
Threat actors from the Democratic People's Republic of Korea (DPRK) are increasingly targeting the cryptocurrency sector as a major revenue generation mechanism since at least 2017 to get around sanctions imposed against the country.
ARTICLES November 2023
H MARCH(103) APRIL(113) MAY(110) JUNE(93) July(113) November(58) December(100) VIRUS BULLETIN 2023
North Korea's Lazarus Group Rakes in $3 Billion from Cryptocurrency Hacks
30.11.23 Cryptocurrency The Hacker News

Threat actors from the Democratic People's Republic of Korea (DPRK) are increasingly targeting the cryptocurrency sector as a major revenue generation mechanism since at least 2017 to get around sanctions imposed against the country.
"Even though movement in and out of and within the country is heavily restricted, and its general population is isolated from the rest of the world, the regime's ruling elite and its highly trained cadre of computer science professionals have privileged access to new technologies and information," cybersecurity firm Recorded Future said in a report shared with The Hacker News.
"The privileged access to resources, technologies, information, and sometimes international travel for a small set of selected individuals with promise in mathematics and computer science equips them with the necessary skills for conducting cyber attacks against the cryptocurrency industry."
The disclosure comes as the U.S. Treasury Department imposed sanctions against Sinbad, a virtual currency mixer that has been put to use by the North Korea-linked Lazarus Group to launder ill-gotten proceeds.
The threat actors from the country are estimated to have stolen $3 billion worth of crypto assets over the past six years, with about $1.7 billion plundered in 2022 alone. A majority of these stolen assets are used to directly fund the hermit kingdom's weapons of mass destruction (WMD) and ballistic missile programs.
"$1.1 billion of that total was stolen in hacks of DeFi protocols, making North Korea one of the driving forces behind the DeFi hacking trend that intensified in 2022," Chainalysis noted earlier this February.
A report published by the U.S. Department of Homeland Security (DHS) as part of its Analytic Exchange Program (AEP) earlier this September also highlighted the Lazarus Group's exploitation of DeFi protocols.

"DeFi exchange platforms allow users to transition between cryptocurrencies without the platform ever taking custody of the customer's funds in order to facilitate the transition," the report said. "This allows DPRK cyber actors to determine exactly when to transition stolen cryptocurrency from one type of cryptocurrency to another, enabling attribution to be more difficult to determine or even trace."
The cryptocurrency sector is among the top targets for state-sponsored North Korean cyber threat actors, as repeatedly evidenced by the myriad campaigns carried out in recent months.
DPRK hackers are known for adeptly pulling off social engineering tricks to target employees of online cryptocurrency exchanges and then lure their victims with the promise of lucrative jobs to distribute malware that grants remote access to the company's network, ultimately allowing them to drain all available assets and move them to various DPRK controlled wallets.
Other campaigns have employed similar phishing tactics to entice users into downloading trojanized cryptocurrency apps to steal their assets as well as watering hole attacks (aka strategic web compromises) as an initial access vector, alongside engaging in airdrop scams and rug pulls.
Another notable tactic adopted by the group is use of mixing services to conceal the financial trail and cloud attribution efforts. Such services are typically offered on cryptocurrency exchange platforms that do not employ know your customer (KYC) policies or anti-money laundering (AML) regulations.
"Absent stronger regulations, cybersecurity requirements, and investments in cybersecurity for cryptocurrency firms, we assess that in the near term, North Korea will almost certainly continue to target the cryptocurrency industry due to its past success in mining it as a source of additional revenue to support the regime," Recorded Future concluded.
CACTUS Ransomware Exploits Qlik Sense Vulnerabilities in Targeted Attacks
30.11.23 Ransom The Hacker News
A CACTUS ransomware campaign has been observed exploiting recently disclosed security flaws in a cloud analytics and business intelligence platform called Qlik Sense to obtain a foothold into targeted environments.
"This campaign marks the first documented instance [...] where threat actors deploying CACTUS ransomware have exploited vulnerabilities in Qlik Sense for initial access," Arctic Wolf researchers Stefan Hostetler, Markus Neis, and Kyle Pagelow said.
The cybersecurity company, which said it's responding to "several instances" of exploitation of the software, noted that the attacks are likely taking advantage of three flaws that have been disclosed over the past three months -
CVE-2023-41265 (CVSS score: 9.9) - An HTTP Request Tunneling vulnerability that allows a remote attacker to elevate their privilege and send requests that get executed by the backend server hosting the repository application.
CVE-2023-41266 (CVSS score: 6.5) - A path traversal vulnerability that allows an unauthenticated remote attacker to transmit HTTP requests to unauthorized endpoints.
CVE-2023-48365 (CVSS score: 9.9) - An unauthenticated remote code execution vulnerability arising due to improper validation of HTTP headers, allowing a remote attacker to elevate their privilege by tunneling HTTP requests.
It's worth noting that CVE-2023-48365 is the result of an incomplete patch for CVE-2023-41265, which along with CVE-2023-41266, was disclosed by Praetorian in late August 2023. A fix for CVE-2023-48365 was shipped on November 20, 2023.
In the attacks observed by Arctic Wolf, a successful exploitation of the flaws is followed by the abuse of the Qlik Sense Scheduler service to spawn processes that are designed to download additional tools with the goal of establishing persistence and setting up remote control.
This includes ManageEngine Unified Endpoint Management and Security (UEMS), AnyDesk, and Plink. The threat actors have also been observed uninstalling Sophos software, changing the administrator account password, and creating an RDP tunnel via Plink.
The attack chains culminate in the deployment of CACTUS ransomware, with the attackers also using rclone for data exfiltration.
The Ever-Evolving Ransomware Landscape#
The disclosure comes as the ransomware threat landscape has become more sophisticated, and the underground economy has evolved to facilitate attacks at scale via a network of initial access brokers and botnet owners who resell access to victim systems to several affiliate actors.
According to data compiled by industrial cybersecurity firm Dragos, the number of ransomware attacks impacting industrial organizations declined from 253 in the second quarter of 2023 to 231 in the third quarter. In contrast, 318 ransomware attacks were reported across all sectors for the month of October 2023 alone.
Despite ongoing efforts by governments across the world to tackle ransomware, the ransomware-as-a-service (RaaS) business model has continued to be an enduring and lucrative pathway to extort money from targets.
Black Basta, a prolific ransomware group that came onto the scene in April 2022, is estimated to have raked in illegal profits to the tune of at least $107 million in Bitcoin ransom payments from more than 90 victims, per new joint research released by Elliptic and Corvus Insurance.
A majority of these proceeds were laundered through Garantex, a Russian cryptocurrency exchange that was sanctioned by the U.S. government in April 2022 for facilitating transactions with the Hydra darknet marketplace.
What's more, the analysis uncovered evidence tying Black Basta to the now-defunct Russian cybercrime group Conti, which discontinued around the same time the former emerged, as well as QakBot, which was used to deploy the ransomware.
"Approximately 10% of the ransom amount was forwarded on to Qakbot, in cases where they were involved in providing access to the victim," Elliptic noted, adding it "traced Bitcoin worth several million dollars from Conti-linked wallets to those associated with the Black Basta operator."
U.S. Treasury Sanctions Sinbad Cryptocurrency Mixer Used by North Korean Hackers
30.11.23 Cryptocurrency The Hacker News

The U.S. Treasury Department on Wednesday imposed sanctions against Sinbad, a virtual currency mixer that has been put to use by the North Korea-linked Lazarus Group to launder ill-gotten proceeds.
"Sinbad has processed millions of dollars' worth of virtual currency from Lazarus Group heists, including the Horizon Bridge and Axie Infinity heists," the department said.
"Sinbad is also used by cybercriminals to obfuscate transactions linked to malign activities such as sanctions evasion, drug trafficking, the purchase of child sexual abuse materials, and additional illicit sales on darknet marketplaces."
The development builds on prior actions undertaken by governments in Europe and the U.S. to blockade mixers such as Blender, Tornado Cash, and ChipMixer, all of which have been accused of providing "material support" to the hacking crew by laundering the stolen assets through their services.
Sinbad, created by an individual who goes by the alias "Mehdi" in September 2022, told WIRED earlier this February that it was a legitimate privacy-preserving initiative and that it was launched as a response to the "growing centralization of cryptocurrency and the erosion of the privacy promises it once appeared to offer."
It also emerged as a replacement for Blender, with the Lazarus Group using it to launder virtual currency plundered following the hacks of Atomic Wallet and Harmony Horizon Bridge.
"Overall, more than one third of funds sent to Sinbad during its lifetime have come from crypto hacks," Chainalysis said. "Following the takedown of Tornado Cash and Blender.io last year, Sinbad emerged as the mixer of choice for DPRK-based hacking activities."
Sinbad has also been used by ransomware actors, darknet markets, and scammers, leveraging it to facilitate illicit transactions by obfuscating their origin, destination, and counterparties.
Blockchain analytics firm Elliptic said there is evidence to suggest that the same individual or group is highly likely behind both Sinbad and Blender based on an examination of on-chain patterns, the way in which the two mixers operate, similarities in their websites, and their connections to Russia.
"Analysis of blockchain transactions shows that, before it was publicly launched, a 'service' address on the Sinbad website received Bitcoin from a wallet believed to be controlled by the operator of Blender – presumably in order to test the service," the company noted.
"A Bitcoin wallet used to pay individuals who promoted Sinbad, itself received Bitcoin from the suspected Blender operator wallet. Almost all of the early incoming transactions to Sinbad originated from the suspected Blender operator wallet."
The development comes as Vitalii Chychasov, a 37-year-old administrator of the now-dismantled online marketplace named SSNDOB, was sentenced to eight years in federal prison in the U.S. for selling personal information, including the names, dates of birth, and Social Security numbers.
Chychasov, an Ukrainian national, was arrested in March 2022 while attempting to enter Hungary. He was subsequently extradited to the U.S. in July 2022. SSNDOB was taken down in a joint operation led by the U.S., Cyprus, and Latvia in June 2022.
Iranian Hackers Exploit PLCs in Attack on Water Authority in U.S.
29.11.23 Exploit The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) revealed that it's responding to a cyber attack that involved the active exploitation of Unitronics programmable logic controllers (PLCs) to target the Municipal Water Authority of Aliquippa in western Pennsylvania.
The attack has been attributed to an Iranian-backed hacktivist collective known as Cyber Av3ngers.
"Cyber threat actors are targeting PLCs associated with [Water and Wastewater Systems] facilities, including an identified Unitronics PLC, at a U.S. water facility," the agency said.
"In response, the affected municipality's water authority immediately took the system offline and switched to manual operations—there is no known risk to the municipality's drinking water or water supply."
According to news reports quoted by the Water Information Sharing & Analysis Center (WaterISAC), CyberAv3ngers is alleged to have seized control of the booster station that monitors and regulates pressure for Raccoon and Potter Townships.
With PLCs being used in the WWS sector to monitor various stages and processes of water and wastewater treatment, disruptive attacks attempting to compromise the integrity of such critical processes can have adverse impacts, preventing WWS facilities from providing access to clean, potable water.
To mitigate such attacks, CISA is recommending that organizations change the Unitronics PLC default password, enforce multi-factor authentication (MFA), disconnect the PLC from the internet, back up the logic and configurations on any Unitronics PLCs to enable fast recovery, and apply latest updates.
Cyber Av3ngers has a history of targeting the critical infrastructure sector, claiming to have infiltrated as many as 10 water treatment stations in Israel. Last month, the group also claimed responsibility for a major cyber assault on Orpak Systems, a prominent provider of gas station solutions in the country.
"Every Equipment 'Made In Israel' Is Cyber Av3ngers Legal Target," the group claimed in a message posted on its Telegram channel on November 26, 2023.
200+ Malicious Android Apps Targeting Iranian Banks: Experts Warn
29.11.23 OS The Hacker News
An Android malware campaign targeting Iranian banks has expanded its capabilities and incorporated additional evasion tactics to fly under the radar.
That's according to a new report from Zimperium, which discovered more than 200 malicious apps associated with the malicious operation, with the threat actor also observed carrying out phishing attacks against the targeted financial institutions.
The campaign first came to light in late July 2023 when Sophos detailed a cluster of 40 credential-harvesting apps targeting customers of Bank Mellat, Bank Saderat, Resalat Bank, and Central Bank of Iran.
The primary goal of the bogus apps is to trick victims into granting them extensive permissions as well as harvest banking login credentials and credit card details by abusing Android's accessibility services.
"The corresponding legitimate versions of the malicious apps are available at Cafe Bazaar, an Iranian Android marketplace, and have millions of downloads," Sophos researcher Pankaj Kohli said at the time.
"The malicious imitations, on the other hand, were available to download from a large number of relatively new domains, some of which the threat actors also employed as C2 servers."
Interestingly, some of these domains have also been observed to serve HTML phishing pages designed to steal credentials from mobile users.
The latest findings from Zimperium illustrate continued evolution of the threat, not only in terms of a broader set of targeted banks and cryptocurrency wallet apps, but also incorporating previously undocumented features that make it more potent.
This includes the use of the accessibility service to grant it additional permissions to intercept SMS messages, prevent uninstallation, and click on user interface elements.
Some variants of the malware have also been found to access a README file within GitHub repositories to extract a Base64-encoded version of the command-and-control (C2) server and phishing URLs.
"This allows attackers to quickly respond to phishing sites being taken down by updating the GitHub repository, ensuring that malicious apps are always getting the latest active phishing site," Zimperium researchers Aazim Yaswant and Vishnu Pratapagiri said.
Another noteworthy tactic is the use of intermediate C2 servers to host text files that contain the encoded strings pointing to the phishing sites.
While the campaign has so far trained its eyes on Android, there is evidence that Apple's iOS operating system is also a potential target based on the fact that the phishing sites verify if the page is opened by an iOS device, and if so, direct the victim to a website mimicking the iOS version of the Bank Saderat Iran app.
It's currently not clear if the iOS campaign is under development stages, or if the apps are distributed through an, as of yet, unidentified source.
The phishing campaigns are no less sophisticated, impersonating the actual websites to exfiltrate credentials, account numbers, device models, and IP addresses to two actor-controlled Telegram channels.
"It is evident that modern malware is becoming more sophisticated, and targets are expanding, so runtime visibility and protection are crucial for mobile applications," the researchers said.
The development comes a little over a month after Fingerprint demonstrated a method by which malicious Android apps can stealthily access and copy clipboard data by leveraging the SYSTEM_ALERT_WINDOW permission to obscure the toast notification that's displayed when a particular app is reading clipboard data.
"It's possible to overdraw a toast either with a different toast or with any other view, completely hiding the original toast can prevent the user from being notified of clipboard actions," Fingerprint said. "Any application with the SYSTEM_ALERT_WINDOW permission can read clipboard data without notifying the user."
Okta Discloses Broader Impact Linked to October 2023 Support System Breach
29.11.23 Incindent The Hacker News
Identity services provider Okta has disclosed that it detected "additional threat actor activity" in connection with the October 2023 breach of its support case management system.
"The threat actor downloaded the names and email addresses of all Okta customer support system users," the company said in a statement shared with The Hacker News.
"All Okta Workforce Identity Cloud (WIC) and Customer Identity Solution (CIS) customers are impacted except customers in our FedRamp High and DoD IL4 environments (these environments use a separate support system NOT accessed by the threat actor). The Auth0/CIC support case management system was not impacted by this incident."
News of the expanded scope of the breach was first reported by Bloomberg.
The company also told the publication that while it does not have any evidence of the stolen information being actively misused, it has taken the step of notifying all customers of potential phishing and social engineering risks.
It also stated that it "pushed new security features to our platforms and provided customers with specific recommendations to defend against potential targeted attacks against their Okta administrators."
Okta, which has enlisted the help of a digital forensics firm to support its investigation, further said it "will also notify individuals that have had their information downloaded."
The development comes more than three weeks after the identity and authentication management provider said the breach, which took place between September 28 to October 17, 2023, affected 1% – i.e., 134 – of its 18,400 customers.
The identity of the threat actors behind the attack against Okta's systems is currently not known, although a notorious cybercrime group called Scattered Spider has targeted the company as recently as August 2023 to obtain elevated administrator permissions by pulling off sophisticated social engineering attacks.
According to a report published by ReliaQuest last week, Scattered Spider infiltrated an unnamed company and gained access to an IT administrator's account via Okta single sign-on (SSO), followed by laterally moving from the identity-as-a-service (IDaaS) provider to their on-premises assets in less than one hour.
The formidable and nimble adversary, in recent months, has also evolved into an affiliate for the BlackCat ransomware operation, infiltrating cloud and on-premises environments to deploy file-encrypting malware for generating illicit profits.
"The group's ongoing activity is a testament to the capabilities of a highly skilled threat actor or group having an intricate understanding of cloud and on-premises environments, enabling them to navigate with sophistication," ReliaQuest researcher James Xiang said.
DJVU Ransomware's Latest Variant 'Xaro' Disguised as Cracked Software
29.11.23 Ransom The Hacker News
A variant of a ransomware strain known as DJVU has been observed to be distributed in the form of cracked software.
"While this attack pattern is not new, incidents involving a DJVU variant that appends the .xaro extension to affected files and demanding ransom for a decryptor have been observed infecting systems alongside a host of various commodity loaders and infostealers," Cybereason security researcher Ralph Villanueva said.
The new variant has been codenamed Xaro by the American cybersecurity firm.
DJVU, in itself a variant of the STOP ransomware, typically arrives on the scene masquerading as legitimate services or applications. It's also delivered as a payload of SmokeLoader.
A significant aspect of DJVU attacks is the deployment of additional malware, such as information stealers (e.g., RedLine Stealer and Vidar), making them more damaging in nature.
In the latest attack chain documented by Cybereason, Xaro is propagated as an archive file from a dubious source that masquerades as a site offering legitimate freeware.
Opening the archive file leads to the execution of a supposed installer binary for a PDF writing software called CutePDF that, in reality, is a pay-per-install malware downloader service known as PrivateLoader.
PrivateLoader, for its part, establishes contact with a command-and-control (C2) server to fetch a wide range of stealer and loader malware families like RedLine Stealer, Vidar, Lumma Stealer, Amadey, SmokeLoader, Nymaim, GCleaner, XMRig, and Fabookie, in addition to dropping Xaro.
"This shotgun-approach to the download and execution of commodity malware is commonly observed in PrivateLoader infections originating from suspicious freeware or cracked software sites," Villanueva explained.
The goal appears to be to gather and exfiltrate sensitive information for double extortion as well as ensure the success of the attack even if one of the payloads gets blocked by security software.
Xaro, besides spawning an instance of the Vidar infostealer, is capable of encrypting files in the infected host, before dropping a ransom note, urging the victim to get in touch with the threat actor to pay $980 for the private key and the decryptor tool, a price that drops by 50% to $490 if approached within 72 hours.
If anything, the activity illustrates the risks involved with downloading freeware from untrusted sources. Last month, Sucuri detailed another campaign called FakeUpdateRU wherein visitors to compromised websites are served bogus browser update notices to deliver RedLine Stealer.
"Threat actors are known to favor freeware masquerading as a way to covertly deploy malicious code," Villanueva said. "The speed and breadth of impact on infected machines should be carefully understood by enterprise networks looking to defend themselves and their data."
GoTitan Botnet Spotted Exploiting Recent Apache ActiveMQ Vulnerability
29.11.23 BotNet The Hacker News
The recently disclosed critical security flaw impacting Apache ActiveMQ is being actively exploited by threat actors to distribute a new Go-based botnet called GoTitan as well as a .NET program known as PrCtrl Rat that's capable of remotely commandeering the infected hosts.
The attacks involve the exploitation of a remote code execution bug (CVE-2023-46604, CVSS score: 10.0) that has been weaponized by various hacking crews, including the Lazarus Group, in recent weeks.
Following a successful breach, the threat actors have been observed to drop next-stage payloads from a remote server, one of which is GoTitan, a botnet designed for orchestrating distributed denial-of-service (DDoS) attacks via protocols such as HTTP, UDP, TCP, and TLS.
"The attacker only provides binaries for x64 architectures, and the malware performs some checks before running," Fortinet Fortiguard Labs researcher Cara Lin said in a Tuesday analysis.
"It also creates a file named 'c.log' that records the execution time and program status. This file seems to be a debug log for the developer, which suggests that GoTitan is still in an early stage of development."

