Articles 2020 July - January February March April May June July August September October November December
WastedLocker: technical analysis
31.7.20 Virus Securelist
The use of crypto-ransomware in targeted attacks has become an ordinary occurrence lately: new incidents are being reported every month, sometimes even more often.
On July 23, Garmin, a major manufacturer of navigation equipment and smart devices, including smart watches and bracelets, experienced a massive service outage. As confirmed by an official statement later, the cause of the downtime was a cybersecurity incident involving data encryption. The situation was so dire that at the time of writing of this post (7/29) the operation of the affected online services had not been fully restored.
According to currently available information, the attack saw the threat actors use a targeted build of the trojan WastedLocker. An increase in the activity of this malware was noticed in the first half of this year.
We have performed technical analysis of a WastedLocker sample.
Command line arguments
It is worth noting that WastedLocker has a command line interface that allows it to process several arguments that control the way it operates.
-p <directory-path>
Priority processing: the trojan will encrypt the specified directory first, and then add it to an internal exclusion list (to avoid processing it twice) and encrypt all the remaining directories on available drives.
-f <directory-path>
Encrypt only the specified directory.
-u username:password \\hostname
Encrypt files on the specified network resource using the provided credentials for authentication.
-r
Launch the sequence of actions:
Delete ;
Copy to %WINDIR%\system32\<rand>.exe using a random substring from the list of subkeys of the registry key SYSTEM\CurrentControlSet\Control\;
Create a service with a name chosen similarly to the method described above. If a service with this name already exists, append the prefix “Ms” (e.g. if the service “Power” already exists, the malware will create a new one with the name “MsPower”). The command line for the new service will be set to “%WINDIR%\system32\<rand>.exe -s”;
Start this service and wait until it finishes working;
Delete the service.
-s:
Start the created service. It will lead to the encryption of any files the malware can find.
UAC bypass
Another interesting feature of WastedLocker is the chosen method of UAC bypass. When the trojan starts, it will check the integrity level it was run on. If this level is not high enough, the malware will try to silently elevate its privileges using a known bypass technique.
Create a new directory in %appdata%; the directory name is chosen at random from the substrings found in the list of subkeys of the registry key SYSTEM\CurrentControlSet\Control\;
Copy a random EXE or DLL file from the system directory to this new directory;
Write the trojan’s own body into the alternate NTFS stream “:bin” of this system file;
Create a new temporary directory and set its mount point to “C:\Windows ” (with a trailing whitespace) using the API function NtFsControlFile with the flag IO_REPARSE_TAG_MOUNT_POINT;
Create a new subdirectory named “system32” inside the temporary directory. As a result of the previous step, this new subdirectory can be equally successfully addressed as “%temp%\<directory_name>\system32” or “C:\Windows \system32” (note the whitespace);
Copy the legitimate winsat.exe and winmm.dll into this subdirectory;
Patch winmm.dll: replace the entry point code with a short fragment of malicious code whose only purpose is to launch the content of the alternate NTFS stream created on step 2;
Launch winsat.exe, which will trigger the loading of the patched winmm.dll as a result of DLL hijacking.
The above sequence of actions results in WastedLocker being relaunched from the alternate NTFS stream with elevated administrative privileges without displaying the UAC prompt.

Procmon log fragment during the launch of WastedLocker
Cryptographic scheme
To encrypt victims’ files, the developers of the trojan employed a combination of the AES and RSA algorithms that has already become a ‘classic’ among different crypto-ransomware families.
The search mask to choose which files will be encrypted, as well as the list of the ignored paths are set in the configuration of the malware.

Part of the trojan config showing the ignored path substrings
For each processed file, WastedLocker generates a unique 256 bit key and a 128 bit IV which will be used to encrypt the file content using the AES-256 algorithm in CBC mode. The implementation of the file operations is worthy of note, as it employs file mapping for data access. It must have been an attempt by the criminals to maximize the trojan’s performance and/or avoid detection by security solutions. Each encrypted file will get a new additional extension: “.garminwasted“.
The trojan also implements a way of integrity control as part of its file encryption routine. The malware calculates an MD5 hash of the original content of each processed file, and this hash may be utilized during decryption to ensure the correctness of the procedure.
WastedLocker uses a publicly available reference implementation of an RSA algorithm named “rsaref”.
The AES key, IV and the MD5 hash of the original content, as well as some auxiliary information, are encrypted with a public RSA key embedded in the trojan’s body. The sample under consideration contains a 4096 bit public RSA key.

The public RSA key format used by WastedLocker
It should be noted that this kind of cryptographic scheme, using one public RSA key for all victims of a given malware sample, could be considered a weakness if WastedLocker were to be mass-distributed. In this case a decryptor from one victim would have to contain the only private RSA key that would allow all the victims to decrypt their files.
However, as we can see, WastedLocker is used in attacks targeted at a specific organization which makes this decryption approach worthless in real-world scenarios.
The result of RSA encryption is Base64 encoded and saved in a new file with the extension .garminwasted_info, and what is notable, a new info file is created for each of the victim’s encrypted files. This is a rare approach that was previously used by the BitPaymer and DoppelPaymer trojans.
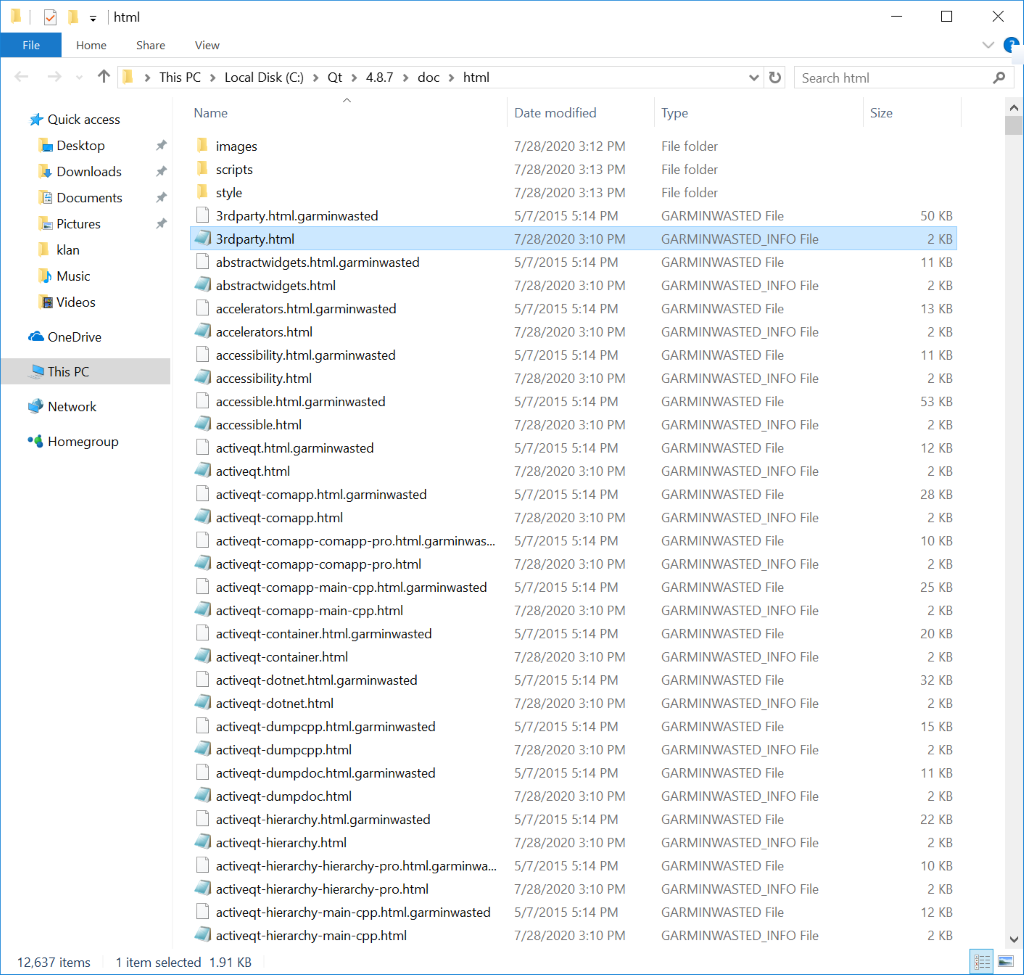
An example list of encrypted files from our test machine
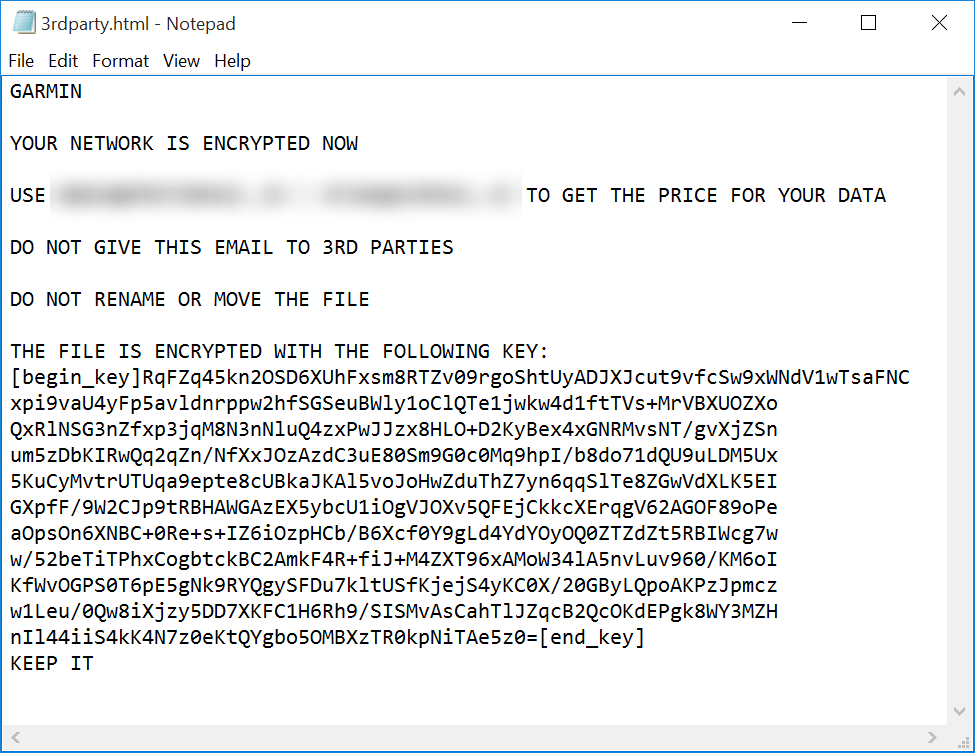
Ransom note left by the trojan
Recommendations
This WastedLocker sample we analyzed is targeted and crafted specifically to be used in this particular attack. It uses a “classic” AES+RSA cryptographic scheme which is strong and properly implemented, and therefore the files encrypted by this sample cannot be decrypted without the threat actors’ private RSA key.
