Phishing Articles - H 2020 1 2 3 4 5 6 7 8 Phishing List - H 2021 2020 2019 2018 1 Phishing blog Phishing blog
Twitter Employees Targeted With Phone Spear-Phishing in Recent Attack
31.7.20 Attack Phishing Securityweek
Twitter on Thursday revealed that several employees were targeted with phone spear-phishing in a social engineering attack leading to the recent security incident.
A total of 130 accounts were targeted in the incident, with hackers abusing internal Twitter systems and tools to reset the passwords for 45 of them. The attackers also accessed the DM inbox of 36 accounts and downloaded the Twitter data of 7.
Supposedly the work of young hackers looking to compromise high-profile, OG accounts, the incident resulted in the inbox of an elected Dutch official being accessed as well.
On Thursday, Twitter confirmed that the hackers targeted several of its employees to gain access to internal systems and gather information on which employees might have access to the tools needed to reset passwords and take over accounts.
“Not all of the employees that were initially targeted had permissions to use account management tools, but the attackers used their credentials to access our internal systems and gain information about our processes. This knowledge then enabled them to target additional employees who did have access to our account support tools,” the social media platform revealed.
Twitter also underlines that its support teams use proprietary tools to resolve issues that users report, to review content, and respond to reports.
“Access to these tools is strictly limited and is only granted for valid business reasons. We have zero tolerance for misuse of credentials or tools, actively monitor for misuse, regularly audit permissions, and take immediate action if anyone accesses account information without a valid business reason,” the company says.
Following the attack, the social platform is looking at means to improve its tools and controls, especially considering the concentrated effort that attackers showed in targeting specific employees.
Twitter also notes that it has already contacted the impacted account owners and worked with them to restore access after initially locking them out to contain the security incident. The company also engaged with law enforcement to investigate the attack.
“Since the attack, we’ve significantly limited access to our internal tools and systems to ensure ongoing account security while we complete our investigation. As a result, some features (namely, accessing the Your Twitter Data download feature) and processes have been impacted. We will be slower to respond to account support needs, reported Tweets, and applications to our developer platform,” the company says.
Twitter also notes that it plans on intensifying employee training and to accelerate improvements to its tools to ensure better security and more efficient detection and prevention of inappropriate access to accounts.
How to protect your business from COVID-19-themed vishing attacks
29.5.2020 Net-Security Phishing
Cybercriminals have been using the COVID-19 pandemic as a central theme in all kinds of crisis-related email phishing campaigns. But because of the dramatic rise of the number of at-home workers, one method that has become increasingly common over the past few months are vishing attacks, i.e., phishing campaigns executed via phone calls.
COVID-19 vishing attacks
Rising success rates are the reason why vishing has become more common, and there are several factors driving this trend:
People are actually at home to receive calls, giving threat actors more hours to connect with live targets
Everyone is on high alert for information about the pandemic, stimulus checks, unemployment compensation, ways to donate to charitable organizations, and other COVID-related topics, providing attackers with an endless supply of vishing social engineering options
Cybercriminals conduct research and use personal information – the last four digits of a social security number, for example – to build credibility and fool their victims into thinking they are speaking with legitimate sources.
Let me expand on this last point. Modern vishing attacks use research-based social engineering to attack targets with convincing scams. How do these attackers know so much about their targets? Typically, cybercriminals obtain personally identifiable information in one of three ways:
1. Social media
Many social media profiles are not protected from public view and they serve as a treasure trove of personal information that can be used for building attacks. For example, listing your place of employment with an employee badge not only lets an attacker know where you work, but what the company badge looks like for replication purposes.
“About You” sections of social media accounts often reveal personal information that can be used for password reset fields – your favorite color, your dog’s name, or the city you were born. And detailed posts outlining work projects, professional affiliations and technologies you’re using all help build a valid pretext scenario.
2. Password dumps
There has been no shortage of public data breaches that have resulted in extensive password dumps containing usernames, email addresses and passwords of compromised accounts. Individuals often reuse passwords across different accounts, which makes it easy for attackers to hack their way in through “credential stuffing.” For example, a LinkedIn password and user email address exposed in a breach could be used to access bank or e-commerce accounts.
3. Search engines
An individual’s name, address and photo of signature can often be found online via local government public records sites. In addition, paid services exist for individuals who want to obtain additional information, such as a target’s date of birth or marital status.
Many people don’t realize how much personal information can be found via a simple online search. As a result, when an attacker uses things like the last four digits of their social security number, the town in which they live, or the names of their children, victims assume the person they are speaking to is a credible source, and they don’t think twice about divulging information that they would otherwise keep private.
Vishing is a business problem, too
On the surface, it might seem like vishing attacks are a consumer problem only. But, in reality, businesses can be impacted too – especially now, as a significant portion of employees across the country are working from home.
These employees not only have corporate information stored on their personal devices, but they also generally have remote access to internal corporate resources. Vishing attacks are designed to build relationships with employees, eventually convincing them to give away confidential information, or to click on malicious links that are sent to them by the visher, who has earned confidence as a “trusted source.” As with other social engineering attacks, the ultimate goal is to gain access to corporate networks and data, or to get other information that can be used to commit fraud.
Tips for mitigating COVID-19 vishing attacks
Mitigating the risk of vishing attacks requires a multi-faceted approach, but it should start with end user awareness and education.
As soon as possible, businesses should roll out employee training sessions (even if they’re virtual) that explain what vishing is, how cybercriminals obtain personal information, and how they’re exploiting the COVID-19 pandemic to trick victims.
They should provide basic security tips, such as keeping social media accounts private and using different passwords for different accounts, as well as best practices for responding to a real-world attack. Incorporating attack simulations into training programs can also be a great way to teach employees how to respond to a vishing campaign using defined internal processes.
Technical controls are another key component of a layered security strategy to protect employees and your business from vishing threats. Web filters, antivirus software, and endpoint detection and response solutions are examples of the types of standard security controls that should be implemented. In addition, password policies must be defined and communicated to employees. And, last but not least, multi-factor authentication can be effective in thwarting attacks, as it forces cybercriminals to crack more than one user credential to gain access to corporate systems.
Defending against vishing during the pandemic and beyond
Even though COVID-19-prompted shelter-in-place orders are lifting across the country, many organizations are maintaining work-at-home policies for the safety of their employees and because they realize the operational and financial benefits that come along with telecommuting programs. This means that protecting the remote workforce should continue to be a top priority for businesses of all sizes and defending against vishing attacks should be a core component of security strategy.
Vishers will continue to come calling long after the COVID-19 pandemic comes to an end, so it’s important to make sure remote workers – and all employees – know how to identify suspicious callers, just like they should know how to identify suspicious emails. Supplementing employee education with the proper security controls is a good starting point to keep your staff and your business safe regardless of who’s on the other end of the line.
Frankenstein's phishing using Google Cloud Storage
27.5.2020 SANS Phishing
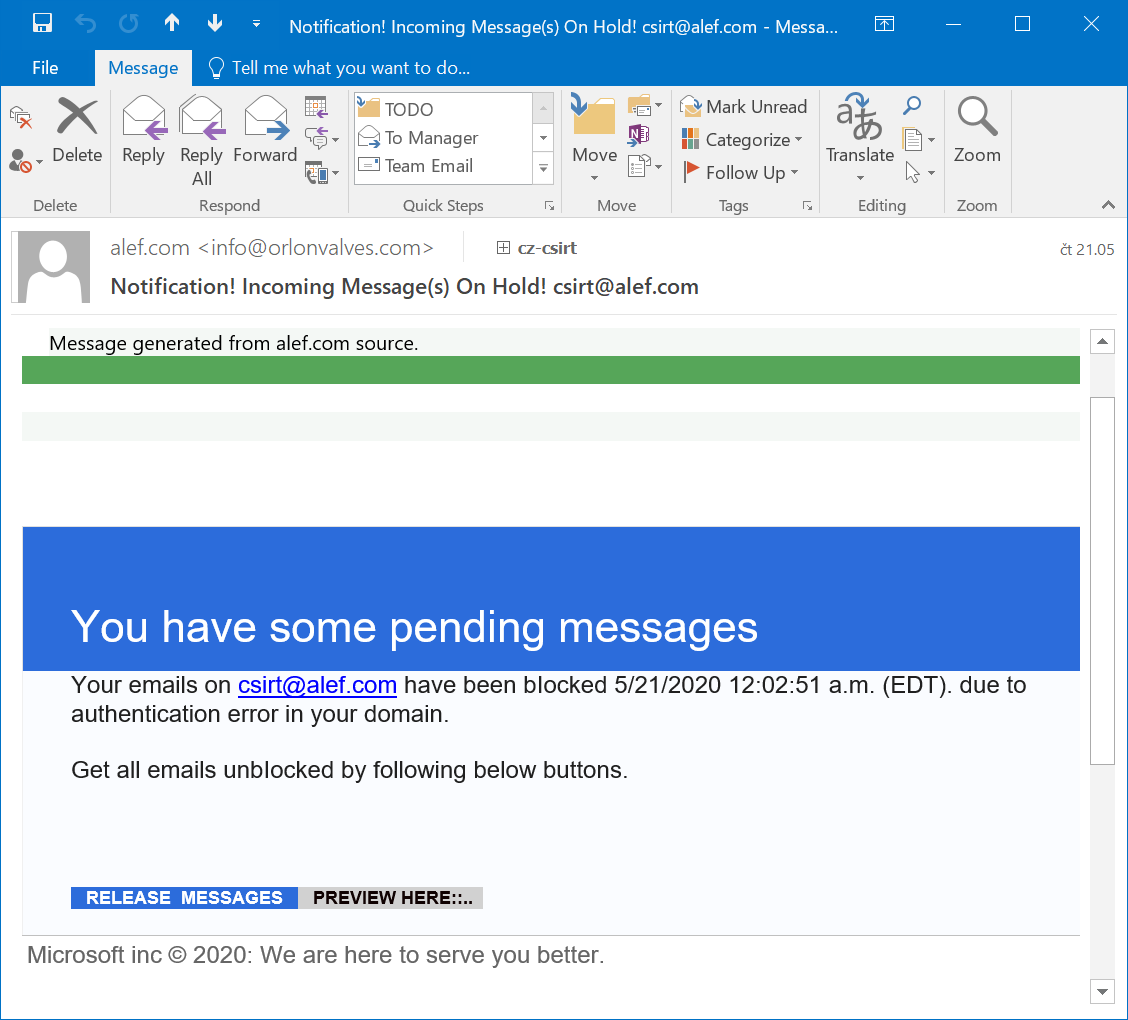
Phishing e-mail messages and/or web pages are often unusual in one way or another from the technical standpoint – some are surprisingly sophisticated, while others are incredibly simple, and sometimes they are a very strange mix of the two. The latter was the case with an e-mail, which our company e-mail gateway caught last week – some aspects of it appeared to be professionally done, but others screamed that the author was a “beginner” at best.
The message appeared to come from info[@]orlonvalves[.]com and passed both SPF and DKIM checks. Contrary to popular belief, it is not that unusual to see a phishing e-mail from an SPF-enabled domain[1,2]. Phishing message with a valid DKIM signature, on the other hand, is something, which is usually seen in connection with a compromised e-mail server. Although it is possible that this was the case in this instance as well, I’m not completely sure about that. The reason is that the domain in question was registered about half a year back using Namecheap, neither it nor any existing subdomain appears to be hosting any content and no company of corresponding name seems to exist. In contrast, a company named Orion Valves, which uses the domain orionvalves[.]com, does exist and although we may only speculate on whether the domain was intended to be used for phishing, since the substitution of characters (i.e. “l” for “i”) in lookalike domain names is a common tactic for phishers, I wouldn’t be surprised if this effect was what the domain holder was actually going for.

As you may see, apart from the potentially interesting sender domain, the message was a fairly low-quality example of a run-of-the-mill phishing. It claimed to be from Microsoft, but also from a source at alef.com (i.e. our company domain). The only further small point of interest connected with it was hidden within its HTML code. Even though it is usually not necessary to analyze the code of phishing messages, it may sometimes provide us with at least some information about their authors. In this case, for example, given that there are attributes “data-cke-saved” and “data-cke-eol” present in the code, we may surmise that the author most likely used the CK Editor to create the HTML code (and that he probably used a historical phishing message which pointed to different phishing pages as a base to build it from).
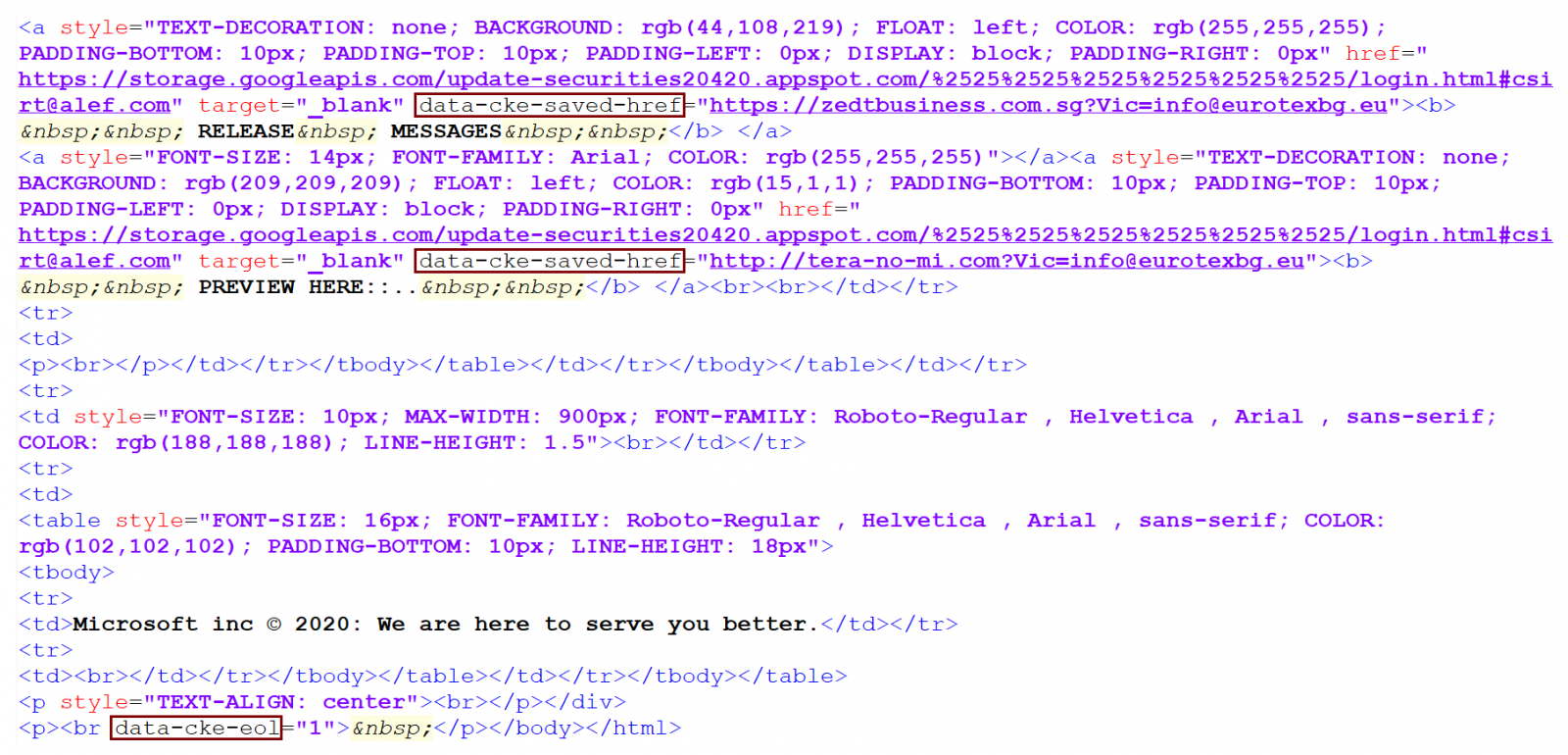
As the code shows, the links in the message lead to the following Google Cloud Storage URL.
hxxps[:]//storage[.]googleapis[.]com/update-securities20420.appspot.com/%2525%2525%2525%2525%2525%2525/login.html
I reported the URL to Google, but since the page is still reachable at the time of writing, you may be able to take a look at it yourself, if you’re interested.