Fortinet said it also observed instances where the susceptible Apache ActiveMQ servers are being targeted to deploy another DDoS botnet called Ddostf, Kinsing malware for cryptojacking, and a command-and-control (C2) framework named Sliver.
Another notable malware delivered is a remote access trojan dubbed PrCtrl Rat that establishes contact with a C2 server to receive additional commands for execution on the system, harvest files, and download and upload files from and to the server.
"As of this writing, we have yet to receive any messages from the server, and the motive behind disseminating this tool remains unclear," Lin said. "However, once it infiltrates a user's environment, the remote server gains control over the system."
Zero-Day Alert: Google Chrome Under Active Attack, Exploiting New Vulnerability
29.11.23 Vulnerebility The Hacker News
Google has rolled out security updates to fix seven security issues in its Chrome browser, including a zero-day that has come under active exploitation in the wild.
Tracked as CVE-2023-6345, the high-severity vulnerability has been described as an integer overflow bug in Skia, an open source 2D graphics library.
Benoît Sevens and Clément Lecigne of Google's Threat Analysis Group (TAG) have been credited with discovering and reporting the flaw on November 24, 2023.
As is typically the case, the search giant acknowledged that "an exploit for CVE-2023-6345 exists in the wild," but stopped short of sharing additional information surrounding the nature of attacks and the threat actors that may be weaponizing it in real-world attacks.
It's worth noting that Google released patches for a similar integer overflow flaw in the same component (CVE-2023-2136) in April 2023 that had also come under active exploitation as a zero-day, raising the possibility that CVE-2023-6345 could be a patch bypass for the former.
CVE-2023-2136 is said to have "allowed a remote attacker who had compromised the renderer process to potentially perform a sandbox escape via a crafted HTML page."
With the latest update, the tech giant has addressed a total of six zero-days in Chrome since the start of the year -
CVE-2023-2033 (CVSS score: 8.8) - Type confusion in V8
CVE-2023-2136 (CVSS score: 9.6) - Integer overflow in Skia
CVE-2023-3079 (CVSS score: 8.8) - Type confusion in V8
CVE-2023-4863 (CVSS score: 8.8) - Heap buffer overflow in WebP
CVE-2023-5217 (CVSS score: 8.8) - Heap buffer overflow in vp8 encoding in libvpx
Users are recommended to upgrade to Chrome version 119.0.6045.199/.200 for Windows and 119.0.6045.199 for macOS and Linux to mitigate potential threats. Users of Chromium-based browsers such as Microsoft Edge, Brave, Opera, and Vivaldi are also advised to apply the fixes as and when they become available.
Design Flaw in Google Workspace Could Let Attackers Gain Unauthorized Access
29.11.23 Vulnerebility The Hacker News
Cybersecurity researchers have detailed a "severe design flaw" in Google Workspace's domain-wide delegation (DWD) feature that could be exploited by threat actors to facilitate privilege escalation and obtain unauthorized access to Workspace APIs without super admin privileges.
"Such exploitation could result in theft of emails from Gmail, data exfiltration from Google Drive, or other unauthorized actions within Google Workspace APIs on all of the identities in the target domain," cybersecurity firm Hunters said in a technical report shared with The Hacker News.
The design weakness – which remains active to this date – has been codenamed DeleFriend for its ability to manipulate existing delegations in the Google Cloud Platform (GCP) and Google Workspace without possessing super admin privileges.
When reached for comment, Google disputed the characterization of the issue as a design flaw. “This report does not identify an underlying security issue in our products,” it said. “As a best practice, we encourage users to make sure all accounts have the least amount of privilege possible (see guidance here). Doing so is key to combating these types of attacks.”
Domain-wide delegation, per Google, is a "powerful feature" that allows third-party and internal apps to access users' data across an organization's Google Workspace environment.
The vulnerability is rooted in the fact that a domain delegation configuration is determined by the service account resource identifier (OAuth ID), and not the specific private keys associated with the service account identity object.
As a result, potential threat actors with less privileged access to a target GCP project could "create numerous JSON web tokens (JWTs) composed of different OAuth scopes, aiming to pinpoint successful combinations of private key pairs and authorized OAuth scopes which indicate that the service account has domain-wide delegation enabled."

To put it differently, an IAM identity that has access to create new private keys to a relevant GCP service account resource that has existing domain-wide delegation permission can be leveraged to create a fresh private key, which can be used to perform API calls to Google Workspace on behalf of other identities in the domain.
Successful exploitation of the flaw could allow exfiltration of sensitive data from Google services like Gmail, Drive, Calendar, and others. Hunters has also made available a proof-of-concept (PoC) that can be utilized to detect DWD misconfigurations.
"The potential consequences of malicious actors misusing domain-wide delegation are severe," Hunters security researcher Yonatan Khanashvili said. "Instead of affecting just a single identity, as with individual OAuth consent, exploiting DWD with existing delegation can impact every identity within the Workspace domain.
Key Cybercriminals Behind Notorious Ransomware Families Arrested in Ukraine
28.11.23 Ransom The Hacker News
A coordinated law enforcement operation has led to the arrest of key individuals in Ukraine who are alleged to be a part of several ransomware schemes.
"On 21 November, 30 properties were searched in the regions of Kyiv, Cherkasy, Rivne, and Vinnytsia, resulting in the arrest of the 32-year-old ringleader," Europol said in a statement today. "Four of the ringleader's most active accomplices were also detained."
The development comes more than two years after 12 people were apprehended in connection with the same operation. The individuals are primarily linked to LockerGoga, MegaCortex, and Dharma ransomware families.
The suspects are estimated to have targeted over 1,800 victims across 71 countries since 2019. They have also been accused of deploying the now-defunct Hive ransomware against high-profile organizations.
Some of the co-conspirators are believed to be involved in penetrating IT networks by orchestrating brute-force attacks, SQL injections, and sending phishing emails bearing malicious attachments in order to steal usernames and passwords.
Following a successful compromise, the attackers stealthily moved within the networks, while dropping additional malware and post-exploitation tools such as TrickBot, Cobalt Strike, and PowerShell Empire to ultimately drop the file-encrypting malware.
The other members of the cybercrime network are suspected to be in charge of laundering cryptocurrency payments made by victims to decrypt their files.
"The investigation determined that the perpetrators encrypted over 250 servers belonging to large corporations, resulting in losses exceeding several hundreds of millions of euros," Europol said.
The collaborative effort involved authorities from France, Germany, the Netherlands, Norway, Switzerland, Ukraine, and the U.S.
The disclosure comes less than two weeks after Europol and Eurojust announced the takedown of a prolific voice phishing gang by Czech and Ukrainian police that's believed to have netted millions in illegal profits by tricking victims into transferring funds from their 'compromised' bank accounts to 'safe' bank accounts under their control.
It also arrives a month after Europol revealed that law enforcement and judicial authorities from eleven countries dismantled the infrastructure associated with Ragnar Locker ransomware and arrested a "key target" in France.
Hackers Can Exploit 'Forced Authentication' to Steal Windows NTLM Tokens
28.11.23 Exploit The Hacker News
Cybersecurity researchers have discovered a case of "forced authentication" that could be exploited to leak a Windows user's NT LAN Manager (NTLM) tokens by tricking a victim into opening a specially crafted Microsoft Access file.
The attack takes advantage of a legitimate feature in the database management system solution that allows users to link to external data sources, such as a remote SQL Server table.
"This feature can be abused by attackers to automatically leak the Windows user's NTLM tokens to any attacker-controlled server, via any TCP port, such as port 80," Check Point security researcher Haifei Li said. "The attack can be launched as long as the victim opens an .accdb or .mdb file. In fact, any more-common Office file type (such as a .rtf ) can work as well."
NTLM, an authentication protocol introduced by Microsoft in 1993, is a challenge-response protocol that's used to authenticate users during sign-in. Over the years, it has been found to be vulnerable to brute-force, pass-the-hash, and relay attacks.
The latest attack, in a nutshell, abuses the linked table feature in Access to leak the NTLM hashes to an actor-controlled server by embedding an .accdb file with a remote SQL Server database link inside of an MS Word document using a mechanism called Object Linking and Embedding (OLE).
"An attacker can set up a server that they control, listening on port 80, and put its IP address in the above 'server alias' field," Li explained. "Then they can send the database file, including the linked table, to the victim."
Should the victim open the file and click the linked table, the victim client contacts the attacker-controlled server for authentication, enabling the latter to pull off a relay attack by launching an authentication process with a targeted NTLM server in the same organization.
The rogue server then receives the challenge, passes it on to the victim, and gets a valid response, which is ultimately transmitted to the sender that challenges the CV as part of the attacker-controlled CV↔ SA authentication process receives valid response and then passes that response to the NTLM server.
While Microsoft has since released mitigations for the problem in the Office/Access version (Current Channel, version 2306, build 16529.20182) following responsible disclosure in January 2023, 0patch has released unofficial fixes for Office 2010, Office 2013, Office 2016, Office 2019, and Office 365.
The development also comes as Microsoft announced plans to discontinue NTLM in Windows 11 in favor of Kerberos for improved security.
N. Korean Hackers 'Mixing' macOS Malware Tactics to Evade Detection
28.11.23 OS The Hacker News
The North Korean threat actors behind macOS malware strains such as RustBucket and KANDYKORN have been observed "mixing and matching" different elements of the two disparate attack chains, leveraging RustBucket droppers to deliver KANDYKORN.
The findings come from cybersecurity firm SentinelOne, which also tied a third macOS-specific malware called ObjCShellz to the RustBucket campaign.
RustBucket refers to an activity cluster linked to the Lazarus Group in which a backdoored version of a PDF reader app, dubbed SwiftLoader, is used as a conduit to load a next-stage malware written in Rust upon viewing a specially crafted lure document.
The KANDYKORN campaign, on the other hand, refers to a malicious cyber operation in which blockchain engineers of an unnamed crypto exchange platform were targeted via Discord to initiate a sophisticated multi-stage attack sequence that led to the deployment of the eponymous full-featured memory resident remote access trojan.
The third piece of the attack puzzle is ObjCShellz, which Jamf Threat Labs revealed earlier this month as a later-stage payload that acts as a remote shell that executes shell commands sent from the attacker server.
Further analysis of these campaigns by SentinelOne has now shown that the Lazarus Group is utilizing SwiftLoader to distribute KANDYKORN, corroborating a recent report from Google-owned Mandiant about how different hacker groups from North Korea are increasingly borrowing each other's tactics and tools.
"The DPRK's cyber landscape has evolved to a streamlined organization with shared tooling and targeting efforts," Mandiant noted. "This flexible approach to tasking makes it difficult for defenders to track, attribute, and thwart malicious activities, while enabling this now collaborative adversary to move stealthily with greater speed and adaptability."
This includes the use of new variants of the SwiftLoader stager that purports to be an executable named EdoneViewer but, in reality, contacts an actor-controlled domain to likely retrieve the KANDYKORN RAT based on overlaps in infrastructure and the tactics employed.
The disclosure comes as the AhnLab Security Emergency Response Center (ASEC) implicated Andariel – a subgroup within Lazarus – to cyber attacks exploiting a security flaw in Apache ActiveMQ (CVE-2023-46604, CVSS score: 10.0) to install NukeSped and TigerRAT backdoors.
Experts Uncover Passive Method to Extract Private RSA Keys from SSH Connections
27.11.23 Safety The Hacker News
A new study has demonstrated that it's possible for passive network attackers to obtain private RSA host keys from a vulnerable SSH server by observing when naturally occurring computational faults that occur while the connection is being established.
The Secure Shell (SSH) protocol is a method for securely transmitting commands and logging in to a computer over an unsecured network. Based on a client-server architecture, SSH uses cryptography to authenticate and encrypt connections between devices.
A host key is a cryptographic key used for authenticating computers in the SSH protocol. Host keys are key pairs that are typically generated using public-key cryptosystems like RSA.
"If a signing implementation using CRT-RSA has a fault during signature computation, an attacker who observes this signature may be able to compute the signer's private key," a group of academics from the University of California, San Diego, and Massachusetts Institute of Technology said in a paper this month.
In other words, a passive adversary can quietly keep track of legitimate connections without risking detection until they observe a faulty signature that exposes the private key. The bad actor can then masquerade as the compromised host to intercept sensitive data and stage adversary-in-the-middle (AitM) attacks.
The researchers described the method as a lattice-based key recovery fault attack, which allowed them to retrieve the private keys corresponding to 189 unique RSA public keys that were subsequently traced to devices from four manufacturers: Cisco, Hillstone Networks, Mocana, and Zyxel.
It's worth noting that the release of TLS version 1.3 in 2018 acts as a countermeasure by encrypting the handshake that establishes the connection, thus preventing passive eavesdroppers from accessing the signatures.
"These attacks provide a concrete illustration of the value of several design principles in cryptography: encrypting protocol handshakes as soon as a session key is negotiated to protect metadata, binding authentication to a session, and separating authentication from encryption keys," the researchers said.
The findings come two months after the disclosure of Marvin Attack, a variant of the ROBOT (short for "Return Of Bleichenbacher's Oracle Threat") Attack which allows a threat actor to decrypt RSA ciphertexts and forge signatures by exploiting security weaknesses in PKCS #1 v1.5.
U.S., U.K., and Global Partners Release Secure AI System Development Guidelines
27.11.23 AI The Hacker News
The U.K. and U.S., along with international partners from 16 other countries, have released new guidelines for the development of secure artificial intelligence (AI) systems.
"The approach prioritizes ownership of security outcomes for customers, embraces radical transparency and accountability, and establishes organizational structures where secure design is a top priority," the U.S. Cybersecurity and Infrastructure Security Agency (CISA) said.
The goal is to increase cyber security levels of AI and help ensure that the technology is designed, developed, and deployed in a secure manner, the National Cyber Security Centre (NCSC) added.
The guidelines also build upon the U.S. government's ongoing efforts to manage the risks posed by AI by ensuring that new tools are tested adequately before public release, there are guardrails in place to address societal harms, such as bias and discrimination, and privacy concerns, and setting up robust methods for consumers to identify AI-generated material.
The commitments also require companies to commit to facilitating third-party discovery and reporting of vulnerabilities in their AI systems through a bug bounty system so that they can be found and fixed swiftly.
The latest guidelines "help developers ensure that cyber security is both an essential precondition of AI system safety and integral to the development process from the outset and throughout, known as a 'secure by design' approach," NCSC said.
This encompasses secure design, secure development, secure deployment, and secure operation and maintenance, covering all significant areas within the AI system development life cycle, requiring that organizations model the threats to their systems as well as safeguard their supply chains and infrastructure.
The aim, the agencies noted, is to also combat adversarial attacks targeting AI and machine learning (ML) systems that aim to cause unintended behavior in various ways, including affecting a model's classification, allowing users to perform unauthorized actions, and extracting sensitive information.
"There are many ways to achieve these effects, such as prompt injection attacks in the large language model (LLM) domain, or deliberately corrupting the training data or user feedback (known as 'data poisoning')," NCSC noted.
New 'HrServ.dll' Web Shell Detected in APT Attack Targeting Afghan Government
25.11.23 APT The Hacker News
An unspecified government entity in Afghanistan was targeted by a previously undocumented web shell called HrServ in what's suspected to be an advanced persistent threat (APT) attack.
The web shell, a dynamic-link library (DLL) named "hrserv.dll," exhibits "sophisticated features such as custom encoding methods for client communication and in-memory execution," Kaspersky security researcher Mert Degirmenci said in an analysis published this week.
The Russian cybersecurity firm said it identified variants of the malware dating all the way back to early 2021 based on the compilation timestamps of these artifacts.
Web shells are typically malicious tools that provide remote control over a compromised server. Once uploaded, it allows threat actors to carry out a range of post-exploitation activities, including data theft, server monitoring, and lateral advancement within the network.
The attack chain involves the PAExec remote administration tool, an alternative to PsExec that's used as a launchpad to create a scheduled task that masquerades as a Microsoft update ("MicrosoftsUpdate"), which subsequently is configured to execute a Windows batch script ("JKNLA.bat").
The Batch script accepts as an argument the absolute path to a DLL file ("hrserv.dll") that's then executed as a service to initiate an HTTP server that's capable of parsing incoming HTTP requests for follow-on actions.
"Based on the type and information within an HTTP request, specific functions are activated," Degirmenci said, adding "the GET parameters used in the hrserv.dll file, which is used to mimic Google services, include 'hl.'"

This is likely an attempt by the threat actor to blend these rogue requests in network traffic and make it a lot more challenging to distinguish malicious activity from benign events.
Embedded within those HTTP GET and POST requests is a parameter called cp, whose value – ranging from 0 to 7 – determines the next course of action. This includes spawning new threads, creating files with arbitrary data written to them, reading files, and accessing Outlook Web App HTML data.
If the value of cp in the POST request equals "6," it triggers code execution by parsing the encoded data and copying it into the memory, following which a new thread is created and the process enters a sleep state.
The web shell is also capable of activating the execution of a stealthy "multifunctional implant" in memory that's responsible for erasing the forensic trail by deleting the "MicrosoftsUpdate" job as well as the initial DLL and batch files.
The threat actor behind the web shell is currently not known, but the presence of several typos in the source code indicates that the malware author is not a native English speaker.
"Notably, the web shell and memory implant use different strings for specific conditions," Degirmenci concluded. "In addition, the memory implant features a meticulously crafted help message."
"Considering these factors, the malware's characteristics are more consistent with financially motivated malicious activity. However, its operational methodology exhibits similarities with APT behavior."
Warning: 3 Critical Vulnerabilities Expose ownCloud Users to Data Breaches
25.11.23 Vulnerebility The Hacker News
The maintainers of the open-source file-sharing software ownCloud have warned of three critical security flaws that could be exploited to disclose sensitive information and modify files.
A brief description of the vulnerabilities is as follows -
Disclosure of sensitive credentials and configuration in containerized deployments impacting graphapi versions from 0.2.0 to 0.3.0. (CVSS score: 10.0)
WebDAV Api Authentication Bypass using Pre-Signed URLs impacting core versions from 10.6.0 to 10.13.0 (CVSS score: 9.8)
Subdomain Validation Bypass impacting oauth2 prior to version 0.6.1 (CVSS score: 9.0)
"The 'graphapi' app relies on a third-party library that provides a URL. When this URL is accessed, it reveals the configuration details of the PHP environment (phpinfo)," the company said of the first flaw.
"This information includes all the environment variables of the web server. In containerized deployments, these environment variables may include sensitive data such as the ownCloud admin password, mail server credentials, and license key."
As a fix, ownCloud is recommending to delete the "owncloud/apps/graphapi/vendor/microsoft/microsoft-graph/tests/GetPhpInfo.php" file and disable the 'phpinfo' function. It is also advising users to change secrets like the ownCloud admin password, mail server and database credentials, and Object-Store/S3 access keys.
The second problem makes it possible to access, modify or delete any file sans authentication if the username of the victim is known and the victim has no signing-key configured, which is the default behavior.
Lastly, the third flaw relates to a case of improper access control that allows an attacker to "pass in a specially crafted redirect-url which bypasses the validation code and thus allows the attacker to redirect callbacks to a TLD controlled by the attacker."
Besides adding hardening measures to the validation code in the oauth2 app, ownCloud has suggested that users disable the "Allow Subdomains" option as a workaround.
The disclosure comes as a proof-of-concept (PoC) exploit has been released for a critical remote code execution vulnerability in the CrushFTP solution (CVE-2023-43177) that could be weaponized by an unauthenticated attacker to access files, run arbitrary programs on the host, and acquire plain-text passwords.
The issue has been addressed in CrushFTP version 10.5.2, which was released on August 10, 2023.
"This vulnerability is critical because it does NOT require any authentication," CrushFTP noted in an advisory released at the time. "It can be done anonymously and steal the session of other users and escalate to an administrator user."
Cybercriminals Using Telekopye Telegram Bot to Craft Phishing Scams on a Grand Scale
25.11.23 Phishing The Hacker News
More details have emerged about a malicious Telegram bot called Telekopye that's used by threat actors to pull off large-scale phishing scams.
"Telekopye can craft phishing websites, emails, SMS messages, and more," ESET security researcher Radek Jizba said in a new analysis.
The threat actors behind the operation – codenamed Neanderthals – are known to run the criminal enterprise as a legitimate company, spawning a hierarchical structure that encompasses different members who take on various roles.
Once aspiring Neanderthals are recruited via advertisements on underground forums, they are invited to join designated Telegram channels that are used for communicating with other Neanderthals and keeping track of transaction logs.
The ultimate goal of the operation is to pull off one of the three types of scams: seller, buyer, or refund.
In the case of the former, Neanderthals pose as sellers and try to lure unwary Mammoths into purchasing a non-existent item. Buyer scams entail the Neaderthals masquerading as buyers so as to dupe the Mammoths (i.e., merchants) into entering their financial details to part with their funds.
Other scenarios fall into a category called refund scams wherein Neaderthals trick the Mammoths a second time under the pretext of offering a refund, only to deduct the same amount of money again.
Singapore headquartered cybersecurity firm Group-IB previously told The Hacker News that the activity tracked as Telekopye is the same as Classiscam, which refers to a scam-as-a-service program that has netted the criminal actors $64.5 million in illicit profits since its emergence in 2019.
"For the Seller scam scenario, Neanderthals are advised to prepare additional photos of the item to be ready if Mammoths ask for additional details," Jizba noted. "If Neanderthals are using pictures they downloaded online, they are supposed to edit them to make image search more difficult."
Choosing a Mammoth for a buyer scam is a deliberate process that takes into account the victim's gender, age, experience in online marketplaces, rating, reviews, number of completed trades, and the type of items they are selling, indicating a preparatory stage that involves extensive market research.
Also utilized by Neanderthals are web scrapers to sift through online marketplace listings and pick an ideal Mammoth who is likely to fall for the bogus scheme.
Should a mammoth prefer in-person payment and in-person delivery for sold goods, the Neanderthals claim "they are too far away or that they are leaving the city for a business trip for a few days," while simultaneously demonstrating heightened interest in the item to increase the likelihood of success of the scam.
Neanderthals have also been observed use VPNs, proxies, and TOR to stay anonymous, while also exploring real estate scams wherein they create bogus websites with apartment listings and entice Mammoths into paying for a reservation fee by clicking on a link that points to a phishing website.
"Neanderthals write to a legitimate owner of an apartment, pretending to be interested and ask for various details, such as additional pictures and what kind of neighbors the apartment has," Jizba said.
"The Neanderthals then take all this information and create their own listing on another website, offering the apartment for rent. They cut the expected market price by about 20%. The rest of the scenario is identical to the Seller scam scenario."
The disclosure comes as Check Point detailed a rug pull scam that managed to pilfer nearly $1 million by luring unsuspecting victims into investing in fake tokens and executing simulated trades to create a veneer of legitimacy.
"Once the token had sufficiently lured in investors, the scammer executed the final move – withdrawal of liquidity from the token pool, leaving token purchasers with empty hands and depleted funds," the company said.
Hamas-Linked Cyberattacks Using Rust-Powered SysJoker Backdoor Against Israel
25.11.23 BigBrothers The Hacker News
Cybersecurity researchers have shed light on a Rust version of a cross-platform backdoor called SysJoker, which is assessed to have been used by a Hamas-affiliated threat actor to target Israel amid the ongoing war in the region.
"Among the most prominent changes is the shift to Rust language, which indicates the malware code was entirely rewritten, while still maintaining similar functionalities," Check Point said in a Wednesday analysis. "In addition, the threat actor moved to using OneDrive instead of Google Drive to store dynamic C2 (command-and-control server) URLs."
SysJoker was publicly documented by Intezer in January 2022, describing it as a backdoor capable of gathering system information and establishing contact with an attacker-controlled server by accessing a text file hosted on Google Drive that contains a hard-coded URL.
"Being cross-platform allows the malware authors to gain advantage of wide infection on all major platforms," VMware said last year. "SysJoker has the ability to execute commands remotely as well as download and execute new malware on victim machines."
The discovery of a Rust variant of SysJoker points to an evolution of the cross-platform threat, with the implant employing random sleep intervals at various stages of its execution, likely in an effort to evade sandboxes.
One noteworthy shift is the use of OneDrive to retrieve the encrypted and encoded C2 server address, which is subsequently parsed to extract the IP address and port to be used.
"Using OneDrive allows the attackers to easily change the C2 address, which enables them to stay ahead of different reputation-based services," Check Point said. "This behavior remains consistent across different versions of SysJoker."
After establishing connections with the server, the artifact awaits further additional payloads that are then executed on the compromised host.
The cybersecurity company said it also discovered two never-before-seen SysJoker samples designed for Windows that are significantly more complex, one of which utilizing a multi-stage execution process to launch the malware.
SysJoker has not yet been formally attributed to any threat actor or group. But newly gathered evidence shows overlaps between the backdoor and malware samples used in connection with Operation Electric Powder, which refers to a targeted campaign against Israeli organizations between April 2016 and February 2017.
This activity was linked by McAfee to a Hamas-affiliated threat actor known as Molerats (aka Extreme Jackal, Gaza Cyber Gang, and TA402).
"Both campaigns used API-themed URLs and implemented script commands in a similar fashion," Check Point noted, raising the possibility that "the same actor is responsible for both attacks, despite the large time gap between the operations."
Kubernetes Secrets of Fortune 500 Companies Exposed in Public Repositories
24.11.23 Incindent The Hacker News
Cybersecurity researchers are warning of publicly exposed Kubernetes configuration secrets that could put organizations at risk of supply chain attacks.
"These encoded Kubernetes configuration secrets were uploaded to public repositories," Aqua security researchers Yakir Kadkoda and Assaf Morag said in a new research published earlier this week.
Some of those impacted include two top blockchain companies and various other fortune-500 companies, according to the cloud security firm, which leveraged the GitHub API to fetch all entries containing .dockerconfigjson and .dockercfg, which store credentials for accessing a container image registry.
Of the 438 records that potentially held valid credentials for registries, 203 records – about 46% – contained valid credentials that provided access to the respective registries. Ninety-three of the passwords were manually set by individuals, as opposed to the 345 that were computer-generated.
"In the majority of cases, these credentials allowed for both pulling and pushing privileges," the researchers noted. "Moreover, we often discovered private container images within most of these registries."
Furthermore, nearly 50% of the 93 passwords were deemed weak. This comprised password, test123456, windows12, ChangeMe, and dockerhub, among others.