The Garmin incident is the next in a series of targeted attacks on large organizations involving crypto-ransomware. Unfortunately, there is no reason to believe that this trend will decline in the near future.
That is why it is crucial to follow a number of recommendations that may help prevent this type of attacks:
Use up-to-date OS and application versions;
Refrain from opening RDP access on the Internet unless necessary. Preferably, use VPN to secure remote access;
Use modern endpoint security solutions, such as Kaspersky Endpoint Security for Business, that support behavior detection, automatic file rollback and a number of other technologies to protect from ransomware.
Improve user education in the field of cybersecurity. Kaspersky Security Awareness offers computer-based training products that combine expertise in cybersecurity with best-practice educational techniques and technologies.
Use a reliable data backup scheme.
Kaspersky products protect from this threat, detecting it as Trojan-Ransom.Win32.Wasted.d and PDM:Trojan.Win32.Generic.
BootHole Patches Causing Many Systems to Become Unbootable
31.7.20 Vulnerebility Securityweek
It appears that the patches released for Linux distributions in response to the GRUB2 bootloader vulnerability are causing problems for many users, making their systems unbootable.
The flaw, tracked as BootHole and CVE-2020-10713, impacts PCs, servers and other devices running Linux and Windows if they use Secure Boot. An attacker with admin privileges on the targeted system can exploit the vulnerability to run malicious code when the device boots up, enabling them to install stealthy and persistent malware.
Completely patching BootHole is not an easy task as it will involve replacing vulnerable bootloaders and updating the Secure Boot revocation list (DBX) to ensure that the old bootloaders cannot be executed, a process that requires collaboration between multiple software and hardware vendors.
BootHole patches causing problems
Linux distributions have already started releasing updates for the grub2, shim and other packages in response to the vulnerability. However, it appears that those packages have been causing problems for many users, resulting in their systems hanging during the boot process.
Red Hat users were the first to report problems, but it appears that other Linux distributions are experiencing similar issues, including Ubuntu, Debian, CentOS and Mint.
Security researcher Kevin Beaumont reported that major cloud providers such as Azure and Digital Ocean are also seeing systems that fail to boot due to the patches.
He pointed out that similar problems were caused by the initial patches released a few years ago for the notorious Meltdown and Spectre vulnerabilities.
“I think there is a genuine conversation to be had about security vulnerabilities and the wider outlook. A primary concern with security (and in business) is availability. As an industry we also need to be better at careful analysis of vulnerabilities, and staggered testing of patches. The provided solution has again, unfortunately, become worse than the vulnerability for most people,” Beaumont noted.
Impacted Linux distributions are working on developing new packages and some of them have provided instructions on how users can restore systems impacted by the buggy patches.
Capsule8’s Kelly Shortridge predicted after BootHole was disclosed, “We might see more damage from people attempting the mitigation rather than attackers leveraging this in dastardly digital crimes.”
Cybercriminals Could Be Cloning Payment Cards Using Stolen EVM Data
31.7.20 CyberCrime Securityweek
Cybercriminals could be stealing data from payment cards with EMV chips and using it to create magnetic stripe cards which they can use for card-present transactions, cybersecurity firm Gemini Advisory reported on Thursday.
EMV technology encrypts the information stored on a card and uses a unique encryption key that is generated for each card-present transaction to prevent malicious actors from conducting other transactions even if the information stored on the chip is compromised.
This has made it impossible for fraudsters to create clones of EMV cards, as they have done with magnetic stripe cards, from which data can be easily obtained and encoded on a blank card.
Many companies still haven’t fully implemented EMV card readers, which has forced card issuers to encode the data needed to make payments on both the magnetic stripe and the EMV chip. The main difference is that the magnetic stripe contains one card security code, or card verification value (CVV), while the chip stores a different code called integrated circuit card verification value (iCVV).
The problem is that some banks don’t check to ensure that the CVV is provided when the magnetic stripe is used and the iCVV is provided when the chip is used for a transaction.
This enables cybercriminals who can steal EMV card data to encode that data on a magnetic stripe, inserting the iCVV instead of the CVV that is expected to be on the magnetic stripe.
Researchers at Cyber R&D Lab conducted an experiment recently using Visa and MasterCard cards issued by 11 banks in the United States, United Kingdom and some EU countries, and found that four of them were not properly verified by banks, enabling fraudsters to make transactions using magnetic stripe cards that were generated with data obtained from EMV chips.
This EMV-bypass cloning technique may already be used by fraudsters in the wild, with Gemini Advisory pointing to two recent security incidents that involved hackers stealing data from cards that were compromised during EMV transactions. The impacted US companies, supermarket chain Key Food Stores and liquor store Mega Package Store, apparently lost more than 720,000 payment cards.
Fraudsters could have used the stolen EMV data, which is believed to have been obtained as a result of a breach into the point-of-sale (PoS) systems at the two companies, to create magnetic stripe clones, which could then be used for fraudulent card-present transactions if the issuing bank fails to properly verify the CVV.
“While analysts have not found dark web chatter highlighting EMV-Bypass Cloning or malware capable of capturing such data from EMV-enabled POS devices, the Key Food Stores and Mega Package Store breaches came from two unrelated dark web sources. This indicates that the technique used to compromise this data is likely spreading across different criminal groups using advanced operational security (OPSEC),” Gemini Advisory explained.
Security blogger Brian Krebs pointed to a recent alert from Visa warning that known PoS malware families such as Alina, Dexter and TinyLoader were successfully used to steal payment card data from EMV chip-enabled PoS terminals.
Gemini Advisory said, “EMV technology may have changed the underground market for CP [card-present] records, but EMV-Bypass Cloning has opened the door for cybercriminals to sidestep the central security features of EMV chips and channel a new source of CP cards back into the underground CP market,”
Twitter Employees Targeted With Phone Spear-Phishing in Recent Attack
31.7.20 Attack Phishing Securityweek
Twitter on Thursday revealed that several employees were targeted with phone spear-phishing in a social engineering attack leading to the recent security incident.
A total of 130 accounts were targeted in the incident, with hackers abusing internal Twitter systems and tools to reset the passwords for 45 of them. The attackers also accessed the DM inbox of 36 accounts and downloaded the Twitter data of 7.
Supposedly the work of young hackers looking to compromise high-profile, OG accounts, the incident resulted in the inbox of an elected Dutch official being accessed as well.
On Thursday, Twitter confirmed that the hackers targeted several of its employees to gain access to internal systems and gather information on which employees might have access to the tools needed to reset passwords and take over accounts.
“Not all of the employees that were initially targeted had permissions to use account management tools, but the attackers used their credentials to access our internal systems and gain information about our processes. This knowledge then enabled them to target additional employees who did have access to our account support tools,” the social media platform revealed.
Twitter also underlines that its support teams use proprietary tools to resolve issues that users report, to review content, and respond to reports.
“Access to these tools is strictly limited and is only granted for valid business reasons. We have zero tolerance for misuse of credentials or tools, actively monitor for misuse, regularly audit permissions, and take immediate action if anyone accesses account information without a valid business reason,” the company says.
Following the attack, the social platform is looking at means to improve its tools and controls, especially considering the concentrated effort that attackers showed in targeting specific employees.
Twitter also notes that it has already contacted the impacted account owners and worked with them to restore access after initially locking them out to contain the security incident. The company also engaged with law enforcement to investigate the attack.
“Since the attack, we’ve significantly limited access to our internal tools and systems to ensure ongoing account security while we complete our investigation. As a result, some features (namely, accessing the Your Twitter Data download feature) and processes have been impacted. We will be slower to respond to account support needs, reported Tweets, and applications to our developer platform,” the company says.
Twitter also notes that it plans on intensifying employee training and to accelerate improvements to its tools to ensure better security and more efficient detection and prevention of inappropriate access to accounts.
New Attack Leverages HTTP/2 for Effective Remote Timing Side-Channel Leaks
31.7.20 Attack Thehackernews
Security researchers have outlined a new technique that renders a remote timing-based side-channel attack more effective regardless of the network congestion between the adversary and the target server.
Remote timing attacks that work over a network connection are predominantly affected by variations in network transmission time (or jitter), which, in turn, depends on the load of the network connection at any given point in time.
But since measuring the time taken to execute cryptographic algorithms is crucial to carrying out a timing attack and consequently leak information, the jitter on the network path from the attacker to the server can make it impractical to successfully exploit timing side-channels that rely on a small difference in execution time.
The new method, called Timeless Timing Attacks (TTAs) by researchers from DistriNet Research Group and New York University Abu Dhabi, instead leverages multiplexing of network protocols and concurrent execution by applications, thus making the attacks immune to network conditions.
"These concurrency-based timing attacks infer a relative timing difference by analyzing the order in which responses are returned, and thus do not rely on any absolute timing information," the researchers said.
Using HTTP/2's Request Multiplexing to Reduce Jitter
Unlike the typical timing-based attacks, wherein the execution times are measured independently and sequentially, the latest technique attempts to extract information from the order and the relative timing difference between two concurrently executed requests without relying on any timing information.
To do so, a bad actor initiates a pair of HTTP/2 requests to the victim server either directly or using a cross-site — such as a malicious advertisement or tricking the victim into visiting an attacker-controlled web page — to launch requests to the server via JavaScript code.