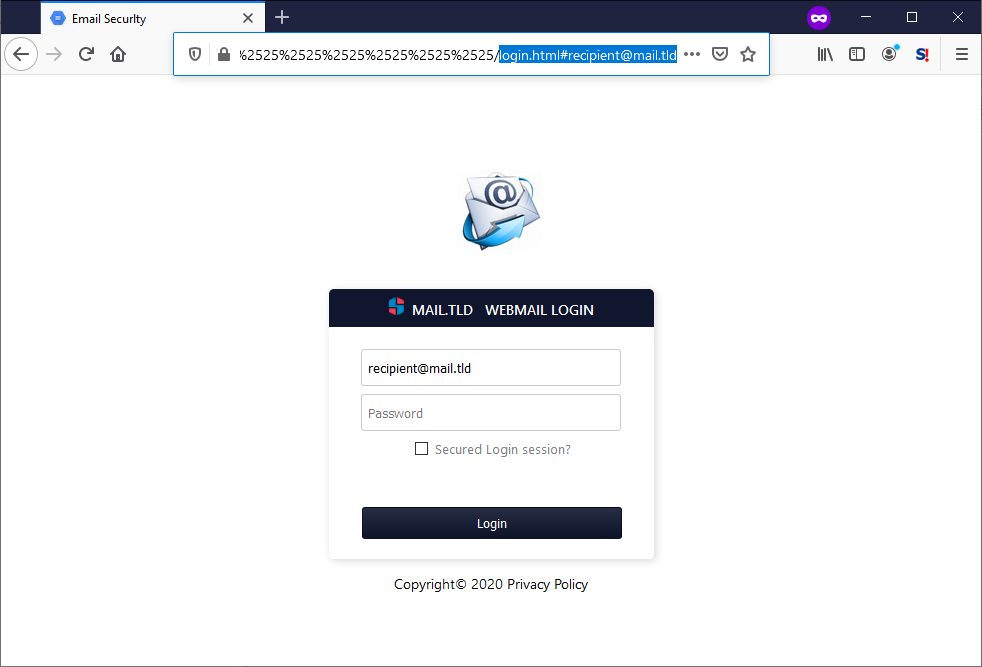
Although web page didn’t look like anything too special at first glance, at the second one it turned out to be quite interesting for multiple reasons.
It was self-contained, with all scripts, styles as well as pictures embedded in the code. This technique is sometimes used by attackers in order to create phishing pages they may use as attachments[4], but isn’t too common for the server-hosted phishing sites (though, given where this page was hosted, use of the technique makes some sort of sense).
It also appeared to be fairly well written – the author expected both a situation when a script blocker would stop JavaScript from executing and a situation when the scripts would be executed. If JS execution was possible, it would “personalize” the contents of the page and pre-fill the users e-mail address in the form, if not, it would stay in a more generic, but still fully functional form.
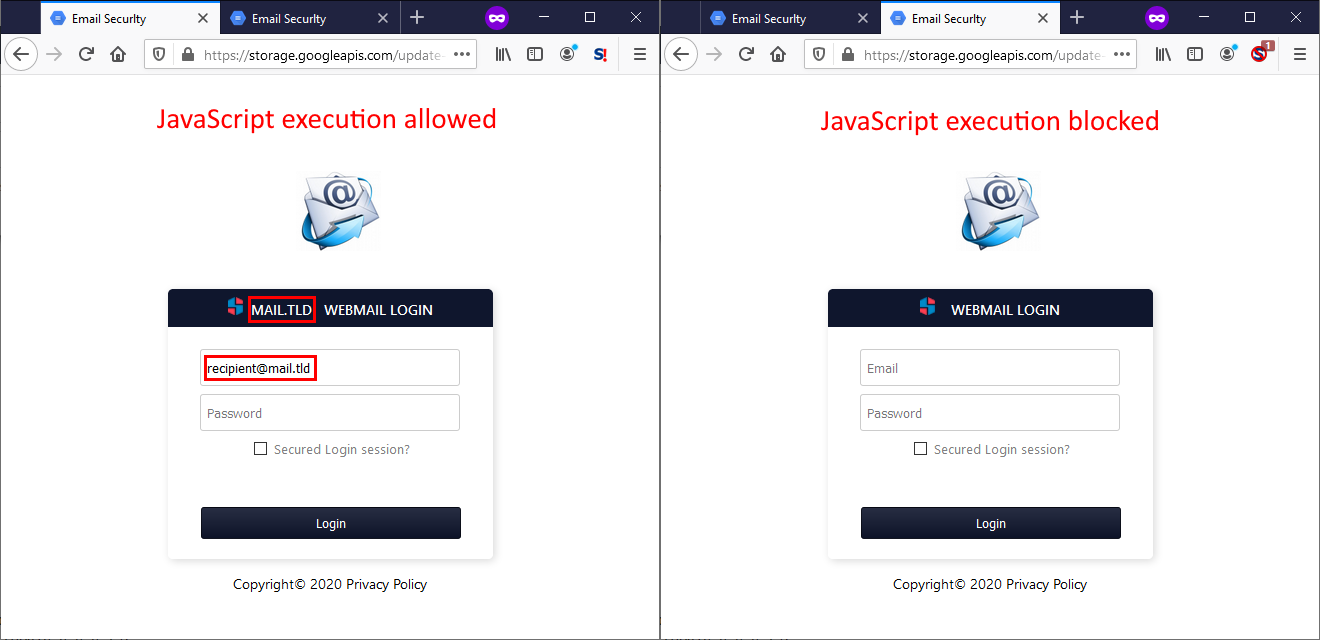
On the other hand, personalization of the page wasn’t the only thing which the embedded JS would try do.
Another piece of JavaScript contained an encoded version of the entire page (i.e. code identical to the one present in the HTML) and it would try to decode it and write it in the body of the document. This would be a bit strange by itself, since – as we’ve mentioned – both versions of the HTML code were the same and if the code were to run, it would result in the entire contents being present twice (i.e. two complete credential stealing forms on one page). But where it got even stranger was the placement of the JavaScript code – it was placed in a style tag within the head portion of the site, which would result in the code never executing (at least not in any browser I’ve tried). It was also probably supposed to be commented out, though it didn’t end up that way as there was a newline after the comment tag instead of a space… In short, there was no reason for the code to be there as it would never run and the way in which it was embedded was completely wrong even if the author intended it as some sort of backup.
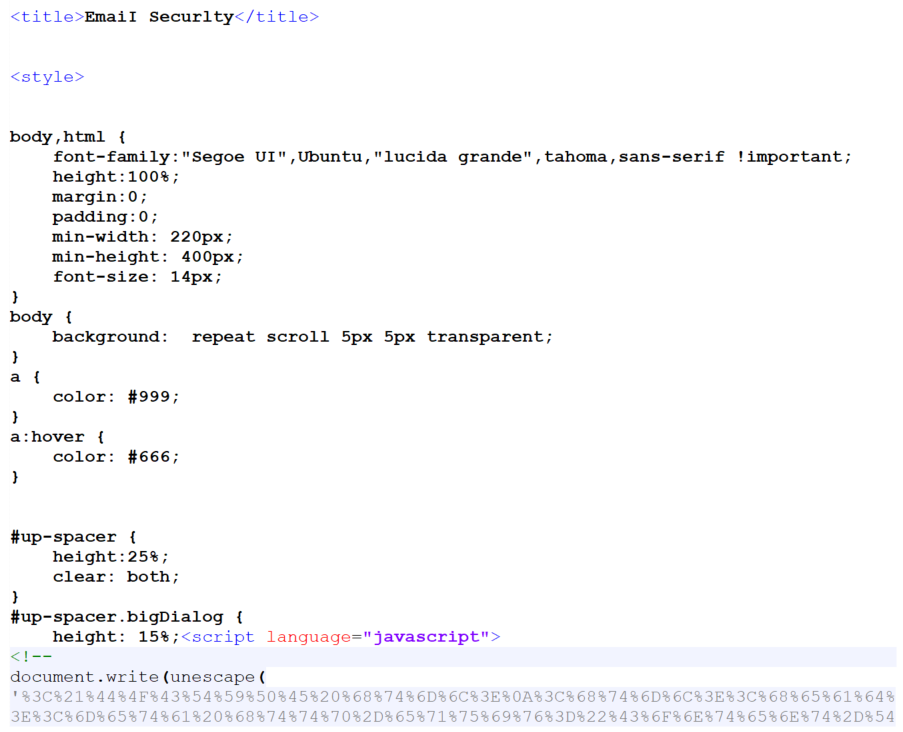
If a target of the phishing were to input his credentials in the page, they would be sent in a POST request to the following URL:
hxxps[:]//hondarebirth[.]com/Zhejiang22320/need.php
After that, the browser would be redirected (HTTP 302) to another PHP script on the same server (go.php) and from there to the domain, to which the e-mail address, which was specified in the form, belonged. Redirection to a legitimate domain after credentials have been gathered by a phishing site is quite a common tactic, since the target may then come to believe that they simply made a mistake while typing the password.
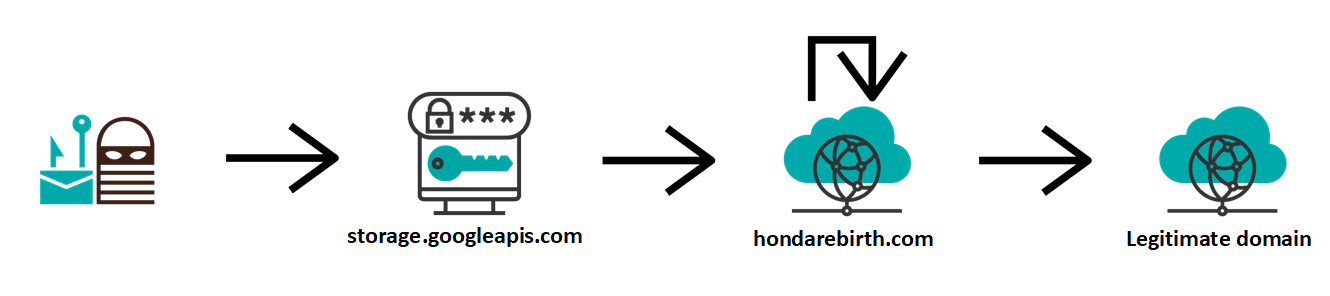
As we may see, the phishing really was a strange mix. On one hand, we have the use of a potential phishing domain with SPF and DKIM set up to send the original e-mail, a well-written phishing page and a fairly standard credential gathering mechanism using a different domain and server from the ones hosting the phishing site itself. On the other hand, we have a very low-quality phishing message trying (though not very hard) to look like it was sent by two different sources at once and a nonsensical inclusion of JavaScript in the phishing page, which would never execute, but if it did, it would completely ruin the appearance of the page as anything even nearly legitimate.
Who knows how this came to be – perhaps the attackers cobbled together pieces of different phishing campaigns they found online and ended up with something functional but resembling the creation of Dr. Frankenstein more than anything else...
Indicators of Compromise (IoCs)
hxxps[:]//storage[.]googleapis[.]com/update-securities20420.appspot.com/%2525%2525%2525%2525%2525%2525/login.html
hxxps[:]//hondarebirth[.]com/Zhejiang22320/need.php
hxxps[:]//hondarebirth[.]com/Zhejiang22320/go.php
[1] https://isc.sans.edu/forums/diary/Phishing+email+spoofing+SPFenabled+domain/25426/
[2] https://isc.sans.edu/forums/diary/Agent+Tesla+delivered+by+the+same+phishing+campaign+for+over+a+year/26062/
[3] https://ckeditor.com/old/forums/CKEditor-3.x
[4] https://isc.sans.edu/forums/diary/Phishing+with+a+selfcontained+credentialsstealing+webpage/25580/
Spam and phishing in Q1 2020
26.5.2020 Securelist Analysis Spam Phishing
Quarterly highlights
Don’t get burned
Burning Man is one of the most eagerly awaited events among fans of spectacular performance and installation art. The main obstacle to attending is the price of admission: a standard ticket will set you back $475, the number is limited, and the buying process is a challenge all by itself (there are several stages, registration data must be entered at a specific time, and if something goes wrong you might not get a second chance). Therefore, half-price fake tickets make for excellent bait.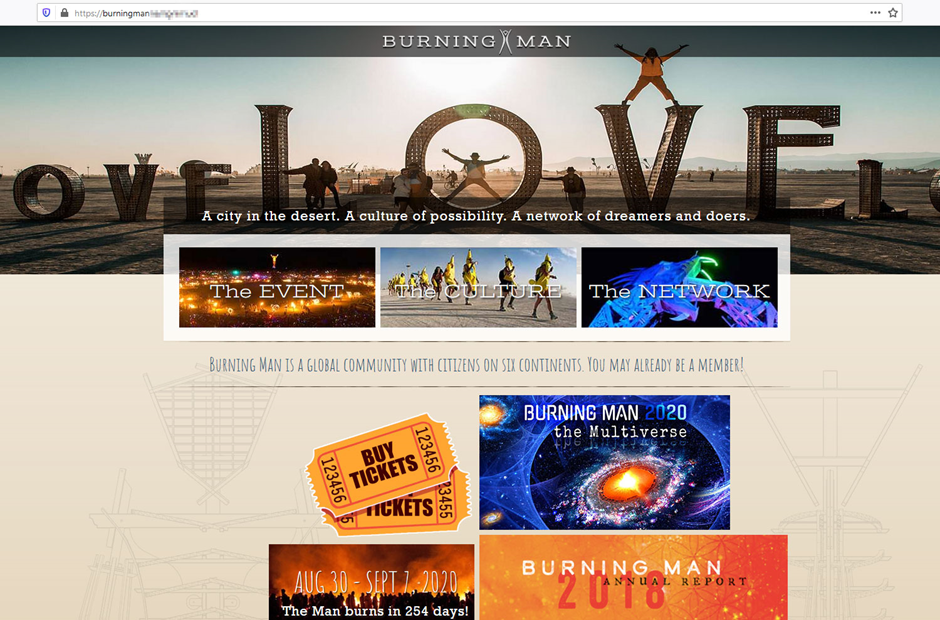
Scammers tried to make their website as close as possible to the original — even the page with the ticket description looked genuine.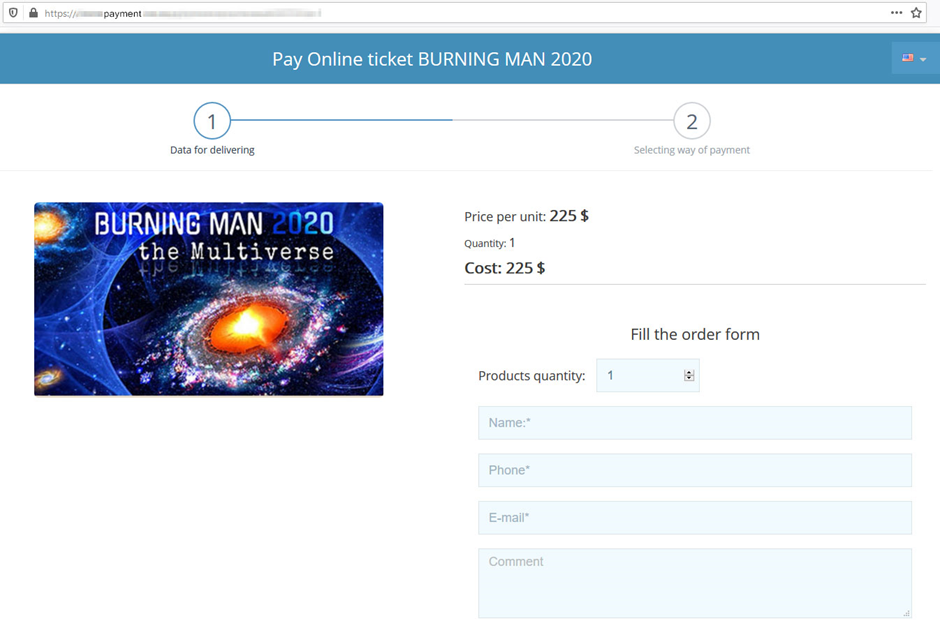
There were just three major differences from the original: only the main page and the ticket purchase section were actually operational, tickets were “sold” without prior registration, and the price was a steal ($225 versus $475).