"This underscores the critical need for organizational password policies that enforce strict password creation rules to prevent the use of such vulnerable passwords," the researchers added.
Aqua said it also found instances where organizations fail to remove secrets from the files that are committed to public repositories on GitHub, leading to inadvertent exposure.
But on a positive note, all the credentials associated with AWS and Google Container Registry (GCR) were found to be temporary and expired, making access impossible. In a similar vein, the GitHub Container Registry required two-factor authentication (2FA) as an added layer against unauthorized access.
"In some cases, the keys were encrypted and thus there was nothing to do with the key," the researchers said. "In some cases, while the key was valid it had minimal privileges, often just to pull or download a specific artifact or image."
According to Red Hat's State of Kubernetes Security Report released earlier this year, vulnerabilities and misconfigurations emerged as top security concerns with container environments, with 37% of the total 600 respondents identifying revenue/customer loss as a result of a container and Kubernetes security incident.
Konni Group Using Russian-Language Malicious Word Docs in Latest Attacks
24.11.23 Virus The Hacker News
A new phishing attack has been observed leveraging a Russian-language Microsoft Word document to deliver malware capable of harvesting sensitive information from compromised Windows hosts.
The activity has been attributed to a threat actor called Konni, which is assessed to share overlaps with a North Korean cluster tracked as Kimsuky (aka APT43).
"This campaign relies on a remote access trojan (RAT) capable of extracting information and executing commands on compromised devices," Fortinet FortiGuard Labs researcher Cara Lin said in an analysis published this week.
The cyber espionage group is notable for its targeting of Russia, with the modus operandi involving the use of spear-phishing emails and malicious documents as entry points for their attacks.
Recent attacks documented by Knowsec and ThreatMon have leveraged the WinRAR vulnerability (CVE-2023-38831) as well as obfuscated Visual Basic scripts to drop Konni RAT and a Windows Batch script capable of collecting data from the infected machines.
"Konni's primary objectives include data exfiltration and conducting espionage activities," ThreatMon said. "To achieve these goals, the group employs a wide array of malware and tools, frequently adapting their tactics to avoid detection and attribution."
The latest attack sequence observed by Fortinet involves a macro-laced Word document that, when enabled, displays an article in Russian that's purportedly about "Western Assessments of the Progress of the Special Military Operation."
The Visual Basic for Application (VBA) macro subsequently proceeds to launch an interim Batch script that performs system checks, User Account Control (UAC) bypass, and ultimately paves the way for the deployment of a DLL file that incorporates information gathering and exfiltration capabilities.
"The payload incorporates a UAC bypass and encrypted communication with a C2 server, enabling the threat actor to execute privileged commands," Lin said.
Konni is far from the only North Korean threat actor to single out Russia. Evidence gathered by Kaspersky, Microsoft, and SentinelOne shows that the adversarial collective referred to as ScarCruft (aka APT37) has also targeted trading companies and missile engineering firms located in the country.
The disclosure also arrives less than two weeks after Solar, the cybersecurity arm of Russian state-owned telecom company Rostelecom, revealed that threat actors from Asia – primarily those from China and North Korea – accounted for a majority of attacks against the country's infrastructure.
"The North Korean Lazarus group is also very active on the territory of the Russian Federation," the company said. "As of early November, Lazarus hackers still have access to a number of Russian systems."
Alert: New WailingCrab Malware Loader Spreading via Shipping-Themed Emails
24.11.23 Virus The Hacker News
Delivery- and shipping-themed email messages are being used to deliver a sophisticated malware loader known as WailingCrab.
"The malware itself is split into multiple components, including a loader, injector, downloader and backdoor, and successful requests to C2-controlled servers are often necessary to retrieve the next stage," IBM X-Force researchers Charlotte Hammond, Ole Villadsen, and Kat Metrick said.
WailingCrab, also called WikiLoader, was first documented by Proofpoint in August 2023, detailing campaigns targeting Italian organizations that used the malware to ultimately deploy the Ursnif (aka Gozi) trojan. It was spotted in the wild in late December 2022.
The malware is the handiwork of a threat actor known as TA544, which is also tracked as Bamboo Spider and Zeus Panda. IBM X-Force has named the cluster Hive0133.
Actively maintained by its operators, the malware has been observed incorporating features that prioritize stealth and allows it to resist analysis efforts. To further lower the chances of detection, legitimate, hacked websites are used for initial command-and-control (C2) communications.
What's more, components of the malware are stored on well-known platforms such as Discord. Another noteworthy change to the malware since mid-2023 is the use of MQTT, a lightweight messaging protocol for small sensors and mobile devices, for C2.
The protocol is something of a rarity in the threat landscape, with it put to use only in a few instances, as observed in the case of Tizi and MQsTTang in the past.
The attack chains commence with emails bearing PDF attachments containing URLs that, when clicked, download a JavaScript file designed to retrieve and launch the WailingCrab loader hosted on Discord.
The loader is responsible for launching the next-stage shellcode, an injector module that, in turn, kick-starts the execution of a downloader to deploy the backdoor ultimately.
"In prior versions, this component would download the backdoor, which would be hosted as an attachment on the Discord CDN," the researchers said.
"However, the latest version of WailingCrab already contains the backdoor component encrypted with AES, and it instead reaches out to its C2 to download a decryption key to decrypt the backdoor."
The backdoor, which acts as the malware's core, is designed to establish persistence on the infected host and contact the C2 server using the MQTT protocol to receive additional payloads.
On top of that, newer variants of the backdoor eschew a Discord-based download path in favor of a shellcode-based payload directly from the C2 via MQTT.
"The move to using the MQTT protocol by WailingCrab represents a focused effort on stealth and detection evasion," the researchers concluded. "The newer variants of WailingCrab also remove the callouts to Discord for retrieving payloads, further increasing its stealthiness."
"Discord has become an increasingly common choice for threat actors looking to host malware, and as such it is likely that file downloads from the domain will start coming under higher levels of scrutiny. Therefore, it is not surprising that the developers of WailingCrab decided on an alternative approach."
The abuse of Discord's content delivery network (CDN) for distributing malware hasn't gone unnoticed by the social media company, which told Bleeping Computer earlier this month that it will switch to temporary file links by the end of the year.
Mirai-based Botnet Exploiting Zero-Day Bugs in Routers and NVRs for Massive DDoS Attacks
24.11.23 BotNet The Hacker News
An active malware campaign is leveraging two zero-day vulnerabilities with remote code execution (RCE) functionality to rope routers and video recorders into a Mirai-based distributed denial-of-service (DDoS) botnet.
"The payload targets routers and network video recorder (NVR) devices with default admin credentials and installs Mirai variants when successful," Akamai said in an advisory published this week.
Details of the flaws are currently under wraps to allow the two vendors to publish patches and prevent other threat actors from abusing them. The fixes for one of the vulnerabilities are expected to be shipped next month.
The attacks were first discovered by the web infrastructure and security company against its honeypots in late October 2023. The perpetrators of the attacks have not been identified as yet.
The botnet, which has been codenamed InfectedSlurs due to the use of racial and offensive language in the command-and-control (C2) servers and hard-coded strings, is a JenX Mirai malware variant that came to light in January 2018.
Akamai said it also identified additional malware samples that appeared to be linked to the hailBot Mirai variant, the latter of which emerged in September 2023, according to a recent analysis from NSFOCUS.
"The hailBot is developed based on Mirai source code, and its name is derived from the string information 'hail china mainland' output after running," the Beijing-headquartered cybersecurity firm noted, detailing its ability to propagate via vulnerability exploitation and weak passwords.
The development comes as Akamai detailed a web shell called wso-ng, an "advanced iteration" of WSO (short for "web shell by oRb") that integrates with legitimate tools like VirusTotal and SecurityTrails while stealthily concealing its login interface behind a 404 error page upon attempting to access it.
One of the notable reconnaissance capabilities of the web shell involves retrieving AWS metadata for subsequent lateral movement as well as searching for potential Redis database connections so as to obtain unauthorized access to sensitive application data.
"Web shells allow attackers to run commands on servers to steal data or use the server as a launch pad for other activities like credential theft, lateral movement, deployment of additional payloads, or hands-on-keyboard activity, while allowing attackers to persist in an affected organization," Microsoft said back in 2021.
The use of off-the-shelf web shells is also seen as an attempt by threat actors to challenge attribution efforts and fly under the radar, a key hallmark of cyber espionage groups that specialize in intelligence gathering.
Another common tactic adopted by attackers is the use of compromised-but-legitimate domains for C2 purposes and malware distribution.
In August 2023, Infoblox disclosed a widespread attack involving compromised WordPress websites that conditionally redirect visitors to intermediary C2 and dictionary domain generation algorithm (DDGA) domains. The activity has been attributed to a threat actor named VexTrio.
North Korean Hackers Distribute Trojanized CyberLink Software in Supply Chain Attack
23.11.23 Hacking The Hacker News

A North Korean state-sponsored threat actor tracked as Diamond Sleet is distributing a trojanized version of a legitimate application developed by a Taiwanese multimedia software developer called CyberLink to target downstream customers via a supply chain attack.
"This malicious file is a legitimate CyberLink application installer that has been modified to include malicious code that downloads, decrypts, and loads a second-stage payload," the Microsoft Threat Intelligence team said in an analysis on Wednesday.
The poisoned file, the tech giant said, is hosted on the updated infrastructure owned by the company while also including checks to limit the time window for execution and bypass detection by security products.
The campaign is estimated to have impacted over 100 devices across Japan, Taiwan, Canada, and the U.S. Suspicious activity associated with the modified CyberLink installer file was observed as early as October 20, 2023.
The links to North Korea stem from the fact that the second-stage payload establishes connections with command-and-control (C2) servers previously compromised by the threat actor.
Microsoft further said it has observed the attackers utilizing trojanized open-source and proprietary software to target organizations in information technology, defense, and media sectors.
Diamond Sleet, which dovetails with clusters dubbed TEMP.Hermit and Labyrinth Chollima, is the moniker assigned to an umbrella group originating from North Korea that's also called Lazarus Group. It's known to be active since at least 2013.
"Their operations since that time are representative of Pyongyang's efforts to collect strategic intelligence to benefit North Korean interests," Google-owned Mandiant noted last month. "This actor targets government, defense, telecommunications, and financial institutions worldwide."
Interestingly, Microsoft said it did not detect any hands-on-keyboard activity on target environments following the distribution of the tampered installer, which has been codenamed LambLoad.
The weaponized downloader and loader inspect the target system for the presence of security software from CrowdStrike, FireEye, and Tanium, and if not present, fetch another payload from a remote server that masquerades as a PNG file.
"The PNG file contains an embedded payload inside a fake outer PNG header that is, carved, decrypted, and launched in memory," Microsoft said. Upon execution, the malware further attempts to contact a legitimate-but-compromised domain for the retrieval of additional payloads.
The disclosures come a day after Palo Alto Networks Unit 42 revealed twin campaigns architected by North Korean threat actors to distribute malware as part of fictitious job interviews and obtain unauthorized employment with organizations based in the U.S. and other parts of the world.
Last month, Microsoft also implicated Diamond Sleet in the exploitation of a critical security flaw in JetBrains TeamCity (CVE-2023-42793, CVSS score: 9.8) to opportunistically breach vulnerable servers and deploy a backdoor known as ForestTiger.
New Flaws in Fingerprint Sensors Let Attackers Bypass Windows Hello Login
23.11.23 Vulnerebility The Hacker News
A new research has uncovered multiple vulnerabilities that could be exploited to bypass Windows Hello authentication on Dell Inspiron 15, Lenovo ThinkPad T14, and Microsoft Surface Pro X laptops.
The flaws were discovered by researchers at hardware and software product security and offensive research firm Blackwing Intelligence, who found the weaknesses in the fingerprint sensors from Goodix, Synaptics, and ELAN that are embedded into the devices.
A prerequisite for the fingerprint reader exploits is that the users of the targeted laptops have fingerprint authentication already set up.
All the three fingerprint sensors are a type of sensor called "match on chip" (MoC), which integrates the matching and other biometric management functions directly into the sensor's integrated circuit.
"While MoC prevents replaying stored fingerprint data to the host for matching, it does not, in itself, prevent a malicious sensor from spoofing a legitimate sensor's communication with the host and falsely claiming that an authorized user has successfully authenticated," researchers Jesse D'Aguanno and Timo Teräs said.
The MoC also does not prevent replay of previously recorded traffic between the host and sensor.
Although the Secure Device Connection Protocol (SDCP) created by Microsoft aims to alleviate some of these problems by creating an end-to-end secure channel, the researchers uncovered a novel method that could be used to circumvent these protections and stage adversary-in-the-middle (AitM) attacks.
Specifically, the ELAN sensor was found to be vulnerable to a combination of sensor spoofing stemming from the lack of SDCP support and cleartext transmission of security identifiers (SIDs), thereby allowing any USB device to masquerade as the fingerprint sensor and claim that an authorized user is logging in.
In the case of Synaptics, not only was SDCP discovered to be turned off by default, the implementation chose to rely on a flawed custom Transport Layer Security (TLS) stack to secure USB communications between the host driver and sensor that could be weaponized to sidestep biometric authentication. The exploitation of Goodix sensor, on the other hand, capitalizes on a fundamental difference in enrollment operations carried out on a machine that's loaded with both Windows and Linux, taking advantage of the fact that the latter does not support SDCP to perform the following actions - Boot to Linux To mitigate such attacks, it's recommended that original equipment manufacturers (OEMs) enable SDCP and ensure that the fingerprint sensor implementation is audited by independent qualified experts. This isn't the first time that Windows Hello biometrics-based authentication has been successfully defeated. In July 2021, Microsoft issued patches for a medium-severity security flaw (CVE-2021-34466, CVSS score: 6.1) that could permit an adversary to spoof a target's face and get around the login screen. "Microsoft did a good job designing SDCP to provide a secure channel between the host and biometric devices, but unfortunately device manufacturers seem to misunderstand some of the objectives," the researchers said. "Additionally, SDCP only covers a very narrow scope of a typical device's operation, while most devices have a sizable attack surface exposed that is not covered by SDCP at all."
Enumerate valid IDs
Enroll attacker's fingerprint using the same ID as a legitimate Windows user
MitM the connection between the host and sensor by leveraging the cleartext USB communication
Boot to Windows
Intercept and rewrite the configuration packet to point to the Linux DB using our MitM
Login as the legitimate user with attacker's print
It's worth pointing out that while the Goodix sensor has separate fingerprint template databases for Windows and non-Windows systems, the attack is possible owing to the fact that the host driver sends an unauthenticated configuration packet to the sensor to specify what database to use during sensor initialization.
North Korean Hackers Pose as Job Recruiters and Seekers in Malware Campaigns
23.11.23 Hacking The Hacker News
North Korean threat actors have been linked to two campaigns in which they masquerade as both job recruiters and seekers to distribute malware and obtain unauthorized employment with organizations based in the U.S. and other parts of the world.
The activity clusters have been codenamed Contagious Interview and Wagemole, respectively, by Palo Alto Networks Unit 42.
While the first set of attacks aims to "infect software developers with malware through a fictitious job interview," the latter is designed for financial gain and espionage.
"The first campaign's objective is likely cryptocurrency theft and using compromised targets as a staging environment for additional attacks," the cybersecurity company said.
The fraudulent job-seeking activity, on the other hand, involves the use of a GitHub repository to host resumes with forged identities that impersonate individuals of various nationalities.
The Contagious Interview attacks pave the way for two hitherto undocumented cross-platform malware named BeaverTail and InvisibleFerret that can run on Windows, Linux, and macOS systems.
It's worth noting that the intrusion set shares tactical overlaps with previously reported North Korean threat activity dubbed Operation Dream Job, which involves approaching employees with potential job offers and tricking them into downloading malicious tools – a rogue npm package hosted on GitHub, in this case – as part of an online interview.
"The threat actor likely presents the package to the victim as software to review or analyze, but it actually contains malicious JavaScript designed to infect the victim's host with backdoor malware," Unit 42 said.
BeaverTail, the JavaScript implant, is a stealer and a loader that comes with capabilities to steal sensitive information from web browsers and crypto wallets, and deliver additional payloads, including InvisibleFerret, a Python-based backdoor with fingerprinting, remote control, keylogging, and data exfiltration features.
InvisibleFerret is also designed to download the AnyDesk client from an actor-controlled server for remote access.
Earlier this month, Microsoft warned that the infamous Lazarus Group sub-cluster referred to as Sapphire Sleet (aka BlueNoroff) has established new infrastructure that impersonates skills assessment portals as part of its social engineering campaigns.

