
Phishing Articles - H 2020 1 2 3 4 5 6 7 8 Phishing List - H 2021 2020 2019 2018 1 Phishing blog Phishing blog
Phish For The Future – spear-phishing attacks target Internet Freedom Activists
1.10.2017 securityaffairs Phishing
EFF published the report on “Phish For The Future,” an advanced persistent spearphishing campaign targeting Freedom Activists.
The Electronic Frontier Foundation (EFF) confirmed that a sophisticated spear-phishing campaign targeted the employees of Internet freedom NGOs “Free Press” and “Fight for the Future”
The EFF revealed that it is aware at least 70 attempts to steal the credentials of net neutrality activists between July 7 and August 8.
Hackers attempted to gather credentials associated with online services, including Google, Dropbox, and LinkedIn, and at least in one case, they succeeded.
The hackers compromised an account and used to launch spear-phishing attacks against other targets.
According to the experts, the campaign was managed by a single threat actor, they pointed out that attackers did not use malware to targets victims.
“This report describes “Phish For The Future,” an advanced persistent spearphishing campaign targeting digital civil liberties activists at Free Press and Fight For the Future. Between July 7th and August 8th of 2017 we observed almost 70 spearphishing attempts against employees of internet freedom NGOs Fight for the Future and Free Press, all coming from the same attackers.” reads the report published by EFF.
The attackers used various social engineering technique to trick victims into providing their credentials.
In some cases, attackers used fake LinkedIn notification messages containing links to Gmail phishing sites.

“Another attack pretended to be from a target’s husband, sharing family photos; the email was forged to include the husband’s name. ” continues the report.
In another attempt, the attackers sent messages related to a YouTube aggressive and hateful comment for a real YouTube video that the target had uploaded.
Who is behind the attack?
The EFF only pointed out that the threat actor appears to be working from an office, with Saturday and Sunday off, during working hours associated with the UTC+3 – UTC+5:30 timezones. This circumstance suggests that attackers may be located in Eastern Europe, Russia, part of the Middle East, or India, but Saturday and Sunday are not weekend days in many Middle Eastern countries.
Unfortunately, the IP from which the one compromised account was accessed did not provide any clues as it was associated with a VPN service.
“The sophistication of the targeting, the accuracy of the credential phishing pages, the working hours, and the persistent nature of the attacks seem to indicate that the attackers are professionals and had a budget for this campaign,” continues the analysis.
Cyber criminals or state-sponsored hackers?
Researchers with the EFF don’t believe the spear-phishing campaign against Freedom Activists has been carried out by a nation-state actor.
“Although this phishing campaign does not appear to have been carried out by a nation-state actor and does not involve malware, it serves as an important reminder that civil society is under attack. It is important for all activists, including those working on digital civil liberties issues in the United States, to be aware that they may be targeted by persistent actors who are well-informed about their targets’ personal and professional connections,” the EFF said.
Sophisticated Phishing Attacks Target Internet Freedom Activists
28.9.2017 securityweek Phishing
The Electronic Frontier Foundation (EFF) revealed on Wednesday that employees of Internet freedom NGOs “Free Press” and “Fight for the Future” have been targeted in sophisticated spear-phishing attacks.
The EFF is aware of nearly 70 attempts to steal the credentials of net neutrality activists between July 7 and August 8. The attacks, believed to be the work of a single entity, were designed to steal credentials associated with Google, Dropbox, LinkedIn and other online services.
At least one account was hijacked and abused to send out more phishing emails to other individuals within the victim organization. The EFF said the attacks did not involve any malware and it’s unclear what the attackers had hoped to accomplish once they obtained account credentials.
The attackers used various tricks to lure targeted individuals to their phishing pages. In some cases, they sent out fake LinkedIn notification messages that contained links to Gmail phishing sites. Other messages showed that the attackers had studied their targets – Fight For The Future Campaign Director Evan Greer was targeted via an email asking about her music, and another employee received malicious emails purporting to be from her husband.
The hackers also sent emails that appeared to notify a user of comments to their YouTube video, ones with clickbait headlines referencing net neutrality and tabloid topics, and fake subscriptions to adult websites.
The EFF has not attributed these attacks to a specific actor or country, but the organization did point out that the individuals behind the attacks appear to be working from an office, with Saturday and Sunday off, during working hours associated with the UTC+3 - UTC+5:30 timezones.
These timezones cover countries and regions such as Eastern Europe, Russia, part of the Middle East, and India. However, it’s worth noting that Saturday and Sunday are not weekend days in many Middle Eastern countries. The IP from which the one compromised account was accessed did not provide any clues as it was associated with a VPN service.
“The sophistication of the targeting, the accuracy of the credential phishing pages, the working hours, and the persistent nature of the attacks seem to indicate that the attackers are professionals and had a budget for this campaign,” the EFF’s Eva Galperin and Cooper Quintin said in a blog post.
However, the EFF does not believe the campaign has been carried out by a nation-state actor.
“Although this phishing campaign does not appear to have been carried out by a nation-state actor and does not involve malware, it serves as an important reminder that civil society is under attack. It is important for all activists, including those working on digital civil liberties issues in the United States, to be aware that they may be targeted by persistent actors who are well-informed about their targets’ personal and professional connections,” the EFF said.