Oscar-winning scammers
February 2020 saw the 92nd Academy Awards ceremony. Even before the big night, websites were popping up offering free viewings of all the nominated films. Fraudsters targeted users eager to see the short-listed movies before the presentation of the awards.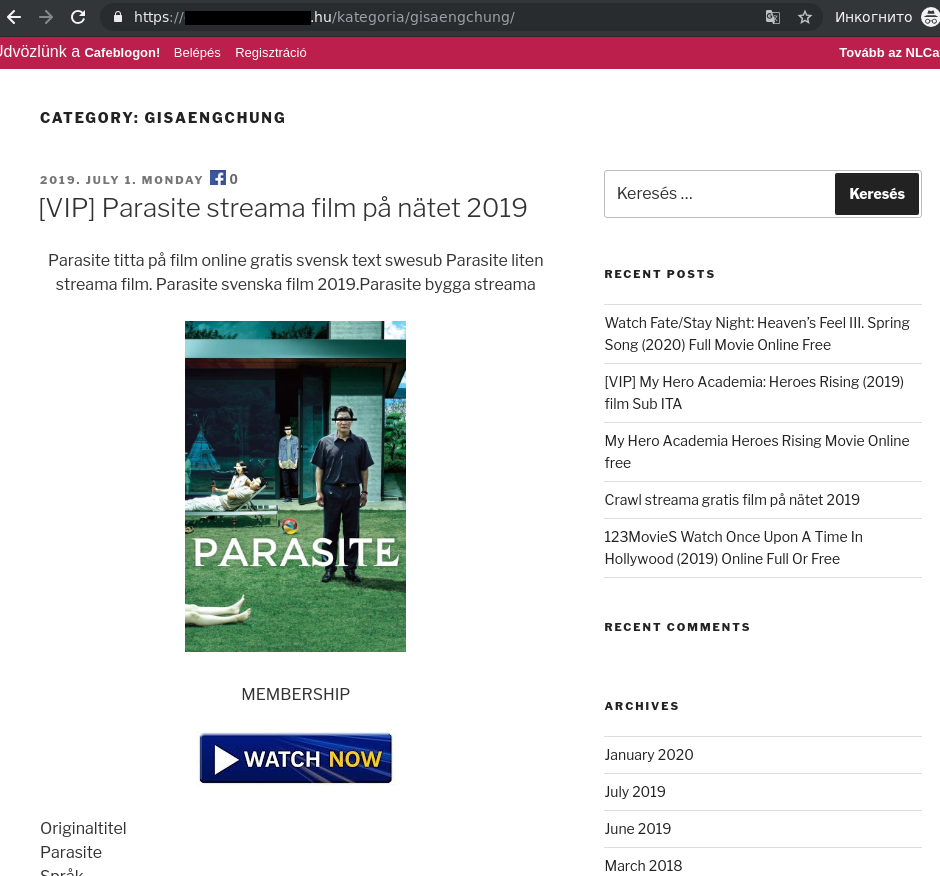
To promote these sites, Twitter accounts were created — one for each nominated film.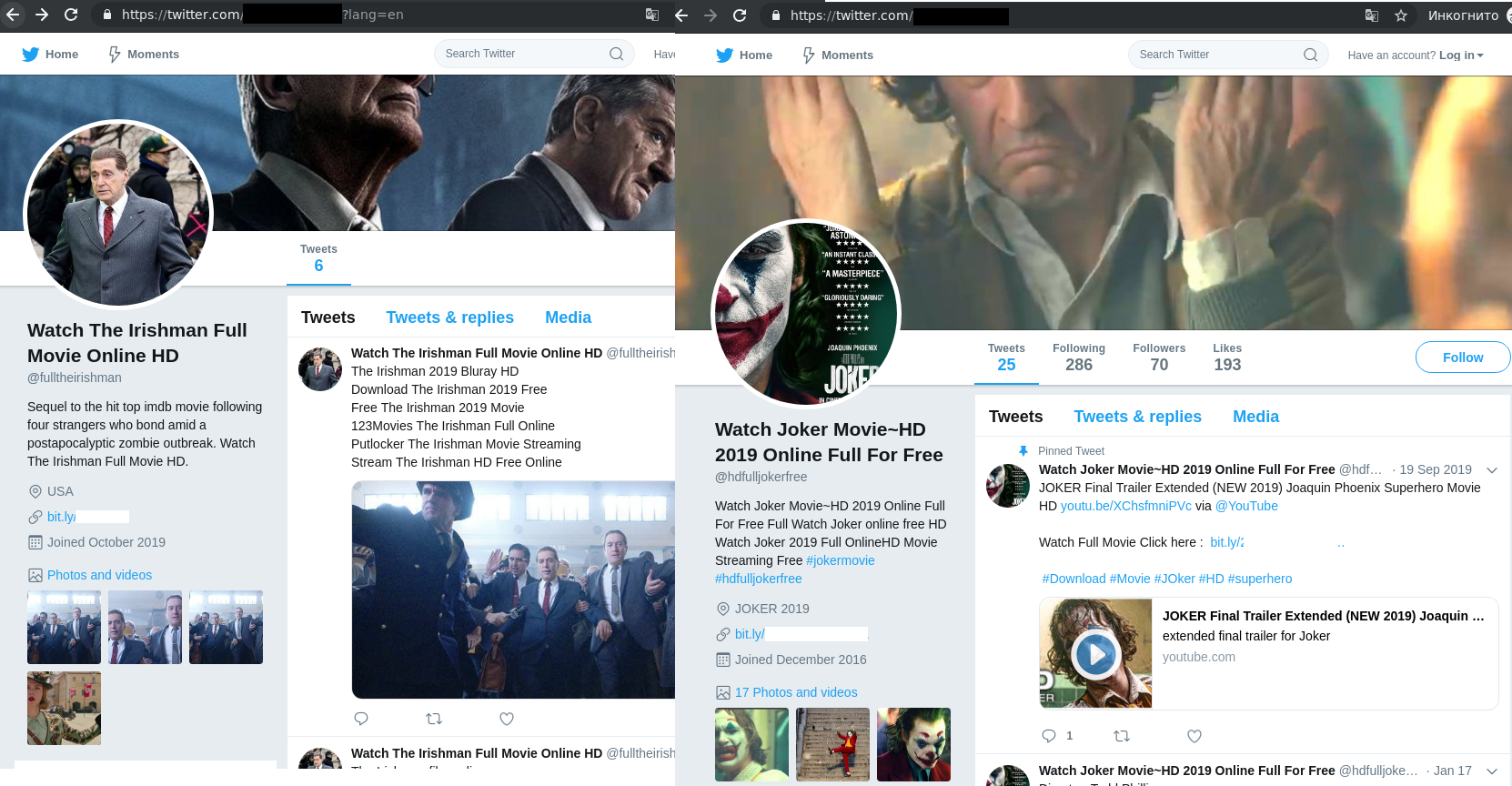
Curious users were invited to visit the resource, where they were shown the first few minutes before being asked to register to continue watching.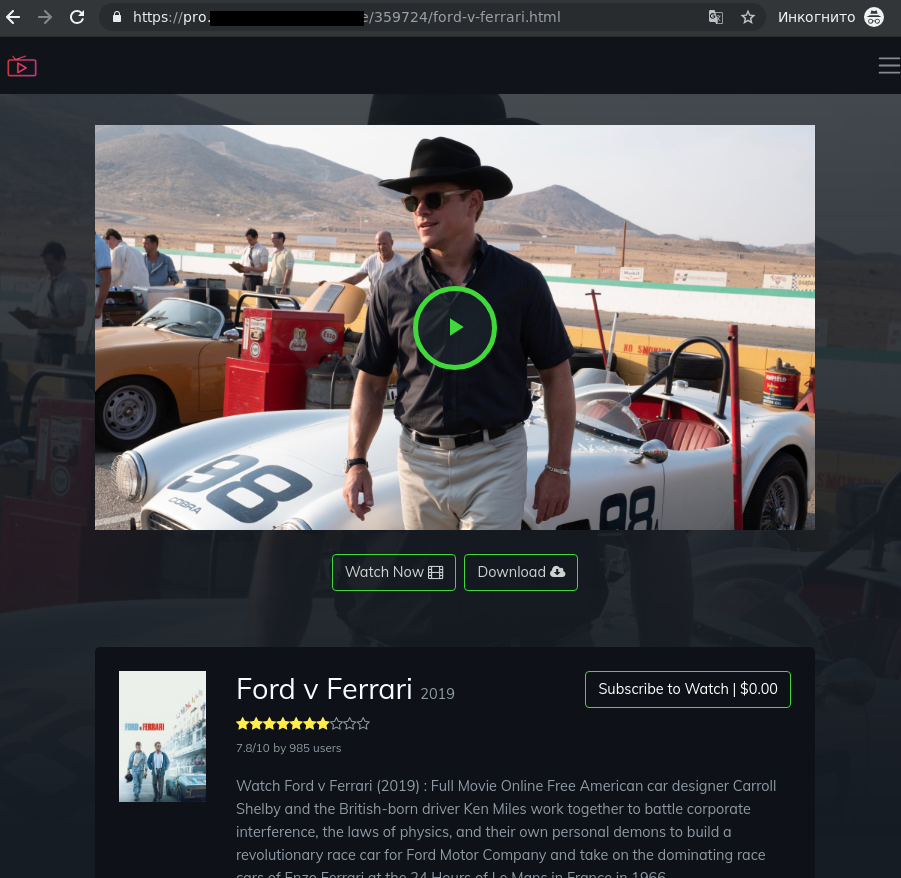
During registration, the victim was prompted to enter their bank card details, allegedly to confirm their region of residence. Unsurprisingly, a short while later a certain amount of money disappeared from their account, and the movie did not resume.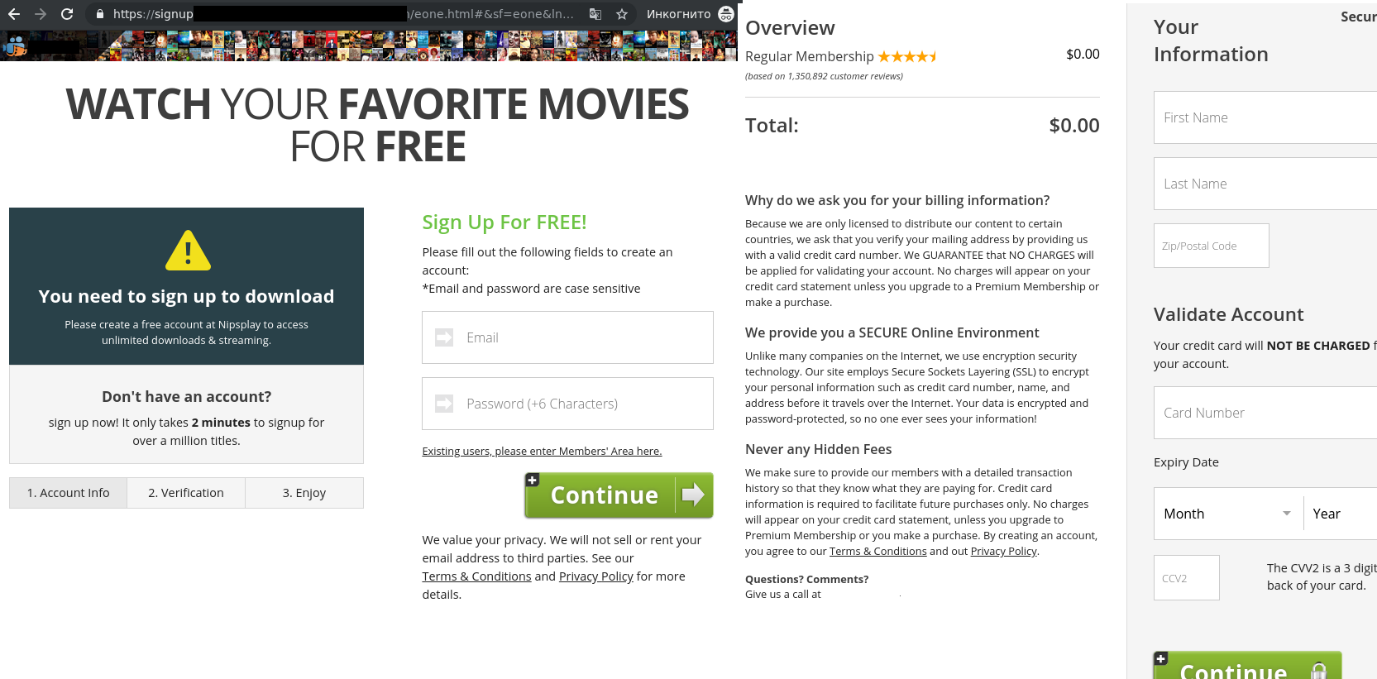
Users should be alert to the use of short links in posts on social networks. Scammers often use them because it’s impossible to see where a shortened URL points without actually following it.
There are special services that let you check what lies behind such links, often with an additional bonus in the form of a verdict on the safety of the website content. It is important to do a proper check on links from untrusted sources.
ID for hire
US companies that leak customer data can be heavily fined by the Federal Trade Commission (FTC). For example, in 2019 Facebook was slapped with a $5 billion penalty; however, users whose data got stolen do not receive any compensation. This is what scammers decided to exploit by sending a fake e-mail offering compensation from the non-existent Personal Data Protection Fund, created by the equally fictitious US Trading Commission.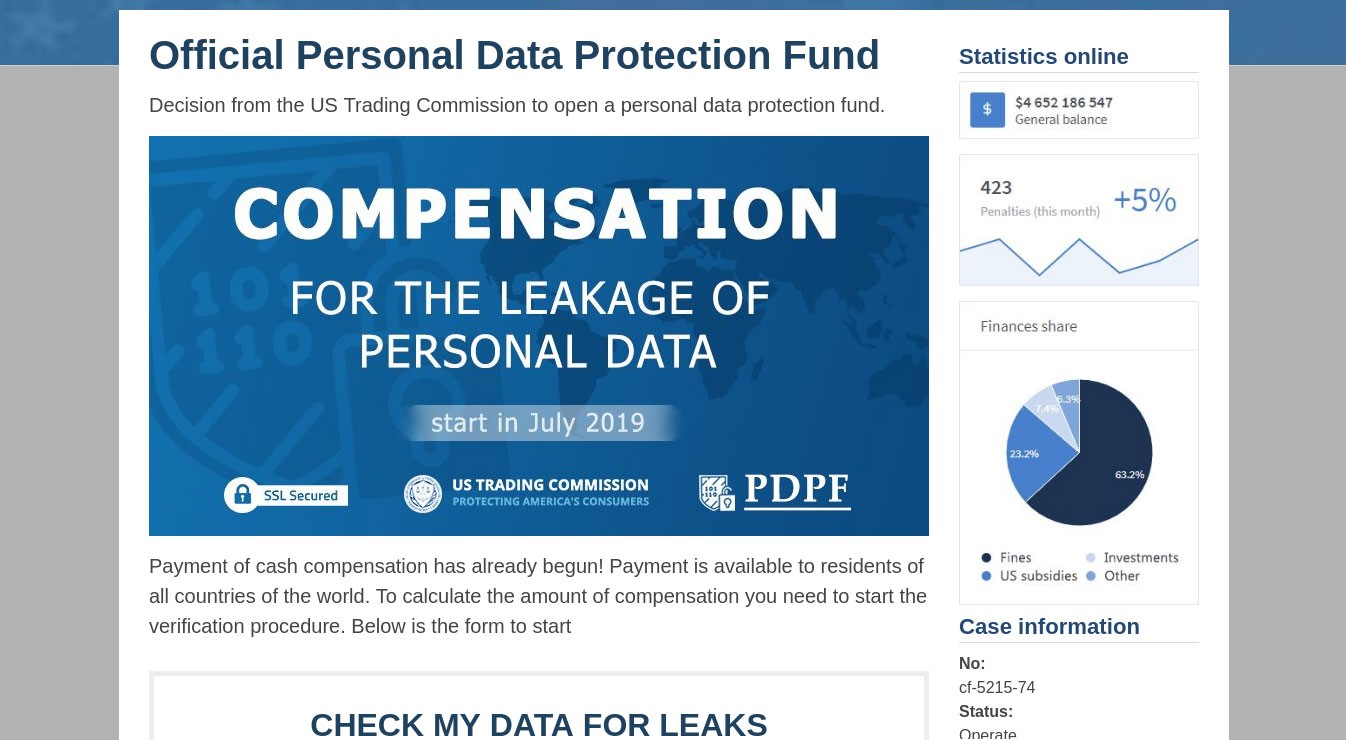
Inspired by the idea of services for checking accounts for leaks, the cybercriminals decided to create their own. Visitors were invited to check whether their account details had been stolen, and if so (the answer was “yes” even if the input was gibberish), they were promised compensation “for the leakage of personal data.”
