Phishing Articles - H 2020 1 2 3 4 5 6 7 8 Phishing List - H 2021 2020 2019 2018 1 Phishing blog Phishing blog
GreatHorn Secures $6.3 Million to Combat Spear-Phishing Attacks
23.6.2017 securityweek Phishing
Belmont, Mass-based start-up GreatHorn announced Wednesday completion of a $6.3 million Series A funding round led by Techstars Venture Capital Fund and .406 Ventures.
The firm, one of Gartner's 'cool cloud vendors', is bringing machine-learning technology to the continuing threat and problem of targeted spear phishing. Spear-phishing, and the related Business E-mail Compromise (BEC) scam, are two of today's most pernicious threats -- the former is the first stage of the majority of successful breaches; and the latter, according to the FBI in May 2016, is responsible for losses "now totaling over $3 billion."
Both threats have proved resilient against traditional defenses because of their use of finely tuned and targeted, narrow-band social engineering. Effectively, each threat is new and unique, probably contains no payload to analyze, and is delivered before it can be recognized and blocked. The same problem exists for malware: new versions are delivered and get through signature-based anti-virus defenses before detection is added to the defense.
The solution against malware has been a shift of emphasis towards the recognition of malware behavior, using machine-learning to understand and detect that behavior. Conceptually, GreatHorn takes a similar approach to spear-phishing and BEC. It monitors email across the cloud both in metadata and content. It builds a behavioral graph that can detect anomalies in email behavior.
"We're not looking for a single smoking gun, we do not rely on any single indicator," CEO Kevin O'Brien told SecurityWeek. "What we do is plug into cloud email systems like Google and O365, and we look at all of the mail that gets sent and received. Then we build a social graph -- we start to understand how, for example, a CFO receives messages from the CEO, what those messages look like, how often they come, are they a bi-directional flow or received only. And we look at all the mechanisms of authentication buried in the metadata. We develop a fingerprint that can be coupled with the social graph.
"When you start to do that, not just for a single company but globally for hundreds of thousands of mailboxes every minute you start to see patterns of how email communication works. From there we think of it in terms of anomaly detection, and we can begin to identify anomalous messages -- things that could be spear-phishing or BEC attempts. We're not looking for things that might match an out of date blacklist, we have a unique lens on how individuals inside of a company, or inside of an industry sector, or even around the world, send mail."
It is this new application of machine-learning on big data to detect the anomalies in e-mail that could detect and prevent spear-phishing that has attracted the investors. "Advanced and targeted social engineering threats represent one of the most pernicious and dangerous challenges to organizations in both the public and private sector," explained Techstars Ventures Partner Ari Newman. "GreatHorn brings fresh thinking and a cloud-native, intelligent platform that can protect these organizations. We've been thrilled with the progress and execution GreatHorn has shown over the last few years and are excited to step up our investment in the company."
"GreatHorn," added .406 Ventures Partner Greg Dracon, "is at the forefront of next-generation cybersecurity, understanding that changing human behavior is difficult and that security awareness training is not nearly enough for employees faced with sophisticated phishing techniques that look real from presumably trusted contacts." Both Newman and Dracon are joining GreatHorn's board of directors.
Existing investors including ff Venture Capital, SoftTech Ventures and RRE Ventures also participated in the funding round.
Spear Phishing Campaign Targets Palestinian Law Enforcement
21.6.2017 securityweek Phishing
Palestinian law enforcement agencies and other targets within Palestine were targeted in a spear phishing campaign delivering malware to remotely control infected systems, Talos researchers reveal.
The actor behind this campaign “has appeared to have used genuine documents stolen from Palestinian sources as well as a controversial music video as part of the attack,” Talos says. The attacker also referenced TV show characters and included German language words within the attack, researchers discovered.
Information on these attacks initially emerged in March from Chinese security firm Qihoo 360, and in early April, when researchers at Palo Alto Networks and ClearSky revealed four malware families being used in targeted campaigns in the Middle East: Windows-based Kasperagent and Micropsia, and Android-focused SecureUpdate and Vamp.
Last week, ThreatConnect shared some additional information on Kasperagent, sayung the threat was mainly used as a reconnaissance tool and downloader, but that newer samples can also steal passwords from browsers, take screenshots, log keystrokes, execute arbitrary commands, and exfiltrate files.
Focusing on Micropsia, Talos’ new report also reveals that Palestinian law enforcement agencies were the main target in the analyzed campaign. The attack featured spear phishing emails purportedly coming from an individual named “Yasser Saad,” but which included a mismatch: the email address suggested “Yasser Saaid” was the sender.
A .r10 file was attached, suggesting it is part of a split archive, but instead it was a disguised RAR, with a malicious “InternetPolicy_xxx_pdf.exe” file inside. When the file is run, a decoy InternetPolicy.pdf file containing 7 pages is displayed, while the Micropsia Remote Administration Tool (RAT) is executed in the background.
Drive-by download campaigns that drop variants of the malware but use different decoy documents were also observed, Talos says.
Written in Delphi, the RAT uses a legitimate binary developed by OptimumX to create a shortcut to ensure persistence. The malware’s configuration file contains the User-Agent, the command and control (C&C) URL and the json keys used for the network communication.
Micropsia can connect to the C&C infrastructure to download and run an executable received in string format and then modified to become a binary file with the Hex2Bin Delphi API. It also uses WMI queries to get information about the anti-virus program running on the machine. These details are sent to the attacker.
The malware registers with the C&C via HTTP, sending information such as the filename of the executed malware and the version; the version of the infected Operating System; and the hostname and username encoded in base64. The server would respond in json format with an ID and 3 other Boolean values.
Talos reports that over 500 systems are already registered with the C&C server (the ID is incremented at each new infection). However, the researchers also suggest that some of these hosts could be security researcher sandbox systems.
Moreover, several German words were found in the network communication: Betriebssystem (operating system), Anwendung (application), and Ausfahrt (exit). This doesn’t mean the actor is German, but that they might be trying to cover their tracks.
“In this [campaign] one of the most surprising elements is the overt naming convention: the author deliberately uses references to several US TV show and intentionally uses German words for malware communication. We have no indication if these inclusions are to confuse attribution, to mock analysts, or a lapse of trade craft. This is in contrast to the highly convincing decoy documents which appear to be copies of genuine documents relating to the current situation in Palestine which suggests a high degree of professionalism,” Talos concludes.
Stanford University Site Hosted Phishing Pages for Months
2.6.2017 securityweek Phishing
Hackers compromised the website of the Paul F. Glenn Center for the Biology of Aging at Stanford University to deploy phishing sites, hacking tools, and defacement pages since January, Netcraft has discovered.
The website was compromised on Jan. 31, and multiple hackers exploited security gaps to deploy their malicious pages over the next several months. During the initial compromise, the hacker placed a rudimentary PHP web shell named wp_conffig.php into the top-level directory of the website, and the naming scheme allowed the shell to remain accessible for four months.
The anonymously accessible web shell on the server allowed for further compromise although the Stanford site was updated to the latest release of WordPress (4.7.5) on 20 April 2017. Thus, a second web shell was deployed on the server by May 14, Netcraft reports. However, the server didn’t run the latest version of PHP.
The second shell was based on the WSO (Web Shell by Orb) script, “which displays directory listings and offers several other hacking tools that can be used to crack passwords and gain access to databases,” Netcraft explains. In an attempt to make the shell difficult to spot, the actor named it config.php.
Six minutes later, an HTML file named Alarg53.html that only displayed the message “Hacked by Alarg53” was also uploaded on the server. Similar defacement pages can be found on dozens of other websites, and the security researchers suggest that “the hacker is well versed at using web shells to compromise websites.”
Within hours, a hacker (possibly the same) uploaded two more PHP scripts to the server: w3mailer.php – which allows attackers to send large amounts of spam or phishing emails, and promailer.php – which provides similar functionality but lacks malicious JavaScript code that the former script includes. The obfuscated code downloads an externally-hosted JavaScript file and is executed every time the hacker accesses the page.
On May 15, another hacker took advantage of the compromise to deploy a Chinese HiNet phishing site on the server, to steal webmail credentials from customers of the Chunghwa Telecom internet service. On May 21, a hacker uploaded a defacement page called TFS.html, and another HiNet phishing site was deployed later the same day.
On May 23, two archives were uploaded to the server and were extracted to multiple locations to create several phishing sites targeting users of Office365 and LinkedIn. The next day an archive containing a generic phishing kit to steal a victim's email address and password was uploaded to the server.
Dubbed ileowosun.zip, a phishing kit uploaded on May 27 was targeting SunTrust Bank users with a fraudulent login form. Each of the kits used a different set of email addresses to collect the stolen credentials, and the security researchers suggest different actors were behind each of them.
Two of the phishing kits were removed from the server on May 29, along with the directories they were unzipped into, and Netcraft believed a rival hacker did this, considering that no other phishing kit or hacking tool was removed. A second SunTrust phishing kit was uploaded the same day.
“A single Stanford University website has ended up hosting several hacking tools that have likely been used by multiple hackers to deploy a similar number of phishing sites onto the server. Failing to notice and remove the hacking tools could well have compounded the problem by facilitating the more recent compromises,” Netcraft concludes.
Spear-Phishing Attacks Increasingly Focused: Report
1.6.2017 securityweek Phishing
Spear-phishing attacks have become increasingly “laser-focused,” with many campaigns aimed at only a small number of inboxes belonging to the targeted organization, according to a report published this week by Israel-based anti-email phishing solutions provider IRONSCALES.
