Phishing Articles - H 2020 1 2 3 4 5 6 7 8 Phishing List - H 2021 2020 2019 2018 1 Phishing blog Phishing blog
Office 365 phishing uses Supreme Court theme and working CAPTCHA
23.5.2020 Bleepingcomputer Phishing
Fraudsters are trying new things to bypass security controls in Office 365 and added a CAPTCHA page in the chain of redirects that ends on a phishing template for login credentials.
To lure potential victims to the malicious page, the threat actor sent them an email purporting to be from the Supreme Court and claiming to deliver a subpoena for a hearing.
Real CAPTCHA, real risk
This attack was not part of a massive campaign, as it was sent to a small number of individuals in targeted organizations, says Chetan Anand, co-founder of Armorblox.
By sending the message to just a few users, there is a good chance that the fraudulent attempt passes unnoticed. Combined with a domain name that has not been analyzed before (zero-day link), the email is likely to bypass protections.
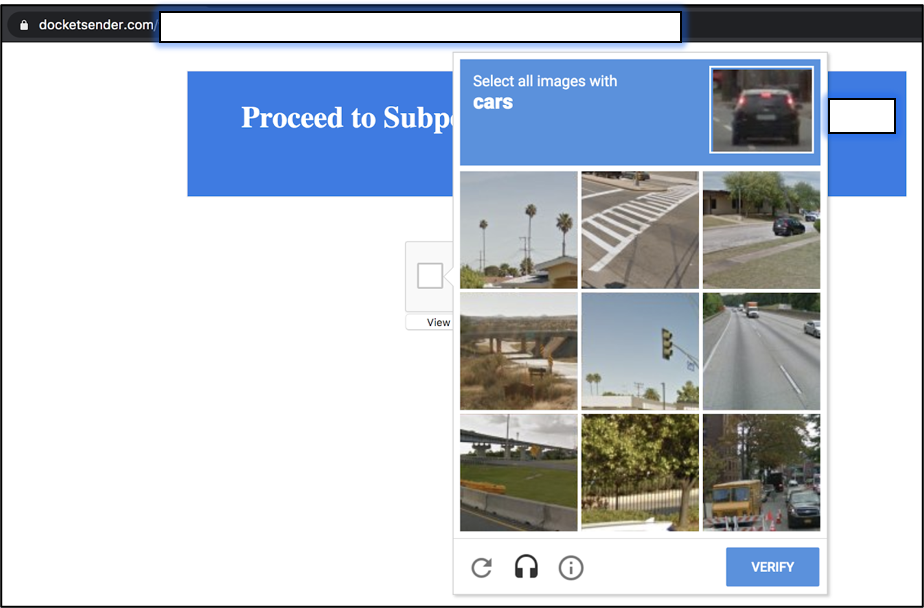
Clicking on the alleged subpoena in the fraudulent message triggered a series of redirects that took the recipient to a working CAPTCHA page, typically used to determine if the user is human or a bot.
The presence of such a challenge-response test would likely make the user believe that the chain of events was legitimate. This is also one of the final steps and it mentions the victim’s name and the reason for the challenge.
Despite some grammar mistakes, the challenge is real and has a test that users need to solve to prove their human condition.
Anand says that including a CAPTCHA makes it more difficult for security solutions that analyze URL redirection to reach the final destination and detect the attempt as malicious.
After going through the redirects and hoops, the user lands on the final phishing page, which is made to look like a valid Office 365 login screen. A look at the URL (invoicesendernow[.]com), though, shows that it is fake.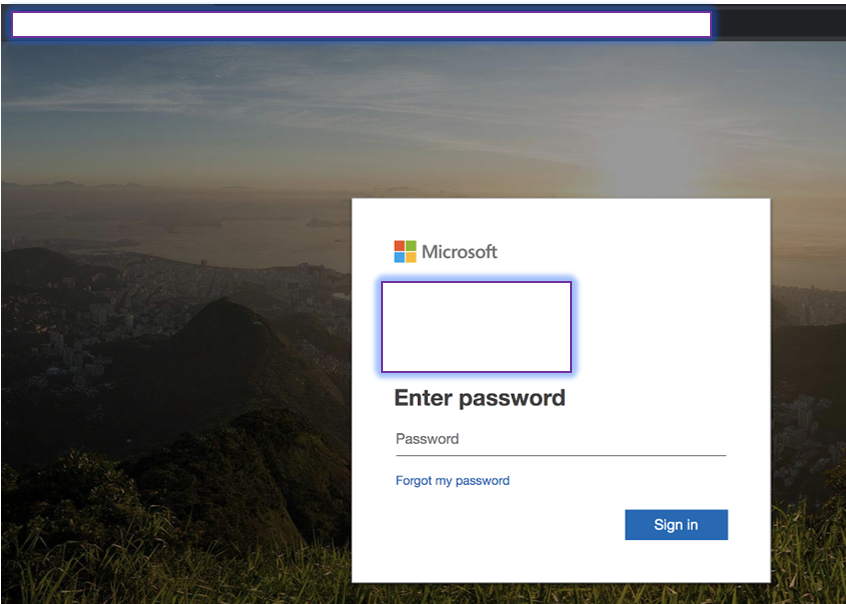
The actors put some effort into making this page look as credible as possible and save from some details, they were successful.
“This page would pass most eye tests during busy mornings, with people happily assuming it to be a legitimate Microsoft page. A closer look at the domain reveals that this is a lookalike page built specifically for the target.”
Users should be suspicious of messages about an urgent task and should take a closer look at the phrasing and grammar mistakes in the text. Before typing in login details, it is wise to check if the URL in the browser address bar matches the resource you're trying to access.
Crooks Tap Google Firebase in Fresh Phishing Tactic
22.5.2020 Threatpost Phishing
Cybercriminals are taking advantage of the Google name and the cloud to convince victims into handing over their login details.
A series of phishing campaigns using Google Firebase storage URLs have surfaced, showing that cybercriminals continue to leverage the reputation of Google’s cloud infrastructure to dupe victims and skate by secure email gateways.
Google Firebase is a mobile and web application development platform. Firebase Storage meanwhile provides secure file uploads and downloads for Firebase apps. Using the Firebase storage API, companies can store data in a Google cloud storage bucket.
