 Apple The Hacker News
Apple on Monday backported fixes for an actively exploited security flaw to older iPhone and iPad models.
The issue, tracked as CVE-2023-23529, concerns a type confusion bug in the WebKit browser engine that could lead to arbitrary code execution.
It was originally addressed by the tech giant with improved checks as part of updates released on February 13, 2023. An anonymous researcher has been credited with reporting the bug.
"Processing maliciously crafted web content may lead to arbitrary code execution," Apple said in a new advisory, adding it's "aware of a report that this issue may have been actively exploited."
Details surrounding the exact nature of exploitation are currently not known, but withholding technical specifics is standard procedure as it helps prevent additional in-the-wild abuse targeting susceptible devices.
The update is available in versions iOS 15.7.4 and iPadOS 15.7.4 for iPhone 6s (all models), iPhone 7 (all models), iPhone SE (1st generation), iPad Air 2, iPad mini (4th generation), and iPod touch (7th generation).
The disclosure comes as Apple rolled out iOS 16.4, iPadOS 16.4, macOS Ventura 13.3, macOS Monterey 12.6.4, macOS Big Sur 11.7.5, tvOS 16.4, and watchOS 9.4 with numerous bug fixes.
20-Year-Old BreachForums Founder Faces Up to 5 Years in Prison
28.3.23 Crime The Hacker News
Conor Brian Fitzpatrick, the 20-year-old founder and the administrator of the now-defunct BreachForums has been formally charged in the U.S. with conspiracy to commit access device fraud.
If proven guilty, Fitzpatrick, who went by the online moniker "pompompurin," faces a maximum penalty of up to five years in prison. He was arrested on March 15, 2023.
"Cybercrime victimizes and steals financial and personal information from millions of innocent people," said U.S. Attorney Jessica D. Aber for the Eastern District of Virginia. "This arrest sends a direct message to cybercriminals: your exploitative and illegal conduct will be discovered, and you will be brought to justice."
The development comes days after Baphomet, the individual who had taken over the responsibilities of BreachForums, shut down the website, citing concerns that law enforcement may have obtained access to its backend. The Department of Justice (DoJ) has since confirmed that it conducted a disruption operation that caused the illicit criminal platform to go offline.
BreachForums, per Fitzpatrick, was created in March 2022 to fill the void left by RaidForums, which was taken down a month before as part of an international law enforcement operation.
It served as a marketplace for trading hacked or stolen data, including bank account information, Social Security numbers, hacking tools, and databases containing personally identifying information (PII).
In new court documents released on March 24, 2023, it has come to light that undercover agents working for the U.S. Federal Bureau of Investigation (FBI) purchased five sets of data offered for sale, with Fitzpatrick acting as a middleman to complete the transactions.
Fitzpatrick's links to pompompurin came from nine IP addresses associated with telecom service provider Verizon that he used to access the account on RaidForums and a major OPSEC failure on the defendant's part.
"The RaidForums records also contained [...] communication between pompompurin and omnipotent [the RaidForums administrator] on or about November 28, 2020, in which pompompurin specifically mentions to omnipotent that he had searched for the email address conorfitzpatrick02@gmail.com and name 'conorfitzpatrick' within a database of breached data from 'Ai.type,'" according to the affidavit.
It's worth noting that the Android keyboard app Ai.type suffered a data breach in December 2017, leading to the accidental leak of emails, phone numbers, and locations pertaining to 31 million users.
Further data obtained from Google showed that Fitzpatrick registered a new Google account with the email address conorfitzpatrick2002@gmail.com in May 2019 to replace conorfitzpatrick02@gmail.com, which was closed around April 2020.
What's more, a search for conorfitzpatrick02@gmail.com on the data breach notification service Have I Been Pwned (HIBP) corroborates the fact the old email address was indeed exposed in the Ai.type breach.
"The recovery email address for conorfitzpatrick2002@gmail.com was funmc59tm@gmail.com," the affidavit reads. "Subscriber records for this account reveal that the account was registered under the name 'a a,' and created on or about December 28, 2018 from the IP address 74.101.151.4."
"Records received from Verizon, in turn, revealed that IP address 74.101.151.4 was registered to a customer with the last name Fitzpatrick at [a residence located on Union Avenue in Peekskill, New York]."
The investigation also turned up evidence of Fitzpatrick logging into various virtual private network (VPN) providers from September 2021 to May 2022 to obscure his true location and connect to different accounts, including the Google Account linked to conorfitzpatrick2002@gmail.com.
One of those masked IP addresses was further used to sign in to a Zoom account under the name of "pompompurin" with an e-mail address of pompompurin@riseup.net, records obtained by the FBI from Zoom reveal. Interestingly, Fitzpatrick is said to have used the pompompurin@riseup.net email address to register on RaidForums.
Also unearthed by the agency is a Purse.io cryptocurrency account that was registered with the email address conorfitzpatrick2002@gmail.com and "was funded exclusively by a Bitcoin address that pompompurin had discussed in posts on RaidForums." Records from Purse.io showed that the account was used to purchase "several items" and ship them to his address in Peekskill.
On top of that, the FBI secured a warrant to get his real-time cell phone GPS location from Verizon, allowing the authorities to determine that he was logged in to BreachForums while his phone's physical location showed he was at his home.
But that's not all. In yet another OPSEC error, Fitzpatrick made the mistake of logging into BreachForums on June 27, 2022, without using a VPN service or the TOR browser, thereby exposing the real IP address (69.115.201.194).
Based on data received from Apple, the same IP address was used to access the iCloud account about 97 times between May 19, 2022, and June 2, 2022.
"Fitzpatrick has used the same VPNs and IP addresses to log into the email account conorfitzpatrick2002@gmail.com, the Conor Fitzpatrick Purse.io account, the pompompurin account on RaidForums, and the pompompurin account on BreachForums, among other accounts," FBI's John Longmire said.
In the aftermath of the release of the affidavit, Baphomet said "you shouldn't trust anyone to handle your own OPSEC," adding "I never made this assumption as an admin, and no one else should have either."
New MacStealer macOS Malware Steals iCloud Keychain Data and Passwords
28.3.23 Apple The Hacker News
A new information-stealing malware has set its sights on Apple's macOS operating system to siphon sensitive information from compromised devices.
Dubbed MacStealer, it's the latest example of a threat that uses Telegram as a command-and-control (C2) platform to exfiltrate data. It primarily affects devices running macOS versions Catalina and later running on M1 and M2 CPUs.
"MacStealer has the ability to steal documents, cookies from the victim's browser, and login information," Uptycs researchers Shilpesh Trivedi and Pratik Jeware said in a new report.
First advertised on online hacking forums for $100 at the start of the month, it is still a work in progress, with the malware authors planning to add features to capture data from Apple's Safari browser and the Notes app.
In its current form, MacStealer is designed to extract iCloud Keychain data, passwords and credit card information from browsers like Google Chrome, Mozilla Firefox, and Brave. It also features support for harvesting Microsoft Office files, images, archives, and Python scripts.
The exact method used to deliver the malware is not known, but it is propagated as a DMG file (weed.dmg) that, when executed, opens a fake password prompt to harvest the passwords under the guise of seeking access to the System Settings app.
MacStealer is one of several info-stealers that have surfaced just over the past few months and adds to an already large number of similar tools currently in the wild.
This also includes another piece of new C#-based malware called HookSpoofer that's inspired by StormKitty and comes with keylogging and clipper abilities and transmits the stolen data to a Telegram bot.
Another browser cookie-stealing malware of note is Ducktail, which also uses a Telegram bot to exfiltrate data and re-emerged in mid-February 2023 with improved tactics to sidestep detection.
This involves "changing the initial infection from an archive containing a malicious executable to an archive containing a malicious LNK file that would start the infection chain," Deep Instinct researcher Simon Kenin said earlier this month.
Stealer malware is typically spread through different channels, including email attachments, bogus software downloads, and other social engineering techniques.
To mitigate such threats, it's recommended that users keep their operating system and security software up to date and avoid downloading files or clicking links from unknown sources.
"As Macs have become increasingly popular in the enterprise among leadership and development teams, the more important the data stored on them is to attackers," SentinelOne researcher Phil Stokes said last week.
Microsoft Issues Patch for aCropalypse Privacy Flaw in Windows Screenshot Tools
28.3.23 Vulnerebility The Hacker News
Microsoft has released an out-of-band update to address a privacy-defeating flaw in its screenshot editing tool for Windows 10 and Windows 11.
The issue, dubbed aCropalypse, could enable malicious actors to recover edited portions of screenshots, potentially revealing sensitive information that may have been cropped out.
Tracked as CVE-2023-28303, the vulnerability is rated 3.3 on the CVSS scoring system. It affects both the Snip & Sketch app on Windows 10 and the Snipping Tool on Windows 11.
"The severity of this vulnerability is Low because successful exploitation requires uncommon user interaction and several factors outside of an attacker's control," Microsoft said in an advisory released on March 24, 2023.
Successful exploitation requires that the following two prerequisites are met -
The user must take a screenshot, save it to a file, modify the file (for example, crop it), and then save the modified file to the same location.
The user must open an image in Snipping Tool, modify the file (for example, crop it), and then save the modified file to the same location.
However, it does not impact scenarios where an image is copied from the Snipping Tool or modified before saving it.
"If you take a screenshot of your bank statement, save it to your desktop, and crop out your account number before saving it to the same location, the cropped image could still contain your account number in a hidden format that could be recovered by someone who has access to the complete image file," Microsoft explains.
"However, if you copy the cropped image from Snipping Tool and paste it into an email or a document, the hidden data will not be copied, and your account number will be safe."
The vulnerability has been addressed in-app version 10.2008.3001.0 of Snip and Sketch installed on Windows 10 and version 11.2302.20.0 of Snipping Tool installed on Windows 11.
aCropalypse first came to light on March 18, 2022, when it was found that a bug in Google Pixel's Markup tool made it possible to retroactively reverse the changes introduced to screenshots, thereby recovering personal information from redacted screenshots and images, including those that have been cropped or had their contents masked.
Credited with discovering the problem are reverse engineers Simon Aarons and David Buchanan. The Pixel-related high-severity flaw, tracked as CVE-2023-21036, was reported to Google on January 2, 2023, and was fixed via an update released on March 6, 2023 for Pixel 4A, 5A, 7, and 7 Pro devices.
The shortcoming has existed since the release of the Markup utility with Android 9 Pie in 2018, and images already shared over the past five years are vulnerable to the Acropalypse attack, raising possible privacy concerns.
"You can patch it, but you can't easily un-share all the vulnerable images you may have sent," Buchanan said in a tweet, describing it as a "bad one."
A similar issue with reversible cropping was recently disclosed in Google Docs as well, allowing users with view-only access to recover original versions of cropped images in shared documents without having the edit permissions to do so.
U.K. National Crime Agency Sets Up Fake DDoS-For-Hire Sites to Catch Cybercriminals
28.3.23 Crime The Hacker News
In what's a case of setting a thief to catch a thief, the U.K. National Crime Agency (NCA) revealed that it has created a network of fake DDoS-for-hire websites to infiltrate the online criminal underground.
"All of the NCA-run sites, which have so far been accessed by around several thousand people, have been created to look like they offer the tools and services that enable cyber criminals to execute these attacks," the law enforcement agency said.
"However, after users register, rather than being given access to cyber crime tools, their data is collated by investigators."
The effort is part of an ongoing international joint effort called Operation PowerOFF in collaboration with authorities from the U.S., the Netherlands, Germany, Poland, and Europol aimed at dismantling criminal DDoS-for-hire infrastructures worldwide.
DDoS-for-hire (aka "Booter" or "Stresser") services rent out access to a network of infected devices to other criminal actors seeking to launch distributed denial-of-service (DDoS) attacks against websites and force them offline.
Such illegal platforms offer a range of membership options, charging their clientele anywhere between $10 to $2,500 per month.
"Their ease of access means these tools and services have made it easier for people with low level cyber skills to commit offences," the NCA noted back in December 2022, when a coordinated exercise led to the dismantling of 48 booter sites.
The NCA said it will not reveal the number of sites it's operating so that individuals who plan on using such services in the future will have to consider if it's worth the risk.
"Booter services are a key enabler of cyber crime," Alan Merrett, a member of the NCA's National Cyber Crime Unit, said in a statement.
"The perceived anonymity and ease of use afforded by these services means that DDoS has become an attractive entry-level crime, allowing individuals with little technical ability to commit cyber offences with ease."
This is not the first time law enforcement agencies have stealthily operated fake services to combat criminal activity in the digital sphere.
In June 2021, the U.S. Federal Bureau of Investigation (FBI) and Australian Federal Police (AFP) revealed that they ran an encrypted chat service called ANoM for nearly three years to intercept 27 million messages exchanged between criminal gang members globally.
Microsoft Warns of Stealthy Outlook Vulnerability Exploited by Russian Hackers
25.3.23 BigBrothers The Hacker News
Microsoft on Friday shared guidance to help customers discover indicators of compromise (IoCs) associated with a recently patched Outlook vulnerability.
Tracked as CVE-2023-23397 (CVSS score: 9.8), the critical flaw relates to a case of privilege escalation that could be exploited to steal NT Lan Manager (NTLM) hashes and stage a relay attack without requiring any user interaction.
"External attackers could send specially crafted emails that will cause a connection from the victim to an untrusted location of attackers' control," the company noted in an advisory released this month.
"This will leak the Net-NTLMv2 hash of the victim to the untrusted network which an attacker can then relay to another service and authenticate as the victim.
The vulnerability was resolved by Microsoft as part of its Patch Tuesday updates for March 2023, but not before Russia-based threat actors weaponized the flaw in attacks targeting government, transportation, energy, and military sectors in Europe.
Microsoft's incident response team said it found evidence of potential exploitation of the shortcoming as early as April 2022.
In one attack chain described by the tech giant, a successful Net-NTLMv2 Relay attack enabled the threat actor to gain unauthorized access to an Exchange Server and modify mailbox folder permissions for persistent access.
The compromised email account was then used to extend the adversary's access within the compromised environment by sending additional malicious messages to target other members of the same organization.
"While leveraging NTLMv2 hashes to gain unauthorized access to resources is not a new technique, the exploitation of CVE-2023-23397 is novel and stealthy," Microsoft said.
"Organizations should review SMBClient event logging, Process Creation events, and other available network telemetry to identify potential exploitation via CVE-2023-23397."
The disclosure comes as the U.S. Cybersecurity and Infrastructure Security Agency (CISA) released a new open source incident response tool that helps detect signs of malicious activity in Microsoft cloud environments.
Dubbed Untitled Goose Tool, the Python-based utility offers "novel authentication and data gathering methods" to analyze Microsoft Azure, Azure Active Directory, and Microsoft 365 environments, the agency said.
Earlier this year, Microsoft also urged customers to keep their on-premises Exchange servers updated as well as take steps to bolster their networks to mitigate potential threats.
OpenAI Reveals Redis Bug Behind ChatGPT User Data Exposure Incident
25.3.23 Incindent The Hacker News
OpenAI on Friday disclosed that a bug in the Redis open source library was responsible for the exposure of other users' personal information and chat titles in the upstart's ChatGPT service earlier this week.
The glitch, which came to light on March 20, 2023, enabled certain users to view brief descriptions of other users' conversations from the chat history sidebar, prompting the company to temporarily shut down the chatbot.
"It's also possible that the first message of a newly-created conversation was visible in someone else's chat history if both users were active around the same time," the company said.
The bug, it further added, originated in the redis-py library, leading to a scenario where canceled requests could cause connections to be corrupted and return unexpected data from the database cache, in this case, information belonging to an unrelated user.
To make matters worse, the San Francisco-based AI research company said it introduced a server-side change by mistake that led to a surge in request cancellations, thereby upping the error rate.
While the problem has since been addressed, OpenAI noted that the issue may have had more implications elsewhere, potentially revealing payment-related information of 1.2% of the ChatGPT Plus subscribers on March 20 between 1-10 a.m. PT.
This included another active user's first and last name, email address, payment address, the last four digits (only) of a credit card number, and credit card expiration date. It emphasized that full credit card numbers were not exposed.
The company said it has reached out to affected users to notify them of the inadvertent leak. It also said it "added redundant checks to ensure the data returned by our Redis cache matches the requesting user."
OpenAI Fixes Critical Account Takeover Flaw#
In another caching-related issue, the company also addressed a critical account takeover vulnerability that could be exploited to seize control of another user's account, view their chat history, and access billing information without their knowledge.
The flaw, which was discovered by security researcher Gal Nagli, bypasses protections put in place by OpenAI on chat.openai[.]com to read a victim's sensitive data.
This is achieved by first creating a specially crafted link that appends a .CSS resource to the "chat.openai[.]com/api/auth/session/" endpoint and tricking a victim to click on the link, causing the response containing a JSON object with the accessToken string to be cached in Cloudflare's CDN.
The cached response to the CSS resource (which has the CF-Cache-Status header value set to HIT) is then abused by the attacker to harvest the target's JSON Web Token (JWT) credentials and take over the account.
Nagli said the bug was fixed by OpenAI within two hours of responsible disclosure, indicative of the severity of the issue.
Malicious Python Package Uses Unicode Trickery to Evade Detection and Steal Data
25.3.23 Virus The Hacker News
A malicious Python package on the Python Package Index (PyPI) repository has been found to use Unicode as a trick to evade detection and deploy an info-stealing malware.
The package in question, named onyxproxy, was uploaded to PyPI on March 15, 2023, and comes with capabilities to harvest and exfiltrate credentials and other valuable data. It has since been taken down, but not before attracting a total of 183 downloads.
According to software supply chain security firm Phylum, the package incorporates its malicious behavior in a setup script that's packed with thousands of seemingly legitimate code strings.
These strings include a mix of bold and italic fonts and are still readable and can be parsed by the Python interpreter, only to activate the execution of the stealer malware upon installation of the package.
"An obvious and immediate benefit of this strange scheme is readability," the company noted. "Moreover, these visible differences do not prevent the code from running, which it does."
This is made possible owing to the use of Unicode variants of what appears to be the same character (aka homoglyphs) to camouflage its true colors (e.g., self vs. 𝘀𝘦𝘭𝘧) among innocuous-looking functions and variables.
The use of Unicode to inject vulnerabilities into source code was previously disclosed by Cambridge University researchers Nicholas Boucher and Ross Anderson in an attack technique dubbed Trojan Source.
What the method lacks in sophistication, it makes up for it by creating a novel piece of obfuscated code, despite exhibiting telltale signs of copy-paste efforts from other sources.
The development highlights continued attempts on part of threat actors to find new ways to slip through string-matching based defenses, leveraging "how the Python interpreter handles Unicode to obfuscate their malware."
On a related note, Canadian cybersecurity company PyUp detailed the discovery of three new fraudulent Python packages – aiotoolbox, asyncio-proxy, and pycolorz – that were downloaded cumulatively over 1,000 times and designed to retrieve obfuscated code from a remote server.
GitHub Swiftly Replaces Exposed RSA SSH Key to Protect Git Operations
24.3.23 Cyber The Hacker News
Cloud-based repository hosting service GitHub said it took the step of replacing its RSA SSH host key used to secure Git operations "out of an abundance of caution" after it was briefly exposed in a public repository.
The activity, which was carried out at 05:00 UTC on March 24, 2023, is said to have been undertaken as a measure to prevent any bad actor from impersonating the service or eavesdropping on users' operations over SSH.
"This key does not grant access to GitHub's infrastructure or customer data," Mike Hanley, chief security officer and SVP of engineering at GitHub, said in a post. "This change only impacts Git operations over SSH using RSA."
The move does not impact Web traffic to GitHub.com and Git operations performed via HTTPS. No change is required for ECDSA or Ed25519 users.
The Microsoft-owned company said there is no evidence that the exposed SSH private key was exploited by adversaries.
It further emphasized that the "issue was not the result of a compromise of any GitHub systems or customer information." It blamed it on an "inadvertent publishing of private information."
It also noted GitHub Actions users may see failed workflow runs if they are using actions/checkout with the ssh-key option, adding it's in the process of updating the action across all tags.
The disclosure comes nearly two months after GitHub revealed that unknown threat actors managed to exfiltrate encrypted code signing certificates pertaining to some versions of GitHub Desktop for Mac and Atom apps.
Researchers Uncover Chinese Nation State Hackers' Deceptive Attack Strategies
24.3.23 BigBrothers The Hacker News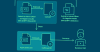
A recent campaign undertaken by Earth Preta indicates that nation-state groups aligned with China are getting increasingly proficient at bypassing security solutions.
The threat actor, active since at least 2012, is tracked by the broader cybersecurity community under Bronze President, HoneyMyte, Mustang Panda, RedDelta, and Red Lich.
Attack chains mounted by the group commence with a spear-phishing email to deploy a wide range of tools for backdoor access, command-and-control (C2), and data exfiltration.
These messages come bearing with malicious lure archives distributed via Dropbox or Google Drive links that employ DLL side-loading, LNK shortcut files, and fake file extensions as arrival vectors to obtain a foothold and drop backdoors like TONEINS, TONESHELL, PUBLOAD, and MQsTTang (aka QMAGENT).
Similar infection chains utilizing Google Drive links have been observed delivering Cobalt Strike as early as April 2021.
"Earth Preta tends to hide malicious payloads in fake files, disguising them as legitimate ones — a technique that has been proven effective for avoiding detection," Trend Micro said in a new analysis published Thursday.
This entry point method, which was first spotted late last year, has since received a slight tweak wherein the download link to the archive is embedded within another decoy document and the file is password-protected in an attempt to sidestep email gateway solutions.
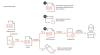
"The files can then be extracted inside via the password provided in the document," the researchers said. "By using this technique, the malicious actor behind the attack can successfully bypass scanning services."
Initial access to the victim's environment is followed by account discovery and privilege escalation phases, with Mustang Panda leveraging custom tools like ABPASS and CCPASS to circumvent User Account Control (UAC) in Windows 10.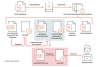
Additionally, the threat actor has been observed deploying malware such as "USB Driver.exe" (HIUPAN or MISTCLOAK) and "rzlog4cpp.dll" (ACNSHELL or BLUEHAZE) to install themselves to removable disks and create a reverse shell with the goal of laterally moving across the network.
Other utilities deployed include CLEXEC, a backdoor capable of executing commands and clearing event logs; COOLCLIENT and TROCLIENT, implants that are designed to record keystrokes as well as read and delete files; and PlugX.
"Apart from well-known legitimate tools, the threat actors also crafted highly customized tools used for exfiltration," the researchers noted. This comprises NUPAKAGE and ZPAKAGE, both of which are equipped to collect Microsoft Office files.
The findings once again highlight the increased operational tempo of Chinese cyber espionage actors and their consistent investment in advancing their cyber weaponry to evade detection.
"Earth Preta is a capable and organized threat actor that is continuously honing its TTPs, strengthening its development capabilities, and building a versatile arsenal of tools and malware," the researchers concluded.
Critical WooCommerce Payments Plugin Flaw Patched for 500,000+ WordPress Sites
24.3.23 Vulnerebility The Hacker News
Patches have been released for a critical security flaw impacting the WooCommerce Payments plugin for WordPress, which is installed on over 500,000 websites.
The flaw, if left unresolved, could enable a bad actor to gain unauthorized admin access to impacted stores, the company said in an advisory on March 23, 2023. It impacts versions 4.8.0 through 5.6.1.
Put differently, the issue could permit an "unauthenticated attacker to impersonate an administrator and completely take over a website without any user interaction or social engineering required," WordPress security company Wordfence said.
The vulnerability appears to reside in a PHP file called "class-platform-checkout-session.php," Sucuri researcher Ben Martin noted.
Credited with discovering and reporting the vulnerability is Michael Mazzolini of Swiss penetration testing company GoldNetwork.
WooCommerce also said it worked with WordPress to auto-update sites using affected versions of the software. Patched versions include 4.8.2, 4.9.1, 5.0.4, 5.1.3, 5.2.2, 5.3.1, 5.4.1, 5.5.2, and 5.6.2.
Furthermore, the maintainers of the e-commerce plugin noted that it's disabling the WooPay beta program owing to concerns that the security defect has the potential to impact the payment checkout service.
There is no evidence that the vulnerability has been actively exploited to date, but it's expected to be weaponized on a large scale once a proof-of-concept becomes available, Wordfence researcher Ram Gall cautioned.
Besides updating to the latest version, users are recommended to check for newly added admin users, and if so, change all administrator passwords and rotate payment gateway and WooCommerce API keys.
Fake ChatGPT Chrome Browser Extension Caught Hijacking Facebook Accounts
24.3.23 Hacking The Hacker News
Google has stepped in to remove a bogus Chrome browser extension from the official Web Store that masqueraded as OpenAI's ChatGPT service to harvest Facebook session cookies and hijack the accounts.
The "ChatGPT For Google" extension, a trojanized version of a legitimate open source browser add-on, attracted over 9,000 installations since March 14, 2023, prior to its removal. It was originally uploaded to the Chrome Web Store on February 14, 2023.
According to Guardio Labs researcher Nati Tal, the extension was propagated through malicious sponsored Google search results that were designed to redirect unsuspecting users searching for "Chat GPT-4" to fraudulent landing pages that point to the fake add-on.
Installing the extension adds the promised functionality – i.e., enhancing search engines with ChatGPT – but it also stealthily activates the ability to capture Facebook-related cookies and exfiltrate it to a remote server in an encrypted manner.
Once in possession of the victim's cookies, the threat actor moves to seize control of the Facebook account, change the password, alter the profile name and picture, and even use it to disseminate extremist propaganda.