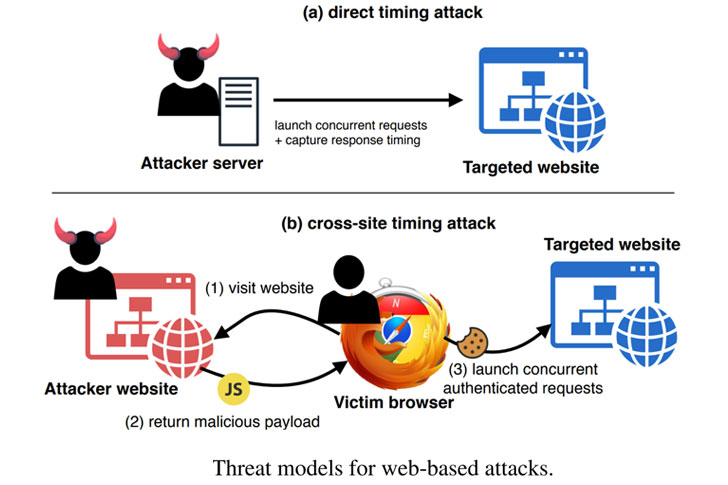
The server returns a result that contains the difference in response time between the second request and the first. The TTA, then, works by taking into account whether this difference is positive or negative, where positive indicates that the processing time of the first request takes less time than processing the second request.
"On web servers hosted over HTTP/2, we find that a timing difference as small as 100ns can be accurately inferred from the response order of approximately 40,000 request-pairs," the researchers noted.
"The smallest timing difference that we could observe in a traditional timing attack over the Internet was 10μs, 100 times higher than our concurrency-based attack."
A limitation of this approach is that attacks aimed at servers using HTTP/1.1 cannot exploit the protocol to coalesce multiple requests in a single network packet, thereby requiring that a concurrent timing attack be performed using multiple connections instead of sending all requests over the same connection.
This stems from HTTP/1.1's use of head-of-line (HOL) blocking, which causes all requests over the same connection to be handled sequentially, whereas HTTP/2 addresses this issue through request multiplexing.
Currently, 37.46% of all desktop websites are served over HTTP/2, a number that increases further to 54.04% for sites that support HTTPS. Although this makes a huge number of websites susceptible to TTAs, the researchers note that many of them rely on content delivery networks (CDN), such as Cloudflare, which still uses HTTP/1.1 for connections between the CDN and the origin site.
Tor Onion Service and Wi-Fi EAP-PWD Vulnerable
But in a twist, the researchers found that concurrency-based timing attacks can also be deployed against Tor onion services, including those that only support HTTP/1.1, allowing an attacker to create two Tor connections to a particular onion service, and then simultaneously send a request on each of the connections to measure a timing difference of 1μs.
That's not all. The EAP-PWD authentication method, which uses a shared password between the server and supplicant when connecting to Wi-Fi networks, is rendered vulnerable to dictionary attacks by exploiting a timing leak in the Dragonfly handshake protocol to reveal the information about the password itself.
Although timing attacks can be countered by ensuring constant-time execution, it's easier said than done, especially for applications that rely on third-party components. Alternatively, the researchers suggest adding a random delay to incoming requests and ensure that different requests are not combined in a single packet.
This is not the first time remote timing attacks have been employed to leak sensitive information. Researchers have previously demonstrated it's possible to exploit cache side-channels to sniff out SSH passwords from Intel CPU cache (NetCAT) and even achieve Spectre-like speculative execution over a network connection (NetSpectre).
"Since the NetSpectre attacks target applications above the network layer, an attacker could, in theory, leverage our concurrency-based timing attacks to improve the timing accuracy," the researchers said.
The findings will be presented at the USENIX Security Symposium later this year. The researchers have also published a Python-based tool to test HTTP/2 servers for TTA vulnerabilities.
Billions of Devices Impacted by Secure Boot Bypass
31.7.20 Vulnerebility Threatpost
The “BootHole” bug could allow cyberattackers to load malware, steal information and move laterally into corporate, OT, IoT and home networks.
Billions of Windows and Linux devices are vulnerable to cyberattacks stemming from a bug in the GRUB2 bootloader, researchers are warning.
GRUB2 (which stands for the GRand Unified Bootloader version 2) is the default bootloader for the majority of computing systems. Its job is to manage part of the start-up process – it either presents a menu and awaits user input, or automatically transfers control to an operating system kernel.
Secure Boot is an industry standard that ensures that a device boots using only trusted software. When a computer starts, the firmware checks the signatures of UEFI firmware drivers, EFI applications and the operating system. If the signatures are valid, the computer boots, and the firmware gives control to the operating system. According to Eclypsium researchers, the bug tracked as CVE-2020-10713 could allow attackers to get around these protections and execute arbitrary code during the boot-up process, even when Secure Boot is enabled and properly performing signature verification.
Dubbed BootHole by Eclypsium because it opens up a hole in the boot process, the new bug is a buffer overflow vulnerability in the way that GRUB2 parses content from the GRUB2 config file (grub.cfg), according to Eclypsium.
“The GRUB2 config file is a text file and typically is not signed like other files and executables,” researchers wrote in the firm’s analysis, released on Wednesday. As a result, Secure Boot doesn’t check it. Thus, an attacker could modify the contents of the GRUB2 configuration file to include attack code. And further, that file is loaded before the operating system is loaded, so the attack code runs first.
“In this way, attackers gain persistence on the device,” explained researchers.
On the technical front, Red Hat noted that the grub.cfg file is composed of several string tokens.
“The configuration file is loaded and parsed at GRUB initialization right after the initial boot loader, called shim, has loaded it,” the project said in an advisory issued on Wednesday. “During the parser stage, the configuration values are copied to internal buffers stored in memory. Configuration tokens that are longer in length than the internal buffer size end up leading to a buffer overflow issue. An attacker may leverage this flaw to execute arbitrary code, further hijacking the machine’s boot process and bypassing Secure Boot protection. Consequently, it is possible for unsigned binary code to be loaded, further jeopardizing the integrity of the system.”
Once in, attackers have “near total control” over a target machine: “Organizations should be monitoring their systems for threats and ransomware that use vulnerable bootloaders to infect or damage systems,” according to the analysis.
The bug carries a high-severity CVSS rating of 8.2 (Red Hat deems it “moderate” in severity, and Microsoft characterizes it as “important”). BootHole likely avoided a critical rating because in order to exploit it, an attacker would need to first gain administrative privileges.
“An attacker would first need to establish access to the system such as gaining physical access, obtain the ability to alter a pxe-boot network, or have remote access to a networked system with root access,” according to Red Hat.
The bad news is that GRUB2 is nearly ubiquitous across the computing landscape.
“The vulnerability is in the GRUB2 bootloader utilized by most Linux systems,” the researchers said. “The problem also extends to any Windows device that uses Secure Boot with the standard Microsoft Third Party UEFI Certificate Authority.”
They added that the majority of computers (laptops, desktops, servers and workstations) are vulnerable, and that the vulnerability also affects network appliances, proprietary gear specific to healthcare, financial and other verticals, internet-of-things (IoT) devices, and operational technology (OT) and SCADA equipment in industrial environments. In all, billions of devices are susceptible.
Worse, no simple patch or firmware update can fix the issue, according to Eclypsium.
“Mitigation is complex and can be risky and will require the specific vulnerable program to be signed and deployed, and vulnerable programs should be revoked to prevent adversaries from using older, vulnerable versions in an attack,” the researchers said. “The three-stage mitigation process will likely take years for organizations to complete patching.”
On the supplier side, the fix will require the release of new installers and bootloaders for all versions of Linux, as well as new versions of vendors’ “shims” (the aforementioned first-stage boot loaders) to be signed by the Microsoft Third-Party UEFI certificate authority, Eclypsium warned. Also, hardware-makers that provision their own keys into their hardware at the factory level (which sign GRUB2 directly) will need to provide updates, and revoke their own vulnerable versions of GRUB2.
“It is important to note that until all affected versions are added to the [Secure Boot revocation list, a.k.a. dbx], an attacker would be able to use a vulnerable version of shim and GRUB2 to attack the system,” researchers explained. “This means that every device that trusts the Microsoft 3rd Party UEFI CA will be vulnerable for that period of time.”
Eclypsium has coordinated responsible disclosure of BootHole with a raft of affected vendors and Linux distros, including Microsoft, the UEFI Security Response Team (USRT), Oracle, Red Hat (Fedora and RHEL), Canonical (Ubuntu), SuSE (SLES and openSUSE), Debian, Citrix, VMware, and various OEMs and software vendors, several of which have issued their own advisories.
Microsoft will be releasing a set of signed dbx updates, which can be applied to systems to block shims that can be used to load the vulnerable versions of GRUB2, according to Eclypsium.
“Due to the risk of bricking systems or otherwise breaking operational or recovery workflows, these dbx updates will initially be made available for interested parties to manually apply to their systems rather than pushing the revocation entries and applying them automatically,” the firm noted. “Organizations should additionally ensure they have appropriate capabilities for monitoring UEFI bootloaders and firmware and verifying UEFI configurations, including revocation lists, in their systems.”
Organizations should also test device-recovery capabilities, including the “reset to factory defaults” functionality, so they can recover it if a device is negatively impacted by an update.
Expert discloses details of 3 Tor zero-day flaws … new ones to come
31.7.20 Vulnerebility Securityaffairs
A security researcher published the details about two Tor zero-day vulnerabilities and plans to release three more flaws.
The security researcher Dr. Neal Krawetz has published technical details about two Tor zero-day vulnerabilities over the past week and promises to release three more. Oppressive regimes could exploit these Tor zero-day flaws to prevent users from accessing the popular anonymizing network.
The expert confirmed that one of these three new issues can de-anonymize Tor servers revealing their real IP address.
Dr. Neal Krawetz decided to publicly disclose details on two zero-day flaws after the Tor Project has repeatedly failed to fix multiple vulnerabilities he reported over the past years.
The researcher also promised to reveal at least three more Tor zero-days, including one that can reveal the real-world IP address of Tor servers.
The researcher operates multiple Tor nodes, last week he published a blog post that describes how internet service providers and organizations could stop Tor connections.
“However, what if there was a distinct packet signature provided by every Tor node that can be used to detect a Tor network connection? Then you could set the filter to look for the signature and stop all Tor connections. As it turns out, this packet signature is not theoretical.” reads the post.
