
The malicious app purports to uninstall after download. Credit: Cisco Talos
Articles 2020 October - January February March April May June July August September October November December
Wisc. GOP’s $2.3M MAGA Hat Debacle Showcases Fraud Concerns
31.10.20 Incindent Threatpost
Scammers bilked Wisconsin Republicans out of $2.3 million in a basic BEC scam — and anyone working on the upcoming election needs to pay attention.
The Wisconsin Republican party’s war chest is lighter by $2.3 million after scammers posing as MAGA-hat vendors were able to spoof invoices in what appears to be a basic business email compromise (BEC) attack. It’s just the latest in a litany of attacks related to the upcoming election, and it showcases a big problem area when it comes to cybersecurity, researchers said.
In a BEC attack, a fraudster impersonates a trusted party to try and trick a business into making payments or wiring money. In a typical BEC attack, criminals will do their research to make their communications seem credible, according to Agari’s recent deep dive on the state of BEC attacks.
“Cybercriminals, using a sophisticated phishing attack, stole funds intended for the re-election of President Trump, altered invoices and committed wire fraud,” Wisconsin state party Chair Andrew Hitt said in a statement announcing the incident. “These criminals exhibited a level of familiarity with state party operations at the end of the campaign to commit this crime.”
Researchers disagreed with the “sophisticated” claim: “While this scam may look sophisticated, this is fairly simple and reflects the vulnerability of any organization that has not digitized their spend management processes,” Alex Saric, CMO of Ivalua said. “Invoicing is an area ripe for fraudsters and cybercriminals, who know employees may not always question their validity, particularly if they look convincing.”
That tracks with Hitt’s explanation about the scammers’ familiarity with party operations. These financially motivated criminals will often sit and monitor inboxes they’ve compromised for quite some time. In this instance they were able to get enough insight into the Wisconsin GOP’s day-to-day dealings that they could doctor MAGA-hat invoices, according to reports. They used the names of existing vendors to the party and made the invoices look close enough to the real thing to get them paid.
The Wisconsin GOP said that no proprietary information was compromised in the attack, and that the state party still has enough cash on hand to keep the operation going.
“While a large sum of money was stolen, our operation is running at full capacity with all the resources deployed to ensure President Donald J. Trump carries Wisconsin on November 3rd,” Hitt added.
Cybercrime Isn’t Partisan
The Wisconsin GOP isn’t alone. According to Agari’s most recent count, BEC attacks make up 40 percent of all cybercrime losses, impacting more than 177 countries across the world.
But as the election approaches and campaign activity amps up to its most furious pace in the final days before the election, political operations will be a particularly juicy target for cybercriminals, warned Ken Liao, vice president of cybersecurity strategy and Abnormal Security.
“Political candidates, their staffs and the organizations they work with will always be targets for malicious actors,” Liao said. “Email-based attacks — and more specifically attacks perpetrating invoice fraud — are one of the more common methods used by hackers to gain access to sensitive information. As we get closer to the election, attackers will count on the fact that staffers will be busier and stretched thin, making it easier to induce a security lapse.”
Which requires political staff and elections officials to be more diligent than normal (especially when things around them are anything but normal). It’s not a simple ask — which is precisely what malicious actors are banking on to help fuel their scams, Liao added.
“All it takes is one errant click from a single member of a campaign staff,” he said. “It’s particularly important for employees to be vigilant and ensure that anything they open or click on is from a trusted source. At the same time, employers need to have detection capabilities that can automatically identify signals coming from email traffic that poses a threat.”
Campaign operations have also largely gone mobile, adding another layer of exposure to attacks, according to Hack Schless, who works in security solutions at Lookout.
“Campaign workers communicate directly with reporters and coordinate with other staffers over messaging apps and SMS,” Schless said. “They also need to run their candidates’ social-media accounts. SMS, social media, and third-party messaging platforms are three of the most popular platforms threat actors use to socially-engineer targets into falling for phishing attempts. It’s gone so far as the DNC warning campaign workers against social engineering through dating apps in a statement issued earlier this year.”
The goal of these attempts is to trick staffers into giving up their credentials, Schless added.
“They want to gain access to the campaign’s infrastructure to steal data or resources normally accessed by that individual,” he said. “The attacker can carry out their campaign through SMS, email, iMessage, social media platforms, third-party messaging apps and more.”
Recent Election-Related Attacks
All of this is against the backdrop of no shortage of attacks on the election this year.
For instance, Iranian actors posing as the hate group “Proud Boys” launched email campaigns against registered Democrats with threatening messages to “vote for Trump or else,” using stolen voter-registration data.
Last week Georgia’s database of voter signatures was impacted by a ransomware attack on Hall County, Ga.
And just days ago the Trump Campaign website was defaced with a cryptocurrency scam, briefly displaying a message from scammers claiming to have “strictly classified information.”
The added fog of highly charged, partisan politics only serves to help criminals, Tom Pendergast, chief learning officer at MediaPro said.
“We must remember as this story unfolds that this is not a partisan issue,” he noted. “Now, it may be partisan in that the cybercriminals behind this attack may prefer one party over the other (though it’s not clear which party is advantaged here). And we can be sure it will get twisted to partisan ends.”
He adds any attacks on our elections need to be met with a unified American front.
“However, the way we respond to it should NOT be partisan,” Pendergast continued. “Making voting and email and digital transactions and the internet safe for everyone should be an issue we can all get behind. No one gains from cybercrime and no one gains from election fraud, if what we ultimately care about is a stable democracy.”
Firestarter Android Malware Abuses Google Firebase Cloud Messaging
31.10.20 Android Threatpost
The DoNot APT threat group is leveraging the legitimate Google Firebase Cloud Messaging server as a command-and-control (C2) communication mechanism.
An APT group is starting fires with a new Android malware loader, which uses a legitimate Google messaging service to bypass detection.
The malware, dubbed “Firestarter,” is used by an APT threat group called “DoNot.” DoNot uses Firebase Cloud Messaging (FCM), which is a cross-platform cloud solution for messages and notifications for Android, iOS and web applications. The service is provided by Firebase, a subsidiary of Google, and has been previously leveraged by cybercriminals.
In this case, the loader uses it as a communication mechanism to connect with DoNot’s command-and-control (C2) servers, helping the group’s activities avoid detection.
“Our research revealed that DoNot has been experimenting with new techniques to keep a foothold on their victim machines,” according to researchers with Cisco Talos in a Thursday analysis. “These experiments, substantiated in the Firestarter loader, are a sign of how determined they are to keep their operations despite being exposed, which makes them a particularly dangerous actor operating in the espionage area.”
The DoNot team continues to focus on India and Pakistan, and is known for targeting Pakistani government officials and Kashmiri non-profit organizations (Kashmiris are a Dardic ethnic group native to the disputed Kashmir Valley).
Users are lured to install a malicious app on their mobile device, likely done via direct messages that utilize social engineering, researchers said. The filename of these Android applications (kashmir_sample.apk or Kashmir_Voice_v4.8.apk) show continued interest in India, Pakistan and the Kashmir crisis.
Once the app — which purports to be a chat platform — is downloaded and opened, users receive a message that chats are continually loading, and that the application is not supported, and that uninstallation is in progress. This is a lure to make the victim believe that there was no malicious install, researchers said. Once the message of uninstallation is shown, the icon is removed from the user interface (though it still shows in the application list in the phone’s settings).

The malicious app purports to uninstall after download. Credit: Cisco Talos
In the background, however, the malicious app is attempting to download a payload using FCM.
According to Firebase, an FCM implementation includes two main components for sending and receiving messages. These include an app server on which to build, target and send messages; and an iOS, Android, or web (JavaScript) client app that receives messages via the corresponding platform-specific transport service.
In this case, the app sends the C2 server a Google FCM token with various device info – including the geographic location, IP address, IMEI and email address from the victims – which then allows operators to decide whether the victim should receive the payload. This ensures that only very specific devices are delivered the malicious payload, researchers said.
The C2 then sends a Google FCM message containing the URL for the malware to download the payload. When the malware receives this message, it checks if it contains a key called “link,” and if that exists, it checks if it starts with “https.” It then uses the link to download the payload from a hosting server.
Of note, researchers said that the Google FCM communication channel is encrypted and mixed among other communications performed by Android OS using the Google infrastructure, which helps it escape notice.
“DoNot team is hiding part of their traffic among legitimate traffic,” said researchers. “Even though the malicious actors still need a [C2] infrastructure, the hardcoded one is only needed at installation time, afterwards it can be discarded and easily replaced by another one. Thus, if their C2 is taken down by law enforcement or deemed malicious, they can still access the victim’s device and instruct it to contact a new C2.”

DoNot’s Firestarter malware attack vector. Credit: Cisco Talos
The final payload, meanwhile, is not embedded in the Android application, making it impossible for analysts to dissect it.
“This approach also makes detection more difficult,” they said. “The application is a loader with a fake user interface that manipulates the target after installing it.”
Wroba Mobile Banking Trojan Spreads to the U.S. via Texts
31.10.20 Android Threatpost
The Roaming Mantis group is targeting the States with a malware that can steal information, harvest financial data and send texts to self-propagate.
The Wroba mobile banking trojan has made a major pivot, targeting people in the U.S. for the first time.
According to researchers at Kaspersky, a wave of attacks are taking aim at U.S. Android and iPhone users in an effort that started on Thursday. The campaign uses text messages to spread, using fake notifications for “package deliveries” as a lure.
The message inside the SMS contains a link and reads, “Your parcel has been sent out. Please check and accept it,” noted researchers from Kaspersky, in an emailed alert on Friday.
If users click on the link, the next thing that happens depends on which operating system is used by the device. A click takes Android users to a malicious site, which in turn surfaces an alert to users saying that the browser is out-of-date and needs to be updated. If the user clicks ‘OK’, next the downloading of a trojanized browser package with the malicious application begins.
But where Android users are served up the full Wroba download, according to researchers, the executable doesn’t work on iPhone. For iOS users the Wroba operators instead engineer a redirect to a phishing page. The page mimics the Apple ID login page in an effort to harvest credentials from Apple aficionados, but no malware is installed.
Apple had more than half of the total U.S. smartphone market share as of May.
Wroba has been around for years, but previously mainly targeted users in APAC. It was first developed as an Android-specific mobile banking trojan, capable of stealing files related to financial transactions, but has since expanded its functionality. Researchers believe the operator behind Wroba are China-based and known as “Roaming Mantis.”
This latest iteration of Wroba can send SMS messages, check which apps are installed, open web pages, harvest any files related to financial transactions, steal contact lists, call specified numbers and show fake phishing pages to steal victim’s credentials, researchers said.
Once it has infected a device, Wroba uses some of its functionality – stolen contact lists and the SMS capability – to propagate, using infected devices to spread further by sending SMS with malicious links, purporting to come from the host.
“Wroba shows how delivering malware to a device can enable longer-term gain for the attack,” according to Hank Schless, senior manager of security solutions at Lookout, which has been tracking Wroba as well.
“A credential-harvesting link only targets you for one purpose, such as when you receive an SMS saying your bank account has been compromised and the intent is to phishing your banking credentials,” he told Threatpost.
“Wroba, on the other hand, can sit silently in the background and deliver credential harvesting pages to your browser at will,” he said. “As long as it goes unnoticed, it can attempt to grab your login data for even your most private accounts.”
The malware has targeted users worldwide since the start of the year, researchers said, mainly in China, Japan and the Russian Federation.
“The USA is currently not at the top of the list but it seems that cybercriminals are heading to this region and the number of users seeing Wroba will increase,” according to Kaspersky. “The wave was detected on 29th of October and targeted users in different states of USA (judging by the phone numbers that were the targets of this campaign).”
The firm added, “Previously seen campaigns targeted users from APAC, so it is interesting to see how cybercriminals expand their targets.”
In 2018, Wroba saw a major reboot when it began targeting Europe and the Middle East in addition to Asian countries. According to Kaspersky researchers at the time, it also expanded its capabilities to include cryptomining as well as the iOS phishing tactic mentioned previously. At that point, it was spreading via DNS hijacking, which redirected users to a malicious webpage that, as in the current campaign distributed a trojanized application (at that time, it was pretending to be either Facebook or Chrome).
Roaming Mantis has swarmed into the U.S. in the past, it should be noted. This summer, it was spotted trotting out a different SMS phishing campaign that spread the FakeSpy infostealer. The malware, which was disguised as legitimate global postal-service apps, also steals SMS messages, financial data and more from the victims’ devices. It started by going after South Korean and Japanese speakers, but then expanded that targeting to China, Taiwan, France, Switzerland, Germany, the United Kingdom and the United States.
Schless told Threatpost that according to Lookout data, 88 percent of U.S. consumer phishing attacks so far in 2020 were attempts to deliver malware to the mobile device.
To avoid becoming a victim of Wroba, or any other mobile malware, users should employ basic security hygiene, researchers stressed, such as only downloading applications from official stores; disabling the installation of applications from third-party sources in smartphone settings; and avoid clicking on suspicious links from unknown senders, or even suspicious links from known senders.
“People are still grasping to avoid phishing attacks by email,” Ray Kelly, principal security engineer at WhiteHat Security, told Threatpost. “Now, SMS messaging is complicating matters further. SMS should be treated the same as email, never click on links from unknown or suspicious senders.”
Microsoft Warns Threat Actors Continue to Exploit Zerologon Bug
31.10.20 Exploit Threatpost
Tech giant and feds this week renewed their urge to organizations to update Active Directory domain controllers.
Threat attackers continue to exploit the Microsoft Zerologon vulnerability, a situation that’s been a persistent worry to both the company and the U.S. government over the last few months. Both on Thursday renewed their pleas to businesses and end users to update Windows systems with a patch Microsoft released in August to mitigate attacks.
Despite patching awareness efforts, Microsoft said it is still receiving “a small number of reports from customers and others” about active exploits of the bug tracked as CVE-2020-1472, or Zerologon, according to a blog post by Aanchal Gupta, vice president of engineering for MSRC, on Thursday.
The zero-day elevation-of-privilege vulnerability—rated as critical and first disclosed and patched on Aug. 11–could allow an attacker to spoof a domain controller account and then use it to steal domain credentials, take over the domain and completely compromise all Active Directory identity services.
The bug is located in a core authentication component of Active Directory within the Windows Server OS and the Microsoft Windows Netlogon Remote Protocol (MS-NRPC). The flaw stems from the Netlogon Remote Protocol, available on Windows domain controllers, which is used for various tasks related to user and machine authentication.
Gupta urged organizations to deploy the Aug.11 patch or later release to every domain controller as the first in a four-step process to fix the vulnerability. Then administrators should monitor event logs to find which devices are making vulnerable connections; address identified non-compliant devices; and enable enforcement to address the bug in the overall environment, he said.
“Once fully deployed, Active Directory domain controller and trust accounts will be protected alongside Windows domain-joined machine accounts,” he said.
In addition to Microsoft’s patches, last month both Samba and 0patch also issued fixes for CVE-2020-1472 to fill in the some of the gaps that the official patch doesn’t address, such as end-of-life versions of Windows.
Microsoft’s latest advisory was enough for the Department of Homeland Security’s (DHS’s) Cybersecurity and Infrastructure Security Agency (CISA) to step in and issue a statement of its own Thursday warning organizations about continued exploit of the bug.
Given the severity of the vulnerability, the government has been nearly as active as Microsoft in urging people to update their systems. Interest from the feds likely has intensified since Microsoft’s warning earlier this month that an Iranian nation-state advanced persistent threat (APT) actor that Microsoft calls MERCURY (also known as MuddyWater, Static Kitten and Seedworm) is now actively exploiting Zerologon.
“CISA urges administrators to patch all domain controllers immediately—until every domain controller is updated, the entire infrastructure remains vulnerable, as threat actors can identify and exploit a vulnerable system in minutes,” according to the CISA alert.
The agency even has released a patch validation script to detect unpatched Microsoft domain controllers to help administers install the update. “If there is an observation of CVE-2020-1472 Netlogon activity or other indications of valid credential abuse detected, it should be assumed that malicious cyber actors have compromised all identity services,” the CISA warned.
Zerologon has been a consistent thorn in Microsoft’s side since its discovery, a scenario that has escalated since early September thanks largely to the publication of four proof-of-concept exploits for the flaw on Github. Soon after the exploits were published, Cisco Talos researchers warned of a spike in exploitation attempts against Zerologon.
The U.S. government first stepped in to rally organizations to update after the publication of the exploits, with the DHS issuing a rare emergency directive that ordered federal agencies to patch their Windows Servers against the flaw by Sept. 21.
Crippling Cyberattacks, Disinformation Top Concerns for Election Day
31.10.20 BigBrothers Threatpost
Cyber-researchers weigh in on what concerns them the most as the U.S. heads into the final weekend before the presidential election — and they also highlight the positives.
What keeps researchers up at night leading up to Nov. 3 isn’t election-day winners and losers. Most cite possible attacks on local infrastructure, crippling ransomware incidents and disinformation campaigns.
There are also many concerned voters this year. Election-related cybersecurity attacks have been making headlines daily, keeping the U.S. electorate worried about possible late-stage cyberattacks.
So, heading into the homestretch weekend before Election Day, Threatpost asked researchers to weigh in on the state of play.
“The last weekend before the election is like the Super Bowl for malicious actors that want to disrupt or influence the election,” said Ray Kelly, principal security engineer at WhiteHat Security. “Authorities and election officials know this is the case and have taken precautions to try to ensure a safe election. These include election infrastructure assessment and securing voting registration systems. However, given the recent hack involving Hall County, Ga., where election data was released to public for failure to pay a ransom, it really brings into question how effective the measures will be in the final stretch of the election.”
That said, just to balance things out, researchers were also asked about what’s going right – it can’t all be a black cloud of worry after all.
Top Concerns
As Kelly intimated, one big area of dread for researchers is the threat to local municipalities and their elections infrastructure.
“The biggest cyber-risks to the election are most likely going to come in the form of disruption to local support services: e-pollbooks, municipal IT infrastructure, informational applications,” said Rob Bathurst, CTO at Digitalware.
Digitalware recently found that the average municipal computer contains more than 30 potential vulnerabilities or risk conditions at any time. And, in an average local government network, an attacker has over 15 ways to penetrate a typical computer and reach an intended target.
“The reason these services would be the most likely to be disrupted is that they are publicly accessible (voter registration/polling place lookup) and common targets of criminals/ransomware actors (municipal IT infrastructure/systems),” Bathurst explained. “The rest of the systems used to support the actual voting process (DRE, ballot markers, tallying) generally has a very limited connectivity timeframe and a small attack surface, meaning the odds of an incident involving them would be small compared to the aforementioned targets.”
Mike Hamilton, CISO at CI Security, also has local elections infrastructure on his radar screen.
“The biggest danger is the threat of counties being hit with ransomware on November 4th. Why? Because at that point in-person voting will have been completed and votes tabulated,” he said. “If ransomware hits a county (only counties conduct elections), the mail-in count will be thrown into question. Because Republicans are known to vote in person on election day and Democrats favor mail-in ballots, this is a danger.”
He added ominously, “It doesn’t matter whether ransomware can actually ‘change vote tallies,’ it’s that if there is enough access to a network to encrypt data, there’s enough access to change it.”
Hamilton isn’t alone in anticipating direct cyberattacks on election infrastructure that could cripple vote-tallying or vote-casting.
“Instead of hacking into voter-registration databases, which are better protected now than they were in 2016, we should be prepared for cyber-attacks that deny access to voter-registration lists on election day,” said Suzanne Spaulding, advisor to Nozomi Networks and former DHS undersecretary of cyber and infrastructure.
She added, “This might be through ransomware attacks that would lock up the data so poll workers could not access it. Or, cyber-activity could disrupt the tabulation or reporting of results. In addition, with a significant increase in mail-in voting expected, we should look for disinformation designed to undermine the public’s trust in that process. We are seeing it already in the Russian propaganda outlets.”
And indeed, another major area of concern for researchers lies in disinformation campaigns, which continue to rage on in the home stretch of the election season. Digital Shadows for instance recently found that China, Iran and Russia are all ramping up their attempts to spread fake news and misinformation about candidates and policies.
“Russia’s Internet Research Agency (IRA), which allegedly takes its direction from the Kremlin, has been primarily responsible for this interconnected ‘carousel of lies, as one former member of the IRA described it,” according to the firm’s report. “In many cases, the fake news stories they spread are more appealing to Americans due to pop culture references, pictures and cartoons.”
The tactic works, too: In September, Facebook took down groups and accounts that were affiliated with the deceptive news organization, Peace Data, but not before hundreds of stories were shared on Facebook.
“At this stage in the election process, the only significant cyber-risk is disinformation with the confidence on the actual result of the election,” opined Joseph Carson, chief security scientist and advisory CISO at Thycotic. “Hacking an election is not about influencing the outcome, it is about hacking democracy. It is always important to determine the ultimate motive and that is about dividing people to create distrust in both government and your fellow citizens.”
Brandon Hoffman, CISO at Netenrich, noted that while it’s important to boost awareness around these types of influence campaigns, the focus in the news on disinformation may also be an intentional distraction for something else.
“We may be creating the smokescreen the real adversaries need to perform the attacks they have been waiting to execute,” he said. “My hunch tells me that there is something waiting in the wings related to voting infrastructure or a major information bomb coming on either Monday or Tuesday. That information bomb may be real or fake, however, as long as it creates chaos and discontent, the effect will be the same.”
Bikash Barai, co-founder of FireCompass, warned that disinformation efforts stretch far beyond just posting or sharing fake news on social media.
“Based on FireCompass’ internet wide monitoring data, there are currently more than 5 million open, vulnerable databases, which include usernames, passwords, emails and personal details,” he said. “When this data gets in the hands of hackers, it can be used to send personalized and targeted misinformation to skew results.”
He added, “In addition, breaking into the ‘information supply chain’ is not a challenge for hackers. In fact, more than 90 percent of organizations have at least one major security vulnerability, which can be used to break in, steal and corrupt data.”
What’s Going Right?
After the hack-and-leak operation against the Democratic National Committee and widely publicized election meddling by foreign actors in 2016, the U.S. population is a bit nervous on the cyberattack front when it comes to ensuring a free and fair election.
And to be sure, there have been plenty of headlines: Iranian actors posing as the hate group “Proud Boys” launching email campaigns against registered Democrats; the aforementioned ransomware attack affecting a Georgia database of voter signatures; the Trump Campaign website defaced with a cryptocurrency scam; scammers bilking Wisconsin Republicans out of $2.3 million; and rampant mobile phishing issues – just to name a few.
But can we hope things will go smoothly in these last few days? Threatpost asked researchers what they consider to be the bright side of cyber for the remaining election season. Most pointed first and foremost to improvements overall in risk awareness.
“Local governments are now aware that their systems could be targeted, and most larger city/county governments have moved to try to shore up their security operations in the run-up to the election,” Digitalware’s Bathurst said. “Some have even taken the proactive approach of attempting to understand their attack surface and how things like misconfigured/unmanaged systems could impact their security.”
Also, so far it’s been pretty quiet in terms of any major bombshells, noted James McQuiggan, security awareness advocate at KnowBe4.
“We haven’t had any significant data breaches with the government or political party systems, like what happened in 2016 with the Democratic party,” he said. “More and more organizations are taking notice of the recent attacks and taking the necessary steps to educate their staff to make sure they can spot social engineering scams. These actions can help to reduce the risk of a cyberattack.”
CI Security’s Hamilton sees other reasons to be positive too. “The cooperation between Microsoft and the Department of Defense at taking down the TrickBot botnet, Microsoft giving Defender/ATP free to counties until the election is over, and the information-sharing that seems to have been stepped up with the FBI and DHS/CISA are all positive,” he said.
On the free protection service front, Spaulding added, “It’s hard to know all the things the political parties may be doing to better protect their data and information systems. I am on the board of an organization, called Defending Digital Campaigns, that got a ruling from the FEC that allows us to work with cybersecurity companies to provide their services to campaigns for free or at a discount. Campaigns have not traditionally focused on cybersecurity and they have a long way to go!”
Netenrich’s Hoffman had a tougher time being positive: “It’s hard to say what’s going right in this election,” he said. “From a place of false comfort, I would say there haven’t been any major cyber issues…but it feels like foreshadowing.”
Google discloses unpatched Windows zero-day exploited in the wild
31.10.20 Exploit Securityaffairs
Google researchers disclosed today a zero-day vulnerability in the Windows operating system that is currently under active exploitation.
Security researchers from Google have disclosed a zero-day vulnerability in the Windows operating system, tracked as CVE-2020-17087, that is currently under active exploitation.
Ben Hawkes, team lead for Google Project Zero team, revealed on Twitter that the vulnerability was chained with another Chrome zero-day flaw, tracked as CVE-2020-15999, that Google recently disclosed.
Google researchers expect a patch for this zero-day flaw to be available on November 10. The Director of Google’s Threat Analysis Group, Shane Huntley (@ShaneHuntley), confirmed that the vulnerability was exploited in targeted attacks that are not related to the forthcoming US election.
Google did not provide info on the attackers that have already exploited the flaw, but experts speculate that they were nation-state actors.
The Chrome zero-day is a sandbox escape issue, it allows attackers to escape Chrome’s secure container and run code on the underlying operating system.
“We have evidence that the following bug is being used in the wild. Therefore, this bug is subject to a 7 day disclosure deadline.” reads Google’s advisory.
“The Windows Kernel Cryptography Driver (cng.sys) exposes a \Device\CNG device to user-mode programs and supports a variety of IOCTLs with non-trivial input structures. It constitutes a locally accessible attack surface that can be exploited for privilege escalation (such as sandbox escape).”
The Google Project Zero team notified Microsoft last week and gave the company seven days to address the vulnerability, but unfortunately, Microsoft has yet to fix it.
The vulnerability affects all Windows versions between Windows 7 and the most recent Windows 10 release.
Google researchers also published a proof of concept code to exploit this vulnerability.
In March 2019, Google disclosed that that threat actors were chaining a Chrome zero-day (CVE-2019-5786) with a Windows zero-day (CVE-2019-0808) in attacks in the wild.
5 Components of the Kubernetes Control Plane that Demand Special Attention in Your Security Strategy
31.10.20 Security Securityaffairs
Organizations and security incidents in Kubernetes environments, these are 5 key components of the control plane that demand special attention
Organizations are no strangers to security incidents in their Kubernetes environments. In its State of Container and Kubernetes Security Fall 2020 survey, StackRox found that 90% of respondents had suffered a security incident in their Kubernetes deployments in the last year. Two-thirds of respondents explained that they had weathered a misconfiguration incident, followed by vulnerability cases, runtime events and failed audits at 22%, 17% and 16%, respectively.
Misconfiguration incidents are so prolific because they can appear in many different aspects of an organization’s Kubernetes environment. For instance, they can affect the Kubernetes control plane. This section of a Kubernetes deployment is responsible for making global decisions about a cluster as well as for detecting and responding to events affecting the cluster, notes Kubernetes.
This raises an important question: how can organizations harden the Kubernetes control plane against digital attacks?
To answer that question, this blog post will discuss five components within the Kubernetes control plane that require special attention within organizations’ security strategy. These are the kube-apiserver, etcd, kube-scheduler, kube-controller-manager and cloud-controller-manager. It will then provide recommendations on how organizations can secure each of these components.
kube-apiserver
What it is
Per Kubernetes’ documentation, kube-apiserver is the front end for the Kubernetes control plane. It functions as the main implementation of a Kubernetes API server. Organizations can scale kube-apiserver horizontally by deploying more instances.
Why it needs to be secured
The Container Journal noted that attackers are committed to scanning the web for publicly accessible API servers. Acknowledging that reality, organizations need to make sure they don’t leave their kube-apiserver instances publicly exposed. If they do, they could provide attackers with an opening for compromising a Kubernetes cluster.
How to secure it
Administrators can follow the Container Journal’s advice by configuring their API servers to allow cluster API access only via the internal network or a corporate VPN. Once they’ve implemented that security measure, they can use RBAC authorization to further limit who has access to the cluster. They can enable this feature specifically via the kube-apiserver.
etcd
What it is
Kubernetes uses etcd as key value backing store for cluster data. In order to use etcd, organizations need to have a backup plan for the highly sensitive configuration data that they’d like to protect with this store.
Why it needs to be secured
As with kube-apiserver, organizations might accidentally leave etcd exposed to the Internet. The New Stack covered the work of one software developer who conducted a search on Shodan to look for exposed etcd servers. This investigation uncovered 2,284 etcd servers that malicious actors could access through the Internet.
How to secure it
Kubernetes notes in its cluster administration resources that etcd is equivalent to root permission in the cluster. In response, administrators should grant permission to only the nodes that require access to etcd clusters. They should also use firewall rules as well as the feature’s inherent security features, notably peer.key/peer.cert and client.key/client.cert, to secure communications between etcd members as well as between etcd and its clients.
kube-scheduler
What it is
The kube-scheduler is a component within the control plane that watches for the creation of new pods with no assigned node. If it detects such a pod, it selects a node for them to run on. It makes these decisions by taking individual and collective resource requirements, data locality and other considerations into consideration, per Kubernetes’ website.
Why it needs to be secured
Any compromise involving the kube-scheduler could affect the performance and availability of a cluster’s pods, explains Packt. Such an event could thereby cause disruptions in an organization’s Kubernetes environment that undermines business productivity.
How to secure it
Administrators can follow Packt’s advise to secure the kube-scheduler by disabling profiling, a feature which exposes system details. They can do this by setting the “–profiling” setting to “false.” Additionally, they can disable external connections to kube-scheduler using the “AllowExtTrafficLocalEndpoints” configuration to prevent outside attackers from gaining access to this control plane component.
kube-controller-manager
What it is
This particular component lives up to its name in that it runs controller processes. Each of those processes, including those run by the node controller, replication controller and others, are separate processes. However, the kube-controller-manager compiles all of those processes and runs them together.
Why it needs to be secured
A security issue in the kube-controller-manager could negatively affect the scalability and resilience of applications that are running in the cluster. Such an event could thus have an effect on the organization’s business.
How to secure it
Organizations can secure the kube-controller-manager by monitoring the number of instances that they have of this feature deployed in their environments. They can also follow the recommendations that StackRox made in September 2020 by restricting the feature’s file permissions, configuring to serve only HTTPs, binding it to a localhost interfact and using Kubernetes RBAC to allow access to individual service accounts per controller.
cloud-controller-manager
What is it?
Last but not least, the cloud-controller-manager enables administrators to link their cluster into their Cloud Service Provider’s (CSP’s) API. They can then use that feature to separate out elements that interact with the CSP’s cloud platform from those that interact with the cluster. Per Kubernetes’ documentation, cloud-controller-manager functions similarly to kube-controller-manager in its ability to compile multiple processes into one. The difference is that the cloud-controller-manager runs controllers that are specific to an organization’s CSP only.
Why it needs to be secured
Issues involving the cloud-controller-manager pose a similar threat to organizations as those that affect the kube-controller-manager.
How to secure it
Acknowledging the similarities between kube-controller-managers and cloud-controller-managers, organizations can use the same measures to secure both.
The Security Work Doesn’t End There
The five control plane components discussed above all demand attention as part of an organization’s overall Kubernetes security efforts. Even so, organizations’ work to secure their Kubernetes architecture doesn’t end there. There are also the Node components.
Operation Earth Kitsune: hackers target the Korean diaspora
31.10.20 BigBrothers Securityaffairs
Experts uncovered a new watering hole attack, dubbed Operation Earth Kitsune, targeting the Korean diaspora that exploits flaws in web browsers.
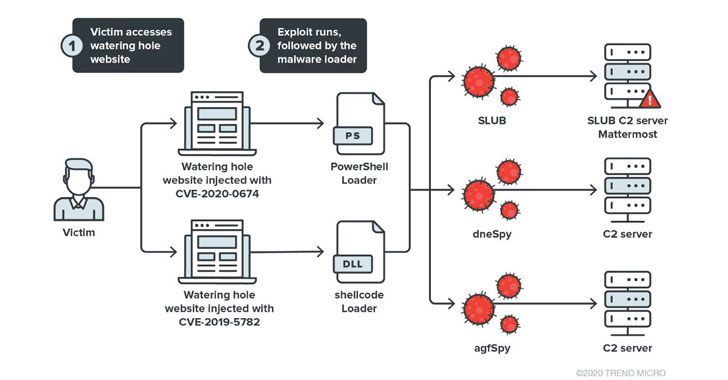
Researchers at Trend Micro have disclosed details about a new watering hole campaign, dubbed Operation Earth Kitsune, targeting the Korean diaspora that exploits flaws in web browsers such as Google Chrome and Internet Explorer to deploy backdoors.
Threat actors behind the Operation Earth Kitsune used SLUB (for SLack and githUB) malware and two new backdoors tracked as dneSpy and agfSpy to exfiltrate data from the infected systems and for taking over them.
The attacks were spotted by the researchers during the months of March, May, and September.
Attackers have deployed the spyware on websites associated with North Korea, but experts pointed out that access to these sites is blocked for visitors from South Korean IP addresses.
“The threat, which we dubbed as such due to its abuse of Slack and GitHub in previous versions, has not abused either of the platforms this time; instead, it employed Mattermost, an open-source online chat service that can be easily deployed on-premise.” reads the analysis published by Trend Micro.

This campaign, unlike other ones, deployed numerous samples (7) to the victim machines and used multiple command-and-control (C&C) servers (5), attackers also employed exploits for four N-day bugs.
Experts were investigating a strange redirection of visitors of the Korean American National Coordinating Council (KANCC) website to the Hanseattle website. Users were redirected to a weaponized version of a proof of concept (POC) for the CVE-2019-5782 Chrome vulnerability published by Google researchers. Experts discovered that the exploit was infecting the victim machine with three separate malware samples.

The attack chain initiates with a connection to the C&C server to receive the dropper, which once executed first checks for the presence of anti-malware solutions on the target system before delivering the three backdoor samples (in “.jpg” format) and executing them.
The attackers used Mattermost server to keep track of the deployment across multiple infected machines and to create a separate channel for each machine for data exfiltration.
The agfSpy backdoor support multiple commands to exfiltrate data, capture screenshots, enumerate directories, upload, download, and execute files.
“One interesting aspect of dneSpy’s design is its C&C pivoting behavior. The central C&C server’s response is actually the next-stage C&C server’s domain/IP, which dneSpy has to communicate with to receive further instructions.” continues the analysis.
agfSpy uses its own C&C server mechanism to receive commands that could instruct the backdoor to execute shell commands and send the execution results back to the server.
agfSpy and dneSpy are very similar except for the use of a different C&C server and various formats in message exchanges.
“Operation Earth Kitsune turned out to be complex and prolific, thanks to the variety of components it uses and the interactions between them,” the researchers concluded. “The campaign’s use of new samples to avoid detection by security products is also quite notable.”
“From the Chrome exploit shellcode to the agfSpy, elements in the operation are custom coded, indicating that there is a group behind this operation. This group seems to be highly active this year, and we predict that they will continue going in this direction for some time.”
Google Discloses Actively Targeted Windows Vulnerability
31.10.20 Vulnerebility Securityweek
Google Project Zero security researchers have identified another Windows vulnerability that has been actively exploited in attacks.
The security bug is an integer overflow with roots in one of the IOCTLs that the Windows Kernel Cryptography Driver (cng.sys) supports, and it could lead to privilege escalation, including a sandbox escape.
Discovered by Google Project Zero researchers Mateusz Jurczyk and Sergei Glazunov and assigned CVE number CVE-2020-17087, the zero-day was discovered in IOCTL 0x390400, in the cng!CfgAdtpFormatPropertyBlock function.
“The Windows Kernel Cryptography Driver (cng.sys) exposes a \Device\CNG device to user-mode programs and supports a variety of IOCTLs with non-trivial input structures. It constitutes a locally accessible attack surface that can be exploited for privilege escalation,” Jurczyk explains.
Details on the vulnerability were submitted to the Google Project Zero discussion board on October 22. Because the flaw was already being exploited in attacks, the information was made public seven days later, as per Google’s policy (for bugs that are not targeted, vendors are given 90 days to patch).
The security researchers have published the source code of a proof-of-concept exploit for the vulnerability, which was tested on “an up-to-date build of Windows 10 1903 (64-bit).”
However, they note that the issue was likely introduced in Windows 7.
“A crash is easiest to reproduce with Special Pools enabled for cng.sys, but even in the default configuration the corruption of 64kB of kernel data will almost surely crash the system shortly after running the exploit,” Jurczyk says.
The vulnerability appears to have been exploited in targeted attacks, but not in incidents related to the U.S. elections.
"Microsoft has a customer commitment to investigate reported security issues and update impacted devices to protect customers. While we work to meet all researchers' deadlines for disclosures, including short-term deadlines like in this scenario, developing a security update is a balance between timeliness and quality, and our ultimate goal is to help ensure maximum customer protection with minimal customer disruption," a Microsoft spokesperson said, replying to a SecurityWeek inquiry.
Google Announces New VPN for Google One Customers
31.10.20 Safety Securityweek
Google announced on Thursday that Google One customers can now use a new virtual private network (VPN) service that will provide them an extra layer of protection when they go online.
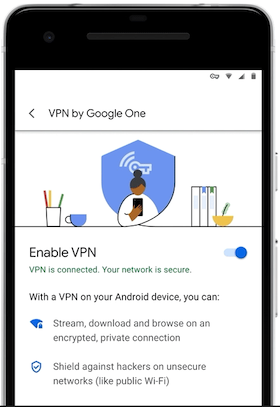
Google One is a subscription-based cloud storage and backup service. The new VPN by Google One is available to customers who have subscribed to a 2 TB plan or higher. The 2 TB plan costs $9.99 per month or $99.99 per year.VPN by Google One
The VPN service will initially only be available in the United States on Android — it will be rolled out over the next weeks and it can be enabled from the Google One app.
However, Google says it plans on expanding it to more countries and operating systems — including Windows, macOS and iOS — in the coming months.
“We already build advanced security into all our products, and the VPN extends that security to encrypt all of your phone’s online traffic, no matter what app or browser you’re using,” said Larissa Fontaine, director of Google One. “The VPN is built into the Google One app, so with just one tap, you can rest assured knowing your connection is safe from hackers.”
Google has also released a whitepaper with some technical details on its new VPN, as well as the source code for the client library to allow users and experts to check how it handles data.
The company says the VPN does not log user activity or data that could reveal personally identifiable information. This includes network traffic, IP address, connection timestamp, or the bandwidth used.
“We will have external security experts audit VPN by Google One end to end, including the server-side implementation, and publish a report on our VPN privacy protections,” Google said in its whitepaper.
While the VPN offer might seem attractive to some users, security experts are not convinced that Google will not use any data for its own benefit.
“A VPN by one of the largest data collection companies in the world is a scary thought,” Joseph Carson, chief security scientist and Advisory CISO at PAM solutions provider Thycotic, told SecurityWeek. “This initially makes me think that it is not exactly a VPN product which is meant to be a virtual private network which typically means that no one can see your data requests. This might be more of a No One Else But Us (NOEBU) will get your data. When products advertise themselves as a VPN, it must be absolutely clear about who it protects against and also whom it is giving access to your entire data communications history to. I hope that this is truly a security motive to make people safe from cybercrime and not one to try and get more data under the disguise of a security solution.”
Dirk Schrader, global VP at New Net Technologies (NNT), a provider of IT security and compliance software, commented, “The Google VPN service is nothing more than a bloated ‘security feature’. It encrypts the last mile, however, that doesn’t solve the issue with these apps that are using weak encryption or no encryption at all. It simply moves the point where the data will be unprotected to a different place, the tunnel end of Google’s side.
“This VPN feature might make it more difficult to conduct Wi-Fi attacks, but not much more. When Google states that the VPN will hide the user’s location to prevent third parties from tracking them, what is the use of this protection if Google sells the collected data to the exact same third party? Google should use its powers and knowledge to help these app developers apply stronger encryption, instead of deviating from the real problem.”
U.S. Cyber Command Shares More Russian Malware Samples
31.10.20 BigBrothers Securityweek
The United States Cyber Command (USCYBERCOM) this week released new malware samples associated with the activity of Russian threat actors Turla and Zebrocy.
Linked to malicious activity dating back two decades and also referred to as Snake, Waterbug, Venomous Bear, Belugasturgeon, and KRYPTON, Turla was most recently observed targeting a European government organization with multiple backdoors.
On Thursday, USCYBERCOM shared on VirusTotal new samples of the ComRAT Trojan, which is believed to be one of the oldest malware families employed by the Russia-linked threat actor.
“FBI has high-confidence that Russian-sponsored APT actor Turla, which is an espionage group active for at least a decade, is using ComRAT malware to exploit victim networks. The group is well known for its custom tools and targeted operations,” a malware analysis report from the Cybersecurity and Infrastructure Security Agency (CISA) reads.
The report shares details on a PowerShell script used to install another script that in turn loads a ComRAT version 4 DLL. CISA explains that the malware includes DLLs employed as communication modules that are injected in the default browser and which communicate with the ComRATv4 file using a named pipe. A Gmail web interface is used to receive commands and exfiltrate data.
A total of five ComRAT files were shared by USCYBERCOM on VirusTotal, alongside two samples associated with the Russian threat actor Zebrocy.
Initially detailed in 2018, the Russian hacking group is considered by some security firms part of the infamous Sofacy APT (also referred to as APT28, Fancy Bear, Pawn Storm, Sednit, and Strontium), while others see it as a separate entity.
In September 2020, new Zebrocy attacks were uncovered, showing continuous targeting of countries associated with the North Atlantic Treaty Organization (NATO).
The two samples that USCYBERCOM shared on VirusTotal are Windows executables believed to be a new variant of the Zebrocy backdoor. The malware provides attackers with remote access to a compromised system and supports various operations, CISA says.
CISA recommends users and administrators apply security best practices to ensure that their systems remain protected from the newly shared malware samples or other threats.
Brooklyn & Vermont US hospitals hit by ransomware attacks
30.10.20 Ransomware Securityaffairs
Wyckoff Heights Medical Center in Brooklyn and the University of Vermont Health Network are the last victims of the Ryuk ransomware operators.
Ryuk ransomware operators continue the target the US healthcare industry, the last victims in order of time are the Wyckoff Heights Medical Center in Brooklyn and the University of Vermont Health Network.
The news of the attack comes a few hours after The FBI, the DHS’s Cybersecurity and Infrastructure Security Agency (CISA), and the Department of Health and Human Services (HHS) have issued a joint alert to warn hospitals and healthcare providers of imminent ransomware attacks from Russia.
This security advisory describes the tactics, techniques, and procedures (TTPs) associated with cyber criminals that could target organizations in the Healthcare and Public Health Sector (HPH) to infect systems with Ryuk ransomware.
The government agencies receive information about imminent attacks, threat actors are using the TrickBot botnet to deliver the infamous ransomware to the infected systems.
This week, the systems at Sky Lakes Medical Center in Oregon and St. Lawrence Health System in New York were infected with the Ryuk ransomware. In September, the Ryuk ransomware gang hit Universal Health Services, one of the largest hospital and healthcare services providers, forcing the company to shut down systems at healthcare facilities in the United States. The incident impacted over 200 medical facilities nationwide.
The news of the Ryuk ransomware attack at the Wycoff hospital was first published by Bleeping Computer that was informed by an employee of the organization.
Wyckoff Heights Medical Center is a 350-bed teaching hospital located in an ethnically diverse residential neighborhood directly on the border of northern Brooklyn and Western Queens, NY.
Wyckoff Hospital shut down portions of its network as part of the incident response procedure.
At the time of publishing this post, it is not known the extent of the incident and the impact on the operations of the hospitals.
University of Vermont Health Network also disclosed a similar cyber attack, the organization is working with the FBI and the Vermont Department of Public Safety on the investigation.
“People who are in urgent need of care are getting it and most appointments are happening,” Dr. Stephen Leffler, president of the University of Vermont Medical Center in Burlington, said at a news conference late Thursday outside the hospital. “Most surgeries will happen tomorrow. We did slow some down today as were switching systems.”
The ransomware attack has caused variable impacts at each of our affiliates, the family of ransomware involved in the attack is yet to be revealed.
“The attack has caused variable impacts at each of our affiliates. Staff are continuing to follow well-practiced standby procedures to ensure safe patient care. We understand the difficulty this causes for our patients and the community and apologize for the impact. There have been some changes to patient appointments and we are attempting to reach those patients who have been affected. We will continue to provide systems and patient service updates when they are available,” read a statement from the University of Vermont Health Network.
According to researchers at CheckPoint, Healthcare is the most targeted industry, by ransomware, in the US in October. Ransomware attacks against the US healthcare sector increased by 71%, experts also reported an increase of 33% in APAC and 36% in EMEA.
DoppelPaymer ransomware gang leaked Hall County, Georgia, voter info
30.10.20 Ransomware Securityaffairs
The DoppelPaymer ransomware operators have released data that was stolen from Hall County, Georgia earlier this month.
The DoppelPaymer ransomware operators have published online data that was stolen from Hall County, Georgia earlier this month.
The attack took place on October 7, it hit Hall County, in the northern part of the state and it disabled the county’s voter signature database.
The ransomware attack hit a Georgia county government and disabled a database used to verify voter signatures in the authentication of absentee ballots. It is a common process to validate absentee ballots sent by mail by analyzing signatures.
The media pointed out that this is the first reported case of a ransomware attack against a system used in the incoming 2020 Presidential election.
Ransomware attacks could have a dramatic impact on the elections, they could disrupt voting systems and raise doubts about the validity of the vote.
While the media reported that the ransomware operators leaked stolen data on their dark web leak site to force the organization to pay the ransom, Hall County stated that there was no indication that the hackers stole any unencrypted data before encrypting the systems.
“At this time, there is no evidence to show that citizen or employee data has been compromised. However, citizens and employees are encouraged to take precautionary measures to monitor and protect their personal information,” Hall County stated.
The DoppelPaymer ransomware gang finally published over 1 GB of files stolen from Hall County systems and revealed that 2,464 devices were encrypted during the attack.

Source Bleeping Computer
According to Bleeping Computer, The dump includes election documents, lobby comment cards, 911 spreadsheets, accounting and financial records.
“The election documents reviewed by BleepingComputer contain ballot proofs, poll worker lists, administrative documents, accounting and financial records, and city bulletins.” reported Bleeping Computer. “Also included are voter registration records containing resident’s voter registration ID, full name, address, and assigned ballot, which is, for the most part, public information.”
Most of the information leaked is public, but can be exploited by threat actors to carry out malicious activities against voters.
Recently the US government revealed that Iran-linked hackers were behind voter intimidation emails that were sent to Democrats in Florida and Alaska that pretended to be from the far-right Proud Boys group.
Microsoft Says Hackers Continue to Target Zerologon Vulnerability
30.10.20 Vulnerebility Securityweek
Microsoft this week revealed that it continues to receive reports from customers of attacks targeting the Zerologon vulnerability.
Patched on August 11, the security flaw was identified in the Microsoft Windows Netlogon Remote Protocol (MS-NRPC). Tracked as CVE-2020-1472, the issue can be exploited to compromise Active Directory domain controllers and gain domain administrator privileges.
The vulnerability came into the spotlight after the DHS ordered federal agencies to immediately apply available patches, with both Microsoft and CISA publishing information on attackers actively exploiting the bug.
At the end of September, Microsoft published a guide to provide organizations with all the necessary details for addressing the issue within their Active Directory deployments, but it appears that some customers continue to be vulnerable.
“If the original guidance is not applied, the vulnerability could allow an attacker to spoof a domain controller account that could be used to steal domain credentials and take over the domain,” Microsoft now says.
The tech giant also reiterates that the first step into addressing the vulnerability is installing the available patches on every domain controller.
“Once fully deployed, Active Directory domain controller and trust accounts will be protected alongside Windows domain-joined machine accounts. We strongly encourage anyone who has not applied the update to take this step now,” the company notes.
To ensure they are fully protected, customers should apply the update and follow Microsoft’s previously published guidance. The company has already updated the FAQs in that guidance, for further clarity.
Following the update, customers are advised to identify any devices that might still be vulnerable, address them, and then enable enforcement mode, to ensure that CVE-2020-1472 is indeed addressed in their environment.
On Thursday, CISA published an alert to warn of the continuous exploitation of Zerologon and to urge administrators to apply the available patches as soon as possible.
Critical OpenEMR Vulnerabilities Give Hackers Remote Access to Health Records
30.10.20 Vulnerebility Securityweek
Several vulnerabilities found by researchers in the OpenEMR software can be exploited by remote hackers to obtain medical records and compromise healthcare infrastructure.
OpenEMR is an open source management software designed for healthcare organizations. The free application is highly popular and it provides a wide range of features for managing health records and medical practices.
Researchers at Swiss-based code quality and security solutions provider SonarSource discovered earlier this year that OpenEMR is affected by four types of vulnerabilities that impact servers using the Patient Portal component.
The list of vulnerabilities includes command injection, persistent cross-site scripting (XSS), insecure API permissions, and SQL injection.
The Patient Portal enables healthcare organizations to allow their patients to perform various tasks online, such as communicating with doctors, filling out new patient registration forms, making appointments, making payments, and requesting prescription refills.
However, SonarSource researchers determined that if the Patient Portal is enabled and accessible from the internet, an attacker could take complete control of the OpenEMR server by chaining the vulnerabilities they’ve found.
According to SonarSource, the Patient Portal has its own API interface, which can be used to control all portal actions. Using this API requires authentication, but the researchers found a way to bypass it, allowing them to access and make changes to patient data, or to change information associated with backend users, such as administrators.
An attacker who is able to change administrator account data can exploit the persistent XSS vulnerability to inject malicious code that would get executed when the targeted admin logs in to their account.
The JavaScript code triggered through the XSS vulnerability can then exploit the command injection vulnerability found by the researchers. The ability to execute arbitrary OS commands enables the attacker to take complete control of the OpenEMR server.
Alternatively, if the attacker targets a user with lower privileges rather than an administrator, they can exploit the SQL injection vulnerability to gain access to the patient database and steal potentially valuable data.
Exploitation of the XSS and command injection flaws requires admin privileges, but the SQL injection bug can be exploited with regular user privileges.
SonarSource discovered the vulnerabilities in OpenEMR 5.0.2.1 and they were patched with the release of version 5.0.2.2 in August. Details of the flaws were only made public now to give users enough time to install the update.
Wisconsin Republican Party Says Hackers Stole $2.3 Million
30.10.20 Incindent Securityweek
Hackers have stolen $2.3 million from the Wisconsin Republican Party’s account that was being used to help reelect President Donald Trump in the key battleground state, the party’s chairman told The Associated Press on Thursday.
The party noticed the suspicious activity on Oct. 22 and contacted the FBI on Friday, said Republican Party Chairman Andrew Hitt.
Hitt said the FBI is investigating. FBI spokesman Brett Banner said that, per policy, “the FBI is not permitted to confirm or deny an investigation.” The Wisconsin Department of Justice, which has a center focused on cyber crime able to assist if requested, has not been asked to investigate, said spokeswoman Rebecca Ballweg.
The alleged hack was discovered less than two weeks before Election Day, as Trump and Democratic rival Joe Biden made their final push to win Wisconsin and its 10 electoral votes. Trump won the state by fewer than 23,000 votes in 2016 and was planning his third visit in seven days on Friday. Biden also planned to campaign in Wisconsin on Friday. Polls have consistently shown a tight race in the state, usually with Biden ahead by single digits and within the margin of error.
Hitt said he was not aware of any other state GOP being targeted for a similar hack, but state parties were warned at the Republican National Convention this summer to be on the lookout for cyber attacks.
“We have been in contact with the state party and are assisting them through this process,” said Republican National Committee spokesman Michael Ahrens. “The RNC never left Wisconsin after 2016, and we are confident that our ground game and the millions we are spending on TV and digital will deliver us another win there in 2020.”
The reported hack exposed new tensions in the final days of the race between the Trump campaign and the state party, which overspent and failed to properly account for its expenditures in 2018, leading to a shakeup in top party leadership.
Campaign officials in Wisconsin learned about the alleged hack from media reports and were furious that state officials had not briefed them on how it might impact operations, according to a Trump campaign official who requested anonymity because the person was not authorized to discuss internal conversations.
But Trump’s director of battleground strategy, Nick Trainer, said the national campaign was notified immediately.
“I personally received a call notifying me as a senior official for the campaign,” he said. “We have complete trust in the Republican Party of Wisconsin and know they will deliver the state for the President in four days.”
There have been more than 800 attempted phishing attacks for financial gain targeting the Wisconsin Democratic Party this campaign cycle, but none has been successful, said party spokeswoman Courtney Beyer.
The alleged hack is “certainly embarrassing” for Republicans, said Matt Rothschild, leader of the Wisconsin Democracy Campaign, an independent group that tracks campaign donations and spending.
“It’s got to hurt them and their ability to function at this crucial moment,” he said. “I can’t see any upside for them in this matter.”
Hitt stressed that the money stolen was for services already rendered.
“While a large sum of money was stolen, our operation is running at full capacity,” he said.
Hitt said the hackers manipulated invoices from four vendors who were being paid for direct mail for Trump’s reelection efforts as well as for pro-Trump material such as hats to be handed out to supporters. Invoices and other documents were altered so when the party paid them, the money went to the hackers instead of the vendors, Hitt said.
It was discovered after someone noticed that an invoice was generated that should not have been, he said.
Hitt said it appears the attack began as a phishing attempt and no data appears to have been stolen, said party spokesman Alec Zimmerman.
The money was stolen from the state party’s federal account, which currently contains about $1.1 million, but that number fluctuates daily because of quick moving resources late in the campaign, Zimmerman said. Money in the federal account can only be spent on federal races and donations are capped at $10,000 per individual each calendar year.
Campaign finance reports filed this week in Wisconsin show Democrats have raised far more money than Republicans. The state Democratic Party raised nearly $59 million over the past two years compared with just $23.7 million for Republicans.
Early voting is in full swing in Wisconsin, with more than 1.6 million ballots returned as of Thursday morning. That is nearly 55% of the total vote cast in 2016.
Britain Fines US Hotel Chain Marriott Over Data Breach
30.10.20 Incindent Securityweek
Britain's data privacy watchdog on Friday said it has fined US hotels group Marriott over a data breach affecting millions of customers worldwide.
The UK Information Commissioner's Office said in a statement it fined Marriott £18.4 million ($23.5 million, 20.1 million euros) for breaches of data that included personal information such as passport numbers since March 2018.
That was when new European Union data protection rules, or GDPR, came into effect.
The final penalty is far less than a figure of around £100 million originally planned by the ICO.
The watchdog said it had taken into account "steps Marriott took to mitigate the effects of the incident and the economic impact of Covid-19 on their business before setting a final penalty".
Since the breach occurred before Britain left the European Union, the ICO investigated on behalf of all EU authorities as lead supervisory authority under the GDPR.
The ICO said Marriott's breach in fact dated back to 2014, uncovering client data including passport numbers.
Marriott estimates that 339 million guest records worldwide were affected following a cyber-attack six years ago on Starwood Hotels and Resorts Worldwide.
The ICO said the precise number of people affected remained unclear as there may have been multiple records for an individual guest.
It added that seven million guest records related to people in the UK.
"The attack, from an unknown source, remained undetected until September 2018, by which time the company had been acquired by Marriott," the watchdog said.
"The personal data involved differed between individuals but may have included names, email addresses, phone numbers, unencrypted passport numbers, arrival/departure information, guests' VIP status and loyalty programme membership number," it said.
Information Commissioner Elizabeth Denham said businesses are required to look after "precious" personal data belonging to clients.
"Millions of people's data were affected by Marriott's failure... When a business fails to look after customers' data, the impact is not just a possible fine, what matters most is the public whose data they had a duty to protect," she said.
Browser Bugs Exploited to Install 2 New Backdoors on Targeted Computers
30.10.20 Virus Thehackernews
Cybersecurity researchers have disclosed details about a new watering hole attack targeting the Korean diaspora that exploits vulnerabilities in web browsers such as Google Chrome and Internet Explorer to deploy malware for espionage purposes.
Dubbed "Operation Earth Kitsune" by Trend Micro, the campaign involves the use of SLUB (for SLack and githUB) malware and two new backdoors — dneSpy and agfSpy — to exfiltrate system information and gain additional control of the compromised machine.
The attacks were observed during the months of March, May, and September, according to the cybersecurity firm.
Watering hole attacks allow a bad actor to compromise a targeted business by compromising a carefully selected website by inserting an exploit with an intention to gain access to the victim's device and infect it with malware.
Operation Earth Kitsune is said to have deployed the spyware samples on websites associated with North Korea, although access to these websites is blocked for users originating from South Korean IP addresses.
A Diversified Campaign
Although previous operations involving SLUB used the GitHub repository platform to download malicious code snippets onto the Windows system and post the results of the execution to an attacker-controlled private Slack channel, the latest iteration of the malware has targeted Mattermost, a Slack-like open-source collaborative messaging system.
"The campaign is very diversified, deploying numerous samples to the victim machines and using multiple command-and-control (C&C) servers during this operation," Trend Micro said. "In total, we found the campaign using five C&C servers, seven samples, and exploits for four N-day bugs."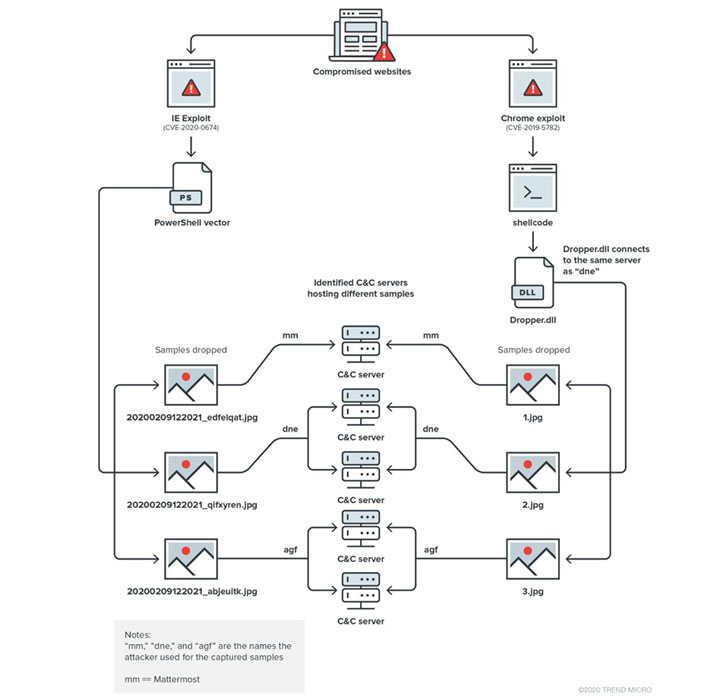
Designed to skip systems that have security software installed on them as a means to thwart detection, the attack weaponizes an already patched Chrome vulnerability (CVE-2019-5782) that allows an attacker to execute arbitrary code inside a sandbox via a specially-crafted HTML page.
Separately, a vulnerability in Internet Explorer (CVE-2020-0674) was also used to deliver malware via the compromised websites.
dneSpy and agfSpy — Fully Functional Espionage Backdoors
The difference in the infection vector notwithstanding, the exploit chain proceeds through the same sequence of steps — initiate a connection with the C&C server, receive the dropper, which then checks for the presence of anti-malware solutions on the target system before proceeding to download the three backdoor samples (in ".jpg" format) and executing them.
What's changed this time around is the use of Mattermost server to keep track of the deployment across multiple infected machines, in addition to creating an individual channel for each machine to retrieve the collected information from the infected host.
Of the other two backdoors, dneSpy, and agfSpy, the former is engineered to amass system information, capture screenshots, and download and execute malicious commands received from the C&C server, the results of which are zipped, encrypted, and exfiltrated to the server.
"One interesting aspect of dneSpy's design is its C&C pivoting behavior," Trend Micro researchers said. "The central C&C server's response is actually the next-stage C&C server's domain/IP, which dneSpy has to communicate with to receive further instructions."
agfSpy, dneSpy's counterpart, comes with its own C&C server mechanism that it uses to fetch shell commands and send the execution results back. Chief among its features include the capability to enumerate directories and list, upload, download, and execute files.
"Operation Earth Kitsune turned out to be complex and prolific, thanks to the variety of components it uses and the interactions between them," the researchers concluded. "The campaign's use of new samples to avoid detection by security products is also quite notable."
"From the Chrome exploit shellcode to the agfSpy, elements in the operation are custom coded, indicating that there is a group behind this operation. This group seems to be highly active this year, and we predict that they will continue going in this direction for some time."
NVIDIA Patches Critical Bug in High-Performance Servers
30.10.20 Vulnerebility Threatpost
NVIDIA said a high-severity information-disclosure bug impacting its DGX A100 server line wouldn’t be patched until early 2021.
NVIDIA released a patch for a critical bug in its high-performance line of DGX servers that could open the door for a remote attacker to take control of and access sensitive data on systems typically operated by governments and Fortune-100 companies.
In all, NVIDIA issued nine patches, each fixing flaws in firmware used by DGX high-performance computing (HPC) systems, which are used for processor-intensive artificial intelligence (AI) tasks, machine learning and data modeling. All of the flaws are tied to its own firmware that runs on its DGX AMI baseboard management controller (BMC), the brains behind a remote monitoring service servers.
“Attacks can be remote (in case of internet connectivity), or if bad guys can root one of the boxes and get access to the BMC they can use the out of band management network to PWN the entire datacenter,” wrote researcher Sergey Gordeychik who is credited for finding the bugs. “If you have access to OOB, it is game is over for the target.”
Given the high-stake computing jobs typically running on the HPC systems, the researcher noted an adversary exploiting the flaw could “poison data and force models to make incorrect predictions or infect an AI model.”
No Patch Until 2021 for One Bug
NVIDIA said a patch fixing one high-severity bug (CVE‑2020‑11487), specifically impacting its DGX A100 server line, would not be available until the second quarter of 2021. The vulnerability is tied to a hard-coded RSA 1024 key with weak ciphers that could lead to information disclosure. A fix for the same bug (CVE‑2020‑11487), impacting other DGX systems (DGX-1, DGX-2) is available.
“To mitigate the security concerns,” NVIDIA wrote, “limit connectivity to the BMC, including the web user interface, to trusted management networks.”
Bugs Highlight Weaknesses in AI and ML Infrastructure
“We found a number of vulnerable servers online, which triggered our research,” the researcher told Threatpost. The bugs were disclosed Wednesday and presented as part of a presentation “Vulnerabilities of Machine Learning Infrastructure” at CodeBlue 2020, a security conference in Tokyo, Japan.
During the session Gordeychik demonstrated how NVIDIA DGX GPU servers used in machine learning frameworks (Pytorch, Keras and Tensorflow), data processing pipelines and applications such as medical imaging and face recognition powered CCTV – could be tampered with by an adversary.
The researcher noted, other vendors are also likely impacted. “Interesting thing here is the supply chain,” he said. “NVIDIA uses a BMC board by Quanta Computers, which is based on AMI software. So to fix issues [NVIDIA] had to push several vendors to get a fix.”
Those vendors include:
IBM (BMC Advanced System Management)
Lenovo (ThinkServer Management Module)
Hewlett-Packard Enterprise Megarac
Mikrobits (Mikrotik)
Netapp
ASRockRack IPMI
ASUS ASMB9-iKVM
DEPO Computers
TYAN Motherboard
Gigabyte IPMI Motherboards
Gooxi BMC
Nine CVEs
As for the actual patches issued by NVIDIA on Wednesday, the most serious is tracked as CVE‑2020‑11483 and is rated critical. “NVIDIA DGX servers contain a vulnerability in the AMI BMC firmware in which the firmware includes hard-coded credentials, which may lead to elevation of privileges or information disclosure,” according to the security bulletin.
Vulnerable NVIDIA DGX server models impacted include DGX-1, DGX-2 and DGX A100.
Four of the NVIDIA bugs were rated high-severity (CVE‑2020‑11484, CVE‑2020‑11487, CVE‑2020‑11485, CVE‑2020‑11486) with the most serious of the four tracked as CVE‑2020‑11484. “NVIDIA DGX servers contain a vulnerability in the AMI BMC firmware in which an attacker with administrative privileges can obtain the hash of the BMC/IPMI user password, which may lead to information disclosure,” the chipmaker wrote.
Three of the other patched vulnerabilities were rated medium severity and one low.
“Hackers are well aware of AI and ML infrastructure issues and use ML infrastructure in attacks,” Gordeychik said.
REvil Gang Promises a Big Video-Game Hit; Claims Massive Revenue
30.10.20 Ransomware Threatpost
In a wide-ranging interview, a REvil leader said the gang is earning $100 million per year, and provided insights into the life of a cybercriminal.
The REvil ransomware gang claims it will rake in $100 million by year’s end. That’s according to a REvil group leader in a rare Q&A with the YouTube Channel for tech blog “Russian OSINT.” During the live interview, the REvil hacker warned of a “big attack coming…linked to a very large video game developer.”
The boasting and threats come on the heels of REvil’s chief rivals, the Maze gang, announcing that it was closing up shop (see below).
The interview (Russian translation provided to Threatpost by Flashpoint) was wide-ranging and touches on the group’s operations, the money it makes, details on its high-profile attacks and the fact that the members are actively being hunted by governments around the world.
Operations
The Q&A first offered details into the group’s operations. For instance, the interviewee signaled an upcoming change in strategy.
While REvil already uses the double-extortion strategy (where companies’ files are not just encrypted but also stolen, with a threatened leak adding pressure to pay the ransom), the leader suggested that the future lie in taking that strategy further.
“Everything ultimately comes down to a shift toward leaking files and not locking them,” he said. “I personally really liked SunCrypt’s idea. DoS [denial of service] the site of the company and their infrastructure, combined with locking the files and threatening to publish them…[it] puts a lot of pressure on them…[We’re] thinking about employing a similar model.”
He also confirmed that REvil employs the ransomware-as-a-service model, where “affiliates” that carry out the attacks receive 70 to 80 percent of the “revenue” from the ransoms. The affiliates themselves are strictly vetted (much like the NetWalker gang), and are responsible for initial network infection, wiping out any backups and downloading files. REvil members meanwhile take care of ransom negotiations, software development and updates, receipt of the payment and the delivery of the decryptor.
When it comes to partners, “we have our own closed family, the selection is very rigorous and we don’t even bother talking to [amateurs],” he said. “Support only helps when it comes to negotiations. They have to master all the technical parts of the job by themselves.”
That said, the group also carries out its own attacks, he said, with a unit devoted to hacking companies – though the ransomware-as-a-service (RaaS) model is more lucrative.
He also said that Android or iOS ransomware is not in the cards for the group, because of the low value of the information stored on phones. “You have to be crazy to get involved in this,” he said. “I’m 100 percent against it.”
High-Profile Attacks
All of that business design has allowed REvil to claim some pretty big headlines. For instance, when asked what the biggest coups were for REvil, he cited, with pride, Travelex, Grubman Shire Meiselas & Sacks, and the 23 Texas municipalities that the gang attacked last summer.
The interviewee also took credit for two rumors associated with REvil. One, that it captured data on President Donald Trump and that REvil was behind Chile’s Banco Estado shutting all of its branches.
In the case of Trump, the files were reportedly lifted as part of the Grubman hack. “We just wished “good luck” to the NSA, FBI, and the U.S. Secret Service with the decryption of the files,” he said. “We didn’t demand money from Trump [directly]…The money for the [stolen] data was paid. I can’t tell you who bought it, though. The data had to do with tax-avoidance scheme affiliated with Trump.”
As for Banco Estado, the initial vector was email to bank employees, he said: “Yes, it really happened – we did it,” he alleged. “Often, companies do not disclose the source of the attack because they are afraid of reputational damage [affecting] their stock position.”
He added that around one-third of all companies quietly negotiate to pay the ransom, and that IT providers, insurance companies, law offices, manufacturing and the agro-industrial sector are the most-lucrative targets.
As for initial access, the interviewee said that harvesting and using administrative credentials with malware, brute-forcing Remote Desktop Protocol connections and exploiting bugs are the best avenues for attack.
“Grubman and Travelex…both were hacked through old versions of Pulsar and Citrix,” he said. “It is actually pretty stupid — we gained access to the [network] in minutes, and all due to one vulnerability that can be patched quickly.”
Attacks are likely to ramp up – and indeed the aforementioned video-game company attack is in the works but under wraps, the REvil operator claimed. But geopolitical realities will add to the momentum, according to Ilia Kolochenko, founder and CEO of web security company ImmuniWeb.
“The pandemic gradually exacerbates the situation, as budgets are being reduced, cybersecurity people are all exhausted, while employees working from home are considerably more vulnerable and susceptible to a wide spectrum of phishing attacks,” he said, via email. “Frequently, it is enough to breach one single user machine to get into a corporate network via VPN. Thus, cybercriminals are now enjoying a windfall of surging profits by effortlessly picking up low-hanging fruits in impunity. Worse, some cybersecurity professionals may sooner or later ponder all pros and cons, and given the unprecedented opportunities and low risks, will readily shift from their daily jobs to generous cyber-gangs.”
Money, Money, Money
All of this activity is in service of course to one thing: Personal enrichment.
The REvil leader noted that life as a cybercriminal started for him with video games.
“Once upon a time, when I was a kid, I installed CHLENIX [cheat config for Counter Strike] and really liked it,” he explained. That legacy lives on. The ransomware’s name is short for “Ransom Evil,” with the nomenclature inspired by the video game “Resident Evil,” according to the interview (only security researchers call it Sodinokibi, he said).
CHLENIX lead to more nefarious things, and now he’s leading a group that claims to be raking in $100 million per year. That’s less than what REvil’s precursor, GandCrab, was making. That group announced a shutdown in June 2019, after claiming to make $2 billion in a year and a half.
REvil was soon developed to take its place, and while the interviewee didn’t confirm the GandCrab connection specifically, he admitted that an earlier project was shut down to make way for a “better product.”
When asked when it would be time to step away form “the life,” he answered. “Personally, I should have stopped a long time ago. I have enough money for hundreds of years, but there is never too much money…[I hope to have] $1 billion, then $2 billion, and then if I’m in a good mood, $5 billion.”
“The [$100 million] number is merely a tip of the cybercrime revenue iceberg,” said Kolochenko. “Concomitant proliferation of cryptocurrencies makes such crimes technically uninvestigable, while law enforcement agencies and joint task forces are already overburdened with nation-state attacks, and transnational targeted attacks aimed to steal intellectual property from the largest Western companies.”
The Downside: Being Hunted
Conventional wisdom says that cyberattackers thrive in dark shadows and anonymity – but comments by the gang leader suggest that REvil members may not be as faceless as they would like.
When asked if group members could travel for instance, the answer was an uncategorical “nope.” The Russian-speaking interviewee added that, contrary to Kolochenko’s claim that being a ransomware operator is “low risk,” no one involved in ransomware would ever travel to Western countries or the United States for fear of being killed.
“We create serious problems and there is no justice for us, so killing us would be the only viable solution,” he said.
He said the group believes they are being hunted by the U.S. Secret Service, Europol and infosec companies on a daily basis, with CIA agents actively trying to infiltrate the group’s operations by posing as an affiliate applicant.
“But generally, their cover falls apart,” he noted. And as for hack-backs, “they have no idea what kind of OS we use on our servers or what kind of web servers we use… They are just hoping to get lucky. Our product…is configured to defend against them.”
Maze Closes Down
During the interview, the REvil leader also touched on its arch rival criminal group Maze, which is reportedly shuttering its operations.
According to someone identifying themselves as a Maze operator told Bleeping Computer this week that the group halted its encryption activities back in September, in order to focus on getting existing victims to pay up.
Soon after, Maze affiliates started porting over to the Egregor ransomware gang, the outlet reported.
Maze was a pioneer in the double-extortion tactic, first emerging last November. Since then, it has made waves with big strikes such as the one against Cognizant. And this summer it formed a cybercrime “cartel” – joining forces with various ransomware strains (including Egregor) sharing code, ideas and resources.
“Criminals don’t just have an epiphany and quit being criminals overnight,” said Lamar Bailey, senior director of security research at Tripwire, via email. “They shut down an operation when the return on their investment drops below the costs of running the ‘program’ or when they are about to get caught. This is no different.”
He added, “They are switching to something new, maybe Egregor, which miraculously came out at the same time Maze started shutting down. This is just like that one furniture store in town that is going out of business every few months only to reopen with a new name but with the same people and product.”
Kegtap, Singlemalt, Winekey Malware Serve Up Ransomware to Hospitals
30.10.20 Ransomware Threatpost
Amid an uptick in attacks on healthcare orgs, malware families, Kegtap, Singlemalt and Winekey are being used to deliver the Ryuk ransomware to already strained systems.
The boozy names might sound like the kind of thing conjured up in a frat-house common room, but malware families Kegtap, Singlemalt and Winekey are being used to gain initial network access in potentially lethal ransomware attacks on healthcare organizations in the midst of a global pandemic, researchers said in newly released findings.
The shot? The rampant spread of COVID-19 has put a tremendous strain on the U.S. healthcare system. The chaser? Cybercriminals are getting better than ever at exploiting that life-and-death crisis to turn a profit.
Who could use a drink?
Mandiant published a report this week laying out the signature tactics of the Kegtap/BEERBOT, Singlemalt/STILLBOT and Winekey/CORKBOT attacks, which researchers said have targeted hospitals, retirement communities and medical centers “… demonstrating a clear disregard for human life,” the report added.
Mandiant researchers observed the ransomware being used to hit a variety of sectors and organizations, in addition to healthcare, and found a few commonalities.
The Malware
Phishing emails, designed to mimic everyday business functions like contracts, personnel paperwork or complaints are sent with a link, not to a malware payload, but to a Google doc, PDF or some other document which would contain the in-line link to the malware.
“Hiding the final payload behind multiple links is a simple yet effective way to bypass some email filtering technologies,” the report said. “Various technologies have the ability to follow links in an email to try to identify malware or malicious domains; however, the number of links followed can vary. Additionally, embedding links within a PDF document further makes automated detection and link-following difficult.”
Kegtap, Singlemalt and Winekey (a.k.a. Bazar variants) act as first-stage loaders, which establish a foothold on a device before fetching malware for the next stage of the attack.
In this case, the criminals use them to download common penetration-testing frameworks like Cobalt Strike, Beacon and/or Powertrick to establish a presence. Following initial compromise, Cobalt Strike helps maintain the malware’s presence after reboot, the report said, and Beacon is the most often observed backdoor in these attacks.
Cobalt Strike, PowerShell Empire, Powersploit and Medasploit are a group of dual-use tools used for both legitimate tasks as well as nefarious ones, according to Cisco researcher Ben Nahorney. These pen-testing tools are intended to help security professionals identify weaknesses in their network defenses, but in the wrong hands they can supercharge attacks.
Beacon has also been used to deploy “PowerLurk’s Register-MaliciousWmiEvent cmdlet to register WMI events used to kill processes related to security tools and utilities, including Task Manager, WireShark, TCPView, ProcDump, Process Explorer, Process Monitor, NetStat, PSLoggedOn, LogonSessions, Process Hacker, Autoruns, AutorunsSC, RegEdit and RegShot,” the report said.
The malware then sets about escalating privileges, most often with valid credentials, according to the report, which are obtained through “exported copies of the ntds.dit Active Directory database and system, and security registry hives from a Domain Controller.”
Beacon, along with publicly available tools like Bloodhound, Sharphound or ADfind, is then deployed for reconnaissance, the researchers added, which enabled the actors to move laterally to expand their footprint across the compromised network.
The Ransomware Payload
The main goal of the mission, according to the report, is to deliver a Ryuk payload.
“There is evidence to suggest that Ryuk ransomware was likely deployed via PsExec, but other scripts or artifacts related to the distribution process were not available for forensic analysis,” the report continued.
This partnership between the developers behind Kegtap, Singlemalt and Winekey with the group behind Ryuk, makes this group particularly noteworthy. Ryuk is operated by an Eastern European actor called UNC1878 according to Mandiant, and continues to be a prolific threat against healthcare organizations — attacks which Charles Carmakal, senior vice president and CTO of Mandiant says pose unprecedented dangers to the U.S.
UNC1878’s Ryuk Threat
UNC1878’s Ryuk has been linked to ransomware spread throughout a Canadian government health organization and just this week was used in ransomware attacks against multiple healthcare systems, including Klamath Falls, Ore.-based Sky Lakes Medical Center and New York-based St. Lawrence Health System.
In September, Universal Health Services, a nationwide hospital operator, was hit by a ransomware attack suspected to have been Ryuk.
“UNC1878 is one of most brazen, heartless and disruptive threat actors I’ve observed over my career, Carmakal told Threatpost.
“Ransomware attacks on our healthcare system may be the most dangerous cybersecurity threat we’ve ever seen in the United States,” Carmakal continued. “Multiple hospitals have already been significantly impacted by Ryuk ransomware and their networks have been taken offline. As hospital capacity becomes more strained by COVID-19, the danger posed by this actor will only increase.”
Kegtap, Singlemalt and Winekey have also caught the attention of U.S. Cyber Command, which tweeted the Mandiant report with the comment, “The public and private sectors are united against ransomware, especially those actors targeting medical facilities during a pandemic.”
Stopping Ransomware Attacks on Healthcare
The key to stopping these attacks, according to the Mandiant report, is moving quickly to harden service accounts, prevent the use of privileged accounts for lateral movement, block internet service to servers where possible, block newly registered domains using DNS filers or web proxies, and update and install patches for Windows in addition to the network (including Zerologon, which has been observed in the attacks).
“The surge of malware campaigns on healthcare organizations is one of the most insidious attacks that can be unleashed by malicious actors — especially during a pandemic,” Jeff Horne, CSO at Order, told Threatpost by email. “These organizations are especially susceptible because many of their mission-critical, internet-connected devices run vulnerable operating systems that cannot be patched. There are nearly 650 million IoT/IoMT devices operating in the healthcare industry right now, and 82 percent of healthcare organizations have had their IoT/IoMT devices attacked.”
Horne adds these healthcare systems are up against a highly professional, well-equipped adversary and need to adapt an appropriate posture to defend their systems.
“These ‘ransomware-as-a-service’ groups are run by sophisticated and malicious developers operating like a criminal company with organized modern customer-focused services, online support, call centers and payment processors — making a considerable amount of money in the process,” Horne added. “This can’t just be addressed with antivirus software — these are focused, motivated and knowledgeable criminal operators that are targeting vulnerable healthcare organizations by exploiting vulnerabilities, gaining a foothold within their networks, and holding their important data hostage.”
Home Depot Confirms Data Breach in Order Confirmation SNAFU
30.10.20 Incindent Threatpost
Hundreds of emailed order confirmations for random strangers were sent to Canadian customers, each containing personal information.
Home Depot has exposed the private order confirmations of hundreds of Canadian consumers, containing names, physical addresses, email addresses, order details and partial credit-card information.
After customers began reporting that they had received hundreds of emails from the home-improvement giant, each containing an order confirmation for a stranger, the company confirmed the issue.
One affected customer posted a screenshot of his inbox on Twitter, filled with random people’s order confirmations, tweeting: “Hey um… I’m pretty sure I received a reminder email for literally every online order that is currently ready for pick up at literally every Home Depot store in Canada. There are 660+ emails. Something has gone wrong.”
He added, “you are almost certainly aware by now that you sent four-to-five-hundred emails to each of 527 people by mistake.”
The company was quick to respond, although it didn’t provide many details.
“Thank you for reaching out to us,” Home Depot Canada tweeted on Wednesday. “We are aware of what occurred this morning and can confirm that this issue has now been fixed. This issue impacted a very small number of our customers who had in-store pick-up orders. Please DM us with any additional questions.”
But the issue seems to have affected multiple hundreds of people, and not just in-store pickup orders:
Home Depot Canada confirmed the impact to online shoppers in a later tweet after being called out on the in-store only claim.
In response to an inquiry asking how the breach happened and asking for more concrete details on who was affected, the DIY specialist told Threatpost: “Tuesday evening, we discovered a systems error on select http://Homedepot.ca orders impacting a small number of our Canadian customers. Some customers may have received multiple emails for orders they did not place. This issue has been fixed. None of the emails contained passwords or un-hashed payment card information.”
It’s unclear exactly what details these particular order confirmations included; Home Depot order confirmations sent in the past to Threatpost staff include full names and addresses, details and cost of the items ordered, phone numbers if provided for delivery purposes, and links to “check order status.” Clicking that link takes customers to an online portal to sign in, which could conceivably lead to the exposure of more information if cyberattackers were able to brute-force the credentials.
If past data exposures are any indication, the information is enough to craft convincing phishing and fraud messages. Additionally, it could even allow someone to show up at a house under the guise of being a delivery person, or conceivably allow someone to pick up an in-store order that wasn’t theirs, if strict ID checking weren’t in place. Threatpost has asked researchers for their take on the seriousness of the issue and will update this post accordingly.
Home Depot was the subject of one of the most high-profile data breaches ever to come to light, with 50 million credit card numbers stolen and 53 million email addresses pilfered by unknown attackers in 2014. The place for “doers” agreed in 2018 to pay $19.5 million to compensate the victims of the incident, which stemmed from attackers using compromised vendor credentials to gain access to its network and then the company’s point-of-sale system.
Oracle WebLogic Server RCE Flaw Under Active Attack
30.10.20 Attack Threatpost
The flaw in the console component of the WebLogic Server, CVE-2020-14882, is under active attack, researchers warn.
If an organization hasn’t updated their Oracle WebLogic servers to protect them against a recently disclosed RCE flaw, researchers have a dire warning: “Assume it has been compromised.”
Oracle WebLogic Server is a popular application server used in building and deploying enterprise Java EE applications. The console component of the WebLogic Server has a flaw, CVE-2020-14882, which ranks 9.8 out of 10 on the CVSS scale. According to Oracle, the attack is “low” in complexity, requires no privileges and no user interaction and can be exploited by attackers with network access via HTTP.
The flaw was fixed by Oracle in the massive October release of its quarterly Critical Patch Update (CPU), which fixed 402 vulnerabilities across various product families. Supported versions that are affected are 10.3.6.0.0, 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0 and 14.1.1.0.0.
The October update was released Oct. 21. Fast forward to this week, Johannes B. Ullrich, dean of research at the SANS Technology Institute, said on Thursday that based on honeypot observations, cybercriminals are now actively targeting the flaw.
“At this point, we are seeing the scans slow down a bit,” said Ullrich in a Thursday post. “But they have reached ‘saturation’ meaning that all IPv4 addresses have been scanned for this vulnerability. If you find a vulnerable server in your network: Assume it has been compromised.”
Ullrich said, the exploits appear to be based on a Wednesday blog post published (in Vietnamese) by “Jang,” who described how to leverage the flaw to achieve remote code execution via only one GET request. Below is a proof of concept (POC) video.
Ullrich said, exploit attempts on the honeypots so far originate from four IP addresses: 114.243.211.182, 139.162.33.228, 185.225.19.240 and 84.17.37.239.
Ullrich and others are urging Oracle WebLogic Server users to update their systems as soon as possible. Users can find a patch availability document for WebLogic and other vulnerable Oracle products, available here.
Oracle WebLogic servers continue to be hard hit with exploits. In May 2020, Oracle urged customers to fast-track a patch for a critical flaw in its WebLogic Server under active attack. The company said it has received numerous reports that attackers were targeting the vulnerability patched last month. In May 2019, researchers warned that malicious activity exploiting a recently disclosed Oracle WebLogic critical deserialization vulnerability (CVE-2019-2725) was surging – including to spread the “Sodinokibi” ransomware. In June 2019, Oracle said that a critical remote code execution flaw in its WebLogic Server (CVE-2019-2729) was being actively exploited in the wild.
Bug-Bounty Awards Spike 26% in 2020
30.10.20 Security Threatpost
The most-rewarded flaw is XSS, which is among those that are relatively cheap for organizations to identify.
Cross-site scripting (XSS) remained the most impactful vulnerability and thus the one reaping the highest rewards for ethical hackers in 2020 for a second year running, according to a list of top 10 vulnerabilities released on Thursday by HackerOne.
The vulnerability — which enables attackers to inject client-side scripts into web pages viewed by other users — earned hackers $4.2 million in total bug-bounty awards in the last year, a 26-percent increase from what was paid out in 2019 for finding XSS flaws, according to the report.
Following XSS on the ethical hacking company’s list of “Top 10 Most Impactful and Rewarded Vulnerability Types of 2020” are: Improper access control, information disclosure, server-side request forgery (SSRF), insecure direct object reference (IDOR), privilege escalation, SQL injection, improper authentication, code injection and cross-site request forgery (CSRF).
In total, organizations paid ethical hackers $23.5 million in bug bounties for all of these flaws this year, according to HackerOne, which maintains a database of 200,000 vulnerabilities found by hackers.
Attackers use XSS vulnerabilities to gain control of an online user’s account and steal personal information such as passwords, bank account numbers, credit card info, personally identifiable information (PII), Social Security numbers and the like. While they account for 18 percent of all reported vulnerabilities, ethical hackers are actually underpaid for finding them, according to HackerOne.
A bug-bounty award for an XSS flaw is about $501, well below the $3,650 average award for a critical flaw, allowing organizations to mitigate the common bug on the cheap, researchers noted.
Indeed, researchers found that the more common a vulnerability is, the less ethical hackers are paid — and thus the less that organizations pay out — to locate and mitigate it, observed HackerOne senior director of product management, Miju Han.
“Finding the most common vulnerability types is inexpensive,” he said in a press statement, noting that only three of the top 10 vulnerabilities on the list — improper access control, server-side request forgery (SSRF) and information disclosure — saw their average bounty awards rise more than 10 percent over the course of the year.
This demonstrates that using ethical hackers to sniff out bugs potentially can be a more cost-effective value proposition for organizations than implementing “traditional security tools and methods, which become more expensive and cumbersome as goals change and attack surface expands,” Han said.
Of the vulnerabilities that saw their stock rise in 2020, improper access control rose from ninth place to second, and information disclosure, which held steady in third place for commonality, became more valuable on the bug-bounty market, researchers noted.
Awards for improper access control increased 134 percent year over year to slightly more than $4 million, while bug bounties for information disclosure rose 63 percent year over year.
Because access-control design decisions have to be made by humans, not technology, the potential for errors is high, researchers said. These flaws also are nearly impossible to detect using automated tools, which makes an ethical hacker’s ability to identify them more valuable, they said.
Indeed, even large tech companies who were historically resistant to being transparent about their product’s security protocols have warmed to the idea of awarding ethical hackers for their work. Both Apple and ByteDance’s TikTok rolled out public, award-based bug-bounty programs in the last 12 months.
Han noted that the boost in interest in ethical hacking in 2020 also has come due to the increased digitalization of organizations’ products and services due to the COVID-19 pandemic and its stay-at-home orders.
“Businesses scrambled to find new revenue streams, creating digital offerings for customers whose lifestyles had dramatically changed,” he said in the statement. “Tens of millions of workers started working remotely whether or not they were ready.”
This “accelerated pace of digital transformation” gave security leaders a new perspective on using ethical hacking to augment existing security resources, making them more willing to support a pay-for-results-based approach, Han added.
Xfinity, McAfee Brands Abused by Parked Domains in Active Campaigns
30.10.20 Virus Threatpost
Malicious redirection websites are using typosquatting and impersonation to attack unwary visitors.
Parked domains, which act as aliases and redirect to other websites, can send visitors to malicious or unwanted landing pages or turn entirely malicious at any point in time – as evidenced by a recent Emotet campaign, a separate effort abusing Comcast and McAfee brands, and an election-themed attack.
Researchers at Palo Alto Networks in an analysis on Thursday noted that domain-parking usually happens in the service of advertising. If someone is searching for “Bread Depot,” (a fictitious example, by the way), the person may end up on Bread Depot.net instead of the official BreadDepot.com, because it popped up in the search results. And if BreadDepot.net is a parked domain that was created in hopes of people making that mistake, it could redirect visitors to a page full of ads in order to drive impressions.
“Parking services either show users a list of ads (and get paid based on the number of user clicks on these ads) or redirect users automatically to the advertisers’ webpages (and get paid based on the number of user visits),” according to Palo Alto Networks. “Often, the parking services and the advertisement networks do not have the means or willingness to filter abusive advertisers (i.e. attackers). Therefore, users are exposed to various threats, such as malware distribution, potentially unwanted program (PUP) distribution and phishing scams. In our experience, we most frequently observe the distribution of grayware.”
That’s shady enough, but sometimes, parked domains are crafted to be malicious from the get-go.
As an example, Palo Alto Networks laid out a domain-parking campaign that was used as part of a global Emotet initiative. Emotet is a trojan that acts as a first-stage malware, capable of fetching and downloading a collection of malware on victim machines, including information stealers, email harvesters, self-propagation mechanisms and ransomware.
In this campaign, a domain called valleymedicalandsurgicalclinic[.]com, which is no longer active, redirected visitors to a malicious page that delivered Emotet. The domain was one of many being used around the world, researchers said, serving up attacks against organizations in various industries (such as education, government, energy, manufacturing, construction and telecommunications), including in France, Italy, Japan, Korea, the U.K. and the U.S.
As mentioned, parked domains usually host or redirect to lists of ads. Such is the case with the still-active domain peoplesvote[.]uk, which claims to be related to the U.S. presidential election. While visiting peoplesvote[.]uk, users are presented with an ad-listing page most of the time. Randomly however, some visitors are sent to a page that hosted an exploit-kit script, before being redirected again to a survey website asking about users’ voting preference between Joe Biden or Donald Trump.
“The exploit-kit script hosted on 0redira[.]com/jr.php fingerprints the browser silently to track users’ web activity and hides the landing URLs to prevent security companies and researchers from analyzing and blocking them,” according to Palo Alto Networks’ analysis, released Thursday.
In yet another case, a still-active typoquatted domain, xifinity[.]com, closely mimics the spelling of Comcast’s xfinity.com website for residential cable customers. When users attempt to visit the real (and highly trafficked) Xfinity website, but accidentally mistype an additional “i,” they’ll be redirected to a suspicious landing page that purports to be owned by McAfee. That page, antivirus-protection[.]com-123[.]xyz, is also still active.
“The landing page tries to fool users into believing that their machine is infected and that their McAfee subscription has expired,” explained the researchers. “Clicking on the ‘Proceed’ button will redirect users to a legitimate McAfee download page offering an antivirus subscription. We believe that attackers are abusing McAfee’s affiliate program to steal ad revenue.”
In looking further into the volume of parked domains out on the web, Palo Alto Networks found that 27,000 newly parked domains are on average identified daily. Overall, the firm has identified 5 million newly parked domains in the past six months.
In the same time frame, the firm observed that 6 million parked domains have transitioned in terms of their classification. For instance, 1 percent were flagged as being malicious (known to host phishing or malware campaigns) after being classified as benign; almost 3 percent changed to not-safe-for-work categories (such as adult or gambling); and 31 percent were changed to being deemed “suspicious.”
Researchers noted that security best practice for enterprises is to keep close track of parked domains, while consumers should make sure that they type domain names correctly and double-check that the domain owners are trusted before entering any site.
US Cyber Command details implants used in attacks on parliaments and embassies
30.10.20 BigBrothers Securityaffairs
US Cyber Command published technical details on malware implants used by Russia-linked APTs on multiple parliaments, embassies
US Cyber Command shared technical details about malware implants employed by Russian hacking groups in attacks against multiple ministries of foreign affairs, national parliaments, and embassies.
Experts from the US Cyber Command’s Cyber National Mission Force (CNMF) unit and the Cybersecurity and Infrastructure Security Agency (CISA) uploaded the samples on the Virus Total online virus scan platform.
CISA also published two joint advisories with the FBI and CNMF that provides info regarding the ComRAT and Zebrocy malware that were used by Russia-linked APT groups, including the APT28 and Turla.
The Turla APT group (aka Snake, Uroburos, Waterbug, Venomous Bear and KRYPTON) has been active since at least 2007 targeting diplomatic and government organizations and private businesses in the Middle East, Asia, Europe, North and South America, and former Soviet bloc nations.
The list of previously known victims is long and includes also the Swiss defense firm RUAG, US Department of State, NASA and the US Central Command.
“FBI has high-confidence that Russian-sponsored APT actor Turla, which is an espionage group active for at least a decade, is using ComRAT malware to exploit victim networks. The group is well known for its custom tools and targeted operations.” reads the advisory published CISA.
Russia-linked cyberespionage groups utilized the Zebrocy backdoor in attacks aimed at embassies and ministries of foreign affairs from Eastern Europe and Central Asia.
“Two Windows executables identified as a new variant of the Zebrocy backdoor were submitted for analysis. The file is designed to allow a remote operator to perform various functions on the compromised system.” reads the CISA’s advisory.
Zebrocy is known to be a malware of the APT28’s arsenal, a Russia linked APT group working under the control of the Russian Main Intelligence Directorate (GRU).
FBI, CISA alert warns of imminent ransomware attacks on healthcare sector
30.10.20 Ransomware Securityaffairs
FBI and the DHS’s CISA agencies published a joint alert to warn hospitals and healthcare providers of imminent ransomware attacks from Russia.
The FBI, the DHS’s Cybersecurity and Infrastructure Security Agency (CISA), and the Department of Health and Human Services (HHS) has issued a joint alert to warn hospitals and healthcare providers of imminent ransomware attacks from Russia.
This security advisory describes the tactics, techniques, and procedures (TTPs) associated with cyber criminals that could target organizations in the Healthcare and Public Health Sector (HPH) to infect systems with Ryuk ransomware.
The government agencies receive information about imminent attacks, threat actors are using the TrickBot botnet to deliver the infamous ransomware to the infected systems.
“CISA, FBI, and HHS have credible information of an increased and imminent cybercrime threat to U.S. hospitals and healthcare providers. CISA, FBI, and HHS are sharing this information to provide warning to healthcare providers to ensure that they take timely and reasonable precautions to protect their networks from these threats.” reads the alert.
TrickBot is a popular banking Trojan that has been around since October 2016, its authors have continuously upgraded it by implementing new features.

In early 2019, researchers spotted a new TrickBot backdoor framework dubbed Anchor that was using the anchor_dns tool for abusing the DNS protocol for C2 communications.
Several groups of experts linked both TrickBot and Ryuk threats to cybercrime gangs operating out of Russia. Ryuk first appeared in the threat landscape in August 2018 as a derivative of the Hermes 2.1 ransomware, that was first spotted in late 2017 and was available for sale on the open market as of August 2018
Unlike other ransomware gangs, Ryuk ransomware operators did not announce to avoid targeting healthcare organizations during the COVID-19
A few weeks ago, Universal Health Services (UHS), one of the largest hospital and healthcare services providers, has shut down systems at healthcare facilities in the United States after they were infected with the Ryuk ransomware.
A few days ago, Microsoft’s Defender team, FS-ISAC, ESET, Lumen’s Black Lotus Labs, NTT, and Broadcom’s cyber-security division Symantec joined the forces and announced a coordinated effort to take down the command and control infrastructure of the infamous TrickBot botnet.
Microsoft has taken down 120 of the 128 servers that were composing the Trickbot infrastructure.
Microsoft announced to have taken down 62 of the original 69 TrickBot C&C servers, seven servers that could not be brought down last week were Internet of Things (IoT) devices.
Threat actors are actively exploiting Zerologon flaw, Microsoft warns
30.10.20 Exploit Securityweek
Microsoft researchers are warning that threat actors are continuing to actively exploit the ZeroLogon vulnerability in attacks in the wild.
Microsoft is warning that threat actors are actively exploiting the ZeroLogon vulnerability in the Netlogon Remote Protocol.
The CVE-2020-1472 flaw is an elevation of privilege that resides in the Netlogon. The Netlogon service is an Authentication Mechanism used in the Windows Client Authentication Architecture which verifies logon requests, and it registers, authenticates, and locates Domain Controllers.
An attacker could exploit the vulnerability to impersonate any computer, including the domain controller itself, and execute remote procedure calls on their behalf.
An attacker could also exploit the flaw to disable security features in the Netlogon authentication process and change a computer’s password on the domain controller’s Active Directory.
“Microsoft has received a small number of reports from customers and others about continued activity exploiting a vulnerability affecting the Netlogon protocol (CVE-2020-1472) which was previously addressed in security updates starting on August 11, 2020.” reads a post published by MSRC VP of Engineering Aanchal Gupta. “If the original guidance is not applied, the vulnerability could allow an attacker to spoof a domain controller account that could be used to steal domain credentials and take over the domain.”
Microsoft strongly encourages administrators of enterprise Windows Servers to install the August 2020 Patch Tuesday as soon as possible to protect their systems from Zerologon attack that exploits the CVE-2020-1472.
Because the initial documentation regarding Zerologon patching process was not clear enough, Microsoft provided the following updates:
UPDATE your Domain Controllers with an update released August 11, 2020 or later.
FIND which devices are making vulnerable connections by monitoring event logs.
ADDRESS non-compliant devices making vulnerable connections.
ENABLE enforcement mode to address CVE-2020-1472 in your environment.
At the end of September, Microsoft issued a similar warning. The IT giant published a series of Tweets to warn of attackers that are actively exploiting the Windows Server Zerologon in attacks in the wild. The IT giant urged Windows administrators to install the released security updates as soon as possible.
In early October, Microsoft spotted a series of Zerologon attacks allegedly launched by the Russian cybercrime group tracked as TA505, CHIMBORAZO and Evil Corp.
Microsoft experts spotted the Zerologon attacks involving fake software updates, the researchers noticed that the malicious code connected to command and control (C&C) infrastructure known to be associated with TA505.
In the same period, Microsoft published a post and a series of tweets to warn of cyber attacks exploiting the Zerologon vulnerability carried out by the Iran-linked APT group known as MuddyWater, aka Mercury.
On September 18, The Department of Homeland Security’s CISA issued an emergency directive to order government agencies to address the Zerologon vulnerability (CVE-2020-1472) by September 21.
Community College Continues to Investigate Cyberattack
30.10.20 Attack Securityweek
A data breach at a North Carolina community college may have affected many of its current and former students.
The Greensboro News & Records reported Tuesday that Guilford Technical Community College was hit with a ransomware cyberattack in mid-September.
The college said it’s investigating the cyberattack “to determine what happened and to remediate impacted systems.” State agencies, cybersecurity experts and the Federal Bureau of Investigation have provided assistance.
The college said it has contacted students, faculty and staff members who were potentially affected. It said it will offer credit monitoring and identity restoration services for a year.
The college declined further comment further “due to the ongoing nature of this investigation.”
GTCC discovered the data breach Sept. 14.
Microsoft Introduces Device Vulnerability Report in Defender for Endpoint
30.10.20 Vulnerebility Securityweek
Microsoft this week announced the availability of a new vulnerability management report in Microsoft Defender, to provide information on vulnerable devices.
The new built-in report complements existing Microsoft Defender for Endpoint (previously known as Microsoft Defender Advanced Threat Protection) threat and vulnerability management capabilities and is catered for those looking to gain insights on devices that pose potential risks due to unpatched vulnerabilities. The feature is currently in preview version.
“The Vulnerable devices report provides extensive insights into your organization’s vulnerable devices with summaries of the current status and customizable trends over time,” Microsoft explains.
Within the report, organizations can access information on the vulnerability security levels of devices, availability of exploits for devices with vulnerabilities, and the age of unpatched security flaws, as well as a list of vulnerable devices, organized by operating system or by Windows 10 version.
Both graphs and bar charts are available in the report, to deliver information on device trends (allows selection of multiple time ranges) and current statistics (only information for the current day).
Data can be filtered based on vulnerability severity or age, availability of exploits, device group, or platform. Additional information can be accessed through selecting a specific bar chart.
According to Microsoft, in each specific graph, devices are only counted once.
The new report is available in the Microsoft Defender Security Center and can be accessed from Reports > Vulnerable devices, but only for those organizations that have the public preview feature enabled.
“This preview version is provided without a service level agreement, and it's not recommended for production workloads. Certain features might not be supported or might have constrained capabilities,” Microsoft notes.
Oracle WebLogic Vulnerability Targeted One Week After Patching
30.10.20 APT Vulnerebility
A vulnerability patched one week ago by Oracle in its WebLogic Server product has already been targeted for exploitation.
The security hole, tracked as CVE-2020-14882 and classified as critical, was patched by Oracle with its October 2020 Critical Patch Update (CPU). The vulnerability can be exploited remotely and without authentication, allowing an attacker to execute arbitrary code.
The issue was reported to Oracle by a researcher at China-based Chaitin Security Research Lab. On Wednesday, a Vietnamese researcher named Jang published a blog post detailing CVE-2020-14882 (written in Vietnamese) and he showed how easily it can be exploited by sending a specially crafted request to the targeted server.
The SANS Technology Institute reported on Thursday that its honeypots have recorded attempts to exploit this WebLogic vulnerability. Johannes B. Ullrich, dean of research at SANS, said the exploitation attempts appeared to be based on the PoC made public by the Vietnamese researcher.
Ullrich said the attacks that hit SANS honeypots only checked if the system was vulnerable, but others reported seeing exploitation attempts that involved downloading an executable file from a remote server and running it.
The attacks seen by SANS came from four IP addresses assigned to organizations in China, the US and Moldova.
“At this point, we are seeing the scans slow down a bit. But they have reached ‘saturation’ meaning that all IPv4 addresses have been scanned for this vulnerability,” Ullrich said. “If you find a vulnerable server in your network: Assume it has been compromised.”
Oracle WebLogic Server vulnerabilities are often targeted by threat actors, including profit-driven cybercriminals and state-sponsored groups. Many of these vulnerabilities are exploited after they are patched, but hackers exploiting zero-days is not unheard of.
Shortly after the April 2020 CPU was released, Oracle warned customers that a critical WebLogic vulnerability, one that was disclosed to the vendor by multiple researchers, including Jang, had been exploited in the wild.
NVIDIA Patches AMI BMC Vulnerabilities Impacting Several Major Vendors
30.10.20 APT Vulnerebility
NVIDIA on Wednesday released patches to address a total of nine vulnerabilities impacting NVIDIA DGX servers.
NVIDIA’s DGX systems are designed for enterprise AI applications. All of the bugs were found in the AMI Baseboard Management Controller (BMC) firmware running on the affected devices. This means the vulnerabilities are not specific to NVIDIA and they impact the products of several other vendors as well.
The vulnerabilities were reported to NVIDIA by members of the SCADA StrangeLove project, which focuses on ICS/SCADA security, as part of their research into machine learning infrastructure vulnerabilities.NVIDIA DGX vulnerabilities
One of the security flaws has been rated critical, five of them are high severity, two are considered medium severity, and one of them is low severity.
The most important of the bugs is related to the inclusion of hardcoded credentials in the AMI BMC firmware of NVIDIA DGX servers. Tracked as CVE‑2020‑11483, the issue has a CVSS score of 9.8 and exploitation could result in elevation of privileges or information leakage.
Next in line is CVE‑2020‑11484, a vulnerability that could allow an attacker that has administrative privileges to obtain the hash of the BMC/IPMI user password. Featuring a CVSS score of 8.4, the security bug could be exploited to access otherwise restricted information.
The third flaw could lead to information disclosure too. Tracked as CVE‑2020‑11487 (CVSS score 8.2), it exists due to the use of a hardcoded RSA 1024 key with weak ciphers.
With a CVSS score of 8.1, the next two vulnerabilities could lead to remote code execution.
The first of them, CVE‑2020‑11485, is a Cross-Site Request Forgery (CSRF) bug that exists because the web application “does not sufficiently verify whether a well-formed, valid, consistent request was intentionally provided by the user who submitted the request,” and which could also lead to information disclosure.
The second, CVE‑2020‑11486, could be abused by attackers “to upload or transfer files that can be automatically processed within the product's environment,” NVIDIA notes in its advisory.
Another high-risk bug that NVIDIA addressed this week is CVE‑2020‑11615 (CVSS score 7.5), where a hardcoded RC4 cipher key used within the firmware could lead to information disclosure.
The medium-severity flaws that NVIDIA patched could lead to information disclosure. The first of them, CVE‑2020‑11488, resides in the RSA 1024 public key used for firmware signature verification not being validated, while the second, CVE‑2020‑11489, exists due to the use of default SNMP community strings.
Last on the list is CVE‑2020‑11616, a low-severity flaw that exists because “the Pseudo-Random Number Generator (PRNG) algorithm used in the JSOL package that implements the IPMI protocol is not cryptographically strong.” Exploitation of the flaw could lead to information disclosure.
NVIDIA says exploitation of these vulnerabilities requires network access to the BMC of the DGX server.
These security holes were found to affect NVIDIA DGX-1, DGX-2, and DGX A100 servers. However, while DGX-1 servers are impacted by all bugs, only some of them affect DGX-2 products and DGX A100 is impacted by a single flaw.
BMC firmware 3.38.30 addresses the issues for DGX-1 servers and BMC firmware 1.06.06 patches the bugs in DGX-2 servers. An update for DGX A100 servers will become available in the second quarter of 2021.
Since the vulnerabilities were found in AMI BMC firmware, SCADA StrangeLove says other vendors appear to be impacted as well, including ASRock Rack, ASUS, DEPO Computers, Gigabyte, Gooxi, Hewlett Packard Enterprise, IBM, Lenovo, Mikrobits (Mikrotik), NetApp, Quanta Computer, and TYAN Computer.
Contacted by SecurityWeek, AMI said it has a close working relationship with NVIDIA, as well as all the other major silicon vendors in the US and abroad. The company said it contracted a third-party security firm to audit its firmware and these vulnerabilities were discovered before NVIDIA brought them to AMI’s attention. Patches have been developed and distributed to customers.
“From our perspective, this incident shows the complexity of the security paradigm in our industry, which requires the industry to work closely together to collaborate, so that we can address these security issues collectively. Over the years, AMI has come up with what we believe to be a robust security framework, which allows us to keep tabs on the security vulnerabilities that are relevant to AMI products, so we can take immediate action. We work together with industry partners on fixes which AMI then distributes to our customers; keeping in close coordination with our partners also makes it easy for AMI customers to apply the fixes that we have developed,” AMI said in an emailed statement.
It added, “In fact, AMI has been working on various mechanisms to simplify this entire process of creating and applying security fixes and patches to vulnerabilities. From our perspective, we don’t see the threat of security issues going away in the future, so we see ourselves as a partner to all silicon manufacturers in many technical and strategic initiatives over the course of many years and we will continue to do so, also to address security vulnerabilities in a timely, coordinated and effective manner.”
Iran-linked Phosphorous APT hacked emails of security conference attendees
29.10.20 APT Securityaffairs
Iran-linked APT group Phosphorus successfully hacked into the email accounts of multiple high-profile individuals and security conference attendees.
Microsoft revealed that Iran-linked APT Phosphorus (aka APT35, Charming Kitten, Newscaster, and Ajax Security Team) successfully hacked into the email accounts of multiple high-profile individuals and attendees at this year’s Munich Security Conference and the Think 20 (T20) summit.
“Today, we’re sharing that we have detected and worked to stop a series of cyberattacks from the threat actor Phosphorous masquerading as conference organizers to target more than 100 high-profile individuals.” reads the post published by Microsoft. “Phosphorus, an Iranian actor, has targeted with this scheme potential attendees of the upcoming Munich Security Conference and the Think 20 (T20) Summit in Saudi Arabia.”
Nation-state actors successfully targeted over 100 individuals, including former ambassadors and other senior policy experts.
According to the experts at Microsoft Security Intelligence Center, the attacks are part of a cyber-espionage campaign aims at gathering intelligence on the victims by exfiltrating data from their mailboxs and contact list.
Data was exfiltrated to the de-ma[.]online domain, and the g20saudi.000webhostapp[.]com, and ksat20.000webhostapp[.]com subdomains.
The attackers have been sending spoofed email invitations to to former government officials, policy experts, academics, and leaders from non-governmental organizations. Attackers attempted to exploit the fears of travel during the Covid-19 pandemic by offering remote sessions.
The emails were written in almost perfect English.
Experts believe that this campaign is not tied to the upcoming U.S. Presidential elections.
Microsoft experts have worked with conference organizers who are warning their attendees about the ongoing attacks and suggesting them to remain vigilant to this approach being used in connection with other conferences or events.
“We recommend people evaluate the authenticity of emails they receive about major conferences by ensuring that the sender address looks legitimate and that any embedded links redirect to the official conference domain. As always, enabling multi-factor authentication across both business and personal email accounts will successfully thwart most credential harvesting attacks like these.” suggest Microsoft. “For anyone who suspects they may have been a victim of this campaign, we also encourage a close review of email-forwarding rules in accounts to identify and remove any suspicious rules that may have been set during a successful compromise.”
The Phosphorus group made the headlines in 2014 when experts at iSight issued a report describing the most elaborate net-based spying campaign organized by Iranian hackers using social media.
Microsoft has been tracking the threat actors at least since 2013, but experts believe that the cyberespionage group has been active since at least 2011. In past campaigns, the APT group launched spear-phishing attacks against activists and journalists focusing on the Middle East, US organizations, and entities located in Israel, the U.K., Saudi Arabia, and Iraq.
Recently Microsoft published a post and a series of tweets to warn of cyber attacks exploiting the Zerologon vulnerability carried out by the Iran-linked APT group known as MuddyWater, aka Mercury.
The IT giant also warned of cyber espionage campaigns carried out by other nation state-sponsored hacking groups operating from Russia and China targeting organizations and individuals involved in this year’s U.S. presidential election.
Russia-linked Turla APT hacked European government organization
29.10.20 APT Securityaffairs
Russia-linked APT Turla has hacked into the systems of an undisclosed European government organization according to Accenture.
According to a report published by Accenture Cyber Threat Intelligence (ACTI), Russia-linked cyber-espionage group Turla has hacked into the systems of an undisclosed European government organization.
The Turla APT group (aka Snake, Uroburos, Waterbug, Venomous Bear and KRYPTON) has been active since at least 2007 targeting diplomatic and government organizations and private businesses in the Middle East, Asia, Europe, North and South America, and former Soviet bloc nations.
The list of previously known victims is long and includes also the Swiss defense firm RUAG, US Department of State, and the US Central Command.
The attack against the undisclosed European government organization is in line with the APT’s espionage motivation, the attacker utilized a combination of remote procedure call (RPC)-based backdoors, such as HyperStack and remote administration trojans (RATs), such as Kazuar and Carbon. ACTI researchers observed the attacks between June and October 2020.
“Notably, Accenture researchers recently identified novel command and control (C&C) configurations for Turla’s Carbon and Kazuar backdoors on the same victim network.” reads the report published by Accenture. “The Kazuar instances varied in configuration between using external C&C nodes off the victim network and internal nodes on the affected network, and the Carbon instance had been updated to include a Pastebin project to receive encrypted tasks alongside its traditional HTTP C&C infrastructure.”
HyperStack is one of several RPC backdoors in the Turla’s arsenal that was first observed in 2018, it is a custom implant developed by the ATP group.
HyperStack leverages named pipes to execute remote procedure calls (RPC) from the command end control to the device running the HyperStack client. Lateral movements are implemented attempting to connect to another remote device’s IPC$ share, either using a null session or default credentials.
“IPC$ is a share that facilitates inter-process communication (IPC) by exposing named pipes to write to or read from. If the implant’s connection to the IPC$ is successful, the implant can forward RPC commands from the controller to the remote device, and likely has the capability to copy itself onto the remote device.” continues the report.
Turla uses a variety of command and control (C&C) implementations for each compromise in an attempt to be resilient to countermeasures implemented by the defenders. The Russia-linked APT group has relied on bot compromised web servers as C&C and legitimate web services like Pastebin as C2. One of the Kazuar sample analyzed by the experts was configured to receive commands sent through likely internal nodes in the government’s network.
Turla continues to extensively use the modular Carbon backdoor framework with advanced peer-to-peer capability. One of the Carbon backdoor analyzed by the researchers used the traditional threat actor-owned C&C infrastructure with tasks served from Pastebin. ACTI analysts discovered a Carbon installer that dropped a Carbon Orchestrator, two communication modules, and an encrypted configuration file.
ACTI also shared Indicators of Compromise (IoCs) for this attack to allow Government entities to check for evidence of compromise within their networks.
“Turla will likely continue to use its legacy tools, albeit with upgrades, to compromise and maintain long-term access to its victims because these tools have proven successful against Windows-based networks,” concludes Accenture.
Microsoft Says Iranian Hackers Targeted Attendees of Major Global Policy Conferences
29.10.20 BigBrothers Securityweek
The Iran-linked state-sponsored threat group known as Charming Kitten was observed targeting potential attendees of two major international conferences, Microsoft reports.
Also referred to as Phosphorous, APT35, Ajax Security Team, ITG18, NewsBeef, and NewsCaster, the threat actor is believed to have been active since at least 2011, targeting entities in the Middle East, the United States, and the United Kingdom.
Recently observed attacks, Microsoft says, targeted over 100 high-profile individuals, potential attendees of two upcoming global policy conferences, namely the Munich Security Conference and the Think 20 (T20) Summit, which is held in Saudi Arabia.
“Based on current analysis, we do not believe this activity is tied to the U.S. elections in any way,” Microsoft reveals.
As part of the assaults, the hackers would masquerade as conference organizers, sending spoofed email invitations to individuals potentially interested in attending. Written in near-perfect English, the emails were sent to academics, former government officials, policy experts, and leaders of non-governmental organizations.
Charming Kitten, the tech company explains, offered remote sessions to potential victims, thus lowering fears associated with travel during the coronavirus pandemic.
The attacks are believed to have been orchestrated for intelligence gathering, with several victims successfully compromised. These include former ambassadors and other senior policy experts.
“We’ve already worked with conference organizers who have warned and will continue to warn their attendees, and we’re disclosing what we’ve seen so that everyone can remain vigilant to this approach being used in connection with other conferences or events,” Microsoft explains.
To stay protected from similar attacks, users are advised to evaluate the authenticity of received messages, use multi-factor authentication, review email-forwarding rules, and enroll in advanced protection programs, where possible.
Microsoft, which has published indicators of compromise (IoC) related to the attacks, underlines that nation-state hackers routinely pursue governmental and non-governmental entities, think tanks, and policy organizations.
“We will continue to use a combination of technology, operations, legal action and policy to disrupt and deter malicious activity, but nothing replaces vigilance from people who are likely targets of these operations,” the company concludes.
U.S. Hospitals Warned of Imminent Ransomware Attacks From Russia
29.10.20 Ransomware Securityweek
The U.S. government has warned hospitals and healthcare providers of an “increased and imminent” ransomware threat, which some experts have attributed to cybercriminals from Eastern Europe.
The alert was issued on Wednesday by the FBI, the DHS’s Cybersecurity and Infrastructure Security Agency (CISA), and the Department of Health and Human Services (HHS). The organizations say they’ve received credible information that threat actors are targeting the healthcare sector with the TrickBot malware in attacks that often lead to ransomware infections, data theft and disruption of healthcare services.
The alert focuses on TrickBot, particularly the Anchor evasion detection modules used in attacks aimed at high-profile organizations, and the Ryuk ransomware, which has often been delivered using the TrickBot botnet. Both TrickBot and Ryuk were previously linked to threat actors operating out of Russia.
Charles Carmakal, SVP and CTO of Mandiant, described it as “the most significant cyber security threat we’ve ever seen in the United States.”
“UNC1878, an Eastern European financially motivated threat actor, is deliberately targeting and disrupting U.S. hospitals, forcing them to divert patients to other healthcare providers. Patients may experience prolonged wait time to receive critical care,” Carmakal told SecurityWeek. “Multiple hospitals have already been significantly impacted by Ryuk ransomware and their networks have been taken offline. UNC1878 is one of most brazen, heartless, and disruptive threat actors I’ve observed over my career.”
While some ransomware operators have decided to avoid targeting healthcare organizations during the COVID-19 pandemic, that does not seem to be the case for Ryuk operators, who, according to what intelligence firm Hold Security told blogger Brian Krebs, have been planning on deploying ransomware at over 400 healthcare facilities in the United States.
According to various local media reports, several hospitals in the United States reported being hit by ransomware over the past days. A few weeks ago, hospital chain Universal Health Services reported that computers at all 250 of its US facilities were disrupted due to a cyberattacks that is believed to have involved Ryuk.
The TrickBot botnet was recently targeted for takedown by Microsoft and its partners, and in a separate operation by the U.S. government. While the operations appear to have been successful, at least to some extent, Ryuk attacks have continued.
Microsoft Defender ATP Users Get False Positive Alerts for Mimikatz, Cobalt Strike
29.10.20 Safety Securityweek
Microsoft rushed to take action on Wednesday after Defender Advanced Threat Protection (ATP) users reported getting Cobalt Strike and Mimikatz alerts that turned out to be false positives.
Cobalt Strike is a commercial penetration testing tool. However, it has often been abused by malicious actors for its advanced capabilities, including in Ryuk, Sodinokibi and other ransomware attacks.
Mimikatz is a post-exploitation tool designed for harvesting passwords from compromised systems. It too has been used by many profit-driven and state-sponsored threat groups.
It’s not surprising that some Microsoft Defender ATP users had a small heart attack on Wednesday when they saw multiple high-severity alerts for Cobalt Strike. Others reported seeing Mimikatz alerts. In both cases they turned out to be false positives.
The issue was likely caused by a bad rule pushed to Defender ATP and Microsoft addressed the issue within hours.
“We’ve addressed the issue that led to false positive alerts and corrected notifications some customers may have received,” a Microsoft spokesperson told SecurityWeek.
However, Jon Hencinski, director of SecOps at cybersecurity company Expel and one of the people who monitored the incident, advised organizations not to immediately dismiss Cobalt Strike alerts in Defender ATP and instead follow their triage process as normal.
Turla Cyber-Spies Target European Government With Multiple Backdoors
29.10.20 CyberSpy Securityweek
The Russia-linked cyber-espionage group known as Turla was recently observed targeting a European government organization with a combination of backdoors, security researchers at Accenture reveal.
Also known as Snake, Waterbug, Venomous Bear, Belugasturgeon, and KRYPTON, Turla is believed to have been active since at least 2006. Earlier this year, the threat actor updated ComRAT, one of its oldest malware families, to ensure it remains efficient.
In a report published this week, Accenture notes that the hackers continue to update legacy tools and to employ custom malware in attacks targeting government organizations.
In fact, in a recent attack on such an organization in Europe, Turla was observed employing a combination of remote procedure call (RPC)-based backdoors, including the HyperStack backdoor, and Kazuar and Carbon remote administration Trojans (RATs).
“The RATs transmit the command execution results and exfiltrate data from the victim's network while the RPC-based backdoors use the RPC protocol to perform lateral movement and issue and receive commands on other machines in the local network. These tools often include several layers of obfuscation and defense evasion techniques,” Accenture explains.
Given the success registered using this combination of tools, Turla is expected to continue employing the ecosystems for the targeting of Windows-based networks. The threat actor was also observed employing various command and control (C&C) implementations for each compromise, to ensure it can regain access if discovered.
The HyperStack backdoor, which was initially identified in 2018, features updated functionality, and employs named pipes for RPC execution. For lateral movement, it attempts to connect to a remote device’s IPC$ share to forward RPC commands.
As part of the campaign, however, Turla was also observed using a variant of HyperStack containing simpler functionality, enabling operators to run commands via a named pipe without IPC$ enumeration.
The malware employed in this campaign revealed the use of traditional C&C implementations, such as compromised web servers and legitimate web services, including Pastebin. One Kazuar variant could receive commands sent via internal nodes in compromised network, while others employed external nodes.
“Turla will likely continue to use its legacy tools, albeit with upgrades, to compromise and maintain long term access to its victims because these tools have proven successful against windows-based networks. Government entities, in particular, should check network logs for indicators of compromise and build detections aimed at thwarting this threat actor,” Accenture concludes.
KashmirBlack Botnet Hijacks Thousands of Sites Running On Popular CMS Platforms
29.10.20 BotNet Thehackernews
An active botnet comprising hundreds of thousands of hijacked systems spread across 30 countries is exploiting "dozens of known vulnerabilities" to target widely-used content management systems (CMS).
The "KashmirBlack" campaign, which is believed to have started around November 2019, aims for popular CMS platforms such as WordPress, Joomla!, PrestaShop, Magneto, Drupal, Vbulletin, OsCommerence, OpenCart, and Yeager.
"Its well-designed infrastructure makes it easy to expand and add new exploits or payloads without much effort, and it uses sophisticated methods to camouflage itself, stay undetected, and protect its operation," Imperva researchers said in a two-part analysis.
The cybersecurity firm's six-month-long investigation into the botnet reveals a complex operation managed by one command-and-control (C2) server and more than 60 surrogate servers that communicate with the bots to send new targets, allowing it to expand the size of the botnet via brute force attacks and installation of backdoors.
The primary purpose of KashmirBlack is to abuse resources of compromised systems for Monero cryptocurrency mining and redirect a website's legitimate traffic to spam pages. But it has also been leveraged to carry out defacement attacks.
Regardless of the motive, the exploitation attempts begin with making use of PHPUnit RCE vulnerability (CVE-2017-9841) to infect customers with next-stage malicious payloads that communicate with the C2 server.
Based on the attack signature it found during once such defacements, Imperva researchers said they believed the botnet was the work of a hacker named Exect1337, a member of the Indonesian hacker crew PhantomGhost.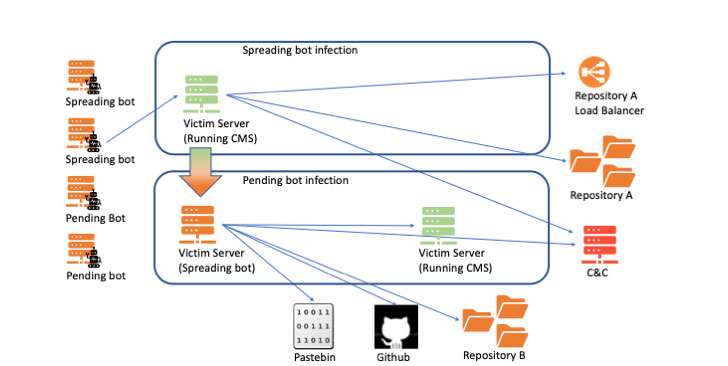
KashmirBlack's infrastructure is complex and comprises a number of moving parts, including two separate repositories — one to host exploits and payloads, and the other to store the malicious script for communication with the C2 server.
The bots themselves are either designated as a 'spreading bot,' a victim server that communicates with the C2 to receive commands to infect new victims, or a 'pending bot,' a newly compromised victim whose purpose in the botnet is yet to be defined.
While CVE-2017-9841 is used to turn a victim into a spreading bot, successful exploitation of 15 different flaws in CMS systems leads to a victim site becoming a new pending bot in the botnet. A separate WebDAV file upload vulnerability has been employed by the KashmirBlack operators to result in defacement.
But just as the botnet grew in size and more bots began fetching payloads from the repositories, the infrastructure was tweaked to make it more scalable by adding a load balancer entity that returns the address of one of the redundant repositories that were newly setup.
The latest evolution of KashmirBlack is perhaps the most insidious one. Last month, the researchers found the botnet using Dropbox as a replacement for its C2 infrastructure, abusing the cloud storage service's API to fetch attack instructions and upload attack reports from the spreading bots.
"Moving to Dropbox allows the botnet to hide illegitimate criminal activity behind legitimate web services," Imperva said. "It is yet another step towards camouflaging the botnet traffic, securing the C&C operation and, most importantly, making it difficult to trace the botnet back to the hacker behind the operation."
Trump Campaign Website Defaced by Cryptocurrency Scam
29.10.20 Cryptocurrency Threatpost
Hackers claim to have access to classified information linking the president to the origin of the coronavirus and criminal collusion with foreign actors.
UPDATE
Hackers took over President Trump’s 2020 election campaign website late Tuesday, replacing parts of the site with a cryptocurrency scam before returning it to its original content several minutes later.
Journalist Gabriel Lorenzo Greschler was the first to notice the attack while he was doing research for a climate-change article, he wrote in a tweet. The accompanying photo showed a message proclaiming “this site was seized” and “the world has had enough of the fake news spread daily by president donald j trump [sic].”
While the hacked page claimed that the threat actors responsible compromised “multiple devices” that gave them “full access” to internal and secret conversations” of “trump and relatives,” there is no evidence that these statements are true, according to the Trump campaign.
The hackers appeared to advocate the ousting of President Trump in the upcoming Nov. 3 election. They claim that the information they obtained prove that Trump and his government are “involved” in the original of the coronavirus as well as engaged in “criminal involvement and cooperation with foreign actors” that “completely discredits” the president. “The US citizens have no choice,” the hackers wrote.
Following the message, attackers posted two addresses for Monero, a cryptocurrency oft used in nefarious cyber activities because it’s easy to send yet difficult to track. Indeed, research has found that illicit Monero-mining malware accounts for more than 4 percent of the XMR in circulation, and has created $57 million in profits for threat actors.

Journalist Gabriel Lorenzo Greschler was the first to notice the attack while he was doing research for a climate-change article.
The addresses allow people to basically buy access to the data with cryptocurrency, giving people the choice of whether they want the classified data shared or not.
“After the deadline we will compare the funds and execute the will of the world,” hackers wrote. “In both cases we will inform you.”
Hackers signed the page with a PGP public key linked to an e-mail address at planet.gov–a domain that does not exist—as a way for people participating in the scam to identify them.
The Trump campaigned acknowledged the hack late Tuesday, saying that the team is working with law enforcement to investigate the source of the attack and asserting that the attackers had zero access to classified data.
“There was no exposure to sensitive data because none of it is actually stored on the site,” campaign communications director Tim Murtaugh said in a statement published on his Twitter page.
Does Trump Embrace Cybersecurity ‘Best Practices’?
Karen Walsh, cyber security compliance expert and CEO of Allegro Solutions, said it is possible the hack is tied to weak password policies and mismanaged account access.
“If Trump’s Twitter account is anything to go by, last week a security researcher ‘guessed’ his Twitter password as ‘maga2020!’ Many have speculated that Trump writes some tweets while staff write others, given the changes in tone that occur throughout the account. Ultimately, this means that we can guess he shares the password with staffers which is not considered a best practice,” wrote Walsh in an email interview with Threatpost. “Most likely, someone assumed that the website used some version of ‘maga2020!’ and manipulated the URL to get the login page. Most WordPress login pages are www[.]website.com/login so the manipulation did not need to be sophisticated.”
One medical professional and Twitter user responded to Murtaugh’s tweet with doubt about the Trump administration’s overall capability to provide security and protection not just online but for the American people.
“If Trump can’t even secure his own campaign website, then how can he secure the country?” tweeted Dr. Eugene Gu, founder and CEO of CoolQuit. “If he can’t protect himself from the coronavirus, how can he protect everyone else? What a joke.”
Big POTUS Target
The hack is not the first time threat attackers have targeted President Trump during the run up to next week’s election. Earlier this month, his Twitter account was allegedly accessed by Dutch ethical hacker Victor Gevers solely by guessing his password, “maga2020!.”
Meanwhile about a year ago, Microsoft researchers observed a group of hackers tied to Iran attempting to break into accounts associated with President Trump’s 2020 reelection campaign.
More attacks are likely to come in the countdown to the final day those eligible can cast their vote in the 2020 election, warned Chris Krebs, director of CISA.gov—the website for government’s Cybersecurity and Infrastructure Security Agency–on Twitter. Rather than targeting candidates, though, threat actors will likely try to attack voting infrastructure, he said.
“Things to keep an eye out for: this week & nxt are prime territory for visible, seemingly disruptive attempts to undermine confidence in voting systems,” Krebs tweeted. “Website defacements are superficial; Denial of Service attacks might deprive you of info, but won’t compromise the vote itself.”
Although no data was stored on the site, Erich Kron, security expert at KnowBe4, said there might likely be lingering exposure risks.
“Exposure risks may exist if the server, database or underlying infrastructure is shared with other websites or services,” he wrote in an email interview with Threatpost. “Once an attacker has administrative credentials, they are likely to attempt to pilfer everything they can, to include credentials for any other accounts and configuration files that may contain static passwords or sensitive information. These could lead to access to other services or sites that do contain sensitive information.”
Russian Espionage Group Updates Custom Malware Suite
29.10.20 BigBrothers Threatpost
Turla has outfitted a trio of backdoors with new C2 tricks and increased interop, as seen in an attack on a European government.
The advanced persistent threat (APT) known as Turla is targeting government organizations using custom malware, including an updated trio of implants that give the group persistence through overlapping backdoor access.
Russia-tied Turla (a.k.a. Ouroboros, Snake, Venomous Bear or Waterbug) is a cyber-espionage group that’s been around for more than a decade. It’s known for its complex collection of malware and interesting command-and-control (C2) implementations. It targets governmental, military and diplomatic targets.
Accenture researchers observed a recent campaign against a foreign government in Europe that ran between June and October, which featured three legacy weapons, all with significant updates. They worked together as a kind of multi-layered threat toolkit.
One of the updated tools is the HyperStack remote procedure call (RPC)-based backdoor (named after the filename that its authors gave it). Accenture has tied it to the group for the first time, thanks to its use alongside the other two tools seen in the campaign: Known Turla second-stage remote-access trojans (RATs), Kazuar and Carbon.
“The RATs transmit the command-execution results and exfiltrate data from the victim’s network, while the RPC-based backdoors [including HyperStack] use the RPC protocol to perform lateral movement and issue and receive commands on other machines in the local network,” according to an Accenture analysis, released on Wednesday. “These tools often include several layers of obfuscation and defense-evasion techniques.”
The upgrades seen in the campaign largely revolved around creating built-in redundancies for remote communication. Turla used disparate C2 configurations, to allow different re-entry points should one of them be blocked.
“[These included] novel [C2] configurations for Turla’s Carbon and Kazuar [RATs] on the same victim network,” according to the analysis. “The Kazuar instances varied in configuration between using external C2 nodes off the victim network and internal nodes on the affected network, and the Carbon instance had been updated to include a Pastebin project to receive encrypted tasks alongside its traditional HTTP C2 infrastructure.”
HyperStack Backdoor
The HyperStack backdoor began life in 2018, but it received a major update in September that allowed Accenture researchers to tie it back to Turla.
“The updated functionality…appears to be inspired by the RPC backdoors previously publicly disclosed by ESET and Symantec researchers, as well as with the Carbon backdoor,” they explained. “Based on these similarities, we assess with high confidence that HyperStack is a custom Turla backdoor.”
The new version of HyperStack uses named pipes to execute RPC calls from a controller to a device hosting the HyperStack client. It leverages IPC$, which is a share function that facilitates inter-process communication (IPC) by exposing named pipes to write to or read from.
“To move laterally, the implant tries to connect to another remote device’s IPC$ share, either using a null session or default credentials,” explained Accenture researchers. “If the implant’s connection to the IPC$ is successful, the implant can forward RPC commands from the controller to the remote device, and likely has the capability to copy itself onto the remote device.”
Kazuar Updates
Meanwhile, a Kazuar sample used in the observed European campaign that Accenture analyzed in mid-September was configured to receive commands via Uniform Resource Identifiers (URI). These pointed to internal C2 nodes in the victim government’s network.
This Kazuar configuration acted alongside another sample, analyzed in early October.
“Based on references to the internal C2 node, the October sample likely acts as a transfer agent used to proxy commands from the remote Turla operators to the Kazuar instances on internal nodes in the network, via an internet-facing shared network location,” according to Accenture. “This set-up allows Turla operators to communicate with Kazuar-infected machines in the victim network that are not accessible remotely.”
Yet another Kazuar sample found on the victim network was configured to communicate directly with a C2 server located outside the victim network, hosted on a compromised legitimate website. This was used by Turla to proxy commands and exfiltrate data to Turla backend infrastructure, researchers said.
Kazuar is a multiplatform trojan discovered in 2017 that allows Turla to remotely load additional plugins to increase its capabilities. It exposes these through an Application Programming Interface (API) to a built-in web server, and it has code lineage that can be traced back to at least 2005, researchers have said. For a while it was believed to have been the successor to Carbon.
Carbon Updates
The aforementioned legacy tool Carbon was also updated for the observed campaign. Carbon is a modular backdoor framework with advanced peer-to-peer capability that Turla has used for several years, well before Kazuar hit the scene.
In June, an updated sample made an appearance which combined the Turla-owned C2 infrastructure with tasks served from Pastebin, researchers found. The installer for the sample contained a configuration file with URLs for compromised web servers hosting a web shell that transmits commands and exfiltrates data from the victim network – as expected. But researchers noted that it also contained a parameter labeled [RENDEZVOUS_POINT], with a URL for a Pastebin project.
“When accessing the Pastebin URL, an encrypted blob is downloaded that requires a corresponding RSA private key from the configuration file,” researchers explained. “The configuration file analyzed did not contain the RSA private key and therefore we were unable to decrypt the contents of the Pastebin link. We assess the decrypted blob was likely a task for the Carbon instance.”
The use of a legitimate web service like Pastebin for C2 activities is an ongoing trend among APTs, the researchers noted, for a few different reasons.
“[For one], web services allow cyber-espionage groups’ malicious network traffic to blend easily with legitimate network traffic,” according to researchers. “Also, threat groups can easily change or create new infrastructure which makes it difficult for defenders to shut down or sinkhole their infrastructure. [And], using web services complicates attribution since the C2 infrastructure is not owned by the threat group.”
Turla will likely continue to use its legacy tools, with upgrades, to compromise and maintain long term access to its victims, researchers said.
“This combination of tools has served Turla well, as some of their current backdoors use code that dates back to 2005,” Accenture researchers noted. “The threat group will likely continue to maintain and rely on this ecosystem, and iterations of it, as long as the group targets Windows-based networks.”
More Hospitals Hit by Growing Wave of Ransomware Attacks
29.10.20 Ransomware Threatpost
Hospitals in New York and Oregon were targeted on Tuesday by threat actors who crippled systems and forced ambulances with sick patients to be rerouted, in some cases.
Two more hospitals were hit with ransomware attacks this week as a growing number of criminals target healthcare facilities during the COVID-19 pandemic.
On Tuesday, Klamath Falls, Ore.-based Sky Lakes Medical Center’s computer systems were compromised by a ransomware attack. On the same day, New York-based St. Lawrence Health System said computers at three of its hospitals (in Canton-Potsdam, Massena and Gouverneur) were attacked by the ransomware variant Ryuk.
Ransomware attacks have become an all-too-familiar reality for hospitals just as COVID-19 has forced many to spread themselves thin and accelerated the adoption of virtual care. This year, as hospitals have scrambled to save lives, cyberattacks targeting healthcare firms have grown 150 percent, according to a report by C5 Alliance.
Sky Lakes Medical Center said that its computer systems were “down” and and that scheduled procedures that require imaging services will need to be delayed. “Emergency and urgent care remain available,” it said in a statement.
The St. Lawrence Health System meanwhile said that within hours of the initial attack, its information systems department “disconnected all systems and shut down the affected network to prevent further propagation,” according to a statement.
Ryuk malware, used in the St. Lawrence attack, is a potent weapon which cybersecurity researchers describe as highly sophisticated. It’s used by threat groups such as North Korea’s Lazarus Group in targeted attacks. The active malware is responsible for a bevy of recent successful attacks, including one that recently shut down Universal Health Services, a Fortune-500 owner of a nationwide network of hospitals.
Cyberattacks in general have become a harrowing reality, threatening patient security tied to not just their data or a missed appointment. A ransomware attack against the Dusseldorf University Hospital in Germany is being blamed for a patient’s death. According to local reports, crippled computer systems forced an ambulance to be diverted to a more distant hospital – resulting in the patient’s death.
Similar to that situation, ambulances were also diverted from the Canton-Potsdam Hospital for a short period of time. And as of Wednesday, the Gouverneur Hospital said it continued to reroute ambulances away from its emergency room.
The attacks come three months after another N.Y.-based hospital, the Samaritan Medical Center, was hit with a ransomware attack on July 25. It took IT workers there 10 weeks to restore systems, the hospital confirmed in a statement. The attack “disrupted” its drug delivery, radiation therapy and medical-imaging services, and forced payroll and accounting to turn to paper records.
“Healthcare-delivery organizations, such as hospitals and clinics, are complex organizations where a broad range of information technology, internet of medical things, operational technology and internet-of-things devices are increasingly interconnected,” pointed out Forescout (PDF) in a recent report on the healthcare sector.
“The growing number and diversity of devices in [healthcare-delivery organizations] have introduced new cybersecurity risks,” according to the firm. “The ability to compromise devices and networks, and the possibility of monetizing patient data, have led to an increase in the number and sophistication of cyberattacks targeting healthcare-delivery organizations in recent years.”
The report said that attackers are attracted to hospitals because of the sheer complexity of their networks. Forescout said many struggle to manage a sprawling number of endpoints, ranging from computer systems, surgical equipment, telemedicine platforms, medical sensors and infusion pumps. All told, the report estimated that healthcare-delivery organizations contain an average of 20,000 devices.
The report urged hospitals to adopt network and device segmentation.
“Segmentation is a foundational control for risk mitigation in networks with a diversity of IT, IoT and OT devices,” according to the report’s authors. They warned, however, that over-segmentation with poorly defined zones only increases complexity with few benefits.
“However, segmentation requires well-defined trust zones based on device identity, risk profiles and compliance requirements for it to be effective in reducing the attack surface and minimizing blast radius,” according to the report.
Microsoft’s SMBGhost Flaw Still Haunts 108K Windows Systems
29.10.20 OS Threatpost
While Microsoft patched the bug known as CVE-2020-0796 back in March, more than one 100,000 Windows systems are still vulnerable.
More than 100,000 Windows systems have not yet been updated to protect against a previously-patched, critical and wormable flaw in Windows called SMBGhost.
Microsoft patched the remote code-execution (RCE) flaw bug tracked as CVE-2020-0796 back in March; it affects Windows 10 and Windows Server 2019, and ranks 10 out of 10 on the CVSS scale. It exists in version 3.1.1 of the Microsoft Server Message Block (SMB) protocol, the same protocol that was targeted by the infamous WannaCry ransomware in 2017.
“I’m unsure what method Shodan uses to determine whether a certain machine is vulnerable to SMBGhost, but if its detection mechanism is accurate, it would appear that there are still over 103,000 affected machines accessible from the internet,” Jan Kopriva, one of the researchers at the SANS Internet Storm Center, said in a post on Wednesday.
According to Kopriva, many of these vulnerable systems (22 percent) are in Taiwan, Japan (20 percent), Russia (11 percent) and the U.S. (9 percent).
Microsoft released its fix, KB4551762, as an update for Windows 10 (versions 1903 and 1909) and Windows Server 2019 (versions 1903 and 1909).
In lieu of a patch, Microsoft in March had noted that administrators can use PowerShell to disable SMBv3 compression, which will block unauthenticated attackers from exploiting the vulnerability against an SMBv3 server. To protect clients from outside attacks, it’s necessary to block TCP port 445 at the enterprise perimeter firewall. Kopriva for his part also tracked a percentage of all IPs with an open port 445 via Shodan, and found that overall approximately 8 percent of all IPs have port 445 open.
The chart below shows the number of vulnerable systems that are open to SMBGhost. Kopriva noted in a message to Threatpost that the “dips” in the data are presumably caused by Shodan re-scanning a large number of IP ranges.