The development makes it the second fake ChatGPT Chrome browser extension to be discovered in the wild. The other extension, which also functioned as a Facebook account stealer, was distributed via sponsored posts on the social media platform.
If anything, the findings are yet another proof that cybercriminals are capable of swiftly adapting their campaigns to cash in on the popularity of ChatGPT to distribute malware and stage opportunistic attacks.
"For threat actors, the possibilities are endless — using your profile as a bot for comments, likes, and other promotional activities, or creating pages and advertisement accounts using your reputation and identity while promoting services that are both legitimate and probably mostly not," Tal said.
Nexus: A New Rising Android Banking Trojan Targeting 450 Financial Apps
23.3.23 Android The Hacker News
An emerging Android banking trojan dubbed Nexus has already been adopted by several threat actors to target 450 financial applications and conduct fraud.
"Nexus appears to be in its early stages of development," Italian cybersecurity firm Cleafy said in a report published this week.
"Nexus provides all the main features to perform ATO attacks (Account Takeover) against banking portals and cryptocurrency services, such as credentials stealing and SMS interception."
The trojan, which appeared in various hacking forums at the start of the year, is advertised as a subscription service to its clientele for a monthly fee of $3,000. Details of the malware were first documented by Cyble earlier this month.
However, there are indications that the malware may have been used in real-world attacks as early as June 2022, at least six months before its official announcement on darknet portals.
It's also said to overlap with another banking trojan dubbed SOVA, reusing parts of its source code and incorporating a ransomware module that appears to be under active development.
A point worth mentioning here is that Nexus is the same malware that Cleafy initially classified as a new variant of SOVA (dubbed v5) in August 2022.
Interestingly, the Nexus authors have laid out explicit rules that prohibit the use of its malware in Azerbaijan, Armenia, Belarus, Kazakhstan, Kyrgyzstan, Moldova, Russia, Tajikistan, Uzbekistan, Ukraine, and Indonesia.
The malware, like other banking trojans, contains features to take over accounts related to banking and cryptocurrency services by performing overlay attacks and keylogging to steal users' credentials.
Furthermore, it's capable of reading two-factor authentication (2FA) codes from SMS messages and the Google Authenticator app through the abuse of Android's accessibility services.
Some new additions to the list of functionalities is its ability to remove received SMS messages, activate or stop the 2FA stealer module, and update itself by periodically pinging a command-and-control (C2) server.
"The [Malware-as-a-Service] model allows criminals to monetize their malware more efficiently by providing a ready-made infrastructure to their customers, who can then use the malware to attack their targets," the researchers said.
Operation Soft Cell: Chinese Hackers Breach Middle East Telecom Providers
23.3.23 APT The Hacker News
Telecommunication providers in the Middle East are the subject of new cyber attacks that commenced in the first quarter of 2023.
The intrusion set has been attributed to a Chinese cyber espionage actor associated with a long-running campaign dubbed Operation Soft Cell based on tooling overlaps.
"The initial attack phase involves infiltrating Internet-facing Microsoft Exchange servers to deploy web shells used for command execution," researchers from SentinelOne and QGroup said in a new technical report shared with The Hacker News.
"Once a foothold is established, the attackers conduct a variety of reconnaissance, credential theft, lateral movement, and data exfiltration activities."
Operation Soft Cell, according to Cybereason, refers to malicious activities undertaken by China-affiliated actors targeting telecommunications providers since at least 2012.
The Soft Cell threat actor, also tracked by Microsoft as Gallium, is known to target unpatched internet-facing services and use tools like Mimikatz to obtain credentials that allows for lateral movement across the targeted networks.
Also put to use by the adversarial collective is a "difficult-to-detect" backdoor codenamed PingPull in its espionage attacks directed against companies operating in Southeast Asia, Europe, Africa, and the Middle East.
Central to the latest campaign is the deployment of a custom variant of Mimikatz referred to as mim221, which packs in new anti-detection features.
"The use of special-purpose modules that implement a range of advanced techniques shows the threat actors' dedication to advancing its toolset towards maximum stealth," the researchers said, adding it "highlights the continuous maintenance and further development of the Chinese espionage malware arsenal."
The attacks ultimately proved to be unsuccessful, with the breaches detected and blocked before any implants could be deployed on the target networks.
Prior research into Gallium suggests tactical similarities [PDF] with multiple Chinese nation-state groups such as APT10 (aka Bronze Riverside, Potassium, or Stone Panda), APT27 (aka Bronze Union, Emissary Panda, or Lucky Mouse), and APT41 (aka Barium, Bronze Atlas, or Wicked Panda).
This once again points to signs of closed-source tool-sharing between Chinese state-sponsored threat actors, not to mention the possibility of a "digital quartermaster" responsible for maintaining and distributing the toolset.
The findings come amid revelations that various other hacking groups, including BackdoorDiplomacy and WIP26, have set their sights on telecom service providers in the Middle East region.
"Chinese cyber espionage threat actors are known to have a strategic interest in the Middle East," the researchers concluded.
"These threat actors will almost certainly continue exploring and upgrading their tools with new techniques for evading detection, including integrating and modifying publicly available code."
German and South Korean Agencies Warn of Kimsuky's Expanding Cyber Attack Tactics
23.3.23 APT The Hacker News
German and South Korean government agencies have warned about cyber attacks mounted by a threat actor tracked as Kimsuky using rogue browser extensions to steal users' Gmail inboxes.
The joint advisory comes from Germany's domestic intelligence apparatus, the Federal Office for the Protection of the Constitution (BfV), and South Korea's National Intelligence Service of the Republic of Korea (NIS).
The intrusions are designed to strike "experts on the Korean Peninsula and North Korea issues" through spear-phishing campaigns, the agencies noted.
Kimsuky, also known Black Banshee, Thallium, and Velvet Chollima, refers to a subordinate element within North Korea's Reconnaissance General Bureau and is known to "collect strategic intelligence on geopolitical events and negotiations affecting the DPRK's interests."
Primary targets of interest include entities in the U.S. and South Korea, particularly singling out individuals working within the government, military, manufacturing, academic, and think tank organizations.
"This threat actor's activities include collecting financial, personal, and client data specifically from academic, manufacturing, and national security industries in South Korea," Google-owned threat intelligence firm Mandiant disclosed last year.
Recent attacks orchestrated by the group suggest an expansion of its cyber activity to encompass Android malware strains such as FastFire, FastSpy, FastViewer, and RambleOn.
The use of Chromium-based browser extensions for cyber espionage purposes is not new for Kimsuky, which has previously used similar techniques as part of campaigns tracked as Stolen Pencil and SharpTongue.

The SharpTongue operation also overlaps with the latest effort in that the latter is also capable of stealing a victim's email content using the rogue add-on, which, in turn, leverages the browser's DevTools API to perform the function.
But in an escalation of Kimsuky's mobile attacks, the threat actor has been observed logging into victims' Google accounts using credentials already obtained in advance through phishing tactics and then installing a malicious app on the devices linked to the accounts.
"The attacker logs in with the victim's Google account on the PC, accesses the Google Play Store, and requests the installation of a malicious app," the agencies explained. "At this time, the target's smartphone linked with the Google account is selected as the device to install the malicious app on."
It's suspected that the apps, which embed FastFire and FastViewer, are distributed using a Google Play feature known as "internal testing" that allows third-party developers to distribute their apps to a "small set of trusted testers."
A point worth mentioning here is that these internal app tests, which are carried out prior to releasing the app to production, cannot exceed 100 users per app, indicating that the campaign is extremely targeted in nature.
Both the malware-laced apps come with capabilities to harvest a wide range of sensitive information by abusing Android's accessibility services. The apps' APK package names are listed below -
com.viewer.fastsecure (FastFire)
com.tf.thinkdroid.secviewer (FastViewer)
The disclosure comes as the North Korean advanced persistent threat (APT) actor dubbed ScarCruft has been linked to different attack vectors that are employed to deliver PowerShell-based backdoors onto compromised hosts.
CISA Alerts on Critical Security Vulnerabilities in Industrial Control Systems
22.3.23 ICS The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has released eight Industrial Control Systems (ICS) advisories on Tuesday, warning of critical flaws affecting equipment from Delta Electronics and Rockwell Automation.
This includes 13 security vulnerabilities in Delta Electronics' InfraSuite Device Master, a real-time device monitoring software. All versions prior to 1.0.5 are affected by the issues.
"Successful exploitation of these vulnerabilities could allow an unauthenticated attacker to obtain access to files and credentials, escalate privileges, and remotely execute arbitrary code," CISA said.
Top of the list is CVE-2023-1133 (CVSS score: 9.8), a critical flaw that arises from the fact that InfraSuite Device Master accepts unverified UDP packets and deserializes the content, thereby allowing an unauthenticated remote attacker to execute arbitrary code.
Two other deserialization flaws, CVE-2023-1139 (CVSS score: 8.8) and CVE-2023-1145 (CVSS score: 7.8) could also be weaponized to obtain remote code execution, CISA cautioned.
Piotr Bazydlo and an anonymous security researcher have been credited with discovering and reporting the shortcomings to CISA.
Another set of vulnerabilities relates to Rockwell Automation's ThinManager ThinServer and affects the following versions of the thin client and remote desktop protocol (RDP) server management software -
6.x – 10.x
11.0.0 – 11.0.5
11.1.0 – 11.1.5
11.2.0 – 11.2.6
12.0.0 – 12.0.4
12.1.0 – 12.1.5, and
13.0.0 – 13.0.1
The most severe of the issues are two path traversal flaw tracked as CVE-2023-28755 (CVSS score: 9.8) and CVE-2023-28756 (CVSS score: 7.5) that could permit an unauthenticated remote attacker to upload arbitrary files to the directory where the ThinServer.exe is installed.
Even more troublingly, the adversary could weaponize CVE-2023-28755 to overwrite existing executable files with trojanized versions, potentially leading to remote code execution.
"Successful exploitation of these vulnerabilities could allow an attacker to potentially perform remote code execution on the target system/device or crash the software," CISA noted.
Users are advised to update to versions 11.0.6, 11.1.6, 11.2.7, 12.0.5, 12.1.6, and 13.0.2 to mitigate potential threats. ThinManager ThinServer versions 6.x – 10.x are retired, requiring that users upgrade to a supported version.
As workarounds, it is also recommended that remote access of port 2031/TCP is limited to known thin clients and ThinManager servers.
The disclosure arrives more than six months after CISA alerted of a high-severity buffer overflow vulnerability in Rockwell Automation ThinManager ThinServer (CVE-2022-38742, CVSS score: 8.1) that could result in arbitrary remote code execution.
ScarCruft's Evolving Arsenal: Researchers Reveal New Malware Distribution Techniques
22.3.23 Virus The Hacker News
The North Korean advanced persistent threat (APT) actor dubbed ScarCruft is using weaponized Microsoft Compiled HTML Help (CHM) files to download additional malware.
According to multiple reports from AhnLab Security Emergency response Center (ASEC), SEKOIA.IO, and Zscaler, the development is illustrative of the group's continuous efforts to refine and retool its tactics to sidestep detection.
"The group is constantly evolving its tools, techniques, and procedures while experimenting with new file formats and methods to bypass security vendors," Zscaler researchers Sudeep Singh and Naveen Selvan said in a new analysis published Tuesday.
ScarCruft, also tracked under the names APT37, Reaper, RedEyes, and Ricochet Chollima, has exhibited an increased operational tempo since the start of the year, targeting various South Korean entities for espionage purposes. It is known to be active since at least 2012.
Last month, ASEC disclosed a campaign that employed HWP files that take advantage of a security flaw in the Hangul word processing software to deploy a backdoor referred to as M2RAT.
But new findings reveal the threat actor is also using other file formats such as CHM, HTA, LNK, XLL, and macro-based Microsoft Office documents in its spear-phishing attacks against South Korean targets.