1.4 Million Phishing Sites Are Created Monthly: Report
23.9.2017 securityweek Phishing
According to a new report, an average of 1.385 million unique new phishing sites are created every month, peaking at 2.3 million in May 2017. The majority of these are online and active for an average of just 4 to 8 hours. This combination of volume and brevity makes it effectively impossible to counter phishing -- especially targeted spear-phishing and whaling -- with block lists. By the time the site is included on a block list, the damage is done and the phishing site is no longer used.
Webroot's latest Quarterly Threat Trends (PDF) report chronicles the increasing sophistication and danger in targeted spear-phishing. According to the Verizon 2017 Data Breaches Investigation Report (DBIR), phishing was found in 90% of security breaches and incidents. And according to the FBI, phishing scams have cost American businesses almost $500 million per year over the last three years.
Phishing emails are becoming more sophisticated. Mass phishing campaigns are being replaced by targeted and tailored campaigns. "Phishing emails see increased impact by using social media to tailor their attacks to the individual target -- sometimes even senior executives -- with messages that are likely to resonate with the individual."
Phishing revolves around social engineering -- which has always appealed to mankind's basic emotions: greed (something for nothing); compassion (over recent natural disasters); fear (respond to this or something dire will happen); and anxiety/panic (instils the need to respond urgently). According to Webroot, the two emotions most frequently used in current phishing emails are fear and panic.
"Typical subjects may imply that there has been unusual activity on an account, a recent purchase must be verified, an account is in danger of being closed, or urgent invoices or tax bills are waiting," warns Webroot. "Often, terms such as 'error', 'warning', 'account closed', 'Microsoft-toll-free', and 'official alert' are included in the subject line."
While the quality of the emails has improved with fewer tell-tale typographical and grammatical errors, so too has the design and implementation of the phishing pages. Webroot provides two example mimicking Microsoft and PayPal. The Microsoft example includes a realistic Windows page combined with the message that the target should telephone support (rather than enter credentials online).
The PayPal example accurately mimics the PayPal login page. The login field tags, however, have been replaced by graphics. This makes it hard for traditional anti-phishing techniques to detect the fraud since web crawlers cannot 'read' the graphics.
Attackers try to fool their targets by using domains and URLs that appear to be related to legitimate and benign organizations. According to Webroot, the most used and abused names are Google, Chase, Dropbox, PayPal and Facebook.
The extent of this problem is verified by High-Tech Bridge's free Trademark Abuse Radar service. This uses its own AI engine to help check how a legitimate domain can be, or is being, abused on the internet. Checking the domains highlighted by Webroot, we find from High-Tech Bridge that 1,426 Google-related websites currently seem to be used to conduct phishing attacks. Chase has 347 websites similarly used, while Dropbox has 3,579; PayPal has 1,162, and Facebook has 3,282.
The report notes that phishing is no longer used simply to steal credentials, but is also increasingly being used to deliver malicious payloads. "Locky ransomware infected more than 400,000 victims in 2016,
and the WanaCrypt0r attack used a combination of phishing, ransomware, and a fast-moving worm to spread rapidly across hundreds of thousands of computers around the globe," says Webroot. "These extended capabilities have increasingly made phishing a vector for advanced threats: some 93% of all phishing emails now lead to ransomware."
Webroot's message is that phishing has become too sophisticated to be detected by traditional block list methods, but too dangerous to ignore. "Today's phishing attacks are incredibly sophisticated, with hackers obfuscating malicious URLs, using psychology, and information gleaned from reconnaissance to get you to click on a link," said Hal Lonas, CTO at Webroot. "Even savvy cybersecurity professionals can fall prey. Instead of blaming the victim, the industry needs to embrace a combination of user education and organizational protection with real-time intelligence to stay ahead of the ever-changing threat landscape."
Webroot's own solution is to employ machine-learning heuristics to provide a verdict on every visited web page within milliseconds of the user's request. "When speed and accuracy are everything, machine learning delivers highly accurate, real-time protection against phishing attacks, as well as contextual threat insights that drive strategic intelligence," says the report.
DMARC in Higher Education: A Formidable Defense Against Targeted Scams
12.9.2017 securityweek Phishing
DMARC Can Be Effective in Defending Against Targeted Phishing Attacks And Student Loan Scams
As the new academic year starts, so starts the "Fresher" phishing scam. Second year students are also targeted, but the new first year university intake is the most vulnerable. It has already begun in the UK where the year starts earlier than in the U.S. -- but will follow wherever there are new students who rely on loans.
ActionFraud, which recently issued a warning, is operated by the City of London Police, the lead agency for action against fraud in the UK. The phishing campaign has leveraged the Student Loan Company (SLC), which governs loans to students. The phishing email claims that there is a problem with the loan, and that new students should log into their account (on a phishing site) to update their information.
"Because tens of thousands of students will be starting university this month," warns John Wilson, field CTO at Agari, "cyber criminals can send out broad, untargeted phishing campaigns to huge databases and be confident they will reach a large number of victims."