An attacker could use the packet signature to block Tor connections from initiating.
Today the expert published a new blog post that provides details about other Tor zero-day issues that could be exploited by attackers to detect indirect connections,
“Direct connections to the Tor network are the most common type of connection. However, there are also indirect ways to connect to the Tor network. These indirect methods are called ‘bridges’. If someone could detect every bridge protocol, then every Tor user could be blocked from accessing the Tor network, or they can be directly surveilled. (If they know your real network address, then they know who you are, and they can monitor or censor your activities.)” reads the report.
“In this blog entry, I’m going to disclose methods to identify Tor bridge network traffic. This includes two new zero-day (0day) exploits — one for detecting obfs4 and one for detecting meek.”
Tor bridges (“Tor bridge relays”) are alternative entry points to the Tor network, some of them are not listed publicly. Using a bridge makes it harder, but not impossible, for the ISP to determine a user is connecting to Tor.
According to Dr. Krawetz, an attacker can easily detect connections to Tor bridges tracking specific packets.
“Between my previous blog entry and this one, you now have everything you need to enforce the policy with a real-time stateful packet inspection system. You can stop all of your users from connecting to the Tor network, whether they connect directly or use a bridge,” continues Dr. Krawetz.
The security researcher reported multiple issues to the Tor Project, but he claims that the maintainers have never addressed them, for this reason, Dr. Krawetz decided to interrupt its collaboration with the organization.
Cisco Patches Serious Vulnerabilities in Data Center Network Manager
31.7.20 Vulnerebility Securityweek
Cisco informed customers on Wednesday that it has patched critical and high-severity vulnerabilities in its Data Center Network Manager (DCNM) network management platform.
One of the security flaws, CVE-2020-3382, has been classified as critical. It allows a remote, unauthenticated attacker to bypass authentication and perform actions with admin privileges on the targeted device.
“The vulnerability exists because different installations share a static encryption key. An attacker could exploit this vulnerability by using the static key to craft a valid session token. A successful exploit could allow the attacker to perform arbitrary actions through the REST API with administrative privileges,” Cisco explained.
The networking giant has fixed several high-severity vulnerabilities in DCNM, including weaknesses that can be exploited for arbitrary command injection, path traversal and arbitrary file writing, and bypassing authorization and escalating privileges. However, exploitation of these bugs requires authentication.
The one high-severity vulnerability that can be exploited by an unauthenticated attacker is CVE-2020-3376. It can be leveraged to bypass authentication and execute arbitrary actions.
“The vulnerability is due to a failure in the software to perform proper authentication. An attacker could exploit this vulnerability by browsing to one of the hosted URLs in Cisco DCNM. A successful exploit could allow the attacker to interact with and use certain functions within the Cisco DCNM,” Cisco explained.
The company has also patched three medium-severity vulnerabilities in DCNM, including XSS, SQL injection and information disclosure issues.
Cisco also announced that it has resolved a critical vulnerability in the management interface of the SD-WAN vManage software. The flaw allows an attacker to access potentially sensitive information, modify the configuration of the system, or cause it to become unavailable. However, exploitation requires authentication.
Cisco says none of these vulnerabilities has been exploited for malicious purposes, which is not surprising considering that the more serious ones were all discovered internally.
APT trends report Q2 2020
30.7.20 APT Securelist
For more than three years, the Global Research and Analysis Team (GReAT) at Kaspersky has been publishing quarterly summaries of advanced persistent threat (APT) activity. The summaries are based on our threat intelligence research and provide a representative snapshot of what we have published and discussed in greater detail in our private APT reports. They are designed to highlight the significant events and findings that we feel people should be aware of.
This is our latest installment, focusing on activities that we observed during Q2 2020.
Readers who would like to learn more about our intelligence reports or request more information on a specific report are encouraged to contact ‘intelreports@kaspersky.com‘.
The most remarkable findings
On May 11, the UK-based supercomputing center, ARCHER, announced that it would shut down access to its network while it investigated a security incident. The website stated that the “ARCHER facility is based around a Cray XC30 supercomputer (with 4920 nodes) that provides the central computational resource”. At the same time, the German-based bwHPC also announced a security incident and decided to restrict access to its resources. The Swiss National Supercomputing Centre, at the time involved in a project to study the small membrane protein of the coronavirus, confirmed that it, and other European high-performance computer facilities, had been attacked and that it had temporarily closed. On May 15, the EGI Computer Security and Incident Response Team (EGI-CSIRT) published an alert covering two incidents that, according to its report, may or may not be related. Both incidents describe the targeting of academic data centers for “CPU mining purposes”. The alert includes a number of IoCs, which complement other OSINT (open-source intelligence) observations. Although we weren’t able to establish with a high degree of certitude that the ARCHER hack and the incidents described by EGI-CSIRT are related, we suspect they might be. Some media speculated that all these attacks might be related to COVID-19 research being carried out at the supercomputing centers.
Interestingly, last July 16th 2020, NCSC published an advisory describing malicious activity targeting institutions related to research to find a vaccine for COVID-19. In this case, the malware used in the attacks belongs to a family called WellMess, as originally described by LAC Co back in 2018. Until recently, this malware was not believed to be related to any APT activity. Surprisingly, NCSC attributes this activity to the APT-29 threat actor. However, it does not provide any public proof.
From our own research, we can confirm that WellMess’s activity seems to follow a cycle, being used in campaigns every three months or so since its discovery. We observed a peak of activity in fall of 2019, followed by an increase in the number of C2s in February 2020. We also observed high-profile targeting, including telcos, government and contractors in MENA and the EU. However, from our side we cannot confirm attribution or targeting of health institutions at the moment.
For more details about WellMess, you can check our presentation from GReAT ideas here: https://youtu.be/xeTYLRCwnFo
Russian-speaking activity
In May, researchers at Leonardo published a report about “Penquin_x64”, a previously undocumented variant of Turla’s Penquin GNU/Linux backdoor. Kaspersky has publicly documented the Penquin family, tracing it back to its Unix ancestors in the Moonlight Maze operation of the 1990s. We followed up on this latest research by generating network probes that detect Penquin_x64 infected hosts at scale, allowing us to discover that tens of internet hoster’s servers in Europe and the US are still compromised today. We think it’s possible that, following public disclosure of Turla’s GNU/Linux tools, the Turla threat actor may have been repurposing Penquin to conduct operations other than traditional intelligence.
In June, we discovered two different domain names, “emro-who[.]in” and “emro-who[.]org”, typo-squatting the World Health Organization (WHO) Regional Office for the Eastern Mediterranean (EMRO). These domains, registered on June 21 using the Njalla.no registrar, seem to be used as sender domains for a spear-phishing campaign. This type of typo-squatting is reminiscent of Sofacy campaigns against other international organizations. Moreover, we have seen Njalla.no recently used to register SPLM and XTUNNEL C2 (command-and-control) servers and we have seen this autonomous system used by Sofacy in the past for a SPLM C2.
Hades is an elusive, highly dynamic threat actor that commonly engages in tailored hacking and special access operations, such as the OlympicDestroyer attack or the ExPetr (aka NotPetya) and Badrabbit attacks. On May 28, the US National Security Agency (NSA) published an alert detailing the use by Hades of an Exim vulnerability (CVE-2019-10149) for what appears to be a potentially large hacking operation designed for mass access. Our own report expanded on the scripts used in this operation, as well as providing other IoCs that we discovered.
Chinese-speaking activity
In late 2019, and again in March this year, we described ongoing malicious activities from a previously unknown threat actor that we named Holy Water. Holy Water notably leveraged a Go language and Google Drive-command-driven implant that we dubbed Godlike12. Following the publication of our report, and notifications to relevant incident response organizations, new Holy Water samples were submitted to VirusTotal. The newly discovered samples include Telegram-controlled and open-source-based Python implants that were probably deployed on the victim’s networks after a successful intrusion.
In March, one of our YARA rules from previous research on ShadowPad attacks detected a recently compiled executable file uploaded to VirusTotal. Later we found a few other samples from our own telemetry. ShadowPad is a modular attack platform consisting of a root module and various plugin modules responsible for diverse functionalities. ShadowPad was first discovered by Kaspersky in 2017. In August of that year, one of our customers detected suspicious network activities. After thorough investigation, we found a legitimate software module that had been compromised and backdoored by an advanced threat actor in a sophisticated software supply-chain attack. We notified the software vendor and also published the outcome of our investigations in a technical white paper. Since then, ShadowPad malware has been deployed in a number of major cyberattacks, with a different subset of plugins used in different attack cases: the CCleaner incident in 2017 and the ShadowHammer attacks in 2018 are the major examples of such attacks.
When analyzing new samples from ShadowPad malware, compiled and used in attacks since late 2019, our investigation revealed a strong connection between these recent ShadowPad malware samples and the CactusPete threat actor. CactusPete started deploying ShadowPad malware to a few victims at the beginning of 2019 through its HighProof backdoor. However, since late 2019, ShadowPad has been commonly used in CactusPete attacks.
This quarter, we described another CactusPete attack campaign which started in December 2019 In this campaign, the CactusPete threat actor used a new method to drop an updated version of the DoubleT backdoor onto the computers. The attackers implanted a new dropper module in the Microsoft Word Startup directory, most likely through a malicious document. This malicious dropper is responsible for dropping and executing a new version of the DoubleT backdoor, which utilizes a new method of encrypting the C2 server address.
While analysing compromised machines in Central Asia, we revealed an additional infection that was unrelated to the initial subject of our investigation. This led us to detect previously unknown malware that we dubbed B&W, which provides an attacker with the capabilities to remotely control a victim’s machine. Further analysis of the samples, infrastructure and other related artefacts allowed us to conclude, with medium confidence, that the newly found malware is related to the SixLittleMonkeys APT. This group is known to have been active for several years, targeting government entities in Central Asia.