The company has analyzed data from 500,000 inboxes belonging to more than 100 of its customers over a period of 12 months. An evaluation of 8,500 emails that bypassed spam filters showed that roughly 77 percent of attacks targeted 10 inboxes or less, and one-third of malicious messages targeted only one inbox.
Experts believe attackers have been targeting fewer inboxes as this can help their operation stay under the radar longer, and it increases their chances of success if the emails are “hyper-personalized.”
The IRONSCALES study showed that 65 percent of email phishing attacks lasted for up to one month, and nearly half of them only lasted for less than 24 hours. Of the campaigns that went on for more than 30 days, roughly one-third spanned across 12 months or more.
Researchers noticed that attackers have increasingly aimed blast campaigns, which are not tailored to the recipient, at less than 10 mailboxes at a time. On the other hand, malware drip campaigns, which are more personalized, are more successful at bypassing traditional spam filters and they typically last longer.
According to the report, nearly 95 percent of phishing emails were part of highly targeted campaigns involving messages that impersonated someone from within the organization. Phishing emails that spoof a popular brand name are less common as they are more likely to be caught by spam filters - IRONSCALES noted that for every five brand-spoofing attacks detected by spam filters, 20 spear-phishing emails went undetected.
The most targeted departments are operations and finance, and the most frequently spoofed brands are DHL and Google.
“Sophisticated email phishing attacks represent the biggest threats to organizations of all sizes,” said Eyal Benishti, founder and CEO of IRONSCALES. “This report verifies that attackers have adopted numerous tools and techniques to circumvent traditional rules-based email security and spam filters. It’s now incumbent upon all organizational leaders to make sure that their employees are well-trained in phishing mitigation and that the cybersecurity technology in place is sophisticated enough to identify, verify and remediate email phishing attacks in real-time.”
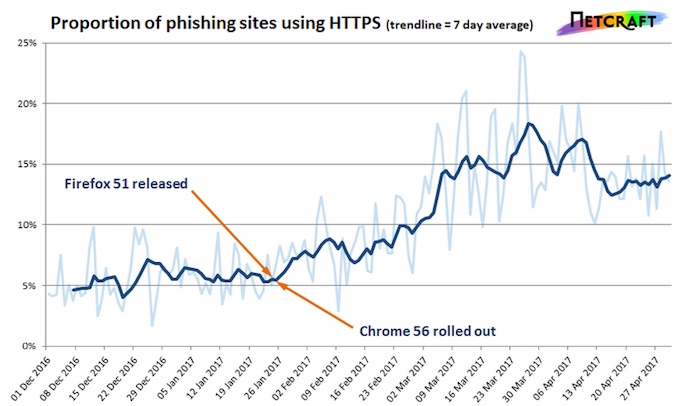
Number of Phishing Sites Using HTTPS Soars
19.5.2017 securityweek Phishing
The number of phishing websites using HTTPS has increased considerably over the past few months since Firefox and Chrome have started warning users when they access login pages that are not secure.
Internet security services firm Netcraft reported on Wednesday that, since late January, the proportion of phishing sites using HTTPS increased from roughly 5% to 15%.
One explanation for the rise is that, in late January, both Google and Mozilla implemented HTTP warnings in their Chrome and Firefox web browsers in an effort to protect their customers against man-in-the-middle (MitM) attacks.
Users of Chrome 56 and later, and Firefox 51 and later are warned when they are about to enter their credentials on a login page that does not use HTTPS. Since most phishing sites had been served over HTTP connections, cybercriminals may have realized that they need to step up their game and move to HTTPS.
“If the new browser behaviour has driven this change — and the timing suggests it might have — then it may have also had the unintended side effect of increasing the efficacy of some phishing sites,” explained Netcraft’s Paul Mutton. “Phishing sites that now use HTTPS and valid third-party certificates can appear more legitimate, and therefore increase the likelihood of snaring a victim.”

Another possible explanation, according to the expert, is that the warnings introduced by Google and Mozilla encouraged website administrators to migrate to HTTPS. Since phishing pages are often hosted on legitimate sites that have been compromised, this may have also been a factor in the significant increase of phishing sites using HTTPS.
On the other hand, Mutton pointed out that some popular browsers, such as Microsoft’s Edge and Internet Explorer, don’t display any warnings for login pages, which means phishing sites served over HTTP will still be efficient in many cases.
Cybercriminals have been coming up with clever ways to phish users’ credentials. One recent campaign aimed at Google customers leveraged a fake Google Docs application. Google quickly killed the operation, but the incident showed that malicious actors continue to improve their methods.
Google Tightens OAuth Rules to Combat Phishing
9.5.2017 securityweek Phishing
Following last week’s phishing attack against Gmail users, Google is planning tightened OAuth rules to prevent similar incidents from occurring.
Phishing emails, which impersonate a trusted source to trick the recipient into opening a malicious attachment or clicking a suspicious link, have long been a favorite tool for attackers. Google’s email service blocks millions of phishing emails each day, but last week’s incident proved that the system isn’t invincible.
The phishing attack tricked users into granting access to their contact information to a third-party application cleverly named “Google Docs.” The incident resulted in the attacker gaining access to all of the affected users’ email content, as well as in the phishing attack immediately propagating to all of the victim’s contacts.
The phishing emails, which appeared to arrive from someone in the victim’s contact list, claimed to contain a link to Google Docs content that the sender wanted to share with the recipient. Once the user clicked on the link, they were taken to a legitimate Google sign-in page, where they were asked to authorize an app called “Google Docs,” thus allowing it to read, send, delete, and manage emails and contacts.
Google was able to spot and block the attack fast, but the incident meant that immediate actions that users might have taken, such as changing passwords, had no effect. Because OAuth was used, the attackers still had access to the account, and only removing permissions for the offending app could solve the issue.
“We have taken action to protect users against an email impersonating Google Docs, and have disabled offending accounts. We've removed the fake pages, pushed updates through Safe Browsing, and our abuse team is working to prevent this kind of spoofing from happening again,” Google said after the incident.
Now, the company reveals that it is updating its policies and enforcement on OAuth applications to prevent similar attacks from happening in the future. Moreover, updates to Google’s anti-spam systems should help prevent similar campaigns, and augmented monitoring of suspicious third-party apps that request information from users should add an extra layer of security.
“We’re committed to keeping your Google Account safe, and have layers of defense in place to guard against sophisticated attacks of all types, from anti-hijacking systems detecting unusual behavior, to machine learning models that block malicious content, to protection measures in Chrome and through Safe Browsing that guard against visiting suspicious sites,” Google says.
What should be noted is that the concept of launching such an attack isn’t new. It was first presented in 2011 by André DeMarre, and then thoroughly detailed by Greg Carson in February 2017.
In fact, the cyber espionage group known as Pawn Storm (aka Fancy Bear, APT28) was observed using the very same technique in the past. Trend Micro recently revealed that this actor’s phishing scheme employed an application dubbed Google Defender, while abusing “the same legitimate OAuth connection to exploit the user’s lack of knowledge of available services.”
In an emailed statement to SecurityWeek, Jaime Blasco, Chief Scientist at AlienVault, shared a similar point of view: “This is similar to what APT28 (the group behind the DNS hack, France election groups attacks, etc) was using a while back. I don't believe they are behind this though because this is way too widespread. Many people/organizations have received similar attempts so this is probably something massive and less targeted.”
According to Google, less than 0.1% of Gmail users were impacted by last week’s “Google Docs” incident, but, as Talos’ Sean Baird and Nick Biasini point out, this proof-of-concept did reveal that a convincing Google phish via OAuth is possible.
To further protect users from such attacks, Google also announced anti-phishing security checks for Gmail for Android. Thus, users will be warned when clicking on suspicious links they receive via email, which should help prevent them from disclosing financial and personal information.
Warning! Don't Click that Google Docs Link You Just Received in Your Email
4.5.2017 thehackernews Phishing
Did someone just share a random Google Doc with you?
First of all — Do not click on that Google Doc link you might have just received in your email and delete it immediately — even if it's from someone you know.
I, my colleagues at The Hacker News, and even people all around the Internet, especially journalists, are receiving a very convincing OAuth phishing email, which says that the person [sender] "has shared a document on Google Docs with you."
Once you clicked the link, you will be redirected to a page which says, "Google Docs would like to read, send and delete emails, as well access to your contacts," asking your permission to "allow" access.
If you allow the access, the hackers would immediately get permission to manage your Gmail account with access to all your emails and contacts, without requiring your Gmail password.
Beware! New GoogleDocs Phishing Email Scam Spreading Across the World — Here's Everything You Need to Know
CLICK TO TWEET
But How? The "Google Docs" app that requests permissions to access your account is fake and malicious, which is created and controlled by the attacker.
You should know that the real Google Docs invitation links do not require your permission to access your Gmail account.
Anything Linked to Compromised Gmail Accounts is at Risk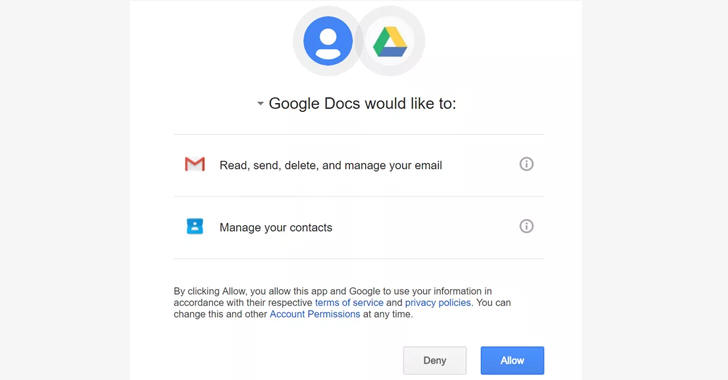
Once the app controlled by the attacker receives permissions to manage your email, it automatically sends same Google Docs phishing email to everyone on your contact list on your behalf.