The phishing effort starts with spam emails that encourage recipients to click on a Firebase link inside the email in order to visit promised content, according to Trustwave researcher Fahim Abbasi, writing in an analysis released Thursday. If the targets click on the link, they’re taken to a supposed login page (mainly for Office 365, Outlook or banking apps) and prompted to enter their credentials – which of course are sent directly to the cybercriminals.
“Credential phishing is a real threat targeting corporates globally,” noted Abbasi. “Threat actors are finding smart and innovative ways to lure victims to covertly harvest their corporate credentials. Threat actors then use these credentials to get a foothold into an organization to further their malicious agendas.”
In this case, that “innovative way” is using the Firebase link.
“Since it’s using Google Cloud Storage, credential-capturing webpages hosted on the service are more likely to make it through security protections like Secure Email Gateways due to the reputation of Google and the large base of valid users,” Karl Sigler, senior security research manager, SpiderLabs at Trustwave., told Threatpost. “The use of cloud infrastructure is rising among cybercriminals in order to capitalize on the reputation and valid uses of those services. They tend to not be immediately flagged by security controls just due to the URL.”
The campaigns were circulating globally, across a range of industries, but the majority of the “hits” have been in Europe and Australia, Sigler said.
“Most of the emails we saw were from late March through the middle of April, but we’ve seen samples as a part of this campaign as far back as February and as recently as mid-May,” he added. “While these tactics of piggy-backing on valid cloud services likely go back to the days those services were invented, this is a current and active trend.”
Major themes for the lures include payment invoices, exhortations to upgrade email accounts, prompts to release pending messages, urging recipients to verify accounts, warnings of account errors, change-password emails and more. In one case, “scammers used the Covid-19 pandemic and internet banking as an excuse to lure the victims into clicking on the fake vendor payment form that leads to the phishing page hosted on Firebase Storage,” according to the analysis.
An example of a phishing email using Firebase. Click to enlarge.
Overall, the phishing messages are convincing, according to Trustwave, with only subtle imperfections that might tip off potential victims that there’s something wrong, such as a few poor graphics.
“Cybercriminals are constantly evolving their techniques and tools to covertly deliver their messages to unwitting victims,” Abbasi said. “In this campaign, threat actors leverage the reputation and service of the Google Cloud infrastructure to conduct phishing by embedding Google firebase storage URLs in phishing emails.”
Using Google to lend an air of legitimacy is an ongoing trend. Earlier this year, an attack surfaced that uses homographic characters to impersonate Google domain names and launch convincing but malicious websites. And last August, a targeted spearphishing campaign hit an organization in the energy sector – after using Google Drive to get around the company’s Microsoft email security stack. The campaign impersonated the CEO of the targeted company, sending email via Google Drive purporting to be “sharing an important message” with the recipients.
“Again, because of the valid uses and large user base of these services, many of these phishing emails can slip through the cracks of the security controls we put in place,” Sigler added. “Educating users about these tactics helps provide defense-in-depth against these techniques when they hit a victim’s inbox.”
Supreme Court Phish Targets Office 365 Credentials
22.5.2020 Threatpost Phishing
Cybercriminals are hunting out victims’ Office 365 credentials — by dishing out Supreme court “summons” in a phishing attack.
A highly-targeted phishing attack pretends to deliver subpoenas, but actually ends up collecting victims’ Office 365 credentials. The ongoing campaign has slipped by Office 365 and gateway security controls to hit several C-Suite level victims thus far.
The phishing emails spoof the U.S. Supreme Court, aiming to capitalize on scare tactics to convince targets to click on an embedded link. The email tells victims that it contains a writ issued by the Supreme Court, to compel them to attend a hearing. To view the subpoena, victims must click on the link.
“Unlike spray-and-pray email fraud attempts, this email was expressly created and sent to trigger the required response,” said researchers with Armorblox in a Thursday analysis, shared exclusively with Threatpost. “The sender name impersonated the Supreme Court, making the email likely to get past eye tests when people glanced through it amidst hundreds of other emails in their overflowing mailboxes. The email language was terse and authoritative, including a CTA (call to action) in the email – View Subpoena – clearly describing the purpose of the email.”
While the email’s sender name labeled as the ‘Supreme Court,’ a closer look at the email addresses showed that they were unrelated (they came from court@flippintoacure[.]com or court@somersethillsevents[.]com).
“From a social-engineering lens, the email was crafted to trigger urgency and fear,” Chetan Anand, co-founder and architect with Armorblox, told Threatpost. “The email keeps things short so that targets click the link without reading (or thinking) too much…. busy employees often don’t have the time or luxury to think about every email in their inbox, and end up following through on the email’s action.”

Clicking the link takes the targets through multiple redirects, including two fully functioning CAPTCHA pages that not only add an air of legitimacy to the phish, but also make it harder for security technologies relying just on URL redirection abilities to follow the URL to its final destination, said researchers.
“The penultimate URL redirect in this attack leads users to a fully functioning CAPTCHA page,” said researchers. “Upon clicking the ‘I’m not a robot’ button, a real CAPTCHA image test pops up, stamping a clear seal of legitimacy on the email communication.”
subpoena phishing attackThe final credential landing page was painstakingly made to resemble an Office 365 login page, designed to collect targets’ Office 365 credentials. However, the domain for the page is ‘invoicesendernow[.]com’ which is clearly not a Microsoft page.
“This page would pass most eye tests during busy mornings, with people happily assuming it to be a legitimate Microsoft page,” said researchers. “A closer look at the domain reveals that this is a lookalike page built specifically for the target.”
While the campaign did take some sophisticated measures, a keen-eyed email recipient might be able to detect several red flags that gave away the phishing attack. For instance, in the CAPTCHA page, the page domains [‘docketsender[.]com’] don’t seem legitimate. The subheading of the CAPTCHA also makes a grammatical error, reading “Kindly verify you human.”
Anand told Threatpost that both the domains associated with the attack (docketsender[.]com and invoicesendernow[.]com) are based out of Kansas and were registered on May 12.

Because the attack was sent to “high-value targets” across organizations – including members of the C-Suite, finance teams, and accounting teams – Anand said the impact could be massive.
“Compromised credentials from these targets can be used to launch secondary attacks on other employees, customers, and third-party vendors,” he told Threatpost. “The credentials could also be used to exfiltrate sensitive or confidential data from the targets’ Office 365 accounts. Attackers are also sure to try the same login credentials to break into other business-critical applications (in case the targets have common passwords across apps).”