HoneyMyte is an APT threat actor that we have been tracking for several years. In February, our fellow researchers at Avira blogged about HoneyMyte PlugX variants that they had recently observed targeting Hong Kong. PlugX has been used by multiple APT groups over the past decade, especially shared among Chinese-speaking threat actors, and has changed in many ways. Avira´s post covers the PlugX loader and backdoor payload, including its USB capabilities. In May, we published an update on this threat actor, specifically providing timely indicators to aid in threat hunting for some of the PlugX variants found in the wild between January and May this year.
In May, we discovered a watering hole on the website of a Southeast Asian top official. This watering hole, set up in March, seemed to leverage whitelisting and social engineering techniques to infect its targets. The final payload was a simple ZIP archive containing a readme file prompting the victim to execute a CobaltStrike implant. The mechanism used to execute CobaltStrike was DLL side-loading, which decrypted and executed a CobaltStrike stager shellcode. Analysis of the code, the infrastructure and the victimology led us to attribute this watering-hole, with high confidence, to the HoneyMyte APT threat actor.
Quarian is a little-known malicious program that Chinese-speaking actors have used since around 2012. We hadn’t spotted any further activity until we observed a resurgence in an attack by the Icefog group in 2019. We tracked the activity of the malware following this and noticed a new variant that was used during several attacks on Middle Eastern and African governments during 2020. In one case, we could see that this variant was deployed following exploitation of the CVE-2020-0688 vulnerability on the network of a government entity. This vulnerability, which was publicly reported in February 2020, allows an authenticated user to run commands as SYSTEM on a Microsoft Exchange server. In this case, the server was indeed compromised and was hosting the ChinaChopper webshell, which was used to obtain, and later launch, the Quarian and PlugX backdoors. Our analysis led us to assume, with medium to high confidence, that the group behind these attacks is one we track under the name CloudComputating – a Chinese-speaking actor that, based on previous reports, has targeted high-profile Middle Eastern diplomatic targets.
In March, researchers at Check Point Research published a report describing an APT campaign that targeted Mongolia’s public sector and leveraged a coronavirus-themed lure to conduct its initial intrusion. We were able to discover further samples and another COVID-themed document with the same targeting, as well as additional targets in Russia. We attribute this activity with medium confidence to IronHusky.
Middle East
The MuddyWater APT was discovered in 2017 and has been active in the Middle East ever since. In 2019, we reported activity against telecoms providers in Iraq and Iran, as well as government bodies in Lebanon. We recently discovered MuddyWater using a new C++ toolchain in a new wave of attacks in which the actor leveraged an open-source utility called Secure Socket Funneling for lateral movement.
At the end of May, we observed that Oilrig had included the DNSExfitrator tool in its toolset. It allows the threat actor to use the DNS over HTTPS (DoH) protocol. Use of the DNS protocol for malware communications is a technique that Oilrig has been using for a long time. The difference between DNS- and DoH-based requests is that, instead of plain text requests to port 53, they would use port 443 in encrypted packets. Oilrig added the publicly available DNSExfiltrator tool to its arsenal, which allows DoH queries to Google and Cloudflare services. This time, the operators decided to use subdomains of a COVID-related domain which are hardcoded in the DNSExfitrator detected samples.
Southеast Asia and Korean Peninsula
BlueNoroff is one of the most prolific financially motivated APT actors and we have published several reports of BlueNoroff campaigns targeting financial institutions. Recently, we uncovered another campaign that has been active since at least 2017. In this campaign, the group sends spear-phishing emails containing an archived Windows shortcut file. The file names are disguised as security or cryptocurrency related files in order to entice users into executing them. The infection chain started from this shortcut file is a complex multi-stage infection procedure. Before delivering the Windows executable payload, the actor uses two VBS and three PowerShell scripts in order to collect system information. The actor very carefully delivers the final payload only to the intended targets. The backdoor payload also utilizes a multi-stage infection procedure. The actor uses it to control infected hosts and implants additional malware for surveillance. These malicious programs are responsible for stealing the user’s keystrokes and saving a screenshot of the infected machine. The main targets of this campaign are financial institutions, such as cryptocurrency businesses, and fintech companies. We identified diverse victims from 10 countries, as well as more potential victims from open source intelligence.
The Lazarus group has been a major threat actor for several years. Alongside goals like cyber-espionage and cyber-sabotage, this threat actor has targeted banks and other financial companies around the globe. The group continues to be very active. We recently observed the Lazarus group attacking a software vendor in South Korea using Bookcode, malware that we evaluate to be a Manuscrypt variant, utilizing a watering-hole attack to deliver it. Manuscrypt is one of the Lazarus group’s tools that is actively being updated and used. The group attacked the same victim twice. Almost a year prior to compromising this victim, Lazarus attempted to infect it by masquerading as a well-known security tool, but failed. We were able to construct the group’s post-exploitation activity, identifying various freeware and red-teaming tools used. Although Lazarus has recently tended to focus more on targeting the financial industry, we believe that in this campaign they were seeking to exfiltrate intellectual property. We also observed that they previously spread Bookcode using a decoy document related to a company working in the defense sector. Based on our observations, we evaluate that the Bookcode malware is being used exclusively for cyber-espionage campaigns.
In April, we released an early warning about the VHD ransomware, which was first spotted in late March. This ransomware stood out because of its self-replication method. The use of a spreading utility compiled with victim-specific credentials was reminiscent of APT campaigns, but at the time we were unable to link the attack to an existing group. However, Kaspersky was able to identify an incident in which the VHD ransomware was deployed, in close conjunction with known Lazarus tools, against businesses in France and Asia. This indicates that Lazarus is behind the VHD ransomware campaigns that have been documented so far. As far as we know, this is also the first time it has been established that the Lazarus group has resorted to targeted ransomware attacks for financial gain.
Last year we created a private report on a malware framework that we named MATA, which we attribute, with low confidence, to the Lazarus group. This framework included several components, such as a loader, orchestrator and plug-ins. Initially, this framework targeted Windows and Linux. However, in April we discovered a suspicious macOS file uploaded to VirusTotal using a rule to detect the MATA malware framework. After looking into this malware, we confirmed that it was a macOS variant of the MATA malware. The malware developers Trojanized an open-source two-factor authentication application and utilized another open-source application template. While investigating, to find more solid evidence for attribution, we found an old Manuscrypt strain that used a similar configuration structure. We also discovered a cluster of C2 servers probably related to this campaign.
The MATA framework was not the only way that Lazarus targeted macOS. We also observed a cluster of activity linked to Operation AppleJeus. The other was similar to the macOS malware used in a campaign that we call TangDaiwbo. This is a multi-platform cryptocurrency exchange campaign: Lazarus utilizes macro-embedded Office documents and spreads PowerShell or macOS malware, depending on the victim’s system.
Early this year, we reported improvements in a Lazarus campaign targeting a cryptocurrency business. In this campaign, Lazarus adopted a downloader that sends compromised host information and selectively fetches the next-stage payload. Recently, we identified a Lazarus campaign with similar strategies, but targeting academic and automotive sectors. Lazarus also adopted new methods to deliver its tools. First of all, the group elaborated its weaponized document by adopting remote template injection techniques. Previously, Lazarus delivered macro-embedded documents to the victim, but the group has now applied one more stage to hinder detection. The group also utilized an open-source PDF reader named Sumatra PDF to make Trojanized applications. They created a Trojanized PDF reader, sending it to the victim with a crafted PDF file. If the victim opens this file, the Trojanised PDF viewer implants malicious files and shows decoy documents to deceive the victim. The actor delivers the final payload very carefully, and executes it in memory. Fortunately, we were able to get the final payload and confirm that it was a Manuscrypt variant that we had already described. We also found that it’s the same malware variant that the US CISA (Cybersecurity and Infrastructure Security Agency) recently reported, named COPPERHEDGE.
Following our report describing the long-standing PhantomLance campaign in Southeast Asia, we published a private report providing detailed attribution based on discovered overlaps with reported campaigns of the OceanLotus APT. In particular, we found multiple code similarities with the previous Android campaign, as well as similarities in macOS backdoors, infrastructure overlap with Windows backdoors and a couple of cross-platform resemblances. Based on our research, we believe, with medium confidence, that PhantomLance is a modern Android campaign conducted by OceanLotus. Apart from the attribution details, we described the actor’s spreading strategy using techniques to bypass app market filters. We also provided additional details about samples associated with previously reported suspected infrastructure, as well as the latest sample deployed in 2020 that uses Firebase to decrypt its payload.
Additionally, OceanLotus has been using new variants of its multi-stage loader since the second half of 2019. The new variants use target-specific information (username, hostname, etc.) of the targeted host that they obtained beforehand, in order to ensure their final implant is deployed on the right victim. The group continues to deploy its backdoor implant, as well as Cobalt Strike Beacon, configuring them with updated infrastructure.
Other interesting discoveries
The Deceptikons APT is a long-running espionage group believed to have been providing mercenary services for almost a decade now. The group is not technically sophisticated and has not, to our knowledge, deployed zero-day exploits. The Deceptikons infrastructure and malware set is clever, rather than technically advanced. It is also highly persistent and in many ways reminds us of WildNeutron. Deceptikon’s repeated targeting of commercial and non-governmental organizations is somewhat unusual for APT actors. In 2019, Deceptikons spear-phished a set of European law firms, deploying PowerShell scripts. As in previous campaigns, the actor used modified LNK files requiring user interaction to initially compromise systems and execute a PowerShell backdoor. In all likelihood, the group’s motivations included obtaining specific financial information, details of negotiations, and perhaps even evidence of the law firms’ clientele.
MagicScroll (aka AcidBox) is the name we’ve given to a sophisticated malware framework, whose main purpose is to decrypt and load an arbitrary payload in kernel mode. The framework consists of several stages. The first stage is a Windows security provider that is loaded by the system on boot and executed in user mode. This decrypts and runs a second payload, which is physically stored in the registry. Although we weren’t able to find a victim with this second stage, we were able to find a file that matches the expected format of the second stage. This second stage payload utilizes a well-known vulnerability in a VirtualBox driver (CVE-2008-3431) to load the third stage, which is designed to run in kernel mode. The kernel mode payload is decrypted from a resource from the second stage, using the key retrieved from the registry. Unfortunately, we couldn’t find a decryption key to decrypt the third stage payload, so we don’t know what the last part of this malware framework looks like. Although the code is quite sophisticated, we couldn’t identify any similarity with other known frameworks.