This is not the first time North Korean threat actors have abused bogus modules in npm and PyPI. In late June and July 2023, Phylum and GitHub detailed a social engineering campaign that targeted the personal GitHub accounts of employees working in technology firms to disseminate a counterfeit npm package under the guise of collaborating on an open-source project.
The attacks have been attributed to another cluster known as Jade Sleet, which is also called TraderTraitor and UNC4899, and has since been implicated in the JumpCloud hack that took place around the same time.
The discovery of Wagehole echoes a recent advisory from the U.S. government, which disclosed North Korea's subterfuge to beat sanctions by dispatching an army of highly-skilled IT workers who obtain employment in several companies globally and funnel back their wages to fund the country's weapons programs.
"Some resumes include links to a LinkedIn profile and links to GitHub content," the cybersecurity company said.
"These GitHub accounts appear well maintained and have a lengthy activity history. These accounts indicate frequent code updates and socialization with other developers. As a result, these GitHub accounts are nearly indistinguishable from legitimate accounts."
"We would create 20 to 50 fake profiles a year until we were hired," a North Korean IT worker who recently defected was quoted as saying to Reuters, which also shared details of the Wagemole campaign.
The development comes as North Korea claimed that it has successfully put a military spy satellite into space, after two unsuccessful attempts in May and August of this year.
It also follows a new attack campaign orchestrated by the North Korea-linked Andariel group – another subordinate element within Lazarus – to deliver Black RAT, Lilith RAT, NukeSped, and TigerRAT by infiltrating vulnerable MS-SQL servers as well as via supply chain attacks using a South Korean asset management software.
"Software developers are often the weakest link for supply chain attacks, and fraudulent job offers are an ongoing concern, so we expect continued activity from Contagious Interview," Unit 42 said. "Furthermore, Wagemole represents an opportunity to embed insiders in targeted companies."
ClearFake Campaign Expands to Deliver Atomic Stealer on Macs Systems
22.11.23 OS The Hacker News
The macOS information stealer known as Atomic is now being delivered to target via a bogus web browser update chain tracked as ClearFake.
"This may very well be the first time we see one of the main social engineering campaigns, previously reserved for Windows, branch out not only in terms of geolocation but also operating system," Malwarebytes' Jérôme Segura said in a Tuesday analysis.
Atomic Stealer (aka AMOS), first documented in April 2023, is a commercial stealer malware family that's sold on a subscription basis for $1,000 per month. It comes with capabilities to siphon data from web browsers and cryptocurrency wallets.
Then in September 2023, Malwarebytes detailed an Atomic Stealer campaign that takes advantage of malicious Google ads, tricking macOS users searching for a financial charting platform known as TradingView into downloading the malware.
ClearFake, on the other hand, is a nascent malware distribution operation that employs compromised WordPress sites to serve fraudulent web browser update notices in hopes of deploying stealers and other malware.
It's the latest addition to a larger pool of threat actors such as TA569 (aka SocGholish), RogueRaticate (FakeSG), ZPHP (SmartApeSG), and EtherHiding that are known to use themes related to fake browser updates for this purpose.
As of November 2023, the ClearFake campaign has been expanded to target macOS systems with a near-identical infection chain, leveraging hacked websites to deliver Atomic Stealer in the form of a DMG file.
The development is a sign that stealer malware continues to rely on fake or poisoned installer files for legitimate software via malicious advertisements, search engine redirects to malicious websites, drive-by downloads, phishing, and SEO poisoning for propagation.
"The popularity of stealers such as AMOS makes it quite easy to adapt the payload to different victims, with minor adjustments," Segura said.
Lumma Stealer Claims to Find a Way to Extract Persistent Google Cookies#
The disclosure also follows updates to the LummaC2 stealer that utilizes a novel trigonometry-based anti-sandbox technique that forces the malware to wait until "human" behavior is detected in the infected machine.
The operators of the malware have also been promoting a new feature that they claim can be used to gather Google Account cookies from compromised computers that will not expire or get revoked even if the owner changes the password.
"This will result in a major shift in the cybercrime world, enabling hackers to infiltrate even more accounts and perform significant attacks," Alon Gal, co-founder and CTO at Hudson Rock, said in a set of posts on LinkedIn.
"The bottom line is that these cookies seem more persistent and could lead to an influx of Google services used by people being hacked, and if the claim that a password change doesn't invalidate the session is true, we're looking at much bigger problems."
LockBit Ransomware Exploiting Critical Citrix Bleed Vulnerability to Break In
22.11.23 Ransom The Hacker News
Multiple threat actors, including LockBit ransomware affiliates, are actively exploiting a recently disclosed critical security flaw in Citrix NetScaler application delivery control (ADC) and Gateway appliances to obtain initial access to target environments.
The joint advisory comes from the U.S. Cybersecurity and Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI), Multi-State Information Sharing and Analysis Center (MS-ISAC), and Australian Signals Directorate's Australian Cyber Security Center (ASD's ACSC).
"Citrix Bleed, known to be leveraged by LockBit 3.0 affiliates, allows threat actors to bypass password requirements and multifactor authentication (MFA), leading to successful session hijacking of legitimate user sessions on Citrix NetScaler web application delivery control (ADC) and Gateway appliances," the agencies said.
"Through the takeover of legitimate user sessions, malicious actors acquire elevated permissions to harvest credentials, move laterally, and access data and resources."
Tracked as CVE-2023-4966 (CVSS score: 9.4), the vulnerability was addressed by Citrix last month but not before it was weaponized as a zero-day, at least since August 2023. It has been codenamed Citrix Bleed.
Shortly after the public disclosure, Google-owned Mandiant revealed it's tracking four different uncategorized (UNC) groups involved in exploiting CVE-2023-4966 to target several industry verticals in the Americas, EMEA, and APJ.
The latest threat actor to join the exploitation bandwagon is LockBit, which has been observed taking advantage of the flaw to execute PowerShell scripts as well as drop remote management and monitoring (RMM) tools like AnyDesk and Splashtop for follow-on activities.
The development once again underscores the fact that vulnerabilities in exposed services continue to be a primary entry vector for ransomware attacks.
The disclosure comes as Check Point released a comparative study of ransomware attacks targeting Windows and Linux, noting that a majority of the families that break into Linux heavily utilize the OpenSSL library along with ChaCha20/RSA and AES/RSA algorithms.
"Linux ransomware is clearly aimed at medium and large organizations compared to Windows threats, which are much more general in nature," security researcher Marc Salinas Fernandez said.
The examination of various Linux-targeting ransomware families "reveals an interesting trend towards simplification, where their core functionalities are often reduced to just basic encryption processes, thereby leaving the rest of the work to scripts and legitimate system tools."
Check Point said the minimalist approach not only renders these ransomware families heavily reliant on external configurations and scripts but also makes them more easier to fly under the radar.
Play Ransomware Goes Commercial - Now Offered as a Service to Cybercriminals
22.11.23 Ransom The Hacker News
The ransomware strain known as Play is now being offered to other threat actors "as a service," new evidence unearthed by Adlumin has revealed.
"The unusual lack of even small variations between attacks suggests that they are being carried out by affiliates who have purchased the ransomware-as-a-service (RaaS) and are following step-by-step instructions from playbooks delivered with it," the cybersecurity company said in a report shared with The Hacker News.
The findings are based on various Play ransomware attacks tracked by Adlumin spanning different sectors that incorporated almost identical tactics and in the same sequence.
This includes the use of the public music folder (C:\...\public\music) to hide the malicious file, the same password to create high-privilege accounts, and both attacks, and the same commands.
Play, also called Balloonfly and PlayCrypt, first came to light in June 2022, leveraging security flaws in Microsoft Exchange Server – i.e., ProxyNotShell and OWASSRF – to infiltrate networks and drop remote administration tools like AnyDesk and ultimately deploy the ransomware.
Besides using custom data gathering tools like Grixba for double extortion, a notable aspect that set Play apart from other ransomware groups was the fact that the operators in charge of developing the malware also carried out the attacks.
The new development, therefore, marks a shift and completes its transformation into a RaaS operation, making it a lucrative option for cybercriminals.
"When RaaS operators advertise ransomware kits that come with everything a hacker will need, including documentation, forums, technical support, and ransom negotiation support, script kiddies will be tempted to try their luck and put their skills to use," Adlumin said.
"And since there are probably more script kiddies than 'real hackers' today, businesses and authorities should take note and prepare for a growing wave of incidents."
New Agent Tesla Malware Variant Using ZPAQ Compression in Email Attacks
22.11.23 Virus The Hacker News
A new variant of the Agent Tesla malware has been observed delivered via a lure file with the ZPAQ compression format to harvest data from several email clients and nearly 40 web browsers.
"ZPAQ is a file compression format that offers a better compression ratio and journaling function compared to widely used formats like ZIP and RAR," G Data malware analyst Anna Lvova said in a Monday analysis.
"That means that ZPAQ archives can be smaller, saving storage space and bandwidth when transferring files. However, ZPAQ has the biggest disadvantage: limited software support."
First appearing in 2014, Agent Tesla is a keylogger and remote access trojan (RAT) written in .NET that's offered to other threat actors as part of a malware-as-a-service (MaaS) model.
It's often used as a first-stage payload, providing remote access to a compromised system and utilized to download more sophisticated second-stage tools such as ransomware.
Agent Tesla is typically delivered via phishing emails, with recent campaigns leveraging a six-year-old memory corruption vulnerability in Microsoft Office's Equation Editor (CVE-2017-11882).
The latest attack chain begins with an email containing a ZPAQ file attachment that purports to be a PDF document, opening which extracts a bloated .NET executable that's mostly padded with zero bytes to artificially inflate the sample size to 1 GB in an effort to bypass traditional security measures.
"The main function of the unarchived .NET executable is to download a file with .wav extension and decrypt it," Lvova explained. "Using commonly used file extensions disguises the traffic as normal, making it more difficult for network security solutions to detect and prevent malicious activity."
The end goal of the attack is to infect the endpoint with Agent Teslathat's obfuscated with .NET Reactor, a legitimate code protection software. Command-and-control (C2) communications is accomplished via Telegram.
The development is a sign that threat actors are experimenting with uncommon file formats for malware delivery, necessitating that users be on the lookout for suspicious emails and keep their systems up-to-date.
"The usage of the ZPAQ compression format raises more questions than answers," Lvova said. "The assumptions here are that either threat actors target a specific group of people who have technical knowledge or use less widely known archive tools, or they are testing other techniques to spread malware faster and bypass security software."
How Multi-Stage Phishing Attacks Exploit QRs, CAPTCHAs, and Steganography
22.11.23 Phishing The Hacker News
Phishing attacks are steadily becoming more sophisticated, with cybercriminals investing in new ways of deceiving victims into revealing sensitive information or installing malicious software. One of the latest trends in phishing is the use of QR codes, CAPTCHAs, and steganography. See how they are carried out and learn to detect them.
Quishing#
Quishing, a phishing technique resulting from the combination of "QR" and "phishing," has become a popular weapon for cybercriminals in 2023.
By concealing malicious links within QR codes, attackers can evade traditional spam filters, which are primarily geared towards identifying text-based phishing attempts. The inability of many security tools to decipher the content of QR codes further makes this method a go-to choice for cybercriminals.
An email containing a QR code with a malicious link
Analyzing a QR code with an embedded malicious link in a safe environment is easy with ANY.RUN:
Simply open this task in the sandbox (or upload your file with a QR code).
Navigate to the Static Discovering section (By clicking on the name of the file in the top right corner).
Select the object containing the QR code.
Click "Submit to Analyze."
The sandbox will then automatically launch a new task window, allowing you to analyze the URL identified within the QR code.
Black Friday Offer
Take advantage of ANY.RUN's Black Friday Offer
Purchase an annual Searcher or Hunter plan subscription and get another for your colleague completely free of charge. Available November 20-26.
Get It Now
CAPTCHA-based attacks#
CAPTCHA is a security solution used on websites to prevent automated bots from creating fake accounts or submitting spam. Attackers have managed to exploit this tool to their advantage.
A phishing attack CAPTCHA page shown in the ANY.RUN sandbox
Attackers are increasingly using CAPTCHAs to mask credential-harvesting forms on fake websites. By generating hundreds of domain names using a Randomized Domain Generated Algorithm (RDGA) and implementing CloudFlare's CAPTCHAs, they can effectively hide these forms from automated security systems, such as web crawlers, which are unable to bypass the CAPTCHAs.
A fake Halliburton login page
The example above shows an attack targeting Halliburton Corporation employees. It first requires the user to pass a CAPTCHA check and then uses a realistic Office 365 private login page that is difficult to distinguish from the real page.
Once the victim enters their login credentials, they are redirected to a legitimate website, while the attackers exfiltrate the credentials to their Command-and-Control server.
Learn more about CAPTCHA attacks in this article.
Steganography malware campaigns#
Steganography is the practice of hiding data inside different media, such as images, videos, or other files.
A typical phishing attack that employs steganography begins with a carefully crafted email designed to appear legitimate. Embedded within the email is an attachment, often a Word document, accompanied by a link to a file-sharing platform like Dropbox. In the example below, you can see a fake email from a Colombian government organization.
A phishing email is typically the first stage of an attack
The unsuspecting user that clicks the link inside the document downloads an archive, which contains a VBS script file. Upon execution, the script retrieves an image file, seemingly harmless but containing hidden malicious code. Once executed, the malware infects the victim's system.
To understand how steganography attacks are carried out and detected, check out this article.
Expose phishing attacks with ANY.RUN#
ANY.RUN is a malware analysis sandbox that is capable of detecting a wide range of phishing tactics and letting users examine them in detail.
Check out ANY.RUN's Black Friday Offer, available November 20-26.
Fully interactive Windows 7,9,10,11 virtual machines
Comprehensive reports with IOCs and malware configs
Private analysis of an unlimited number of files and links
Kinsing Hackers Exploit Apache ActiveMQ Vulnerability to Deploy Linux Rootkits
22.11.23 Virus The Hacker News
The Kinsing threat actors are actively exploiting a critical security flaw in vulnerable Apache ActiveMQ servers to infect Linux systems with cryptocurrency miners and rootkits.
"Once Kinsing infects a system, it deploys a cryptocurrency mining script that exploits the host's resources to mine cryptocurrencies like Bitcoin, resulting in significant damage to the infrastructure and a negative impact on system performance," Trend Micro security researcher Peter Girnus said.
Kinsing refers to a Linux malware with a history of targeting misconfigured containerized environments for cryptocurrency mining, often utilizing compromised server resources to generate illicit profits for the threat actors.
The group is also known to quickly adapt its tactics to include newly disclosed flaws in web applications to breach target networks and deliver crypto miners. Earlier this month, Aqua disclosed the threat actor's attempts to exploit a Linux privilege escalation flaw called Looney Tunables to infiltrate cloud environments.
The latest campaign entails the abuse of CVE-2023-46604 (CVSS score: 10.0), an actively exploited critical vulnerability in Apache ActiveMQ that enables remote code execution, permitting the adversary to download and install the Kinsing malware.
This is followed by retrieving additional payloads from an actor-controlled domain while simultaneously taking steps to terminate competing cryptocurrency miners already running on the infected system.
"Kinsing doubles down on its persistence and compromise by loading its rootkit in /etc/ld.so.preload, which completes a full system compromise," Girnus said.
In light of the continued exploitation of the flaw, organizations running affected versions of Apache ActiveMQ are recommended to update to a patched version as soon as possible to mitigate potential threats.
The disclosure comes as the AhnLab Security Emergency response Center (ASEC) is warning of cyber attacks targeting vulnerable Apache web servers for a cryptojacking campaign that leverages Cobalt Strike or Gh0st RAT to deliver a cryptocurrency miner.
Malicious Apps Disguised as Banks and Government Agencies Targeting Indian Android Users
21.11.23 OS The Hacker News
Android smartphone users in India are the target of a new malware campaign that employs social engineering lures to install fraudulent apps that are capable of harvesting sensitive data.
"Using social media platforms like WhatsApp and Telegram, attackers are sending messages designed to lure users into installing a malicious app on their mobile device by impersonating legitimate organizations, such as banks, government services, and utilities," Microsoft threat intelligence researchers Abhishek Pustakala, Harshita Tripathi, and Shivang Desai said in a Monday analysis.
The ultimate goal of the operation is to capture banking details, payment card information, account credentials, and other personal data.
The attack chains involve sharing malicious APK files via social media messages sent on WhatsApp and Telegram by falsely presenting them as banking apps and inducing a sense of urgency by claiming that the targets' bank accounts will be blocked unless they update their permanent account number (PAN) issued by the Indian Income Tax Department through the bogus app.
Upon installation, the app urges the victim to enter their bank account information, debit card PIN, PAN card numbers, and online banking credentials, which are subsequently transmitted to an actor-controlled command-and-control (C2) server and a hard-coded phone number.
"Once all the requested details are submitted, a suspicious note appears stating that the details are being verified to update KYC," the researchers said.
"The user is instructed to wait 30 minutes and not to delete or uninstall the app. Additionally, the app has the functionality to hide its icon, causing it to disappear from the user's device home screen while still running in the background."
Another notable aspect of the malware is that it requests the user to grant it permission to read and send SMS messages, thereby enabling it to intercept one-time passwords (OTPs) and send the victims' messages to the threat actor's phone number via SMS.
Variants of the banking trojan discovered by Microsoft have also been found to steal credit card details along with personally identifiable information (PII) and incoming SMS messages, exposing unsuspecting users to financial fraud.
However, it's worth noting that for these attacks to be successful, users will have to enable the option to install apps from unknown sources outside of the Google Play Store.
"Mobile banking trojan infections can pose significant risks to users' personal information, privacy, device integrity, and financial security," the researchers said. "These threats can often disguise themselves as legitimate apps and deploy social engineering tactics to achieve their goals and steal users' sensitive data and financial assets."
The development comes as the Android ecosystem has also come under attack from the SpyNote trojan, which has targeted Roblox users under the guise of a mod to siphon sensitive information.
In another instance, fake adult websites are being used as lures to entice users into downloading an Android malware called Enchant that specifically focuses on pilfering data from cryptocurrency wallets.
"Enchant malware uses the accessibility service feature to target specific cryptocurrency wallets, including imToken, OKX, Bitpie Wallet, and TokenPocket wallet," Cyble said in a recent report.
"Its primary objective is to steal critical information such as wallet addresses, mnemonic phrases, wallet asset details, wallet passwords, and private keys from compromised devices."
Last month, Doctor Web uncovered several malicious apps on the Google Play Store that displayed intrusive ads (HiddenAds), subscribed users to premium services without their knowledge or consent (Joker), and promoted investment scams by masquerading as trading software (FakeApp).
The onslaught of Android malware has prompted Google to announce new security features such as real-time code-level scanning for newly encountered apps. It also launched restricted settings with Android 13 that prohibits apps from obtaining access to critical device settings (e.g., accessibility) unless it's explicitly enabled by the user.
It's not just Google. Samsung, in late October 2023, unveiled a new Auto Blocker option that prevents app installations from sources other than Google Play Store and Galaxy Store, and blocks harmful commands and software installations through the USB port.
To avoid downloading malicious software from Google Play and other trusted sources, users are advised to check the legitimacy of the app developers, scrutinize reviews, and vet the permissions requested by the apps.
Mustang Panda Hackers Targets Philippines Government Amid South China Sea Tensions
21.11.23 BigBrothers The Hacker News
The China-linked Mustang Panda actor has been linked to a cyber attack targeting a Philippines government entity amid rising tensions between the two countries over the disputed South China Sea.
Palo Alto Networks Unit 42 attributed the adversarial collective to three campaigns in August 2023, primarily singling out organizations in the South Pacific.
"The campaigns leveraged legitimate software including Solid PDF Creator and SmadavProtect (an Indonesian-based antivirus solution) to sideload malicious files," the company said.
"Threat authors also creatively configured the malware to impersonate legitimate Microsoft traffic for command and control (C2) connections."
Mustang Panda, also tracked under the names Bronze President, Camaro Dragon, Earth Preta, RedDelta, and Stately Taurus, is assessed to be a Chinese advanced persistent threat (APT) active since at least 2012, orchestrating cyber espionage campaigns targeting non-governmental organizations (NGOs) and government bodies across North America, Europe, and Asia.
In late September 2023, Unit 42 also implicated the threat actor to attacks aimed at an unnamed Southeast Asian government to distribute a variant of a backdoor called TONESHELL.
The latest campaigns leverage spear-phishing emails to deliver a malicious ZIP archive file that contains a rogue dynamic-link library (DLL) that's launched using a technique called DLL side-loading. The DLL subsequently establishes contact with a remote server.
It's assessed that the Philippines government entity was likely compromised over a five-day period between August 10 and 15, 2023.
The use of SmadavProtect is a known tactic adopted by Mustang Panda in recent months, having deployed malware expressly designed to bypass the security solution.
"Stately Taurus continues to demonstrate its ability to conduct persistent cyberespionage operations as one of the most active Chinese APTs," the researchers said.
"These operations target a variety of entities globally that align with geopolitical topics of interest to the Chinese government."
The disclosure comes as a South Korean APT actor named Higaisa has been uncovered targeting Chinese users through phishing websites mimicking well-known software applications such as OpenVPN.
"Once executed, the installer drops and runs Rust-based malware on the system, subsequently triggering a shellcode," Cyble said late last month. "The shellcode performs anti-debugging and decryption operations. Afterward, it establishes encrypted command-and-control (C&C) communication with a remote Threat Actor (TA)."
NetSupport RAT Infections on the Rise - Targeting Government and Business Sectors
21.11.23 Virus The Hacker News
Threat actors are targeting the education, government and business services sectors with a remote access trojan called NetSupport RAT.
"The delivery mechanisms for the NetSupport RAT encompass fraudulent updates, drive-by downloads, utilization of malware loaders (such as GHOSTPULSE), and various forms of phishing campaigns," VMware Carbon Black researchers said in a report shared with The Hacker News.
The cybersecurity firm said it detected no less than 15 new infections related to NetSupport RAT in the last few weeks.
While NetSupport Manager started off as a legitimate remote administration tool for technical assistance and support, malicious actors have misappropriated the tool to their own advantage, using it as a beachhead for subsequent attacks.
NetSupport RAT is typically downloaded onto a victim's computer via deceptive websites and fake browser updates.
In August 2022, Sucuri detailed a campaign in which compromised WordPress sites were being used to display fraudulent Cloudflare DDoS protection pages that led to the distribution of NetSupport RAT.

