30.4.23 Security The Hacker News

OpenAI, the company behind ChatGPT, has officially made a return to Italy after the company met the data protection authority's demands ahead of April 30, 2023, deadline.
ARTICLES APRIL H MARCH(103) APRIL(113) MAY(110) JUNE(93) July(113) November(58) December(100)
CISA Warns of Critical Flaws in Illumina's DNA Sequencing Instruments
30.4.23 Vulnerebility The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has released an Industrial Control Systems (ICS) medical advisory warning of a critical flaw impacting Illumina medical devices.
The issues impact the Universal Copy Service (UCS) software in the Illumina MiSeqDx, NextSeq 550Dx, iScan, iSeq 100, MiniSeq, MiSeq, NextSeq 500, NextSeq 550, NextSeq 1000/2000, and NovaSeq 6000 DNA sequencing instruments.
The most severe of the flaws, CVE-2023-1968 (CVSS score: 10.0), permits remote attackers to bind to exposed IP addresses, thereby making it possible to eavesdrop on network traffic and remotely transmit arbitrary commands.
The second issue relates to a case of privilege misconfiguration (CVE-2023-1966, CVSS score: 7.4) that could enable a remote unauthenticated malicious actor to upload and execute code with elevated permissions.
"Successful exploitation of these vulnerabilities could allow an attacker to take any action at the operating system level," CISA said. "A threat actor could impact settings, configurations, software, or data on the affected product; a threat actor could interact through the affected product via a connected network."
The Food and Drug Administration (FDA) said an unauthorized user could weaponize the shortcoming to impact "genomic data results in the instruments intended for clinical diagnosis, including causing the instruments to provide no results, incorrect results, altered results, or a potential data breach."
There is no evidence that the two vulnerabilities have been exploited in the wild. Users are recommended to apply the fixes released on April 5, 2023, to mitigate potential threats.
This is not the first time severe flaws have come to light in Illumina's DNA Sequencing Devices. In June 2022, the company disclosed multiple similar vulnerabilities that could have been abused to seize control of affected systems.
The disclosure comes almost a month after the FDA issued new guidance that will require medical device makers to adhere to a set of cybersecurity requirements when submitting an application for a new product.
This includes a plan to monitor, identify, and address "postmarket" cybersecurity vulnerabilities and exploits within a reasonable time period, and design and maintain processes to ensure the security of such devices via regular and out-of-band patches.
ChatGPT is Back in Italy After Addressing Data Privacy Concerns
30.4.23 Security The Hacker News
OpenAI, the company behind ChatGPT, has officially made a return to Italy after the company met the data protection authority's demands ahead of April 30, 2023, deadline.
The development was first reported by the Associated Press. OpenAI's CEO, Sam Altman, tweeted, "we're excited ChatGPT is available in [Italy] again!"
The reinstatement comes following Garante's decision to temporarily block access to the popular AI chatbot service in Italy on March 31, 2023, over concerns that its practices are in violation of data protection laws in the region.
Generative AI systems like ChatGPT and Google Bard primarily rely on huge amounts of information freely available on the internet as well as the data its users provide over the course of their interactions.
OpenAI, which published a new FAQ, said it filters and removes information such as hate speech, adult content, sites that primarily aggregate personal information, and spam.
It also emphasized that it doesn't "actively seek out personal information to train our models" and that it "will not use any personal information in training information to build profiles about people, to contact them, to advertise to them, to try to sell them anything, or to sell the information itself."
That said, the company acknowledged that ChatGPT responses may include personal information about public figures and other individuals whose details are accessible on the public internet.
European users who wish to object to such processing of their personal information can do so by filling out an online form, and even exercise their right to correct, restrict, delete, or transfer their personal information contained within its training dataset.
The Garante, in a related announcement, said OpenAI also agreed to include an option to verify users' ages to confirm they are above 18 prior to gaining access to ChatGPT, or, alternatively, have obtained the consent of parents or guardians if aged between 13 and 18.
OpenAI is further expected to implement a more robust age verification system to screen minors from accessing the service, with the watchdog noting that it will continue its "fact-finding activities regarding OpenAI" as part of a task force set up by the European Data Protection Board (EDPB).
The move also follows OpenAI's introduction of a new privacy setting that allows users to turn off chat history as well as an export option to access the kinds of information stored by ChatGPT.
New Atomic macOS Malware Steals Keychain Passwords and Crypto Wallets
28.4.23 Apple The Hacker News
Threat actors are advertising a new information stealer for the Apple macOS operating system called Atomic macOS Stealer (or AMOS) on Telegram for $1,000 per month, joining the likes of MacStealer.
"The Atomic macOS Stealer can steal various types of information from the victim's machine, including Keychain passwords, complete system information, files from the desktop and documents folder, and even the macOS password," Cyble researchers said in a technical report.
Among other features include its ability to extract data from web browsers and cryptocurrency wallets like Atomic, Binance, Coinomi, Electrum, and Exodus. Threat actors who purchase the stealer from its developers are also provided a ready-to-use web panel for managing the victims.
The malware takes the form of an unsigned disk image file (Setup.dmg) that, when executed, urges the victim to enter their system password on a bogus prompt to escalate privileges and carry out its malicious activities -- a technique also adopted by MacStealer.
The initial intrusion vector used to deliver the malware is immediately not clear, although it's possible that users are manipulated into downloading and executing it under the guise of legitimate software.
The Atomic stealer artifact, submitted to VirusTotal on April 24, 2023, also bears the name "Notion-7.0.6.dmg," suggesting that it's being propagated as the popular note-taking app. Other samples unearthed by the MalwareHunterTeam are distributed as "Photoshop CC 2023.dmg" and "Tor Browser.dmg."
"Malware such as the Atomic macOS Stealer could be installed by exploiting vulnerabilities or hosting on phishing websites," Cyble noted.
Atomic then proceeds to harvest system metadata, files, iCloud Keychain, as well as information stored in web browsers (e.g., passwords, autofill, cookies, credit card data) and crypto wallet extensions, all of which are compressed into a ZIP archive and sent to a remote server. The ZIP file of the compiled information is then sent to pre-configured Telegram channels.
The development is another sign that macOS is increasingly becoming a lucrative target beyond nation-state hacking groups to deploy stealer malware, making it imperative that users only download and install software from trusted sources, enable two-factor authentication, review app permissions, and refrain from opening suspicious links received via emails or SMS messages.
Zyxel Firewall Devices Vulnerable to Remote Code Execution Attacks Patch Now
28.4.23 Vulnerebility The Hacker News
Networking equipment maker Zyxel has released patches for a critical security flaw in its firewall devices that could be exploited to achieve remote code execution on affected systems.
The issue, tracked as CVE-2023-28771, is rated 9.8 on the CVSS scoring system. Researchers from TRAPA Security have been credited with reporting the flaw.
"Improper error message handling in some firewall versions could allow an unauthenticated attacker to execute some OS commands remotely by sending crafted packets to an affected device," Zyxel said in an advisory on April 25, 2023.
Products impacted by the flaw are -
ATP (versions ZLD V4.60 to V5.35, patched in ZLD V5.36)
USG FLEX (versions ZLD V4.60 to V5.35, patched in ZLD V5.36)
VPN (versions ZLD V4.60 to V5.35, patched in ZLD V5.36), and
ZyWALL/USG (versions ZLD V4.60 to V4.73, patched in ZLD V4.73 Patch 1)
Zyxel has also addressed a high-severity post-authentication command injection vulnerability affecting select firewall versions (CVE-2023-27991, CVSS score: 8.8) that could permit an authenticated attacker to execute some OS commands remotely.
The shortcoming, which impacts ATP, USG FLEX, USG FLEX 50(W) / USG20(W)-VPN, and VPN devices, has been resolved in ZLD V5.36.
Lastly, the company also shipped fixes for five high-severity flaws affecting several firewalls and access point (AP) devices (from CVE-2023-22913 to CVE-2023-22918) that could result in code execution and cause a denial-of-service (DoS) condition.
Nikita Abramov from Russian cybersecurity company Positive Technologies has been credited for reporting the issues. Abramov, earlier this year, also discovered four command injection and buffer overflow vulnerabilities in CPE, fiber ONTs, and WiFi extenders.
The most severe of the flaws is CVE-2022-43389 (CVSS score: 9.8), a buffer overflow vulnerability impacting 5G NR/4G LTE CPE devices.
"It did not require authentication to be exploited and led to arbitrary code execution on the device," Abramov explained at the time. "As a result, an attacker could gain remote access to the device and fully control its operation."
ViperSoftX InfoStealer Adopts Sophisticated Techniques to Avoid Detection
28.4.23 Virus The Hacker News
A significant number of victims in the consumer and enterprise sectors located across Australia, Japan, the U.S., and India have been affected by an evasive information-stealing malware called ViperSoftX.
ViperSoftX was first documented in 2020, with cybersecurity company Avast detailing a campaign in November 2022 that leveraged the malware to distribute a malicious Google Chrome extension capable of siphoning cryptocurrencies from wallet applications.
Now a new analysis from Trend Micro has revealed the malware's adoption of "more sophisticated encryption and basic anti-analysis techniques, such as byte remapping and web browser communication blocking."
The arrival vector of ViperSoftX is typically a software crack or a key generator (keygen), while also employing actual non-malicious software like multimedia editors and system cleaner apps as "carriers."
One of the key steps performed by the malware before downloading a first-stage PowerShell loader is a series of anti-virtual machine, anti-monitoring, and anti-malware checks.
The loader then decrypts and executes a second-stage PowerShell script retrieved from a remote server, which then takes care of launching the main routine responsible for installing rogue browser extensions to exfiltrate passwords and crypto wallet data.
The primary command-and-control (C&C) servers used for the second stage download have been observed to change on a monthly basis, suggesting attempts on the part of the actor to sidestep detection.
"It also uses some basic anti-C&C analyses by disallowing communications using web browsers," Trend Micro researcher Don Ovid Ladores said, adding the updated version of ViperSoftX scans for the presence of KeePass 2 and 1Password password managers.
As mitigations, it's advised that users download software only from official platforms and sources, and avoid downloading illegal software.
"The cybercriminals behind ViperSoftX are also skilled enough to execute a seamless chain for malware execution while staying under the radar of authorities by selecting one of the most effective methods for delivering malware to consumers," Ovid Ladores added.
Attention Online Shoppers: Don't Be Fooled by Their Sleek, Modern Looks It's Magecart!
28.4.23 CyberCrime The Hacker News
An ongoing Magecart campaign has attracted the attention of cybersecurity researchers for leveraging realistic-looking fake payment screens to capture sensitive data entered by unsuspecting users.
"The threat actor used original logos from the compromised store and customized a web element known as a modal to perfectly hijack the checkout page," J้r๔me Segura, director of threat intelligence at Malwarebytes, said. "The remarkable thing here is that the skimmer looks more authentic than the original payment page."
The term Magecart is a catch-all that refers to several cybercrime groups which employ online skimming techniques to steal personal data from websites most commonly, customer details and payment information on e-commerce websites.
The name originates from the groups' initial targeting of the Magento platform. According to data shared by Sansec, the first Magecart-like attacks were observed as early as 2010. As of 2022, more than 70,000 stores are estimated to have been compromised with a web skimmer.
These digital skimming attacks, also called formjacking, traditionally leverage various kinds of JavaScript trickery to siphon sensitive information from website users.
The latest iteration, as observed by Malwarebytes on an unnamed Parisian travel accessory store running on the PrestaShop CMS, involved the injection of a skimmer called Kritec to intercept the checkout process and display a fake payment dialog to victims.
Kritec, previously detailed by Akamai and Malwarebytes in February 2023, has been found to impersonate legitimate third-party vendors like Google Tag Manager as an evasion technique.
The cybersecurity firm said the skimmer is both complex and heavily obfuscated, with the malicious modal loaded upon selecting a credit card as the payment option from the compromised website.
Once the payment card details are harvested, a fake error message about payment cancellation is briefly displayed to the victim before redirecting to the actual payment page, at which point the payment will go through.
"The skimmer will drop a cookie which will serve as an indication that the current session is now marked as completed," Segura explained. "If the user was to go back and attempt the payment again, the malicious modal would no longer be displayed."
The threat actors behind the operation are said to be using different domains to host the skimmer, which are given similar names: "[name of store]-loader.js," suggesting that the attacks are targeting different online stores with custom modals.
"Discerning whether an online store is trustworthy has become very difficult and this case is a good example of a skimmer that would not raise any suspicion," Segura said.
The findings come a little over two months after Malwarebytes unearthed another web skimmer that collects browser fingerprint data, such as IP addresses and User-Agent strings, along with credit card information, likely in an attempt to monitor invalid users such as bots and security researchers.
Tonto Team Uses Anti-Malware File to Launch Attacks on South Korean Institutions
28.4.23 Virus The Hacker News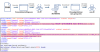
South Korean education, construction, diplomatic, and political institutions are at the receiving end of new attacks perpetrated by a China-aligned threat actor known as the Tonto Team.
"Recent cases have revealed that the group is using a file related to anti-malware products to ultimately execute their malicious attacks," the AhnLab Security Emergency Response Center (ASEC) said in a report published this week.
Tonto Team, active since at least 2009, has a track record of targeting various sectors across Asia and Eastern Europe. Earlier this year, the group was attributed to an unsuccessful phishing attack on cybersecurity company Group-IB.
The attack sequence discovered by ASEC starts with a Microsoft Compiled HTML Help (.CHM) file that executes a binary file to side-load a malicious DLL file (slc.dll) and launch ReVBShell, an open source VBScript backdoor also put to use by another Chinese threat actor called Tick.
ReVBShell is subsequently leveraged to download a second executable, a legitimate Avast software configuration file (wsc_proxy.exe), to side-load a second rogue DLL (wsc.dll), ultimately leading to the deployment of the Bisonal remote access trojan.
"The Tonto Team is constantly evolving through various means such as using normal software for more elaborate attacks," ASEC said.
The use of CHM files as a distribution vector for malware is not limited to Chinese threat actors alone. Similar attack chains have been adopted by a North Korean nation-state group known as ScarCruft in attacks aimed at its southern counterpart to backdoor targeted hosts.
The adversary, also known as APT37, Reaper, and Ricochet Chollima, has since also utilized LNK files to distribute the RokRAT malware, which is capable of collecting user credentials and downloading additional payloads.
Google Gets Court Order to Take Down CryptBot That Infected Over 670,000 Computers
28.4.23 BotNet The Hacker News
Google on Wednesday said it obtained a temporary court order in the U.S. to disrupt the distribution of a Windows-based information-stealing malware called CryptBot and "decelerate" its growth.
The tech giant's Mike Trinh and Pierre-Marc Bureau said the efforts are part of steps it takes to "not only hold criminal operators of malware accountable, but also those who profit from its distribution."
CryptBot is estimated to have infected over 670,000 computers in 2022 with the goal of stealing sensitive data such as authentication credentials, social media account logins, and cryptocurrency wallets from users of Google Chrome.
The harvested data is then exfiltrated to the threat actors, who then sell the data to other attackers for use in data breach campaigns. CryptBot was first discovered in the wild in December 2019.
The malware has been traditionally delivered via maliciously modified versions of legitimate and popular software packages such as Google Earth Pro and Google Chrome that are hosted on fake websites.
What's more, a CryptBot campaign unearthed by Red Canary in December 2021 entailed the use of KMSPico, an unofficial tool that's used to illegally activate Microsoft Office and Windows without a license key, as a delivery vector.
Then in March 2022, BlackBerry disclosed details of a new and improved version of the malicious infostealer that was distributed via compromised pirate sites that purport to offer "cracked" versions of various software and video games.
The major distributors of CryptBot, per Google, are suspected to be operating a "worldwide criminal enterprise" based out of Pakistan.
Google said it intends to use the court order, granted by a federal judge in the Southern District of New York, to "take down current and future domains that are tied to the distribution of CryptBot," thereby kneecapping the spread of new infections.
To mitigate risks posed by such threats, it's advised to only download software from well-known and trusted sources, scrutinize reviews, and ensure that the device's operating system and software are kept up-to-date.
The disclosure comes weeks after Microsoft, Fortra, and Health Information Sharing and Analysis Center (Health-ISAC) legally joined hands to dismantle servers hosting illegal, legacy copies of Cobalt Strike to prevent the tool's abuse by threat actors.
It also follows Google's endeavors to shut down the command-and-control infrastructure associated with a botnet dubbed Glupteba in December 2021. The malware, however, staged a return six months later as part of an "upscaled" campaign.
Separately, ESET and Microsoft-owned GitHub announced the temporary disruption of a commodity information stealer malware named RedLine Stealer after finding that its command-and-control panels leveraged four different GitHub repositories as dead drop resolvers.
"The removal of these repositories should break authentication for panels currently in use," the Slovak cybersecurity company said. "While this doesn't affect the actual back-end servers, it will force the RedLine operators to distribute new panels to their customers."
Paperbug Attack: New Politically-Motivated Surveillance Campaign in Tajikistan
28.4.23 BigBrothers The Hacker News
A little-known Russian-speaking cyber-espionage group has been linked to a new politically-motivated surveillance campaign targeting high-ranking government officials, telecom services, and public service infrastructures in Tajikistan.
The intrusion set, dubbed Paperbug by Swiss cybersecurity company PRODAFT, has been attributed to a threat actor known as Nomadic Octopus (aka DustSquad).
"The types of compromised machines range from individuals' computers to [operational technology] devices," PRODAFT said in a deep dive technical report shared with The Hacker News. "These targets make operation 'Paperbug' intelligence-driven."
The ultimate motive behind the attacks is unclear at this stage, but the cybersecurity firm has raised the possibility that it could be the work of opposition forces within the country or, alternatively, an intelligence-gathering mission carried out by Russia or China.
Nomadic Octopus first came to light in October 2018 when ESET and Kaspersky detailed a series of phishing attacks mounted by the actor against several countries in Central Asia. The group is estimated to have been active since at least 2014.
The cyber offensives have involved the use of custom Android and Windows malware to strike a mix of high-value entities like local governments, diplomatic missions, and political bloggers, raising the possibility that the threat actor is likely involved in cyber surveillance operations.
The Windows malware, dubbed Octopus and which masqueraded as an alternative version of the Telegram messaging app, is a Delphi-based tool that allows the adversary to surveil victims, siphon sensitive data, and gain backdoor access to their systems via a command-and-control (C2) panel.
A subsequent analysis by Gcow Security in December 2019 highlighted the advanced persistent threat (APT) group's attacks against the Ministry of Foreign Affairs of Uzbekistan to deploy Octopus.
PRODAFT's findings are the result of the discovery of an operational environment managed by Nomadic Octopus since 2020, making Paperbug the first campaign orchestrated by the group since Octopus.
According to data gathered by the company, the threat actor managed to gain access to a telecommunication firm network, before moving laterally to over a dozen targets focusing on government networks, executives, and OT devices with publicly known vulnerabilities. Exactly how and when the telecommunication network was infiltrated is unknown.
"Operation Paperbug aligns with the common trend of attacking into Central Asia government infrastructure that recently became more prominent," PRODAFT noted.
Nomadic Octopus is believed to exhibit some level of cooperation with another Russian nation-state actor known as Sofacy (aka APT28, Fancy Bear, Forest Blizzard, or FROZENLAKE), based on victimology overlaps.
The latest attacks further entailed the use of an Octopus variant that comes with features to take screenshots, run commands remotely, and download and upload files to and from the infected host to a remote server. One such artifact was uploaded to VirusTotal on April 1, 2021.
A closer look at the command-and-control (C2) server reveals that the group managed to successfully backdoor a total of 499 systems as of January 27, 2022, some of which include government network devices, gas stations, and a cash register.
The group, however, doesn't seem to possess advanced toolsets or be too concerned about covering their tracks on victim machines despite the high-stakes nature of the attacks.
"As they operate on the compromised machines to steal information, they sometimes inadvertently caused permission pop-ups on victim computers, which resulted in suspicion from the victim," the company pointed out. "However, this was resolved due to the group diligently naming the files they transfer as benign and inconspicuous programs."
The same tactic extends to naming their malicious tools as well, what with the group camouflaging them as popular web browsers such as Google Chrome, Mozilla Firefox, and Yandex to fly under the radar.
That having said, Paperbug attack chains are largely characterized by the use of public offensive tools and generic techniques, effectively acting as a "cloak" for the group and making attribution a lot more challenging.
"This imbalance between the operator skills and importance of the mission might indicate that the operators have been recruited by some entity which provided them a list of commands that need to be executed on each machine exactly," PRODAFT said, adding "the operator follows a checklist and is forced to stick to it."
LimeRAT Malware Analysis: Extracting the Config
28.4.23 Virus The Hacker News
Remote Access Trojans (RATs) have taken the third leading position in ANY. RUN's Q1 2023 report on the most prevalent malware types, making it highly probable that your organization may face this threat.
Though LimeRAT might not be the most well-known RAT family, its versatility is what sets it apart. Capable of carrying out a broad spectrum of malicious activities, it excels not only in data exfiltration, but also in creating DDoS botnets and facilitating crypto mining. Its compact footprint allows it to elude endpoint detection systems, making it a stealthy adversary. Interestingly, LimeRAT shares similarities with njRAT, which ANY.RUN ranks as the third most popular malware family in terms of uploads during Q1 2023.
ANY.RUN researchers have recently conducted an in-depth analysis of a LimeRAT sample and successfully extracted its configuration. In this article, we'll provide a brief overview of that analysis.
Collected artifacts#
SHA1 14836dd608efb4a0c552a4f370e5aafb340e2a5d
SHA256 6d08ed6acac230f41d9d6fe2a26245eeaf08c84bc7a66fddc764d82d6786d334
MD5 d36f15bef276fd447e91af6ee9e38b28
SSDEEP 3072:DDiv2GSyn88sH888wQ2wmVgMk/211h36vEcIyNTY4WZd/w1UwIwEoTqPMinXHx+i:XOayyIPv4:
IOC Description
20[.]199.13.167:8080 LimeRAT's Command and Control serverDomains:
IOC Description
https://pastebin[.]com/raw/sxNJt2ek PasteBin used by LimeRAT to hide its original Command and Control serverMITRE ATT&CKฎ
Tactic Technique Description
TA0005: Defense Evasion T1027: Obfuscated Files or Information Malware is using obfuscator to strip its method names, class names, etc.
TA0005: Defense Evasion T1027: Obfuscated Files or Information Malware uses Base64 algorithm to encode and decode data
TA0005: Defense Evasion T1027: Obfuscated Files or Information Malware uses AES algorithm to encrypt and decrypt data
ANY.RUN is running a limited-time offer, celebrating the 7th Cyberbirthdsay#
ANY.RUN is an interactive cloud malware sandbox that can extract malware configs automatically for numerous families, saving researchers hours of effort.
The service is celebrating its 7th anniversary and inviting all researchers to try out advanced analysis features typically reserved for pro plans, completely free until May 5th. This includes configuring the execution environment with Windows 8, 10, or 11.
If you discover that ANY.RUN enhances your malware analysis workflow, they are also offering a limited promotion, available until May 5th: receive 6 or 12 months of free usage when you sign up for a yearly or two-year subscription, respectively.

Breaking down LimeRAT's decryption algorithm#
We'll share a condensed version of the article here. For a complete walkthrough and the extended analysis, head over to ANY. RUN's blog if you're interested in learning more about the workflow they employed.
Since the sample under review was written in .NET, researchers utilized DnSpy to examine the code. Immediately, it was obvious that obfuscation techniques were being employed:

Sample overview in DnSpy; note that use of obfuscation techniques
Closer examination of the code revealed a class resembling the malware configuration. Within this class, was a field containing a string that was both base64 encoded and encrypted.
Possibly, malware configuration class
Continuing the code inspection, ANY.RUN researchers pinpointed a function responsible for decrypting the string. By employing the "Read by" filter in DnSpy, they tracked down methods where the string was being read, which led to a total of two methods. The first method proved unfruitful, but the second one looked interesting:

The second x-ref is more interesting. It seems that it uses our string in WebClient.DownloadString method
This method turned out to be responsible for decryption. By closely examining it, it was possible to reconstruct the process by which LimeRAT decrypts its configuration:
Instances of the RijndaelManaged and MD5CryptoServiceProvider classes are instantiated. As per MSDN, RijndaelManaged is an outdated implementation of the AES encryption algorithm (MITRE T1027), while MD5CryptoServiceProvider computes MD5 hashes.
A 32-byte array, initialized with zeros, is generated to store the AES key.
The key is created by first calculating the MD5 hash of a distinct string within the configuration class (in our analysis, the string is "20[.]199.13.167").
The initial 15 bytes, followed by the first 16 bytes of the calculated hash, are copied into the previously established array. The final element of the array remains zero.
The derived key is assigned to the key property of the RijndaelManaged instance, while the Mode property is configured as CipherMode.ECB.
Ultimately, the primary string undergoes decoding via the Base64 algorithm and decryption using the AES256-ECB algorithm.
Decrypting the string revealed a link to a PasteBin note: https://pastebin[.]com/raw/sxNJt2ek. Within this note, was LimeRAT's Command and Control (C2) server:

LimeRATs C2 discovered with decrypted data
To wrap up#
We hope you found this brief overview of our LimeRAT configuration decryption process insightful. For a more comprehensive examination, head over to the full article on ANY.RUN's blog, to get additional context on the steps and check the decryption process using CyberChef.
Also, remember that ANY. RUN's currently offering limited-time deals, featuring discounts on subscriptions and an expanded feature set for free plans, including the ability to configure execution environments with Windows 8, 10, and 11 operating systems. This offer expires on May 5th.
This is an ideal opportunity to test out ANY.RUN and determine if it streamlines your workflow, or to secure a subscription at an unbeatable price and reap the benefits of significant time savings through static and behavioral analysis.
To learn more about this offer, visit ANY.RUN plans.
RTM Locker's First Linux Ransomware Strain Targeting NAS and ESXi Hosts
28.4.23 Ransomware The Hacker News
The threat actors behind RTM Locker have developed a ransomware strain that's capable of targeting Linux machines, marking the group's first foray into the open source operating system.
"Its locker ransomware infects Linux, NAS, and ESXi hosts and appears to be inspired by Babuk ransomware's leaked source code," Uptycs said in a new report published Wednesday. "It uses a combination of ECDH on Curve25519 (asymmetric encryption) and Chacha20 (symmetric encryption) to encrypt files."
RTM Locker was first documented by Trellix earlier this month, describing its developers as a private ransomware-as-a-service (RaaS) provider. It has its roots in a cybercrime group called Read The Manual (RTM) that's known to be active since at least 2015.
The group is notable for deliberately avoiding high-profile targets such as critical infrastructure, law enforcement, and hospitals so as to draw as little attention as possible. It also leverages affiliates to ransom victims, in addition to leaking stolen data should they refuse to pay up.
The Linux flavor is specifically geared to single out ESXi hosts by terminating all virtual machines running on a compromised host prior to commencing the encryption process. The exact initial infector employed to deliver the ransomware is currently unknown.

"It is statically compiled and stripped, making reverse engineering more difficult and allowing the binary to run on more systems," Uptycs explained. "The encryption function also uses pthreads (aka POSIX threads) to speed up execution."
Following successful encryption, victims are urged to contact the support team within 48 hours via Tox or risk getting their data published. Decrypting a file locked with RTM Locker requires the public key appended to the end of the encrypted file and the attacker's private key.
The development comes as Microsoft revealed that vulnerable PaperCut servers are being actively targeted by threat actors to deploy Cl0p and LockBit ransomware.
Microsoft Confirms PaperCut Servers Used to Deliver LockBit and Cl0p Ransomware
28.4.23 Ransomware The Hacker News
Microsoft has confirmed that the active exploitation of PaperCut servers is linked to attacks that are designed to deliver Cl0p and LockBit ransomware families.
The tech giant's threat intelligence team is attributing a subset of the intrusions to a financially motivated actor it tracks under the name Lace Tempest (formerly DEV-0950), which overlaps with other hacking groups like FIN11, TA505, and Evil Corp.
"In observed attacks, Lace Tempest ran multiple PowerShell commands to deliver a TrueBot DLL, which connected to a C2 server, attempted to steal LSASS credentials, and injected the TrueBot payload into the conhost.exe service," Microsoft said in a series of tweets.
The next phase of the attack entailed the deployment of Cobalt Strike Beacon implant to conduct reconnaissance, move laterally across the network using WMI, and exfiltrate files of interest via the file-sharing service MegaSync.
Lace Tempest is a Cl0p ransomware affiliate that's said to have previously leveraged Fortra GoAnywhere MFT exploits as well as initial access gained via Raspberry Robin infections (attributed to another actor dubbed DEV-0856).
Raspberry Robin, also called QNAP worm, is believed to be an access-as-a-service malware that's used as a delivery vehicle for next-stage payloads such as IcedID, Cl0p, and LockBit. It's known to incorporate various obfuscation, anti-debugging, and anti-virtual machine measures to evade detection.
Microsoft said the threat actor subsumed PaperCut flaws (2023-27350 and CVE-2023-27351) into its attack toolkit as early as April 13, corroborating the Melbourne-based print management software provider's earlier assessment.
Successful exploitation of the separate clustertwo security vulnerabilities could allow unauthenticated remote attackers to achieve arbitrary code execution and gain unauthorized access to sensitive information.
A separate cluster of activity has also been detected weaponizing the same flaws, including those that lead to LockBit ransomware infections, Redmond further added.
According to an update shared by cybersecurity firm Huntress, the PaperCut flaws have come under broader exploitation by opportunistic threat actors looking to deploy Monero cryptocurrency miners on infected systems.
FIN7 Exploits Veeam Flaw CVE-2023-27532#
The development comes as the Russian cybercrime group monitored as FIN7 has been connected to attacks exploiting unpatched Veeam backup software instances to distribute POWERTRASH, a staple PowerShell-based in-memory dropper that executes an embedded payload.

The activity, detected by WithSecure on March 28, 2023, likely involved the abuse of CVE-2023-27532, a high-severity flaw in Veeam Backup & Replication that permits an unauthenticated attacker to obtain encrypted credentials stored in the configuration database and gain access to the infrastructure hosts. It was patched last month.
"The threat actor used a series of commands as well as custom scripts to gather host and network information from the compromised machines," the Finnish cybersecurity company said. "Furthermore, a series of SQL commands were executed to steal information from the Veeam backup database."
Also utilized in the attacks were custom PowerShell scripts to retrieve stored credentials from the backup servers, gather system information, and set up an active foothold in the compromised host by executing DICELOADER (aka Lizar or Tirion) every time the device boots up.
The hitherto undocumented persistence script has been codenamed POWERHOLD, with the DICELOADER malware decoded and executed using another unique loader referred to as DUBLOADER.
"The goal of these attacks were unclear at the time of writing, as they were mitigated before fully materializing," security researchers Neeraj Singh and Mohammad Kazem Hassan Nejad said, adding the findings point to the group's evolving tradecraft and modus operandi.
POWERHOLD and DUBLOADER are far from the only new pieces of malware added by FIN7 to its attack arsenal. IBM Security X-Force recently shed light on a loader and backdoor called Domino that's designed to facilitate follow-on exploitation.
Mirai Botnet Adds TP-Link Archer Wi-Fi Router Bug to the Mix#
In a related development, the Zero Day Initiative (ZDI) disclosed that the Mirai botnet authors have updated their malware to include CVE-2023-1389, a high-severity flaw in TP-Link Archer AX21 routers that could allow an unauthenticated adversary to execute arbitrary code on affected installations.