Aarogya Setu is the name of a mandatory COVID-19 mobile tracking app developed by the National Informatics Centre, an organization that comes under the Ministry of Electronics and Information Technology in India. It allows its users to connect to essential health services in India. With cyber criminals and APT actors taking advantage of pandemic-tracking applications to distribute Trojanized mobile apps, we investigated and identified apps that mimic the appearance and behavior of the legitimate Aarogya Setu app while deploying Android RATs. We consider one of these to be a new version of a RAT that we previously reported being used by the Transparent Tribe threat actor.
Final thoughts
The threat landscape isn’t always full of “groundbreaking” events. However, a review of the activities of APT threat actors indicates that there are always interesting developments. Our regular quarterly reviews are intended to highlight these key developments.
Here are the main trends that we’ve seen in Q2 2020.
Geo-politics remains an important motive for some APT threat actors, as shown in the activities of MuddyWater, the compromise of the Middle East Eye website and the campaigns of CloudComputating and HoneyMyte groups.
As is clear from the activities of Lazarus and BlueNoroff, financial gain is another driver for some threat actors – including the use of ransomware attacks.
While Southeast Asia continues to be an active region for APT activities, this quarter we have also observed heavy activity by Chinese-speaking groups, including ShadowPad, HoneyMyte, CactusPete, CloudComputating and SixLittleMonkeys.
APT threat actors continue to exploit software vulnerabilities – examples this quarter include Hades and MagicScroll.
We have noted before that the use of mobile implants is no longer a novelty, and this quarter is no exception, as illustrated by the PhantomLance campaign.
It is clear that APT actors, like opportunistic cybercriminals, continue to exploit the COVID-19 pandemic as a theme to lure potential victims. However, we would note once again that this doesn’t represent a shift in TTPs.
As always, we would note that our reports are the product of our visibility into the threat landscape. However, it should be borne in mind that, while we strive to continually improve, there is always the possibility that other sophisticated attacks may fly under our radar.
Operation North Star – North-Korea hackers targeted US defense and aerospace companies
30.7.20 BigBrothers Securityweek
North Korea-linked hackers continue to be very active in this period, researchers reported a campaign aimed at the US defense and aerospace sectors.
Security experts from McAfee uncovered a new cyber-espionage campaign carried out by North Korean hackers that targeted the US defense and aerospace sectors. Threat actors used fake job offers to deceive employees looking for new job opportunities and compromise the network of their organizations.
The campaign tracked ‘Operation North Star,’ was active between late March and May 2020.

The threat actors’ job postings messages were crafted to target the following specific US defense programs and groups:
F-22 Fighter Jet Program
Defense, Space and Security (DSS)
Photovoltaics for space solar cells
Aeronautics Integrated Fighter Group
Military aircraft modernization programs
The researchers noticed that the infrastructure and TTPs (Techniques, Tactics, and Procedures) used in this campaign overlaps with the ones previously associated with Hidden Cobra.
The attackers sent out spear-phishing emails using boobytrapped documents leveraging the fake job offer as bait.
Threat actors behind this campaign are utilizing compromised infrastructure from multiple European countries to host their C2 infrastructure and distribute the malware to the targets.
The Techniques, Tactics, and Procedures (TTPs) of the Operation North Star operations are very similar to those observed in 2017 and 2019 campaigns that targeted key military and defense technologies.

“Our analysis indicates that one of the purposes of the activity in 2020 was to install data gathering implants on victims’ machines. These DLL implants were intended to gather basic information from the victims’ machines with the purpose of victim identification.” states the report published by the experts. “The data collected from the target machine could be useful in classifying the value of the target. McAfee ATR noticed several different types of implants were used by the adversary in the 2020 campaigns.”
It is not clear how efficient was a “new job” theme campaign due to the ongoing Coronavirus pandemic.
Recently, security experts from Kaspersky Lab reported that North Korea-linked hackers are attempting to spread a new ransomware strain known as VHD.
In a separate report, Kaspersky also reported that Lazarus APT Group has used a new multi-platform malware framework, dubbed MATA, to target entities worldwide,
U.S. experts claim China-linked hackers have infiltrated Vatican networks
30.7.20 BigBrothers Securityweek
U.S. cybersecurity firm revealed that China-linked hackers have infiltrated Vatican computer networks ahead of talks.
China-linked hackers have infiltrated the Vatican computer networks, reads a report published by the U.S. cybersecurity firm Recorded Future that focuses on the analysis of nation-state actors.
According to the experts, the cyber espionage campaign began in May ahead the talk between the Vatican and the Chinese government.
The hackers also targeted the Catholic diocese of Hong Kong, including the head of the Hong Kong Study Mission.
“It said the attacks began in May. The Vatican and Beijing were expected to engage in talks this year over the renewal of a landmark 2018 deal that stabilised relations between China and the Church.” reads the article published by the Reuters.
“U.S. cybersecurity firm Recorded Future said in the report that the attacks targeted the Vatican and the Catholic diocese of Hong Kong, including the head of the Hong Kong Study Mission, who is seen as Pope Francis’ de facto representative to China.”
Hackers focused on communications between the Hong Kong diocese and the Vatican. Techniques, tactics, and procedures are aligned with the ones used by China-linked APT groups.
China’s Foreign Ministry spokesman Wang Wenbin, recently speaking at a daily news conference in Beijing, declared that its country always defended the cybersecurity and never used an offensive approach.
Beijing always denied any engagement in any nation-state campaign against foreign governments.
The Vatican, either the Hong Kong Study Mission, did not comment on the claims of the US cybersecurity firm.
“The reported hacking follows an extremely rare meeting between Beijing and the Vatican’s foreign minister earlier this year in Germany, marking the highest-level official encounter between the two sides in decades.” continues the Reuters.
“Relations between the two have been improving and they have been expected to renew the provisional two-year deal on the operation of the Catholic Church in China this September.”
A Chinese delegation is expected to visit the Vatican as part of ongoing talks, but at the time there is no indication of the exact calendar of the talks. We have also to consider the ongoing Coronavirus outbreak that could have an impact on the talks between the two states.
Companies Respond to 'BootHole' Vulnerability
30.7.20 Vulnerebility Securityweek
Companies affected by the recently disclosed GRUB2 bootloader vulnerability dubbed BootHole have started releasing advisories to inform customers about the impact of the issue on their products.
Firmware security company Eclypsium revealed on Wednesday that billions of Windows and Linux devices are affected by a potentially serious vulnerability that can be exploited to install stealthy and persistent malware. The firm says the weakness affects devices that use Secure Boot, a feature designed to protect the boot process against untrusted code execution.
The security hole, officially tracked as CVE-2020-10713, impacts laptop, desktop, workstation and server devices, as well as network appliances and equipment used in the healthcare, industrial and financial sectors.
BootHole
The vulnerability is a buffer overflow related to how GRUB2 parses its grub.cfg configuration file. An attacker with admin privileges on the targeted system can modify this file so that their malicious code is executed in the UEFI environment before the OS is loaded.
Several other flaws related to GRUB2 have been identified during investigations into BootHole.
Secure Boot is designed to ensure that the code executed when a device boots is trusted. For this purpose it uses two databases containing lists of digital signatures associated with trusted code (DB) and digital signatures associated with prohibited code (DBX).
Preventing BootHole attacks will require replacing vulnerable bootloaders with an updated version and releasing an update for the DBX database to ensure that the vulnerable bootloaders can no longer be executed. This process requires collaboration between software and hardware vendors.
Shortly after Eclypsium published its report on the BootHole vulnerability, several companies and organizations released advisories to address the issue.
CERTs
Some Computer Emergency Response Teams (CERTs) have already released advisories, including CERT/CC in the United States and SingCERT in Singapore.
CERT/CC explained, “Linux distributions and other vendors using GRUB2 will need to update their installers, boot loaders, and shims. New shims will need to be signed by the Microsoft 3rd Party UEFI Certificate Authority. Administrators of affected devices will need to update installed versions of operating systems as well as installer images, including disaster recovery media. Until all affected versions are added to the dbx revocation list, an attacker would be able to use a vulnerable version of shim and GRUB2. Eventually the UEFI revocation list (dbx) needs to be updated in the firmware of each affected system to prevent running this vulnerable code during boot.”
UEFI Forum
The UEFI Forum has made available the files needed to update the Secure Boot DBX database, which includes the now-revoked signatures of previously approved and signed firmware and software. However, the revocation list file is work in progress and at this point it’s mainly recommended for testing purposes.
“Distribution of the data in these files to running systems could cause instability and should only be attempted by security experts and IT professionals. System OEMs can use these files to test their platform firmware,” the UEFI Forum warned.
Microsoft
Microsoft says BootHole impacts Windows 10, 8.1, Server 2012, Server 2016, Server 2019 and Server versions 1903, 1909 and 2004. The company is working on an update that will be rolled out to users via the Windows Update system.
In the meantime, the company tells customers that they can prevent attacks on Surface devices by changing some UEFI settings.
Windows users can manually install the Secure Boot DBX update from the UEFI Forum, but Microsoft has warned that this update has not been tested and it’s only recommended for professionals and enthusiasts since installing it can result in “unrecoverable failure to boot.”
Red Hat
Red Hat says BootHole impacts Red Hat Enterprise Linux 7 and 8, Atomic Host, and the OpenShift Container Platform 4. The company has advised users to update their grub2 packages and customers using Secure Boot need to update the kernel, fwupdate, fwupd, shim and dbxtool packages, which contain newly validated keys and certificates.
Canonical
Canonical, whose security team has identified additional GRUB2 vulnerabilities following Eclypsium’s research, has released updated packages for Ubuntu, and says it will provide a packaged DBX update in the future, but told users that until then they can apply a third-party DBX update.
SUSE
SUSE has published a blog post and provided the following statement to SecurityWeek:
“We’re aware of the Linux vulnerability called BootHole shared by Eclypsium today, and our customers and partners can rest assured we have released fixed grub2 packages which close the BootHole vulnerability for all SUSE Linux products today, and are releasing corresponding updates to Linux kernel packages, cloud image and installation media.