Phishing Scams Target Universitities
But there is a solution to this type of phishing, where the scammer pretends to be a specific organization -- such as the SLC or a particular university. Those organizations should implement Domain-based Message Authentication, Reporting and Conformance (DMARC).
DMARC effectively whitelists the genuine emails from genuine domains, so that ISPs and receiving organizations (such as universities) can reject or block spoofed mails. "DMARC is an open source email authentication standard that will reject unauthorized messages using the domain, preventing them from ever being delivered," explains Wilson.
The UK government is a big supporter, and DMARC is used, for example, by the UK tax office (HMRC). Last year, Ian Levy, technical director of the National Cyber Security Centre (NCSC, part of GCHQ) said that all 5,700 domains used by the UK government will be adopting DMARC. Once this is achieved, he intends to apply pressure on industry in general to force them to do the same. "I'm going to point and laugh at everybody who doesn't do the same -- publicly," said Levy. "Because there is no excuse not to do DMARC on a high value domain anymore."
The NCSC did not respond to SecurityWeek's inquiry over whether it now recommends that SLC and UK universities should implement DMARC. SecurityWeek also asked SLC whether it uses DMARC to protect the students, and was told, "Due to the sensitivity of the topic we wouldn't comment on the range of tools and methods that we use to counter fraud."
However, when SecurityWeek spoke to the security industry, there was less reluctance to comment. Is the same issue a problem in America? Yes, says Dan Lohrmann, chief security officer at Security Mentor -- although he hasn't seen any elevated concern yet this year (he's more concerned with Hurricanes Harvey- and Irma-related phishing scams right now).
"The back-to-school timeframe is perfect for malicious actors, as students are headed back to the classroom with their latest devices and are expecting a number of emails to be hitting their inboxes from faculty and staff," comments Jordan Wright, senior R&D engineer at Duo Security. "This scenario is just as prevalent in the US as it is anywhere else, with bogus emails purporting to have a student's grades ready for viewing, the latest assignment(s) for completion, student loan changes or simply a call to update personal information for the university's system."
"We see this type of phishing attack every year," adds Lohrmann, "especially in the Fall in 'back-to-school' season. Going after new University students with financial scams has been happening for years, and specific loan-related phishing is an ongoing challenge."
DMARC Implementation
Asaf Cidon, VP of content security at Barracuda, agrees. "Phishing is a growing problem for educational institutions. We've seen a particularly sharp increase in Office 365 account compromise attacks -- where criminals attempt to steal login credentials and ultimately gain access to launch attacks from within an organization. One customer we spoke with recently had some 200 accounts hijacked -- including the Dean and multiple faculty, students, and staff."
Should universities and related organizations (such as SLC in the UK) implement DMARC?
"Universities should absolutely implement DMARC," Cidon adds. "Universities send a wide variety of messages, often from multiple departments, alumni, and third-parties. DMARC is a great tool to prevent domain spoofing, and also to ensure deliverability of legitimate mail (which is important for EDUs looking at planned giving, recruitment, and other activities)."
DMARC is, however, complex to implement. Martin Zinaich, information security officer for the City of Tampa, told SecurityWeek, "it goes a long way to reducing spoofed messages (which is usually how an account gets compromised in the first place). But," he added, "even dmarc.org recognizes that fully deploying this framework is not easy: 'Many senders have a complex email environment with many systems sending email, often including 3rd party service providers. Ensuring that every message can be authenticated using SPF or DKIM is a complex task, particularly given that these environments are in a perpetual state of flux.'"
Alan Levine, a security advisor to phishing specialist Wombat, adds, "DMARC does help in terms of domain authentication, but it is not close to a panacea. Any attacker with a particular target will register a 'like' domain, something close to and almost indiscernible from the targeted organization's domain. Then, DMARC won't help, because the domain will appear legit, even though the mission is malicious."
So, while the first step would be to implement DMARC, an important second step would be to seek control over potential look-alike domains that could be used as phishing sites. While this is in progress, users such as students will remain vulnerable. At this point, security awareness training is an important option.
"Universities should create internal awareness and education programs within their institution," says Wright. "Teaching users how to spot, report and prevent phishing attacks and emails can be a great way to reduce the risk of falling prey to such attacks. Universities can assist this by setting up dedicated web pages that flag ongoing phishing attacks for students and, whenever a phishing attack is detected as targeting their university, the IT Team can send out alerts for students."
But there is an important addendum to this. While this phishing scam is targeted against students, student loan organizations and universities, nobody and no organization is ignored by the scammers.
"Young and old alike," explains Tim Ayling, a fraud and risk intelligence director at RSA Security, "the public needs to have greater awareness of spoofing attacks and take better care to protect themselves online. Much of this comes down to basic security hygiene. Our advice would be: first and foremost, avoid clicking on links to websites from emails and any unknown sources. If in any doubt, search for the website using an engine -- particularly in cases like this where the email would've come from a random email alias, with a generic introduction that suggests it was sent to others. Secondly, the devil is in the detail. Always be sure to check the URL of a site that you are visiting to make sure that it is correct -- often spoofed sites have typos in their address that will give clues that it is not official. Lastly, check the address bar to ensure you are visiting a secure site and there are no warnings."