Since your personal and business email accounts are commonly being used as the recovery email for many online accounts, there are possibilities that hackers could potentially get control over those online accounts, including Apple, Facebook, and Twitter.
In short, anything linked to a compromised Gmail account is potentially at risk and even if you enabled two factor authentication, it would not prevent hackers to access your data.
Meanwhile, Google has also started blacklisting malicious apps being used in the active phishing campaign.
"We are investigating a phishing email that appears as Google Docs. We encourage you to not click through & report as phishing within Gmail," Google tweeted.
This Google Docs phishing scheme is spreading incredibly quickly, hitting employees at multiple organizations and media outlets that use Google for email, as well as thousands of individual Gmail users who are reporting the same scam at the same time.
If by anyhow you have clicked on the phishing link and granted permissions, you can remove permissions for the fraudulent "Google Docs" app from your Google account. Here’s how you can remove permissions:
Go to your Gmail accounts permissions settings at https://myaccount.google.com and Sign-in.
Go to Security and Connected Apps.
Search for "Google Docs" from the list of connected apps and Remove it. It's not the real Google Docs.
Stay tuned to our Facebook Page for more updates ! Stay Safe!
New insidious Google Docs phishing scheme is rapidly spreading on the web
4.5.2017 securityaffairs Phishing
Don’t click Google Docs link! A Google Docs phishing scheme is quickly spreading across the Internet targeting a large number of users.
Did you receive an unsolicited Google Doc from someone?
First, do not click on that Google Doc link embedded in the email you have received and delete the message, even if it’s from someone you know.
A Google Docs phishing scheme is quickly spreading across the Internet targeting a large number of users and employees at multiple media outlets and organizations that Gmail.
Some of the websites associated with this campaign appear to have been shut down.
A large number of users are receiving a very insidious OAuth phishing email, which informs the recipient that sender “has shared a document on Google Docs” with the,
Once the recipient clicked the link, he will be redirected to a page which says, “Google Docs would like to read, send and delete emails, as well access to your contacts,” asking the victim’s permission to “allow” access.

If the user will allow the access, the attackers would get access to the recipient’s Gmail account without providing any Gmail password.
At this point, the attackers have the key of your kingdom and anything linked to the compromised Gmail Accounts is at risk.
Once the victim gives the attacker’s applications the permissions to manage his email account, it automatically sends same Google Docs phishing email to everyone on the contact list on behalf of the victim.
The attack technique used in this Google Docs phishing scheme was also associated recently with and Pawn Storm ongoing espionage campaign. The cyber spies are abusing OAuth, presenting a legitimate Google dialogue box requesting authorization, then asks permission for access to “view and manage your e-mail” and “view and manage the files in your Google Drive.”
Google also already started blocking any malicious apps leveraging this subtle trick.
Follow
Google Docs ✔ @googledocs
We are investigating a phishing email that appears as Google Docs. We encourage you to not click through & report as phishing within Gmail.
10:08 PM - 3 May 2017
4,378 4,378 Retweets 2,325 2,325 likes
“We have taken action to protect users against an email impersonating Google Docs, and have disabled offending accounts,” said a Google spokesperson in an email.
“We’ve removed the fake pages, pushed updates through Safe Browsing, and our abuse team is working to prevent this kind of spoofing from happening again. We encourage users to report phishing emails in Gmail.”
“There’s a very clever phishing scam going around at the moment – originally thought to be targeting journalists given the sheer number of them mentioning it on their Twitter feeds, it’s also been slinging its way across unrelated mailboxes – from orgs to schools / campuses,” explained Christopher Boyd, malware intelligence analyst at Malwarebytes, today.
“This doesn’t mean it didn’t begin with a popped journo mailbox and spread its way out from there, or that someone didn’t intentionally send it to a number of journalists of course – but either way, this one has gone viral and not in a ‘look at the cute cat pic’ fashion.”
If you have already clicked on the phishing link and granted permissions you can remove them for the bogus “Google Docs” app directly from your Google account.
Below the procedure to remove permissions:
Go to your Gmail accounts permissions settings at https://myaccount.google.com and Sign-in.
Go to Security and Connected Apps.
Search for “Google Docs” from the list of connected apps and Remove it.
Google Docs Phishing Scam Doused After Catching Fire
4.5.2017 securityweek Phishing
A phishing scam that tricked people with what appeared to be Google Docs links was doused by the internet giant after spreading wildly on Wednesday.
The purpose of the scam, and the culprits behind it, remained unknown late in the day.
"We have taken action to protect users against an email impersonating Google Docs, and have disabled offending accounts," a Google spokesperson said in an email response to an AFP inquiry.
"We've removed the fake pages, pushed updates through Safe Browsing, and our abuse team is working to prevent this kind of spoofing from happening again."
The scam combined "a phishing attack and a worm," using a deceptive email to get people to open the door to malicious code that wriggled into their messaging programs to spread itself to others, according to Electronic Frontier Foundation staff technologist Cooper Quintin.
Email sent from a known contact's real address would arrive containing a link it claimed led to a file to be shared at Google Docs online service, according to a rundown of the chicanery.
Clicking the link led to a real Google web address and asked for authorization to run an application the attacker had cleverly called 'Google Docs.'
Permissions granted to the application included allowing it to read or send email on a person's behalf.
"It doesn't immediately look like a phishing email," Quintin said.
"When you authorize the app, the very next thing it does is send the same emails to everyone in your contacts."
The application, along with online domains it was connecting to, were disabled within hours of it starting to spread wildly, according to Quintin.
"I suspect that it was far more successful than whoever released it into the world hoped or expected, and was maybe undone by its own success," he said.
"The domains went down pretty quickly. Google disabled the app, so it is no longer a threat."
FIN7 group has enhanced its phishing techniques
29.4.2017 securityaffairs Phishing
According to the experts from security firm FireEye, the financially-motivated FIN7 group is changing hacking techniques.
The group that has been active since late 2015, and was recently spotted to have been targeting personnel involved with United States Securities and Exchange Commission (SEC) filings at various organizations with a new PowerShell backdoor dubbed POWERSOURCE.
The FIN7 group has adopted new phishing techniques, it is leveraging on hidden shortcut files (LNK files) to compromise targets.
Experts from FireEye highlighted that attacks were launched by FIN7 group and not the Carbanak Group as suspected by other security experts.
“FIN7 is a financially-motivated threat group that has been associated with malicious operations dating back to late 2015. FIN7 is referred to by many vendors as “Carbanak Group”, although we do not equate all usage of the CARBANAK backdoor with FIN7.” reads the analysis published by FireEye. “FireEye recently observed a FIN7 spear phishing campaign targeting personnel involved with United States Securities and Exchange Commission (SEC) filings at various organizations.”
Experts from FireEye distinguish the activity associated with the FIN7 group to the one attributed to CARBANAK.
Security experts discovered a string of fileless malware attacks last month that have been powered by the same hacking framework.
The last attacks attributed to FIN7 recently spotted did not use weaponized Microsoft Office, hackers switched to hidden shortcut files (LNK files) as an attack vector to launch “mshta.exe”. Then FIN7 hackers used the VBScript functionality launched by mshta.exe to compromise the victim’s system.
“In a newly-identified campaign, FIN7 modified their phishing techniques to implement unique infection and persistence mechanisms. FIN7 has moved away from weaponized Microsoft Office macros in order to evade detection. This round of FIN7 phishing lures implements hidden shortcut files (LNK files) to initiate the infection and VBScript functionality launched by mshta.exe to infect the victim.” reads the analysis.
Hackers leveraged on spear phishing emails using malicious DOCX or RTF files, each being a different variant of the same LNK file and VBScript technique.
The DOCX and RTF files attempt to convince the user to double-click included images.
“both the malicious DOCX and RTF attempt to convince the user to double-click on the image in the document” states the analysis.

“In this ongoing campaign, FIN7 is targeting organizations with spear phishing emails containing either a malicious DOCX or RTF file – two versions of the same LNK file and VBScript technique.”
The ongoing campaign targeted large restaurant chains, hospitality, and financial service organizations, threat actors used phishing messages themed as complaints, catering orders, or resumes. To improve the efficiency of the campaign the FIN7 hackers were also calling the targets to make sure they received the email.
According to the experts, this new phishing scheme is more effective respect previous ones.
“Overall, this is a more effective phishing tactic since the malicious content is embedded in the document content rather than packaged in the OLE object. By requiring this unique interaction – double-clicking on the image and clicking the “Open” button in the security warning popup – the phishing lure attempts to evade dynamic detection as many sandboxes are not configured to simulate that specific user action,” state the researchers.
Hackers used a multilayer obfuscated PowerShell script that once launched executes shellcode for a Cobalt Strike stager. The shellcode downloads an additional payload from a specific C&C server using DNS aaa.stage.14919005.www1.proslr3[.]com, if the reply is successful, the PowerShell executes the embedded Cobalt Strike.
The FIN7 group also used the HALFBAKED backdoor in the ongoing attacks.
FireEye researchers examined shortcut LNK files created by attackers that allowed them to reveal valuable information attackers environment.
One of the LNK files used by hackers in the last campaign revealed some specific information about the attackers, for example, that the hackers likely generated this file on a VirtualBox system with hostname “andy-pc” on March 21, 2017.