The use of bogus web browser updates is a tactic often associated with the deployment of a JavaScript-based downloader malware known as SocGholish (aka FakeUpdates), which has also been observed propagating a loader malware codenamed BLISTER.
The Javascript payload subsequently invokes PowerShell to connect to a remote server and retrieve a ZIP archive file containing NetSupport RAT that, upon installation, beacons out to a command-and-control (C2) server.
"Once installed on a victim's device, NetSupport is able to monitor behavior, transfer files, manipulate computer settings, and move to other devices within the network," the researchers said.
DarkGate and PikaBot Malware Resurrect QakBot's Tactics in New Phishing Attacks
21.11.23 Virus The Hacker News
Phishing campaigns delivering malware families such as DarkGate and PikaBot are following the same tactics previously used in attacks leveraging the now-defunct QakBot trojan.
"These include hijacked email threads as the initial infection, URLs with unique patterns that limit user access, and an infection chain nearly identical to what we have seen with QakBot delivery," Cofense said in a report shared with The Hacker News.
"The malware families used also follow suit to what we would expect QakBot affiliates to use."
QakBot, also called QBot and Pinkslipbot, was shut down as part of a coordinated law enforcement effort codenamed Operation Duck Hunt earlier this August.
The use of DarkGate and PikaBot in these campaigns is not surprising as they can both act as conduits to deliver additional payloads to compromised hosts, making them both an attractive option for cybercriminals.
PikaBot's parallels to QakBot were previously highlighted by Zscaler in its analysis of the malware in May 2023, noting similarities in the "distribution methods, campaigns, and malware behaviors."
DarkGate, for its part, incorporates advanced techniques to evade detection by antivirus systems, alongside capabilities to log keystrokes, execute PowerShell, and implement a reverse shell that allows its operators to commandeer an infected host remotely.
"The connection is bidirectional, meaning the attackers can send commands and receive responses in real-time, enabling them to navigate the victim's system, exfiltrate data, or perform other malicious actions," Sekoia said in a new technical report of the malware.
Cofense's analysis of the high-volume phishing campaign shows that it targets a wide range of sectors, with the attack chains propagating a booby-trapped URL pointing to a ZIP archive in hijacked email threads.
The ZIP archive contains a JavaScript dropper that, in turn, contacts a second URL to download and run either the DarkGate or PikaBot malware.
A noteworthy variant of the attacks has been observed taking advantage of Excel add-in (XLL) files in lieu of JavaScript droppers to deliver the final payloads.
"A successful DarkGate or PikaBot infection could lead to the delivery of advanced crypto mining software, reconnaissance tools, ransomware, or any other malicious file the threat actors wish to install on a victim's machine," Cofense said.
LummaC2 Malware Deploys New Trigonometry-Based Anti-Sandbox Technique
20.11.23 Virus The Hacker News
The stealer malware known as LummaC2 (aka Lumma Stealer) now features a new anti-sandbox technique that leverages the mathematical principle of trigonometry to evade detection and exfiltrate valuable information from infected hosts.
The method is designed to "delay detonation of the sample until human mouse activity is detected," Outpost24 security researcher Alberto Marín said in a technical report shared with The Hacker News.
Written in the C programming language, LummaC2 has been sold in underground forums since December 2022. The malware has since received iterative updates that make it harder to analyze via control flow flattening and even allow it to deliver additional payloads.
The current version of LummaC2 (v4.0) also requires its customers to use a crypter as an added concealing mechanism, not to mention prevent it from being leaked in its raw form.
Another noteworthy update is the reliance on trigonometry to detect human behavior on the infiltrated endpoint.
"This technique takes into consideration different positions of the cursor in a short interval to detect human activity, effectively preventing detonation in most analysis systems that do not emulate mouse movements realistically," Marín said.
To do so, it extracts the current cursor position for five times after a predefined interval of 300 milliseconds, and checks if every captured position is different from its preceding one. The process is repeated indefinitely until all consecutive cursor positions differ.
Once all the five cursor positions (P0, P1, P2, P3, and P4) meet the requirements, LummaC2 treats them as Euclidean vectors and calculates the angle that's formed between two consecutive vectors (P01-P12, P12-P23, and P23-P34).
"If all the calculated angles are lower than 45º, then LummaC2 v4.0 considers it has detected 'human' mouse behavior and continues with its execution," Marín said.
"However, if any of the calculated angles is bigger than 45º, the malware will start the process all over again by ensuring there is mouse movement in a 300-millisecond period and capturing again 5 new cursor positions to process."
The development comes amid the emergence of new strains of information stealers and remote access trojans such as BbyStealer, Trap Stealer, Predator AI, and Sayler RAT that are designed to extract a wide range of sensitive data from compromised systems.
Predator AI, an actively maintained project, is also notable for the fact that it can be used to attack many popular cloud services such as AWS, PayPal, Razorpay, and Twilio, in addition to incorporating a ChatGPT API to "make the tool easier to use," SentinelOne noted earlier this month.
"The malware-as-a-service (MaaS) model, and its readily available scheme, remains to be the preferred method for emerging threat actors to carry out complex and lucrative cyberattacks," Marín said.
"Information theft is a significant focus within the realm of MaaS, [and] represents a considerable threat that can lead to substantial financial losses for both organizations and individuals."
Randstorm Exploit: Bitcoin Wallets Created b/w 2011-2015 Vulnerable to Hacking
20.11.23 Exploit The Hacker News
Bitcoin wallets created between 2011 and 2015 are susceptible to a new kind of exploit called Randstorm that makes it possible to recover passwords and gain unauthorized access to a multitude of wallets spanning several blockchain platforms.
"Randstorm() is a term we coined to describe a collection of bugs, design decisions, and API changes that, when brought in contact with each other, combine to dramatically reduce the quality of random numbers produced by web browsers of a certain era (2011-2015)," Unciphered disclosed in a report published last week.
It's estimated that approximately 1.4 million bitcoins are parked in wallets that were generated with potentially weak cryptographic keys. Customers can check whether their wallets are vulnerable at www.keybleed[.]com.
The cryptocurrency recovery company said it re-discovered the problem in January 2022 while it was working for an unnamed customer who had been locked out of its Blockchain.com wallet. The issue was first highlighted way back in 2018 by a security researcher who goes by the alias "ketamine."
The crux of the vulnerability stems from the use of BitcoinJS, an open-source JavaScript package used for developing browser-based cryptocurrency wallet applications.
Especially, Randstorm is rooted in the package's reliance on the SecureRandom() function in the JSBN javascript library coupled with cryptographic weaknesses that existed at that time in the web browsers' implementation of the Math.random() function, which allowed for weak pseudorandom number generation. BitcoinJS maintainers discontinued the use of JSBN in March 2014.
As a result, the lack of enough entropy could be exploited to stage brute-force attacks and recover the wallet private keys generated with the BitcoinJS library (or its dependent projects). The easiest wallets to crack open were those that had been generated before March 2012.
The findings once again cast fresh light on the open-source dependencies powering software infrastructure and how vulnerabilities in such foundational libraries can have cascading supply chain risks, as previously laid bare in the case of Apache Log4j in late 2021.
"The flaw was already built into wallets created with the software, and it would stay there forever unless the funds were moved to a new wallet created with new software," Unciphered noted.
Indian Hack-for-Hire Group Targeted U.S., China, and More for Over 10 Years
20.11.23 BigBrothers The Hacker News
An Indian hack-for-hire group targeted the U.S., China, Myanmar, Pakistan, Kuwait, and other countries as part of a wide-ranging espionage, surveillance, and disruptive operation for over a decade.
The Appin Software Security (aka Appin Security Group), according to an in-depth analysis from SentinelOne, began as an educational startup offering offensive security training programs, while carrying out covert hacking operations since at least 2009.
In May 2013, ESET disclosed a set of cyber attacks targeting Pakistan with information-stealing malware. While the activity was attributed to a cluster tracked as Hangover (aka Patchwork or Zinc Emerson), evidence shows that the infrastructure is owned and controlled by Appin.
"The group has conducted hacking operations against high value individuals, governmental organizations, and other businesses involved in specific legal disputes," SentinelOne security Tom Hegel said in a comprehensive analysis published last week.
"Appin's hacking operations and overall organization appear at many times informal, clumsy, and technically crude; however, their operations proved highly successful for their customers, impacting world affairs with significant success."
The findings are based on non-public data obtained by Reuters, which called out Appin for orchestrating data theft attacks on an industrial scale against political leaders, international executives, sports figures, and others. The company, in response, has dismissed its connection with the hack-for-hire business.
One of the core services offered by Appin was a tool "MyCommando" (aka GoldenEye or Commando) that allowed its customers to log in to view and download campaign-specific data and status updates, communicate securely, and choose from various task options that range from open-source research to social engineering to a trojan campaign.
The targeting of China and Pakistan is confirmation that an Indian-origin mercenary group has been roped in to conduct state-sponsored attacks. Appin has also been identified as behind the macOS spyware known as KitM in 2013.
What's more, SentinelOne said it also identified instances of domestic targeting with the goal of stealing login credentials of email accounts belonging to Sikhs in India and the U.S.

"In an unrelated campaign, the group also used the domain speedaccelator[.]com for an FTP server, hosting malware used in their malicious phishing emails, one of which was used on an Indian individual later targeted by the ModifiedElephant APT," Hegel noted. It's worth noting that Patchwork's links to ModifiedElephant were previously identified by Secureworks.
Besides leveraging a large infrastructure sourced from a third-party for data exfiltration, command-and-control (C2), phishing, and setting up decoy sites, the shadowy private-sector offensive actor (PSOA) is said to have relied on private spyware and exploit services provided by private vendors like Vervata, Vupen, and Core Security.
In another noteworthy tactic, Appin is said to have leveraged a California-based freelancing platform referred to as Elance (now called Upwork) to purchase malware from external software developers, while also using its in-house employees to develop a custom collection of hacking tools.
"The research findings underscore the group's remarkable tenacity and a proven track record of successfully executing attacks on behalf of a diverse clientele," Hegel said.
The development comes as Aviram Azari, an Israeli private investigator, was sentenced in the U.S. to nearly seven years in federal prison on charges of computer intrusion, wire fraud, and aggravated identity theft in connection with a global hack-for-hire scheme between November 2014 to September 2019. Azari was arrested in September 2019.
"Azari owned and operated an Israeli intelligence firm," the Department of Justice (DoJ) said last week. "Clients hired Azari to manage 'Projects' that were described as intelligence gathering efforts but were, in fact, hacking campaigns specifically targeting certain groups of victims."
Aviram has also been accused of using mercenary hackers in India, a company called BellTroX Infotech (aka Amanda or Dark Basin), to help clients gain an advantage in court battles via spear-phishing attacks and ultimately gain access to victims' accounts and steal information.
BellTrox was founded by Sumit Gupta in May 2013. Reuters disclosed in June 2022 that prior to launching the company, Gupta had worked for Appin.
8Base Group Deploying New Phobos Ransomware Variant via SmokeLoader
18.11.23 Virus The Hacker News
The threat actors behind the 8Base ransomware are leveraging a variant of the Phobos ransomware to conduct their financially motivated attacks.
The findings come from Cisco Talos, which has recorded an increase in activity carried out by cybercriminals.
"Most of the group's Phobos variants are distributed by SmokeLoader, a backdoor trojan," security researcher Guilherme Venere said in an exhaustive two-part analysis published Friday.
"This commodity loader typically drops or downloads additional payloads when deployed. In 8Base campaigns, however, it has the ransomware component embedded in its encrypted payloads, which is then decrypted and loaded into the SmokeLoader process' memory."
8Base came into sharp focus in mid-2023, when a similar spike in activity was observed by the cybersecurity community. It's said to be active at least since March 2022.
A previous analysis from VMware Carbon Black in June 2023 identified parallels between 8Base and RansomHouse, in addition to discovering a Phobos ransomware sample that was found using the ".8base" file extension for encrypted files.
This raised the likelihood that 8Base is either a successor to Phobos or that the threat actors behind the operation are merely using already existing ransomware strains to conduct their attacks, akin to the Vice Society ransomware group.
The latest findings from Cisco Talos show that SmokeLoader is used as a launchpad to execute the Phobos payload, which then carries out steps to establish persistence, terminate processes that may keep the target files open, disable system recovery, and delete backups as well as shadow copies.
Another notable characteristic is the full encryption of files that are below 1.5 MB and partial encryption of files above the threshold to speed up the encryption process.
Furthermore, the artifact incorporates a configuration with over 70 options that's encrypted using a hard-coded key. The configuration unlocks additional features such as User Account Control (UAC) bypass and reporting of a victim infection to an external URL.
There is also a hard-coded RSA key used to protect the per-file AES key used in the encryption, which Talos said could help enable decryption of files locked by the ransomware.
"Once each file is encrypted, the key used in the encryption along with additional metadata is then encrypted using RSA-1024 with a hard-coded public key, and saved to the end of the file," Venere elaborated.
"It implies, however, that once the private RSA key is known, any file encrypted by any Phobos variant since 2019 can reliably be decrypted."
Phobos, which first emerged in 2019, is an evolution of the Dharma (aka Crysis) ransomware, with the ransomware predominantly manifesting as the variants Eking, Eight, Elbie, Devos, and Faust, based on the volume of artifacts unearthed on VirusTotal.
"The samples all contained the same source code and were configured to avoid encrypting files that other Phobos affiliated already locked, but the configuration changed slightly depending on the variant being deployed," Venere said. "This is based on a file extension block list in the ransomware's configuration settings."
Cisco Talos assesses that Phobos is closely managed by a central authority, while being sold as a ransomware-as-a-service (RaaS) to other affiliates based on the same RSA public key, the variations in the contact emails, and regular updates to the ransomware's extension block lists.
"The extension blocklists appear to tell a story of which groups used that same base sample over time," Venere said.
"The extension block lists found in the many Phobos samples [...] are continually updated with new files that have been locked in previous Phobos campaigns. This may support the idea that there is a central authority behind the builder who keeps track of who used Phobos in the past. The intent could be to prevent Phobos affiliates from interfering with one another's operations."
The development comes as FalconFeeds disclosed that a threat actor is advertising a sophisticated ransomware product called UBUD that's developed in C and features "strong anti-detection measures against virtual machines and debugging tools."
It also follows a formal complaint filed by the BlackCat ransomware group with the U.S. Securities and Exchange Commission (SEC), alleging that one of its victims, MeridianLink, failed to comply with new disclosure regulations that require impacted companies to report the incident within four business days, DataBreaches.net reported.
The financial software company has since confirmed it was targeted in a cyber attack on November 10, but noted it found no evidence of unauthorized access to its systems.
While the SEC disclosure rules don't take effect until next month on December 18, the unusual pressure tactic is a sign that threat actors are closely watching the space and are willing to bend government regulations to their advantage and compel victims to pay up.
That said, it's worth noting that the enforcement exclusively applies in situations where the companies have identified that the attacks have had a "material" impact on their bottom lines.
Another prolific ransomware gang LockBit, in the meanwhile, has instituted new negotiation rules starting October 2023, citing less-than-expected settlements and larger discounts offered to victims due to the "different levels of experience of affiliates."
"Establish a minimum ransom request depending on the company's yearly revenue, for example at 3%, and prohibit discounts of more than 50%," the LockBit operators said, according to a detailed report from Analyst1.
"Thus, if the company's revenue is $100 million USD, the initial ransom request should start from $3 million USD with the final payout must be no less than $1.5 million USD."
Russian Cyber Espionage Group Deploys LitterDrifter USB Worm in Targeted Attacks
18.11.23 Virus The Hacker News
Russian cyber espionage actors affiliated with the Federal Security Service (FSB) have been observed using a USB propagating worm called LitterDrifter in attacks targeting Ukrainian entities.
Check Point, which detailed Gamaredon's (aka Aqua Blizzard, Iron Tilden, Primitive Bear, Shuckworm, and Winterflounder) latest tactics, branded the group as engaging in large-scale campaigns that are followed by "data collection efforts aimed at specific targets, whose selection is likely motivated by espionage goals."
The LitterDrifter worm packs in two main features: automatically spreading the malware via connected USB drives as well as communicating with the threat actor's command-and-control (C&C) servers. It's also suspected to be an evolution of a PowerShell-based USB worm that was previously disclosed by Symantec in June 2023.
Written in VBS, the spreader module is responsible for distributing the worm as a hidden file in a USB drive together with a decoy LNK that's assigned random names. The malware gets its name LitterDrifter owing to the fact that the initial orchestration component is named "trash.dll."
"Gamaredon's approach towards the C&C is rather unique, as it utilizes domains as a placeholder for the circulating IP addresses actually used as C2 servers," Check Point explained.
LitterDrifter is also capable of connecting to a C&C server extracted from a Telegram channel, a tactic it has repeatedly put to use since at least the start of the year.
The cybersecurity firm said it also detected signs of possible infection outside of Ukraine based on VirusTotal submissions from the U.S., Vietnam, Chile, Poland, Germany, and Hong Kong.
Gamaredon has had an active presence this year, while continuously evolving its attack methods. In July 2023, the adversary's rapid data exfiltration capabilities came to light, what with the threat actor transmitting sensitive information within an hour of the initial compromise.
"It's clear that LitterDrifter was designed to support a large-scale collection operation," the company concluded. "It leverages simple, yet effective techniques to ensure it can reach the widest possible set of targets in the region."
The development comes as Ukraine's National Cybersecurity Coordination Center (NCSCC) revealed attacks orchestrated by Russian state-sponsored hackers targeting embassies across Europe, including Italy, Greece, Romania, and Azerbaijan.
The intrusions, attributed to APT29 (aka BlueBravo, Cloaked Ursa, Cozy Bear, Iron Hemlock, Midnight Blizzard, and The Dukes), involve the exploitation of the recently disclosed WinRAR vulnerability (CVE-2023-38831) via benign-looking lures that claim to offer BMWs for sale, a theme it has employed in the past.
The attack chain commences with sending victims phishing emails containing a link to a specially crafted ZIP file that, when launched, exploits the flaw to retrieve a PowerShell script from a remote server hosted on Ngrok.
"A concerning trend of exploiting CVE-2023-38831 vulnerability by Russian intelligence services hacking groups demonstrates its growing popularity and sophistication," NCSCC said.
Earlier this week, the Computer Emergency Response Team of Ukraine (CERT-UA) unearthed a phishing campaign that propagates malicious RAR archives that masquerades as a PDF document from the Security Service of Ukraine (SBU) but, in reality, is an executable that leads to the deployment of Remcos RAT.
CERT-UA is tracking the activity under the moniker UAC-0050, which was also linked to another spate of cyber attacks aimed at state authorities in the country to deliver Remcos RAT in February 2023.
Beware: Malicious Google Ads Trick WinSCP Users into Installing Malware
17.11.23 Virus The Hacker News
Threat actors are leveraging manipulated search results and bogus Google ads that trick users who are looking to download legitimate software such as WinSCP into installing malware instead.
Cybersecurity company Securonix is tracking the ongoing activity under the name SEO#LURKER.
"The malicious advertisement directs the user to a compromised WordPress website gameeweb[.]com, which redirects the user to an attacker-controlled phishing site," security researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov said in a report shared with The Hacker News.
The threat actors are believed to leverage Google's Dynamic Search Ads (DSAs), which automatically generates ads based on a site's content to serve the malicious ads that take the victims to the infected site.
The ultimate goal of the complex multi-stage attack chain is to entice users into clicking on the fake, lookalike WinSCP website, winccp[.]net, and download the malware.
"Traffic from the gaweeweb[.]com website to the fake winsccp[.]net website relies on a correct referrer header being set properly," the researchers said. "If the referrer is incorrect, the user is 'Rickrolled' and is sent to the infamous Rick Astley YouTube video."
The final payload takes the form of a ZIP file ("WinSCP_v.6.1.zip") that comes with a setup executable, which, when launched, employs DLL side-loading to load and execute a DLL file named python311.dll that's present within the archive.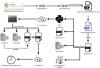
The DLL, for its part, downloads and executes a legitimate WinSCP installer to keep up the ruse, while stealthily dropping Python scripts ("slv.py" and "wo15.py") in the background to activate the malicious behavior. It's also responsible for setting up persistence.
Both the Python scripts are designed to establish contact with a remote actor-controlled server to receive further instructions that allow the attackers to run enumeration commands on the host.
"Given the fact that the attackers were leveraging Google Ads to disperse malware, it can be believed that the targets are limited to anyone seeking WinSCP software," the researchers said.
"The geoblocking used on the site hosting the malware suggests that those in the U.S. are victims of this attack."
This is not the first time Google's Dynamic Search Ads have been abused to distribute malware. Late last month, Malwarebytes lifted the lid on a campaign that targets users searching for PyCharm with links to a hacked website hosting a rogue installer that paves the way for the deployment of information-stealing malware.
Malvertising has grown in popularity among cybercriminals in the past few years, with numerous malware campaigns using the tactic for attacks in recent months.
Earlier this week, Malwarebytes revealed an uptick in credit card skimming campaigns in October 2023 that's estimated to have compromised hundreds of e-commerce websites with an aim to steal financial information by injecting convincing counterfeit payment pages.
FCC Enforces Stronger Rules to Protect Customers Against SIM Swapping Attacks
17.11.23 Attack The Hacker News
The U.S. Federal Communications Commission (FCC) is adopting new rules that aim to protect consumers from cell phone account scams that make it possible for malicious actors to orchestrate SIM-swapping attacks and port-out fraud.
"The rules will help protect consumers from scammers who target data and personal information by covertly swapping SIM cards to a new device or porting phone numbers to a new carrier without ever gaining physical control of a consumer's phone," FCC said this week.
While SIM swapping refers to transferring a user's account to a SIM card controlled by the scammer by convincing the victim's wireless carrier, port-out fraud occurs when the bad actor, posing as the victim, transfers their phone number from one service provider to another without their knowledge.
The new rules, first proposed in July 2023, mandate wireless providers to adopt secure methods of authenticating a customer before redirecting a customer's phone number to a new device or provider.
Another requirement ensures that customers are immediately notified whenever a SIM change or port-out request is made on their accounts so that they can take appropriate action to secure against such attacks.
SIM swapping has emerged as a serious threat, enabling threat actors like LAPSUS$ and Scattered Spider to infiltrate corporate networks. Migrating the service to an actor-controlled device gives the attackers the ability to divert SMS-based two-factor authentication codes and take over victims' online accounts.
"Because we so frequently use our phone numbers for two-factor authentication, a bad actor who takes control of a phone can also take control of financial accounts, social media accounts, the list goes on," FCC Commissioner Geoffrey Starks said.
"Consumers must be able to count on secure verification procedures and reliable privacy guarantees from their wireless providers. And they should be able to go about their day without fearing that someone, somewhere, might take control of their phone without a single warning sign."
The development comes as the FCC said it's also launching an inquiry to understand the impact of artificial intelligence (AI) on robocalls and robotexts.
"AI could improve analytics tools used to block unwanted calls and texts and restore trust in our networks," the agency said. "But AI could also permit bad actors to more easily defraud consumers through calls and text messages, such as by using technology to mimic voices of public officials or other trusted sources."
27 Malicious PyPI Packages with Thousands of Downloads Found Targeting IT Experts
17.11.23 Virus The Hacker News
An unknown threat actor has been observed publishing typosquat packages to the Python Package Index (PyPI) repository for nearly six months with an aim to deliver malware capable of gaining persistence, stealing sensitive data, and accessing cryptocurrency wallets for financial gain.
The 27 packages, which masqueraded as popular legitimate Python libraries, attracted thousands of downloads, Checkmarx said in a new report. A majority of the downloads originated from the U.S., China, France, Hong Kong, Germany, Russia, Ireland, Singapore, the U.K., and Japan.
"A defining characteristic of this attack was the utilization of steganography to hide a malicious payload within an innocent-looking image file, which increased the stealthiness of the attack," the software supply chain security firm said.
Some of the packages are pyefflorer, pyminor, pyowler, pystallerer, pystob, and pywool, the last of which was planted on May 13, 2023.
A common denominator to these packages is the use of the setup.py script to include references to other malicious packages (i.e., pystob and pywool) that deploy a Visual Basic Script (VBScript) in order to download and execute a file named "Runtime.exe" to achieve persistence on the host.
Embedded within the binary is a compiled file that's capable of gathering information from web browsers, cryptocurrency wallets, and other applications.
An alternate attack chain observed by Checkmarx is said to have hidden the executable code within a PNG image ("uwu.png"), which is subsequently decoded and run to extract the public IP address and the universally unique identifier (UUID) of the affected system.
Pystob and Pywool, in particular, were published under the guise of tools for API management, only to exfiltrate the data to a Discord webhook and attempt to maintain persistence by placing the VBS file in the Windows startup folder.
"This campaign serves as another stark reminder of the ever-present threats that exist in today's digital landscape, particularly in areas where collaboration and open exchange of code are foundational," Checkmarx said.
The development comes as ReversingLabs uncovered a new wave of protestware npm packages that "hide scripts broadcasting messages of peace related to the conflicts in Ukraine and in Israel and the Gaza Strip."
One of the packages, named @snyk/sweater-comb (version 2.1.1), determines the geographic location of the host, and if it's found to be Russia, displays a message criticizing the "unjustified invasion" of Ukraine through another module called "es5-ext."
Another package, e2eakarev, has the description "free palestine protest package" in the package.json file, and carries out similar checks to see if the IP address resolves to Israel, and if so, log what's described as a "harmless protest message" that urges developers to raise awareness about the Palestinian struggle.
It's not just threat actors infiltrating open-source ecosystems. Earlier this week, GitGuardian revealed the presence of 3,938 total unique secrets across 2,922 PyPI projects, of which 768 unique secrets were found to be valid.
This includes AWS keys, Azure Active Directory API keys, GitHub OAuth app keys, Dropbox keys, SSH keys, and credentials associated with MongoDB, MySQL, PostgreSQL, Coinbase, and Twilio.
What's more, many of these secrets were leaked more than once, spanning multiple release versions, bringing the total number of occurrences to 56,866.
"Exposing secrets in open-source packages carries significant risks for developers and users alike," GitGuardian's Tom Forbes said. "Attackers can exploit this information to gain unauthorized access, impersonate package maintainers, or manipulate users through social engineering tactics."
The continuous wave of attacks targeting the software supply chain has also prompted the U.S. government to issue new guidance this month for software developers and suppliers to maintain and provide awareness about software security.
"It is recommended that acquisition organizations assign supply chain risk assessments to their buying decisions given the recent high profile software supply chain incidents," the Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA), and the Office of the Director of National Intelligence (ODNI) said.
"Software developers and suppliers should improve their software development processes and reduce the risk of harm to not just employees and shareholders, but also to their users."
U.S. Cybersecurity Agencies Warn of Scattered Spider's Gen Z Cybercrime Ecosystem
17.11.23 BigBrothers The Hacker News
U.S. cybersecurity and intelligence agencies have released a joint advisory about a cybercriminal group known as Scattered Spider that's known to employ sophisticated phishing tactics to infiltrate targets.
"Scattered Spider threat actors typically engage in data theft for extortion using multiple social engineering techniques and have recently leveraged BlackCat/ALPHV ransomware alongside their usual TTPs," the agencies said.
The threat actor, also tracked under the monikers Muddled Libra, Octo Tempest, 0ktapus, Scatter Swine, Star Fraud, and UNC3944, was the subject of an extensive profile from Microsoft last month, with the tech giant calling it "one of the most dangerous financial criminal groups."
Considered as experts in social engineering, Scattered Spider is known to rely on phishing, prompt bombing, and SIM swapping attacks to obtain credentials, install remote access tools, and bypass multi-factor authentication (MFA).
Scattered Spider, like LAPSUS$, is said to be part of a larger Gen Z cybercrime ecosystem that refers to itself as the Com (alternately spelled Comm), which has resorted to violent activity and swatting attacks.
A report from Reuters earlier this week disclosed that the U.S. Federal Bureau of Investigation (FBI) is aware of the identities of at least a dozen members of the cybercrime gang.
One of the notable tricks in its arsenal is the impersonation of IT and helping desk staff use phone calls or SMS messages to target employees and gain elevated access to the networks.
Successful initial access is followed by the deployment of legitimate remote access tunneling tools such as Fleetdeck.io, Ngrok, and Pulseway, as well as remote access trojans and stealers like AveMaria (aka Warzone RAT), Raccoon Stealer, and Vidar Stealer.
Furthermore, the English-speaking extortion crew leverages living-off-the-land (LotL) techniques to skirt detection and navigate compromised networks with an ultimate aim to steal sensitive information in exchange for a payment.
"The threat actors frequently join incident remediation and response calls and teleconferences, likely to identify how security teams are hunting them and proactively develop new avenues of intrusion in response to victim defenses," the agencies noted.
As of mid-2023, Scattered Spider has also acted as an affiliate for the BlackCat ransomware gang, monetizing its access to victims for extortion-enabled ransomware and data theft.
The U.S. government is urging companies to implement phishing-resistant MFA, enforce a recovery plan, maintain offline backups, and adopt application controls to prevent the execution of unauthorized software on endpoints.
CISA Adds Three Security Flaws with Active Exploitation to KEV Catalog
17.11.23 Vulnerebility The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added three security flaws to its Known Exploited Vulnerabilities (KEV) catalog based on evidence of active exploitation in the wild.
The vulnerabilities are as follows -
CVE-2023-36584 (CVSS score: 5.4) - Microsoft Windows Mark-of-the-Web (MotW) Security Feature Bypass Vulnerability
CVE-2023-1671 (CVSS score: 9.8) - Sophos Web Appliance Command Injection Vulnerability
CVE-2023-2551 (CVSS score: 8.8) - Oracle Fusion Middleware Unspecified Vulnerability
CVE-2023-1671 relates to a critical pre-auth command injection vulnerability that allows for the execution of arbitrary code. CVE-2023-2551 is a flaw in the WLS Core Components that allows an unauthenticated attacker with network access to compromise the WebLogic Server.
There are currently no public reports documenting in-the-wild attacks leveraging the two flaws.
On the other hand, the addition of CVE-2023-36584 to the KEV catalog is based on a report from Palo Alto Networks Unit 42 earlier this week, which detailed spear-phishing attacks mounted by pro-Russian APT group known as Storm-0978 (aka RomCom or Void Rabisu) targeting groups supporting Ukraine's admission into NATO in July 2023.
CVE-2023-36584, patched by Microsoft as part of October 2023 security updates, is said to have been used alongside CVE-2023-36884, a Windows remote code execution vulnerability addressed in July, in an exploit chain to deliver PEAPOD, an updated version of RomCom RAT.
In light of active exploitation, federal agencies are recommended to apply the fixes by December 7, 2023, to secure their networks against potential threats.
Fortinet Discloses Critical Command Injection Bug in FortiSIEM#
The development comes as Fortinet is alerting customers of a critical command injection vulnerability in FortiSIEM report server (CVE-2023-36553, CVSS score: 9.3) that could be exploited by attackers to execute arbitrary commands.
CVE-2023-36553 has been described as a variant of CVE-2023-34992 (CVSS score: 9.7), a similar flaw in the same product that was remediated by Fortinet in early October 2023.
"An improper neutralization of special elements used in an OS command vulnerability [CWE-78] in FortiSIEM report server may allow a remote unauthenticated attacker to execute unauthorized commands via crafted API requests," the company said in an advisory this week.
The vulnerability, which impacts FortiSIEM versions 4.7, 4.9, 4.10, 5.0, 5.1, 5.2, 5.3, and 5.4, has been fixed in versions 7.1.0, 7.0.1, 6.7.6, 6.6.4, 6.5.2, 6.4.3, or later.
Zero-Day Flaw in Zimbra Email Software Exploited by Four Hacker Groups
17.11.23 Vulnerebility The Hacker News
A zero-day flaw in the Zimbra Collaboration email software was exploited by four different groups in real-world attacks to pilfer email data, user credentials, and authentication tokens.
"Most of this activity occurred after the initial fix became public on GitHub," Google Threat Analysis Group (TAG) said in a report shared with The Hacker News.
The flaw, tracked as CVE-2023-37580 (CVSS score: 6.1), is a reflected cross-site scripting (XSS) vulnerability impacting versions before 8.8.15 Patch 41. It was addressed by Zimbra as part of patches released on July 25, 2023.
Successful exploitation of the shortcoming could allow execution of malicious scripts on the victims' web browser simply by tricking them into clicking on a specially crafted URL, effectively initiating the XSS request to Zimbra and reflecting the attack back to the user.
Google TAG, whose researcher Clément Lecigne was credited with discovering and reporting the bug, said it discovered multiple campaign waves starting June 29, 2023, at least two weeks before Zimbra issued an advisory.
Three of the four campaigns were observed prior to the release of the patch, with the fourth campaign detected a month after the fixes were published.
The first campaign is said to have targeted a government organization in Greece, sending emails containing exploit URLs to their targets that, when clicked, delivered an email-stealing malware previously observed in a cyber espionage operation dubbed EmailThief in February 2022.
The intrusion set, which Volexity codenamed as TEMP_HERETIC, also exploited a then-zero-day flaw in Zimbra to carry out the attacks.