Researchers pointed to a similar phishing attack from last year, which claimed to deliver emailed subpoenas is targeting insurance and retail companies. The phishing emails spoofed the U.K. Ministry of Justice in order to ultimately infect victims with Predator the Thief, a publicly available information-stealing malware that’s not often seen in phishing campaigns.
Attackers continue to leverage phishing lures that might trigger anxiety in victims and spur them to hand over their credentials. That includes recent coronavirus-themed cyberattacks as panic around the global pandemic continues – including malware attacks, booby-trapped URLs and credential-stuffing scams. Researchers warned that users should continue to be on the lookout for phishing emails playing into fears around the coronavirus pandemic.
“We are seeing a big increase in credential phishing attacks against small, medium businesses,” said Anand. “These allow the attackers to then launch vendor email compromise or supply chain fraud kind of attacks from those organizations to larger companies that they work with. This attack was very much in line with that pattern.”
Beware of phishing emails urging for a LogMeIn security update
22.5.2020 Net-security Phishing
LogMeIn users are being targeted with fake security update requests, which lead to a spoofed phishing page.
“Should recipients fall victim to this attack, their login credentials to their LogMeIn account would be compromised. Additionally, since LogMeIn has SSO with Lastpass as LogMeIn is the parent company, it is possible the attacker may be attempting to obtain access to this user’s password manager,” Abnormal Security noted.
The fake LogMeIn security update request
The phishing email has been made to look like it’s coming from LogMeIn. Not only does the company logo feature prominently in the email body, but the sender’s identity has been spoofed and the phishing link looks, at first glance, like it might be legitimate:

“The link attack vector was hidden using an anchor text impersonation to make it appear to actually be directing to the LogMeIn domain,” Abnormal Security explained.
“Other collaboration platforms have been under scrutiny for their security as many have become dependent on them to continue their work given the current pandemic. Because of this, frequent updates have become common as many platforms are attempting to remedy the situation. A recipient may be more inclined to update because they have a strong desire to secure their communications.”
Advice for users
This LogMeIn-themed phishing campaign is a small one, but users should know that the company has seen an “incredible uptick” in collaboration software impersonations in the past month.
Be careful when perusing unsolicited email, even if it looks like it’s coming from a legitimate source. If you have to enter login credentials into a web page, make sure you landed on that page by entering the correct URL yourself or by opening a bookmark – and not by following a link in an email.
In this particular case, you can be sure that if LogMeIn asks you to update something, the request/reminder will be shown once you access your account, so you’re not losing anything by ignoring the email and the link in it.
Microsoft warns of 'massive' phishing attack pushing legit RAT
21.5.2020 Bleepingcomputer Phishing Virus
Microsoft is warning of an ongoing COVID-19 themed phishing campaign that installs the NetSupport Manager remote administration tool.
In a series of tweets, the Microsoft Security Intelligence team outlines how this "massive campaign" is spreading the tool via malicious Excel attachments.
The attack starts with emails pretending to be from the Johns Hopkins Center, which is sending an update on the number of Coronavirus-related deaths there are in the United States.
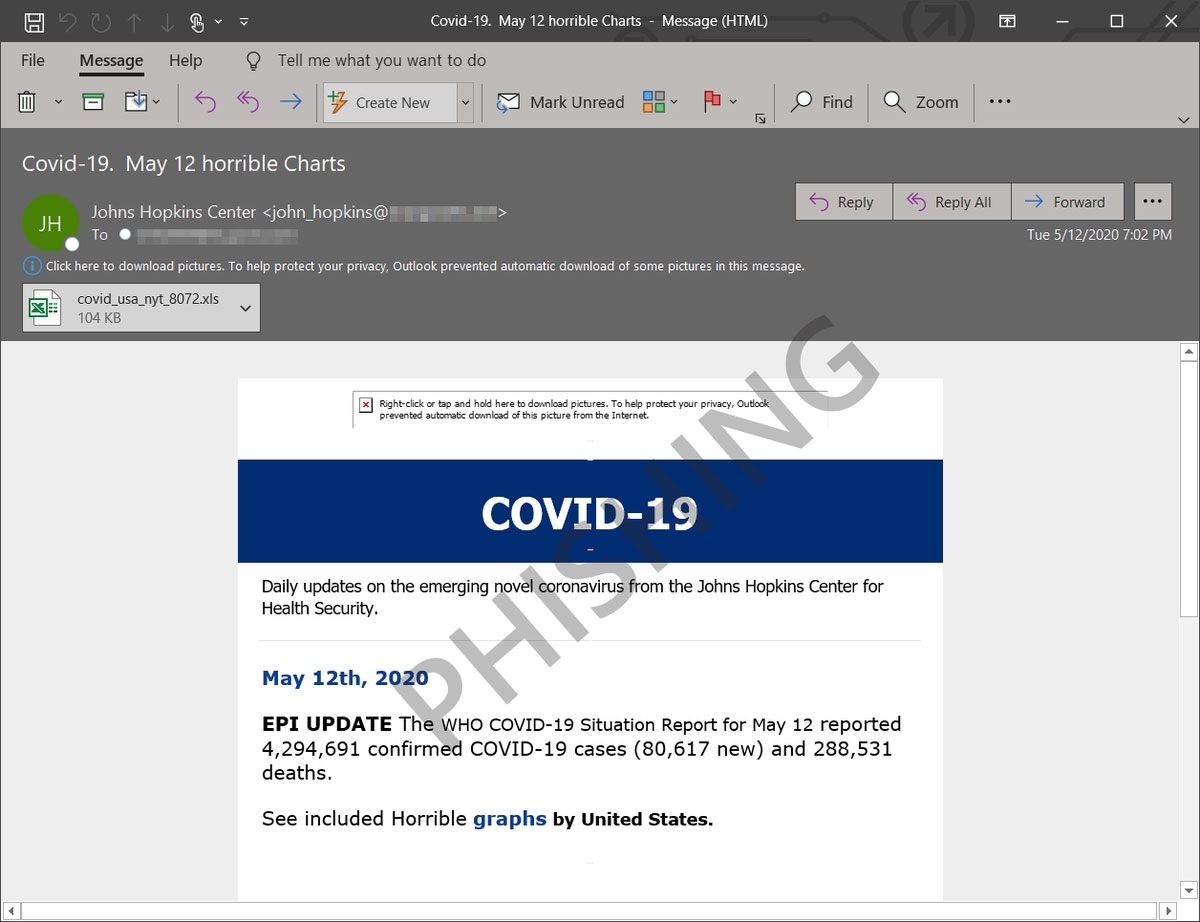
Malicious COVID-19 themed email
Attached to this email is an Excel file titled 'covid_usa_nyt_8072.xls', that when opened, displays a chart showing the number of deaths in the USA based on data from the New York Times.