It's not just Freshers who get phished.
Researchers Devise Hopeful Defense Against Credential Spear Phishing Attacks
5.9.2017 securityweek Phishing
Security Researchers Have Proposed a New and Effective Way to Detect Credential Spearphishing Attacks in the Enterprise
A new research paper, 'Detecting Credential Spearphishing Attacks in Enterprise Settings', was awarded the Facebook Internet Defense Prize at the 26th USENIX Security Symposium in Vancouver, BC, August 16-18, 2017. The paper proposes and evaluates a methodology for effectively detecting credential spear phishing attacks in corporate networks while achieving a very low number of false positives.
The paper (PDF) was authored by Grant Ho, University of California, Berkeley; Aashish Sharma, Lawrence Berkeley National Laboratory; Mobin Javed, University of California, Berkeley and International Computer Science Institute; and Professor Vern Paxson, University of California, Berkeley, International Computer Science Institute.
The paper is important because it promises an effective mitigation for one of cybersecurity's most pernicious threats: credential spear phishing. While malicious attachment spearphishing has something that can be sought and detected by increasingly sophisticated security controls, credential spear phishing contains nothing but a link to an URL that probably has a good reputation.
Credential spear phishing is, furthermore, an issue that does not lend itself to a machine learning (ML) solution -- the difficulty is that there are too few known anomalies in any given dataset from which the algorithm can successfully learn. Since machine learning 'learns' from past behaviors, any previously unseen attacker is to some extent invisible to machine learning algorithms because there is no prior history from which to learn.
Using a dataset of 4 years of emails -- about 370 million -- supplied by the Lawrence Berkeley National Laboratory (LBNL), the researchers first analyzed the different stages of an attack, and then developed a new anomaly detection technique called DAS. The dataset used contained 19 known spearphishing campaigns.
"With such a small number of known spearphishing instances, standard machine learning approaches seem unlikely to succeed: the training set is too small and the class imbalance too extreme," notes the paper.
But by breaking down the taxonomy of credential spear phishing, the researchers demonstrate that enterprises can develop their own form of reputation monitoring from enterprise traffic monitoring. For example, a spearphishing email might seek to persuade a user to visit a particular URL.
The researchers suggest that the traditional reputation of an URL is not as important as how often, if ever, this user (or all users) have visited the same URL. Such information is usually already available from existing controls, such as network intrusion detection systems (NIDS). This basic approach of working with data that is generally -- certainly within an enterprise environment -- already available means that the cost of implementing DAS should not be overly expensive. "Our work draws on the SMTP logs, NIDS logs, and
LDAP logs from LBNL," point out the researchers.
The bane of all anomaly detection systems is the number of false positives. While anomaly detection systems -- especially those designed to detect malware -- are frequently analyzed by third-party testing organizations, there are few statistics specifically around the false positive rate (FPR) for spear phishing detection.
SecurityWeek asked Simon Edwards, director at independent testing organization SE Labs Ltd (and chairman of the board at the Anti Malware Testing Standards Organization) for his view. Although he had no relevant statistics, he has personal experience of the false positive problem in anomaly detection.
"Whereas you and I might expect a product to block an installation and alert the user," Edwards told SecurityWeek, "what I've found is that the legitimate software appears to install correctly but then crashes or otherwise fails at some point in the future."
He installed a new scanner on Windows 10. "Everything appeared to be fine until I tried to actually scan something. I received an error and no output. After a long time troubleshooting I eventually checked the logs of the next-gen product I had running on the same system. Lo and behold, a DLL had been quarantined. I marked it as clean, reinstalled and all was well again. Very annoying!"
This made him wonder what else had been quarantined. "The logs also showed all sorts of other legitimate components (rarely the full app) had been quarantined. Most of this was for the rubbish you see pre-installed on Lenovo laptops, so I'd not experienced any problems." The point, however, is clear: false positives are a major problem for machine learning detectors.
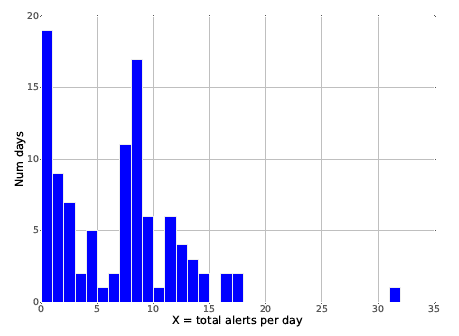
Credential Spear Phishing AttacksEvery one of the false positives needs to be triaged by the security team. One common statistic often quoted is an FPR of between 1% and 10%. The paper's researchers point out that this is not acceptable. "Although quite low, an FPR of even 1% is too high for practical enterprise settings; our dataset contains over 250,000 emails per day, so an FPR of 1% would lead to 2,500 alerts each day." If an average of 5 minutes were spent on these alerts, it would require more than 200 hours labor every day.