The second threat actor to exploit CVE-2023-37580 is Winter Vivern, which targeted government organizations in Moldova and Tunisia shortly after a patch for the vulnerability was pushed to GitHub on July 5.
It's worth noting that the adversarial collective has been linked to the exploitation of security vulnerabilities in Zimbra Collaboration and Roundcube by Proofpoint and ESET this year.
TAG said it spotted a third, unidentified group weaponizing the bug before the patch was pushed on July 25 to phish for credentials belonging to a government organization in Vietnam.
"In this case, the exploit URL pointed to a script that displayed a phishing page for users' webmail credentials and posted stolen credentials to a URL hosted on an official government domain that the attackers likely compromised," TAG noted.
Lastly, a government organization in Pakistan was targeted using the flaw on August 25, resulting in the exfiltration of the Zimbra authentication token to a remote domain named "ntcpk[.]org."
Google further pointed out a pattern in which threat actors are regularly exploiting XSS vulnerabilities in mail servers, necessitating that such applications are audited thoroughly.
"The discovery of at least four campaigns exploiting CVE-2023-37580, three campaigns after the bug first became public, demonstrates the importance of organizations applying fixes to their mail servers as soon as possible," TAG said.
"These campaigns also highlight how attackers monitor open-source repositories to opportunistically exploit vulnerabilities where the fix is in the repository, but not yet released to users."
Experts Uncover DarkCasino: New Emerging APT Threat Exploiting WinRAR Flaw
17.11.23 APT The Hacker News
A hacking group that leveraged a recently disclosed security flaw in the WinRAR software as a zero-day has now been categorized as an entirely new advanced persistent threat (APT).
Cybersecurity company NSFOCUS has described DarkCasino as an "economically motivated" actor that first came to light in 2021.
"DarkCasino is an APT threat actor with strong technical and learning ability, who is good at integrating various popular APT attack technologies into its attack process," the company said in an analysis.
"Attacks launched by the APT group DarkCasino are very frequent, demonstrating a strong desire to steal online property."
DarkCasino was most recently linked to the zero-day exploitation of CVE-2023-38831 (CVSS score: 7.8), a security flaw that can be weaponized to launch malicious payloads.
In August 2023, Group-IB disclosed real-world attacks weaponizing the vulnerability and aimed at online trading forums at least since April 2023 to deliver a final payload named DarkMe, which is a Visual Basic trojan attributed to DarkCasino.
The malware is equipped to collect host information, take screenshots, manipulate files and Windows Registry, execute arbitrary commands, and self-update itself on the compromised host.
While DarkCasino was previously classified as a phishing campaign orchestrated by the Evilnum group targeting European and Asian online gambling, cryptocurrency, and credit platforms, NSFOCUS said its continuous tracking of the adversary's activities has allowed it rule out any potential connections with known threat actors.
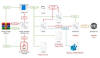
The exact provenance of the threat actor is currently unknown.
"In the early days, DarkCasino mainly operated in countries around the Mediterranean and other Asian countries using online financial services," it said.
"More recently, with the change of phishing methods, its attacks have reached users of cryptocurrencies worldwide, even including non-English-speaking Asian countries such as South Korea and Vietnam."
Multiple threat actors have joined the CVE-2023-38831 exploitation bandwagon in recent months, including APT28, APT29, APT40, Dark Pink, Ghostwriter, Konni, and Sandworm.
Ghostwriter's attack chains leveraging the shortcoming have been observed to pave the way for PicassoLoader, an intermediate malware that acts as a loader for other payloads.
"The WinRAR vulnerability CVE-2023-38831 brought by the APT group DarkCasino brings uncertainties to the APT attack situation in the second half of 2023," NSFOCUS said.
"Many APT groups have taken advantage of the window period of this vulnerability to attack critical targets such as governments, hoping to bypass the protection system of the targets and achieve their purposes."
CISA and FBI Issue Warning About Rhysida Ransomware Double Extortion Attacks
16.11.23 Ransom The Hacker News
The threat actors behind the Rhysida ransomware engage in opportunistic attacks targeting organizations spanning various industry sectors.
The advisory comes courtesy of the U.S. Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the Multi-State Information Sharing and Analysis Center (MS-ISAC).
"Observed as a ransomware-as-a-service (RaaS) model, Rhysida actors have compromised organizations in education, manufacturing, information technology, and government sectors and any ransom paid is split between the group and affiliates," the agencies said.
"Rhysida actors leverage external-facing remote services, such as virtual private networks (VPNs), Zerologon vulnerability (CVE-2020-1472), and phishing campaigns to gain initial access and persistence within a network."
First detected in May 2023, Rhysida makes use of the time-tested tactic of double extortion, demanding a ransom payment to decrypt victim data and threatening to publish the exfiltrated data unless the ransom is paid.
It's also said to share overlaps with another ransomware crew known as Vice Society (aka Storm-0832 or Vanilla Tempest), owing to similar targeting patterns and the use of NTDSUtil as well as PortStarter, which has been exclusively employed by the latter.
According to statistics compiled by Malwarebytes, Rhysida has claimed five victims for the month of October 2023, putting it far behind LockBit (64), NoEscape (40), PLAY (36), ALPHV/BlackCat (29), and 8BASE (21).
The agencies described the group as engaging in opportunistic attacks to breach targets and taking advantage of living-off-the-land (LotL) techniques to facilitate lateral movement and establish VPN access.
In doing so, the idea is to evade detection by blending in with legitimate Windows systems and network activities.
Vice Society's pivot to Rhysida has been bolstered in the wake of new research published by Sophos earlier last week, which said it observed the same threat actor using Vice Society up until June 2023, when it switched to deploying Rhysida.
The cybersecurity company is tracking the cluster under the name TAC5279.
"Notably, according to the ransomware group's data leak site, Vice Society has not posted a victim since July 2023, which is around the time Rhysida began reporting victims on its site," Sophos researchers Colin Cowie and Morgan Demboski said.
The development comes as the BlackCat ransomware Gang is attacking corporations and public entities using Google ads laced with Nitrogen malware, per eSentire.
"This affiliate is taking out Google ads promoting popular software, such as Advanced IP Scanner, Slack, WinSCP and Cisco AnyConnect, to lure business professionals to attacker-controlled websites," the Canadian cybersecurity company said.
The rogue installers, which come fitted with Nitrogen, which is an initial access malware capable of delivering next-stage payloads onto a compromised environment, including ransomware.
Cybersecurity
"Known examples of ransomware-associated initial access malware that leverage browser-based attacks include GootLoader, SocGholish, BATLOADER, and now Nitrogen," eSentire said. "Interestingly, ALPHV has been observed as an end-game for at least two of these browser-based initial access pieces of malware: GootLoader and Nitrogen."
The ever-evolving nature of the ransomware landscape is further evidenced by the fact that 29 of the 60 ransomware groups currently active began operations this year, per WithSecure, in part driven by the source code leaks of Babuk, Conti, and LockBit over the years.
"Data leaks aren't the only thing that leads to older groups cross-pollinating younger ones," WithSecure said in a report shared with The Hacker News.
"Ransomware gangs have staff just like an IT company. And like an IT company, people change jobs sometimes, and bring their unique skills and knowledge with them. Unlike legit IT companies, however, there's nothing stopping a cyber criminal from taking proprietary resources (such as code or tools) from one ransomware operation and using it at another. There's no honor among thieves."
Hackers Could Exploit Google Workspace and Cloud Platform for Ransomware Attacks
16.11.23 Ransom The Hacker News
A set of novel attack methods has been demonstrated against Google Workspace and the Google Cloud Platform that could be potentially leveraged by threat actors to conduct ransomware, data exfiltration, and password recovery attacks.
"Starting from a single compromised machine, threat actors could progress in several ways: they could move to other cloned machines with GCPW installed, gain access to the cloud platform with custom permissions, or decrypt locally stored passwords to continue their attack beyond the Google ecosystem," Martin Zugec, technical solutions director at Bitdefender, said in a new report.
A prerequisite for these attacks is that the bad actor has already gained access to a local machine through other means, prompting Google to mark the bug as not eligible for fixing "since it's outside of our threat model and the behavior is in line with Chrome's practices of storing local data."
However, the Romanian cybersecurity firm has warned that threat actors can exploit such gaps to extend a single endpoint compromise to a network-wide breach.
The attacks, in a nutshell, rely on an organization's use of Google Credential Provider for Windows (GCPW), which offers both mobile device management (MDM) and single sign-on (SSO) capabilities.
This enables administrators to remotely manage and control Windows devices within their Google Workspace environments, as well as allows users to access their Windows devices using the same credentials that are used to login to their Google accounts.
GCPW is designed to use a local privileged service account named Google Accounts and ID Administration (GAIA) to seamlessly facilitate the process in the background by connecting to Google APIs for verifying a user's credentials during the sign-in step and storing a refresh token to obviate the need for re-authentication.
With this setup in place, an attacker with access to a compromised machine can extract an account's refresh OAuth tokens, either from the Windows registry or from the user's Chrome profile directory, and bypass multi-factor authentication (MFA) protections.
The refresh token is subsequently utilized to construct an HTTP POST request to the endpoint "https://www.googleapis[.]com/oauth2/v4/token" to obtain an access token, which, in turn, can be abused to retrieve, manipulate, or delete sensitive data associated with the Google Account.
A second exploit concerns what's called the Golden Image lateral movement, which focuses on virtual machine (VM) deployments and takes advantage of the fact that creating a machine by cloning another machine with pre-installed GCPW causes the password associated with the GAIA account to be cloned as well.
"If you know the password to a local account, and local accounts on all machines share the same password, then you know the passwords to all machines," Zugec explained.
"This shared-password challenge is similar to having the same local administrator password on all machines that has been addressed by Microsoft's Local Administrator Password Solution (LAPS)."
The third attack entails access to plaintext credentials by leveraging the access token acquired using the aforementioned technique to send an HTTP GET request to an undocumented API endpoint and get hold of the private RSA key that is required to decrypt the password field.
"Having access to plaintext credentials, such as usernames and passwords, represents a more severe threat," Zugec said. "This is because it enables attackers to directly impersonate legitimate users and gain unrestricted access to their accounts, potentially leading to complete account takeover."
Russian Hackers Linked to 'Largest Ever Cyber Attack' on Danish Critical Infrastructure
16.11.23 BigBrothers The Hacker News
Russian threat actors have been possibly linked to what's been described as the "largest cyber attack against Danish critical infrastructure," in which 22 companies associated with the operation of the country's energy sector were targeted in May 2023.
"22 simultaneous, successful cyberattacks against Danish critical infrastructure are not commonplace," Denmark's SektorCERT said [PDF]. "The attackers knew in advance who they were going to target and got it right every time. Not once did a shot miss the target."
The agency said it found evidence connecting one or more attacks to Russia's GRU military intelligence agency, which is also tracked under the name Sandworm and has a track record of orchestrating disruptive cyber assaults on industrial control systems. This assessment is based on artifacts communicating with IP addresses that have been traced to the hacking crew.
The unprecedented and coordinated cyber attacks took place on May 11 by exploiting CVE-2023-28771 (CVSS score: 9.8), a critical command injection flaw impacting Zyxel firewalls that was disclosed in late April 2023.
On the 11 companies that were successfully infiltrated, the threat actors executed malicious code to conduct reconnaissance of the firewall configurations and determine the next course of action.
"This kind of coordination requires planning and resources," SektorCERT said in a detailed timeline of events. "The advantage of attacking simultaneously is that the information about one attack cannot spread to the other targets before it is too late."
"This puts the power of information sharing out of play because no one can be warned in advance about the ongoing attack since everyone is attacked at the same time. It is unusual – and extremely effective."
A second wave of attacks targeting more organizations was subsequently recorded from May 22 to 25 by an attack group with previously unseen cyber weapons, raising the possibility that two different threat actors were involved in the campaign.
That said, it's currently unclear if the groups collaborated with each other, worked for the same employer, or were acting independently.