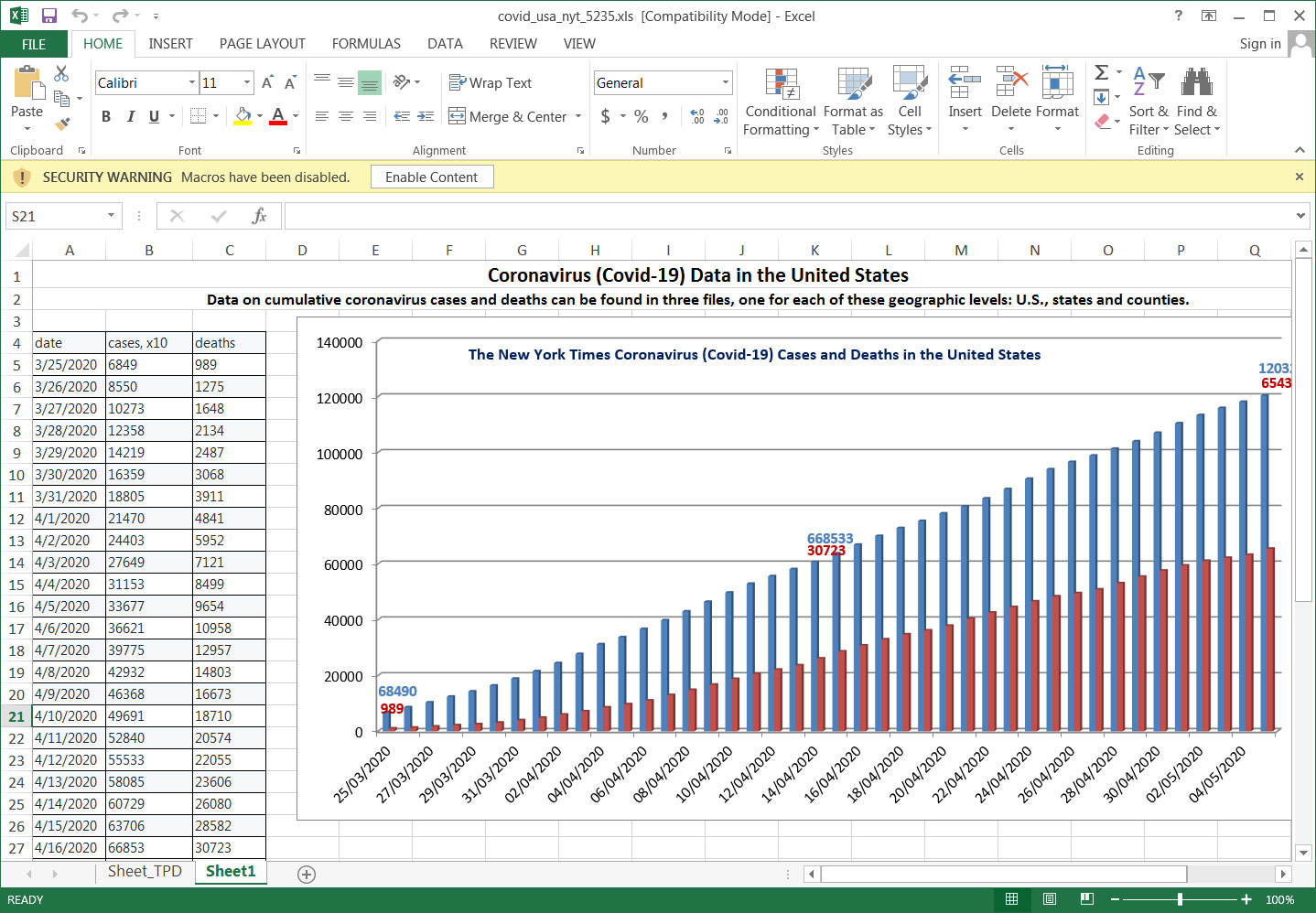
Malicious Excel document
As this document contains malicious macros, it will prompt the user to 'Enable Content'. Once clicked, malicious macros will be executed to download and install the NetSupport Manager client from a remote site.
"The hundreds of unique Excel files in this campaign use highly obfuscated formulas, but all of them connect to the same URL to download the payload. NetSupport Manager is known for being abused by attackers to gain remote access to and run commands on compromised machines," Microsoft tweeted.
The NetSupport Manager is a legitimate remote administration tool commonly distributed among the hacker communities to use as a remote access trojan.
When installed, it allows a threat actor to gain complete control over the infected machine and execute commands on it remotely.
In this particular attack, the NetSupport Manager client will be saved as the dwm.exe file under a random %AppData% folder and launched.
As the remote administration tool is masquerading as the legitimate Desktop Windows Manager executable, it may not be noticed as unusual by users viewing Task Manager.
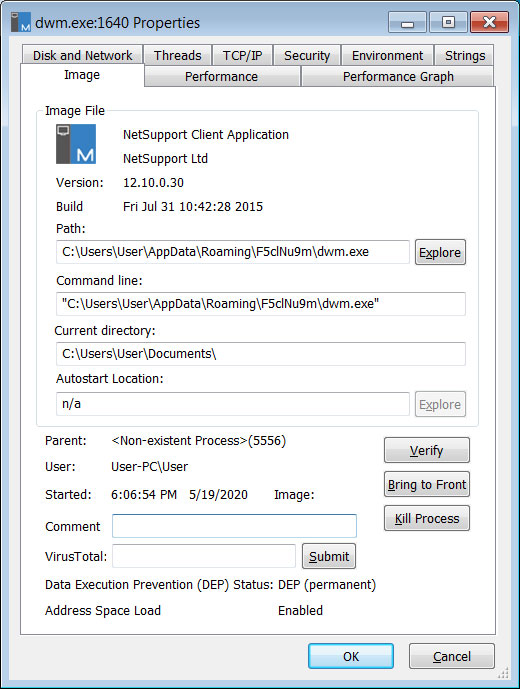
Netsupport Manager running as DWM.exe
After some time, the NetSupport Manager RAT will be used to further compromise the victim's computer by installing other tools and scripts.