These infection chains often serve to display a decoy file and deploy an updated version of a PowerShell-based implant known as Chinotto, which is capable of executing commands sent by a server and exfiltrating sensitive data.
Some of the new capabilities of Chinotto include capturing screenshots every five seconds and logging keystrokes. The captured information is saved in a ZIP archive and sent to a remote server.
The insights about ScarCruft's various attack vectors come from a GitHub repository maintained by the adversarial collective to host malicious payloads since October 2020.
"The threat actor was able to maintain a GitHub repository, frequently staging malicious payloads for more than two years without being detected or taken down," Zscaler researchers said.
Outside of malware distribution, ScarCruft has also been observed serving credential phishing webpages targeting multiple email and cloud services such as Naver, iCloud, Kakao, Mail.ru, and 163.com.

It's however not clear how these pages are accessed by the victims, raising the possibility that they may have been embedded inside iframes on websites controlled by the attacker or sent as HTML attachments via email.
Also discovered by SEKOIA.IO is a piece of malware named AblyGo, a backdoor written in Go that utilizes the Ably real-time messaging framework to receive commands.
The use of CHM files to smuggle malware appears to be catching on with other North Korea-affiliated groups as well, with ASEC uncovering a phishing campaign orchestrated by Kimsuky to distribute a backdoor responsible for harvesting clipboard data and recording keystrokes.
Rogue NuGet Packages Infect .NET Developers with Crypto-Stealing Malware
22.3.23 Virus The Hacker News
The NuGet repository is the target of a new "sophisticated and highly-malicious attack" aiming to infect .NET developer systems with cryptocurrency stealer malware.
The 13 rogue packages, which were downloaded more than 160,000 times over the past month, have since been taken down.
"The packages contained a PowerShell script that would execute upon installation and trigger a download of a 'second stage' payload, which could be remotely executed," JFrog researchers Natan Nehorai and Brian Moussalli said.
While NuGet packages have been in the past found to contain vulnerabilities and be abused to propagate phishing links, the development marks the first-ever discovery of packages with malicious code.
Three of the most downloaded packages – Coinbase.Core, Anarchy.Wrapper.Net, and DiscordRichPresence.API – alone accounted for 166,000 downloads, although it's also possible that the threat actors artificially inflated the download counts using bots to make them appear more legitimate.
The use of Coinbase and Discord underscores the continued reliance on typosquatting techniques, in which fake packages are assigned names that are similar to legitimate packages, in order to trick developers into downloading them.
The malware incorporated within the software packages functions as a dropper script and is designed to automatically run a PowerShell code that retrieves a follow-on binary from a hard-coded server.
As an added obfuscation mechanism, some packages did not embed a malicious payload directly, instead fetching it via another booby-trapped package as a dependency.
Even more troublingly, the connection to the command-and-control (C2) server occurs over HTTP (as opposed to HTTPS), rendering it vulnerable to an adversary-in-the-middle (AiTM) attack.
The second-stage malware is what JFrog describes as a "completely custom executable payload" that can be dynamically switched at will since it's retrieved from the C2 server.
The second-stage delivers several capabilities that include a crypto stealer and an auto-updater module that pings the C2 server for an updated version of the malware.
The findings come as the software supply chain has become an increasingly lucrative pathway to compromise developers' systems and stealthily propagate backdoored code to downstream users.
"This proves that no open source repository is safe from malicious actors," Shachar Menashe, senior director at JFrog Security Research, said in a statement shared with The Hacker News.
".NET developers using NuGet are still at high risk of malicious code infecting their environments and should take caution when curating open-source components for use in their builds – and at every step of the software development lifecycle – to ensure the software supply chain remains secure."
NAPLISTENER: New Malware in REF2924 Group's Arsenal for Bypassing Detection
22.3.23 Virus The Hacker News
The threat group tracked as REF2924 has been observed deploying previously unseen malware in its attacks aimed at entities in South and Southeast Asia.
The malware, dubbed NAPLISTENER by Elastic Security Labs, is an HTTP listener programmed in C# and is designed to evade "network-based forms of detection."
REF2924 is the moniker assigned to an activity cluster linked to attacks against an entity in Afghanistan as well as the Foreign Affairs Office of an ASEAN member in 2022.
The threat actor's modus operandi suggests overlaps with another hacking group dubbed ChamelGang, which was documented by Russian cybersecurity company Positive Technologies in October 2021.
Attacks orchestrated by the group are said to have exploited internet-exposed Microsoft Exchange servers to deploy backdoors such as DOORME, SIESTAGRAPH, and ShadowPad.
DOORME, an Internet Information Services (IIS) backdoor module, provides remote access to a contested network and executes additional malware and tools.
SIESTAGRAPH employs Microsoft's Graph API for command-and-control via Outlook and OneDrive, and comes with capabilities to run arbitrary commands through Command Prompt, upload and download files to and from OneDrive, and take screenshots.
ShadowPad is a privately sold modular backdoor and a successor of PlugX, enabling threat actors to maintain persistent access to compromised computers and run shell commands and follow-on payloads.
The use of ShadowPad is noteworthy as it indicates a potential link to China-based hacking groups, which are known to utilize the malware in various campaigns over the years.
To this list of expanding malware arsenal used by REF2924 joins NAPLISTENER ("wmdtc.exe"), which masquerades as a legitimate service Microsoft Distributed Transaction Coordinator ("msdtc.exe") in an attempt to fly under the radar and establish persistent access.
"NAPLISTENER creates an HTTP request listener that can process incoming requests from the internet, reads any data that was submitted, decodes it from Base64 format, and executes it in memory," security researcher Remco Sprooten said.
Code analysis suggests the threat actor borrows or repurposes code from open source projects hosted on GitHub to develop its own tools, a sign that REF2924 may be actively honing a raft of cyber weapons.
The findings also come as a Vietnamese organization was targeted in late December 2022 by a previously unknown Windows backdoor codenamed PIPEDANCE to facilitate post-compromise and lateral movement activities, including deploying Cobalt Strike.
BreachForums Administrator Baphomet Shuts Down Infamous Hacking Forum
22.3.23 Crime The Hacker News
In a sudden turn of events, Baphomet, the current administrator of BreachForums, said in an update on March 21, 2023, that the hacking forum has been officially taken down but emphasized that "it's not the end."
"You are allowed to hate me, and disagree with my decision but I promise what is to come will be better for us all," Baphomet noted in a message posted on the BreachForums Telegram channel.
The shutdown is suspected to have been prompted by suspicions that law enforcement may have obtained access to the site's configurations, source code, and information about the forum's users.
The development follows the arrest of its administrator Conor Brian Fitzpatrick (aka "pompompurin"), who has been charged with a single count of conspiracy to commit access device fraud.
Over the past few months, BreachForums filled the void left by RaidForums last year, becoming a lucrative destination to purchase and sell stolen databases from various companies and organizations.
But with the shuttering of BreachForums, the move could spur cybercriminals to migrate to underground forums to peddle their warez.
The development also comes as Telegram continues to be a hub for cybercrime activities, facilitating the sale of malware, personal and corporate data dumps, and other illicit goods such as counterfeits and drugs.
"Threat actors will likely continue to have an appetite for breached databases, and it remains to be seen if this can be through an alternative venue, or requires a new forum entirely," cybersecurity firm Flashpoint said.
New 'Bad Magic' Cyber Threat Disrupts Ukraine's Key Sectors Amid War
22.3.23 Virus The Hacker News
Amid the ongoing war between Russia and Ukraine, government, agriculture, and transportation organizations located in Donetsk, Lugansk, and Crimea have been attacked as part of an active campaign that drops a previously unseen, modular framework dubbed CommonMagic.
"Although the initial vector of compromise is unclear, the details of the next stage imply the use of spear phishing or similar methods," Kaspersky said in a new report.
The Russian cybersecurity company, which detected the attacks in October 2022, is tracking the activity cluster under the name "Bad Magic."
Attack chains entail the use of booby-trapped URLS pointing to a ZIP archive hosted on a malicious web server. The file, when opened, contains a decoy document and a malicious LNK file that culminates in the deployment of a backdoor named PowerMagic.
Written in PowerShell, PowerMagic establishes contact with a remote server and executes arbitrary commands, the results of which are exfiltrated to cloud services like Dropbox and Microsoft OneDrive.
PowerMagic also serves as a conduit to deliver the CommonMagic framework, a set of executable modules that are designed to carry out specific tasks such as interacting with the command-and-control (C2) server, encrypting and decrypting C2 traffic, and executing plugins.
Two of the plugins discovered so far come with capabilities to capture screenshots every three seconds and gather files of interest from connected USB devices.
Kaspersky said it found no evidence linking the operation and its tooling to any known threat actor or group. The earliest ZIP archive attachment dates back to September 2021, indicating that the campaign may have flown under the radar for more than 1.5 years.
"Geopolitics always affect the cyberthreat landscape and lead to the emergence of new threats," Kaspersky's Leonid Besverzhenko said. "Although the malware and techniques employed in the CommonMagic campaign are not particularly sophisticated, the use of cloud storage as the command-and-control infrastructure is noteworthy."
New ShellBot DDoS Malware Variants Targeting Poorly Managed Linux Servers
22.3.23 Virus The Hacker News
Poorly managed Linux SSH servers are being targeted as part of a new campaign that deploys different variants of a malware called ShellBot.
"ShellBot, also known as PerlBot, is a DDoS Bot malware developed in Perl and characteristically uses IRC protocol to communicate with the C&C server," AhnLab Security Emergency response Center (ASEC) said in a report.
ShellBot is installed on servers that have weak credentials, but only after threat actors make use of scanner malware to identify systems that have SSH port 22 open.
A list of known SSH credentials is used to initiate a dictionary attack to breach the server and deploy the payload, after which it leverages the Internet Relay Chat (IRC) protocol to communicate with a remote server.
This encompasses the ability to receive commands that allows ShellBot to carry out DDoS attacks and exfiltrate harvested information.
ASEC said it identified three different ShellBot versions – LiGhT's Modded perlbot v2, DDoS PBot v2.0, and PowerBots (C) GohacK – the first two of which offer a variety of DDoS attack commands using HTTP, TCP, and UDP protocols.
PowerBots, on the other hand, comes with more backdoor-like capabilities to grant reverse shell access and upload arbitrary files from the compromised host.
The findings come nearly three months after ShellBot was employed in attacks aimed at Linux servers that also distributed cryptocurrency miners via a shell script compiler.
"If ShellBot is installed, Linux servers can be used as DDoS Bots for DDoS attacks against specific targets after receiving a command from the threat actor," ASEC said. "Moreover, the threat actor could use various other backdoor features to install additional malware or launch different types of attacks from the compromised server."
The development also comes as Microsoft revealed a gradual increase in the number of DDoS attacks targeting healthcare organizations hosted in Azure, surging from 10-20 attacks in November 2022 to 40-60 attacks daily in February 2023.
From Ransomware to Cyber Espionage: 55 Zero-Day Vulnerabilities Weaponized in 2022
22.3.23 BigBrothers The Hacker News
As many as 55 zero-day vulnerabilities were exploited in the wild in 2022, with most of the flaws discovered in software from Microsoft, Google, and Apple.
While this figure represents a decrease from the year before, when a staggering 81 zero-days were weaponized, it still represents a significant uptick in recent years of threat actors leveraging unknown security flaws to their advantage.
The findings come from threat intelligence firm Mandiant, which noted that desktop operating systems (19), web browsers (11), IT and network management products (10), and mobile operating systems (six) accounted for the most exploited product types.
Of the 55 zero-day bugs, 13 are estimated to have been abused by cyber espionage groups, with four others exploited by financially motivated threat actors for ransomware-related operations. Commercial spyware vendors were linked to the exploitation of three zero-days.
Among state-sponsored groups, those attributed to China have emerged as the most prolific, exploiting seven zero-days – CVE-2022-24682, CVE-2022-1040, CVE-2022-30190, CVE-2022-26134, CVE-2022-42475, CVE-2022-27518, and CVE-2022-41328 – during the year.
Much of the exploitation has focused on vulnerabilities in edge network devices such as firewalls for obtaining initial access. Various China-nexus clusters have also been spotted leveraging a flaw in Microsoft Diagnostics Tool (aka Follina) as part of disparate campaigns.
"Multiple separate campaigns may indicate that the zero-day was distributed to multiple suspected Chinese espionage clusters via a digital quartermaster," Mandiant said, adding it points to the "existence of a shared development and logistics infrastructure and possibly a centralized coordinating entity."

North Korean and Russian threat actors, on the other hand, have been linked to the exploitation of two zero-days each. This includes CVE-2022-0609, CVE-2022-41128, CVE-2022-30190, and CVE-2023-23397.
The disclosure comes as threat actors are also getting better at turning newly disclosed vulnerabilities into powerful exploits for breaching a wide range of targets across the world.
"While the discovery of zero-day vulnerabilities is a resource-intensive endeavor and successful exploitation is not guaranteed, the total number of vulnerabilities disclosed and exploited has continued to grow, the types of targeted software, including Internet of Things (IoT) devices and cloud solutions, continue to evolve, and the variety of actors exploiting them has expanded," Mandiant said.
The Mandiant report also follows a warning from Microsoft's Digital Threat Analysis Center about Russia's persistent kinetic and cyber targeting as the war in Ukraine continues into the second year.
The tech giant said since January 2023 it has observed "Russian cyber threat activity adjusting to boost destructive and intelligence gathering capacity on Ukraine and its partners' civilian and military assets."
It further warned of a possible "renewed destructive campaign" mounted by the nation-state group known as Sandworm (aka Iridium) on organizations located in Ukraine and elsewhere.
What's more, Kremlin-backed hackers have deployed at least two ransomware and nine wiper families against over 100 Ukrainian entities. No less than 17 European countries have been targeted in espionage campaigns between January and mid-February 2023, and 74 countries have been targeted since the start of the war.
Other key traits associated with Russian threat activity include the use of ransomware as weapons of cyber sabotage, gaining initial access through diverse methods, and leveraging real and pseudo hacktivist groups to expand the reach of Moscow's cyber presence.
Hackers Steal Over $1.6 Million in Crypto from General Bytes Bitcoin ATMs Using Zero-Day Flaw
22.3.23 Cryptocurrency The Hacker News
Bitcoin ATM maker General Bytes disclosed that unidentified threat actors stole cryptocurrency from hot wallets by exploiting a zero-day security flaw in its software.
"The attacker was able to upload his own java application remotely via the master service interface used by terminals to upload videos and run it using 'batm' user privileges," the company said in an advisory published over the weekend.
"The attacker scanned the Digital Ocean cloud hosting IP address space and identified running CAS services on ports 7741, including the General Bytes Cloud service and other GB ATM operators running their servers on Digital Ocean," it further added.
The company said that the server to which the malicious Java application was uploaded was by default configured to start applications present in the deployment folder ("/batm/app/admin/standalone/deployments/").
In doing so, the attack allowed the threat actor to access the database; read and decrypt API keys used to access funds in hot wallets and exchanges; send funds from the wallets; download usernames, password hashes, and turn off two-factor authentication (2FA); and even access terminal event logs.
It also warned that its own cloud service as well as other operators' standalone servers were infiltrated as a result of the incident, prompting the company to shutter the service.
In addition to urging customers to keep their crypto application servers (CASs) behind a firewall and a VPN, it's also recommending to rotate all users' passwords and API keys to exchanges and hot wallets.
"The CAS security fix is provided in two server patch releases, 20221118.48 and 20230120.44," General Bytes said in the advisory.
The company further emphasized that it had conducted multiple security audits since 2021 and that none of them flagged this vulnerability. It appears to have been unpatched since version 20210401.
General Bytes did not disclose the exact amount of funds stolen by the hackers, but an analysis of the cryptocurrency wallets used in the attack reveals the receipt of 56.283 BTC ($1.5 million), 21.823 ETH ($36,500), and 1,219.183 LTC ($96,500).
The ATM hack is the second breach targeting General Bytes in less than a year, with another zero-day flaw in its ATM servers exploited to steal crypto from its customers in August 2022.
New DotRunpeX Malware Delivers Multiple Malware Families via Malicious Ads
21.3.23 Virus The Hacker News
A new piece of malware dubbed dotRunpeX is being used to distribute numerous known malware families such as Agent Tesla, Ave Maria, BitRAT, FormBook, LokiBot, NetWire, Raccoon Stealer, RedLine Stealer, Remcos, Rhadamanthys, and Vidar.
"DotRunpeX is a new injector written in .NET using the Process Hollowing technique and used to infect systems with a variety of known malware families," Check Point said in a report published last week.
Said to be in active development, dotRunpeX arrives as a second-stage malware in the infection chain, often deployed via a downloader (aka loader) that's transmitted through phishing emails as malicious attachments.
Alternatively, it's known to leverage malicious Google Ads on search result pages to direct unsuspecting users searching for popular software such as AnyDesk and LastPass to copycat sites hosting trojanized installers.
The latest DotRunpeX artifacts, first spotted in October 2022, add an extra obfuscation layer by using the KoiVM virtualizing protector.
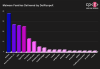
It's worth pointing out that the findings dovetail with a malvertising campaign documented by SentinelOne last month in which the loader and the injector components were collectively referred to as MalVirt.
Check Point's analysis has further revealed that "each dotRunpeX sample has an embedded payload of a certain malware family to be injected," with the injector specifying a list of anti-malware processes to be terminated.
This, in turn, is made possible by abusing a vulnerable process explorer driver (procexp.sys) that's incorporated into dotRunpeX so as to obtain kernel mode execution.
There are signs that dotRunpeX could be affiliated to Russian-speaking actors based on the language references in the code. The most frequently delivered malware families delivered by the emerging threat include RedLine, Raccoon, Vidar, Agent Tesla, and FormBook.
Mispadu Banking Trojan Targets Latin America: 90,000+ Credentials Stolen
21.3.23 Virus The Hacker News