To receive “compensation,” the victim’s citizenship was of no consequence — what mattered was their first name, last name, phone number, and social network accounts. For extra authenticity, a warning message about the serious consequences of using other people’s data to claim compensation popped up obsessively on the page.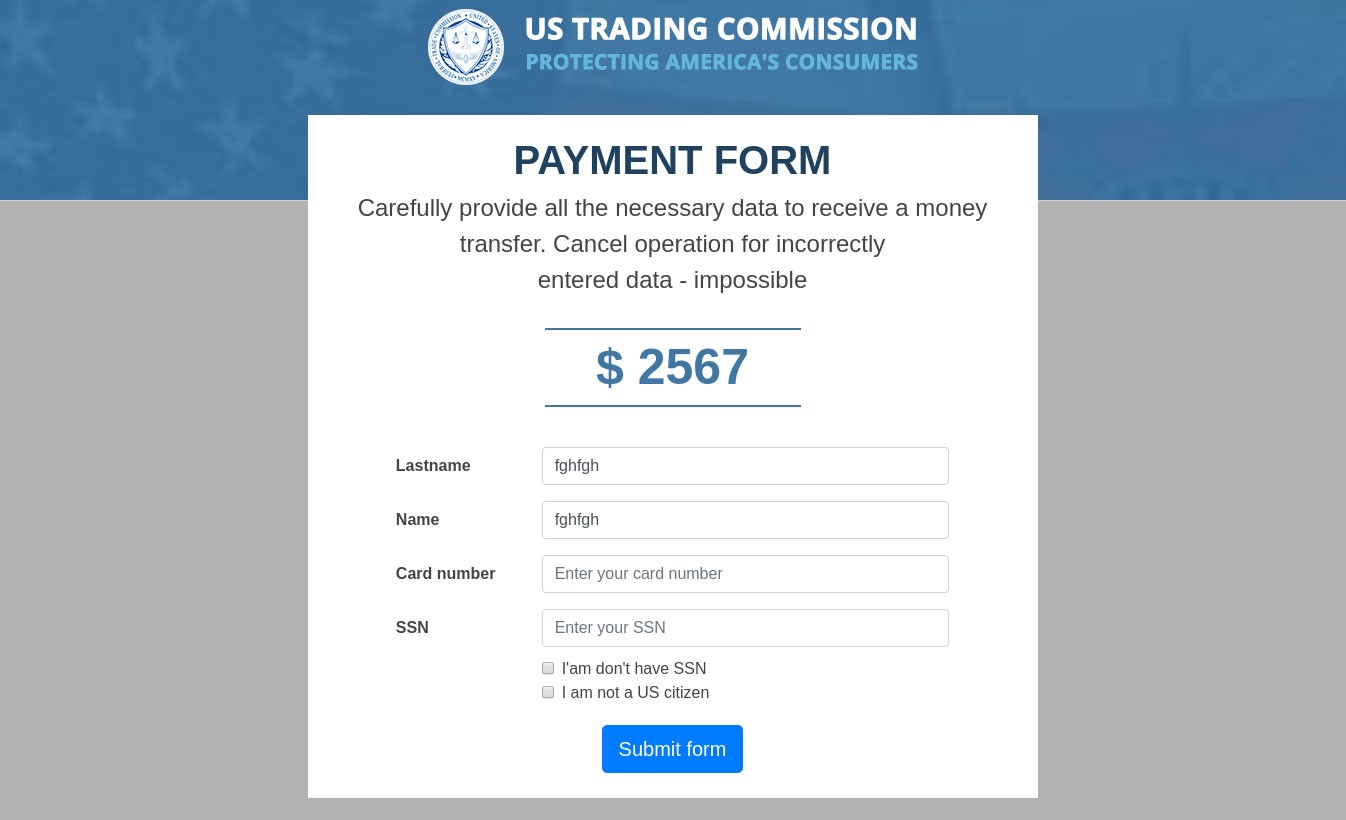
To receive the payment, US citizens were asked to enter their Social Security Number (SSN). Everyone else had to check the box next to the words “I’am don’t have SSN” (the mistakes are a good indicator of a fake), whereupon they were invited to “rent” an SSN for $9. Interestingly, even if the user already had an SSN, they were still pestered to get another one.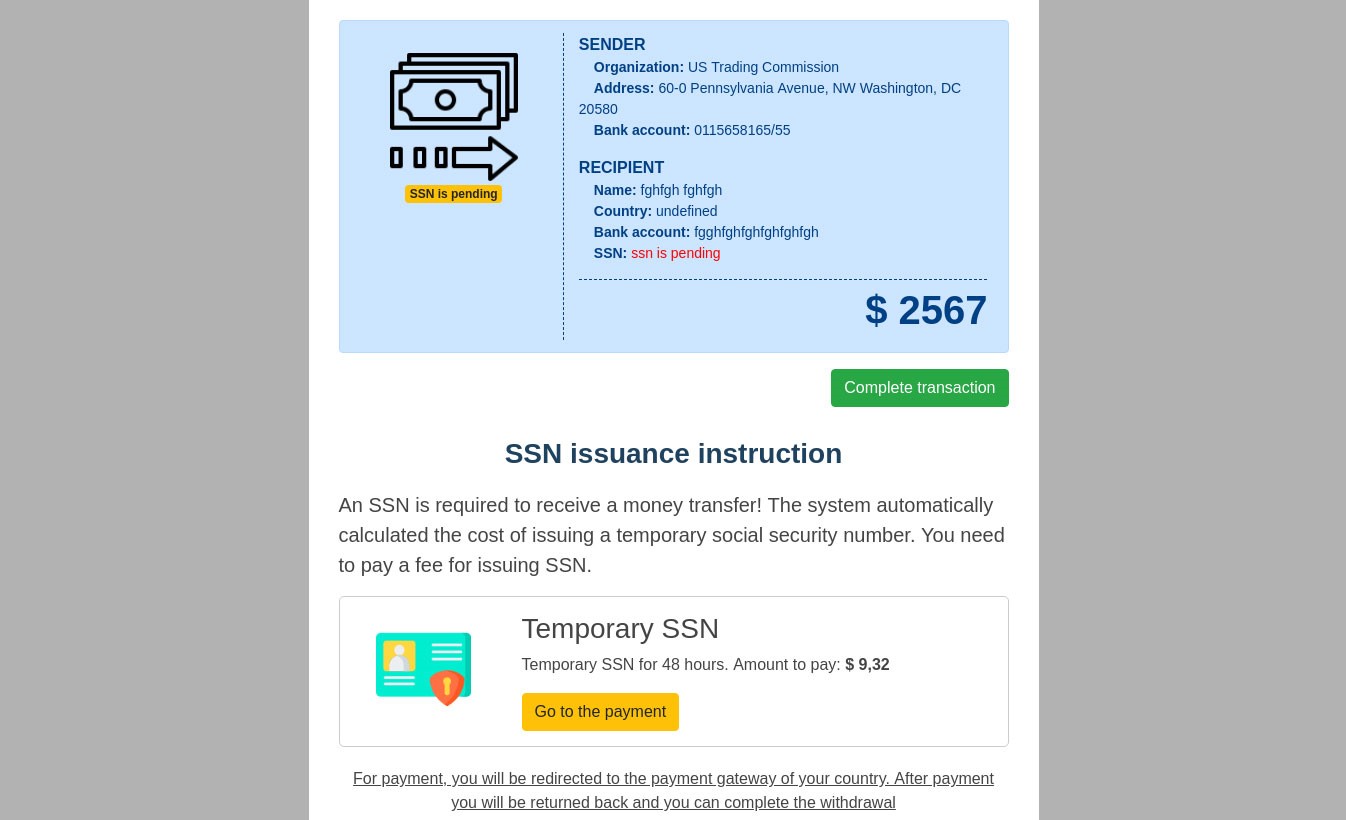
After that, the potential victim was redirected to a payment page with the amount and currency based on the user’s location. For instance, users in Russia were asked to pay in rubles.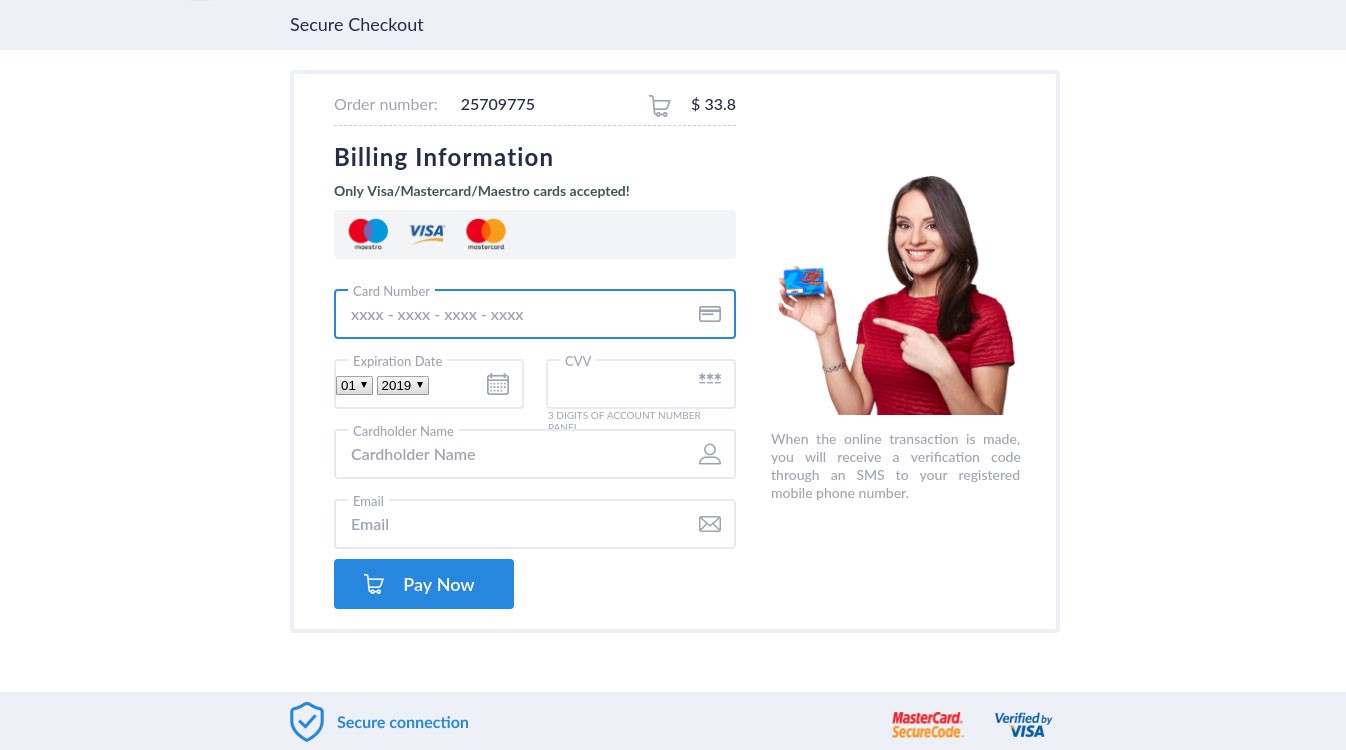
The scam deployed the conventional scheme (especially common in the Runet) of asking the victim to pay a small commission or down payment for the promise of something much bigger. In Q1, 14,725,643 attempts to redirect users to such websites were blocked.
Disaster and pandemic
Fires in Australia
The natural disaster that hit the Australian continent was another get-rich opportunity for scammers. For example, one “Nigerian prince”-style e-mail scam reported that a millionaire dying of cancer was ready to donate her money to save the Australian forests. The victim was asked to help withdraw the funds from the dying woman’s account by paying a fee or making a small contribution to pay for the services of a lawyer, for which they would be rewarded handsomely at a later date.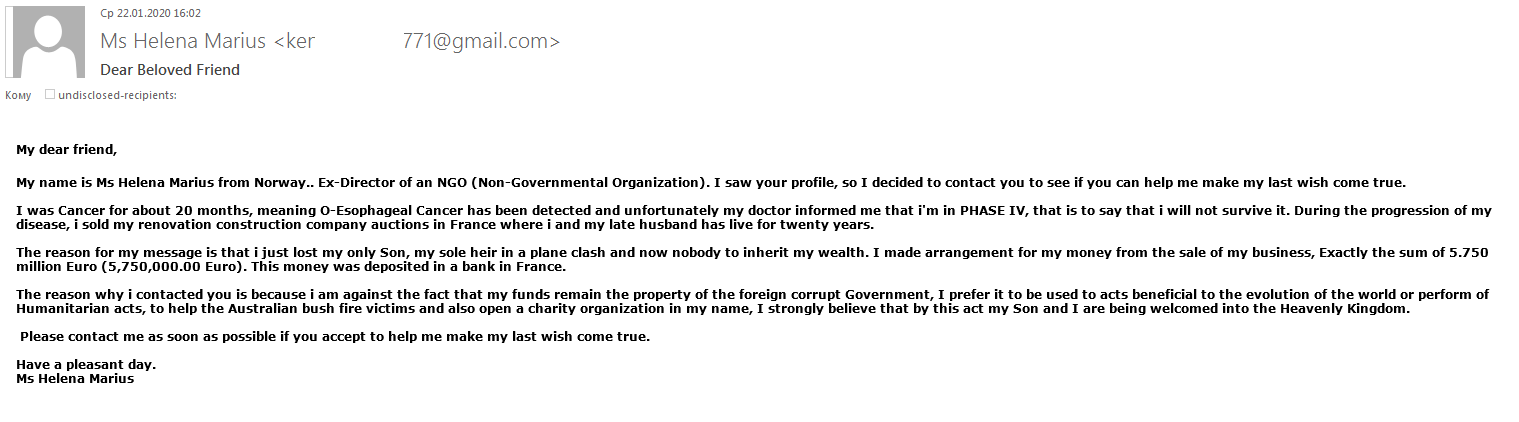
Besides the fictional millionaire, other “nature lovers” were keen to help out — their e-mails were more concise, but the scheme was essentially the same.