IP addresses detected as vulnerable to SMBGhost by Shodan. Credit: Jan Kopriva
The pressure is on for system administrators to patch their systems against SMBGhost, with various proof of concepts (PoCs) for the flaw being released over the past few months. While many attempts to exploit SMBGhost resulted only in denial of service or local privilege escalation, a PoC released in June by someone who goes by “Chompie,” who announced his exploit to achieve RCE on Twitter.
“Since release of this PoC was again met with wide attention from the media, one might reasonably expect that by now, most of the vulnerable machines would have been patched – especially those accessible from the internet,” according to Kopriva.
These PoCs have also spurred the Department of Homeland Security to urge companies to update in June, saying that cybercriminals are targeting the unpatched systems: The agency “strongly recommends using a firewall to block server message block ports from the internet and to apply patches to critical- and high-severity vulnerabilities as soon as possible.”
‘Copyright Violation’ Notices Lead to Facebook 2FA Bypass
29.10.20 Social Threatpost
Fraudulent Facebook messages allege copyright infringement and threaten to take down pages, unless users enter logins, passwords and 2FA codes.
Scammers have hatched a new way to attempt to bypass two-factor authentication (2FA) protections on Facebook.
Cybercriminals are sending bogus copyright-violation notices with the threat of taking pages down unless the user attempts to appeal. The first step in the “appeal?” The victim is asked to submit a username, password and 2FA code from their mobile device, according to Sophos researcher Paul Ducklin, allowing fraudsters bypass 2FA.
2FA is an added layer of protection on top of a username and password that usually involves sending a unique code to a mobile device, which must be entered to access a platform. But crooks are increasingly finding ways around it.
Ducklin explained in a recent post about his findings that Sophos regularly receives social media copyright infringement scam emails, but this one distinguished itself by launching a plausible attack using fraudulent pages generated on Facebook, giving their phishing emails an added air of legitimacy.
“None of these tactics are new — this scam was just an interesting and informative combination,” Ducklin wrote to Threatpost in an email about his findings. “Firstly, the email is short and simple; secondly, the link in the email goes to a legitimate site, namely Facebook; thirdly, the workflow on the scam site is surprisingly believable.”
The fake Facebook emails offer clues that they’re not legit, but Ducklin points out it’s convincing enough to goad social-media administrators into wanting to gather more information on the supposed copyright violation complaints, which means clicking on the phishing link in the email.
The email’s message threatens to delete the victim’s page unless an appeal is filed within 24 hours.
“You’ll see when you hover over the ‘continue’ [it] does indeed take you to facebook.com,” he said. “The catch is that the Facebook address is the fraudulent page set up to look like an official Facebook page dedicated to handling copyright violation issues.”
From there, even though the linked text looks like clicks are sent to another Facebook page — ostensibly so victims can file an “appeal” — Ducklin looked and found the target URL is different from the linked text. It instead sends the victim to a .CF domain based in the Central African Republic.
“That’s an old trick used by crooks – and even by some legitimate sites,” Ducklin added.
The site was set up temporarily on a cloud web hosting service, which generates an HTTPS certificate once the site is online, making detection a bit trickier, he added.
“The certificate’s validity started at midnight today, and the scam email we received arrived at 01:53 UTC, which is early evening on the West Coast of America, and late evening on the East Coast,” Ducklin wrote. “As you can see, cybercrooks move fast!”
Once on the site, users were asked to enter their password, twice, access the Facebook app on their mobile device and enter in the 2FA code, which is found in the “Settings & Privacy > Code Generator” section of the app. Ducklin wrote this could result in “potentially giving them a one-shot chance to login as you, directly from their server, even if you have 2FA enabled.”
Once they have access to a victim’s Facebook credentials, the attackers can sell off the info on the dark web, use it to hijack or take down pages, hold user data for ransom or even make fraudulent in-app purchases.
Facebook responded to Threatpost’s request for comment, saying the company recommends being careful to not click on any suspicious links, adding if a user does get hacked, they can get help securing their account at facebook.com/hacked. The company added that they recommend using a third-party authenticator app as a primary security method. Facebook also has a list of tips to avoid phishing attempts on its platform.
Is 2FA Broken?
Bypassing 2FA has emerged as a disturbing trend.
Cybercriminal group Rampant Kitten was discovered just last month, after years of operating undetected, to have developed Android malware that gathers 2FA security codes sent to devices in addition to Telegram login information, while launching Google phishing attacks.
At about the same time a trojan called “Alien” targeted banks with a novel notification sniffer which gave scammers the ability to access new device updates, including 2FA codes, to bypass the protection.
In May, another attack on Office 365 attempted to trick users into granting permissions to a rogue application, which would then bypass 2FA protections.
The list of 2FA breaches goes on. It remains up to the user to make sure they don’t fall for these types of phishing scams. Ducklin added that using a web filter and avoiding email requests for login details are also good policies to follow.
“2FA has never been a silver bullet that will eliminate phishing and fraud — but it does make things harder for the crooks, and it gives you one more opportunity to stop and think when you are logging in, ‘Do I really want to put my password and my login code in *on this very site*?” Ducklin said. Always check where emails came from and where web links have taken you — because the only thing worse than being scammed is being scammed and then realizing that the telltale signs were there all along.”
He added, “As any carpenter will tell you: measure twice; cut once.”
Iran-linked APT Targets T20 Summit, Munich Security Conference Attendees
29.10.20 APT Threatpost
The Phosphorous APT has launched successful attacks against world leaders who are attending the Munich Security Conference and the Think 20 (T20) Summit in Saudi Arabia, Microsoft warns.
Microsoft said that an Iranian threat actor has successfully compromised attendees of two global conferences – including ambassadors and senior policy experts – in an effort to steal their email credentials.
The two conferences targeted include the Munich Security Conference, slated for Feb. 19 to 21, 2021 and the Think 20 (T20) Summit in Saudi Arabia, taking place Oct. 31 to Nov. 1 2020. Both conferences are majority virtual this year and are both longstanding and well respected venues to discuss global and regional security policies, among other things.
Microsoft linked the attack, which targeted more than 100 conference attendees, to Phosphorus, which it said is operating from Iran. The group – also known as APT 35, Charming Kitten and Ajax Security Team – has been known to use phishing as an attack vector.
“We believe Phosphorus is engaging in these attacks for intelligence collection purposes,” wrote to Tom Burt, corporate vice president, Customer Security and Trust at Microsoft, in post outlining the plots on Wednesday. “The attacks were successful in compromising several victims, including former ambassadors and other senior policy experts who help shape global agendas and foreign policies in their respective countries.”
Burt said the attackers have been sending possible attendees spoofed invitations by email. These emails use near-perfect English and were sent to former government officials, policy experts, academics and leaders from non-governmental organizations, he said. They purport to help assuage fears of travel during the Covid-19 pandemic by offering remote sessions.
The emails come from fake conference organizers using the email addresses t20saudiarabia[@]outlook.sa, t20saudiarabia[@]gmail.com and munichconference[@]outlook.com.
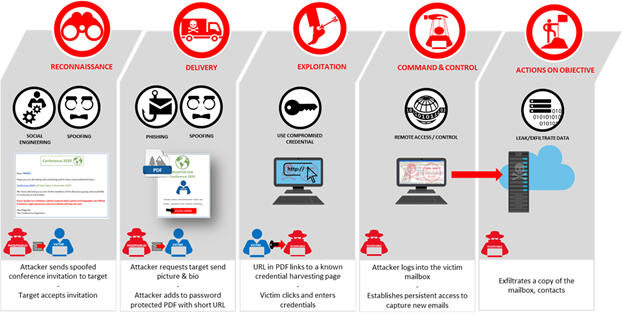
The attack vector: Credit: Microsoft
If the target accepts the invitation, the attacker is then asked to send a picture of themselves and bio. The attacker’s request is embedded in an attached password-protected PDF and comes in the form of a short link (inside the PDF). Naturally, the link links to one of several known credential harvesting pages meant to trick targets into handing over their email account credentials via a fake account login page. Malicious domains include de-ma[.]online, g20saudi.000webhostapp[.]com and ksat20.000webhostapp[.]com.
The attackers uses those credentials to log into the victims’ mailbox, where they can then gather further sensitive information and launch more malicious attacks.
“The attacks were successful in compromising several victims, including former ambassadors and other senior policy experts who help shape global agendas and foreign policies in their respective countries,” Burt wrote.
Microsoft said it’s working with conference organizers who have warned their attendees.
Threatpost has reached out to both conference organizers for further information.
Meanwhile, Microsoft recommends that conference-goers evaluate the authenticity of emails they receive about major conferences by ensuring that the sender address looks legitimate and that any embedded links redirect to the official conference domain.
“As always, enabling multi-factor authentication across both business and personal email accounts will successfully thwart most credential harvesting attacks like these,” Burt said. “For anyone who suspects they may have been a victim of this campaign, we also encourage a close review of email-forwarding rules in accounts to identify and remove any suspicious rules that may have been set during a successful compromise.”
The Iran-linked Phosphorus hacking group has made waves this year targeting campaign staffers of both Trump and Biden with phishing attacks. In February the group discovered targeting public figures in phishing attacks that stole victims’ email-account information. Earlier this year, Microsoft also took control of 99 websites utilized by the threat group in attacks. Last year, Phosphorus was also discovered attempting to break into accounts associated with the 2020 reelection campaign of President Trump. And most recently, it was seen using WhatsApp and LinkedIn messages to impersonate journalists.
North Korea-Backed Spy Group Poses as Reporters in Spearphishing Attacks, Feds Warn
29.10.20 Attack Threatpost
The Kimsuky/Hidden Cobra APT is going after the commercial sector, according to CISA.
The North Korean advanced persistent threat (APT) group known as Kimsuky is actively attacking commercial-sector businesses, often by posing as South Korean reporters, according to an alert from the U.S. Cybersecurity and Infrastructure Security Agency (CISA).
Kimsuky (a.k.a. Hidden Cobra) has been operating as a cyberespionage group since 2012 under the auspices of the regime in Pyongyang. Its mission is global intelligence gathering, CISA noted, which usually starts with spearphishing emails, watering-hole attacks, torrent shares and malicious browser extensions, in order to gain an initial foothold in target networks.
Primary targets include think-tanks, and diplomatic and high-level organizations in Japan, South Korea and the United States, with a focus on foreign policy and national-security issues related to the Korean peninsula, nuclear policy and sanctions, CISA added. It also targets the cryptocurrency industry.
In recent campaigns seen over the summer, the group ultimately sent malicious attachments embedded in spearphishing emails to gain initial access to victim organizations, according to an analysis, published on Tuesday. But the malicious content was deployed only after several initial exchanges with the target meant to build trust.
“Posing as South Korean reporters, Kimsuky exchanged several benign interview-themed emails with their intended target to ostensibly arrange an interview date and possibly build rapport,” according to CISA. “The emails contained the subject line, ‘Skype Interview requests of [redacted TV show] in Seoul,’ and began with a request to have the recipient appear as a guest on the show. The APT group invited the targets to a Skype interview on the topic of inter-Korean issues and denuclearization negotiations on the Korean Peninsula.”
After a recipient agreed to an interview, Kimsuky sent a subsequent email with a malicious document. And when the date of the interview got closer, the purported “reporter” sent an email canceling the interview.
After obtaining initial access, the APT group ultimately deployed the BabyShark malware and PowerShell or the Windows Command Shell for execution.
“This is another example of the seriousness of the modern cybercrime world and the resources behind them,” said Erich Kron, security awareness advocate at KnowBe4, via email. “With billions of dollars at stake every year and with warfare expanding to the digital realm in such a large way, it is no surprise that nation-states are involved. The days of thick manila envelopes full of papers, traditional dossiers on people or stealthy microfilm cameras whisking away our information are gone. Now, it is all a bunch of ones and zeros in easily searched databases.”
Lateral Movement
The infection routine typically used by the North Korean APT is multi-staged, according to CISA, which included a deep-dive into the group’s recent tactics, techniques and procedures (TTPs).
“First, the compromised host system uses the native Microsoft Windows utility, mshta.exe, to download and execute an HTML application (HTA) file from a remote system,” CISA explained. “The HTA file then downloads, decodes and executes the encoded BabyShark VBS file. The script maintains persistence by creating a registry key that runs on startup. It then collects system information, sends it to the operator’s command-and-control (C2) servers, and awaits further commands.”
Kimsuky is a fan of fileless attacks: It uses PowerShell to run executables from the internet without touching the physical hard disk on a computer by using the target’s memory.
It also uses well-known methods for privilege escalation to move laterally, including placing scripts in the Startup folder, creating and running new services, changing default file associations and injecting malicious code in explorer.exe, CISA said. In addition, the group makes use of Win7Elevate—an exploit from the Metasploit framework—to bypass the User Account Control to inject malicious code into explorer.exe.
“This malicious code decrypts its spying library—a collection of keystroke-logging and remote-control access tools, and remote-control download and execution tools—from resources, regardless of the victim’s operating system,” according to CISA. “It then saves the decrypted file to a disk with a random but hardcoded name in the user’s temporary folder and loads this file as a library, ensuring the tools are then on the system even after a reboot. This allows for the escalation of privileges.”
Kimsuky uses stolen web-hosting credentials — from victims outside of its usual targets—to host its arsenal of weapons and harvest credentials from web browsers, files and keyloggers.
“Kimsuky likely obtained the credentials from the victims via spearphishing and credential-harvesting scripts,” according to the CISA alert. “On the victim domains, they have created subdomains mimicking legitimate sites and services they are spoofing, such as Google or Yahoo mail.”
Weapons
In terms of the tools in its espionage library, CISA also noted that Kimsuky uses a raft of legitimate tools mixed with proprietary weapons.
For instance, “Kimsuky uses memory-dump programs instead of using well-known malicious software and performs the credential extraction offline,” according to the alert. “Kimsuky uses ProcDump, a Windows command line administration tool, also available for Linux, that allows a user to create crash dumps/core dumps of processes based upon certain criteria, such as high central processing unit (CPU) utilization. ProcDump monitors for CPU spikes and generates a crash dump when a value is met; it passes information to a Word document saved on the computer. It can be used as a general process dump utility that actors can embed in other scripts, as seen by Kimsuky’s inclusion of ProcDump in the BabyShark malware.”
CISA found that Kimsuky also uses modified versions of PHProxy, an open-source web proxy written in PHP, to examine web traffic between victims and the websites accessed by the victims, and to collect any credentials entered.
Meanwhile, Kimsuky leverages the victim’s operating system command prompt to enumerate the file structure and system information.
“The information is directed to C:\WINDOWS\msdatl3.inc, read by malware and likely emailed to the malware’s command server,” according to CISA.
Legitimate tools aside, it has its own set of malicious tools as well. For instance, Kimsuky has been seen abusing a Chrome extension to steal passwords and cookies from browsers.
“The spearphishing email directs a victim to a phishing site, where the victim is shown a benign PDF document but is not able to view it,” according to CISA. “The victim is then redirected to the official Chrome Web Store page to install a Chrome extension, which has the ability to steal cookies and site passwords and loads a JavaScript file, named jQuery.js, from a separate site.”
Kimsuky also uses a PowerShell-based keylogger and cryptominer named MECHANICAL, and a network-sniffing tool, named Nirsoft SniffPass, which is capable of obtaining passwords sent over non-secure protocols.
“The keylogger intercepts keystrokes and writes them to C:\Program Files\Common Files\System\Ole DB\msolui80.inc and records the active window name where the user pressed keys,” according to CISA. “There is another keylogger variant that logs keystrokes into C:\WINDOWS\setup.log.”
Kimsuky meanwhile collects data from the victim’s system through a HWP document malware, which changes the default program association in the Registry to open HWP documents.
“When a user opens an HWP file, the Registry key change triggers the execution of malware that opens the HWP document and then sends a copy of the HWP document to an account under the adversary’s control,” according to the alert. “The malware then allows the user to open the file as normal without any indication to the user that anything has occurred.”
And on the macOS front, Kimsuky has used a Python implant that gathers data from macOS systems and sends it to a C2 server. The Python program also downloads various implants based on C2 options.
Anti-Detection and C2
Kimsuky has been seen using a modified TeamViewer client for C2 communications, but Kimsuky’s preferred method for sending or receiving exfiltrated information is through email, according to CISA. Malware on the victim machine encrypts the data before sending it to a C2 server. Kimsuky also sets up auto-forward rules within a victim’s email account.
Kimsuky uses well-known and widely available methods for defense evasion, according to CISA. These methods include disabling security tools, deleting files and using Metasploit.
The group also uses a malicious DLL that runs at startup to disable the Windows system firewall and turn off the Windows Security Center service.
“[We] recommend individuals and organizations within this target profile increase their defenses and adopt a heightened state of awareness,” according to the alert. “Particularly important mitigations include safeguards against spearphishing, use of multi-factor authentication, and user awareness training.”
TrickBot operators employ Linux variants in attacks after recent takedown
29.10.20 BotNet Securityaffairs
A few days after the TrickBot takedown, Netscout researchers spotted a new TrickBot Linux variant that was used by its operators.
A few days ago, Microsoft’s Defender team, FS-ISAC, ESET, Lumen’s Black Lotus Labs, NTT, and Broadcom’s cyber-security division Symantec joined the forces and announced a coordinated effort to take down the command and control infrastructure of the infamous TrickBot botnet.
Microsoft has taken down 120 of the 128 servers that were composing the Trickbot infrastructure.
Microsoft announced to have taken down 62 of the original 69 TrickBot C&C servers, seven servers that could not be brought down last week were Internet of Things (IoT) devices.
Microsoft also revealed that operators tried to resume the operations, The company brought down 58 of the 59 servers the operators attempted to bring online after the recent takedown.
According to a new report published by researchers from security firm Netscout, TrickBot’s operators have started to use a new variant of their malware in an attempt to Linux systems and expand the list of its targets.
TrickBot is a popular banking Trojan that has been around since October 2016, its authors have continuously upgraded it by implementing new features.
At the end of 2019, researchers spotted a new TrickBot backdoor framework dubbed Anchor that was using the DNS protocol for C2 communications.
Stage 2 Security researcher Waylon Grange first spotted the new Linux variant of Anchor_DNS in July and called it “Anchor_Linux.”
“The actors behind Trickbot, a high profile banking trojan, have recently developed a Linux port of their new DNS command and control tool known as Anchor_DNS.” explained Grange.
“Often delivered as part of a zip, this malware is a lightweight Linux backdoor. Upon execution it installs itself as a cron job, determines the public IP [address] for the host and then begins to beacon via DNS queries to its C2 server.”
Researchers from Netscout now published an analysis of the variant detailing the communication flow between the bot and the C2 server.
The client sends “c2_command 0” to the server along with information about the compromised system and the bot ID, the server, in turn, responds with the message “signal /1/” back to the bot.

The infected host responds by sending the same message back to the C2, which in turn sends the command to be executed by the bot. Once executed the command, the bot sends the result of the execution to the C2 server.
“The complexity of Anchor’s C2 communication and the payloads that the bot can execute reflect not only a portion of the Trickbot actors’ considerable capabilities, but also their ability to constantly innovate, as evidenced by their move to Linux.” concludes the report. “It is important to note that Trickbot operators aren’t the only adversaries to realize the value of targeting other operation systems”
U.S. Shares Information on North Korean Threat Actor 'Kimsuky'
29.10.20 BigBrothers Securityweek
An alert released by the United States this week provides information on Kimsuky, a threat actor focused on gathering intelligence on behalf of the North Korean government.
Issued by the Cybersecurity and Infrastructure Security Agency (CISA), the FBI, and the Cyber Command Cyber National Mission Force (CNMF), the advisory notes that the adversary has been active since at least 2012, engaging in social engineering, spear-phishing, and watering hole attacks.
The malicious cyber activity associated with the North Korean government is typically referred to as HIDDEN COBRA by the United States.
Kimsuky, the alert says, targets individuals and organizations located in Japan, South Korea, and the United States, and is mainly focused on gathering intelligence on “foreign policy and national security issues related to the Korean peninsula, nuclear policy, and sanctions.”
Targets include entities associated with the South Korean government, individuals who are believed to be experts in various fields, and think tanks.
For initial access, Kimsuky uses spear-phishing with malicious attachments, and various social engineering methods. However, the threat actor would also send benign emails to gain victims’ trust. Malicious scripts and tools are hosted using stolen web hosting credentials, the alert reads.
The adversary was observed posing as South Korean reporters and engaging with intended targets to claim to be arranging interviews on inter-Korean issues and denuclearization negotiations. To one recipient who agreed to an interview, Kimsuky sent a malicious document in a subsequent email, to infect the victim with a variant of the BabyShark malware.
The employed spear-phishing emails were tailored to topics deemed relevant to the target, including the current COVID-19 crisis, the North Korean nuclear program, and media interviews.
Kimsuky, the advisory reads, also uses login-security-alert-themed phishing emails for initial access, along with watering hole attacks, malware delivered via torrent sharing sites, and malicious browser extensions served to their victims.
Following initial access, the threat actor uses mshta.exe to fetch and execute an HTML application (HTA) file that downloads and runs the encoded BabyShark VBS file. The script achieves persistence through a registry key, and collects system information and sends it to the operator’s command and control (C&C) servers.
The adversary would also employ PowerShell for the execution of files directly in memory and to achieve persistence through malicious browser extensions, altered system processes, Remote Desktop Protocol (RDP), and by changing the autostart execution and default file association for an application.
In 2018, during a campaign referred to as STOLEN PENCIL, Kimsuky used the GREASE malware, which adds a Windows administrator account and abuses RDP to provide attackers with access to the compromised systems.
For information gathering purposes, Kimsuky targets Hangul Word Processor (HWP) and Microsoft Office documents, and uses web shells for file upload, download, and deletion.
To escalate privileges, the threat actor uses scripts placed in the Startup folder, newly created services, modified file associations, and malicious code injected into explorer.exe. The Win7Elevate exploit from the Metasploit framework was used to bypass the User Account Control to inject code into explorer.exe.
In their joint alert, CISA, the FBI and USCYBERCOM also provide information on methods Kimsuky employs for defense evasion, its use of various tools for credential harvesting, memory dumping, and system information enumeration, how system data is collected, and the targeting of macOS systems.
The advisory also provides details on the employed C&C and data exfiltration, also noting that the threat actor’s activities are limited to information harvesting, and are not destructive in nature.
FBI, DHS Warn Of Possible Major Ransomware Attacks On Healthcare Systems
29.10.20 Ransomware Thehackernews
The US Federal Bureau of Investigation (FBI), Departments of Homeland Security, and Health and Human Services (HHS) issued a joint alert Wednesday warning of an "imminent" increase in ransomware and other cyberattacks against hospitals and healthcare providers.
"Malicious cyber actors are targeting the [Healthcare and Public Health] Sector with TrickBot malware, often leading to ransomware attacks, data theft, and the disruption of healthcare services," the Cybersecurity and Infrastructure Security Agency said in its advisory.
The infamous botnet typically spreads via malicious spam email to unsuspecting recipients and can steal financial and personal data and drop other software, such as ransomware, onto infected systems.
It's worth noting that cybercriminals have already used TrickBot against a major healthcare provider, Universal Health Services, whose systems were crippled by Ryuk ransomware late last month.
TrickBot has also seen a severe disruption to its infrastructure in recent weeks, what with Microsoft orchestrating a coordinated takedown to make its command-and-control (C2) servers inaccessible.
"The challenge here is because of the attempted takedowns, the TrickBot infrastructure has changed and we don't have the same telemetry we had before," Hold Security's Alex Holden told The New York Times.
Although the federal report doesn't name any threat actor, the advisory makes a note of TrickBot's new Anchor backdoor framework, which has been recently ported to Linux to target more high-profile victims.
"These attacks often involved data exfiltration from networks and point-of-sale devices," CISA said. "As part of the new Anchor toolset, Trickbot developers created Anchor_DNS, a tool for sending and receiving data from victim machines using Domain Name System (DNS) tunneling."
As The Hacker News reported yesterday, Anchor_DNS is a backdoor that allows victim machines to communicate with C2 servers via DNS tunneling to evade network defense products and make their communications blend in with legitimate DNS traffic.
Also coinciding with the warning is a separate report by FireEye, which has called out a financially-motivated threat group it calls "UNC1878" for the deployment of Ryuk ransomware in a series of campaigns directed against hospitals, retirement communities, and medical centers.
Urging the HPH sector to patch operating systems and implement network segmentation, CISA also recommended not paying ransoms, adding it may encourage bad actors to target additional organizations.
"Regularly back up data, air gap, and password protect backup copies offline," the agency said. "Implement a recovery plan to maintain and retain multiple copies of sensitive or proprietary data and servers in a physically separate, secure location."
DDoS attacks in Q3 2020
28.10.20 Attack Securelist
News overview
Q3 was relatively calm from a DDoS perspective. There were no headline innovations, although cybercriminals did continue to master techniques and develop malware already familiar to us from the last reporting period. For example, another DDoS botnet joined in the assault on Docker environments. The perpetrators infiltrated the target server, created an infected container, and placed in it the Kaiten bot (also known as Tsunami), paired with a cryptominer.
The Lucifer botnet, which first appeared on researchers’ radar last quarter, and knows all about DDoS attacks and cryptocurrency mining, got an update, and now infects not only Windows, but also Linux devices. In DDoS attacks, the new version can use all major protocols (TCP, UDP, ICMP, HTTP) and spoof the IP address of the traffic source.
Mirai enthusiasts supplemented their brainchild with exploits for new vulnerabilities. In July, our colleagues at Trend Micro told about a variant of the botnet that exploited the bug CVE-2020-10173 in Comtrend VR-3033 routers, allowing sections of the network connected to vulnerable routers to be compromised. Then in August, news broke of a Mirai variant attacking BIG-IP products through the CVE-2020-5902 vulnerability. The BIG-IP family includes firewalls, load management and access control apps, and fraud and botnet protection systems. The vulnerability can be used to execute arbitrary commands, upload and delete files, disable services, and run JavaScript scripts.
On the topic of actual DDoS attacks, Q3 was not that eventful. The most newsworthy were extortion attacks allegedly carried out by actors known for hiding behind variously named APT groups: FancyBear, Armada Collective, Lazarus, and others. The ransomers send bitcoin ransom emails to organizations around the world, demanding from 5 BTC to 20 BTC, and threatening a powerful and sustained DDoS attack in case of non-payment. After that, the victim is flooded with junk traffic to demonstrate that the threats are far from empty.
In August and early September, several organizations in New Zealand were hit, including the New Zealand Stock Exchange (NZX), which was taken offline for several days. Also among the victims were the Indian bank YesBank, PayPal, Worldpay, Braintree, and other financial companies. Another DDoS wave of bitcoin ransom demands affected a number of European ISPs; however, it’s not known for sure whether this was the work of the same group. At the end of September, financial and telecommunications companies in Hungary were rocked by a powerful DDoS attack. According to Magyar Telekom, the junk traffic came from Russia, China, and Vietnam. Whether the cybercriminals sent ransom messages as part of the attack is unknown.
The back end of September saw a series of DDoS attacks on public flight-tracking services. The victims included the Swedish website Flightradar24 and the UK platform Plane Finder, which monitor the movement of aircraft in real time. These services are in great demand: meeters and greeters can check if a flight is on time, and media use the information when reporting on aircraft incidents. As a result, the services worked only intermittently, and their Twitter accounts posted messages that an attack had taken place. A tweet from Flightradar24, for instance, reported that the resource had suffered no fewer than three attacks in a short space of time. US company FlightAware also reported service availability issues, but did not specify whether it was an attack or just a malfunction.
Q3 was not without traditional attacks on the media. Russian TV station Dozhd reported a DDoS incident on August 24. Unknown cyberactors attempted to take the resource offline during daytime and evening news broadcasts. In early September, cybercriminals targeted the news agency UgraPRO. According to media reports, the junk traffic originated from Russian and foreign IP addresses at a rate of more than 5,000 requests per second. In late September, the news portals Chronicles of Turkmenistan and Sputnik Armenia reported attacks on their websites.
Lastly, due to the coronavirus pandemic and related restrictions in Russia, the Unified State Exam, sat by final grade students in Russian schools, was this year postponed to July. This could hardly fail to impact the DDoS landscape: in the middle of the month, the Federal Service for Supervision in Education and Science (Rosobrnadzor) reported an attempt to disrupt the exam results portal. Fortunately, the results had not yet been uploaded, so the attack was a wasted effort.
More school-related attacks were predictably seen at the start of the academic year. For example, in Miami-Dade County, Florida, a DDoS wave swept across the websites of local educational institutions, disrupting online classes. However, one of the juvenile cybercriminals met with near-instant karma: the schools brought in the FBI, and by September 3 the delinquent had been arrested. The other perpetrators are still being traced.
On the topic of the FBI, in Q2 the agency issued two anti-DDoS alerts for businesses. In July, a document was released containing a brief description of new amplification methods, as well as recommendations for detecting attacks and measures to prevent them. And in late August, it published a fairly detailed report on DDoS extortionists activity, again with tips for countering such attacks.
Quarter trends
In Q3, we observed a significant drop in all indicators relative to the previous reporting period. This is more likely due to the anomalous DDoS activity seen in Q2 than any unusual lull this quarter, which becomes clear when comparing the current picture with data for the same period in 2019: total attacks increased by 1.5 times, while the number of smart attacks almost doubled.
Comparative amount of DDoS attacks, Q2/Q3 2020 and Q3 2019. Data for Q3 2019 is taken as the 100% reference value (download)
Unlike the previous quarter, Q3 can be described as normal: we are finally witnessing the traditional summer decline in the attack market, which did not happen in May and June. We expected such picture in early 2020, but the abnormally high Q2 figures upset the applecart. The current normalization of DDoS activity can be explained by two factors:
Global market stabilization amid the coronavirus pandemic. It is now nine months since the introduction of quarantine measures, and the mass transition to remote working has ceased to be news. Companies have adapted to the new work format, and IT departments have plugged holes in remote infrastructure and strengthened key nodes. As a result, there are fewer targets fit for attack.
Cryptocurrency market growth. For instance, the Ethereum price chart (see below) shows a clear jump in Q3. Cryptocurrency mining and DDoS attacks are competing markets. Many botnets can do both, and their operators choose where to direct resources at any particular moment depending on the potential yield. In Q3, some botnets could have been switched over to mining.
Ethereum price dynamics from October 13, 2019, to October 13, 2020. Source: coindesk.com
Quarter statistics
Methodology
Kaspersky has a long history of combating cyber threats, including DDoS attacks of all types and complexity. Company experts monitor botnets using the Kaspersky DDoS Intelligence system.
The DDoS Intelligence system is part of the Kaspersky DDoS Protection solution, and intercepts and analyzes commands sent to bots from C&C servers. The system is proactive, not reactive, meaning that it does not wait for a user device to get infected or a command to be executed.
This report contains DDoS Intelligence statistics for Q3 2020.
In the context of this report, the incident is counted as a single DDoS-attack only if the interval between botnet activity periods does not exceed 24 hours. For example, if the same web resource was attacked by the same botnet with an interval of 24 hours or more, then this is considered as two attacks. Bot requests originating from different botnets but directed at one resource also count as separate attacks.
The geographical location of DDoS victims is determined by their IP addresses. The number of unique targets of DDoS attacks in this report is counted by the number of unique IP addresses in the quarterly statistics.
DDoS Intelligence statistics are limited to botnets detected and analyzed by Kaspersky. Note that botnets are just one of the tools used for DDoS attacks, and that this section does not cover every single DDoS attack that occurred during the review period.
Quarter results
The TOP 3 by number of attacks and targets remain unchanged: China (71.20 and 72.83%), the US (15.30 and 15.75%), and the Hong Kong Special Administrative Region (4.47 and 4.27%).
The Netherlands and Vietnam are new faces in the Top 10 by number of attacks.
As for the ranking by number of targets, there was a noticeable decline of interest in Asia: Hong Kong lost 2.07 p.p. and Singapore 0.3 p.p., while Japan and South Korea did not even show. The exception is China, where the share of targets rose by 6.81 p.p.
After the Q2 upturn, the number of attacks in Q3 dipped again. What’s more, the difference between the peak (323 attacks per day) and anti-peak (1 registered attack) figures increased sharply.
In Q3, we observed a two-week drop in late August and early September. During this period, there were three anti-peaks (August 31, September 1/7) with one attack per day, and another five days with fewer than 10.
DDoS botnet flooding was most active on Thursdays, with a noticeable dip on Fridays.
Although Q3 lags far behind Q1 in terms of duration, there were two registered attacks of more than 10 days (246 and 245 hours), and the number of attacks lasting 5–9 days (12 attacks lasting 121–236 hours) increased.
The distribution of attacks by type did not undergo any changes: SYN flooding is still the main tool (94.6%), its share remaining virtually unchanged since the previous quarter. ICMP attacks comprised 3.4%, while HTTP flooding scored less than 0.1% of attacks.
Linux botnets still dominate over their Windows counterparts, accounting for 95.39% of attacks (up 0.61 p.p. on the previous quarter).
Attack geography
Q3 2020 brought no surprises in terms of the geographical distribution of attacks. The TOP 3 by number of attacks this year is surprisingly stable: China (71.2%, up 6.08 p.p. against Q2), the US (15.3%, down 4.97 p.p.), and Hong Kong (4.47%, down 1.61 p.p.). Despite some fluctuations, the huge gap between China and the US, and Hong Kong’s markedly lower share, remain unchanged. We saw a similar state of play in Q3 2019.
Singapore, Australia, and India all climbed one line higher (from fifth to fourth, sixth to fifth, and seventh to sixth place, respectively), knocking South Africa from fourth to eighth. The reason has less to do with the rising share of attacks in these countries, rather the relative calm in South Africa itself: in July-September, the share of attacks there fell by 0.88 p.p. to 0.4%. At the same time, there were fewer registered attacks in Singapore, in relative terms, than in the previous reporting period: 0.85% of DDoS attacks (-0.28 p.p.). The shares of Australia and India increased by roughly the same amount (+0.27 p.p. and +0.24 p.p., respectively), delivering a 0.65% share for the former and 0.57% for the latter.
In seventh place in the ranking, wedged between India and South Africa, is the Netherlands, absent from the TOP 10 since Q3 2019. In the reporting period, this country accounted for 0.49% of attacks.
The TOP 10 by number of attacks is rounded out by Vietnam and the UK. The share of attacks in the former increased by 0.23 p.p. against Q2, giving Vietnam a TOP 10 finish for the second time this year with 0.39% of attacks (its previous entry was at the start of the year). As for the UK, it remains relatively stable: from 0.18% of attacks in Q2, its share rose only slightly, to 0.25%.
Distribution of DDoS attacks by country, Q2 and Q3 2020 (download)
The geographical distribution of targets also changed insignificantly: only two newcomers entered the TOP 10, although the reshuffling of last quarter’s ranking is more pronounced than in the distribution of attacks.
The TOP 3 remained the same as in the previous quarter: China, the US, Hong Kong. The share of targets in China continues to grow — up 6.81 p.p. against the last reporting period, approaching three-quarters of all registered targets: 72.83%. Having shed 3.57 p.p., the US was left with 15.75% of targets. Hong Kong lost 2.07 p.p., its share of targets falling to 4.27%.
Fourth place was taken by Singapore. Despite the reduced number of targets there (down 0.3 p.p. to 0.74%), it moved up one notch, displacing South Africa. In fifth position was Vietnam with 0.5% of registered targets (in the previous reporting period it ranked seventh). The already mentioned South Africa claimed sixth place with 0.47% of targets.
The next two positions, seventh and eighth, went to a couple of newbies: the UK (0.35%) and the Netherlands (0.27%). It was their first inclusion in the ranking since Q4 and Q3 2019, respectively. These European countries ousted Asia’s Japan and South Korea, which had occupied the bottom two lines in last quarter’s TOP 10 countries by number of targets. In Q3, these lines were filled by Australia (0.25%) and India (0.23%), which had previously sat in sixth and eighth position, respectively.
Distribution of unique DDoS-attack targets by country, Q3 and Q4 2020 (download)
Dynamics of the number of DDoS attacks
The number of attacks this quarter varied significantly. On the one hand, at peak activity, DDoS operators broke the previous period’s record: on July 2, we registered 323 attacks (compared to 298 in April). On the other, this quarter had a few surprisingly calm days: August 31 and September 1/7 saw only one registered attack each. Overall, late August–early September was quite mild: during the two weeks from August 25 to September 7, the number of attacks exceeded 100 on just one day (181 on September 5), and as many as eight days registered fewer than 10.
Another curiosity is the difference between the peak and the indicators closest to it. In the past few quarters, there has been no significant difference in the number of attacks on the 2–3 most active days. Q3 broke the mold: the next most attack-intensive day after July 2 — July 13 — scored almost 20% fewer attacks, 260 in total. On average, there were approximately 106 attacks per day in Q3, which is 10 fewer than in the previous quarter.
Dynamics of the number of DDoS attacks, Q3 2020 (download)
Cybercriminals’ most and least favored days shifted again this quarter. Active Wednesdays were replaced by active Thursdays (19.02%), and quiet Saturdays by quiet Fridays (10.11%). The gap between them widened: 8.91 p.p. against 4.93 p.p. in the previous reporting period. This is largely due to Thursday being the most active day of the quarter.
Besides Saturday and Thursday, Monday also increased its share of attacks, although not significantly, while the remaining days saw their percentage fall accordingly.
Distribution of DDoS attacks by day of the week, Q2 and Q3 2020 (download)
Duration and types of DDoS attacks
The average attack duration in Q3 continued to shorten. This can be explained by the increase in the share of ultra-short attacks (this time by a significant 5.09 p.p.). However, unlike in the previous reporting period, the share of long (100–139 hours) attacks decreased inappreciably (by just 0.08 p.p.), while the share of ultra-long attacks even rose slightly (by 0.18 p.p.). Whereas in Q2, the longest attacks did not even reach nine days, this quarter we registered two lasting over 10 days (246 and 245 hours), and the number of attacks lasting 5–10 days increased by 1.5 times.
As such, the following picture emerged: the bulk of attacks (91.06%) lasted up to four hours; 4.89% lasted 5–9 hours; 2.25% lasted 10–19 hours; 2.09% lasted 20–49 hours; 0.4% lasted 50–99 hours; and just 0.08% lasted 100–139 hours. Unusually, this quarter the number of attacks lasting 140 hours or more is actually greater than the number of attacks in the bracket before it, accounting for 0.23% of the total number of DDoS attacks.
Distribution of DDoS attacks by duration (hours), Q2 and Q3 2020 (download)
The distribution of attacks of different types is unchanged from the last reporting period, as is the share of the most common type — SYN flooding: 94.6% in Q3 versus 94.7% in Q2. ICMP flooding decreased slightly (3.4% against the previous 4.9%), but did not surrender its positions. TCP attacks comprised 1.4% of the total number registered (up by a considerable 1.2 p.p.); UDP attacks accounted for 0.6%, while HTTP attacks were so few that their share did not even stretch to 0.1%.
Distribution of DDoS attacks by type, Q3 2020 (download)
In Q3, the share of Windows botnets continued to fall: this time their number dropped by 0.61 p.p. against the previous quarter to 4.61%. The percentage of Linux botnets grew accordingly.
Ratio of Windows/Linux botnet attacks, Q2 and Q3 2020 (download)
Conclusion
If Q2 2020 surprised us with an unusually high number of DDoS attacks for this period, the Q3 figures point to a normalization. Judging by the number of unique targets, in comparison with last quarter, cybercriminals were more attracted by European, and less by the Asian countries, such as Japan and South Korea, although interest in China is still high and continues to grow in terms both of unique targets and of attacks. Growth was observed in the number of short and ultra-short attacks, as well as multi-day ones. The sharp contrast between the highest and lowest number of attacks per day is curious. Taken together, these indicators mark Q3 2020 out as somewhat contradictory from a DDoS viewpoint.
It will be interesting to see what Q4 has in store. Barring major shocks, we expect to see indicators comparable to those at end-2019. Back then, after almost two years of growth, the DDoS market more or less stabilized.
Q4 is usually a hot time due to the Christmas and New Year sales frenzy. End-of-year figures are typically around 30% higher than those of Q3. We expect to see a similar picture this year, although, after the abnormally active Q2, it would be foolhardy to make cast-iron predictions. That said, if nothing else extraordinary happens in this more-than-extraordinary year, we see no reason for the DDoS market to experience a significant swing in either direction in Q4.
Hackers Can Open Doors by Exploiting Vulnerabilities in Hörmann Device
28.10.20 Exploit Securityweek
Hackers could remotely open garage doors and gates by exploiting vulnerabilities found in a gateway device made by Hörmann, researchers warned on Wednesday.
Hörmann is a Germany-based company that specializes in home and industrial doors. The company’s products are sold in more than 50 countries across North America, Europe and Asia, and according to Wikipedia, it’s the fourth largest door manufacturer in the world.
Customers who want to control garage doors, entrance gates and other smart systems from a smartphone are provided the BiSecur gateway device, a wireless access control system that includes a Hörmann key fob and comes with Wi-Fi and Ethernet interfaces.Hörmann gateway vulnerabilities
Researchers at Austria-based cybersecurity company SEC Consult have discovered a total of 15 vulnerabilities in the gateway device, including issues related to encryption, poorly protected communications, and the associated mobile application.

The flaws can be exploited for both attacks that require access to the local network and attacks that can be launched remotely from the internet. Based on its research, SEC Consult has created an open source Python-based communication library for BiSecur devices.
In one attack scenario described by SEC Consult for SecurityWeek, an attacker who is able to connect to the local network can open doors connected to the Hörmann gateway by executing a small script. The attack does not require authentication and it can be conducted from a mobile phone.
Another scenario involves an attacker on the local network rendering the door-opening hardware unresponsive. In order to restore the system, a manual reset of the device is required, but the device is typically behind the door, which in case of an attack cannot be opened by the victim.
As for attacks that can be launched remotely over the internet, the vulnerabilities found by SEC Consult only allow unauthenticated hackers to impersonate a device and send false status information to the owner. For instance, they can notify the victim via the app that their garage door is opening or that it’s open, when in fact it’s not.
A remote attacker can also impersonate a device over the internet and cause Hörmann’s servers to send the victim’s device username and password to the attacker instead of the door opener.
These remote attacks require the attacker to extract the client certificate and private key from any Hörmann door opener hardware, and then use the extracted key to connect to the vendor’s server. The attacker can then run a script to switch the identity of their device to the targeted user’s device, which is possible due to Hörmann’s failure to ensure that certificates matched the device.
SEC Consult says it has not checked how many potentially vulnerable systems are exposed to the internet due to legal reasons — doing so required accessing the vendor’s servers — but the vulnerable product has been on the market for years and is highly popular.
SEC Consult says Hoermann has taken steps to address the vulnerabilities after being notified. SecurityWeek has reached out to the vendor for comment and will update this article if it responds.
This is not the first time researchers have found vulnerabilities in the Hoermann BiSecur device. Back in 2017, experts showed how hackers could have cloned a legitimate transmitter to take control of gates and doors.
EXCLUSIVE: Medical Records of 3.5 Million U.S. Patients Can be Accessed and Manipulated by Anyone
28.10.20 Incindent Securityweek
More Than 2 Petabytes of Unprotected Medical Data Found on Picture Archiving and Communication System (PACS) Servers
The results of 13 million medical examinations relating to around 3.5 million U.S. patients are unprotected and available to anyone on the internet, SecurityWeek has learned. This is despite the third week of this year's National Cybersecurity Awareness Month (week beginning 19 October 2020) majoring on 'Securing Internet-Connected Devices in Healthcare'.
The details were disclosed to SecurityWeek by Dirk Schrader, global vice president at New Net Technologies (NNT -- a security and compliance software firm headquartered in Naples, Florida). He demonstrated that the records can be accessed via an app that can be downloaded from the internet by anyone. The records found are in files that are still actively updated, and provide three separate threats: personal identity theft (including the more valuable medical identity theft), personal extortion, and healthcare company breaches.
Schrader examined a range of radiology systems that include an image archive system -- PACS, or picture archiving and communication system. These contain not only imagery but metadata about individual patients. The metadata includes the name, data of birth, date and reason for the medical examination, and more. Within a hospital, the imaging systems (X-rays, MRIs etc) are also stored in the PACS. The treating physician needs ready access to the images to confirm the current treatment. Schrader simply used Shodan to locate systems using the DICOM medical protocol. Individual unprotected PACS systems within the return of 3,000 servers were located manually. One, for example, contained the results of over 800,000 medical examinations, probably relating to about 250,000 different patients.
Although unprotected servers were found manually by Schrader, he chose this route to demonstrate that no hacking skills are required in this process. An attacker could have written a script to separate the protected from the unprotected servers in a fraction of the time. In total, he had access to more than 2 petabytes of medical data.
He found three ways to access the stored data. The first is what the physician would do, via a configurable freeware DICOM Viewer app downloaded from the internet and configured by the user. Viewers can be found simply by searching for 'DICOM viewer'. Schrader specifically used the Radiant DICOM Viewer. An even simpler method is directly via the web browser. The server is located via Shodan, and because it is unprotected, an attacker can often both download and upload to that server, and manipulate the content. "I can upload false data," Shrader told SecurityWeek, "without hacking." The third method is that some of the servers offer a full download of the entire dataset directly through the browser.
The level of detail on individuals includes names and sometimes social security numbers -- potentially allowing identity theft. The type and result of the medical examination is also included, allowing an attacker to collect details on patients who have proved COVID or HIV positive, or had a mastectomy procedure -- potentially allowing personal extortion. In some cases, active folders can be accessed -- and updated -- by an attacker simply through a browser. If these folders are updated with a weaponized PDF or JPG, then the attacker has a potential route to deliver malware and ultimately ransomware to the healthcare institution concerned. Where a physician is using the content of the PACS server to check on a patient's current treatment, and downloads a weaponized file, he or she could potential open route for malware to infect the institution, ultimately leading to a major ransomware attack.
Schrader has been investigating this issue for several years, looking at healthcare institutions around the world. In December 2019, he sent disclosure notices to the administrators of 120 unprotected systems in the U.S. Sixty-nine administrators completely ignored the warnings, including 19 children's hospitals. Elsewhere, responses have been better. In general, the response from Europe and the UK has been positive, and the data has been secured. The U.S., India and Brazil are the primary culprits today, but other unprotected PACS systems exist in Australia and Canada - and one in France. The figures he gave to SecurityWeek relate entirely to the U.S.; and rather than exposed systems being removed, new systems are still being added without adequate or any authentication requirements.
Having obtained the IP addresses from Shodan, Schrader went on to run vulnerability checks against the U.S. institutions, and found, he told SecurityWeek, "around 600 high severity vulnerabilities in around 170 U.S. systems connected to the internet;" suggesting that the systems are not just unprotected, but also unmanaged. "There are numerous end-of-life vulnerabilities, and several Microsoft vulnerabilities at the highest risk level. There is no reason for a picture archiving system to remain unpatched -- it's like these systems have been connected to the internet and just forgotten."
Schrader has found no hard evidence that PACS content has been abused by criminals, "But my suspicion," he told SecurityWeek, "is that criminals are already using this method because it is so easy." The solution to the problem is simple -- PACS servers should require adequate access authentication, or be removed from the internet. In the meantime, many millions of sensitive medical records can be accessed by anyone at any time.
Compromised CMS Credentials Likely Used to Hack Trump Campaign Website
28.10.20 Hacking Securityweek
Security researchers believe that compromised credentials were used by hackers to access the content management system behind Donald Trump’s campaign website.
On Tuesday, hackers managed to break into the website and change content on it. For a short period of time, the message “This site was seized” was displayed on donaldjtrump.com.
The incident has been confirmed by Trump campaign spokesman Tim Murtaugh, who also revealed that law enforcement had been called in to investigate. He also said that no sensitive information had been compromised.
In the message posted on the website, the hackers claimed they managed to compromise sensitive information on President Trump. They also included two cryptocurrency wallet IDs, saying they would release the information if visitors sent money to them.
The message also contained a Pretty Good Privacy (PGP) public key, which can be used to verify future messages supposedly coming from the hackers.
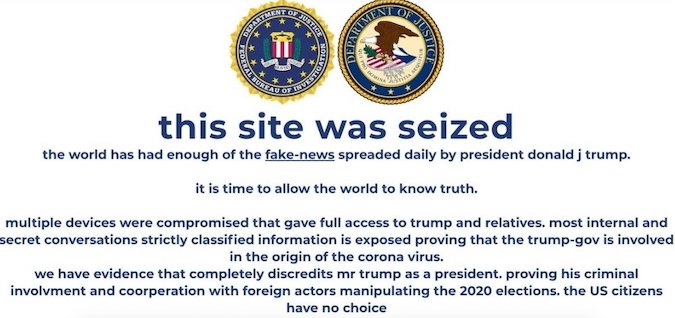
According to WordPress security solutions provider Defiant, which develops the Wordfence product, the hackers most likely used compromised credentials for access, supposedly targeting the underlying Expression Engine content management system (CMS), which is an alternative to WordPress.
While the site content was quickly restored, the “Privacy Policy” and “Terms & Conditions” pages were still delivering a “404 page not found” error hours after the incident was resolved.
“This indicates that something changed on the content management system itself, rather than on the Cloudflare configuration. So we believe that the CMS being compromised is therefore a higher probability than Cloudflare being compromised,” Defiant notes.
The site uses Cloudflare as a content delivery network (CDN), and Defiant says that this could have been used as a point of access only if the attackers knew the IP of the server hosting the site, which is hidden. Thus, this attack vector is less likely to have been used.
If the attackers had access to the campaign’s Cloudflare account and were able to point the domain to their own IP address, the entire website would have been restored by simply pointing it to the right IP address.
However, the issues with the “Privacy Policy” and the “Terms & Conditions” pages suggest this was not the attack vector.
Of even lower probability would be the use of compromised credentials to access the account where the domain donaldjtrump.com was registered; a possible access via FTP or SSH (would require not only FTP or SSH credentials, but also knowledge of the site’s origin IP address); or the use of a zero-day flaw in Expression Engine, which has had few known vulnerabilities, Defiant says.
“Almost every possible scenario includes reused credentials being exploited to gain access to the donaldjtrump.com site. In almost every case, having 2-Factor Authentication enabled would have prevented such a scenario from occurring. It’s also a reminder that it is important to enable 2-Factor Authentication not only on your website’s administrative panel, but on every service that offers it, including services you might not think of as being vulnerable,” Defiant concludes.
The attack comes shortly after a Dutch security researcher claimed that he gained access to Donald Trump’s Twitter account by guessing its password, which he said was “maga2020!”. The White House and Twitter have denied the claims and the researcher has yet to provide any definitive proof.
Researchers: LinkedIn, Instagram Vulnerable to Preview-Link RCE Security Woes
28.10.20 Social Threatpost
Popular chat apps, including LINE, Slack, Twitter DMs and others, can also leak location data and share private info with third-party servers.
UPDATE
Link previews in popular chat apps on iOS and Android are a firehose of security and privacy issues, researchers have found. At risk are Facebook Messenger, LINE, Slack, Twitter Direct Messages, Zoom and many others. In the case of Instagram and LinkedIn, it’s even possible to execute remote code on the companies’ servers through the feature, according to an analysis.
Link previews are standard in most chat apps, and they can be very useful. When a user sends a link through, it renders a short summary and a preview image in-line in the chat, so other users don’t have to click the link to see what it points to.
Unfortunately, there’s a downside. According to independent researchers Talal Haj Bakry and Tommy Mysk, the feature can leak IP addresses, expose links sent in end-to-end encrypted chats and has been caught “unnecessarily downloading gigabytes of data quietly in the background.”
The issues go back to how the previews are generated, according to the researchers. There are three ways to do that: The sender can generate it; the receiver can generate it; or the server can generate it. The last two are problematic, with the server-generated version being the most concerning.
“How does the app know what to show in the summary?” Bakry and Mysk explained. “It must somehow automatically open the link to know what’s inside. But is that safe? What if the link contains malware? Or what if the link leads to a very large file that you wouldn’t want the app to download and use up your data.”
Sender-Generated Links
If the sender generates the preview, the app will go and download what’s in the link, create a summary and a preview image of the website, and it will send this as an attachment along with the link.
A typical link preview. Source: Google.
“When the app on the receiving end gets the message, it’ll show the preview as it got from the sender without having to open the link at all,” explained the researchers, in a posting this week. “This way, the receiver would be protected from risk if the link is malicious.”
iMessage, Signal (if the link preview option is turned on in settings), Viber and WhatsApp all follow this best-practice approach, they noted. But, there is a caveat when it comes to Viber.
“If you send a link to a large file, your phone will automatically try to download the whole file even if it’s several gigabytes in size,” researchers noted.
They added, “it’s also worth mentioning that even though Viber chats are end-to-end encrypted, tapping on a link will cause the app to forward that link to Viber servers for the purposes of fraud protection and personalized ads.”
Receiver-Generated Links
When the receiver generates the preview, it means that the app will open any link that’s sent to it, automatically, with no user interaction needed.
“This one is bad,” said the researchers, noting that the process can leak location data.
“Let’s briefly explain what happens when an app opens a link,” they wrote. “First, the app has to connect to the server that the link leads to and ask it for what’s in the link. This is referred to as a GET request. In order for the server to know where to send back the data, the app includes your phone’s IP address in the GET request.”
They added, “If you’re using an app that follows this approach, all an attacker would have to do is send you a link to their own server where it can record your IP address. Your app will happily open the link even without you tapping on it, and now the attacker will know where you are [down to a city block].”
A second issue is that a link could potentially point to a large video or archive file.
“A buggy app might try to download the whole file, even if it’s gigabytes in size, causing it to use up your phone’s battery and data plan,” the researchers warned.
Server-Generated Links
Finally, in the third approach, the app sends the link to an external server and asks it to generate a preview, then the server will send the preview back to both the sender and receiver.
While this avoids the IP address-leaking issue found in the receiver-generating scenario, it potentially exposes information to third parties, according to the researchers, and can allow for code execution if the link points to a malicious website with JavaScript.
As far as data exposure, the server will need to make a copy (or at least a partial copy) of what’s in the link to generate the preview.
“Say you were sending a private Dropbox link to someone, and you don’t want anyone else to see what’s in it,” researchers wrote. “The question becomes…are the servers downloading entire files, or only a small amount to show the preview? If they’re downloading entire files, do the servers keep a copy, and if so for how long? And are these copies stored securely, or can the people who run the servers access the copies?”
Multiple apps use this approach for previewing links. But in testing, they vary widely in terms of how much data the servers downloaded, researchers said:
Discord: Downloads up to 15 MB of any kind of file.
Facebook Messenger: Downloads entire files if it’s a picture or a video, even files gigabytes in size.
Google Hangouts: Downloads up to 20 MB of any kind of file.
Instagram: Just like Facebook Messenger, but not limited to any kind of file. The servers will download anything no matter the size.
LINE: Downloads up to 20 MB of any kind of file.
LinkedIn: Downloads up to 50 MB of any kind of file.
Slack: Downloads up to 50 MB of any kind of file.
Twitter: Downloads up to 25 MB of any kind of file.
Zoom: Downloads up to 30 MB of any kind of file.
“Though most of the app servers we’ve tested put a limit on how much data gets downloaded, even a 15 MB limit still covers most files that would typically be shared through a link (most pictures and documents don’t exceed a few MBs in size),” the researchers noted. “So if these servers do keep copies, it would be a privacy nightmare if there’s ever a data breach of these servers.”
The issue is of particular concern to LINE users, according to Bakry and Mysk, because LINE claims to have end-to-end encryption where only the sender and receiver can read the messages.
“When the LINE app opens an encrypted message and finds a link, it sends that link to a LINE server to generate the preview,” according to the researchers. “We believe that this defeats the purpose of end-to-end encryption, since LINE servers know all about the links that are being sent through the app, and who’s sharing which links to whom. Basically, if you’re building an end-to-end encrypted app, please don’t follow [the server-generated] approach.”
After the researchers sent a report to the LINE security team, the company updated its FAQ to include a disclosure that they use external servers for preview links, along with information on how to disable them.
Facebook Messenger and its sister app Instagram Direct Messages are the only ones in the testing that put no limit on how much data is downloaded to generate a link preview. Facebook responded to the researchers’ concerns, saying that it considers the feature to be working as intended, but did not confirm how long it holds onto the data. Twitter gave the same response.
“As we explained to the researcher weeks ago, these are not security vulnerabilities,” a facebook company spokesperson told Threatpost. “The behavior described is how we show previews of a link on Messenger or how people can share a link on Instagram, and we don’t store that data. This is consistent with our data policy and terms of service.”
Slack meanwhile confirmed that it only caches link previews for around 30 minutes, which is also explained in its documentation.
Zoom told the researchers that it is looking into the issue and that it’s discussing ways to ensure user privacy.
The researchers also contacted Discord, Google Hangouts and LinkedIn to report their findings, but said they have not received a response from these two.
Remote Code-Execution Woes
As far as the code-execution issue, the researchers posted a video with a proof-of-concept of how hackers can run any JavaScript code on Instagram servers. And in LinkedIn Messages case, the servers were also vulnerable to running JavaScript code, which allowed them to bypass the 50 MB download limit in a test.
“You can’t trust code that may be found in all the random links that get shared in chats,” Bakry and Mysk explained. “We did find, however, at least two major apps that did this: Instagram and LinkedIn. We tested this by sending a link to a website on our server which contained JavaScript code that simply made a callback to our server. We were able to confirm that we had at least 20 seconds of execution time on these servers. It may not sound like much, and our code didn’t really do anything bad, but hackers can be creative.”
When reached via Twitter DM, Mysk told Threatpost that “In our testing, an attacker can run any JavaScript code on these servers. While it may not be immediately obvious how this can cause real harm, allowing JavaScript code to run leaves the door wide open for a team of dedicated attackers. The simplest attack would be something like mining cryptocurrencies on these servers and using up their resources.”
Neither company responded to the researchers’ concerns. But the Facebook spokesperson told Threatpost that the feature works as intended, and that it’s not a security vulnerability. The person added that way the functionality is presented does not take into account industry-standard security measures that Instagram has put in place to protect against code-execution risks, and that when the concern was reported, it “found no risk of RCE.”
As for LinkedIn, a spokesperson told Threatpost via email: “To help keep our members safe, we use a sandbox environment to evaluate the security risk of the links being shared. These environments are ephemeral and have strict access controls that are designed to discover malicious code execution. To this end, we do execute JavaScript in the URL contents for completeness of evaluation. We also don’t cache the content of these URLs. All these steps are taken to inspect content of link for safety.”
But Mysk noted that such protections may not be good enough.
“Server-side mitigations such as running JavaScript code in a sandbox environment is effective in thwarting most attacks, but more sophisticated attacks could allow the attacker to leave the sandbox and execute code outside the protected environment, which could potentially allow the attacker to steal data and secret keys,” he told Threatpost. “We’ve seen many successful attempts to escape the JavaScript sandbox in apps like Chrome, and these link preview servers are no different.”
Looking for Safety
The link-preview issue is just one more concern when it comes to the security of the collaboration apps that have become intrinsic to the work-from-home reality caused by the COVID-19 pandemic.
The good news is that some apps don’t render previews at all, such as Signal (if the link preview option is turned off in settings), Threema, TikTok and WeChat.
“This is the safest way to handle links, since the app won’t do anything with the link unless you specifically tap on it,” researchers noted.
However, they also warned that link previews are a widespread phenomenon: “There are many email apps, business apps, dating apps, games with built-in chat, and other kinds of apps that could be generating link previews improperly, and may be vulnerable to some of the problems we’ve covered.”
Lax Security Exposes Smart-Irrigation Systems to Attack Across the Globe
28.10.20 Attack Threatpost
Systems designed by Mottech Water Management were misconfigured and put in place and connected to the internet without password protections.
More than 100 smart-irrigation systems deployed across the globe were installed without changing the factory’s default, passwordless setting, leaving them vulnerable to malicious attacks, according to recent findings from Israeli security research firm Security Joes.
The researchers immediately alerted CERT Israel, the affected companies and the irrigation system vendor, Mottech Water Management, which did not immediately respond to a request for comment from Threatpost.
Mottech’s system allows for real-time control and monitoring of irrigation for both agricultural and turf/landscaping installations, via desktop and mobile phone. Sensor networks allow for the flexible and real-time allocation of water and fertilizer to different valves in the system. Access to the network could result in an attacker being able to flood fields or over-deliver fertilizer, for instance.
Security Joes regularly scans for Israeli open devices on the internet to check for vulnerabilities, the firm’s co-founder Ido Naor told Threatpost. Recently, its researchers discovered that 55 irrigation systems within Israel were visible on the open internet without password protections. After expanding their search, they found 50 others scattered around the world in countries including France, South Korea, Switzerland and the U.S.
“We’re talking about full-fledged irrigation systems, they could be entire cities,” Naor said. “We don’t look closely at what’s behind the address, because we don’t want to cause any trouble.”
Naor said that at last check, only about 20 percent of the identified vulnerable irrigation devices have had mitigation efforts taken to protect them so far.
Israel’s Water Systems Under Attack
There’s good reason for alarm about water systems not being secured, particularly in Israel. Just last April, a cyberattack on Israeli water systems, reportedly launched by Iran, attempted to increase the mix of chlorine in the water to poison the civilian population and ultimately interrupt the population’s water supply, The Times of Israel reported.
Yigal Unna, the head of the country’s National Cyber Directorate addressed the CybertechLive Asia conference in late May with the ominous warning that the direct cyberattack on people represented a new chapter in cyberwarfare, according to The Times of Israel.
“Cyber-winter is coming and coming even faster than I suspected,” he told the conference, according to the report. “We are just seeing the beginning.”
Unna was correct. Just weeks later in July, the Israeli Water Authority said that it was able to stop an attack on agricultural water pumps in Galilee, and another on water-supply infrastructure in the “center of the country,” reports.
The irrigation systems which were discovered without password protection aren’t related to the previous attacks, Naor said.
Locking Down Utilities Beyond Israel
These types of vulnerabilities certainly aren’t limited to Israel.
Last month, six critical flaws in CodeMeter, software used to power industrial systems in the U.S., including water and electric utilities, were discovered which could be exploited to launch attacks or even allow third-party takeovers of systems.
Over the summer, researchers found that VPNs used for remote access to operational technology (OT) networks in industrial environments left field devices open to attacks, which could cause shutdowns or even physical damage.
Governments are making attempts to keep up with the proliferation of internet-of-things (IoT) devices throughout critical-infrastructure systems. In the U.S., the House of Representatives passed legislation in September establishing minimum requirements for IoT devices within the federal government.
“Most experts expect tens of billions of devices operating on our networks within the next several years as the [IoT] landscape continues to expand,” the legislation’s so-sponsor Senator Cory Gardner (R-Co.) said in a press release. “We need to make sure these devices are secure from malicious cyberattacks as they continue to transform our society and add countless new entry points into our networks, particularly when they are integrated into the federal government’s networks.”
Naor told Threatpost that minimum security standards for IoT devices are an important step toward locking down critical infrastructure. But operators need to take security seriously, he added, noting that two-factor authentication should be a bare minimum requirement for accessing these systems from a mobile device. But more generally, he adds, “We should be way more careful about what we put on the internet.”
Amazon Fires Employee Who Leaked Customer Names, Emails
28.10.20 Security Threatpost
Amazon notified customers and law enforcement of the insider-threat incident this week.
Amazon has fired an employee who shared customers’ names and email addresses with a third party.
An Amazon spokesperson told Threatpost that it has systems in place to limit and control access to information, and processes in place for identifying and investigating suspicious behavior. These systems notified Amazon of “suspicious behavior.” After the company investigated the incident, it fired the employee, referred them to law enforcement and is working with law enforcement in their criminal prosecution.
“No other information related to your account was shared,” according to the note, shared on Twitter by several Amazon customers. “This is not a result of anything you have done and there is no need for you to take any action. We apologize for this incident.”
Amazon did not comment on an inquiry from Threatpost asking how many customers were impacted, and what the role of the Amazon employee was.
“It is critical for businesses to recognize that threats from legitimate users have always been more elusive and harder to detect or prevent than traditional external threats,” said Orion Cassetto, director of product marketing at Exabeam, in an emailed statement. “Though the extent of the leak is currently unknown, a number of Amazon customers have been notified that their email addresses have been passed on to a third-party by an employee, which has resulted in their termination. Organizations must be armed with the tools to prevent threats from within their walls from launching attacks.”
Researchers for their part say that a combination of training, organizational alignment and technology can help companies prevent insider threats. Behavioral analytics tools are one type preventative technology that tracks, collects and analyzes user data to detect threats, said Cassetto.
“This is typically done by collecting data over a period of time to understand what normal user behavior looks like, then flagging behavior that does not fit that pattern,” said Cassetto. “It can often spot unusual online behaviors – credential abuse, unusual access patterns, large data uploads – that are telltale signs of insider threats. More importantly, it can often spot these unusual behaviors among compromised insiders long before criminals have gained access to critical systems.”
Insider threats continue to plague tech companies. Last year, Trend Micro said that a rogue employee sold the data of 68,000 customers to a malicious third party, who then used that data to target customers with scam calls. In May 2019, a report outlined how Snap employees were abusing their access to private user data – which includes location data, saved Snaps and phone numbers. And a report in 2018 found that Facebook had fired an employee who allegedly abused access privileges to data to stalk women.
Enel Group suffered the second ransomware attack this year
28.10.20 Ransomware Securityaffairs
Multinational energy company Enel Group has been hit by Netwalker ransomware operators that are asking a $14 million ransom.
Systems at the multinational energy company Enel Group has been infected with Netwalker ransomware, it is the second ransomware attack suffered by the energy giant this year. Netwalker ransomware operators are asking a $14 million ransom for the decryption key, the hackers claim to have stolen several terabytes from the company and threaten to leak them if the ransom will be not paid.
Enel S.p.A., or the Enel Group, is an Italian multinational energy company that is active in the sectors of electricity generation and distribution, as well as in the distribution of natural gas.
The company has more than 61 million customers in 40 countries, it ranks 87 in Fortune Global 500, with $90 billion in revenues in 2019.
In June, Enel was hit by Snake ransomware, but the attack was quickly contained and the malware was not able to spread within its network.
The news of a possible ransomware attack against Enel Group was reported to BleepingComputer by a researcher on October 19.
The researcher shared with BleepingComputer a Netwalker ransom note that appeared to be used in the attack on Enel Group.

Source Bleeping Computer
BleepingComputer attempted to notify Enel Group last week without success. A few days later, Netwalker announced the leak of the company data through their support chat.
Enel never replied to the message of the ransomware operators, for this reason, the attackers started leaking a portion of the stolen data as proof of the data breach.
The operators are asking $14 million worth of Bitcoin (roughly 1234.02380000 BTC).

Source Bleeping Computer
Today, the Netwalker ransomware operators added Enel Group to their data leak site and some screenshots of unencrypted files stolen from the company.
The Italian cyber security firm TG soft publicly shared the news of the attack in a tweet:
The hackers stole about 5 terabytes of documents from the company and announced that they will “analyze every file for interesting things” and publish it on their leak site.
At the time of publishing this post, the company have yet to confirm the incident, let’s remember that the company conduct will have to be in compliance with the current EU privacy legislation GDPR.
Steelcase office furniture giant hit by Ryuk ransomware attack
28.10.20 Ransomware Securityaffairs
Office furniture company Steelcase was hit by Ryuk ransomware attack that forced it to shut down its network to avoid the malware from spreading.
Steelcase is a US-based furniture company that produces office furniture, architectural and technology products for office environments and the education, health care and retail industries. It is the largest office furniture manufacturer in the world. It has facilities, offices, and factories in the Americas, Europe, Asia, the Middle East, Australia and Africa.
Steelcase has 13,000 employees and $3.7 billion in 2020. The company is the last victim of the Ryuk ransomware operators, the attack forced the firm to shut down its network to avoid the malware from spreading.
In an 8-K form filed with the Securities and Exchange Commission (SEC), the company has disclosed the ransomware attack that took place on October 22nd, 2020.
“On October 22, 2020, Steelcase Inc. (the “Company”) detected a cyberattack on its information technology systems. The Company promptly implemented a series of containment measures to address this situation including temporarily shutting down the affected systems and related operations.” reads the 8-K form.
The company immediately started the incident response procedure in an attempt to restore the affected systems and return to normal operations as soon as possible. The company is not aware of data loss caused by the ransomware attack.
Bleeping Computer, citing a source in the cybersecurity industry, confirmed that Steelcase suffered a Ryuk ransomware attack.
“At this time, the Company is not aware of any data loss from its systems or any other loss of assets as a result of this attack. Although cyberattacks can be unpredictable, the Company does not currently expect this incident will have a material impact on its business operations or its financial results.” continues the form.
Ryuk ransomware operators were very active during the recent weeks, recently the gang infected systems at the Universal Health Services and French IT outsourcer Sopra Steria.
In March, the City of Durham shut down its network after Ryuk Ransomware attack.
A few days before, EVRAZ, one of the world’s largest multinational vertically integrated steel making and mining companies, has been hit by the Ryuk ransomware.
The list of the victims of the Ryuk ransomware is very long and includes the US government contractor Electronic Warfare Associates (EWA), US railroad company Railworks, Croatian petrol station chain INA Group, and parts manufacturer Visser Precision.
Threat actors behind Ryuk attacks often used the BazarLoader or TrickBot infections to gain a foothold in the target networks and then deploy Ryuk.
Trump Campaign Website Broken Into by Hackers
28.10.20 BigBrothers Securityweek
Hackers briefly broke into Donald Trump's campaign website on Tuesday, just a week before Election Day, officials and reports said.
"This site was seized," said a message that popped up on donaldjtrump.com, which normally carries details of rallies and fundraising appeals.

"The world has had enough of the fake-news spreaded daily by president donald j trump", the message went to say, US media reported.
Trump campaign spokesman Tim Murtaugh said the site was quickly fixed and no sensitive data was compromised.
"The Trump campaign website was defaced and we are working with law enforcement authorities to investigate the source of the attack," Murtaugh said.
The technology website Techcrunch said the hack appeared to be a scam intended to collect hard-to-trace cypto-currency Monero.
In their message, the hackers claimed to have confidential information on Trump and his relatives.
They instructed people to send crypto-currency to one address if they wanted the information revealed and to another to keep it secret.
21 Malicious Apps Downloaded 8 Million Times From Google Play
28.10.20 Android Securityweek
Despite Google’s best efforts to keep Android users safe, malware does manage to slip into Google Play from time to time, and the 21 malicious apps that Avast identified recently are proof of that.
Catered for gamers, the apps were found to include adware that is part of the HiddenAds family. The offending applications appear to have been downloaded roughly 8 million times before being discovered.
The HiddenAds malware, Avast explains, poses as fun or useful apps but in reality delivers intrusive ads outside the application. Often, the malware would make detection difficult by hiding behind relevant-looking advertisements and would attempt to prevent removal by hiding icons.
In this case, the threat was disguised as games promising to provide users with highly engaging actions.
“Developers of adware are increasingly using social media channels, like regular marketers would. This time, users reported they were targeted with ads promoting the games on YouTube. In September, we saw adware spread via TikTok. The popularity of these social networks make them an attractive advertising platform, also for cybercriminals, to target a younger audience,” notes Jakub Vávra, threat analyst at Avast.
To stay protected, users are advised to always double-check any application they want to download and install on their devices, even those listed in Google Play.
Just as HiddenAds managed to bypass Google’s protections and enter the mobile app store, other malware families did and may continue to do so as well. Checking the app’s reviews, price, and ratings in the store and paying attention to the requested permissions should help users identify suspicious apps.
“Users need to be vigilant when downloading applications to their phones and are advised to check the applications’ profile, reviews and to be mindful of extensive device permission requests,” Vávra notes.
Avast also advises users to educate themselves to identify scammers in areas they most often visit, such as online social platforms, YouTube, and the like. Applying rules where children need an adult’s permission before downloading an app should also help keep scammers and malware away.
TrickBot Linux Variants Active in the Wild Despite Recent Takedown
28.10.20 BotNet Thehackernews
Efforts to disrupt TrickBot may have shut down most of its critical infrastructure, but the operators behind the notorious malware aren't sitting idle.
According to new findings shared by cybersecurity firm Netscout, TrickBot's authors have moved portions of their code to Linux in an attempt to widen the scope of victims that could be targeted.
TrickBot, a financial Trojan first detected in 2016, has been traditionally a Windows-based crimeware solution, employing different modules to perform a wide range of malicious activities on target networks, including credential theft and perpetrate ransomware attacks.
But over the past few weeks, twin efforts led by the US Cyber Command and Microsoft have helped to eliminate 94% of TrickBot's command-and-control (C2) servers that were in use and the new infrastructure the criminals operating TrickBot attempted to bring online to replace the previously disabled servers.
Despite the steps taken to impede TrickBot, Microsoft cautioned that the threat actors behind the botnet would likely make efforts to revive their operations.
TrickBot's Anchor Module
At the end of 2019, a new TrickBot backdoor framework called Anchor was discovered using the DNS protocol to communicate with C2 servers stealthily.
The module "allows the actors — potential TrickBot customers — to leverage this framework against higher-profile victims, said SentinelOne, adding the "ability to seamlessly integrate the APT into a monetization business model is evidence of a quantum shift."
Indeed, IBM X-Force spotted new cyberattacks earlier this April revealing collaboration between FIN6 and TrickBot groups to deploy the Anchor framework against organizations for financial profit.
The variant, dubbed "Anchor_DNS," enables the infected client to utilize DNS tunneling to establish communications with the C2 server, which in turn transmits data with resolved IPs as a response, NTT researchers said in a 2019 report.
But a new sample uncovered by Stage 2 Security researcher Waylon Grange in July found that Anchor_DNS has been ported to a new Linux backdoor version called "Anchor_Linux."
"Often delivered as part of a zip, this malware is a lightweight Linux backdoor," Grange said. "Upon execution it installs itself as a cron job, determines the public IP [address] for the host and then begins to beacon via DNS queries to its C2 server."
How the C2 Communication Works Using Anchor
Netscout's latest research decodes this flow of communication between the bot and the C2 server. During the initial setup phase, the client sends "c2_command 0" to the server along with information about the compromised system and the bot ID, which then responds with the message "signal /1/" back to the bot.
As an acknowledgment, the bot sends the same message back to the C2, following which the server remotely issues the command to be executed on the client. In the last step, the bot sends back the result of the execution to the C2 server.
"Every part of communication made to the C2 follows a sequence of 3 different DNS queries," Netscout security researcher Suweera De Souza said.
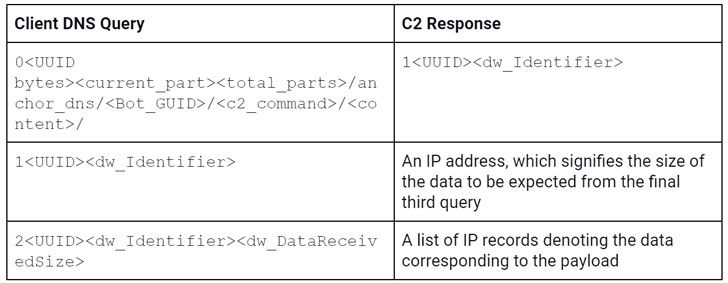
A list of IP records denoting the data corresponding to the payload
The result of the third query is a list of IP addresses that are subsequently parsed by the client to build the executable payload.
The last piece of data sent by the C2 server corresponds to a range of commands (numbered 0-14 in Windows, and 0-4, 10-12, and 100 in Linux) for the bot to execute the payload via cmd.exe or by injecting it into multiple running processes such as Windows File Explorer or Notepad.
"The complexity of Anchor's C2 communication and the payloads that the bot can execute reflect not only a portion of the Trickbot actors' considerable capabilities, but also their ability to constantly innovate, as evidenced by their move to Linux," De Souza said.
Hacker was identified after the theft of $24 million from Harvest Finance
27.10.20 Incindent Securityaffairs
A threat actor has stolen roughly $24 million worth of cryptocurrency assets from decentralized finance service Harvest Finance.
A hacker has stolen approximately $24 million worth of cryptocurrency assets from decentralized finance service Harvest Finance, a web portal that lets users finding the farming opportunities that will maximize their yield(APY) returns.
The hack took place earlier today and was almost immediately confirmed by Harvest Finance administrators in messages posted on the company’s Twitter account and Discord channel.
“On October 26, 02:53:31 AM +UTC, an attacker executed a theft of funds from the USDC and USDT vaults of Harvest Finance.” reads the security breach notification published by the company. “The attacker exploited an arbitrage and impermanent loss that influences the value of individual assets inside the Y pool of Curve.fi, which is where the funds of Harvest’s vaults were invested.”
The attackers initially invested large quantities of cryptocurrency assets in the company service and then used a cryptographic exploit to stole the platform’s funds and transfer them to wallets under its control.
The attacker successfully transferred 13,000,000 USD Coin (USDC) and 11,000,000 Tether (USDT) from the attacking contract to the address “0x3811765a53c3188c24d412daec3f60faad5f119b.”
Experts noticed that shortly after the attack, the hacker returned roughly $2.5 million back to Harvest Finance, but they ignore the reason.
The company immediately launched an investigation into the cyber heist, it claims to have linked the fraudulent activities to an individual “well-known in the crypto community.”
The company claims to have collected “a significant amount of personally identifiable information on the attacker initially offered a $400,000 bounty to anyone who will allow recovering the stolen funds. The bounty will be lowered to $100,000 after 36 hours of the announcement.
The company hopes that the attacker will return the stolen funds:
Harvest Finance explained that the attack was the result of an error it has made, anyway if the attacker will return the stolen funds it will not take legal action against the hacker.
“We made an engineering mistake, we own up to it,” explained the company.
“You’ve proven your point. If you can return the funds to the users, it would be greatly appreciated by the community, and let’s move on.”
Fragomen law firm data breach exposed Google employee’s data
27.10.20 Incindent Securityaffairs
Immigration law firm Fragomen has disclosed a data breach that exposed current and former Google employees’ personal information.
Immigration law firm Fragomen, Del Rey, Bernsen & Loewy, LLP, one of the most prominent US law firms covering immigration law, disclosed a data breach.
The security breach exposed current and former Google employees’ personal information after an unauthorized third party gained access to a single file containing personal information relating to I-9 employment verification services.
The firm discovered the intrusion on September 24, 2020 and engaged a digital forensic investigation firm to assist with this investigation.
“We recently became aware of suspicious activity within our computer network. While our investigation is ongoing, we discovered that an unauthorized third party gained access to a single file containing personal information relating to I-9 employment verification services. This file contained personal information for a discrete number of Googlers (and former Googlers), including you,” reads the data breach notification sent to the impacted people.
A Form I-9 is filled out by all US employees to verify their identity and employment authorization for employment in the United States.
The form contains employee’s information, including full name, date of birth, phone number, social security number, passport numbers, mailing address, and email address,
Exposed data could be abused by crooks to carry out multiple malicious activities, including identity theft. Users should be vigilant and report to the authorities any suspicious activities.
Fragomen is offering one year of free credit monitoring to the affected Google’s employees.
“We are offering complimentary identity theft protection and credit monitoring services to all Googlers (and former Googlers) who may have been affected by this incident in countries where these services are available. These services are available through IDX, the data breach and recovery services expert.” continues the notification notice. “IDX identity protection services include: 12 months of credit and CyberScan monitoring, a $1,000,000 insurance reimbursement policy, and fully managed ID theft recovery services. With this protection, IDX will help you resolve issues if your identity is compromised.”
Microsoft Introduces New Password Spray Detection for Azure
27.10.20 Safety Securityweek
Microsoft this week announced the availability of a new password spray detection for Azure AD Identity Protection customers.
Password spraying represents one of the most common forms of attack, where threat actors attempt to breach organizations by trying common passwords against multiple accounts. According to Microsoft, one-third of account compromises are the result of such an attack.
“Instead of trying many passwords against one user, they try to defeat lockout and detection by trying many users against one password. Effective forms of this attack are ‘low and slow,’ where the bad actor uses thousands of IP addresses (such as from a botnet) to attack many tenants with a few common passwords,” the tech giant explains.
With one or two attempts per day, which fall within the normal login patterns, such attacks typically go undetected and traditional protections such as password lockout and IP blocking are bypassed too.
According to Microsoft, password spray attacks yield a 1% success rate, but only if the targeted accounts don’t use password protection.
A look at such attacks across Azure Active Directory (AD) tenants around the world can reveal the patterns of a password spray: the attempts that use the same password generate the same hash, making them traceable.
“The huge elevation of a single hash failing across many accounts indicates a single password being attempted against hundreds of thousands of usernames from many tenants—a password spray attack in progress,” Microsoft explains.
Using this approach, the tech company came up with a heuristic detection for password spray, which allowed it to warn tenants “of hundreds of thousands of attacks monthly.” Based on this, the company built a new tool for password spray risk detection.
The new detection can identify twice as many compromised accounts compared to the previous heuristic algorithm, but maintains a 98% precision. The new risk detection is being introduced in the Azure AD Identity Protection portal and APIs for Identity Protection.
Some Ballot Requests May Be Affected by County Cyber Attack
27.10.20 Attack Securityweek
A hacker attack against an upstate New York county’s computer system raised concern that some emailed absentee ballot applications may not be processed, but the state Board of Elections said voting won’t be affected overall.
The cyber attack on Oct. 18 encrypted about 200 computers operated by Chenango County and hackers demanded ransom of $450 per computer to unlock the files, Herman Ericksen, the county’s information technology director, said Monday. “We are not paying the ransom,” he said.
Last week, the county board of elections released a public statement urging anyone who had sent an absentee ballot application by email since Oct. 15 to call the board to verify it had been received. The statement said the cyber attack would not otherwise impact voting because “the board has redundancies in place that will allow the secure and effective administration of the general election.”
“It was not an attack on the election system,” said state Board of Elections spokesman John Conklin.
Erickson said affected computers are being wiped clean to remove the malware and all software is being reinstalled. The county’s email system was down for several days but is back in operation, he said.
State police and the U.S. Department of Homeland Security are investigating the attack, which appears to have originated in Hong Kong, Erickson said.
Chenango County is part of the 22nd Congressional District in central New York, where Republican Claudia Tenney is in a tight race to reclaim her seat from U.S. Rep. Anthony Brindisi, a Democrat who ousted her by fewer than 4,500 votes two years ago.
Flaws in Winston Privacy Devices Can Expose Networks to Remote Attacks
27.10.20 Vulnerebility Securityweek
Researchers say they’ve uncovered a series of potentially serious vulnerabilities in devices made by online privacy firm Winston Privacy. The vendor has released patches that are automatically being sent to devices.
Winston Privacy provides a hardware-based service designed to boost online privacy and security. The company says it can block online surveillance, accelerate browsing, and block ads and trackers, and it also advertises its services as an alternative to traditional VPNs.Vulnerabilities found in Winston Privacy devices
A consultant at offensive security testing company Bishop Fox and an independent researcher discovered a total of 9 vulnerabilities in the device provided by Winston Privacy to customers. Many of the flaws have been assigned a severity rating of critical or high.
The types of security holes identified in the device include command injection, cross-site request forgery (CSRF), improper access control, insecure cross-origin resource sharing (CORS), default credentials, insufficient authorization controls, and undocumented SSH services.

They can be exploited for arbitrary code execution, privilege escalation, changing device settings and launching DoS attacks.
Chris Davis, the Bishop Fox researcher credited for finding the vulnerabilities, told SecurityWeek that an attacker could exploit some of these weaknesses to hack a Winston Privacy device remotely from the internet by convincing the targeted user to access a malicious webpage.
“Alternatively, if an attacker was on the local area network, an unauthenticated API request would also compromise the device,” Davis explained.
Justin Paglierani, the independent researcher credited for finding the vulnerabilities, explained that successful exploitation of the flaws can give an attacker root access to a device.
“In some configurations, this would allow an unauthenticated attacker direct access to your internal network, bypassing NAT, firewalls, etc,” Paglierani said via email. “In other configurations, it would allow an attacker to intercept any unencrypted traffic passing through the device.”
The vulnerabilities were reported to Winston Privacy in July and the vendor told SecurityWeek that it released a critcal hotfix within 24 hours. Patches were then gradually rolled out through last week, when version 1.5.8 was released to patch a remaining minor issue. Firmware updates containing the patches are automatically sent to devices and users do not need to take any action.
“The cost and effort required to mitigate these vulnerabilities was substantial, especially for a small startup,” Richard Stokes, CEO of Winston Privacy, said in an emailed statement. “As a result of these disclosures, we proactively conducted a thorough internal audit of the device and decided that rebuilding and updating the kernel to incorporate leading edge security patches was the best course of action for our users. This led to significant hardening of the device. This underscores the importance of ongoing investment in security which vendors must accept as part of their responsibility to their users. We are proud of the responsiveness we have demonstrated in addressing these issues.”
Bishop Fox has published an advisory with technical details for each of the identified vulnerabilities.
Swedish Authorities, Banks Hit by Security Data Leak: Report
27.10.20 Incindent Securityweek
Details of bank vault floor plans, alarm systems and the security arrangements for Swedish authorities have been leaked online after a security company was hacked, local media reported Tuesday.
A total of 19 gigabytes of information and around 38,000 files were stolen from security group Gunnebo by one or more hackers in August, according to newspaper Dagens Nyheter.
"It's of course unfortunate that we've had a theft of data," Gunnebo CEO Stefan Syren was quoted as telling the paper.
"We are now reviewing the material and in the cases where there is sensitive information we are contacting the client," he said.
Among the leaked documents are details of the security arrangements for the Swedish parliament and confidential plans of the Swedish Tax Agency's new office on the outskirts of Stockholm, the paper said.
Plans for bank vaults in at least two German banks were leaked, while other documents show the alarm systems and surveillance cameras at a branch of the SEB bank in Sweden, it reported.
Headquartered in Sweden, Gunnebo is a multinational company with nuclear power plants, hospitals and airports among its international customers.
The hack was reported to the Swedish Security Service in August.
"We can only speculate on what the target of the attack was, but as we cannot rule out that it was an attempt at industrial espionage, it has been important to follow the regulations and we have therefore decided to inform Sapo," Syren said in a statement at the time.
The company also said it had concluded that the attack was "well organized," but no details of what data had been compromised was disclosed.
AFP has contacted Gunnebo for a comment.
Dagens Nyheter said hacking attacks based on extortion have hit many companies in recent times, in which criminals steal sensitive information and then demand a ransom not to leak the data online.
Neighboring Finland is currently dealing with an unprecedented hack after the private records of thousands of psychotherapy patients were stolen from the private healthcare company Vastaamo.
The records were first used to try to blackmail the company but then emails demanding ransoms were sent directly to patients at the weekend.
Google Removes 21 Malicious Android Apps from Play Store
27.10.20 Android Thehackernews
Google has stepped in to remove several Android applications from the official Play Store following the disclosure that the apps in question were found to serve intrusive ads.
The findings were reported by the Czech cybersecurity firm Avast on Monday, which said the 21 malicious apps (list here) were downloaded nearly eight million times from Google's app marketplace.
The apps masqueraded as harmless gaming apps and came packed with HiddenAds malware, a notorious Trojan known for its capabilities to serve intrusive ads outside of the app. The group behind the operation relies on social media channels to lure users into downloading the apps.
Earlier this June, Avast discovered a similar HiddenAds campaign involving 47 gaming apps with over 15 million downloads that were leveraged to display device-wide intrusive ads.
"Developers of adware are increasingly using social media channels, like regular marketers would," Avast's Jakub Vávra said. "This time, users reported they were targeted with ads promoting the games on YouTube."
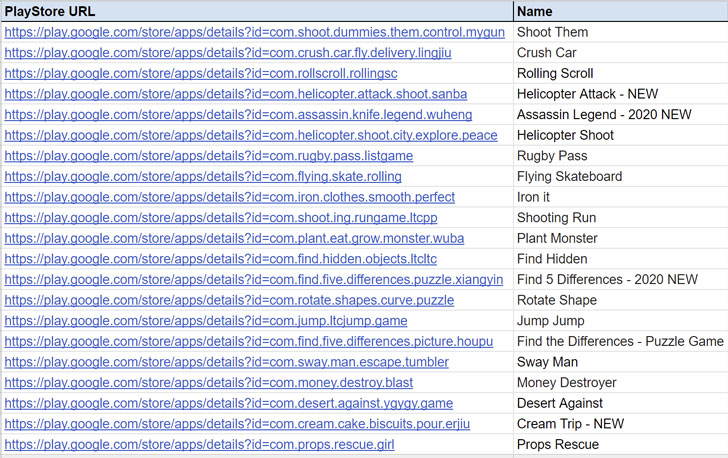
"In September, we saw adware spread via TikTok. The popularity of these social networks make them an attractive advertising platform, also for cybercriminals, to target a younger audience."
Once installed, the apps not only hide their icons to prevent deletion but also hide behind relevant-looking advertisements, making them hard to identify.
In addition, the apps also have the ability to draw over other apps to show timed ads that cannot be skipped, and in some cases, even open the browser to bombard users with ads.
Although such apps can be uninstalled through the app manager features of the device, it puts the onus on the users to search for the exact app that's the source of the ads and remove them.
Google, for its part, has been actively trying to stop rogue Android apps from infiltrating the Google Play Store. It has leveraged Google Play Protect as a means to screen potentially harmful applications and also forged an "App Defense Alliance" last year in partnership with cybersecurity firms ESET, Lookout, and Zimperium to reduce the risk of app-based malware.
If anything, the latest news is another reason why users need to scrutinize the reviews, developer details, and the list of requested permissions before installing any app.
Nando’s Hackers Feast on Customer Accounts
27.10.20 Incindent Threatpost
Multiple chicken diners said their usernames and passwords were stolen and the accounts used to place high-volume orders.
Diners at a popular chicken-dinner chain have seen hundreds of dollars siphoned out of their bank accounts, after cybercriminals were able to access their restaurant ordering credentials. The issue though is that payment-card information is not stored within Nando’s accounts, leaving some questions as to how the hacks occurred.
The Nando’s chain of Peri-Peri chicken eateries is a fixture on most main drags in U.K. and European cities, with dozens of locations in the U.S. as well. It confirmed a credential-stuffing attack on Friday.
Credential-stuffing is accomplished by hackers who take advantage of users who often reuse the same passwords across multiple online accounts. The cyberattackers use stolen passwords and usernames from previous data breaches to brute-force accounts on a wide scale, and when a match is found, they can take over the victim’s account.
Multiple Nando’s customers said their usernames and passwords were stolen and the accounts used to place high-volume orders, according to reports. The mobile numbers were also changed on the impacted accounts.
“We can confirm that while our systems have not been hacked, unfortunately some individual Nando customer accounts have been accessed by a party or parties using a technique called credential-stuffing, whereby the customer’s email address and password have been stolen from somewhere else and, if they use the same details with us, used to access their Nando’s accounts,” Nando’s said in a press statement. “We take immediate action to refund anyone who has been impacted and secure those affected Nando’s accounts.”
It added, “We have made and are continuing to make investments to improve our detection and prevention of suspicious and malicious activity. We apologize to our customers who have been impacted by this.”
Because of COVID-19, Nando’s customers must place an order online or by using a QR code. They’re then prompted for their payment details, but customers said that those details aren’t stored in the account.
“We quite quickly received a refund after complaining on Twitter, however we’re yet to receive any explanation as to how the attack happened,” one U.K. victim told the Daily Mirror.
The sums were not insignificant – one woman received an email confirmation for two orders totaling around $150 (£114.50) that she had never placed. After checking her banking app and confirming that the money was taken out, she talked to the manager at the store, located in the Kensington neighborhood of greater London.
“We eventually found the telephone number for the Kensington High Street branch and after a while managed to talk to the manager who confirmed that there were a group of young people who’d placed the same orders in store,” she told the Mirror. “They said they’d had numerous attempts blocked while trying to purchase further orders. They’d just left the branch with all the food from the original two orders. He said he had CCTV and we had to contact head office to obtain a refund.”
Other victims told U.K. media outlets that they were robbed of even more – one man was robbed of about $870 (£670).
Threatpost has reached out to Nando’s for more information on how the fraudsters were able to access payment-card details.
Between July 2018 and June of this year, there were more than 100 billion credential-stuffing attacks in total, according to a recent Akamai report. In the commerce category specifically – comprising the retail, travel, and hospitality industries – there were 64 billion recorded. More than 90 percent of those attacks targeted the retail industry, which includes fast-food chains like Nando’s.
‘Among Us’ Mobile Game Under Siege by Attackers
27.10.20 Attack Threatpost
Ongoing attacks on the wildly popular game Among Us are testing developers’ ability to keep up.
The meteoric rise of the game Among Us appears to be outpacing its developer’s ability to keep up with malicious actors. On Sunday night, a specific ongoing attack forced InnerSloth, the company behind the game, to hastily roll out an update designed to kick bad actors off the game’s servers — likely along with some innocent players as well.
Among Us takes place in a space setting, where some platers are “crewmates,” and others are “imposters” that live among us. As crewmates prepare their ship for departure, they must locate and eliminate the imposters before they’re taken out themselves. It so far has 5.3 million downloads on Google Play alone.
InnerSloth is asking for patience while the company addresses this and other ongoing security concerns. InnerSloth is run by a three-person team consisting of one developer, one animator and game designer, and one artist. The game was released almost two years ago, but thanks to a long summer spent largely under quarantine its audience has exploded over the past few months.
Eris Loris Takes Over Among Us
This most recent round of attacks spammed players with ads from a player named Eris Loris, rendering the game useless. Players flooded the Among Us subreddit to report the activity.
“So far every single server I’ve joined is hacked by Eris Loris today,” one user with a NSFW handle name wrote two days ago. “I have tried maybe 40-plus games. Not a single one wasn’t hacked within 10-30 seconds.”
The breach uses bots to overwhelm the game with messages promoting a YouTube channel and Discord operated under the name Eris Loris, threatening to “blow up your phone,” and concluding with a “Trump 2020” endorsement.
Among Us Server Update
Forest Willard, InnerSloth’s resident programmer, announced a server update Sunday night that tries to identify bad actors on the game and kick them out before they cause trouble. But the move comes with a downside, some players might get kicked off inadvertently, which Willard added in a tweet is for the “greater good,” that players should view as “emergency maintenance.”
“The reason I didn’t roll this update out sooner is that I was afraid of false positives: You totally might see the game think you’re hacking when you’re not,” Willard said in a subsequent tweet. “I’ve done my best to find this kind of bug, but my hand is forced this time.”
Threatpost wasn’t able to contact the person behind the Eris Loris breach by the time of publication, but he told Kokatu he attacked Among Us because he thinks it’s funny to rile people up. He added that the blame for the damage to the game falls on InnerSloth and the team’s inability to scale up quickly enough.
“Among Us may be a small developer team, but that’s not my fault,” he added. “The game is at a scale bigger than most games. There is nothing stopping them from getting more developers, so the ‘it’s three people’ reasoning means nothing to me.”
Can Among Us Scale?
InnerSloth’s recent record might back up Eris Loris’ point about scale. A scroll through the Among Us subreddit shows breaches on the game are frequent, in addition to rampant cheating.
In early October, a massive spike in traffic kept shutting down the Among Us servers, according to Screen Rant.
But that hasn’t stunted the game’s growth yet. Among Us was the most downloaded mobile game in the world during September, with 83.8 million installs, according to SensorTower, which added that’s 40 times more than the same month last year.
And just last week New York Representative Alexandria Ocasio-Cortez went live on Twitch to play Among Us and promote voting, an event that drew in 435,000 viewers just to her stream alone, TechCrunch reported.
InnerSloth is in a bit of a pickle here. If the owners make major changes to the game, they could ruin the magic that made it explode in popularity and drive away the audience. If they leave it as-is, malicious actors could drive away players.
Prior to the new fix, InnerSloth posted on Twitter that it is “…super duper aware” of the issue and reminded users to, “Please play private games or with people you trust!!! We’re doing what we can!!”
While InnerSloth works out the security bugs on Among Us, the company has decided to delay the release of its sequel, Among Us 2 and instead work on improving the original.
“The main reason we are shooting for a sequel is because the codebase of Among Us 1 is so outdated and not built to support adding so much new content,” InnerSloth said in a recent blog post. “However, seeing how many people are enjoying Among Us 1 really makes us want to be able to support the game and take it to the next level. We have decided to cancel Among Us 2 and instead put all our focus into improving Among Us 1.”
Containerd Bug Exposes Cloud Account Credentials
27.10.20 Vulnerebility Threatpost
The flaw (CVE-2020-15157) is located in the container image-pulling process.
A security vulnerability can be exploited to coerce the containerd cloud platform into exposing the host’s registry or users’ cloud-account credentials.
Containerd bills itself as a runtime tool that “manages the complete container lifecycle of its host system, from image transfer and storage to container execution and supervision to low-level storage to network attachments and beyond.” As such, it offers deep visibility into a user’s cloud environment, across multiple vendors.
The bug (CVE-2020-15157) is located in the container image-pulling process, according to Gal Singer, researcher at Aqua. Adversaries can exploit this vulnerability by building dedicated container images designed to steal the host’s token, then using the token to take over a cloud project, he explained.
“A container image is a combination of a manifest file and some individual layer files,” he wrote in a recent post. “The manifest file [in Image V2 Schema 2 format]…can contain a ‘foreign layer’ which is pulled from a remote registry. When using containerd, if the remote registry responds with an HTTP 401 status code, along with specific HTTP headers, the host will send an authentication token that can be stolen.”
He added, “the manifest supports an optional field for an external URL from which content may be fetched, and it can be any registry or domain.”
The attackers can thus exploit the problem by crafting a malicious image in a remote registry, and then convincing the user to access it through containerd (this can be done through email and other social-engineering avenues), according to the National Vulnerability Database writeup.
“If an attacker publishes a public image with a manifest that directs one of the layers to be fetched from a web server they control, and they trick a user or system into pulling the image, they can obtain the credentials used for pulling that image,” according to the bug advisory. “In some cases, this may be the user’s username and password for the registry. In other cases, this may be the credentials attached to the cloud virtual instance which can grant access to other cloud resources in the account.”
Non-Trivial Exploitation
Researcher Brad Geesaman at Darkbit, who did original research into the vulnerability (which he calls “ContainerDrip”), put together a proof-of-concept (PoC) exploit for a related attack vector.
One of the hurdles for exploitation is the fact that containerd clients that pull images may be configured to authenticate to a remote registry in order to fetch private images, which would prevent it from accessing the malicious content. Instead, an attacker would need to place the tainted image into a remote registry that the user already authenticates to.
“The question became: ‘How do I get them to send their credentials to me [for remote-registry authentication]?'” he said in a posting earlier this month. “As it turns out, all you have to do is ask the right question.”
The Google Kubernetes Engine (GKE) is a managed environment for running containerized applications, which can be integrated with containerd. When GKE clusters running COS_CONTAINERD and GKE 1.16 or below are given a deployment to run, a Basic Auth header shows up, which when base64 decoded, turns out to be the authentication token for the underlying Google Compute Engine, used to create virtual machines. This token is attached to the GKE cluster/nodepool.
“By default in GKE, the [Google Cloud Platform] service account attached to the nodepool is the default compute service account and it is granted Project Editor,” explained Geesaman.
That said, also by default, a function called GKE OAuth Scopes “scopes down” the available permissions of that token. Geesaman also found a workaround for that.
“If the defaults were modified when creating the cluster to grant the [“any”] scope to the nodepool, this token would have no OAuth scope restrictions and would grant the full set of Project Editor IAM permissions in that GCP project,” he explained.
And from there, attackers can escalate privileges to “Project Owner” using a known attack vector demonstrated at DEF CON 2020.
He added that the GKE path is one of many possible.
containerd patched the bug, which is listed as medium in severity, in version 1.2.4; containerd 1.3.x is not vulnerable.
Cloud security continues to be a challenge for organizations. Researchers earlier in October disclosed two flaws in Microsoft’s Azure web hosting application service, App Services, which if exploited could enable an attacker to take over administrative servers. Over the summer, malware like the Doki backdoor was found to be infesting Docker containers.
In April, a simple Docker container honeypot was used in a lab test to see just how quickly cybercriminals will move to compromise vulnerable cloud infrastructure. It was quickly attacked by four different criminal campaigns over the span of 24 hours.
Microsoft IE Browser Death March Hastens
27.10.20 IT Threatpost
Internet Explorer end of support browser transition
Internet Explorer redirects more traffic to Edge Chromium browser as Microsoft warns of the upcoming demise of the once dominant browser.
As the death of the once dominant Internet Explorer (IE) draws closer, Microsoft is quickly pounding more nails into the browser’s coffin.
On Monday, Microsoft hastened its IE-to-Edge browser-transition strategy and announced new controls for users and IT staff when it comes to how the lame-duck browser will handle a growing list of websites incompatible with IE. Those include YouTube, Twitter, Yahoo Mail and 1,153 other leading internet destinations.
Microsoft also announced that in two short weeks, its own services would no longer be supported by 25-year-old browser that once crushed Netscape and other competitors. In 2004 IE enjoyed 95 percent market share. Today, an estimated 5 percent of users rely on it.
As a point of reference, the Microsoft Edge web browser comes built into Windows 10. In 2015 Microsoft said it would replace IE with Edge in an effort to support modern browser functions, such as extensions. In 2018, it announced further efforts to streamline its development — Edge be rebuilt on the Chromium rendering engine, which is the same code that Google’s Chrome browser uses.
Internet Explorer alert regarding Edge BrowserIE: The Long Goodbye
Part of IE’s shuttering entails redirecting users to the Microsoft Edge 87, to be released November 17. However, BleepingComputer reported that the redirects have already begun.
Last Monday, Microsoft explained that users of IE who visited an incompatible website would be presented with an interstitial webpage alerting them they were being redirected to Microsoft Edge. An opt-in prompt asks consent to copy a user’s browsing data and preferences from Internet Explorer to Microsoft Edge. In addition to that, a website incompatibility banner will appear below the address bar for every redirection, Microsoft said.
On Monday, Microsoft released instructions on how IT staff can change the behavior of Internet Explorer when it lands on an incompatible site.
One option is configuring IE to not redirect to Edge “RedirectSitesFromInternetExplorerPreventBHOInstall”.
A second option “RedirectSitesFromInternetExplorerRedirectMode” allows IE to open sites in Edge – and browser data and user preferences are automatically imported.
The third option doesn’t import browser data and user preferences, but hides any incompatibility warning message and redirects IE to Edge.
“Redirection from Internet Explorer to Microsoft Edge requires an Internet Explorer Browser Helper Object (BHO) named ‘IEtoEdge BHO,'” Microsoft explained.
“These policies will be available as ADMX file updates by October 26, 2020 and will be available in Intune by November 9, 2020,” wrote Microsoft. ADMX files are Windows registry-based policy settings that are XML-based and define policy settings and browser behaviors.

Security and Privacy Concerns?
For many, there will be few tears when IE is finally put out to pasture. The browser, which was the centerpiece to a 2001 antitrust lawsuit between United States and Microsoft, has a spotty history when it comes to security, privacy and compatibility.
There are more than a few reasons there will be no love lost with the expiration of IE. Since 2000, there have been over 1,000 serious vulnerabilities tied to it. The majority (28 percent) are tied to code-execution bugs, 25 percent related to IE memory-corruption flaws and 20 percent buffer-overflow vulnerabilities, according to CVE Details.
For an exhaustive look at the history of major IE bugs, Paul Szabo has an impressive collection.
The browser, often standardized within corporations, was the bane of many security teams because of Microsoft’s chronic foot dragging when it came to patching. In 2014, the U.S. Department of Homeland Security advised companies and Windows XP users to ditch IE until Microsoft fixed a use-after-free bug that allowed unauthorized remote code execution.
Privacy concerns have also been paramount for users of IE, with many feeling that Microsoft’s access to browsing data coupled with services and application data was unsettling. Those Microsoft anxieties have been muted over time as massive data collected by Google, Facebook and Amazon have normalized the behavior.
Things have come full circle, with some arguing switching to Microsoft’s Edge Chromium browser is a way to avoid Google’s data collection, while still being able to reap the benefits the same browser engine.
“Microsoft Edge gives more privacy than Chrome, Google Chrome uses its user’s data to give a personalized advertisement for its revenue which would also make,” wrote a Microsoft contributor to its Tech Community.
That’s not to say Microsoft Edge doesn’t have security concerns.
On Monday, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned of a Microsoft Edge memory-corruption flaw (CVE-2020-15999) rated high-risk. However, unlike with IE, this bug was tied to Google Chromium code and was patched last week. At the time, Google warned that adversaries were exploiting the bug in the wild.
Final Farewell
“Internet Explorer 11 is the last major version of Internet Explorer. Internet Explorer 11 will continue receiving security updates and technical support for the lifecycle of the version of Windows on which it is installed,” wrote Microsoft. Mainstream support for Windows 10 ends Oct. 13, 2020. Extended support, according to Microsoft, ends on Oct. 14, 2025.
Nitro PDF data breach might impact major companies, including Microsoft, Google, and Apple
27.10.20 Incindent Securityaffairs
Nitro PDF suffered a massive data breach that impacts many major organizations, including Apple, Chase, Citibank, Google, and Microsoft.
A massive data breach suffered by the Nitro PDF might have a severe impact on well-known organizations, including Google, Apple, Microsoft, Chase, and Citibank.
Nitro Software, Inc. develops commercial software used to create, edit, sign, and secure Portable Document Format (PDF) files and digital documents. The company has over 650,000 business customers worldwide, and claims millions of users across the globe.
According to the following the security advisory issued by the software maker and unauthorized third party gained limited access to a company database.
"NITRO ADVISES OF LOW IMPACT SECURITY INCIDENT
* AN ISOLATED SECURITY INCIDENT INVOLVING LIMITED ACCESS TO NITRO DATABASE BY AN UNAUTHORISED THIRD PARTY
* DATABASE DOES NOT CONTAIN USER OR CUSTOMER DOCUMENTS.
* INCIDENT HAS HAD NO MATERIAL IMPACT ON NITRO'S ONGOING OPERATIONS.
* INVESTIGATION INTO INCIDENT REMAINS ONGOING
* NO EVIDENCE CURRENTLY THAT ANY SENSITIVE OR FINANCIAL DATA RELATING TO CUSTOMERS IMPACTED OR IF INFO MISUSED
* DOES NOT ANTICIPATE A MATERIAL FINANCIAL IMPACT TO ARISE FROM INCIDENT
* INCIDENT IS NOT EXPECTED TO IMPACT CO'S PROSPECTUS FORECAST FOR FY2020"
Cybersecurity intelligence firm Cyble came across a threat actor that was selling a database, allegedly stolen from Nitro Software’s cloud service, that includes users’ data and documents. The huge archive contains 1TB of documents, the threat actor is attempting to sell it in a private auction with the starting price of $80,000.

The database contains a table named ‘user_credential’ that contains 70 million user records, including email addresses, full names, bcrypt hashed passwords, titles, company names, IP addresses, and other system-related data.
Cyble shared the database with Bleeping Computer that was able to determine the authenticity of the database.
“From the samples of the database shared with BleepingComputer, the document titles alone disclose a great deal of information about financial reports, M&A activities, NDAs, or product releases.” states BleepingComputer.
The records in the document database contain a file’s title, whether it was created, signed, what account owns the document, and whether it’s public.
I have reached Cyber for a comment, below their statement:
“Considering the scale and extent of the breach, this is one of the worst breaches Cyble has seen in the last few years. The cybercriminals were not only able to access sensitive account details, but also the information related to shared documents as well. Majority of the Fortune 500 organizations are affected by this breach.”
The databases contain a large number of records belonging to well-known companies:
Company # of accounts # of documents
Amazon 5,442 17,137
Apple 584 6,405
Citi 653 137,285
Chase 85 177
Google 3,678 32,153
Microsoft 3,330 2,390
M&A documents
Cyble has added the data related to the NITRO PDF data breach to its AmIBreached.com data breach notification service.
KashmirBlack, a new botnet in the threat landscape that rapidly grows
27.10.20 BotNet Securityaffairs
Security experts spotted a new botnet, tracked as KashmirBlack botnet, that likely infected hundreds of thousands of websites since November 2019.
Security experts from Imperva have spotted a new sophisticated botnet, tracked as KashmirBlack is believed to have already infected hundreds of thousands of websites by exploiting vulnerabilities in their content management system (CMS) platforms.
The KashmirBlack botnet has been active at least since November 2019, operators leverages dozens of known vulnerabilities in the target servers.
Experts believe that the botmaster of the KashmirBlack botnet is a hacker that goes online with moniker “Exect1337,” who is a member of the Indonesian hacker crew ‘PhantomGhost’.
The experts observed millions of attacks per day on average, on thousands of victims in more than 30 different countries around the world.
“It has a complex operation managed by one C&C (Command and Control) server and uses more than 60 – mostly innocent surrogate – servers as part of its infrastructure. It handles hundreds of bots, each communicating with the C&C to receive new targets, perform brute force attacks, install backdoors, and expand the size of the botnet.” reads the first part of two reports published by the experts detailing the DevOps implementation behind the botnet.