"The NetSupport RAT used in this campaign further drops multiple components, including several .dll, .ini, and other .exe files, a VBScript, and an obfuscated PowerSploit-based PowerShell script. It connects to a C2 server, allowing attackers to send further commands," Microsoft explained.
Anyone who was affected by this phishing campaign should operate under the assumption that their data has been compromised and that the threat actor attempted to steal their passwords.
It is also possible that the threat actor used the infected machine to spread laterally throughout the network.
After cleaning the infected device, passwords should be changed, and the rest of the computers on the network should be investigated for infections.
Clever Phishing Attack Bypasses MFA to Nab Microsoft Office 365 Credentials
20.5.2020 Threatpost Phishing
The attack discovered by Cofense can steal sensitive user data stored on the cloud as well as find other victims to target.
A new phishing campaign can bypass multi-factor authentication (MFA) on Office 365 to access victims’ data stored on the cloud and use it to extort a Bitcoin ransom or even find new victims to target, security researchers have found.
Researchers at Cofense Phishing Defense Center discovered the tactic, which leverages the OAuth2 framework and OpenID Connect (OIDC) protocol and uses a malicious SharePoint link to trick users into granting permissions to a rogue application, researcher Elmer Hernandez wrote in a blog post published Tuesday.
The attack is different than a typical credential harvester in that it attempts to trick users into granting permissions to the application, which can bypass MFA, he said. MFA is used as back-up security to a user’s password in case the password is compromised and is meant to protect an account in such a scenario.
“This is not the first time the tactic has been observed, but it’s a stark reminder that phishing isn’t going to be solved by multi-factor authentication,” Hernandez noted.
If attackers are successful, they can engage in a number of threat behaviors, researchers said. The most basic attack can steal all the victims’ email and access cloud hosted documents containing sensitive or confidential information. But attackers wouldn’t have to stop there, he said.
“Once the attacker has sensitive information, they can use it to extort victims for a Bitcoin ransom,” Hernandez wrote. “The same permissions can also be used to download the user’s contact list to be used against fresh victims. Using the address book and old emails would allow the attacker to create hyper-realistic Reply-Chain phishing emails.”
The email used in the attack appears like a typical invite to a SharePoint hosted file; in the example cited in the research, the file seemed to be offering information about a salary bonus, creating an effective lure, Hernandez noted.
After clicking on the link, users are taken to the legitimate Microsoft Office 365 login page at https://login.microsoftonline.com. However, a closer inspection of the full, long-form URL showed that there are clues to its nefarious intentions that someone without technical experience might not notice, but which are more obvious to security experts.
Applications that want to access Office 356 data on behalf of a user do so through Microsoft Graph authorizations, but must first obtain an access token from the Microsoft Identity Platform, Hernandez explained.
“This is where OAuth2 and OIDC come in,” he said. “The latter is used to authenticate the user who will be granting the access, and if authentication is successful, the former authorizes (delegates) access for the application. All of this is done without exposing any credentials to the application.”
The entire URL used in the attack includes key parameters that show how the attacker can trick a victim into giving a rogue application permissions to access his or her account.
A parameter called “response_type” denotes the type of access being requested to the Microsoft Identity Platform /authorize endpoint. In the case of the attack examined by Hernandez, both an ID token and an authorization code (id_token+code) are requested.
“The latter will be exchanged for an access token which will, in turn, be presented by the application to Microsoft Graph for data access,” he explained.
In the next phase, the “redirect uri” parameter indicates the location to which authorization responses are sent, including tokens and authorization codes. In the attack outlined in the post, responses are sent to hxxps://officehnoc[.]com/office, a domain masquerading as a legitimate Office 365 entity. The domain’s location is 88[.]80[.]148[.]31 in Sofia, Bulgaria, where it is hosted by BelCloud, Hernandez noted.
Then, the “scope” parameter shows a list of permissions the user gives to the application that allow the application to read and/or modify specific resources for the signed-in user. If this parameter shows an “all” constraint, these permissions apply for all such resources in a directory, Hernandez said. Attackers also can ask for specific permissions using this parameter, he noted.
“For example “contacts.read” enables the application to read only the user’s contacts, whereas “notes.read.all” allows it to read all OneNote notebooks the user has access to, and “Files.ReadWrite.All” to both read and modify (create, update and delete) all files accessible to the user, not only his or her own,” he wrote.
The last and “most concerning” parameter that Hernandez identified in the extended URL is “offline_access,” he explained, which allows the application to obtain refresh tokens that can be exchanged for new access tokens once they expire. This would allow an attacker to need only to authenticate and approve permissions once to potentially enable indefinite access to a victim’s data, he explained.
In the final step of the attack OpenID and profile parameters come into play, used to provide user authentication and profile information–such as the user’s name, profile picture, gender and locale among others. “This information, known as claims, is sent to the application in the ID token issued by the /authorize endpoint,” Hernandez wrote.
If a user falls for the malicious SharePoint link and signs in, he or she then will be asked to confirm one last time that he or she wants to grant the application the aforementioned permissions.
“If users fail to act, it will be up to domain administrators to spot and deal with any suspicious applications their users might have misguidedly approved,” Hernandez noted.
Hernandez said that the novel phishing campaign is evidence of attackers adapting and finding new ways to steal people’s credentials and use it for foul play, creating scenarios in which they can trick victims into working against themselves.
“Not only is there no need to compromise credentials, but touted security measures such as MFA are also bypassed; it is users themselves who unwittingly approve malicious access to their data,” he noted.
Phishers are trying to bypass Office 365 MFA via rogue apps
19.5.2020 Net-security Phishing
Phishers are trying to bypass the multi-factor authentication (MFA) protection on users’ Office 365 accounts by tricking them into granting permissions to a rogue application.

The app allows attackers to access and modify the contents of the victim’s account, but also to retain that access indefinitely, Cofense researchers warn.
