
An example of an AT&T phishing Google Form page. Credit: Zimperium
Phishing Articles - H 2020 1 2 3 4 5 6 7 8 Phishing List - H 2021 2020 2019 2018 1 Phishing blog Phishing blog
Google Forms Abused to Phish AT&T Credentials
5.11.20 Phishing Threatpost
More than 200 Google Forms impersonate top brands – including Microsoft OneDrive, Office 365, and Wells Fargo – to steal victims’ credentials.
Researchers are warning of phishing attacks that leverage Google Forms as a landing page to collect victims’ credentials. The forms masquerade as login pages from more than 25 different companies, brands and government agencies.
So far, 265 different Google Forms used in these attacks have been uncovered, which are likely sent to victims via email (using social engineering tactics). More than 70 percent of these forms purported to be from AT&T. However, other big brands – including financial orgs like Citibank and Capital One, collaboration apps like Microsoft OneDrive and Outlook, and government agencies like the Internal Revenue Service (IRS) and even the Mexican government – were also seen (a full list of impersonated brands is available here).
“According to our findings, the links remained active for several months after being added to public phishing databases,” according to Zimperium researchers in a Tuesday analysis. “All of the Google Forms were removed by Google after we reported it to them.”
Google Forms is a survey administration app – utilized for quizzes, RSVPs and otherwise – that are part of Google’s Docs Office Suite and Classroom. Many of the phishing Google Forms – like the AT&T form below – utilize the company’s brand, and tell users to “sign in” with their email and password, then to click “submit.”
Researchers said that cybercriminals’ use of Google Forms is clever from a phishing perspective, as they are easy to create and are hosted under the Google domain. The Google domain host gives victims the false sense that they are legitimate and avoids phishing detection tactics.

An example of an AT&T phishing Google Form page. Credit: Zimperium
Google Forms also provide a valid SSL certificate, which can fool users who rely on the “secure” indication of the browsers. While this “secure” icon next to the URL gives users the impression that the page is not malicious, it merely shows that it is an encrypted HTTPS connection using a valid SSL certificate.
There are two red flags that pop up when a user is presented with a Google Form phishing page – first of all, though the impersonated brand is used, the forms can look strange and not like the legitimate page. For instance, the final button always said “Submit” (instead of the typical Login), and the default completion or message on all fields was “Your answer” (instead of “your username” and “your password”).
“There are several differences that will alert some experienced users, but lots of users will write their credentials on any form showing a company logo, unless the browser or a security tool warns them,” said researchers.
Second of all, Google Forms state automatically at the base of each form “never submit password via Google forms.” However, this is evidentially ignored by many victims, said researchers.
“This form wasn’t detected as phishing using most of the common industry techniques since it used a high-reputation domain, established several years ago and it used a valid SSL certificate,” said researchers.
With the ongoing pandemic, worries about cyberattackers leveraging various brands like Microsoft Teams, Zoom and Skype have been piqued. In May, a convincing campaign that impersonated notifications from Microsoft Teams in order to steal the Office 365 credentials of employees circulated, with two separate attacks that targeted as many as 50,000 different Teams users. Earlier in October, researchers warned of a phishing campaign that pretends to be an automated message from Microsoft Teams. In reality, the attack aims to steal Office 365 recipients’ login credentials.
Microsoft Teams phishing campaign targeted up to 50,000 Office 365 users
24.10.20 Phishing Securityaffairs
Experts warn of a phishing campaign that already targeted up to 50,000 Office 365 users with a fake automated message from Microsoft Teams.
Secruity researchers reported that up to 50,000 Office 365 users have been targeted by a phishing campaign that pretends to be automated message from Microsoft Teams. The bait message uses fake notifications of a “missed chat” from Microsoft Teams, the campaigns aims at stealing Office 365 recipients’ login credentials.
Like other collaboration and communications platforms, the popularity of Microsoft Teams has risen since the beginning of the Covid-19 pandemic because a growing number of organizations started using the remote working model. Threat actors are adapting their attack techniques to exploit the ongoing situation, researchers from Abnormal Security observed campaign that hit between 15,000 to 50,000 Office 365 users.
“This attack impersonates an automated message from Microsoft Teams in order to steal recipient’s login credentials.” reads the report published by Abnormal Security. “The email is sent from the display name, ‘There’s new activity in Teams’, making it appear like an automated notification from Microsoft Teams. It appears to notify the recipient that their teammates are trying to reach them and urges the recipient to click on ‘Reply in Teams’. However, this leads to a phishing page.”
The bait email displays the name “There’s new activity in Teams” to trick the victims into believing that it is an automated notification from Microsoft Teams.
The email tells the recipient that they have missed Microsoft Team chats and show an example of a teammate chat that asks them to submit something by Wednesday of next week.
The researchers that the campaing is not targeted in nature as the employee referenced in the chats doesn’t appear to be an employee of the company that was targeted by the attackers.
Recipient could respond to the email by click on the “Reply in Teams” button that is present in the content of the message, but as a consequence of this action, the victim is redirected to a phishing page.
“Within the body of the email, there are three links appearing as ‘Microsoft Teams’, ‘(contact) sent a message in instant messenger’, and ‘Reply in Teams’,” continues the analysis. “Clicking on any of these leads to a fake website that impersonates the Microsoft login page. The phishing page asks the recipient to enter their email and password.”
The phishing landing looks like a Microsoft login page, its URL begins with the “microsftteams” to appear as legitimate.
“The attacker spoofed employee emails and also impersonated Microsoft Teams. The recipient is more likely to fall prey to an attack when it is believed to originate from within the company and also from a trusted brand.” concludes the report.
Microsoft Teams Phishing Attack Targets Office 365 Users
23.10.20 Phishing Threatpost
Up to 50,000 Office 365 users are being targeted by a phishing campaign that purports to notify them of a “missed chat” from Microsoft Teams.
Researchers are warning of a phishing campaign that pretends to be an automated message from Microsoft Teams. In reality, the attack aims to steal Office 365 recipients’ login credentials.
Teams is Microsoft’s popular collaboration tool, which has particularly risen in popularity among remote workforces during the pandemic – making it an attractive brand for attackers to impersonate. This particular campaign was sent to between 15,000 to 50,000 Office 365 users, according to researchers with Abnormal Security on Thursday.
“Because Microsoft Teams is an instant-messaging service, recipients of this notification might be more apt to click on it so that they can respond quickly to whatever message they think they may have missed based on the notification,” said researchers in a Thursday analysis.
The initial phishing email displays the name “There’s new activity in Teams,” making it appear like an automated notification from Microsoft Teams.