COVID-19
“Nigerian prince” scheme
COVID-19 was (and continues to be) a boon to scammers: non-existent philanthropists and dying millionaires are popping up everywhere offering rewards for help to withdraw funds supposedly for humanitarian purpsoses. Some recipients were even invited to help finance the production of a miracle vaccine, or take part in a charity lottery, the proceeds of which, it was said, would be distributed to poor people affected by the pandemic.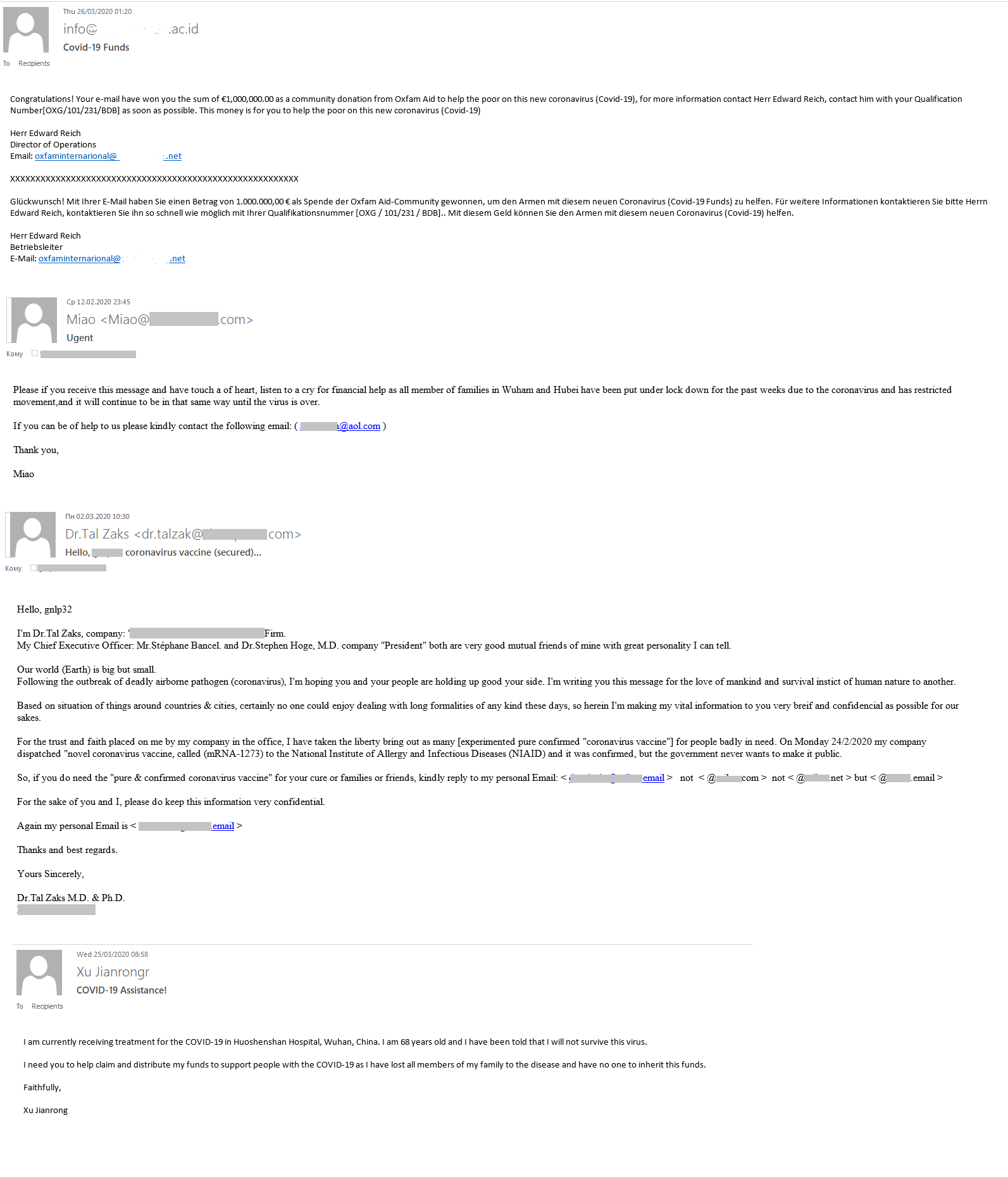
Bitcoin for coronavirus
Having introduced themselves as members of a healthcare organization, the scammers appealed to the victim to transfer a certain sum to the Bitcoin wallet specified in the message. The donation would allegedly go toward fighting the coronavirus outbreak and developing a vaccine, as well as helping victims of the pandemic.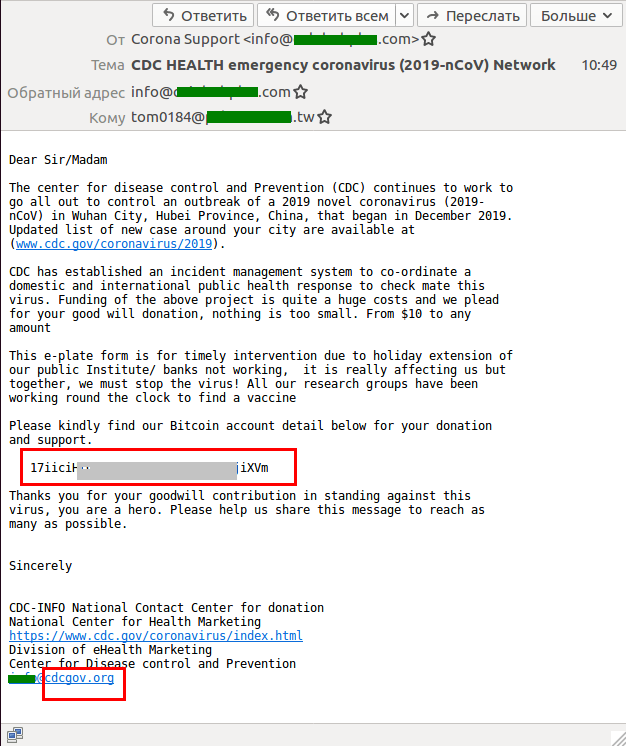
In one e-mail, the attackers played on people’s fear of contracting COVID-19: the message was from an unnamed “neighbor” claiming to be dying from the virus and threatening to infect the recipient unless the latter paid a ransom (which, it was said, would help provide a comfortable old age for the ransomer’s parents).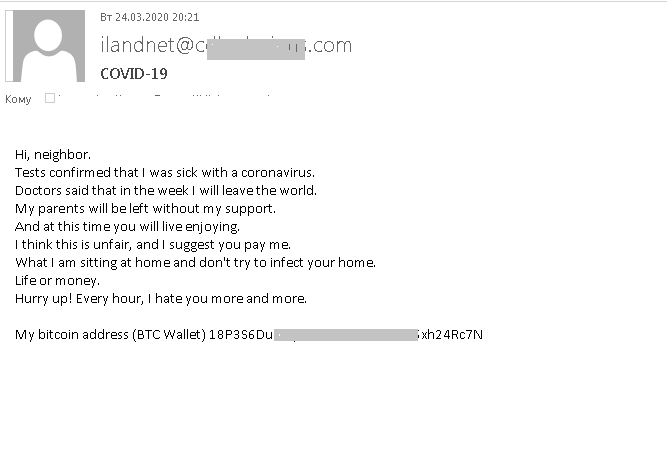
Dangerous advice from the WHO
One fraudulent mailing disguised as a WHO newsletter offered tips about staying safe from COVID-19.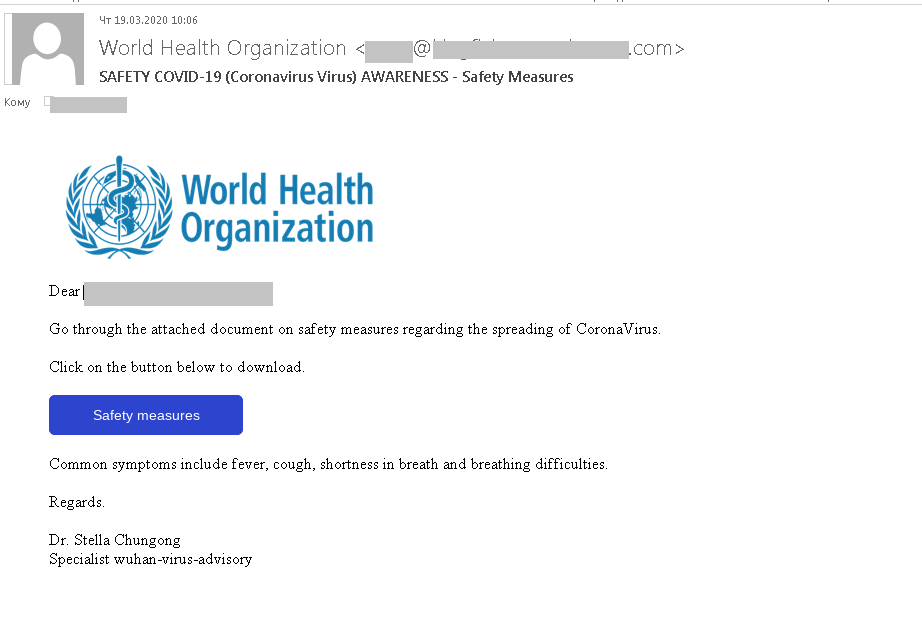
To get the information, the recipient had to click a link pointing to a fake WHO website. The design was so close to the original that only the URL gave away the scam. The cybercriminals were after login credentials for accounts on the official WHO site. Whereas in the first mailings only a username and password were asked for, in later ones a phone number was also requested.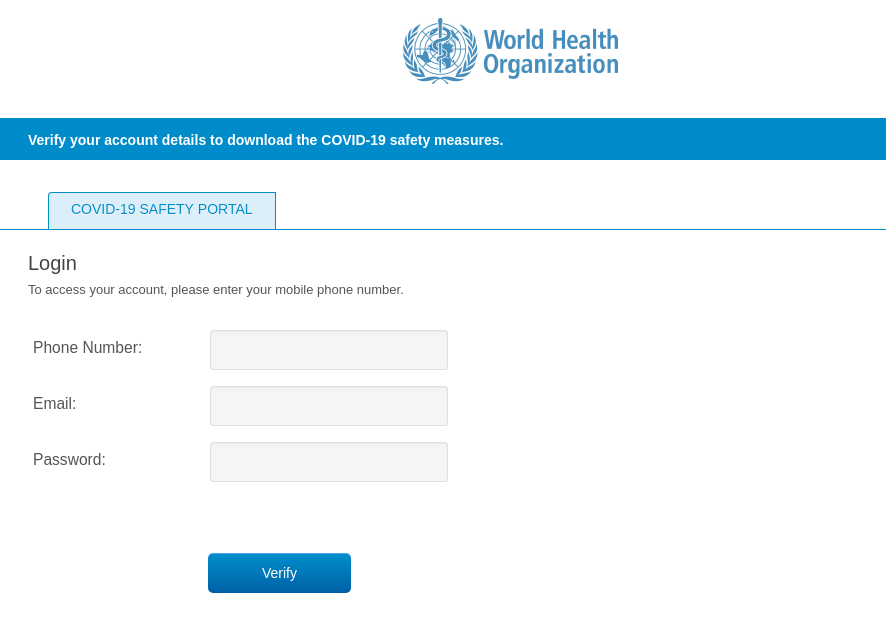
In addition, we detected several e-mails supposedly from the WHO containing documents with malware. The recipient was asked to open the attachment (in DOC or PDF format), which allegedly offered coronavirus prevention advice. For example, this message contained Backdoor.Win32.Androm.tvmf:
There were other, less elaborate mailings with harmful attachments, including ones containing Trojan-Spy.Win32.Noon.gen: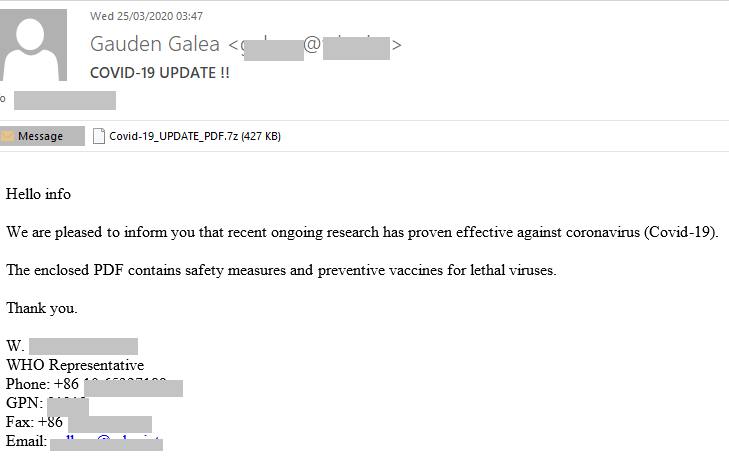
Corporate segment
The coronavirus topic was also exploited in attacks on the corporate sector. For example, COVID-19 was cited in fraudulent e-mails as a reason for delayed shipments or the need to reorder. The authors marked the e-mails as urgent and required to check attached files immediately.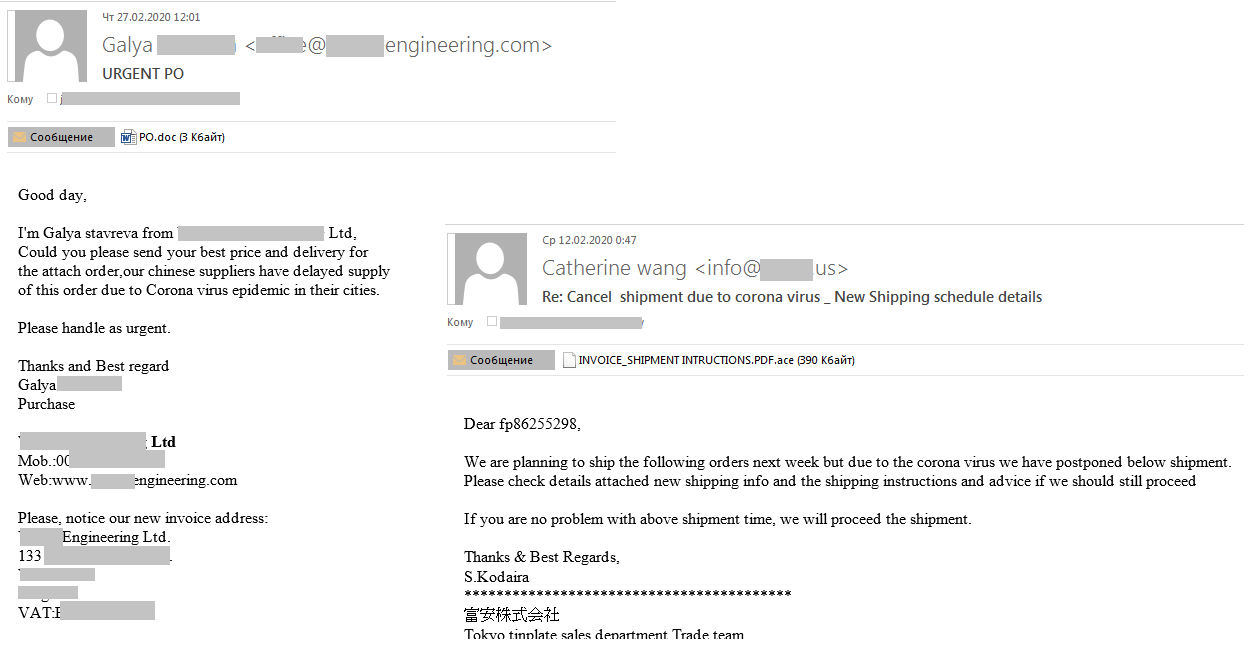
Another mailing prompted recipients to check whether their company was in a list of firms whose activities were suspended due to the pandemic. After which it asked for a form to be filled out, otherwise the company could be shut down. Both the list of companies and the form were allegedly in the archives attached to the message. In actual fact, the attachments contained Trojan-PSW.MSIL.Agensla.a: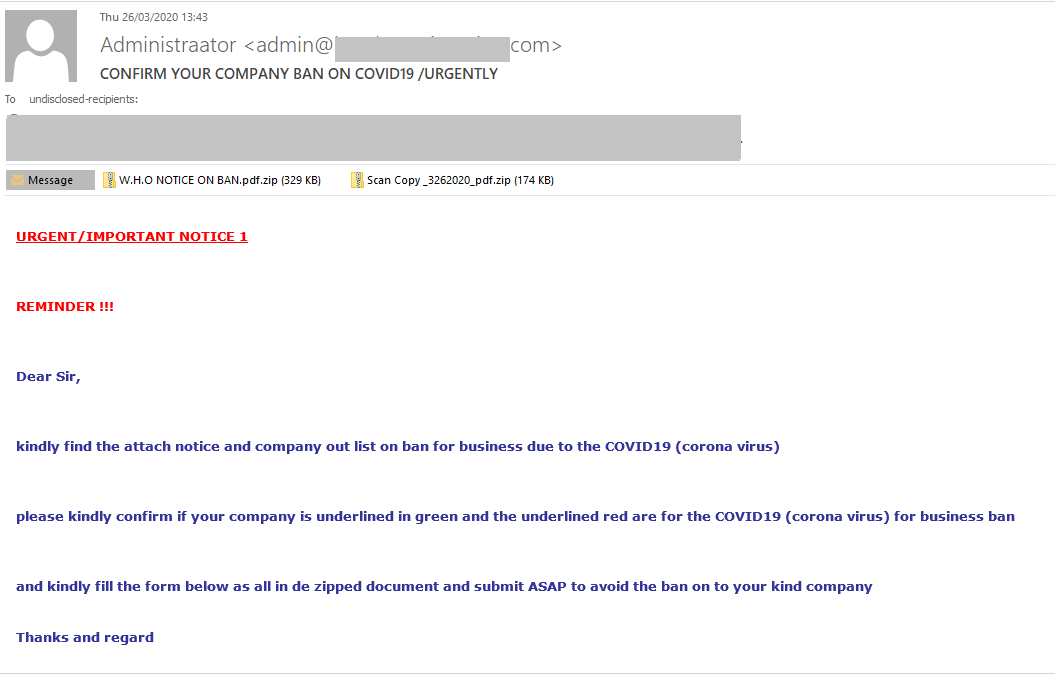
We also registered a phishing attack on corporate users. On a fake page, visitors were invited to monitor the coronavirus situation across the world using a special resource, for which the username and password of the victim’s corporate mail account were required.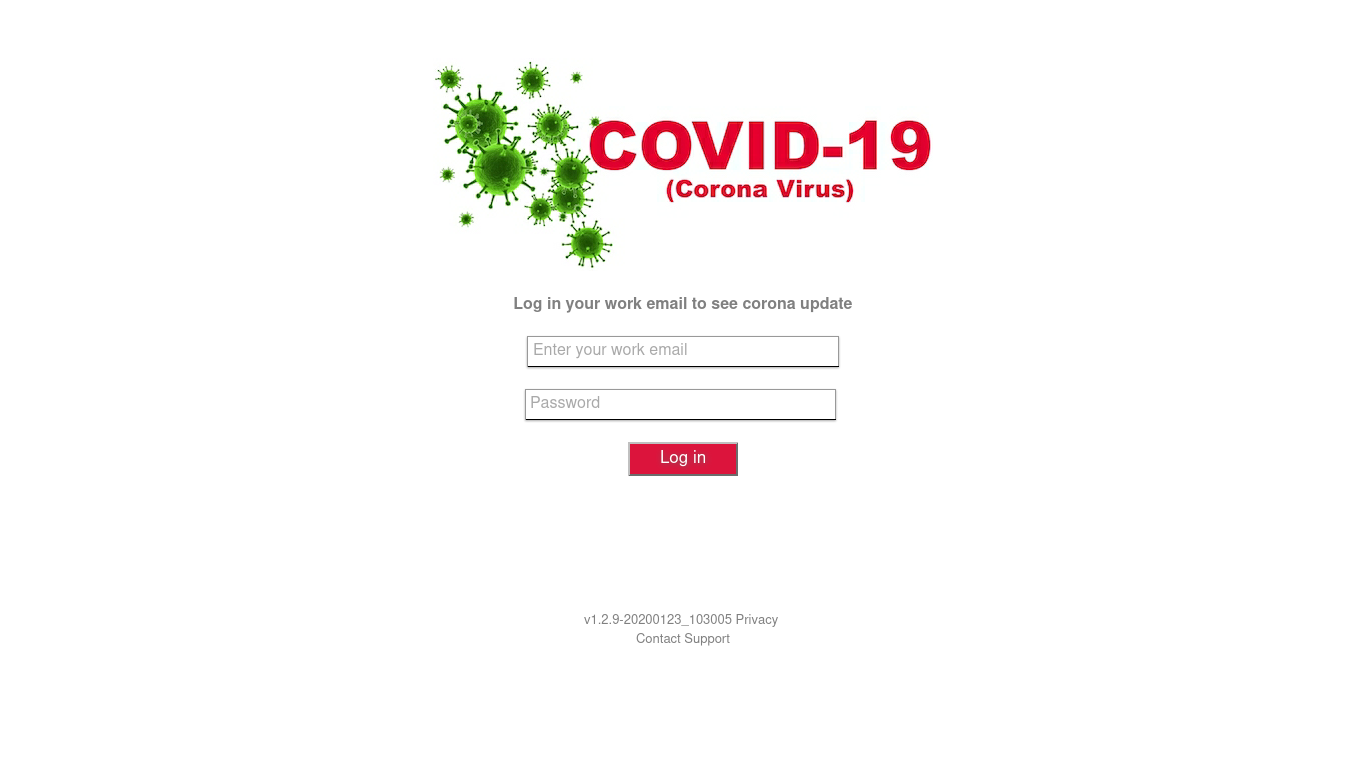
Government compensation
The introduction of measures to counter the pandemic put many people in a difficult financial situation. Forced downtime in many industries has had a negative impact on financial well-being. In this climate, websites offering compensation from the government pose a particular danger.