The primary purpose of the KashmirBlack botnet is to abuse resources of compromised systems for cryptocurrency mining and redirecting a site’s legitimate traffic to spam pages.
Experts observed a continuous growth of the botnet since its discovery along with an increasing level of complexity.
In May experts observed an increase in the command-and-control (C&C) infrastructure and the exploits used by botnet operators.
KashmirBlack scans the internet for sites using vulnerable CMS versions and attempting to exploit known vulnerabilities to them and take over the underlying server.
Below a list of vulnerabilities exploited by the botnet operators to compromise websites running multiple CMS platforms, including WordPress, Joomla!, PrestaShop, Magneto, Drupal, vBulletin, osCommerce, OpenCart, and Yeager:
PHPUnit Remote Code Execution – CVE-2017-9841
jQuery file upload vulnerability – CVE-2018-9206
ELFinder Command Injection – CVE-2019-9194
Joomla! remote file upload vulnerability
Magento Local File Inclusion – CVE-2015-2067
Magento Webforms Upload Vulnerability
CMS Plupload Arbitrary File Upload
Yeager CMS vulnerability – CVE-2015-7571
Multiple vulnerabilities including File Upload & RCE for many plugins in multiple platforms here
WordPress TimThumb RFI Vulnerability – CVE-2011-4106
Uploadify RCE vulnerability
vBulletin Widget RCE – CVE-2019-16759
WordPress install.php RCE
WordPress xmlrpc.php Login Brute-Force attack
WordPress multiple Plugins RCE (see full list here)
WordPress multiple Themes RCE (see full list here)
Webdav file upload vulnerability
“During our research we witnessed its evolution from a medium-volume botnet with basic abilities to a massive infrastructure that is here to stay,” Imperva concludes.
The second part of the report also includes Indicators of Compromise (IoCs) for this botnet.
IT Services Giant Sopra Steria Hit by Ransomware
27.10.20 Ransomware Securityweek
European IT services provider Sopra Steria on Monday said its systems were recently infected with a new variant of the notorious Ryuk ransomware.
France-based Sopra Steria, which claims to have 46,000 employees across 25 countries, offers a wide range of IT services, including consulting, technology, software, system integration, business process, infrastructure management and cybersecurity.
The company reported on October 21 that it had detected an intrusion on its IT network the day before and that it had started working on containing the incident.
In an update shared on Monday, the IT giant said it was targeted in a cyberattack that involved a new variant of the Ryuk ransomware, a variant that allegedly was “previously unknown to antivirus software providers and security agencies.”
“Sopra Steria’s investigation teams immediately provided the competent authorities with all information required. The Group was able to quickly make this new version’s virus signature available to all antivirus software providers, in order for them to update their antivirus software,” the company said. “Moreover, it has also been established that the cyberattack was only launched a few days before it was detected.”
The fact that the attackers only gained access to Sopra Steria systems just days before the attack was uncovered is not surprising. The DFIR Report said recently that in one of the attacks it observed, only 29 hours passed between the first email being sent by the hackers and systems becoming fully compromised and encrypted.
Sopra Steria said the incident only impacted a “limited part” of its infrastructure and claimed that it had found no evidence of data leaks or damage to customer systems. However. the firm expects that it will take a few weeks until all operations return to normal.
Russia-linked cybercriminals who use the Ryuk ransomware have been known to also steal data from victims in an effort to increase their chances of getting paid.
The Ryuk ransomware has often been delivered via the TrickBot botnet, whose infrastructure was recently targeted for takedown by both the U.S. government and private sector companies. While the operation against TrickBot appears to have been successful — at least to some degree — it was reported just days before Sopra Steria was targeted that Ryuk attacks continued.
NVIDIA Patches Code Execution Flaws in GeForce Experience
27.10.20 Vulnerebility Securityweek
Patches released by NVIDIA last week for the GeForce Experience software address two arbitrary code execution bugs assessed with a severity rating of high.
The GeForce Experience software is a companion application that is being installed alongside NVIDIA’s GeForce drivers. Functioning as a GPU management tool, it allows users to record and share videos and screenshots, update drivers, and ensure game settings are always optimized.
Tracked as CVE‑2020‑5977 and with a CVSS score of 8.2, the first of the newly addressed issues was identified in the NVIDIA Web Helper NodeJS Web Server and exists because an uncontrolled search path is used to load a node module.
An attacker able to exploit the flaw could execute code in the context of the vulnerable software, could cause denial of service, escalate privileges, or access restricted information, NVIDIA notes in an advisory.
The second vulnerability has the identifier CVE‑2020‑5990 and a CVSS score of 7.3. According to NVIDIA, the flaw was identified in the ShadowPlay component and may lead to code execution, local privilege escalation, denial of service, or information disclosure.
A third vulnerability patched with the new release is CVE‑2020‑5978 (CVSS score of 3.2), identified in the GeForce Experience services. The bug exists because “a folder is created by nvcontainer.exe under normal user login with LOCAL_SYSTEM privileges,” NVIDIA explains.
The flaw could be exploited to achieve denial of service or to escalate privileges.
All three vulnerabilities, NVIDIA explains, impact GeForce Experience versions prior to 3.20.5.70. To keep their systems protected, users are advised to update to version 3.20.5.70 or newer of the software.
US Insists on Need to Ban TikTok
27.10.20 BigBrothers Securityweek
US President Donald Trump's administration has insisted on the need to ban TikTok due to national security concerns in a new court filing ahead of a plan to make the video app unavailable on November 12.
The filing comes as the court considers the legality of the administration's bid to make the Chinese-owned app unavailable in the United States, where it has 100 million users.
"The president should not be prevented from regulating national security threats simply because a foreign adversary cloaks its activities within a media company," the filing on Friday at a federal court in Washington says.
The Trump administration is seeking to persuade the judge in the case to allow it to move forward with restrictions on the video-sharing app, which it claims has links to the Chinese government through its parent firm ByteDance.
In September, a temporary injunction prevented the government from removing TikTok from mobile application download platforms.
That Trump administration order had sought to ban new downloads of the app but continue to allow use of TikTok until November 12, when all usage would be blocked.
The judge at the time denied TikTok's request to suspend the November 12 ban, but the court has yet to consider the merits of the legal arguments on whether the social platform should remain available to Americans.
TikTok has repeatedly defended itself against allegations of data transfers to the Chinese government.
It says its servers where user information is stored are located in the United States and Singapore.
The company has also said the ban is unnecessary since negotiations are underway to restructure the ownership of TikTok to address national security issues raised by the administration.
A tentative deal has been unveiled that would make Silicon Valley giant Oracle the technology partner for TikTok and a stakeholder in a new entity to be known as TikTok Global.
Link Previews in Chat Apps Pose Privacy, Security Issues: Researchers
27.10.20 Privacy Securityweek
An analysis of the manner in which popular chat applications handle link previews has revealed several privacy and security issues, including some that still need addressing, security researchers warn.
Link previews provide users with information on what a link received in chat would lead them to, regardless of whether it is a file or a web page.
However, link previews can be abused for nefarious purposes, and security researchers Talal Haj Bakry and Tommy Mysk claim to have identified several cases in which popular chat apps for iOS and Android fail to provide their users with the necessary protections against such abuses.
Due to the manner in which link previews are implemented, some applications were found to leak users’ IP addresses, others to leak links that have been sent in conversations encrypted end-to-end, while some would unnecessarily download large amounts of data, even gigabytes, in the background.
The analyzed applications include Discord, Facebook Messenger, Google Hangouts, iMessage, Instagram, LINE, LinkedIn, Reddit, Signal, Slack, Threema, TikTok, Twitter, Viber, WeChat, WhatsApp, and Zoom.
Four of the apps, namely Signal (if the link preview option is turned off in settings), Threema, TikTok, and WeChat, do not generate previews. In iMessage, Signal (if the link preview option is enabled), Viber, and WhatsApp, the previews are generated on the sender’s side.
In Reddit (only in the chat, not when viewing posts and comments), previews are generated by the receiver, before the user taps on the link, which the researchers found to be a major privacy concern, as it may result in the receiver’s IP address being leaked to the sender.
An attacker can obtain a user’s IP address, which can also enable them to obtain an approximate geographical location, by sending them a link that points to a server they control. When the app generates the preview, it needs to connect to the attacker’s server in order to fetch the content, allowing the server to record the victim’s IP.
Reddit has released fixes for the issue. A second chat app was found vulnerable, but the researchers refrained from providing details on it, pending a fix.
In some applications, the previews are generated server-side, with Discord, Facebook Messenger, Google Hangouts, Instagram, LINE, LinkedIn, Slack, Twitter, and Zoom falling in this category. The problem with this approach, the researchers say, is that the server may store a copy of the sent file, which could contain sensitive information.
“Although these servers are trusted by the app, there’s no indication to users that the servers are downloading whatever they find in a link. Are the servers downloading entire files, or only a small amount to show the preview? If they’re downloading entire files, do the servers keep a copy, and if so for how long? And are these copies stored securely, or can the people who run the servers access the copies?” the researchers said.
Another issue that the researchers identified was that many of the analyzed chat applications stored the files on their servers regardless of their size. Specifically, Facebook Messenger and Instagram, both Facebook applications, were found to store entire files on the company’s servers, even if they weigh gigabytes.
This behavior could lead to a server reaching its capacity, which in theory can result in service disruptions. However, Facebook says this is a feature that works as intended.
“As we explained to the researcher weeks ago, these are not security vulnerabilities. The behavior described is how we show previews of a link on Messenger or how people can share a link on Instagram, and we don’t store that data. This is consistent with our data policy and terms of service,” a Facebook spokesperson told SecurityWeek.
Another concerning matter, the researchers say, is the fact that although many of the analyzed apps offer end-to-end encryption, the LINE app finds no issue with sending links from within the encrypted messages to an internal server to generate a preview.
“Well, it appears that when the LINE app opens an encrypted message and finds a link, it sends that link to a LINE server to generate the preview. We believe that this defeats the purpose of end-to-end encryption, since LINE servers know all about the links that are being sent through the app, and who’s sharing which links to whom,” the researchers explain.
They also underline the fact that chat apps should avoid running JavaScript code when generating previews, as malicious websites may abuse this for nefarious purposes. In LinkedIn’s case, the researchers were able to leverage such code to bypass the app’s limit of downloading 50 MB of a file when generating the preview.
SecurityWeek has also reached out to LINE, LinkedIn, and Reddit for comments on the researchers’ findings, but hasn’t received responses by the time of publication.
Ransomware attack disabled Georgia County Election database
26.10.20 Ransomware Securityaffairs
A ransomware attack recently hit Georgia county government and reportedly disabled a database used to verify voter signatures.
A ransomware attack hit a Georgia county government early this month and disabled a database used to verify voter signatures in the authentication of absentee ballots. It is a common process to validate absentee ballots sent by mail by analyzing signatures.
The media pointed out that this is the first reported case of a ransomware attack against a system used in the incoming 2020 Presidential election.
Ransomware attacks could have a dramatic impact on the elections, they could disrupt voting systems and raise doubts about the validity of the vote.
The attack took place on October 7, it hit Hall County, in the northern part of the state and it disabled the county’s voter signature database.
“One of the databases the county uses to verify voter signatures on absentee ballots is not working after some county network outages due to a ransomware attack on Oct. 7.” reported the Gainesville Times. “Registration Coordinator Kay Wimpye with the county elections office said employees can still verify voter signatures by manually pulling hard copies of voter registration cards, which is more time-consuming. Most voter signatures can be verified using a state database that has been unaffected by the outages, she said.”
The media reported that the Hall County attack was carried out by Doppelpaymer ransomware operators that also leaked stolen data on their dark web leak site to force the organization to pay the ransom.
The county website published an update to announce that the attack did not impact the voting process for citizens, a situation that is differed from the scenario reported by the Times.
Is the Abaddon RAT the first malware using Discord as C&C?
26.10.20 Virus Securityaffairs
Abaddon is the first RAT that uses the freeware instant messaging and VoIP app and digital distribution platform Discord as a command & control server.
Researchers from MalwareHunterTeam have spotted a new piece of remote access trojan (RAT) dubbed ‘Abaddon’ that is likely the first malware using the Discord platform as command and control. The Abaddon malware connects to the Discord command and control server to check for new commands to execute.
Experts also warn that the author of the malware also developed a malware feature.
In the past, other threat actors already abused the Discord platform for different purposes, such as using it as a stolen data drop.
“In the past, we have reported on how threat actors use Discord as a stolen data drop or have created malware that modifies the Discord client to have it steal credentials and other information.” reported Bleeping Computer that first reported the news.
Abaddon implements data-stealing feature, it was designed to steal multiple data from the infected host, including Chrome cookies, saved credit cards, and credentials, Steam credentials, Discord tokens and MFA information.
The malware also collects system information such as country, IP address, and hardware information.
According to Bleeping Computer the malware supports the following commands:
Steal a file or entire directories from the computer
Get a list of drives
Open a reverse shell that allows the attacker to execute commands on the infected PC.
Launch in-development ransomware (more later on this).
Send back any collected information and clear the existing collection of data.
The malicious code connects to the Command & Control every ten seconds for new tasks to execute.
Experts pointed out that the malware also implements the commands to encrypt files of the infected system and decrypt them.
The ransomware feature appears to be under development.
HPE addresses critical auth bypass issue in SSMC console
26.10.20 Vulnerebility Securityaffairs
HPE fixed a remote authentication bypass vulnerability in HPE StoreServ Management Console (SSMC) data center storage management solution.
Hewlett Packard Enterprise (HPE) has addressed a maximum severity (rated 10/10) remote authentication bypass vulnerability, tracked as CVE-2020-7197, affecting the HPE StoreServ Management Console (SSMC) data center storage management solution.
HPE SSMC is a management and reporting console for HPE Primera (data storage for mission-critical apps) and HPE 3PAR StoreServ systems (AI-powered storage cloud service providers) data center arrays.
The CVE-2020-7197 flaw is a remote authentication bypass vulnerability that affects HPE 3PAR StoreServ Management and Core Software Media prior to 3.7.0.0.
“HPE StoreServ Management Console 3.7.0.0 is an off node multiarray manager web application and remains isolated from data on the managed arrays. SSMC is vulnerable to remote authentication bypass.” reads the advisory.
The flaw can be exploited by threat actors with no privileges and doesn’t require user interaction.
HPE has addressed the issue with the release of the HPE 3PAR StoreServ Management Console 3.7.1.1.
“This SSMC release includes important security and quality improvement defect fixes that strengthen the security posture of SSMC appliances,” reads the changelog.
Hewlett Packard Enterprise acknowledged the researchers Elwood Buck from MindPoint Group for reporting the flaw.
U.S. Treasury Sanctions Russian Institute Linked to Triton Malware
26.10.20 BigBrothers Securityweek
The United States Department of the Treasury’s Office of Foreign Assets Control (OFAC) has announced sanctions against a Russian government institute connected to the destructive Triton malware.
Initially identified in 2017 on the systems of a Saudi Arabian oil and gas company and also referred to as Trisis and HatMan, Triton is known for the targeting of Schneider Electric’s Triconex Safety Instrumented System (SIS) controllers.
Referred to by some as Xenotime, the threat actor behind the malware is believed to have been active since at least 2014, and at one point it expanded activities to Australia, Europe, and the US, and added electric utilities to its target list.
In 2018, FireEye associated Triton with the Russian technical research organizations Central Scientific Research Institute of Chemistry and Mechanics (CNIIHM).
At SecurityWeek’s 2019 ICS Cyber Security Conference in Singapore, FireEye revealed that evidence connecting Triton with CNIIHM started disappearing following the publishing of their 2018 report, including photos, details on internal structure, and information on associated IP addresses.
OFAC, which notes that Triton has been labeled “the most dangerous activity publicly known,” announced on Friday sanctions against CNIIHM, or TsNIIKhM (the State Research Center of the Russian Federation FGUP Central Scientific Research Institute of Chemistry and Mechanics), essentially prohibiting Americans from engaging with the institution.
This Russian government-controlled research organization, the Treasury Department says, is responsible for the development of customized tools that made possible the 2017 attack against the Saudi Arabian petrochemical facility.
Pursuant to section 224 of the Countering America’s Adversaries Through Sanctions Act (CAATSA), the Treasury Department designated TTsNIIKhM “for knowingly engaging in significant activities undermining cybersecurity against any person, including a democratic institution, or government on behalf of the Government of the Russian Federation.”
The Triton malware, OFAC says, was specifically created to target industrial control systems (ICS) that are used within critical infrastructure facilities to ensure immediate shutdown in the event of an emergency.
Deployed via phishing emails, the malware was designed to manipulate these safety controllers, providing attackers with full control over the infected systems. The malware can cause “significant physical damage and loss of life,” the US government said.
In an emailed comment, Robert M. Lee, CEO and co-founder of industrial cybersecurity firm Dragos, said, “An OFAC sanction by the U.S. Treasury is significant and compelling; not only will it impact this research institution in Russia, but anyone working with them will have their ability to be successful on the international stage severely hampered.”
“The most important aspect of this development, however, is the attribution to Russia for the TRISIS attack by the USG officially and the explicit call out of industrial control systems in the sanction. This is a norm setting moment and the first time an ICS cyber-attack has ever been sanctioned. This is entirely appropriate as this cyber-attack was the first ever targeted explicitly towards human life. We are fortunate no one died and I'm glad to see governments take a strong stance condemning such attacks," he continued.
Nathan Brubaker, senior manager of analysis at Mandiant Threat Intelligence, commented, “TRITON malware was designed to disable the safety systems which form one of the last lines of protection in industrial systems. With control of these safety systems hackers could potentially allow an unsafe state to occur or worse yet, use their access to other control systems to cause an unsafe state, then allow that state to continue, potentially causing dangerous conditions and threaten human life.
“Fortunately, TRITON was discovered when safety systems recognized an abnormality during an intrusion and shut operations down at a plant. In the following months, Mandiant was able to track the intrusion to the Russian lab that is being sanctioned and publicly expose their involvement. This was a dangerous tool that may have been used to do real physical harm. We’re fortunate that it was found in the manner it was, giving us a chance to dig into the actors behind the scenes.”
Finland Shocked by Therapy Center Hacking, Client Blackmail
26.10.20 Hacking Securityweek
Finland’s interior minister summoned key Cabinet members into an emergency meeting Sunday after hundreds — and possibly thousands — of patient records at a private Finnish psychotherapy center were accessed by a hacker or hackers now demanding ransoms.
Finnish Interior Minister Maria Ohisalo tweeted that authorities would “provide speedy crisis help to victims” of the security breach at the Vastaamo psychotherapy center, an incident she called “shocking and very serious.”
Vastaamo, which has branches throughout the Nordic country of 5.5 million and operates as a sub-contractor for Finland’s public health system, said its client register with intimate patient information was likely stolen during two attacks that started almost two years ago.
The first incursion probably took place in November 2018 and “it is likely that our (data) systems were penetrated also between the end of November 2018 and March 2019,” Vastaamo said in a statement late Saturday.
The center said the unknown perpetrator or perpetrators had published at least 300 patient records containing names and contact information using the anonymous Tor communication software. “The blackmailer has started to approach victims of the security breach directly with extortion letters,” it said.
The National Bureau of Investigation said Sunday up to “tens of thousands” of Vastaamo clients may have had their personal data compromised. Police were looking for the possible culprits both in Finland and abroad.
It was not immediately clear if the stolen information included diagnoses, notes from therapy sessions or other potentially damaging information. Also, it wasn’t clear why the information was surfacing only now.
“What makes this case exceptional is the contents of the stolen material,” Marko Leponen, the National Bureau of Investigation’s chief investigator assigned to the case, told reporters.
Vastaamo urged clients who receive demands to pay money in exchange for keeping their information private — allegedly dozens already — to immediately contact Finnish police.
Finnish media reported that cyber-criminals have demanded ransoms of 200 euros ($240) paid in Bitcoin, with the amount increased to 500 euros unless paid within 24 hours. The psychotherapy center also reportedly received a ransom demand for 450,000 euros ($534,000) in Bitcoin.
Citizens reacted to the news with disbelief. It also prompted comments from Finland’s leaders. President Sauli Niinisto called the blackmailing “cruel” and “repulsive.” Prime Minister Sanna Marin said the hacking of such sensitive information was ”shocking in many ways.”
The chief research officer of Finnish data security company F-Secure, Mikko Hypponen, told Finnish public broadcaster YLE that the case was exceptional even on an international level.
“I’m not aware of any such case anywhere in the world with such gross misuse of patient records,” said Hypponen, one of Finland’s leading data security experts and an internationally known lecturer on cyber-threats.
Hypponen also tweeted that he knew of “only one other patient blackmail case that would be even remotely similar: the Center for Facial Restoration incident in Florida in 2019. This was a different medical area and had a smaller number of victims, but the basic idea was the same.”
Various Finnish organizations have rapidly mobilized ways to help the victims of the breach, including direct dial-in numbers with churches and therapy services.
Microsoft Teams phishing campaign targeted up to 50,000 Office 365 users
24.10.20 Phishing Securityaffairs
Experts warn of a phishing campaign that already targeted up to 50,000 Office 365 users with a fake automated message from Microsoft Teams.
Secruity researchers reported that up to 50,000 Office 365 users have been targeted by a phishing campaign that pretends to be automated message from Microsoft Teams. The bait message uses fake notifications of a “missed chat” from Microsoft Teams, the campaigns aims at stealing Office 365 recipients’ login credentials.
Like other collaboration and communications platforms, the popularity of Microsoft Teams has risen since the beginning of the Covid-19 pandemic because a growing number of organizations started using the remote working model. Threat actors are adapting their attack techniques to exploit the ongoing situation, researchers from Abnormal Security observed campaign that hit between 15,000 to 50,000 Office 365 users.
“This attack impersonates an automated message from Microsoft Teams in order to steal recipient’s login credentials.” reads the report published by Abnormal Security. “The email is sent from the display name, ‘There’s new activity in Teams’, making it appear like an automated notification from Microsoft Teams. It appears to notify the recipient that their teammates are trying to reach them and urges the recipient to click on ‘Reply in Teams’. However, this leads to a phishing page.”
The bait email displays the name “There’s new activity in Teams” to trick the victims into believing that it is an automated notification from Microsoft Teams.
The email tells the recipient that they have missed Microsoft Team chats and show an example of a teammate chat that asks them to submit something by Wednesday of next week.
The researchers that the campaing is not targeted in nature as the employee referenced in the chats doesn’t appear to be an employee of the company that was targeted by the attackers.
Recipient could respond to the email by click on the “Reply in Teams” button that is present in the content of the message, but as a consequence of this action, the victim is redirected to a phishing page.
“Within the body of the email, there are three links appearing as ‘Microsoft Teams’, ‘(contact) sent a message in instant messenger’, and ‘Reply in Teams’,” continues the analysis. “Clicking on any of these leads to a fake website that impersonates the Microsoft login page. The phishing page asks the recipient to enter their email and password.”
The phishing landing looks like a Microsoft login page, its URL begins with the “microsftteams” to appear as legitimate.
“The attacker spoofed employee emails and also impersonated Microsoft Teams. The recipient is more likely to fall prey to an attack when it is believed to originate from within the company and also from a trusted brand.” concludes the report.
Boyne Resorts ski and golf resort operator hit with WastedLocker ransomware
24.10.20 Ransomware Securityaffairs
The systems at the US-based ski and golf resort operator were infected with the WastedLocker ransomware, the incident impacted reservation systems.
Boyne Resorts is a collection of mountain and lakeside resorts, ski areas, and attractions spanning from British Columbia to Maine. The company owns and operates eleven properties and an outdoor lifestyle equipment/apparel retail division with stores in cities throughout Michigan. An industry leader in multiple U.S. regions, operations include snowsports and year-round mountain recreation, golf, an indoor waterpark, spas, food and beverage, lodging and real estate development.
Boyne Resorts was the victim of WastedLocker ransomware attack, the incident has impacted reservation systems.
According to BleepingComputer, the ransomware initially breached the corporate offices and then moved laterally targeting the IT systems of the resorts they operate. As result of the attack the company was forced to shut down portions of its network to prevent the ransomware from spreading.
Customers of the company were not able to make reservations at the resorts operated by the company. .
The ransomware encrypted files and renamed their filenames by adding the “.easy2lock” extension, this extension was previously associated with recent WastedLocker ransomware infections.
In July, Smartwatch and wearable device maker Garmin had to shut down some of its connected services and call centers following a WastedLocker Ransomware attack.
In June, security experts from Symantec reported that at least 31 organizations in the United States have been targeted with the recently discovered WastedLocker ransomware.
Researchers from the NCC Group’s report and later Symantec confirmed that malware was developed by the Russian cybercrime crew known as Evil Corp, which was behind the Dridex Trojan, and multiple ransomware like Locky , Bart, Jaff, and BitPaymer.
Most of the victims belong to the manufacturing industry, followed by IT and media and telecommunications sectors.
This group has been active since at least 2007, in December 2019, the U.S. Treasury Department imposed sanctioned on Evil Corp for causing more than $100 million in financial damages.
The U.S. Department of Justice (DoJ) has charged Russian citizens Maksim V. (32) and Igor Turashev (38) for distributing the infamous Dridex banking Trojan, and for their involvement in international bank fraud and computer hacking schemes.
Ransom payments to WastedLocker is not allowed by US authorities, this means that Boyne Resorts could face severe sanctions if it will pay the ransom.
US Treasury imposes sanctions on a Russian research institute behind Triton malware
24.10.20 Virus Securityaffairs
US Treasury Department announced sanctions against Russia’s Central Scientific Research Institute of Chemistry and Mechanics behind Triton malware.
The US Treasury Department announced sanctions against a Russian research institute for its alleged role in the development of the Triton malware.
“Today, the Department of the Treasury’s Office of Foreign Assets Control (OFAC) designated, pursuant to Section 224 of the Countering America’s Adversaries Through Sanctions Act (CAATSA), a Russian government research institution that is connected to the destructive Triton malware.” reads a press release published by the Department of the Treasury.
Triton is a strain of malware specifically designed to target industrial control systems (ICS) system that has been spotted by researchers at FireEye in December 2017.
The malware was first spotted after it was employed in 2017 in an attack against a Saudi petrochemical plant owned by the privately-owned Saudi company Tasnee. According to the experts, the infection caused an explosion.
“In August 2017, a petrochemical facility in the Middle East was the target of a cyber-attack involving the Triton malware. This cyber-attack was supported by the State Research Center of the Russian Federation FGUP Central Scientific Research Institute of Chemistry and Mechanics (TsNIIKhM), a Russian government-controlled research institution that is responsible for building customized tools that enabled the attack.” continues the press release.
The Triton malware is designed to target Schneider Electric’s Triconex Safety Instrumented System (SIS) controllers that are used in industrial environments to monitor the state of a process and restore it to a safe state or safely shut it down if parameters indicate a potentially hazardous situation.
“Mandiant recently responded to an incident at a critical infrastructure organization where an attacker deployed malware designed to manipulate industrial safety systems. The targeted systems provided emergency shutdown capability for industrial processes.” reads the analysis published by FireEye in 2017.
“We assess with moderate confidence that the attacker was developing the capability to cause physical damage and inadvertently shutdown operations. This malware, which we call TRITON, is an attack framework built to interact with Triconex Safety Instrumented System (SIS) controllers.”
![]()
Once gained access to the SIS system, the threat actor deployed the TRITON malware, a circumstance that indicates that attackers had a knowledge of such systems. According to FireEye the attackers pre-built and tested the tool which would require access to hardware and software that is not widely available. TRITON is also designed to communicate using the proprietary TriStation protocol which is not publicly documented, this implies that the attackers reverse engineered the protocol to carry out the attack.
The Triton malware interacts with Triconex SIS controllers., it is able to read and write programs and functions to and from the controller.
Triton Malware Triconex
The hackers deployed the Triton malware on a Windows-based engineering workstation, the malicious code added its own programs to the execution table. In case of a failure, the malware attempts to return the controller to a running state, it also overwrites the malicious program with junk data if the attempt fails, likely to delete any track of the attack.
The US Treasury Department imposed sanctions on the State Research Center of the Russian Federation FGUP Central Scientific Research Institute of Chemistry and Mechanics (also known as CNIIHM or TsNIIKhM).
In October 2018, FireEye experts discovered a link between the Triton malware, tracked by the company as TEMP.Veles, and the Central Scientific Research Institute of Chemistry and Mechanics (CNIIHM), a Russian government research institute in Moscow.
FireEye collected strong evidence suggesting that the Russian CNIIHM institute has been involved in the development of some of the tools used in the Triton attack.
“FireEye Intelligence assesses with high confidence that intrusion activity that led to deployment of TRITON was supported by the Central Scientific Research Institute of Chemistry and Mechanics (CNIIHM; a.k.a. ЦНИИХМ), a Russian government-owned technical research institution located in Moscow. The following factors supporting this assessment are further detailed in this post.” reads the analysis published by FireEye.
FireEye uncovered malware development activity that is very likely supporting TEMP.Veles activity. This includes testing multiple versions of malicious software, some of which were used by TEMP.Veles during the TRITON intrusion.
Investigation of this testing activity reveals multiple independent ties to Russia, CNIIHM, and a specific person in Moscow. This person’s online activity shows significant links to CNIIHM.
An IP address registered to CNIIHM has been employed by TEMP.Veles for multiple purposes, including monitoring open-source coverage of TRITON, network reconnaissance, and malicious activity in support of the TRITON intrusion.
Behavior patterns observed in TEMP.Veles activity are consistent with the Moscow time zone, where CNIIHM is located.
We judge that CNIIHM likely possesses the necessary institutional knowledge and personnel to assist in the orchestration and development of TRITON and TEMP.Veles operations.”
Experts pointed out that Triton is linked to Russia, the CNIIHM, and an individual located in Moscow. Some of the TEMP.Veles hacking tools were tested using an unnamed online scan service. A specific user of the service who has been active since 2013 has tested various tools across the time.
The user also tested several customized versions of widely available tools, including Metasploit, Cobalt Strike, PowerSploit, the PowerShell-based WMImplant, and cryptcat.
In many cases, the custom versions of the tools were used in TEMP.Veles attacks just days after being submitted to the testing environment.
The experts discovered that a PDB path contained in a tested file included a string that appears to be an online moniker associated with a Russia-based individual active in Russian information security communities since at least 2011.
According to a now-defunct social media profile, the individual was a professor at CNIIHM.
FireEye also discovered that one IP address registered to the Russian research institute was involved in the Triton attacks.
The sanctions prohibit US entities from engaging with CNIIHM and also seize any asset on the US soil belonging to the research institute.
“The Russian Government continues to engage in dangerous cyber activities aimed at the United States and our allies,” said Secretary Steven T. Mnuchin. “This Administration will continue to aggressively defend the critical infrastructure of the United States from anyone attempting to disrupt it.”
“TsNIIKhM is being designated pursuant to Section 224 of CAATSA for knowingly engaging in significant activities undermining cybersecurity against any person, including a democratic institution, or government on behalf of the Government of the Russian Federation.” concludes the press release.
“As a result of today’s designation, all property and interests in property of TsNIIKhM that are in or come within the possession of U.S. persons are blocked, and U.S. persons are generally prohibited from engaging in transactions with them. Additionally, any entities 50 percent or more owned by one or more designated persons are also blocked. Moreover, non-U.S. persons who engage in certain transactions with TsNIIKhM may themselves be exposed to sanctions.”
On Thursday, the Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) issued a joint report that provides details about a hacking campaign of a Russian hacking group known as Energetic Bear.
The EU Council also imposed sanctions on two Russian intelligence officers for their role in the 2015 Bundestag hack.
New Emotet attacks use a new template urging recipients to upgrade Microsoft Word
24.10.20 Virus Securityaffairs
Emotet operators have started using a new template this week that pretends to be a Microsoft Office message urging a Microsoft Word update.
Researchers this week observed Emotet attacks employing a new template that pretends to be a Microsoft Office message urging the recipient to update their Microsoft Word to add a new feature.
Source Bleeping Computer
Emotet spam messages leverage templates to trick the victims into enabling macros to start the infection.
Upon installing the malware, Emotet will download additional payloads on the machine, including ransomware, and use it to send spam emails.
The Emotet banking trojan has been active at least since 2014, the botnet is operated by a threat actor tracked as TA542. In the middle-August, the malware was employed in fresh COVID19-themed spam campaign
Recent spam campaigns used messages with malicious Word documents, or links to them, pretending to be an invoice, shipping information, COVID-19 information, resumes, financial documents, or scanned documents.
The infamous banking trojan is also used to deliver other malicious code, such as Trickbot and QBot trojan or ransomware such as Conti (TrickBot) or ProLock (QBot).
Emotet is a modular malware, its operators could develop new Dynamic Link Libraries to update its capabilities.
Recently, the Cybersecurity and Infrastructure Security Agency (CISA) issued an alert to warn of a surge of Emotet attacks that have targeted multiple state and local governments in the U.S. since August.
During that time, the agency’s EINSTEIN Intrusion Detection System has detected roughly 16,000 alerts related to Emotet activity.
In a recent campaign observed on October 14th, the attackers are using multiple lures, including invoices, purchase orders, shipping information, COVID-19 information, and information about President Trump’s health.
The spam messages come with malicious Word (.doc) attachments or include links to download the bait document.
“Emotet switched to a new template this week that pretends to be a Microsoft Office message stating that Microsoft Word needs to be updated to add a new feature.” reported BleepingComputer.
Below the messages displayed to the recipient to trick him into opening enabling the macros.
Upgrade your edition of Microsoft Word
Please click Enable Editing and then click
Enable Content.
Upon enabling the macros, the Emotet malware is downloaded and installed into the victim’s %LocalAppData% folder, as shown below.
“Due to this, it is important that all email users recognize malicious document templates used by Emotet so that you do not accidentally become infected.” concludes Bleeping computer.
Report: Ransomware Disables Georgia County Election Database
24.10.20 Vulnerebility Securityweek
A ransomware attack that hobbled a Georgia county government in early October reportedly disabled a database used to verify voter signatures in the authentication of absentee ballots.
It is the first reported case of a ransomware attack affecting an election-related system in the 2020 cycle. Federal officials and cybersecurity experts are especially concerned that ransomware attacks — even ones that don’t intentionally target election infrastructure — could disrupt voting and damage confidence in the integrity of the Nov. 3 election.
The Oct. 7 attack on Hall County, in the northern part of the state, hit critical systems and interrupted phone services, the county said in a statement posted on its website. County spokeswoman Katie Crumley did not return multiple requests for comment from The Associated Press.
But according to a report in the Gainesville Times, the attack also disabled the county’s voter signature database. Crumley was also quoted in an online CNN story saying that the attack affected both the signature database and a voting precinct map.
Ransomware scrambles affected computer networks with encryption that can only be unlocked with keys provided once the victim has paid up. Deloitte analyst Srini Subramanian said ransoms local governments pay in such cases average about $400,000.
An update Thursday evening on the county website said “the voting process for citizens has not been impacted by the attack.” However, a county official quoted by the Times said signature verification was slowed because employees had to manually pull hard copies of voter registration cards in many cases. The official was quoted as saying that most voter signatures could still be verified using a state database unaffected by the attack. The county has 129,000 registered voters.
In most states, signatures are used to validate absentee ballots sent by mail. Written on the envelopes that sheath the ballots, they are matched by election workers against signatures on file with state and local election authorities.
Federal officials recently announced that Russian hackers have infiltrated dozens of state and local government networks and could be poised to launch disruptive attacks.
An international ransomware syndicate known as Doppelpaymer appears to be involved in the Hall County attack. It posted documents purportedly stolen from Hall County on a dark web site as proof of responsibility.
Crumley, the county spokeswoman, did not respond to an email asking how much ransom that attackers had demanded and whether the county had paid a ransom.
Brett Callow, a threat analyst at Emsisoft cybersecurity firm, said the attack could augur other similar actions exploiting the proximity of Election Day.
“The real question is how many local government networks are already compromised? Threat actors frequently delay deploying ransomware on compromised networks until what they consider to be the most opportune moment — and that may well be in the days immediately prior to the election,” he said. “What better time to extort money from a government by holding its systems hostage than when those systems are most needed?”
A worsening ransomware plague is afflicting U.S. cities, counties and school districts, exacerbated by the COVID-19 pandemic.
At least 82 government bodies in the U.S. have been hit by ransomware so far this year. Eighteen of those incidents have occurred since the beginning of September, according to Emsisoft.
Nvidia Warns Gamers of Severe GeForce Experience Flaws
24.10.20 Vulnerebility Threatpost
Versions of Nvidia GeForce Experience for Windows prior to 3.20.5.70 are affected by a high-severity bug that could enable code execution, denial of service and more.
Nvidia, which makes gaming-friendly graphics processing units (GPUs), has issued fixes for two high-severity flaws in the Windows version of its GeForce Experience software.
GeForce Experience is a supplemental application to the GeForce GTX graphics card — it keeps users’ drivers up-to-date, automatically optimizes their game settings and more. GeForce Experience is installed by default on systems running NVIDIA GeForce products, Nvidia’s brand of GPUs.
The most severe flaw of the two (CVE-2020-5977) can lead to a slew of malicious attacks on affected systems – including code execution, denial of service, escalation of privileges and information disclosure. It ranks 8.2 out of 10 on the CVSS scale, making it high severity.
In a Thursday security advisory, the graphics giant said users can “download the updates from the GeForce Experience Downloads page or open the client to automatically apply the security update.”
The flaw specifically stems from the Nvidia Web Helper NodeJS Web Server. When users install GeForce Experience, Node.js runs on startup and provides a webserver connection with Nvidia. The issue here is that an uncontrolled search path is used to load a node module, which occurs when an application uses fixed search paths to find resources – but one or more locations of the path are under control of malicious user. Attackers can leverage tactics like DLL preloading, binary planting and insecure library loading in order to exploit this vulnerability.
While further details regarding this specific flaw are not available from Nvidia, the company did say that attackers can leverage the flaw to execute code, launch a DoS attack, escalate their privileges or view sensitive data. Xavier DANEST with Decathlon was credited with discovering the flaw.
Nvidia on Thursday also issued patches for another high-severity flaw in the ShadowPlay component of GeForce Experience (CVE‑2020‑5990), which may lead to local privilege escalation, code execution, DoS or information disclosure. Hashim Jawad of ACTIVELabs was credited with discovering the flaw.
Versions of Nvidia GeForce Experience for Windows prior to 3.20.5.70 are affected; users are urged to update to version 3.20.5.70.
Nvidia has previously warned of security issues affecting its GeForce brand, including an issue affecting GeForce Experience in 2019 that could lead to code execution or denial of service of products if exploited.
In June, Nvidia fixed two high-severity flaws that affected drivers for Windows and Linux users, including ones that use Nvidia’s GeForce, Quadro and Tesla software. And in March, Nvidia issued patches for high-severity bugs in its graphics driver, which can be exploited by a local attacker to launch DoS or code-execution attacks, and also affected display drivers used in GeForce (as well as Quadro and Tesla-branded) GPUs for Windows.
Ransomware Takes Down Network of French IT Giant
24.10.20 Ransomware Threatpost
Sopra Steria hit with cyber attack that reportedly encrypted parts of their network on Oct. 20 but has remained mostly mum on details.
French IT giant Sopra Steria was hit with a cyber attack this week that disrupted the business of the firm and is widely believed to be the work of the threat actors behind Ryuk ransomware.
The company revealed the attack in a brief press statement released Oct. 22, two days after officials said the attack—which reportedly encrypted parts of the firm’s network—occurred.
“A cyberattack has been detected on Sopra Steria’s IT network on the evening of 20th October,” officials said. “Security measures have been implemented in order to contain risks.”
Sopra Steria employs 46,000 people in 25 countries and even has a cybersecurity arm that specializes in helping customers implement “reliable security and resiliency,” according to its website.
However the company, which did $4.4 billion in business last year, divulged nothing of exactly what type of attack it was and what services, systems and data were affected, sources in the French media claim it was Ryuk ransomware that took down the company.
If that’s true than the attackers behind Ryuk have been quite active lately. Earlier this week the group—also responsible for the TrickBot and BazarLoader infections used together with the ransomware—also struck in an unusually swift attack that went from sending a phishing email to complete encryption across the victim’s network in just five hours.
Ryuk also is behind a ransomware attack less than a month ago that shut down Universal Health Services, a Fortune-500 owner of a nationwide network of hospitals.
Sopra Steria is currently working to recover its systems “for a return to normal as quickly as possible” after the attack, as well as making “every effort … to ensure business continuity,” officials said in a statement. The company is working with authorities on the matter as well as staying in touch with customers and partners.
Still, it’s unfortunate that a company that specializes in IT services and cybersecurity would keep the public in the dark about key details of what went down during the attack and how it might affect their affiliates, observed Chloe Messdaghi, vice president of strategy for Point3 Security.
“One thing that is disappointing however is that Sopra Steria didn’t inform its customers in their public notification of exactly what types of data were exposed,” she said in an e-mail to Threatpost. “They also didn’t offer any advice on the kinds of attack attempts that end users whose data was exposed might expect and should be prepared to spot. Those potential attack strategies are dependent on the data exposed.”
This type of transparency with customers who could have been affected and exposed to risk is especially important for companies that specialize in IT services to uphold in these circumstances, Messdaghi said.
“As a digital transformation company, Sopra Steria is no doubt aware of these risks,” she said. “It’s crucially important that they share them, and quickly, with those whose data was exposed.”
U.S. Levies Sanctions Against Russian Research Institution Linked to Triton Malware
24.10.20 BigBrothers Threatpost
The latest in a flurry of actions this week, tied to foreign threats against U.S. computer systems, includes sanctions by the Department of the Treasury.
The Trump administration sanctioned a Russia government research institution on Friday claiming it was behind a series of cyberattacks using the highly destructive Triton malware.
The Department of the Treasury’s Office of Foreign Assets Control (OFAC) said the Triton malware had been used in various attacks against U.S. partners in the Middle East and spotted probing U.S. facilities.
Triton (aka TRISIS or HatMan) is most notoriously known for a series of 2017 attacks on a Saudi Arabian petrochemical facility, where it targeted safety systems with the intent of causing loss of life or physical damage, according to researchers at the time.
“This cyber-attack was supported by the State Research Center of the Russian Federation FGUP Central Scientific Research Institute of Chemistry and Mechanics (TsNIIKhM), a Russian government-controlled research institution that is responsible for building customized tools that enabled the attack,” according to a Treasury Department statement issued Friday.
“This Administration will continue to aggressively defend the critical infrastructure of the United States from anyone attempting to disrupt it,” said secretary of the Treasury Steven Mnuchin in a statement.
Over the years, the advanced persistent threat (APT) group identified as XENOTIME was believed to be behind the Triton malware attacks. About a year ago the APT expanded beyond its initial focus of Saudi Arabian petrochemical firms.
According to a 2019 analysis by Dragos, the group had begun to target dozens of electric power utilities in North American and Asia-Pacific regions. Dragos said, at the time, it expected Triton to be used to attack industrial controls systems that managed water plants and manufacturing industries.
On Friday, the Department of Treasury accused the TsNIIKhM of “knowingly engaging in significant activities undermining cybersecurity against any person, including a democratic institution, or government on behalf of the Government of the Russian Federation”, pursuant to Section 224 of the Countering America’s Adversaries Through Sanctions Act.
Friday’s sanctions against Russia cap a busy week for U.S. cyber defenses. On Wednesday, federal officials claim that Iranian threat actors are behind two separate email campaigns that assailed Democratic voters this week with threats to “vote for Trump or else.” The campaigns claimed to be from violent extremist group Proud Boys.
On Thursday, the Trump administration claimed Iran and Russia hacked local governments local governments and obtained voter registration and other personal data, first reported by NBC News. On Tuesday, the National Security Agency released an advisory (PDF) warning Chinese state-sponsored actors were exploiting 25 publicly known vulnerabilities. On Monday, the Department of Justice announced charges against six Russian nationals who are allegedly tied to the Sandworm APT.
IoT Device Takeovers Surge 100 Percent in 2020
24.10.20 IoT Threatpost
The COVID-19 pandemic, coupled with an explosion in the number of connected devices, have led to a swelling in IoT infections observed on wireless networks.
Connected cameras, refrigerators and other seemingly-mundane internet-of-things (IoT) devices are a cybercriminal favorite this year, with new research showing a sharp increase (100 percent) in IoT infections observed on wireless networks.
IoT devices are now responsible for 32.72 percent of all infections observed in mobile and Wi-Fi networks – up from 16.17 percent in 2019. And researchers with Nokia’s Threat Intelligence Lab said, in the Threat Intelligence Report 2020 released this week, that they believe that number of IoT infections will continue to grow “dramatically” as connected devices continue to populate in homes and enterprise settings alike.
“It’s not a surprise that IoT devices are the crown jewels for cybercriminals,” Dirk Schrader, global vice president at New Net Technologies, told Threatpost. “Businesses around the world are transforming their processes, their production lines using digitalized assets. Having control over these assets means that a cybercriminal’s hand is – literally – at the main switch of a digitally transformed company. ”
IoT devices are even a target for ransomware, he added: “The danger of being shut down almost completely is the reason why companies are more likely to pay even higher ransoms.”
Researchers pointed to the visibility of devices connected to the internet as a barometer for IoT infection rates, with high IoT infection rates occurring when devices are connected to publicly facing internet IP addresses. In networks where carrier grade network address translation (NAT) is enabled on a firewall or router, the infection rate is reduced, as the connected devices are not visible to network scanning, they said. While standard NAT translates a private IPv4 address to public IPv4 address, carrier-grade adds an additional translation layer as an extra security measure.
There are more and more devices for cybercriminals to scan: Brandon Hoffman, CISO at Netenrich, pointed out that due to the pandemic, people are also not spending money on vacations and therefore buying more connected “things” for their homes.
“As devices at home and other ‘things’ become smarter, and have computing capacity they don’t need, cybercriminals can snap that computing power up and use it to perform attacks, transfer data anonymously, and store it in places people aren’t looking,” Hoffman told Threatpost.
Overall, in 2020, Android devices were the most commonly targeted by malware, researchers found, making up 26.64 percent of all infections. Meanwhile, Windows devices and PCs, which are increasingly connected to mobile networks via USB dongles and Wi-Fi, made up 38.92 percent.
Researchers said that the coronavirus pandemic caused a surge (a 30 percent increase over 2019, specifically) in mobile-malware infections, saying the volume and type of attacks have also seen “profound” changes.
“The situation is certainly worsened during the pandemic, as the IT operations and information security teams had to organize, setup and secure a remote workforce more or less in no time,” Schrader said. “Plans for digital transformation need to be altered to reflect this ‘new normal,’ and such the problem is likely to worsen.”
IoT devices have long been under scrutiny for their lack of security measures, with researchers finding in March that more than half of all IoT devices are vulnerable to medium- or high-severity attacks, for instance.
In September, researchers found a Bluetooth Low Energy (BLE) vulnerability that impacted billions of IoT devices and remained unpatched in Android devices. And in August, researchers urged connected-device manufacturers to ensure they applied patches addressing a flaw in a module used by millions of IoT devices.
Meanwhile, the growth in IoT is far from over: The introduction of 5G is also expected to continue to increase not just the number of IoT devices, but the share of connected devices accessible directly from the internet.
Louisiana Calls Out National Guard to Fight Ransomware Surge
24.10.20 Ransomware Threatpost
An investigation showed a custom backdoor RAT and the Emotet trojan in the networks of municipal victims of the attacks.
The National Guard has been called in to help stop a series of government-focused ransomware attacks in Louisiana, according to a report.
Local government offices across the Pelican State have been besieged by ransomware strikes, according to a cybersecurity consultant speaking to Reuters, with “evidence suggesting a sophisticated hacking group was involved.”
The paper reported that a forensic investigation into the attacks unearthed a remote access trojan (RAT) buried in affected networks, which is often the calling card of an advanced persistent threat (APT) group known to be an arm of the North Korean government. That said, the “KimJongRat” backdoor has had its source code partially leaked, which could allow cyberattackers to copy it – thus casting doubt on that attribution.
The Emotet trojan was also found in victim networks, sources said, which can load other malware and self-propagate through networks. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued a warning earlier this month that state and local governments need to fortify their systems against the malware, amid a dramatic uptick in Emotet phishing attacks on municipalities since July.
“This increase has rendered Emotet one of the most prevalent ongoing threats,” the CISA alert read.
Sources said that the attacks were successful in locking up networks in several government offices in northern Louisiana, after staff were socially engineered via email into opening an attachment and triggering the infection chain. Further, the attackers took over victim email accounts to send malware to other employees under the guise of legitimate communications.
However, that cyberattack was stopped “in its early stages before significant harm was done,” according to the report.
It’s unclear which ransomware family was used in the attacks. The Louisiana National Guard has declined to comment on the incidents.
This is not the first time that Louisiana has called out the National Guard to combat cyberattacks. In July 2019, Louisiana’s governor declared a statewide state of emergency after ransomware hits on at least three school districts – Monroe City, Morehouse Parish and Sabine Parish. Declaring the state of emergency allowed coordination between cybersecurity experts from the National Guard, Louisiana State Police and the Office of Technology Services.
Ransomware attacks continue to surge in all sectors. Just this month, Software AG was struck by the Clop ransomware; French IT giant Sopra Steria was afflicted with Ryuk; and a county in Georgia found its voter-registration database caught up in an attack.
Georgia Election Data Hit in Ransomware Attack
24.10.20 Ransomware Threatpost
With Election Day approaching, local governments need to be prepared for malware attacks on election infrastructure.
Ransomware gangs have officially entered the 2020 election fray, with reports of one of the first breaches of the voting season, on Hall County, Ga. The county’s database of voter signatures was impacted in the attack along with other government systems.
Although the county said the voting process hasn’t been impacted by the ransomware attack, the incident is a warning to other municipalities to lock down their systems, particularly in these last days leading up to the election.
Hall County sits about an hour north of Atlanta and first reported the attack on Oct. 7.
Ransomware attacks involve a criminal introducing malware into the target’s systems, which then takes over an organization’s data and encrypts it until a ransom is paid.
Hall County’s Ransomware Attack
On Oct. 21, the Gainesville Times reported the county’s precinct map was down as a result of a ransomware attack, in addition to a voter-signature database.
It wasn’t until Oct. 22 that the county announced, “The voting process for citizens has not been impacted by the attack.”
“A ransomware attack has occurred involving critical systems within the Hall County government networks, including an interruption of phone services,” according to a news release. “As soon as it occurred, the county began working to investigate the cause, to restore operations and determine the effects of the incident.”
Hall County registration coordinator Kay Wimpye old the paper that some of the systems are already back up and running and if there is a question about a ballot signature, county employees are still able to pull voter-registration cards manually. But with record numbers of mail-in ballots being submitted, that could prove to be a time-consuming process.
Wimpye told the Times that her office sent out 27,573 absentee ballots as of Oct. 21, and 11,351 had been sent back. The Georgia Secretary of State reported that by Oct. 21, 2016, 103,239 mail-in ballots had been returned, compared to 805,442 on the same day in 2020, showing an explosion in the number of voters opting for mail-in voting this election cycle. Although the signatures are being verified now, the ballots won’t be tabulated until Election Day, according to the Times.
Ransomware & the Public Sector
Ransomware attacks timed this close to Election Day threaten to throw an already contentious competition into total disarray.
Brandon Hoffman, CIO at Netentrich, called the attack on voting infrastructure “inevitable.”
“The ransomware spree has gone essentially unchecked and it stands to reason that type of malware would be the one to hit,” he added. “On the other hand, with ransomware, election infrastructure probably wasn’t the main target.”
But, Hoffman warns, that could change.
“The fact that this was successful validates the attack path,” he said. “Attack-path validation is a key step in any attack sequence, and testing it on small-scale scenarios always makes sense. If security professionals working with voting technology were not already extra-vigilant, there’s no time to waste in getting over-prepared.”
Public-sector organizations are already a juicy target for malware attacks. More than half (52 percent) of public-sector organizations have been attacked and saw malware spread from a compromised user to colleagues, according to a recent report on public sector email security from Mimecast.
The report added that 9 percent of those attacked experienced more than a week of downtime as a result, the most of any other industry. And with the election just over a week away, that could spell disaster for getting votes tabulated in time.
Matthew Gardiner, cybersecurity strategist at Mimecast, told Threatpost by email that attackers see an easy payday in local governments.
“Ransomware-centric cybercriminals are focused on money,” he said. “Thus, they focus on hitting organizations that are relatively easy to get into and have an ability/willingness to pay the ransom. In general, cities, municipalities, towns, and school districts score high here.”
Once a ransom is paid, Gardiner compared it to “blood in the water for sharks,” drawing in more predators. The election deadline may up the price for the data or motivate targets to pay more quickly, but besides that, Gardiner doesn’t see the election outcome as a specific motivator for cybercriminals.
Patching & Training
To keep systems protected at such a sensitive time, two simple things can make a big difference: Patching and employee training, according to Daniel Norman, senior solutions analyst at Information Security Forum.
“Moving forward, end users should receive ample security awareness, education and training on the threat of ransomware, particularly its delivery mechanism,” Norman said in an emailed statement. “Typically, the success of ransomware is reliant on whether or not the target organization has patched its devices properly. Therefore, having all systems patched and up-to-date is a minimal for security.”
Ransomware is on the rise across the globe thanks to the pandemic, up more than 109 percent over last year, according to SonicWall’s 2020 Cyber Threat Report.
Hank Schless, senior manager with security solutions at Lookout, pointed out that workers scattered across the globe on mobile devices are more vulnerable than ever to socially engineered ploys as they toggle between personal and professional applications.
“As workers across the globe began working from home, organizations enabled their employees to stay productive by using mobile devices, and attackers know this,” Schless said.
“Organizations that are proactive about securing mobile devices with mobile security are at the forefront of innovation and demonstrate that they are adapting to today’s rapidly evolving threat landscape,” he added.
As for Hall County, their spokeswoman Katie Crumley declined to provide a comment to Threatpost, beyond the press release, “for security purposes.” The statement said the county “has enlisted the assistance of third-party cyber security professionals to expedite the recovery.”
Iran-Linked Seedworm APT target orgs in the Middle East
24.10.20 APT Securityaffairs
The Iran-linked cyber espionage group tracked as Seedworm started using a new downloader and is conducting destructive attacks.
The Iran-linked cyber-espionage group Seedworm (aka MuddyWater MERCURY, and Static Kitten) was observed using a new downloader in a new wave of attacks. Security experts pointed out that the threat actor started conducting destructive attacks.
Also referred to as MuddyWater, MERCURY, and Static Kitten, the cyber-espionage group was initially analyzed in 2017.
The first MuddyWater campaign was observed in late 2017, then researchers from Palo Alto Networks were investigating a mysterious wave of attacks in the Middle East.
The experts called the campaign ‘MuddyWater’ due to the confusion in attributing these attacks that took place between February and October 2017 targeting entities in Saudi Arabia, Iraq, Israel, United Arab Emirates, Georgia, India, Pakistan, Turkey, and the United States to date.
In September 2018, experts from Symantec found evidence of Seedworm and the espionage group APT28 on a computer in the Brazil-based embassy of an oil-producing nation.
Earlier this month, the Iranian APT group was observed actively targeting the Zerologon flaw.
According to security firm ClearSky and Symantec, Seedworm recently started using a new downloader dubbed PowGoop. Experts noticed that the threat actors used the downloader to deliver the Thanos ransomware in an attack aimed at an organization in the Middle East.
“PowGoop is a loader that was exposed in a PaloAlto report and later used in Operation Quicksand. PowGoop is comprised of a DLL Loader and a PowerShell-based downloader.” reads the report published by ClearSky. “The malicious file impersonates a legitimate goopdate.dll file that is signed as a Google Update executable”
The experts observed the attacks between July 6 and July 9, 2020, the hackers employed a strain of ransomware that was able to evade security tools and that implemented a destructive feature by overwriting the MBR.
Experts pointed out that the primary objectives of previous MuddyWater campaigns were espionage and cyber espionage, but in the latest campaign, tracked as ‘Operation Quicksand’ threat actors used for the first time the destructive malware in attacks on prominent organizations in Israel and in other countries around the world.
“We assess that the group is attempting to employ destructive attacks (the likes of the NotPetya attack from 2017), via a disguised as ransomware attacks” continnues the report.
“Although we didn’t see execution of the destruction in the wild, due to the presence of the destructive capabilities, the attribution to nation-state sponsored threat actor, and the realization of this vector in the past, a destructive purpose is more likely than a ransomware that is being deployed for financial goals.”
Another report published by Symantec connected the dots between MuddyWater and the PowGoopdownlaoder.
“In several recent Seedworm attacks, PowGoop was used on computers that were also infected with known Seedworm malware (Backdoor.Mori). In addition to this, activity involving Seedworm’s Powerstats (aka Powermud) backdoor appears to have been superseded by DLL side-loading of PowGoop.” reads the report published by Symantec.
“Additionally, during PowGoop activity, we also observed the attackers downloading tools and some unknown content from GitHub repos, similar to what has been reported on Seedworm‘s Powerstats in the past.”
Symantec researchers noticed that on the same machine where Seedworm was active, the attackers deployed the PowGoop downloader which is known to be a malware that is part of Seedworm’s arsenal.
PowGoop appears to have been employed in attacks aimed at governments, education, oil and gas, real estate, technology, and telecoms organizations in Afghanistan, Azerbaijan, Cambodia, Iraq, Israel, Georgia, Turkey, and Vietnam.
Symantec’s analysis revealed that the PowGoop was masquerading as a Google tool and noticed the use of SSF and Chisel.
Experts speculate the PowGoop downloader might be an evolution of Powerstats tool employed by MuddyWater in previous attacks.
“Symantec has not found any evidence of a wiper or ransomware on computers infected with PowGoop.”Symantec concludes. “This suggests that either the simultaneous presence of PowGoop and Thanos in one attack was a coincidence or, if the two are linked, that PowGoop is not used exclusively to deliver Thanos,”
Sopra Steria hit by the Ryuk ransomware gang
24.10.20 Ransomware Securityaffairs
French IT outsourcer Sopra Steria hit by ‘cyberattack’, Ryuk ransomware suspected
French IT outsourcer Sopra Steria has been hit by a ransomware attack, while the company did not reveal the family of malware that infected its systems, local media speculate the involvement of the Ryuk ransomware.
“A cyber attack was detected on the Sopra Steria computer network on the evening of October 20. Security measures have been taken to limit the risk of propagation.” reads the press release published by the company. “The Group’s teams are fully mobilized to ensure a return to normal as quickly as possible and everything is done to ensure business continuity. Sopra Steria is in close contact with its customers and partners as well as with the competent authorities.”
The European IT firm has 46,000 employees operating in 25 countries worldwide. It provides a wide range of IT services, including software development and consulting.
“According to our sources, the incident started to spread during the course of last night. The Active Directory infrastructure would be affected. And part of the information system would have been encrypted.” reported the website LeMagit. “Two sources tell us that the ransomware involved is none other than Ryuk. Surprise, researcher JamesWT_MHT found on VirusTotal a copy of an executable which two sources have confirmed to us is used internally at ESN for the generation of email signatures.”
French authorities are investigating the incident.
Sopra Steria is a member of France’s Cyber Campus, a French initiative to spread cybersecurity awareness, training, and product sales.
The Ryuk ransomware operators were very active early this year, in March they targeted hospitals even as these organizations are involved in the fight against the Coronavirus pandemic.
In September, the Universal Health Services (UHS) healthcare providers has reportedly shut down systems at healthcare facilities after a Ryuk ransomware attack.
In March, the City of Durham shut down its network after Ryuk Ransomware attack.
A few days before, EVRAZ, one of the world’s largest multinational vertically integrated steel making and mining companies, has been hit by the Ryuk ransomware.
The list of the victims of the Ryuk ransomware is very long and includes the US government contractor Electronic Warfare Associates (EWA), US railroad company Railworks, Croatian petrol station chain INA Group, and parts manufacturer Visser Precision.
Microsoft, MITRE Release Adversarial Machine Learning Threat Matrix
24.10.20 Safety Securityweek
Microsoft and MITRE, in collaboration with a dozen other organizations, have developed a framework designed to help identify, respond to, and remediate attacks targeting machine learning (ML) systems.
Such attacks, Microsoft says, have increased significantly over the past four years, and are expected to continue evolving. Despite that, however, organizations have yet to come to terms with adversarial machine learning, Microsoft says.
In fact, a recent survey conducted by the tech giant among 28 organizations has revealed that most of them (25) don’t have the necessary tools to secure machine learning systems and are explicitly looking for guidance.
“We found that preparation is not just limited to smaller organizations. We spoke to Fortune 500 companies, governments, non-profits, and small and mid-sized organizations,” Microsoft says.
The Adversarial ML Threat Matrix, which Microsoft has released in collaboration with MITRE, IBM, NVIDIA, Airbus, Bosch, Deep Instinct, Two Six Labs, Cardiff University, the University of Toronto, PricewaterhouseCoopers, the Software Engineering Institute at Carnegie Mellon University, and the Berryville Institute of Machine Learning, is an industry-focused open framework that aims to address this issue.
The framework provides information on the techniques employed by adversaries when targeting ML systems and is primarily aimed at security analysts. Structured like the ATT&CK framework, the Adversarial ML Threat Matrix is based on observed attacks that have been vetted as effective against production ML systems.
Attacks targeting these systems are possible because of inherent limitations underlying ML algorithms and require a new approach to security and a shift in how cyber adversary behavior is modelled, to ensure the accurate reflection of emerging threat vectors, as well as the fast evolving adversarial machine learning attack lifecycle.
“MITRE has deep experience with technically complex multi-stakeholder problems. […] To succeed, we know we need to bring the experience of a community of analysts sharing real threat data and improving defenses. And for that to work, all the organizations and analysts involved need to be assured they have a trustworthy, neutral party who can aggregate these real-world incidents and maintain a level of privacy—and they have that in MITRE,” Charles Clancy, senior vice president and general manager of MITRE Labs, said.
The newly released framework is a first attempt at creating a knowledge base on the manner in which ML systems can be attacked and the partnering companies will modify it with input received from the security and machine learning community. Thus, the industry is encouraged to help fill the gaps, and to participate in discussions in this Google Group.
“This effort is aimed at security analysts and the broader security community: the matrix and the case studies are meant to help in strategizing protection and detection; the framework seeds attacks on ML systems, so that they can carefully carry out similar exercises in their organizations and validate the monitoring strategies,” Microsoft explains.
FBI and CISA joint alert blames Russia’s Energetic Bear APT for US government networks hack
23.10.20 BigBrothers Securityaffairs
The US government declared that Russia-linked APT group Energetic Bear has breached US government networks and exfiltrated data.
A joint security advisory published by The Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) revealed that Russia-linked APT group Energetic Bear has breached US government networks and exfiltrated data.
The Energetic Bear APT group (aka DragonFly, Crouching Yeti, TEMP.Isotope, Berserk Bear, TeamSpy, Havex, Koala). has been active since at least 2010 most of the victims of the group are organizations in the energy and industrial sectors.
In March 2018, the Department of Homeland Security and Federal Bureau of Investigation issued a joint technical alert to warn of attacks on US critical infrastructure powered by Russian threat actors. The US-CERT blamed the APT group tracked as Dragonfly, Crouching Yeti, and Energetic Bear.
This joint advisory provides information on Russia-linked APT actor activity targeting various U.S. state, local, territorial, and tribal (SLTT) government networks, as well as aviation networks.
Officials said the group has been targeting dozens of US state, local, territorial, and tribal (SLTT) government networks since at least February 2020.
Energetic Bear successfully compromised the infrastructure and as of October 1, 2020, exfiltrated data from at least two victim servers.
“Since at least September 2020, a Russian state-sponsored APT actor—known variously as Berserk Bear, Energetic Bear, TeamSpy, Dragonfly, Havex, Crouching Yeti, and Koala in open-source reporting—has conducted a campaign against a wide variety of U.S. targets.” reads the advisory. “The Russian state-sponsored APT actor has targeted dozens of SLTT government and aviation networks, attempted intrusions at several SLTT organizations, successfully compromised network infrastructure, and as of October 1, 2020, exfiltrated data from at least two victim servers.”
The Russian-sponsored APT actor uses previously obtained user and administrator credentials to access the target network and then perform lateral movement to locate high-value assets and exfiltrate data. In at least one compromise, the APT actor laterally traversed an SLTT victim network and accessed documents related to sensitive network configurations and passwords, standard operating procedures (SOP), IT instructions, such as requesting password resets, vendors and purchasing information. printing access badges.
This advisory updates another joint CISA-FBI cybersecurity advisory, which warned of attackers combining VPN and Windows Zerologon flaws to target government networks.
The new advisory attributes the cyber attacks to the Russian threat actor and included technical details about the Energetic Bear’s TTPs.
The state-sponsored hackers scanned for vulnerable Citrix (CVE-2019-19781) and Microsoft Exchange services (CVE-2020-0688) and identified vulnerable installs for future exploitation.
According to the technical advisory, Russian hackers used publicly known vulnerabilities to breach networking gear, pivot to internal networks, elevate privileges, and steal sensitive data.
Hackers also targeted Exim mail agents (CVE 2019-10149) and Fortinet SSL VPNs (CVE-2018-13379).
Once gained access to the target networks, Russian hackers moved laterally exploiting the Zerologon vulnerability in Windows Servers (CVE-2020-1472) to access and steal Windows Active Directory (AD) credentials to take over the target’s internal network.
“To date, the FBI and CISA have no information to indicate this APT actor has intentionally disrupted any aviation, education, elections, or government operations. However, the actor may be seeking access to obtain future disruption options, to influence US policies and actions, or to delegitimize SLTT government entities,” continues the alert.
“As this recent malicious activity has been directed at SLTT government networks, there may be some risk to elections information housed on SLTT government networks. However, the FBI and CISA have no evidence to date that integrity of elections data has been compromised.”
Destructive Malware Spotted in Recent Attacks Launched by Iranian Cyberspies
23.10.20 BigBrothers Securityweek
The Iran-linked cyber-espionage group known as Seedworm appears to have added a new downloader to its arsenal and to have started conducting destructive attacks, security researchers report.
Also referred to as MuddyWater, MERCURY, and Static Kitten, the cyber-espionage group was initially analyzed in 2017. Seedworm shows a focus on targeting Middle Eastern organizations, or those in nearby regions.
The threat actor is highly active and is known for the use of a broad and varied toolset. Earlier this month, the group was observed actively targeting the Zerologon vulnerability that Microsoft patched in August.
According to recent reports from ClearSky and Symantec, MuddyWater recently added to its arsenal a downloader called PowGoop, which earlier this year was used in attacks employing the Thanos ransomware against an organization in the Middle East.
PowGoop contains a DLL loader and a PowerShell-based downloader, with the latter designed to decrypt and run the former. The downloader is a fake Google Update mechanism similar to the MoriAgent / PudPoul DLL loader, which was previously attributed to MuddyWater.
“While we cannot confirm the connection, we believe the actors deploying the Thanos ransomware at the Middle Eastern state-run organization also used a downloader that we call PowGoop. The actors would use the PowGoop downloader to reach out to a remote server to download and execute additional PowerShell scripts,” Palo Alto Networks noted in a September 4 report.
The attacks, which were observed on July 6 and July 9, 2020, feature a ransomware variant that was capable of better evading analysis tools, could monitor for newly attached storage devices, and was also able to overwrite the MBR, functionality that would make Thanos rather destructive in nature.
Last week, in a report linking PowGoop to MuddyWater, ClearSky noted that the hacking group appears to have started employing wipers in assaults hidden behind apparent ransomware operations. Other Iranian hackers too have employed wipers, Shamoon being the most infamous of them.
“Although we didn’t see execution of the destruction in the wild, due to the presence of the destructive capabilities, the attribution to nation-state sponsored threat actor, and the realization of this vector in the past, a destructive purpose is more likely than a ransomware that is being deployed for financial goals,” ClearSky noted.
Now, Symantec too says it was able to draw a connection between MuddyWater and PowGoop, after discovering the downloader on systems where one of the group’s backdoors was installed. Furthermore, MuddyWater’s Powerstats (Powermud) backdoor was apparently superseded by DLL side-loading of PowGoop.
“On the same machine where Seedworm was active, a tool known as PowGoop was deployed. This same tool was also deployed against several of the organizations attacked by Seedworm in recent months,” Symantec says.
PowGoop appears to have been used in attacks targeting governments, education, oil and gas, real estate, technology, and telecoms organizations in Afghanistan, Azerbaijan, Cambodia, Iraq, Israel, Georgia, Turkey, and Vietnam.
Symantec’s analysis revealed the use of the Remadmin remote code execution tool to deploy PowGoop, and also led to the identification of artefacts suggesting that PowGoop was masquerading as a Google tool and noticed the use of SSF and Chisel.
Analysis of PowGoop activity would suggest that the downloader might be “an evolution of Powerstats rather than a completely new tool,” Symantec notes, adding that there isn’t enough evidence to confirm the hypothesis. Furthermore, the security firm is unsure of the destructive purpose of the attacks.
“Symantec has not found any evidence of a wiper or ransomware on computers infected with PowGoop. This suggests that either the simultaneous presence of PowGoop and Thanos in one attack was a coincidence or, if the two are linked, that PowGoop is not used exclusively to deliver Thanos,” Symantec says.
U.S. Says Russian Hackers Stole Data From Two Government Servers
23.10.20 BigBrothers Securityweek
The United States says Russian state-sponsored hacking group Energetic Bear has successfully compromised state, local, territorial, and tribal (SLTT) government networks and stole data from at least two servers.
Also referred to as Berserk Bear, Crouching Yeti, Dragonfly, Havex, Koala, and TeamSpy, the hacking group has been active for at least a decade, mainly focused on the energy sector in the United States and Europe.
In a Thursday alert, the FBI and the Cybersecurity and Infrastructure Security Agency (CISA) revealed that the threat actor has been observed targeting the networks of various U.S. SLTT governments, as well as those of aviation organizations.
The attacks, conducted since at least September 2020, “targeted dozens of SLTT government and aviation networks, attempted intrusions at several SLTT organizations, successfully compromised network infrastructure, and as of October 1, 2020, exfiltrated data from at least two victim servers,” the alert reads.
Using stolen credentials for initial access and lateral movement, the hackers then locate high value assets and exfiltrate data of interest.
In at least one incident involving an SLTT network, Energetic Bear was able to access documents related to sensitive network configurations and passwords; standard operating procedures (SOP); IT instructions; vendors and purchasing information; and printing access badges.
According to the FBI and CISA, the threat actor does not appear to have intentionally disrupted the operations of organizations in aviation, education, elections, or government sectors.
“However, the actor may be seeking access to obtain future disruption options, to influence U.S. policies and actions, or to delegitimize SLTT government entities,” the alert reads.
The attacks might also be seen as a risk to elections information that is stored on SLTT government networks, but there’s no evidence that such data has been compromised, the FBI and CISA note. Monitoring of the activity will continue, the two agencies say.
In an emailed comment, John Hultquist, senior director of analysis at Mandiant Threat Intelligence, said that the threat actor behind this activity has been observed targeting election-related organizations before. However, it does not appear capable of altering votes.
“The actor, who we call TEMP.Isotope, has successfully breached systems in the US, EU, and elsewhere and have targeted energy providers, water infrastructure, and even airports. Though we have not seen them disrupt these systems, we believe they are compromising them to hold them under threat, as a contingency, and possibly a warning. On one occasion we have seen them target an election related organization,” Hultquist said.
“We have actively tracked targeting of state and local systems by this actor in the lead up to the election. The timing of these incidents, the targeting of organizations with ties to election administration, and the aggressive past behavior of this actor, all underscore the seriousness of this activity. However, we have no information which suggests these actors are capable or even willing to alter votes. Access to these systems could enable disruption or could be an end in itself, allowing the actor to seize on perceptions of election insecurity and undermine the democratic process,” he concludes.
As part of the observed attacks, Turkish IP addresses were used to connect to the compromised networks. The hackers were seen attempting brute force logins, SQL injections, as well as scanning for or exploiting known vulnerabilities, such as CVE-2019-19781 (Citrix ADC and Gateway), CVE-2020-0688 (Microsoft Exchange), CVE 2019-10149 (Exim SMTP), CVE-2018-13379 (Fortinet VPN), and CVE-2020-1472 (Windows Netlogon).
The FBI and CISA also list a series of steps organizations can take to mitigate the risks posed by the threat actor, including applying the available patches for the targeted applications and remote access services, isolating Internet-facing servers, implementing application controls, and blocking RDP connections, among others.
“Organizations must maintain a robust layered defense network with monitoring and detection to reduce an attack's risk by a known vulnerability and exploit. The recent attacks from nation-state cybersecurity operatives use known vulnerabilities to access an organization's networks and systems to steal data,” James McQuiggan, security awareness advocate at KnowBe4, commented. “Essentially, without patching or updating external facing systems or network devices, it's like leaving a car door wide open in the middle of a street. It makes it easy for criminals to jump in and steal it.”
EU Slaps Sanctions on 2 Russians Over Germany Cyberattack
23.10.20 BigBrothers Securityweek
The European Union on Thursday imposed sanctions on two Russian officials and part of Russia’s GRU military intelligence agency over a cyberattack against the German parliament in 2015.
EU headquarters said in a statement that travel bans and asset freezes have been imposed on the two men: Igor Kostyukov, head of the Main Directorate of the General Staff of the Russian Armed Forces, and Dmitry Badin, a military intelligence officer.
The EU said that Badin, who is also being sought by U.S. authorities, was part of a team that launched the attacks on the Bundestag.
“This cyber-attack targeted the parliament’s information system and affected its operation for several days. A significant amount of data was stolen and the email accounts of several MPs as well as of Chancellor Angela Merkel were affected,” it said.
The part of the intelligence agency targeted is known as “military unit 26165,” or more commonly by monikers like APT28, Fancy Bear, Pawn Storm and Strontium. The EU said it “is responsible for cyber-attacks with a significant effect constituting an external threat to the Union or its Member States.”
The same unit stands accused of trying to hack into the Wi-Fi network of the Organization for the Prohibition of Chemical Weapons, based in the Netherlands, in 2018.
The sanctions were imposed under a set of measures designed to “prevent, discourage, deter and respond to continuing and increasing malicious behavior in cyberspace.” EU citizens and organizations are banned from making funds available to those listed.
A total of eight people and four organizations now appear on the list.
Russian officials have repeatedly denied any involvement by Moscow in the hacking attack. They have similarly dismissed charges of Russian meddling in the 2016 U.S. presidential election and alleged cyberattacks on other Western nations and institutions.
Diplomatic ties between Germany and Russia are already tense, following the brazen killing of a Georgian man on the streets of Berlin last year. Prosecutors have suggested the hit was ordered either by Moscow or authorities in the Russian republic of Chechnya.
Microsoft Teams Phishing Attack Targets Office 365 Users
23.10.20 Phishing Threatpost
Up to 50,000 Office 365 users are being targeted by a phishing campaign that purports to notify them of a “missed chat” from Microsoft Teams.
Researchers are warning of a phishing campaign that pretends to be an automated message from Microsoft Teams. In reality, the attack aims to steal Office 365 recipients’ login credentials.
Teams is Microsoft’s popular collaboration tool, which has particularly risen in popularity among remote workforces during the pandemic – making it an attractive brand for attackers to impersonate. This particular campaign was sent to between 15,000 to 50,000 Office 365 users, according to researchers with Abnormal Security on Thursday.
“Because Microsoft Teams is an instant-messaging service, recipients of this notification might be more apt to click on it so that they can respond quickly to whatever message they think they may have missed based on the notification,” said researchers in a Thursday analysis.
The initial phishing email displays the name “There’s new activity in Teams,” making it appear like an automated notification from Microsoft Teams.
As seen in the picture below, the email tells recipient that their teammates are trying to reach them, warning them they have missed Microsoft Team chats and showing an example of a teammate chat that asks them to submit something by Wednesday of next week.
Erin Ludert, data scientist at Abnormal Security, told Threatpost researchers suspect attackers are using more of a “spray” tactic here, as the employee referenced in the chats doesn’t appear to be an employee of the company that received the attack.

The phishing emails. Credit: Abnormal Security
To respond, the email urges the recipient to click on the “Reply in Teams” button – However, this leads to a phishing page.
“Within the body of the email, there are three links appearing as ‘Microsoft Teams’, ‘(contact) sent a message in instant messenger’, and ‘Reply in Teams’,” according to researchers. “Clicking on any of these leads to a fake website that impersonates the Microsoft login page. The phishing page asks the recipient to enter their email and password.”
Researchers said that the phishing landing page also looks convincingly like a Microsoft login page with the start of the URL containing “microsftteams.” If recipients are convinced to input their Microsoft credentials into the page, they are unwittingly handing them over to attackers, who can then use them for an array of malicious purposes – including account takeover.
With the ongoing pandemic, worries about cyberattackers leveraging enterprise friendly collaboration brands like Microsoft Teams, Zoom and Skype have been piqued. In May, a convincing campaign that impersonated notifications from Microsoft Teams in order to steal the Office 365 credentials of employees circulated, with two separate attacks that targeted as many as 50,000 different Teams users.
Microsoft is top of the heap when it comes to hacker impersonations – with Microsoft products and services featuring in nearly a fifth of all global brand phishing attacks in the third quarter of this year. Attackers are also using sophisticated tactics – including visual CAPTCHAS to target Office 365 users and token-based authorization methods.
Feds: Iran Behind ‘Proud Boys’ Email Attacks on Democratic Voters
23.10.20 BigBrothers Threatpost
Messages that threaten people to ‘vote for Trump or else’ are part of foreign adversaries’ attempts to interfere with the Nov. 3 election, according to feds.
Federal officials claim that Iranian threat actors are behind two separate email campaigns that assailed Democratic voters this week with threats to “vote for Trump or else.” The campaigns claimed to be from violent extremist group Proud Boys.
Two specific email campaigns — one on Tuesday Oct. 20 and one on Wednesday, Oct. 21 — threatened Democratic voters in Alaska, Arizona and Florida that attackers accessed “all of your information.” They warned that there would be dire repercussions if voters didn’t cast their ballot for President Trump in the upcoming election, according to a Wednesday Proofpoint report. The research came on the heels of a report from WUFT in Florida that the FBI was investigating threatening emails sent to Democratic voters in the state.
The emails of both campaigns were sent from addresses linked to the far-right, male-only group Proud Boys — “Proud Boys <info[@]officialproudboys[.]com>” on Oct. 20 messages and “Proud Boys <info[@]proudboysusa[.]com>” on Oct. 21 messages. However, federal officials claimed in a press conference late Wednesday that Iran had obtained some voter registration information and was actually behind the attack.
“We have already seen Iran sending spoofed emails designed to intimidate voters, incite voters and damage President Trump,” Director of National Intelligence John Ratcliffe said in the briefing.
Iran also is distributing other content to mislead voters, including a video that implies that individuals can cast fraudulent ballots, even from overseas, Ratcliffe said. “These videos are not true,” he said, calling the actions of Iran to interfere with the election “desperate attempts by desperate adversaries.”
Of note, Reuters has reported that governments sources say, while U.S. officials suspect the Iranian government was involved, concrete evidence remains inconclusive. Meanwhile, others in the security research community told ZDNet that they could not confirm the attribution to Iran.
Proud Boys Content
The video in question is a Proud Boys-branded video demonstrating a Kali Linux user filling out voter registration and absentee ballots for Alaskan citizens, according to the report from Proofpoint, whose researchers obtained a copy.
“We only observed two intended recipients of these messages, both of whom appear to reside in Florida,” wrote researchers. The video appeared to be taken off the Internet not long after researchers viewed it, they said.
The emails observed by Proofpoint demonstrates that attackers did obtain sensitive personal information of voters and also shows those behind the threats changing up their tactics to avoid detection.
Messages in the Oct. 20 campaign — which Proofpoint separated into two sets — show that the threat actors have the home addresses of some of their victims. Researchers traced messages in set one to a PHPmailer script hosted on a likely compromised Saudi Arabian insurance company website, while set two was routed through the website of an Estonian textbook publisher, as previously reported by Vice.
The email attacks and attempts to spread misinformation are a departure from recent and more typical tactics used by threat actors to interfere in the U.S. elections, such as impersonation of the Democratic National Committee and various fraudulent voter registration portals, researchers said.
“Previous activity used political themes to entice users to click on links or open attachments but did not appear especially politically motivated,” they wrote in the report.
Indeed, this election season has seen a ramp up and variation in methods by state-sponsored actors to interfere with the 2020 U.S. Elections, which has been complicated by the COVID-19 pandemic.
This election will see many more voters choose to vote by mail, increasing the load of votes the postal system will handle. People also have opted to vote early to avoid long lines on election day, a scenario that could invite attacks on voting machines. These various scenarios provide a wider playing field for attackers to target in the run-up to the official election day on Nov. 3, experts observed.
EU Council sanctions two Russian military intelligence officers over 2015 Bundestag hack
23.10.20 BigBrothers Securityaffairs
The Council of the European Union announced sanctions imposed on Russian military intelligence officers for 2015 Bundestag hack.
The Council of the European Union announced sanctions imposed on Russian military intelligence officers, belonging to the 85th Main Centre for Special Services (GTsSS), for their role in the 2015 attack on the German Federal Parliament (Deutscher Bundestag).
The 85th Main Centre for Special Services (GTsSS) is the military unit of the Russian government also tracked as APT28 (aka Fancy Bear, Pawn Storm, Sofacy Group, Sednit, and STRONTIUM).
The APT28 group (aka Fancy Bear, Pawn Storm, Sofacy Group, Sednit, and STRONTIUM) has been active since at least 2007 and it has targeted governments, militaries, and security organizations worldwide. The group was involved also in the string of attacks that targeted 2016 Presidential election.
“The Council today imposed restrictive measures on two individuals and one body that were responsible for or took part in the cyber-attack on the German Federal Parliament (Deutscher Bundestag) in April and May 2015.” reads the press release published by the Council. “This cyber-attack targeted the parliament’s information system and affected its ability to operate for several days. A significant amount of data was stolen and the email accounts of several members of parliament, including that of Chancellor Angela Merkel, were affected.”
Immediately after the attack the daily Der Spiegel speculated that the Russian Government was behind the attack.
Bundestag German politicians
The attackers used a sophisticated strain of malware to violated the Bundestag network and syphoned sensitive data. The experts that analyzed the malicious code employed in the hack found many similarities with a piece of malware used in a previous attack against a German Government network that took place in 2014.
“The cyber attack on the “Parlakom” network was discovered in early May. At the parliamentary IT network 20,000 Bundestag accounts are connected – including German Chancellor Angela Merkel and other government officials.” continues the Der Spiegel.
EU’s sanctions imposed on Russian military officers include travel bans and asset freezes, they also block EU organizations and individuals from transferring funds to sanctioned entities and individuals.
The Council’s sanctions target a total of 8 persons and 4 entities and bodies.
“Sanctions are one of the options available in the Union’s framework for a joint diplomatic response to malicious cyber activities (the so-called cyber diplomacy toolbox), and are intended to prevent, discourage, deter and respond to continuing and increasing malicious behaviour in cyberspace,” a press release published earlier reads. “The relevant legal acts, including the names of the individuals and the body concerned, have been published in the Official Journal.”
Two of the officers sanctioned by the Council of the European Union are Dmitry Sergeyevich Badin and Igor Olegovich Kostyukov are known members of the GTsSS.
The two officers were also indicted by US DoJ in October 2018, along with other five members of the Russian Main Intelligence Directorate (GRU), for hacking, wire fraud, identity theft, and money laundering.
Kostyukov was also reached by an executive order issued by President Barack Obama in 2016 to impose sanctions on a number of Russian military and intelligence officials in response to the alleged hacking campaigns against the 2016 US Presidential Election.
Kostyukov is the current chief of the Main Directorate of the General Staff of the Armed Forces of the Russian Federation (GU/GRU).
“In this capacity, Igor Kostyukov is responsible for cyber-attacks carried out by the GTsSS, including those with a significant effect constituting an external threat to the Union or its Member States,” states the Council. “In particular, military intelligence officers of the GTsSS took part in the cyber-attack against the German federal parliament (Deutscher Bundestag) which took place in April and May 2015 and the attempted cyber-attack aimed at hacking into the Wi-Fi network of the Organisation for the Prohibition of Chemical Weapons (OPCW) in the Netherlands in April 2018.”
In July 2020, for the first-ever time, the EU has imposed economical sanctions on Russia, China, and North Korea following cyber-attacks aimed at the EU and its member states.
The EU Council announced sanctions imposed on a Russia-linked military espionage unit, as well as companies operating for Chinese and North Korean threat actors that launched cyber-attacks against the EU and its member states.
The sanctions were imposed as part of a legal framework established on May 17, 2019, which allows the EU to impose targeted restrictive measures to deter and respond to cyber-attacks aimed at the EU or its member states.
US whistleblower Edward Snowden received permanent residency by Russian authorities
23.10.20 BigBrothers Securityaffairs
The popular US whistleblower Edward Snowden has been granted permanent residency in Russia, the announcement was made by his lawyer.
The former CIA employee and National Security Agency contractor Edward Snowden (37) has been granted permanent residency in Russia, his lawyer announced on Thursday.
In 2013, Edward Snowden shed the light on the mass surveillance program operated by the US government to spy on its citizens and allies.
The man expressed his desire to return to the United States where he is considered a criminal and a threat to homeland security due to his revelation. Snowden is wanted in the United States on espionage charges after he revealed details on the surveillance apparatus used by the National Security Agency (NSA) to collect telephone records of millions of US citizens.
According to his lawyer Anatoly Kucherena, Snowden’s residency permit was extended as the result of recent changes introduced to Russia’s immigration law. The residency permit and is now indefinite, as reported by AFP press.
“Kucherena said it was “natural” that Snowden wanted to return to the United States but will only do so when the case against him is closed.” reported AFP.
Edward snowden
The application was filed in April, but the decision of the Russian authorities was made public only this week due to a delay in the process caused by the ongoing COVID-19 pandemic.
It is not clear if Snowden plans to apply for Russian citizenship.
Earlier this year, US President Donald Trump announced that he was evaluating the possibility of pardoning Snowden but he did not provide further details on the case.
In 2015 the White House rejected a petition calling on then-president Barack Obama to pardon the popular US whistleblower.
In September 2019, the US DoJ filed a lawsuit against Edward Snowden to prevent the former CIA employee and National Security Agency contractor from receiving the payment for his book, Permanent Record.
According to the civil lawsuit, filed in the Eastern District of Virginia, Snowden violated non-disclosure agreements signed when he was an employee at the US intelligence agencies.
FDA Approves Use of New Tool for Medical Device Vulnerability Scoring
23.10.20 ICS Securityweek
The U.S. Food and Drug Administration (FDA) this week announced that it has approved the use of a new rubric specifically designed by the MITRE Corporation for assigning CVSS scores to vulnerabilities found in medical devices.
The Common Vulnerability Scoring System (CVSS) was originally designed to convey the severity of vulnerabilities found in IT systems, and it may not be as relevant in some areas, such as industrial control systems (ICS) or medical devices.
That is why the FDA contracted MITRE to create a special rubric for assigning CVSS scores to medical device vulnerabilities. MITRE developed the new rubric last year and the FDA announced this week that it has qualified as a Medical Device Development Tool (MDDT).
The MDDT program enables the organization to qualify tools that can be used in the development and evaluation of medical devices. In order for a tool to qualify, it must be evaluated by the FDA, which must agree that it “produces scientifically-plausible measurements and works as intended within the specified context of use.”
The FDA believes that using MITRE’s rubric for applying CVSS to medical devices, together with CVSS v3.0, “allows a common framework for risk evaluation and communication between all parties involved in a security vulnerability disclosure, particularly when discussing its severity and urgency.”
The FDA’s approval of the tool means “that vendors can communicate measurements from the rubric about their devices with the FDA for pre-market security and risk assessments,” Elad Luz, head of research at New York-based healthcare cybersecurity firm CyberMDX, told SecurityWeek.
CyberMDX has identified more than ten vulnerabilities in medical devices over the past year and it has seen first hand how misleading CVSS can be if it’s not adapted. For instance, a vulnerability it discovered last year in some of GE Healthcare’s hospital anesthesia devices was assigned a CVSS score of only 5.3 but, as the vendor itself admitted, exploitation of the flaw posed a direct risk to patients, which made it highly serious.
“[The vulnerability] was not scored as high severity because you could not execute remote code, or remotely access information, just remotely alter limited specific functionality,” Luz explained. “The problem is — when you look at the medical aspect of this — those remote functions altered might just be the most severe thing to compromise on this device, so this must be expressed for anyone doing a risk assessment for it.”
Luz says the new rubric addresses these and other issues. The expert says the new guidelines are clear and easy to use, with real-world examples taken from medical devices used worldwide.
“When doing disclosures there are many disagreements regarding the interpretation of CVSS because it was not always clear how one should project those measurements that were meant for computers/mobiles software to medical devices,” he explained. “The rubric goes through all CVSS measurements and clears them out in the form of a Q&A flowchart. This makes things much more clear and will hopefully spare much of the arguments.”
Luz also pointed out that the new rubric gives the environmental metric group “the place it deserves.”
“When people get exposed to CVSS scores they mostly consume the ‘base metric group’. This is unfortunate because the base score only gives a general impression of the risk,” he said. “The ‘environmental metric group’ is another group on CVSS that adjusts the score to your specific case. The environment where the device is deployed and used greatly affects the actual risk and this must be taken into account. Almost half of the rubric talks about this environmental group and finally it gets the right attention it deserves.”
U.S. Voter Data Traded on Hacker Forums: Researchers
23.10.20 BigBrothers Securityweek
A database with information on virtually the entire US voting population has been circulated on hacker forums, opening up the potential for disinformation and scams that could impact the November 3 election, security researchers say.
A report released Wednesday by the security firm Trustwave said its researchers "discovered massive databases with detailed information about US voters and consumers offered for sale on several hacker forums."
The databases "include a shocking level of detail about citizens including their political affiliation," and the sellers claim to have 186 million records, which would mean nearly all US voters, the security researchers said in a blog post.
"The information found in the voter database can be used to conduct effective social engineering scams and spread disinformation to potentially impact the elections, particularly in swing states," said the post from Trustwave analysts Ziv Mador and Nikita Kazymirskyi.
The analysts said at least some of the data comes from public records, but that other information appears to have come from data leaks or breaches. The researchers said they also discovered other databases on the entire US consumer population and on residents of Britain, Canada, Ireland and South Africa.
Cybercriminals appear to be working "to monetize the upcoming elections" in the United States, the researchers added, by selling databases that include addresses, age, gender and political affiliation of American voters, and phone numbers in some cases.
The news comes a day after US authorities said Russian and Iran had obtained voter information and taken actions to influence public opinion including with "spoofed" emails designed to intimidate voters and create unrest.
On the trail of the XMRig miner
22.10.20 Cryptocurrency Securelist
As protection methods improve, the developers of miners have had to enhance their own creations, often turning to non-trivial solutions. Several such solutions (previously unseen by us) were detected during our analysis of the open source miner XMRig.
How it all began: ransominer
Alongside well-known groups that make money from data theft and ransomware (for example, Maze, which is suspected of the recent attacks on SK Hynix and LG Electronics), many would-be attackers are attracted by the high-profile successes of cybercrime. In terms of technical capabilities, such amateurs lag far behind organized groups and therefore use publicly available ransomware, targeting ordinary users instead of the corporate sector.
The outlays on such attacks are often quite small, so the miscreants have to resort to various stratagems to maximize the payout from each infected machine. For example, in August of this year, we noticed a rather curious infection method: on the victim’s machine, a Trojan (a common one detected by our solutions as Trojan.Win32.Generic) was run, which installed administration programs, added a new user, and opened RDP access to the computer. Next, the ransomware Trojan-Ransom.Win32.Crusis started on the same machine, followed by the loader of the XMRig miner, which then set about mining Monero cryptocurrency.
As a result, the computer would already start earning money for the cybercriminals just as the user saw the ransom note. In addition, RDP access allowed the attackers to manually study the victim’s network and, if desired, spread the ransomware to other nodes.
Details about Trojan files:
Mssql — PC Hunter x64 (f6a3d38aa0ae08c3294d6ed26266693f)
mssql2 — PC Hunter x86 (f7d94750703f0c1ddd1edd36f6d0371d)
exe — nmap-like network scanner (597de376b1f80c06d501415dd973dcec)
bat — removes shadow copy
bat — creates a new user, adds it to the administrators group, opens the port for RDP access, and starts the Telnet server
exe — IOBIT Unlocker (5840aa36b70b7c03c25e5e1266c5835b)
EVER\SearchHost.exe — Everything software (8add121fa398ebf83e8b5db8f17b45e0)
EVER\1saas\1saas.exe — ransomware Trojan-Ransom.Win32.Crusis (0880430c257ce49d7490099d2a8dd01a)
EVER\1saas \LogDelete — miner loader (6ca170ece252721ed6cc3cfa3302d6f0, HEUR:Trojan-Downloader.Win32.Generic)
Batch script systembackup.bat adds a user and opens access via RDP
We decided to use KSN to examine how often XMRig and its modifications get bundled with malware. It emerged that in August 2020 there were more than 5,000 attempts to install it on users’ computers. The parties responsible for its distribution turned out to be the Prometei malware family and a new family called Cliptomaner.
Prometei backdoor
The Prometei family has been known since 2016, but spotted together with XMRig for the first time in February 2020. What’s more, the backdoor was distributed in an unusual way: whereas during ordinary attacks the cybercriminals gain server access through various exploits, this time they used brute-force attacks. Having thus obtained usernames and passwords for computers with MS SQL installed, the attackers used the T-SQL function xp_cmdshell to run several PowerShell scripts and elevated the privileges of the current user by exploiting the CVE-2016-0099 vulnerability. After that, Purple Fox Trojan and Prometei itself were installed on the victim’s machine. The whole attack, starting with the brute-forcing of credentials to connect to the SQL server and ending with the installation of Prometei, was carried out in fully automatic mode.
The installation process is of interest: the .NET executable file, packed into an ELF file using standard .NET Core tools (Apphost), sends information about the infected machine to the C&C server, and then downloads the cryptocurrency miner and its configuration. The versions of the loaders for Windows and Linux differ only slightly: the .NET build for different platforms saved the attackers from having to create a separate loader for Linux and allowed cryptocurrency mining on powerful Windows and Linux servers.
Cliptomaner miner
Detected in September 2020, Cliptomaner is very similar to its fellows: like them, it not only mines cryptocurrency, but can also substitute cryptowallet addresses in the clipboard. The miner version is selected according to the computer configuration and downloaded from C&C. The malware is distributed under the guise of software for Realtek audio equipment. On the whole, we saw no new techniques, but interestingly Cliptomaner is written entirely in the AutoIT scripting language. Most of the time, families with similar behavior are written in compiled languages, such as C# or C, but in this case the authors opted for a more creative approach, and wrote a lengthy script that selects the required version of the miner and receives cryptowallet addresses from C&C for substitution.
Substituting cryptowallets in the clipboard
Kaspersky security solutions detect the above malicious programs with the following verdicts: HEUR:Trojan.MSIL.Prometei.gen, HEUR:Trojan.Script.Cliptomaner.gen, HEUR:Trojan-Downloader.Win32.Generic, Trojan-Ransom.Win32.Crusis, Trojan.Win64.Agentb, not-a-virus:RiskTool.Win64.XMRigMiner
Indicators of compromise (IoC)
Domains
taskhostw[.]com
svchost[.]xyz
sihost[.]xyz
srhost[.]xyz
2fsdfsdgvsdvzxcwwef-defender[.]xyz
Cryptowallets used for substitution
LTC: LPor3PrQHcQv4obYKEZpnbqQEr8LMZoUuX
BTC: 33yPjjSMGHPp8zj1ZXySNJzSUfVSbpXEuL
ETH: 0x795957d9753e854b62C64cF880Ae22c8Ab14991b
ZEC: t1ZbJBqHQyytNYtCpDWFQzqPQ5xKftePPt8
DODGE: DEUjj7mi5N67b6LYZPApyoV8Ek8hdNL1Vy
MD5
1273d0062a9c0a87e2b53e841b261976
16b9c67bc36957062c17c0eff03b48f3
d202d4a3f832a08cb8122d0154712dd1
6ca170ece252721ed6cc3cfa3302d6f0
1357b42546dc1d202aa9712f7b29aa0d
78f5094fa66a9aa4dc10470d5c3e3155
ENISA Threat Landscape Report 2020
22.10.20 Analysis Securityaffairs
According to the ENISA Threat Landscape Report 2020, cyberattacks are becoming more sophisticated, targeted, and in many cases undetected.
I’m proud to present the ENISA Threat Landscape Report 2020, the annual report published by the ENISA that provides insights on the evolution of cyber threats for the period January 2019-April 2020.
The 8th annual ENISA Threat Landscape (ETL) report was compiled by the European Union Agency for Cybersecurity (ENISA), with the support of the European Commission, EU Member States and the CTI Stakeholders Group.
It is an amazing work that identifies and evaluates the top cyber threats for the period January 2019-April 2020.
This year the report has a different format that could allow the readers to focus on the threat of interest. The publication is divided into 22 different reports, which are available in both pdf form and ebook form.
The report provides details on threats that characterized the period of the analysis and highlights the major change from the 2018 threat landscape as the COVID-19-led transformation of the digital environment.
“During the pandemic, cyber criminals have been seen advancing their capabilities, adapting quickly and targeting relevant victim groups more effectively. (Infographic – Threat Landscape Mapping during COVID-19). states the report.
ENISA Threat Landscape Report 2020
The ETL report provides strategic and technical analysis of the events, it was created to provide relevant information to both technical and non-technical readers.
For a better understanding of how the ETL is structured, we recommend the initial reading of “The Year in Review” report, the following table could help readers to focus on the section of their interest included in the publication.
The report highlights the importance of cyber threat intelligence to respond to increasingly automated attacks leveraging automated tools and skills.
Another element of concern is the diffusion of IoT devices, in many cases, smart objects are exposed online without protection.
Below the main trends reported in the document:
Attack surface in cybersecurity continues to expand as we are entering a new phase of the digital transformation.
There will be a new social and economic norm after the COVID-19 pandemic even more dependent on a secure and reliable cyberspace.
The use of social media platforms in targeted attacks is a serious trend and reaches different domains and types of threats.
Finely targeted and persistent attacks on highvalue data (e.g. intellectual property and state secrets) are being meticulously planned and executed by state-sponsored actors.
Massively distributed attacks with a short duration and wide impact are used with multiple objectives such as credential theft.
The motivation behind the majority of cyberattacks is still financial.
Ransomware remains widespread with costly consequences to many organisations.
Still many cybersecurity incidents go unnoticed or take a long time to be detected.
With more security automation, organisations will be invest more in preparedness using Cyber Threat Intelligence as its main capability.
The number of phishing victims continues to grow since it exploits the human dimension being the weakest link.
Let me close with the Top Threats 2020, for each threat the report includes detailed information on trends and observed evolution.

Enjoy it!
Snowden Granted Permanent Residency in Russia
22.10.20 BigBrothers Securityweek
Fugitive US whistleblower Edward Snowden has been granted permanent residency in Russia, his lawyer said on Thursday.
Snowden, the former US intelligence contractor who revealed in 2013 that the US government was spying on its citizens, has been living in exile in Russia since the revelations.
The 37-year-old has said he would like to return to the United States.
His lawyer Anatoly Kucherena told AFP on Thursday that his residency permit was extended and is now indefinite, a situation made possible by recent changes to Russia's immigration law.
Kucherena said the application was filed in April but the process was delayed by the coronavirus pandemic.
Snowden is wanted in the United States on espionage charges after he leaked information showing that agents from the National Security Agency (NSA) were collecting telephone records of millions of US citizens.
When asked whether Snowden planned to apply for Russian citizenship, Kucherena said: "He will make the decision himself."
Kucherena said it was "natural" that Snowden wanted to return to the United States but will only do so when the case against him is closed.
Earlier this year, US President Donald Trump said he would "take a look" at pardoning Snowden but has not made further comment on the matter.
A 2015 petition calling on then president Barack Obama to pardon the whistleblower and privacy advocate was rejected by the White House.
Cisco Patches 17 High-Severity Vulnerabilities in Security Appliances
22.10.20 Vulnerebility Securityweek
Cisco on Wednesday announced the release of patches for 17 high-severity vulnerabilities in its security appliances as part of its Security Advisory Bundled Publication for October 2020.
The vulnerabilities have been found to impact Adaptive Security Appliance (ASA), Firepower Threat Defense (FTD), and Firepower Management Center (FMC).
A majority of the flaws can be exploited remotely without authentication, including to alter data between FMC and FTD devices via an MitM attack, conduct actions on behalf of a user via a CSRF attack, and bypass FMC authentication.
However, most of the vulnerabilities that can be exploited remotely without authentication allow an attacker to cause a denial-of-service (DoS) condition. In some cases, recovering from this DoS condition requires a manual reboot of the device.
The flaws whose exploitation requires local access or authentication can be exploited to read or write files on a device, cause a DoS condition, bypass the secure boot mechanism, and escape containers and execute commands with root privileges.
A majority of these security holes were found internally and Cisco says it has found no evidence that any of them has been exploited in attacks.
The company did, however, warn customers this week that a Discovery Protocol vulnerability disclosed earlier this year has been exploited in attacks. The U.S. National Security Agency included the flaw, tracked as CVE-2020-3118, in a list of vulnerabilities exploited by Chinese state-sponsored hackers.
Last month, the networking giant released a patch bundle that fixed 34 high-severity vulnerabilities in its IOS and IOS XE software.
QNAP Issues Advisory on Zerologon Vulnerability
22.10.20 Vulnerebility Securityweek
Storage solutions provider QNAP this week published an advisory to warn customers that certain versions of QTS, the operating system for its network-attached storage (NAS) devices, are affected by the Zerologon vulnerability.
Residing in the Microsoft Windows Netlogon Remote Protocol (MS-NRPC) and addressed on August 2020 Patch Tuesday, the flaw started gaining attention after CISA on September 18 issued an Emergency Directive requiring federal agencies to install the available patches within three days.
Soon after, Microsoft and CISA revealed that threat actors were already targeting the vulnerability in their attacks, urging organizations to patch all domain controllers to ensure their environments are protected.
To date, both Iranian and Russian adversaries were observed abusing Zerologon, and CISA issued an alert to warn of attacks chaining exploits for this flaw with those targeting bugs in Fortinet FortiOS VPN and MobileIron MDM solutions.
This week, QNAP revealed that it too released patches for Zerologon, to ensure that its devices can’t be abused to take over entire networks.
NAS devices can be used as Windows domain controllers to allow administrators to leverage them for operations such as authentication and user account management.
“If exploited, this elevation of privilege vulnerability allows remote attackers to bypass security measures via a compromised QTS device on the network. The NAS may be exposed to this vulnerability if users have configured the device as a domain controller in Control Panel > Network & File Services > Win/Mac/NFS > Microsoft Networking,” the company explains.
QTS 4.5.1.1456 build 20201015 and later, QTS 4.4.3.1439 build 20200925 and later, QTS 4.3.6.1446 build 20200929 and later, QTS 4.3.4.1463 build 20201006 and later, and QTS 4.3.3.1432 build 20201006 and later contain fixes for the vulnerability. QTS 2.x and QES, QNAP notes, are not impacted.
Users are advised to update QTS to the latest available version and to ensure that all other applications on their devices are up to date. Users can check for new updates for their NAS model on the product support status page.
QNAP’s advisory also includes details on how users can apply the newly released QTS updates, as well as on how to update all of the installed applications.
XSS Vulnerability Exploited in Tech Support Scam
22.10.20 Spam Securityweek
Malwarebytes security researchers have identified a new campaign in which tech support scammers are exploiting a cross-site scripting (XSS) vulnerability and are relying exclusively on links posted on Facebook to reach potential victims.
The scam starts with malicious bit.ly shortened links that are being distributed on the social media platform, and which ultimately take the intended victims to a browser locker page. According to Malwarebytes, certain games and applications on Facebook appear to be abused for the distribution of these links.
Over a period of three months, the researchers found a total of 50 different bit.ly links that were being used in this campaign. This, they say, suggests that the tech support scammers were regularly changing these links to avoid blacklisting.
The bit.ly URLs would trigger a second stage redirection where a Peruvian news website (rpp[.]pe) containing a cross-site scripting (XSS) vulnerability is abused for an open redirect. The legitimate site has more than 23 million visits per month.
“Besides redirecting users to other sites, an attacker could exploit the XSS to rewrite the current page into anything they like,” Malwarebytes notes.
In this attack, the next step involves code being passed into the URL to load external JavaScript code from the malicious domain buddhosi[.]com. The script was designed to create a redirection to the browser locker landing page.
Initially, the attackers were directly loading decoy cloaking domains designed to check incoming traffic and deliver the malicious content to legitimate victims only. Later on in the campaign, the attackers added exploitation of the open redirect flaw instead.
At the end of the redirection chain, the user is served a browser locker that shows an animation suggesting system files are being scanned, and threatening to delete the hard drive after five minutes.
The trick is likely convincing enough that some people do call the toll-free number that is listed on the page. Malwarebytes identified approximately 40 different phone numbers used in the campaign, but notes that the list might be longer.
The researchers say they did not call any of the numbers, but the next step of the tech support scam is well known: the victim is told their computer has been infected and is urged to immediately purchase expensive software or services to clean up their system.
Bug Parade: NSA Warns on Cresting China-Backed Cyberattacks
22.10.20 BigBrothers Threatpost
The Feds have published a Top 25 exploits list, rife with big names like BlueKeep, Zerologon and other notorious security vulnerabilities.
Chinese state-sponsored cyberattackers are actively compromising U.S. targets using a raft of known security vulnerabilities – with a Pulse VPN flaw claiming the dubious title of “most-favored bug” for these groups.
That’s according to the National Security Agency (NSA), which released a “top 25” list of the exploits that are used the most by China-linked advanced persistent threats (APT), which include the likes of Cactus Pete, TA413, Vicious Panda and Winniti.
The Feds warned in September that Chinese threat actors had successfully compromised several government and private sector entities in recent months; the NSA is now driving the point home about the need to patch amid this flurry of heightened activity.
“Many of these vulnerabilities can be used to gain initial access to victim networks by exploiting products that are directly accessible from the internet,” warned the NSA, in its Tuesday advisory. “Once a cyber-actor has established a presence on a network from one of these remote exploitation vulnerabilities, they can use other vulnerabilities to further exploit the network from the inside.”
APTs – Chinese and otherwise – have ramped up their cyberespionage efforts in the wake of the pandemic as well as in the leadup to the U.S. elections next month. But Chloé Messdaghi, vice president of strategy at Point3 Security, noted that these vulnerabilities contribute to an ongoing swell of attacks.
“We definitely saw an increase in this situation last year and it’s ongoing,” she said. “They’re trying to collect intellectual property data. Chinese attackers could be nation-state, could be a company or group of companies, or just a group of threat actors or an individual trying to get proprietary information to utilize and build competitive companies…in other words, to steal and use for their own gain.”
Pulse Secure, BlueKeep, Zerologon and More
Plenty of well-known and infamous bugs made the NSA’s Top 25 cut. For instance, a notorious Pulse Secure VPN bug (CVE-2019-11510) is the first flaw on the list.
It’s an arbitrary file-reading flaw that opens systems to exploitation from remote, unauthenticated attackers. In April of this year, the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) warned that attackers are actively using the issue to steal passwords to infiltrate corporate networks. And in fact, this is the bug at the heart of the Travelex ransomware fiasco that hit in January.
Pulse Secure issued a patch in April 2019, but many companies impacted by the flaw still haven’t applied it, CISA warned.
Another biggie for foreign adversaries is a critical flaw in F5 BIG-IP 8 proxy/load balancer devices (CVE-2020-5902). This remote code-execution (RCE) bug exists in the Traffic Management User Interface (TMUI) of the device that’s used for configuration. It allows complete control of the host machine upon exploitation, enabling interception and redirection of web traffic, decryption of traffic destined for web servers, and serving as a hop-point into other areas of the network.
At the end of June, F5 issued urgent patches the bug, which has a CVSS severity score of 10 out of 10 “due to its lack of complexity, ease of attack vector, and high impacts to confidentiality, integrity and availability,” researchers said at the time. Thousands of devices were shown to be vulnerable in a Shodan search in July.
The NSA also flagged several vulnerabilities in Citrix as being Chinese faves, including CVE-2019-19781, which was revealed last holiday season. The bug exists in the Citrix Application Delivery Controller (ADC) and Gateway, a purpose-built networking appliance meant to improve the performance and security of applications delivered over the web. An exploit can lead to RCE without credentials.
When it was originally disclosed in December, the vulnerability did not have a patch, and Citrix had to scramble to push fixes out – but not before public proof-of-concept (PoC) exploit code emerged, along with active exploitations and mass scanning activity for the vulnerable Citrix products.
Other Citrix bugs in the list include CVE-2020-8193, CVE-2020-8195 and CVE-2020-8196.
Meanwhile, Microsoft bugs are well-represented, including the BlueKeep RCE bug in Remote Desktop Services (RDP), which is still under active attack a year after disclosure. The bug tracked as CVE-2019-0708 can be exploited by an unauthenticated attacker connecting to the target system using RDP, to send specially crafted requests and execute code. The issue with BlueKeep is that researchers believe it to be wormable, which could lead to a WannaCry-level disaster, they have said.
Another bug-with-a-name on the list is Zerologon, the privilege-escalation vulnerability that allows an unauthenticated attacker with network access to a domain controller to completely compromise all Active Directory identity services. It was patched in August, but many organizations remain vulnerable, and the DHS recently issued a dire warning on the bug amid a tsunami of attacks.
The very first bug ever reported to Microsoft by the NSA, CVE-2020-0601, is also being favored by Chinese actors. This spoofing vulnerability, patched in January, exists in the way Windows CryptoAPI (Crypt32.dll) validates Elliptic Curve Cryptography (ECC) certificates. An attacker could exploit the vulnerability by using a spoofed code-signing certificate to sign a malicious executable, making it appear that the file was from a trusted, legitimate source.
Two proof-of-concept (PoC) exploits were publicly released just a week after Microsoft’s January Patch Tuesday security bulletin addressed the flaw.
Then there’s a high-profile Microsoft Exchange validation key RCE bug (CVE-2020-0688), which stems from the server failing to properly create unique keys at install time.
It was fixed as part of Microsoft’s February Patch Tuesday updates – and admins in March were warned that unpatched servers are being exploited in the wild by unnamed advanced persistent threat (APT) actors. But as of Sept. 30, at least 61 percent of Exchange 2010, 2013, 2016 and 2019 servers were still vulnerable to the flaw.
The Best of the Rest
The NSA’s Top 25 list covers plenty of ground, including a nearly ubiquitous RCE bug (CVE-2019-1040) that, when disclosed last year, affected all versions of Windows. It allows a man-in-the-middle attacker to bypass the NTLM Message Integrity Check protection.
CVE-2018-4939 in certain Adobe ColdFusion versions.
CVE-2020-2555 in the Oracle Coherence product in Oracle Fusion Middleware.
CVE-2019-3396 in the Widget Connector macro in Atlassian Confluence Server
CVE-2019-11580 in Atlassian Crowd or Crowd Data Center
CVE-2020-10189 in Zoho ManageEngine Desktop Central
CVE-2019-18935 in Progress Telerik UI for ASP.NET AJAX.
CVE-2019-0803 in Windows, a privilege-escalation issue in the Win32k component
CVE-2020-3118 in the Cisco Discovery Protocol implementation for Cisco IOS XR Software
CVE-2020-8515 in DrayTek Vigor devices
The advisory also covers three older bugs, in Exim mail transfer (CVE-2018-6789); Symantec Messaging Gateway (CVE-2017-6327); and the WLS Security component in Oracle WebLogic Server (CVE-2015-4852).
“We hear loud and clear that it can be hard to prioritize patching and mitigation efforts,” NSA Cybersecurity Director Anne Neuberger said in a media statement. “We hope that by highlighting the vulnerabilities that China is actively using to compromise systems, cybersecurity professionals will gain actionable information to prioritize efforts and secure their systems.”
US Officials Link Iran to Emails Meant to Intimidate Voters
22.10.20 BigBrothers Securityweek
Iran is responsible for emails sent to Democratic voters in multiple states aimed at intimidating the recipients into voting for President Donald Trump, U.S. officials said Wednesday night in calling out both Tehran and Russia for activities meant to interfere in the upcoming presidential election.
The activities attributed to Iran mark a significant escalation for a nation that some cybersecurity experts regard as a second-rate player in online espionage. Most public election interference discussion has centered on Russia, which hacked Democratic emails during the 2016 election, and China. The announcement at a rare, hastily called news conference just two weeks before the election underscored the concern within the U.S. government about efforts by foreign countries to spread false information meant to suppress voter turnout and undermine American confidence in the vote.
“These actions are desperate attempts by desperate adversaries,” said John Ratcliffe, the government’s top intelligence official, who, along with FBI Director Chris Wray, insisted the U.S. would impose costs on any foreign countries that interfere in the 2020 U.S. election and that the integrity of the election is still sound.
“You should be confident that your vote counts,” Wray said. “Early, unverified claims to the contrary should be viewed with a healthy dose of skepticism.”
Wray and Ratcliffe did not describe the emails linked to Iran, but officials familiar with the matter said the U.S. has linked Tehran to messages sent to Democratic voters in at least four battleground states that falsely purported to be from the neo-fascist group Proud Boys and that warned “we will come after you” if the recipients didn’t vote for Trump.
Ratcliffe said the spoofed emails were intended to hurt Trump, though he did not elaborate on how. An intelligence assessment released in August said: “Iran seeks to undermine U.S. democratic institutions, President Trump, and to divide the country in advance of the 2020 elections. Iran’s efforts along these lines probably will focus on online influence, such as spreading disinformation on social media and recirculating anti-U.S. content.”
Trump, speaking at a rally in North Carolina, made no reference to the press conference but repeated a familiar campaign assertion that Iran is opposed to his reelection. He promised that if he wins another term he will swiftly reach a new accord with Iran over its nuclear program.
“Iran doesn’t want to let me win. China doesn’t want to let me win,” Trump said. “The first call I’ll get after we win, the first call I’ll get will be from Iran saying let’s make a deal.”
Both Russia and Iran also obtained voter registration information, though such data is considered easily, publicly accessible. Tehran used the information to send out the spoofed emails, which were sent to voters in states including Pennsylvania and Florida.
Asked about the emails during an online forum Wednesday, Pennsylvania Secretary of State Kathy Boockvar said she lacked specific information. “I am aware that they were sent to voters in multiple swing states and we are working closely with the attorney general on these types of things and others,” she said.
While state-backed Russian hackers are known to have infiltrated U.S. election infrastructure in 2016, there is no evidence that Iran has ever done so.
The voter intimidation operation apparently used email addresses obtained from state voter registration lists, which include party affiliation and home addresses and can include email addresses and phone numbers. Those addresses were then used in an apparently widespread targeted spamming operation. The senders claimed they would know which candidate the recipient was voting for in the Nov. 3 election, for which early voting is ongoing.
Federal officials have long warned about the possibility of this type of operation, as such registration lists are not difficult to obtain.
“These emails are meant to intimidate and undermine American voters’ confidence in our elections,” Christopher Krebs, the top election security official at the Department of Homeland Security, tweeted Tuesday night after reports of the emails first surfaced.
Microsoft Says Most TrickBot Servers Are Down
22.10.20 BotNet Securityweek
Most of the servers associated with the TrickBot botnet have been taken down following the technical and legal effort announced last week, Microsoft says.
The takedown was meant to disable Trickbot’s infrastructure and prevent its operators from reviving the botnet, but initial reports claimed that the network of infected machines continued operations unhindered.
The TrickBot operators, which some say are the hackers that also use Ryuk and Conti ransomware, appeared largely unaffected by the takedown attempt, with only a relatively small percentage of the bots being isolated.
On Tuesday, threat intelligence company Intel 471 revealed that newly observed TrickBot control servers were unable to respond to bot requests, and Microsoft now says its actions have successfully prevented newly registered servers from becoming operational.
The tech giant explains that it managed to take down 62 of the 69 initial TrickBot servers around the world, as well as 58 of the 59 new servers that the malware operators attempted to add to their infrastructure.
“In sum, from the time we began our operation until October 18, we have taken down 120 of the 128 servers we identified as Trickbot infrastructure around the world,” Tom Burt, Corporate Vice President of Customer Security & Trust at Microsoft, says.
Burt also notes that, due to the botnet’s unique architecture, Microsoft and its partners are taking a “persistent and layered approach to addressing Trickbot’s operations around the world.” Furthermore, he says, the same action will continue throughout election day on November 3.
Microsoft’s partners, he says, are working to clean and remediate compromised Internet of Things (IoT) devices that are being used as non-traditional command and control (C&C) infrastructure.
“These compromised routers pose a unique challenge for the internet service providers (ISPs) as they must simultaneously work to remediate devices while keeping legitimate traffic uninterrupted, and this delicate work is underway. Finally, we’re working with ISPs and others to also clean devices in people’s homes and businesses that might be infected,” Burt notes.
The focus of this effort, he adds, is to disrupt TrickBot during peak election activity, and so far the company feels confident with the progress it has made, as the cybercriminals need to invest a lot into rebuilding their server infrastructure.
“We fully expect that Trickbot’s operators will continue looking for ways to stay operational, and we and our partners will continue to monitor them and take action. We encourage others in the security community who believe in protecting the elections to join the effort and share their intelligence directly with hosting providers and ISPs that can take Trickbot’s infrastructure offline,” Burt concludes.
Oracle's October 2020 CPU Contains 402 New Security Patches
22.10.20 Vulnerebility Securityweek
Oracle on Tuesday released its Critical Patch Update (CPU) for October 2020, which includes 402 new security patches released across the company’s product portfolio.
The advisory for the latest CPU includes information on the patches released after the previous CPU, but the patches are typically cumulative, Oracle notes. Thus, customers are advised to review information on previously released patches, to ensure their systems are protected.
This month, Oracle released two versions of the advisory: a new one where details on patches for security flaws in third-party components that are not exploitable as implemented in Oracle products are listed beneath the product's risk matrix, and the traditional advisory (which mentions a total of 421 patches).
More than half of the 402 new security patches included in this month’s CPU can be exploited remotely without authentication.
More than 80 of the patches address critical-severity bugs, most of them with CVSS scores of 9.8. Two of them, namely CVE-2020-1953, impacting Healthcare Foundation, and CVE-2020-14871, affecting Solaris, have CVSS scores of 10.
Oracle products that saw the highest number of new security patches are Financial Services Applications: 53 patches – 49 of the vulnerabilities can be exploited by remote, unauthenticated attackers; MySQL: 53 fixes – 4 bugs remotely exploitable without the need of credentials; Communications: 52 patches – 41 remotely exploitable flaws; and Fusion Middleware: 46 patches – 36 vulnerabilities exploitable remotely without authentication.
Next in line are Retail Applications (28 patches – 25 flaws exploitable remotely without credentials), E-Business Suite (27 fixes – 25 remotely exploitable bugs), Database Server (18 – 4), PeopleSoft (15 – 12), Enterprise Manager (11 – 10), Communications Applications (9 – 8), Construction and Engineering (9 – 7), Hyperion (9 – 1), Java SE (8 – 8), Systems (8 – 3), Virtualization (7 – 0), Insurance Applications (6 – 6), Policy Automation (6 – 6), and Hospitality Applications (6 – 3).
Products that saw less than five new patches this month include Utilities Applications (5 – 3 vulnerabilities exploitable by remote, unauthenticated attackers), REST Data Services (5 – 2), Health Sciences Applications (4 – 4), TimesTen In-Memory Database (4 – 4), Food and Beverage Applications (4 – 3), Supply Chain (4 – 3), Siebel CRM (3 – 3), Big Data Graph (1 – 1), and GraalVM (1 – 1).
Many of the fixes Oracle lists in each of the products’ risk matrix address various other vulnerabilities, some even tens of issues. For instance, the patch for CVE-2020-14734, a high-severity flaw in the Text component of Database Server, also includes fixes for 38 additional CVEs.
Oracle encourages customers to apply the available patches to ensure their systems remain protected. The company also notes that it continues to receive reports of active targeting of previously addressed issues, underscoring the need for timely patching.
“Due to the threat posed by a successful attack, Oracle strongly recommends that customers apply Critical Patch Update security patches as soon as possible. Until you apply the Critical Patch Update patches, it may be possible to reduce the risk of successful attack by blocking network protocols required by an attack,” Oracle notes.
New Chrome 0-day Under Active Attacks – Update Your Browser Now
22.10.20 Attack Thehackernews
Attention readers, if you are using Google Chrome browser on your Windows, Mac, or Linux computers, you need to update your web browsing software immediately to the latest version Google released earlier today.
Google released Chrome version 86.0.4240.111 today to patch several security high-severity issues, including a zero-day vulnerability that has been exploited in the wild by attackers to hijack targeted computers.
Tracked as CVE-2020-15999, the actively exploited vulnerability is a type of memory-corruption flaw called heap buffer overflow in Freetype, a popular open source software development library for rendering fonts that comes packaged with Chrome.
The vulnerability was discovered and reported by security researcher Sergei Glazunov of Google Project Zero on October 19 and is subject to a seven-day public disclosure deadline due to the flaw being under active exploitation.
Glazunov also immediately reported the zero-day vulnerability to FreeType developers, who then developed an emergency patch to address the issue on October 20 with the release of FreeType 2.10.4.
Without revealing technical details of the vulnerability, the technical lead for Google's Project Zero Ben Hawkes warned on Twitter that while the team has only spotted an exploit targeting Chrome users, it's possible that other projects that use FreeType might also be vulnerable and are advised to deploy the fix included in FreeType version 2.10.4.
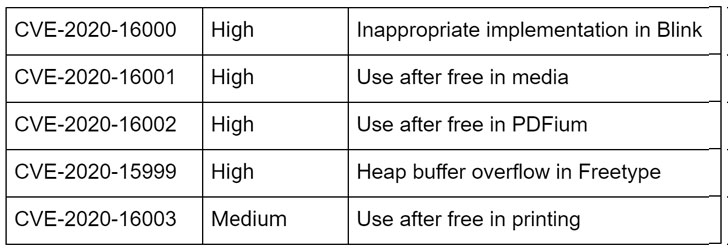
"While we only saw an exploit for Chrome, other users of freetype should adopt the fix discussed here: https://savannah.nongnu.org/bugs/?59308 -- the fix is also in today's stable release of FreeType 2.10.4," Hawkes writes.
According to details shared by Glazunov, the vulnerability exists in the FreeType's function "Load_SBit_Png," which processes PNG images embedded into fonts. It can be exploited by attackers to execute arbitrary code just by using specifically crafted fonts with embedded PNG images.
"The issue is that libpng uses the original 32-bit values, which are saved in `png_struct`. Therefore, if the original width and/or height are greater than 65535, the allocated buffer won't be able to fit the bitmap," Glazunov explained.
Glazunov also published a font file with a proof-of-concept exploit.
Google released Chrome 86.0.4240.111 as Chrome's "stable" version, which is available to all users, not just to opted-in early adopters, saying that the company is aware of reports that "an exploit for CVE-2020-15999 exists in the wild," but did not reveal further details of the active attacks.
Besides the FreeType zero-day vulnerability, Google also patched four other flaws in the latest Chrome update, three of which are high-risk vulnerabilities—an inappropriate implementation bug in Blink, a use after free bug in Chrome's media, and use after free bug in PDFium—and one medium-risk use after free issue in browser's printing function.
Although the Chrome web browser automatically notifies users about the latest available version, users are recommended to manually trigger the update process by going to "Help → About Google Chrome" from the menu.
Google Patches Actively-Exploited Zero-Day Bug in Chrome Browser
21.10.20 Vulnerebility Threatpost
The memory-corruption vulnerability exists in the browser’s FreeType font rendering library.
Google released an update to its Chrome browser that patches a zero-day vulnerability in the software’s FreeType font rendering library that was actively being exploited in the wild.
Security researcher Sergei Glazunov of Google Project Zero discovered the bug which is classified as a type of memory-corruption flaw called a heap buffer overflow in FreeType. Glazunov informed Google of the vulnerability on Monday. Project Zero is an internal security team at the company aimed at finding zero-day vulnerabilities.
By Tuesday, Google already had released a stable channel update, Chrome version 86.0.4240.111, that deploys five security fixes for Windows, Mac & Linux–among them a fix for the zero-day, which is being tracked as CVE-2020-15999 and is rated as high risk.
“Google is aware of reports that an exploit for CVE-2020-15999 exists in the wild,” Prudhvikumar Bommana of the Google Chrome team wrote in a blog post announcing the update Tuesday. Google did not reveal further details of the active attacks that researchers observed.
Andrew R. Whalley, a member of the Chrome security team, gave his team kudos on Twitter for the “super-fast” response to the zero-day.
Still, Ben Hawkes, technical lead for the Project Zero team, warned that while Google researchers only observed the Chrome exploit, it’s possible that other implementations of FreeType might be vulnerable as well since Google was so quick in its response to the bug. He referred users to a fix by Glazunov posted on the FreeType Project page and urged them to update other potentially vulnerable software.
“The fix is also in today’s stable release of FreeType 2.10.4,” Hawkes tweeted.
Meanwhile, security researchers took to Twitter to encourage people to update their Chrome browsers immediately to avoid falling victim to attackers aiming to exploit the flaw.
“Make sure you update your Chrome today! (restart it!),” tweeted London-based application security consultant Sam Stepanyan.
In addition to the FreeType zero day, Google patched four other bugs—three of high risk and one of medium risk–in the Chrome update released this week.
The high-risk vulnerabilities are: CVE-2020-16000, described as “inappropriate implementation in Blink;” CVE-2020-16001, described as “use after free in media;” and CVE-2020-16002, described as “use after free in PDFium,” according to the blog post. The medium-risk bug is being tracked as CVE-2020-16003, described as “use after free in printing,” Bommana wrote.
So far in the last 12 months Google has patched three zero-day vulnerabilities in its Chrome browser. Prior to this week’s FreeType disclosure, the first was a critical remote code execution vulnerability patched last Halloween night and tracked as CVE-2019-13720, and the second was a type of memory confusion bug tracked as CVE-2020-6418 that was fixed in February.
Ransomware Group Makes Splashy $20K Donation to Charities
21.10.20 Ransomware Threatpost
Cybercriminal gang Darkside sent $20K in donations to charities in a ‘Robin Hood’ effort that’s likely intended to draw attention to future data dumps, according to experts.
The Darkside ransomware group has distinguished itself from its cybercriminal counterparts not by technical innovation, but by slapping a shiny corporate veneer on its attacks. The latest evolution in Darkside’s ransomware-as-a-corporation gimmick is a hefty $20,000 donation that the group made with stolen Bitcoin to two international charitable organizations, The Water Project and Children International, which they then mysteriously announced by a press release.
“Altruism isn’t a common trait in criminal extortion gangs, so it’s difficult to take their motivations at their word,” Chris Clements with Cerberus Sentinel said in a statement about the donations.
The Water Project did not immediately respond to Threatpost’s inquiries. Children’s International told Threatpost that the matter is being investigated.
“We are aware of the situation and are researching it internally,” Lauren Jurgens from Children’s International told Threatpost by email. “If the donation is linked to a hacker, we have no intention of keeping it.”
Darkside announced the deposits on October 13 through one of its corporatized “press releases” posted on a dark web portal, according to BBC, along with tax receipts for the donations for .88 Bitcoin for each group, or $10,000 apiece.
“The most troubling realization here is that the cybercriminals have made so much money through extortion that donating $20,000 is chump change to them,” Clements added.
Darkside’s Branding Effort
Darkside has devoted much of its time to trying to carve out a position as an altruistic, digital Robin Hood. The public relations ploy isn’t likely to have much sway with law-enforcement, and public sentiment has little to do with criminal activity.
“As we said in the first press release — we are targeting only large, profitable corporations,” the group wrote. “We think it’s fair that some of the money they’ve paid will go to charity. No matter how bad you think our work is, we are pleased to know that we helped change someone’s life.”
Javvad Malik, security awareness advocate with KnowBe4, told Threatpost that regardless of the messaging, the goal of ransomware crimes remains the same: To drive better outcomes for their breaches and steal more money.
“This [steal from the rich, give to the poor tactic] is not so much a shift in the narrative as a shift in the business model driving these criminal organizations,” he said, adding that bigger corporations give them more of what they want. “The more systems that can be disrupted, the more data that can be stolen, and the more public pressure that can be mounted on organizations — which means a greater likelihood for payout out and greater profit.”
Ransomware Goes Corporate
Digital Shadows has been tracking Darkside since it popped up last August, and a recent report pointed out that their tactics follow typical ransomware patterns. The exception is their chosen targets.
Stefano De Blasi with Digital Shadows said in that report that the group tries to differentiate itself by vowing not to attack organizations like schools, hospitals or governments, instead focusing on companies based on revenue.
Darkside uses customized ransomware for each attack and, according to Digital Shadows, combs through company’s financial data to pinpoint what they believe to be an appropriate ransom.
“The ransomware executes a PowerShell command that deletes shadow volume copies on the system. DarkSide then proceeds to terminate various databases, applications, and mail clients to prepare for encryption,” De Blasi wrote.
Personalized ransom notes from Darkside are then issued to the breached company with details on the type of data stolen, as well as how much and a link to their leak site, where the data will be published if ransom demands aren’t met.
Getting the criminal gang’s name in the headlines is one way to help make sure published, stolen data gets the most attention possible, causing the most damage possible to targets.
“Whether or not they’ll succeed in breaking the mold – only time will tell,” De Blasi added. “While the cyber-threat landscape can be unpredictable and volatile, a trend is a trend, and we will continue to monitor the cybercriminal bandwagon closely.”
Most researchers are not impressed by Darkside’s seeming altruism and careful victim selection.
“This latest ‘donation’ effort by ransomware operators is just an attempt to improve their image publicly,” Katie Nickels, director of intelligence at Red Canary, said via email. “When the pandemic first started, we saw ransomware operators claim that they wouldn’t target hospitals — yet we know many of them have. If ransomware operators truly cared about making the world a better place, they would stop ransoming victims, not make donations.”
Office 365 OAuth Attack Targets Coinbase Users
21.10.20 Attack Threatpost
Attackers are targeting Microsoft Office 365 users with a Coinbase-themed attack, aiming to take control of their inboxes via OAuth.
Office 365 users are receiving emails purporting to come from cryptocurrency platform Coinbase, which ask them to download updated Terms of Service via an OAuth consent app. But when they agree to do so, users are unknowingly giving attackers full access to their email.
OAuth is an open standard for token-based authorization, which enables a user’s account information to be used by third-party services without exposing their password. For instance, instead of opting to create a new account from scratch, users may decide to sign into a website using a “Sign in with Google” or “Sign in with Facebook” option.
However, this feature – which lays bare victims’ mailboxes – has also attracted cybercriminals, who use OAuth to gain permissions using malicious third-party apps. These types of “consent” attacks are not new, but the tactic is gaining ground, as seen in this particular incident, said researchers in an analysis.
“We’ve seen consent app-based attacks since the beginning of this year,” said Stu Sjouwerman, CEO of KnowBe4, in a Tuesday analysis. “Users need to be educated via security-awareness training that they should be looking for these kinds of attacks and only grant access to legitimate app publishers (such as Outlook for mobile devices).”
In this particular attack, users receive an email impersonating Coinbase, a platform allowing users to buy and sell cryptocurrency like Bitcoin. It has 35 million users – making for a sizable target audience for attackers. The email also asks users to update their Terms of Service. Here, attackers are betting that they are targeting Office 365 users who are also Coinbase users, researchers said.
Upon clicking the link in the email to review the new Terms of Service, users are then taken to a legitimate Office 365 login page, said researchers.

The OAuth app request used in the attack. Credit: BleepingComputer
They are then presented with the OAuth consent request for read-and-write access to their mailboxes, emails, profiles and other information, citing “coinbaseterms.app” as the requestor – keeping up with the ruse that the request is from Coinbase as part of its updated Terms of Service.
If Office 365 users fall for this trick and click “yes,” they are unwittingly giving attackers access to their inboxes, allowing for them to view sensitive data, use their email in subsequent phishing or spearphishing attacks and other malicious purposes.
“Once access is granted, the app now has access to read the victim’s emails, delete messages and more,” said researchers. “The only way to remove access is administratively.”
Microsoft has previously warned of risky OAuth apps, in July warning that widespread remote working and the increased use of collaboration apps are leading attackers to ramp up application-based attacks that exploit OAuth.
“When users install these apps, they often click accept without closely reviewing the details in the prompt, including granting permissions to the app,” Microsoft has said in a previous post. “Accepting third-party app permissions is a potential security risk to your organization.”
In September, an APT known as TA2552 was spotted using OAuth or other token-based authorization methods to access Office 365 accounts, in order to steal users’ contacts and mail.
In another incident, disclosed in October, a medical research unit at a university was targeted with a phishing lure that promoted a free calendar optimization and time-management app. After one person took the bait and installed the malicious OAuth app, the attackers had complete access to Office 365 and used it to send internal phishing emails, taking advantage of trusted identities and communications to spread further inside the university.
Microsoft for its part recommends that users investigate any OAuth apps by using the abilities and information provided in the Cloud App Security portal (Microsoft’s security offering for its cloud apps) to filter out apps with a low chance of being risky, and focus on the suspicious apps. The tech giant also warned users to be on the lookout for the following tell-tale signs of a risky OAuth app:
The less common or used an app is, the less likely it is to be safe.
An app should require only permissions that are related to the app’s purpose. If that’s not the case, the app may potentially be risky.
Apps that require high privileges or admin consent are more likely to be risky.
Threatpost has reached out to both Microsoft and Coinbase for further comment on this incident.
Life of Maze ransomware
21.10.20 Ransomware Securelist
In the past year, Maze ransomware has become one of the most notorious malware families threatening businesses and large organizations. Dozens of organizations have fallen victim to this vile malware, including LG, Southwire, and the City of Pensacola.
The history of this ransomware began in the first half of 2019, and back then it didn’t have any distinct branding – the ransom note included the title “0010 System Failure 0010”, and it was referenced by researchers simply as ‘ChaCha ransomware’.
Ransom note of an early version of Maze/ChaCha ransomware
Shortly afterwards, new versions of this Trojan started calling themselves Maze and using a relevantly named website for the victims instead of the generic email address shown in the screenshot above.
Website used by a recent version of Maze ransomware
Infection scenarios
Mass campaigns
The distribution tactic of the Maze ransomware initially involved infections via exploit kits (namely, Fallout EK and Spelevo EK), as well as via spam with malicious attachments. Below is an example of one of these malicious spam messages containing an MS Word document with a macro that’s intended to download the Maze ransomware payload.
If the recipient opens the attached document, they will be prompted to enable editing mode and then enable the content. If they fall for it, the malicious macro contained inside the document will execute, which in turn will result in the victim’s PC being infected with Maze ransomware.
Tailored approach
In addition to these typical infection vectors, the threat actors behind Maze ransomware started targeting corporations and municipal organizations in order to maximize the amount of money extorted.
The initial compromise mechanism and subsequent tactics vary. Some incidents involved spear-phishing campaigns that installed Cobalt Strike RAT, while in other cases the network breach was the result of exploiting a vulnerable internet-facing service (e.g. Citrix ADC/Netscaler or Pulse Secure VPN). Weak RDP credentials on machines accessible from the internet also pose a threat as the operators of Maze may use this flaw as well.
Privilege escalation, reconnaissance and lateral movement tactics also tend to differ from case to case. During these stages, the use of the following tools has been observed: mimikatz, procdump, Cobalt Strike, Advanced IP Scanner, Bloodhound, PowerSploit, and others.
During these intermediate stages, the threat actors attempt to identify valuable data stored on the servers and workstations in the compromised network. They will then exfiltrate the victim’s confidential files in order to leverage them when negotiating the size of the ransom.
At the final stage of the intrusion, the malicious operators will install the Maze ransomware executable onto all the machines they can access. This results in the encryption of the victim’s valuable data and finalizes the attack.
Data leaks/doxing
Maze ransomware was one of the first ransomware families that threatened to leak the victims’ confidential data if they refused to cooperate.
In fact, this made Maze something of a trendsetter because this approach turned out to be so lucrative for the criminals that it’s now become standard for several notorious ransomware gangs, including REvil/Sodinokibi, DoppelPaymer, JSWorm/Nemty/Nefilim, RagnarLocker, and Snatch.
The authors of the Maze ransomware maintain a website where they list their recent victims and publish a partial or a full dump of the documents they have managed to exfiltrate following a network compromise.
Website with leaked data published by Maze operators
Ransomware cartel
In June 2020, the criminals behind Maze teamed up with two other threat actor groups, LockBit and RagnarLocker, essentially forming a ‘ransomware cartel’. The data stolen by these groups now gets published on the blog maintained by the Maze operators.
It wasn’t just the hosting of exfiltrated documents where the criminals pooled their efforts – apparently they are also sharing their expertise. Maze now uses execution techniques that were previously only used by RagnarLocker.
Brief technical overview
The Maze ransomware is typically distributed as a PE binary (EXE or DLL depending on the specific scenario) which is developed in C/C++ and obfuscated by a custom protector. It employs various tricks to hinder static analysis, including dynamic API function imports, control flow obfuscation using conditional jumps, replacing RET with JMP dword ptr [esp-4], replacing CALL with PUSH + JMP, and several other techniques.
To counter dynamic analysis, this Trojan will also terminate processes typically used by researchers, e.g. procmon, procexp, ida, x32dbg, etc.
The cryptographic scheme used by Maze consists of several levels:
To encrypt the content of the victim’s files, the Trojan securely generates unique keys and nonce values to use with the ChaCha stream cipher;
The ChaCha keys and nonce values are encrypted by a session public RSA-2048 key which is generated when the malware is launched;
The session private RSA-2048 key is encrypted by the master public RSA-2048 key hardcoded in the Trojan’s body.
This scheme is a variation of a more or less typical approach used by developers of modern ransomware. It allows the operators to keep their master private RSA key secret when selling decryptors for each individual victim, and it also ensures that a decryptor purchased by one victim won’t help others.
When executing on a machine, Maze ransomware will also attempt to determine what kind of PC it has infected. It tries to distinguish between different types of system (‘backup server’, ‘domain controller’, ‘standalone server’, etc.). Using this information in the ransom note, the Trojan aims to further scare the victims into thinking that the criminals know everything about the affected network.
Strings that Maze uses to generate the ransom note
Fragment of the procedure that generates the ransom note
How to avoid and prevent
Ransomware is evolving day by day, meaning a reactive approach to avoid and prevent infection is not profitable. The best defense against ransomware is proactive prevention because often it is too late to recover data once they have been encrypted.
There are a number of recommendations that may help prevent attacks like these:
Keep your OS and applications patched and up to date.
Train all employees on cybersecurity best practices.
Only use secure technology for remote connection in a company local network.
Use endpoint security with behavior detection and automatic file rollback, such asKaspersky Endpoint Security for Business.
Use the latest threat intelligence information to detect an attack quickly, understand what countermeasures are useful, and prevent it from spreading.
Detection
Kaspersky products protect against this ransomware, detecting it as Trojan-Ransom.Win32.Maze; it is blocked by Behavior-based Protection as PDM:Trojan.Win32.Generic.
We safeguard our customers with the best Ransomware Protection technologies.
TIP Cloud Sandbox report summary and execution map with mapping on MITRE ATT&CK Framework
Hackers are targeting CVE-2020-3118 flaw in Cisco devices
21.10.20 Vulnerebility Securityaffairs
Cisco warns of attacks attempting to exploit the CVE-2020-3118 vulnerability that affects multiple carrier-grade routers running Cisco IOS XR Software.
Cisco is warning of attacks targeting the CVE-2020-3118 high severity vulnerability that affects multiple carrier-grade routers running the Cisco IOS XR Software.
The flaw resides in the Cisco Discovery Protocol implementation for Cisco IOS XR Software and could allow an unauthenticated, adjacent attacker to execute arbitrary code or cause a reload an affected device.
“The vulnerability is due to improper validation of string input from certain fields in Cisco Discovery Protocol messages. An attacker could exploit this vulnerability by sending a malicious Cisco Discovery Protocol packet to an affected device.” reads the advisory. “A successful exploit could allow the attacker to cause a stack overflow, which could allow the attacker to execute arbitrary code with administrative privileges on an affected device.”
Cisco experts pointed out that the flaw can be exploited by unauthenticated adjacent attackers (Layer 2 adjacent) in the same broadcast domain as the vulnerable devices.
It is listed in top 25 vulnerabilities, shared by the NSA, exploited by Chinese state-sponsored hacking groups in attacks in the wild.
The IOS XR Network OS runs on several Cisco router families including NCS 540 & 560, NCS 5500, 8000, and ASR 9000 series routers.
The vulnerability also impacts third-party white box routers and Cisco products that have the Cisco Discovery Protocol enabled both on at least one interface and globally. Below the list of impacted devices:
ASR 9000 Series Aggregation Services Routers
Carrier Routing System (CRS)
IOS XRv 9000 Router
Network Convergence System (NCS) 540 Series Routers
Network Convergence System (NCS) 560 Series Routers
Network Convergence System (NCS) 1000 Series Routers
Network Convergence System (NCS) 5000 Series Routers
Network Convergence System (NCS) 5500 Series Routers
Network Convergence System (NCS) 6000 Series Routers
Cisco addressed the CVE-2020-3118 flaw in February 2020, along with four other severe issues collectively tracked as CDPwn.
“In October 2020, the Cisco Product Security Incident Response Team (PSIRT) received reports of attempted exploitation of this vulnerability in the wild,” states the updated advisory.
“Cisco recommends that customers upgrade to a fixed Cisco IOS XR Software release to remediate this vulnerability.”
The following table reports the fixed release for this flaw:
CISCO IOS XR SOFTWARE RELEASE FIRST FIXED RELEASE FOR THIS VULNERABILITY
Earlier than 6.6 Appropriate SMU
6.61 6.6.3 or appropriate SMU
7.0 7.0.2 (Mar 2020) or appropriate SMU
7.1 Not vulnerable
The advisory includes mitigation to address the flaw, the company suggests disabling Cisco Discovery Protocol Globally and on an Interface for customers who can immediately apply the security updates.
Microsoft took down 120 of 128 Trickbot servers in recent takedown
21.10.20 BotNet Securityaffairs
Microsoft brought down TrickBot infrastructure last week, but a few days later the botmasters set up a new command and control (C&C) servers.
Microsoft’s Defender team, FS-ISAC, ESET, Lumen’s Black Lotus Labs, NTT, and Broadcom’s cyber-security division Symantec joined the forces and announced last week a coordinated effort to take down the command and control infrastructure of the infamous TrickBot botnet.
Even if Microsoft and its partners have brought down the TrickBot infrastructure TrickBot operators attempted to resume the operations by setting up new command and control (C&C) servers online.

Microsoft provided an update on its takedown efforts and announced a new wave of takedown actions against TrickBot.
According to the IT giant, the operation conducted last week has taken down 94% of the servers composing the Trickbot infrastructure. Trickbot enables ransomware attacks which have been identified as one of the biggest threats to the upcoming U.S. elections.
“We initially identified 69 servers around the world that were core to Trickbot’s operations, and we disabled 62 of them. The seven remaining servers are not traditional command-and-control servers but rather internet of things (IoT) devices Trickbot infected and was using as part of its server infrastructure; these are in the process of being disabled. As expected, the criminals operating Trickbot scrambled to replace the infrastructure we initially disabled. We tracked this activity closely and identified 59 new servers they attempted to add to their infrastructure.” said Tom Burt, CVP of Customer Security and Trust at Microsoft. “We’ve now disabled all but one of these new servers. In sum, from the time we began our operation until October 18, we have taken down 120 of the 128 servers we identified as Trickbot infrastructure around the world.”
Microsoft has taken down 120 of the 128 servers that were composing the Trickbot infrastructure.
Microsoft announced to have taken down 62 of the original 69 TrickBot C&C servers, seven servers that could not be brought down last week were Internet of Things (IoT) devices.
Microsoft also revealed that operators tried to resume the operations, The company brought down 58 of the 59 servers the operators attempted to bring online after the recent takedown.
Burt praised the role of Microsoft’s lawyers who quickly requested new court orders to take down the new servers set up by the Trickbot operators in response to the takedown.
“We have identified new Trickbot servers, located their respective hosting provider, determined the proper legal methodology to take action, and completely disabled those servers in less than three hours. Our global coordination has allowed a provider to take quick action as soon as we notify them – in one case, in less than six minutes.” continues the expert. “What we’re seeing suggests Trickbot’s main focus has become setting up new infrastructure, rather than initiating fresh attacks, and it has had to turn elsewhere for operational help.”
Currently, a few Trickbot C2 servers are still active and operators are using them to control the botnet. Researchers from cyber-security firm Intel 471 reported that these servers are based in Brazil, Colombia, Indonesia, and Kyrgyzstan, and that they still are able to respond to Trickbot bot requests.
“This small number of working control servers was not listed in the most recent distributed Trickbot sample.” states Intel 471.
Burt pointed out that TrickBot operators are working to restore their infrastructure instead of conducting new attacks.
“We fully expect that Trickbot’s operators will continue looking for ways to stay operational, and we and our partners will continue to monitor them and take action.” Microsoft concludes. “We encourage others in the security community who believe in protecting the elections to join the effort and share their intelligence directly with hosting providers and ISPs that can take Trickbot’s infrastructure offline.”
NSA details top 25 flaws exploited by China-linked hackers
21.10.20 BigBrothers Securityaffairs
The US National Security Agency (NSA) has shared the list of top 25 vulnerabilities exploited by Chinese state-sponsored hacking groups in attacks in the wild.
The US National Security Agency (NSA) has published a report that includes details of the top 25 vulnerabilities that are currently being exploited by China-linked APT groups in attacks in the wild.
The knowledge of these vulnerabilities could allow IT and security staffs at organizations worldwide to protect their infrastructure against Chinese state-sponsored hacking campaigns.
The report includes well known vulnerabilites that have been already addressed by their vendors.
“This advisory provides Common Vulnerabilities and Exposures (CVEs) known to be recently leveraged, or scanned-for, by Chinese state-sponsored cyber actors to enable successful hacking operations against a multitude of victim networks. Most of the vulnerabilities listed below can be exploited to gain initial access to victim networks using products that are directly accessible from the Internet and act as gateways to internal networks.” reads the report. “The majority of the products are either for remote access (T1133)1 or for external web services (T1190), and should be prioritized for immediate patching.”
The report includes a description of the vulnerability and the recommended mitigations.
The exploits for many of these vulnerabilities are publicly available and are employed by multiple threat actors, including China-linked hackers, in attacks in the wild.
The majority of the vulnerabilities can be exploited to gain initial access to the target networks, they affect systems that are directly accessible from the Internet, such as firewalls and gateways.
NSA confirmed that it is aware that National Security Systems, Defense Industrial Base, and Department of Defense networks are consistently scanned, targeted, and exploited by Chinese state-sponsored cyber actors. The US agency recommends that critical system owners will address the above vulnerabilities to mitigate the risk of loss of sensitive information that could have a significant impact on U.S. policies, strategies, plans, and competitive advantage.
The
These include:
1) CVE-2019-11510 – In Pulse Secure VPNs, ® 7 an unauthenticated remote attacker can send a specially crafted URI to perform an arbitrary file reading vulnerability. This may lead to exposure of keys or passwords.
2) CVE-2020-5902– In F5 BIG-IP® 8 proxy / load balancer devices, the Traffic Management User Interface (TMUI) – also referred to as the Configuration utility – has a Remote Code Execution (RCE) vulnerability in undisclosed pages.
3) CVE-2019-19781 – An issue was discovered in Citrix® 9 Application Delivery Controller (ADC) and Gateway. They allow directory traversal, which can lead to remote code execution without credentials.
4+5+6) CVE-2020-8193, CVE-2020-8195, CVE-2020-8196– Improper access control and input validation, in Citrix® ADC and Citrix® Gateway and Citrix® SDWAN WAN-OP, allows unauthenticated access to certain URL endpoints and information disclosure to low-privileged users
7) CVE-2019-0708 (aka BlueKeep) – A remote code execution vulnerability exists within Remote Desktop Services®10 when an unauthenticated attacker connects to the target system using RDP and sends specially crafted requests
8) CVE-2020-15505 – A remote code execution vulnerability in the MobileIron®13 mobile device management (MDM) software that allows remote attackers to execute arbitrary code and take over remote company servers.
9) CVE-2020-1350 (aka SIGRed) – A remote code execution vulnerability exists in Windows Domain Name System servers when they fail to properly handle requests.
10) CVE-2020-1472 (aka Netlogon) – An elevation of privilege vulnerability exists when an attacker establishes a vulnerable Netlogon secure channel connection to a domain controller using the Netlogon Remote Protocol (MS-NRPC).
11) CVE-2019-1040 – A tampering vulnerability exists in Microsoft Windows when a man-in-the-middle attacker is able to successfully bypass the NTLM MIC (Message Integrity Check) protection.
12) CVE-2018-6789 – Sending a handcrafted message to an Exim mail transfer agent may cause a buffer overflow. This can be used to execute code remotely and take over email servers.
13) CVE-2020-0688 – A Microsoft Exchange® validation key remote code execution vulnerability exists when the software fails to properly handle objects in memory
14) CVE-2018-4939 – Certain Adobe ColdFusion versions have an exploitable Deserialization of Untrusted Data vulnerability. Successful exploitation could lead to arbitrary code execution.
15) CVE-2015-4852 – The WLS Security component in Oracle WebLogic 15 Server allows remote attackers to execute arbitrary commands via a crafted serialized Java object
16) CVE-2020-2555 – A vulnerability exists in the Oracle Coherence product of Oracle Fusion Middleware. This easily exploitable vulnerability allows unauthenticated attacker with network access via T3 to compromise Oracle Coherence systems.
17) CVE-2019-3396– The Widget Connector macro in Atlassian Confluence 17 Server allows remote attackers to achieve path traversal and remote code execution on a Confluence Server or Data Center instance via server-side template injection.
18) CVE-2019-11580 – Attackers who can send requests to an Atlassian Crowd or Crowd Data Center instance can exploit this vulnerability to install arbitrary plugins, which permits remote code execution.
19) CVE-2020-10189 – Zoho ManageEngine Desktop Central allows remote code execution because of deserialization of untrusted data.
20) CVE-2019-18935 – Progress Telerik UI for ASP.NET AJAX contains a .NET deserialization vulnerability. Exploitation can result in remote code execution.
21) CVE-2020-0601 (aka CurveBall) – A spoofing vulnerability exists in the way Windows CryptoAPI (Crypt32.dll) validates Elliptic Curve Cryptography (ECC) certificates. An attacker could exploit the vulnerability by using a spoofed code-signing certificate to sign a malicious executable, making it appear that the file was from a trusted, legitimate source.
22) CVE-2019-0803– An elevation of privilege vulnerability exists in Windows when the Win32k component fails to properly handle objects in memory.
23) CVE-2017-6327– The Symantec Messaging Gateway can encounter a remote code execution issue.
24) CVE-2020-3118 – A vulnerability in the Cisco Discovery Protocol implementation for Cisco IOS XR Software could allow an unauthenticated, adjacent attacker to execute arbitrary code or cause a reload an affected device.
25) CVE-2020-8515 – DrayTek Vigor devices allow remote code execution as root (without authentication) via shell metacharacters.
MMO game Street Mobster leaking data of 1.9 million users due to critical vulnerability
21.10.20 Incindent Securityaffairs
Researchers discovered that MMO game Street Mobster is leaking data of 1.9 million users due to SQL Injection critical vulnerability.
Attackers could exploit the SQL Injection flaw to compromise the game’s database and steal user data.
Original Post: https://cybernews.com/street-mobster-game-leaking-data-of-2-million-players
The CyberNews.com Investigation team discovered a critical vulnerability in Street Mobster, a browser-based massively multiplayer online game created by Bulgarian development company BigMage Studios.
Street Mobster is a free to play, browser-based online game in the mafia empire genre where players manage a fictional criminal enterprise. The game boasts a 1.9+ million player base and stores a user record database that can be accessed by threat actors by committing an SQL Injection (SQLi) attack on the game’s website.
The records that can be compromised by exploiting the SQLi vulnerability in Street Mobster potentially include the players’ usernames, email addresses, and passwords, as well as other game-related data that is stored on the database.
Fortunately, after we reported the vulnerability to BigMage Studios, CERT Bulgaria, and the Bulgarian data protection authority, the issue has been fixed by the developers and the user database is no longer accessible to potential attackers.

What is SQL Injection?
First found back in 1998, SQLi is deemed by the Open Web Application Security Project (OWASP) as the number one web application security risk.
Even though this vulnerability is relatively easy to fix, researchers found that 8% of websites and web applications are still vulnerable to SQLi attacks in 2020. Which, from a security perspective, is inexcusable. So much so, in fact, that UK internet service provider TalkTalk was hit with a record £400,000 fine over succumbing to a cyberattack that involved SQLi.
The vulnerability works by injecting an unexpected payload (a piece of code) into the input box on the website or in its URL address. Instead of reading the text as part of the URL, the website’s server reads the attacker’s payload as code and then proceeds to execute the attacker’s command or output data that would otherwise be inaccessible to unauthorized parties. Attackers can exploit SQLi even further by uploading pieces of code or even malware to the vulnerable server.
The fact that Street Mobster is susceptible to SQLi attacks clearly shows the disappointing and dangerous neglect of basic security practices on the part of the developers at BigMage Studios.
How we found this vulnerability
Our security team identified an SQL Injection vulnerability on the Street Mobster website and were able to confirm the vulnerability by performing a simple command injection test on the website URL. The CyberNews team did not extract any data from the vulnerable Street Mobster database.
What’s the impact of the vulnerability?
The data in the vulnerable Street Mobster database can be used in a variety of ways against the players whose information was exposed:
By injecting malicious payloads on Street Mobster’s server, attackers can potentially gain access to said server, where they can install malware on the game’s website and cause harm to the visitors – from using the players’ devices to mine cryptocurrency to redirecting them to other malicious websites, installing malware, and more.
The 1.9 million user credentials stored on the database can net the attackers user email addresses and passwords, which they can potentially use for credential stuffing attacks to hack the players’ accounts on other gaming platforms like Steam or other online services.
Because Street Mobster is a free-to-play game that incorporates microtransactions, bad actors could also make a lot of money from selling hacked player accounts on gray market websites.
What to do if you’ve been affected?
If you have a Street Mobster account, make sure to change your password immediately and make it as complex as possible. If you’ve been using your Street Mobster password on any other websites or services, change that password as well. This will prevent potential attackers from accessing your accounts on these websites in case they try to reuse your password for credential stuffing attacks.
However, it’s ultimately up to BigMage Studios to completely secure your Street Mobster account against attacks like SQLi.
Disclosure and lack of communication from BigMage Studios
Following our vulnerability disclosure guidelines, we notified the BigMage Studios about the leak on August 31, 2020. However, we received no reply. Our follow-up emails were left unanswered as well.
We then reached out to CERT Bulgaria on September 11 in order to help secure the website. CERT contacted the BigMage Studios and informed the company about the misconfiguration.
Throughout the disclosure process, BigMage Studios stayed radio silent and refused to get in touch with CyberNews.com. Due to this reason, we also notified the Bulgarian data protection agency about the incident on October 9 in the hopes that the agency would be able to pressure the company into fixing the issue.
Eventually, however, BigMage Studios appear to have fixed the SLQi vulnerability on streetmobster.com, without informing either CyberNews.com or CERT Bulgaria about that fact.
Chrome 86.0.4240.111 fixes actively exploited CVE-2020-15999 zero-day
21.10.20 Exploit Securityaffairs
Google has released Chrome version 86.0.4240.111 that also addresses the CVE-2020-15999 flaw which is an actively exploited zero-day.
Google has released Chrome version 86.0.4240.111 that includes security fixes for several issues, including a patch for an actively exploited zero-day vulnerability tracked as CVE-2020-15999.
The CVE-2020-15999 flaw is a memory corruption bug that resides in the FreeType font rendering library, which is included in standard Chrome releases.
White hat hackers from the Google Project Zero team spotted attacks exploiting the vulnerability in the wild.
The researchers did not disclose technical details about the attacks exploiting the CVE-2020-15999 in the wild to avoid mass exploitation from threat actors.
Google Project Zero is recommending other app development teams who use the same FreeType library to update their software as well.
The FreeType version 2.10.4 address this issue.
Chrome users can update their install to v86.0.4240.111 via the browser’s built-in update function.
Experts pointed out that since the patch for this zero-day is visible in the source code of the FreeType open-source library, threat actors will be able to make a reverse-engineering of the code and develop working exploits for the issue.
In the recent twelve months, Google addressed another two zero-day vulnerabilities tracked as CVE-2019-13720 (Oct. 2019) and CVE-2020-6418 (Feb. 2020) respectively
Chrome Update Patches Actively Exploited FreeType Vulnerability
21.10.20 Exploit Securityweek
A Chrome 86 update released by Google on Tuesday patches several high-severity vulnerabilities, including a zero-day that has been exploited in the wild.
The actively exploited vulnerability is tracked as CVE-2020-15999 and it has been described as a heap buffer overflow bug affecting FreeType, a popular software library for rendering fonts.
In addition to Chrome and Chrome OS, FreeType is used in Linux and UNIX distributions, Android, iOS, ReactOS, and Ghostscript, which means the font engine is present on over a billion devices, according to its developers.
CVE-2020-15999 was discovered by Google Project Zero researcher Sergei Glazunov on October 19. It was immediately also reported to FreeType developers, who created an emergency fix on October 20, which has been included in FreeType 2.10.4.
Glazunov, who shared details about the vulnerability on the FreeType bug tracked, noted that while the emergency fix appears to be working, a long-term patch will require a thorough code review.
The issue is related to Load_SBit_Png, a function that processes PNG images embedded into fonts. Buffer overflow vulnerabilities often allow an attacker to execute arbitrary code. In this case, exploitation apparently involves specially crafted font files.
No information has been shared by Project Zero on the attacks involving this security bug.
Google Project Zero’s Ben Hawkes noted on Twitter that while they have only spotted an exploit aimed at Chrome, other projects that use FreeType should also adopt the fix that was included in version 2.10.4.
Hawkes also clarified that the vulnerability may impact Chrome on Android as well, but Project Zero has yet to confirm this.
This is the second zero-day flaw patched this year in Chrome. The first was addressed in February with a Chrome 80 update.
Euronext Says Stock Market Glitch Was Not a Cyber Attack
21.10.20 Attack Securityweek
A problem that halted trading on the Paris stock market and others across Europe was a "middleware" issue and not a cyber attack, operator Euronext said Tuesday.
Trading ground to a halt for around three hours early Monday in Amsterdam, Brussels, Dublin, Lisbon and Paris, and the French market closed late, before issuing a statement that most trades made after 5:30 local time (1530 GMT) would be annulled.
"It was not a cyber attack," a Euronext spokesman insisted.
"It was a technical problem that has been resolved at the middleware level, one of the systems that ensures the persistance of data," he told AFP.
Euronext also issued a statement in which it presented its excuses for the problems and said that action had been taken to ensure similar problems do not occur again.
Trading proceeded without incident in the first half of the session on Tuesday.
NSA Lists 25 Vulnerabilities Currently Targeted by Chinese State-Sponsored Hackers
21.10.20 BigBrothers Securityweek
The U.S. National Security Agency this week released an advisory containing information on 25 vulnerabilities that are being actively exploited or targeted by Chinese state-sponsored threat actors.
Most of these security bugs, the NSA says, can be used for initial access to networks, through exploiting Internet-facing assets. Post compromise, the adversaries can target additional vulnerabilities for exploitation.
The list shared by the NSA this week contains a total of 25 vulnerabilities, including CVE-2019-11510 (Pulse Secure VPN), CVE-2020-5902 (F5 BIG-IP), CVE-2019-0708 (BlueKeep), CVE-2020-1350 (SIGRed), CVE-2020-1472 (Zerologon), CVE-2020-0601 (CurveBall), CVE-2018-6789 (Exim mail server), CVE-2015-4852 (Oracle WebLogic), and CVE-2019-19781, CVE-2020-8193, CVE-2020-8195, and CVE-2020-8196 (Citrix ADC and Gateway).
The list also mentions CVE-2020-15505 (MobileIron MDM), CVE-2019-1040 (Windows), CVE-2020-0688 (Microsoft Exchange), CVE-2018-4939 (Adobe ColdFusion), CVE-2020-2555 (Oracle Coherence), CVE-2019-3396 (Atlassian Confluence), CVE-2019-11580 (Atlassian Crowd), CVE-2020-10189 (Zoho ManageEngine Desktop Central), CVE-2019-18935 (Progress Telerik UI for ASP.NET AJAX), CVE-2019-0803 (Windows), CVE-2017-6327 (Symantec Messaging Gateway), CVE-2020-3118 (Cisco IOS XR Software), and CVE-2020-8515 (DrayTek Vigor devices).
The NSA notes that it has observed Chinese threat actors scanning for or attempting to exploit these vulnerabilities against multiple victims. However, the agency also points out that the same adversaries might be targeting other vulnerabilities as well.
While the vulnerabilities mentioned by the NSA have been detailed publicly, not all of them were previously known as being targeted by hackers. This includes a Cisco Discovery Protocol flaw disclosed earlier this year.
For each of these bugs, the NSA also mentioned previously published guidance, some focused on different actors.
The agency notes that National Security Systems (NSS), U.S. Defense Industrial Base (DIB), and Department of Defense (DoD) systems are constantly being targeted by Chinese hackers, and encourages owners to ensure their systems are protected from exploitation.
The NSA underlines the threat that government-backed hackers from China pose to NSS, DIB, and DoD information networks in their attempts to compromise computer networks of interest to gather intellectual property and economic, military, and political information. Thus, patching of known vulnerabilities is highly important to keep systems protected.
“We hear loud and clear that it can be hard to prioritize patching and mitigation efforts. We hope that by highlighting the vulnerabilities that China is actively using to compromise systems, cyber-security professionals will gain actionable information to prioritize efforts and secure their systems,” NSA Cybersecurity Director Anne Neuberger said.
Satnam Narang, staff research engineer at Tenable, said in an emailed comment, “If you’re experiencing déjà vu from the National Security Agency (NSA) advisory listing the top 25 vulnerabilities being leveraged by foreign threat actors, your feeling is warranted. Many of the vulnerabilities in the advisory align with similar alerts that have been published by the Cybersecurity and Infrastructure Security Agency (CISA) over the last year. It’s unmistakably clear that unpatched vulnerabilities remain a valuable tool for cybercriminals and state-sponsored threat actors. With many of the vulnerabilities listed in the advisory residing in remote access tools or external web services, it is extremely critical for organizations to prioritize patching these vulnerabilities.”
“The breadth of products covered by this list of CVEs would indicate that the NSA has curated this list through the observation of many attacks undertaken by these actors,” Oliver Tavakoli, chief technology officer at Vectra, commented. “The exploits themselves also cover a broad range of steps in the cyberattack lifecycle indicating that many of the attacks in which these exploits were observed were already pretty deep into the attack progression – and many were likely found only after-the-fact through deep forensic efforts rather than having been identified while the attacks were active.”
Chinese Hackers Target Cisco Discovery Protocol Vulnerability
21.10.20 BigBrothers Securityweek
Chinese state-sponsored hackers are targeting a Cisco Discovery Protocol vulnerability that was disclosed earlier this year, the networking giant and the U.S. National Security Agency revealed on Tuesday.
An advisory published by the NSA on Tuesday lists 25 vulnerabilities that have been exploited or targeted by threat actors believed to be sponsored by Beijing. The list includes several vulnerabilities that were not known to have been targeted, including CVE-2020-3118, which impacts Cisco products.
CVE-2020-3118 is one of the five vulnerabilities in the Cisco Discovery Protocol (CDP) implementation of IOS XR software that were disclosed in February by IoT security firm Armis. The company reported at the time that the flaws, collectively tracked as CDPwn, impacted tens of millions of Cisco devices deployed in enterprise environments, including IP phones, switches, routers and cameras.
Just as the NSA issued its warning on the vulnerabilities targeted by Chinese hackers, Cisco updated its advisory to inform customers that it received reports earlier this month of attackers attempting to exploit CVE-2020-3118 in the wild. The company has advised customers to install the available IOS XR patches.
While it’s unclear which Chinese threat actor has targeted the flaw, the group tracked as APT41 is known to have exploited Cisco product vulnerabilities in its attacks.
The high-severity vulnerability can be exploited without authentication for arbitrary code execution with admin privileges and denial-of-service (DoS) attacks, but the attacker needs to have network access to the targeted device. Specifically, Cisco says, they need to be on the same broadcast domain as the impacted system.
When it disclosed the CDPwn vulnerabilities, Armis warned that they could allow an attacker to move from one network segment to another, intercept network traffic, and exfiltrate sensitive information.
Over the past few months, Cisco has also warned customers about attempts to exploit vulnerabilities affecting its firewalls and carrier-grade routers.
Sweden Bans Huawei, ZTE From 5G, Calls China Biggest Threat
21.10.20 BigBrothers Securityweek
Sweden is banning Chinese tech companies Huawei and ZTE from building new high-speed wireless networks after a top security official called China one of the country’s biggest threats.
The Swedish telecom regulator said Tuesday that four wireless carriers bidding for frequencies in an upcoming spectrum auction for the new 5G networks must not use equipment from Huawei or ZTE.
Wireless carriers that plan to use existing telecommunications infrastructure for 5G networks must also rip out any existing gear from Huawei or ZTE, the Swedish Post and Telecom Authority said.
The agency said the conditions were based on assessments by the Swedish military and security service. Huawei said it was “surprised and disappointed” by the rules.
Sweden is the latest country to prohibit Huawei from playing a role in building 5G networks and its decision is likely to add to tensions between the Chinese government and Western powers. U.S. officials have waged an intense lobbying campaign in Europe to persuade allies to shun the company, saying Huawei could be compelled by China’s communist rulers to facilitate cyberespionage. The company has consistently denied the accusations.
The ban means more opportunities for Huawei’s main rivals, Swedish company Ericsson and Finland’s Nokia.
New 5G networks, which are expected to usher in a wave of innovation such as smart factories and remote surgery, are considered critical infrastructure. Klas Friberg, the head of Sweden’s domestic security service, known as SAPO, said Tuesday that foreign powers have intensified their intelligence activity in recent years so 5G networks should be built in a secure way from the start.
“China is one of the biggest threats to Sweden,” Friberg said. “The Chinese state is conducting cyber espionage to promote its own economic development and develop its military capabilities. This is done through extensive intelligence gathering and theft of technology, research and development. This is what we must consider when building the 5G network of the future.”
Huawei denied it was a security risk.
“Huawei has never caused even the slightest shred of threat to Swedish cyber security and never will,” it said. “Excluding Huawei will not make Swedish 5G networks any more secure. Rather, competition and innovation will be severely hindered.
New TrickBot Control Servers Unable to Respond to Bot Requests
21.10.20 BotNet Securityweek
Control servers included in the configuration file of new TrickBot samples fail to respond to bot requests, according to researchers at threat intelligence company Intel 471.
Released in 2016 by the Dyre gang, TrickBot has evolved into one of the most prevalent malware families out there, having ensnared in excess of one million systems to date and being employed by both nation-state and cybercrime actors for malicious operations.
Last week, Microsoft announced that, together with industry partners, it was able to legally take over and disrupt infrastructure used by TrickBot, as well as to block efforts from the its operators to register new infrastructure and revive the botnet.
Days after the announcement, however, Intel 471’s researchers revealed that TrickBot resumed operations, and that Emotet was observed serving TrickBot payloads to infected machines.
CrowdStrike too confirmed that TrickBot was still operational, saying that only approximately 10,000 bots were seen becoming unreachable after being served a non-standard configuration file.
On Tuesday, Intel 471 revealed that, starting Monday, October 19, Emotet has distributed TrickBot samples that include new control servers in their configuration, but that these servers were not able to respond to bot requests.
Most of these controllers, the security firm reveals, are located in the United States and Germany, with some of them based in Bosnia and Herzegovina, Romania, the Netherlands, and Turkmenistan.
“On Oct. 19, 2020, when this latest Trickbot sample was distributed, none of the above listed control servers were able to respond to Trickbot bot requests, a state that continued at the time of this report. Intel 471 believes disruption operations against Trickbot are currently global in nature and have had success against Trickbot infrastructure,” Intel 471 says.
The researchers also note that there are other controllers that do work, and these are located in Brazil, Colombia, Indonesia, and Kyrgyzstan. These control servers, however, were not listed in the most recently distributed TrickBot samples.
Russia Dismisses Hacking Allegations as 'Russophobia'
21.10.20 BigBrothers Securityweek
The Kremlin on Tuesday denied US claims that Russian military intelligence was behind cyber attacks targeting Ukraine's power grid, the 2017 French election and the 2018 Winter Olympic Games.
President Vladimir Putin's spokesman Dmitry Peskov described US charges against six Russian intelligence officers as "rampant Russophobia which, of course, have nothing to do with reality."
The US Justice Department, which announced the charges against the GRU agents Monday, also said Russian intelligence was behind the "NotPetya" malware attack that infected computers of businesses worldwide, causing nearly $1 billion in losses to three US companies alone.
At the same time, UK Foreign Secretary Dominic Raab accused Russian military intelligence services of carrying out internet reconnaissance missions against targets linked to the Tokyo Olympics, before they were postponed until 2021 by the coronavirus pandemic.
"The Russian Federation, Russian security services have never undertaken any hacker attacks, especially in connection with the Olympics," Peskov told reporters.
Windows GravityRAT Malware Now Also Targets macOS and Android Devices
21.10.20 Android Thehackernews
A Windows-based remote access Trojan believed to be designed by Pakistani hacker groups to infiltrate computers and steal users' data has resurfaced after a two-year span with retooled capabilities to target Android and macOS devices.
According to cybersecurity firm Kaspersky, the malware — dubbed "GravityRAT" — now masquerades as legitimate Android and macOS apps to capture device data, contact lists, e-mail addresses, and call and text logs and transmit them to an attacker-controlled server.
First documented by the Indian Computer Emergency Response Team (CERT-In) in August 2017 and subsequently by Cisco Talos in April 2018, GravityRAT has been known to target Indian entities and organizations via malware-laced Microsoft Office Word documents at least since 2015.
Noting that the threat actor developed at least four different versions of the espionage tool, Cisco said, "the developer was clever enough to keep this infrastructure safe, and not have it blacklisted by a security vendor."
Then last year, it emerged that Pakistani spies used fake Facebook accounts to reach out to more than 98 officials from various defence forces and organizations, such as the Indian Army, Air Force, and Navy, and trick them into installing the malware disguised as a secure messaging app called Whisper.