"In contrast," the paper claims, "our detector can detect real-world attacks, including those from a previously unseen attacker, with a budget of 10 alerts per day." While 10 alerts per day was the target, the achieved figure was a little different. From a random selection of 100 days, DAS returned figures ranging from 19 to zero alerts per day -- the median, however, was 7 alerts per day (well below the target of 10).
Of course, such figures are meaningless if the alerts are false positives, and real spearphishing attempts are missed. However, since the dataset used to develop and test the technique was historical data supplied by LBNL, the incidence of spearphishing was largely already known. The researchers' tests discovered all but one of the known spearphishing attacks in the dataset; but also uncovered two previously undiscovered spearphishing attacks against LBNL.
"Ultimately," conclude the researchers, "our detector's ability to identify both known and novel attacks, and the low volume and burden of alerts it imposes, suggests that our approach provides a practical path towards detecting credential spearphishing attacks."
DAS works. The only remaining question is whether this is simply theoretical research, or something that realistically can be implemented. One real-life implementation already exists. "Because of our approach's ability to detect a wide range of attacks, including previously undiscovered attacks, and its low false positive cost, LBNL has implemented and deployed a version of our detector."
One of the authors, Professor Vern Paxson, is also co-founder and chief scientist at Corelight (a network visibility company). "We're looking at DAS to see whether it can complement our existing products," he told SecurityWeek. "But," he added, "our research is free and publicly available, and we hope that other vendors will take it up."
US CERT is warning of potential Hurricane Harvey Phishing Scams
29.8.2017 securityaffairs Phishing
After the Hurricane Harvey hit Texas causing deaths and destructions, authorities are warning of potential Phishing Scams.
The US CERT is warning of Potential Hurricane Harvey phishing scams, the experts fear crooks may start using malicious emails purportedly tied to the storm.
“US-CERT warns users to remain vigilant for malicious cyber activity seeking to capitalize on interest in Hurricane Harvey. Users are advised to exercise caution in handling any email with subject line, attachments, or hyperlinks related to Hurricane Harvey, even if it appears to originate from a trusted source.” reads the advisory issued by the US CERT. “Fraudulent emails will often contain links or attachments that direct users to phishing or malware-infected websites. Emails requesting donations from duplicitous charitable organizations commonly appear after major natural disasters.”
US-CERT is advising users to remain vigilant when receiving unsolicited emails with attachments or links purporting to be related to the Hurricane Harvey that recently hit the Texas killing at least five people and injuring a dozen of people over the weekend.
US experts warn of phishing emails requesting donations from allegedly charity organizations, a tactic observed after other major disasters and incidents.
Typically these messages used malicious attachments or embed links to websites hosting exploits or to phishing pages.
A good practice to avoid scams is to contact the charity organizations by calling them directly.
US-CERT encourages users and administrators to use caution receiving messages linked to the Hurricane Harvey and adopt the following best practices:
Review the Federal Trade Commission’s information on Wise Giving in the Wake of Hurricane Harvey.
Do not follow unsolicited web links in email messages.
Use caution when opening email attachments. Refer to the US-CERT Tip Using Caution with Email Attachments for more information on safely handling email attachments.
Keep antivirus and other computer software up-to-date.
Refer to the Avoiding Social Engineering and Phishing Attacks for more information on social engineering attacks.
Verify the legitimacy of any email solicitation by contacting the organization directly through a trusted contact number. You can find trusted contact information for many charities on the BBB National Charity Report Index.
Cyber criminals have no scruples and often exploit any tragic event in their favor.
In October, as the Hurricane Matthew was battering the South Carolina coast, authorities warned of a series of cyber attacks against residents.
In the past crooks exploited the media interest in tragic events like the Boston Marathon attack and the crash of the flight MH17 of Malaysian Airline, they used the news as bait themes for massive spam attacks and spear phishing campaigns.
Mortgage Phishing Scams Target Big Payouts
31.7.2017 securityweek Phishing
Over the last few years, business email compromise (BEC) scams have rocketed -- costing victims $1.45 billion in 2016 alone (FBI report). Now a new related threat has emerged -- the mortgage phishing scam -- that seems likely to follow a similar trajectory.
It is early days and the scam -- like BEC in its early days -- goes by various names: mortgage phish, mortgage escrow scam, real estate wire transfer scam, and mortgage wiring scam. But it is growing. In June 2017, during National Homeownership Month, the FTC issued a warning: "the FTC and the National Association of Realtors want to remind you that scammers sometimes use emails to rob home buyers of their closing costs and personal information."
Like BEC, the scam seeks to trick its victims into wiring funds to a criminally operated account. The difference here is that it people rather than businesses that are conned -- and they can end up losing their life savings and/or their home.
The FTC warning explains the basic scam: "Hackers break into the email accounts of buyers or real estate professionals to get information about upcoming real estate transactions. The hacker then sends an email to the buyer, posing as the real estate professional or title company. The bogus email says there has been a last-minute change to the wiring instructions, and tells the buyer to wire closing costs to a different account. But it's the scammer's account. If the buyer takes the bait, their bank account could be cleared out in a matter of minutes."