CVE-2023-1389 (CVSS score: 8.8) was demonstrated at the Pwn2Own hacking contest held in Toronto in December 2022 by researchers from Team Viettel and Qrious Security, prompting the vendor to issue fixes in March 2023.
The first signs of in-the-wild exploitation, per ZDI, emerged on April 11, 2023, with the threat actors leveraging the flaw to make an HTTP request to the Mirai command-and-control (C2) servers to download and execute payloads responsible for co-opting the device into the botnet and launch DDoS attacks against game servers.
"This is nothing new for the maintainers of the Mirai botnet, who are known for quickly exploiting IoT devices to maintain their foothold in an enterprise," ZDI threat researcher Peter Girnus said. "Applying this patch is the only recommended action to address this vulnerability."
Chinese Hackers Spotted Using Linux Variant of PingPull in Targeted Cyberattacks
28.4.23 Virus The Hacker News
The Chinese nation-state group dubbed Alloy Taurus is using a Linux variant of a backdoor called PingPull as well as a new undocumented tool codenamed Sword2033.
That's according to findings from Palo Alto Networks Unit 42, which discovered recent malicious cyber activity carried out by the group targeting South Africa and Nepal.
Alloy Taurus is the constellation-themed moniker assigned to a threat actor that's known for its attacks targeting telecom companies since at least 2012. It's also tracked by Microsoft as Granite Typhoon (previously Gallium).
Last month, the adversary was attributed to a campaign called Tainted Love targeting telecommunication providers in the Middle East as part of a broader operation referred to as Soft Cell.
Recent cyber espionage attacks mounted by Alloy Taurus have also broadened their victimology footprint to include financial institutions and government entities.
PingPull, first documented by Unit 42 in June 2022, is a remote access trojan that employs the Internet Control Message Protocol (ICMP) for command-and-control (C2) communications.
The Linux flavor of the malware, which was uploaded to VirusTotal on March 7, 2023, boasts of similar functionalities as its Windows counterpart, allowing it to carry out file operations and run arbitrary commands by transmitting from the C2 server a single upper case character between A and K, and M.
"Upon execution, this sample is configured to communicate with the domain yrhsywu2009.zapto[.]org over port 8443 for C2," Unit 42 said. "It uses a statically linked OpenSSL (OpenSSL 0.9.8e) library to interact with the domain over HTTPS."
Interestingly, PingPull's parsing of the C2 instructions mirrors that of China Chopper, a web shell widely used by Chinese threat actors, suggesting that the threat actor is repurposing existing source code to devise custom tools.
A closer examination of the aforementioned domain has also revealed the existence of another ELF artifact (i.e., Sword2033) that supports three basic functions, including uploading and exfiltrating files to and from the system, and executing commands.
The malware's links to Alloy Taurus stems from the fact that the domain resolved to an IP address that was previously identified as an active indicator of compromise (IoC) associated with a 2021 campaign targeting companies operating in Southeast Asia, Europe, and Africa.
The targeting of South Africa, per the cybersecurity company, comes against the backdrop of the country holding a joint 10-day naval drill with Russia and China earlier this year.
"Alloy Taurus remains an active threat to telecommunications, finance, and government organizations across Southeast Asia, Europe, and Africa," Unit 42 said.
"The identification of a Linux variant of PingPull malware, as well as recent use of the Sword2033 backdoor, suggests that the group continues to evolve their operations in support of their espionage activities."
Charming Kitten's New BellaCiao Malware Discovered in Multi-Country Attacks
26.4.23 Virus The Hacker News
The prolific Iranian nation-state group known as Charming Kitten targeted multiple victims in the U.S., Europe, the Middle East and India with a novel malware dubbed BellaCiao, adding to its ever-expanding list of custom tools.
Discovered by Bitdefender Labs, BellaCiao is a "personalized dropper" that's capable of delivering other malware payloads onto a victim machine based on commands received from an actor-controlled server.
"Each sample collected was tied up to a specific victim and included hard-coded information such as company name, specially crafted subdomains, or associated public IP address," the Romanian cybersecurity firm said in a report shared with The Hacker News.
Charming Kitten, also known as APT35, Cobalt Illusion, Educated Manticore, ITG18, Mint Sandstorm (n้e Phosphorus), TA453, and Yellow Garuda, is an Iranian state-sponsored APT group associated with the Islamic Revolutionary Guard Corps (IRGC).
Over the years, the group has utilized various means to deploy backdoors in systems belonging to a wide range of industry verticals.
The development comes as the threat actor was attributed by Microsoft to retaliatory attacks aimed at critical infrastructure entities in the U.S. between late 2021 to mid-2022 using bespoke malware such as harmPower, Drokbk, and Soldier.
Then earlier this week, Check Point disclosed Mint Sandstorm's use of an updated version of the PowerLess implant to strike organizations located in Israel using Iraq-themed phishing lures.
"Custom-developed malware, also known as 'tailored' malware, is generally harder to detect because it is specifically crafted to evade detection and contains unique code," Bitdefender researcher Martin Zugec noted.
The exact modus operandi used to achieve initial intrusion is currently undetermined, although it's suspected to entail the exploitation of known vulnerabilities in internet-exposed applications like Microsoft Exchange Server or Zoho ManageEngine.
A successful breach is followed by the threat actor attempting to disable Microsoft Defender using a PowerShell command and establishing persistence on the host via a service instance.
Bitdefender said it also observed Charming Kitten downloading two Internet Information Services (IIS) modules capable of processing incoming instructions and exfiltrating credentials.
BellaCiao, for its part, is also notable for performing a DNS request every 24 hours to resolve a subdomain to an IP address that's subsequently parsed to extract the commands to be executed on the compromised system.
"The resolved IP address is like the real public IP address, but with slight modifications that allow BellaCiao to receive further instructions," Zugec explained.
Depending on the resolved IP address, the attack chain leads to the deployment of a web shell that supports the ability to upload and download arbitrary files as well as run commands.
Also spotted is a second variant of BellaCiao that substitutes the web shell for a Plink tool a command-line utility for PuTTY that's designed to establish a reverse proxy connection to a remote server and implements similar backdoor features.
"The best protection against modern attacks involves implementing a defense-in-depth architecture," Zugec concluded. "The first step in this process is to reduce the attack surface, which involves limiting the number of entry points that attackers can use to gain access to your systems and prompt patching of newly discovered vulnerabilities."
Chinese Hackers Using MgBot Malware to Target International NGOs in Mainland China
26.4.23 Virus The Hacker News
The advanced persistent threat (APT) group referred to as Evasive Panda has been observed targeting an international non-governmental organization (NGO) in Mainland China with malware delivered via update channels of legitimate applications like Tencent QQ.
The attack chains are designed to distribute a Windows installer for MgBot malware, ESET security researcher Facundo Muñoz said in a new report published today. The activity commenced in November 2020 and continued throughout 2021.
Evasive Panda, also known as Bronze Highland and Daggerfly, is a Chinese-speaking APT group that has been attributed to a series of cyber espionage attacks targeting various entities in China, Hong Kong, and other countries located in East and South Asia since at least late December 2012.
The group's hallmark is the use of the custom MgBot modular malware framework, which is capable of receiving additional components on the fly to expand on its intelligence-gathering capabilities.
Some of the prominent capabilities of the malware include stealing files, logging keystrokes, harvesting clipboard data, recording audio streams, and credential theft from web browsers.
ESET, which discovered the campaign in January 2022 after a legitimate Chinese application was used to deploy an installer for the MgBot backdoor, said the targeted users were located in the Gansu, Guangdong, and Jiangsu provinces and are members of an unnamed international NGO.
The trojanized application is the Tencent QQ Windows client software updater ("QQUrlMgr.exe") hosted on the domain "update.browser.qq[.]com." It's not immediately clear how the threat actor managed to deliver the implant through legitimate updates.
MgBot Malware
But it points to either of the two scenarios, a supply chain compromise of Tencent QQ's update servers or a case of an adversary-in-the-middle (AitM) attack, as detailed by Kaspersky in June 2022 involving a Chinese hacking crew dubbed LuoYu.
In recent years, many software supply chain attack has been orchestrated by nation-state groups from Russia, China, and North Korea. The ability to gain a large malicious footprint quickly has not been lost on these attackers, who are increasingly targeting the IT supply chain to breach enterprise environments.
"AitM styles of interception would be possible if the attackers either LuoYu or Evasive Panda were able to compromise vulnerable devices such as routers or gateways," Muñoz elaborated.
"With access to ISP backbone infrastructure through legal or illegal means Evasive Panda would be able to intercept and reply to the update requests performed via HTTP, or even modify packets."
This is significant as the findings come less than a week after Broadcom-owned Symantec detailed attacks mounted by the threat actor against telecom service providers in Africa using the MgBot malware framework.
Apache Superset Vulnerability: Insecure Default Configuration Exposes Servers to RCE Attacks
26.4.23 Vulnerebility The Hacker News
The maintainers of the Apache Superset open source data visualization software have released fixes to plug an insecure default configuration that could lead to remote code execution.
The vulnerability, tracked as CVE-2023-27524 (CVSS score: 8.9), impacts versions up to and including 2.0.1 and relates to the use of a default SECRET_KEY that could be abused by attackers to authenticate and access unauthorized resources on internet-exposed installations.
Naveen Sunkavally, the chief architect at Horizon3.ai, described the issue as "a dangerous default configuration in Apache Superset that allows an unauth attacker to gain remote code execution, harvest credentials, and compromise data."
It's worth noting that the flaw does not affect Superset instances that have changed the default value for the SECRET_KEY config to a more cryptographically secure random string.
The cybersecurity firm, which found that the SECRET_KEY is defaulted to the value "\x02\x01thisismyscretkey\x01\x02\\e\\y\\y\\h" at install time, said that 918 out of 1,288 publicly-accessible servers were using the default configuration in October 2021.
An attacker who had knowledge of the secret key could then sign in to these servers as an administrator by forging a session cookie and seize control of the systems.
On January 11, 2022, the project maintainers attempted to rectify the problem by rotating the SECRET_KEY value to "CHANGE_ME_TO_A_COMPLEX_RANDOM_SECRET" in the Python code along with user instructions to override it.
Horizon3.ai said it further found two additional SECRET_KEY configurations that were assigned the default values "USE_YOUR_OWN_SECURE_RANDOM_KEY" and "thisISaSECRET_1234."
An expanded search conducted in February 2023 with these four keys unearthed 3,176 instances, out of which 2,124 were using one of the default keys. Some of those affected include large corporations, small companies, government agencies, and universities.
Following responsible disclosure to the Apache security team a second time, a new update (version 2.1) was released on April 5, 2023, to plug the security hole by preventing the server from starting up altogether if it's configured with the default SECRET_KEY.
"This fix is not foolproof though as it's still possible to run Superset with a default SECRET_KEY if it's installed through a docker-compose file or a helm template," Sunkavally said.
"The docker-compose file contains a new default SECRET_KEY of TEST_NON_DEV_SECRET that we suspect some users will unwittingly run Superset with. Some configurations also set admin/admin as the default credential for the admin user."
Horizon3.ai has also made available a Python script that can be used to determine if Superset instances are susceptible to the flaw.
"It's commonly accepted that users don't read documentation and applications should be designed to force users along a path where they have no choice but to be secure by default," Sunkavally concluded. "The best approach is to take the choice away from users and require them to take deliberate actions to be purposefully insecure."
VMware Releases Critical Patches for Workstation and Fusion Software
26.4.23 Vulnerebility The Hacker News
VMware has released updates to resolve multiple security flaws impacting its Workstation and Fusion software, the most critical of which could allow a local attacker to achieve code execution.
The vulnerability, tracked as CVE-2023-20869 (CVSS score: 9.3), is described as a stack-based buffer-overflow vulnerability that resides in the functionality for sharing host Bluetooth devices with the virtual machine.
"A malicious actor with local administrative privileges on a virtual machine may exploit this issue to execute code as the virtual machine's VMX process running on the host," the company said.
Also patched by VMware is an out-of-bounds read vulnerability affecting the same feature (CVE-2023-20870, CVSS score: 7.1), that could be abused by a local adversary with admin privileges to read sensitive information contained in hypervisor memory from a virtual machine.
Both vulnerabilities were demonstrated by researchers from STAR Labs on the third day of the Pwn2Own hacking contest held in Vancouver last month, earning them an $80,000 reward.
VMware has also patched two additional shortcomings, which include a local privilege escalation flaw (CVE-2023-20871, CVSS score: 7.3) in Fusion and an out-of-bounds read/write vulnerability in SCSI CD/DVD device emulation (CVE-2023-20872, CVSS score: 7.7).
While the former could enable a bad actor with read/write access to the host operating system to obtain root access, the latter could result in arbitrary code execution.
VMware
"A malicious attacker with access to a virtual machine that has a physical CD/DVD drive attached and configured to use a virtual SCSI controller may be able to exploit this vulnerability to execute code on the hypervisor from a virtual machine," VMware said.
The flaws have been addressed in Workstation version 17.0.2 and Fusion version 13.0.2. As a temporary workaround for CVE-2023-20869 and CVE-2023-20870, VMware is suggesting that users turn off Bluetooth support on the virtual machine.
As for mitigating CVE-2023-20872, it's advised to remove the CD/DVD device from the virtual machine or configure the virtual machine not to use a virtual SCSI controller.
The development comes less than a week after the virtualization services provider fixed a critical deserialization flaw impacting multiple versions of Aria Operations for Logs (CVE-2023-20864, CVSS score: 9.8).
New SLP Vulnerability Could Let Attackers Launch 2200x Powerful DDoS Attacks
25.4.23 Vulnerebility The Hacker News
Details have emerged about a high-severity security vulnerability impacting Service Location Protocol (SLP) that could be weaponized to launch volumetric denial-of-service attacks against targets.
"Attackers exploiting this vulnerability could leverage vulnerable instances to launch massive Denial-of-Service (DoS) amplification attacks with a factor as high as 2200 times, potentially making it one of the largest amplification attacks ever reported," Bitsight and Curesec researchers Pedro Umbelino and Marco Lux said in a report shared with The Hacker News.
The vulnerability, which has been assigned the identifier CVE-2023-29552 (CVSS score: 8.6), is said to impact more than 2,000 global organizations and over 54,000 SLP instances that are accessible over the internet.
This includes VMWare ESXi Hypervisor, Konica Minolta printers, Planex Routers, IBM Integrated Management Module (IMM), SMC IPMI, and 665 other product types.
The top 10 countries with the most organizations having vulnerable SLP instances are the U.S., the U.K., Japan, Germany, Canada, France, Italy, Brazil, the Netherlands, and Spain.
SLP is a service discovery protocol that makes it possible for computers and other devices to find services in a local area network such as printers, file servers, and other network resources.
Successful exploitation of CVE-2023-29552 could allow permit an attacker to take advantage of susceptible SLP instances to launch a reflection amplification attack and overwhelm a target server with bogus traffic.
To do so, all an attacker needs to do is find an SLP server on UDP port 427 and register "services until SLP denies more entries," followed by repeatedly spoofing a request to that service with a victim's IP as the source address.
An attack of this kind can produce an amplification factor of up to 2,200, resulting in large-scale DoS attacks. To mitigate against the threat, users are recommended to disable SLP on systems directly connected to the internet, or alternatively filter traffic on UDP and TCP port 427.
"It is equally important to enforce strong authentication and access controls, allowing only authorized users to access the correct network resources, with access being closely monitored and audited," the researchers said.
Web security company Cloudflare, in an advisory, said it "expects the prevalence of SLP-based DDoS attacks to rise significantly in the coming weeks" as threat actors experiment with the new DDoS amplification vector.
The findings come as a now-patched two-year-old flaw in VMware's SLP implementation was exploited by actors associated with the ESXiArgs ransomware in widespread attacks earlier this year.
Iranian Hackers Launch Sophisticated Attacks Targeting Israel with PowerLess Backdoor
25.4.23 BigBrothers The Hacker News
An Iranian nation-state threat actor has been linked to a new wave of phishing attacks targeting Israel that's designed to deploy an updated version of a backdoor called PowerLess.
Cybersecurity firm Check Point is tracking the activity cluster under its mythical creature handle Educated Manticore, which exhibits "strong overlaps" with a hacking crew known as APT35, Charming Kitten, Cobalt Illusion, ITG18, Mint Sandstorm (formerly Phosphorus), TA453, and Yellow Garuda.
"Like many other actors, Educated Manticore has adopted recent trends and started using ISO images and possibly other archive files to initiate infection chains," the Israeli company said in a technical report published today.
Active since at least 2011, APT35 has cast a wide net of targets by leveraging fake social media personas, spear-phishing techniques, and N-day vulnerabilities in internet-exposed applications to gain initial access and drop various payloads, including ransomware.
The development is an indication that the adversary is continuously refining and retooling its malware arsenal to expand their functionality and resist analysis efforts, while also adopting enhanced methods to evade detection.
The attack chain documented by Check Point begins with an ISO disk image file that makes use of Iraq-themed lures to drop a custom in-memory downloader that ultimately launches the PowerLess implant.
The ISO file acts as a conduit to display a decoy document written in Arabic, English, and Hebrew, and purports to feature academic content about Iraq from a legitimate non-profit entity called the Arab Science and Technology Foundation (ASTF), indicating that the research community may have been the target of the campaign.
Iranian Hackers
The PowerLess backdoor, previously spotlighted by Cybereason in February 2022, comes with capabilities to steal data from web browsers and apps like Telegram, take screenshots, record audio, and log keystrokes.
"While the new PowerLess payload remains similar, its loading mechanisms have significantly improved, adopting techniques rarely seen in the wild, such as using .NET binary files created in mixed mode with assembly code," Check Point said.
"PowerLess [command-and-control] communication to the server is Base64-encoded and encrypted after obtaining a key from the server. To mislead researchers, the threat actor actively adds three random letters at the beginning of the encoded blob."
The cybersecurity firm said it also discovered two other archive files used as part of a different intrusion set that shares overlaps with the aforementioned attack sequence owing to the use of the same Iraq-themed PDF file.
Further analysis has revealed that the infection chains arising from these two archive files culminate in the execution of a PowerShell script that's engineered to download two files from a remote server and run them.
"Educated Manticore continues to evolve, refining previously observed toolsets and delivering mechanisms," Check Point said, adding "the actor adopts popular trends to avoid detection" and keeps "developing custom toolsets using advanced techniques."
"Because it is an updated version of previously reported malware, [...] it is important to note that it might only represent the early stages of infection, with significant fractions of post-infection activity yet to be seen in the wild."
Lazarus Subgroup Targeting Apple Devices with New RustBucket macOS Malware
25.4.23 APT The Hacker News
A financially-motivated North Korean threat actor is suspected to be behind a new Apple macOS malware strain called RustBucket.
"[RustBucket] communicates with command and control (C2) servers to download and execute various payloads," Jamf Threat Labs researchers Ferdous Saljooki and Jaron Bradley said in a technical report published last week.
The Apple device management company attributed it to a threat actor known as BlueNoroff, a subgroup within the infamous Lazarus cluster that's also tracked under the monikers APT28, Nickel Gladstone, Sapphire Sleet, Stardust Chollima, and TA444.
The connections stem from tactical and infrastructure overlaps with a prior campaign exposed by Russian cybersecurity company Kaspersky in late December 2022 likely aimed at Japanese financial entities using fake domains impersonating venture capital firms.
BlueNoroff, unlike other constituent entities of the Lazarus Group, is known for its sophisticated cyber-enabled heists targeting the SWIFT system as well as cryptocurrency exchanges as part of an intrusion set tracked as CryptoCore.
Earlier this year, the U.S. Federal Bureau of Investigation (FBI) implicated the threat actor for the theft of $100 million in cryptocurrency assets from Harmony Horizon Bridge in June 2022.
BlueNoroff's attack repertoire is also said to have witnessed a major shift over the past few months, what with the group making use of job-themed lures to trick email recipients into entering their credentials on fake landing pages.
The macOS malware identified by Jamf masquerades as an "Internal PDF Viewer" application to activate the infection, although it bears noting that the success of the attack banks on the victim manually overriding Gatekeeper protections.
In reality, it's an AppleScript file that's engineered to retrieve a second-stage payload from a remote server, which also carries the same name as its predecessor. Both the malicious apps are signed with an ad-hoc signature.
The second-stage payload, written in Objective-C, is a basic application that offers the ability to view PDF files and only initiates the next phase of the attack chain when a booby-trapped PDF file is opened through the app.
One such nine-page PDF document identified by Jamf purports to offer an "investment strategy," that when launched, reaches out to the command-and-control (C2) server to download and execute a third-stage trojan, a Mach-O executable written in Rust that comes with capabilities to run system reconnaissance commands.
"This PDF viewer technique used by the attacker is a clever one," the researchers explained. "At this point, in order to perform analysis, not only do we need the stage-two malware but we also require the correct PDF file that operates as a key in order to execute the malicious code within the application."
It's not currently not clear how initial access is obtained and if the attacks were successful, but the development is a sign that threat actors are adapting their toolsets to accommodate cross-platform malware by using programming languages like Go and Rust.
The findings also come off a busy period of attacks orchestrated by the Lazarus Group aimed at organizations across countries and industry verticals for collecting strategic intelligence and performing cryptocurrency theft.
Lazarus Group (aka Hidden Cobra and Diamond Sleet) is less a distinct outfit and more of an umbrella term for a mixture of state-sponsored and criminal hacking groups that sit within the Reconnaissance General Bureau (RGB), North Korea's primary foreign intelligence apparatus.
Recent activity undertaken by the threat actor has offered fresh evidence of the threat actor's growing interest in exploiting trust relationships in the software supply chain as entry points to corporate networks.
Last week, the adversarial collective was linked to a cascading supply chain attack that weaponized trojanized installers versions of a legitimate app known as X_TRADER to breach enterprise communications software maker 3CX and poison its Windows and macOS apps.
Around the same time, ESET detailed Lazarus Group's use of a Linux malware dubbed SimplexTea against the backdrop of a recurring social engineering campaign referred to as Operation Dream Job.
"It is also interesting to note that Lazarus can produce and use native malware for all major desktop operating systems: Windows, macOS, and Linux," ESET malware researcher Marc-Etienne M.L้veill้ pointed out last week.
Lazarus is far from the only RGB-affiliated state-sponsored hacking group known to conduct operations on behalf of the sanctions-hit country. Another equally prolific threat actor is Kimsuky (aka APT43 or Emerald Sleet), a subgroup of which is monitored by Google's Threat Analysis Group (TAG) as ARCHIPELAGO.
"The actor primarily targets organizations in the U.S. and South Korea, including individuals working within the government, military, manufacturing, academic, and think tank organizations that possess subject matter expertise in defense and security, particularly nuclear security and nonproliferation policy," Google-owned Mandiant noted last year.
Other lesser known targets of Kimsuky include Indian and Japanese government and educational institutions, a set of attacks tracked by Taiwnese cybersecurity company TeamT5 under the name KimDragon.
The group has a history of deploying a raft of cyber weapons to exfiltrate sensitive information through a wide range of tactics such as spear-phishing, fraudulent browser extensions, and remote access trojans.
Latest findings released by VirusTotal highlight Kimsuky's heavy reliance on malicious Microsoft Word documents to deliver its payloads. A majority of the files have been submitted to the malware-scanning platform from South Korea, the U.S., Italy, and Israel, and the U.K.
"The group uses a variety of techniques and tools to conduct espionage, sabotage, and theft operations, including spear-phishing and credential harvesting," the Google Chronicle subsidiary said.
Google Cloud Introduces Security AI Workbench for Faster Threat Detection and Analysis
25.4.23 Security The Hacker News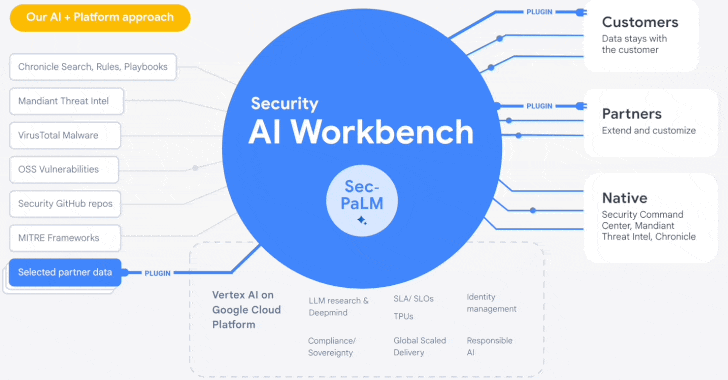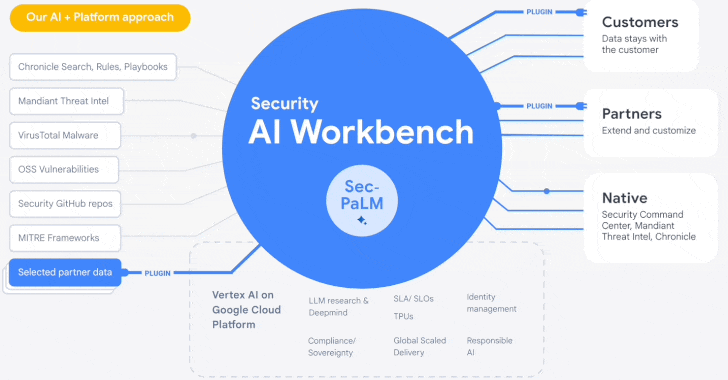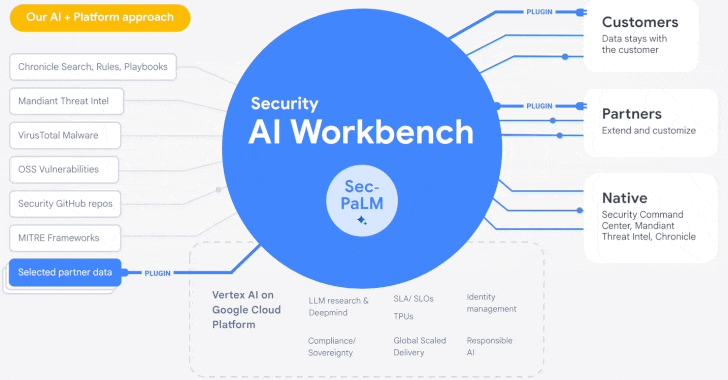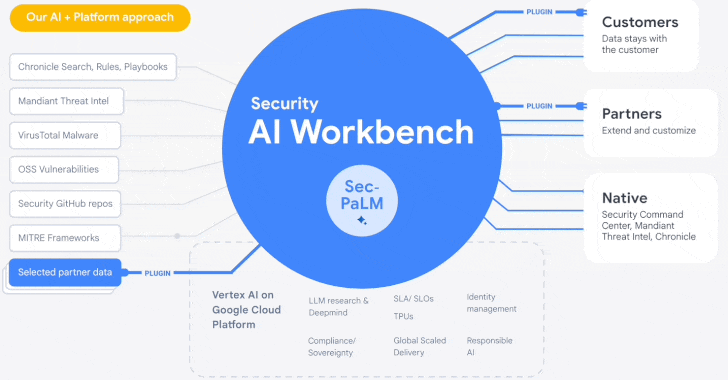
Google's cloud division is following in the footsteps of Microsoft with the launch of Security AI Workbench that leverages generative AI models to gain better visibility into the threat landscape.
Powering the cybersecurity suite is Sec-PaLM, a specialized large language model (LLM) that's "fine-tuned for security use cases."
The idea is to take advantage of the latest advances in AI to augment point-in-time incident analysis, threat detection, and analytics to counter and prevent new infections by delivering intelligence that's trusted, relevant, and actionable.
To that end, the Security AI Workbench spans a wide range of new AI-powered tools, including VirusTotal Code Insight and Mandiant Breach Analytics for Chronicle, to analyze potentially malicious scripts and alert customers of active breaches in their environments.
Users, like with Microsoft's GPT-4-based Security Copilot, can "conversationally search, analyze, and investigate security data" with an aim to reduce mean time-to-respond as well as quickly determine the full scope of events.
Threat Detection and Analysis
On the other hand, the Code Insight feature in VirusTotal is designed to generate natural language summaries of code snippets so as to detect and mitigate potential threats. It can also be used to flag false negatives and clear false positives.
Another key offering is Security Command Center AI, which utilizes Sec-PaLM to provide operators with "near-instant analysis of findings and possible attack paths" as well as impacted assets and recommended mitigations.
Google is also making use of machine learning models to detect and respond to API abuse and business logic attacks, wherein an adversary weaponizes a legitimate functionality to achieve a nefarious goal without triggering a security alert.
"Because Security AI Workbench is built on Google Cloud's Vertex AI infrastructure, customers control their data with enterprise-grade capabilities such as data isolation, data protection, sovereignty, and compliance support," Google Cloud's Sunil Potti said.
The development comes days after Google announced the creation of a new unit called Google DeepMind that brings together its AI research groups from DeepMind and the Brain team from Google Research to "build more capable systems more safely and responsibly."
News of Google's Security AI Workbench also follows GitLab's plans to integrate AI into its platform to help developers from leaking access tokens and avoid false positives during security testing.
Google Authenticator App Gets Cloud Backup Feature for TOTP Codes
25.4.23 Security The Hacker News
Search giant Google on Monday unveiled a major update to its 12-year-old Authenticator app for Android and iOS with an account synchronization option that allows users to back up their time-based one-time passwords (TOTPs) to the cloud.
"This change means users are better protected from lockout and that services can rely on users retaining access, increasing both convenience and security," Google's Christiaan Brand said.
The update, which also brings a new icon to the two-factor authenticator (2FA) app, finally brings it in line with Apple's iCloud Keychain and addresses a long-standing complaint that it's tied to the device on which it's installed, making it a hassle when switching between phones.
Even worse, as Google puts it, users who lose access to their devices completely "lost their ability to sign in to any service on which they'd set up 2FA using Authenticator."
The cloud sync feature is optional, meaning users can opt to use the Authenticator app without linking it to a Google account.
That said, it's always worth keeping in mind the pitfalls associated with cloud backups, as a malicious actor with access to a Google account could leverage it to break into other online services.
The development comes days after Swiss privacy-focused company Proton, which surpassed 100 million active accounts last week, unveiled an end-to-end encrypted password manager solution called Proton Pass.
The open source and publicly auditable tool, which makes use of the bcrypt password hashing function and a hardened version of the Secure Remote Password (SRP) protocol for authentication, also comes with 2FA integration.
Russian Hackers Tomiris Targeting Central Asia for Intelligence Gathering
25.4.23 BigBrothers The Hacker News
The Russian-speaking threat actor behind a backdoor known as Tomiris is primarily focused on gathering intelligence in Central Asia, fresh findings from Kaspersky reveal.
"Tomiris's endgame consistently appears to be the regular theft of internal documents," security researchers Pierre Delcher and Ivan Kwiatkowski said in an analysis published today. "The threat actor targets government and diplomatic entities in the CIS."
The Russian cybersecurity firm's latest assessment is based on three new attack campaigns mounted by the hacking crew between 2021 and 2023.
Tomiris first came to light in September 2021 when Kaspersky highlighted its potential connections to Nobelium (aka APT29, Cozy Bear, or Midnight Blizzard), the Russian nation-state group behind the SolarWinds supply chain attack.
Similarities have also been unearthed between the backdoor and another malware strain dubbed Kazuar, which is attributed to the Turla group (aka Krypton, Secret Blizzard, Venomous Bear, or Uroburos).
Spear-phishing attacks mounted by the group have leveraged a "polyglot toolset" comprising a variety of low-sophistication "burner" implants that are coded in different programming languages and repeatedly deployed against the same targets.
Besides using open source or commercially available offensive tools like RATel and Warzone RAT (aka Ave Maria), the custom malware arsenal used by the group falls into one of the three categories: downloaders, backdoors, and information stealers -
Telemiris - A Python backdoor that uses Telegram as a command-and-control (C2) channel.
Roopy - A Pascal-based file stealer that's designed to hoover files of interest every 40-80 minutes and exfiltrate them to a remote server.
JLORAT - A file stealer written in Rust that gathers system information, runs commands issued by the C2 server, upload and download files, and capture screenshots.
Kaspersky's investigation of the attacks has further identified overlaps with a Turla cluster tracked by Google-owned Mandiant under the name UNC4210, uncovering that the QUIETCANARY (aka TunnusSched) implant had been deployed against a government target in the CIS by means of Telemiris.
"More precisely, on September 13, 2022, around 05:40 UTC, an operator attempted to deploy several known Tomiris implants via Telemiris: first a Python Meterpreter loader, then JLORAT and Roopy," the researchers explained.
"These efforts were thwarted by security products, which led the attacker to make repeated attempts, from various locations on the filesystem. All these attempts ended in failure. After a one-hour pause, the operator tried again at 07:19 UTC, this time using a TunnusSched/QUIETCANARY sample. The TunnusSched sample was blocked as well."
That said, despite the potential ties between the two groups, Tomiris is said to be separate from Turla owing to differences in their targeting and tradecrafts, once again raising the possibility of a false flag operation.
On the other hand, it's also highly probable that Turla and Tomiris collaborate on select operations or that both the actors rely on a common software provider, as exemplified by Russian military intelligence agencies' use of tools supplied by a Moscow-based IT contractor named NTC Vulkan.
"Overall, Tomiris is a very agile and determined actor, open to experimentation," the researchers said, adding "there exists a form of deliberate cooperation between Tomiris and Turla."
Ransomware Hackers Using AuKill Tool to Disable EDR Software Using BYOVD Attack
25.4.23 Ransomware The Hacker News
Threat actors are employing a previously undocumented "defense evasion tool" dubbed AuKill that's designed to disable endpoint detection and response (EDR) software by means of a Bring Your Own Vulnerable Driver (BYOVD) attack.
"The AuKill tool abuses an outdated version of the driver used by version 16.32 of the Microsoft utility, Process Explorer, to disable EDR processes before deploying either a backdoor or ransomware on the target system," Sophos researcher Andreas Klopsch said in a report published last week.
Incidents analyzed by the cybersecurity firm show the use of AuKill since the start of 2023 to deploy various ransomware strains such as Medusa Locker and LockBit. Six different versions of the malware have been identified to date. The oldest AuKill sample features a November 2022 compilation timestamp.
The BYOVD technique relies on threat actors misusing a legitimate, but out-of-date and exploitable, driver signed by Microsoft (or using a stolen or leaked certificate) to gain elevated privileges and turn off security mechanisms.
By using valid, susceptible drivers, the idea is to bypass a key Windows safeguard known as Driver Signature Enforcement that ensures kernel-mode drivers have been signed by a valid code signing authority before they are allowed to run.
"The AuKill tool requires administrative privileges to work, but it cannot give the attacker those privileges," Klopsch noted. "The threat actors using AuKill took advantage of existing privileges during the attacks, when they gained them through other means."
This is not the first time the Microsoft-signed Process Explorer driver has been weaponized in attacks. In November 2022, Sophos also detailed LockBit affiliates' use of an open source tool called Backstab that abused outdated versions of the driver to terminate protected anti-malware processes.
Then earlier this year, a malvertising campaign was spotted utilizing the same driver as part of an infection chain distributing a .NET loader named MalVirt to deploy the FormBook information-stealing malware.
The development comes as the AhnLab Security Emergency response Center (ASEC) revealed that poorly managed MS-SQL servers are being weaponized to install the Trigona ransomware, which shares overlaps with another strain referred to as CryLock.
It also follows findings that the Play ransomware (aka PlayCrypt) actors have been observed using custom data harvesting tools that make it possible to enumerate all users and computers on a compromised network and copy files from the Volume Shadow Copy Service (VSS).
Grixba, a .NET-based information stealer, is designed to scan a machine for security programs, backup software, and remote administration tools, and exfiltrate the gathered data in the form of CSV files that are then compressed into ZIP archives.
Also used by the cybercriminal gang, tracked by Symantec as Balloonfly, is a VSS Copying Tool written in .NET that makes use of the AlphaVSS framework to list files and folders in a VSS snapshot and copy them to a destination directory prior to encryption.
Play ransomware is notable for not only utilizing intermittent encryption to speed up the process, but also for the fact that it's not operated on a ransomware-as-a-service (RaaS) model. Evidence gathered so far points to Balloonfly carrying out the ransomware attacks as well as developing the malware themselves.
Grixba and VSS Copying Tool are the latest in a long list of proprietary tools such as Exmatter, Exbyte, and PowerShell-based scripts that are used by ransomware actors to establish more control over their operations, while also adding extra layers of complexity to persist in compromised environments and evade detection.
Another technique increasingly adopted by financially-motivated groups is the use of the Go programming language to develop cross-platform malware and resist analysis and reverse engineering efforts.
Indeed, a report from Cyble last week documented a new GoLang ransomware called CrossLock that employs the double-extortion technique to increase the likelihood of payment from its victims, alongside taking steps to sidestep event tracing for Windows (ETW).
"This functionality can enable the malware to avoid detection by security systems that depend on event logs," Cyble said. "CrossLock Ransomware also performs several actions to reduce the chances of data recovery while simultaneously increasing the attack's effectiveness."
Hackers Exploit Outdated WordPress Plugin to Backdoor Thousands of WordPress Sites
24.4.23 Exploit The Hacker News
Threat actors have been observed leveraging a legitimate but outdated WordPress plugin to surreptitiously backdoor websites as part of an ongoing campaign, Sucuri revealed in a report published last week.
The plugin in question is Eval PHP, released by a developer named flashpixx. It allows users to insert PHP code pages and posts of WordPress sites that's then executed every time the posts are opened in a web browser.
While Eval PHP has never received an update in 11 years, statistics gathered by WordPress show that it's installed on over 8,000 websites, with the number of downloads skyrocketing from one or two on average since September 2022 to 6,988 on March 30, 2023.
On April 23, 2023, alone, it was downloaded 2,140 times. The plugin has racked up 23,110 downloads over the past seven days.
GoDaddy-owned Sucuri said it observed some infected websites' databases injected with malicious code into the "wp_posts" table, which stores a site's posts, pages, and navigation menu information. The requests originate from these three IP addresses based in Russia.
"This code is quite simple: It uses the file_put_contents function to create a PHP script into the docroot of the website with the specified remote code execution backdoor," security researcher Ben Martin said.
"Although the injection in question does drop a conventional backdoor into the file structure, the combination of a legitimate plugin and a backdoor dropper in a WordPress post allows them to easily reinfect the website and stay hidden. All the attacker needs to do is to visit one of the infected posts or pages and the backdoor will be injected into the file structure."
Sucuri said it detected over 6,000 instances of this backdoor in the last 6 months alone, describing the pattern of inserting the malware directly into the database as a "new and interesting development."
The attack chain entails installing the Eval PHP plugin on compromised sites and misusing it to establish persistent backdoors across multiple posts that are sometimes also saved as drafts.
"The way the Eval PHP plugin works it's enough to save a page as a draft in order to execute the PHP code inside the [evalphp] shortcodes," Martin explained, adding the rogue pages are created with a real site administrator as their author, suggesting the attackers were able to successfully sign in as a privileged user.
The development once again points to how malicious actors are experimenting with different methods to maintain their foothold in compromised environments and evade server-side scans and file integrity monitoring.
Site owners are advised to secure the WP Admin dashboard as well as watch out for any suspicious logins to prevent threat actors from gaining admin access and install the plugin.
New All-in-One "EvilExtractor" Stealer for Windows Systems Surfaces on the Dark Web
24.4.23 Virus The Hacker News
A new "all-in-one" stealer malware named EvilExtractor (also spelled Evil Extractor) is being marketed for sale for other threat actors to steal data and files from Windows systems.
"It includes several modules that all work via an FTP service," Fortinet FortiGuard Labs researcher Cara Lin said. "It also contains environment checking and Anti-VM functions. Its primary purpose seems to be to steal browser data and information from compromised endpoints and then upload it to the attacker's FTP server."
The network security company said it has observed a surge in attacks spreading the malware in the wild in March 2023, with a majority of the victims located in Europe and the U.S. While marketed as an educational tool, EvilExtractor has been adopted by threat actors for use as an information stealer.
Sold by an actor named Kodex on cybercrime forums like Cracked since October 22, 2022, it's continually updated and packs in various modules to siphon system metadata, passwords and cookies from various web browsers as well as record keystrokes and even act as a ransomware by encrypting files on the target system.
The malware is also said to have been used as part of a phishing email campaign detected by the company on March 30, 2023. The emails lure recipients into launching an executable that masquerades as a PDF document under the pretext of confirming their "account details."
The "Account_Info.exe" binary is an obfuscated Python program designed to launch a .NET loader that uses a Base64-encoded PowerShell script to launch EvilExtractor. The malware, besides gathering files, can also activate the webcam and capture screenshots.
"EvilExtractor is being used as a comprehensive info stealer with multiple malicious features, including ransomware," Lin said. "Its PowerShell script can elude detection in a .NET loader or PyArmor. Within a very short time, its developer has updated several functions and increased its stability."
The findings come as Secureworks Counter Threat Unit (CTU) detailed a malvertising and SEO poisoning campaign used to deliver the Bumblebee malware loader via trojanized installers of legitimate software.
Dark Web
Bumbleebee, documented first a year ago by Google's Threat Analysis Group and Proofpoint, is a modular loader that's primarily propagating through phishing techniques. It's suspected to be developed by actors associated with the Conti ransomware operation as a replacement for BazarLoader.
The use of SEO poisoning and malicious ads to redirect users searching for popular tools like ChatGPT, Cisco AnyConnect, Citrix Workspace, and Zoom to rogue websites hosting tainted installers has witnessed a spike in recent months after Microsoft began blocking macros by default from Office files downloaded from the internet.
In one incident described by the cybersecurity firm, the threat actor used the Bumblebee malware to obtain an entry point and move laterally after three hours to deploy Cobalt Strike and legitimate remote access software like AnyDesk and Dameware. The attack was ultimately disrupted before it proceeded to the final ransomware stage.
"To mitigate this and similar threats, organizations should ensure that software installers and updates are only downloaded from known and trusted websites," Secureworks said. "Users should not have privileges to install software and run scripts on their computers."
Russian Hackers Suspected in Ongoing Exploitation of Unpatched PaperCut Servers
24.4.23 BigBrothers The Hacker News
Print management software provider PaperCut said that it has "evidence to suggest that unpatched servers are being exploited in the wild," citing two vulnerability reports from cybersecurity company Trend Micro.
"PaperCut has conducted analysis on all customer reports, and the earliest signature of suspicious activity on a customer server potentially linked to this vulnerability is 14th April 01:29 AEST / 13th April 15:29 UTC," it further added.
The update comes as the U.S. Cybersecurity and Infrastructure Security Agency (CISA) added a critical improper access control flaw (CVE-2023-27350, CVSS score: 9.8) in PaperCut MF and NG to the Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation.
Cybersecurity company Huntress, which found about 1,800 publicly exposed PaperCut servers, said it observed PowerShell commands being spawned from PaperCut software to install remote management and maintenance (RMM) software like Atera and Syncro for persistent access and code execution on the infected hosts.
Additional infrastructure analysis has revealed the domain hosting the tools windowservicecemter[.]com was registered on April 12, 2023, also hosting malware like TrueBot, although the company said it did not directly detect the deployment of the downloader.
TrueBot is attributed to a Russian criminal entity known as Silence, which in turn has historical links with Evil Corp and its overlapping cluster TA505, the latter of which has facilitated the distribution of Cl0p ransomware in the past.
"While the ultimate goal of the current activity leveraging PaperCut's software is unknown, these links (albeit somewhat circumstantial) to a known ransomware entity are concerning," Huntress researchers said.
"Potentially, the access gained through PaperCut exploitation could be used as a foothold leading to follow-on movement within the victim network, and ultimately ransomware deployment."
Users are recommended to upgrade to the fixed versions of PaperCut MF and NG (20.1.7, 21.2.11, and 22.0.9) as soon as possible, regardless of whether the server is "available to external or internal connections," to mitigate potential risks.
Customers who are unable to upgrade to a security patch are advised to lock down network access to the servers by blocking all inbound traffic from external IPs and limiting IP addresses to only those belonging to verified site servers.
Lazarus X_TRADER Hack Impacts Critical Infrastructure Beyond 3CX Breach
22.4.23 ICS The Hacker News
Lazarus, the prolific North Korean hacking group behind the cascading supply chain attack targeting 3CX, also breached two critical infrastructure organizations in the power and energy sector and two other businesses involved in financial trading using the trojanized X_TRADER application.
The new findings, which come courtesy of Symantec's Threat Hunter Team, confirm earlier suspicions that the X_TRADER application compromise affected more organizations than 3CX. The names of the organizations were not revealed.
Eric Chien, director of security response at Broadcom-owned Symantec, told The Hacker News in a statement that the attacks took place between September 2022 and November 2022.
"The impact from these infections is unknown at this time more investigation is required and is on-going," Chien said, adding it's possible that there's "likely more to this story and possibly even other packages that are trojanized."
The development comes as Mandiant disclosed that the compromise of the 3CX desktop application software last month was facilitated by another software supply chain breach targeting X_TRADER in 2022, which an employee downloaded to their personal computer.
It's currently unclear how UNC4736, a North Korean nexus actor, tampered with X_TRADER, a piece of trading software developed by a company named Trading Technologies. While the service was discontinued in April 2020, it was still available for download on the company's website as recently as last year.
Mandiant's investigation has revealed that the backdoor (dubbed VEILEDSIGNAL) injected into the corrupted X_TRADER app allowed the adversary to gain access to the employee's computer and siphon their credentials, which were then used it to breach 3CX's network, move laterally, and compromise the Windows and macOS build environments to insert malicious code.
The sprawling interlinked attack appears to have substantial overlap with previous North Korea-aligned groups and campaigns that have historically targeted cryptocurrency companies and conducted financially motivated attacks.
The Google Cloud subsidiary has assessed with "moderate confidence" that the activity is linked to AppleJeus, a persistent campaign targeting crypto companies for financial theft. Cybersecurity firm CrowdStrike previously attributed the attack to a Lazarus cluster it calls Labyrinth Chollima.
The same adversarial collective was previously linked by Google's Threat Analysis Group (TAG) to the compromise of Trading Technologies' website in February 2022 to serve an exploit kit that leveraged a then zero-day flaw in the Chrome web browser.
ESET, in an analysis of a disparate Lazarus Group campaign, disclosed a new piece of Linux-based malware called SimplexTea that shares the same network infrastructure identified as used by UNC4736, further expanding on existing evidence that the 3CX hack was orchestrated by North Korean threat actors.
"[Mandiant's] finding about a second supply-chain attack responsible for the compromise of 3CX is a revelation that Lazarus could be shifting more and more to this technique to get initial access in their targets' network," ESET malware researcher Marc-Etienne M.L้veill้ told The Hacker News.
The compromise of the X_TRADER application further alludes to the attackers' financial motivations. Lazarus (also known as HIDDEN COBRA) is an umbrella term for a composite of several subgroups based in North Korea that engage in both espionage and cybercriminal activities on behalf of the Hermit Kingdom and evade international sanctions.
Symantec's breakdown of the infection chain corroborates the deployment of the VEILEDSIGNAL modular backdoor, which also incorporates a process-injection module that can be injected into Chrome, Firefox, or Edge web browsers. The module, for its part, contains a dynamic-link library (DLL) that connects to the Trading Technologies' website for command-and-control (C2).
"The discovery that 3CX was breached by another, earlier supply chain attack made it highly likely that further organizations would be impacted by this campaign, which now transpires to be far more wide-ranging than originally believed," Symantec concluded.
CISA Adds 3 Actively Exploited Flaws to KEV Catalog, including Critical PaperCut Bug
22.4.23 BigBrothers The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday added three security flaws to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation.
The three vulnerabilities are as follows -
CVE-2023-28432 (CVSS score - 7.5) - MinIO Information Disclosure Vulnerability
CVE-2023-27350 (CVSS score - 9.8) - PaperCut MF/NG Improper Access Control Vulnerability
CVE-2023-2136 (CVSS score - TBD) - Google Chrome Skia Integer Overflow Vulnerability
"In a cluster deployment, MinIO returns all environment variables, including MINIO_SECRET_KEY and MINIO_ROOT_PASSWORD, resulting in information disclosure," MinIO maintainers said in an advisory published on March 21, 2023.
Data gathered by GreyNoise shows that as many as 18 unique malicious IP addresses from the U.S., the Netherlands, France, Japan, and Finland have attempted to exploit the flaw over the past 30 days.
The threat intelligence company, in an alert published late last month, also noted how a reference implementation provided by OpenAI for developers to integrate their plugins to ChatGPT relied on an older version of MinIO that's vulnerable to CVE-2023-28432.
"While the new feature released by OpenAI is a valuable tool for developers who want to access live data from various providers in their ChatGPT integration, security should remain a core design principle," GreyNoise said.
Also added to the KEV catalog is a critical remote code execution bug affecting PaperCut print management software that allows remote attackers to bypass authentication and run arbitrary code.
The vulnerability has been addressed by the vendor as of March 8, 2023, with the release of PaperCut MF and PaperCut NG versions 20.1.7, 21.2.11, and 22.0.9. Zero Day Initiative, which reported the issue on January 10, 2023, is expected to release additional technical details on May 10, 2023.
According to an update shared by the Melbourne-based company earlier this week, evidence of active exploitation of unpatched servers emerged in the wild around April 18, 2023.
Cybersecurity firm Arctic Wolf said it "has observed intrusion activity associated with a vulnerable PaperCut Server where the RMM tool Synchro MSP was loaded onto a victim system."
Lastly added to the list of actively exploited flaws is a Google Chrome vulnerability affecting the Skia 2D graphics library that could enable a threat actor to perform a sandbox escape via a crafted HTML page.
Federal Civilian Executive Branch (FCEB) agencies in the U.S. are recommended to remediate identified vulnerabilities by May 12, 2023, to secure their networks against active threats.
Kubernetes RBAC Exploited in Large-Scale Campaign for Cryptocurrency Mining
22.4.23 Cryptocurrency The Hacker News
A large-scale attack campaign discovered in the wild has been exploiting Kubernetes (K8s) Role-Based Access Control (RBAC) to create backdoors and run cryptocurrency miners.
"The attackers also deployed DaemonSets to take over and hijack resources of the K8s clusters they attack," cloud security firm Aqua said in a report shared with The Hacker News. The Israeli company, which dubbed the attack RBAC Buster, said it found 60 exposed K8s clusters that have been exploited by the threat actor behind this campaign.
The attack chain commenced with the attacker gaining initial access via a misconfigured API server, followed by checking for evidence of competing miner malware on the compromised server and then using RBAC to set up persistence.
"The attacker created a new ClusterRole with near admin-level privileges," the company said. "Next, the attacker created a 'ServiceAccount', 'kube-controller' in the 'kube-system' namespace. Lastly, the attacker created a 'ClusterRoleBinding', binding the ClusterRole with the ServiceAccount to create a strong and inconspicuous persistence."
In the intrusion observed against its K8s honeypots, the attacker attempted to weaponize the exposed AWS access keys to obtain an entrenched foothold into the environment, steal data, and escape the confines of the cluster.