But even as the latest evolution of GravityRAT goes beyond anti-malware evasion capabilities to gain multi-platform support — including Android and macOS — the overall modus operandi remains the same: sending targets links to booby-trapped Android (e.g., Travel Mate Pro) and macOS apps (Enigma, Titanium) to distribute the malware.
Kaspersky said it found over ten versions of GravityRAT that were being distributed under the guise of legitimate applications by cross-referencing the command-and-control (C2) addresses used by the Trojan.
In all, the trojanized applications spanned across travel, file sharing, media players, and adult comics categories, catering to users of Android, macOS, and Windows, thereby allowing the attackers to grab system information, documents with specific extensions, a list of running processes, record keystrokes and take screenshots, and even execute arbitrary Shell commands.
"Our investigation indicated that the actor behind GravityRAT is continuing to invest in its spying capacities," Kaspersky's Tatyana Shishkova said.
"Cunning disguise and an expanded OS portfolio not only allow us to say that we can expect more incidents with this malware in the APAC region, but this also supports the wider trend that malicious users are not necessarily focused on developing new malware, but developing proven ones instead, in an attempt to be as successful as possible."
Popular Mobile Browsers Found Vulnerable To Address Bar Spoofing Attacks
21.10.20 Attack Thehackernews
Cybersecurity researchers on Tuesday disclosed details about an address bar spoofing vulnerability affecting multiple mobile browsers, such as Apple Safari and Opera Touch, leaving the door open for spear-phishing attacks and delivering malware.
Other impacted browsers include UCWeb, Yandex Browser, Bolt Browser, and RITS Browser.
The flaws were discovered by Pakistani security researcher Rafay Baloch in the summer of 2020 and jointly reported by Baloch and cybersecurity firm Rapid7 in August before they were addressed by the browser makers over the past few weeks.
UCWeb and Bolt Browser remain unpatched as yet, while Opera Mini is expected to receive a fix on November 11, 2020.
The issue stems from using malicious executable JavaScript code in an arbitrary website to force the browser to update the address bar while the page is still loading to another address of the attacker's choice.
Original PoC demo
"The vulnerability occurs due to Safari preserving address bar of the URL when requested over an arbitrary port, the set interval function reloads bing.com:8080 every 2 milliseconds and hence user is unable to recognize the redirection from the original URL to spoofed URL," Rafay Baloch said in technical analysis.
"What makes this vulnerability more effective in Safari by default does not reveal port number in URL unless and until focus is set via cursor."
Put differently; an attacker can set up a malicious website and lure the target into opening the link from a spoofed email or text message, thereby leading an unsuspecting recipient into downloading malware or risk getting their credentials stolen.
The research also found the macOS version of Safari to be vulnerable to the same bug, which according to Rapid7 has been addressed in a Big Sur macOS update released last week.
This is not the first time such vulnerability has been spotted in Safari. Back in 2018, Baloch disclosed a similar kind of address bar spoofing flaw that caused the browser to preserve the address bar and to load the content from the spoofed page through a JavaScript-induced timing delay.
"With ever growing sophistication of spear phishing attacks, exploitation of browser-based vulnerabilities such as address bar spoofing may exacerbate the success of spear-phishing attacks and hence prove to be very lethal," Baloch said.
"First and foremost, it is easy to persuade the victim into stealing credentials or distributing malware when the address bar points to a trusted website and giving no indicators forgery, secondly since the vulnerability exploits a specific feature in a browser, it can evade several anti-phishing schemes and solutions."
Ryuk Ransomware Gang Uses Zerologon Bug for Lightning-Fast Attack
20.10.20 Ransomware Threatpost
Researchers said the group was able to move from initial phish to full domain-wide encryption in just five hours.
The Ryuk threat actors have struck again, moving from sending a phishing email to complete encryption across the victim’s network in just five hours.
That breakneck speed is partially the result of the gang using the Zerologon privilege-escalation bug (CVE-2020-1472), less than two hours after the initial phish, researchers said.
The Zerologon vulnerability allows an unauthenticated attacker with network access to a domain controller to completely compromise all Active Directory identity services, according to Microsoft. It was patched in August, but many organizations remain vulnerable.
In this particular attack, after the attackers elevated their privileges using Zerologon, they used a variety of commodity tools like Cobalt Strike, AdFind, WMI and PowerShell to accomplish their objective, according to the analysis from researchers at the DFIR Report, issued Sunday.
The Attack Begins
The attack started with a phishing email containing a version of the Bazar loader, researchers said. From there, the attackers performed basic mapping of the domain, using built-in Windows utilities such as Nltest. However, they needed to escalate their privileges to do any real damage, so they exploited the recently disclosed Zerologon vulnerability, researchers said.
Having gained elevated admin privileges, the cybercriminals were able to reset the machine password of the primary domain controller, according to the analysis.
Then, they moved laterally to the secondary domain controller, carrying out more domain discovery via Net and the PowerShell Active Directory module.
“From there, the threat actors appeared to use the default named pipe privilege escalation module on the server,” researchers said. “At this point, the threat actors used [Remote Desktop Protocol] RDP to connect from the secondary domain controller to the first domain controller, using the built-in administrator account.”
Cobalt Strike
Lateral movement was initiated via Server Message Block (SMB) and Windows Management Instrumentation (WMI) executions of Cobalt Strike beacons, researchers said. SMB is a networking file-share protocol included in Windows 10 that provides the ability to read and write files to network devices. WMI meanwhile enables management of data and operations on Windows-based operating systems.
Cobalt Strike belongs to a group of dual-use tools that are typically leveraged for both exploitation and post-exploitation tasks. Other examples in circulation include PowerShell Empire, Powersploit and Metasploit, according to recent findings from Cisco.
“From memory analysis, we were also able to conclude the actors were using a trial version of Cobalt Strike with the EICAR string present in the network configuration for the beacon. Both portable executable and DLL beacons were used,” researchers added.
Once on the main domain controller, another Cobalt Strike beacon was dropped and executed.
The analysis of the attack revealed that after about four hours and 10 minutes, the Ryuk gang pivoted from the primary domain controller, using RDP to connect to backup servers.
“Then more domain reconnaissance was performed using AdFind. Once this completed…the threat actors were ready for their final objective,” according to DFIR’s report.
Five Hours Later: Ryuk
For the final phase of the attack, the Ryuk operators first deployed their ransomware executable onto backup servers. After that, the malware was dropped on other servers in the environment, and then workstations.
Ryuk is a highly active malware, responsible for a string of recent hits, including a high-profile attack that shut down Universal Health Services (UHS), a Fortune-500 owner of a nationwide network of hospitals.
“The threat actors finished their objective by executing the ransomware on the primary domain controller, and at the five-hour mark, the attack completed,” researchers said.
The use of Zerologon made the cybrcriminals’ efforts much easier, since the attack didn’t need to be aimed at a high-privileged user who would likely have more security controls.
In fact, the toughest part of the campaign was the start of the attack – the successful installation of Bazar from the initial phishing email, which required user interaction. Researchers note that the user was a Domain User and did not have any other permissions – but that proved to be a non-issue, thanks to Zerologon.
The attack shows that organizations need to be ready to move more quickly than ever in response to any detected malicious activity.
“You need to be ready to act in less than an hour, to make sure you can effectively disrupt the threat actor,” according to researchers.
Zerologon Attacks Surge
The case study comes as exploitation attempts against Zerologon spike. Government officials last week warned that advanced persistent threat actors (APTs) are now leveraging the bug to target elections support systems.
That came just days after Microsoft sounded the alarm that an Iranian nation-state actor was actively exploiting the flaw (CVE-2020-1472). The APT is MERCURY (also known as MuddyWater, Static Kitten and Seedworm). And, Cisco Talos researchers also recently warned of a spike in exploitation attempts against Zerologon.
In September, the stakes got higher for risks tied to the bug when four public proof-of-concept exploits for the flaw were released on Github. This spurred the Secretary of Homeland Security to issue a rare emergency directive, ordering federal agencies to patch their Windows Servers against the flaw by Sept. 2.
Microsoft Exchange, Outlook Under Siege By APTs
20.10.20 APT Threatpost
A new threat report shows that APTs are switching up their tactics when exploiting Microsoft services like Exchange and OWA, in order to avoid detection.
New, sophisticated adversaries are switching up their tactics in exploiting enterprise-friendly platforms — most notably Microsoft Exchange, Outlook Web Access (OWA) and Outlook on the Web – in order to steal business credentials and other sensitive data.
Both Microsoft’s Exchange mail server and calendaring server and its Outlook personal information manager web app provide authentication services – and integration with other platforms – that researchers say are prime for attackers to leverage for launching attacks.
Accenture’s 2020 Cyber Threatscape report, released Monday, shed light on how actors are leveraging Exchange and OWA – and evolving their tactics to develop new malware families that target these services, or using new detection evasion techniques.
“Web-facing, data-intense systems and services that typically communicate externally can make it easier for adversaries to hide their traffic in the background noise, while authentication services could open up a credential-harvesting opportunity for cybercriminals,” according to Accenture researchers on Monday.
APTs Flock Exchange, OWA
One threat group that has been targeting Exchange and OWA is what researchers dub “BELUGASTURGEON” (aka Turla or Whitebear). Researchers say that this group operates from Russia, has been active for more than 10 years and is associated with numerous cyberattacks aimed at government agencies, foreign-policy research firms and think tanks across the globe.
The group is targeting these Microsoft services and using them as beachheads to hide traffic, relay commands, compromise e-mail, exfiltrate data and gather credentials for future espionage attacks, said researchers. For instance, they are manipulating legitimate traffic that’s traversing Exchange in order to relay commands or exfiltrate sensitive data.
“Hosts supporting Exchange and associated services frequently relay large volumes of data to external locations— representing a prime opportunity for malicious actors to hide their traffic within this background noise,” said researchers.
Another group, which researchers call SOURFACE (aka APT39 or Chafer), appears to have developed similar techniques to conceal malicious traffic, manipulating local firewalls and proxying traffic over non-standard ports using native commands, tools and functions, researchers said. Researchers said this group has been active since at least 2014 and is known for its cyberattacks on the oil and gas, communications, transportation and other industries in the Australia, Europe, Israel, Saudi Arabia, the U.S. and other regions.
In addition, threat groups are also creating new malware designed to specifically target Exchange and OWA. Researchers said they discovered several malicious files in the wild in 2019 that they assessed “with moderate confidence” were associated to a group called BLACKSTURGEON, used in targeting government and public sector orgs.
That includes a file that seemed like a version of the group’s customized version of the “RULER” tool, which is designed to abuse Microsoft Exchange services. This file exploits the CVE- 2017-11774 Outlook vulnerability, a security-feature bypass vulnerability that affects Microsoft Outlook and enables attackers to execute arbitrary commands, researchers said.
Other Services Under Attack
Cybercriminals are also targeting services that support Exchange and OWA. For instance, client-access servers (CAS), which handle all client connections to Exchange Server 2010 and Exchange 2013, typically operate in web-login portals for services including OWA. Attackers with access to CAS may be able to deploy capabilities to steal user login credentials, researchers said.
“Notably, an advanced persistent threat actor reportedly deployed web shells to harvest credentials from OWA users as they logged in,” they said.
The Windows Internet Information Services (IIS) platform, which supports OWA, is another increasing target. IIS is a web server software created by Microsoft for use with the Windows family. Researchers said they have observed SOURFACE, for instance, deploying custom Active Server Page Extended (ASPX) Web shells to IIS directories within the victim’s OWA environment. These web shells would include discrete file names, to resemble legitimate files on the victim’s system (for instance “login2.aspx” instead of “login.aspx”). And, to evade static detection, they typically contained limited functionality, often only file upload and download or command execution.
“SOURFACE operators altered their approach as the intrusion progressed. Instead of placing additional files to accomplish malicious functionality, the adversary appended web shell code to legitimate files within IIS,” said researchers. “It is likely they did this to reduce the identification by network defenders and ensure persistent access, even if other web shell files were identified and removed.”
Researchers said moving forward, attackers will continue to innovate their techniques in attacking Microsoft services, like Exchange, in ways that will naturally challenge network defenders. Beyond malware, Microsoft is top of the heap when it comes to hacker impersonations – with Microsoft products and services featuring in nearly a fifth of all global brand phishing attacks in the third quarter of this year, according to Check Point researchers.
“State-aligned operators could continue — in most cases — to need to emphasize stealth and persistence to meet their intelligence- gathering goals,” according to Accenture. “Such capabilities and detection evasion approaches underline the importance of identifying and tracking priority adversaries and then threat hunting against the specific behaviors employed by the priority adversaries.”
DOJ Charges 6 Sandworm APT Members in NotPetya Cyberattacks
20.10.20 BigBrothers Threatpost
DOJ charges six Russian nationals for their alleged part in the NotPetya, Ukraine power grid and Olympics cyberattacks.
The Department of Justice (DOJ) on Monday announced charges against six Russian nationals who are allegedly tied to the Sandworm APT. The threat group is believed to have launched several high-profile cyberattacks over the past few years – including the destructive NotPetya cyberattack that targeted hundreds of firms and hospitals worldwide in 2017.
According to the DOJ complaint, the six Russian nationals are tied to a division of the Russian military intelligence service and also affiliated with the APT Sandworm, also known as TeleBots. The DOJ said cyberattacks linked to the six defendants were “breathtaking” in their scope and “harmed ordinary people around the world,” said Scott Brady, U.S. attorney with the Western District of Pennsylvania, in a DOJ press conference on Monday.
The six defendants are: Yuriy Sergeyevich Andrienko (32); Sergey Vladimirovich Detistov (35); Pavel Valeryevich Frolov (28); Anatoliy Sergeyevich Kovalev (29); Artem Valeryevich Ochichenko (27) and Petr Nikolayevich Pliskin (32).
A breakdown of the charges against each defendant. Credit: DoJ
Each were charged in seven counts: conspiracy to conduct computer fraud and abuse, conspiracy to commit wire fraud, wire fraud, damaging protected computers, and aggravated identity theft, according to the DOJ.
According to the DOJ, the alleged malicious activity of the six dates back to November 2015, with the group developing malware known as BlackEnergy, Industroyer and KillDisk. The group used the malware in attacks against Ukraine’s electric power grid, Ministry of Finance, and State Treasury Service from Dec. 2015 to Dec. 2016, according to the DOJ.
In April and May 2017 the group allegedly launched spearphishing campaigns targeting French President Macron’s “La République En Marche!” (En Marche!) political party prior to the 2017 French elections.

The six defendants. Credit: DoJ
They were also allegedly behind the June 2017 destructive malware attacks that infected computers worldwide, using the NotPetya malware, resulting in the infection of 400 computers. The malware crippled many critical systems, including mission critical systems used by hospitals like the Pennsylvania-based Heritage Valley Health Systems.
In February 2018, the group allegedly sent spearphishing campaigns and malicious mobile applications targeting South Korean citizens and officials, Olympic athletes, partners, and visitors, and International Olympic Committee (IOC) officials; they then allegedly compromised computers supporting the 2018 PyeongChang Winter Olympic Games. This led to the Feb. 9, 2018, destructive malware attack against the opening ceremony, using malware known as Olympic Destroyer.
Finally, the group is alleged to have sent spearphishing emails to government organizations investigating the poisoning of a former GRU officer and his daughter in the United Kingdom in April 2018; and to have targeted the country of Georgia in 2018 with a spearphishing attack that led to the defacement of 15,000 websites.
“Groups like this use tactics, such as spearphishing, that are just as likely to reach targets on both computers, smartphones, or tablets,” Hank Schless, Senior Manager, Security Solutions at Lookout, told Threatpost. “They know that the likelihood of a successful phishing attack increases dramatically if the target receives it on a mobile device. They can phish login credentials from particular users that would allow them to get into the corporate infrastructure, then move laterally around the infrastructure for surveillance purposes or to exfiltrate valuable data.”
Threat researchers applauded the crackdown, saying that, while the arrest and extraction of the six Russian nationals seems unlikely, the indictments will limit their ability to use the Western financial system or travel to any country that may have an extradition agreement with the US.
“The charges filed against Sandworm represent not only the first criminal charges against Sandworm for its most destructive attacks but the first time that most of the charged threat actors have been publicly identified as members of the cybercriminal group,” Kacey Clark, Threat Researcher at Digital Shadows, told Threatpost. “They also represent Sandworm’s first global law enforcement reaction to their deployment of the NotPetya ransomware that has crippled networks worldwide.”
Google’s Threat Analysis Group (TAG), Cisco’s Talos Intelligence Group, Facebook and Twitter were credited in helping the DOJ with its investigation.
Overlay Malware Targets Windows Users with a DLL Hijack Twist
20.10.20 Virus Threatpost
Brazilians are warned of a new Vizom malware masquerading as video conferencing and browser software.
Brazilians are being warned of a new overlay malware targeting Windows users in order to siphon victims’ financial data and drain their bank accounts. Researchers say what the malware, dubbed Vizom, lacks in sophistication it makes up for in its creative abuse of the Windows ecosystem.
Trusteer, a Boston-based research arm of IBM Security, said the new code is being actively used in campaigns targeting online bank users in Brazil. Overlay malware, it said, is prevalent in Latin America and a top offender for the past decade.
Vizom is similar to other overlay malware strains in that its attack vector is via malspam and phishing campaigns delivered to potential victims’ inboxes.
“Typically delivered by spam, once Vizom is downloaded by an unwitting user, it finds its way into the [Windows] AppData directory and launches the infection process,” wrote Chen Nahman, security threat researcher at Trusteer.
He explained the malware is called “Vizom” because it leverages some legitimate computer code used by the Chromium browser Vivaldi, and binaries from a popular videoconferencing software, which researchers did not identify by name.
First, the dropper downloads an executable, then unpacks the video conferencing software and a malware DLL payload, explained Nahman in a breakdown of the malware infection chain posted Monday.
“What we found interesting about Vizom, is the way it infects and deploys on user devices. It uses ‘DLL hijacking’ to sneak into legitimate directories on Windows-based machines, masked as a legitimate, popular video conferencing software, and tricks the operating system’s inherent logic to load its malicious Dynamic Link Libraries (DLLs) before it loads the legitimate ones that belong in that address space. It uses similar tactics to operate the attack,” Nahman wrote.
Once infected, Vizom uses the above technique to piggyback on Windows in a variety of ways, such pre-loading malicious files from the various OS directories as the malware executes.
Anti-Virus Sidestep
“In this case, the malicious DLL’s name was taken from a popular videoconferencing software: ‘Cmmlib.dll.’ To make sure that the malicious code is executed from ‘Cmmlib.dll,’ the malware’s author copied the real export list of that legitimate DLL but made sure to modify it and have all the functions direct to the same address – the malicious code’s address space,” he wrote.
Similarly, to sneak past endpoint mitigations, the legitimate browser Vivaldi is dropped to the target system alongside the malware’s malicious DLLs – also used to carry out the attack, according to the report.
The malware’s persistence is maintained via modifying the “browser shortcuts so that they will all lead to its own executables and keep it running in the background no matter what browser the user attempted to run.”
Now, when a victim launches their browser, the Vizom malware is loaded and disguised as a Vivaldi browser process in order to increase its odds of not being detected.
“Since so many people have shifted to working from home, and almost everyone is using videoconferencing… Vizom uses the binaries of a popular videoconferencing software to pave its way into new devices,” he wrote.
“Vizom uses the files of yet another legitimate software, this time the Internet browser Vivaldi, which helps to disguise the malware’s activity and avoid detection from operating system controls and anti-virus software,” he added.
Post Infection Pest
Post infection, the malware monitors browser activity, communicates to the attackers’ command-and-control (C2) server, captures keystrokes and deploys its overlay screen above a bank’s website that the attackers have preselected.
“After it begins fully running on an infected device, Vizom, like other overlay malware, monitors the user’s online browsing, waiting for a match for its target list,” the researcher wrote. “Since Vizom does not hook the browser like other, more sophisticated malware typically does, it monitors activity by comparing the window title the user is accessing to key target strings the attacker is interested in. This comparison happens continually in a loop.”
Once a victim visits a desired bank’s website, the attacker is alerted in real time to the open banking session. Vizom triggers the attacker by opening a TCP socket and linking C2 server. The communication with the C2 server is a reverse shell that the infected machine uses to communicate back to the attacking server, where a listener port receives the connection.
Phase RAT
Next, the attacker leverages a remote access trojan component of it malware to launch the overlay interface and take control of the browser session. Researchers said victims are then tricked into providing personal identifiable information (PII) and financial information, which helps the attacker complete fraudulent transactions from the target’s bank account.
The actual data pilfered from targets is collected with a keylogger and then sent to the attacker’s C2. Of note, according to Nahman, is that Vizom “generates an HTML file from encrypted strings, then opens it with the ‘Vivaldi’ browser in application mode.” This, he said, is not typical of similar overlay malware and allows the application to be executed on a single web page without the typical browser’s user interface – preventing the infected victim from taking on-screen actions.
“Vizom focuses on large Brazilian banks, however, the same tactics are known to be used against users across South America and has already been observed targeting banks in Europe as well,” he warned.
Game Titles Watch Dogs: Legion, Albion Both Targeted by Hackers
20.10.20 Hacking Threatpost
In both cases, cybercriminals claim to have reams of information for the popular gaming titles.
A ransomware gang that just emerged this month dubbed Egregor claims to have hacked the source code to the upcoming gaming release, Watch Dogs: Legion.
And in separate gaming news, a popular fantasy title called Albion — a massive multiplayer online role-playing game (MMORPG) — has been hacked. Cybercriminals are offering what they claim are game databases in underground forums.
Source Code Leaked
Watch Dogs: Legion is due to be released a couple of weeks from now, on Oct. 29 – a highly anticipated release thanks to its 4K visuals, “ray tracing” capabilities and a planned Assassin’s Creed crossover.
The Egregor gang claims to have lifted both the code and some proprietary files from the game’s publisher, Ubisoft. Release of the source code would allow fans to develop game hacks and perform all kinds of “modding” (i.e., development of custom features) and jailbreaks.
The group also said that it has files Crytek relating to gaming titles like Arena of Fate and Warface.
According to a look at Egregor’s leak site portal by ZDNet, partial leaks for the hacks appear to have been posted. The operators emailed the outlet as well, noting that they only hacked Ubisoft and didn’t deploy its ransomware. Crytek, meanwhile, “has been encrypted fully.” In both cases, the companies haven’t responded to the incidents, according to the email.
“In case Ubisoft will not contact us we will begin posting the source code of upcoming Watch Dogs and their engine,” the hackers told ZDNet.
The data posted is somewhat inconclusive – the code in the portal could be from an older Watch Dogs version, for instance. In all, the data totals 20 MB from Ubisoft, and 300 MB from Crytek.
Egregor was first spotted in the wild in early October and late September, using a tactic of siphoning off corporate information and threatening a “mass-media” release of it before encrypting all files.
Egregor is an occult term meant to signify the collective energy or force of a group of individuals, especially when the individuals are united toward a common purpose — apropos for a ransomware gang. According to a recent analysis from Appgate, the code seems to be a spinoff of the Sekhmet ransomware (itself named for the Egyptian goddess of healing).
Neither company has acknowledged an attack. Threatpost has reached out for more information.
There is some precedent for hacking claims like these to be bogus. In September, reports surfaced that 500,000 Activision accounts may have been hacked, impacting online Call of Duty (CoD) players. The alleged breach was first flagged by the #oRemyy account on Twitter, and was quickly amplified by others, who claimed that accounts were being taken over and credentials changed, so that the legitimate users couldn’t recover them. The claims were picked up by gaming news outlet Dexterto.com and many others.
The gaming giant categorically disputed the claim as a widespread hoax.
Data Breach for Albion
Meanwhile, the Albion has disclosed a data breach resulting from an outside hack of its forum’s user database.
Albion is a fantasy-themed sandbox game in which players can go to battle, farm, forge alliances, defend territory, take on dragons and other monsters, and even invest in real estate. According to one tracker site, around 225,000 people play per day globally, and it has a total player base of 2.4 million active users.
According to game-owner Sandbox Interactive, the intruder was able to access forum-user profiles, including email addresses, encrypted (hashed and salted) passwords. No payment information was accessed, but the email addresses could be used in brute-force attacks on accounts.
Source: Albion Online
“If you have a forum account, you should, as a precaution, change the password to your Albion Online account,” the company noted. “Should you have also used the same password on other webpages or services, we strongly encourage you to change it there as well, and use unique passwords going forward.”
However, a hacker taking responsibility for the incident claims to have accessed much more than just emails and encrypted passwords. On an underground forum, someone is offering what they claim to be databases for payments, the main game and the forum; and source code for the Albion website and the forum.
For its part, Albion said that has closed off hacker access and is now “running additional checks to ensure the integrity of our systems. Because the safety of your data is a top priority for us, we will also be executing a full security review of all our systems to ensure your information remains absolutely safe.”
Threatpost has reached out to Ubisoft, Crytek and Albion/Sandbox Interactive for more details on all of these incidents.
Pay it safe: Group-IB aids Paxful in repelling a series of web-bot attacks
20.10.20 Attack Securityaffairs
Group-IB assisted Paxful, an international peer-to-peer cryptocurrency marketplace, in countering web-bot and social engineering attacks
Group-IB, a global threat hunting and intelligence company headquartered in Singapore, has assisted Paxful, an international peer-to-peer cryptocurrency marketplace, in countering a wave of web-bot and social engineering attacks, and customer account takeovers. Powered with Group-IB’s solution for online fraud prevention Secure Portal, the platform has managed to fight off over 220,000 requests from web-bots in just two months, shielding its 4.5 million customers against possible attacks. The figure suggests that bitcoin platforms remain of great interest to threat actors.
Cryptocurrencies, in general, are the apple of cybercriminals’ eye: Group-IB has alerted cryptocurrency holders to various scams on numerous occasions: fake giveaways, non-existent cryptocurrency investment platforms, as well as personal data-exposing schemes, have found hundreds of thousands of people as their victims.
The scope of online threats that Paxful faced before acquiring Secure Portal ranged from social engineering attacks to customer account takeover, which is not surprising given the popularity of cryptocurrencies. But it was the detection and prevention of bad bot activity that pushed Paxful to adopt an additional layer of cybersecurity and resort to Group-IB. Bots, which are reported to generate about a quarter of global Web traffic, are de facto programs that emulate the actions of a real device for the purposes needed. They are a big headache for eCommerce businesses today, with cybercriminals using them to steal money, brute-force user credentials or carry out DDoS attacks.
The brute-forcing of user credentials was the case with Paxful. To successfully thwart bad-bot activity, Group-IB Secure Portal creates a unique fingerprint of a device that is based on over a dozen of indicators and metrics, including info on the user-agent, platform, operation system, the time zone from which the user operates, device language, and others. Based on this fingerprinting and behavioral analysis, Group-IB Secure Portal identifies and issues an alert for any suspicious activity in real-time, after which this detection is used by Paxful to block bad bots.
Trojans have also been spotted in the attacks on the marketplace: Group-IB Secure Portal has identified at least 1,200 user devices infected with Trojans. The detection of malware is considerably facilitated by the fact that Secure Portal is fueled by the information on threat actors, different malware strains’ behavior, malicious IPs and compromised data, such as login credentials or bank card data, from Group-IB attribution-based Threat Intelligence, a proprietary system that holds the most up-to-date data on advanced attackers and their TTPs.
Group-IB Secure Portal also managed to identify over 100,000 accounts with three or more logins from the same device. Some of these accounts were simply compromised, others were used to boost rank on the platform for further fraud activity or were just resold.
“For Paxful, Group-IB was the perfect solution; we were particularly impressed by the accuracy of Group-IB’s device fingerprint technology,” comments Dmitry Moiseev, the Chief Information Security Officer at Paxful. “The unique technology that easily detects suspicious devices is exactly what we were looking for. Interactive graph visualization tools and strong API create a truly comprehensive experience when it comes to fraud investigation. With reliable and helpful technical support, Group-IB is a well-rounded cybersecurity solution that works for us.”
With the deployment of Group-IB Secure Portal, Paxful is now even better equipped to mitigate fraud and prevent digital crimes well before they are even close to affecting the company’s multimillion customer base.
“Businesses are struggling more than ever today and to ensure that their customers are safe from fraud when using online services is the new normal,” comments Group-IB International Business Development Director Nicholas Palmer. “Online fraud is one of the biggest hurdles on the path toward achieving a positive client experience. For online platforms, it is extremely important to ensure the safety of its users and the integrity of its cybersecurity, whose perimeter should extend to end-point devices and the protection of its clients. Group-IB Secure Portal is implementing this philosophy through its patented clientless detection technology, which protects clients’ customers without need for the latter to install any additional apps.”
The forum of the popular Albion Online game was hacked
20.10.20 Hacking Securityaffairs
Albion Online game maker discloses a data breach, hackers gained access to the company forum database by exploiting a known vulnerability.
Albion Online (AO) is a free medieval fantasy MMORPG developed by Sandbox Interactive, a studio based in Berlin, Germany
A threat actor has breached the forum of Albion Online and stole usernames and password hashes from its database.
According to Sandbox Interactive, the intrusion took place on Friday, October 16, and the hacker exploited a vulnerability in its forum platform, known as WoltLab Suite.
“Unfortunately, we have become aware of a data breach in one of our systems, in which a malicious actor gained access to parts of our forum’s user database.” reads the message published on the forum.
“The intruder was able to access forum user profiles, which include the e-mail addresses connected to those forum accounts. On top of that, the attacker gained access to encrypted passwords (in technical terms: hashed and salted passwords).”

The moderator of the forum pointed out that the intruder did not access to payment information.
According to Sandbox Interactive, the passwords were hashed with the Bcrypt hashing function and then salted with random data, which makes it hard to crack if the password is not weak.
“However, there is a small possibility they could be used to identify accounts with particularly weak passwords.” continues the German game maker.
In response to the data breach, the game maker notified the forum members about the intrusion and asked them to reset passwords.
The company notified the authorities, but did not reveal the number of impacted users. The game maker announced to have addressed the flaw exploited in the attack.
“So far we have prioritized fixing vulnerabilities and informing players about this incident,” Sandbox Interactive said.
The game is believed to have more than 2.5 million players, while the number of registered members of the forum was 293,602 at the time of the attack.
Nefilim ransomware gang published Luxottica data on its leak site
20.10.20 Ransomware Securityaffairs
The Nefilim ransomware operators have posted a long list of files that appear to belong to Italian eyewear and eyecare giant Luxottica.
Luxottica Group S.p.A. is an Italian eyewear conglomerate and the world’s largest company in the eyewear industry. As a vertically integrated company, Luxottica designs, manufactures, distributes and retails its eyewear brands, including LensCrafters, Sunglass Hut, Apex by Sunglass Hut, Pearle Vision, Target Optical, Eyemed vision care plan, and Glasses.com. Its best known brands are Ray-Ban, Persol, and Oakley. Luxottica also makes sunglasses and prescription frames for designer brands such as Chanel, Prada, Giorgio Armani, Burberry, Versace, Dolce and Gabbana, Miu Miu, and Tory Burch.
Luxottica employs over 80,000 people and generated 9.4 billion in revenue for 2019.
On September 18, the company was hit by a cyberattack, some of the web sites operated by the company were not reachable, including Ray-Ban, Sunglass Hut, LensCrafters, EyeMed, and Pearle Vision.
Italian media outlets reported that the operations at the plants of Luxottica in Agordo and Sedico (Italy) were disrupted due to a computer system failure. Union sources confirmed that the personnel at the plants received an SMS in which they were notified that “the second workshift of today 21 September is suspended” due to “serious IT problems”.
BleepingComputer website, citing the security firm Bad Packets, speculates that the Italian was using a Citrix ADX controller device vulnerable to the critical CVE-2019-19781 vulnerability in Citrix devices.
At the time Luxottica has yet to release any official statement on the attack.
Security experts believe that threat actor exploited the above flaw to infect the systems at the company with ransomware.
Now we have more information about the incident, that seems to be the result of a ransomware attack.
The popular Italian cyber security expert Odysseus first revealed on the web site “Difesa e Sicurezza” that the Nefilim ransomware operators have posted a long list of files that appear to belong to Luxottica.
The huge trove of files appears to be related to the personnel office and finance departments.

The analysis of the leaked files revealed that they contain confidential information regarding the recruitment process, professional resumes, and info about the internal structures of the Group’s human resource department.
The exposed financial data includes budgets, marketing forecast analysis, and other sensitive data.
Nefilim ransomware operators also published a message which accuses Luxottica of having failed the properly manage the attack.
In the past months, the number of ransomware attacks surged, numerous ransomware gangs made the headlines targeting organizations worldwide and threating the victims of releasing the stolen data if the ransom was not paid.
“Extortion it’s the “new deal” of the cybercrime: now, more than in the past, companies can’t “hide” the cyber attack anymore. Now it becomes mandatory “manage” the breach from the communication perspective: dissembling is useless and harmful.” explained Odysseus. “And again, defend the companies from the cyber attacks becomes even more strategic: data leaks damages can generate tremendus amount of costs for companies worldwide.”
One of the crews that adopted this double-extortion model is the Nefilim ransomware gang that targeted several organizations including the mobile network operator Orange, the independent European leader in multi-technical services The SPIE Group, the German largest private multi-service provider Dussman Group.
UK Says Russia Launched Cyberattacks Against 2020 Olympic, Paralympic Games
20.10.20 BigBrothers Securityweek
The United Kingdom on Monday exposed and condemned cyberattacks that the Russian military intelligence service GRU allegedly launched against organizations involved in the 2020 Olympic and Paralympic Games that were set to take place in Tokyo this summer, but were postponed due to the COVID-19 pandemic.
The GRU is known for launching numerous hacking campaigns for the benefit of Moscow, including high-profile attacks such as those involving the BlackEnergy, Industroyer, and NotPetya malware families.
On Monday, the United States announced charges against six officers of the GRU, which is also said to have orchestrated the cyberattacks on the PyeongChang Winter Olympics with the Olympic Destroyer malware. Russia has also been blamed for attacks on Georgian companies and government organizations.
On Monday, the UK officially accused the GRU of launching malicious cyber-operations targeting the Olympic and Paralympic Games, including the now-postponed 2020 Summer Olympics and the 2018 Winter Olympic and Paralympic Games in Pyeongchang, South Korea.
“The National Cyber Security Centre (NCSC) assesses with high confidence that these attacks were carried out by the GRU’s Main Centre for Specialist Technologies (GTsST), also known as Sandworm and VoodooBear,” the NCSC says.
GTsST, which is known by its field post number 74455, is also referred to as BlackEnergy Group, Telebots, Iron Viking, Quedagh, Electrum, and G0034.
The Russian hackers attempted to disguise themselves as North Korean and Chinese threat actors and targeted the opening ceremony of the 2018 Winter Games, as well as broadcasters, Olympic officials, a ski resort, and sponsors of the 2018 games, the UK says.
According to the NCSC, the 2018 attack was meant to sabotage the Winter Olympic and Paralympic Games through the use of malware meant to disable computers and networks and wipe data.
“The GRU’s actions against the Olympic and Paralympic Games are cynical and reckless. We condemn them in the strongest possible terms. The UK will continue to work with our allies to call out and counter future malicious cyber-attacks,” British Foreign Secretary Dominic Raab said.
Furthermore, the Russian military intelligence service is blamed for spear-phishing attacks targeting the UK’s Defence Science and Technology Laboratory (DSTL) in 2018.
“We condemn these attacks carried out by the GRU and fully support the criminal charges announced today by the US Department of Justice. These attacks have had very real consequences around the world – both to national economies and the everyday lives of people,” Paul Chichester, the NCSC’s Director of Operations, said.
Ryuk Ransomware Attacks Continue Following TrickBot Takedown Attempt
20.10.20 Ransomware Securityweek
The threat actor behind the Ryuk ransomware continues to conduct attacks following the recent attempts to disrupt the TrickBot botnet, CrowdStrike reports.
Referred to as WIZARD SPIDER, the adversary has been widely using TrickBot for the distribution of ransomware, and the recent attempts by the U.S. Cyber Command and Microsoft to disrupt the botnet were expected to put an end to such operations.
However, the efforts had little effect on the botnet, and the threat actor is apparently able to continue operations at the same pace as before. With over one million infected machines, TrickBot represents a serious threat.
According to CrowdStrike, an initial swing at the botnet was observed on September 21, when a non-standard configuration file was being delivered to some of the infected machines, to instruct them to connect to a command and control (C&C) server address at 0.0.0.1 on TCP port 1.
As a result of this move, an unknown number of bots remained isolated from the network and became unreachable through the normal C&C channel. The non-standard config file was downloaded approximately 10,000 times, which translates into roughly one percent of systems infected with TrickBot being separated from the botnet.
“The operation against the TrickBot network was orchestrated to take down the botnet, thus reducing BGH infections by WIZARD SPIDER’s Ryuk and Conti ransomware families, with an ultimate goal of protecting the forthcoming U.S. elections from ransomware operations,” CrowdStrike notes.
TrickBot’s operators quickly switched to secondary channels to ensure their operations could continue. Emotet started deploying TrickBot last week, and WIZARD SPIDER added BazarLoader into the mix, an initial access tool the threat actor has used before.
Distributed through spam emails leading to Google Docs, BazarLoader features a backdoor component that provides the threat actor with the ability to run payloads and arbitrary scripts.
Starting September 2018, CrowdStrike notes, the Ryuk ransomware has been the most lucrative operation run by WIZARD SPIDER, as victims are believed to have paid over $61 million in ransom to recover files encrypted by Ryuk.
For an unknown reason, in March 2020, the group moved away from Ryuk and switched to the Conti ransomware, which emerged in an attack in June 2020. Conti, which has received weekly updates and improvements, is estimated to have been used to compromise more than 120 networks to date, most of them located in North America and Europe.
“Additional features, obfuscation techniques and code changes are integrated on an almost weekly basis. In August 2020, Conti’s technique shifted from fully encrypting files with AES-256 to a more strategic and efficient approach of selectively encrypting files with the ChaCha stream cipher. Conti’s host discovery and network share targeting functionality has also continued to evolve and is now comparable to that of Ryuk’s,” the security firm notes.
In September 2020, however, WIZARD SPIDER resumed Ryuk deployments and little code changes were observed between the ransomware’s April 2020 and September 2020 variants. The most notable of these modifications is the introduction of code obfuscation, although these are not as advanced as those used in Conti and BazarLoader.
“The ultimate goal of the disruption operation against the TrickBot network was to impact and prevent ransomware infections […]. While the valiant efforts of the cybersecurity teams involved in this complex operation undoubtedly had a short-term impact on WIZARD SPIDER’s TrickBot network, the response by the criminal actors has been swift, effective and efficient,” Crowdstrike concludes.
Android, macOS Versions of GravityRAT Spyware Spotted in Ongoing Campaign
20.10.20 Virus Securityweek
Kaspersky security researchers have identified versions of the GravityRAT spyware that are targeting Android and macOS devices.
Initially detailed in 2018, the RAT was previously employed in attacks targeting the Indian military, as part of a campaign that is believed to have been active since 2015. Targeting Windows systems, the tool has mainly been used for spying purposes.
In a report published on Monday, Kaspersky reveals that the malware’s authors have invested a lot into making their tool cross-platform, and that, as part of an ongoing campaign, both Android and macOS are now being targeted, in addition to Windows.
The investigation into the new samples has revealed over 10 variants of GravityRAT, which have been distributed masquerading as legitimate apps, including secure file sharing software and media players.
Spyware capabilities packed within GravityRAT allow the malware to retrieve device information, contact lists, call logs, email addresses, and SMS messages, and even to find and exfiltrate files based on extensions: .docx, .doc, .ppt, .pptx, .txt, .pdf, .xml, .jpg, .jpeg, .log, .png, .xls, .xlsx, and .opus.
The malware, which is believed to have been developed by a Pakistani group, is also capable of retrieving a list of running processes on the system, log keystrokes, take screenshots, execute shell commands, record audio, and scan for open ports.
“Our investigation indicated that the actor behind GravityRAT is continuing to invest in its spying capacities. Cunning disguise and an expanded OS portfolio not only allow us to say that we can expect more incidents with this malware in the APAC region, but this also supports the wider trend that malicious users are not necessarily focused on developing new malware, but developing proven ones instead, in an attempt to be as successful as possible,” Tatyana Shishkova, security expert at Kaspersky, said.
Analysis of some of the apps the Trojan has been distributed as revealed similar functionality between samples and also allowed the security researchers to identify command and control (C&C) servers used by the attackers, such as nortonupdates[.]online, windowsupdates[.]eu, mozillaupdates[.]com, mozillaupdates[.]us, msoftserver[.]eu, microsoftupdate[.]in, and others.
The domains distributing the malware, Kaspersky reveals, are hidden behind Cloudflare, thus making it difficult for security researchers to discover their IPs.
Kaspersky’s researchers also discovered that GravityRAT’s operators have developed .NET, Python, and Electron variants of the threat, which allows them to easily target both Windows and macOS devices. The Android variant features similar functionality.
Previously reported GravityRAT attacks employed fake Facebook accounts for distribution, with the intended victims contacted through the social platform and asked to install a malware masquerading as a secure messenger application. Approximately 100 victims were identified, including employees in defense, police, and other departments and organizations.
“It is safe to assume that the current GravityRAT campaign uses similar infection methods — targeted individuals are sent links pointing to malicious apps. The main modification seen in the new GravityRAT campaign is multiplatformity: besides Windows, there are now versions for Android and macOS. The cybercriminals also started using digital signatures to make the apps look more legitimate,” Kaspersky concludes.
CISA Warns of Remote Code Execution Bugs in Visual Studio, Windows Codecs Library
20.10.20 Virus Vulnerebility
The Cybersecurity and Infrastructure Security Agency (CISA) on Friday informed users about the availability of patches for two remote code execution vulnerabilities that affect Windows Codecs Library and Visual Studio Code.
Fixes for both of the bugs were released days after Microsoft’s October 2020 Patch Tuesday updates, and CISA published its alert to encourage users and administrators alike to install the available patches.
Tracked as CVE-2020-17022, the first of the issues exists in the manner in which the Codecs Library in Microsoft Windows handles objects in memory.
The bug can be triggered during the processing of a specially crafted image file and could allow an attacker to successfully execute arbitrary code on a vulnerable machine.
Residing in Visual Studio Code and tracked as CVE-2020-17023, the second vulnerability can be triggered when the user opens a malicious 'package.json' file. An attacker can trick the victim into cloning a repository and then opening it using Visual Studio Code, which would result in the attacker’s code being executed on the victim’s device.
“An attacker who successfully exploited the vulnerability could run arbitrary code in the context of the current user. If the current user is logged on with administrative user rights, an attacker could take control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights,” Microsoft explains.
Microsoft says there are no mitigations or workarounds for either of the two vulnerabilities. Both issues have been assigned a CVSS score of 7.8 and neither appears to have been exploited in the wild.
The vulnerability in Visual Studio was identified by Justin Steven, who in early October revealed on Twitter that Microsoft last month released a botched fix for CVE-2020-16881, a remote code execution bug in Visual Studio Code that could be triggered in a similar manner, through malicious 'package.json' files.
“Microsoft Visual Studio Code seems to have botched the fix for CVE-2020-16881, a ‘remote code execution’ vulnerability regarding ‘malicious package.json files’. The patch can be trivially bypassed,” Steven said, complaining that Microsoft isn’t forthcoming about the bug’s details.
Users who have automatic updates enabled on their computers will receive the patches for CVE-2020-17022 and CVE-2020-17023 without having to take additional steps.
French Court Tries Russian for Multi-Million-Euro Cyberfraud
20.10.20 BigBrothers Securityweek
A Russian goes on trial in Paris Monday accused of having defrauded nearly 200 victims across the world of 135 million euros using ransomware.
Prosecutors say Alexander Vinnik sent emails to his targets masquerading as invoices, whose attached document, when opened, activated malware that shut down the computer and encrypted its contents.
A message would appear on the hacked computer with instructions to pay a ransom in the online currency Bitcoin to regain control of the machine.
Among the 188 victims of the attacks -- which happened between 2016 and 2018 -- were local authorities, businesses and individuals across the world.
In France, many of the victims were local councils, law or insurance firms and small local businesses such as driving schools or pharmacies.
Vinnik, who has denied charges of extortion and money laundering, has refused to answer questions put by investigating magistrates.
He is also wanted in both the United States and his native Russia.
Investigators described the system he allegedly used as extremely elaborate, involving the mass mail-shots of the "contaminated" emails via a botnet: a network of already infected computers.
The way that the paid ransoms were subsequently laundered to make it difficult to trace was equally sophisticated, says the indictment.
Prosecutors identified 20 businesses in six cities across France among the victims and following the money trail through various bank accounts -- as much as $8 million -- identified one as belonging to Vinnik.
US investigators suspect the 41-year-old of being the mastermind of what they say has become one the main ways cybercriminals launder their illegal gains.
Vinnik was extradited to France in January from Greece, where he had been arrested on an American warrant in 2017.
He allegedly operated the BTC-e bitcoin exchange until his arrest at the northern Greek tourist resort of Halkidiki, which set off a three-way extradition tussle between the United States, France and Russia.
Greece eventually preferred the European warrant issued by France.
A US indictment accuses Vinnik of 21 charges ranging from identity theft and facilitating drug trafficking to money laundering.
He tried unsuccessfully to be extradited to Russia, where he is wanted on lesser fraud charges involving just 9,500 euros ($11,000).
Google Targeted in Record-Breaking 2.5 Tbps DDoS Attack in 2017
20.10.20 Attack Securityweek
Google revealed last week that its infrastructure was targeted in a record-breaking distributed denial-of-service (DDoS) attack back in September 2017.
When measuring DDoS attacks, Google looks at three main metrics: bits per second (bps) for attacks targeting network links, requests per second (rps) for attacks targeting application servers, and packets per second (pps) for attacks targeting DNS servers and network devices.
The tech giant says DDoS attacks have increased significantly over the past years in each of these metric categories.
In terms of bits per second, Google spotted the largest attack in September 2017. The attack was aimed at the company’s infrastructure and it reached 2.5 Tbps, being described by Google as “the culmination of a six-month campaign that utilized multiple methods of attack.”
“Despite simultaneously targeting thousands of our IPs, presumably in hopes of slipping past automated defenses, the attack had no impact,” explained Damian Menscher, a security reliability engineer at Google, whose team focuses on DDoS defenses. “The attacker used several networks to spoof 167 Mpps (millions of packets per second) to 180,000 exposed CLDAP, DNS, and SMTP servers, which would then send large responses to us.”
AWS reported this summer that a DDoS attack it mitigated in February 2020 peaked at 2.3 Tbps. When AWS disclosed the incident, it was considered the largest DDoS attack ever recorded, but apparently, bigger attacks were seen much earlier. Google now says that the attack it observed in 2017 is still the “highest-bandwidth attack reported to date.”
“[Even] though the 2.5 Tbps attack in 2017 didn't cause any impact, we reported thousands of vulnerable servers to their network providers, and also worked with network providers to trace the source of the spoofed packets so they could be filtered,” Menscher said.
In terms of packets per second, the largest attack seen by Google reached 690 Mpps and it was generated by an IoT botnet earlier this year. While this was a significant attack, Akamai reported in June that it had seen a DDoS attack peaking at 809 Mpps.
As for attacks that involved sending a large number of HTTP/HTTPS requests, Google provided as example an incident from March 2014, when malicious actors injected JavaScript code into thousands of websites, causing the sites to flood YouTube with requests. The attack peaked at 2.7 Mrps (million requests per second). However, Google says it’s also aware of a more recent attack, aimed at a Google Cloud customer, which peaked at 6 Mrps.
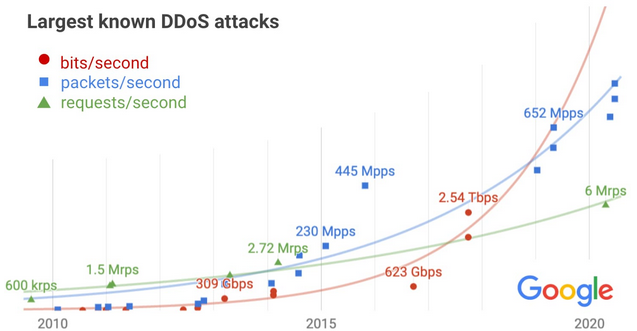
Google has various tools and mechanisms designed to protect its customers against DDoS attack, but the company called on users and businesses to join the fight against such threats by ensuring that botnets cannot abuse their devices for attacks and, in the case of organizations, by analyzing attacks, reporting them to law enforcement, and sharing information with the community.
U.S. Charges 6 Russian Intelligence Officers Over Destructive Cyberattacks
20.10.20 BigBrothers Thehackernews
The US government on Monday formally charged six Russian intelligence officers for carrying out destructive malware attacks with an aim to disrupt and destabilize other nations and cause monetary losses.
The individuals, who work for Unit 74455 of the Russian Main Intelligence Directorate (GRU), have been accused of perpetrating the "most disruptive and destructive series of computer attacks ever attributed to a single group," according to the Justice Department (DoJ).
All the six men — Yuriy Sergeyevich Andrienko, Sergey Vladimirovich Detistov, Pavel Valeryevich Frolov, Anatoliy Sergeyevich Kovalev, Artem Valeryevich Ochichenko, and Petr Nikolayevich Pliskin — have been charged with seven counts of conspiracy to conduct computer fraud and abuse, conspiracy to commit wire fraud, wire fraud, damaging protected computers, and aggravated identity theft.
"The object of the conspiracy was to deploy destructive malware and take other disruptive actions, for the strategic benefit of Russia, through unauthorized access ('hacking') of victim computers," the prosecutors said.
"In furtherance of the conspiracy, Andrienko, Detistov, Frolov, Kovalev, Ochichenko, Pliskin, and others known and unknown to the grand jury procured, maintained, and utilized servers, email accounts, malicious mobile applications, and related hacking infrastructure to engage in spear-phishing campaigns and other network intrusion methods against computers used by the victims."
Five years ago, Russian hackers belonging to Sandworm (aka APT28, Telebots, Voodoo Bear or Iron Viking) group attacked Ukraine's power grid, Ministry of Finance, and State Treasury Service using malware such as BlackEnergy, Industroyer, and KillDisk, before embarking on a spree of destructive cyberattacks — including unleashing NotPetya in 2017 and targeting the Pyeongchang Winter Olympics with phishing campaigns and "Olympic Destroyer" malware.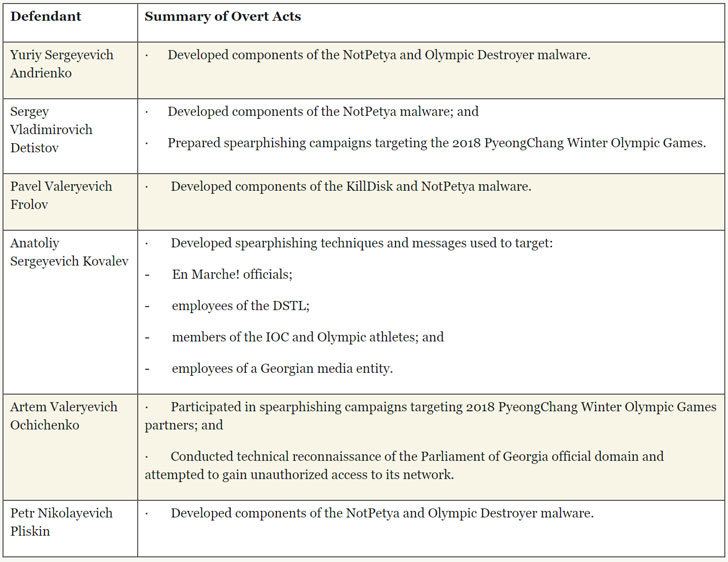
The six individuals have been accused of developing components for NotPetya, Olympic Destroyer, KillDisk malware, as well as preparing spear-phishing campaigns directed against the 2018 PyeongChang Winter Olympic Games, resulting in damage and disruption to computer networks across France, Georgia, the Netherlands, Republic of Korea, Ukraine, the UK, and the US.
"For example, the NotPetya malware impaired Heritage Valley's provision of critical medical services to citizens of the Western District of Pennsylvania through its two hospitals, 60 offices, and 18 community satellite facilities," the DoJ said. "The attack caused the unavailability of patient lists, patient history, physical examination files, and laboratory records."
"Heritage Valley lost access to its mission-critical computer systems (such as those relating to cardiology, nuclear medicine, radiology, and surgery) for approximately one week and administrative computer systems for almost one month, thereby causing a threat to public health and safety," it added.
The total damages brought about by NotPetya is pegged to more than $10 billion to date, crippling several multinational companies like Maersk, Merck, FedEx's TNT Express, Saint-Gobain, Mondelēz, and Reckitt Benckiser.
In a similar development, the UK government also formally accused the GRU of perpetrating cyber reconnaissance against officials and organizations at the 2020 Tokyo Olympic and Paralympic Games earlier this summer before they were postponed next year due to COVID-19.
This is not the first time GRU has come under the DoJ scanner. Two years back, the US government charged seven officers working for the military intelligence agency for conducting sophisticated computer intrusions against US entities as part of an influence and disinformation campaign designed to counter anti-doping efforts.
GravityRAT: The spy returns
19.10.20 Virus Securelist
In 2018, researchers at Cisco Talos published a post on the spyware GravityRAT, used to target the Indian armed forces. The Indian Computer Emergency Response Team (CERT-IN) first discovered the Trojan in 2017. Its creators are believed to be Pakistani hacker groups. According to our information, the campaign has been active since at least 2015, and previously targeted Windows machines. However, it underwent changes in 2018, with Android devices being added to the list of targets.
Malicious guide
In 2019, on VirusTotal, we encountered a curious piece of Android spyware which, when analyzed, seemed connected to GravityRAT. The cybercriminals had added a spy module to Travel Mate, an Android app for travelers to India, the source code of which is available on Github.

Clean Travel Mate app on Google Play
The attackers used a version of the app published on Github in October 2018, adding malicious code and changing the name to Travel Mate Pro.
The app requests permissions at startup
The Trojan’s manifest file includes Services and Receiver, which are not in the app from Github
List of Trojan classes
The spyware’s functions are fairly standard: it sends device data, contact lists, e-mail addresses, and call and text logs to the C&C server. In addition, the Trojan searches for files in the device memory and on connected media with the extensions .jpg, .jpeg, .log, .png, .txt, .pdf, .xml, .doc, .xls, .xlsx, .ppt, .pptx, .docx, and .opus, and sends these to C&C as well.
The malware does not resemble a “typical” Android spy in that the choice of app is rather specific and the malicious code is not based on that of any known spyware app, as is often the case. As such, we decided to look for connections with known APT families.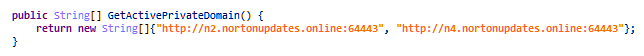
C&C addresses hardcoded into the Trojan
The simplest thing to do is to check the C&C addresses used by the Trojan:
nortonupdates[.]online:64443
nortonupdates[.]online:64443
As it turned out, n3.nortonupdates[.]online:64443 was used by another piece of malware to download data about files found on the computer (.doc, .ppt, .pdf, .xls, .docx, .pptx, .xlsx) together with data about the infected machine. With the aid of Threat Intelligence, we found this malware: a malicious PowerShell script called Enigma.ps1 that executes C# code.
The PowerShell script was run using a VBS script: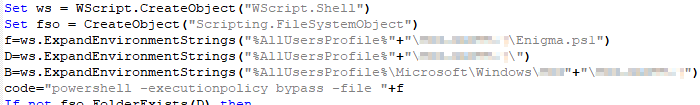
Next, we detected a very similar VBS script template with no specifiedpaths under the name iV.dll: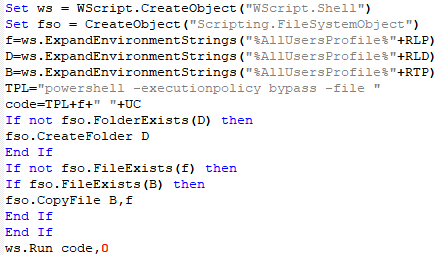
It was located inside the PyInstaller container enigma.exe signed by E-Crea Limited on 09.05.2019. The installer was downloaded from the site enigma.net[.]in under the guise of a secure file sharing app to protect against ransomware Trojans:
Besides the VBS template, inside the container were XML templates for Windows Task Scheduler under the names aeS.dll, rsA.dll, eA.dll, and eS.dll:
And in the main program, the required paths and names were written into the templates and a scheduled task had been added:
The program communicated with the server at the address download.enigma.net[.]in/90954349.php (note that 90954349A is the start of the MD5 hash of the word “enigma”). It featured a simple graphical interface and encryption and file exchange logic:
The Mac version has a similar functionality and adds a cron job:
Similar in functionality to enigma.exe is the app Titanium (titaniumx.co[.]in), signed on 04.14.2019 by Plano Logic Ltd, certificate revoked on 09.08.2019.
Alongside the Enigma and Titanium payloads were the following spyware Trojans:
Wpd.exe, signed 09.17.2018 by Plano Logic Ltd, certificate revoked
Taskhostex.exe, signed 02.18.2020 by Theravada Solutions Ltd
WCNsvc.exe, signed on 09.17.2018 by Plano Logic Ltd, certificate revoked
SMTPHost.exe, signed 12.21.2018 by Plano Logic Ltd, certificate revoked
CSRP.exe
Their C&Cs:
windowsupdates[.]eu:46769
windowsupdates[.]eu:46769
mozillaupdates[.]com:46769
mozillaupdates[.]com:46769
mozillaupdates[.]us
We focused on port 46769, used by the above Trojans. The same port was used by the GravityRAT family. A further search of nortonupdates[.]online led us to the PE file Xray.exe:
This version collected data and sent it to n1.nortonupdates[.]online and n2.nortonupdates[.]online.
The domains n*.nortonupdates[.]online resolved to the IP address 213.152.161[.]219. We checked our Passive DNS database for other domains previously found at this address, and discovered the suspicious looking u01.msoftserver[.]eu. A search of this domain led us to the app ZW.exe, written in Python and packaged using the same PyInstaller (signed on 04.10.2019 by Plano Logic Ltd, certificate revoked on 09.08.2019).
The C&C addresses called by ZW.exe are decrypted by the AES algorithm from the file Extras\SystemEventBrokerSettings.dat:
msoftserver[.]eu:64443
msoftserver[.]eu:64443
msoftserver[.]eu:64443
msoftserver[.]eu:64443
Communication with the server takes place at the relative address /ZULU_SERVER.php.
The spyware receives commands from the server, including to:
get information about the system
search for files on the computer and removable disks with the extensions .doc, .docx, .ppt, .pptx, .xls, .xlsx, .pdf, .odt, .odp, and .ods, and upload them to the server
get a list of running processes
intercept keystrokes
take screenshots
execute arbitrary shell commands
record audio (not implemented in this version)
scan ports
The code is multiplatform:
The characteristic path also confirms that we are dealing with a new version of GravityRAT:
The newer variants of the malware with similar functionality that we detected using Threat Intelligence — RW.exe and TW.exe — were signed by Theravada Solutions Ltd on 10.01.2019 and 02.20.2020, respectively; the certificates are valid.
RW.exe called the C&C server at the relative address /ROMEO/5d907853.php, and TW.exe at /TANGO/e252a516.php, so we can assume that the first letter in the name of the executable file indicates the version of the C&C server.
C&Cs of this instance:
mozillaupdates[.]us
mozillaupdates[.]us
mozillaupdates[.]us
mozillaupdates[.]us
microsoftupdate[.]in
microsoftupdate[.]in
microsoftupdate[.]in
microsoftupdate[.]in
Other versions of GravityRAT
lolomycin&Co
An older version of GravityRAT, Whisper, in addition to the string “lolomycin2017” (whose byte representation was used as a salt for AES encryption in the component lsass.exe), contained in the component whisper.exe the string “lolomycin&Co” for use as a password to unpack downloaded ZIP archives with the payload:
Through this string, we found newer .NET versions of GravityRAT in the apps:
WeShare
TrustX
Click2Chat
Bollywood
New versions of GravityRAT
All sites that distribute malware examined below are hidden behind Cloudflare to make it hard to determine the real IP.
.NET versions
Sharify
MelodyMate (signed by E-Crea Limited on 11.05.2019)
Python version
GoZap
Another PyInstaller container. Note that the code explicitly mentions the names of the potential payload already familiar to us:
Depending on the specific payload, the destination directory is selected, as well as the name of the task for Windows Task Scheduler:
Payload Name Path Task Name
ZW %APPDATA%\Programs WinUpdate
SMTPHost %APPDATA%\WinUpdates Disksynchronization
WCNsvc %APPDATA%\System Windows_startup_update
CSRP %APPDATA%\Applications Antivirus_Update
Windows-Portable-Devices %APPDATA%\ System Updates System_Update
Electron versions
The following versions are multiplatform for Windows and Mac based on the Electron framework. The logic is as before: the Trojan checks if it is running on a virtual machine, collects information about the computer, downloads the payload from the server, and adds a scheduled task.
StrongBox (signed by E-Crea Limited on 11.20.2019)
TeraSpace (signed by E-Crea Limited on 11.20.2019)
OrangeVault
CvStyler (signed by E-Crea Limited 02.20.2020)
Android versions
SavitaBhabi exists for Windows and Android.
The Windows version is based on .NET. The functionality is standard: the Trojan checks if it is running on a virtual machine and if security software is installed on the computer, transmits information about the computer to the server, and receives commands in response. It uses Windows Task Scheduler to launch the payload. Communication with the server is through POST requests to download.savitabhabi.co[.]in/A5739ED5.php.
The second file, downloaded from the same site, is the Android app Savitabhabi.apk, which is an adult comic strip with an embedded spyware module. Unlike the Travel Mate Pro version, this time it seems that the cybercriminals took a bottom-up approach and wrote the app themselves.
The app requests suspicious permissions at startup
The malicious functionality of this Android app is identical to that of Travel Mate Pro; the C&C addresses and code (save for minor details) also coincide:
List of Trojan classes
Conclusion
In 2019, The Times of India published an article about the cybercriminal methods used to distribute GravityRAT during the period 2015-2018. Victims were contacted through a fake Facebook account, and asked to install a malicious app disguised as a secure messenger in order to continue the conversation. Around 100 cases of infection of employees at defense, police, and other departments and organizations were identified.
It is safe to assume that the current GravityRAT campaign uses similar infection methods — targeted individuals are sent links pointing to malicious apps.
The main modification seen in the new GravityRAT campaign is multiplatformity: besides Windows, there are now versions for Android and macOS. The cybercriminals also started using digital signatures to make the apps look more legitimate.
IoCs
MD5
Travel Mate Pro — df6e86d804af7084c569aa809b2e2134
iV.dll — c92a03ba864ff10b8e1ff7f97dc49f68
enigma.exe — b6af1494766fd8d808753c931381a945
Titanium — 7bd970995a1689b0c0333b54dffb49b6
Wpd.exe — 0c26eb2a6672ec9cd5eb76772542eb72
Taskhostex.exe — 0c103e5d536fbd945d9eddeae4d46c94
WCNsvc.exe — cceca8bca9874569e398d5dc8716123c
SMTPHost.exe — 7bbf0e96c8893805c32aeffaa998ede4
CSRP.exe — e73b4b2138a67008836cb986ba5cee2f
Chat2Hire.exe — 9d48e9bff90ddcae6952b6539724a8a3
AppUpdater.exe — 285e6ae12e1c13df3c5d33be2721f5cd
Xray.exe — 1f484cdf77ac662f982287fba6ed050d
ZW.exe — c39ed8c194ccf63aab1db28a4f4a38b9
RW.exe — 78506a097d96c630b505bd3d8fa92363
TW.exe — 86c865a0f04b1570d8417187c9e23b74
Whisper — 31f64aa248e7be0be97a34587ec50f67
WeShare —e202b3bbb88b1d32dd034e6c307ceb99
TrustX — 9f6c832fd8ee8d8a78b4c8a75dcbf257
Click2Chat — defcd751054227bc2dd3070e368b697d
Bollywood — c0df894f72fd560c94089f17d45c0d88
Sharify — 2b6e5eefc7c14905c5e8371e82648830
MelodyMate — ee06cfa7dfb6d986eef8e07fb1e95015
GoZap — 6689ecf015e036ccf142415dd5e42385
StrongBox — 3033a1206fcabd439b0d93499d0b57da (Windows), f1e79d4c264238ab9ccd4091d1a248c4 (Mac)
TeraSpace — ee3f0db517f0bb30080a042d3482ceee (Windows), 30026aff23b83a69ebfe5b06c3e5e3fd (Mac)
OrangeVault — f8da7aaefce3134970d542b0e4e34f7b (Windows), 574bd60ab492828fada43e88498e8bd2 (Mac)
CvStyler — df1bf7d30a502e6388e2566ada4fe9c8
SavitaBhabi — 092e4e29e784341785c8ed95023fb5ac (Windows), c7b8e65e5d04d5ffbc43ed7639a42a5f (Android)
URLs
daily.windowsupdates[.]eu
nightly.windowsupdates[.]eu
dailybuild.mozillaupdates[.]com
nightlybuild.mozillaupdates[.]com
u01.msoftserver[.]eu
u02.msoftserver[.]eu
u03.msoftserver[.]eu
u04.msoftserver[.]eu
n1.nortonupdates[.]online
n2.nortonupdates[.]online
n3.nortonupdates[.]online
n4.nortonupdates[.]online
sake.mozillaupdates[.]us
gyzu.mozillaupdates[.]us
chuki.mozillaupdates[.]us
zen.mozillaupdates[.]us
ud01.microsoftupdate[.]in
ud02.microsoftupdate[.]in
ud03.microsoftupdate[.]in
ud04.microsoftupdate[.]in
chat2hire[.]net
wesharex[.]net
click2chat[.]org
x-trust[.]net
bollywoods[.]co[.]in
enigma[.]net[.]in
titaniumx[.]co[.]in
sharify[.]co[.]in
strongbox[.]in
teraspace[.]co[.]in
gozap[.]co[.]in
orangevault[.]net
savitabhabi[.]co[.]in
melodymate[.]co[.]in
cvstyler[.]co[.]in
New Emotet campaign uses a new ‘Windows Update’ attachment
19.10.20 Virus Securityaffairs
After a short pause, a new Emotet malware campaign was spotted by the experts on October 14th, crooks began using a new ‘Windows Update’ attachment.
After a short interruption, a new Emotet malware campaign was spotted by the experts in October. Threat actors began using new Windows Update attachments in a spam campaign aimed at users worldwide.
The spam campaign uses a new malicious attachment that pretends to be a message from Windows Update and attempts to trick the victims recommending to upgrade Microsoft Word.
The Emotet banking trojan has been active at least since 2014, the botnet is operated by a threat actor tracked as TA542. In the middle-August, the malware was employed in fresh COVID19-themed spam campaign
Recent spam campaigns used messages with malicious Word documents, or links to them, pretending to be an invoice, shipping information, COVID-19 information, resumes, financial documents, or scanned documents.
The infamous banking trojan is also used to deliver other malicious code, such as Trickbot and QBot trojan or ransomware such as Conti (TrickBot) or ProLock (QBot).
Emotet is a modular malware, its operators could develop new Dynamic Link Libraries to update its capabilities.
Recently, the Cybersecurity and Infrastructure Security Agency (CISA) issued an alert to warn of a surge of Emotet attacks that have targeted multiple state and local governments in the U.S. since August.
During that time, the agency’s EINSTEIN Intrusion Detection System has detected roughly 16,000 alerts related to Emotet activity.
The new campaign was observed on October 14th, the attackers are using multiple lures, including invoices, purchase orders, shipping information, COVID-19 information, and information about President Trump’s health.
The spam messages come with malicious Word (.doc) attachments or include links to download the bait document.
Upon opening the attachments users are instructed to ‘Enable Content,’ in this way the malicious macros will be executed starting the infection process.
“To trick users into enabling the macros, Emotet uses various document templates, including pretending to be created on iOS devices, Windows 10 Mobile, or that the document is protected.” reported BleepingComputer.
The recent campaign employed a new template that pretends to be a message from Windows Update urging the update of Microsoft Word to correctly view the document.
Below the message displayed to the users:
Windows Update
Some apps need to be updated
These programs need to be upgrade because they aren't compatible with this file format.
* Microsoft Word
You need to click Enable Editing and then click Enable Content.
Researchers recommend sharing knowledge about malicious document templates used by Emotet in order to quickly identify them and avoid being infected.
FIN11 gang started deploying ransomware to monetize its operations
19.10.20 Ransomware Securityaffairs
The financially-motivated hacker group FIN11 has started spreading ransomware to monetize its cyber criminal activities.
The financially-motivated hacker group FIN11 has switched tactics starting using ransomware as the main monetization method.
The group carried out multiple high-volume operations targeting companies across the world, most of them in North America and Europe.
In recent attacks, the group was observed deploying the Clop ransomware into the networks of its victims.
Since August, FIN11 started targeting organizations in many industries, including defense, energy, finance, healthcare, legal, pharmaceutical, telecommunications, technology, and transportation.
Researchers from FireEye’s Mandiant observed FIN11 hackers using spear-phishing messages distributing a malware downloader dubbed FRIENDSPEAK.
“Recently, FIN11 has deployed CLOP ransomware and threatened to publish exfiltrated data to pressure victims into paying ransom demands.” reads the analysis published by FireEye. “The group’s shifting monetization methods—from point-of-sale (POS) malware in 2018, to ransomware in 2019, and hybrid extortion in 2020—is part of a larger trend in which criminal actors have increasingly focused on post-compromise ransomware deployment and data theft extortion.”
The attack chain starts when the victims enable the macro embedded in an Excel spreadsheet that came with the phishing e-mails.
The macros download and execute the FRIENDSPEAK code, which in turn downloads the MIXLABEL malware.
Experts also reported that the threat actor modified the macros in Office documents used as bait and also added geofencing techniques.
Mandiant researchers highlighted an important with operations conducted by the TA505 cybercrime gang (aka Evil Corp), which has been active since 2014 focusing on retail and banking sectors.
TA505 also deployed the Clop ransomware in its malware campaigns and recently started exploiting the ZeroLogon critical flaw to compromise targeted organizations.
“Attribution of both historic TA505 activity and more recent FIN11 activity is complicated by the actors’ use of criminal service providers. Like most financially motivated actors, FIN11 doesn’t operate in a vacuum. We believe that the group has used services that provide anonymous domain registration, bulletproof hosting, code signing certificates, and private or semi-private malware.” reads the analysis. “Outsourcing work to these criminal service providers likely enables FIN11 to increase the scale and sophistication of their operations.”

The experts pointed out that the FIN11 actors after dropped the Clop ransomware did not abandon the target after losing access, at least in one case they re-compromised the target organization a few months later.
The researchers believe FIN11 operates from the Commonwealth of Independent States (CIS – former Soviet Union countries).
The experts observed Russian-language file metadata in the code of the malware and reported that the Clop ransomware was only deployed on machines with a keyboard layout used outside CIS countries.
Mandiant researchers speculate FIN11 will continue to target organizations with sensitive proprietary data and that will likely pay the ransom to recover their operations after the attacks.
Microsoft released out-of-band Windows fixes for 2 RCE issues
19.10.20 Vulnerebility Securityaffairs
Microsoft released two out-of-band security updates to address remote code execution (RCE) bugs in the Microsoft Windows Codecs Library and Visual Studio Code.
Microsoft has released two out-of-band security updates to address two remote code execution (RCE) vulnerabilities that affect the Microsoft Windows Codecs Library and Visual Studio Code.
The two vulnerabilities, tracked as CVE-2020-17022 and CVE-2020-17023, have been rated as important severity.
The CVE-2020-17022 is a remote code execution vulnerability that exists in the way that Microsoft Windows Codecs Library handles objects in memory. An attacker can exploit the vulnerability to execute arbitrary code.
“Exploitation of the vulnerability requires that a program process a specially crafted image file.” reads the advisory. “The update addresses the vulnerability by correcting how Microsoft Windows Codecs Library handles objects in memory.”
The CVE-2020-17022 vulnerability affects all devices running Windows 10, version 1709 or later, and a vulnerable library version.
Windows 10 devices are not affected in their default configuration and that “only customers who have installed the optional HEVC or ‘HEVC from Device Manufacturer’ media codecs from Microsoft Store may be vulnerable.”
The CVE-2020-17022 flaw was reported to Microsoft by Dhanesh Kizhakkinan from FireEye.
The CVE-2020-17023 vulnerability is a remote code execution vulnerability that exists in Visual Studio Code. An attacker can trigger the flaw by tricking a user into opening a malicious ‘package.json’ file, then he could run arbitrary code in the context of the current user.
“If the current user is logged on with administrative user rights, an attacker could take control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.” reads the advisory.
“To exploit this vulnerability, an attacker would need to convince a target to clone a repository and open it in Visual Studio Code. Attacker-specified code would execute when the target opens the malicious ‘package.json’ file. The update address the vulnerability by modifying the way Visual Studio Code handles JSON files.”
The CVE-2020-17023 vulnerability was reported by Justin Steven.
The IT giant did not provide any mitigating measures or workarounds for the two vulnerabilities.
According to Microsoft, both vulnerabilities are not being exploited in the wild.
Iran-linked Silent Librarian APT targets universities again
19.10.20 APT Securityaffairs
Iran-linked cyberespionage group Silent Librarian has launched a new phishing campaign aimed at universities around the world.
Iran-linked APT group Silent Librarian has launched another phishing campaign targeting universities around the world.
The Silent Librarian, also tracked as Cobalt Dickens and TA407, targeted tens of universities in four continents in the last couple of years.
In August 2018, the security firm SecureWorks uncovered a phishing campaign carried out by the APT group targeting universities worldwide. The operation involved sixteen domains hosting more than 300 spoofed websites for 76 universities in 14 countries, including Australia, Canada, China, Israel, Japan, Switzerland, Turkey, the United Kingdom, and the United States.
Since mid-September, researchers from Malwarebytes observed a new spear-phishing campaign carried out by the group that is expanding its target list to include more countries.
Silent Librarian hackers targeted both employees and students at the universities, experts noticed that the threat actor set up a new infrastructure to avoid a takeover.
“Considering that Iran is dealing with constant sanctions, it strives to keep up with world developments in various fields, including that of technology. As such, these attacks represent a national interest and are well funded,” states Malwarebytes. “The new domain names follow the same pattern as previously reported, except that they swap the top level domain name for another.”
The threat actor used domain names following a pattern observed in past campaigns, although they use a different top-level domain name (the “.me” TLD instead of “.tk” and “.cf”).

The hackers use Cloudflare for phishing hostnames in an attempt to hide the real hosting origin. Anyway, Malwarebytes was able to identify some of the infrastructure which was located in Iran, likely because it is considered a bulletproof hosting option due to the lack of cooperation between US and European law enforcement and local police in Iran.
“Clearly we only uncovered a small portion of this phishing operation. Although for the most part the sites are taken down quickly, the attacker has the advantage of being one step ahead and is going for many possible targets at once,” Malwarebytes concludes.
The security firm also published Indicators of Compromise (IoCs) for this campaign.
QQAAZZ crime gang charged for laundering money stolen by malware gangs
19.10.20 CyberCrime Securityaffairs
Multiple members of QQAAZZ multinational cybercriminal gang were charged for providing money-laundering services to high-profile malware operations.
20 members of the multinational cybercriminal group QQAAZZ were charged this week in the US, Portugal, Spain, and the UK for providing money-laundering services.
The arrests are the result of an unprecedented international law enforcement operation, coordinated by the Europol and dubbed Operation 2BaGoldMule, involving agencies from 16 countries. The police executed more than 40 house searches in Latvia, Bulgaria, the United Kingdom, Spain, and Italy.
The police also seized an extensive bitcoin mining operation in Bulgaria associated with QQAAZZ.
According to law enforcement bodies, the gang provides services to multiple malware operations, including Dridex, GozNym, and Trickbot.
QQAAZZ attempted to launder tens of millions stolen from victims starting with 2016 by the world’s foremost cybercriminals.
“Comprised of several layers of members mainly from Latvia, Georgia, Bulgaria, Romania, and Belgium, the QQAAZZ network opened and maintained hundreds of corporate and personal bank accounts at financial institutions throughout the world to receive money from cybercriminals who stole it from accounts of victims.” reads the press release published by Europol. “The funds were then transferred to other QQAAZZ-controlled bank accounts and sometimes converted to cryptocurrency using ‘tumbling’ services designed to hide the original source of the funds. After taking a fee of up to 50-percent, QQAAZZ returned the balance of the stolen funds to their cybercriminal clientele.”
The QQAAZZ gang advertised its services as a ‘global, complicit bank drops service’ on multiple Russian-speaking online cybercriminal forums.

The member of the gang used instant messaging apps to instruct their client on how to transfer the stolen funds to bank accounts under their control. The bank accounts were opened by money mules using fake and legitimate Polish and Bulgarian ID documents.
QQAAZZ also leverages dozens of shell companies to open other bank accounts.
The money laundering operation involved hundreds of corporate and personal bank accounts at financial institutions throughout the world.
Some of the money was also “converted to cryptocurrency using ‘tumbling’ services designed to hide the original source of the funds.”
“The funds were then transferred to other QQAAZZ-controlled bank accounts and sometimes converted to cryptocurrency using “tumbling” services designed to hide the original source of the funds.” states the DoJ. “After taking a fee of up to 40 to 50 percent, QQAAZZ returned the balance of the stolen funds to their cybercriminal clientele.”
“Cybercriminals are constantly exploring new possibilities to abuse technology and financial frameworks to victimise millions of users in a moment from anywhere in the world,” said Edvardas Šileris, Head of Europol’s European Cybercrime Centre.
“Today’s operation shows how through a proper law enforcement international coordination we can turn the table on these criminals and bring them to justice.”
Four npm packages found opening shells and collecting info on Linux, Windows systems
18.10.20 Security Securityaffairs
On Thursday, four JavaScript packages have been removed from the npm portal because they have been found containing malicious code.
NPM staff removed four JavaScript packages from the npm portal because were containing malicious code. Npm is the largest package repository for any programming language.
The four packages, which had a total of one thousand of downloads, are:
plutov-slack-client
nodetest199
nodetest1010
npmpubman
“Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer,” the npm security team said.
“The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it,”
The researcher AX Sharma, who analyzed the packages, revealed that plutov-slack-client, nodetest1010, and nodetest199 share identical code.
Experts warn that systems running applications that imported one of these packages should be potentially compromised because the three JavaScript libraries opened web shells on the computers running them.
A web shell is a code, often written in typical web development programming languages (e.g., ASP, PHP, JSP), that attackers implant on web servers to gain remote access and code execution.
The npmpubman, unlike the other packages, was found collecting user data from the environment variables and uploads the gathered info to a remote host.
The malicious code could work on both Windows and *nix operating systems, including major distros, including Linux, FreeBSD, OpenBSD.
One of the packages was uploaded on the npm portal in May, while the remaining ones were uploaded in September 2018.
“It is possible that all four packages were authored by the same attacker(s) despite conflicting data provided in the package.json manifests.” reported Bleeping Computer.
“In a real-world scenario, npmpubman could be used as a part of an attacker’s reconnaissance efforts to collect information about a system, whereas the other packages establish a direct connection between the attacker’s and the victim’s computers.”
In August, the npm security team has removed the JavaScript library “fallguys” from the npm portal because it was containing a malicious code used to steal sensitive files from an infected users’ browser and Discord application.
Google warned users of 33,015 nation-state attacks since January
18.10.20 Attack Securityaffairs
Google delivered over 33,000 alerts to its users during the first three quarters of 2020 to warn them of attacks from nation-state actors.
Google delivered 33,015 alerts to its users during the first three quarters of 2020 to warn them of phishing attacks, launched by nation-state actors, targeting their accounts.
Google sent 11,856 government-backed phishing warnings during Q1 2020, 11,023 in Q2 2020, and 10,136 in Q3 2020.
Shane Huntley, Director at Google’s Threat Analysis Group (TAG), revealed that her team has shared its findings with the campaigns and the Federal Bureau of Investigation.
The IT giant pointed out that major events like elections and COVID-19 represent opportunities for threat actors.
The trend in the nation-state attacks is consistent with what others have subsequently reported.

“Overall, we’ve seen increased attention on the threats posed by APTs in the context of the U.S. election. U.S government agencies have warned about different threat actors, and we’ve worked closely with those agencies and others in the tech industry to share leads and intelligence about what we’re seeing across the ecosystem.” reads the report published by Google TAG.
Since last summer, TAG team has tracked a large spam network linked to China that is running an influence operation on multiple platforms, primarily on YouTube. The threat actor behind this campaign was primarily acquiring or hijacking existing accounts and using them to spread content crafted for their intent.
According to Google, the alerts are shown to up to 0.1% of all Gmail accounts. The company’s alert advises Gmail users to take several measures to secure their accounts, such as enrolling in the Advanced Protection Program, keeping software up to date, enabling Gmail 2-step verification, as well as using Google Authenticator and/or a physical security key for 2-step verification.
As the course of the COVID-19 pandemic evolves, Google experts warn of threat actors evolving their tactics as well. During the last summer, Google observed threat actors from China, Russia, and Iran targeting pharmaceutical companies and researchers involved in the development of a vaccine.
In September, Google experts started to observe attacks carried out by multiple North Korea-linked APT groups aimed at COVID-19 researchers and pharmaceutical companies, especially those based in South Korea.
This week, the Google Cloud team revealed that in September 2017 it has mitigated DDoS attack that reached 2.54 Tbps, the largest DDoS attack of ever.
This attack is the largest DDoS attack recorded to date and according to a report published by the Google Threat Threat Analysis Group (TAG) it was carried out by a state-sponsored threat actor.
Dickey’s BBQ Breach: Meaty 3M Payment Card Upload Drops on Joker’s Stash
17.10.20 Incindent Threatpost
After cybercriminals smoked out 3 million compromised payment cards on the Joker’s Stash marketplace, researchers linked the data to a breach at the popular barbecue franchise.
Popular U.S. smoked-meat franchise Dickey’s Barbecue Pit has been hit with a data breach, with cybercriminals posting the fat cap of the compromised data – 3 million payment cards – on the popular Joker’s Stash underground marketplace this week.
The Dallas-based franchise, which is a subsidiary of Dickey’s Capital Group, has 469 locations (411 of which are currently open during the pandemic) across 42 states. Researchers believe that the meat of the compromised data came from 156 of these locations across 30 states. They also believe the exposure window appears to be between July 2019 and August 2020.
In a statement sent to Threatpost, Dickey’s confirmed the breach and said it is currently focused on determining the locations affected and time frames involved.17.10.20
“We are taking this incident very seriously and immediately initiated our response protocol and an investigation is underway,” according to the statement. “We are utilizing the experience of third parties who have helped other restaurants address similar issues and also working with the FBI and payment card networks. We understand that payment card network rules generally provide that individuals who timely report unauthorized charges to the bank that issued their card are not responsible for those charges.”

The affected Dickey’s locations. Credit: Gemini Research
Researchers with Gemini Advisory shed light on the details of the breach when they discovered the upload on the Joker’s Stash, a popular underground destination that specializes in trading in payment-card data. This marketplace is known for advertising and uploading major breaches containing millions of compromised cards, including the Wawa breach – which dropped 30 million payment cards – from January.
Researchers said they observed the marketplace administrator setting the compromised data live on Oct. 12. The administrators claimed the breached data, which they called BLAZINGSUN, is comprised of 3 million compromised cards with a median price of $17 per card.
Gemini Advisory researchers claim that payment transactions of the franchise may have been processed on point-of-sale (PoS) systems via the outdated magnetic stripe card method – which they said is prone to malware attacks.
Security experts have advocated for retailers to switch over to chip-card readers, which contain an embedded microprocessor that encrypts the card data, implement the EMV standard (which stands for Europay, MasterCard and Visa, and is a global standard for chip cards’ compatibility with point-of-sale terminals), and are in theory a more secure alternative to magnetic stripe cards.
“It remains unclear if the affected restaurants were using outdated terminals or if the EMV terminals were misconfigured; either of these possibilities may hold serious liability for Dickey’s,” researchers said.
Another piece of the equation is that because Dickey’s operates on a franchise model, each location may have been able to dictate the type of POS device and processors that they utilize – so some locations may be affected by the breach, while others may not be, said researchers.
“However, given the widespread nature of the breach, the exposure may be linked to a breach of the single central processor, which was leveraged by over a quarter of all Dickey’s locations,” said researchers. “The current exposure by location does not exactly align with the restaurant’s distribution across states, although with the exception of Texas, which hosts 123 restaurant locations but only three compromised locations, the exposure is approximately reflective of the overall distribution.”
Dickey’s did not provide any further information on the cause of the breach when reached out to by Threatpost.
Warren Poschman, senior solutions architect with data-security specialist comforte AG, said that store merchants need to require the use of secure connections – from the PoS device to the backend – using point-to-point encryption and tokenization. Backend payment processors (and the merchants that outsource to them) must also tokenize all data to ensure that any breach will not result in exposure, he stressed.
“As the breach at Dickey’s BBQ reminds us, there is still plenty of meat left on the bone of credit card fraud despite the dramatic shift in coverage to privacy and identity theft,” he said. “With COVID-19 pushing businesses in the fast casual restaurant segment to the brink, attackers are taking advantage of lax security while many are in survival mode. Regardless of the ill timing, organizations need to ensure that every step in the payment cycle is secured from acquisition to settlement.”
It’s not the first security incident for Dickey’s, which experienced a ransomware attack in 2015 with a $6,000 extortion demand. Gemini Advisory researchers said, based on previous major breaches uploaded to Joker’s Stash, the records from Dickey’s Barbecue Pit will likely continue to be added to this marketplace over several months. Regardless, the incident shows that PoS security issues continue to pose a threat to merchants, they said.
“This represents a broader challenge for the industry, and Dickey’s may become the latest cautionary tale of facing lawsuits in addition to financial damage from cybersecurity attacks,” they said.
Critical Magento Holes Open Online Shops to Code Execution
17.10.20 Vulnerebility Threatpost
Adobe says the two critical flaws (CVE-2020-24407 and CVE-2020-24400) could allow arbitrary code execution as well as read or write access to the database.
Two critical flaws in Magento – Adobe’s e-commerce platform that is commonly targeted by attackers like the Magecart threat group – could enable arbitrary code execution on affected systems.
Retail is set to boom in the coming months – between this week’s Amazon Prime Day and November’s Black Friday – which puts pressure on Adobe to rapidly patch up any holes in the popular Magento open-source platform, which powers many online shops.
The company on Thursday disclosed two critical flaws, six important-rated errors and one moderate-severity vulnerability plaguing both Magento Commerce (which is aimed at enterprises that need premium support levels, and has a license fee starting at $24,000 annually) and Magento Open Source (its free alternative).17.10.20
The most severe of these include a vulnerability that allows for arbitrary code execution. The issue stems from the application not validating full filenames when using an “allow list” method to check the file extensions. This could enable an attacker to bypass the validation and upload a malicious file. In order to exploit this flaw (CVE-2020-24407), attackers would not need pre-authentication (meaning the flaw is exploitable without credentials) – however, they would need administrative privileges.
The other critical flaw is an SQL injection vulnerability. This is a type of web security flaw that allows an attacker to interfere with the queries that an application makes to its database. An attacker without authentication – but also with administrative privileges – could exploit this bug in order to gain arbitrary read or write access to a database.
Adobe also issued patches for various important improper-authorization vulnerabilities, which occur when an application does not properly check that a user is authorized to access functionality — which could ultimately expose data. These include a flaw that could allow unauthorized modification of Magento content management system (CMS) pages (CVE-2020-24404), one that could enable the unauthorized modification of an e-commerce business customer list (CVE-2020-24402) and two that could allow for unauthorized access to restricted resources (CVE-2020-24405 and CVE-2020-24403).
Another important vulnerability stems from an insufficient validation of a User Session, which could give an attacker unauthorized access to restricted resources (CVE-2020-24401).
For all of the flaws above, an attacker would need to have administrative privileges, but wouldn’t need pre-authentication to exploit the flaw, according to Adobe.
Finally, an important-severity cross-site scripting flaw (CVE-2020-24408) was also addressed, which could allow for arbitrary JavaScript execution in the browser. To exploit this, an attacker wouldn’t need administrative privileges, but they would need credentials.
Specifically affected are Magento Commerce, versions 2.3.5-p1 and earlier and 2.4.0 and earlier; as well as Magento Open Source, versions 2.3.5-p1 and earlier and 2.4.0 and earlier. Adobe has issued patches (below) in Magento Commerce and Magento Open Source versions 2.4.1 and 2.3.6, and “recommends users update their installation to the newest version.”

The update for all vulnerabilities is a priority 2, meaning they exist in a product that has historically been at elevated risk – but for which there are currently no known exploits.
“Based on previous experience, we do not anticipate exploits are imminent. As a best practice, Adobe recommends administrators install the update soon (for example, within 30 days),” according to the firm.
Indeed, Magento has had its share of security flaws over the past year. In July, Adobe fixed two critical vulnerabilities and two important-severity flaws that could have enabled code execution and a signature-verification bypass. And in April, Adobe patched several critical flaws in Magento, which if exploited could lead to arbitrary code execution or information disclosure.
The issue also comes after Magento 1 reached end-of-life (EOL) in June, with Adobe making a last-ditch effort to urge the 100,000 online stores still running the outdated version to migrate to Magento 2. E-commerce merchants must migrate to Magento 2, which was released five years ago.
Phishers Capitalize on Headlines with Breakneck Speed
17.10.20 Phishing Threatpost
Marking a pivot from COVID-19 scams, researchers track a single threat actor through the evolution from the pandemic to PayPal, and on to more timely voter scams — all with the same infrastructure.
The speed with which phishers are able to adapt to new messaging based on the latest headlines is accelerating, according to the Proofpoint Threat Research Team, which was able to track backend data from a recent voter-registration scam to uncover just how quickly cybercriminals can pivot to capitalize on current events. It turns out, all it takes to launch a potent phishing scam is a new wrapper.
“The range of information credential-phishing themes — PayPal, COVID-19, voting — illustrate how actors often simply pivot from one theme to the next, all while using similar (often the same) infrastructure and backend functionality,” Sherrod DeGrippo, senior director of threat research and detection for Proofpoint, told Threatpost. “It’s clear that threat actors are continuing to try and reach as many intended recipients as possible by capitalizing on a popular topic. We’ve seen throughout the global COVID-19 situation that threat actors are able to adjust quickly to timely news and current events.”
A recent voter registration scheme, first discovered by KnowBe4, sent emails out telling voters their registration information was incomplete. The logos in the communications were from the U.S. Election Assistance Commission (EAC), leading them to a fraudulent page asking them for their personal data.
Tracking Phishing Kit Data
By tracking data from phishing kits, which are easy, one-stop packages for phishing, the Proofpoint Threat Research Team found a trail of scams, all connected to the same infrastructure, with little more than a messaging swap differentiating them.
“Phishkits can be highly technical or not very sophisticated, but they have been evolving slowly over time to offer more features and capabilities,” DeGrippo said by email. “Phishkits are traded, sold and given away for free in various forums.”
Tracking phishing kit data isn’t new, but the Proofpoint team noticed that the same infrastructure was being used to support various scams, making it easy to lure in as many victims as possible.
“The major changes observed are in branding only – the actor continues to use similar [user-interface] elements and backend code, evidenced by the POST of user-supplied information to the same email address across multiple information-phishing operations,” according to Proofpoint’s findings, issued this week.
Evolution of a Phishing Scam
In the voter-registration scam, which blasted out hundreds of typo-ridden phishing emails through SendGrid, the message posed as an official communication and asked recipients to “confirm” their details. One clicked, the link led to what the report said is a “compromised WordPress install,” impersonating the Arizona voter-registration system, ServiceArizona.
Phishing page. Source: Proofpoint
A search of the phishing kit data led to an email address, obiri409[@]gmail[.]com, which researchers were able to follow to other sites that this fraudster used in scams of the past, including a previous PayPal account-verification phishing lure.
From there they tracked the same criminals to a different October voter-registration messaging approach, branding the pages with the EAC logo instead of the Maricopa County government logo, asking for everything from Social Security numbers to tax IDs.
“…and though we were unable to capture POST data for this page, the striking similarity in both the look of the page and use of a compromised WordPress install suggests that it is the same threat actor,” the report added.
Phishing Flavors
It’s safe to expect new fraud schemes rapidly coming into circulation related to recent headlines, according to Proofpoint. Already in October, several major campaigns have launched centered on news hooks. The president’s COVID-19 diagnosis, the Democratic National Committee and other recent news lures have also been used as cover for recent fraud schemes, according to Proofpoint.
The deadline for Americans to file for coronavirus relief is approaching and criminals hatched a scheme to get people to serve up their personal information for the promised of a check, for instance. In another case, a recent announcement by Facebook that it was awarding $100 million in grants for small businesses sparked a round of attacks, luring users through Telegram and WhatsApp with the promise of easy money.
And, unsurprisingly, Amazon Prime Day was a field day for fraud, with attempts to dupe unsuspecting bargain hunters.
Fads and headlines come and go, which is why smart cybercriminals have learned to quickly adapt to the latest hot topics to keep their attacks fresh and relatively obscured by news traffic spikes. The challenge for the security community is to stay one step ahead of the next rebranding of the same old social-engineering tactics.
“The last messages we observed from this actor using voter-registration themes were sent on October 7,” Proofpoint added. “This suggests that the actor may have already shifted to another type of lure.”
Microsoft Fixes RCE Flaws in Out-of-Band Windows Update
17.10.20 Vulnerebility Threatpost
The two important-severity flaws in Microsoft Windows Codecs Library and Visual Studio Code could enable remote code execution.
Microsoft has issued out-of-band patches for two “important” severity vulnerabilities, which if exploited could allow for remote code execution.
One flaw (CVE-2020-17023) exists in Microsoft’s Visual Studio Code is a free source-code editor made by Microsoft for Windows, Linux and macOS. The other (CVE-2020-17022) is in the Microsoft Windows Codecs Library; the codecs module provides stream and file interfaces for transcoding data in Windows programs.
“Microsoft has released security updates to address remote code execution vulnerabilities affecting Windows Codecs Library and Visual Studio Code,” according to a Friday CISA alert on the patches. “An attacker could exploit these vulnerabilities to take control of an affected system.”17.10.20
According to Microsoft, one “important” severity flaw (CVE-2020-17022) stems from the way that Microsoft Windows Codecs Library handles objects in memory. This vulnerability has a CVSS score of 7.8 out of 10.
An attacker who successfully exploited the vulnerability could execute arbitrary code, according to Microsoft. While an attacker could be remote to launch the attack, exploitation requires that a program process a specially crafted image file.
Only customers who have installed the optional HEVC or “HEVC from Device Manufacturer” media codecs from Microsoft Store may be vulnerable. The secure Microsoft installed packed versions are 1.0.32762.0, 1.0.32763.0, and later.
“The update addresses the vulnerability by correcting how Microsoft Windows Codecs Library handles objects in memory,” according to Microsoft.
The other “important” severity flaw (which also has a CVSS score of 7.8 out of 10) exists in Visual Studio Code, when a user is tricked into opening a malicious ‘package.json’ file.
According to Microsoft, an attacker who successfully exploited this flaw (CVE-2020-17023) could run arbitrary code in the context of the current user. An attacker would first need to convince a target to clone a repository and open it in Visual Studio Code (via social engineering or otherwise). The attacker’s malicious code would execute when the target opens the malicious ‘package.json’ file.
“If the current user is logged on with administrative user rights, an attacker could take control of the affected system,” said Microsoft. “An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.”
Microsoft’s update addresses the vulnerability by modifying the way Visual Studio Code handles JSON files.
In a Twitter thread, Justin Steven, who reported the flaw, said that the issue stems from a bypass of a previously deployed patch for an RCE flaw in Visual Studio Code (CVE-2020-16881).
Neither flaw has been observed being exploited in the wild according to Microsoft. Microsoft also did not offer mitigations or workarounds for other flaws – but updates will be automatically installed for users.
“Affected customers will be automatically updated by Microsoft Store,” according to Microsoft. “Customers do not need to take any action to receive the update.”
The fixes come days after Microsoft’s October Patch Tuesday updates, during which it released fixes for 87 security vulnerabilities, 11 of them critical – and one potentially wormable.
In the case of these bugs, “servicing for store apps/components does not follow the monthly ‘Update Tuesday’ cadence, but are offered whenever necessary,” according to Microsoft.
Biden Campaign Staffers Targeted in Cyberattack Leveraging Antivirus Lure, Dropbox Ploy
17.10.20 BigBrothers Threatpost
Google’s Threat Analysis Group sheds more light on targeted credential phishing and malware attacks on the staff of Joe Biden’s presidential campaign.
Hackers sent Joe Biden’s presidential campaign staffers malicious emails that impersonated anti-virus software company McAfee, and used a mix of legitimate services (such as Dropbox) to avoid detection. The emails were an attempt to steal staffers’ credentials and infect them with malware.
The unsuccessful advanced persistent threat group (APT) attacks on Biden’s campaign were first uncovered in June, along with cyberattacks targeting Donald Trump’s campaign. However, the details of the attacks themselves, and the tactics used, were scant until Google Threat Analysis Group’s (TAG) Friday analysis.
“In one example, attackers impersonated McAfee,” said researchers on Friday. “The targets would be prompted to install a legitimate version of McAfee anti-virus software from GitHub, while malware was simultaneously silently installed to the system.”17.10.20
The campaign was based on email based links that would ultimately download malware hosted on GitHub, researchers said. The malware was specifically a python-based implant using Dropbox for command and control (C2), which once downloaded would allow the attacker to upload and download files and execute arbitrary commands.
Every malicious piece of this attack was hosted on legitimate services – making it harder for defenders to rely on network signals for detection, researchers noted.

The McAfee lure used in the Biden cyberattack. Credit: Google
Google attributed the attack on Biden’s campaign staff to APT 31 (also known as Zirconium). According to reports, this threat actor is tied to the Chinese government.
Beyond staffers on the “Joe Biden for President” campaign, APT 31 has also been targeting “prominent individuals in the international affairs community, academics in international affairs from more than 15 universities,” according to previous Microsoft research.
The threat group’s TTPs include using web “beacons” that are tied to an attacker-controlled domain. The group then sends the URL of the domain to targets via email text (or attachment) and persuades them to click the link via social engineering.
“Although the domain itself may not have malicious content, [this] allows Zirconium [APT 31] to check if a user attempted to access the site,” said Microsoft. “For nation-state actors, this is a simple way to perform reconnaissance on targeted accounts to determine if the account is valid or the user is active.”
On the other side of the coin, the personal email accounts of staffers associated with the “Donald J. Trump for President” campaign have also been targeted by another threat group called APT 35 (also known as Phosphorus and Charming Kitten), which researchers said operates out of Iran. The Iran-linked hacking group has been known to use phishing as an attack vector, and in February was discovered targeting public figures in phishing attacks that stole victims’ email-account information.

Government backed attacker warnings sent in 2020. Credit: Google
However, researchers said the good news is that there’s increased attention on the threats posed by APTs in the context of the U.S. election. Google for its part said it removed 14 Google accounts that were linked to Ukrainian Parliament member Andrii Derkach shortly after the U.S. Treasury sanctioned Derkach for attempting to influence the U.S. elections.
“U.S government agencies have warned about different threat actors, and we’ve worked closely with those agencies and others in the tech industry to share leads and intelligence about what we’re seeing across the ecosystem,” said Google researchers.
With the 2020 U.S. Presidential Election just around the corner, cybersecurity concerns are under the spotlight – including worries about the integrity of voting machines, the expected expansion of mail-in voting due to COVID-19 and disinformation campaigns.
Google mitigated a 2.54 Tbps DDoS attack in 2017, the largest DDoS ever seen
17.10.20 Attack Securityaffairs
The Google Cloud team revealed that in September 2017 it has mitigated DDoS attack that reached 2.54 Tbps, the largest DDoS attack of ever.
The Google Cloud team revealed that back in September 2017 it has mitigated a powerful DDoS attack that clocked at 2.54 Tbps.
This attack is the largest distributed denial of service attack recorded to date.
“Our infrastructure absorbed a 2.5 Tbps DDoS in September 2017, the culmination of a six-month campaign that utilized multiple methods of attack. Despite simultaneously targeting thousands of our IPs, presumably in hopes of slipping past automated defenses, the attack had no impact.” reads the post published by Damian Menscher, a Security Reliability Engineer for Google Cloud.
“The attacker used several networks to spoof 167 Mpps (millions of packets per second) to 180,000 exposed CLDAP, DNS, and SMTP servers, which would then send large responses to us.”

Google researchers pointed out that the attack they mitigated was four times larger than the 623 Gbps attack launched from the Mirai botnet in 2016.
Experts noticed that this attack is bigger than the 2.3 Tbps DDoS attack mitigated by Amazon’s AWS in February.
A report published by the Google Threat Threat Analysis Group (TAG) speculates that the attack was carried out by a state-sponsored threat actor.
“we’ve seen bigger players increase their capabilities in launching large-scale attacks in recent years. For example in 2017, our Security Reliability Engineering team measured a record-breaking UDP amplification attack sourced out of several Chinese ISPs (ASNs 4134, 4837, 58453, and 9394), which remains the largest bandwidth attack of which we are aware.” reads the report published by Google.
Menscher revealed that the attack was part of a campaign that leveraged multiple DDoS amplification methods to hit Google’s servers.
Google decided to disclose the DDoS attack today to warn of an increasing trend of state-sponsored actors abusing DDoS attacks to target online resources.
Experts believe that DDoS attacks are becoming even more dangerous and would intensify in the coming years.
Juniper fixes tens of flaws affecting the Junos OS
17.10.20 Vulnerebility Securityaffairs
Juniper Networks has addressed tens of vulnerabilities, including serious flaws that can be exploited to take over vulnerable systems.
Juniper Networks has addressed tens of vulnerabilities, including serious issues that can be exploited to take control of vulnerable systems.
The vendor has published 40 security advisories related to security vulnerabilities in the Junos OS operating system that runs on Juniper’s firewalls and other third-party components.
The vendor addressed multiple critical flaws in the Juniper Networks Mist Cloud UI. The vulnerabilities affect the Security Assertion Markup Language (SAML) authentication, they could be exploited by a remote attacker to bypass SAML authentication.
“Juniper Networks Mist Cloud UI, when SAML authentication is enabled, may incorrectly handle SAML responses, allowing a remote attacker to bypass SAML authentication security controls.” reads the security advisory published by Juniper.
“If SAML authentication is not enabled, the product is not affected. These vulnerabilities can be exploited alone or in combination. The CVSS score below represents the worst case chaining of these vulnerabilities.”
Multiple vulnerabilities in Juniper Networks Junos OS have been fixed by updating third party software included with Junos OS devices.
Juniper fixed a critical remote code execution vulnerability in Telnet server tracked as CVE-2020-10188.
“A vulnerability in the telnetd Telnet server allows remote attackers to execute arbitrary code via short writes or urgent data, because of a buffer overflow involving the netclear and nextitem functions.” reads the advisory.
“This issue only affects systems with inbound Telnet service enabled. SSH service is unaffected by this vulnerability.”
The company also addressed high-severity denial-of-service (DoS) and arbitrary code execution issues.
The good news is that Juniper is not aware of attacks in the wild exploiting the vulnerabilities.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) also urges organizations to apply the security updates released by the vendor.
“Juniper Networks has released security updates to address vulnerabilities affecting multiple products. An attacker could exploit some of these vulnerabilities to take control of an affected system.” reads alert issued by CISA.
“The Cybersecurity and Infrastructure Security Agency (CISA) encourages users and administrators to review the Juniper Networks security advisories page and apply the necessary updates.”
UK NCSC recommends organizations to fix CVE-2020-16952 SharePoint RCE flaw asap
17.10.20 Vulnerebility Securityaffairs
The U.K. National Cyber Security Centre (NCSC) issued an alert to urge organizations to patch CVE-2020-16952 RCE vulnerability in MS SharePoint Server.
The U.K. National Cyber Security Centre (NCSC) issued an alert to warn of the risks of the exploitation for the CVE-2020-16952 remote code execution (RCE) vulnerability in Microsoft SharePoint Server and urges organizations to address the flaw.
Attackers could exploit this vulnerability to run arbitrary code and execute operations in the context of the local administrator on vulnerable SharePoint servers.
The issue is caused by the improper validation in user-supplied data and can be exploited when a user uploads a specially crafted SharePoint application package to a vulnerable version of SharePoint.
The vulnerability affects Microsoft SharePoint Foundation 2013 Service Pack 1, Microsoft SharePoint Enterprise Server 2016, and Microsoft SharePoint Server 2019, while SharePoint Online as part of Office 365 is not impacted.
“The NCSC strongly advises that organizations refer to the Microsoft guidance referenced in this alert and ensure the necessary updates are installed in affected SharePoint products,” reads the alert. “The NCSC generally recommends following vendor best practice advice in the mitigation of vulnerabilities. In the case of this SharePoint vulnerability, it is important to install the latest updates as soon as practicable.”
The server-side include (SSI) vulnerability CVE-2020-16952 was reported by the researcher Steven Seeley from Qihoo 360 Vulcan Team, who also provided a proof-of-concept exploit for the RCE flaw.
An exploit module for the open-source Metasploit penetration testing framework was also available, it works on SharePoint 2019 on Windows Server 2016.
Security experts recommend applying the October 2020 SharePoint security updates ([1],[2],[3]).
Experts pointed out that SharePoint servers are used in enterprise environments, for this reason, such kind of vulnerabilities is very dangerous.
The UK NCSC confirms that both CVE-2020-16952 and CVE-2015-1641 flaws are included in the list of most exploited vulnerabilities since 2016 published in a joint advisory by the US Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI).
Juniper Networks Patches Tens of Vulnerabilities
17.10.20 Vulnerebility Securityweek
Juniper Networks informed customers this week that it has patched tens of vulnerabilities, including serious issues that can be exploited to take control of affected systems.
Juniper Networks has published 40 security advisories describing vulnerabilities in its Junos OS operating system, which powers the company’s firewalls, and various third-party components.
Several vulnerabilities that have collectively been assigned a critical severity rating have been found in the Juniper Networks Mist Cloud UI. The bugs, related to Security Assertion Markup Language (SAML) authentication, allow a remote attacker to bypass SAML authentication.
Juniper has also informed customers of a critical remote code execution vulnerability affecting the Telnet server used by Junos OS.
The other flaws rated critical affect third-party components, including SQLite and the PyYAML YAML parser.
The company has released over a dozen advisories for high-severity vulnerabilities. Many of these weaknesses can be exploited for denial-of-service (DoS) attacks, but some could allow arbitrary code execution, including by sending specially crafted messages or via cross-site scripting (XSS).
Updates have also been released to address crypto-related issues, including in OpenSSL, and vulnerabilities such as SACK Panic (in Linux kernel) and ZombieLoad variant 2 (in Intel processors).
While Juniper says that it has found no evidence of malicious exploitation, the advisories for some of the flaws do inform users about the public availability of exploits.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has advised organizations to review the Juniper advisories and apply the updates.
Dickey's Barbecue Pit Investigating Possible Breach Affecting 3M Payment Cards
17.10.20 Incindent Securityweek
A data set of millions of payment card records apparently stolen from US-based restaurant franchise Dickey’s Barbecue Pit has emerged on a Dark Web marketplace, Gemini Advisory reports.
The data, posted on the Joker’s Stash underground marketplace, appears to have been harvested from over a hundred compromised locations. The data seems to come from 35 US states and several countries in Europe and Asia.
The data set, which is titled BLAZINGSUN, supposedly contains 3 million payment records, with an average price of $17 per card.
There are 469 locations across 42 states that are operating under the Dickey’s Barbecue Pit franchise, each of them allowed to use the type of point-of-sale (POS) device they like, as well as their preferred processors.
According to Gemini Advisory, the data that emerged on Joker’s Stash suggests that 156 Dickey’s locations across 30 states may have been compromised. The data was supposedly harvested between July 2019 and August 2020.
“Dickey’s operates on a franchise model, which often allows each location to dictate the type of point-of-sale (POS) device and processors that they utilize. However, given the widespread nature of the breach, the exposure may be linked to a breach of the single central processor, which was leveraged by over a quarter of all Dickey’s locations,” Gemini Advisory says.
The security firm also notes that the exposure by location does not exactly align with the restaurant’s distribution across states, although with the exception of Texas, which hosts 123 restaurant locations but only three compromised locations, the exposure is approximately reflective of the overall distribution.
Gemini also says that the payment transactions in this breach were processed via the magstripe method, which is outdated and prone to attacks. However, it’s unclear whether the affected restaurants employed outdated or misconfigured terminals.
“Based on previous Joker’s Stash major breaches, the records from Dickey’s will likely continue to be added to this marketplace over several months,” the security firm notes.
The restaurant chain says it’s aware of a possible data breach and it has launched an investigation.
"We received a report indicating that a payment card security incident may have occurred. We are taking this incident very seriously and immediately initiated our response protocol and an investigation is underway. We are currently focused on determining the locations affected and time frames involved. We are utilizing the experience of third parties who have helped other restaurants address similar issues and also working with the FBI and payment card networks. We understand that payment card network rules generally provide that individuals who timely report unauthorized charges to the bank that issued their card are not responsible for those charges," Dickey's said, responding to a SecurityWeek inquiry.
Almost 800,000 SonicWall VPN appliances online are vulnerable to CVE-2020-5135
16.10.20 Vulnerebility Securityaffairs
The Tripwire VERT security team spotted almost 800,000 SonicWall VPN appliances exposed online that are vulnerable to the CVE-2020-5135 RCE flaw.
Security experts from the Tripwire VERT security team have discovered 795,357 SonicWall VPN appliances that were exposed online that are vulnerable to the CVE-2020-5135 RCE flaw.
“A buffer overflow vulnerability in SonicOS allows a remote attacker to cause Denial of Service (DoS) and potentially execute arbitrary code by sending a malicious request to the firewall. This vulnerability affected SonicOS Gen 6 version 6.5.4.7, 6.5.1.12, 6.0.5.3, SonicOSv 6.5.4.v and Gen 7 version 7.0.0.0.” reads the advisory published by SonicWall.
The CVE-2020-5135 is a stack-based buffer overflow that affects the SonicWall Network Security Appliance (NSA). The vulnerability can be exploited by an unauthenticated HTTP request involving a custom protocol handler.
The flaw resides in the HTTP/HTTPS service used for product management as well as SSL VPN remote access.
“An unskilled attacker can use this flaw to cause a persistent denial of service condition. Tripwire VERT has also confirmed the ability to divert execution flow through stack corruption indicating that a code execution exploit is likely feasible.” reads the analysis published by Tripwire. “This flaw exists pre-authentication and within a component (SSLVPN) which is typically exposed to the public Internet.”
This vulnerability is very dangerous, especially during the COVID-19 pandemic because SonicWall NSA devices are used as firewalls and SSL VPN portals allow employees to access corporate networks.
The vulnerability affects the following versions:
SonicOS 6.5.4.7-79n and earlier
SonicOS 6.5.1.11-4n and earlier
SonicOS 6.0.5.3-93o and earlier
SonicOSv 6.5.4.4-44v-21-794 and earlier
SonicOS 7.0.0.0-1
Security experts from Tenable have published a post detailing the flaw, they also shared Shodan dorks for searching SonicWall VPNs.
“Our own Shodan search for vulnerable SonicWall devices led us to two specific search queries:
product:”SonicWALL firewall http config”
product:”SonicWALL SSL-VPN http proxy”
The combined results from Shodan using these search queries led to a total of 795,674 hosts. In the VERT advisory, they specified that 795,357 hosts were vulnerable.” wrote Tenable.
At the time of this post, the first search query provides 448,400 results, the second one 24,149, most of the vulnerable devices are in the United States.
SonicWall has already released updates to address the flaw, the company also recommends to disconnect SSL VPN portals from the Internet as temporary mitigation before installing one of the following versions:
SonicOS 6.5.4.7-83n
SonicOS 6.5.1.12-1n
SonicOS 6.0.5.3-94o
SonicOS 6.5.4.v-21s-987
Gen 7 7.0.0.0-2 and onwards
The CVE-2020-5135 is a critical vulnerability rated as 9.4 out of 10, it could be easily exploited by unauthenticated attackers.
At the time this post was published, no PoC exploit code was available for the CVE-2020-5135 flaw.
Breach at Dickey’s Barbecue Pit compromises 3 million Cards
16.10.20 Incindent Securityaffairs
Dickey’s Barbecue Pit, the largest barbecue restaurant chain in the US, suffered a POS breach, card details for 3 Million customers were posted online.
Dickey’s Barbecue Pit is a family-owned American barbecue restaurant chain, the company suffered a POS breach and card details of more than three million customers have been posted on the carding portal Joker’s Stash.
The huge trove of payment card data was spotted by researchers from the cyber-security firm Gemini Advisory.
The Joker’s Stash dark web marketplace is one of the most popular carding websites, it is known for advertising and card details from major breaches.
The card details of Dickey’s Barbecue Pit‘s customers were included in a dump titled “BLAZINGSUN.” JokerStash originally claimed that the breach would be available in August, then again in September, and finally it was posted online on October 12.
“Gemini Advisory determined that the compromised point of purchase (CPP) was Dickey’s Barbecue Pit, a US-based restaurant franchise.” reads the post published by Gemini Advisory.
“The advertisement claimed that BLAZINGSUN would contain 3 million compromised cards with both track 1 and track 2 data. They purportedly came from 35 US states and “some” countries across Europe and Asia.”
This BLAZINGSUN breach contains 3 million compromised payment records that are available for a median price of $17 per card.
The experts worked with several partner financial institutions who independently confirmed the authenticity of the stolen data.
According to Gemini, the hackers obtained the card details after compromised the in-store Point-of-Sale (POS) system used at Dickey’s Barbecue Pit restaurants.
Crooks compromised 156 of Dickey’s 469 locations across 30 states, most of them in California and Arizona.
Dickey’s locations are marked by the blue restaurant icon while the locations confirmed to be compromised are marked in red.
The compromise took place between July 2019 and August 2020. Gemini reported that the root cause of the security breach was the use of the outdated magstripe method for payment transactions, which exposed car holders to PoS malware attacks.
The company published an official statement that confirmed that it has immediately started the incident response procedure.
“We received a report indicating that a payment card security incident may have occurred. We are taking this incident very seriously and immediately initiated our response protocol and an investigation is underway. We are currently focused on determining the locations affected and time frames involved.” reads the statement provided by the company. “We are utilizing the experience of third parties who have helped other restaurants address similar issues and also working with the FBI and payment card networks. We understand that payment card network rules generally provide that individuals who timely report unauthorized charges to the bank that issued their card are not responsible for those charges.”
The payment card records are mostly for cards using outdated magstripe technologies and are being sold for a median price of $17 per card.
“Based on previous Joker’s Stash major breaches, the records from Dickey’s will likely continue to be added to this marketplace over several months.”concludes the post.
Twitter Hack: 24 Hours From Phishing Employees to Hijacking Accounts
16.10.20 Social Securityweek
New York Financial Regulator Concludes Investigation Into Twitter Hack
Hackers needed roughly 24 hours to take over high-profile Twitter accounts in the July attack, a report from the New York Department of Financial Services reveals.
The attack started on July 14 and was over the next day, when it became apparent that numerous high-profile accounts, including those of Bill Gates, Elon Musk, Barack Obama, and Jeff Bezos, were hijacked and leveraged to promote a cryptocurrency scam.
The hackers, which were identified shortly after the incident, leveraged internal Twitter systems to change email addresses and login credentials for targeted accounts and take control of them. A total of 130 accounts were targeted and the passwords for 45 of them were changed.
A couple of weeks after the incident, Twitter revealed that hackers targeted some employees with phone phishing until gaining access to the account support tools they needed.
In a report summarizing an investigation into the incident, the New York Department of Financial Services, which launched a probe on July 16, reveals that the attack lasted roughly 24 hours from when the phishing calls were placed until the targeted accounts were compromised.
“It was surprising how easily the Hackers were able to penetrate Twitter’s network and gain access to internal tools allowing them to take over any Twitter user’s account. The extraordinary access the Hackers obtained with this simple technique underscores Twitter’s cybersecurity vulnerability and the potential for devastating consequences,” the report reads.
The attack was allegedly carried out by 17-year-old Graham Ivan Clark (aka Kirk#5270), of Tampa, Florida, who is said to be the mastermind behind the incident, 19-year-old Mason John Sheppard (aka Chaewon and “ever so anxious#001”) of the United Kingdom, and 22-year-old Nima Fazeli (aka Rolex, Rolex#0373, and Nim F) of Orlando, Florida.
In the afternoon of July 14, pretending to be calling from the IT department at Twitter in response to some issues with the VPN (not uncommon, due to the massive switch to remote working), the hackers called several of the social platform’s employees and directed them to enter credentials on a phishing page. The page would also generate a fake multi-factor authentication notification.
“The Department found no evidence the Twitter employees knowingly aided the Hackers. Rather, the Hackers used personal information about the employees to convince them that the Hackers were legitimate and could, therefore, be trusted. While some employees reported the calls to Twitter’s internal fraud monitoring team, at least one employee believed the Hackers’ lies,” the report reveals.
While the first victim did not have access to the targeted internal systems, the hackers used their credentials to navigate the network and identify employees that did. On July 15, they targeted such employees, including some of those who were responsible for dealing with sensitive global legal requests.
Soon after gaining the ability to take over Twitter accounts (including OG – “original gangster” accounts), the hackers started discussing the sale of OG usernames, and then began publicly demonstrating their access to Twitter’s internal systems: on July 15, just before 2:00 p.m., they hijacked multiple OG accounts and posted screenshots of a Twitter internal tool.
Next, the hackers switched to verified accounts, likely aiming to make their demands for cryptocurrency seem legitimate, the report points out. Within the next couple of hours, they hit the accounts of cryptocurrency trader @AngeloBTC, crypto-exchange Binance, and ten other cryptocurrency-related accounts, such as Coinbase, Gemini Trust Company, and Square, Inc.
Over the next couple of hours, the hackers started tweeting from verified accounts that had millions of followers, including those of Apple, Uber, Bill Gates, Elon Musk, Kanye West, Kim Kardashian West, Joseph R. Biden, Jr., Warren Buffet, and Floyd Mayweather Jr.
“The Hackers also used some of the compromised accounts to resend the same bitcoin scam tweets multiple times. Given the number of followers for each high-profile user account, the fraudulent tweets reached millions of potential victims across the globe. The Hackers stole approximately $118,000 worth of bitcoin through the Twitter Hack,” the report notes.
In their report, which provides a visual timeline of the events, the Department of Financial Services also points out that the non-public information of some users was compromised and that Twitter failed to publicly report real-time updates on the incident – although the company “severely limited or revoked its employees’ access to its internal systems” to contain the breach.
The report also underlines the incident’s impact on cryptocurrency-related entities and their customers, dissects the cybersecurity weaknesses that made the hack possible, and provides details on the best practices critical institutions should adopt to prevent or mitigate similar incidents.
“The Twitter Hack brought a social media giant to its knees. The David to this Goliath was a group of unsophisticated cyber crooks who exploited social media to create widespread disruption for hundreds of millions of users. The election weeks away puts a spotlight on the need to improve cybersecurity to prevent misuse of social media platforms,” the report concludes.
Iran-Linked 'Silent Librarian' Back at Phishing Universities
16.10.20 BigBrothers Securityweek
Iran-linked state-sponsored threat actor 'Silent Librarian' has launched another phishing campaign targeting universities around the world.
Also tracked as TA407 and COBALT DICKENS, the adversary was previously observed launching similar attacks for two years in a row.
In 2018, the group set up fake login pages for 76 universities. In 2019, Silent Librarian targeted more than 60 universities in Australia, Canada, Hong Kong, Switzerland, the United States, and the United Kingdom.
Observed in mid-September, the new round of attacks revealed that the threat actor is expanding its target list to include more countries. One of the victims is the Nanyang Technological University in Singapore, cybersecurity researcher Peter Kruse says.
Silent Librarian, Malwarebytes’ security researchers reveal, has sent spear-phishing emails to both staff and students at the targeted universities, and the threat actor was observed setting up new infrastructure to counter efforts to take down its domains.
“Considering that Iran is dealing with constant sanctions, it strives to keep up with world developments in various fields, including that of technology. As such, these attacks represent a national interest and are well funded,” Malwarebytes says.
Domain names used in the new attacks follow the pattern observed before, although they use a different top level domain name: the adversary switched from the “.me” TLD that was previously employed to “.tk” and “.cf” in recent attacks.
Considering Silent Librarian’s use of similar domains to target universities in the past, Malwarebytes researchers are confident the new domains were registered by the same group.
The threat actor uses Cloudflare for hostnames, which helps them hide the real hosting origin. Despite that, however, the researchers were able to identify some of the infrastructure, which was hosted in Iran.
While the use of infrastructure located in the attacker’s own country might seem surprising, the researchers explain that it only shows that the adversary can leverage yet another bulletproof hosting option, the result of a lack of cooperation between US and European law enforcement and local police in Iran.
“Clearly we only uncovered a small portion of this phishing operation. Although for the most part the sites are taken down quickly, the attacker has the advantage of being one step ahead and is going for many possible targets at once,” Malwarebytes concludes.
Google Warns of Zero-Click Bluetooth Flaws in Linux-based Devices
16.10.20 Vulnerebility Thehackernews
Google security researchers are warning of a new set of zero-click vulnerabilities in the Linux Bluetooth software stack that can allow a nearby unauthenticated, remote attacker to execute arbitrary code with kernel privileges on vulnerable devices.
According to security engineer Andy Nguyen, the three flaws — collectively called BleedingTooth — reside in the open-source BlueZ protocol stack that offers support for many of the core Bluetooth layers and protocols for Linux-based systems such as laptops and IoT devices.
The first and the most severe is a heap-based type confusion (CVE-2020-12351, CVSS score 8.3) affecting Linux kernel 4.8 and higher and is present in the Logical Link Control and Adaptation Protocol (L2CAP) of the Bluetooth standard, which provides multiplexing of data between different higher layer protocols.
"A remote attacker in short distance knowing the victim's [Bluetooth device] address can send a malicious l2cap packet and cause denial of service or possibly arbitrary code execution with kernel privileges," Google noted in its advisory. "Malicious Bluetooth chips can trigger the vulnerability as well."
The vulnerability, which is yet to be addressed, appears to have been introduced in a change to the "l2cap_core.c" module made in 2016.
Intel, which has significantly invested in the BlueZ project, has also issued an alert characterizing CVE-2020-12351 as a privilege escalation flaw.
The second unpatched vulnerability (CVE-2020-12352) concerns a stack-based information disclosure flaw affecting Linux kernel 3.6 and higher.
A consequence of a 2012 change made to the core Alternate MAC-PHY Manager Protocol (A2MP) — a high-speed transport link used in Bluetooth HS (High Speed) to enable the transfer of larger amounts of data — the issue permits a remote attacker in short distance to retrieve kernel stack information, using it to predict the memory layout and defeat address space layout randomization (KASLR)
Lastly, a third flaw (CVE-2020-24490) discovered in HCI (Host Controller Interface), a standardized Bluetooth interface used for sending commands, receiving events, and for transmitting data, is a heap-based buffer overflow impacting Linux kernel 4.19 and higher, causing a nearby remote attacker to "cause denial of service or possibly arbitrary code execution with kernel privileges on victim machines if they are equipped with Bluetooth 5 chips and are in scanning mode."
The vulnerability, which has been accessible since 2018, has been patched in versions 4.19.137 and 5.7.13.
For its part, Intel has recommended installing the kernel fixes to mitigate the risk associated with these issues.
"Potential security vulnerabilities in BlueZ may allow escalation of privilege or information disclosure," Intel said of the flaws. "BlueZ is releasing Linux kernel fixes to address these potential vulnerabilities."
Carnival Corp. Ransomware Attack Affects Three Cruise Lines
16.10.20 Ransomware Threatpost
Hackers accessed personal information of guests, employees and crew for Carnival Cruise, Holland America and Seabourn as well as casino operations.
Hackers accessed personal information of guests, employees and crew for three cruise line brands and the casino operations of Carnival Corp. in a ransomware attack the company suffered on Aug. 15, officials have confirmed.
Carnival Cruise Line, Holland America Line and Seabourn were the brands affected by the attack, which Carnival is still investigating, the company said in an update on the situation this week. Carnival has been working with cybersecurity consultants to recover its files and believes there is a a “low likelihood of the data being misused,” the company said.
Carnival had already revealed that it was the target of a ransomware attack two days after the incident, on Aug. 17. At the time acknowledged that hackers had accessed and encrypted a portion of one brand’s information technology systems, as well as downloaded data files from the company.
Carnival continues to work “as quickly as possible to identify the guests, employees, crew and other individuals whose personal information may have been impacted,” according to the update. Within 30 to 60 days, Carnival plans to complete the process and notify those known to be affected, provided the company has their current contact information.
In the meantime, anyone who believes they may have been affected can contact a dedicated call center the company set up to answer questions regarding the event, Carnival said. “When the investigation is complete, callers may confirm whether or not their information was affected,” the company said.
Cruise operators, like many other touristic services-oriented companies, have been hit hard during the COVID-19 pandemic, which has inspired hackers to take advantage of their troubled situation. Indeed, threat actors have been on nearly constant attack across industries since March when news of the pandemic first hit across the world, inspiring business closures and stay-at-home orders that left organizations vulnerable.
Calling the attack “yet another example of the importance of proper investment in cyber security programs to protect company and customer data,” Terence Jackson, CISO at cloud privileged access management solution provider Thycotic, stressed continued vigilance as the pandemic persists.
“Attackers are not taking it easy during the pandemic,” he said in an e-mail to Threatpost. “They are stepping the attacks up and we have to be ready.”
Business continuity and disaster recovery are two areas companies should consider bolstering during this unique time of vulnerability to attacks, noted Steve Durbin, managing director of the Information Security Forum.
“Established plans that depend on employees being able to work from home, for example, do not stand up to an attack that removes connectivity or personally targets individuals as a means of dropping ransomware into the corporate infrastructure,” he said in an e-mail to Threatpost. “Revised plans should cover threats to periods of operational downtime caused by attacks.”
For its part, Carnival said it is indeed taking proactive steps to bolster its security position, reviewing security and privacy policies and procedures and implementing changes when needed to enhance information security and privacy controls as it continues its review of the incident.
Broadvoice Leak Exposes 350M Records, Personal Voicemail Transcripts
16.10.20 Incindent Threatpost
Companies that use Broadvoice’s cloud-based VoIP platform may find their patients, customers, suppliers and partners to be impacted by a massive data exposure.
UPDATE
Broadvoice, a well-known VoIP provider that serves small- and medium-sized businesses, has leaked more than 350 million customer records related to the company’s “b-hive” cloud-based communications suite.
The data includes hundreds of thousands of voicemail transcripts, many involving sensitive information such as details about medical prescriptions and financial loans.
Broadvoice provides one of the more popular business platforms for communications, which includes voice, contact-center technology, remote-workforce help, Salesforce.com integration, unified communications, SIP trunking and more. Much of this is offered via b-hive, which it hosts on behalf of customers such as doctors’ offices, law firms, retail stores, community organizations and more.
Because its technology underpins these customers’ basic interactions with patients, clients, partners, suppliers and others, plenty of personal data flows through Broadvoice’s cloud-based systems. And that data is apparently retained by the company, so that its business clients can access it if needed, for analytics and call-center quality control, among other things.
Unfortunately, according to researchers at Comparitech, Broadvoice left an Elasticsearch database cluster containing such information open to the internet, accessible to anyone, with no authentication required. The cache of data included records with personal details of Broadvoice clients’ customers, they noted.
The misconfigured cluster included 10 separate collections of data, related to b-hive.
The largest collection (275 million records) included full caller name, caller ID, phone number, and city and state. Meanwhile, a collection entitled “people-production” contained account ID numbers for Broadvoice’s own customers, which allowed researchers to cross-reference entries with records in other collections.
But the most concerning one held 2 million voicemail records, with more than 200,000 transcripts.
“Many of the transcripts included select personal details such as full name, phone number and date of birth, as well as some sensitive information,” according to a Comparitech posting on Thursday. “For example, some transcripts of voicemails left at medical clinics included names of prescriptions or details about medical procedures. In one transcript, the caller identified themselves by their full name and discussed a positive COVID-19 diagnosis.”
Researchers added, “Other voicemails left for financial-service companies included details about mortgages and other loans, while there was at least one instance of an insurance-policy number being disclosed.”