A banking trojan dubbed Mispadu has been linked to multiple spam campaigns targeting countries like Bolivia, Chile, Mexico, Peru, and Portugal with the goal of stealing credentials and delivering other payloads.
The activity, which commenced in August 2022, is currently ongoing, Ocelot Team from Latin American cybersecurity firm Metabase Q said in a report shared with The Hacker News.
Mispadu (aka URSA) was first documented by ESET in November 2019, describing its ability to perpetrate monetary and credential theft and act as a backdoor by taking screenshots and capturing keystrokes.
"One of their main strategies is to compromise legitimate websites, searching for vulnerable versions of WordPress, to turn them into their command-and-control server to spread malware from there, filtering out countries they do not wish to infect, dropping different type of malware based on the country being infected," researchers Fernando García and Dan Regalado said.
It's also said to share similarities with other banking trojans targeting the region, like Grandoreiro, Javali, and Lampion. Attack chains involving the Delphi malware leverage email messages urging recipients to open fake overdue invoices, thereby triggering a multi-stage infection process.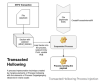
Should a victim open the HTML attachment sent via the spam email, it verifies that the file was opened from a desktop device and then redirects to a remote server to fetch the first-stage malware.
The RAR or ZIP archive, when launched, is designed to make use of rogue digital certificates – one which is the Mispadu malware and the other, an AutoIT installer – to decode and execute the trojan by abusing the legitimate certutil command-line utility.
Mispadu is equipped to gather the list of antivirus solutions installed on the compromised host, siphon credentials from Google Chrome and Microsoft Outlook, and facilitate the retrieval of additional malware.
This includes an obfuscated Visual Basic Script dropper that serves to download another payload from a hard-coded domain, a .NET-based remote access tool that can run commands issued by an actor-controlled server, and a loader written in Rust that, in turn, executes a PowerShell loader to run files directly from memory.
What's more, the malware utilizes malicious overlay screens to obtain credentials associated with online banking portals and other sensitive information.
Metabase Q noted that the certutil approach has allowed Mispadu to bypass detection by a wide range of security software and harvest over 90,000 bank account credentials from over 17,500 unique websites.
Researchers Shed Light on CatB Ransomware's Evasion Techniques
21.3.23 Ransomware The Hacker News
The threat actors behind the CatB ransomware operation have been observed using a technique called DLL search order hijacking to evade detection and launch the payload.
CatB, also referred to as CatB99 and Baxtoy, emerged late last year and is said to be an "evolution or direct rebrand" of another ransomware strain known as Pandora based on code-level similarities.
It's worth noting that the use of Pandora has been attributed to Bronze Starlight (aka DEV-0401 or Emperor Dragonfly), a China-based threat actor that's known to employ short-lived ransomware families as a ruse to likely conceal its true objectives.
One of the key defining characteristics of CatB is its reliance on DLL hijacking via a legitimate service called Microsoft Distributed Transaction Coordinator (MSDTC) to extract and launch the ransomware payload.
"Upon execution, CatB payloads rely on DLL search order hijacking to drop and load the malicious payload," SentinelOne researcher Jim Walter said in a report published last week. "The dropper (versions.dll) drops the payload (oci.dll) into the System32 directory."
The dropper is also responsible for carrying out anti-analysis checks to determine if the malware is being executed within a virtual environment, and ultimately abusing the MSDTC service to inject the rogue oci.dll containing the ransomware into the msdtc.exe executable upon system restart.
"The [MSDTC] configurations changed are the name of the account under which the service should run, which is changed from Network Service to Local System, and the service start option, which is changed from Demand start to Auto start for persistency if a restart occurs," Minerva Labs researcher Natalie Zargarov explained in a previous analysis.
One striking aspect of the ransomware is its absence of a ransom note. Instead, each encrypted file is updated with a message urging the victims to make a Bitcoin payment.
Another trait is the malware's ability to harvest sensitive data such as passwords, bookmarks, history from web browsers Google Chrome, Microsoft Edge (and Internet Explorer), and Mozilla Firefox.