As seen in the picture below, the email tells recipient that their teammates are trying to reach them, warning them they have missed Microsoft Team chats and showing an example of a teammate chat that asks them to submit something by Wednesday of next week.
Erin Ludert, data scientist at Abnormal Security, told Threatpost researchers suspect attackers are using more of a “spray” tactic here, as the employee referenced in the chats doesn’t appear to be an employee of the company that received the attack.

The phishing emails. Credit: Abnormal Security
To respond, the email urges the recipient to click on the “Reply in Teams” button – However, this leads to a phishing page.
“Within the body of the email, there are three links appearing as ‘Microsoft Teams’, ‘(contact) sent a message in instant messenger’, and ‘Reply in Teams’,” according to researchers. “Clicking on any of these leads to a fake website that impersonates the Microsoft login page. The phishing page asks the recipient to enter their email and password.”
Researchers said that the phishing landing page also looks convincingly like a Microsoft login page with the start of the URL containing “microsftteams.” If recipients are convinced to input their Microsoft credentials into the page, they are unwittingly handing them over to attackers, who can then use them for an array of malicious purposes – including account takeover.
With the ongoing pandemic, worries about cyberattackers leveraging enterprise friendly collaboration brands like Microsoft Teams, Zoom and Skype have been piqued. In May, a convincing campaign that impersonated notifications from Microsoft Teams in order to steal the Office 365 credentials of employees circulated, with two separate attacks that targeted as many as 50,000 different Teams users.
Microsoft is top of the heap when it comes to hacker impersonations – with Microsoft products and services featuring in nearly a fifth of all global brand phishing attacks in the third quarter of this year. Attackers are also using sophisticated tactics – including visual CAPTCHAS to target Office 365 users and token-based authorization methods.
Phishers Capitalize on Headlines with Breakneck Speed
17.10.20 Phishing Threatpost
Marking a pivot from COVID-19 scams, researchers track a single threat actor through the evolution from the pandemic to PayPal, and on to more timely voter scams — all with the same infrastructure.
The speed with which phishers are able to adapt to new messaging based on the latest headlines is accelerating, according to the Proofpoint Threat Research Team, which was able to track backend data from a recent voter-registration scam to uncover just how quickly cybercriminals can pivot to capitalize on current events. It turns out, all it takes to launch a potent phishing scam is a new wrapper.
“The range of information credential-phishing themes — PayPal, COVID-19, voting — illustrate how actors often simply pivot from one theme to the next, all while using similar (often the same) infrastructure and backend functionality,” Sherrod DeGrippo, senior director of threat research and detection for Proofpoint, told Threatpost. “It’s clear that threat actors are continuing to try and reach as many intended recipients as possible by capitalizing on a popular topic. We’ve seen throughout the global COVID-19 situation that threat actors are able to adjust quickly to timely news and current events.”
A recent voter registration scheme, first discovered by KnowBe4, sent emails out telling voters their registration information was incomplete. The logos in the communications were from the U.S. Election Assistance Commission (EAC), leading them to a fraudulent page asking them for their personal data.
Tracking Phishing Kit Data
By tracking data from phishing kits, which are easy, one-stop packages for phishing, the Proofpoint Threat Research Team found a trail of scams, all connected to the same infrastructure, with little more than a messaging swap differentiating them.
“Phishkits can be highly technical or not very sophisticated, but they have been evolving slowly over time to offer more features and capabilities,” DeGrippo said by email. “Phishkits are traded, sold and given away for free in various forums.”
Tracking phishing kit data isn’t new, but the Proofpoint team noticed that the same infrastructure was being used to support various scams, making it easy to lure in as many victims as possible.
“The major changes observed are in branding only – the actor continues to use similar [user-interface] elements and backend code, evidenced by the POST of user-supplied information to the same email address across multiple information-phishing operations,” according to Proofpoint’s findings, issued this week.
Evolution of a Phishing Scam
In the voter-registration scam, which blasted out hundreds of typo-ridden phishing emails through SendGrid, the message posed as an official communication and asked recipients to “confirm” their details. One clicked, the link led to what the report said is a “compromised WordPress install,” impersonating the Arizona voter-registration system, ServiceArizona.
Phishing page. Source: Proofpoint
A search of the phishing kit data led to an email address, obiri409[@]gmail[.]com, which researchers were able to follow to other sites that this fraudster used in scams of the past, including a previous PayPal account-verification phishing lure.
From there they tracked the same criminals to a different October voter-registration messaging approach, branding the pages with the EAC logo instead of the Maricopa County government logo, asking for everything from Social Security numbers to tax IDs.
“…and though we were unable to capture POST data for this page, the striking similarity in both the look of the page and use of a compromised WordPress install suggests that it is the same threat actor,” the report added.
Phishing Flavors
It’s safe to expect new fraud schemes rapidly coming into circulation related to recent headlines, according to Proofpoint. Already in October, several major campaigns have launched centered on news hooks. The president’s COVID-19 diagnosis, the Democratic National Committee and other recent news lures have also been used as cover for recent fraud schemes, according to Proofpoint.
The deadline for Americans to file for coronavirus relief is approaching and criminals hatched a scheme to get people to serve up their personal information for the promised of a check, for instance. In another case, a recent announcement by Facebook that it was awarding $100 million in grants for small businesses sparked a round of attacks, luring users through Telegram and WhatsApp with the promise of easy money.
And, unsurprisingly, Amazon Prime Day was a field day for fraud, with attempts to dupe unsuspecting bargain hunters.
Fads and headlines come and go, which is why smart cybercriminals have learned to quickly adapt to the latest hot topics to keep their attacks fresh and relatively obscured by news traffic spikes. The challenge for the security community is to stay one step ahead of the next rebranding of the same old social-engineering tactics.
“The last messages we observed from this actor using voter-registration themes were sent on October 7,” Proofpoint added. “This suggests that the actor may have already shifted to another type of lure.”
Amazon Prime Day Spurs Spike in Phishing, Fraud Attacks
9.10.20 Phishing Threatpost
A spike in phishing and malicious websites aimed at defrauding Amazon.com customers aim to make Prime Day a field day for hackers.
Cybercriminals are tapping into Amazon’s annual discount shopping campaign for subscribers, Prime Day, with researchers warning of a recent spike in phishing and malicious websites that are fraudulently using the Amazon brand.
There has been a spike in the number of new monthly phishing and fraudulent sites created using the Amazon brand since August, the most significant since the COVID-19 pandemic forced people indoors in March, according to a Thursday report from Bolster Research.