One such popular scheme was highlighted by a colleague of ours from Brazil. A WhatsApp messages about financial or food assistance were sent that appeared to come from a supermarket, bank, or government department. To receive the aid, the victim had to fill out the attached form and share the message with a certain number of contacts. After the form was filled out, the data was sent to the cybercriminals, while the victim got redirected to a page with advertising, a phishing site, a site offering a paid SMS subscription, or similar.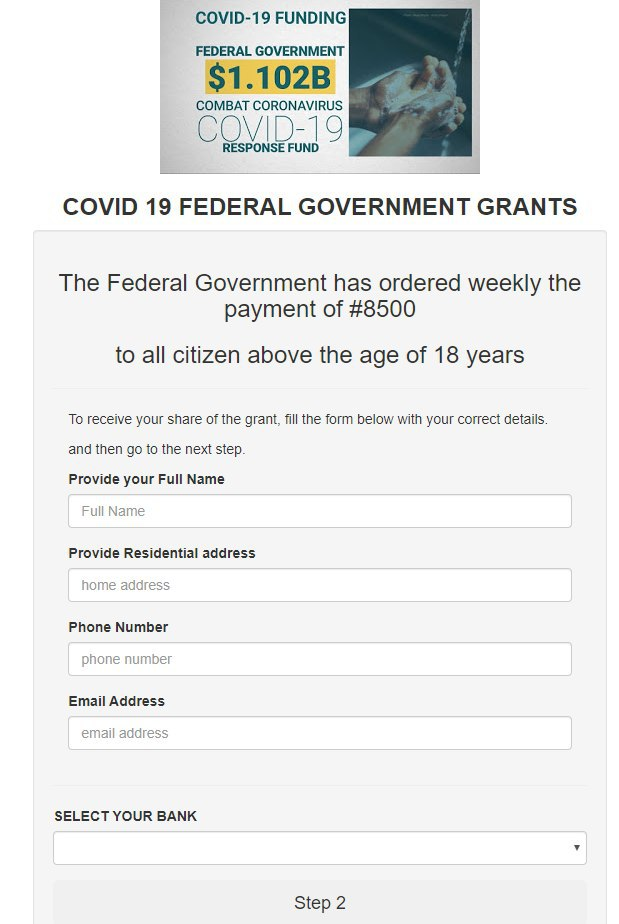

Given that the number of fake sites offering government handouts seems likely only to increase, we urge caution when it comes to promises of compensation or material assistance.
Anti-coronavirus protection with home delivery
Due to the pandemic, demand for antiseptics and antiviral agents has spiked. We registered a large number of mailings with offers to buy antibacterial masks.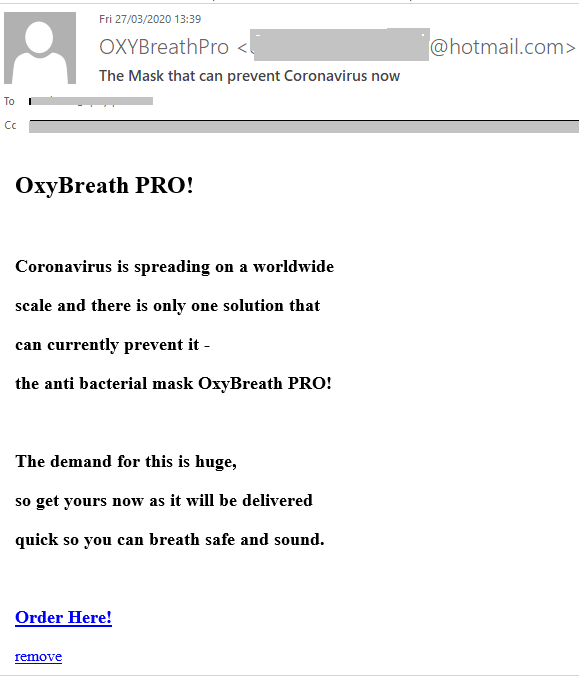
In Latin America, WhatsApp mass messages were used to invite people to take part in a prize draw for hand sanitizer products from the brewing company Ambev. The company has indeed started making antiseptics and hand gel, but exclusively for public hospitals, so the giveaway was evidently the work of fraudsters.
The number of fake sites offering folk remedies for the treatment of coronavirus, drugs to strengthen the immune system, and non-contact thermometers and test kits has also risen sharply. Most of the products on offer have no kind of certification whatsoever.
On average, the daily share of e-mails mentioning COVID-19 in Q1 amounted to around 6% of all junk traffic. More than 50% of coronavirus-related spam was in the English language. We anticipate that the number of phishing sites and pandemic-related scams will only increase, and that cybercriminals will use new attack schemes and strategies.
Statistics: spam
Proportion of spam in mail traffic
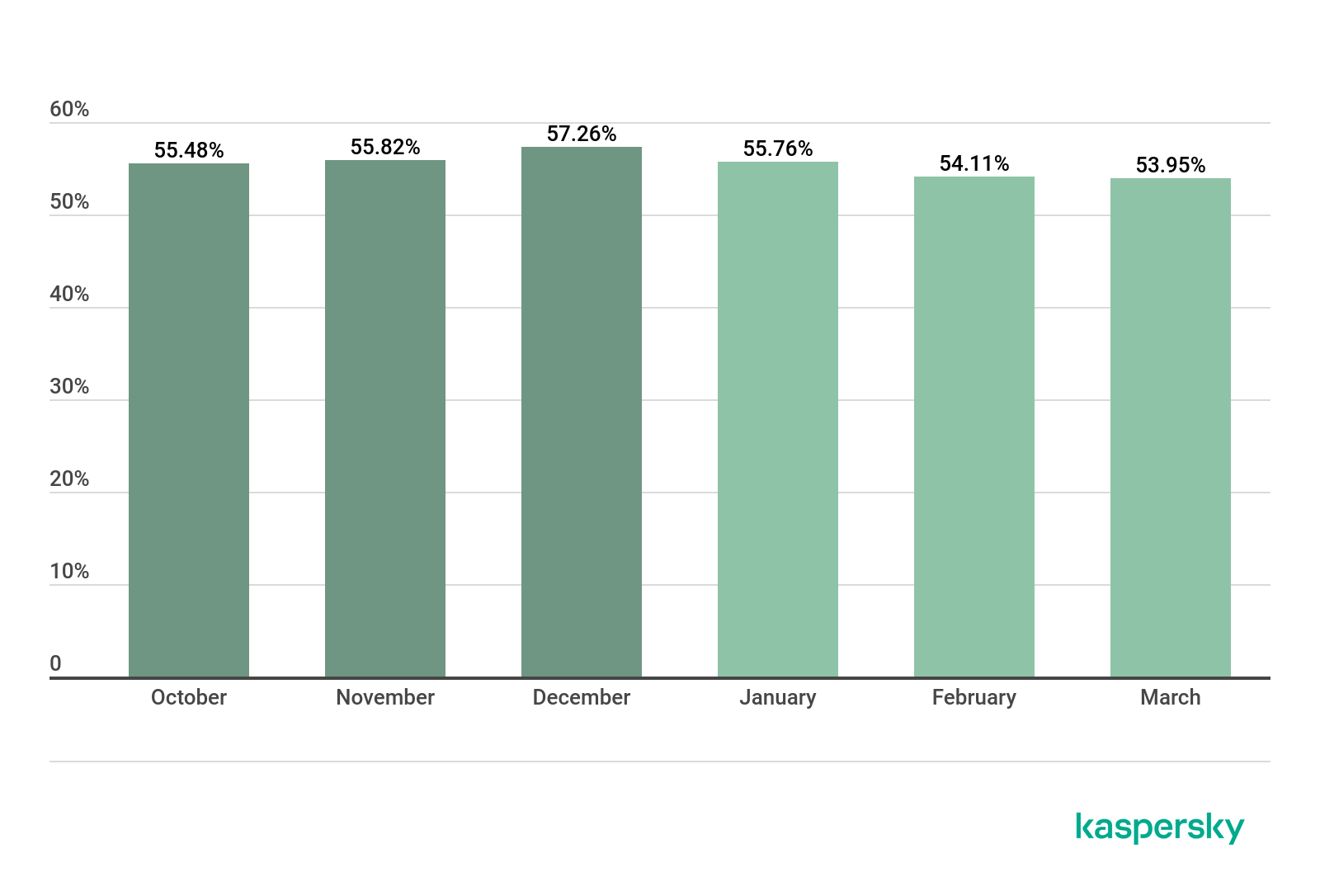
Proportion of spam in global mail traffic, Q4 2019 – Q1 2020 (download)
In Q1 2020, the largest share of spam was recorded in January (55.76%). The average percentage of spam in global mail traffic was 54.61%, down 1.58 p.p. against the previous reporting period.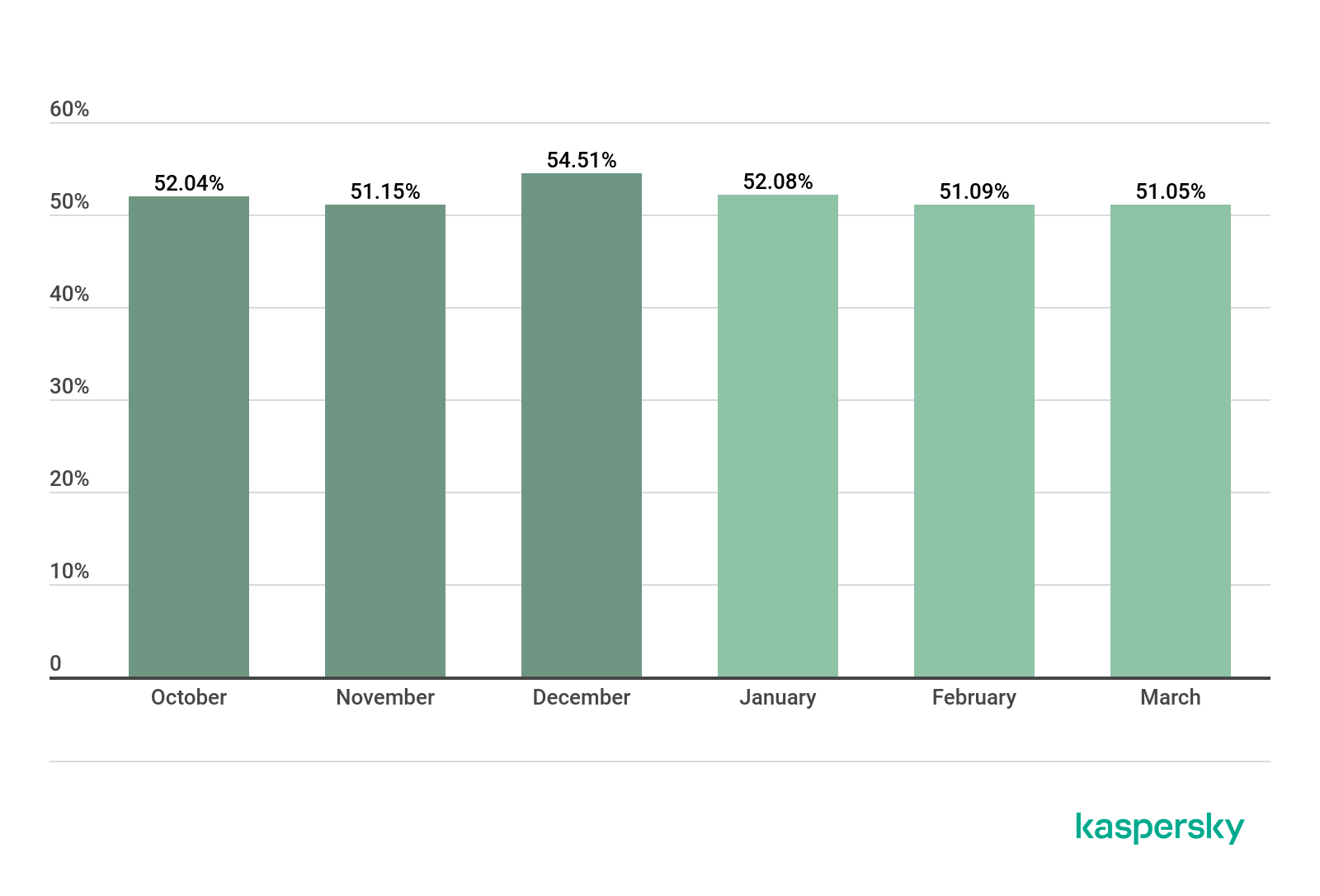
Proportion of spam in Runet mail traffic, Q4 2019 – Q1 2020 (download)
In Q1, the share of spam in Runet traffic (the Russian segment of the Internet) likewise peaked in January (52.08%). At the same time, the average indicator, as in Q4 2019, remains slightly lower than the global average (by 3.20 p.p.).