The final step of the attack entailed the threat actor creating a DaemonSet to deploy a container image hosted on Docker ("kuberntesio/kube-controller:1.0.1") on all nodes. The container, which has been pulled 14,399 times since its upload five months ago, harbors a cryptocurrency miner.
"The container image named 'kuberntesio/kube-controller' is a case of typosquatting that impersonates the legitimate 'kubernetesio' account," Aqua said. "The image also mimics the popular 'kube-controller-manager' container image, which is a critical component of the control plane, running within a Pod on every master node, responsible for detecting and responding to node failures."
Interestingly, some of the tactics described in the campaign bear similarities to another illicit cryptocurrency mining operation that also took advantage of DaemonSets to mint Dero and Monero. It's currently not clear whether the two sets of attacks are related.
GhostToken Flaw Could Let Attackers Hide Malicious Apps in Google Cloud Platform
21.4.23 Vulnerebility The Hacker News
Cybersecurity researchers have disclosed details of a now-patched zero-day flaw in Google Cloud Platform (GCP) that could have enabled threat actors to conceal an unremovable, malicious application inside a victim's Google account.
Israeli cybersecurity startup Astrix Security, which discovered and reported the issue to Google on June 19, 2022, dubbed the shortcoming GhostToken.
The issue impacted all Google accounts, including enterprise-focused Workspace accounts. Google deployed a global-patch more than nine months later on April 7, 2023.
"The vulnerability [...] allows attackers to gain permanent and unremovable access to a victim's Google account by converting an already authorized third-party application into a malicious trojan app, leaving the victim's personal data exposed forever," Astrix said in a report.
In a nutshell, the flaw makes it possible for an attacker to hide their malicious app from a victim's Google account application management page, thereby effectively preventing users from revoking its access.
This is achieved by deleting the GCP project associated with the authorized OAuth application, causing it to go in a "pending deletion" state. The threat actor, armed with this capability, could then unhide the rogue app by restoring the project and use the access token to obtain the victim's data, and make it invisible again.
Google Cloud Platform
"In other words, the attacker holds a 'ghost' token to the victim's account," Astrix said.
The kind of data that can be accessed depends on the permissions granted to the app, which the adversaries can abuse to delete files from Google Drive, write emails on the victim's behalf to perform social engineering attacks, track locations, and exfiltrate sensitive data from Google Calendar, Photos, and Drive.
"Victims may unknowingly authorize access to such malicious applications by installing a seemingly innocent app from the Google Marketplace or one of the many productivity tools available online," Astrix added.
"Once the malicious app has been authorized, an attacker exploiting the vulnerability can bypass Google's "Apps with access to your account" management feature, which is the only place where Google users can view third-party apps connected to their account."
Google's patch addresses the problem by now displaying apps that are in a pending deletion state on the third-party access page, allowing users to revoke the permission granted to such apps.
The development comes as Google Cloud fixed a privilege escalation flaw in the Cloud Asset Inventory API dubbed Asset Key Thief that could be exploited to steal user-managed Service Account private keys and gain access to valuable data. The issue, which was discovered by SADA earlier this February, was patched by the tech giant on March 14, 2023.
The findings come a little over a month after cloud incident response firm Mitiga revealed that adversaries could take advantage of "insufficient" forensic visibility into GCP to exfiltrate sensitive data.
N.K. Hackers Employ Matryoshka Doll-Style Cascading Supply Chain Attack on 3CX
21.4.23 Attack The Hacker News
The supply chain attack targeting 3CX was the result of a prior supply chain compromise associated with a different company, demonstrating a new level of sophistication with North Korean threat actors.
Google-owned Mandiant, which is tracking the attack event under the moniker UNC4736, said the incident marks the first time it has seen a "software supply chain attack lead to another software supply chain attack."
The Matryoshka doll-style cascading attack against 3CX first came to light on March 29, 2023, when it emerged that Windows and macOS versions of its communication software were trojanized to deliver a C/C++-based data miner named ICONIC Stealer by means of a downloader, SUDDENICON, that used icon files hosted on GitHub to extract the server containing the stealer.
"The malicious application next attempts to steal sensitive information from the victim user's web browser," the U.S. Cybersecurity and Infrastructure Security Agency (CISA) said in an analysis of the malware. "Specifically it will target the Chrome, Edge, Brave, or Firefox browsers."
Select attacks targeting cryptocurrency companies also entailed the deployment of a next-stage backdoor referred to as Gopuram that's capable of running additional commands and interacting with the victim's file system.
Mandiant's investigation into the sequence of events has now revealed the patient zero to be a malicious version of a now-discontinued software provided by a fintech company called Trading Technologies, which was downloaded by a 3CX employee to their personal computer.
It described the initial intrusion vector as "a malware-laced software package distributed via an earlier software supply chain compromise that began with a tampered installer for X_TRADER."
This rogue installer, in turn, contained a setup binary that dropped two trojanized DLLs and an innocuous executable, the latter of which is used to side-load one of the DLLs that's camouflaged as a legitimate dependency.
The attack chain then made use of open source tools like SIGFLIP and DAVESHELL to ultimately extract and execute VEILEDSIGNAL, a multi-stage modular backdoor written in C that's capable of sending data, executing shellcode, and terminating itself.
The initial compromise of the employee's personal computer using VEILEDSIGNAL enabled the threat actor to obtain the individual's corporate credentials, two after which the first unauthorized access to its network took place via a VPN by taking advantage of the stolen credentials.
Besides identifying tactical similarities between the compromised X_TRADER and 3CXDesktopApp apps, Mandiant found that the threat actor subsequently laterally moved within the 3CX environment and breached the Windows and macOS build environments.
"On the Windows build environment, the attacker deployed a TAXHAUL launcher and COLDCAT downloader that persisted by performing DLL side-loading through the IKEEXT service and ran with LocalSystem privileges," Mandiant said. "The macOS build server was compromised with POOLRAT backdoor using Launch Daemons as a persistence mechanism."
POOLRAT, previously classified by the threat intelligence firm as SIMPLESEA, is a C/C++ macOS implant capable of collecting basic system information and executing arbitrary commands, including carrying out file operations.
UNC4736 is suspected to be a threat group with North Korean nexus, an assessment that's been reinforced by ESET's discovery of an overlapping command-and-control (C2) domain (journalide[.]org) employed in the supply chain attack and that of a Lazarus Group campaign called Operation Dream Job.
Evidence gathered by Mandiant shows that the group exhibits commonalities with another intrusion set tracked as Operation AppleJeus, which has a track record of carrying out financially motivated attacks.
What's more, the breach of Trading Technologies' website is said to have taken place in early February 2022 by weaponizing a then zero-day flaw in Google Chrome (CVE-2022-0609) to activate a multi-stage infection chain responsible for serving unknown payloads to the site visitors.
"The site www.tradingtechnologies[.]com was compromised and hosting a hidden IFRAME to exploit visitors, just two months before the site was known to deliver a trojanized X_TRADER software package," Mandiant explained.
Another link connecting it to AppleJeus is the threat actor's previous use of an older version of POOLRAT as part of a long-running campaign disseminating booby-trapped trading applications like CoinGoTrade to facilitate cryptocurrency theft.
The entire scale of the campaign remains unknown, and it's currently not clear if the compromised X_TRADER software was used by other firms. The platform was purportedly decommissioned in April 2020, but it was still available to download from the site in 2022.
3CX, in an update shared on April 20, 2023, said it's taking steps to harden its systems and minimize the risk of nested software-in-software supply chain attacks by enhancing product security, incorporating tools to ensure the integrity of its software, and establishing a new department for Network Operations and Security.
"Cascading software supply chain compromises demonstrate that North Korean operators can exploit network access in creative ways to develop and distribute malware, and move between target networks while conducting operations aligned with North Korea's interests," Mandiant said.
Cisco and VMware Release Security Updates to Patch Critical Flaws in their Products
21.4.23 Vulnerebility The Hacker News
Cisco and VMware have released security updates to address critical security flaws in their products that could be exploited by malicious actors to execute arbitrary code on affected systems.
The most severe of the vulnerabilities is a command injection flaw in Cisco Industrial Network Director (CVE-2023-20036, CVSS score: 9.9), which resides in the web UI component and arises as a result of improper input validation when uploading a Device Pack.
"A successful exploit could allow the attacker to execute arbitrary commands as NT AUTHORITY\SYSTEM on the underlying operating system of an affected device," Cisco said in an advisory released on April 19, 2023.
The networking equipment major also resolved a medium-severity file permissions vulnerability in the same product (CVE-2023-20039, CVSS score: 5.5) that an authenticated, local attacker could abuse to view sensitive information.
Patches have been made available in version 1.11.3, with Cisco crediting an unnamed "external" researcher for reporting the two issues.
Also fixed by Cisco is another critical flaw in the external authentication mechanism of the Modeling Labs network simulation platform. Tracked as CVE-2023-20154 (CVSS score: 9.1), the vulnerability could permit an unauthenticated, remote attacker to access the web interface with administrative privileges.
"To exploit this vulnerability, the attacker would need valid user credentials that are stored on the associated external authentication server," the company noted.
"If the LDAP server is configured in such a way that it will reply to search queries with a non-empty array of matching entries (replies that contain search result reference entries), this authentication bypass vulnerability can be exploited."
While there are workarounds that plug the security hole, Cisco cautions customers to test the effectiveness of such remediations in their own environments before administering them. The shortcoming has been patched with the release of version 2.5.1.
VMware ships updates for Aria Operations for Logs#
VMware, in an advisory released on April 20, 2023, warned of a critical deserialization flaw impacting multiple versions of Aria Operations for Logs (CVE-2023-20864, CVSS score: 9.8).
"An unauthenticated, malicious actor with network access to VMware Aria Operations for Logs may be able to execute arbitrary code as root," the virtualization services provider said.
VMware Aria Operations for Logs 8.12 fixes this vulnerability along with a high-severity command injection flaw (CVE-2023-20865, CVSS score: 7.2) that could allow an attacker with admin privileges to run arbitrary commands as root.
"CVE-2023-20864 is a critical issue and should be patched immediately," the company said. "It needs to be highlighted that only version 8.10.2 is impacted by this vulnerability."
The alert comes almost three months after VMware plugged two critical issues in the same product (CVE-2022-31704 and CVE-2022-31706, CVSS scores: 9.8) that could result in remote code execution.
With Cisco and VMware appliances turning out to be lucrative targets for threat actors, it's recommended that users move quickly to apply the updates to mitigate potential threats.
Two Critical Flaws Found in Alibaba Cloud's PostgreSQL Databases
21.4.23 Vulnerebility The Hacker News
A chain of two critical flaws has been disclosed in Alibaba Cloud's ApsaraDB RDS for PostgreSQL and AnalyticDB for PostgreSQL that could be exploited to breach tenant isolation protections and access sensitive data belonging to other customers.
"The vulnerabilities potentially allowed unauthorized access to Alibaba Cloud customers' PostgreSQL databases and the ability to perform a supply chain attack on both Alibaba database services, leading to an RCE on Alibaba database services," cloud security firm Wiz said in a new report shared with The Hacker News.
The issues, dubbed BrokenSesame, were reported to Alibaba Cloud in December 2022, following mitigations were deployed by the company on April 12, 2023. There is no evidence to suggest that the weaknesses were exploited in the wild.
In a nutshell, the vulnerabilities a privilege escalation flaw in AnalyticDB and a remote code execution bug in ApsaraDB RDS made it possible to elevate privileges to root within the container, escape to the underlying Kubernetes node, and ultimately obtain unauthorized access to the API server.
Armed with this capability, an attacker could retrieve credentials associated with the container registry from the API server and push a malicious image to gain control of customer databases belonging to other tenants on the shared node.
"The credentials used to pull images were not scoped correctly and allowed push permissions, laying the foundation for a supply-chain attack," Wiz researchers Ronen Shustin and Shir Tamari said.
This is not the first time PostgreSQL vulnerabilities have been identified in cloud services. Last year, Wiz uncovered similar issues in Azure Database for PostgreSQL Flexible Server (ExtraReplica) and IBM Cloud Databases for PostgreSQL (Hell's Keychain).
The findings come as Palo Alto Networks Unit 42, in its Cloud Threat Report, revealed that "threat actors have become adept at exploiting common, everyday issues in the cloud," including misconfigurations, weak credentials, lack of authentication, unpatched vulnerabilities and malicious open source software (OSS) packages.
"76% of organizations don't enforce MFA [multi-factor authentication] for console users, while 58% of organizations don't enforce MFA for root/admin users," the cybersecurity firm said.
Lazarus Group Adds Linux Malware to Arsenal in Operation Dream Job
20.4.23 APT The Hacker News
The notorious North Korea-aligned state-sponsored actor known as the Lazarus Group has been attributed to a new campaign aimed at Linux users.
The attacks are part of a persistent and long-running activity tracked under the name Operation Dream Job, ESET said in a new report published today.
The findings are crucial, not least because it marks the first publicly documented example of the adversary using Linux malware as part of this social engineering scheme.
Operation Dream Job, also known as DeathNote or NukeSped, refers to multiple attack waves wherein the group leverages fraudulent job offers as a lure to trick unsuspecting targets into downloading malware. It also exhibits overlaps with two other Lazarus clusters known as Operation In(ter)ception and Operation North Star.
The attack chain discovered by ESET is no different in that it delivers a fake HSBC job offer as a decoy within a ZIP archive file that's then used to launch a Linux backdoor named SimplexTea distributed via an OpenDrive cloud storage account.
While the exact method used to distribute the ZIP file is not known, it's suspected to be either spear-phishing or direct messages on LinkedIn. The backdoor, written in C++, bears similarities to BADCALL, a Windows trojan previously attributed to the group.
Furthermore, ESET said it identified commonalities between artifacts used in the Dream Job campaign and those unearthed as part of the supply chain attack on VoIP software developer 3CX that came to light last month.
This also includes the command-and-control (C2) domain "journalide[.]org," which was listed as one of the four C2 servers used by malware families detected within the 3CX environment.
Indications are that preparations for the supply chain attack had been underway since December 2022, when some of the components were committed to the GitHub code-hosting platform.
The findings not only strengthen the existing link between Lazarus Group and the 3CX compromise, but also demonstrates the threat actor's continued success with staging supply chain attacks since 2020.
Fortra Sheds Light on GoAnywhere MFT Zero-Day Exploit Used in Ransomware Attacks
20.4.23 Exploit The Hacker News
Fortra, the company behind Cobalt Strike, shed light on a zero-day remote code execution (RCE) vulnerability in its GoAnywhere MFT tool that has come under active exploitation by ransomware actors to steal sensitive data.
The high-severity flaw, tracked as CVE-2023-0669 (CVSS score: 7.2), concerns a case of pre-authenticated command injection that could be abused to achieve code execution. The issue was patched by the company in version 7.1.2 of the software in February 2023, but not before it was weaponized as a zero-day since January 18.
Fortra, which worked with Palo Alto Networks Unit 42, said it was made aware of suspicious activity associated with some of the file transfer instances on January 30, 2023.
"The unauthorized party used CVE-2023-0669 to create unauthorized user accounts in some MFTaaS customer environments," the company said. "For a subset of these customers, the unauthorized party leveraged these user accounts to download files from their hosted MFTaaS environments."
The threat actor further abused the flaw to deploy two additional tools, dubbed "Netcat" and "Errors.jsp," between January 28, 2023 and January 31, 2023, although not every installation attempt is said to have been successful.
Fortra said it directly reached out to affected customers, and that it has not found any sign of unauthorized access to customer systems that have been reprovisioned a "clean and secure MFTaaS environment."
While Netcat is a legitimate program for managing reading and writing data over a network, it's currently not known how the JSP file was used in the attacks.
The investigation also found that CVE-2023-0669 was exploited against a small number of on-premise implementations running a specific configuration of the GoAnywhere MFT solution.
As recommendations, the company is recommending that users rotate the Master Encryption Key, reset all credentials, review audit logs, and delete any suspicious admin or user accounts.
The development comes as Malwarebytes and NCC Group reported a spike in ransomware attacks during the month of March, largely driven by active exploitation of the GoAnywhere MFT vulnerability.
A total of 459 attacks were recorded last month alone, a 91% increase from February 2023 and a 62% jump when compared to March 2022.
"The ransomware-as-a-service (RaaS) provider, Cl0p, successfully exploited the GoAnywhere vulnerability and was the most active threat actor observed, with 129 victims in total," NCC Group said.
Cl0p's exploitation spree marks the second time LockBit has been knocked off the top spot since September 2021. Other prevalent ransomware strains included Royal, BlackCat, Play, Black Basta, and BianLian.
It's worth noting that the Cl0p actors previously exploited zero-day flaws in Accellion File Transfer Appliance (FTA) to breach several targets in 2021.
Daggerfly Cyberattack Campaign Hits African Telecom Services Providers
20.4.23 BigBrothers The Hacker News
Telecommunication services providers in Africa are the target of a new campaign orchestrated by a China-linked threat actor at least since November 2022.
The intrusions have been pinned on a hacking crew tracked by Symantec as Daggerfly, and which is also tracked by the broader cybersecurity community as Bronze Highland and Evasive Panda.
The campaign makes use of "previously unseen plugins from the MgBot malware framework," the cybersecurity company said in a report shared with The Hacker News. "The attackers were also seen using a PlugX loader and abusing the legitimate AnyDesk remote desktop software."
Daggerfly's use of the MgBot loader (aka BLame or MgmBot) was spotlighted by Malwarebytes in July 2020 as part of phishing attacks aimed at Indian government personnel and individuals in Hong Kong.
According to a profile published by Secureworks, the threat actor uses spear-phishing as an initial infection vector to drop MgBot as well as other tools like Cobalt Strike, a legitimate adversary simulation software, and an Android-based remote access trojan (RAT) named KsRemote.
The group is suspected to conduct espionage activities against domestic human rights and pro-democracy advocates and nations neighboring China as far back as 2014.
Attack chains analyzed by Symantec show the use of living-off-the-land (LotL) tools like BITSAdmin and PowerShell to deliver next-stage payloads, including a legitimate AnyDesk executable and a credential harvesting utility.
The threat actor subsequently moves to set up persistence on the victim system by creating a local account and deploys the MgBot modular framework, which comes with a wide range of plugins to harvest browser data, log keystrokes, capture screenshots, record audio, and enumerate the Active Directory service.
"All of these capabilities would have allowed the attackers to collect a significant amount of information from victim machines," Symantec said. "The capabilities of these plugins also show that the main goal of the attackers during this campaign was information-gathering."
The all-encompassing nature of MgBot indicates that it's actively maintained and updated by the operators to obtain access to victim environments.
The disclosure arrives almost a month after SentinelOne detailed a campaign called Tainted Love in Q1 2023 aimed at telecommunication providers in the Middle East. It was attributed to a Chinese cyberespionage group that shares overlaps with Gallium (aka Othorene).
Symantec further said it identified three additional victims of the same activity cluster that are located in Asia and Africa. Two of the victims, which were breached in November 2022, are subsidiaries of a telecom firm in the Middle East region.
"Telecoms companies will always be a key target in intelligence gathering campaigns due to the access they can potentially provide to the communications of end-users," Symantec said.
NSO Group Used 3 Zero-Click iPhone Exploits Against Human Rights Defenders
20.4.23 Apple The Hacker News
Israeli spyware maker NSO Group deployed at least three novel "zero-click" exploits against iPhones in 2022 to infiltrate defenses erected by Apple and deploy Pegasus, according to the latest findings from Citizen Lab.
"NSO Group customers widely deployed at least three iOS 15 and iOS 16 zero-click exploit chains against civil society targets around the world," the interdisciplinary laboratory based at the University of Toronto said.
NSO Group is the manufacturer of Pegasus, a sophisticated cyber weapon that's capable of extracting sensitive information stored in a device e.g., messages, locations, photos, and call logs, among others in real-time. It's typically delivered to targeted iPhones using zero-click and/or zero-day exploits.
While it has been pitched as a tool for law enforcement agencies to combat serious crimes such as child sexual abuse and terrorism, it has also been deployed illegally by authoritarian governments to spy on human rights defenders, democracy advocates, journalists, dissidents, and others.
The misuse of Pegasus prompted the U.S. government to add NSO Group to its trade blocklist in late 2021, with Apple filing a lawsuit of its own against the company for targeting its users.
In July 2022, it emerged that the spyware was used against Thai activists involved in the country's pro-democracy protests between October 2020 and November 2021 using two zero-click exploits named KISMET and FORCEDENTRY.
Two of the targets of the latest campaign unearthed by Citizen Lab include human rights defenders from Centro PRODH, which represents victims of the Mexican Army's extrajudicial killings and disappearances. The intrusions occurred in June 2022.
This entailed the use of three disparate exploit chains dubbed LATENTIMAGE, FINDMYPWN, and PWNYOURHOME that weaponized various flaws in iOS 15 and iOS 16 as zero-days to penetrate the devices and ultimately launch Pegasus -
LATENTIMAGE (iOS version 15.1.1, detected in January 2022) - An exploit that's suspected to involve the iPhone's Find My feature and SpringBoard
FINDMYPWN (iOS versions 15.5 and 15.6, detected in June 2022) - A two-phase exploit that makes use of the Find My service and iMessage
PWNYOURHOME (iOS version 16.0.3, detected in October 2022) - A two-phase exploit that combines the HomeKit functionality built into iPhones and iMessage to bypass BlastDoor protections
In an encouraging sign, Citizen Lab said it found evidence of Lockdown Mode stepping in to thwart an attempted PWNYOURHOME attack, warning users that it blocked unknown parties with Gmail and Yahoo! accounts from trying to "access a Home."
The development marks the first publicly documented instance where Lockdown Mode, which is specifically designed to reduce the iPhone's attack surface, has successfully protected an individual from a compromise.
Zero-Click iPhone
That said, Citizen Lab pointed out that NSO Group "may have figured out a way to correct the notification issue, such as by fingerprinting Lockdown Mode." Apple has since shipped several security improvements to HomeKit in iOS 16.3.1 and sent out notifications to targeted victims in November and December 2022, and March 2023.
The findings are the latest example of NSO's evolving attack techniques to break into iPhones without requiring any targets to take any action to trigger the infection.
They also coincide with a new investigation from the New York Times uncovering Mexico's use of Pegasus to target human rights defenders in recent months, detailing how the country became the first and most prolific user of the spyware.
In yet another indication of the pervasive nature of such campaigns, Jamf Threat Labs uncovered evidence of a human rights activist based in the Middle East as well as a Hungarian journalist being targeted with spyware. Their names were not disclosed.
The attack targeting the journalist's iPhone is also significant for the fact that the device was an iPhone 6s, which is no longer compatible with the latest iOS version, indicating threat actors' penchant for exploiting known and unknown vulnerabilities to meet their goals.
While Apple does back-port fixes for critical flaws to older devices (the current version supported by iPhone 6s is iOS 15.7.5), it's important to note that not all vulnerabilities are addressed for legacy devices.
"As a result, threat actors can continue to exploit unpatched vulnerabilities that have been patched on newer supported devices, potentially giving attackers more time and more information to gain remote access to targeted devices," Jamf said.
To safeguard against spyware attacks, it's recommended to apply the latest operating system updates, upgrade outdated devices to newer iPhone or iPad models, and consider enabling Lockdown Mode.
The U.K. National Cyber Security Centre (NCSC), in an advisory released on April 19, 2023, cautioned the "proliferation of commercial cyber tools will pose a growing threat to organizations and individuals globally."
"The commercial proliferation of cyber tools and services lowers the barrier to entry to state and non-state actors in obtaining capability and intelligence that they would not otherwise be able to develop or acquire," the agency said.
Google TAG Warns of Russian Hackers Conducting Phishing Attacks in Ukraine
20.4.23 BigBrothers The Hacker News
Elite hackers associated with Russia's military intelligence service have been linked to large-volume phishing campaigns aimed at hundreds of users in Ukraine to extract intelligence and influence public discourse related to the war.
Google's Threat Analysis Group (TAG), which is monitoring the activities of the actor under the name FROZENLAKE, said the attacks continue the "group's 2022 focus on targeting webmail users in Eastern Europe."
The state-sponsored cyber actor, also tracked as APT28, Fancy Bear, Forest Blizzard, Iron Twilight, Sednit, and Sofacy, is both highly active and proficient. It has been active since at least 2009, targeting media, governments, and military entities for espionage.
The latest intrusion set, starting in early February 2023, involved the use of reflected cross-site scripting (XSS) attacks on various Ukrainian government websites to redirect users to phishing domains and capture their credentials.
The disclosure comes as U.K. and U.S. intelligence and law enforcement agencies released a joint advisory warning of APT28's attacks exploiting an old, known vulnerability in Cisco routers to deploy malware known as Jaguar Tooth.
FROZENLAKE is far from the only actor focused on Ukraine since Russia's military invasion of the country over a year ago. Another notable adversarial collective is FROZENBARENTS aka Sandworm, Seashell Blizzard (n้e Iridium), or Voodoo Bear which has engaged in a sustained effort to target organizations affiliated to the Caspian Pipeline Consortium (CPC) and other energy sector entities in Eastern Europe.
Phishing Attacks in Ukraine
Both groups have been attributed to the General Staff Main Intelligence Directorate (GRU), with APT28 tied to the 85th Special Service Center (GTsSS) military intelligence unit 26165. Sandworm, on the other hand, is believed to be part of GRU's Unit 74455.
The credential harvesting campaign targeted CPC employees with phishing links delivered via SMS. The attacks against the energy vertical distributed links to fake Windows update packages that ultimately executed an information stealer known as Rhadamanthys to exfiltrate passwords and browser cookies.
FROZENBARENTS, dubbed the "most versatile GRU cyber actor," has also been observed launching credential phishing attacks targeting the Ukrainian defense industry, military, and Ukr.net webmail users beginning in early December 2022.
The threat actor is said to have further created online personas across YouTube, Telegram, and Instagram to disseminate pro-Russian narratives, leak data stolen from compromised organizations, and post targets for distributed denial-of-service (DDoS) attacks.
"FROZENBARENTS has targeted users associated with popular channels on Telegram," TAG researcher Billy Leonard said. "Phishing campaigns delivered via email and SMS spoofed Telegram to steal credentials, sometimes targeting users following pro-Russia channels."
A third threat actor of interest is PUSHCHA (aka Ghostwriter or UNC1151), a Belarusian government-backed group that's known to act on behalf of Russian interests and which carried out targeted phishing attacks singling out Ukrainian webmail providers such as i.ua and meta.ua to siphon credentials.
Lastly, Google TAG also highlighted a set of attacks mounted by the group behind Cuba ransomware to deploy RomCom RAT in the Ukrainian government and military networks.
"This represents a large shift from this actor's traditional ransomware operations, behaving more similarly to an actor conducting operations for intelligence collection," Leonard pointed out.
The development also follows a new alert from the U.K. National Cyber Security Centre (NCSC) about emerging threats to critical national infrastructure organizations from state-aligned groups, particularly those that are "sympathetic" to Russia's invasion of Ukraine.
"These groups are not motivated by financial gain, nor subject to control by the state, and so their actions can be less predictable and their targeting broader than traditional cyber crime actors," the agency said.
Blind Eagle Cyber Espionage Group Strikes Again: New Attack Chain Uncovered
20.4.23 APT The Hacker News
The cyber espionage actor tracked as Blind Eagle has been linked to a new multi-stage attack chain that leads to the deployment of the NjRAT remote access trojan on compromised systems.
"The group is known for using a variety of sophisticated attack techniques, including custom malware, social engineering tactics, and spear-phishing attacks," ThreatMon said in a Tuesday report.
Blind Eagle, also referred to as APT-C-36, is a suspected Spanish-speaking group that chiefly strikes private and public sector entities in Colombia. Attacks orchestrated by the group have also targeted Ecuador, Chile, and Spain.
Infection chains documented by Check Point and BlackBerry this year have revealed the use of spear-phishing lures to deliver commodity malware families like BitRAT and AsyncRAT, as well as in-memory Python loaders capable of launching a Meterpreter payload.
The latest discovery from ThreatMon entails the use of a JavaScript downloader to execute a PowerShell script hosted in Discord CDN. The script, in turn, drops another PowerShell script and a Windows batch file, and saves a VBScript file in the Windows startup folder to achieve persistence.
New Attack Chain
The VBScript code is then run to launch the batch file, which is subsequently deobfuscated to run the PowerShell script that was previously delivered along with it. In the final stage, the PowerShell script is used to execute njRAT.
"njRAT, also known as Bladabindi is a remote access tool (RAT) with user interface or trojan which allows the holder of the program to control the end-user's computer," the cybersecurity firm said.
Google Chrome Hit by Second Zero-Day Attack - Urgent Patch Update Released
20.4.23 Vulnerebility The Hacker News
Google on Tuesday rolled out emergency fixes to address another actively exploited high-severity zero-day flaw in its Chrome web browser.
The flaw, tracked as CVE-2023-2136, is described as a case of integer overflow in Skia, an open source 2D graphics library. Cl้ment Lecigne of Google's Threat Analysis Group (TAG) has been credited with discovering and reporting the flaw on April 12, 2023.
"Integer overflow in Skia in Google Chrome prior to 112.0.5615.137 allowed a remote attacker who had compromised the renderer process to potentially perform a sandbox escape via a crafted HTML page," according to the NIST's National Vulnerability Database (NVD).
The tech giant, which also fixed seven other security issues with the latest update, said it's aware of active exploitation of the flaw, but did not disclose additional details to prevent further abuse.
The development marks the second Chrome zero-day vulnerability to be exploited by malicious actors this year, and comes merely days after Google patched CVE-2023-2033 last week. It's not immediately clear if the two zero-days have been chained together as part of in-the-wild attacks.
Users are recommended to upgrade to version 112.0.5615.137/138 for Windows, 112.0.5615.137 for macOS, and 112.0.5615.165 for Linux to mitigate potential threats. Users of Chromium-based browsers such as Microsoft Edge, Brave, Opera, and Vivaldi are also advised to apply the fixes as and when they become available.
Pakistani Hackers Use Linux Malware Poseidon to Target Indian Government Agencies
19.4.23 BigBrothers The Hacker News
The Pakistan-based advanced persistent threat (APT) actor known as Transparent Tribe used a two-factor authentication (2FA) tool used by Indian government agencies as a ruse to deliver a new Linux backdoor called Poseidon.
"Poseidon is a second-stage payload malware associated with Transparent Tribe," Uptycs security researcher Tejaswini Sandapolla said in a technical report published this week.
"It is a general-purpose backdoor that provides attackers with a wide range of capabilities to hijack an infected host. Its functionalities include logging keystrokes, taking screen captures, uploading and downloading files, and remotely administering the system in various ways."
Transparent Tribe is also tracked as APT36, Operation C-Major, PROJECTM, and Mythic Leopard, and has a track record of targeting Indian government organizations, military personnel, defense contractors, and educational entities.
It has also repeatedly leveraged trojanized versions of Kavach, the Indian government-mandated 2FA software, to deploy a variety of malware, such as CrimsonRAT and LimePad to harvest valuable information.
Another phishing campaign detected late last year took advantage of weaponized attachments to download malware designed to exfiltrate database files created by the Kavach app.
Linux Malware Poseidon
The latest set of attacks entail the use of a backdoored version of Kavach to target Linux users working for Indian government agencies, indicating attempts made by the threat actor to expand its attack spectrum beyond Windows and Android ecosystems.
"When a user interacts with the malicious version of Kavach, the genuine login page is displayed to distract them," Sandapolla explained. "Meanwhile, the payload is downloaded in the background, compromising the user's system."
The starting point of the infections is an ELF malware sample, a compiled Python executable that's engineered to retrieve the second-stage Poseidon payload from a remote server.
The cybersecurity firm noted that the fake Kavach apps are primarily distributed through rogue websites that are disguised as legitimate Indian government sites. This includes www.ksboard[.]in and www.rodra[.]in.
With social engineering being the primary attack vector used by Transparent Tribe, users working within the Indian government are advised to double-check URLs received in emails before opening them.
"Repercussions of this APT36 attack could be significant, leading to loss of sensitive information, compromised systems, financial losses, and reputational damage," Sandapolla said.
U.S. and U.K. Warn of Russian Hackers Exploiting Cisco Router Flaws for Espionage
19.4.23 BigBrothers The Hacker News
U.K. and U.S. cybersecurity and intelligence agencies have warned of Russian nation-state actors exploiting now-patched flaws in networking equipment from Cisco to conduct reconnaissance and deploy malware against targets.
The intrusions, per the authorities, took place in 2021 and targeted a small number of entities in Europe, U.S. government institutions, and about 250 Ukrainian victims.
The activity has been attributed to a threat actor tracked as APT28, which is also known as Fancy Bear, Forest Blizzard (formerly Strontium), FROZENLAKE, and Sofacy, and is affiliated with the Russian General Staff Main Intelligence Directorate (GRU).
"APT28 has been known to access vulnerable routers by using default and weak SNMP community strings, and by exploiting CVE-2017-6742," the National Cyber Security Centre (NCSC) said.
CVE-2017-6742 (CVSS score: 8.8) is part of a set of remote code execution flaws that stem from a buffer overflow condition in the Simple Network Management Protocol (SNMP) subsystem in Cisco IOS and IOS XE Software.
In the attacks observed by the agencies, the threat actor weaponized the vulnerability to deploy a non-persistent malware dubbed Jaguar Tooth on Cisco routers that's capable of gathering device information and enabling unauthenticated backdoor access.
While the issues were patched in June 2017, they have since come under public exploitation as of January 11, 2018, underscoring the need for robust patch management practices to limit the attack surface.
Besides updating to the latest firmware to mitigate potential threats, the company is also recommending that users switch from SNMP to NETCONF or RESTCONF for network management.
Cisco Talos, in a coordinated advisory, said the attacks are part of a broader campaign against aging networking appliances and software from a variety of vendors to "advance espionage objectives or pre-position for future destructive activity."
This includes the installation of malicious software into an infrastructure device, attempts to surveil network traffic, and attacks mounted by "adversaries with preexisting access to internal environments targeting TACACS+/RADIUS servers to obtain credentials."
The alert comes months after the U.S. government sounded the alarm about China-based state-sponsored cyber actors leveraging network vulnerabilities to exploit public and private sector organizations since at least 2020.
Then earlier this year, Google-owned Mandiant highlighted efforts undertaken by Chinese state-sponsored threat actors to deploy bespoke malware on vulnerable Fortinet and SonicWall devices.
"Advanced cyber espionage threat actors are taking advantage of any technology available to persist and traverse a target environment, especially those technologies that do not support [endpoint detection and response] solutions," Mandiant said.
Iranian Government-Backed Hackers Targeting U.S. Energy and Transit Systems
19.4.23 BigBrothers The Hacker News
An Iranian government-backed actor known as Mint Sandstorm has been linked to attacks aimed at critical infrastructure in the U.S. between late 2021 to mid-2022.
"This Mint Sandstorm subgroup is technically and operationally mature, capable of developing bespoke tooling and quickly weaponizing N-day vulnerabilities, and has demonstrated agility in its operational focus, which appears to align with Iran's national priorities," the Microsoft Threat Intelligence team said in an analysis.
Targeted entities consist of seaports, energy companies, transit systems, and a major U.S. utility and gas company. The activity is suspected to be retaliatory and in response to attacks targeting its maritime, railway, and gas station payment systems that took place between May 2020 and late 2021.
It's worth noting here that Iran subsequently accused Israel and the U.S. of masterminding the attacks on the gas stations in a bid to create unrest in the nation.
Mint Sandstorm is the new name assigned to the threat actor Microsoft was previously tracking under the name Phosphorus, and also known as APT35, Charming Kitten, ITG18, TA453, and Yellow Garuda.
The change in nomenclature is part of Microsoft's shift from chemical elements-inspired monikers to a new weather-themed threat actor naming taxonomy, in part driven by the increasing "complexity, scale, and volume of threats."
Unlike MuddyWater (aka Mercury or Mango Sandstorm), which is known to operate on behalf of Iran's Ministry of Intelligence and Security (MOIS), Mint Sandstorm is said to be associated with Islamic Revolutionary Guard Corps (IRGC).
The attacks detailed by Redmond demonstrate the adversary's ability to constantly refine its tactics as part of highly-targeted phishing campaigns to obtain access to targeted environments.
This includes rapid adoption of publicly disclosed proof-of-concepts (PoCs) linked to flaws in internet-facing applications (e.g., CVE-2022-47966 and CVE-2022-47986) into their playbooks for initial access and persistence.
A successful breach is followed by the deployment of a custom PowerShell script, which is then used to activate one of the two attack chains, the first of which relies on additional PowerShell scripts to connect to a remote server and steal Active Directory databases.
The other sequence entails the use of Impacket to connect to an actor-controlled server and deploy a bespoke implant called Drokbk and Soldier, with the latter being a multistage .NET backdoor with the ability to download and run tools and uninstall itself.
Drokbk was previously detailed by Secureworks Counter Threat Unit (CTU) in December 2022, attributing it to a threat actor known as Nemesis Kitten (aka Cobalt Mirage, TunnelVision, or UNC2448), a sub-cluster of Mint Sandstorm.
Microsoft also called out the threat actor for conducting low-volume phishing campaigns that culminate in the use of a third custom and modular backdoor referred to as CharmPower, a PowerShell-based malware that can read files, gather host information, and exfiltrate the data.
"Capabilities observed in intrusions attributed to this Mint Sandstorm subgroup are concerning as they allow operators to conceal C2 communication, persist in a compromised system, and deploy a range of post-compromise tools with varying capabilities," the tech giant added.
Critical Flaws in vm2 JavaScript Library Can Lead to Remote Code Execution
19.4.23 Vulnerebility The Hacker News
A fresh round of patches has been made available for the vm2 JavaScript library to address two critical flaws that could be exploited to break out of the sandbox protections.
Both the flaws CVE-2023-29199 and CVE-2023-30547 are rated 9.8 out of 10 on the CVSS scoring system and have been addressed in versions 3.9.16 and 3.9.17, respectively.
Successful exploitation of the bugs, which allow an attacker to raise an unsanitized host exception, could be weaponized to escape the sandbox and run arbitrary code in the host context.
"A threat actor can bypass the sandbox protections to gain remote code execution rights on the host running the sandbox," the maintainers of the vm2 library said in an alert.
Credited with discovering and reporting the vulnerabilities is security researcher SeungHyun Lee, who has also released proof-of-concept (PoC) exploits for the two issues in question.
The disclosure comes a little over a week after vm2 remediated another sandbox escape flaw (CVE-2023-29017, CVSS score: 9.8) that could lead to the execution of arbitrary code on the underlying system.
It's worth noting that researchers from Oxeye detailed a critical remote code execution vulnerability in vm2 late last year (CVE-2022-36067, CVSS score: 9.8) that was codenamed Sandbreak.
YouTube Videos Distributing Aurora Stealer Malware via Highly Evasive Loader
19.4.23 Virus The Hacker News
Cybersecurity researchers have detailed the inner workings of a highly evasive loader named "in2al5d p3in4er" (read: invalid printer) that's used to deliver the Aurora information stealer malware.
"The in2al5d p3in4er loader is compiled with Embarcadero RAD Studio and targets endpoint workstations using advanced anti-VM (virtual machine) technique," cybersecurity firm Morphisec said in a report shared with The Hacker News.
Aurora is a Go-based information stealer that emerged on the threat landscape in late 2022. Offered as a commodity malware to other actors, it's distributed through YouTube videos and SEO-poised fake cracked software download websites.
Clicking the links present in YouTube video descriptions redirects the victim to decoy websites where they are enticed into downloading the malware under the garb of a seemingly-legitimate utility.
The loader analyzed by Morphisec is designed to query the vendor ID of the graphics card installed on a system, and compared it against a set of allowlisted vendor IDs (AMD, Intel, or NVIDIA). If the value doesn't match, the loader terminates itself.
The loader ultimately decrypts the final payload and injects it into a legitimate process called "sihost.exe" using a technique called process hollowing. Alternatively, some loader samples also allocate memory to write the decrypted payload and invoke it from there.
"During the injection process, all loader samples resolve the necessary Win APIs dynamically and decrypt these names using a XOR key: 'in2al5d p3in4er,'" security researchers Arnold Osipov and Michael Dereviashkin said.