Threatpost Webinar Promo Retail Security
Click to Register!
“As shoppers gear up for two days of great deals, cyber criminals are preparing to prey on the unwary, taking advantage of those who let their guard down to snap up bargains,” researchers wrote.
Prime Day actually happens over two days—this year the event falls on Oct. 13 to 14. Amazon Prime customers enjoy special sales and discounts on top brands to mark the biggest shopping event of the year on the online retail giant’s site.
Amazon last year yielded over $7 billion in sales during the 36-hour event, which could go even bigger this year due to “the decline of brick and mortar retail and the close proximity to the holidays,” researchers noted. Indeed, mandatory stay-at-home orders globally that began with the COVID-19 pandemic in March have significantly boosted Amazon’s business, a trend that shows no signs of abating.
Researchers analyzed hundreds of millions of web pages to track the number of new phishing and fraudulent sites using the Amazon brand and logos. Its research shows threat actors taking advantage of both Amazon features and consumer behaviors to try to lure online shoppers to fraudulent sites that can steal their credentials, financial information and other sensitive data.
One new campaign targets “returns” or “order cancellations” related to Prime Day using a fraudulent site, www.amazoncustomersupport[.]net, that mimics a legitimate Amazon site. However, closer examination of the site shows it is clearly designed to defraud consumers, researchers noted.
One clear evidence is its use of a phone number, as “Amazon does not encourage customer service by phone, and takes a great effort to find phone support on the real Amazon site,” researchers wrote.
The form on the site also requests bank or credit card information from customers–a clear intent to steal this information, since Amazon always offers refunds to original form of payment or gift cards. Further, the site also does not ask for a customer password, something Amazon always requires for purchases and returns.
Other smaller issues that might be overlooked—such as broken links attached to the Amazon Prime Logo and a “Get Started” button–also appear on the site. These also are clues to fraudulent behavior that shoppers should look out for in general as they shop on Prime Day, researchers noted.
Another malicious site recently observed by researchers takes advantage of most consumers’ inherent love of a free gift. The site, www.fr-suivre[.]vip, promotes an Amazon loyalty program and offers a free iPhone 11 Pro if people answer a few survey questions. After answering these questions, people are directed to a simple game that they win, after which they’re asked to enter credit card info so the site can charge them $1 to receive the iPhone.
The site even includes a screenshot in which “the free iPhone is validated by many others who have already received their phones,” researchers wrote. “Despite the glowing reviews, the $999 phone will never arrive, and the shopper begins to see strange charges on the credit card number provided,” they warned.
Fortunately for Amazon Prime customers who plan to take advantage of the event this year—or anyone else shopping Amazon these days—avoiding online fraud is not that difficult, researchers said. All shoppers should start directly at the source—Amazon.com—and pay close attention to their experience to ensure that nothing is out of the ordinary.
“Shoppers need to be aware of cyber criminals prepared to take advantage of the situation,” researchers noted. “With some diligence and attention to detail, shoppers will be able to get those deals without getting scammed.”
Amazon, too, can take even more security steps to protect customers as its business continues to boom, with cybercrime inevitably following suit, observed Kevin Beasley, CIO at enterprise management software provider VAI.
“To minimize the risk of data breaches or security issues, retailers, like Amazon, must install additional multi-factor authentication for logins and policies to protect passwords and who has access to data,” he said in an email to Threatpost.
Online retailers across the board also should get out ahead of the busy holiday season by making their platform “a security-first environment,” Beasley said.
This can be done “by installing additional layers of security infrastructure between the operating system and hardware platform, and continuous security testing and automating scans of hardware and software systems to seek out vulnerabilities and patch potential issues as they arise,” he told Threatpost.
Voter Registration ‘Error’ Phish Hits During U.S. Election Frenzy
3.10.20 Phishing Threatpost
Phishing emails tell recipients that their voter’s registration applications are incomplete – but instead steal their social security numbers, license data and more.
Cybercriminals this week are tapping into this week’s political frenzy with a new phishing lure that warns U.S. targets that their voter registration data needs extra details.
The emails purport to come from the U.S. Election Assistance Commission, an independent agency of the United States government that serves as a national resource of information regarding election administration. Utilizing this organization as a sender shows that cybercriminals are tapping into the vast database of U.S. citizens who are preparing to vote in the U.S. presidential election, which is right around the corner.
The email contains a URL, which leads to a spoofed web page that steals a variety of targets’ personal data, including name, date of birth, mailing address, email address, Social Security number and driver’s license data.
“Whatever the intent behind this particular phishing attack, it should serve as a reminder that human beings — users, employees, citizens and voters — are ‘soft targets’ for malicious actors,’ said Eric Howes with KnowBe4, in a Friday analysis. “This is especially true in turbulent times such as the present — when fear, confusion and doubt are surging in the run-up to a historic election that just happens to fall in the middle of a catastrophic pandemic.”
The emails subject says “voter registration application details couldnt be confirmed,” and the body of the email tells users: “Your Arizona voter’s registration application submitted has been reviewed by your County Clerk and some few details couldnt be comfirmed” (Note a suspicious lack of capitalization, spelling and grammar, which serve as a tip that the email is malicious).

The initial phishing email. Credit: KnowBe4
The email then asks recipients to reconfirm their details to allow for processing, saying it could take up to two days to reflect in the system, and points to a URL.
“The social-engineering tactic being used here is a classic one in which email recipients are told of a problem with one of their accounts (usually a bank account) and are then offered a link to fix or redress the problem,” said researchers.
Though the email pretends to come from the U.S. Election Assistance Commission, the link in the email sends users to a web page that spoofs ServiceArizona, which is part of the state government of Arizona. The page includes images pulled directly from the state’s official site.
“Arizona, it should be noted, is considered a potentially important swing state in the upcoming U.S. presidential election,” said researchers. “The state also happens to be hosting a hotly contested election for one of the state’s two U.S. Senate seats.”
However, it should be noted that the phishing email reported to KnowBe4 was submitted by a target in Wisconsin – who wouldn’t submit a voter registration application in Arizona – another potential error on the side of the cybercriminals.
“Curiously, the copy of the email we received was submitted by a customer in Kenosha County, WI — a locality that has been in the news recently due to widely reported civil unrest in the area,” said researchers. “Moreover, like Arizona, Wisconsin is expected to play an important role in the upcoming election.”
Of note, the email was sent through Sendgrid, which researchers say suggests it could have been delivered to a large number of email addresses. Sendgrid is a popular email service provider, which researchers say is currently dealing with a significant problem with compromised accounts that have been exploited by malicious actors to deliver large volumes of phishing emails.