"CatB joins a long line of ransomware families that embrace semi-novel techniques and atypical behaviors such as appending notes to the head of files," Walter said. "These behaviors appear to be implemented in the interest of detection evasion and some level of anti-analysis trickery."
This is not the first time the MSDTC service has been weaponized for malicious purposes. In May 2021, Trustwave disclosed a novel malware dubbed Pingback that leveraged the same technique to achieve persistence and bypass security solutions.
Emotet Rises Again: Evades Macro Security via OneNote Attachments
21.3.23 Virus The Hacker News
The notorious Emotet malware, in its return after a short hiatus, is now being distributed via Microsoft OneNote email attachments in an attempt to bypass macro-based security restrictions and compromise systems.
Emotet, linked to a threat actor tracked as Gold Crestwood, Mummy Spider, or TA542, continues to be a potent and resilient threat despite attempts by law enforcement to take it down.
A derivative of the Cridex banking worm – which was subsequently replaced by Dridex around the same time GameOver Zeus was disrupted in 2014 – Emotet has evolved into a "monetized platform for other threat actors to run malicious campaigns on a pay-per-install (PPI) model, allowing theft of sensitive data and ransom extortion."
While Emotet infections have acted as a conduit to deliver Cobalt Strike, IcedID, Qakbot, Quantum ransomware, and TrickBot, its return in late 2021 was facilitated by means of TrickBot.
"Emotet is known for extended periods of inactivity, often occurring multiple times per year, where the botnet maintains a steady-state but does not deliver spam or malware," Secureworks notes in its profile of the actor.
The dropper malware is commonly distributed through spam emails containing malicious attachments. But with Microsoft taking steps to block macros in downloaded Office files, OneNote attachments have emerged as an appealing alternative pathway.
"The OneNote file is simple but yet effective at social engineering users with a fake notification stating that the document is protected," Malwarebytes disclosed in a new alert. "When instructed to double-click on the View button, victims will inadvertently double-click on an embedded script file instead."
The Windows Script File (WSF) is engineered to retrieve and execute the Emotet binary payload from a remote server. Similar findings have been echoed by Cyble, IBM X-Force, and Palo Alto Networks Unit 42.
That said, Emotet still continues to use booby-trapped documents containing macros to deliver the malicious payload, employing social engineering lures to entice users into enabling macros to activate the attack chain.
Such documents have been observed to leverage a technique called decompression bomb to conceal a very large file (over 550 MB) within ZIP archive attachments to fly under the radar, according to multiple reports from Cyble, Deep Instinct, Hornetsecurity, and Trend Micro.
This is achieved by padding 00-byte at the end of the document to artificially inflate the file size so as to exceed the limitations imposed by anti-malware solutions.
The latest development is a sign of the operators' flexibility and agility in switching attachment types for initial delivery to evade detection signatures. It also comes amid a spike in threat actors using OneNote documents to distribute a wide range of malware such as AsyncRAT, Icedid, RedLine Stealer, Qakbot, and XWorm.
According to Trellix, a majority of the malicious OneNote detections in 2023 have been reported in the U.S., South Korea, Germany, Saudi Arabia, Poland, India, the U.K., Italy, Japan, and Croatia, with manufacturing, high-tech, telecom, finance, and energy emerging as the top targeted sectors.
Chinese Hackers Exploit Fortinet Zero-Day Flaw for Cyber Espionage Attack
21.3.23 Exploit The Hacker News
The zero-day exploitation of a now-patched medium-severity security flaw in the Fortinet FortiOS operating system has been linked to a suspected Chinese hacking group.
American cybersecurity company Mandiant, which made the attribution, said the activity cluster is part of a broader campaign designed to deploy backdoors onto Fortinet and VMware solutions and maintain persistent access to victim environments.
The Google-owned threat intelligence and incident response firm is tracking the malicious operation under its uncategorized moniker UNC3886, describing it as a China-nexus threat actor.
"UNC3886 is an advanced cyber espionage group with unique capabilities in how they operate on-network as well as the tools they utilize in their campaigns," Mandiant researchers said in a technical analysis.
"UNC3886 has been observed targeting firewall and virtualization technologies which lack EDR support. Their ability to manipulate firewall firmware and exploit a zero-day indicates they have curated a deeper-level of understanding of such technologies."
It's worth noting that the adversary was previously tied to another intrusion set targeting VMware ESXi and Linux vCenter servers as part of a hyperjacking campaign designed to drop backdoors such as VIRTUALPITA and VIRTUALPIE.
The latest disclosure from Mandiant comes as Fortinet revealed that government entities and large organizations were victimized by an unidentified threat actor by leveraging a zero-day bug in Fortinet FortiOS software to result in data loss and OS and file corruption.
The vulnerability, tracked as CVE-2022-41328 (CVSS score: 6.5), concerns a path traversal bug in FortiOS that could lead to arbitrary code execution. It was patched by Fortinet on March 7, 2023.
According to Mandiant, the attacks mounted by UNC3886 targeted Fortinet's FortiGate, FortiManager, and FortiAnalyzer appliances to deploy two different implants such as THINCRUST and CASTLETAP. This, in turn, was made possible owing to the fact that the FortiManager device was exposed to the internet.
THINCRUST is a Python backdoor capable of executing arbitrary commands as well as reading and writing from and to files on disk.
The persistence afforded by THINCRUST is subsequently leveraged to deliver FortiManager scripts that weaponize the FortiOS path traversal flaw to overwrite legitimate files and modify firmware images.
This includes a newly added payload called "/bin/fgfm" (referred to as CASTLETAP) that beacons out to an actor-controlled server so as to accept incoming instructions that allow it to run commands, fetch payloads, and exfiltrate data from the compromised host.
"Once CASTLETAP was deployed to the FortiGate firewalls, the threat actor connected to ESXi and vCenter machines," the researchers explained. "The threat actor deployed VIRTUALPITA and VIRTUALPIE to establish persistence, allowing for continued access to the hypervisors and the guest machines."
Alternatively, on FortiManager devices that implement internet access restrictions, the threat actor is said to have pivoted from a FortiGate firewall compromised with CASTLETAP to drop a reverse shell backdoor named REPTILE ("/bin/klogd") on the network management system to regain access.
Also employed by UNC3886 at this stage is a utility dubbed TABLEFLIP, a network traffic redirection software to connect directly to the FortiManager device regardless of the access-control list (ACL) rules put in place.
This is far from the first time Chinese adversarial collectives have targeted networking equipment to distribute bespoke malware, with recent attacks taking advantage of other vulnerabilities in Fortinet and SonicWall devices.
The revelation also comes as threat actors are developing and deploying exploits faster than ever before, with as many as 28 vulnerabilities exploited within seven days of public disclosure — a 12% rise over 2021 and an 87% rise over 2020, according to Rapid7.
This is also significant, not least because China-aligned hacking crews have become "particularly proficient" at exploiting zero-day vulnerabilities and deploying custom malware to steal user credentials and maintain long-term access to target networks.
"The activity [...] is further evidence that advanced cyber espionage threat actors are taking advantage of any technology available to persist and traverse a target environment, especially those technologies that do not support EDR solutions," Mandiant said.
Pompompurin Unmasked: Infamous BreachForums Mastermind Arrested in New York
18.3.23 Crime The Hacker News
U.S. law enforcement authorities have arrested a New York man in connection with running the infamous BreachForums hacking forum under the online alias "Pompompurin."
The development, first reported by Bloomberg Law, comes after News 12 Westchester, earlier this week, said that federal investigators "spent hours inside and outside of a home in Peekskill."
"At one point, investigators were seen removing several bags of evidence from the house," the New York-based local news service added.
According to an affidavit filed by the Federal Bureau of Investigation (FBI), the suspect identified himself as Conor Brian Fitzpatrick and that he admitted to being the owner of the BreachForums website.
"When I arrested the defendant on March 15, 2023, he stated to me in substance and in part that: a) his name was Conor Brian Fitzpatrick; b) he used the alias 'pompompurin,' and c) he was the owner and administrator of 'BreachForums,'" FBI Special Agent, John Longmire, said.
Fitzpatrick has been charged with one count of conspiracy to solicit individuals with the purpose of selling unauthorized access devices.
The defendant was released a day later on a $300,000 bond signed by his parents and is scheduled to appear before the District Court for the Eastern District of Virginia on March 24, 2023.
Besides being barred from obtaining a passport or other international travel document, Fitzpatrick has been restricted from contacting his co-conspirators and using a narcotic drug or other controlled substances unless prescribed by a licensed medical practitioner.
BreachForums emerged last year three weeks after a coordinated law enforcement operation seized control of RaidForums in March 2022.
"In the threat actor's welcoming thread, 'pompompurin' stated that they had created BreachForums as an alternative to RaidForums but that it was 'not affiliated with RaidForums in any capacity,'" cybersecurity firm Flashpoint said at the time.
The forum has since attracted notoriety for hosting stolen databases belonging to several companies, often including sensitive personal information.
In the wake of Fitzpatrick's arrest, another forum user named Baphomet said they were taking ownership of the website, noting that there is no evidence of "access or modifications to Breached infra."
"My only response to [law enforcement], or any media outlet is that I have no concerns for myself at the moment," Baphomet said in the announcement. "OPSEC has been my focus from day one, and thankfully I don't think any mountain lions will be attacking me in my little fishing boat."
The development comes as the Cyber Police of Ukraine announced the arrest of a 25-year-old developer who created a remote access trojan that infected over 10,000 computers under the guise of gaming apps.
LockBit 3.0 Ransomware: Inside the Cyberthreat That's Costing Millions
18.3.23 Ransomware The Hacker News
U.S. government agencies have released a joint cybersecurity advisory detailing the indicators of compromise (IoCs) and tactics, techniques, and procedures (TTPs) associated with the notorious LockBit 3.0 ransomware.
"The LockBit 3.0 ransomware operations function as a Ransomware-as-a-Service (RaaS) model and is a continuation of previous versions of the ransomware, LockBit 2.0, and LockBit," the authorities said.
The alert comes courtesy of the U.S. Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), and the Multi-State Information Sharing & Analysis Center (MS-ISAC).
Since emerging in late 2019, the LockBit actors have invested significant technical efforts to develop and fine-tune its malware, issuing two major updates — LockBit 2.0, released in mid-2021, and LockBit 3.0, released in June 2022. The two versions are also known as LockBit Red and LockBit Black, respectively.
"LockBit 3.0 accepts additional arguments for specific operations in lateral movement and rebooting into Safe Mode," according to the alert. "If a LockBit affiliate does not have access to passwordless LockBit 3.0 ransomware, then a password argument is mandatory during the execution of the ransomware."
The ransomware is also designed to infect only those machines whose language settings do not overlap with those specified in an exclusion list, which includes Romanian (Moldova), Arabic (Syria), and Tatar (Russia).
Initial access to victim networks is obtained via remote desktop protocol (RDP) exploitation, drive-by compromise, phishing campaigns, abuse of valid accounts, and weaponization of public-facing applications.
Upon finding a successful ingress point, the malware takes steps to establish persistence, escalate privileges, carry out lateral movement, and purge log files, files in the Windows Recycle Bin folder, and shadow copies, before initiating the encryption routine.
"LockBit affiliates have been observed using various freeware and open source tools during their intrusions," the agencies said. "These tools are used for a range of activities such as network reconnaissance, remote access and tunneling, credential dumping, and file exfiltration."
One defining characteristic of the attacks is the use of a custom exfiltration tool referred to as StealBit, which the LockBit group provides to affiliates for double extortion purposes.
In November, the U.S. Department of Justice reported that the LockBit ransomware strain has been used against at least 1,000 victims worldwide, netting the operation over $100 million in illicit profits.
Industrial cybersecurity firm Dragos, earlier this year, revealed that LockBit 3.0 was responsible for 21% of 189 ransomware attacks detected against critical infrastructure in Q4 2022, accounting for 40 incidents. A majority of those attacks impacted food and beverage and manufacturing sectors.
The FBI's Internet Crime Complaint Center (IC3), in its latest Internet Crime Report, listed LockBit (149), BlackCat (114), and Hive (87) as the top three ransomware variants victimizing critical infrastructure in 2022.
Despite LockBit's prolific attack spree, the ransomware gang suffered a huge blow in late September 2022 when a disgruntled LockBit developer released the builder code for LockBit 3.0, raising concerns that other criminal actors could take advantage of the situation and spawn their own variants.
The advisory comes as the BianLian ransomware group has shifted its focus from encrypting its victims' files to pure data-theft extortion attacks, months after cybersecurity company Avast released a free decryptor in January 2023.
In a related development, Kaspersky has published a free decryptor to help victims who have had their data locked down by a version of ransomware based on the Conti source code that leaked after Russia's invasion of Ukraine last year led to internal friction among the core members.
"Given the sophistication of the LockBit 3.0 and Conti ransomware variants, it is easy to forget that people are running these criminal enterprises," Intel 471 noted last year. "And, as with legitimate organizations, it only takes one malcontent to unravel or disrupt a complex operation."
FakeCalls Vishing Malware Targets South Korean Users via Popular Financial Apps
18.3.23 Virus The Hacker News
An Android voice phishing (aka vishing) malware campaign known as FakeCalls has reared its head once again to target South Korean users under the guise of over 20 popular financial apps.
"FakeCalls malware possesses the functionality of a Swiss army knife, able not only to conduct its primary aim but also to extract private data from the victim's device," cybersecurity firm Check Point said.
FakeCalls was previously documented by Kaspersky in April 2022, describing the malware's capabilities to imitate phone conversations with a bank customer support agent.
In the observed attacks, users who install the rogue banking app are enticed into calling the financial institution by offering a fake low-interest loan.
At the point where the phone call actually happens, a pre-recorded audio with instructions from the real bank is played. Simultaneously, the malware conceals the phone number with the bank's legitimate number to give the impression that a conversation is happening with an actual bank employee on the other end.
The ultimate goal of the campaign to get the victim's credit card information, which the threat actors claim is required to qualify for the non-existent loan.
The malicious app also requests for intrusive permissions so as to harvest sensitive data, including live audio and video streams, from the compromised device, which are then exfiltrated to a remote server.
The latest FakeCalls samples further implement various techniques to stay under the radar. One of the methods involves adding a large number of files inside nested directories to the APK's asset folder, causing the length of the file name and path to breach the 300-character limit.
"The malware developers took special care with the technical aspects of their creation as well as implementing several unique and effective anti-analysis techniques," Check Point said. "In addition, they devised mechanisms for disguised resolution of the command-and-control servers behind the operations."
While the attack exclusively focuses on South Korea, the cybersecurity company has warned that the same tactics can be repurposed to target other regions across the world.
The findings also come as Cyble shed light on two Android banking trojans dubbed Nexus and GoatRAT that can harvest valuable data and carry out financial fraud.
Nexus, a rebranded version of SOVA, also incorporates a ransomware module that encrypts the stored files and can abuse Android's accessibility services to extract seed phrases from cryptocurrency wallets.
In contrast, GoatRAT is designed to target Brazilian banks and joins the likes of BrasDex and PixPirate to commit fraudulent money transfer over the PIX payments platform while displaying a fake overlay window to hide the activity.
The development is part of a growing trend where threat actors have unleashed increasingly sophisticated banking malware to automate the whole process of unauthorized money transfers on infected devices.
Cybersecurity company Kaspersky said it detected 196,476 new mobile banking trojans and 10,543 new mobile ransomware trojans in 2022, with China, Syria, Iran, Yemen, and Iraq emerging as the top countries attacked by mobile malware, including adware.
Spain, Saudi Arabia, Australia, Turkey, China, Switzerland, Japan, Colombia, Italy, and India lead the list of top countries infected by mobile financial threats.
"Despite the decline in overall malware installers, the continued growth of mobile banking Trojans is a clear indication that cybercriminals are focusing on financial gain," Kaspersky researcher Tatyana Shishkova said.
New GoLang-Based HinataBot Exploiting Router and Server Flaws for DDoS Attacks
17.3.23 Exploit The Hacker News
A new Golang-based botnet dubbed HinataBot has been observed to leverage known flaws to compromise routers and servers and use them to stage distributed denial-of-service (DDoS) attacks.
"The malware binaries appear to have been named by the malware author after a character from the popular anime series, Naruto, with file name structures such as 'Hinata-<OS>-<Architecture>,'" Akamai said in a technical report.
Among the methods used to distribute the malware are the exploitation of exposed Hadoop YARN servers and security flaws in Realtek SDK devices (CVE-2014-8361), Huawei HG532 routers (CVE-2017-17215, CVSS score: 8.8).
Unpatched vulnerabilities and weak credentials have been a low-hanging fruit for attackers, representing an easy, well-documented entry point that does not require sophisticated social engineering tactics or other methods.
The threat actors behind HinataBot are said to have been active since at least December 2022, with the attacks first attempting to use a generic Go-based Mirai variant before switching to their own custom malware starting from January 11, 2023.
Since then, newer artifacts have been detected in Akamai's HTTP and SSH honeypots as recently as this month, packing in more modular functionality and added security measures to resist analysis. This indicates that HinataBot is still in active development and evolving.
The malware, like other DDoS botnets of its kind, is capable of contacting a command-and-control (C2) server to listen for incoming instructions and initiate attacks against a target IP address for a specified duration.
While early versions of the botnet utilized protocols such as HTTP, UDP, TCP, and ICMP to carry out DDoS attacks, the latest iteration is limited to just HTTP and UDP. It's not immediately known why the other two protocols were axed.
Akamai, which conducted 10-second attack tests using HTTP and UDP, revealed that the HTTP flood generated 3.4 MB of packet capture data and pushed 20,430 HTTP requests. The UDP flood, on the other hand, created 6,733 packets for a total of 421 MB of packet capture data.
In a hypothetical real-world attack with 10,000 bots, a UDP flood would peak at more than 3.3 terabit per second (Tbps), resulting in a potent volumetric attack. An HTTP flood would generate a traffic of roughly 27 gigabit per second (Gbps)
The development makes it the latest to join the ever-growing list of emerging Go-based threats such as GoBruteforcer and KmsdBot.
"Go has been leveraged by attackers to reap the benefits of its high performance, ease of multi-threading, its multiple architecture and operating system cross-compilation support, but also likely because it adds complexity when compiled, increasing the difficulty of reverse engineering the resulting binaries," Akamai said.
The findings also come as Microsoft revealed that TCP attacks emerged as the most frequent form of DDoS attack encountered in 2022, accounting for 63% of all attack traffic, followed by UDP floods and amplification attacks (22%), and packet anomaly attacks (15%).
Besides being used as distractions to conceal extortion and data theft, DDoS attacks are also expected to rise due to the arrival of new malware strains that are capable of targeting IoT devices and taking over accounts to gain unauthorized access to resources.
"With DDoS attacks becoming more frequent, sophisticated, and inexpensive to launch, it's important for organizations of all sizes to be proactive, stay protected all year round, and develop a DDoS response strategy," the tech giant's Azure Network Security Team said.
Lookalike Telegram and WhatsApp Websites Distributing Cryptocurrency Stealing Malware
17.3.23 Cryptocurrency The Hacker News
Copycat websites for instant messaging apps like Telegram and WhatApp are being used to distribute trojanized versions and infect Android and Windows users with cryptocurrency clipper malware.
"All of them are after victims' cryptocurrency funds, with several targeting cryptocurrency wallets," ESET researchers Lukáš Štefanko and Peter Strýèek said in a new analysis.
While the first instance of clipper malware on the Google Play Store dates back to 2019, the development marks the first time Android-based clipper malware has been built into instant messaging apps.
"Moreover, some of these apps use optical character recognition (OCR) to recognize text from screenshots stored on the compromised devices, which is another first for Android malware."
The attack chain begins with unsuspecting users clicking on fraudulent ads on Google search results that lead to hundreds of sketchy YouTube channels, which then direct them to lookalike Telegram and WhatsApp websites.
What's novel about the latest batch of clipper malware is that it's capable of intercepting a victim's chats and replacing any sent and received cryptocurrency wallet addresses with addresses controlled by the threat actors.
Another cluster of clipper malware makes use of OCR to find and steal seed phrases by leveraging a legitimate machine learning plugin called ML Kit on Android, thereby making it possible to empty the wallets.
A third cluster is designed to keep tabs on Telegram conversations for certain Chinese keywords, both hard-coded and received from a server, related to cryptocurrencies, and if so, exfiltrate the complete message, along with the username, group or channel name, to a remote server.
Lastly, a fourth set of Android clippers come with capabilities to switch the wallet address as well as harvest device information and Telegram data such as messages and contacts.
The rogue Android APK package names are listed below -
org.telegram.messenger
org.telegram.messenger.web2
org.tgplus.messenger
io.busniess.va.whatsapp
com.whatsapp
ESET said it also found two Windows clusters, one which is engineered to swap wallet addresses and a second group that distributes remote access trojans (RATs) in place of clippers to gain control of infected hosts and perpetrate crypto theft.
All the analyzed RAT samples are based on the publicly available Gh0st RAT, barring one, which employs more anti-analysis runtime checks during its execution and uses the HP-socket library to communicate with its server.
It's also worth pointing out that these clusters, despite following a similar modus operandi, represent disparate sets of activity likely developed by different threat actors.
The campaign, like a similar malicious cyber operation that came to light last year, is geared towards Chinese-speaking users, primarily motivated by the fact that both Telegram and WhatsApp are blocked in the country.
"People who wish to use these services have to resort to indirect means of obtaining them," the researchers said. "Unsurprisingly, this constitutes a ripe opportunity for cybercriminals to abuse the situation."
Winter Vivern APT Group Targeting Indian, Lithuanian, Slovakian, and Vatican Officials
17.3.23 APT The Hacker News
The advanced persistent threat known as Winter Vivern has been linked to campaigns targeting government officials in India, Lithuania, Slovakia, and the Vatican since 2021.
The activity targeted Polish government agencies, the Ukraine Ministry of Foreign Affairs, the Italy Ministry of Foreign Affairs, and individuals within the Indian government, SentinelOne said in a report shared with The Hacker News.
"Of particular interest is the APT's targeting of private businesses, including telecommunications organizations that support Ukraine in the ongoing war," senior threat researcher Tom Hegel said.
Winter Vivern, also tracked as UAC-0114, drew attention last month after the Computer Emergency Response Team of Ukraine (CERT-UA) detailed a new malware campaign aimed at state authorities of Ukraine and Poland to deliver a piece of malware dubbed Aperetif.
Previous public reports chronicling the group show that it has leveraged weaponized Microsoft Excel documents containing XLM macros to deploy PowerShell implants on compromised hosts.
While the origins of the threat actor are unknown, the attack patterns suggest that the cluster is aligned with objectives that support the interests of Belarus and Russia's governments.
UAC-0114 has employed a variety of methods, ranging from phishing websites to malicious documents, that are tailored to the targeted organization to distribute its custom payloads and gain unauthorized access to sensitive systems.
In one batch of attacks observed in mid-2022, Winter Vivern set up credential phishing web pages to lure users of the Indian government's legitimate email service email.gov[.]in.
Typical attack chains involve using batch scripts masquerading as virus scanners to trigger the deployment of the Aperetif trojan from actor-controlled infrastructure such as compromised WordPress sites.
Aperetif, a Visual C++-based malware, comes with features to collect victim data, maintain backdoor access, and retrieve additional payloads from the command-and-control (C2) server.
"The Winter Vivern APT is a resource-limited but highly creative group that shows restraint in the scope of their attacks," Hegel said.
"Their ability to lure targets into the attacks, and their targeting of governments and high-value private businesses demonstrate the level of sophistication and strategic intent in their operations."
While Winter Vivern may have managed to evade the public eye for extended periods of time, one group that's not too concerned about staying under the radar is Nobelium, which shares overlaps with APT29 (aka BlueBravo, Cozy Bear, or The Dukes).
The Kremlin-backed nation-state group, notorious for the SolarWinds supply chain compromise in December 2020, has continued to evolve its toolset, developing new custom malware like MagicWeb and GraphicalNeutrino.
It has also been attributed to yet another phishing campaign directed against diplomatic entities in the European Union, with specific emphasis on agencies that are "aiding Ukrainian citizens fleeing the country, and providing help to the government of Ukraine."
"Nobelium actively collects intelligence information about the countries supporting Ukraine in the Russia-Ukraine war," BlackBerry said. "The threat actors carefully follow geopolitical events and use them to increase their possibility of a successful infection."
The phishing emails, spotted by the company's research and intelligence team, contain a weaponized document that includes a link pointing to an HTML file.
The weaponized URLs, hosted on a legitimate online library website based in El Salvador, features lures related to LegisWrite and eTrustEx, both of which are used by E.U. nations for secure document exchange.
The HTML dropper (dubbed ROOTSAW or EnvyScout) delivered in the campaign embeds an ISO image, which, in turn, is designed to launch a malicious dynamic link library (DLL) that facilitates the delivery of a next-stage malware via Notion's APIs.
The use of Notion, a popular note-taking application, for C2 communications was previously revealed by Recorded Future in January 2023. It's worth noting that APT29 has employed various online services like Dropbox, Google Drive, Firebase, and Trello in an attempt to evade detection.
"Nobelium remains highly active, executing multiple campaigns in parallel targeting government organizations, non-governmental organizations (NGOs), intergovernmental organizations (IGOs), and think tanks across the U.S., Europe, and Central Asia," Microsoft stated last month.
The findings also come as enterprise security firm Proofpoint disclosed aggressive email campaigns orchestrated by a Russia-aligned threat actor called TA499 (aka Lexus and Vovan) since early 2021 to trick targets into participating in recorded phone calls or video chats and extract valuable information.
"The threat actor has engaged in steady activity and expanded its targeting to include prominent businesspeople and high-profile individuals that have either made large donations to Ukrainian humanitarian efforts or those making public statements about Russian disinformation and propaganda," the company said.
Google Uncovers 18 Severe Security Vulnerabilities in Samsung Exynos Chips
17.3.23 Vulnerebility The Hacker News
Google is calling attention to a set of severe security flaws in Samsung's Exynos chips, some of which could be exploited remotely to completely compromise a phone without requiring any user interaction.
The 18 zero-day vulnerabilities affect a wide range of Android smartphones from Samsung, Vivo, Google, wearables using the Exynos W920 chipset, and vehicles equipped with the Exynos Auto T5123 chipset.
Four of the 18 flaws make it possible for a threat actor to achieve internet-to-Samsung, Vivo, and Google, as well as wearables using the Exynos W920 chipset and vehicleses in late 2022 and early 2023, said.
"[The] four vulnerabilities allow an attacker to remotely compromise a phone at the baseband level with no user interaction, and require only that the attacker know the victim's phone number," Tim Willis, head of Google Project Zero, said.
In doing so, a threat actor could gain entrenched access to cellular information passing in and out of the targeted device. Additional details about the bugs have been withheld.
The attacks might sound prohibitive to execute, but, to the contrary, they are well within reach of skilled attackers, who can quickly devise an operational exploit to breach affected devices "silently and remotely."
The remaining 14 flaws are said to be not as severe, as it necessitates a rogue mobile network insider or an attacker with local access to the device.
While Pixel 6 and 7 handsets have already received a fix as part of March 2023 security updates, patches for other devices are expected to vary depending on the manufacturer's timeline.
Until then, users are recommended to switch off Wi-Fi calling and Voice over LTE (VoLTE) in their device settings to "remove the exploitation risk of these vulnerabilities."
Chinese and Russian Hackers Using SILKLOADER Malware to Evade Detection
17.3.23 APT The Hacker News
Threat activity clusters affiliated with the Chinese and Russian cybercriminal ecosystems have been observed using a new piece of malware that's designed to load Cobalt Strike onto infected machines.
Dubbed SILKLOADER by Finnish cybersecurity company WithSecure, the malware leverages DLL side-loading techniques to deliver commercial adversary simulation software.
The development comes as improved detection capabilities against Cobalt Strike, a legitimate post-exploitation tool used for red team operations, is forcing threat actors to seek alternative options or concoct new ways to propagate the framework to evade detection.
"The most common of these include adding complexity to the auto-generated beacon or stager payloads via the utilization of packers, crypters, loaders, or similar techniques," WithSecure researchers said.
SILKLOADER joins other loaders such as KoboldLoader, MagnetLoader, and LithiumLoader that have been recently discovered incorporating Cobalt Strike components.
It also shares overlaps with LithiumLoader in that both employ the DLL side-loading method to hijack a legitimate application with the goal of running a separate, malicious dynamic link library (DLL).
SILKLOADER achieves this via specially crafted libvlc.dll files that are dropped alongside a legitimate but renamed VLC media player binary (Charmap.exe).
"Cobalt Strike beacons are very well known and detections against them on a well-protected machine are all but guaranteed," WithSecure researcher Hassan Nejad said.
"However, by adding additional layers of complexity to the file content and launching it through a known application such as VLC Media Player via side-loading, the attackers hope to evade these defense mechanisms."
WithSecure said it identified the shellcode loader following an analysis of "several human-operated intrusions" targeting various entities spanning a wide range of organizations located in Brazil, France, and Taiwan in Q4 2022.
Although these attacks were unsuccessful, the activity is suspected to be a lead-up to ransomware deployments, with the tactics and tooling "heavily overlapping" with those attributed to the operators of the Play ransomware.
In one attack aimed at an unnamed French social welfare organization, the threat actor gained a foothold into the network by exploiting a compromised Fortinet SSL VPN appliance to stage Cobalt Strike beacons.
"The threat actor maintained a foothold in this organization for several months," WithSecure said. "During this time, they performed discovery and credential stealing activities, followed by deployment of multiple Cobalt Strike beacons."
But when this attempt failed, the adversary switched to using SILKLOADER to bypass detection and deliver the beacon payload.
That's not all. Another loader known as BAILLOADER, which is also used to distribute Cobalt Strike beacons, has been linked to attacks involving Quantum ransomware, GootLoader, and the IcedID trojan in recent months.
BAILLOADER, for its part, is said to exhibit similarities with a crypter codenamed Tron that has been put to use by different adversaries to distribute Emotet, TrickBot, BazarLoader, IcedID, Conti ransomware, and Cobalt Strike.
This has given rise to the possibility that disparate threat actors are sharing Cobalt Strike beacons, crypters, and infrastructure provided by third-party affiliates to service multiple intrusions utilizing different tactics.
In other words, SILKLOADER is likely being offered as an off-the-shelf loader through a Packer-as-a-Service program to Russian-based threat actors.
"This loader is being provided either directly to ransomware groups or possibly via groups offering Cobalt Strike/Infrastructure-as-a-Service to trusted affiliates," WithSecure said.
"Most of these affiliates appear to have been part of or have had close working relationships with the Conti group, its members, and offspring after its alleged shutdown."
SILKLOADER samples analyzed by the company show that early versions of the malware date back to the start of 2022, with the loader exclusively put to use in different attacks targeting victims in China and Hong Kong.
The shift from East Asian targets to other countries such as Brazil and France is believed to have occurred around July 2022, after which all SILKLOADER-related incidents have been attributed to Russian cybercriminal actors.
This has further given way to a hypothesis that "SILKLOADER was originally written by threat actors acting within the Chinese cybercriminal ecosystem" and that the "loader was used by the threat actors within this nexus at least as early as May 2022 till July 2022."
"The builder or source code was later acquired by a threat actor within the Russian cybercriminal ecosystem between July 2022 and September 2022," WithSecure said, adding, "the original Chinese author sold the loader to a Russian threat actor once they no longer had any use for it."
Both SILKLOADER and BAILLOADER are just the latest examples of threat actors refining and retooling their approaches to stay ahead of the detection curve.
"As the cybercriminal ecosystem becomes more and more modularized via service offerings, it is no longer possible to attribute attacks to threat groups simply by linking them to specific components within their attacks," WithSecure researchers concluded.
Cryptojacking Group TeamTNT Suspected of Using Decoy Miner to Conceal Data Exfiltration
17.3.23 Cryptocurrency The Hacker News
The cryptojacking group known as TeamTNT is suspected to be behind a previously undiscovered strain of malware used to mine Monero cryptocurrency on compromised systems.
That's according to Cado Security, which found the sample after Sysdig detailed a sophisticated attack known as SCARLETEEL aimed at containerized environments to ultimately steal proprietary data and software.
Specifically, the early phase of the attack chain involved the use of a cryptocurrency miner, which the cloud security firm suspected was deployed as a decoy to conceal the detection of data exfiltration.
The artifact – uploaded to VirusTotal late last month – "bear[s] several syntactic and semantic similarities to prior TeamTNT payloads, and includes a wallet ID that has previously been attributed to them," a new analysis from Cado Security has revealed.
TeamTNT, active since at least 2019, has been documented to repeatedly strike cloud and container environments to deploy cryptocurrency miners. It's also known to unleash a crypto mining worm capable of stealing AWS credentials.
While the threat actor willingly shut down their operations in November 2021, cloud security firm Aqua disclosed in September 2022 a fresh set of attacks mounted by the group targeting misconfigured Docker and Redis instances.
That said, there are also indications that rival crews such as WatchDog might be mimicking TeamTNT's tactics, techniques, and procedures (TTPs) to foil attribution efforts.
Another activity cluster of note is Kiss-a-dog, which also relies on tools and command-and-control (C2) infrastructure previously associated with TeamTNT to mine cryptocurrency.
There is no concrete evidence to tie the new malware to the SCARLETEEL attack. But Cado Security pointed out that the sample surfaced around the same time the latter was reported, raising the possibility that this could be the "decoy" miner that was installed.
The shell script, for its part, takes preparatory steps to reconfigure resource hard limits, prevent command history logging, accept all ingress or egress traffic, enumerate hardware resources, and even clean up prior compromises before commencing the activity.
Like other TeamTNT-linked attacks, the malicious payload also leverages a technique referred to as dynamic linker hijacking to cloak the miner process via a shared object executable called libprocesshider that uses the LD_PRELOAD environment variable.
Persistence is achieved by three different means, one of which modifies the .profile file, to ensure that the miner continues to run across system reboots.
The findings come as another crypto miner group dubbed the 8220 Gang has been observed using a crypter called ScrubCrypt to carry out illicit cryptojacking operations.
What's more, unknown threat actors have been found targeting vulnerable Kubernetes container orchestrator infrastructure with exposed APIs to mine the Dero cryptocurrency, marking a shift from Monero.
Cybersecurity company Morphisec, last month, also shed light on an evasive malware campaign that leverages the ProxyShell vulnerabilities in Microsoft Exchange servers to drop a crypto miner strain codenamed ProxyShellMiner.
"Mining cryptocurrency on an organization's network can lead to system performance degradation, increased power consumption, equipment overheating, and can stop services," the researchers said. "It allows threat actors access for even more nefarious ends."
Authorities Shut Down ChipMixer Platform Tied to Crypto Laundering Scheme
16.3.23 Cryptocurrency The Hacker News
A coalition of law enforcement agencies across Europe and the U.S. announced the takedown of ChipMixer, an unlicensed cryptocurrency mixer that began its operations in August 2017.
"The ChipMixer software blocked the blockchain trail of the funds, making it attractive for cybercriminals looking to launder illegal proceeds from criminal activities such as drug trafficking, weapons trafficking, ransomware attacks, and payment card fraud," Europol said in a statement.
The coordinated exercise, besides dismantling the clearnet and dark web websites associated with ChipMixer, also resulted in the seizure of $47.5 million in Bitcoin and 7 TB of data.
Mixers, also called tumblers, offer full anonymity for a fee by commingling cryptocurrency from different users – both legitimate and criminally-derived funds – in a manner that makes it hard to trace the origins.
This is achieved by funneling different payments into a single pool before splitting up each amount and transmitting them to designated recipients, thereby turning it into an attractive option for criminals looking to cash out and exchange the tainted money for fiat currency.
According to a report from Chainalysis in January 2023, "mixers processed a total of $7.8 billion in 2022, 24% of which came from illicit addresses," and "the vast majority of illicit value processed by mixers is made up of stolen funds, the majority of which were stolen by North Korea-linked hackers."
ChipMixer, the world's largest centralized crypto mixer service, is estimated to have laundered no less than $3.75 billion worth of digital assets (152,000 BTC) to further a wide range of criminal schemes.
Blockchain analytics firm Elliptic said ChipMixer has been used to launder over $844 million in Bitcoin that can be linked directly to criminal activity.
"ChipMixer was one of a variety of mixers used to launder the proceeds of hacks perpetrated by North Korea's Lazarus Group," Elliptic's co-founder and chief scientist, Tom Robinson, said.
This comprises the KuCoin theft in September 2020 as well as the Axie Infinity Ronin Bridge and Harmony Horizon Bridge hacks that took place last year.