Another crucial aspect of the loader is its use of Embarcadero RAD Studio to generate executables for multiple platforms, thereby enabling it to evade detection.
"Those with the lowest detection rate on VirusTotal are compiled using 'BCC64.exe,' a new Clang based C++ compiler from Embarcadero," the Israeli cybersecurity company said, pointing out its ability to evade sandboxes and virtual machines.
"This compiler uses a different code base such as 'Standard Library' (Dinkumware) and 'Runtime Library' (compiler-rt) and generates optimized code which changes the entry point and execution flow. This breaks security vendors' indicators, such as signatures composed from 'malicious/suspicious code block.'"
In a nutshell, the findings show that the threat actors behind in2al5d p3in4er are leveraging social engineering methods for a high-impact campaign that employs YouTube as a malware distribution channel and directs viewers to convincing-looking fake websites to distribute the stealer malware.
The development comes as Intel 471 unearthed another malware loader AresLoader that's marketed for $300/month as a service for criminal actors to push information stealers disguised as popular software using a binder tool. The loader is suspected to be developed by a group with ties to Russian hacktivism.
Some of the prominent malware families spread using AresLoader since January 2023 include Aurora Stealer, Laplas Clipper, Lumma Stealer, Stealc, and SystemBC.
Goldoson Android Malware Infects Over 100 Million Google Play Store Downloads
18.4.23 Android The Hacker News
A new Android malware strain named Goldoson has been detected in the official Google Play Store spanning more than 60 legitimate apps that collectively have over 100 million downloads.
An additional eight million installations have been tracked through ONE store, a leading third-party app storefront in South Korea.
The rogue component is part of a third-party software library used by the apps in question and is capable of gathering information about installed apps, Wi-Fi and Bluetooth-connected devices, and GPS locations.
"Moreover, the library is armed with the functionality to perform ad fraud by clicking advertisements in the background without the user's consent," McAfee security researcher SangRyol Ryu said in a report published last week.
What's more, it includes the ability to stealthily load web pages, a feature that could be abused to load ads for financial profit. It achieves this by loading HTML code in a hidden WebView and driving traffic to the URLs.
Following responsible disclosure to Google, 36 of the 63 offending apps have been pulled from the Google Play Store. The remaining 27 apps have been updated to remove the malicious library.
Some of the prominent apps include -
L.POINT with L.PAY
Swipe Brick Breaker (removed)
Money Manager Expense & Budget
TMAP - 대리,주차,전기차 충전,킥보드를 티맵에서!
롯데시네마
지니뮤직 - genie
컬쳐랜드[컬쳐캐쉬]
GOM Player
메가박스 (removed), and
LIVE Score, Real-Time Score
The findings highlight the need for app developers to be transparent about the dependencies used in their software, not to mention take adequate steps to safeguard users' information against such abuse.
"Attackers are becoming more sophisticated in their attempts to infect otherwise legitimate applications across platforms," Kern Smith, vice president of sales engineering for the Americas at Zimperium, said.
"The use of third-party SDKs and code, and their potential to introduce malicious code into otherwise legitimate applications is only continuing to grow as attackers start to target the software supply chain to gain the largest footprint possible."
The development comes as Cyble took the wraps off a new Android banking trojan dubbed Chameleon that has been active since January 2023 and is targeting users in Australia and Poland.
The trojan is no different from other banking malware spotted in the wild owing to its abuse of Android's accessibility services to harvest credentials and cookies, log keystrokes, prevent its uninstallation, and perform other nefarious activities.
It's also designed to display rogue overlays on top of a specific list of apps, intercept SMS messages, and even comprises an unused functionality that allows it to download and execute another payload.
Chameleon, true to its name, has a penchant for evasion by incorporating anti-emulation checks to detect if the device is rooted or it's being executed in a debugging environment, and if so, terminate itself.
To mitigate such threats, users are recommended to only download apps from trusted sources, scrutinize app permissions, use strong passwords, enable multi-factor authentication, and exercise caution when receiving SMS or emails from unknown senders.
Iranian Hackers Using SimpleHelp Remote Support Software for Persistent Access
18.4.23 Hacking The Hacker News
The Iranian threat actor known as MuddyWater is continuing its time-tested tradition of relying on legitimate remote administration tools to commandeer targeted systems.
While the nation-state group has previously employed ScreenConnect, RemoteUtilities, and Syncro, a new analysis from Group-IB has revealed the adversary's use of the SimpleHelp remote support software in June 2022.
MuddyWater, active since at least 2017, is assessed to be a subordinate element within Iran's Ministry of Intelligence and Security (MOIS). Some of the top targets include Turkey, Pakistan, the U.A.E., Iraq, Israel, Saudi Arabia, Jordan, the U.S., Azerbaijan, and Afghanistan.
"MuddyWater uses SimpleHelp, a legitimate remote device control and management tool, to ensure persistence on victim devices," Nikita Rostovtsev, senior threat analyst at Group-IB, said.
"SimpleHelp is not compromised and is used as intended. The threat actors found a way to download the tool from the official website and use it in their attacks."
The exact distribution method used to drop the SimpleHelp samples is currently unclear, although the group is known to send spear-phishing messages bearing malicious links from already compromised corporate mailboxes.
Group-IB's findings were corroborated by Slovak cybersecurity firm ESET earlier this January, detailing MuddyWater's attacks in Egypt and Saudi Arabia that entailed the use of SimpleHelp to deploy its Ligolo reverse tunneling tool and a credential harvester dubbed MKL64.
The Singapore-headquartered company further said it was able to identify hitherto unknown infrastructure operated by the group as well as a PowerShell script that's capable of receiving commands from a remote server, the results of which are sent back to the server.
The disclosure comes weeks after Microsoft detailed the group's modus operandi of carrying out destructive attacks on hybrid environments under the guise of a ransomware operation.
LockBit Ransomware Now Targeting Apple macOS Devices
18.4.23 Ransomware The Hacker News
Threat actors behind the LockBit ransomware operation have developed new artifacts that can encrypt files on devices running Apple's macOS operating system.
The development, which was reported by the MalwareHunterTeam over the weekend, appears to be the first time a big-game ransomware crew has created a macOS-based payload.
Additional samples identified by vx-underground show that the macOS variant has been available since November 11, 2022, and has managed to evade detection by anti-malware engines until now.
LockBit is a prolific cybercrime crew with ties to Russia that has been active since late 2019, with the threat actors releasing two major updates to the locker in 2021 and 2022.
According to statistics released by Malwarebytes last week, LockBit emerged as the second most used ransomware in March 2023 after Cl0p, accounting for 93 successful attacks.
An analysis of the new macOS version ("locker_Apple_M1_64"_ reveals that it's still a work in progress, relying on an invalid signature to sign the executable. This also means that Apple's Gatekeeper protections will prevent it from being run even if it's downloaded and launched on a device.
The payload, per security researcher Patrick Wardle, packs in files like autorun.inf and ntuser.dat.log, suggesting that the ransomware sample was originally designed to target Windows.
"While yes it can indeed run on Apple Silicon, that is basically the extent of its impact," Wardle said. "Thus macOS users have nothing to worry about ...for now!"
Wardle also pointed out additional safeguards implemented by Apple, such as System Integrity Protection (SIP) and Transparency, Consent, and Control (TCC) that prevent the execution of unauthorized code and require apps to seek users' permission to access protected files and data.
"This means that without an exploit or explicit user-approval users files will remain protected," Wardle pointed out. "Still an additional layer or detection/protection may be warranted."
The findings, despite the artifacts' overall bugginess, are a definite sign that threat actors are increasingly setting their sights on macOS systems.
A LockBit representative has since confirmed to Bleeping Computer that the macOS encryptor is "actively being developed," indicating that the malware is likely to pose a serious threat to the platform.
Israeli Spyware Vendor QuaDream to Shut Down Following Citizen Lab and Microsoft Expose
18.4.23 Virus The Hacker News
Israeli spyware vendor QuaDream is allegedly shutting down its operations in the coming days, less than a week after its hacking toolset was exposed by Citizen Lab and Microsoft.
The development was reported by the Israeli business newspaper Calcalist, citing unnamed sources, adding the company "hasn't been fully active for a while" and that it "has been in a difficult situation for several months."
The company's board of directors are looking to sell off its intellectual property, the report further added.
QuaDream, which specializes in hacking Apple devices using "zero-click" infections which do not require any action on the part of the victim, is also said to have fired all its employees, with the firm undergoing significant downsizing, according to Haaretz and The Jerusalem Post.
News of the purported shutdown comes as the firm's spyware framework dubbed REIGN was outed as having been used against journalists, political opposition figures, and NGO workers across North America, Central Asia, Southeast Asia, Europe, and the Middle East.
Microsoft described REIGN as a "suite of exploits, malware, and infrastructure designed to exfiltrate data from mobile devices."
The attacks entailed the exploitation of a now-patched flaw in iOS to deploy sophisticated surveillanceware capable of surreptitiously gathering sensitive information, including audio, pictures, passwords, files, and locations.
Apple told The Hacker News last week that there was no indication to suggest that the exploit, codenamed ENDOFDAYS, had been put to use since the company released iOS 14.4.2 in March 2021.
QuaDream, like its Israeli counterparts NSO Group and Candiru, is a private-sector offensive actor (PSOA) that markets end-to-end hacking tools for use by its customers to run their targeted cyber operations.
While the company has largely managed to stay under the shadows, Haaretz reported in June 2021 that its spyware technology was sold to Saudi Arabia to carry out zero-click attacks against targets of interest.
Then last year, Reuters revealed that QuaDream had independently developed an exploit to break into iPhones that's comparable to the one provided by NSO Group by leveraging a flaw in iMessage. Apple addressed the vulnerability in September 2021.
The upcoming closure also comes a little over a month after Haaretz shed light on a previously unknown Israeli cyber mercenary company called NFV Systems for selling its surveillance technologies to foreign countries without obtaining a license from the Ministry of Defense.
New QBot Banking Trojan Campaign Hijacks Business Emails to Spread Malware
18.4.23 Virus The Hacker News
A new QBot malware campaign is leveraging hijacked business correspondence to trick unsuspecting victims into installing the malware, new findings from Kaspersky reveal.
The latest activity, which commenced on April 4, 2023, has primarily targeted users in Germany, Argentina, Italy, Algeria, Spain, the U.S., Russia, France, the U.K., and Morocco.
QBot (aka Qakbot or Pinkslipbot) is a banking trojan that's known to be active since at least 2007. Besides stealing passwords and cookies from web browsers, it doubles up as a backdoor to inject next-stage payloads such as Cobalt Strike or ransomware.
Distributed via phishing campaigns, the malware has seen constant updates during its lifetime that pack in anti-VM, anti-debugging, and anti-sandbox techniques to evade detection. It has also emerged as the most prevalent malware for the month of March 2023, per Check Point.
"Early on, it was distributed through infected websites and pirated software," Kaspersky researchers said, explaining QBot's distribution methods. "Now the banker is delivered to potential victims through malware already residing on their computers, social engineering, and spam mailings."
Email thread hijacking attacks are not new. It occurs when cybercriminals insert themselves into existing business conversations or initiate new conversations based on information previously gleaned by compromised email accounts.
The goal is to entice victims into opening malicious links or malicious attachments, in this case, an enclosed PDF file that masquerades as a Microsoft Office 365 or Microsoft Azure alert.
Opening the document leads to the retrieval of an archive file from an infected website that, in turn, contains an obfuscated Windows Script File (.WSF). The script, for its part, incorporates a PowerShell script that downloads malicious DLL from a remote server. The downloaded DLL is the QBot malware.
The findings come as Elastic Security Labs unearthed a multi-stage social engineering campaign that employs weaponized Microsoft Word documents to distribute Agent Tesla and XWorm by means of a custom .NET-based loader.
FIN7 and Ex-Conti Cybercrime Gangs Join Forces in Domino Malware Attacks
18.4.23 Virus The Hacker News
A new strain of malware developed by threat actors likely affiliated with the FIN7 cybercrime group has been put to use by the members of the now-defunct Conti ransomware gang, indicating collaboration between the two crews.
The malware, dubbed Domino, is primarily designed to facilitate follow-on exploitation on compromised systems, including delivering a lesser-known information stealer that has been advertised for sale on the dark web since December 2021.
"Former members of the TrickBot/Conti syndicate [...] have been using Domino since at least late February 2023 to deliver either the Project Nemesis information stealer or more capable backdoors such as Cobalt Strike," IBM Security X-Force security researcher Charlotte Hammond said in a report published last week.
FIN7, also called Carbanak and ITG14, is a prolific Russian-speaking cybercriminal syndicate that's known to employ an array of custom malware to deploy additional payloads and broaden its monetization methods.
Recent analyses by Google-owned Mandiant, SentinelOne, and PRODAFT have revealed the group's role as a precursor for Maze and Ryuk ransomware attacks, not to mention exposing its connections to Black Basta, DarkSide, REvil, and LockBit families.
The latest intrusion wave, spotted by IBM Security X-Force two months ago, involves the use of Dave Loader, a crypter previously attributed to the Conti group (aka Gold Blackburn, ITG23, or Wizard Spider), to deploy the Domino backdoor.
Domino Malware Attacks
Domino's potential connections to FIN7 comes from source code overlaps with DICELOADER (aka Lizar or Tirion), a time-tested malware family attributed to the group. The malware, for its part, is designed to gather basic sensitive information and retrieve encrypted payloads from a remote server.
This next-stage artifact is a second loader codenamed Domino Loader, which harbors an encrypted .NET information stealer referred to as Project Nemesis that's capable of amassing sensitive data from clipboard, Discord, web browsers, crypto wallets, VPN services, and other apps.
"Domino has been active in the wild since at least October 2022, which notably is when Lizar observations began to decrease," Hammond pointed out, indicating that the threat actors may be phasing out the latter in favor of the new malware.
Another crucial link bridging Domino to FIN7 comes from a December 2022 campaign that leveraged another loader called NewWorldOrder Loader to deliver both the Domino and Carbanak backdoors.
The Domino backdoor and loader both 64-bit DLLs written in Visual C++ are said to have been used to install Project Nemesis since at least October 2022, prior to its use by ex-Conti members earlier this year.
"This leads us to assess that the ITG14 members responsible for developing Domino probably had a relationship with Project Nemesis and offered Domino and the infostealer to the ex-Conti threat actors as a package," Hammond said. "The ex-Conti members in turn likely used the Project Nemesis infostealer against lower value targets."
The use of stealer malware by ransomware distributors is not without precedent. In November 2022, Microsoft revealed intrusions mounted by a threat actor known as DEV-0569 that leveraged BATLOADER malware to deliver Vidar and Cobalt Strike, the latter of which eventually facilitated human-operated ransomware attacks distributing Royal ransomware.
This has raised the possibility that information stealers are deployed during lower priority infections (e.g., personal computers), while those belonging to an Active Directory domain are served with Cobalt Strike.
"The use of malware with ties to multiple groups in a single campaign such as Dave Loader, Domino Backdoor, and Project Nemesis infostealer highlights the complexity involved in tracking threat actors but also provides insight into how and with whom they operate," Hammond concluded.
Google Uncovers APT41's Use of Open Source GC2 Tool to Target Media and Job Sites
17.4.23 APT The Hacker News