Phishing landing page. Credit: KnowBe4
At this point, researchers are unsure if the end goal of this phishing attack is identity theft-related, versus specifically targeting U.S. voter registration data.
While it is common for bad actors to solicit data from targets in order to support a variety of fraudulent endeavors, “given the election angle…we cannot ignore the possibility that this phish may be part of an attempt by parties unknown to intervene in the election, either by seeding confusion and chaos in the election process or engaging in some form of election fraud,” said researchers.
With the U.S. presidential election only 31 days away – coupled with this week’s presidential debate and news of Pres. Donald Trump testing positive for COVID-19 – political tensions are at an all-time high.
Cybercriminals have wasted no time utilizing these tensions as a lure. On Thursday, hundreds of U.S. organizations were targeted by an Emotet spear-phishing campaign, which sent thousands of emails purporting to be from the Democratic National Committee and recruiting potential Democratic volunteers. Meanwhile, the U.S. election campaigns of both Donald Trump and Joe Biden were targeted in a slew of recent cyberattacks, Microsoft warned earlier in September.
Maryland Officials Warn Gun Dealers About Phishing Scams
15.8.20 Phishing Securityweek
Authorities in Maryland have issued an advisory about an apparent email phishing scam targeting firearms dealers in the state.
Maryland State Police said it was issued after the Maryland State Police Licensing Division was notified Tuesday about emails received by at least two firearms dealers.
The emails had addresses that made it look like they were sent from employees of the licensing division.
The release says they also contain an attachment that has a computer virus. Officials say firearm dealers should verify the emails are coming from the correct address prior to opening them.
Homoglyph attacks used in phishing campaign and Magecart attacks
9.8.20 CyberCrime Phishing Securityaffairs
Researchers detailed a new evasive phishing technique that leverages modified favicons to inject e-skimmers and steal payment card data covertly.
Researchers from cybersecurity firm Malwarebytes have analyzed a new evasive phishing technique used by attackers in the wild in Magecart attacks. The hackers targeted visitors of several sites using typo-squatted domain names, and modified favicons to inject software skimmers used to steal payment card information.
The technique is known as homoglyph attack, it was involved in phishing scams with IDN homograph attacks.
“The idea is simple and consists of using characters that look the same in order to dupe users,” reads the analysis published by Malwarebytes researchers. “Sometimes the characters are from a different language set or simply capitalizing the letter ‘i’ to make it appear like a lowercase ‘l’.”
The internationalized domain name (IDN) homograph attack technique has been used by a Magecart group on multiple domains to load the Inter software skimmer inside a favicon file.
The visual trick leverages on the similarities of character scripts to and register fraudulent domains that appear similar to legitimate ones, then attackers trick victims into visiting them.
While analyzing homoglyph attacks, experts also found legitimate websites (e.g., “cigarpage.com”) that were compromised and injected with an innocuous loader for an icon file that loaded a copycat version of the favicon from the typo-squatted domain (“cigarpaqe[.]com”).
This favicon loaded from the homoglyph domain allowed the attackers to inject the Inter JavaScript skimmer.![]()
Experts noticed that one of the fraudulent domains (“zoplm.com”) involved in this type of attack has been previously tied to Magecart Group 8, the crew that was behind the attacks on NutriBullet, and MyPillow.
“A fourth domain stands out from the rest: zoplm.com. This is also an homoglyph for zopim.com, but that domain has a history. It was previously associated with Magecart Group 8 (RiskIQ)/CoffeMokko (Group-IB) and was recently registered again after several months of inactivity.” continues the analysis.
“In addition, Group 8 was documented in high-profile breaches, including one that is relevant here: the MyPillow compromise. This involved injecting a malicious third-party JavaScript hosted on mypiltow.com (note the homoglyph on mypillow.com). While homoglyph attacks are not restricted to one threat actor, especially when it comes to spoofing legitimate web properties, it is still interesting to note in correlation with infrastructure reuse.”
The combination of attack techniques allows threat actors to implement layers of evasion. Code re-use poses a problem for defenders makes the attribution of the attacks harder.
To avoid phishing attacks that are even more sophisticated users have to scrutinize the website URLs that intend to visit, avoid clicking links from emails, chat messages, and other publicly available content, and enable multi-factor authentication for their accounts to secure accounts from being hijacked.
Spam and phishing in Q2 2020
7.8.2020 Phishing Spam Securelist
Quarterly highlights
Targeted attacks
The second quarter often saw phishers resort to targeted attacks, especially against fairly small companies. To attract attention, scammers imitated email messages and websites of companies whose products or services their potential victims could be using.
The scammers did not try to make any of the website elements appear credible as they created the fake. The login form is the only exception. One of the phishing websites we discovered even used a real captcha on that form.
The main pretext that scammers use to prompt the target to enter their information is offering an online catalog that purportedly only becomes available once the target provides the login and password to their email account.
In one instance, phishers used Microsoft Sway, the service for creating and sharing presentations, to hunt for logins and passwords for corporate accounts. The user was offered to view presentations belonging to another company in the same industry by following a link and entering the login and password for their work email account.
A fake website can be recognized by its design. The workmanship is often rough, and the chunks of information on the various pages are disjointed due to being pulled from diverse sources. Besides, pages like that are created on free hosting websites, as cybercriminals are not prepared to invest too much money in the fakes.
A targeted phishing attack may lead to serious consequences: after gaining access to an employee’s mailbox, cybercriminals can use it for further attacks on the company itself, or its employees or partners.
Waiting for your package: keeping your data secure and your computer, clean
As the pandemic reached its peak, mail service between countries became complicated and delivery times noticeably increased. Organizations responsible for delivery of letters and parcels rushed to notify recipients about all kinds of possible delays and hiccups. This is exactly the type of email messages that scammers started to imitate: the target was offered to open the attachment to find out the address of the warehouse with the package that had failed to reach them.
Another, relatively original, trick employed by cybercriminals was a message containing a miniature image of a postal receipt. The scammers expected the curious recipient to take the attachment, which was an ACE archive despite its name containing “jpg”, for the real thing and open it. The mailshots we detected used this as a method of spreading the Noon spyware. The scam can only be detected if the email client displays the full names of attachments.
In another fraudulent scheme, the target was to told that their order could not be dispatched due to a restriction on mailing of certain types of goods, but the processing of the package would be resumed once the restrictions were lifted. All required documents and a new tracking number could purportedly be found in the attached archive. In reality, the attachment contained a copy of the Androm backdoor, which opened remote access to the victim’s computer.