The Lazarus Group is far from the only infamous client to have used the service to obfuscate the financial tracks. The other prominent actors consist of ransomware crews like LockBit, Sodinokibi (aka REvil), Zeppelin, Mamba, Dharma, and SunCrypt.
Additionally, ChipMixer is said to have attracted more than $200 million in Bitcoin linked to purchases originating from darknet markets, including $60 million from customers of the now-defunct Hydra.
The mixer platform, per the U.S. Department of Justice (DoJ), also processed cryptocurrency used by the Russia-linked APT28 hacking group (aka Fancy Bear or Strontium) to procure infrastructure employed in connection with a malware called Drovorub.
Coinciding with the crackdown, the DoJ further charged a 49-year-old Vietnamese national, Minh Quốc Nguyễn, for his role in creating and running ChipMixer's online infrastructure and advertising its services.
"ChipMixer facilitated the laundering of cryptocurrency, specifically Bitcoin, on a vast international scale, abetting nefarious actors and criminals of all kinds in evading detection," U.S. Attorney Jacqueline C. Romero said.
"Platforms like ChipMixer, which are designed to conceal the sources and destinations of staggering amounts of criminal proceeds, undermine the public's confidence in cryptocurrencies and blockchain technology."
The development is the latest in a string of law enforcement actions undertaken by governments across the world to tackle cybercrime, and comes weeks after "penal procedures" were initiated against suspected core members of the DoppelPaymer ransomware gang.
ChipMixer is also the fourth mixer service to be outlawed over the past few years following the disruption of Bestmixer, Blender, and Tornado Cash, the latter two of which were sanctioned by the U.S. Treasury Department last year for abetting Lazarus Group and other threat actors in laundering ill-gotten proceeds.
Multiple Hacker Groups Exploit 3-Year-Old Vulnerability to Breach U.S. Federal Agency
16.3.23 Exploit The Hacker News
Multiple threat actors, including a nation-state group, exploited a critical three-year-old security flaw in Progress Telerik to break into an unnamed federal entity in the U.S.
The disclosure comes from a joint advisory issued by the Cybersecurity and Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI), and Multi-State Information Sharing and Analysis Center (MS-ISAC).
"Exploitation of this vulnerability allowed malicious actors to successfully execute remote code on a federal civilian executive branch (FCEB) agency's Microsoft Internet Information Services (IIS) web server," the agencies said.
The indicators of compromise (IoCs) associated with the digital break-in were identified from November 2022 through early January 2023.
Tracked as CVE-2019-18935 (CVSS score: 9.8), the issue relates to a .NET deserialization vulnerability affecting Progress Telerik UI for ASP.NET AJAX that, if left unpatched, could lead to remote code execution.
It's worth noting here that CVE-2019-18935 has previously found a place among some of the most commonly exploited vulnerabilities abused by various threat actors in 2020 and 2021.
CVE-2019-18935, in conjunction with CVE-2017-11317, has also been weaponized by a threat actor tracked as Praying Mantis (aka TG2021) to infiltrate the networks of public and private organizations in the U.S.
Last month, CISA also added CVE-2017-11357 – another remote code execution bug affecting Telerik UI – to the Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation.
Threat actors are said to have leveraged the flaw to upload and execute malicious dynamic-link library (DLL) files masquerading as PNG images via the w3wp.exe process.
The DLL artifacts are designed to gather system information, load additional libraries, enumerate files and processes, and exfiltrate the data back to a remote server.
Another set of attacks, observed as early as August 2021 and likely mounted by a cybercriminal actor dubbed XE Group, entailed the use of aforementioned evasion techniques to sidestep detection.
These DLL files dropped and executed reverse (remote) shell utilities for unencrypted communications with a command-and-control domain to drop additional payloads, including an ASPX web shell for persistent backdoor access.
The web shell is equipped to "enumerate drives; to send, receive, and delete files; and to execute incoming commands" and "contains an interface for easily browsing files, directories, or drives on the system, and allows the user to upload or download files to any directory."
To counter such attacks, it's recommended that organizations upgrade their instances of Telerik UI ASP.NET AJAX to the latest version, implement network segmentation, and enforce phishing-resistant multi-factor authentication for accounts that have privileged access.
CISA Issues Urgent Warning: Adobe ColdFusion Vulnerability Exploited in the Wild
16.3.23 BigBrothers The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on March 15 added a security vulnerability impacting Adobe ColdFusion to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation.
The critical flaw in question is CVE-2023-26360 (CVSS score: 8.6), which could be exploited by a threat actor to achieve arbitrary code execution.
"Adobe ColdFusion contains an improper access control vulnerability that allows for remote code execution," CISA said.
The vulnerability impacts ColdFusion 2018 (Update 15 and earlier versions) and ColdFusion 2021 (Update 5 and earlier versions). It has been addressed in versions Update 16 and Update 6, respectively, released on March 14, 2023.
It's worth noting that CVE-2023-26360 also affects ColdFusion 2016 and ColdFusion 11 installations, both of which are no longer supported by the software company as they have reached end-of-life (EoL).
While the exact details surrounding the nature of the attacks are unknown, Adobe said in an advisory that it's aware of the flaw being "exploited in the wild in very limited attacks."
Federal Civilian Executive Branch (FCEB) agencies are required to apply the updates by April 5, 2023, to safeguard their networks against potential threats.
Charlie Arehart, a security researcher credited with discovering and reporting the flaw alongside Pete Freitag, described it as a "grave" issue that could result in "arbitrary code execution" and "arbitrary file system read."
YoroTrooper Stealing Credentials and Information from Government and Energy Organizations
15.3.23 Virus The Hacker News

A previously undocumented threat actor dubbed YoroTrooper has been targeting government, energy, and international organizations across Europe as part of a cyber espionage campaign that has been active since at least June 2022.
"Information stolen from successful compromises include credentials from multiple applications, browser histories and cookies, system information and screenshots," Cisco Talos researchers Asheer Malhotra and Vitor Ventura said in a Tuesday analysis.
Prominent countries targeted include Azerbaijan, Tajikistan, Kyrgyzstan, Turkmenistan, and other Commonwealth of Independent States (CIS) nations.
The threat actor is believed to be Russian-speaking owing to the victimology patterns and the presence of Cyrillic snippets in some of the implants.
That said, the YoroTrooper intrusion set has been found to exhibit tactical overlaps with the PoetRAT team that was documented in 2020 as leveraging coronavirus-themed baits to strike government and energy sectors in Azerbaijan.
YoroTrooper's data gathering goals are realized through a combination of commodity and open source stealer malware such as Ave Maria (aka Warzone RAT), LodaRAT, Meterpreter, and Stink, with the infection chains using malicious shortcut files (LNKs) and decoy documents wrapped in ZIP or RAR archives that are propagated via spear-phishing.
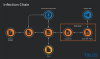
The LNK files function as simple downloaders to execute an HTA file retrieved from a remote server, which is then used to display a lure PDF document, while stealthily launching a dropper to deliver a custom stealer that uses Telegram as an exfiltration channel.
The use of LodaRAT is notable as it indicates that the malware is being employed by multiple operators despite its attribution to another group called Kasablanka, which has also been observed distributing Ave Maria in recent campaigns targeting Russia.
Other auxiliary tools deployed by YoroTrooper consist of reverse shells and a C-based custom keylogger that's capable of recording keystrokes and saving them to a file on disk.
"It is worth noting that while this campaign began with the distribution of commodity malware such as Ave Maria and LodaRAT, it has evolved significantly to include Python-based malware," the researchers said.
"This highlights an increase in the efforts the threat actor is putting in, likely derived from successful breaches during the course of the campaign."
New Cryptojacking Operation Targeting Kubernetes Clusters for Dero Mining
15.3.23 Cryptocurrency The Hacker News
Cybersecurity researchers have discovered the first-ever illicit cryptocurrency mining campaign used to mint Dero since the start of February 2023.
"The novel Dero cryptojacking operation concentrates on locating Kubernetes clusters with anonymous access enabled on a Kubernetes API and listening on non-standard ports accessible from the internet," CrowdStrike said in a new report shared with The Hacker News.
The development marks a notable shift from Monero, which is a prevalent cryptocurrency used in such campaigns. It's suspected it may have to do with the fact that Dero "offers larger rewards and provides the same or better anonymizing features."
The attacks, attributed to an unknown financially motivated actor, commence with scanning for Kubernetes clusters with authentication set as --anonymous-auth=true, which allows anonymous requests to the server, to drop initial payloads from three different U.S.-based IP addresses.
This includes deploying a Kubernetes DaemonSet named "proxy-api," which, in turn, is used to drop a malicious pod on each node of the Kubernetes cluster to kick-start the mining activity.