A Chinese nation-state group targeted an unnamed Taiwanese media organization to deliver an open source red teaming tool known as Google Command and Control (GC2) amid broader abuse of Google's infrastructure for malicious ends.
The tech giant's Threat Analysis Group (TAG) attributed the campaign to a threat actor it tracks under the geological and geographical-themed moniker HOODOO, which is also known by the names APT41, Barium, Bronze Atlas, Wicked Panda, and Winnti.
The starting point of the attack is a phishing email that contains links to a password-protected file hosted on Google Drive, which, in turn, incorporates the GC2 tool to read commands from Google Sheets and exfiltrate data using the cloud storage service.
"After installation on the victim machine, the malware queries Google Sheets to obtain attacker commands," Google's cloud division said in its sixth Threat Horizons Report. "In addition to exfiltration via Drive, GC2 enables the attacker to download additional files from Drive onto the victim system."
Google said the threat actor previously utilized the same malware in July 2022 to target an Italian job search website.
The development is notable for two reasons: First, it suggests that Chinese threat groups are increasingly relying on publicly available tooling like Cobalt Strike and GC2 to confuse attribution efforts.
Secondly, it also points to the growing adoption of malware and tools written in the Go programming language, owing to its cross-platform compatibility and its modular nature.
Google further cautioned that the "undeniable value of cloud services" have made them a lucrative target for cybercriminals and government-backed actors alike, "either as hosts for malware or providing the infrastructure for command-and-control (C2)."
A case in point is the use of Google Drive for storing malware such as Ursnif (aka Gozi) and DICELOADER (aka Lizar or Tirion) in the form of ZIP archive files as part of disparate phishing campaigns.
"The most common vector used to compromise any network, including cloud instances is to take over an account's credentials directly: either because there is no password, as with some default configurations, or because a credential has been leaked or recycled or is generally so weak as to be guessable," Google Cloud's Christopher Porter said.
The findings come three months after Google Cloud detailed APT10's (aka Bronze Riverside, Cicada, Potassium, or Stone Panda) targeting of cloud infrastructure and VPN technologies to breach enterprise environments and exfiltrate data of interest.
Vice Society Ransomware Using Stealthy PowerShell Tool for Data Exfiltration
17.4.23 Ransomware The Hacker News
Threat actors associated with the Vice Society ransomware gang have been observed using a bespoke PowerShell-based tool to fly under the radar and automate the process of exfiltrating data from compromised networks.
"Threat actors (TAs) using built-in data exfiltration methods like [living off the land binaries and scripts] negate the need to bring in external tools that might be flagged by security software and/or human-based security detection mechanisms," Palo Alto Networks Unit 42 researcher Ryan Chapman said.
"These methods can also hide within the general operating environment, providing subversion to the threat actor."
Vice Society, tracked by Microsoft under the name DEV-0832, is an extortion-focused hacking group that emerged on the scene in May 2021. It's known to rely on ransomware binaries sold on the criminal underground to meet its goals.
In December 2022, SentinelOne detailed the group's use of a ransomware variant, dubbed PolyVice, that implements a hybrid encryption scheme that combines asymmetric and symmetric encryption to securely encrypt files.
Vice Society Ransomware
The PowerShell script discovered by Unit 42 (w1.ps1) works by identifying mounted drives on the system, and then recursively searching through each of the root directories to facilitate data exfiltration over HTTP.
The tool also makes use of exclusion criteria to filter out system files, backups, and folders pointing to web browsers as well as security solutions from Symantec, ESET, and Sophos. The cybersecurity firm said the overall design of the tool demonstrates a "professional level of coding."
The discovery of the data exfiltration script illustrates the ongoing threat of double extortion in the ransomware landscape. It also serves as a reminder for organizations to prioritize robust security protections and stay vigilant against evolving threats.
"Vice Society's PowerShell data exfiltration script is a simple tool for data exfiltration," Chapman said. "Multi-processing and queuing are used to ensure the script does not consume too many system resources."
"However, the script's focus on files over 10 KB with file extensions and in directories that meet its include list means that the script will not exfiltrate data that doesn't fit this description."
New Zaraza Bot Credential-Stealer Sold on Telegram Targeting 38 Web Browsers
17.4.23 BotNet The Hacker News
A novel credential-stealing malware called Zaraza bot is being offered for sale on Telegram while also using the popular messaging service as a command-and-control (C2).
"Zaraza bot targets a large number of web browsers and is being actively distributed on a Russian Telegram hacker channel popular with threat actors," cybersecurity company Uptycs said in a report published last week.
"Once the malware infects a victim's computer, it retrieves sensitive data and sends it to a Telegram server where the attackers can access it immediately."
A 64-bit binary file compiled using C#, Zaraza bot is designed to target as many as 38 different web browsers, including Google Chrome, Microsoft Edge, Opera, AVG Browser, Brave, Vivaldi, and Yandex. It's also equipped to capture screenshots of the active window.
It's the latest example of malware that's capable of capturing login credentials associated with online bank accounts, cryptocurrency wallets, email accounts, and other websites deemed of value to the operators.
Stolen credentials pose a serious risk as they not only allow threat actors to gain unauthorized access to victims' accounts, but also conduct identity theft and financial fraud.
Zaraza Bot
Evidence gathered by Uptycs points to Zaraza bot being offered as a commercial tool for other cybercriminals for a subscription. It's currently not clear how the malware is propagated, but information stealers have typically leveraged several methods such as malvertising and social engineering in the past.
Zaraza Bot
The findings come as eSentire's Threat Response Unit (TRU) disclosed a GuLoader (aka CloudEyE) campaign targeting the financial sector via phishing emails by employing tax-themed lures to deliver information stealers and remote access trojans (RATs) like Remcos RAT.
The development also follows a spike in malvertising and search engine poisoning techniques to distribute a growing number of malware families by enticing users searching for legitimate applications into downloading fake installers containing stealer payloads.
Russian cybersecurity firm Kaspersky, in a new analysis, revealed the use of trojanized cracked software downloaded from BitTorrent or OneDrive to deploy CueMiner, a .NET-based downloader that acts as a conduit to installer a cryptocurrency miner known as SilentCryptoMiner.
To mitigate risks stemming from stealer malware, it's recommended that users enable two-factor authentication (2FA) and apply software and operating systems updates as and when they become available.
Russia-Linked Hackers Launches Espionage Attacks on Foreign Diplomatic Entities
15.4.23 APT The Hacker News
The Russia-linked APT29 (aka Cozy Bear) threat actor has been attributed to an ongoing cyber espionage campaign targeting foreign ministries and diplomatic entities located in NATO member states, the European Union, and Africa.
According to Poland's Military Counterintelligence Service and the CERT Polska team, the observed activity shares tactical overlaps with a cluster tracked by Microsoft as Nobelium, which is known for its high-profile attack on SolarWinds in 2020.
Nobelium's operations have been attributed to Russia's Foreign Intelligence Service (SVR), an organization that's tasked with protecting "individuals, society, and the state from foreign threats."
That said, the campaign represents an evolution of the Kremlin-backed hacking group's tactics, indicating persistent attempts at improving its cyber weaponry to infiltrate victim systems for intelligence gathering.
"New tools were used at the same time and independently of each other, or replacing those whose effectiveness had declined, allowing the actor to maintain a continuous, high operational tempo," the agencies said.

The attacks commence with spear-phishing emails impersonating European embassies that aim to entice targeted diplomats into opening malware-laced attachments under the guise of an invitation or a meeting.
Embedded within the PDF attachment is a booby-trapped URL that leads to the deployment of an HTML dropper called EnvyScout (aka ROOTSAW), which is then used as a conduit to deliver three previously unknown strains SNOWYAMBER, HALFRIG, and QUARTERRIG.
SNOWYAMBER, also referred to as GraphicalNeutrino by Recorded Future, leverages the Notion note-taking service for command-and-control (C2) and downloading additional payloads such as Brute Ratel.
QUARTERRIG also functions as a downloader capable of retrieving an executable from an actor-controlled server. HALFRIG, on the other hand, acts as a loader to launch the Cobalt Strike post-exploitation toolkit contained within it.
It's worth noting that the disclosure dovetails with recent findings from BlackBerry, which detailed a Nobelium campaign targeting European Union countries, with a specific emphasis on agencies that are "aiding Ukrainian citizens fleeing the country, and providing help to the government of Ukraine."
Google Releases Urgent Chrome Update to Fix Actively Exploited Zero-Day Vulnerability
15.4.23 Exploit The Hacker News
Google on Friday released out-of-band updates to resolve an actively exploited zero-day flaw in its Chrome web browser, making it the first such bug to be addressed since the start of the year.
Tracked as CVE-2023-2033, the high-severity vulnerability has been described as a type confusion issue in the V8 JavaScript engine. Clement Lecigne of Google's Threat Analysis Group (TAG) has been credited with reporting the issue on April 11, 2023.
"Type confusion in V8 in Google Chrome prior to 112.0.5615.121 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page," according to the NIST's National Vulnerability Database (NVD).
The tech giant acknowledged that "an exploit for CVE-2023-2033 exists in the wild," but stopped short of sharing additional technical specifics or indicators of compromise (IoCs) to prevent further exploitation by threat actors.
CVE-2023-2033 also appears to share similarities with CVE-2022-1096, CVE-2022-1364, CVE-2022-3723, and CVE-2022-4262 four other actively abused type confusion flaws in V8 that were remediated by Google in 2022.
Google closed out a total of nine zero days in Chrome last year. The development comes days after Citizen Lab and Microsoft disclosed the exploitation of a now-patched flaw in Apple iOS by customers of a shadowy spyware vendor named QuaDream to target journalists, political opposition figures, and an NGO worker in 2021.
Users are recommended to upgrade to version 112.0.5615.121 for Windows, macOS, and Linux to mitigate potential threats. Users of Chromium-based browsers such as Microsoft Edge, Brave, Opera, and Vivaldi are also advised to apply the fixes as and when they become available.
Kodi Confirms Data Breach: 400K User Records and Private Messages Stolen
14.4.23 Incindent The Hacker News
Open source media player software provider Kodi has confirmed a data breach after threat actors stole the company's MyBB forum database containing user data and private messages.
What's more, the unknown threat actors attempted to sell the data dump comprising 400,635 Kodi users on the now-defunct BreachForums cybercrime marketplace.
"MyBB admin logs show the account of a trusted but currently inactive member of the forum admin team was used to access the web-based MyBB admin console twice: on 16 February and again on 21 February," Kodi said in an advisory.
The threat actors then abused the account to create database backups that were then downloaded and deleted. Also downloaded were existing nightly full backups of the database. The account in question has now been disabled.
The nightly backups contained all public forum posts, team forum posts, messages sent through the user-to-user messaging system, and user information such as forum username, email address used for notifications, and an encrypted (hashed and salted) password generated by the MyBB software.
Kodi said there is no evidence threat actors managed to obtain unauthorized access to the underlying server hosting the MyBB software. It further emphasized that the legitimate account owner did not perform malicious actions on the admin console, suggesting credential theft.
Out of an abundance of caution, the maintainers said work is underway to initiate a global password reset. Users are recommended to change their passwords on other sites if the same password has been used.
In the interim, the company has taken down the Kodi forum and noted that it's in the process of commissioning a new server, an activity that's expected to last "several days." It's also planning to redeploy the forum on the latest version of MyBB software.
As additional security measures, Kodi is hardening access to the MyBB admin console, revising admin roles to limit privileges, and improving audit logging and backup processes.
Severe Android and Novi Survey Vulnerabilities Under Active Exploitation
14.4.23 Android The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added two vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation.
The two flaws are listed below -
CVE-2023-20963 (CVSS score: 7.8) - Android Framework Privilege Escalation Vulnerability
CVE-2023-29492 (CVSS score: TBD) - Novi Survey Insecure Deserialization Vulnerability
"Android Framework contains an unspecified vulnerability that allows for privilege escalation after updating an app to a higher Target SDK with no additional execution privileges needed," CISA said in an advisory for CVE-2023-20963.
Google, in its monthly Android Security Bulletin for March 2023, acknowledged "there are indications that CVE-2023-20963 may be under limited, targeted exploitation."
The development comes as tech news site Ars Technica disclosed late last month that Android apps digitally signed by China's e-commerce company Pinduoduo weaponized the flaw to seize control of the devices and steal sensitive data, citing analysis from mobile security firm Lookout.
Chief among the capabilities of the malware-laced app includes inflating the number of Pinduoduo daily active users and monthly active users, uninstalling rival apps, accessing notifications and location information, and preventing itself from being uninstalled.
CNN, in a follow-up report published at the start of the month, said an analysis of the 6.49.0 version of the app revealed code designed to achieve privilege escalation and even track user activity on other shopping apps.
The exploits allowed the malicious app to access users' contacts, calendars, and photo albums without their consent and requested a "large number of permissions beyond the normal functions of a shopping app," the news channel said.
It's worth pointing out that Google suspended Pinduoduo's official app from the Play Store in March, citing malware identified in "off-Play versions" of the software.
That said, it's still not clear how these APK files were signed with the same key used to sign the legitimate Pinduoduo app. This either points to a key leak, the work of a rogue insider, a compromise of Pinduoduo's build pipeline, or a deliberate attempt by the Chinese company to distribute malware.
The second vulnerability added to the KEV catalog relates to an insecure deserialization vulnerability in Novi Survey software that allows remote attackers to execute code on the server in the context of the service account.
The issue, which impacts Novi Survey versions prior to 8.9.43676, was addressed by the Boston-based provider earlier this week on April 10, 2023. It's currently not known how the flaw is being abused in real-world attacks.
To counter the risks posed by the vulnerabilities, Federal Civilian Executive Branch (FCEB) agencies in the U.S. are advised to apply necessary patches by May 4, 2023.
Google Launches New Cybersecurity Initiatives to Strengthen Vulnerability Management
14.4.23 Security The Hacker News
Google on Thursday outlined a set of initiatives aimed at improving the vulnerability management ecosystem and establishing greater transparency measures around exploitation.
"While the notoriety of zero-day vulnerabilities typically makes headlines, risks remain even after they're known and fixed, which is the real story," the company said in an announcement. "Those risks span everything from lag time in OEM adoption, patch testing pain points, end user update issues and more."
Security threats also stem from incomplete patches applied by vendors, with a chunk of the zero-days exploited in the wild turning out to be variants of previously patched vulnerabilities.
Mitigating such risks requires addressing the root cause of the vulnerabilities and prioritizing modern secure software development practices to eliminate entire classes of threats and block potential attack avenues.
Taking these factors into consideration, Google said it's forming a Hacking Policy Council along with Bugcrowd, HackerOne, Intel, Intigriti, and Luta Security to "ensure new policies and regulations support best practices for vulnerability management and disclosure."
The company further emphasized that it's committing to publicly disclose incidents when it finds evidence of active exploitation of vulnerabilities across its product portfolio.
Lastly, the tech giant said it's instituting a Security Research Legal Defense Fund to provide seed funding for legal representation for individuals engaging in good-faith research to find and report vulnerabilities in a manner that advances cybersecurity.
The goal, the company noted, is to escape the "doom loop" of vulnerability patching and threat mitigation by "focusing on the fundamentals of secure software development, good patch hygiene, and designing for security and ease of patching from the start."
Google's latest security push speaks to the need for looking beyond zero-days by making exploitation difficult in the first place, driving patch adoption for known vulnerabilities in a timely manner, setting up policies to address product life cycles, and making users aware when products are actively exploited.
It also serves to highlight the importance of applying secure-by-design principles during all phases of the software development lifecycle.
The disclosure comes as Google launched a free API service called deps.dev API in a bid to secure the software supply chain by providing access to security metadata and dependency information for over 50 million versions of five million open source packages found on the Go, Maven, PyPI, npm, and Cargo repositories.
In a related development, Google's cloud division has also announced the general availability of the Assured Open Source Software (Assured OSS) service for Java and Python ecosystems.
RTM Locker: Emerging Cybercrime Group Targeting Businesses with Ransomware
14.4.23 Ransomware The Hacker News
Cybersecurity researchers have detailed the tactics of a "rising" cybercriminal gang called "Read The Manual" (RTM) Locker that functions as a private ransomware-as-a-service (RaaS) provider and carries out opportunistic attacks to generate illicit profit.
"The 'Read The Manual' Locker gang uses affiliates to ransom victims, all of whom are forced to abide by the gang's strict rules," cybersecurity firm Trellix said in a report shared with The Hacker News.
"The business-like set up of the group, where affiliates are required to remain active or notify the gang of their leave, shows the organizational maturity of the group, as has also been observed in other groups, such as Conti."
RTM, first documented by ESET in February 2017, started off in 2015 as a banking malware targeting businesses in Russia via drive-by downloads, spam, and phishing emails. Attack chains mounted by the group have since evolved to deploy a ransomware payload on compromised hosts.
In March 2021, the Russian-speaking group was attributed to an extortion and blackmail campaign that deployed a trifecta of threats, including legitimate remote access tools, a financial trojan, and a ransomware strain called Quoter.
Trellix told The Hacker News that there is no relationship between Quoter and the RTM Locker ransomware executable used in the latest attacks.

A key trait of the threat actor is its ability to operate under the shadows by deliberately avoiding high-profile targets that could draw attention to its activities. To that end, CIS countries, as well as morgues, hospitals, COVID-19 vaccine-related corporations, critical infrastructure, law enforcement, and other prominent companies are off-limits for the group.
"The RTM gang's goal is to attract as little attention as possible, which is where the rules help them to avoid hitting high-value targets," security researcher Max Kersten said. "Their management of affiliates to accomplish that goal requires some level of sophistication, though it's not a high level per se."
RTM Locker malware builds are bound by strict mandates that forbid affiliates from leaking the samples, or else risk facing a ban. Among the other rules laid out is a clause that locks out affiliates should they remain inactive for 10 days sans a notification upfront.
"The effort the gang put into avoiding drawing attention was the most unusual," Kersten explained. "The affiliates need to be active as well, making it harder for researchers to infiltrate the gang. All in all, the gang's specific efforts in this area are higher than normally observed compared to other ransomware groups."
It's suspected that the locker is executed on networks that are already under the adversary's control, indicating that the systems may have been compromised by other means, such as phishing attacks, malspam, or the exploitation of internet-exposed vulnerable servers.
The threat actor, like other RaaS groups, uses extortion techniques to compel victims into paying up. The payload, for its part, is capable of elevating privileges, terminating antivirus and backup services, and deleting shadow copies before commencing its encryption procedure.
It's also designed to empty the Recycle Bin to prevent recovery, change the wallpaper, wipe event logs, and execute a shell command that self-deletes the locker as a last step.
The findings suggest that cybercrime groups will continue to "adopt new tactics and methods to avoid the headlines and help them fly under the radar of researchers and law enforcement alike," Kersten noted.
WhatsApp Introduces New Device Verification Feature to Prevent Account Takeover Attacks
14.4.23 Social The Hacker News
Popular instant messaging app WhatsApp on Thursday announced a new account verification feature that ensures that malware running on a user's mobile device doesn't impact their account.
"Mobile device malware is one of the biggest threats to people's privacy and security today because it can take advantage of your phone without your permission and use your WhatsApp to send unwanted messages," the Meta-owned company said in an announcement.
Called Device Verification, the security measure is designed to help prevent account takeover (ATO) attacks by blocking the threat actor's connection and allowing targets of the malware infection to use the app without any interruption.
In other words, the goal is to deter attackers' use of malware to steal WhatsApp authentication keys and hijack victim accounts, and subsequently impersonate them to distribute spam and phishing links to other contacts.
This, in turn, is achieved by introducing a security-token that's stored locally on the device, a cryptographic nonce to identify if a WhatsApp client is contacting the server to retrieve incoming messages, and an authentication-challenge that acts as an "invisible ping" from the server to a user's device.
The client is required to send the security-token every time it connects to the server so as to detect potentially suspicious connections. The security-token, for its part, is updated every time it fetches an offline message from the server.
An authentication-challenge is considered a failure when the client responds to the challenge from a different device, indicating an anomalous connection originating from an attacker. This causes the connection to be blocked.
Should there be no response from the client, the process is retried a "few more times," after which the connection will be blocked if the client still doesn't respond.
"These three parameters help prevent malware from stealing the authentication key and connecting to WhatsApp server from outside the users' device," Meta's Attaullah Baig and Archis Apte explained.
WhatsApp said Device Verification has been rolled out to all Android users and that it's in the process of being rolled out to iOS users.
The feature is part of a broader set of new enhancements that are designed to authenticate and verify users' identities, including displaying alerts when there is an attempt to migrate a WhatsApp account from one device to another.
Also launched by WhatsApp is a Key Transparency feature to automatically confirm whether chats are end-to-end encrypted without requiring any additional actions from the user.
To do so, it's implementing a new Auditable Key Directory (AKD) that's based on existing protocols like CONIKS and SEEMless to help users verify their conversation security.
"The AKD will enable WhatsApp clients to automatically validate that a user's encryption key is genuine and enables anyone to verify audit-proofs of the directory's correctness," the company said.
Verification currently requires users in a chat to manually compare the security code (which exists as a QR code and a 60-digit number) by sending it to the participant on the other end via SMS or email, or alternatively by scanning the QR code if the parties are physically next to each other.
The security code is nothing but a unique hash of both the public/private key pair that's generated to facilitate end-to-end encrypted messaging. Complicating matters further, it can change when users switch devices or reinstall WhatsApp.
Key Transparency streamlines the verification process by making use of an automated flow that obviates the need for the long code, instead maintaining a record of public key changes in a directory and allowing a client to check against it.
"Key transparency describes a protocol in which the [WhatsApp] server maintains an append-only record of the mapping between a user's account and their public identity key," Meta explained. "This allows the generation of inclusion proofs to assert that a given mapping exists in the directory at the time of the most recent update."
WhatsApp intends to make this feature live in the coming months, although it's already hosting and operating an Auditable Key Directory of all its users. "This is an important mechanism that empowers security-conscious users to verify an end-to-end encrypted personal conversation quickly," the company added.
New Python-Based "Legion" Hacking Tool Emerges on Telegram
14.4.23 Hacking The Hacker News
An emerging Python-based credential harvester and a hacking tool named Legion is being marketed via Telegram as a way for threat actors to break into various online services for further exploitation.
Legion, according to Cado Labs, includes modules to enumerate vulnerable SMTP servers, conduct remote code execution (RCE) attacks, exploit unpatched versions of Apache, and brute-force cPanel and WebHost Manager (WHM) accounts.
The malware is said to bear similarities to another malware family called AndroxGh0st that was first documented by cloud security services provider Lacework in December 2022.
Cybersecurity firm SentinelOne, in an analysis published late last month, revealed that AndroxGh0st is part of a comprehensive toolset called AlienFox that's offered to threat actors to steal API keys and secrets from cloud services.
"Legion appears to be part of an emerging generation of cloud-focused credential harvester/spam utilities," security researcher Matt Muir told The Hacker News. "Developers of these tools often steal each other's code, making attribution to a particular group difficult."
Besides using Telegram as a data exfiltration point, Legion is designed to exploit web servers running content management systems (CMS), PHP, or PHP-based frameworks like Laravel.
"It can retrieve credentials for a wide range of web services, such as email providers, cloud service providers, server management systems, databases, and payment platforms like Stripe and PayPal," Cado Labs said.
Some of the other targeted services include SendGrid, Twilio, Nexmo, AWS, Mailgun, Plivo, ClickSend, Mandrill, Mailjet, MessageBird, Vonage, Exotel, OneSignal, Clickatell, and TokBox.
The primary goal of the malware is to enable threat actors to hijack the services and weaponize the infrastructure for follow-on attacks, including mounting mass spam and opportunistic phishing campaigns.
The cybersecurity firm said it also discovered a YouTube channel containing tutorial videos on how to use Legion, suggesting that the "tool is widely distributed and is likely paid malware." The YouTube channel, which was created on June 15, 2021, remains active as of writing.
Furthermore, Legion retrieves AWS credentials from insecure or misconfigured web servers and deliver SMS spam messages to users of U.S. mobile networks such as AT&T, Sprint, T-Mobile, Verizon, and Virgin.
"To do this, the malware retrieves the area code for a U.S. state of the user's choosing from the website www.randomphonenumbers.com," Muir said. "A rudimentary number generator function is then used to build up a list of phone numbers to target."
Furthermore, Legion can retrieve AWS credentials from insecure or misconfigured web servers and deliver SMS spam messages to users of U.S. mobile networks such as AT&T, Sprint, T-Mobile, Verizon, and Virgin by leveraging the stolen SMTP credentials.
"To do this, the malware retrieves the area code for a U.S. state of the user's choosing from the website www.randomphonenumbers[.]com," Muir said. "A rudimentary number generator function is then used to build up a list of phone numbers to target."
Another notable aspect of Legion is its ability to exploit well-known PHP vulnerabilities to register a web shell for persistent remote access or execute malicious code.
The origins of the threat actor behind the tool, who goes by the alias "forzatools" on Telegram, remain unknown, although the presence of Indonesian-language comments in the source code indicates that the developer may be Indonesian or based in the country.
SentinelOne security researcher Alex Delamotte told The Hacker News the latest discovery "highlights some new functionality" that was not previously observed in AlienFox samples and that the two pieces of malware are two distinct toolsets.
"There are many feature overlaps, yet the tools are developed independently and implementation varies," Delamotte explained. "I believe the actors are practicing their own form of business intelligence, watching the features developed by other toolsets and implementing similar features in their own tools."
"Since this malware relies heavily on misconfigurations in web server technologies and frameworks such as Laravel, it's recommended that users of these technologies review their existing security processes and ensure that secrets are appropriately stored," Muir said.
Pakistan-based Transparent Tribe Hackers Targeting Indian Educational Institutions
14.4.23 BigBrothers The Hacker News
The Transparent Tribe threat actor has been linked to a set of weaponized Microsoft Office documents in intrusions directed against the Indian education sector to deploy a continuously maintained piece of malware called Crimson RAT.
While the suspected Pakistan-based threat group is known to target military and government entities in the country, the activities have since expanded to include the education vertical.
The hacking group, also called APT36, Operation C-Major, PROJECTM, and Mythic Leopard, has been active as far back as 2013. Educational institutions have been at the receiving end of the adversary's attacks since late 2021.
"Crimson RAT is a consistent staple in the group's malware arsenal the adversary uses in its campaigns," SentinelOne researcher Aleksandar Milenkoski said in a report shared with The Hacker News.
The .NET malware has the functionality to exfiltrate files and system data to an actor-controlled server. It's also built with the ability to capture screenshots, terminate running processes, and download and execute additional payloads to log keystrokes and steal browser credentials.
Last month, ESET attributed Transparent Tribe to a cyber espionage campaign aimed at infecting Indian and Pakistani Android users with a backdoor called CapraRAT.
An analysis of Crimson RAT samples has revealed the presence of the word "Wibemax," corroborating a previous report from Fortinet. While the name matches that of a Pakistani software development company, it's not immediately clear if it shares any direct connection to the threat actor.
That said, it bears noting that Transparent Tribe has in the past leveraged infrastructure operated by a web hosting provider called Zain Hosting in attacks targeting the Indian education sector.
The documents analyzed by SentinelOne feature education-themed content and names like assignment or Assignment-no-10, and make use of malicious macro code to launch the Crimson RAT. Another method concerns the use of OLE embedding to stage the malware.
"Malicious documents that implement this technique require users to double-click a document element," Milenkoski explained. "These documents distributed by Transparent Tribe typically display an image (a 'View Document' graphic) indicating that the document content is locked."
This, in turn, tricks users into double-clicking the graphic to view the content, thereby activating an OLE package that stores and executes the Crimson RAT masquerading as an update process.
Crimson RAT variants have also been observed to delay their execution for a specific time period spanning anywhere between a minute and four minutes, not to mention implement different obfuscation techniques using tools like Crypto Obfuscator and Eazfuscator.
"Transparent Tribe is a highly motivated and persistent threat actor that regularly updates its malware arsenal, operational playbook, and targets," Milenkoski said. "Transparent Tribe's constantly changing operational and targeting strategies require constant vigilance to mitigate the threat posed by the group."
Lazarus Hacker Group Evolves Tactics, Tools, and Targets in DeathNote Campaign
14.4.23 Hacking The Hacker News
The North Korean threat actor known as the Lazarus Group has been observed shifting its focus and rapidly evolving its tools and tactics as part of a long-running campaign called DeathNote.
While the nation-state adversary is known for persistently singling out the cryptocurrency sector, recent attacks have also targeted automotive, academic, and defense sectors in Eastern Europe and other parts of the world, in what's perceived as a "significant" pivot.
"At this point, the actor switched all the decoy documents to job descriptions related to defense contractors and diplomatic services," Kaspersky researcher Seongsu Park said in an analysis published Wednesday.
The deviation in targeting, along with the use of updated infection vectors, is said to have occurred in April 2020. It's worth noting that the DeathNote cluster is also tracked under the monikers Operation Dream Job or NukeSped. Google-owned Mandiant has also tied a subset of the activity to a group it calls UNC2970.
The phishing attacks directed against crypto businesses typically entail using bitcoin mining-themed lures in email messages to entice potential targets into opening macro-laced documents in order to drop the Manuscrypt (aka NukeSped) backdoor on the compromised machine.
The targeting of the automotive and academic verticals is tied to Lazarus Group's broader attacks against the defense industry, as documented by the Russian cybersecurity firm in October 2021, leading to the deployment of BLINDINGCAN (aka AIRDRY or ZetaNile) and COPPERHEDGE implants.