Scammers posing as courier service employees sent out email warning that packages could not be delivered due to failure to pay for the shipping. The “couriers” accepted codes for prepaid cards issued by Paysafecard as payment. These cards range from €10 to €100 and can be used in stores that accept this payment method. The victim was offered to email a €50 card code – incidentally, an activity that the payment system’s rules explicitly forbid. The cybercriminals chose this payment method for a reason: blocking or revoking a Paysafecard payment is next to impossible.
Banking phishing amid a pandemic
Banking phishing attacks in the second quarter of the year often employed emails that offered borrowers various pandemic-related discounts and bonuses. Accessing the benefits involved downloading a file with a manual or following a link. As a result, the scammers could access the user’s computer, personal data or credentials for various services, depending on the scheme.
The COVID-19 theme was present, too, in the widely known fake bank emails informing customers that their accounts had been blocked, and that they needed to enter their login and password on a special page to get back their access.
The pandemic saw the revival of a more-than-a-decade-old scheme, in which scammers sent victims emails offering to open the attachment to get the details of a low-rate loan. This time, the rate reduction was linked to the pandemic.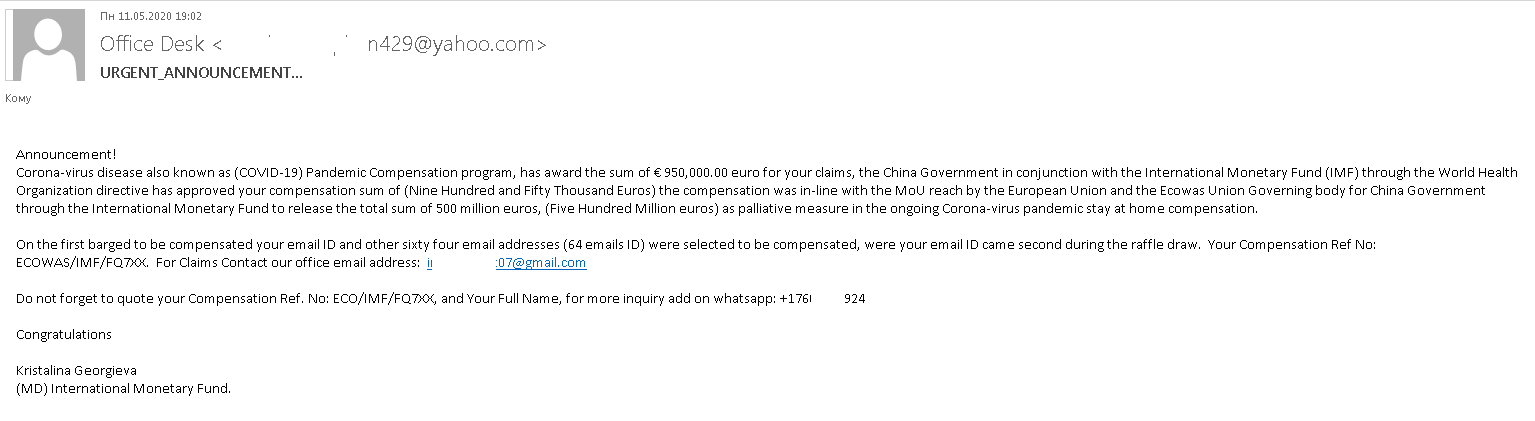
Taxes and exemptions
The beginning of the second quarter is the time for submitting tax forms in many countries. This year, tax authorities in some countries reduced the tax burden or exempted citizens from paying taxes. Scammers naturally grabbed the opportunity: mailshots we detected reported that the government had approved a compensation payout, and claiming it involved following a link to the tax agency’s website, which, unsurprisingly, proved to be fake. Some of the email messages were not too well crafted, and looking closely at the From field was all it took to detect a fake.
More ingenious scammers made up a whole legend: in an email presented as being from the IRS (United States Internal Revenue Service), they said there was a $500,000 “pandemic payment”, authorized jointly by the UN and the World Bank, that could be transferred to the recipient if it had not been for a woman named Annie Morton. The lady, the email said, had showed up at an IRS office carrying a warrant for the payment. She purportedly said that the intended recipient had succumbed to COVID-19, and she was the one to receive the $500,000. The message insisted that the victim contact a certain IRS employee – and not any other, so as to avoid a mistake – to prove that they were alive.
Subsequent steps would most likely be identical to the well-known inheritance scam, where the victim would be offered to pay for the services of a lawyer, who would then disappear with the advance money. One might guess that instead of the advance, the scammers would ask for a fee for executing papers that would prove the victim was still alive.
Getting refunded and losing it all
Tax refunds are not the only type of aid that states have been providing to individuals and companies distressed by the pandemic. And not the only type the scammers have been using. Thus, Brazilians were “allowed” not to pay their energy bills, and all they had to do was register on a website by following a link in an “email from the government”. The hyperlink had an appearance designed to trick the user into thinking that they were being redirected to a government portal, whereas in reality, the victim had a trojan installed on their computer, which downloaded and then ran another trojan, Sneaky.
Personal information leak is another hazard faced by those who risk registering for “compensation” on a suspicious website. For example, one mailshot offered individuals aged over seventy to go to a website and fill out a form, which contained fields for the last name, first name, gender, mailing address and SSN (social security number, for US citizens).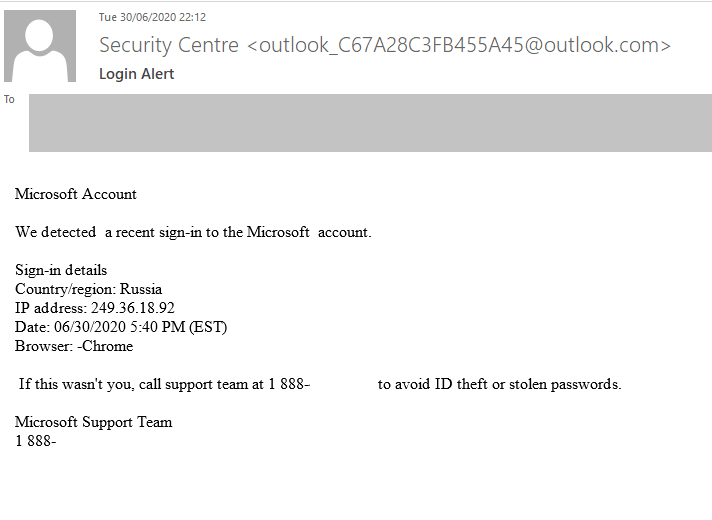
Identifying a fake email is easy. One just needs to take a closer look at the From field and the subject, which appears odd for an official email.