To that end, the DaemonSet's YAML file is orchestrated to run a Docker image that contains a "pause" binary, which is actually the Dero coin miner.
"In a legitimate Kubernetes deployment, 'pause' containers are used by Kubernetes to bootstrap a pod," the company noted. "Attackers may have used this name to blend in to avoid obvious detection."
The cybersecurity company said it identified a parallel Monero-mining campaign also targeting exposed Kubernetes clusters by attempting to delete the existing "proxy-api" DaemonSet associated with the Dero campaign.
This is an indication of the ongoing tussle between cryptojacking groups that are vying for cloud resources to take and retain control of the machines and consume all of its resources.
"Both campaigns are trying to find undiscovered Kubernetes attack surfaces and are battling it out," CrowdStrike threat researchers Benjamin Grap and Manoj Ahuje said.
Tick APT Targeted High-Value Customers of East Asian Data-Loss Prevention Company
15.3.23 APT The Hacker News
A cyberespionage actor known as Tick has been attributed with high confidence to a compromise of an East Asian data-loss prevention (DLP) company that caters to government and military entities.
"The attackers compromised the DLP company's internal update servers to deliver malware inside the software developer's network, and trojanized installers of legitimate tools used by the company, which eventually resulted in the execution of malware on the computers of the company's customers," ESET researcher Facundo Muñoz said.
Tick, also known as Bronze Butler, REDBALDKNIGHT, Stalker Panda, and Stalker Taurus, is a suspected China-aligned collective that has primarily gone after government, manufacturing, and biotechnology firms in Japan. It's said to be active since at least 2006.
Other lesser-known targets include Russian, Singaporean, and Chinese enterprises. Attack chains orchestrated by the group have typically leveraged spear-phishing emails and strategic web compromises as an entry point.
In late February 2021, Tick emerged as one of the threat actors to capitalize on the ProxyLogon flaws in Microsoft Exchange Server as a zero-day to drop a Delphi-based backdoor in a web server belonging to a South Korean IT company.
Around the same time, the adversarial collective is believed to have gained access to the network of an East Asian software developer company through unknown means. The name of the company was not disclosed.
This was followed by the deployment of a tampered version of a legitimate application called Q-Dir to drop an open source VBScript backdoor named ReVBShell, in addition to a previously undocumented downloader named ShadowPy.
ShadowPy, as the name indicates, is a Python downloader that's responsible for executing a Python script retrieved from a remote server.
Also delivered during the intrusion were variants of a Delphi backdoor called Netboy (aka Invader or Kickesgo) that comes with information gathering and reverse shell capabilities as well as another downloader codenamed Ghostdown.
"To maintain persistent access, the attackers deployed malicious loader DLLs along with legitimate signed applications vulnerable to DLL search-order hijacking," Muñoz said. "The purpose of these DLLs is to decode and inject a payload into a designated process."
Subsequently, in February and June 2022, the trojanized Q-Dir installers were transferred via remote support tools like helpU and ANYSUPPORT to two of the company's customers, an engineering and a manufacturing firm located in East Asia.
The Slovak cybersecurity company said the goal here was not to perform a supply chain attack against its downstream customers, but rather that the rogue installer was "unknowingly" used as part of technical support activities.
The incident is also likely related to another unattributed cluster detailed by AhnLab in May 2022 that involved the use of Microsoft Compiled HTML Help (.CHM) files to drop the ReVBShell implant.
Microsoft Rolls Out Patches for 80 New Security Flaws — Two Under Active Attack
15.3.23 Vulnerebility The Hacker News
Microsoft's Patch Tuesday update for March 2023 is rolling out with remediations for a set of 80 security flaws, two of which have come under active exploitation in the wild.
Eight of the 80 bugs are rated Critical, 71 are rated Important, and one is rated Moderate in severity. The updates are in addition to 29 flaws the tech giant fixed in its Chromium-based Edge browser in recent weeks.
The two vulnerabilities that have come under active attack include a Microsoft Outlook privilege escalation flaw (CVE-2023-23397, CVSS score: 9.8) and a Windows SmartScreen security feature bypass (CVE-2023-24880, CVSS score: 5.1).
CVE-2023-23397 is "triggered when an attacker sends a message with an extended MAPI property with a UNC path to an SMB (TCP 445) share on a threat actor-controlled server," Microsoft said in a standalone advisory.
A threat actor could leverage this flaw by sending a specially crafted email, activating it automatically when it is retrieved and processed by the Outlook client for Windows. As a result, this could lead to exploitation without requiring any user interaction and before even the message is viewed in the Preview Pane.
Microsoft credited the Computer Emergency Response Team of Ukraine (CERT-UA) with reporting the flaw, adding it is aware of "limited targeted attacks" mounted by a Russia-based threat actor against government, transportation, energy, and military sectors in Europe.
CVE-2023-24880, on the other hand, concerns a security bypass flaw that could be exploited to evade Mark-of-the-Web (MotW) protections when opening untrusted files downloaded from the internet.
It is also the consequence of a narrow patch released by Microsoft to resolve another SmartScreen bypass bug (CVE-2022-44698, CVSS score: 5.4) that came to light last year and which was exploited by financially motivated actors to deliver Magniber ransomware.
"Vendors often release narrow patches, creating an opportunity for attackers to iterate and discover new variants," Google Threat Analysis Group (TAG) researcher Benoit Sevens said in a report.
"Because the root cause behind the SmartScreen security bypass was not addressed, the attackers were able to quickly identify a different variant of the original bug."
TAG said it observed over 100,000 downloads of malicious MSI files signed with malformed Authenticode signature since January 2023, thereby permitting the adversary to distribute Magniber ransomware without raising any security warnings. A majority of those downloads have been associated with users in Europe.
The disclosure comes as the U.S. Cybersecurity and Infrastructure Security Agency (CISA) added the two flaws to the Known Exploited Vulnerabilities (KEV) catalog and announced a new pilot program that aims to warn critical infrastructure entities about "vulnerabilities commonly associated with known ransomware exploitation."
Also closed out by Microsoft are a number of critical remote code execution flaws impacting HTTP Protocol Stack (CVE-2023-23392, CVSS score: 9.8), Internet Control Message Protocol (CVE-2023-23415, CVSS score: 9.8), and Remote Procedure Call Runtime (CVE-2023-21708, CVSS score: 9.8).
Other notable mentions include patches for four privilege escalation bugs identified in the Windows Kernel, 10 remote code execution flaws affecting Microsoft PostScript and PCL6 Class Printer Driver, and a WebView2 spoofing vulnerability in the Edge browser.
Microsoft also remedied two information disclosure flaws in OneDrive for Android (CVE-2023-24882 and CVE-2023-24923, CVSS scores: 5.5), one spoofing vulnerability in Office for Android (CVE-2023-23391, CVSS score: 5.5), one security bypass bug in OneDrive for iOS (CVE-2023-24890, CVSS score: 4.3), and one privilege escalation issue in OneDrive for macOS (CVE-2023-24930, CVSS score: 7.8).
Rounding off the list are patches for two high-severity vulnerabilities in the Trusted Platform Module (TPM) 2.0 reference library specification (CVE-2023-1017 and CVE-2023-1018, CVSS scores: 8.8) that could lead to information disclosure or privilege escalation.
GoBruteforcer: New Golang-Based Malware Breaches Web Servers Via Brute-Force Attacks
14.3.23 Virus The Hacker News
A new Golang-based malware dubbed GoBruteforcer has been found targeting web servers running phpMyAdmin, MySQL, FTP, and Postgres to corral the devices into a botnet.
"GoBruteforcer chose a Classless Inter-Domain Routing (CIDR) block for scanning the network during the attack, and it targeted all IP addresses within that CIDR range," Palo Alto Networks Unit 42 researchers said.
"The threat actor chose CIDR block scanning as a way to get access to a wide range of target hosts on different IPs within a network instead of using a single IP address as a target."
The malware is mainly designed to single out Unix-like platforms running x86, x64 and ARM architectures, with GoBruteforcer attempting to obtain access via a brute-force attack using a list of credentials hard-coded into the binary.
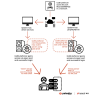
If the attack proves to be successful, an internet relay chat (IRC) bot is deployed on the victim server to establish communications with an actor-controlled server.
GoBruteforcer also leverages a PHP web shell already installed in the victim server to glean more details about the targeted network.
That said, the exact initial intrusion vector used to deliver both GoBruteforcer and the PHP web shell is undetermined as yet. Artifacts collected by the cybersecurity company suggest active development efforts to evolve its tactics and evade detection.
The findings are yet another indication of how threat actors are increasingly adopting Golang to develop cross-platform malware. What's more, GoBruteforcer's multi-scan capability enables it to breach a broad set of targets, making it a potent threat.
"Web servers have always been a lucrative target for threat actors," Unit 42 said. "Weak passwords could lead to serious threats as web servers are an indispensable part of an organization. Malware like GoBruteforcer takes advantage of weak (or default) passwords."
Microsoft Warns of Large-Scale Use of Phishing Kits to Send Millions of Emails Daily
14.3.23 Phishing The Hacker News
An open source adversary-in-the-middle (AiTM) phishing kit has found a number of takers in the cybercrime world for its ability to orchestrate attacks at scale.
Microsoft Threat Intelligence is tracking the threat actor behind the development of the kit under its emerging moniker DEV-1101.
An AiTM phishing attack typically involves a threat actor attempting to steal and intercept a target's password and session cookies by deploying a proxy server between the user and the website.
Such attacks are more effective owing to their ability to circumvent multi-factor authentication (MFA) protections.
DEV-1101, per the tech giant, is said to be the party behind several phishing kits that can be purchased or rented by other criminal actors, thereby reducing the effort and resources required to launch a phishing campaign.
"The availability of such phishing kits for purchase by attackers is part of the industrialization of the cybercriminal economy and lowers the barrier of entry for cybercrime," Microsoft said in a technical report.
The service-based economy that fuels such offerings can also result in double theft, wherein the stolen credentials are sent to both the phishing-as-a-service provider as well as their customers.
The open source kit from DEV-1101 comes with features that make it possible to set up phishing landing pages mimicking Microsoft Office and Outlook, not to mention manage campaigns from mobile devices and even use CAPTCHA checks to evade detection.
The service, since its debut in May 2022, has undergone several enhancements, chief among them being the ability to manage servers running the kit through a Telegram bot. It currently has a price tag of $300 for a monthly licensing fee, with VIP licenses costing $1,000.
Microsoft said it has detected numerous high-volume phishing campaigns spanning millions of phishing emails per day from various actors that leverage the tool.
This includes an activity cluster dubbed DEV-0928 that Redmond described as one of "DEV-1101's more prominent patrons" and which has been linked to a phishing campaign comprising over one million emails since September 2022.
The attack sequence commences with document-themed email messages containing a link to a PDF document, that when clicked, directs the recipient to a login page that masquerades as Microsoft's sign-in portal, but not before urging the victim to complete a CAPTCHA step.
"Inserting a CAPTCHA page into the phishing sequence could make it more difficult for automated systems to reach the final phishing page, while a human could easily click through to the next page," Microsoft said.
Although these AiTM attacks are designed to bypass MFA, it's crucial that organizations adopt phishing-resistant authentication methods, such as using FIDO2 security keys, to block suspicious login attempts.
Fortinet FortiOS Flaw Exploited in Targeted Cyberattacks on Government Entities
14.3.23 Vulnerebility The Hacker News
Government entities and large organizations have been targeted by an unknown threat actor by exploiting a security flaw in Fortinet FortiOS software to result in data loss and OS and file corruption.
"The complexity of the exploit suggests an advanced actor and that it is highly targeted at governmental or government-related targets," Fortinet researchers Guillaume Lovet and Alex Kong said in an advisory last week.
The zero-day flaw in question is CVE-2022-41328 (CVSS score: 6.5), a medium security path traversal bug in FortiOS that could lead to arbitrary code execution.
"An improper limitation of a pathname to a restricted directory vulnerability ('path traversal') [CWE-22] in FortiOS may allow a privileged attacker to read and write arbitrary files via crafted CLI commands," the company noted.
The shortcoming impacts FortiOS versions 6.0, 6.2, 6.4.0 through 6.4.11, 7.0.0 through 7.0.9, and 7.2.0 through 7.2.3. Fixes are available in versions 6.4.12, 7.0.10, and 7.2.4 respectively.
The disclosure comes days after Fortinet released patches to address 15 security flaws, including CVE-2022-41328 and a critical heap-based buffer underflow issue impacting FortiOS and FortiProxy (CVE-2023-25610, CVSS score: 9.3).
According to the Sunnyvale-based company, multiple FortiGate devices belonging to an unnamed customer suffered from a "sudden system halt and subsequent boot failure," indicating an integrity breach.

Further analysis of the incident revealed that the threat actors modified the device's firmware image to include a new payload ("/bin/fgfm") such that it's always launched before the booting process began.
The /bin/fgfm malware is designed to establish contact with a remote server to download files, exfiltrate data from the compromised host, and grant remote shell access.
Additional changes introduced to the firmware are said to have provided the attacker with persistent access and control, not to mention even disable firmware verification at startup.
Fortinet said the attack was highly targeted, with evidence pointing to governmental or government-affiliated organizations.
Given the complexity of the exploit, it's suspected that the attacker has a "deep understanding of FortiOS and the underlying hardware" and possesses advanced capabilities to reverse engineer different aspects of the FortiOS operating system.
It's not immediately clear if the threat actor has any connections to another intrusion set that was observed weaponizing a flaw in FortiOS SSL-VPN (CVE-2022-42475) earlier this January to deploy a Linux implant.
Large-scale Cyber Attack Hijacks East Asian Websites for Adult Content Redirects
14.3.23 Attack The Hacker News
A widespread malicious cyber operation has hijacked thousands of websites aimed at East Asian audiences to redirect visitors to adult-themed content since early September 2022.
The ongoing campaign entails injecting malicious JavaScript code to the hacked websites, often connecting to the target web server using legitimate FTP credentials the threat actor previously obtained via an unknown method.
"In many cases, these were highly secure auto-generated FTP credentials which the attacker was somehow able to acquire and leverage for website hijacking," Wiz said in a report published this month.
The fact that the breached websites – owned by both small firms and multinational corporations – utilize different tech stacks and hosting service providers has made it difficult to trace a common attack vector, the cloud security company noted.
That having said, one of the common denominators between the websites is that a majority of them are either hosted in China or hosted in a different country but are primed for Chinese users.
What's more, the URLs hosting the rogue JavaScript code are geofenced to limit its execution in certain East Asian countries.
There are also indications that the campaign has set its sights on Android as well, with the redirection script leading visitors to gambling websites that urge them to install an app (APK package name "com.tyc9n1999co.coandroid").
The identity of the threat actor is unknown as yet, and although their precise motives are yet to be identified, it is suspected that the goal is to carry out ad fraud and SEO manipulation, or alternatively, drive inorganic traffic to these websites.
Another notable aspect of the attacks is the absence of phishing, web skimming, or malware infection.
"We remain unsure as to how the threat actor has been gaining initial access to so many websites, and we have yet to identify any significant commonalities between the impacted servers other than their usage of FTP," researchers Amitai Cohen and Barak Sharoni said.
"Although it's unlikely that the threat actor is using a 0-day vulnerability given the apparently low sophistication of the attack, we can't rule this out as an option."
KamiKakaBot Malware Used in Latest Dark Pink APT Attacks on Southeast Asian Targets
13.3.23 APT The Hacker News

The Dark Pink advanced persistent threat (APT) actor has been linked to a fresh set of attacks targeting government and military entities in Southeast Asian countries with a malware called KamiKakaBot.
Dark Pink, also called Saaiwc, was extensively profiled by Group-IB earlier this year, describing its use of custom tools such as TelePowerBot and KamiKakaBot to run arbitrary commands and exfiltrate sensitive information.
The threat actor is suspected to be of Asia-Pacific origin and has been active since at least mid-2021, with an increased tempo observed in 2022.
"The latest attacks, which took place in February 2023, were almost identical to previous attacks," Dutch cybersecurity company EclecticIQ disclosed in a new report published last week.
"The main difference in the February campaign is that the malware's obfuscation routine has improved to better evade anti-malware measures."
The attacks play out in the form of social engineering lures that contain ISO image file attachments in email messages to deliver the malware.
The ISO image includes an executable (Winword.exe), a loader (MSVCR100.dll), and a decoy Microsoft Word document, the latter of which comes embedded with the KamiKakaBot payload.