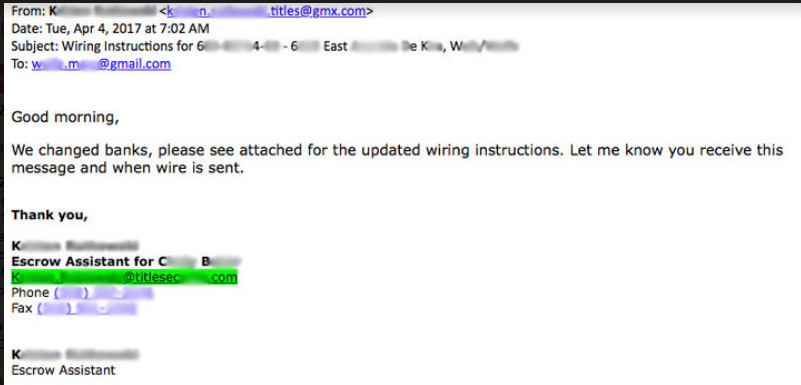
Barracuda Networks has described a real-life example that, in this instance, failed. "On the day that the buyers were set to wire funds, they received an email from their mortgage company stating that they switched banks, and to follow the updated wiring instructions in the email attachment."
Home buyers are particularly vulnerable at this point. They may have spent many stressful months in arranging the purchase, and there is now one relatively simple task before they can collect the keys to their new home. In this instance, the scam failed. It raised a red flag for the buyer who looked more closely at the email -- and noticed that the actual sender's email address didn't quite match the one listed in the real mortgage agent's email signature.
The text of the email read, "We changed banks, please see the attached for the updated wiring instructions. Let me know you receive this message and when wire is sent."
The attachment gives the attacker an extra shot at the target. If he opens the attachment but decides against making the wire, he could still find himself infected with a banking trojan or, potentially, ransomware. In this instance, however, the target did the right thing: he "immediately called his mortgage agent to confirm that the message was in fact a scam. What he found even more alarming with his situation," adds Barracuda, "was the reaction that he received from the mortgage company. They mentioned that it's a wide-spread problem, but they didn't seem interested in looking into the issue any further."
House prices have consistently grown since the 2006 crash, and now stand at similar or above their previous high. This makes it a lucrative market for scammers. "Scams like these have been around for a few years," reported HousingWire in June this year." Last year, the Contra Costa Association of Realtors warned Bay Area homebuyers that they could be targets of similar schemes, one of which cost a local buyer nearly $1 million."
The mortgage phish is just another social engineering spear-phish; but the stakes are high and the targets are vulnerable. The Contra Costa Association warns, "Because buyers often put their complete faith in the real estate professionals who guide them through transactions, they very rarely challenge any advice and direction provided. Moreover, they are so comfortable making daily online transactions, they rarely, if ever question the authenticity of email or text messages." It adds, "there is no means to retrieve the funds once wired."
Last month Barracuda launched Sentinel, described as "an artificial intelligence (AI) powered spear-phishing and business email compromise (BEC) real-time detection and prevention solution."
Google Takes Second Swing at OAuth Worm
27.7.2017 securityweek Phishing
Mitigations put in place by Google in May 2017 to help block phishing attacks such as the recent OAuth worm weren’t enough to completely mitigate the issue, as Google's platform still allowed malicious OAuth clients to be submitted under deceiving names, Proofpoint security researchers say.
The OAuth worm was possible because malicious developers could create seemingly legitimate apps and trick users into granting access to email and cloud service accounts. Lack of validation allowed an attacker to impersonate Google Docs and impacted more than one million G Suite users.
The attack, however, prompted Google to tighten OAuth rules and introduce validations around the choice of name for new apps. The company updated policies and announced enforcement on OAuth applications in an attempt to prevent similar attacks from happening.
Proofpoint now explains that while Google was able to respond to the attack fast, it didn’t address the issue properly, and malicious developers were still able “to submit any name for new OAuth clients — including scripts, third-party apps and extensions.” The security company discovered that Google’s validations could be bypassed to serve “a Google OAuth client with a name of its choice from script.google[.]com.”
The issue, Proofpoint says, was that Google resolved the vulnerability that made the May attack possible, but didn’t address the root of the technique. As a result, it was still possible for users “to serve their own content with a URL at ‘script.google.com’, itself at least in part a factor of the openness of the OAuth clients space.”
Because the OAuth clients space historically had no checks on the actions developers could perform, it allowed the creation of any application and the request of any permission considered necessary. App developers were also allowed to send their applications to anyone else and serve them with a URL at script.google.com in the process.
In addition to alerting the public on the risk these applications pose, the May 2017 attack could also be mitigated because it included an identifiable URL. This, however, didn’t eliminate the exploit itself, allowing future versions to avoid the mitigations by not including a return URL or by using a URL that can’t be distinguished from a valid Google script URL.
"[The] OAuth worm employed a rare email permission often used only by select email clients (e.g. Outlook) in combination with another permission. That specific combination was unique and not used by any other OAuth client Proofpoint has previously examined,” the security researchers say.
Effective defense would build on the analysis of the app to determine permissions, app creator, recipient (or victim), app name, context, and other features. By performing such analysis, Proofpoint discovered another flaw within Google Apps and says that an attacker could exploit it to carry a similar attack as the OAuth worm, despite the mitigations put in place by Google.