Once the target filled out the entire form, they were redirected to the official Web page of the World Health Organization’s COVID-19 Solidarity Response Fund, a real organization, to give a donation. This helped the scammers to create an illusion that the questionnaire was official and to build a vast database containing the details of individuals over seventy years of age.
Fake emails promising government compensations carried one more threat: instead of getting paid, the victim risked losing their own money to the cybercriminals. Thus, a fake email from the International Monetary Fund announced that the recipient and sixty-four other “lucky” individuals had been selected to receive compensations from a five-hundred-million-dollar fund set up by the IMF, China and the European Union for supporting victims of the pandemic. Getting €950,000 was a matter of contacting the IMF office at the address stated in the message. Subsequent events followed the lottery-scam script: getting the money required paying a commission first.
Fake HR: getting dismissed by professional spammers
The pandemic-related economic downturns in several countries caused a surge in unemployment, an opportunity that cybercriminals were quick to take advantage of. One mailshot, sent in the name of the US Department of Labor, offered looking at the latest changes to the parental leave and sick leave laws. The sender said these laws had been amended following the adoption of the coronavirus relief act, and all details on the amendments were available in the attachment. What the attachment really contained was Trojan-Downloader.MSOffice.SLoad.gen, a trojan mostly used for downloading and installing ransomware.
Another way scammers “surprised” potential victims was dismissal notices. The employee was informed that the company had been forced to discharge them due to the pandemic-induced recession. The dismissal “followed the book”, in that the attachment, according to the author of the email, contained a request form for two months’ worth of pay. Needless to say, the victim only found malware attached.
Your data wanted, now
The share of voice phishing in email traffic rose noticeably at the end of Q2 2020. One mailshot warned of a suspicious attempt at logging in to the target’s Microsoft account, originating in another country, and recommended that the target contact support by phone at the supplied number. This spared the scammers the need to create a large number of fake pages, as they tried to get all the information they needed over the phone.
An even less conventional way of obtaining personal data could be found in emails that offered subscription to COVID-19 updates, where the target only needed to verify their email address. Besides personal data theft, forms like this can be used for collecting mailbox usage statistics.
Statistics: spam
Proportion of spam in email traffic
Proportion of spam in global email traffic, Q1 2020 – Q2 2020 (download)
In Q2 2020, the largest share of spam (51.45 percent) was recorded in April. The average percentage of spam in global email traffic was 50,18%, down by 4.43 percentage points from the previous reporting period.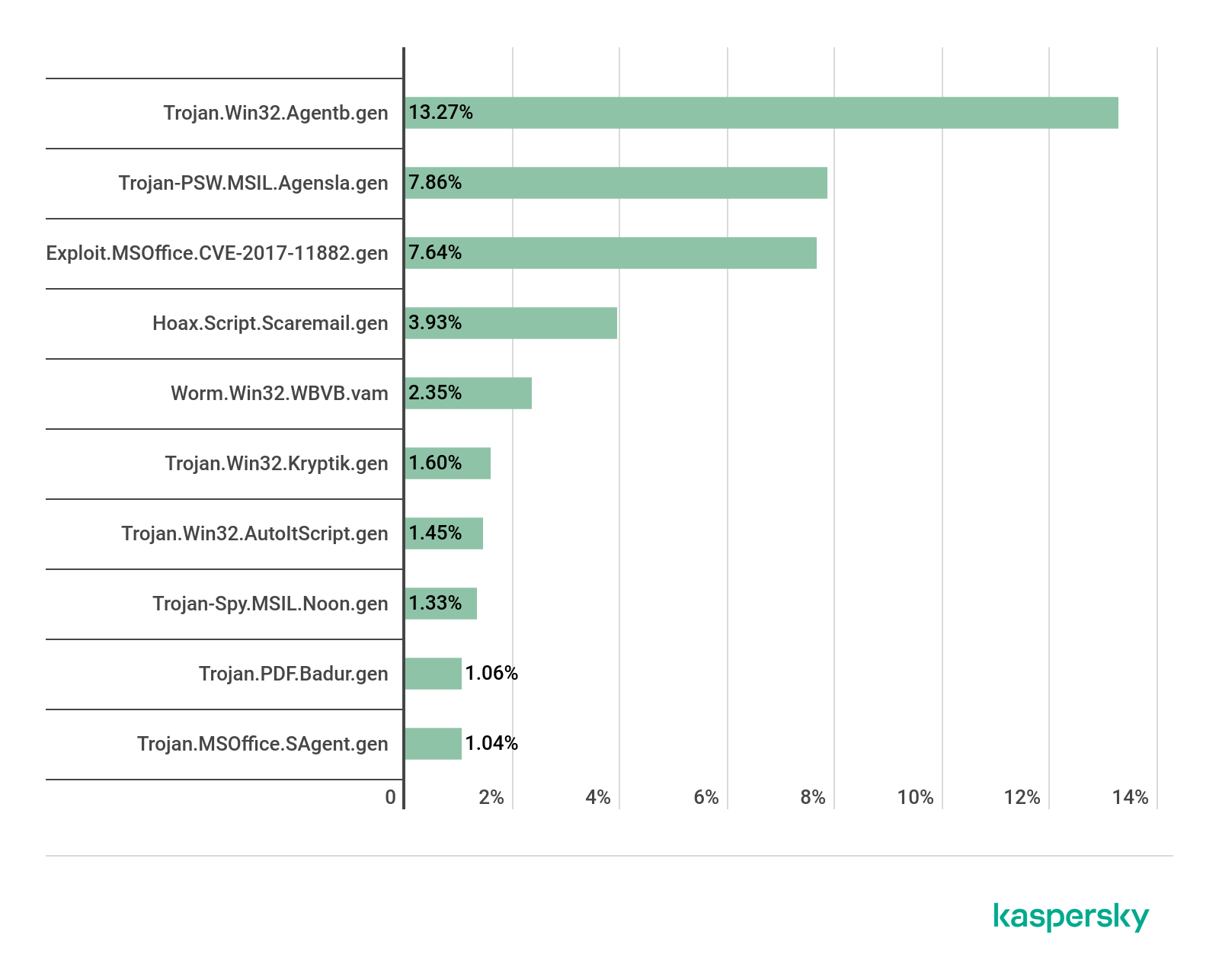
Proportion of spam in Runet email traffic, Q1 2020 – Q2 2020 (download)
The Russian segment of the World Wide Web presents the opposite picture, with the end of the quarter accounting for the larger share of spam: spam peaked in June as it reached 51.23 percent. The quarterly average was 50.35 percent, 1.06 p.p. lower that the first quarter’s average.