The loader, for its part, is designed to load the KamiKakaBot malware by leveraging the DLL side-loading method to evade security protections and load it into the memory of the Winword.exe binary.
KamiKakaBot is primarily engineered to steal data stored in web browsers and execute remote code using Command Prompt (cmd.exe), while also embracing evasion techniques to blend in with victim environments and hinder detection.
Persistence on the compromised host is achieved by abusing the Winlogon Helper library to make malicious Windows Registry key modifications. The gathered data is subsequently exfiltrated to a Telegram bot as a ZIP archive.
"The use of legitimate web services as a command-and-control (C2) server, such as Telegram, remains the number one choice for different threat actors, ranging from regular cyber criminals to advanced persistent threat actors," the Amsterdam-based company said.
"The Dark Pink APT group is very likely a cyber espionage-motivated threat actor that specifically exploits relations between ASEAN and European nations to create phishing lures during the February 2023 campaign."
Researchers Uncover Over a Dozen Security Flaws in Akuvox E11 Smart Intercom
13.3.23 Vulnerebility The Hacker News 
More than a dozen security flaws have been disclosed in E11, a smart intercom product made by Chinese company Akuvox.
"The vulnerabilities could allow attackers to execute code remotely in order to activate and control the device's camera and microphone, steal video and images, or gain a network foothold," Claroty security researcher Vera Mens said in a technical write-up.
Akuvox E11 is described by the company on its website as a "SIP [Session Initiation Protocol] video doorphone specially designed for villas, houses, and apartments."
The product listing, however, has been taken down from the website, displaying an error message: "Page does not exist." A snapshot captured by Google shows that the page was live as recently as March 12, 2023, 05:59:51 GMT.
The attacks can manifest either through remote code execution within the local area network (LAN) or remote activation of the E11's camera and microphone, allowing the adversary to collect and exfiltrate multimedia recordings.
A third attack vector takes advantage of an external, insecure file transfer protocol (FTP) server to download stored images and data.
The most severe of the issues are as follows -
CVE-2023-0344 (CVSS score: 9.1) - Akuvox E11 appears to be using a custom version of dropbear SSH server. This server allows an insecure option that by default is not in the official dropbear SSH server.
CVE-2023-0345 (CVSS score: 9.8) - The Akuvox E11 secure shell (SSH) server is enabled by default and can be accessed by the root user. This password cannot be changed by the user.
CVE-2023-0352 (CVSS score: 9.1) - The Akuvox E11 password recovery webpage can be accessed without authentication, and an attacker could download the device key file. An attacker could then use this page to reset the password back to the default.
CVE-2023-0354 (CVSS score: 9.1) - The Akuvox E11 web server can be accessed without any user authentication, and this could allow an attacker to access sensitive information, as well as create and download packet captures with known default URLs.
A majority of the 13 security issues remain unpatched to date, with the industrial and IoT security company noting that Akuvox has since addressed the FTP server permissions issue by disabling the "the ability to list its content so malicious actors could not enumerate files anymore."
The findings have also prompted the U.S. Cybersecurity and Infrastructure Security Agency (CISA) to release an Industrial Control Systems (ICS) advisory of its own last week.
"Successful exploitation of these vulnerabilities could cause loss of sensitive information, unauthorized access, and grant full administrative control to an attacker," the agency cautioned.
In the absence of patches, organizations using the doorphone are advised to disconnect it from the internet until the vulnerabilities are fixed to mitigate potential remote attacks.
It's also advised to change the default password used to secure the web interface and "segment and isolate the Akuvox device from the rest of the enterprise network" to prevent lateral movement attacks.
The development comes as Wago released patches for several of its programmable logic controllers (PLCs) to address four vulnerabilities (CVE-2022-45137, CVE-2022-45138, CVE-2022-45139, and CVE-2022-45140) two of which could be exploited to achieve full system compromise.
Warning: AI-generated YouTube Video Tutorials Spreading Infostealer Malware
13.3.23 Virus The Hacker News 
Threat actors have been increasingly observed using AI-generated YouTube Videos to spread a variety of stealer malware such as Raccoon, RedLine, and Vidar.
"The videos lure users by pretending to be tutorials on how to download cracked versions of software such as Photoshop, Premiere Pro, Autodesk 3ds Max, AutoCAD, and other products that are licensed products available only to paid users," CloudSEK researcher Pavan Karthick M said.
Just as the ransomware landscape comprises core developers and affiliates who are in charge of identifying potential targets and actually carrying out the attacks, the information stealer ecosystem also consists of threat actors known as traffers who are recruited to spread the malware using different methods.
One of the popular malware distribution channels is YouTube, with CloudSEK witnessing a 200-300% month-over-month increase in videos containing links to stealer malware in the description section.
These links are often obfuscated using URL shorteners like Bitly and Cuttly, or alternatively hosted on MediaFire, Google Drive, Discord, GitHub, and Telegram's Telegra.ph.
In several instances, threat actors leverage data leaks and social engineering to hijack legitimate YouTube accounts and push malware, often targeting popular accounts to reach a large audience in a short span of time.
"Uploading to such accounts lends video legitimacy as well," Karthick explained. "However, such Youtubers will report their account taker to YouTube and gain access back to their accounts within a few hours. But in a few hours, hundreds of users could have fallen prey."
More ominously, anywhere between five to 10 crack download videos are uploaded to the video platform every hour, with the threat actors employing search engine optimization (SEO) poisoning techniques to make the videos appear at the top of the list.
Threat actors have also been observed to add fake comments to the uploaded videos to further mislead and entice users into downloading the cracked software.
The development comes amid a surge in new information stealer variants like SYS01stealer, S1deload, Stealc, Titan, ImBetter, WhiteSnake, and Lumma that are offered for sale and come with capabilities to plunder sensitive data under the guise of popular apps and services.
The findings also follow the discovery of a ready-to-use toolkit called R3NIN Sniffer that can enable threat actors to siphon payment card data from compromised e-commerce websites.
To mitigate risks posed by stealer malware, users are recommended to enable multi-factor authentication, refrain from clicking on unknown links, and avoid downloading or using pirated software.
Fake ChatGPT Chrome Extension Hijacking Facebook Accounts for Malicious Advertising
13.3.23 Hacking The Hacker News 
A fake ChatGPT-branded Chrome browser extension has been found to come with capabilities to hijack Facebook accounts and create rogue admin accounts, highlighting one of the different methods cyber criminals are using to distribute malware.
"By hijacking high-profile Facebook business accounts, the threat actor creates an elite army of Facebook bots and a malicious paid media apparatus," Guardio Labs researcher Nati Tal said in a technical report.
"This allows it to push Facebook paid ads at the expense of its victims in a self-propagating worm-like manner."
The "Quick access to Chat GPT" extension, which is said to have attracted 2,000 installations per day since March 3, 2023, has since been pulled by Google from the Chrome Web Store as of March 9, 2023.
The browser add-on is promoted through Facebook-sponsored posts, and while it offers the ability to connect to the ChatGPT service, it's also engineered to surreptitiously harvest cookies and Facebook account data using an already active, authenticated session.
This is achieved by making use of two bogus Facebook applications – portal and msg_kig – to maintain backdoor access and obtain full control of the target profiles. The process of adding the apps to the Facebook accounts is fully automated.
The hijacked Facebook business accounts are then used to advertise the malware, thereby effectively expanding its army of Facebook bots.

The development comes as threat actors are capitalizing on the massive popularity of OpenAI's ChatGPT since its release late last year to create fake versions of the artificial intelligence chatbot and trick unsuspecting users into installing them.
Last month, Cyble revealed a social engineering campaign that relied on an unofficial ChatGPT social media page to direct users to malicious domains that download information stealers, such as RedLine, Lumma, and Aurora.
Also spotted are fake ChatGPT apps distributed via the Google Play Store and other third-party Android app stores to push SpyNote malware onto people's devices.
"Unfortunately, the success of the viral AI tool has also attracted the attention of fraudsters who use the technology to conduct highly sophisticated investment scams against unwary internet users," Bitdefender disclosed last week.
CASPER attack steals data using air-gapped computer's internal speaker
12.3.23 Attack Bleepingcomputer
Researchers at the School of Cyber Security at Korea University, Seoul, have presented a new covert channel attack named CASPER can leak data from air-gapped computers to a nearby smartphone at a rate of 20bits/sec.
The CASPER attack leverages the internal speakers inside the target computer as the data transmission channel to transmit high-frequency audio that the human ear cannot hear and convey binary or Morse code to a microphone up to 1.5m away.
The receiving microphone can be in a smartphone recording sound inside the attacker's pocket or a laptop in the same room.
Researchers have previously developed similar attacks leveraging external speakers. However, air-gapped, network-isolated systems used in critical environments, such as government networks, energy infrastructure, and weapon control systems, are unlikely to have external speakers.
On the other hand, internal speakers that provide audio feedback, such as boot-up beeps, are still considered necessary, so they're commonly present, making them better candidates.
Infecting the target
As is the case with almost all secret channel attacks targeting network-isolated computers, a rogue employee or a stealthy intruder with physical access to the target must first infect it with malware.
Although this scenario may seem impractical or even far-fetched, there have been multiple instances of such attacks being successfully carried out in the past, with notable examples including the Stuxnet worm, which targeted Iran's uranium enrichment facility at Natanz, the Agent.BTZ malware that infected a U.S. military base, and the Remsec modular backdoor, which secretly collected information from air-gapped government networks for over five years.
The malware can autonomously enumerate the target's filesystem, locate files or file types that match a hardcoded list and attempt to exfiltrate them.
More realistically, it can perform keylogging, which is more suitable for such a slow data transmission rate.
The malware will encode the data to be exfiltrated from the target in binary or Morse code and transmit it through the internal speaker using frequency modulation, achieving an imperceptible ultrasound in a range between 17 kHz and 20 kHz.

CASPER attack diagram (Korea University)
The results
The researchers experimented with the described model using a Linux-based (Ubuntu 20.04) computer as the target, and a Samsung Galaxy Z Flip 3 as the receiver, running a basic recorder application with a sampling frequency of up to 20 kHz.
In the Morse code experiment, the researchers set the length per bit to 100 ms and used 18 kHz for dots and 19 kHz for the dash. The smartphone was located 50cm away and was able to decode the sent word "covert."
In the binary data experiment, the length per bit was set to 50 ms, transferring zeros at a frequency of 18 kHz and 1s at 19 kHz. A 50 ms start/end bit was also used at 17 kHz to indicate the beginning of a new message.
Data transmitted through generated sound frequencies (Korea University)
Based on the conducted tests, the maximum distance of the receiver is 1.5 meters (4.9 ft), using a length per bit of 100 ms.
The overall results of the experiment, however, show that the length per bit affects the bit error rate, and a maximum reliable transmitting bit rate of 20 bits/s is achievable when the length per bit is 50 ms.

Bit error rate calculations (Korea University)
At this data transfer rate, the malware could transmit a typical 8-character length password in about 3 seconds and a 2048-bit RSA key in 100 seconds.
Anything above that, like a small 10 KB file, for example, would need over an hour to exfiltrate from the air-gapped system, even if the conditions are ideal and no interruptions occur during the transmission.
"Our method is slower in transferring data compared to other covert channel technologies using optical methods or electromagnetic methods because the speed of data transfer by sound is limited." - Korea University.
A solution to the slow data rate would be to vary the frequency band for multiple simultaneous transmissions; however, internal speakers can only produce sound in a single frequency band, so the attack is practically limited.
The researchers shared ways to defend against the CASPER attack, with the simplest being to remove the internal speaker from mission-critical computers.
If that's impossible, defenders could implement a high-pass filter to keep all generated frequencies within the audible sound spectrum, blocking ultrasound transmissions.
If you're interested in other covert channel attacks against air-gapped systems, check out COVID-bit, which uses the PSU to generate electromagnetic waves that carry data.
Other examples of similar attacks are ETHERLED, which relies on the LED lights of the target's network card to transmit Morse code signals, and one named SATAn, which uses SATA cables as wireless antennas.
Clop ransomware gang begins extorting GoAnywhere zero-day victims
12.3.23 Ransomware Bleepingcomputer
The Clop ransomware gang has begun extorting companies whose data was stolen using a zero-day vulnerability in the Fortra GoAnywhere MFT secure file-sharing solution.
In February, the GoAnywhere MFT file transfer solution developers warned customers that a zero-day remote code execution vulnerability was being exploited on exposed administrative consoles.
GoAnywhere is a secure web file transfer solution that allows companies to securely transfer encrypted files with their partners while keeping detailed audit logs of who accessed the files.
While no details were publicly shared on how the vulnerability was exploited, a proof-of-concept exploit was soon released, followed by a patch for the flaw.
The day after the release of the GoAnywhere patch, the Clop ransomware gang contacted BleepingComputer and said they were responsible for the attacks.
The extortion group said they used the flaw over ten days to steal data from 130 companies. At the time, BleepingComputer could not independently confirm these claims, and Fortra did not respond to our emails.
Since then, two companies, Community Health Systems (CHS) and Hatch Bank, disclosed that data was stolen in the GoAnywhere MFT attacks.
Clop begins extorting GoAnywhere customers
Last night, the Clop ransomware gang began publicly exploiting victims of the GoAnywhere attacks by adding seven new companies to their data leak site.
Only one of the victims, Hatch Bank, is publicly known to have been breached using the vulnerability. However, BleepingComputer has learned that at least two other listed companies had their data stolen using this flaw as well.
The entries on the data leak site all state that the release of data is "coming soon" but include screenshots of allegedly stolen data.
Hatch Bank listed on Clop's data leak site
Source: BleepingComputer
Furthermore, BleepingComputer has been told that victims have begun to receive ransom demands from the ransomware gang.
While it is unclear how much the threat actors are demanding, they had previously demanded $10 million in ransoms in similar attacks using an Accellion FTA zero-day vulnerability in December 2020.
During these attacks, the extortion group stole large amounts of data from nearly 100 companies worldwide, with the threat actors slowly leaking data from companies while demanding million-dollar ransoms.
Organizations that had their Accellion servers hacked include, among others, energy giant Shell, cybersecurity firm Qualys, supermarket giant Kroger, and multiple universities worldwide such as Stanford Medicine, University of Colorado, University of Miami, University of California, and the University of Maryland Baltimore (UMB).
CISA warns of actively exploited Plex bug after LastPass breach
12.3.23 Exploit Bleepingcomputer
CISA has added an almost three-year-old high-severity remote code execution (RCE) vulnerability in the Plex Media Server to its catalog of security flaws exploited in attacks.
Tracked as CVE-2020-5741, this security flaw allows threat actors with admin privileges to execute arbitrary Python code remotely in low-complexity attacks that don't require user interaction.
Attackers with "admin access to a Plex Media Server could abuse the Camera Upload feature to make the server execute malicious code," according to an advisory published by the Plex Security Team in May 2020 when it patched the bug with the release of Plex Media Server 1.19.3.
"This could be done by setting the server data directory to overlap with the content location for a library on which Camera Upload was enabled. This issue could not be exploited without first gaining access to the server's Plex account."
While CISA didn't provide any info on the attacks where the CVE-2020-5741 was exploited, this is likely linked to LastPass recently disclosing that a senior DevOps engineer's computer was hacked last year to install a keylogger by abusing a third-party media software RCE bug.
The attackers eventually gained access to the engineer's credentials and LastPass corporate vault. This led to a massive August 2022 data breach after the threat actors exfiltrated LastPass production backups and critical database backups.
Plex RCE reportedly used to hack LastPass engineer
Even though LastPass didn't disclose what software flaw was exploited to hack into the engineer's computer, Ars Technica reported that the software package exploited on the employee's home computer was Plex.
Coincidentally, in August, Plex also notified customers of a data breach and asked them to reset their passwords after LastPass disclosed a second breach of its own.
On Friday, CISA also added a critical severity vulnerability in VMware's Cloud Foundation (tracked as CVE-2021-39144), exploited in the wild since early December, to its Known Exploited Vulnerabilities (KEV) catalog.
According to a November 2021 binding operational directive (BOD 22-01), the U.S. federal agencies are now also required to secure their systems against attacks until March 31st to block attack attempts that might target their networks by exploiting the two flaws.
Although the BOD 22-01 only applies to federal agencies, CISA strongly urged all organizations to patch these bugs to defend against ongoing attacks.
Brazil seizing Flipper Zero shipments to prevent use in crime
12.3.23 Crime Bleepingcomputer 
The Brazilian National Telecommunications Agency is seizing incoming Flipper Zero purchases due to its alleged use in criminal activity, with purchasers stating that the government agency has rejected all attempts to certify the equipment.
Flipper Zero is a portable multi-function cybersecurity tool that allows pentesters and hacking enthusiasts to tinker with a wide range of hardware by supporting RFID emulation, digital access key cloning, radio communications, NFC, infrared, Bluetooth, and more.
Since it was released, security researchers have demonstrated Flipper Zero's features on social media, showing how it can trigger doorbells, perform replay attacks to open garage doors and unlock cars, and be used as a digital key.
Brazil requiring certification
Multiple people in Brazil who purchased the Flipper Zero hacking tool have reported that their shipments are being redirected to Brazil's telecommunications agency, Anatel, due to a lack of certification with the country's Radio Frequencies department.
This type of seizure is usually associated with compliance with the country's electronic and telecommunications standards for devices emitting radio signals.
Because Flipper Devices INC is not certified in Brazil according to this standard, it's not allowed to circulate freely in the Brazilian market.
Flipper Zero shippment seized by Anatel
Source: Reddit
However, as the Electronic Frontier Foundation (EFF) explains in a recent report and from emails seen by BleepingComputer, the Anatel agency has flagged the device as a tool used for criminal purposes, making its clearance complicated and preventing it from reaching its final destination.
Flipper Zero has gained a reputation from users who showcased its hacking capabilities on social media to perform illegal activities such as unlocking cars, changing gas pump prices, intercepting and storing remote control signals, opening garage doors, and more.
Although the device does not use hardware that is illegal or impossible to find elsewhere, its market success fueled a wave of negative media attention that portrayed it as a risk to society.
The unexpected interceptions of the $169 portable multi-functional tool created for pen-testers and hacking enthusiasts began at the start of the year and are still ensuing.
Buyers from Brazil have been exchanging advice on Reddit in the past couple of months, trying to get their items cleared by Anatel.
A user has posted analytical instructions on applying to Anatel for a personal homologation certificate for Flipper Zero, which should make it usable by the buyer, albeit preventing resells to others in Brazil.
However, many buyers report that the agency has rejected this certification procedure because Flipper Zero is allegedly being used to facilitate crime.
"Anatel's certification area informs that the equipment called FLIPPER ZERO has been used in the country by malicious users in facilitating a crime or criminal misdemeanor and, as provided for in item II of Art. 60 of the Regulation for Conformity Assessment and Homologation of Telecommunications Products (annex to Resolution No. 715, of October 23, 2019), Anatel has rejected all homologation requests for the product in question, in order to collaborate in the protection of Brazilian citizens against criminal actions," reads a letter received by Flipper Zero customers in Brazil.
Anatel concludes the message by saying that the item will be sent back to the post office with the suggestion to return it to the sender.

Anatel rejecting a certification request
(HiroshiSakamoto1)
EFF argues that the Brazilian authorities outright banning Flipper Zero in the country will limit the security researchers' access to powerful portable cybersecurity tools, harming their work and negatively impacting the field.
"The Flipper Zero has clear uses: penetration testing to facilitate hardening of a home network or organizational infrastructure, hardware research, security research, protocol development, use by radio hobbyists, and many more," argues EFF.
"The creation, possession or distribution of tools related to security research should not be criminalized or otherwise restricted."
Those who purchased the devices from Joomf and have had their Flipper Zero seized have been told they would be reimbursed.
BleepingComputer has requested comment on the above from Anatel and FlipperZero, but we have not heard back by publication time.