Most of these records also contained a full name, business name or a generic name such as “wireless caller”; phone number; a name or identifier for the voice mailbox (such as “appointments”); and internal identifiers, according to Comparitech.
When reached for comment about Broadvoice’s data-retention policies, and whether its business customers will be issuing data-breach notifications to their own affected customers, Rebecca Rosen, vice president of marketing, told Threatpost that the number of impacted businesses is likely less than 10,000.
“To provide some perspective, we believe that the researcher accessed a sub-set of data that potentially impacted less than 10,000 customers,” she said. “Our investigation is otherwise ongoing, and we are not otherwise commenting or speculating other than what we have posted online.”
Aside from the privacy implications, the data paves the way for convincing fraud attempts, researchers noted.
“The leaked database represents a wealth of information that could help facilitate targeted phishing attacks,” according to Comparitech. “In the hands of fraudsters, it would offer a ripe opportunity to dupe Broadvoice clients and their customers out of additional information and possibly into handing over money. For example, criminals could pose as Broadvoice or one of its clients to convince customers to provide things like account login credentials or financial information.”
Meanwhile, “information about things like medical prescriptions and loan enquiries could be used to make messages extremely convincing and persuasive.”
The collections were discovered by researcher Bob Diachenko on Oct. 1, and were secured the same day, according to Broadvoice. The cluster had been uploaded on Sept. 28, meaning it was exposed for about four days.
“Broadvoice takes data privacy and security seriously,” Broadvoice CEO Jim Murphy said in a statement. He added, “At this point, we have no reason to believe that there has been any misuse of the data. We are currently engaging a third-party forensics firm to analyze this data and will provide more information and updates to our customers and partners. We cannot speculate further about this issue at this time.”
He also said that Broadvoice is working with Diachenko to ensure that the retained data is destroyed.
Iran acknowledged cyberattacks on two governmental departments
16.10.20 BigBrothers Securityaffairs
Iran ’s cybersecurity authority revealed that two governmental departments were hit by cyberattacks this week, state media reported.
State media reported on Thursday that Iran’s cybersecurity authority acknowledged cyberattacks on two unnamed governmental departments.
The state-owned IRAN daily newspaper revealed that the cyberattacks took place on Tuesday and Wednesday respectively.
Iranian authorities are investigating the attacks that were defined as important.
Other governmental departments temporarily took down their online operation as a precaution measure.
Iran’s cybersecurity authority did not attribute the attack to a specific threat actor
This isn’t the first time that Irans‘ authorities claim to have been targeted by cyber attacks. In December 2019, the Iran telecommunications minister announced for two times in a week to have foiled a cyber attack against its infrastructure.
At the time, the Iranian minister Mohammad Javad Azari-Jahromi confirmed that the attack was neutralized by the national cyber shield, it also added that the attack was launched by the China-linked APT27 group seeking for gathering intelligence its country.
In October 2019, Iran announced it was fearing retaliation from Western countries that are accusing it to carry out physical and cyber attacks against their infrastructure and countries in the Middle East.
At the time, Iran’s oil ministry said that the Government of Washington has launched a full-scale economic war” against the Islamic Republic in retaliation for the shooting down of a US drone as well as attacks on oil tankers that the US has blamed Iran.
Tensions between Tehran and Washington have escalated since 2018 when President Trump reimposed sanctions on Iran. The situation went out of control after a US drone strike killed top Iranian general Qasem Soleimani in January.
The order to kill Soleimani was issued by President Trump that said Soleimani was planning an “imminent” attack on US personnel in Baghdad.
In January, the U.S. Department of Homeland Security (DHS) has issued warnings about the possibility of cyber-attacks launched by Iran-linked threat actors. The attacks could be the response of Teheran after Maj. Gen. Qassim Suleimani was killed by a U.S. drone airstrike at the Baghdad airport in Iraq.
Crooks hit Puerto Rico Firefighting Department Servers
16.10.20 Hacking Securityaffairs
Puerto Rico’s firefighting department discloses a security breach, hackers breached its database and demanded $600,000.
Puerto Rico’s firefighting department discloses a security breach, hackers breached its database and demanded a $600,000 ransom.
According to the department’s director, Alberto Cruz, the ability of the department to respond to emergencies was not impacted by the attack.
The department received an email from the threat actors that notifies it that they had encrypted its servers and demanded the payment of a ransom to release them.
Local police launched an investigation into the incident, while the department decided to don’t pay the ransom.
“The department contacted police and have not paid the money, officials said. The investigation is ongoing.” reported the Associated Press.
Egregor ransomware gang leaked data alleged stolen from Ubisoft, Crytek
16.10.20 Ransomware Securityaffairs
The Egregor ransomware gang has hit the game developer Crytek and leaked files allegedly stolen from the systems of the gaming firm Ubisoft.
A previously unknown ransomware gang dubbed Egregor has hit the game developer Crytek and leaked files allegedly stolen from the internal network of another leading gaming firm, Ubisoft.
A few days ago, the Egregor ransomware operators posted archives containing unencrypted files allegedly stolen in two distinct attacks from the two gaming firms.
Data allegedly stolen from the two companies were published on the Egregor’s gang dark web leak site. The ransomware operators leaked 300 MB from Crytek and 20 MB from Ubisoft.
The files stolen from Crytek contained data related to the development of games like Arena of Fate and Warface, along with the company’s old Gface social gaming network.

Source ZDNet
At the time of writing the post, media outlets only confirmed the ransomware attack against Crytek, while it is not clear if Ubisoft suffered a security breach.
Files of the gaming firm were encrypted and the ransomware appended the’.CRYTEK’ extension to their filenames.
Egregor Ransomware operators also threatened to leak the source code of a popular upcoming Ubisoft game, the Watch Dogs: Legion.
Security researcher MalwareHunterTeam has attempted, without success, to warn Ubisoft for almost a year that their employees were the victims of phishing attacks.
Critical Vulnerability Allows Hackers to Disrupt SonicWall Firewalls
16.10.20 Vulnerebility Securityweek
A significant number of SonicWall firewalls may be affected by a critical vulnerability that can be exploited for denial-of-service (DoS) attacks and possibly arbitrary code execution.
The vulnerability, identified as CVE-2020-5135, impacts various versions of SonicOS, the operating system powering SonicWall firewalls. The vendor has credited researchers at Tripwire and Positive Technologies for finding the security bug.
Tripwire discovered the flaw, which it described as a stack-based buffer overflow, in the SonicWall Network Security appliance (NSa), a firewall solution designed for medium size networks. The product also includes VPN capabilities that can be used by organizations to ensure secure remote access for employees.

Tripwire explained in a blog post that the vulnerability exists in the HTTP/HTTPS service that is used for device management and VPN access. An unauthenticated attacker can exploit it by sending specially crafted HTTP requests with a custom protocol handler.
While the security hole can definitely be exploited for DoS attacks, Tripwire says arbitrary code execution is “likely feasible” as the company has “confirmed the ability to divert execution flow through stack corruption.”
Even for DoS attacks, the vulnerability can pose a serious threat to organizations as an attacker can leverage it to force a targeted firewall to reboot.
“An attacker can keep the system rebooting by continuously sending the malicious request,” Tripwire’s Craig Young told SecurityWeek. “You could imagine an extortion scheme where someone threatens to keep your VPN workforce offline until you pay them to stop attacking. Particularly during COVID, it could be difficult for the organization to patch a device while under attack as it may require physical device access and prolonged downtime.”
Nikita Abramov, application analysis specialist at Positive Technologies, explained that a DoS attack leads to the “collapse” of the main firewall application, which he says is responsible for all the logic work, including the web interface, command-line interface and other services.
Tripwire said it identified nearly 800,000 exposed SonicWall systems on Shodan, but Young clarified that this list likely also includes devices that are not vulnerable.
Positive Technologies, on the other hand, told SecurityWeek that it identified roughly 460,000 vulnerable devices.
SonicWall has released an advisory that provides information on affected SonicOS versions as well as the availability of updates that should patch CVE-2020-5135.
Positive Technologies has also been credited by SonicWall this week for finding a dozen other vulnerabilities in SonicOS, including several high-severity DoS flaws that can be exploited remotely without authentication to crash a firewall, and less severe DoS, XSS, brute forcing, and admin username enumeration issues.
Cybercrime Money-launders Busted by European Police, FBI
16.10.20 BigBrothers Securityweek
European and American officials said Thursday that they have arrested 20 people in several countries for allegedly belonging to an international ring that laundered millions of euros stolen by cybercriminals through malware schemes.
The international police operation “2BaGoldMule” led by Portuguese investigators and the FBI included 14 more European countries, under the umbrella of Europol. Europol said that more than 40 homes were searched by agents in Spain, Italy, Bulgaria and Latvia in the operation.
Most of the house searches were carried out in Latvia, where six arrests were made. Another six arrests were made in Britain, four in Spain, and one each in Portugal, Poland, the U.S. and Australia, according to Europol.
The ring “QQAAZZ” allegedly laundered cybercriminals’ stolen funds, transferring them between hundreds of bank accounts held in banks across the world, officials said. The ring included citizens of Russia, Latvia, Georgia, Bulgaria, Romania, and Belgium, according to the U.S. Justice Department. The ring laundered money stolen from victims in the U.S. and European countries. The suspects face criminal investigations in the U.S., Portugal, Spain and the U.K.
“This operation has shown that through this cooperation we can collectively tackle the global nature of cybercrime. This is the only way forward,” said Carlos Cabreiro, director of Portugal’s National Unit for Fighting Cybercrime.
TrickBot Botnet Survives Takedown Attempt
16.10.20 BotNet Securityweek
The TrickBot botnet appears to have resumed normal operations days after Microsoft announced that it managed to take it down using legal means.
On October 12, Microsoft and several partners announced that they were able to disrupt the TrickBot infrastructure by legally disabling IP addresses, making servers inaccessible and suspending services employed by the botnet. The effort was also aimed at preventing operators from registering new infrastructure.
Only three days after the announcement, however, security researchers with Intel 471 revealed that the botnet has resumed operations, despite Microsoft’s takedown attempt and efforts from the U.S. Cyber Command to hack TrickBot’s servers.
On October 14, the Emotet botnet began distributing malicious Word documents meant to download and execute a copy of Emotet. The Emotet bots, the researchers say, received commands to fetch and run Trickbot on victim machines.
Intel 471 also notes that the Trickbot plugin server configuration file has received an update which added fifteen server addresses and retained two old servers, along with the server’s .onion address.
The change, the researchers believe, was likely performed as a fix that would ensure that the botnet’s infrastructure remains operational.
“The fact that Trickbot has resumed normal operations despite the best efforts of U.S. Cyber Command and Microsoft shows how resilient of an operation Trickbot is and how much more effort is needed to fully take the botnet offline for good,” Intel 471 said.
The researchers, who have been tracking the botnet’s activity for months, assess that TrickBot’s operators have IT support that any legitimate enterprise takes advantage of, including automated deployment, backups, continuity planning, and a dedicated team behind, which allows them to react to disruptions fast.
“About 10 years ago it was much easier to completely take over or significantly disrupt a botnet, but cybercriminals are students of takedowns and have learned to make their operations more resilient to takedown efforts. That’s why every takedown attempt has some potential of giving ground to the adversary. You’re teaching them where the weaknesses in their armor are and they have a team of developers ready to act on that information. So unless you strike a killing blow, you’re not going to impact them long term,” Intel 471 COO Jason Passwaters said.
To fully disrupt TrickBot, the researchers say, a multi-prolonged effort is needed. Multinational law enforcement support with focus on arresting operators, an aim at the botnet’s main infrastructure, and tight collaboration between governments and the private sector for de-infection are required for a successful takedown.
Hackers Target Puerto Rico Firefighting Department Servers
16.10.20 Hacking Securityweek
Puerto Rico’s firefighting department said Wednesday that its database was hacked by unknown people demanding $600,000 in an act of alleged extortion.
The department’s director, Alberto Cruz, said in a statement the situation has not affected its ability to respond to emergencies.
Police said the department received an email notifying it that hackers had encrypted its servers and wouldn’t release them until they got paid.
The department contacted police and have not paid the money, officials said. The investigation is ongoing.
Barnes & Noble Informs Customers of Cyberattack
16.10.20 Attack Securityweek
Bookselling giant Barnes & Noble has sent email notifications to its customers to inform them of a recent cyberattack.
A Fortune 1000 company, Barnes & Noble is the bookseller with the largest number of retail outlets in the United States. The company is also known for the NOOK e-readers and for the collection of e-books it offers for the device.
In the email to its users, Barnes & Noble revealed that it discovered the breach on October 10, 2020, and that unauthorized actors managed to access certain corporate systems, likely compromising some user information.
“We write now out of the greatest caution to let you know how this may have exposed some of the information we hold of your personal details,” the company said.
Payment card and other financial data, the email notification reveals, hasn’t been compromised, as it is stored “encrypted and tokenized and not accessible.”
User data likely affected in the incident includes email addresses, billing and shipping addresses, along with phone numbers, where supplied by the user.
“While we do not know if any personal information was exposed as a result of the attack, we do retain in the impacted systems your billing and shipping addresses, your email address and your telephone number if you have supplied these,” the company noted.
The compromised systems also store transaction history, which includes purchase information related to books and other products bought from Barnes & Noble.
“We currently have no evidence of the exposure of any of this data, but we cannot at this stage rule out the possibility,” the notification reads.
The company says users should not fear that their emails have been compromised, although email addresses might have been exposed, meaning that users could receive unsolicited messages.
Good e-Reader reported that the incident involved a “virus,” which could indicate that this was a ransomware attack.
Iran Acknowledges Cyberattacks on Government Departments
16.10.20 BigBrothers Securityweek
Iran’s cybersecurity authority acknowledged cyberattacks on two governmental departments this week, state media reported Thursday.
The cyberattacks occurred Tuesday and Wednesday and were under investigation, the state-owned IRAN daily newspaper said.
While the report did not say which government departments were targeted, it called the attacks “important” and said some other departments temporarily took down their online services as a precaution against further attacks.
The brief report did not blame any group or country for the attacks.
Iran occasionally says it has thwarted cyberattacks on its infrastructure, although it has disconnected much of its infrastructure from the internet after the Stuxnet computer virus, widely believed to be a joint U.S.-Israeli creation, disrupted thousands of Iranian centrifuges in the country’s nuclear sites in the late 2000s.
In December, Iran said it halted a massive cyberattack on unspecified “electronic infrastructure” but provided no specifics on the purported attack.
Last year, Washington officials said that U.S. military cyber forces launched a strike against Iranian military computer systems, as President Donald Trump backed away from plans for a more conventional military strike in response to Iran’s downing of a U.S. surveillance drone in the strategic Persian Gulf.
Tensions have escalated between the U.S. and Iran since Trump in 2018 withdrew America from Iran’s nuclear deal with world powers and began a policy of “maximum pressure” on Tehran.
Tensions rose further after a U.S. airstrike killed a top Iranian general at Baghdad’s airport in January. Iran retaliated with a ballistic missile strike on Iraqi bases housing American troops, wounding dozens of U.S. troops.
IAmTheKing and the SlothfulMedia malware family
15.10.20 APT Securelist
On October 1, 2020, the DHS CISA agency released information about a malware family called SlothfulMedia, which they attribute to a sophisticated threat actor. We have been tracking this set of activity through our private reporting service, and we would like to provide the community with additional context.
In June 2018, we published the first report on a new cluster of activities that we named IAmTheKing, based on malware strings discovered in a malware sample from an unknown family. Amusingly, other strings present inside of it invited “kapasiky antivirus” to “leave [them] alone”.
Over time, we identified three different malware families used by this threat actor, one of which was SlothfulMedia. The aim of this blog post is to introduce all of them and to provide data we have been able to gather about the attackers’ interests.
IAmTheKing’s toolset
KingOfHearts
This C++ backdoor, which contains the character strings discussed above, is the first element of this toolset we encountered. It comes in EXE or DLL variants, and we have been able to find traces of this family dating back to 2014. We believe it was distributed through spear-phishing e-mails containing malicious Word documents, but have been unable to obtain samples of these. The infection process relies on a PowerShell script that downloads from a remote server a base64-encoded payload hidden in an image file.
In terms of capabilities, KingOfHearts offers nothing more than the basic features you would expect from a backdoor:
Arbitrary command execution
File system manipulation: listing drives and files, deleting, uploading and downloading data, etc.
Listing of running processes with the option to terminate any of them
Capturing screenshots using a custom standalone utility, described below
Rather than developing sophisticated features, the malware developers instead opted to include anti-debugging and virtualization detection routines. Communications with the C2 server take place over HTTP(S), implemented with the wsdlpull open source library. The backdoor looks for new orders every second by sending a heartbeat to the C2 (the “HEART” command, hence the name).
We identified two main development branches: one of them sends url-encoded POST data, and the other one sends JSON objects. Both have been used concurrently and otherwise display the same capabilities: we cannot say what motivates attackers to choose the one or the other.
QueenOfHearts
Following our initial discovery, we identified another, more widespread malware family linked to the same threat actor. While it does not contain the anti-analysis countermeasures of its cousin, the rest of its features and overall design decisions map to King of Hearts almost one to one. QueenOfHearts seems to have appeared somewhere in 2017. It is the family designated as PowerPool by our esteemed colleagues from ESET.
QueenOfHearts also interacts with its C2 server over HTTP. It sends simple GET requests containing a backdoor identifier and optional victim machine information, then reads orders located in the cookie header of the reply. Orders come in the form of two-letter codes (e.g.: “xe” to list drives) which tend to vary between samples. As of today, this family is still in active development, and we have observed code refactoring as well as incremental upgrades over 2020. For instance, earlier backdoor responses were sent as base64-encoded payloads in POST requests. They are now compressed beforehand, and additionally supplied through the cookie header.
QueenOfClubs
In the course of our investigations, we discovered another malware strain that appeared to fill the same role as QueenOfHearts. This C++ backdoor also offers similar features as KingOfHearts, as well as the ability to execute arbitrary Powershell scripts. One minute difference is that in this one, screenshot capture capabilities are embedded directly into the program instead of being handled by a separate utility.
It contains a number of links to QueenOfHearts, namely:
Identical hardcoded file names can be found in both malware strains.
We observed a number of command and control servers concurrently handling traffic originating from both families.
QueenOfHearts and QueenOfClubs were on occasion deployed simultaneously on infected machines.
However, it is also our belief that they originate from two separate codebases, although their authors shared common development practices.
The malware designated as SlothfulMedia by US-CERT is an older variant of this family.
JackOfHearts
Astute readers will notice that we did not discuss persistence mechanisms for any of the two aforementioned families. In fact, both of them expect to run in an environment that has already been prepared for them. JackOfHearts is the dropper associated with QueenOfHearts: its role is to write the malware somewhere on the disk (for instance: %AppData%\mediaplayer.exe) and create a Windows service pointing to it as well as a shortcut in the startup folder that is also used to immediately launch QueenOfHearts. This shortcut is the one that contains references to a “david” user highlighted by the DHS CISA report.
Finally, the dropper creates a self-deletion utility in the %TEMP% folder to remove itself from the filesystem.
As of 2020, JackOfHearts is still used to deploy QueenOfHearts.
Screenshot capture utility
A simple program that captures screenshots and saves them as “MyScreen.jpg”. It is sometimes embedded directly inside QueenOfHearts but has also been seen in conjunction with KingOfHearts.
Powershell backdoor
In addition to these malware families, IAmTheKing also leverages an extensive arsenal of Powershell scripts. Recent infection vectors have involved archives sent over e-mail which contain LNK files masquerading as Word documents. Clicking on these links results in the execution of a Powershell backdoor that hides inside custom Windows event logs and retrieves additional scripts over HTTPS, DNS or even POP3S.
The C2 server provides PNG files, which contain additional Powershell scripts hidden through steganography. The code performing this operation comes from the open-source project Invoke-PSImage. This allows operators to stage components on the victim machine, such as:
An information-stealing utility written in Powershell that collects all documents found on the victim’s machine and sends them in password-protected RAR archives. These archives are sent back to the attackers over e-mail.
A command execution utility which obtains orders from DNS TXT records. The code to accomplish this is derived from another open-source project, Nishang.
An information-gathering utility tasked with collecting running processes, disk drives and installed programs with WMI queries. It may also steal passwords saved by the Chrome browser.
A spreader script that lists computers connected to the domain, and tries to open a share on each of them to copy a binary and create a remote scheduled task.
A home-made keylogger.
QueenOfHearts, one of the malware families described above.
Lateral movement
Once the attackers have gained access to a machine through any of the tools described above, they leverage well-known security testing programs to compromise additional machines on the network. In particular, we found evidence of the following actions on the target:
Microsoft’s SysInternals suite: ProcDump to dump the exe process and PsExec to run commands on remote hosts.
LaZagne and Mimikatz to collect credentials on infected machines.
Built-in networking utilities such as ipconfig.exe, net.exe and ping.exe, etc. for network discovery.
Victimology
Until very recently, IAmTheKing has focused exclusively on collecting intelligence from high-profile Russian entities. Victims include government bodies and defense contractors, public agencies for development, universities and companies in the energy sector. This threat actor’s geographic area of interest is so specific that KingOfHearts, QueenOfHearts and even recent versions of JackOfHearts include code referring specifically to the Russian language character set:
In 2020, we discovered rare incidents involving IAmTheKing in central Asian and Eastern European countries. The DHS CISA also reports activity in Ukraine and Malaysia. Our data however indicates that Russia overwhelmingly remains IAmTheKing’s primary area of operation.
There is currently debate within our team on whether this constitutes a slight shift in this threat actor’s targeting, or if its toolset is now shared with other groups. We are unable to provide a definitive answer to this question at this juncture.
Conclusion
While the public has only recently discovered this set of activity, IAmTheKing has been very active for a few years. Considering the type of organizations that cybercriminals have been targeting, we felt that there was little public interest in raising awareness about this group beyond our trusted circle of industry partners. However, now that researchers have started investigating this threat actor, we want to assist the community as much as possible by providing this brief summary of our knowledge of IAmTheKing.
Based on the type of information IAmTheKing is after, we believe that it is state-sponsored. Its toolset is rapidly evolving, and it is not afraid to experiment with non-standard communications channels. The group is characterized by a mastery of traditional pentesting methodologies and a solid command of Powershell. Data available to us indicates that it has achieved operational success on numerous occasions.
Kaspersky will keep investigating incidents related to this group in the foreseeable future and has gathered a detailed view of their 2020 activity so far. We invite individuals or companies who think they might be – or have been – targeted by IAmTheKing to get in touch with us for additional information, or otherwise request access to our Threat Intelligence Portal for regular updates on this threat actor.
YARA rules
In virtually all our investigations, we write YARA rules to hunt for additional malware samples and get a better idea of each family’s prevalence. In the spirit of sharing knowledge with the community and assisting research efforts on this threat actor, we are happy to release a few of these rules, which will allow defenders to identify recent samples from the families described above. If you are unfamiliar with YARA or would like to learn more about the art of writing rules, please check out the online training written by members of GReAT.
Indicators of Compromise
00E415E72A4FC4C8634D4D3815683CE8 KingOfHearts (urlencode variant)
4E2C2E82F076AD0B5D1F257706A5D579 KingOfHearts (JSON variant)
AB956623B3A6C2AC5B192E07B79CBB5B QueenOfHearts
4BBD5869AA39F144FADDAD85B5EECA12 QueenOfHearts
4076DDAF9555031B336B09EBAB402B95 QueenOfHearts
096F7084D274166462D445A7686D1E5C QueenOfHearts
29AA501447E6E20762893A24BFCE05E9 QueenOfClubs
97c6cfa181c849eb87759518e200872f JackOfHearts
7DB4F1547D0E897EF6E6F01ECC484314 Screenshot capture utility
60D78B3E0D7FFE14A50485A19439209B Malicious LNK
90EF53D025E04335F1A71CB9AA6D6592 Keylogger
U.S. Bookstore giant Barnes & Noble hit by cyberattack
15.10.20 CyberCrime Securityaffairs
U.S. Bookstore giant Barnes & Noble has disclosed a cyber attack and that the threat actors have exposed the customers’ data.
Barnes & Noble, Inc., is an American bookseller with the largest number of retail outlets in the United States in fifty states.
The bookseller also operated the Nook Digital, which is a spin-off division that sells eBook and e-Reader platform.
Barnes & Noble
Over the weekend, users have been complaining on Nook’s Facebook page and Twitter that they were not able to access their library of purchased eBooks and magazine subscriptions.
A series of messages published on Barnes & Noble’s Nook social media accounts state that it had suffered a system failure and is working to restore operations by restoring their server backups.
In a statement to Fast Company Barnes & Noble confirmed that financial data of its customers were not compromised.
“We have a serious network issue and are in the process of restoring our server backups,” Barnes & Noble told Fast Company in a statement. “Our systems are back online in our stores and on BN.com, and we are investigating the cause. Please be assured that there is no compromise of customer payment details, which are encrypted and tokenized.”
In a series of updates, GoodReader revealed that according to store managers Barnes & Noble had a “virus in their networks”
“Various Barnes and Noble Store managers have contacted me and stated that there is a virus in their networks. It intitially came down from the corporate and filtered down to the stores and also affected the Nook. Cash registers, in physical bookstores are attached to the same network, so no orders can be placed or processed.” states GoodReader. “Some people in the comment section said some of their Nook accounts have been compromised and their credit cards are being used by third parties. The Nook Cloud continues to be down, you can’t sync or access it on the Nook e-reader or the Nook apps, so you can’t see any of the purchases you might have made in the past week.”
BleepingComputer confirmed that the company was hit by a cyber attack on October 10th, 2020, and cited as a source an email sent to customers late Wednesday night that is has seen.
Threat actors compromised the network of Barnes & Noble and gained access to its corporate systems.
“It is with the greatest regret we inform you that we were made aware on October 10, 2020 that Barnes & Noble had been the victim of a cybersecurity attack, which resulted in unauthorized and unlawful access to certain Barnes & Noble corporate systems.” reads the email sent to the customers.
“We write now out of the greatest caution to let you know how this may have exposed some of the information we hold of your personal details,” Barnes & Noble stated in their email.”
The company revealed that hackers had access to customers’ email addresses, billing addresses, shipping addresses, and purchase history.
At the time of writing this post, the company hasn’t provided details of the attack, such as the family of malware that infected its systems. Information shared about the cyber attacks suggests that the company was the victim of a ransomware attack.
In August, the website ZDNet reported in exclusive that a list of passwords for 900+ enterprise VPN servers has been shared on a Russian-speaking hacker forum. The experts pointed out that the list of Pulse VPN credentials, gathered by exploiting the CVE-2019-11510 flaw, also contained accounts belonging to Barnes & Noble.
Depending on the family of ransomware that allegedly infected the company systems we cannot exclude that ransomware operators will leak stolen data on a leak site to threaten Barnes & Noble.
Zoom Announces Technical Preview of End-to-End Encryption
15.10.20 Safety Securityweek
Video conferencing platform Zoom next week will start rolling out end-to-end encryption (E2EE) in technical preview.
The company revealed plans to provide users with end-to-end encryption in May, and announced in June that it would make the feature available to all users, although it was initially planning on leaving free users out.
Now, the company has reinforced the fact that both free and paid users will be offered encryption, and that they will be able to host E2EE meetings with up to 200 participants, thus benefiting from increased privacy and security.
“We’re excited to announce that starting next week, Zoom’s end-to-end encryption (E2EE) offering will be available as a technical preview, which means we’re proactively soliciting feedback from users for the first 30 days,” the company said earlier this week.
This, Zoom says, is only the first phase of its four-phase rollout plan, which is aimed at providing robust protections “to help prevent the interception of decryption keys that could be used to monitor meeting content.”
With E2EE, Zoom says, users will take advantage of the same encryption already available in Zoom meetings, with the main difference being where the encryption keys are stored. Typically, these keys are generated in Zoom cloud and distributed to meeting participants, but with Zoom E2EE, the keys are generated and distributed by the meeting’s host.
With these keys being distributed using public key cryptography, Zoom’s servers never see the encryption keys that are used to decrypt the meeting contents.
Zoom users will need to enable encrypted meetings at the account level and also opt-in to the new feature on a per-meeting basis.
The company also explains that enabling E2EE disables certain features in Zoom, such as 1:1 private chat, Breakout Rooms, cloud recording, join before host, live transcription, streaming, polling, and meeting reactions.
When end-to-end encryption is enabled, participants in a Zoom meeting will see a green shield logo with a padlock in the middle in the upper left corner of the screen. The symbol is similar to that of the GCM encryption, but features a lock instead of a checkmark.
“Participants will also see the meeting leader’s security code that they can use to verify the secure connection. The host can read this code out loud, and all participants can check that their clients display the same code,” Zoom says.
Phase two of the E2EE rollout is planned for 2021 and will include better identity management and E2EE SSO integration.
“End-to-end encryption is another stride toward making Zoom the most secure communications platform in the world. This phase of our E2EE offering provides the same security as existing end-to-end-encrypted messaging platforms, but with the video quality and scale that has made Zoom the communications solution of choice for hundreds of millions of people and the world’s largest enterprises,” said Zoom CEO Eric S. Yuan.
US Cyber Command Urges Users to Patch New 'Ping of Death' Windows Flaw
15.10.20 BigBrothers Securityweek
The United States Cyber Command (USCYBERCOM) warns that users should apply the latest patches for Microsoft software to ensure they won’t fall victim to exploitation attempts.
The most important of these issues, US Cyber Command points out, is CVE-2020-16898, a critical bug in the Windows TCP/IP stack that can be triggered remotely to potentially achieve remote code execution on the victim machine.
While remote code execution might not be easy to achieve, Sophos has demonstrated how the vulnerability can be exploited to cause a Blue Screen of Death (BSoD), which is why the company has described it as a “Ping of Death” vulnerability.
Addressed on October 2020 Patch Tuesday, the flaw can be exploited through specially crafted ICMPv6 Router Advertisement packets sent to a vulnerable system, as these packets are not handled properly. Both Windows 10 and Windows Server are susceptible to exploitation.
“Update your Microsoft software now so your system isn't exploited: CVE-2020-16898 in particular should be patched or mitigated immediately, as vulnerable systems could be compromised remotely,” USCYBERCOM says.
McAfee, which calls the vulnerability “Bad Neighbor” due to the fact that it is located within an ICMPv6 Neighbor Discovery Protocol, explains that consumer Windows 10 systems will likely be impacted the most, as there are only hundreds of Windows Server 2019 machines with IPv6 addresses.
“We believe this vulnerability can be detected with a simple heuristic that parses all incoming ICMPv6 traffic, looking for packets with an ICMPv6 Type field of 134 – indicating Router Advertisement – and an ICMPv6 Option field of 25 – indicating Recursive DNS Server (RDNSS). If this RDNSS option also has a length field value that is even, the heuristic would drop or flag the associated packet, as it is likely part of a ‘Bad Neighbor’ exploit attempt,” the security firm says.
On Tuesday, Microsoft released patches to address not only this flaw, but also CVE-2020-16899, a second bug in the TCP/IP driver, which could be abused to cause denial of service.
Users are advised to apply the available patches as soon as possible. If that’s not a viable option, available workarounds include disabling IPv6, or blocking or dropping ICMPv6 Router Advertisements at the network perimeter.
“Windows Defender and Windows Firewall fail to block the proof-of-concept when enabled. It is unknown yet if this attack can succeed by tunneling the ICMPv6 traffic over IPv4 using technologies like 6to4 or Teredo. Our efforts to repeat the attack in this manner have not been successful to date,” McAfee says.
Google, Intel Warn on ‘Zero-Click’ Kernel Bug in Linux-Based IoT Devices
15.10.20 IoT Threatpost
Intel and Google are urging users to update the Linux kernel to version 5.9 or later.
Google and Intel are warning of a high-severity flaw in BlueZ, the Linux Bluetooth protocol stack that provides support for core Bluetooth layers and protocols to Linux-based internet of things (IoT) devices.
Threatpost Webinar Promo Retail Security
Click to Register!
According to Google, the vulnerability affects users of Linux kernel versions before 5.9 that support BlueZ. BlueZ, which is an open-source project distributed under GNU General Public License (GPL), features the BlueZ kernel that has been part of the official Linux kernel since version 2.4.6.
The flaw, which Google calls “BleedingTooth,” can be exploited in a “zero-click” attack via specially crafted input, by a local, unauthenticated attacker. This could potentially allow for escalated privileges on affected devices.
“A remote attacker in short distance knowing the victim’s bd [Bluetooth] address can send a malicious l2cap [Logical Link Control and Adaptation Layer Protocol] packet and cause denial of service or possibly arbitrary code execution with kernel privileges,” according to a Google post on Github. “Malicious Bluetooth chips can trigger the vulnerability as well.”
The flaw (CVE-2020-12351) ranks 8.3 out of 10 on the CVSS scale, making it high-severity. It specifically stems from a heap-based type confusion in net/bluetooth/l2cap_core.c. A type-confusion vulnerability is a specific bug that can lead to out-of-bounds memory access and can lead to code execution or component crashes that an attacker can exploit. In this case, the issue is that there is insufficient validation of user-supplied input within the BlueZ implementation in Linux kernel.
Intel, meanwhile, which has placed “significant investment” in BlueZ, addressed the security issue in a Tuesday advisory, recommending that users update the Linux kernel to version 5.9 or later.
“Potential security vulnerabilities in BlueZ may allow escalation of privilege or information disclosure,” according to the security advisory. “BlueZ is releasing Linux kernel fixes to address these potential vulnerabilities.”
Google has also published proof-of-concept exploit code for the flaw on GitHub. See a video demo of BleedingTooth below:
Intel also issued a fix for two medium-severity flaws that affect BlueZ, both of which stem from improper access control. That includes CVE-2020-12352, which could enable an unauthenticated user to potentially enable information disclosure via adjacent access.
“A remote attacker in short distance knowing the victim’s bd address can retrieve kernel-stack information containing various pointers that can be used to predict the memory layout and to defeat KASLR,” according to a description on GitHub. “The leak may contain other valuable information such as the encryption keys.”
Another flaw (CVE-2020-24490) could allow an unauthenticated user to potentially enable denial of service via adjacent access. The flaw can be exploited by a remote attacker in short distance, who can broadcast extended advertising data and cause a denial-of-service state, or possibly arbitrary code execution with kernel privileges on victim machines (if they are equipped with Bluetooth 5 chips and are in scanning mode), according to Google.
Andy Nguyen, security engineer with Google, was credited with discovering the flaw. Further details will soon be available on Google’s security blog.
FIN11 Cybercrime Gang Shifts Tactics to Double-Extortion Ransomware
15.10.20 CyberCrime Threatpost
The Clop ransomware has become a tool of choice for the financially motivated group.
The FIN11 financial crime gang is shifting its tactics from phishing and credential-theft to ransomware, researchers said.
According to FireEye Mandiant researchers, FIN11 is notable for its “sheer volume of activity,” known to run up to five disparate wide-scale email phishing campaigns per week. “At this point, it would be difficult to name a client that FIN11 hasn’t targeted,” Mandiant researchers noted, in a posting on Tuesday.
But lately, it has used the Clop ransomware to up its monetary gains.
Threatpost Webinar Promo Retail Security
Click to Register!
Researchers have recently observed attacks in which FIN11 threatened to publish exfiltrated data to pressure victims into paying ransom demands, in a tactic known as double extortion. Clop (which emerged in February 2019) is often used in these kinds of attacks, putting it in the company of the Maze, DoppelPaymer and Sodinokibi ransomware families.
Clop recently made headlines as the malware behind double-extortion attacks on Germany’s Software AG (which carried a $23 million ransom) and a biopharmaceutical firm called ExecuPharm.
FIN11 has been around for at least four years, conducting widespread phishing campaigns. However, it continues to evolve – it’s use of Clop and double extortion is only the latest change in its tactics and tools. It added point-of-sale (POS) malware to its arsenal in 2018, according to Mandiant; and started conducting run-of-the-mill ransomware attacks in 2019.
It’s changed its victimology, too, researchers said: “From 2017 through 2018, the threat group primarily targeted organizations in the financial, retail, and hospitality sectors. However, in 2019 FIN11’s targeting expanded to include a diverse set of sectors and geographic regions.”
Mandiant’s analysis noted that the changes may have been implemented to supplement the ongoing phishing efforts because the latter aren’t wildly successful.
“We’ve only observed the group successfully monetize access in few instances,” researchers said. “This could suggest that the actors cast a wide net during their phishing operations, then choose which victims to further exploit based on characteristics such as sector, geolocation or perceived security posture.”
Also, FIN11 is a subset of the larger TA505 group (a.k.a. Hive0065), which is a financially motivated cybercrime group that has been actively targeting various industries, including finance, retail and restaurants, since at least 2014. It’s known for using a wide range of tactics (in March, IBM X-Force observed TA505 using COVID-19 themed phishing emails) — plus ongoing malware authoring and development.
Its wares include fully-fledged backdoors and RATs – including the recently spotted SDBbot code. And in January, a new backdoor named ServHelper was spotted in the wild, acting as both a remote desktop agent as well as a downloader for a RAT called FlawedGrace.
These campaigns deliver a variety of payloads, including the Dridex and TrickBot trojans, and, yes, ransomware. The latter includes Clop, but also Locky and MINEBRIDGE.
All of this could also explain FIN11’s adoption of new malware.
“Like most financially motivated actors, FIN11 doesn’t operate in a vacuum,” Mandiant researchers concluded. “We believe that the group has used services that provide anonymous domain registration, bulletproof hosting, code signing certificates, and private or semi-private malware. Outsourcing work to these criminal service providers likely enables FIN11 to increase the scale and sophistication of their operations.”
Brandon Hoffman, CISO at Netenrich, told Threatpost that this use of service providers in the underground iis common. “There is a whole marketplace of providers that cater to and operate in what some refer to as the dark web. These services are not limited to the ones described as in use by FIN11 but include code-writing services, monetary exchanges and more,” he said.
Hoffman also pointed out that this evolution to ransomware and extortion has become common for cybercriminals everywhere.
“Broad-based phishing campaigns with the hope of hooking ransomware into an organization for the purpose of extortion, while leveraging malicious service providers, is at the basic footprint of cybercrime today,” he said. “What makes this group special or different remains to be seen for those of us on the outside.”
Critical SonicWall VPN Portal Bug Allows DoS, Worming RCE
15.10.20 Vulnerebility Threatpost
The CVE-2020-5135 stack-based buffer overflow security vulnerability is trivial to exploit, without logging in.
A critical security bug in the SonicWall VPN portal can be used to crash the device and prevent users from connecting to corporate resources. It could also open the door to remote code execution (RCE), researchers said.
The flaw (CVE-2020-5135) is a stack-based buffer overflow in the SonicWall Network Security Appliance (NSA). According to the researchers at Tripwire who discovered it, the flaw exists within the HTTP/HTTPS service used for product management and SSL VPN remote access.
An unskilled attacker could trigger a persistent denial-of-service condition using an unauthenticated HTTP request involving a custom protocol handler, wrote Craig Young, a computer security researcher with Tripwire’s Vulnerability and Exposures Research Team (VERT), in a Tuesday analysis. But the damage could go further.
“VPN bugs are tremendously dangerous for a bunch of reasons,” he told Threatpost. “These systems expose entry points into sensitive networks and there is very little in the way of security introspection tools for system admins to recognize when a breach has occurred. Attackers can breach a VPN and then spend months mapping out a target network before deploying ransomware or making extortion demands.”
Adding insult to injury, this particular flaw exists in a pre-authentication routine, and within a component (SSL VPN) which is typically exposed to the public internet.
“The most notable aspect of this vulnerability is that the VPN portal can be exploited without knowing a username or password,” Young told Threatpost. “It is trivial to force a system to reboot…An attacker can simply send crafted requests to the SonicWALL HTTP(S) service and trigger memory corruption.”
However, he added that a code-execution attack does require a bit more work.
“Tripwire VERT has also confirmed the ability to divert execution flow through stack corruption, indicating that a code-execution exploit is likely feasible,” he wrote, adding in an interview that an attacker would need to also leverage an information leak and a bit of analysis to pull it off.
That said, “If someone takes the time to prepare RCE payloads, they could likely create a sizeable botnet through a worm,” he said.
There’s no sign of exploitation so far, Young said, but a Shodan search for the affected HTTP server banner indicated 795,357 vulnerable hosts as of Tuesday.
SonicWall has issued a patch; SSL VPN portals may be disconnected from the internet as a temporary mitigation before the patch is applied.
The following versions are vulnerable: SonicOS 6.5.4.7-79n and earlier; SonicOS 6.5.1.11-4n and earlier; SonicOS 6.0.5.3-93o and earlier; SonicOSv 6.5.4.4-44v-21-794 and earlier; and SonicOS 7.0.0.0-1.
“Organizations exposing VPN portals to the web should not consider these systems as impenetrable fortresses,” Young told Threatpost. “If the last 18 months has shown anything, it is that enterprise VPN firewalls can be just as insecure as a cheap home router. It is crucial to employ a tiered security model to recognize and respond to unauthorized activity.”
Travelex, Other Orgs Face DDoS Threats as Extortion Campaign Rages On
15.10.20 Attack Threatpost
Organizations worldwide – including Travelex – have been sent letters threatening to launch DDoS attacks on their network unless a $230K ransom is paid.
Companies worldwide have continued to receive extortion emails threatening to launch a distributed denial-of-service (DDoS) attack on their network, unless they pay up – with British foreign-exchange company Travelex reportedly being one recent high-profile threat recipient.
Researchers said that since mid-August, several companies have been sent emails that warn that their company network will be hit by a DDoS attack in about a week. The initial ransom demand is set at 20 BTC – which translates to about $230,000 at the time of writing – and cybercriminals threaten to increase that ransom by 10 BTC for each day not paid, said researchers.
While a high level of activity was first tracked in August, that activity then slowed down in the first half of September – only to “grow significantly” in the end of September and beginning of October, Radware researchers told Threatpost.
Travelex (which has undergone its fair share of security woes over the past year, starting with a New Year’s ransomware attack) was one such org threatened with a DDoS attack, unless it paid 20 bitcoins (BTC), Intel471 researchers reported on Tuesday. A bitcoin wallet address in the email shows that Travelex did not pay the attackers at any point, they said.
“Following the extortion email, the threat actor conducted a volumetric attack on a custom port of four IP addresses serving the company’s subdomains,” according to Intel471 researchers. “Two days later, the attackers carried out another DNS amplification attack against Travelex using Google DNS servers.”
Threatpost has reached out to Travelex for further comment on the DDoS extortion threat.
Ongoing DDoS Extortion Threats
While the ransom DDoS campaign has been ongoing since August and has received widespread coverage, researchers with Radware said in a Wednesday post that they are continuing to see companies worldwide receive the extortion emails – and that attackers are becoming more sophisticated.
“There is no way to communicate with the blackmailers, so there is no option to negotiate and the only way to get a message through is by sending BTC to the bitcoin address mentioned in the letter,” researchers said.
The extortion emails claim that the threat group has already launched a small DDoS attack on the victim’s IPs (of the ASN number mentioned in the letter) to give the threat legitimacy. The attackers also claim that they have the ability to perform volumetric attacks that peak at 2Tbps – almost reaching the levels of the 2.3Tbps attack targeting an Amazon Web Services client in February that was the largest volumetric DDoS attack on record.
“These threats are not hoaxes, and the actors have followed up with attacks,” Pascal Geenens, director of threat intelligence at Radware, told Threatpost. “While we have not observed the 2TBps attack threatened in the letter included the report, organizations have seen attacks ranging up to 300GBps and combining multiple attack vectors. These attacks can be devastating for many organizations.”

A sample DDoS ransom letter. Credit: Radware
Of note, the extortion threats were sent to generic email addresses within the companies, which did not always reach the right person in the organization – and were even sometimes received by subsidiaries of companies in the wrong country. However, while earlier iterations of the ransom note were elementary, researchers observed the threat actor increasing their sophistication.
“The letters have been improved since the start of the campaign by fixing some typos, rephrasing some actions for better clarity, and press coverage of earlier DDoS attacks that impacted financial organizations has been added to instill more fear,” said researchers.
The threat actor purports to be various APTs, posing as Fancy Bear, Armada Collective and Lazarus Group. The actors seem to have a preference of APT depending on the vertical they are trying to convince to pay a ransom: The cybercriminals purport to be Lazarus Group when targeting financial organizations, (such as in Travelex’s case, for instance), while they pretend to be Fancy Bear while targeting technology and manufacturing orgs.
However, researchers pointed to discrepencies that show that the threat actors are merely posing as these APTs as opposed to being the real deal: “Based on what we know about the standard tactics, techniques and procedures of these APT groups, the threat activity that we are seeing does not match up,” Geenens told Threatpost. “Attribution is mostly guesswork, and it’s impossible to make an absolute statement one way or another. Even if an APT group were to admit to these threats, it would be impossible to confirm whether they are even telling the truth.”
It’s worth noting that these ransom threats are nothing new. In 2019, cybercriminals posing as Fancy Bear launched DDoS attacks against companies in the financial sector and demanded ransom payments. And back in 2016, a group (who also called themselves the Armada Collective) sent extortion emails to various online businesses threatening to launch DDoS attacks if they weren’t paid in Bitcoin. All the way back in 2015, the FBI said that it was seeing an increase in the number of companies being targeted by scammers threatening to launch DDoS attacks if they don’t pay a ransom.
In their ransom letters, attackers claim there are no counter-measures to protect against their attacks. Researchers said this isn’t the case, and advised organizations to not pay the ransom demand: “There is no guarantee blackmailers will honor the terms of their letter,” they said. “Paying only funds future operations, allows them to improve their capabilities and motivates them to continue the campaign.”
BEC Attacks: Nigeria No Longer the Epicenter as Losses Top $26B
15.10.20 Spam Threatpost
BEC fraudsters now have bases of operation across at least 39 counties and are responsible for $26 billion in losses annually — and growing.
A study of more than 9,000 instances of business email compromise (BEC) attacks all over the world shows that the number has skyrocketed over the past year, and that the social-engineering scam has expanded well beyond its historic roots in Nigeria.
The report from Agari’s Cyber Intelligence Division (ACID), entitled The Global Reach of Business Email Compromise, found that these attacks cost businesses a staggering $26 billion every year. And that trend appears to be accelerating. In fact, researchers found BEC attacks currently make up a full 40 percent of cybercrime losses globally, impacting at least 177 countries.
For context, the Anti-Phishing Working Group recently found that the average wire transfer in a BEC scam is around $80,000.
Beyond Nigeria
In a BEC attack, a scammer impersonates a company executive or other trusted party, and tries to trick an employee responsible for payments or other financial transactions into wiring money to a bogus account. Attackers usually conduct a fair amount of recon work, studying executive styles and uncovering the organization’s vendors, billing system practices and other information to help mount a convincing attack.
It started as an evolution from the old-school lures used by Nigerian cybergangs to trick people into giving them money: Fake princes, the promise of finding true love or even work-from-home gigs that sound too good to be true.
“Most of the seasoned actors have some nexus to Nigeria,” the report said. “It is here, after all, where BEC first gained global notoriety back in 2015, when email-fraud rings first began defrauding organizations by impersonating their CEOs and CFOs in email scams targeting employees.”
The rising payoff for these crimes has led to a period of innovation, according to the report, which identified a new “flavor” of attack, called vendor email compromise, which Agari credits to the criminal organization Silent Starling, located in West Africa.
In a VEC attack, crooks will first compromise accounts belonging to employees of suppliers, then target the vendors’ customers by purporting to be the owner of the compromised account and asking clients to transfer money to the “supplier” – which is actually a mule account.
Meanwhile, these types of attacks have evolved to become more potent and more difficult to stop, largely because these operations have proliferated worldwide, beyond their Nigerian roots.
More Money, More BEC Attacks
Insights gained by Agari in analyzing 9,000 defense engagements between May 2019 and July 2020 found that only half of the instances examined originated in Nigeria. Law-enforcement crackdowns have driven these fraudsters elsewhere and rising returns are enticing other criminal gangs into the fray, meaning the bases of operations from these scams can come from anywhere.
What researchers found instead was that 25 percent of these attacks originated in the U.S., specifically clustered in the states of California, Florida, Georgia, New York and Texas. Not coincidentally, these are the same states targeted by the U.S. Department of Justice’s BEC crackdown.
On Sept. 10, the DOJ announced that 281 arrests had been made across the globe under “Operation ReWired,” and detailed where investigators found U.S.-based scammers, including the metro areas of Atlanta, Chicago, Dallas, and Miami.
BEC Money Mules
Perhaps the most crucial aspect of any BEC gang scam is the role of “money mule.” These people, either wittingly or unwittingly, do the scammers dirty work for them, like setting up bank accounts and transferring money. As further evidence of BEC’s growing global presence, Agari identified mules scattered around 39 countries.
However, most of these mule accounts are located in the U.S. (80 percent) and clustered around many of the same metro areas as the scammers themselves — but, the report added, these accounts were found in every state and the District of Columbia.
Interestingly, they also noticed that mule-account deposit amounts in the U.S. were substantially smaller than in other countries. The report said that out of 2,900 mule accounts analyzed, the average amount requested by American-based scammers was $39,500, which is just a fraction of what was requested in other spots around the world. By comparison, Hong Kong had an average wire transfer amount of of $257,300.
“BEC actors can now be found in 50 countries, and while half of these actors still have a home base in Nigeria, the geographical distribution of these threat actors is much higher than was just a few years ago,” the report concluded. “This signals that cybercriminal organizations are healthy, growing, becoming more diversified and showing little signs of weakness.”
Silent Librarian Goes Back to School with Global Research-Stealing Effort
15.10.20 Cyber Threatpost
The Iranian hacker group is targeting universities in 12 countries.
The Silent Librarian campaign has re-emerged for the fall school session, actively targeting students and faculty at universities via spear-phishing campaigns.
The threat group (also known as TA407 and Cobalt Dickens), which operates out of Iran, has been on the prowl since the start of the 2019 school year, launching low-volume, highly-targeted, socially engineered emails that eventually trick victims into handing over their login credentials. The goal is to harvest not just logins to sell online, but also proprietary university research and data, researchers said.
An example of a Silent Librarian phishing portal. Source: Proofpoint.
The emails typically masquerade as messages from university library systems or other on-campus divisions. Over the course of the last school year, the cyberattackers honed their efforts, and began using shortened URL links in their phishing emails, which make it more difficult to detect that victims are being redirected to an attacker-hosted landing page. The attackers also revamped their landing pages with new university-specific banners, based on weather alerts or emergency notifications, to make them look more authentic.
Now, this APT group is going back to school with a fresh campaign that seems to be targeting institutions globally, according to an analysis Tuesday from Malwarebytes. Targets stretch across a dozen countries and so far have included: The University of Adelaide in Australia; Glasgow Caledonian, University of Kent, University of York, King’s College London, Cambridge and others in the U.K.; the University of Toronto and McGill in Canada; and Stony Brook University, University of North Texas and others in the U.S.
The modus operandi seen last year remains in place, with Silent Librarian hosting a series of phishing sites that are built to mimic legitimate university domains. For instance, emails purporting to be from the University of Adelaide Library directed victims to a “library.adelaide.crev[dot]me” URL, which is very close to the legitimate “library.adelaide.edu.au” domain of the school.
“Many of these have been identified and taken down, [but] the threat actor has built enough of them to continue with a successful campaign against staff and students alike,” according to the analysis. “Clearly we only uncovered a small portion of this phishing operation. Although for the most part the sites are taken down quickly, the attacker has the advantage of being one step ahead and is going for many possible targets at once.”
The APT is using the Cloudflare content delivery network to host most of the phishing hostnames, in order to hide the real hosting origin.
“However, with some external help we were able to identify some of their infrastructure located on Iran-based hosts,” researchers noted. “It may seem odd for an attacker to use infrastructure in their own country, possibly pointing a finger at them. However, here it simply becomes another bulletproof hosting option based on the lack of cooperation between U.S. or European law enforcement and local police in Iran.”
In March 2018, nine Iranians were indicted by the U.S. Department of Justice for conducting attacks against universities and other organizations with the goal of stealing research and proprietary data. The Silent Librarian attacks are likely part of the same ongoing effort, according to Malwarebytes.
“Considering that Iran is dealing with constant sanctions, it strives to keep up with world developments in various fields, including that of technology,” the researchers added, noting that as such, these attacks represent a national interest and are well-funded. “IT administrators working at universities have a particularly tough job considering that their customers, namely students and teachers, are among the most difficult to protect due to their behaviors. Despite that, they also contribute to and access research that could be worth millions or billions of dollars.”
Intel Adds Memory Encryption, Firmware Security to Ice Lake Chips
15.10.20 Safety Threatpost
Intel’s addition of memory encryption to its upcoming 3rd generation Xeon Scalable processors matches AMD’s Secure Memory Encryption (SME) feature.
Intel’s third-generation Xeon Scalable server processors, code-named Ice Lake, will be rolled out with new security upgrades that the chip giant claims will better protect devices from firmware attacks.
The upcoming chips are based on Ice Lake, Intel’s 10nm CPU microarchitecture, which was first launched in 2019. Intel is targeting initial production shipments for its Xeon scalable processors for servers at the end of the year – but just announced that they will come with new security features.
One such feature is called Intel Total Memory Encryption (Intel TME), which Intel said helps ensure that all memory accessed from the CPU is encrypted – such as customer credentials, encryption keys and other IP or personal information on the external memory bus.
“Intel developed this feature to provide greater protection for system memory against hardware attacks, such as removing and reading the dual in-line memory module (DIMM) after spraying it with liquid nitrogen or installing purpose-built attack hardware,” according to Intel on Wednesday.
Of note, this feature already exists in other competing chip platforms, with AMD first proposing its own version, Secure Memory Encryption (SME), back in 2016.
Intel TME utilizes the storage encryption standard, AES XTS, from the National Institute of Standards and Technology (NIST). Intel said an encryption key is generated using a hardened random number generator in the processor without exposure to software, allowing existing software to run unmodified while better protecting memory.
Intel also claims that another new feature can protect against sophisticated adversaries who may attempt to compromise or disable the platform’s firmware to intercept data or take down the server. The Intel Platform Firmware Resilience (Intel PFR) will be part of the Xeon Scalable platform, which Intel claims will help protect against platform firmware attacks by detecting them before they can compromise or disable the machine.
Intel PFR will use an Intel field-programmable gate array (FPGA) as a “platform root of trust,” which will validate critical-to-boot platform firmware components before any firmware code is executed, according to Intel. An Intel FPGA is an integrated circuit designed to be configured by a customer or a designer after manufacturing.
The firmware components protected “can include BIOS Flash, BMC Flash, SPI Descriptor, Intel Management Engine and power supply firmware.”
The chip giant is also bringing its existing Intel Software Guard Extensions (SGX) feature to Ice Lake. Intel SGX, a set of security-related instruction codes that are built into Intel CPUs, shields sensitive data – such as AES encryption keys – inside “enclaves,” which are physically separate from other CPU memory and are protected by software encryption.
Of note, Intel SGX is not an end-all-be-all solution – researchers have previously been able to bypass SGX in various attacks, from the Plundervolt security issue revealed in 2019 to speculative execution design flaws in Intel CPUs revealed in 2018.
The new security features come as Intel processors have been plagued by various security issues over the past years – including Meltdown and Spectre as well as other speculative execution and side-channel attacks.
Cybercriminals Steal Nearly 1TB of Data from Miami-Based International Tech Firm
15.10.20 Incindent Threatpost
Databases of sensitive, financial and personally identifiable info and documents from Intcomex were leaked on Russian-language hacker forum after a ransomware attack.
Hackers have stolen nearly a terabyte of data from a Miami-based tech firm, leaking a number of the pilfered files (including full credit-card information, scans of sensitive documents such as passports, bank statements and financial documents, and even customer databases) on a Russian hacker forum.
An investigation uncovered leaked data belonging to Intcomex, a very large value-added reseller (VAR) which provides technology products and services targeting Latin America and the Caribbean. The leaks occurred on Sept. 14 and Sept. 20, when hackers dumped it in two parts on the forum.
“So far, the first release was a collection called ‘Internal Audit’ with a size of 16.6GB, while the second release is titled ‘Finance_ER,’ totaling 18GB,” according to a report on the CyberNews website. “Based on folder names, the most recent data comes from July 2020.”
The data appears to have been stolen as the result of a ransomware attack. Hackers promised to leak “the more interesting data”— which — at a later time, according to the report. A Russian-language note left along with the leaked data alludes to the hackers waiting to see if the company will pay up before releasing the rest of the data, which likely will be more full credit-card information, a treasure trove for hackers, according to the report.
CyberNews said it contacted Intcomex on Sept. 21 about the leak, which confirmed that the database researchers saw on the forum is indeed theirs.
Intcomex said it took “decisive steps to address the situation and protect our systems” upon learning about the leak and is working with third-party cybersecurity experts in the investigation of what happened, according to a media statement. The company also notified law enforcement and is in the process of letting “affected parties” know about the leak “as appropriate,” the company said.
The breach did not impact the services Intcomex provides to its partners, the company said. However, its sheer size, the sensitivity of the info, and the lack of breach detection by the company are extremely worrisome from a cybersecurity position, experts noted.
“Not only is this leak significant in the volume of data that was leaked, but also the sensitive contents of the data as well,” observed Erich Kron, security awareness advocate for security firm KnowBe4, in an email to Threatpost. “This is not a simple matter of an email address and a name; when sensitive information such as passport numbers and license scans along with payroll information are lost, these can cause significant damage to the users of the service, up to and including real identity theft.”
Threat actors also were able to steal the data and dump it online before the company even noticed, observed Chris Clements, vice president of solutions architecture for security firm Cerberus Sentinel.
“This highlights the ongoing shortcomings of businesses in detecting that a breach has occurred before the attacker has been able to do significant damage,” he said in an email to Threatpost. “In this case, attackers were apparently able to exfiltrate nearly a terabyte of sensitive information without detection.”
Indeed, the data leaked by the team is extensive and could be used by cybercriminals to launch further and comprehensive attacks on the company’s employees, customers or partners. Credit cards include the full number, expiration date, CVV2, and the holder’s full name, and document scans include full passport info for both U.S. and Latin American passport holders, as well as people’s Social Security numbers and full driver-license info.
The fact that the company operates across country borders also could mean a very messy and expensive clean-up operation on the backend of the leak, Kron noted.
“Between legal fees, fines and identity-theft protection services being provided to the victims, these types of attacks can be very costly for organizations,” he said. “In addition, with this organization serving 41 countries, they are going to have a mess of notification requirements and additional fines are likely from foreign entities.”
German authorities raid the offices of the FinFisher surveillance firm
15.10.20 BigBrothers Securityaffairs
Earlier this month, German authorities have raided the offices of FinFisher, the German surveillance software firm, accused of providing its software to oppressive regimes.
German authorities have raided the offices of FinFisher, the popular German surveillance firm as part of an investigation into the alleged sale of their software to oppressive regimes.
The news was first reported by the German news agency Tagesschau, which claims FinFisher had been using satellite companies to evade restrictions on the exportation of its surveillance tools.
The Munich Public Prosecutor’s Office ordered the police to raid 15 locations around Munich and at a connected company in Romania on October 6 and October 8.
The authorities started the investigation last year after the German blog Netzpolitik and some advocacy groups (Reporters Without Borders, Society for Freedom Rights, and the European Center for Constitutional and Human Rights), filed a complaint with Munich prosecutors in the summer of 2019.
The complaint claims that the popular surveillance firm FinFisher eluded the restrictions for the sale of the software to oppressive regimes that used it to spy on activists, political dissidents, privacy advocates, and citizens.
The company denied accusations and sued the German blog and requested the removal of the article on the case.
In September, Amnesty International uncovered a new surveillance campaign that targeted Egyptian civil society organizations with previously undisclosed versions of the infamous FinSpy surveillance spyware.
The new versions employed in this campaign allow its operators to spy on both Linux and macOS systems.
Finisher, aka FinFisher, is a multiplatform surveillance software used by government and law enforcement agencies for their investigations, but unfortunately, it made the headlines because it was also used by oppressive regimes to spy on dissidents, activists, and Journalists.
Since 2011 it was employed in attacks aimed at Human Rights Defenders (HRDs) in many countries, including Bahrain, Ethiopia, UAE, and more.
FinSpy can spy on most popular desktop and mobile operating systems, including Android, iOS, Windows, macOS, and Linux. It allows to use the users’ devices as a spying tool, it can control both webcam and microphone, to spy on communications and exfiltrate data stored on the infected systems.
The new versions of FinSpy spyware were used by a new unknown hacking group, Amnesty International speculates the involvement of a nation-state actor that employed them since September 2019.

FinFisher was officially designed for law enforcement investigations and intelligence agencies, but across the years, security experts have found on the devices of dissidents and journalists in countries many countries, including Ethiopia, Bahrain, Egypt, and Turkey where this surveillance software cannot be exported.
Talos experts disclosed unpatched DoS flaws in Allen-Bradley adapter
15.10.20 ICS Securityaffairs
Cisco Talos found several remotely exploitable denial-of-service (DoS) vulnerabilities in a Rockwell Automation industrial automation product.
A researcher from Cisco Talos released technical details of several remotely exploitable denial-of-service (DoS) vulnerabilities in an industrial automation product made by Rockwell Automation.
The product affected by the flaw is the Allen-Bradley 1794-AENT Flex I/O series B adapter, the issue resides in the Ethernet/IP request path port/data/logical segment functionality.
Cisco Talos researcher has found five high-severity buffer overflow vulnerabilities that impact Allen-Bradley devices running versions 4.003 and earlier.
“The Allen-Bradley Flex input/output system contains multiple denial-of-service vulnerabilities in its ENIP request path data segment. These bugs exist specifically in the 1794-AENT FLEX I/O modular platform. It provides many I/O operations and servers as a smaller physical device compared to other similar hardware.” reads the Cisco Advisory.
An attacker could exploit the above vulnerabilities by sending a specially crafted, malicious packet to the vulnerable device, this will causing a loss of communication between the victim’s network and the device resulting in denial-of-service.
Talos reported the flaws to Rockwell Automation in February and for two times the vendor requested disclosure extensions. When Rockwell Automation requested a third extension, Talos decided to disclose the issues on October 12 regardless of whether or not the vendor has released security updates.
Rockwell Automation published a security advisory for its registered customers on October 12 that includes general recommendations to prevent attacks exploiting the above flaws.
The vendor recommends configuring the devices to accept CIP connections only from trusted sources on port 44818. The company also suggests implementing network segmentation and security controls to minimize exposure of affected devices. Other recommendations include the use of firewalls, VPNs and other network infrastructure controls.
Google researcher found BleedingTooth flaws in Linux Bluetooth
15.10.20 Vulnerebility Securityaffairs
Google security researcher discovered Bluetooth vulnerabilities (BleedingTooth) in the Linux kernel that could allow zero-click attacks.
Andy Nguyen, a Google security researcher, has found Bluetooth vulnerabilities, referred to as BleedingTooth, in the Linux kernel that could be exploited by attackers to run arbitrary code or access sensitive information.
The BleedingTooth flaws are tracked as CVE-2020-12351, CVE-2020-12352, and CVE-2020-24490.
The most severe of the vulnerabilities is a heap-based type confusion flaw (CVE-2020-12351) that has been rated as high severity and received a CVSS score of 8.3 out of 10.
A remote attacker within the Bluetooth range of the victim can exploit the flaw by knowing the bd address of the target device. The attacker can trigger the vulnerability by sending a malicious l2cap packet, which can lead to denial of service or even execution of arbitrary code, with kernel privileges.
According to the Google security researcher, the issue is a zero-click flaw that means that it does not require user interaction to be exploited.
Nguyen released a Proof-of-concept code for this vulnerability an exploit along with a video PoC demonstrating the issue.
The second issue found by the expert is a stack-based information leak that is tracked as CVE-2020-12352. The flaw impacts Linux kernel 3.6 and higher, it is classified as medium severity and received a CVSS score of 5.3.
“A remote attacker in short distance knowing the victim’s bd address can retrieve kernel stack information containing various pointers that can be used to predict the memory layout and to defeat KASLR. The leak may contain other valuable information such as the encryption keys,” reads the security advisory published by Google.
The third vulnerability tracked as CVE-2020-24490, is a heap-based buffer overflow that resides in net/bluetooth/hci_event.c. and affects Linux kernel 4.19 and higher.
The vulnerability is classified as medium risk and received a CVSS score of 5.3.
“A remote attacker in short distance can broadcast extended advertising data and cause denial of service or possibly arbitrary code execution with kernel privileges on victim machines if they are equipped with Bluetooth 5 chips and are in scanning mode. Malicious or vulnerable Bluetooth chips (e.g. compromised by BLEEDINGBIT or similar) can trigger the vulnerability as well.” reads the security advisory.
The researchers published the PoC code for both issue on GitHub.
Tactical vs Strategic: CISOs and Boards Narrow Communication Gap
15.10.20 Cyber Securityweek
91% of Survey Respondents Say Their Boards Have Increased Cybersecurity Investment in Response to COVID-19 Pandemic
A global survey of almost 1000 CISO/Senior IT decision makers shows positive signs of Boards' willingness to invest in cybersecurity -- with perhaps one major rider.
The purpose of the survey, commissioned by Thycotic, was to examine the primary drivers in cybersecurity spend decision-making. The resulting survey report shows that 91% of the respondents say their Board has increased cybersecurity investment in response to the COVID-19 pandemic, and around 60% believe they will receive more security budget next year because of COVID-19. This is a welcome sign that Boards are taking cybersecurity seriously.
More than three-quarters of the respondents report they have received investment for new projects either in response to a security incident, or through fear of compliance audit failures. This is the rider in the Boards' willingness to invest -- all three of these investment triggers (COVID, incident response and compliance) are reactive; that is, they are tactical responses rather than strategic plans.
For security teams to adequately defend their systems, they need to get ahead of the adversaries. That requires strategic thinking and planning rather than tactical reaction -- which seems to be less acceptable to boardrooms. Indeed, 37% of the respondents have had proposed investments turned down because the threat was perceived as low risk or because the technology had a lack of demonstrable ROI.
The extent to which this is a failure of CISOs to explain threats in business language, or a simple reluctance of the Board to be proactive rather than reactive, is impossible to determine from the survey.
“The fact Boards mainly approve investments after a security incident or through fear of regulatory penalties for non-compliance," comments Terence Jackson, CISO for the privilege management firm Thycotic, "shows that cybersecurity investment decisions are more about insurance than about any desire to lead the field which, in the long run, limits the industry’s ability to keep pace with the cybercriminals.”
A reactive approach to cybersecurity can have two further negative effects. Firstly, it can lead to excessive 'shelfware', where a point product is purchased but never fully utilized; and secondly it can lead to the purchase of inadequate solutions. For the former, half of the organizations taking part in the survey admit that new technology solutions they purchase are never fully utilized, and become shelfware. For the latter, reaction to an issue can lead to a failure to think through the problem. Joseph Carson, chief security scientist and advisory CISO at Thycotic, gives the following example. "Companies can react to the weak password issue by buying password managers," he told SecurityWeek, "without realizing that what they actually need is an integrated system that can rotate passwords and manage privileges." When they realize they need a full privilege management system, the password managers become redundant.
Carson nevertheless finds a lot of positivity in the survey results. "One area that I think is key," he said, "is that the communication between the CISO and the executive Board is getting better. In previous research we found that there was a language barrier between the CISO and the Board -- the CISO would think very much about fear and doubt and threats and risk and tend to stress that fear factor. However, this report now shows that CISOs are both being listened to, but also getting the follow through budget. In the past, CISOs and the Board weren't speaking the same language. This report shows that the communication gap between the CISO and the Board is closing."
Despite the increased budget to COVID being a reactive decision, Carson nevertheless believes it is a positive response from the Board. "That 91% of respondents say the Board is now adequately supporting the team with the follow-up investments is significant. But there is some bad news that goes with that as well -- that with that investment, 50% of the purchased security solutions are not being fully utilized." He recognizes the reactive nature of security decision-making in much of the world, but sees an interesting cultural difference in Asia. "The factors are a little different in Asia," he told SecurityWeek, "where they are focusing more on the return on investment. There's this interesting cultural difference in places like Australia, Singapore and Malaysia where purchasing decision focuses more on ROI."
The survey also shows that product choice is often geared to benchmarking against what peer companies are doing. This is particularly prevalent in the UK and Europe. In the U.S. and Australia, choice is very much dominated by industry analysts and expertise, where they tend to look at the analysts such as Gartner and Forrester for direction. "Another surprise for me," he continued, "is that I would have thought the security team would have a strong say in the final decision-making process for new solutions, but in fact in most places it is the operations teams that have a bigger say in what the final solution will be. I think this is because the security teams can look at the problem from a threat and risk perspective, but ultimately the operations teams have to implement, deploy, maintain and upgrade it."
In the final analysis, the difficulty with all surveys is that the statistics returned are objective facts; but the interpretation of those statistics is subjective. Joseph Carson is fairly upbeat and positive about how the Boards are beginning to take cybersecurity seriously and fund what is necessary. However, it is equally possible to point to the examples given in the survey and suggest that the Boards are merely reacting to what is visibly happening today. There is little in the survey to suggest that boardrooms are ready to support their security teams with longer term strategic rather than tactical approaches to cybersecurity -- and it is the strategic approach that is necessary to thwart the adversaries.
BleedingTooth: Vulnerabilities in Linux Bluetooth Allow Zero-Click Attacks
15.10.20 Vulnerebility Securityweek
Bluetooth vulnerabilities that a Google security researcher has identified in the Linux kernel could be exploited to run arbitrary code or access sensitive information.
Referred to as BleedingTooth, the issues were identified by Andy Nguyen, a security engineer from Google, and are tracked as CVE-2020-12351, CVE-2020-12352, and CVE-2020-24490. They were introduced in 2016, 2012, and 2018, respectively.
The most severe of these flaws is CVE-2020-12351, a heap-based type confusion that affects Linux kernel 4.8 and higher. The issue features a high severity rating (CVSS score of 8.3).
The bug can be exploited by a remote attacker within Bluetooth range of the victim and which knows the bd address of the target device. To trigger the flaw, the attacker would have to send a malicious l2cap packet, which can lead to denial of service or even execution of arbitrary code, with kernel privileges.
An attacker looking to trigger the vulnerability can also use a malicious Bluetooth chip for that. Proof-of-concept code for an exploit can be found on GitHub.
The bug, Nguyen explains, does not require user interaction to be exploited (it is a zero-click vulnerability). A video demonstrating the issue is embedded below.
The second issue, CVE-2020-12352, is a stack-based information leak that impacts Linux kernel 3.6 and higher. The bug is considered medium severity (CVSS score of 5.3).
“A remote attacker in short distance knowing the victim's bd address can retrieve kernel stack information containing various pointers that can be used to predict the memory layout and to defeat KASLR. The leak may contain other valuable information such as the encryption keys,” Google’s researchers explain.
Tracked as CVE-2020-24490 and considered medium risk (CVSS score of 5.3), the third vulnerability is a heap-based buffer overflow that affects Linux kernel 4.19 and higher.
A remote attacker within short range of a vulnerable device can trigger the flaw through broadcasting extended advertising data. This could lead to denial of service or even arbitrary code execution with kernel privileges.
Only devices that feature Bluetooth 5 chips and which are in scanning mode are vulnerable to this flaw, but an attacker could also use malicious chips to trigger the vulnerability, Google’s researchers note.
PoC code for both medium-severity flaws has been published on GitHub.
BlueZ, the official Linux Bluetooth protocol stack, has announced Linux kernel fixes that patch all three of these security issues, Intel reveals. The company notes that the vulnerabilities affect “all Linux kernel versions before 5.9 that support BlueZ.”
The tech giant recommends updating Linux kernel to version 5.9 or later. Provided that an update is not possible, several kernel fixes are available to address the issues.
Microsoft Patches New Windows 'Ping of Death' Vulnerability
15.10.20 OS Securityweek
One of the vulnerabilities that Microsoft addressed as part of the October 2020 Patch Tuesday is a critical bug in Windows’ TCP/IP driver that could lead to the remote execution of code.
Tracked as CVE-2020-16898, the issue is triggered when the TCP/IP stack doesn’t handle ICMPv6 Router Advertisement packets properly. An attacker could send specially crafted ICMPv6 Router Advertisement packets to a remote Windows machine to exploit the flaw and execute arbitrary code, Microsoft explains.
The tech company notes that Windows 10 and Windows Server are vulnerable to attacks and that there are no mitigations. However, one workaround is available.
A second issue in the TCP/IP driver, which is tracked as CVE-2020-16899, could be exploited to cause the target computer to stop responding. This flaw too can be exploited through crafted packets, but would not result in code execution, Microsoft says. The company rated the flaw as important.
SophosLabs’ security researchers have published a video to demonstrate how the first vulnerability (CVE-2020-16898) can be exploited to trigger a Blue Screen of Death (BSoD). They described it as a so-called “Ping of Death” vulnerability.
The issue, they say, resides in the tcpip.sys kernel driver and is caused by a logic error in how ICMP (Internet Control Message Protocol) messages are parsed. To trigger the flaw, an attacker would need to send “a crafted IPv6 router advertisement packet containing a Recursive DNS Server (RDNSS) option.”
The packet, they explain, would contain more data than expected, thus resulting in the driver “putting more bytes of data on its memory stack than provided for in the driver’s code, resulting in a buffer overflow.”
While both denial of service and remote code execution are possible by exploiting the bug, in practice, the latter would be extremely difficult to achieve, the researchers say. SophosLabs’ researchers created proof-of-concept (PoC) code to exploit the issue but won’t release details on it yet, to prevent exploitation.
“Once we understood the bug, developing a ‘Blue Screen of Death’ proof-of-concept was fairly straightforward. But taking it to the level that Microsoft has warned is possible—remote code execution (RCE)—is not. Modern defensive coding standards and practices would slow down an effort to build a reliable generic RCE exploit, for two reasons,” SophosLabs notes.
Cyber Warriors Sound Warning on Working From Home
15.10.20 Cyber Securityweek
Cyber warriors on NATO's eastern edge are warning that the growing number of people working from home globally due to the pandemic is increasing vulnerability to cyber attacks.
The Baltic state of Estonia hosts two cyber facilities for the Western military alliance -- set up following a series of cyber attacks from neighbour Russia more than a decade ago.
"Large scale use of remote work has attracted spies, thieves and thugs," Jaak Tarien, head of NATO's Cooperative Cyber Defence Centre of Excellence (CCDCOE), told AFP in an interview.
The increased amount of information travelling between institutional servers and home networks is creating new challenges for employers.
"Tackling these new challenges is complicated and requires a lot of resources as well as a different kind of approach," Tarien said.
"We are likely only scratching the surface in assessing the magnitude of malicious activities taking place in the Covid-era busy cyberspace."
An EU-wide survey in September found that around a third of employees were working from home.
- Boom in online courses -
The concerns are echoed at NATO's Cyber Range -- a heavily-guarded facility protected by barbed wire in the centre of the capital Tallinn run by Estonian defence forces.
The server rooms inside serve as a platform for NATO cyber security exercises and training.
"Specialists have set up the work infrastructure, but they cannot control the way people use their home internet or how secure it is," said Mihkel Tikk, head of the Estonian defence ministry's cyber policy department.
Tikk said the latest cyberattacks have targeted Estonia's health sector and Mobile-ID -- the mobile phone based digital ID.
The coronavirus pandemic has also affected operations at the cyber facilities themselves, forcing the cancellation of offline exercises.
But the NATO Cyber Defence Centre said the silver lining is the growing popularity of the cyber security courses it is putting online.
The online courses include "Fighting a Botnet Attack", "Operational Cyber Threat Intelligence" and "IT Systems Attack and Defence".
There were 6,411 students by September 1 and the centre is aiming for 10,000 by the end of 2020.
- 'A massive mistake' -
The Cyber Defence Centre was set up following a series of cyberattacks of unprecedented sophistication on Estonian websites in 2007.
The Russian pro-Kremlin youth organisation Nashi later claimed responsibility.
These days, Estonia faces a "continuous flow of attacks" and repelling them requires constant work, Defence Minister Juri Luik told AFP.
But he said the country was in "a pretty good situation" since it has had time to learn from past experience.
"We have worked diligently to guarantee that the computer networks are difficult to break in and the communication is encrypted –- both military but also civilian communication.
"So I think it is relatively more difficult to harm Estonia than many other countries who perhaps are not so used to working via cyberspace and haven't given too much attention to cyber defence," he said.
The minister underlined that all this work would be for nothing without basic cyber hygiene, including password protection.
"This is extremely important and should be remembered -- especially now that many people work from home via computer.
"At home you might let your guard down and that's of course a massive mistake."
FIN11 Spun Out From TA505 Umbrella as Distinct Attack Group
15.10.20 CyberCrime Securityweek
FIN11 is a new designation for a financially motivated threat actor that may previously have been obscured within the activity set and group usually referred to as TA505. Although there are similarities and overlaps in the TTPs of both groups, researchers have discovered enough differences to separate the groups.
TA505 is largely defined by its large-scale phishing campaigns. It has distributed Dridex and dropped multiple types of ransomware, including GlobeImposter and Philadelphia. The group now defined by Mandiant (FireEye) Threat Intelligence researchers as FIN11 similarly uses large-scale phishing campaigns, but is primarily defined by its unique use of the CLOP ransomware. The researchers also believe that the code families known as FlawedAmmyy, FRIENDSPEAK and MIXLABEL are unique to FIN11.
It is possible that some earlier attacks attributed to TA505 were actually undertaken by FIN11 -- especially those that used any of the malware now uniquely attributed to FIN11. Examples could include the use of FlawedAmmyy and the CLOP ransomware. An example of the latter could be the CLOP ransomware attack in December 2019 against the University of Maastricht (Netherlands); although Kimberly Goody, FireEye's manager of cyber crime analysis said that she could not confirm this without first seeing the attack forensics.
"I would think of TA505 as a really big umbrella, while FIN11 is a portion of that activity," she said. "So, the TA505 attribution isn't necessarily incorrect, it's just another name that other companies use for this activity. We would caution against just saying we attribute that attack to FIN11 because we don't have the technical artifacts. We need to see the full life cycle of the tactics and malware that attackers use within an environment before we would make an attribution." Nevertheless, it is tempting on the basis of this new report to suggest that the Maastricht attack would be better attributed to FIN11 than to TA505.
FIN11 primarily now focuses its efforts on ransomware and extortion. "Recent FIN11 intrusions have most commonly led to data theft, extortion and the disruption of victim networks via the distribution of CLOP ransomware," say the FireEye researchers in their report. This demonstrates FIN11's willingness and ability to change tactics over time. "In 2018," Goody told SecurityWeek, "we saw FIN11 deploying point of sale malware. But in 2019, they pivoted towards CLOP and ransomware." This shift from POS to extortion was quite common with other groups during the same timeframe -- Mandiant saw an increase in ransomware of around 300% over the same period.
It isn't known how many organizations have fallen victim to FIN11 because of the apparently growing tendency for victims to simply pay for a decryption key. This can be assumed because of the rapidly increasing ransomware demands. While the Dutch university paid $240,000, it seems that this month's attack on Software AG may have been accompanied by a demand for $23 million. It is unlikely that the demands would have increased to this extent if lower demands were not being met.
The CLOP group engages in what is sometimes referred to as 'double extortion'. Before encrypting data, the gang steals it. If the victim fails to pay the decryption fee, the gang then threatens to release the stolen data if payment is not received. Data is released via the gang's dark website called CL0P^_- LEAKS. While we don't necessarily know how many CLOP victims have paid a ransomware, this site gives a good indication of victims that have declined to pay.
The CL0P^_- LEAKS website suggests that there have been FIN11 victims in North America, India and Europe. The majority are located in Europe, and about half of those in Germany. "FIN11," say the researchers, has used German-language lures in many of their 2020 campaigns, suggesting that they have actively targeted German organizations." This is slightly unusual, since ransomware attackers more usually target American firms above others. FireEye does not believe that the gang specifically targets either operations or IT. It told SecurityWeek that the malware includes many process killers across both IT and OT, suggesting that the CLOP gang simply tries to extort from wherever it lands.
The lack of victims in Commonwealth of Independent States (CIS) countries is part of the reason that FireEye believes the CLOP gang operates out of this region. It is generally considered that the Russian government largely turns a blind eye towards cybercriminals that do not operate within Russia or the associated CIS. This is further supported by FIN11 files containing metadata suggesting that the operators are using a language with a Cyrillic alphabet, and a dramatic drop in activity during the Russian New Year holiday and Orthodox Christmas (January 1-8). Further clues include the use of Russian language resource files by some of the malware, and some of the phishing emails using a Cyrillic language code page.
The CLOP group seems to combine the spray and pray approach to compromising targets with a more targeted approach. It operates large scale phishing campaigns, but then selects which of the networks it compromises to target for monetization. "Once access to a company’s network has been obtained," write the researchers, "FIN11 may selectively choose whether the access is worth exploiting based on criteria such as their geolocation, sector or perceived security posture." This selection may indicate that the gang is only interested in targeting wealthier organizations, especially if they are likely to have very sensitive or personal data, or it may simply be a capacity issue. FireEye warns that this may prompt the CLOP group to effectively sub-contract exploitation of those victims it doesn't exploit itself to other criminal groups in order to maximize its revenues.
Police Raided German Spyware Company FinFisher Offices
15.10.20 BigBrothers Thehackernews
German investigating authorities have raided the offices of Munich-based company FinFisher that sells the infamous commercial surveillance spyware dubbed 'FinSpy,' reportedly in suspicion of illegally exporting the software to abroad without the required authorization.
Investigators from the German Customs Investigation Bureau (ZKA), ordered by the Munich Public Prosecutor's Office, searched a total of 15 properties in Munich, including business premises of FinFisher GmbH, two other business partners, as well as the private apartments of the managing directors, along with a partner company in Romania from October 6 to 8.
For those unaware, FinSpy is extremely powerful spying software that is being sold as a legal law enforcement tool to governments around the world but has also been found in use by oppressive and dubious regimes to spy on activists, political dissidents and journalists.
FinSpy malware can target both desktop and mobile operating systems, including Android, iOS, Windows, macOS, and Linux, and gives its operator spying capabilities, including secretly turning on victims' webcams and microphones, recording everything they types on the keyboard, intercepting calls, and exfiltration of sensitive data.
However, a new report from BR (Bayerischer Rundfunk) and (Norddeutscher Rundfunk) NDR suggests the spying firm illegally exported FinSpy to other countries without the correct export license issued by the federal government.

The Munich public prosecutor's office is now investigating "suspected violations of the Foreign Trade Act against managing directors and employees of FinFisher GmbH and at least two other companies," said a spokeswoman to BR and NDR.
The raids were part of a criminal complaint [pdf] filed by the GFF, Netzpolitik, Reporters Without Borders (ROG), and the European Center for Constitutional Rights and Human Rights (ECCHR) against the managing directors of FinFisher GmbH in July 2019.
In 2015, a permit requirement for exports of FinSpy to non-EU countries was introduced across Europe, but even after the federal government not issued a single export license, the surveillance software was found on a Turkish website in 2017 to spy on members of the opposition and was used in Egypt to target NGOs.
This strongly suggests that the surveillance company illegally exported the FinSpy software despite the existing permit requirements.
Unfortunately, the German media site has taken down the original report it posted last year after FinFisher sued the publication and won the case.
We will update the article as and when new information becomes available.
FIN11 Hackers Spotted Using New Techniques In Ransomware Attacks
15.10.20 Ransomware Thehackernews
A financially-motivated threat actor known for its malware distribution campaigns has evolved its tactics to focus on ransomware and extortion.
According to FireEye's Mandiant threat intelligence team, the collective — known as FIN11 — has engaged in a pattern of cybercrime campaigns at least since 2016 that involves monetizing their access to organizations' networks, in addition to deploying point-of-sale (POS) malware targeting financial, retail, restaurant, and pharmaceutical sectors.
"Recent FIN11 intrusions have most commonly led to data theft, extortion and the disruption of victim networks via the distribution of CLOP ransomware," Mandiant said.
Although FIN11's activities in the past have been tied to malware such as FlawedAmmyy, FRIENDSPEAK, and MIXLABEL, Mandiant notes significant overlap in TTPs with another threat group that cybersecurity researchers call TA505, which is behind the infamous Dridex banking Trojan and Locky ransomware that's delivered through malspam campaigns via the Necurs botnet.
It's worth pointing that Microsoft orchestrated the takedown of the Necurs botnet earlier this March in an attempt to prevent the operators from registering new domains to execute further attacks in the future.
High-Volume Malspam Campaigns
FIN11, in addition to leveraging a high-volume malicious email distribution mechanism, has expanded its targeting to native language lures coupled with manipulated email sender information, such as spoofed email display names and email sender addresses, to make the messages appear more legitimate, with a strong bent towards attacking German organizations in their 2020 campaigns.
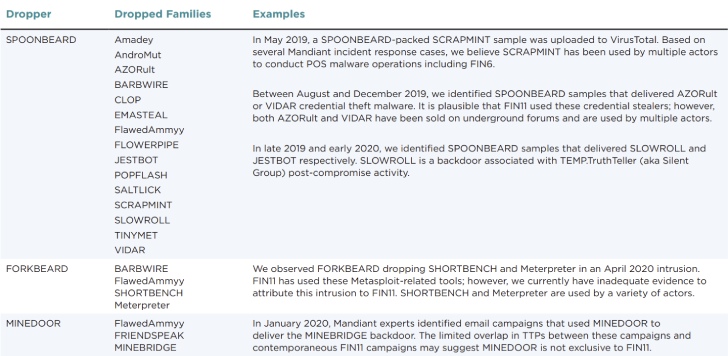
For instance, the adversary triggered an email campaign with email subjects such as "research report N-[five-digit number]" and "laboratory accident" in January 2020, followed by a second wave in March using phishing emails with the subject line "[pharmaceutical company name] 2020 YTD billing spreadsheet."
"FIN11's high-volume email distribution campaigns have continually evolved throughout the group's history," Andy Moore, senior technical analyst at Mandiant Threat Intelligence, told The Hacker News via email.
"Although we have not independently verified the connection, there is substantial public reporting to suggest that until sometime in 2018, FIN11 relied heavily on the Necurs botnet for malware distribution. Notably, observed downtime of the Necurs botnet has directly corresponded to lulls in the activity we attribute to FIN11."
Indeed, as per Mandiant's research, FIN11's operations appear to have ceased entirely from mid-March 2020 through late May 2020, before picking up again in June via phishing emails containing malicious HTML attachments to deliver malicious Microsoft Office files.
The Office files, in turn, made use of macros to fetch the MINEDOOR dropper and the FRIENDSPEAK downloader, which then dispatched the MIXLABEL backdoor on the infected device.
A Shift to Hybrid Extortion
In recent months, however, FIN11's monetization efforts have resulted in a number of organizations infected by CLOP ransomware, in addition to resorting to hybrid extortion attacks — combining ransomware with data theft — in a bid to force businesses into acquiescing to extortion payments that range from a few hundred thousand dollars up to 10 million dollars.
"FIN11's monetization of intrusions via ransomware and extortion follows a broader trend among financially motivated actors," Moore said.
"Monetization strategies that have been more common historically, such as the deployment of point-of-sale malware, limit criminals to targeting victims in certain industries, whereas ransomware distribution can allow actors to profit from an intrusion into the network of nearly any organization.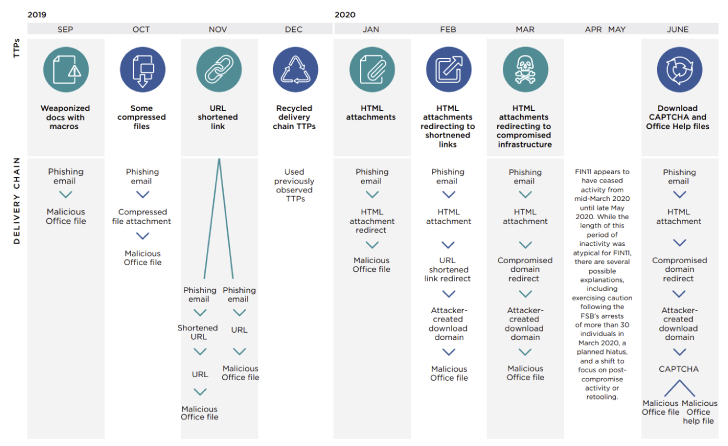
That flexibility, in combination with increasingly frequent reports of ballooning ransom payments, makes it an extremely attractive scheme for financially motivated actors," he added.
What's more, FIN11 is purported to have made use of a wide variety of tools (e.g., FORKBEARD, SPOONBEARD, and MINEDOOR) purchased from underground forums, thereby making attribution difficult or accidentally conflating activities of two disparate groups based on similar TTPs or indicators of compromise.
An Actor of Likely CIS Origin
As for the roots of FIN11, Mandiant stated with "moderate confidence" that the group operates out of the Commonwealth of Independent States (CIS) owing to the presence of Russian-language file metadata, avoidance of CLOP deployments in CIS countries, and the dramatic fall in activity coinciding the Russian New Year and Orthodox Christmas holiday period between January 1-8.
"Barring some sort of disruption to their operations, it is highly likely that FIN11 will continue to attack organizations with an aim to deploy ransomware and steal data to be used for extortion," Moore said.
"As the group has regularly updated their TTPs to evade detections and increase the effectiveness of their campaigns, it is also likely that these incremental changes will continue. Despite these changes, however, recent FIN11 campaigns have consistently relied on the use of macros embedded in malicious Office documents to deliver their payloads."
"Along with other security best practices, organizations can minimize the risk of being compromised by FIN11 by training users to identify phishing emails, disabling Office macros, and implementing detections for the FRIENDSPEAK downloader."
Election Systems Under Attack via Microsoft Zerologon Exploits
14.10.20 Exploit Threatpost
Cybercriminals are chaining Microsoft’s Zerologon flaw with other exploits in order to infiltrate government systems, putting election systems at risk, a new CISA and FBI advisory warns.
U.S. government officials have warned that advanced persistent threat actors (APTs) are now leveraging Microsoft’s severe privilege-escalation flaw, dubbed “Zerologon,” to target elections support systems.
Days after Microsoft sounded the alarm that an Iranian nation-state actor was actively exploiting the flaw (CVE-2020-1472), the Cybersecurity Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) published a joint advisory warning of further attacks.
The advisory details how attackers are chaining together various vulnerabilities and exploits – including using VPN vulnerabilities to gain initial access and then Zerologon as a post-exploitation method – to compromise government networks.
“This recent malicious activity has often, but not exclusively, been directed at federal and state, local, tribal and territorial (SLTT) government networks,” according to the security advisory. “Although it does not appear these targets are being selected because of their proximity to elections information, there may be some risk to elections information housed on government networks.”
With the U.S. November presidential elections around the corner – and cybercriminal activity subsequently ramping up to target election infrastructure and presidential campaigns – election security is top of mind. While the CISA and FBI’s advisory did not detail what type of elections systems were targeted, it did note that there is no evidence to support that the “integrity of elections data has been compromised.”
Microsoft released a patch for the Zerologon vulnerability as part of its August 11, 2020 Patch Tuesday security updates. Exploiting the bug allows an unauthenticated attacker, with network access to a domain controller, to completely compromise all Active Directory identity services, according to Microsoft.
Despite a patch being issued, many companies have not yet applied the patches to their systems – and cybercriminals are taking advantage of that in a recent slew of government-targeted attacks.
The CISA and FBI warned that various APT actors are commonly using a Fortinet vulnerability to gain initial access to companies. That flaw (CVE-2018-13379) is a path-traversal glitch in Fortinet’s FortiOS Secure Socket Layer (SSL) virtual private network (VPN) solution. While the flaw was patched in April 2019, exploitation details were publicized in August 2019, opening the door for attackers to exploit the error.
Other initial vulnerabilities being targeted in the attacks include ones in Citrix NetScaler (CVE-2019-19781), MobileIron (CVE-2020-15505), Pulse Secure (CVE-2019-11510), Palo Alto Networks (CVE-2020-2021) and F5 BIG-IP (CVE-2020-5902).
After exploiting an initial flaw, attackers are then leveraging the Zerologon flaw to escalate privileges, researchers said. They then use legitimate credentials to log in via VPN or remote-access services, in order to maintain persistence.
“The actors are leveraging CVE-2020-1472 in Windows Netlogon to escalate privileges and obtain access to Windows AD servers,” they said. “Actors are also leveraging the opensource tools such as Mimikatz and the CrackMapExec tool to obtain valid account credentials from AD servers.”
The advisory comes as exploitation attempts against Zerologon spike, with Microsoft recently warned of exploits by an advanced persistent threat (APT) actor, which the company calls MERCURY (also known as MuddyWater, Static Kitten and Seedworm). Cisco Talos researchers also recently warned of a spike in exploitation attempts against Zerologon.
Earlier in September, the stakes got higher for risks tied to the bug when four public proof-of-concept exploits for the flaw were released on Github. This spurred the Secretary of Homeland Security to issue a rare emergency directive, ordering federal agencies to patch their Windows Servers against the flaw by Sept. 2.
CISA and the FBI stressed that organizations should ensure their systems are patched, and adopt an “assume breach” mentality. Satnam Narang, staff research engineer with Tenable, agreed, saying that “it seems clear that Zerologon is becoming one of the most critical vulnerabilities of 2020.”
“Patches are available for all of the vulnerabilities referenced in the joint cybersecurity advisory from CISA and the FBI,” said Narang in a Monday analysis. “Most of the vulnerabilities had patches available for them following their disclosure, with the exception of CVE-2019-19781, which received patches a month after it was originally disclosed.”
Lemon Duck Cryptocurrency-Mining Botnet Activity Spikes
14.10.20 Cryptocurrency Threatpost
Researchers warn of a spike in the cryptocurrency-mining botnet since August 2020.
Researchers are warning of a recent dramatic uptick in the activity of the Lemon Duck cryptocurrency-mining botnet, which targets victims’ computer resources to mine the Monero virtual currency.
Researchers warn that Lemon Duck is “one of the more complex” mining botnets, with several interesting tricks up its sleeve. While the botnet has been active since at least the end of December 2018, researchers observed an increase in DNS requests connected with its command-and-control (C2) and mining servers since the end of August, in a slew of attacks centered on Asia (including ones targeting Iran, Egypt, Philippines, Vietnam and India).
“Cisco Talos has identified activity in our endpoint telemetry associated with Lemon Duck cryptocurrency mining malware, affecting three different companies in the government, retail, and technology sectors,” said researchers with Cisco Talos, in Tuesday research. “We observed the activity spanning from late March 2020 to present.”
More recent attacks have included less-documented modules that are loaded by the main PowerShell component – including a Linux branch and a module allowing further spread by sending emails to victims with COVID-19 lures.
Threatpost has reached out to researchers for further information about how many victims have been targeted and the extent to which the botnet’s operators have profited off of the cryptomining attacks.
Lemon Duck
Lemon Duck has at least 12 independent infection vectors – more than most malware. These capabilities range from Server Message Block (SMB) and Remote Desktop Protocol (RDP) password brute-forcing, sending emails with exploit attachments or targeting the RDP BlueKeep flaw (CVE-2019-0708) in Windows machines; or targeting vulnerabilities in Redis (an open-source, in-memory data structure store used as a database, cache and message broker) and YARN Hadoop (a resource-management and job-scheduling technology) in Linux machines.

Lemon Duck botnet August activity. Credit: Cisco Talos
After the initial infection, a PowerShell loading script is downloaded, which utilizes the function “bpu” to disable Windows Defender real-time detection and put powershell.exe on the list of processes excluded from scanning.
“bpu” also checks if the script is running with administrative privileges. If it is, the payload is downloaded and run using the Invoke-Expression cmdlet (a function that can be utilized for calling code within a script or building commands to be executed later). If not, it leverages existing system executables to launch the next stage.
“This is a good starting point for analysis and retrieval of additional modules,” said researchers. “Almost all PowerShell modules are obfuscated with four or five layers of obfuscation, likely generated by the Invoke-Obfuscation module. Although they are relatively easy to remove, they still slow down the analysis process and make detection using regular signatures more difficult.”
These executable modules, which are downloaded and driven by the main module, communicates with the C2 server over HTTP.
Modular Functionalities
The modules include a main loader, which checks the level of user privileges and components relevant for mining, such as the type of the available graphic card (including GTX, Nvidia, GeForce, AMD and Radeon). If these GPUs are not detected, the loader downloads and runs the commodity XMRig CPU-based mining script.
Other modules include a main spreading module (with what researchers say include “a rather ambitious piece of code” containing more than 10,000 lines of coding), a Python-based module packaged using Pyinstaller, and a killer module designed to disable known competing mining botnets.
Lemon Duck also includes an email-spreading module. These spread emails using a mix of COVID-19-related subject lines and text, as well as other emotion-driven lures (such as an email subject “WTF” with the text “What’s wrong with you?are you out of your mind!!!!!!!”). These emails contain an infected attachments sent using Outlook automation to every contact in the affected user’s address book.

An example of an email sent by the Lemon Duck module. Credit: Cisco Talos
Linux Branch
Researchers also shed light on a less documented Linux branch of the Lemon Duck malware. These Lemon Duck bash scripts are executed after the attacker successful compromises a Linux host (via Redis, YARN or SSH). There are two main bash scripts, said researchers: The first collects some data about the infected host and attempts to download a Linux version of the XMRig miner, before attempting to delete various system logs. The second attempts to terminate and remove competing cryptocurrency miners already present on the system.
“The script also attempts to terminate and uninstall processes related to Alibaba and Tencent cloud security agents. The script seems to be shared between several Linux-based cryptomining botnets,” said researchers.
Lemon Duck was previously spotted in 2020 in a campaign targeting printers, smart TVs and automated guided vehicles that depend on Windows 7. Researchers in February warned that the processor-intensive mining efforts are taking their toll on gear and triggering equipment malfunctions along with exposing devices to safety issues, disruption of supply chains and data loss.
Defenders can stomp out the threat of cryptocurrency attacks by monitoring system behavior to spot any resource-sucking threats.
“Cryptocurrency-mining botnets can be costly in terms of the stolen computing cycles and power consumption costs,” they said. “While organizations need to be focused on protecting their most valuable assets, they should not ignore threats that are not particularly targeted toward their infrastructure.”
Software AG Data Released After Clop Ransomware Strike – Report
14.10.20 Ransomware Threatpost
The Clop group attacked Software AG, a German conglomerate with operations in more than 70 countries, threatening to dump stolen data if the whopping $23 million ransom isn’t paid.
Clop and the group’s signature malware has struck again — this time hitting a giant target in the form of German software conglomerate Software AG. The company isn’t paying a mammoth $23 million ransom (so far), and over the weekend it confirmed that the crooks were releasing company data, according to reports.
The Clop ransomware cybercriminals were able to infiltrate the company’s systems in early October. The company released a statement on October 5 publicly announcing the attack, adding, “While services to its customers, including its cloud-based services, remain unaffected, as a result, Software AG has shut down the internal systems in a controlled manner in accordance with the company’s internal security regulations,” the statement read.
But that assessment turned out to be prematurely rosy. Just days later, the company had to admit that Clop was, in fact, able to access and download customer data. And on Saturday, it admitted that the data was being released, according to Bloomberg.
“Today, Software AG has obtained first evidence that data was downloaded from Software AG’s servers and employee notebooks,” the company said in its follow-up statement. “There are still no indications for services to the customers, including the cloud-based services, being disrupted.”
The company has shut down internal systems as a security precaution – as of the time of this writing, the effects of the cyberattack are dragging on.
“Ransomware gangs are becoming bolder and more sophisticated, going after larger and more lucrative targets with their criminal attacks,” said Saryu Nayyar, CEO at Gurucul, via email. “This recent attack against Germany’s Software AG is one of the largest ransomware attacks, but it will certainly not be the last. Even with a complete security stack and a mature security operations team, organizations can still be vulnerable. The best we can do is keep our defenses up to date, including behavioral analytics tools that can identify new attack vectors, and educate our users to reduce the attack surface.”
She added, “With little risk of punishment and potentially multi-million dollar payoffs, these attacks will continue until the equation changes.”
Clop’s Clout
“Scale and clout do not make an organization immune from ransomware attacks, and often make them a more vulnerable target,” Dan Piazza, technical product manager for Stealthbits Technologies said, via email. “An organization having deep pockets means attackers will devote vast resources towards compromising them, and more employees and networks means a larger attack surface. This also shows that threat actors are more motivated than ever and feel confident requesting exorbitant sums — likely due to past successes.”
Clop has emerged as a potent ransomware threat. First discovered in Feb. 2019 by the MalwareHunterTeam, the group continues to terrorize companies with a tactic called “double extortion,” meaning it steals the data and if their ransom demands aren’t met, the data is dumped on a criminal website for anyone to access.
Besides, Software AG, Clop recently hit ExecuPharm, a biopharmaceutical company, in April. And after the company refused to pay, the criminals leaked the compromised data. Other ransomware groups engage in similar tactics, including Maze, DoppelPaymer and Sodinokibi.
Just last month, the Maze gang dumped the personal information of students in Las Vegas on a shady underground forum, after the Clark County School District didn’t pay the ransom.
But Clop is distinguishing itself by going after top-flight companies, rather than the small- to midsize school districts and municipalities, which have emerged as the bread and butter of ransomware crooks everywhere.
MalwareHunterTeam shared excerpts from the ransom note sent by Clop to Software AG, which included the warm greeting, “HELLO DEAR SOFTWARE AG.” The ransom note continued more ominously, “If you refuse to cooperate, all data will be published for free download on our portal…”
Inside the Clop Malware
Researchers Alexandre Mundo and Marc Rivero Lopez at McAfee explained how Clop malware works in a recent blog post.
“The Clop ransomware is usually packed to hide its inner workings,” they wrote. “Signing a malicious binary, in this case ransomware, may trick security solutions to trust the binary and let it pass.” They also said the malware is equipped with the ability to terminate itself if it isn’t successfully installed as a service.
Once deployed, it compares the victim’s computer keyboard against hardcoded values.
“The malware checks that the layout is bigger than the value 0x0437 (Georgian), makes some calculations with the Russian language (0x0419) and with the Azerbaijan language (0x082C). This function will return 1 or 0, 1 if it belongs to Russia or another CIS country, or 0 in every other case,” Mundo and Lopez explained.
If it returns 0, the malware functions normally. If not, it fetches the entire screen context. It also determines whether the system uses a Russian character set, and if it does, the malware deletes itself. Otherwise, the malware marches on.
“This double-check circumvents users with a multisystem language, i.e. they have the Russian language installed but not active in the machine to avoid this type of malware,” they added.
Next, Clop’s ransomware creates a new thread and creates a folder entitled “Favorite” in a shared folder with the malware. It will then make a dummy call that the researchers think is intended to produce an error message, and loops for 666,000 times. If the malware discovers antivirus protections, it goes to sleep for five seconds, only to later continue its nefarious operation.
“The next action is to write this batch file in the same folder where the malware stays with the function ‘CreateFileA,'” they said. “The file created has the name ‘clearsystems-11-11.bat’. Later will launch it with ‘ShellExecuteA,’ wait for five seconds to finish, and delete the file with the function ‘DeleteFileA.'”
Clop’s use of .bat files indicates to Mundo and Lopez the authors aren’t very sophisticated programmers.
“All these actions could have been performed in the malware code itself, without the need of an external file that can be detected and removed,” they wrote.
A second version of Clop analyzed by the researchers shows an evolution of the malware, but with the same basic structure and intent.
Companies Wrangle with Clop
As Clop and other ransomware groups appear to be upping the ante on attacks, Piazza advises compromised organizations to be honest and up-front with customers about the security of their data. He points to Software AG’s clean up statement on Oct. 5 as a prime example of what not to do and that overly optimistic prognostications that must be recanted later are poisonous to the customer relationship.
“Customers want to be reassured their data is safe when an organization they do business with is the victim of ransomware, however when statements need to be later walked back it ends up doing more harm to an organization’s reputation than if they hadn’t issued the statement to begin with (at least until the extent of the attack is known),” Piazza advised, “Although statements such as these are typically done with good intentions, they can still have consequences if proven wrong and sensitive data is leaked.”
Software AG has not responded to inquiries.
TrickBot Takedown Disrupts Major Crimeware Apparatus
14.10.20 BotNet Threatpost
Microsoft and partners went after the botnet using a copyright infringement tactic and hunting down C2 servers.
The TrickBot trojan has been dealt a serious blow thanks to a coordinated action led by Microsoft that disrupted the botnet that spreads it. However, researchers warn that the operators will quickly try to revive their operations.
TrickBot is known for spreading other malware, especially ransomware. Microsoft said this week that the United States District Court for the Eastern District of Virginia granted a request for a court order to halt TrickBot’s operations, which it carried out in concert with other firms, including ESET, Lumen’s Black Lotus Labs, NTT Ltd., Symantec and others.
“We disrupted TrickBot through a court order we obtained, as well as technical action we executed in partnership with telecommunications providers around the world,” wrote Tom Burt, corporate vice president, Customer Security & Trust, at Microsoft, in a Monday posting. “We have now cut off key infrastructure so those operating TrickBot will no longer be able to initiate new infections or activate ransomware already dropped into computer systems.”
TrickBot is a well-known and sophisticated trojan first developed in 2016 as a banking malware – it has a history of transforming itself and adding new features to evade detection. Moving far beyond its banking roots, it has developed over the years into a full-fledged, module-based crimeware solution typically aimed at attacking corporations and public infrastructure.
Users infected with the TrickBot Trojan will see their device become part of a botnet that can allow attackers to gain complete control of the device. Typical consequences of TrickBot infections are bank account takeover, high-value wire fraud and ransomware attacks. It’s often seen working in concert with Emotet, another concerning and widespread trojan that’s known for its modular design.
“What makes [TrickBot] so dangerous is that it has modular capabilities that constantly evolve, infecting victims for the operators’ purposes through a ‘malware-as-a-service’ model,” Burt said. “Its operators could provide their customers access to infected machines and offer them a delivery mechanism for many forms of malware, including ransomware. Beyond infecting end user computers, TrickBot has also infected a number of Internet of Things devices, such as routers, which has extended TrickBot’s reach into households and organizations.”
TrickBot has infected more than 1 million computing devices around the world since late 2016, according to Microsoft.
The Takedown
Microsoft and partners were able to thwart TrickBot’s mechanisms to evade detection and uncover its command-and-control (C2) infrastructure, including the location of its servers.
ESET for example said that it analyzed more than 125,000 malicious samples and downloaded and decrypted more than 40,000 configuration files used by the different Trickbot modules, which gave the team a window into the C2 setup.
TrickBot accounts for infections globally. Source: ESET.
According to ESET, one of the keys to the investigation was the fact that TrickBot’s modular architecture uses a variety of plugins to perform its vast array of malicious actions.
“One of the oldest plugins developed for the platform allows TrickBot to use web injects, a technique allowing the malware to dynamically change what the user of a compromised system sees when visiting specific websites,” according to the post. “To operate, this plugin relies on configuration files downloaded by the main module. These contain information about which websites should be modified and how.”
These decrypted configuration files contain targeted URLs and the malicious C2 URLs the bot should contact when a victim accesses a targeted site.
“As we observed the infected computers connect to and receive instructions from command-and-control servers, we were able to identify the precise IP addresses of those servers,” Microsoft’s Burt explained. “With this evidence, the court granted approval for Microsoft and our partners to disable the IP addresses, render the content stored on the command-and-control servers inaccessible, suspend all services to the botnet operators, and block any effort by the TrickBot operators to purchase or lease additional servers.”
This is a different approach than the takedown of the Necurs peer-to-peer botnet, which Microsoft led in March. The firm worked with technical and legal partners in 35 countries to disrupt that malware.
“By analyzing the algorithm Necurs used to systematically generate new domains, Microsoft was able to accurately predict the 6+ million unique domains that would be created within the next 25 months,” said Nozomi Networks co-founder Andrea Carcano, via email. “Microsoft reported these domains to their respective registries worldwide, allowing the websites to be blocked and preventing them from becoming part of the Necurs infrastructure.”
Copyright Claim
Interestingly, Microsoft’s request for legal approval hinges on a copyright claim against TrickBot’s malicious use of its software code. It’s the first time the computing giant has used this approach, Burt said, adding that the tactic “allowed us to take civil action to protect customers in the large number of countries around the world that have these laws in place.”
He added that because TrickBot retains its focus on online banking websites, and stealing funds from people and financial institutions, the Financial Services Information Sharing and Analysis Center (FS-ISAC) was a co-plaintiff in the legal action.
“While botnet operators are using every trick in the book to expand their malicious activity, defenders for obvious reasons have to comply with the law when implementing the countermeasures,” said Carcano. “But as Microsoft’s actions show, this doesn’t mean that you cannot be creative with the technical and non-technical tools available. The beauty of this latest approach is that while defenders have to suffer the asymmetry of attackers operating behind the limits of the law, by taking the case to court, Microsoft gained a legal advantage to regain control.”

TrickBot may be disrupted for now, but researchers pointed out that the operators have other projects going on.
“One of these projects is the so-called Anchor project, a platform mostly geared towards espionage rather than crimeware,” according to ESET. “They are also likely involved in the development of the Bazar malware — a loader and backdoor used to deploy malware, such as ransomware, and to steal sensitive data from compromised systems.”
“Prior to the disruption, we had already observed some actors that were previously distributing TrickBot switch to BazaLoader, which has been linked by code similarity to TrickBot,” said Sherrod DeGrippo, senior director of threat research at Proofpoint, via email.
TrickBot itself will likely re-emerge, according to Burt.
“We fully anticipate TrickBot’s operators will make efforts to revive their operations, and we will work with our partners to monitor their activities and take additional legal and technical steps to stop them,” he said.
DeGrippo went further and noted that the takedown’s efficacy remains to be seen.
“Typically, these types of actions don’t result in a direct reduction of threat activity,” the researcher noted. “Threat actors will often replace the lost infrastructure quickly and easily out of a different country so we will need to wait and see what the direct impact will be…We believe it’s unlikely we’ll see any immediate significant changes in Trickbot email delivery volumes…The most recent Trickbot campaigns are already using new command-and-control channels, which shows the threat actors are actively adapting their campaigns.”
Office 365: A Favorite for Cyberattack Persistence
14.10.20 Attack Threatpost
Bad actors are leveraging legitimate services and tools within Microsoft’s productivity suite to launch cyberattacks on COVID-19 stay-at-home workers, new research finds.
Threat actors are consistently leveraging legitimate services and tools from within Microsoft Office 365 to pilfer sensitive data and launch phishing, ransomware, and other attacks across corporate networks from a persistent position inside the cloud-based suite, new research has found.
Office 365 user account takeover – particularly during the COVID-19 pandemic with so many working from home – is one of the most effective ways for an attacker to gain a foothold in an organization’s network, said Chris Morales, head of security analytics at Vectra AI.
From there, attackers can move laterally to launch attacks, something that researchers observed in 96 percent of the 4 million Office 365 customers sampled between June to August 2020. The company revealed the findings of this research in a 2020 Spotlight Report, released Tuesday.
“We expect this trend to magnify in the months ahead,” Morales said in an email interview with Threatpost.
The report takes a dive into some of the most popular ways that attackers leverage Office 365 services and tools to compromise corporate networks. Indeed, Office 365 presents a wide playing field for attackers; the leading software-as-a-service (SaaS) productivity suite has more than 250 million active users each month, which has made it a historically consistent target for attacks.
Many of those users are currently working from home due to COVID-19 restrictions, often on networks that don’t have the same protections as the corporate cloud. This adds another aspect of accessibility for attackers, Morales said.
Cybercriminal Tactics
Researchers found three key features of the suite that attackers exploit to take over accounts and go on to perform a variety of attacks: OAuth, Power Automate and eDiscovery.
“OAuth is used for establishing a foothold, Power Automate is used for command and control and lateral movement, and eDiscovery is used for reconnaissance and exfiltration,” Morales told Threatpost.
OAuth is an open standard for access authentication used in Office 365 and already has been observed by researchers as a way for attackers to gain access to the cloud-based suite. Third-party applications use the standard to authenticate users by employing Office 365 login services and the user’s associated credentials so that they don’t have “to continuously log into every app every time the user and app requires access,” Morales said.
Unfortunately, this convenience also is a boon for threat actors because it allows an attacker to steal OAuth credentials or access them by convincing a legitimate user to approve a malicious app (via phishing email), he said. This can allow attackers to maintain persistent and undetected access to Office 365 accounts.
Power Automate lets users create custom integrations and automated workflows between Office 365 applications, is enabled by default, and includes connectors to hundreds of third-party applications and services—also giving it appeal for both users and hackers, Morales noted.
It allows users to automate mundane tasks but can also be leveraged by attackers, not only because of its default on status, but also because it allows them to make lateral movements within the app and execute malicious command-and-control behaviors, he said.
“There is no way to turn off individual connectors — it is all or nothing,” Morales told Threatpost. “Attackers can sign up for free trials to get access to premium connectors that do even more.”
Vectra found that 71 percent of customers sampled in their research exhibited suspicious Office 365 Power Automate behaviors.
Meanwhile, Microsoft eDiscovery searches across Office 365 applications and data and exports the results. Once inside Office 365, attackers are using this feature as an internal reconnaissance and data exfiltration tool to find critical data to steal that can be used with malicious intent. Fifty-six percent of customers sampled in Vectra’s research exhibited suspicious Office 365 eDiscovery behaviors, researchers found.
Account Compromise Impact
Once attackers use these features and services to take over Office 365 accounts, there are a number of techniques they use to compromise networks. They can search through emails, chat histories, and files looking for passwords or interesting data to exfiltrate, or set up forwarding rules to get access to a steady stream of email without needing to sign-in again, researchers said.
Threat actors also can leverage the trusted communication channel to send socially engineered phishing emails to employees, customers, or partners. For instance, researchers observed (and helped mitigate) an incident where a medical research unit at a university was targeted with a phishing lure that promoted a free calendar optimization and time-management app.
After one person took the bait and installed the malicious OAuth app, the attackers had complete access to Office 365 and used it to send internal phishing emails, taking advantage of trusted identities and communications to spread further inside the university.
Other attacks that can occur due to Office 365 account takeover include the ability to plant malware or malicious links in documents that many people trust and use; or steal or hold files and data for ransom.
To mitigate these threats, researchers recommend that organizations move away from employing static, prevention-based, policy control-centric or one-off mitigations and move to a more contextual security approach, Morales said.
“These approaches continue to fail,” he told Threatpost. “Security teams must have detailed context that explains how entities utilize their privileges – known as observed privilege – within SaaS applications like Office 365. Just as attackers observe or infer interactions between entities, defenders should think similarly about their adversaries. It is about the usage patterns and behaviors, not the static access.”
Microsoft October 2020 Patch Tuesday fixes 87 flaws, including 21 RCEs
14.10.20 Vulnerebility Securityaffairs
Microsoft October 2020 Patch Tuesday security updates address 87 vulnerabilities, including 21 remote code execution (RCE) issues.
The remote code execution (RCE) flaws fixed by Microsoft affects multiple products, including Excel, Outlook, the Windows Graphics component, and the Windows TCP/IP stack.
The most severe vulnerability is an RCE issue tracked as CVE-2020-16898. that resides in the Windows TCP/IP stack. The vulnerability can be exploited by the attackers to take over Windows systems by sending malicious ICMPv6 Router Advertisement packets to an unpatched system via a network connection.
“A remote code execution vulnerability exists when the Windows TCP/IP stack improperly handles ICMPv6 Router Advertisement packets. An attacker who successfully exploited this vulnerability could gain the ability to execute code on the target server or client.” reads the security advisory published by Microsoft.
“To exploit this vulnerability, an attacker would have to send specially crafted ICMPv6 Router Advertisement packets to a remote Windows computer.”
The vulnerability received a score of 9.8 out of a maximum of 10, it affects Windows 10 and Windows Server 2019.
Microsoft also provided some workarounds such as disabling ICMPv6 RDNSS support.
Another severe RCE flaw, tracked as CVE-2020-16947, affects MS Outlook and can be exploited by attackers by tricking a user to open a specially crafted file with a vulnerable version of Outlook.
“A remote code execution vulnerability exists in Microsoft Outlook software when the software fails to properly handle objects in memory. An attacker who successfully exploited the vulnerability could run arbitrary code in the context of the System user. If the current user is logged on with administrative user rights, an attacker could take control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.” reads the advisory.
“Exploitation of the vulnerability requires that a user open a specially crafted file with an affected version of Microsoft Outlook software.”
The list of the vulnerabilities addressed with the release of the October 2020 Patch Tuesday updates is available on the Security Update Guide portal.
The British government aims at improving its offensive cyber capability
14.10.20 BigBrothers Securityaffairs
Britain’s most senior cyber general declared that the UK has implemented an advanced offensive cyberwar capability that could destroy its enemies.
Gen Sir Patrick Sanders, the UK’s strategic command chief, announced that that the UK has implemented an advanced offensive cyberwar capability that could potentially “degrade, disrupt and destroy” the critical infrastructure of its adversaries.
Boris Johnson tasked Gen Sanders to enhance both defensive and offensive cyber capabilities to ensure Britain is a “leading, full-spectrum cyber power.”
Sanders explained that its cyber army was supported by the GCHQ intelligence agency to deliver offensive cyber capabilities.
“[offensive cyber capability could] degrade, disrupt and even destroy critical capabilities and infrastructure of those who would do us harm, ranging from strategic to tactical targets” both in isolation or alongside traditional military force.” Sanders confirmed.
Experts don’t exclude that Boris Johnson will order the creation of National Cyber Force, a special military cyber division that will work with local intelligence agencies as the US Cyber Command does in the US.
The news is not surprising for people working in the cyber security sector, the British military claims to have had an offensive cyber capability for a decade.
Intelligence experts pointed out that the British government already conducted offensive hacking operations, including the one that targeted the ISIS in 2017.
“Cyber operations are in part run from a control room near Corsham, near Chippenha m, the historical site of the secret nuclear bunker to which the British government could relocate in an emergency.” reported The Guardian.
Clearly the UK military is under incessant cyber attacks from multiple threat actors, Sanders said, the UK military was targeted by an average of 60 attacks that require human intervention to be mitigated.
“The binary distinction between war and peace as we have approached it no longer applies,” Gen Sanders concluded. “Our adversaries are applying all means to gain advantage below the threshold of war and are accruing advantage insidiously and inevitably.”
Leading Law firm Seyfarth Shaw discloses ransomware attack
14.10.20 Ransomware Securityaffairs
Seyfarth Shaw, one of the leading global legal firms announced that it was a victim of an “aggressive malware” attack, likely a ransomware attack.
Seyfarth Shaw LLP is an international AmLaw 100 law firm headquartered in Chicago, Illinois, its clients include over 300 of the Fortune 500 companies, and its practice reflects virtually every industry and segment of the economy.
Seyfarth Shaw announced it was the victim of an “aggressive malware” attack, but the media immediately reported a ransomware infection later confirmed by the firm.
According to a statement published by the company, the attack took place on October 10, 2020.
“On October 10, 2020, Seyfarth was the victim of a sophisticated and aggressive malware attack. At this time, our email system remains down.” reads the statement published by the company.
“We understand that a number of other entities were simultaneously hit with this same attack. Our monitoring systems detected the unauthorized activity, and our IT team acted quickly to prevent its spread and protect our systems.”
The firm confirmed that many of its systems were encrypted and it is not aware of unauthorized access to its client or firm data,
“We have found no evidence that any of our client or firm data were accessed or removed.” continues the statement. “However, many of our systems were encrypted, and we have shut them down as a precautionary measure.”
The company notified law enforcement and it is supporting the investigation conducted by the FBI.
The firm added that an undisclosed number of companies was hit “simultaneously” by the same threat actors.
At the time of this post, the law firm did not disclose details about the attack, it is not clear the family of ransomware that hit the company and the extent of the security incident.
In the past other law firms suffered ransomware attacks, sometimes with dramatic consequences for their business like the Mossack Fonseca case.
In May, the Sodinokibi ransomware gang has stolen gigabytes of legal documents from the law firm of the stars, Grubman Shire Meiselas & Sacks (GSMLaw). In June 2017, the global law firm DLA Piper experienced severe issues at its systems after a ransomware attack.
Governments Use Pandemic to Crack Down on Online Dissent: Watchdog
14.10.20 BigBrothers Securityweek
Governments around the world are using the pandemic as a justification to expand surveillance and crack down on dissent online, resulting in a 10th consecutive annual decline in internet freedom, a human rights watchdog report said Wednesday.
The report by Washington-based Freedom House said authorities in dozens of countries have cited the Covid-19 outbreak "to justify expanded surveillance powers and the deployment of new technologies that were once seen as too intrusive."
This is leading to increasing censorship of dissent and the expansion of technological systems for social control, according to the report.
"The pandemic is accelerating society's reliance on digital technologies at a time when the internet is becoming less and less free," said Michael Abramowitz, president of the nonprofit group.
"Without adequate safeguards for privacy and the rule of law, these technologies can be easily repurposed for political repression."
Freedom House's index of internet based on a score assigned on a 100-point scale to 65 countries shows a drop in internet freedom for a 10th straight year.
The scale is based on 21 indicators pertaining to obstacles to access, limits on content and violations of user rights.
China was the worst-ranked country for the sixth consecutive year, according to the report.
It said Chinese authorities "combined low- and high-tech tools not only to manage the outbreak of the coronavirus, but also to deter internet users from sharing information from independent sources and challenging the official narrative."
The report said these trends are showing a growing trend toward Chinese-style "digital authoritarianism" globally and a "splintering" of the internet as each government imposes its own regulations.
Freedom House said that of the estimated 3.8 billion people using the internet, just 20 percent live in countries with a free internet, 32 percent in countries "partly free," while 35 percent were in places where online activities are not free. The remainder live in countries that weren't among the 65 assessed.
The report cited notable declines in countries where authorities have imposed internet shutdowns including Myanmar, Kyrgyzstan and India, and in Rwanda for its use of "sophisticated spyware to monitor and intimidate exiled dissidents."
The United States remained among those counties ranked free but saw its score decline in light of increased surveillance used by law enforcement against protest movements, executive orders on social media regulations, disinformation propagated by President Donald Trump and moves to ban Chinese-owned apps TikTok and WeChat.
The app bans were described as "an arbitrary and disproportionate response to the genuine risks" from those services.
Microsoft Patches Several Publicly Disclosed Windows Vulnerabilities
14.10.20 Vulnerebility Securityweek
Microsoft has fixed nearly 90 vulnerabilities with its October 2020 Patch Tuesday updates and while none of them has been exploited in attacks, several of the flaws were publicly disclosed before the patches were released.
The publicly disclosed vulnerabilities have been classified as important severity and their exploitation can lead to information disclosure or privilege escalation. A majority impact Windows and one affects the .NET framework.
The .NET vulnerability allows an authenticated attacker to access the targeted system’s memory, specifically memory layout. Exploitation requires executing a specially crafted application.
Another disclosed flaw impacts the Windows Error Reporting (WER) component and it can be leveraged for privilege escalation. While this particular weakness does not appear to have been exploited, Malwarebytes reported earlier this month that it had spotted an attack in which the payload was injected into the WER service to evade defenses.
Two of the disclosed vulnerabilities affect the Windows kernel. An authenticated attacker could exploit them to obtain information that can be useful to further compromise impacted systems.
One of the flaws whose details have been made public impacts Windows 10 Setup and it can only be exploited for privilege escalation by a local attacker while the computer is upgrading to a newer version of Windows.
The last disclosed issue impacts the Windows Storage VSP Driver and it can allow an authenticated attacker to escalate privileges.
Nearly a dozen of the vulnerabilities patched by Microsoft this month have been rated critical. They impact Windows, Outlook, the Base3D rendering engine, and SharePoint. They can all lead to remote code execution.
One interesting security bug that has been rated critical is CVE-2020-16947, which affects Outlook and allows an attacker to execute arbitrary code by sending a specially crafted email to the targeted user.
“The Preview Pane is an attack vector here, so you don’t even need to open the mail to be impacted,” explained the Zero Day Initiative’s Dustin Childs. “The specific flaw exists within the parsing of HTML content in an email. The issue results from the lack of proper validation of the length of user-supplied data before copying it to a fixed-length heap-based buffer. Although Microsoft gives this an XI rating of 2, we have a working proof-of-concept. Patch this one quickly.”
Another noteworthy vulnerability that was patched this month is CVE-2020-16898, which is related to how the Windows TCP/IP stack handles ICMPv6 Router Advertisement packets. An attacker can exploit the flaw for code execution on a server or client by sending specially crafted packets to the targeted device.
Bharat Jogi, senior manager of vulnerability and threat research at Qualys, warned that this flaw could be wormable.
“An attacker can exploit this vulnerability without any authentication, and it is potentially wormable,” Jogi said in an emailed comment. “We expect a PoC for this exploit would be dropped soon, and we highly encourage everyone to fix this vulnerability as soon as possible. Microsoft has also provided a workaround for this vulnerability and strongly recommends installing updates for this vulnerability quickly.”
It’s worth noting that the number of vulnerabilities fixed this Patch Tuesday is slightly smaller compared to the previous months. Between March and September, the number of patched vulnerabilities never dropped below 110.
Todd Schell, senior product manager for security at Ivanti, pointed out that there do not appear to be any Edge or Internet Explorer patches this month. “Not sure I remember the last time that has happened,” he told SecurityWeek.
Adobe’s October 2020 Patch Tuesday updates only address one critical code execution vulnerability in Flash Player.
G7 Raises Concerns About Rising Cyberattacks Amid Pandemic
14.10.20 BigBrothers Securityweek
Finance ministers from the G7 industrialized countries expressed "concern" on Tuesday over the rise in "malicious cyber-attacks" in the midst of the Covid-19 pandemic, including some involving cryptocurrencies.
These ransomware attacks demanding payments often to facilitate money laundering "have been growing in scale, sophistication, and frequency" over the past two years, causing "significant economic damage and (threatening) customer protection and data privacy," the ministers said.
"The G7 is concerned by the rising threat of ransomware attacks, particularly in light of malicious actors targeting critical sectors amid the COVID-19 pandemic," said the statement from the US Treasury issued on the G7's behalf following their virtual meeting.
"These attacks, which often involve payments in crypto-assets, jeopardize essential functions along with our collective security and prosperity."
The ministers and central bank governors repeated their call for caution in the deployment of cryptocurrencies, while recognizing digital currencies issued by central banks could play a role in providing financial services.
"The G7 continues to maintain that no global stablecoin project should begin operation until it adequately addresses relevant legal, regulatory and oversight requirements through appropriate design and by adhering to applicable standards," the statement said.
Finance ministers from the major euro area economies in September unveiled rules that could limit the development of digital currencies like Facebook's Libra project.
French Minister of Finance, Bruno Le Maire, long a vocal critic of the project, warned that, "We will not accept the deployment of Libra... under current conditions."
The G7 on Tuesday stressed that confidence in the payments system "is underpinned by credible and longstanding public sector commitments to transparency, the rule of law, and sound economic governance."
Norway Says Russia Behind Cyber Attack on Parliament
14.10.20 BigBrothers Securityweek
Norway's government on Tuesday said that it believes Russia was behind an August cyber attack targeting the email system of the country's parliament.
The attack was detected in August, when Norway announced hackers had attacked the parliament's email system, gaining access to some lawmakers' messages.
"Based on the information the government has, it is our view that Russia is responsible for these activities," foreign minister Ine Eriksen Soreide said in a statement.
The foreign ministry did not specify what information prompted its conclusions, but encouraged companies to follow guidelines on cyber security.
"This is a very serious incident, affecting our most important democratic institution," she added.
In its annual threat assessment published in February, Norway's PST domestic intelligence service warned of "computer network operations" which they said represented a "persistent and long-term threat to Norway".
In 2018, NATO member Norway arrested a Russian national suspected of gathering information on the parliament's internet network, but released him several weeks later due to lack of evidence.
The two countries, which share a common border in the Arctic, have generally enjoyed good relations but those have become strained since Russian annexation of the Crimean peninsula in 2014.
Remotely Exploitable DoS Vulnerabilities Found in Allen-Bradley Adapter
14.10.20 ICS Securityweek
Cisco Talos this week released the details of several remotely exploitable denial-of-service (DoS) vulnerabilities found by one of its researchers in an industrial automation product made by Rockwell Automation.
The affected product is the Allen-Bradley 1794-AENT Flex I/O series B adapter, specifically the device’s Ethernet/IP request path port/data/logical segment functionality.
Cisco Talos and Rockwell Automation say a total of five high-severity buffer overflow vulnerabilities have been identified. They impact adapters running versions 4.003 and earlier.DoS vulnerabilities in Allen-Bradley adapters
A remote, unauthenticated attacker can exploit these flaws to cause the targeted device to enter a DoS condition by sending it specially crafted packets.
Cisco noted in its advisories that “all remote communications with the device are stopped and a physical power cycle is required to regain functionality.”
The vulnerabilities were reported to Rockwell Automation in February and the vendor requested two disclosure extensions, but when it asked for a third extension, Talos informed it that the vulnerabilities would be disclosed on October 12 regardless of whether or not a patch is available.
Learn more about vulnerabilities in industrial systems at SecurityWeek’s 2020 ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
Rockwell Automation also published an advisory (account required) for these vulnerabilities on October 12 and while a patch does not appear to be available, the company has provided specific and general recommendations to prevent attacks.
Specific recommendations include only accepting CIP connections from trusted sources on port 44818, employing network segmentation and security controls to minimize exposure of affected devices, and the use of firewalls, VPNs and other network infrastructure controls.
Microsoft Releases Patches For Critical Windows TCP/IP and Other Bugs
14.10.20 OS Thehackernews
Microsoft on Tuesday issued fixes for 87 newly discovered security vulnerabilities as part of its October 2020 Patch Tuesday, including two critical remote code execution (RCE) flaws in Windows TCP/IP stack and Microsoft Outlook.
The flaws, 11 of which are categorized as Critical, 75 are ranked Important, and one is classified Moderate in severity, affect Windows, Office and Office Services and Web Apps, Visual Studio, Azure Functions, .NET Framework, Microsoft Dynamics, Open Source Software, Exchange Server, and the Windows Codecs Library.
Although none of these flaws are listed as being under active attack, six vulnerabilities are listed as publicly known at the time of release.
Chief among the most critical bugs patched this month include CVE-2020-16898 (CVSS score 9.8). According to Microsoft, an attacker would have to send specially crafted ICMPv6 Router Advertisement packets to a remote Windows computer to exploit the RCE flaw in the TCP/IP stack to execute arbitrary code on the target client or server.
According to McAfee security experts, 'this type of bug could be made wormable,' allowing hackers to launch an attack that can spread from one vulnerable computer to another without any human interaction.
A second vulnerability to keep track of CVE-2020-16947, which concerns an RCE flaw on affected versions of Outlook that could allow code execution just by viewing a specially crafted email.
"If the current user is logged on with administrative user rights, an attacker could take control of the affected system," Microsoft noted in its advisory. "An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights."
Another critical RCE vulnerability in Windows Hyper-V (CVE-2020-16891, CVSS score 8.8) exists due to improper validation of input from an authenticated user on a guest operating system.
As a result, an adversary could exploit this flaw to run a specially crafted program on a guest operating system that could cause the Hyper-V host operating system to execute arbitrary code.
Two other critical RCE flaws (CVE-2020-16967 and CVE-2020-16968) affect Windows Camera Codec Pack, permitting an attacker to send a malicious file that, when opened, exploits the flaw to run arbitrary code in the context of the current user.
Finally, the patch also addresses a privilege escalation flaw (CVE-2020-16909) associated with Windows Error Reporting (WER) component that could allow an authenticated attacker to execute malicious applications with escalated privileges and gain access to sensitive information.
Other critical flaws fixed by Microsoft this month include RCE flaws in SharePoint, Media Foundation Library, Base3D rendering engine, Graphics Components, and the Windows Graphics Device Interface (GDI).
It's highly recommended that Windows users and system administrators apply the latest security patches to mitigate the threats associated with these issues.
For installing the latest security updates, Windows users can head to Start > Settings > Update & Security > Windows Update, or by selecting Check for Windows updates.
Ransomware Attackers Buy Network Access in Cyberattack Shortcut
13.10.20 Ransomware Threatpost
Network access to various industries is being offered in underground forums at as little as $300 a pop – and researchers warn that ransomware groups like Maze and NetWalker could be buying in.
For prices between $300 and $10,000, ransomware groups have the opportunity to easily buy initial network access to already-compromised companies on underground forums. Researchers warn this opportunity gives groups like Maze or Sodinokibi the ability to more easily kickstart ransomware attacks across various industries.
The ability to purchase initial network access gives cybercriminals a quicker handle on infiltrating corporate and government networks, so that they can focus in on establishing persistence and moving laterally.
“Network-access selling has progressed from a niche underground offering throughout 2017 to a central pillar of criminal underground activity in 2020,” said Thomas Willkan and Paul Mansfield, senior analysts with Accenture’s CTI Reconnaissance team, in a Monday post.
The salespeople behind this activity typically first develop an initial network vulnerability and infiltrate the victim network to gain complete corporate network access. Once that access is gained, the threat groups then sell it on dark web forums. The pricing depends on the size and revenue of the victim.
Network-access offerings are typically advertised on underground forums with victim industry info (such as banking or retail), the type of access for sale (VPN, Citrix or remote-desktop protocol, for instance), the number of the machines on the network, the country the victim operates in and more (such as the number of employees or revenue of the company).
In September, researchers tracked more than 25 persistent network-access sellers – with more entering the scene on a weekly basis. These sellers are operating on the same forums as actors associated with the ransomware gangs Maze, Lockbit, Avaddon, Exorcist, NetWalker, Sodinokibi and others, they said.
“Although it is difficult to prove that an advertised network access is linked to a specific ransomware attack, from analysis of threat-actor activity we assess with high confidence that some of the accesses are being purchased by ransomware groups and affiliates, thereby enabling potentially devastating ransomware attacks on corporate entities,” they said.
Upon closer inspection of these network access sellers, researchers noted that compromised RDP connections continue to be the most common attack vector – however, cybercriminals are increasingly offering up other vectors, including compromised Citrix and Pulse Secure VPN clients.
“We assess that network-access sellers are taking advantage of remote working tools as more of the workforce works from home as a result of the COVID-19 pandemic,” said researchers.
Another trend is that network-access sellers are starting to use zero-day exploits and sell the network access itself, as opposed to selling the zero-day exploit on its own. One threat actor named Frankknox, for instance, started by advertising for a zero-day targeting a popular mail server for $250,000 – however, he later killed that sale and started exploiting the zero-day himself, and went on to offer corporate network access to 36 companies instead. This network access has been marketed for between $2,000 up to $20,000 – and the threat group claimed to have sold access to at least 11 organizations.
Companies can protect themselves from network compromise and ransomware attacks by setting up monitoring capabilities, regularly backing up their data and employing best practices for using RDP, said researchers.
“We assess with high confidence that the relationship between initial access broker and ransomware group will continue to thrive in 2020 and beyond, earning the threat actors behind it huge profits,” they said. “This symbiotic relationship facilitates continuous targeting of government and corporate entities and streamlines the network compromise process, allowing cyber criminals to act quicker and more efficiently.”
Five Eyes nations plus India and Japan call for encryption backdoor once again
13.10.20 BigBrothers Securityaffairs
Members of the Five Eyes intelligence alliance once again call for tech firms to engineer backdoors into end-to-end and device encryption.
States of the Five Eyes intelligence alliance (US, UK, Canada, Australia, and New Zealand), plus Japan and India, once again call for tech firms to implement backdoors into end-to-end and device encryption.
“We, the undersigned, support strong encryption, which plays a crucial role in protecting personal data, privacy, intellectual property, trade secrets and cyber security,” reads the joint “International Statement.” “Encryption is an existential anchor of trust in the digital world and we do not support counter-productive and dangerous approaches that would materially weaken or limit security systems.”
The statements reinforce the importance of the encryption in protecting data, privacy, and IP, but highlights the risks of abusing it for criminal and terrorist purposes. The Five Eyes argued that encryption could interfere with the ability of the same tech firms to identify and respond to violations of their terms of service or respond to the most serious illegal content and activity on their platform.
“Particular implementations of encryption technology … pose significant challenges to public safety, including to highly vulnerable members of our societies like sexually exploited children.” continues the statement.
Last year, Five Eyes states called on tech firms to implement a mechanism to bypass encryption in their solutions to support law enforcement requests for access to encrypted data on suspects.
On the other end, tech firms always refused to introduce backdoors in their systems because they violate terms of service.
The Statement ends with the call to protect public safety, even sacrificing privacy or cyber security.
“We reiterate that data protection, respect for privacy and the importance of encryption as technology changes and global internet standards are developed remain at the forefront of each state’s legal framework,” concluded the statement.
“However, we challenge the assertion that public safety cannot be protected without compromising privacy or cybersecurity. We strongly believe that approaches protecting each of these important values are possible and strive to work with industry to collaborate on mutually agreeable solutions.”
Microsoft partnered with other security firms to takedown TrickBot botnet
13.10.20 BotNet Securityaffairs
A joint operation conducted by FS-ISAC, ESET, Lumen’s Black Lotus Labs, NTT, Symantec, and Microsoft aimed at takedown the TrickBot botnet.
Microsoft’s Defender team, FS-ISAC, ESET, Lumen’s Black Lotus Labs, NTT, and Broadcom’s cyber-security division Symantec joint the forces and announced today a coordinated effort to take down the command and control infrastructure of the infamous TrickBot botnet.
The experts that participated in the takedown have supported the investigation into TrickBot’s backend infrastructure for several months.
“Through our monitoring of Trickbot campaigns, we collected tens of thousands of different configuration files, allowing us to know which websites were targeted by Trickbot’s operators. The targeted URLs mostly belong to financial institutions,” Jean-Ian Boutin, Head of Threat Research at ESET.
“Trying to disrupt this elusive threat is very challenging as it has various fallback mechanisms, and its interconnection with other highly active cybercriminal actors in the underground makes the overall operation extremely complex.”
The security firms have collected more than 125,000 TrickBot malware samples and mapped the command and control infrastructure. The TrickBot botnet was considered by security experts one of the biggest botnets.