Sources of spam by country
Countries where spam originated in Q2 2020 (download)
The composition of the top five Q1 2020 spam leaders remained unchanged in the second quarter. Russia kept the lead with 18.52 percent, followed by Germany with 11.94 percent, which had overtaken the US, now third with 10.65 percent. France (7.06 percent) and China (7.02 percent) remained fourth and fifth, respectively.
Sixth was the Netherlands (4.21 percent), closely followed by Brazil (2.91 percent), Turkey (2.89 percent), Spain (2.83 percent) and lastly, Japan (2.42 percent).
Spam email size
Spam email size, Q1 – Q2 2002 (download)
The share of extra small emails kept going down, dropping by 8.6 p.p. to 51.30 percent in Q2 2020. Emails between 5 KB and 10 KB decreased slightly (by 0.66 p.p.) compared to the previous quarter, to 4.90 percent. Meanwhile, the share of spam messages within the range of 10 KB to 20 KB rose by 4.73 p.p. to 11.09 percent. The share of larger messages between 100 KB and 200 KB in the second quarter fell by 1.99 p.p. to 2.51 percent compared to Q1 2020.
Malicious attachments: malware families
Number of Mail Anti-Virus triggerings, Q1 2020 – Q2 2020 (download)
Our security solutions detected a total of 43,028,445 malicious email attachments in Q2 2020, an increase of six and a half million year-on-year.
TOP 10 malicious attachments in mail traffic, Q2 2020 (download)
Trojan.Win32.Agentb.gen (13.27 percent) was the most widespread malware in email attachments in the second quarter of the year, followed by Trojan-PSW.MSIL.Agensla.gen (7.86 percent) in second place and Exploit.MSOffice.CVE-2017-11882.gen (7.64 percent) in third place.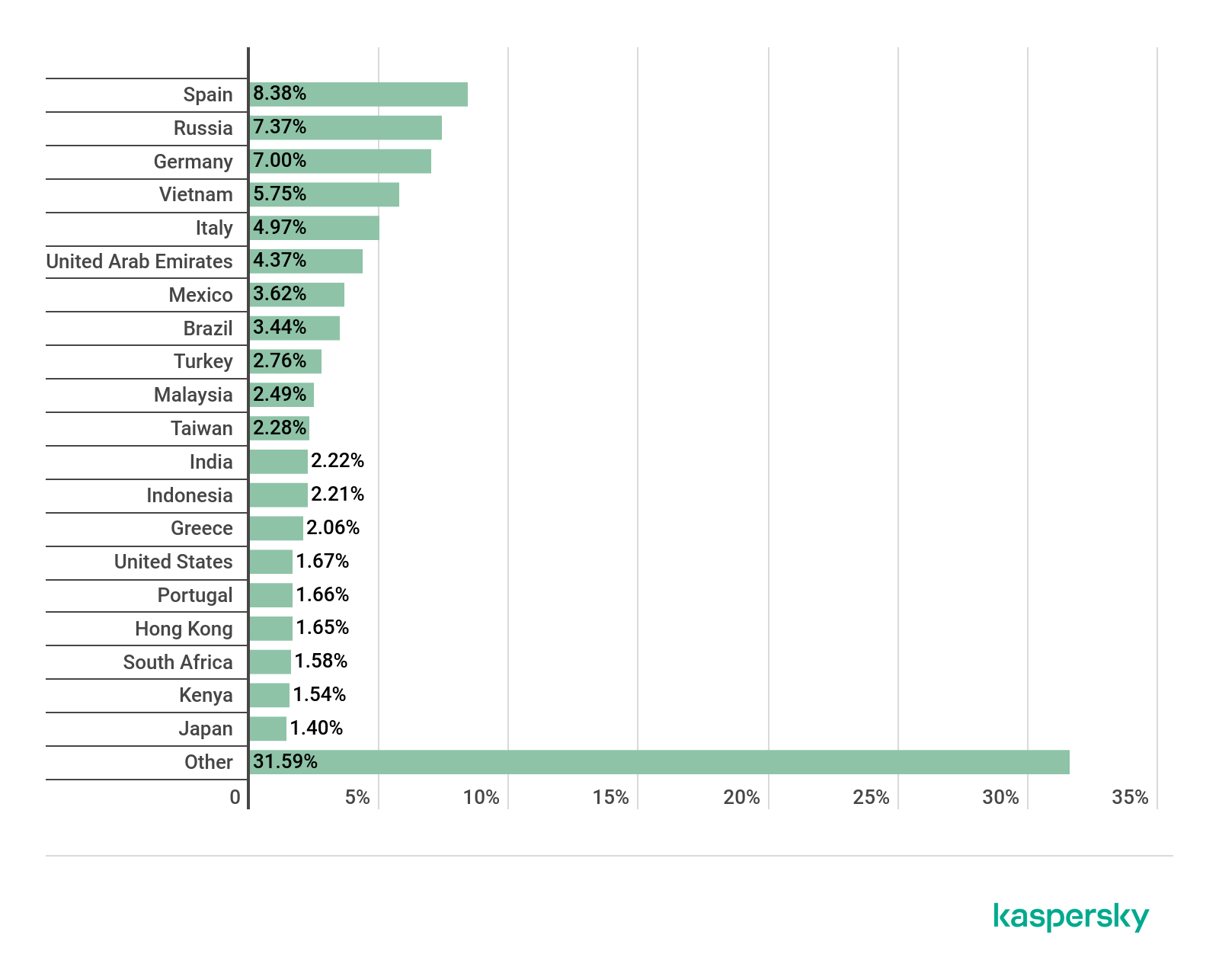
TOP 10 malware families in mail traffic, Q2 2020 (download)
The most widespread malware family in the second quarter, as in the previous one, was Trojan.Win32.Agentb (13.33 percent), followed by Trojan-PSW.MSIL.Agensla (9.40 percent) and Exploit.MSOffice.CVE-2017-11882 (7.66 percent).
Countries targeted by malicious mailshots
Distribution of Mail Anti-Virus triggerings by country, Q2 2020 (download)
Spain (8.38%) took the lead in Mail Anti-Virus triggerings in Q2 2020, just as in Q1 2020. Second came Russia with 7.37 percent of attacks, and third came Germany with 7.00 percent.
Statistics: phishing
Kaspersky Anti-Phishing helped to prevent 106,337,531 attempts at redirecting users to phishing Web pages in Q2 2020, a figure that is almost thirteen million lower than that for the first quarter. The share of unique attacked users accounted for 8.26 percent of the total Kaspersky users in the world, with 1,694,705 phishing wildcards added to the system database.