Given the need for physical access to the bootloader, the most likely exposure is when untrusted users can access a machine, e.g. bad actors in classified computing scenarios or computers in public spaces operating in unattended kiosk mode. To ensure that sophisticated attackers cannot reinstall old versions of grub2, software and hardware vendors are working together. SUSE Linux Enterprise provides unprecedented reliability, stability and security to the enterprise, and we are committed to keeping our customers’ and partners’ systems up to date and ready to handle everyday business challenges.”
Debian
Debian told customers that since Debian 10 (buster) was the first release to include support for Secure Boot, older versions of the operating system may not receive updates. For Debian 10 (buster), developers have already released updated GRUB2, linux, shim, fwupdate and fwupd packages.
VMware
VMware says CVE-2020-10713 affects Photon OS when configured with Secure Boot, as well as virtual machines running impacted operating systems. The company is working on an update for Photon OS.
The virtualization giant pointed out that exploitation of BootHole inside a VM cannot allow an attacker to compromise the host, but noted that available patches will need to be deployed on both guest and host machines.
HP
HP says it will be providing a SoftPaq to allow users to update the DBX database. The company has shared a long list of business notebook PCs, business desktop PCs, workstations, retail point-of-sale products, Thin Client devices, home notebook PCs, and home desktop PCs impacted by the vulnerability.
Britain Names Turkish Speaker as New Top Spy
30.7.20 BigBrothers Securityweek
Britain on Wednesday named its former ambassador to Turkey as the new director of the MI6 Secret Intelligence Service.
Richard Moore succeeds Alex Younger, who was a career intelligence officer and became Britain's top spy in 2014.
Moore, a fluent Turkish speaker, has served as the political director of the Foreign Office, deputy national security adviser, and ambassador to Ankara from 2014 to 2017.
Prior to becoming a diplomat, Moore worked for MI6 "where he undertook a range of roles across the Service both in the UK and overseas," according to his official profile.
"I am pleased and honoured to be asked to return to lead my Service," Moore said in a statement.
"SIS plays a vital role... in keeping the British people safe and promoting UK interests overseas."
Younger identified cyber-security as a top priority for Britain during his term, describing the internet as "an existential threat" to intelligence work in a rare public address in 2016.
He has also raised concern about the safety of China's private telecoms giant Huawei, which Britain this month decided to phase out of its 5G network.
Foreign Secretary Dominic Raab said Younger "carefully and effectively guided the service during a time of increased and more diverse threats."
Moore's brief official biography says he was born in Libya and is married with two children.
"Outside of work, Richard's interests include playing golf and watching cricket and rugby," says the biography.
"He speaks fluent Turkish."
It does not give his age.
'BootHole' Flaw Allows Installation of Stealthy Malware, Affects Billions of Devices
30.7.20 Android Securityweek
Billions of Windows and Linux devices are affected by a serious GRUB2 bootloader vulnerability that can be exploited to install persistent and stealthy malware, firmware security company Eclypsium revealed on Wednesday.
The vulnerability, tracked as CVE-2020-10713 and dubbed BootHole, has a CVSS score of 8.2 and Eclypsium says it affects all operating systems that use GRUB2 with Secure Boot, a mechanism designed to protect the boot process from attacks. In fact, the company says the flaw impacts machines that use Secure Boot even if they’re not using GRUB2.
“Almost all signed versions of GRUB2 are vulnerable, meaning virtually every Linux distribution is affected,” Eclypsium explained in its report. “In addition, GRUB2 supports other operating systems, kernels and hypervisors such as Xen. The problem also extends to any Windows device that uses Secure Boot with the standard Microsoft Third Party UEFI Certificate Authority.”BootHole vulnerability found in GRUB2 bootloader
The company says the vulnerability affects a majority of laptop, desktop, workstation and server devices, as well as network appliances and equipment used in the healthcare, industrial and financial sectors.
Threat actors could exploit this vulnerability to install bootkits or malicious bootloaders that would give them control of the targeted device. Eclypsium researchers noted that exploiting the vulnerability requires administrator privileges on the targeted device, but successful exploitation enables the attacker to obtain even higher privileges and achieve persistence.
BootHole has been described as a buffer overflow flaw related to how GRUB2 parses its grub.cfg configuration file. An attacker can modify this file, which is an unsigned text file typically found in the EFI system partition, to ensure that their malicious code is executed in the UEFI execution environment, before the operating system is loaded. This enables the attacker to run malware, modify the boot process, or directly patch the operating system kernel.
Following Eclypsium’s discovery of the BootHole vulnerability, the Canonical security team also analyzed GRUB2 and identified several other security holes, all of which have been classified as medium severity.
Eclypsium has coordinated the disclosure of the vulnerability with Microsoft, Linux distributions, the UEFI Security Response Team, OEMs, CERTs, VMware, Oracle and other impacted software vendors. Many of them are expected to release advisories or updates addressing BootHole and other GRUB2 issues.
“Mitigation will require new bootloaders to be signed and deployed, and vulnerable bootloaders should be revoked to prevent adversaries from using older, vulnerable versions in an attack. This will likely be a long process and take considerable time for organizations to complete patching,” the company explained.
'Ghostwriter' – Widespread Disinformation Campaign Associated with Russia
30.7.20 BigBrothers Securityweek
FireEye security researchers have linked a series of disinformation operations that have been ongoing since at least March 2017.
Referred to as Ghostwriter, the influence campaign mainly targeted audiences in Lithuania, Latvia, and Poland with themes referencing the North Atlantic Treaty Organization (NATO) presence in Eastern Europe, often using compromised websites or spoofed email accounts to distribute the fake content.
Aligned with Russian security interests, the campaign also leveraged anti-United States narratives and themes related to the COVID-19 pandemic. Adversaries created at least 14 fake online personas posing as locals, journalists, and analysts to distribute the falsified content via articles and op-eds published to third-party websites such as OpEdNews.com, BalticWord.com, and TheDuran.com, among others.
While some of these incidents have already received attention from researchers, news outlets, and government entities, others remain obscure. Although the attacks haven’t been attributed to a specific actor, the operations are “part of a larger, concerted, and ongoing influence campaign,” FireEye says in its report (PDF).
“It appears, based on the limited public information available regarding the website compromises we have tied to Ghostwriter, that the actors behind the campaign are relatively well-resourced, either directly possessing traditional cyber threat capabilities themselves or having ready access to operational support from others who do. It is plausible that Ghostwriter operations are conducted by overlapping actors or groups that are also behind other influence campaigns or incidents of cyber threat activity,” FireEye says.
While some of the aspects of the campaign resemble those of the Secondary Infektion operation, the researchers did not observe cyber threat activity to support the previously detailed operations, and many other attributes of the newly detailed attacks are different.
Overall, the observed Ghostwriter operations employ a combination of tactics and dissemination of fake content that often changes from one incident to another. However, each operation begins with the creation of a falsified narrative and fake source documentation.
The false narratives distributed in this campaign rely on fabricated quotes supposedly attributed to officials, as well as falsified official correspondence presented as source for the narratives. Modified images have been employed as well.
Many of the operations abused compromised websites, such as those of news outlets, to publish fake news or documentation. In some cases, the adversaries appear to have replaced existing content on the compromised sites with the fabricated content.
The adversaries disseminated the Ghostwriter narratives and articles via email, published fabricated articles and op-eds on sites that accept user-generated content, and promoted the content through blogs and pages on Blogspot, Wix, and Wordpress. In some cases, social media was used for dissemination.
According to FireEye, some of the personas abused in the campaign have been coordinating with each other, and many were observed publishing content as part of the same operation. The 14 personas associated with the campaign have been active in at least 15 suspected Ghostwriter operations since 2017.
“The Ghostwriter campaign leverages traditional cyber threat activity and information operations tactics to promote narratives intended to chip away at NATO’s cohesion and undermine local support for the organization in Lithuania, Latvia, and Poland. While the operations so far have targeted audiences in this limited set of countries, we caution that the same tactics employed in the Ghostwriter campaign can be readily repurposed and used against other target geographies,” FireEye concludes.
EU Sanctions on Russian, Chinese 'Cyber Attackers'
30.7.20 BigBrothers Securityweek
The European Union imposed its first ever sanctions against alleged cyber attackers on Thursday, targeting Russian and Chinese individuals and a specialist unit of Moscow's GRU military intelligence agency.
An export firm based in North Korea and technology company from Tiajin, China, were also listed.
The member states said measures would be taken against six individuals and three entities involved in various actions, including the attempt to hack into the Organisation for the Prohibition of Chemical Weapons (OPCW).
They also included suspects said to be involved in the major cyber assaults known by the nicknames "WannaCry", "NotPetya" and "Operation Could Hopper".
The individuals will be banned from travel to the European Union and all the targets will be subject to an asset freeze for any funds in areas under EU jurisdiction.
In addition, the European Council of member states said: "EU persons and entities are forbidden from making funds available to those listed."
EU foreign policy chief Josep Borrell said the action had been taken "to better prevent, discourage, deter and respond to such malicious behaviour in cyberspace".
These attacks, he said, represented "an external threat to the European Union or its member states" or had "a significant effect against third States or international organisations".
The best known of the targeted entities is the Main Centre for Special Technologies, a unit of the Main Directorate of the General Staff of the Armed Forces of the Russian Federation -- better known as the GRU.
This unit, based on Kirova Street in Moscow, is said to have carried out attacks known as NotPetya and EternalPetya in June 2017, hitting EU private companies with ransomware and blocking data.
The sanctions list also accuses GRU agents of carrying out an attack on the Ukrainian power grid in the winters of 2015 and 2016, resulting in parts of it being shut down.
Four alleged Russian GRU agents -- two "human intelligence support" officers and two "cyber operators" -- are also named, for their roles in the April 2018 attempt to penetrate the OPCW agency in The Hague.
The watchdog was investigating reports that Russian-backed Syrian forces carried out chemical attacks when alleged GRU agents were intercepted trying to penetrate the agency's wifi from a hire car parked near its headquarters.
"With these sanctions, the EU is taking a big step towards safer cyber space. The price for bad behaviour is being increased, because the bad guys still get away with it too often," said Dutch foreign minister Stef Blok.
"Now the EU shows that it can take effective action against these and other malicious parties," he said.