Internet service providers (ISPs) and computer emergency readiness teams (CERTs) around the world also supported the operation by notifying all infected users.
The information gathered by the security firm was used by Microsoft to receive a warrant to takedown the TrickBot servers.
“We took today’s action after the United States District Court for the Eastern District of Virginia granted our request for a court order to halt Trickbot’s operations.” reads the post published by Microsoft.
“With this evidence, the court granted approval for Microsoft and our partners to disable the IP addresses, render the content stored on the command and control servers inaccessible, suspend all services to the botnet operators, and block any effort by the TrickBot operators to purchase or lease additional servers,”
This is the second-ever major botnet takedown operation this year, after Necurs one in March.
Microsoft pointed out that this takedown represents a new legal approach that its DCU used for the first time, it includes copyright claims against Trickbot’s operators that have illegally used the software code of the IT giant. Microsoft has chosen this approach to take civil action against botnet operators and protect its customers across the world.
According to the security firms that took part in the operation, the TrickBot botnet had infected more than one million devices at the time of its takedown.
Trickbot has been active since 2016, at the time the authors of the author designed it to steal banking credentials. Over the years, the threat evolved and its operators implemented a modular structure that allowed them to offer the threat as malware-as-a-service. The Trickbot infrastructure was used by crooks to compromise systems and carry out human-operated campaigns, notably its use for the deployment of the Ryuk ransomware.
The malware first started out in 2016 as a banking trojan before shifting into a multi-purpose malware downloader that infected systems and provided access to other criminal groups using a business model known as MaaS (Malware-as-a-Service).
The TrickBot operators also deployed banking trojans and info-stealer trojans and were providing access to corporate networks for crooks focused on scams and cyber espionage.
“The action against Trickbot is one of the ways in which Microsoft provide real-world protection against threats. This action will result in protection for a wide range of organizations, including financial services institutions, government, healthcare, and other verticals from malware and human-operated campaigns delivered via the Trickbot infrastructure.” concludes Microsoft.
Anatomy of Ryuk Attack: 29 Hours From Initial Email to Full Compromise
13.10.20 Ransomware Securityweek
An attack involving the Ryuk ransomware required 29 hours from an email being sent to the target to full environment compromise and the encryption of systems, according to the DFIR Report, a project that provides threat intelligence from real attacks observed by its honeypots.
Initially detailed in 2018, Ryuk was believed to be the work of North Korean hackers at first, due to similarities with the Hermes ransomware, but was then associated with Russian cybercriminals.
Over the past two years, Ryuk has been responsible for a significant number of high-profile attacks, including incidents involving Pennsylvania-based UHS and Alabama hospital chain DCH Health System.
In the case of the attack observed by the DFIR Report, it all started with a malicious email that carried a link to download the Bazar/Kegtap loader, which injects into multiple processes, and which performs reconnaissance on the infected system, using Windows utilities like nltest and net group, as well as third-party tool AdFind.
The malware remained quiet for roughly one day, after which a second reconnaissance phase was launched, using the same tools, plus Rubeus. Data was exfiltrated to a remote server and the attackers started lateral movement.
To compromise additional systems on the network, the attackers used various methods, including remote WMI, remote service execution with PowerShell, and a Cobalt Strike beacon dropped over SMB. Next, the Cobalt Strike beacon was used as the main pivotal point.
Additional beacons were then established across the environment and PowerShell was employed to disable Windows Defender. Ryuk was executed one minute after being transferred over SMB from the pivot and, once encryption started, the servers used to store backups were hit first.
The DFIR Report, which provides a comprehensive technical analysis of the attack, reveals that Ryuk was also transferred to the remaining hosts on the network via SMB, and that an RDP connection was leveraged to execute it from the pivot domain controller.
“In total, the campaign lasted 29 hours–from initial execution of the Bazar, to domain wide ransomware. If a defender missed the first day of recon, they would have had a little over 3 hours to respond before being ransomed,” The DFIR Report notes.
After the systems were encrypted, the attackers demanded approximately 600 Bitcoins (roughly $6 million) in ransom. However, the threat actors were willing to negotiate.
On Monday, Microsoft announced that it shut down the infrastructure of TrickBot, the botnet used as the main delivery channel for Ryuk ransomware.
Law Firm Seyfarth Shaw Hit by Damaging Ransomware Attack
13.10.20 Ransomware Securityweek
International law firm Seyfarth Shaw LLP has shut down many of its systems after being hit with a ransomware attack.
Founded in 1945 in Chicago, Illinois, Seyfarth has over 900 lawyers across 17 offices, providing clients all around the world with advisory, litigation, and transactional legal services. The Am Law 100 firm serves more than 300 of the Fortune 500 companies.
Over the weekend, the company fell victim to a ransomware attack that spread aggressively across its network and forced it to shut down its email service and other systems.
The firm says it was able to stop the attack soon after detection, but not before data on many systems was encrypted by the malware.
“On Saturday, October 10, 2020, Seyfarth was the victim of a sophisticated and aggressive malware attack that appears to be ransomware. […] many of our systems were encrypted, and we have shut them down as a precautionary measure,” Seyfarth announced.
The company claims that this appears to have been a coordinated attack targeting multiple entities at the same time.
“We understand that a number of other entities were simultaneously hit with this same attack. Our monitoring systems detected the unauthorized activity, and our IT team acted quickly to prevent its spread and protect our systems,” the law firm says.
Seyfarth also notes that it found no evidence that client or firm data was accessed or exfiltrated, but many recent ransomware attacks have resulted in sensitive information being stolen to convince the victim to pay the ransom.
As its email service remains inaccessible at the moment, the company advises clients to contact it via phone. An online contact form is also available.
“Our clients remain our top priority, and we will continue to do everything necessary to protect their confidential information and continue to serve them. We are coordinating with the FBI and are working around the clock to bring our systems back online as quickly and safely as possible,” Seyfarth continues.
Microsoft and Other Tech Companies Take Down TrickBot Botnet
13.10.20 BotNet Thehackernews
Days after the US Government took steps to disrupt the notorious TrickBot botnet, a group of cybersecurity and tech companies has detailed a separate coordinated effort to take down the malware's back-end infrastructure.
The joint collaboration, which involved Microsoft's Digital Crimes Unit, Lumen's Black Lotus Labs, ESET, Financial Services Information Sharing and Analysis Center (FS-ISAC), NTT, and Broadcom's Symantec, was undertaken after their request to halt TrickBot's operations were granted by the US District Court for the Eastern District of Virginia.
The development comes after the US Cyber Command mounted a campaign to thwart TrickBot's spread over concerns of ransomware attacks targeting voting systems ahead of the presidential elections next month. Attempts aimed at impeding the botnet were first reported by KrebsOnSecurity early this month.
Microsoft and its partners analyzed over 186,000 TrickBot samples, using it to track down the malware's command-and-control (C2) infrastructure employed to communicate with the victim machines and identify the IP addresses of the C2 servers and other TTPs applied to evade detection.
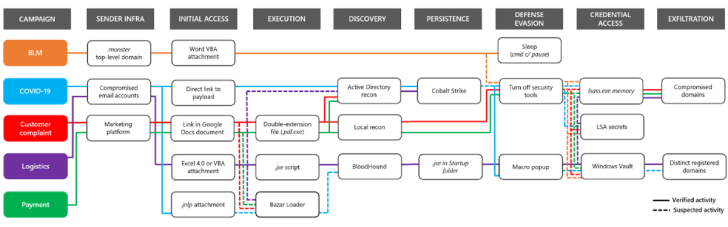
"With this evidence, the court granted approval for Microsoft and our partners to disable the IP addresses, render the content stored on the command and control servers inaccessible, suspend all services to the botnet operators, and block any effort by the TrickBot operators to purchase or lease additional servers," Microsoft said.
Since its origin as a banking Trojan in late 2016, TrickBot has evolved into a Swiss Army knife capable of pilfering sensitive information, and even dropping ransomware and post-exploitation toolkits on compromised devices, in addition to recruiting them into a family of bots.
"Over the years, TrickBot's operators were able to build a massive botnet, and the malware evolved into a modular malware available for malware-as-a-service," Microsoft said.
"The TrickBot infrastructure was made available to cybercriminals who used the botnet as an entry point for human-operated campaigns, including attacks that steal credentials, exfiltrate data, and deploy additional payloads, most notably Ryuk ransomware, in target networks."
Typically delivered via phishing campaigns that leverage current events or financial lures to entice users into open malicious file attachments or click links to websites hosting the malware, TrickBot has also been deployed as a second-stage payload of another nefarious botnet called Emotet.
The cybercrime operation has infected over a million computers to date.
Microsoft, however, cautioned that it did not expect the latest action to permanently disrupt TrickBot, adding that the cybercriminals behind the botnet will likely make efforts to revive their operations.
According to Swiss-based Feodo Tracker, eight TrickBot control servers, some of which were first seen last week, are still online after the takedown.
APT groups chain VPN and Windows Zerologon bugs to attack US government networks
12.10.20 APT Securityaffairs
US government networks are under attack, threat actors chained VPN and Windows Zerologon flaws to gain unauthorized access to elections support systems.
The Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) published a joint security alert to warn of attackers combining VPN and Windows Zerologon flaws to target government networks.
According to government experts, the attacks aimed at federal and state, local, tribal, and territorial (SLTT) government networks, the agencies also reported attacks against non-government networks.
The alert didn’t provide details about the attackers, it only classify them as “advanced persistent threat (APT) actors, a circumstance that suggests the involvement of state-sponsored hackers.
“CISA is aware of some instances where this activity resulted in unauthorized access to elections support systems; however, CISA has no evidence to date that integrity of elections data has been compromised,” the security alert published by the two agencies reads.
The joint alert includes information on the vulnerabilities exploited by the hackers and recommended mitigation actions for affected organizations.
The agencies warn of risk to elections information housed on government networks.
According to the Alert (AA20-283A), advanced persistent threat (APT) actors are exploiting multiple legacy vulnerabilities in combination with a the recently discovered Zerologon vulnerability (CVE-2020-1472).
The CVE-2020-1472 flaw is an elevation of privilege that resides in the Netlogon. The Netlogon service is an Authentication Mechanism used in the Windows Client Authentication Architecture which verifies logon requests, and it registers, authenticates, and locates Domain Controllers.
An attacker could exploit the vulnerability to impersonate any computer, including the domain controller itself, and execute remote procedure calls on their behalf.
An attacker could also exploit the flaw to disable security features in the Netlogon authentication process and change a computer’s password on the domain controller’s Active Directory.
“CISA has recently observed advanced persistent threat (APT) actors exploiting multiple legacy vulnerabilities in combination with a newer privilege escalation vulnerability—CVE-2020-1472—in Windows Netlogon.” reads the report. “The commonly used tactic, known as vulnerability chaining, exploits multiple vulnerabilities in the course of a single intrusion to compromise a network or application.”
Experts believe that the targets are not being selected because of their proximity to elections information, anyway, the agencies warn of the risk to elections systems operated by the government.
“CISA is aware of some instances where this activity resulted in unauthorized access to elections support systems; however, CISA has no evidence to date that integrity of elections data has been compromised.” continues the alert.
CISA and FBI have observed attacks carried out by APT actors that combined two the CVE-2018-13379 and CVE-2020-1472 flaws.
The CVE-2018-13379 is a path traversal vulnerability in the FortiOS SSL VPN web portal that could be exploited by an unauthenticated attacker to download FortiOS system files, to upload malicious files on unpatched systems and take over Fortinet VPN servers.
Government experts explained that attackers are combining these two flaws to hijack Fortinet servers and use them as an entry point in government networks, then take over internal networks using the Zerologon flaw to compromise all Active Directory (AD) identity services.
Threat actors have then been observed using legitimate remote access tools, including Remote Desktop Protocol (RDP) and VPN, to access the targeted environment with the compromised credentials.
Recently Microsoft observed Iran-linked APT Mercury and the Russian cybercrime gang TA505 exploiting the Zerologon flaw in attacks in the wild.
Microsoft publicly shared some file indicators for the attacks along with variations of the ZeroLogon exploits its experts have detected. Many of these exploits were recompiled versions of well-known, publicly available proof-of-concept code.
Both CISA and the FBI recommend private organizations and public agencies to patch systems and equipment promptly and diligently.
The alert also warns of other vulnerabilities that could be exploited by threat actors and urge to patch vulnerable systems immediately.
“CISA recommends network staff and administrators review internet-facing infrastructure for these and similar vulnerabilities that have or could be exploited to a similar effect, including Juniper CVE-2020-1631, Pulse Secure CVE-2019-11510, Citrix NetScaler CVE-2019-19781, and Palo Alto Networks CVE-2020-2021 (this list is not considered exhaustive).” concludes the alert.
Tech Companies Take Down TrickBot Botnet Infrastructure
12.10.20 BotNet Securityweek
Microsoft on Monday revealed that it worked together with industry partners to shut down the infrastructure used by TrickBot operators and block efforts to revive the botnet.
The Washington Post reported last week that the U.S. Cyber Command too attempted to hack TrickBot's C&C servers, in an attempt to take the botnet down to prevent attacks seeking to disrupt the U.S. presidential elections. This is said to have been a separate operation that was not coordinated with Microsoft.
TrickBot emerged in 2016 as a banking Trojan, supposedly from the same group that operated the Dyre Trojan, and has become one of the most prevalent threats out there, with more than one million infected machines all around the world.
Over time, TrickBot has received updates that expanded its capabilities, evolved into a modular threat that ensnared computers into a botnet being offered under a malware-as-a-service model. Both nation-states and criminal networks are believed to have employed it for nefarious purposes.
The network of infected machines has been leveraged in malicious campaigns aimed at stealing credentials and data, and delivering additional malware, such as the Ryuk ransomware.
TrickBot has been distributed in email campaigns that leveraged current events as lures, with malicious documents attached. The attacks targeted a wide range of verticals in numerous regions, Microsoft says. Other distribution methods included lateral movement via Server Message Block (SMB), or deployment via other malware, such as Emotet.
“Over the years we’ve tracked it, Trickbot compromises have been reported in a steady manner, making it one of the largest and longest-lived botnets out there. Trickbot is one of the most prevalent banking malware families, and this malware strain represents a threat for internet users globally,” Jean-Ian Boutin, Head of Threat Research at ESET, explains.
As part of one TrickBot attack, once the victim was enticed to open the malicious attachment, a script was executed to gather system information, perform queries to the affected organization’s domain controller, and gather data about the Active Directory.
Additional payloads were executed to eventually gain control over the affected system, gather information on potentially high-value devices on the network, and move laterally. TrickBot was used to steal credentials from the Windows Vault and Credentials Manager, so that security mechanisms could be evaded. The attackers added the initial script to Startup for persistence.
Microsoft says that its investigation into TrickBot involved the analysis of roughly 61,000 malware samples, which revealed constantly evolving modular capabilities, and support for infecting Internet of Things (IoT) devices.
Various TrickBot modules are meant for banking credentials theft, reconnaissance, data theft, password grabbing, cookies theft, information stealing, point-of-sale reconnaissance, remote control, SMB spreading, Outlook theft, lateral movement, and RDP brute-force.
Microsoft notes that it managed to disrupt TrickBot’s infrastructure “after United States District Court for the Eastern District of Virginia granted our request for a court order to halt Trickbot’s operations.”
The company worked together with industry partners to take action against TrickBot, and received help from the Financial Services Information Sharing and Analysis Center (FS-ISAC), ESET, Lumen’s Black Lotus Labs, NTT, and Broadcom-owned Symantec. Internet service providers (ISPs) and computer emergency readiness teams (CERTs) around the world were also contacted, to help with remediation efforts.
“The court granted approval for Microsoft and our partners to disable the IP addresses, render the content stored on the command and control servers inaccessible, suspend all services to the botnet operators, and block any effort by the Trickbot operators to purchase or lease additional servers,” Microsoft says.
The company expects that TrickBot’s operators will attempt to revive their operation, but says that it will work with its partners to monitor such activities and take further action when necessary. The malware has various fallback mechanisms and its operators are connected to other highly active cybercriminal actors, which made the disruption difficult, ESET notes.
As Symantec explains, the takedown “relied upon intellectual-property laws to effectively evict the botnet operators from the command-and-control servers they need to maintain access to victim machines.”
Zerologon Chained With Fortinet, MobileIron Vulnerabilities in U.S. Government Attacks
12.10.20 BigBrothers Securityweek
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has warned that government networks have been targeted in attacks exploiting the Zerologon vulnerability in combination with flaws affecting Fortinet and MobileIron products.
“This recent malicious activity has often, but not exclusively, been directed at federal and state, local, tribal, and territorial (SLTT) government networks. Although it does not appear these targets are being selected because of their proximity to elections information, there may be some risk to elections information housed on government networks,” CISA said in an advisory written with contributions from the FBI.
It added, “CISA is aware of some instances where this activity resulted in unauthorized access to elections support systems; however, CISA has no evidence to date that integrity of elections data has been compromised.”
According to CISA, the attacks, which appear to be ongoing, have in many cases involved exploitation of CVE-2018-13379, a Fortinet FortiOS VPN vulnerability, and in some cases CVE-2020-15505, a recently detailed issue affecting MobileIron’s mobile device management (MDM) solutions.
These security holes were exploited by malicious actors to gain initial access to the targeted network, and then they used Zerologon to escalate privileges and compromise Active Directory identity services. CISA has described the attackers as “APT actors.”
While the attacks spotted by US agencies involved the Fortinet and MobileIron vulnerabilities, organizations have been warned that attackers could also leverage flaws in Citrix, Pulse Secure, Palo Alto Networks and F5 Networks products for the same purpose.
The Zerologon vulnerability, officially tracked as CVE-2020-1472, is a privilege escalation issue affecting Windows Server. It allows an attacker who has access to the targeted network to hack domain controllers without credentials.
Microsoft patched the flaw in August, but it appears many organizations have failed to install the patches and threat actors are increasingly exploiting it in their operations.
CISA issued its first warning about Zerologon being exploited in attacks in late September, shortly after it issued an emergency directive instructing federal agencies to immediately install the patches.
According to Microsoft, the Zerologon vulnerability has been exploited by both profit-driven cybercriminals and state-sponsored groups.
Carnival Corp. Confirms Personal Information Compromised in Ransomware Incident
12.10.20 Ransomware Securityweek
Leisure travel company Carnival Corporation last week confirmed that personal information pertaining to guests, employees, and crew was compromised in an August 2020 ransomware attack.
Carnival, which owns 10 global cruise line brands and a tour company, employs more than 120,000 people and has a fleet of 102 ships. Prior to the COVID-19 pandemic, which forced the company to suspend operations, Carnival served more than 11 million guests per year.
In mid-August, the company announced that it detected a ransomware attack that resulted not only in some of its systems being encrypted, but also in the unauthorized download of some files.
In an 8-K form filed at the time with the U.S. Securities and Exchange Commission to announce the security incident, the company said the attack affected the technology systems for a cruise line brand, but did not mention which. An investigation was launched and law enforcement was alerted.
Last week, Carnival filed a 10-Q form with the SEC, confirming that certain personal data was compromised. However, it did not reveal the number of affected people or what type of information was accessed.
“On August 15, 2020, we detected a ransomware attack and unauthorized access to our information technology systems,” the filing reads. “While the investigation is ongoing, early indications are that the unauthorized third-party gained access to certain personal information relating to some guests, employees and crew for some of our operations.”
In the filing, Carnival also notes that it is not aware of the compromised data being misused.
“There is currently no indication of any misuse of this information. While at this time we do not believe that this information will be misused going forward or that this incident will have a material adverse effect on our business, operations or financial results, no assurances can be given and further we may be subject to future attacks or incidents that could have such a material adverse effect,” the company also said.
In March 2020, the cruise operator revealed a data breach that was initially identified in May 2019, and which resulted in large amounts of sensitive data pertaining to its guests being accessed by an unauthorized party.
Hackers Publish Public School District's Stolen Data Online
12.10.20 Incindent Securityweek
Computer hackers who obtained information about a Virginia public school district’s students and employees have posted stolen data online, school officials said Friday in an email to parents and staff.
The Fairfax County Public Schools didn’t specify the nature or volume of the data that was stolen in the ransomware attack last month. Hackers use ransomware software to steal data and threaten to publish or block access to it unless a target pays a ransom.
The Washington Post reports that Schools Superintendent Scott Brabrand’s email on Friday said the criminal cyber organization known as the Maze group had claimed responsibility for the attack and posted stolen data on the dark web.
Braband said the district was cooperating with the Virginia State Police and the FBI.
“We are working around the clock to identify the information that was taken and will notify impacted individuals as appropriate,” he wrote.
School district spokeswoman Lucy Caldwell said officials believe “only a subset of individuals, including a limited number of students” were affected by the ransomware attack. Caldwell said the district will offer free credit-monitoring services to all district employees and their spouses and any others who were affected.
A Self-Service Password Reset Project Can Be A Quick Win For IT
12.10.20 Security Thehackernews
Since the beginning of this year, organizations' IT staff have faced numerous challenges and an increased workload as a result of the global pandemic and shift to a mainly remote workforce.
Supporting end-users that are now working from home has introduced new challenges in troubleshooting since it isn't as simple as visiting an end user's desk to resolve issues as they arise.
One support issue common to both on-premises and remote end-users is password resets and other account-related activities. These include accounts that are locked out, passwords that have expired, and password changes.
Implementing a self-service password reset (SSPR) solution can be a quick win for IT staff who are now supporting both on-premises and remote workers and taking care of other normal daily tasks.
Let's look at why SSPR solutions can lead to quick results in lowering the overall support burden on IT staff.
Increased Strain On IT Staff
The global pandemic this year has been challenging for just about everyone. Most have seen adjustments, cutbacks, increased duties, and other changes resulting from the impact of Covid-19. Earlier this year, as the global pandemic unfolded, IT staff were tasked with effectively providing remote access to resources almost overnight. This led to many tense days as IT staff may have struggled to make this possible for all remote employees technically.
After the initial provisioning of a remote work solution, IT has been responsible for supporting end-users who are now reliant on home Internet connectivity and, in some cases, even on personal devices to connect to corporate resources. Like many others, IT departments may also have been subject to downsizing due to business downturns associated with the pandemic. All of these factors have led to tremendous workloads on IT staff, among others.
This sheds light on a couple of important considerations that emerge to help IT support staff keep up with increased duties and activities.
These include prioritizing:
Minimizing high volume calls to the IT service desk
Projects that optimize efficiency quickly
Implementing a self-service password reset (SSPR) solution can achieve both objectives. Adopting an SSPR solution helps to minimize the overall number of calls to the IT service desk. Additionally, IT will see a quick time to value for an SSPR solution which is easy to implement and will start yielding results almost immediately.
How Much Do Account-related Activities Cost Your Business?
According to analyst firms the Gartner Group and Forrester Research, between 20%-50% of help desk calls are related to password resets, and a single password reset call can cost about $70. So, to put some context to those numbers, if your service desk triages 500 calls a month, potentially 250 of those calls are password related accounting for $17,500 in support costs per month!
Implementing a self-service password reset (SSPR) solution could essentially eliminate the 250 calls in the example and save the organization tens of thousands per month while freeing up IT staff to triage other issues in the environment. Another cost-saving that is not accounted for is end-user productivity, which is a bit harder to quantify.
What is a Self-Service Password Reset (SSPR) Solution?
A self-service password reset solution provides a way for end-users to resolve their account issues, including password resets, account unlocks, and password changes in an automated way, without the need to interact with the service desk.
With SSPR, end-users enroll in the system and provide information that can later be used to verify their identity when the need arises to unlock their account or reset their password. Common SSPR identity verification methods include security questions and one-time passcodes delivered over text or email.
For example, users will enroll into the system with answers to predetermined questions or with their mobile or email address. Before being able to perform account-related actions, users will have to identify themselves using the enrolled identity verification method to ensure that they are whom they say they are. The workflow includes a fully automated approach without IT staff interaction and allows end-users to get a resolution to their issue almost immediately.
Full-featured SSPR solutions generally provide the following benefits to your organization:
Fast implementation – They are easy to implement and generally provide a small footprint from an infrastructure perspective.
Measurable cost savings – Statistically speaking, SSPR solutions could potentially cut service desk calls by up to 50%. With the high cost of password resets, this can amount to tremendous savings in time and effort from service desk professionals. This has a trickle-down effect of allowing more time allocation for other issues.
Higher quality experience – End users no longer have to wait for service desk technicians to work through the queue and triage their password issue. Account-related activities and password resets can be resolved immediately with the self-service process made possible by the SSPR solution. This is easily accomplished via an intuitive web-based interface.
Increased security – Given that IT service desk user verification is often non-existent or highly insecure, SSPR fills this gap by ensuring users are whom they say they are before performing a password reset.
Not All SSPR Solutions Are Created Equal
Implementing an effective SSPR solution can certainly result in a quick win for IT departments that are already stretched thin due to the COVID-19 pandemic. However, not all SSPR solutions are created equal. A large part of the success of an SSPR implementation depends on the features and functionality of the solution itself.
Some essential features you should look for include:
Enrollment specific features – pre-enrollment, admin enrollment, and forced enrollment options.
Usability – ability to access and utilize the solution easily from multiple entry points (login screen, Internet, apps, etc.)
Ability to use existing MFA tools – supports existing forms of authentication that users use to access other applications at work.
For an SSPR solution in your environment to truly be successful and lead to a quick win for IT, you need to have 100% compliance from an enrollment standpoint. As such, the solution needs to either remove the enrollment process from end-users or make the enrollment process mandatory while being simple to use and access.
Specops uReset is an example of a fully-featured and secure SSPR solution that can ensure 100% user enrollment and usage. Request a free trial today.
Researchers received $288,500 for 32 out of 55 issues reported to Apple
12.10.20 Apple Securityaffairs
Researchers received hundreds of thousands of dollars in bug bounties for reporting 55 vulnerabilities as part of the Apple bug bounty program.
A team of researchers composed of Sam Curry, Brett Buerhaus, Ben Sadeghipour, Samuel Erb and Tanner Barnes reported a total of 55 flaws to Apple as part of the company bug bounty program.
The flaws were all covered by Apple’s bug bounty program, 11 vulnerabilities have been rated critical and 29 rated high severity.
Some of the flaws were addressed by Apple a few hours after they have been reported by the researchers.
The researchers already received for these issues 32 payrolls for a total of $288,500, but likely will receive more for the other flaws reported.
The experts published technical details for some of the vulnerabilities they found.
“During our engagement, we found a variety of vulnerabilities in core portions of their infrastructure that would’ve allowed an attacker to fully compromise both customer and employee applications, launch a worm capable of automatically taking over a victim’s iCloud account, retrieve source code for internal Apple projects, fully compromise an industrial control warehouse software used by Apple, and take over the sessions of Apple employees with the capability of accessing management tools and sensitive resources.” reported the experts.
The experts discovered how to fully compromise the Apple Distinguished Educators Program via Authentication and bypass authorization and hot to fully compromise the DELMIA Apriso Application via authentication bypass.
The experts also detailed wormable Stored Cross-Site Scripting vulnerabilities that could allow attackers to steal iCloud data through a modified email and a command injection issue in Author’s ePublisher.
The experts also reported a full response SSRF on iCloud that could allow attackers to retrieve Apple Source Code.
The experts pointed out that many of the flaws could have been exploited by threat actors to gain access to Apple’s internal network and execute arbitrary commands on the company’s web servers.
“Overall, Apple was very responsive to our reports. The turn around for our more critical reports was only four hours between time of submission and time of remediation,” concludes Curry.
“Since no-one really knew much about their bug bounty program, we were pretty much going into unchartered territory with such a large time investment. Apple has had an interesting history working with security researchers, but it appears that their vulnerability disclosure program is a massive step in the right direction to working with hackers in securing assets and allowing those interested to find and report vulnerabilities,”
Underestimating the FONIX – Ransomware as a Service could be an error
12.10.20 Ransomware Securityaffairs
FONIX is a new Ransomware as a Service available in the threat landscape that was analyzed by SentinelLabs researchers.
FONIX is a relatively new Ransomware as a Service (RaaS) analyzed by researchers from Sentinel Labs, its operators were previously specialized in the developers of binary crypters/packers.
The actors behind FONIX RaaS advertised several products on various cybercrime forums.
FONIX first appeared in the threat landscape in July 2020, fortunately, the number of infections associated with this threat is still small.
Experts pointed out that the ransomware authors don’t require the payment of a fee to become an affiliate of the service, the operators only keep a percentage of any ransoms from their affiliate network.
Experts believe that However the FONIX RaaS can quickly become rampant if security firms and authorities underestimate it.
“Notably, FONIX varies somewhat from many other current RaaS offerings in that it employs four methods of encryption for each file and has an overly-complex post-infection engagement cycle.” reads the analysis published by Sentinel Labs.

The communications with the RaaS operators are carried out via email. Any affiliate has to provide the operators files from a victim system to obtain the decryptor and key for the victim, in turn the operators keep for them 25% of the ransom.
“Based on current intelligence, we know that FONIX affiliates do not get provided with a decryptor utility or keys at first. Instead, victims first contact the affiliate (buyer) via email as described above. The affiliate then requests a few files from the victim. These include two small files for decryption: one is to provide proof to the victim, the other is the file “cpriv.key” from the infected host. The affiliate is then required to send those files to the FONIX authors, who decrypt the files, after which they can be sent to the victims.” continues the analysis.
“Presumably, once the victim is satisfied that decryption is possible, the affiliate provides a payment address (BTC wallet). The victim then pays the affiliate, with the affiliate in turn supplying the FONIX authors with their 25% cut.”
Obviously, the above process is a bit convoluted and far less user-friendly than most RaaS services.
The FONIX ransomware only targets Windows systems, by default it encrypts all file types, excluding critical Windows OS files.
The ransomware uses a combination of AES, Chacha, RSA, and Salsa20 to encrypt a victim’s files, it adds a .XINOF extension. Experts pointed out that the use of multiple encryption protocols makes the encryption process significantly slower than that of other ransomware.
Upon executing the payload with administrative privileges, the following system changes are made:
Task Manager is disabled
Persistence is achieved via scheduled task, Startup folder inclusion, and the registry (Run AND RunOnce)
System file permissions are modified
Persistent copies of the payload have their attributed set to hidden
A hidden service is created for persistence (Windows 10)
Drive / Volume labels are changed (to “XINOF”)
Volume Shadow Copies are deleted (vssadmin, wmic)
System recovery options are manipulated/disabled (bcdedit)
Safeboot options are manipulated
“a FONIX infection is notably aggressive – encrypting everything other than system files – and can be difficult to recover from once a device has been fully encrypted. Currently, FONIX does not appear to be threatening victims with additional consequences (such as public data exposure or DDoS attacks) for non-compliance.” concludes the report.
Hackers targeted the US Census Bureau network, DHS report warns
12.10.20 BigBrothers Securityaffairs
The US DHS’s Homeland Threat Assessment (HTA) report revealed that threat actors have targeted the US Census network during the last year.
The US Department of Homeland Security revealed that unknown threat actors have targeted the network of the US Census Bureau during the last year.
The attacks were reported in the first Homeland Threat Assessment (HTA) report released earlier this week.
The US Census Bureau is the largest US federal government statistical agency responsible dedicated to providing current facts and figures about America’s people, places, and economy.
Data collected by the agency is used by the federal government to allocate over $675 billion in federal funds to tribal, local, and state governments every year.
According to the DHS, threat actors will likely interfere with the upcoming 2020 US Presidential election, as well as to compromise the 2020 US Census.
DHS warns of nation-state actors linked to China, Russia, Iran, and North Korea that will attempt to compromise or disrupt critical 2020 elections infrastructure, as well as try to interfere with the final vote.
“Advanced persistent threat or other malicious cyber actors likely will target election-related infrastructure as the 2020 Presidential election approaches, focusing on voter PII, municipal or state networks, or state election officials directly.” reads the DHS HTA.
The report mentions multiple attempts of gaining access to systems on the US Census network.
“Unidentified cyber actors have engaged in suspicious communications with the U.S. Census public-facing network over at least the last year, including conducting vulnerability scans and attempting unauthorized access,” continues the report. “Cyber activity directed at the U.S. Census could include attempts to gain illicit access to census-gathered bulk data; to alter census registration data; to compromise the census infrastructure supply chain, or conducting denial-of-service attacks.”
In the past, the US Census has been hit by attacks, such as hacks and DDoS attacks during a 2018 test of census systems attributed to Russia-linked hackers and a 2015 hack attributed to the Anonymous collective.
The HTA report warns of an intensification of malicious activities conducted by both nation-states and cybercrime groups. The document warns of destructive attacks against U.S. critical infrastructure.
“Federal, state, local, tribal and territorial governments, as well as the private sector, will experience an array of cyber-enabled threats designed to access sensitive information, steal money, and force ransom payments,” continues the HTA report.
The report pointed out the nation-state actors have different motivations.
Russia, China, and Iran are more focused on cyber-espionage while North Korea is “confined to criminal generation of revenue.”
This HTA annual report provides information of threats targeting the US to government and private sector partners.
Let me suggest to read it.
Tyler Technologies finally paid the ransom to receive the decryption key
12.10.20 Ransomware Securityaffairs
Tyler Technologies has finally decided to paid a ransom to obtain a decryption key and recover files encrypted in a recent ransomware attack.
Tyler Technologies, Inc. is the largest provider of software to the United States public sector. At the end of September, the company disclosed a ransomware attack and its customers reported finding suspicious logins and previously unseen remote access tools on their networks.
The ransomware attack took place on September 23, the threat actors breached the network of the company and deployed the malware.
Tyler notified law enforcement and hired a forensics firm to investigate the incident and determine the extent of the incident.
Immediately after the attack company representatives declared that the incident only impacted the internal network and phone systems.
Some reports circulating online speculate the company was infected with the RansomExx ransomware.
The RansomEXX is human-operated ransomware, this means that attackers manually infected the systems after gained access to the target network.
In June 2020, the same ransomware was employed in an attack on the Texas Department of Transportation, in September it infected the systems at the IPG Photonics high-performance laser developer.
According to BleepingComputer, which cited a source informed on the event, Tyler Technologies paid a ransom of an unspecified amount to receive the decryption key and recover encrypted files.
“When the ransomware encrypted Tyler Technologies’ files, they appended an extension similar to ‘.tylertech911-f1e1a2ac.'” reported BleepingComputer.
“To prove that the decryptor was valid, BleepingComputer was able to decrypt encrypted files [1, 2] uploaded to VirusTotal at the time of the ransomware attack.”
When decrypted, the Arin.txt file contained a list of IP ranges used by the company.
Experts pointed out that many school districts, court systems, and local and statement governments in the United States uses Tyler Technologies software, this means that the disclosure of data stolen during the ransomware attack could have serious consequences.
For this reason, the company decided to pay the ransom.
Researchers found alleged sensitive documents of NATO and Turkey
12.10.20 Security Securityaffairs
Security experts from Cyble found alleged sensitive documents of NATO and Turkey, is it a case of cyber hacktivism or cyber espionage?
Researchers from the US-based firm Cyble recently came across a post shared by an unknown threat actor that goes online with the moniker Spectre123, where he has allegedly leaked the sensitive documents of NATO and Havelsan (Turkish Military/defence manufacturer).
Cyble analyzed the leaked sensitive documents and reported that they include Statement of Work files, proposals, contracts, 3d designs, resumes, excel sheets containing raw materials information, and financial statements.
It is unclear if the threat actors acted for cyber espionage purposes or hacktivism, the content of the message advertising the leak suggests that it was the work of hacktivists, but we cannot exclude that it is the result of a nation-state actor.
“Based on the message body of the leak, the cyber attack indicates hacktivism, but last year, around May 23, 2019, UK warned NATO allies of hacking activities of Russia -> Link. Also, in September 2020, it was reported that Russian hackers targeted government agencies in NATO member countries, and nations who cooperate with NATO -> Link.” reads the post published by Cyble. “These events ensue an unsatisfying narrative – Is it really hacktivism or cyber espionage?”
The availability of sensitive documents like the ones discovered by the experts could allow threat actors to gather intelligence on potential targets and use the leaked information to carry out spear-phishing campaigns.
Cyber researchers are still investigating the data leak and will provide updates on the story.
'Five Eyes' Alliance Demands Ways to Access Encrypted Apps
12.10.20 Security Securityweek
The "Five Eyes" intelligence alliance demanded Sunday that tech companies insert "backdoors" in encrypted apps to allow law enforcement agencies the access they say they need to police online criminality.
The top justice officials of the United States, Britain, Australia, Canada and New Zealand said in a statement that the growth of end-to-end encrypted apps that make official oversight impossible -- like Signal, Telegram, FaceBook Messenger and WhatsApp -- "pose significant challenges to public safety."
"There is increasing consensus across governments and international institutions that action must be taken," they said.
"While encryption is vital and privacy and cyber security must be protected, that should not come at the expense of wholly precluding law enforcement, and the tech industry itself, from being able to act against the most serious illegal content and activity online."
They called on tech companies to "embed the safety of the public in system designs," providing access to law enforcement "in a readable and usable format."
It was the strongest call yet for programmers to include "backdoor" access to encrypted communications programs.
India and Japan, which cooperate in intelligence with the Five Eyes group, added their names to the statement.
Law enforcement globally has complained of the difficulty encrypted communications poses to criminal investigations.
But end-to-end encryption also offers protection to all sorts of activities from business to political dissent.
Pro-privacy advocates say encoding the means for law enforcement to access a user's communications can endanger democracy activists and empower dictatorial governments.
Pressure has built in recent years in the US and Europe to force the makers of encryption apps to provide access to law enforcement.
According to the Electronic Frontier Foundation, which advocates for privacy on the internet, European countries have moved closer to regulating such apps.
In an article last week, the EFF said that recently leaked European Union documents indicate a plan to introduce anti-encryption laws forcing backdoor access to the European Parliament "within the next year."
It would be "a drastically invasive step," EFF said.
The Five Eyes statement says that its proposal would require safeguards and oversight so that authorities cannot take advantage of their access without cause.
They justified the need based on the prevalence of child sexual abuse material on the internet.
In the United States, most prominent cases in which law enforcement said it was stymied by encrypted devices and communications have been related to violent extremism.
Enterprise Solutions Provider 'Software AG' Hit by Clop Ransomware
12.10.20 Ransomware Securityweek
German enterprise solutions giant Software AG revealed last week that it had been targeted by cybercriminals with the Clop ransomware.
Software AG operates across more than 70 countries around the world and it has over 5,000 employees. It claims that its solutions are used by more than 10,000 of the world’s biggest brands.
The company disclosed the incident on October 5, when it reported being hit by a malware attack on October 3. Software AG said at the time that it had shut down some internal systems in response to the breach.
The company said its helpdesk services and internal communications were impacted, but claimed that cloud-based services were not affected and that it found no evidence of customer information being compromised.
However, in an update shared on October 8, the company said the malware had not been fully contained and it had found evidence that the attackers did in fact download data from servers and employee notebooks.
Researchers at MalwareHunterTeam said on Saturday that the attack involved the Clop ransomware, and they noticed what appeared to be a new feature — the use of wevtutil.exe to clear event logs. They also noted that the sample that hit Software AG checked for the presence of McAfee software and attempted to uninstall it, but it’s unclear if the attackers somehow learned that the target was using McAfee products or if this functionality was added to the malware for a different target.
The Tor-hosted website where the group behind the Clop ransomware leaks data stolen from victims that refuse to pay the ransom claims that the first part of the stolen files will be made public soon.
Screenshots posted by the hackers show that they have obtained tens of gigabytes of data representing more than one million files. They appear to have obtained passport copies, invoices, and emails.
Bleeping Computer has learned from the Clop payment page associated with Software AG that the attackers have asked for more than 2,000 bitcoin, which is roughly $23 million.
SecurityWeek has reached out to Software AG for confirmation of the ransom demand and will update this article if the company responds.
The Clop ransomware is also known to have targeted the University of Maastricht in the Netherlands, which revealed earlier this year that it had paid a $240,000 ransom in response to the attack.
Watch Out — Microsoft Warns Android Users About A New Ransomware
12.10.20 Ransomware Thehackernews
Microsoft has warned about a new strain of mobile ransomware that takes advantage of incoming call notifications and Android's Home button to lock the device behind a ransom note.
The findings concern a variant of a known Android ransomware family dubbed "MalLocker.B" which has now resurfaced with new techniques, including a novel means to deliver the ransom demand on infected devices as well as an obfuscation mechanism to evade security solutions.
The development comes amid a huge surge in ransomware attacks against critical infrastructure across sectors, with a 50% increase in the daily average of ransomware attacks in the last three months compared to the first half of the year, and cybercriminals increasingly incorporating double extortion in their playbook.
MalLocker has been known for being hosted on malicious websites and circulated on online forums using various social engineering lures by masquerading as popular apps, cracked games, or video players.
Previous instances of Android ransomware have exploited Android accessibility features or permission called "SYSTEM_ALERT_WINDOW" to display a persistent window atop all other screens to display the ransom note, which typically masquerade as fake police notices or alerts about purportedly finding explicit images on the device.
But just as anti-malware software began detecting this behavior, the new Android ransomware variant has evolved its strategy to overcome this barrier. What's changed with MalLocker.B is the method by which it achieves the same goal via an entirely new tactic.
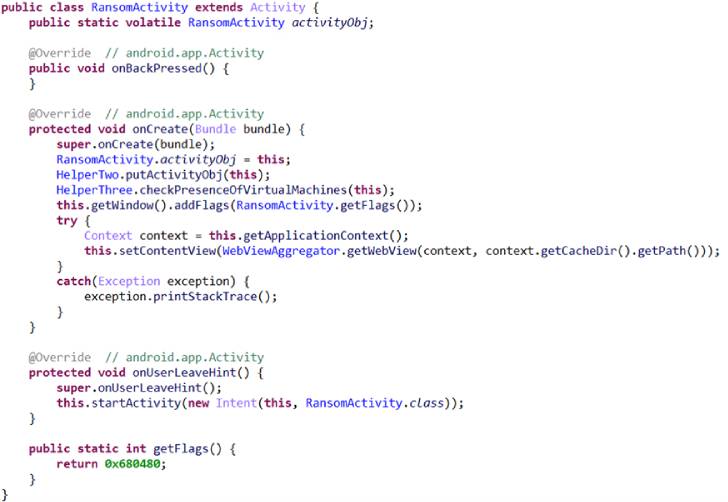
To do so, it leverages the "call" notification that's used to alert the user about incoming calls in order to display a window that covers the entire area of the screen, and subsequently combines it with a Home or Recents keypress to trigger the ransom note to the foreground and prevent the victim from switching to any other screen.
"This creates a chain of events that triggers the automatic pop-up of the ransomware screen without doing infinite redraw or posing as a system window," Microsoft said.
Aside from incrementally building on an array of aforementioned techniques to show the ransomware screen, the company also noted the presence of a yet-to-be-integrated machine learning model that could be used to fit the ransom note image within the screen without distortion, hinting at the next stage evolution of the malware.
Furthermore, in an attempt to mask its true purpose, the ransomware code is heavily obfuscated and made unreadable through name mangling and deliberate use of meaningless variable names and junk code to thwart analysis, the company said.
"This new mobile ransomware variant is an important discovery because the malware exhibits behaviors that have not been seen before and could open doors for other malware to follow," Microsoft 365 Defender Research Team said.
"It reinforces the need for comprehensive defense powered by broad visibility into attack surfaces as well as domain experts who track the threat landscape and uncover notable threats that might be hiding amidst massive threat data and signals."
Sophisticated Android Ransomware Executes with the Home Button
11.10.20 Ransomware Threatpost
The malware also has a unique machine-learning module.
A fresh variant of a sophisticated Android ransomware known as MalLocker locks up mobile devices – surfacing its ransom note when a user hits the Home button.
According to research from Microsoft, MalLocker is spreading via malicious website downloads (disguised as popular apps, cracked games or video players) and peddled in online forums, as it always has. However, “the new variant caught our attention because it’s an advanced malware with unmistakable malicious characteristic and behavior and yet manages to evade many available protections, registering a low detection rate against security solutions,” Microsoft researchers said, in a Thursday posting.
Android ransomware differs from its desktop counterparts by blocking access to the device with overlay screens containing ransom notes that prevent users from taking any action – it doesn’t actually encrypt anything. In MalLocker’s case, the overlay screen is surfaced using never-before-seen techniques that make use of certain Android features.
And, it has an open-source machine-learning module used to automatically fit the overlay screen to the device.
New Permissions
Researchers noted that typical Android ransomware uses a special permission called “SYSTEM_ALERT_WINDOW.” The note is hooked to that permission, so that whenever an app is opened that has this permission, the ransom note is presented and can’t be dismissed.
“No matter what button is pressed, the window stays on top of all other windows,” researchers said. “The notification was intended to be used for system alerts or errors, but Android threats misused it to force the attacker-controlled UI to fully occupy the screen, blocking access to the device. Attackers create this scenario to persuade users to pay the ransom so they can gain back access to the device.”
MalLocker is different though: It uses the “call” notification, among several categories of notifications that Android supports, which requires immediate user attention. It combines this with the “onUserLeaveHint()” callback method of the Android Activity, which is a bedrock Android function. It surfaces the typical GUI screen that Android users see after closing an app or when the user presses the Home key to send current activity to the background.
“The malware connects the dots and uses these two components to create a special type of notification that triggers the ransom screen via the callback,” according to Microsoft. “The malware overrides the onUserLeaveHint() callback function [and] triggers the automatic pop-up of the ransomware screen without…posing as system window.”
The analysis added, “The malware creates a notification builder [and builds] a very important notification that needs special privilege. The setFullScreenIntent()…API wires the notification to a GUI so that it pops up when the user taps on it.”
Machine Learning
MalLocker’s machine-learning module indicates continuous evolution of this Android ransomware family, researchers said.
“This ransomware is the latest variant of a malware family that has undergone several stages of evolution,” researchers said. “We expect it to churn out new variants with even more sophisticated techniques. In fact, recent variants contain code forked from an open-source machine-learning module used by developers to automatically resize and crop images based on screen size, a valuable function given the variety of Android devices.”
The latest MalLocker variant is also indicative that mobile threat actors continuously attempt to sidestep technological barriers and creatively find ways to accomplish their goal – and can open the door to new malware trends.
“This new mobile ransomware variant is an important discovery because the malware exhibits behaviors that have not been seen before and could open doors for other malware to follow,” Microsoft added.
Fitbit Spyware Steals Personal Data via Watch Face
11.10.20 Virus Threatpost
Immersive Labs Researcher takes advantage of lax Fitbit privacy controls to build a malicious spyware watch face.
A wide-open app-building API would allow an attacker to build a malicious application that could access Fitbit user data, and send it to any server.
Kev Breen, director of cyber threat research for Immersive Labs, created a proof-of-concept for just that scenario, after realizing that Fitbit devices are loaded with sensitive personal data.
“Essentially, [the developer API] could send device type, location and user information including gender, age, height, heart rate and weight,” Breen explained. “It could also access calendar information. While this doesn’t include PII profile data, the calendar invites could expose additional information such as names and locations.”
Since all of this information is available via the Fitbit application developer API, it was a simple process to create an application to carry out the attack. Breen’s efforts resulted in a malicious watch face, which he was then able to make available through the Fitbit Gallery (where Fitbit showcases various third-party and in-house apps). Thus, the spyware appears legitimate, and increases the likelihood it would be downloaded.
“Using a dashboard used by development teams to preview apps, I submitted our spyware and soon had our own URL at https://gallery.fitbit.com/details/<redacted>,” he explained. “Our spyware was now live on fitbit.com. It is important to note that while Fitbit doesn’t count this as ‘available for public download’, the link was still accessible in the public domain and our ‘malware’ was still downloadable. ”
Increasing the air of legitimacy, when the link was clicked on any mobile device, it opened inside the Fitbit app with “all thumbnails perfectly rendered as if it were a legitimate app,” Breen said. “From there, it was just a quick click to download and install, which I did with both Android and iPhone.”
Breen also found that Fitbit’s fetch API allows the use of HTTP to internal IP ranges, which he abused to turn the malicious watch face into a primitive network scanner.
“With this functionality, our watch face could become a threat to the enterprise,” he said. “It could be used to do everything from identifying and accessing routers, firewalls and other devices, to brute-forcing passwords and reading the company intranet – all from inside the app on the phone.”
Fitbit Fixes
After contacting Fitbit about the issues, Breen said the company was responsive and vowed to make the necessary changes to mitigate future breaches.
“The trust of our customers is paramount, and we are committed to protecting consumer privacy and keeping data safe,” Fitbit told Threatpost, in a statement. “We responded immediately when contacted by this researcher and worked quickly and collaboratively to address the concerns they raised. We are not aware of any actual compromise of user data.”
Fitbit has added a warning message for users within the UI when installing an app from a private link, and it has made it easier for consumers to identify which installed apps/clocks on the mobile device are not publicly listed.
Breen said that Fitbit also has committed to adjusting default permission settings during the authorization flow to being opted out by default.
As for the ease of uploading the malicious app to the gallery, “we we were advised that apps submitted to the Fitbit Gallery for public download undergo manual review and that obvious spyware or applications masquerading as something else are likely to be caught and blocked from being published.”
However, Breen’s malicious watch face was still publicly accessible as of early Friday.
“We encourage consumers to only install applications from sources they know and trust and to be mindful of what data they’re sharing with third parties,” Fitbit concluded. “We give our users control over what data they share and with whom.”
Fitbit isn’t alone in representing an internet-of-things threat surface. The sheer exploding numbers of IoT devices coming online every day is making it hard for the security community to stay ahead of malicious actors.
Last month, researchers realized the Mozi botnet peer-to-peer malware accounted for a full 90 percent of traffic on IoT devices. And Bluetooth spoofing bug was recently found to leave billions of devices vulnerable. Even a connected male chastity device was recently discovered to be easily hacked, leaving the unsuspecting user stuck and in need of rescue.
As the rest of the industry catches up, it is end users who need to be empowered to take precautions to protect their data.
Breen offers this advice; “if in doubt, don’t install it.”
Wormable Apple iCloud Bug Allows Automatic Photo Theft
11.10.20 Apple Threatpost
Ethical hackers so far have earned nearly $300K in payouts from the Apple bug-bounty program for discovering 55 bugs, 11 of them critical, during a three-month hack.
A group of ethical hackers cracked open Apple’s infrastructure and systems and, over the course of three months, discovered 55 vulnerabilities, a number of which would have given attackers complete control over customer and employee applications.
Of note, a critical, wormable iCloud account takeover bug would allow attackers to automatically steal all of a victim’s documents, photos, videos and more.
The discovery by hackers Sam Curry, Brett Buerhaus, Ben Sadeghipour, Samuel Erb and Tanner Barnes demonstrated key weaknesses in the company’s “massive” infrastructure while it also earned the team nearly $300,000 to date in rewards for their efforts, Curry wrote in an extensive blog post detailing the team’s findings.
Among the flaws found in core portions of Apple’s infrastructure includes ones that would have allowed an attacker to: “fully compromise both customer and employee applications; launch a worm capable of automatically taking over a victim’s iCloud account; retrieve source code for internal Apple projects; fully compromise an industrial control warehouse software used by Apple; and take over the sessions of Apple employees with the capability of accessing management tools and sensitive resources,” he wrote.
Of the 55 vulnerabilities discovered, 11 were rated with critical severity, 29 with high severity, 13 with medium severity and two with low severity. Researchers rated the bugs based on the CvSS vulnerability-severity rating, and “our understanding of the business-related impact,” Curry said.
The wormable iCloud bug is a cross-site scripting (XSS) issue, according to the writeup. iCloud is an automatic storage mechanism for photos, videos, documents, and app related data for Apple products. Additionally, this platform provides services like Mail and Find my iPhone.
“The mail service is a full email platform where users can send and receive emails similar to Gmail and Yahoo,” explained Curry. “Additionally, there is a mail app on both iOS and Mac which is installed by default on the products. The mail service is hosted on www.icloud.com alongside all of the other services like file and document storage.”
He added, “This meant, from an attackers perspective, that any cross-site scripting vulnerability would allow an attacker to retrieve whatever information they wanted to from the iCloud service.”
He discovered such a bug after hunting around for a while: “When you had two style tags within the email, the contents of the style tags would be concatenated together into one style tag,” he said. “This meant that if we could get ‘</sty’ into the first tag and ‘le>’ into the second tag, it would be possible to trick the application into thinking our tag was still open when it really wasn’t.”
The team was ultimately able to create a proof of concept that demonstrated code that steals all of the victim’s personal iCloud information (photos, calendar information and documents) then forwards the same exploit to all of their contacts.
Ilia Kolochenko, founder and CEO of web security company ImmuniWeb, said that the success of the bounty-hunters should be a wake-up call.
“Unfortunately, there is no warranty that these vulnerabilities have not been exploited by sophisticated threat actors to silently compromise VIP victims,” he said via email. “Worse, likely more similar vulnerabilities exist undiscovered and may be known to hacking groups that make a lot of money by their exploitation. Modern web applications open the door to corporate networks with the most critical information, and their breach can be fatal for a company.”
Apple Response and $300K
For its part, Apple responded quickly to the bug reports, fixing the majority of them by the time the post went live, with typical remediation upon learning of the flaws occurring within one to two business days, and response to some critical vulnerabilities within as little as four to six hours, he acknowledged.
“Overall, Apple was very responsive to our reports,” Curry said, adding that, “as of now, October 8th, we have received 32 payments totaling $288,500 for various vulnerabilities.” That number could go higher as Apple tends to pay in “batches,” so the hackers anticipate more payments in the coming months, he said.
Apple’s public bug-bounty program – in which all interested parties can participate – is a fairly recent affair. The company opened up a historically private program to the public last December after years of criticism from developers, who argued that the company needed to be more transparent about flaws in its hardware and software. It also included a $1 million maximum payout to sweeten the deal.
Indeed, Curry – who calls himself a full-time bug-bounty hunter – said he was inspired to assemble the team of hackers to peer under the hood of Apple’s infrastructure after learning on Twitter of a researcher’s award of $100,000 from Apple for discovering an authentication bypass that allowed for arbitrary access any Apple customer account.
“This was surprising to me, as I previously understood that Apple’s bug bounty program only awarded security vulnerabilities affecting their physical products and did not payout for issues affecting their web assets,” he wrote.
Once he found out that Apple was willing to pay for vulnerabilities “with significant impact to users” regardless of whether or not the asset was explicitly listed in scope, it was game on, he said.
“This caught my attention as an interesting opportunity to investigate a new program which appeared to have a wide scope and fun functionality,” Curry wrote in the post. He decided to invite hackers he’d worked with in the past on the project, even though everyone on board knew there was no guarantee of payouts for their discoveries.
The critical vulnerabilities the team discovered in their work are the following: Full Compromise of Apple Distinguished Educators Program via Authentication and Authorization Bypass; Full Compromise of DELMIA Apriso Application via Authentication Bypass; Wormable Stored Cross-Site Scripting Vulnerabilities Allow Attacker to Steal iCloud Data through a Modified Email; Command Injection in Author’s ePublisher; Full Response SSRF on iCloud allows Attacker to Retrieve Apple Source Code; Nova Admin Debug Panel Access via REST Error Leak; AWS Secret Keys via PhantomJS iTune Banners and Book Title XSS; Heap Dump on Apple eSign Allows Attacker to Compromise Various External Employee Management Tools; XML External Entity processing to Blind SSRF on Java Management API; GBI Vertica SQL Injection and Exposed GSF API; Various IDOR Vulnerabilities; and Various Blind XSS Vulnerabilities.
The hackers received permission from the Apple security team to publish details on the critical bugs, all of which have been fixed and re-tested, Curry said.
The findings are an alarming reminder that even the largest tech companies considerably underestimate their web application security, according to Kolochenko.
“Most organizations merely invest into some automated scanning tools and recurrent penetration testing but without implementing a comprehensive application security program,” he said. “Such a program shall include regular secure coding trainings for software developers, introducing security controls aimed to detect vulnerabilities at the early stage of development – the so-called ‘shift-left’ approach – and providing strict security guidelines for software developed by third-parties. Finally, modern software shall incorporate privacy by design to enable seamless compliance with regulations like CCPA or GDRP.”
Facebook Debuts Bug-Bounty ‘Loyalty Program’
11.10.20 Vulnerebility Threatpost
Facebook bounty hunters will be placed into tiers by analyzing their score, signal and number of submitted bug reports — which will dictate new bonus percentages.
Facebook has lifted the curtain on what it claims is an industry first: A loyalty program as part of its bug-bounty offering, which aims to further incentivize researchers to find vulnerabilities in its platform.
The loyalty program, called “Hacker Plus,” offers bonuses on top of bounty awards, access to more products and features that researchers can stress-test, and invites to Facebook annual events. It adds another layer to Facebook’s bug-bounty effort, which has been around since 2011.
“Hacker Plus is designed to help build community among the researchers who participate in our bug-bounty program, in addition to incentivizing quality reporting,” Dan Gurfinkel, security engineering manager with Facebook, said in a Friday post.
Hacker Plus will have five “leagues” – from an entry-level Bronze tier all the way up to the highest-level Diamond tier (Silver, Gold and Platinum are in-between). Gurfinkel said that researchers have been placed into different leagues based on the cumulative quantity of their submissions and scores over the last 24 months.
Based on their league, researchers are eligible to receive bonuses on top of the standard bounty award. For instance, Bronze tier members will receive a 5 percent bonus on top of each bounty they receive – while Diamond tier members will earn a 20 percent bonus. Diamond-level researchers also gain access to various events, including live hacking events, Facebook’s F8 conference and DEFCON.
Facebook also said that researchers who submitted at least one valid vulnerability report and received a payout according to the bug-bounty program terms and conditions are eligible to participate in the Hacker Plus program. Researchers can view their tiers on their profile page.
“Starting today [Friday], we’ll regularly evaluate researchers’ league placement by analyzing their score, signal and number of submitted bug reports within the last 12 months,” said Gurfinkel. “This means researchers can move up a league if they submit more high-quality bug submissions. Once a researcher meets a higher league’s criteria, they will immediately be placed into that league.”
The announcement comes as bug-bounty programs have come under scrutiny in the cybersecurity community. Security experts worry that if improperly implemented, the programs merely promote marketing hype and flashy rewards – forgetting important backend logistics for securing the company, such as triage.
For its part, Facebook continues to flesh out its bug-bounty offerings for the security research community.
In 2018, Facebook said it will expand its bug-bounty program in an attempt to crackdown on data misuse by third-party app developers. Also in 2018 the social media company announced an expansion to sniff out vulnerabilities related to access-token exposure. More recently, this past year, Facebook awarded a security researcher $20,000 for discovering a cross-site scripting (XSS) vulnerability in the Facebook Login SDK, which is used by developers to add a “Continue with Facebook” button to a page as an authentication method.
Carnival confirms data breach as a result of the August ransomware attack
11.10.20 Ransomware Securityaffairs
Carnival Corporation, the world’s largest cruise line operator, has confirmed a data breach as a result of the august ransomware attack.
Carnival Corporation, the world’s largest cruise line operator, has confirmed a data breach as a result of the ransomware attack that took place in August. Ransomware operators have stolen the personal information of customers, employees, and ship crews during the attack.
Carnival Corporation & plc is a British-American cruise operator, currently the world’s largest travel leisure company, with a combined fleet of over 100 vessels across 10 cruise line brands. A dual-listed company,
Carnival Corporation has over 150,000 employees and 13 million guests annually. The cruise line operates under the brands Carnival Cruise Line, Costa, P&O Australia, P&O Cruises, Princess Cruises, Holland American Line, AIDA, Cunard, and their ultra-luxury cruise line Seabourn.

Source: Orlando Weekly
The company operates nine cruise line brands (Carnival Cruise Line, Costa, P&O Australia, P&O Cruises, Princess Cruises, Holland American Line, AIDA, Cunard, Seabourn) and a travel tour company (Holland America Princess Alaska Tours).
In an 8-K filing with the US Securities Exchange Commission (SEC), the cruise line operators revealed that the incident took place on August 15.
“On August 15, 2020, Carnival Corporation and Carnival plc (together, the “Company,” “we,” “us,” or “our”) detected a ransomware attack that accessed and encrypted a portion of one brand’s information technology systems. The unauthorized access also included the download of certain of our data files,” states the 8-K form filed with the SEC.
“Nonetheless, we expect that the security event included unauthorized access to personal data of guests and employees, which may result in potential claims from guests, employees, shareholders, or regulatory agencies,”
The company also notified law enforcement agencies and data regulators.
At the time, the company revealed that only one of its cruise line brands was affected by the security breach.
Upon the discovery of the security incident, the Company launched an investigation and notified law enforcement, it also hired legal counsel and cyber security professionals. The company also announced to have already implemented a series of containment and remediation measures to respond to the incident and reinforce the security of its information technology systems.
Now the company filed a new In a 10-Q form with the SEC, it confirmed that an unknown ransomware gang also stole the personal information of its customers and employees. The company added that it is not aware of any misuse of the exposed information.
“On August 15, 2020, we detected a ransomware attack and unauthorized access to our information technology systems. We engaged a major cybersecurity firm to investigate the matter and notified law enforcement and regulators of the incident.” reads the 10-Q form.
“While the investigation is ongoing, early indications are that the unauthorized third-party gained access to certain personal information relating to some guests, employees, and crew for some of our operations.” “There is currently no indication of any misuse of this information.”
The company warns its customers of future attacks or incidents that could be linked to this security breach.
“While at this time we do not believe that this information will be misused going forward or that this incident will have a material adverse effect on our business, operations, or financial results, no assurances can be given, and further, we may be subject to future attacks or incidents that could have such a material adverse effect.” states the company.
In August, researchers from cybersecurity intelligence firm Bad Packets noticed that Carnival was utilizing vulnerable Citrix devices at the time of the attack. The experts speculate that the vulnerable equipment was targeted by the attacker to access the corporate network.
BadPackets also speculate that another entry point in the Carnival network could be CVE-2020-2021 issue in the the PAN-OS operating system.
In March 2020, Carnival Corporation disclosed another data breach that took place in 2019. The company informed customers of the incident, a third-party gained unauthorized access to their personal information.
Exposed guests’ personal information included name, address, Social Security number, government identification number, such as passport number or driver’s license number, and health-related information. For some clients, credit card and financial account information might have been exposed
Russian Cybercrime group is exploiting Zerologon flaw, Microsoft warns
11.10.20 APT Securityaffairs
Microsoft has uncovered Zerologon attacks that were allegedly conducted by the infamous TA505 Russia-linked cybercrime group.
Microsoft spotted a series of Zerologon attacks allegedly launched by the Russian cybercrime group tracked as TA505, CHIMBORAZO and Evil Corp.
Microsoft experts spotted the Zerologon attacks involving fake software updates, the researchers noticed that the malicious code connected to command and control (C&C) infrastructure known to be associated with TA505.
TA505 hacking group has been active since 2014 focusing on Retail and banking sectors. The group is also known for some evasive techniques they put in place over time to avoid the security controls and penetrate corporate perimeters with several kinds of malware, for instance abusing the so-called LOLBins (Living Off The Land Binaries), legit programs regularly used by victim, or also the abuse of valid cryptographically signed payloads.
The TA505 group was involved in campaigns aimed at distributing the Dridex banking Trojan, along with Locky, BitPaymer, Philadelphia, GlobeImposter, and Jaff ransomware families.
Security experts from cyber-security firm Prevailion reported that TA505 has compromised more than 1,000 organizations.
The malicious updates employed in the Zerologon attacks are able to bypass the user account control (UAC) security feature in Windows and abuse the Windows Script Host tool (wscript.exe) to execute malicious scripts.
The experts explained that the threat actors abuse MSBuild.exe to compile Mimikatz updated with built-in ZeroLogon functionality.
“Attacks showing up in commodity malware like those used by the threat actor CHIMBORAZO indicate broader exploitation in the near term.” states Microsoft.
This is the second alert published by Microsoft related to Zerologon attack in the wild. Early this week the IT giant published a post and a series of tweets warning of cyber attacks exploiting the Zerologon vulnerability carried out by the Iran-linked APT group known as MuddyWater, aka Mercury.
The CVE-2020-1472 Zerologon flaw is an elevation of privilege that resides in the Netlogon. The Netlogon service is an Authentication Mechanism used in the Windows Client Authentication Architecture which verifies logon requests, and it registers, authenticates, and locates Domain Controllers.
An attacker could exploit the vulnerability to impersonate any computer, including the domain controller itself, and execute remote procedure calls on their behalf.
An attacker could also exploit the flaw to disable security features in the Netlogon authentication process and change a computer’s password on the domain controller’s Active Directory.
At the end of September, DHS CISA issued an emergency directive to tells government agencies to address the Zerologon vulnerability (CVE-2020-1472) by Monday.
Microsoft Warns of Russian Cybercriminals Exploiting Zerologon Vulnerability
11.10.20 APT Securityweek
Microsoft reported this week that it has spotted Zerologon attacks apparently conducted by TA505, a notorious Russia-linked cybercrime group.
According to Microsoft, the Zerologon attacks it has observed involve fake software updates that connect to command and control (C&C) infrastructure known to be associated with TA505, which the company tracks as CHIMBORAZO.
The fake updates are designed to bypass the user account control (UAC) security feature in Windows and they abuse the Windows Script Host tool (wscript.exe) to execute malicious scripts.
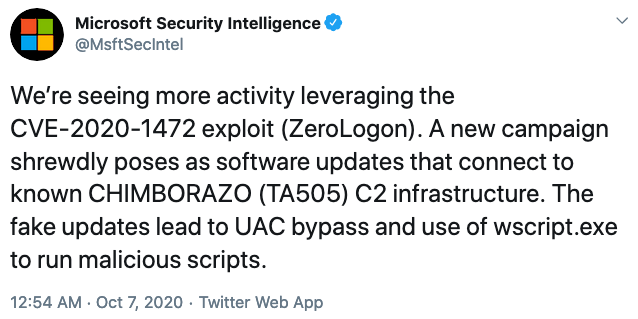
“To exploit the vulnerability, attackers abuse MSBuild.exe to compile Mimikatz updated with built-in ZeroLogon functionality,” Microsoft said.
The tech giant added, “Attacks showing up in commodity malware like those used by the threat actor CHIMBORAZO indicate broader exploitation in the near term.”
TA505, also known as Evil Corp, has been active for nearly a decade and it’s mainly known for operations involving banking trojans and ransomware. This is not the first time the group has exploited Windows vulnerabilities in its attacks, and researchers recently found some links between campaigns conducted by TA505 and North Korean hackers.
Microsoft first warned users about malicious actors exploiting the Zerologon vulnerability on September 24. Earlier this week, it issued another warning after seeing that the flaw had also been exploited by an Iranian state-sponsored threat actor.
The Zerologon vulnerability, officially tracked as CVE-2020-1472 and described as a privilege escalation issue, affects Windows Server and it has been rated critical. It was patched by Microsoft in August with its monthly security updates.
The flaw allows an attacker who has access to the targeted organization’s network to compromise domain controllers without the need for credentials.
Microsoft has informed customers that applying the patches released in August is only the first phase of addressing the Zerologon vulnerability. The second phase, which will involve placing domain controllers in enforcement mode, will start in February 2021.
A few weeks after the vulnerability was fixed by Microsoft, the DHS issued an emergency directive requiring federal agencies to immediately install the available patches.
Researchers Get Big Bounties From Apple For Critical Vulnerabilities
11.10.20 Vulnerebility Securityweek
A team of researchers has received hundreds of thousands of dollars in bug bounties from Apple for reporting 55 vulnerabilities, including ones that exposed source code, employee and customer apps, warehouse software, and iCloud accounts.
Researchers Sam Curry, Brett Buerhaus, Ben Sadeghipour, Samuel Erb and Tanner Barnes decided in early July to take part in Apple’s bug bounty program and attempt to find as many vulnerabilities as possible in the tech giant’s systems and services.
Between July 6 and October 6, they discovered and reported a total of 55 issues, including 11 rated critical and 29 rated high severity. To date, Apple made 32 payments to the researchers totaling $288,500, but they expect to receive more for their findings in the coming months.
The researchers said in a blog published this week that a vast majority of the vulnerabilities they reported to Apple have been patched. The company fixed some of the more serious issues within a few hours.
With Apple’s permission, the white hat hackers disclosed the details of a dozen interesting vulnerabilities they found during the three-month project.
For example, they found a way to bypass authentication and authorization on the Apple Distinguished Educators website, which ultimately could have allowed an attacker to execute arbitrary commands on an Apple web server, access an internal user account management service, and access “the majority of Apple’s internal network.”
They also analyzed a third-party warehouse management solution used by Apple and discovered vulnerabilities that could have been exploited to obtain highly sensitive information or cause significant disruption.
In addition, they found stored cross-site scripting (XSS) flaws in the iCloud platform, which could have been exploited to execute arbitrary code in a user’s browser or create an email-based worm that could silently modify or steal information from iCloud accounts, including photos and videos.
Also related to iCloud, there was a server-side request forgery (SSRF) bug that could have been exploited to gain access to some Apple source code and breach Apple’s internal network.
Actually, there were several vulnerabilities that could have been exploited to gain access to Apple’s internal network and execute arbitrary commands on some of the company’s web servers.
The researchers also reported finding secret keys that could have allowed an attacker to obtain data from Apple’s internal AWS environment, IDOR flaws that could have been leveraged to obtain or modify data, and XSS vulnerabilities that may have provided access to sensitive user data.
“Overall, Apple was very responsive to our reports. The turn around for our more critical reports was only four hours between time of submission and time of remediation,” Curry explained.
“Since no-one really knew much about their bug bounty program, we were pretty much going into unchartered territory with such a large time investment. Apple has had an interesting history working with security researchers, but it appears that their vulnerability disclosure program is a massive step in the right direction to working with hackers in securing assets and allowing those interested to find and report vulnerabilities,” he added.
Cisco addresses three high-severity issues in Webex, IP Cameras and ISE
10.10.20 Vulnerebility Securityaffairs
Cisco fixed three high-severity flaws in Webex video conferencing system, Video Surveillance 8000 Series IP Cameras and Identity Services Engine.
Cisco has addressed three high-severity flaws and eleven medium-severity vulnerabilities in its Webex video conferencing system, Video Surveillance 8000 Series IP Cameras and Identity Services Engine.
The most severe of these vulnerabilities is a Remote Code Execution and Denial of Service issue in Cisco’s Video Surveillance 8000 Series IP Cameras.
The vulnerabilty, tracked as Remote Code Execution and Denial of Service Vulnerability. received a CVSS score of 8.8 out of 10.
“A vulnerability in the Cisco Discovery Protocol implementation for Cisco Video Surveillance 8000 Series IP Cameras could allow an unauthenticated, adjacent attacker to execute arbitrary code on an affected device or cause the device to reload.” reads the Cisco’s security advisory.
“This vulnerability is due to missing checks when an IP camera processes a Cisco Discovery Protocol packet.”
An attacker could exploit this vulnerability by sending a malicious Cisco Discovery Protocol packet to a vulnerable device. The flaw could allow an attacker to execute code on the affected IP camera or triggering a DoS condition by forcing the device to reload unexpectedly, resulting in a denial of service (DoS) condition.
Cisco also addressed a high-severity flaw, tracked as CVE-2020-3535, in its Webex platform that is caused by the incorrect handling of directory paths at run time.
An authenticated, local attacker could exploit the flaw to load a malicious library, experts pointed out that to exploit this vulnerability, the attacker needs valid credentials on the Windows system.
“The vulnerability is due to incorrect handling of directory paths at run time. An attacker could exploit this vulnerability by placing a malicious DLL file in a specific location on the targeted system. This file will execute when the vulnerable application launches.” reads the advisory published by Cisco. “A successful exploit could allow the attacker to execute arbitrary code on the targeted system with the privileges of another user’s account.”
The vulnerability affects Cisco Webex Teams for Windows releases 3.0.13464.0 through 3.0.16040.0, the IT giant confirmed that the issue does not affect Webex Teams for Android, Mac or iPhone and iPad.
The third high-severity flaw, tracked as CVE-2020-3467, resides in the web-based management interface of Cisco Identity Services Engine (ISE).
The ISE is a tool that enables the creation and enforcement of security and access policies for endpoint devices connected to the company’s network devices. The vulnerability allows an authenticated, remote attackers to modify parts of the configuration on an affected device.
“The vulnerability is due to improper enforcement of role-based access control (RBAC) within the web-based management interface. An attacker could exploit this vulnerability by sending a crafted HTTP request to an affected device. A successful exploit could allow the attacker to modify parts of the configuration. The modified configuration could either allow unauthorized devices onto the network or prevent authorized devices from accessing the network.” according to reads the Cisco’s advisory “To exploit this vulnerability, an attacker would need valid Read-Only Administrator credentials.”
The good news is that the Cisco Product Security Incident Response Team (PSIRT) is not aware attacks exploiting the above flaws in the wild.
Hacker who helped the ISIS will remain in US prison
10.10.20 BigBrothers Securityaffairs
The hacker who shared with the ISIS personal data of more than 1,300 U.S. government and military personnel will remain in a federal prison.
Ardit Ferizi, aka Th3Dir3ctorY, is the hacker that supported the ISIS organization by handing over data for 1,351 US government and military personnel.
Ferizi is the first man charged with cyber terrorism that was extradited to the US early 2016.
The man was charged with hacking crimes and providing support to a terrorist organization. The 24-year-old man was accused of supporting the ISIS terrorist organization, he was the subject of extradition from the Malaysian government, where he lived. The man of Kosovar origin was studying computer science in Malaysia.
He was arrested in Malaysia in September 2015 and transferred to the US to face trial.
Now Ardit Ferizi has been sentenced to 20 years in a U.S. prison. According to the US investigators, he provided the data to the popular IS militant Junaid Hussain, which disclosed it on the web. The collaboration between the IS hackers Hussain and Ferizi started in April 2015, according to the US authorities.
The details of the Ferizi’s case are described in s court filings [PDF].
Leaked data included names, e-mail addresses, passwords, locations and phone numbers of 1,351 U.S. military and other government personnel.

The ISIS-linked hacker obtained the data by hacking into the US web hosting company’s servers on June 13, 2015.
The US authorities suspected that Ferizi is a member of a Kosovan hacking team known as KHS, he used the pseudonym of “Th3Dir3ctorY”. The KHS breached a database of a US retailer was able to identify the records belonging to military and government personnel.
The Kosova Hacker’s Security (KHS) hit numerous organizations across the world, including Serbian Government websites, Israeli websites under the #OpIsrael campaign, The Interpol, IBM Research, Hotmail, US National Weather Service Website and numerous targets in Ukraine.

I wrote about Ferizi in October 2015, when the man was arrested by Malaysian authorities because for the first time ever the US Justice Department has charged a suspect for terrorism and hacking (cyber terrorism).
Ferizi was pleaded guilty on June 15, 2016, now is serving a 20-year sentence at a federal prison in Lewisburg, Pennsylvania, and is scheduled for release in 2032 if he gets credit for good behavior.
Ferizi asked a federal judge in Alexandria to release him from prison due to his health status.
“In a handwritten motion from prison, he said his asthma and obesity place him at greater risk of contracting COVID-19.” reads the post published by Associated Press. “He also said special restrictions at the prison require him to check in with staff every two hours, increasing his contact with guards and his risk of contracting the virus.”
Now prosecutors refused the request of hacker and opposed his release. The U.S. District Judge Leonie Brinkema rejected Ferizi’s request at a hearing Tuesday, the authorities believe that the man could teiterate his criminal activity.
German tech firm Software AG hit by ransomware attack
10.10.20 Ransomware Securityaffairs
German tech firm Software AG has suffered a ransomware attack that took place during last weekend, media blamed the Clop ransomware gang.
The website ZDNet revealed in exclusive that German tech firm Software AG was hit by the Clop ransomware, the criminal gang is demanding more than $20 million ransom.
Software AG is an enterprise software company with over 10,000 enterprise customers in over 70 countries. The company is the second largest software vendor in Germany, and the seventh largest in Europe.
The incident took place on Saturday, October 3, and the company has not yet fully recovered from the ransomware infection.
“Earlier today, after negotiations failed, the Clop gang published screenshots of the company’s data on a website the hackers operate on the dark web (a so-called leak site).” reported ZDNet.
The screenshots shared by the Clop ransomware operators show employee passport and ID scans, employee emails, financial documents, and directories from the company’s internal network.

On Monday, the software giant disclosed the ransomware attack and revealed that that the malware disrupted part of its internal network.
“The IT infrastructure of Software AG is affected by a malware attack since the evening of 3 October 2020. While services to its customers, including its cloud-based services, remain unaffected, as a result, Software AG has shut down the internal systems in a controlled manner in accordance with the company’s internal security regulations.” reads a statement released by the company. “The company is in the process of restoring its systems and data in order to resume orderly operation. However, helpdesk services and internal communication at Software AG are currently still being affected.”
NATO Chief calls for a new strategic to address new challenges
9.10.20 BigBrothers Securityaffairs
NATO Chief calls for a new strategic to mitigate the risks related to the threats to the rising technologies, new forms of terrorism, and the role of China
The rapid and continuous changes in our society needs to be properly addressed, NATO warns, NATO Chief call for a new strategic to address the global rise of new technologies, the evolution of terrorism and role of China in the global politics.
The new strategy has to replace the one developed a decade ago by the Atlantic alliance.
Among the advocates of change there is the French President Emmanuel Macron that also aims at the reopening dialogue with Russia and empower the efforts to fight the Islamist terrorism.
“My thought is that the existing Strategic Concept, which we agreed in 2010, has served NATO well. And it has actually served us well for many years. And we have also seen over the last year that the Strategic Concept we already have has not prevented us from adapting and changing NATO. Having said that, I think we all have to realise that since we agreed the Strategic Concept back in 2010, the world has fundamentally changed.” Secretary General Jens Stoltenberg said at the GLOBSEC security forum in Bratislava, Slovakia.
“The time has come to develop a new strategic concept for NATO, a new blueprint for how NATO can adapt and respond to a changing security environment.”
The overall process of change is part of a program that the NATO chief indicated as NATO 2030.
Stoltenberg recommends to maintain alliance’s technological edge, while developing common principles and standards for new technologies. The Alliance have to enhance cooperation between Allies in areas like joint research and development.
NATO Chief states that the alliance does not see any imminent threats and does’t regard China as an enemy or an adversary’. Anyway the role of China in the global economy have to be properly addressed because the state has is the biggest market in the world and they have the second largest defence budget.
Beijing is investing heavily in new technologies, including missiles, nuclear weapons, Artificial Intelligence. NATO is also concerned about the investments of China in disruptive technologies and the related implications for the Alliance.
“We see a much more assertive Russia than we did in 2010, with illegal annexation of Crimea destabilising eastern Ukraine, the military build-up. We see a new and more brutal form of terrorism, more instability to the south of our Alliance – Middle East, North Africa. And we see, of course, a fundamental shift in the global balance of power with the rise of China. And we see the development of new destructive technologies which affect our security.” Stoltenberg added.
Stoltenberg highlighted the concept to enhance the resilience of our society across the member states, because “our military cannot be strong if our societies are weak.”
“So our first line of defence must be strong societies able to prevent, endure, adapt and bounce back from whatever happens,” he explained with a clear reference to the ongoing pandemic and the related difficulties that member states are facing with.
“And any attempt to try to divide Europe from North America will not only weaken NATO, but it will also divide Europe. So we need to work together as Europe, as NATO. That’s the only way we can stand together and meet all the challenges we see in the future.” concludes NATO chief.
New MalLocker.B ransomware displays ransom note in innovative way
9.10.20 Ransomware Securityaffairs
Microsoft warns of Android ransomware that activates when you press the Home button
Microsoft spotted a new strain of Amdroid ransomware tracked as MalLocker.B that activates when the users press the Home button.
Researchers from Microsoft spotted a new strain of Android ransomware that abuses the mechanisms behind the “incoming call” notification and the “Home” button to lock the screen on the victim’s device.
AndroidOS/MalLocker.B is distributed through tainted Android apps available for download on online forums and third-party websites.
The new variant also manages to evade many available protections, registering a low detection rate against security solutions.
Experts believe the malware is particularly sophisticated, but implements novel techniques and behavior.
Like other Android ransomware, MalLocker.B doesn’t actually encrypt the files on the devices but only inhibits the access to the phone.
Once installed, the ransomware displays a ransom note on the phone’s screen and prevents the victim from dismissing. The ransom note pretends to be a message from Russian law enforcement notifying users they have violated the law and must compensate by paying a fine.
Across time, security firms have spotted multiple mobile malware strains that have abused various features implemented by the Android operating systems to lock out the owners of the devices. For example, in 2017 ESET experts observed the DoubleLocker that was both encrypting user data and changing PIN Lock and that abused the Accessibility service to re-activate itself after users pressed the Home button.
What’s innovative about the MalLocker.B ransomware is how it displays its ransom note.
In the past, Android ransomware used the “SYSTEM_ALERT_WINDOW” a special permission to display their ransom note.
This permission allows apps to draw a window that belongs to the system group and can’t be dismissed, independently from any button pressed by the victims.
The actual mechanism implemented by the MalLocker.B ransomware to display the ransom note is composed of two parts.
The first part abuses the “call” notification that activates for incoming calls to show info about the caller. The ransomware abuses this feature to show a window that covers the entire screen of the device. The second part abuses the “onUserLeaveHint()” function which is called when users want to push an app into the background and switch to a new app. This feature is triggered everytime the users press buttons like Home or Recents. MalLocker.B abuses this function to prevent the victims from leaving the ransom note for the home screen or another app.
“The malware connects the dots and uses these two components to create a special type of notification that triggers the ransom screen via the callback.” reads the analysis published by Microsoft. “As the code snippet shows, the malware overrides the onUserLeaveHint() callback function of Activity class. The function onUserLeaveHint() is called whenever the malware screen is pushed to background, causing the in-call Activity to be automatically brought to the foreground. Recall that the malware hooked the RansomActivity intent with the notification that was created as a “call” type notification. This creates a chain of events that triggers the automatic pop-up of the ransomware screen without doing infinite redraw or posing as system window.”
This is the first time that experts observed the concurrent abuse of these two features in a ransomware that hijacks the Home button.
In order to avoid being infected with MalLocker.B and similar malware users are advised to avoid installing Android apps from third-party stores or forums.
Cybercriminals Target Conference Platform With Payment Card Skimmer
9.10.20 CyberCrime Securityweek
Cybercriminals have planted a payment card skimmer on the websites of several organizations using the Playback Now conference platform, Malwarebytes reported on Thursday.
Playback Now enables organizations to record events and deliver the content via live streaming or on demand. It also provides a virtual conference hall and helps companies market their events.
Malwarebytes researchers noticed that a server owned by Playback Now, which hosts conference materials for the company’s customers, was compromised. The customer websites hosted on it — customers receive a dedicated website which they can use to serve their content — had been injected with a payment card skimmer that allowed the attackers to steal the financial information of users purchasing conference materials from those sites.
Tens of these websites appear to be impacted, many of them belonging to educational or medical organizations. It’s worth noting that Playback Now’s official website, playbacknow.com, does not appear to be affected.
Based on Malwarbytes’ analysis, the attackers likely used a previously documented piece of malware designed to provide access to e-commerce websites by brute-forcing credentials. The cybercriminals then inserted one line of code that fetched malicious JavaScript from a domain with a name similar to the official Playback Now website, specifically playbacknows.com, which they registered only a few weeks ago.
The affected websites were reportedly powered by Magento version 1, which is no longer supported. Tens of thousands of e-commerce websites are still powered by this outdated version of the platform.
Digital skimming protection solutions provider Sansec reported last month that hundreds of Magento stores were hacked daily in what the company described as the largest ever skimming campaign.
The company said at the time that the attackers possibly used a new exploit that had been sold for $5,000. The exploit, which allows users to hack Magento 1 websites, may have been used in this attack as well, possibly by the same group that was monitored by Sansec.
Malwarebytes said it reported its findings to Playback Now, but it’s unclear if any action has been taken. SecurityWeek has reached out to the vendor for comment and will update this article if they respond.
C&C Panels of 10 IoT Botnets Compromised by Researchers
9.10.20 BotNet Securityweek
At the Virus Bulletin Conference last week, two security researchers explained how they were able to compromise the command and control (C&C) panels of 10 Internet of Things (IoT) botnets.
The researchers, Aditya K. Sood of F5 Networks and Rohit Bansal of SecNiche Security Labs, revealed at the online conference that they were able to access the C&C panels of the Mana, Vivid, Kawaii, Verizon, Goon, 911-Net, Purge Net, Direct, 0xSec, and Dark botnets.
According to Sood and Bansal, possible approaches to such compromise would first involve mapping the remote servers that are distributing binaries, or extracting the binaries dropped onto compromised IoT devices, and then extracting the hardcoded IP addresses from these files, to learn where those panels are located.
However, it is also possible to extract artefacts from network traffic, including IP addresses, or even extract C&C information from malicious processes running on the compromised devices (effective if the address is generated on the fly).
One other approach involves mass scanning the Internet for potentially suspicious IoT devices, finding exposed administrative interfaces and attempting to compromise them to extract information on C&C servers. Scanning for remote servers based on known indicators is also possible.
The next step after identifying the attacker’s server is accessing the C&C panel, which can be done through the frontend admin interface by brute-forcing credentials. Access can also be obtained by compromising a backend database to gain access to administrative credentials, finding and exploiting vulnerabilities in the C&C panel, or using cracked credentials, the researchers said.
In the event that the C&C interface cannot be breached, one could also attempt to crash the server, or kill it. By analyzing the source code of botnet malware, such as that for Mirai, which is available online, one could identify the buffer allocation for various functions, discover vulnerable ones to trigger overflows, craft a buffer and then send it to the target to see if the crash happens.
At the VB 2020 conference, the two researchers revealed that they used these approaches to access the C&C panels of the aforementioned IoT botnets, which then allowed them to learn more about the capabilities of these threats and the manner in which they are operated.
They obtained information on the commands supported by the botnets, the various options available for administrators, including those employed for launching distributed denial of service (DDoS) or similar attacks, as well as the similarities and differences between the different panels.
The two researchers also detailed specific techniques which, they say, could be used to create additional attack scenarios, not only to hack back at IoT botnets, but also to build defensive measures against them.
In fact, they argue, compromising these C&C panels is highly important for gathering threat intelligence and building defenses against IoT botnets, pointing out that otherwise it would be difficult to understand how exactly the botnets operate.
Stuck in Your 'Smart' Chastity Device? Use a Screwdriver, Manufacturer Says
9.10.20 Security Securityweek
The maker of a 'smart' male chastity device has recommended using a screwdriver to break them open after warnings they can be locked remotely by hackers.
Chinese firm Qiui, whose Bluetooth-controlled Cellmate device can only be unlocked via an app, issued a video called "When nothing else works", showing the screwdriver fix.
It follows a warning from researchers that the Cellmate, which clamps a metal ring around the genitals, is vulnerable to hackers who could lock them en masse, potentially trapping thousands of users.
Company founder and CEO Jake Guo said it was "simply not true" that users could get stuck in the Cellmate, which is marketed both for anti-cheating and submission sex play.
"In case you cannot contact our customer support, the second option is to break open the Cellmate cap with a screwdriver or similar, as demonstrated in the video on our website," he said in a statement sent to AFP.
"This will allow you to remove the pin lock and device."
Guo added: "Compared to Cellmate, wearing a traditional chastity cage –- often made of steel -– with a classic padlock is much riskier.
"If you lose the key, you actually would need a grinder or bolt-cutter to remove the cage."
Learn More About IoT Security at SecurityWeek's IoT Lockdown Virtual Event
Alex Lomas of Pen Test Partners, which released the research report, questioned the screwdriver manoeuvre, wondering whether the required angle was possible while wearing a Cellmate.
"Also, it's a bit close for comfort!" he wrote on Twitter. "Have you tried this for real?"
His colleague Ken Munro told the BBC: "The forceful use of a screwdriver in close proximity to a very sensitive area of the anatomy seems very unwise."
- Internet of things -
PTP also found other security flaws in the Cellmate -- listed for $189 on Qiui's website -- that could expose user information such as names, phone numbers, birthdays and location data.
Smart sex toys and devices are among the wave of new "internet of things" products and appliances introduced in recent years that are online and capable of being operated remotely.
Their connectivity has also made them vulnerable to security breaches and privacy violations.
To guard against hacks, Guo advised Cellmate users to remove the Qiui app on their phones and replace it with an updated version.
"Every modern device can potentially be hacked nowadays," he said.
"When a possible security leak with a game console, PC, smart phone or social media app is discovered and reported, people don't seem to have the tendency to stop using them."
55 New Security Flaws Reported in Apple Software and Services
9.10.20 Apple Thehackernews
A team of five security researchers analyzed several Apple online services for three months and found as many as 55 vulnerabilities, 11 of which are critical in severity.
The flaws — including 29 high severity, 13 medium severity, and 2 low severity vulnerabilities — could have allowed an attacker to "fully compromise both customer and employee applications, launch a worm capable of automatically taking over a victim's iCloud account, retrieve source code for internal Apple projects, fully compromise an industrial control warehouse software used by Apple, and take over the sessions of Apple employees with the capability of accessing management tools and sensitive resources."
The flaws meant a bad actor could easily hijack a user's iCloud account and steal all the photos, calendar information, videos, and documents, in addition to forwarding the same exploit to all of their contacts.
The findings were reported by Sam Curry along with Brett Buerhaus, Ben Sadeghipour, Samuel Erb, and Tanner Barnes over a three month period between July and September.
After they were responsibly disclosed to Apple, the iPhone maker took steps to patch the flaws within 1-2 business days, with a few others fixed within a short span of 4-6 hours.
So far, Apple has processed about 28 of the vulnerabilities with a total payout of $288,500 as part of its bug bounty program.
The critical bugs pointed out by Sam Curry, and the team are as follows:
Remote Code Execution via Authorization and Authentication Bypass
Authentication Bypass via Misconfigured Permissions allows Global Administrator Access
Command Injection via Unsanitized Filename Argument
Remote Code Execution via Leaked Secret and Exposed Administrator Tool
Memory Leak leads to Employee and User Account Compromise allowing access to various internal applications
Vertica SQL Injection via Unsanitized Input Parameter
Wormable Stored XSS allows Attacker to Fully Compromise Victim iCloud Account
Wormable Stored XSS allows Attacker to Fully Compromise Victim iCloud Account
Full Response SSRF allows Attacker to Read Internal Source Code and Access Protected Resources
Blind XSS allows Attacker to Access Internal Support Portal for Customer and Employee Issue Tracking
Server Side PhantomJS Execution allows an attacker to Access Internal Resources and Retrieve AWS IAM Keys
One of the Apple domains that were impacted included the Apple Distinguished Educators site ("ade.apple.com") that allowed for an authentication bypass using a default password ("###INvALID#%!3"), thus permitting an attacker to access the administrator console and execute arbitrary code.
Likewise, a flaw in the password reset process associated with an application called DELMIA Apriso, a warehouse management solution, made it possible to create and modify shipments, inventory information, validate employee badges, and even take full control over the software by creating a rogue user.
A separate vulnerability was also discovered in Apple Books for Authors service that's used by authors to help write and get their books published on the Apple Books platform. Specifically, using the ePub file upload tool, the researchers were able to manipulate the HTTP requests with an aim to run arbitrary commands on the "authors.apple.com" server.
Among the other critical risks revealed by the researchers were those that stemmed from cross-site scripting (XSS) vulnerability in the "www.icloud.com" domain, which operates by just sending a target with iCloud.com or Mac.com address a specially-crafted email that, when opened via Apple Mail in the browser, allowed the attacker to steal all the photos and contacts.
What's more, the XSS vulnerability was wormable, meaning it could be easily propagating by sending a similar email to every iCloud.com or Mac.com address stored in the victim's contacts.
"When we first started this project we had no idea we'd spend a little bit over three months working towards its completion," Sam Curry noted in his blog post. "This was originally meant to be a side project that we'd work on every once in a while, but with all of the extra free time with the pandemic we each ended up putting a few hundred hours into it."
Amazon Prime Day Spurs Spike in Phishing, Fraud Attacks
9.10.20 Phishing Threatpost
A spike in phishing and malicious websites aimed at defrauding Amazon.com customers aim to make Prime Day a field day for hackers.
Cybercriminals are tapping into Amazon’s annual discount shopping campaign for subscribers, Prime Day, with researchers warning of a recent spike in phishing and malicious websites that are fraudulently using the Amazon brand.
There has been a spike in the number of new monthly phishing and fraudulent sites created using the Amazon brand since August, the most significant since the COVID-19 pandemic forced people indoors in March, according to a Thursday report from Bolster Research.
“As shoppers gear up for two days of great deals, cyber criminals are preparing to prey on the unwary, taking advantage of those who let their guard down to snap up bargains,” researchers wrote.
Prime Day actually happens over two days—this year the event falls on Oct. 13 to 14. Amazon Prime customers enjoy special sales and discounts on top brands to mark the biggest shopping event of the year on the online retail giant’s site.
Amazon last year yielded over $7 billion in sales during the 36-hour event, which could go even bigger this year due to “the decline of brick and mortar retail and the close proximity to the holidays,” researchers noted. Indeed, mandatory stay-at-home orders globally that began with the COVID-19 pandemic in March have significantly boosted Amazon’s business, a trend that shows no signs of abating.
Researchers analyzed hundreds of millions of web pages to track the number of new phishing and fraudulent sites using the Amazon brand and logos. Its research shows threat actors taking advantage of both Amazon features and consumer behaviors to try to lure online shoppers to fraudulent sites that can steal their credentials, financial information and other sensitive data.
One new campaign targets “returns” or “order cancellations” related to Prime Day using a fraudulent site, www.amazoncustomersupport[.]net, that mimics a legitimate Amazon site. However, closer examination of the site shows it is clearly designed to defraud consumers, researchers noted.
One clear evidence is its use of a phone number, as “Amazon does not encourage customer service by phone, and takes a great effort to find phone support on the real Amazon site,” researchers wrote.
The form on the site also requests bank or credit card information from customers–a clear intent to steal this information, since Amazon always offers refunds to original form of payment or gift cards. Further, the site also does not ask for a customer password, something Amazon always requires for purchases and returns.
Other smaller issues that might be overlooked—such as broken links attached to the Amazon Prime Logo and a “Get Started” button–also appear on the site. These also are clues to fraudulent behavior that shoppers should look out for in general as they shop on Prime Day, researchers noted.
Another malicious site recently observed by researchers takes advantage of most consumers’ inherent love of a free gift. The site, www.fr-suivre[.]vip, promotes an Amazon loyalty program and offers a free iPhone 11 Pro if people answer a few survey questions. After answering these questions, people are directed to a simple game that they win, after which they’re asked to enter credit card info so the site can charge them $1 to receive the iPhone.
The site even includes a screenshot in which “the free iPhone is validated by many others who have already received their phones,” researchers wrote. “Despite the glowing reviews, the $999 phone will never arrive, and the shopper begins to see strange charges on the credit card number provided,” they warned.
Fortunately for Amazon Prime customers who plan to take advantage of the event this year—or anyone else shopping Amazon these days—avoiding online fraud is not that difficult, researchers said. All shoppers should start directly at the source—Amazon.com—and pay close attention to their experience to ensure that nothing is out of the ordinary.
“Shoppers need to be aware of cyber criminals prepared to take advantage of the situation,” researchers noted. “With some diligence and attention to detail, shoppers will be able to get those deals without getting scammed.”
Amazon, too, can take even more security steps to protect customers as its business continues to boom, with cybercrime inevitably following suit, observed Kevin Beasley, CIO at enterprise management software provider VAI.
“To minimize the risk of data breaches or security issues, retailers, like Amazon, must install additional multi-factor authentication for logins and policies to protect passwords and who has access to data,” he said in an email to Threatpost.
Online retailers across the board also should get out ahead of the busy holiday season by making their platform “a security-first environment,” Beasley said.
This can be done “by installing additional layers of security infrastructure between the operating system and hardware platform, and continuous security testing and automating scans of hardware and software systems to seek out vulnerabilities and patch potential issues as they arise,” he told Threatpost.
HEH P2P Botnet Sports Dangerous Wiper Function
9.10.20 BotNet Threatpost
The P2P malware is infecting any and all types of endpoints via brute-forcing, with 10 versions targeting desktops, laptops, mobile and IoT devices.
A freshly discovered botnet dubbed HEH by researchers is casting a wide net, looking to infect any and all devices that use Telnet on ports 23/2323. It’s particularly destructive: It contains code that wipes all data from infected systems.
Perhaps ironically, its operators also have a penchant for civil advocacy – a loading of the Universal Declaration of Human Rights, visible to researchers during analysis, accompanies each infection.
According to a 360Netlab analysis, samples of the bot are being found on a wide range of CPU architectures, including x86(32/64), ARM(32/64), MIPS(MIPS32/MIPS-III) and PPC – meaning it’s infecting desktops, laptops, mobile and internet-of-things (IoT) devices. It’s looking to brute-force Telnet credentials, and once in, it infects the target with a Go language binary that communicates with other bot nodes using a proprietary peer-to-peer protocol, researchers said.
Craig Young, computer security researcher for Tripwire’s vulnerability and exposure research team (VERT), noted that the use of Golang is an ongoing trend in malware development.
“Golang has been steadily rising in popularity including among IoT malware authors,” he said via email. “Go offers a strong feature set with the ability to easily produce self-contained executables across most popular architectures. This marks a shift from IoT malware like Mirai which uses C to produce very compact binaries compared to a Go executable.”
From a technical perspective, the botnet, which gets its name from phrasing inside the code samples, contains three functional modules, according to 360Netlab: A propagation module, a local HTTP service module and the P2P module.
Infection Routine
Once a device has been successfully brute-forced (its dictionary includes 171 usernames and 504 passwords), a malicious shell script named wpqnbw.txt is executed on the host, according to the analysis. This propagation module is an initial loader, which goes on to download and execute multiple versions of the second-stage binaries – one for each possible device type.
The malicious scripts and binary programs are fetched from a legitimate pomf.cat site, which has been compromised, researchers explained.
“[There are downloads for] every single one of the malicious programs, for all different CPU architectures, there is no environment checking or things like that, [it] just run[s] all the programs in turn,” explained 360Netlab researchers, in a posting this week.
After the correct version of the code for the CPU architecture is determined, the sample is started. It first starts an HTTP server on the local port :80, researchers said – which is where the human-rights angle comes in.
“The initial state of this HTTP server will be set :80/0 to :80/9 a total of 10 URIs,” according to the post. “Correspondingly, the Universal Declaration of Human Rights in eight languages – and two empty contents – are displayed. For example, the :80/0 returns the Chinese version of the Universal Declaration of Human Rights.”
After this, the sample pulls data for the P2P module over the port, which overwrites the declaration. This is where the botnet gets down to business.
P2P Module
In a P2P botnet, each node (a.k.a. “peer”) has the capability to talk to other peers by what’s known as a ping-pong mechanism. Through this, peers share the own command-and-control functions in a distributed way; maintain their own lists of other peers; and can spread other payloads or components to each other.
In the case of HEH, the P2P module itself includes three components, starting with one that pings for all other nodes (peers) in the botnet at 0.1-second intervals (via a UDP service port) and waits for a pong back; and one that updates the node with the latest peer addresses.
On the latter front, this peer update component receives commands every 10 seconds containing new peer addresses; the node will check whether its peer list already contains the peer address information, and if not, adds it to its peer list.
The third component, a UDP service component, does most of the work, researchers explained: It monitors data or instructions sent by other peers, analyzes the instructions and performs corresponding operations.
“This component has two key functions: UDP service port number generation and command parsing,” according to 360Netlab.
For the former, “the UDP service port of HEH botnet is not fixed, nor is it randomly generated, but is calculated based on [the] peer’s own public network IP,” explained the firm. “Each time HEH bot receives a new peer’s IP address, it will calculate the peer’s UDP port according to the algorithm, and pack this information into its peer list.”
Meanwhile, the instructions that the HEH bot can parse come from a command-and-control server (C2), meaning that the botnet isn’t a true P2P architecture – yet.
“The P2P implementation still has flaws,” the researchers said. “The bot does maintain a peer list internally, and there is ongoing Ping<–>Pong communication between peers, but the entire botnet still is considered centralized, as currently the bot node cannot send control commands.”
Commands and Self-Destruction
The commands that peers can parse are divided into two categories: P2P protocol-related functional instructions, which essentially keep the node updated and continuously connected to other peers; and a module responsible for control instructions (“Bot Cmd”).
The Bot Cmd list supported by HEH bot includes commands for restarting or exiting; executing shell commands; updating the peer list; updating the malware itself; and, crucially, something called “SelfDestruct,” which is the wiper function.
SelfDestruct, which is command No. 8, will tell the bot to wipe out everything on all the disks on the host. Wipers like this are usually seen targeting critical infrastructure and nation-state types of targets, which makes this aspect of HEH stand out.
Two other commands, “launch attacks” and “Misc,” are listed but not implemented in the samples analyzed by 360Netlab – potentially meaning that the botnet is still in the development stages. That’s not to say it doesn’t pose a threat.
“The operating mechanism of this botnet is not yet mature,” researchers noted. “With that being said, the new and developing P2P structure, the multiple CPU architecture support, the embedded self-destruction feature, all make this botnet potentially dangerous.”
It’s unclear how many devices make up the botnet, or if the operators have hit the self-destruct button on any of them yet. Threatpost has reached out to 360Netlab for more information.
Users can protect themselves by making sure Telnet ports 23/2323 aren’t open to the public internet, and by ensuring strong passwords on devices.
P2P Botnets on the Rise
P2P architectures are attractive for botnets because they introduce redundancy and decentralization, making them difficult to dismantle. Also, a single communication to a single node is all it takes to propagate a new command or feature, allowing operators more opportunities for stealth when it comes to their control infrastructure.
As such, P2P botnets have been on the rise. For instance, the coin-mining botnet known as DDG for instance adopted a proprietary peer-to-peer (P2P) mechanism in April that has turned the DDG into a highly sophisticated, “seemingly unstoppable” threat, according to researchers.
Meanwhile, in September, news came that the Mozi botnet, a P2P malware known previously for taking over Netgear, D-Link and Huawei routers, has swollen in size to account for 90 percent of observed traffic flowing to and from all IoT devices, according to researchers.
And in October, a new variant of the InterPlanetary Storm P2P botnet emerged, which comes with fresh detection-evasion tactics and now targets Mac and Android devices (in addition to Windows and Linux, which were targeted by previous variants of the malware).
MontysThree APT Takes Unusual Aim at Industrial Targets
9.10.20 APT Threatpost
The newly discovered APT specializes in espionage campaigns against industrial holdings — a rare target for spyware.
SAS@Home 2020 – A series of highly targeted attacks by an APT group called MontysThree against industrial targets has been uncovered, with evidence that the campaign dates back to 2018.
That’s according to researchers from Kaspersky, who noted that the group uses a variety of techniques to evade detection, including using public cloud services for command-and-control (C2) communications, and hiding its main malicious espionage module using steganography.
Spy attacks on industrial holdings are far more unusual than campaigns against diplomats and other nation-state targets, according to the firm.
“Government entities, diplomats and telecom operators tend to be the preferred target for APTs, since these individuals and institutions naturally possess a wealth of highly confidential and politically sensitive information,” according to a Kaspersky analysis, issued on Thursday in tandem with its virtual Security Analyst Summit conference, SAS@Home. “Far more rare are targeted espionage campaigns against industrial entities—but, like any other attacks against industries, they can have devastating consequences for the business.”
The APT uses a toolset that it calls MT3, which consists of separate modules. The first—the loader—is initially spread using RAR self-extracted (SFX) archives. These, delivered via email, contain savvy lures related to employees’ contact lists, technical documentation and medical analysis, to trick industrial employees into downloading the files.
The loader obfuscates itself using steganography, which is the practice of hiding electronic information inside images.
“Steganography is used by actors to hide the fact that data is being exchanged,” according to Kaspersky. “In the case of MontysThree, the main malicious payload is disguised as a bitmap file. If the right command is inputted, the loader will use a custom-made algorithm to decrypt the content from the pixel array and run the malicious payload.”
The main malicious payload uses several encryption techniques of its own to evade detection, namely the use of an RSA algorithm to encrypt communications with the control server and to decrypt the main “tasks” assigned from the malware.
Once installed, it sets about searching for documents with specific extensions (MontysThree is designed to specifically target Microsoft and Adobe Acrobat documents) and in specific company directories. It also takes screenshots and fingerprints compromised devices by gathering information about their network settings, host name and so on, to determine if the target is of interest to the attackers.
Meanwhile, C2 communications are hosted on public cloud services like Google, Microsoft and Dropbox, which, as Kaspersky pointed out, makes the communications traffic difficult to detect as malicious.
“Because no antivirus blocks these services, it ensures the control server can execute commands uninterrupted,” according to the firm.
MontysThree also uses a simple method for gaining persistence on the infected system—a modifier for Windows Quick Launch. Users inadvertently run the initial module of the malware by themselves every time they run legitimate applications, such as browsers, when using the Quick Launch toolbar, researchers explained.
“MontysThree is interesting not just because of the fact that it’s targeting industrial holdings, but because of the combination of sophisticated and somewhat amateurish TTPs,” said Denis Legezo, senior security researcher with Kaspersky’s Global Research and Analysis Team, in a posting on Thursday. “In general, the sophistication varies from module to module, but it can’t compare to the level used by the most advanced APTs.”
Despite the less-complex aspects of the campaign, “they use strong cryptographic standards and there are indeed some tech-savvy decisions made, including the custom steganography,” Legezo said. “Perhaps most importantly, it’s clear that the attackers have put significant effort into developing the MontysThree toolset, suggesting they are determined in their aims—and that this is not meant to be a short-lived campaign.”
As far as attribution, that remains a mystery; Kaspersky has not been able to find any similarities in the malicious code or the infrastructure with any known APTs.
Kaspersky researchers will be presenting technical details on the MontysThree toolset as well as more information on targeting and other aspects of the campaign during SAS@Home on Thursday; Threatpost will update this posting with more information as it surfaces.
RAINBOWMIX Apps in Google Play Serve Up Millions of Ad Fraud Victims
9.10.20 Android Threatpost
Collectively, 240 fraudulent Android apps — masquerading as retro game emulators — account for 14 million installs.
Researchers with White Ops have uncovered a scam to deliver millions of out-of-context (OOC) ads through a group of more than 240 Android applications on the official Google Play store, which the team said were collectively delivering more than 15 million impressions per day at their peak.
The apps have since been purged from Google Play, but users should delete them off their phones as well. The full list is available here.
The apps worked the way they were supposed to, for the most part, making them all the more effective at hiding in plain sight. Most were simple retro games like Nintendo NES emulators, and used “packer” software to bypass protections. The apps would then deliver OOC ads disguised to appear as if they were from reputable sources like Chrome and YouTube, according to the White Ops team.
“The main tool in the adware developer’s arsenal are the packers,” Gabriel Cirlig, principal threat intelligence analyst for White Ops, told Threatpost. “They cloak and allow a threat to exist under the guise of intellectual property protection. However, once they passed any antivirus [protections] a user might have, the OOC ads were able to stay undetected for a period of time by pretending to be coming from popular applications and social-media platforms, such as YouTube and Chrome. Because of this, users think the ads are coming from legitimate platforms and do not get suspicious.”
The White Ops team of researchers, including Cirling, Michael Gethers, Lisa Gansky and Dina Haines, — who named the investigation “RAINBOWMIX,” inspired by the 8-16 bit color palate running throughout the retro game apps — found that these fraudulent apps were downloaded more than 14 million times by unsuspecting users.
How RAINBOWMIX Infiltrated User Devices
The various applications’ reviews show there wasn’t a lot of attention being paid to the RAINBOWMIX group.
“Most of the RAINBOWMIX apps have a “C-shaped rating distribution curve (with primarily one- and five-star reviews, which is common with suspect apps),” the team reported.
All of the RAINBOWMIX apps were loaded with the Tencent Legu packer, they add, noting that some did give clues to their nefarious intent, if you looked hard enough.
“It is worth noting that even while packed, these apps exhibit some potentially suspicious behavior corresponding to the interstitial component of the ad SDKs, which are renamed with labels that point to well-known apps,” the researchers said.
How RAINBOWMIX Fooled the System
The team also noticed triggers for services and receivers inside the apps’ manifests which shouldn’t have been there, including upon system boot, during connection changes, when a charging chord is plugged in or out, and during app installations. The assessment is that these were used to “confuse analysts and trick static-analysis engines,” the report read.
The analysts were able to pinpoint that the trigger for OOC ads “resides in the service com.timuz.a,” adding it was present in every one of the RAINBOWMIX group of applications.
“The receiver com.google.android.gms.common.license.a is a simple wrapper that tries to keep the service com.timuz.a running and sets up the out-of-context ad loop. It is contained in all bundles in the appendix,” the report said.
The service com.timuz.a gets its orders from a command-and-control server (C2), the researchers were able to discover, despite the C2 URL being buried behind base64 coding. After that connection with the C2 is established, another service takes over (com.ironsource.sdk.handlers.a.a), and attempts to deliver an OOC ad every 10 minutes, according to the report findings.
“It is important to note that while com.ironsource.sdk.handlers.a.a is a legit SDK, ironSource is unlikely involved or aware of the abuse,” researchers said.
The C2 domain (api[.]pythonexample[.]com) meanwhile has been identified by the group as a “likely hacked website.” Research showed that the site was posted with a question on an online forum two years ago, but now it defaults to a Ngnix page.
Once the C2 connection is made, a secondary URL (hxxp://api[.]pythonexample[.]com/xyyx?pn=com.androidapk.gbaemulator) is contacted and a JSON payload downloaded. After that, researchers could see ads being played on a compromised device, with nothing from than a small icon to alert the user was getting data from another app than the one they were running.
“This is used as the C2 of the ad SDK, which determines which ad network to use as well as the interstitials frequency,” the report read. “The same C2 architecture is used across all of the RAINBOWMIX apps identified in this investigation.”
The RAINBOWMIX apps were also able to boost their ad-delivery counts by monitoring when users turned their screen on and off, the analysts also discovered. “The code responsible for detecting screen on/off events was placed inside a fake Unity class ‘com.unity.b.’,” they explained.
The Impact of RAINBOWMIX & OOC Ads
Outside of the nuisance factor for users, delivering OOC ads damages every legit advertiser out there relying on consumers to trust the messages they consume online, White Ops pointed out.
“Alongside the usual fraudulent aspect of delivering ads that don’t have the same impact as a legitimate ones with users dismissing them on the spot, they also lower brand trust by masquerading as legitimate applications that would never spam the user in such as manner as the one presented,” Cirlig said.
The team found the majority (nearly 21 percent) of traffic came from Brazil, followed closely by Indonesia and Vietnam. The U.S. represented 7.7 percent of the traffic to RAINBOWMIX OOC ads.
Keywords: Out of Context ads, OOC ads, malware, RAINBOWMIX, White Ops, Google Play, emulator, Nintendo, retro games, 8-16 bit color palate, android, google play, malicious ads, ad fraud, white ops
Cisco Fixes High-Severity Webex, Security Camera Flaws
9.10.20 Vulnerebility Threatpost
Three high-severity flaws exist in Cisco’s Webex video conferencing system, Cisco’s Video Surveillance 8000 Series IP Cameras and Identity Services Engine.
Cisco has issued patches for high-severity vulnerabilities plaguing its popular Webex video-conferencing system, its video surveillance IP cameras and its Identity Services Engine network administration product.
Overall, Cisco on Wednesday issued the three high-severity flaws along with 11 medium-severity vulnerabilities.
The most severe of these is a flaw (CVE-2020-3544) in Cisco’s Video Surveillance 8000 Series IP Cameras, which ranks 8.8 out of 10 on the CVSS scale.
“A vulnerability in the Cisco Discovery Protocol [CDP] implementation for Cisco Video Surveillance 8000 Series IP Cameras could allow an unauthenticated, adjacent attacker to execute arbitrary code on an affected device or cause the device to reload,” according to Cisco’s security advisory.
The CDP is a network-discovery tool that helps network administrators identify neighboring Cisco devices. The vulnerability is due to missing checks when an IP camera processes a CDP packet.
To exploit the flaw, an attacker does not need to be authenticated. However, the person must be in the same broadcast domain as the affected device — because CDP is a Layer 2 protocol, attackers must be Layer 2-adjacent.
“An attacker could exploit this vulnerability by sending a malicious [CDP] packet to an affected device,” according to Cisco. “A successful exploit could allow the attacker to execute code on the affected IP camera or cause it to reload unexpectedly, resulting in a denial of service (DoS) condition.”
The vulnerability affects cameras running a firmware release earlier than Release 1.0.9-5 that have the CDP enabled, said Cisco. Of note, Cisco Video Surveillance 8000 Series IP Cameras are no longer being sold as of July 24; however, vulnerability and security support does not end until July 24, 2023.
Webex Bug
Cisco also patched a high-severity flaw affecting its Webex platform. This issue is severe given the troves of workforces turning to video conferencing systems during the pandemic – however, it is significantly complex to exploit, as an attacker would need to be both authenticated (needing valid credentials on the Windows system) and local.
The vulnerability stems from the incorrect handling of directory paths at run time. An attacker could exploit this vulnerability by placing a malicious DLL file in a specific location on the targeted system, which would then execute when the vulnerable application launches.
“A successful exploit could allow the attacker to execute arbitrary code on the targeted system with the privileges of another user’s account,” according to Cisco.
The flaw (CVE-2020-3535) affects Cisco Webex Teams for Windows releases 3.0.13464.0 through 3.0.16040.0; it does not affect Webex Teams for Android, Mac or iPhone and iPad.
Identity Services Flaw
A final high-severity flaw (CVE-2020-3467) exists in the web-based management interface of Cisco Identity Services Engine (ISE), a tool that enables the creation and enforcement of security and access policies for endpoint devices connected to the company’s routers and switches. The flaw enables authenticated (with valid Read-Only Administrator credentials), remote attackers to modify parts of the configuration on an affected device.
The bug stems from an improper enforcement of role-based access control (RBAC) within the web-based management interface.
“An attacker could exploit this vulnerability by sending a crafted HTTP request to an affected device,” according to Cisco. “A successful exploit could allow the attacker to modify parts of the configuration. The modified configuration could either allow unauthorized devices onto the network or prevent authorized devices from accessing the network.”
Cisco said it is not aware of any public exploits for any of the three bugs
Microsoft Azure Flaws Open Admin Servers to Takeover
9.10.20 Vulnerebility Threatpost
Two flaws in Microsoft’s cloud-based Azure App Services could have allowed server-side forgery request (SSFR) and remote code-execution attacks.
Researchers have disclosed two flaws in Microsoft’s Azure web hosting application service, App Services, which if exploited could enable an attacker to take over administrative servers.
Azure App Services is an HTTP-based service for hosting web applications, and is available in both Microsoft Azure Cloud and on-premise installations. Researchers found two vulnerabilities in the cloud service that specifically affect Linux servers.
“The two vulnerabilities we found allow us to combine them and enable any attacker with the ability to forge post requests (SSRF) or [remote] code execution on an Azure App Service to take over the Azure App Service administration server,” said Paul Litvak, researcher with Intezer, in a Thursday post.
Both flaws were discovered three months ago and reported to Microsoft. Microsoft has since issued a fix. The vulnerabilities do not have CVE assignments.
KuduLite Bugs
The first flaw stems from an open-source project called KuduLite within Azure App Services. This Linux project manages the administration page that’s used to register admins into the App Service Plan (to start using App Services a user must first create an App Service Plan).
After discovering that the KuduLite instance’s SSH service uses hardcoded credentials “root:Docker!” to access the application node, researchers were able to log in as root.
“As a reminder, the developers of the App Service KuduLite made sure admins were only able to log into it as a low privileged user, so we knew this was unintended.”
After taking control of the KuduLite instance, researchers could then gain control over the Software Configuration Management (SCM) web server, which systematically manages and controls changes in the documents and codes during the Software Development Life Cycle. This allowed them to then listen to a user’s HTTP requests to the SCM web page, add their own pages and inject malicious Javascript into the user’s web page.
“The user may also choose to let App Services manage the git server, in which case the server will be managed by KuduLite,” said researchers. “The attacker could then add malicious code to the repository to achieve persistence and spread to other instances using the same git server.”
The second flaw exists in the KuduLite API. The issue here stems from the application node being able to send requests to the KuduLite API sans access validation – an error that is especially problematic when considering a web app with an SSRF vulnerability, researchers said.
“An attacker who manages to forge a GET request may access the application node’s file system via the KuduLite VFS API,” said researchers. “This would enable an attacker to easily steal source code and other assets on the application node.”
An attacker who manages to forge a POST request, meanwhile, may achieve remote code execution on the application node via the command API, they said. And, in Windows (where Kudu is used), packets sent from the application node to the manager node are dropped.
These two vulnerabilities can be chained together, since once an attacker achieves code execution with the second vulnerability, they can then exploit the first one. One potential attack vector here is for an attacker to use this flaw to implant a phishing page in what’s supposed to be the SCM web page (as seen in the video below).
Researchers stressed that cloud security is still relatively new, making it essential to research and document new attack surfaces that arise when using these services.
“As a general best practice, runtime cloud security is an important last line of defense and one of the first actions you can to reduce risk, since it can detect malicious code injections and other in-memory threats that take place after a vulnerability has been exploited by an attacker,” they said.
Springfield Public Schools district hit with ransomware
9.10.20 Ransomware Securityaffairs
The Springfield Public Schools district in Massachusetts was forced to shut down its systems after a ransomware attack and closed the schools.
The Springfield Public Schools district, the third largest school district in Massachusetts, was forced to shut down its systems after a ransomware attack. The district, which has over 25,000 students, 4,500 employees, and more than sixty schools that were closed after the incident.
Due to the ongoing COVID-19 pandemic, the schools of the district were using remote learning model.
The district initially announced that the schools were closed due to “issues” with their network, but later it conformed that the problems were the result of a ransomware attack.
“Out of an abundance of caution the Springfield Public Schools have issued an early dismissal from school today and have temporarily suspended remote learning due to potential threats to the network that have been identified,” Mayor Domenic J. Sarno and Superintendent Daniel Warwick said in a statement.
Mayor Sarno and Superintendent Warwick, who initially announced the suspension of remote learning, has also confirmed the ransomware infection.
“Early this morning, the Springfield Public Schools identified a potential threat to their IT network. To ensure that the District can effectively mitigate the potential incident and restore access to all software and services as quickly as possible, school and remote learning activities are canceled for the remainder of today, Thursday, October 8th, 2020.” reads the official announcement. “It is anticipated that the risk will be cleared and resolved in the near future so that remote learning may continue,”
Bleeping computer, citing a source in the cyber security industry, was the first media to attribute the issues to a ransomware attack.
At the time the Springfield Public Schools has yet to reveal the family of ransomware that infected its systems and the number of devices impacted.
Unfortunately, it is likely that such kind of incident will become even more frequent in the incoming months.
In early September, the Hartford School District in Connecticut also suffered a ransomware attack that caused the delay of the school’s opening.
Hacker Who Helped Islamic State to Remain in US Prison
9.10.20 BigBrothers Securityweek
A computer hacker who gave the Islamic State group personal data of more than 1,300 U.S. government and military personnel will remain in a federal prison after a judge rejected his request for compassionate release.
Ardit Ferizi, 24, is serving a 20-year sentence. The native of Kosovo is the first person convicted in the U.S. of both computer hacking and terrorism charges. He is currently held at a federal prison in Lewisburg, Pennsylvania, and is scheduled for release in 2032 if he gets credit for good behavior.
Ferizi asked a federal judge in Alexandria to release him from prison. In a handwritten motion from prison, he said his asthma and obesity place him at greater risk of contracting COVID-19. He also said special restrictions at the prison require him to check in with staff every two hours, increasing his contact with guards and his risk of contracting the virus.
Prosecutors opposed his release, and U.S. District Judge Leonie Brinkema rejected Ferizi’s request at a hearing Tuesday, citing concerns that he might resume hacking if released, among other issues.
Microsoft Warns of Android Ransomware Abusing Notification Services
9.10.20 Ransomware Securityweek
Microsoft warned users on Thursday that it has spotted a sophisticated piece of Android ransomware that abuses notification services to display a ransom note.
Android ransomware typically allows cybercriminals to make a profit not by encrypting files — such as in the case of ransomware targeting desktop systems — but by displaying a full-screen ransom note that is difficult for the user to remove.
Microsoft says this particular Android ransomware family has been around for a while and its developers have continued to make improvements. Previous variants of the malware abused Android accessibility features or system alert windows to display the ransom note. However, Google has been taking steps to prevent abuse of these features, and some methods used by attackers can be easily spotted or bypassed by the victim.Android ransomware
In an effort to increase its chances of success, the latest version of the Android ransomware, which Microsoft tracks as AndroidOS/MalLocker.B, uses a new technique to display the ransom note and make it more difficult to remove.

The ransomware note is usually a fake police notice informing the victim that explicit images had been found on their device and instructing them to pay a fine within 24 hours.
The malware displays the ransom note using a “call” notification, which requires immediate attention from the user, combined with the “onUserLeaveHint()” callback method of the Activity class, which is called when an application is about to go into the background after the user has pressed the home key on their smartphone.
“The malware overrides the onUserLeaveHint() callback function of Activity class. The function onUserLeaveHint() is called whenever the malware screen is pushed to background, causing the in-call Activity to be automatically brought to the foreground,” explained Microsoft researcher Dinesh Venkatesan.
This ensures that the ransom note continues to be displayed on the screen regardless of what the victim does.
Microsoft also noted that it spotted a piece of code in the latest version that leverages an open source machine learning module which allows developers to automatically resize and crop an image based on the size of the device’s screen.
This code does not appear to be used in current versions of the ransomware, but if it’s fully implemented, it will ensure that the ransom note is displayed on the screen without being distorted, which Microsoft says makes the threats more believable and increases the chances of the ransom being paid.
Microsoft has published a blog post with technical details on how the malware works and how organizations can protect themselves against such threats.
MontysThree: Industrial espionage with steganography and a Russian accent on both sides
8.10.20 BigBrothers Securelist
In summer 2020 we uncovered a previously unknown multi-module C++ toolset used in highly targeted industrial espionage attacks dating back to 2018. Initially the reason for our interest in this malware was its rarity, the obviously targeted nature of the campaign and the fact that there are no obvious similarities with already known campaigns at the level of code, infrastructure or TTPs. To date, we consider this toolset and the actor behind it to be new. The malware authors named the toolset “MT3”; following this abbreviation we have named the toolset “MontysThree”.

Following the MT3 abbreviation we named the toolset MontysThree
The malware includes a set of C++ modules used for persistence, obtaining data from a bitmap with steganography, decryption of configuration tasks (making screenshots, fingerprinting the target, getting the file, etc.) and their execution, and network communications with major legitimate public cloud services such as Google, Microsoft and Dropbox. MontysThree is configured to search for specific Microsoft Office and Adobe Acrobat documents stored in current documents directories and on removable media. The malware uses custom steganography and several encryption schemes: besides custom XOR-based encryption, the modules rely on 3DES and RSA algorithms for configuration decryption and communications.
MontysThree contains natural language artifacts of proper Russian language and configuration that seek directories that exist only on Cyrilic localised Windows versions. While most external public cloud communications use token-based authorisation, some samples contain email-based accounts for them, which pretend to be a Chinese lookalike. We consider these names to be false flags. Many more artifacts suggest that the malware was developed by a Russian-speaking actor and is targeting Cyrillic Windows versions.
How the malware spreads
The initial loader module is spread inside RAR self-extracting archives (SFX) with names related to employees’ phones list, technical documentation and medical test results. There are no lures, only PE files (masquerading a .pdf or .doc file), but such titles are now a typical trick used in spear-phishing – “corporate info update” or “medical analysis results”. One of the loaders (MD5 da49fea229dd2dedab2b909f24fb24ab) has the name “Список телефонов сотрудников 2019.doc” (“Employee phone list”, in Russian). Other loaders have the names “Tech task.pdf” and “invitro-106650152-1.pdf”. The latter is the name of a medical laboratory in Russia. All of them seem like typical spear-phishing tricks. The SFX script is as follows:
Path=%TEMP%\
SavePath
Setup=rundll32.exe "invitro-106650152-1.pdf",Open
Silent=1
Overwrite=1
Update=U
Delete=invitro-106650152-1.pdf
On execution, the SFX script calls the Open() function (we’ll return to this exported name) of the decompressed loader executable in the %TEMP% directory and deletes it. Judging by the filename, it most likely imitates medical analysis results, given that “Invitro” is a prominent medical laboratory in Russia. This initial PE32 is the first loader module.
How modules work and communicate
Execution flow of MontysThree’s modules
The diagram above shows the overall execution flow of the MontysThree modules. Four modules and their features are listed in the table below. The modules share common communication conventions. When dealing with shared data, such as the configuration and detailed execution log, the malware initializes the structure in thread local storage (TLS), which in its turn refers to heap structures. Interestingly, besides RAM, the execution log is stored on disk in a file, encrypted with a one-byte XOR.
The entry point DllEntryPoint() works just like a construtor, which allocates the structure with TlsAlloc() and saves it in a global variable. Modules must export a function named Open(), which takes no parameters (but could parse the command line) and returns a four-byte error code.
Module name Features
Loader This anti-detection module is in charge of custom steganography, kernel module decryption.
Kernel This kernel (main) module is in charge of decrypting the config XML, then parsing and executing the corresponding tasks in it.
HttpTransport Network module to communicate with Google, Microsoft, Dropbox legitimate public cloud services, as well as with WebDAV sources. The module is able to make requests through RDP and Citrix in a naive way using legitimate clients.
LinkUpdate Persistence module is a Windows Quick Launch .lnk modifier. With this naive persistence method users would run the Loader module by themselves every time along with the browsers from the Windows Quick Launch toolbar.
Now let’s take a look how the developers mixed strong modern cryptography standards with custom XOR-based ones.
Task Encryption in use
Steganography To decrypt the kernel module the initial loader uses a custom algorithm.
Logs encryption The malware logs exist in memory as well as in encrypted files on disk at the same time. In RAM the developers store the logs in plaintext, on disk they use one-byte XOR.
Config encryption Kernel module uses strong encryption algorithms. Configuration data is encrypted with 3DES and the key is encrypted using RSA. All the keys – RSA public/private as well as encrypted 3DES – are stored inside the module’s .data section.
Network module encryption Initially encrypted HttpTransport is made of four binary blobs stored in the kernel module. The kernel concatenates them and decrypts them with a custom XOR-based algorithm. A round key of four bytes length is used
Communications encryption The encryption algorithm is RSA using the same public and private keys stored inside the kernel module .data section.
| Module name | Features |
| Loader | This anti-detection module is in charge of custom steganography, kernel module decryption. |
| Kernel | This kernel (main) module is in charge of decrypting the config XML, then parsing and executing the corresponding tasks in it. |
| HttpTransport | Network module to communicate with Google, Microsoft, Dropbox legitimate public cloud services, as well as with WebDAV sources. The module is able to make requests through RDP and Citrix in a naive way using legitimate clients. |
| LinkUpdate | Persistence module is a Windows Quick Launch .lnk modifier. With this naive persistence method users would run the Loader module by themselves every time along with the browsers from the Windows Quick Launch toolbar. |
| Task | Encryption in use |
| Steganography | To decrypt the kernel module the initial loader uses a custom algorithm. |
| Logs encryption | The malware logs exist in memory as well as in encrypted files on disk at the same time. In RAM the developers store the logs in plaintext, on disk they use one-byte XOR. |
| Config encryption | Kernel module uses strong encryption algorithms. Configuration data is encrypted with 3DES and the key is encrypted using RSA. All the keys – RSA public/private as well as encrypted 3DES – are stored inside the module’s .data section. |
| Network module encryption | Initially encrypted HttpTransport is made of four binary blobs stored in the kernel module. The kernel concatenates them and decrypts them with a custom XOR-based algorithm. A round key of four bytes length is used |
| Communications encryption | The encryption algorithm is RSA using the same public and private keys stored inside the kernel module .data section. |
Loader module: Bitmap decryptor and next stage launcher
If the filename of the bitmap containing the steganography-encrypted data is provided to the loader as an argument, the loader decrypts the next stager from the pixel array. In the first iteration, it extracts the steganography parameter data. To do so, the algorithm takes the last bits of the bytes.
The IID, IParam and ISize parameters are kept in the first 384 bytes of the pixel array, meaning that only the last bit of every pixel array’s byte is needed. As a result, the module gathers 48 bytes of steganography configuration structure with the fields, determining the next decryption stages.
Field Offset Features
IID 0x00 Determines one or two decryption layers would apply to the following pixel array.
IParam 0x04 Determines which bits from pixel arrays bytes would form the next kernel module.
ISize 0x28 The decrypted kernel module’s resulting size.
After extracting the steganography parameters, the next stager is decrypted using a two-step algorithm. Firstly, the IParam algorithm chooses the bits from the pixel array’s bytes. Then, if IID equals 2, a custom dexoring operation using a four-byte round key is applied on the gathered bytes. The initial key for the first four-byte decryption has the hardcoded value 0x23041920. Then the formula for the round XOR key for the next bytes is:
key ^= 8 * (key ^ (key << 20))
We consider this steganography algorithm to be custom made and not taken from some open source third-party repository. Surprisingly, the decryption result is not injected into some process’s memory, but dropped to disk as a file named msgslang32.dll. The loader then simply uses the Windows API functions LoadLibraryW() and GetProcAddress() to run the next stager’s Open() function, as we previously saw with the loader module.
Kernel module: Config decryptor and tasks dispatcher
The kernel module contains three encryption keys used for configuration decryption and C2 communications. Public and private RSA keys are stored in the .data section as PUBLICKEYBLOB and PRIVATEKEYBLOB respectively. These are used to encrypt C2 communications and to decrypt the 3DES key as well. The third 3DES key is also stored in the .data section in its encrypted form; this key is used to decrypt an embedded .cab archive containing the XML config. To decompress the .cab archive the module uses Window’s standard system utility, “expand.exe”. We’ll see another common software usage in the HttpTransport module.
The XML configuration contains valuable data that helps us understand the campaign operator’s interest. It is structured using various “tasks” for the malware, such as fingerprinting the target using its OS version, process list and capturing screenshots; but also grabs the list of users’ recent documents with any of the extensions .doc, .docx, .xls, .xlsx, .rtf, .pdf, .odt, .psw, .pwd from the several recent documents directories in %USERPROFILE% and %APPDATA%, including %APPDATA%\Microsoft\Office\Последние файлы. This folder name translates to “Recent files” in Russian, suggesting that the malware is aimed at Cyrillic localised Windows versions.
Config holds the tasks scheduling (screenshot top), access tokens (here Dropbox, redacted), directories and extensions of interest. One directory exists only on Cyrillic Windows localized versions
We observed several Cyrillic text strings such as “Снимок рабочего стола” (desktop snapshot), “Системная информация” (system information), “Время выхода” (exit time).
Config tasks description starts with MT3D and contains proper short phrases in Russian
The decrypted config structure is as follows:
Field Size Content
Magic 4 bytes MT3D. All parsed files must have this as a prefix to be valid
Creation time 4 bytes Timestamp, task config creation time stored as Epoch time
Header size 4 bytes Header size has to be greater than 18. Observed value is e.g. 0x7E
XML size 4 bytes XML task description has to be greater than zero. Observed value is e.g. 0x662D
XML body XML size The task’s description and schedule in XML format
While the samples we looked at didn’t contain RTTI information, the execution logs allowed us to recover the C++ class names. After the kernel module parses the tasks from the configuration into memory, the main class that processes the instruction is CTask. CTask’s IoControl() method is in charge of handling the corresponding tasks and in turn runs the following methods:
CTask method Features
MainIoControl() Handler of “Main” task in XML. In case of a RESET command the file, serving as a “pipe”, will be deleted. Any other command here will be logged, but not executed
FileIoControl() Handler of “File” task with PUT, DEL, FIND, WATCH, WATCH_REMOVABLE, RUN and LOGS subcommands
SysInfoIoControl() Handler of “SysInfo” task with SCREENSHOT, INFO and TASKLIST subcommands
HttpIoControl() Handler of “Http” task with SENDRECV subcommand
GDriveIoControl() Handler of “GDrive” task with SENDRECV subcommand
DropboxIoControl() Handler of “Dropbox” task with SENDRECV subcommand
All methods used for external communications first decrypt the HttpTransport module and use it to transmit the corresponding data RSA-encrypted. The RSA keys in use are the same aforementioned keys used to decrypt the 3DES config key. In a separate Window procedure, the malware monitors if a USB device is plugged in, searching for files of interest.
HttpTransport module: network tasks
The HttpTransport module exists as four encrypted chunks of data inside the .text section of the kernel module. When the kernel needs to communicate, it decrypts this module and, as usual for MontysThree, runs the Open() function, passing command line arguments.
Depending on the arguments transmitted from the kernel module, the module may upload or download content using RDP, WebDAV, Citrix and HTTP protocols. Downloading data from Google and Dropbox public services using user tokens is implemented in HttpTransport as well. In case of HTTP GET/POST requests, the malware would receive a steganography bitmap picture using Windows API HTTP-related functions from a corresponding URL.
The aforementioned communication protocols themselves aren’t implemented inside the module. The malware authors make use of legitimate Windows programs like RDP, Citrix clients and Internet Explorer already installed on the target’s machine. For example, the module executes a task to send some data to a URL and receive the reply through an RDP connection as follows: edit the .rdp file to silently run Internet Explorer on the remote machine; paste the URL to the browser via the clipboard; wait and paste the contents to the opened web page via the clipboard as well; wait and receive the result through the clipboard again.
To copy data, the malware literally sends Ctrl+C, Ctrl+V and Ctrl+A. Perhaps it’s the first time we have seen such a method of “RDP communication”. The Citrix communication is done using a similar procedure: the malware doesn’t implement the protocol but rather searches for Windows Quick Launch .lnk for XenApp pnagent.exe, runs Internet Explorer remotely and communicates with it through the clipboard using special keyboard shortcuts.
Dropbox and Google data upload and download relies on another principle: its implementation uses the custom class CSimpleHttp to authenticate and send HTTP requests. For WebDAV communication, the developers simply use the “net use” Windows command.
LinkUpdate
This auxiliary module is in charge of achieving persistence on the host. It changes the .lnk files in the Windows Quick Launch panel to run the loader along with legitimate applications such as browsers when the user executes them using the modified link.
Who is behind this malware
As we mentioned at the beginning, to date we have observed no similarities or overlaps with known campaigns in terms of TTPs, infrastructure or malware code. So far, we attribute this activity and the use of MontysThree to a new actor. Some samples contain account details used for communicating with public cloud services, which pretend to be of Chinese origin. Taking into consideration all the aforementioned Cyrilic artefacts, we consider these account names to be false flags.
We assume that the actor behind MontysThree is both Russian-speaking and is going after Russian-speaking targets. Some of the filenames of the RAR SFX archives used for spreading the malware were written in Russian and referenced a Russian medical laboratory, used to entice the user to open the file. The XML configuration showcased data fields and Windows titles written in Russian, as well as specific folder paths that exist on Cyrilic localised versions of Windows. We also saw some grammatical errors in the malware’s English log message strings.
Let’s sum up
Typically we see targeted malware that is mostly going after governmental entities, diplomats and telecom operators, which are fruitful for state-sponsored actors. Industrial espionage cases like MontysThree are far more rare.
The overall campaign sophistication doesn’t compare to top notch APT actors in terms of spreading, persistence method. And some aspects of the malware – logging in RAM and files at the same time, keeping the encryption keys in the same file, running an invisible browser on the remote RDP host – seem immature and amateurish in terms of malware development.
On the other hand, the amount of code and therefore effort invested, in MontysThree is significant. The toolset demonstrates some tech-savvy decisions: Storing 3DES key under RSA encryption, custom steganography to avoid IDS and the use of legitimate cloud storage providers to hide the C2 traffic.
File Hashes
Loader
1B0EE014DD2D29476DF31BA078A3FF48
0976C442A06D2D8A34E9B6D38D45AE42
A2AA414B30934893864A961B71F91D98
Kernel
A221671ED8C3956E0B9AF2A5E04BDEE3
3A885062DAA36AE3227F16718A5B2BDB
3AFA43E1BC578460BE002EB58FA7C2DE
HttpTransport
017539B3D744F7B6C62C94CE4BCA444F
501E91BA1CE1532D9790FCD1229CBBDA
D6FB78D16DFE73E6DD416483A32E1D72
Domains and IPs
autosport-club.tekcities[.]com
dl10-web-stock[.]ru
dl16-web-eticket[.]ru
dl166-web-eticket[.]ru
dl55-web-yachtbooking[.]xyz
QNAP addresses 2 critical flaws that can allow hackers to take over NASs
8.10.20 Vulnerebility Securityaffairs
QNAP has addressed two critical security vulnerabilities in the Helpdesk app that could enable potential attackers to take over NAS devices.
QNAP has addressed two critical security vulnerabilities in the Helpdesk app that can potential allow threat actors to take over vulnerable QNAP network-attached storage (NAS) devices.
Helpdesk is a built-in app that allows owners of QNAP NAS to directly submit help requests to the vendor from their NAS, to do this, the app has specific permission.
According to a security advisory published by the company, both flaws, tracked as CVE-2020-2506 and CVE-2020-2507, are improper access control vulnerabilities.
The Taiwanese vendor confirmed that if exploited, the two improper access control vulnerabilities could allow attackers to obtain control of a QNAP device.
QNAP has addressed these issues with the release of Helpdesk 3.0.3 and later versions, below the step by step instructions to update the helpdesk:
Log on to QTS as administrator.
Open the App Center, and then click .
A search box appears.
Type “Helpdesk”, and then press ENTER.
The Helpdesk application appears in the search results.
Click Update.
A confirmation message appears.
Note: The Update button is not available if you are using the latest version.
Click OK.
The application is updated.
Recently QNAP published a security advisory urging its customers to update the firmware and apps installed on their network-attached storage (NAS) devices to prevent AgeLocker ransomware infections.
The name AgeLocker comes from the use of the Actually Good Encryption (AGE) algorithm to encrypt files, experts warn that encrypted files can’t be recovered without paying the ransom to the ransomware operators.
Security experts are observing the new strain of ransomware that is targeting QNAP devices since June.
In early August, the Taiwanese company urged its users to update the Malware Remover app to prevent NAS devices from being infected by the QSnatch malware.
At the time, the United States Cybersecurity and Infrastructure Security Agency (CISA) and the United Kingdom’s National Cyber Security Centre (NCSC) also issued a joint advisory about a massive ongoing campaign spreading the QSnatch data-stealing malware.
Earlier this year, the company issued another alert to warn its users of a wave of attacks spreading a ransomware strain tracked as eCh0raix.
Data from Airlink International UAE leaked on multiple dark web forums
8.10.20 BigBrothers Securityaffairs
Cybersecurity researchers from Cyble have spotted a threat actor sharing leaked data of Airlink International UAE for free on two different platforms.
Cybersecurity researchers from Cyble have found a threat actor sharing leaked data of Airlink International UAE for free on two platforms on the dark web.
The availability of the data on the dark web could pose organizations to serious risk, threat actors could use this data to carry out multiple malicious attacks.
Cyble discovered the data leak as part of its daily monitoring.
Airlink International U.A.E. is a leading company for any travel and logistics requirements. It has more than than 200 employees with around $250 million in revenue.
The data leak is the result of a misconfigured server containing 60 directories with approximately 5,000 files each.
The data leak was first reported on May 30, 2020, the data have been posted online by the collective KelvinSecTeam.
“The files present accommodation reservations, airline tickets and other logistics services that the company provides on a global scale. In a quick inspection by sampling, it was possible to observe customers of different nationalities and services provided in Africa, Asia and Europe.” reported the media.
According to Cyble, now, another threat actor is spreading the same data on multiple dark web forums in an attempt to gain fame.
Leaked data includes 14 folders and 53,555 files divided into the following categories:
Passport scans
Flight bookings
Hotel bookings
Email communications between Airlink International Group employees and customers
Insurance policy for international travel
Cyble provides recommends the following recommendation to the organizations:
Configure server to prevent unauthorized access, directory listing
Review old backup and unreferenced files for sensitive information
Test file permissions
Enumeration of infrastructure and application administrator interfaces
Consider running scans and doing audits periodically to help detect future misconfigurations or missing patches
U.S. Seizes Domain Names Used by Iran for Disinformation
8.10.20 BigBrothers Securityweek
U.S. Seizes Domain Names Used by Iran for Disinformation
The United States this week announced that it seized a total of 92 domain names that an Iran-linked adversary was leveraging in a global disinformation campaign.
Although four of the domains pretended to be genuine news outlets, they were controlled by Iran’s Islamic Revolutionary Guard Corps (IRGC) to spread Iranian propaganda targeting the United States, while the remaining websites were spreading propaganda to other countries.
The manner in which these domains were being used was in violation of sanctions the U.S. imposed on both the government of Iran and the IRGC.
As of April 2019, the United States has designated the IRGC as a foreign terrorist organization. The organization was found to have provided material support to terrorist groups such as Hizballah, Hamas, and the Taliban.
On October 7, pursuant to a seizure warrant, the United States seized 92 domain names that were being operated in violation of federal law. Four of these were seized pursuant to the Foreign Agents Registration Act (FARA), which requires the submission of periodic registration statements about activities and income.
“The four domains purported to be independent news outlets, but were actually operated by or on behalf of the IRGC to target the United States with pro-Iranian propaganda in an attempt to influence the American people to change United States foreign and domestic policy toward Iran and the Middle East,” the U.S. Department of Justice says.
These domains, the DoJ explains, targeted an audience in the U.S. without proper registration pursuant to FARA and also failed to inform the audience that the IRGC and the government of Iran were in control of the published content.
Also masquerading as news outlets, the remaining 88 domains targeted audiences in Western Europe, the Middle East, and South East Asia, spreading pro-Iranian disinformation.
All of the domains were found to be owned and operated by companies in the U.S., but the government of Iran and the IRGC used them without a license from the Office of Foreign Assets Control (OFAC). Pursuant to the International Emergency Economic Powers Act (IEEPA), a license is required to provision services to the government of Iran.
The activity associated with these domains was initially reported on in 2018, but the Department of Justice has now linked it to the IRGC, John Hultquist, Senior Director of Analysis, Mandiant Threat Intelligence, said in an emailed comment.
“The DOJ has just linked Iranian information operations that FireEye publicly reported in 2018 to the Islamic Revolutionary Guard Corps, Iran’s aggressive security service. The IRGC is very comfortable with asymmetric tools and they have increasingly adopted cyber capabilities as a means to disrupt and manipulate their enemies abroad. Iran has become a prolific actor in the information operations space and similar to their cyberattack capability, they have evolved over a series of brash operations,” Hultquist said.
Russia-Linked Hackers Targeting Russian Industrial Organizations
8.10.20 BigBrothers Securityweek
A previously unknown threat group whose members speak Russian has been launching attacks against Russian industrial organizations in a highly targeted espionage campaign, Kaspersky reported on Thursday.
According to Kaspersky, the group calls its toolset MT3 and based on this the cybersecurity company has named the threat actor MontysThree. The campaign will be detailed on Thursday at Kaspersky’s second SAS@Home event.
MontysThree has been active since at least 2018, but Kaspersky has not found any links between this group and other known advanced persistent threats (APTs).MontysThree
Denis Legezo, senior security researcher with Kaspersky’s Global Research and Analysis Team, told SecurityWeek that the hackers have only been seen targeting the IT networks of industrial entities and there is no indication that they have also targeted industrial control systems (ICS).
MontysThree, Kaspersky says, relies on a piece of malware that has four modules. One of them has loader functionality and is responsible for delivering the main payload. The loader is hidden inside a self-extracting RAR archive that references contact lists, medical test results or technical documentation in order to convince the employees of the targeted organization to download the file.