Attack geography
Venezuela was traditionally the country with the largest share of users attacked by phishers (17.56 percent).
Geography of phishing attacks, Q2 2020 (download)
Portugal was 4.05 p.p. behind with 13.51 percent, closely followed by Tunisia with 13.12 percent.
Country %*
Venezuela 17.56%
Portugal 13.51%
Tunisia 13.12%
France 13.08%
Brazil 12.91%
Qatar 11.94%
Bahrain 11.88%
Guadeloupe 11.73%
Belgium 11.56%
Martinique 11.34%
*Share of users on whose computers Anti-Phishing was triggered out of all Kaspersky users in the country
Top-level domains
Starting with this quarter, we have decided to maintain statistics on top-level domains used in phishing attacks. Quite predictably, COM led by a huge margin, with 43.56 percent of the total number of top-level domain names employed in attacks. It was followed by NET (3.96 percent) and TOP (3.26 percent). The Russia-specific RU domain took fourth place with 2.91 percent, followed by ORG with 2.55 percent.
Top-level domains most popular with phishers, Q2 2020 (download)
Organizations under attack
The rating of attacks by phishers on different categories of organizations is based on detections by Kaspersky Anti-Phishing component. This component detects pages with phishing content that the user tried to access by following email or Web links, regardless of how the user got to the page: by clicking a link in a phishing email or in a message on a social network, or after being redirected by a malicious program. When the component is triggered, a banner is displayed in the browser warning the user about a potential threat.
As in the first quarter, the Online Stores category accounted for the largest share of phishing attacks, its share increasing by 1.3 p.p. to 19.42 percent. Global Web Portals again received the second-largest share of attacks, virtually unchanged at 16.22 percent. Banks (11.61 percent) returned to third place, pushing Social Networks (10.08 percent) to fourth place.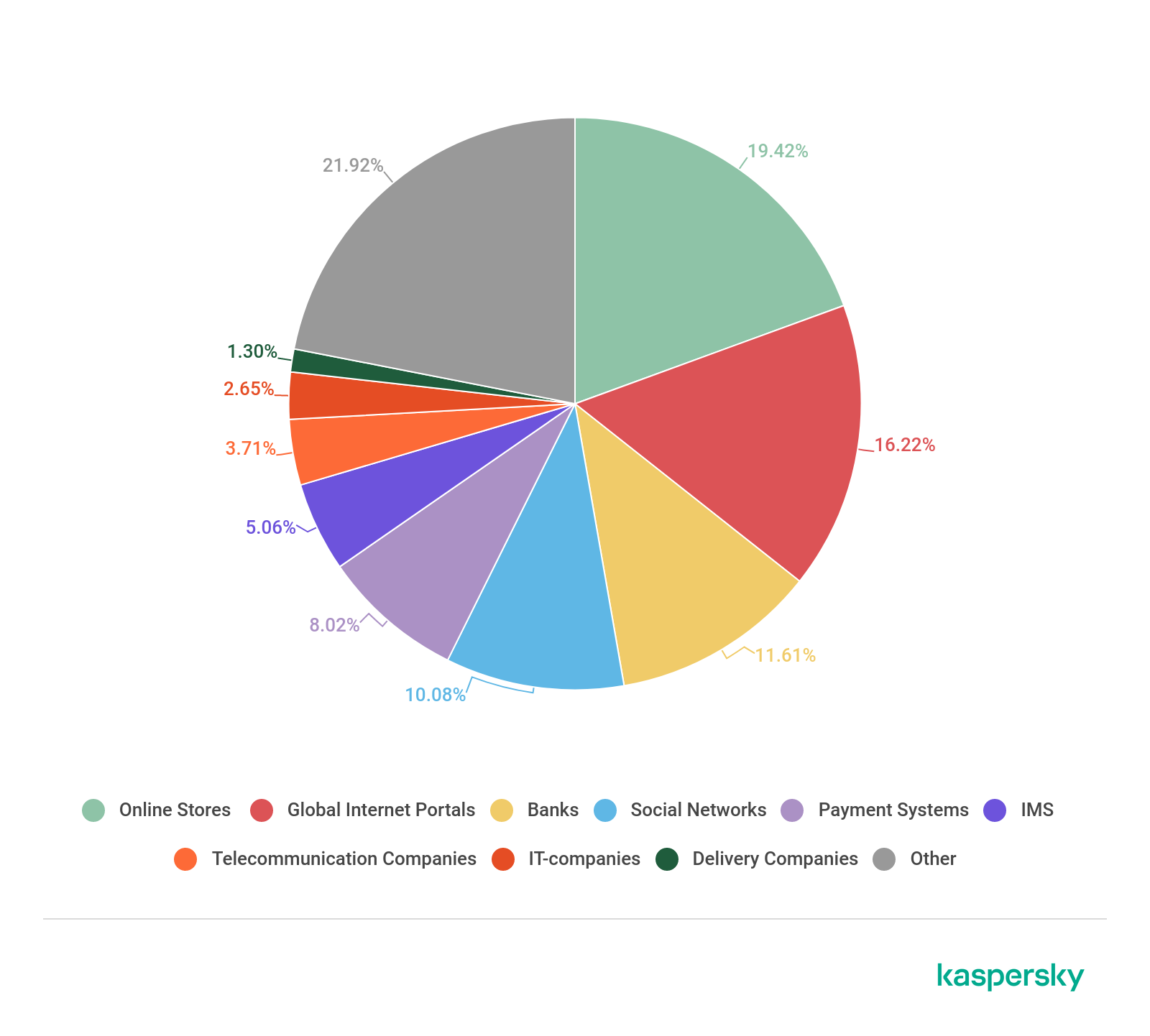
Distribution of organizations subjected to phishing attacks by category, Q2 2020 (download)
Conclusion
In our summary of the first quarter, we hypothesized that COVID-19 would remain spammers’ and fishers’ key theme in the future. That is exactly what happened: seldom did a mailshot fail to mention the pandemic as phishers added relevance to their tried and tested schemes and came up with brand-new ones.
The average share of spam in global email traffic in Q2 2020 dropped by 4.43 p.p. to 50.18 percent compared to the previous reporting period, and attempts to access phishing pages amounted to 106 million.
First place in the list of spam sources in Q2 went to Russia with a share of 18.52 percent. Our security solutions blocked a total of 43,028,445 malicious email attachments, with the most widespread “email-specific” malware family being Trojan.Win32.Agentb.gen, which infected 13.33 percent of the total email traffic.