In an alternative attack chain, the threat actor employed a trojanzied version of a legitimate PDF reader application called SumatraPDF Reader to initiate its malicious routine. The Lazarus Group's use of rogue PDF reader apps was previously revealed by Microsoft.
The targets of these attacks included an IT asset monitoring solution vendor based in Latvia and a think tank located in South Korea, the latter of which entailed the abuse of legitimate security software that's widely used in the country to execute the payloads.
The twin attacks "point to Lazarus building supply chain attack capabilities," Kaspersky noted at the time. The adversarial crew has since been blamed for the supply chain attack aimed at enterprise VoIP service provider 3CX that came to light last month.
Kaspersky said it discovered another attack in March 2022 that targeted several victims in South Korea by exploiting the same security software to deliver downloader malware capable of distributing a backdoor as well as an information stealer for harvesting keystroke and clipboard data.
"The newly implanted backdoor is capable of executing a retrieved payload with named-pipe communication," Park said, adding it's also "responsible for collecting and reporting the victim's information."
Around the same time, the same backdoor is said to have been utilized to compromise a defense contractor in Latin America using DLL side-loading techniques upon opening a specially-crafted PDF file using a trojanized PDF reader.
The Lazarus Group has also been linked to a successful breach of another defense contractor in Africa last July in which a "suspicious PDF application" was sent over Skype to ultimately drop a variant of a backdoor dubbed ThreatNeedle and another implant known as ForestTiger to exfiltrate data.
"The Lazarus group is a notorious and highly skilled threat actor," Park said. "As the Lazarus group continues to refine its approaches, it is crucial for organizations to maintain vigilance and take proactive measures to defend against its malicious activities."
ChatGPT Security: OpenAI's Bug Bounty Program Offers Up to $20,000 Prizes
14.4.23 Security The Hacker News
OpenAI, the company behind the massively popular ChatGPT AI chatbot, has launched a bug bounty program in an attempt to ensure its systems are "safe and secure."
To that end, it has partnered with the crowdsourced security platform Bugcrowd for independent researchers to report vulnerabilities discovered in its product in exchange for rewards ranging from "$200 for low-severity findings to up to $20,000 for exceptional discoveries."
It's worth noting that the program does not cover model safety or hallucination issues, wherein the chatbot is prompted to generate malicious code or other faulty outputs. The company noted that "addressing these issues often involves substantial research and a broader approach."
Other prohibited categories are denial-of-service (DoS) attacks, brute-forcing OpenAI APIs, and demonstrations that aim to destroy data or gain unauthorized access to sensitive information beyond what's necessary to highlight the problem.
"Please note that authorized testing does not exempt you from all of OpenAI's terms of service," the company cautioned. "Abusing the service may result in rate limiting, blocking, or banning."
What's in scope, however, are defects in OpenAI APIs, ChatGPT (including plugins), third-party integrations, public exposure of OpenAI API keys, and any of the domains operated by the company.
The development comes in response to OpenAI patching account takeover and data exposure flaws in the platform, prompting Italian data protection regulators to take a closer look at the platform.
Italian Data Protection Authority Proposes Measures to Lift ChatGPT Ban#
The Garante, which imposed a temporary ban on ChatGPT on March 31, 2023, has since outlined a set of measures the Microsoft-backed firm will have to agree to implement by the end of the month in order for the suspension to be lifted.
"OpenAI will have to draft and make available, on its website, an information notice describing the arrangements and logic of the data processing required for the operation of ChatGPT along with the rights afforded to data subjects," the Garante said.
Additionally, the information notice should be readily available for Italian users before signing up for the service. Users will also need to be required to declare they are over the age of 18.
OpenAI has also been ordered to implement an age verification system by September 30, 2023, to filter out users aged below 13 and have provisions in place to seek parental consent for users aged 13 to 18. The company has been given time till May 31 to submit a plan for the age-gating system.
As part of efforts to exercise data rights, both users and non-users of the service should be able to request for "rectification of their personal data" in cases where it's incorrectly generated by the service, or alternatively, erase the data if corrections are technically infeasible.
Non-users, per the Garante, should further be provided with easily accessible tools to object to their personal data being processed by OpenAI's algorithms. The company is also expected to run an advertising campaign by May 15, 2023, to "inform individuals on use of their personal data for training algorithms."
Update: Spain Opens Probe into OpenAI ChatGPT#
The Spanish Data Protection Authority (AEPD), on April 13, 2023, said it has initiated a preliminary investigation into OpenAI ChatGPT service for suspected breaches of E.U. data protection laws.
The European Data Protection Board (EDPB), in a related announcement, said it's launching a "dedicated task force to foster cooperation and to exchange information on possible enforcement actions conducted by data protection authorities."
Israel-based Spyware Firm QuaDream Targets High-Risk iPhones with Zero-Click Exploit
12.4.23 Apple The Hacker News
Threat actors using hacking tools from an Israeli surveillanceware vendor named QuaDream targeted at least five members of civil society in North America, Central Asia, Southeast Asia, Europe, and the Middle East.
According to findings from a group of researchers from the Citizen Lab, the spyware campaign was directed against journalists, political opposition figures, and an NGO worker in 2021. The names of the victims were not disclosed.
It's also suspected that the company abused a zero-click exploit dubbed ENDOFDAYS in iOS 14 to deploy spyware as a zero-day in version 14.4 and 14.4.2. There is no evidence that the exploit has been used after March 2021.
ENDOFDAYS "appears to make use of invisible iCloud calendar invitations sent from the spyware's operator to victims," the researchers said.
The Microsoft Threat Intelligence team is tracking QuaDream as DEV-0196, describing the cyber mercenary company as a private sector offensive actor (PSOA). While QuaDream is not directly involved in targeting, it is known to sell its "exploitation services and malware" to government customers, the tech giant assessed with high confidence.
The malware, named KingsPawn, contains a monitor agent and the primary malware agent, both of which are Mach-O files written in Objective-C and Go, respectively.
While the monitor agent is responsible for reducing the forensic footprint of the malware to evade detection, the main agent comes with capabilities to gather device information, cellular and Wi-Fi data, harvest files, access camera in the background, access location, call logs, and iOS Keychain, and even generate an iCloud time-based one-time password (TOTP).
Other samples support recording audio from phone calls and the microphone, running queries in SQL databases, and cleaning up forensic trails, such as deleting all calendar events from two years prior to the current time. The data is exfiltrated via HTTPS POST requests.
Internet scans carried out by the Citizen Lab reveal that QuaDream's customers operated 600 servers from several countries around the world between late 2021 and early 2023, including Bulgaria, Czech Republic, Hungary, Romania, Ghana, Israel, Mexico, Singapore, the U.A.E., and Uzbekistan.
Despite attempts made by the spyware to cover its tracks, the interdisciplinary laboratory said it was able to uncover unspecified traces of what it calls the "Ectoplasm Factor" that could be used to track QuaDream's toolset in the future.
This is not the first time QuaDream has attracted attention. In February 2022, Reuters reported that the company weaponized the FORCEDENTRY zero-click exploit in iMessage to deploy a spyware solution named REIGN.
Then in December 2022, Meta disclosed that it took down a network of 250 fake accounts on Facebook and Instagram controlled by QuaDream to infect Android and iOS devices and exfiltrate personal data.
If anything, the development is yet another indication that despite the notoriety attracted by NSO Group, commercial spyware firms continue to fly under the radar and develop sophisticated spyware products for use by government clients.
"Until the out-of-control proliferation of commercial spyware is successfully curtailed through systemic government regulations, the number of abuse cases is likely to continue to grow, fueled both by companies with recognizable names, as well as others still operating in the shadows," the Citizen Lab said.
Calling the growth of mercenary spyware companies as a threat to democracy and human rights, Microsoft said combating such offensive actors requires a "collective effort" and a "multistakeholder collaboration."
"Moreover, it is only a matter of time before the use of the tools and technologies they sell spread even further," Amy Hogan-Burney, the company's associate general counsel for cybersecurity policy and protection, said.
"This poses real risk to human rights online, but also to the security and stability of the broader online environment. The services they offer require cyber mercenaries to stockpile vulnerabilities and search for new ways to access networks without authorization."
Urgent: Microsoft Issues Patches for 97 Flaws, Including Active Ransomware Exploit
12.4.23 Vulnerebility The Hacker News
It's the second Tuesday of the month, and Microsoft has released another set of security updates to fix a total of 97 flaws impacting its software, one of which has been actively exploited in ransomware attacks in the wild.
Seven of the 97 bugs are rated Critical and 90 are rated Important in severity. Interestingly, 45 of the shortcomings are remote code execution flaws, followed by 20 elevation of privilege vulnerabilities. The updates also follow fixes for 26 vulnerabilities in its Edge browser that were released over the past month.
The security flaw that's come under active exploitation is CVE-2023-28252 (CVSS score: 7.8), a privilege escalation bug in the Windows Common Log File System (CLFS) Driver.
"An attacker who successfully exploited this vulnerability could gain SYSTEM privileges," Microsoft said in an advisory, crediting researchers Boris Larin, Genwei Jiang, and Quan Jin for reporting the issue.
CVE-2023-28252 is the fourth privilege escalation flaw in the CLFS component that has come under active abuse in the past year alone after CVE-2022-24521, CVE-2022-37969, and CVE-2023-23376 (CVSS scores: 7.8). At least 32 vulnerabilities have been identified in CLFS since 2018.
According to Russian cybersecurity firm Kaspersky, the vulnerability has been weaponized by a cybercrime group to deploy Nokoyawa ransomware against small and medium-sized businesses in the Middle East, North America, and Asia.
"CVE-2023-28252 is an out-of-bounds write (increment) vulnerability that can be exploited when the system attempts to extend the metadata block," Larin said. "The vulnerability gets triggered by the manipulation of the base log file."
In light of ongoing exploitation of the flaw, CISA has added the Windows zero-day to its catalog of Known Exploited Vulnerabilities (KEV), ordering Federal Civilian Executive Branch (FCEB) agencies to secure their systems by May 2, 2023.
Active Ransomware Exploit
Also patched are critical remote code execution flaws impacting DHCP Server Service, Layer 2 Tunneling Protocol, Raw Image Extension, Windows Point-to-Point Tunneling Protocol, Windows Pragmatic General Multicast, and Microsoft Message Queuing (MSMQ).
The MSMQ bug, tracked as CVE-2023-21554 (CVSS score: 9.8) and dubbed QueueJumper by Check Point, could lead to unauthorized code execution and take over a server by sending a specially crafted malicious MSMQ packet to an MSMQ server.
"The CVE-2023-21554 vulnerability allows an attacker to potentially execute code remotely and without authorization by reaching the TCP port 1801," Check Point researcher Haifei Li said. "In other words, an attacker could gain control of the process through just one packet to the 1801/tcp port with the exploit, triggering the vulnerability."
Two other flaws discovered in MSMQ, CVE-2023-21769 and CVE-2023-28302 (CVSS scores: 7.5), could be exploited to cause a denial-of-service (DoS) condition such as a service crash and Windows Blue Screen of Death (BSoD).
Microsoft has also updated its advisory for CVE-2013-3900, a 10-year-old WinVerifyTrust signature validation vulnerability, to include the following Server Core installation versions -
Windows Server 2008 for 32-bit Systems Service Pack 2
Windows Server 2008 for x65-based Systems Service Pack 2
Windows Server 2008 R2 for x64-based Systems Service 1
Windows Server 2012
Windows Server 2012 R2
Windows Server 2016
Windows Server 2019, and
Windows Server 2022
The development comes as North Korea-linked threat actors have been observed leveraging the flaw to incorporate encrypted shellcode into legitimate libraries without invalidating the Microsoft-issued signature.
Microsoft Issues Guidance for BlackLotus Bootkit Attacks#
In tandem with the update, the tech giant also issued guidance for CVE-2022-21894 (aka Baton Drop), a now-fixed Secure Boot bypass flaw that has been exploited by threat actors using a nascent Unified Extensible Firmware Interface (UEFI) bootkit called BlackLotus to establish persistence on a host.
Some indicators of compromise (IoCs) include recently created and locked bootloader files in the EFI system partition (ESP), event logs associated with the stoppage of Microsoft Defender Antivirus, presence of the staging directory ESP:/system32/, and modifications to the registry key HKLM:\SYSTEM\CurrentControlSet\Control\DeviceGuard\Scenarios\HypervisorEnforcedCodeIntegrity.
"UEFI bootkits are particularly dangerous as they run at computer startup, prior to the operating system loading, and therefore can interfere with or deactivate various operating system (OS) security mechanisms," the Microsoft Incident Response team said.
Microsoft further recommends that compromised devices be removed from the network and examined for evidence of follow-on activity, reformat or restore the machines from a known clean backup that includes the EFI partition, maintain credential hygiene, and enforce the principle of least privilege (PoLP).
North Korean Hackers Uncovered as Mastermind in 3CX Supply Chain Attack
12.4.23 Attack The Hacker News
Enterprise communications service provider 3CX confirmed that the supply chain attack targeting its desktop application for Windows and macOS was the handiwork of a threat actor with North Korean nexus.
The findings are the result of an interim assessment conducted by Google-owned Mandiant, whose services were enlisted after the intrusion came to light late last month. The threat intelligence and incident response unit is tracking the activity under its uncategorized moniker UNC4736.
It's worth noting that cybersecurity firm CrowdStrike has attributed the attack to a Lazarus sub-group dubbed Labyrinth Chollima, citing tactical overlaps.
The attack chain, based on analyses from multiple security vendors, entailed the use of DLL side-loading techniques to load an information stealer known as ICONIC Stealer, followed by a second-stage called Gopuram in selective attacks aimed at crypto companies.
Mandiant's forensic investigation has now revealed that the threat actors infected 3CX systems with a malware codenamed TAXHAUL that's designed to decrypt and load shellcode containing a "complex downloader" labeled COLDCAT.
"On Windows, the attacker used DLL side-loading to achieve persistence for TAXHAUL malware," 3CX said. "The persistence mechanism also ensures the attacker malware is loaded at system start-up, enabling the attacker to retain remote access to the infected system over the internet."
The company further said the malicious DLL (wlbsctrl.dll) was loaded by the Windows IKE and AuthIP IPsec Keying Modules (IKEEXT) service through svchost.exe, a legitimate system process.
macOS systems targeted in the attack are said to have been backdoored using another malware strain referred to as SIMPLESEA, a C-based malware that communicates via HTTP to run shell commands, transfer files, and update configurations.
The malware families detected within the 3CX environment have been observed to contact at least four command-and-control (C2) servers: azureonlinecloud[.]com, akamaicontainer[.]com, journalide[.]org, and msboxonline[.]com.
3CX CEO Nick Galea, in a forum post last week, said the company is only aware of a "handful of cases" where the malware was actually activated and that it's working to "strengthen our policies, practices, and technology to protect against future attacks." An updated app has since been made available to customers.
It's currently not determined how the threat actors managed to break into 3CX's network, and if it entailed the weaponization of a known or unknown vulnerability. The supply chain compromise is being tracked under the identifier CVE-2023-29059 (CVSS score: 7.8).
Newly Discovered "By-Design" Flaw in Microsoft Azure Could Expose Storage Accounts to Hackers
11.4.23 Vulnerebility The Hacker News
A "by-design flaw" uncovered in Microsoft Azure could be exploited by attackers to gain access to storage accounts, move laterally in the environment, and even execute remote code.
"It is possible to abuse and leverage Microsoft Storage Accounts by manipulating Azure Functions to steal access-tokens of higher privilege identities, move laterally, potentially access critical business assets, and execute remote code (RCE)," Orca said in a new report shared with The Hacker News.
The exploitation path that underpins this attack is a mechanism called Shared Key authorization, which is enabled by default on storage accounts.
According to Microsoft, Azure generates two 512-bit storage account access keys when creating a storage account. These keys can be used to authorize access to data via Shared Key authorization, or via SAS tokens that are signed with the shared key.
"Storage account access keys provide full access to the configuration of a storage account, as well as the data," Microsoft notes in its documentation. "Access to the shared key grants a user full access to a storage account's configuration and its data."
The cloud security firm said these access tokens can be stolen by manipulating Azure Functions, potentially enabling a threat actor with access to an account with Storage Account Contributor role to escalate privileges and take over systems.
Specifically, should a managed identity be used to invoke the Function app, it could be abused to execute any command. This, in turn, is made possible owing to the fact that a dedicated storage account is created when deploying an Azure Function app.
"Once an attacker locates the storage account of a Function app that is assigned with a strong managed identity, it can run code on its behalf and as a result acquire a subscription privilege escalation (PE)," Orca researcher Roi Nisimi said.
In other words, by exfiltrating the access-token of the Azure Function app's assigned managed identity to a remote server, a threat actor can elevate privileges, move laterally, access new resources, and execute a reverse shell on virtual machines.
"By overriding function files in storage accounts, an attacker can steal and exfiltrate a higher-privileged identity and use it to move laterally, exploit and compromise victims' most valuable crown jewels," Nisimi explained.
As mitigations, it's recommended that organizations consider disabling Azure Shared Key authorization and using Azure Active Directory authentication instead. In a coordinated disclosure, Microsoft said it "plans to update how Functions client tools work with storage accounts."
"This includes changes to better support scenarios using identity. After identity-based connections for AzureWebJobsStorage are generally available and the new experiences are validated, identity will become the default mode for AzureWebJobsStorage, which is intended to move away from shared key authorization," the tech giant further added.
The findings arrive weeks after Microsoft patched a misconfiguration issue impacting Azure Active Directory that made it possible to tamper with Bing search results and a reflected XSS vulnerability in Azure Service Fabric Explorer (SFX) that could lead to unauthenticated remote code execution.
Cybercriminals Turn to Android Loaders on Dark Web to Evade Google Play Security
11.4.23 Android The Hacker News
Malicious loader programs capable of trojanizing Android applications are being traded on the criminal underground for up to $20,000 as a way to evade Google Play Store defenses.
"The most popular application categories to hide malware and unwanted software include cryptocurrency trackers, financial apps, QR-code scanners, and even dating apps," Kaspersky said in a new report based on messages posted on online forums between 2019 and 2023.
Dropper apps are the primary means for threat actors looking to sneak malware via the Google Play Store. Such apps often masquerade as seemingly innocuous apps, with malicious updates introduced upon clearing the review process and the applications have amassed a significant user base.
This is achieved by using a loader program that's responsible for injecting malware into a clean app, which is then made available for download from the app marketplace. Users who install the tampered app are prompted to grant it intrusive permissions to facilitate malicious activities.
The apps, in some instances, also incorporate anti-analysis features to detect if they are being debugged or installed in a sandboxed environment, and if so, halt their operations on the compromised devices.
As another option, threat actors can purchase a Google Play developer account either hacked or newly created by the sellers for anywhere between $60 and $200, depending on the number of already published apps and download counts.
App developer accounts lacking in strong password or two-factor authentication (2FA) protections can be trivially cracked and put up for sale, thereby allowing other actors to upload malware to existing apps.
A third alternative is the use of APK binding services, which are responsible for hiding a malicious APK file in a legitimate application, for distributing the malware through phishing texts and dubious websites advertising cracked games and software.
Binding services, as opposed to loaders, cost less owing to the fact that the poisoned apps are not available via the Google Play Store. Notably, the technique has been used to deliver Android banking trojans like SOVA and Xenomorph in the past.
Some other illicit services offered for sale on cybercrime markets include malware obfuscation ($30), web injects ($25-$80), and virtual private servers ($300), the latter of which can be used to control infected devices or to redirect user traffic.
Furthermore, attackers can buy installs for their Android apps (legitimate or otherwise) through Google Ads for $0.5 on average. Installation costs vary based on the targeted country.
To mitigate risks posed by Android malware, users are recommended to refrain from installing apps from unknown sources, scrutinize app permissions, and keep their devices up-to-date.
Cryptocurrency Stealer Malware Distributed via 13 NuGet Packages
11.4.23 Cryptocurrency The Hacker News
Cybersecurity researchers have detailed the inner workings of the cryptocurrency stealer malware that was distributed via 13 malicious NuGet packages as part of a supply chain attack targeting .NET developers.
The sophisticated typosquatting campaign, which was detailed by JFrog late last month, impersonated legitimate packages to execute PowerShell code designed to retrieve a follow-on binary from a hard-coded server.
The two-stage attack culminates in the deployment of a .NET-based persistent backdoor, called Impala Stealer, which is capable of gaining unauthorized access to users' cryptocurrency accounts.
"The payload used a very rare obfuscation technique, called '.NET AoT compilation,' which is a lot more stealthy than using 'off the shelf' obfuscators while still making the binary hard to reverse engineer," JFrog told The Hacker News in a statement.
.NET AoT compilation is an optimization technique that allows apps to be ahead-of-time compiled to native code. Native AOT apps also have faster startup time and smaller memory footprints, and can run on a machine without .NET runtime installed.
The second-stage payload comes with an auto-update mechanism that enables it to retrieve new versions of the executable from a remote location. It further achieves persistence by injecting JavaScript code into Discord or Microsoft Visual Studio Code apps, thereby activating the launch of the stealer binary.

The binary then proceeds to search for the installation of the Exodus Wallet desktop application and inserts JavaScript code into various HTML files in order to harvest and exfiltrate sensitive data to a hard-coded Discord webhook.
The JavaScript snippet, for its part, is fetched from an online paste website from where it's already been deleted. That said, it's suspected that the code may have been used to steal user credentials and access other information of interest.
"The bad actors used typosquatting techniques to deploy a custom malicious payload [...] which targets the Exodus crypto wallet and leaks the victim's credentials to cryptocurrency exchanges, by using code injection," Shachar Menashe, senior director at JFrog Security Research, said.
"Our investigation proves no open source software repository is completely trust-worthy, so safety measures should be taken at every step of the software development lifecycle to ensure the software supply chain remains secure."
The findings come as Phylum unearthed a malicious npm package named mathjs-min that was uploaded to the repository on March 26, 2023, and found to harbor a credential stealer that grabs Discord passwords from the official app as well as web browsers like Google Chrome, Brave, and Opera.
"This package is actually a modified version of the widely used Javascript math library mathjs, and was injected with malicious code after being forked," the software supply chain security firm said. "The modified version was then published to NPM with the intention of passing it off as a minified version of the genuine mathjs library."
Estonian National Charged in U.S. for Acquiring Electronics and Metasploit Pro for Russian Military
11.4.23 BigBrothers The Hacker News
An Estonian national has been charged in the U.S. for purchasing U.S.-made electronics on behalf of the Russian government and military.
The 45-year-old individual, Andrey Shevlyakov, was arrested on March 28, 2023, in Tallinn. He has been indicted with 18 counts of conspiracy and other charges. If found guilty, he faces up to 20 years in prison.
Court documents allege that Shevlyakov operated front companies that were used to import sensitive electronics from U.S. manufacturers. The goods were then shipped to Russia, bypassing export restrictions.
The purchased items included analog-to-digital converters and low-noise pre-scalers and synthesizers that are found in defense systems. Shevlyakov is also accused of attempting to acquire hacking tools like Rapid7 Metasploit Pro, a legitimate penetration testing and adversary simulation software.
Although Shevlyakov was placed in Entity List in 2012 by the U.S. government for acting as a procurement agent for Russia, he is said to have used "false names and a web of front companies" to sidestep the regulations and run an "intricate logistics operation involving frequent smuggling trips across the Russian border."
Shevlyakov is estimated to have exported at least $800,000 worth of items from U.S. electronics manufacturers and distributors between about October 2012 and January 2022 through his shell companies like Yaxart, Anmarna, and Marnik.
"As alleged, for more than a decade, the defendant has been acquiring sensitive electronics from U.S. manufacturers on behalf of the Russian government, in defiance of U.S. export controls," U.S. Attorney Breon Peace said.
Hackers Flood NPM with Bogus Packages Causing a DoS Attack
11.4.23 Attack The Hacker News
Threat actors flooded the npm open source package repository for Node.js with bogus packages that briefly even resulted in a denial-of-service (DoS) attack.
"The threat actors create malicious websites and publish empty packages with links to those malicious websites, taking advantage of open-source ecosystems' good reputation on search engines," Checkmarx's Jossef Harush Kadouri said in a report published last week.
"The attacks caused a denial-of-service (DoS) that made NPM unstable with sporadic 'Service Unavailable' errors."
While similar campaigns were recently observed propagating phishing links, the latest wave pushed the number of package versions to 1.42 million, a dramatic uptick from the approximate 800,000 packages released on npm.
The attack technique leverages the fact that open source repositories are ranked higher on search engine results to create rogue websites and upload empty npm modules with links to those sites in the README.md files.
"Since the open source ecosystems are highly reputed on search engines, any new open-source packages and their descriptions inherit this good reputation and become well-indexed on search engines, making them more visible to unsuspecting users," Harush Kadouri explained.
Given that the whole process is automated, the load created by publishing numerous packages led to NPM intermittently experiencing stability issues towards the end of March 2023.
Checkmarx points out that while there may be multiple actors behind the activity, the end goal is to infect the victim's system with malware such as RedLine Stealer, Glupteba, SmokeLoader, and cryptocurrency miners.
Other links take users through a series of intermediate pages that ultimately lead to legitimate e-commerce sites like AliExpress with referral IDs, earning the actors a profit when the victim makes a purchase on the platform. A third category entails inviting Russian users to join a Telegram channel that specializes in cryptocurrency.
"The battle against threat actors poisoning our software supply chain ecosystem continues to be challenging, as attackers constantly adapt and surprise the industry with new and unexpected techniques," Harush Kadouri said.
To prevent such automated campaigns, Checmarx has recommended npm to incorporate anti-bot techniques during user account creation.
Over 1 Million WordPress Sites Infected by Balada Injector Malware Campaign
11.4.23 Virus The Hacker News
Over one million WordPress websites are estimated to have been infected by an ongoing campaign to deploy malware called Balada Injector since 2017.
The massive campaign, per GoDaddy's Sucuri, "leverages all known and recently discovered theme and plugin vulnerabilities" to breach WordPress sites. The attacks are known to play out in waves once every few weeks.
"This campaign is easily identified by its preference for String.fromCharCode obfuscation, the use of freshly registered domain names hosting malicious scripts on random subdomains, and by redirects to various scam sites," security researcher Denis Sinegubko said.
The websites include fake tech support, fraudulent lottery wins, and rogue CAPTCHA pages urging users to turn on notifications to 'Please Allow to verify, that you are not a robot,' thereby enabling the actors to send spam ads.
The report builds on recent findings from Doctor Web, which detailed a Linux malware family that exploits flaws in more than two dozen plugins and themes to compromise vulnerable WordPress sites.
In the interim years, Balada Injector has relied on over 100 domains and a plethora of methods to take advantage of known security flaws (e.g., HTML injection and Site URL), with the attackers primarily attempting to obtain database credentials in the wp-config.php file.
Additionally, the attacks are engineered to read or download arbitrary site files including backups, database dumps, log and error files as well as search for tools like adminer and phpmyadmin that could have been left behind by site administrators upon completing maintenance tasks.
WordPress
The malware ultimately allows for the generation of fake WordPress admin users, harvests data stored in the underlying hosts, and leaves backdoors for persistent access.
Balada Injector further carries out broad searches from top-level directories associated with the compromised website's file system to locate writable directories that belong to other sites.
"Most commonly, these sites belong to the webmaster of the compromised site and they all share the same server account and the same file permissions," Sinegubko said. "In this manner, compromising just one site can potentially grant access to several other sites 'for free.'"
Should these attack pathways turn out to be unavailable, the admin password is brute-forced using a set of 74 predefined credentials. WordPress users are, therefore, recommended to keep their website software up-to-date, remove unused plugins and themes, and use strong WordPress admin passwords.
The findings come weeks after Palo Alto Networks Unit 42 unearthed a similar malicious JavaScript injection campaign that redirects site visitors to adware and scam pages. More than 51,000 websites have been affected since 2022.
The activity, which also employs String.fromCharCode as an obfuscation technique, leads victims to booby-trapped pages that trick them into enabling push notifications by masquerading as a fake CAPTCHA check to serve deceptive content.
"The injected malicious JS code was included on the homepage of more than half of the detected websites," Unit 42 researchers said. "One common tactic used by the campaign's operators was to inject malicious JS code on frequently used JS filenames (e.g., jQuery) that are likely to be included on the homepages of compromised websites."
"This potentially helps attackers target the website's legitimate users, since they are more likely to visit the website's home page."
CISA Warns of 5 Actively Exploited Security Flaws: Urgent Action Required
11.4.23 BigBrothers The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday added five security flaws to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation in the wild.
This includes three high-severity flaws in the Veritas Backup Exec Agent software (CVE-2021-27876, CVE-2021-27877, and CVE-2021-27878) that could lead to the execution of privileged commands on the underlying system. The flaws were fixed in a patch released by Veritas in March 2021.
CVE-2021-27876 (CVSS score: 8.1) - Veritas Backup Exec Agent File Access Vulnerability
CVE-2021-27877 (CVSS score: 8.2) - Veritas Backup Exec Agent Improper Authentication Vulnerability
CVE-2021-27878 (CVSS score: 8.8) - Veritas Backup Exec Agent Command Execution Vulnerability
Google-owned Mandiant, in a report published last week, revealed that an affiliate associated with the BlackCat (aka ALPHV and Noberus) ransomware operation is targeting publicly exposed Veritas Backup Exec installations to gain initial access by leveraging the aforementioned three bugs.
The threat intelligence firm, which is tracking the affiliate actor under its uncategorized moniker UNC4466, said it first observed exploitation of the flaws in the wild on October 22, 2022.
In one incident detailed by Mandiant, UNC4466 gained access to an internet-exposed Windows server, followed by carrying out a series of actions that allowed the attacker to deploy the Rust-based ransomware payload, but not before conducting reconnaissance, escalating privileges, and disabling Microsoft Defender's real-time monitoring capability.
Also added by CISA to the KEV catalog is CVE-2019-1388 (CVSS score: 7.8), a privilege escalation flaw impacting Microsoft Windows Certificate Dialog that could be exploited to run processes with elevated permissions on an already compromised host.
The fifth vulnerability included in the list is an information disclosure flaw in Arm Mali GPU Kernel Driver (CVE-2023-26083) that was revealed by Google's Threat Analysis Group (TAG) last month as abused by an unnamed spyware vendor as part of an exploit chain to break into Samsung's Android smartphones.
Federal Civilian Executive Branch (FCEB) agencies have time till April 28, 2023, to apply the patches to secure their networks against potential threats.
The advisory also comes as Apple released updates for iOS, iPadOS, macOS, and Safari web browser to address a pair of zero-day flaws (CVE-2023-28205 and CVE-2023-28206) that it said has been exploited in real-world attacks.
Update:#
CISA, on April 10, 2023, added the two Apple zero-day vulnerabilities to the KEV catalog, urging FCEB agencies to secure iOS, iPadOS, and macOS devices by May 1, 2023.
Taiwanese PC Company MSI Falls Victim to Ransomware Attack
9.4.23 Ransomware The Hacker News
Taiwanese PC company MSI (short for Micro-Star International) officially confirmed it was the victim of a cyber attack on its systems.
The company said it "promptly" initiated incident response and recovery measures after detecting "network anomalies." It also said it alerted law enforcement agencies of the matter.
That said, MSI did not disclose any specifics about when the attack took place and if it entailed the exfiltration of any proprietary information, including source code.
"Currently, the affected systems have gradually resumed normal operations, with no significant impact on financial business," the company said in a brief notice shared on Friday.
In a regulatory filing with the Taiwan Stock Exchange, it said that it's setting up enhanced controls of its network and infrastructure to ensure the security of data.
MSI is further urging users to obtain firmware/BIOS updates only from its official website, and refrain from downloading files from other sources.
The disclosure comes as a new ransomware gang known as Money Message added the company to its list of victims. The threat actor was spotlighted by Zscaler late last month.
"The group utilizes a double extortion technique to target its victims, which involves exfiltrating the victim's data before encrypting it," Cyble noted in an analysis published this week. "The group uploads the data on their leak site if the ransom is unpaid."
The development comes a month after Acer confirmed a breach of its own that resulted in the theft of 160 GB of confidential data. It was advertised on March 6, 2023, for sale on the now-defunct BreachForums.
Iran-Based Hackers Caught Carrying Out Destructive Attacks Under Ransomware Guise
8.4.23 BigBrothers The Hacker News
The Iranian nation-state group known as MuddyWater has been observed carrying out destructive attacks on hybrid environments under the guise of a ransomware operation.
That's according to new findings from the Microsoft Threat Intelligence team, which discovered the threat actor targeting both on-premises and cloud infrastructures in partnership with another emerging activity cluster dubbed DEV-1084.
"While the threat actors attempted to masquerade the activity as a standard ransomware campaign, the unrecoverable actions show destruction and disruption were the ultimate goals of the operation," the tech giant revealed Friday.
MuddyWater is the name assigned to an Iran-based actor that the U.S. government has publicly connected to the country's Ministry of Intelligence and Security (MOIS). It's been known to be active since at least 2017.
It's also tracked by the cybersecurity community under various names, including Boggy Serpens, Cobalt Ulster, Earth Vetala, ITG17, Mercury, Seedworm, Static Kitten, TEMP.Zagros, and Yellow Nix.
Attacks mounted by the group have primarily singled out Middle Eastern nations, with intrusions observed over the past year leveraging the Log4Shell flaw to breach Israeli entities.
The latest findings from Microsoft reveal the threat actor probably worked together with DEV-1084 to pull off the attack, the latter of which conducted the destructive actions after MuddyWater successfully gained a foothold onto the target environment.
"Mercury likely exploited known vulnerabilities in unpatched applications for initial access before handing off access to DEV-1084 to perform extensive reconnaissance and discovery, establish persistence, and move laterally throughout the network, oftentimes waiting weeks and sometimes months before progressing to the next stage," Microsoft said.
In the activity detected by Redmond, DEV-1084 subsequently abused highly privileged compromised credentials to perform encryption of on-premise devices and large-scale deletion of cloud resources, including server farms, virtual machines, storage accounts, and virtual networks.
Furthermore, the threat actors gained full access to email inboxes through Exchange Web Services, using it to perform "thousands of search activities" and impersonate an unnamed high-ranking employee to send messages to both internal and external recipients.
All these actions are actions are estimated to have transpired over a roughly three-hour timeframe starting at 12:38 a.m. (when the attacker logged into the Microsoft Azure environment via compromised credentials) and ending at 3:21 a.m. (when the attacker sent emails to other parties after the successful cloud disruption).
It's worth noting here that DEV-1084 refers to the same threat actor that assumed the "DarkBit" persona as part of a ransomware and extortion attack aimed at Technion, a leading research university in Israel, in February. The Israel National Cyber Directorate, last month, attributed the attack to MuddyWater.
"DEV-1084 [...] presented itself as a criminal actor interested in extortion, likely as an attempt to obfuscate Iran's link to and strategic motivation for the attack," Microsoft added.
The links between Mercury and DEV-1084 originate from infrastructure, IP address, and tooling overlaps, with the latter observed using a reverse tunneling utility called Ligolo, a staple MuddyWater artifact.
That said, there is not ample evidence to determine if DEV-1084 operates independently of MuddyWater and collaborates with other Iranian actors, or if it's a sub-team that's only summoned when there is a need to conduct a destructive attack.
Cisco Talos, early last year, described MuddyWater as a "conglomerate" comprising several smaller clusters rather than a single, cohesive group. The emergence of DEV-1084 suggests a nod in this direction.
"While these teams seem to operate independently, they are all motivated by the same factors that align with Iranian national security objectives, including espionage, intellectual theft, and destructive or disruptive operations based on the victims they target," Talos noted in March 2022.
Apple Releases Updates to Address Zero-Day Flaws in iOS, iPadOS, macOS, and Safari
8.4.23 Apple The Hacker News
Apple on Friday released security updates for iOS, iPadOS, macOS, and Safari web browser to address a pair of zero-day flaws that are being exploited in the wild.
The two vulnerabilities are as follows -
CVE-2023-28205 - A use after free issue in WebKit that could lead to arbitrary code execution when processing specially crafted web content.
CVE-2023-28206 - An out-of-bounds write issue in IOSurfaceAccelerator that could enable an app to execute arbitrary code with kernel privileges.
Apple said it addressed CVE-2023-28205 with improved memory management and the second with better input validation, adding it's aware the bugs "may have been actively exploited."
Credited with discovering and reporting the flaws are Cl้ment Lecigne of Google's Threat Analysis Group (TAG) and Donncha ำ Cearbhaill of Amnesty International's Security Lab.
Details about the two vulnerabilities have been withheld in light of active exploitation and to prevent more threat actors from abusing them.
The updates are available in version iOS 16.4.1, iPadOS 16.4.1, macOS Ventura 13.3.1, and Safari 16.4.1. The fixes also span a wide range of devices -
iPhone 8 and later, iPad Pro (all models), iPad Air 3rd generation and later, iPad 5th generation and later, and iPad mini 5th generation and later
Macs running macOS Big Sur, Monterey, and Ventura
Apple has patched three zero-days since the start of the year. In February, Apple addressed another actively exploited zero-day (CVE-2023-23529) in WebKit that could result in arbitrary code execution.
The development also comes as Google TAG disclosed that commercial spyware vendors are leveraging zero-days in Android and iOS to infect mobile devices with surveillance malware.
Researchers Uncover Thriving Phishing Kit Market on Telegram Channels
7.4.23 Phishing The Hacker News
In yet another sign that Telegram is increasingly becoming a thriving hub for cybercrime, researchers have found that threat actors are using the messaging platform to peddle phishing kits and help set up phishing campaigns.
"To promote their 'goods,' phishers create Telegram channels through which they educate their audience about phishing and entertain subscribers with polls like, 'What type of personal data do you prefer?'," Kaspersky web content analyst Olga Svistunova said in a report published this week.
The links to these Telegram channels are distributed via YouTube, GitHub, and the phishing kits that are developed by the crooks themselves. The Russian cybersecurity firm said it detected over 2.5 million malicious URLs generated using phishing kits in the past six months.
One of the prominent services offered is to provide threat actors with Telegram bots that automate the process of generating phishing pages and collecting user data.
Although it's the scammer's responsibility to distribute the fake login pages to targets of interest, the credentials captured in those pages are sent back by means of another Telegram bot.
Other bot services go a step further by advertising options to generate phishing pages that mimic a legitimate service, which are then used to lure potential victims under the pretext of giving away free likes on social media services.
"Scammer-operated Telegram channels sometimes post what appears to be exceptionally generous offers, for example, zipped up sets of ready-to-use phishing kits that target a large number of global and local brands," Svistunova said.
In some cases, phishers have also been observed sharing users' personal data with other subscribers for free in hopes of attracting aspiring criminals, only to sell paid kits to those who wish to pull off more such attacks. The scammers further offer to teach "how to phish for serious cash."
Using free propositions is also a way for scammers to trick cash-strapped and newbie criminals into using their phishing kits, resulting in double theft, where the stolen data is also sent to the creator without their knowledge.
Paid services, on the other hand, include advanced kits that boast of an appealing design and features like anti-bot detection, URL encryption and geoblocking that threat actors could use to commit more advanced social engineering schemes. Such pages cost anywhere between $10 to $280.
Another paid category entails the sale of personal data, with credentials of bank accounts advertised at different rates based on the balance. For example, an account with a balance of $49,000 was put up for $700.
What's more, phishing services are marketed via Telegram on a subscription basis (i.e., phishing-as-a-service or PhaaS), wherein the developers rent the kits for a monthly fee in return for providing regular updates.
Also promoted as a subscription is a one-time password (OTP) bot that calls users and convinces them to enter the two-factor authentication code on their phones to help bypass account protections.
Setting up these services are relatively straightforward. What's more difficult is earning the trust and loyalty of the customers. And some vendors go out of their way to assure that all the information is encrypted so that no third-parties, including themselves, can read it.
The findings also follow an advisory from Cofense earlier this January, which revealed an 800% increase year-over-year in the use of Telegram bots as exfiltration destinations for phished information.
"Wannabe phishers used to need to find a way onto the dark web, study the forums there, and do other things to get started," Svistunova said. "The threshold to joining the phisher community lowered once malicious actors migrated to Telegram and now share insights and knowledge, often for free, right there in the popular messaging service."
Microsoft Takes Legal Action to Disrupt Cybercriminals' Illegal Use of Cobalt Strike Tool
7.4.23 Ransomware The Hacker News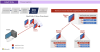
Microsoft said it teamed up with Fortra and Health Information Sharing and Analysis Center (Health-ISAC) to tackle the abuse of Cobalt Strike by cybercriminals to distribute malware, including ransomware.
To that end, the tech giant's Digital Crimes Unit (DCU) revealed that it secured a court order in the U.S. to "remove illegal, legacy copies of Cobalt Strike so they can no longer be used by cybercriminals."
While Cobalt Strike, developed and maintained by Fortra (formerly HelpSystems), is a legitimate post-exploitation tool used for adversary simulation, illegal cracked versions of the software have been weaponized by threat actors over the years.
Ransomware actors, in particular, have leveraged Cobalt Strike after obtaining initial access to a target environment to escalate privileges, lateral move across the network, and deploy file-encrypting malware.