The loader uses steganography to evade detection, with the main payload being hidden inside a bitmap image file. The main payload uses encryption to evade detection and protect C&C communications.
The malware allows the attackers to steal Microsoft Office and PDF documents, capture screenshots, and collect information on the compromised machine in order to help the hackers determine if it might be of interest to them. The stolen information is hosted on public cloud services from Google, Microsoft and Dropbox, making it more difficult to detect attacks, Kaspersky said.
Based on the lures used by the hackers, the language artifacts found in the malware, and the fact that it only targets Windows devices configured to use Cyrillic script, Kaspersky believes the members of the MontysThree group are Russian speakers and they target Russian entities.
“Some samples contain account details used for communicating with public cloud services, which pretend to be of Chinese origin. Taking into consideration all the aforementioned Cyrilic artefacts, we consider these account names to be false flags,” Kaspersky said in its report. “We also saw some grammatical errors in the malware’s English log message strings.”
The cybersecurity firm says MontysThree is not as sophisticated as other groups it has seen, but it’s still not a threat that should be ignored.
“Some aspects of the malware – logging in RAM and files at the same time, keeping the encryption keys in the same file, running an invisible browser on the remote RDP host – seem immature and amateurish in terms of malware development,“ Kaspersky said. “On the other hand, the amount of code and therefore effort invested, in MontysThree is significant. The toolset demonstrates some tech-savvy decisions: Storing 3DES key under RSA encryption, custom steganography to avoid IDS and the use of legitimate cloud storage providers to hide the C2 traffic.”
Google Readies Redesigned Security Alerts for Google Accounts
8.10.20 Security Securityweek
Google this week revealed that it’s working on redesigning the security alerts for Google accounts and that it will make them available directly in the applications users are logged into.
The company has already built numerous protections into Google accounts and other Google products, with Safe Browsing delivering protection for over 4 billion devices, Gmail blocking in excess of 100 million daily phishing attempts, and Google Play Protect scanning more than 100 billion apps per day.
However, the company plans to continue investing in such protections, and keeping users notified on suspicious activity on their Google accounts is one of the areas to receive improvements.
Since 2015, notifications regarding critical issues in Google accounts are delivered to Android devices, and Google says that an increasing number of users has been engaging with these alerts within one hour after receiving them.
“Soon we’ll be introducing a redesigned critical alert and a new way of delivering it. When we detect a serious Google Account security issue, we’ll automatically display an alert within the Google app you’re using and help you address it—no need to check email or your phone’s alerts,” Google says.
The company claims that the new alerts are resistant to spoofing, and that the warnings will be rolled out to a limited set of users in the coming weeks, with more users receiving them early next year.
In the coming weeks, Google will also introduce for Google Assistant on home devices a ‘Guest mode,’ where interactions won’t be saved to the user’s account. The Guest mode can be easily turned on or off, and users also have the possibility to delete any interaction with the Assistant using voice commands only.
Google is also rolling out new security and privacy protections for Google Workplace, along with updated password protections in Chrome. Furthermore, the company is also advancing on implementing a Privacy Sandbox in the browser, in an attempt to further improve user privacy online.
“To make it easier to control your privacy, you'll soon be able to directly edit your Location History data in Timeline by adding or editing places you’ve visited with just a few taps, and because Search is the starting point for so many questions, starting today we’ll display your personal security and privacy settings when you ask things like ‘Is my Google Account secure?’,” the company says.
Android 11, which started arriving on devices last month, includes security and privacy improvements as well, including the training of new word prediction models and AI models without having data leaving devices.
NATO Chief Calls for New Strategy on Cyber, China
8.10.20 BigBrothers Securityweek
NATO needs a new strategic concept adjusted to the global rise of new technologies, terrorism and China to replace a plan developed a decade ago, the head of the alliance said on Wednesday.
French President Emmanuel Macron famously branded the alliance "brain dead" last year, demanding a new strategy that would, among other things, reopen dialogue with Russia -- stifled after it annexed part of Ukraine -- and refocus on the fight against Islamist terrorism.
As part of a "reflection process" triggered by the French leader's controversial remarks, NATO will revise its strategic concept -- its overarching statement of the threats it faces and how it might respond, Secretary General Jens Stoltenberg told a conference in Slovakia's capital Bratislava.
"The time has come to develop a new strategic concept for NATO, as the world has fundamentally changed," Stoltenberg said at the GLOBSEC security forum.
He dubbed the initiative "NATO 2030".
Stoltenberg urged the Western defensive alliance of 30 states to "develop common principles and standards for new technologies" to meet security challenges related to "disruptive technologies" using big data and cyber telecommunications.
The NATO chief also highlighted the need to address the "fundamental shift in the global balance of power with the rise of China" as well as the rise of a "more brutal form of terrorism, more instability to the south of our Alliance, in the Middle East and North Africa."
At a summit in London last year, NATO leaders for the first time formally recognised the "challenges" posed by China.
While the transatlantic alliance remains focused on its European and North American core, Stoltenberg has argued it is impossible to ignore Beijing's booming military investment and geopolitical assertiveness.
Stoltenberg also underscored the importance of maintaining resilient societies across the alliance, insisting that "our military cannot be strong if our societies are weak.
"So our first line of defence must be strong societies able to prevent, endure, adapt and bounce back from whatever happens," he added in an apparent nod to the unprecedented impact of the coronavirus pandemic on NATO members.
Since the Ukraine conflict erupted in 2014, NATO has sought ways to boost its members' resilience to the kind of hybrid warfare -- combining irregular forces, cyber tactics and disinformation -- seen there.
Juniper Launches Adaptive Threat Profiling, New VPN Features
8.10.20 Safety Securityweek
Juniper Networks has introduced three new capabilities to improve network visibility, access control and VPN-based remote working.
The three new features provide adaptive threat profiling for Juniper's ATP Cloud, the integration of WootCloud HyperContext for device profiling, and Secure Connect VPN for remote working beyond the branch office. The purpose is to improve network visibility and provide consistent policy enforcement across all connected devices.
Juniper Networks logoSamantha Madrid, VP of security business and strategy at Juniper Networks, sees security's primary problem as one of visibility. "As a security industry," she told SecurityWeek, "we have being doing a phenomenal job in understanding threats, and how threats take shape in networks -- we've been great about ensuring the collective understanding of those threats. But one of the things I don't think we have really scratched the surface on has been about how do we secure the network by providing customers with the visibility that allows them to not only understand their overall risk profile but also gives them the visibility to make any necessary changes -- whether through technology, policy or whatever -- so that they're coming from a vantage point of knowledge versus reaction." The new additions to the Juniper portfolio are designed to provide that visibility and control by bringing security to every point of connection and allowing CISOs to know who and what is on the network.
Adaptive Threat Profiling makes use of Juniper's SRX series firewalls to act as sensors throughout the network. The result is a series of security intelligence feeds populated by data on potential intrusions. The intelligence can be shared with in-line devices that can enforce policy automatically in real time and at scale. "All of our firewalls," explains Madrid, "through our ATP Cloud, have the ability to assess, in real time, changes to the environment, and can customize threat intelligence and distribute it not just to the firewalls, but to all the networking devices. As changes occur, whether that's a new device or a new threat, we can automatically adapt to those changes with network-specific intelligence." This is particularly relevant at a time when adversaries are customizing their attacks to specific targets. As soon as a targeted attack is recognized anywhere on the network, information on that threat is distributed to every Juniper device on the network, and the relevant response can be taken.
The WootCloud HyperContext integration provides visibility of all IoT connected devices, and their susceptibility to compromise. "Network visibility is an important issue that security teams have struggled with," explains Madrid in an associated blog. "With each new connection, risk increases -- especially when it comes to IoT devices. Not all connected devices can run secure operating systems, be patched or run endpoint agents."
WootCloud is a company that provides agent-less device-focused segmentation, access control and threat response across the network. The system will automatically detect IoT devices and place them in separate VLANs to inhibit the propagation of any compromise. This segmentation can be used to enforce secondary authentication and limit access to high risk devices. "This allows us," said Madrid, "to see any device that comes on the network, that is an internet-based device. So, think of soda machines, a casino slot machine, any internet connected IoT device -- anything that has internet connectivity can be seen and risk assessed through behavioral analytics." Policy can then automatically take action against any device that is indicating new or unacceptable risk. Segmentation can be used to effectively remove that device from the network. The point at which automated response is taken can be left to the baselines provided by the system, or can be modified by users according to their own risk tolerance.
The COVID-19 pandemic has thrown the increasing move to remote working into hyperdrive. The need for secure VPN connection from remote or home devices to the corporate network is not new, but now essential and immediate for more organizations. The new Secure Connect offering, which simply requires the installation of an app on the remote device, supports both IPSEC and SSL-VPN.
The new VPN allows remote users to stay securely connected to the corporate network. Juniper's Mist AI on the network allows organizations to scale quickly and easily, adapting to changes to the network perimeter and attack surface. "This will enable a customer," Madrid told SecurityWeek, "to extend the connected security capabilities and the threat aware network that we introduced two years ago to every user and device no matter where they are."
"We’re extending security," Madrid said, "in ways that turn 'dumb pipes' into intelligent sensors and enforcement points that are able to dynamically optimize protections as attacks are happening. We can provide comprehensive visibility across an organization into who and what is on the network and give our customers the means to limit their risk with minimal impact to their end users."
Researchers Find Vulnerabilities in Microsoft Azure Cloud Service
8.10.20 Vulnerebility Thehackernews
As businesses are increasingly migrating to the cloud, securing the infrastructure has never been more important.
Now according to the latest research, two security flaws in Microsoft's Azure App Services could have enabled a bad actor to carry out server-side request forgery (SSRF) attacks or execute arbitrary code and take over the administration server.
"This enables an attacker to quietly take over the App Service's git server, or implant malicious phishing pages accessible through Azure Portal to target system administrators," cybersecurity firm Intezer said in a report published today and shared with The Hacker News.
Discovered by Paul Litvak of Intezer Labs, the flaws were reported to Microsoft in June, after which the company subsequently addressed them.
Azure App Service is a cloud computing-based platform that's used as a hosting web service for building web apps and mobile backends.
When an App Service is created via Azure, a new Docker environment is created with two container nodes — a manager node and the application node — along with registering two domains that point to the app's HTTP web server and the app service's administration page, which in turn leverages Kudu for continuous deployment of the app from source control providers such as GitHub or Bitbucket.
Likewise, Azure deployments on Linux environments are managed by a service called KuduLite, which offers diagnostic information about the system and consists of a web interface to SSH into the application node (called "webssh").
The first vulnerability is a privilege escalation flaw that allows for a takeover of KuduLite via hard-coded credentials ("root:Docker!") that makes it possible to SSH into the instance and log in as root, thereby allowing an attacker complete control over the SCM (aka Software Configuration Management) webserver.
According to the researchers, this could enable an adversary to "listen to a user's HTTP requests to the SCM web page, add our own pages, and inject malicious Javascript into the user's web page."
The second security vulnerability concerns the way the application node sends requests to the KuduLite API, potentially permitting a web app with an SSRF vulnerability to access the node's file system and steal source code and other sensitive assets.
"An attacker who manages to forge a POST request may achieve remote code execution on the application node via the command API," the researchers said.
What's more, successful exploitation of the second vulnerability implies the attacker can chain the two issues to leverage the SSRF flaw and elevate their privileges to take over the KuduLite web server instance.
For its part, Microsoft has been steadily working to improve security in the cloud and the internet of things (IoT) space. After making available its security-focused IoT platform Azure Sphere earlier this year, it has also opened it up for researchers to break into the service with an aim to "identify high impact vulnerabilities before hackers."
"The cloud enables developers to build and deploy their applications at great speed and flexibility, however, often the infrastructure is susceptible to vulnerabilities out of their control," Intezer said. "In the case of App Services, applications are co-hosted with an additional administration container, and [...] additional components can bring additional threats."
"As a general best practice, runtime cloud security is an important last line of defense and one of the first actions you can to reduce risk, since it can detect malicious code injections and other in-memory threats that take place after a vulnerability has been exploited by an attacker."
Comcast TV Remote Hack Opens Homes to Snooping
8.10.20 Hacking Threatpost
Researchers disclosed the ‘WarezTheRemote’ attack, affecting Comcast’s XR11 voice remote control.
A security flaw allowing attackers to remotely snoop in on victims’ private conversations was found to stem from an unexpected device – their TV remotes.
The flaw stems from Comcast’s XR11, a popular voice-activated remote control for cable TV, which has more than 18 million units deployed across the U.S. The remote enables users to say the channel or content they want to watch rather than keying in the channel number or typing to search.
However, researchers found a serious vulnerability in the remote, allowing attackers to take it over (details below). Worse, the ensuing attack, dubbed WarezTheRemote, does not require any interaction from the victim — it’s extremely cheap to carry out (a hacker merely needs a low-priced RF transceiver and antenna), and can be launched remotely (from up to 65 feet away).
Threatpost Webinar Promo Retail Security
Click to Register!
Researchers worked with Comcast’s security team after finding the flaw and fixes have been released that remediate the issues that make the attack possible – however, in a disclosure post on Wednesday, they stressed that the incident is an important reminder of the inherent security and privacy issues plaguing even the least-suspected internet of things (IoT) devices.
“Few people think of their television remote controls as ‘connected devices,’ fewer still would guess that they can be vulnerable to attackers, and almost no one would imagine that they can jeopardize their privacy,” said researchers with Guardicore, in a Wednesday post. “In this case, the recent development of RF-based communication and voice control makes this threat real. Even more so in these strange times: With so many of us working from home, a home-recording device is a credible means to snoop on trade secrets and confidential information.”
The Flaw
By extensively reverse-engineering both the remote’s firmware and the software it communicates with on the set-top box, researchers found an error in the way the remote handles incoming RF packets.

The Comcast remote. Credit: Guardicore
To understand the flaw, it’s first important to look at how XR11 voice remotes work. The remote communicates with the television set-top box over the RF4CE (Radio Frequency for Consumer Electronics) protocol. RF4CE, which is a subset of the Zigbee family of power-saving RF protocols, has a feature called, straightforwardly, “security” — which should encrypt the contents of RF4CE packets to bar attackers from injecting malicious packets into the connection.
However, in the XR11’s implementation, the RF4CE “security” feature is set on a packet-by-packet basis. Each packet has a “flags” byte, and when one of its bits is set to 1, its contents will be encrypted – and if the bit isn’t set, the packet will be sent in plaintext.
The vulnerability lies in the fact that the original XR11 firmware didn’t verify that responses to encrypted requests are encrypted as well, said researchers. That means an attacker within RF range (about 65 feet away) could view requests from the remote in plaintext – allowing them to easily formulate a malicious response to that request.
“WarezTheRemote used a man-in-the-middle attack to exploit remote’s RF communication with the set-top box and over-the-air firmware upgrades – by pushing a malicious firmware image back the remote, attackers could have used the remote to continuously record audio without user interaction,” they said.
The Attack
Researchers say that the remote’s firmware queries the box it is paired with – be default – for a new firmware once every 24 hours. That means in a real-life attack, a bad actor would need to wait for the a firmware upgrade query to occur.
“The request packet is encrypted, so an attacker can’t actually read its contents, but there is a non-encrypted byte in the packet’s header that indicates that this request is firmware-related, which allows the attack to guess its contents without actually decrypting it,” they said.
Following this initial exchange, the remote then sends out a series of requests asking for the contents of the firmware image, chunk by chunk. The order these chunk requests are sent in is entirely predictable – meaning attackers can easily guess which chunk of the firmware the remote is asking for.
“By carefully timing our responses, we were able to send exactly the right firmware chunk to the remote each time,” they said. “Furthermore, we found a way to temporarily crash the software running on the cable box using a malformed RF4CE packet. This simple DoS prevented the box from interfering over the course of the attack.”
Researchers said an attacker would only need a basic RF transceiver, which is cheap – a Texas Instruments CC2531 costs only a few dollars for a whole development kit – as well as a cheap 2 dBi antenna (researchers used a 16dBi antenna for better results).
“We didn’t push this to the limit, but we were easily able to push firmware to the remote around 65 feet away from outside the apartment it was in,” they said. “This is the alarming part – it conjures up the famous ‘van parked outside’ scene in every espionage film in recent memory.”
Researchers disclosed the vulnerability to Comcast April 21, and Comcast began to release a patch on July 24. On Sept. 24, Comcast confirmed that all devices were patched.
“Nothing is more important than keeping our customers safe and secure, and we appreciate Guardicore for bringing this issue to our attention,” said Comcast in a press statement. “As detailed in this report, we fixed this issue for all affected Xfinity X1 voice remotes, which means the issue described here has been addressed and the attack exploiting it is not possible.”
PoetRAT Resurfaces in Attacks in Azerbaijan Amid Escalating Conflict
8.10.20 Virus Threatpost
Spear-phishing attacks targeting VIPs and others show key malware changes and are likely linked to the current conflict with Armenia.
A new iteration of the PoetRAT spyware, sporting improvements to operational security, code efficiency and obfuscation, is making the rounds in Azerbaijan, targeting the public sector and other key organizations as the country’s conflict with Armenia over disputed territory intensifies.
Threat intelligence researchers have observed multiple new strikes using the malware that show a “change in the actor’s capabilities” and “maturity toward better operational security,” while maintaining the tactic of spear-phishing to lure users into downloading malicious documents, Cisco Talos researchers revealed in a blog post, published Tuesday.
Threatpost Webinar Promo Retail Security
Click to Register!
PoetRAT scurried onto the scene in April as a region-specific backdoor that acted as the tip of the spear for a greater espionage framework. In that case, the operator deployed additional post-exploitation tools on the targeted systems, including a tool, “dog.exe,” that monitors hard drive paths to exfiltrate the information via an email account or a File Transfer Protocol (FTP), depending on the configuration. Another tool, “Bewmac,” enables the attacker to record the victim’s camera. Researchers also came across other tools, including a keylogger, a browser credential stealer, an open-source framework for privilege escalation (WinPwnage) and an open-source pentesting and network scanning tool (Nmap).
This time around, the attacks use Microsoft Word documents alleged to be from the Azerbaijan government — complete with the National Emblem of Azerbaijan in the top corners — to install PoetRAT in two separate files on victims’ machines, according to researchers Warren Mercer, Paul Rascagneres and Vitor Ventura.
“These Word documents continue to contain malicious macros, which in turn download additional payloads once the attacker sets their sites on a particular victim,” they wrote. However, the malicious document included in the spear-phishing emails drops PoetRAT, with some notable changes to the malware, researchers said.

Differences between the previous and most recent campaigns include a change in the programming language used for the malware from Python to Lua script. In previous campaigns, a Python interpreter was installed along with the main payload. This change adds efficiency to the code and reduces the file size of the malware, researchers explained — even if in and of itself it retains a lack of complexity, as demonstrated in earlier campaigns, researchers noted.
“Previous versions of PoetRAT deployed a Python interpreter to execute the included source code, which resulted in a much larger file size compared to the latest version’s switch to Lua script,” they said. “The code is easy to parse — nothing advanced — but our analysis showed us that the campaigns are efficient.”
The latest campaign also features some new tactics to evade detection, researchers noted. These include a new exfiltration protocol to hide attackers’ activities, as well as “additional obfuscation to avoid detection based on strings or signatures,” including a Base64 and an LZMA compression algorithm, researchers noted.
Developers also have improved the operational security (OpSec) by performing reconnaissance on compromised systems, and by changing the protocol used to download and upload files from FTP to HTTP, they said.
Victims and Conflict
Victims of the campaign include Azerbaijani VIPs and organizations in the public sector, with attackers demonstrating access to sensitive information, such as diplomatic passports belonging to some of the country’s citizens.
Cisco Talos researchers first discovered PoetRAT in April in attacks against energy companies in Azerbaijan that included post-exploitation tools to log keystrokes, record footage from webcams and steal browser credentials. The malware operators also targeted other victims in the public and private Azerbaijan sectors as well as SCADA systems.
Researchers believe the rising conflict between Azerbaijan and Armenia is most likely to blame for the new attacks, according to the post.
“As the geopolitical tensions grow in Azerbaijan with neighboring countries, this is no doubt a stage of espionage with national-security implications being deployed by a malicious actor with a specific interest in various Azerbajiani government departments,” they wrote.
The malware gets its name from various references to sonnets by English playwright William Shakespeare that were included throughout the macros that are embedded in the malicious Word documents that were part of the initial campaign. The literature references found in the macros this time around—from the novel “The Brothers Karamazov” by Russian novelist Fyodor Dostoevsky –also may be a veiled reference to the current conflict. Both Azerbaijan and Armenia used to be a part of the former Soviet Union, and Russia has close ties with both countries, and is also a military ally of Armenia.
IRS COVID-19 Relief Payment Deadlines Anchor Convincing Phish
8.10.20 BigBrothers Threatpost
The upcoming deadlines for applying for coronavirus relief are the lure for a phish that gets around email security gateways by using a legitimate SharePoint page for data-harvesting.
A credential-phishing email campaign is making the rounds, using the lure of coronavirus tax relief to scam people into giving up their personal information.
The data-harvesting cybercriminals are looking to take advantage of the Internal Revenue Service (IRS) deadlines that are approaching for consumers who haven’t received an Economic Impact Payment. While most Americans got their one-time $1,200 payment in the spring, those who don’t usually file tax returns (such as those on Social Security) weren’t automatically included in that payout. These individuals have until Nov. 21 to register for their assistance check. Meanwhile, taxpayers who requested an extension of time to file their 2019 tax return have a deadline of October 15.
The emails purport to contain an important document about COVID-19 relief funds from the IRS. Clicking the link in the email leads readers to a SharePoint form that they were told to complete before accessing the document, according to Chetan Anand, co-founder and architect at Armorblox.
Threatpost Webinar Promo Retail Security
Click to Register!
The SharePoint form asks for email credentials, Social Security numbers, driver license numbers and tax ID numbers.
The sneaky use of the SharePoint form as an interim step helped the emails get past email gateways, Anand noted, in a blog posted Wednesday.
“This email got past existing Office 365 email security controls because it didn’t follow the tenets of more traditional phishing attacks,” he wrote. “When victims clicked the link in the email, they were led to a SharePoint form that asked for email credentials along with a host of other personal information…Since the phishing link pointed to a legitimate SharePoint page, it got past any email security filters designed to block known bad domains. The familiar Microsoft branding on the page might also put victims’ minds at ease as they subconsciously buy into the legitimacy of the email. It’s worth noting the irony-laden footer asking people not to share passwords or give away personal information.”
The phishing page was in fact hosted on a compromised user’s SharePoint account, lending legitimacy. Closer inspection revealed that the SharePoint account belonged to an employee of the Reproductive Medicine Associates of Connecticut (RMACT).
The campaign, which hit multiple email inboxes in the Armorblox telemetry, also used better-than-average social engineering, Anand noted, with the email language and context including multiple emotional triggers.
For instance, the email subject line read “IRS Covid Relief Fund Update,” and the sender name was “IRS Covid Relief Funds.”
“Both [are] very specific and related to topics that elicit quick actions from victims,” the researcher wrote, noting that the use of the IRS is an “authority” trigger. “Discerning readers will stop short of sharing the wealth of personal information asked in this SharePoint form. However, given the context of the communication – IRS sharing COVID relief fund details – victims might rationalize the extent of personal information asked in the form.”
The email language also included urgency triggers by talking about “important updates,” and ends with a simple but effective request: asking victims to click the link if they want to view the document – this, along with the aforementioned boilerplate confidentiality footer, makes it seem more legitimate, according to Anand.
That’s not to say that the phish is perfect – as always, some red flags pop up.
“A closer look reveals some grammatical irregularities in the email, as well as a non-capitalized ‘Irs’ in the email sender name, both of which can be red flags to anyone who stops and reads the email closely,” he noted.
To avoid falling victim, users should remain vigilant, and be wary of entering any personal information – including Social Security numbers and the like – after clicking on a link in an email.
“Perform a second factor of authentication by calling or texting the email sender to confirm the requests are legitimate,” Anand pointed out. “Whenever possible, engage with emails related to money and data in a rational manner. Subject the email to an eye test that includes inspecting the sender name, sender email address, language within the email, and any logical inconsistencies within the email.”
Feds Sound Alarm Over Emotet Attacks on State, Local Govs
8.10.20 BigBrothers Threatpost
CISA warned already-strained public-sector entities about disturbing spikes in Emotet phishing attacks aimed at municipalities.
A dramatic uptick in Emotet phishing attacks since July has led the U.S. Cybersecurity and Infrastructure Security Agency (CISA) to issue a warning that state and local governments need to fortify their systems against the trojan.
“This increase has rendered Emotet one of the most prevalent ongoing threats,” the CISA alert, issued Tuesday, read.
The alarm comes at a time when municipalities are already strained, juggling the concurrent crises of the COVID-19 pandemic, widespread social unrest and a caustic election season. Emotet, which can load other malware and self-propagate, is the last thing they need.
Threatpost Webinar Promo Retail Security
Click to Register!
“Emotet is one of the reasons why you should never click on links in emails you don’t recognize,” Bryan Becker, product manager at WhiteHat Security, told Threatpost. “Among other things, Emotet turns your computer into a ‘bot’ or ‘zombie’ that can be controlled by the hacker group to perform other crimes — without your OS or anti-malware noticing – one of which is sending more spam emails infecting more people with Emotet.”
Since July, CISA’s executive branch security protection tool, the EINSTEIN Intrusion Detection System, has found more than 16,000 instances of Emotet activity. These attacks are being executed in phases, indicating “possible targeted campaigns,” according to CISA, using tainted .doc Word files to deliver the malware.
CISA also said that Emotet-related domains and IPs seemed to be the most common on ports 80, 8080 and 443.
“In one instance, traffic from an Emotet-related IP attempted to connect to a suspected compromised site over port 445, possibly indicating the use of Server Message Block [SMB] exploitation frameworks along with Emotet,” the CISA report added.
That attack-volume data tracks with what’s being observed across the rest of the world. According to Check Point, the Emotet trojan tops its index of the most potent threats in circulation for the third consecutive month: It impacted 14 percent of organizations globally, followed by Trickbot at 4 percent and Dridex at 3 percent.
CISA Tracks the Threat
Starting last February, CISA said cybercriminals were targeting foreign countries using COVID-19 phishing emails to deliver malware. By July, researchers saw those emails and Emotet URLs being targeted against U.S. business, once again using COVID-19 communications for cover.
In August, CISA saw a 1,000-percent spike in Emotet loader downloads, and the attacks started to include state and local governments. By September, Canada, France, Japan, New Zealand, Italy and the Netherlands had seen breaches by Emotet, which then dropped Trickbot to deliver ransomware, and Qakbot trojans to steal banking information and other sensitive data.
Researchers also have noticed that Emotet has picked up a couple of new tricks over the course of the year. First, Emotet’s attachments started to include password-protected archive files to bypass email security gateways. Soon after, Palo Alto Networks reported to CISA that researchers are now seeing instances of “thread jacking” — that is, intercepting an existing email chain via an infected host and simply replying with an attachment to deliver the malware to an unsuspecting recipient.
And the threat isn’t limited to desktop computers. Steve Banda, senior manager of security solutions at Lookout, told Threatpost Emotet has gone mobile this year.
“While the Emotet is an advanced trojan primarily seen to affect desktops, our data shows mobile users encountering phishing attacks at a rate of over 30 percent on their personal devices,” Banda said. “It’s become more evident through our threat research that adversaries are extending their attacks to mobile. In many cases, desktop and mobile malware will have connections to the same command-and-control infrastructure. Cybercriminals are taking full advantage of this expanded attack surface.”
Local municipalities, from tribal and territorial governments to state authorities, as well as private businesses, are being encouraged by CISA to review existing security protocols and make necessary updates to prepare for the next Emotet phishing attempt.
Emotet, an Evolving Threat
Emotet was first detected in 2014 as a threat targeted at banks. But it has continued to evolve into something much more widespread and sophisticated, with the ability to deliver a range of secondary malware to compromised systems. In late 2019 it re-emerged with new social-engineering tools and the novel ability to customize phishing emails with messages tied to recent holidays, headlines and happenings. This version of Emotet also added an export function.
In February, the trojan got a code makeover and gained the ability to spread over Wi-Fi Networks.
But later that same month, researcher James Quinn with Binary Defense won a brief victory over Emotet, when he was able to exploit a vulnerability and develop a killswitch, shutting the malware down until early August, Threatpost reported. There’s also an anonymous vigilante combating Emotet by replacing payloads with memes and GIFs.
Despite those, and other, efforts, Emotet continues to proliferate. In fact, earlier in October it was spotted hitting hundreds of U.S. organizations with emails purporting to come from the Democratic National Committee, in a new politically charged spear-phishing attack.
“It’s mature, having been around in various forms since 2014, but it is always mutating and continues to evade detection by antivirus (AV),” Mark Kedgley, CTO at New Net Technologies, told Threatpost. “It has strong downloader capabilities, so it’s a carrier or conduit for other hacking tools and malware, such as credential-theft or ransomware. And it has worm capabilities too, designed to spread the malware laterally within a network once it has breached defenses, usually via phishing.”
The key for local governments trying to protect their systems, Kedgley said, is to understand the nature of the threat.
“Because of the polymorphic nature of Emotet, AV and other signature-based detection technologies will not be effective,” he said. “Therefore, the best action is to harden the infrastructure and reduce functionality used to infect systems, and also to leverage breach-detection capabilities…which will place a trojan like this right in the cross-hairs.”
CISA also offered mitigation best practices like blocking email attachments associated with malware, blocking attachments which can’t be scanned by antivirus software, using multifactor authentication and restricting browser access to risky sites.
BAHAMUT Spies-for-Hire Linked to Extensive Nation-State Activity
8.10.20 BigBrothers Threatpost
Researchers uncovered a sophisticated, incredibly well-resourced APT that has its fingers in wide-ranging espionage and disinformation campaigns.
A cyberespionage group known as BAHAMUT has been linked to a “staggering” number of ongoing attacks against government officials and private-sector VIPs in the Middle East and South Asia, while also engaging in wide-ranging disinformation campaigns.
That’s according to BlackBerry researchers, who said that the highly resourced group is probably operating on a mercenary basis, offering their services to the highest bidder.
“BAHAMUT is behind a number of extremely targeted and elaborate phishing and credential-harvesting campaigns, hundreds of new Windows malware samples, use of zero-day exploits, anti-forensic/AV evasion tactics, and more,” said Eric Milam, vice president of research operations at BlackBerry, in a report issued on Wednesday.
He added, “They rely on malware as a last resort, are highly adept at phishing, tend to aim for mobile phones of specific individuals as a way into an organization, show an exceptional attention to detail and above all are patient – they have been known to watch their targets and wait for a year or more in some cases.”
Researchers also found that BAHAMUT is running reams of fake-news entities – ranging from fraudulent social-media personae to stewarding entire news websites built to include disinformation.
“The sophistication and sheer scope of malicious activity that our team was able to link to BAHAMUT is staggering,” said Milam.
BAHAMUT – the name, in Arabic lore, of a sea monster that provides the support structure that holds up the earth – focuses mainly on carrying out classic espionage activity, according to researchers.
Mobile and Phishing Cyberattacks
While it distributes custom Windows malware and uses various zero-days, the group has notably recently embraced mobile: The report uncovered nine malicious iOS applications that had been available in the Apple App Store, and an assortment of Android applications that BlackBerry said are “directly attributable” to BAHAMUT, based on unique fingerprints.
“The applications were complete with well-designed websites, privacy policies and written terms of service – often overlooked by threat actors – which helped them bypass safeguards put in place by both Google and Apple,” the researchers said.
The apps in reality functioned as backdoors, with espionage capabilities that fluctuated across samples. All of them had the ability to enumerate filetypes on the devices and upload any potential file of interest. Other functionalities included the ability to enumerate device information, access contacts, access call records, access SMS messages, record phone calls, record audio, record video, download and update the backdoor, and track GPS location, researchers said.
They added that some of the targets for the mobile apps were specific to the United Arab Emirates (downloads were region-locked to the UAE); also, they observed Ramadan-themed applications and those pertaining to a Sikh separatist movement.
Phishing is another part of the group’s core competency, and its methods are unique.
“BAHAMUT’s phishing and credential harvesting tradecraft is significantly better than the majority of other publicly known APT groups,” the firm noted. “This is principally due to the group’s speed, their dedication to single-use and highly compartmentalized infrastructure, and their ability to adapt and change, particularly when their phishing tools are exposed.”
The phishing exercises that the group carries out for credential harvesting happen only after “concerted and robust reconnaissance operations” aimed at very precise targets, researchers noted.
BAHAMUT also stands up new phishing infrastructure on an ongoing basis, with targeted spear-phishing operations lasting anywhere from a few hours to a few months, depending on the domain and success rates.
“This embrace of ever-fleeting infrastructure makes real-time detection all but impossible,” according to the report.
Fake Websites for Attacks and Disinformation
In addition to its more traditional efforts, BAHAMUT is also distinctive in its use of original, painstakingly crafted websites, applications and personae to carry out cyberattacks, as well as spread fake news and misinformation, according to researchers.
Dozens of the fake sites were seen to serve up malware or exploits; while others tied into BAHAMUT phishing servers, or acted as command-and-control domains for BAHMAUT backdoors.
On the disinformation front, several of the fake websites researchers identified deal directly with a common theme: The 2020 Sikh Referendum, which has been a hotbed issue within India since late last year. This is essentially a secessionist movement, the brainchild of an organization called “Sikhs for Justice” (SFJ), which was banned by the government of India in July of 2019.
In some cases, social-media accounts were created and linked to the news sites, to make them seem more legitimate.
One site, called Techsprouts, was once a legitimate technology news site run by a journalist from India, which is now defunct. Its purpose left researchers scratching their heads.
“The group took over the domain of what was originally an information security news website and began pushing out content focused on geopolitics, research, industry news about other hack-for-hire groups,” according to the report – along with news about exploit brokers like the NSO Group.
Fake contributor to Techsprouts. Source: BlackBerry
“Within the past year…BAHAMUT appears to have re-registered the Techsprouts domain and continued to operate it,” according to the report – which added that the new site has an impressive list of “contributors.”
“Their biographies are impressive, but upon further inspection, it is apparent that the thumbnail photos of each author seen throughout the site have been appropriated from other sites and other people with quite different names,” the report explained. “For example, the image of ‘Alice Jane,’ a senior writer, was actually that of Julie Luck, the evening anchor at the local CBS station in Greensboro, N.C.”
In this case, the content isn’t overtly fake or malicious, leaving researchers wondering what its purpose is.
“[Other researchers] posited that the group used sites like this (though not Techsprouts specifically) as a way to discern the click habits of their targets,” according to the report. “BlackBerry is unable to verify this theory, though it certainly seems well within the realm of possibility.”
Hackers for Hire
The group overall is using a wide range of tools, tactics and techniques (TTPs), and researchers said that “at least one zero-day developer reflects a skill-level beyond most other known threat-actor groups today” – all of which suggests that the group is extremely well-funded and well-resourced.
This is borne out further by BAHAMUT’s startlingly good operational security (OpSec). Notably, there is no domain or IP address cross-over between operational functions in the group’s current tradecraft.
“We find, for example, that no domains or IP addresses used to control or distribute Windows malware are used for phishing or to administer malware designed for any other operating system,” according to the report. “Similarly, it is rare that any single server is used for more than a single mobile application at any given time. BAHAMUT ensures that no hosting provider is leveraged too heavily and spreads its current active infrastructure across more than 50 different hosting providers, thereby ensuring operational continuity if any single campaign is identified or a set of malware samples is disclosed. This is likely enormously time consuming, expensive, and requires considerable attention to detail.”
As for the victimology, apart from somewhat clustered targeting in South Asia and the Middle East, the targets run the gamut in terms of political ideology, which lends credence to the “hacker for hire” theory – the targeting “is all over the place,” according to researchers.
In looking at code-based similarities and unique string-based similarities, researchers said they was able to connect the dots between shadowy, “unsolved” APT incidents that have been spotted going back for years.
“BAHAMUT leverages publicly available tools, imitates other threat groups and changes its tactics frequently, which has made attribution difficult in the past,” researchers said. “However, BlackBerry reports with high confidence that the threat group is behind exploits researched by over 20 different security companies and nonprofits.”
Specifically, the threat groups identified as EHDevel, Windshift, Urpage and the White Company, along with the unnamed threat group in Kaspersky’s 2016 “InPage zero-day” research.
In all, given the extensive capabilities, links to disparate nation-state-linked APT activity, and lack of focused targeting, researchers concluded that BAHAMUT is one sprawling group that sells services to the highest bidder, including governments.
“Operational security will become increasingly important as more and more intelligence functions are outsourced by governments, corporations, and private individuals to groups like BAHAMUT,” according to the report. “These third parties add a layer of plausible deniability for those who employ them.”
Google’s Chrome 86: Critical Payments Bug, Password Checker Among Security Notables
8.10.20 Security Threatpost
Google is rolling out 35 security fixes, and a new password feature, in Chrome 86 versions for Windows, Mac, Android and iOS users.
Google’s latest version of its browser, Chrome 86, is now being rolled out with 35 security fixes – including a critical bug – and a feature that checks if users have any compromised passwords.
As of Tuesday, Chrome 86 is being promoted to the stable channel for Windows, Mac and Linux and will roll out over the coming days. The versions of the browser for Android and iOS were also released Tuesday, and will become available on Google Play and the App Store this week.
Threatpost Webinar Promo Retail Security
Click to Register!
Included in the newest browser version is a critical flaw (CVE-2020-15967) existing in Chrome’s payments component. The flaw, reported by Man Yue Mo of GitHub Security Lab, is a use-after-free vulnerability. Use after free is a memory-corruption flaw where an attempt is made to access memory after it has been freed. This can cause an array of malicious impacts, from causing a program to crash, to potentially leading to execution of arbitrary code.
Use-after-free bugs have plagued Google Chrome in the past year. In fact, all seven high-severity vulnerabilities fixed by Google in Chrome 86 were use-after-free flaws – ranging from ones affecting Chrome’s printing (CVE-2020-15971), audio (CVE-2020-15972), password manager (CVE-2020-15991) and WebRTC (CVE-2020-15969) components (WebRTC is a protocol for rich-media web communication).
Further details of the bugs are not yet available, as “access to bug details and links may be kept restricted until a majority of users are updated with a fix,” according to Google’s Tuesday post.
Password Check
The Android and iOS versions of Chrome 86 will also come with a new security feature, which will send a copy of user’s usernames and passwords using a “special form of encryption.” That then lets Google check them against list of passwords known to be compromised.
“Passwords are often the first line of defense for our digital lives,” Abdel Karim Mardini, senior product manager with Chrome, said in a Tuesday post. “Today, we’re improving password security on both Android and iOS devices by telling you if the passwords you’ve asked Chrome to remember have been compromised, and if so, how to fix them.”
At the back end, when Google detects a username and password exposed by a data breach, it stores a strongly hashed and encrypted copy of the data. Then, when Chrome users log into a website, the feature sends a strongly hashed and encrypted version of their username and password to Google – meaning the company never derives usernames or passwords from the encrypted copy, it said.
Google then fetches the encrypted database of every “unsafe” username and password – and shares the same anonymous hash prefix of account detail, ensuring, it said, that the username and password details are not revealed during the process.
Google rolled out an iteration of this feature in 2019, when it unveiled the Password Checkup Chrome extension, to alert Chrome browser users of weak or compromised passwords. The company has now embedded this functionality directly into Chrome for Android and iOS for better ease of use. It has also added support for “well-known/change-password” URLs, letting Chrome take users directly to the right “change password” form after they’ve been alerted that their password has been compromised.
“We notify you when you have compromised passwords on websites, but it can be time-consuming to go find the relevant form to change your password,” said Mardini.
The password-reuse issue continues to be a staple problem in the security industry, and has led to a slew of attacks, most notably credential stuffing. A Google study released in August 2019 – which was actually based on data collected from Google’s Password Checkup Chrome extension – found that 1.5 percent – or 316,000 users – of website logins on the browser are utilizing already-hacked passwords.
Google’s password checkup feature joins other similar services including Have I Been Pwned and Mozilla’s Firefox Monitor in fighting against stolen password problems.
Other Features
Chrome 86 also comes with a slew of other security features, including Safety Check on iOS and Android. This feature is used to check for compromised passwords, tell users if Safe Browsing is enabled and whether the version of Chrome being run is updated with the latest security protections.
Chrome 86 will also include mixed-form warnings on desktop and Android to alert and warn users before submitting a non-secure form that’s embedded in an HTTPS page. And, the browser will now block or warn on some insecure downloads initiated by secure pages.
“Currently, this change affects commonly abused file types, but eventually secure pages will only be able to initiate secure downloads of any type,” according to Google.
Kraken fileless attack technique abuses Microsoft Windows Error Reporting (WER)
8.10.20 Attack Securityaffairs
An unidentified group of hackers is using a new fileless attack technique, dubbed Kraken, that abuses the Microsoft Windows Error Reporting (WER).
Malwarebytes researchers Hossein Jazi and Jérôme Segura have documented a new fileless attack technique, dubbed Kraken, that abuses the Microsoft Windows Error Reporting (WER) service. The hacking technique was employed by an unidentified hacking group to avoid detection.
“On September 17th, we discovered a new attack called Kraken that injected its payload into the Windows Error Reporting (WER) service as a defense evasion mechanism.” states the blog post published by Malwarebytes.
“That reporting service, WerFault.exe, is usually invoked when an error related to the operating system, Windows features, or applications happens.”
Threat actors employed anti-analysis and evasion techniques, including, code obfuscation and performing some checks for sandbox or debugger environments.
The threat actor that employed the Kraken technique, likely an APT group, launched a phishing attack that used messages with a .ZIP file attachment.
The .ZIP archive, titled, “Compensation manual.doc,” claims to contain information relating to worker compensation rights.
Upon opening the document, a macro is triggered, the malicious code uses a custom version of the CactusTorch VBA module to perform a fileless attack.
Unlike CactusTorch VBA that specifies the target process to inject the payload into it within the macro, but the threat actor behind this campaign modified the macro and specified the target process within the .Net payload.
The payload loaded is a .Net DLL internally named “Kraken.dll” and compiled on 2020-06-12.
This DLL acts as a loader that injects an embedded shellcode into WerFault.exe. According to the experts the loader has two main classes named “Kraken” and “Loader“.
The last shellcode in the attack chain is composed of a set of instructions that make an HTTP request to a hard-coded domain to download a malicious payload and inject it into a process.
At the time of the analysis, the hard-coded target URL of the malware was not reachable making it impossible to attribute the Kraken technique to a specific threat actor. However, Malwarebytes researchers have found some links with APT32, which is a Vietnam-linked cyberespionage group.
The APT32 group has been active since at least 2012, it has targeted organizations across multiple industries and foreign governments, dissidents, and journalists.
Since at least 2014, experts at FireEye have observed APT32 targeting foreign corporations with an interest in Vietnam’s manufacturing, consumer products, and hospitality sectors. The APT32 also targeted peripheral network security and technology infrastructure corporations, and security firms that may have connections with foreign investors.
Malwarebytes’s report includes Indicators of Compromise (IoCs).
'Smart' Male Chastity Device Vulnerable to Locking by Hackers: Researchers
8.10.20 Vulnerebility Securityweek
A security flaw in an internet-connected male chastity device could allow hackers to remotely lock it -- leaving users trapped, researchers have warned.
The Cellmate, produced by Chinese firm Qiui, is a cover that clamps on the base of the male genitals with a hardened steel ring, and does not have a physical key or manual override.
The locking mechanism is controlled with a smartphone app via Bluetooth -- marketed as both an anti-cheating and a submission sex play device -- but security researchers have found multiple flaws that leave it vulnerable to hacking.
"We discovered that remote attackers could prevent the Bluetooth lock from being opened, permanently locking the user in the device. There is no physical unlock," British security firm Pen Test Partners said Tuesday.
"An angle grinder or other suitable heavy tool would be required to cut the wearer free."
The firm also found other security flaws in the Cellmate -- listed for $189 on Qiui's website -- that could expose sensitive user information such as names, phone numbers, birthdays and location data.
"It wouldn't take an attacker more than a couple of days to exfiltrate the entire user database and use it for blackmail or phishing," PTP's Alex Lomas wrote in their report on the device.
"A number of countries have oppressive laws that may expose users of these types of devices to unwarranted interest from law enforcement and bigots."
Qiui did not immediately respond to AFP's request for comment.
PTP said it reached out to Qiui in April this year, identifying the flaws.
Qiui fixed most of the issues by updating the software, but left the older version active and its users still vulnerable, PTP added, saying other researchers had found similar issues.
Such smart sex toys and devices are among the wave of new "internet of things" products and appliances introduced in recent years that are online and capable of being operated remotely.
Their connectivity has also made them vulnerable to security breaches and privacy violations.
In 2017, the Canadian maker of a smart vibrator agreed to a multi-million-dollar settlement after it was sued for collecting sensitive user information, though it did not admit any wrongdoing.
Next year, cybersecurity firm SEC Consult reported multiple vulnerabilities that hackers could exploit to hijack and control a smartphone-controlled vibrator called Vibratissimo. Sensitive user data was also left exposed.
CISA Warns of Emotet Trojan Targeting State, Local Governments
8.10.20 BigBrothers Securityweek
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) warns of an increase in attacks targeting state and local governments with the Emotet Trojan.
Active for over a decade, Emotet is a Trojan mainly used to drop additional malware onto compromised systems. Previously, it also functioned as a banking Trojan and as an information stealer.
Emotet has been silent for nearly half a year in 2020, but resumed activity in July, with the number of attacks surrounding it surging the next month. In early August, Binary Defense security researchers revealed that a vaccine deployed in February kept Emotet away for six months.
In an alert published this week, CISA and the Multi-State Information Sharing & Analysis Center (MS-ISAC) explain that, since August, cyber-criminals have been increasingly targeting state and local governments with phishing emails meant to drop Emotet.
“Emotet is difficult to combat because of its “worm-like” features that enable network-wide infections. Additionally, Emotet uses modular Dynamic Link Libraries to continuously evolve and update its capabilities,” the alert reads.
According to CISA, approximately 16,000 Emotet-related alerts were observed since July, with the malware being executed in phases in what appear to be targeted campaigns. Malicious Word documents attached to phishing emails were used as the initial attack vector.
The agency also observed Emotet-related traffic over ports 80, 8080, and 443, as well as one instance where an Emotet-related IP attempted to connect over port 445, suggesting the possible use of Server Message Block (SMB).
In February and July, CISA says, Emotet was using COVID-19-themed phishing to target victims in the United States and abroad. In August, the malware operators changed tactics to improve campaign efficiency, and the number of attacks in the United States increased.
In September, the number of Emotet attacks surged worldwide, with the malware dropping Trickbot to deliver ransomware in some cases, or Qakbot to steal banking credentials and other information from victims.
Emotet operators also switched to using password-protected archives as attachments, to bypass email security gateways and security researchers noticed that hackers leveraged thread hijacking for the delivery of Emotet.
In their alert, CISA and MS-ISAC also provide a list of ATT&CK techniques that Emotet employs, along with Snort signatures to help with detection, and recommendations to network defenders (regardless of whether in federal, local, state, territorial, or tribal governments, or from the private sector) on how to improve security posture.
Android's October 2020 Security Update Patches 48 Vulnerabilities
8.10.20 Android Securityweek
The October 2020 security updates for Android patch a total of 48 vulnerabilities, including critical-severity flaws that affect Qualcomm closed-source components.
Twenty of the vulnerabilities described in the latest Android Security Bulletin were patched as part of the 2020-10-01 security patch level, the most important of which is a high-risk bug in System that could allow a remote attacker to gain additional permissions.
A total of ten issues were fixed in Android System this month, all rated high severity. Two of these are elevation of privilege bugs, while the remaining eight are information disclosure vulnerabilities.
Other impacted components include Android runtime (a high-risk elevation of privilege bug that could allow attackers to run arbitrary code), Framework (two elevation of privilege bugs and three information disclosure issues, all high severity), and Media Framework (three high-risk information disclosure and one medium-severity elevation of privilege).
The second part of this month’s update arrives on devices as the 2020-10-05 security patch level and addresses 28 bugs in Kernel (one flaw), MediaTek components (five issues), Qualcomm components (four vulnerabilities), and Qualcomm closed-source components (18 flaws).
While 22 of these bugs have a severity rating of high, six of the vulnerabilities in Qualcomm closed-source components were rated critical.
Devices that run a patch level of October 5 include fixes for all of the vulnerabilities mentioned above, as well as those addressed in previous monthly updates.
Pixel devices are automatically updated to the 2020-10-05 security patch level. No security patches specific to Pixel devices were released this month.
Last month, Google started rolling out Android 11, which arrived with various new security improvements, including many designed specifically for the work profile that has been present on the operating system since 2014.
Smoke and Mirrors – Hack-for-Hire Group Builds Fake Online Empire
8.10.20 Hacking Securityweek
Hack-for-hire group BAHAMUT managed to build a fake online empire to leverage in cyber-espionage operations targeting the Middle East and other regions around the world, BlackBerry reports.
Dubbed BAHAMUT, but also tracked as EHDEVEL, WINDSHIFT, URPAGE, and THE WHITE COMPANY, the cyber-espionage group was initially detailed in 2017, but its activity spans a much longer period of time.
In fact, the threat actor’s activities appear to have been described in several other reports that lack attribution, including a 2016 Kaspersky report on attacks exploiting InPage word processor vulnerabilities.
“BlackBerry assesses that the InPage zero-day exploit first identified by Kaspersky in 2016 and given CVE-2017-12824 but never attributed, was in fact used by BAHAMUT. We also assess that it was first developed by a Chinese threat group in 2009 for use in targeting a group in diaspora perceived to be a potential threat to the power of the Chinese Communist Party,” BlackBerry notes in a new report.
The threat actor was able to fly under the radar through the use of a large number of fake identities, including social media personas, websites, and applications, some of which had original content and were meant to distort reality, but did not immediately show a malicious purpose.
In fact, the use of original websites, applications, and personas across a wide array of industries and regions is what sets this group apart from similar threats. Its fake empire suggests legitimacy and is able to distort consumers’ perception of reality.
Furthermore, the adversary strives to ensure campaigns, network infrastructure, and phishing tools are kept separate, it builds anti-analysis tools directly into backdoors and exploit shellcode, and immediately changes tactics when exposed. The group is also believed to be re-using tools from other groups and to mimic their tradecraft, to hinder attribution.
BAHAMUT, BlackBerry says, has a diverse and long list of targets, including government officials, politicians, human rights activists and organizations, human rights NGOs, financial services and technology companies, Egypt-focused media and foreign press, military organizations, aerospace entities, and scholars.
The group mainly focuses on South Asia (particularly India and Pakistan) and the Middle East (UAE and Qatar in particular), but victims were also identified in China and Northern and Eastern Europe. The hackers appear to be avoiding targets located in the United States.
“BAHAMUT’s targeting is all over the map, which makes it difficult to concoct a single victimology. BAHAMUT appears to be not only well-funded and well-resourced, but also well-versed in security research and the cognitive biases analysts often possess. Taken together, these aspects present a considerable attribution challenge,” BlackBerry notes.
The group is also believed to have access to at least one zero-day developer and to be operating over a dozen malicious apps for Android and iOS. Some of these apps were previously mentioned by Trend Micro in a report on Urpage.
New applications were also identified, all accompanied by well-designed websites, privacy policies, and terms of service, thus increasing the sense of legitimacy. They were able to bypass Google’s static code safeguards and five of them were still in Google Play as of July 2020 (they appeared designed specifically for targets in UAE).
Several other websites were employed for the distribution of additional applications, including seven of which were being distributed in recent campaigns. These included VPN and compass applications, but also apps that catered to the Sikh separatist movement.
“A variety of modifications were made to the APKs we found, and most had limited to no detection in a commonly used malware repository. In most cases the APK files were comprised of completely legitimate code and well-known Android libraries which helped cloak the underlying activity from common static detection methods,” BlackBerry says.
A total of nine malicious iOS applications attributed to BAHAMUT were identified in the Apple App Store, all of which were still available as of August 2020. The apps had generic themes with universal appeal: messaging, VOIP, prayer, file management, and password saver applications.
According to BlackBerry, the threat actor also masters the art of phishing, at a level superior to other groups, with targeted spear-phishing operations lasting anywhere between a few hours to months. Additionally, the adversary has the ability to learn from its mistakes and constantly improves its tradecraft.
The security firm, which claims to have “a solid grasp of BAHAMUT’s existing infrastructure,” assesses that BAHAMUT is a hack-for-hire group, just as independent security researchers Collin Anderson and Claudi Guarnieri suggested before.
“For a group that historically set themselves apart by employing above-average operational security and extremely skilled technical capabilities, BAHAMUT operators are, at the end of the day, still human. While their mistakes have been few, they have also proven devastating. BlackBerry found that the idiom “old habits die hard” applies to even the most advanced of threat groups,” BlackBerry concludes.
ALERT! Hackers targeting IoT devices with a new P2P botnet malware
8.10.20 BotNet IoT Thehackernews
Cybersecurity researchers have taken the wraps off a new botnet hijacking Internet-connected smart devices in the wild to perform nefarious tasks, mostly DDoS attacks, and illicit cryptocurrency coin mining.
Discovered by Qihoo 360's Netlab security team, the HEH Botnet — written in Go language and armed with a proprietary peer-to-peer (P2P) protocol, spreads via a brute-force attack of the Telnet service on ports 23/2323 and can execute arbitrary shell commands.
The researchers said the HEH botnet samples discovered so far support a wide variety of CPU architectures, including x86(32/64), ARM(32/64), MIPS(MIPS32/MIPS-III), and PowerPC (PPC).
The botnet, despite being in its early stages of development, comes with three functional modules: a propagation module, a local HTTP service module, and a P2P module.
Initially downloaded and executed by a malicious Shell script named "wpqnbw.txt," the HEH sample then uses the Shell script to download rogue programs for all different CPU architectures from a website ("pomf.cat"), before eventually terminating a number of service processes based on their port numbers.

The second phase commences with the HEH sample starting an HTTP server that displays the Universal Declaration of Human Rights in eight different languages and subsequently initializing a P2P module that keeps track of the infected peers and allows the attacker to run arbitrary shell commands, including the ability to wipe all data from the compromised device by triggering a self-destruct command.
Other commands make it possible to restart a bot, update the list of peers, and exit the current running bot, although an "Attack" command is yet to be implemented by the botnet authors.
"After the Bot runs the P2P module, it will execute the brute-force task against the Telnet service for the two ports 23 and 2323 in a parallel manner, and then complete its own propagation," the researchers said.
In other words, if the Telnet service is opened on port 23 or 2323, it attempts a brute-force attack using a password dictionary consisting of 171 usernames and 504 passwords. On a successful break-in, the newly infected victim is added to the botnet, thereby amplifying it.
"The operating mechanism of this botnet is not yet mature, [and] some important functions such as the attack module have not yet been implemented," the researchers concluded.
"With that being said, the new and developing P2P structure, the multiple CPU architecture support, the embedded self-destruction feature, all make this botnet potentially dangerous."
John McAfee has been arrested in Spain and is awaiting extradition
7.10.20 Crime Securityaffairs
The legendary cyber security expert John McAfee has been indicted on charges of tax evasion by the DoJ, authorities arrested him in Spain
The popular cyber security expert and cryptocurrency evangelist John McAfee has been indicted on charges of tax evasion by the Department of Justice (DOJ). The expert has been arrested in Spain and is awaiting extradition.

According to the indictment, the expert earned millions in income from promoting cryptocurrencies, consulting work, speaking engagements, and selling the rights to his life story for a documentary.
The authorities claim that the McAfee failed to file tax returns for incomes related to a period between 2014 and 2018.
“From 2014 to 2018, McAfee allegedly failed to file tax returns, despite receiving considerable income from these sources.” reads the press release published by DoJ.
“According to the indictment, McAfee allegedly evaded his tax liability by directing his income to be paid into bank accounts and cryptocurrency exchange accounts in the names of nominees.”
The investigators suppose that the income was directed into bank accounts and cryptocurrency exchange accounts in the names of nominees.
According to prosecutors, McAfee allegedly attempted to evade the IRS by concealing assets, including real property, a vehicle, and a yacht, in the names of others.
The indictment does not allege that during these years McAfee received any income or had any connection with the anti-virus company bearing his name.
The DoJ announced the charges after the US Securities and Exchange Commission (SEC) also charged McAfee with fraudulently touting ICOs.
“The Securities and Exchange Commission today charged businessman and computer programmer John McAfee for promoting investments in initial coin offerings (ICOs) to his Twitter followers without disclosing that he was paid to do so.” reads the SEC’s press release.
“According to the SEC’s complaint, McAfee promoted multiple ICOs on Twitter, allegedly pretending to be impartial and independent even though he was paid more than $23 million in digital assets for the promotions.”
McAfee could face a maximum sentence of five years in prison on each count of tax evasion and a maximum sentence of one year in prison on each count of willful failure to file a tax return. The popular expert also faces a period of supervised release, restitution, and monetary penalties.
Let’s remind that a defendant is presumed innocent until proven guilty beyond a reasonable doubt.
A sophisticated cyberattack hit the International Maritime Organization (IMO)
7.10.20 BigBrothers Securityaffairs
The United Nations International Maritime Organization (IMO) disclose a cyber attack that disrupted its IT systems.
The United Nations International Maritime Organization (IMO) is a global standard-setting authority for the safety, security and environmental performance of international shipping. The UN Maritime Organization is the United Nations that develops a regulatory framework that is adopted on a global scale to ensure the safety and security of shipping and the prevention of marine and atmospheric pollution by ships.
According to the agency, a first cyberattack caused the unavailability of the IMO website, and other web services on September 30.
The agency initially attributed the problem to technical issues, but on October 2, it revealed that the real cause of the problems was a cyberattack.
“A number of IMO’s web-based services became unavailable on Wednesday 30 September. The systems impacted included the IMO public website and other web-based services.” reads a statement published by the organization on its website.
“The email system, including other Internal and external collaboration platforms, are working as normal. The platform used for virtual meeting with simultaneous interpretation has been unaffected and continued to function, without issue, during Wednesday’s Facilitation Committee (FAL) session and is expected to continue to function during today’s final FAL session.”
The access to the website www.imo.org has been restored on Friday 2 October. Initial investigation revealed that the IT systems at the IMO was hit by a sophisticated cyber-attack.
“The interruption of web-based services was caused by a sophisticated cyber-attack against the Organization’s IT systems that overcame robust security measures in place.” continues the statement.
IMO did not share technical details about the attack, the Secretariat is working with international security experts to identify the source of the attack, and further enhance the security of its infrastructure.
At the end of September, the French maritime transport and logistics giant CMA CGM S.A. revealed it was the victim of a malware attack that affecting some servers on its network.
The company currently ranks fourth behind Maersk Line, MSC, and COSCO Shipping Lines, all companies that have been curiously hit by malware attacks in the past.
CISA alert warns of Emotet attacks on US govt entities
7.10.20 BigBrothers Securityaffairs
The CISA agency is warning of a surge in Emotet attacks targeting multiple state and local governments in the US since August.
The Cybersecurity and Infrastructure Security Agency (CISA) issued an alert to warn of a surge of Emotet attacks that have targeted multiple state and local governments in the U.S. since August.
During that time, the agency’s EINSTEIN Intrusion Detection System has detected roughly 16,000 alerts related to Emotet activity.
According to the experts from CISA the Emotet attacks were targeted on US government entities.
The Emotet banking trojan has been active at least since 2014, the botnet is operated by a threat actor tracked as TA542. In the middle-August, the malware was employed in fresh COVID19-themed spam campaign
Recent spam campaigns used messages with malicious Word documents, or links to them, pretending to be an invoice, shipping information, COVID-19 information, resumes, financial documents, or scanned documents.
The infamous banking trojan is also used to deliver other malicious code, such as Trickbot and QBot trojan or ransomware such as Conti (TrickBot) or ProLock (QBot).
Emotet is a modular malware, its operators could develop new Dynamic Link Libraries to update its capabilities.
The alert published by CISA was based on data provided by the Multi-State Information Sharing & Analysis Center (MS-ISAC) and the CISA itself since July 2020.
“Since August, CISA and MS-ISAC have seen a significant increase in malicious cyber actors targeting state and local governments with Emotet phishing emails. This increase has rendered Emotet one of the most prevalent ongoing threats.” reads that alert published by CISA.
“To secure against Emotet, CISA and MS-ISAC recommend implementing the mitigation measures described in this Alert, which include applying protocols that block suspicious attachments, using antivirus software, and blocking suspicious IPs.”
According to CISA, the surge in the attacks has rendered this malware one of the most prevalent ongoing threats.
In mid-September, cybersecurity agencies across Asia and Europe warned of Emotet spam campaigns targeting businesses in France, Japan, and New Zealand. At the end of September, agencies in Italy and the Netherlands, and researchers from Microsoft issued new alerts about the spike in Emotet activity.
CISA and MS-ISAC recommend admins and users to use antimalware solutions to block suspicious attachments and to block suspicious IPs addresses.
The report includes mitigations, Indicators of Compromise (IoCs) and MITRE ATT&CK Techniques.
Iran-linked APT is exploiting the Zerologon flaw in attacks
6.10.20 APT Securityaffairs
Microsoft researchers reported that Iranian cyber espionage group MuddyWater is exploiting the Zerologon vulnerability in attacks in the wild.
Microsoft published a post and a series of tweets to warn of cyber attacks exploiting the Zerologon vulnerability carried out by the Iran-linked APT group known as MuddyWater, aka Mercury.
The Zerologon vulnerability, tracked as CVE-2020-1472, is an elevation of privilege that resides in the Netlogon. The Netlogon service is an Authentication Mechanism used in the Windows Client Authentication Architecture which verifies logon requests, and it registers, authenticates, and locates Domain Controllers.
An attacker could exploit the vulnerability to impersonate any computer, including the domain controller itself, and execute remote procedure calls on their behalf.
An attacker could also exploit the flaw to disable security features in the Netlogon authentication process and change a computer’s password on the domain controller’s Active Directory.
The only limitation on how to carry out a Zerologon attack is that the attacker must have access to the target network.
Administrators of enterprise Windows Servers have to install the August 2020 Patch Tuesday to mitigate “unacceptable risk” posed by the flaw to federal networks.
According to Microsoft’s Threat Intelligence Center (MSTIC) the attacks exploiting this vulnerability surged since September 13.

“One of the adversaries noticed by our analysts was interesting because the attacker leveraged an older vulnerability for SharePoint (CVE-2019-0604) to exploit remotely unpatched servers (typically Windows Server 2008 and Windows Server 2012) and then implant a web shell to gain persistent access and code execution.” reads the analysis published by Microsoft. “Following the web shell installation, this attacker quickly deployed a Cobalt Strike-based payload and immediately started exploring the network perimeter and targeting domain controllers found with the ZeroLogon exploit.”
Microsoft linked the attacks to the Iranian cyberespionge group MERCURY, also known as MuddyWater, SeedWorm and TEMP.Zagros.
The first MuddyWater campaign was observed in late 2017 when targeted entities in the Middle East.
The experts called the campaign ‘MuddyWater’ due to the confusion in attributing a wave of attacks that took place between February and October 2017 targeting entities in Saudi Arabia, Iraq, Israel, United Arab Emirates, Georgia, India, Pakistan, Turkey, and the United States to date.
The group evolved over the years by adding new attack techniques to its arsenal.
Microsoft publicly shared some file indicators for the attacks along with variations of the ZeroLogon exploits its experts have detected. Many of these exploits were recompiled versions of well-known, publicly available proof-of-concept code. Microsoft pointed out that MS Defender for Endpoint can also detect certain file-based versions of the CVE-2020-1472 exploit when executed on devices protected by Microsoft Defender for Endpoints.
The MuddyWater attackers have begun around one week after the first proof-of-concept code was published, and Microsoft began detecting the first Zerologon exploitation attempts.
At the time, the Department of Homeland Security’s CISA issued an emergency directive to order government agencies to address the Zerologon vulnerability (CVE-2020-1472) by Monday, September 21.
Analyzing the evolution of MageCart cybercrime groups’ TTPs
6.10.20 CyberCrime Securityaffairs
Researchers from RiskIQ and FlashPoint analyzed the evolution of Magecart groups, in particular of a gang tracked as Group 4 that appears to be very sophisticated.
Security firms have monitored the activities of a dozen Magecart groups at least since 2015. The gangs use to implant skimming script into compromised online stores in order to steal payment card data on, but they are quite different from each other.
According to a joint report published by RiskIQ and FlashPoint, some groups are more advanced than others, in particular, the gang tracked as Group 4 appears to be very sophisticated.
Experts at RiskIQ, was able to discover and bring down parts of the infrastructure used by the Magecars Group 4, the researchers were also able to monitor the evolution of the gang across the time.
The group uses about one hundred domains registered and a pool of servers to route traffic and deliver the skimming code to victims.
“Group 4 is advanced. Once the group has access, it is extremely careful about how it places the skimmer. This group focuses on high volumes of compromises with the goal of getting as many cards as possible without specific targeting. However, it doesn’t shy away from targeting altogether.” states the report.
“The way Group 4 uses its skimmer is different from other Magecart groups. The skimmer isn’t shown to just anyone—you can’t request it without knowing a victim and having a valid user-agent at the bare minimum. However, there’s more to it.”
The researchers consider this gang as one of the most advanced Magecart groups, they argue it originates from another crime business involved in malware distribution and hijacking of banking sessions using web injects.
As said the Group 4 evolved tactics, it uses only up to five domains associated with a single IP address.
“The domains associated with Group 4’s skimming operation are simply proxies pointing towards a large internal network. After applying some initial filtering, these proxies upstream skimmer requests towards a backend that provides the skimmer script (or benign script when a visitor isn’t performing a payment),” reads a blog post published by RiskIQ.
Magecart gangs attempt to hide the skimmer on a payment page by using
multiple benign libraries, experts observed a continuous update for the skimmer, vxers constantly implements new features.
The latest version of the skimmer is only 150 lines of code, which is ten times less than the first release, anyway, it implements more event listeners to hook into the payment process and steal payment card data.
“The previous version of Group 4’s skimmer wasn’t actually a skimmer—it was an overlay payment phishing system.” wrote the experts.
“Group 4’s new skimmer also adds one more event listener to hook into the process of the payment-completion process. Usually, this involves a ‘submit button’ of some kind, but In this case, they hook the keyboard key-events and search for usage of the return/enter key. This is just one more option they added to the skimmer with a feature flag which, until now, we have only seen turned off, which likely indicates Group 4 is still experimenting with it.”
The experts also observed that coders deactivated some feature, a circumstance that suggests that are making some tests with their skimmer.
The option comes deactivated, which supports the theory that it starts as an experiment.
Experts observed an improvement in the way the exfiltration URL is created, it uses a pre-configured domain and passes the exfiltrated payment data as arguments. The URL is included as an image element and removed after it’s loaded.
Initially the data was encoded using the base64 scheme, currently, Magecart hackers use RSA public-private key cryptography before the base64 encoding process.
The list of victims of Magecart groups is long and includes several major platforms such as British Airways, Newegg, Ticketmaster, and Feedify.
Further information, including IoCs associated with different groups, are reported in the analysis published by the experts.
Fullz House hacked the website of Boom! Mobile provider to steal credit cards
6.10.20 Hacking Securityaffairs
The credit card skimming group Fullz House has compromised the website of US mobile virtual network operator (MVNO) Boom! Mobile.
The credit card skimming group Fullz House has compromised the website of US mobile virtual network operator (MVNO) Boom! Mobile in a classic MageCart attack.
Boom! Mobile offers postpaid and prepaid no-contract wireless service plans to its customers that allow them to use the lines of the nation’s largest cellular networks including AT&T, T-Mobile, and Verizon.
The Fullz House hackers injected an e-skimmer into the website and unfortunately, the malicious software has yet to be removed.
The e-skimmer was first spotted by researchers at Malwarebytes’ Threat Intelligence Team, the researchers noticed a single line of code that is used to load an external JavaScript library from paypal-debit[.]com/cdn/ga.js.
“Our crawlers recently detected that their website, boom[.]us, had been injected with a one-liner that contains a Base64 encoded URL loading an external JavaScript library.” reads the analysis published by Malwarebytes. “Once decoded, the URL loads a fake Google Analytics script from paypal-debit[.]com/cdn/ga.js. We quickly recognize this code as a credit card skimmer that checks for input fields and then exfiltrates the data to the criminals.”
The malicious software collects payment card information provided by the users, then exfiltrates the harvested data as a Base64 encoded GET request.
Researchers believe that the Fullz House Magecart group has compromised the Boom’s website by exploiting a vulnerability in the PHP version 5.6.40 used by the company, which is no more supported since January 2019.
The experts attempted to report the compromise to Boom! Mobile without success.
The Fullz House group was first spotted by security experts at RiskIQ in November 2019, when it was using phishing and web skimming for its attacks. Since August-September of 2019, the group started using a hybrid technique that leverages on MiTM and phishing attacks to target sites using external payment processors.
Hacker groups under the Magecart umbrella continue to target to steal payment card data with so-called software skimmers. Security firms have monitored the activities of a dozen groups at least since 2010.
According to a joint report published by RiskIQ and FlashPoint in 2019, some groups are more advanced than others, in particular, the gang tracked as Group 4 appears to be very sophisticated.
MalwareBytes researchers also shared Indicators of Compromise for this attack in its analysis.
Cisco Ordered to Pay $1.9 Billion in Cybersecurity Patent Infringement Case
6.10.20 IT Securityweek
A US district judge has ordered Cisco to pay $1.9 billion to Centripetal Networks, Inc., for infringing on four patents related to cybersecurity.
Founded in 2009, Centripetal focuses on cyber threat intelligence, providing solutions that help organizations defeat cyber-attacks. The company has developed technology for operationalizing and automating threat intelligence and has been awarded various patents in the United States and abroad.
In a lawsuit filed in the Eastern District of Virginia in March 2018, the company claimed that numerous Cisco product series have been infringing on five of its patents for years.
“Cisco has willfully infringed each of the Asserted Patents. Centripetal is informed and believes that Cisco had knowledge of the Asserted Patents through various channels and despite its knowledge of Centripetal’s patent rights, engaged in egregious behavior warranting enhanced damages,” the company said in the initial filing.
The company also claimed that, although it knew of the Centripetal patented technology, Cisco continued to sell products infringing on those patents and made no effort to avoid infringement.
On Monday, District Judge Henry C. Morgan, Jr., ordered Cisco to pay a total of $1,903,239,287.50 to Centripetal, ruling that four of the five asserted patents were infringed.
Damages suffered by Centripetal amounted to $755,808,545, but Cisco’s infringement was “willful and egregious,” and the judge decided to multiply the figure by 2.5, to $1,889,521,362.50. To this, an interest of $13,717,925 is applied.
Furthermore, the court imposed a three-year running royalty of 10% of sales of the accused products and their successors, followed by a running royalty of 5% on those sales, for another three years. At the termination of the second three-year term, Centripetal won’t receive any further relief, the judge ruled.
Cisco expressed disappointment and said it would appeal the decision to the U.S. Federal Circuit Court of Appeals.
"We are disappointed with the trial court's decision given the substantial evidence of non-infringement, invalidity and that Cisco's innovations predate the patents by many years," Cisco said.
Microsoft Says Iranian Hackers Exploiting Zerologon Vulnerability
6.10.20 Exploit Securityweek
The Iran-linked threat actor known as MuddyWater is actively targeting the Zerologon vulnerability in Windows Server, Microsoft warns.
Also known as Seedworm, MERCURY, and Static Kitten, and initially analyzed in 2017, MuddyWater is mainly focused on organizations in the Middle East and regions nearby. Highly active, the group was observed expanding its target list and leveraging a broad and varied toolset.
Although further details on the threat actor’s operations emerged last year (after an unknown entity published documents on multiple Iranian groups), and despite security researchers’ scrutiny, MuddyWater continues to evolve its strategies.
According to Microsoft, one of the latest changes in the group’s tactics is the adoption of exploits for Zerologon, a Netlogon remote protocol (MS-NRPC) vulnerability that was addressed in August 2020.
By exploiting the bug, an unauthenticated attacker could gain domain administrator access, resulting in full takeover.
“MSTIC has observed activity by the nation-state actor MERCURY using the CVE-2020-1472 exploit (ZeroLogon) in active campaigns over the last 2 weeks. We strongly recommend patching,” Microsoft said on Twitter.
Both Microsoft and CISA previously issued alerts on attackers targeting the vulnerability, urging administrators to apply the available patches as soon as possible, to all domain controllers in their environments.
In fact, CISA even issued an Emergency Directive requiring all federal agencies to apply the patches immediately. Samba too released fixes for the bug.
The patching of this vulnerability will be done in two stages, Microsoft has revealed. The initial one involves applying the August 2020 fixes, while the second one is an enforcement phase that will start on February 9, 2021.
Last week, Microsoft also announced that the exploitation of Zerologon is now being detected by Microsoft Defender for Identity (previously Azure Advanced Threat Protection) and Microsoft 365 Defender (previously Microsoft Threat Protection).
EU Court Curbs Mass Phone Data Grab by Spy Agencies
6.10.20 BigBrothers Securityweek
The EU's top court on Tuesday put limits on how European spy and security agencies could harvest troves of personal data, but said this could be done under a serious threat to national security.
At the request of the courts in France, Belgium and Britain, the European Court of Justice confirmed that "EU law precludes national legislation" that requires telcos and tech companies to carry out the "indiscriminate retention" of data, a statement said
However, it does allow for exemptions in cases of "serious threat to national security" or the "fight against serious crime", under the supervision of a judge or an independent administrative authority.
This lifting of the ban would have to be "limited in time to what is strictly necessary," the court added.
The decision will be closely looked at by privacy activists who fear wide loopholes that would allow unfettered data spying by state agencies.
Data privacy is a highly sensitive issue in Europe, where activists have put the legality of Facebook and other big tech operations into jeopardy over similar concerns.
The legal onslaught began after revelations by Edward Snowden of mass digital spying by US agencies that also revealed cooperation with Washington by the UK's spy agencies.
The mass harvesting of data is a central part of anti-terror laws passed in several Western countries in the wake of September 11 and other attacks.
Rare Bootkit Malware Targets North Korea-Linked Diplomats
6.10.20 Attack Threatpost
The MosaicRegressor espionage framework is newly discovered and appears to be the work of Chinese-speaking actors.
A firmware bootkit has been spotted in the wild, targeting diplomats and members of non-governmental organizations (NGOs) from Africa, Asia and Europe. It has turned out to be part of a newly uncovered framework called MosaicRegressor.
According to researchers from Kaspersky, code artifacts in some of the framework’s components and overlaps in command-and-control (C2) infrastructure suggest that a Chinese-speaking group with connections to the Winnti backdoor is behind the attacks.
Kaspersky observed several dozen victims who received components from the MosaicRegressor framework between 2017 and 2019 – all of whom had ties to North Korea.
“Based on the affiliation of the discovered victims, we could determine that all had some connection to the DPRK, be it non-profit activity related to the country or actual presence within it,” Kaspersky said.
This focus on North Korea-related victims was reinforced by emails used to deliver the malware. These contained self-extracting (SFX) archives pretending to be documents discussing various subjects related to North Korea. Those were bundled with both an actual document and MosaicRegressor variants, both of which execute when the archive is opened.
Modifying UEFI Malware
Initially, the researchers discovered rogue UEFI firmware images within Kaspersky’s telemetry that were modified from their benign counterparts to incorporate several malicious modules.
“The modules were used to drop malware on the victim machines,” researchers explained, in a posting on Monday. “This malware was part of a wider malicious framework that we dubbed MosaicRegressor.”
UEFI is a specification that constitutes the structure and operation of low-level platform firmware, including the loading of the operating system itself. It can also be used when the OS is already up and running, for example in order to update the firmware.
“UEFI firmware makes for a perfect mechanism of persistent malware storage,” Kaspersky researchers explained. “A sophisticated attacker can modify the firmware in order to have it deploy malicious code that will be run after the operating system is loaded.”
A deeper inspection revealed that the malicious firmware images contained four components: Two [driver execution environment] DXE drivers and two UEFI applications. Delving even deeper, they found that the components were all based on a customized version of the leaked source code of HackingTeam’s VectorEDK bootkit.
“The goal of these added modules is to invoke a chain of events that would result in writing a malicious executable named ‘IntelUpdate.exe’ to the victim’s Startup folder,” according to the research. “Thus, when Windows is started, the written malware would be invoked as well.”
The team wasn’t able to determine the exact infection vector that allowed the attackers to overwrite the original UEFI firmware. However, options include physical access to the victim’s machine, using a malicious USB key with a special update utility, or a remote infection, perhaps through a compromised update mechanism.
“Such a [remote] scenario would typically require exploiting vulnerabilities in the BIOS update authentication process,” researchers said.
4 Components
One of the two uncovered DXE drivers is named Ntfs. It’s called such because it’s used to detect and parse the NT File System (NTFS), in order to conduct file and directory operations on the disk.
SmmReset meanwhile is a UEFI application intended to mark the firmware image as infected.
“This is done by setting the value of a variable named ‘fTA’ to a hard-coded [globally unique identifier] GUID,” researchers said. “The application is based on a component from the original Vector-EDK code base that is named ‘ReSetfTA.'”
The second DXE driver is called SmmInterfaceBase, and is based on Hacking Team’s “rkloader” component. It’s used as a first-stage tool to deploy the main bootkit component, SmmAccessSub, later on in the attack chain.
“This is done by registering a callback that will be invoked upon an event of type EFI_EVENT_GROUP_READY_TO_BOOT. The event occurs at a point when control can be passed to the operating system’s bootloader, effectively allowing the callback to take effect before it. The callback will in turn load and invoke the ‘SmmAccessSub’ component,” according to the research.
SmmAccessSub serves as a persistent dropper for a user-mode malware, and takes care of writing a binary embedded within it as a file named ‘IntelUpdate.exe’ to the startup directory on disk. This allows the binary to execute whenever Windows is up and running.
“This is the only proprietary component amongst the ones we inspected, which was mostly written from scratch and makes only slight use of code from a Vector-EDK application named ‘fsbg,'” researchers wrote.
SmmAccessSub Component
SMMAccessSub runs through a series of actions that culminate in dropping the IntelUpdate.exe file to disk, Kaspersky explained.
First, it bootstraps pointers for the SystemTable, BootServices and RuntimeServices global structures, and uncovers the currently loaded UEFI image. The module then attempts to find the root drive in which Windows is installed, and makes sure that the \Windows\System32 directory is present.
“A global EFI_FILE_PROTOCOL object that corresponds to the drive will be created at this point and referenced to open any further directories or files in this drive,” researchers said.
The module also looks for a marker file named ‘setupinf.log’ under the Windows directory and proceeds only if it doesn’t exist. It then creates a file with the same name, and goes on to check if the “Users” directory exists under the same drive.
If that directory exists, it writes the IntelUpdate.exe file (embedded in the UEFI application’s binary) under the ProgramData\Microsoft\Windows\Start Menu\Programs\Startup directory in the root drive.
The MosaicRegressor Framework
The IntelUpdate executable unpacks a new piece of malware, a downloader, which hadn’t been seen in the wild before, Kaspersky said. The analysts however were able to use code fingerprints to determine that the binary belongs to a wider, multi-stage and modular framework called MosaicRegressor.
This is “a framework aimed at espionage and data-gathering,” explained the researchers. “It consists of downloaders, and occasionally multiple intermediate loaders, that are intended to fetch and execute payload on victim machines….we were able to obtain only a handful of payload components during our investigation.”
Most of the components are merely downloaders that fetch other payloads. For instance, one installs in the autorun registry values and acts as another loader for components that themselves are also just intermediate loaders for the next stage DLLs.
Researchers said that this modular nature of the framework allows the attackers to conceal the wider framework from analysis, and deploy components to target machines only on demand.
Kaspersky did uncover one example of a late-stage component, an info-stealer called “load.rem.” It fetches files from the “Recent Documents” directory and archives them with a password, “likely as a preliminary step before exfiltrating the result to the C2 by another component,” according to Kaspersky.
Chinese-Language Attribution
Kaspersky suspects the threat actor to be Chinese-speaking, based on several pieces of forensic evidence.
For instance, certain strings used in the system-information log contain a Unicode character that appears to be translated from either the Chinese or Korean code pages. Also, the researchers found a file resource in some of the samples that contained a language identifier set to 2052 (“zh-CN”). They also uncovered the use of an OLE2 object-builder commonly used by Chinese-speaking threat actors.
Meanwhile, one of the C2 addresses used by one of MosaicRegressor’s variants has been observed in the past being used by the Winnti umbrella and linked groups, which are APTs that have been linked to the Chinese government.
“It is highly uncommon to see compromised UEFI firmware in the wild, usually due to the low visibility into attacks on firmware, the advanced measures required to deploy it…and the high stakes of burning sensitive toolset or assets when doing so. With this in mind, we see that UEFI continues to be a point of interest to APT actors, while at large being overlooked by security vendors.”
Malware Families Turn to Legit Pastebin-Like Service
6.10.20 Virus Threatpost
AgentTesla, W3Cryptolocker and Redline Stealer using Paste.nrecom
AgentTesla, LimeRAT, W3Cryptolocker and Redline Stealer are now using Paste.nrecom in spear-phishing attacks.
Cybercriminals are increasingly turning to a legitimate, Pastebin-like web service for downloading malware — such as AgentTesla and LimeRAT — in spear-phishing attacks.
Pastebin, a code-hosting service that enables users to share plain text through public posts called “pastes,” currently has 17 million unique monthly users and is popular among cybercriminals (such as the FIN5 APT group and Rocke threat group) for hosting their payloads or command-and-control (C2) infrastructure. But now, more malware and ransomware families are starting to utilize another service, with the domain Paste.nrecom[.]net.
This service been around since May 2014, and has a similar function as Pastebin. It also has an API (powered by open-source PHP based pastebin Stikked) that allows for scripting. Researchers with Juniper Networks said that the API feature is lucrative for cybercriminals, who can leverage it to easily insert and update their data programmatically.
“Although using legitimate web services is not novel, this is the first time that we have seen threat actors use paste.nrecom[.]net,” said Paul Kimayong, researcher with Juniper Networks, in a Monday analysis. “Among the malware we have identified are AgentTesla, LimeRAT, [W3Cryptolocker] Ransomware and Redline Stealer.”
AgentTesla RAT pastebin
The number of malware families using the new Pastebin-like service. Credit: Juniper Networks
Researchers said that the attacks utilizing the service generally start with a spear-phishing email that includes an attachment (such as a document, archive or an executable). The recipient is tricked into opening a malicious attachment (as the first stage of the attack), which then downloads the next stages from paste.nrecom[.]net.
“We have also seen malware hosting their configuration data in the same service,” said researchers.
AgentTesla is the most active malware family using this service, researchers said. The spyware is capable of stealing personal data from web browsers, mail clients and FTP servers, as well as collecting screenshots and videos, and capturing clipboard data.
Researchers highlighted specific AgentTesla campaigns that target multiple industries related to shipping, supply chains and banks, using spear-phishing emails with archive attachments (such as .iso, .rar or .uue). These attachments, once opened, then install AgentTesla using paste.nrecom.
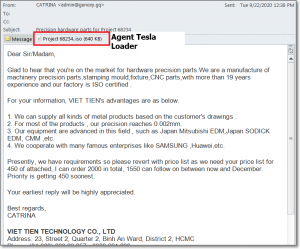
The AgentTesla malware attack that uses paste.nrecom. Credit: Juniper Networks
The developers of LimeRAT, an open-source remote administration trojan coded in .NET (used recently by the APT-C-36 group to target Colombian government institutions) have also utilized the web service to download malware.
Other, newer malware and ransomware are also turning to paste.nrecom. One of these is W3Cryptolocker, a relatively new ransomware that surfaced in July. Researchers found that the initial-stage loader was hosted on a potentially hacked site, italake.com. Once the loader was downloaded, W3Cryptolocker was executed, after which it encrypted most files in all drives and created a “Read_Me.txt” file on each folder with the ransom message.
And, Redline Stealer, a malware that surfaced as recently as March and has targeted healthcare and manufacturing firms in the U.S., also makes use of the service. Researchers said they found samples posing as a Bitcoin miner archived into a RAR file. The RAR file contained an executable (MinerBitcoin.exe) that downloaded the Redline Stealer payload from paste.nrecom.
Looking ahead, researchers warned that more malware families will turn to legitimate web services to host their malicious infrastructure.
“Using legitimate web-services like pastebin or paste.nrecom for malware infrastructure gives cybercriminals an advantage, as these services cannot be easily taken down due to their legitimate use,” said researchers.
Black-T Malware Emerges From Cryptojacker Group TeamTNT
6.10.20 Cryptocurrency Threatpost
The cryptojacking malware variant builds on the TeamTNT group’s typical approach, with a few new — and sophisticated — extras.
Researchers have discovered the latest cryptojacking malware gambit from TeamTNT, called Black-T. The variant builds on the group’s typical approach, with a few new — and sophisticated — extras.
TeamTNT is known for its targeting of Amazon Web Services (AWS) credentials, to break into the cloud and use it to mine for the Monero cryptocurrency. But according to researchers with Palo Alto Network’s Unit 42, with Black-T, the group has added in additional capabilities to its tactics, techniques and procedures (TTPs). These include the addition of sophisticated network scanners; the targeting of competitor XMR mining tools on the network; and the use of password scrapers.
What TeamTNT plans to do with the saved passwords and additional capabilities is still unclear, but the development signals that the group doesn’t plan to slow down anytime soon.
In August, TeamTNT was identified by researchers as the first cryptojacking group to specifically target AWS. With increasingly sophisticated TTPs, the cybercriminal gang appears to be gaining steady momentum. Just last month, TeamTNT was discovered to have been leveraging a common open-source cloud monitoring tool called Weave Scope, to infiltrate the cloud and execute commands without breaching the server.
Black-T represents a notable jump forward in the operation’s sophistication, researchers said.
Once deployed, the first order of business for Black-T is to disable any other malware competing for processing power, including Kinsing, Kswapd0, ntpd miner, redis-backup miner, auditd miner, Migration miner, the Crux worm and Crux worm miner. Ironically, the fact that TeamTNT identified these competitors in their malware gives security professionals a critical heads-up to be on the lookout for potential threats from these groups, Unit 42 said.
This kind of cyberjacking turf warfare isn’t new, but it appears to be accelerating.
“The battle for cloud resources will continue well into the future,” Nathaniel Quist, senior threat researcher for Unit 42 said. “In the past, attacker groups like Rocke and Pacha would battle for resources. TeamTNT is battling with Kinsing malware and Crux worm today. I believe that this battle for resources will increase and attacker groups will look for other opportunities to use cloud resources. We can see this now with TeamTNT collecting passwords and AWS credentials in an attempt to expand and maintain a cloud presence.”
After it eliminates the competition, Black-T installs masscan, libpcap to listen to various resources on the network, including pnscan, zgrab, Docker and jq (the latter is a flexible command-line JSON processor, according to Unit 42).
“TeamTNT is investing more resources into scanning operations, likely with the intent to identify and compromise more cloud systems,” Quist added. “Zmap is a known open-source scanning solution and with the creation of zgrab, a GoLang tool written for zmap, it is attempting to capitalize on the added benefits of the Go programming language, such as speed and performance increases. It is likely that TeamTNT actors are attempting to refine their scanning capabilities to make them faster, more accurate and less resource-intensive.”
Next, Black-T fetches various downloads: Beta to create a new directory; the mimipy and mimipenquin password scraping tools; and the XMR mining software called bd.
“The inclusion of memory password-scraping tools should be considered an evolution of tactics,” Quist said. “TeamTNT has already integrated the collection and exfiltration of AWS credentials from compromised cloud systems, which provides post-exploitation capabilities. By adding memory password-scraping capabilities, TeamTNT actors are increasing their chances in gaining persistence within cloud environments.”
The use of worms like masscan or pnscan by TeamTNT isn’t new, but Unit 42 noticed Black-T adds a new scanning port. Researchers wonder whether this signals the group has figured out how to target Android devices as well.
As remote work and cost savings continue to drive computing to the cloud, more groups like TeamTNT are sure to emerge ready to take advantage, according to Quist. Admins should take steps to ensure that Docker and daemon APIs, as well as any other sensitive network services, aren’t exposed, so that the cloud can be protected from the next evolution of cloud cryptojackers, he added.
Tenda Router Zero-Days Emerge in Spyware Botnet Campaign
6.10.20 BotNet Threatpost
A variant of the Mirai botnet, called Ttint, has added espionage capabilities to complement its denial-of-service functions.
Two former Tenda router zero-days are anchoring the spread of a Mirai-based botnet called Ttint. In addition to denial-of-service (DoS) attacks, this variant also has remote-access trojan (RAT) and spyware capabilities.
According to 360Netlab, the botnet is unusual in a few ways. For one, on the RAT front, researchers said that it implements 12 remote access functions, that combine with custom command-and-control (C2) server commands to carry out tasks like setting up a Socket5 proxy for router devices, tampering with router DNS, setting iptables and executing custom system commands.
In addition, Ttint also uses encrypted channels to communicate with the C2 – specifically, using the WebSocket over TLS (WSS) protocol. Researchers said that this allows the traffic to avoid detection while providing additional security.
And finally, the infrastructure seems to migrate. 360Netlab first observed the attackers using a Google cloud service IP, before switching to a hosting provider in Hong Kong.
Zero-Days
Tenda routers are available at big-box stores and are used in homes and small offices. The first vulnerability used to spread Ttint samples (CVE-2018-14558) has been exploited since at least November of last year; but it wasn’t disclosed until July. There’s now a firmware update available to address it.
The bug is a critical command-injection vulnerability, rated 9.8 out of 10 on the CvSS vulnerability-severity scale. It allows attackers to execute arbitrary OS commands via a crafted goform/setUsbUnload request. It arises because the “formsetUsbUnload” function executes a dosystemCmd function with untrusted input.
In late August, a second critical Tenda router vulnerability (CVE-2020-10987) emerged in the campaign. It’s also rated 9.8 out of 10 and was initially disclosed in July by Independent Security Evaluators, after it had tried since January to get a patch from Tenda. It was able to exploit the bug in order to cause a DoS condition.
The bug exists because the goform/setUsbUnload endpoint of Tenda AC15 AC1900 version 15.03.05.19 allows remote attackers to execute arbitrary system commands via the deviceName POST parameter, according to the CVE description.
360Netlab also tried to warn Tenda about issues with the bug, this time for use in botnet infections.
“On August 28, 2020, we reported the details of the second 0-day vulnerability and the PoC [proof of concept] to the router manufacturer Tenda via email, but the manufacturer has not yet responded,” researchers said.
Threatpost has reached out to the manufacturer for more information.
Ttint RAT
Ttint as a malware can carry out 10 typical Mirai DDoS attack instructions (including multiple attack vectors), along with 12 RAT instructions and 22 custom C2 commands that work together.
“Generally speaking, at the host level, Ttint’s behavior is relatively simple,” according to the researchers. “When running, it deletes its own files, manipulates the watchdog and prevents the device from restarting, it runs as a single instance by binding the port; then modifies the process name to confuse the user…it finally establishes a connection with the decrypted C2, reporting device information, waiting for C2 to issue instructions, and executing corresponding attacks or custom functions.”
Researchers said, among the most notable of the RAT functions is the command to bind a specific port issued by C2 to enable Socket5 proxy service. This allows attackers to remotely access the router’s intranet, and roam across the network.
“Generally speaking, Ttint will combine multiple custom functions to achieve specific attack goals,” the researchers explained. “Take the two adjacent commands we captured, the first command is iptables -I INPUT -p tcp –dport 51599 -j ACCEPT, to allow access to port 51599 of the affected device. The next command is to enable the Socket5 proxy function on port 51599 of the affected device. The combination of the two commands enabled and allowed the attacker to use the Socket5 proxy.”
Another command tells the malware to tamper with the router DNS by modifying the resolv.conf file, allowing it to hijack the network access of any of the router’s users. This in turn allows attackers to monitor or steal sensitive information.
Meanwhile, by setting iptables up, the operators can achieve traffic forwarding and target address conversion, which could expose internal network services and lead to information disclosure. And, by implementing a reverse shell through socket, the author of Ttint can operate the shell of the affected routing device as a local shell.
And finally, the custom commands also allow the malware to self-update and self-destruct.
The C2 information of the Ttint Bot sample is encrypted and stored in the configuration information table in the Mirai format, protected with a XOR key, researchers said.
“When the bot is running, it decrypts to obtain the C2 address,…and then communicates with C2 securely through the WebSocket over TLS protocol,” according to the researchers. “When Ttint C2 replies to the bot with a response code of 101, it means that the protocol handshake is completed, and then the bot can communicate using the WebSocket protocol.”
There has of late been a resurgence of Mirai-based malware capable of building large botnets through the exploitation of poorly secured IoT devices. This has contributed to a significant uptick in the number of distributed denial-of-service (DDoS) attacks in the first half of the year, compared to the same period last year. The addition of the RAT and concerning C2 commands marks a change for the Mirai world, however.
“Two zero-days, 12 remote-access functions for the router, encrypted traffic protocol and infrastructure IP that that moves around,” the firm wrote in a recent blog. “This botnet does not seem to be a very typical player.”
MosaicRegressor: Lurking in the Shadows of UEFI
6.10.20 APT Securelist
UEFI (or Unified Extensible Firmware Interface) has become a prominent technology that is embedded within designated chips on modern day computer systems. Replacing the legacy BIOS, it is typically used to facilitate the machine’s boot sequence and load the operating system, while using a feature-rich environment to do so. At the same time, it has become the target of threat actors to carry out exceptionally persistent attacks.
One such attack has become the subject of our research, where we found a compromised UEFI firmware image that contained a malicious implant. This implant served as means to deploy additional malware on the victim computers, one that we haven’t come across thus far. To the best of our knowledge, this is the second known public case where malicious UEFI firmware in use by a threat actor was found in the wild.
Throughout this blog we will elaborate on the following key findings:
We discovered rogue UEFI firmware images that were modified from their benign counterpart to incorporate several malicious modules;
The modules were used to drop malware on the victim machines. This malware was part of a wider malicious framework that we dubbed MosaicRegressor;
Components from that framework were discovered in a series of targeted attacks pointed towards diplomats and members of an NGO from Africa, Asia and Europe, all showing ties in their activity to North Korea;
Code artefacts in some of the framework’s components and overlaps in C&C infrastructure used during the campaign suggest that a Chinese-speaking actor is behind these attacks, possibly having connections to groups using the Winnti backdoor;
The attack was found with the help of Firmware Scanner, which has been integrated into Kaspersky products since the beginning of 2019. This technology was developed to specifically detect threats hiding in the ROM BIOS, including UEFI firmware images.
Current State of the Art
Before we dive deep into our findings, let us have a quick recap of what UEFI is and how it was leveraged for attacks thus far. In a nutshell, UEFI is a specification that constitutes the structure and operation of low-level platform firmware, so as to allow the operating system to interact with it at various stages of its activity.
This interaction happens most notably during the boot phase, where UEFI firmware facilitates the loading of the operating system itself. That said, it can also occur when the OS is already up and running, for example in order to update the firmware through a well-defined software interface.
Considering the above, UEFI firmware makes for a perfect mechanism of persistent malware storage. A sophisticated attacker can modify the firmware in order to have it deploy malicious code that will be run after the operating system is loaded. Moreover, since it is typically shipped within SPI flash storage that is soldered to the computer’s motherboard, such implanted malware will be resistant to OS reinstallation or replacement of the hard drive.
This type of attack has occurred in several instances in the past few years. A prominent example is the LowJax implant discovered by our friends at ESET in 2018, in which patched UEFI modules of the LoJack anti-theft software (also known as Computrace) were used to deploy a malicious user mode agent in a number of Sofacy \ Fancy Bear victim machines. The dangers of Computrace itself were described by our colleagues from the Global Research and Analysis Team (GReAT) back in 2014.
Another example is source code of a UEFI bootkit named VectorEDK which was discovered in the Hacking Team leaks from 2015. This code consisted of a set of UEFI modules that could be incorporated into the platform firmware in order to have it deploy a backdoor to the system which will be run when the OS loads, or redeploy it if it was wiped. Despite the fact that VectorEDK’s code was made public and can be found in Github nowadays, we hadn’t witnessed actual evidence of it in the wild, before our latest finding.
Our Discovery
During an investigation, we came across several suspicious UEFI firmware images. A deeper inspection revealed that they contained four components that had an unusual proximity in their assigned GUID values, those were two DXE drivers and two UEFI applications. After further analysis we were able to determine that they were based on the leaked source code of HackingTeam’s VectorEDK bootkit, with minor customizations.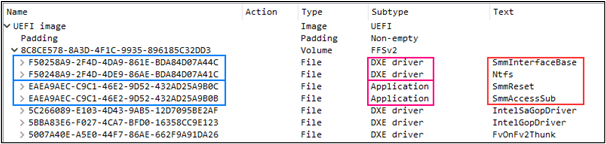
Rogue components found within the compromised UEFI firmware
The goal of these added modules is to invoke a chain of events that would result in writing a malicious executable named ‘IntelUpdate.exe’ to the victim’s Startup folder. Thus, when Windows is started the written malware would be invoked as well. Apart from that, the modules would ensure that if the malware file is removed from the disk, it will be rewritten. Since this logic is executed from the SPI flash, there is no way to avoid this process other than eliminating the malicious firmware.
Following is an outline of the components that we revealed:
SmmInterfaceBase: a DXE driver that is based on Hacking Team’s ‘rkloader’ component and intended to deploy further components of the bootkit for later execution. This is done by registering a callback that will be invoked upon an event of type EFI_EVENT_GROUP_READY_TO_BOOT. The event occurs at a point when control can be passed to the operating system’s bootloader, effectively allowing the callback to take effect before it. The callback will in turn load and invoke the ‘SmmAccessSub’ component.
Ntfs: a driver written by Hacking Team that is used to detect and parse the NTFS file system in order to allow conducting file and directory operations on the disk.
SmmReset: a UEFI application intended to mark the firmware image as infected. This is done by setting the value of a variable named ‘fTA’ to a hard-coded GUID. The application is based on a component from the original Vector-EDK code base that is named ‘ReSetfTA’.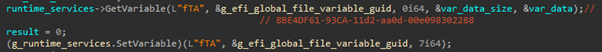
Setting of the fTA variable with a predefined GUID to mark the execution of the bootkit
SmmAccessSub: the main bootkit component that serves as a persistent dropper for a user-mode malware. It is executed by the callback registered during the execution of ‘SmmInterfaceBase’, and takes care of writing a binary embedded within it as a file named ‘IntelUpdate.exe’ to the startup directory on disk. This allows the binary to execute when Windows is up and running.
This is the only proprietary component amongst the ones we inspected, which was mostly written from scratch and makes only slight use of code from a Vector-EDK application named ‘fsbg’. It conducts the following actions to drop the intended file to disk:
Bootstraps pointers for the SystemTable, BootServices and RuntimeServices global structures.
Tries to get a handle to the currently loaded image by invoking the HandleProtocol method with the EFI_LOADED_IMAGE_PROTOCOL_GUID argument.
If the handle to the current image is obtained, the module attempts to find the root drive in which Windows is installed by enumerating all drives and checking that the ‘\Windows\System32’ directory exists on them. A global EFI_FILE_PROTOCOL object that corresponds to the drive will be created at this point and referenced to open any further directories or files in this drive.
If the root drive is found in the previous stage, the module looks for a marker file named ‘setupinf.log’ under the Windows directory and proceeds only if it doesn’t exist. In the absence of this file, it is created.
If the creation of ‘setupinf.log’ succeeds, the module goes on to check if the ‘Users’ directory exists under the same drive.
If the ‘Users’ directory exists, it writes the ‘IntelUpdate.exe’ file (embedded in the UEFI application’s binary) under the ‘ProgramData\Microsoft\Windows\Start Menu\Programs\Startup’ directory in the root drive.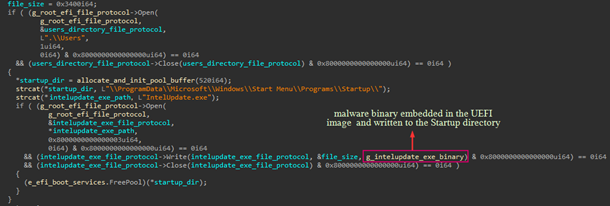
Code from ‘SmmAccessSub’ used to write the embedded ‘IntelUpdate.exe’ binary to the Windows Startup directory
Unfortunately, we were not able to determine the exact infection vector that allowed the attackers to overwrite the original UEFI firmware. Our detection logs show that the firmware itself was found to be malicious, but no suspicious events preceded it. Due to this, we can only speculate how the infection could have happened.
One option is through physical access to the victim’s machine. This could be partially based on Hacking Team’s leaked material, according to which the installation of firmware infected with VectorEDK requires booting the target machine from a USB key. Such a USB would contain a special update utility that can be generated with a designated builder provided by the company. We found a Q-flash update utility in our inspected firmware, which could have been used for such a purpose as well.
Furthermore, the leaks reveal that the UEFI infection capability (which is referred to by Hacking Team as ‘persistent installation’) was tested on ASUS X550C laptops. These make use of UEFI firmware by AMI which is very similar to the one we inspected. For this reason we can assume that Hacking Team’s method of patching the firmware would work in our case as well.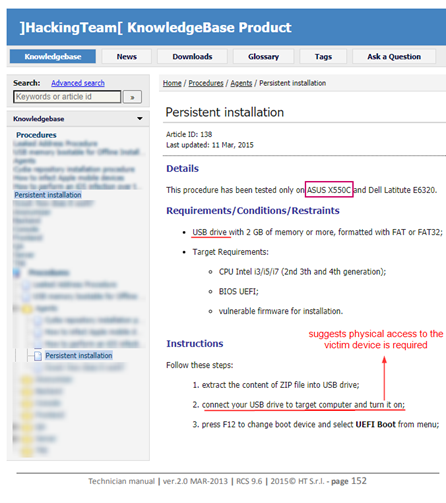
Excerpt from a Hacking Team manual for deployment of infected UEFI firmware, also known as ‘persistent installation’
Of course, we cannot exclude other possibilities whereby rogue firmware was pushed remotely, perhaps through a compromised update mechanism. Such a scenario would typically require exploiting vulnerabilities in the BIOS update authentication process. While this could be the case, we don’t have any evidence to support it.
The Bigger Picture: Enter MosaicRegressor Framework
While Hacking Team’s original bootkit was used to write one of the company’s backdoors to disk, known as ‘Soldier’, ‘Scout’ or ‘Elite’, the UEFI implant we investigated deployed a new piece of malware that we haven’t seen thus far. We decided to look for similar samples that share strings and implementation traits with the dropped binary. Consequently, the samples that we found suggested that the dropped malware was only one variant derived from a wider framework that we named MosaicRegressor.
MosaicRegressor is a multi-stage and modular framework aimed at espionage and data gathering. It consists of downloaders, and occasionally multiple intermediate loaders, that are intended to fetch and execute payload on victim machines. The fact that the framework consists of multiple modules assists the attackers to conceal the wider framework from analysis, and deploy components to target machines only on demand. Indeed, we were able to obtain only a handful of payload components during our investigation.
The downloader components of MosaicRegressor are composed of common business logic, whereby the implants contact a C&C, download further DLLs from it and then load and invoke specific export functions from them. The execution of the downloaded modules usually results in output that can be in turn issued back to the C&C.
Having said that, the various downloaders we observed made use of different communication mechanisms when contacting their C&Cs:
CURL library (HTTP/HTTPS)
BITS transfer interface
WinHTTP API
POP3S/SMTPS/IMAPS, payloads transferred in e-mail messages
The last variant in the list is distinct for its use of e-mail boxes to host the requested payload. The payload intended to run by this implant can also generate an output upon invocation, which can be later forwarded to a ‘feedback’ mail address, where it will likely be collected by the attackers.
The mail boxes used for this purpose reside on the ‘mail.ru’ domain, and are accessed using credentials that are hard-coded in the malware’s binary. To fetch the requested file from the target inbox, MailReg enters an infinite loop where it tries to connect to the “pop.mail.ru” server every 20 minutes, and makes use of the first pair of credentials that allow a successful connection. The e-mails used for login (without their passwords) and corresponding feedback mail are specified in the table below:
Login mail Feedback mail
thtgoolnc@mail.ru thgetmmun@mail.ru
thbububugyhb85@mail.ru thyhujubnmtt67@mail.ru
The downloaders can also be split in two distinct types, the “plain” one just fetching the payload, and the “extended” version that also collects system information:
Structure of the log file written by BitsRegEx, strings marked in red are the original fields that appear in that file
We were able to obtain only one variant of the subsequent stage, that installs in the autorun registry values and acts as another loader for the components that are supposed to be fetched by the initial downloader. These components are also just intermediate loaders for the next stage DLLs. Ultimately, there is no concrete business logic in the persistent components, as it is provided by the C&C server in a form of DLL files, most of them temporary.
We have observed one such library, “load.rem“, that is a basic document stealer, fetching files from the “Recent Documents” directory and archiving them with a password, likely as a preliminary step before exfiltrating the result to the C&C by another component.
The following figure describes the full flow and connection between the components that we know about. The colored elements are the components that we obtained and gray ones are the ones we didn’t:
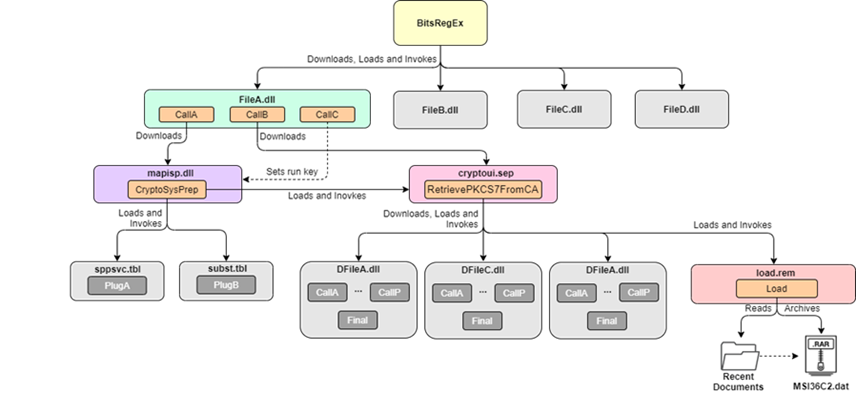
Flow from BitsRegEx to execution of intermediate loaders and final payload
Who were the Targets?
According to our telemetry, there were several dozen victims who received components from the MosaicRegressor framework between 2017 and 2019. These victims included diplomatic entities and NGOs in Africa, Asia and Europe. Only two of them were also infected with the UEFI bootkit in 2019, predating the deployment of the BitsReg component.
Based on the affiliation of the discovered victims, we could determine that all had some connection to the DPRK, be it non-profit activity related to the country or actual presence within it. This common theme can be reinforced through one of the infection vectors used to deliver the malware to some of the victims, which was SFX archives pretending to be documents discussing various subjects related to North Korea. Those were bundled with both an actual document and MosaicRegressor variants, having both executed when the archive is opened. Examples for the lure documents can be seen below.
Examples of lure documents bundled to malicious SFX archives sent to MosaicRegressor victims, discussing DPRK related topics
Who is behind the attack?
When analyzing MosaicRegressor’s variants, we noticed several interesting artefacts that provided us with clues on the identity of the actor behind the framework. As far as we can tell, the attacks were conducted by a Chinese-speaking actor, who may have previously used the Winnti backdoor. We found the following evidence to support this:
We spotted many strings used in the system information log generated by the BitsRegEx variant that contain the character sequence ‘0xA3, 0xBA’. This is an invalid sequence for a UTF8 string and the LATIN1 encoding translates these symbols to a pound sign followed by a “masculine ordinal indicator” (“£º”). An attempt to iterate over all available iconv symbol tables, trying to convert the sequence to UTF-8, produces possible candidates that give a more meaningful interpretation. Given the context of the string preceding the symbol and line feed symbols following it, the best match is the “FULL-WIDTH COLON” Unicode character translated from either the Chinese or Korean code pages (i.e. CP936 and CP949).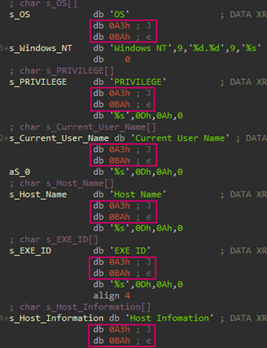
Figure: The BitsRegEx system information log making use of the character sequence 0xA3, 0xBA, likely used to represent a full-width colon, according to code pages CP936 and CP949.
Another artefact that we found was a file resource found in CurlReg samples that contained a language identifier set to 2052 (“zh-CN”)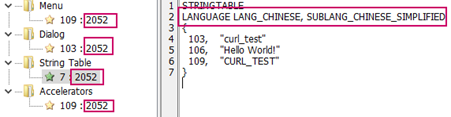
Chinese language artefact in the resource section of a CurlReg sample
We detected an OLE2 object taken out of a document armed with the CVE-2018-0802 vulnerability, which was produced by the so-called ‘Royal Road’ / ‘8.t’ document builder and used to drop a CurlReg variant. To the best of our knowledge, this builder is commonly used by Chinese-speaking threat actors.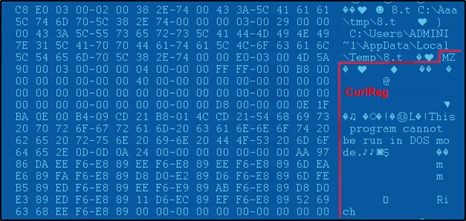
Excerpt from the OLE2 object found within a ‘Royal Road’ weaponized document, delivering the CurlReg variant
A C&C address (103.82.52[.]18) which was found in one of MosaicRegressor’s variants (MD5:3B58E122D9E17121416B146DAAB4DB9D) was observed in use by the ‘Winnti umbrella and linked groups’, according to a publicly available report. Since this is the only link between our findings and any of the groups using the Winnti backdoor, we estimate with low confidence that it is indeed responsible for the attacks.
Conclusion
The attacks described in this blog post demonstrate the length an actor can go in order to gain the highest level of persistence on a victim machine. It is highly uncommon to see compromised UEFI firmware in the wild, usually due to the low visibility into attacks on firmware, the advanced measures required to deploy it on a target’s SPI flash chip, and the high stakes of burning sensitive toolset or assets when doing so.
With this in mind, we see that UEFI continues to be a point of interest to APT actors, while at large being overlooked by security vendors. The combination of our technology and understanding of the current and past campaigns leveraging infected firmware, helps us monitor and report on future attacks against such targets.
The full details of this research, as well as future updates on the underlying threat actor, are available to customers of the APT reporting service through our Threat Intelligence Portal.
IoCs
The followings IoC list is not complete. If you want more information about the APT discussed here, a full IoC list and YARA rules are available to customers of Kaspersky Threat Intelligence Reports. Contact: intelreports@kaspersky.com
UEFI Modules
F5B320F7E87CC6F9D02E28350BB87DE6 (SmmInterfaceBase)
B53880397D331C6FE3493A9EF81CD76E (SmmAccessSub)
91A473D3711C28C3C563284DFAFE926B (SmmReset)
DD8D3718197A10097CD72A94ED223238 (Ntfs)
RAR SFX droppers
0EFB785C75C3030C438698C77F6E960E
12B5FED367DB92475B071B6D622E44CD
3B3BC0A2772641D2FC2E7CBC6DDA33EC
3B58E122D9E17121416B146DAAB4DB9D
70DEF87D180616406E010051ED773749
7908B9935479081A6E0F681CCEF2FDD9
AE66ED2276336668E793B167B6950040
B23E1FE87AE049F46180091D643C0201
CFB072D1B50425FF162F02846ED263F9
Decoy documents
0D386EBBA1CCF1758A19FB0B25451AFE
233B300A58D5236C355AFD373DABC48B
449BE89F939F5F909734C0E74A0B9751
67CF741E627986E97293A8F38DE492A7
6E949601EBDD5D50707C0AF7D3F3C7A5
92F6C00DA977110200B5A3359F5E1462
A69205984849744C39CFB421D8E97B1F
D197648A3FB0D8FF6318DB922552E49E
BitsReg
B53880397D331C6FE3493A9EF81CD76E
AFC09DEB7B205EADAE4268F954444984 (64-bit)
BitsRegEx
DC14EE862DDA3BCC0D2445FDCB3EE5AE
88750B4A3C5E80FD82CF0DD534903FC0
C63D3C25ABD49EE131004E6401AF856C
D273CD2B96E78DEF437D9C1E37155E00
72C514C0B96E3A31F6F1A85D8F28403C
CurlReg
9E182D30B070BB14A8922CFF4837B94D
61B4E0B1F14D93D7B176981964388291
3D2835C35BA789BD86620F98CBFBF08B
CurlRegEx
328AD6468F6EDB80B3ABF97AC39A0721
7B213A6CE7AB30A62E84D81D455B4DEA
MailReg
E2F4914E38BB632E975CFF14C39D8DCD
WinHTTP Based Downloaders
08ECD8068617C86D7E3A3E810B106DCE
1732357D3A0081A87D56EE1AE8B4D205
74DB88B890054259D2F16FF22C79144D
7C3C4C4E7273C10DBBAB628F6B2336D8
BitsReg Payload (FileA.z)
89527F932188BD73572E2974F4344D46
2nd Stage Loaders
36B51D2C0D8F48A7DC834F4B9E477238 (mapisp.dll)
1C5377A54CBAA1B86279F63EE226B1DF (cryptui.sep)
9F13636D5861066835ED5A79819AAC28 (cryptui.sep)
3rd Stage Payload
FA0A874926453E452E3B6CED045D2206 (load.rem)
File paths
%APPDATA%\Microsoft\Credentials\MSI36C2.dat
%APPDATA%\Microsoft\Internet Explorer\%Computername%.dat
%APPDATA%\Microsoft\Internet Explorer\FileA.dll
%APPDATA%\Microsoft\Internet Explorer\FileB.dll
%APPDATA%\Microsoft\Internet Explorer\FileC.dll
%APPDATA%\Microsoft\Internet Explorer\FileD.dll
%APPDATA%\Microsoft\Internet Explorer\FileOutA.dat
%APPDATA%\Microsoft\Network\DFileA.dll
%APPDATA%\Microsoft\Network\DFileC.dll
%APPDATA%\Microsoft\Network\DFileD.dll
%APPDATA%\Microsoft\Network\subst.sep
%APPDATA%\Microsoft\WebA.dll
%APPDATA%\Microsoft\WebB.dll
%APPDATA%\Microsoft\WebC.dll
%APPDATA%\Microsoft\Windows\LnkClass.dat
%APPDATA%\Microsoft\Windows\SendTo\cryptui.sep
%APPDATA%\Microsoft\Windows\SendTo\load.dll %APPDATA%\Microsoft\Windows\load.rem
%APPDATA%\Microsoft\Windows\mapisp.dll
%APPDATA%\Microsoft\exitUI.rs
%APPDATA%\Microsoft\sppsvc.tbl
%APPDATA%\Microsoft\subst.tbl
%APPDATA%\newplgs.dll
%APPDATA%\rfvtgb.dll
%APPDATA%\sdfcvb.dll
%APPDATA%\msreg.dll
%APPDATA\Microsoft\dfsadu.dll
%COMMON_APPDATA%\Microsoft\Windows\user.rem
%TEMP%\BeFileA.dll
%TEMP%\BeFileC.dll
%TEMP%\RepairA.dll
%TEMP%\RepairB.dll
%TEMP%\RepairC.dll
%TEMP%\RepairD.dll
%TEMP%\wrtreg_32.dll
%TEMP%\wrtreg_64.dll
%appdata%\dwhost.exe
%appdata%\msreg.exe
%appdata%\return.exe
%appdata%\winword.exe
Domains and IPs
103.195.150[.]106
103.229.1[.]26
103.243.24[.]171
103.243.26[.]211
103.30.40[.]116
103.30.40[.]39
103.39.109[.]239
103.39.109[.]252
103.39.110[.]193
103.56.115[.]69
103.82.52[.]18
117.18.4[.]6
144.48.241[.]167
144.48.241[.]32
150.129.81[.]21
43.252.228[.]179
43.252.228[.]252
43.252.228[.]75
43.252.228[.]84
43.252.230[.]180
menjitghyukl.myfirewall[.]org
Additional Suspected C&Cs
43.252.230[.]173
185.216.117[.]91
103.215.82[.]161
103.96.72[.]148
122.10.82[.]30
Mutexes
FindFirstFile Message Bi
set instance state
foregrounduu state
single UI
Office Module
process attach Module
Australian social news platform leaks 80,000 user records
6.10.20 Social Securityaffairs
Cybernews has found an exposed data bucket that belongs to the Australian news sharing platform Snewpit containing around 80,000 user records.
Original post at https://cybernews.com/security/australian-social-news-platform-leaks-80000-user-records/
To increase efforts to secure user data, Snewpit will be reviewing “all server logs and access control settings” to confirm that no unauthorized access took place and to ensure that “user data is secure and encrypted.”
The CyberNews investigations team discovered an exposed data bucket that belongs to Snewpit, an Australian news sharing platform. The unsecured bucket contains close to 80,000 user records, including usernames, full names, email addresses, and profile pictures.
The files that contain the records were stored on a publicly accessible Amazon Web Services (AWS) server, which means that anyone with a direct URL to the files could access and download the data that was left out in the open.
On September 24, the sensitive files in the Snewpit bucket were secured by the company and are no longer accessible.
To see if your email address has been exposed in this or other security breaches, use ourpersonal data leak checker.
What data is in the bucket?
The exposed Snewpit Amazon AWS bucket contained 26,203 files, including:
256 video files filmed and uploaded by Snewpit users and developers
23,586 image files of photos documenting local events that were apparently uploaded by the users
4 CSV files, one of which contained 79,725 user records, including full names, email addresses, usernames, user descriptions, last login times, and total time spent in the Snewpit app, among other metrics
Aside from the user records, the bucket also contained thousands of user profile pictures.
Examples of exposed records
Here are some examples of the user records, videos, and images left on the exposed Snewpit bucket.
The CSV file contains user records for what we assume to be users who downloaded and installed the Snewpit app, which currently has 50,000+ installs on Apple’s App Store and Google’s Play store.
The video files stored in the bucket seem to show raw footage from news posts, including criminal incidents.
There were also user profile pictures among the files stored in the bucket.
Who owns the bucket?
The publicly available Amazon bucket appears to belong to Snewpit, a software company based in Australia. Snewpit is a map-based peer-to-peer app that allows users to create, find, and share real-time news updates, as well as receive notifications for news posted within 5 kilometers of their location.
According to the developers, the app is aimed at helping users “form a worldwide community of citizen journalists, reporting and discovering local news and events happening around them.”
The app is mostly used by Australians, with small userbases currently located in the US and the UK.
Who had access to the data?
According to Snewpit founder Charlie Khoury, the bucket has been exposed for 5 weeks since the development team made server changes to the system reporting. While Snewpit have not noticed any suspicious activity, the company is reviewing all server logs to confirm that this is the case.
”We will be reviewing all access control settings and ensuring our user data is secure and encrypted. We take our data and security seriously and will endeavour to make sure this does not happen again.” -Charlie Khoury
With that said, the files were stored on a publicly accessible Amazon S3 server, and bad actors can find unprotected Amazon buckets relatively easily. Since these buckets lack any sort of protection from unauthorized access, there is a possibility that the data may have been accessed by bad actors for malicious purposes during the 5-week period.
What’s the impact of the leak?
Fortunately, the files stored in the exposed Snewpit bucket don’t contain any deeply sensitive information like personal document scans, passwords, or social security numbers. However, even this data can be enough for bad actors to abuse for a variety of malicious purposes:
Contact details like full names and email addresses can be used by phishers and scammers to commit targeted attacks against the exposed Snewpit users by sending them malicious spam emails
Particularly determined cybercriminals can combine the data found in this bucket with previous breaches in other verticals in order to build more accurate profiles of potential targets for identity theft
What happened to the data?
We discovered the Snewpit bucket on September 24 and immediately reached out to the company in order to help secure the bucket. The Snewpit team responded within minutes and secured the files containing user records on the same day.
What to do if you’ve been affected by the leak?
If you have a Snewpit account, there is a high chance that your records may have been exposed in this breach. To secure your data and avoid any potential harm from bad actors, we recommend doing the following:
Use our personal data leak checker to see if your email address has been leaked.
Immediately change your email password and consider using a password manager.
Enable two-factor authentication (2FA) on your email and other online accounts.
Look out for incoming spam emails and phishing messages. Don’t click on anything that looks even remotely suspicious, including emails from senders you do not recognize.
Hackers stole a six-figure amount from Swiss universities
6.10.20 Hacking Securityaffairs
Threat actors have hacked at least three Swiss universities, including the University of Basel and managed to drain employee salary transfers.
Threat actors have managed to steal employee salary payments at several Swiss universities, including the University of Basel.
“According to our information, several universities in Switzerland have been affected,” explained Martina Weiss, Secretary General of the Rectors’ Conference of the Swiss Universities.
The hackers carried out spear-phishing attacks against the Swiss universities in an attempt of tricking its employees into providing their access data.
According to the SonntagsZeitung, the Basel public prosecutor’s office confirmed that hackers compromised the systems at the universities, then the threat actors hijacked the employee salary transfers by changing the beneficiaries’ accounts.
The SonntagsZeitung also added that hackers attempted to breach the University of Zurich, but the employees at the university recognised the phishing attempts and neutralized them.
It seems that the hackers stolen a six-figure amount and immediately moved the funds abroad.
“The cybercriminals embezzled a six-figure amount, the office said. It added that part of the misappropriated funds was now in foreign accounts.” reads the site SwissInfo.
“Umbrella organisation swissuniversities has sent a warning email to keep universities on their guard.”
Second-ever UEFI rootkit used in North Korea-themed attacks
6.10.20 BigBrothers Securityaffairs
A China-linked threat actor used UEFI malware based on code from Hacking Team in attacks aimed at organizations with an interest in North Korea.
Researchers from Kaspersky have spotted a UEFI malware that was involved in attacks on organizations with an interest in North Korea.
The experts were investigating several suspicious UEFI firmware images when discovered four components, some of which were borrowing the source code a Hacking Team spyware.
In 2015, the hacker who breached the systems of the Italian surveillance firm Hacking Team leaked a 400GB package containing hacking tools and exploits codes. The archive included a number of zero-day exploits for Adobe Flash Player and Microsoft IE, these codes are just part of the hacking arsenal of the surveillance firm, which developed the popular Remote Control System (RCS) spyware, also known as Galileo. RCS has a modular structure that allows it to compromise several targets by loading the necessary zero-day exploits.
Trend Micro was the first security firm to discover the availability of a UEFI BIOS rootkit in the arsenal of the Hacking Team that allowed the company’s spyware to ensure the persistence even if the victims had formatted their hard disk to reinstall the Operating System.
“Hacking Team uses a UEFI BIOS rootkit to keep their Remote Control System (RCS) agent installed in their targets’ systems. This means that even if the user formats the hard disk, reinstalls the OS, and even buys a new hard disk, the agents are implanted after Microsoft Windows is up and running.” stated Trend Micro.
The firmware malware is based on code associated with HackingTeam’s VectorEDK bootkit, with minor changes.
Experts revealed that they were not able to determine the exact infection vector that allowed the attackers to overwrite the original UEFI firmware.
Experts speculate that the threat actors need to have physical access in order to deploy the implant into the victim’s machine. However, researchers don’t exclude that a rogue firmware was pushed remotely through a supply chain attack.
“Of course, we cannot exclude other possibilities whereby rogue firmware was pushed remotely, perhaps through a compromised update mechanism. Such a scenario would typically require exploiting vulnerabilities in the BIOS update authentication process. While this could be the case, we don’t have any evidence to support it,” reads the analysis published by Kaspersky.
The UEFI implant spotted by Kaspersky was used to deploy a new piece of malware that experts classified as a variant derived from a wider framework that they tracked as MosaicRegressor.
The MosaicRegressor framework was developed for cyber espionage purposes, its modular architecture allows operators to perform multiple actions.
Kaspersky researchers revealed to have found MosaicRegressor components at several dozen entities between 2017 and 2019. The list of victims included NGOs and diplomatic entities in Asia, Africa and Europe.
Researchers speculate the threat actors behind these attacks are linked with the Winnti APT.
“The attacks described in this blog post demonstrate the length an actor can go in order to gain the highest level of persistence on a victim machine. It is highly uncommon to see compromised UEFI firmware in the wild, usually due to the low visibility into attacks on firmware, the advanced measures required to deploy it on a target’s SPI flash chip, and the high stakes of burning sensitive toolset or assets when doing so.” concludes the report.
“With this in mind, we see that UEFI continues to be a point of interest to APT actors, while at large being overlooked by security vendors.”
Ttint Botnet Targets Zero-Day Vulnerabilities in Tenda Routers
6.10.20 BotNet Securityweek
A new Mirai-based botnet is targeting zero-day vulnerabilities in Tenda routers, according to researchers at 360 Netlab, a unit of Chinese cybersecurity company Qihoo 360.
Dubbed Ttint, the Remote Access Trojan (RAT) contains distributed denial of service capabilities, just as any Mirai offspring does, but also implements 12 remote access functions, including a Socket5 proxy, modifying router DNS and iptables, and running system commands.
In order to circumvent detection of typical traffic generated by Mirai botnets, Ttint uses the WSS (WebSocket over TLS) protocol for communication with the command and control (C&C) server, and also uses encryption.
The botnet’s activity was initially detected in November 2019, when the attackers started abusing the first zero-day vulnerability in Tenda routers (CVE-2020-10987). The second bug started being exploited in August 2020, but 360 Netlab says the vendor has not responded to its emails reporting the flaw.
“We analyzed and compared Ttint samples in the two periods and found that their C2 instructions were exactly the same, but they had some differences in the 0-day vulnerability, XOR Key, and C2 protocol used,” 360 Netlab says.
Ttint, the researchers say, has a relatively simple behavior, where it deletes its own files when running, modifies its process name, manipulates the watchdog, and can prevent device restarts. After establishing a connection to the C&C, it sends device information and starts waiting for instructions.
The malware has many of the features previously observed in Mirai, such as a random process name, encryption of configuration information, support for multiple DDoS attack vectors, or the fact that only a single malware instance is running at a time. However, unlike Mirai, it uses the websocket protocol.
Functions implemented in Ttint allow attackers to remotely access the router's intranet, hijack network access to possibly steal sensitive information, set traffic forwarding rules, and leverage a reverse shell as a local shell. The malware can also update itself or kill its own process, and can execute commands issued by the C&C.
The threat supports a total of 22 commands, including many for launching DDoS attacks.
Tenda router users are advised to check the firmware on their devices and make sure that available updates are installed if necessary. They should also monitor and block the related IoCs shared by 360 Netlab.
China-Linked Hackers Used UEFI Malware in North Korea-Themed Attacks
6.10.20 BigBrothers Securityweek
A threat actor linked to China has used UEFI malware based on code from Hacking Team in attacks aimed at organizations with an interest in North Korea, Kaspersky reported on Monday.
Kaspersky researchers analyzed the malware and the malicious activity after stumbling upon several suspicious UEFI firmware images. A deeper investigation revealed the existence of four components, many of which were based on source code leaked in 2015 by a hacker who had breached the systems of the now-defunct Italian surveillance solutions provider Hacking Team. The firmware implant appeared to be based on code associated with the Vector-EDK bootkit, with only some minor modifications.
Kaspersky has not been able to determine how the attackers managed to rewrite the firmware on targeted machines. However, considering that the firmware implant is based on Hacking Team code, it’s possible that deployment involved physical access to the targeted device and attaching a USB key — Hacking Team’s Vector-EDK bootkit was designed to be deployed via a USB key.
“Of course, we cannot exclude other possibilities whereby rogue firmware was pushed remotely, perhaps through a compromised update mechanism. Such a scenario would typically require exploiting vulnerabilities in the BIOS update authentication process. While this could be the case, we don’t have any evidence to support it,” Kaspersky researchers said.
The implant’s main bootkit component is designed to act as a persistent dropper for a piece of Windows malware. This allows the attackers to ensure that the Windows malware cannot be removed from the compromised system — the malware is rewritten to disk if removed, unless the malicious firmware is also removed.
The malware delivered by the bootkit was determined to be a variant from a framework that Kaspersky has dubbed MosaicRegressor, which is designed for espionage. The framework is modular, enabling the attackers to carry out various tasks, such as stealing documents from the compromised computer.
Kaspersky detected MosaicRegressor components at “several dozen” entities between 2017 and 2019. Victims included NGOs and diplomatic entities in Asia, Africa and Europe, and one thing they had in common was a connection to North Korea — in some cases they had a presence in the country, while others were involved in non-profit activity related to North Korea. However, only two of these victims were targeted with the UEFI implant.
Evidence uncovered by Kaspersky suggests that the hackers behind these attacks are Chinese speakers, and a connection has been found to Winnti, but no definitive links have been found to a known threat actor.
There aren’t too many known attacks involving UEFI malware. ESET reported in 2018 that the Russia-linked threat group Fancy Bear had been using a UEFI rootkit in its attacks.
Visa Warns of Attack Involving Mix of POS Malware
6.10.20 Virus Securityweek
A North American merchant’s point-of-sale (POS) terminals were infected with a mix of POS malware earlier this year, Visa reports.
In May and June 2020, the company analyzed malware variants used in independent attacks on two North American merchants, one of which employed a TinyPOS variant, while the other involved a mix of malware families such as MMon (aka Kaptoxa), PwnPOS, and RtPOS.
As part of the first attack, phishing emails were sent to a North American hospitality merchant’s employees to compromise user accounts, including an administrator account, and legitimate administrative tools were used to access the cardholder data environment (CDE) within the network.
Next, the attackers deployed the TinyPOS memory scraper to gather Track 1 and Track 2 payment card data and leveraged a batch script to deploy the malware en masse across the network. The analyzed malware sample did not contain network or exfiltration functions.
In addition to harvesting card data and preparing it for exfiltration, the malware can enumerate processes running on the system to identify those pertaining to specific POS software.
As for the second attack, while Visa’s researchers couldn’t identify the exact intrusion vector, they managed to gather evidence suggesting the adversary used remote access tools and credential dumpers for initial access, lateral movement, and malware deployment.
“The malware utilized in these stages of the compromise was not recovered. The POS malware variants used in this attack targeted track 1 and track 2 payment account data,” Visa explains in a technical report.
The RtPOS sample used in this attack iterates the available processes to identify those of interest, gains access to the compromised system’s memory space, and attempts to validate all Track 1 and Track 2 data that it finds, using a Luhn algorithm.
MMon (“memory monitor”), also referred to as Картоха on underground forums, has been around for roughly a decade, and so far powered POS scraping malware such as JavalinPOS, BlackPOS, POSRAM, and more.
PwnPOS can achieve persistence through installing itself as a service, employs the Luhn algorithm to identify card data and writes the data to a file in plain text, and logs its own general behavior to a log file.
To reduce the risk of exposure to POS malware, merchants are advised to use available IOCs to improve detection and remediation, secure remote access, employ unique credentials for each administrative account, monitor network traffic, implement network segmentation, enable behavioral detection, and ensure all software is up-to-date with the latest patches.
Hackers Steal Swiss University Salaries
6.10.20 Hacking Securityweek
As yet unidentifed hackers have managed to steal employee salary payments at several Swiss universities, officials said Sunday.
"According to our information, several top schools in Switzerland have been affected," Martina Weiss, director general of the rectors group of Switzerland's public universities, told AFP.
The hackers used information obtained by phishing -- tricking a person into passing on their personal details -- for their attacks on at least three universities, including the University of Basel.
According to the SonntagsZeitung newspaper, they accessed the universities' payment systems and changed the instructions on salary transfers, stealing a six-figure sum.
The University of Zurich managed to fend off the hackers after employees recognised their modus operandi, SonntagsZeitung reported.
DoD, DHS Warn of Attacks Involving SLOTHFULMEDIA Malware
6.10.20 BigBrothers Securityweek
The U.S. Department of Defense’s Cyber National Mission Force (CNMF) and the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) last week published a malware analysis report for what they described as a new malware variant named SLOTHFULMEDIA.
SLOTHFULMEDIA is described as a dropper that deploys two files when executed, including a RAT designed to allow hackers to control compromised devices, and a component that removes the dropper once the RAT achieves persistence on the targeted computer.
The RAT is capable of running arbitrary commands, terminating processes, taking screenshots, modifying the registry, and making changes to files.
The U.S. government’s malware analysis report includes technical details about how the malware works, indicators of compromise (IoC) and recommendations for securing systems against such threats.
“Users or administrators should flag activity associated with the malware and report the activity to the CISA or the FBI Cyber Watch (CyWatch), and give the activity the highest priority for enhanced mitigation,” the agencies said.
It’s not uncommon for these types of malware analysis reports made public by U.S. agencies to include information about the threat actor believed to be behind the attacks, including if it’s a nation-state actor. However, the report on SLOTHFULMEDIA doesn’t provide any information on the possible origin of the attackers.
CISA and CNMF say the malware has been used in attacks launched by a sophisticated threat actor against entities in India, Kazakhstan, Kyrgyzstan, Malaysia, Russia, and Ukraine.
A sample of the malware was also made available on VirusTotal by the U.S Cyber Command, which regularly posts samples of malware linked to foreign threat actors. A majority of the samples shared by USCYBERCOM have been linked to North Korea, and some have been attributed to Russia and Iran, but this summer it also started sharing Chinese samples.
ESET last week published a report on XDSpy, a previously unknown threat actor that has been active for at least 9 years and which has also targeted Russia and Ukraine, as well as Belarus, Moldova and Russia. This group has mainly targeted government organizations, and its main goal appears to be the theft of sensitive documents.
SecurityWeek has asked ESET if it has found any links between XDSpy and SLOTHFULMEDIA given the timing of the reports and the fact that they both target Russia and Ukraine. However, the cybersecurity firm says SLOTHFULMEDIA is actually related to PowerPool, a threat actor whose activities were detailed by the company back in 2018 after it was spotted exploiting a Windows zero-day vulnerability.
ESET at the time reported seeing attacks against a relatively small number of users located in the US, UK, Germany, Ukraine, Chile, India, Russia, Poland and the Philippines.
UN Maritime Agency Hit by 'Sophisticated Cyberattack'
6.10.20 BigBrothers Securityweek
The United Nations’ International Maritime Organization (IMO) last week said some of its systems were disrupted as a result of a cyberattack.
IMO describes itself as the “global standard-setting authority for the safety, security and environmental performance of international shipping.” The organization says its main role is to develop a fair and effective regulatory framework that is universally adopted and implemented.
IMO’s website and other web services were first disrupted on September 30, when the agency announced on Twitter that its team was working on fixing some “technical issues.” Then, on October 2, it admitted that the problems were caused by a cyberattack, and said that it was working on restoring impacted systems.
“IMO has ISO/IEC 27001:2013 certification for its information security management system. IMO was the first UN organization to get this certification in 2015,” IMO stated. “The IMO Headquarters file servers are located in the UK, with extensive backup systems in Geneva. The backup and restore system is regularly tested.”
It added, “Following the attack the Secretariat shut down key systems to prevent further damage from the attack.”
IMO has not shared any technical information about the attack. It may have been a distributed denial-of-service (DDoS) attack, a ransomware attack, or a different type of breach.
While it has described it as a “sophisticated cyberattack against the Organization’s IT systems that overcame robust security measures in place,” it’s not uncommon for organizations to describe even DDoS attacks as “sophisticated.”
SecurityWeek has reached out to IMO to find out exactly what type of attack it was and we will update this article if the organization responds.
The news came less than a week after French shipping giant CMA CGM was hit by a cyberattack that forced it to shut down some systems. According to reports, the attack involved a piece of file-encrypting ransomware named Ragnar Locker.
New Flaws in Top Antivirus Software Could Make Computers More Vulnerable
6.10.20 Vulnerebility Thehackernews
Cybersecurity researchers today disclosed details of security vulnerabilities found in popular antivirus solutions that could enable attackers to elevate their privileges, thereby helping malware sustain its foothold on the compromised systems.
According to a report published by CyberArk Labs today and shared with The Hacker News, the high privileges often associated with anti-malware products render them more vulnerable to exploitation via file manipulation attacks, resulting in a scenario where malware gains elevated permissions on the system.
The bugs impact a wide range of antivirus solutions, including those from Kaspersky, McAfee, Symantec, Fortinet, Check Point, Trend Micro, Avira, and Microsoft Defender, each of which has been fixed by the respective vendor.
Chief among the flaws is the ability to delete files from arbitrary locations, allowing the attacker to delete any file in the system, as well as a file corruption vulnerability that permits a bad actor to eliminate the content of any file in the system.
Per CyberArk, the bugs result from default DACLs (short for Discretionary Access Control Lists) for the "C:\ProgramData" folder of Windows, which are by applications to store data for standard users without requiring additional permissions.
Given that every user has both write and delete permission on the base level of the directory, it raises the likelihood of a privilege escalation when a non-privileged process creates a new folder in "ProgramData" that could be later accessed by a privileged process.
Antivirus
Vulnerability
Kaspersky Security Center CVE-2020-25043, CVE-2020-25044, CVE-2020-25045
McAfee Endpoint Security and McAfee Total Protection CVE-2020-7250, CVE-2020-7310
Symantec Norton Power Eraser CVE-2019-1954
Fortinet FortiClient CVE-2020-9290
Check Point ZoneAlarm and Check Point Endpoint Security CVE-2019-8452
Trend Micro HouseCall for Home Networks CVE-2019-19688, CVE-2019-19689, and three more unassigned flaws
Avira CVE-2020-13903
Microsoft Defender CVE-2019-1161
In one case, it was observed that two different processes — one privileged and the other run as an authenticated local user — shared the same log file, potentially allowing an attacker to exploit the privileged process to delete the file and create a symbolic link that would point to any desired arbitrary file with malicious content.
Subsequently, CyberArk researchers also explored the possibility of creating a new folder in "C:\ProgramData" before a privileged process is executed.
In doing so, they found that when McAfee antivirus installer is run after creating the "McAfee" folder, the standard user has full control over the directory, allowing the local user to gain elevated permissions by performing a symlink attack.
To top it all, a DLL hijacking flaw in Trend Micro, Fortinet, and other antivirus solutions could have been exploited by an attacker to place a malicious DLL file into the application directory and elevate privileges.
Urging that access control lists must be restrictive to prevent arbitrary delete vulnerabilities, CyberArk stressed the need to update the installation frameworks to mitigate DLL Hijacking attacks.
While these issues may have been addressed, the report serves as a reminder that weaknesses in software, including those that aim to offer antivirus protection, can be a conduit for malware.
"The implications of these bugs are often full privilege escalation of the local system," CyberArk researchers said. Due to the high privilege level of security products, an error in them could help malware to sustain its foothold and cause more damage to the organization."
Visa shares details for two attacks on North American hospitality merchants
5.10.20 Attack Securityaffairs
Visa revealed that two unnamed North American hospitality merchants have been infected with some strains of point-of-sale (POS) malware.
US payments processor Visa revealed that two North American hospitality merchants have been hacked, threat actors infected the systems of the two unnamed organizations with some strains of point-of-sale (POS) malware.
According to a security alert published last week, the attacks took place in May and June 2020, respectively.
“In May and June 2020, respectively, Visa Payment Fraud Disruption (PFD) analyzed malware samples recovered from the independent compromises of two North American merchants.” reads the VISA security alert.”In these incidents, criminals targeted the merchants’ point-of-sale (POS) terminals in an effort to harvest and exfiltrate payment card data. Subsequent to analysis, the first attack was attributed to the malware variant TinyPOS, and the second to a mix of POS malware families including RtPOS, MMon (aka Kaptoxa, BlackPOS), and PwnPOS.”
The US payments processor investigated the security breached and provided technical details about the malware employed in the attacks to allow other companies in the hospitality sector to check for the presence of the same threat actors in their networks.
In the May incident, attackers compromised the network a North American hospitality merchant with the TinyPOS POS malware. The attackers targeted the employees at the merchant with a phishing campaign to obtain credentials for user accounts and were able to take over an administrator account. Then the threat actors used legitimate administrative tools to access the cardholder data environment (CDE).
“Once access to the CDE was established, the actors deployed a memory scraper to harvest track 1 and track 2 payment account data, and later used a batch script to mass deploy the malware across the merchant’s network to target various locations and their respective POS environments. The memory scraper harvested the payment card data and output the data into a log file.” continues the report. “At the time of analysis, no network or exfiltration functions were present within the sample. Therefore, the actors would likely remove the output log file from the network using other means.”
In the second compromise, which took place in June, threat actors employed three different strains of POS malware. Experts found samples of RtPOS, MMon, and PwnPOS on the victim network.
“While less is known about the tactics used by the threat actors in this attack, there is evidence to suggest that the actors employed various remote access tools and credential dumpers to gain initial access, move laterally, and deploy the malware in the POS environment.” continues the report.
The recent attacks demonstrate that the threat actors continue to target merchant POS systems to harvest card present payment account data.
The report includes the indicators of compromise associated with both attacks, it is essential to share the report to prevent other compromises.
New Ttint IoT botnet exploits two zero-days in Tenda routers
5.10.20 BotNet IoT Securityaffairs
Security researchers provided technical details about an IoT botnet dubbed Ttint that has been exploiting two zero-days in Tenda routers
Security researchers at Netlab, the network security division Qihoo 360, have published a report that details an IoT botnet dubbed Ttint.
The experts are monitoring the Mirai-based botnet since November 2019 and observed it exploiting two Tenda router 0-day vulnerabilities to spread a Remote Access Trojan (RAT).