Sources of spam by country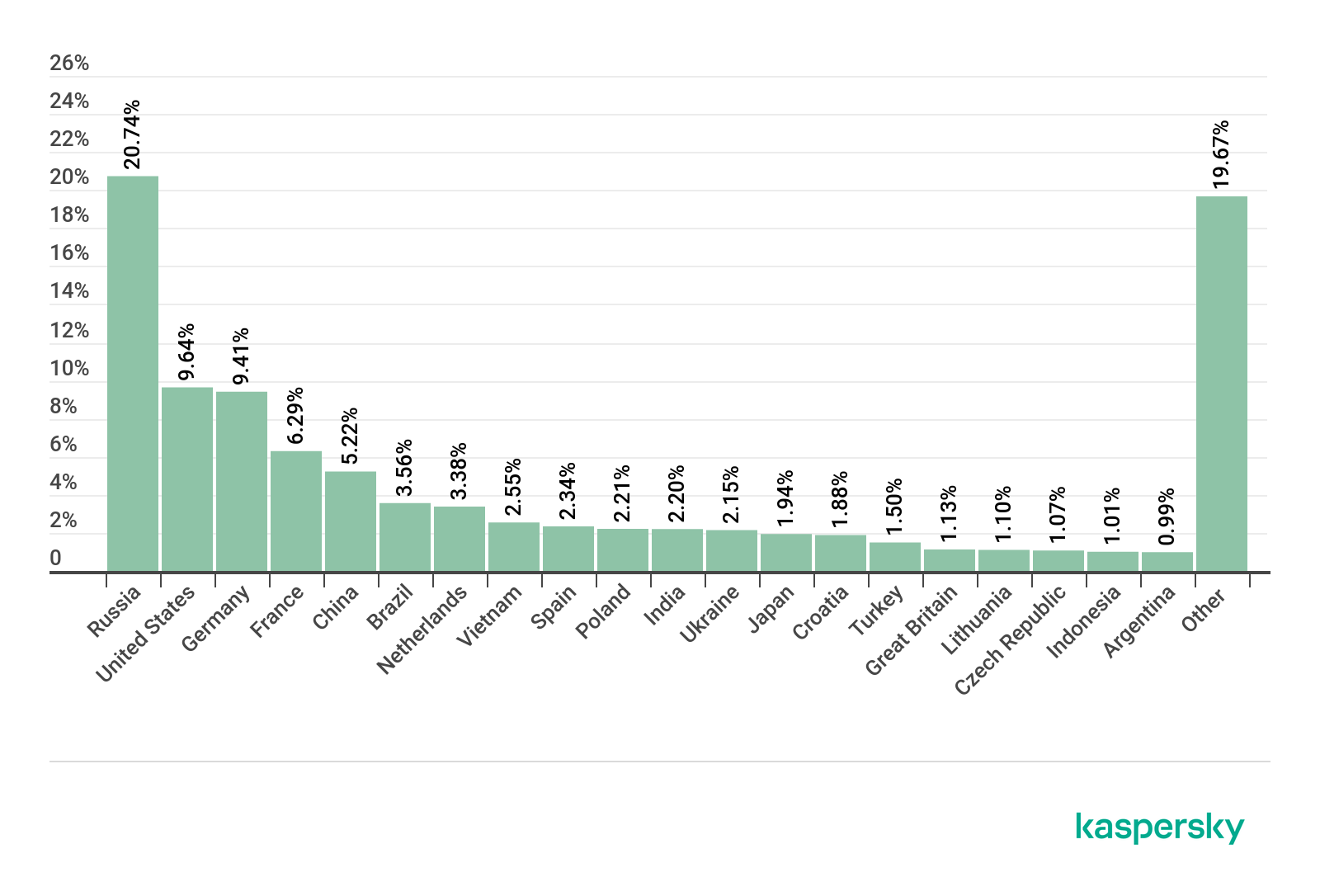
Sources of spam by country, Q1 2020 (download)
In Q1 2020, Russia led the TOP 5 countries by amount of outgoing spam. It accounted for 20.74% of all junk traffic. In second place came the US (9.64%), followed by Germany (9.41%) just 0.23 p.p. behind. Fourth place goes to France (6.29%) and fifth to China (5.22%), which is usually a TOP 3 spam source.
Brazil (3.56%) and the Netherlands (3.38%) took sixth and seventh positions, respectively, followed by Vietnam (2.55%), with Spain (2.34%) and Poland (2.21%) close on its heels in ninth and tenth.
Spam e-mail size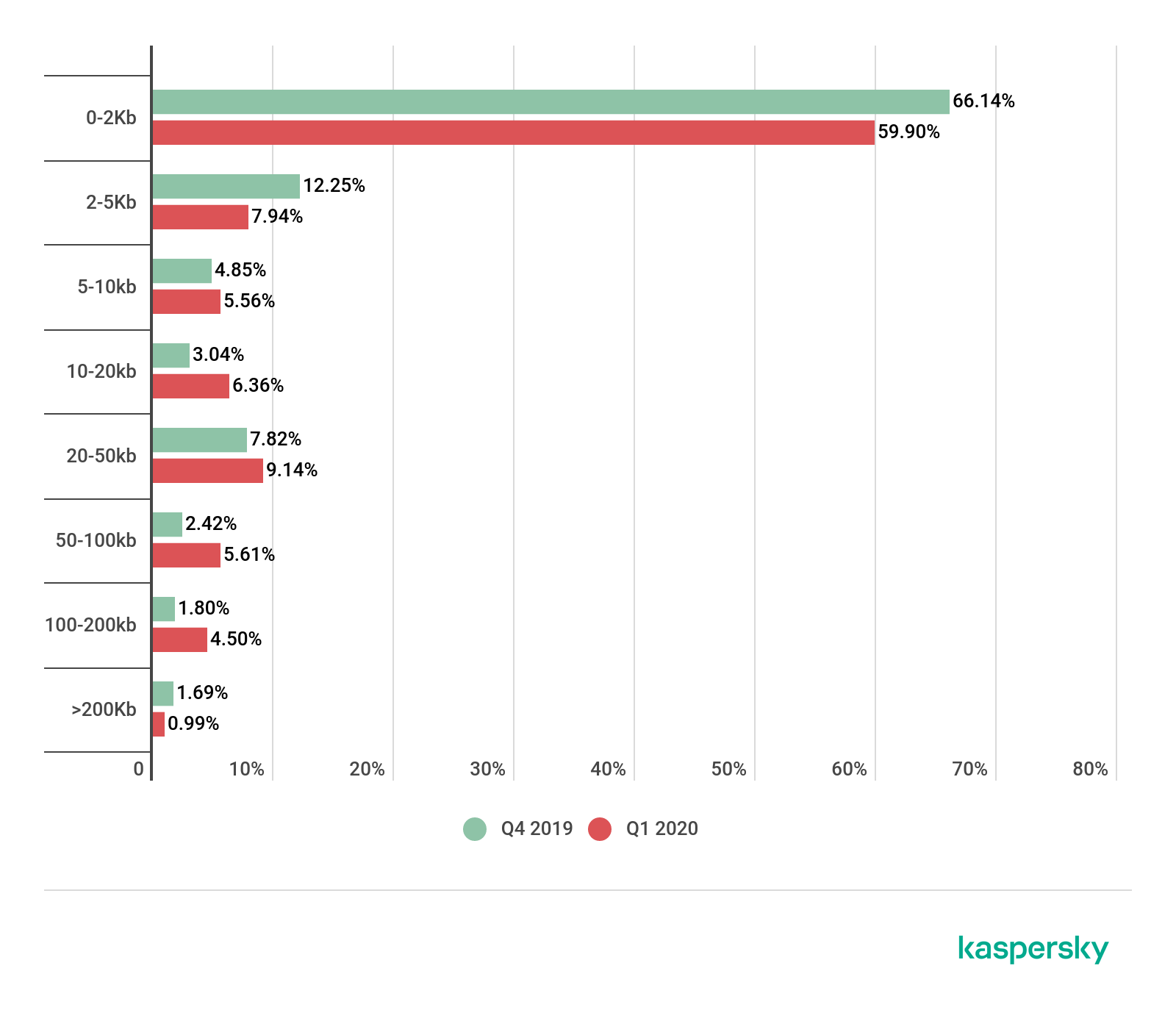
Spam e-mail size, Q4 2019 – Q1 2020 (download)
Compared to Q4 2019, the share of very small e-mails (up to 2 KB) in Q1 2020 fell by more than 6 p.p. and amounted to 59.90%. The proportion of e-mails sized 5-10 KB grew slightly (by 0.72 p.p.) against the previous quarter to 5.56%.
Meanwhile, the share of 10-20 KB e-mails climbed by 3.32 p.p. to 6.36%. The number of large e-mails (100–200 KB) also posted growth (+2.70 p.p.). Their slice in Q1 2020 was 4.50%.
Malicious attachments in e-mail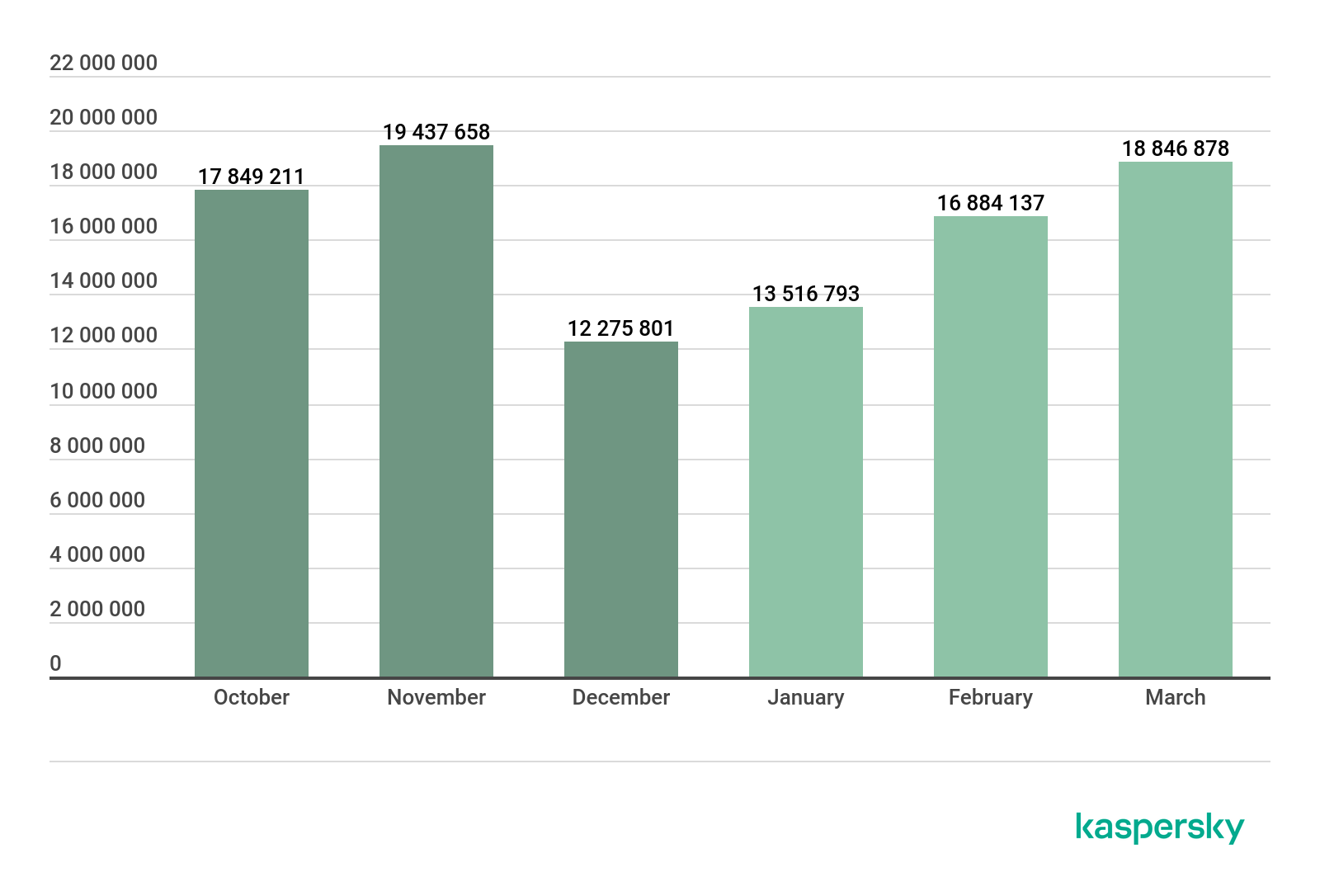
Number of Mail Anti-Virus triggerings, Q4 2019 – Q1 2020 (download)
In Q1 2020, our security solutions detected a total of 49,562,670 malicious e-mail attachments, which is almost identical to the figure for the last reporting period (there were just 314,862 more malicious attachments detected in Q4 2019).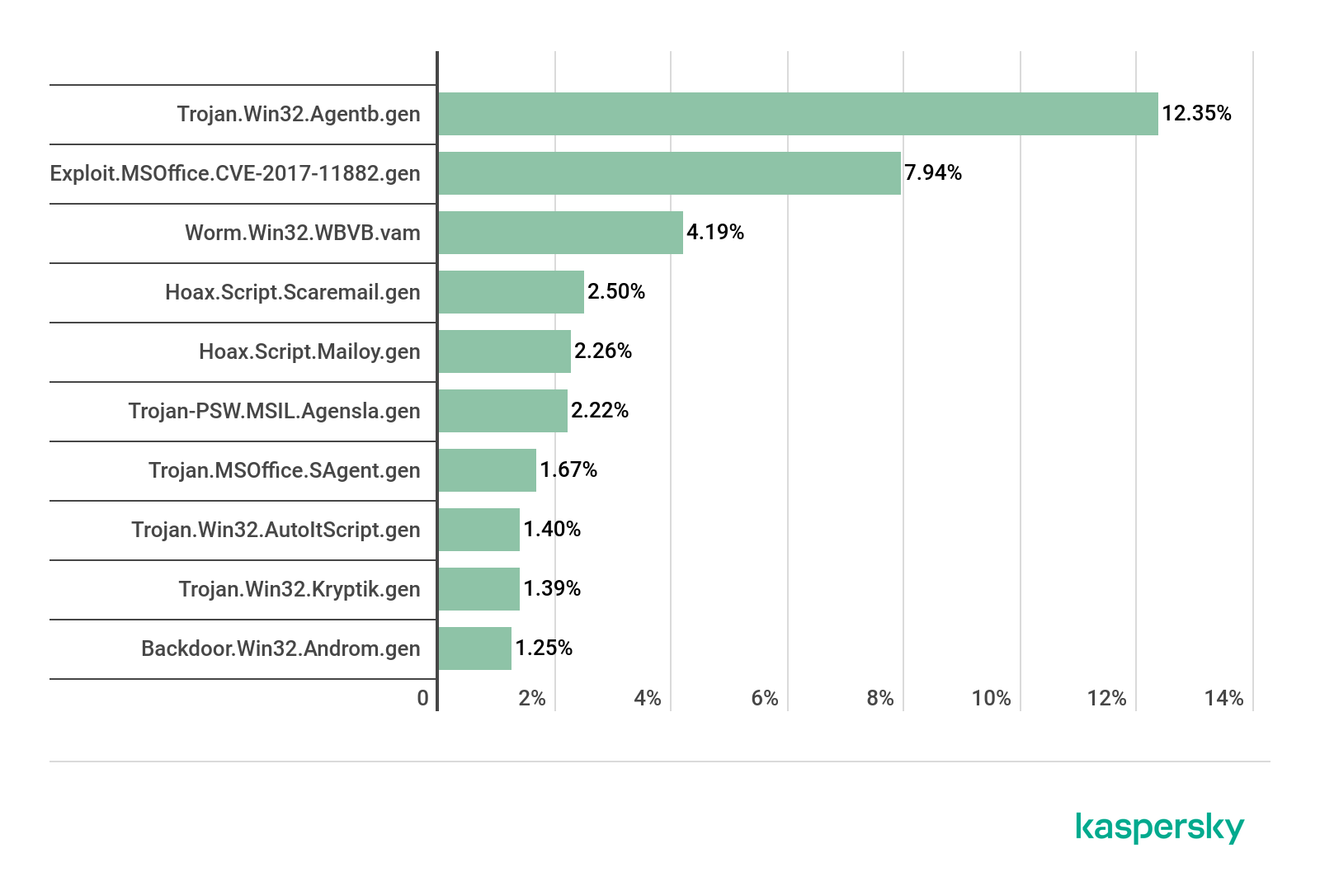
TOP 10 malicious attachments in mail traffic, Q1 2020 (download)
In Q1, first place in terms of prevalence in mail traffic went to Trojan.Win32.Agentb.gen (12.35%), followed by Exploit.MSOffice.CVE-2017-11882.gen (7.94%) in second and Worm.Win32.WBVB.vam (4.19%) in third.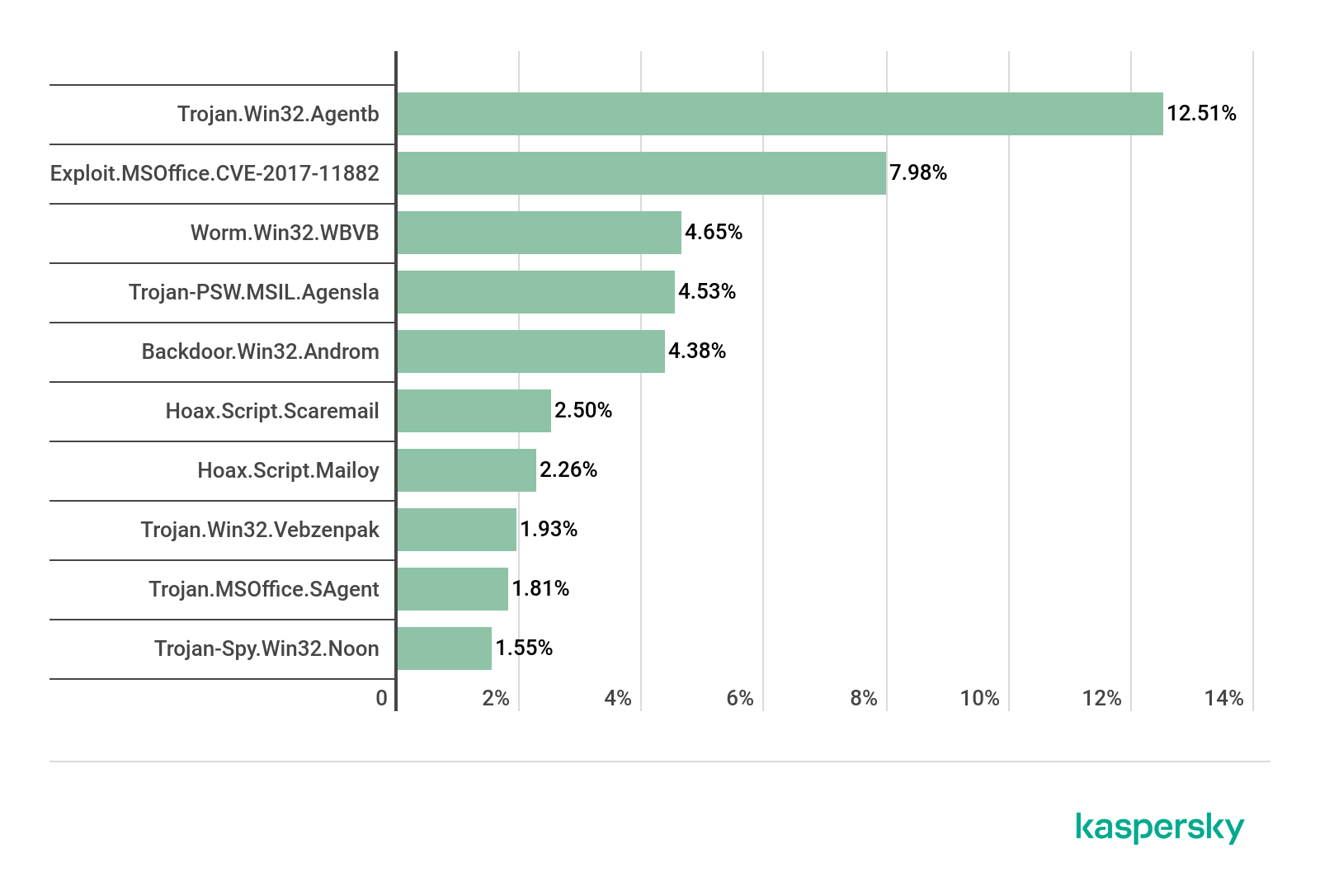
TOP 10 malicious families in mail traffic, Q1 2020 (download)
As regards malware families, the most widespread this quarter was Trojan.Win32.Agentb (12.51%), with Exploit.MSOffice.CVE-2017-11882 (7.98%), whose members exploit a vulnerability in Microsoft Equation Editor, in second place and Worm.Win32.wbvb (4.65%) in third.