"The ransomware families associated with or deployed by cracked copies of Cobalt Strike have been linked to more than 68 ransomware attacks impacting healthcare organizations in more than 19 countries around the world," Amy Hogan-Burney, general manager of DCU, said.
By disrupting the use of legacy copies of Cobalt Strike and compromised Microsoft software, the goal is to hinder the attacks and force the adversaries to rethink their tactics, the company added.
Redmond further noted the misuse of Cobalt Strike by nation-state groups whose operations align with that of Russia, China, Vietnam, and Iran, adding it detected malicious infrastructure hosting Cobalt Strike across the globe, counting China, the U.S., and Russia.
The legal crackdown comes months after Google Cloud identified 34 different hacked release versions of the Cobalt Strike tool in the wild in an attempt to "make it harder for bad guys to abuse."
FBI Cracks Down on Genesis Market: 119 Arrested in Cybercrime Crackdown
6.4.23 BigBrothers The Hacker News
A coordinated international law enforcement operation has dismantled Genesis Market, an illegal online marketplace that specialized in the sale of stolen credentials associated with email, bank accounts, and social media platforms.
Coinciding with the infrastructure seizure, the major crackdown, which involved authorities from 17 countries, culminated in 119 arrests and 208 property searches in 13 nations. However, the .onion mirror of the market appears to be still up and running.
The "unprecedented" law enforcement exercise has been codenamed Operation Cookie Monster.
Genesis Market, since its inception in March 2018, evolved into a major hub for criminal activities, offering access to data stolen from over 1.5 million compromised computers across the world totaling more than 80 million credentials.
A majority of infections associated with Genesis Market related malware have been detected in the U.S., Mexico, Germany, Turkey, Sweden, Italy, France, Spain, Poland, Ukraine, Saudi Arabia, India, Pakistan, and Indonesia, among others, per data gathered by Trellix.
Some of the prominent malware families that were leveraged to compromise victims encompass AZORult, Raccoon, RedLine, and DanaBot, which are all capable of stealing sensitive information from users' systems. Also delivered through DanaBot is a rogue Chrome extension designed to siphon browser data.
"Account access credentials advertised for sale on Genesis Market included those connected to the financial sector, critical infrastructure, and federal, state, and local government agencies," the U.S. Department of Justice (DoJ) said in a statement.
The DoJ called Genesis Market one of the "most prolific initial access brokers (IABs) in the cybercrime world." The U.S. Treasury Department, in a coordinated announcement, sanctioned the criminal shop, describing it as a "key resource" used by threat actors to target U.S. government organizations.
Besides credentials, Genesis also peddled device fingerprints which include unique identifiers and browser cookies so as to help threat actors circumvent anti-fraud detection systems used by many websites.
"The combination of stolen access credentials, fingerprints, and cookies allowed purchasers to assume the identity of the victim by tricking third party websites into thinking the Genesis Market user was the actual owner of the account," the DoJ added.
Court documents reveal that the U.S. Federal Bureau of Investigation (FBI) gained access to Genesis Market's backend servers twice in December 2020 and May 2022, enabling the agency to access information pertaining to about 59,000 users of the cybercrime bazaar.
The packages of stolen information harvested from infected computers (aka "bots") were sold for anywhere between $0.70 to several hundreds of dollars depending on the nature of the data, according to Europol and Eurojust.
"The most expensive would contain financial information which would allow access to online banking accounts," Europol noted, stating the criminals purchasing the data were also provided with additional tools to use it without attracting attention.
"Buyers were provided with a custom browser which would mimic the one of their victim. This allowed the criminals to access their victim's account without triggering any of the security measures from the platform the account was on."
The proprietary Chromium-based browser, referred to as Genesium, is cross-platform, with the maintainers claiming features such as "anonymous surfing" and other advanced functionalities that permit its users to bypass anti-fraud systems.
Genesis Market, unlike Hydra and other illicit marketplaces, was also accessible over the clearnet, thereby lowering the barrier of entry for lesser-skilled threat actors looking to obtain digital identities in order to breach individual accounts and enterprise systems.
The takedown is expected to have a "ripple effect throughout the underground economy" as threat actors search for alternatives to fill the void left by Genesis Market.
Genesis Market is the latest in a long line of illegitimate services that have been taken down by law enforcement. It also arrives exactly a year after the dismantling of Hydra, which was felled by German authorities in April 2022 and created a "seismic shift in the Russian-language darknet marketplace landscape."
"Almost a year after Hydra's takedown, five markets Mega, Blacksprut, Solaris, Kraken, and OMG!OMG! Market have emerged as the biggest players based on the volume of offers and the number of sellers," Flashpoint said in a new report.
The development also follows the launch of a new dark web marketplace known as STYX that's primarily geared towards financial fraud, money laundering, and identity theft. It's said to have opened its doors around January 19, 2023.
"Some examples of the specific service offerings marketed on STYX include cash-out services, data dumps, SIM cards, DDOS, 2FA/SMS bypass, fake and stolen ID documents, banking malware, and much more," Resecurity said in a detailed writeup.
Like Genesis Market, STYX also offers utilities that are designed to get around anti-fraud solutions and access compromised accounts by using granular digital identifiers like stolen cookie files, physical device data, and network settings to spoof legitimate customer logins.
The emergence of STYX as a new platform in the commercial cybercriminal ecosystem is yet another sign that the market for illegal services continues to be a fruitful business, allowing bad actors to profit from credential theft and payment data.
"The majority of STYX Marketplace vendors specialize in fraud and money laundering services targeting popular digital banking platforms, online-marketplaces, e-commerce and other payment applications," Resecurity noted. "The geographies targeted by these threat actors are global, spanning the U.S., E.U., U.K., Canada, Australia and multiple countries in APAC and Middle East."
Google Mandates Android Apps to Offer Easy Account Deletion In-App and Online
6.4.23 Android The Hacker News
Google is enacting a new data deletion policy for Android apps that allow account creation to also offer users with a setting to delete their accounts in an attempt to provide more transparency and control over their data.
"For apps that enable app account creation, developers will soon need to provide an option to initiate account and data deletion from within the app and online," Bethel Otuteye, senior director of product management for Android App Safety, said.
"This web requirement, which you will link in your Data safety form, is especially important so that a user can request account and data deletion without having to reinstall an app."
The goal, the search behemoth said, is to have a "readily discoverable option" to initiate an app account deletion process from both within an app and outside of it.
To that end, developers are to provide users with an in-app path as well as a web link resource to request app account deletion and associated data. Should users submit such a request, it's required of app developers to purge all data associated with that account.
In addition, users may be provided with alternatives to selectively delete only portions of the data (e.g., activity history, images, or videos) instead of entirely deleting their accounts.
Developers who wish to retain certain data for valid reasons such as security, fraud prevention, or regulatory compliance are mandated to disclose such data retention practices upfront.
"Temporary account deactivation, disabling, or 'freezing' the app account does not qualify as account deletion," Google explicitly spells out.
The new policy is expected to go into effect early next year, with developers having time till December 7, 2023, to submit answers to the data deletion questions in the app's Data safety form. Developers can file for an extension until May 31, 2024.
The development also puts Android in line with Apple's iOS and iPadOS operating systems, which instituted a similar policy starting June 30, 2022. It, however, doesn't require that users should be able to delete their accounts via the web as well.
That said, it remains to be seen if any enforcement actions will be taken if a developer fails to follow the rules. Earlier this year, Mozilla called out Google after discovering serious discrepancies between the top 20 most popular free apps' privacy policies and the information they self-reported in the Play Store.
In a related privacy measure, Google has also imposed additional guardrails that prohibit personal loan apps from accessing sensitive data, such as user contacts, photos, and locations, in an attempt to curb blackmail and extortion.
CryptoClippy: New Clipper Malware Targeting Portuguese Cryptocurrency Users
6.4.23 Virus The Hacker News
Portuguese users are being targeted by a new malware codenamed CryptoClippy that's capable of stealing cryptocurrency as part of a malvertising campaign.
The activity leverages SEO poisoning techniques to entice users searching for "WhatsApp web" to rogue domains hosting the malware, Palo Alto Networks Unit 42 said in a new report published today.
CryptoClippy, a C-based executable, is a type of cryware known as clipper malware that monitors a victim's clipboard for content matching cryptocurrency addresses and substituting them with a wallet address under the threat actor's control.
"The clipper malware uses regular expressions (regexes) to identify what type of cryptocurrency the address pertains to," Unit 42 researchers said.
"It then replaces the clipboard entry with a visually similar but adversary-controlled wallet address for the appropriate cryptocurrency. Later, when the victim pastes the address from the clipboard to conduct a transaction, they actually are sending cryptocurrency directly to the threat actor."

The illicit scheme is estimated to have netted its operators about $983 so far, with victims found across manufacturing, IT services, and real estate industries.
It's worth noting that the use of poisoned search results to deliver malware has been adopted by threat actors associated with the GootLoader malware.
Another approach used to determine suitable targets is a traffic direction system (TDS), which checks if the preferred browser language is Portuguese, and if so, takes the user to a rogue landing page.
Users who do not meet the requisite criteria are redirected to the legitimate WhatsApp Web domain without any further malicious activity, thereby avoiding detection.
The findings arrive days after SecurityScorecard detailed an information stealer called Lumma that's capable of harvesting data from web browsers, cryptocurrency wallets, and a variety of apps such as AnyDesk, FileZilla, KeePass, Steam, and Telegram.
Hackers Using Self-Extracting Archives Exploit for Stealthy Backdoor Attacks
5.4.23 Virus The Hacker News
An unknown threat actor used a malicious self-extracting archive (SFX) file in an attempt to establish persistent backdoor access to a victim's environment, new findings from CrowdStrike show.
SFX files are capable of extracting the data contained within them without the need for dedicated software to display the file contents. It achieves this by including a decompressor stub, a piece of code that's executed to unpack the archive.
"However, SFX archive files can also contain hidden malicious functionality that may not be immediately visible to the file's recipient, and could be missed by technology-based detections alone," CrowdStrike researcher Jai Minton said.
In the case investigated by the cybersecurity firm, compromised credentials to a system were used to run a legitimate Windows accessibility application called Utility Manager (utilman.exe) and subsequently launch a password-protected SFX file.
This, in turn, is made possible by configuring a debugger (another executable) in the Windows Registry to a specific program (in this case, utilman.exe) so that the debugger is automatically started every time the program is launched.
The abuse of utilman.exe is also noteworthy as it can be launched directly from the Windows login screen by using the Windows logo key + U keyboard shortcut, potentially enabling threat actors to configure backdoors via the Image File Execution Options Registry key.
"Closer inspection of the SFX archive revealed that it functions as a password-protected backdoor by abusing WinRAR setup options rather than containing any malware," Minton explained.
Specifically, the file is engineered to run PowerShell (powershell.exe), Command Prompt (cmd.exe), and Task Manager (taskmgr.exe) with NT AUTHORITY\SYSTEM privileges by providing the right password to the archive.
"This type of attack is likely to remain undetected by traditional antivirus software that is looking for malware inside of an archive (which is often also password-protected) rather than the behavior from an SFX archive decompressor stub," Minton added.
This is not the first time SFX files have been employed in attacks as a means for attackers to stay undetected. In September 2022, Kaspersky disclosed a malware campaign that utilized links to such password-protected files to propagate RedLine Stealer.
A month later, the infamous Emotet botnet was observed sending out an SFX archive that, once opened by a user, would automatically extract a second password-protected SFX archive, enter the password, and execute its content without further user interaction using a batch script.
To mitigate threats posed by this attack vector, it's recommended that SFX archives are analyzed through unarchiving software to identify any potential scripts or binaries that are set to extract and run upon execution.
Google TAG Warns of North Korean-linked ARCHIPELAGO Cyberattacks
5.4.23 BigBrothers The Hacker News
A North Korean government-backed threat actor has been linked to attacks targeting government and military personnel, think tanks, policy makers, academics, and researchers in South Korea and the U.S.
Google's Threat Analysis Group (TAG) is tracking the cluster under the name ARCHIPELAGO, which it said is a subset of another threat group tracked by Mandiant under the name APT43.
The tech giant said it began monitoring the hacking crew in 2012, adding it has "observed the group target individuals with expertise in North Korea policy issues such as sanctions, human rights, and non-proliferation issues."
The priorities of APT43, and by extension ARCHIPELAGO, are said to align with North Korea's Reconnaissance General Bureau (RGB), the primary foreign intelligence service, suggesting overlaps with a group broadly known as Kimsuky.
Attack chains mounted by ARCHIPELAGO involve the use of phishing emails containing malicious links that, when clicked by the recipients, redirect to fake login pages that are designed to harvest credentials.
These messages purport to be from media outlets and think tanks and seek to entice targets under the pretext of requesting for interviews or additional information about North Korea.
"ARCHIPELAGO invests time and effort to build a rapport with targets, often corresponding with them by email over several days or weeks before finally sending a malicious link or file," TAG said.
The threat actor is also known to employ the browser-in-the-browser (BitB) technique to render rogue login pages inside an actual window to steal credentials.
What's more, the phishing messages have posed as Google account security alerts to activate the infection, with the adversarial collective hosting malware payloads like BabyShark on Google Drive in the form of blank files or ISO optical disc images.
Another notable technique adopted by ARCHIPELAGO is the use of fraudulent Google Chrome extensions to harvest sensitive data, as evidenced in prior campaigns dubbed Stolen Pencil and SharpTongue.
The development comes as AhnLab Security Emergency Response Center (ASEC) detailed Kimsuky's use of Alternate Data Stream (ADS) and weaponized Microsoft Word files to deliver info-stealer malware.
Typhon Reborn Stealer Malware Resurfaces with Advanced Evasion Techniques
5.4.23 Virus The Hacker News
The threat actor behind the information-stealing malware known as Typhon Reborn has resurfaced with an updated version (V2) that packs in improved capabilities to evade detection and resist analysis.
The new version is offered for sale on the criminal underground for $59 per month, $360 per year, or alternatively, for $540 for a lifetime subscription.
"The stealer can harvest and exfiltrate sensitive information and uses the Telegram API to send stolen data to attackers," Cisco Talos researcher Edmund Brumaghin said in a Tuesday report.
Typhon was first documented by Cyble in August 2022, detailing its myriad features, including hijacking clipboard content, capturing screenshots, logging keystrokes, and stealing data from crypto wallet, messaging, FTP, VPN, browser, and gaming apps.
Based on another stealer malware called Prynt Stealer, Typhon is also capable of delivering the XMRig cryptocurrency miner. In November 2022, Palo Alto Networks Unit 42 unearthed an updated version dubbed Typhon Reborn.
"This new version has increased anti-analysis techniques and it was modified to improve the stealer and file grabber features," Unit 42 said, pointing out the removal of existing features like keylogging and cryptocurrency mining in an apparent attempt to lower the chances of detection.
The latest V2 variant, per Cisco Talos, was marketed by its developer on January 31, 2023, on the Russian language dark web forum XSS.
"Typhon Reborn stealer is a heavily refactored and improved version of the older and unstable Typhon Stealer," the malware author said, in addition to touting its inexpensive price and the absence of any backdoors.
Like other malware, V2 comes with options to avoid infecting systems that are located in the Commonwealth of Independent States (CIS) countries. It, however, notably excludes Ukraine and Georgia from the list.
Typhon Reborn Stealer Malware
Besides incorporating more anti-analysis and anti-virtualization checks, Typhon Reborn V2 removes its persistence features, instead opting to terminate itself after exfiltrating the data.
The malware ultimately transmits the collected data in a compressed archive via HTTPS using the Telegram API, marking continued abuse of the messaging platform.
"Once the data has been successfully transmitted to the attacker, the archive is then deleted from the infected system," Brumaghin said. "The malware then calls [a self-delete function] to terminate execution."
The findings come as Cyble disclosed a new Python-based stealer malware named Creal that targets cryptocurrency users via phishing sites mimicking legitimate crypto mining services like Kryptex.
The malware is no different from Typhon Reborn in that it's equipped to siphon cookies and passwords from Chromium-based web browsers as well as data from instant messaging, gaming, and crypto wallet apps.
That said, the malware's source code is available on GitHub, thereby allowing other threat actors to alter the malware to suit their needs and making it a potent threat.
"Creal Stealer is capable of exfiltrating data using Discord webhooks and multiple file-hosting and sharing platforms such as Anonfiles and Gofile," Cyble said in a report published last week.
"The trend of using open source code in malware is increasing among cybercriminals, since it allows them to create sophisticated and customized attacks with minimal expenses."
Rorschach Ransomware Emerges: Experts Warn of Advanced Evasion Strategies
5.4.23 Ransomware The Hacker News
Cybersecurity researchers have taken the wraps off a previously undocumented ransomware strain called Rorschach that's both sophisticated and fast.
"What makes Rorschach stand out from other ransomware strains is its high level of customization and its technically unique features that have not been seen before in ransomware," Check Point Research said in a new report. "In fact, Rorschach is one of the fastest ransomware strains ever observed, in terms of the speed of its encryption."
The cybersecurity firm said it observed the ransomware deployed against an unnamed U.S.-based company, adding it found no branding or overlaps that connect it to any previously known ransomware actors.
However, further analysis of Rorschach's source code reveals similarities to Babuk ransomware, which suffered a leak in September 2021, and LockBit 2.0. On top of that, the ransom notes sent out to the victims appear to be inspired by that of Yanluowang and DarkSide.
The most significant aspect of the intrusion is the use of a technique called DLL side-loading to load the ransomware payload, a method rarely observed in such attacks. The development marks a new sophistication in the approaches adopted by financially motivated groups to sidestep detection.
Specifically, the ransomware is said to have been deployed by abusing Palo Alto Network's Cortex XDR Dump Service Tool (cy.exe) to sideload a library named "winutils.dll."
Another unique characteristic is its highly customizable nature and the use of direct syscalls to manipulate files and bypass defense mechanisms.
Rorschach ransomware is also tasked with terminating a predefined list of services, deleting shadow volumes and backups, clearing Windows events logs to erase forensic trail, disabling the Windows firewall, and even deleting itself after completing its actions.
Internal propagation is achieved by compromising the domain controller and creating a group policy, according to Check Point and South Korean cybersecurity company AhnLab, which erroneously attributed the infection chain to DarkSide earlier this February.
The ransomware, like other malware strains observed in the wild, skips machines that are located in the Commonwealth of Independent States (CIS) countries by checking the system language.
"The Rorschach ransomware employs a highly effective and fast hybrid-cryptography scheme, which blends the curve25519 and eSTREAM cipher hc-128 algorithms for encryption purposes," researchers Jiri Vinopal, Dennis Yarizadeh, and Gil Gekker explained.
This process is designed to only encrypt a specific portion of the original file content instead of the entire file, and employs additional compiler optimization methods that make it a "speed demon."
In five separate tests carried out by Check Point in a controlled environment, 220,000 files were encrypted using Rorschach within four minutes and 30 seconds on average. LockBit 3.0, on the other hand, took approximately seven minutes.
"Its developers implemented new anti-analysis and defense evasion techniques to avoid detection and make it more difficult for security software and researchers to analyze and mitigate its effects," the researchers said.
"Additionally, Rorschach appears to have taken some of the 'best' features from some of the leading ransomwares leaked online, and integrated them all together. In addition to Rorschach's self-propagating capabilities, this raises the bar for ransom attacks."
The findings come as the Fortinet FortiGuard Labs detailed two emerging ransomware families called PayMe100USD, a Python-based file-locking malware, and Dark Power, which is written in the Nim programming language.
Rorschach (aka BabLock) Attacks Spotted in Asia, Europe, and the Middle East#
Singapore-headquartered Group-IB said it has identified Rorschach attacks targeting small and medium-sized companies and industrial firms across Asia, Europe, and the Middle East.
The cybersecurity company has christened the ransomware strain BabLock, so named for its source code similarities to Babuk and LockBit. It's said to be active since at least June 2022 and has capabilities to strike ESXi and Linux systems as well.
"The absence of [a data leak site], along with relatively modest ransom requests ranging from 50,000 to 1,000,000 USD, allows the group to operate stealthily and remain under the radar," Group-IB researchers Andrey Zhdanov and Vladislav Azersky said.
In the incident aimed at an unnamed industrial sector company in Europe, the threat actors leveraged a remote code execution flaw impacting Zimbra Collaboration (CVE-2022-41352, CVSS score: 9.8) to gain initial access.
The attack entailed no data exfiltration prior to encryption, instead pressurizing victims to pay up by threatening to "attack your company again in the future" and "delete all your data from your networks."
The Linux counterpart, according to Group-IB, is an 32-bit ELF binary written in Go 1.18.3, whereas the ESXi variant is a 64-bit program for Linux in ELF format compiled using GNU Compiler (GCC). Both the versions are based on the leaked Babuk ransomware source code.
"It would make more sense for the threat actors to use a simpler program based on Babuk to encrypt Windows systems, but they preferred developing their own, more sophisticated program, which overall is not similar to other families," the researchers said.
Palo Alto Networks, in an informational bulletin released on April 4, said it's aware of attacks leveraging its Cortex XDR Dump Service Tool to load the Rorschach payload, adding they don't affect macOS and Linux platforms. It's also expected to release a patch to address the issue next week.
"When removed from its installation directory, the Cortex XDR Dump Service Tool (cydump.exe), which is included with Cortex XDR agent on Windows, can be used to load untrusted dynamic link libraries (DLLs) with a technique known as DLL side-loading," the cybersecurity company said.
"Rorschach ransomware uses a copy of this tool and this technique to evade detection on systems that do not have sufficient endpoint protection. When the Cortex XDR agent is installed on Windows and the Cortex XDR Dump Service Tool process is running from the installation path, it is not possible to side-load DLLs with this technique."
New Rilide Malware Targeting Chromium-Based Browsers to Steal Cryptocurrency
5.4.23 Cryptocurrency The Hacker News
Chromium-based web browsers are the target of a new malware called Rilide that masquerades itself as a seemingly legitimate extension to harvest sensitive data and siphon cryptocurrency.
"Rilide malware is disguised as a legitimate Google Drive extension and enables threat actors to carry out a broad spectrum of malicious activities, including monitoring browsing history, taking screenshots, and injecting malicious scripts to withdraw funds from various cryptocurrency exchanges," Trustwave SpiderLabs Research said in a report shared with The Hacker News.
What's more, the stealer malware can display forged dialogs to deceive users into entering a two-factor authentication code to withdraw digital assets.
Trustwave said it identified two different campaigns involving Ekipa RAT and Aurora Stealer that led to the installation of the malicious browser extension.
While Ekipa RAT is distributed via booby-trapped Microsoft Publisher files, rogue Google Ads act as the delivery vector for Aurora Stealer a technique that's become increasingly common in recent months.
Both the attack chains facilitate the execution of a Rust-based loader that, in turn, modifies the browser's LNK shortcut file and makes use of the "--load-extension" command line switch to launch the add-on.
The exact origins of Rilide is unknown, but Trustwave said it was able to find an underground forum post made in March 2022 by a threat actor advertising the sale of a botnet with similar functionalities.
A portion of the malware's source code has since found its way to the forums following what appears to be an unresolved payment dispute.
One notable feature implemented in the leaked source code is the ability to swap cryptocurrency wallet addresses in the clipboard with an actor-controlled address hard-coded in the sample.
Furthermore, a command-and-control (C2) address specified in the Rilide code has made it possible to identify various GitHub repositories belonging to a user named gulantin that contain loaders for the extension. GitHub has taken down the account in question.
"The Rilide stealer is a prime example of the increasing sophistication of malicious browser extensions and the dangers they pose," Trustwave concluded.
"While the upcoming enforcement of manifest v3 may make it more challenging for threat actors to operate, it is unlikely to solve the issue entirely as most of the functionalities leveraged by Rilide will still be available."
Arid Viper Hacking Group Using Upgraded Malware in Middle East Cyber Attacks
5.4.23 Virus The Hacker News
The threat actor known as Arid Viper has been observed using refreshed variants of its malware toolkit in its attacks targeting Palestinian entities since September 2022.
Symantec, which is tracking the group under its insect-themed moniker Mantis, said the adversary is "going to great lengths to maintain a persistent presence on targeted networks."
Also known by the names APT-C-23 and Desert Falcon, the hacking group has been linked to attacks aimed at Palestine and the Middle East at least since 2014.
Mantis has used an arsenal of homemade malware tools such as ViperRat, FrozenCell (aka VolatileVenom), and Micropsia to execute and conceal its campaigns across Windows, Android, and iOS platforms.
The threat actors are believed to be native Arabic speakers and based in Palestine, Egypt, and Turkey, according to a report published by Kaspersky in February 2015. Prior public reporting has also tied the group to the cyber warfare division of Hamas.
In April 2022, high-profile Israeli individuals employed in sensitive defense, law enforcement, and emergency services organizations were observed being targeted with a novel Windows backdoor dubbed BarbWire.
Attack sequences mounted by the group typically employ spear-phishing emails and fake social credentials to lure targets into installing malware on their devices.
The most recent attacks detailed by Symantec entail the use of updated versions of its custom Micropsia and Arid Gopher implants to breach targets before engaging in credential theft and exfiltration of stolen data.
Arid Gopher, an executable coded in the Go programming language, is a variant of the Micropsia malware that was first documented by Deep Instinct in March 2022. The shift to Go is not unusual as it allows the malware to stay under the radar.
Micropsia, alongside its ability to launch secondary payloads (like Arid Gopher), is also designed to log keystrokes, take screenshots, and save Microsoft Office files within RAR archives for exfiltration using a bespoke Python-based tool.
"Arid Gopher, like its predecessor Micropsia, is an info-stealer malware, whose intent is to establish a foothold, collect sensitive system information, and send it back to a C2 (command-and-control) network," Deep Instinct said at the time.
Evidence gathered by Symantec shows that Mantis moved to deploy three distinct versions of Micropsia and Arid Gopher on three sets of workstations between December 18, 2022, and January 12, 2023, as a way of retaining access.
Arid Gopher, for its part, has received regular updates and complete code rewrites, with the attackers "aggressively mutating the logic between variants" as a detection evasion mechanism.
"Mantis appears to be a determined adversary, willing to put time and effort into maximizing its chances of success, as evidenced by extensive malware rewriting and its decision to compartmentalize attacks against single organizations into multiple separate strands to reduce the chances of the entire operation being detected," Symantec concluded.
Microsoft Tightens OneNote Security by Auto-Blocking 120 Risky File Extensions
4.4.23 Security The Hacker News
Microsoft has announced plans to automatically block embedded files with "dangerous extensions" in OneNote following reports that the note-taking service is being increasingly abused for malware delivery.
Up until now, users were shown a dialog warning them that opening such attachments could harm their computer and data, but it was possible to dismiss the prompt and open the files.
That's going to change going forward. Microsoft said it intends to prevent users from directly opening an embedded file with a dangerous extension and display the message: "Your administrator has blocked your ability to open this file type in OneNote."
The update is expected to start rolling out with Version 2304 later this month and only impacts OneNote for Microsoft 365 on devices running Windows. It does not affect other platforms, including macOS, Android, and iOS, as well as OneNote versions available on the web and for Windows 10.
"By default, OneNote blocks the same extensions that Outlook, Word, Excel, and PowerPoint do," Microsoft said. "Malicious scripts and executables can cause harm if clicked by the user. If extensions are added to this allow list, they can make OneNote and other applications, such as Word and Excel, less secure."
The list of 120 extensions are as follows -
.ade, .adp, .app, .application, .appref-ms, .asp, .aspx, .asx, .bas, .bat, .bgi, .cab, .cer, .chm, .cmd, .cnt, .com, .cpl, .crt, .csh, .der, .diagcab, .exe, .fxp, .gadget, .grp, .hlp, .hpj, .hta, .htc, .inf, .ins, .iso, .isp, .its, .jar, .jnlp, .js, .jse, .ksh, .lnk, .mad, .maf, .mag, .mam, .maq, .mar, .mas, .mat, .mau, .mav, .maw, .mcf, .mda, .mdb, .mde, .mdt, .mdw, .mdz, .msc, .msh, .msh1, .msh2, .mshxml, .msh1xml, .msh2xml, .msi, .msp, .mst, .msu, .ops, .osd, .pcd, .pif, .pl, .plg, .prf, .prg, .printerexport, .ps1, .ps1xml, .ps2, .ps2xml, .psc1, .psc2, .psd1, .psdm1, .pst, .py, .pyc, .pyo, .pyw, .pyz, .pyzw, .reg, .scf, .scr, .sct, .shb, .shs, .theme, .tmp, .url, .vb, .vbe, .vbp, .vbs, .vhd, .vhdx, .vsmacros, .vsw, .webpnp, .website, .ws, .wsc, .wsf, .wsh, .xbap, .xll, and .xnk
Users who opt to still open the embedded file can do so by first saving the file locally to their device and then opening it from there.
The development comes as Microsoft's decision to block macros by default in Office files downloaded from the internet spurred threat actors to switch to OneNote attachments to deliver malware via phishing attacks.
According to cybersecurity firm Trellix, the number of malicious OneNote samples has been gradually increasing since December 2022, before ramping up in February 2023.
Cryptocurrency Companies Targeted in Sophisticated 3CX Supply Chain Attack
4.4.23 Cryptocurrency The Hacker News
The adversary behind the supply chain attack targeting 3CX deployed a second-stage implant specifically singling out a small number of cryptocurrency companies.
Russian cybersecurity firm Kaspersky, which has been internally tracking the versatile backdoor under the name Gopuram since 2020, said it observed an increase in the number of infections in March 2023 coinciding with the 3CX breach.
Gopuram's primary function is to connect to a command-and-control (C2) server and await further instructions that allow the attackers to interact with the victim's file system, create processes, and launch as many as eight in-memory modules.
The backdoor's links to North Korea stem from the fact that it "co-existed on victim machines with AppleJeus, a backdoor attributed to the Korean-speaking threat actor Lazarus," detailing an attack on an unnamed crypto firm located in Southeast Asia in 2020.
The targeting of cryptocurrency companies is another telltale sign of the Lazarus Group's involvement, given the threat actor's recurring focus on the financial industry to generate illicit profits for the sanctions-hit nation.
Kaspersky further said it identified a C2 overlap with a server ("wirexpro[.]com") that was previously identified as employed in an AppleJeus campaign documented by Malwarebytes in December 2022.
"As the Gopuram backdoor has been deployed to less than ten infected machines, it indicates that attackers used Gopuram with surgical precision," the company pointed out, adding the highest infection rates have been detected in Brazil, Germany, Italy, and France.
While the attack chain discovered so far entails the use of rogue installers to distribute an information stealer (known as ICONIC Stealer), the latest findings suggest that the ultimate goal of the campaign may have been to infect targets with the full-fledged modular backdoor.
That said, it's not known how successful the campaign has been, and if it has led to the actual theft of sensitive data or cryptocurrency. It, however, raises the possibility that ICONIC Stealer was used as a reconnaissance utility to cast a wide net and identify targets of interest for follow-on exploitation.
The development comes as BlackBerry revealed that "the initial phase of this operation took place somewhere between the end of summer and the beginning of fall 2022."
A majority of the attack attempts, per the Canadian company, have been registered in Australia, the U.S., and the U.K., with healthcare, pharma, IT, and finance emerging as the top targeted sectors.
It's currently unclear how the threat actor obtained initial access to the 3CX network, and if it entailed the exploitation of a known or unknown vulnerability. The compromise is being tracked under the identifier CVE-2023-29059.
Evidence collected to date indicates that the attackers poisoned 3CX's development environment and delivered trojanized versions of the legitimate app to the company's downstream customers in a SolarWinds or Kaseya-like supply chain attack.
One of the malicious components responsible for retrieving the info-stealer, a library named "d3dcompiler_47.dll," has also been spotted weaponizing a 10-year-old Windows flaw (CVE-2013-3900) to incorporate encrypted shellcode without invalidating its Microsoft-issued signature.
A point worth noting here is that the same technique was adopted by a ZLoader malware campaign unearthed by Israeli cybersecurity firm Check Point Research in January 2022.
Multiple versions of the desktop app 18.12.407 and 18.12.416 for Windows and 18.11.1213, 18.12.402, 18.12.407, and 18.12.416 for macOS have been impacted. 3CX has since pinned the attack on a "highly experienced and knowledgeable hacker."
CrowdStrike has tied the incident to a North Korea-aligned nation-state group it tracks under the moniker Labyrinth Chollima, a sub-cluster within the Lazarus Group.
Western Digital Hit by Network Security Breach - Critical Services Disrupted!
4.4.23 Incindent The Hacker News
Data storage devices maker Western Digital on Monday disclosed a "network security incident" that involved unauthorized access to its systems.
The breach is said to have occurred on March 26, 2023, enabling an unnamed third party to gain access to a "number of the company's systems."
Following the discovery of the hack, Western Digital said it has initiated incident response efforts and enlisted the help of cybersecurity and forensic experts to conduct an investigation.
It also said it's coordinating with law enforcement agencies on the matter, adding the probe is in its initial stages.
The company has taken several of its services offline, noting that the threat actor may have obtained "certain data from its systems" and that it's working on estimating the nature and scope of the data accessed.
While Western Digital did not reveal the exact services that are impacted, the My Cloud status page shows that cloud, proxy, web, authentication, emails, and push notification services are down.
"Western Digital is currently experiencing a service outage impacting the following products: My Cloud, My Cloud Home, My Cloud Home Duo, My Cloud OS5, SanDisk ibi, SanDisk Ixpand Wireless Charger," the company said in a message posted on April 2.
Update#
Western Digital, in a message shared on April 3, said that it's "currently experiencing a service interruption that is preventing customers from accessing the My Cloud, My Cloud Home, My Cloud Home Duo, My Cloud OS 5, SanDisk ibi, SanDisk Ixpand Wireless Charger service."
It also noted that it's "working urgently to resolve the issue and restore access as soon as possible."
Italian Watchdog Bans OpenAI's ChatGPT Over Data Protection Concerns
4.4.23 BigBrothers The Hacker News
The Italian data protection watchdog, Garante per la Protezione dei Dati Personali (aka Garante), has imposed a temporary ban of OpenAI's ChatGPT service in the country, citing data protection concerns.
To that end, it has ordered the company to stop processing users' data with immediate effect, stating it intends to investigate the company over whether it's unlawfully processing such data in violation of the E.U. General Data Protection Regulation (GDPR) laws.
"No information is provided to users and data subjects whose data are collected by Open AI," the Garante noted. "More importantly, there appears to be no legal basis underpinning the massive collection and processing of personal data in order to 'train' the algorithms on which the platform relies."
ChatGPT, which is estimated to have reached over 100 million monthly active users since its release late last year, has not disclosed what it used to train its latest large language model (LLM), GPT-4, or how it trained it.
That said, its predecessor GPT-3 utilizes text sourced from books, Wikipedia, and Common Crawl, the latter of which maintains an "open repository of web crawl data that can be accessed and analyzed by anyone."
The Garante also pointed to the lack of any age verification system to prevent minors from accessing the service, potentially exposing them to "inappropriate" responses. Google's own chatbot, called Bard, is only open to users over the age of 18.
Additionally, the regulator raised questions about the accuracy of the information surfaced by ChatGPT, while also highlighting a data breach the service suffered earlier last month that exposed some users' chat titles and payment-related information.
In response to the order, OpenAI has blocked its generative AI chatbot from being accessed by users with an Italian IP address. It also said it's issuing refunds to subscribers of ChatGPT Plus, in addition to pausing subscription renewals.
The San Francisco-based company further emphasized that it provides ChatGPT in compliance with GDPR and other privacy laws. ChatGPT is already blocked in China, Iran, North Korea, and Russia.
In a statement shared with Reuters, OpenAI said it actively works to "reduce personal data in training our AI systems like ChatGPT because we want our AI to learn about the world, not about private individuals."
OpenAI has 20 days to notify the Garante of the measures it has taken to bring it in compliance, or risk facing fines of up to 20 million or 4% of the total worldwide annual turnover, whichever is higher.
The ban, however, is not expected to impact applications from other companies that employ OpenAI's technology to augment their services, including Microsoft's Bing search engine and its Copilot offerings.
The development also comes as Europol warned that LLMs like ChatGPT are likely to help generate malicious code, facilitate fraud, and "offer criminals new opportunities, especially for crimes involving social engineering, given its abilities to respond to messages in context and adopt a specific writing style."
This is not the first time AI-focused companies have come under the radar. Last year, controversial facial recognition firm Clearview AI was fined by multiple European regulators for scraping users' publicly available photos without consent to train its identity-matching service.
It has also run afoul of privacy laws in Australia, Canada, and the U.S., with several countries ordering the company to delete all of the data it obtained in such a manner.
Clearview AI told the BBC News last week that it has run nearly a million searches for U.S. law enforcement agencies, despite being permanently banned from selling its faceprint database within the country.
Microsoft Fixes New Azure AD Vulnerability Impacting Bing Search and Major Apps
1.4.23 Vulnerebility The Hacker News
Microsoft has patched a misconfiguration issue impacting the Azure Active Directory (AAD) identity and access management service that exposed several "high-impact" applications to unauthorized access.
"One of these apps is a content management system (CMS) that powers Bing.com and allowed us to not only modify search results, but also launch high-impact XSS attacks on Bing users," cloud security firm Wiz said in a report. "Those attacks could compromise users' personal data, including Outlook emails and SharePoint documents."
The issues were reported to Microsoft in January and February 2022, following which the tech giant applied fixes and awarded Wiz a $40,000 bug bounty. Redmond said it found no evidence that the misconfigurations were exploited in the wild.
The crux of the vulnerability stems from what's called "Shared Responsibility confusion," wherein an Azure app can be incorrectly configured to allow users from any Microsoft tenant, leading to a potential case of unintended access.
Interestingly, a number of Microsoft's own internal apps were found to exhibit this behavior, thereby permitting external parties to obtain read and write to the affected applications.
This includes the Bing Trivia app, which the cybersecurity firm exploited to alter search results in Bing and even manipulate content on the homepage as part of an attack chain dubbed BingBang.