The attack
The attack starts with an invitation email that directs potential victims to a file hosted on Microsoft SharePoint (a web-based collaborative platform that integrates with Microsoft Office).
The name of the document implies that the email recipient will get a bonus on their salary for Q1 2019.
Users who follow the link will land on a legitimate Microsoft Office 365 login page, but only those careful enough to check the URL might see something out of the ordinary – and only if they know what to look for:

The long URL holds a number of parameters that, “translated”, show that by entering the login credentials and pressing the login button, the user will “ask” the Microsoft Identity Platform for an ID token and an authorization code, which will be sent to domain masquerading as a legitimate Office 365 entity (hxxps://officehnoc[.]com/office).
It also shows that the app for which the request is made will gain permission to access the victim’s account, read and modify its contents (documents, files) and use associated resources, access and use the victim’s contacts, and prolong that access indefinitely.
How? The aforementioned authorization code is exchanged for an access token that is presented by the rogue application to Microsoft Graph, which will authorize its access.
How can attackers bypass MFA protection on Office 365?
“Applications that want to access Office 356 data on behalf of a user do so through Microsoft Graph authorizations. However, they must first obtain an access token from the Microsoft Identity Platform,” Cofense researchers explained.
“This is where OAuth2 and OIDC come in. The latter is used to authenticate the user who will be granting the access, and if authentication is successful, the former authorizes (delegates) access for the application. All of this is done without exposing any credentials to the application.”
So the attacker doesn’t have to know the victim’s login credentials and this tactic allows them to gain access to the victim’s account without having to use the credentials or the MFA code.
The access token the rogue app receives and uses will expire after a while, but the app has also been granted the permission to obtain refresh tokens, which can be exchanged for new access tokens, meaning that the app will able to retain access potentially indefinitely.
After signing in, the user will be asked to confirm that he or she wants to grant the application all those permissions. Ideally, that’s the moment most users will balk and refuse but, unfortunately, many don’t understand the danger of giving random apps access to their account.
Remediation
“The OAuth2 phish is a relevant example of adversary adaptation. Not only is there no need to compromise credentials, but touted security measures such as MFA are also bypassed; it is users themselves who unwittingly approve malicious access to their data,” the researchers noted.
“If users fail to act, it will be up to domain administrators to spot and deal with any suspicious applications their users might have misguidedly approved.”
Once the rogue app’s access is revoked, victims must change their O365 account password and check whether the attackers have switched off MFA protection or modified some of its settings/options.
New Microsoft 365 sign-in pages already spoofed for phishing
17.5.2020 Bleepingcomputer Phishing
Microsoft says that attackers have already adapted their phishing campaigns to use the newly updated design for Azure AD and Microsoft 365 sign-in pages.
"Office 365 ATP data shows that attackers have started to spoof the new Azure AD sign-in page in multiple phishing campaigns," Microsoft tweeted earlier. "We have so far seen several dozens of phishing sites used in these campaigns."
The new Azure AD sign-in experience design for Microsoft customers was updated roughly three months ago, at the end of February, and has started rolling out during the first week of April.
While the change was designed to lower the bandwidth requirements needed to load Azure AD sign-in pages, it inadvertently also made it easier for potential victims to figure out a lot easier when they were targeted by an attacker who forgot to update his phishing tools.
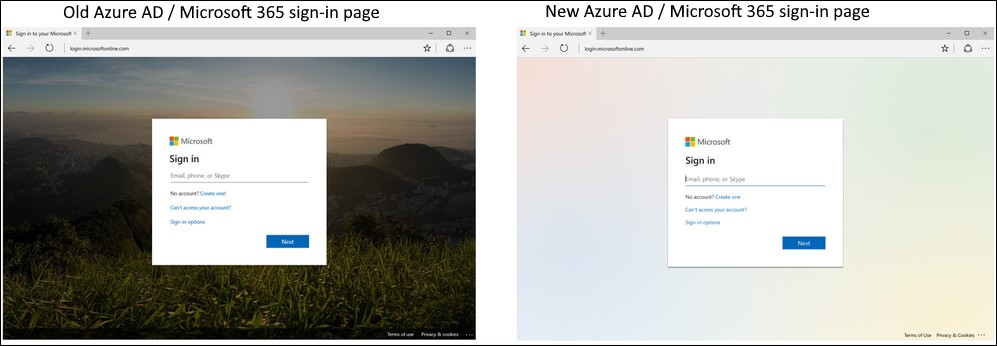
Phishing attacks adapt to changes to prevent effectiveness drop
Microsoft's discovery shows just how quick threat actors are at adapting to changes made to resources and experiences they try to impersonate in their attacks.
This makes their attacks a lot more convincing and allows them to trick their targets into opening booby-trapped attachments and hand over their sensitive information on phishing landing pages that clone the current designs of services they're mimicking.
One of these recent phishing campaigns is delivering emails with the 'Business Document Received' subject line and PDF attachments that attempt to pass as OneDrive documents that require the potential victims to sign in for viewing.
If the recipients click the 'Access Document' button prominently displayed on the malicious PDF camouflaged as an OneDrive shared file, they will be redirected to a phishing landing page that perfectly mimics the new Azure AD and Microsoft 365 sign-in page design.