The other two entities targeted were Tianjin Huaying Haitai Science and Technology Development Company Ltd, said to be the actor known to cyber war observers as "Advanced Persistent Threat 10" or APT10.
Haitai is said to have been the source of "Operation Cloud Hopper", which the European Council said "targeted information systems of multinational companies in six continents ... and gained unauthorised access to commercially sensitive data, resulting in significant economic loss".
Another target was Chosun Expo, an export company from North Korea which, under the "WannaCry" banner, is said to have helped hack the Polish Financial Supervision Authority and Sony Pictures Entertainment.
It is alleged to have carried out cyber-theft from the Bangladesh Bank and attempted cyber-theft from the Vietnam Tien Phong Bank.
Critical GRUB2 Bootloader Bug Affects Billions of Linux and Windows Systems
30.7.20 Vulnerebility Thehackernews
A team of cybersecurity researchers today disclosed details of a new high-risk vulnerability affecting billions of devices worldwide—including servers and workstations, laptops, desktops, and IoT systems running nearly any Linux distribution or Windows system.
Dubbed 'BootHole' and tracked as CVE-2020-10713, the reported vulnerability resides in the GRUB2 bootloader, which, if exploited, could potentially let attackers bypass the Secure Boot feature and gain high-privileged persistent and stealthy access to the targeted systems.
Secure Boot is a security feature of the Unified Extensible Firmware Interface (UEFI) that uses a bootloader to load critical components, peripherals, and the operating system while ensuring that only cryptographically signed code executes during the boot process.
"One of the explicit design goals of Secure Boot is to prevent unauthorized code, even running with administrator privileges, from gaining additional privileges and pre-OS persistence by disabling Secure Boot or otherwise modifying the boot chain," the report explained.
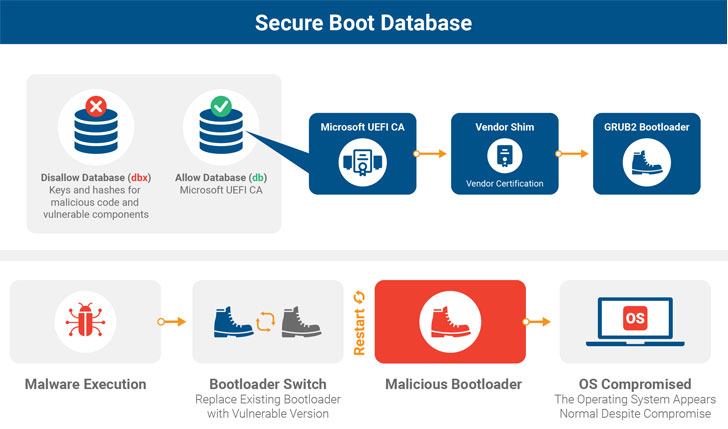
Discovered by researchers from Eclypsium, BootHole is a buffer overflow vulnerability that affects all versions of GRUB2 and exists in the way it parses content from the config file, which typically is not signed like other files and executables—leaving an opportunity for attackers to break the hardware root of trust mechanism.
grub2 bootloader malware
To be noted, the grub.cfg file is located in the EFI system partition, and thus, to modify the file, an attacker still needs an initial foothold on the targeted system with admin privileges that would eventually provide the attacker with an additional escalation of privilege and persistence on the device.
Though GRUB2 is the standard bootloader used by most Linux systems, it supports other operating systems, kernels, and hypervisors like XEN as well.
"The buffer overflow allows the attacker to gain arbitrary code execution within the UEFI execution environment, which could be used to run malware, alter the boot process, directly patch the OS kernel, or execute any number of other malicious actions," researchers said.
Thus, to exploit BootHole flaw on Windows systems, attackers can replace the default bootloaders installed on Windows systems with a vulnerable version of GRUB2 to install the rootkit malware.
"The problem also extends to any Windows device that uses Secure Boot with the standard Microsoft Third Party UEFI Certificate Authority," the report says.
According to the detailed report researchers shared with The Hacker News, this vulnerability can lead to major consequences, and that's primarily because the attack allows hackers to execute malicious code even before the operating system boots, making it difficult for security software to detect the presence of malware or remove it.
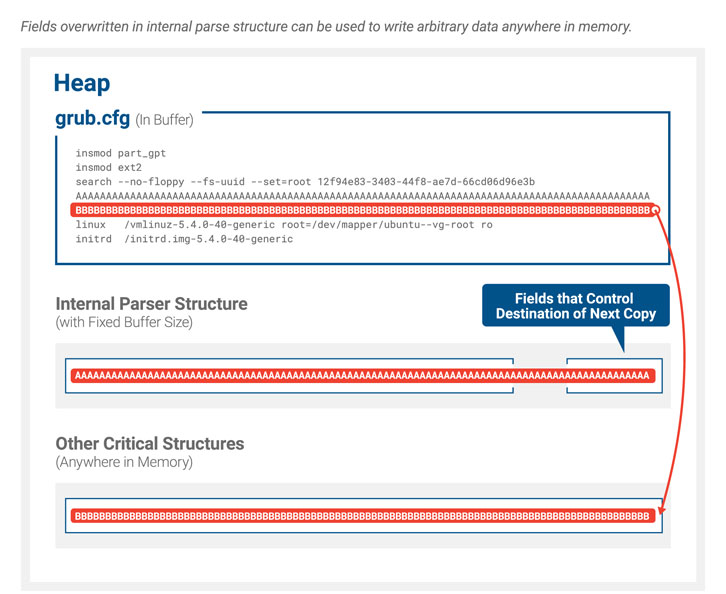
Besides this, the researcher also added that "the UEFI execution environment does not have Address Space Layout Randomization (ASLR) or Data Execution Prevention (DEP/NX) or other exploit mitigation technologies typically found in modern operating systems, so creating exploits for this kind of vulnerability is significantly easier."
Just Installing Updates and Patches Wouldn't Resolve the Issue
Experts at Eclypsium have already contacted related industry entities, including OS vendors and computer manufacturers, to help them patch the issue.
However, it doesn't appear to be an easy task to patch the issue altogether.
Just installing patches with updated GRUB2 bootloader would not resolve the issue, because attackers can still replace the device's existing bootloader with the vulnerable version.
According to Eclypsium, even "mitigation will require new bootloaders to be signed and deployed, and vulnerable bootloaders should be revoked to prevent adversaries from using older, vulnerable versions in an attack."
So, the affected vendors would need first to release the new versions of their bootloader shims to be signed by the Microsoft 3rd Party UEFI CA.
Eventually, the UEFI revocation list (dbx) then also needs to be updated in the firmware of each affected system to prevent running this vulnerable code during boot.
This multi-stage mitigation process will likely take years for organizations to complete patching.
"However, full deployment of this revocation process will likely be very slow. UEFI-related updates have had a history of making devices unusable, and vendors will need to be very cautious. If the revocation list (dbx) is updated before a given Linux bootloader and shim are updated, then the operating system will not load," researchers warned.
In an advisory released today, Microsoft acknowledged the issue, informing that it's "working to complete validation and compatibility testing of a required Windows Update that addresses this vulnerability."
It also recommended users to apply security patches as soon as they are rolled out in the coming weeks.
Besides Microsoft, many popular Linux distributions have also released related advisories explaining the flaw, possible mitigations, and timeline on the upcoming security patches.
Here's a list for all advisories:
Red Hat (Fedora and RHEL)
Canonical (Ubuntu)
SuSE (SLES and OpenSUSE)
Debian
VMware
Microsoft
HP
Zoom Bug Allowed Snoopers Crack Private Meeting Passwords in Minutes
30.7.20 Vulnerebility Thehackernews
Popular video conferencing app Zoom recently fixed a new security flaw that could have allowed potential attackers to crack the numeric passcode used to secure private meetings on the platform and snoop on participants.
Zoom meetings are by default protected by a six-digit numeric password, but according to Tom Anthony, VP Product at SearchPilot who identified the issue, the lack of rate limiting enabled "an attacker to attempt all 1 million passwords in a matter of minutes and gain access to other people's private (password protected) Zoom meetings."
It's worth noting that Zoom began requiring a passcode for all meetings back in April as a preventive measure to combat Zoom-bombing attacks, which refers to the act of disrupting and hijacking Zoom meetings uninvited to share obscene and racist content.
Anthony reported the security issue to the company on April 1, 2020, along with a Python-based proof-of-concept script, a week after Zoom patched the flaw on April 9.
The fact that meetings were, by default, secured by a six-digit code meant there could be only a maximum of one million passwords.
But in the absence of no checks for repeated incorrect password attempts, an attacker can leverage Zoom's web client (https://zoom.us/j/MEETING_ID) to continuously send HTTP requests to try all the one million combinations.
"With improved threading, and distributing across 4-5 cloud servers you could check the entire password space within a few minutes," Anthony said.
The attack worked with recurring meetings, implying that bad actors could have had access to the ongoing meetings once the passcode was cracked.
The researcher also found that the same procedure could be repeated even with scheduled meetings, which have the option to override the default passcode with a longer alphanumeric variant, and run it against a list of top 10 million passwords to brute-force a login.
Separately, an issue was uncovered during the sign-in process using the web client, which employed a temporary redirect to seek customers' consent to its terms of service and privacy policy.
"There was a CSRF HTTP header sent during this step, but if you omitted it then the request still seemed to just work fine anyway," Anthony said. "The failure on the CSRF token made it even easier to abuse than it would be otherwise, but fixing that wouldn't provide much protection against this attack."
Following the findings, Zoom took the web client offline to mitigate the issues on April 2 before issuing a fix a week later.
The video conferencing platform, which drew scrutiny for a number of security issues as its usage soared during the coronavirus pandemic, has quickly patched the flaws as they were uncovered, even going to the extent of announcing a 90-day freeze on releasing new features to "better identify, address, and fix issues proactively."
Just earlier this month, the company addressed a zero-day vulnerability in its Windows app that could allow an attacker to execute arbitrary code on a victim's computer running Windows 7 or older.
It also fixed a separate flaw that could have allowed attackers to mimic an organization and trick its employees or business partners into revealing personal or other confidential information via social engineering attacks.