These attacks are suspected to have weaponized two more critical bugs in Zyxel gear (CVE-2023-33009 and CVE-2023-33010, CVSS scores: 9.8) as zero-days to co-opt the firewalls into Mirai and MooBot botnets, given that patches for them were released by the company on May 24, 2023.
The compromised devices, in some cases, were used to conduct distributed denial-of-service (DDoS) attacks against unnamed companies in the U.S. and Hong Kong.
"After the exploit code for some of the vulnerabilities became publicly known around 30/5, attack attempts against the Danish critical infrastructure exploded – especially from IP addresses in Poland and Ukraine," SektorCERT explained.
The onslaught of attacks prompted the affected entities to disconnect from the internet and go into island mode, the agency further added.
But it's not only nation-state actors. The energy sector is also increasingly becoming a focus for ransomware groups, with initial access brokers (IABs) actively promoting unauthorized access to nuclear energy firms, according to a report from Resecurity earlier this week.
The development comes as Censys discovered six hosts belonging to NTC Vulkan, a Moscow-based IT contractor that's alleged to have supplied offensive cyber tools to Russian intelligence agencies, including Sandworm.
Furthermore, the research uncovered a connection to a group called Raccoon Security via an NTC Vulkan certificate.
"Racoon Security is a brand of NTC Vulkan and that it is possible that Raccoon Security's activities include either previous or current participation in the previously-mentioned leaked initiatives contracted by the GRU," Matt Lembright, director of Federal Applications at Censys, said.
U.S. Takes Down IPStorm Botnet, Russian-Moldovan Mastermind Pleads Guilty
16.11.23 BigBrothers The Hacker News
The U.S. government on Tuesday announced the takedown of the IPStorm botnet proxy network and its infrastructure, as the Russian and Moldovan national behind the operation pleaded guilty.
"The botnet infrastructure had infected Windows systems then further expanded to infect Linux, Mac, and Android devices, victimizing computers and other electronic devices around the world, including in Asia, Europe, North America and South America," the Department of Justice (DoJ) said in a press statement.
Sergei Makinin, who developed and deployed the malicious software to infiltrate thousands of internet-connected devices from June 2019 through December 2022, faces a maximum of 30 years in prison.
The Golang-based botnet malware, prior to its dismantling, turned the infected devices into proxies as part of a for-profit scheme, which was then offered to other customers via proxx[.]io and proxx[.]net.
"IPStorm is a botnet that abuses a legitimate peer-to-peer (p2p) network called InterPlanetary File System (IPFS) as a means to obscure malicious traffic," cybersecurity firm Intezer noted in October 2020.
The botnet was first documented by Anomali in May 2019, and, over the years, broadened its focus to target other operating systems such as Linux, macOS, and Android.
Threat actors who wish to hide their malicious activities could purchase illegitimate access to more than 23,000 bots for "hundreds of dollars a month" to route their traffic. Makinin is estimated to have netted at least $550,000 from the scheme.
Pursuant to the plea agreement, Makinin is expected to forfeit cryptocurrency wallets linked to the offense.
"The InterPlanetary Storm botnet was complex and used to power various cybercriminal activities by renting it as a proxy as a service system over infected IoT devices," Alexandru Catalin Cosoi, senior director of investigation and forensics unit at Bitdefender, said in a statement shared with The Hacker News.
"Our initial research back in 2020 uncovered valuable clues to the culprit behind its operation, and we are extremely pleased it helped lead to arrests. This investigation is another primary example of law enforcement and the private cybersecurity sector working together to shut down illegal online activities and bring those responsible to justice."
New PoC Exploit for Apache ActiveMQ Flaw Could Let Attackers Fly Under the Radar
16.11.23 Exploit The Hacker News
Cybersecurity researchers have demonstrated a new technique that exploits a critical security flaw in Apache ActiveMQ to achieve arbitrary code execution in memory.
Tracked as CVE-2023-46604 (CVSS score: 10.0), the vulnerability is a remote code execution bug that could permit a threat actor to run arbitrary shell commands.
It was patched by Apache in ActiveMQ versions 5.15.16, 5.16.7, 5.17.6, or 5.18.3 released late last month.
The vulnerability has since come under active exploitation by ransomware outfits to deploy ransomware such as HelloKitty and a strain that shares similarities with TellYouThePass as well as a remote access trojan called SparkRAT.
According to new findings from VulnCheck, threat actors weaponizing the flaw are relying on a public proof-of-concept (PoC) exploit originally disclosed on October 25, 2023.
The attacks have been found to use ClassPathXmlApplicationContext, a class that's part of the Spring framework and available within ActiveMQ, to load a malicious XML bean configuration file over HTTP and achieve unauthenticated remote code execution on the server.
VulnCheck, which characterized the method as noisy, said it was able to engineer a better exploit that relies on the FileSystemXmlApplicationContext class and embeds a specially crafted SpEL expression in place of the "init-method" attribute to achieve the same results and even obtain a reverse shell.
"That means the threat actors could have avoided dropping their tools to disk," VulnCheck said. "They could have just written their encryptor in Nashorn (or loaded a class/JAR into memory) and remained memory resident."
However, it's worth noting that doing so triggers an exception message in the activemq.log file, necessitating that the attackers also take steps to clean up the forensic trail.
"Now that we know attackers can execute stealthy attacks using CVE-2023-46604, it's become even more important to patch your ActiveMQ servers and, ideally, remove them from the internet entirely," Jacob Baines, chief technology officer at VulnCheck, said.
Reptar: New Intel CPU Vulnerability Impacts Multi-Tenant Virtualized Environments
15.11.23 Vulnerebility The Hacker News
Intel has released fixes to close out a high-severity flaw codenamed Reptar that impacts its desktop, mobile, and server CPUs.
Tracked as CVE-2023-23583 (CVSS score: 8.8), the issue has the potential to "allow escalation of privilege and/or information disclosure and/or denial of service via local access."
Successful exploitation of the vulnerability could also permit a bypass of the CPU's security boundaries, according to Google Cloud, describing it as an issue stemming from how redundant prefixes are interpreted by the processor.
"The impact of this vulnerability is demonstrated when exploited by an attacker in a multi-tenant virtualized environment, as the exploit on a guest machine causes the host machine to crash resulting in a Denial of Service to other guest machines running on the same host," Google Cloud's Phil Venables said.
"Additionally, the vulnerability could potentially lead to information disclosure or privilege escalation."
Security researcher Tavis Normandy, in a separate analysis of Reptar, said it can be abused to corrupt the system state and force a machine-check exception.
Intel, as part of November 2023 updates, has published updated microcode for all affected processors. The complete list of Intel CPUs impacted by CVE-2023-23583 is available here. There is no evidence of any active attacks using this vulnerability.
"Intel does not expect this issue to be encountered by any non-malicious real-world software," the company said in a guidance issued on November 14. "Malicious exploitation of this issue requires execution of arbitrary code."
The disclosure coincides with the release of patches for a security flaw in AMD processors called CacheWarp (CVE-2023-20592) that lets malicious actors break into AMD SEV-protected VMs to escalate privileges and gain remote code execution.
Alert: Microsoft Releases Patch Updates for 5 New Zero-Day Vulnerabilities
15.11.23 Vulnerebility The Hacker News
Microsoft has released fixes to address 63 security bugs in its software for the month of November 2023, including three vulnerabilities that have come under active exploitation in the wild.
Of the 63 flaws, three are rated Critical, 56 are rated Important, and four are rated Moderate in severity. Two of them have been listed as publicly known at the time of the release.
The updates are in addition to more than 35 security shortcomings addressed in its Chromium-based Edge browser since the release of Patch Tuesday updates for October 2023.
The five zero-days that are of note are as follows -
CVE-2023-36025 (CVSS score: 8.8) - Windows SmartScreen Security Feature Bypass Vulnerability
CVE-2023-36033 (CVSS score: 7.8) - Windows DWM Core Library Elevation of Privilege Vulnerability
CVE-2023-36036 (CVSS score: 7.8) - Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability
CVE-2023-36038 (CVSS score: 8.2) - ASP.NET Core Denial of Service Vulnerability
CVE-2023-36413 (CVSS score: 6.5) - Microsoft Office Security Feature Bypass Vulnerability
Both CVE-2023-36033 and CVE-2023-36036 could be exploited by an attacker to gain SYSTEM privileges, while CVE-2023-36025 could make it possible to bypass Windows Defender SmartScreen checks and their associated prompts.
"The user would have to click on a specially crafted Internet Shortcut (.URL) or a hyperlink pointing to an Internet Shortcut file to be compromised by the attacker," Microsoft said about CVE-2023-36025.
CVE-2023-36025 is the third Windows SmartScreen zero-day vulnerability exploited in the wild in 2023 and the fourth in the last two years. In December 2022, Microsoft patched CVE-2022-44698 (CVSS score: 5.4), while CVE-2023-24880 (CVSS score: 5.1) was patched in March and CVE-2023-32049 (CVSS score: 8.8) was patched in July.
The Windows maker, however, has not provided any further guidance on the attack mechanisms employed and the threat actors that may be weaponizing them. But the active exploitation of the privilege escalation flaws suggests that they are likely used in conjunction with a remote code execution bug.
"There have been 12 elevation of privilege vulnerabilities in the DWM Core Library over the last two years, though this is the first to have been exploited in the wild as a zero-day," Satnam Narang, senior staff research engineer at Tenable, said in a statement shared with The Hacker News.
The development has prompted the U.S. Cybersecurity and Infrastructure Security Agency (CISA) to add the three issues to its Known Exploited Vulnerabilities (KEV) catalog, urging federal agencies to apply the fixes by December 5, 2023.
Also patched by Microsoft are two critical remote code execution flaws in Protected Extensible Authentication Protocol and Pragmatic General Multicast (CVE-2023-36028 and CVE-2023-36397, CVSS scores: 9.8) that a threat actor could leverage to trigger the execution of malicious code.
The November update further includes a patch for CVE-2023-38545 (CVSS score: 9.8), a critical heap-based buffer overflow flaw in the curl library that came to light last month, as well as an information disclosure vulnerability in Azure CLI (CVE-2023-36052, CVSS score: 8.6).
"An attacker that successfully exploited this vulnerability could recover plaintext passwords and usernames from log files created by the affected CLI commands and published by Azure DevOps and/or GitHub Actions," Microsoft said.
Palo Alto Networks researcher Aviad Hahami, who reported the issue, said the vulnerability could enable access to credentials stored in the pipeline's log and permit an adversary to potentially escalate their privileges for follow-on attacks.
In response, Microsoft said it has made changes to several Azure CLI commands to harden Azure CLI (version 2.54) against inadvertent usage that could lead to secrets exposure.
Urgent: VMware Warns of Unpatched Critical Cloud Director Vulnerability
15.11.23 Vulnerebility The Hacker News
VMware is warning of a critical and unpatched security flaw in Cloud Director that could be exploited by a malicious actor to get around authentication protections.
Tracked as CVE-2023-34060 (CVSS score: 9.8), the vulnerability impacts instances that have been upgraded to version 10.5 from an older version.
"On an upgraded version of VMware Cloud Director Appliance 10.5, a malicious actor with network access to the appliance can bypass login restrictions when authenticating on port 22 (ssh) or port 5480 (appliance management console)," the company said in an alert.
"This bypass is not present on port 443 (VCD provider and tenant login). On a new installation of VMware Cloud Director Appliance 10.5, the bypass is not present."
The virtualization services company further noted that the impact is due to the fact that it utilizes a version of sssd from the underlying Photon OS that is affected by CVE-2023-34060.
Dustin Hartle from IT solutions provider Ideal Integrations has been credited with discovering and reporting the shortcomings.
While VMware has yet to release a fix for the problem, it has provided a workaround in the form of a shell script ("WA_CVE-2023-34060.sh").
It also emphasized implementing the temporary mitigation will neither require downtime nor have a side-effect on the functionality of Cloud Director installations.
The development comes weeks after VMware released patches for another critical flaw in the vCenter Server (CVE-2023-34048, CVSS score: 9.8) that could result in remote code execution on affected systems.
CacheWarp Attack: New Vulnerability in AMD SEV Exposes Encrypted VMs
15.11.23 Attack The Hacker News
A group of academics has disclosed a new "software fault attack" on AMD's Secure Encrypted Virtualization (SEV) technology that could be potentially exploited by threat actors to infiltrate encrypted virtual machines (VMs) and even perform privilege escalation.
The attack has been codenamed CacheWarp (CVE-2023-20592) by researchers from the CISPA Helmholtz Center for Information Security and the Graz University of Technology. It impacts AMD CPUs supporting all variants of SEV.
"For this research, we specifically looked at AMD's newest TEE, AMD SEV-SNP, relying on the experience from previous attacks on Intel's TEE," security researcher Ruiyi Zhang told The Hacker News. "We found the 'INVD' instruction [flush a processor's cache contents] could be abused under the threat model of AMD SEV."
SEV, an extension to the AMD-V architecture and introduced in 2016, is designed to isolate VMs from the hypervisor by encrypting the memory contents of the VM with a unique key.
The idea, in a nutshell, is to shield the VM from the possibility that the hypervisor (i.e., the virtual machine monitor) could be malicious and thus cannot be trusted by default.
SEV-SNP, which incorporates Secure Nested Paging (SNP), adds "strong memory integrity protection to help prevent malicious hypervisor-based attacks like data replay, memory re-mapping, and more in order to create an isolated execution environment," according to AMD. But CacheWarp, according to Zhang, makes it possible to defeat the integrity protections and achieve privilege escalation and remote code execution in the targeted virtual machine - The instruction `INVD` drops all the modified content in the cache without writing them back to the memory. Hence, the attacker can drop any writes of guest VMs and the VM continues with architecturally stale data. In the paper, we demonstrate that via two primitives, "timewarp" and "dropforge." For the timewarp, we can reset what the computer has memorized as the next step. This makes the computer execute code that it executed before because it reads an outdated so-called return address from memory. The computer thus travels back in time. However, the old code is executed with new data (the return value of another function), which leads to unexpected effects. We use this method to bypass OpenSSH authentication, logging in without knowing the password. Another method, called "Dropforge," lets the attacker reset changes of guest VMs made to data. With one or multiple drops, the attacker can manipulate the logic flow of guest execution in an exploitable way. Take the `sudo` binary as an example, a return value is stored in the memory (stack) so that the attacker can reset it to an initial value. However, the initial value "0" gives us administrator privilege even when we are not. Cybersecurity Successful exploitation of the architectural bug could permit an attacker to hijack the control flow of a program by reverting to a previous state, and seize control of the VM. AMD has since released a microcode update to fix the "instruction misuse." "A team of Google Project Zero and Google Cloud security has audited the newest version of AMD's TEE (SEV-SNP) last year," Zhang noted. "AMD also claims that SEV-SNP prevents all attacks on the integrity. However, our attack breaks the integrity of it." CISPA researchers, earlier this August, also revealed a software-based power side-channel attack targeting Intel, AMD, and Arm CPUs dubbed Collide+Power (CVE-2023-20583) that could be weaponized to leak sensitive data by breaking isolation protections.
With this combination, we have unlimited access to the virtual machine.
Alert: OracleIV DDoS Botnet Targets Public Docker Engine APIs to Hijack Containers
14.11.23 BotNet The Hacker News
Publicly-accessible Docker Engine API instances are being targeted by threat actors as part of a campaign designed to co-opt the machines into a distributed denial-of-service (DDoS) botnet dubbed OracleIV.
"Attackers are exploiting this misconfiguration to deliver a malicious Docker container, built from an image named 'oracleiv_latest' and containing Python malware compiled as an ELF executable," Cado researchers Nate Bill and Matt Muir said.
The malicious activity starts with attackers using an HTTP POST request to Docker's API to retrieve a malicious image from Docker Hub, which, in turn, runs a command to retrieve a shell script (oracle.sh) from a command-and-control (C&C) server.
Oracleiv_latest purports to be a MySQL image for docker and has been pulled 3,500 times to date. In a perhaps not-so-surprising twist, the image also includes additional instructions to fetch an XMRig miner and its configuration from the same server.
That said, the cloud security firm said it did not observe any evidence of cryptocurrency mining performed by the counterfeit container. The shell script, on the other hand, is concise and incorporates functions to conduct DDoS attacks such as slowloris, SYN floods, and UDP floods.
Exposed Docker instances have become a lucrative attack target in recent years, often used as conduits for cryptojacking campaigns.
"Once a valid endpoint is discovered, it's trivial to pull a malicious image and launch a container from it to carry out any conceivable objective," the researchers said. "Hosting the malicious container in Docker Hub, Docker's container image library, streamlines this process even further."
It's not just Docker, as vulnerable MySQL servers have emerged as the target of another DDoS botnet malware known as Ddostf, according to the AhnLab Security Emergency Response Center (ASEC).
"Although most of the commands supported by Ddostf are similar to those from typical DDoS bots, a distinctive feature of Ddostf is its ability to connect to a newly received address from the C&C server and execute commands there for a certain period," ASEC said.
"Only DDoS commands can be performed on the new C&C server. This implies that the Ddostf threat actor can infect numerous systems and then sell DDoS attacks as a service."
Compounding matters further is the emergence of several new DDoS botnets, such as hailBot, kiraiBot, and catDDoS that are based on Mirai, whose source code leaked in 2016.
"These newly developed Trojan horses either introduce new encryption algorithms to hide critical information or better hide themselves by modifying the go-live process and designing more covert communication methods," cybersecurity company NSFOCUS revealed last month.
Another DDoS malware that has resurfaced this year is XorDdos, which infects Linux devices and "transforms them into zombies" for follow-on DDoS attacks against targets of interest.
Palo Alto Networks Unit 42 said the campaign began in late July 2023, before peaking around August 12, 2023.
"Before malware successfully infiltrated a device, the attackers initiated a scanning process, employing HTTP requests to identify potential vulnerabilities in their targets," the company noted. "To evade detection, the threat turns its process into a background service that runs independently of the current user session."
New Campaign Targets Middle East Governments with IronWind Malware
14.11.23 Virus The Hacker News
Government entities in the Middle East are the target of new phishing campaigns that are designed to deliver a new initial access downloader dubbed IronWind.
The activity, detected between July and October 2023, has been attributed by Proofpoint to a threat actor it tracks under the name TA402, which is also known as Molerats, Gaza Cyber Gang, and shares tactical overlaps with a pro-Hamas hacking crew known as APT-C-23 (aka Arid Viper).
"When it comes to state-aligned threat actors, North Korea, Russia, China, and Iran generally reap the lion's share of attention," Joshua Miller, senior threat researcher at Proofpoint, said in a statement shared with The Hacker News.
"But TA402, a Middle Eastern advanced persistent threat (APT) group that historically has operated in the interests of the Palestinian Territories, has consistently proven to be an intriguing threat actor capable of highly sophisticated cyber espionage with a focus on intelligence collection."
Coinciding with the use of IronWind are consistent updates to its malware delivery mechanisms, using Dropbox links, XLL file attachments, and RAR archives to distribute IronWind.
The use of IronWind is a shift from prior attack chains, which were linked to the propagation of a backdoor codenamed NimbleMamba in intrusions targeting Middle Eastern governments and foreign policy think tanks.
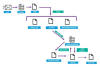
TA402's latest campaigns are characterized by the use of a compromised email account belonging to the Ministry of Foreign Affairs to send phishing lures pointing to Dropbox links that facilitate the deployment of IronWind.
The downloader is engineered to contact an attacker-controlled server to fetch additional payloads, including a post-exploitation toolkit called SharpSploit, following a multi-stage sequence.
Subsequent social engineering campaigns in August and October 2023 have been found to leverage XLL file and RAR archive attachments embedded in email messages to trigger the deployment of IronWind. Another notable tactic employed by the group is the reliance on geofencing techniques to complicate detection efforts.
"The ongoing conflict in the Middle East does not appear to have hindered their ongoing operations, as they continue to iterate and use new and clever delivery methods to bypass detection efforts," Miller said.
"Using complex infection chains and drumming up new malware to attack their targets, TA402 continues to engage in extremely targeted activity with a strong focus on government entities based in the Middle East and North Africa."