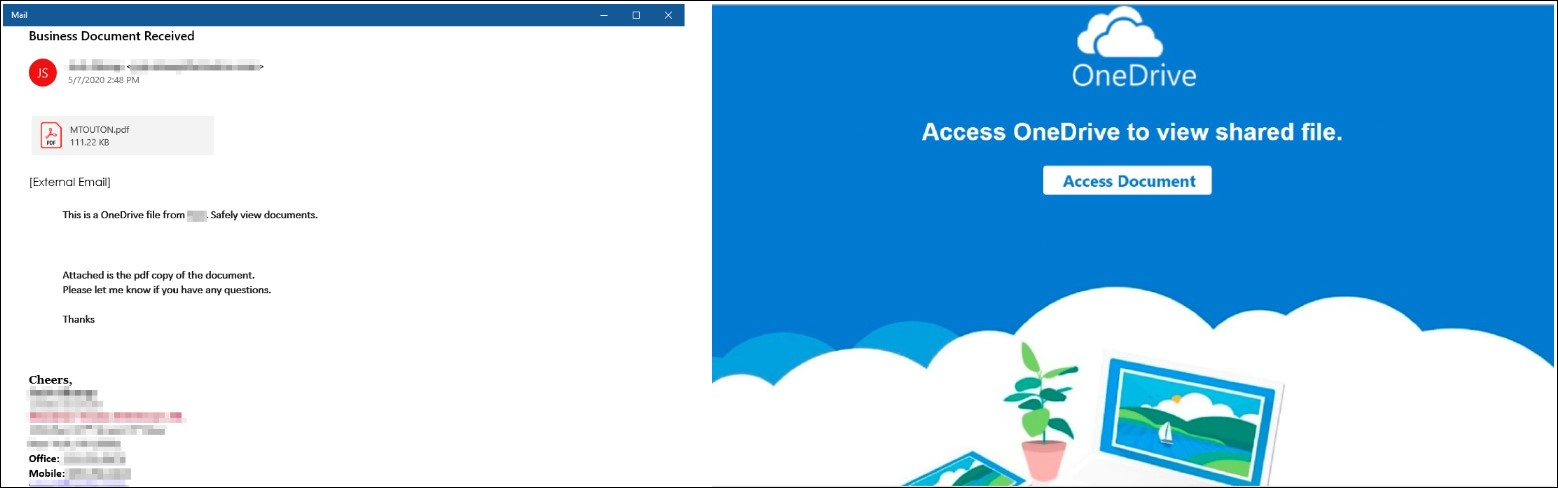
Phishing email and PDF attachment (Microsoft)
Phishing campaigns targeting Microsoft customers
Azure AD and Microsoft 365 are not the only Microsoft products malicious actors have used as lures in recent attacks.
Another highly convincing series of phishing attacks were observed while using cloned imagery from automated Microsoft Teams notifications to harvest Office 365 credentials from tens of thousands of potential victims.
Microsoft's Sway service was also impersonated in a highly targeted spear-phishing campaign dubbed PerSwaysion to deceive recipients into sending their Office 365 credentials to multiple threat actors.
To date, the operators behind the PerSwaysion managed to collect more than 20 Office 365 accounts belonging to executives companies in the U.S., the U.K., Germany, the Netherlands, Canada, Hong Kong, and Singapore.
Microsoft warns of COVID-19 phishing spreading info-stealing malware
17.5.2020 Bleepingcomputer Phishing
Microsoft has discovered a new COVID-19 themed phishing campaign using economic concerns to target businesses with the LokiBot information-stealing Trojan.
In tweets published today by Microsoft Security Intelligence, Microsoft explains that a recent phishing campaign was detected using COVID-19 lures to spread the LokiBot information-stealing Trojan.
When infected, LokiBot will steal saved login credentials from a variety of browsers, FTP, mail, and terminal programs, and then send them back to the attackers' servers where they can be later retrieved.
Microsoft was able to detect the attack with the help of Microsoft Threat Protection's machine learning algorithms, with all customers running Microsoft Defender being automatically protected.
Phishing campaigns utilize COVID-19 lures
According to Microsoft, both of the new phishing campaigns utilized COVID-19 lures to trick recipients into opening the malicious attachments.
The first phishing email seen by Microsoft illustrates how threat actors are following the latest news and concerns to adapt their lures to what's most concerning to businesses.
In this email, the threat actors pretend to be from the Centers for Disease Control (CDC) with the latest information on the virus and a new "BUSINESS CONTINUITY PLAN ANNOUNCEMENT STARTING MAY 2020".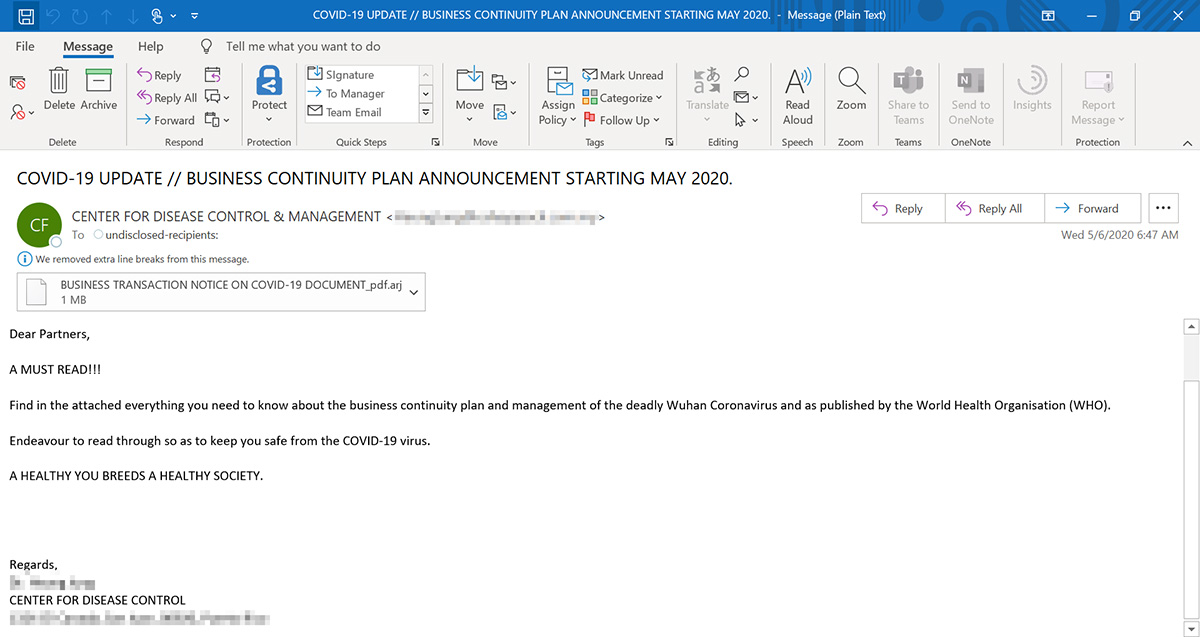
The second email is following more common COVID-19 lures that pretend to be from a vendor asking for updated banking information to process payments.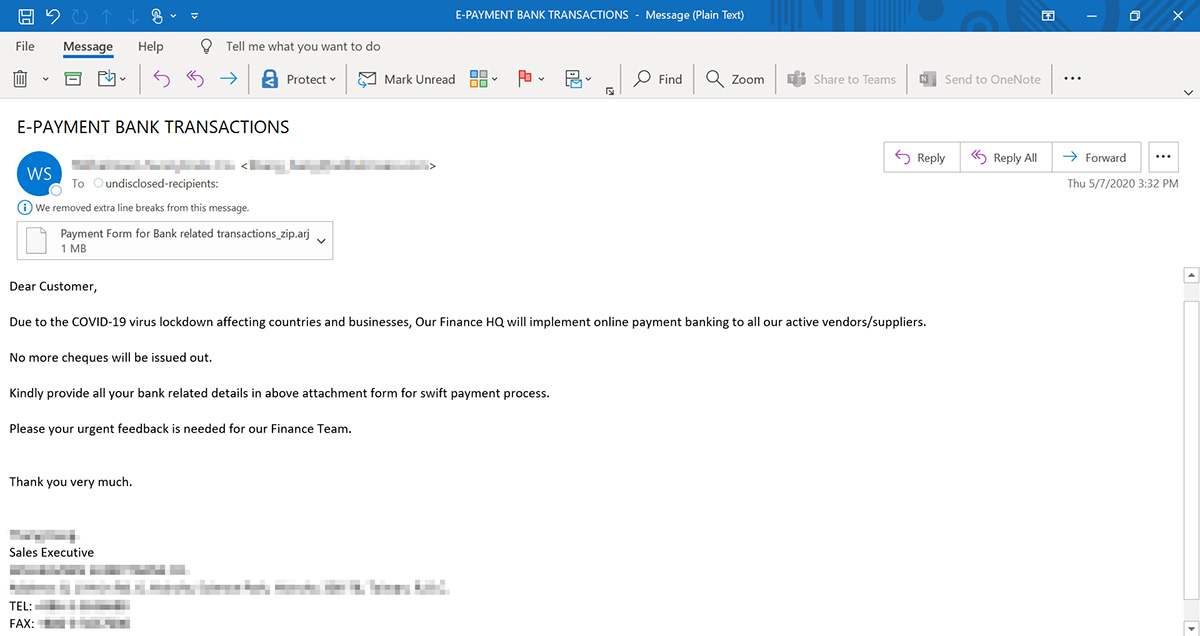
Both of these emails include ARJ attachments that contain executables disguised as PDF files.
"ARJ files are archive files which some antimalware scanners will skip when scanning – especially if a password is used to encrypt the files. Microsoft Defender and Office 365 scan these files when they are attached on email, and are scanned when the file is downloaded or unzipped," Tanmay Ganacharya, director of security research of Microsoft Threat Protection, told BleepingComputer via email.
If a victim attempted to open the enclosed files, they would have been infected with the LokiBot Trojan, and their saved browser and app passwords would have been collected and exfiltrated to a remote server.
"Microsoft Defender's advanced detection technologies, including behavior learning and machine learning, started blocking this attack right away. We used deeper analysis of the blocked attacks, which helped us to identify the end-to-end campaign detailed," Ganacharya explained.
Machine learning plays an important role
Using signals received through the Microsoft Intelligent Security Graph, Microsoft is able to capture trillions of signals from program behavior, scanning engines, customers, and partners and feed them into machine learning algorithms to detect new threats.