Countries targeted by malicious mailshots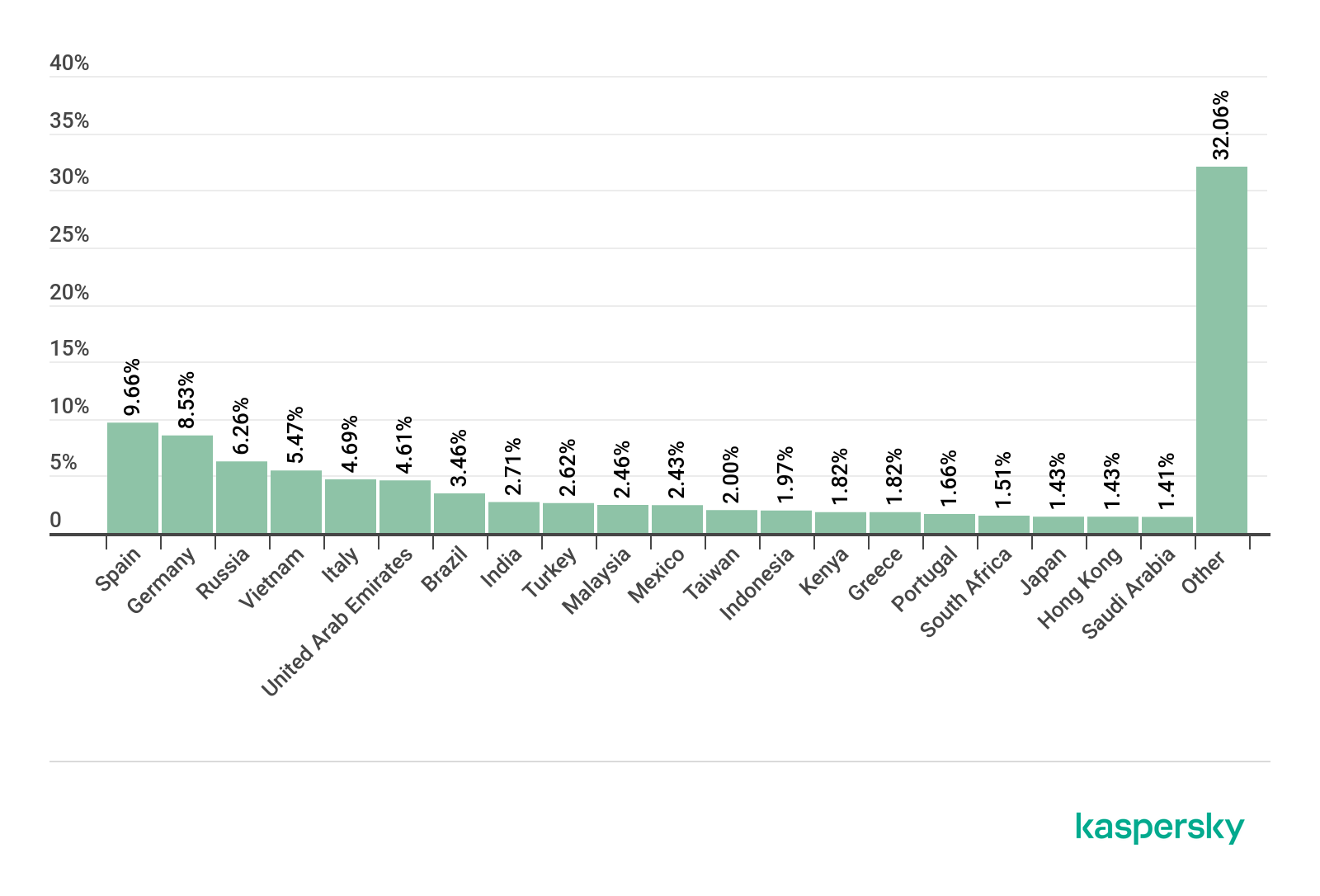
Distribution of Mail Anti-Virus triggerings by country, Q1 2020 (download)
First place by number of Mail Anti-Virus triggerings in Q1 2020 was claimed by Spain. This country accounted for 9.66% of all users of Kaspersky security solutions who encountered e-mail malware worldwide. Second place went to Germany (8.53%), and Russia (6.26%) took bronze.
Statistics: phishing
In Q1 2020, the Anti-Phishing system prevented 119,115,577 attempts to redirect users to scam websites. The percentage of unique attacked users was 8.80% of the total number of users of Kaspersky products in the world.
Attack geography
The country with the largest proportion of users attacked by phishers, not for the first time, was Venezuela (20.53%).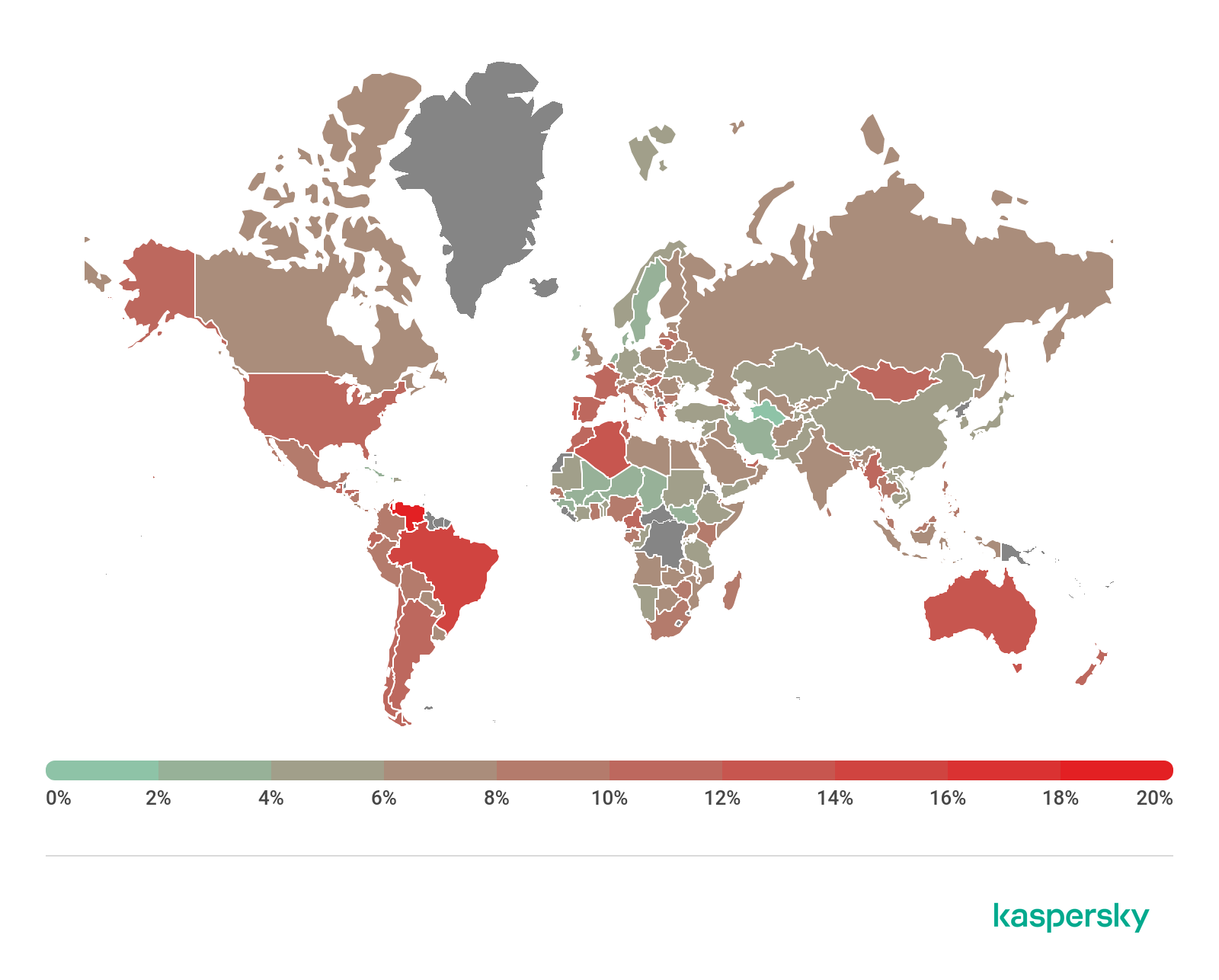
Geography of phishing attacks, Q1 2020 (download)
In second place, by a margin of 5.58 p.p., was Brazil (14.95%), another country that is no stranger to the TOP 3. Next came Australia (13.71%), trailing by just 1.24 p.p.
Country %*
Venezuela 20.53%
Brazil 14.95%
Australia 13.71%
Portugal 12.98%
Algeria 12.12%
France 11.71%
Honduras 11.62%
Greece 11.58%
Myanmar 11.54%
Tunisia 11.53%
* Share of users on whose computers Anti-Phishing was triggered out of all Kaspersky users in the country
Organizations under attack
The rating of attacks by phishers on different categories of organizations is based on detections by Kaspersky products Anti-Phishing component. This component detects pages with phishing content that the user gets redirected to. It does not matter whether the redirect is the result of clicking a link in a phishing e-mail or in a message on a social network, or the result of a malicious program activity. When the component is triggered, a banner is displayed in the browser warning the user about a potential threat.
The largest share of phishing attacks in Q1 2020 fell to the Online Stores category (18.12%). Second place went to Global Internet Portals (16.44%), while Social Networks (13.07%) came in third.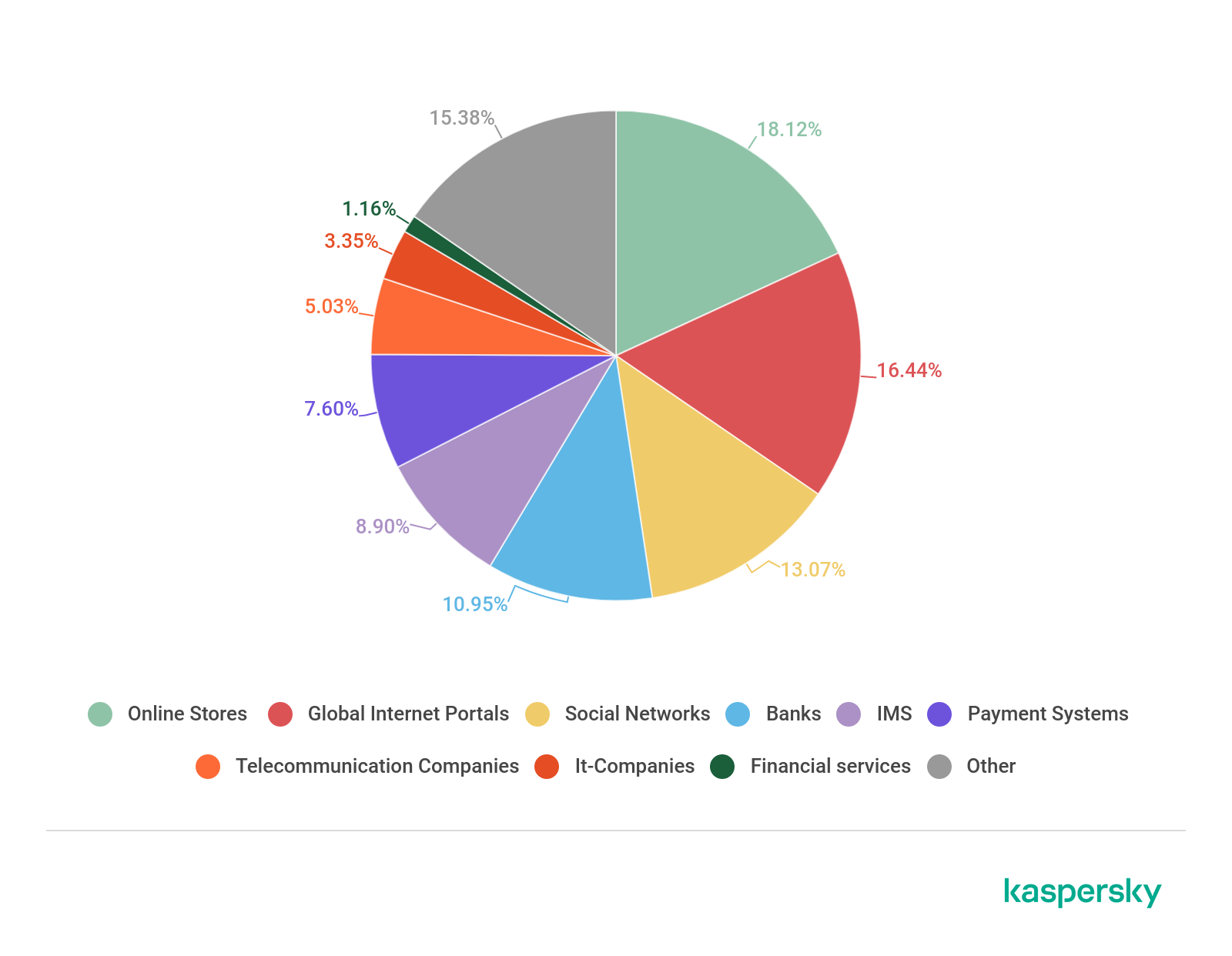
Distribution of organizations affected by phishing attacks by category, Q1 2020 (download)
As for the Banks category, a TOP 3 veteran, this time it placed fourth with 10.95%.
Conclusion
Glancing at the results of Q1 2020, we anticipate that the COVID-19 topic will continue to be actively used by cybercriminals for the foreseeable future. To attract potential victims, the pandemic will be mentioned even on “standard” fake pages and in spam mailings.
The topic is also used extensively in fraudulent schemes offering compensation and material assistance.
It is highly likely that this type of fraud will become more frequent.
The average share of spam in global mail traffic (54.61%) this quarter decreased by 1.58 p.p. against the previous reporting period, while the number of attempted redirects totaled nearly 120 million.
Top of this quarter’s list of spam-source countries is Russia, with a share of 20.74%. Our security solutions blocked 49,562,670 malicious mail attachments, while the most common mail-based malware family, with a 12.35% share of mail traffic, was Trojan.Win32.Agentb.gen.