The development comes as Cisco Talos revealed that cybercriminals have been observed exploiting the "Release scores" feature of Google Forms quizzes to deliver email and orchestrate elaborate cryptocurrency scams, highlighting the creative ways threat actors resort to in order to meet their objectives.
"The emails originate from Google's own servers and consequently may have an easier time bypassing anti-spam protections and finding the victim's inbox," security researcher Jaeson Schultz said last week.
Vietnamese Hackers Using New Delphi-Powered Malware to Target Indian Marketers
14.11.23 Virus The Hacker News
The Vietnamese threat actors behind the Ducktail stealer malware have been linked to a new campaign that ran between March and early October 2023, targeting marketing professionals in India with an aim to hijack Facebook business accounts.
"An important feature that sets it apart is that, unlike previous campaigns, which relied on .NET applications, this one used Delphi as the programming language," Kaspersky said in a report published last week.
Ducktail, alongside Duckport and NodeStealer, is part of a cybercrime ecosystem operating out of Vietnam, with the attackers primarily using sponsored ads on Facebook to propagate malicious ads and deploy malware capable of plundering victims' login cookies and ultimately taking control of their accounts.
Such attacks primarily single out users who may have access to a Facebook Business account. The fraudsters then use the unauthorized access to place advertisements for financial gain, perpetuating the infections further.
In the campaign documented by the Russian cybersecurity firm, potential targets looking for a career change are sent archive files containing a malicious executable that's disguised with a PDF icon to trick them into launching the binary.
Doing so results in the malicious file saving a PowerShell script named param.ps1 and a decoy PDF document locally to the "C:\Users\Public" folder in Windows.
"The script uses the default PDF viewer on the device to open the decoy, pauses for five minutes, and then terminates the Chrome browser process," Kaspersky said.
The parent executable also downloads and launches a rogue library named libEGL.dll, which scans the "C:\ProgramData\Microsoft\Windows\Start Menu\Programs" and "C:\ProgramData\Microsoft\Internet Explorer\Quick Launch\User Pinned\TaskBar\" folders for any shortcut (i.e., LNK file) to a Chromium-based web browser.
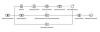
The next stage entails altering the browser's LNK shortcut file by suffixing a "--load-extension" command line switch to launch a rogue extension that masquerades as the legitimate Google Docs Offline add-on to fly under the radar.
The extension, for its part, is designed to send information about all open tabs to an actor-controlled server registered in Vietnam and hijack the Facebook business accounts.
Google Sues Scammers for Using Bard Lures to Spread Malware#
The findings underscore a strategic shift in Ducktail's attack techniques and come as Google filed a lawsuit against three unknown individuals in India and Vietnam for capitalizing on the public's interest in generative AI tools such as Bard to spread malware via Facebook and pilfer social media login credentials.
"Defendants distribute links to their malware through social media posts, ads (i.e., sponsored posts), and pages, each of which purport to offer downloadable versions of Bard or other Google AI products," the company alleged in its complaint.
"When a user logged into a social media account clicks the links displayed in Defendants' ads or on their pages, the links redirect to an external website from which a RAR archive, a type of file, downloads to the user's computer."
The archive files include an installer file that's capable of installing a browser extension adept at pilfering victims' social media accounts.
Earlier this May, Meta said it observed threat actors creating deceptive browser extensions available in official web stores that claim to offer ChatGPT-related tools and that it detected and blocked over 1,000 unique URLs from being shared across its services.
CISA Sets a Deadline - Patch Juniper Junos OS Flaws Before November 17
14.11.23 Vulnerebility The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has given a November 17, 2023, deadline for federal agencies and organizations to apply mitigations to secure against a number of security flaws in Juniper Junos OS that came to light in August.
The agency on Monday added five vulnerabilities to the Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation -
CVE-2023-36844 (CVSS score: 5.3) - Juniper Junos OS EX Series PHP External Variable Modification Vulnerability
CVE-2023-36845 (CVSS score: 5.3) - Juniper Junos OS EX Series and SRX Series PHP External Variable Modification Vulnerability
CVE-2023-36846 (CVSS score: 5.3) - Juniper Junos OS SRX Series Missing Authentication for Critical Function Vulnerability
CVE-2023-36847 (CVSS score: 5.3) - Juniper Junos OS EX Series Missing Authentication for Critical Function Vulnerability
CVE-2023-36851 (CVSS score: 5.3) - Juniper Junos OS SRX Series Missing Authentication for Critical Function Vulnerability
The vulnerabilities, per Juniper, could be fashioned into an exploit chain to achieve remote code execution on unpatched devices. Also added to the list is CVE-2023-36851, which has been described as a variant of the SRX upload flaw.
Juniper, in an update to its advisory on November 8, 2023, said it's "now aware of successful exploitation of these vulnerabilities," recommending that customers update to the latest versions with immediate effect.
The details surrounding the nature of the exploitation are currently unknown.
In a separate alert, CISA has also warned that the Royal ransomware gang may rebrand as BlackSuit owing to the fact that the latter shares a "number of identified coding characteristics similar to Royal."
The development comes as Cyfirma disclosed that exploits for critical vulnerabilities are being offered for sale on darknet forums and Telegram channels.
"These vulnerabilities encompass elevation of privilege, authentication bypass, SQL injection, and remote code execution, posing significant security risks," the cybersecurity firm said, adding, "ransomware groups are actively searching for zero-day vulnerabilities in underground forums to compromise a large number of victims."
It also follows revelations from Huntress that threat actors are targeting multiple healthcare organizations by abusing the widely-used ScreenConnect remote access tool used by Transaction Data Systems, a pharmacy management software provider, for initial access.
"The threat actor proceeded to take several steps, including installing additional remote access tools such as ScreenConnect or AnyDesk instances, to ensure persistent access to the environments," Huntress noted.
New Ransomware Group Emerges with Hive's Source Code and Infrastructure
14.11.23 Ransom The Hacker News
The threat actors behind a new ransomware group called Hunters International have acquired the source code and infrastructure from the now-dismantled Hive operation to kick-start its own efforts in the threat landscape.
"It appears that the leadership of the Hive group made the strategic decision to cease their operations and transfer their remaining assets to another group, Hunters International," Martin Zugec, technical solutions director at Bitdefender, said in a report published last week.
Hive, once a prolific ransomware-as-a-service (RaaS) operation, was taken down as part of a coordinated law enforcement operation in January 2023.
While it's common for ransomware actors to regroup, rebrand, or disband their activities following such seizures, what can also happen is that the core developers can pass on the source code and other infrastructure in their possession to another threat actor.
Reports about Hunters International as a possible Hive rebrand surfaced last month after several code similarities were identified between the two strains. It has since claimed five victims to date.
The threat actors behind it, however, have sought to dispel these speculations, stating that it purchased the Hive source code and website from its developers.
"The group appears to place a greater emphasis on data exfiltration," Zugec said. "Notably, all reported victims had data exfiltrated, but not all of them had their data encrypted," making Hunters International more of a data extortion outfit.
Bitdefender's analysis of the ransomware sample reveals its Rust-based foundations, a fact borne out by Hive's transition to the programming language in July 2022 for its increased resistance to reverse engineering.
"In general, as the new group adopts this ransomware code, it appears that they have aimed for simplification," Zugec said.
"They have reduced the number of command line parameters, streamlined the encryption key storage process, and made the malware less verbose compared to earlier versions."
The ransomware, besides incorporating an exclusion list of file extensions, file names, and directories to be omitted from encryption, runs commands to prevent data recovery as well as terminate a number of processes that could potentially interfere with the process.
"While Hive has been one of the most dangerous ransomware groups, it remains to be seen if Hunters International will prove equally or even more formidable," Zugec noted.
"This group emerges as a new threat actor starting with a mature toolkit and appears eager to show its capabilities, [but] faces the task of demonstrating its competence before it can attract high-caliber affiliates."
Chinese Hackers Launch Covert Espionage Attacks on 24 Cambodian Organizations
13.11.23 BigBrothers The Hacker News
Cybersecurity researchers have discovered what they say is malicious cyber activity orchestrated by two prominent Chinese nation-state hacking groups targeting 24 Cambodian government organizations.
"This activity is believed to be part of a long-term espionage campaign," Palo Alto Networks Unit 42 researchers said in a report last week.
"The observed activity aligns with geopolitical goals of the Chinese government as it seeks to leverage their strong relations with Cambodia to project their power and expand their naval operations in the region."
Targeted organizations include defense, election oversight, human rights, national treasury and finance, commerce, politics, natural resources, and telecommunications.
The assessment stems from the persistent nature of inbound network connections originating from these entities to a China-linked adversarial infrastructure that masquerades as cloud backup and storage services over a "period of several months."
Some of the command-and-control (C2) domain names are listed below -
api.infinitycloud[.]info
connect.infinitycloud[.]info
connect.infinitybackup[.]net
file.wonderbackup[.]com
login.wonderbackup[.]com
update.wonderbackup[.]com
The tactic is likely an attempt on the part of the attackers to fly under the radar and blend in with legitimate network traffic.
What's more, the links to China are based on the fact that the threat actor's activity has been observed primarily during regular business hours in China, with a drop recorded in late September and early October 2023, coinciding with the Golden Week national holidays, before resuming to regular levels on October 9.

China-nexus hacking groups such as Emissary Panda, Gelsemium, Granite Typhoon, Mustang Panda, RedHotel, ToddyCat, and UNC4191 have launched an array of espionage campaigns targeting public- and private sectors across Asia in recent months.
Last month, Elastic Security Labs detailed an intrusion set codenamed REF5961 that was found leveraging custom backdoors such as EAGERBEE, RUDEBIRD, DOWNTOWN, and BLOODALCHEMY in its attacks directed against the Association of Southeast Asian Nations (ASEAN) countries.
The malware families "were discovered to be co-residents with a previously reported intrusion set, REF2924," the latter of which is assessed to be a China-aligned group owing to its use of ShadowPad and tactical overlaps with Winnti and ChamelGang.
The disclosures also follow a report from Recorded Future highlighting the shift in Chinese cyber espionage activity, describing it as more mature and coordinated, and with a strong focus on exploiting known and zero-day flaws in public-facing email servers, security, and network appliances.
Since the beginning of 2021, Chinese state-sponsored groups have been attributed to the exploitation of 23 zero-day vulnerabilities, including those identified in Microsoft Exchange Server, Solarwinds Serv-U, Sophos Firewall, Fortinet FortiOS, Barracuda Email Security Gateway, and Atlassian Confluence Data Center and Server.
The state-sponsored cyber operations have evolved "from broad intellectual property theft to a more targeted approach supporting specific strategic, economic, and geopolitical goals, such as those related to the Belt and Road Initiative and critical technologies," the company said.
Major Phishing-as-a-Service Syndicate 'BulletProofLink' Dismantled by Malaysian Authorities
13.11.23 Phishing The Hacker News
Malaysian law enforcement authorities have announced the takedown of a phishing-as-a-service (PhaaS) operation called BulletProofLink.
The Royal Malaysia Police said the effort, which was carried out with assistance from the Australian Federal Police (AFP) and the U.S. Federal Bureau of Investigation (FBI) on November 6, 2023, was based on information that the threat actors behind the platform were based out of the country.
To that end, eight individuals aged between 29 and 56, including the syndicate's mastermind, have been arrested across different locations in Sabah, Selangor, Perak, and Kuala Lumpur, New Straits Times reported.
Along with the arrests, authorities confiscated servers, computers, jewelry, vehicles, and cryptocurrency wallets containing approximately $213,000.
BulletProofLink, also called BulletProftLink, is known for offering ready-to-use phishing templates on a subscription basis to other actors for conducting credential harvesting campaigns. These templates mimic the login pages of well-known services like American Express, Bank of America, DHL, Microsoft, and Naver.
According to an analysis from Microsoft in September 2021, BulletProofLink actors also engaged in what's called double theft wherein the stolen credentials are sent to both their customers and the core developers, resulting in additional monetization avenues.
"BulletProftLink is associated with the threat actor AnthraxBP who also went by the online nicknames TheGreenMY and AnthraxLinkers," cybersecurity firm Intel 471 said last week.
"The actor maintained an active website advertising phishing services. The actor has an extensive underground footprint and operated on a number of clear web underground forums and Telegram channels using multiple handles."
Believed to be active since at least 2015, BulletProftLink's online storefront is estimated to have no less than 8,138 active clients and 327 phishing pages templates as of April 2023.
Another noteworthy feature is its integration of the Evilginx2 to facilitate adversary-in-the-middle (AiTM) attacks that make it possible for threat actors to steal session cookies and bypass multi-factor authentication protections.
"PhaaS schemes like BulletProftLink provide the fuel for further attacks," Intel 471 said. "Stolen login credentials are one of the primary ways that malicious hackers gain access to organizations."
In a sign that threat actors are constantly updating tactics in response to disruptions and taking more sophisticated approaches, AiTM attacks have also been observed employing intermediary links to documents hosted on file-sharing solutions like DRACOON that contain the URLs to adversary-controlled infrastructure.
"This new method can bypass email security mitigations since the initial link appears to be from a legitimate source and no files are delivered to the victim's endpoint as the hosted document containing the link can be interacted with via the file-sharing server within the browser," Trend Micro said.
The development comes as a 33-year-old Serbian and Croatian national, Milomir Desnica, pleaded guilty in the U.S. to operating a drug trafficking platform called Monopoly Market on the dark web and for conspiring to distribute over 30 kilograms of methamphetamine to U.S. customers.
The illicit marketplace, which was set up by Desnica in 2019, was taken offline in December 2021 as part of a coordinated exercise in partnership with Germany and Finland. Desnica was arrested in Austria in November 2022 and extradited to the U.S. to face drug trafficking charges in June 2023.
New BiBi-Windows Wiper Targets Windows Systems in Pro-Hamas Attacks
13.11.23 Virus The Hacker News
Cybersecurity researchers have warned about a Windows version of a wiper malware that was previously observed targeting Linux systems in cyber attacks aimed at Israel.
Dubbed BiBi-Windows Wiper by BlackBerry, the wiper is the Windows counterpart of BiBi-Linux Wiper, which has been put to use by a pro-Hamas hacktivist group in the wake of the Israel-Hamas war last month.
"The Windows variant [...] confirms that the threat actors who created the wiper are continuing to build out the malware, and indicates an expansion of the attack to target end user machines and application servers," the Canadian company said Friday.
Slovak cybersecurity firm is tracking the actor behind the wiper under the name BiBiGun, noting that the Windows variant (bibi.exe) is designed to overwrite data in the C:\Users directory recursively with junk data and appends .BiBi to the filename.
The BiBi-Windows Wiper artifact is said to have been compiled on October 21, 2023, two weeks after the onset of the war. The exact method by which it is distributed is currently unknown.
Besides corrupting all files with the exception of those with .exe, .dll, and .sys extensions, the wiper deletes shadow copies from the system, effectively preventing the victims from recovering their files.
Another notable similarity with its Linux variant is its multithreading capability.
"For the fastest possible destruction action, the malware runs 12 threads with eight processor cores," Dmitry Bestuzhev, senior director of cyber threat intelligence at BlackBerry, said.
It's not immediately clear if the wiper has been deployed in real-world attacks, and if so, who the targets are.
The development comes as Security Joes, which first documented BiBi-Linux Wiper, said the malware is part of a "larger campaign targeting Israeli companies with the deliberate intent to disrupt their day-to-day operations using data destruction."
The cybersecurity firm said it identified tactical overlaps between the hacktivist group, who call themselves Karma, and another geopolitically motivated actor codenamed Moses Staff (aka Cobalt Sapling), which is suspected to be of Iranian origin.
"Although the campaign has primarily centered around Israeli IT and government sectors up to this point, some of the participating groups, such as Moses Staff, have a history of simultaneously targeting organizations across various business sectors and geographical locations," Security Joes said.
Microsoft Warns of Fake Skills Assessment Portals Targeting IT Job Seekers
12.11.23 OS The Hacker News
A sub-cluster within the infamous Lazarus Group has established new infrastructure that impersonates skills assessment portals as part of its social engineering campaigns.
Microsoft attributed the activity to a threat actor it calls Sapphire Sleet, describing it as a "shift in the persistent actor's tactics."
Sapphire Sleet, also called APT38, BlueNoroff, CageyChameleon, and CryptoCore, has a track record of orchestrating cryptocurrency theft via social engineering.
Earlier this week, Jamf Threat Labs implicated the threat actor to a new macOS malware family called ObjCShellz that's assessed to be a late-stage payload delivered in connection with another macOS malware known as RustBucket.
"Sapphire Sleet typically finds targets on platforms like LinkedIn and uses lures related to skills assessment," the Microsoft Threat Intelligence team said in a series of posts on X (formerly Twitter).
"The threat actor then moves successful communications with targets to other platforms."
The tech giant said past campaigns mounted by the hacking crew involved sending malicious attachments directly or embedding links to pages hosted on legitimate websites like GitHub.
However, the swift detection and deletion of these payloads may have forced Sapphire Sleet to flesh out its own network of websites for malware distribution.
"Several malicious domains and subdomains host these websites, which entice recruiters to register for an account," the company added. "The websites are password-protected to impede analysis."
Russian Hackers Sandworm Cause Power Outage in Ukraine Amidst Missile Strikes
11.11.23 APT The Hacker News
The notorious Russian hackers known as Sandworm targeted an electrical substation in Ukraine last year, causing a brief power outage in October 2022.
The findings come from Google's Mandiant, which described the hack as a "multi-event cyber attack" leveraging a novel technique for impacting industrial control systems (ICS).
"The actor first used OT-level living-off-the-land (LotL) techniques to likely trip the victim's substation circuit breakers, causing an unplanned power outage that coincided with mass missile strikes on critical infrastructure across Ukraine," the company said.
"Sandworm later conducted a second disruptive event by deploying a new variant of CaddyWiper in the victim's IT environment."
The threat intelligence firm did not reveal the location of the targeted energy facility, the duration of the blackout, and the number of people who were impacted by the incident.
The development marks Sandworm's continuous efforts to stage disruptive attacks and compromise the power grid in Ukraine since at least 2015 using malware such as Industroyer.
The exact initial vector used for the cyber-physical attack is presently unclear, and it's believed that the threat actor's use of LotL techniques decreased the time and resources required to pull it off.
The intrusion is thought to have happened around June 2022, with the Sandworm actors gaining access to the operational technology (OT) environment through a hypervisor that hosted a supervisory control and data acquisition (SCADA) management instance for the victim's substation environment.
On October 10, 2022, an optical disc (ISO) image file was used to launch malware capable of switching off substations, resulting in an unscheduled power outage.
"Two days after the OT event, Sandworm deployed a new variant of CaddyWiper in the victim's IT environment to cause further disruption and potentially to remove forensic artifacts," Mandiant said.
CaddyWiper refers to a piece of data-wiping malware that first came to light in March 2022 in connection with the Russo-Ukrainian war.
The eventual execution of the attack, Mandiant noted, coincided with the start of a multi-day set of coordinated missile strikes on critical infrastructure across a number of Ukrainian cities, including the city in which the unnamed victim was situated.
"This attack represents an immediate threat to Ukrainian critical infrastructure environments leveraging the MicroSCADA supervisory control system," the company said.
"Given Sandworm's global threat activity and the worldwide deployment of MicroSCADA products, asset owners globally should take action to mitigate their tactics, techniques, and procedures against IT and OT systems."
Alert: 'Effluence' Backdoor Persists Despite Patching Atlassian Confluence Servers
11.11.23 Virus The Hacker News
Cybersecurity researchers have discovered a stealthy backdoor named Effluence that's deployed following the successful exploitation of a recently disclosed security flaw in Atlassian Confluence Data Center and Server.
"The malware acts as a persistent backdoor and is not remediated by applying patches to Confluence," Aon's Stroz Friedberg Incident Response Services said in an analysis published earlier this week.
"The backdoor provides capability for lateral movement to other network resources in addition to exfiltration of data from Confluence. Importantly, attackers can access the backdoor remotely without authenticating to Confluence."
The attack chain documented by the cybersecurity entity entailed the exploitation of CVE-2023-22515 (CVSS score: 10.0), a critical bug in Atlassian that could be abused to create unauthorized Confluence administrator accounts and access Confluence servers.
Atlassian has since disclosed a second flaw known as CVE-2023-22518 (CVSS score: 10.0) that an attacker can also take advantage of to set up a rogue administrator account, resulting in a complete loss of confidentiality, integrity, and availability.
What makes the latest attack stand out is that the adversary gained initial access via CVE-2023-22515 and embedded a novel web shell that grants persistent remote access to every web page on the server, including the unauthenticated login page, without the need for a valid user account.
The web shell, made up of a loader and payload, is passive, allowing requests to pass through it unnoticed until a request matching a specific parameter is provided, at which point it triggers its malicious behavior by executing a series of actions.
This comprises creating a new admin account, purging logs to cover up the forensic trail, running arbitrary commands on the underlying server, enumerating, reading, and deleting files, and compiling extensive information about the Atlassian environment.
The loader component, per Aon, acts as a normal Confluence plugin and is responsible for decrypting and launching the payload.
"Several of the web shell functions depend on Confluence-specific APIs," security researcher Zachary Reichert said.
"However, the plugin and the loader mechanism appear to depend only on common Atlassian APIs and are potentially applicable to JIRA, Bitbucket, or other Atlassian products where an attacker can install the plugin."
Iran-Linked Imperial Kitten Cyber Group Targeting Middle East's Tech Sectors
11.11.23 APT The Hacker News
A group with links to Iran targeted transportation, logistics, and technology sectors in the Middle East, including Israel, in October 2023 amid a surge in Iranian cyber activity since the onset of the Israel-Hamas war.
The attacks have been attributed by CrowdStrike to a threat actor it tracks under the name Imperial Kitten, and which is also known as Crimson Sandstorm (previously Curium), TA456, Tortoiseshell, and Yellow Liderc.
The latest findings from the company build on prior reports from Mandiant, ClearSky, and PwC, the latter of which also detailed instances of strategic web compromises (aka watering hole attacks) leading to the deployment of IMAPLoader on infected systems.
"The adversary, active since at least 2017, likely fulfills Iranian strategic intelligence requirements associated with IRGC operations," CrowdStrike said in a technical report. "Its activity is characterized by its use of social engineering, particularly job recruitment-themed content, to deliver custom .NET-based implants."
Attack chains leverage compromised websites, primarily those related to Israel, to profile visitors using bespoke JavaScript and exfiltrate the information to attacker-controlled domains.
Besides watering hole attacks, there's evidence to suggest that Imperial Kitten resorts to exploitation of one-day exploits, stolen credentials, phishing, and even targeting upstream IT service providers for initial access.
Phishing campaigns involve the use of macro-laced Microsoft Excel documents to activate the infection chain and drop a Python-based reverse shell that connects to a hard-coded IP address for receiving further commands.
Among some of the notable post-exploitation activities entail achieving lateral movement through the use of PAExec, the open-source variant of PsExec, and NetScan, followed by the delivery of the implants IMAPLoader and StandardKeyboard.
Also deployed is a remote access trojan (RAT) that uses Discord for command-and-control, while both IMAPLoader and StandardKeyboard employ email messages (i.e., attachments and email body) to receive tasking and send results of the execution.
"StandardKeyboard's main purpose is to execute Base64-encoded commands received in the email body," the cybersecurity company pointed out. "Unlike IMAPLoader, this malware persists on the infected machine as a Windows Service named Keyboard Service."
The development comes as Microsoft noted that malicious cyber activity attributed to Iranian groups after the start of the war on October 7, 2023, is more reactive and opportunistic.
"Iranian operators [are] continuing to employ their tried-and-true tactics, notably exaggerating the success of their computer network attacks and amplifying those claims and activities via a well-integrated deployment of information operations," Microsoft said.
"This is essentially creating online propaganda seeking to inflate the notoriety and impact of opportunistic attacks, in an effort to increase their effects."
The disclosure also follows revelations that a Hamas-affiliated threat actor named Arid Viper has targeted Arabic speakers with an Android spyware known as SpyC23 through weaponized apps masquerading as Skipped and Telegram, according to Cisco Talos and SentinelOne.