"We see a lot of benefits of leveraging machine learning and we are in a very unique position here at Microsoft because of the quality and diversity of our 8.2 trillion signals we process daily through the Microsoft Intelligent Security Graph," Ganacharya explained.
"While anyone can build machine learning models, the quality of the training set as well as the labeled data we have is what drives the quality of the output of these models and is a unique strength for Microsoft."
"The quality of the machine learning models is a key differentiator because these machine learning models help catch the latest strains of malware and attack methods. As attackers change their lures and payloads to capitalize on our fears and desire for information related to COVID-19, this is especially important."
"We've been making quite a lot of investments in terms of adding machine learning detection engines to Defender, around capturing the sequence of behaviors, scanning memory, capturing metadata and relevant details of the files and leveraging these signals in our client- and cloud-side machine learning models to deliver protection for everyone including patient zero," Ganacharya concluded.
Microsoft's machine learning algorithms have also been used in the past to stop a large scale spear-phishing attack attempting to deploy LokiBot payloads in July 2019.
Criminals boost their schemes with COVID-19 themed phishing templates
15.5.20 Net-security Phishing
Phishers are incessantly pumping out COVID-19 themed phishing campaigns and refining the malicious pages the targets are directed to.
“Credential phishing attackers often tailor their email lures with themes they believe will be the most effective and use general websites for actual credential harvesting. The recent move to create custom COVID-19 payment phishing templates indicates that buyers view them as effective enough to warrant custom tactics to harvest credentials,” ProofPoint researchers have noted.
The COVID-19 themed phishing templates
Cybercriminals have eagerly embraced the opportunities brought on by the COVID-19 pandemic. One of those is the fact that many governments and non-governmental organizations are offering crucial information about the virus and/or financial assistance.
The crooks have put in a lot of effort into creating convincing phishing page templates to impersonate these organizations and make it easier to quickly set up new pages once current ones get blacklisted.
Most of the templates aren’t exact copies of the impersonated websites, but they do copy their look and feel – and that’s often enough to fool many targets.
For example: the multi-layered template that spoofs the legitimate Canadian government website starts with a page that asks users to chose whether they want to continue using the site in English or French (the country’s two official languages), and then offers the credential phishing pages in the chosen language.

Another template that impersonates the US Internal Revenue Service (IRS) first tells the potential victim they are eligible for financial aid as part of the COVID-19 relief program and then leads them to the page asking for their personal information.
Similar schemes are used to impersonate Her Majesty’s Revenue and Customs (HMRC) in the United Kingdom, the French government, the World Health Organization (WHO), the US Centers for Disease Control (CDC), and so on.

The crooks are exploiting people’s anxiety and despair to steal login credentials for a variety of online accounts – Gmail, Office 365, Outlook, etc. – as well as sensitive information such as names, addresses, social security/insurance numbers, payment card information, and so on.
So far, ProofPoint researchers have seen more than 300 different COVID-19 campaigns this year and, as the COVID-19 situation continues to unfold, they expect these kinds of attacks to continue and threat actors to offer additional tools that can make those attacks easier to carry out.