FIN7 Hackers Change Phishing Techniques
28.4.2017 securityweek Phishing
A recently uncovered threat group referred to as FIN7 has adopted new phishing techniques and is now using hidden shortcut files (LNK files) to compromise targets, FireEye security researchers reveal.
The financially-motivated threat group has been active since late 2015 and was recently found to have been targeting personnel involved with United States Securities and Exchange Commission (SEC) filings at various organizations with a new PowerShell backdoor dubbed POWERSOURCE.
While some security firms refer to the operation as the “Carbanak Group,” FireEye says that not all CARBANAK backdoor activity can be attributed to FIN7. Interestingly, the group’s recent fileless attacks were said last month to have been launched from an attack framework used in various other seemingly unrelated attacks as well.
In the recently observed campaign, FIN7 was no longer using malicious Microsoft Office macros to evade detection, but switched to hidden shortcut files (LNK files) as the initial infection vector, while using the VBScript functionality launched by mshta.exe to infect the victim, FireEye reveals.
The campaign featured spear phishing emails that contained malicious DOCX or RTF files, each being a different variant of the same LNK file and VBScript technique. The group targeted various locations of large restaurant chains, hospitality, and financial service organizations with emails themed as complaints, catering orders, or resumes. On top of that, the group was also calling the targets to make sure they received the email.
The DOCX and RTF files attempt to convince the user to double-click included images. When that happens, the hidden embedded malicious LNK file in the document launches “mshta.exe” with a specific argument. The script in the argument combines all text box contents in the document, executes them, and creates a scheduled task for persistence.
“Overall, this is a more effective phishing tactic since the malicious content is embedded in the document content rather than packaged in the OLE object. By requiring this unique interaction – double-clicking on the image and clicking the “Open” button in the security warning popup – the phishing lure attempts to evade dynamic detection as many sandboxes are not configured to simulate that specific user action,” the researchers note.
A multilayer obfuscated PowerShell script is dropped and launched, which in turn executes shellcode for a Cobalt Strike stager. The shellcode retrieves an additional payload by connecting to a specific command and control (C&C) server using DNS, the researchers discovered. If a successful reply is received from the C&C, the PowerShell executes the embedded Cobalt Strike.
The campaign was also observed using a HALFBAKED backdoor variant, capable of performing various operations based on commands received from the server: send victim machine information (OS, Processor, BIOS and running processes) using WMI queries; take screenshots of victim machine; execute a VB script, EXE file, or PowerShell script; and delete or update a specified file.
One of the LNK files used by FIN7 in this campaign revealed some specific information about the attackers, namely that the shortcut launched within the string data, and that the actor likely generated this file on a VirtualBox system with hostname “andy-pc” on March 21, 2017, the researchers note.
Chrome Addresses Threat of Unicode Domain Spoofing
21.4.2017 securityweek Phishing
Chrome 58 Resolves Unicode Domain Spoofing
Google on Wednesday released Chrome 58 to the stable channel for Windows, Mac and Linux to address 29 vulnerabilities, including an issue that rendered users vulnerable to Unicode domain phishing.
Demonstrated by web developer Xudong Zheng, the bug resides in the use of Unicode characters in Internet hostnames through Punycode. By using characters that may look the same but are represented differently in Punycode, malicious actors can spoof legitimate websites and use them in phishing attacks.
The issue was also demonstrated by Avanan researchers in December 2016, when they stumbled upon live phishing attacks targeting Office 365 business email users. Using Unicode characters, attackers could create a site looking like http://www.pаypal.com/, but which actually resolved to http://www.xn--pypal-4ve.com/, thus bypassing Office 365’ anti-phishing defenses, the researchers explained.
Chrome 58 addresses the bug, which Google refers to as an URL spoofing in Omnibox (CVE-2017-5060). Assessed only a Medium severity rating, the vulnerability earned Xudong Zheng a $2000 bounty.
Two other Medium risk URL spoofing in Omnibox flaws were addressed as well: CVE-2017-5061, discovered by Haosheng Wang (awarded $2000), and CVE-2017-5067, credited to Khalil Zhani (awarded $500).
Only 12 of the 29 security fixes in Chrome 28 were for flaws discovered by external researchers: three rated High severity, 8 Medium risk, and one Low severity.
The High risk flaws include a Type confusion in PDFium (CVE-2017-5057), found by Guang Gong of Alpha Team, Qihoo 360 ($3000); a Heap use after free in Print Preview (CVE-2017-5058), discovered by Khalil Zhani ($2000); and a Type confusion in Blink (CVE-2017-5059), credited to SkyLined working with Trend Micro's Zero Day Initiative.
The Medium severity bugs also included a Use after free in Chrome Apps (CVE-2017-5062), a Heap overflow in Skia (CVE-2017-5063), a Use after free in Blink (CVE-2017-5064), Incorrect UI in Blink (CVE-2017-5065), and Incorrect signature handing in Networking (CVE-2017-5066).
The Low severity vulnerability was a Cross-origin bypass in Blink tracked as CVE-2017-5069 and was discovered by Michael Reizelman.
Tracking Pixels Used in Phishing Campaigns
19.4.2017 securityweek Phishing
Tracking Pixels Used in Phishing Campigns
Very small image files that can track user behavior have started to emerge in phishing campaigns, where hackers use them to gather information on their targets, Check Point researchers warn.
These very small image files are designed to send a string of code to an outside website. Usually of only one pixel in size, these images can also be hidden by setting them to the same color as the background of a web page, which allows them to go unnoticed by the user. They can also be used in emails, with the same purpose, and are called tracking pixels because of their small size and obvious purpose.
The code in these pixels is meant to ping the website when the image is downloaded, and can be designed to “capture information such as IP addresses, hostnames, operating systems, Web-browser types, dates the image was viewed, use of cookies, and other information,” Check Point explains.
This information is most often used by marketers to fine tune their advertising, but cybercriminals can also abuse the technique to gather information on cloud-platform components and discover known software vulnerabilities they can exploit in a later attack.
Check Point also explains that phishers can use tracking pixels in their attacks to learn which recipients are most likely to open their scam emails. Phishing attacks that leverage tracking pixels as a surveillance tool have been already observed in the wild, Check Point says.
“Since some scammers retool mass phishing attacks against random users to target high-value enterprise users, scammers are turning to pixel tracking to increase the odds a spear phishing attack will succeed,” the researchers reveal.
The researchers observed tracking pixels in phishing emails in August 2016, when in-place filters prevented the image from loading, which resulted in a red x placeholder image being displayed instead. These small images, Check Point says, threaten privacy in more than emails and web pages.
“For well over a decade, it has been understood that you can utilize tracking pixels in Microsoft Office files like Word documents, Excel spreadsheets and PowerPoint presentations. This works because Office files can link to an image located on a remote Web server. Putting a tracking pixel in an Office document allows you to be able to track a document’s activity as it moves through an organization,” the security firm notes.
While not found to be the direct cause of any specific security breach, tracking pixels are used for their surveillance capabilities in activities that precede attacks against users and infrastructure. The good news, however, is that it’s easy to stay protected.
Enterprises are advised to deploy email and anti-phishing security controls as part of their cloud-security arsenal, as well as to ensure that any software running in a cloud environment is patched at all times. Using web application security to protect any unpatched software should also help prevent intrusion. Looking for anomalous image placeholders when downloading pictures in advertising emails is also a good idea.
Chrome, Firefox Users Exposed to Unicode Domain Phishing
19.4.2017 securityweek Phishing
Malicious actors can create legitimate-looking phishing domains by leveraging the fact that some popular web browsers fail to properly protect their users against homograph attacks.
Web developer Xudong Zheng has demonstrated how an attacker could have registered the domain name “xn--80ak6aa92e.com,” which is displayed by web browsers such as Chrome, Opera and Firefox as “apple.com.”
Unicode is a standard for encoding and representing all characters and glyphs from all languages. Unicode characters can be used in Internet hostnames through Punycode. For instance, the Chinese word “短” is equivalent to “xn--s7y.”
Characters such as the Cyrillic “а” and the Latin “a” may look the same, but they are represented differently in Punycode, allowing malicious actors to create domains where Latin letters are replaced with similar-looking Greek or Cyrillic characters. This is known as an internationalized domain name (IDN) homograph attack.
Modern web browsers are designed to prevent these types of attacks – for example, "xn--pple-43d.com" will be displayed as "xn--pple-43d.com" instead of “apple.com.” However, Zheng discovered that this filter can be bypassed in Chrome, Firefox and Opera by creating the entire domain name using Cyrillic characters, leading to "xn--80ak6aa92e.com” being displayed as “apple.com.”
For a proof-of-concept (PoC), the expert registered the domain “xn--80ak6aa92e.com” and obtained a free digital certificate for it from Let’s Encrypt. When the domain is accessed via Opera, Chrome or Firefox, the user sees the domain name “apple.com” with a certificate issued for “apple.com.”
Wordfence has demonstrated the attack technique by spoofing the healthcare website “epic.com,” and experts at SANS have also provided some examples.
Zheng reported his findings to Google and Mozilla on January 20, and while the upcoming Chrome 58 will resolve the issue, Mozilla is still trying to figure out how to address the problem.
Mozilla initially classified the vulnerability report as “WONTFIX,” but later reopened it and assigned it a low severity rating. Until the organization comes up with a fix, Firefox users can protect themselves against potential attacks by typing “about:config” in the address bar to access advanced settings, and changing the “network.IDN_show_punycode” preference to “true.”
Edge, Internet Explorer and Safari are not affected. However, it’s worth noting that researchers did report recently that cybercriminals had been targeting Office 365 business email users by exploiting a weakness in how Office 365 handles Punycode.