Unlike other IoT DDoS botnets, Ttint implements 12 remote access functions such as Socket5 proxy for router devices, tampering with router firewall and DNS settings, executing remote custom system commands.
The botnet uses the WSS (WebSocket over TLS) protocol for C2 communication to circumvent the typical Mirai traffic detection and provide secure encrypted communication for command and control.
“About the infrastructure, the attacker first used a Google cloud service IP, and then switched to a hosting provider in Hong Kong” reads the analysis published by Netlab.
“Two zero days, 12 remote access functions for the router, encrypted traffic protocol, and infrastructure IP that that moves around. This botnet does not seem to be a very typical player.”
When the botnet was first detected in 2019, experts noticed it was exploiting the Tenda zero-day flaw tracked as CVE-2020-10987.
The vulnerability was detailed in July 2020 by the security researchers Sanjana Sarda.
On August 21, Netlab researchers observed the Ttint botnet exploiting a second zero-day flaw in the family of Tenda routers.
On August 28, 2020, Netlab reported the details of this second 0-day flaw and the PoC to Tenda, but the vendor has not yet responded.
According to the experts, Tenda routers running a firmware version between AC9 to AC18 are vulnerable to the attack.
The report published by Netlab includes Indicators of Compromise (IoCs).
“We recommend that Tenda router users check their firmware and make necessary update.” concludes the report. “We also recommend that our readers monitor and block related IoCs.”
SILENTFADE a long-running malware campaign targeted Facebook AD platform
4.10.20 Virus Securityaffairs
Facebook shared details about a long-running ad-fraud campaign that’s been ongoing since 2016 targeting Facebook users with SilentFade malware.
Facebook detailed an ad-fraud cyberattack that’s been ongoing since 2016, crooks are using a malware tracked as SilentFade (short for “Silently running Facebook Ads with Exploits”) to steal Facebook credentials and browser cookies.
The social network giant revealed that malware has a Chinese origin and allowed hackers to siphon $4 million from users’ advertising accounts.
Threat actors initially compromised Facebook accounts, then used them to steal browser cookies and carry out malicious activities, including the promotion of malicious ads.
Facebook spotted the campaign in December 2018 when noticed a surge in suspicious traffic across a number of Facebook endpoints.
“Our investigation uncovered a number of interesting techniques used to compromise people with the goal to commit ad fraud. The attackers primarily ran malicious ad campaigns, often in the form of advertising pharmaceutical pills and spam with fake celebrity endorsements.” explained this week Facebook researchers Sanchit Karve and Jennifer Urgilez in a talk at the Virus Bulletin 2020 conference.
Facebook confirmed that the initial attack vector isn’t its platform, in fact, SilentFade was not spreading via Facebook or its products. The experts noticed that it was usually bundled with potentially unwanted programs (PUPs).
Once installed, SilentFade allows attackers to steal only Facebook-specific stored credentials and cookies from major browsers, including Internet Explorer, Chromium, and Firefox.
“However, unlike the others, SilentFade’s credential-stealing component only retrieved Facebook-specific stored credentials and cookies located on the compromised machine” reads the paper published by the experts.
“Cookies are more valuable than passwords because they contain session tokens, which are post-authentication tokens. This use of compromised credentials runs the risk of encountering accounts that are protected with two-factor authentication, which SilentFade cannot bypass.”
Experts explained that All Chromium and Firefox-based browsers store credentials and cookies in SQLite databases. A malware running on an infected endpoint could access cookie store if has the knowledge of its location in the various browsers.
The malware is composed of three to four components, its main downloader component is included in PUP bundles.
“The downloader application either downloads a standalone malware component or a Windows service installed as either ‘AdService’ or ‘HNService’. The service is responsible for persistence across reboots and for dropping 32-bit and 64-bit version DLLs in Chrome’s application directory.” continues the paper.
“The DLL proxies all make requests to the real winhttp.dll but makes requests to facebook.com through the Chrome process, evading dynamic behavior-based anti-malware detection by mimicking innocuous network requests.”
Upon stealing Facebook-related credentials, SilentFade retrieves the metadata of the Facebook account (i.e. payment information and the total amount previously spent on Facebook ads) using the Facebook Graph API.
The malware sends the data to the C2 servers in the form of an encrypted JSON blob through custom HTTP headers.

SilentFade implements multiple evasion techniques, it is able to detect virtual machines and to disable Facebook notification alerts from compromised accounts.
The C2 server stored the data it received from the infected node and logged the IP address of the incoming request for the purpose of geolocation.
The geolocation is crucial in the fraudulent scheme implemented by crooks because the attackers intentionally used the stolen credentials in the proximity of the city of the infected machine.
Facebook accounts with associated credit cards were used to promote malicious ads on Facebook.
Facebook experts pointed out that financial data such as bank account and credit card numbers were never exposed to the attackers because Facebook does not make them visible through the desktop website or the Graph API.
The experts also uncovered other Chinese malware campaigns some of which are still ongoing. Threat actors employed multiple malicious codes dubbed StressPaint, FacebookRobot, and Scranos.

“We anticipate more platform-specific malware to appear for platforms serving large and growing audiences, as the evolving ecosystem targeting Facebook demonstrates,” concludes Facebook. “Only through user education and strong partnerships across the security industry will we measure the scale of malicious campaigns and effectively respond to them.”
University Hospital New Jersey paid a $670K ransom
4.10.20 Ransomware Securityaffairs
University Hospital New Jersey paid a $670,000 ransom this month to prevent the leak of 240 GB of stolen data, including patient information.
The University Hospital New Jersey (UHNJ) in Newark (New Jersey) has finally paid a $670,000 ransom to prevent the publishing of 240 GB of stolen data, including patient info.
In September, systems at the University Hospital New Jersey (UHNJ) were encrypted with the SunCrypt ransomware, threat actors also stolen documents from the institution and leaked a small portion of them online.
The UHNJ is a New Jersey state-owned teaching hospital with over 3,500 employees that was established in 1994. The hospital has a $626 million budget with over 172,000 annual outpatient visits.
SunCrypt ransomware operators first appeared in the threat landscape in October 2019, and over the past few months, they launched a dedicated leak site where they started publishing the data stolen from the victims.
BleepingComputer first reported the attack on the UHNJ, the SunCrypt Ransomware leaked a 1.7 GB archive containing over 48,000 documents, they claimed to have stolen 240 GB of data.
“This data leak includes patient information release authorization forms, copies of driving licenses, Social Security Numbers (SSNs), date of birth (DOB), and records about the Board of Directors.” reported Bleeping Computer.
A BleepingComputer’s source informed about the incident revealed that an employee of UHNJ was infected with the TrickBot trojan at the end of August before the ransomware attack took place.
The hospital contacted the ransomware operators via their Tor payment site, according to BleepingComputer the initial ransom demand was $1.7 million. Anyway, the threat actors were open to a negotiation of the ransom “due to COVID-19 situation.”
“We want to prevent any further leakage of our data and that is why we are here talking with you,” UHNJ told the ransomware operators.
The two parts finally agreed to pay a ransom of $672,744, approximately 61.90 bitcoins on September 19th.
SunCrypt ransomware operators provided to the University Hospital New Jersey a decryptor, the stolen data, a security report, and an agreement not to disclose any stolen data or attack UHNJ again.
The report states that the entry point was a phishing email that tricked an employee into providing the network credentials that allowed the attackers to log into UHNJ’s Citrix server and gain access to the network.
Years-Long ‘SilentFade’ Attack Drained Facebook Victims of $4M
3.10.20 Social Threatpost
Facebook detailed an ad-fraud cyberattack that’s been ongoing since 2016, stealing Facebook credentials and browser cookies.
Facebook has detailed a wide-scale Chinese malware campaign that targeted its ad platform for years and siphoned $4 million from users’ advertising accounts.
Dubbed SilentFade (short for “Silently running Facebook Ads with Exploits”), the malware compromised Facebook accounts and used them to promote malicious ads, steal browser cookies and more. The social-media giant said that the Chinese malware campaign started in 2016, but it was first discovered in December 2018, due to a suspicious traffic spike across a number of Facebook endpoints. After an extensive investigation, Facebook shut down the campaign and pursued legal action against the cybercriminals behind the attack in December 2019.
“Our investigation uncovered a number of interesting techniques used to compromise people with the goal to commit ad fraud,” said Sanchit Karve and Jennifer Urgilez with Facebook, in a Thursday analysis unveiled this week at the Virus Bulletin 2020 conference. “The attackers primarily ran malicious ad campaigns, often in the form of advertising pharmaceutical pills and spam with fake celebrity endorsements.”
Facebook said that SilentFade was not downloaded or installed by using Facebook or any of its products. It was instead usually bundled with potentially unwanted programs (PUPs). PUPs are software programs that a user may perceive as unwanted; they may use an implementation that can compromise privacy or weaken user security. In this case, researchers believe the malware was spread via pirated copies of popular software (such as the Coreldraw Graphics graphic design software for vector illustration and page layout, as seen below).
Once installed, SilentFade stole Facebook credentials and cookies from various browser credential stores, including Internet Explorer, Chromium and Firefox.
“Cookies are more valuable than passwords because they contain session tokens, which are post-authentication tokens,” said researchers. “This use of compromised credentials runs the risk of encountering accounts that are protected with two-factor authentication, which SilentFade cannot bypass.”
facebook malware campaign silentfade
An example of a web page leading to the download of SilentFade. Credit: Facebook
The malware itself consists of three to four components, with the main downloader component being included in PUP bundles, researchers said. This downloader component is either a standalone malware component or a Windows service (installed as either “AdService” or ‘”HNService”). It’s responsible for persistence across reboots and for dropping 32-bit and 64-bit version dynamic library links (DLLs) in Chrome’s application directory, which are usually named winhttp.dll and launch DLL hijacking attacks.
“The DLL proxies all make requests to the real winhttp.dll but makes requests to facebook.com through the Chrome process, evading dynamic behavior-based anti-malware detection by mimicking innocuous network requests,” said researchers.
After stealing credentials, the malware retrieves the metadata about the Facebook account (such as payment information and the total amount previously spent on Facebook ads), using the Facebook Graph API, which is a legitimate Facebook feature allowing users to read and write data to and from the Facebook social graph. This data is then sent back to the malware’s C2 servers (as an encrypted JSON blob through custom HTTP headers).
SilentFade has varying persistence and detection-evasion tactics, including code to detect virtual machines (checking the description field of all available display drivers against “Virtual” or “VM” ) and halt execution when detected. It also disables Facebook notification alerts from compromised accounts, which could potentially alert the victim of suspicious activity.
And, in a unique anti-detection tactic, the C2 server stores the data and logs the IP address of the incoming request for the purpose of geolocation. “This was crucial as the attackers intentionally used the stolen credentials from the same or a nearby city to the infected machine to appear as though the original account owner has traveled within their city,” said researchers.
facebook malware campaign silentfade
Ad fraud process using cloaking and legitimate user sessions retrieved by SilentFade. Credit: Facebook
While users’ Facebook credentials are valuable, users with credit cards linked accounts (for business accounts, for instance) also gave cybercriminals the ability to use those payment cards to promote malicious ads on Facebook.
However, “it should be noted that payment-information details (such as bank account and credit card numbers) were never exposed to the attackers, as Facebook does not make them visible through the desktop website or the Graph API,” said researchers.
As part of its investigations into SilentFade, Facebook also uncovered other Chinese malware campaigns, including ones dubbed StressPaint, FacebookRobot and Scranos. Some of these malware attacks remained active as recently as June, Facebook warned.
The company has faced security and privacy issues over the past year, and on Thursday filed a lawsuit in the U.S. against two companies that used scraping to engage in an international data harvesting operation, including scraping data from Facebook, Instagram, Twitter, YouTube, LinkedIn and Amazon, to sell “marketing intelligence.” The data involved includes names, user IDs, genders, dates of birth, relationship status, location information and more.
In the midst of all this, Facebook warns that it expects cybercriminals to continue to up the ante when it comes to launching attacks on its platform.
“We anticipate more platform-specific malware to appear for platforms serving large and growing audiences, as the evolving ecosystem targeting Facebook demonstrates,” said Facebook. “Only through user education and strong partnerships across the security industry will we measure the scale of malicious campaigns and effectively respond to them.”
Researchers Mixed on Sanctions for Ransomware Negotiators
3.10.20 Ransomware Threatpost
Financial institutions, cyber-insurance firms, and security firms have all been put on notice by the U.S. Department of the Treasury.
Ransomware negotiators may have to pay up in new ways if they intercede with cybercriminals on companies’ behalf. Several researchers weighed in on the wisdom of the move, with mixed reactions.
The U.S. Department of the Treasury said Thursday that companies that facilitate ransomware payments to cyber-actors on behalf of victims may face sanctions for encouraging crime and future ransomware payment demands. These facilitators can fall into multiple camps, including financial institutions, cyber-insurance firms, and security firms involved in digital forensics and incident response.
The department has added multiple crimeware gangs to its sanctions program, prohibiting U.S. entities or citizens from doing business with them (i.e., pay a ransom). These include the developer of CryptoLocker, Evgeniy Mikhailovich Bogachev; the SamSam ransomware group; North Korea-linked Lazarus Group; and Evil Corp and its leader, Maksim Yakubets. This latest policy expands the sanctions’ applicability to anyone dealing with ransomware operators in general.
“Ransomware payments made to sanctioned persons or to comprehensively sanctioned jurisdictions could be used to fund activities adverse to the national security and foreign policy objectives of the United States. Ransomware payments may also embolden cyber-actors to engage in future attacks,” according to a website notice on the policy. “In addition, paying a ransom to cyber-actors does not guarantee that the victim will regain access to its stolen data.”
The Tresasury Department added that a lack of knowledge of the sanctions’ existence is not an excuse, and that people could still be held civilly liable in that case. However, if a company makes a “self-initiated, timely and complete report of a ransomware attack to law enforcement,” this will be taken into account and could lower any penalties for the organization.
The department did not specify the amount of any potential penalty.
To Pay or Not to Pay
While the feds have always recommended not paying ransoms, in reality, the decision to pay up or to not is an individual choice that has to be made given the context of any given situation, researchers said. Businesses that don’t have backups may be desperate to get their data back, for instance; or, many times, the ransomware payment is less than alternate investigation and remediation would cost (and often, firms can intercede for them and reduce the amount being extorted). Also, many gangs are stealing data as well, so sensitive data exposure is another consideration.
Because of that, the Treasury Department’s move could end up being counterproductive, some said.
“Penalizing businesses that pay off attackers sounds like it will make ransomware less lucrative,” said Melody Kaufmann, cybersecurity specialist for Saviynt, said via email. “The converse is true. This advisory will propagate ransomware rather than reduce it for three key reasons. First, it disincentivizes reporting ransomware attacks, robbing law enforcement, security professionals, and analysts of data vital to combat future attacks. Second, it fails to provide an effective data recovery alternative. Third, it favors big corporations while crushing small- to medium-sized businesses beneath its heel.”
Small and medium businesses are notorious for having weak security because maintaining an information security team is often cost-prohibitive. Lack of security increases their risk and the likelihood of infection, she added.
“This advisory discourages them from contacting law enforcement by increasing the chance of a fine,” she added. “Often paying the ransom is cheaper than the cost of losing their data or recovering from back-ups, which few small businesses even maintain. The treasury department will only learn of a ransomware attack on a small or medium business via a disgruntled employee or a media outlet reporting it.”
Tim Erlin, vice president of product management and strategy at Tripwire, added that ransomware affects every segment.
“It’s not just commercial organizations that have paid out for ransomware incidents,” he said via email. “There have been government agencies, cities and police departments that have fallen victim and ultimately paid the ransom as well. It’s easy to say that you should never pay the ransom because it just encourages more ransomware, but it’s much harder to follow one’s own advice when faced with the potential for sensitive data loss, publication, or the loss of your business.”
Not everyone saw the move as problematic.
“We need to change the economics of the bad guys if we want anything to change,” CynergisTek CEO Caleb Barlow said. “Ransomware payment got so much more difficult to do. The fact they’re using the Treasury Department to do this is brilliant. The reach of US Treasury is far broader – [and] applies to U.S. companies, allies, citizens – that they cannot aid and abet the enemy. A ransomware payment is no longer a get out of free jail card. Enterprises have to invest in defenses.”
He added that the fact that Garmin recently, knowingly paid an adversary on the sanction list “likely accelerated this decision.”
Nozomi Networks CEO Edgard Capdevielle also fell into the “don’t pay” camp.
“While it might be tempting to pay a ransom, doing so only fuels the fire,” he said via email. “We are seeing more instances where the public and private sector respond to the pressure and pay the ransom…choosing to pay a ransom is too often a short-sighted response that could come at a high cost. Research has shown that paying a ransom can double the cost of recovery. Building, maintaining and constantly improving an organization’s cybersecurity program is always the best approach and there are certainly tools available today that provide cost effective solutions.”
He added, “Organizations that give into hackers’ demands are only supporting the profitability and growth of ransomware activity. When it comes to ransomware attacks, prevention will always be better than a cure.”
One thing is certain – ransomware has reached epidemic proportions, according to Charles Carmakal, SVP and CTO of FireEye Mandiant.
“Ransomware is the most significant and prevalent cybersecurity threat facing corporations today,” he said. “Today’s ransomware and extortion problem is unbearable. Many ransomware operators steal a large volume of sensitive data from organizations prior to deploying encryptors and locking organizations out of their systems and data. Threat actors may ask for money for a decryption tool, a promise to not publish the stolen data, and a walkthrough of how they broke into the network.”
He said that these types of extortion demands are in the six-figure range for smaller companies and between seven and eight figures for larger companies.
“We are aware of several victim organizations that paid extortion demands between $10 million and $30 million,” he said. “Mandiant is aware of over 100 organizations in which ransomware operators had network access to in September alone, more than double what we were aware of in September of the previous year.”
Egregor Ransomware Threatens ‘Mass-Media’ Release of Corporate Data
3.10.20 Ransomware Threatpost
The newly discovered ransomware is hitting companies worldwide, including the GEFCO global logistics company.
A freshly discovered family of ransomware called Egregor has been spotted in the wild, using a tactic of siphoning off corporate information and threatening a “mass-media” release of it before encrypting all files.
Egregor is an occult term meant to signify the collective energy or force of a group of individuals, especially when the individuals are united toward a common purpose — apropos for a ransomware gang. According to an analysis from Appgate, the code seems to be a spinoff of the Sekhmet ransomware (itself named for the Egyptian goddess of healing) – a link that was also noted by other researchers..
“We found similarities in both Sekhmet and Egregor ransomware, such as obfuscation techniques, functions, API calls and strings, such as %Greetings2target% and %sekhmet_data% changing to %egregor_data%,” Gustavo Palazolo, security researcher at Appgate, told Threatpost. “Furthermore, the ransom note is also fairly similar.”
As far as other technical details, “The sample we analyzed has many anti-analysis techniques in place, such as code obfuscation and packed payloads,” according to the firm’s research, announced Friday. “Also, in one of the execution stages, the Egregor payload can only be decrypted if the correct key is provided in the process’ command line, which means that the file cannot be analyzed, either manually or using a sandbox, if the exact same command line that the attackers used to run the ransomware isn’t provided.”
Further, “we have found that Egregor can receive additional parameters via command line, such as ‘nomimikatz,’ ‘killrdp,’ ‘norename,’ among others,” Palazolo said. “At the moment, our team is still revers- engineering the malware to get the whole picture. Furthermore, we will continue to monitor any possible variant emerging from this family.”
Overall, he said, it has the same sophistication level as other ransomware families, however Egregor implements a high number of anti-analysis techniques, such as code obfuscation and payload encryption.
While Appgate researchers don’t know how long Egregor has been circulating, its first public appearance of Egregor was September 18 on Twitter, after it was spotted by @demonslay335 and @PolarToffee
Appgate researchers also found that the ransom note demands payment within three days – otherwise, the sensitive data will be leaked. In a twist from the usual double-extortion tactics used by ransomware families like NetWalker, the Egregor operators threaten to distribute stolen via “mass media,” so that a victim company’s partners and clients will know that the company was attacked.
This part of the ransom note, shared with Threatpost, reads: “What does it mean? It means that soon mass media, your partners and clients WILL KNOW about your PROBLEM.”
So far though, no mass-media events have occurred. “The only evidence we have is the deep web site in which they are publishing details about attacked companies, we have not identified any other news or information on data being released to any media organizations,” Palazolo said.
And indeed, the analysis uncovered a self-billed “Egregor news” website, hosted on the deep web, which the criminal group uses to leak stolen data.
“At the time of this advisory, there are at least 13 different companies listed in their ‘hall of shame,’ including the global logistics company GEFCO, which suffered a cyberattack last week,” according to the firm.
The Egregor ransom note also says that aside from decrypting all the files in the event the company pays the ransom, the operators will provide recommendations for securing the company’s network, “helping” them to avoid being breached again, “acting as some sort of black-hat pen-test team,” according to the Appgate research.
The note reads: “(In case the payment is done) … You WILL GET full DECRYPTION of your machines in the network, FULL FILE LISTING of downloaded data, confirmation of downloaded data DELETION from our servers, RECOMMENDATIONS for securing your network perimeter.”
“The ‘security recommendations’ caught our attention since it’s something unusual for a criminal group, they are trying to play good guys by suggesting they would try to help secure your network,” Palazolo said.
There’s no word yet on the initial infection vector for the malware, but ransomware seems to be equal-opportunity in terms of its targets, with samples affecting corporations in France, Germany, Italy, Japan, Mexico, Saudi Arabia and the US, according to the researcher.
As for the size of the ransom, the crimeware operators make victims jump through hoops.
“Unfortunately, there are no details on [the ransom payment amount] in the ransom note or on the Egregor website,” the researcher told Threatpost. “To get payment details, the victim needs to navigate to the deep web link Egregor provided and get instructions from the attacker through a live chat, which we have not performed.”
Voter Registration ‘Error’ Phish Hits During U.S. Election Frenzy
3.10.20 Phishing Threatpost
Phishing emails tell recipients that their voter’s registration applications are incomplete – but instead steal their social security numbers, license data and more.
Cybercriminals this week are tapping into this week’s political frenzy with a new phishing lure that warns U.S. targets that their voter registration data needs extra details.
The emails purport to come from the U.S. Election Assistance Commission, an independent agency of the United States government that serves as a national resource of information regarding election administration. Utilizing this organization as a sender shows that cybercriminals are tapping into the vast database of U.S. citizens who are preparing to vote in the U.S. presidential election, which is right around the corner.
The email contains a URL, which leads to a spoofed web page that steals a variety of targets’ personal data, including name, date of birth, mailing address, email address, Social Security number and driver’s license data.
“Whatever the intent behind this particular phishing attack, it should serve as a reminder that human beings — users, employees, citizens and voters — are ‘soft targets’ for malicious actors,’ said Eric Howes with KnowBe4, in a Friday analysis. “This is especially true in turbulent times such as the present — when fear, confusion and doubt are surging in the run-up to a historic election that just happens to fall in the middle of a catastrophic pandemic.”
The emails subject says “voter registration application details couldnt be confirmed,” and the body of the email tells users: “Your Arizona voter’s registration application submitted has been reviewed by your County Clerk and some few details couldnt be comfirmed” (Note a suspicious lack of capitalization, spelling and grammar, which serve as a tip that the email is malicious).

The initial phishing email. Credit: KnowBe4
The email then asks recipients to reconfirm their details to allow for processing, saying it could take up to two days to reflect in the system, and points to a URL.
“The social-engineering tactic being used here is a classic one in which email recipients are told of a problem with one of their accounts (usually a bank account) and are then offered a link to fix or redress the problem,” said researchers.
Though the email pretends to come from the U.S. Election Assistance Commission, the link in the email sends users to a web page that spoofs ServiceArizona, which is part of the state government of Arizona. The page includes images pulled directly from the state’s official site.
“Arizona, it should be noted, is considered a potentially important swing state in the upcoming U.S. presidential election,” said researchers. “The state also happens to be hosting a hotly contested election for one of the state’s two U.S. Senate seats.”
However, it should be noted that the phishing email reported to KnowBe4 was submitted by a target in Wisconsin – who wouldn’t submit a voter registration application in Arizona – another potential error on the side of the cybercriminals.
“Curiously, the copy of the email we received was submitted by a customer in Kenosha County, WI — a locality that has been in the news recently due to widely reported civil unrest in the area,” said researchers. “Moreover, like Arizona, Wisconsin is expected to play an important role in the upcoming election.”
Of note, the email was sent through Sendgrid, which researchers say suggests it could have been delivered to a large number of email addresses. Sendgrid is a popular email service provider, which researchers say is currently dealing with a significant problem with compromised accounts that have been exploited by malicious actors to deliver large volumes of phishing emails.

Phishing landing page. Credit: KnowBe4
At this point, researchers are unsure if the end goal of this phishing attack is identity theft-related, versus specifically targeting U.S. voter registration data.
While it is common for bad actors to solicit data from targets in order to support a variety of fraudulent endeavors, “given the election angle…we cannot ignore the possibility that this phish may be part of an attempt by parties unknown to intervene in the election, either by seeding confusion and chaos in the election process or engaging in some form of election fraud,” said researchers.
With the U.S. presidential election only 31 days away – coupled with this week’s presidential debate and news of Pres. Donald Trump testing positive for COVID-19 – political tensions are at an all-time high.
Cybercriminals have wasted no time utilizing these tensions as a lure. On Thursday, hundreds of U.S. organizations were targeted by an Emotet spear-phishing campaign, which sent thousands of emails purporting to be from the Democratic National Committee and recruiting potential Democratic volunteers. Meanwhile, the U.S. election campaigns of both Donald Trump and Joe Biden were targeted in a slew of recent cyberattacks, Microsoft warned earlier in September.
Account Takeover Fraud Losses Total Billions Across Online Retailers
3.10.20 CyberCrime Threatpost
Account takeover fraud (ATO) attacks are on the rise, up nearly 300 percent since last year.
Account takeover (ATO) attacks are on the rise, and in fact have become a go-to attack of choice cybercriminals of all stripes. In fact, in 2019 alone, ATO attacks cost consumers and e-commerce retailers a whopping $16.9 billion in losses.
To be clear, ATO fraud isn’t new, it’s been a concern for online retailers for a decade. But Sift recently released its 2020 Digital Trust & Safety Index, which found that ATO attacks have jumped dramatically, by 282 percent, between Q2 2019 and Q2 2020, driven by a rise in digital business and a jump in online shopping since the COVID-19 outbreak last spring. The number of stolen credentials for sale on the dark web is meanwhile up 300 percent.
In a typical ATO attack, criminals use automated bots to crisscross the web and enter stolen credentials into online accounts – and they also try to search for clues to crack passwords and security codes to cash in further.
Undoubtedly, COVID-19 has driven more online retail activity, creating an even more target-rich environment for ATO fraudsters. But retailers are unintentionally making themselves more susceptible, too, according to Sift’s report. One-click, on-demand and mobile solutions, intended to make the shopping experience simple, also have the unintended consequence of making consumer data easier to steal. Sift’s report calls this a “Catch-22” for retailers in trying to balance “concerns of fraud and friction.”
The “friction” is the series barriers to fraud; tools like two-factor and multifactor authentication, biometrics, CAPTCHA codes and the like. The “catch” is that the more of these barriers you place in front of a shopper, the more likely retailers are to see a jump in abandoned carts and irritated customers repeatedly being asked to input their sensitive data.
ATO fraud victims have been exposed across all kinds of sites — dating, travel, banking and social media — meaning consumers are at risk almost anywhere they go online shop or buy services.
But hardest hit, according to Sift’s report, have been online sellers of physical goods. ATO fraud is up 378 percent among physical e-commerce marketplaces. Criminals have also become adept at exploiting new buy online, pick up in store sales models (BOPIS) which have become a go-to solution for low-contact shopping during the pandemic. Fraudsters buy goods online with stolen credentials, pick them up, then return them to resell for a quick profit.
And the cost to online retailers goes far beyond the initial fraud. More than half (56 percent), of customers surveyed by Sift said that if they discovered that their personal data was compromised, they would stop doing business with site and choose another provider.So, ATO fraud is a real threat to brand loyalty.
Also, forget the tired stereotype of the hoodie-wearing hacker trying to steal credentials from a basement. ATO criminals have evolved into well-funded, well-organized, state-sponsored actors, according to Sift.
“The lonely, disgruntled, hacker trope has mutated into far-reaching, state-sponsored teams of fraudsters who are just as focused on efficiency, expansion and ROI as any e-commerce merchant,” the report said.
They’ve also become adept at hiding their fraud behind periodic traffic spikes. In Sept. 2019, cybercriminals used the back-to-school and start of the holiday shopping seasons to hide their nefarious activity behind already bogged-down systems, Sift said.
The 2020 Digital Trust and Safety Index was complied through a survey of Sift’s global network of more than 34,000 sites and apps, in addition to more than 1,000 customers contacted throughout August.
LatAm Banking Trojans Collaborate in Never-Before-Seen Effort
3.10.20 Virus Threatpost
Eleven different malware families are coordinating on distribution, features, geo-targeting and more.
Virus Bulletin 2020 — A loose affiliation of cybercriminals are working together to author and distribute multiple families of banking trojans in Latin America – a collaborative effort that researchers say is highly unusual.
Multiple, distinct malware families have plagued Latin American banking customers for years – the variants include Amavaldo, Casbaneiro, Grandoreiro, Guildma, Krachulka, Lokorrito, Mekotio, Mispadu, Numando, Vadokrist and Zumanek, according to ESET.
In examining these families over time, ESET researchers began to notice “some similarities between multiple families in our series, such as using the same uncommon algorithm to encrypt strings or suspiciously similar DGAs [domain-generation algorithms] to obtain C2 server addresses,” according to a Thursday analysis.
The trojans also share “practically identical implementation[s] of the banking trojans’ cores,” including sending notifications to operators, periodically scanning active windows based on name or title and using carefully designed pop-up windows designed to mimic banking apps and harvest information.
The families also share uncommon third-party libraries, string encryption algorithms, and string and binary obfuscation techniques, researchers said.
Flowchart of a typical distribution chain used by Latin American banking trojans. Click to enlarge. Source: ESET
What also caught the researchers’ eye is the fact that the banking trojans all use a very similar distribution flow. With typical malware, “a lot of time, we can predict which banking trojan is going to download based on the distribution flow,” said ESET researcher Jakub Souèek, speaking on the research at the Virus Bulletin 2020 conference this week along with his colleague, Martin Jirkal. This isn’t the case with the Latin American trojans, he added.
“They usually check for a marker (an object, such as a file or registry key value used to indicate that the machine has already been compromised), and download data in ZIP archives,” according to the researcher. “Besides that, we have observed identical distribution chains ending up distributing multiple Latin American banking trojans. It is also worth mentioning that since 2019, the vast majority of these malware families started to utilize Windows Installer (MSI files) as the first stage of the distribution chain.”
Most Latin American banking trojans also share execution methods, including DLL side-loading of the same set of vulnerable software applications, and abusing a legitimate AutoIt interpreter. And, the collaboration also appears to extend to geo-targeting.
“Since late 2019, we see several [banking trojans] adding Spain and Portugal to the list of countries they target,” researchers said. “Moreover, different families use similar spam email templates in their latest campaigns, almost as if this were a coordinated move as well.”
It’s highly unlikely that separate malware gangs developed so many families with such a depth of similarities – which extend to “coding mistakes and things that don’t work,” Souèek said. However, he stressed that it’s also unlikely that it’s one single group authoring all of the trojans.
This is borne out by the fact that one of the unique attributes of each trojan is the fake pop-up windows that they use.
“Even though the windows look similar (since they are designed to fool customers of the same financial institutions), we have not spotted multiple families using identical windows,” according to the research.
Given all of the evidence, it seems clear that with so many common ideas, as well as some personalization between the malwares, multiple threat actors are likely closely cooperating with each other.
Source: ESET
“Even though the sharing of knowledge among cybercriminals is not unusual, seeing so many examples of it in region-specific malware families with the same focus caught our attention,” Souèek said, adding that it’s a phenomenon that hasn’t been seen elsewhere.
“Since we believe it is impossible for 11 different authors to have come up with so many common ideas and we don’t believe that one group is deliberately maintaining 11 different families at the same time, we conclude that the authors of these banking trojans communicate with each other,” he said. “This cooperation is extensive and it affects the vast majority of the families we have analysed. Such tight collaboration between malware families that share the same goal, are region-specific and are, in fact, expected to be competitors, is something we have never encountered before.”
IPStorm botnet evolves to infect Android, Linux, and Mac devices
3.10.20 BotNet Securityaffairs
Researchers from Intezer reported that the IPStorm botnet has evolved to infect other operating systems, including Android, Linux, and Mac devices.
The IPStorm botnet was first uncovered in May 2019 while targeting Windows systems, not experts from Intezer reported that the bot evolved to infect other platforms, including Android, Linux, and Mac devices.
IPStorm botnet continues to infect systems across the world, its size passed from around 3,000 infected systems in May 2019 to more than 13,500 devices this month.
The name IPStorm is the abbreviation of InterPlanetary Storm that came from the InterPlanetary File System (IPFS), which is a peer-to-peer protocol used by the bot for communications with the intent to obscure the malicious traffic.
The bot was written in the Go programming language, it was initially designed to compromise Windows systems only. In June security firms Bitdefender and Barracuda discovered new IPStorm versions that are able to target also Android, Linux, and Mac.
The experts from both security firms reported that IPStorm was infecting Android systems with ADB (Android Debug Bridge) port exposed online.
The bot was also targeting Linux and Mac devices performs dictionary attacks against SSH services to guess their username and passwords.
Once a connection is established, the malware will check the presence of a honeypot by comparing the hostname of the attacked server to the string “svr04”, which is the default hostname of Cowrie SSH honeypot.
“The Linux variant has additional features over the documented Windows version, such as using SSH brute-force as a means to spread to additional victims and fraudulent network activity abusing Steam gaming and advertising platforms.” reads the Intezer’s report. “The Linux variant has adjusted some features in order to account for the fundamental differences that exist between this operating system and Windows.”
The IPStorm bot also kills a list of processes that could potentially interfere with its operations.
Experts noticed that IPStorm versions for both Linux and Windows systems implement a reverse shell mechanism.
“The Windows variant has a package called powershell which contains functions for achieving reverse shell. The same package is present in the Linux variant but it contains only one function: storm_powershell__ptr_Backend_StartProcess. The function is used to get a reverse shell on the infected system.” continues the analysis.

Curiously, until now, the researchers have not seen the IPStorm operators doing malicious activities, such as performing DDoS attacks or relaying malicious traffic.
“Platforms that are compromised by IPStorm are not only exposed to a backdoor to their services but are also added to the IPStorm Botnet which attempts to spread to other victims.” concludes Intezer. “The attackers behind IPStorm are very active evidenced by the frequent release of updated versions with new features and improvements, as well as the expansion to several different platforms and architectures.”
Wacky Indoor Amazon Drone Takes on Privacy Skeptics
3.10.20 Privacy Securityweek
It could be the wackiest product yet from Amazon -- a tiny indoor drone which buzzes around people's homes as a security sentry.
The introduction of the Ring Always Home Cam planned for 2021 has opened up fresh debate on the potential for intrusive surveillance and privacy infringement.
Amazon says the tiny drone is "built with privacy in mind" and operates at the direction of its customers. Nestled in a charging dock, the drone can be deployed remotely and send up to five minutes of video to the user.
But some activists express concerns about the device -- part of a family of Ring-branded home security technology which has been scrutinized over its links to law enforcement.
John Verdi, vice president of policy at the Future of Privacy Forum, a Washington think tank, said the deployment may contribute to a "normalization of surveillance" in everyday life as more consumers install devices that listen and see inside the home.
"When cameras and microphones and other sensors are deployed in private spaces like living rooms and bedrooms, that leads to an acceptance of everyday surveillance," Verdi said.
Nonetheless, Verdi noted that "Amazon has put some thought into privacy protections for this product both in the hardware and in the software policies."
University of Washington law professor and privacy researcher Ryan Calo noted that even the perception of being watched can make people change behavior.
With any form of electronic monitoring, "you feel like there is a social agent in your midst," Calo said.
"A camera like this can make people feel observed and threatens one of the few remaining opportunities for solitude."
Calo said the flying cam "could be incrementally more harmful than a regular camera" by allowing someone to monitor other people without their consent.
Although it is marketed as a home device, Calo said it could be used in a workplace as well and "allows the person who controls it to check in on anyone -- and there isn't anywhere to hide."
This could enable an abusive spouse to monitor a partner, for example.
British-based privacy group Big Brother Watch was more blunt, calling the cam "arguably Amazon's most chilling surveillance product yet."
- Feeling safe or threatened? -
An Amazon spokesperson said of the new device: "Our customers are looking for ways to keep their homes and families safe, connected, and secure -- and our new products and features, including the Always Home Cam, help do just that."
Amazon, which purchased Ring in 2018, has faced a wave of criticism over its sharing of surveillance footage from its doorbell camera and partnerships with police departments which have encouraged homeowners to use the devices.
But Amazon said Ring indoor cameras are not subject to law enforcement requests and have no microphone to record audio.
Calo said that despite Amazon's pledge not to share video with law enforcement, "it may not be up to Amazon -- it might be up to a court if police request a warrant."
Separately, some fear these monitoring devices could be surreptitiously used to gather data for marketing by Amazon or its partners.
While it was not clear how data from the drones might be used, Calo said that "Amazon has a long track record of attempting to monetize what it knows about you from search history or purchase history. It's part of their business model."
XDSpy APT remained undetected since at least 2011
2.10.20 APT Securityaffairs
Researchers from ESET uncovered the activity of a new APT group, tracked as XDSpy, that has been active since at least 2011.
XDSpy is the name used by ESET researchers to track a nation-state actor that has been active since at least 2011. The APT group, recently discovered by ESET, targeted government and private companies in Belarus, Moldova, Russia, Serbia, and Ukraine, including militaries and Ministries of Foreign Affairs.
The activity of the cyber espionage group was first documented by ESET experts Matthieu Faou and Francis Labelle in a talk at the Virus Bulletin 2020 security conference.
“Early in 2020, ESET researchers discovered a previously undisclosed cyber espionage operation targeting several governments in Eastern Europe, the Balkans and Russia. Unusually, our research shows that this campaign has been active since at least 2011 with next to no changes in TTPs.” reads the abstract from the talk. “It is very uncommon to find a cyber espionage operation without any public reporting after almost 10 years of activity.”
Experts believe that the hacker group could have targeted many other countries and a good portion of its operations has yet to be discovered.
In February 2020 Belarussian CERT published a security advisory about an ongoing spear-phishing campaign, linked by ESET to XDSpy, targeting several Belarussian ministries and agencies. At the time, the threat actors were interested into collecting documents from government staff such as diplomats or military personnel, private companies and academic institutions. The nature of the targets suggests that the threat actor is also responsible for economic espionage operations.
Since the publishing of the advisory, the group’s operations have now gone dark.
The tools in the arsenal of the XDSpy APT are quite basic, although efficient, their primary tool is a downloader dubbed named XDDown.
The malware samples analyzed by the researchers are slightly obfuscated using string obfuscation and dynamic Windows API library loading. The malware supports multiple features, including the monitoring of removable drives, taking screenshots, exfiltrating documents, and collecting nearby Wi-Fi access point identifiers.
Experts also noticed that hackers also used NirSoft utilities to recover passwords from web browsers and email clients.
Experts observed the threat actor exploiting a remote code issue in Internet Explorer tracked as CVE-2020-0968 that was addressed by Microsoft with the release of Patch Tuesday security updates for April 2020.
“At the time it was exploited by XDSpy, no proof-of-concept and very little information about this specific vulnerability was available online,” explained ESET. “We think that XDSpy either bought this exploit from a broker or developed a 1-day exploit themselves by looking at previous exploits for inspiration.”
ESET described XDDown as a “downloader” used to infect a victim and then download secondary modules that would perform various specialized tasks.
The XDDown malware has a modular structure, some of the plugins analyzed by ESET are:
XDRecon: Gathers basic information about the victim machine (the computer name, the current username and the Volume Serial Number of the main drive).
XDList: Crawls the C: drive for interesting files (.accdb, .doc, .docm, .docx, .mdb, .xls, .xlm, .xlsx, .xlsm, .odt, .ost, .ppt, .pptm, .ppsm, .pptx, .sldm, .pst, .msg, .pdf, .eml, .wab) and exfiltrates the paths of these files. It can also take screenshots.
XDMonitor: Similar to XDList. It also monitors removable drives to exfiltrate the files matching an interesting extension.
XDUpload: Exfiltrates a hardcoded list of files from the filesystem to the C&C server, as shown in Figure 5. The paths were sent to the C&C servers by XDList and XDMonitor.
XDLoc: Gathers nearby SSIDs (such as Wi-Fi access points), probably in order to geo-locate the victim machines.
XDPass: Grabs saved passwords from various applications such as web browsers and email programs.
XDSpy
The analysis of the spear-phishing campaigns linked to the APT group revealed that the hackers used email subject lines with lures related to lost and found objects and the COVID-19 pandemic. These messages came with malicious attachments such as Powerpoint, JavaScript, ZIP, or shortcut (LNK) files.
ESET researchers noted that many XDSpy malware samples were compiled in the UTC+2 or UTC+3 time zone from Monday to Friday, a circumstance that suggests the involvement of professionals.
“XDSpy is a cyberespionage group mostly undetected for more than nine years while being very busy over the past few months.” concludes the report. “The group’s technical proficiency tends to vary a bit. It has used the same basic malware architecture for nine years, but it also recently exploited a vulnerability patched by the vendor but for which no public proof-of-concept exists, a so-called 1-day exploit.”
The report includes additional technical details, such as Indicators of Compromise (IoCs).
Internet Engineering Task Force Proposes Standard for Network Time Security
2.10.20 Security Securityweek
IETF Publishes New Proposal to Add Security to Network Timing
The Internet Engineering Task Force (IETF) has published RFC8915, its proposed standard for network time security (NTS). It has been five years in the making and is designed to remedy the issues and vulnerabilities that exist in the current network time protocol (NTP).
Accurately synchronized time between different computers over packet-switched, variable-latency data networks is essential. This becomes even more critical in the age of the fourth industrial revolution, where the accurate timing and sequence of different processes is vital. Since its launch in 1985, NTP has served this purpose well. However, over the last 35 years it has become apparent that various vulnerabilities and issues in NTP demonstrate that it requires an increased level of security. NTS is designed to provide that security.
The existing issues affecting basic NTP include DDoS amplification, packet manipulation, and replay attacks -- the last two being implemented by man-in-the-middle (MiTM) attacks that can forge messages and falsify the time.
The primary solution has been the introduction of asymmetric cryptography to the initial server authentication. This can prevent MiTM attacks. That it operates slower than symmetric encryption opens an increased possibility of DDoS attacks against NTP servers. However, as RFC8915 notes, "a successful DDoS attack on an NTS-KE server separated from the NTP service it supports will not affect NTP users that have already performed initial authentication, AEAD key extraction, and cookie exchange."
The proposed standard also warns that NTS does not fully protect against attacks from on-path adversaries. "In addition to dropping packets and attacks... an on-path attacker can send spoofed Kiss-o'-Death replies, which are not authenticated, in response to NTP requests."
However, NTS does largely prevent the use of some NTP implementations in DDoS amplification attacks. "Certain nonstandard and/or deprecated features of the Network Time Protocol enable clients to send a request to a server that causes the server to send a response much larger than the request," notes the standard. NTS avoids contributing to this problem by ensuring that NTS-related extension fields included in server responses are the same size as the fields sent by the client.
This is not a hundred-percent accurate statement since RFC7822 requires that extensions be padded and aligned to four-octet boundaries -- meaning that response size may in some cases exceed request by up to three octets. But as the IETF comments, "This is sufficiently inconsequential that we have declined to address it."
"The publication of RFC8915 is an important moment both for the development of NTS and for security on the Internet in general," comments Lars Michael Jogback, the CEO of Netnod. Netnod is a Swedish firm that provides NTP, NTS and Precision Time Protocol (PTP) services. "Netnod is proud to have been at the forefront of developing the NTS standard and implementations. We will continue to focus on services such as NTS to make the Internet as secure and robust as possible for everyone."
Hacked Hospital Chain Says All 250 US Facilities Affected
2.10.20 Hacking Securityweek
The hospital chain Universal Health Services said Thursday that computer services at all 250 of its U.S. facilities were hobbled in last weekend’s malware attack and efforts to restore hospital networks were continuing.
Doctors and nurses at affected hospitals and clinics, many already burdened with coronavirus care, have had to rely on manual record-keeping, with lab work slowed. Employees have described chaotic conditions impeding patient care.
The chain has not commented on reports it was hit by ransomware, though its description of the attack in a statement Thursday was consistent with malware variety that encrypts data into gibberish that can only be restored with software keys after ransoms are paid.
King of Prussia, Pennsylvania-based UHS said its “systems were quickly disconnected and the network was shut down in order to prevent further propagation.”
The company, with 90,000 employees, said electronic medical records systems were not impacted by the attack and it was making steady progress restoring and reconnecting systems. Company spokeswoman Jane Crawford said via email that all 250 U.S. facilities were affected.
UHS workers reached by The Associated Press at company facilities in Texas and Washington, D.C., earlier in the week described mad scrambles after the outage began to render care, including longer emergency room waits and anxiety over determining which patients might be infected with the virus that causes COVID-19.
BleepingComputer, an online cybersecurity news site, spoke to UHS employees who described ransomware with the characteristics of Ryuk, which has been widely linked to Russian cybercriminals and used against large enterprises.
UHS operates hospitals and clinics, many treating behavioral health and addiction problem. Its acute care hospitals are concentrated in states including California, Texas, Nevada and Florida.
Facebook Details Malware Campaign Targeting Its Ad Platform
2.10.20 Social Virus Securityweek
Facebook on Thursday released a detailed technical report on a malware campaign that targeted its ad platform for years.
Referred to as SilentFade (Silently running Facebook ADs with Exploits), the malware was identified in late 2018 and the vulnerability it was exploiting to stay undetected was patched soon after. Facebook took legal action against the malware operators in December 2019.
The malware exploited a server-side flaw to persistently suppress notifications and ensure that the infected users would not be made aware of suspicious activity related to their accounts. This allowed SilentFade to abuse the compromised accounts and run malicious ads without the victims noticing anything.
Although the malware was first detected in the final week of 2018, the cyber-crime group behind it is believed to have been operating since 2016, constantly adapting to new Facebook features and likely expanding to other social platforms and web services as well.
Distribution channels for SilentFade include potentially unwanted program (PUP) bundles within pirated copies of legitimate software and other malware families. The PUP bundles would include a downloader component that would fetch a standalone malware component meant to achieve persistence and download malicious DLLs into Chrome’s application directory, to perform DLL hijacking.
Next, the malware would steal Facebook login credentials from Internet browsers, would retrieve metadata about the Facebook account, and send the information to the command and control (C&C) servers. The victim’s IP address was logged as well, for geolocation purposes.
“Based on a review of the data collected by SilentFade, it’s likely that compromised user accounts that had at least a linked payment method were deemed more valuable. SilentFade, or its customers, would then be able to use the compromised user’s payment method (credit card, bank account, or PayPal account) to run malicious ads on Facebook,” the social media platform explains.
If no page or linked payment information was attached to the account, the attackers used stolen credit card data to create pages and run ads. According to Facebook, however, no user payment information details were exposed to the attackers.
The malware included anti-VM checks and targeted Facebook-specific credentials and cookies stored on the local machine only. It also leveraged access to the Graph API to gather additional information on the victim, and took specific action to get around the security checks that Facebook had in place, such as asking for user permission.
Notification alerts were completely turned off for the compromised accounts, thus preventing users from receiving alerts on the suspicious activity taking place. Login alerts and Facebook Business pages were blocked as well.
After identifying the malicious activity, Facebook patched a server-side validation flaw, reverted the blocked notification state on all affected accounts, forced password resets, invalidated sessions, added more fixes and detection mechanisms, and reimbursed affected users.
Facebook’s investigation into SilentFade, which saw collaboration from Radware, Bitdefender, Atlassian/BitBucket and Google/VirusTotal, enabled attribution, and in December 2019 the company sued Chinese firm ILikeAd Media International Company Ltd. and two of its employees, namely Chen Xiao Cong and Huang Tao, for creating and operating the malware.
SilentFade authors, however, modified their code to ensure it can work even with Facebook’s new mechanisms in place, and started employing obfuscation to hinder detection.
The social platform also discovered additional Chinese malware that are part of an ecosystem targeting Facebook users and says that such attacks were active as of June 2020. Some of the names it mentions in a report made public on Thursday include StressPaint, FacebookRobot, and Scranos.
“We believe this ecosystem spread its wings again in early 2019 with the release of two newer malware families, ‘Scranos’ and ‘FacebookRobot’, first seen in April and June 2019, respectively,” the company notes.
Blackbaud Says Bank Account Data, SSNs Impacted in Ransomware Incident
2.10.20 Ransomware Securityweek
Documents filed by cloud software provider Blackbaud with the United States Securities and Exchange Commission (SEC) this week reveal that bank account details and social security numbers might have been affected in a ransomware attack earlier this year.
In June 2020, Blackbaud, which is mainly known for the fundraising suites employed by charities and educational institutions, but which also offers payment services, announced publicly that it managed to stop a ransomware attack, but not before some data was stolen.
At the time, the company admitted to paying ransomware operators so that they would delete the data exfiltrated during the attack, but said that no personally identifiable information (PII) or bank account details were compromised.
In a Form 8-K filing this week, the cloud software company said a subsequent investigation revealed that the attackers were able to access data related to bank accounts, social security numbers, and login credentials.
“After July 16, further forensic investigation found that for some of the notified customers, the cybercriminal may have accessed some unencrypted fields intended for bank account information, social security numbers, usernames and/or passwords. In most cases, fields intended for sensitive information were encrypted and not accessible,” the company said.
Blackbaud said it took steps to inform the potentially impacted users in July, but that the new findings do not apply to all of those who were affected by the ransomware attack.
“Customers who we believe are using these fields for such information are being contacted the week of September 27, 2020 and are being provided with additional support,” Blackbaud noted in the filing.
The company also said that the investigation into the incident will continue, just as will security improvements to its systems. Customers, stockholders and other stakeholders will be informed of any new details that are uncovered during the investigation.
“Ransomware's double jeopardy factor is an effective attack vector for cybercriminals in this situation. It exfiltrates valuable original research data and IP for later sale on the dark web while locking the authors out of files that could potentially contain 100s of hours of irreplaceable work,” Matt Lock, UK Technical Director at Varonis, said in an emailed comment.
Researchers Fingerprint Exploit Developers Who Help Several Malware Authors
2.10.20 Exploit Virus Thehackernews
Writing advanced malware for a threat actor requires different groups of people with diverse technical expertise to put them all together. But can the code leave enough clues to reveal the person behind it?
To this effect, cybersecurity researchers on Friday detailed a new methodology to identify exploit authors that use their unique characteristics as a fingerprint to track down other exploits developed by them.
By deploying this technique, the researchers were able to link 16 Windows local privilege escalation (LPE) exploits to two zero-day sellers "Volodya" (previously called "BuggiCorp") and "PlayBit" (or "luxor2008").
"Instead of focusing on an entire malware and hunting for new samples of the malware family or actor, we wanted to offer another perspective and decided to concentrate on these few functions that were written by an exploit developer," Check Point Research's Itay Cohen and Eyal Itkin noted.
Fingerprinting an Exploit Writer's Characteristics
The idea, in a nutshell, is to fingerprint an exploit for specific artifacts that can uniquely tie it to a developer. It could be in using hard-coded values, string names, or even how the code is organized and certain functions are implemented.
Check Point said their analysis began in response to a "complicated attack" against one of its customers when they encountered a 64-bit malware executable that exploited CVE-2019-0859 to gain elevated privileges.
Noticing the fact that the exploit and the malware were written by two different sets of people, the researchers used the binary's properties as a unique hunting signature to find at least 11 other exploits developed by the same developer named "Volodya" (or "Volodimir").
"Finding a vulnerability, and reliably exploiting it, will most probably be done by specific teams or individuals who specialize in a particular role. The malware developers for their part don't really care how it works behind the scenes, they just want to integrate this [exploits] module and be done with it," the researchers said.
Interestingly, Volodya — likely of Ukrainian origin — has been previously linked to selling Windows zero-days to cyberespionage groups and crimeware gangs for anywhere between $85,000 to $200,000.
Chief among them was an LPE exploit that leveraged a memory corruption in "NtUserSetWindowLongPtr" (CVE-2016-7255), which has been widely used by ransomware operators like GandCrab, Cerber, and Magniber. It's now believed that Volodya advertised this LPE zero-day on the Exploit.in cybercrime forum in May 2016.
In all, five zero-day and six one-day exploits were identified as developed by Volodya over a period of 2015-2019. Subsequently, the same technique was employed to identify five more LPE exploits from another exploit writer known as PlayBit.
An Extensive Clientele
Stating the exploit samples shared code level similarities to grant SYSTEM privileges to the desired process, the researchers said, "both of our actors were very consistent in their respective exploitation routines, each sticking to their favorite way."
What's more, Volodya also appears to have switched up his tactics during the intervening years, with the developer shifting from selling the exploits as embeddable source code in the malware to an external utility that accepts a specific API.
Besides ransomware groups, Volodya has been found to cater to an extensive clientele, including the Ursnif banking trojan, and APT groups such as Turla, APT28, and Buhtrap.
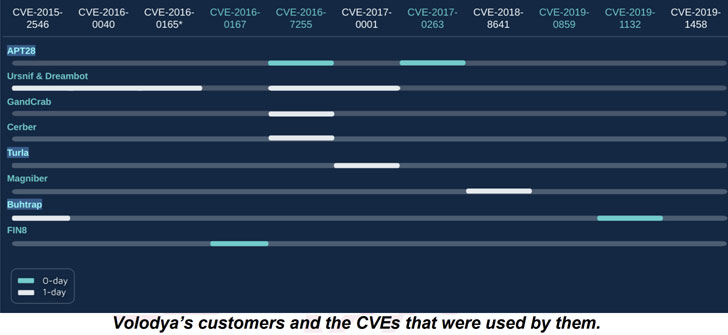
"The APT customers, Turla, APT28, and Buhtrap, are all commonly attributed to Russia and it is interesting to find that even these advanced groups purchase exploits instead of developing them in-house," Check Point observed in its analysis. "This is another point which further strengthens our hypothesis that the written exploits can be treated as a separate and distinct part of the malware."
With cyberattacks expanding in scope, frequency, and magnitude, using an exploit developer's code signature as a means to track down bad actors could provide valuable insight into the black exploit market.
"When Check Point finds a vulnerability, we demonstrate its severity, report it to the appropriate vendor, and make sure it's patched, so it doesn't pose a threat," Cohen said. "However, for individuals trading these exploits, it's a completely different story. For them, finding the vulnerability is just the beginning. They need to reliably exploit it on as many versions as possible, in order to monetize it to a customer's satisfaction."
"This research provides insight into how that is achieved, and the buyers in this market, which often include nation-state actors. We believe that this research methodology can be used to identify additional exploit writers."
InterPlanetary Storm Botnet Infects 13K Mac, Android Devices
2.10.20 BotNet Threatpost
In addition to Windows and Linux machines, a new variant of the malware now targets Mac and Android devices.
A new variant of the InterPlanetary Storm malware has been discovered, which comes with fresh detection-evasion tactics and now targets Mac and Android devices (in addition to Windows and Linux, which were targeted by previous variants of the malware).
Researchers say, the malware is building a botnet with a current estimated 13,500 infected machines across 84 countries worldwide – and that number continues to grow. Half of the infected machines are in Hong Kong, South Korea and Taiwan. Other infected systems are in Russia, Brazil, the U.S., Sweden and China.
“While the botnet that this malware is building does not have clear functionality yet, it gives the campaign operators a backdoor into the infected devices so they can later be used for cryptomining, DDoS, or other large-scale attacks,” said researchers with Barracuda in a Thursday analysis.
The first variant of InterPlanetary Storm was discovered in May 2019 and targeted Windows machines. In June, a variant targeting Linux machines was also reported targeting IoT devices, such as TVs that run on Android operating systems, and Linux-based machines, such as routers with ill-configured SSH service.
The botnet, which is written in Go, uses the Go implementation of libp2p, which is a network framework that allows users to write decentralized peer-to-peer (P2P) applications. This framework was originally the networking protocol of InterPlanetary File System (IPFS), on which researchers based the malware’s name.
“The malware is called InterPlanetary Storm because it uses the InterPlanetary File System (IPFS) p2p network and its underlying libp2p implementation,” said researchers. “This allows infected nodes to communicate with each other directly or through other nodes (i.e. relays).”
The malware spreads via brute force attacks on devices with Secure Shell (SSH), a cryptographic network protocol for operating network services securely over an unsecured network. Researchers noted this is similar to FritzFrog, another P2P malware. Another method of infection is by accessing open Apple Desktop Bus (ADB) ports, which connect low-speed devices to computers.
“The malware detects the CPU architecture and running OS of its victims, and it can run on ARM-based machines, an architecture that is quite common with routers and other IoT devices,” said researchers.

Machines infected worldwide by Interplanetary botnet. Credit: Barracuda
The newest variant of the malware has various big changes, most notably extending its targeting to include Mac and Android devices. However, the new variant can also auto-update to the latest available malware version and kill other processes on the machine that present a threat, like debuggers or competing malware (by looking at strings such as “rig,” “xig” and “debug”).
And, it now can detect honeypots by looking for the string “svr04” in the default shell prompt, for instance.
Once infected, devices communicate with the command-and-control (C2) server to inform that they are part of the botnet. Researchers said, the IDs of each infected machine are generated during initial infection and will be reused if the machine restarts or the malware updates. Once downloaded, it also serves malware files to other nodes in the network. The malware also enables reverse shell and can run bash shell, said researchers.
“Libp2p applications handle incoming connection (streams) based on a logical address (i.e. unknown to the transport layer) called protocol ID,” said researchers. “By convention, protocol ids have a path-like structure, with a version number as the final component.”
Botnets – particularly P2P botnets like Mozi, Roboto and DDG – continue to appear in the threat landscape. To avoid infection, researchers suggest end users properly configure SSH access on all devices and use a cloud security posture management tool to monitor SSH access control, eliminating any potential configuration mistakes.
“When password login is enabled and the service itself is accessible, the malware can exploit the ill-configured attack surface,” they said. “This is an issue common with routers and IoT devices, so they make easy targets for this malware.”
NFL, NBA Players Hacked in Would-Be Cyber-Slam-Dunk
2.10.20 Hacking Threatpost
Federal prosecutors charged two men with crimes that carry up to 20 years in prison.
NFL and NBA athletes whose social-media accounts were taken over have been thrown the ball of justice.
Multiple professional and semi-pro athletes were victimized by two men who infiltrated their personal accounts, according to testimony in federal court on Wednesday. Trevontae Washington of Thibodaux, La., and Ronnie Magrehbi, of Orlando, Fla., faced separate judges in the Eastern District of Louisiana and the Middle District of Florida, respectively, and were charged with one count of conspiracy to commit wire fraud, and one count of conspiracy to commit computer fraud and abuse.
Federal prosecutors alleged that between December 2017 and April 2019, Washington and Magrehbi actively took part in illegal schemes to gain access to social media and other personal online accounts of the players.
Washington allegedly specialized in NBA and NFL players, and phished for their credentials by taking advantage of public platforms like Instagram. He would send them messages with embedded links to what appeared to be legitimate social media log-in sites, prosecutors said, but these were actually phishing pages used to steal the athletes’ user names and passwords. Once the athletes entered their credentials, they would be sent to Washington, who, along with others allegedly locked the athletes out of their accounts. They also used the credentials against other accounts, banking on password reuse. Prosecutors claimed that Washington then sold access to the compromised accounts to others for amounts ranging from $500 to $1,000.
Magrehbi, meanwhile, is alleged to have obtained access to accounts belonging to one professional football player, including an Instagram account and personal email account. Magrehbi took a ransomware-like tack, prosecutors said, and extorted the player. He demanded payment in return for restoring access to the accounts – and was paid, according to Department of Justice documents. However, even though the player sent funds on at least one occasion, portions of which were transferred to a personal bank account controlled by Magrehbi – he was double-crossed and the athlete never regained access, prosecutors said.
The DoJ has not released the names of the affected players.
“Instagram is built as a mobile-first experience, which means that these attackers knew they could build a mobile-specific phishing campaign to increase the likelihood of success,” Hank Schless, senior manager of security solutions at Lookout, told Threatpost. “Since we carry our mobile devices with us all the time, we trust them to be inherently secure. Threat actors know this and socially engineer targets through SMS, social media and third-party messaging apps and convince them to click a malicious link.”
It’s more difficult to spot phishing targets on mobile, he added.
“Smaller screens, a simplified user experience and shortened URLs make it difficult to tell if a site is legitimate or not,” he said. “It’s also much easier to create a legitimate-looking account or phone number that could convince a target that the communication is real. Lookout discovered a mobile-specific phishing campaign earlier this year that intended to phish individual mobile banking login credentials through SMS.”
The wire fraud conspiracy charges carry a statutory maximum of 20 years in prison and a fine of up to $250,000. The computer fraud conspiracy charges carry a statutory maximum of five years in prison and a fine of up to $250,000.
To avoid being a victim of a mobile phishing scam, “first and foremost, be aware,” Shahrokh Shahidzadeh, CEO at Acceptto, told Threatpost. “Do not click on texts or respond to texts if you are not sure who they’re coming from. Even if it does come from a reputable source, but still seems off, consider checking in with them to make sure it was meant to be sent to you before clicking. Companies and end-users that are relying solely on binary authentication tactics, such as two-factor authentication (2FA) or multifactor authentication (MFA) via SMS, need to understand that these items are static and stored somewhere, waiting to be compromised time and time again. The best way to avoid these scams is to assume all credentials, even those yet to be created have been compromised.”
Meanwhile, account takeovers of high-profile accounts have been in the news lately, after hackers “mislead certain employees” to gain access to internal tools at Twitter to take over celebrity and company handles and push out a Bitcoin scam.
In that case, the attackers targeted 130 Twitter accounts, ultimately tweeting from 45, accessing the direct messages of 36 and downloading the Twitter Data of seven. Accounts for Joe Biden, Bill Gates, Elon Musk, Apple and Uber were all hijacked in the scheme.
Emotet Emails Strike Thousands of DNC Volunteers
2.10.20 Virus Threatpost
Hundreds of U.S. organizations on Thursday received emails purporting to come from the Democratic National Committee, in a new politically charged Emotet spear-phishing attack.
On Thursday, hundreds of U.S. organizations were targeted by an Emotet spear-phishing campaign, which sent thousands of emails purporting to be from the Democratic National Committee and recruiting potential Democratic volunteers.
Emotet has historically utilized a variety of lure themes leveraging current events – from COVID-19 to Greta Thunberg. However, the threat actor behind the malware, TA542, has not directly leveraged political themes in their messaging before. That changed with Thursday’s email campaign, which featured Word Document attachments labeled “Team Blue Take Action,” which actually infected victims with Emotet.
“The shift to using politically themed lures comes days after the first of several 2020 U.S. presidential debates,” said researchers with Proofpoint in a Thursday post. “The debate received widespread media coverage, and as Election Day draws nearer, many voters are likely feeling compelled to volunteer for political causes or for the election in some way.”
The email messages had the subject line “Team Blue Take Action,” with a message body taken directly from a page on the Democratic National Committee’s (DNC) website (democrats.org/team-blue) said researchers. This message body describes Team Blue, which is the DNC’s 2018 volunteer recruitment program – and says that Team Blue is being relaunched for the 2020 campaign. The email then asks the recipient to open the attached document.
This Word Document contains macros, which, if enabled, will download and install Emotet. Currently, researchers said they are also seeing a second stage payload following Emotet infections within this campaign, which either come in the form of the Qbot trojan or The Trick.
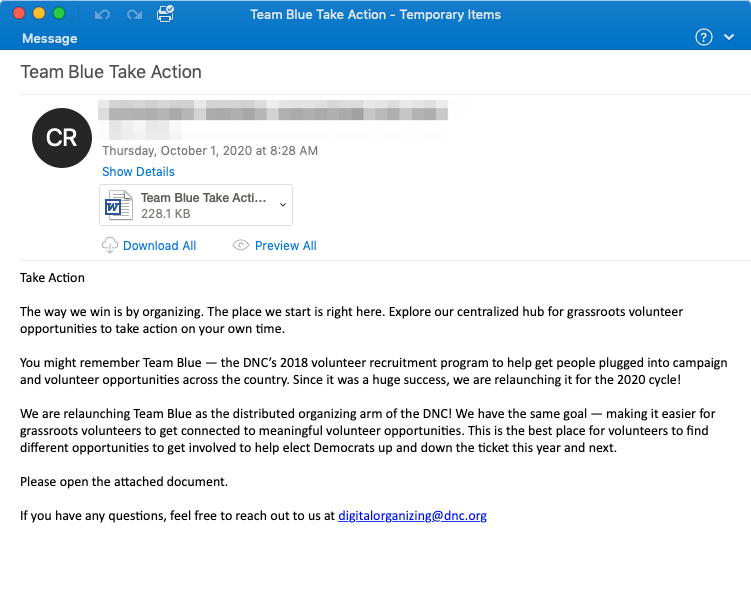
A sample spear-phishing email. Credit: Proofpoint
Beyond the email subject line “Team Blue Take Action,” researchers also observed other subject lines, including “Valanters 2020,” “List of Works” and more, with varying file names such as “Detailed information.doc” and “Volunteer.doc.”
Though disinformation is a key concern for many as the November U.S. presidential elections draw near, researchers believe that this lure was simply used to convince as many voters – fired up after Tuesday evening’s debate – to click as possible.
“It’s unlikely that this shift is driven by any specific political ideology,” they said. “Like earlier use of COVID-19 or Greta Thunberg lure themes, TA542 is attempting to reach as many intended recipients as possible by capitalizing on a popular topic.”
Emotet started life as a banking trojan in 2014 and has continually evolved to become a full-service threat-delivery mechanism. It can install a collection of malware on victim machines, including information stealers, email harvesters, self-propagation mechanisms and ransomware.
Emotet returned earlier in July after a five-month hiatus, when researchers spotted the malware in a campaign that has spammed Microsoft Office users with hundreds of thousands of malicious emails since Friday. The malware first emerged in 2014, but has since then evolved into a full fledged botnet that’s designed to steal account credentials and download further malware.
Emotet was last seen in February 2020, in a campaign that sent SMS messages purporting to be from victims’ banks. Once victims clicked on the links in the text messages, they are asked to hand over their banking credentials and download a file that infects their systems with the Emotet malware. Also in February, researchers uncovered an Emotet malware sample with the ability to spread to insecure Wi-Fi networks that are located nearby to an infected device.
Spammers Smuggle LokiBot Via URL Obfuscation Tactic
2.10.20 BotNet Threatpost
Researchers say that the campaign sidesteps end user detection and security solutions.
Spammers have started using a tricky URL obfuscation technique that sidesteps detection – and ultimately infects victims with the LokiBot trojan.
The tactic was uncovered in recent spear-phishing emails with PowerPoint attachments, which contain a malicious macro. When the PowerPoint file is opened, the document attempts to access a URL via a Windows binary (mshta.exe), and this leads to various malware being installed onto the system.
This process is not unusual for macro downloaders. However, because the domains associated with the campaign are already known to host malicious files and data, the attackers used a unique semantic attack on the campaign’s URLs to trick the email recipient and avoid being flagged by email and AV scanners. A semantic URL attack is when a client manually adjusts the parameters of its request by maintaining the URL’s syntax – but altering its semantic meaning. More on that, below.
“We found it interesting that the attackers were using URIs in this way, which essentially is an attack on the user’s preconceived notion of what a URI should look like,” said researchers with Trustwave in a Thursday report. “It may also defeat security solutions, which may be expecting URIs in a certain format.”
The malicious email that was observed by researchers is titled: “URGENT: REQUEST FOR OFFER (University of Auckland)” and the attached PowerPoint is titled “Request For Offer.” The University of Auckland is a public research university in Auckland, New Zealand. Threatpost has reached out to Trustwave for further details on the targeting and lure of this attack.
Obfuscation Tactic
It’s important to distinguish between a URL versus URI here. A URI is an identifier of a specific resource, such as a page, book or a document. A URL, meanwhile, is the most common type of URI that also tells users how to access it (such as HTTPs or FTP).
A URI is made up of a scheme, host and path. The scheme identifies the protocol to be used to access the resource on the internet, while the host identifies the host that holds the resource, and the path identifies the specific resource in the host that the web client wants to access.

The spear phishing email lure. Credit: Trustwave
The spammers behind this attack have horned in on one component of the URI scheme called an Authority component, which holds an optional user-information part. If the “userinfo” subcomponent is present, it is preceded by two slashes and followed by an “@” character. An example of this Authority structure is as follows: authority = [userinfo@]host[:port].
Because “userinfo” is not commonly used, it is sometimes ignored by servers, researchers said. In this specific campaign, attackers took advantage of this fact, utilizing what researchers called a “dummy” userinfo in order to hide their true intent.
The end result is that at face value, end users who click on the link may believe they are being led to one domain, but the URL is actually for another.
In this specific campaign, the URL used (j[.]mp/kassaasdskdd) actually utilizes a URL shortening service offered by Bit.ly and leads to Pastebin, which is a website that allows users to share plain text through public posts called “pastes.” Both the use of URL shortening services and Pastebin are commonly leveraged by cybercriminals; so to avoid being characterized as a short URL and to evade detection signatures, the attackers repeatedly use a randomized, short string (“%909123id”) in the userinfo portion of their URL (see picture below).
Because userinfo is not required to gain access to any resources, the userinfo data will be ignored when the URL is accessed – meaning that at face value, it’s unclear that the URL is shortened, and will redirect the users to Pastebin despite security gates.
“The bad guys are attempting to make the domains unnoticeable yet still conforming with the generic URI syntax,” said researchers.
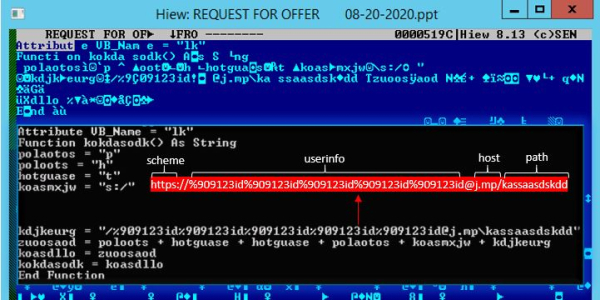
The PowerPoint attachment and its macro code where the initial malicious URL is formulated. Credit: Trustwave
Researchers conducted a deeper analysis of four URLs associated in the campaign. The first URL, accessed by the PowerPoint attachment, redirects to an obfuscated VBScript hosted on Pastebin. A second URL contains VBScript, which is a dropper that writes a PowerShell downloader into the registry and sets up persistence, said researchers. This PowerShell then downloads and processes the raw data on two more Pastebin URLs, and then executes the output binaries, they said.
The content at the third URL meanwhile contains an obfuscated PowerShell code, which then executes two DotNet compiled Dynamic Link Libraries (DLLs). These DLLs bypass the Windows Anti-Malware Scan Interface (AMSI) on the machine, which is an interface standard allowing user applications and services to integrate with any anti-malware product on a machine.
They then load a DLL injector into the memory. Finally, the last URL contains an obfuscated malware LokiBot sample, which is injected into a legitimate process (notedpad.exe) by the aforementioned DLL injector.
LokiBot Malware
LokiBot is a prolific trojan that’s infamous for being simple and effective with its capabilities to covertly steal information from compromised endpoints. It’s currently being distributed in various forms that can hitch a ride inside other file formats—as is the case in the current campaign. Various versions of LokiBot also in the past were sold on underground markets for as little as $300.
The new tactic comes just a week after The U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned that LokiBot is seeing a surge across the enterprise landscape. The uptick started in July, according to the agency, and activity has remained “persistent” ever since.
“LokiBot has stolen credentials from multiple applications and data sources, including Windows operating system credentials, email clients, File Transfer Protocol and Secure File Transfer Protocol clients,” according to the alert, issued Tuesday. “LokiBot has [also] demonstrated the ability to steal credentials from…Safari and Chromium and Mozilla Firefox-based web browsers.”
How to check if an email or a domain was used in Emotet attacks?
2.10.20 Virus Securityaffairs
Cyber security firm launches a new service that allows users to check if an email domain or address was part of an Emotet spam campaign.
Experts worldwide warn about a surge in the Emotet activity, recently Microsoft along Italy and the Netherlands CERT/CSIRT agencies reported a significant increase of Emotet attacks targeting the private sector and public administration entities. Similar alerts were issued in the same period by Computer Emergency Response Teams (CERTs) in France, Japan, and New Zealand.
Emotet is a malware infection that spreads through spam emails containing malicious Word or Excel documents. When opened and macros are enabled, it will install the Emotet trojan on a victim’s computer.
The recent Emotet campaign uses spam messages with password-protected attachments.
The Emotet banking trojan has been active at least since 2014, the botnet is operated by a threat actor tracked as TA542. In the middle-August, the malware was employed in fresh COVID19-themed spam campaign
Recent spam campaigns used messages with malicious Word documents, or links to them, pretending to be an invoice, shipping information, COVID-19 information, resumes, financial documents, or scanned documents.
Emotet malware is also used to deliver other malicious code, such as Trickbot and QBot trojan or ransomware such as Conti (TrickBot) or ProLock (QBot).
Now I’m very happy to announce that the Italian cybersecurity company TG Soft launched a new service called Have I Been Emotet that allows users and organizations to check if a domain or email address was involved/targeted in Emotet spam campaigns.
TG Soft has monitored Emotet spam emails sent between August and September 23rd, 2020. The experts analyzed more than 700,000 outgoing emails and collected over 2.1 million email addresses.
The use of the service is very simple, the users have to provide a domain or email address, in turn, the platform will report how many times the email address or domain was used as the sender of an email or the recipient.
Querying the Have I Been Emotet service, the email address or domain can be marked as a SENDER (FAKE or REAL), as a RECIPIENT, or any combination of the three. A REAL SENDER suggests that the computer using this email account has been compromised and used to send out spam messages. A FAKE SENDER indicates that the email address provided by the users was compromised and used in spam campaigns. RECIPIENT indicates that the email address provided by the users was the recipient of an Emotet spam email. Watch out, the presence of an email address or domain that has been used as a recipient, does not necessarily mean that the user’s organization has been infected.
A recipient could have been infected in case it has opened the attachments used in the spam email and enabled macros.
If a domain was marked as a ‘REAL’ sender it is suggested to check if it has been compromised.
Let’s consider for example the mail shared by the Italian CSIRT in his alert, we can verify that the domain “pro-teca.com” was involved in Emotet campaigns monitored by TG Soft.


Netwalker ransomware operators leaked files stolen from K-Electric
2.10.20 Ransomware Securityaffairs
K-Electric, Pakistan’s largest private power company, did not pay the ransom and the Netwalker ransomware operators have leaked the stolen data.
In early September, K-Electric (KE), the electricity provider for the city of Karachi, Pakistan, was hit by a Netwalker ransomware attack that blocked billing and online services.
K-Electric is the largest power supplier in the country with 2.5 million customers and around 10,000 people.
Starting on September 7, the customers of the company were not able to access the services for their accounts. The good news is that the power supply has not been affected. In response to the incident, K-Electric is attempting to reroute users through a staging site, but the problems have yet to be solved.
The news of the incident was first reported by BleepingComputer which was informed by the ransomware researcher Ransom Leaks.
After being informed about this ransomware attack, security researchers confirmed that the Netwalker ransomware operators were behind the attack.
Netwalker ransomware operators are demanding the payment of $3,850,000 worth of Bitcoin. As usual, if the company will not pay the ransom within another seven days, the ransom will increase to $7.7 million.
Source BleepingComputer
The gang also claimed on the ‘Stolen data’ page of their Tor leak site that they have stolen unencrypted files from K-Electric before encrypting its systems. At the time it is not clear how many documents were stolen and which kind of information they contained.
News of the day is that Netwalker ransomware operators have released the victim’s data stolen during the attack, an 8.5 GB archive.
Researchers from cybersecurity firm Rewterz, who analyzed the content of the archive, told BleepingComputer that it contains some company’s sensitive information, including financial data, customer information, engineering reports, engineering diagrams for turbines, maintenance logs, and more.
Experts pointed out that threat actors had access to customer’s personal information that could be used to carry out multiple malicious activities.
Recently the Netwalker ransomware operators hit Argentina’s official immigration agency, Dirección Nacional de Migraciones, the attack caused the interruption of the border crossing into and out of the country for four hours.
Another victim of the group is the University of California San Francisco (UCSF), who decided to pay a $1.14 million ransom to recover its files.
Recently the FBI has issued a security alert about Netwalker ransomware attacks targeting U.S. and foreign government organizations.
The feds are recommending victims, not to pay the ransom and reporting incidents to their local FBI field offices.
The flash alert also includes indicators of compromise for the Netwalker ransomware along with mitigations.
The FBI warns of a new wave of Netwalker ransomware attacks that began in June, the list of victims includes the UCSF School of Medicine and the Australian logistics giant Toll Group.
The Netwalker ransomware operators have been very active since March and also took advantage of the ongoing COVID-19 outbreak to target organizations.
Below the recommended mitigations provided by the FBI:
Back-up critical data offline.
Ensure copies of critical data are in the cloud or on an external hard drive or storage device.
Secure your back-ups and ensure data is not accessible for modification or deletion from the system where the data resides.
Install and regularly update anti-virus or anti-malware software on all hosts.
Only use secure networks and avoid using public Wi-Fi networks.
Consider installing and using a VPN.
Use two-factor authentication with strong passwords.
Keep computers, devices, and applications patched and up-to-date.
Treasury Department Warns Ransomware Payment Facilitators of Legal Implications
2.10.20 Ransomware Securityweek
The U.S. Department of the Treasury this week issued an advisory to warn companies that facilitate ransomware payments of the potential legal implications resulting from sending money to sanctioned entities.
The Treasury Department’s Office of Foreign Assets Control (OFAC) says there has been a rise in ransomware attacks on U.S. organizations, which has resulted in an increase in the demand for ransomware payments.
Many organizations from around the world, including several cities and universities in the U.S., have paid significant amounts of money to recover their files following a ransomware attack.
However, the Treasury Department warns, companies that facilitate ransomware payments to cybercriminals on behalf of victims not only encourage future attacks, but also risk violating OFAC regulations. The advisory specifically lists cyber insurance companies, financial institutions, and providers of incident response and digital forensics services as organizations that can facilitate ransomware payments.
The OFAC noted that many cyber threat actors have been sanctioned over the past years, including for attacks involving malware such as Cryptolocker (linked to a Russian individual), SamSam (linked to Iranians), WannaCry (linked to North Korea) and Dridex (linked to a Russian organization).
Companies are informed that making a ransomware payment to sanctioned people or countries could be used to fund activities “adverse to the national security and foreign policy objectives of the United States.” The advisory also points out that paying the ransom not only encourages the threat actor to launch more attacks, but there is also no guarantee that the victim will regain access to the compromised data.
“OFAC may impose civil penalties for sanctions violations based on strict liability, meaning that a person subject to U.S. jurisdiction may be held civilly liable even if it did not know or have reason to know it was engaging in a transaction with a person that is prohibited under sanctions laws and regulations administered by OFAC,” the advisory notes.
In a fireside chat at SecurityWeek’s recent CISO Forum, Evan Wolff, a cyber-attorney and partner at international law firm Crowell & Moring, talked about the legal issues that CISOs could personally face due to their actions, and one of the examples he mentioned was paying to recover from a ransomware infection. The advisory from the Treasury Department reinforces Wolff’s warning about personal liability.
The advisory recommends that companies “implement a risk-based compliance program to mitigate exposure to sanctions-related violations,” and points out that reporting a ransomware attack to law enforcement in a timely manner and cooperating with law enforcement is considered a “significant mitigating factor in determining an appropriate enforcement outcome if the situation is later determined to have a sanctions nexus.”
“OFAC already provides a list of sanctioned entities. Victim organizations are required to check the list prior to paying extortion demands. However, the true identity of the cyber criminals extorting victims is usually not known, so it’s difficult for organizations to determine if they are unintentionally violating U.S. Treasury sanctions. Sometimes victims pay threat actors before they are sanctioned. For example, many victims have paid the ‘SamSam’ ransomware operators in the past, not knowing they were based in Iran at the time,” Charles Carmakal, SVP & CTO at FireEye Mandiant, told SecurityWeek.
“In recent months, the individuals (referred to as “EvilCorp”) involved with the Dridex banking malware have been connected with the WastedLocker ransomware family. Some extortion payment organizations have decided that they would not pay extortion demands associated with WastedLocker incidents out of fear of violating U.S. Treasury sanctions,” he added.
German Privacy Watchdog Fines H&M $41M for Spying on Workers
2.10.20 BigBrothers Securityweek
A German privacy watchdog said Thursday that it is fining clothing retailer H&M 35.3 million euros ($41 million) after the company was found to have spied on some of its employees in Germany.
Hamburg’s data protection commissioner said in a statement that the Swedish company collected private information about employees at a customer service center in Nuremberg, “ranging from rather harmless details to family issues and religious beliefs.”
The information was recorded on a network drive accessible to up to 50 managers and “used, among other things, to obtain a detailed profile of employees for measures and decisions regarding their employment.”
The data protection commissioner, Johannes Caspar, said that “the combination of collecting details about their private lives and the recording of their activities led to a particularly intensive encroachment on employees’ civil rights.”
The privacy violation was discovered after the data briefly became visible to all people on the company network, resulting in news reports about the information gathering.
H&M said in a statement that the practices in Nuremberg didn’t correspond to company guidelines but that it nevertheless took full responsibility and had apologized unreservedly to the employees. The company said it would examine the fine issued.
Casper welcomed H&M’s decision to pay compensation to employees at the Nuremberg service center and take measures to prevent future privacy breaches, saying the steps “show the intention to give the employees the respect and appreciation they deserve as dependent workers in their daily work for their company.”
Flaws in leading industrial remote access systems allow disruption of operations
1.10.20 ICS Securityaffairs
Experts found critical security flaws in two popular industrial remote access systems that could be exploited by threat actors for malicious purposes.
Security researchers from Israeli firm OTORIO found critical vulnerabilities in leading industrial remote access systems that could be exploited by attackers to ban access to industrial production floors, hack into company networks, tamper with data, and even steal sensitive business secrets.
Remote access has crucial in the modern industry, especially due to the increased demands of industrial remote access systems sustained during the ongoing COVID-19 pandemic.
The issues affect the popular industrial remote access systems B&R Automation’s SiteManager and GateManager broadly used in multiple sectors, including in automotive, energy, oil & gas, and metal.
The experts found six vulnerabilities in B&R Automation’s SiteManager and GateManager (CVE-2020-11641, CVE-2020-11642, CVE-2020-11643, CVE-2020-11644, CVE-2020-11645, CVE-2020-11646) that could potentially disrupt operations.
“Exploiting the 6 new vulnerabilities, an attacker who has gained authorized access to the solution could view sensitive information about other users, their assets and their processes (even when they belong to an external organization).” reads the advisory published by the company. “Additionally, hackers can fool users to malicious foreign sites through fictive system messages and alerts, and trigger a repeated restart of both the GateManager and the SiteManager, leading eventually to a loss of availability, and halt production.”
“Leveraging all three vulnerabilities would have enabled attackers to devise a worst-case scenario to an operations floor which relied on remote access employees.”
The US CISA agency also published a security advisory to warn of risks associated with the successful exploitation of the flaws in the B&R Automation systems. The Agency confirmed that an authenticated attacker with access to the solution via a general license could exploit the flaws to trigger a DoS condition or to achieve arbitrary information disclosure and data manipulation.
The vulnerabilities impact all versions of SiteManager prior to v9.2.620236042, GateManager 4260, and 9250 before v9.0.20262, and GateManager 8250 prior to v9.2.620236042.
Experts also found security vulnerabilities in mymbCONNECT24 and mbCONNECT24 that could be exploited by authenticated attackers to access arbitrary information via SQL injection, steal session details by carrying out a cross-site request forgery (CSRF).
The vulnerabilities, tracked as (CVE-2020-24569, CVE-2020-24568, CVE-2020-24570), impact mymbCONNECT24 and mbCONNECT24 versions v2.6.1 and prior.
The most severe issue is an IMPROPER NEUTRALIZATION OF SPECIAL ELEMENTS USED IN A COMMAND (‘COMMAND INJECTION’) vulnerability that received a CVSS score of 9.8.
CISA also published a security advisory for these vulnerabilities, the US agency provided the following recommendations to the users:
Minimize network exposure for all control system devices and/or systems, and ensure that they are not accessible from the Internet.
Locate control system networks and remote devices behind firewalls, and isolate them from the business network.
When remote access is required, use secure methods, such as Virtual Private Networks (VPNs), recognizing that VPNs may have vulnerabilities and should be updated to the most current version available. Also recognize that VPN is only as secure as the connected devices.
FBI, CISA Say DDoS Attacks Won't Prevent Voting
1.10.20 BigBrothers Securityweek
While they might hinder access to information, distributed denial-of-service (DDoS) attacks against election infrastructure won’t prevent voting, the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) said in an alert issued this week.
DDoS attacks would either slow down election-related public-facing websites or render them inaccessible, thus preventing voters from staying updated with voting information or from accessing voting results.
Such attacks are meant to disrupt activities for a period of time through flooding Internet-accessible servers with requests and preventing legitimate users from connecting to online resources, such as online accounts or websites.
“The public should be aware that if foreign actors or cyber criminals were able to successfully conduct DDoS attacks against election infrastructure, the underlying data and internal systems would remain uncompromised, and anyone eligible to vote would still be able to cast a ballot,” the FBI and CISA note.
Furthermore, the two agencies warn that threat actors might falsely claim that they successfully compromised voting systems through DDoS attacks and that they were able to prevent voters from casting their ballots or that they managed to modify already-cast votes.
Such disinformation attempts, the two agencies say, would undermine the public’s trust in the country’s democratic institutions and seek to discredit the electoral process. Two other similar alerts issued over the past couple of weeks warn of disinformation regarding the security of voting systems and the validity of election results.
“The FBI and CISA have no reporting to suggest a DDoS attack has ever prevented a registered voter from casting a ballot, or compromised the integrity of any ballots cast,” the alert reads.
The agencies also note that they’ve worked closely with election officials to identify additional channels through which they could keep voters informed, including traditional media, verified social media accounts, and other resources.
“Election officials have multiple safeguards and plans in place to limit the impact and recover from a DDoS incident with minimal disruption to the voting process,” the agencies say.
Citizens are advised to get informed on vote procedures and polling places ahead of election day, to make sure that information comes from trustworthy sources only, and to only rely on state and local government election officials when it comes to details on how to vote, on polling locations, and on final election results.
HP Offering Big Rewards for Cartridge Vulnerabilities
1.10.20 Vulnerebility Securityweek
HP announced on Thursday that it has expanded its bug bounty program, inviting several white hat hackers to find vulnerabilities in its office-class ink and toner cartridges.
The printer giant says it’s working with Bugcrowd to run this program for three months. The program is private and only four researchers have been invited to find vulnerabilities in original HP cartridges.
HP says it has invested roughly $200,000 into this initiative and it’s prepared to award an extra $10,000 for each vulnerability, in addition to the researchers’ base fee.HP adds cartridge vulnerabilities to its bug bounty program
HP has been running a bug bounty program for its printers since 2018 — the company claimed at the time that this was the industry’s first printer bug bounty program. The company says there has been an increase in attacks on embedded systems, and printer firmware may also be targeted.
The company has warned that, in addition to poor printing results and the financial damage they cause to the industry, imitation and fake cartridges can introduce unknown and untrusted electrical hardware into an organization’s network.

“While the industry has become sophisticated at spotting and blocking software-based intrusions, the same can’t be said for hardware. In fact, it is well understood in the IT industry that counterfeit hardware can become the source of hardware-based exploitation,” said Shivaun Albright, chief technologist for print security at HP.
HP says it has taken steps to prevent cartridge chips from being replaced or altered in the supply chain.
“Only Original HP cartridges contain a chip with HP proprietary firmware that is designed to be secure and resistant to tampering. Non-HP supplies include chips of unknown origin that may employ untrusted firmware,” Albright explained. “Given that there is a data interface from the chip to the printer, an attacker with the right skills and resources may be able to uncover and exploit a vulnerability, taking advantage of this interface to inject malicious code.”
Twitter Removes Iran-Linked Accounts Aimed at Disrupting U.S. Presidential Debate
1.10.20 APT Social Securityweek
Twitter on Wednesday announced that it removed 130 accounts originating from Iran that were aimed at disrupting the first 2020 U.S. presidential debate.
The accounts, the social media platform reveals, were removed after the Federal Bureau of Investigation (FBI) alerted it on the suspicious activity.
“Based on intel provided by the @FBI, last night we removed approximately 130 accounts that appeared to originate in Iran. They were attempting to disrupt the public conversation during the first 2020 US Presidential Debate,” Twitter announced.
The social platform also explains that it was able to quickly identify the accounts and remove them. The accounts had low engagement and weren’t able to impact the public conversation.
The company says that, once its investigation into these accounts has been completed, it will publish all of the necessary details on its Transparency portal.
“As standard, the accounts and their content will be published in full once our investigation is complete. We’re providing this notice to keep people updated in real time about our actions. We wish to thank the @FBI for their assistance,” Twitter said.
The removal of these accounts comes roughly one month after Microsoft warned of attempts from state-sponsored threat actors, including Iranian ones, to disrupt the 2020 U.S. presidential elections. Iran responded swiftly, claiming the allegations were absurd.
Last week, Facebook announced that it shut down a network of fake accounts out of China that were aiming at the US presidential race.
In June, Twitter announced the removal of a total of 30,000 state-linked accounts originating from China, Turkey, and Russia that engaged in manipulation.
Over the past couple of weeks, the FBI and CISA issued several alerts to warn of disinformation campaigns aimed hurting the population’s trust in the election results and the security of voting systems.
Microsoft Publishes Guide to Securing Systems Vulnerable to Zerologon Attacks
1.10.20 Attack Securityweek
Microsoft has published a support article to provide guidance on what organizations need to do to ensure that they are not exposed to attacks targeting the Zerologon vulnerability.
Addressed on August 2020 Patch Tuesday, the flaw was identified in the Microsoft Windows Netlogon Remote Protocol (MS-NRPC) and can be abused by remote attackers to compromise Active Directory domain controllers and gain administrator access.
To exploit the flaw, which is tracked as CVE-2020-1472, an unauthenticated attacker would need to run a specially crafted application on a device on the network.
On September 18, the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) issued an Emergency Directive requiring all federal agencies to apply the available patches within three days, and Samba also issued patches for the bug.
Last week, Microsoft said it was seeing adversaries attempting to exploit the vulnerability and this week CISA warned of similar attacks, urging administrators to patch all of their domain controllers.
In a guide aimed at administrators looking to keep their organization’s environment secure, Microsoft explains that patching for the bug is being performed in two stages: an initial deployment stage, starting with the August 11 release of patches, and an enforcement phase that will start on February 9, 2021.
To mitigate the vulnerability, Microsoft says, admins should apply the August update on all domain controllers and read-only domain controllers, monitor log events to identify any devices that might still make vulnerable connections, and address these non-compliant devices, and then enable enforcement mode to address the flaw.
“The February 9, 2021 release marks the transition into the enforcement phase. The DCs will now be in enforcement mode regardless of the enforcement mode registry key. This requires all Windows and non-Windows devices to use secure RPC with Netlogon secure channel or explicitly allow the account by adding an exception for the non-compliant device,” Microsoft notes.
The tech giant also provides information on the type of log errors to look for to identify vulnerable Netlogon secure channel connections, what group policies to apply, and what happens following the installation of the August 11 patches or when the enforcement phase starts.
Russian Who Hacked LinkedIn, Dropbox Sentenced to 7 Years in Prison
1.10.20 Crime Thehackernews
A Russian hacker who was found guilty of hacking LinkedIn, Dropbox, and Formspring over eight years ago has finally been sentenced to 88 months in United States prison, that's more than seven years by a federal court in San Francisco this week.
Yevgeniy Aleksandrovich Nikulin, 32, of Moscow hacked into servers belonging to three American social media firms, including LinkedIn, Dropbox, and now-defunct social-networking firm Formspring, and stole data on over 200 million users.
Between March and July 2012, Nikulin hacked into the computers of LinkedIn, Dropbox, and Formspring, and installed malware on them, which allowed him to remotely download user databases of over 117 Million LinkedIn users and more than 68 Million Dropbox users.
According to the prosecutor, Nikulin also worked with unnamed co-conspirators of a Russian-speaking cybercriminal forum to sell customer data he stole as a result of his hacks.
Besides hacking into the three social media firms, Nikulin has also been accused of gaining access to LinkedIn and Formspring employees' credentials, which helped him carry out the computer hacks.
"The Court also found that Automattic, parent company of Wordpress.com, was the victim of an intrusion by defendant, although there was no evidence that defendant stole any customer credentials," the Justice Department said.
Nikulin was arrested in Prague on October 5, 2016, by Interpol agents working in collaboration with the FBI, and extradited to the United States in March 2018 after a long extradition battle between the U.S. and Russia.
In 2016, the hacker was charged with nine felony counts of computer intrusion, aggravated identity theft, causing damage to a protected computer, trafficking in unauthorized access devices, and conspiracy.
However, after a long delay of trials due to the coronavirus pandemic, Nikulin was found guilty by a federal jury of the United States in early July this year and was sentenced to 88 months in prison on September 29.
U.S. District Judge William H. Alsup convicted Nikulin of selling stolen usernames and passwords, installing malware on protected computers, conspiracy, computer intrusion, and aggravated identity theft.
Prior to the sentencing hearing on September 29, federal prosecutors sought a sentence of 145 months in prison, that's over 12 years in prison, three years of supervised release, and restitution.
Nikulin has been in U.S. custody since his extradition from the Czech Republic and will be serving his sentence effect immediately.
Critical Flaws Discovered in Popular Industrial Remote Access Systems
1.10.20 ICS Thehackernews
Cybersecurity researchers have found critical security flaws in two popular industrial remote access systems that can be exploited to ban access to industrial production floors, hack into company networks, tamper with data, and even steal sensitive business secrets.
The flaws, discovered by Tel Aviv-based OTORIO, were identified in B&R Automation's SiteManager and GateManager, and MB Connect Line's mbCONNECT24, two of the popular remote maintenance tools used in automotive, energy, oil & gas, metal, and packaging sectors to connect to industrial assets from anywhere across the world.
Six Flaws in B&R Automation's SiteManager and GateManager
According to an advisory published by the US Cybersecurity and infrastructure Security Agency (CISA) on Wednesday, successful exploitation of the B&R Automation vulnerabilities could allow for "arbitrary information disclosure, manipulation, and a denial-of-service condition."
The flaws, ranging from path traversal to improper authentication, impact all versions of SiteManager prior to v9.2.620236042, GateManager 4260, and 9250 before v9.0.20262, and GateManager 8250 prior to v9.2.620236042.
OTORIO's Nikolay Sokolik and Hay Mizrachi found that by exploiting these six vulnerabilities (CVE-2020-11641 through CVE-2020-11646), an authenticated attacker with access to the solution via a general license could view sensitive information about other users, their assets, and their processes, even when they belong to a different organization from that of the adversary.
"This information can be used by attackers to target other organizations and their industrial systems," OTORIO said.
"Additionally, hackers can fool users into malicious foreign sites through fake system messages and alerts. The attacker can also trigger a repeated restart of both the GateManager and the SiteManager, leading eventually to a loss of availability and halt production."
An RCE Flaw in mbCONNECT24
Likewise, mymbCONNECT24 and mbCONNECT24 versions v2.6.1 and prior have been found vulnerable to four different security issues that could make it possible for a logged-in attacker to access arbitrary information via SQL injection, steal session details by carrying out a cross-site request forgery (CSRF) attack with merely a specifically crafted link, and leverage outdated and unused third-party libraries bundled with the software to gain remote code execution.
The RCE vulnerability is the severest of all, with a CVSS score of 9.8 out of a maximum of 10.
Although these flaws have since been fixed, the development is another reminder of how weaknesses in remote access solutions can have destructive consequences on critical infrastructure.
For its part, CISA has recommended minimizing network exposure for all control system devices, in addition to putting control system networks and remote devices behind firewalls, and isolating them from the business network.
"When remote access is required, use secure methods, such as Virtual Private Networks (VPNs), recognizing that VPNs may have vulnerabilities and should be updated to the most current version available," the agency cautioned. Also, recognize that VPN is only as secure as the connected devices."
Beware: New Android Spyware Found Posing as Telegram and Threema Apps
1.10.20 Android Thehackernews
A hacking group known for its attacks in the Middle East, at least since 2017, has recently been found impersonating legitimate messaging apps such as Telegram and Threema to infect Android devices with a new, previously undocumented malware.
"Compared to the versions documented in 2017, Android/SpyC23.A has extended spying functionality, including reading notifications from messaging apps, call recording and screen recording, and new stealth features, such as dismissing notifications from built-in Android security apps," cybersecurity firm ESET said in a Wednesday analysis.
First detailed by Qihoo 360 in 2017 under the moniker Two-tailed Scorpion (aka APT-C-23 or Desert Scorpion), the mobile malware has been deemed "surveillanceware" for its abilities to spy on the devices of targeted individuals, exfiltrating call logs, contacts, location, messages, photos, and other sensitive documents in the process.
In 2018, Symantec discovered a newer variant of the campaign that employed a malicious media player as a lure to grab information from the device and trick victims into installing additional malware.
Then earlier this year, Check Point Research detailed fresh signs of APT-C-23 activity when Hamas operators posed as young teenage girls on Facebook, Instagram, and Telegram to lure Israeli soldiers into installing malware-infected apps on their phones.
The latest version of the spyware detailed by ESET expands on these features, including the ability to collect information from social media and messaging apps via screen recording and screenshots, and even capture incoming and outgoing calls in WhatsApp and read the text of notifications from social media apps, including WhatsApp, Viber, Facebook, Skype, and Messenger.
The infection begins when a victim visits a fake Android app store called "DigitalApps," and downloads apps such as Telegram, Threema, and weMessage, suggesting that the group's motivation behind impersonating messaging apps is to "justify the various permissions requested by the malware."
In addition to requesting invasive permissions to read notifications, turn off Google Play Protect, and record a user's screen under the guise of security and privacy features, the malware communicates with its command-and-control (C2) server to register the newly infected victim and transmit the device information.
The C2 servers, which typically masquerade as websites under maintenance, are also responsible for relaying the commands to the compromised phone, which can be used to record audio, restart Wi-Fi, uninstall any app installed on the device, among others.
What's more, it also comes equipped with a new feature that allows it to stealthily make a call while creating a black screen overlay to mask the call activity.
"Our research shows that the APT-C-23 group is still active, enhancing its mobile toolset and running new operations. Android/SpyC32.A – the group's newest spyware version — features several improvements making it more dangerous to victims," ESET said.
Apps downloaded from fraudulent third-party app stores has been a conduit for Android malware in recent years. It's always essential to stick to official sources to limit risk, and scrutinize permissions requested by apps before installing them on the device.
Microsoft Exchange Servers Still Open to Actively Exploited Flaw
1.10.20 Exploit Threatpost
Despite Microsoft issuing patches almost eight months ago, 61 percent of Exchange servers are still vulnerable.
Over half of exposed Exchange servers are still vulnerable to a severe bug that allows authenticated attackers to execute code remotely with system privileges – even eight months after Microsoft issued a fix.
The vulnerability in question (CVE-2020-0688) exists in the control panel of Exchange, Microsoft’s mail server and calendaring server. The flaw, which stems from the server failing to properly create unique keys at install time, was fixed as part of Microsoft’s February Patch Tuesday updates – and admins in March were warned that unpatched servers are being exploited in the wild by unnamed advanced persistent threat (APT) actors.
However, new telemetry found that out of 433,464 internet-facing Exchange servers observed, at least 61 percent of Exchange 2010, 2013, 2016 and 2019 servers are still vulnerable to the flaw.
“There are two important efforts that Exchange administrators and infosec teams need to undertake: verifying deployment of the update and checking for signs of compromise,” said Tom Sellers with Rapid7 in a Tuesday analysis.
Researchers warned in a March advisory that unpatched servers are being exploited in the wild by unnamed APT actors. Attacks first started in late February and targeted “numerous affected organizations,” researchers said. They observed attackers leverage the flaw to run system commands to conduct reconnaissance, deploy webshell backdoors and execute in-memory frameworks, post-exploitation.
Previously, in April, Rapid7 researchers found that more than 80 percent of servers were vulnerable; out of 433,464 internet-facing Exchange servers observed, at least 357,629 were open to the flaw (as of March 24). Researchers used Project Sonar, a scanning tool, to analyze internet-facing Exchange servers and sniff out which were vulnerable to the flaw.

Exchange build number distribution status for flaw. Credit: Rapid7
Sellers urged admins to verify that an update has been deployed. The most reliable method to do so is by checking patch-management software, vulnerability-management tools or the hosts themselves to determine whether the appropriate update has been installed, he said.
“The update for CVE-2020-0688 needs to be installed on any server with the Exchange Control Panel (ECP) enabled,” he said. “This will typically be servers with the Client Access Server (CAS) role, which is where your users would access the Outlook Web App (OWA).”
With the ongoing activity, admins should also determine whether anyone has attempted to exploit the vulnerability in their environment. The exploit code that Sellers tested left log artifacts in the Windows Event Log and the IIS logs (which contain HTTP server API kernel-mode cache hits) on both patched and unpatched servers: “This log entry will include the compromised user account, as well as a very long error message that includes the text invalid viewstate,” he said.
Admins can also review their IIS logs for requests to a path under /ecp (usually /ecp/default.aspx), Sellers said, These should contain the string __VIEWSTATE and __VIEWSTATEGENERATOR – and will have a long string in the middle of the request that is a portion of the exploit payload.
“You will see the username of the compromised account name at the end of the log entry,” he said. “A quick review of the log entries just prior to the exploit attempt should show successful requests (HTTP code 200) to web pages under /owa and then under /ecp.”
Facebook Small Business Grants Spark Identity-Theft Scam
1.10.20 Spam Threatpost
The cybercrooks spread the COVID-19 relief scam via Telegram and WhatsApp, and ultimately harvest account credentials and even pics of IDs.
Cybercriminals are exploiting a $100 million Facebook grant program designed for small businesses impacted by the pandemic, to phish personal information and take over Facebook accounts.
The perpetrators are trying to dupe people into thinking that the social network is handing out free money to any user affected by COVID-19, according to a Kaspersky analysis. It’s using messaging platforms to proliferate.
“This is an attack that was caught propagating via messengers, such as Telegram,” Vladislav Tushkanov, senior data scientist at Kaspersky, told Threatpost. “This seems to be a common trend – we even see some attacks where after asking for your private info, the perpetrators ask you to forward the scam link to your WhatsApp contacts (e.g. ‘to spread awareness about these benefits’).”
Despite the “must be too good to be true” aspect of the game that should tip most people off, the cybercriminals are taking steps to make the offer seem legit.
“Samples detected by Kaspersky indicate that potential victims viewed an article appearing to come from a prominent media outlet [CNBC] and were prompted to follow a link to apply for the grant,” researchers explained, in a Tuesday post. They pointed out that there is in fact, a real CNBC article about coronavirus-related Facebook grants, but the legitimate program is for small businesses, not individuals.
The bogus CNBC article. Source: Kaspersky
If people were sucked into clicking the link, they were taken to a phishing page and asked to enter personal information, even including a scan of both sides of their ID.
“First you’ll be asked for your Facebook username and password,” according to Kaspersky. “If you enter them, they’ll go straight to the cybercriminals. Then, to accept your application, the site requires a lot more information, supposedly to verify your account: Your address, Social Security number (for U.S. citizens), and even a scan of both sides of your ID. No fields can be left blank, and the site diligently prompts you about any omissions.”
The portal mimics the official site of Mercy Corps, a charity that helps victims of natural disasters and armed conflicts.
“However, the only topic on this one is Facebook grants, and the victim is asked to specify how many years they have been a user of the social network,” researchers noted. “The collected information allowed the scammers to gain access of their victims’ Facebook accounts, which they could use to pull off other crimes, including identity theft.”
There are a few red flags along the way; for instance, the headline in the purported CNBC article is filled with grammar mistakes.
“The grammar should give away the game, and the URL, which does not start with cnbc.com, is another suspicious element,” according to the posting.
Also, the grammar on the phishing website “stinks,” the researchers said, and most of the links don’t work. “And, of course, the site URL does not contain facebook.com, so it clearly has nothing to do with Facebook,” they added.
Once the information is submitted, the crooks log into the victim’s Facebook account and then try to message friends or leave postings that ultimately are aimed at extracting money from them.
“Facebook accounts can be used to scam victims’ friends and relatives directly or to promote further scam,” Tushkanov said.
However, the form fields provide the crooks with enough personal information to steal full identities, researchers warned. “Armed with this and scans of your documents, they will likely be able to get into any of your accounts, including online banking.”
These types of scams aren’t going away anytime soon, Tushkanov said, so people should be vigilant and careful in vetting “offers” like these.
“We have seen numerous attempts to lure people by promising them some kind of coronavirus-related compensations – for following by stay-at-home orders, payments for children etc.,” he told Threatpost, adding that these kinds of simple scams are the most common. “More sophisticated attacks are by definition more difficult to carry out. So yes, these more simplistic attacks seem to still be the most common ones. Ultimately, almost all scammers are driven by some kind of financial incentive.”
OAuth Consent Phishing Ramps Up with Microsoft Office 365 Attacks
1.10.20 Attack Threatpost
Attackers gain read-only permissions to snoop around Office 365 accounts, including emails, contacts and more.
An APT known as TA2552 has been spotted using OAuth2 or other token-based authorization methods to access Office 365 accounts, in order to steal users’ contacts and mail.
OAuth is an open standard for access delegation, commonly used as a way for people to sign into services without entering a password — using signed-in status on another, trusted service or website. The most visible example might be the “Sign in with Google” or “Sign in with Facebook” that many websites use in lieu of asking visitors to create a new account.
According to researchers from Proofpoint, targets receive a well-crafted lures asking them to click a link which carries them to the legitimate Microsoft third-party apps consent page.
“Once signed into their O365 (Office 365) account, the user is redirected to the official O365 consent process that prompts them to grant permissions to the actor’s application,” they explained. “The domains that catch the OAuth tokens are often registered via Namecheap and hosted on Cloudflare.”
There, they’re asked to grant read-only permissions to a (malicious) third-party application that’s masquerading as a real organization’s app.
Proofpoint researchers added that users should be aware of the permissions that these, and any, third-party apps are asking for. In the case of this campaign, the malicious apps are asking for read-only access to the user’s contacts, profile and mail – all of which could be used to snoop around accounts, silently steal data or even intercept password reset messages from other accounts, like online banking.
“Even read-only access comes with considerable risk,” according to a Proofpoint posting on Tuesday. “The ability to perform reconnaissance on an O365 account supplies an actor with valuable information that can later be weaponized in business email compromise (BEC) attacks or account takeovers…The minimal [read-only] permissions requested by these apps also likely help them appear inconspicuous if an organization’s O365 administrator audits connected apps for their users’ accounts.”
They added, “The apps don’t request many permissions, and those they do might not appear particularly far-reaching, allowing them to blend in with other benign apps.”
If consent is granted, the third-party application will be allowed to access the currently authenticated Office 365 account. If consent is denied, the browser is still redirected to an attacker-controlled page, giving the actor the opportunity to try again with a different tactic.
Further, if the browser is not already authenticated to Office 365 in the first place, the user is sent to the official Office 365 login page to sign in, researchers added, and then are asked to grant permissions again.
Proofpoint researchers said that organizations worldwide have received messages, but TA2552 seems to favor Spanish speakers in Mexico for this effort. For instance, the impersonation of the Servicio de Administración Tributaria (SAT), Mexico’s tax authority, is a common message theme.
“When SAT is used in the phish lure, the email suggests that the recipient needs to update their contact information and is presented with what appears to be a link to do so,” Proofpoint noted. “Some subjects, like ‘Аcսse dе Сіta – Aсlaracіоոes 2020. (Acknowledgment of Appointment – Clarifications 2020.),’ make use of non-ASCII characters, possibly to evade simple spam filters.”
The firm added that while Mexican tax- and government-themed messages are the normal spoofing targets for the campaign, researchers also observed lures and apps impersonating Netflix Mexico and Amazon Prime Mexico.
“Threat actors often find creative ways to harvest information,” Proofpoint researchers said. “In these attacks, TA2552 doesn’t rely on techniques like more traditional credential-phishing or dropping malware on a system. Instead, they gain permissions to view the content and activity of resources available through a user’s O365 account. The departure from such traditional techniques gives this actor an advantage, as users likely aren’t trained to spot or inspect suspicious applications.”
OAuth Attacks on the Rise
In July, Microsoft warned against these kinds of attacks, which Agnieszka Girling, Partner Group PM Manager at Microsoft, warned were on the rise. Also known as consent phishing, it’s an easy attack to carry out, she said. Attackers need only to register a malicious app with an OAuth 2.0 provider, such as Microsoft’s own Azure Active Directory.
“The app is configured in a way that makes it seem trustworthy, like using the name of a popular product used in the same ecosystem,” explained Girling at the time. “The attacker gets a link in front of users, which may be done through conventional email-based phishing, by compromising a non-malicious website or other techniques. The user clicks the link and is shown an authentic consent prompt asking them to grant the malicious app permissions to data.”
If a user clicks accept, they will grant the bad app permissions to access their credentials and potentially other sensitive data, as in the campaign flagged by Proofpoint.
“The app gets an authorization code which it redeems for an access token, and potentially a refresh token,” Girling explained. “The access token is used to make API calls on behalf of the user. If the user accepts, the attacker can gain access to their mail, forwarding rules, files, contacts, notes, profile and other sensitive data and resources.”
Users can protect themselves by ensuring that whatever app they’re signing into is actually legitimate. They can also apply basic phishing-awareness strategies, such as looking for poor spelling and grammar in the original emails. Also, app names and domain URLs can offer red flags.
Developer successfully compiled leaked source code for MS Windows XP and Windows Server 2003 OSs
1.10.20 Incindent Securityaffairs
Last week, the source code for MS Windows XP and Windows Server 2003 OSs were leaked online, now a developer successfully compiled them.
Last week, the source code for Microsoft’s Windows XP and Windows Server 2003 operating systems was published as a torrent file on the bulletin board website 4chan. This is the first time that the source code of Microsoft’s 19-year-old operating system was leaked online.
The leaker goes online with the moniker billgates3 and claims to have collected the source code over the course of the last few months.
The leaker also added that the source code for multiple Microsoft operating systems is circulating in the hacking community for years.
The collection of torrent files leaked online is 43GB in size and include the source code for Windows Server 2003 and other older operating systems developed by Microsoft, including:
Windows 2000
Windows CE 3
Windows CE 4
Windows CE 5
Windows Embedded 7
Windows Embedded CE
Windows NT 3.5
Windows NT 4
MS-DOS 3.30
MS-DOS 6.0
Now a Windows developer that goes online with the moniker ‘NTDEV‘ announced to have successfully compiled both Windows XP and Windows Server 2003 using the leaked source code.
And the final proof…
I'm so excited! It's been such an amazing journey! pic.twitter.com/d0wLp1OdRQ
— NTDEV (@NTDEV_) September 29, 2020
I have compiled Server 2003 and, it seems like it's more complete than XP… Let's make it an ISO and see how far it goes…
(for comparison, the "CD" from the compiled XP took only 68MB) pic.twitter.com/ncCwTjCS1f
— NTDEV (@NTDEV_) September 28, 2020
‘NTDEV‘ also published a video to show how to compile both Windows operating systems. The expert has no problem while compiling the source code for Windows server 2003.
The developer explained that the source code for Windows XP doesn’t contain critical files, including the Winlogon.exe.
“So, upon further inspection, the XP source code might not be as complete as we previously thought, as it doesn’t compile a critical file, winlogon.exe However, there is also an Server 2003 sc in that leak, so let’s see how far that goes… Stay tuned!” added the developer.
So, upon further inspection, the XP source code might not be as complete as we previously thought, as it doesn't compile a critical file, winlogon.exe
However, there is also an Server 2003 sc in that leak, so let's see how far that goes… Stay tuned!
— NTDEV (@NTDEV_) September 28, 2020
The expert provided multiple updates on its attempts and successes through its Twitter account.
The availability of the source code of the Windows XP could allow threat actors to search for zero-day issues that could be exploited in attacks against the tens of millions of PCs are still based on the popular Microsoft OS.
Russian national Yevgeniy Aleksandrovich Nikulin sentenced to 88 months in prison
1.10.20 Crime Securityaffairs
Russian national Yevgeniy Aleksandrovich Nikulin was sentenced to 88 months in prison for hacking LinkedIn, Dropbox, and Formspring in 2012.
The Russian national Yevgeniy Aleksandrovich Nikulin was sentenced to 88 months in prison in the United States for hacking LinkedIn, Dropbox, and Formspring in 2012.
Let’s summarize the criminal activities of the man who was arrested in Prague in October 2016 in an international joint operation with the FBI.

Source: US Defense Watch.com
Nikulin first breached LinkedIn between March 3 and March 4, 2012, the hacker first infected an employee’s laptop with malware then used the employee’s VPN to access LinkedIn’s internal network.
The Russian man stole roughly 117 million user records, including usernames, passwords, and emails.
Nikulin used data stolen from Linkedin to launch spear-phishing attacks against employees at other companies, including Dropbox.
Between May 14, 2012 and July 25, 2012, Nikulin obtained the records belonging 68 million Dropbox users containing usernames, emails, and hashed passwords.
Nikulin also hacked into an employee account of a Formspring engineer and used it to access the company network between June 13, 2012, and June 29, 2012. The hacker stole 30 million user details from the company database.
The data stolen by Nikulin were available on the cybercrime underground between 2015 and 2016, they were offered for sale by multiple traders.
The man always refused to cooperate with the authorities or to plead guilty while he was in prison.
The Russian man was found guilty by a United States jury in early July, he was previously sentenced to 145 months in prison, three years of supervised release, and restitution.
The lawyers of the hacker, Adam Gasner and Valery Nechay, claimed that their client had been already in custody for a total of 48 months already.
Nikulin was sentenced to 88 months in prison, of which he will or 74 months, minus the time already served.
“Nikulin’s sentence breaks down to 64 months on counts two, six and eight related to trafficking in unauthorized access devices and causing damage to a protected computer, and 60 months for counts one, four, five and seven related to computer intrusion and conspiracy. These will all be served concurrently. He will also serve 24 months for aggravated identity theft.” reported the CourtHouseNews website.
“The sentence imposed was 88 months, of which he will serve 85% of that time – meaning he needs to serve 74.8 months of actual custody,” Gasner said. “After deducting the 48 months he has already served, he has 26.8 additional months remaining. So, a little over two years before he is returned home. We wish him well.”
Nikulin was also sentenced to three years of supervised release and the judge ordered him to pay restitution of $1 million to LinkedIn, $514,000 to Dropbox, $20,000 to Formspring, and $250,000 to WordPress parent company Automattic.
Over 61% of Exchange servers vulnerable to CVE-2020-0688 attacks
1.10.20 Attack Securityaffairs
More than 247,000 Microsoft Exchange servers are still vulnerable to attacks exploiting the CVE-2020-0688 RCE issue impacting Exchange Server.
The CVE-2020-0688 vulnerability resides in the Exchange Control Panel (ECP) component, the root cause of the problem is that Exchange servers fail to properly create unique keys at install time.
“Knowledge of a the validation key allows an authenticated user with a mailbox to pass arbitrary objects to be deserialized by the web application, which runs as SYSTEM.” reads the advisory published by Microsoft.
A remote, authenticated attacker could exploit the CVE-2020-0688 vulnerability to execute arbitrary code with SYSTEM privileges on a server and take full control.
Security experts Simon Zuckerbraun from Zero Day Initiative published technical details on how to exploit the Microsoft Exchange CVE-2020-0688 along with a video PoC.
Microsoft addressed the vulnerability with the release of the Microsoft February Patch Tuesday updates, but more than 247,000 Microsoft Exchange servers (61% percent of Exchange servers installs) are yet to be fixed.
Rapid7 reported that 87% of almost 138,000 Exchange 2016 servers and 77% of around 25,000 Exchange 2019 servers are still vulnerable to CVE-2020-0688 attacks, and roughly 54,000 Exchange 2010 servers have not been updated in six years.
After Microsoft addressed the flaw experts reportedly observed that APT actors exploiting the flaw.
Researchers from Rapid7 reported that 61 percent of Exchange 2010, 2013, 2016 and 2019 servers are still vulnerable to the vulnerability.
“It’s been just under eight months since Microsoft released the patches to address CVE-2020-0688, so we thought it would be a good time to revisit patch deployment to see whether organizations have addressed this particular risk.” explained Tom Sellers with Rapid7 in a blog post. “Unfortunately, as of our study on Sept. 21, 2020, it appears that 61% of the target population (Exchange 2010, 2013, 2016, and 2019) is still vulnerable to exploitation.”
In March researchers from the cybersecurity firm Volexity warned of nation-state actors that were attempting to exploit the CVE-2020-0688 flaw.
Experts reccoments to determine whether Exchange has been updated and to install the update on any server with the Exchange Control Panel (ECP) enabled.
“The most reliable method to determine whether the update is installed is by checking patch management software, vulnerability management tools, or the hosts themselves to determine whether the appropriate update has been installed.” continues the post.”Note that these tools will likely not indicate that the update is missing if the Exchange Server isn’t running a current version of the Exchange Cumulative Update or Rollup. These servers are still vulnerable.”
According to the experts, admins could check the presence of compromised accounts used in attacks against Exchange servers by reviewing Windows Event and IIS logs for parts of encoded payloads including the “Invalid viewstate” text or the __VIEWSTATE and __VIEWSTATEGENERATOR strings for requests to a path under /ecp (usually /ecp/default.aspx).
Don’t waste time, check if your install is up to date.
North Korea APT group targeted tens of UN Security Council officials
1.10.20 APT Securityaffairs
North Korea-linked APT group targeted UN Security Council officials over the past year, states a report from the United Nations organ.
A North-Korea-linked cyber espionage group has launched spear-phishing attacks aimed at compromising tens of officials from the United Nations Security Council.
The campaign targeted at least 28 UN officials, including at least 11 individuals representing six countries of the UN Security Council.
The campaign was disclosed in a UN report published at the end of August, the attacks took place this year and were spotted by an unnamed UN member state that reported it to the UN Security Council.
“According to information from another Member State, at least 28 individuals, including at least 11 officials from six members of the Security Council, became the targets of a spear-phishing campaign in 2020 which appeared to have been conducted by a Kimsuky advanced persistent threat group.” reads the report. “According to the information, these Democratic People’s Republic of Korea cyberactors launched a “security alert” – themed spear-phishing campaign in mid-March against Gmail accounts of the targeted individuals by placing malicious links in the email, utilizing a link to bypass spam blockers of the potential victims.”
The UN Security Council attributes the attack to the KimSuky APT group.
The Kimsuky APT group has been analyzed by several security teams, it was first spotted by Kaspersky researcher in 2013, recently its activity was detailed by ESTsecurity and by the malware researchers from Cybaze ZLab.
The campaign took place between March and April, threat actors attempted to compromise the Gmail accounts of UN officials by carrying out spear-phishing messages.
The spear-phishing messages were posing as UN security alerts or requests for interviews from journalists, a UN member also reported that the attacks were also launched through WhatsApp.

The emails were designed to look like UN security alerts or requests for interviews from reporters, both designed to convince officials to access phishing pages or run malware files on their systems.
The country which reported the Kimsuky attacks to the UN Security Council also said that similar campaigns were also carried out against members of its own government, with some of the attacks taking place via WhatsApp, and not just email.
The UN Security Council also published another report in March that detailed two other Kimsuky campaigns against its officials.
The first campaign targeted 38 email addresses belonging to members of the Security Council, while the second campaign targeted officials from China, France, Belgium, Peru, and South Africa in August.
“Cyberattacks against the Panel continued. An expert received a phishing email with a fake security alert from the United Nations, and multiple experts received an email in which the attacker spoofed as a member of the editing staff of a journal soliciting an article from experts. The Panel notes the similar cyberattacks against the expert community on the Democratic People’s Republic of Korea in 2020.” concludes the report. “The Panel reiterates its view that cyberattacks, both past and ongoing, against such United Nations bodies as the Committee and the Panel, which are mandated to monitor the implementation of United Nations sanctions, amount to sanctions evasion, considering the persistent and highly disruptive nature of the attacks.”
Cisco Issues Patches For 2 High-Severity IOS XR Flaws Under Active Attacks
1.10.20 Attack Thehackernews
Cisco yesterday released security patches for two high-severity vulnerabilities affecting its IOS XR software that were found exploited in the wild a month ago.
Tracked as CVE-2020-3566 and CVE-2020-3569, details for both zero-day unauthenticated DoS vulnerabilities were made public by Cisco late last month when the company found hackers actively exploiting Cisco IOS XR Software that is installed on a range of Cisco's carrier-grade and data center routers.
Both DoS vulnerabilities resided in Cisco IOS XR Software's Distance Vector Multicast Routing Protocol (DVMRP) feature and existed due to incorrect implementation of queue management for Internet Group Management Protocol (IGMP) packets on affected devices.
IGMP is a communication protocol typically used by hosts and adjacent routers to efficiently use resources for multicasting applications when supporting streaming content such as online video streaming and gaming.
"These vulnerabilities affect any Cisco device that is running any release of Cisco IOS XR Software if an active interface is configured under multicast routing and it is receiving DVMRP traffic," Cisco said in an advisory.
"An administrator can determine whether multicast routing is enabled on a device by issuing the show igmp interface command."
Successful exploitation of these vulnerabilities could allow remote unauthenticated hackers to send specially crafted IGMP packets to affected devices to either immediately crash the IGMP process or exhaust process memory and eventually crash.
The memory consumption may negatively result in instability of other processes running on the device, including routing protocols for both internal and external networks.
The vulnerabilities affect all Cisco devices running any release of Cisco IOS XR Software if an active interface is configured under multicast routing, and it is receiving DVMRP traffic.
At the time Cisco initially made these vulnerabilities public, the company provided some mitigation to resolve the issues and block the active exploitation attempts, but now it has finally released Software Maintenance Upgrades (SMUs) to address the vulnerabilities completely.
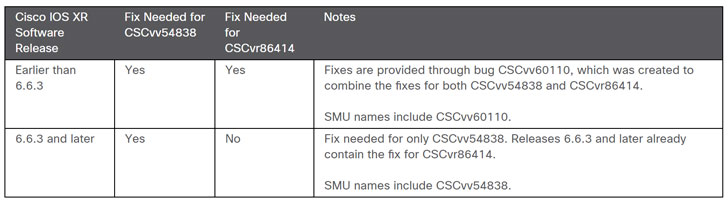
"Although there are no workarounds for these vulnerabilities, there are multiple mitigations available to customers depending on their needs," the company said.
"When considering mitigations, it should be understood that for the memory exhaustion case, the rate limiter and the access control methods are effective. For the immediate IGMP process crash case, only the access control method is effective."
Cisco customers are highly recommended to make sure they are running the latest Cisco IOS XR Software release earlier than 6.6.3 and Cisco IOS XR Software release 6.6.3 and later.