“In this case, our researchers were able to create an app called ‘Google Docs’ or ‘Google Drive’, bypassing some of the protections Google introduced following the May 2017 attack. Using this technique, an attacker can then launch a similar phishing campaign, but this time with links that are less suspicious -- and more potentially enticing -- than possible in the May campaign,” Proofpoint says.
The security company reported the issue to Google, which resolved it within a day. The Internet giant released an update to alert users on new web applications and Apps Scripts that require verification. Previously, an ‘error’ page was displayed for unverified web apps. In the following months, the verification process will be expanded to existing applications as well.
SMS Phishing induces victims to photograph its own token card
17.7.2017 securityaffairs Phishing
Renato Marinho detailed an unusual SMS phishing campaign that hit Brazilian users. All started with an SMS message supposedly sent from his bank.
Introduction
Today I faced quite an unusual SMS phishing campaign here in Brazil. A friend of mine received an SMS message supposedly sent from his bank asking him to update his registration data through the given URL. Otherwise, he could have his account blocked, as seen in Figure 1.

.png?ssl=1)
Figure 1 – SMS message received
Telling you the truth, my friend doesn’t have any account on the informed bank and, even so, we know that those kinds of message are hardly ever sent by banks and are, most of the time, related to malware propagation and information stealing. However, instead of discarding the message, we decided to give it a try and the results, as you are going to read in this diary, surprised us. This campaign involves no malware propagation – just creativity in favor of evil.
SMS Phishing analysis
The link in the message aims to take the victim to a fake and very simplistic mobile version of a well-known bank website. First, it asks for the “CPF” (a kind of social security card number) and a password, as seen in Figure 2.

Figure 2 – Fake bank website asking for CPF and password
It is interesting noting that there is a data input validation. The user must obey to the CPF number composition rules otherwise he can’t proceed. This validation is done by the JavaScript code shown in Figure 3.

Figure 3 – CPF validation rules
This kind of validation is certainly used to give a bit of legitimacy to the fake website and, perhaps, to do not overload crooks with much “data-mining” work.
In the next page, the fake website informs that the device used on that connection needs to be authorized, as seen in Figure 4.

Figure 4 – Fake website: user must authorize the device
By clinking on “Habilitar Aparelho” which means “enable device”, a new page is shown asking for the victim to inform the 4-digit password, as seen in Figure 5.

Figure 5 – Fake website asking for the 4-digit password
Again, there is a minimum validation to avoid the user trying very simple passwords like “1234” as seen in Figure 6.

Figure 6 – 4-digit password “validation” code
Next, the step that caught our attention. The fake website asks the victim to take a picture of its token card and upload it. To be precisely, asks to take a picture of the side with all security codes used to validate banking transactions as a second-factor authenticator, as seen in Figure 7.

Figure 7 – Asking for the token card picture
By clicking on “Finalizar Habilitação” which means “proceed with the device authorization”, the victim’s smartphone will prompt the user to select a picture from its library or take a new one – which is exactly what the user is induced to do, as seen in Figure 8.

Figure 8 – Taking the token card picture
Once the victim ends up the whole process, including the token card picture, the criminals will have all the information needed to make fraudulent transactions on the compromised bank account and the user is forwarded to the real bank login page.
Final words
Using victim’s smartphone to take pictures to steal information or, who knows, things, scares me a little bit. I can explain. Earlier this month, reading Bruce Schneier’s blog I saw a post entitled “Now It’s Easier than Ever to Steal Someone’s Keys” [1] which says, “The website key.me will make a duplicate key from a digital photo.”.
While writing this diary, I was reported about similar SMS Phishing campaigns targeting other banks costumers here in Brazil. Stay tuned.
References
[1] https://www.schneier.com/blog/archives/2017/07/now_its_easier_.html
Hackshit PhaaS platform, even more easy to power Phishing campaigns
16.7.2017 securityaffairs Phishing
The experts from Netskope Threat Research Labs discovered the Hackshit PhaaS platform, another interesting case of crimeware-as-a-service.
A few days ago, we discussed the Katyusha scanner,a powerful and fully automated SQLi vulnerability scanner discovered by researchers at security firm Recorded Future that was available for $500 in the cyber crime underground.
The Katyusha scanner is just one of the numerous hacking tools and crimeware-as-a-service available in the hacking community.
Today I desire to present you another crimeware-as-a-service that was discovered by the experts from Netskope Threat Research Labs dubbed Hackshit.
The Hackshit is a Phishing-as-a-Service (PhaaS) platform that offers low cost, “automated solution for the beginner scammers,” it allows wannabe crooks to easily launch a phishing campaign.
Dubbed Hackshit, the PhaaS platform attracts new subscribers by offering them free trial accounts to review their limited set of hacking tutorials and tricks to make easy money.
“Netskope Threat Research Labs recently discovered a Phishing-as-a-Service (PhaaS) platform named Hackshit, that records the credentials of the phished bait victims. The phished bait pages are packaged with base64 encoding and served from secure (HTTPS) websites with “.moe” top level domain (TLD) to evade traditional scanners. “.moe” TLD is intended for the purpose of ‘The marketing of products or services deemed’. The victim’s credentials are sent to the Hackshit PhaaS platform via websockets. ” states a blog post published by Netskope.