Homograph Phishing Attacks are almost impossible to detect on major browsers
19.4.2017 securityaffairs Phishing
The Chinese security Xudong Zheng is warning of Homograph Phishing Attacks are “almost impossible to detect” also to experts.
The Chinese security researcher Xudong Zheng has devised a phishing technique that is “almost impossible to detect.”
Hackers can exploit a known vulnerability in the popular web browsers Chrome, Firefox and Opera to display to the users fake domain names as apparently legitimate services, like Apple and Google.
This attack is known as homograph attack, hackers can register domains such as “xn--pple-43d.com”, which is equivalent to “аpple.com”. This is possible if the address uses a foreign language, for example using the Cyrillic “а” (U+0430) rather than the ASCII “a” (U+0041).
To give you an idea of the technique reported by Zheng give a look at this demo web page created by the expert.
Well it displays in the address bar the URL
https://www.apple.com/
and also uses the HTTPs protocol.
However, if you try to copy and paste the URL in another page you will see the following address:
https://www.xn--80ak6aa92e.com/
So, in case the displayed page is a clone of the legitimate page there is no reason to doubt regarding its authenticity.

Despite the Homograph attack has been known since 2001, major browsers still haven’t solved the issue and are still vulnerable to Homograph Phishing Attacks.
“Chrome’s (and Firefox’s) homograph protection mechanism unfortunately fails if every characters is replaced with a similar character from a single foreign language. The domain “аррӏе.com”, registered as “xn--80ak6aa92e.com”, bypasses the filter by only using Cyrillic characters.” Xudong Zheng said in a blog post. “You can check this out yourself in the proof-of-concept using Chrome or Firefox. In many instances, the font in Chrome and Firefox makes the two domains visually indistinguishable. It becomes impossible to identify the site as fraudulent without carefully inspecting the site’s URL or SSL certificate. This program nicely demonstrates the difference between the two sets of characters. Internet Explorer and Safari are fortunately not vulnerable.”
Anther PoC page was created by researchers at security firm Wordfence, in this case, the experts spoofed the “epic.com” domain.
Major web browsers use ‘Punycode’ encoding by default to represent Unicode characters in the URL.
Punycode converts Unicode characters to the limited character set of ASCII (A-Z, 0-9), supported by International Domain Names (IDNs) system.
The Chinese domain “短.co” is represented in Punycode as “xn--s7y.co“. The xn-- prefix, aka ‘ASCII compatible encoding’ prefix, indicates web browser that the domain uses ‘punycode’ encoding to represent Unicode characters.
The flaw reported by the Chinese researcher could be exploited to register a domain having characters that are interpreted by major browsers in the wrong way. This trick could allow bypassing phishing protections implemented by several browsers, including Chrome, Firefox, and Opera.
Zheng reported this issue to the affected browser vendors early this year. Google has solved the problem in the experimental Chrome Canary 59 and will release a stable fix with the release of Chrome Stable 58.
The only way to prevent the Homograph Phishing Attacks is to disable Punycode support in your web browsers waiting for a fix, unfortunately only Firefox allows it.
“Firefox users can limit their exposure to this bug by going to about:config and setting network.IDN_show_punycode to true. This will force Firefox to always display IDN domains in its Punycode form, making it possible to identify malicious domains. Thanks to /u/MARKZILLA on reddit for this solution.” wrote Zheng.
“A simple way to limit the damage from bugs such as this is to always use a password manager. In general, users must be very careful and pay attention to the URL when entering personal information. I hope Firefox will consider implementing a fix to this problem since this can cause serious confusion even for those who are extremely mindful of phishing.”
This Phishing Attack is Almost Impossible to Detect On Chrome, Firefox and Opera
18.4.2017 thehackernews Phishing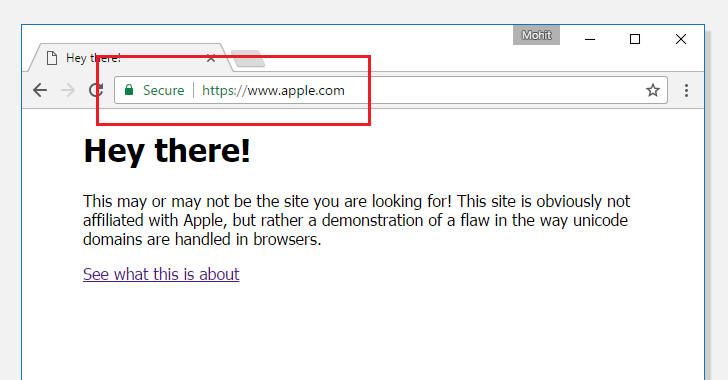
A Chinese infosec researcher has discovered a new "almost impossible to detect" phishing attack that can be used to trick even the most careful users on the Internet.
He warned, Hackers can use a known vulnerability in the Chrome, Firefox and Opera web browsers to display their fake domain names as the websites of legitimate services, like Apple, Google, or Amazon to steal login or financial credentials and other sensitive information from users.
What is the best defence against phishing attack? Generally, checking the address bar after the page has loaded and if it is being served over a valid HTTPS connection. Right?
Okay, then before going to the in-depth details, first have a look at this demo web page (note: you may experience downtime due to high traffic on demo server), set up by Chinese security researcher Xudong Zheng, who discovered the attack.
“It becomes impossible to identify the site as fraudulent without carefully inspecting the site's URL or SSL certificate.” Xudong Zheng said in a blog post.
If your web browser is displaying "apple.com" in the address bar secured with SSL, but the content on the page is coming from another server (as shown in the above picture), then your browser is vulnerable to the homograph attack.
There is another proof-of-concept website created by security experts from Wordfence to demonstrate this browsers' vulnerability. It spoof "epic.com" domain.
Homograph attack has been known since 2001, but browser vendors have struggled to fix the problem. It’s a kind of spoofing attack where a website address looks legitimate but is not because a character or characters have been replaced deceptively with Unicode characters.
Doesn't matter how much aware you're, anyone can fall victim to this "Almost Impossible to Detect" Phishing Attack.
CLICK TO TWEET
Many Unicode characters, which represents alphabets like Greek, Cyrillic, and Armenian in internationalised domain names, look the same as Latin letters to the casual eye but are treated differently by computers with the completely different web address.
For example, Cyrillic "а" (U+0430) and Latin "a" (U+0041) both are treated different by browsers but are displayed "a" in the browser address.
Punycode Phishing Attacks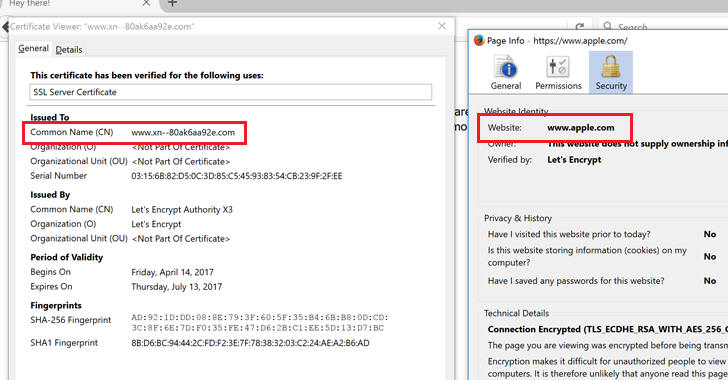
By default, many web browsers use ‘Punycode’ encoding to represent Unicode characters in the URL to defend against Homograph phishing attacks. Punycode is a special encoding used by the web browser to convert Unicode characters to the limited character set of ASCII (A-Z, 0-9), supported by International Domain Names (IDNs) system.
For example, the Chinese domain "短.co" is represented in Punycode as "xn--s7y.co".
According to Zheng, the vulnerability relies on the fact that web browsers render only Punycode URLs in one language as Unicode (like only Chinese or only Japanese), but they fail if a domain name contains characters from multiple languages.
This loophole allowed the researcher to register a domain name xn--80ak6aa92e.com and bypass protection, which appears as “apple.com” by all vulnerable web browsers, including Chrome, Firefox, and Opera, though Internet Explorer, Microsoft Edge, Apple Safari, Brave, and Vivaldi are not vulnerable.
Here, xn-- prefix is known as an ‘ASCII compatible encoding’ prefix, which indicates web browser that the domain uses ‘punycode’ encoding to represent Unicode characters, and Because Zheng uses the Cyrillic "а" (U+0430) rather than the ASCII "a" (U+0041), the defence approach implemented by web browser fails.
Zheng has reported this issue to the affected browser vendors, including Google and Mozilla in January.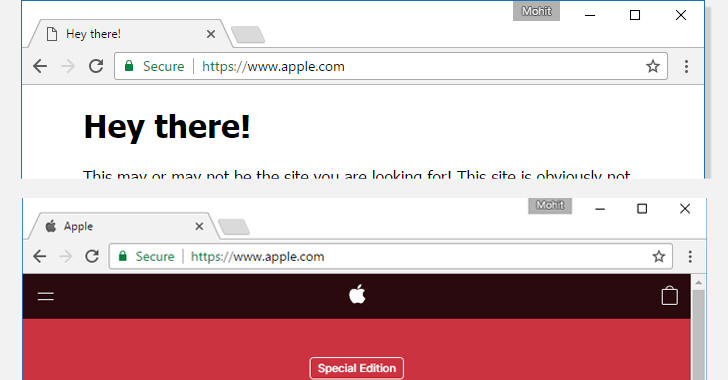
Fake Page (top) and Original Apple.com (bottom), but exactly same URL
While Mozilla is currently still discussing a fix, Google has already patched the vulnerability in its experimental Chrome Canary 59 and will come up with a permanent fix with the release of Chrome Stable 58, set to be launched later this month.