To make matters worse, the exploit could be weaponized to trigger a cross-site scripting (XSS) attack on Bing.com and extract a victim's Outlook emails, calendars, Teams messages, SharePoint documents, and OneDrive files.
"A malicious actor with the same access could've hijacked the most popular search results with the same payload and leak sensitive data from millions of users," Wiz researcher Hillai Ben-Sasson noted.
Other apps that were found susceptible to the misconfiguration issue include Mag News, Central Notification Service (CNS), Contact Center, PoliCheck, Power Automate Blog, and COSMOS.
The development comes as enterprise penetration testing firm NetSPI revealed details of a cross-tenant vulnerability in Power Platform connectors that could be abused to gain access to sensitive data.
Following responsible disclosure in September 2022, the deserialization vulnerability was resolved by Microsoft in December 2022.
The research also follows the release of patches to remediate Super FabriXss (CVE-2023-23383, CVSS score: 8.2), a reflected XSS vulnerability in Azure Service Fabric Explorer (SFX) that could lead to unauthenticated remote code execution.
Cacti, Realtek, and IBM Aspera Faspex Vulnerabilities Under Active Exploitation
1.4.23 Vulnerebility The Hacker News
Critical security flaws in Cacti, Realtek, and IBM Aspera Faspex are being exploited by various threat actors in hacks targeting unpatched systems.
This entails the abuse of CVE-2022-46169 (CVSS score: 9.8) and CVE-2021-35394 (CVSS score: 9.8) to deliver MooBot and ShellBot (aka PerlBot), Fortinet FortiGuard Labs said in a report published this week.
CVE-2022-46169 relates to a critical authentication bypass and command injection flaw in Cacti servers that allows an unauthenticated user to execute arbitrary code. CVE-2021-35394 also concerns an arbitrary command injection vulnerability impacting the Realtek Jungle SDK that was patched in 2021.
While the latter has been previously exploited to distribute botnets like Mirai, Gafgyt, Mozi, and RedGoBot, the development marks the first time it has been utilized to deploy MooBot, a Mirai variant known to be active since 2019.
The Cacti flaw, besides being leveraged for MooBot attacks, has also been observed serving ShellBot payloads since January 2023, when the issue came to light.
At least three different versions of ShellBot have been detected viz. PowerBots (C) GohacK, LiGhT's Modded perlbot v2, and B0tchZ 0.2a the first two of which were recently disclosed by the AhnLab Security Emergency response Center (ASEC).

All three variants are capable of orchestrating distributed denial-of-service (DDoS) attacks. PowerBots (C) GohacK and B0tchZ 0.2a also feature backdoor capabilities to carry out file uploads/downloads and launch a reverse shell.
"Compromised victims can be controlled and used as DDoS bots after receiving a command from a C2 server," Fortinet researcher Cara Lin said. "Because MooBot can kill other botnet processes and also deploy brute force attacks, administrators should use strong passwords and change them periodically."
Active Exploitation of IBM Aspera Faspex Flaw#
A third security vulnerability that has come under active exploitation is CVE-2022-47986 (CVSS score: 9.8), a critical YAML deserialization issue in IBM's Aspera Faspex file exchange application.
The bug, patched in December 2022 (version 4.4.2 Patch Level 2), has been co-opted by cybercriminals in ransomware campaigns associated with Buhti and IceFire since February, shortly after the release of the proof-of-concept (PoC) exploit.
Cybersecurity firm Rapid7, earlier this week, revealed that one of its customers was compromised by the security flaw, necessitating that users move quickly to apply the fixes to prevent potential risks.
"Because this is typically an internet-facing service and the vulnerability has been linked to ransomware group activity, we recommend taking the service offline if a patch cannot be installed right away," the company said.
Hackers Exploiting WordPress Elementor Pro Vulnerability: Millions of Sites at Risk!
1.4.23 Exploit The Hacker News
Unknown threat actors are actively exploiting a recently patched security vulnerability in the Elementor Pro website builder plugin for WordPress.
The flaw, described as a case of broken access control, impacts versions 3.11.6 and earlier. It was addressed by the plugin maintainers in version 3.11.7 released on March 22.
"Improved code security enforcement in WooCommerce components," the Tel Aviv-based company said in its release notes. The premium plugin is estimated to be used on over 12 million sites.
Successful exploitation of the high-severity flaw allows an authenticated attacker to complete a takeover of a WordPress site that has WooCommerce enabled.
"This makes it possible for a malicious user to turn on the registration page (if disabled) and set the default user role to administrator so they can create an account that instantly has the administrator privileges," Patchstack said in an alert of March 30, 2023.
"After this, they are likely to either redirect the site to another malicious domain or upload a malicious plugin or backdoor to further exploit the site."
Credited with discovering and reporting the vulnerability on March 18, 2023, is NinTechNet security researcher Jerome Bruandet.
Patchstack further noted that the flaw is currently being abused in the wild from several IP addresses intending to upload arbitrary PHP and ZIP archive files.
Users of the Elementor Pro plugin are recommended to update to 3.11.7 or 3.12.0, which is the latest version, as soon as possible to mitigate potential threats.
The advisory comes over a year after the Essential Addons for Elementor plugin was found to contain a critical vulnerability that could result in the execution of arbitrary code on compromised websites.
Last week, WordPress issued auto-updates to remediate another critical bug in the WooCommerce Payments plugin that allowed unauthenticated attackers to gain administrator access to vulnerable sites.
Winter Vivern APT Targets European Government Entities with Zimbra Vulnerability
1.4.23 APT The Hacker News
The advanced persistent threat (APT) actor known as Winter Vivern is now targeting officials in Europe and the U.S. as part of an ongoing cyber espionage campaign.
"TA473 since at least February 2023 has continuously leveraged an unpatched Zimbra vulnerability in publicly facing webmail portals that allows them to gain access to the email mailboxes of government entities in Europe," Proofpoint said in a new report.
The enterprise security firm is tracking the activity under its own moniker TA473 (aka UAC-0114), describing it as an adversarial crew whose operations align with that of Russian and Belarussian geopolitical objectives.
What it lacks in sophistication, it makes up for in persistence. In recent months, the group has been linked to attacks targeting state authorities of Ukraine and Poland as well as government officials in India, Lithuania, Slovakia, and the Vatican.
The NATO-related intrusion wave entails the exploitation of CVE-2022-27926 (CVSS score: 6.1), a now-patched medium-severity security flaw in Zimbra Collaboration that could enable unauthenticated attackers to execute arbitrary JavaScript or HTML code.
This also involves employing scanning tools like Acunetix to identify unpatched webmail portals belonging to targeted organizations with the goal of sending phishing email under the guise of benign government agencies.
The messages come with booby-trapped URLs that exploit the cross-site scripting (XSS) flaw in Zimbra to execute custom Base64-encoded JavaScript payloads within the victims' webmail portals to exfiltrate usernames, passwords, and access tokens.
It's worth noting that each JavaScript payload is tailored to the targeted webmail portal, indicating that the threat actor is willing to invest time and resources to reduce the likelihood of detection.
"TA473's persistent approach to vulnerability scanning and exploitation of unpatched vulnerabilities impacting publicly facing webmail portals is a key factor in this actor's success," Proofpoint said.
"The group's focus on sustained reconnaissance and painstaking study of publicly exposed webmail portals to reverse engineer JavaScript capable of stealing usernames, passwords, and CSRF tokens demonstrates its investment in compromising specific targets."
The findings come amid revelations that at least three Russian intelligence agencies, including FSB, GRU (linked to Sandworm), and SVR (linked to APT29), likely use software and hacking tools developed by a Moscow-based IT contractor named NTC Vulkan.
This includes frameworks like Scan (to facilitate large-scale data collection), Amesit (to conduct information operations and manipulate public opinion), and Krystal-2B (to simulate coordinated IO/OT attacks against rail and pipeline control systems).
"Krystal-2B is a training platform that simulates OT attacks against different types of OT environments in coordination with some IO components by leveraging Amesit 'for the purpose of disruption,'" Google-owned Mandiant said.
"The contracted projects from NTC Vulkan provide insight into the investment of Russian intelligence services into developing capabilities to deploy more efficient operations within the beginning of the attack lifecycle, a piece of operations often hidden from our view," the threat intelligence firm added.
Cyber Police of Ukraine Busted Phishing Gang Responsible for $4.33 Million Scam
1.4.23 Crime The Hacker News
The Cyber Police of Ukraine, in collaboration with law enforcement officials from Czechia, has arrested several members of a cybercriminal gang that set up phishing sites to target European users.
Two of the apprehended affiliates are believed to be organizers, with 10 others detained in other territories across the European Union.
The suspects are alleged to have created more than 100 phishing portals aimed at users in France, Spain, Poland, Czechia, Portugal, and other nations in the region.
These websites masqueraded as online portals offering heavily discounted products below market prices to lure unsuspecting users into placing fake "orders."
In reality, the financial information entered on those websites to complete the payments were used to siphon money from the victims' accounts.
"For the fraudulent scheme, the participants also created two call centers, in Vinnytsia and in Lviv, and involved operators in their work," the Cyber Police said. "Their role was to convince customers to make purchases."
The nefarious scheme is estimated to have duped over 1,000 individuals, earning the operators approximately $4.33 million in illicit profits.
As part of the probe, law enforcement authorities carried out over 30 searches and confiscated mobile phones, SIM cards, and computer equipment used to carry out the activities.
Criminal proceedings have been initiated against the perpetrators, who may face a maximum sentence of up to 12 years in prison.
3CX Supply Chain Attack Here's What We Know So Far
1.4.23 Attack The Hacker News
Enterprise communications software maker 3CX on Thursday confirmed that multiple versions of its desktop app for Windows and macOS are affected by a supply chain attack.
The version numbers include 18.12.407 and 18.12.416 for Windows and 18.11.1213, 18.12.402, 18.12.407, and 18.12.416 for macOS. The issue has been assigned the CVE identifier CVE-2023-29059.
The company said it's engaging the services of Google-owned Mandiant to review the incident. In the interim, it's urging its customers of self-hosted and on-premise versions of the software to update to version 18.12.422.
"3CX Hosted and StartUP users do not need to update their servers as we will be updating them over the night automatically," 3CX CEO Nick Galea said in a blog post. "Servers will be restarted and the new Electron App MSI/DMG will be installed on the server."
Evidence available so far points to either a compromise of 3CX's software build pipeline to distribute Windows and macOS versions of the app package, or alternatively, the poisoning of an upstream dependency. The scale of the attack is currently unknown.
Telemetry data shared by Fortinet shows that the geographic spread of victim machines calling out to known actor controlled infrastructure chiefly spans Italy, Germany, Austria, the U.S., South Africa, Australia, Switzerland, the Netherlands, Canada, and the U.K.
The earliest period of potentially malicious activity is said to have been detected on or around March 22, 2023, according to a post on the 3CX forum, although preparations for the sophisticated campaign commenced no later than February 2022.
3CX said the initial alert flagging a potential security problem in its app last week was treated as a "false positive" owing to the fact that none of the antivirus engines on VirusTotal labeled it as suspicious or malware.
The Windows version of the attack leveraged a technique called DLL side-loading to load a rogue library referred to as "ffmpeg.dll" that's designed to read encrypted shellcode from another DLL called "d3dcompiler_47.dll."
SUDDENICON downloading a new executable
This involved accessing a GitHub repository to retrieve an ICO file containing URLs hosting the final-stage payload, an information stealer (dubbed ICONIC Stealer or SUDDENICON) capable of harvesting system information and sensitive data stored in web browsers.
British cybersecurity vendor Sophos pointed out that the shellcode utilized in the attack is a "byte-to-byte match" to prior samples seen in incidents exclusively attributed to the Lazarus Group.
"The choice of these two DLLs ffmpeg and d3dcompiler_47 by the threat actors behind this attack was no accident," ReversingLabs security researcher Karlo Zanki said.
"The target in question, 3CXDesktopApp, is built on the Electron open source framework. Both of the libraries in question usually ship with the Electron runtime and, therefore, are unlikely to raise suspicion within customer environments."
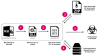
The macOS attack chain, in the same vein, bypassed Apple's notarization checks to download an unknown payload from a command-and-control (C2) server that's currently unresponsive.
"The macOS version does not use GitHub to retrieve its C2 server," Volexity said, which is tracking the activity under the cluster UTA0040. "Instead, a list of C2 servers is stored in the file encoded with a single byte XOR key, 0x7A."
Cybersecurity firm CrowdStrike, in an advisory of its own, has attributed the attack with high confidence to Labyrinth Chollima (aka Nickel Academy), a North Korea-aligned state-sponsored actor.
"The activity, which targets many organizations across a broad range of verticals without any obvious patterns, has been attributed to Labyrinth Chollima based on observed network infrastructure uniquely associated with that adversary, similar installation techniques, and a reused RC4 key," Adam Meyers, senior vice president of intelligence at CrowdStrike, told The Hacker News.
"The trojanized 3CX applications invoke a variant of ArcfeedLoader, malware uniquely attributed to Labyrinth Chollima."
Labyrinth Chollima, per the Texas-based company, is a subset of the Lazarus Group, which also constitutes Silent Chollima (aka Andariel or Nickel Hyatt) and Stardust Chollima (aka BlueNoroff or Nickel Gladstone).
The threat actor "has been active at least since 2009 and typically tries to generate revenue by targeting crypto and financial organizations," Meyers said, adding it's "likely affiliated with Bureau 121 of the DPRK's Reconnaissance General Bureau (RGB) and primarily conducts espionage operations and revenue generation schemes."
Google Chrome blocks latest 3CX MSI installer#
3CX, in an update shared on Friday, said Google is prohibiting downloads of the MSI installer files through its Chrome web browser. It also noted that antivirus engines from several companies are blocking any software signed with the old security certificate.
The following MSI installers have been blocked: SBC for Windows, Windows desktop app, and Call Flow Designer. However, there are indications that the restriction may have been lifted as some customers report being able to download the latest version (18.12.422) through Chrome.
In response, the company said it's making new MSI installers with a new certificate and a new build server, a process that's expected to take at least eight hours. It's further encouraging its customers to use the web app (PWA) version instead.
Researchers Detail Severe "Super FabriXss" Vulnerability in Microsoft Azure SFX
1.4.23 Vulnerebility The Hacker News
Details have emerged about a now-patched vulnerability in Azure Service Fabric Explorer (SFX) that could lead to unauthenticated remote code execution.
Tracked as CVE-2023-23383 (CVSS score: 8.2), the issue has been dubbed "Super FabriXss" by Orca Security, a nod to the FabriXss flaw (CVE-2022-35829, CVSS score: 6.2) that was fixed by Microsoft in October 2022.
"The Super FabriXss vulnerability enables remote attackers to leverage an XSS vulnerability to achieve remote code execution on a container hosted on a Service Fabric node without the need for authentication," security researcher Lidor Ben Shitrit said in a report shared with The Hacker News.
XSS refers to a kind of client-side code injection attack that makes it possible to upload malicious scripts into otherwise trusted websites. The scripts then get executed every time a victim visits the compromised website, thereby leading to unintended consequences.
While both FabriXss and Super FabriXss are XSS flaws, Super FabriXss has more severe implications in that it could be weaponized to execute code and potentially gain control of susceptible systems.
Super FabriXss, which resides in the "Events" tab associated with each node in the cluster from the user interface, is also a reflected XSS flaw, meaning the script is embedded into a link, and is only triggered when the link is clicked.
"This attack takes advantage of the Cluster Type Toggle options under the Events Tab in the Service Fabric platform that allows an attacker to overwrite an existing Compose deployment by triggering an upgrade with a specially crafted URL from XSS Vulnerability," Ben Shitrit explained.
"By taking control of a legitimate application in this way, the attacker can then use it as a platform to launch further attacks or gain access to sensitive data or resources."
The flaw, according to Orca, impacts Azure Service Fabric Explorer version 9.1.1436.9590 or earlier. It has since been addressed by Microsoft as part of its March 2023 Patch Tuesday update, with the tech giant describing it as a spoofing vulnerability.
"The vulnerability is in the web client, but the malicious scripts executed in the victim's browser translate into actions executed in the (remote) cluster," Microsoft noted in its advisory. "A victim user would have to click the stored XSS payload injected by the attacker to be compromised."
The disclosure comes as NetSPI revealed a privilege escalation flaw in Azure Function Apps, enabling users with "read only" permissions to access sensitive information and gain command execution.
It also follows the discovery of a misconfiguration in Azure Active Directory that exposed a number of applications to unauthorized access, including a content management system (CMS) that powers Bing.com.
Cloud security firm Wiz, which codenamed the attack BingBang, said it could be weaponized to alter search results in Bing, and worse, even perform XSS attacks on its users.
Chinese RedGolf Group Targeting Windows and Linux Systems with KEYPLUG Backdoor
1.4.23 Virus The Hacker News
A Chinese state-sponsored threat activity group tracked as RedGolf has been attributed to the use of a custom Windows and Linux backdoor called KEYPLUG.
"RedGolf is a particularly prolific Chinese state-sponsored threat actor group that has likely been active for many years against a wide range of industries globally," Recorded Future told The Hacker News.
"The group has shown the ability to rapidly weaponize newly reported vulnerabilities (e.g. Log4Shell and ProxyLogon) and has a history of developing and using a large range of custom malware families."
The use of KEYPLUG by Chinese threat actors was first disclosed by Google-owned Manidant in March 2022 in attacks targeting multiple U.S. state government networks between May 2021 and February 2022.
Then in October 2022, Malwarebytes detailed a separate set of attacks targeting government entities in Sri Lanka in early August that leveraged a novel implant dubbed DBoxAgent to deploy KEYPLUG.
Both these campaigns were attributed to Winnti (aka APT41, Barium, Bronze Atlas, or Wicked Panda), which Recorded Future said "closely overlaps" with RedGolf.
"We have not observed specific victimology as part of the latest highlighted RedGolf activity," Recorded Future said. "However, we believe this activity is likely being conducted for intelligence purposes rather than financial gain due to the overlaps with previously reported cyberespionage campaigns."
The cybersecurity firm, in addition to detecting a cluster of KEYPLUG samples and operational infrastructure (codenamed GhostWolf) used by the hacking group from at least 2021 to 2023, noted its use of other tools like Cobalt Strike and PlugX.
The GhostWolf infrastructure, for its part, consists of 42 IP addresses that function as KEYPLUG command-and-control. The adversarial collective has also been observed utilizing a mixture of both traditionally registered domains and Dynamic DNS domains, often featuring a technology theme, to act as communication points for Cobalt Strike and PlugX.
"RedGolf will continue to demonstrate a high operational tempo and rapidly weaponize vulnerabilities in external-facing corporate appliances (VPNs, firewalls, mail servers, etc.) to gain initial access to target networks," the company said.
"Additionally, the group will likely continue to adopt new custom malware families to add to existing tooling such as KEYPLUG."
To defend against RedGolf attacks, organizations are recommended to apply patches regularly, monitor access to external facing network devices, track and block identified command-and-control infrastructure, and configure intrusion detection or prevention systems to monitor for malware detections.
The findings come as Trend Micro revealed that it discovered more than 200 victims of Mustang Panda (aka Earth Preta) attacks as part of a far-reaching cyber espionage effort orchestrated by various sub-groups associated with the threat actor since 2022.
A majority of the cyber strikes have been detected in Asia, followed by Africa, Europe, the Middle East, Oceania, North America, and South America.
"There are strong indications of intertwined traditional intelligence tradecraft and cyber collection efforts, indicative of a highly coordinated and sophisticated cyber espionage operation," Trend Micro said.
New Wi-Fi Protocol Security Flaw Affecting Linux, Android and iOS Devices
1.4.23 Vulnerebility The Hacker News
A group of academics from Northeastern University and KU Leuven has disclosed a fundamental design flaw in the IEEE 802.11 Wi-Fi protocol standard, impacting a wide range of devices running Linux, FreeBSD, Android, and iOS.
Successful exploitation of the shortcoming could be abused to hijack TCP connections or intercept client and web traffic, researchers Domien Schepers, Aanjhan Ranganathan, and Mathy Vanhoef said in a paper published this week.
The approach exploits power-save mechanisms in endpoint devices to trick access points into leaking data frames in plaintext, or encrypt them using an all-zero key.
"The unprotected nature of the power-save bit in a frame's header [...] also allows an adversary to force queue frames intended for a specific client resulting in its disconnection and trivially executing a denial-of-service attack," the researchers noted.
In other words, the goal is to leak frames from the access point destined to a victim client station by taking advantage of the fact that most Wi-Fi stacks do not adequately dequeue or purge their transmit queues when the security context changes.
Besides manipulating the security context to leak frames from the queue, an attacker can override the client's security context used by an access point to receive packets intended for the victim. This attack pre-supposes that the targeted party is connected to a hotspot-like network.
"The core idea behind the attack is that the manner in which clients are authenticated is unrelated to how packets are routed to the correct Wi-Fi client," Vanhoef explained.
"A malicious insider can abuse this to intercept data towards a Wi-Fi client by disconnecting a victim and then connecting under the MAC address of the victim (using the credentials of the adversary). Any packets that were still underway to the victim, such website data that the victim was still loading, will now be received by the adversary instead."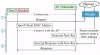
Cisco, in an informational advisory, described the vulnerabilities as an "opportunistic attack and the information gained by the attacker would be of minimal value in a securely configured network."
However, the company acknowledged that the attacks presented in the study may be successful against Cisco Wireless Access Point products and Cisco Meraki products with wireless capabilities.
To reduce the probability of such attacks, it's recommended to implement transport layer security (TLS) to encrypt data in transit and apply policy enforcement mechanisms to restrict network access.
The findings arrive months after researchers Ali Abedi and Deepak Vasisht demonstrated a location-revealing privacy attack called Wi-Peep that also exploits the 802.11 protocol's power-saving mechanism to localize target devices.
The research also follows other recent studies that have leveraged the Google Maps' Geolocation API to launch location spoofing attacks in urban areas, not to mention use Wi-Fi signals to detect and map human movement in a room.
AlienFox Malware Targets API Keys and Secrets from AWS, Google, and Microsoft Cloud Services
1.4.23 Virus The Hacker News
A new "comprehensive toolset" called AlienFox is being distributed on Telegram as a way for threat actors to harvest credentials from API keys and secrets from popular cloud service providers.
"The spread of AlienFox represents an unreported trend towards attacking more minimal cloud services, unsuitable for crypto mining, in order to enable and expand subsequent campaigns," SentinelOne security researcher Alex Delamotte said in a report shared with The Hacker News.
The cybersecurity company characterized the malware as highly modular and constantly evolving to accommodate new features and performance improvements.
The primary use of AlienFox is to enumerate misconfigured hosts via scanning platforms like LeakIX and SecurityTrails, and subsequently leverage various scripts in the toolkit to extract credentials from configuration files exposed on the servers.
Specifically, it entails searching for susceptible servers associated with popular web frameworks, including Laravel, Drupal, Joomla, Magento, Opencart, Prestashop, and WordPress.
Recent versions of the tool incorporate the ability to establish persistence on an Amazon Web Services (AWS) account and escalate privileges as well as automate spam campaigns through the compromised accounts.
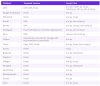
Attacks involving AlienFox are said to be opportunistic, with the scripts capable of gathering sensitive data pertaining to AWS, Bluemail, Exotel, Google Workspace, Mailgun, Mandrill, Microsoft 365, Sendgrid, Twilio, Zimbra, and Zoho.
Two such scripts are AndroxGh0st and GreenBot, which were previously documented by Lacework and Permiso p0 Labs.
While Androxgh0st is designed to parse a configuration file for specific variables and pull out their values for follow-on abuse, GreenBot (aka Maintance) contains an "AWS persistence script that creates a new administrator account and deletes the hijacked legitimate account."
Maintance further incorporates licensing checks, suggesting that the script is being offered as a commercial tool, and the ability to perform reconnaissance on the web server.
SentinelOne said it identified three different variants of the malware (from v2 to v4) dating back to February 2022. A notable functionality of AlienFoxV4 is its ability to check if an email address is already linked to an Amazon.com retail account, and if not, create a new account using that address.
To mitigate threats posed by AlienFox, organizations are recommended to adhere to configuration management best practices and follow the principle of least privilege (PoLP).
"The AlienFox toolset demonstrates another stage in the evolution of cybercrime in the cloud," Delamotte said. "For victims, compromise can lead to additional service costs, loss in customer trust, and remediation costs."
3CX Desktop App Supply Chain Attack Leaves Millions at Risk - Urgent Update on the Way!
1.4.23 Attack The Hacker News
3CX said it's working on a software update for its desktop app after multiple cybersecurity vendors sounded the alarm on what appears to be an active supply chain attack that's using digitally signed and rigged installers of the popular voice and video conferencing software to target downstream customers.
"The trojanized 3CX desktop app is the first stage in a multi-stage attack chain that pulls ICO files appended with Base64 data from GitHub and ultimately leads to a third-stage infostealer DLL," SentinelOne researchers said.
The cybersecurity firm is tracking the activity under the name SmoothOperator, stating the threat actor registered a massive attack infrastructure as far back as February 2022. There are indications that the attack may have commenced around March 22, 2023.
3CX, the company behind 3CXDesktopApp, claims to have more than 600,000 customers and 12 million users in 190 countries, some of which include well-known names like American Express, BMW, Honda, Ikea, Pepsi, and Toyota, among others.
While the 3CX PBX client is available for multiple platforms, telemetry data shows that the attacks observed so far are confined to the Windows Electron client (versions 18.12.407 and 18.12.416) and macOS versions of the PBX phone system.
The infection chain, in a nutshell, takes advantage of the DLL side-loading technique to load a rogue DLL (ffmpeg.dll) that's designed to retrieve an icon file (ICO) payload. The GitHub repository hosting the file has since been taken down.

The final payload is an information stealer capable of gathering system information and sensitive data stored in Google Chrome, Microsoft Edge, Brave, and Mozilla Firefox browsers.
The macOS sample (a 381 MB file), according to security researcher Patrick Wardle, carries a valid signature and is notarized by Apple, meaning it can be run without the operating system blocking it.
The malicious app, similar to the Windows counterpart, includes a Mach-O binary named libffmpeg.dylib that's designed to reach out to an external server "pbxsources[.]com" to download and execute a file named UpdateAgent. The server is currently offline.
Huntress reported that there are 242,519 publicly exposed 3CX phone management systems. Broadcom-owned Symantec, in its own advisory, said "the information gathered by this malware presumably allowed the attackers to gauge if the victim was a candidate for further compromise."
"Due to its widespread use and its importance in an organization's communication system, threat actors can cause major damage (for example, by monitoring or rerouting both internal and external communication) to businesses that use this software," Trend Micro said.
Cybersecurity firm CrowdStrike said it's attributing the attack with high confidence to a North Korean nation-state actor it tracks as Labyrinth Chollima (aka Nickel Academy), a sub-cluster within the notorious Lazarus Group.
"The malicious activity includes beaconing to actor-controlled infrastructure, deployment of second-stage payloads, and, in a small number of cases, hands-on-keyboard activity," CrowdStrike added.
In a forum post, 3CX's CEO Nick Galea said it's in the process of issuing a new build over the next few hours, and noted that Android and iOS versions are not impacted. "Unfortunately this happened because of an upstream library we use became infected," Galea said, without specifying more details.
As a workaround, the company is urging its customers to uninstall the app and install it again, or alternatively use the PWA client.
3CX, in a follow-up update, said the "issue appears to be one of the bundled libraries that we compiled into the Windows Electron app via git" and that it's further investigating the matter.
(This is a developing story and has been updated with new information about the macOS infection chain.)