The researchers discovered the PhaaS platform during a research about the trends of CloudPhishing attacks. They observed a phishing page using data URI scheme to serve base64 encoded content (data:text/html;base64) delivered from “https://a.safe.moe,” accessing the link the researchers were presented a phished login page for Google Docs.
Once the victims have provided their credentials, they presented another phishing page whose source uses a data URI scheme to serve base64 encoded content (data:text/html;base64) again from https://a.safe.moe.
This second phished page was designed to trick victims into providing recovery details of their email account. Once the victim has provided his details, he is redirected to the original Google recovery page.
The experts decoded the two phishing pages and discovered that the credentials are sent to the attacker via a websocket to https://pod[.]logshit[.]com and https://pod-1[.]logshit[.]com.
“Accessing logshit[.]com led us to the discovery of the PhaaS website named Hackshit as shown in Figure 6. Further research concluded the website is serving as a PhaaS platform.” continues the blog post.

Hackshit is a PhaaS platform that offers several phishing services and it also implements a black marketplace to buy and sell such kind of services.
“The marketplace is a portal that offers services to purchase and sell for carrying out the phishing attacks,” Netskope researcher Ashwin Vamshi explained.
“The attacker then generates a phished page from the page/generator link and logs into the email account of the compromised victim, views all the contacts and sends an email embedded with the phished link.”
Crooks can purchase site login accounts of compromised victim from the marketplace using Perfect Money or bitcoins.
Using the Hackshit, subscribers can easily generate their unique phishing pages for many popular services, including Yahoo, Facebook, and Gmail.
Experts also noticed that the Hackshit website uses an SSL certificate issued by the open certificate authority Let’s Encrypt.
Let’s see which is the pricing model behind the PhaaS, Hackshit offers several subscription tiers from Starter to Master, ranging from 40 USD per week to 250 USD for 2 months.
Hackshit demonstrated that crimeware-as-a-service represent a serious risk for businesses and end-users, it is bringing wannabe hackers into the cybercrime arena.
Barracuda Launches AI-based Spear Phishing Detection
29.6.2017 securityweek Phishing
Barracuda Networks this week announced its new Sentinel product: an artificial intelligence (AI) powered spear-phishing and business email compromise (BEC) realtime detection and prevention solution. It marks the second company in a week, following GreatHorn, to use AI to combat social engineering.
"The threat has grown exponentially over the last few years," Asaf Cidon, vice president of content security services at Barracuda, told SecurityWeek. "According to the FBI's latest figures, more than $5 billion has been lost to BEC fraud between 2013 and 2016 -- with a 2,370% growth in spear-phishing between the beginning of 2015 and the end of 2016. BEC has become so pervasive because it is simple to do: anyone with an email account and a little on-line research into the target can produce a compelling fraudulent email."
Not only is BEC easy to produce, it is also hard to detect. While many other email-based attacks include a payload -- from a link in the body to malware in the attachment -- BEC fraud has neither. It relies entirely upon social engineering that traditional defenses cannot detect.
"This problem led us to build Sentinel," said Cidon; "an AI-based platform for real-time spear-phishing and cyber fraud defense. It relies on three individual layers to provide a comprehensive solution: artificial intelligence for fraud detection; DMARC for protection against domain spoofing and brand hijacking; and simulated attack training for identified high-risk staff."
The AI layer is the most important, he suggested. With access to millions of mailboxes, Barracuda has taught its AI to recognize fraudulent emails. It does this in two ways. Firstly, it fingerprints communication patterns within the customer organization. It learns, for example, how the CEO normally communicates with the finance team. Deviations from this pattern -- such as the sudden use of an email address not used before -- immediately flag the communication as worrying.
But Sentinel also analyzes the email content for style. In an example given by Cidon, the AI engine detected urgency (use of the word 'need', and termination with a question-mark) and sensitivity (use of 'bank transfer'). 'Urgency' is an archetypal element of social engineering. When the content analysis is coupled with the metadata fingerprint, other indicators such as the use of an external email address in either the from or reply-to fields are sufficient for the AI to recognize and quarantine the fraud.
The second layer of Sentinel sets up DMARC (Domain-based Message Authentication Reporting & Conformance) to prevent outbound domain spoofing. One common technique used by criminals is to spoof the organization's domain in order to send apparently official messages to customers and partners to steal credentials and gain access to accounts. This layer of Sentinel helps prevent spoofing-based spear phishing and brand hijacking.
The final layer is anti-fraud training for high risk staff. The AI part of the product is used to identify high risk personnel. The product then offers a set of tools to periodically and automatically train and test the security awareness of these employees with simulated spear phishing attacks.
Sentinel currently works with Office 365. However, Barracuda also offers a set of APIs designed to make to make the functionality easily extensible beyond email to additional messaging platforms such as G Suite, Slack, social media, and others: "In fact," said Cidon, "to any platform used by organizations for business communication."