Meanwhile, millions of Internet users who are at risk of this sophisticated hard-to-detect phishing attack are recommended to disable Punycode support in their web browsers in order to temporarily mitigate this attack and identify such phishing domains.
Mitigation For Firefox Users (Not FIX For Chrome)
Firefox uses can follow below-mentioned steps to manually apply temporarily mitigation:
Type about:config in address bar and press enter.
Type Punycode in the search bar.
Browser settings will show parameter titled: network.IDN_show_punycode, double-click or right-click and select Toggle to change the value from false to true.
Unfortunately, there is no similar setting available in Chrome or Opera to disable Punycode URL conversions manually, so Chrome users have to wait for next few weeks to get patched Stable 58 release.
Internet users are always advised to manually type website URLs in the address bar for important sites like Gmail, Facebook, Twitter, Yahoo or banking websites, instead of clicking any link mentioned on some website or email, to prevent against such undetectable attacks.
Phishing campaigns target airline consumers seeking business credentials
3.4.2017 securityaffairs Phishing
A series of phishing campaigns is targeting airline consumers with messages crafted to trick victims into handing over personal or business credentials.
A wave string of phishing campaigns is targeting airline consumers with messages crafted to trick victims into handing over personal or business credentials.
The phishing messages pretend to be sent from a travel agency or a someone inside the target firm, they include a weaponized document or embed a malicious link.
“Over the past several weeks, we have seen a combination of attack techniques. One, where an attacker impersonates a travel agency or someone inside a company. Recipients are told an email contains an airline ticket or e-ticket,” explained Asaf Cidon, vice president, content security services at Barracuda Networks. 
According to Barracuda Networks, aviation-themed phishing attacks contain links to spoofed airline sites, threat actors personalize the phishing page in a way to trick victims into providing business information.
The attackers show a deep knowledge of the targets, hackers are targeting logistic, manufacturing and shipping industries.
“It’s clear there is some degree of advanced reconnaissance that takes place before targeting individuals within these companies,” Cidon added.
Recently the U.S. Computer Emergency Readiness Team issued an alert of phishing campaigns targeting airline consumers.
“US-CERT has received reports of email-based phishing campaigns targeting airline consumers. Systems infected through phishing campaigns act as an entry point for attackers to gain access to sensitive business or personal information.” reads the US-CERT warning.
“US-CERT encourages users and administrators to review an airline Security Advisory(link is external) and US-CERT’s Security Tip ST04-014 for more information on phishing attacks.”
The US-CERT specifically references the security advisory published by Delta Air Lines that warned its consumers of fraudulent activities.
“Delta has received reports of attempts by parties not affiliated with us to fraudulently gather customer information in a number of ways including: fraudulent emails, social media sites, postcards, Gift Card promotional websites claiming to be from Delta Air Lines and letters or prize notifications promising free travel,” states the Delta Air Lines warning.
Barracuda confirmed that these campaigns have a high success rate:
“Our analysis shows that for the airline phishing attack, attackers are successful over 90 percent of the time in getting employees to open airline impersonation emails,” concluded Cidon. “This is one of the highest success rates for phishing attacks.”
Spear phishing campaign targeted Saudi Arabia Government organizations
25.3.2017 Securityaffairs Phishing
Security researchers at MalwareBytes have uncovered a spearphishing campaign that targeted Saudi Arabia Government organizations.
Security experts at MalwareBytes have spotted a new spear phishing campaign that is targeting Saudi Arabia governmental organizations.
According to the experts, the campaign already targeted about a dozen Saudi agencies. Attackers used weaponized Word document and tricked victims into opening them and enabling macros.

The document is in Arabic language, if the victim opens it up, it will be infected and the phishing document is sent to their contact via Outlook inbox.
The malicious payload is embedded in the macro as Base64 code and leverages the certutil application for decoding into a PE file that is finally executed.
The binary dropped on the infected machine is coded in .NET and its code is encrypted but not obfuscated. The malware was designed to steal information from the victims and upload it to a remote server.
“Decrypting it we can see the main payload (neuro_client.exe renamed to Firefox-x86-ui.exe here) and two helper DLLs” reads the analysis published by MalwareBytes.

The malicious code gains persistence via the Task Scheduler.
MalwareBytes is still monitoring the campaign and plans to provide further information in the future.
I suggest reading the analysis that also includes the IoCs.
Phishing Trends Report – 2016 ended as the worst year for phishing in history
2.3.2017 securityaffairs Phishing
The Anti-Phishing Working Group (APWG) published the Phishing Trends Report for Q4 2016. APWG reported 1.2 million phishing attacks in 2016.
The Anti-Phishing Working Group (APWG) published the Phishing Trends Report for Q4 2016. The data are worrisome, 2016 ended as the worst year for phishing in history. The experts reported the total number of phishing attacks in 2016 was 1,220,523, a 65 percent increase over 2015.
The analysis of data across the years could give us precious information about the evolution of phishing activities.
In little more than a decade, the number of phishing attacks per month observed in Q4 is passed from 1,609 in 2004, up to 92,564 phishing attacks per month in 2016 (+5,753 percent).
The most targeted industry sectors in the fourth quarter of 2016 are the Retail and Financial services.

The Phishing Trends Report for Q4 2016 includes data provided by the company Axur that is located in Brazil. Axur focused on monitoring phishing attacks on financial organizations, technology firms, airlines, and online marketplaces located in the country.
“Fraudsters in Brazil are using both traditional phishing and social media to defraud Internet users. They are also using technical tricks to make it harder for responders to stop theses scams. ” states the APWG.
According to the APWG, the overall number of brands targeted by phishers during the holiday season dropped in a significant way, likely because crooks concentrated on fewer targets.
The company RiskIQ that monitored thousands of phishing attack revealed that the top-10 TLDs where phishing attacks occurred in 4Q2016 were:

The report shows that very few phishers registered domain names that were confusingly similar to the legitimate brands. The crooks mostly used URL with brand names, or misspellings thereof, in subdomains.
“A relatively low percentage of phishing websites targeting a brand attempt to spoof that brand in the domain name—whether at the second-level or in the fully-qualified domain name,” says Jonathan Matkowsky, VP for intellectual property & brand security at RiskIQ. This is evidence that phishers do not need to use deceptive domains names to fool Internet users into visiting their sites. Instead, users are often fooled by hyperlinks (which must be hovered over to even see the destination domain), URL shorteners, which mask the destination domain, or brand names inserted elsewhere in the URL.
Let’s close with a look at the country most plagued by malware, China it the top with 47.09% of infected machines, followed by Turkey (42.88%) and Taiwan (38.98%).
Corporate email addresses are 6.2x more targeted by phishing
21.2.2017 securityaffairs Phishing
At the RSA security conference in San Francisco, the experts at Google Research explained that Corporate email addresses are privileged targets for hackers.
At the RSA security conference in San Francisco, the experts at the Google Research team at the Google Research team have shared the results of an interesting study on cyber attacks against emails accounts.
Corporate email addresses are 4.3 more likely to receive malicious codes compared to personal accounts, 6.2 times more likely to receive phishing lures, and 0.4 times less likely to receive spam messages.

The Google Research team analyzing more than one billion emails that passed through its Gmail service, the experts discovered that corporate inboxes are a privileged target for threat actors. The result is not surprising because corporate email accounts contain more valuable information for attackers. Cyber criminals can steal information and resell them on the Dark Web, meanwhile, nation-state actors could use them for espionage activities.
Which is the most targeted industry?
This result is very interesting, organizations in the real estate sector were the most targeted with malicious codes, while spam emails proposing products and services mostly targeted companies in entertainment and IT industries.

Organizations in the financial sector are the privileged target of phishing campaigns, the experts at Google believe that phishing attacks will continue to increase in the future.
Anyway, there is a good news for Gmail.users, as announced by Elie Bursztein, the head of Google’s anti-abuse research team, the company is going to implement the SMTP Strict Transport Security to the email service.
The SMTP STS will provide a further security measure to protect Gmail users from man-in-the-middle attacks that leverage on rogue certificates. Google, Microsoft,
“Google, Microsoft, Yahoo and Comcast are expected to adopt the standard this year, a draft of which was submitted to the IETF in March 2016.” wrote ThreatPost.
Amnesty Warns of Phishing Attacks on Qatar Activists
15.2.2017 securityweek Phishing
Human rights watchdog Amnesty International has uncovered a sophisticated phishing campaign targeting journalists, activists and other entities in Nepal and Qatar interested in migrants' rights.
The campaign, dubbed Operation Kingphish, involves an online persona named “Safeena Malik” – Malik can mean “king” in Arabic. Amnesty International learned that Safeena Malik had contacted several individuals via email and social media over the course of 2016.
Safeena Malik, who claimed to be an activist interested in human rights, had accounts on several social media websites, including Twitter, Facebook and LinkedIn. “She” reached out to dozens of people, many involved in the issue of migrants’ rights in Qatar.
Qatar has attracted the attention of several human and labor rights organizations for its exploitation of migrant workers, many of which are from Nepal. Some of the documented cases are related to the construction of stadiums and infrastructure for the FIFA World Cup competition that will be hosted by Qatar in 2022.
According to Amnesty, many of the attacks launched using the fake Safeena Malik profiles attempted to lure targeted individuals to realistic Google phishing pages. In order to avoid raising suspicion, the phishing pages displayed the email address and profile picture of the targeted user, and a legitimate document was displayed once the password had been handed over to the attacker.
Documents on human trafficking and ISIS funding, and fake Google Hangouts invitations were used to lure targeted users to the phishing pages. Safeena Malik also sent out private messages on Facebook to obtain the Gmail addresses of the targets.
The persona had hundreds of connections on social media and often joined groups focusing on migrant workers and forced labor in an effort to identify potential targets and make it appear as if “she” was part of the community.
Amnesty identified 30 different targets by analyzing the profile pictures hosted on the server used by the attacker to deliver the phishing pages, although the organization believes the actual number is much higher.
“Most identified targets were activists, journalists, and labour union members. While some of targets had published critical opinions about Qatar’s international affairs, the majority of identified targets were affiliated with organisations supporting migrant workers in Qatar,” said activist and security researcher Claudio Guarnieri. “Interestingly, a significant number of them are from Nepal, which is one of the largest nationalities amongst migrant workers in Qatar, and a country that has featured prominently in the migrant worker narrative on Qatar.”
While experts could not find too much evidence, they believe the attacks were likely carried out by a state-sponsored actor. One of the IP addresses used to access some of the compromised email accounts had been associated with an ISP headquartered in Doha, Qatar.
However, when contacted by Amnesty, the government of Qatar denied any involvement and expressed interest in stopping the attacks. Experts pointed out that the operation could be the work of an actor that seeks to damage Qatar’s reputation.
This is not the only social engineering campaign targeting human and labor rights organizations focusing on the situation in Qatar. In December, Amnesty International published a report detailing a fake human rights organization named Voiceless Victims. It is unclear if the two campaigns are directly connected.
PayPal Phishing Attack Immediately Verifies Credentials
3.2.2017 securityweek Phishing
A newly observed phishing campaign targeting PayPal users employs checks to immediately verify whether the entered login credentials are legitimate or not, Proofpoint reveals.
Using email as the distribution method, attackers lured users to a well-crafted phishing page that appeared to be a legitimate PayPal login page, but was actually the first step in an elaborate scheme meant to trick users into revealing their banking and personal information. (The attack is different from a separate sophisticated phishing campaign targeting PayPal users detailed earlier this week.)
The phishing page, researchers say, returns a “vaguely worded error message” if the wrong credentials are entered, something that doesn’t usually happen with phishing landing pages, as they tend to accept any credentials that users enter. The newly observed page, however, verifies the entered credentials with PayPal before moving forth with the scheme.
To perform the check, the crooks were using a decommissioned service in PayPal, meant to allow one to purchase a gift card from a user. “If the queried email account does not exist, the login supplied to the phishing landing page is discarded, helping to ensure that the phisher gets a higher percentage of valid credentials. The code does not check the password, only that the email account exists on PayPal,” Proofpoint researchers note.
Usually, scammers verify the stolen credentials after they managed to acquire a larger number of potential logins, but the new approach eliminates the need to perform the validation at a later date. On top of that, researchers say, this specific approach can fool automated analysis tools.
Once a valid PayPal email address is used, the victim is presented with a reassuring welcome page, followed by a phishing page on which users are required to confirm the credit card information they have associated with their PayPal account. Because the phishing kit comes with support for multiple languages, it can appear legitimate to users in many locations.
The phishing kit was also designed to check the credit card number that the victim supplies, making sure it passes the Luhn algorithm, as well as to perform a lookup against the card number to retrieve additional information. After validating the credit card, the kit asks the victim to enter security information about their card.
Users are also asked to link their bank accounts to their PayPal account, and are offered a number of well-known retail banks to choose from. Stolen bank branding gives the phishing page a legitimate look. Next, the user is asked to enter login credentials for their bank, claiming that the information is not saved, which is, of course, fraud.
“The user is then prompted for routing information for the bank account. Finally, the phishing kit prompts the user for identity information such as a driver's license number or other identifying document that can be uploaded directly to the phishing kit. If the victim clicks the ‘Don't have your ID now?’ button, they simply skip this screen,” Proofpoint said.
After attempting to gather all of the aforementioned personal and financial information from the victims, the phishing kit then redirects them to the legitimate PayPal website. According to Proofpoint, in addition to using inventive phishing pages, the scheme uses an administrative backend similar to what remote access Trojans (RATs) usually employ.
Through this panel, attackers can view visitor information, the option to access stolen credentials, and a simple interface for the administrator to modify settings. There is even the option to enable a “selfie page” where Flash is used to interact with the victim's webcam, most probably to allow the phisher to snap a photo of the victim for later use. The admin panel even features a page for Trojans, but the feature appears to be under development.
“As attackers continue to turn away from the use of exploits and other means of compromising victim PCs and stealing information via malware, they are developing increasingly sophisticated means of collecting credentials and other data directly through phishing schemes. The use of phishing kits like the one detailed here provides threat actors with ready access to turnkey templates and administrative backends that make harvesting data from unsuspecting victims all too easy,” Proofpoint says.
The phishing kit also illustrates the advanced state of “crimeware as a service” and how straightforward conducting phishing scams can be. The existence of an admin panel with the aforementioned options is quite rare among credential phishing kits at the moment, but similar panels were previously associated with APT activities. However, this type of admin panel is expected to become more common and, understandably, popular with phishing actors, Proofpoint concludes.
PayPal Users Targeted in Sophisticated Phishing Attack
1.2.2017 securityweek Phishing
A recently observed phishing campaign is targeting PayPal users with fake pages that are well designed and difficult to distinguish from the real ones, ESET researchers warn.
The attack was observed only a couple of weeks after Gmail users were targeted in a phishing campaign that used legitimate-looking URLs capable of tricking even tech-savvy people. The attackers were even able to bypass two-factor authentication protection by accessing the compromised email accounts immediately.
The attack against PayPal users, ESET reveals, uses a very convincing bait as well, with fake websites and email messages meant to trick users into revealing their login credentials and other personal information.
The phishing emails include logos and wording that seems legitimate, yet users paying attention can immediately spot grammar and syntax errors that suggest the author isn’t a native English speaker, which is a clue that something is not right.
The email urges the user to log into their account and includes what looks like a “Log In” button, which in fact takes the victims to a landing page that presents them with a fake login screen. Because it uses an SSL certificate, the page attempts to fool users into believing it is authentic.
The domain, however, has nothing to do with PayPal sites, and are clearly scam URLs. After the user enters their information, another message with fake information is presented to them, asking for more personal details. Thus, the security researchers suggest that the attackers aren’t looking only for the victims’ money, but also after their identities.
To give a sense of urgency, the page claims that the user won’t be able to access the PayPal account until the requested information is provided. The page, however, contains more clues that something isn’t right, as it even asks for the user’s Social Security Number, which applies to US citizens only, but also asks which country the victim is from.
“If you’re concerned about PayPal security, you should log directly into PayPal.com itself and update your security settings, and if you know someone who has fallen victim, the first step should be to change their PayPal password before more damage occurs,” ESET notes.
Users should keep in mind that attackers spend a lot of time and effort to make their phishing pages look exactly like those of real vendors. Users of well-known online services such as Gmail, PayPal, and many more are more likely to be targeted in such attacks.
To stay protected, users should avoid opening attachments or clicking on links included in unsolicited emails. When an alert appears while browsing the Internet, users should immediately check the URL in the address bar, to make sure they are on the expected website (it should be http://www․paypal․com/ or https://www․paypal․com/ when PayPal is involved).
“Since phishing becomes more of a problem when the same password is utilized across multiple sites and services, consider deploying two-factor authentication (2FA). By requiring a one-time password generated by a user’s smartphone as a second form of authentication, 2FA helps block unauthorized access,” ESET also notes.
A sophisticated spear phishing campaign is targeting NATO Governments
30.1.2017 securityaffeirs Phishing
Researchers from Cisco’s Talos security intelligence and research group.discovered a sophisticated spear phishing campaign on NATO Governments.
Security experts at Cisco Talos are warning of a new sophisticated espionage campaign targeting NATO Governments with specially designed documents used to deliver Flash exploits. The campaign started during the Christmas and New Year holidays, the hackers used Word document titled “Statement by the NATO Secretary General following a meeting of the NATO-Russia Council” as bait.
The attacks aim to perform reconnaissance activity on infected systems and avoid sandboxes. The researchers dubbed the framework “Matryoshka Doll Reconnaissance Framework” due to its complexity.
NATO Matryoshka Doll Reconnaissance Framework attack
The content of the document has been copied from an official NATO statement published on its website and the RTF file does not contain any exploits, both circumstances make hard for the victims to detect the attack.
The malicious document contains a succession of embedded objects, including OLE and Adobe Flash objects, that are extracted in a specific order.
“The OLE object contains an Adobe Flash object. The purpose of the Adobe Flash is to extract a binary blob embedded in itself via ActionScript execution,” reads a blog post . “This blob is a second encoded and compressed Adobe Flash object. The encoded algorithm is based on XOR and zlib compression. This is the second Adobe Flash in the final payload located within the document.”
The analysis of the payload revealed its most relevant component is located in the ActionScript. The first action of the ActionScript is to contact a specific URL of the C&C.
In this way, the attacker gathers information about the target, including the OS version or the Adobe Flash version that are used to evaluate if attack the machine or not.
The collected data can allow the attacker to determine if the infected system is a sandbox or a virtual machine and stop the operations.
At this point, the malicious code performs two additional nested requests that use data obtained from the response to the previous request.
In the final phase of the attack, a Flash exploit is fetched, decoded and executed.
Talos observed a significant traffic on the C&C domain starting with January 16, it was mainly composed of requests coming from the security research community.
The attacker noticed the source of the request and decided to replace the malicious payload with junk data in order to interfere with an investigation conducted by the principal security firms.
“It’s important to note that the actor realized security researchers were poking around their infrastructure and then rigged the infrastructure to create resource issues for some security devices. These are the characteristics of reasonably advanced attackers who have designed an efficient minimalist framework that was able to adapt purposes on the fly.” states the analysis.
Insidious phishing attack leverages on fake attachments to steal Gmail credentials
16.1.2017 securityaffairs Phishing
Cybercriminals are adopting specially crafted URLs to trick users into entering their Gmail credentials in a new sophisticated phishing campaign.
Security experts discovered a new effective Gmail phishing attack that is able to deceive also tech-savvy people. Crooks leverage on specially crafted URLs to trick victims into providing their Gmail credentials on a phishing page.
The malicious messages are sent from one of the victim’s contacts and pretend to carry a PDF document that can be previewed directly from Gmail. When the victim clicks on the “attachment” image included in the body of the message it is redirected to a Gmail phishing page.
The URL to which the images of attachments point is crafted to appear legitimate:
“data:text/html,https://accounts/google.com,”
The web browser does not display any certificate warning, experts noticed that the apparently legitimate part of the URL is followed by white spaces, which prevent the victims from seeing suspicious strings and an obfuscated script that opens a Gmail phishing page in a new tab. A technical description of the Chrome/Gmail attack has been published on Github.

“You click on the image, expecting Gmail to give you a preview of the attachment. Instead, a new tab opens up and you are prompted by Gmail to sign in again. You glance at the location bar and you see accounts.google.com in there. It looks like this….” states a blog post published by WordFence. “Once you complete sign-in, your account has been compromised.”
This technique is not new, several victims reported similar attacks in July.
One of the main characteristics of the attacks that have been recently detected by the experts is that crooks immediately accessed the compromised accounts and used them to send out phishing emails to all the victim’s contacts. It is still unclear if the attackers have found a way to automate the process.
View image on Twitter
View image on Twitter
Follow
Tom Scott ✔ @tomscott
This is the closest I've ever come to falling for a Gmail phishing attack. If it hadn't been for my high-DPI screen making the image fuzzy…
12:54 PM - 23 Dec 2016
6,132 6,132 Retweets 5,310 5,310 likes
As usual, let me suggest to enable two-factor authentication (2FA) on Gmail in order to avoid being victims of this powerful phishing scheme. However, if the cyber criminals immediately access the compromised account they could also include in a phishing page the 2FA code.
“2FA would make it harder to exploit, but phishing attacks are getting fancier. They capture the 2FA code you enter and immediately start a session elsewhere with your password and 2FA. Hardware 2FA, a security key, (such as a Yubikey) is the only likely way to prevent phishing (excluding targets of state actors)” wrote a user in a discussion on Hacker News.
Google has been aware of this new phishing tactic at least March 2016, for this reason, the Chrome security team suggested introducing a “Not Secure” tag in the address bar for data:, blob: and other URLs that may be exploited by phishers in hacking campaigns.
Phishing campaign on Office 365 Business users leverages Punycode
15.12.2016 securityaffairs Phishing
Security researchers discovered a new phishing campaign leveraging Punycode and a bug in Office 365 defense systems to deceive victims.
Office 365 business email users continue to be the target of phishing campaigns, a new wave of attacks was leveraging Punycode to avoid detection of Microsoft’s default security and desktop email filters.
Punycode is a method added to the Domain Name System (DNS) in order to support non-ASCII characters within a web URL.
Security researchers from Avanan security warn of a new phishing campaign that aims to steal Office 365 credentials and abuses a vulnerability in how Office 365 anti-phishing and URL-reputation security layers deal with Punycode.
Office 365 is even popular as corporate email solution, for this reason, hackers are increasing their interest on it.
“Avanan’s cloud security researchers uncovered a new attack method against Office 365 business email that goes undetected by Microsoft’s Office 365 default security and bypasses desktop email filters.” states a blog post published by Avanan.”The attack includes a phishing scheme to steal Office 365 credentials, and leverages what appears to be a vulnerability in how Office 365 anti-phishing and URL-reputation security layers translate Punycode”
Punycode was already exploited in past attacks in order to trick victims into clicking links that looked legitimate, in this last attack it was designed to bypass the Office 365 anti-phishing filters and email phishing protection systems instead.
The researchers explained that this specific attack is possible due to a gap in the Office 365 phishing filters.
“What makes this attack different is that instead of fooling the user, it was designed to fool the anti-phishing filters found in Office 365 and other email phishing protection systems. Hackers have identified a gap in the Office 365 phishing filters and are starting to leverage it in order to compromise accounts.” continues the analysis.
The phishing campaign detected by Avanan leverages on fake FedEx emails that URLs that appear to be legitimate.
Leveraging on the vulnerability in the phish-detection engine, the URL actually resolves to two different domains, one followed by the malware protection filter and the second one followed by the browser when the user clicks on it.
The legitimate and safe URL is the one followed by protection systems implemented in Office 365, while the malicious one is followed by the browser redirecting the victims to a bogus domain.
“What makes this attack nefarious is that by using Punycode and a flaw in the phish-detection engine, the URL actually goes to TWO different sites, one followed by the malware protection filter and the other followed by the end-user’s browser when he or she clicks on it.” states the analysis.
The experts discovered that Office 365’s default security systems check domain reputation by analyzing it as plain ASCII.
The rapid diffusion of the Office 365 solution in the business environments will continues attract cyber criminal syndicates.
Scammers advertise backdoored phishing templates on YouTube
27.11.2016 securityaffairs Phishing
Security experts from Proofpoint firm observed scammers exploiting YouTube to promote their backdoored phishing templates.
According to experts from the security firm Proofpoint, scammers are advertising on YouTube backdoored phishing templates offering also “how-to” videos and manuals.
It is not a novelty, cyber criminals are switching on legitimate websites to propose their products and services.
Proofpoint researchers have observed scammers distributing phishing templates and related kits via YouTube, a query for “paypal scama” returns over 114,000 results.
The kits offered for sale through YouTube include a backdoor that automatically sends the phished information back to the author.
“A simple search for “paypal scama” returns over 114,000 results. There’s a catch, though, for criminals downloading the software: a backdoor sends the phished information back to the author. While backdoors on these templates aren’t new, the use of YouTube to advertise and distribute them is a new trend.” reads a blog post published by Proofpoint.
The videos show the appearance of the templated and provide instruct to the potential buyers on how to steal information from the victims with phishing attacks.
The post shows as an example of these malicious kits, an Amazon phishing template that replicates the legitimate login page of the popular website.
The researchers downloaded one of the kits advertised on YouTube and analyzed it discovering that the clumsy scammer left his Gmail address hardcoded in the template alongside with an email address used to receive the stolen credentials from the template.

The researchers also analyzed a template for PayPal scammers that was improved to avoid suspicion.
“In this PayPal scam, the author attempts to avoid raising suspicions by adding a PHP include for a file called style.js just before the PHP “mail” command is used to ship off the stolen credentials.” reads the analysis.
The researchers noticed that many videos have been posted for months, a circumstance that suggests the lack of filtering mechanisms implemented by YouTube.
“Many of the video samples we found on YouTube have been posted for months, suggesting that YouTube does not have an automated mechanism for detection and removal of these types of videos and links. They remain a free, easy-to-use method for the authors of phishing kits and templates to advertise, demonstrate, and distribute their software,” states Proofpoint.
Security expert presented a PhishLulz tool for professional phishing pen test
21.11.2016 securityaffairs Phishing
The security expert Michele Orru from FortConsult has released an automated phishing toolkit dubbed ‘PhishLulz’ for penetration testing activities.
The security expert Michele Orru from FortConsult, aka @antisnatchor, has released an automated phishing toolkit dubbed ‘PhishLulz’ for penetration testing activities. The PhishLulz tool was presented at the Kiwicon hacking event held Wellington New Zealand last week.
PhishLulz is a tool written in Ruby, it leverages Amazon EC2 cloud instances for its phishing campaigns. The toolkit provides a GUI from the PhishingFrenzy kit and combines it with the Browser Exploitation Framework Project (BeEF).
The tool also includes a self-signed certificate authority and new phishing templates that could be used by penetration testers fro their analysis, Orry also announced as a future improvement the automatic domain registration capability that in the current version is limited to registrar NameCheap.
The toolkit allows an attacker to easily compose efficient phishing campaigns, it is quite easy to compose malicious messages that appear as legitimate. The tools will promptly alert the attacker when a victim takes the bait. The BeEF allows the PhishLulz is also able to and send exploits and gather user target configuration information such as the operating system, browser versions, and running applications.
The tool includes MailBoxBug and also works with Office365 accounts to send out phishing messages.
Orru presented the results of the tests conducted an unnamed Australian Government agency, PhishLulz has deceived 40 percent of its staff who revealed corporate VPN credentials.
“I was in Poland, and they were in Australia, so I had to send the emails at the right time,” Orru told the hacking conference.
“With five minutes to run the PhishLulz VM, five minutes to start modify the template and upload the certificates you need, you’re ready to go.”
Orru provided interesting insights on phishing campaigns, for example, attackers will have an hour to exploit the dozen or so logins they receive before the victims will notice the attack and revoke them.
Another info shared by the expert during the presentation is related to the best times to launch phishing campaigns, the emails sent in the morning or just after the lunch have a greater likelihood to trick victims into providing sensitive data.
The experts highlighted that employees often fail to distinguish dots from dashes in the URLs.